Image encryption method and device, image decryption method and device, electronic equipment and storage medium
An encryption method and image technology, applied in the field of information transmission, can solve problems such as slow encryption speed, low security, and complex encryption algorithm, and achieve the effect of fast operation speed and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0124] Taking a JPEG image as an example, the image encryption operation is performed, in which the marker matrix is embedded into the DCT coefficient of the JPEG image, and the image encryption process is as follows:
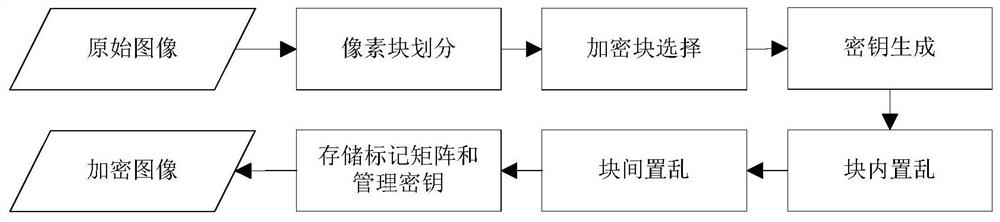
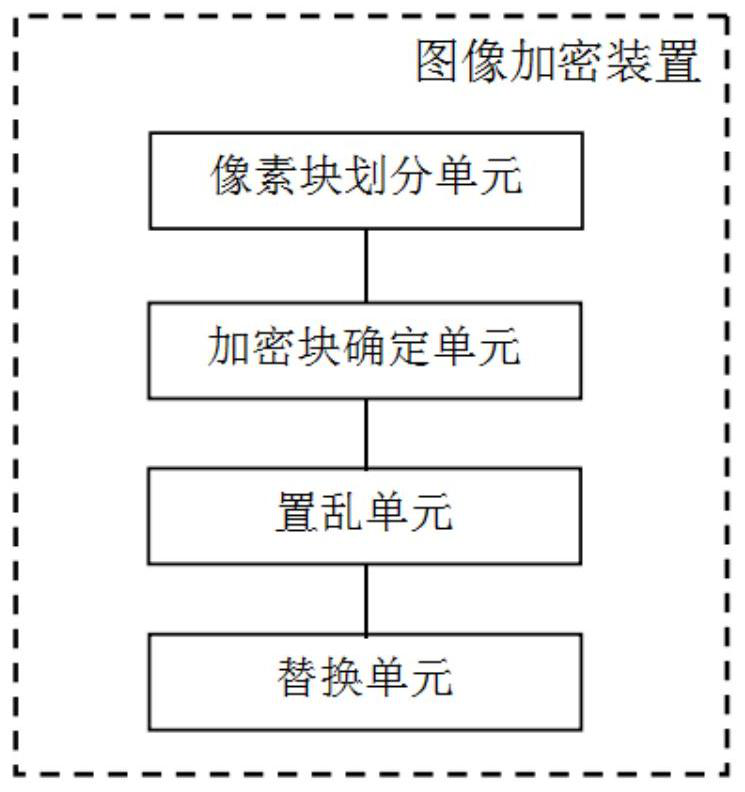
[0125] Pixel block division: the encryptor first decompresses the JPEG image into the airspace to obtain the airspace pixel matrix. Then divide the spatial domain pixel matrix into rectangular blocks. Since there may be cases where the division cannot be done exactly, the image can be scaled or cut in advance to fit the division.
[0126] Encryption block selection: according to the content to be encrypted, the encryptor sets the rectangular block covered by the encrypted content as an encryption block, thus obtaining a marked matrix.
[0127] Key Generation: The encryptor uses the original key to generate key sequences for subsequent intra-block and inter-block scrambling respectively.
[0128] Built-in block scrambling: The encryptor uses the key to scramb...
Embodiment 2
[0132] Also take a JPEG image as an example to perform an image decryption operation, where the marker matrix is embedded into the DCT coefficients of the JPEG image. The image decryption process is as follows:
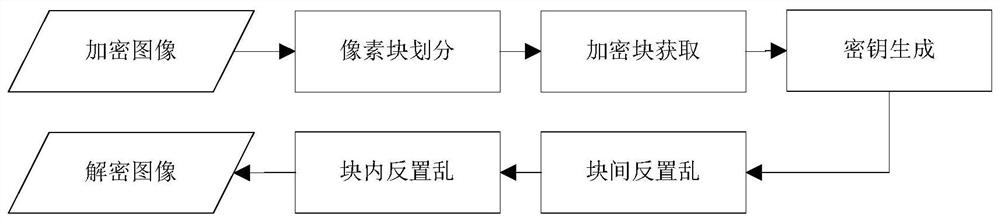
[0133] Pixel block division: the decryptor first decompresses the encrypted JPEG image into the airspace to obtain the airspace pixel matrix. Then divide the spatial domain pixel matrix into rectangular blocks.
[0134] Encrypted block acquisition: the decryptor extracts the marker matrix from the DCT coefficients of the JPEG image, and combines the marker matrix to obtain the encrypted scrambling matrix.
[0135] Key generation: The decryptor uses the original key to generate a key sequence, which is used for subsequent intra-block and inter-block anti-scrambling respectively.
[0136] Inter-block anti-scrambling: The decryptor uses the key to perform inter-block anti-scrambling on all encrypted blocks. After anti-scrambling, each rectangular block will return to...
Embodiment 3
[0140] Taking a video image as an example, the video image encryption and decryption operations are performed, where the marker matrix is embedded in the DCT coefficients of the video image, and the video image encryption process is as follows:
[0141] Pixel block division: the encryptor first decompresses the video image into the airspace to obtain the airspace pixel matrix. Then divide the spatial domain pixel matrix into rectangular blocks. Since there may be cases where the division cannot be done exactly, the video can be scaled or cut in advance to fit the division.
[0142] The encryption process is exactly the same as that of ordinary images. After the encryption is completed, the encrypted video images are obtained and input into the video encoder to generate video encoding streams.
[0143] Store the marking matrix and manage the key: the encryptor embeds the marking matrix into the DCT coefficient of the video image, and then makes the encrypted video public or s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com