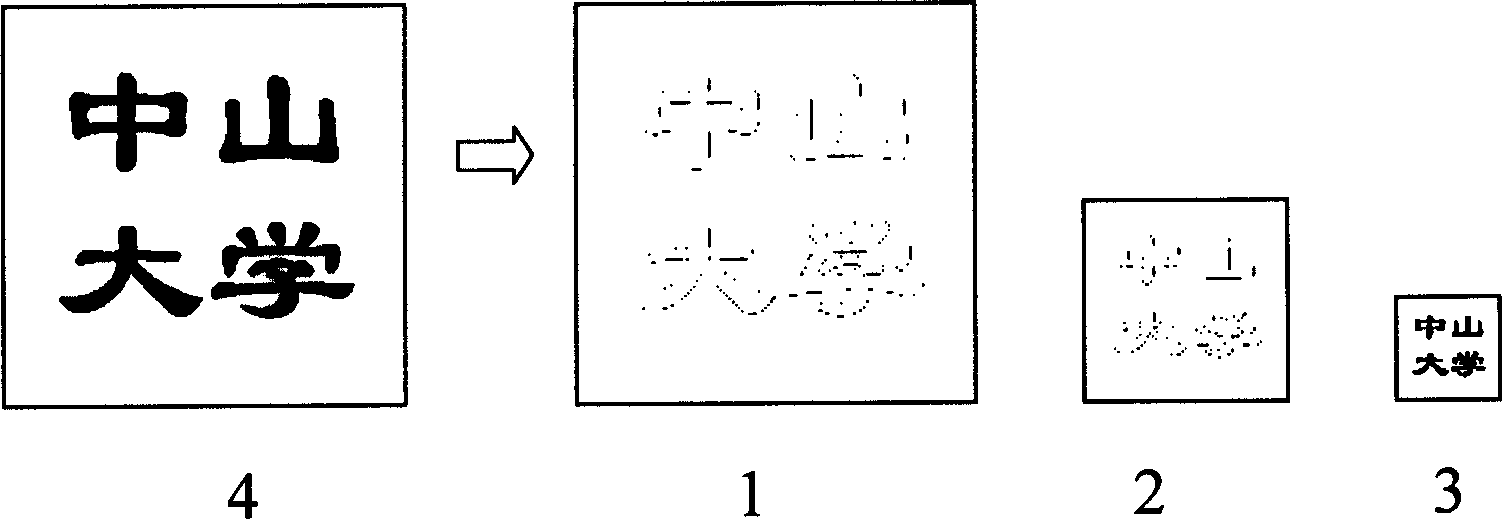
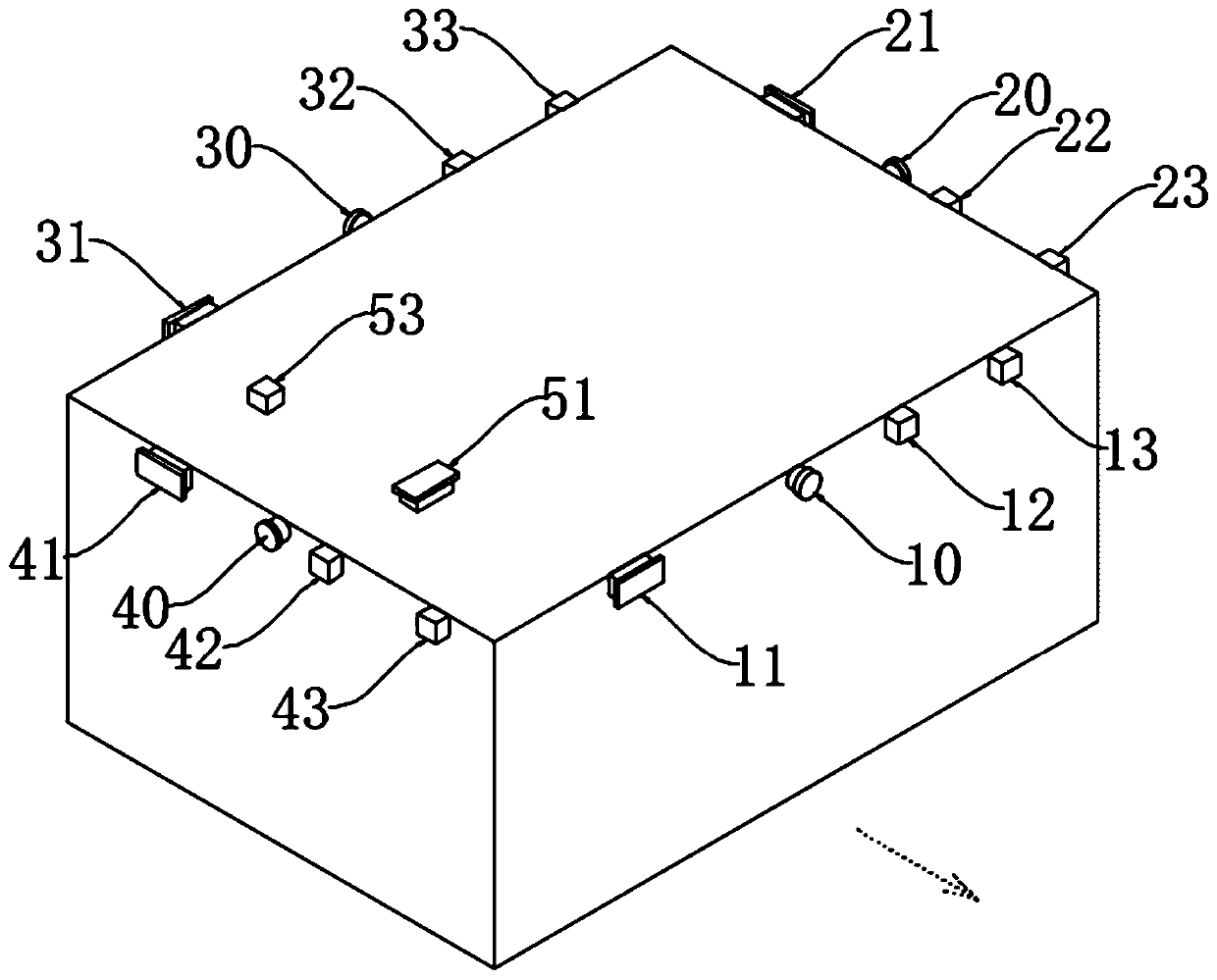
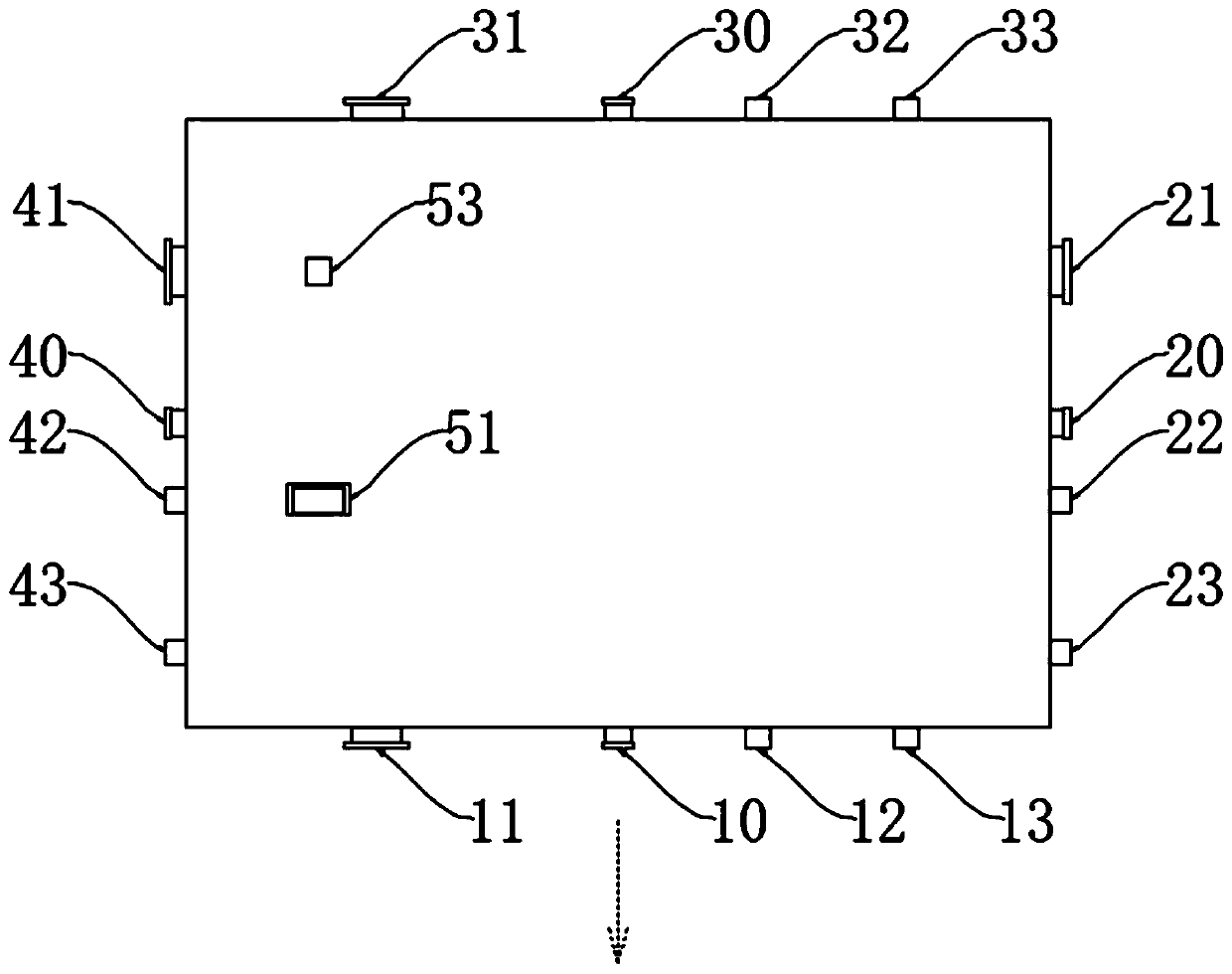
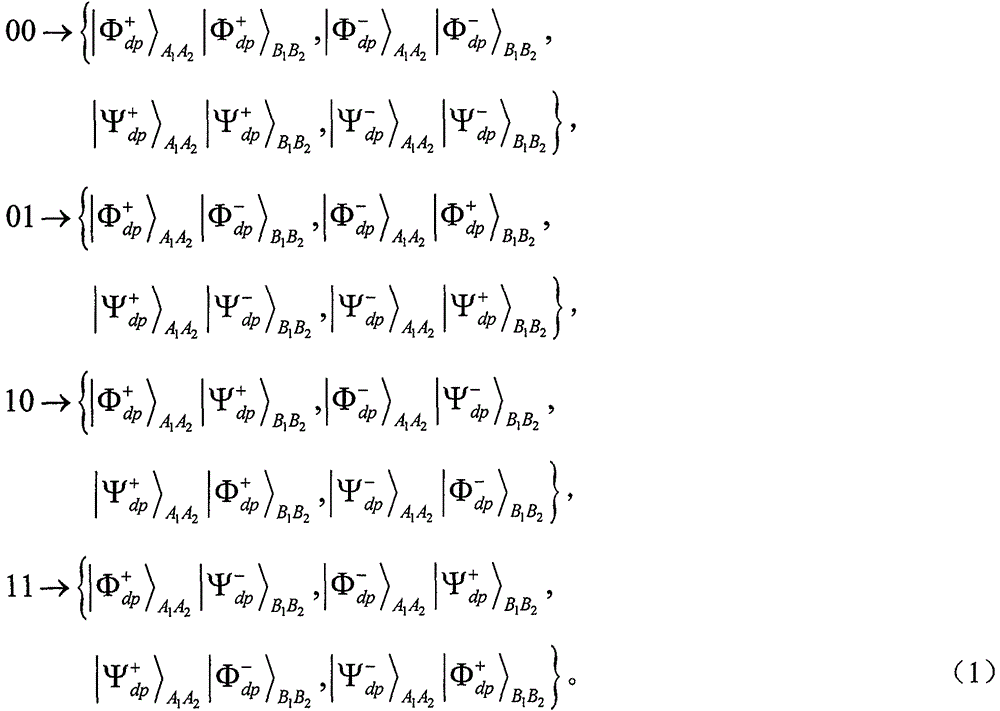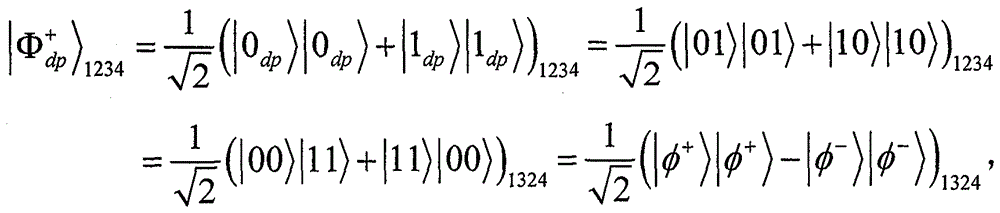Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40results about How to "Guaranteed invisibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
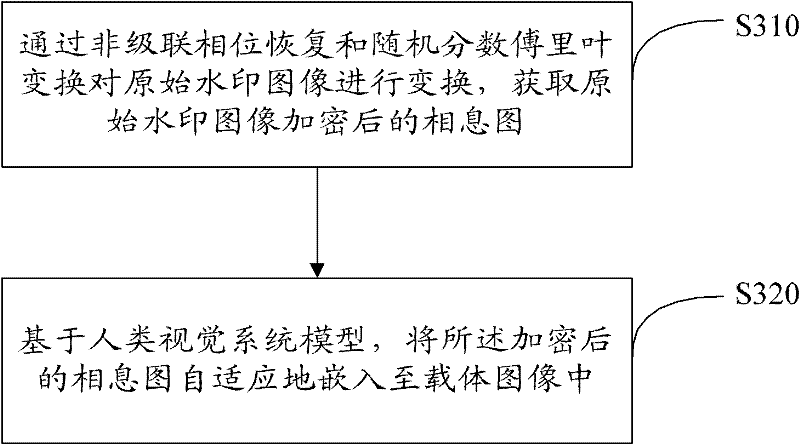
Encrypted kinoform based digital image watermarking embedding and extracting methods and systems
ActiveCN102142131AReduce data volumeGood clipping resistanceImage data processing detailsHuman visual system modelKinoform
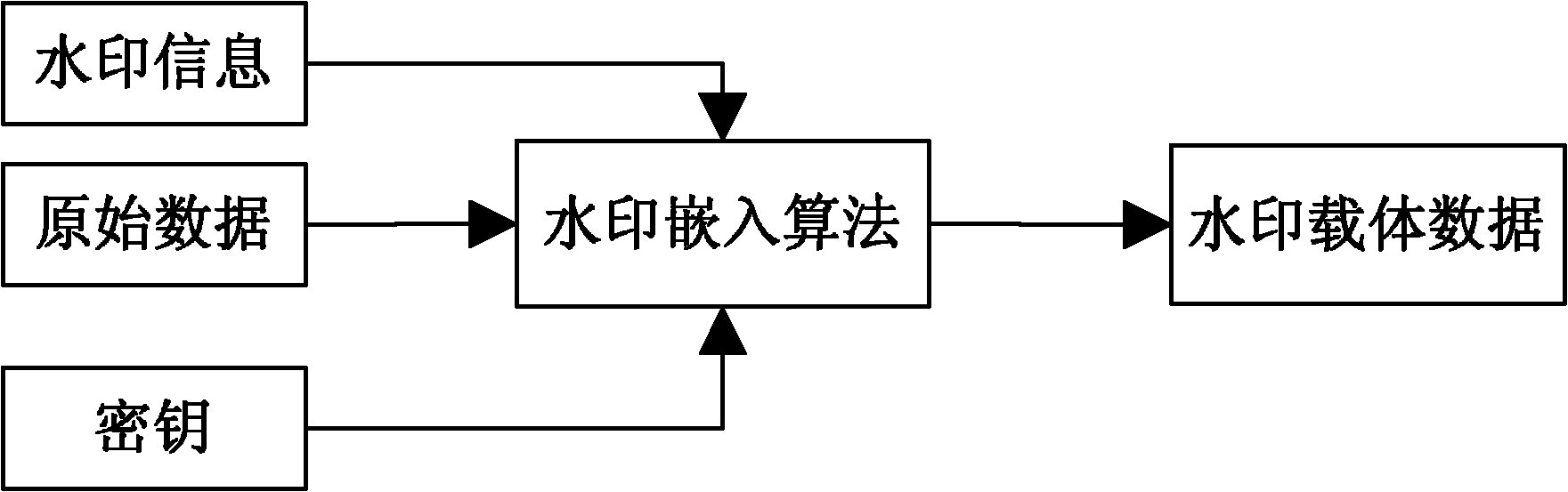
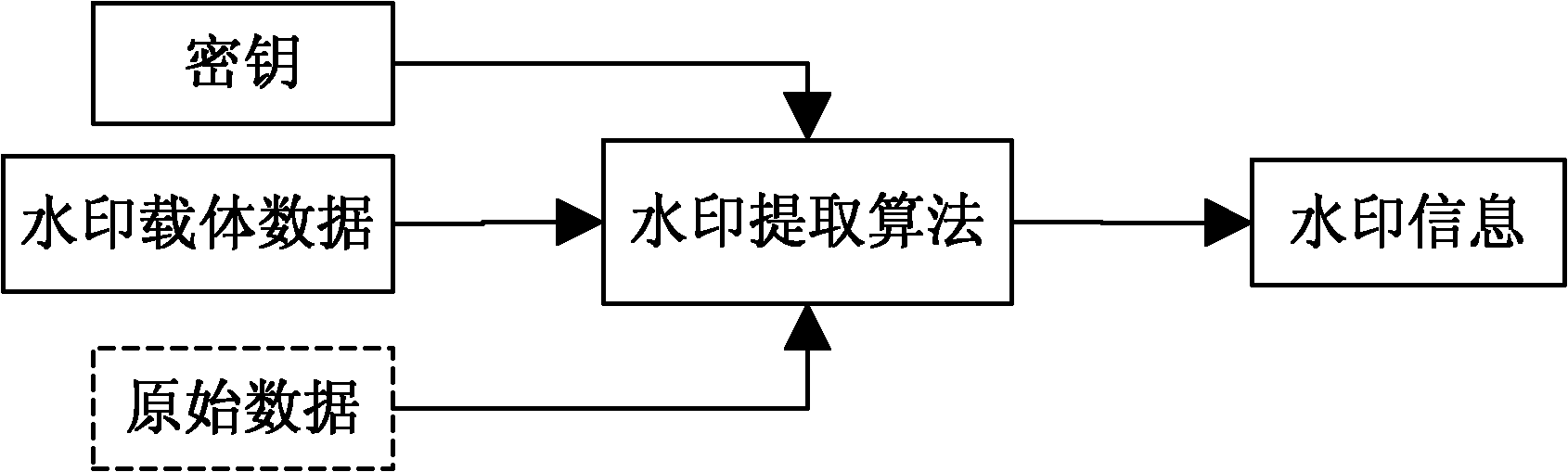
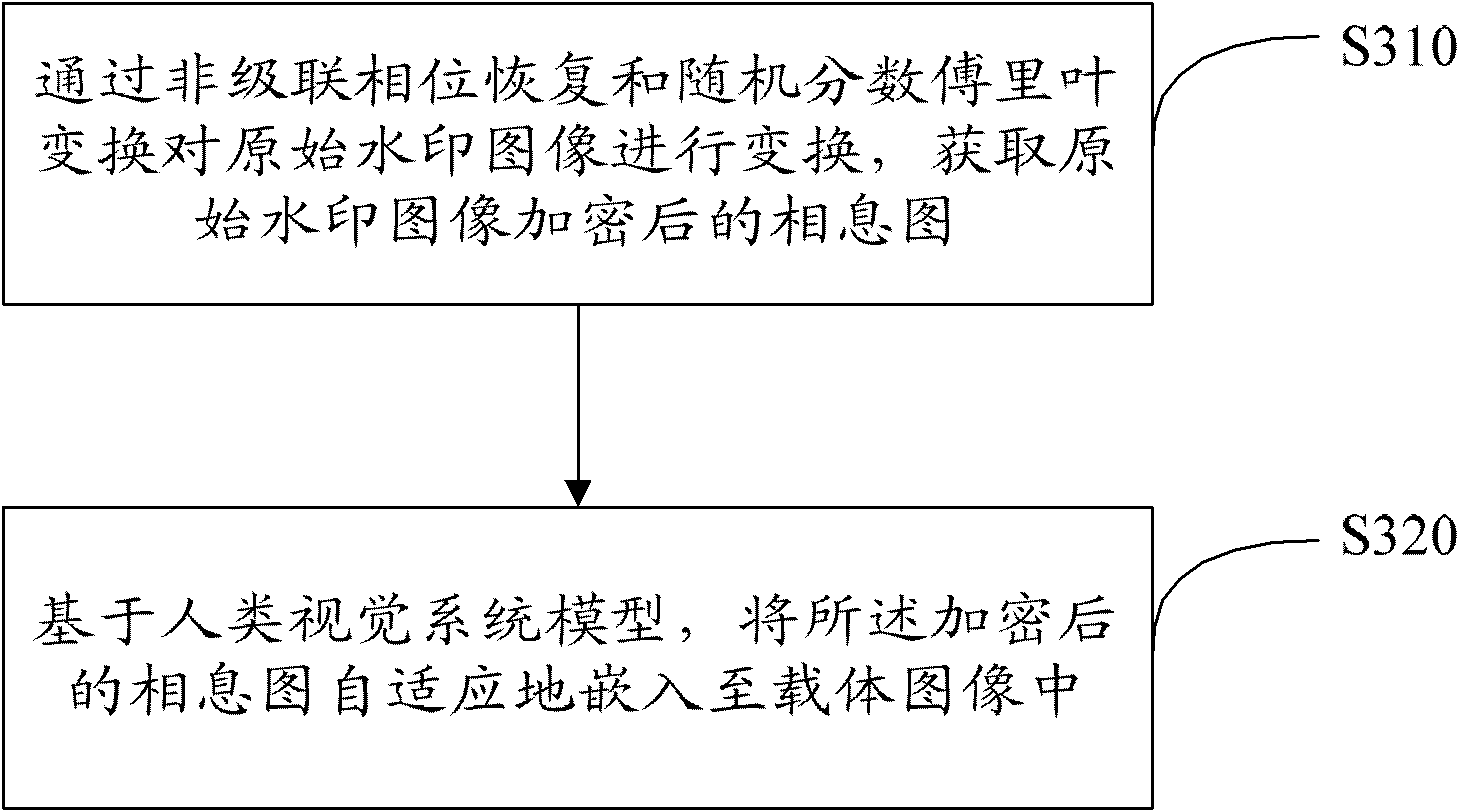
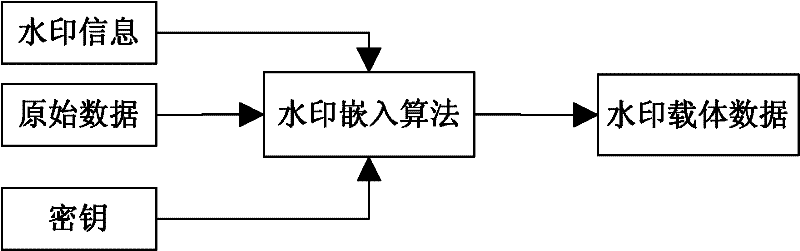
The invention discloses encrypted kinoform based digital image watermarking embedding and extracting methods and systems. The digital image watermarking embedding method comprises the following steps of: transforming an original watermarking image through non-cascaded phase recovery and random fractional fourier transform (RFrFT) to acquire an encrypted kinoform of the original watermarking image; and adaptively embedding the encrypted kinoform into a carrier image based on a human visual system (MVS) model. In the invention, the safety of the watermarking of the kinoform is enhanced by using a non-cascaded iterative encryption method; meanwhile, blink watermarking is realized by adopting an adaptive embedding algorithm; and experiments verify that extremely high robustness against various attacks is achieved, and the safety performance is extremely high.
Owner:PEKING UNIV
Method for embedding and extracting strong robustness hologram watermark on the basis of DWT-SVD (Discrete Wavelet Transform-Singular Value Decomposition)
InactiveCN104680470AImprove robustnessImprove securityImage data processing detailsSingular value decompositionAlgorithm
The invention discloses a method for embedding and extracting a strong robustness hologram watermark on the basis of DWT-SVD (Discrete Wavelet Transform-Singular Value Decomposition). The method comprises the following steps: 1) carrying out transform on an original watermark image to generate a Fourier transform encryption hologram digital watermark, and carrying out singular value decomposition to obtain a singular value matrix; 2) carrying out channel separation on an RGB (Red Green Blue) colorful carrier image, carrying out second-level wavelet decomposition on a B component, and carrying out the singular value decomposition on a low-frequency coefficient matrix to obtain the singular value matrix; 3) embedding, multiplying the singular value matrix generated in the step 1) by an embedding coefficient K, embedding the obtained value into the singular value matrix generated in the step 2) through a gray level adding method, carrying out reduction and wavelet inverse transform on the generated singular value matrix, and combining channels to obtain the RGB colorful carrier image which contains the digital watermark; and 4) carrying out extraction, carrying out channel separation on the RGB colorful carrier image which contains the digital watermark, carrying out the second-level wavelet decomposition and the singular value decomposition to obtain the singular value matrix, subtracting the singular value matrix generated in the step 2) from the singular value matrix obtained in the step 4), dividing the obtained value by the embedding coefficient K, and carrying out the inverse transform to obtain original watermark information.
Owner:SHANGHAI BAOYIN METAL DECORATION +1
Active mode digital image content identification method based on wavelet and DCT dual domain
InactiveCN101042769AGuaranteed ChangesGuaranteed invisibilityImage codingImage data processing detailsDigital imageWavelet
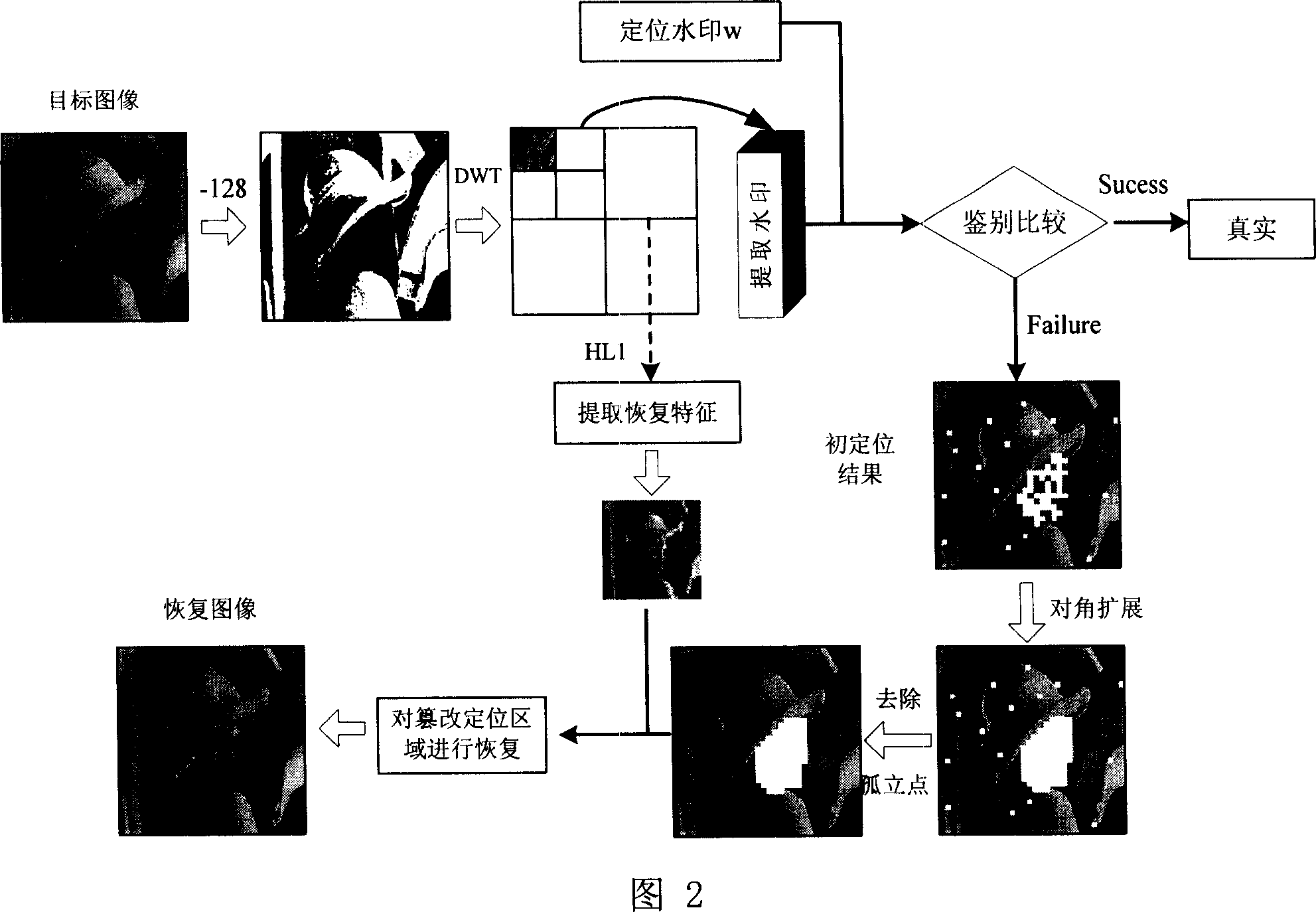
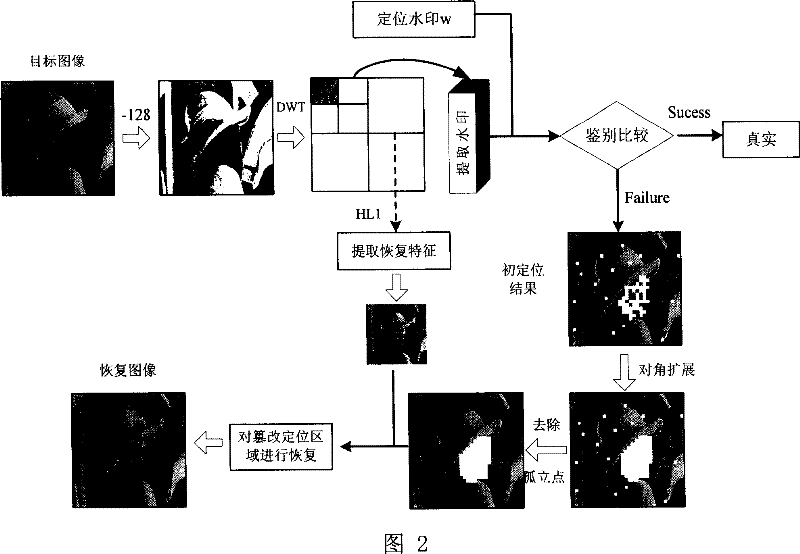
This invention discloses one active digital image content identification method based on wavelet and DCT double areas, which comprises the following steps: send end processes water mark generation, imbedding and image identification and modification initial position, wherein, through above position to generate water mark images to restore property extraction and imbedding water mark and restoring.
Owner:NAT UNIV OF DEFENSE TECH
Robust watermark technique of digital image selected from space domain of images
InactiveCN101004830AGuaranteed accuracyImprove confidentialityImage data processing detailsMultimedia signal processingVariable length
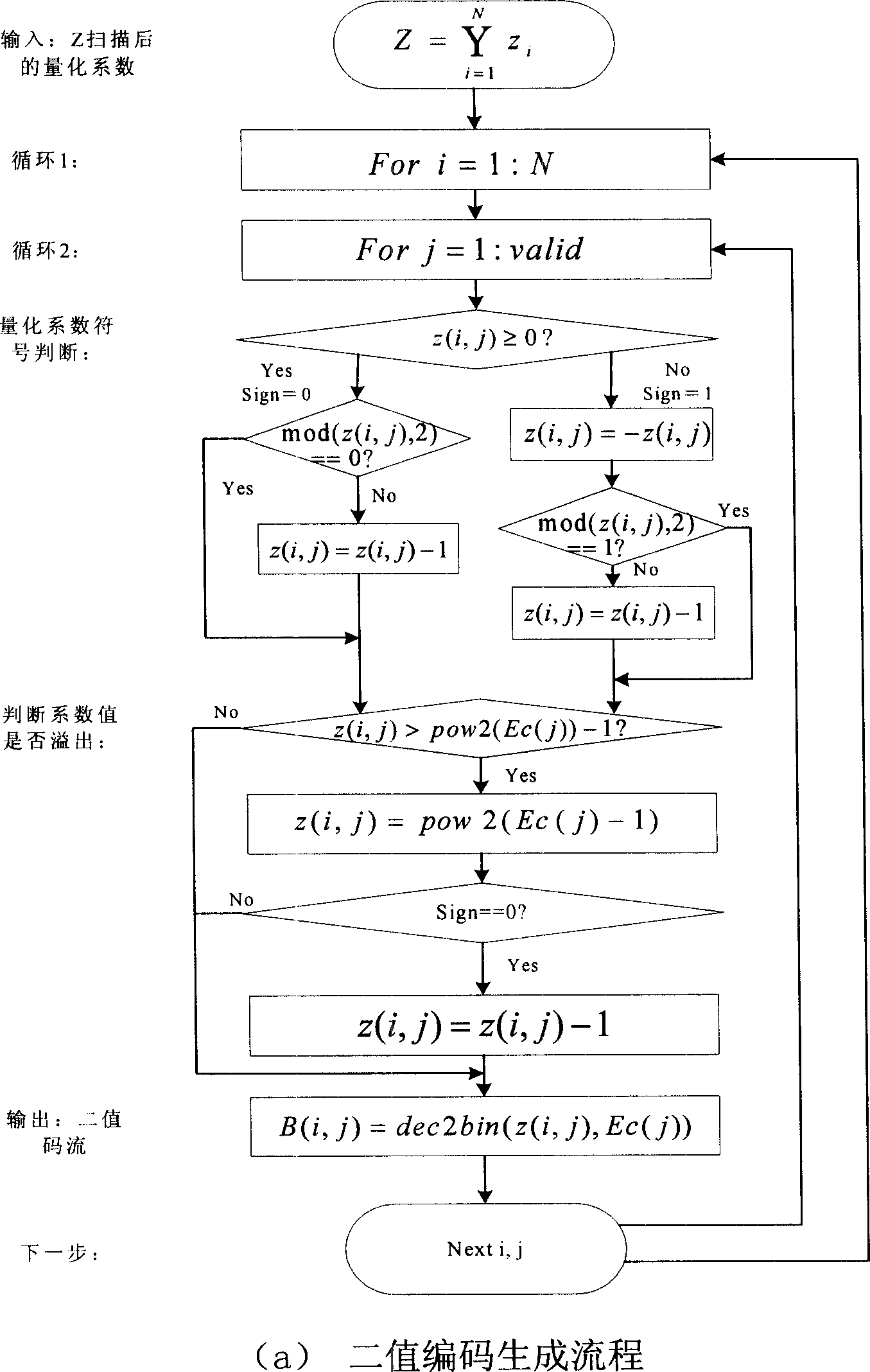
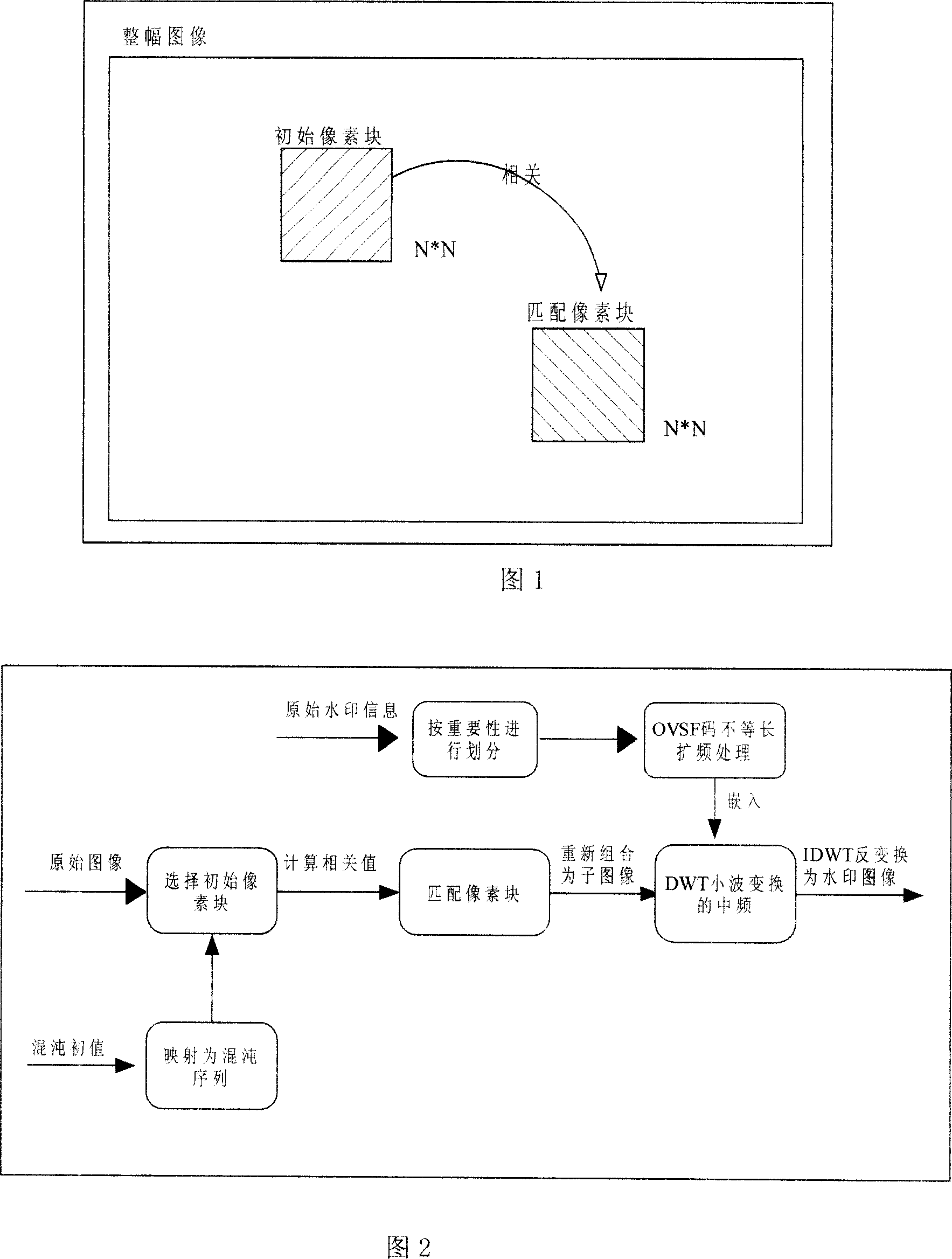
A method for embedding watermark on robust digital image of airspace image includes using chose sequence generated by cipher key to select initial image pixel block, seeking optimum matched block with said pixel block in complete image, recombining them as per their generated order and making DWT conversion, dividing watermark information as per their importance, realizing unequal error protection by utilizing orthogonal variable length OVSF code spread spectrum treatment and embedding spread spectrum watermark into DWT wavelet coefficient. The method for picking up watermark is also disclosed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
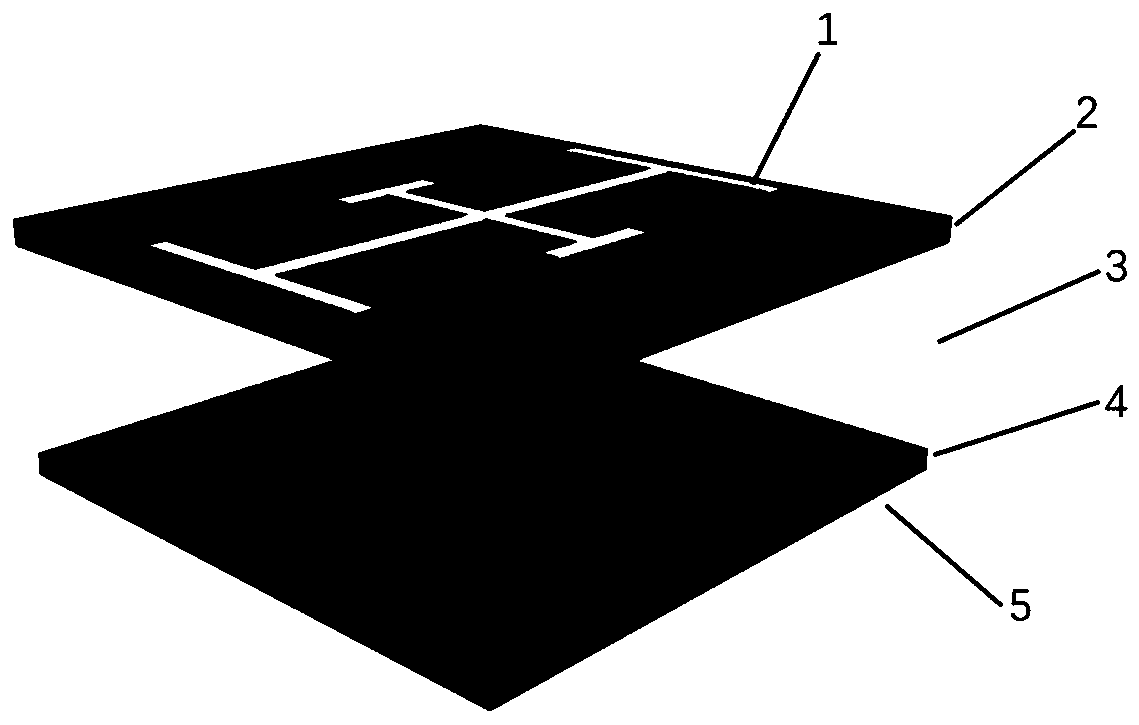
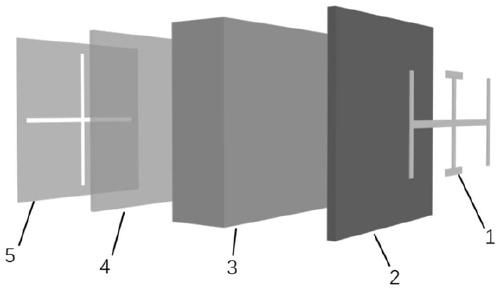
Scattering and wave-transmitting integrated electromagnetic coding metamaterial integrated with multiple phase regulation and control
The invention discloses a scattering and wave-transmitting integrated electromagnetic coding metamaterial integrated with multiple phase regulation and control. The scattering and wave-transmitting integrated electromagnetic coding metamaterial is composed of metamaterial basic units of a multi-layer stacked structure. Each basic unit comprises a first metal layer, a first dielectric layer, a honeycomb layer, a second dielectric layer and a second metal layer which are arranged in sequence, wherein the first metal layer comprises a deformed Jerusalem cross, and the second metal layer comprisesa cross groove. Due to the special structural design, the units have anisotropism, and different reflection and transmission characteristics are shown under incidence of x and y polarized waves. According to the invention, the structure is simple, the processing is easy, the RCS reduction can be realized by using a scattering mechanism in a broadband, and a wave-transparent frequency point with high transmissivity exists in an RCS reduction band, so that the working environment of radio equipment is effectively improved.
Owner:NANJING UNIV
QR (Quick Response) code watermarking algorithm with strong robustness
InactiveCN103150701AImprove robustnessGuaranteed invisibilityImage data processing detailsWatermark robustnessAlgorithm
The invention provides a digital watermarking algorithm for the enhancement of the robustness of a watermarking system, wherein the algorithm comprises the steps of coding specific marking information as a quick response matrix code (QR (Quick Response) code), as a digital watermark, and making use of discrete wavelet transform to embed the QR code into an intermediate frequency coefficient after secondary wavelet decomposition of a carrier image. Therefore, under the premise of assurance of the invisibility of the watermark, the enhancement of the watermark robustness is achieved. The simulation experimental result of a watermark attack indicates that as the digital watermark, the QR code is capable of largely enhancing the robustness of the watermarking system. The digital watermarking algorithm can be widely used in the fields of copyright protection, anti-counterfeiting and the like, and has certain practical value.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
EVD-HG and DWT-SVD adaptive watermark image processing method
ActiveCN109544436ABalance constraintsGuaranteed robustnessImage watermarkingSingular value decompositionFeature vector
The invention belongs to the field of digital watermarking technology and copyright protection, in order to realize self-adaptive simultaneous embedding of a plurality of color watermarks, balance theinvisibility of the embedded watermark image and the robustness of the concealment method to various geometric attacks or image processing attacks. To this end, the technical scheme adopted by the invention is that EVD-HG and DWT-SVD adaptive watermark image processing method, the image to be hidden is firstly scrambled and encrypted by Arnold transform and rotator Gyrator transform; Then, the carrier image is transformed by wavelet transform, the selected frequency part is decomposed by singular value decomposition, and the encrypted color watermarks are embedded into the singular value partof the carrier image. Finally, the singular value part of the secret image is combined with the eigenvector and then the inverse wavelet transform is performed to obtain the carrier image containingthe secret image. The invention is mainly applied to digital watermarking occasions.
Owner:TIANJIN UNIV
Vulnerable watermark method for protecting electronic signet
InactiveCN1540599AGuaranteed invisibilityIntegrity guaranteedCoding/ciphering apparatusPictoral communicationComputer hardwareWatermark method
Treating original watermark in binary form, the invention constructs pyramidal watermark with descended resolution layer by layer. Meanwhile, using wavelet transform decomposes multimedia data. Then, according to certain rule, some special wavelet coefficients are selected to embed to watermark. Finally, multimedia data with watermark being embedded into can be obtained through wavelet inverse transform. The invention possesses capability of detecting interpolation including interpolation characteristic and region. The invention also discloses rules of classifying interpolation to distinguish occasional interpolation from vicious interpolation. Thus, vulnerable watermark can resist such as JPEG loss compression etc. content lockout operation. The invention insures reliability of multimedia data released or transferred on network so that it is applicable to authentication possibly.
Owner:SUN YAT SEN UNIV
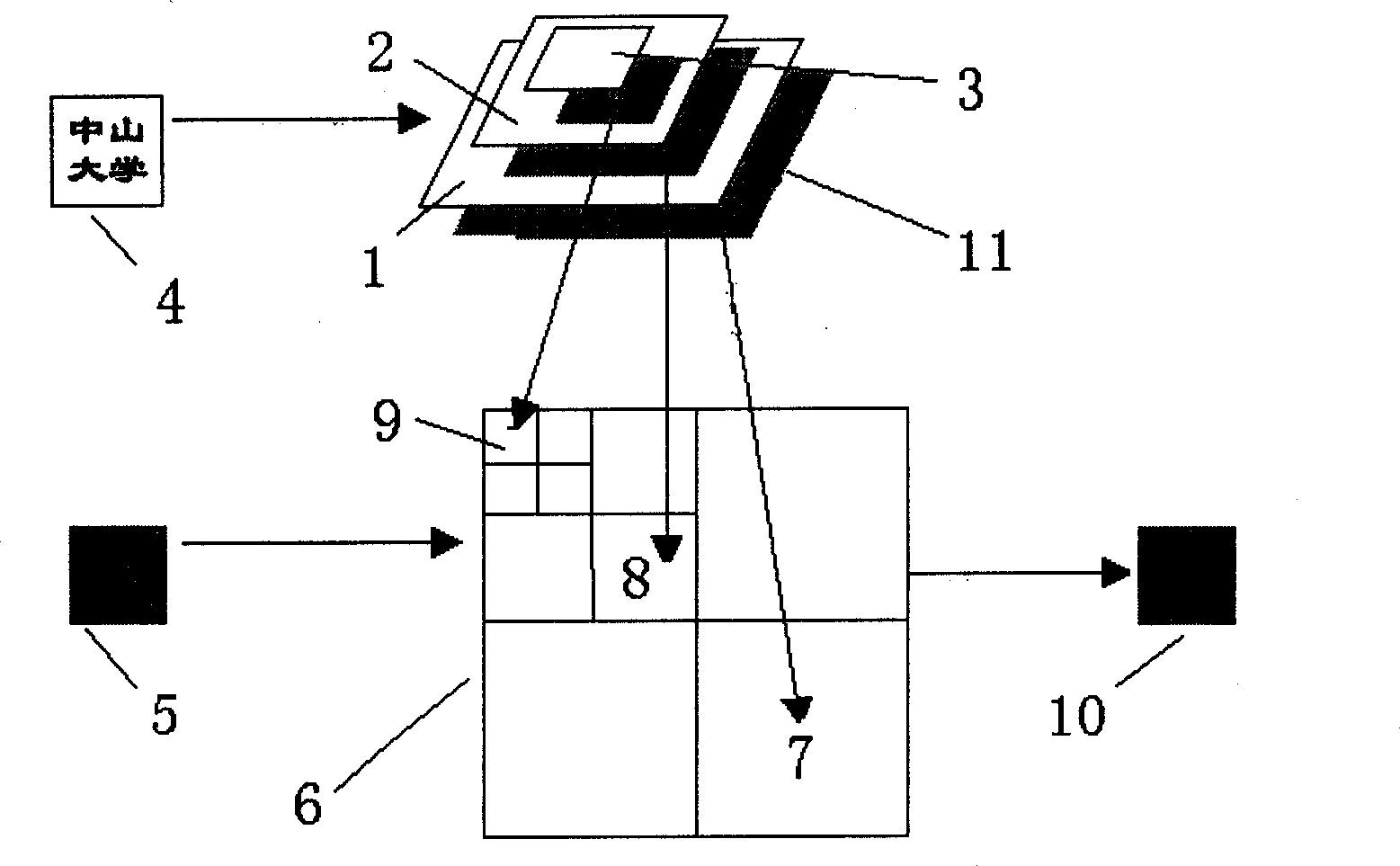
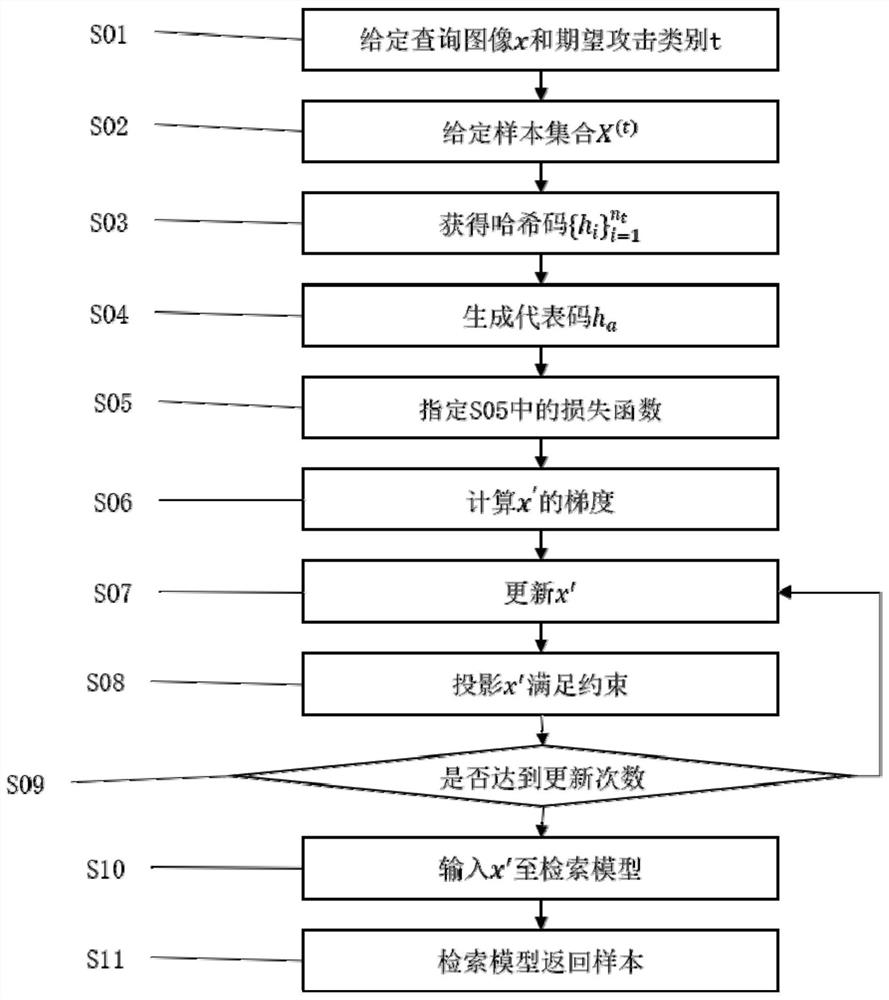
Targeted attack method for deep hash retrieval and terminal equipment
PendingCN112115317AOptimized against noiseGood targeted attack effectDigital data protectionOther databases queryingEngineeringAlgorithm
The invention discloses a targeted attack method for deep hash retrieval and terminal equipment, and the method comprises the steps: providing a sample set with a label t, inputting all samples in thesample set into a deep hash retrieval model, and generating a corresponding hash code; obtaining a representative hash code ha by adopting a bit voting algorithm; specifying the size of the hyper-parameter alpha to be 0-1, and designing a loss function; calculating the gradient of x' by using a gradient descent method and updating x' by using the gradient; projecting the generated adversarial sample x' to enable the x' to meet infinite constraints and image space; judging whether a preset updating frequency is reached or not, and if so, obtaining an adversarial sample x'; and inputting the adversarial sample x' into the deep hash retrieval model, and returning a sample of an expected category. When the deep hash retrieval model is designed, the attack method is adopted, the safety and robustness of the model can be improved, and the generated adversarial sample can enable the retrieval model to return to a category sample expected by an attacker.
Owner:PENG CHENG LAB +1
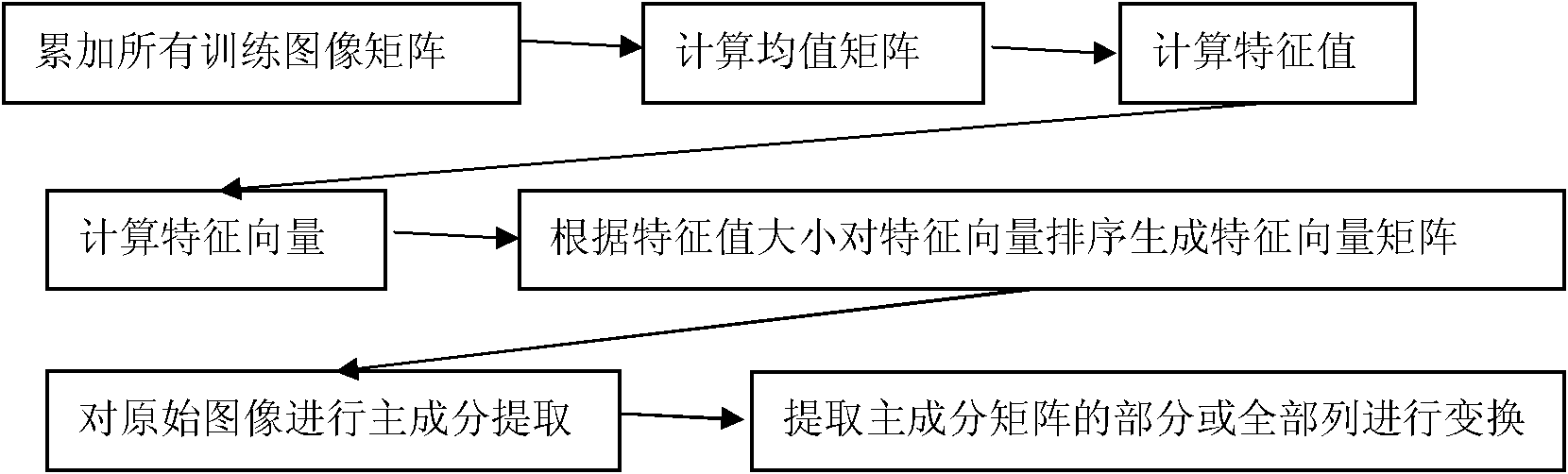
Digital watermarking method based on 2DPCA (two-dimensional principal component analysis)
InactiveCN102184516AGuaranteed robustnessReduce bit error rateImage data processing detailsFeature vectorKernel principal component analysis
The invention provides a digital watermarking method based on 2DPCA (two-dimensional principal component analysis), belonging to the field of digital watermarking. The method comprises the following steps of: pre-processing an image: performing various non-linear geometrical transform to the primary image to obtain a new image after each transform, extracting an image characteristic vector matrix and an image principal component matrix; watermarking pre-processing; watermarking embedding; recovering the image; and watermarking extracting. As the characteristic vector matrix which is used for extracting the image principal component matrix is unchanged, even though each valve of the image principal component matrix is changed, the fluctuation range of the data in the image principal component matrix is approximately similar; i leading out principal components are selected from the principal component matrix of the primary image; namely, weight values of i different principal components representing image information are accumulated, and the accumulation sum is within the range of 0.4-0.9; and the i leading out principal components are subjected from discrete cosine transform or Fourier transform. The invention, under the precondition of ensuring robustness and invisibility of the digital watermarking, effectively resists attack from the non-linear geometry.
Owner:BEIJING UNIV OF TECH
Transparent kinesiology tape and production technology thereof
ActiveCN103519936AReach is not obviousAchieve the invisible effectLayered productsAdhesive dressingsKinesiologyChemistry
The invention discloses transparent kinesiology tape and a production technology thereof. The transparent kinesiology tape comprises transparent elastic base material, a medical acrylic acid glue layer and release paper, wherein the medical acrylic acid glue layer is combined to one surface of the transparent elastic base material, and the release paper covers the medical acrylic acid glue layer. The elasticity value of the transparent elastic base material is greater than 160%, and the thickness is greater than or equal to 8dmm. According to the transparent kinesiology tape, the transparent elastic base material with the elasticity value in an elasticity value range meeting the requirement of the transparent kinesiology tape is adopted, the release paper on the reverse surface of the transparent kinesiology tape can be removed, glue is also transparent, and therefore the full-transparent elastic base material adheres to the back of the human body finally, and the unapparent or invisible effect is achieved perfectly.
Owner:嘉兴好事帮医疗器械有限公司
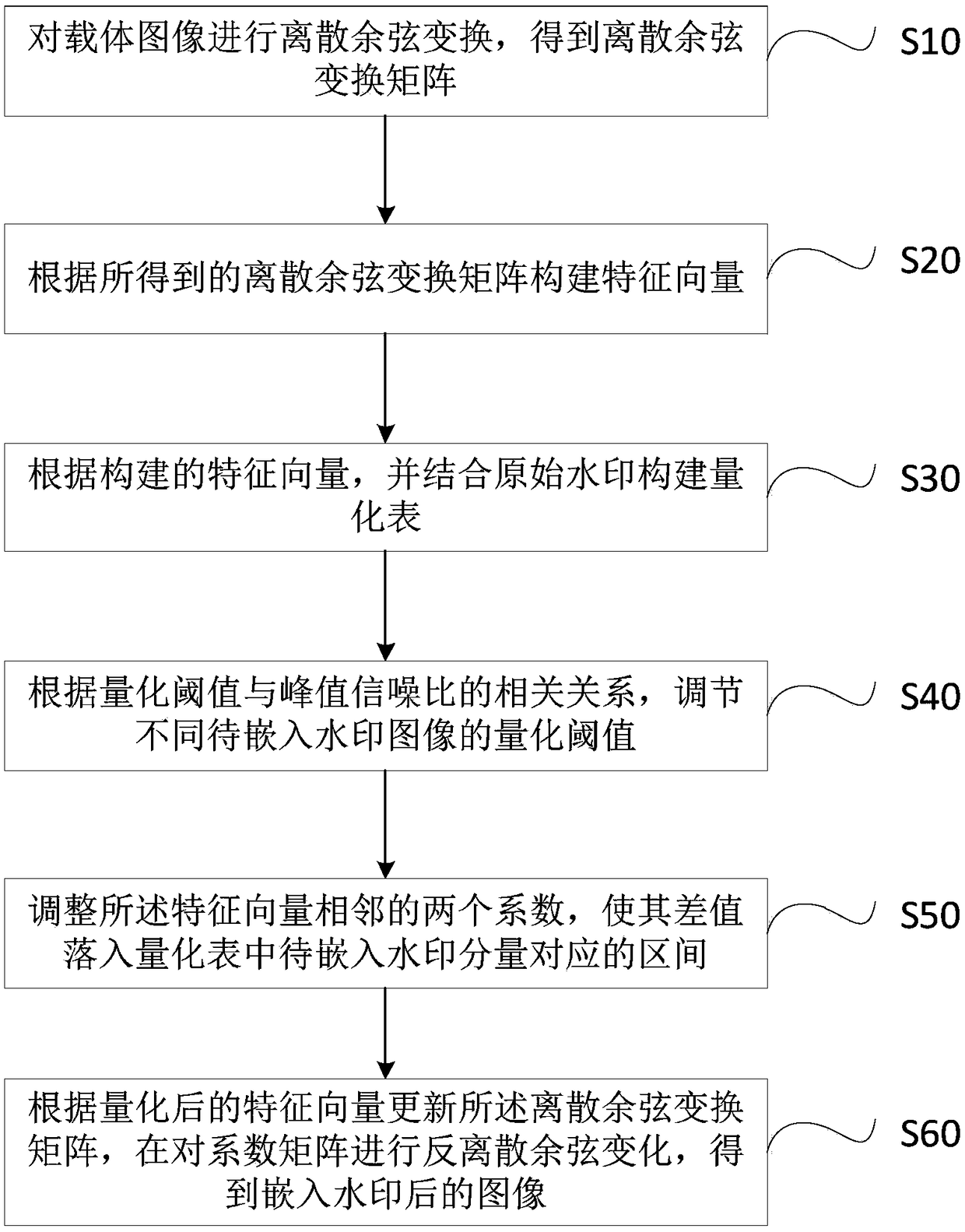
Image difference quantization watermark embedding method and extraction method, equipment and storage medium
ActiveCN109493271AGuaranteed invisibilityImprove visibilityImage watermarkingWatermark methodPeak value
The invention discloses an image difference quantization watermark embedding method and extraction method, equipment and a computer readable storage medium, the method utilizes the stability of difference values among certain coefficients in a DCT transform domain to design a difference quantization scheme, and can effectively overcome the defect that the quantization method is difficult to resistscaling attack; the relationship between the quantization threshold and the peak signal-to-noise ratio is theoretically derived; by utilizing the relational expression, the quantization threshold canbe adaptively adjusted according to different carrier images, so that each image can obtain a specified peak signal-to-noise ratio before and after watermark embedding, the robustness of the watermark method is maximized, and meanwhile, the invisibility of the watermark in each image can be ensured. The method provided by the invention is efficient in execution, not only can overcome the defect that a quantization method is difficult to resist scaling attacks, but also can show very good robustness for various common attacks, and can enable all watermarks embedded in an image to obtain good invisibility.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Blind watermark implantation method and device, blind watermark detection method and device, equipment and storage medium
ActiveCN111932432AGuaranteed robustnessGuaranteed invisibilityImage data processing detailsPattern recognitionImaging processing
The invention discloses a blind watermark implantation method and device, a blind watermark detection method and device, equipment and a storage medium, and relates to the field of image processing. The blind watermark implantation method comprises the steps of obtaining a target image frame in a to-be-encrypted video; determining the implantation position of a blind watermark in the frequency domain of the target image frame; calculating a blind watermark pixel value through a Sobel operator according to the watermark matrix of the blind watermark and the frequency domain coefficient at the implantation position; filling the frequency domain pixel point of the implantation position with the blind watermark pixel value to obtain an image frame after the blind watermark is implanted; and performing flag bit filling in the spatial domain of the implanted image frame to obtain an encrypted image frame. According to the method, the blind watermark implanted in the image frame can simultaneously achieve high robustness and high resistance to cutting attack.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Stereoscopic video oriented frequency domain parallax coherent watermarking method
InactiveCN107222750AGuaranteed invisibilityResistance robustnessDigital video signal modificationStereoscopic videoParallax
The invention discloses a stereoscopic video oriented frequency domain parallax coherent watermarking method. At a watermark embedding part, watermark information blocks of which value distribution is consistent with standard normal distribution is generated; copyright information can be selected as a key for scrambling the watermark information blocks; a video into which a watermark is about to be embedded is decoded into continuous sequence frames; 4*4 DCT is carried out on each frame; watermark information is repeatedly embedded into each sequence frame; and the sequence frames are recoded into the video. At a watermark detection part, a to-be-detected video is provided; I frames are extracted from the to-be-detected video; and the watermark information is determined by caring out statistics on the watermark energy of each I frame on each parallax. In the whole watermark detection process, the to-be-detected video is compared with a target watermark and no any other assistant information is required, namely the detection process is full blind. Compared with the existing method, the method has the advantage that on the basis of ensuring the invisibility and resisting a DIBR (Depth Image Based Rendering) attack, a video compression attack can be effectively resisted.
Owner:BEIJING UNIV OF TECH
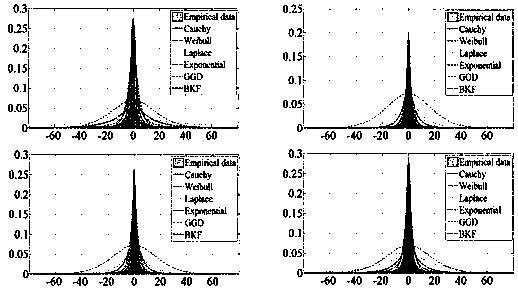
Digital image watermarking detection method based on robust difference
InactiveCN107918924AGuaranteed invisibilityImprove robustnessImage watermarkingHigh energyLocator Parameter
The invention discloses a digital image watermarking detection method based on robust difference. The digital image watermarking detection method based on robust difference includes the steps: performing secondary non down-sampling Contourlet transformation on a host image, in the same direction, making difference between the father coefficients and the sub coefficients, of two scales, being obtained through decomposition, obtaining the difference sub-bands, and selecting the difference sub-band with the highest energy as the carrier; by means of a multiplicative method, performing watermarking embedding, and obtaining an image with watermarking through reconstruction; extracting the watermarking, performing modeling of a statistic model on the difference sub-band with the watermarking bymeans of a Cauchy distribution probability density function, obtaining a shape parameter Gamma and a positional parameter, and performing parameter estimation on the difference sub-band coefficient with the watermarking by means of a sample fractile estimation method; and according to the decision criterion, constructing a local optimal LMP detector and a Rao detector, and utilizing the decision threshold to determine whether the watermarking exists or not.
Owner:LIAONING NORMAL UNIVERSITY
Remote-sensing image digital watermarking embedding and extraction method based on QR codes
InactiveCN106373081AGuaranteed invisibilityGuaranteed detection effectImage data processing detailsData compressionGeneration process
The present invention discloses a remote-sensing image digital watermarking embedding and extraction method based on QR codes. The QR codes are taken as watermarking information and are embedded in a carrier image; in the generation process of the QR codes, on the basis of removing the corresponding fixed information, dividing the residual watermarking information into two parts of data encoding and error correction encoding. The carrier image is subjected to 8*8 blocking DCT transformation, on the premise of embedding the feature watermarking, based on the QR code self error correction principle, the error correction encoding part of the QR codes is embedded into the low-frequency coefficient with high robustness, and the data encoding part of the QR codes is embedded into the medium-frequency coefficient which has weak influence on the image quality. The present invention further discloses a watermarking information extraction method. Through adoption of the encoding mechanism and the self error correction principle of the QR codes, the remote-sensing image digital watermarking embedding and extraction method based on the QR codes can perform data compression and preprocessing of the watermarking information so as to reduce the embedding data volume; and moreover, the remote-sensing image digital watermarking embedding and extraction method based on the QR codes can effectively resist general attack such as compression, cutting and the like and combined attack on the basis of realizing the invisibility and the blind detection of the watermarking, and has high robustness.
Owner:NANJING NORMAL UNIVERSITY
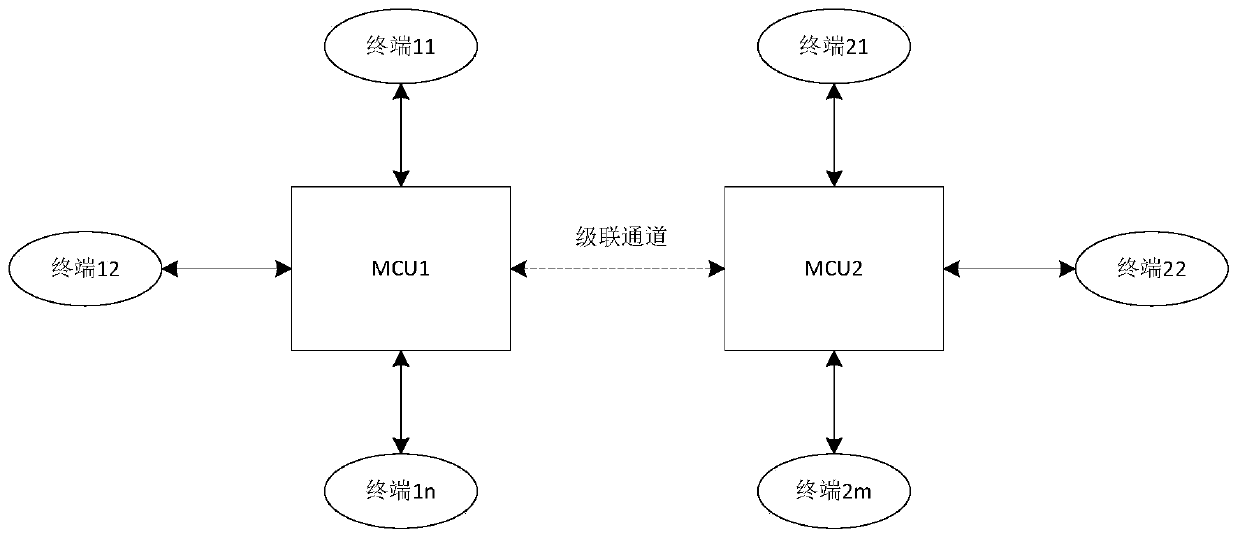
Conference cascading method and electronic equipment
ActiveCN110225293AImprove efficiencyAvoid cascading failure problemsTelevision conference systemsTwo-way working systemsCascading failureNetwork connection
The invention relates to the technical field of video conferences, in particular to a conference cascading method and electronic equipment, and the method comprises the steps: sending a request message for opening a logic channel to second conference control equipment; receiving a response message of opening the logic channel fed back by the second conference control equipment based on the requestmessage; analyzing the response message to obtain a second network address; and based on the second network address, sending a network connection request to the second conference control device to establish a network connection with the second conference control device. Cascading capability negotiation is carried out before network connection is established, so that the problem of cascading failure caused by the cascading capability in the subsequent process can be avoided; the second network address of the second conference control device is utilized to realize the network connection, the network address acquired by the first conference control equipment is the current network address of the second conference control equipment, and the network address is used for establishing the networkconnection, so that the conference cascading efficiency can be improved.
Owner:SUZHOU KEYUAN SOFTWARE TECH DEV +1
Encrypted kinoform based digital image watermarking embedding and extracting methods and systems
ActiveCN102142131BReduce data volumeGood clipping resistanceImage data processing detailsPattern recognitionHuman visual system model
The invention discloses encrypted kinoform based digital image watermarking embedding and extracting methods and systems. The digital image watermarking embedding method comprises the following steps of: transforming an original watermarking image through non-cascaded phase recovery and random fractional fourier transform (RFrFT) to acquire an encrypted kinoform of the original watermarking image; and adaptively embedding the encrypted kinoform into a carrier image based on a human visual system (MVS) model. In the invention, the safety of the watermarking of the kinoform is enhanced by usinga non-cascaded iterative encryption method; meanwhile, blink watermarking is realized by adopting an adaptive embedding algorithm; and experiments verify that extremely high robustness against various attacks is achieved, and the safety performance is extremely high.
Owner:PEKING UNIV
Adaptive image watermark embedding method and system and extraction method and system
InactiveCN111062853AGuaranteed correctnessGuaranteed visual qualityImage watermarkingPattern recognitionComputer vision
The invention relates to a texture-based adaptive image watermark embedding method, a texture-based adaptive image watermark embedding system, a texture-based adaptive image watermark extracting method and a texture-based adaptive image watermark extracting system. The adaptive image watermark embedding method comprises the following steps: determining a watermark embedding area in a carrier imageinto which a watermark is to be embedded, the watermark embedding area being a plurality of non-overlapping texture rough areas; utilizing a multiple regression analysis method to establish a texture-based adaptive parameter adjustment model for adjusting embedding parameters in the watermark embedding method; and embedding a watermark into each watermark embedding region by using the watermark embedding method. According to the invention, the richness of image textures can be truly measured; accurately positioning a texture rough area in the image; through multiple regression analysis, a function relationship between a watermark embedding parameter and a global texture value and a local texture value of a texture rough region is established, and the watermark embedding parameter is adaptively adjusted according to the texture value of the region, so that the invisibility of the watermark is ensured to the greatest extent, and the robustness of the watermark is enhanced.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI +1
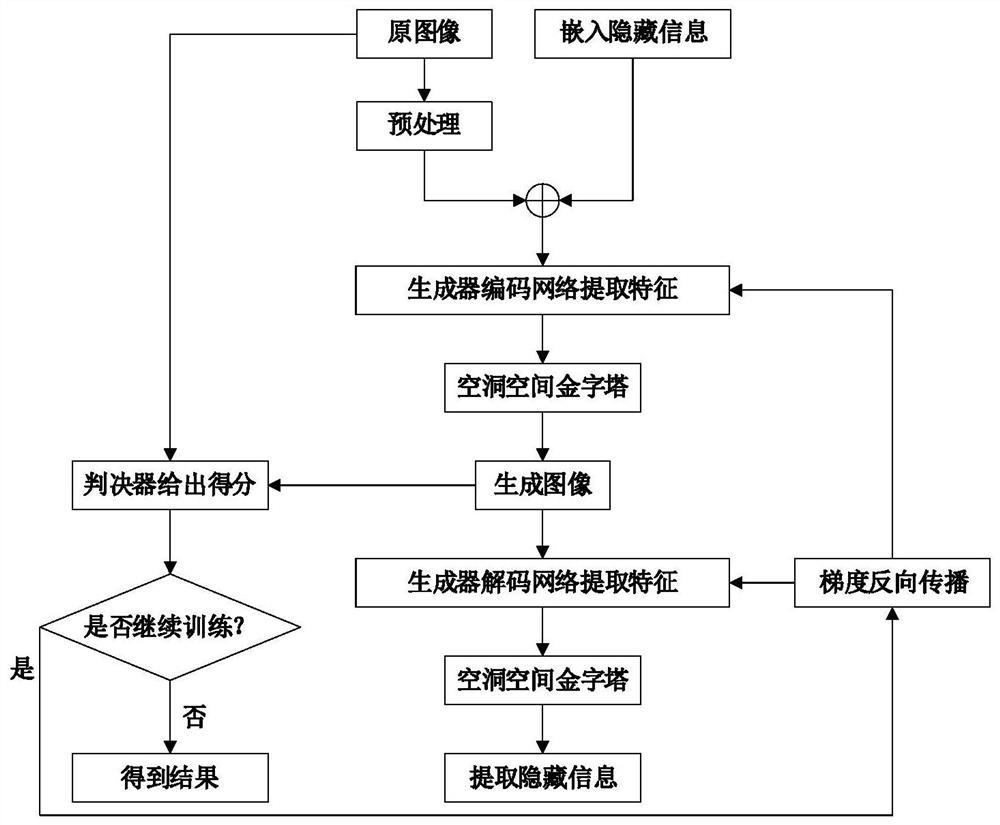
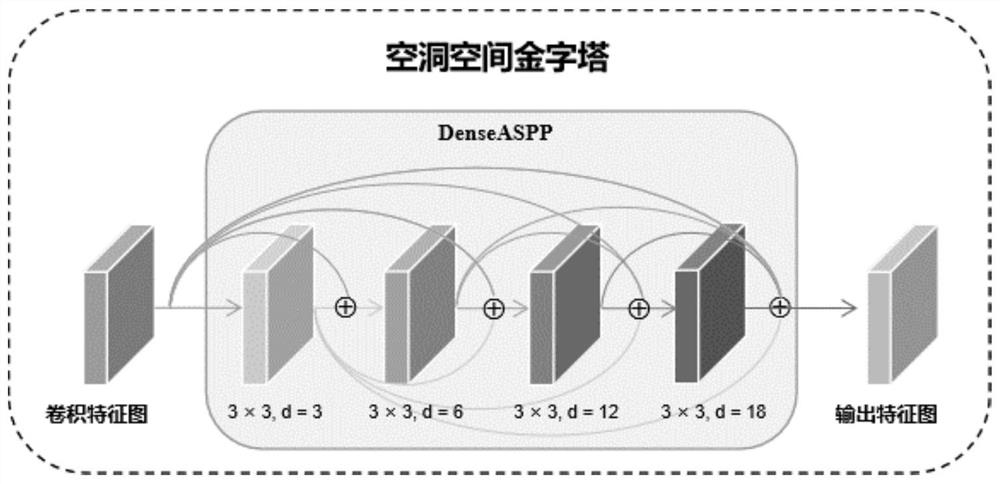
Information hiding method, device and system based on cavity space pyramid
ActiveCN113254891ASolve the problem of low embeddable informationIncrease hidden capacityImage data processing detailsNeural architecturesData privacy protectionAlgorithm
In order to solve the problems of low image information hiding capacity and distortion in the aspect of data privacy protection, the invention provides an information hiding method, device and system based on a cavity spatial pyramid, which are used for embedding and extracting watermark information in a protected image to realize image version authentication and protection. According to the method, a cavity space pyramid module is built by adopting cascaded and parallel cavity convolution layers, the receptive field is expanded, the multi-scale and multi-cavity-rate characteristics are extracted, information is more accurately hidden in a semantic redundancy position, and the decoding capability of a network on embedded information is improved; meanwhile, the decoding accuracy is improved by using cross entropy loss; in addition, the quality of the generated image is improved through residual error and linear operation confrontation in the discrimination network; finally, in order to improve the network stability, updating of different scales, cosine annealing adjustment and an intensive connection strategy are used in training. According to the method, high-capacity information hiding is achieved, meanwhile, it is guaranteed that images are not distorted, and experiments prove that the method has high information hiding capacity.
Owner:SHANDONG UNIV
Self-adaptive stealth system and method for square cabin
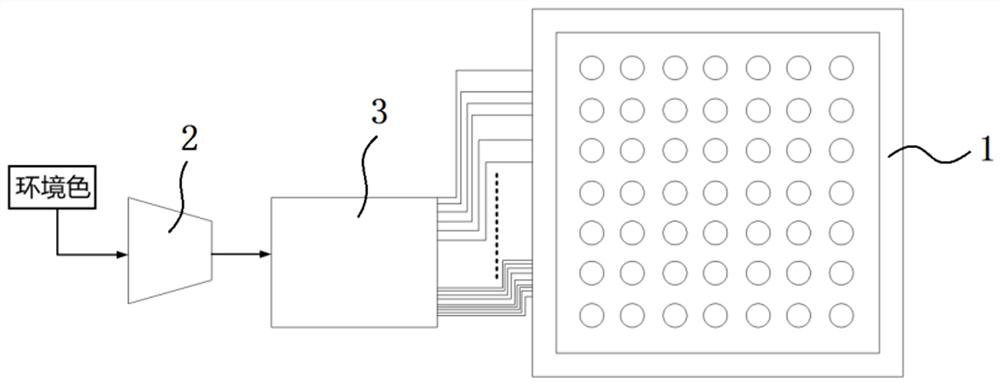
InactiveCN110145968AGuaranteed invisibilitySimple structureCamouflage devicesProtective buildings/sheltersSelf adaptiveProject environment
The invention discloses a self-adaptive stealth system and method for a square cabin. The system comprises projection devices and cabin surface brightness detection devices which are arranged on sidesurfaces and a top surface of the square cabin, image acquisition devices and environment brightness detection devices which are arranged on the side surfaces of the square cabin, the system further comprises a projection control module and a brightness control module, wherein the projection control module is used for projecting environment images onto the side surfaces and the top surface of thesquare cabin, and the brightness control module is used for adjusting projection brightness. The method comprises the following steps that a plurality of environment images around the square cabin arecollected in real time, for any side surface, an ambient image which is opposite to the side surface is projected onto the side surface, and brightness of projection is adjusted by utilizing the brightness of the side surface and the brightness of the environment; the image which is facing the side surface is projected to the top surface of the square cabin, and the projection brightness of the top surface is adjusted by utilizing the brightness of the top surface and the brightness of the environment. According to the self-adaptive stealth system for the square cabin, the square cabin can beintegrated with environment anytime and anywhere, and the system has the outstanding advantages of being high in environmental adaptability, good in fusion effect, low in cost and the like.
Owner:郑州佛光发电设备股份有限公司
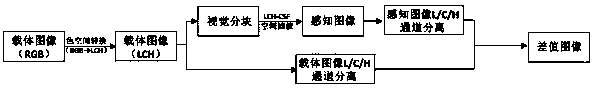
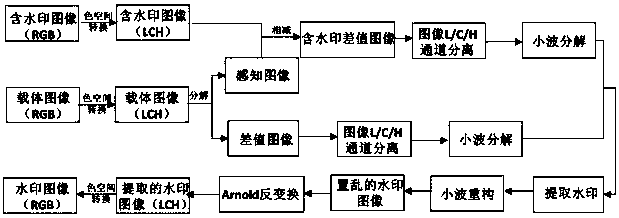
Color watermark embedding and extracting method based on human eye vision characteristics
ActiveCN107862648AAvoid the problem of hue shiftGuaranteed invisibilityImage watermarkingIntellectual propertyHue
The invention provides a color watermark embedding and extracting method based on human eye vision characteristics. According to the method, the human eye vision characteristics are sufficiently considered, carrier images are decomposed to obtain perception images and difference images, watermarks are embedded into the difference images and extracted from the difference images, and transparency, robustness, safety and the like after embedding of the watermarks are improved. The constancy of a hue is kept in the whole embedding and extracting process of the watermarks, the method solves the problem that the hue is shifted when color digit watermarks are embedded into the carrier images, and legitimate rights of intellectual property owners are furthest protected. According to the method, the constancy of H channels is kept, the watermarks are embedded into the difference images and extracted from the difference images, and the method is different from a traditional method that watermarks are embedded into three channels and extracted from the three channels in space of colors such as RGB, CIE, Lab and YUV. The method further has the advantages that calculation amount is less, calculation time is saved, use of users is facilitated and the like.
Owner:山东济清科技服务有限公司
Digital watermarking method based on 2DPCA (two-dimensional principal component analysis)
InactiveCN102184516BGuaranteed robustnessReduce bit error rateImage data processing detailsPrincipal component analysisFourier transform on finite groups
The invention provides a digital watermarking method based on 2DPCA (two-dimensional principal component analysis), belonging to the field of digital watermarking. The method comprises the following steps of: pre-processing an image: performing various non-linear geometrical transform to the primary image to obtain a new image after each transform, extracting an image characteristic vector matrixand an image principal component matrix; watermarking pre-processing; watermarking embedding; recovering the image; and watermarking extracting. As the characteristic vector matrix which is used for extracting the image principal component matrix is unchanged, even though each valve of the image principal component matrix is changed, the fluctuation range of the data in the image principal component matrix is approximately similar; i leading out principal components are selected from the principal component matrix of the primary image; namely, weight values of i different principal componentsrepresenting image information are accumulated, and the accumulation sum is within the range of 0.4-0.9; and the i leading out principal components are subjected from discrete cosine transform or Fourier transform. The invention, under the precondition of ensuring robustness and invisibility of the digital watermarking, effectively resists attack from the non-linear geometry.
Owner:BEIJING UNIV OF TECH
Vulnerable watermark method for protecting electronic signet
InactiveCN1234230CGuaranteed invisibilityIntegrity guaranteedCoding/ciphering apparatusPictoral communicationWatermark methodImage resolution
The invention relates to a fragile watermark technology based on wavelet transform, which belongs to the field of multimedia signal processing. The invention first processes the original watermark in binary format, constructs a watermark pyramid with decreasing resolution layer by layer, and uses wavelet transform to decompose multimedia data, and then selects some special wavelet coefficients to embed watermark according to certain rules. Finally, the multimedia data embedded with watermark is obtained by inverse wavelet transform. The present invention has multi-resolution tampering detection capability, ensures accurate detection of tampering characteristics and tampering areas, and the present invention also provides a tampering classification rule, so as to distinguish malicious tampering from accidental tampering, so that the fragile watermark can resist such as JPEG Content preservation operations such as lossy compression meet actual needs. The invention can authenticate the authenticity and integrity of the multimedia data or files propagated through the network, so as to ensure the credibility of the multimedia data when it is transmitted and released through the network.
Owner:SUN YAT SEN UNIV
A theft-proof device for cars
InactiveCN101712312APlay the role of anti-theftGuaranteed invisibilityAnti-theft devicesLatching locksEngineeringGear drive
The invention discloses a theft-proof device for cars, which comprises a member suitable for being attached to a gear shift rod or a gear driving arm (33) on design; the member comprises a circular hole (26) of a locking bolt (7) that can be used for inserting into a lockset (1). When the lockset (1) that can move in a casing tube (6) is pressed, an inner mechanism is started, and the locking bolt (7) extends out from the lockset so as to lock the device. The casing tube (6) is mounted on a noumenon near to bottom of the automobile, and is hidden in an operation desk of a gear shift rod (33). When on lock position, the potential thief cannot shift gear by moving the gear shift rod (33), hence cannot drive the car away.
Owner:SOLEX INT (THAILAND) CO LTD
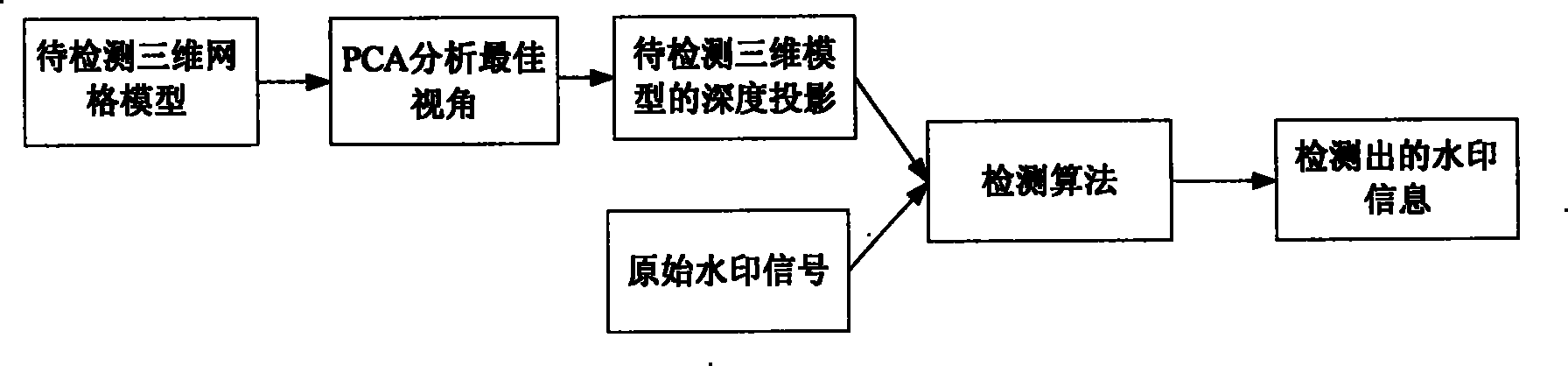
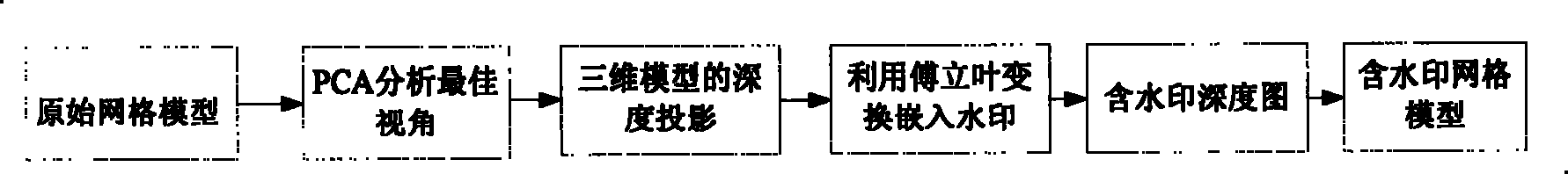
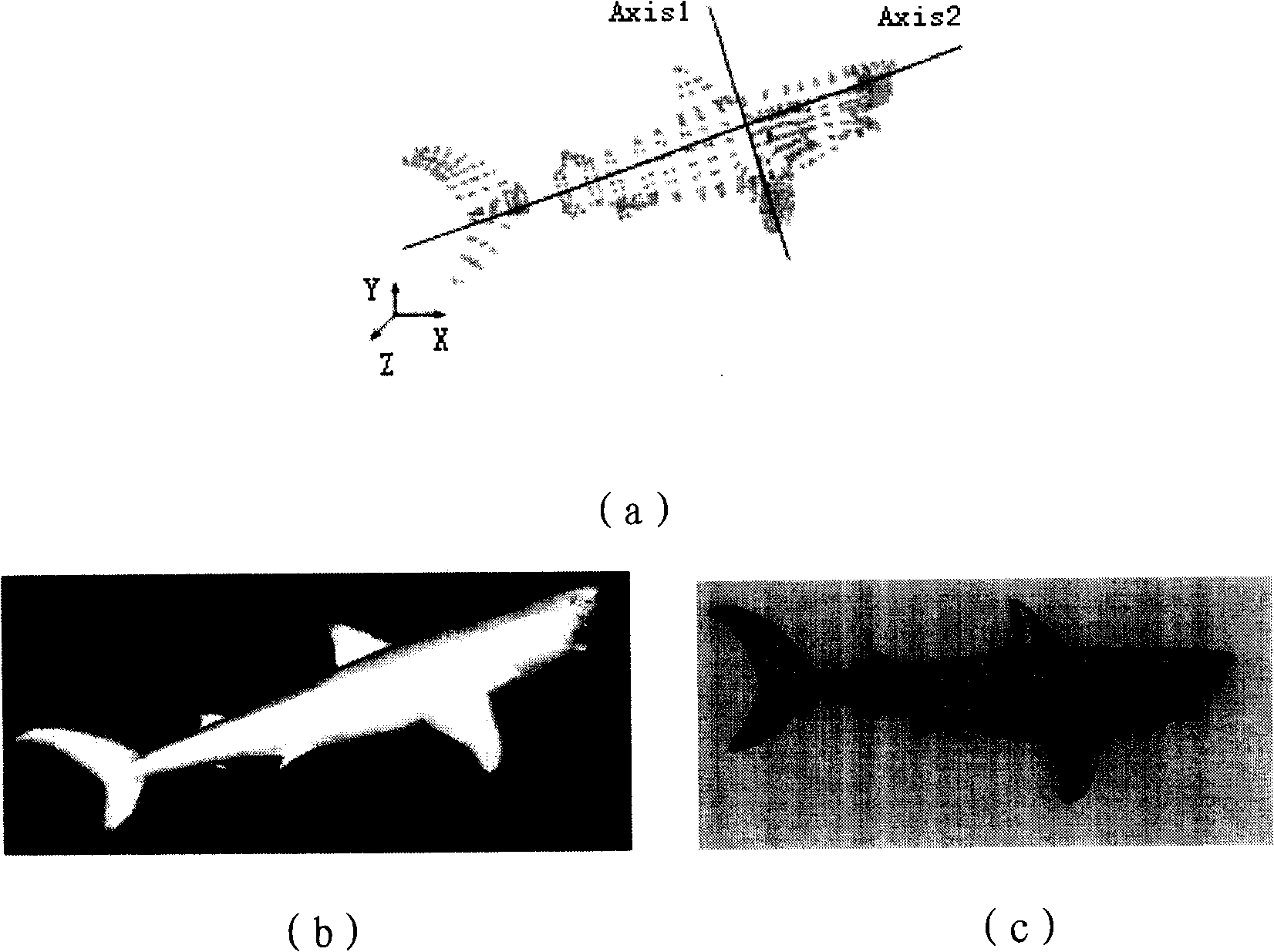
Three-dimensional digital watermarking method and apparatus based on three-dimensional model depth projection
InactiveCN101251931BGuaranteed invisibilityImprove confidentialityImage data processing details3D modellingThree dimensional modelProjection image
Owner:WUHAN UNIV OF TECH
Preparation method of invisible wing surface component
ActiveCN114193863AInvisibility GuaranteeReduce the risk of obsolescenceSynthetic resin layered productsLaminationDielectric plateMeasuring instrument
The invention discloses a preparation method of a stealth airfoil component, the stealth airfoil component is composed of a dielectric layer material, a wave-absorbing functional material and a shielding bottom layer material, and the wave-absorbing functional material is rapidly detected before the stealth airfoil component is manufactured and formed. A device used for testing comprises a reflectivity field measuring instrument, a standard reference medium layer plate and a shielding bottom plate, and the testing is carried out according to the following steps that a wave-absorbing functional material, the standard reference medium plate and the shielding bottom plate form a multi-layer structure, and the layering sequence of the multi-layer structure is required to be consistent with the actual layering sequence of an invisible wing surface component; the standard reference dielectric plate is made of a dielectric layer material, and the thickness of the standard reference dielectric plate is consistent with the designed thickness of the dielectric layer material in an actual laying layer. A reflectivity field measuring instrument is pressed on the outer surface of the multi-layer composite structure for reflectivity testing, and whether the stealth performance of the wave-absorbing functional material used for forming the stealth wing surface part reaches an expected index or not is judged according to whether the test result R reaches the standard or not.
Owner:BEIJING RES INST OF MECHANICAL & ELECTRICAL TECH
Active mode digital image content identification method based on wavelet and DCT dual domain
InactiveCN101042769BGuaranteed invisibilityReduce data volumeImage codingImage data processing detailsDigital imageWavelet
This invention discloses one active digital image content identification method based on wavelet and DCT double areas, which comprises the following steps: send end processes water mark generation, imbedding and image identification and modification initial position, wherein, through above position to generate water mark images to restore property extraction and imbedding water mark and restoring.
Owner:NAT UNIV OF DEFENSE TECH
Pixelated thermochromic liquid crystal array system for light stealth
PendingCN112992084AGuaranteed invisibilityImprove mobilityStatic indicating devicesControl cellEngineering
The invention discloses a pixelated thermochromic liquid crystal array system for light stealth, which comprises: a thermochromic liquid crystal color developing array, wherein the array is provided with a color developing element, and the color developing element is composed of a substrate layer, an electric heating layer, a color changing layer and a packaging layer; an image sensor which is used for sampling surrounding environment images; and a control unit which is used for adjusting the electric heating temperature of the electric heating layer in each color developing element according to the surrounding environment image from the image sensor so as to change the color of the color changing layer in each color developing element and achieve the purpose that the thermochromic liquid crystal color developing array adapts to the surrounding environment image. The system has the beneficial effects that the color of the device can be adaptively adjusted in time according to environmental changes, the dynamic stealth effect is achieved by reducing the color contrast of the device and the surrounding environment, the stealth performance of military equipment in the complex and changeable environment is guaranteed, and the maneuverability and combat performance of weaponry are improved.
Owner:SHANGHAI AVIATION ELECTRIC
Error Tolerant Quantum Steganography Applicable to Collectively Dephasing Noise Channels
ActiveCN104125054BCollective dephasing noise overcomesGuaranteed invisibilitySecuring communicationBell statePhase noise
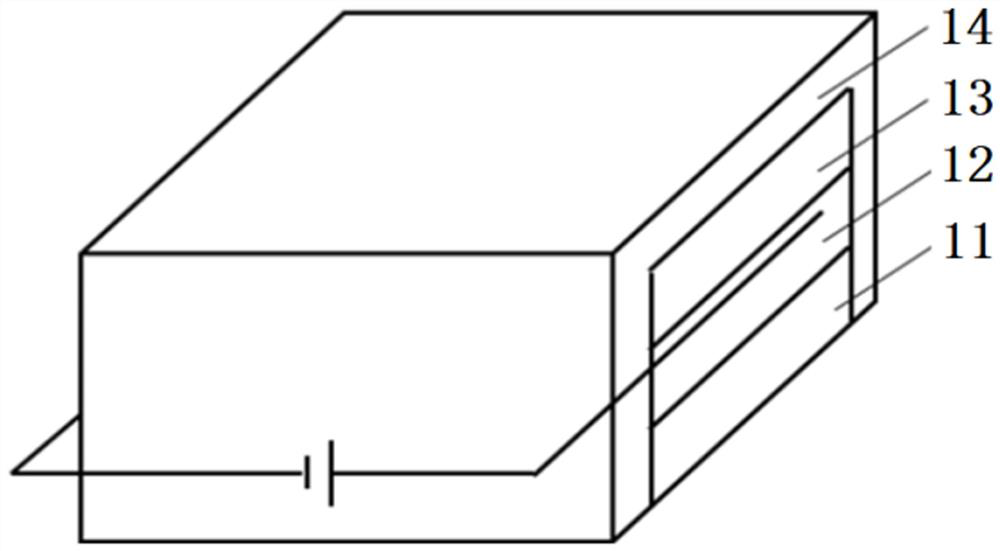
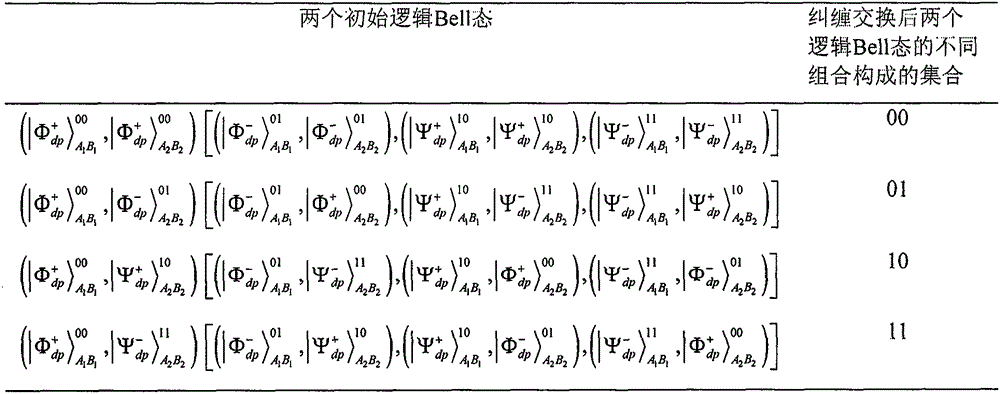
The invention provides an error tolerance quantum steganography sub-protocol applicable to collective dephasing noise channels. Logic Bell states are utilized to overcome collective dephasing noise. A quantum covert channel constructed in normal quantum communication and utilized for distributing secret messgaes is established by means of exchange of the two logic Bell states. The Bell state measurement rather than quadri-quantum bit united measurement is utilized for decoding. The error tolerance quantum steganography sub-protocol applicable to the collective dephasing noise channels has the advantages that the channel capacity of the protocol reaches to 4 bits for every turn of covert communication, and invisibility and safety are guaranteed.
Owner:浙江海宁经编产业园区开发有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com