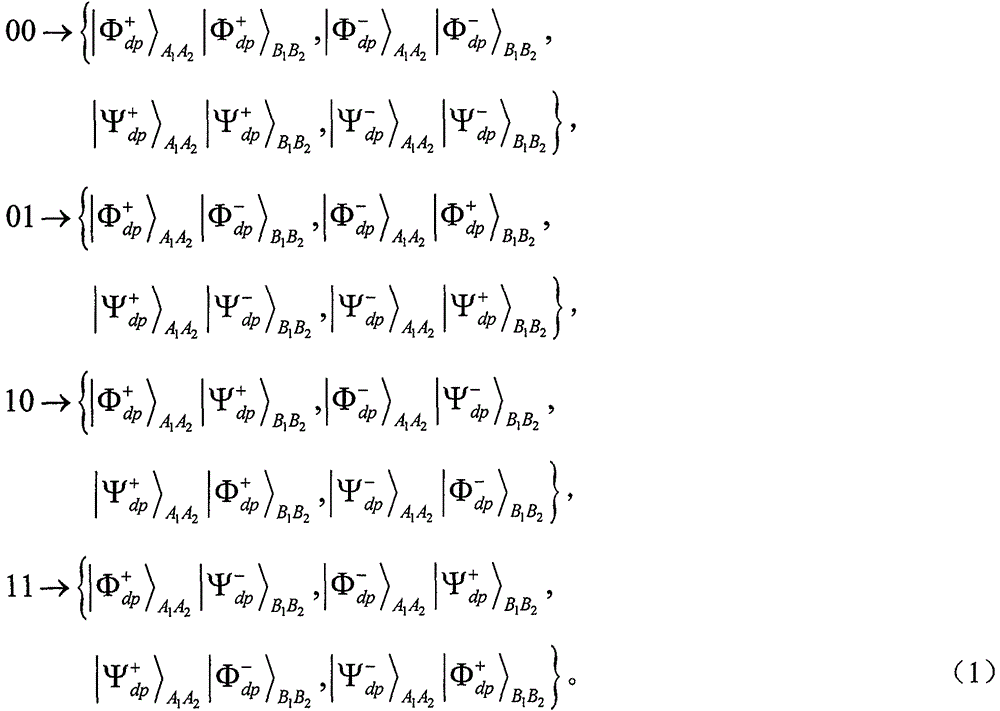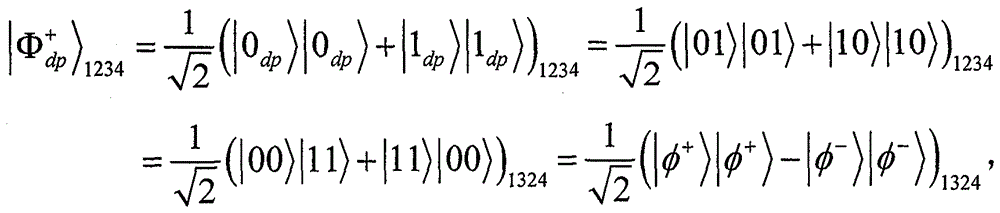Error Tolerant Quantum Steganography Applicable to Collectively Dephasing Noise Channels
A technology of phase noise and quantum steganography, which is applied in the direction of secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as noise interference, and achieve the effect of invisibility and security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0106] 1. Application examples of quantum steganography
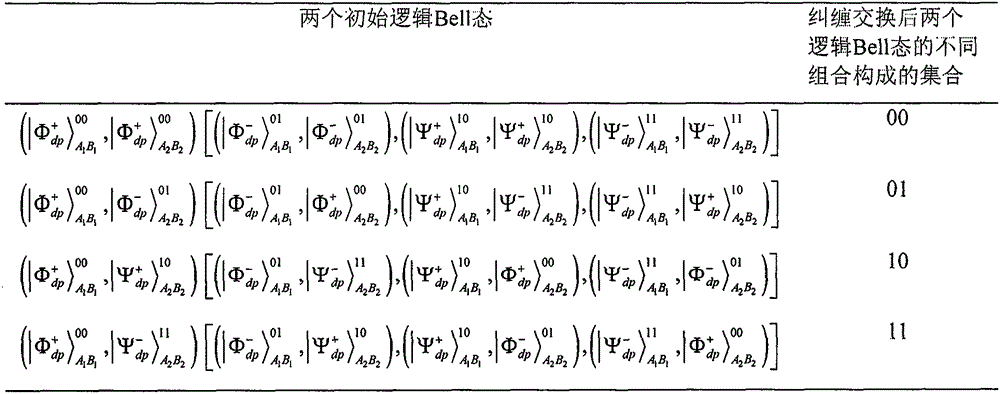
[0107] Here, a concrete example under collectively dephased noise channel is given to further explain the concealment and decoding modes of information and secret messages. Suppose the two-bit secret message sent by Alice to Bob is 01. According to Table 2, Alice generates the information bit sequence...00 01 ...01 00 ...10 11 ...11 10 ...to help hide two-bit secret messages (information in groups of four bits, where each two bits represent a logical unitary operation). Suppose 00 01 、01 00 、10 11 and 11 10 The group numbers are 2, 4, 6 and 9 respectively. Without loss of generality, take the second group of the information sequence as an example. At S3, Alice makes m=5 to satisfy the consistency of Table 2. Thus, A' 4 B' 4 and A' 5 B' 5 will be respectively with Moreover, the two-bit secret message 01 passes through A' 5 B' 5 and A' 6 B' 6 Entanglement exchange between to teleport. It should be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com