Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
236 results about "Non users" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Non user. NON USER. The neglect to make use of a thing. 2. A right which may be acquired by use, may be lost by non-user, and an absolute discontinuance of the use for twenty years affords presumption of the extinguishment of the right, in favor of some others adverse right.
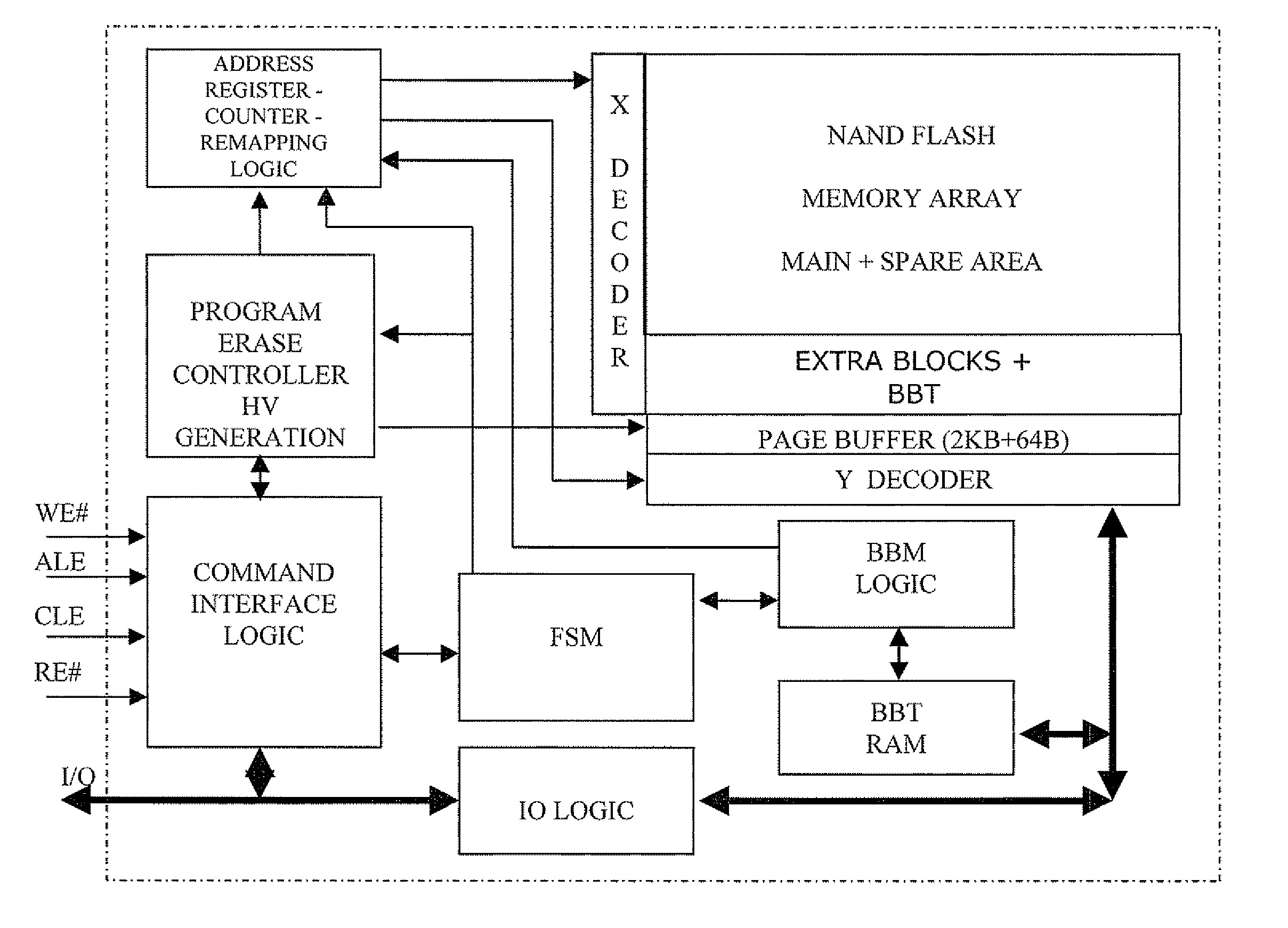
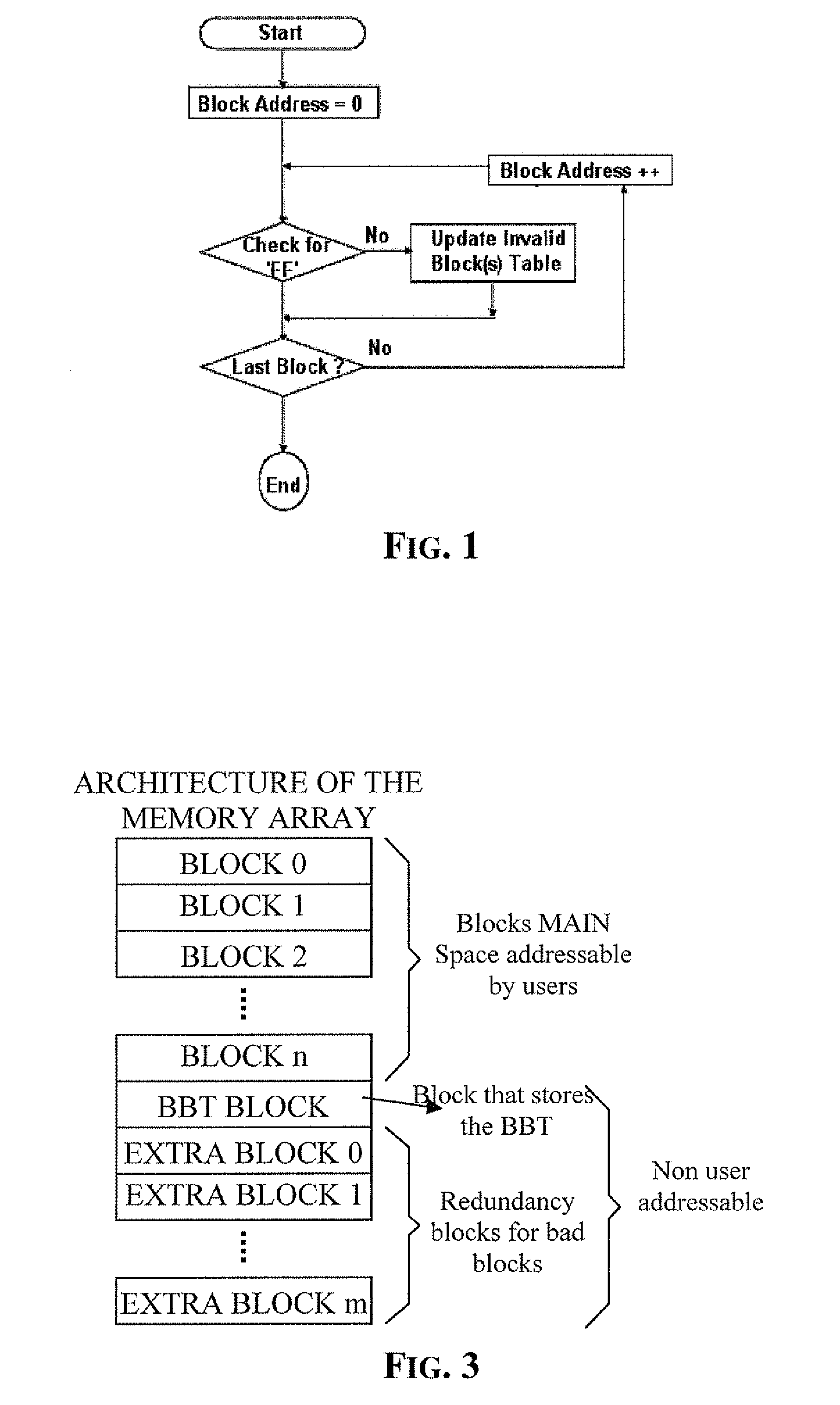
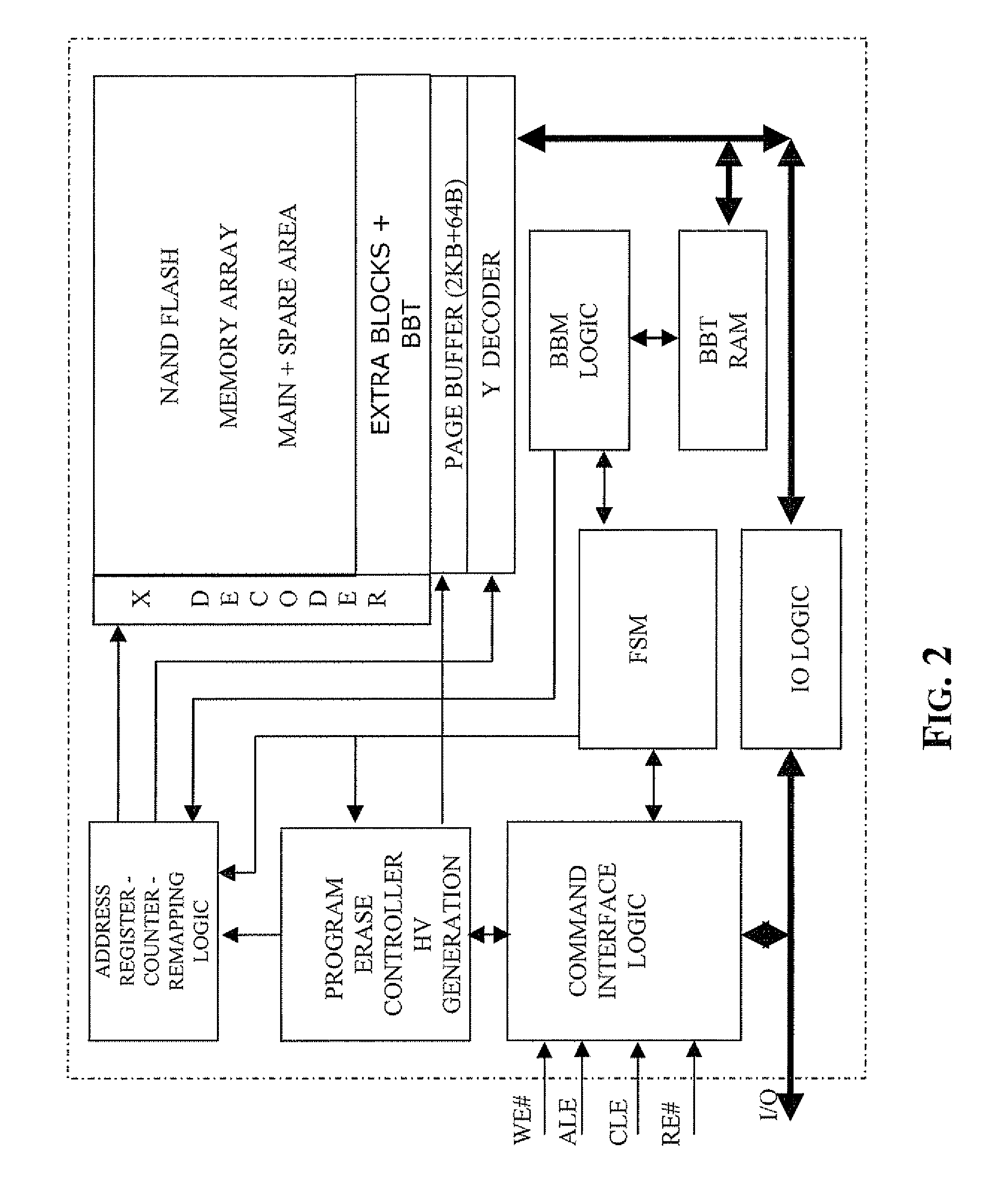
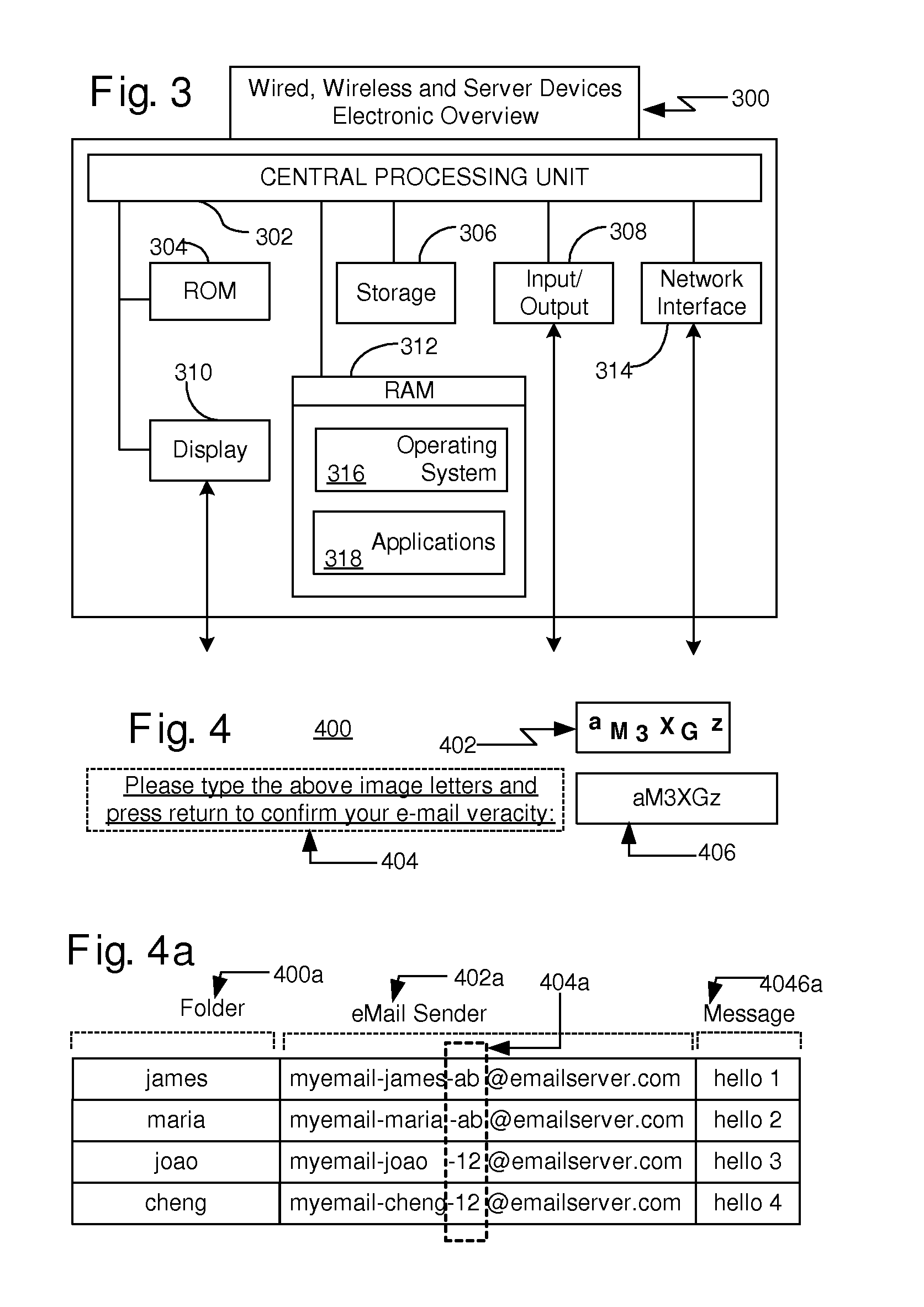
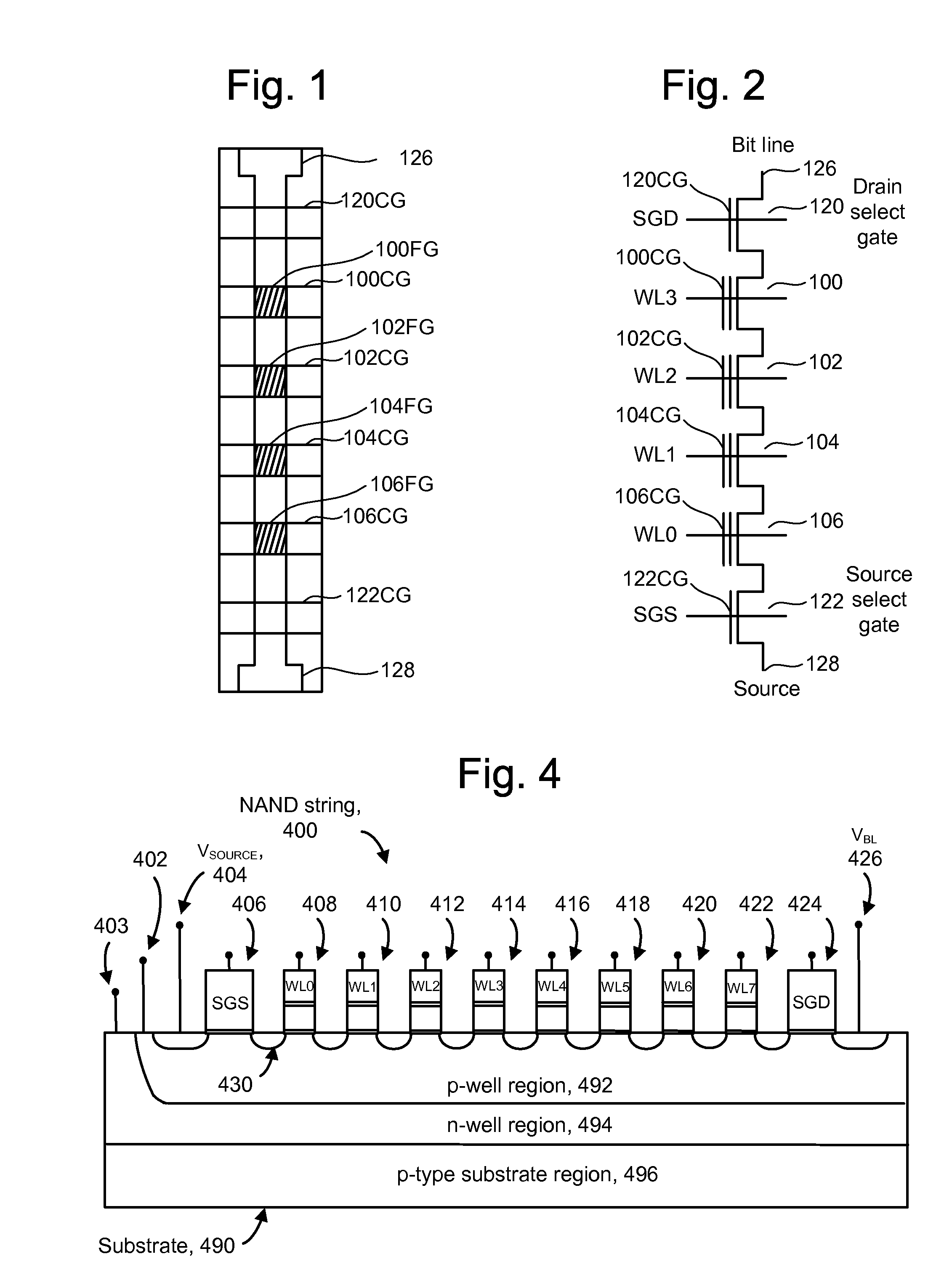
Method of managing fails in a non-volatile memory device and relative memory device
ActiveUS20070109856A1Easy to implementLow costRead-only memoriesDigital storageElectricityWorking life
A method of managing fails in a non-volatile memory device including an array of cells grouped in blocks of data storage cells includes defining in the array a first subset of user addressable blocks of cells, and a second subset of redundancy blocks of cells. Each block including at least one failed cell in the first subset is located during a test on wafer of the non-volatile memory device. Each block is marked as bad, and a bad block address table of respective codes is stored in a non-volatile memory buffer. At power-on, the bad block address table is copied from the non-volatile memory buffer to the random access memory. A block of memory cells of the first subset is verified as bad by looking up the bad block address table, and if a block is bad, then remapping access to a corresponding block of redundancy cells. A third subset of non-user addressable blocks of cells is defined in the array for storing the bad block address table of respective codes in an addressable page of cells of a block of the third subset. Each page of the third subset is associated to a corresponding redundancy block. If during the working life of the memory device a block of cells previously judged good in a test phase becomes failed, each block is marked as bad and the stored table in the random access memory is updated.
Owner:MICRON TECH INC
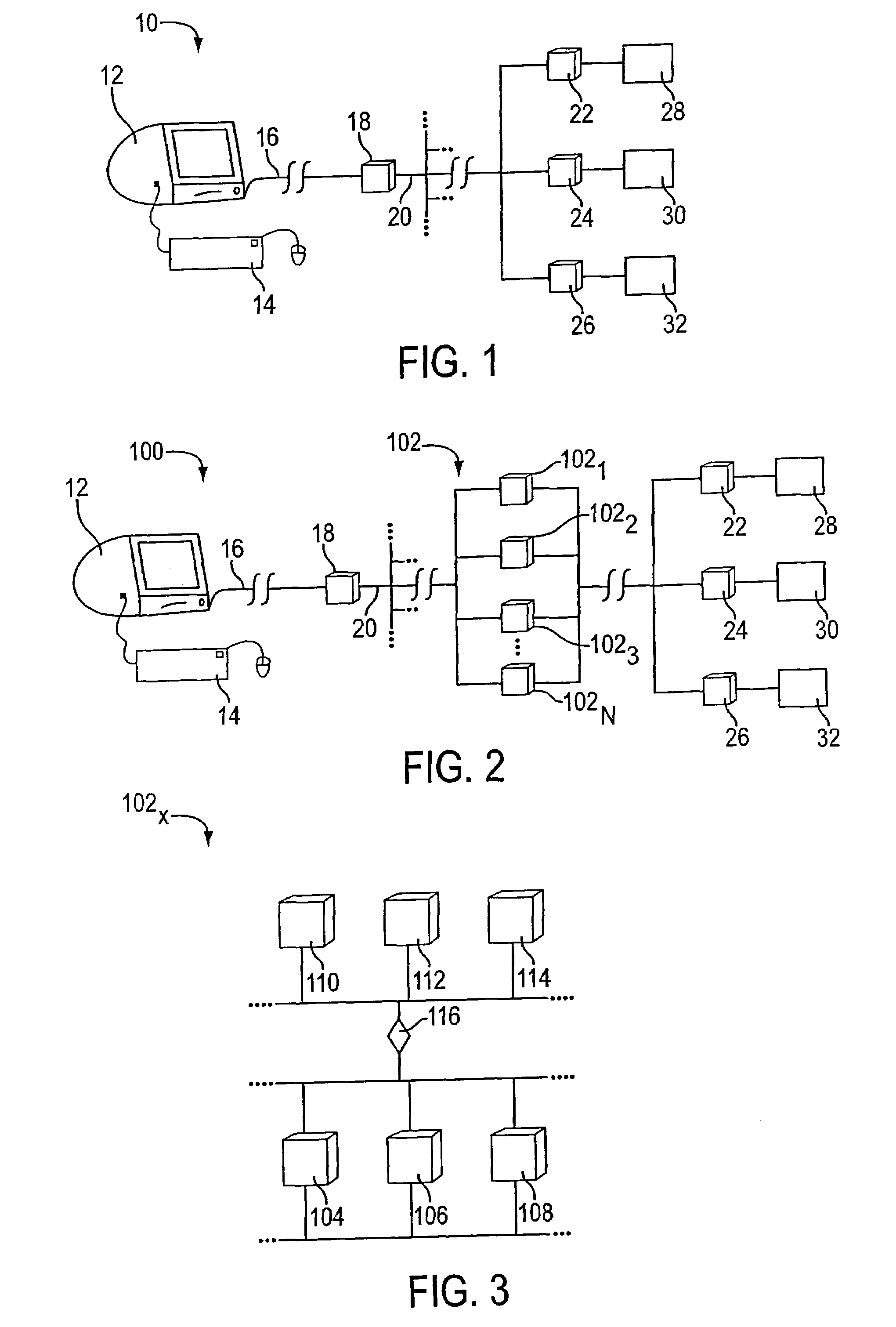
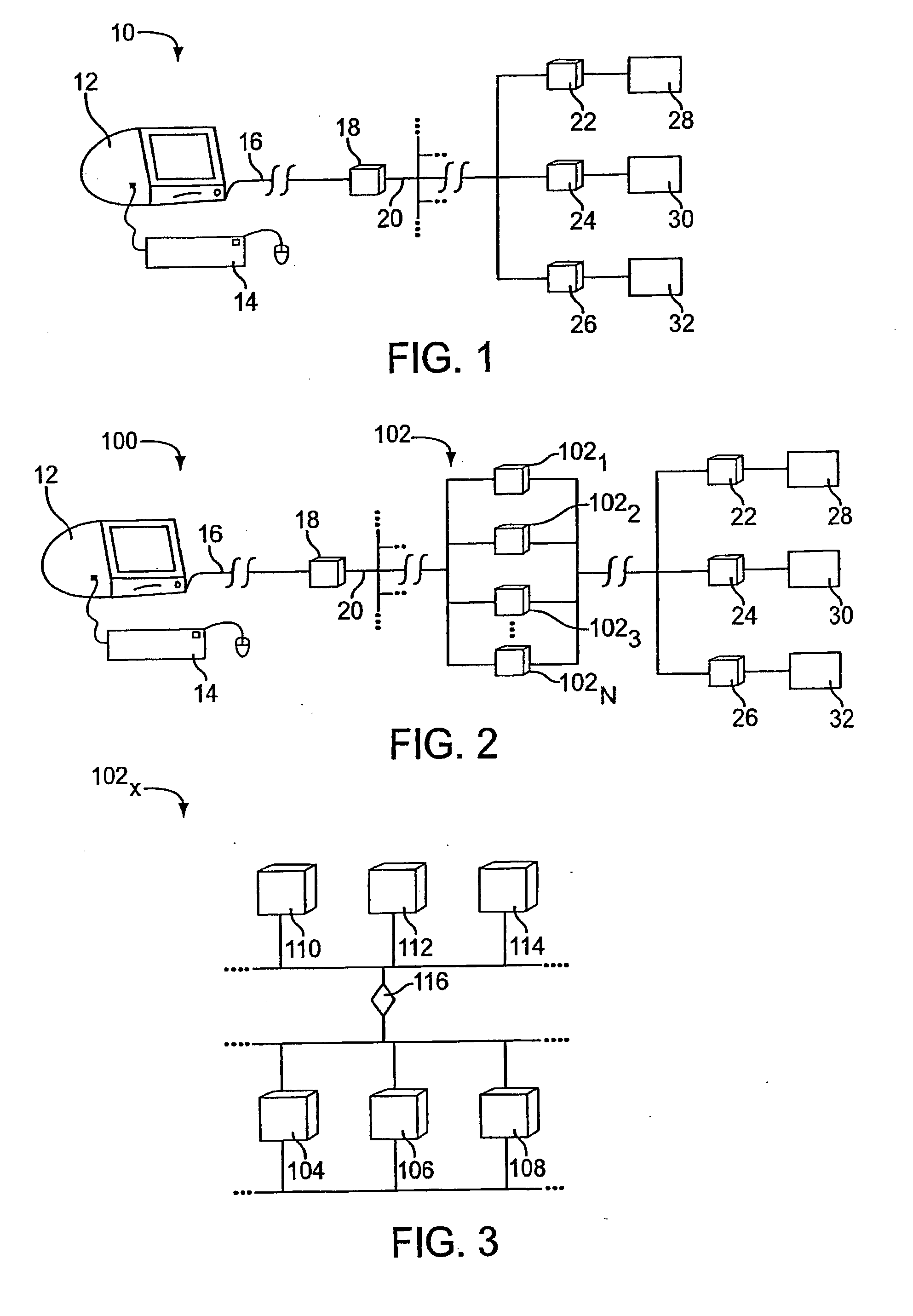
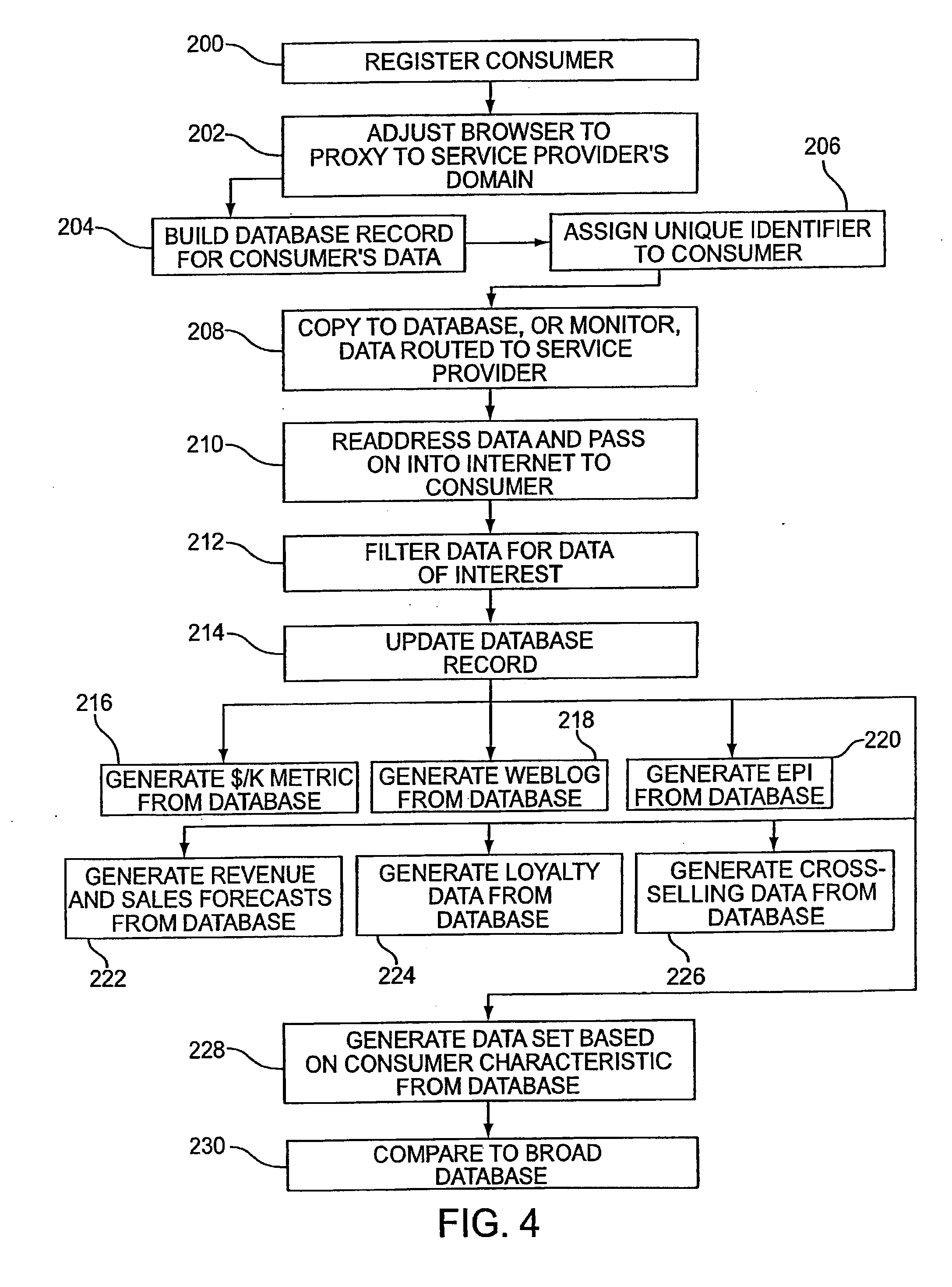
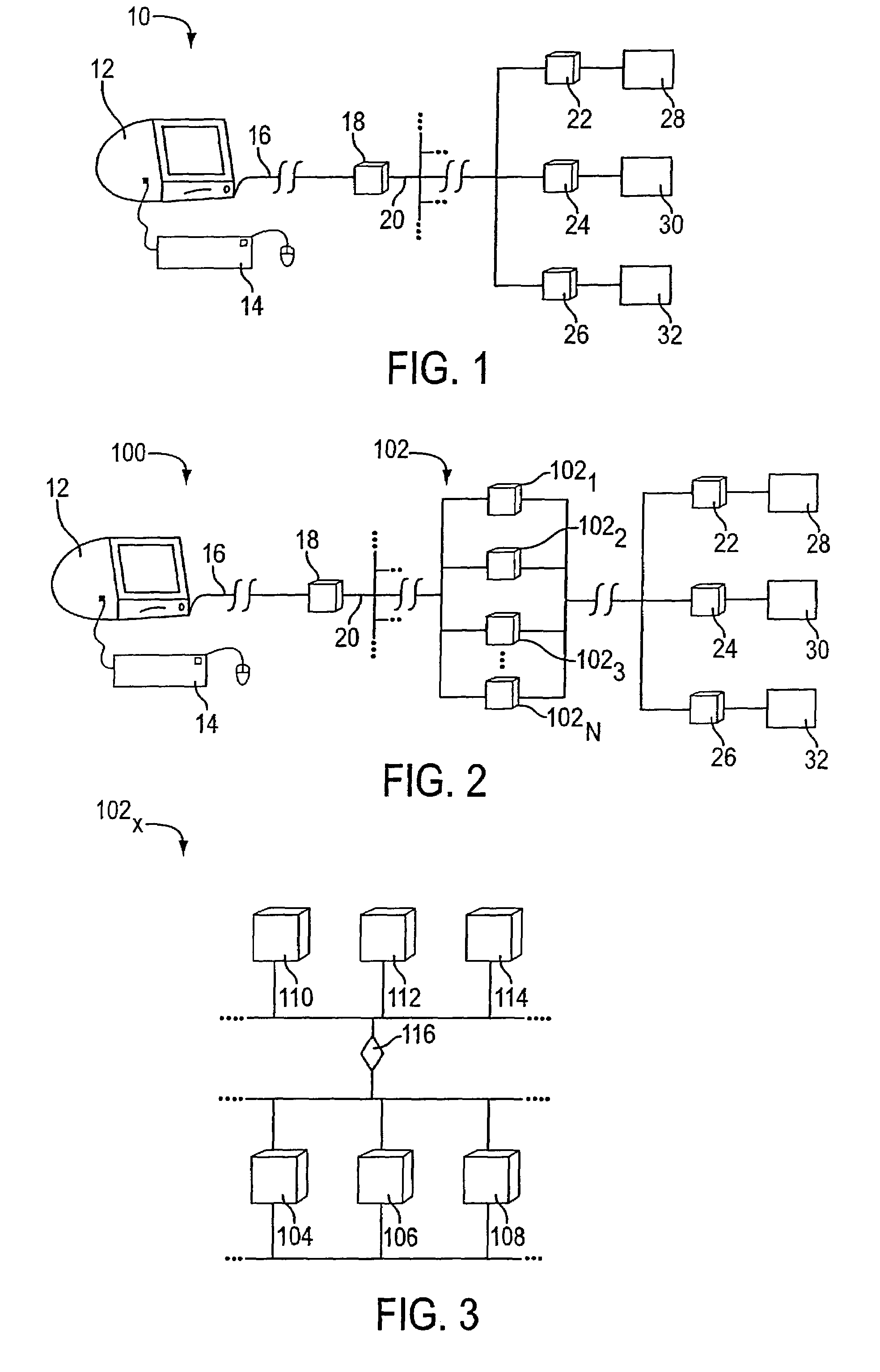
Systems and methods for user identification, user demographic reporting and collecting usage data usage biometrics
InactiveUS7260837B2Digital data information retrievalDigital data processing detailsData setDatabase server
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
User identification in the header of data packets
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE NETWORKS
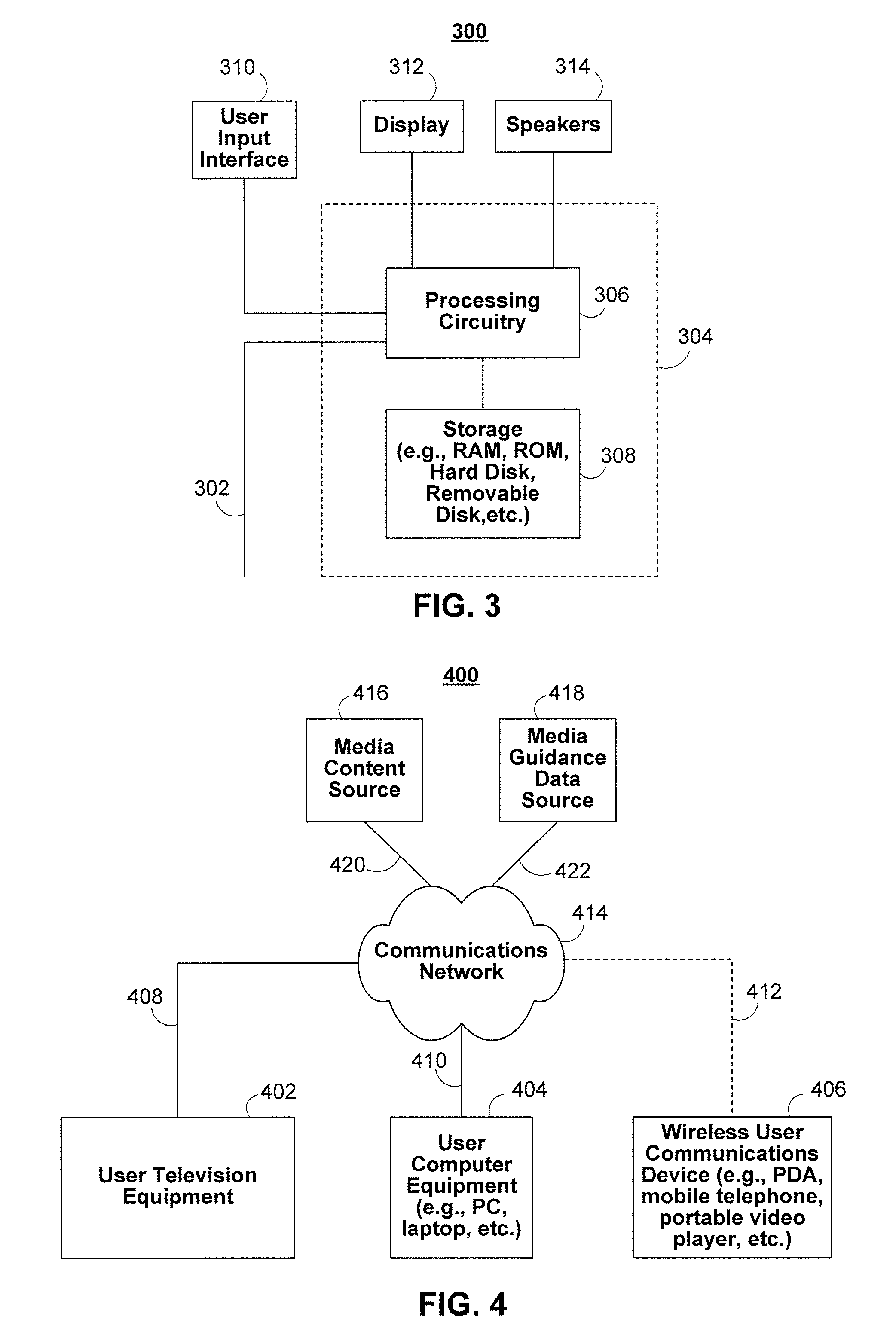
Display device, corresponding systems, and methods therefor
A display system includes a display and a control circuit operable with the display. The display is configured to provide visual output having a presentation orientation. When user input is received, the control circuit can alter the presentation orientation from an initial orientation in response to user input. When non-user events or device events are detected, the control circuit can revert the presentation orientation to the initial orientation in response to the non-user event or device event. Where the presentation orientation has a user input configuration associated therewith, the user input configuration can either be altered with the presentation orientation or retained in an initial disposition.
Owner:GOOGLE TECH HLDG LLC
Systems for and methods of placing user identification in the header of data packets usable in user demographic reporting and collecting usage data
InactiveUS7493655B2Digital data processing detailsMultiple digital computer combinationsData setMarket place
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
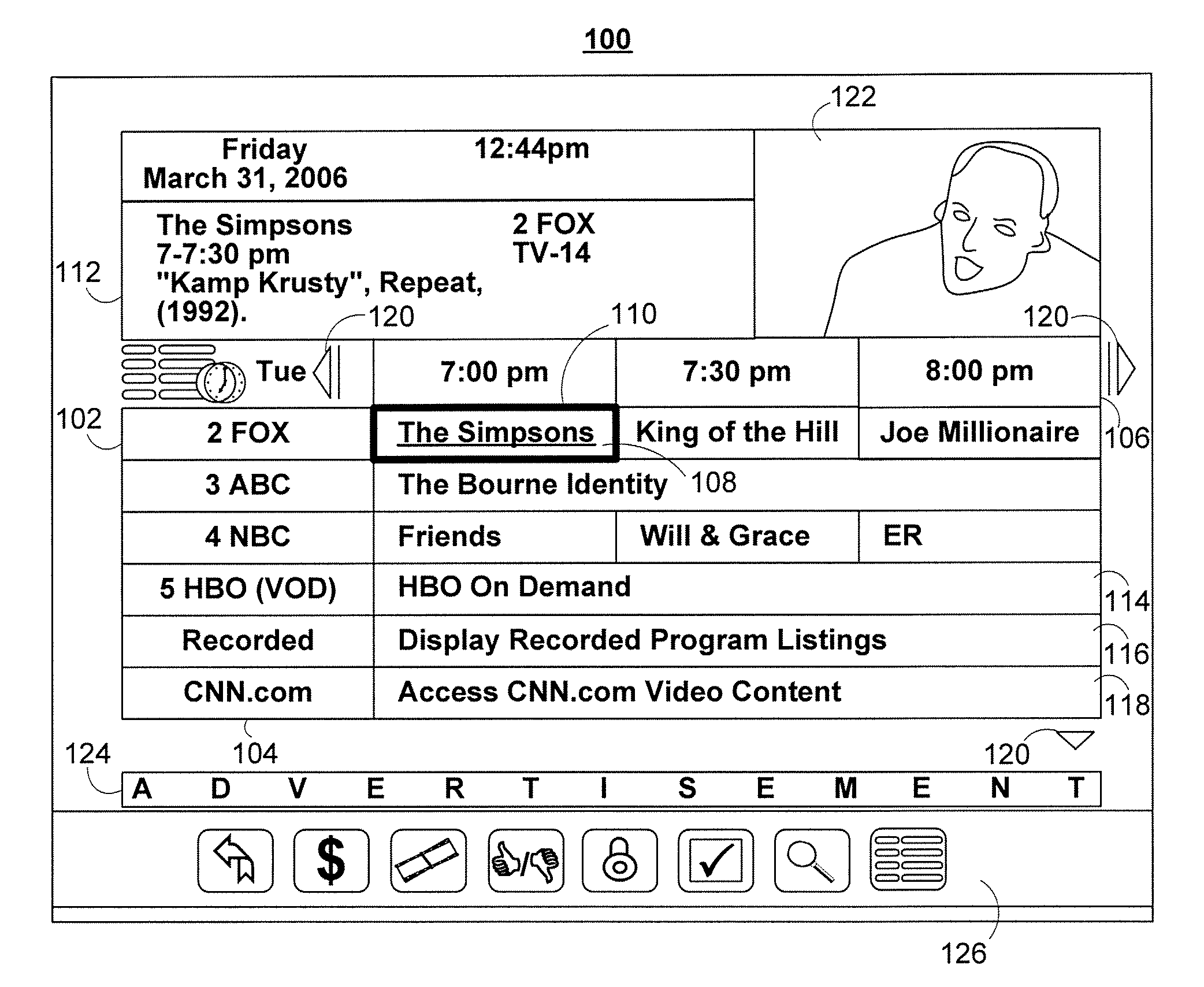
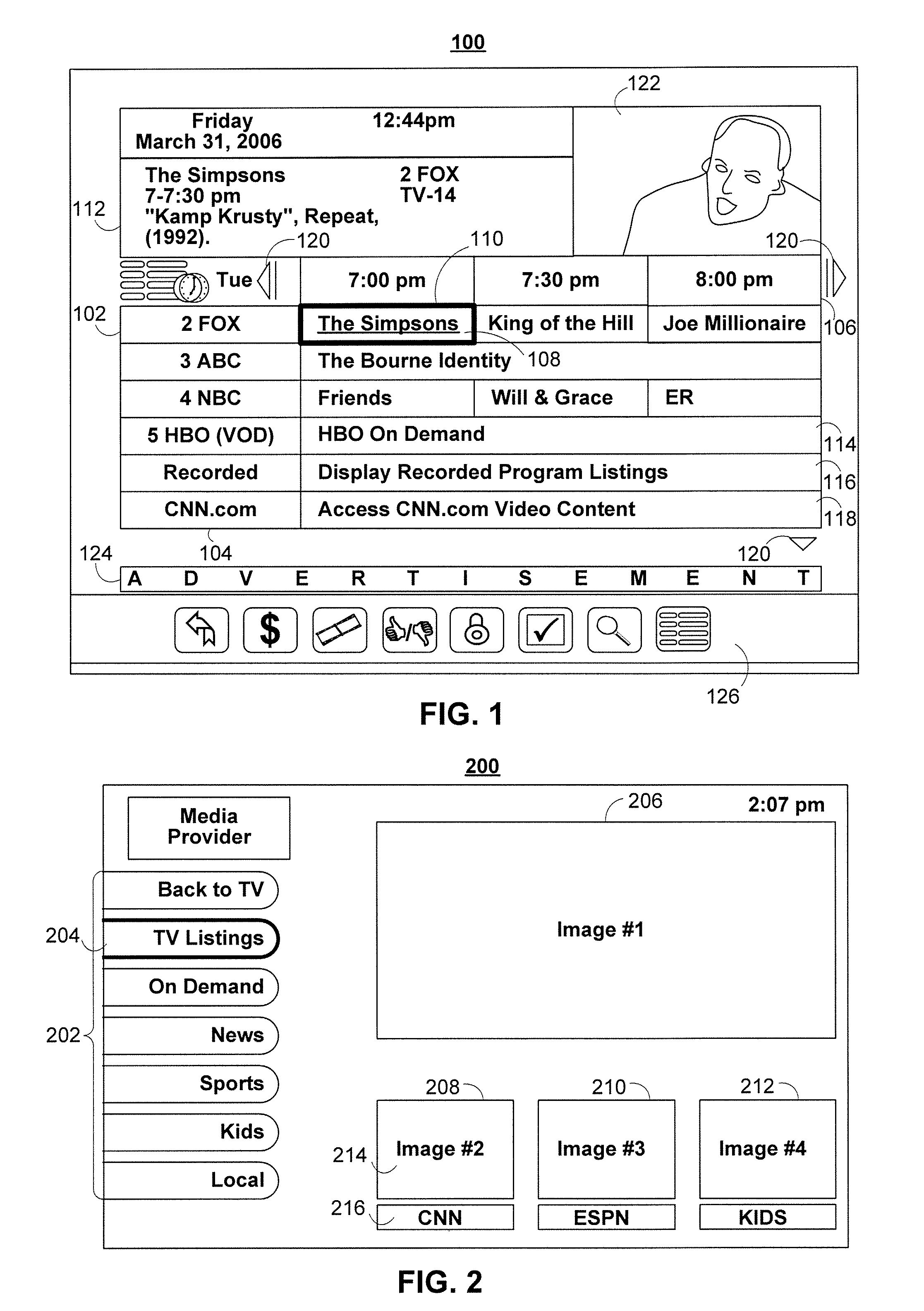
Systems and methods for generating a user profile based customized media guide that includes an internet source
ActiveUS20130305287A1Television system detailsColor television detailsUser-generated contentThe Internet
Systems and methods for presenting user-generated content in an easily accessible manner using an interactive media guide are provided. In particular, a user may be able to peruse user-generated content through an interactive media guide which is also used to access non-user-generated media content such as linear programming (e.g., over-the-air broadcast, cable, and satellite scheduled programming) and on-demand media. The interactive media guide may include a provider of user-generated content populated with user-generated content according to the user's interests or most recently added to the provider.
Owner:ROVI GUIDES INC
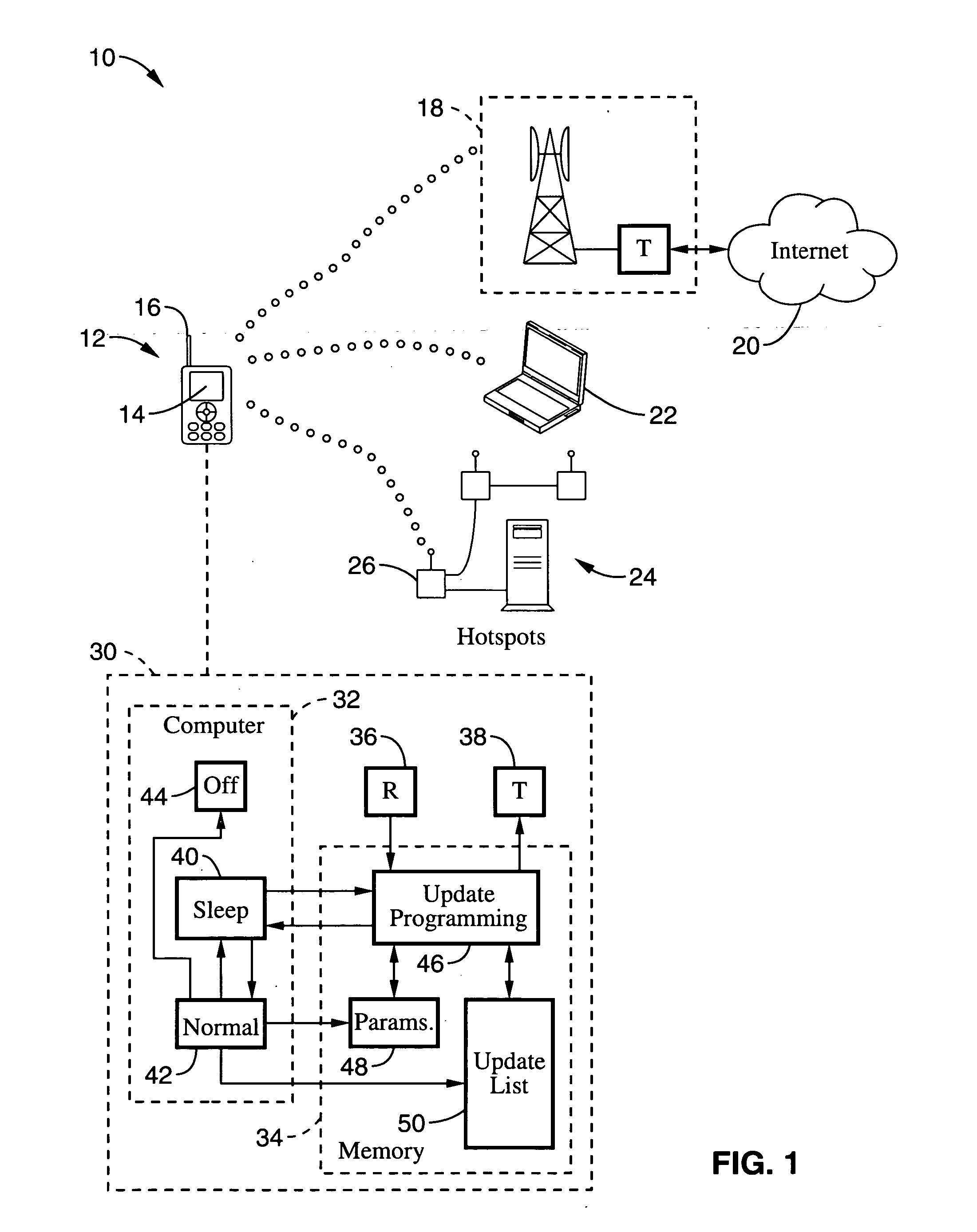
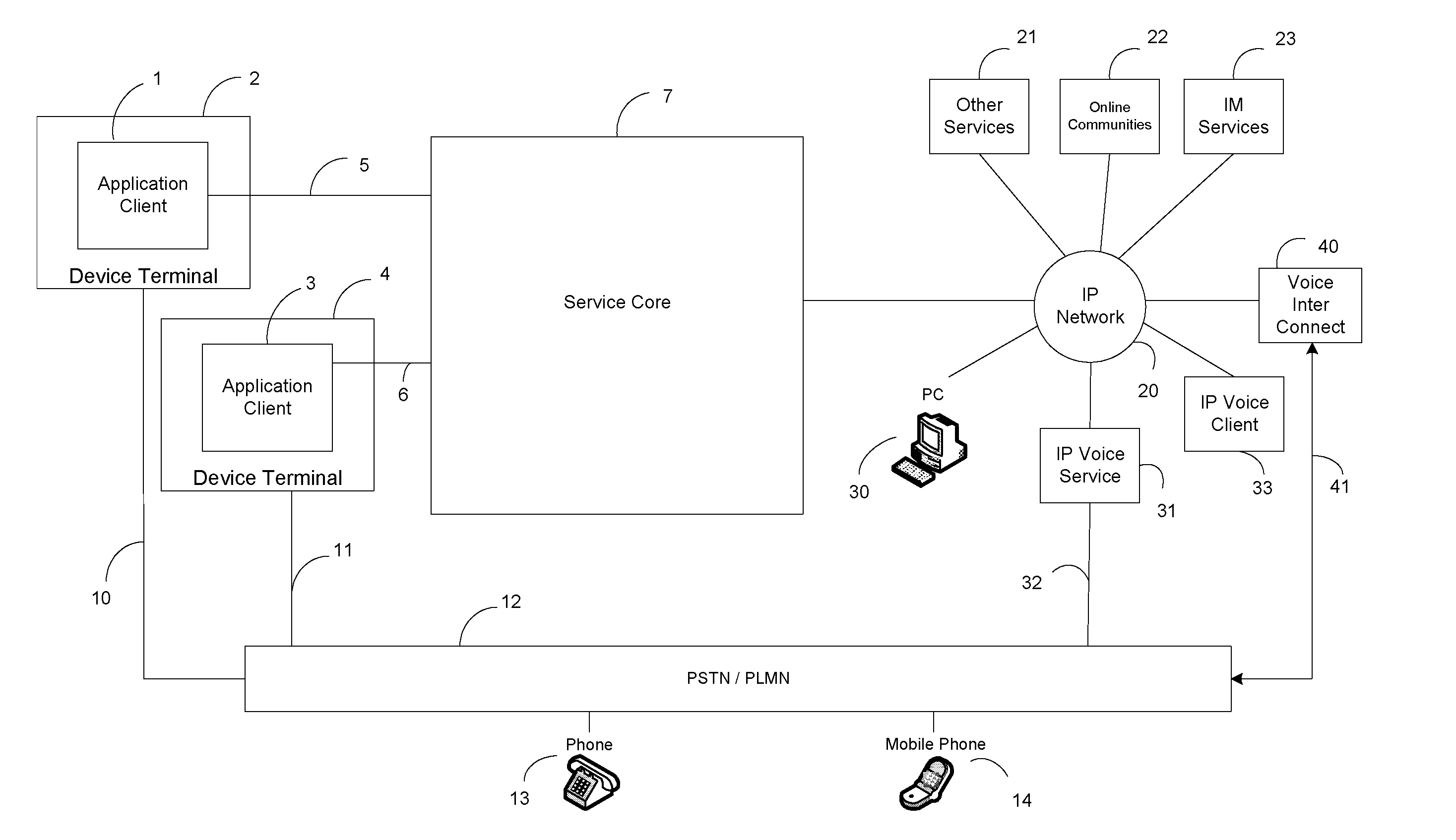
Method for data synchronization with mobile wireless devices
InactiveUS20060056336A1Network traffic/resource managementMultiple digital computer combinationsData synchronizationNetwork communication
A system and method of non-interactive communication with wireless networks for a mobile wireless device such as a telephone, personal digital assistant (PDA), laptop, or other device configured for performing data transfers with an unreliable network, and the playing back of multimedia received over said network. The invention allows a user to send and receive email, web and other data updates in physical areas and locations of limited signal coverage without the user periodically activating the device for updating data. Furthermore, the invention allows non-interactive receipt of multimedia content for viewing when a network communication outage arises. In one embodiment a second (or subsequent) multimedia stream is received and stored in a data repository for playback when an outage arises. The programming of the device is configured to retrieve the content within the second multimedia stream in response to device programming, user set parameters, learned behaviors and / or non-user based selections.
Owner:SONY CORP +1
Systems and methods for user identification, user demographic reporting and collecting usage data using biometrics
InactiveUS20070276940A1Digital data information retrievalDigital computer detailsData setInternet traffic
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE NETWORKS
Display Device, Corresponding Systems, and Methods for Orienting Output on a Display
A display system includes a display and a control circuit operable with the display. The display is configured to provide visual output having a presentation orientation. When user input is received, the control circuit can alter the presentation orientation from an initial orientation in response to user input. When non-user events or device events are detected, the control circuit can revert the presentation orientation to the initial orientation in response to the non-user event or device event. Where the presentation orientation has a user input configuration associated therewith, the user input configuration can either be altered with the presentation orientation or retained in an initial disposition.
Owner:GOOGLE TECH HLDG LLC
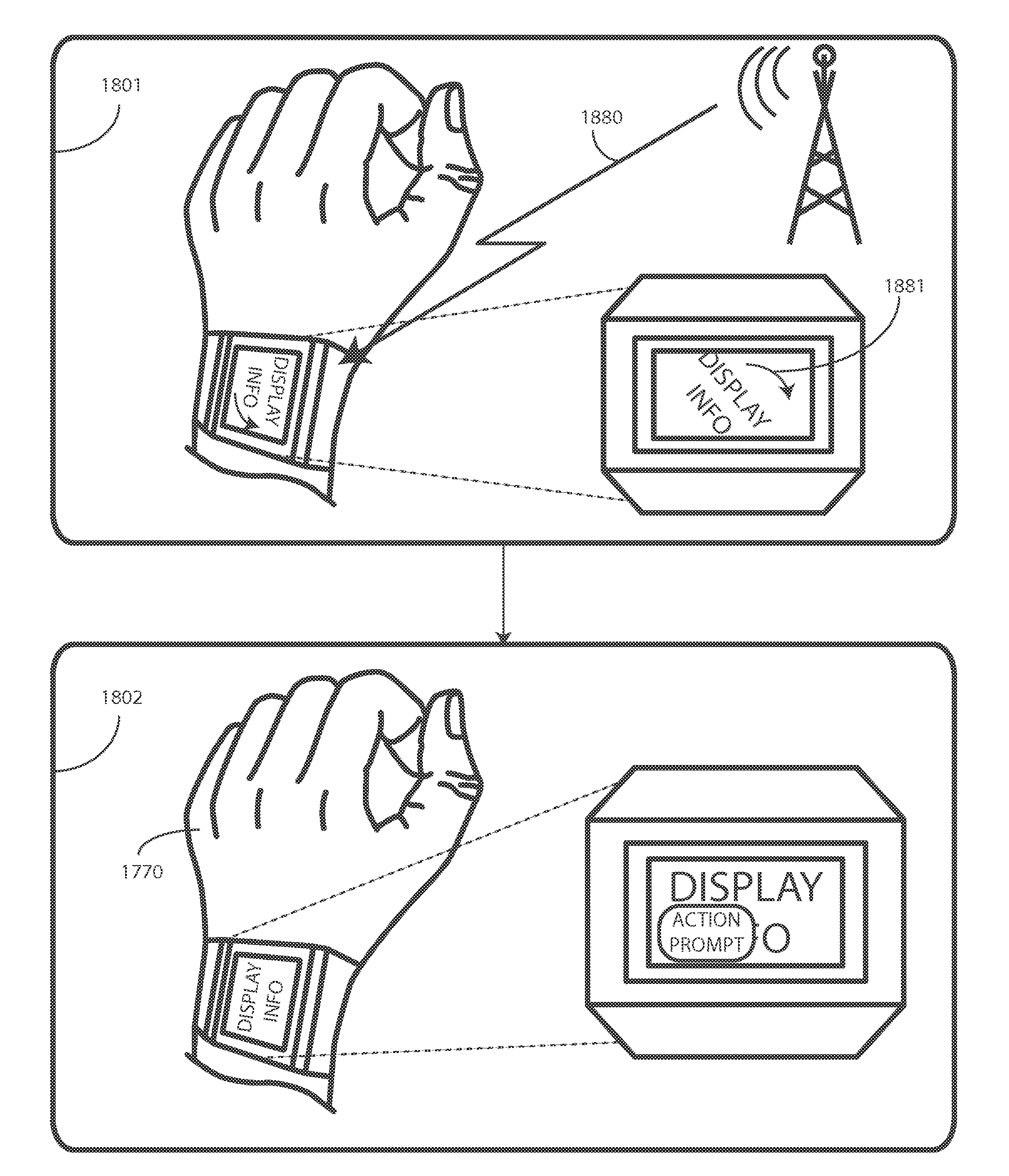
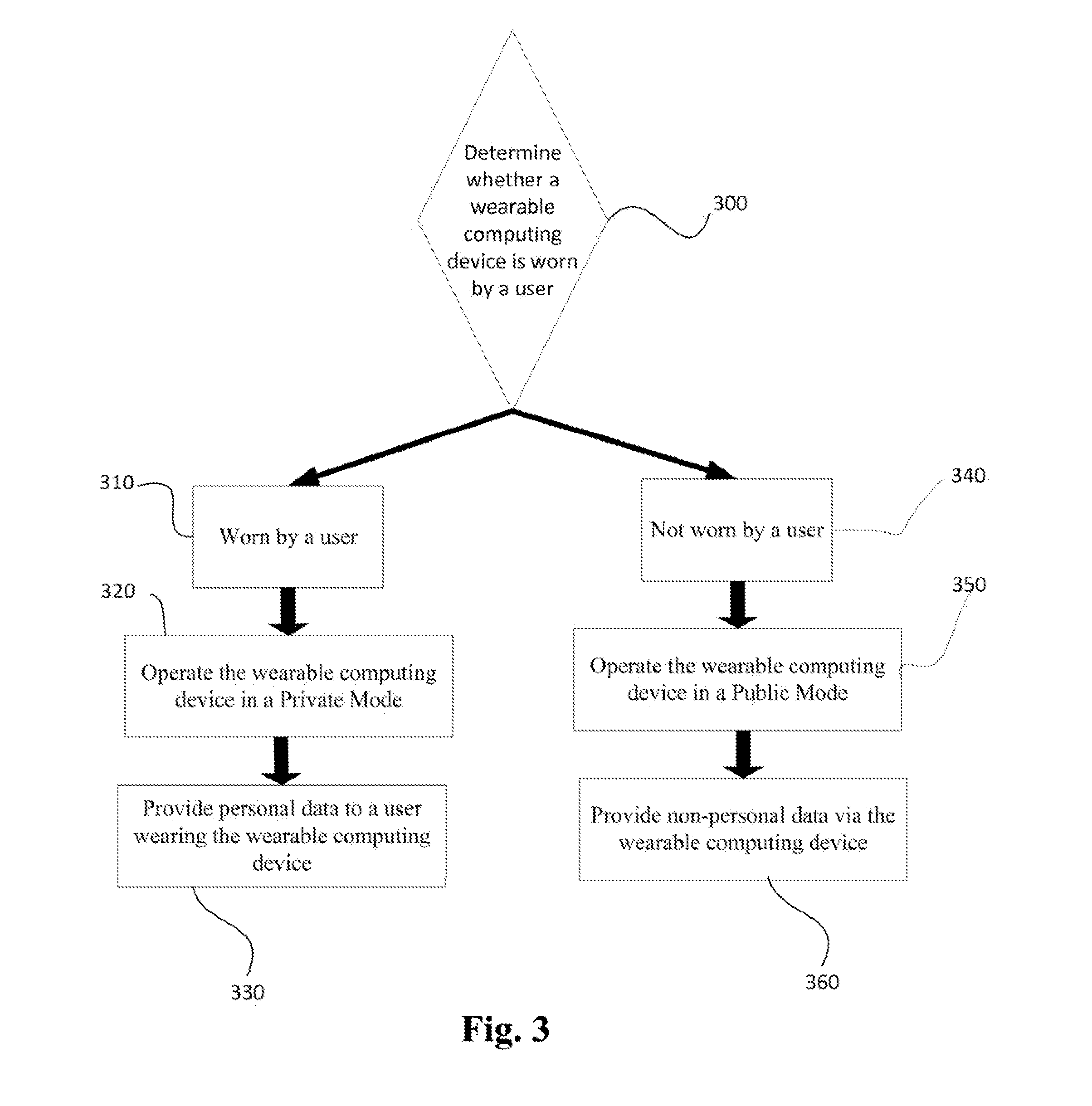
Wearable Device Multi-mode System
ActiveUS20140366123A1Digital data processing detailsUnauthorized memory use protectionHuman–computer interactionNon users
Systems and techniques are disclosed for detecting whether a wearable computing device is worn by a user or not. The detection can be made based on whether the device is secured to a user or based on a sensor. A device worn by a user may be operated in a private mode such that the user wearing the device is provided information that is useful while wearing the device. For example, the user may receive message notifications, news updates, telephone call information, or the like. A wearable computing device maybe operated in a public mode while not being worn by a user. While in the public mode, the device may provide non user specific information such as a current time, media items, or the like.
Owner:GOOGLE LLC
Method and system for providing 'what's next' data
ActiveUS20100094866A1Efficient and quicker displayDigital data processing detailsMetadata video data retrievalData miningNon users
A system and method for generating a list of content is disclosed. A processor may store in memory at least one content preference of a user, may store at least one non-user content preference of at least one entity other than the user, may associate the at least one non-user content preference with the user, and may generate the content list based on a combination of the at least one content preference of the user and the at least one non-user content preference for output to the user.
Owner:HOME BOX OFFICE INC
Gestures Beyond Skeletal
Systems, methods and computer readable media are disclosed for gesture input beyond skeletal. A user's movement or body position is captured by a capture device of a system. Further, non-user-position data is received by the system, such as controller input by the user, an item that the user is wearing, a prop under the control of the user, or a second user's movement or body position. The system incorporates both the user-position data and the non-user-position data to determine one or more inputs the user made to the system.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for making the use of head-mounted displays less obvious to non-users
ActiveUS20140078175A1Cathode-ray tube indicatorsInput/output processes for data processingComputer graphics (images)Display device
Owner:QUALCOMM INC
User interface display system
InactiveUS20060085759A1Special data processing applicationsInput/output processes for data processingHuman–computer interactionUser interface
A user interface system for presenting information to a user involves a display processor for initiating generation of data representing an image. The image includes multiple adjacent rows of visible user selectable tabs individually incorporating a tab function identifier identifying a function associated with a respective tab. An individual tab is selectable by a user to initiate presentation of an image area in an image window and presents information concerning a function identified by a tab function identifier of a selected tab. An individual row of visible user selectable tabs includes multiple user selectable tabs together with a non-user selectable label. The non-user selectable label includes information associated with the multiple user selectable tabs on the individual row. A command processor initiates generation of data representing an update of the image to include an image area in an image window and present information concerning a function identified by a tab function identifier of the selected tab in response to user selection of the selected tab.
Owner:SIEMENS MEDICAL SOLUTIONS HEALTH SERVICES CORPORAT
System and Method for Device Bound Public Key Infrastructure
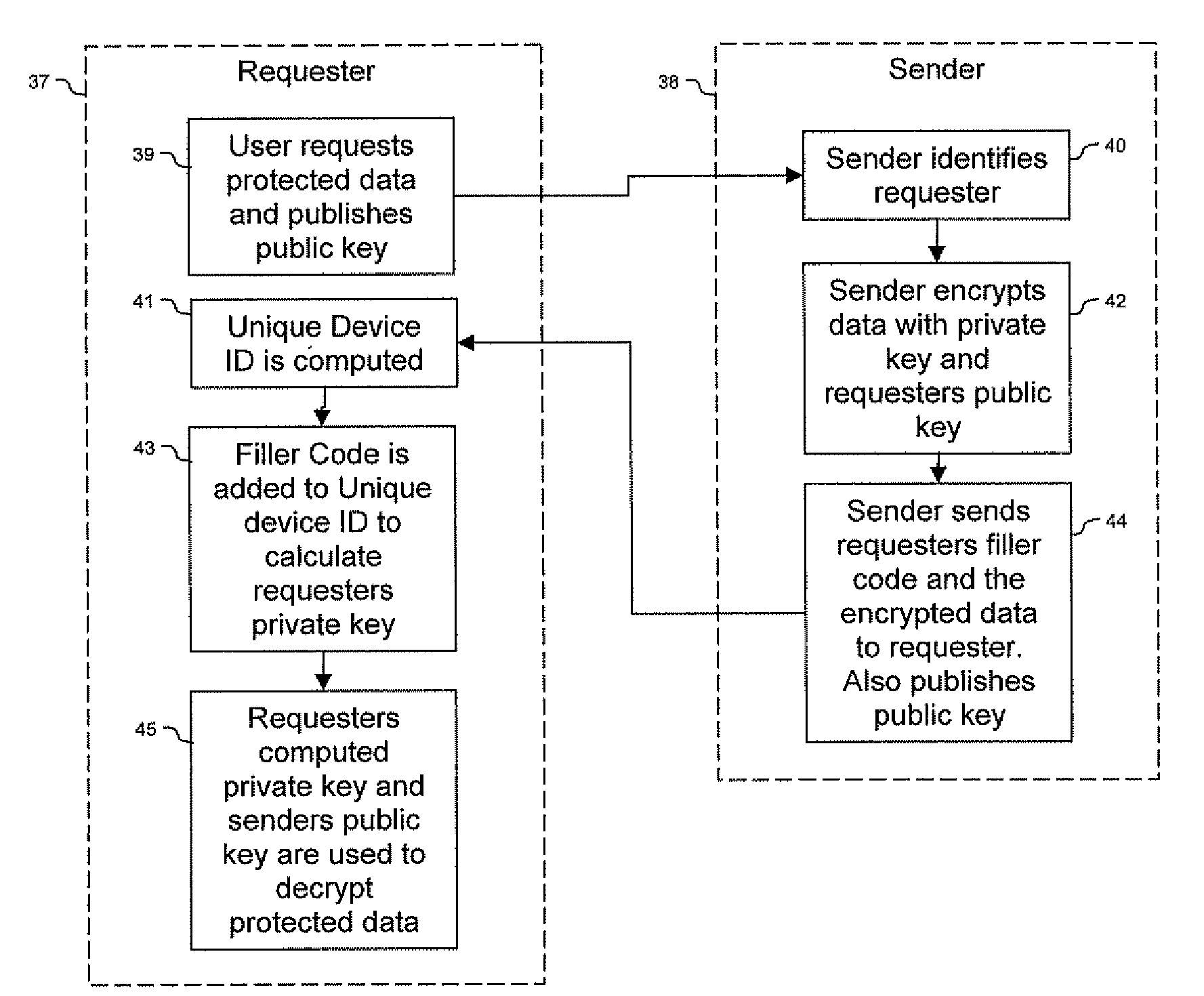
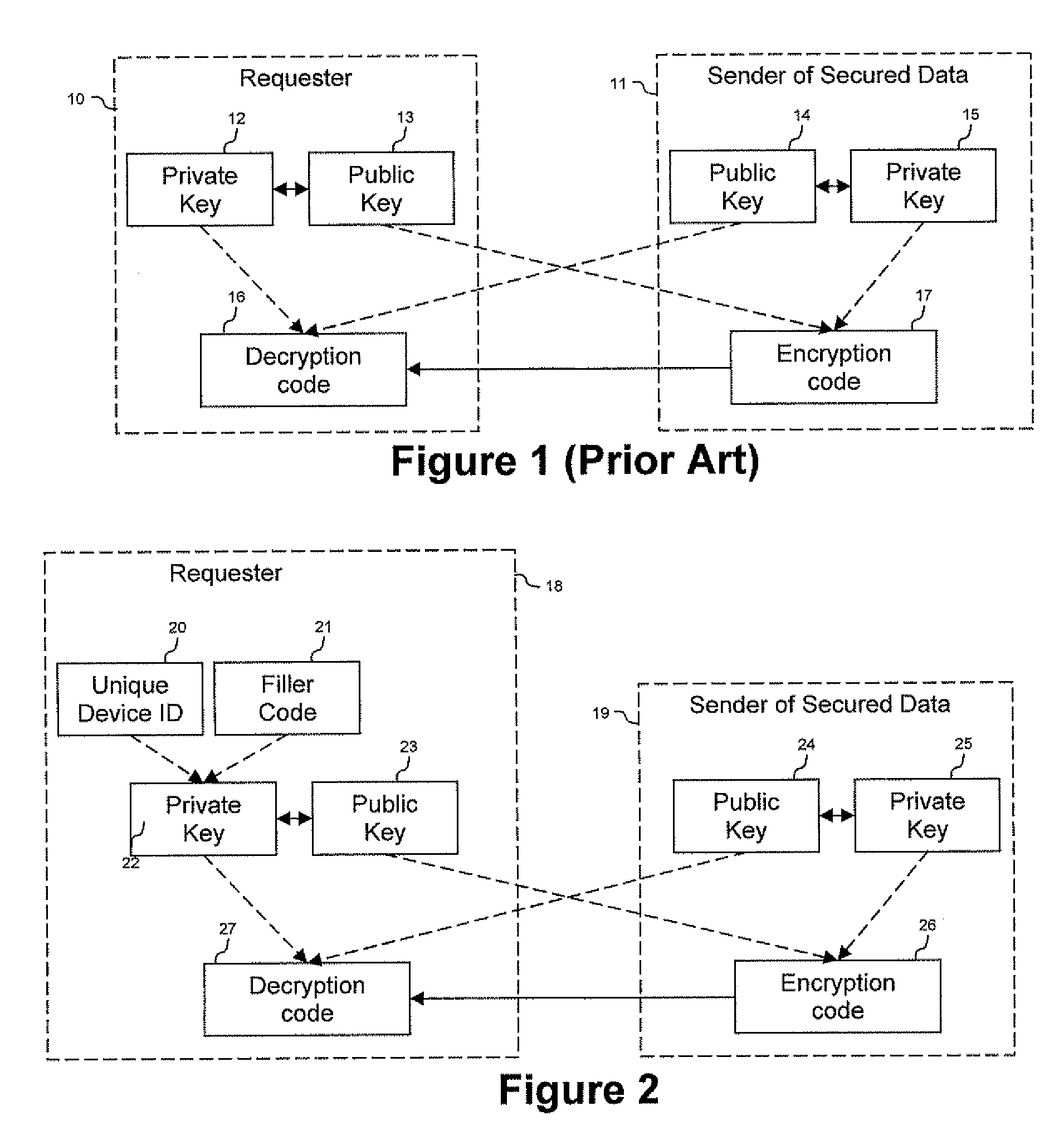
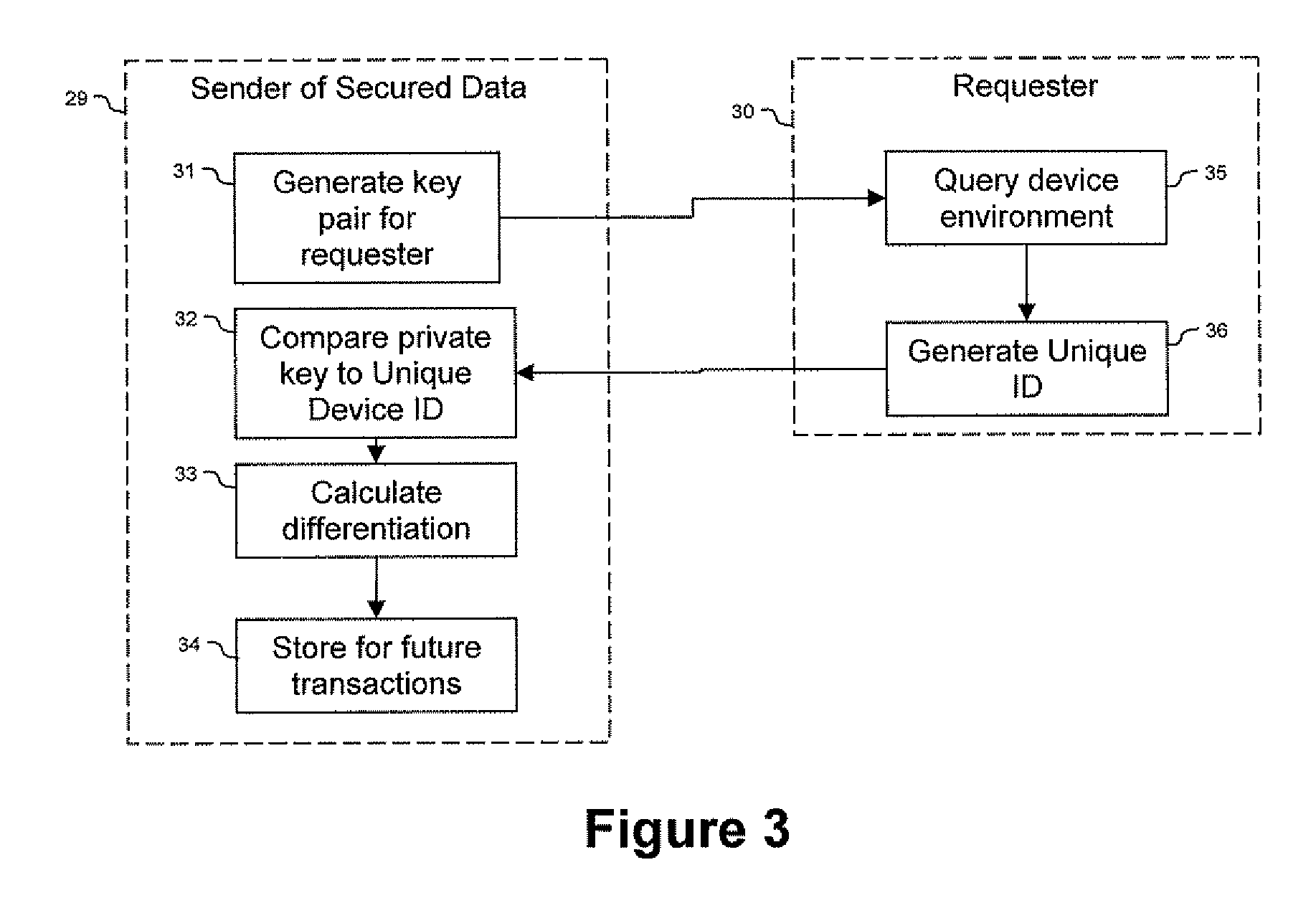
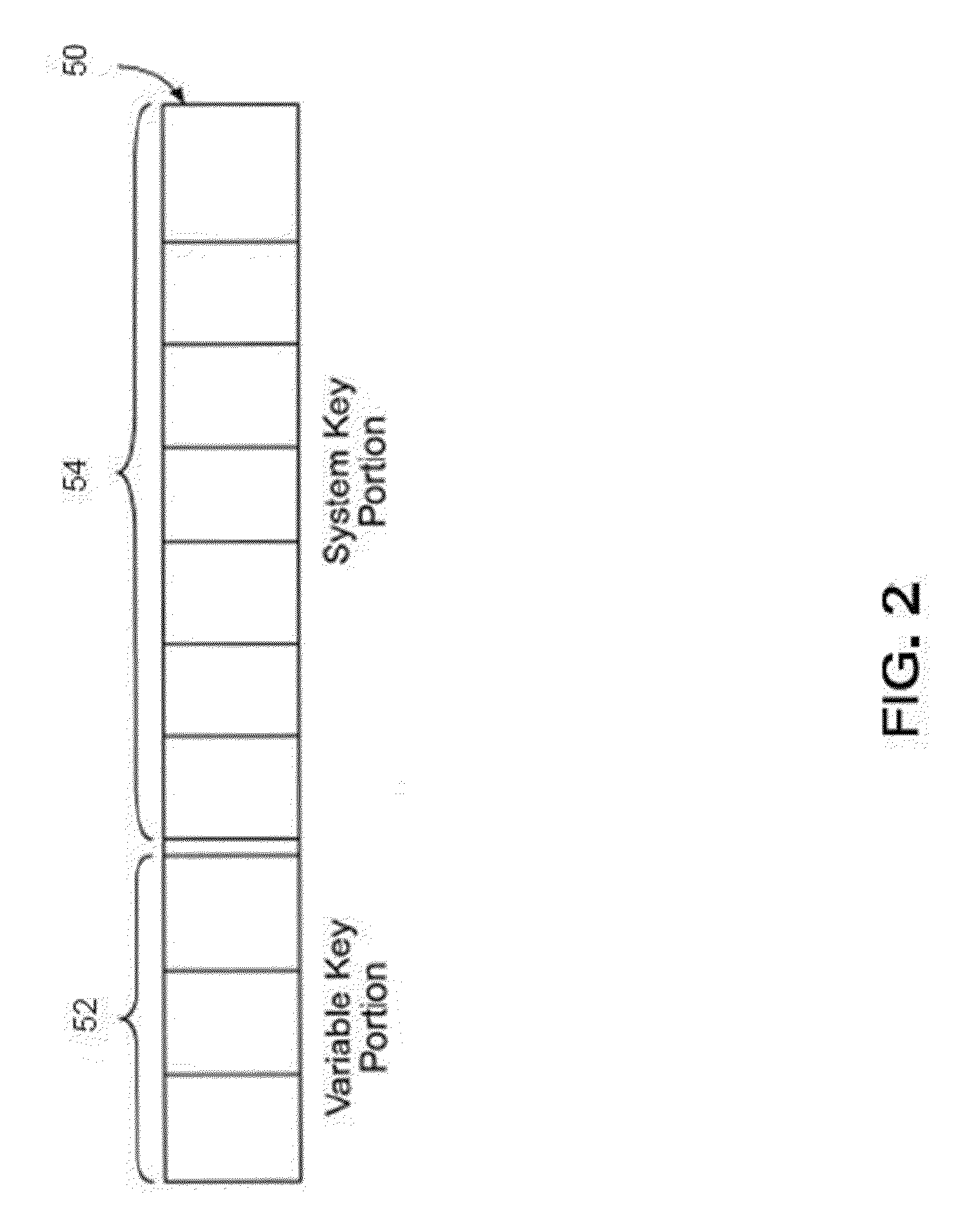
ActiveUS20090150674A1Not easy to copyNot easy to be stolenDigital data processing detailsUser identity/authority verificationSecure communicationUnique device identifier
Techniques are provided secured communication of data, such as in the context of a public key infrastructure (PKI). In one embodiment, the technique may involve using a private key that is bound to the device requesting the secure data, thereby making it harder for someone to copy, steal or fake. The private key may be generated by adding a filler code to a unique device identifier. The identifier may be based on at least one user-configurable parameter and at least one non-user-configurable parameter of the device.
Owner:DEVICE AUTHORITY LTD
System and method for adding and associating users on contact addressbook
InactiveUS20080292080A1Easy to installEasy to useSpecial service for subscribersSubstation equipmentAddress bookService user
Systems and methods are disclosed that allow a service user to add other service users and non-users into the service user's address book based on contact telephone numbers. This method allows a first service user to be associated either automatically or through an invitation process with a second service user via their telephone numbers for them to be service contacts on each other's service phonebook. Systems and methods for growing a service user base are also provided.
Owner:NELTURA TECH
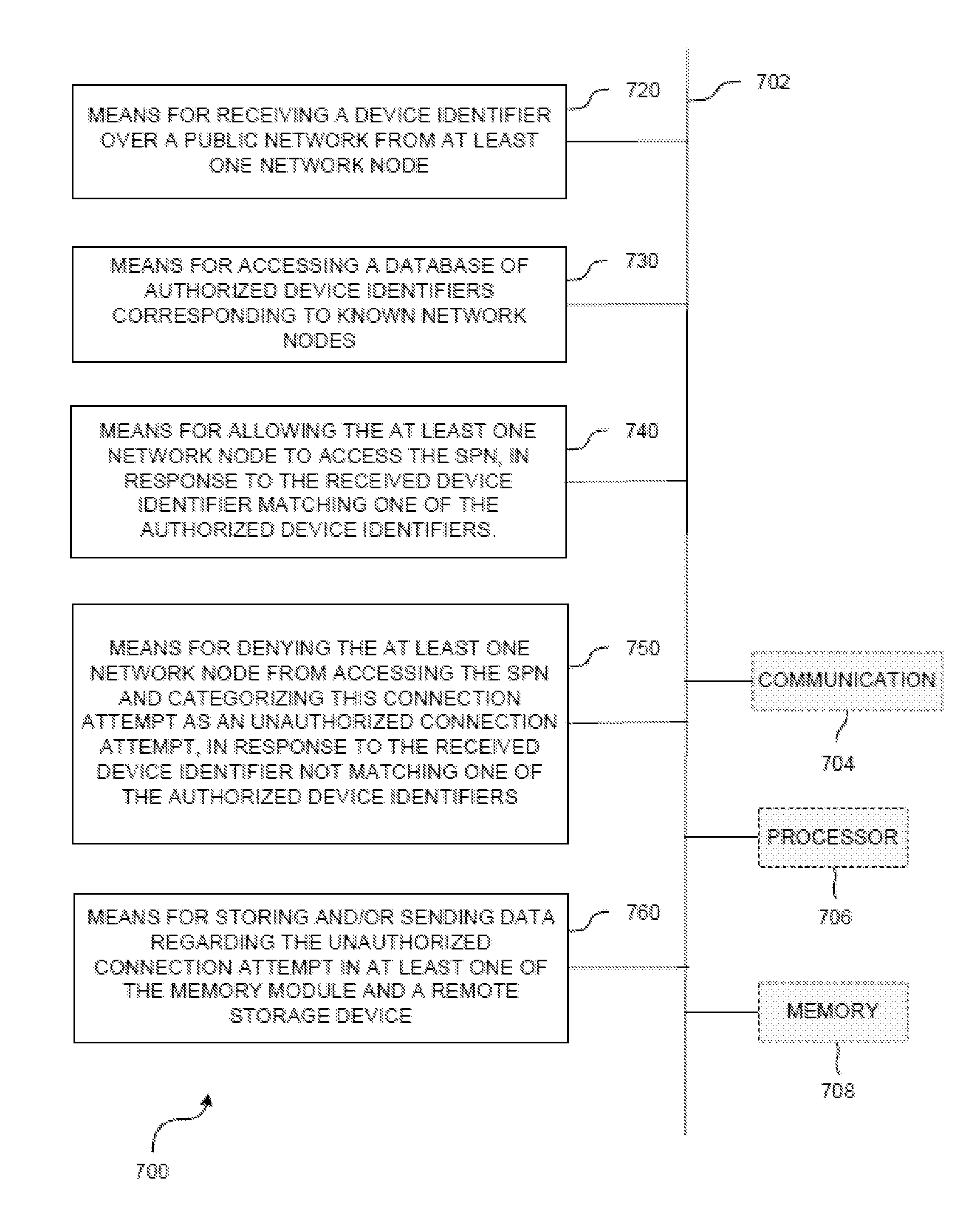
System and Method for Monitoring Attempted Network Intrusions
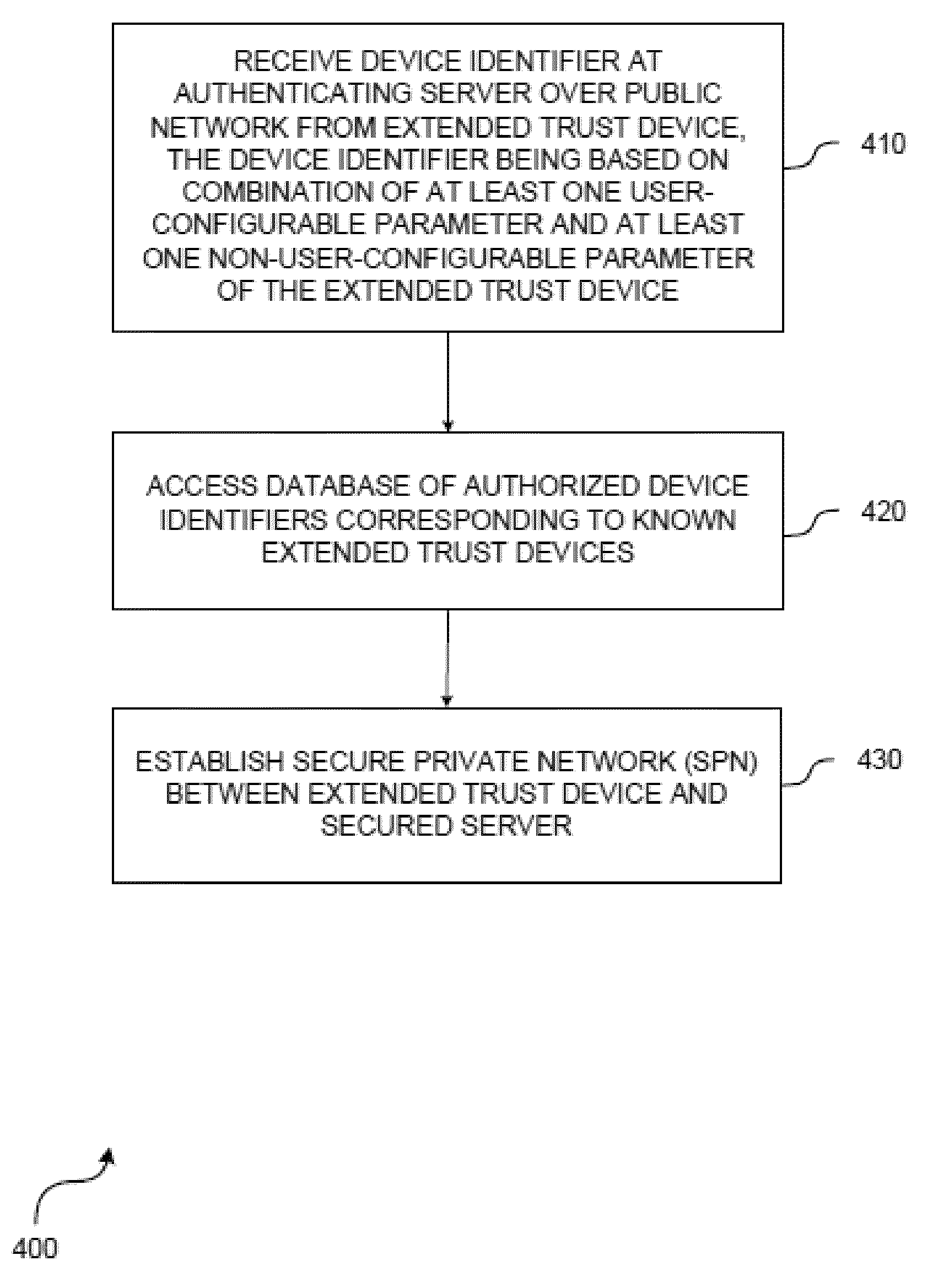
InactiveUS20100325720A1Well formedDigital data processing detailsUnauthorized memory use protectionTransceiverPrivate network
A system for monitoring attempted intrusions into a secure private network (SPN) includes a transceiver adapted to receive a device identifier over a public network from a network node, the device identifier based on a user-configurable parameter and a non-user-configurable parameter of the network node, and a processor coupled to the transceiver and to memory storing executable code. When executed, the code enables the processor to: access a database of authorized device identifiers corresponding to known network nodes, allow, in response to the received device identifier matching one of the authorized device identifiers, the network node to access the SPN, deny, in response to the received device identifier not matching one of the authorized device identifiers, the network node from accessing the SPN and categorize a connection attempt as an unauthorized connection attempt, and store information regarding the unauthorized connection attempt in local or remote memory.
Owner:UNILOC LUXEMBOURG
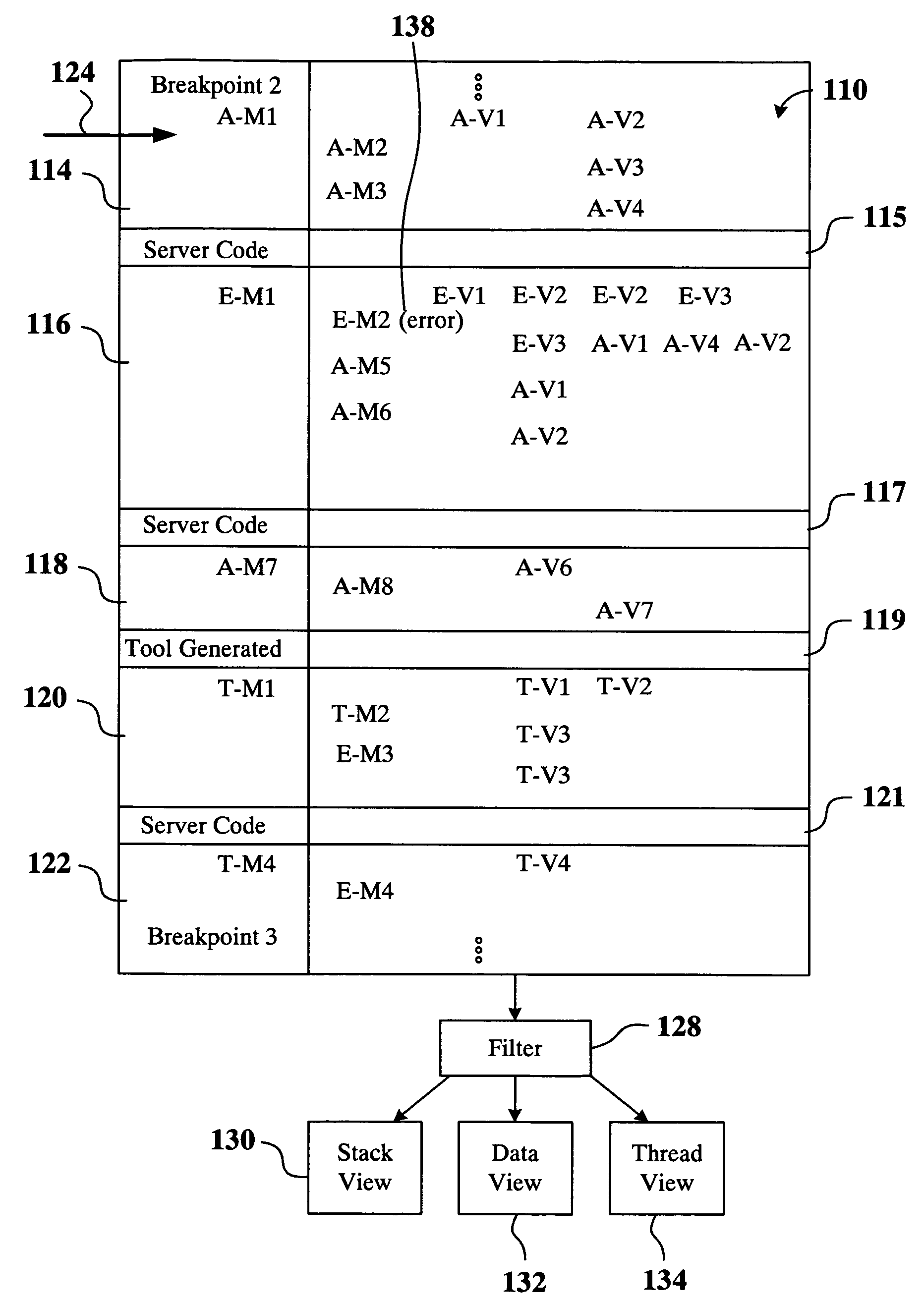
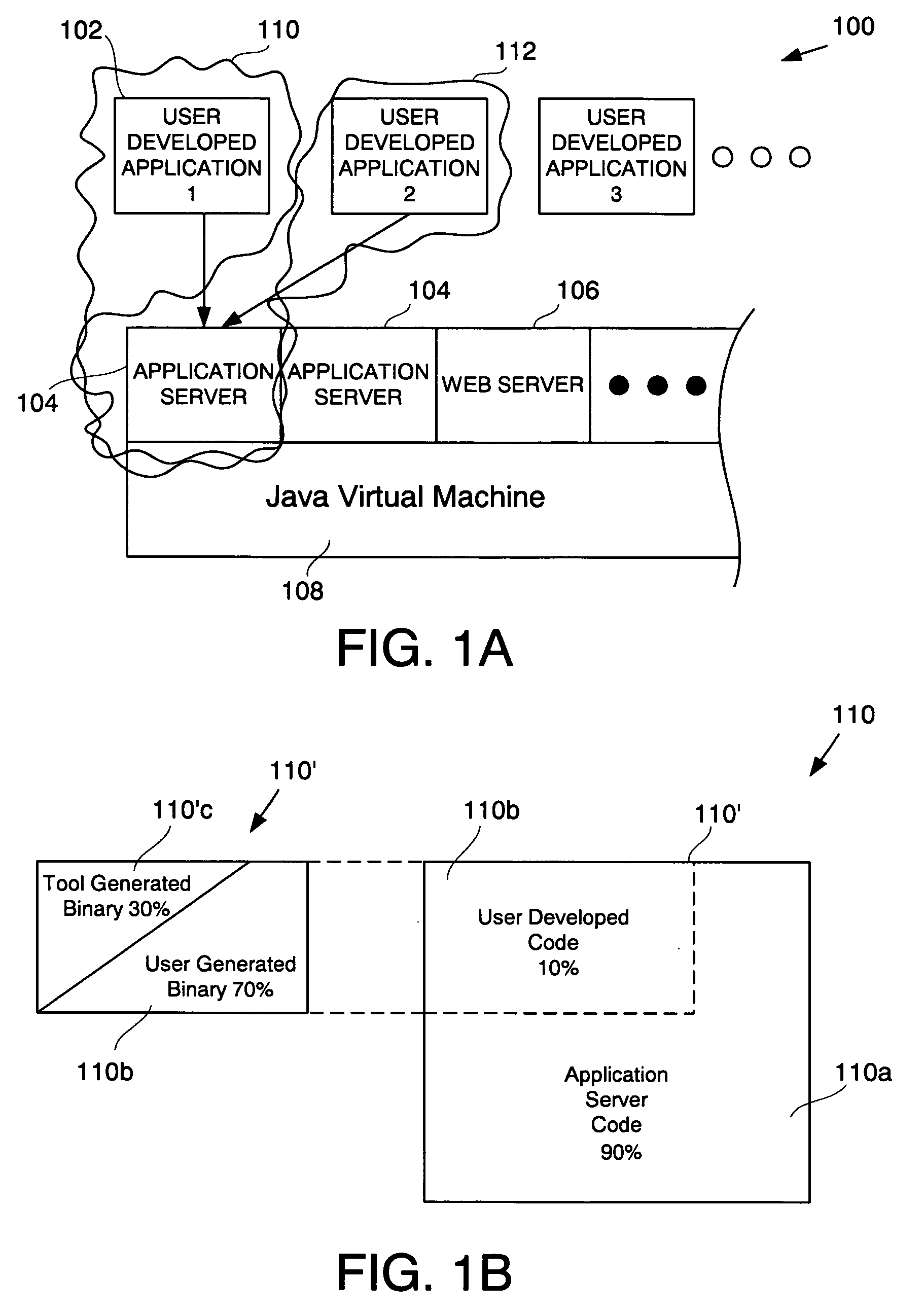
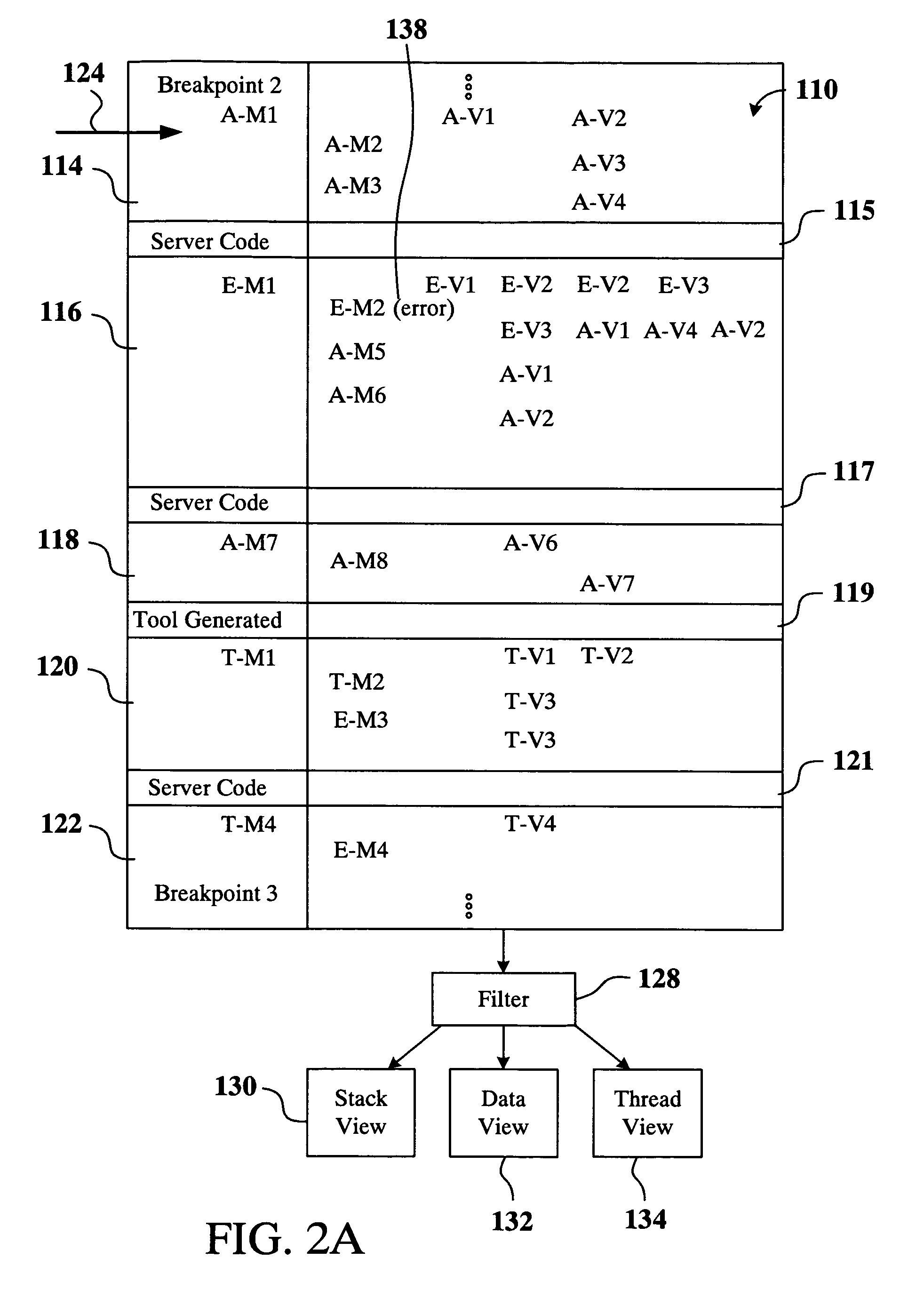
Intelligent computer program debugger, and system and method for implementing the same
ActiveUS20090210862A1Error detection/correctionSpecific program execution arrangementsApplication softwareComputer software
A method for displaying a user-defined artifact in a debugger view is provided. The user-defined artifact is defined in a software application that is developed by a computer software application developer. The software application is included in a packaged application that includes instructions, with each instruction being either a user-defined instruction or a non-user defined instruction. A breakpoint is defined at a desired instruction of the packaged application. The method includes initiating debugging of the packaged application and hitting the breakpoint defined at the desired instruction. Also included is identifying the user-defined artifact in the software application and obtaining data to populate the debugger view. Further included is filtering-in data associated with the user-defined artifact and displaying the debugger view showing the filtered-in data. The method also includes marking data not associated with the user-defined artifact and stepping through the user-defined instruction.
Owner:ORACLE INT CORP
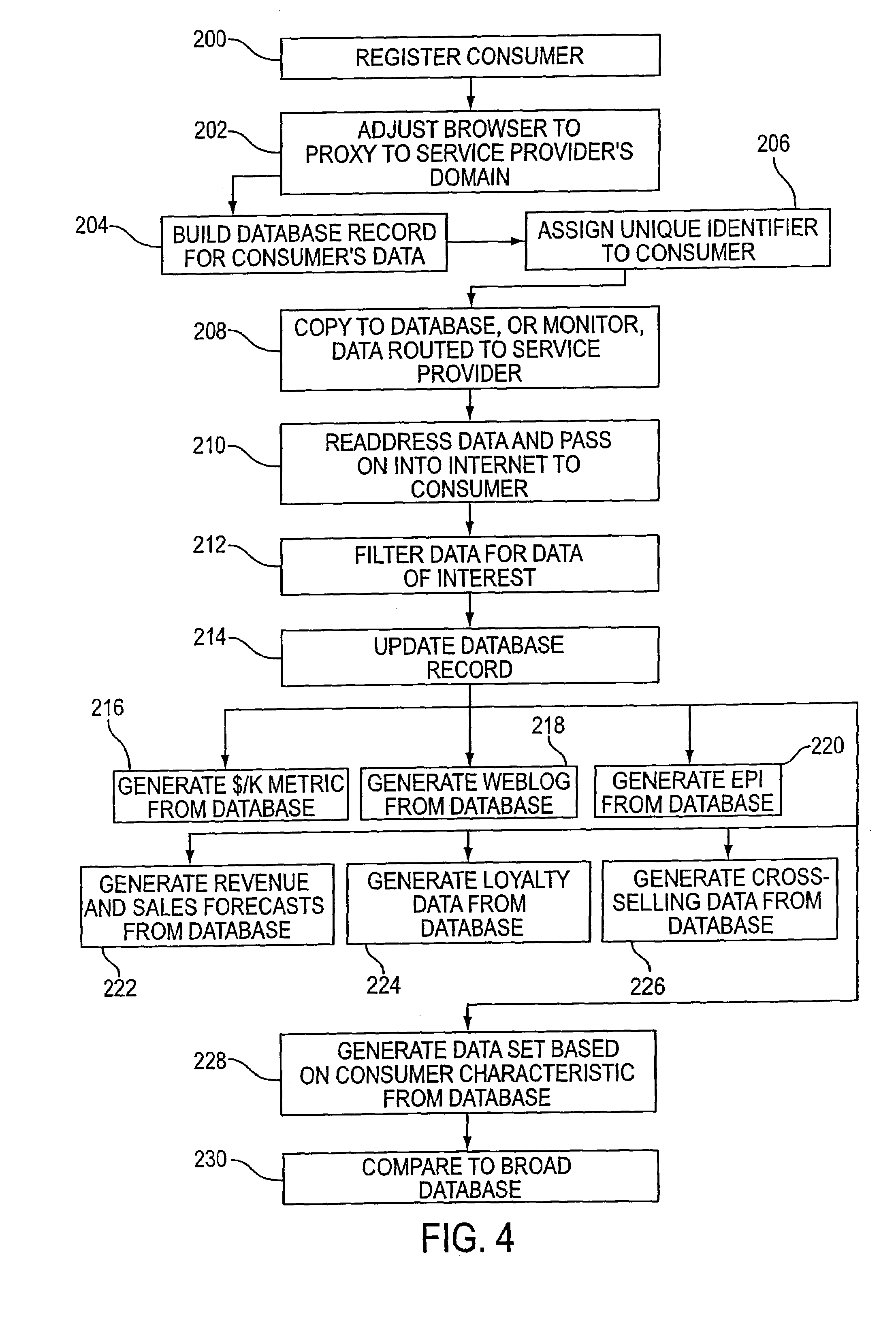
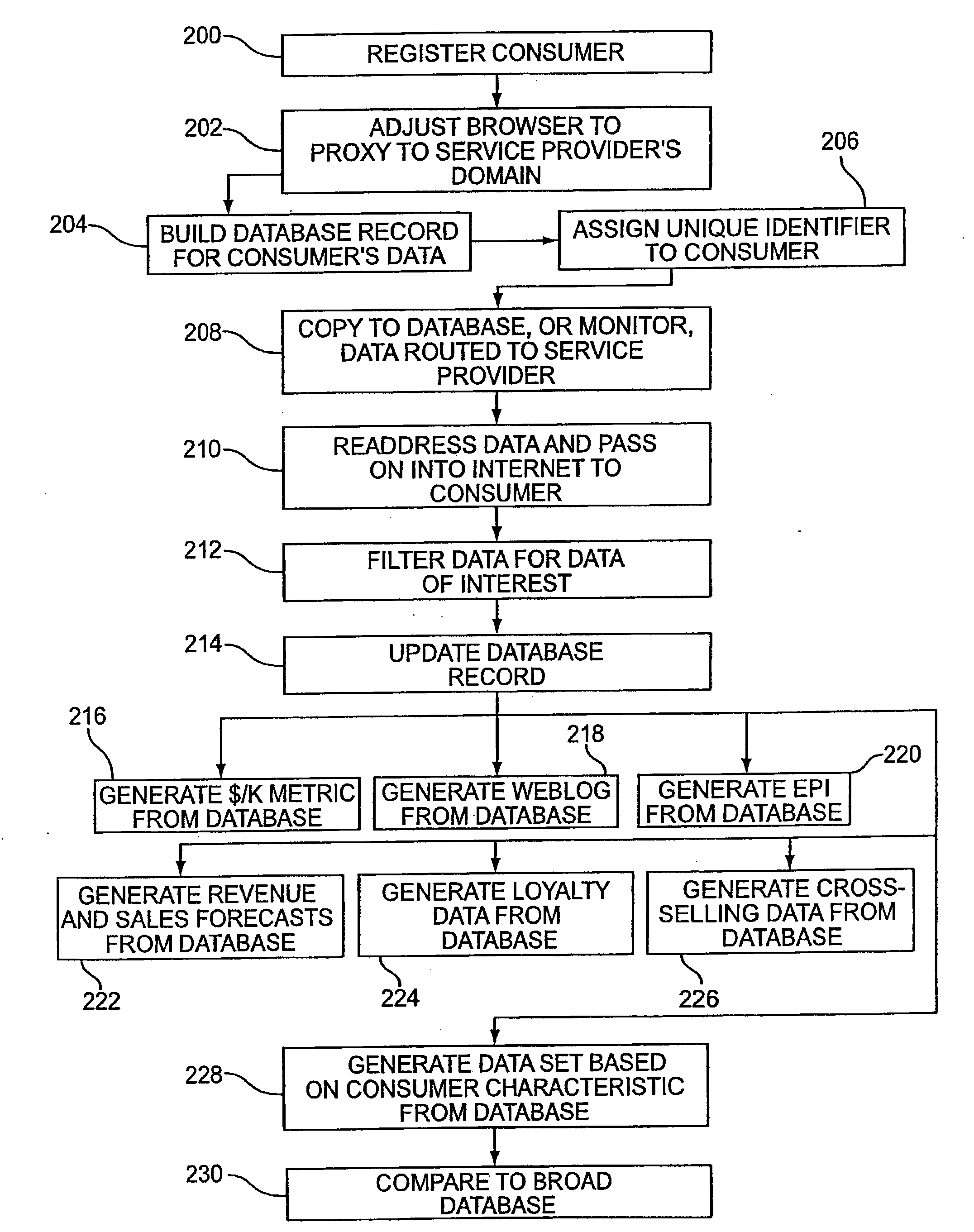
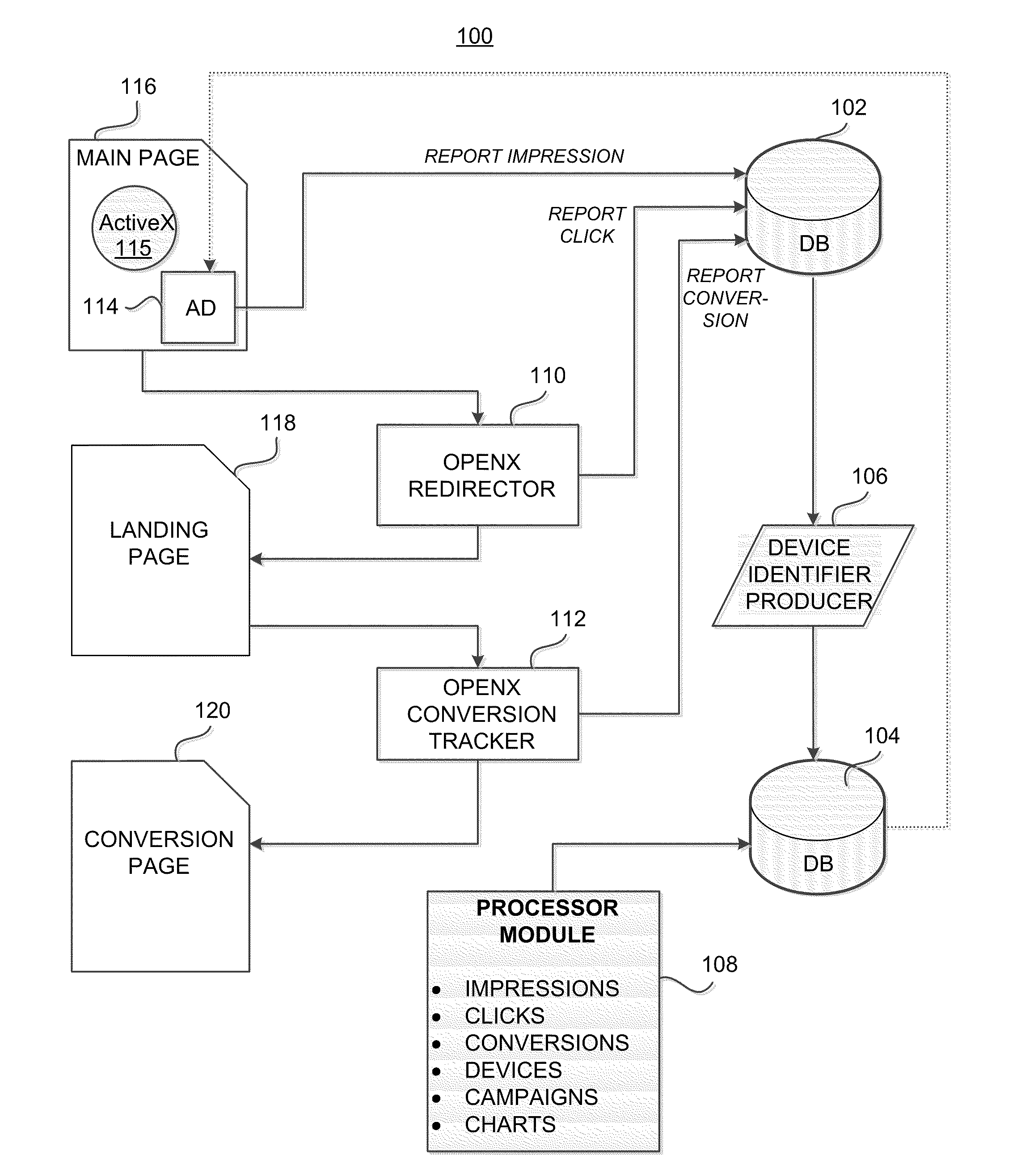
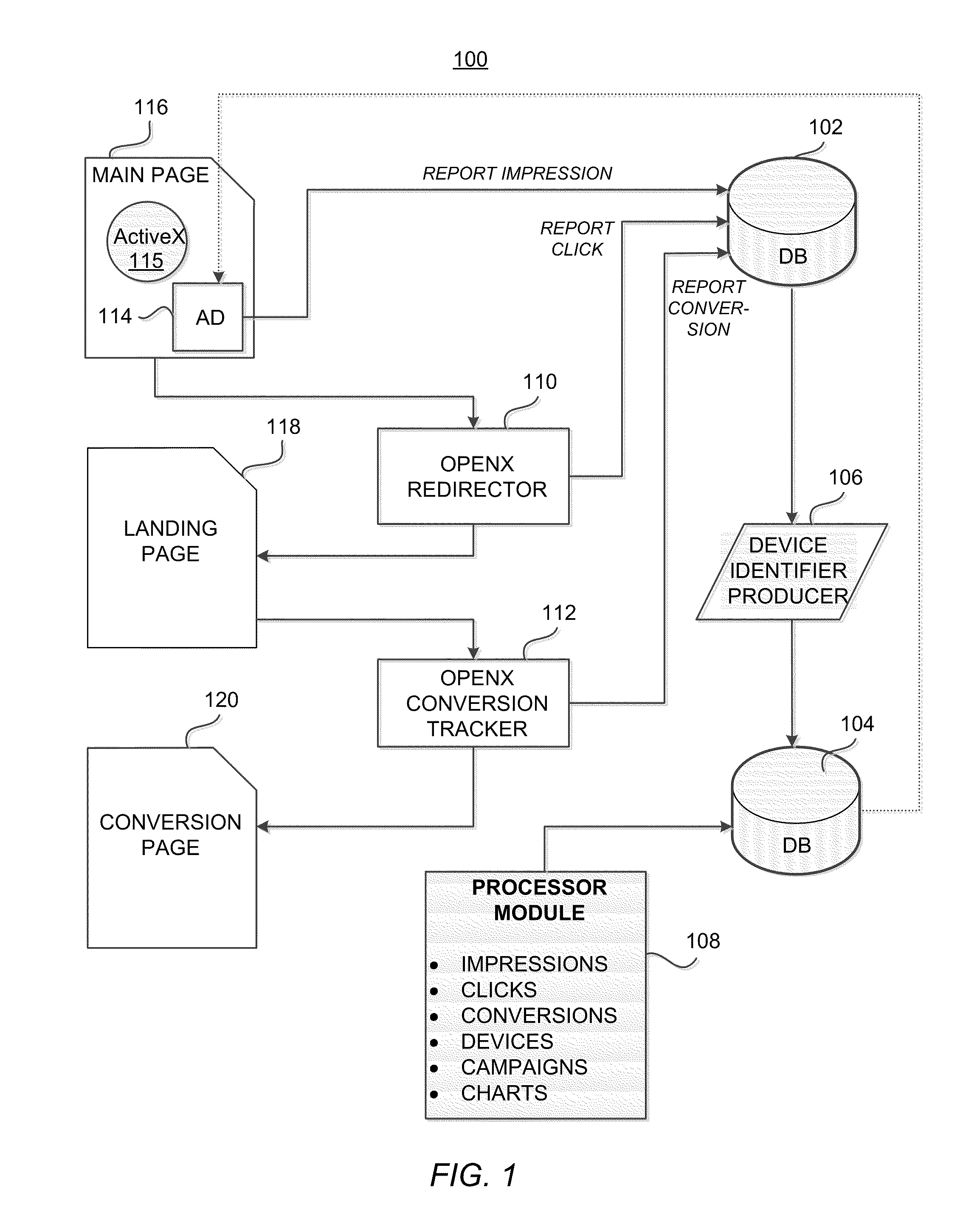
System and Method for Monitoring Efficacy of Online Advertising
InactiveUS20100324989A1Well formedMultiple digital computer combinationsMarketingUnique device identifierOnline advertising
A system for determining efficacy of online advertising includes a server connected to a computer network. The server is specially adapted to provide functions for communicating with a web resource that provides a web media that contains links or JavaScript calls for causing a client device to generate a device identifier in response to a user of the client device retrieving the web media, receiving the device identifier via a network, associating and caching any impressions, clicks or conversions by the user with the device identifier, calculating total cached impressions, total cached clicks and total cached conversions associated with each unique device identifier, and displaying, for each unique device identifier, at least one of the total cached impressions, the total cached clicks, and the total cached conversions. The device identifier may be derived from a combination of a user-configurable machine parameter and a non-user-configurable machine parameter.
Owner:UNILOC 2017 LLC
Virtual email method for preventing delivery of unsolicited and undesired electronic messages
ActiveUS20100198928A1Simple methodAvoid receivingMultiple digital computer combinationsTransmissionEmail addressElectronic mail
A method is used to filter an electronic message using virtual email sent to a server using a virtual email address created by the server for a recipient-identified. The virtual email address comprises a sender identification in combination with the recipient's non-encoded email address. The server identifies the email recipient using the recipient's non-encoded email address, identifies the email sender as authorized, stores the email sender's identification, stores email comprising the virtual email address; enables the recipient to access the email; enables the recipient to create a virtual email address, receives the virtual email; receives a second electronic message from a non-user-identified sender at the server, responds to the non-user-identified sender requesting an answer that only a human could provide; and, receives the answer from the non-user-identified sender and if the answer is correct, then creates an electronic account on the server for the non-user-identified.
Owner:PILOANDIA LLC
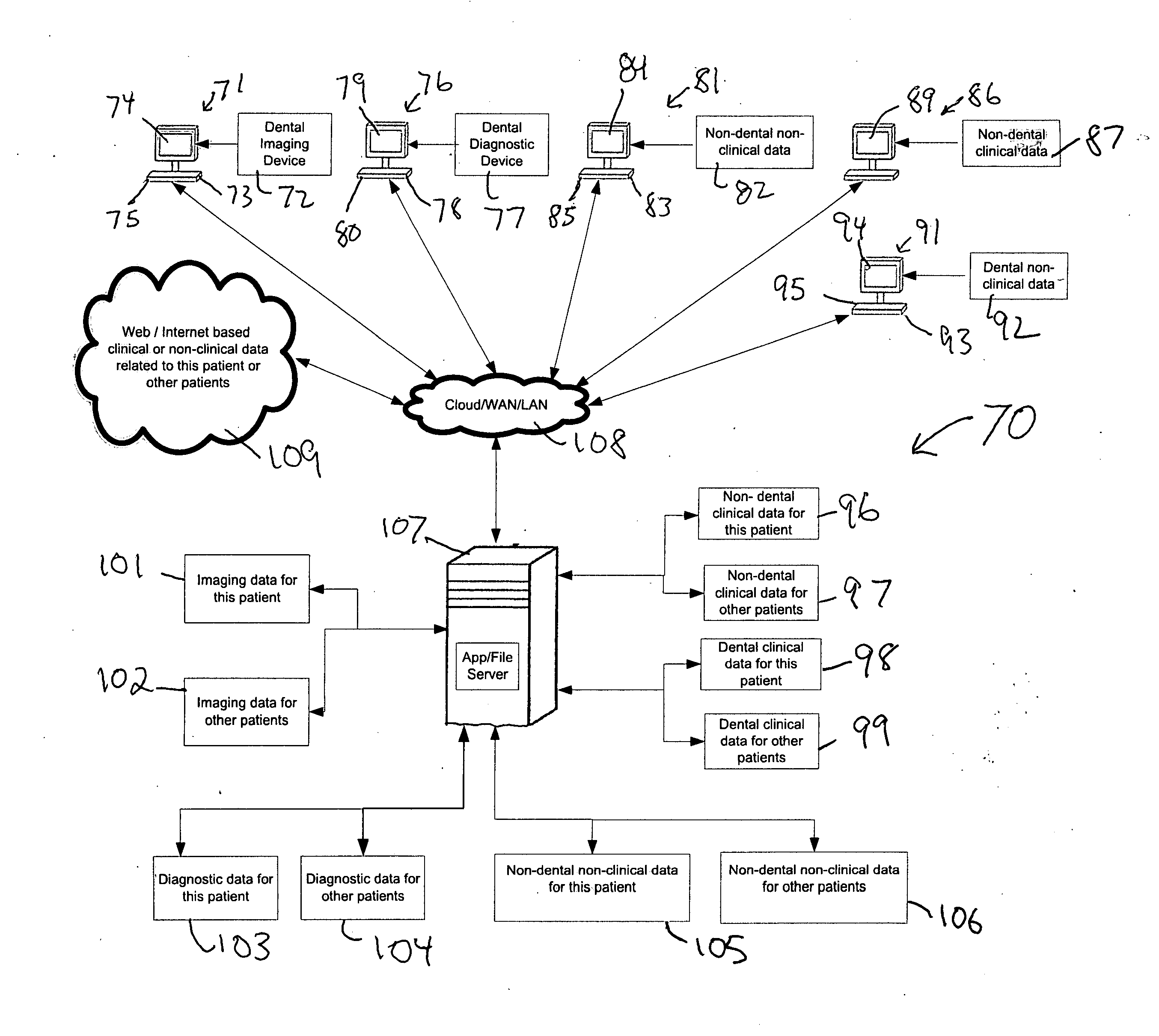
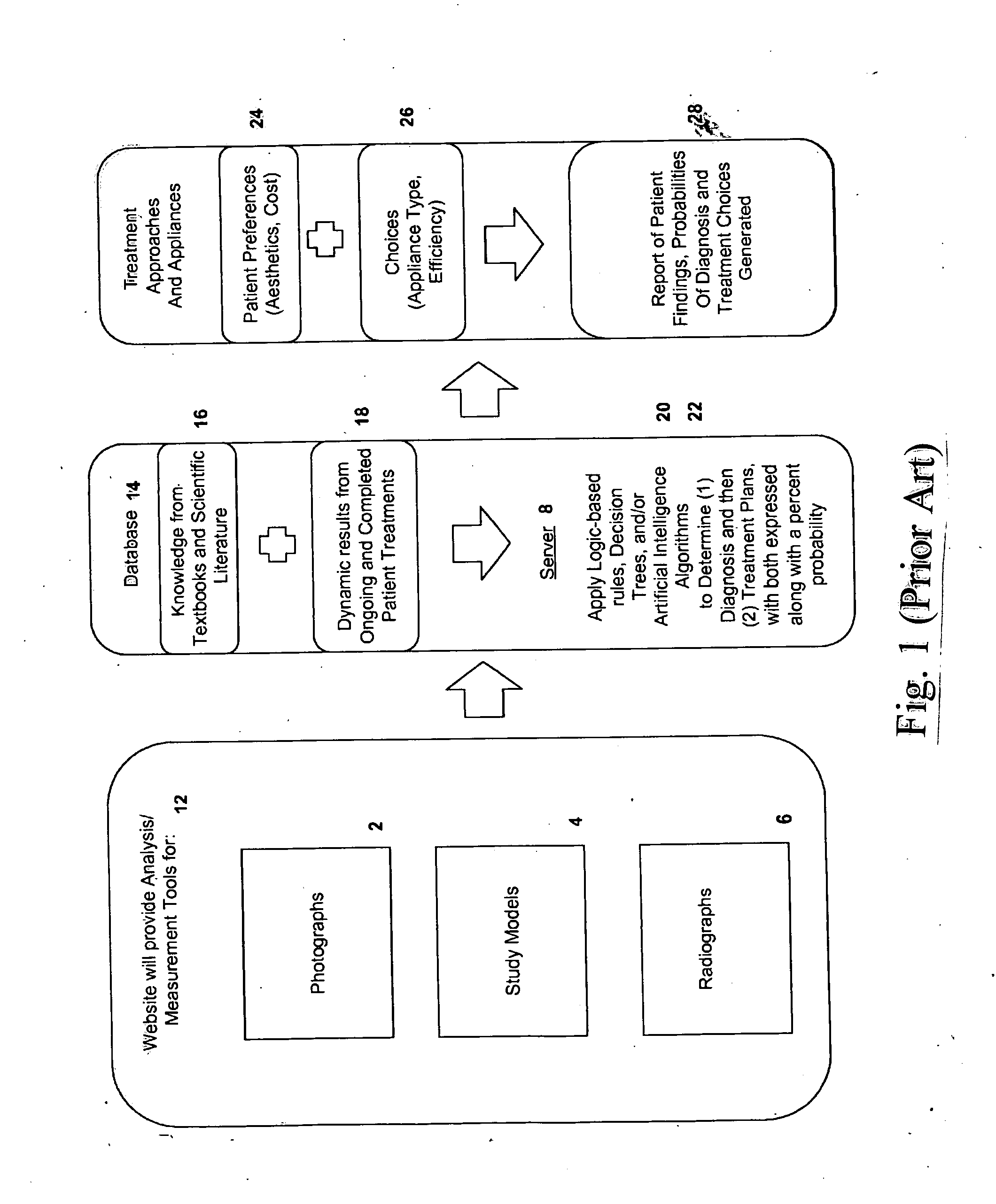
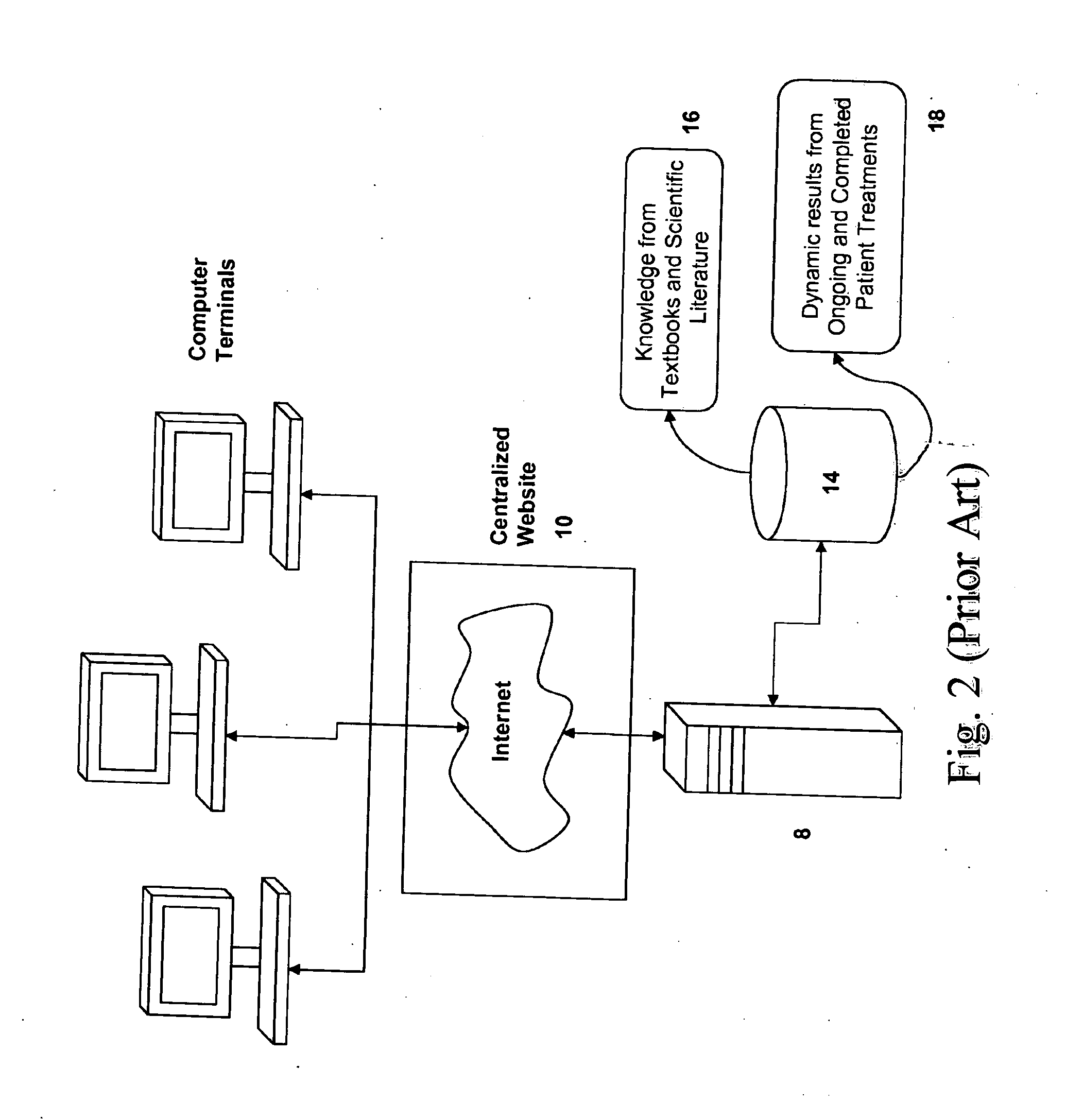
Applying non-real time and non-user attended algorithms to stored non-imaging data and existing imaging data for obtaining a dental diagnosis
A method of making a diagnosis of a dental condition of a patient includes the steps of collecting non-imaging data relating to the patient, storing the non-imaging data in a storage medium containing stored non-imaging data and existing imaging data for this patient and for a plurality of other patients and applying non-real time and non-user attended algorithms to the stored non-imaging data and the existing imaging data of this patient and other patients. The algorithms determine the diagnosis of the dental condition of the patient. The diagnosis either is complete or determines what new dental imaging data for the patient is required to be acquired to diagnose the dental condition of the patient. The non-imaging data includes non-clinical data and non-dental clinical data.
Owner:GOLAY DOUGLAS A
Communication device, system, method, and computer program product for sorting data based on proximity
InactiveUS20020147717A1Simple taskDigital data processing detailsSubstation equipmentMotion detectorUser device
A proximity sorting system, method and computer program product for sorting data is provided including a communication device featuring a processor operative to access a plurality of records and position information. The communication device can include a processor operative to sort the plurality of records based on a first detected position and is operative to resort the records based on a second detected position. The device can further feature a detector that detects a change in position of a user device. The communication device can feature a detector having a positioning device; a global positioning system; a receiver operative to receive position information; or three or more receivers operative to detect by triangulating the position. The communication device can further include a transmitter that can transmit a change in position of the user device, a storage device operative to store and retrieve said records and position information, or a zone detector operative to receive zone information. The communication device can feature a zone detector that can respond to the zone information wherein the zone information is externally definable and responsive to a user signal; or network signal. The communication device can further feature a user interface wherein the zone detector features detecting a zone responsive to a user input signal; a network signal; a position detector; a user identifiable zone; and a non-user identifiable zone.
Owner:GOOGLE TECH HLDG LLC
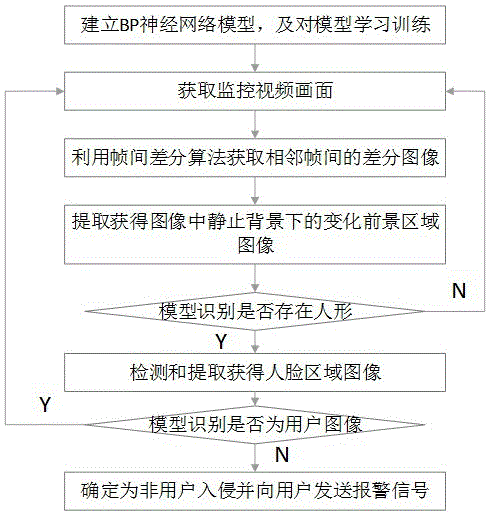
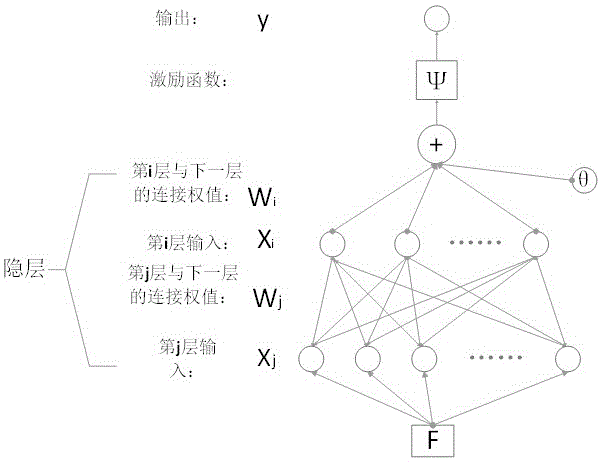
Deep learning-based intelligent indoor intrusion detection method and system
InactiveCN106372576AReduce overheadAvoid interferenceBiological neural network modelsCharacter and pattern recognitionFrame differenceNetwork model
The invention discloses a deep learning-based intelligent indoor intrusion detection method and system. The method comprises the following steps of establishing a BP neural network model; obtaining difference images between adjacent frames in a monitoring video picture by utilizing a frame difference algorithm; carrying out binarization processing on the obtained difference images and extracting change foreground area images, under a static background, in the processed images; detecting and identifying whether human shapes exist in the extracted change foreground images or not; when the human shapes exist, detecting and extracting face area images from the change foreground areas; identifying whether the extracted face area images are user images or not; and when the face area images are not the user images, determining the face area images as non-user intrusion and sending alarm signals to the users. The method and system are strong in ability of resisting the interference of other moving objects and low in mis-judgement rate, and can be used for carrying out massive video data analysis and correctly carrying out intrusion detection and identification.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for scrambling data in which scrambling data and scrambled data are stored in corresponding non-volatile memory locations
ActiveUS20100070681A1Memory architecture accessing/allocationMemory adressing/allocation/relocationData storeNon-volatile memory
A method in which data is randomized before being stored in a non-volatile memory to minimize data pattern-related read failures. Predetermined randomized non-user data is stored in a block or other location of a memory array, and accessed as needed by a memory device controller to randomize user data before it is stored in other blocks of the array. Each portion of the user data which is stored in a block is randomized using a portion of the non-user data which is stored in the same relative location in another block.
Owner:SANDISK TECH LLC
System and Method for Secured Communications
InactiveUS20100325424A1Well formedDigital data processing detailsUser identity/authority verificationTransceiverAuthentication server
A system for secured communications includes a control center, a network transceiver, an authentication server communicatively coupled between the control center and the network transceiver, and an extended trust device communicatively coupled between the authentication server and a client, the extended trusted device being configured to send a device identifier to the authentication server via the network transceiver, the device identifier being based on a combination of a user-configurable parameter and a non-user-configurable parameter of the extended trust device, wherein the authentication server is configured to determine access privilege of a client to the control center by authenticating the device identifier received from extended trust device.
Owner:DEVICE AUTHORITY LTD
Method for Detecting False Wake Conditions of a Portable Electronic Device
There is described a portable electronic device capable of detecting false wake conditions, and a method thereof. The portable electronic device comprises a sensor circuit and a display. The sensor circuit detects double tap data associated with user input and motion data subsequent to the double tap data within a predetermined time period. The sensor circuit also determines whether the motion data corresponds to at least one criterion associated with non-user input. The display wakes from a sleep state in response to the sensor circuit determining that the motion data corresponds to the at least one criterion. For some embodiments, the sensor circuit includes a motion sensor to detect the motion data and a sensor hub to determine whether the motion data corresponds to the at least one criterion.
Owner:GOOGLE TECH HLDG LLC
Method, server and system for managing personal area network
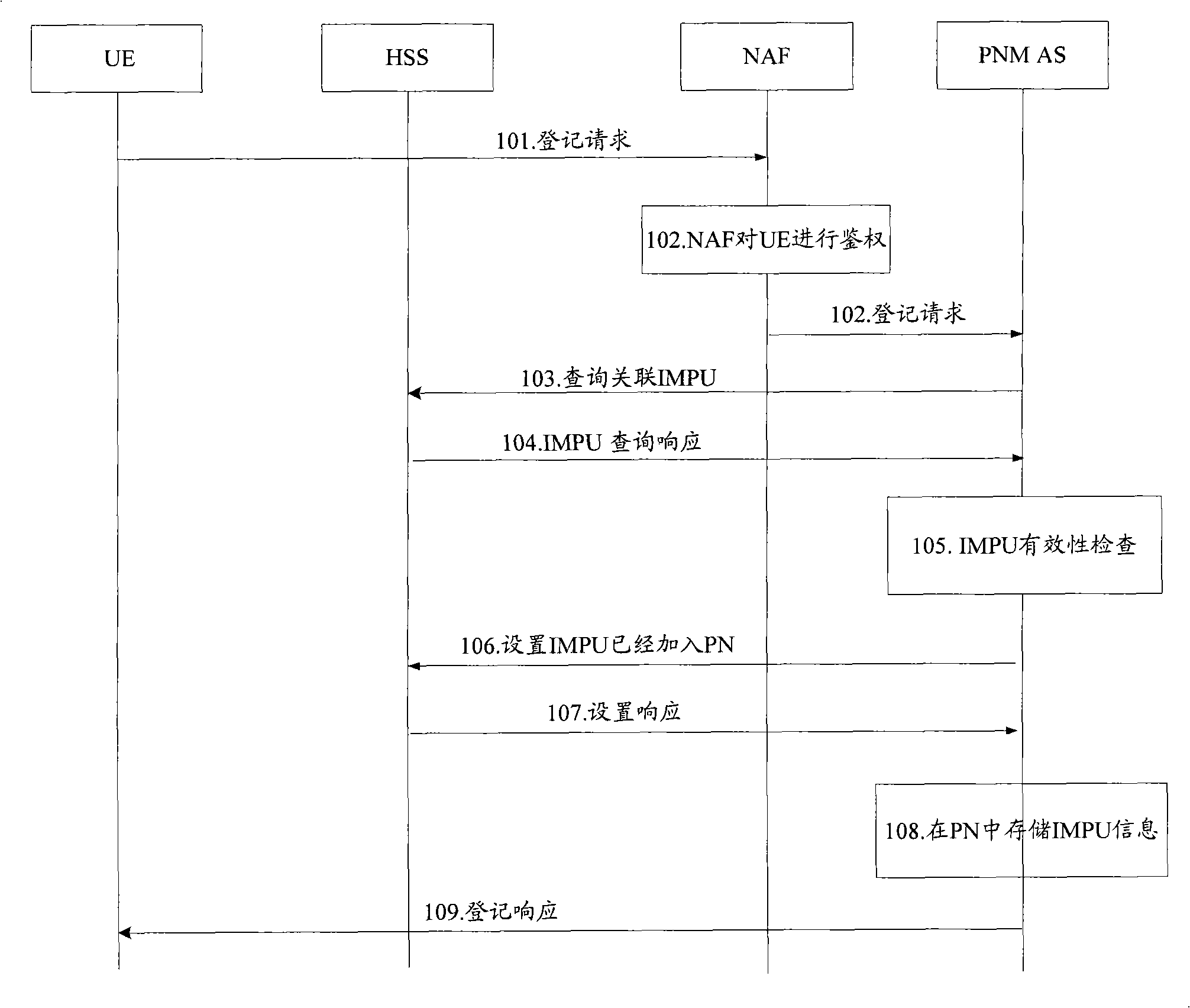
InactiveCN101299859AManagement granularityRadio/inductive link selection arrangementsData switching networksGranularityPersonal network
The inventive embodiment provides a personal area network management method, including: the personal area network management (PANM) server receives the request which requires personal network element (PNE) of non user equipment (UE) to add in the Personal Area Network (PAN) where the UE locates; the PANM server uses the information carried in the request to authenticate the request, and allows the PNE to join the PAN after passing the authentication. The inventive embodiment also provides a personal area network management server and system. The technical scheme provided by the inventive embodiment gives out a specific management scheme to the PNE of non-UE in the PAN, so as to embody the association between the PNE of UE and non-UE in the PAN, thereby further thinning the management granularity to PN, and replenishing the specific implementing program of 3GPP in the PANM field.
Owner:HUAWEI TECH CO LTD
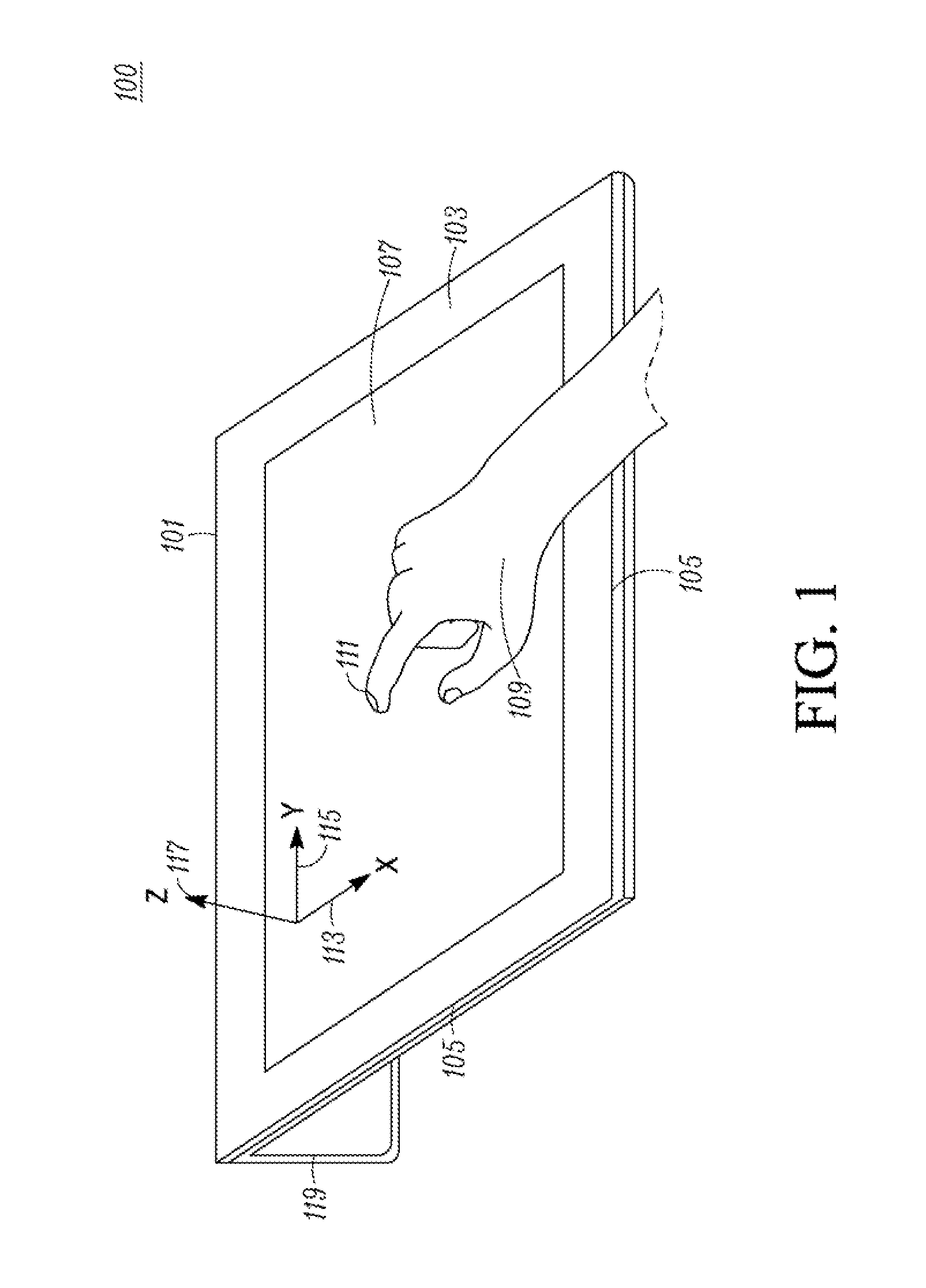
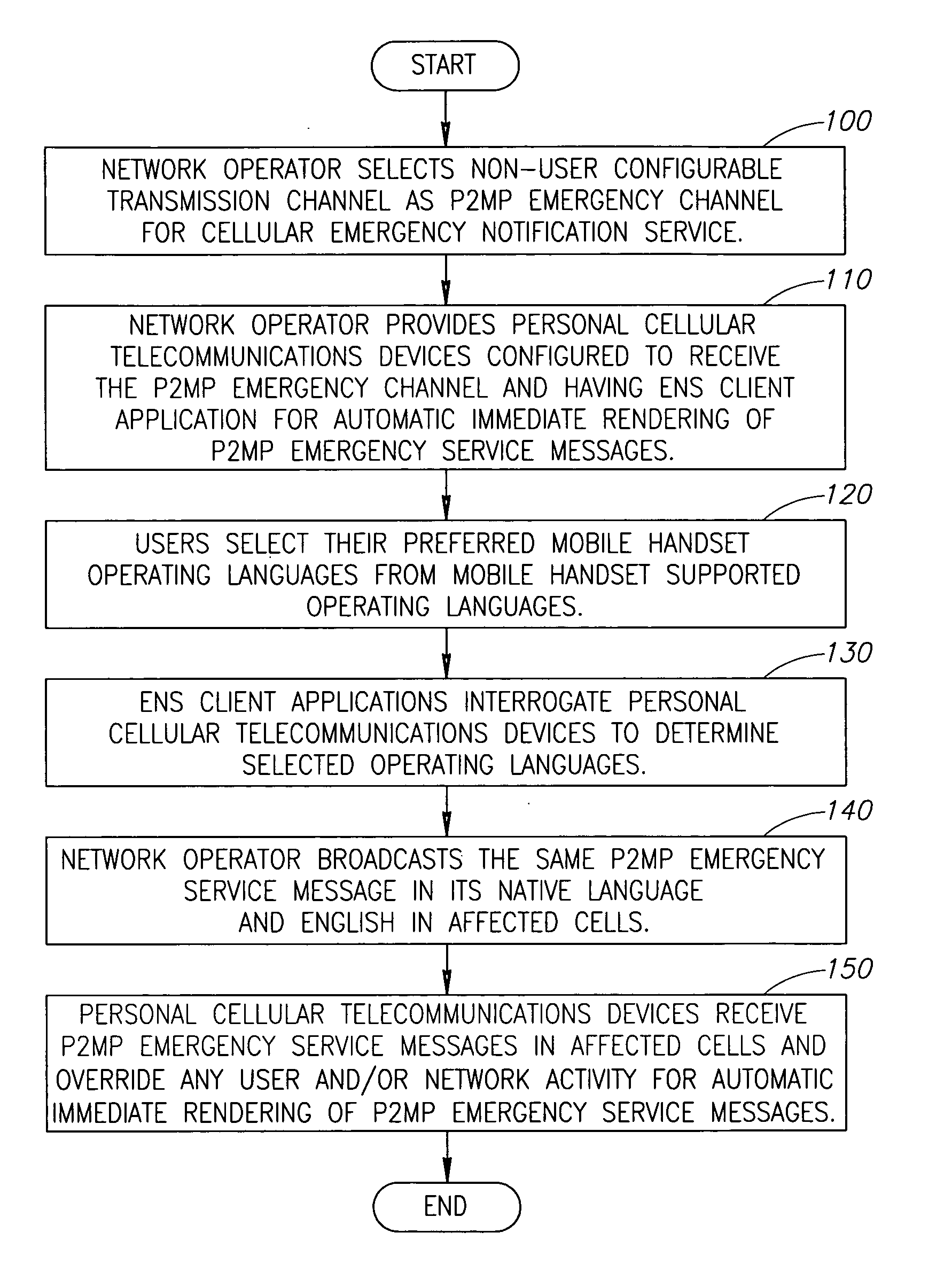
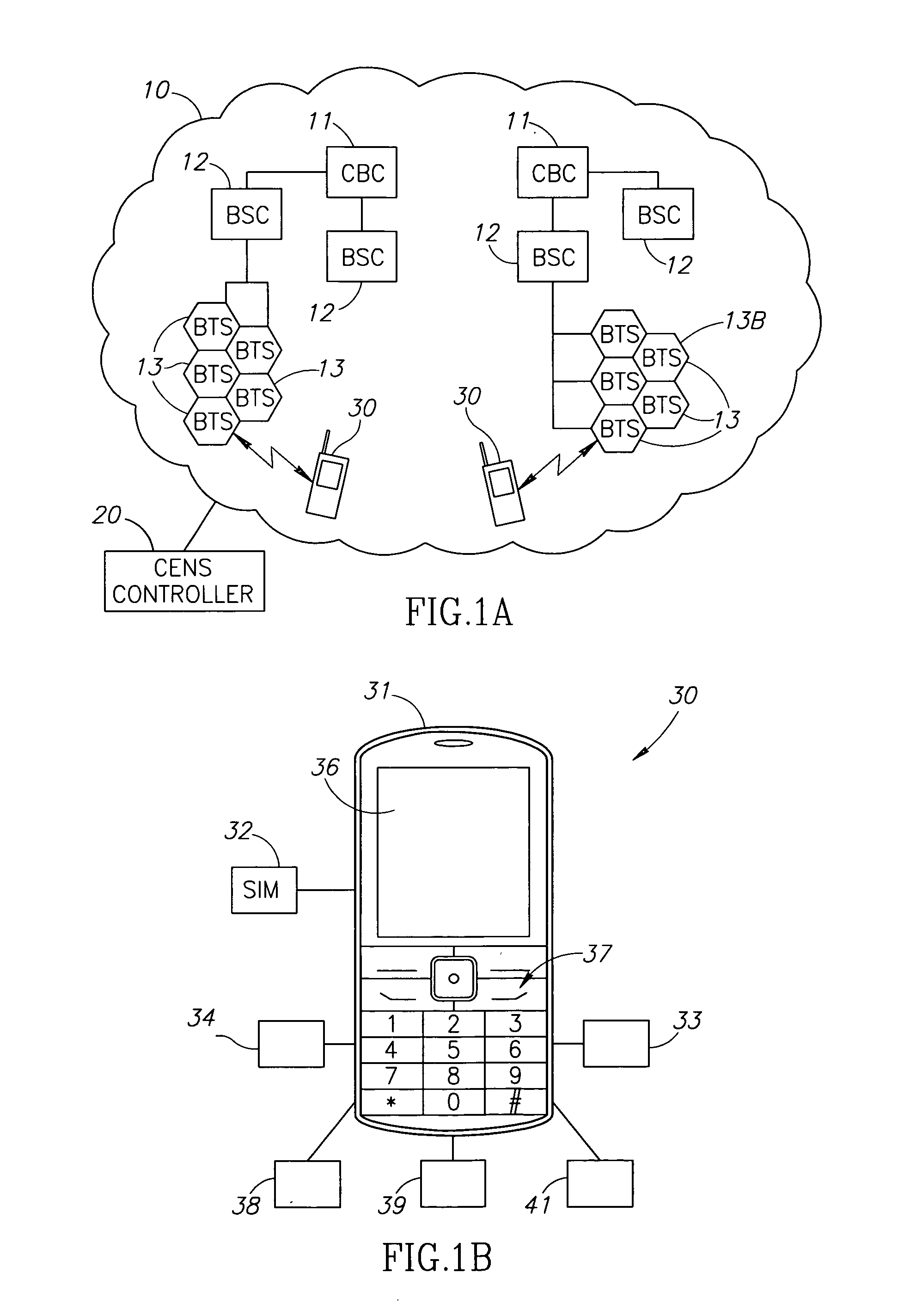
Cellular emergency notification service
InactiveUS20100003945A1Emergency connection handlingNetwork topologiesTelecommunications DeviceNon users
Cellular emergency notification service transmitting Point-To-MultiPoint (P2MP) emergency service messages on one or more mandatory non-user configurable P2MP emergency channels to all available personal cellular telecommunications devices in one or more selected cells thereby ensuring mandatory reception.
Owner:CELLTICK TECH
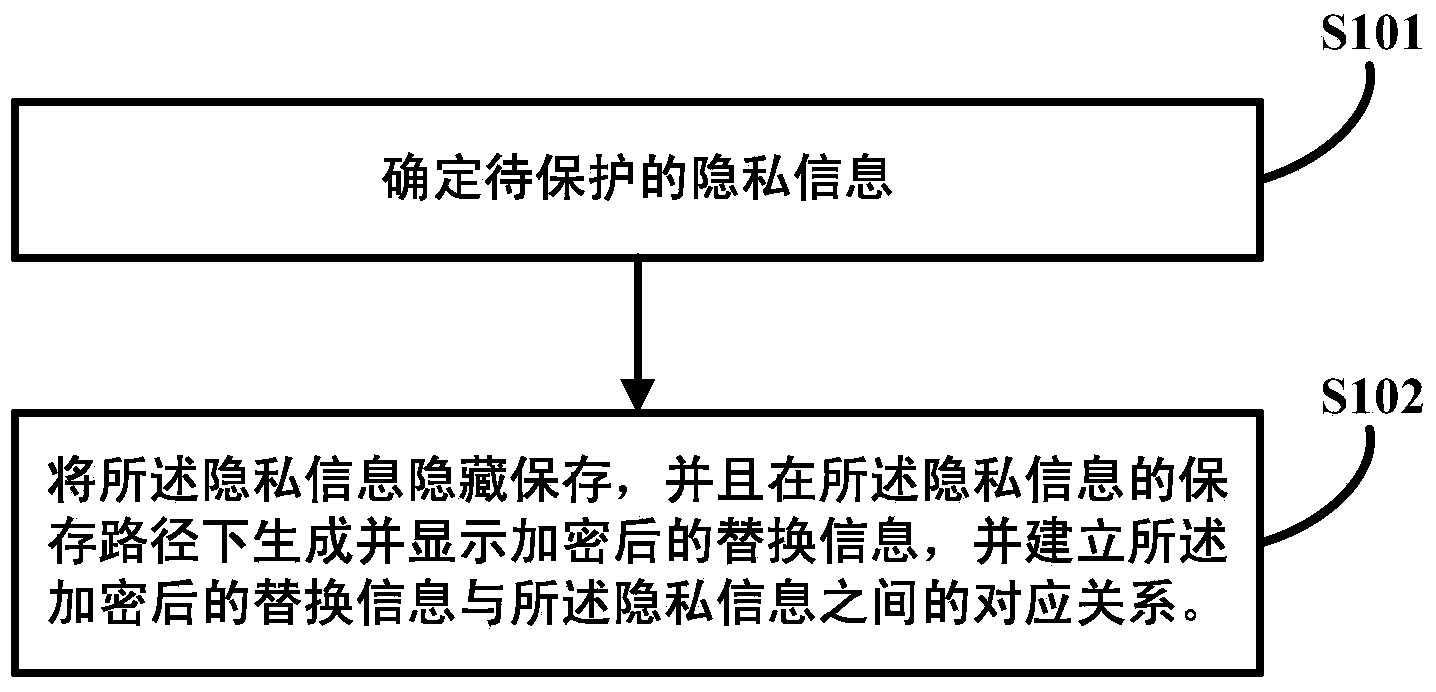
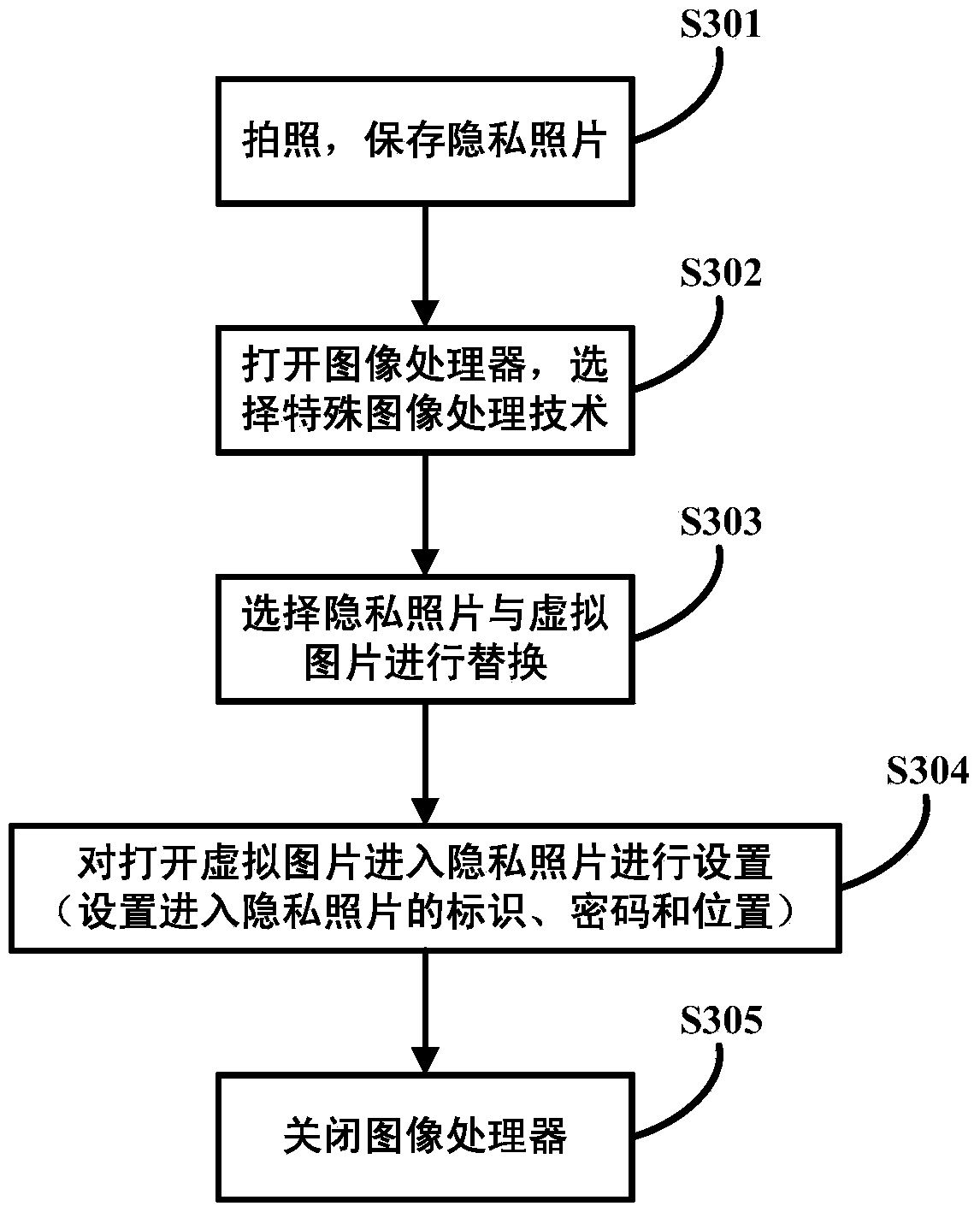
Method and device for protecting and displaying privacy information
InactiveCN103559451AEliminate the leading roleProtect personal privacy informationDigital data protectionInternet privacyInformation hiding
The invention discloses a method and a device for protecting and displaying privacy information. The method comprises the steps of: determining to-be-protected privacy information; saving the privacy information in a hiding manner and generating and displaying encrypted replaced information in a save path of the privacy information, and establishing a corresponding relationship between the encrypted replaced information and the privacy information. Through the technical scheme, the problem of privacy information leakage due to that the conventional encryption protection method may generate and display an encryption mark on the privacy information to guide a non-user is solved. The privacy information is displayed as non-privacy normal information by generating and displaying the encrypted replaced information in the save path of the privacy information, the guide function of the conventional encryption mark for a non-user is removed, the user per se is helped to save the privacy information on the terminal in the hiding manner, random encryption and recovery functions are achieved, and personal privacy information of the user per se is protected at any time.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
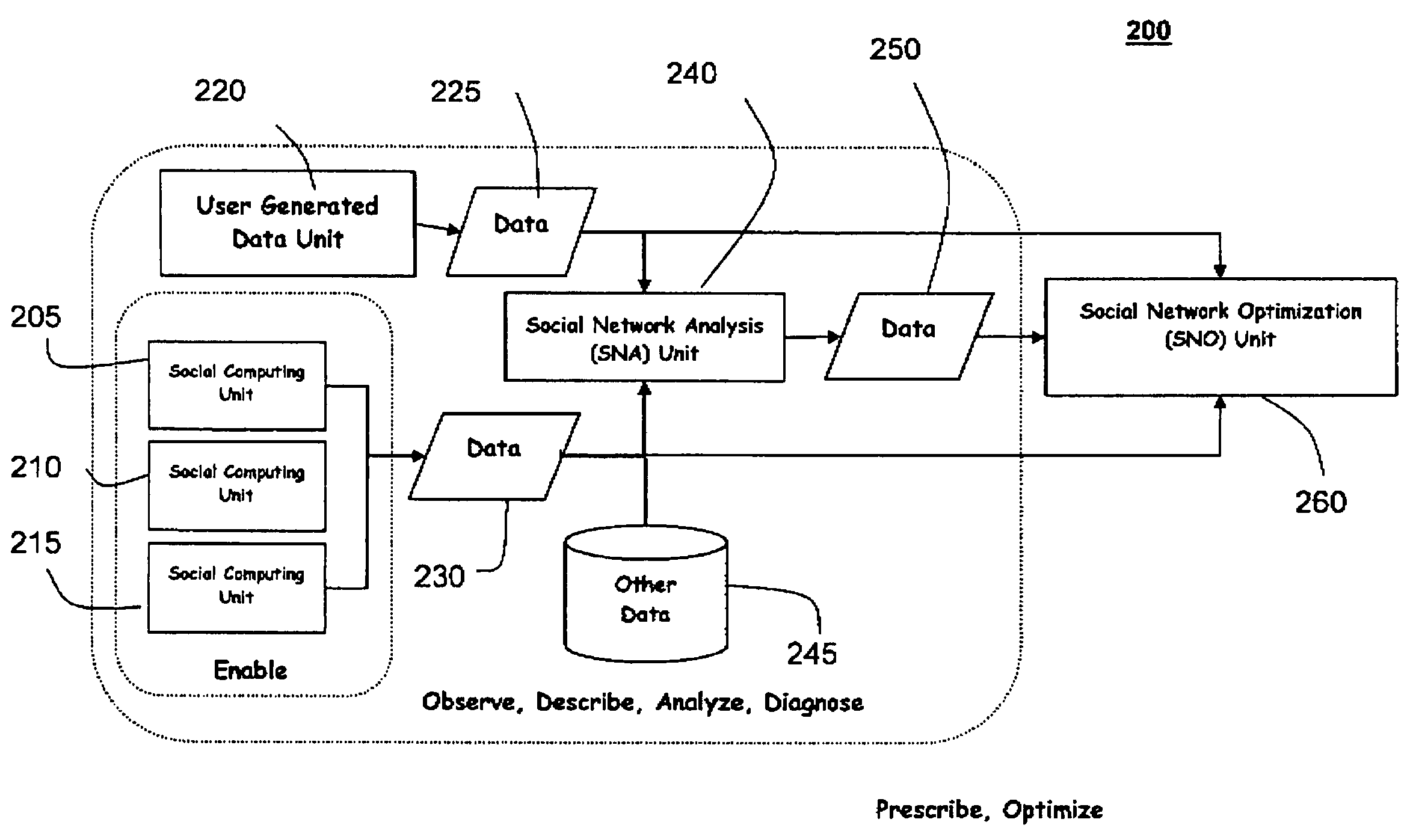
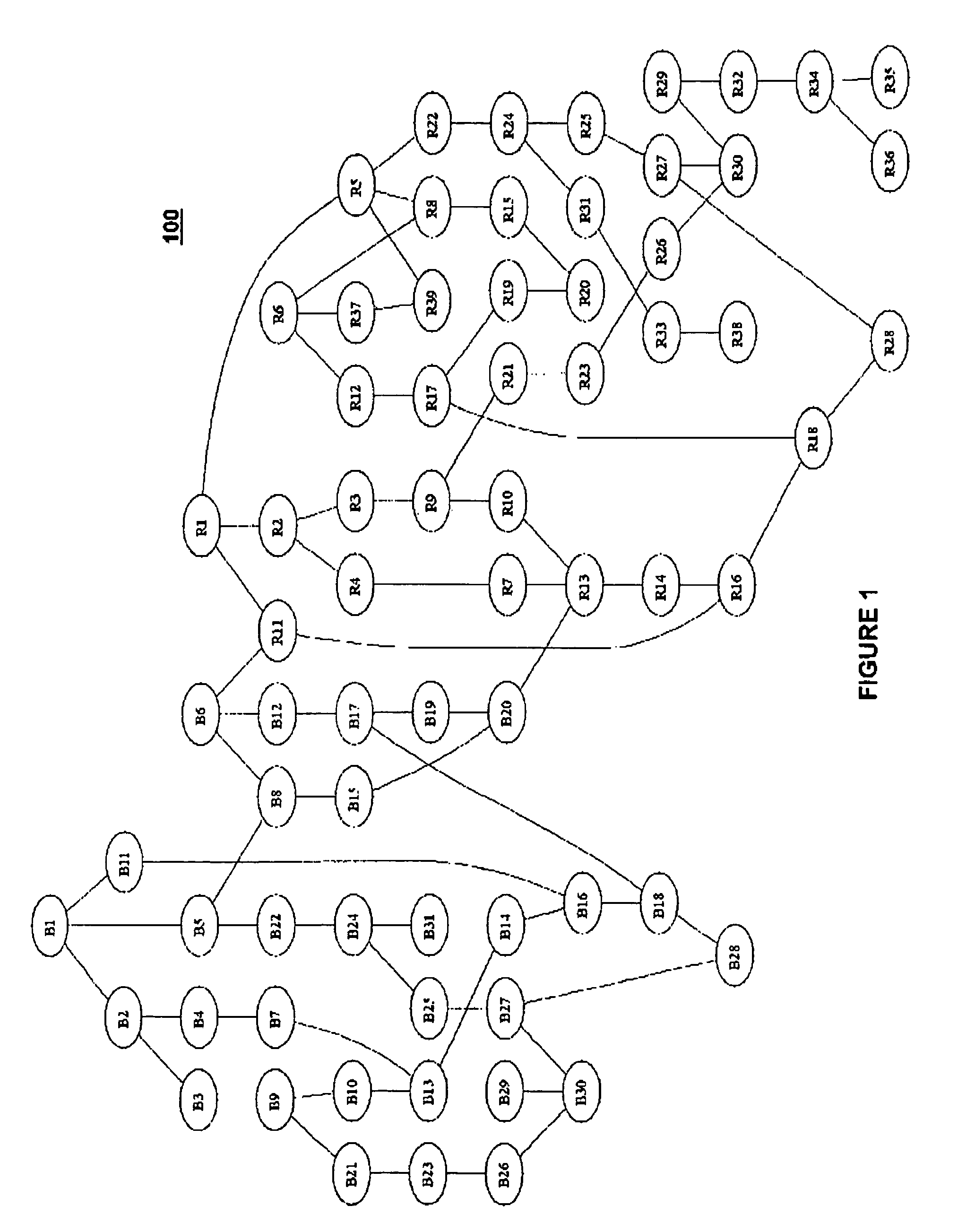
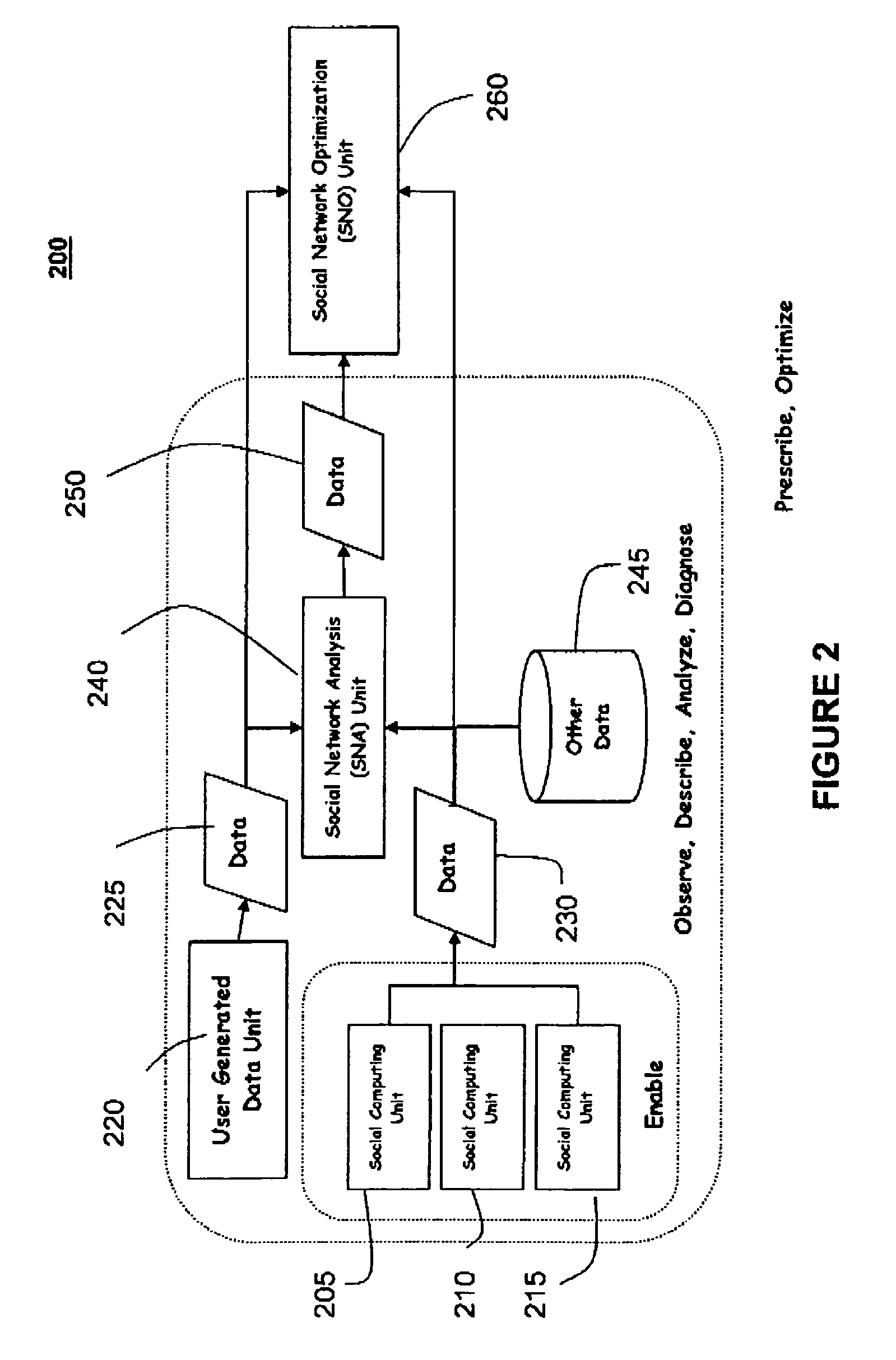
System and method for constructing a social network from multiple disparate, heterogeneous data sources
InactiveUS7512628B2Easy to analyzeAnalysis is limitedDigital data processing detailsResourcesData sourceData mining
A computer implemented method of constructing a social network, the method including constructing the social network from a plurality of disparate, heterogenous data sources, wherein at least one of the plurality of disparate, heterogenous data sources includes a user generated data source; identifying a plurality of nodes and linkages; determining attributes of the nodes and linkages based on a plurality of disparate, heterogenous data sources, wherein the plurality of disparate, heterogenous data sources includes a combination of the user generated data source and at least one non-user generated source, wherein the attributes include at least one of a deterministic attribute, a probabilistic attribute, and a dynamic attribute; populating a mathemetical decision-making model based on the plurality of nodes and linkages, and the determined attributes of the plurality of nodes and linkages; determining attributes of the nodes and links at a second point in time; re-populating the mathematical decision-making model based on the plurality of nodes and linkages, and the determined attributes of the plurality of nodes and linkages at the second point in time.
Owner:CHESS CATHERINE ANNE +7
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com