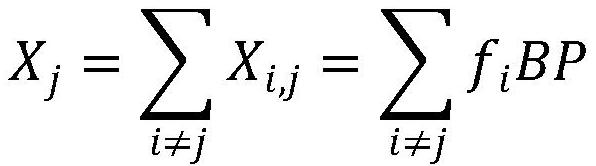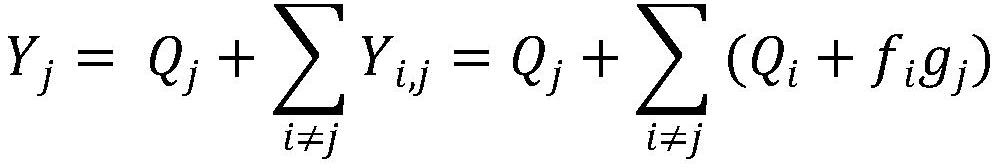Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39results about How to "Solve security deficiencies" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
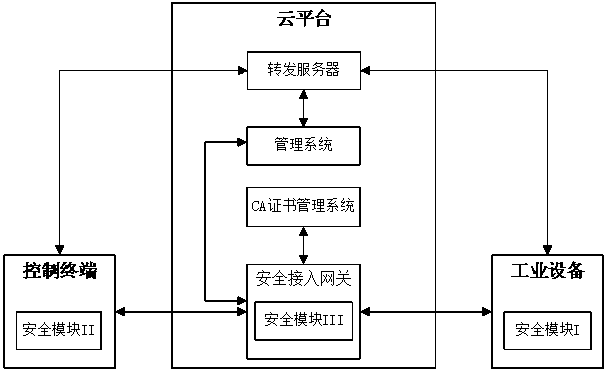
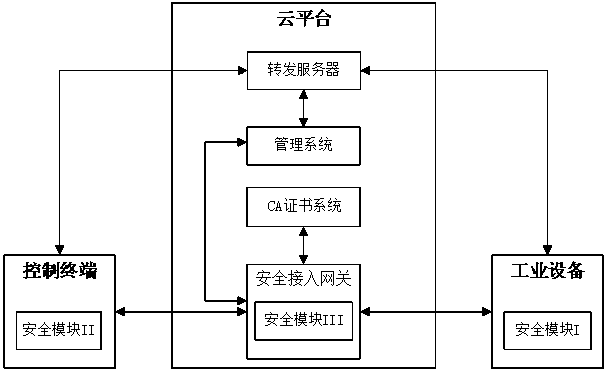
Security remote control system and method for industrial equipment
ActiveCN108390851AHighlight substantiveSignificant progressKey distribution for secure communicationUser identity/authority verificationRemote controlControl system
The invention provides a security remote control system and method for industrial equipment. The system comprises industrial equipment, a control terminal and a cloud platform, wherein a security module I is arranged in the industrial equipment, a security module II is inserted into or arranged in the control terminal, the cloud platform comprises a security access gateway, a management system, aCA certificate management system and a forwarding server, and a security module III is arranged in the security access gateway. In remote control, the industrial equipment and the security access gateway perform bidirectional identity authentication and key negotiation and create a first session key; the control terminal and the security access gateway perform bidirectional identity authenticationand key negotiation and create a second session key; the control terminal and the industrial equipment perform bidirectional identity authentication and key negotiation through the forwarding serverand then create a third session key; and the control terminal performs security remote control on the industrial equipment by using the third session key through the forwarding server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
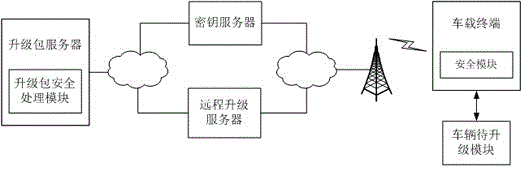
Secure remote upgrade system and upgrade method for vehicles
InactiveCN106648626ASafe remote upgrade is safe and reliableGuaranteed confidentialityVersion controlProgram loading/initiatingDigital signatureConfidentiality
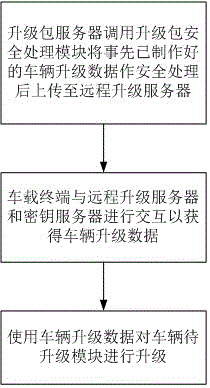
The invention discloses a secure remote upgrade system and upgrade method for vehicles. The system comprises an upgrade pack server, a vehicle-mounted terminal, a remote upgrade server and a key server. The upgrade method comprises following steps: 1, the upgrade pack server calls an upgrade pack secure processing module to carry out secure processing on preset vehicle upgrade data and then upload the data to the remote upgrade server; 2,the vehicle-mounted terminal and the remote upgrade server interacts with the key server to obtain vehicle upgrade data; 3, the vehicle modules to be upgraded are upgraded by means of the vehicle upgrade data. According to the secure remote upgrade system and upgrade method for vehicles of the invention, through the addition of the hardware-security-chip-based secure module to the upgrade pack server and the vehicle-mounted terminal and the combination of the key server and the remote upgrade server, encryption and digital signature and verification services are provided for the data upgrading and the confidentiality and integrity of data upgrading are guaranteed.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
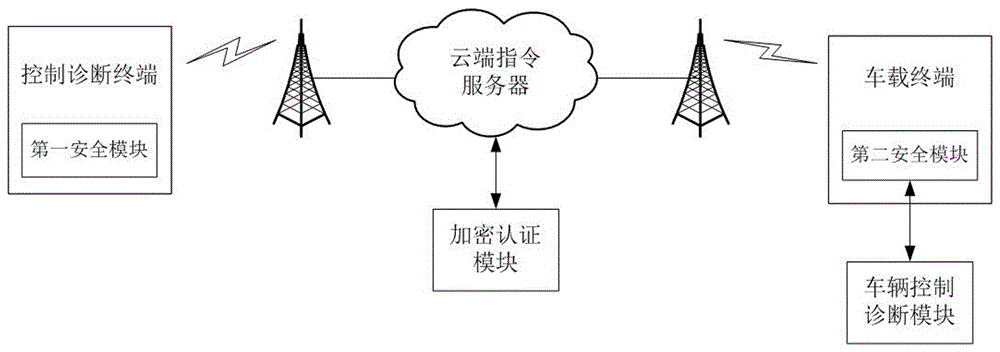
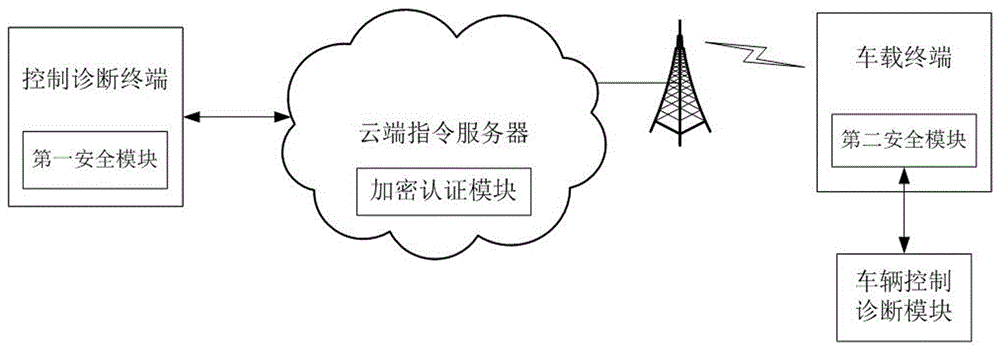
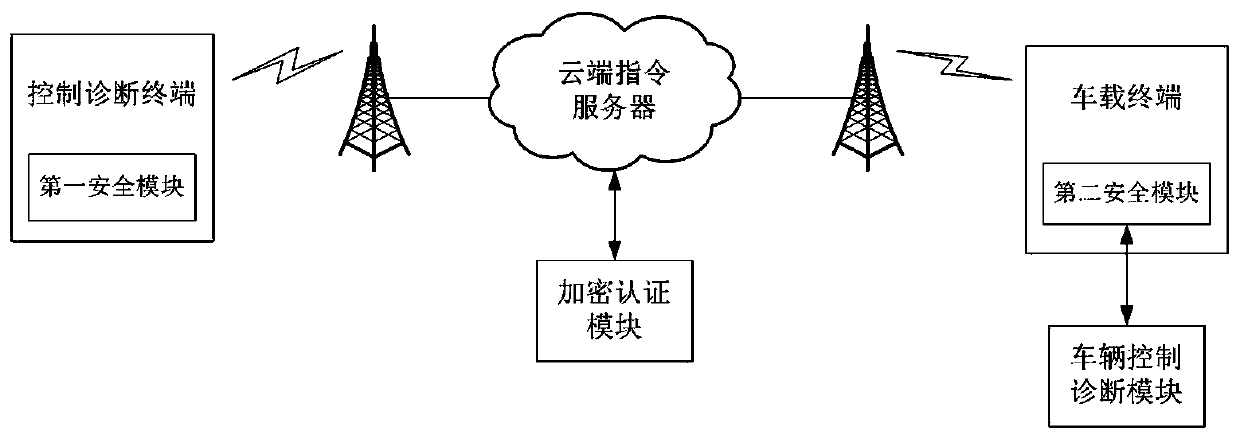
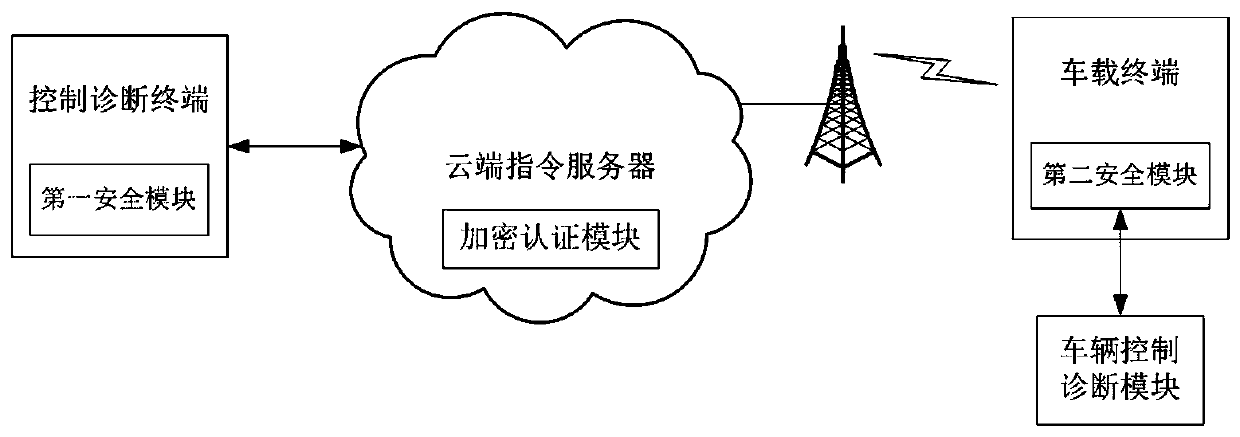
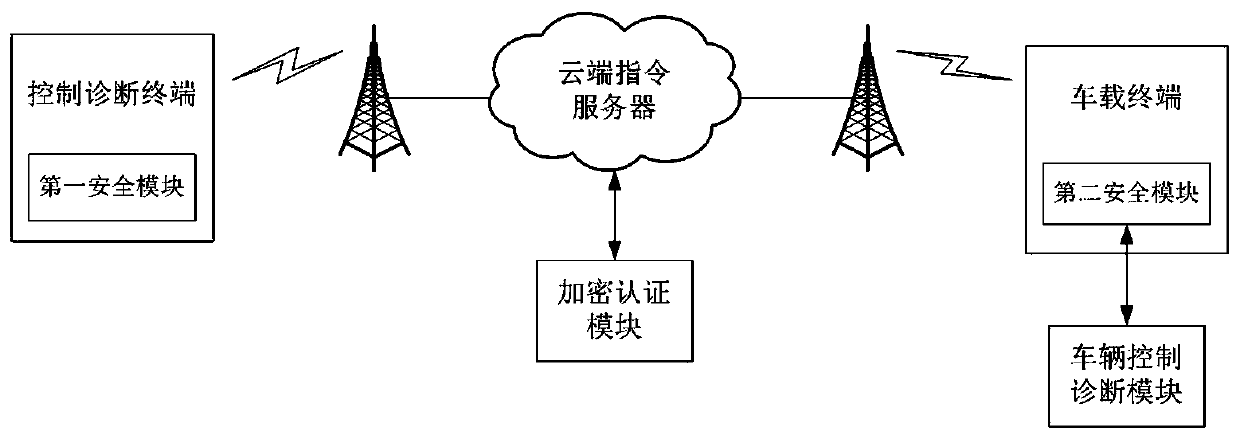
Method for vehicle safety remote control and diagnosis and system thereof
ActiveCN106713264APrevent access to the systemGuarantee information securityKey distribution for secure communicationUser identity/authority verificationRemote controlComputer terminal
The invention provides a method for vehicle safety remote control and diagnosis and a system thereof. A control and diagnosis terminal and a cloud side instruction server perform first identity authentication and key agreement; a vehicle-mounted terminal and the cloud side instruction server perform second identity authentication and key agreement; and the control and diagnosis terminal establishes communication connection with the vehicle-mounted terminal through the cloud side instruction server and performs remote control or remote diagnosis on a vehicle according to the control and diagnosis instruction of a user. Different secret keys are adopted between the control and diagnosis terminal and the cloud side instruction server and between the vehicle-mounted terminal and the cloud side instruction server and so that the information security of remote control and diagnosis information can be guaranteed, and the problem of security insufficiency in the prior art can be effectively solved. The system for vehicle safety remote control and diagnosis has the advantages of being scientific in design, high in practicality, convenient and rapid, high in security and high in reliability.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
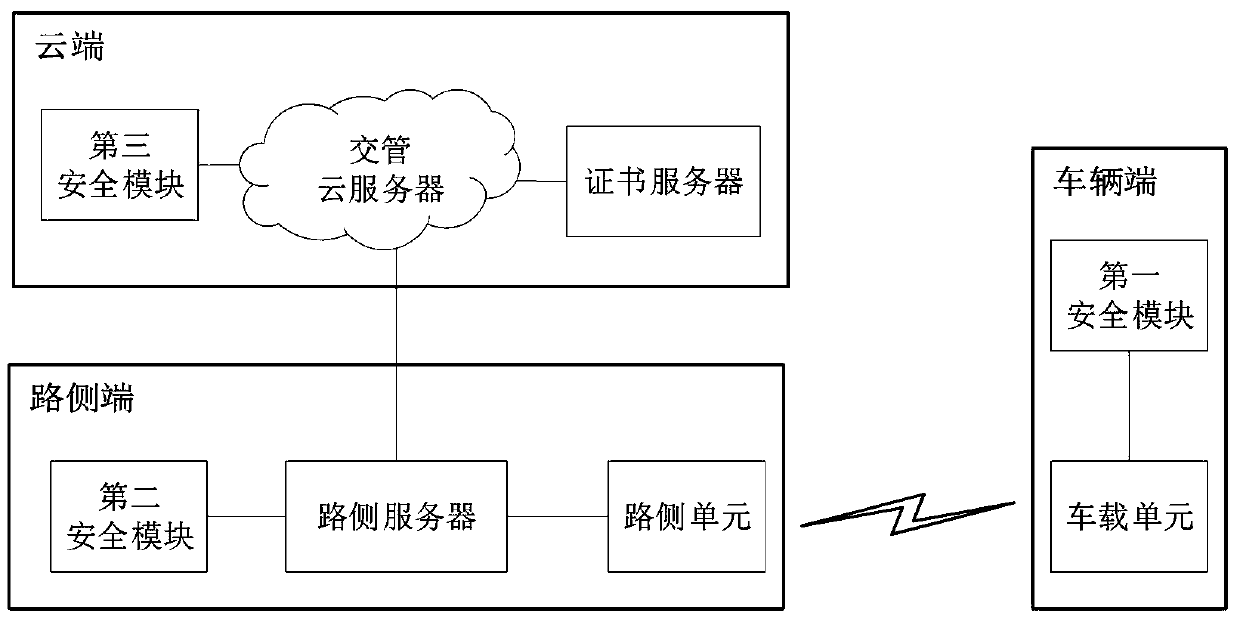
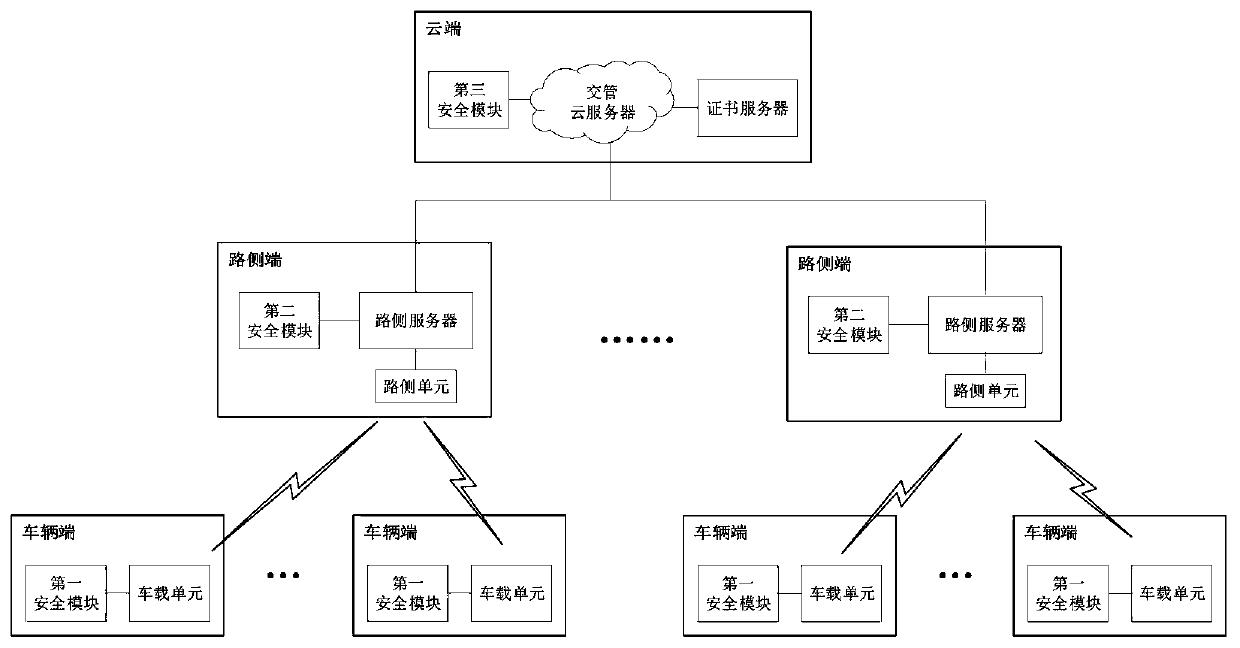
V2I Internet-of-Vehicles identity authentication system and method
ActiveCN111479244AImprove mobilityImprove dynamic performanceParticular environment based servicesVehicle infrastructure communicationIn vehicleEngineering
The invention provides a V2I Internet-of-Vehicles identity authentication system and method. The V2I Internet-of-Vehicles identity authentication system comprises a cloud end, at least one roadside end and at least one vehicle end, the cloud comprises a traffic management cloud server, a certificate server and a third security module; each roadside end comprises a roadside server, a roadside unitand a second security module; the vehicle terminal comprises a vehicle-mounted unit and a first safety module. The traffic management cloud server is connected with the certificate server and the third security module. When identity authentication is carried out on the cloud, the roadside end and the vehicle end, identity authentication is carried out. According to the embodiment of the invention,the cloud is adopted to respectively carry out identity authentication on the roadside end and the vehicle end, and then the roadside end and the vehicle end respectively carry out identity authentication on the cloud, so that direct mutual authentication between the vehicle end and the roadside end is avoided, and the consumption of vehicle end resources and the burden of processing related information by the vehicle end are reduced.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
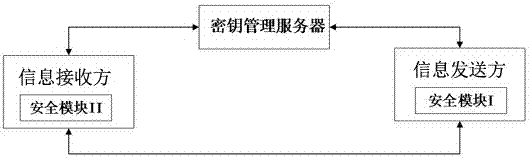
Secure communication system and communication method for smart home
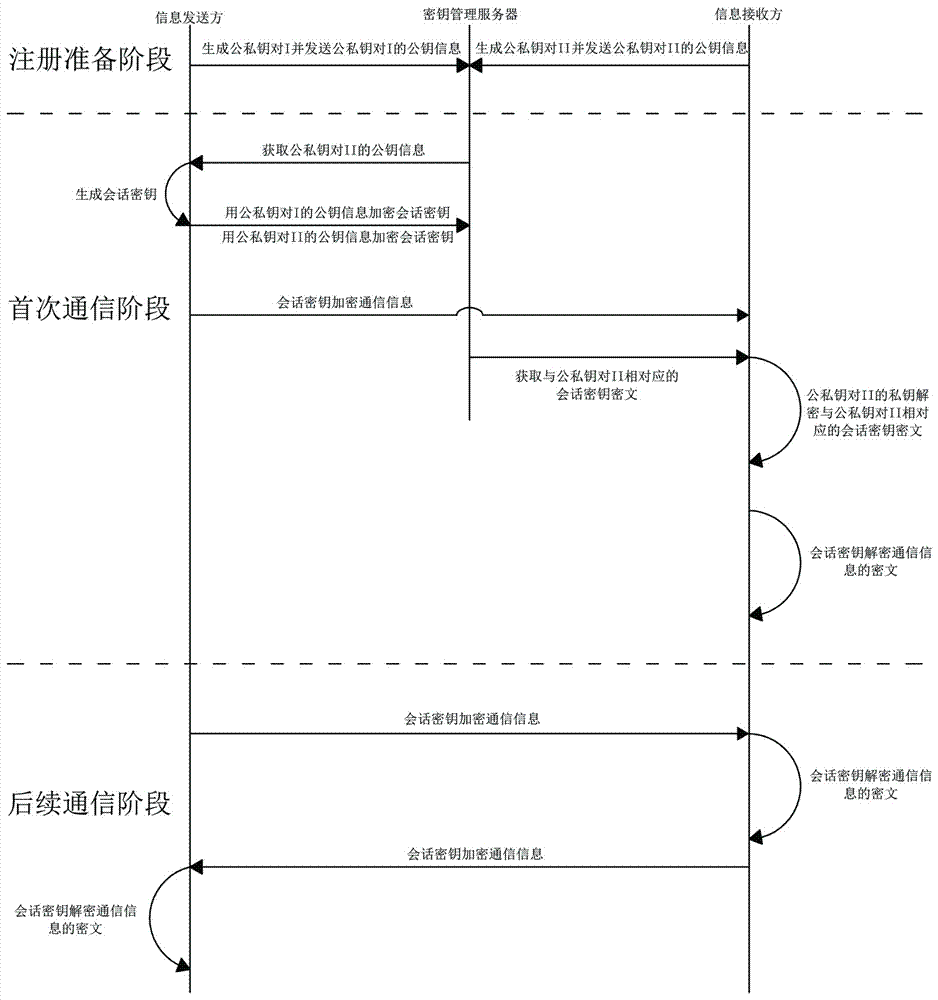
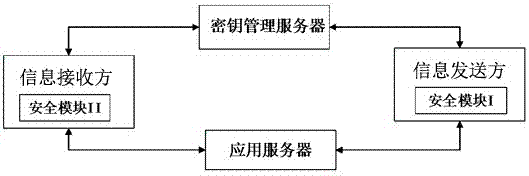
ActiveCN107094138AEnsure safetyHighlight substantive featuresHome automation networksCiphertextComputer module
The invention provides a secure communication system and communication method for a smart home. The secure communication system comprises an information sender, an information receiver and a key management server, wherein the information sender is provided with a security module I, and the information receiver is provided with a security module II; the information sender is registered in the key management server; the information receiver is registered in the key management server; the information sender generates a session key, encrypts the session key according to the registration information of the information receiver, and then sends the encrypted session key to the key management server; the information receiver acquires a ciphertext of the session key from the key management server, and decrypts the ciphertext of the session key to obtain the session key; and the information sender and the information receiver carry out remote communication by using the same session key.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
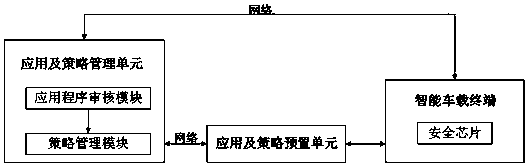
Security authorized access system for automobile functional interfaces, and security authorized access method
ActiveCN107147646AImplement secure authorized accessOutstanding FeaturesKey distribution for secure communicationUser identity/authority verificationManagement unitAccess method
The invention provides a security authorized access system for automobile functional interfaces, and a security authorized access method. The security authorized access system for the automobile functional interfaces comprises an application and strategy management unit, an application and strategy pre-setting unit and an intelligent vehicular terminal with a built-in security chip; the application and strategy management unit is separately connected to the application and strategy pre-setting unit and the intelligent vehicular terminal through a network; and the intelligent vehicular terminal is connected with the application and strategy pre-setting unit. Due to arrangement, distribution, security storage and execution of application program security strategies, security authorized access of the intelligent vehicular terminal to different types of automobile functional interfaces can be realized; therefore, hackers cannot access the automobile functional interfaces through a malicious program; automobile functional interface data is obtained or execution of an automobile ECU is controlled; therefore, the automobile functional interface access security of the intelligent vehicular terminal through an application program can be improved; and the security authorized access system has the advantages of being scientific in design, safe and reliable.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Operator cab for construction machine
ActiveCN1693594AExpand field of viewInhibit sheddingSoil-shifting machines/dredgersWing suspension devicesEngineeringExcavator
Owner:TAKEUCHI SEISAKUSHOKK +1
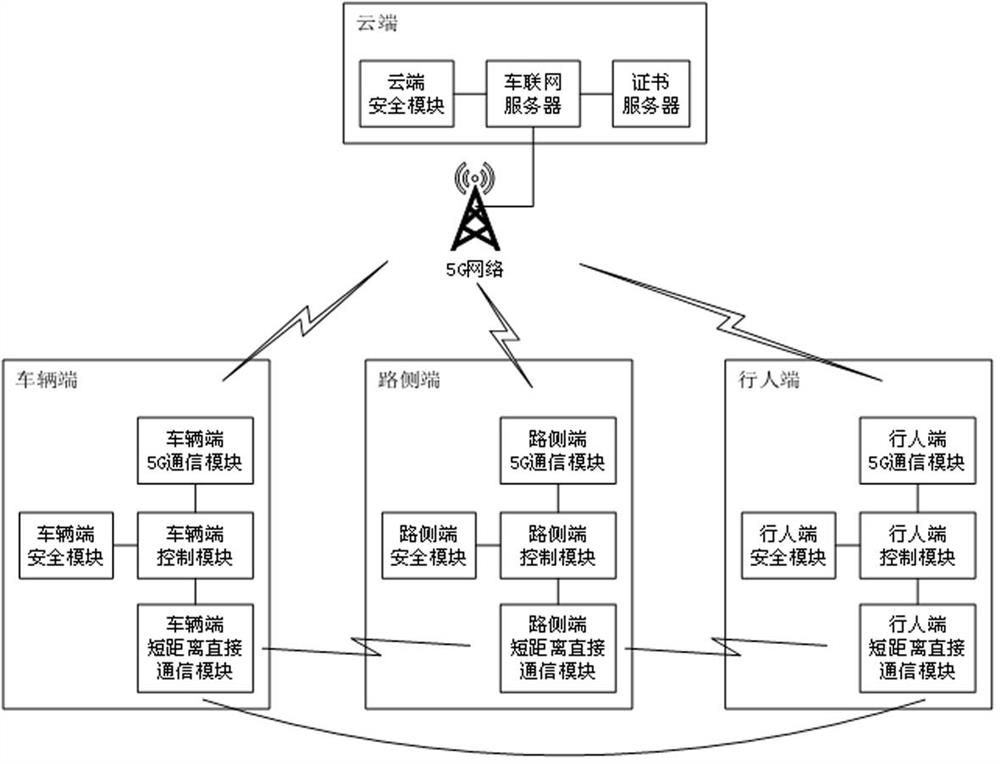
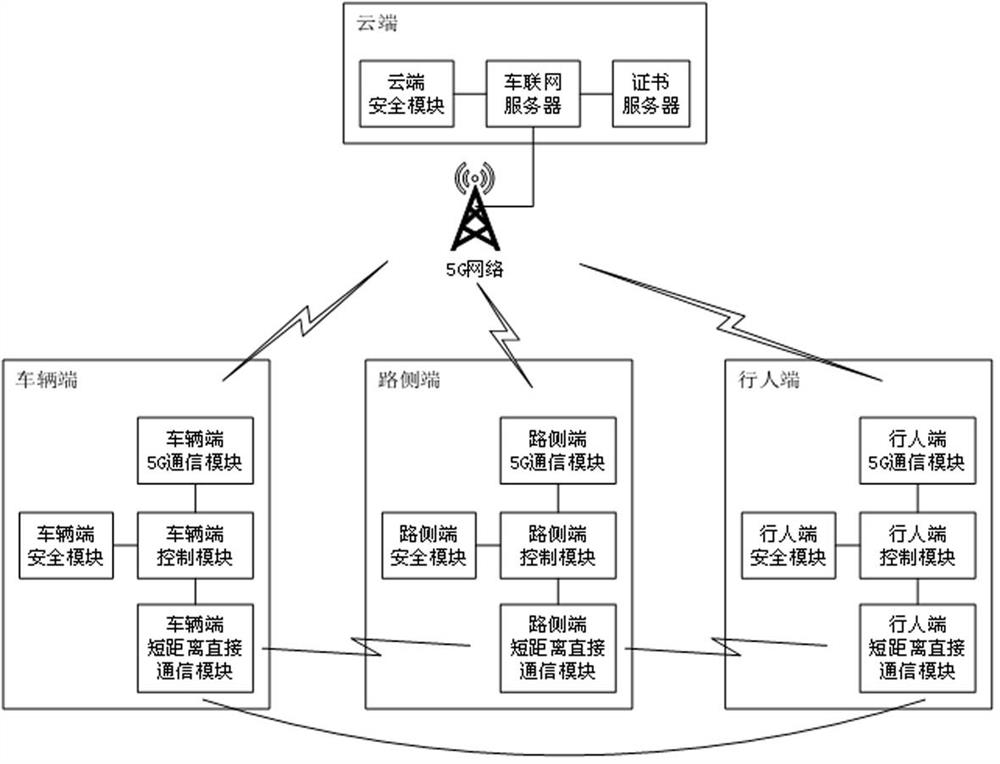
V2X Internet-of-vehicles safety communication system and method based on 5G
ActiveCN112055330AEasy to useImprove securityKey distribution for secure communicationPublic key for secure communicationEmbedded systemSecure communication
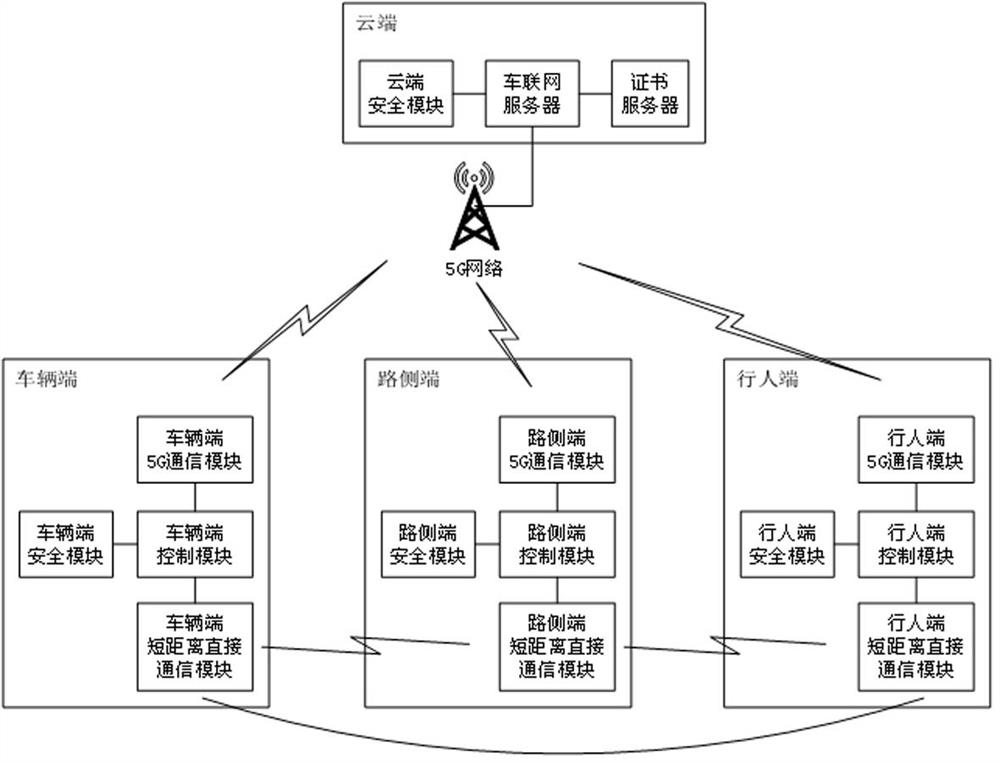
The invention relates to a V2X Internet-of-vehicles safety communication system and method based on 5G. The V2X Internet-of-vehicles safety communication system comprises a cloud terminal, a vehicle terminal, a road side terminal and at least two pedestrian terminals, wherein the sum of the number of the road side terminals and the number of the pedestrian terminals is at least two; the cloud terminal comprises a certificate server, a cloud security module and an Internet-of-vehicle server; the vehicle end comprises a vehicle end short-distance direct communication module, a vehicle end 5G communication module, a vehicle terminal safety module and a vehicle terminal control module; the roadside end comprises a roadside end short-distance direct communication module, a roadside end 5G communication module, a roadside terminal safety module and a roadside terminal control module; the pedestrian terminal comprises a pedestrian end short-distance direct communication module, a pedestrian end 5G communication module, a pedestrian end safety module and a pedestrian end control module; V2X Internet-of-vehicles identity authentication and group security encryption communication are realized according to the characteristics of 5G and V2X Internet-of-vehicles, so that the V2X Internet-of-vehicles identity authentication and group security encryption communication are safe, reliable, simple and efficient.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
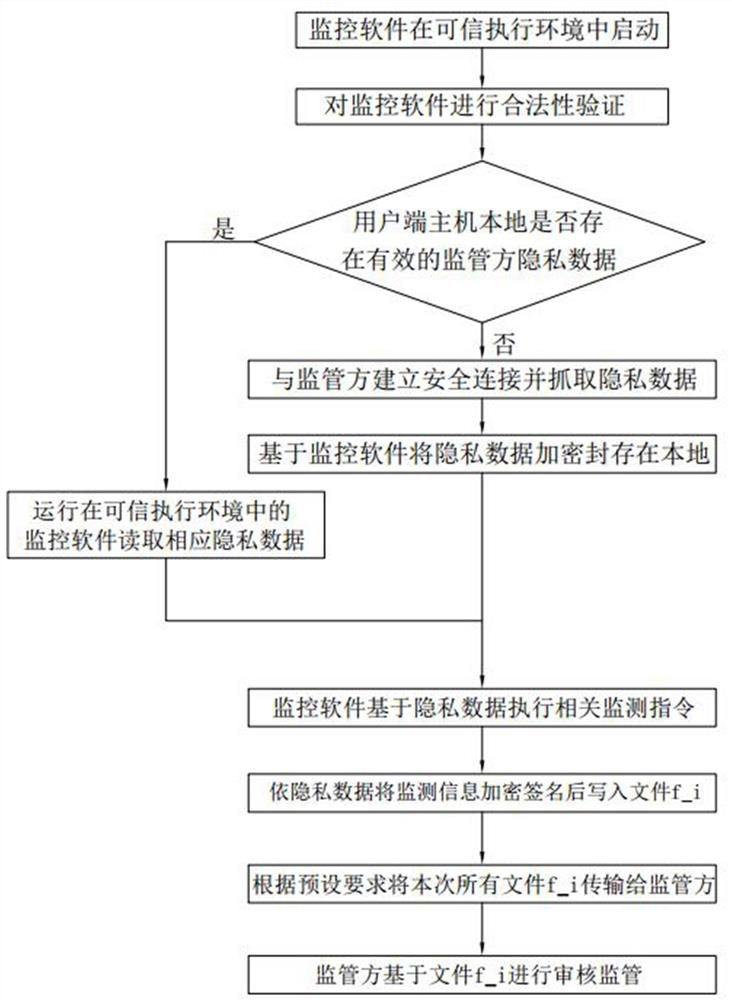
Host remote monitoring method based on chip hierarchy privacy calculation
ActiveCN113569266ASolve security deficienciesFlexible deliveryDigital data protectionPlatform integrity maintainanceEncryptionReliability engineering
The invention discloses a host remote monitoring method based on chip hierarchy privacy calculation. The host remote monitoring method comprises: S1, starting monitoring software in a client host in a trusted execution environment based on chip hierarchy; S2, judging whether valid private data exists in the local of the user side host, if so, directly entering a step S4, and otherwise, entering a step S3; S3, establishing secure connection with a supervisor and capturing privacy data; and S4, executing a related monitoring instruction by the monitoring software operating in the trusted execution environment based on the privacy data, encrypting and signing a monitoring result, and transmitting the monitoring result to a supervisor. According to the scheme, the validity, non-tampering property and monitoring safety of the monitoring information of the user side are ensured by utilizing a trusted execution environment based on privacy calculation, and the monitoring information is encrypted and signed based on the encryption key and the signature key of the supervisor, so that the supervisory information can be stored locally, and high overhead cost caused by real-time connection is avoided.
Owner:NANHU LAB
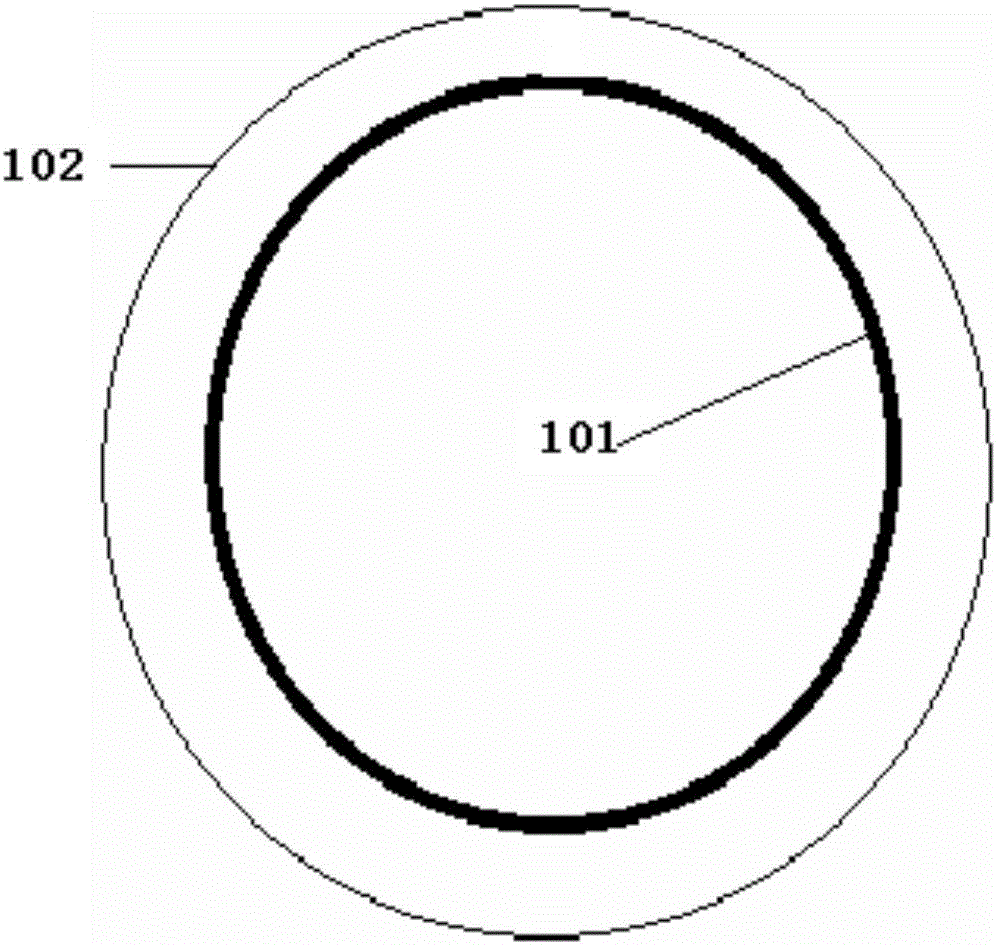
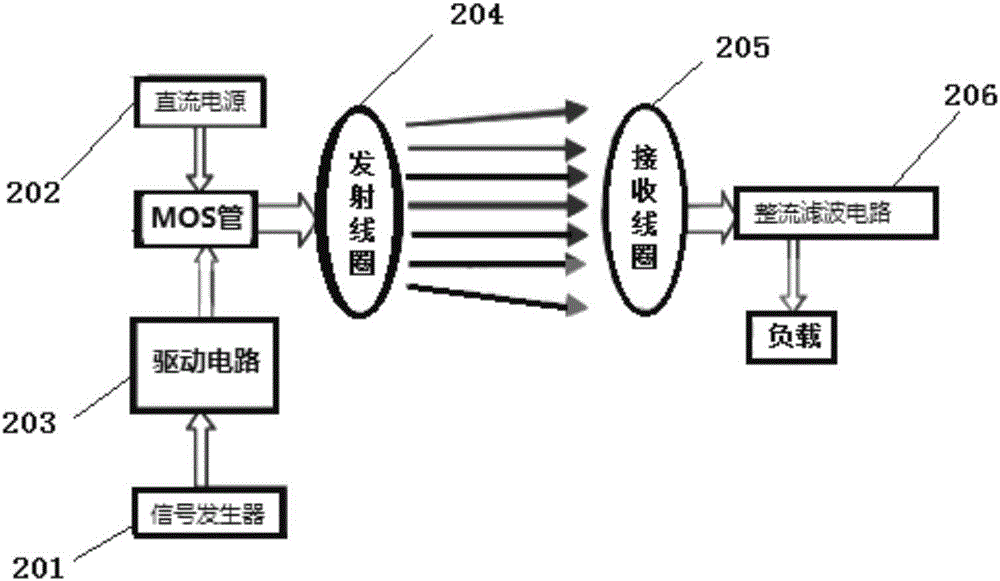
Magnetic coupling wireless charging device having properties of high efficiency and high safety factor
PendingCN106602741AAddressing security deficienciesImprove work efficiencyBatteries circuit arrangementsElectric powerInductive chargingSafety coefficient
The invention relates to a magnetic coupling wireless charging device having properties of high efficiency and a high safety factor. The charging device comprises a magnetic coupling wireless charging solenoid and further comprises an annular solenoid arranged outside the magnetic coupling wireless charging solenoid, wherein height of the annular solenoid is not lower than the magnetic coupling wireless charging solenoid, an output power of a compensation power source is quite smaller than a power of a magnetic field power source generated by the magnetic coupling wireless charging solenoid, the annular solenoid can cover a solenoid of a main loop, and a magnetic field direction generated after providing a current to the additional annular solenoid is guaranteed to be opposite to a leakage magnetic field direction at an outer side of the main loop. The charging device is advantaged in that parallel leakage prevention and compensation design concept is employed, so not only can poor safety existing in wireless charging in the prior art be well solved, but also work efficiency of the wireless charging technology is substantially enhanced, and application prospects of the wireless charging technology are improved.
Owner:伽行科技(北京)有限公司
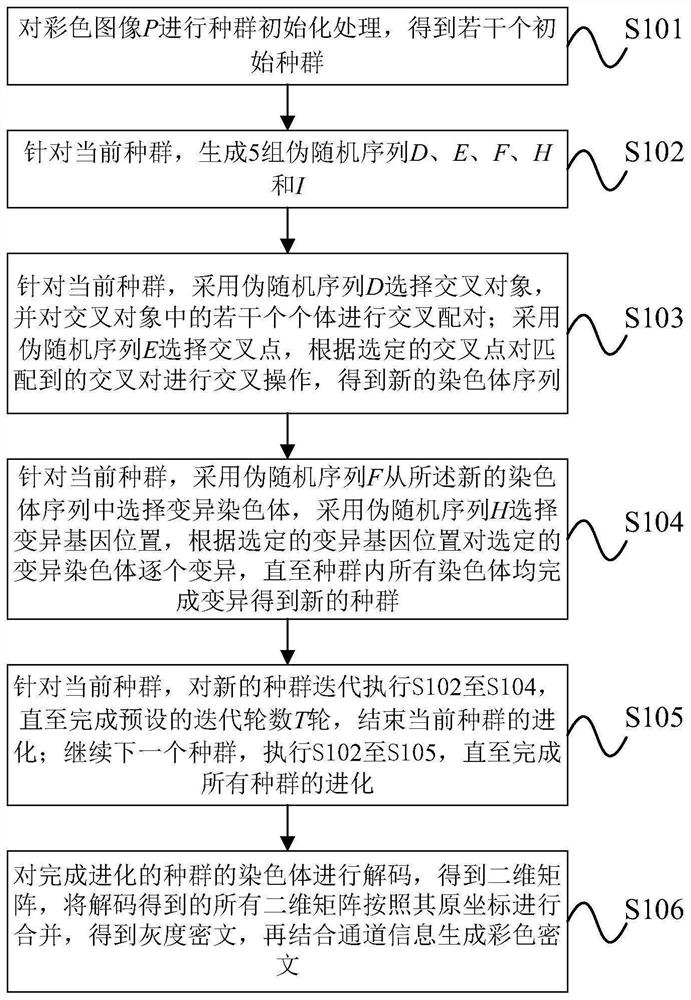
Color image storage thumbnail encryption algorithm based on genetic algorithm
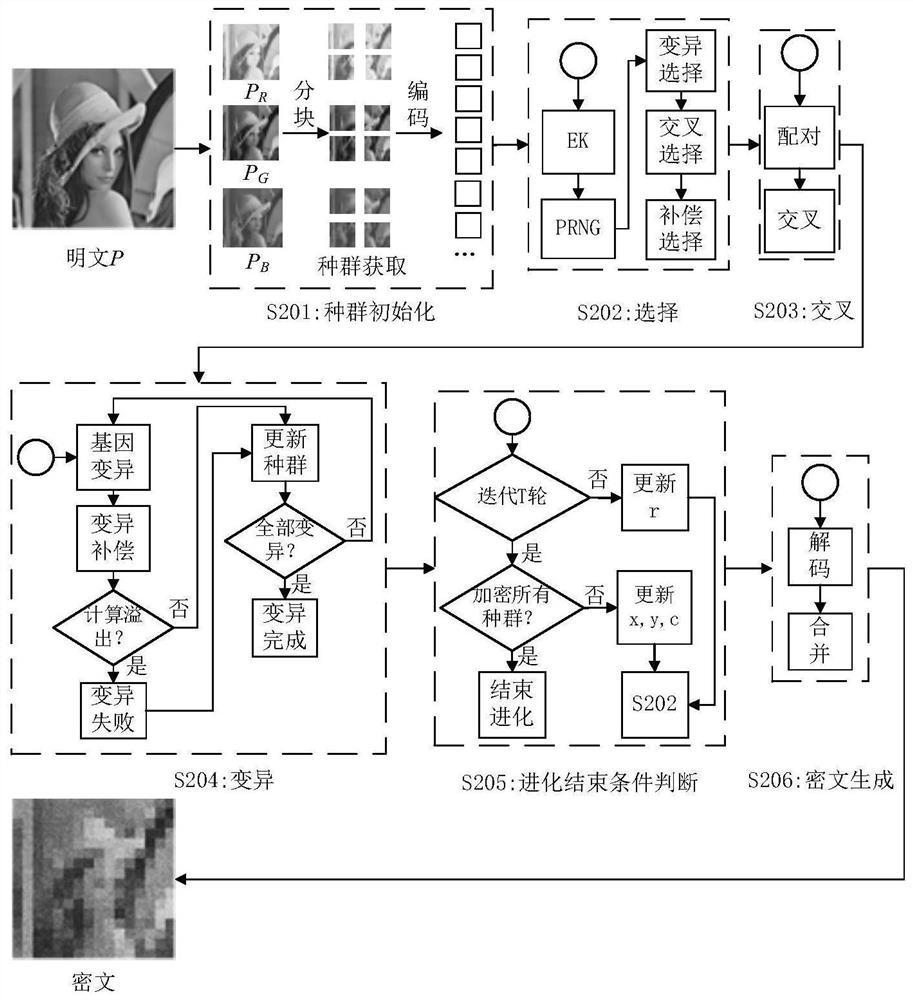
PendingCN112116672AAchieving the goal of invariance to the meanImplement encryptionImage codingGenetic algorithmsColor imageAlgorithm
The invention provides a color image storage thumbnail encryption algorithm based on a genetic algorithm. The algorithm comprises the following steps: 1, performing population initialization processing on a color image P to obtain a plurality of initial populations; 2, generating five groups of pseudorandom sequences D, E, F, H and I; 3, selecting a cross object by adopting D, selecting a cross point by adopting E, and carrying out cross operation on the cross pair to obtain a new chromosome sequence A '; 4, selecting variant chromosomes from the A' by adopting F, selecting variant gene positions by adopting H, and mutating the variant chromosomes one by one until all chromosomes in the population are mutated to obtain a new population; 5, executing step 2 to the step 4 on the new population iteratively until a preset iteration round number T is completed, and ending the evolution of the current population; continuing the next population, and executing the step 2 to the step 5 until the evolution of all populations is completed; and 6, decoding the chromosomes of the evolved population, and generating a color ciphertext in combination with the channel information.
Owner:HENAN UNIVERSITY
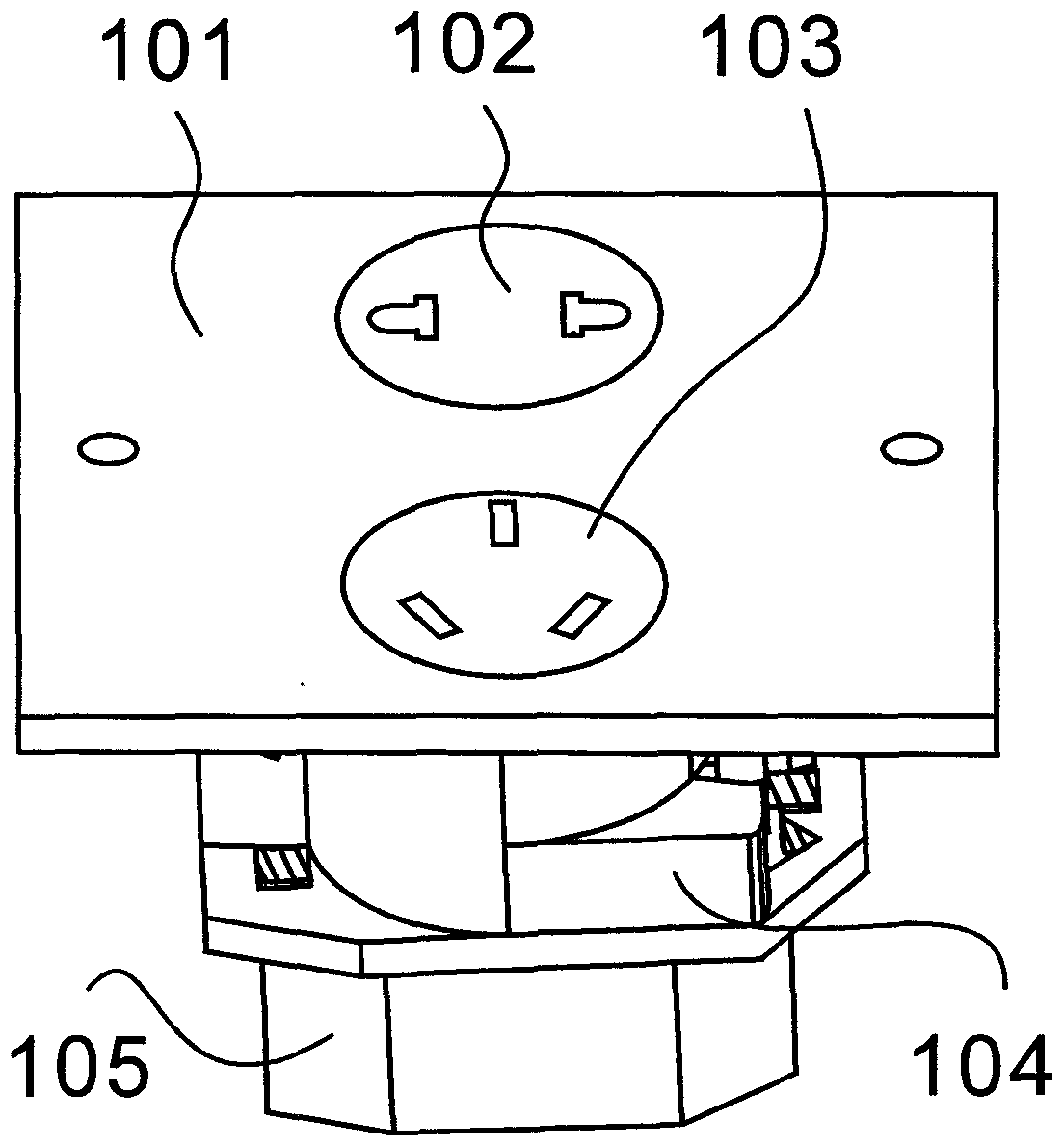
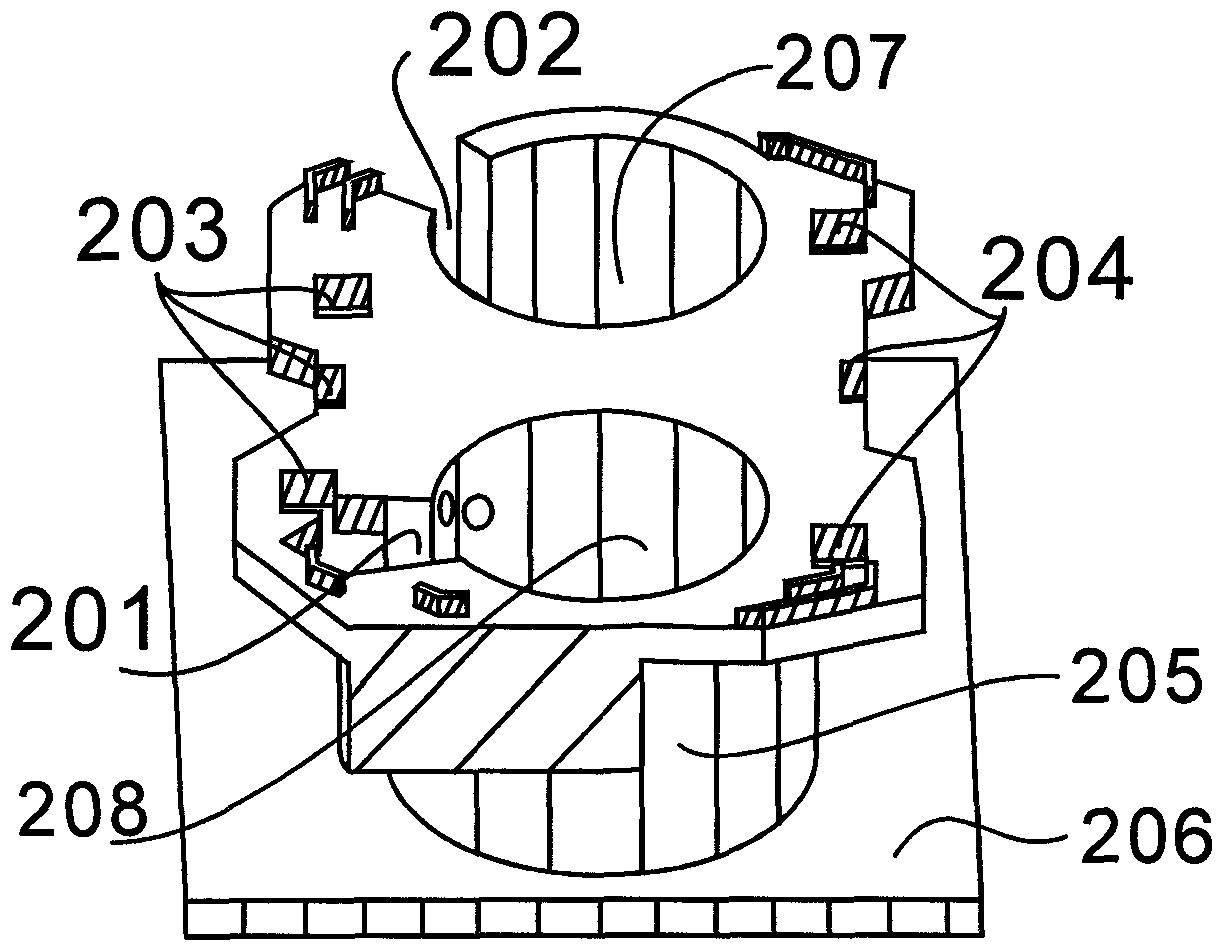
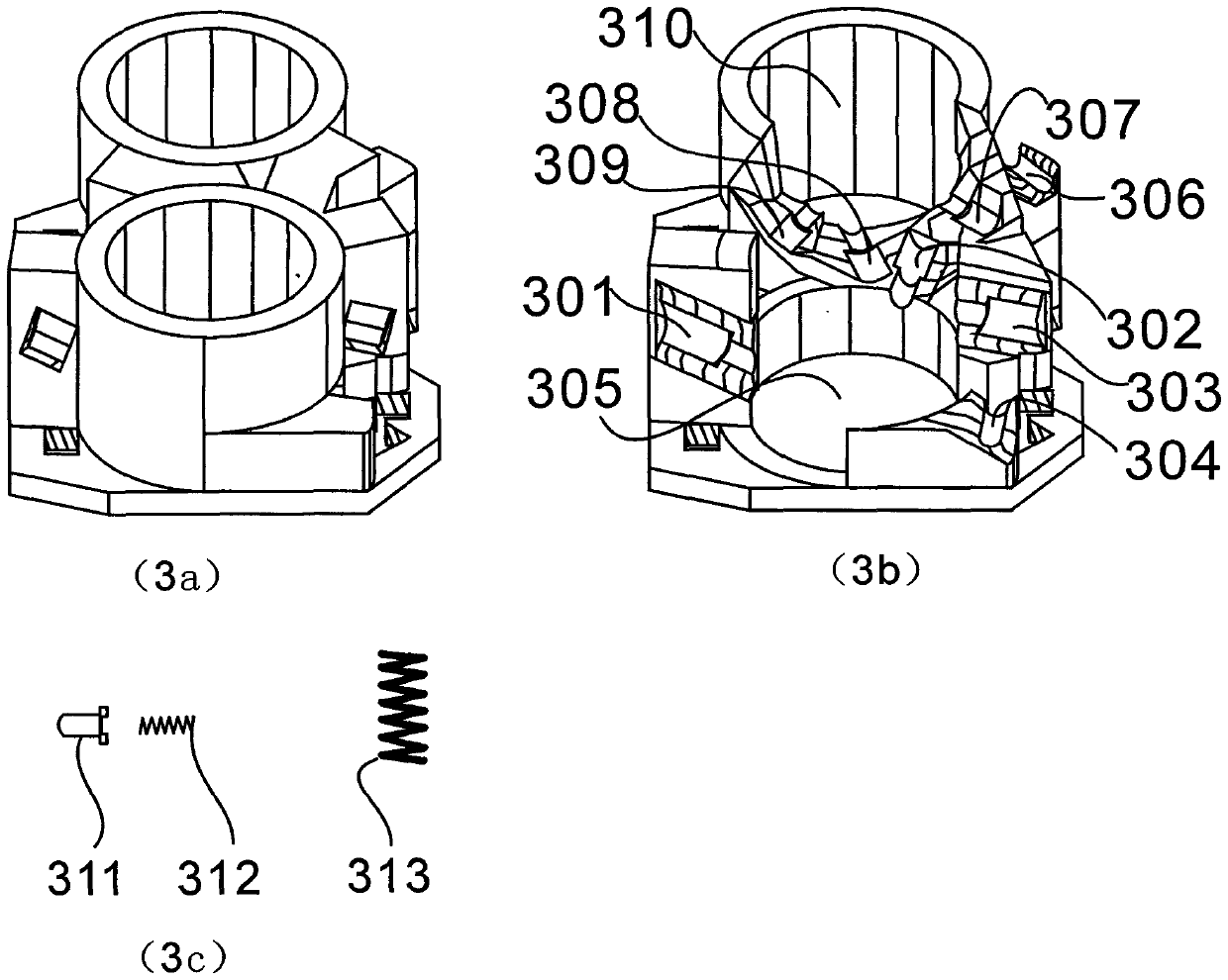
Safe anti-electric shock socket
PendingCN109560427AImprove electricity safetySolve security deficienciesCoupling device detailsEngineeringElectric shock
The invention discloses a safe anti-electric shock socket. The safe anti-electric shock socket comprises a socket panel cover, a socket core, a socket core sleeve and a bottom box, and is characterized in that a user cannot suffer from an electric shock when holding metal to be inserted into the socket; a plug is electrified only when the socket core rotates in place, firstly the socket core rotates after the socket core is unlocked in un unlocking condition that a lock shaft is pushed out by a wobble wheel, the socket core is unlocked if a standard plug is plugged into the socket, the socketsuffers from the resistance of a reset spring when the socket core rotates, and the plug is electrified after the socket core rotates in place; after the plug is pulled out, the socket core automatically rotates in place in the counterclockwise direction, and the socket is powered off; if the user holds the metal to be inserted into a single socket, the socket core cannot be unlocked; if the userholds the metal to be inserted into the socket and the socket core is unlocked, but the socket core does not rotate, the human body cannot suffer from the electric shock; the socket is electrified under multiple conditions, so that the user is effectively prevented from holding the metal to be inserted into the socket by mistake for the electric shock, and the life safety of people is guaranteed effectively.
Owner:何锐平
Industrial control safety communication system and method based on 5G
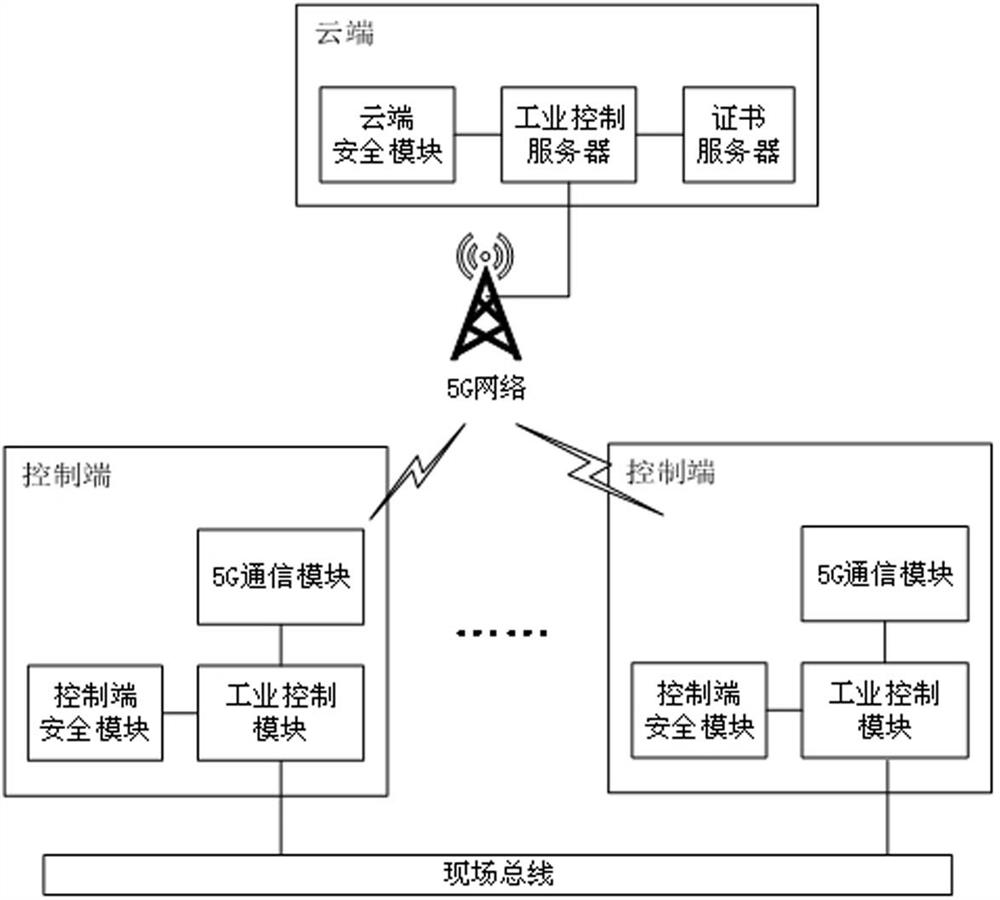
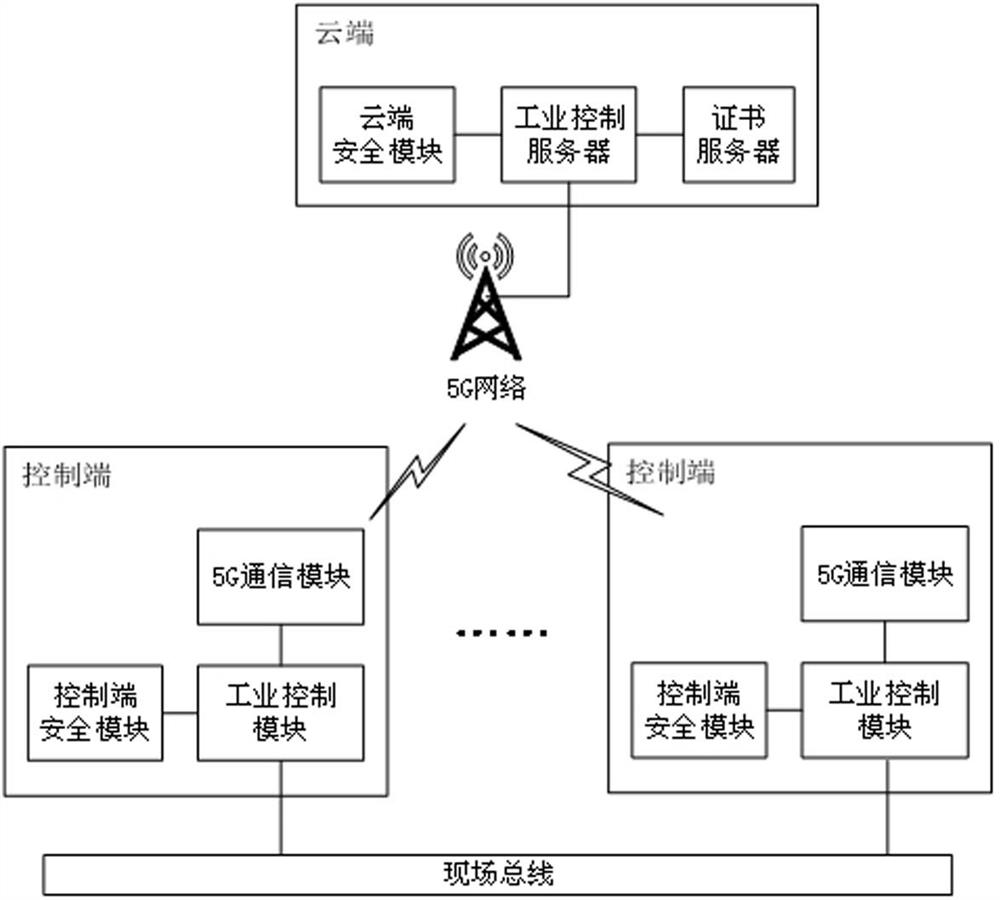
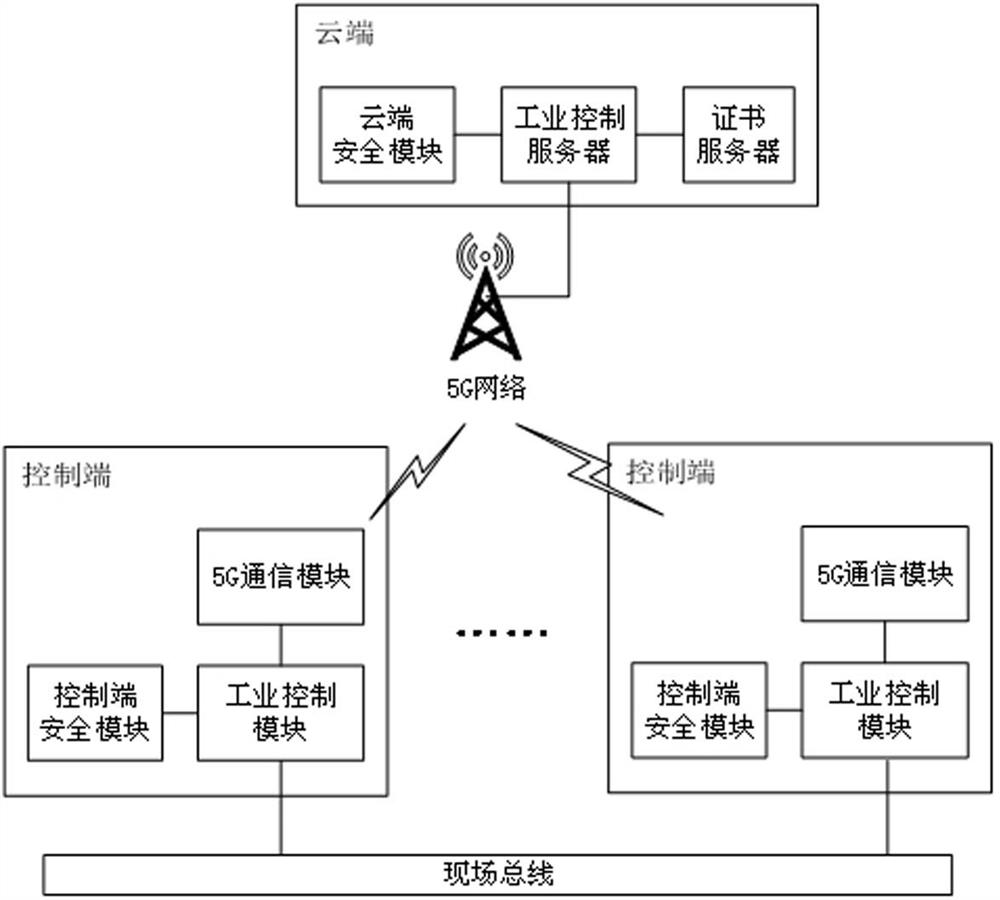
ActiveCN112055071ASolve the problem of limited storage resourcesSolve the problem of mutual secure communicationKey distribution for secure communicationPublic key for secure communicationSecure communicationPassword
The invention relates to an industrial control safety communication system and method based on 5G. The system comprises a cloud and at least two control terminals. The cloud comprises a certificate server, a cloud security module and an industrial control server; the control terminal comprises a 5G communication module, a control end safety module and an industrial control module; wherein the industrial control server is in communication connection with the 5G communication module through a 5G network, the control end is connected through a field bus, the cloud security module and the controlend security module provide password and storage services, and the password services comprise random number generation, signature verification operation, encryption and decryption operation, session key generation and hash operation; the industrial control server calls a cloud security module password service, and the industrial control module calls a control end security module password and a storage service; the certificate server generates a public key certificate for the cloud and the control terminal, and writes a public key of the public key certificate into the control terminal securitymodule; and the cloud security module and the control end security module store corresponding private keys to realize identity authentication and group security encryption communication between the control modules.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
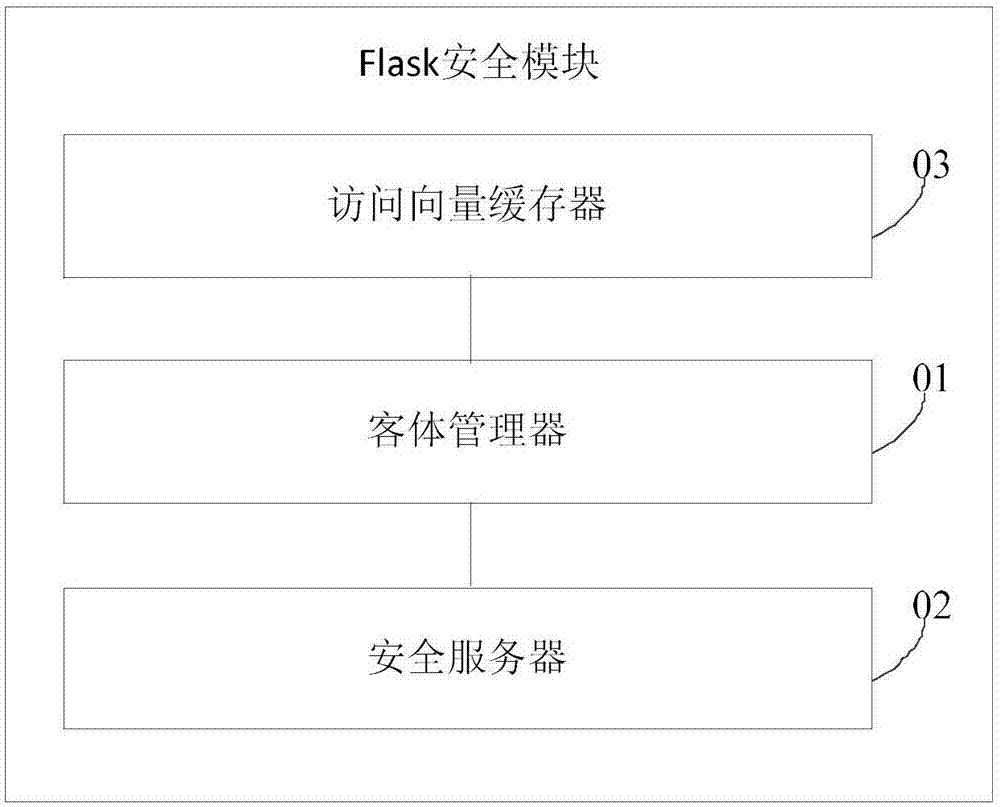
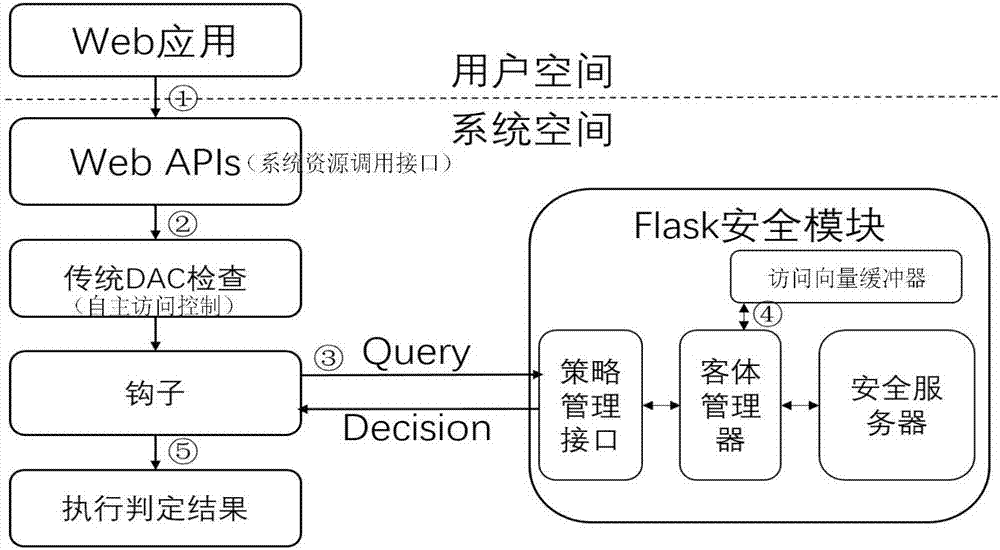
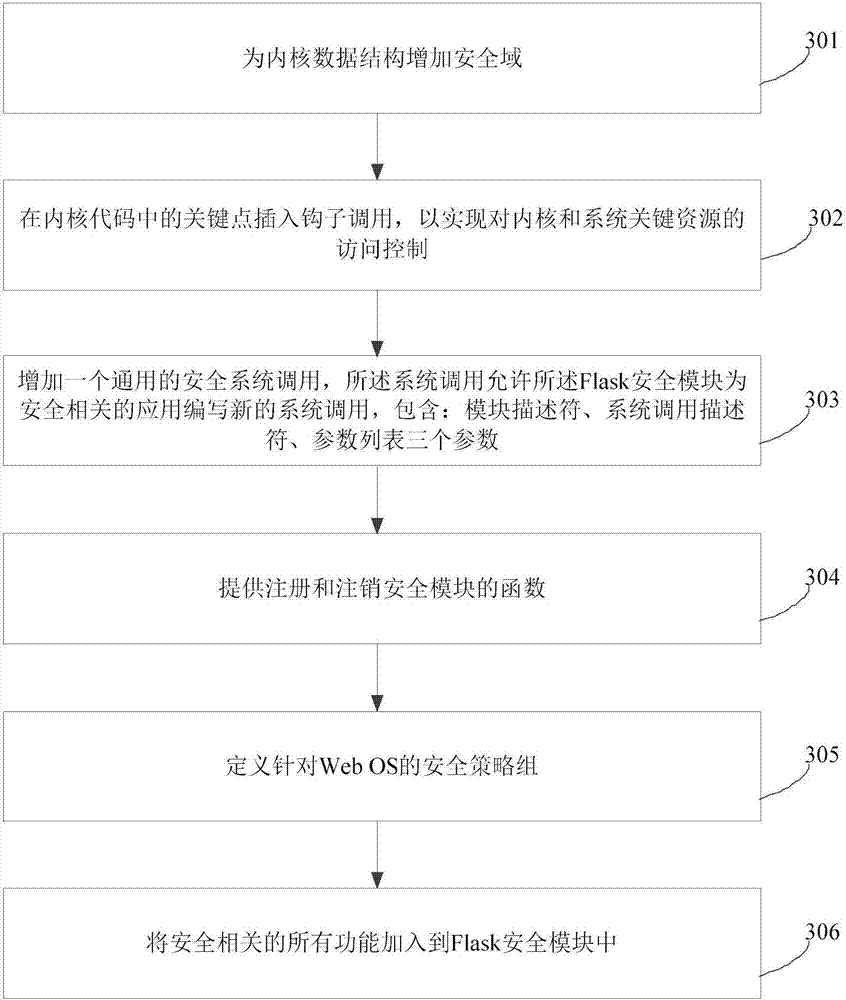
Flask safety module, construction method and mobile Web system
InactiveCN107547520ASolve security deficienciesImprove securityTransmissionUser identifierSecurity policy
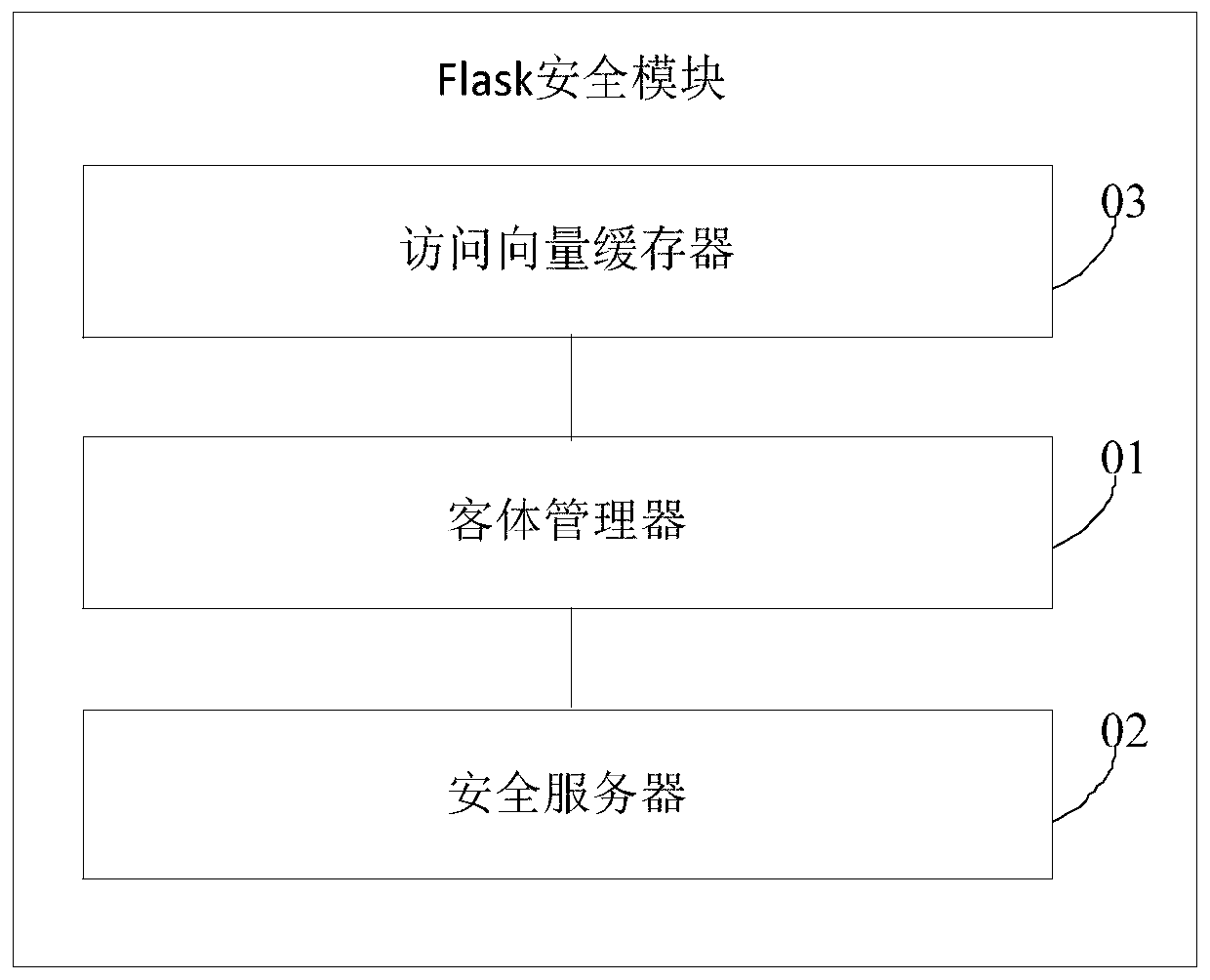
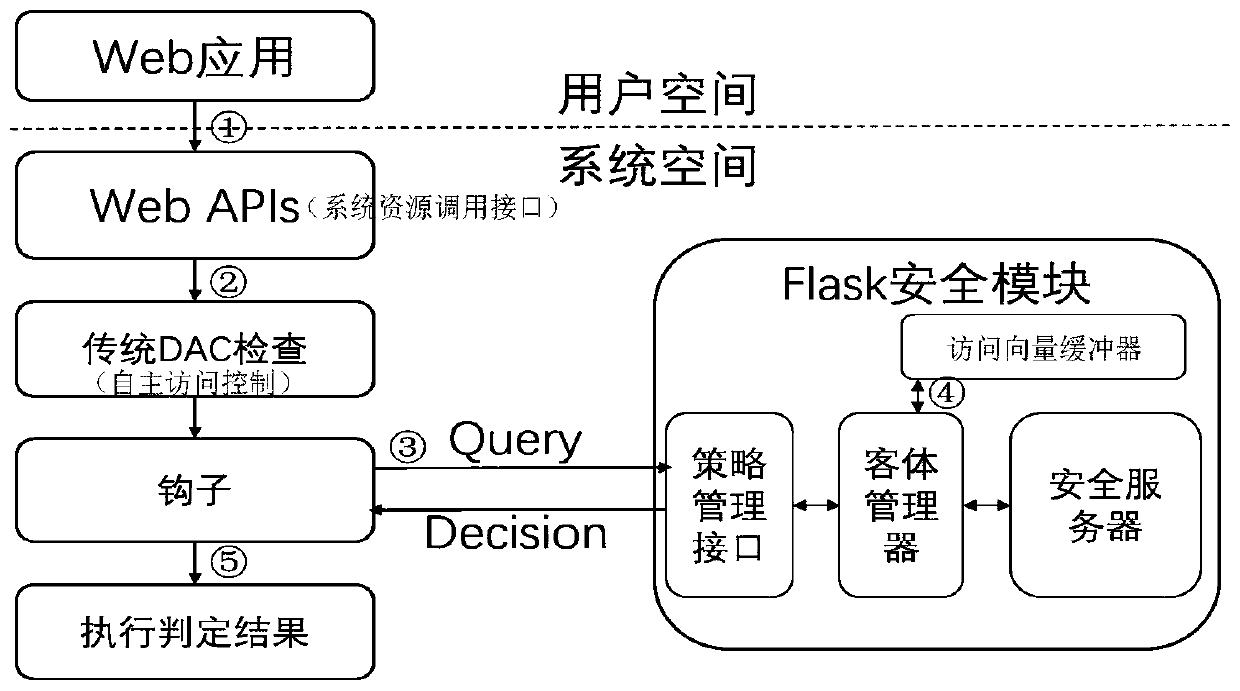
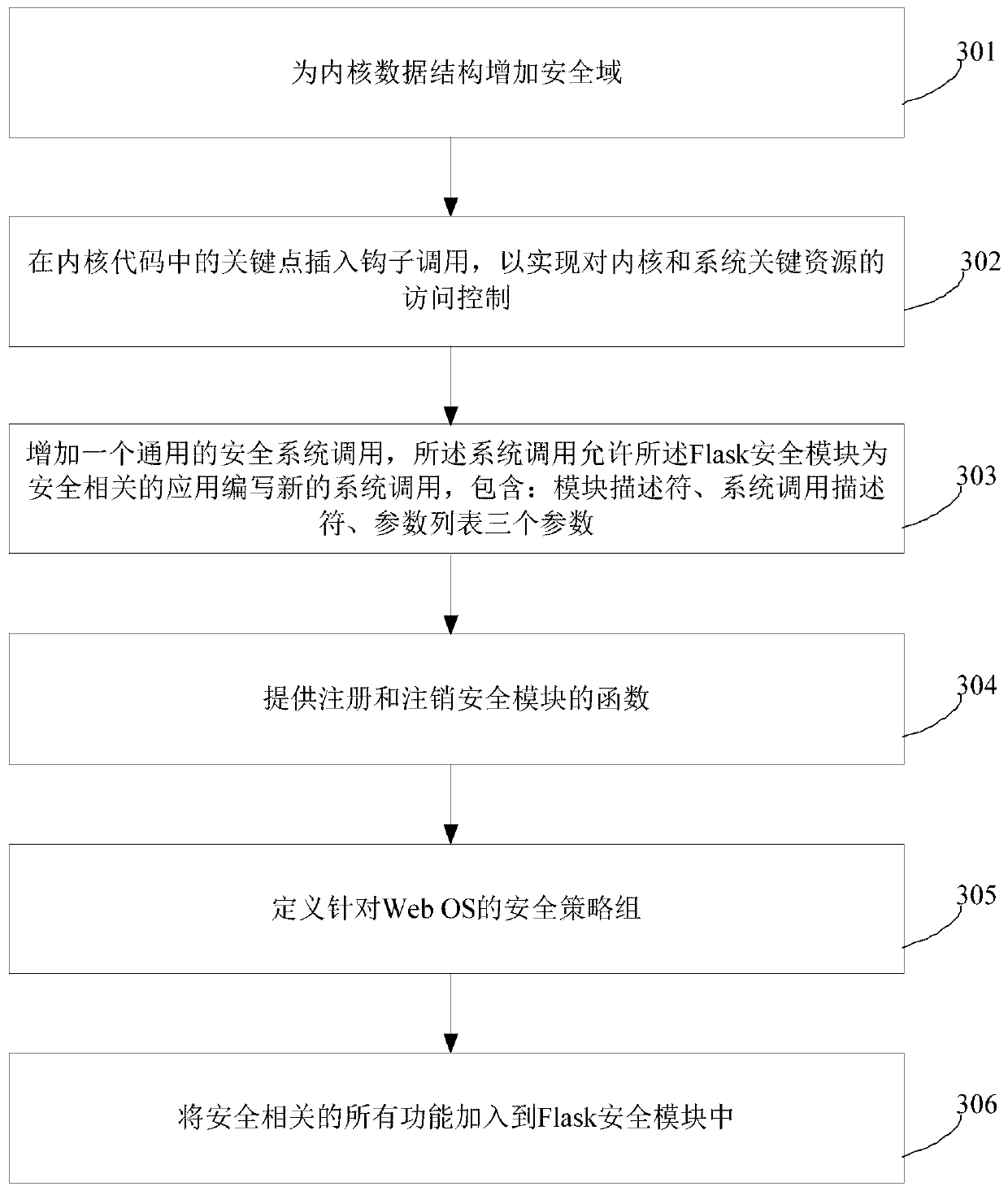
The invention provides a Flask safety module, a construction method and a mobile Web system. The Flask safety module comprises a safety server, an object manager and an access vector buffer, wherein the safety server is used for providing a safety strategy decision, keeping mapping between a safety identifier and a safety context, allocating the safety identifier to a newly established object, controlling contents of the access vector buffer to be correct and consistent; the object manager is respectively in communication connection with the safety server, the access vector buffer and a hook in the mobile Web system, and is used for providing an interface for carrying out re-access, marking and multi-instance decision from one safety server, providing one access vector buffer to allow theobject manager to buffer an access decision result and providing the object manager to receive and process a safety strategy change notification, wherein the multi-instance decision stipulates which member of a multi-instance resource set is accessed to by a specific request; and the access vector buffer is used for buffering a preset safety strategy. The problem of poor safety caused by a case that an existing mobile Web system adopts discretionary access control can be solved.
Owner:INST OF INFORMATION ENG CAS
A method and system for vehicle safety remote control and diagnosis
ActiveCN106713264BPrevent access to the systemGuarantee information securityKey distribution for secure communicationUser identity/authority verificationRemote controlInformation security
The invention provides a method for vehicle safety remote control and diagnosis and a system thereof. A control and diagnosis terminal and a cloud side instruction server perform first identity authentication and key agreement; a vehicle-mounted terminal and the cloud side instruction server perform second identity authentication and key agreement; and the control and diagnosis terminal establishes communication connection with the vehicle-mounted terminal through the cloud side instruction server and performs remote control or remote diagnosis on a vehicle according to the control and diagnosis instruction of a user. Different secret keys are adopted between the control and diagnosis terminal and the cloud side instruction server and between the vehicle-mounted terminal and the cloud side instruction server and so that the information security of remote control and diagnosis information can be guaranteed, and the problem of security insufficiency in the prior art can be effectively solved. The system for vehicle safety remote control and diagnosis has the advantages of being scientific in design, high in practicality, convenient and rapid, high in security and high in reliability.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Pit type furnace lifting device
PendingCN110108129AEasy to pick and placeEasy to operateFurnace doorsHydraulic cylinderIndustrial engineering
The invention discloses a pit type furnace lifting device. The pit type furnace lifting device comprises a wall body and a furnace door, a motor is fixed on the outer wall of the wall body through a mounting seat, the output end of the motor is rotationally connected with a shaft rod, the outer wall of the shaft rod is sequentially sleeved with limiting seats, the limiting seats are arranged at the outer end of the wall body, a top beam is fixed to the top end of the shaft rod through a reinforcing plate, a hydraulic cylinder is arranged on the top beam, a control rod is fixed at the output end of the bottom of the hydraulic cylinder, a lifting table is arranged at the lower end of the control rod, the furnace door is fixed on the lifting table, and each limiting seat internally comprisesa limiting seat body and a base. According to the pit type furnace lifting device, the motor, the limiting seats, a spiral groove, the shaft rod, the reinforcing plate, the top beam, the hydraulic cylinder, the lifting table, a spring, a limiting cavity, a ball and a limiting through hole are arranged, so that the problems that when a pit type furnace lifting device is used at the present stage, lifting and rotating can not be performed at the same time, the stability is poor, and potential safety hazards exist during use are solved.
Owner:HENAN TIANLI THERMOTECHNICAL EQUIP CO LTD
A secure remote control system and method for industrial equipment
ActiveCN108390851BHighlight substantiveSignificant progressKey distribution for secure communicationUser identity/authority verificationAccess networkControl system
The invention provides a security remote control system and method for industrial equipment. The system comprises industrial equipment, a control terminal and a cloud platform, wherein a security module I is arranged in the industrial equipment, a security module II is inserted into or arranged in the control terminal, the cloud platform comprises a security access gateway, a management system, aCA certificate management system and a forwarding server, and a security module III is arranged in the security access gateway. In remote control, the industrial equipment and the security access gateway perform bidirectional identity authentication and key negotiation and create a first session key; the control terminal and the security access gateway perform bidirectional identity authenticationand key negotiation and create a second session key; the control terminal and the industrial equipment perform bidirectional identity authentication and key negotiation through the forwarding serverand then create a third session key; and the control terminal performs security remote control on the industrial equipment by using the third session key through the forwarding server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Removable outdoor environment-friendly detecting device
InactiveCN108508153ARapid assessmentConvenient collection workWithdrawing sample devicesAnalysing gaseous mixturesGas detectorStorage tank
The invention discloses a removable outdoor environment-friendly detecting device. The removable outdoor environment-friendly detecting device comprises detecting main bodies, storage main bodies andmain supporting plates, wherein a protective shell is fixedly sleeved and arranged on the upper end surfaces of the main supporting plates; four groups of the storage main bodies are arranged and arerectangularly and fixedly inserted in the upper end surface of the protective shell; the inner parts of the storage main bodies are fixedly connected with supporting frames; the central positions of the upper end surfaces of the supporting frames are fixedly connected with the protective shell in a clamping way; the inner part of the protective shell is fixedly connected with gas storage tanks; the detecting main bodies are inserted in the central positions of the upper end surfaces of the storage main bodies in a penetrating way; the inner parts of the detecting main bodies are fixedly connected with gas temporary storage tanks; the central positions of the upper end surface of the gas temporary storage tanks are connected with exhaust fans in the penetrating way; the central positions ofthe side end surfaces of the exhaust fans are connected with gas detectors in the penetrating way. According to the removable outdoor environment-friendly detecting device disclosed by the invention,through the arrangement of the detecting main bodies, the storage main bodies and the main supporting plates, the practicability of the removable outdoor environment-friendly detecting device can beimproved, so that the sealed connecting performance of the removable outdoor environment-friendly detecting device is improved.
Owner:SUZHOU UNIV OF SCI & TECH
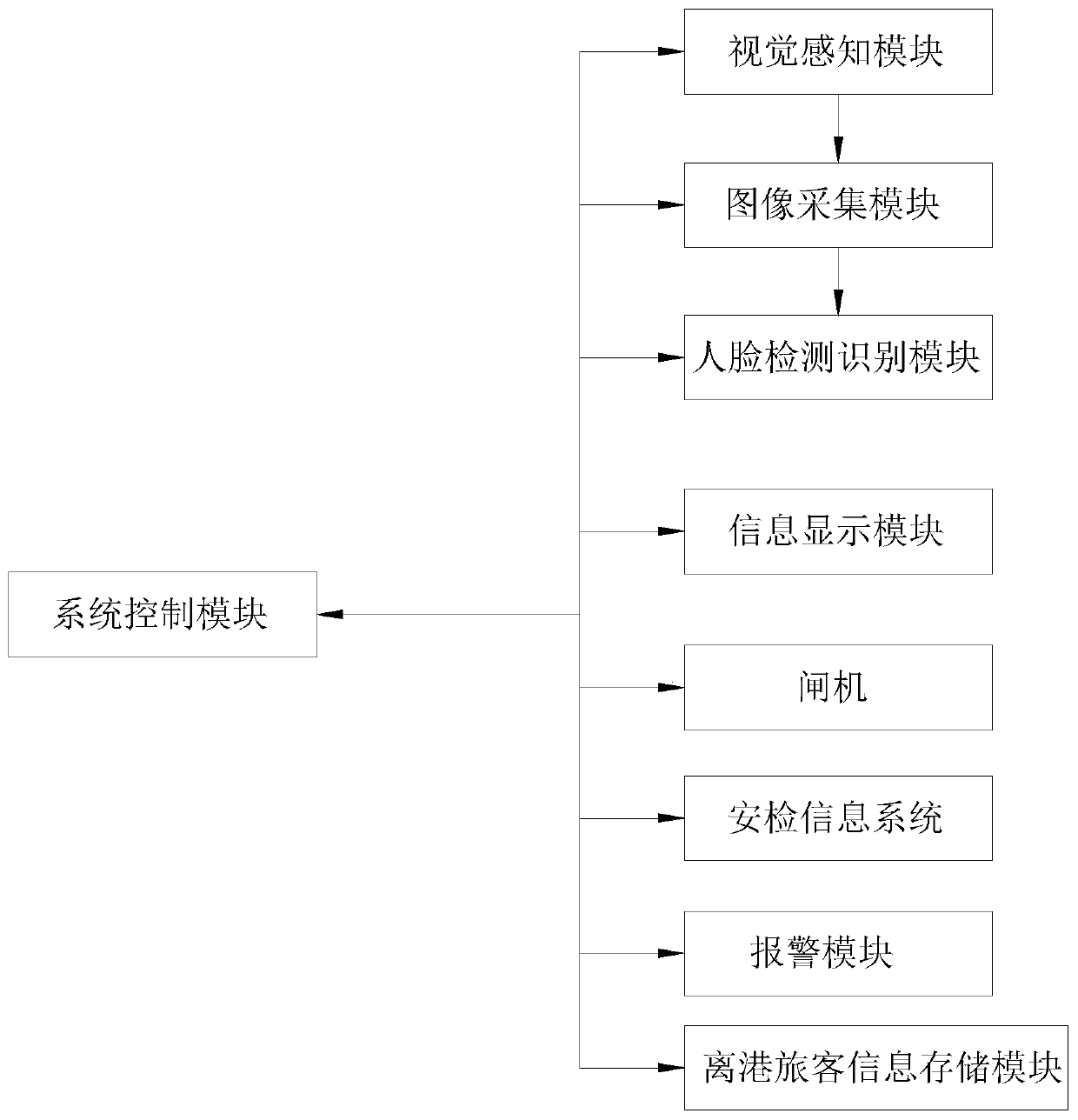
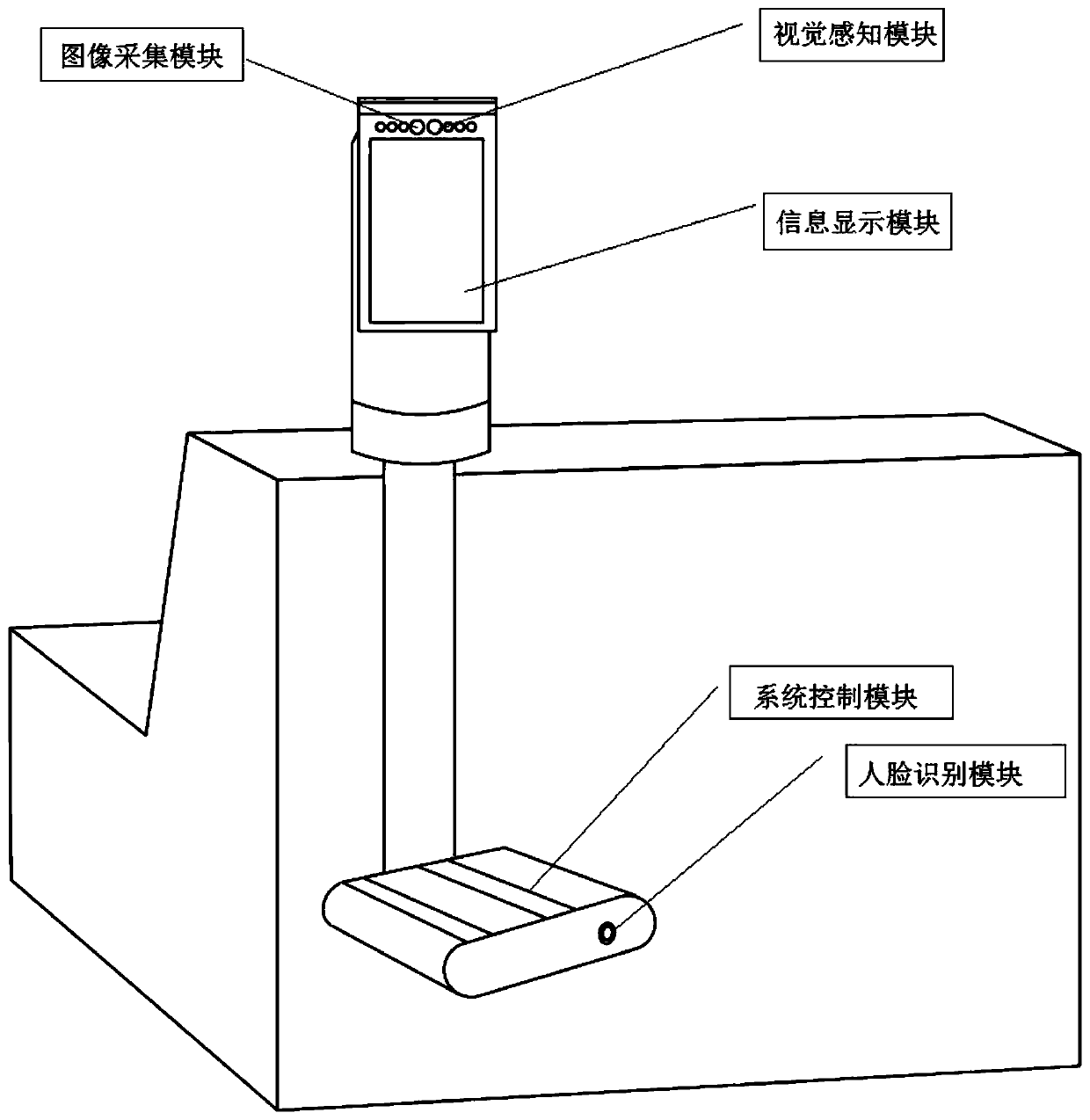
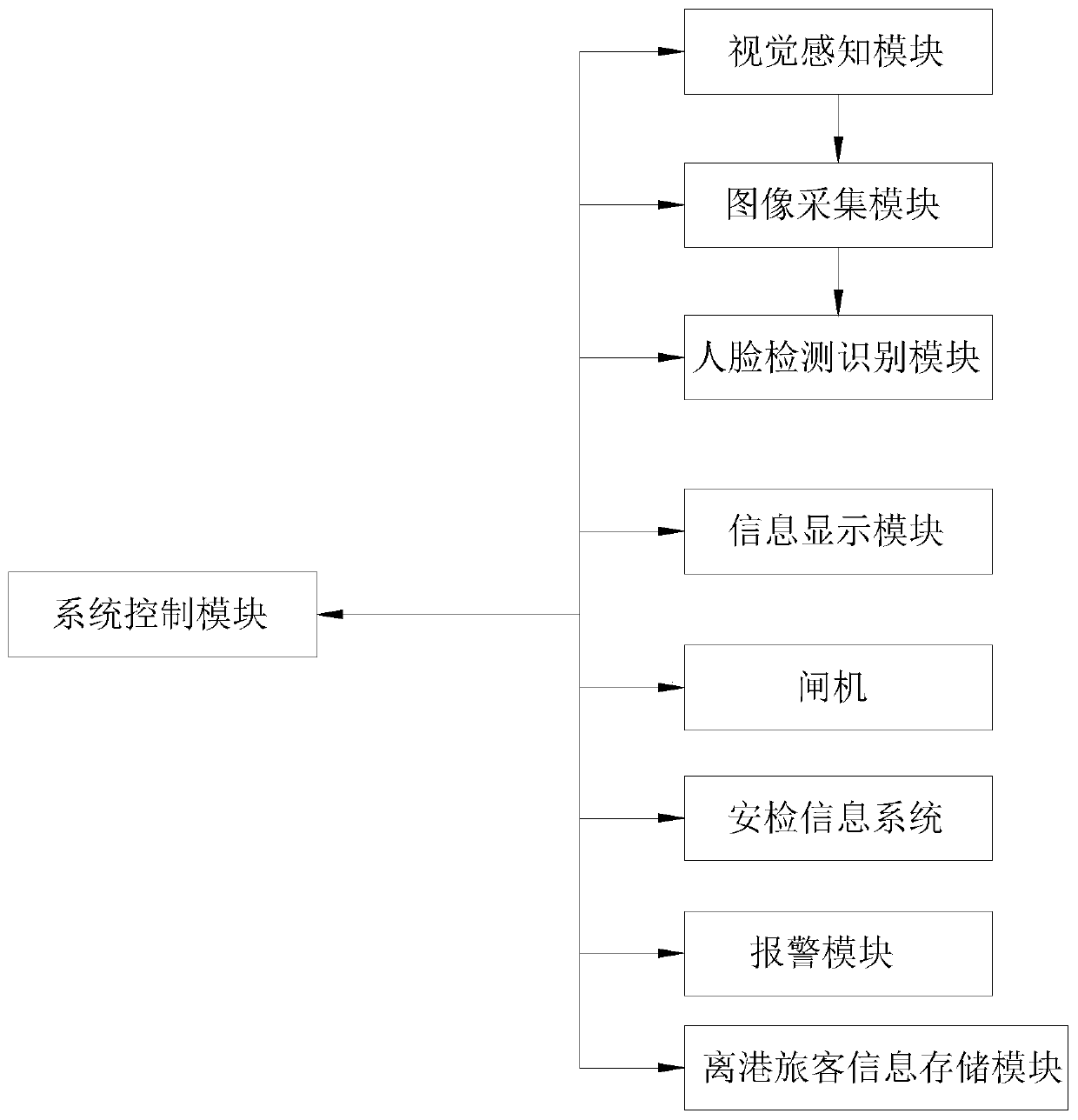
Human face departure information equipment based on visual perception
PendingCN111126267ASolve security deficienciesConsolidate air defense securityData processing applicationsCharacter and pattern recognitionVision basedInformation system
The invention is applicable to the technical field of departure information systems in aircraft ports and provides human face departure information equipment based on visual perception. A visual perception module, an image acquisition module, a face detection and recognition module, a system control module and an information display module are arranged; the visual perception module is used in front of a boarding gate in an aircraft port. Passenger postures and physiological characteristics are detected; the image acquisition module is used for acquiring passenger face information after the passenger posture and physiological characteristics detected by the visual perception module meet a preset posture condition and a preset physiological characteristic condition respectively; the face detection and recognition module is used for processing the passenger face information acquired by the image acquisition module, detecting the specific position of a face and extracting face features; the system control module is used for controlling the visual perception module, the image acquisition module and the face detection and recognition module, and the problem that in the prior art, the safety is insufficient in the boarding pass authentication process can be solved.
Owner:RECONOVA TECH CO LTD
A security authorization access system and a security authorization access method for an automobile function interface
ActiveCN107147646BImplement secure authorized accessSignificant progressKey distribution for secure communicationUser identity/authority verificationManagement unitAccess method
The invention provides a security authorized access system for automobile functional interfaces, and a security authorized access method. The security authorized access system for the automobile functional interfaces comprises an application and strategy management unit, an application and strategy pre-setting unit and an intelligent vehicular terminal with a built-in security chip; the application and strategy management unit is separately connected to the application and strategy pre-setting unit and the intelligent vehicular terminal through a network; and the intelligent vehicular terminal is connected with the application and strategy pre-setting unit. Due to arrangement, distribution, security storage and execution of application program security strategies, security authorized access of the intelligent vehicular terminal to different types of automobile functional interfaces can be realized; therefore, hackers cannot access the automobile functional interfaces through a malicious program; automobile functional interface data is obtained or execution of an automobile ECU is controlled; therefore, the automobile functional interface access security of the intelligent vehicular terminal through an application program can be improved; and the security authorized access system has the advantages of being scientific in design, safe and reliable.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
A 5G-based industrial control security communication system and method
ActiveCN112055071BSolve the problem of limited storage resourcesSolve the problem of mutual secure communicationKey distribution for secure communicationPublic key for secure communicationSecure communicationCommunications system
The present invention relates to a 5G-based industrial control security communication system and method, including a cloud and at least two control terminals; the cloud includes a certificate server, a cloud security module and an industrial control server; the control terminal includes a 5G communication module, a control terminal security module and Industrial control module; the industrial control server communicates with the 5G communication module through the 5G network, and the control terminal is connected by the field bus. The cloud security module and the control terminal security module provide password and storage services. The password service includes random number generation, signature verification calculation, Encryption and decryption operations, session key generation and hash operations; the industrial control server calls the cloud security module password service, and the industrial control module calls the control terminal security module password and storage services; the certificate server generates public key certificates for the cloud and the control terminal, and the public key The certificate public key is written into the security module of the control terminal; the cloud security module and the security module of the control terminal store the corresponding private key to realize identity authentication and group secure encrypted communication between control modules.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Industrial control security communication system and communication method
ActiveCN112787819ASolve the problem of mutual secure communicationSolve authentication problemsUser identity/authority verificationSecurity arrangementCommunications securitySecure communication
The invention relates to an industrial control security communication system and communication method. The system comprises a cloud end and at least two control ends. The cloud comprises a certificate server, a cloud security module and an industrial control server; the control end comprises a 5G communication module, a control end safety module and an industrial control module; the industrial control server is connected with the 5G communication module, the control ends are in communication connection through a field bus, and the cloud security module and the control end security module provide password service and a security storage function; the password service function comprises random number generation, signature verification operation, encryption and decryption operation, session key generation and hash operation; the industrial control server calls the cloud security module to provide a password service function; the industrial control module calls the control end security module to provide a password service function and a security storage function; the certificate server generates and stores a public key certificate for the cloud end, and writes a public key into the control end security module; and the cloud security module stores a corresponding private key to ensure that communication between the industrial control modules is safe, reliable, simple and efficient.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
A method for safe communication of Internet of Vehicles
ActiveCN112804659BSolve the problem of mutual secure communicationSolve authentication problemsKey distribution for secure communicationPublic key for secure communicationSecure communicationInternet privacy
The invention relates to a secure communication method for the V2X network of vehicles that can realize secure encrypted communication in the V2X network of vehicles. Through an identity-based public key cryptography system, a safe and efficient group session key negotiation protocol is proposed to establish a protocol between parties involved in V2X communication. The group session key used for secure communication solves the problem of secure communication between V2X communication parties in the V2X Internet of Vehicles environment; through ultra-high reliability and ultra-low latency communication during the group session key negotiation process The 5G network generates the system parameters required for negotiation by the cloud, and provides the required relevant data for each participant, and assists all parties to solve the problem of identity authentication in the process of group session key negotiation. The present invention is based on 5G and V2X The characteristics of the Internet of Vehicles realize the V2X Internet of Vehicles identity authentication and group security encrypted communication, which effectively solves the problem of insufficient security in the existing technology, making the V2X Internet of Vehicles identity authentication and group security encrypted communication safe, reliable, simple and efficient.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Equipment binding method, device and system, storage medium and electronic device
PendingCN113596005AAddressing security deficienciesImprove securityKey distribution for secure communicationEngineeringReal-time computing
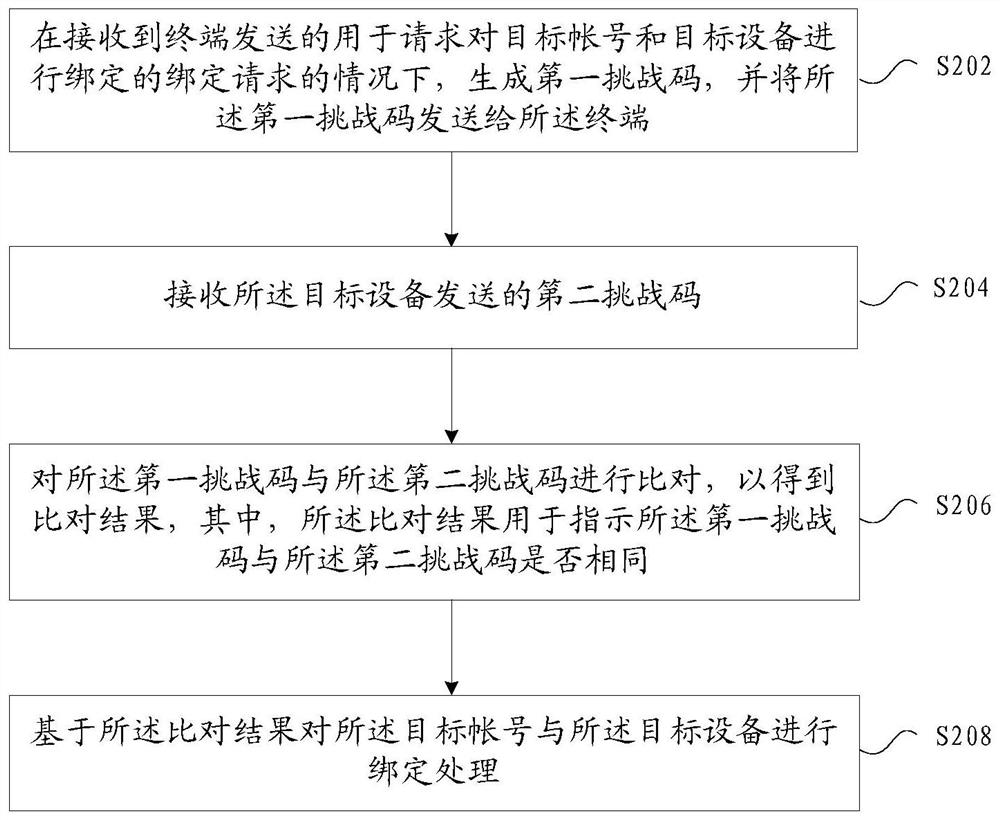
The embodiment of the invention provides an equipment binding method, device and system, a storage medium and an electronic device. The method comprises the steps that under the condition that a binding request sent by a terminal and used for requesting binding of a target account and target equipment is received, a first challenge code is generated, and the first challenge code is sent to the terminal; a second challenge code sent by the target equipment is received; the first challenge code and the second challenge code are compared to obtain a comparison result, and the comparison result is used for indicating whether the first challenge code and the second challenge code are the same or not; and binding processing is performed on the target account and the target equipment based on a comparison result. Through application of the equipment binding method and device, the problem of insufficient safety of the equipment binding method in the related technology is solved, and the effect of improving the binding safety is achieved.
Owner:杭州华橙软件技术有限公司
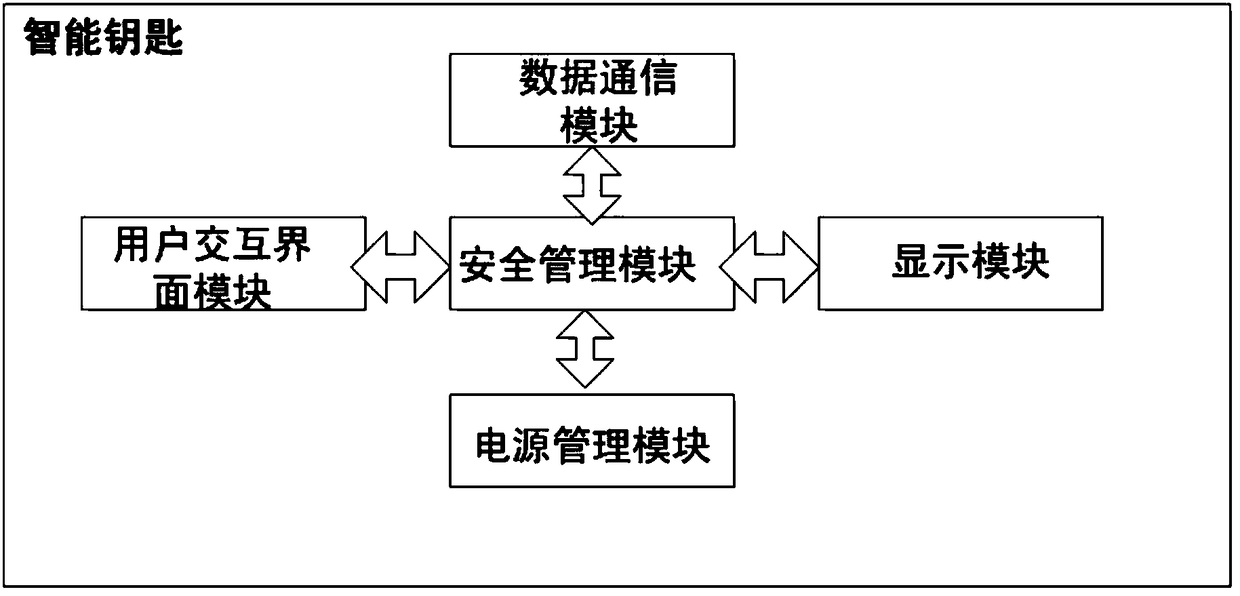
Smart key
InactiveCN109191117ASolve security deficienciesDigital data authenticationProtocol authorisationMobile paymentQuantum
The invention provides a smart key based on the quantum communication technology, wherein the problem that the security of the existing smart key used for mobile payment is insufficient is solved by setting a security management module based on the quantum key.
Owner:CAS QUANTUM NETWORK CO LTD
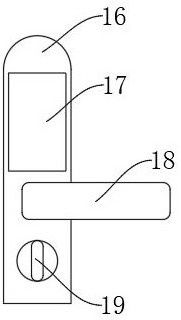
Intelligent door lock with visual function
InactiveCN111911007AImprove ease of useImprove home securityKeyhole guardsNon-mechanical controlsEngineeringFingerprint recognition
The invention discloses an intelligent door lock with a visual function in the technical field of door locks. The intelligent door lock comprises a door plate, a handle I and a clamping block. One side of the middle of one side wall of the door plate is connected with a shell I through a screw. A camera is embedded in the upper end of one side wall, far away from the door plate, of the shell I. Adisplay screen I is arranged below the camera. An operation panel is arranged below the display screen I. The shell I is provided with the handle I under the operation panel. A fingerprint identifieris embedded in one side wall, far away from the shell I, of the handle I. By arranging an NFC module, the unlocking modes of the intelligent door lock are more diversified, thus, a user has more standby unlocking modes, and the using convenience of the intelligent door lock is improved; and by arranging the camera, a microprocessor, a wireless network card and a display screen I, the user can check the picture outside a door in real time, the home safety of the user can be greatly improved, the user can further remotely check the picture shot by the intelligent door lock through a network, andthe intelligent door lock is quite practical.
Owner:唐翠华
A 5G-based V2X vehicle networking security communication system and method
ActiveCN112055330BEasy to useImprove securityKey distribution for secure communicationPublic key for secure communicationSecure communicationCommunications system
The present invention relates to a 5G-based V2X Internet of Vehicles security communication system and method, including a cloud, a vehicle terminal, a roadside terminal, and a pedestrian terminal, and the sum of the vehicle terminal, roadside terminal, and pedestrian terminal is at least two; the cloud includes a certificate Server, cloud security module and Internet of Vehicles server; the vehicle end includes the short-distance direct communication module of the vehicle end, the 5G communication module of the vehicle end, the security module of the vehicle end and the control module of the vehicle end; the roadside end includes the short-distance direct communication module of the roadside end, Roadside terminal 5G communication module, roadside terminal security module and roadside terminal control module; pedestrian terminal includes pedestrian terminal short-distance direct communication module, pedestrian terminal 5G communication module, pedestrian terminal security module and pedestrian terminal control module; according to 5G and V2X The characteristics of the Internet of Vehicles realize the V2X Internet of Vehicles identity authentication and group secure encrypted communication, making the V2X Internet of Vehicles identity authentication and group secure encrypted communication safe, reliable, simple and efficient.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Electronic antitheft cabinet
The invention discloses an electronic antitheft cabinet. The electronic antitheft cabinet comprises a lower fixing plate, the outer wall of the upper end of the lower fixing plate is fixedly connected with a three-phase asynchronous motor, the outer wall of the upper end of the three-phase asynchronous motor is fixedly connected with an upper transmission shaft, the outer wall of the upper end of the upper transmission shaft is fixedly connected with an upper supporting plate, and the outer wall of the upper end of the upper supporting plate is fixedly connected with rotatable file cabinets; and each rotatable file cabinet comprises a fixing wrench, a rotating turning-over cover, a rotating shaft, a protection outer shell, a fixing clamping plate and fixing connection belts, the fixing wrenches are fixedly connected to the middles of the outer walls of the upper ends of the rotating turning-over covers, the rotating turning-over covers are rotatably connected to the side walls of the upper ends of the protection outer shells, and the rotating shafts are fixedly connected to the side walls of the lower ends of the protection outer shells. Through the arrangement of an adjustable stretchable cover and the rotatable file cabinets, safety performance of the electronic antitheft cabinet can be greatly improved, and meanwhile operators can sort various files conveniently.
Owner:岳西县吉奥电子器件有限公司
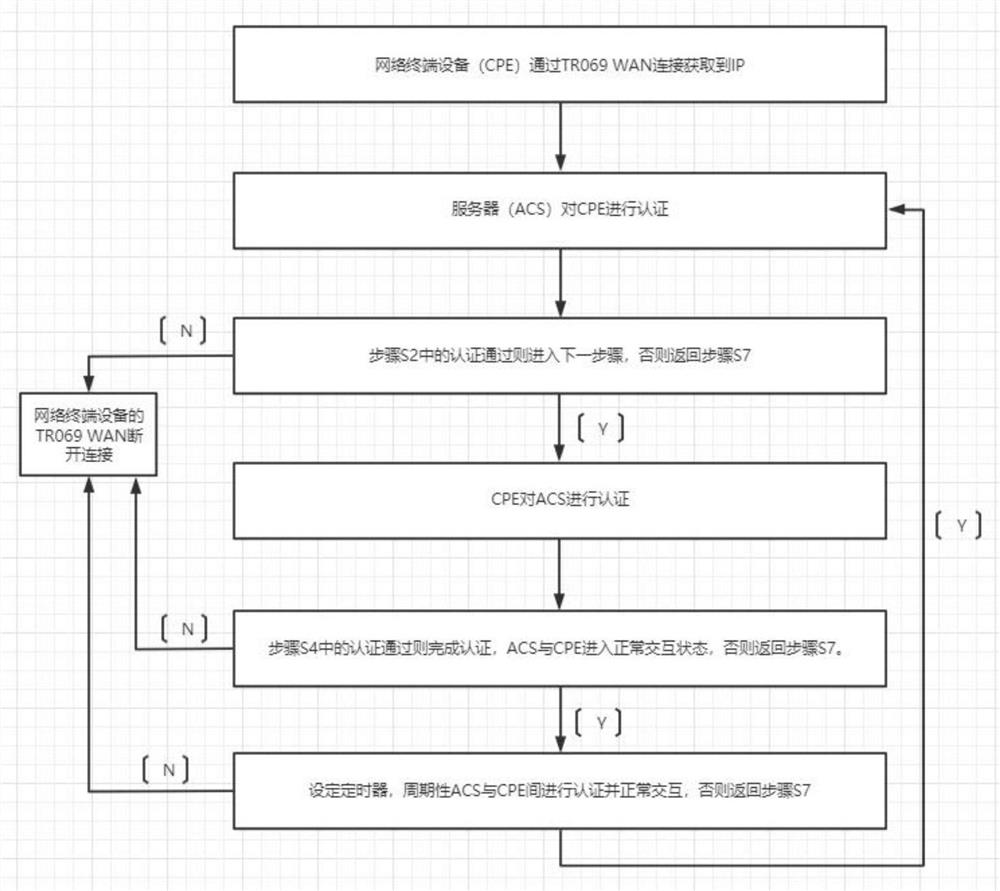
Method for authentication between CPE and ACS based on MD5 algorithm
The invention discloses a method for authentication between CPE and ACS based on an MD5 algorithm, and relates to the field of authentication methods. According to the method for authentication between the CPE and the ACS based on the MD5 algorithm, network terminal equipment (CPE) obtains an IP through TR069 WAN connection, and a server (ACS) authenticates the CPE; (matching an inform message special node, and generating a secret key through MD5 calculation of a set meaningful string of characters), if the authentication in the step S2 is passed, entering the next step, otherwise, returning to the step S7; (the ACS replies an InformResponse message Message node: whether the CPE passes the authentication or not, and a set string of characters are calculated by MD5 to generate a key). According to the authentication method between the CPE and the ACS based on the MD5 algorithm and the authentication method between the CPE and the ACS based on the MD5 algorithm, while the cost is relatively low and the method has general applicability, the problem that the security is insufficient when a server based on a TR069 protocol communicates with network terminal equipment is solved, and the risks that the server is easy to crack and communication contents are tampered or intercepted are avoided.
Owner:SHENZHEN C-DATA TECH CO LTD
How to build the flask security module
InactiveCN107547520BSolve security deficienciesImprove securityTransmissionMobile WebDiscretionary access control
The invention provides a Flask safety module, a construction method and a mobile Web system. The Flask safety module comprises a safety server, an object manager and an access vector buffer, wherein the safety server is used for providing a safety strategy decision, keeping mapping between a safety identifier and a safety context, allocating the safety identifier to a newly established object, controlling contents of the access vector buffer to be correct and consistent; the object manager is respectively in communication connection with the safety server, the access vector buffer and a hook in the mobile Web system, and is used for providing an interface for carrying out re-access, marking and multi-instance decision from one safety server, providing one access vector buffer to allow theobject manager to buffer an access decision result and providing the object manager to receive and process a safety strategy change notification, wherein the multi-instance decision stipulates which member of a multi-instance resource set is accessed to by a specific request; and the access vector buffer is used for buffering a preset safety strategy. The problem of poor safety caused by a case that an existing mobile Web system adopts discretionary access control can be solved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com