Method for authentication between CPE and ACS based on MD5 algorithm
An algorithm and equipment technology, applied in the field of authentication between CPE and ACS based on the MD5 algorithm, it can solve the problems of non-universal applicability, security and increase equipment cost, and achieve the effect of saving process and labor, reducing cost and improving service life.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
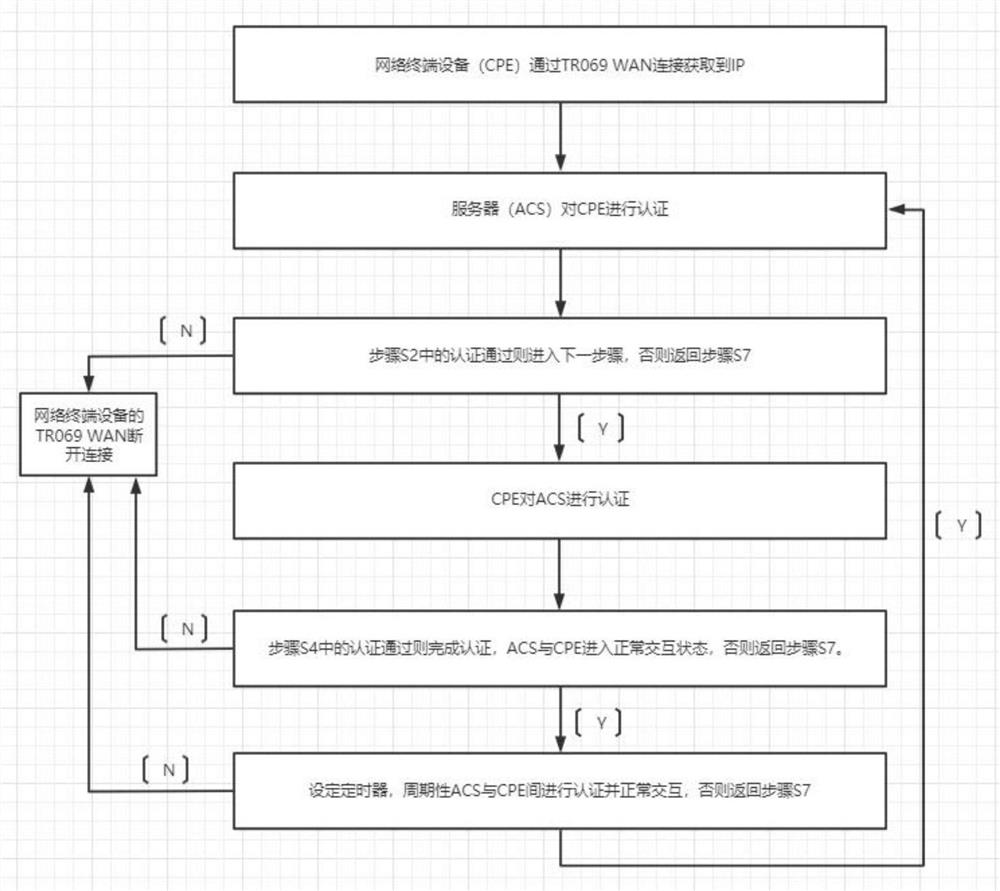
[0023] The embodiment of the present invention provides an intelligent network diagnosis method based on the HGU home gateway, such as figure 1 Shown, below in conjunction with accompanying drawing, the present invention is described in further detail, comprises the following steps:
[0024] Step S1: The network terminal equipment (CPE) obtains the IP through the TR069 WAN connection; (after the TCP protocol interaction is completed);
[0025] Step S2: the server (ACS) authenticates the CPE; (matching the special node of the inform message, and generating a key after MD5 calculation of a default meaningful string of characters);
[0026] Step S3: if the authentication in step S2 is passed, enter the next step, otherwise return to step S7; (ACS replies to the InformResponse message Message node: whether the CPE is authenticated, and a string of default characters generates a key after MD5 calculation);
[0027] Step S4: The CPE authenticates the ACS (matching the Message key c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com