Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72results about How to "Prevent repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
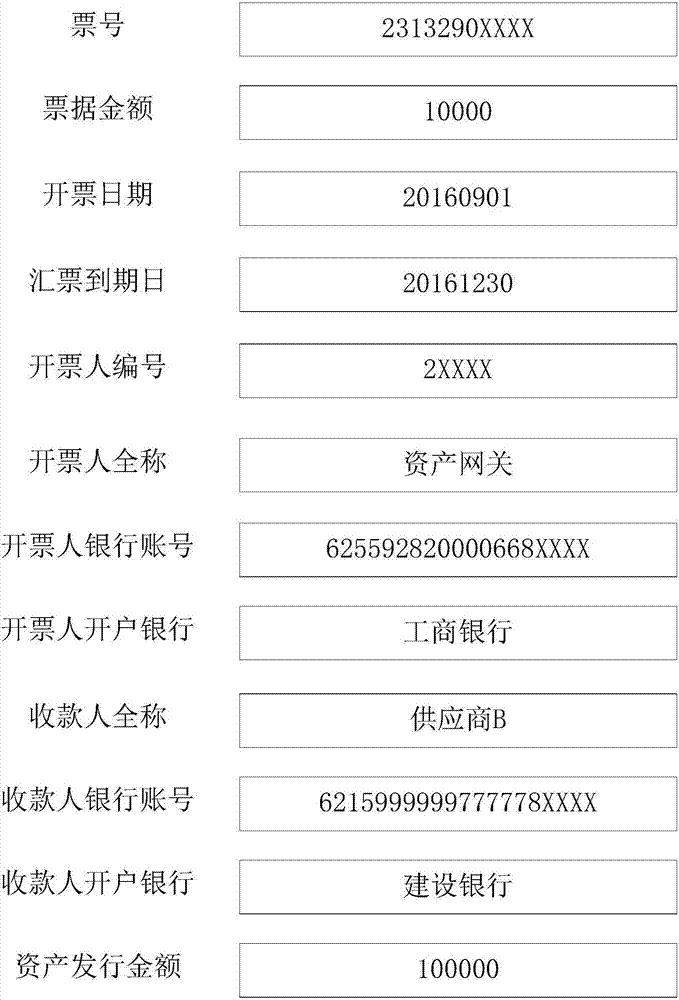
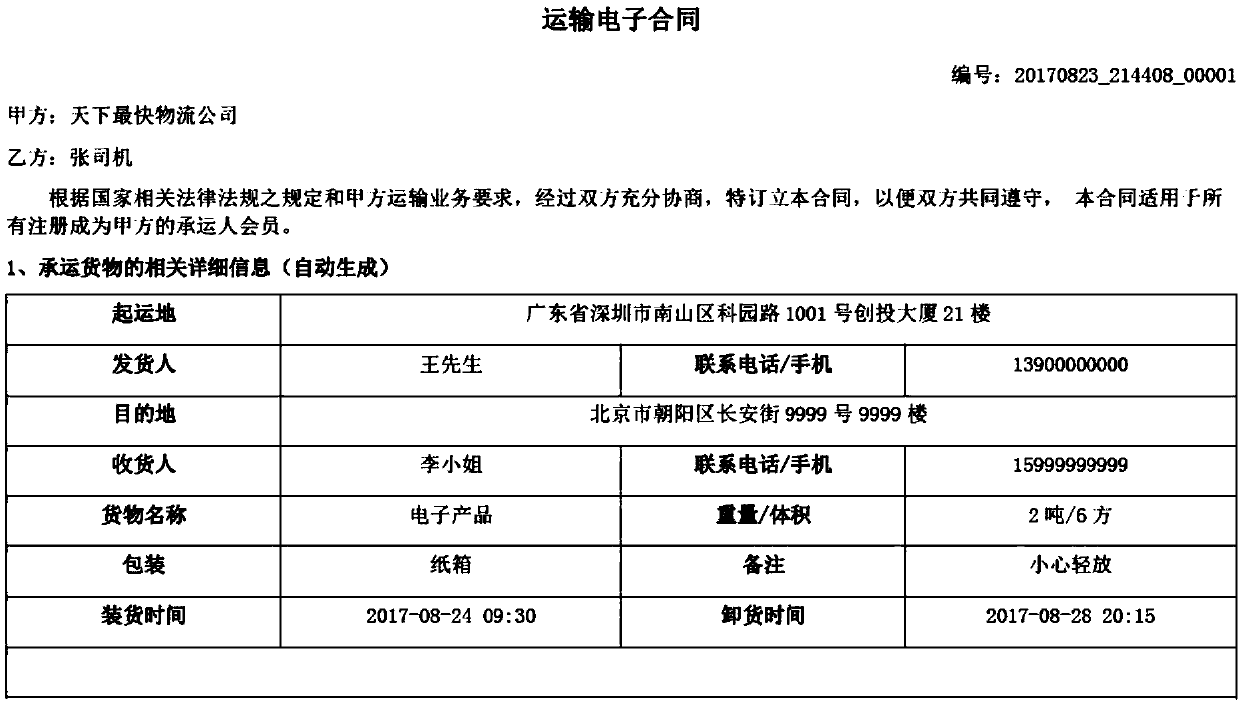
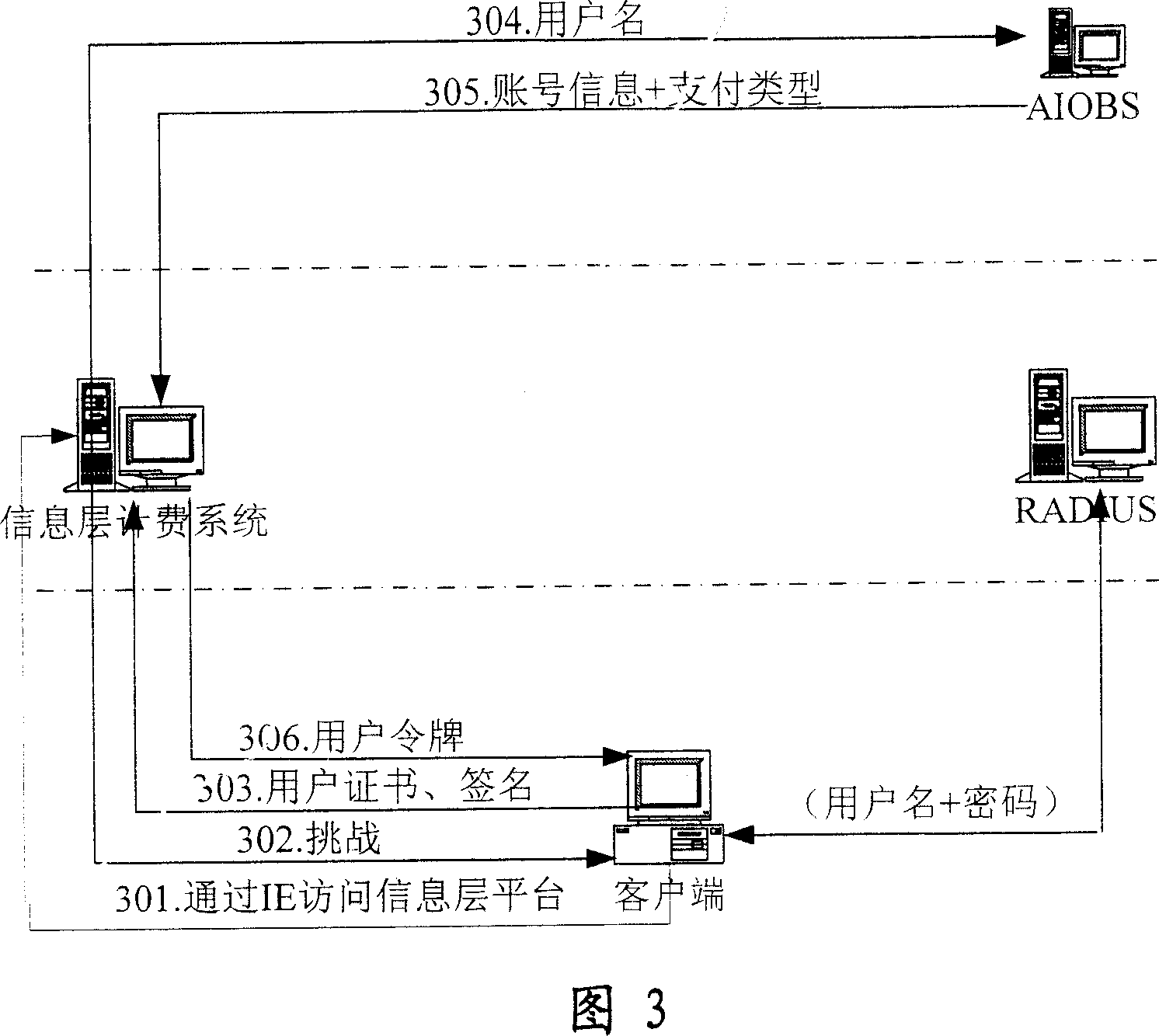
Electronic bill management method and device
ActiveCN106952094APrevent tamperingPrevent repudiationCryptography processingBilling/invoicingDatabaseManagement system
The invention discloses an electronic bill management method and device, and belongs to the technical field of network. The method comprises the steps that a bill issuing request of a first user is received, wherein the bill issuing request carries original bill information; a first bill account corresponding to the first user is generated based on the original bill information, and the account information of the first bill account is stored in the account table in an electronic bill management system; a second block is generated based on the bill issuing request, the first bill account and the block header feature value of the first block in the block chain in the electronic bill management system, wherein the first block is the previous block of the second block on the block chain, and the second block is used for recording the bill issuing event of the first user; and an issuing success message is transmitted to the first user, wherein the issuing success message carries the first bill account. The security and the reliability of transaction information can be guaranteed by the electronic bill management method and device.
Owner:TENCENT TECH (SHENZHEN) CO LTD
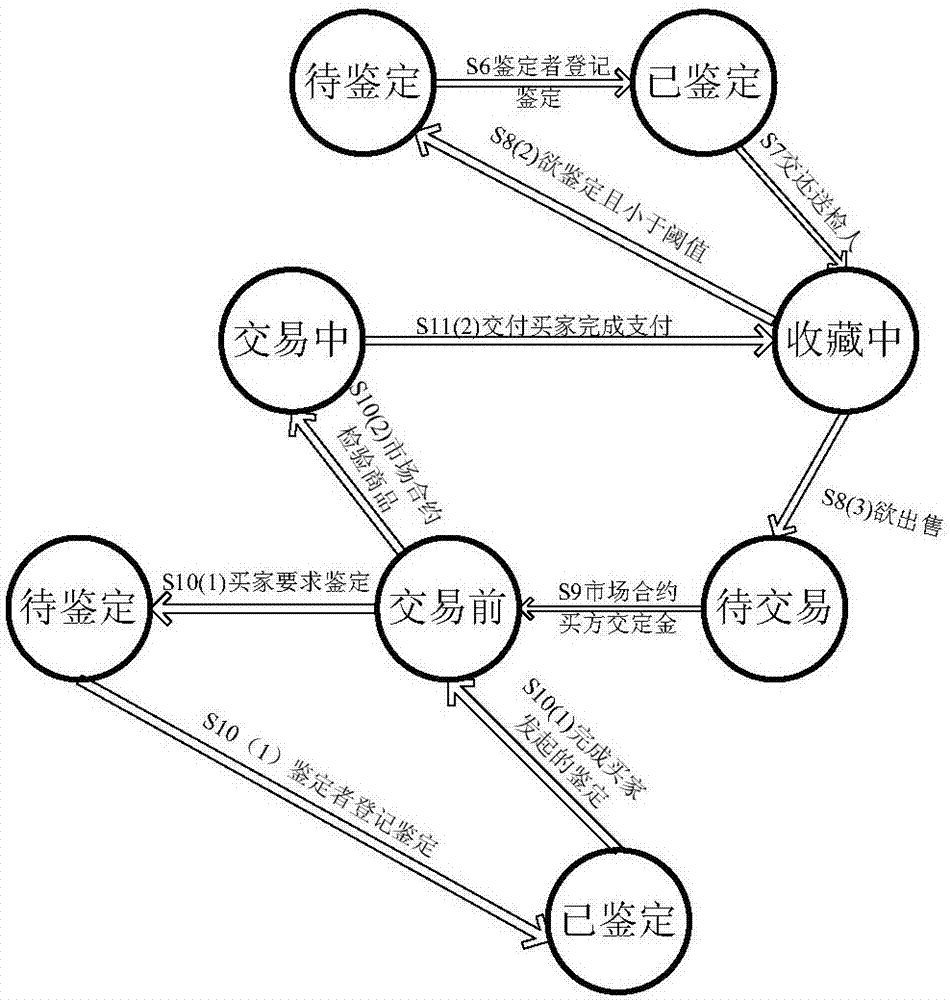
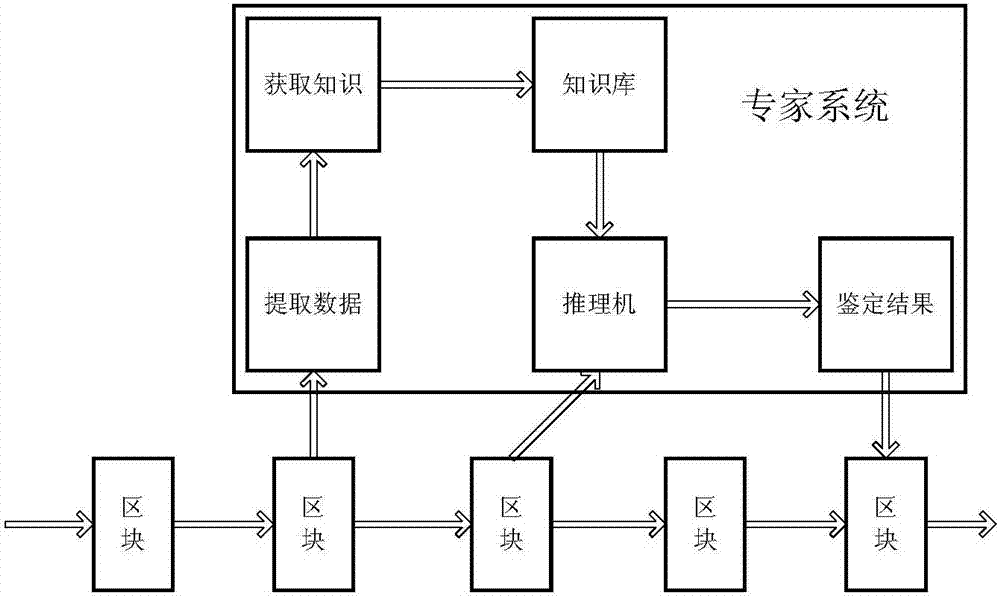
Artwork circulation, authentication and registration method based on blockchain and expert system
InactiveCN107194587APrevent repudiationAvoid harmBuying/selling/leasing transactionsResourcesSmart contractIdentity privacy
The invention discloses an artwork circulation, authentication and registration method based on a blockchain and an expert system. According to the method, registration for an authentication result of an artwork is completed by smart contracts of authentication markets, and then the artwork is allowed to be circulated and recorded in smart contracts of trading markets. According to the method, block information accumulated in the smart contracts of the authentication markets is utilized, and knowledge is acquired outside the blockchain by machine learning of authentication information, the expert system is established, and a need for the commodity authentication validity and authentication result checking is met through providing an authentication suggestion for the artwork of which an inquiry is to the expert system. In addition, under the premise of protecting the identity privacy of a trader from disclosure, the smart contracts of the trading markets and the smart contracts of the authentication markets are combined, and cultural relic registration is established to specifically record a circulation state and an authentication result of a cultural relic. Ultimately, decentralization is realized in a trading process of the artwork by virtue of the above-mentioned method, and gain effects of creditability, convenience and a low cost are achieved at the same time.
Owner:JINAN UNIVERSITY
Big data oriented ownership confirmation method
ActiveCN107196762AIntegrityFairKey distribution for secure communicationUser identity/authority verificationThird partyData source
The invention discloses a big data oriented ownership confirmation method. An ownership confirmation process comprises an initialization phase, a sampling challenge phase and an ownership confirmation result chaining phase. The initialization phase comprises the steps that a certificate authority CA finishes signing various participating entity public key certificates of a network system, a data source provider P finishes selecting a signing key pair and an encryption key pair, blocking data and generating data block authentication information, and a third party ownership confirmation center T finishes authenticating block chain ownership registration commercial network B. The sampling challenge phase comprises the step that the third party ownership confirmation center T finishes sampling and authenticating data blocks. The ownership confirmation result chaining phase comprises the step that the block chain ownership registration commercial network B finishes registering an ownership confirmation result. The ownership confirmation method is the big data oriented ownership confirmation method based on the third party ownership confirmation center and a block chain, and the data ownership definition fairness and the completeness and credibility of the ownership result can be effectively ensured.
Owner:GUIZHOU UNIV
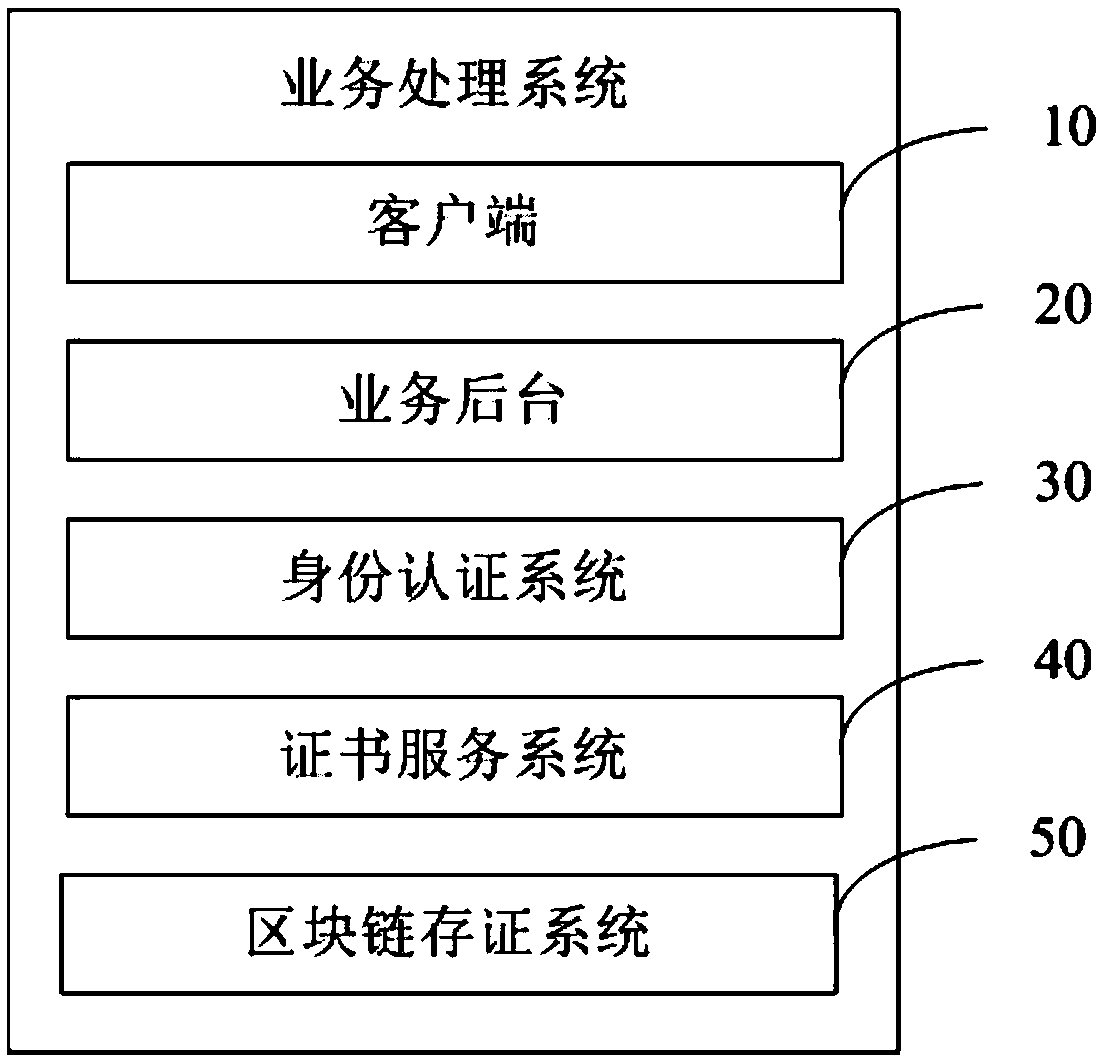
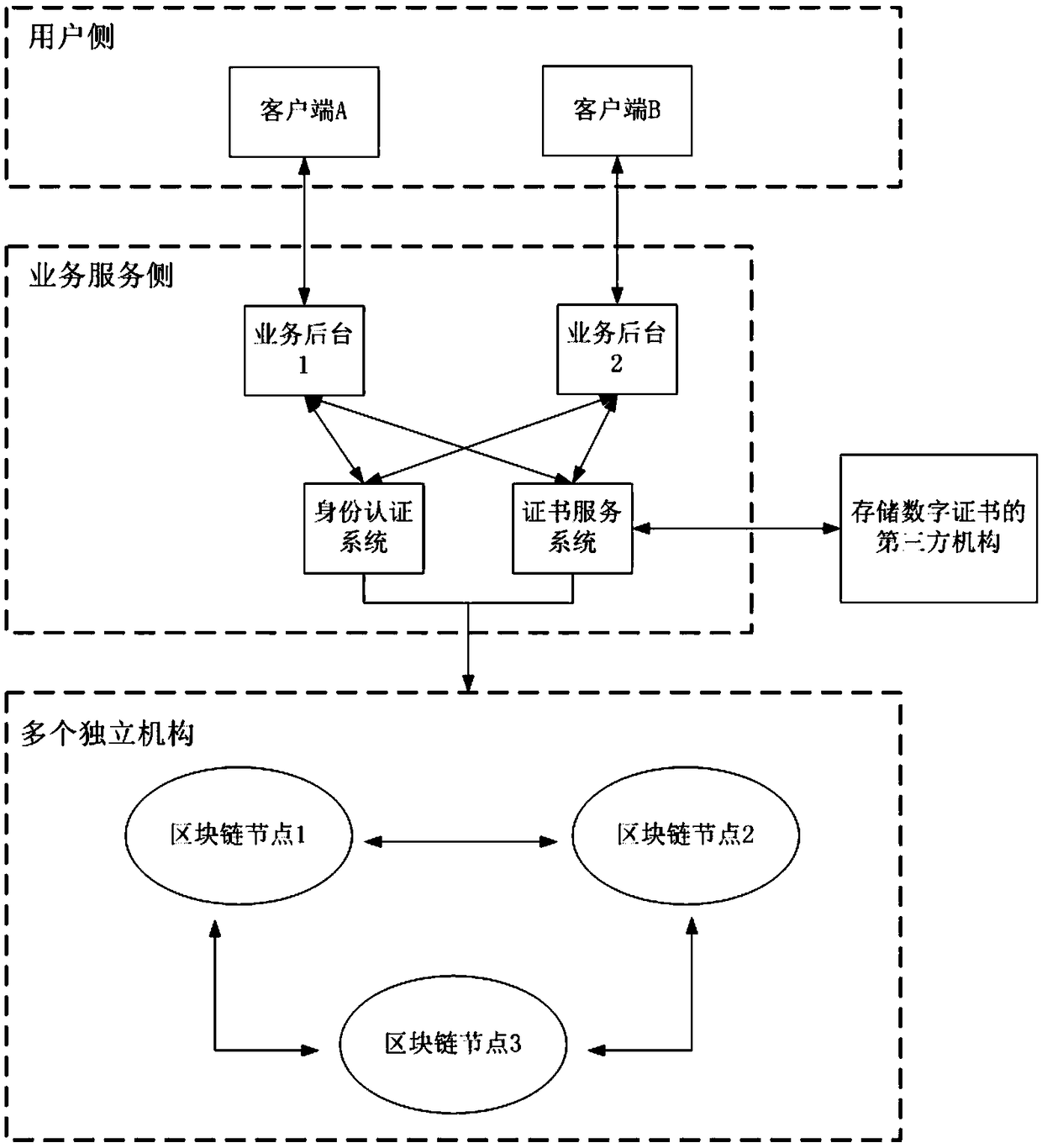
Digital certificate use method, system and storage medium based on block chain
ActiveCN108881290AImprove the safety of usePrevent repudiationUser identity/authority verificationThird partyDigital signature
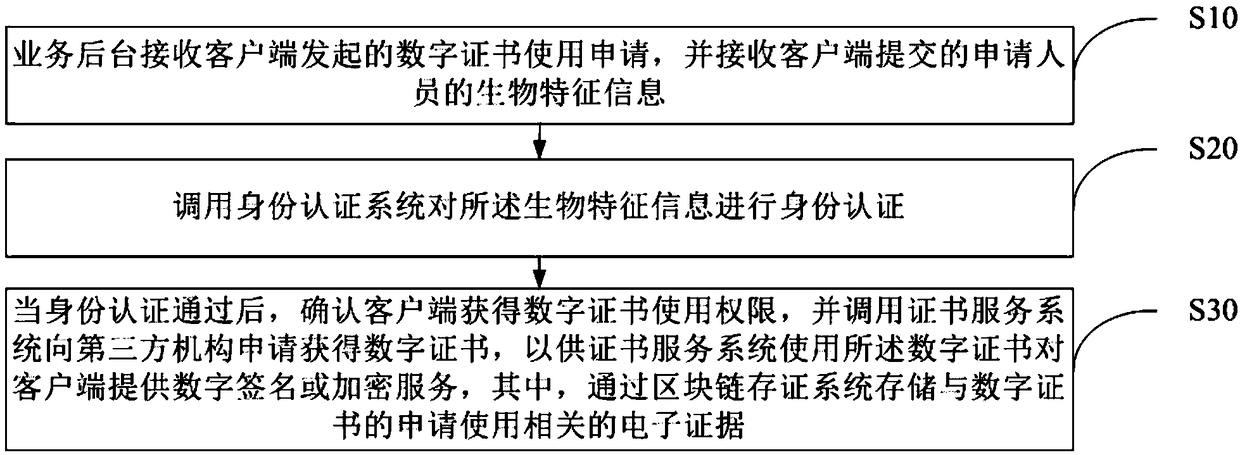
The invention discloses a digital certificate use method based on a block chain. The method comprises the following steps: receiving a digital certificate use application initiated by a client througha business background, and receiving biological feature information, submitted by the client, of application personnel; calling an identity authentication system to perform identity authentication onthe biological feature information; when the identity authentication is passed, confirming that the client acquires the digital certificate use permission, and calling a certificate service system toapply a digital certificate from a third-party mechanism, thereby enabling the certificate service system to provide digital signature or encryption service for the client by using the digital certificate, wherein the block chain storage system stores an electronic evidence related to the application use of the digital certificate. The invention further discloses a business processing system anda computer readable storage medium. The security and the convenience of the digital certificate use are improved, and the issuing cost and the use cost of the certificate are saved at the same time.
Owner:WEBANK (CHINA)
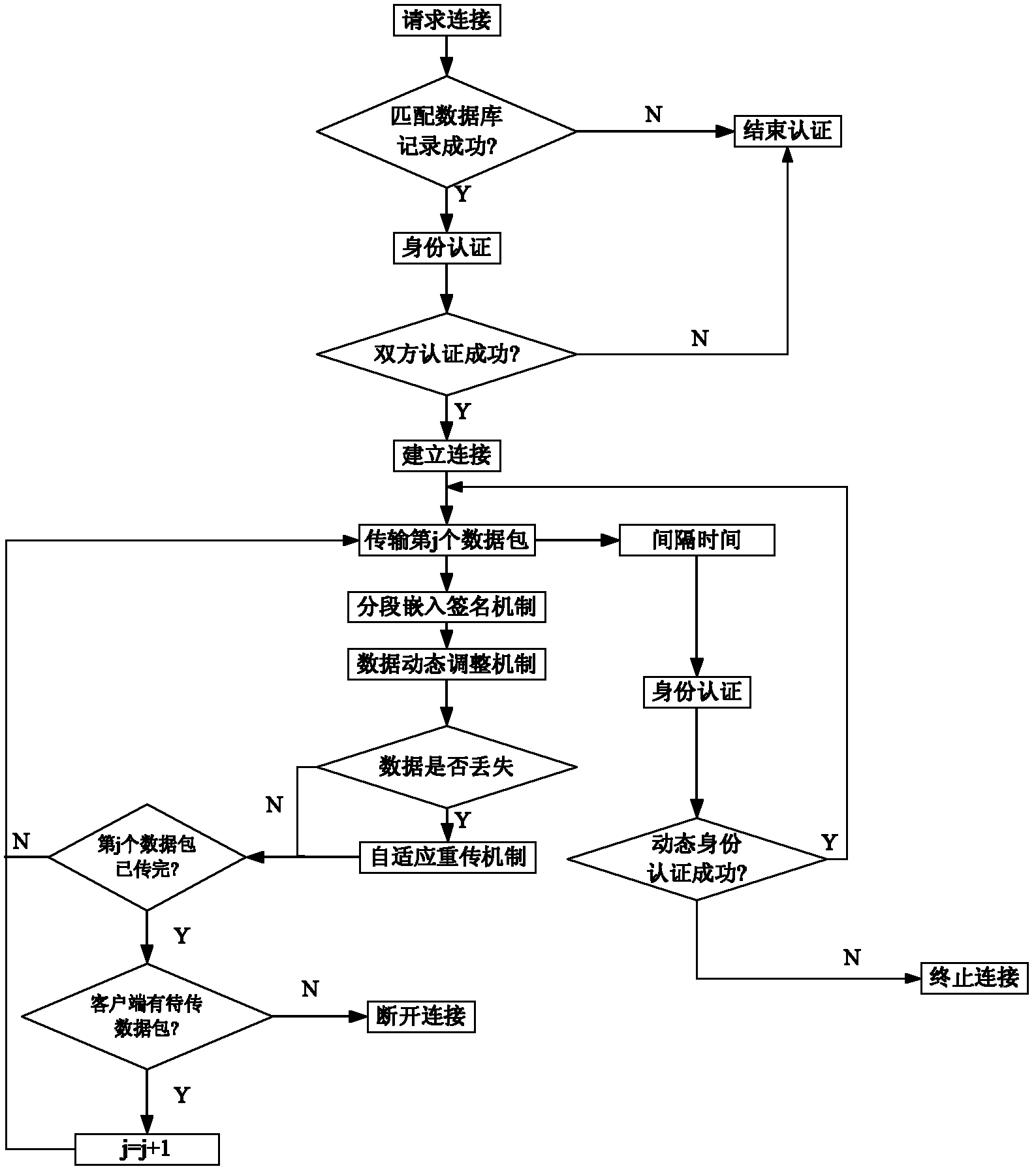
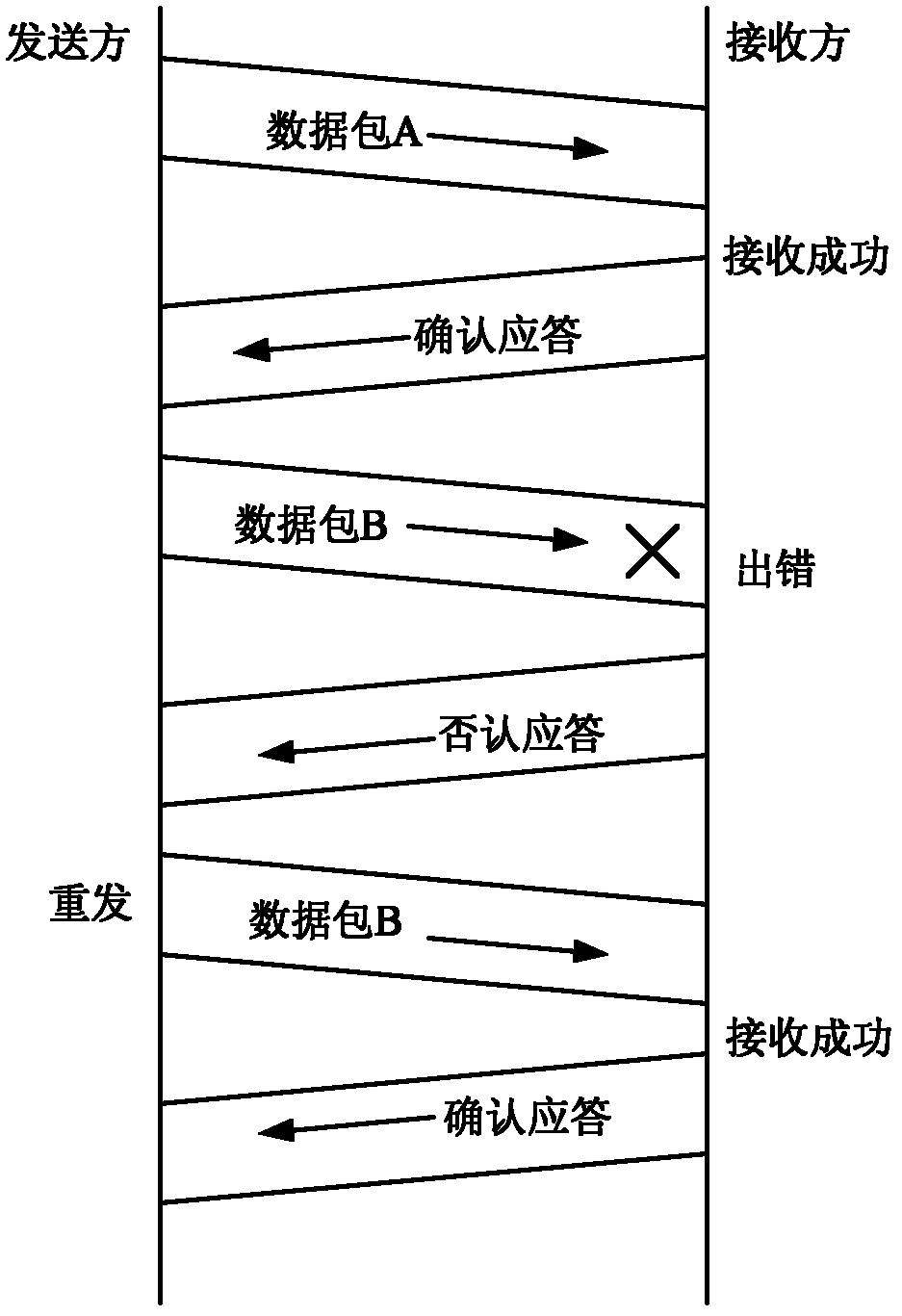
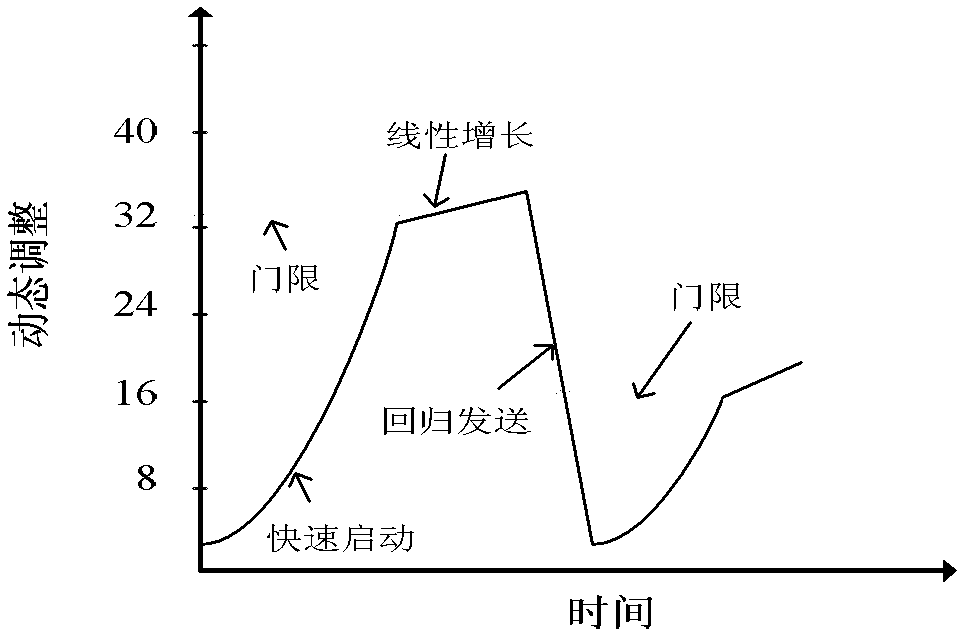
Adaptive retransmission and signature segmented embedding data transmission method
InactiveCN102664893AIntegrity guaranteedFirmly connectedError prevention/detection by using return channelUser identity/authority verificationSelf adaptiveData transmission
The invention discloses an adaptive retransmission and signature segmented embedding data transmission method, which is characterized by comprising the following steps of: matching the identity information of a user in a safety database by using a server, and finishing the method if the identity information of the user fails to be matched; performing mutual identity authentication on the user and the server, and finishing the method if the mutual identity authentication of the user and the server fails; and performing data transmission, and in a data transmission process, performing the steps of performing dynamic identity authentication on the server and the user at random time intervals, terminating connection if the dynamic identity authentication of the server and the user fails, embedding a signature in a segmented way, judging whether transmitted data has an error or is lost or not in an acknowledgement way, performing data retransmission if the transmitted data has the error or is lost, judging whether the data transmission is finished or not, and terminating the connection when the data transmission is finished.
Owner:CHONGQING UNIV OF TECH
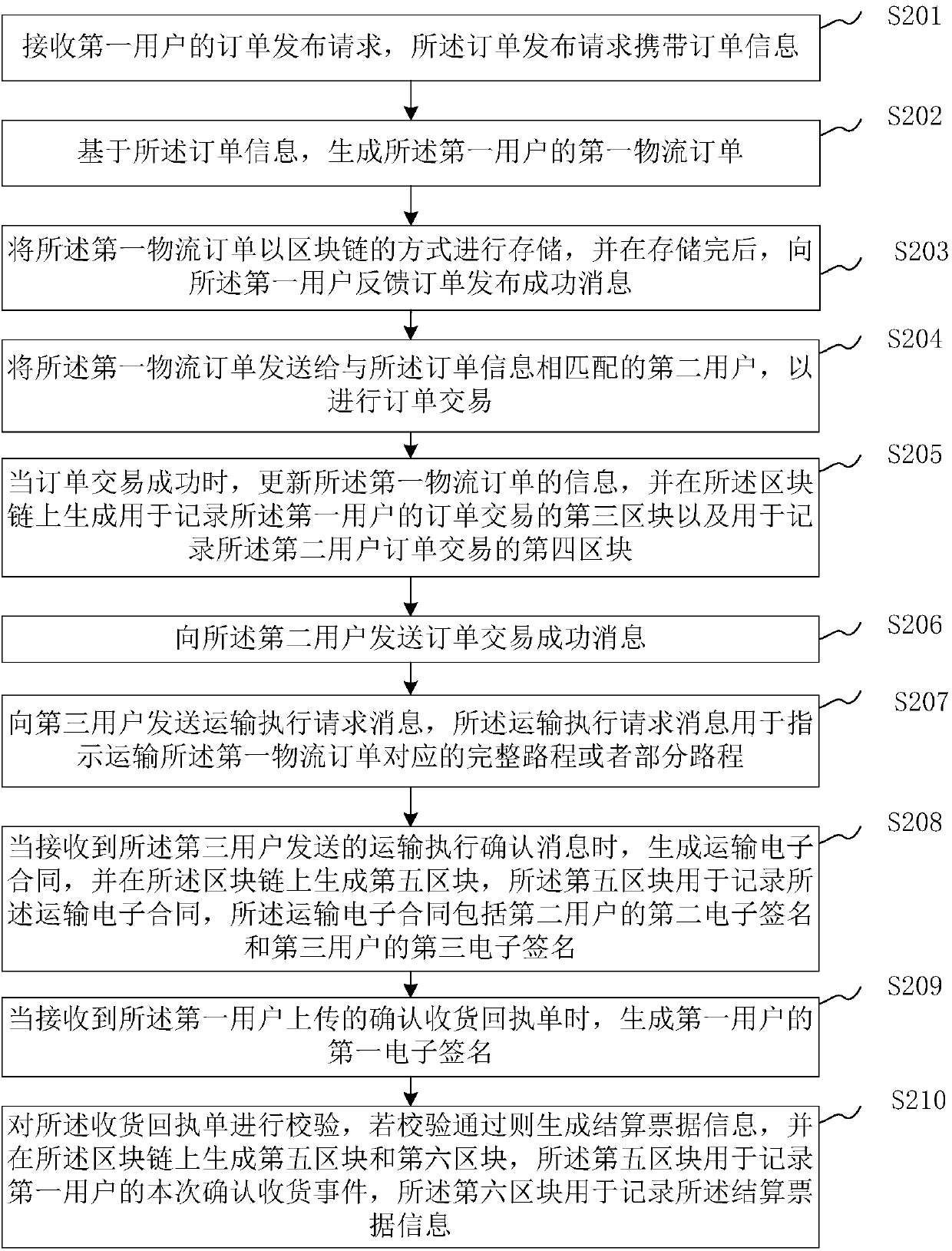
Electronic logistics document management method and device
InactiveCN107730165APrevent tamperingPrevent repudiationLogisticsLogistics managementNetwork communication
The invention is applicable to the technical field of network communication, and provides an electronic logistics document management method and an electronic logistics document management device. Theelectronic logistics document management method comprises the steps of: receiving an order release request of a first user, wherein the order release request carries order information; generating a first logistics order of the first user based on the order information; and storing the first logistics order in a blockchain mode, and feeding back an order release success message to the first user after completion of storage. According to the electronic logistics document management method and the electronic logistics document management device, the generated first logistics order is stored in ablockchain mode, thus the tampering can be detected by means of the blockchain when the logistics order information is tampered, thereby avoiding the user from tampering or denying the released orderinformation, and ensuring the security and reliability of electronic logistics document information.
Owner:前海云链科技(深圳)有限公司
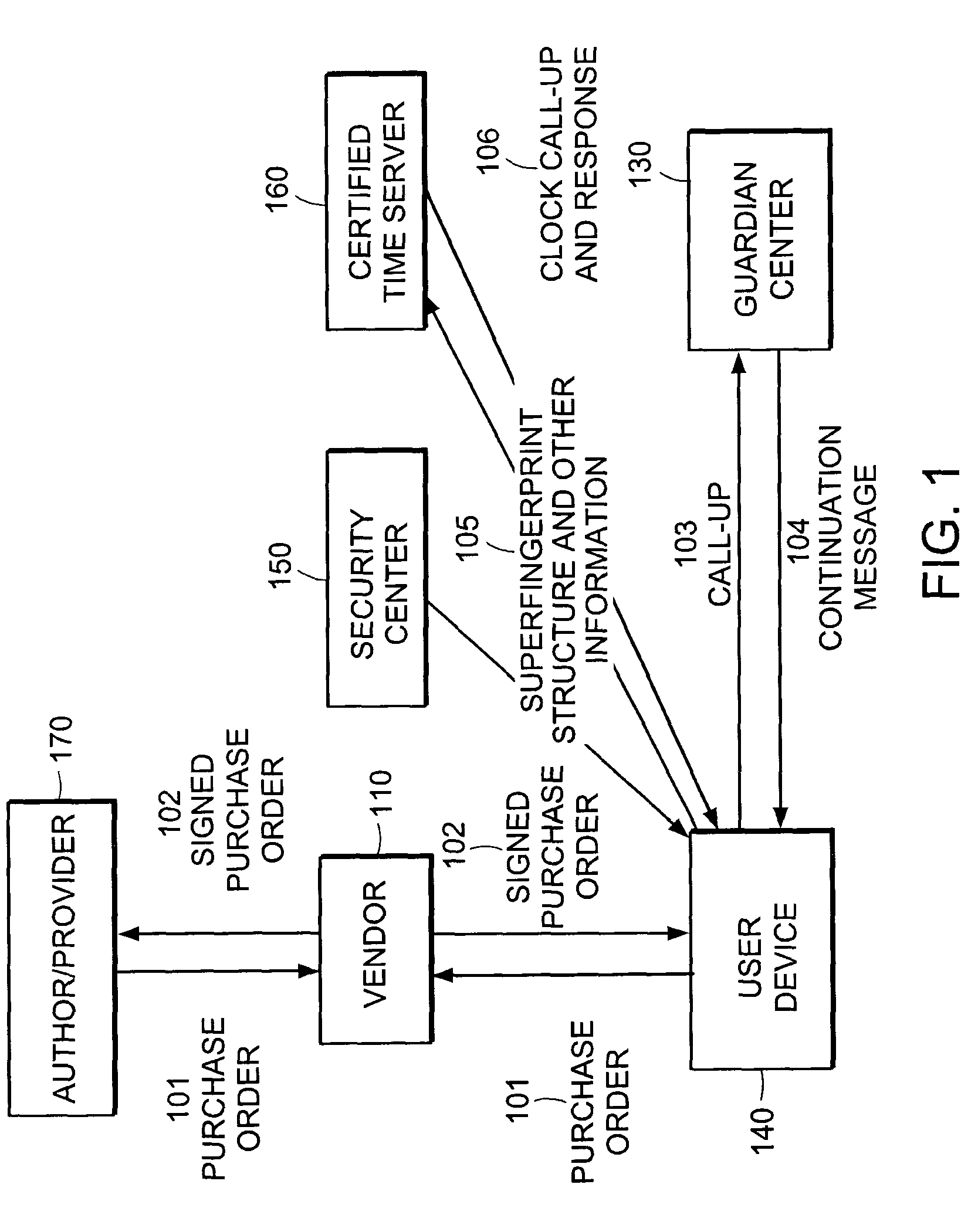
Method and apparatus for protecting information and privacy
InactiveUS7406593B2Reduce in quantityRepudiation of a call-up message is preventedDigital data processing detailsUnauthorized memory use protectionUser deviceProtection system
A system for protecting software against piracy while protecting a user's privacy enables enhancements to the protection software in a user device and extended protections against piracy. The protection system allows the user device to postpone validation of purchased tags stored in a tag table for installed software and to re-establish ownership of a tag table to recover from invalidation of a tag table identifier value resulting from revelation of a tag table identifier value. Continued use of the tag table is provided by the use of credits associated with a tag table. A protection center is protected against denial of service attacks by making calls to the protection center cost time or money to the attackers.
Owner:RPX CORP
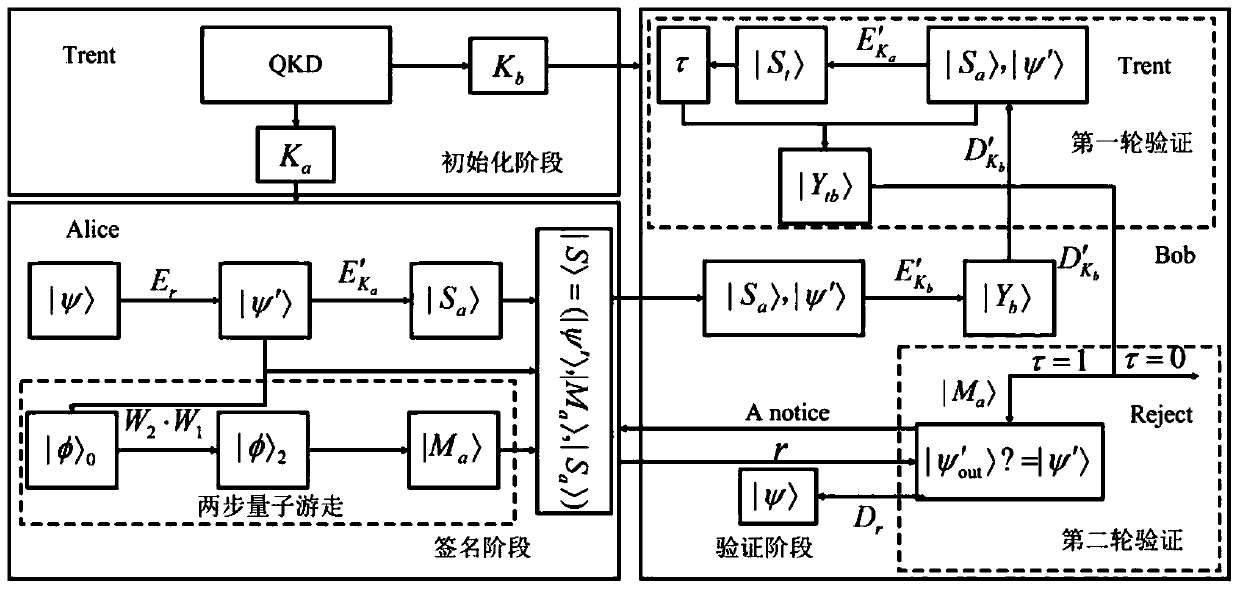
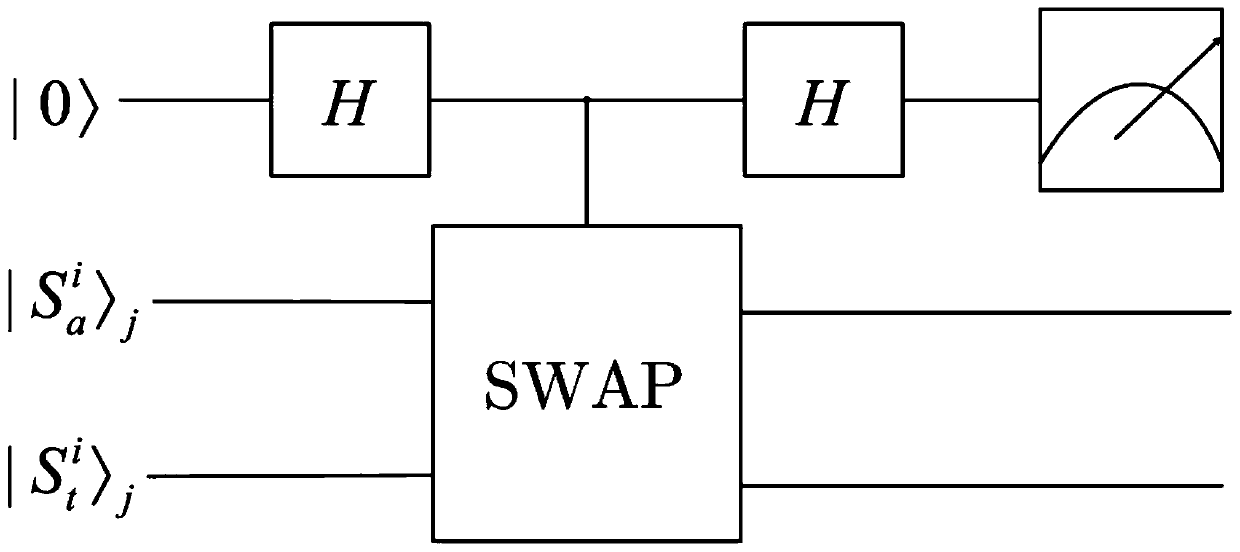
Arbitration quantum signature method based on glass color sampling random unitary operation
ActiveCN111162913AReduce overheadImprove efficiencyKey distribution for secure communicationUser identity/authority verificationCommunications systemInformation design
The invention discloses an arbitration quantum signature method based on glass color sampling random unitary operation. The arbitration quantum signature method comprises an initialization stage, a signature stage and a verification stage. The initialization stage is used for preparing a secret key and establishing a communication system; the signature stage is used for selecting a proper signature algorithm to design the signature of the transmission information; and the verification stage is used for verifying the validity of the signer and the integrity and authenticity of original information. According to the invention, unitary operation encryption based on glass color sampling is adopted in the signature of transmission information designed in arbitration quantum signature; an m-modequantum state is transferred by adopting quantum walk invisible transmission based on a graph, a necessary entanglement state for invisible transmission does not need to be prepared in advance, the safety is higher by adopting a common channel and a random tuple, and a glass color sampling model and a quantum walk invisible transmission model are proved to be realized through a linear optical network; and therefore, the method disclosed by the invention is high in safety, resource-saving and easy to implement in experiment.
Owner:CENT SOUTH UNIV
Safety product license management method based on XML encryption and digital certificate
InactiveCN101694685AGuaranteed confidentialityPrevent tamperingDigital data authenticationTransmissionTamper resistanceSoftware development process
The invention relates to a safety product license management method based on XML encryption and a digital certificate, which comprises the steps of applying a license, generating the license, verifying the license and checking the license. The invention ensures the confidentiality, the non-repudiation and the tamper resistance during the software distribution based on the safety of symmetric key / public key and private key theory; a product has a certain popularity in the product inside an enterprise and can be repeatedly used by every product, thereby effectively lowering the software development cost of the enterprise, improving the efficiency of the critical development of the enterprise, and promoting the image of the product of the enterprise.
Owner:LINKAGE SYST INTEGRATION
Internet access system and method
InactiveCN1925401AEasy to usePromote business developmentKey distribution for secure communicationUser identity/authority verificationClient-sideIdentification device
This invention provides one network interface system, which comprises the following parts: outlet identification device to store user identification information to provide to customer terminal; customer terminal to provide network interface service and to provide interface network or business to network. This invention also provides one interface method, which comprises the following steps: getting user identification information from outside device; customer ends uses identification to load network to determine user legal information to realize network interface.
Owner:中国联合网络通信有限公司北京市分公司
A mail receiving and sending system based on a block chain
ActiveCN109831374AEnsure safetyPrevent repudiationData switching networksSecuring communicationChain systemBlockchain
The invention belongs to the technical field of block chains, and particularly relates to a mail receiving and sending system based on a block chain. Wherein the mail receiving and sending system comprises a block chain mail client and a mail block chain system, and the block chain mail client is used for receiving and sending mails, encrypting sent mail contents and decrypting the received mail contents; the mail block chain system is used for storing transaction data generated in the mail receiving and sending process through each block chain node. Through the system, the user mail plaintextdata are encrypted at the block chain mail client, so that the security of the data at the sending and transmission stages is ensured. Even if the data is intercepted by a malicious program, the ciphertext is obtained, if the ciphertext data is tampered, the check code is invalid, the verification of the block chain node is not passed, and the repudiation behavior of the user can be effectively prevented due to the characteristics of decentralized storage, non-tampering and the like of the block chain.
Owner:SHENZHEN LIANBAO TECH CO LTD
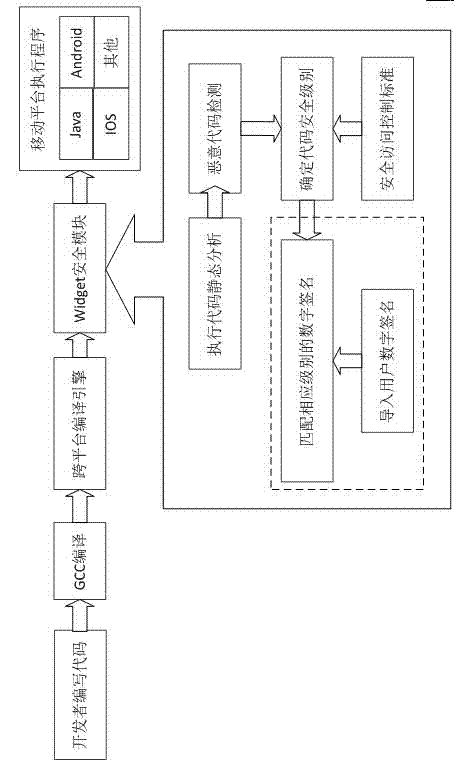
Digital signature authentication method facing mobile widget
The invention provides a digital signature authentication method facing a mobile widget, which comprises the following steps that: a certificate is generated; a developer submits a developer certificate application to a registration authority RA in a certification authority, the RA audits related contents and determines whether to examine and approve a request of the certificate application, the RA submits the application request and information that the approval is passed to a certificate authority CA after the certificate application passes the approval, and the CA signs and issues the certificate; the signature is carried out; after the certificate application is approved to register, an application program at the RA end initializes information of an applicant, issues the certificate to the developer, sends a privacy key, the CA adds related information of the certificate applicant in a LDAP (Lightweight Directory Access Protocol) directory server, the developer signs a program passing compilation on a development platform after receiving the privacy key and uploads the signed program to a Web server; and the verification is carried out. The invention combines a public key infrastructure PKI and an oval curve encryption mechanism and implements the certificate application, the certificate issuing, the certificate acquisition, the widget signature and the widget verification of the mobile widget developer are implemented.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
A data exchange method
InactiveCN102281303APrevent repudiationPublic key for secure communicationUser identity/authority verificationDigital dataData terminal
A data exchange method provided by the present invention includes the steps: a data sending end sends a data exchange request to a server; the server generates a session key according to the above request, and encrypts the session key and sends it to the data sending end ; The data sending end imports the ciphertext of the session key into the USBKEY of the data sending end, and after digitally signing and encrypting the data to be exchanged, designate the data receiving end that receives the data; the data The sending end packages the public key certificate of the data receiving end, the data ciphertext and the digital signature of the data and sends it to the server; the server parses the public key of the data receiving end from the public key certificate of the data receiving end, and uses the public key Encrypting the session key and adding the ciphertext of the session key into the data packet and sending it to the data receiving end; the data receiving end decrypts the data ciphertext in the data packet. This enables efficient enterprise-level data exchange.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Methods and devices for generating and distinguishing anti-counterfeiting paper document
ActiveCN104361293ASolve the problem that it is impossible to verify whether the paper anti-counterfeiting document is signed by the signer himselfPrevent repudiationDigital data protectionDigital data authenticationCiphertextElectronic signature
The invention provides methods and devices for generating and distinguishing an anti-counterfeiting paper document. In the method for generating the anti-counterfeiting paper document, document information, an electronic signature, an anti-counterfeiting ciphertext, an anti-counterfeiting signature picture and a data storage carrier are bound together, so that the generated anti-counterfeiting paper document has functions of preventing repudiation, preventing tampering and preventing copying. In addition, the distinguishing method can distinguish whether the anti-counterfeiting paper document is signed by a signer, tampered and copied; further, the anti-counterfeiting paper document can be comprehensively protected, and the safety of the anti-counterfeiting paper document is improved.
Owner:BEIJING CERTIFICATE AUTHORITY
E-mail transmitting method and system thereof
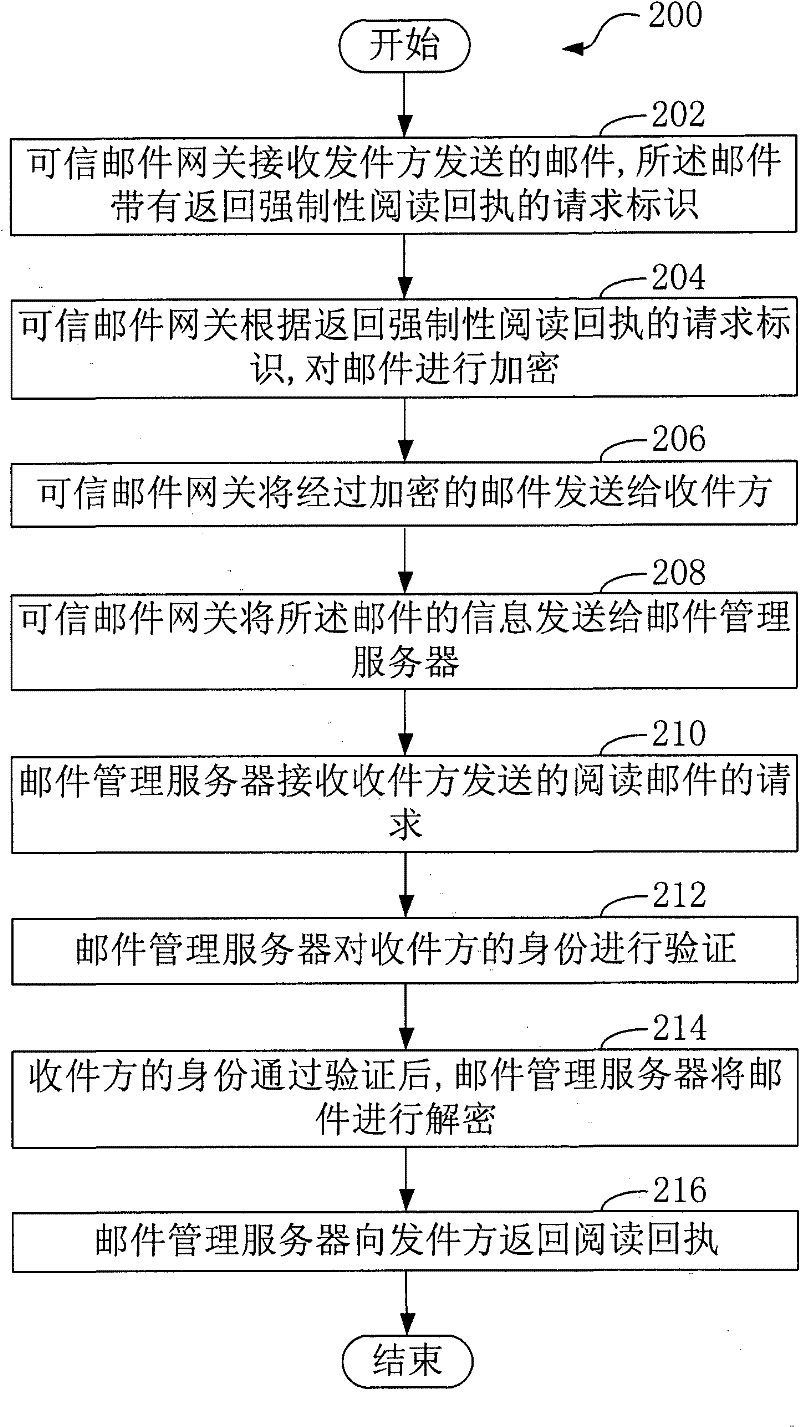
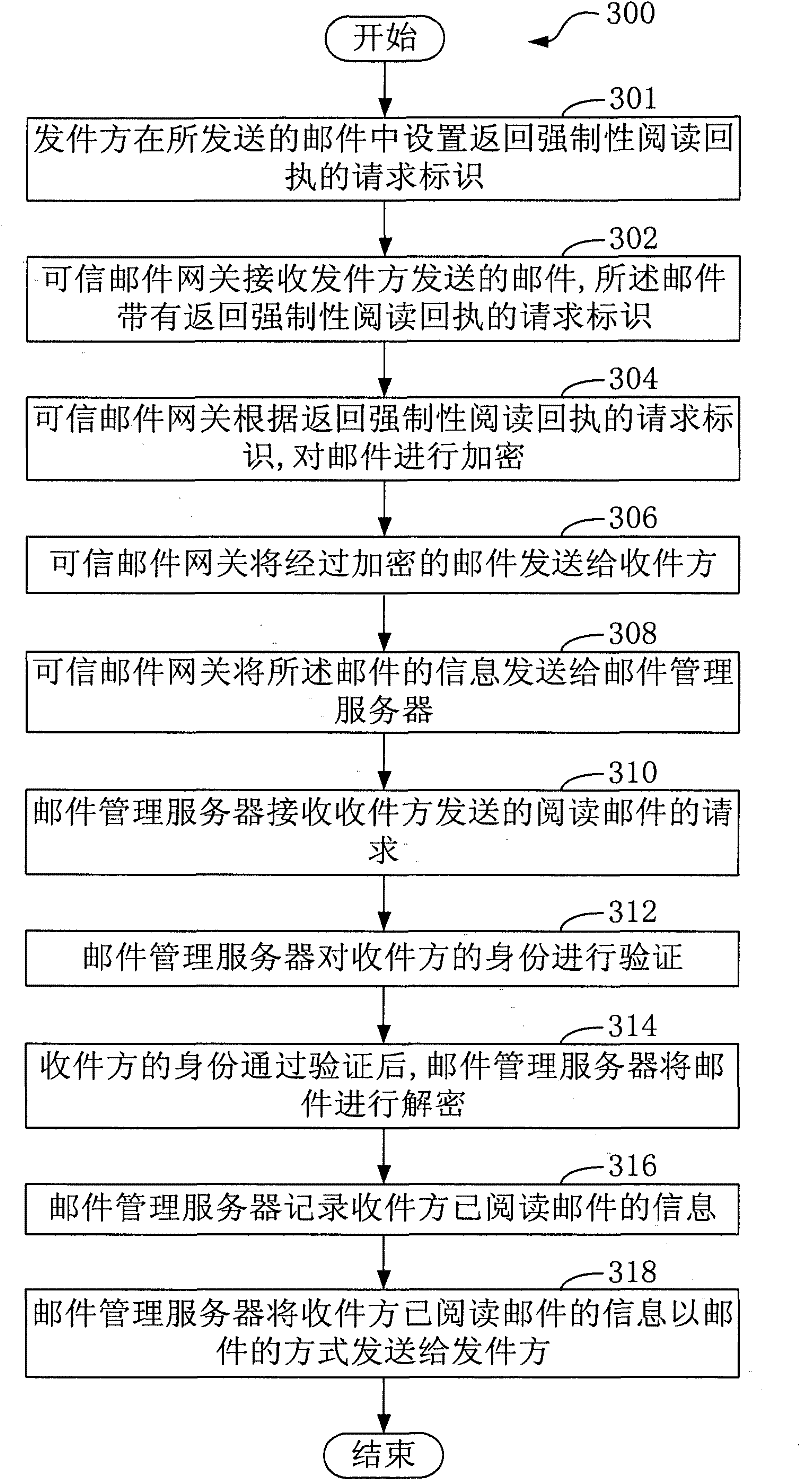
ActiveCN102571627APrevent repudiationImprove securityData switching networksInternet privacyThe Internet
The invention, which relates to the internet technology, provides an e-mail transmitting method and a system thereof. The e-mail transmitting method comprises the following steps that: a trusted e-mail gateway receives an e-mail sent by an e-mail sending party, wherein the e-mail carries a request identifier of mandatory reading receipt return; according to the request identifier of mandatory reading receipt return, the trusted e-mail gateway carries out encryption on the e-mail; the trusted e-mail gateway sends the encrypted e-mail to an e-mail receiving party; the trusted e-mail gateway sends information of the e-mail to an e-mail management server; the e-mail management server receives a request on e-mail reading sent by the e-mail receiving party; the e-mail management server carries out authentication on the identity of the e-mail receiving party; after the authentication on the identity of the e-mail receiving party is completed successfully, the e-mail management server carries out decryption; and the e-mail management server returns a reading receipt to the e-mail sending party. According to the invention, security of e-mail transmission can be improved; and it can be prevented that an e-mail receiving party denies that a received e-mail has been read.
Owner:CHINA TELECOM CORP LTD
Method and device for playing back operation process, equipment and storage medium
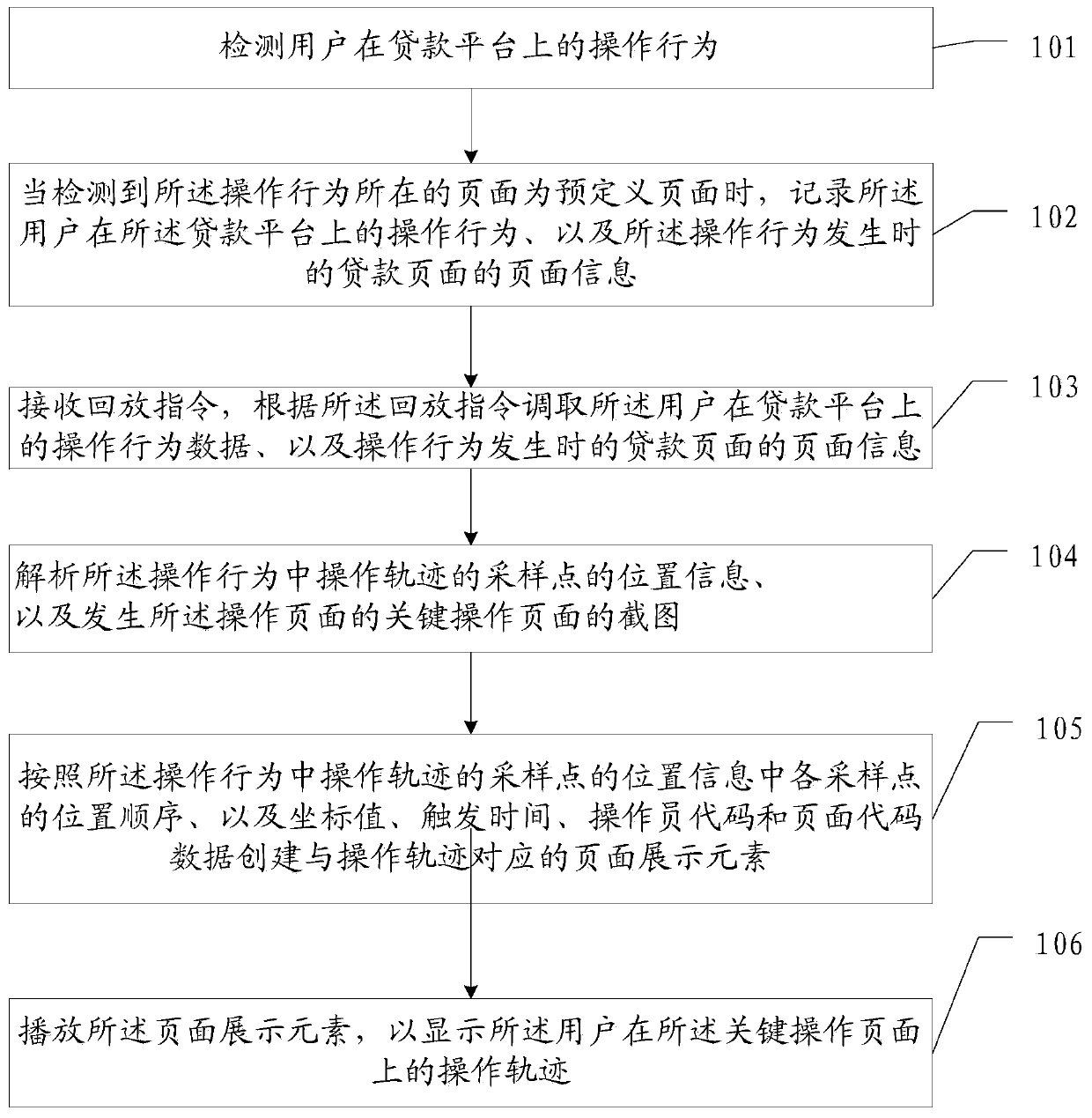
PendingCN110647321APrevent repudiationDatabase management systemsFinanceData scienceSystems engineering
The invention relates to the field of data processing. The invention provides a method and device for playing back an operation process, equipment and a storage medium. The method comprises: detectingan operation behavior of a user on a loan platform, and when it is detected that a page where the operation behavior is located is a predefined page, recording the operation behavior of the user on the loan platform and page information of a loan page when the operation behavior occurs, wherein the predefined page comprises a key operation page of a loan, and the key operation page is used for recording or replaying an operation behavior when the user applies for the loan on the loan platform; receiving a playback instruction, and calling operation behavior data of the user on the loan platform and page information of a loan page when the operation behavior occurs according to the playback instruction; analyzing and playing the operation behavior data of the user on the loan platform andthe page information of the loan page when the operation behavior occurs; by adopting the scheme, the customer operation process can be traced back.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
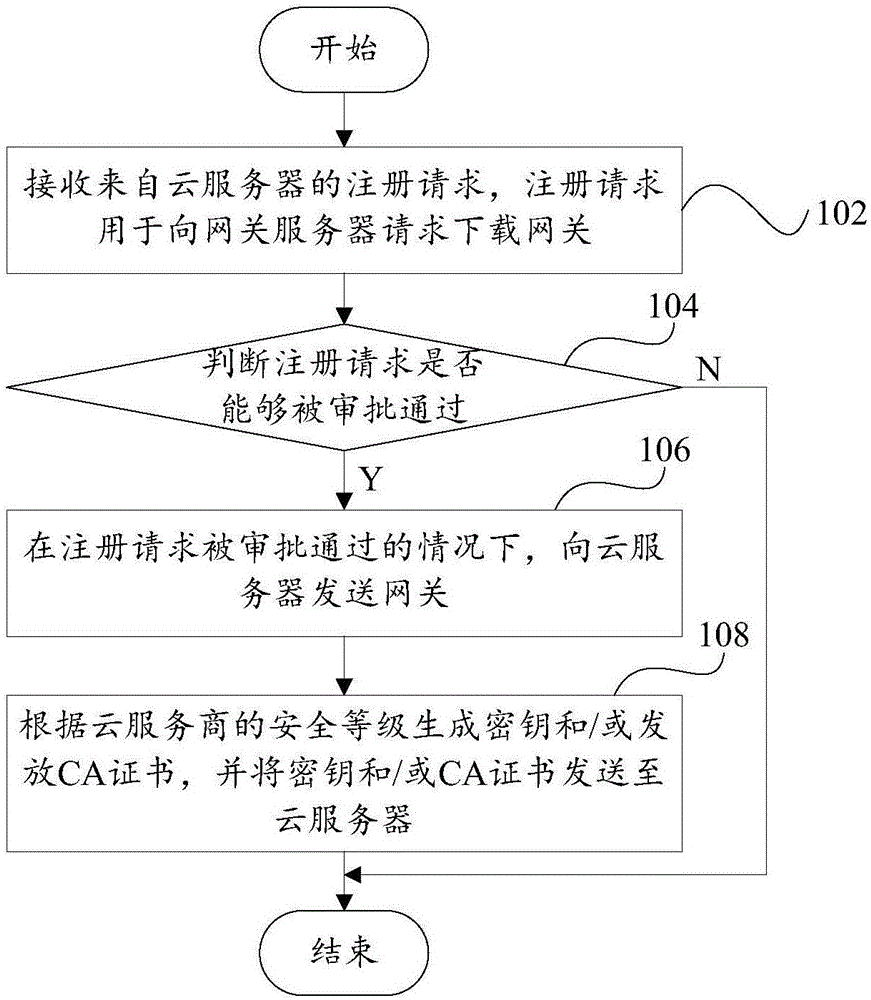
Safety communication method and device and safety communication system
ActiveCN106534179ABuild flexibilityReduce docking workloadTransmissionCloud service providerThird party
The invention provides a safety communication method and device and a safety communication system. The safety communication method is used for a gateway server. The gateway server is integrated with a safety component provided by a third-party CA authentication center. The safety communication method comprises the steps of: receiving a registration request from a cloud server, wherein the registration request is used for requesting for the gateway server to download a gateway; judging whether the registration request can pass examination and approval; in a case that the registration request passes examination and approval, sending the gateway to the cloud server; generating a secret key and / or issuing a CA certificate according to a safety level of a cloud service provider, and sending the secret key and / or the CA certificate to the cloud server. By the technical scheme of the invention, safe, reliable and efficient communication among different cloud services is implemented.
Owner:YONYOU NETWORK TECH
A method and apparatus for matching information
ActiveCN109104410AGuarantee authenticityPrevent repudiationUser identity/authority verificationCommunication with homomorphic encryptionAlgorithmOperations research
The invention provides an information matching method and a device, the methods include: a match initiating side sends information matching request to a match initaiating recipient, the matching recipient verifies the information in the information matching request, if the verification passes, a first response to the information matching request is constituted, sending to the matching initiator, verifying the information in the first response after the matching initiator receives the first response, if the verification passes, sending a second response to the matching receiver, obtaining a first calculation result according to the first commitment and the second commitment by the matching initiator, obtaining a second calculation result according to the first commitment and the second commitment by the matching receiver; after receiving the second response, the matching receiver compares the first calculation result with the second calculation result. If the comparison result is equal,the matching is successful. If the comparison result is not equal, the matching fails. The invention solves the technical problem that the accuracy of the matching result is not high in the prior art.
Owner:HUBEI UNIV OF TECH
Registration-free access control and smart lock registration and unlocking method, device and system
InactiveCN107172041APrevent repudiationPrivacy protectionIndividual entry/exit registersTransmissionComputer hardwareFree access
The invention discloses a registration-free access control and smart lock registration and unlocking method, device and system. The method comprises the steps that S1, a mobile smart device obtains a two-dimensional bar code in a first display screen of a registration device; S2, the two-dimensional bar code is sent to a server; S3, the server receives the two-dimensional bar code, carries out networking query and verification on real name information registered by a mobile smart device user, generates a ciphertext two-dimensional bar code instruction after the query and verification are successful and passes back the ciphertext two-dimensional bar code instruction to the mobile smart device, and the server stores operation time, verification content and result; S4, the mobile smart device displays the received ciphertext two-dimensional bar code in a second display screen;S5, the registration device identifies the ciphertext two-dimensional bar code; and S6, the registration device decrypts the ciphertext two-dimensional bar code, if the decryption is successful, registration verification is finished, and if the decryption is unsuccessful, the verification is terminated and prompt is sent. According to the method provided by the invention, the privacy of a visitor is protected through network verification.
Owner:刘兴丹
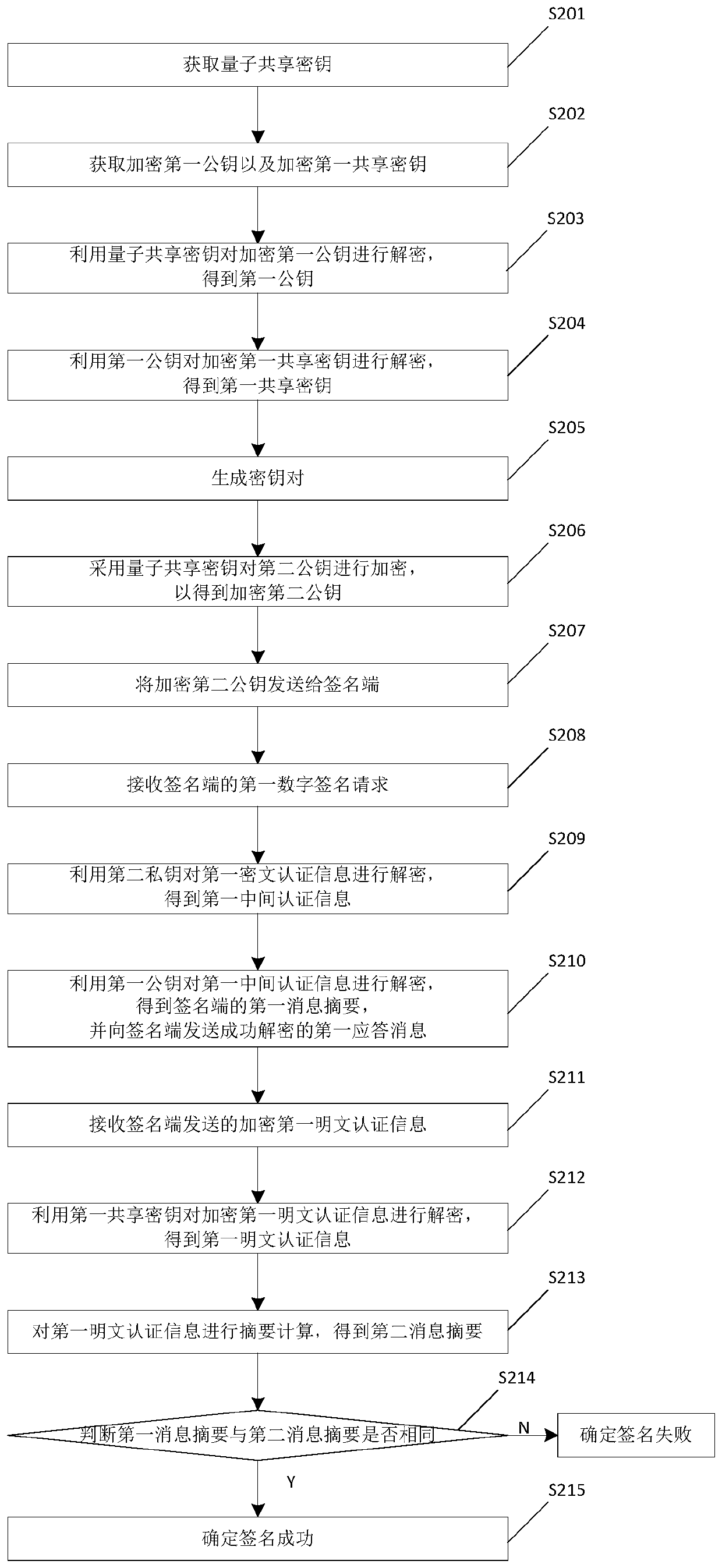
Digital signature method and device
ActiveCN109818747AImprove efficiencyAvoid multiple negotiationsKey distribution for secure communicationUser identity/authority verificationCiphertextDigital signature
The invention relates to the technical field of communication, in particular to a digital signature method and device, and the method comprises the steps: receiving a first digital signature request of a signature end; Decrypting the first ciphertext authentication information by using the second private key to obtain first intermediate authentication information; Decrypting the first intermediateauthentication information by utilizing the first public key to obtain a first message abstract of the signature end, and sending a first response message which is successfully decrypted to the signature end; Decrypting the first intermediate authentication information by utilizing the first public key to obtain a first message abstract of the signature end, and sending a first response message which is successfully decrypted to the signature end; Decrypting the encrypted first plaintext authentication information by using the first shared key to obtain first plaintext authentication information; Judging whether the first message digest is the same as the second message digest or not; And when the first message digest is the same as the second message digest, determining that the signature is successful. According to the method, confirmation is performed after identity authentication is successful, so that the safety of authentication information is ensured, and the digital signatureefficiency is improved.
Owner:SUZHOU KEDA TECH
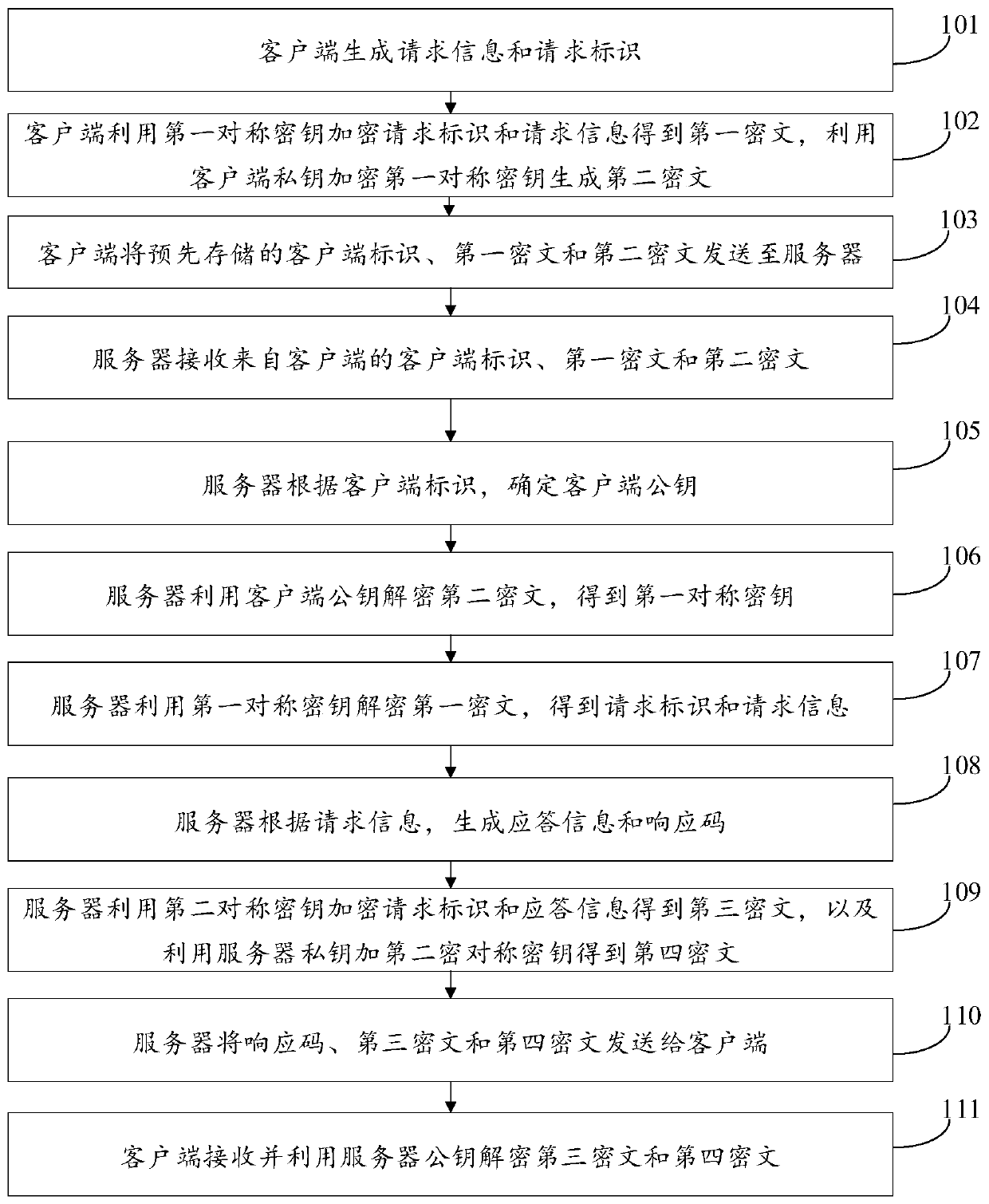
Anti-repudiation method of transaction information, client and server
ActiveCN111080299AEnsure safetyReduce occupancyPayment protocolsTransmissionInternet privacyCiphertext
The invention discloses an anti-repudiation method of transaction information, a client and a server, and the method comprises the steps: generating a client private key, a client public key, requestinformation and a request identification, transmitting the client public key to the server, and receiving a server public key generated by the server; encrypting the request identifier and the requestinformation by using a first symmetric key to generate a first ciphertext; encrypting the first symmetric key by using the client private key to generate a second ciphertext; sending the first ciphertext and the second ciphertext to the server; and receiving and decrypting the information returned by the server by using the server public key to obtain the request identifier and the response information. According to the method provided by the invention, repudiation of a client or a server can be prevented, so that normal transaction is ensured, and the user experience of two communication parties is improved.
Owner:广州骏伯网络科技有限公司
Motorcade ETC payment information processing system and method based on blockchain
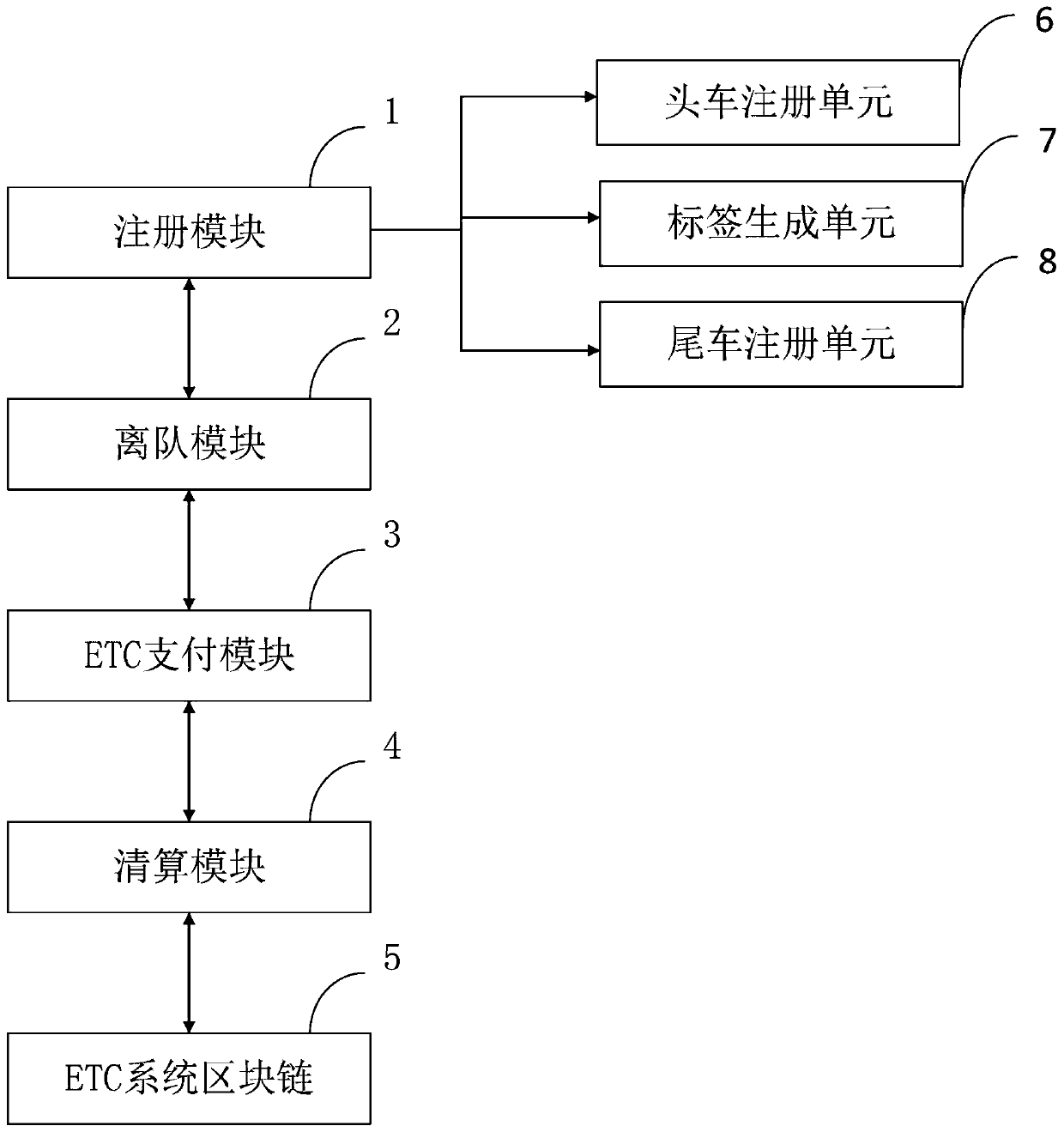
PendingCN110782348ASolve the problem of mutual distrust and team formationSolve traffic jamsTicket-issuing apparatusFinancePaymentComputer network
The invention belongs to the technical field of road toll collection or congestion toll collection devices for vehicles and vehicle owners, and discloses a motorcade ETC payment information processingsystem and method based on a blockchain, and the system comprises a registration module which is used for registering a head vehicle and a tail vehicle, and generating a label; a dequeuing module used for the head vehicle or the tail vehicle to apply for quitting the fleet; an ETC payment module used for a motorcade to pay ETC fees for transaction; a clearing module used for each node of the vehicle account to initiate a request to the intelligent contract storing the virtual currency of each vehicle account, realizing recharging and withdrawal of the virtual currency, and performing exchange rate conversion between the virtual currency and the real currency; an ETC system block chain which comprises a plurality of nodes and an intelligent contract; and a node interaction platform used for running the intelligent contract. According to the invention, the characteristic of public trust removal of the blockchain is utilized, and the problem that fleet members complete unified payment and quickly pass through an ETC toll station under the condition of mutual trust is solved.
Owner:ANHUI UNIVERSITY
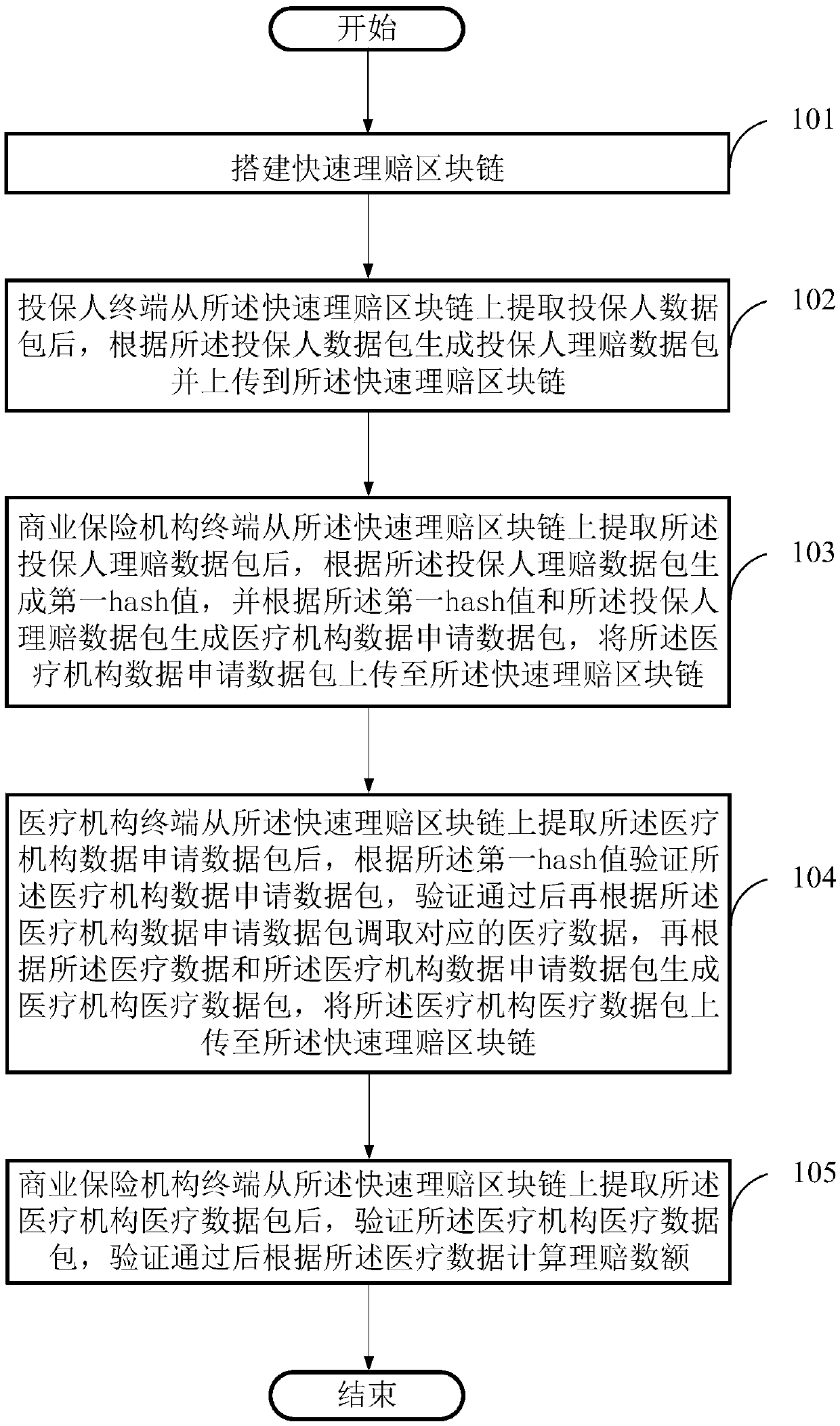
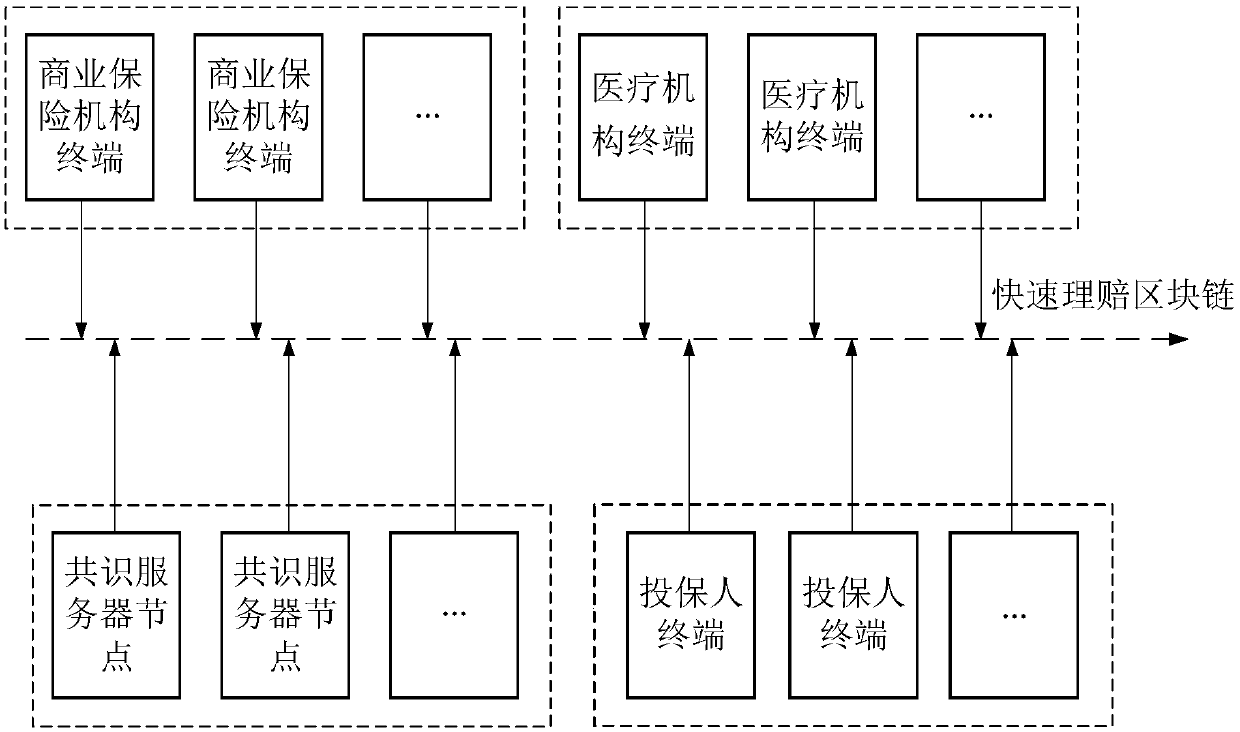
Business insurance rapid claim settlement method based on a block chain, a storage medium and equipment
ActiveCN109658273AGuarantee authenticityGuarantee fairnessFinanceDigital data protectionNetwork packetComputer terminal
The invention provides a business insurance rapid claim settlement method based on a block chain, a storage medium and equipment. The method comprises the following steps: a rapid claim settlement block chain is established; The applicant terminal generates an applicant claim settlement data packet according to the applicant data packet and uploads the data packet to the rapid claim settlement block chain; The commercial insurance institution terminal obtains a first hash value of the insurance applicant claim settlement data packet by using a hash algorithm, and generates a medical institution data application data packet according to the first hash value and the insurance applicant claim settlement data packet; The medical institution terminal verifies the medical institution data application data packet according to the first hash value, calls corresponding medical data according to the medical institution data application data packet after verification is passed, and generates a medical institution medical data packet according to the medical data and the medical institution data application data packet; And the commercial insurance institution terminal verifies the medical data packet of the medical institution, and calculates the claim settlement amount according to the medical data after the verification is passed. The claim settlement time is shortened, and transparencyof the claim settlement process is realized.
Owner:易保互联医疗信息科技(北京)有限公司
Method, system and device for information acquisition and extraction by means of biological characteristics
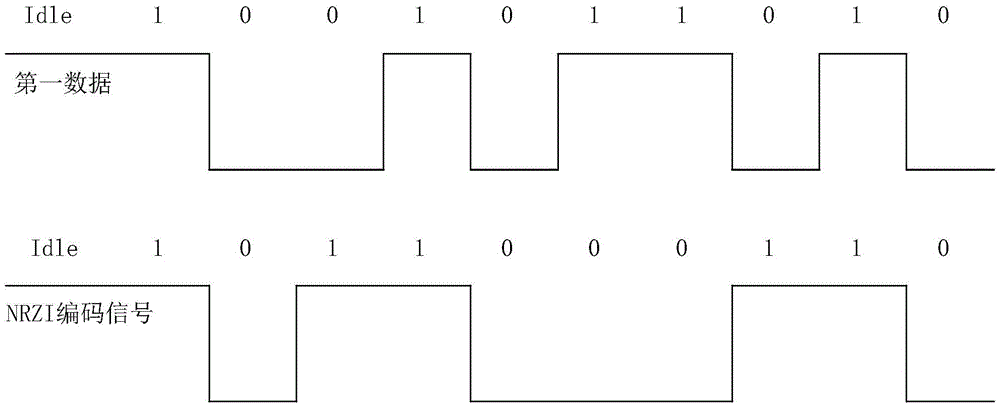
The invention provides a method, system and device for information acquisition and extraction by means of biological characteristics. The method for information acquisition and extraction by means of biological characteristics includes that a terminal acquires first data, the terminal controls a light source to generate light signals with variable intensity and projects the light signals with variable intensity on an iris the terminal acquires first iris information at least including first iris contraction information, the first iris contraction information is generated based on the light signals with variable intensity, and the first iris contraction information includes first iris contraction movement.
Owner:TENDYRON CORP
A method of intelligent contract generation and execution based on banking service flow
ActiveCN109285066ATime-consuming to solveImprove efficiencyFinancePayment protocolsClient-sideService flow
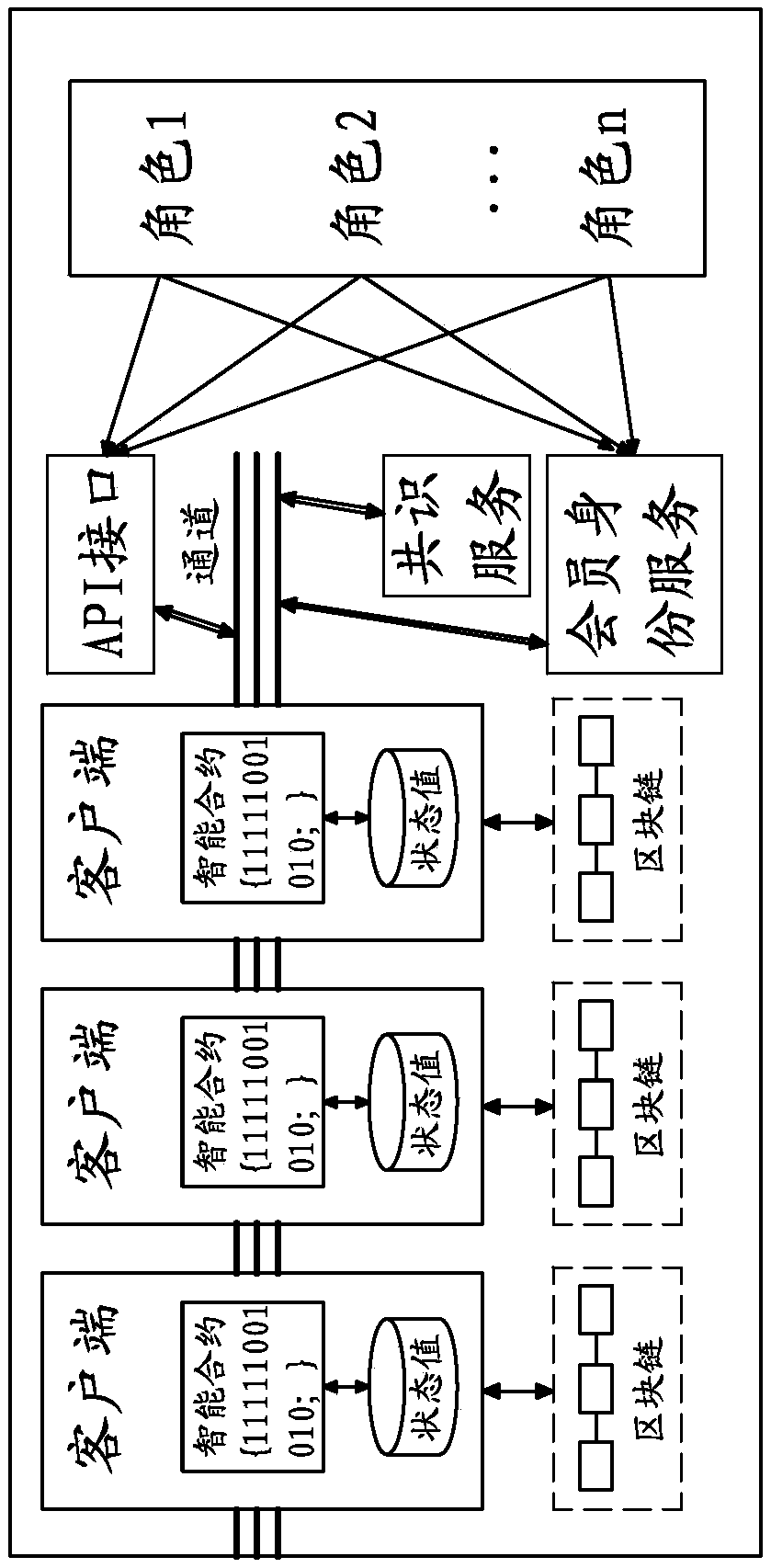
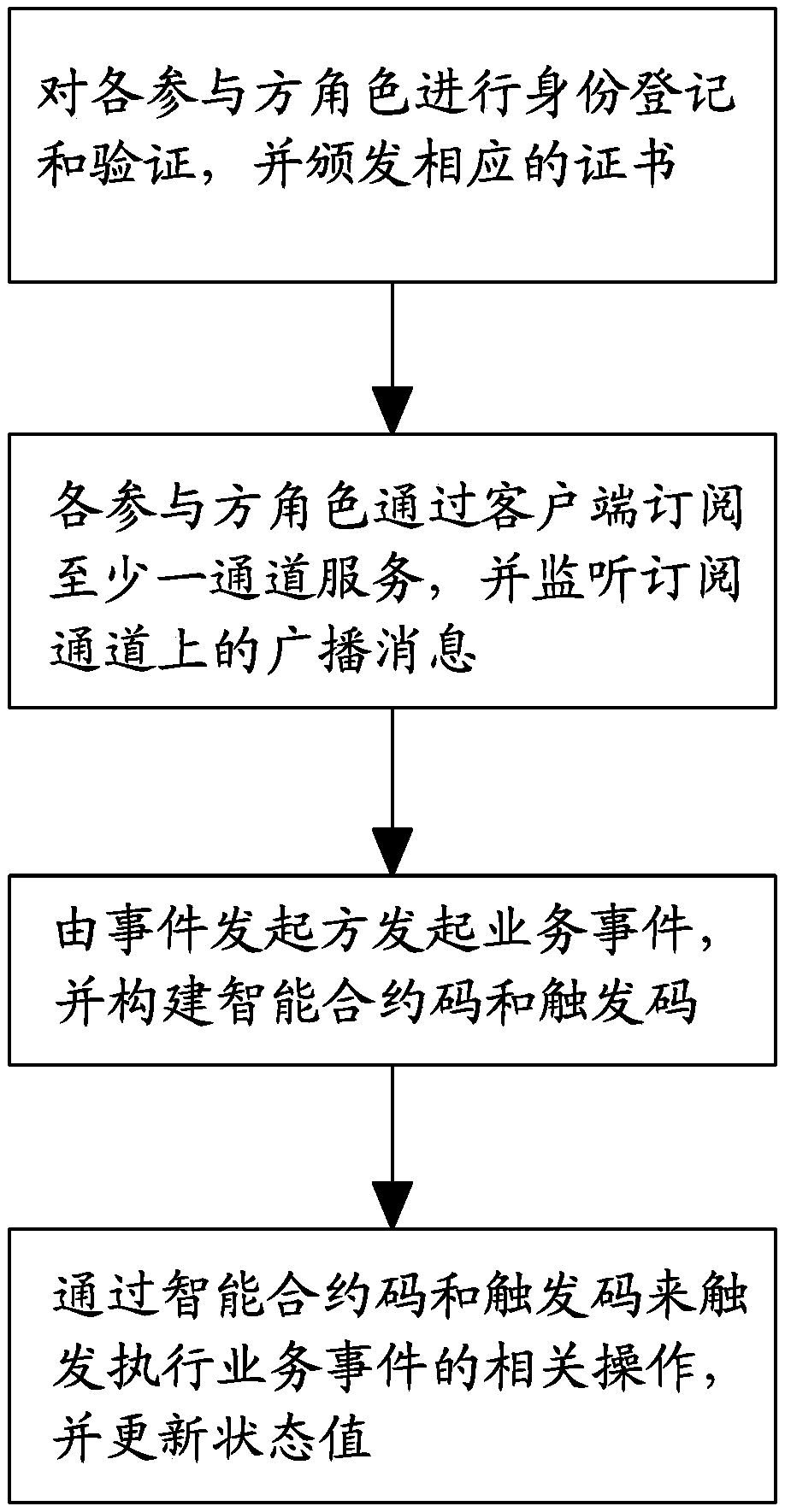
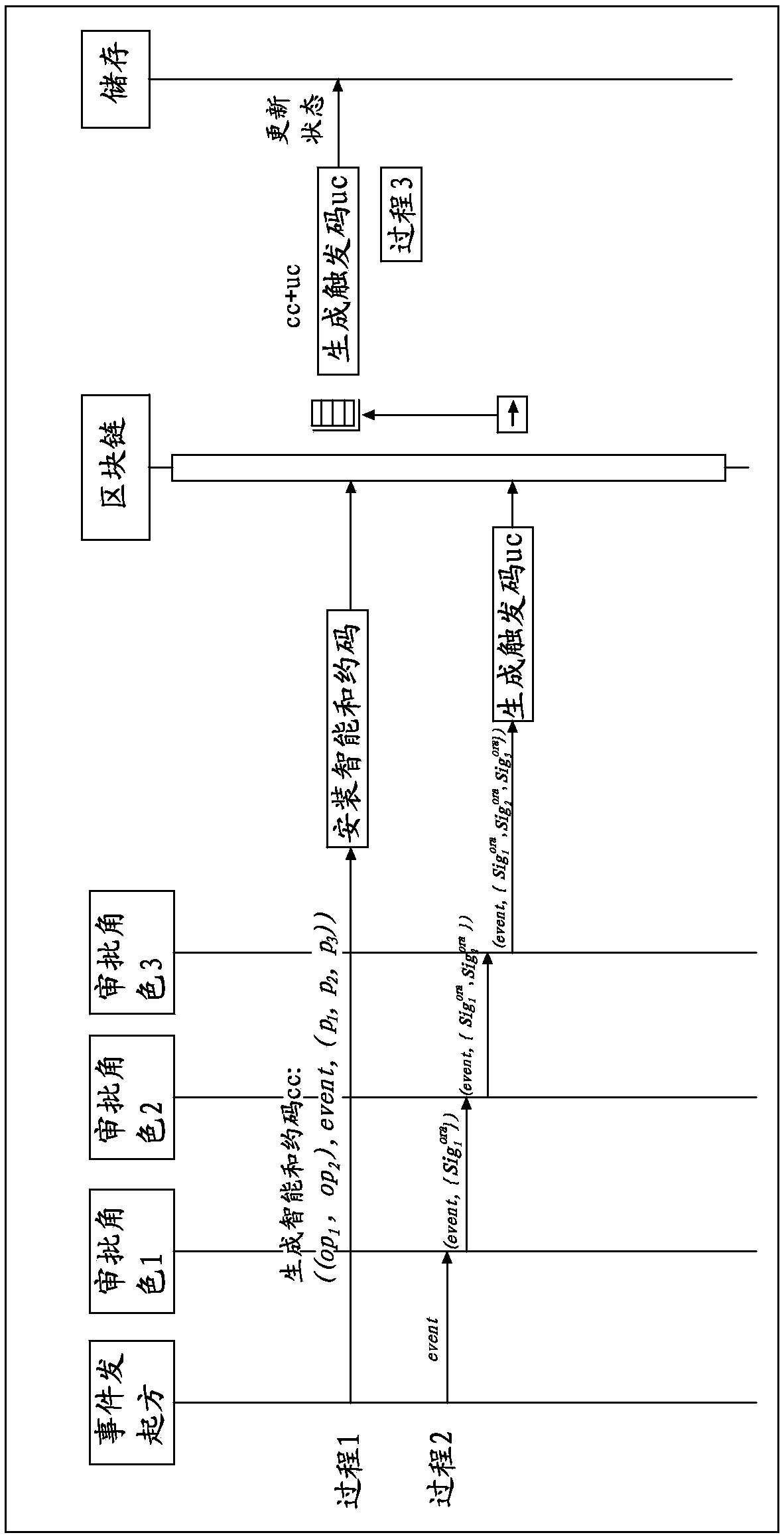
The invention provides a method for intelligent contract generation and execution based on a banking service flow. The method comprises the steps of: S1, registering and verifying the identities of each participant role and issuing corresponding certificates; S2, that role of each participant subscribe to at least one channel service through the client, and monitoring broadcast message on the subscribe channel; S3, initiate a service event by that event initiator, and constructing an intelligent contract code and a trig code; S4, triggering the related operation of executing the service eventthrough the intelligent contract code and the trigger code, and updating the status value. The invention also provides a system for generating and executing intelligent contract based on banking service flow. The invention has the advantages of solving the problems of long time consuming, slow examination and approval, complex process and the like of the traditional banking service flow, and effectively improving the efficiency of service processing and also ensures the integrity of the transaction and the security of the data.
Owner:FUJIAN RURAL CREDIT UNION
Anti-counterfeiting identification method and device for preventing identification code from being repeatedly used, and electronic equipment
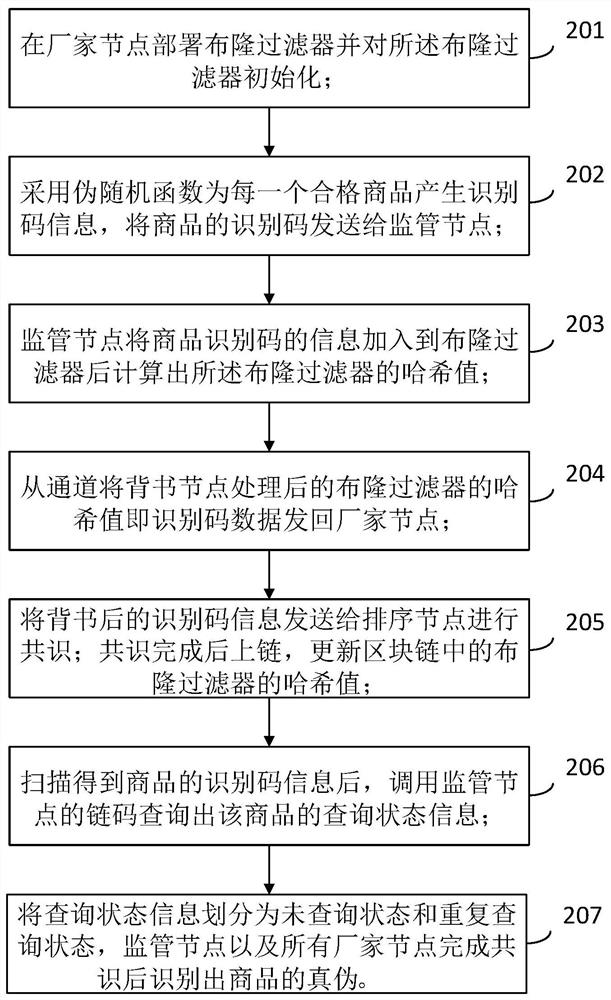
PendingCN113269565AMemory saving functionPrevent repudiationDigital data information retrievalCommerceBloom filterChain code
The invention belongs to a block chain anti-counterfeiting technology, and particularly relates to an anti-counterfeiting identification method and device for preventing an identification code from being repeatedly used, and electronic equipment. The method comprises the following steps: generating identification code information for each qualified commodity by adopting a pseudo-random function, and sending the identification code of the commodity to a supervision node; after receiving the identification code information of the commodity, the supervision node sending the hash value processed by the endorsement node back to the manufacturer node from the channel; sending the endorsed identification code information to a sorting node for consensus, uploading after the consensus is completed, and storing the hash value of the identification code of the commodity; and after identification code information of the commodity is obtained through scanning, the chain code of the supervision node being called to inquire authenticity information of the commodity. According to the invention, the Bloom filter is arranged on the block chain, and the consensus algorithm is adopted, so that the repudiation behavior of merchant nodes can be prevented, and the accuracy of the traceability technology is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
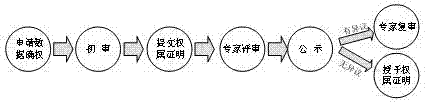
Method for enhancing network lottery trade safety based on credible third party
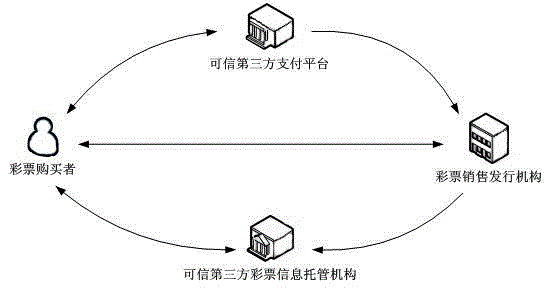
InactiveCN102722809AImprove securityPrevent repudiationPayments involving neutral partyThird partyThird-Party Payments
The invention relates to a method for enhancing the network lottery trade safety based on a credible third party. The method relates to four objects which are respectively a lottery purchaser, a lottery sale and issue mechanism, a credible third party payment platform and a credible third party lottery information deposit mechanism, wherein the lottery purchaser is an initiator of lottery purchase, the lottery sale and issue mechanism is a unit in charge of sale and issue work of lotteries, the credible third part payment platform is used for completing safe payment settlement between the lottery purchaser and the lottery sale and issue mechanism, and the credible third party lottery information deposit mechanism stores lottery signature information between the lottery purchaser and the lottery sale and issue mechanism to prevent the occurrence of denial, the measure can effectively prevent the denial behaviors of the lottery sale and issue mechanism, and the lottery purchase is supported by lottery data evidences after the credible third party lottery information deposit mechanism is introduced, so that the problem that the lottery purchaser is afraid of paying first or refuses to pay after receiving the lottery can be effectively solved.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Anonymous auction method and device based on blockchain, and medium
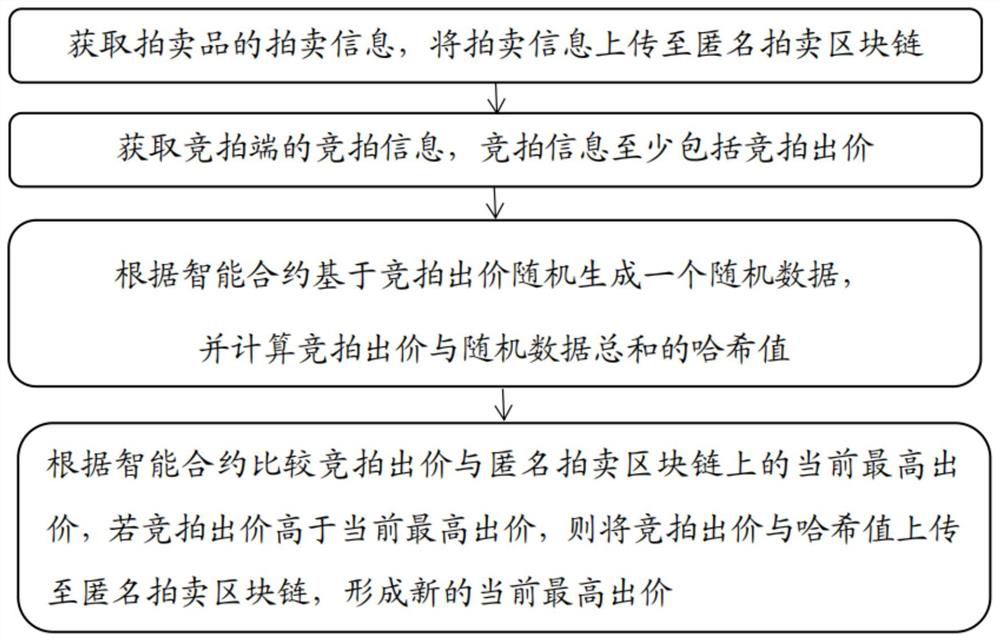
InactiveCN112288555AVerify correctnessPrevent repudiationDatabase distribution/replicationDigital data protectionThird partyComputer network
The invention discloses an anonymous auction method and device based on a block chain and a medium. The method comprises the steps of obtaining auction information of auction products, and uploading the auction information to an anonymous auction block chain; obtaining auction information of an auction end, wherein the auction information at least comprises auction bids; randomly generating randomdata based on the auction bid according to the smart contract, and calculating a hash value of the sum of the auction bid and the random data; and comparing the auction bid with the current highest bid on the anonymous auction block chain according to the smart contract, and if the auction bid is higher than the current highest bid, uploading the auction bid and the hash value to the anonymous auction block chain to form a new current highest bid. According to the method disclosed by the invention, the privacy leakage risk in the traditional auction process can be effectively reduced, and theauction end is anonymous on the premise that the whole process is public and verifiable; and in the auction process, the third-party supervision terminal can obtain key data in the auction process, and the auction end can verify the correctness of the auction result.
Owner:山东爱城市网信息技术有限公司
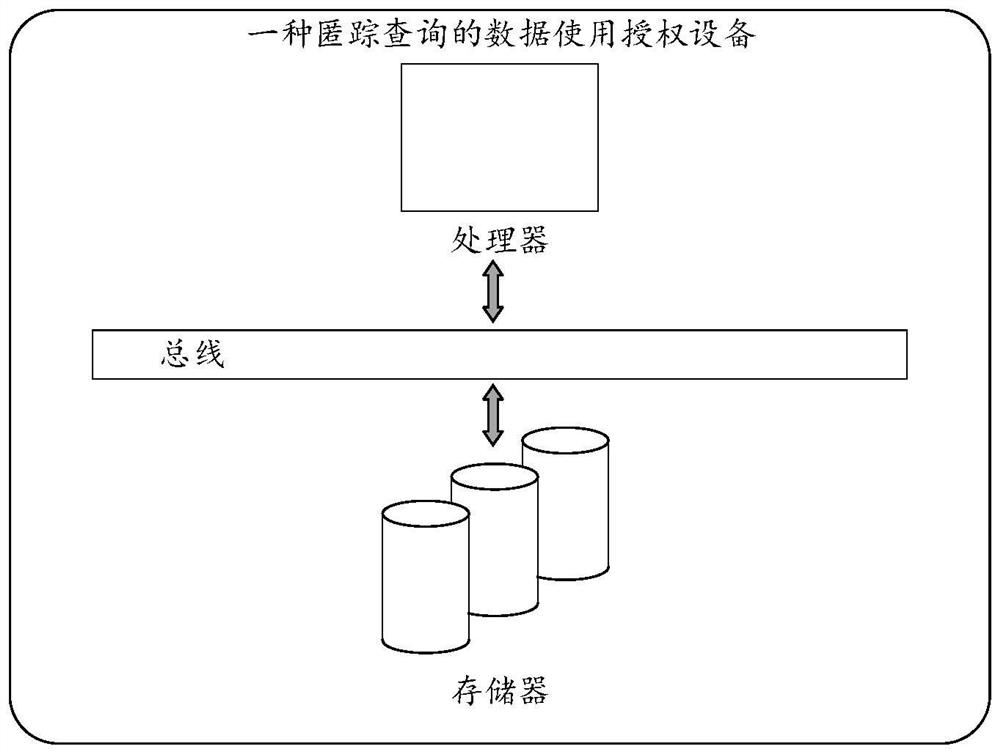
Data use authorization method and device for hidden trace query, and storage medium
The invention discloses a data use authorization method and device for hidden trace query, and a storage medium. The method comprises the following steps: a data user sends n identities (IDs) including a to-be-queried identity to an authorization center; the authorization center applies for authorization to the inquired object; the authorization center generates keys for the n IDs, an effective key is encrypted to form an encryption key, the effective key is replaced by the encryption key, and then the n IDs and the keys thereof are sent to a data user after digital signature; the data user sends the data returned by the authorization center to the data provider; after verifying the authenticity of the data, the data provider decrypts n keys including encryption keys, then queries information corresponding to n IDs, encrypts n query results, and then sends the encrypted n query results to the data user; and the data user decrypts the query result of the to-be-queried identity ID by using the effective key to obtain the query result.
Owner:山东数据交易有限公司
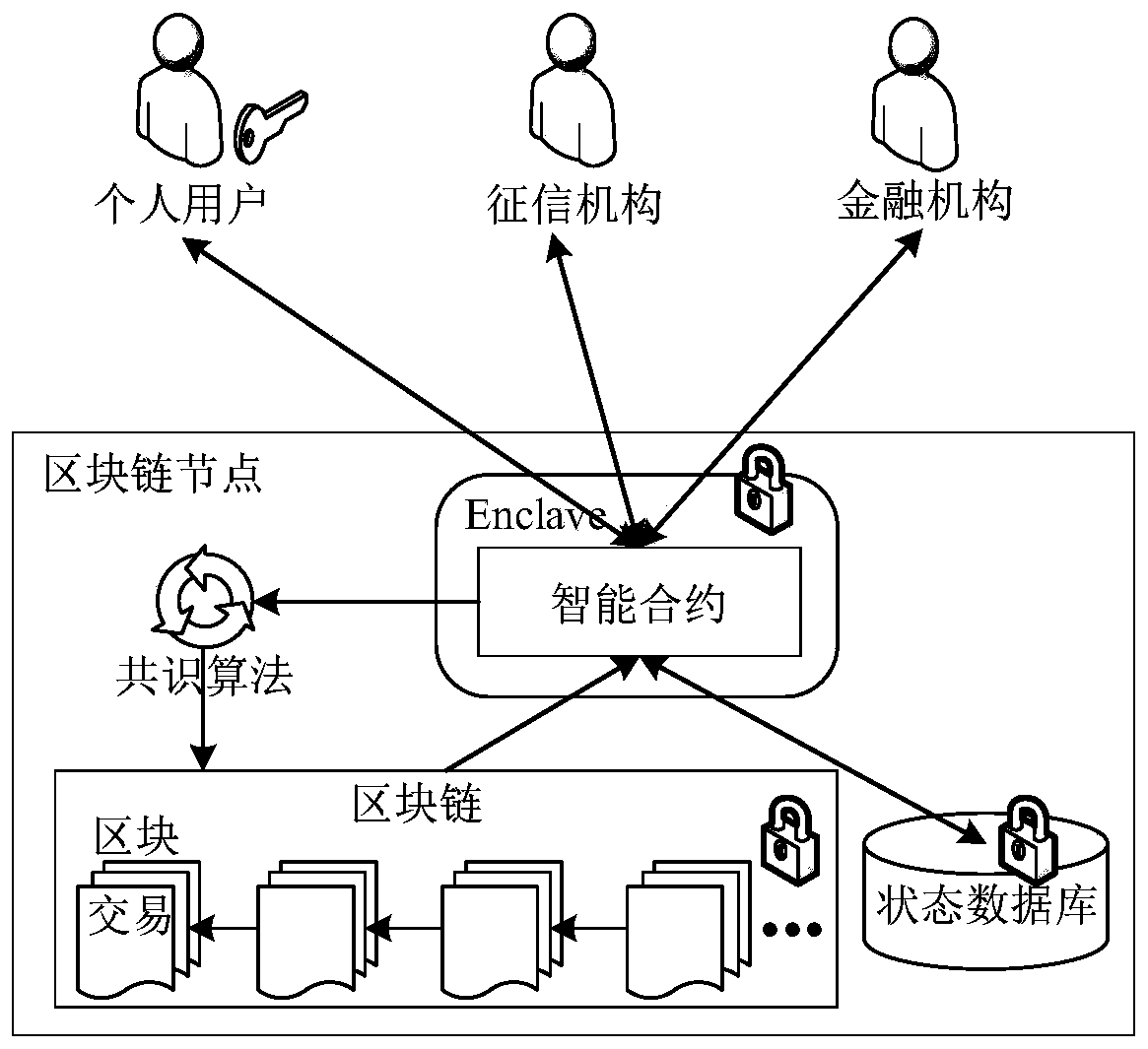
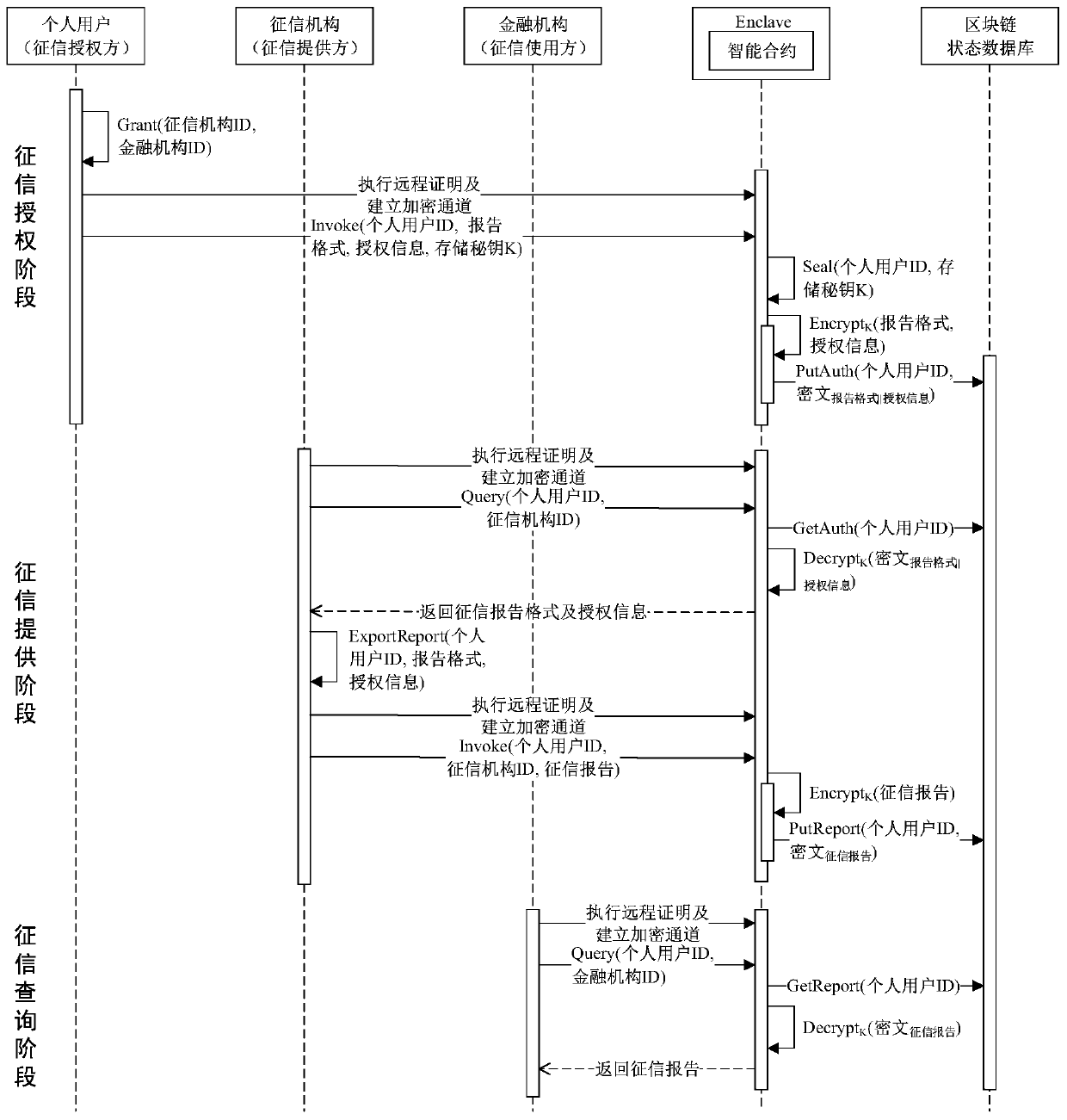
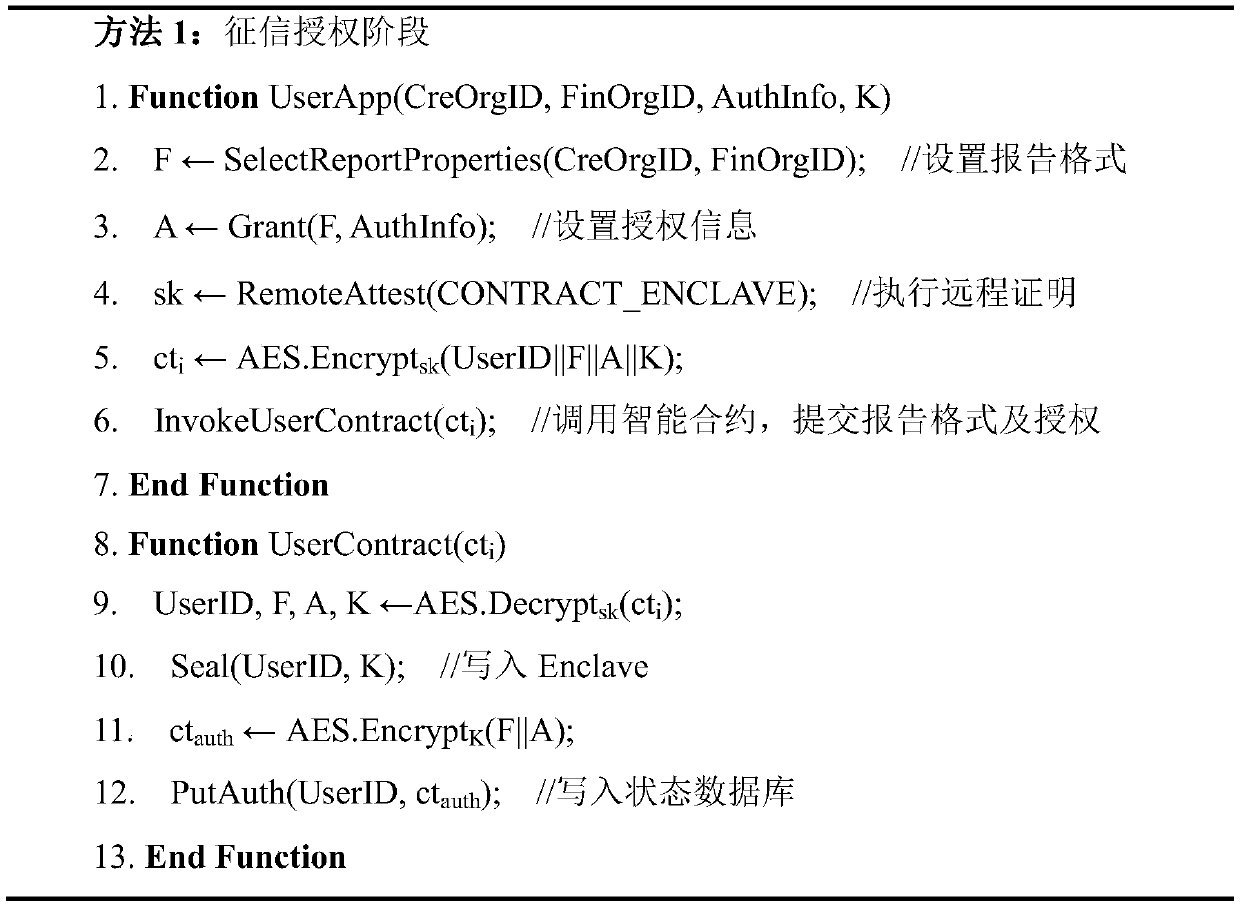
A credit report transfer method based on blockchain and intel SGX
ActiveCN109766712BPrevent casual abuseRealize electronicFinanceDigital data protectionPrivacy protectionUser privacy
The invention discloses a credit investigation report circulation method based on a block chain and Intel SGX. The method comprises a credit investigation authorization stage, a credit investigation providing stage and a credit investigation query stage. In the credit investigation authorization stage, a credit investigation report format is customized by a personal user, and the specific authorization information is set; in the credit investigation providing stage, a credit investigation mechanism generates a credit investigation report according to a report format defined by a personal userand authorization information; and the credit investigation stage is used for inquiring and auditing a credit investigation report provided by a credit investigation mechanism by a financial institution. The report formats, the authorization information, the credit reports and the report query records involved in the flow process are encrypted through SGX and stored on the block chain. By combining the block chain and Intel SGX, the non-tampering, traceability and privacy protection of data in the credit report transfer process are realized, and the problems that a paper report is easy to tamper and forge, the user privacy attention is low, and a management and control credit report cannot be abused due to a traditional transfer method are solved.
Owner:EAST CHINA NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com