Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
213 results about "Network verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
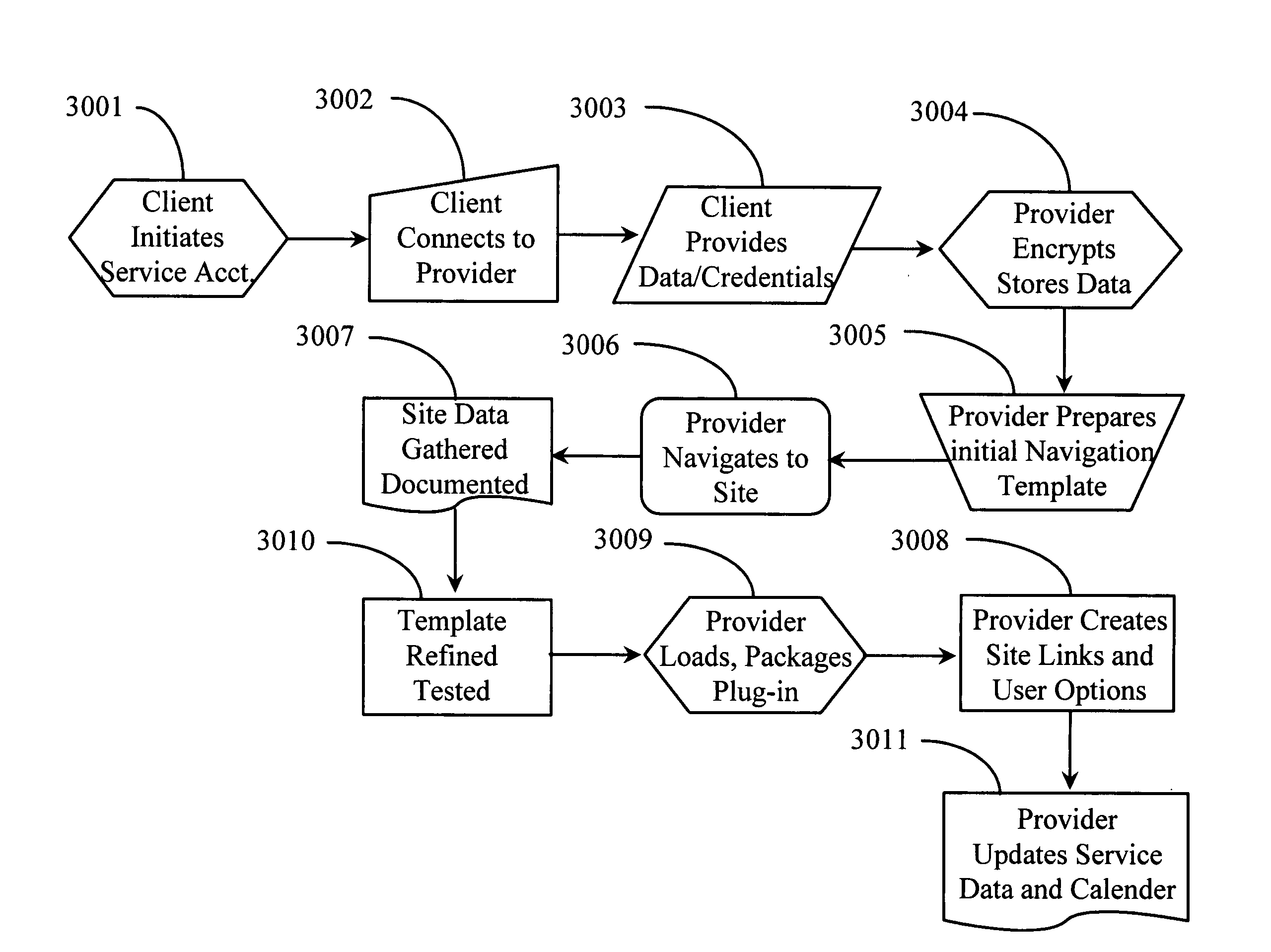
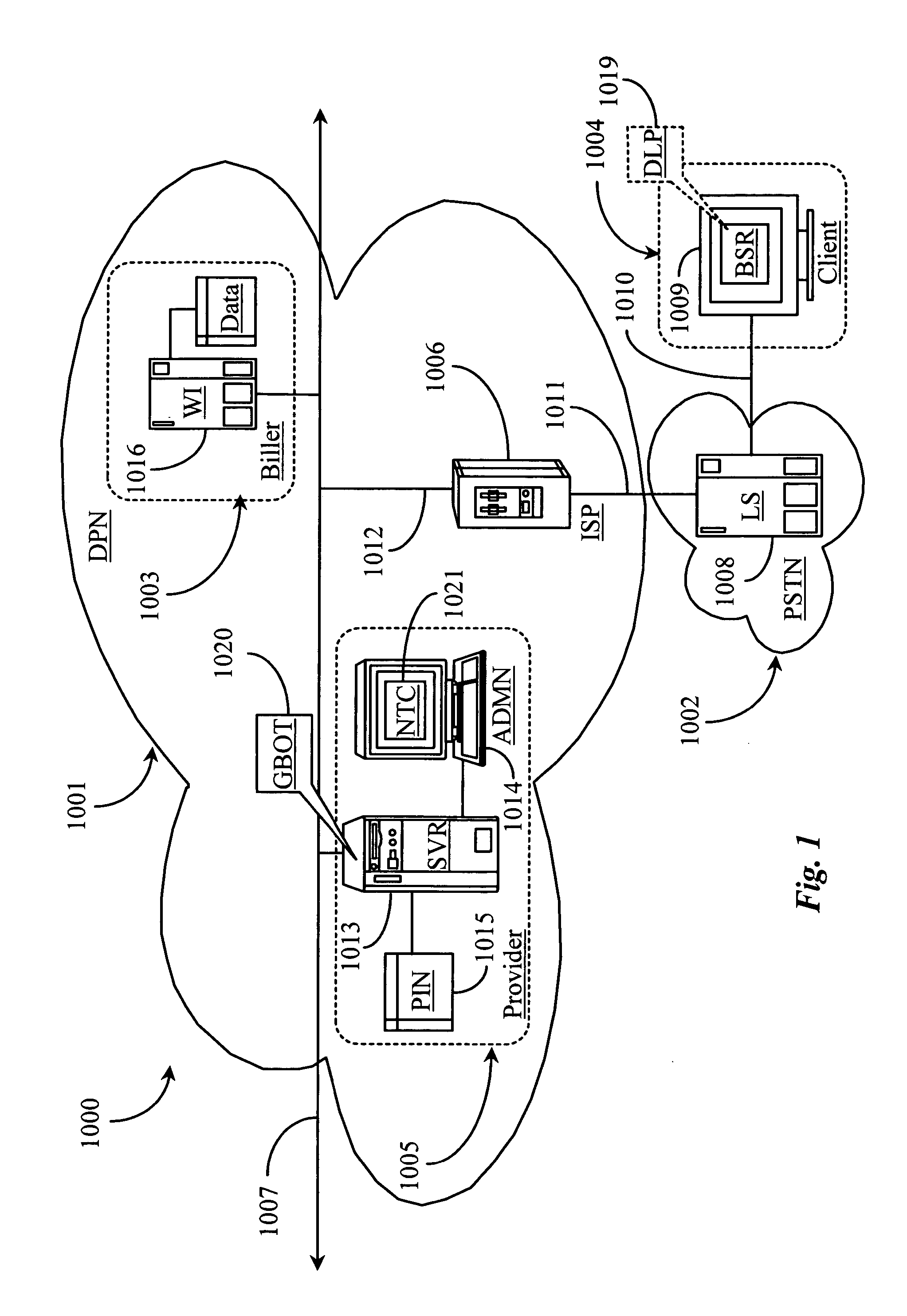
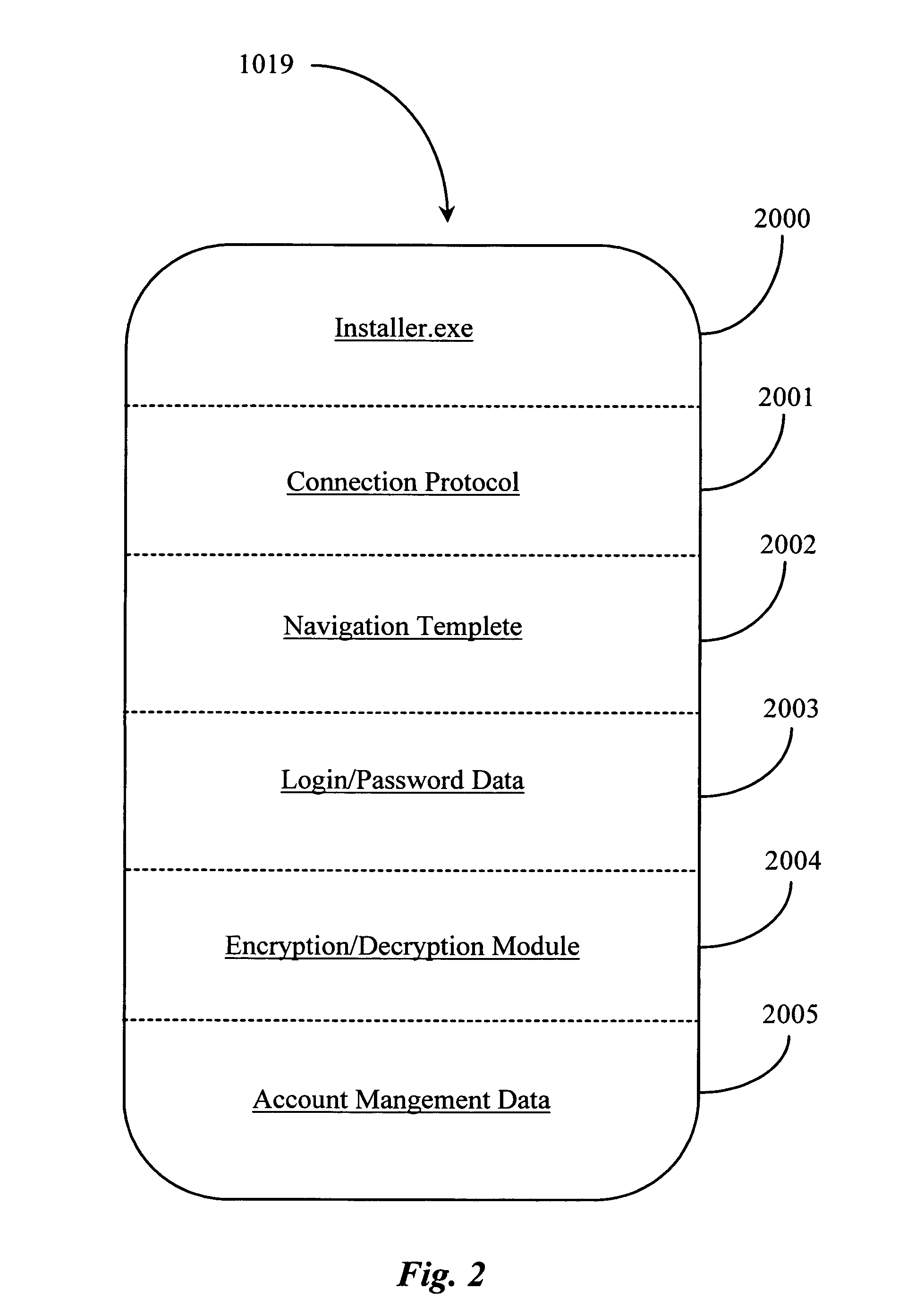
Method and system for verifying state of a transaction between a client and a service over a data-packet-network
InactiveUS20050198377A1Multiple digital computer combinationsPayment architectureWeb navigationClient-side
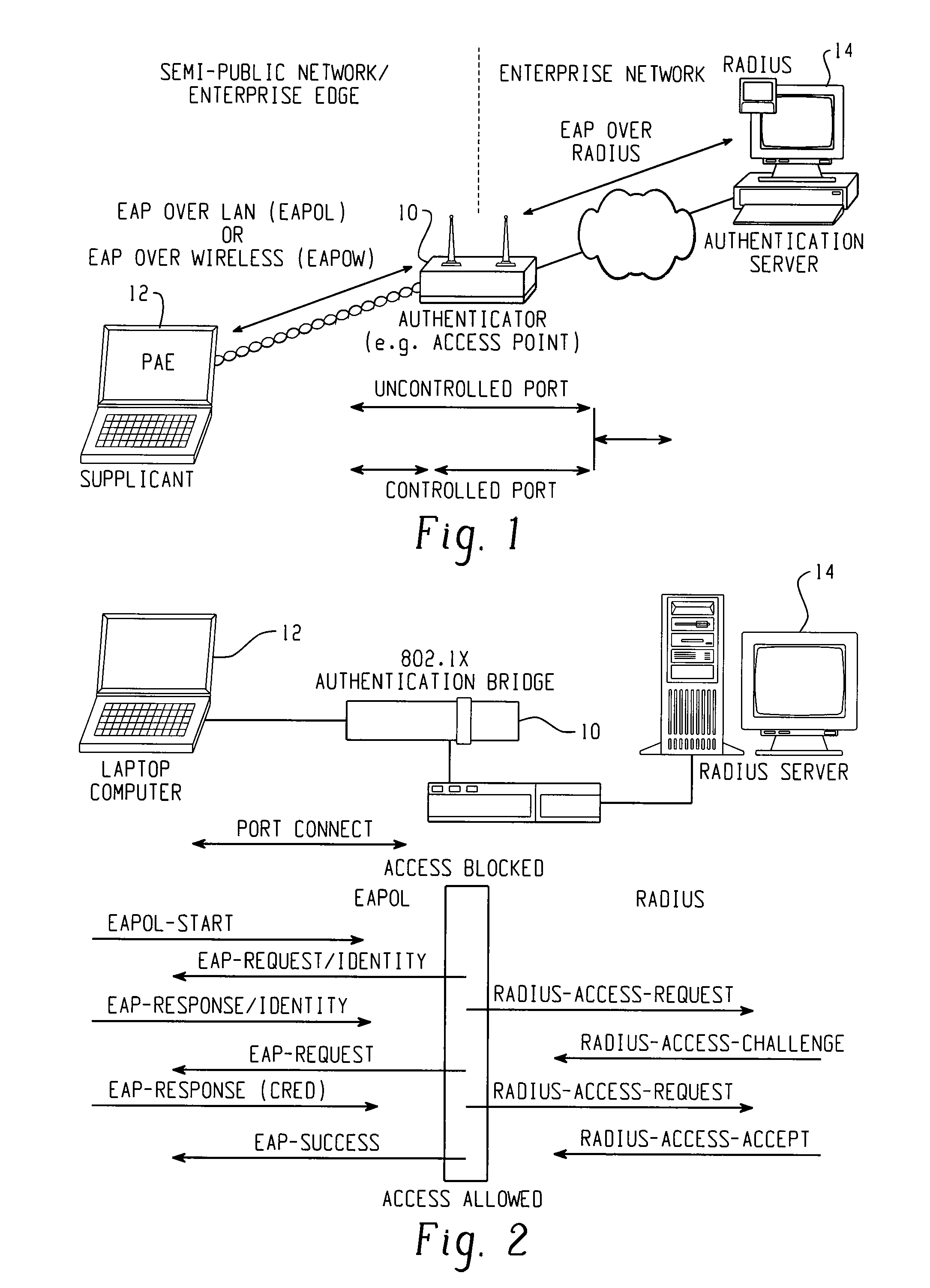
A system for verifying communication established between a first and a second node over a data-packet-network includes a third network node accessible from the first node over the data-packet-network, the third node containing network location information of the second node and the network location information of at least one resource accessible there from; and a navigation agent directed by the third network node for navigating over the network to the second node and to the at least one resource to gather information. In a preferred embodiment, the information gathered includes indication of receipt of data sent from the first node at the second node and indication of confirmation or authorization to access services.
Owner:YODLEE COM INC
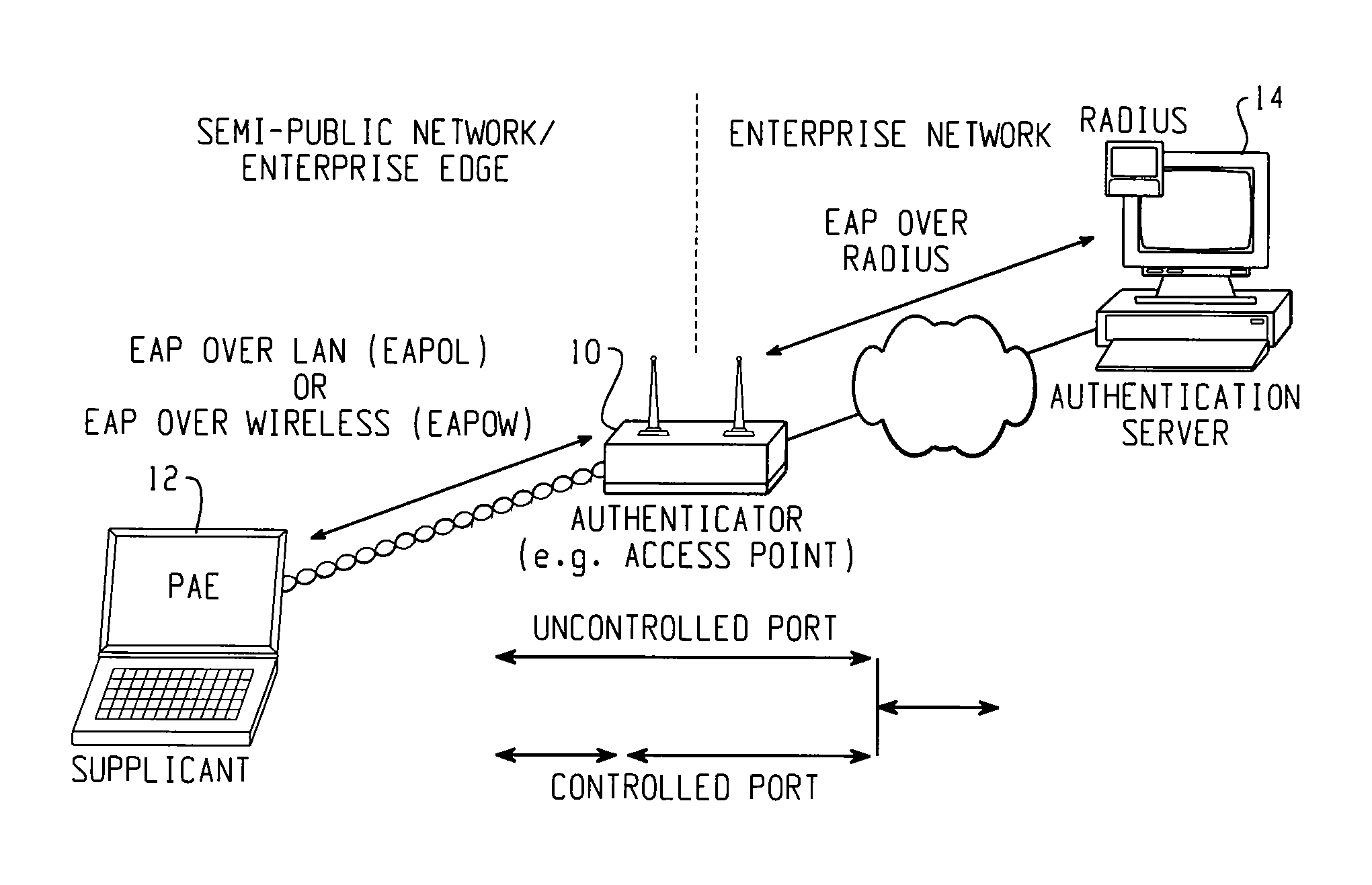
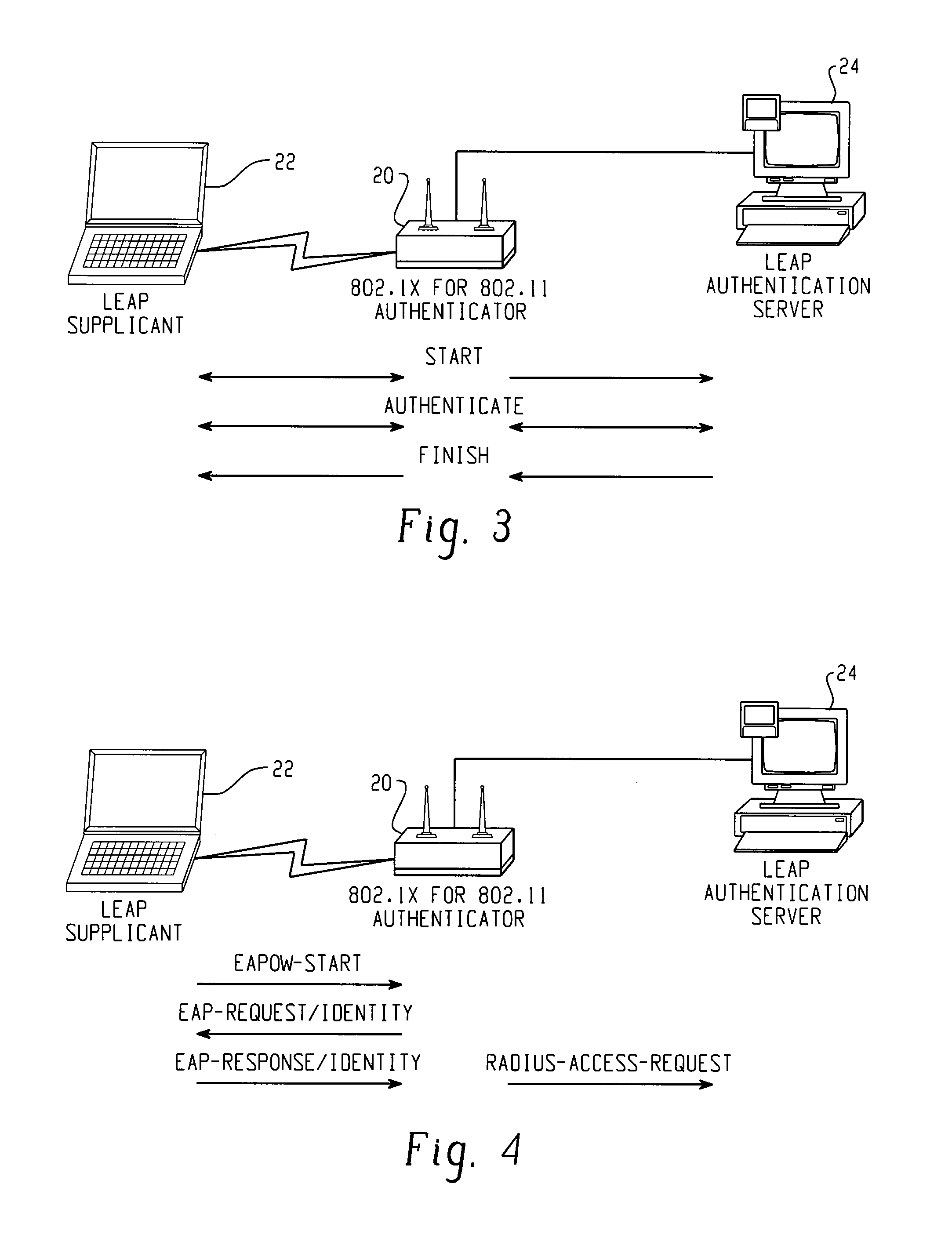
Rogue AP detection
InactiveUS7181530B1Quick launchReduce complexityMultiple digital computer combinationsTransmissionRogue access pointNetwork access point
A method of detecting a rogue access point is disclosed. A message is directed from a supplicant to a network through an access point. A network response message is received by the supplicant from the access point. A step of determining whether the access point is one of a valid network access point and a rogue access point is performed based on whether the received network response message is respectively in conformity or nonconformity with predetermined expectations. If the access point is determined to be a rogue access point, it is reported to the network. If the access point is determined to be a valid network access point, the supplicant is authenticated to the network.
Owner:CISCO TECH INC
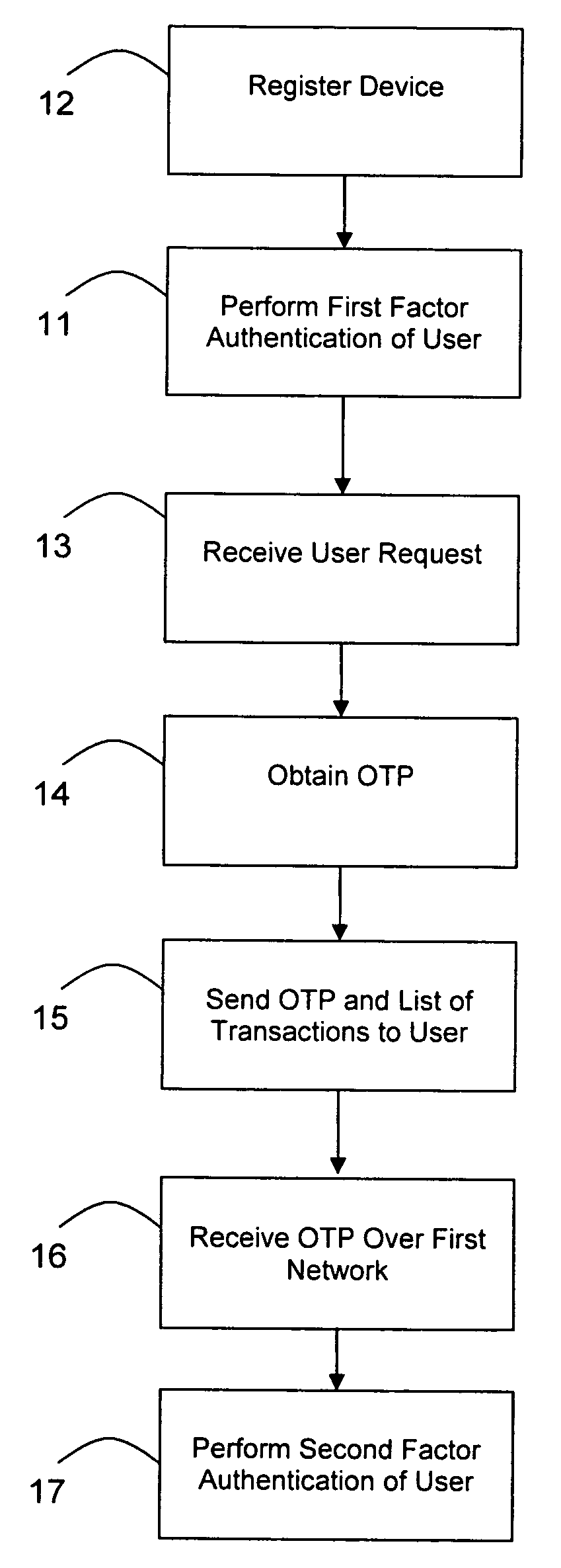
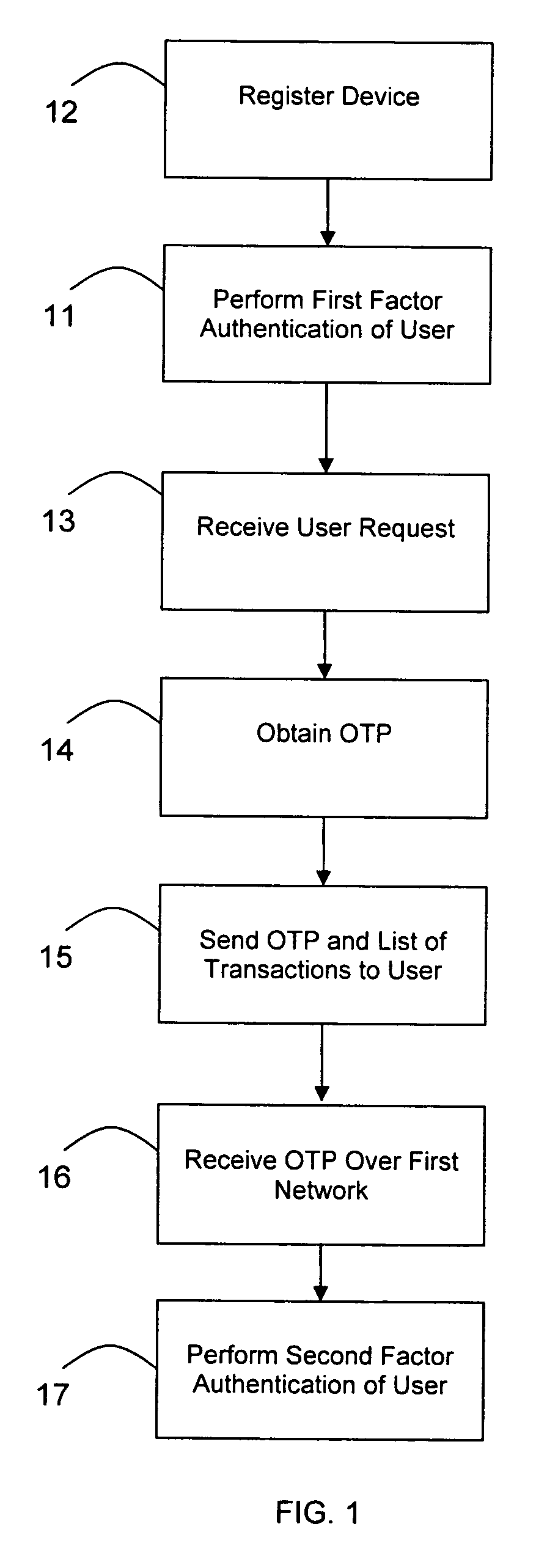
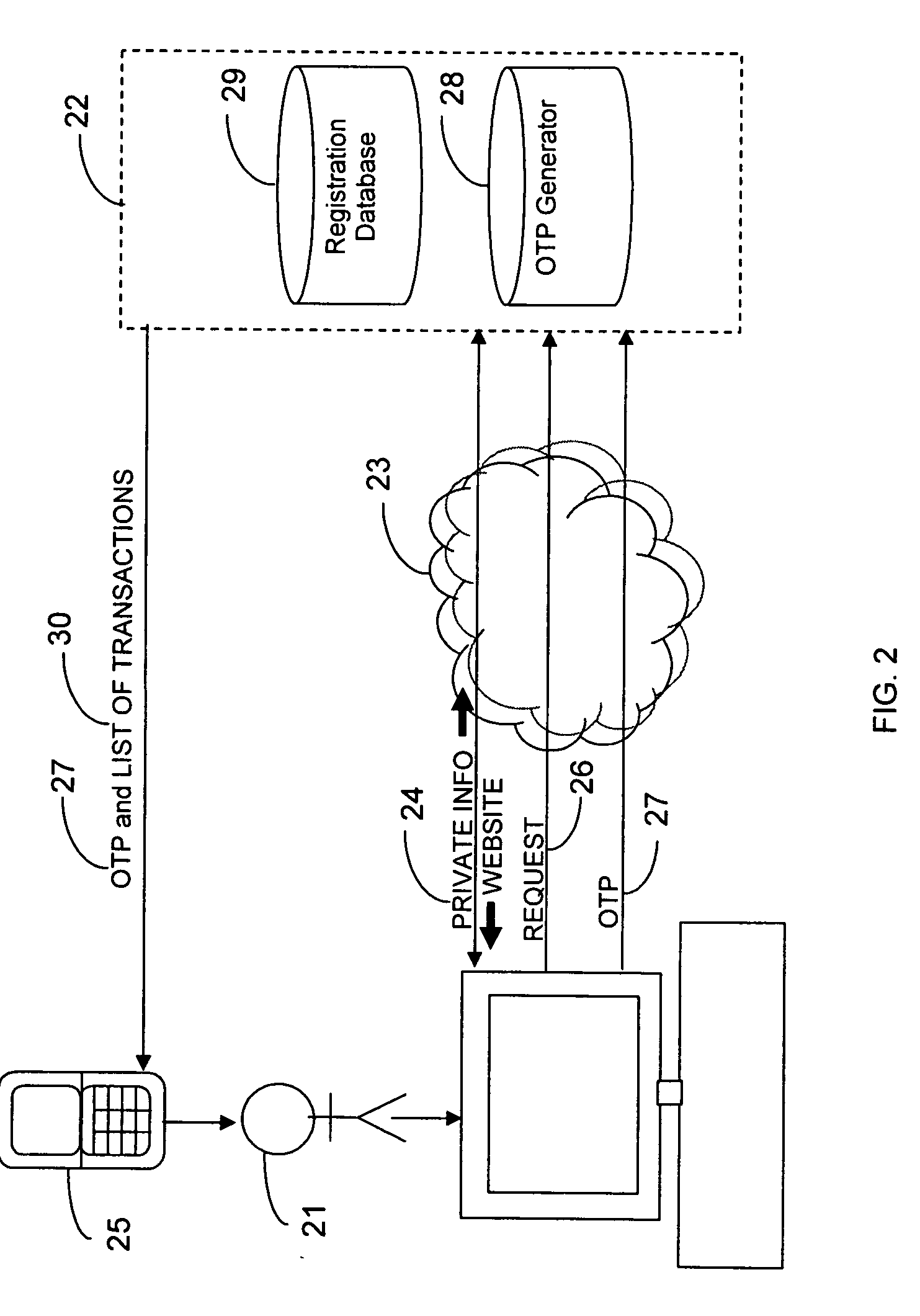
Transaction authentication over independent network
InactiveUS20090106138A1Accelerating transactionFinanceProtocol authorisationOne-time passwordCommunication device
A method of authenticating an online transaction over a first network uses 2-factor authentication of the user to defeat hacker attacks. A communication device is registered for use with the method. The communication device is configured to receive messages over a second network independent of the first network. The user is authenticated over the first network using a first factor, such as a username and password, and then initiates the transaction. A request to execute the transaction is received and a one-time password is obtained to be used as a second factor of authentication. The one-time password and details describing the transaction are sent to the communication device over the second network. The one-time password is received from the user over the first network to complete the second factor of authentication.
Owner:CLAREITY VENTURES INC
Centralized identity authentication for electronic communication networks
InactiveUS7140036B2Easy to carryReduce demandDigital data processing detailsUser identity/authority verificationWeb authenticationElectronic communication
A method of centralized identity authentication for use in connection with a communications network includes registering users of the communications network such that each registered user's identity is uniquely defined and determinable, and registering a plurality of vendors having a presence on the communications network. The registered vendors selectively transact with registered users, wherein the transactions include: (i) the registered vendor selling goods and / or services to the registered user; (ii) the registered vendor granting the registered user access to personal records maintained by the registered vendor; and / or (iii) the registered vendor communicating to the registered user personal information maintained by the registered vendor. The method also includes each user's identity being authenticated over the communications network prior to completion of transactions between registered vendors and registered users.
Owner:CARDINALCOMMERCE CORP +2
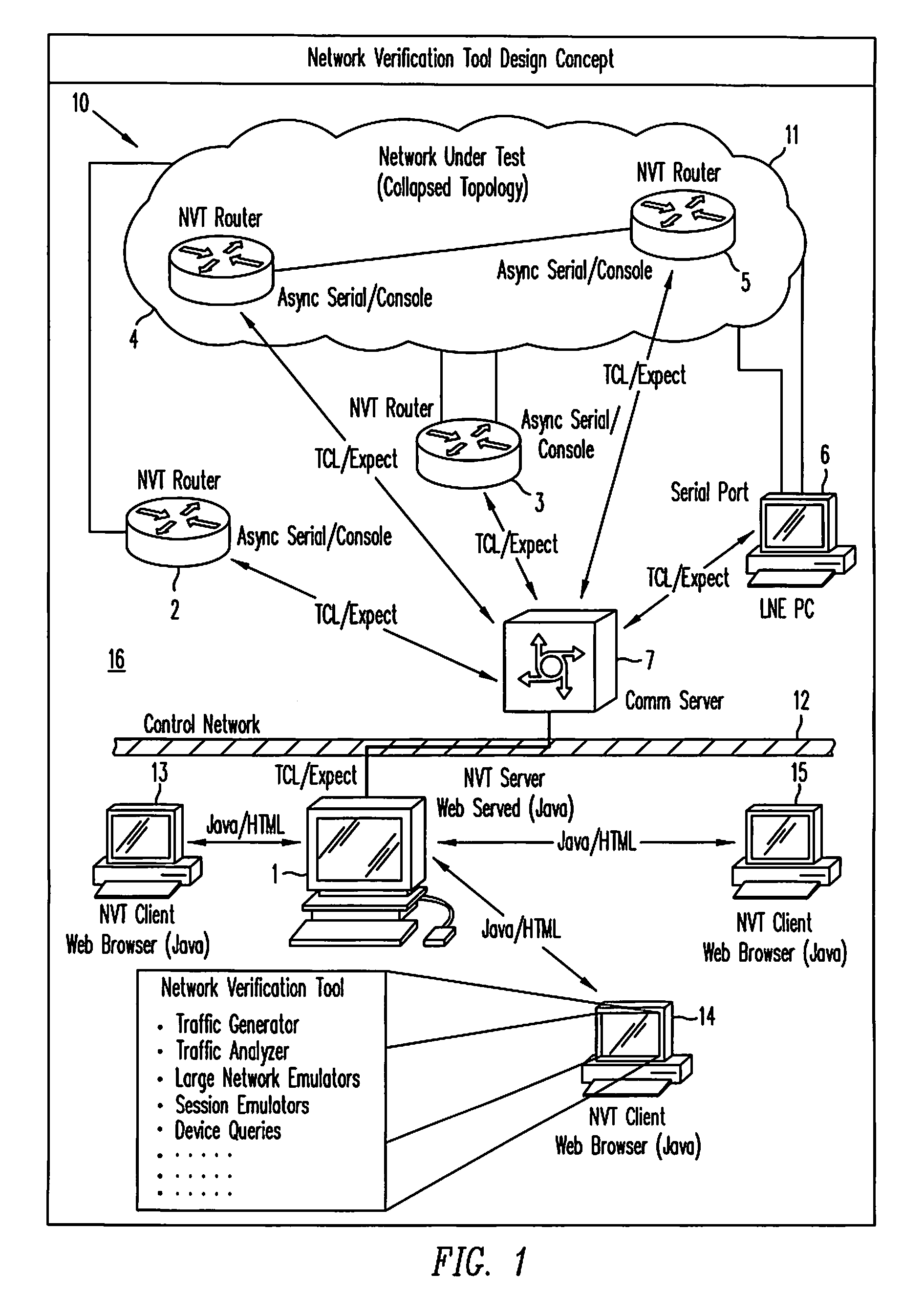
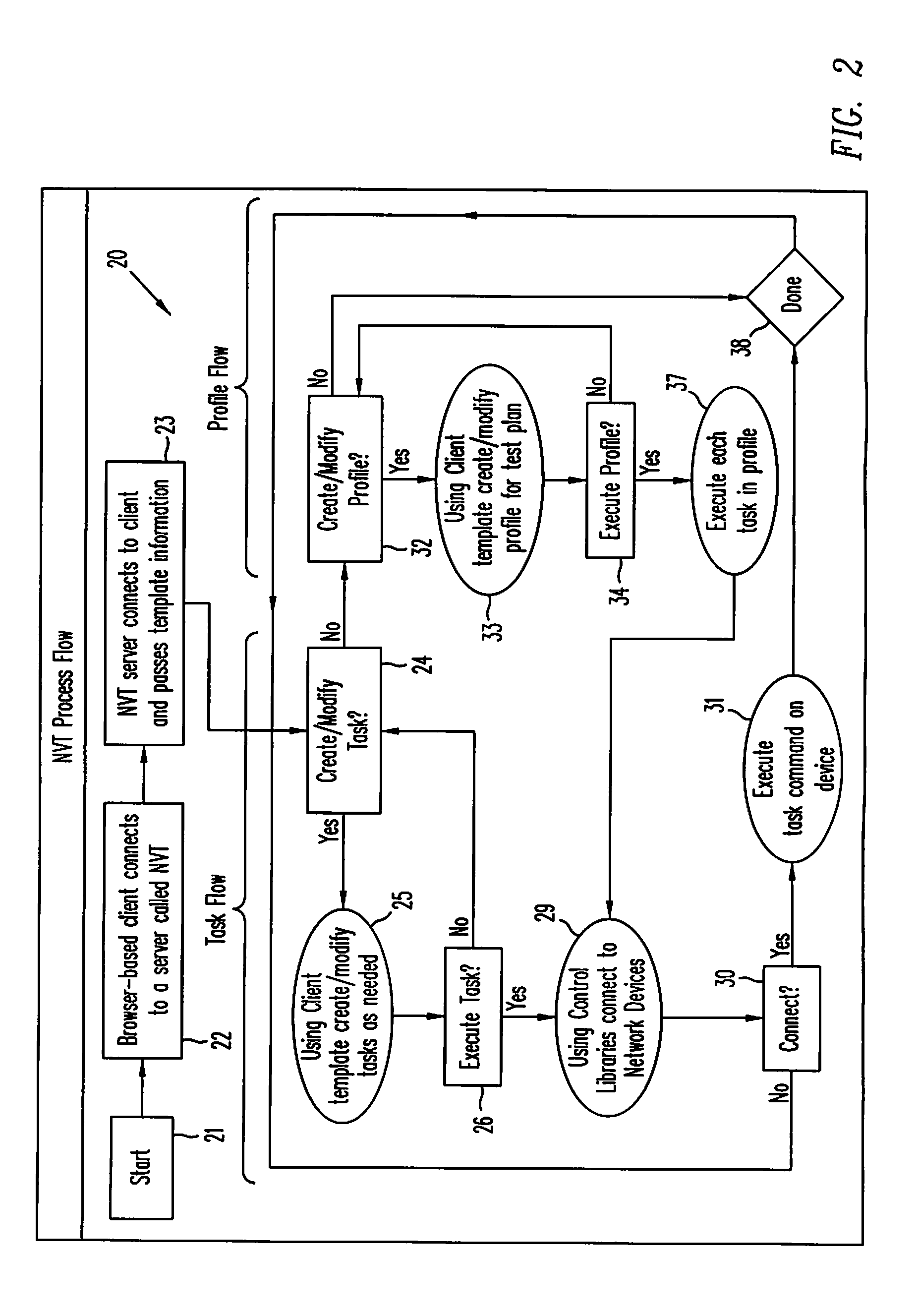
Network verification tool
InactiveUS7342897B1Easily set parameter requiredFacilitate joint resolutionError preventionFrequency-division multiplex detailsTraffic capacityClient-side
A network verification tool is presented that allows a user to easily create tasks for a collection of task types. The collection of task types are hosted by probe network devices that are coupled to a network under test. The network under test includes network devices executing generic network software and particular hardware or software that is being tested. The probe network devices are coupled to an NVT server, which transmits tasks to the task types and interfaces with one or more NVT clients. The NVT clients can create tasks by entering the appropriate parameters within templates supplied by the NVT server. Any collection of task types can be included in the network verification tool, including traffic generators, traffic analyzers, large network emulators, session emulators, device queries and script tasks.
Owner:CISCO SYSTEMS INC
Method and system for biometric based access control of media content presentation devices
InactiveUS20060271791A1Strong claimBroadcast-related systemsBroadcast transmission systemsInternet privacyMedia access control
A centralized biometric system for verifying the identity of a user over a communications network includes a device that stores biometric information in association with information that identifies users. The system further includes a receiver that receives, from a media content presentation device via a communications network, a biometric sample provided by a user requesting media content from a provider. The provider delivers the media content requested by the user from the communications network to the media content presentation device for receipt by the user contingent upon the identity of the user being verified. The system further includes a processor that compares the biometric sample provided by the user to stored biometric information of the user. The processor verifies the identity of the user upon a sufficient correspondence between the biometric sample provided by the user and the stored biometric information of the user.
Owner:SBC KNOWLEDGE VENTURES LP
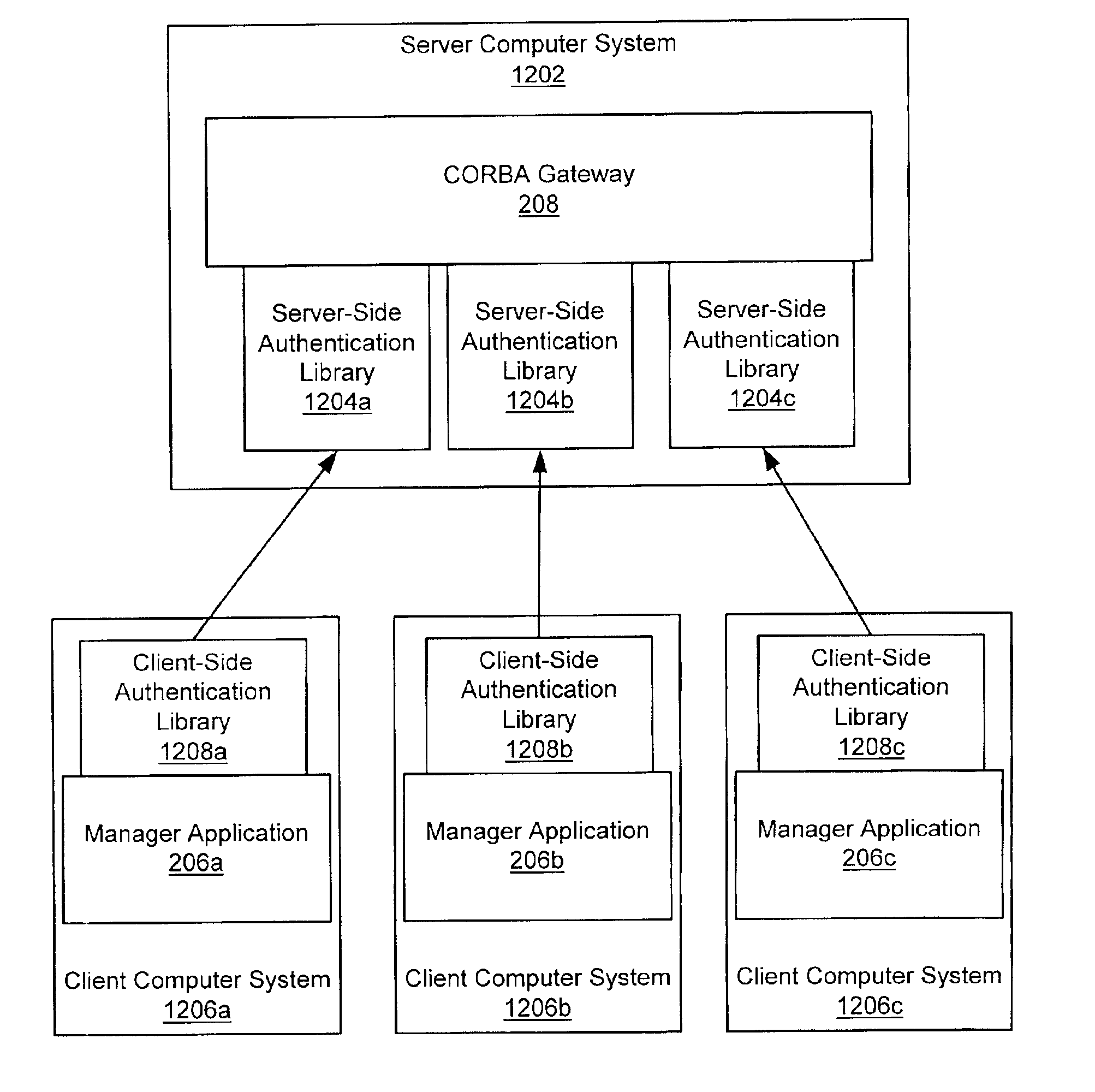
Pluggable authentication modules for telecommunications management network
InactiveUS6950935B1User identity/authority verificationMultiple digital computer combinationsApplication softwareNetwork service
A system and method for authenticating users over a network. At least one pluggable authentication module (PAM) is used to authenticate users of network services. Each PAM includes a client-side authentication library and a server-side authentication library which may each be implemented in accordance with a specification expressed in an interface definition language (IDL), wherein the IDL is operable to define interfaces across a plurality of platforms and programming languages. The client-side authentication library is implemented for a particular client platform and deployed on the client computer system to provide a client-side interface to retrieve and encrypt a user profile. The server-side authentication library is implemented for a particular server platform and deployed on the server computer system to provide a server-side interface to receive the encrypted user profile from the client-side authentication library and decrypt the user profile to authenticate the user for network services. The client-side authentication library may be shared by a plurality of management applications and the server-side authentication library may be shared by a plurality of gateway components.
Owner:ORACLE INT CORP
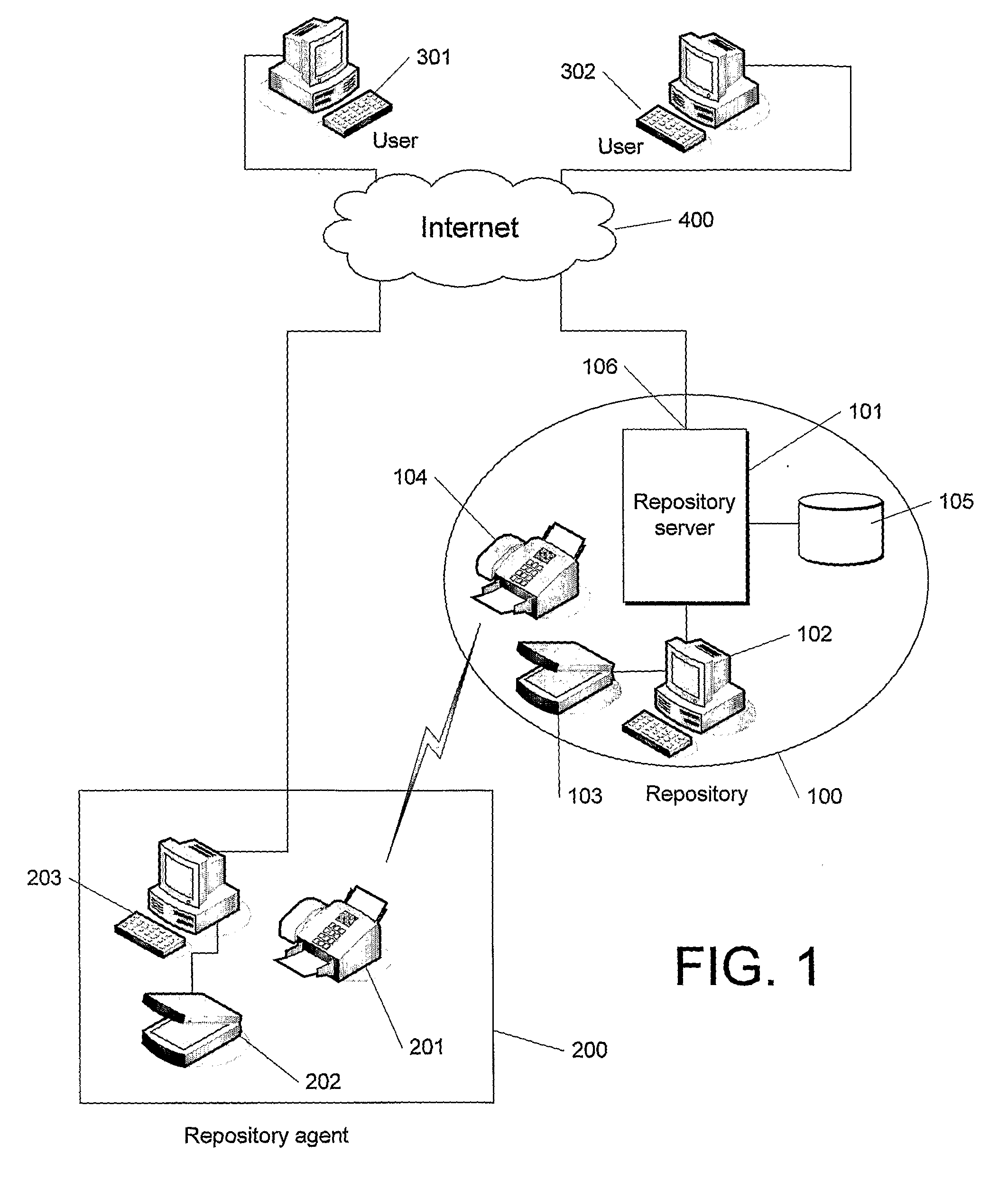
Method and System for Verifying Documents
InactiveUS20080028220A1SpeedLow costPaper-money testing devicesUser identity/authority verificationInformation supportThe Internet
A method and system for verifying the authenticity documents using an international computer network. Documents are processed by a central repository (100) and verification information supporting their authenticity generated. Paper documents are scanned into electronic image data and uploaded to a server (101) together with verification information where they can be viewed by persons using client computers (301, 302) on an international computer network such as the Internet (400).
Owner:THE THAYN FIRM LIMITED LIABILITY
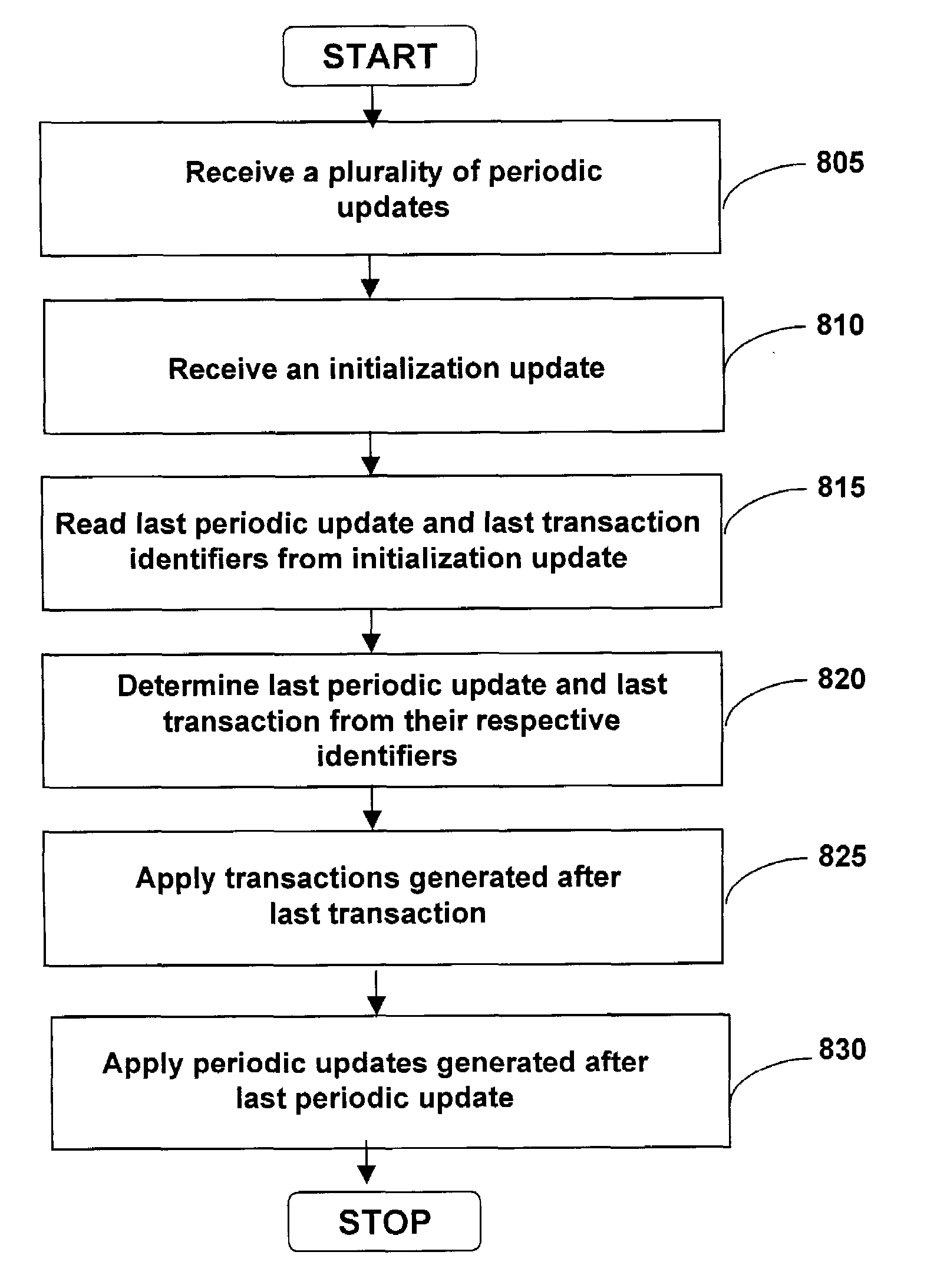
Method and system for validating remote database updates
InactiveUS7047258B2Data processing applicationsDigital data information retrievalDatabaseNetwork verification
Embodiments of the present invention provide a method and system for validating remote database updates over a network. A local database record and a remote database record may be compared and exceptions may be generated. Each exception may describe a discrepancy between the remote and local database records. An exception identifier may be associated with each exception, where the exception identifier may be associated with an identifier of the record. An event identifier may be associated with each event in the update, where the event identifier may be associated with an identifier of the record. The events and exceptions that correspond to the record may be compared to determine whether the update is valid.
Owner:VERISIGN
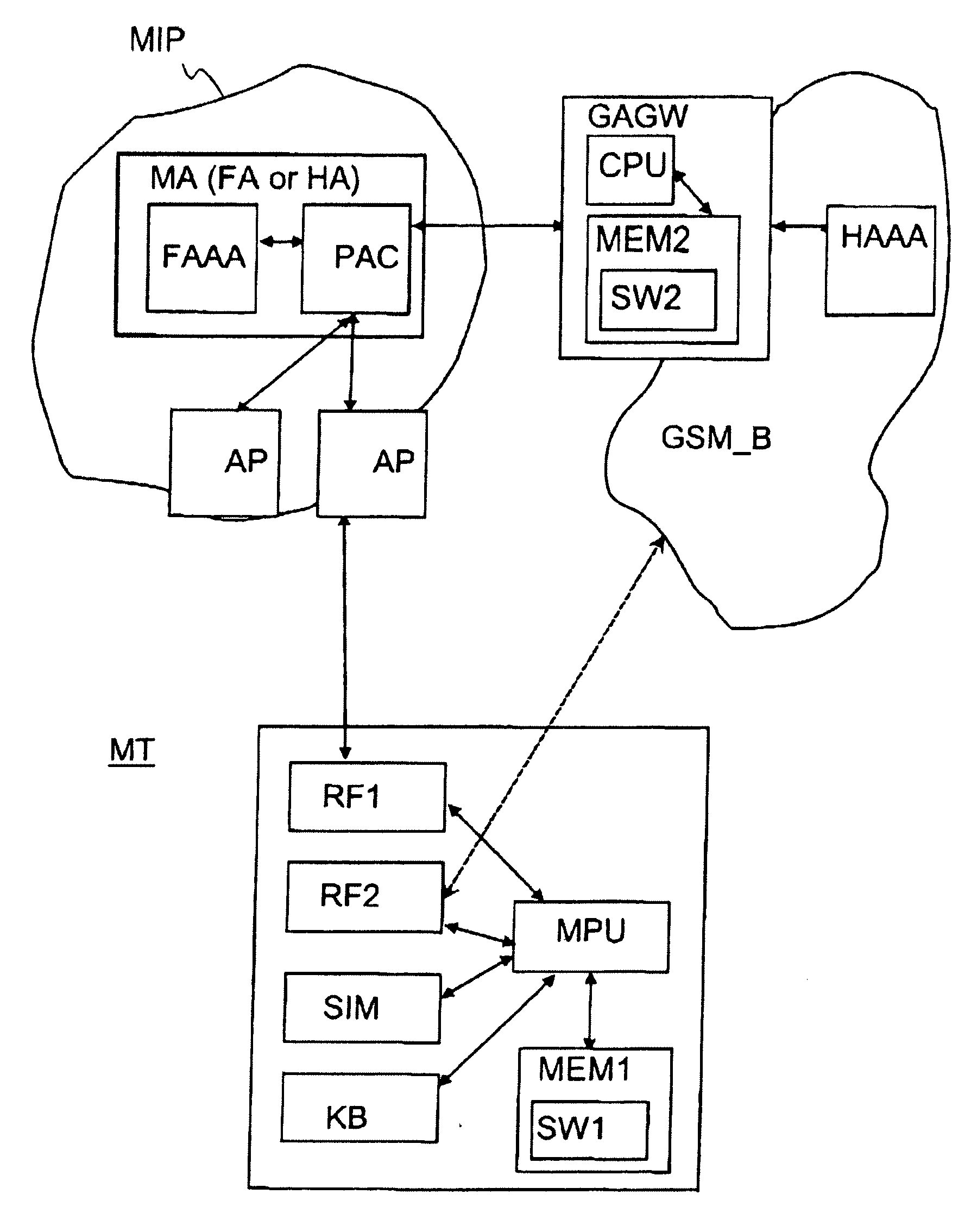
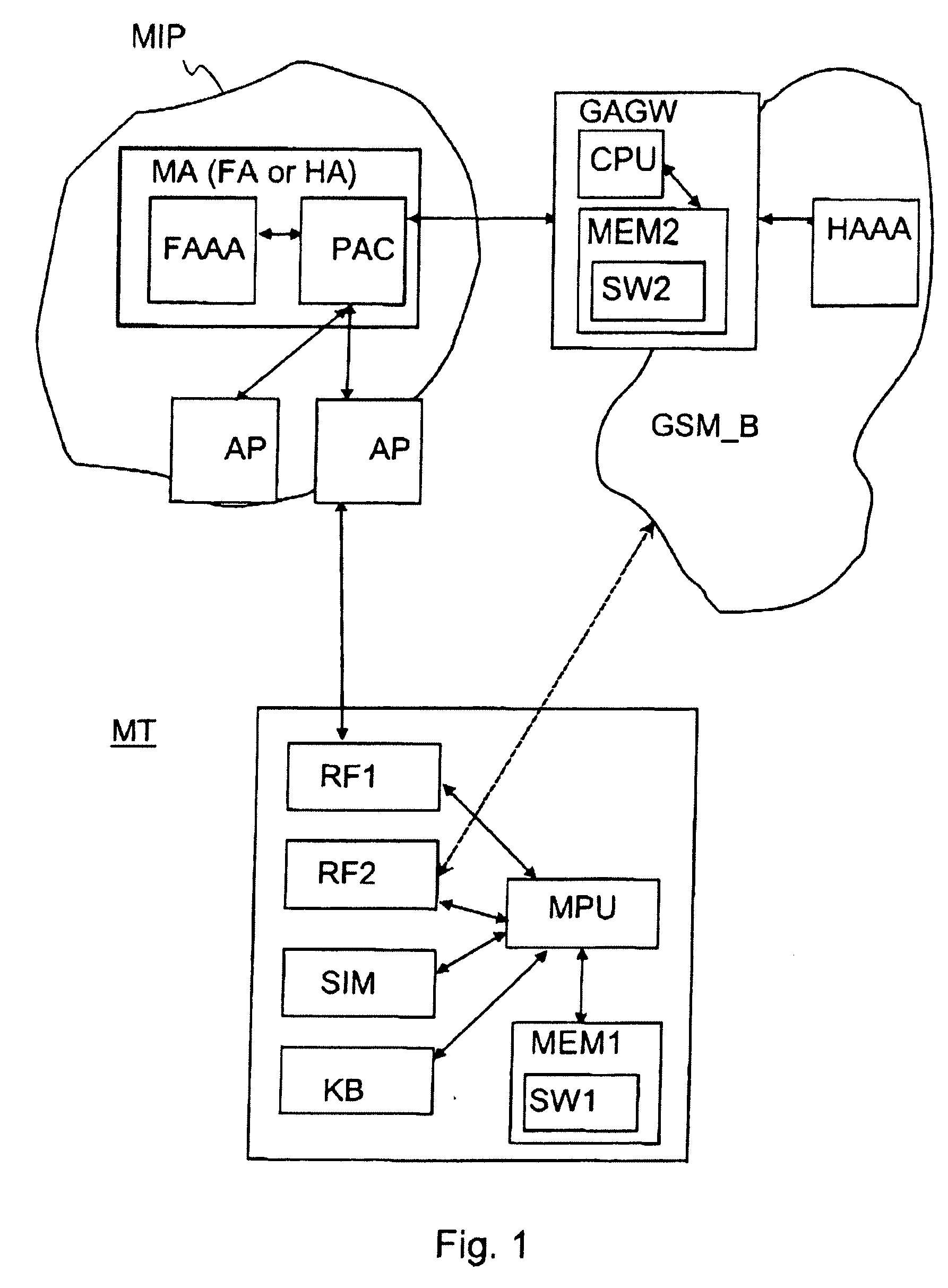
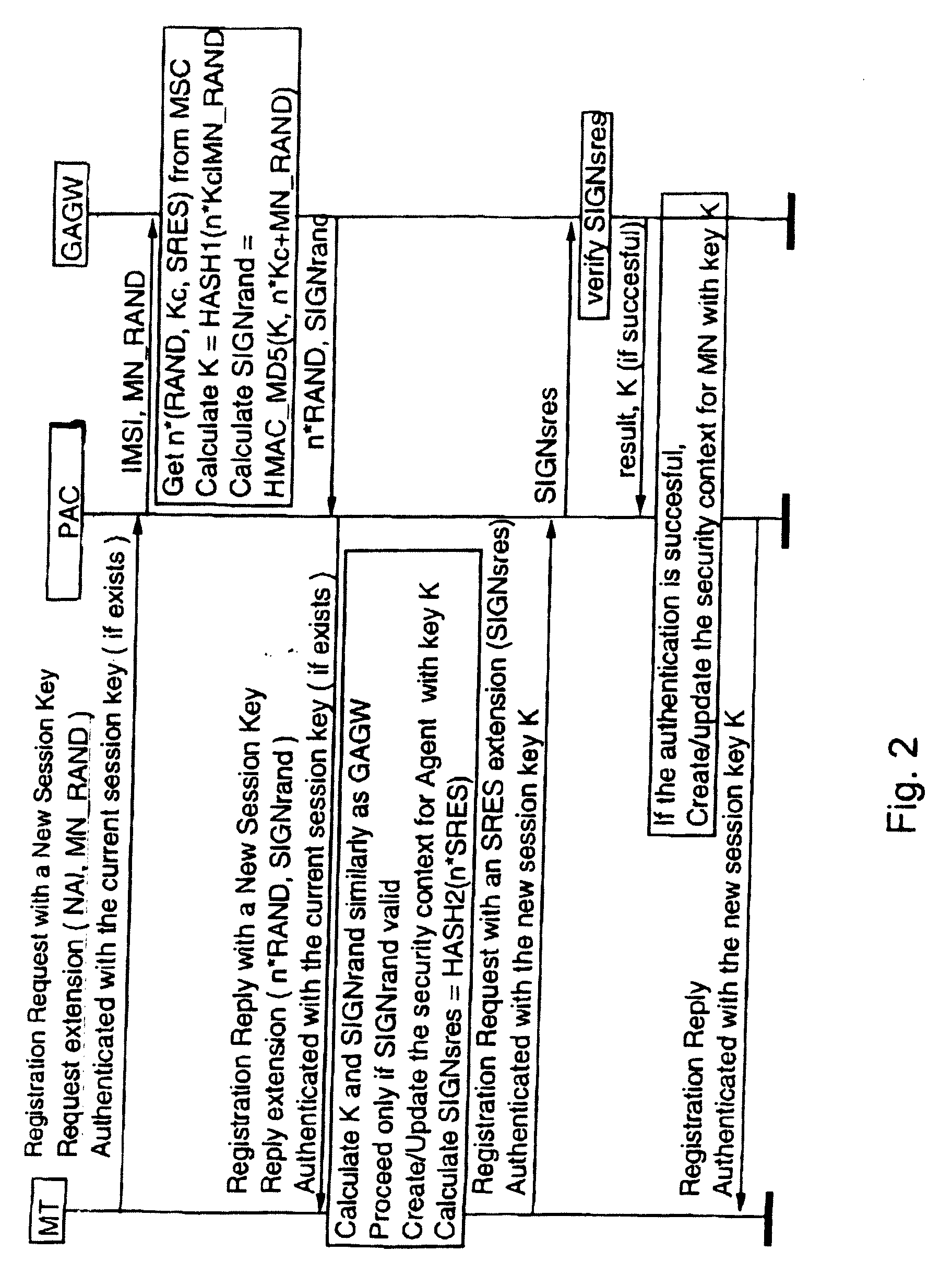
Authentication in a packet data network
InactiveUS20070060106A1Key distribution for secure communicationUnauthorised/fraudulent call preventionTelecommunications networkSession key
Owner:NOKIA CORP
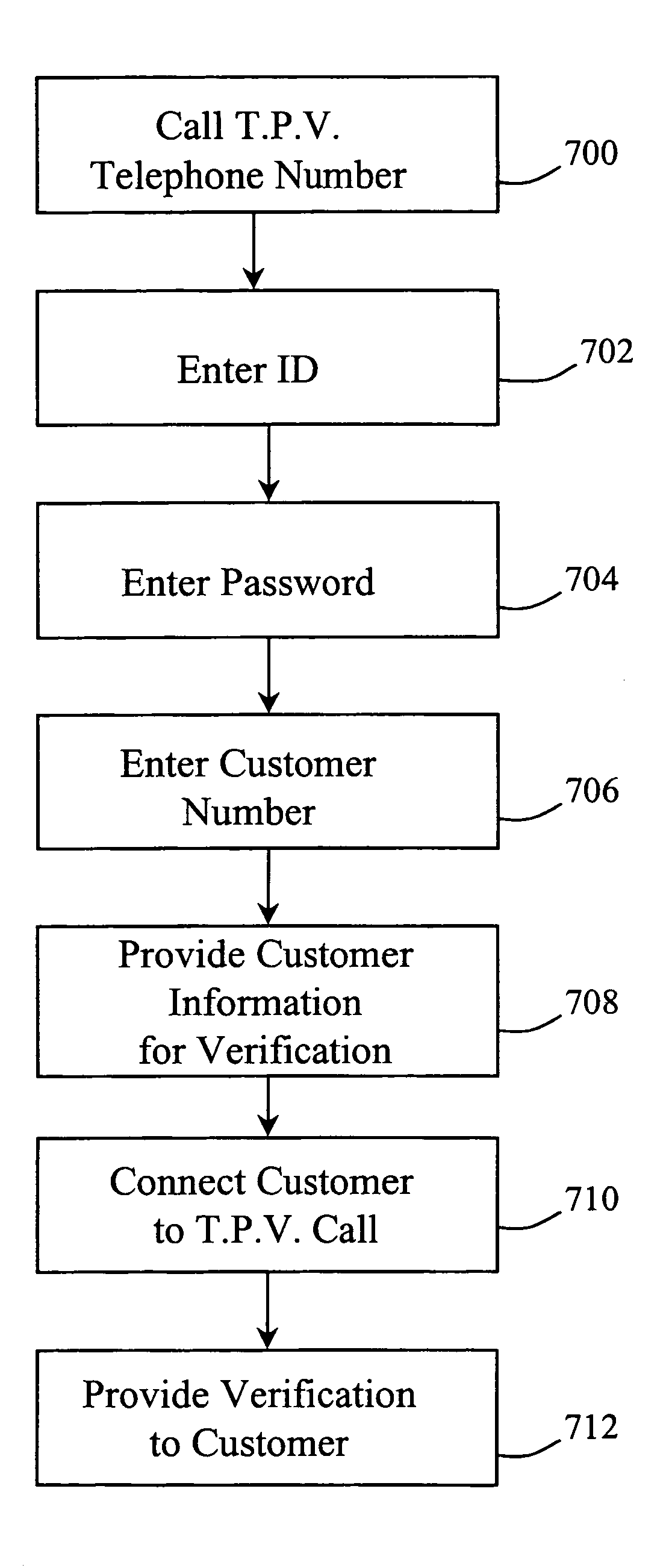
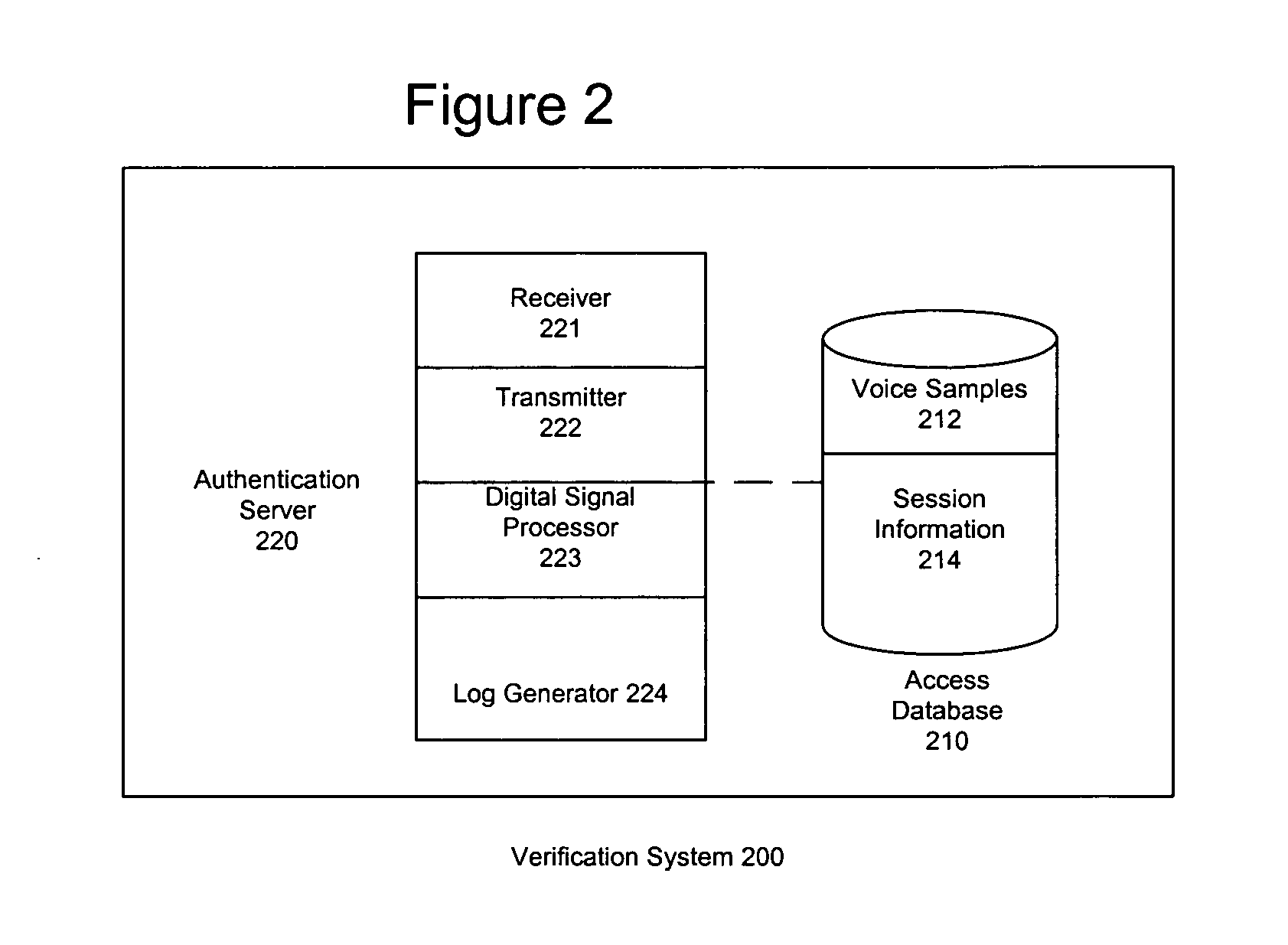
Automated third party verification system
InactiveUS7203653B1Easy accessAutomatic call-answering/message-recording/conversation-recordingDigital data authenticationThird partyData access
A computer based verification retrieval system comprises a communication network to facilitate communication between a first computer and a data access computer, a data access computer connected to said communication network, said data access computer configured to serve as an interface for said first computer and transmit said verification over said communication network to said first computer, and a data storage computer in communication with said data access computer, said data storage computer configured to store said verification and provide said verification to said data access computer upon request.
Owner:RED HAT
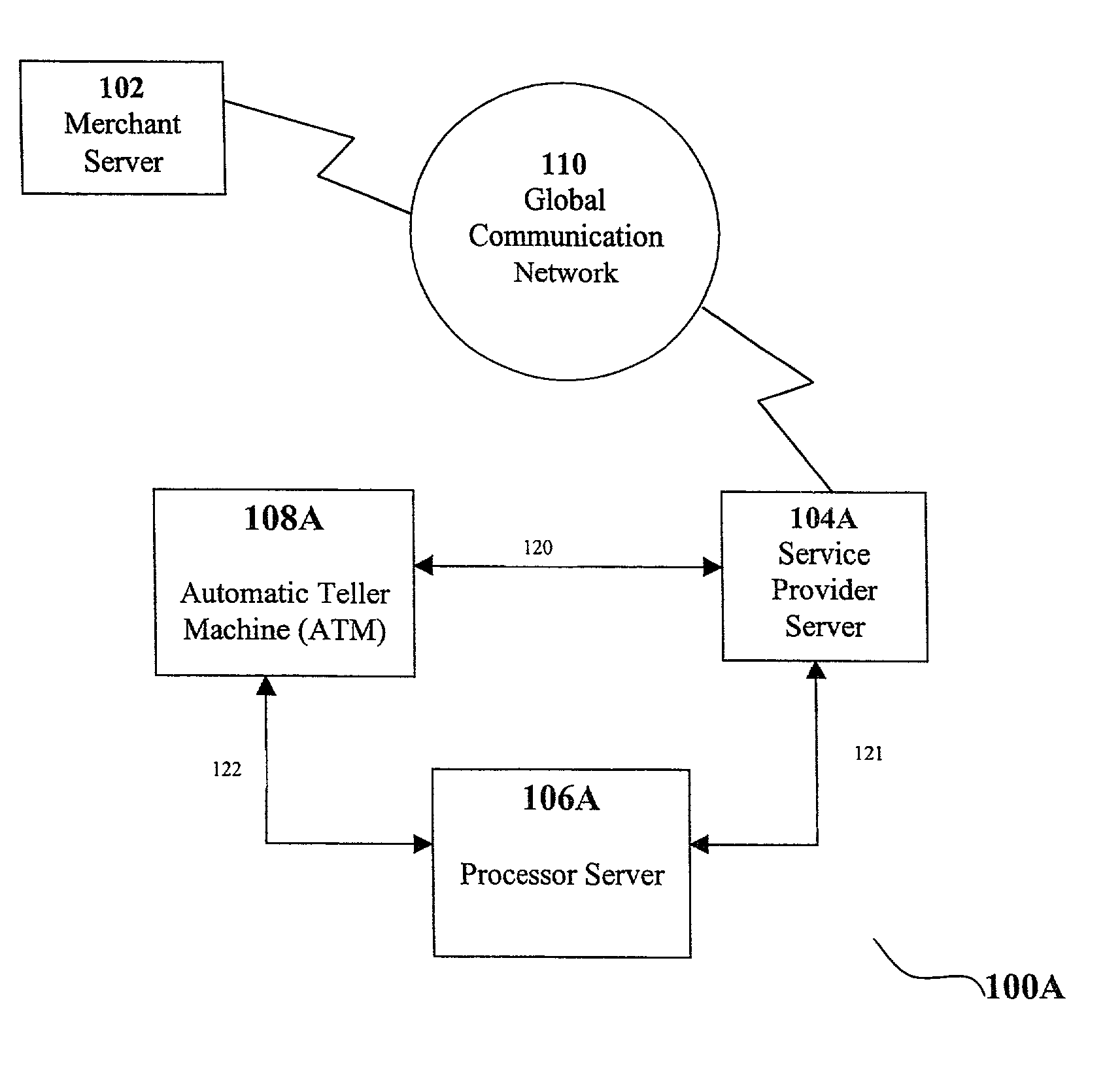
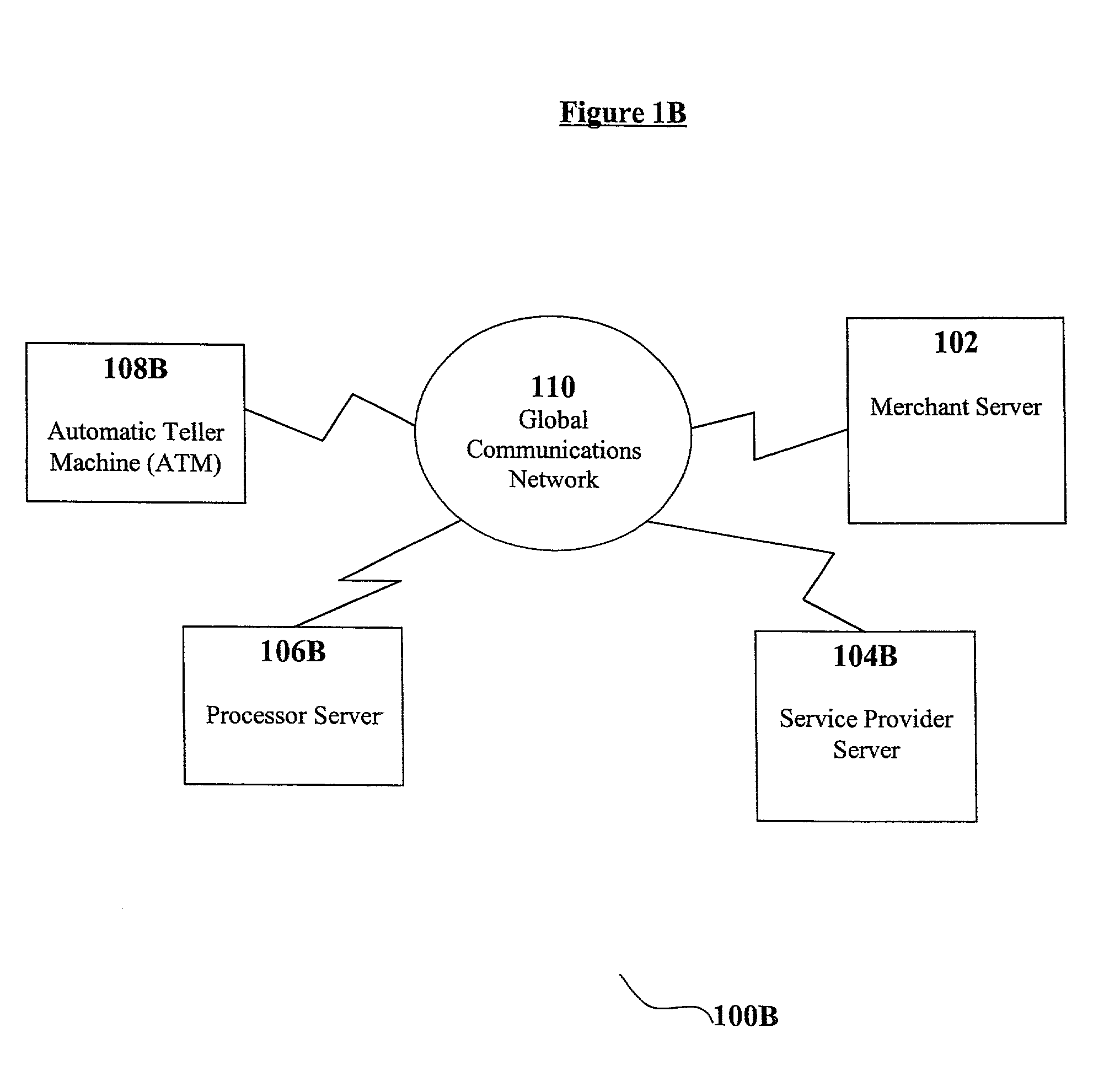
System and method for facilitating electronic commerce transactions at an automatic teller machine
A method and system facilitate an electronic commerce transaction between an ATM and an electronic commerce merchant via a global communications network. Transaction data is received at a server and verified with a processing network. The transaction data is reformatted, such that the data can be utilized by a server located on a global communications network, and transmitted over the global communications network to the servers of an electronic commerce merchant. Data is then received from the merchant, reformatted into a format that is capable of being utilized by the ATM, and transmitted back to the ATM.
Owner:IATMGLOBAL NET
VoIP call through tester
ActiveUS20060188080A1Interconnection arrangementsSpecial service for subscribersTester deviceCall routing
According to various embodiments of the present invention, systems and methods for verifying the routing of a call through a network, including: generating an outbound call from a test tool in a first network, the outbound call including a test key and a destination number, the destination number being associated with a communication device accessible to first network, routing the outbound call to second network, receiving outbound call from second network in the form of inbound call to first network, the inbound call including the test key and the destination number, accessing the test key, and based at least in part on the test key, routing the inbound call to the test tool. In some instances, call tracking information may be collected, analyzed, and / or displayed.
Owner:LEVEL 3 COMM LLC
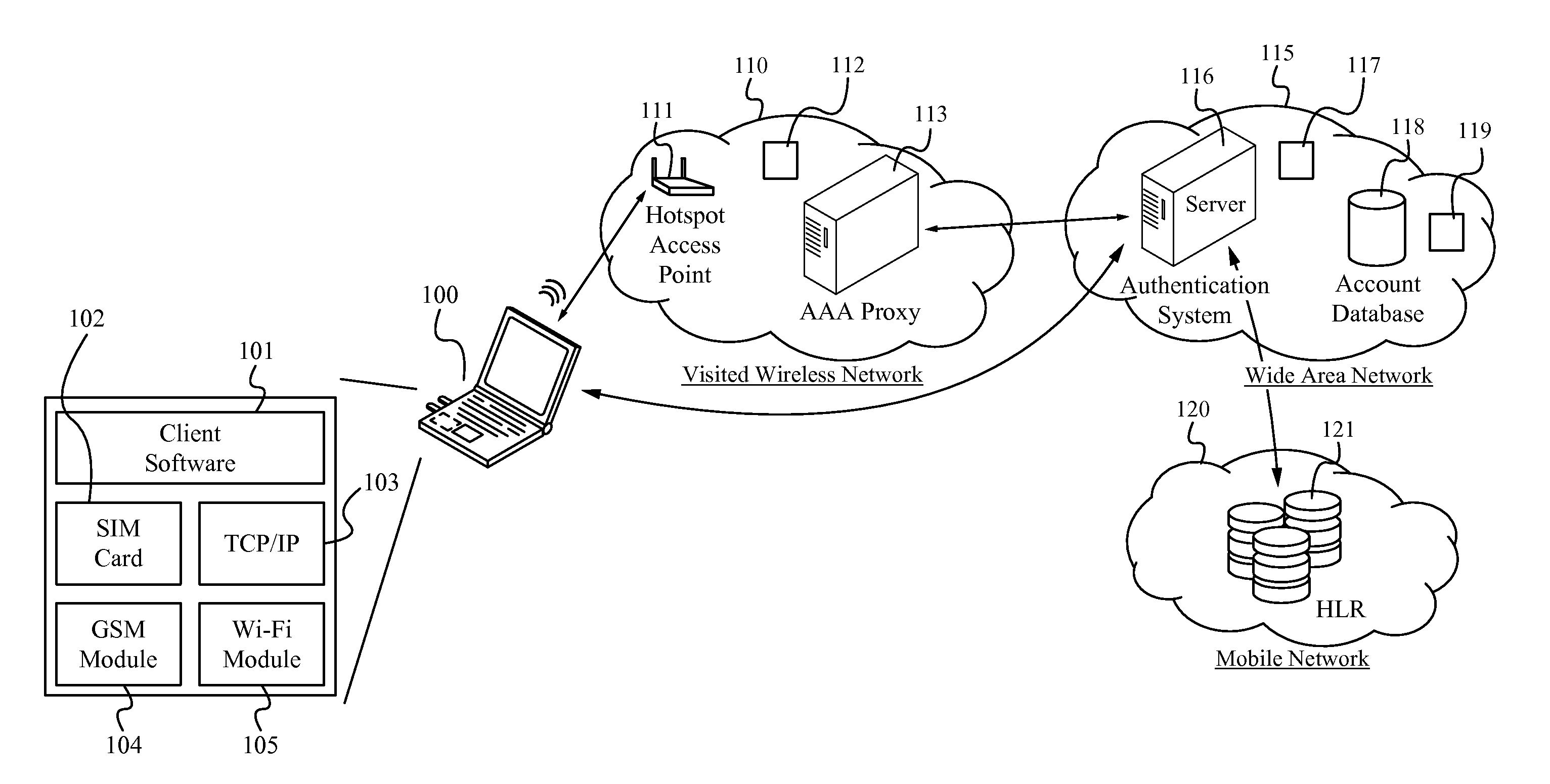
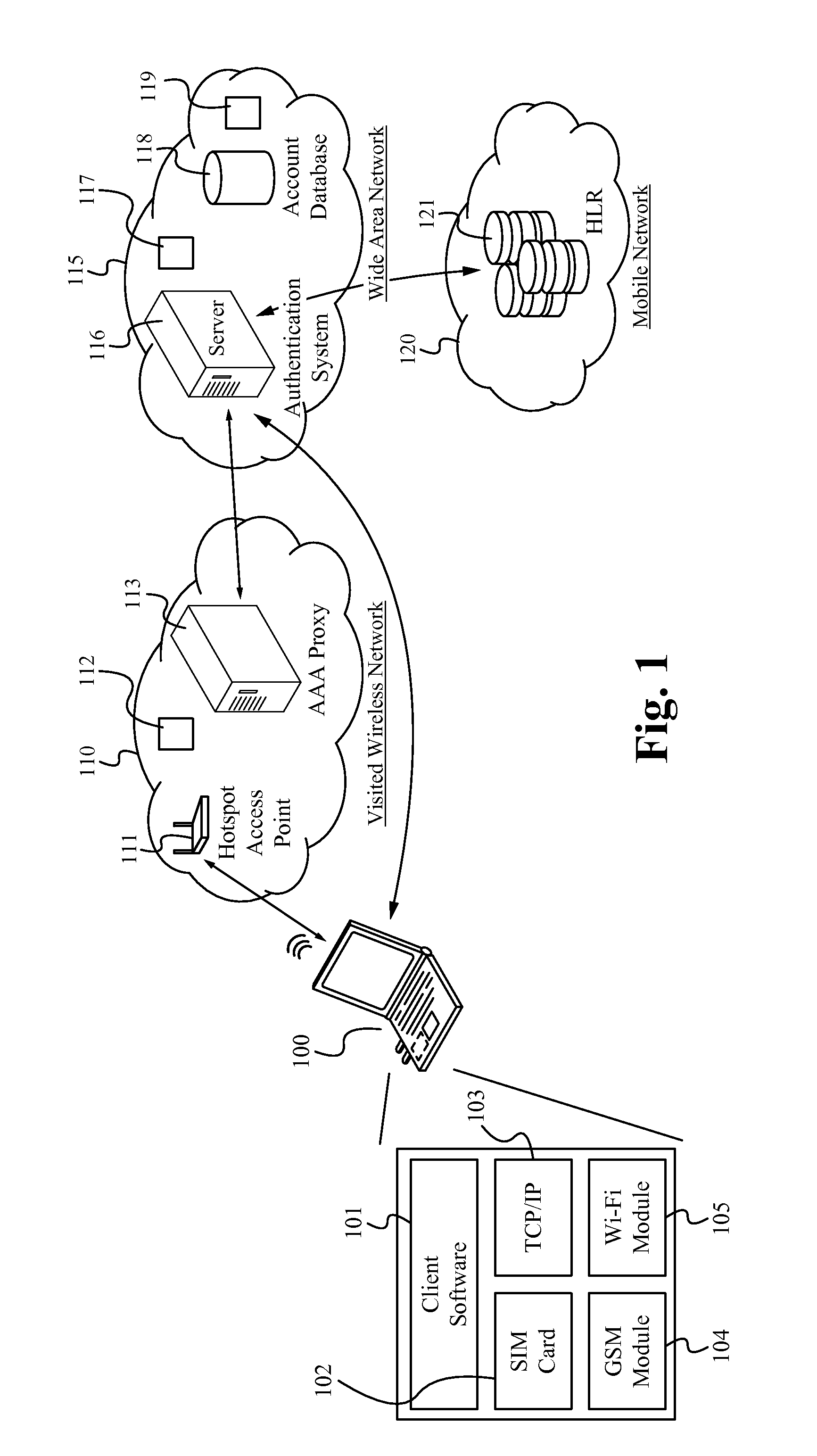
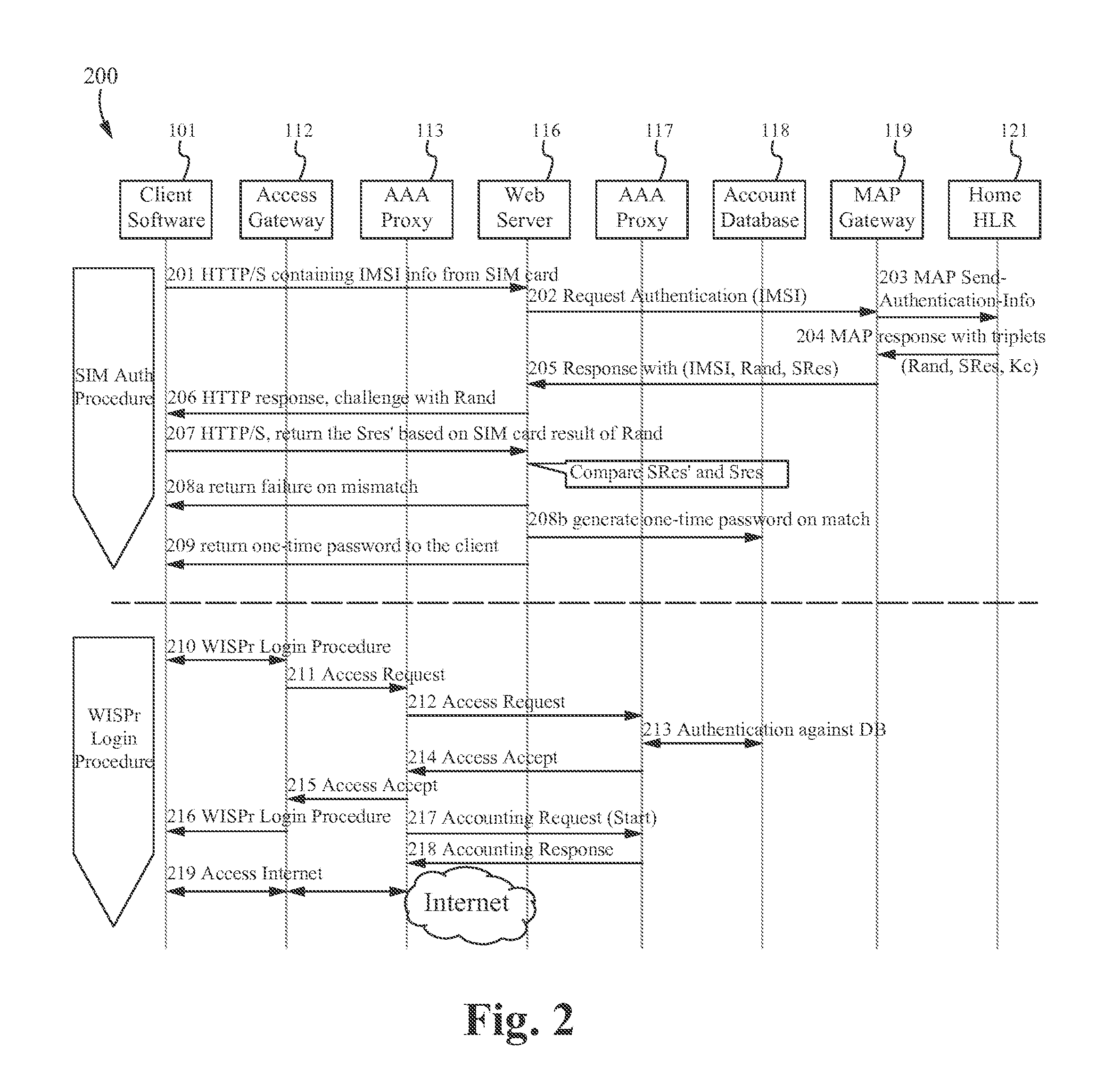
METHOD OF AND SYSTEM FOR EXTENDING THE WISPr AUTHENTICATION PROCEDURE
ActiveUS20120149334A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareWi-Fi
A method and system for completing the authentication process of a user device in a second communication network (such as Wi-Fi or WiMAX) utilizes the user credential (such as a SIM card, a USIM card, or a RUIM card) of a first communication network (such as GSM, CDMA, EDGE, or LTE). A client, such as a software module, executes on the wireless device. An authentication platform retrieves the SIM card credential information in the first communication network and passes the information to the authentication platform of the second communication network, thereby granting the client access to the second communication after the authentication platform validates with the first communication network.
Owner:SYNIVERSE COMM
Centralized biometric authentication
ActiveUS7107220B2Electric signal transmission systemsKey distribution for secure communicationNetwork communicationCommunication device
A centralized biometric system is provided for verifying an individual's identity over a communications network. The system includes a storage that stores biometric information in association with information that identifies an individual. The system also includes a receiver that receives, from one of a communications device and a network communications platform, a biometric sample from a party attempting to obtain a service from the one of the communications device and the network communications platform. The service is provided contingent on authentication of the party as the individual. The system also includes a processor that compares the biometric sample to the biometric information to authenticate the identity of the party as the individual.
Owner:INTERACTIONS LLC (US)
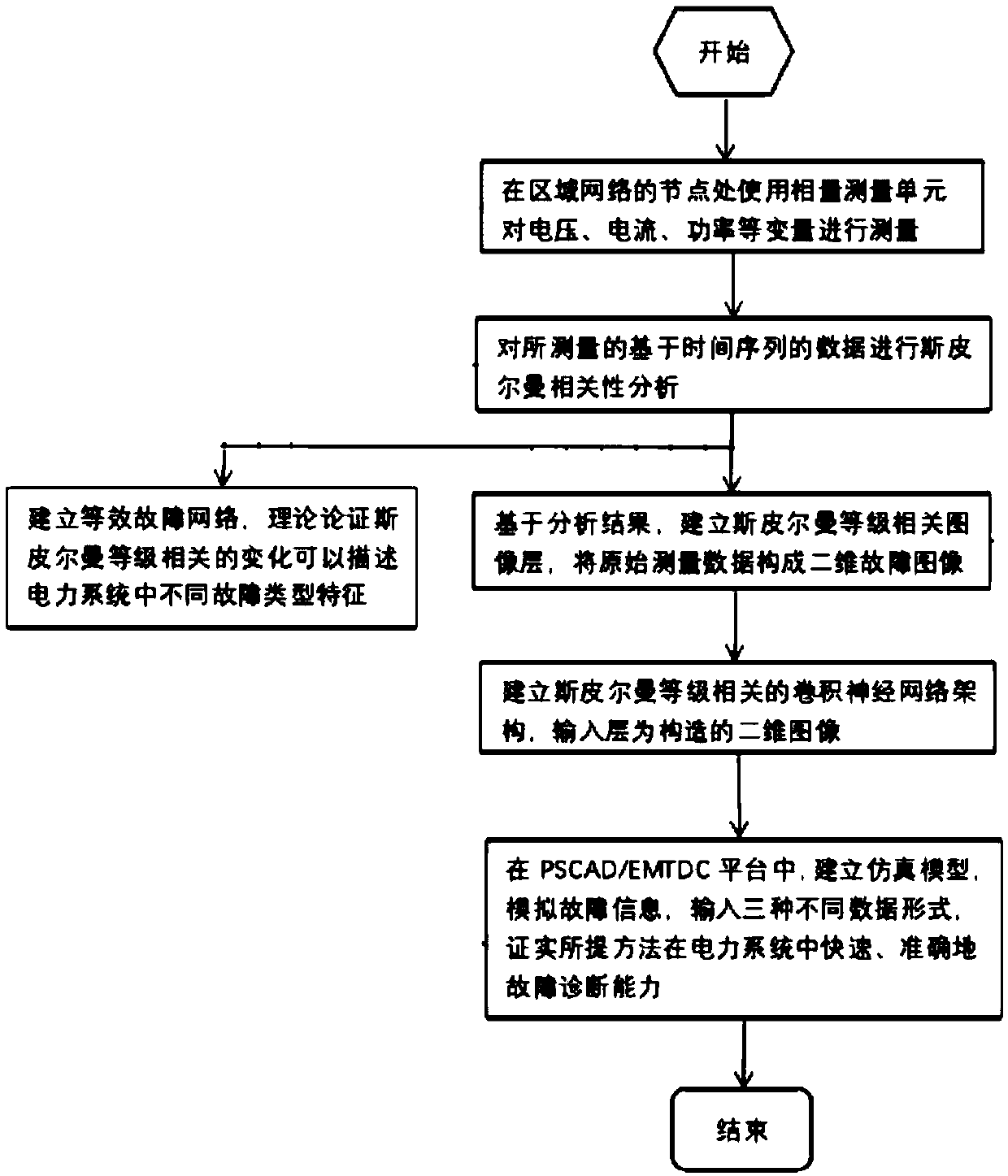
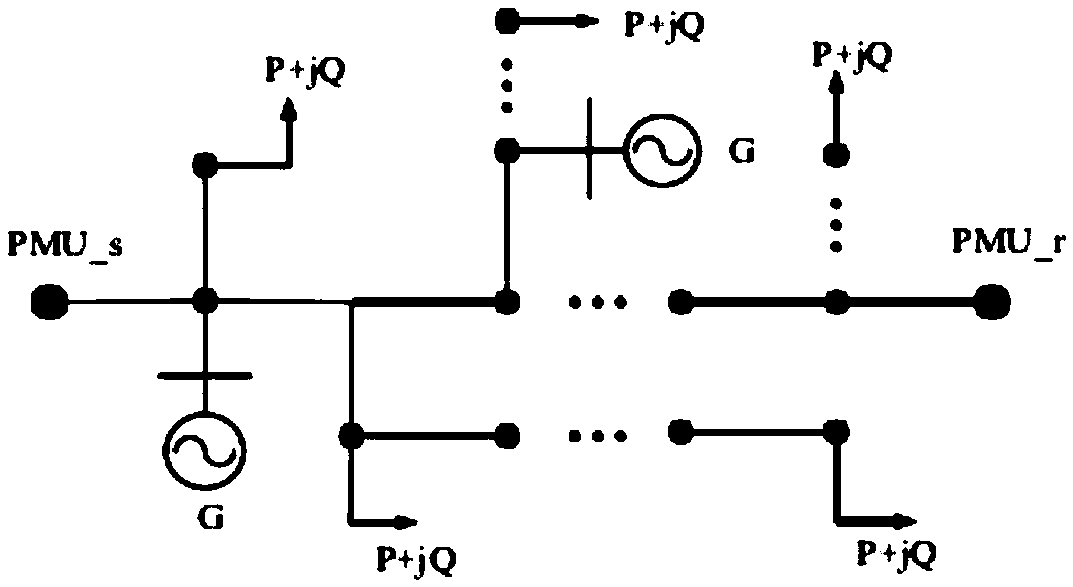
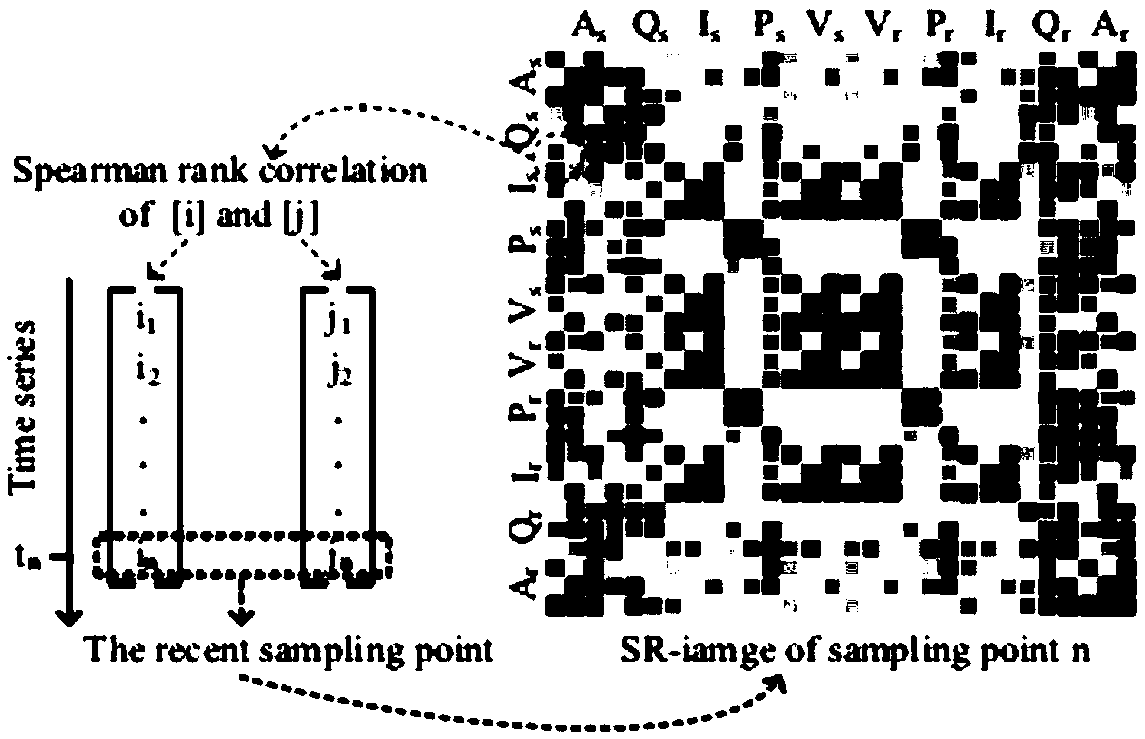
Convolutional neural network power system intelligent fault detection method and system based on Spearman level correlation
ActiveCN109614981AImprove reliabilityRealize analysisCharacter and pattern recognitionDesign optimisation/simulationNODALElectric power system
The invention provides a convolutional neural network power system intelligent fault detection method and system based on Spearman level correlation, and the method comprises the steps: setting a phasor measurement unit at a regional network node, and carrying out the measurement of data; performing Spearman correlation analysis on the acquired data, and proposing an image generation method basedon an analysis result; establishing an equivalent fault network, verifying the relation between the fault characteristics and the Spearman level correlation, and demonstrating the feasibility of the method; taking the generated image as an initial convolutional layer, and establishing a convolutional neural network architecture based on Spearman level correlation; and verifying the rationality andsuperiority of the method based on PSCAD / EMTDC according to the established architecture. A plurality of types of electric quantity data are comprehensively used for fault diagnosis, the position ofa fault in the power system can be quickly and accurately identified through the convolutional neural network, the problems that the power system has volatility and the traditional detection method isinaccurate due to addition of a distributed power supply and the like are solved, and the robustness and the self-adaptability of the power system are higher.
Owner:NORTHEASTERN UNIV
Verification of a communication path between networks
A system and method for verification of a communication path between a first and a second network by turning on and off a loop back mode. Firstly, verification begins by requesting verification of a communication path by the first network. The second network then acknowledges the verification request and places the communication path in a loop back mode. The first network sends a verification signal over the communication path, which is returned by the second network over the communication path. The second network then terminates the loop back mode. Timers can be included for the acknowledgment and termination steps to ensure the temporary nature of the loop back mode.
Owner:MOTOROLA INC
Searching data
InactiveUS20110131419A1Digital data information retrievalDigital data processing detailsEngineeringLabeled data
A device or “dongle” (32) is provided for coupling to a Windows-based PC (23). The dongle (32) includes a subscriber identity module (SIM) (15), such as the type used in GSM or UMTS cellular or mobile telecommunications networks. A search engine (40) is accessed by the PC (23) by means of a client application (38) on the PC. The search engine (40) generates a list of search results in response to search criteria in a known manner. Further, the search engine is able to return search results relating to data for which there is restricted access (for example, encrypted data). Such data is identified with a tag which may, for example indicated which users or entities are able to access that data. A user's dongle (32) authenticates that user with the network (3) using a authentication arrangement similar to that employed for authenticating users of a GSM or UMTS mobile telecommunications network. The authenticated identity of the user is communicated to the search engine. The search engine then includes in the search results tagged data items for which the tag indicates that the authenticated user has permission to view. Tagged data items that the authenticated user does not have permission to view are not returned in the search results. Therefore, the user not entitled to view data is not distracted by search results corresponding to data that the user is unable to access. The network (3) may include a key store (51) which stores keys that allow encrypted data items identified by the search engine (40) to be decrypted.
Owner:VODAFONE GRP PLC
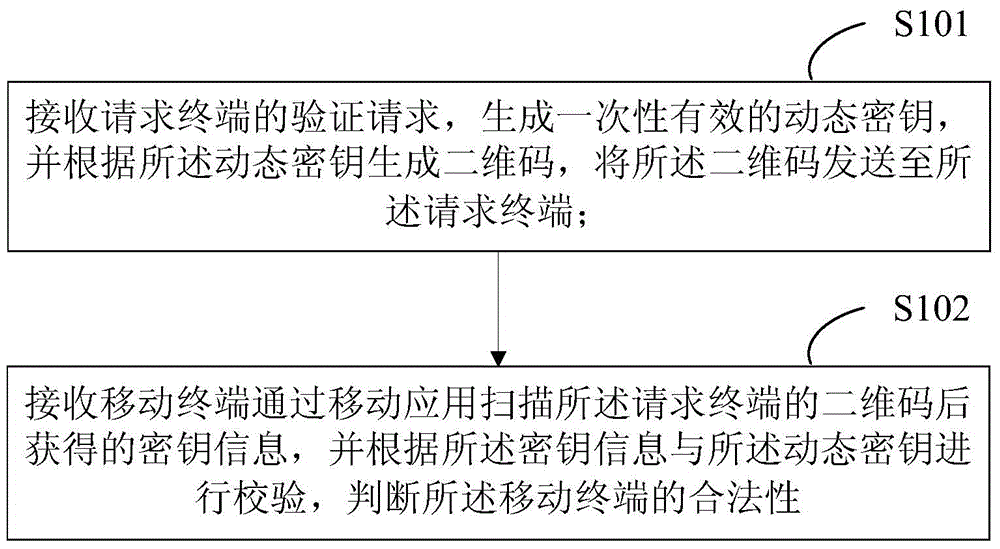
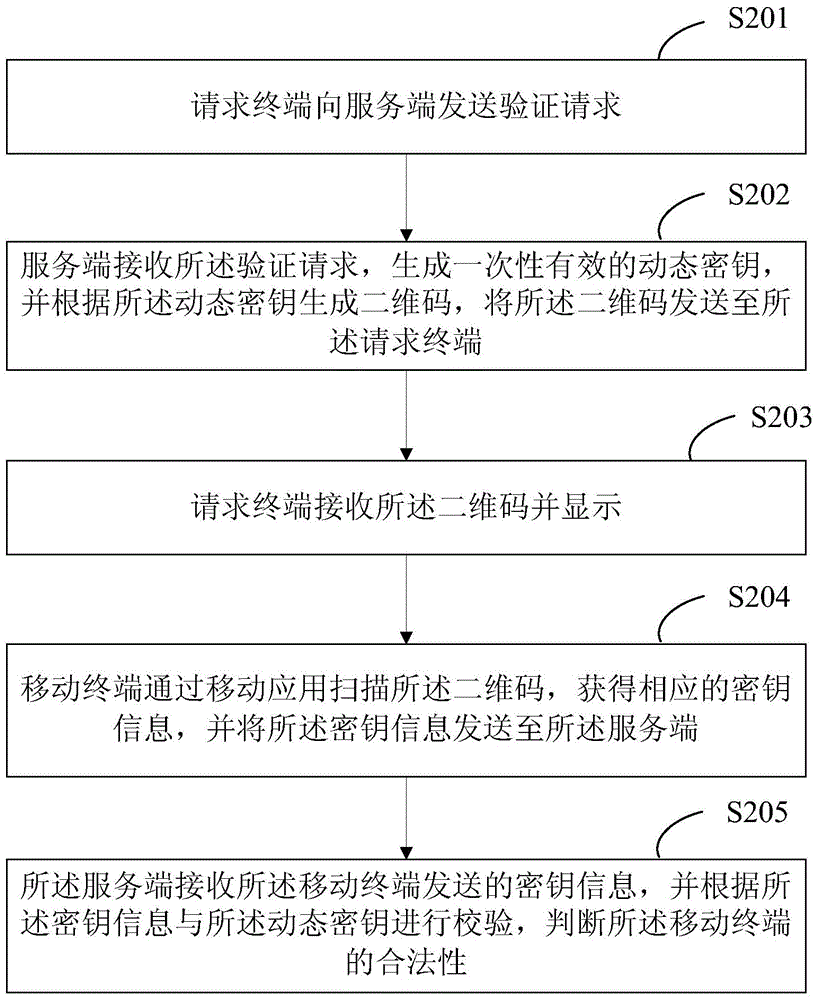
Method and system for controlling verification server and method and system for controlling verification
InactiveCN105282088AEasy to operateImprove securityUser identity/authority verificationSecurity arrangementComputer terminalNetwork verification
The invention discloses a method and a system for controlling a verification server and a method and a system for controlling verification. According to the invention, a one-time effective dynamic key is generated on the verification server, a two-dimensional code is generated according to the dynamic key, the two-dimensional key is sent to a request terminal, a mobile terminal can acquire corresponding key information through scanning the two-dimensional code of the request terminal through a mobile application, the server carries out verification according to the key information returned by the mobile terminal and the locally stored dynamic key, and the legality of the mobile terminal can be judged. The methods and the systems disclosed by the invention enable the key to be difficult to be forged or stolen in the network verification process, can improve the safety of network verification, and are more convenient.
Owner:TENCENT TECH (SHENZHEN) CO LTD
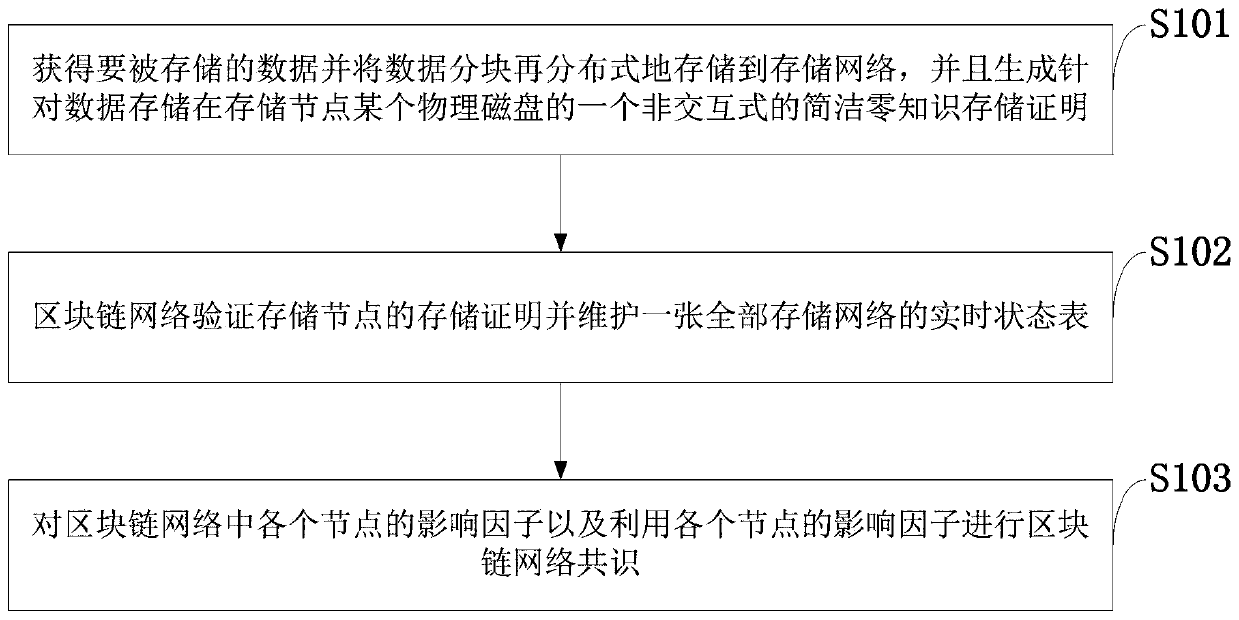
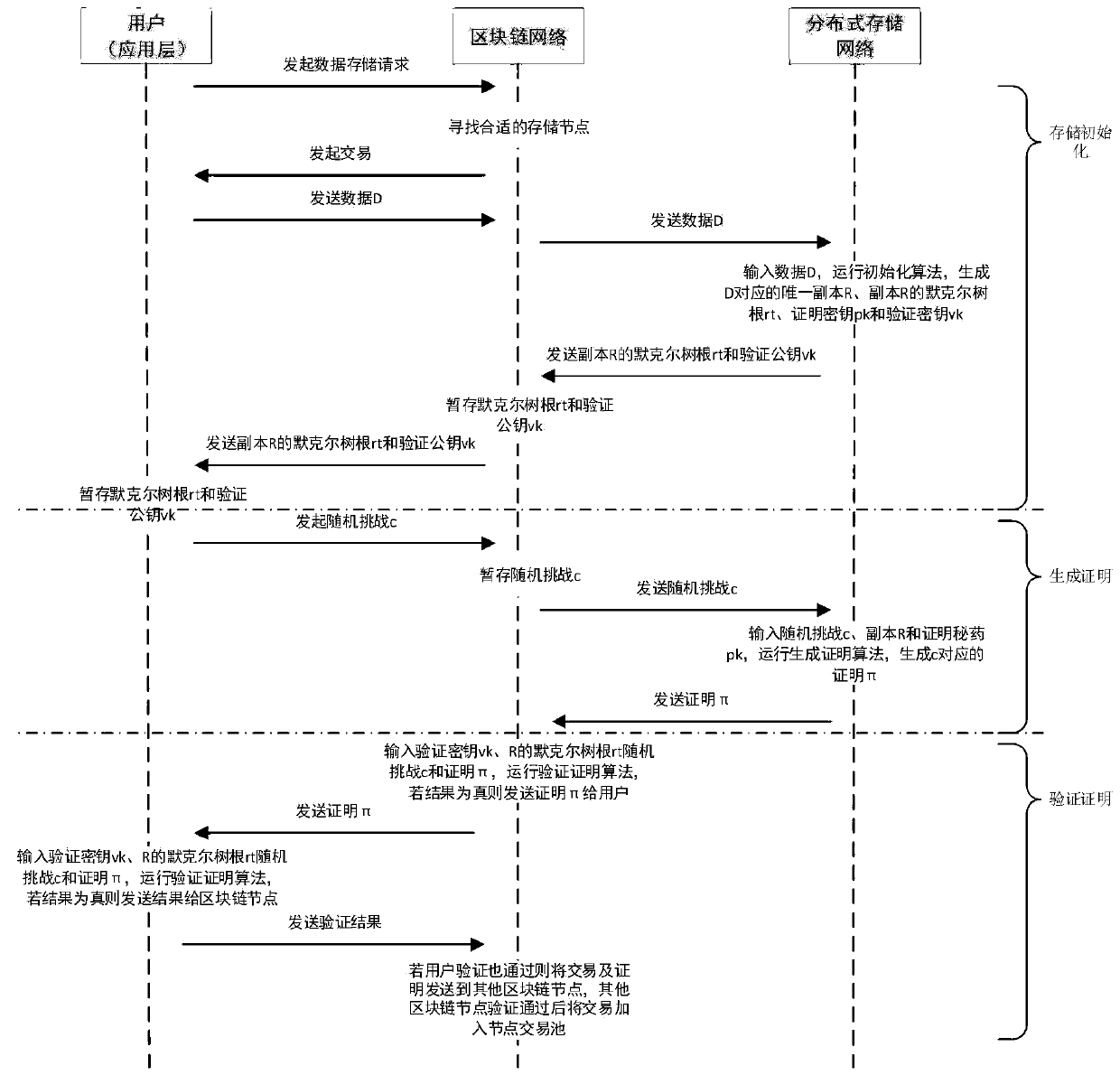
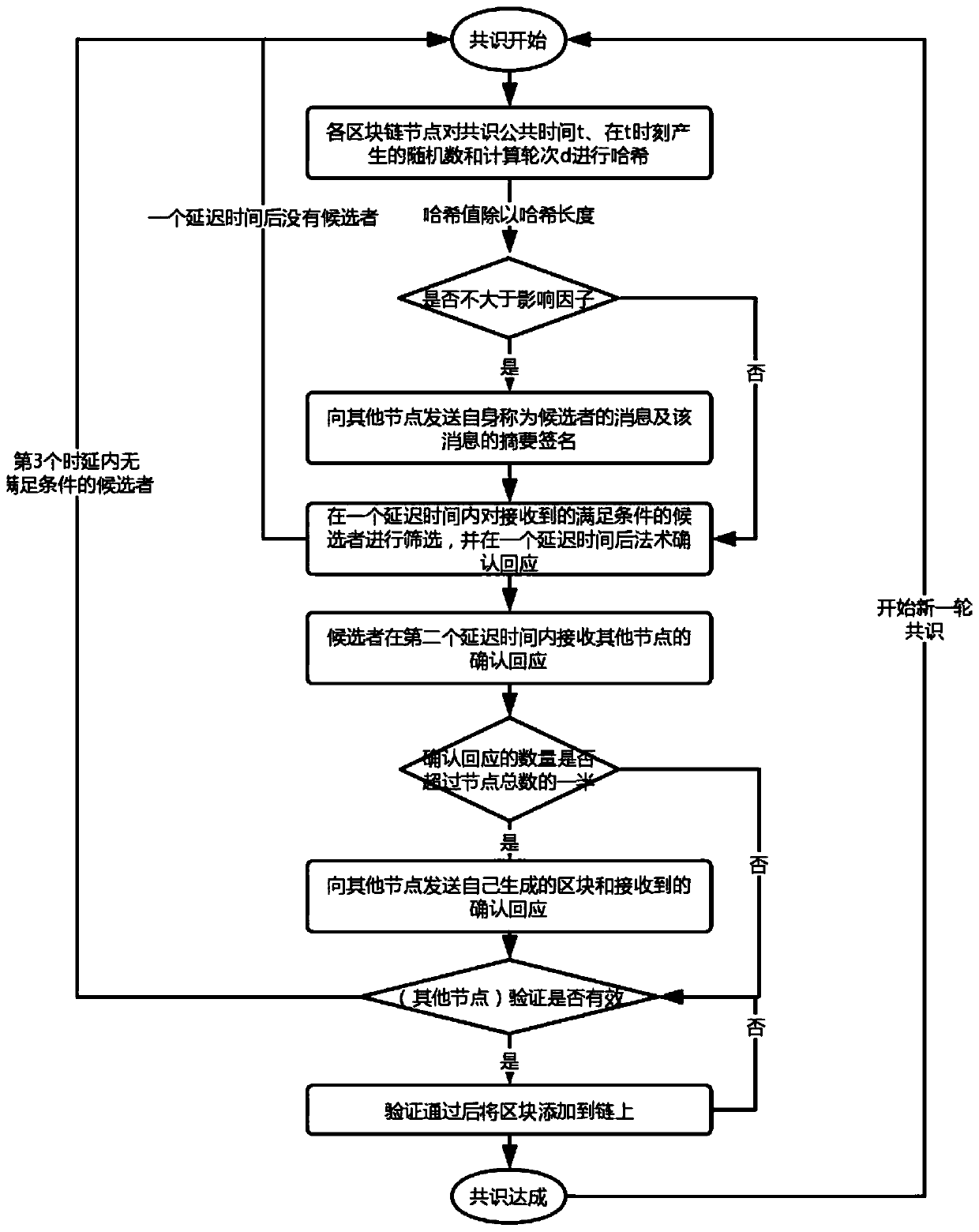
Consensus method for secure storage certification based on block chain and distributed storage system
ActiveCN110321074APromote healthy developmentReduce wasteInput/output to record carriersSecuring communicationChain networkStorage area network
The invention belongs to the technical field of distributed storage technology and block chain application. The invention discloses a consensus method for secure storage certification based on a blockchain and a distributed storage system. The method comprises the following steps: firstly, obtaining data to be stored, partitioning the data, then storing the partitioned data in a storage network in a distributed manner, and generating a non-interactive concise zero-knowledge storage proof for storing the data in a certain physical disk of a storage node; then the block chain network verifyingthe storage proof of the storage node and maintaining a real-time state table of all storage networks; and finally, carrying out block chain network consensus on the influence factor of each node in the block chain network and by utilizing the influence factor of each node. According to the distributed network storage system, an extensible system structure is adopted, a plurality of storage servers are used for sharing the storage load, and the position server is used for positioning the storage information, so that the reliability, the availability and the access efficiency of the system areimproved, and the system is easy to extend.
Owner:XIDIAN UNIV +1
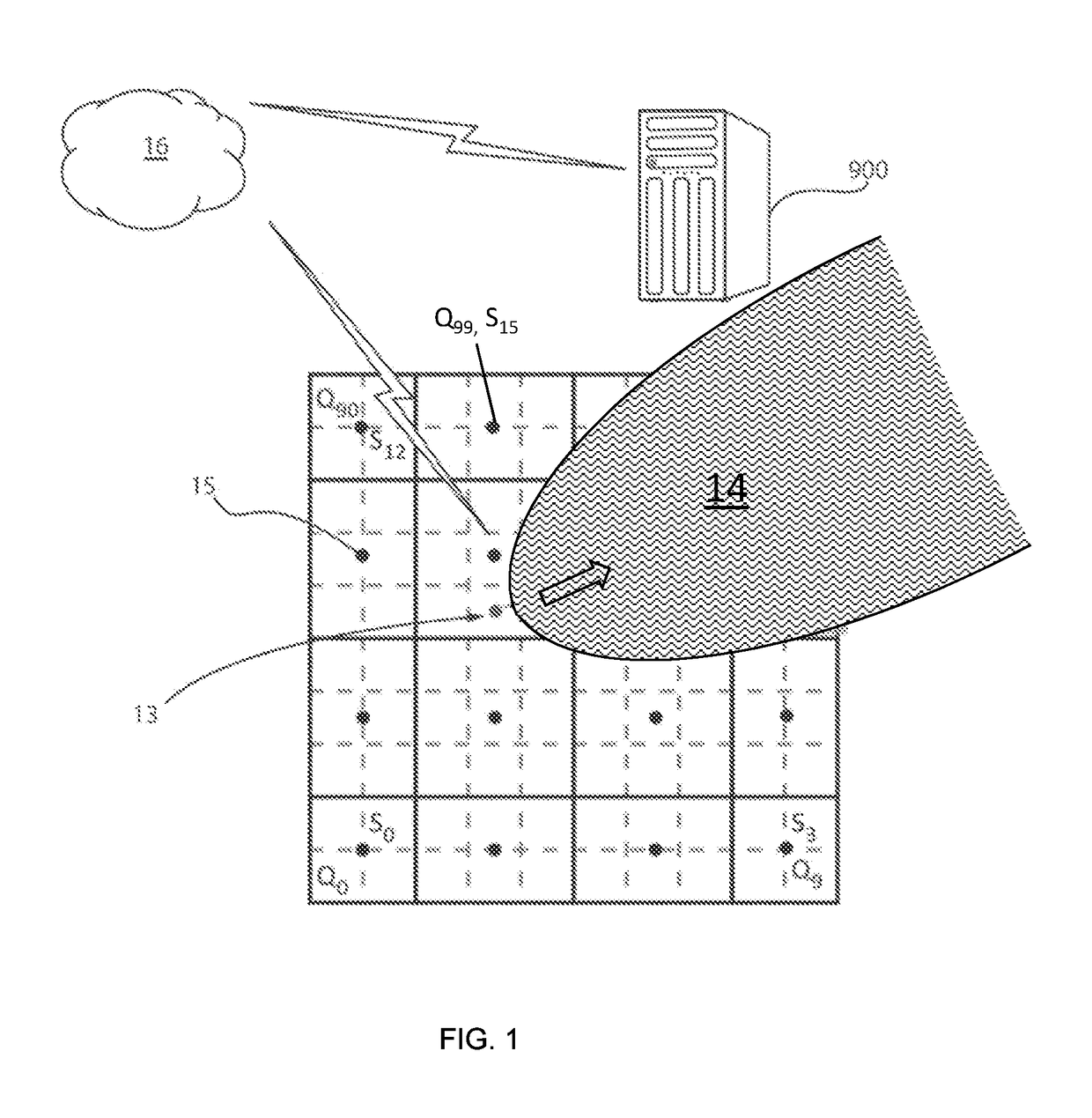
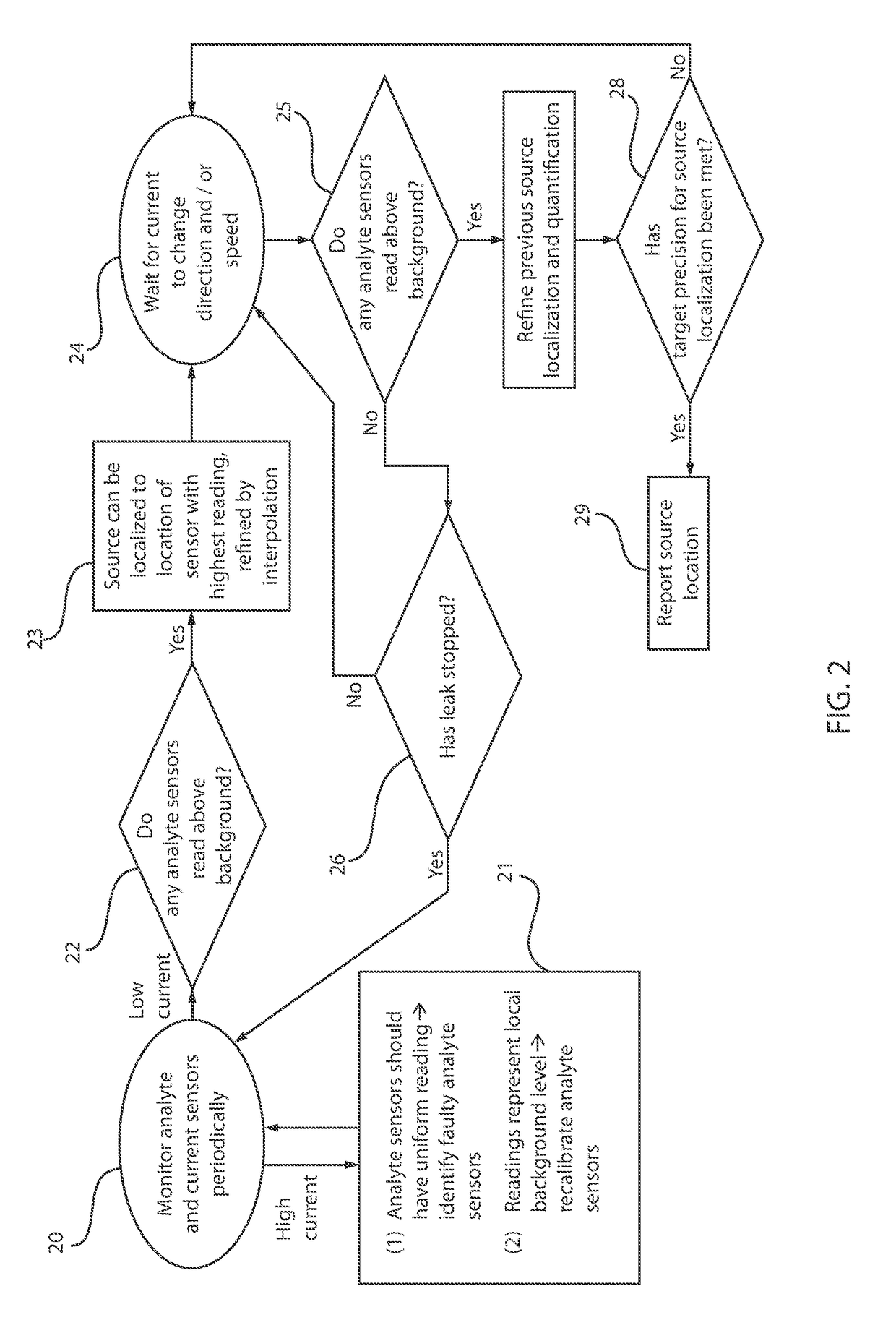
Leveraging air/water current variability for sensor network verification and source localization
A method for measuring pollution that includes providing a plurality of analyte sensors arranged in a grid over a sensing area, wherein the analyte sensors measure a pollutant, and positioning at least one current sensor in the sensing area. A pollution source is localized using a pollution source locator including a dispersion model and at least one hardware processor to interpolate a location of a pollution source from variations in current measured from the current sensors and measurements of pollutants from the analyte sensors.
Owner:IBM CORP
Ink Edge Anti-counterfeiting Method and Ink Edge Anti-counterfeiting Network Verification System
ActiveUS20180178579A1Overcome defectsEasy to identifyStampsPattern printingEngineeringNetwork verification
Disclosed are an ink edge anti-counterfeiting method and an ink edge anti-counterfeiting network identification system. Tiny sawteeth (6) are randomly produced on ink edges of a product code (4) and / or an image-text and the sawteeth (6) are zoomed in on and photographed, feature information about the sawteeth (6) on the ink edges acquired through photographing is stored in an ink edge anti-counterfeiting network identification system database as anti-counterfeiting feature information, and sawtooth feature information to be checked is compared with the sawtooth feature information in the database to identify the authenticity. The method and system are simple and easy to implement, do not need to increase equipment investment, can realize an effective anti-counterfeiting function, and can avoid the problem in the existing digital anti-counterfeiting techniques, such as a telegram code, that the anti-counterfeiting feature information can be easily copied and stolen by internal staff.
Owner:KHAINAN YAYUAN ANTI TSOUNTERFEIT TECH RES INST
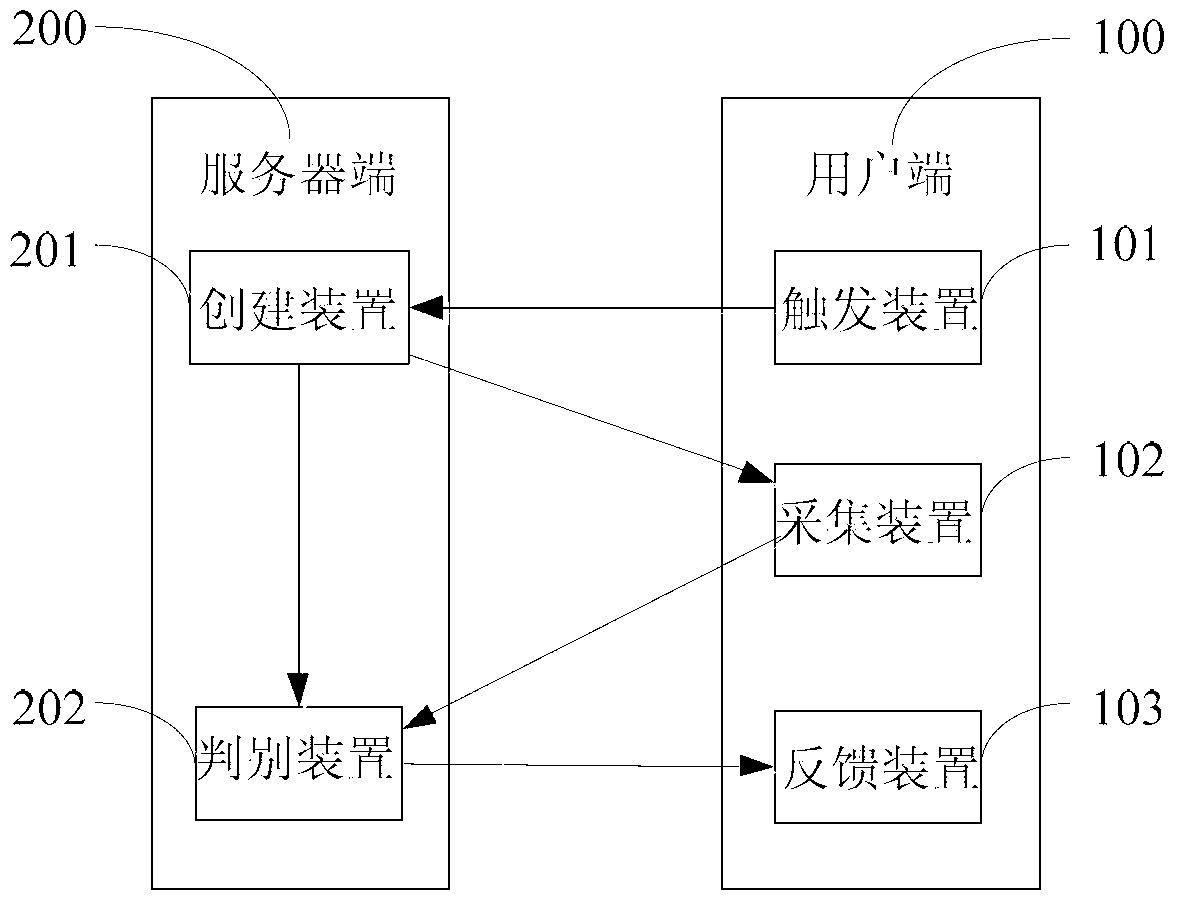
Network authentication method and system based on behavior mode
InactiveCN102801735AImprove experienceAvoid the problems of cracking traditional captchasUser identity/authority verificationAuthentication systemComputer software
The invention discloses a network authentication method and a network authentication system based on a behavior mode. The network authentication method comprises the following steps of: triggering a behavior authentication request, establishing a behavior sandbox according to the behavior authentication request, displaying the behavior sandbox to a user, and acquiring behavior information of the user; judging whether the behavior information of the user corresponds to a behavior required in the behavior sandbox; if so, allowing to pass authentication, otherwise refusing to pass the authentication. The behavior which can be identified and made by human thinking serves as the basis for judging whether the authentication is passed, and compared with the existing security code mode in a character form, the method has the advantages that the passing defects are easily identified by computer software, and the human user is uniquely determined.
Owner:WUHAN JIYI NETWORK TECH CO LTD
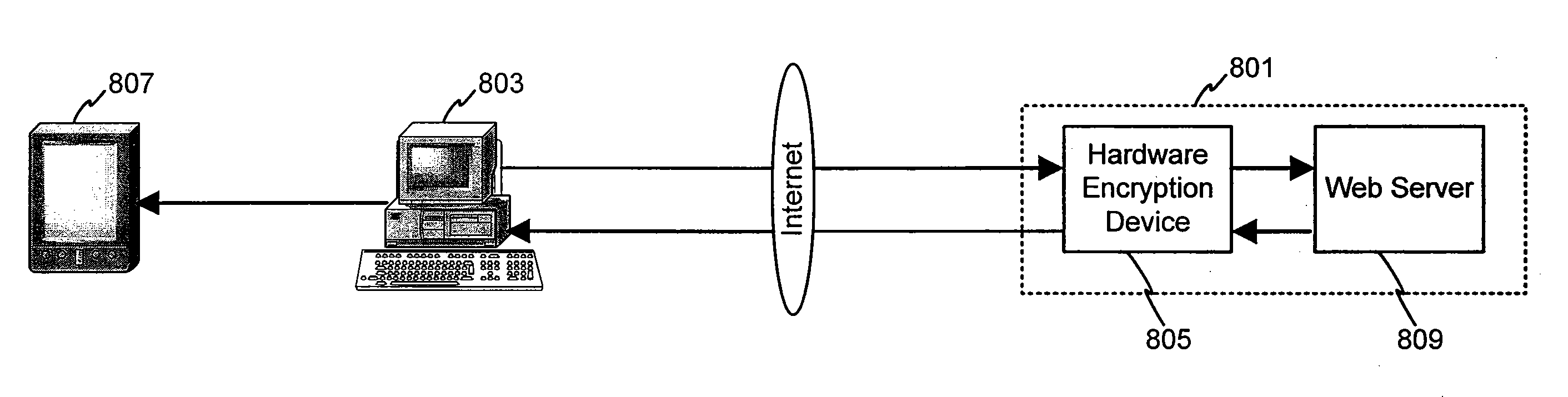
System and Method for Securing Data Through a PDA Portal
InactiveUS20090089581A1Easy to purchaseFacilitate loyalty processFinanceUser identity/authority verificationWeb siteSecured transaction
Consumers may utilize computing devices to assist in the purchase and / or loyalty process, and in particular, the consumer may utilize a PDA to facilitate the purchase and / or loyalty process. During the purchase and / or loyalty process, the consumer may need to insure that any content downloaded or used in association with the PDA is secure in how it is collected, assembled, and delivered to the PDA device. This system and method secures the data from its source to when it is actually viewed or used by the authorized user. The PDA may have direct access to an Internet web site portal that offers secure personal content from a content provider, such as, for example, an on-line banking or financial institution. Using the web site portal, the content provider may offer personal or confidential data, such as financial information, to PDA users in a secure (e.g., encrypted) environment. The exemplary system and method may establish a PDA portal link to the web site for collecting specified information for a user and transmitting the information to the remote device. To receive the information, the PDA contacts the portal and establishes a connection, authenticates itself to the network and allows the user to complete secured transactions or transmissions over the network.
Owner:LIBERTY PEAK VENTURES LLC
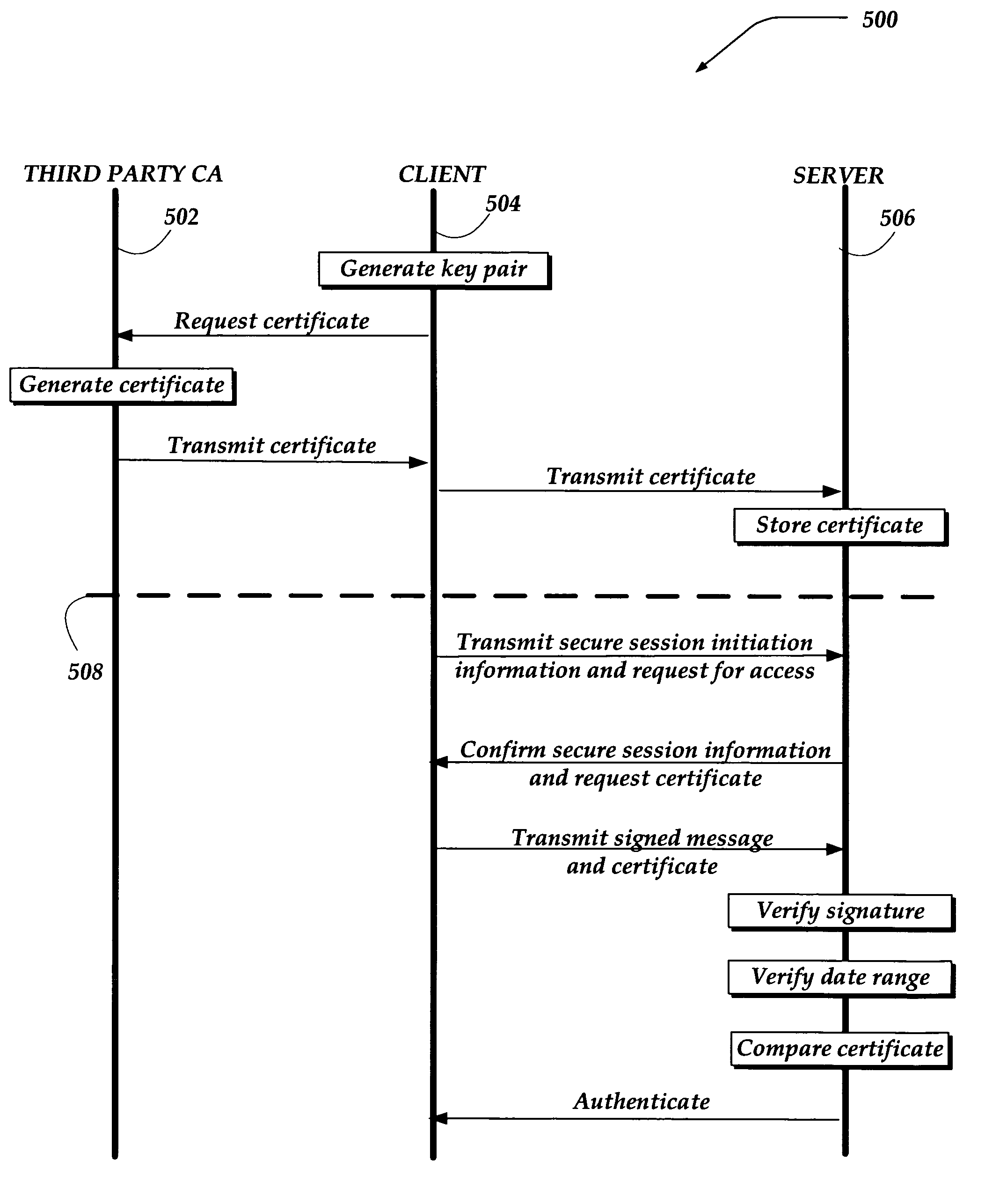
Method and system for authentication using infrastructureless certificates
ActiveUS7321970B2User identity/authority verificationSpecial data processing applicationsThird partyWeb authentication
Methods and systems are directed to authenticating a client over a network. The client generates a certificate and sends it to a server through a trusted mechanism. The server is configured to store the received certificate. When the client requests authentication over the network, it provides the certificate again, along with a parameter associated with a secure session. The server verifies the parameter associated with the secure session and determines if the certificate is substantially the same as the stored certificate. The server authenticates the client over the network, if the certificate is determined to be stored. In another embodiment, the client transmits the certificate that is generated by a third party Certificate Authority (CA) based, in part, on the client's public key.
Owner:WSOU INVESTMENTS LLC
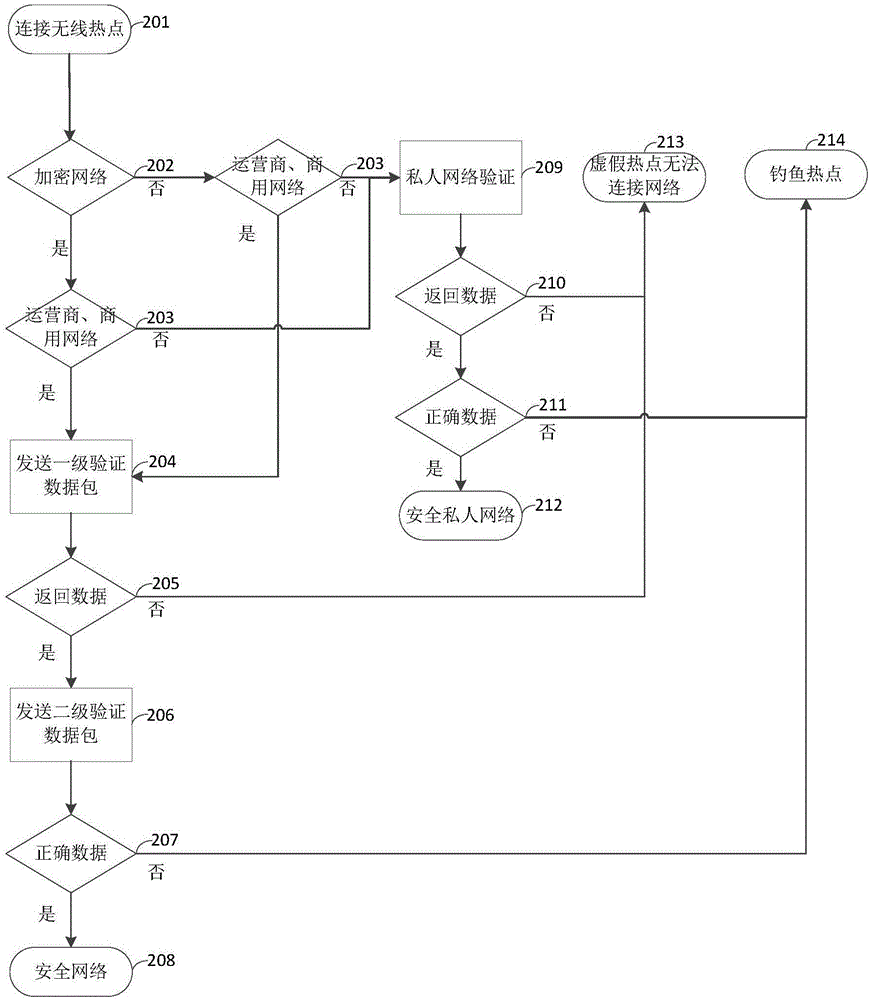
Method and system for detecting phishing hotspot
The invention discloses a method for detecting a phishing hotspot, which comprises the steps of connecting a terminal to a wireless hotspot, and judging the type of the wireless hotspot according to attribute information of the wireless hotspot; sending a network verification data packet to the wireless hotspot according to the type of hotspot, and judging whether the wireless hotspot is a phishing wireless hotspot or not through data fed back by the wireless hotspot according to the network verification data packet; and prompting a user to disconnect connection between the terminal and the wireless hotspot if the wireless hotspot is a phishing wireless hotspot. The invention further provides a system for detecting the phishing hotspot, which comprises a hotspot type judgment unit, a phishing hotspot judgment unit and a prompt unit. The method and the system disclosed by the invention can accurately detect phishing wireless hotspots with high camouflage performance, display a phishing mode of camouflaged hotspots, prompt users to timely disconnect dangerous hotspots, and protect the security of information in an intelligent terminal.
Owner:INST OF INFORMATION ENG CAS
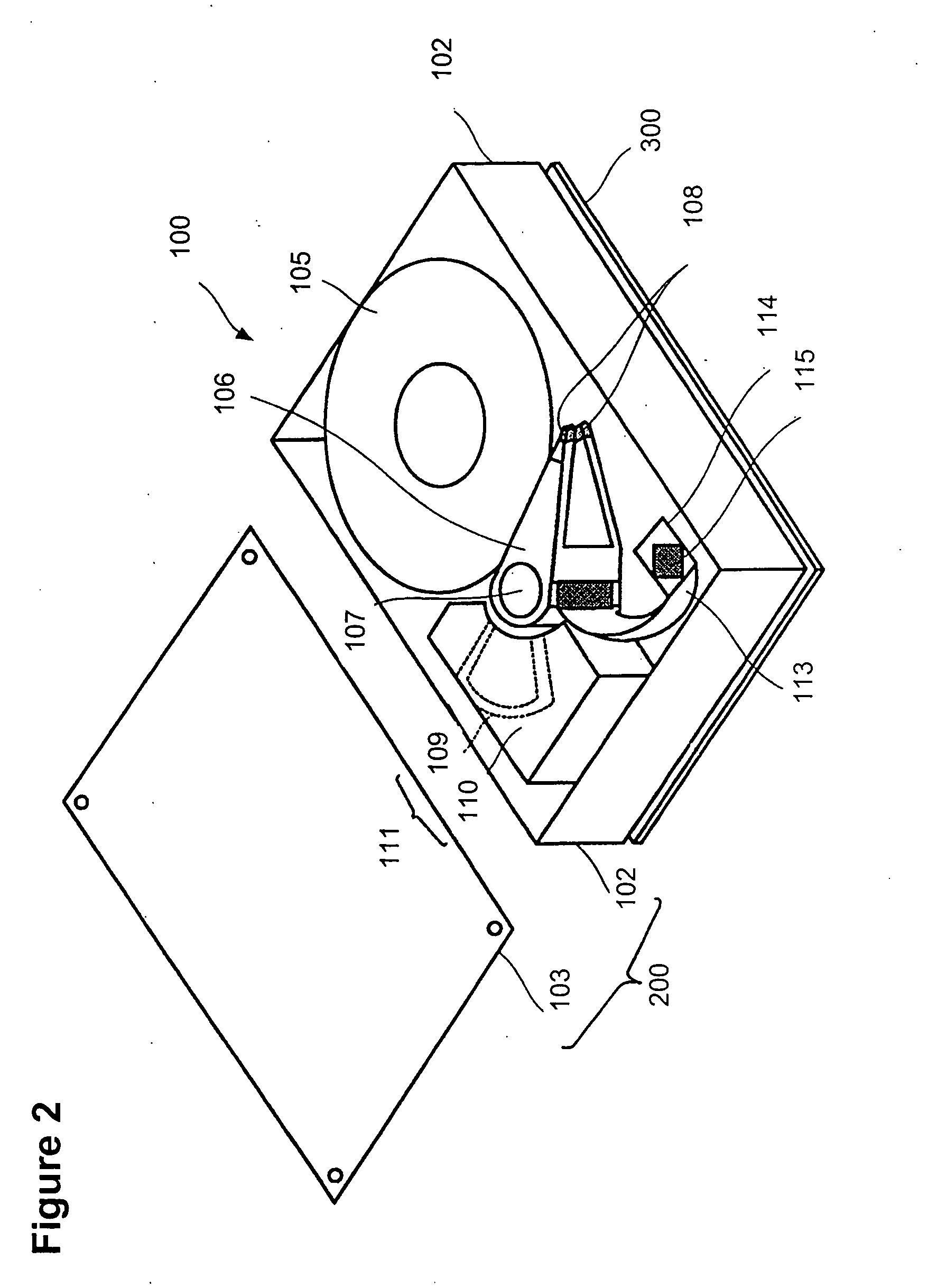
Certified HDD with network validation
InactiveUS20070266443A1Prevent undesired duplicationAvoid replacementDigital data processing detailsUser identity/authority verificationNetwork verificationComputer security
A data storage device can be validated through a network before the data storage device can be operated. In one embodiment, the data storage device includes a magnetic disk and a head assembly having a read / write head which reads and writes data from / on the magnetic disk. The data storage device further includes a controller configured to control the head assembly to read / write data to / from the magnetic disk. In addition, the data storage device includes a secure area of the magnetic disk containing a private key. The private key is one of a pair of cryptographically linked keys and the other of the cryptographically linked keys is a public key. Furthermore, the data storage device includes a memory located within the controller containing an auxiliary key, the auxiliary key being used to encrypt or decrypt the private key.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
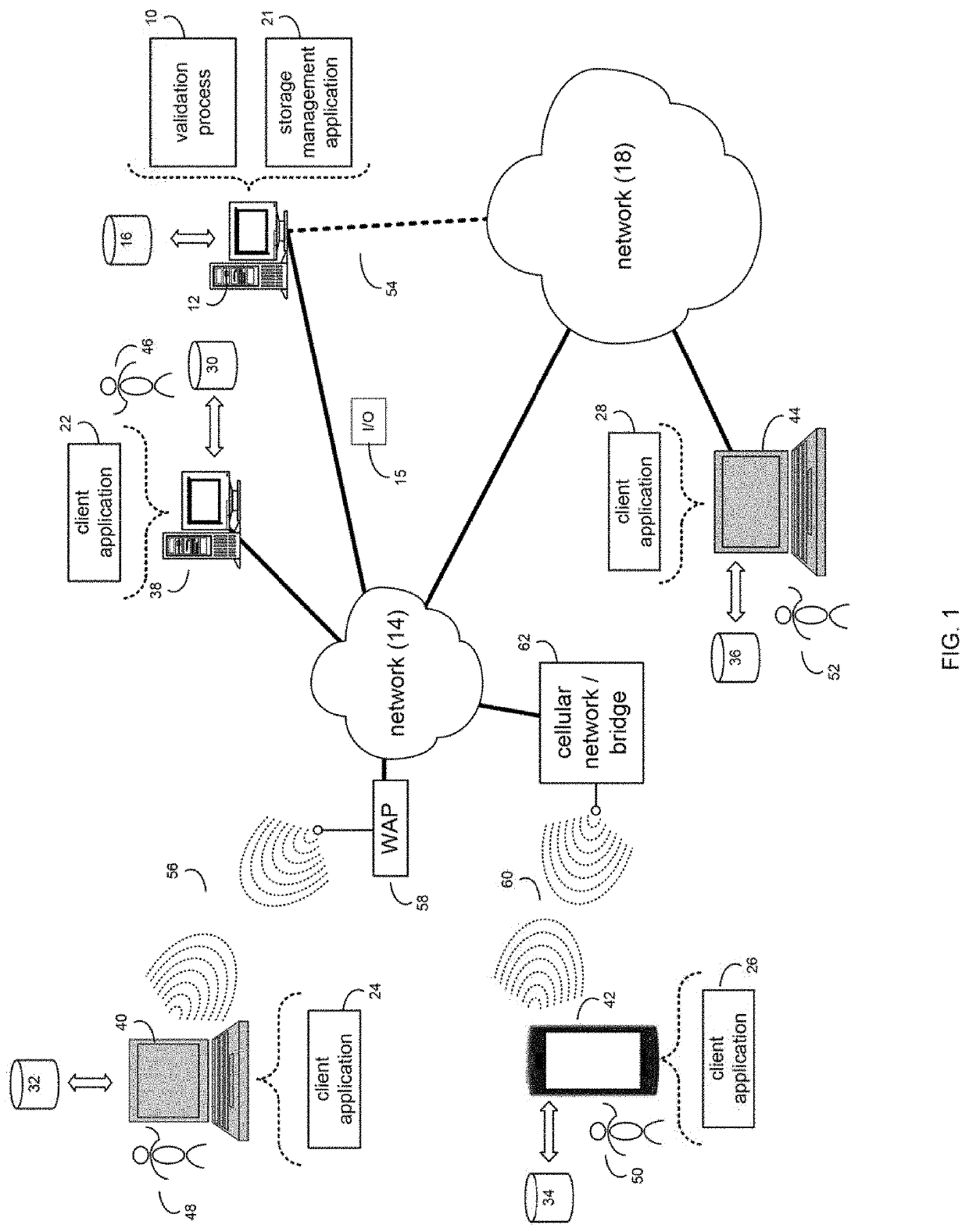
System and method for network validation architecture for clustered and federated storage systems
A method, computer program product, and computer system for performing, by a single unified architecture, an initial network validation, wherein the initial network validation may be performed before a storage cluster is fully configured. The single unified architecture may perform a cluster expansion validation, wherein the cluster expansion validation may be performed before at least one of a new storage application and a new storage controller is added into the storage cluster. The single unified architecture may perform a pre-reconfiguration validation, wherein the pre-reconfiguration validation may be performed as a network reconfiguration operation in the storage cluster before a network reconfiguration request is processed. The single unified architecture may perform ongoing network validation, wherein the ongoing network validation may be performed periodically as a background process.
Owner:EMC IP HLDG CO LLC
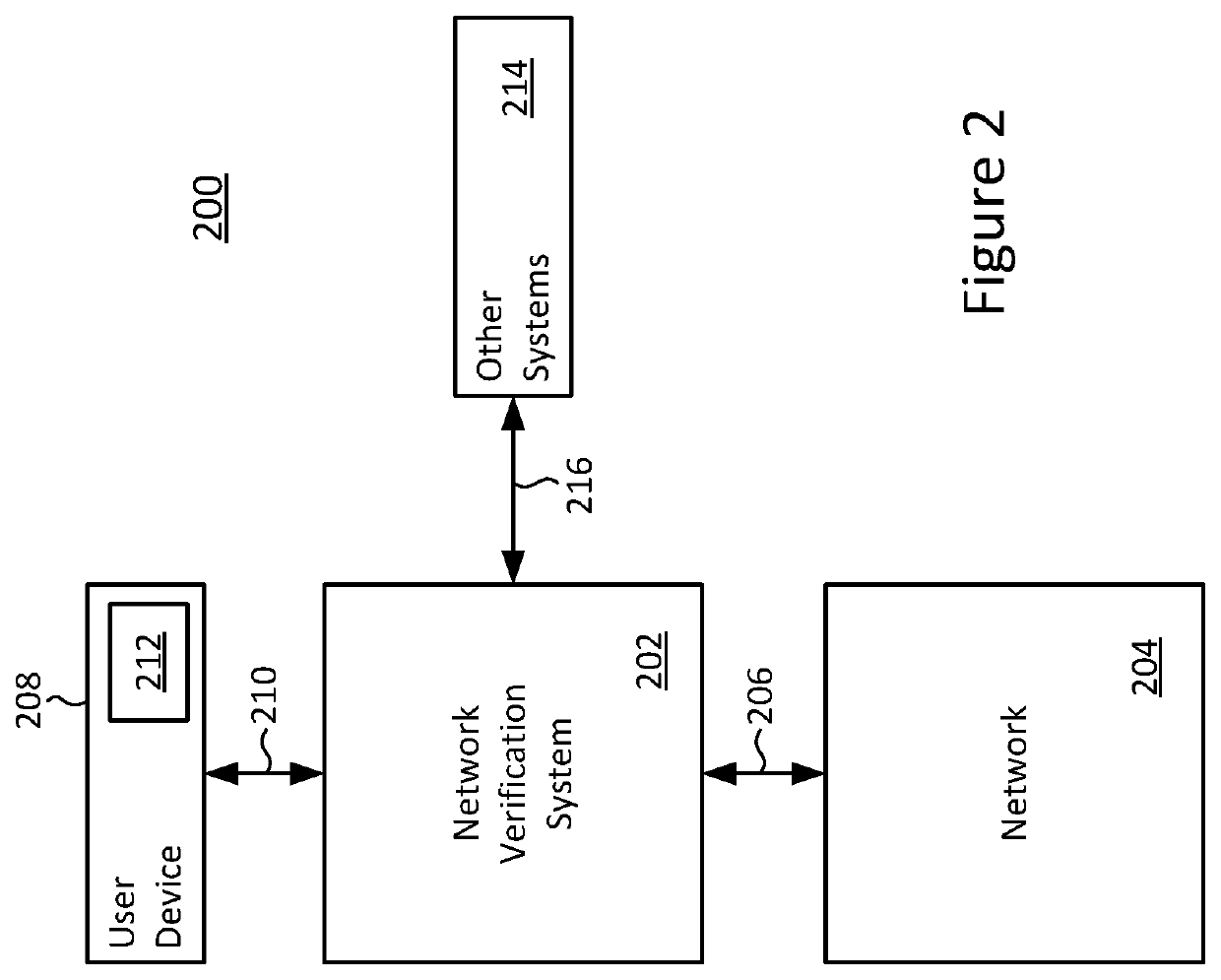
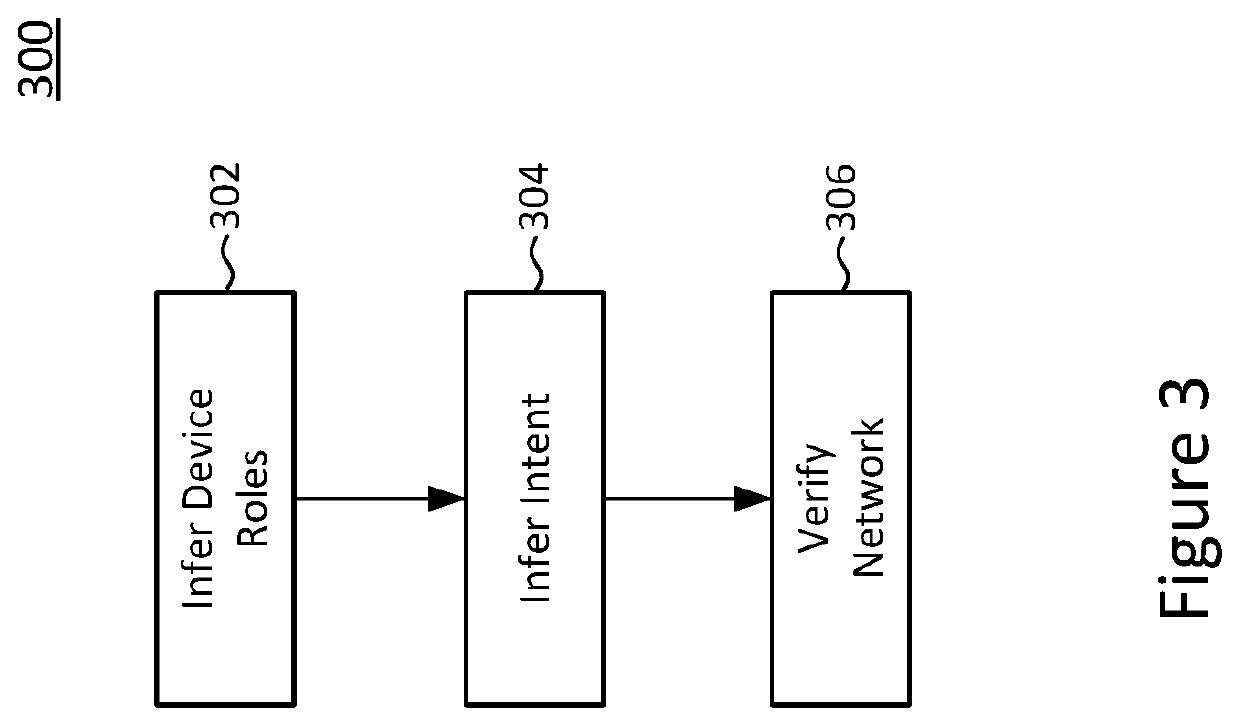
Systems for and methods of network management and verification using intent inference
A system for managing a network using intent inference includes a network interface that is configured to obtain device information regarding a plurality of hardware devices within a data communication network. A processor is configured to infer intended packet handling behavior of a plurality of the devices. A network verification system models packet handling behavior of the devices within the network and compares the inferred intended behavior to the modeled packet handling behavior. The system can take action in response to the results of the comparison, which can include initiating a configuration change to one or more of the hardware devices of the data communication network.
Owner:VMWARE INC
Byzantine agreement in open networks
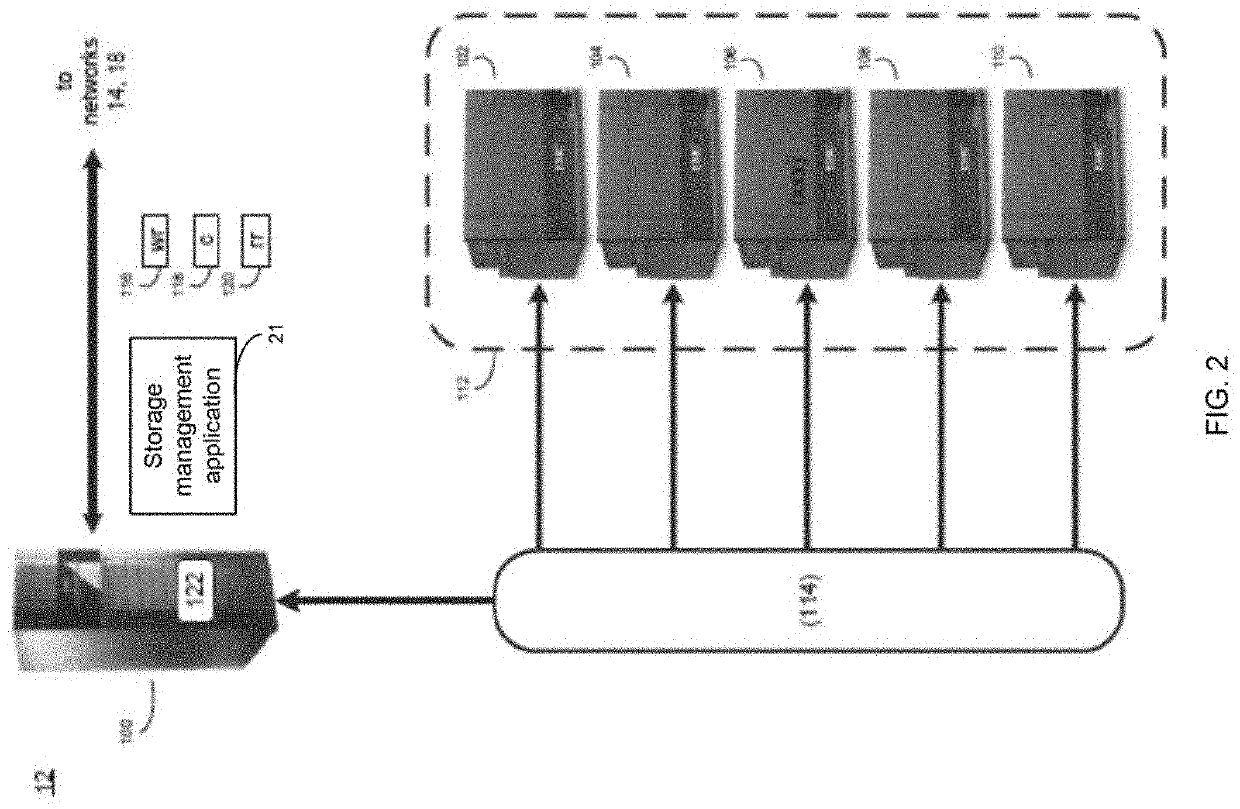
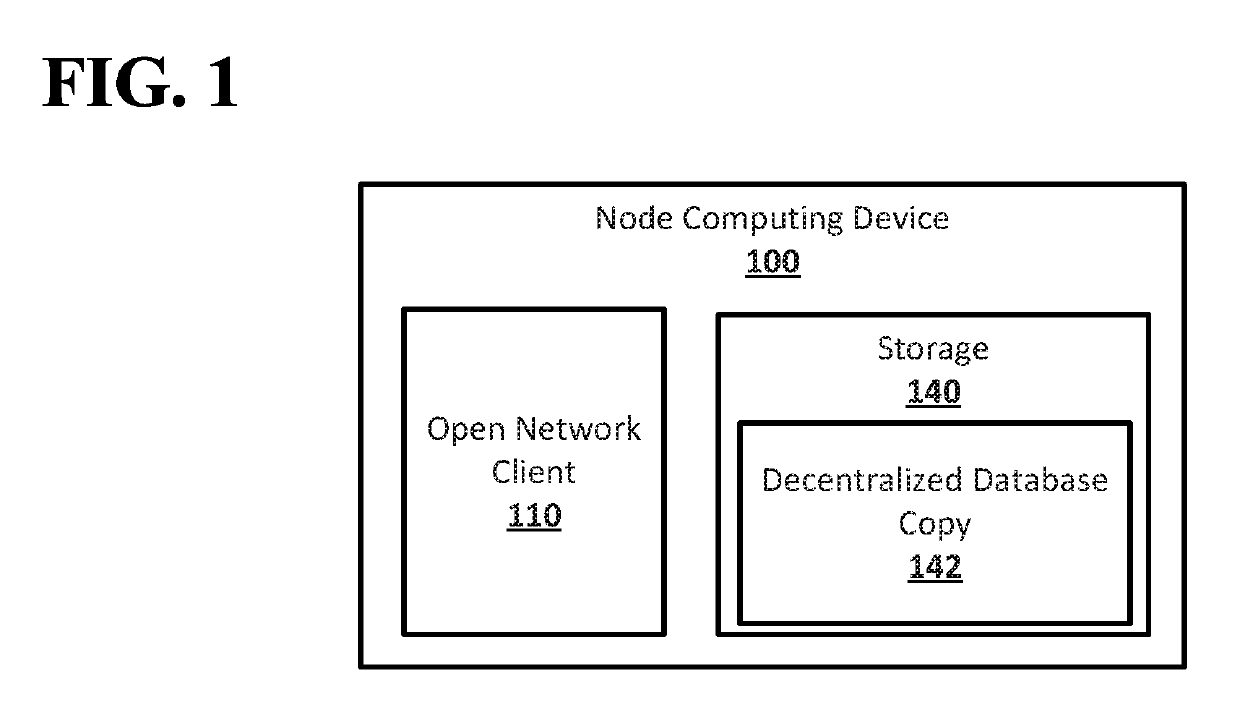
ActiveUS20190251007A1User identity/authority verificationDatabase distribution/replicationBroadcastingProtocol for Carrying Authentication for Network Access
Systems and techniques are provided for Byzantine agreement in open networks. An indication to change a validation network for an open network from a current validation network to a next validation network may be broadcast. An agreement to change to the validation network to the next validation network may be. An instance of external validity multi-valued Byzantine agreement may be run to determine a continuing sequence number to be used by the next validation network based on the sequence numbers of amendments applied to decentralized database copies stored node computing devices of the open network. The next validation network may be switched to as the validation network for the open network after the continuing sequence number is determined. An amendment validated by the next validation network may be applied to a decentralized database copy. The amendment may include a sequence number that is higher than the continuing sequence number.
Owner:RIPPLE LABS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com