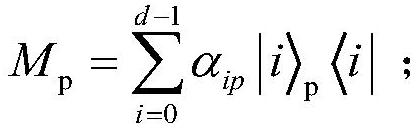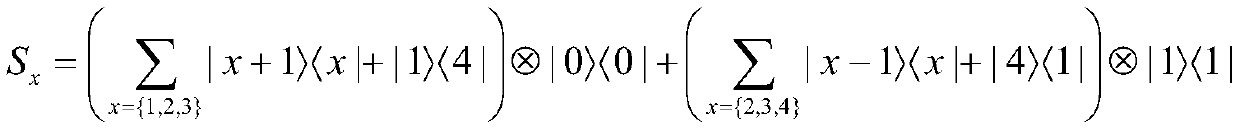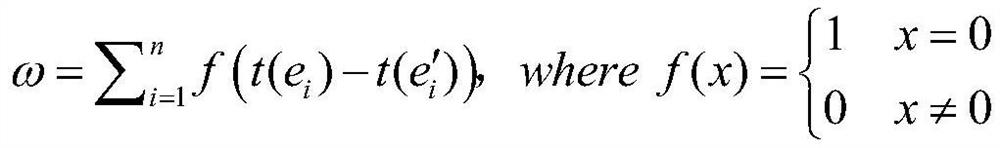Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54 results about "Quantum walk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Quantum walks are quantum analogues of classical random walks. In contrast to the classical random walk, where the walker occupies definite states and the randomness arises due to stochastic transitions between states, in quantum walks randomness arises through: (1) quantum superposition of states, (2) non-random, reversible unitary evolution and (3) collapse of the wave function due to state measurements.
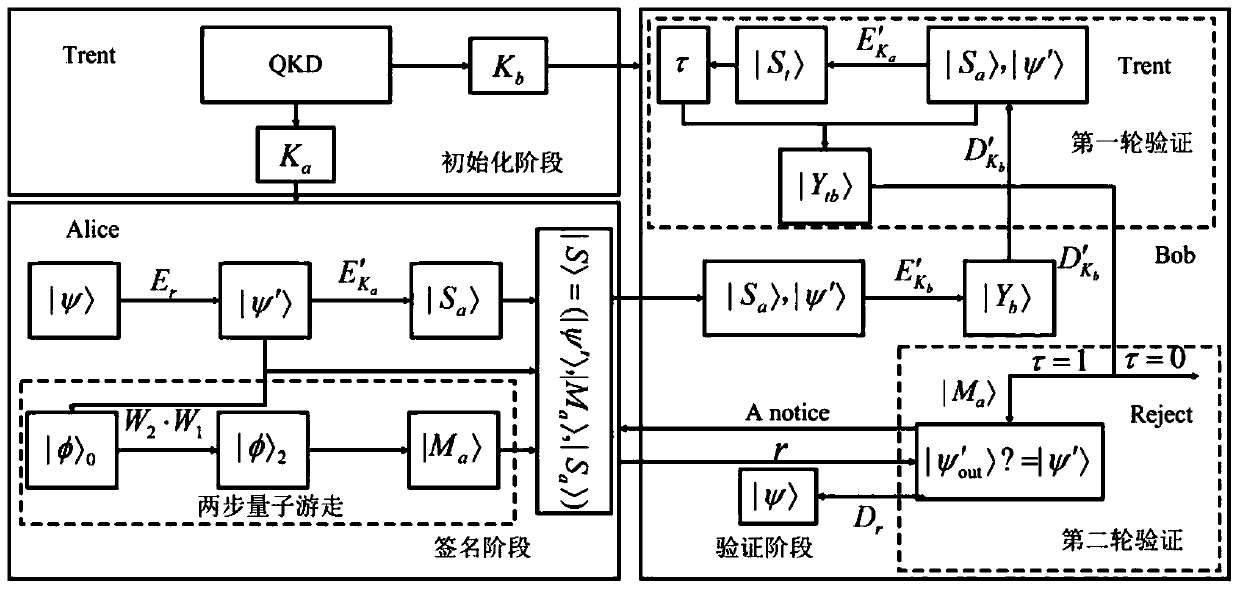
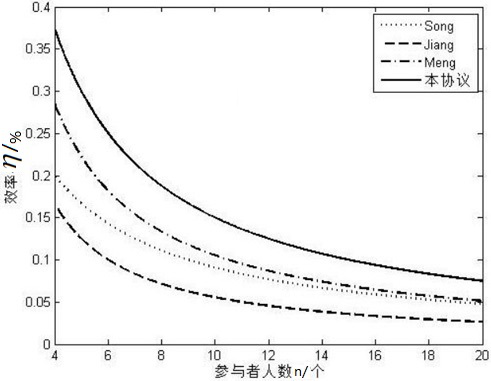
Arbitration quantum signature method based on glass color sampling random unitary operation
ActiveCN111162913AReduce overheadImprove efficiencyKey distribution for secure communicationUser identity/authority verificationCommunications systemInformation design
The invention discloses an arbitration quantum signature method based on glass color sampling random unitary operation. The arbitration quantum signature method comprises an initialization stage, a signature stage and a verification stage. The initialization stage is used for preparing a secret key and establishing a communication system; the signature stage is used for selecting a proper signature algorithm to design the signature of the transmission information; and the verification stage is used for verifying the validity of the signer and the integrity and authenticity of original information. According to the invention, unitary operation encryption based on glass color sampling is adopted in the signature of transmission information designed in arbitration quantum signature; an m-modequantum state is transferred by adopting quantum walk invisible transmission based on a graph, a necessary entanglement state for invisible transmission does not need to be prepared in advance, the safety is higher by adopting a common channel and a random tuple, and a glass color sampling model and a quantum walk invisible transmission model are proved to be realized through a linear optical network; and therefore, the method disclosed by the invention is high in safety, resource-saving and easy to implement in experiment.
Owner:CENT SOUTH UNIV
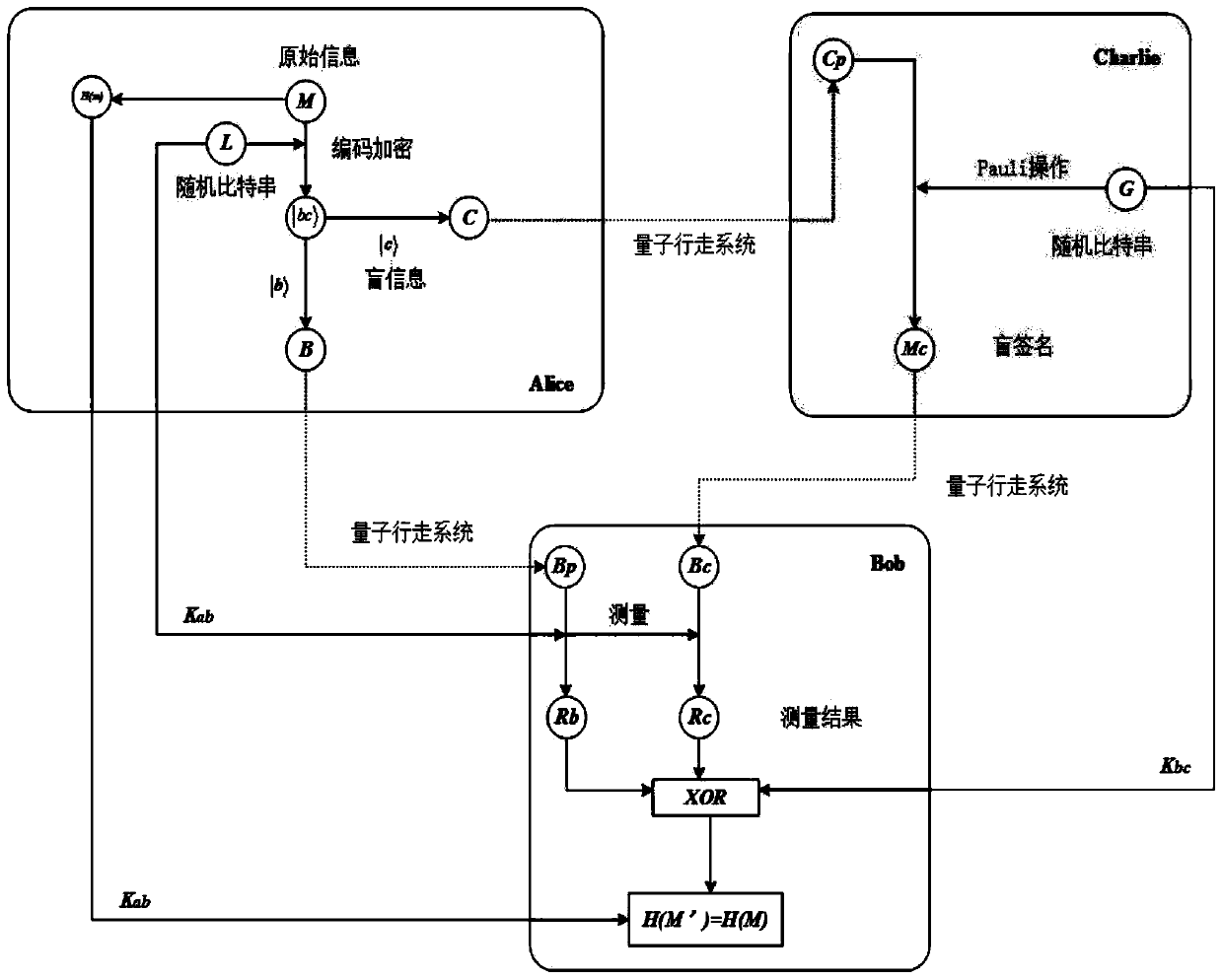
Unentangled quantum blind signature method and system based on quantum walking
ActiveCN110213060AProven robustnessAchieve the effect of one-time pad (OTP)Key distribution for secure communicationUser identity/authority verificationE-commerceBlind signature
The invention belongs to the technical field of quantum information processing, and discloses an unentangled quantum blind signature method and system based on quantum walking, and the method comprises the steps: carrying out the coding and blind information through employing four single event states in combination with a blind coding rule of a message in the coding stage of the message; in the invisible transmission process of the coded particles, using quantum walking to achieve invisible transmission of the coded particles, wherein entanglement is spontaneously generated on the invisible transmission seed particles, which is used for resisting negative attacks of signers and denial attacks of verifiers and further used for preventing attackers from forgery signatures. The method comprises secret key updating, the effect of one-time encryption (OTP) is achieved, and therefore a next execution scheme does not need secret key redistribution any more; security analysis shows that the scheme of the invention satisfies the characteristics of unforgeability, undeniable property and blindness, can also resist entanglement attack, and is very suitable for use in electronic commerce or electronic payment systems.
Owner:芽米科技(广州)有限公司
High-speed traffic flow distribution analog quantum computing method considering destination selection
ActiveCN111126611AImprove accuracyImprove efficiencyQuantum computersData processing applicationsSimulationNetwork structure
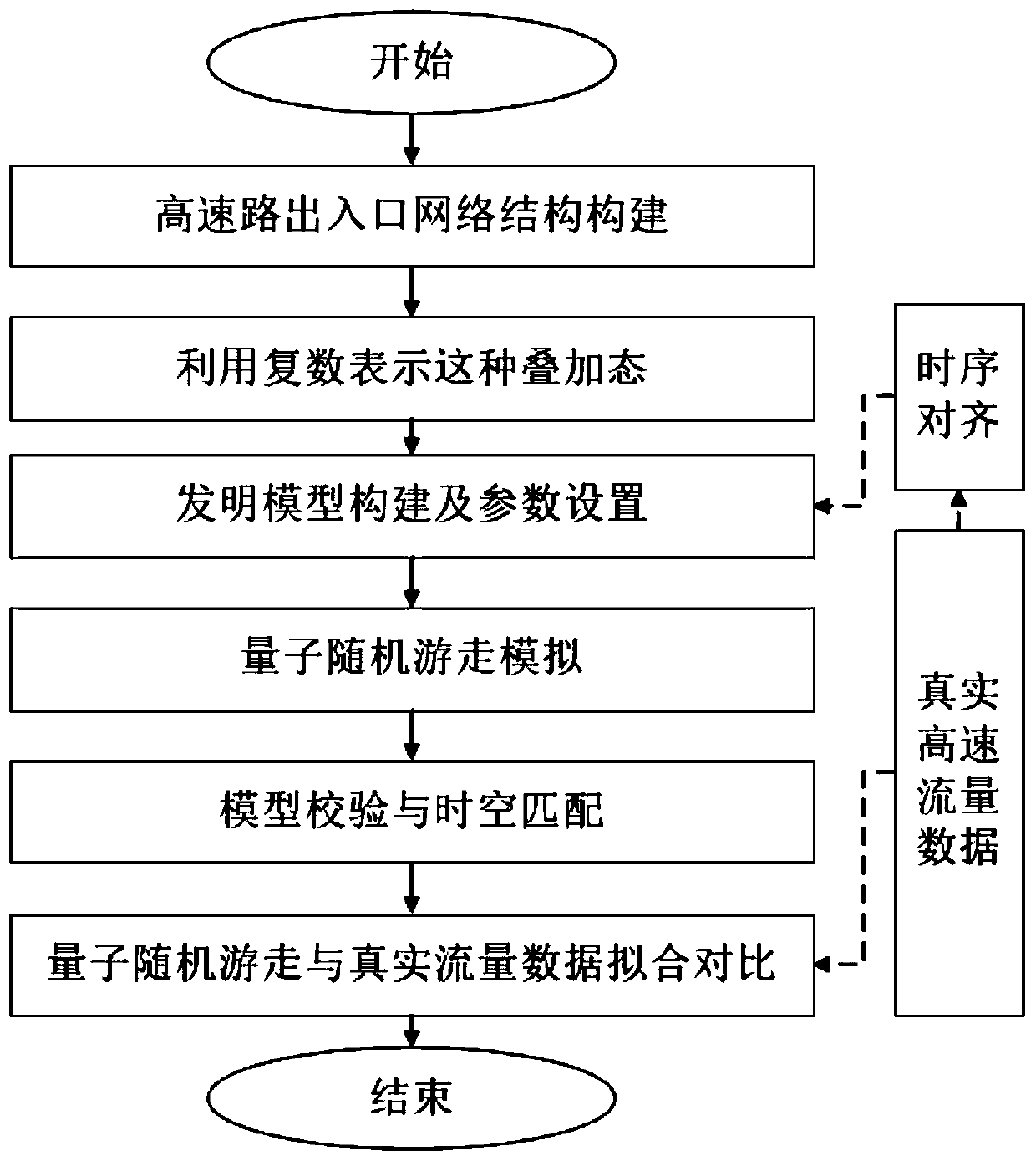
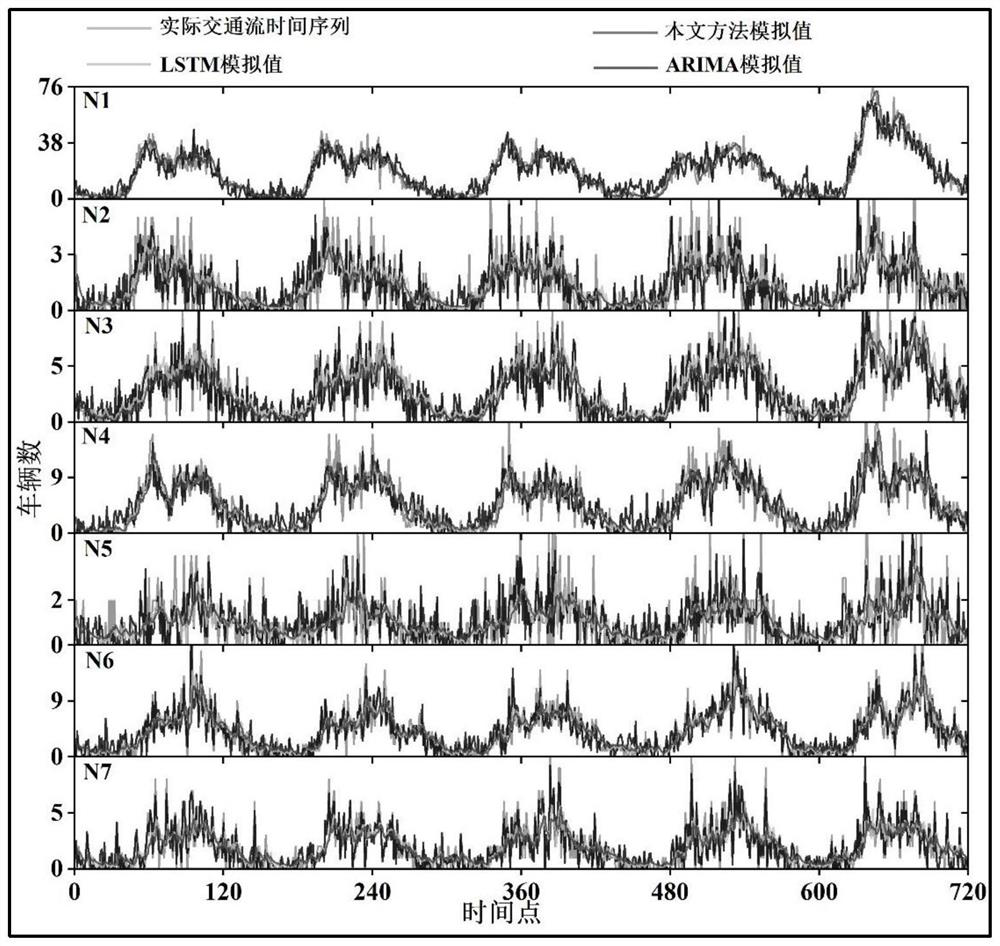
The invention discloses a high-speed traffic flow distribution analog quantum computing method considering destination selection. The method comprises the following steps: (1) constructing a highway gateway network structure; (2) representing a vehicle flow direction and flow superposition state by utilizing a plurality of numbers; (3) constructing a model and setting parameters; (4) simulating quantum random walk; (5) performing model verification and space-time matching; and (6) fitting and comparing the quantum random walk with real flow data. Quasi-periodic vibration and irregular characteristics in highway traffic flow can be simulated, traffic observation data are closely integrated, deep characteristics of traffic behaviors are revealed from a new perspective, and the accuracy and efficiency of highway flow simulation are improved.
Owner:NANJING NORMAL UNIVERSITY
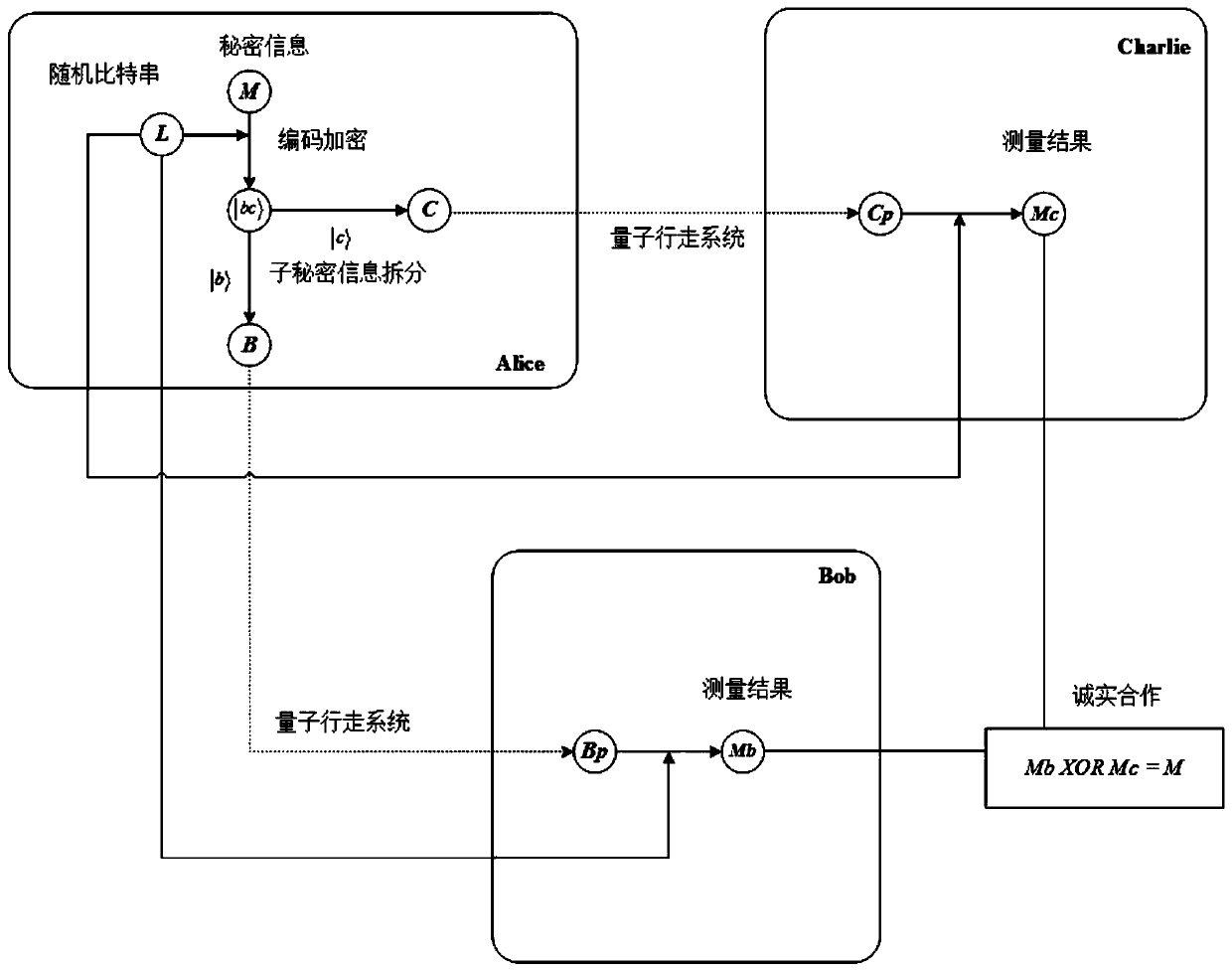
Quantum secret sharing method and sharing system based on quantum walking
ActiveCN110445609ARealize teleportationSafe and feasible technologyKey distribution for secure communicationQuantum secret sharingComputer network
The invention belongs to the technical field of quantum information sharing, and discloses a quantum secret sharing method and sharing system based on quantum walk, and the method comprises the steps:enabling a secret distributor to encode secret information to be shared into a quantum state according to a rule, and enabling an encoding particle to be split into two parts; invisibly transferringthe two pieces of encrypted information to a first participant and a second participant through a quantum walking system; and the first participant and the second participant decrypt the secret information of the secret distributor through cooperation. Characteristics of the quantum walking system are used for invisible state transfer of unknown particles, entanglement is spontaneously generated among the particles, and preparation of entangled particles in a particle preparation stage is avoided to complete invisible state transfer of the particles. According to the quantum secret sharing method based on quantum walking, an invisible state transfer method based on quantum walking is combined with a coding rule, and the quantum secret sharing method based on quantum walking is completed.
Owner:HEFEI LONGTUTEM INFORMATION TECH CO LTD
Universal quantum walk analog chip structure based on integrated optics
ActiveCN111478735AQuantum computersKey distribution for secure communicationParticle physicsAnalog chip
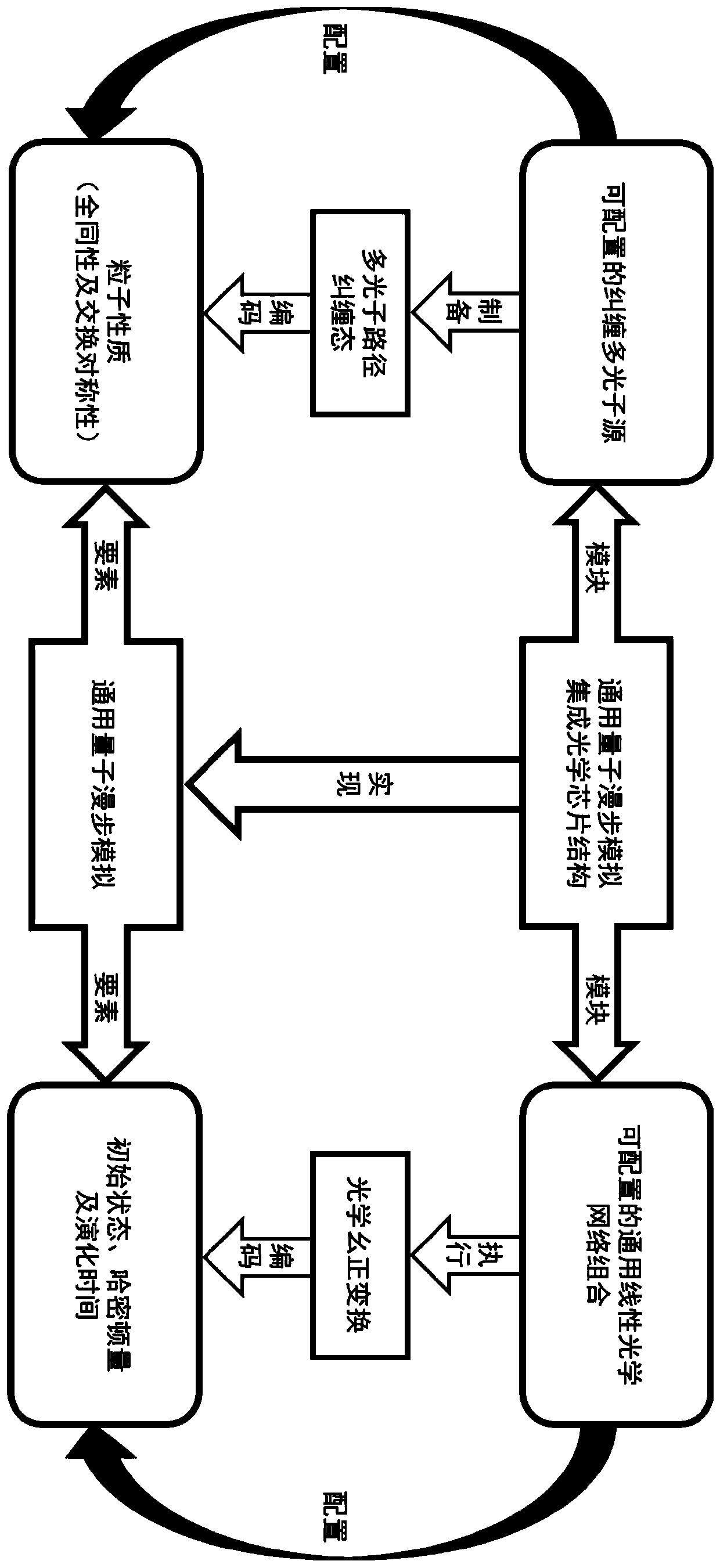
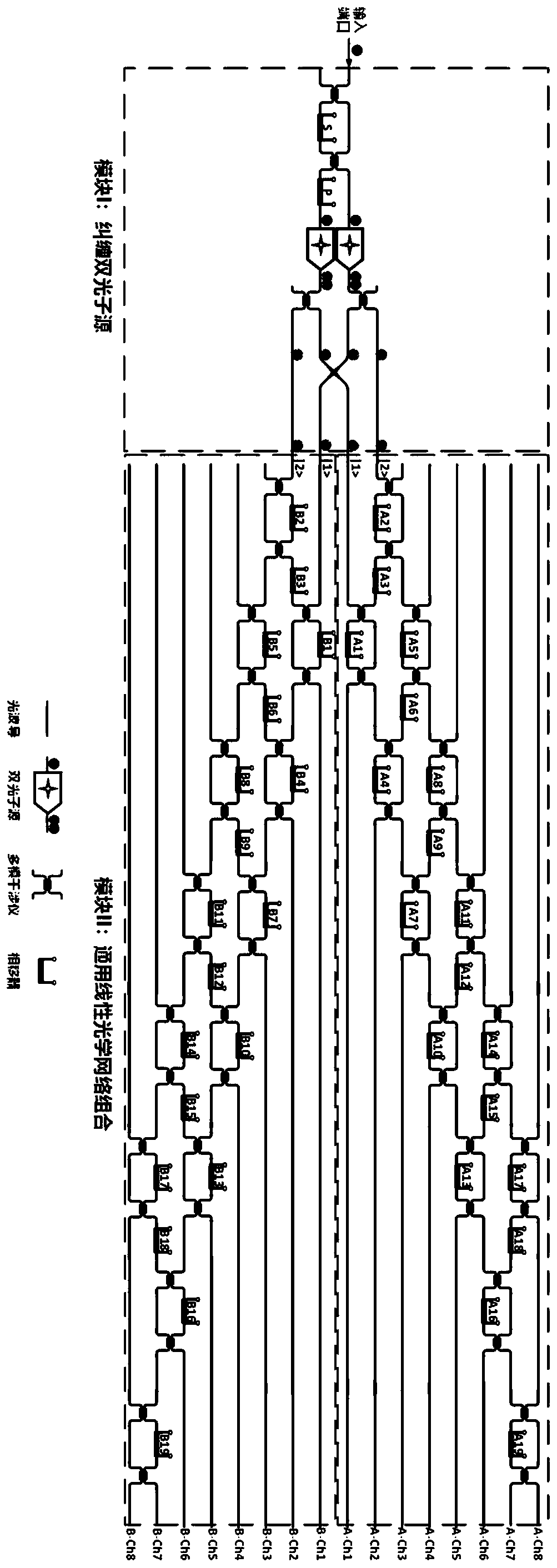
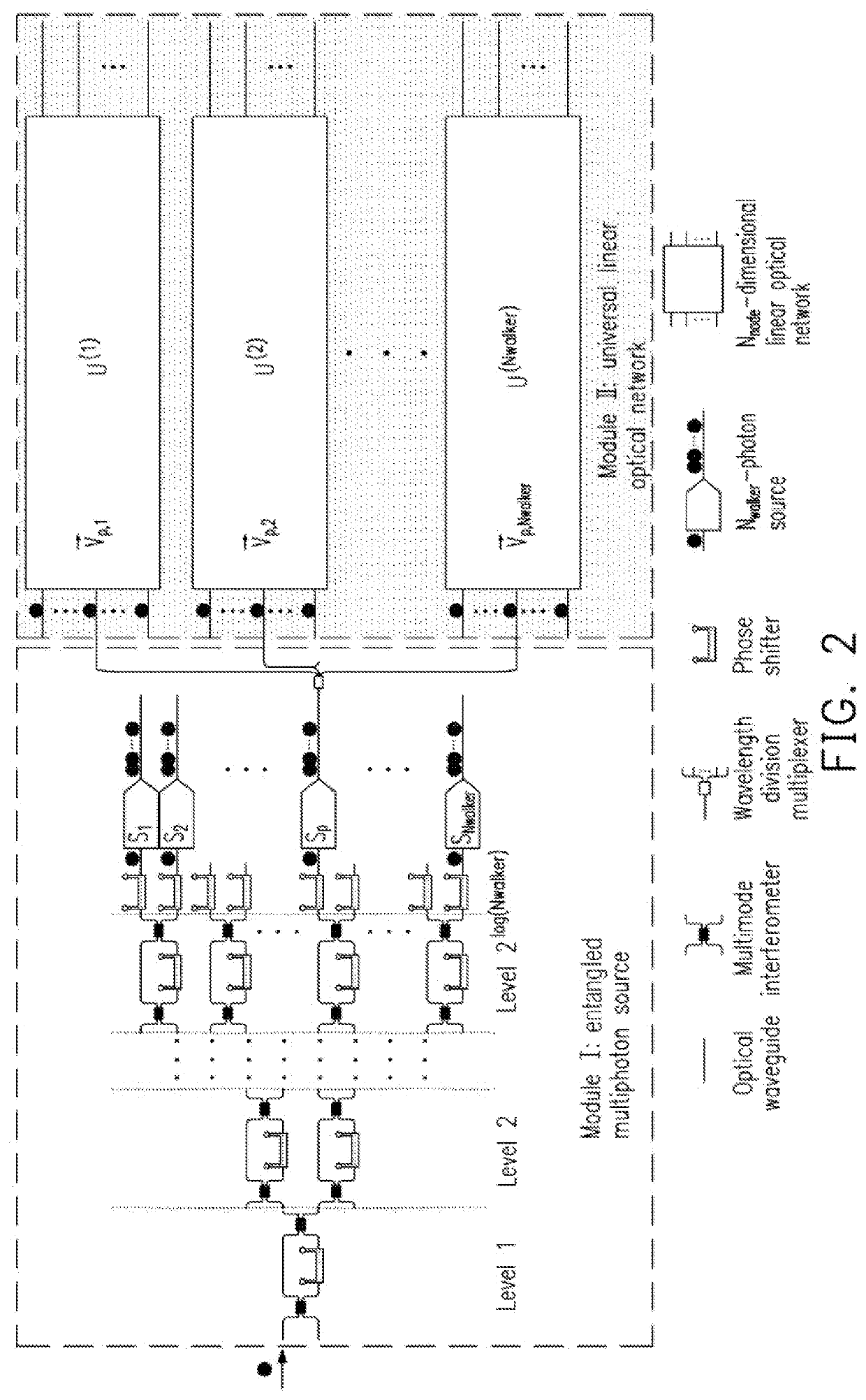
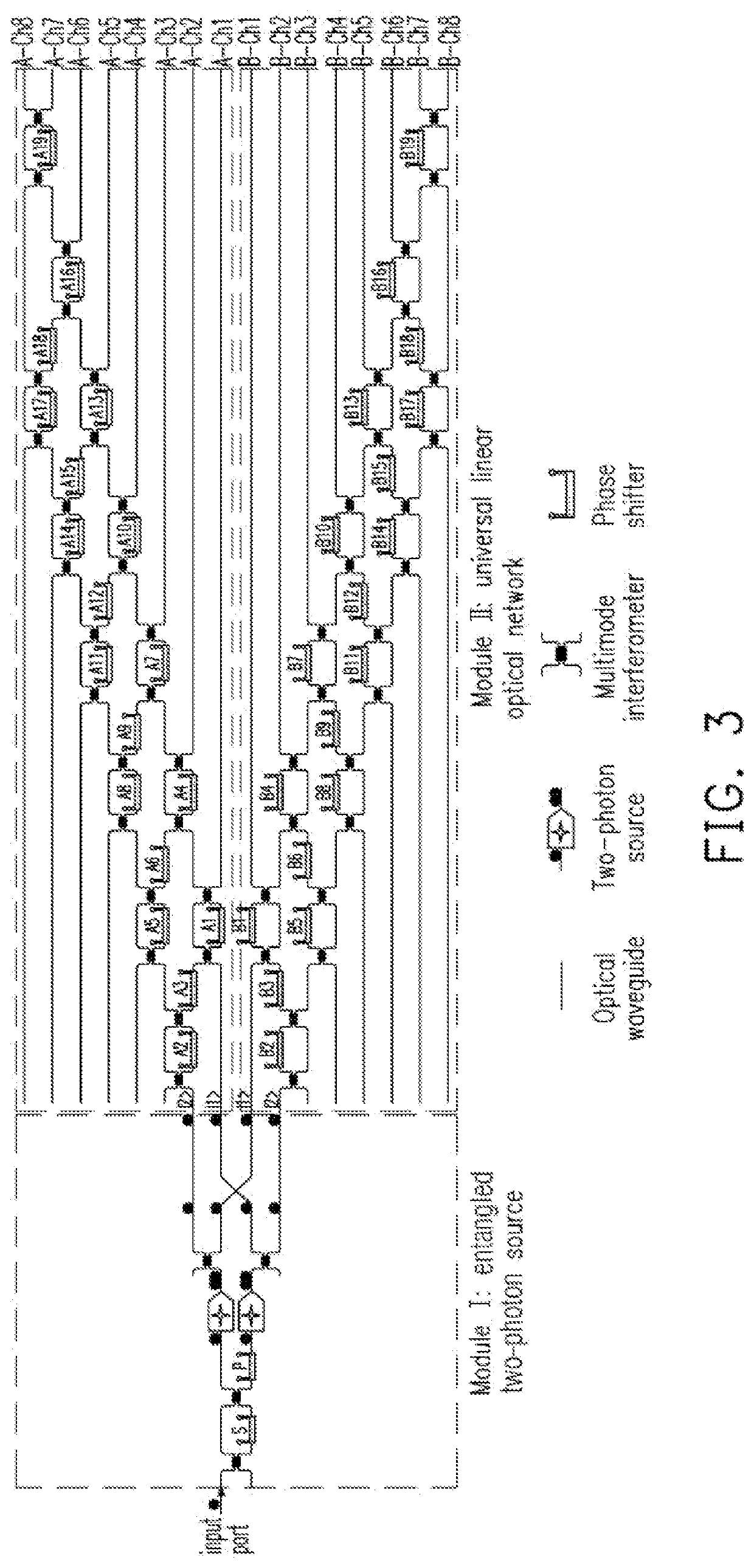
The invention discloses a universal quantum walk analog chip structure based on integrated optics. A multi-photon source capable of preparing a multi-photon path entangled state and a linear optical network capable of achieving unitary transformation are organically combined and used in cooperation, and the corresponding relation among the on-chip multi-photon path entangled state, the unitary transformation, the quantum walking state of multi-particle quantum walking and the walking process is established. Optical unitary transformation is realized by regulating and controlling a multi-photonpath entangled state prepared by a multi-photon source and a universal linear optical network; the chip structure can carry out general quantum walk simulation with configurable elements such as evolution Hamiltonian quantity, evolution time, initial evolution state, particle properties (such as particle isotropy and particle exchange symmetry) and the like of multi-particle quantum walk.
Owner:NAT UNIV OF DEFENSE TECH
Image encryption compression method based on discrete quantum walk and Chinese remainder theorem
InactiveCN103957418ALarge key spaceCiphertext correlation is lowDigital video signal modificationKey spaceArnold transformation
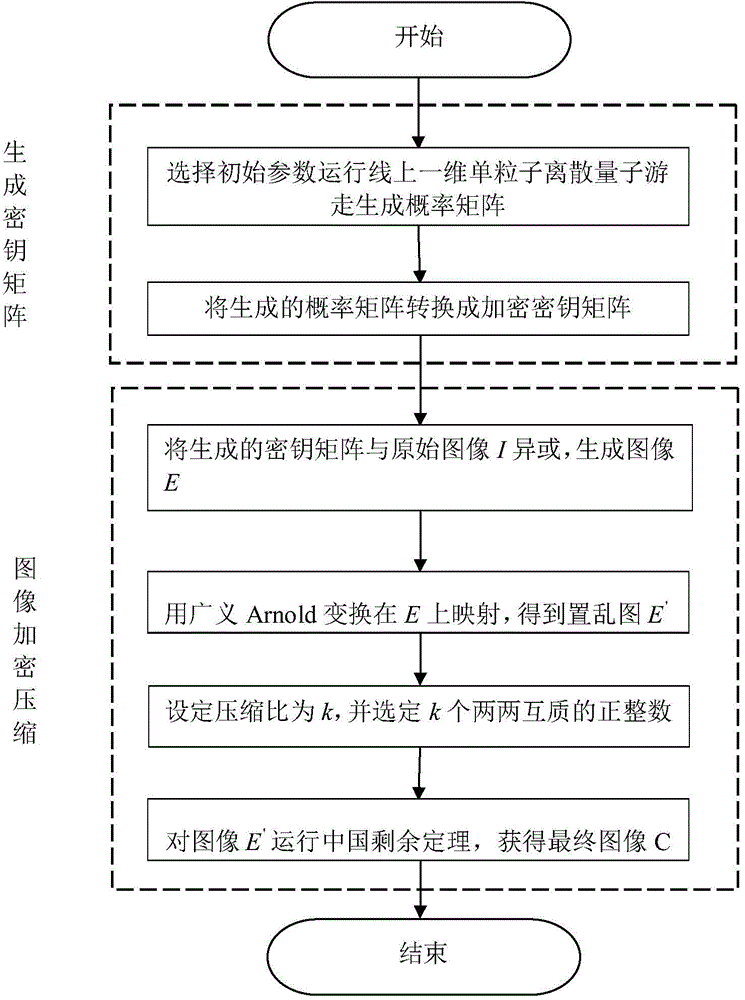
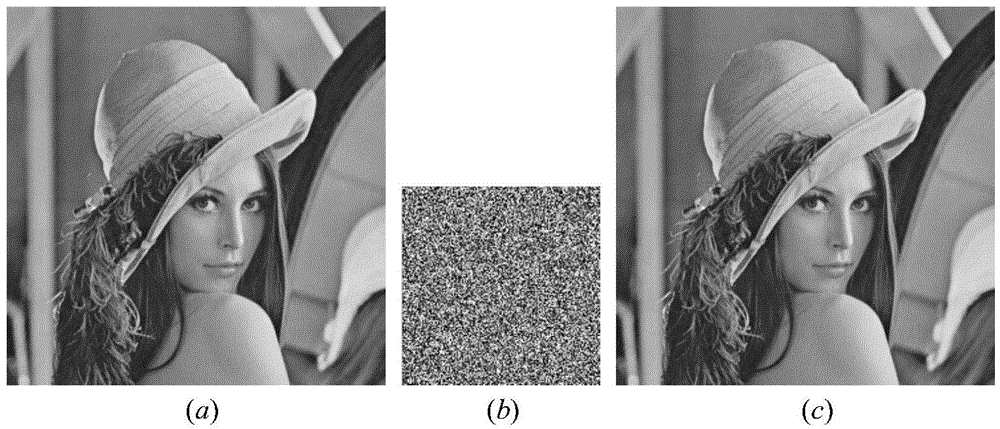
The invention relates to an image encryption compression method based on a discrete quantum walk and a Chinese remainder theorem. The method comprises two phases: a secret key generation phase, i.e., generating probability distribution by use of a linear single particle one-dimensional discrete quantum random walk (QRW), and converting the probability distribution into a secret key matrix capable of encryption; and an image encryption compression phase, i.e., compressing an image by use of the generated secret key matrix and the Chinese remainder theorem. XOR operation is performed on an obtained encryption secret key and an original image, afterwards, Arnold transformation is performed on an obtained image. Diffusion and compression are carried out on a scrambling image according to a given compression ratio k by use of the Chinese remainder theorem. Compared to an image encryption compression scheme based on chaos and optics, the method provided by the invention has higher safety and better compression performance. The greatest advantage of the algorithm is that a theoretical infinite large secret key space can be generated so as to oppose a violent attack capability. Various performance comparisons indicate that the algorithm is better than prior research and can better satisfy actual demands.
Owner:BEIJING UNIV OF TECH
Integratable light quantum walking device based on photonic crystal auto-collimation effect
ActiveCN103675993AEasy to integrateImprove coupling efficiencyOptical light guidesBeam splitterDielectric cylinder
The invention discloses an integratable light quantum walking device based on the photonic crystal auto-collimation effect. Tetragonal lattice air holes or an energy band structure and an equi-frequency line of a dielectric cylinder photonic crystal are utilized, a first or a second energy band is taken to establish beam splitters in the Gamma-X or Gamma-M direction and arrange the beam splitters in the Gamma-M or Gamma-X direction, wherein beam splitter nodes in the Gamma-X or Gamma-M direction are increased at intervals of fixed transmission distances. The integratable light quantum walking device utilizes the advantages that auto-collimation light beams in the photonic crystal do not diverge during transmission and are free of crosstalk when being crossed, adopts a 3dB beam splitter array to form a micronanoelectronic device capable of being used for light quantum walking and belongs to the fields of semiconductor integrated optical technologies and quantum information science.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Semi-quantum group signature method and system based on quantum walk
ActiveCN110166251AReduce demandEnsure safetyKey distribution for secure communicationUser identity/authority verificationInformation transmissionSecurity analysis
The invention belongs to the technical field of quantum communication, and discloses a semi-quantum group signature method and system based on quantum walk, and the method comprises the steps: carrying out the group internal communication through employing a semi-quantum communication mode; using a quantum walking-based mode to carry out communication outside a group, entangled particles being automatically generated in a walking process, and transmitting a communication message by adopting a quantum walking-based invisible transmission state; when the distributed information is signed by group members, performing blind processing on the message by using a certain coding rule, so that the blind information is not acquired by other group members and external potential attackers; and carrying out anti-repudiation, anti-denial, anti-forgery, interception retransmission attack and entanglement attack security analysis on the blind information. According to the method, single-photon-based information transmission is adopted for communication in the group, so that quantum preparation and detection are relatively easy, and the communication cost is greatly saved in the actual applicationprocess.
Owner:CHENGDU UNIV OF INFORMATION TECH
Image encryption method based on on-ring two particle one-dimensional discrete quantum walk
InactiveCN103871016AImprove encryption qualityReduce correlationImage data processing detailsExclusive orComputer science
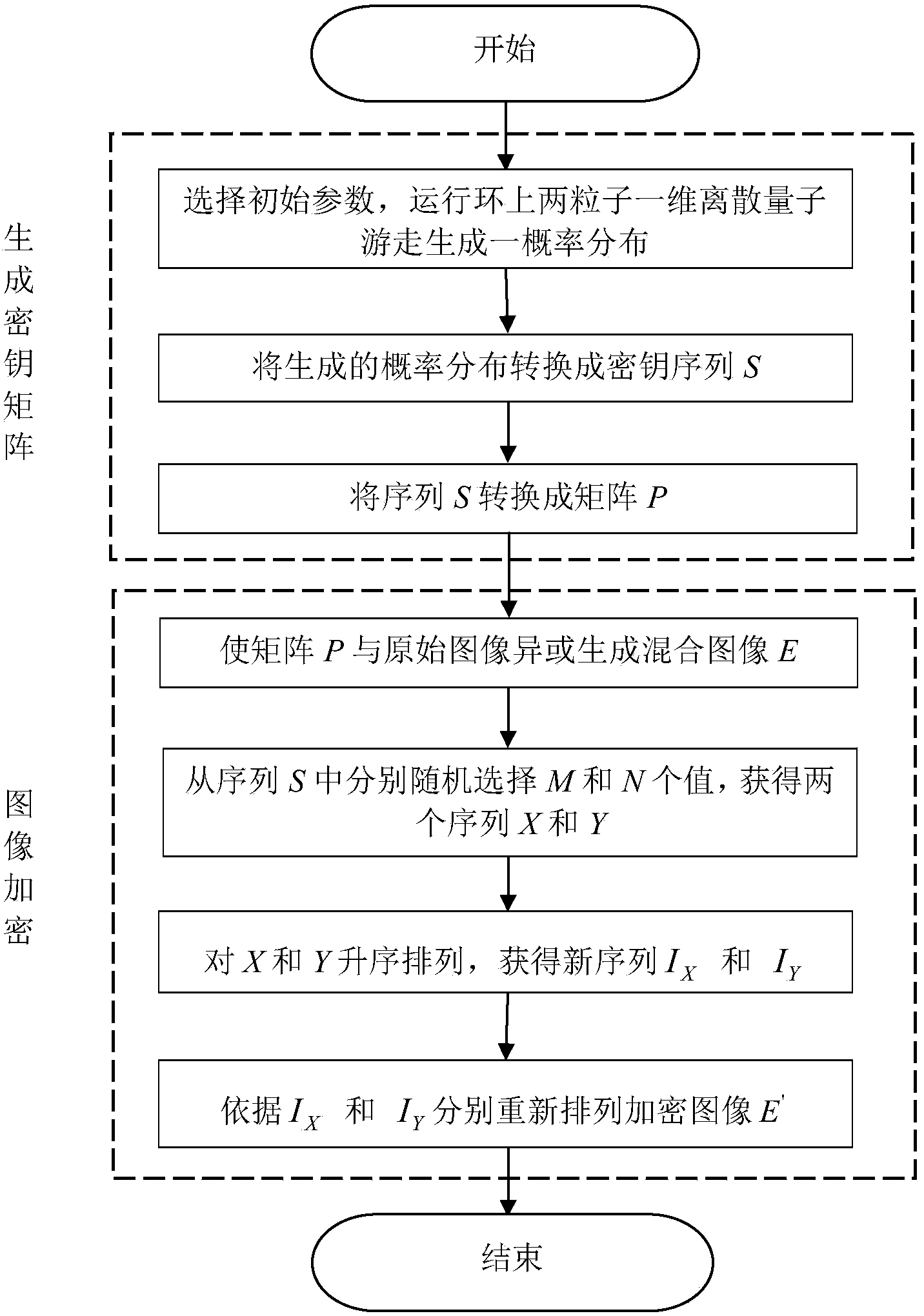
The invention relates to an image encryption method based on on-ring two particle one-dimensional discrete quantum walk. The purpose is to guarantee safety and high efficiency of an image encryption algorithm and effectively protect an image. The method includes the steps that (1), on-ring two particle one-dimensional discrete quantum walk is used for generating a secrete key matrix; the on-ring two particle one-dimensional discrete quantum walk is operated to generate probability distribution which is converted to a secrete key sequence S, and the sequence S is converted into a matrix P; (2), the image is encrypted, logic exclusive or is performed on the matrix P and the original image I to generate a mixed image E, M values and N values are randomly and respectively selected from the sequence S, so that a sequence X and a sequence Y are respectively obtained, and ascending sort is performed on the two sequences to respectively obtain two new sequences. The two new sequences IX and IY are used for rearranging the encrypted image E to obtain a final encrypted image E'. Compared with an existing image encryption method, the image encryption method is easier to operate, higher in speed, better in performance and encryption quality and capable of meeting practical needs better.
Owner:BEIJING UNIV OF TECH
Method for constructing quantum hash function based on controlled alternate quantum walks on two-dimensional plane
ActiveCN107359984ACollision avoidance behaviorCollision behavior without scruplesEncryption apparatus with shift registers/memoriesHash functionOriginal data
The invention discloses a method for constructing a quantum hash function based on controlled alternate quantum walks on a two-dimensional plane. Based on the proposed controlled alternate quantum walks, an information sequence is used to control coin throwing operations, the controlled alternate quantum walks are used to achieve a unidirectional compression process of quantum hash, and the probability obtained by measuring the location of a walker are used as original data and then processed as a hash value. The method adopts the controlled alternate quantum walks, and controls the walks on the two-dimensional plane with a two-dimensional coin. Thus, the method not only avoids a predictable collision behavior in a previous quantum hash mechanism, but also facilitates the physical experiment. A reliable and practical quantum hash mechanism is realized.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Photonic crystal-based integratable quantum walking device
The invention discloses a photonic crystal-based integratable quantum walking device. By utilizing the limit characteristic of photonic crystal to light fields, intercoupling and interference among the light fields of a wider range are realized, so that quantum walking of photons is realized on an integrated optical device of which the dimension is extremely small. The invention belongs to the field of semiconductor integrated optical technology and the quantum information science.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Quantum walking-based quantum secret sharing method and system with credible authentication
ActiveCN111404691ADetermine securityAvoid attackKey distribution for secure communicationUser identity/authority verificationQuantum secret sharingEngineering
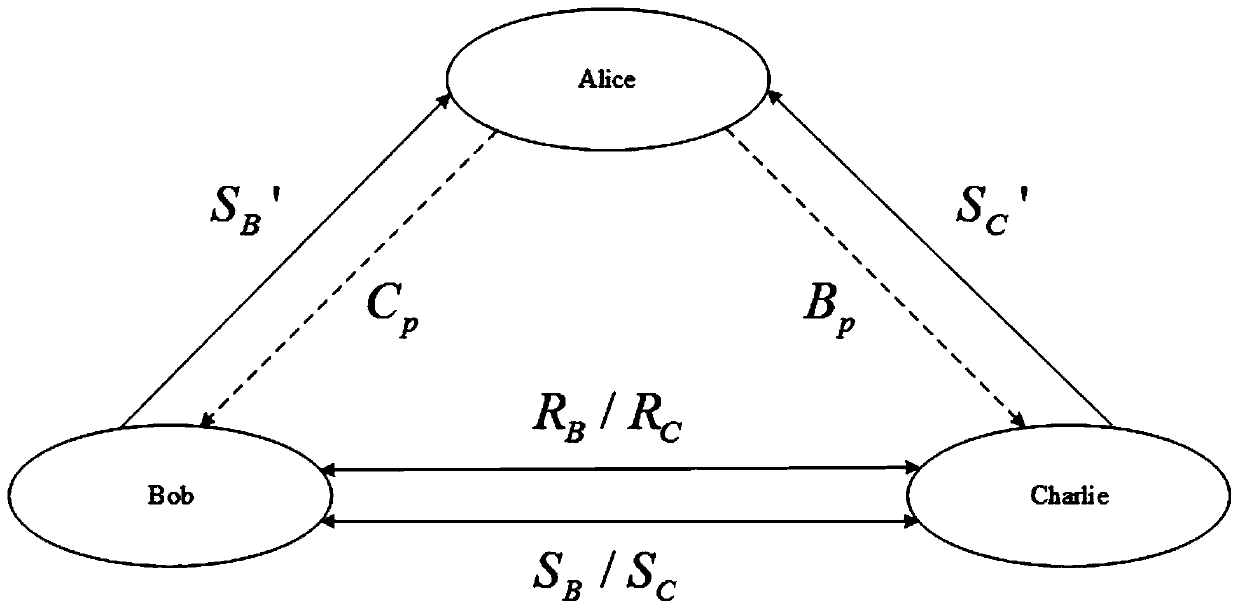
The invention provides a quantum walking-based quantum secret sharing method with credible authentication. The method comprises the following steps: a secret participation end preparing single photonsequences SB and SC, encoding the SB and SC according to an identity authentication key of the secret participation end to obtain SB' and SC ', and sending the SB' and SC' to a secret distribution end; the secret distribution end authenticating the identity of the secret distribution end based on the identity authentication key of the secret participation end; the secret distribution end constructing two quantum walking systems based on the SB and the SC, encoding secret information to be shared to the SB and the SC, and recording secret information encoding particles as MB and MC; the secretdistribution end invisibly transmitting the MB and the MC to the secret participation end; the secret participation ends cooperating with each other to complete identity authentication of the secret distribution end and reconstruction of secret information. According to the trusted identity authentication function and the quantum walking circuit, the safety and practicability of the quantum secretsharing method and system can be improved, and interception / retransmission attacks, entanglement attacks, participant attacks and pretending attacks from the inside and the outside are avoided.
Owner:龙图腾网科技(合肥)股份有限公司
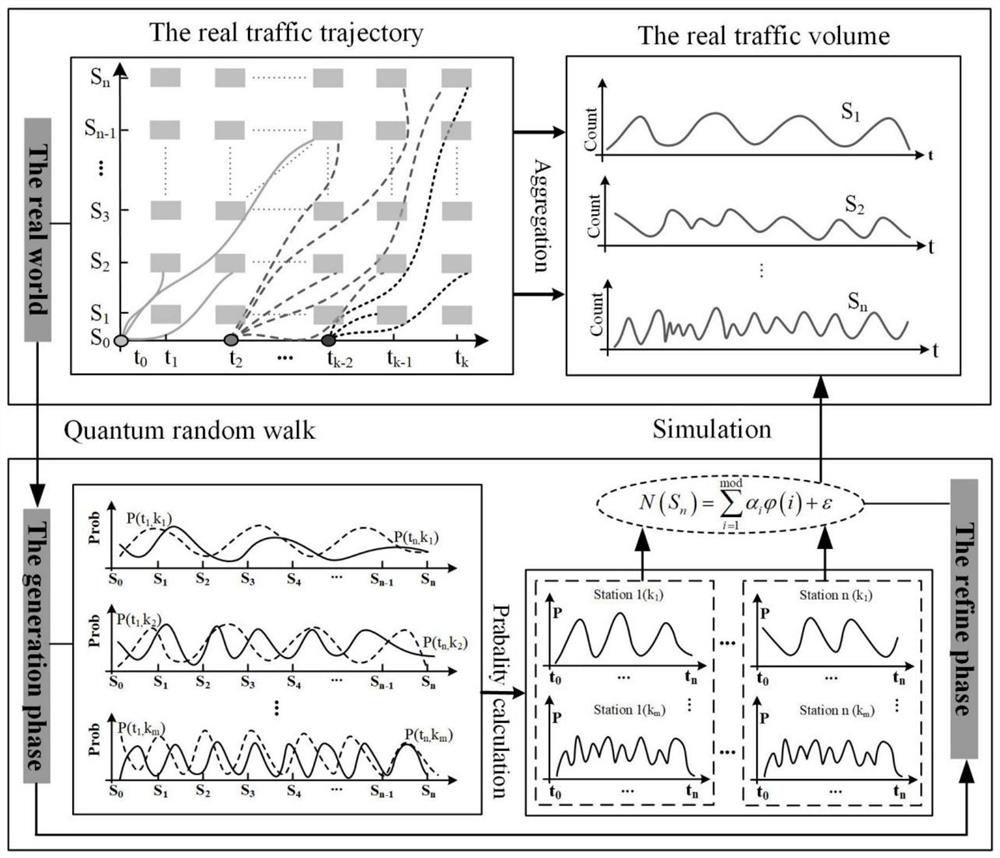
Traffic flow modal fitting method based on quantum random walk
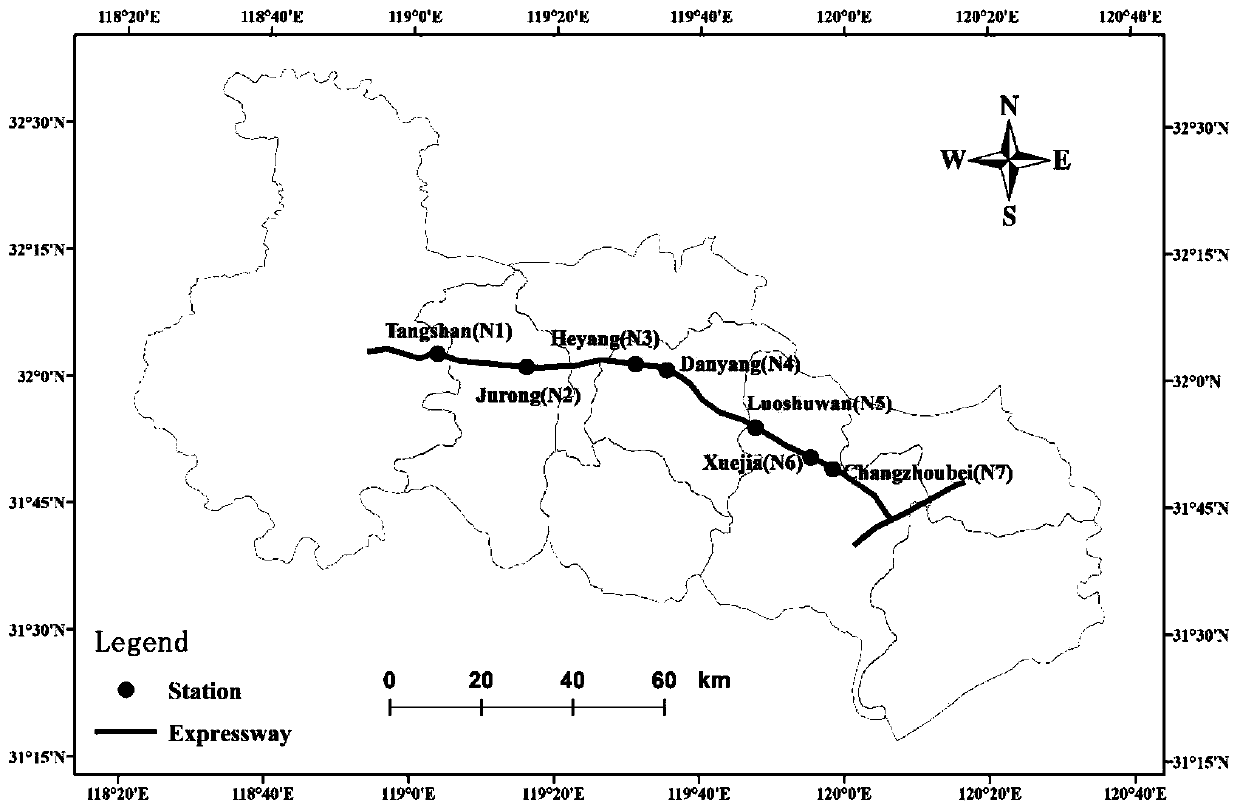
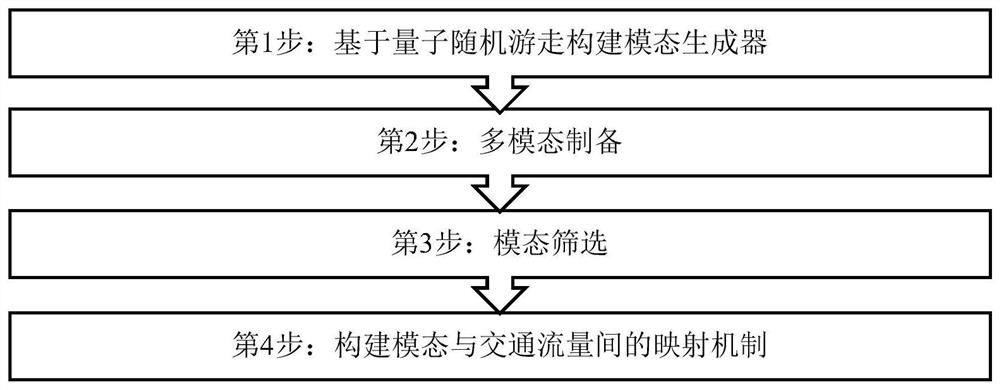
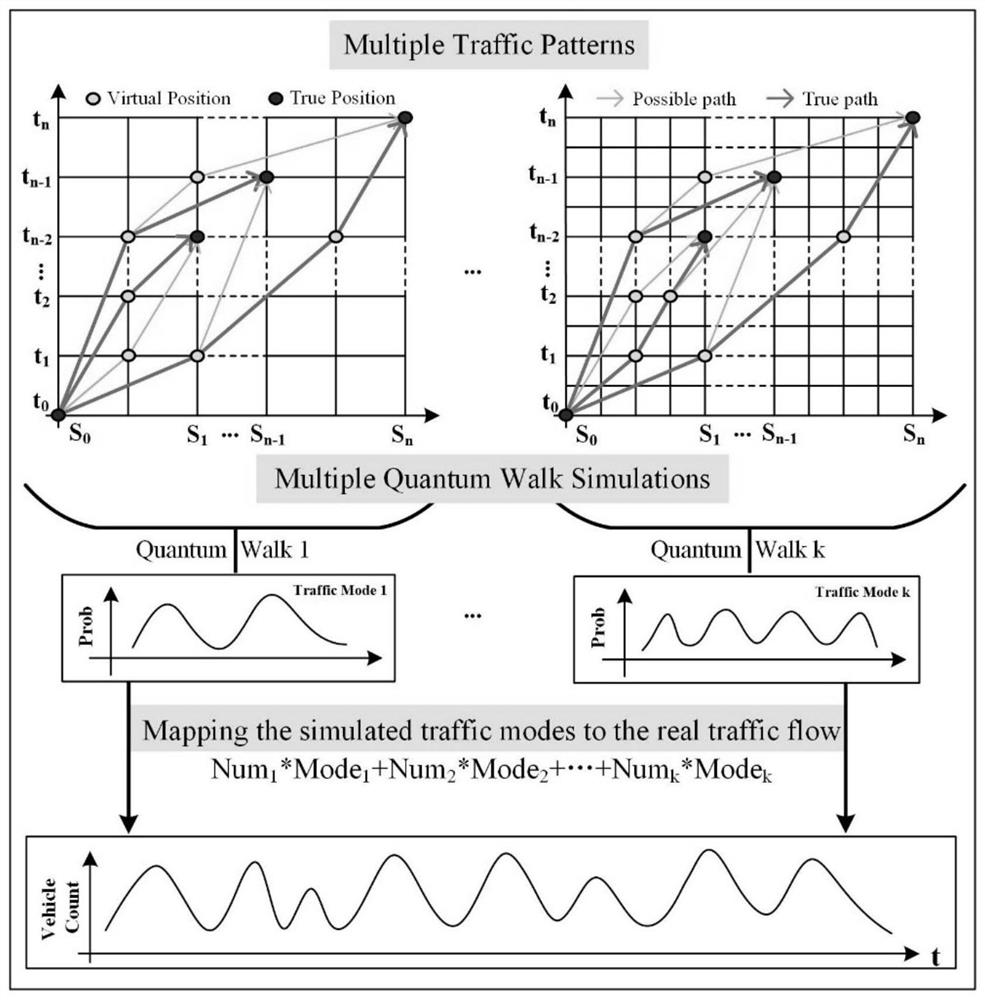
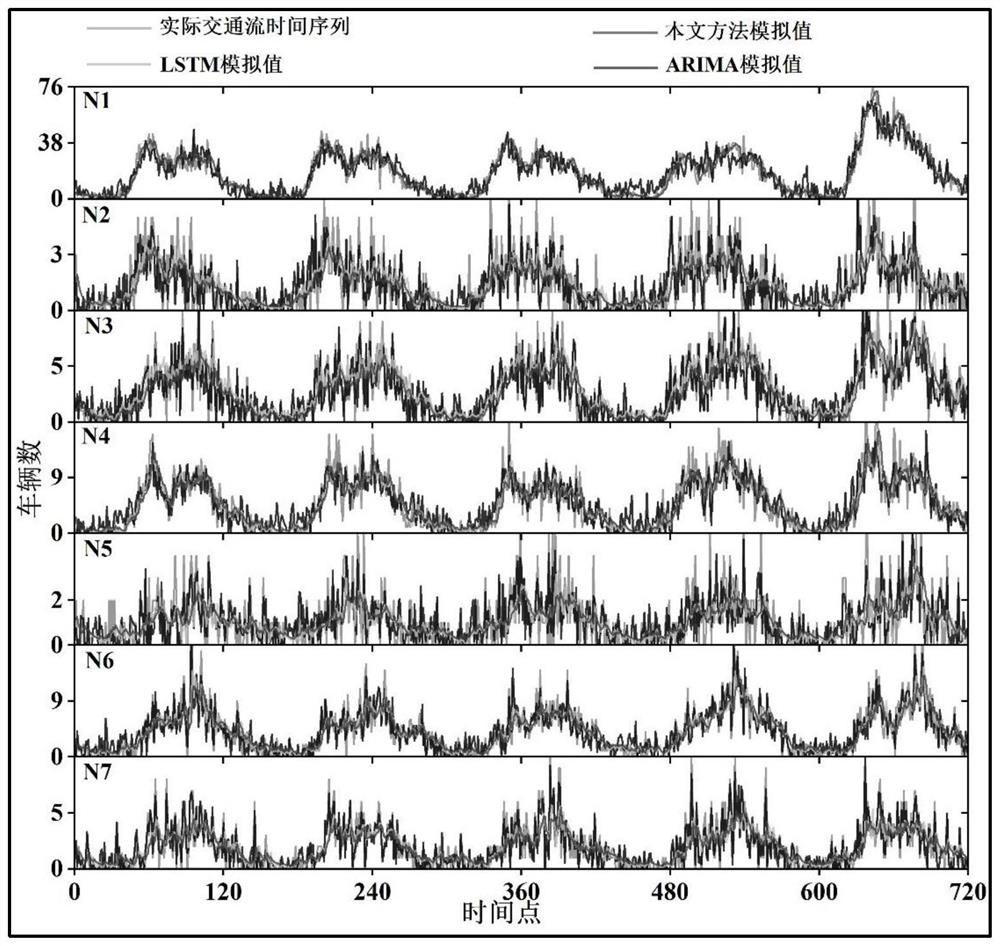
ActiveCN112614336ARealize modeling simulationGeometric CADDetection of traffic movementAlgorithmEngineering
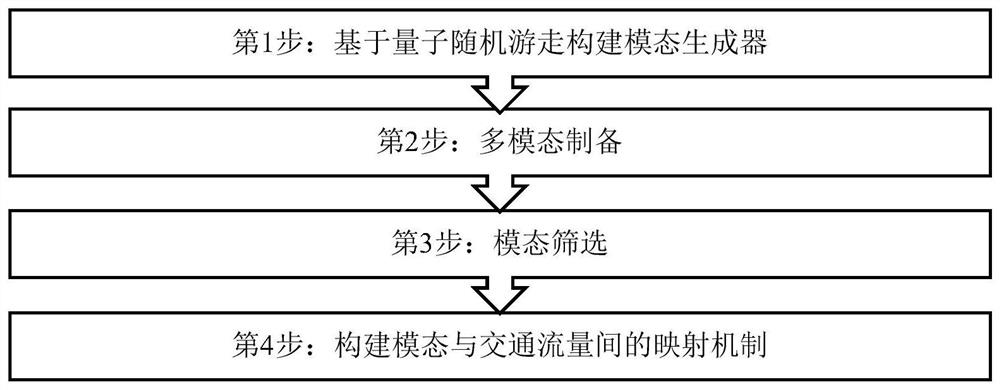
The invention discloses a traffic flow modal fitting method based on quantum random walk. The method comprises the following steps: (1) constructing a modal generator based on quantum random walk; (2) multi-modal preparation; (3) modal screening; and (4) constructing a mapping mechanism between the mode and the traffic flow. According to the method, the high-speed traffic flow is considered to be a complex geographic space-time process formed by aliasing and coupling a plurality of traffic flow modes with different structures, and modeling simulation of the traffic flow is attempted to be realized from the perspective of multi-scale analysis; all possible traffic flow modes in high-speed traffic flow are generated by utilizing quantum random walk under a basic framework of an expressway network topological structure; under the constraint of an actual traffic flow time sequence, modal screening is achieved based on a specific screening rule, a conversion coupling mechanism between a traffic flow modal and traffic flow is explored, and modeling simulation of high-speed traffic flow is achieved.
Owner:NANJING NORMAL UNIVERSITY
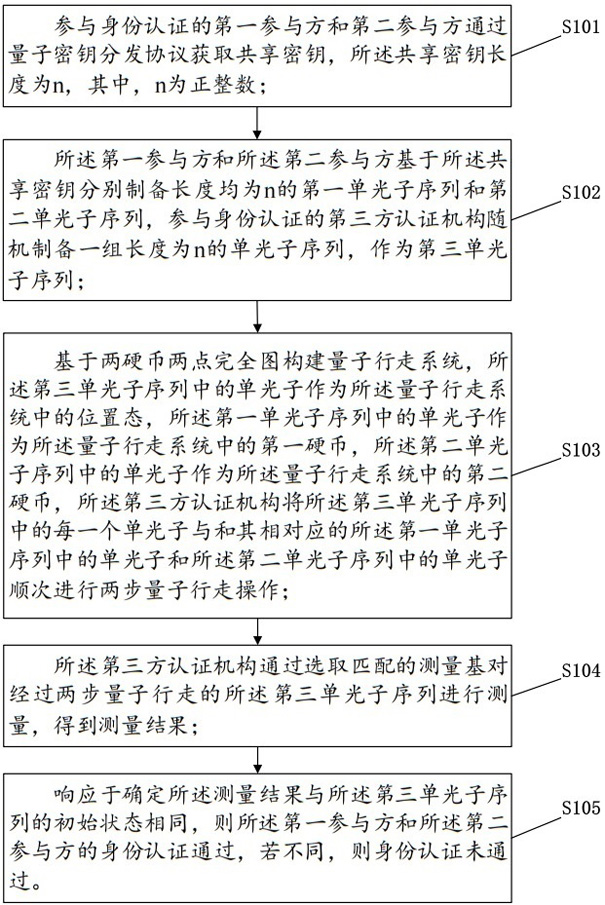
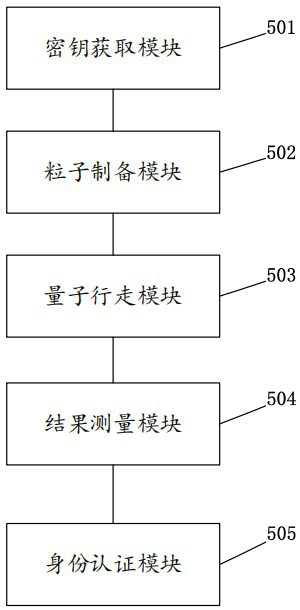
Identity authentication method based on quantum walking and related equipment
ActiveCN113517986AHigh feasibilityImprove practicalityKey distribution for secure communicationUser identity/authority verificationAlgorithmSimulation
The invention provides an identity authentication method based on quantum walking and related equipment. The method comprises the steps: carrying out the two-step quantum walking operation in a constructed quantum walking system through preparing a single photon sequence, carrying out the Z-base measurement of the single photon sequence after the two-step quantum walking, and judging whether a participant passes the identity authentication or not through a measurement result. The identity authentication method provided by the invention is higher in feasibility and practicability, easy to prepare and less in physical resource consumption, and does not need to prepare entangled quantum in the early stage, so that risk leakage caused in the authentication process is avoided, and the security of identity authentication is improved. Meanwhile, according to the identity authentication method provided by the invention, experimental verification is carried out on an IBM quantum cloud platform, and a verification result accords with theoretical derivation, so that the identity authentication method provided by the invention is more practical.
Owner:HUNAN NORMAL UNIVERSITY
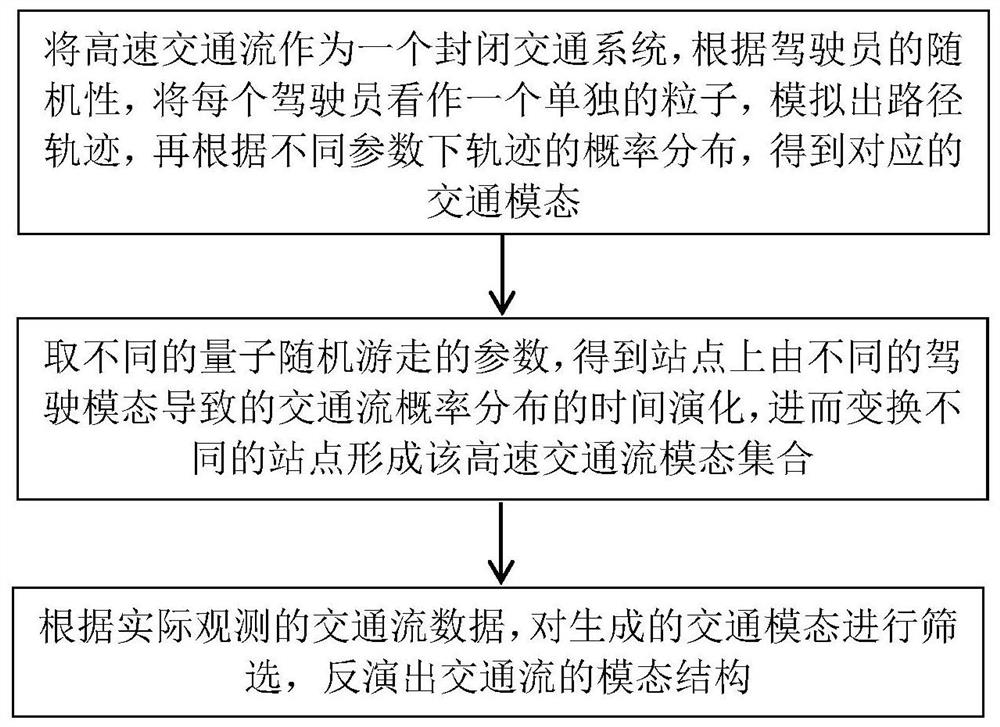
Traffic flow characteristic modal decomposition method based on generation-filtering mechanism
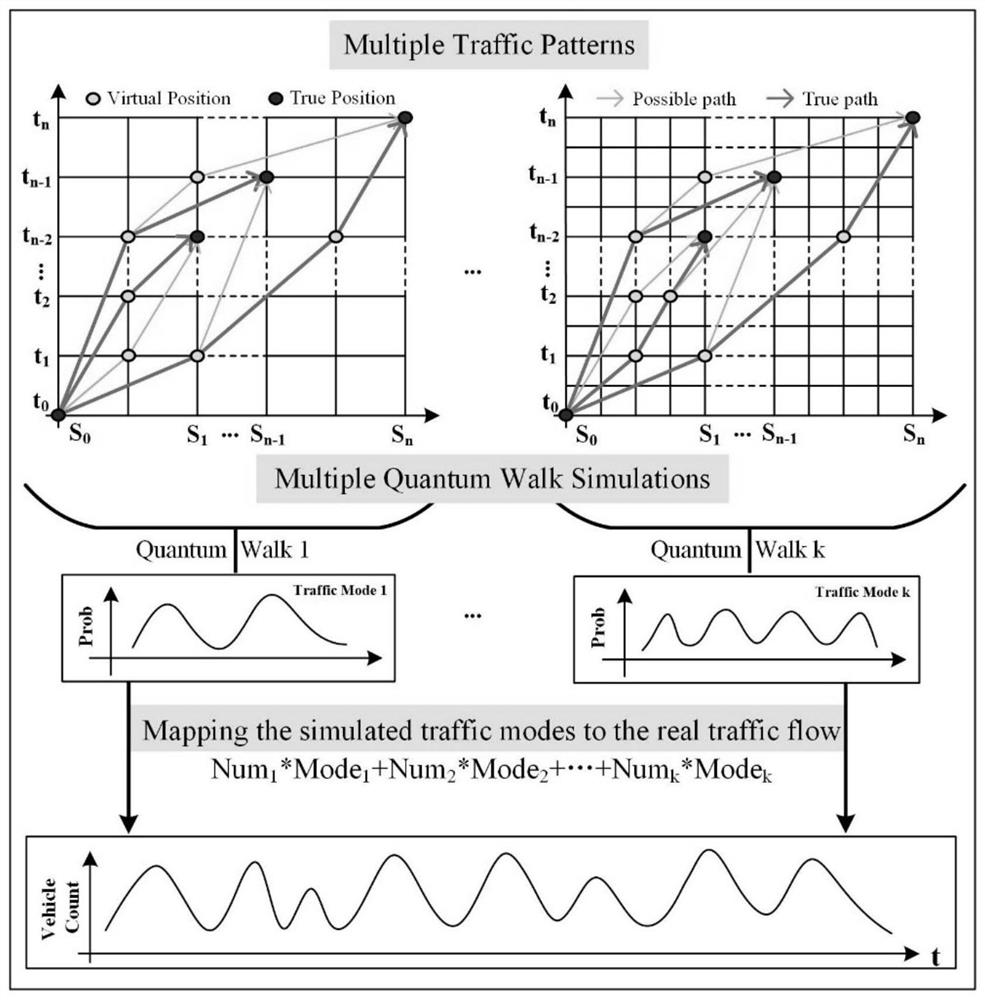
ActiveCN112614335AImprove understandingIncrease awarenessQuantum computersDetection of traffic movementMultiscale decompositionDriver/operator
The invention discloses a traffic flow characteristic modal decomposition method based on a generation-filtering mechanism, and the method comprises the steps: firstly enabling a high-speed traffic flow to serve as a closed traffic system, enabling each driver to serve as an independent particle according to the randomness of the drivers, simulating a path track, and calculating the probability distribution of the track according to the probability distribution of the track under different parameters; obtaining a corresponding traffic mode; secondly, taking different quantum random walk parameters, obtaining time evolution of traffic flow probability distribution caused by different driving modes on the stations, and then transforming the different stations to form the high-speed traffic flow mode set; and finally, screening the generated traffic modes according to the actually observed traffic flow data, and inverting to obtain the mode structure of the traffic flow. The complex structure and multi-modal characteristics of the traffic flow are disclosed from the perspective of multi-scale decomposition, a certain reference is provided for traffic management, prediction and regulation, and the method has great significance in solving various traffic problems faced by the current society.
Owner:NANJING NORMAL UNIVERSITY
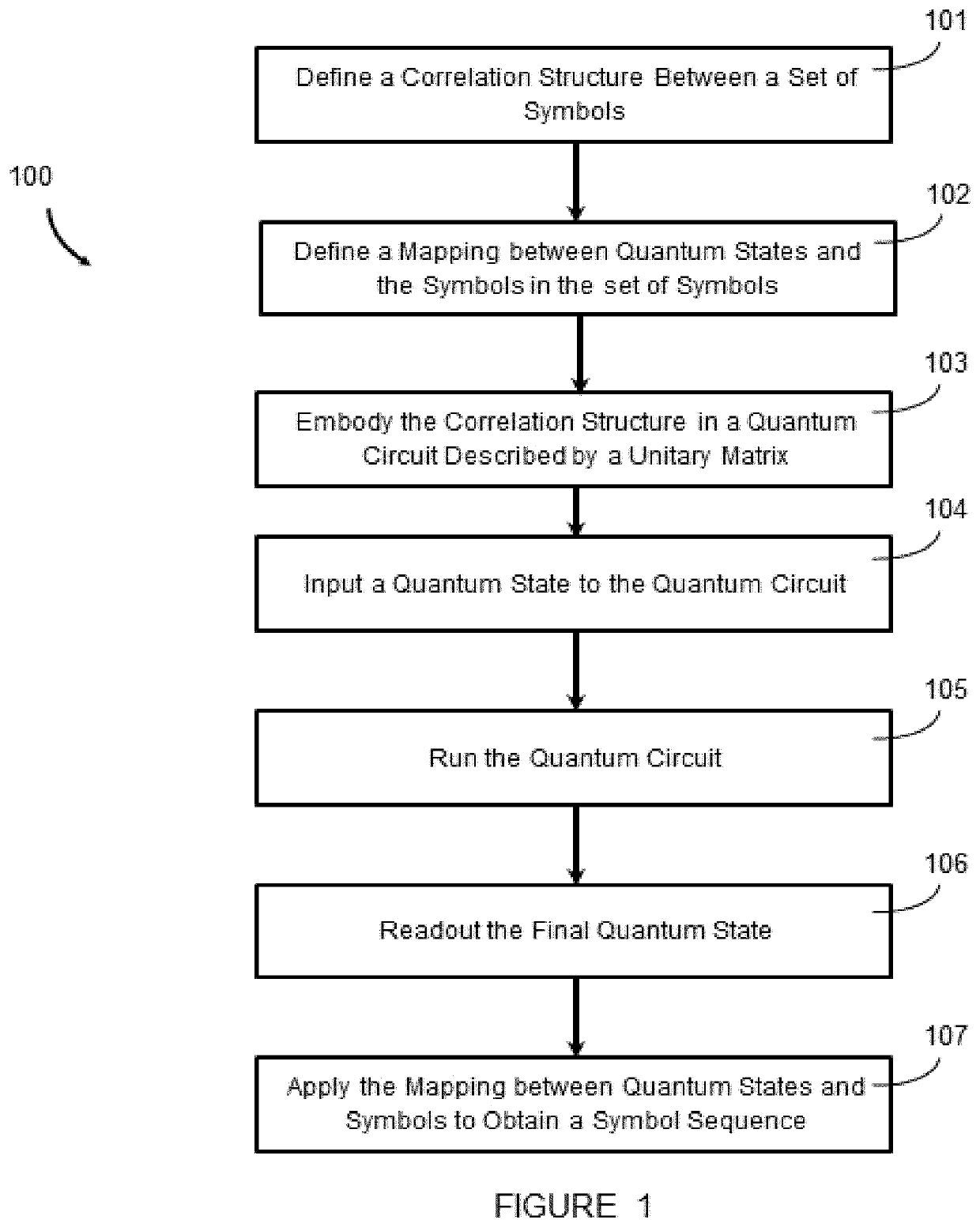
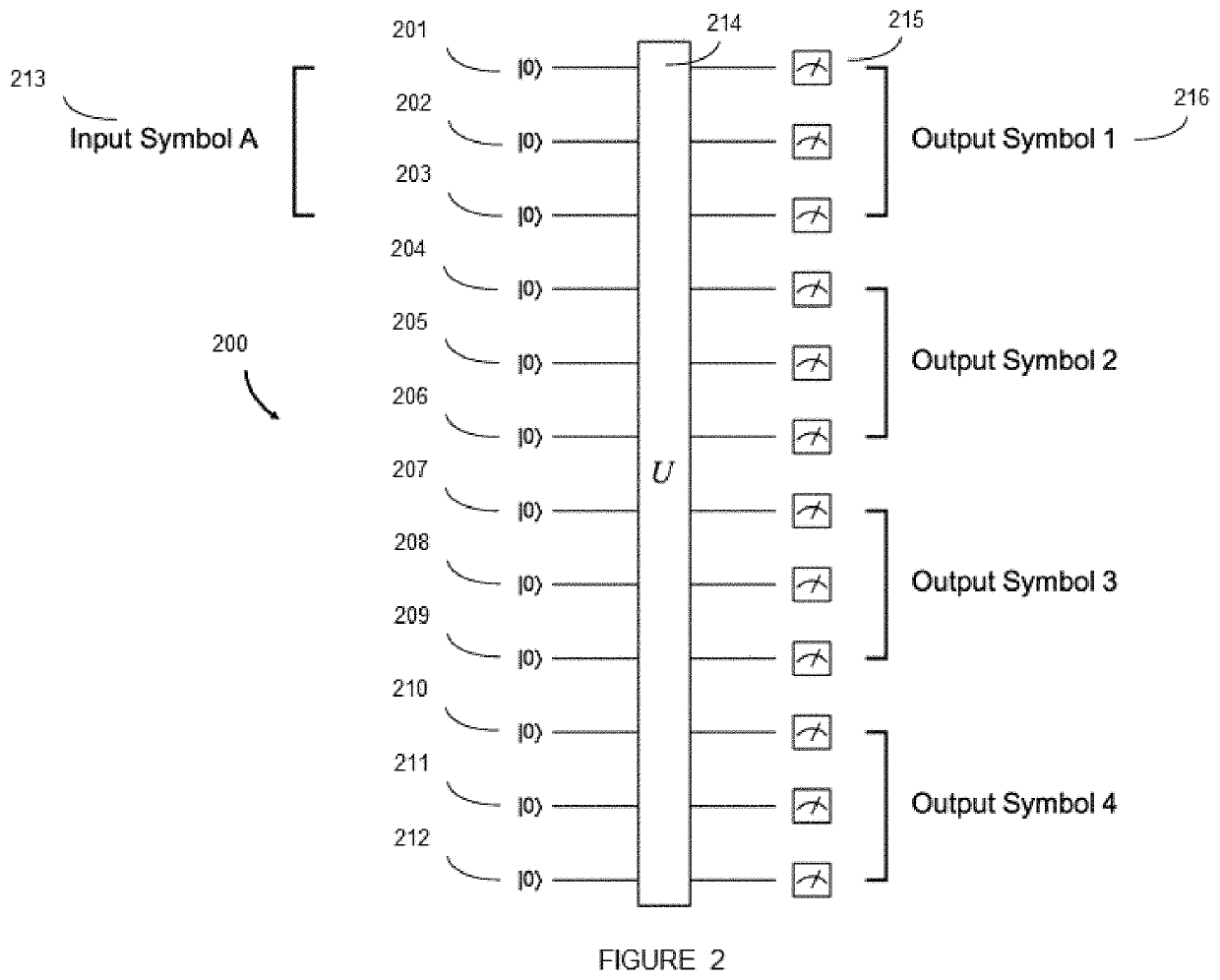
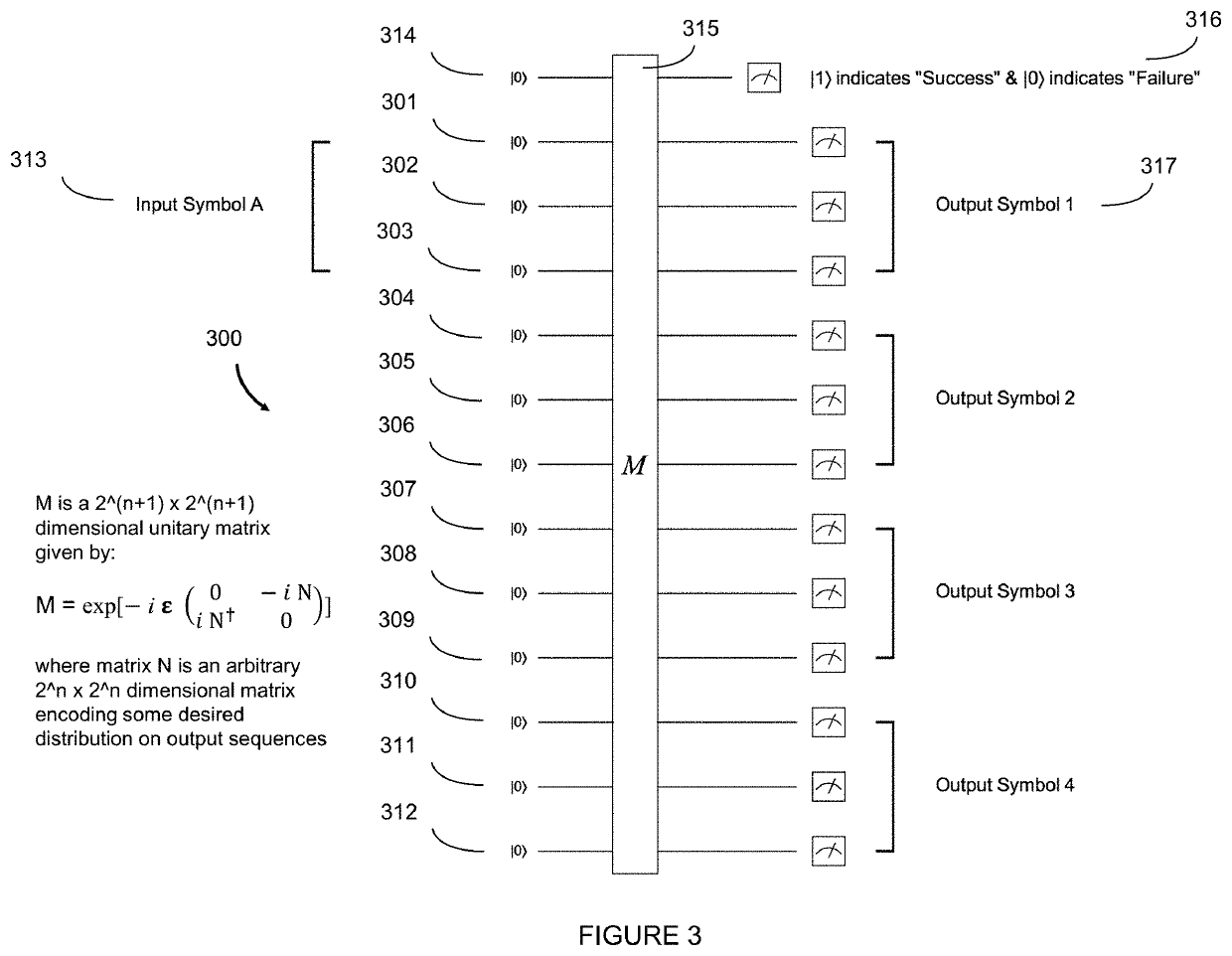
Systems, devices, and methods for generating symbol sequences and families of symbol sequences
PendingUS20220114994A1Quantum computersElectrophonic musical instrumentsQuantum computerQuantum walk
The present systems, devices, and methods generally relate to generating families of symbol sequences with controllable degree of correlation within and between them using quantum computers, and particularly to the exploitation of this capability to generate families of symbol sequences representing musical events such as, but not limited to, musical notes, musical chords, musical percussion strikes, musical time intervals, musical note intervals, and musical key changes that comprise a musical composition. Quantum random walks on graphs representing allowed transitions between musical events are also employed in some implementations.
Owner:OBEEBO LABS LTD
Multi-party quantum secret sharing method based on quantum walk and system thereof
ActiveCN113645034AThe number of people can be expandedVerify correctnessKey distribution for secure communicationComputer networkSecret share
The invention provides a multi-party quantum secret sharing method based on quantum walk and a system thereof, and the method comprises the following steps: S1, firstly constructing a quantum walk subsystem by a secret distributor Alice, and executing the quantum walk to generate an entangled state for secret sharing; S2, enabling a secret distributor Alice splits secret to share and distribute the secret shares to participants, and executing wiretapping detection; after eavesdropping detection, measuring particles in the hand by the participant; and S3, enabling the Alice to randomly select a part of measurement results as samples for verification, and recovering all original secret messages after verification is passed. According to the invention, quantum walking multi-party secret sharing is realized by using the on-ring quantum walking principle.
Owner:HUNAN NORMAL UNIVERSITY
A method for generating random numbers based on controlled alternating quantum walkson a two-dimensional plane
PendingCN109190766AImprove production efficiencyWon't convergeRandom number generatorsFuzzy logic based systemsQuantum evolutionComputer science
The invention discloses a method for generating random numbers based on controlled alternating quantum walks on a two-dimensional plane, which utilizes the controlled alternating quantum walks to process the generated probability distribution as a random number, and then uses the random number to control the evolution of the quantum walks. The method provided by the invention has high efficiency of generating random numbers, and is a reliable random number generation method because the quantum evolution is unitary and there is no defect of random number convergence.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
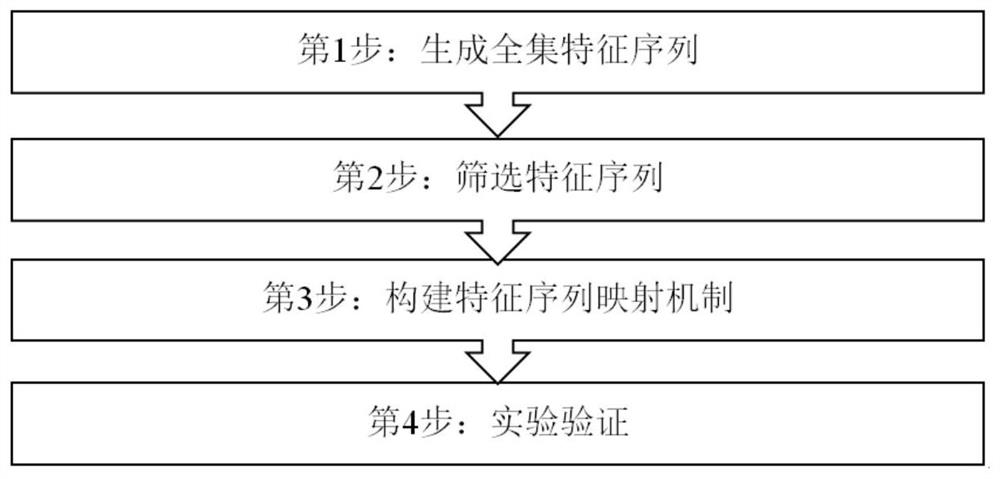
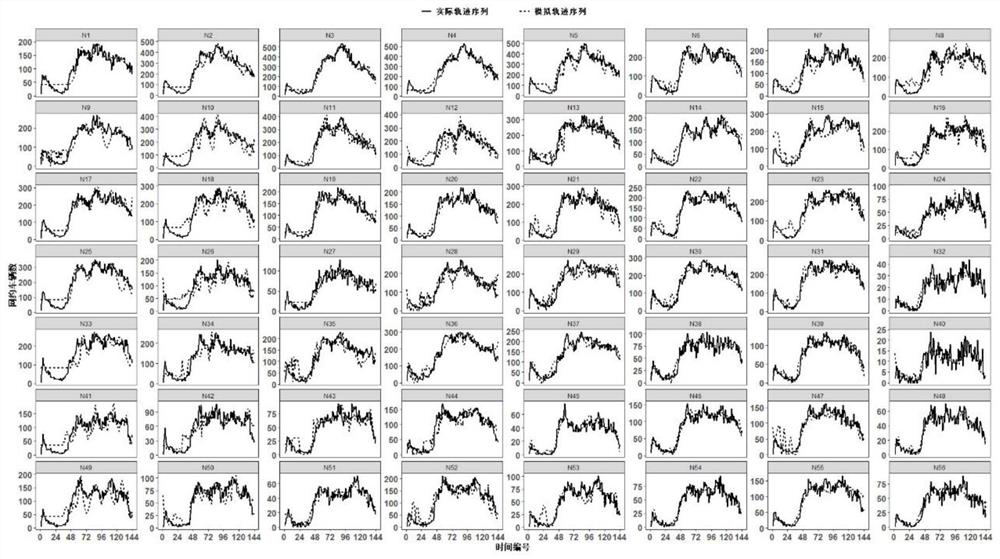
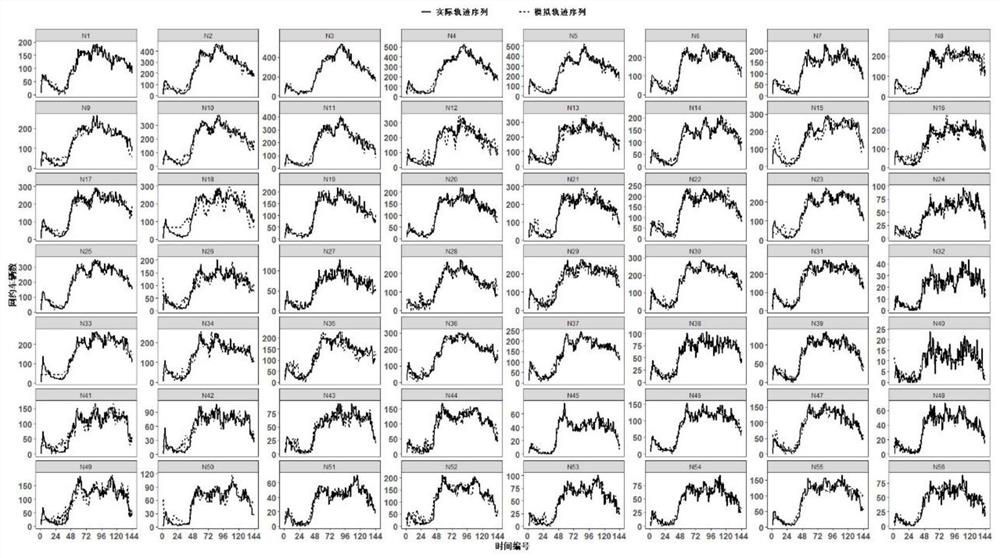
Behavior trajectory sequence multi-feature simulation method based on quantum walk
The invention discloses a behavior trajectory sequence multi-feature simulation method based on quantum walk. The method comprises the following steps: (1) generating a complete set feature sequence; (2) screening a feature sequence; (3) constructing a feature sequence mapping mechanism; (4) executing the experimental verification. According to the method, on the basis of conversion combination characteristics between individual behaviors and group behaviors, the feature structures of similar individuals are simulated from the perspective of multi-scale analysis by utilizing quantum migration, and behavior tracks are simulated.
Owner:NANJING NORMAL UNIVERSITY
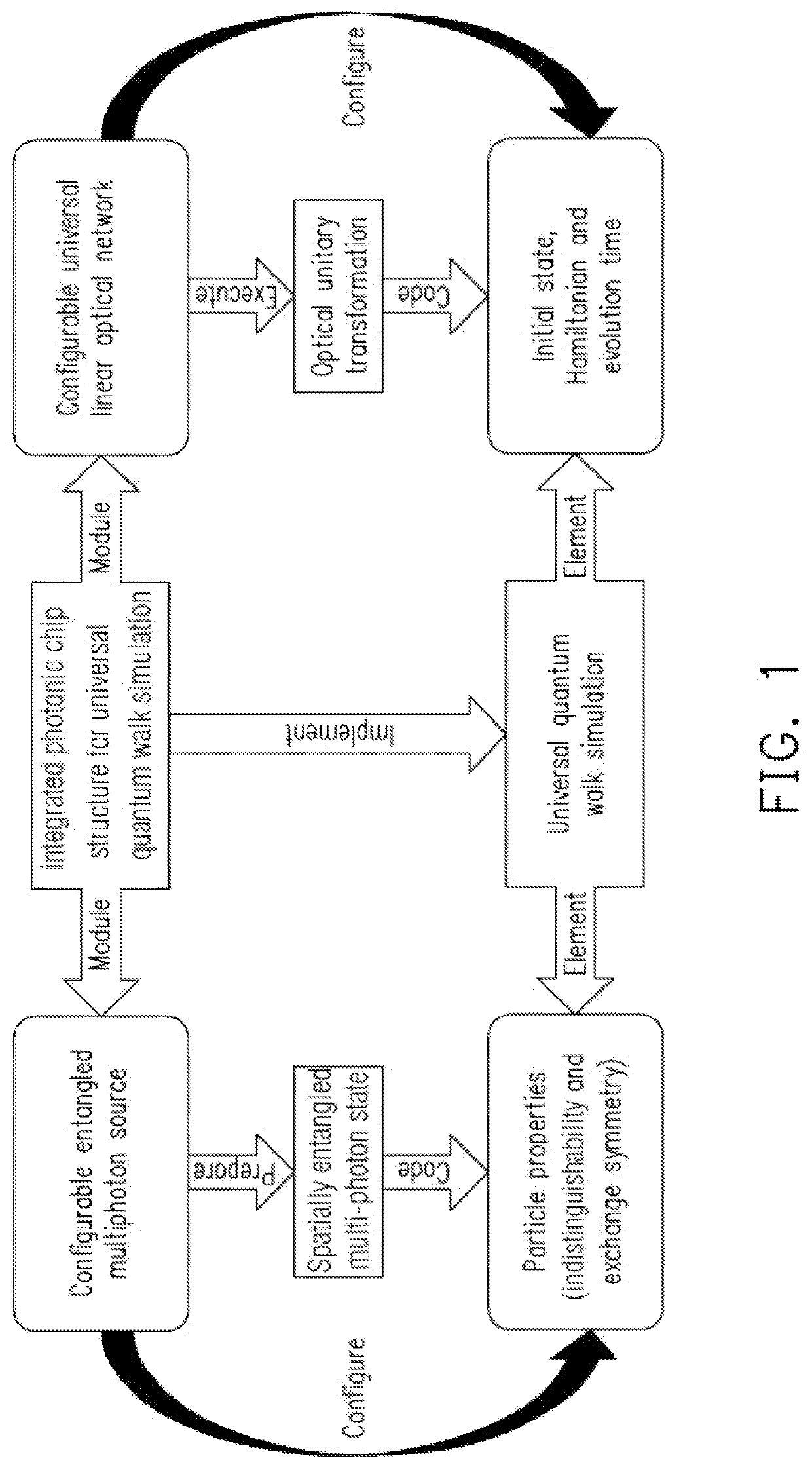
Integrated photonic chip structure for universal quantum walk simulation
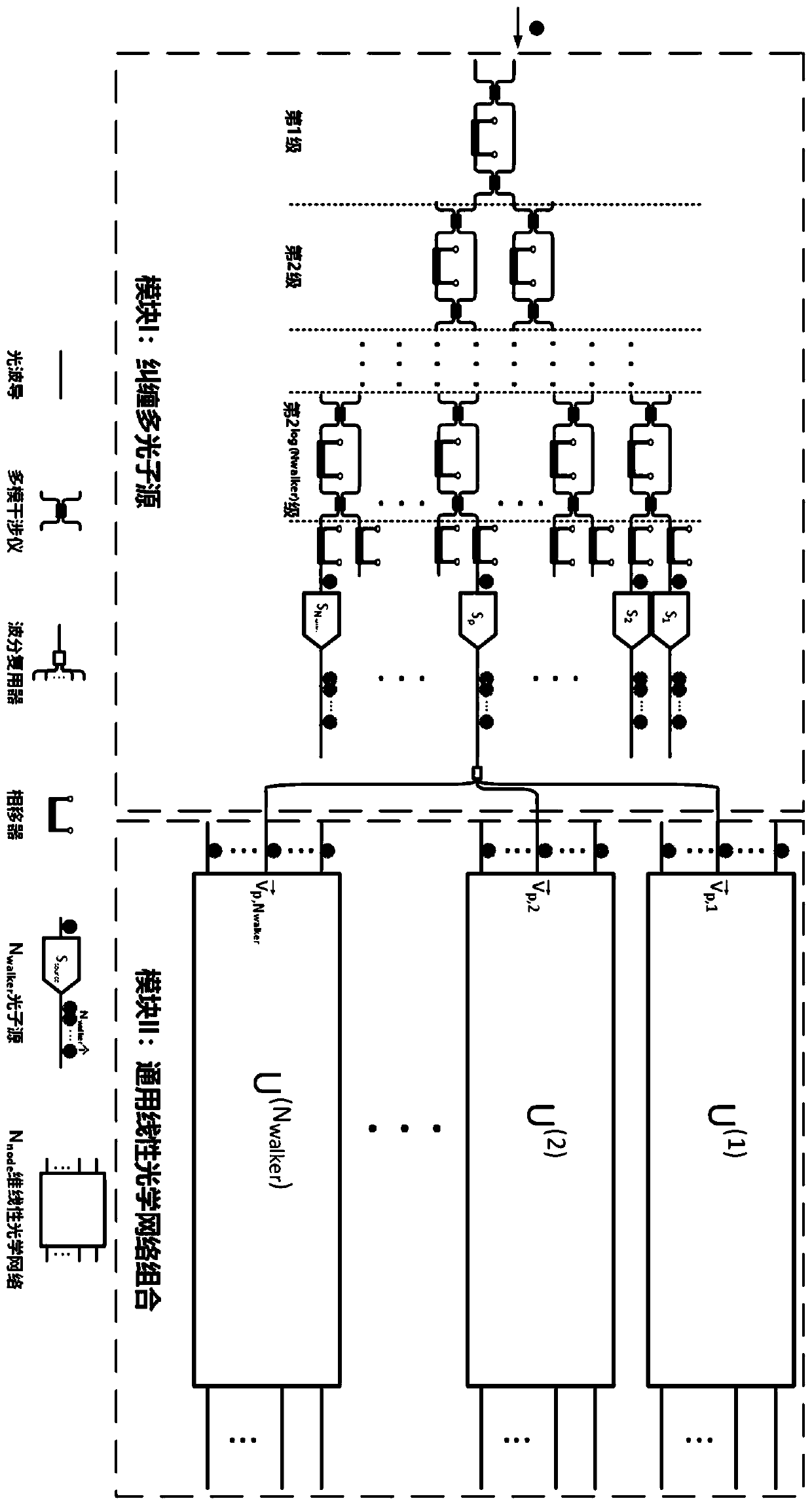
The present invention discloses an integrated photonic chip structure for universal quantum walk simulation which combines the multiphoton source that can generate the spatially entangled multi-photon state and the linear optical network that can implement the unitary transformation, and establishes mapping between on-chip spatial-entangled multi-photon state and quantum walk state and mapping between on-chip linear optical unitary transformation and the evolution process of multi-particle quantum walk. By manipulating the spatially entangled multi-photon state generated via the multi-photon sources and the optical unitary transformation implemented via the universal linear optical networks, the chip structure can implement universal quantum walk simulation with the control over all parameters of multiple-particle quantum walks including such as evolution Hamiltonian, evolution time, initial evolution state and particle properties (i.e., particle indistinguishability and particle exchange symmetry).
Owner:NAT UNIV OF DEFENSE TECH
Quantum privacy comparison method and system based on unidirectional quantum walking and storage medium
ActiveCN114710270AImprove securityImprove efficiencyKey distribution for secure communicationQuantum walkThird party
Owner:BEIJING UNIV OF POSTS & TELECOMM
A Method for Constructing Quantum Hash Functions Based on Controlled Alternating Quantum Walks on a Two-dimensional Plane
ActiveCN107359984BCollision avoidance behaviorCollision behavior without scruplesEncryption apparatus with shift registers/memoriesHash functionOriginal data
The invention discloses a method for constructing a quantum hash function based on controlled alternate quantum walks on a two-dimensional plane. Based on the proposed controlled alternate quantum walks, an information sequence is used to control coin throwing operations, the controlled alternate quantum walks are used to achieve a unidirectional compression process of quantum hash, and the probability obtained by measuring the location of a walker are used as original data and then processed as a hash value. The method adopts the controlled alternate quantum walks, and controls the walks on the two-dimensional plane with a two-dimensional coin. Thus, the method not only avoids a predictable collision behavior in a previous quantum hash mechanism, but also facilitates the physical experiment. A reliable and practical quantum hash mechanism is realized.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
A Traffic Flow Mode Fitting Method Based on Quantum Random Walk
ActiveCN112614336BRealize modeling simulationGeometric CADDetection of traffic movementComputational physicsTraffic flow
Owner:NANJING NORMAL UNIVERSITY
Image Encryption Method Based on Controlled Alternating Quantum Walk and DNA Sequence Manipulation
ActiveCN111031191BEnsure safetyKey distribution for secure communicationDigital data protectionAlgorithmA-DNA
The invention discloses an image encryption method based on controlled alternate quantum walk and DNA sequence operation. The pixel value of the original image is changed by adding DNA sequence to the key matrix, and the pixel position is generated by the controlled alternate quantum walk. The random number sequence after distribution processing is perturbed. The scheme proposed by the invention has good encryption effect. It is highly sensitive to keys, can resist common attacks, such as statistical attacks, differential attacks, etc., and has high security, so it is a reliable image encryption method.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Robust image watermarking method based on quantum random walk and discrete wavelet transform
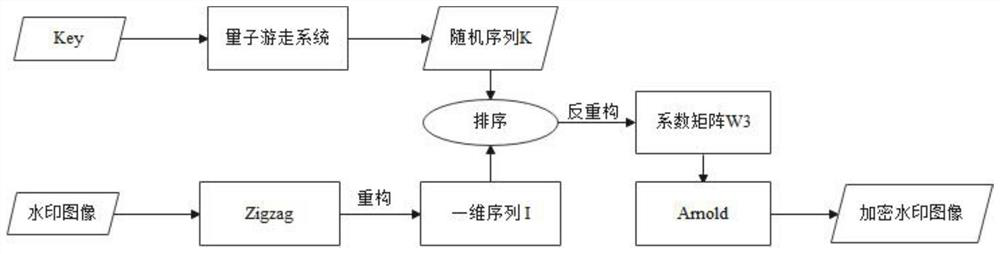
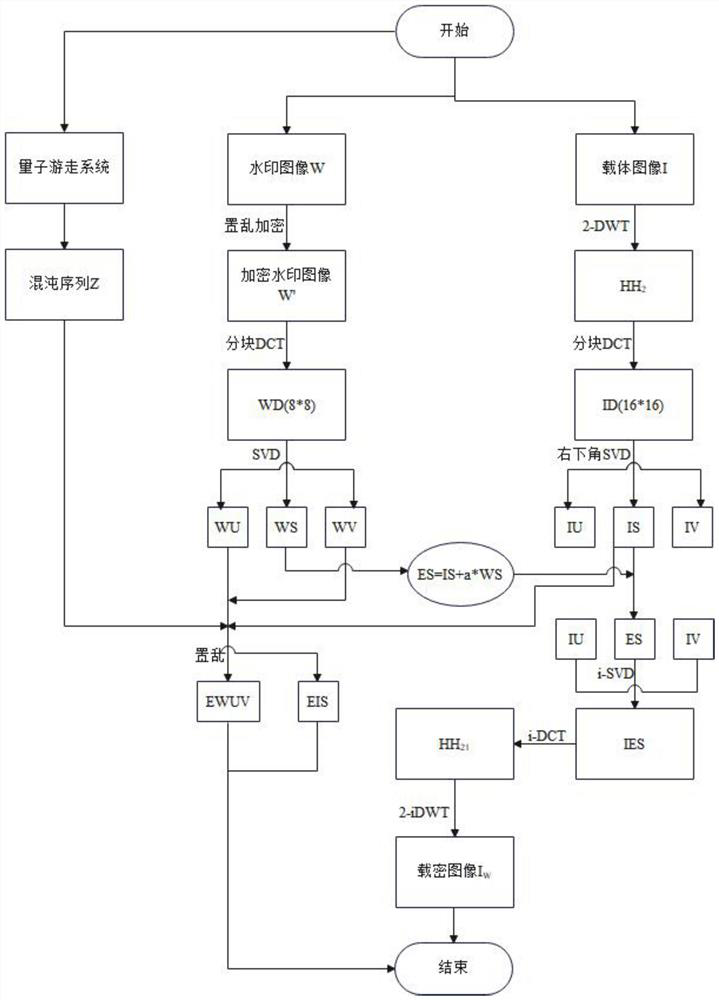
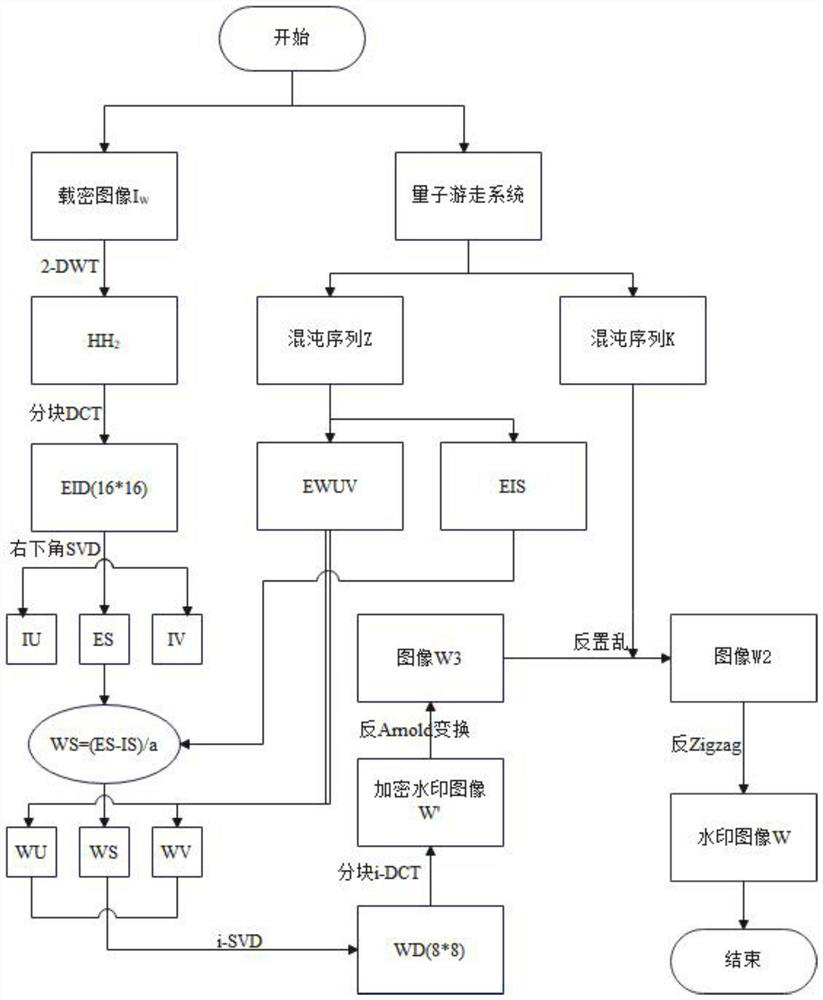
PendingCN114170062AImprove robustnessGuaranteed robustnessImage enhancementImage analysisPattern recognitionSingular value decomposition
The invention discloses a robust image watermarking method based on quantum random walk and discrete wavelet transform, and aims to improve robustness and select to embed watermarks in a frequency domain. The discrete wavelet transform has the advantages that the discrete wavelet transform has good discreteness and spatial locality; important information in the image is compressed through discrete cosine transform, and the important information is concentrated and stepwise on the upper left portion of a coefficient matrix. The SVD coefficients provide high robustness, visual quality, and data payload. Second-level discrete wavelet transform is applied to a carrier image, and watermark embedding is completed in a high-frequency coefficient HH2 of the carrier image, so that the robustness of the watermark is ensured, and better visual quality of the carrier image is kept. After 2-DWT is carried out on a carrier image, the carrier image is divided into blocks, DCT operation is carried out on each block, and main energy of the image is further extracted. In order to not influence the visual quality as far as possible, the watermarking is embedded in the alternating current coefficient, and the watermarking is embedded into the singular value of the block by performing singular value decomposition on the watermarking.
Owner:BEIJING UNIV OF TECH
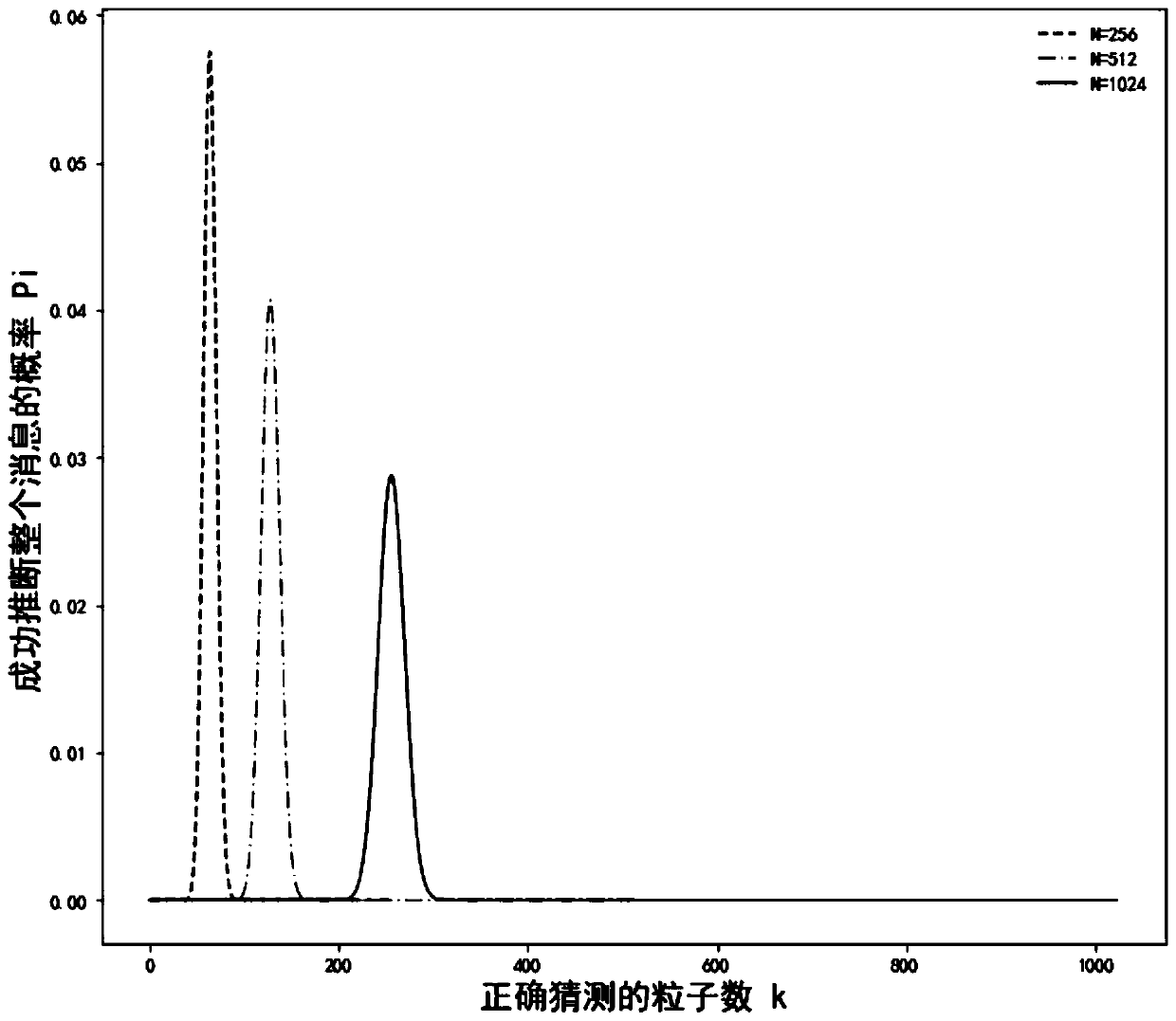
Method for realizing information integrity based on continuous quantum walk hash algorithm
ActiveCN112564886AImprove securityImprove execution efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signaturePassword
The invention discloses a method for realizing information integrity based on a continuous quantum walk hash algorithm. The method comprises the following steps: selecting a Hamiltonian operator according to the bit of a binary message; secondly, constructing a quantum hash algorithm by message control based on continuous quantum walk on bounded one-dimensional crystal lattices to realize information integrity; and finally, analyzing the safety and the efficiency of the constructed quantum hash algorithm by using a simulation experiment. The hash algorithm based on continuous quantum walk hasthe advantages that the efficiency of the quantum hash algorithm is obviously improved when files with the same size are calculated; and the collision performance is lower. According to the method, people can be promoted to construct a new quantum computing model and explore the application of the hash algorithm in the cryptology field to realize information integrity, and the fusion of quantum computing and traditional cryptography is further promoted. Meanwhile, the method can also be used as a key technology for password application such as digital signature and message authentication, andis widely applied to the fields of finance, securities, electronic commerce and the like.
Owner:BEIJING UNIV OF TECH
Integrated photonic quantum walking device based on photonic crystal self-collimation effect
ActiveCN103675993BEasy to integrateImprove coupling efficiencyOptical light guidesBeam splitterDielectric cylinder
The invention discloses an integratable light quantum walking device based on the photonic crystal auto-collimation effect. Tetragonal lattice air holes or an energy band structure and an equi-frequency line of a dielectric cylinder photonic crystal are utilized, a first or a second energy band is taken to establish beam splitters in the Gamma-X or Gamma-M direction and arrange the beam splitters in the Gamma-M or Gamma-X direction, wherein beam splitter nodes in the Gamma-X or Gamma-M direction are increased at intervals of fixed transmission distances. The integratable light quantum walking device utilizes the advantages that auto-collimation light beams in the photonic crystal do not diverge during transmission and are free of crosstalk when being crossed, adopts a 3dB beam splitter array to form a micronanoelectronic device capable of being used for light quantum walking and belongs to the fields of semiconductor integrated optical technologies and quantum information science.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
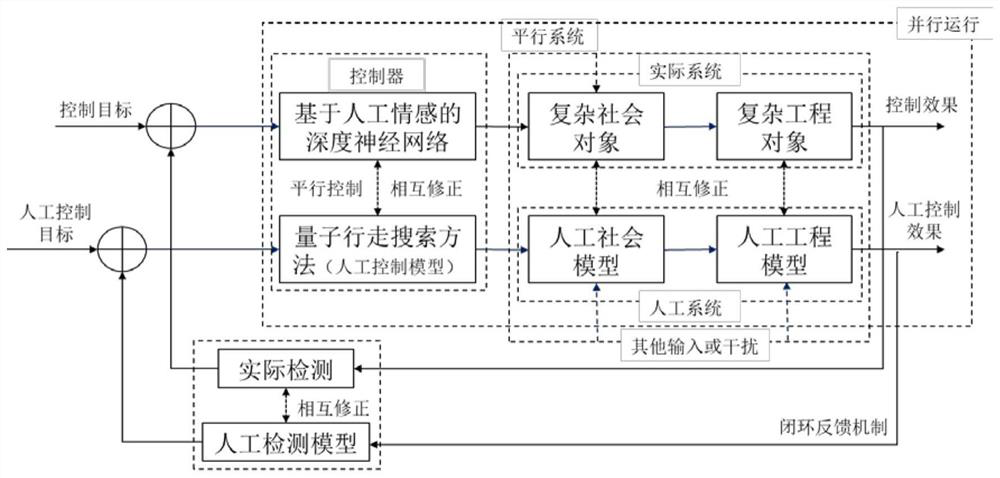
Multi-layer voltage control method for parallel quantum artificial emotion deep learning
ActiveCN112800667APrediction data is accurateOptimizing Voltage Control StrategyQuantum computersDesign optimisation/simulationData streamAlgorithm
The invention provides a multi-layer voltage control method for parallel quantum artificial emotion deep learning, which combines a quantum walking search method with an artificial emotion-based deep neural network and is used for multilayer voltage control of a power system. Firstly, a quantum walking method serves as a manual control model in a parallel control system to carry out probability statistics on historical voltage data, and is used for rapidly obtaining a target control strategy through quantum and obtaining more original voltage data at the same time. And secondly, features are extracted by using voltage data generated by a quantum walking method and historical voltage data based on an artificial emotion deep neural network method, and accurate prediction of the voltage is realized. And finally, the power system decision optimization model realizes optimal control according to the predicted voltage. The method can effectively solve the problem of insufficient voltage data samples of a power system, and achieves the precise control of the voltage of a power grid. Parallel data stream transmission is adopted, and data exchange between parallel systems is efficiently completed.
Owner:GUANGXI UNIV
A multi-party quantum secret sharing method and system based on quantum walk
ActiveCN113645034BThe number of people can be expandedVerify correctnessKey distribution for secure communicationSecret shareQuantum secret sharing
Owner:HUNAN NORMAL UNIVERSITY
An entanglement-free quantum blind signature method and system based on quantum walks
ActiveCN110213060BProven robustnessAchieve the effect of one-time pad (OTP)Key distribution for secure communicationUser identity/authority verificationInformation processingAttack
The invention belongs to the technical field of quantum information processing, and discloses an entanglement-free quantum blind signature method and system based on quantum walking. Blind information; in the process of teleportation of encoded particles, quantum walking is used to realize teleportation of encoded particles, and entanglement occurs spontaneously in the teleportation seed particles, which is used to resist the signer's denial attack and the verifier's denial attack , also used to prevent attackers from forging signatures. The present invention includes key update, which achieves the effect of One Time One Pad (OTP), which makes it unnecessary to redistribute keys for the next execution of the scheme; security analysis shows that the scheme of the present invention satisfies the requirements of unforgeable, undeniable, and blinded It is also resistant to entanglement attacks, so it is very suitable to use this scheme in e-commerce or electronic payment systems.
Owner:芽米科技(广州)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com