Identity authentication method based on quantum walking and related equipment
A quantum walk, identity authentication technology, applied in user identity/authority verification, key distribution, can solve the problems of encryption algorithm no longer safe, multiple physical resources, leakage, etc., to achieve less physical resource consumption, improve security, and avoid risks leaked effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
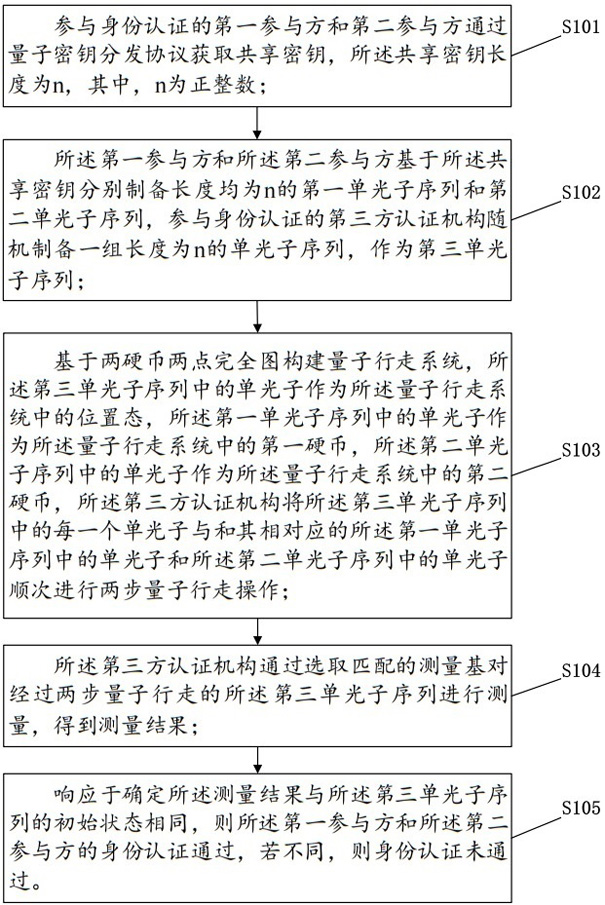
[0090] Identity authentication pass case:
[0091] The single photon sequence obtained by the participants Alice and Bob is as follows:
[0092]
[0093]
[0094] Prepared by the third-party certification body Charlie As follows:
[0095]
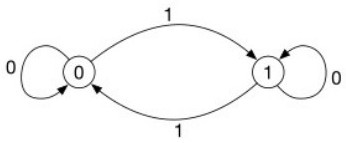
[0096] At the same time, assuming first with Perform a quantum walk, and then with Do a quantum walk. The results after the two-step quantum walk are shown in Table 2.
[0097] Table 2 Execution process of certified cases
[0098]
[0099] It can be seen from Table 2 that The measurement result is the same as the initial state, and the parties Alice and Bob are authenticated.
Embodiment 2
[0101] Identity authentication failed case:
[0102] Assume that the single photon sequence obtained by the participants Alice and Bob is as follows:
[0103]
[0104]
[0105] Prepared by the third-party certification body Charlie As follows:
[0106]
[0107] At the same time, assuming first with Perform a quantum walk, and then with Do a quantum walk. The results after the two-step quantum walk are shown in Table 3.
[0108] Table 3 Execution process of cases that fail certification
[0109]
[0110] due to the single photon sequence and middle and different, causing the authentication process to fail.
[0111] The invention not only proposes an identity authentication method based on quantum walking, but also verifies the method on the IBM quantum cloud platform. Experiments Simulate Controlled Shift Operators in Quantum Walks Using Quantum CNOT Gates T , using the Pauli operator mock coin operator C , using the operator X and single ph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com