Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
77results about How to "Improve encryption and decryption efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
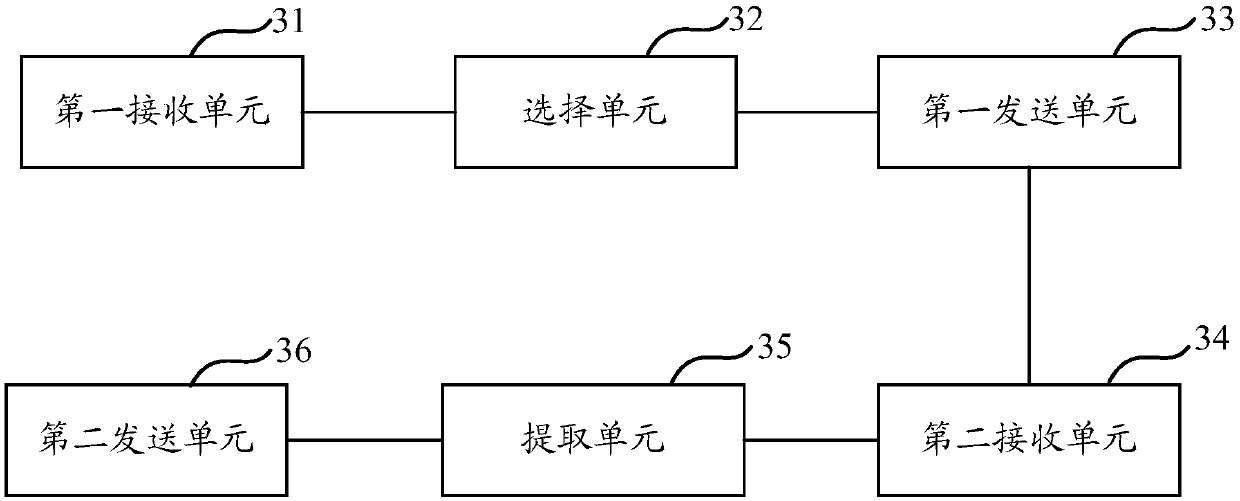
Data transmission method, device and system
ActiveCN107040369AAvoid the defect of long encryption and decryption timeSimplify the encryption processKey distribution for secure communicationMultiple keys/algorithms usagePaymentCiphertext
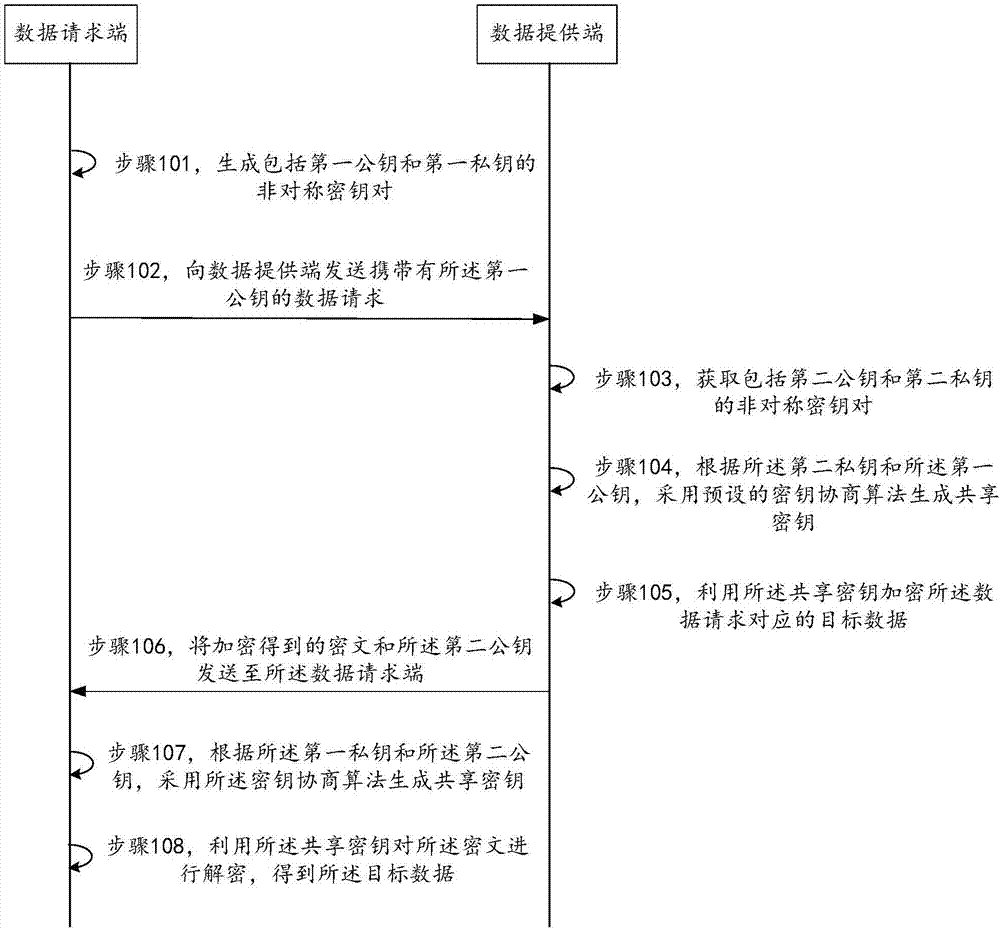
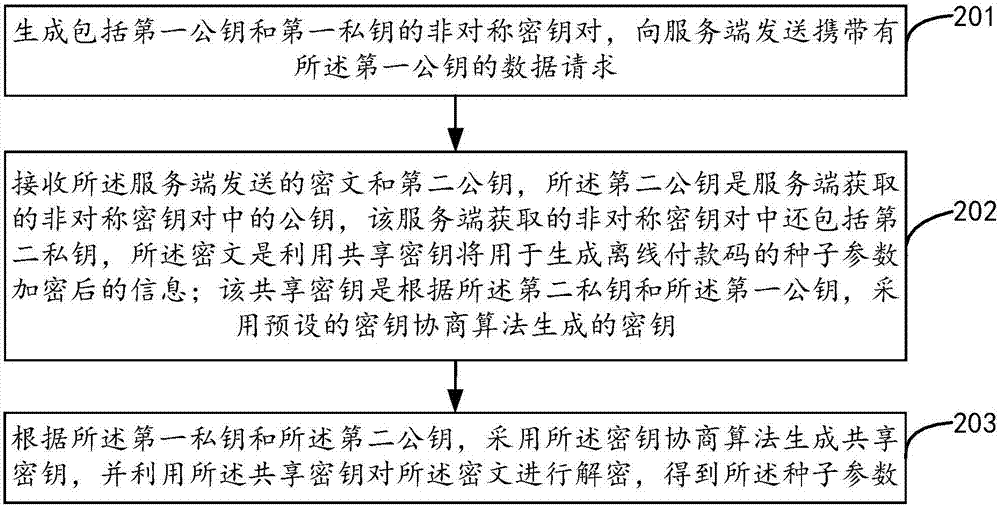
The invention provides a data transmission method, a data transmission device and a data transmission system. The method comprises the steps of generating an asymmetrical secret key pair including a first public key and a first private key, and sending a data request carrying the first public key to a server side; receiving a ciphertext and a second public key sent by the server side, wherein the second public key is the public key in the asymmetrical secret key pair acquired by the server side, the asymmetrical secret key pair acquired by the server side also comprises a second private key, the ciphertext is information generated by encrypting a seed parameter used for generating an offline payment code by using a sharing secret key, and the sharing secret key is the secret key by using a preset secret key negotiation algorithm according to the second private key and the first public key; and generating the sharing secret key by using the secret key negotiation algorithm according to the first private key and the second public key, using the sharing secret key to decrypt the ciphertext, thus acquiring the seed parameter. According to the method, the device and the system provided by the invention, security of the data during a whole transmission process is ensured, and decryption and encryption efficiency is also improved.
Owner:ADVANCED NEW TECH CO LTD
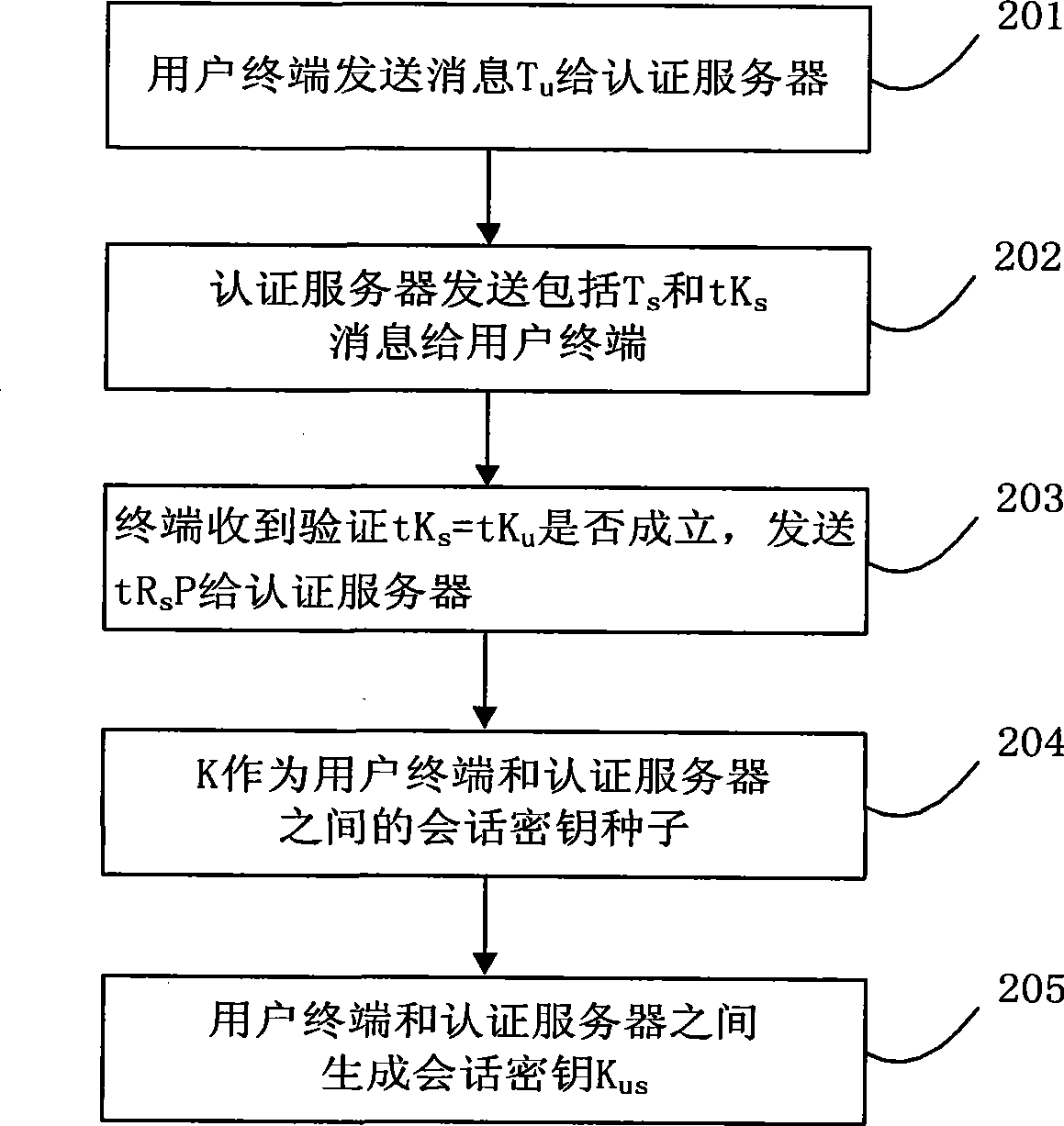
Bidirectional authentication method
InactiveCN101431415AImprove encryption efficiencyShort ciphertext lengthKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
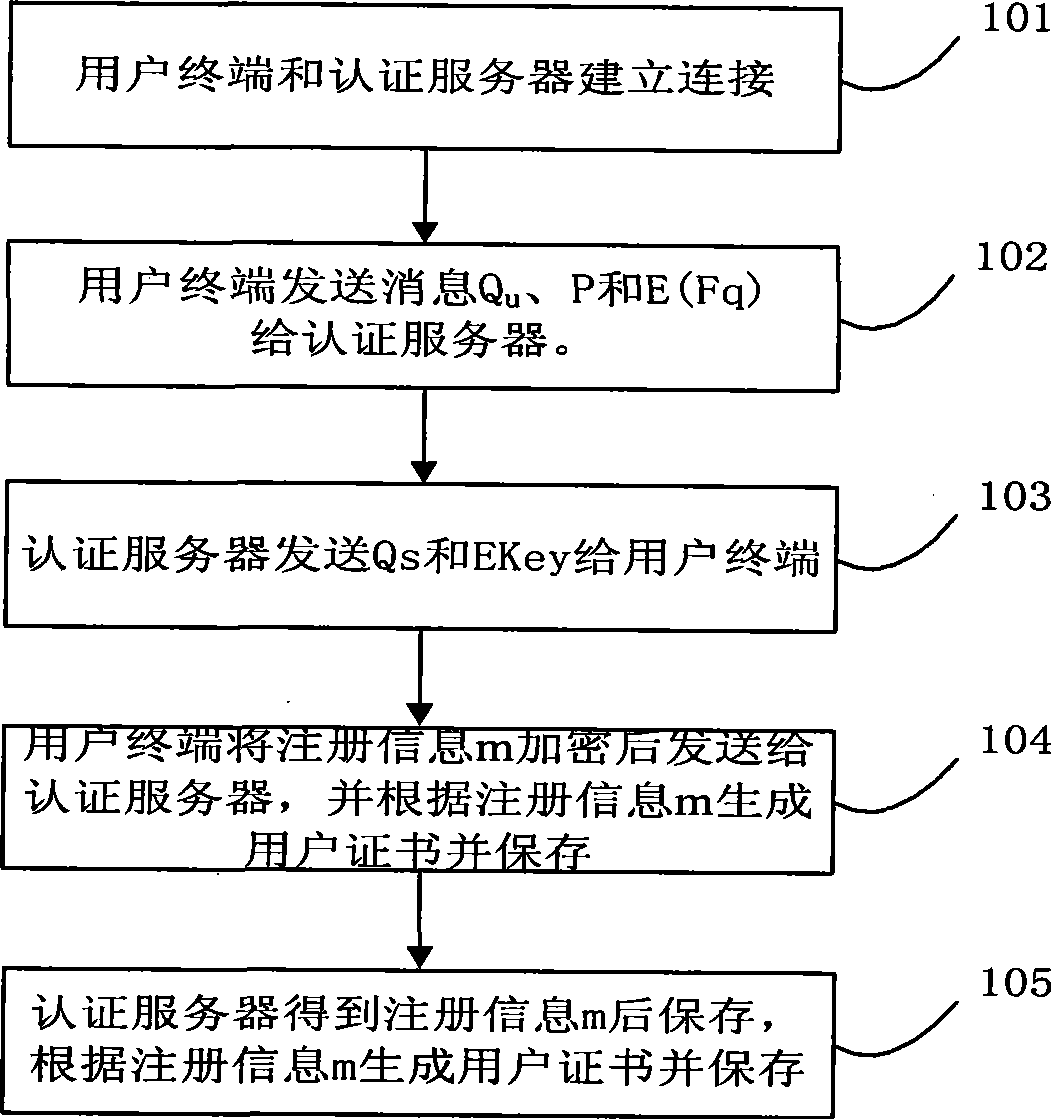
The present invention discloses a method of mutual authentication which is suitable for digital right management domain of interactive network TV. The invention comprises the following procedures: registering in an authentication server by a user terminal; executing key agreement between user terminal and authentication server; executing mutual authentication between user terminal and authentication server; obtaining license certificate for content broadcasting by user terminal. Mutual authentication is established between server of IPTVDRM and client taking advantage of high encryption efficiency of ECC and short length of cipher text by adopting the technical scheme described in the invention; obtaining session key from key protocol agreement before mutual authentication, authenticating ID of mutual parties through certificate mutually, and preventing certificate from tampering attack in transmitting process; making authentication valid and encryption and decryption efficiency higher than RSA mutual authentication by adopting mutual authentication of the certificate, and obtaining information of counterpart in plaintext by both parties for mutual confirmation without leaking plaintext simultaneously.
Owner:天柏宽带网络技术(北京)有限公司
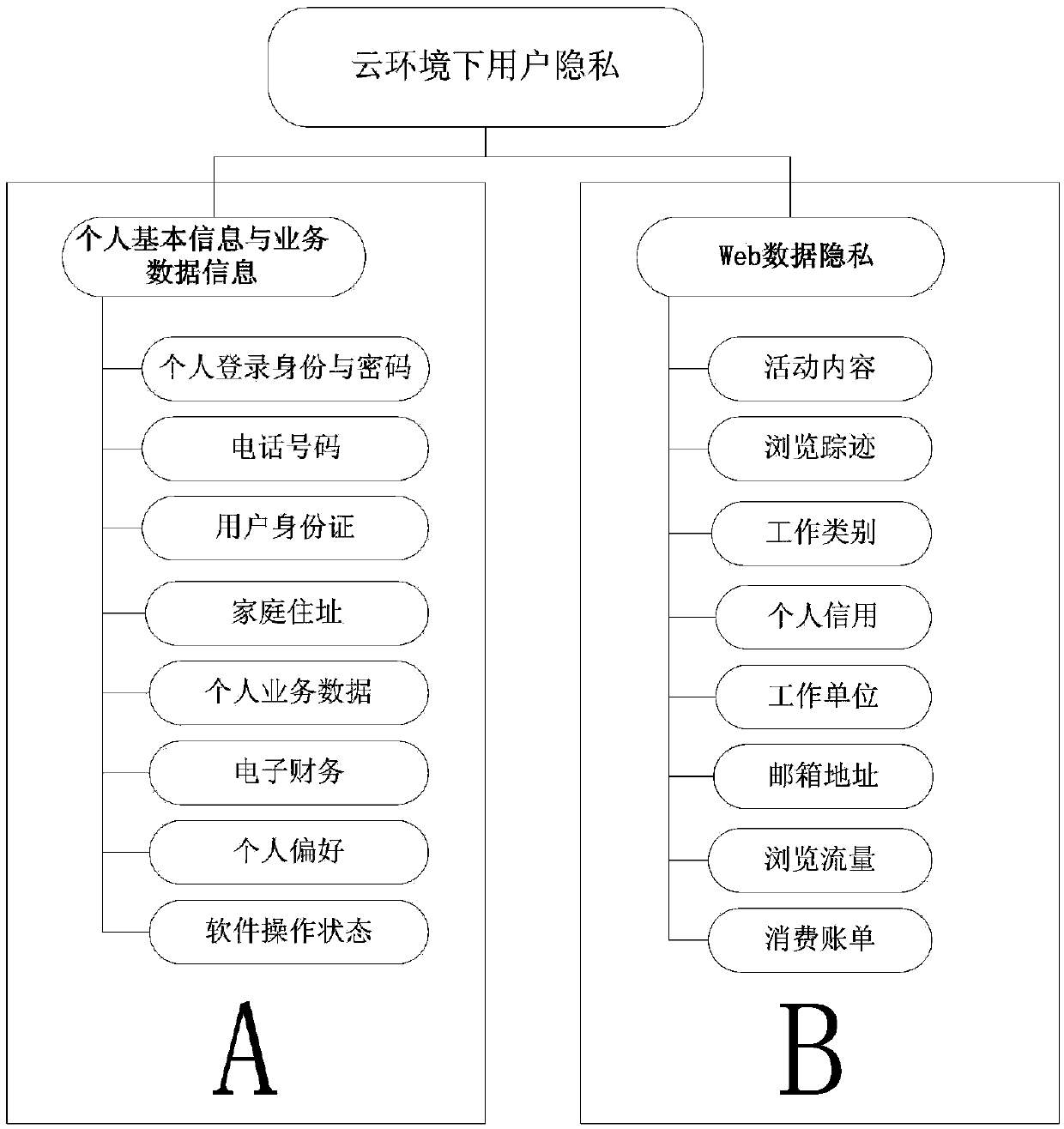
User privacy protection method based on attribute and homomorphism mixed encryption under cloud environment
ActiveCN104079574AGuaranteed fair accessEnsure safetyTransmissionAttribute-based encryptionInternet privacy
The invention provides a user privacy protection method based on attribute and homomorphism mixed encryption under a cloud environment. The method is mainly used for solving the safety problem of user privacy under the cloud environment. Firstly, a user sends the information of the user to a cloud service provider, and the cloud service provider clarifies the user privacy. Secondly, the user adopts different encryption modes for different types, namely a homomorphism encryption mode and an encryption mode based on the attribute. It is guaranteed that important privacy information is more difficult to be leaked out and stolen through the homomorphism encryption mode for the user, and the user can conduct operation on the privacy information of the user. Through the encryption mode based on the attribute, it is guaranteed that certain network resources can be shared with other users. Finally, the user downloads and decodes cryptograph. Through the mixed encryption mode, safety of the user data privacy is further guaranteed. Meanwhile, the user can operate important service data of the user conveniently. Moreover, coding efficiency and decoding efficiency are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
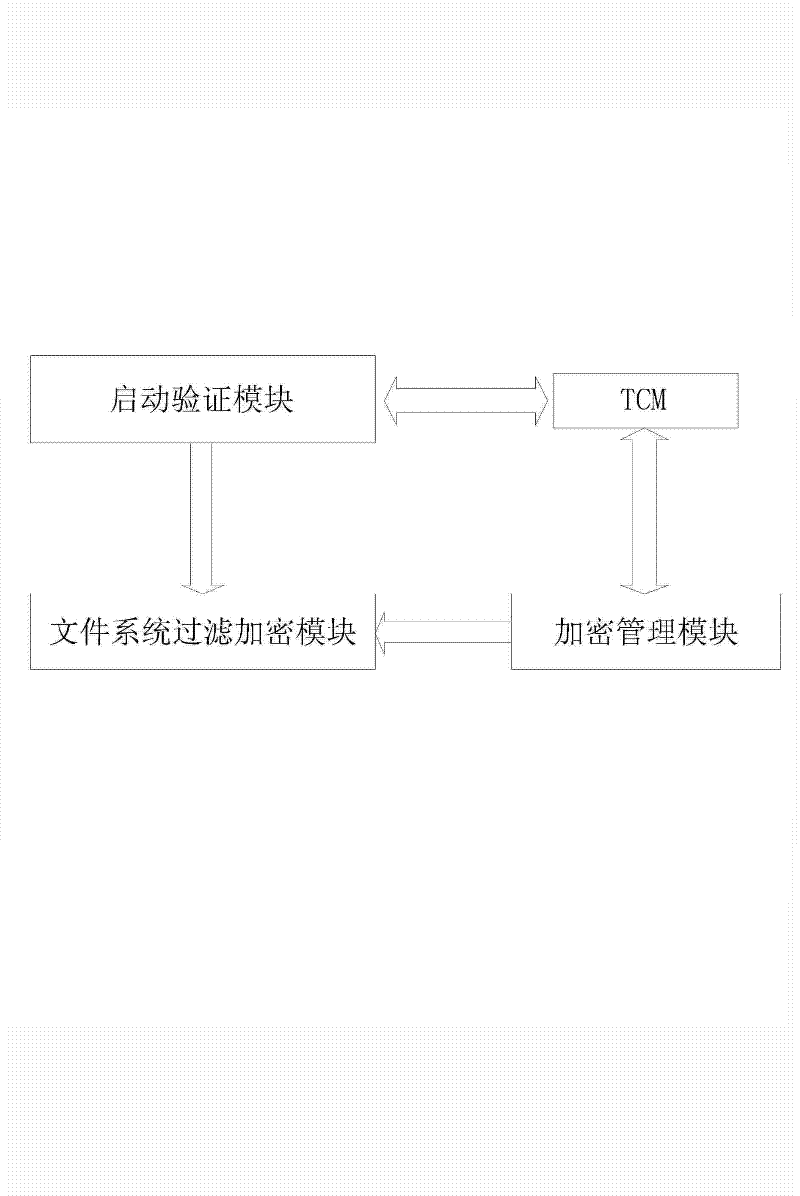
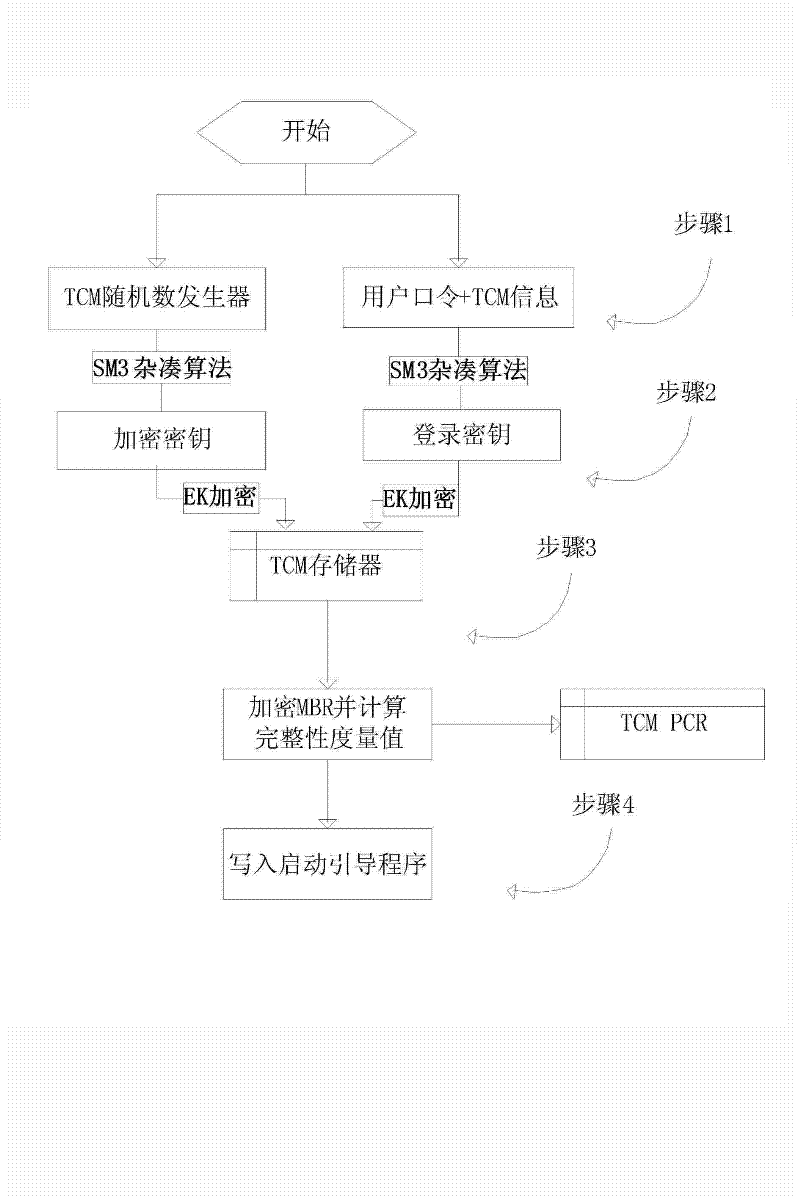
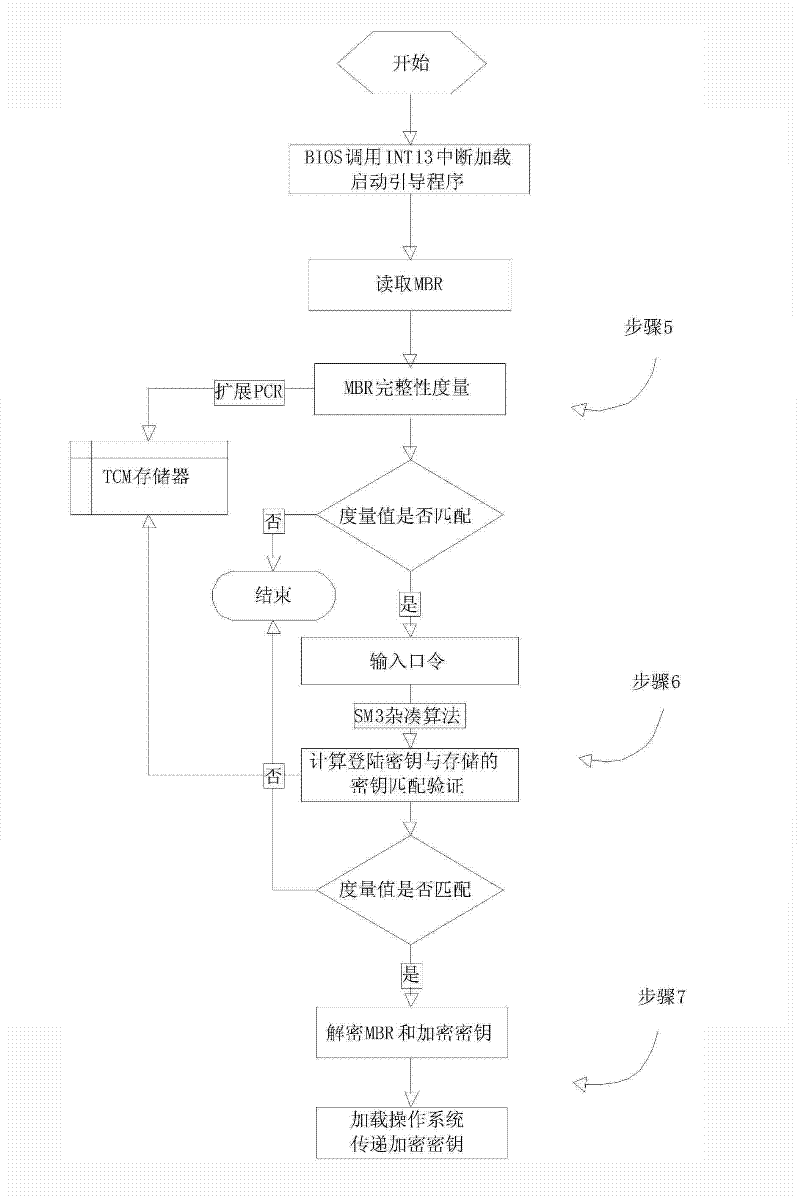
Method for full-disk encryption based on trusted cryptography module
ActiveCN102646077AImprove securityImprove encryption efficiencyUnauthorized memory use protectionInternal/peripheral component protectionFile systemPassword
The invention provides a method for full-disk encryption based on a trusted cryptography module. A logging-in key and a storage key are protected by a trusted cryptography module, a file system is designed for filtering and driving an encryption module to encrypt or decrypt the I / O data of a disk, the real-time transparent encryption of full-disk data is realized, the trusted cryptography module (TCM) is invoked to carry out authentication and integrality verification on an encryption system by adding a starting and verifying module into a first magnetic track of the disk, and the keys and integrality verification information are stored in the TCM. Compared with the prior art, the operation of storage is not carried out in the disk according to the method for the full-disk encryption based on the trusted cryptography module, so that the safety is high; and TCM authentication and integrality inspection are needed for logging in a system, so that the condition that a user password is intercepted by implanting a malicious program can be prevented.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
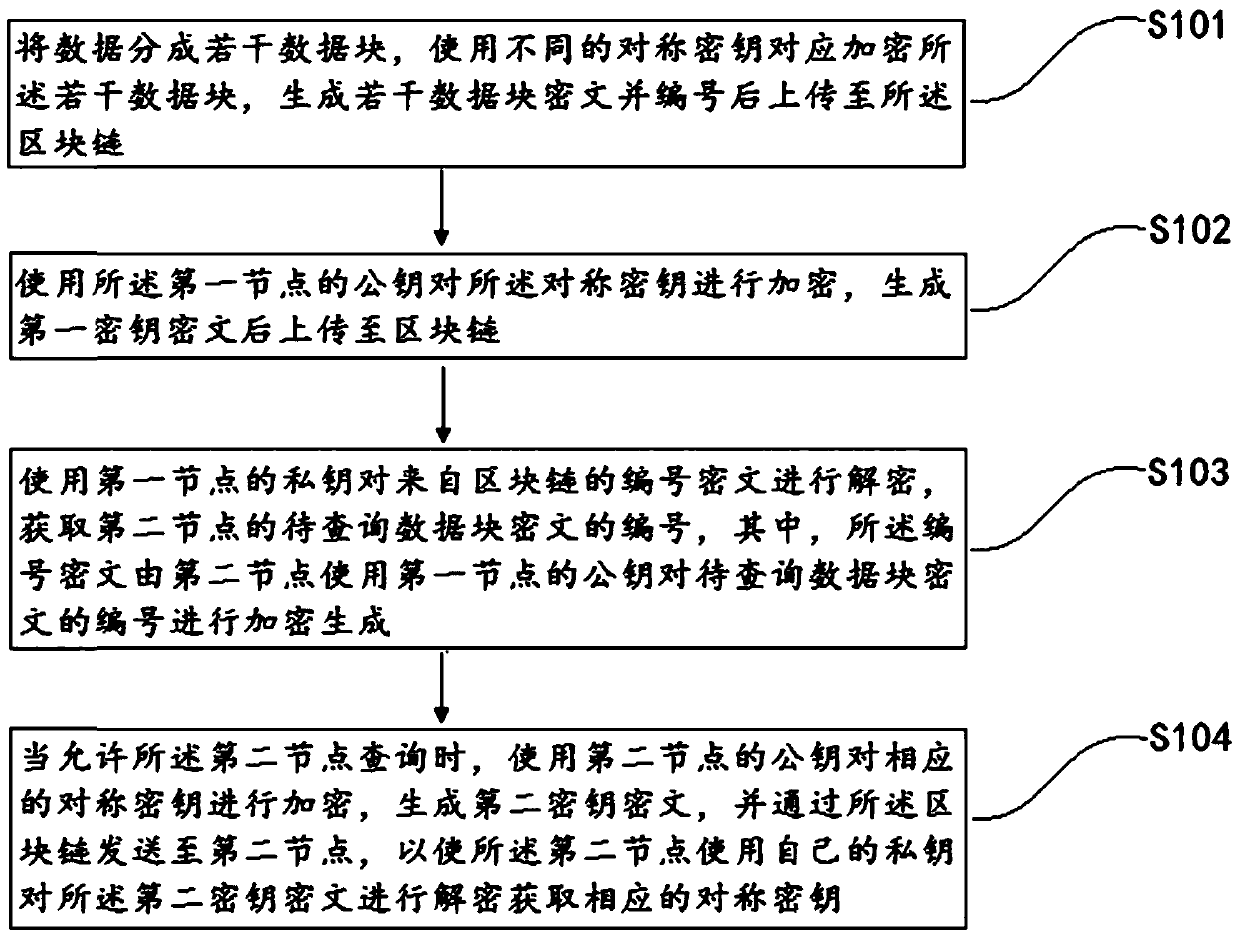
Data transmission method and device based on alliance chain
ActiveCN109587132AEnsure controllabilityEnsure safetyKey distribution for secure communicationMultiple keys/algorithms usageData transmissionBlockchain
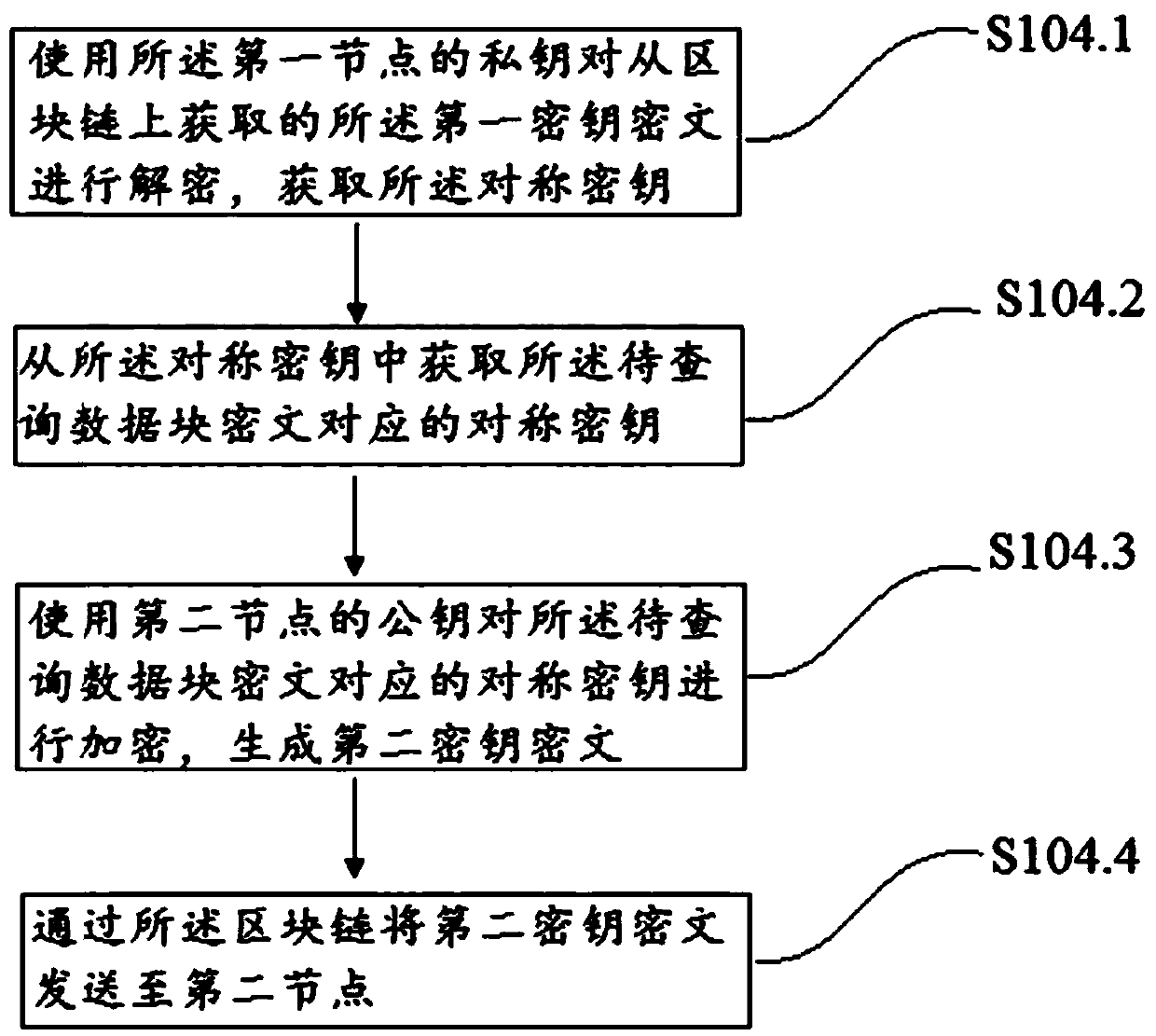
The invention discloses a data transmission method and device based on an alliance chain. The method comprises the following steps of dividing data into several data blocks, using different symmetricsecret keys to correspond to encrypted data blocks, generating and numbering several data block ciphertexts, and then uploading to a blockchain; using the public key of a first node to encrypt the symmetric secret keys, generating a first secret key ciphertext and then uploading to the blockchain; using the private key of the first node to decrypt a numbered ciphertext from the blockchain, and obtaining the ciphertext number of the data block to be inquired of a second node; and when the second node is allowed to inquire, using the public key of the second node to encrypt the corresponding symmetric secret key to generate a second secret key ciphertext, sending to the second node through the blockchain so that the second node decrypts the second secret key ciphertext by using the private key to obtain the corresponding symmetric secret key. in the invention, the safety, the controllability and the restorability of the data are ensured, and simultaneously the efficiency of encryption and decryption is increased.
Owner:NANJING SUNING SOFTWARE TECH CO LTD
Data encryption method and system
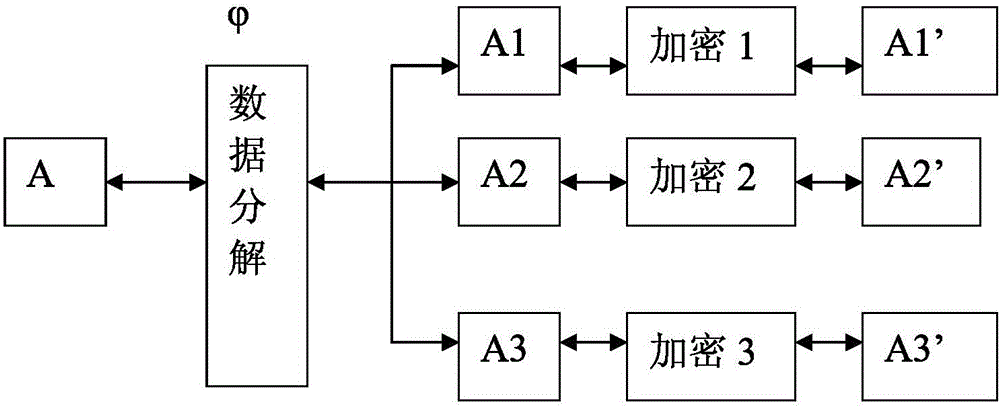
InactiveCN102567687AEncryption guaranteedGood encryptionDigital data protectionSecuring communicationComputer hardwareData transmission
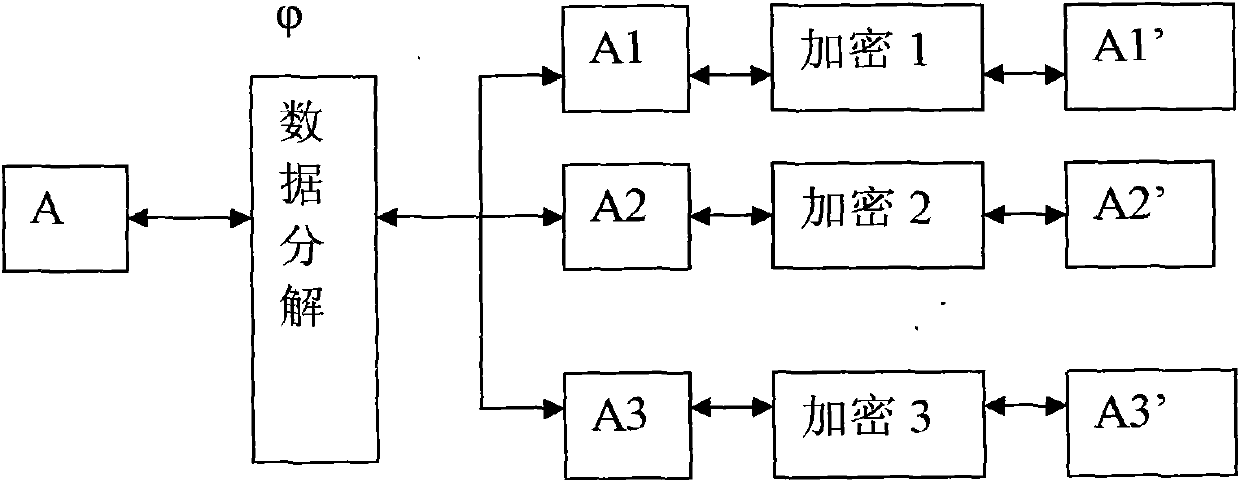
The invention relates to a data encryption method and a system. The data encryption method is characterized in that raw data is decomposed into at least two parts of data according to a preset function relationship. A data encryption storage method is characterized in that the preset function relationship is decomposed into at least parts of data, and the disassembled data is respectively stored in different memories. A data encryption transmission method is characterized in that a sending end decomposes raw data A into at least two parts according to the preset function relationship; the two parts are sent to a data receiving end via different data transmitting channels; and the data receiving end respectively receives the data, and combines and reduces the data into the raw data A according to the corresponding function relationship. As various combination modes are provided, the decryption difficulty is high after encryption, and the original encryption index is enhanced by times to guarantee the encryption effect of numbers. Only disassembly is required, and therefore, good encryption effect is achieved. In addition, the data encryption method has the advantages of low calculation amount and high encryption and decryption efficiency.
Owner:成都科创知识产权研究所
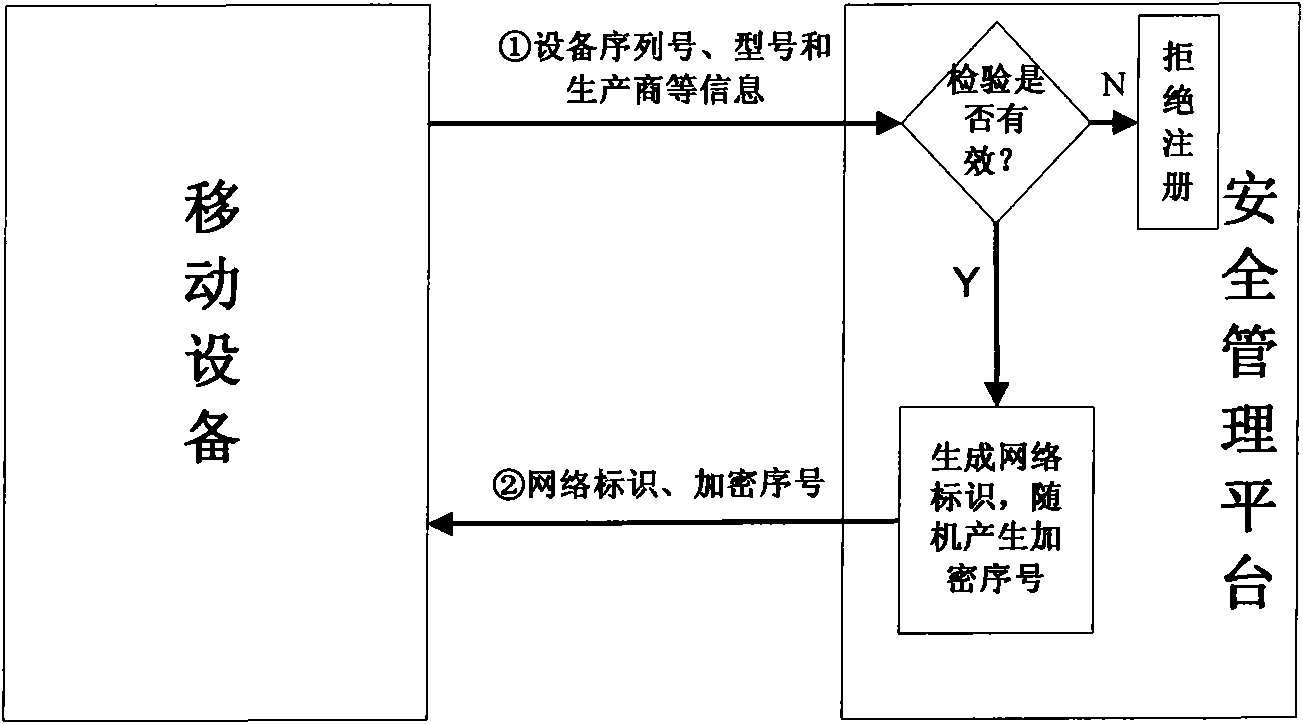
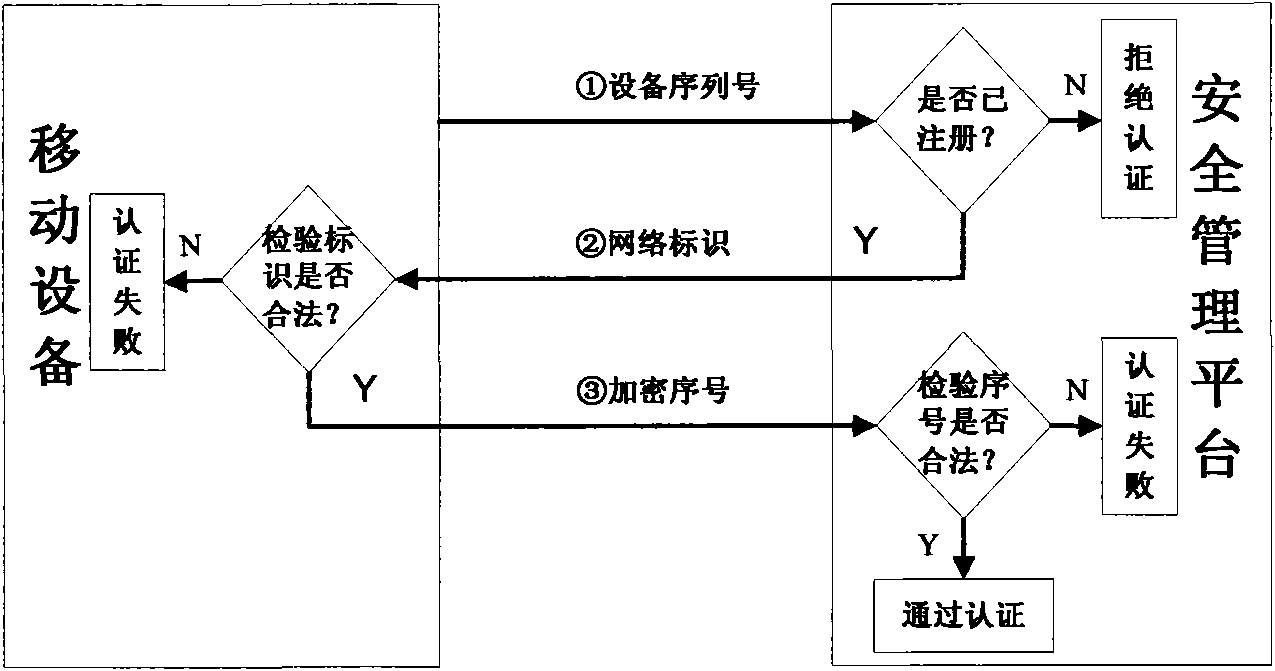
Realization system and method for safely visiting and storing intranet data by mobile equipment
InactiveCN101800738AAchieve authenticationDefend against impersonation attacksUser identity/authority verificationData switching by path configurationConfidentialityMobile device
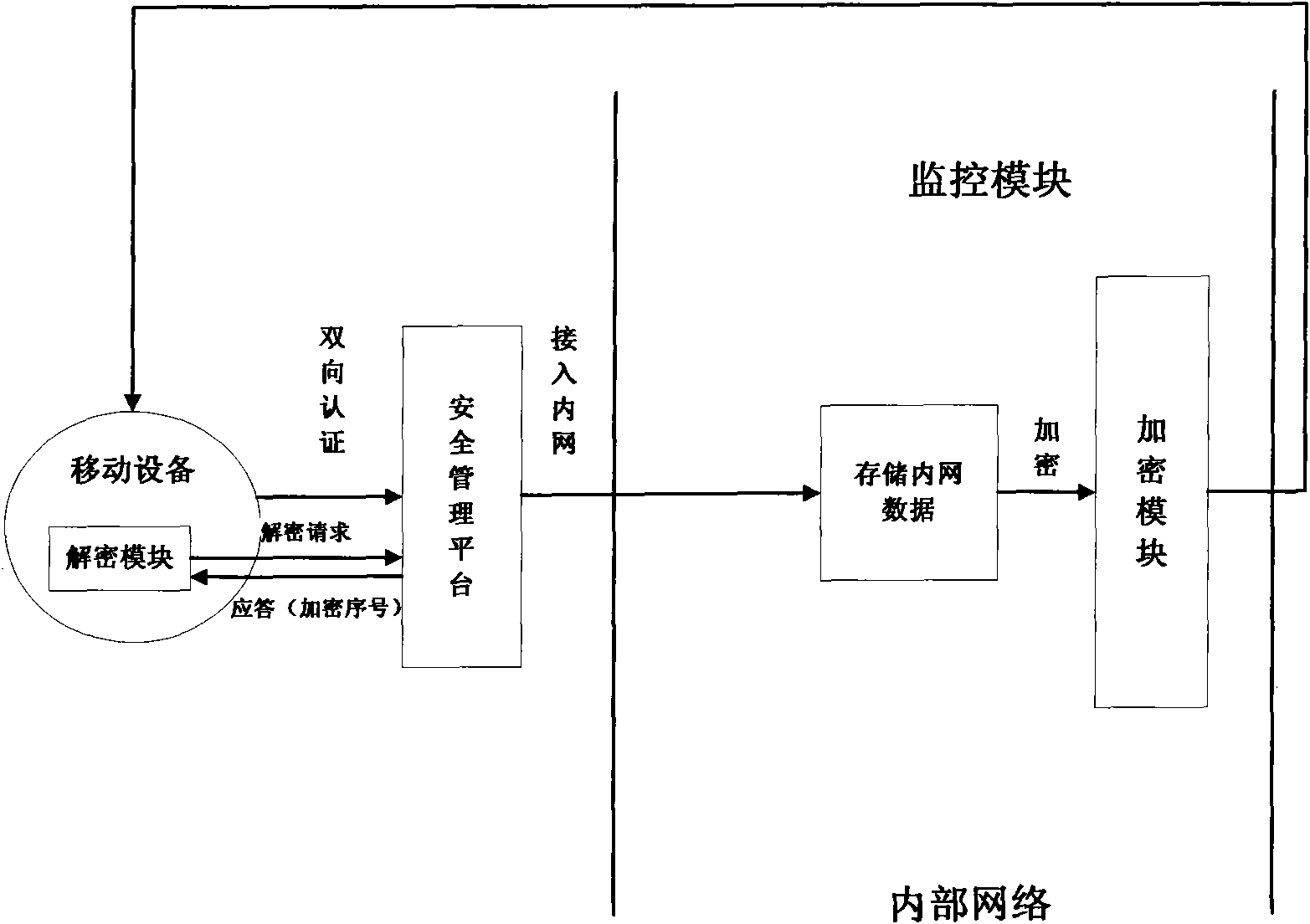
The invention discloses a realization system and a method for safely visiting and storing intranet data by mobile equipment. The method comprises the following steps: judging whether the mobile equipment is registered or not by a security management platform; carrying out mutual authentication on the registered mobile equipment; allowing the accession to the intranet after the authentication success; rejecting the accession to the intranet of unregistered mobile equipment and authentication failed mobile equipment; invoking an encryption module when a monitoring module discovers that the mobile equipment is about to store the intranet data in the intranet into the mobile equipment per se; selecting corresponding encryption methods by the encryption module under the monitoring of the monitoring module according to the confidentiality levels of the intranet data for encrypting the intranet data to be stored into the mobile equipment; and inquiring whether the encryption data is confidentiality data or not by a decryption module to the monitoring module in the intranet when the encryption data stored in the mobile equipment needs to be decrypted, and then, selecting corresponding methods for decrypting the encryption data. The invention implements different encryption and decryption methods according to different confidentiality levels, improves the encryption and decryption efficiency and data confidentiality, integrally utilizes the mutual authentication method and the encryption and decryption method, and improves the security of the intranet data.
Owner:JINAN UNIVERSITY
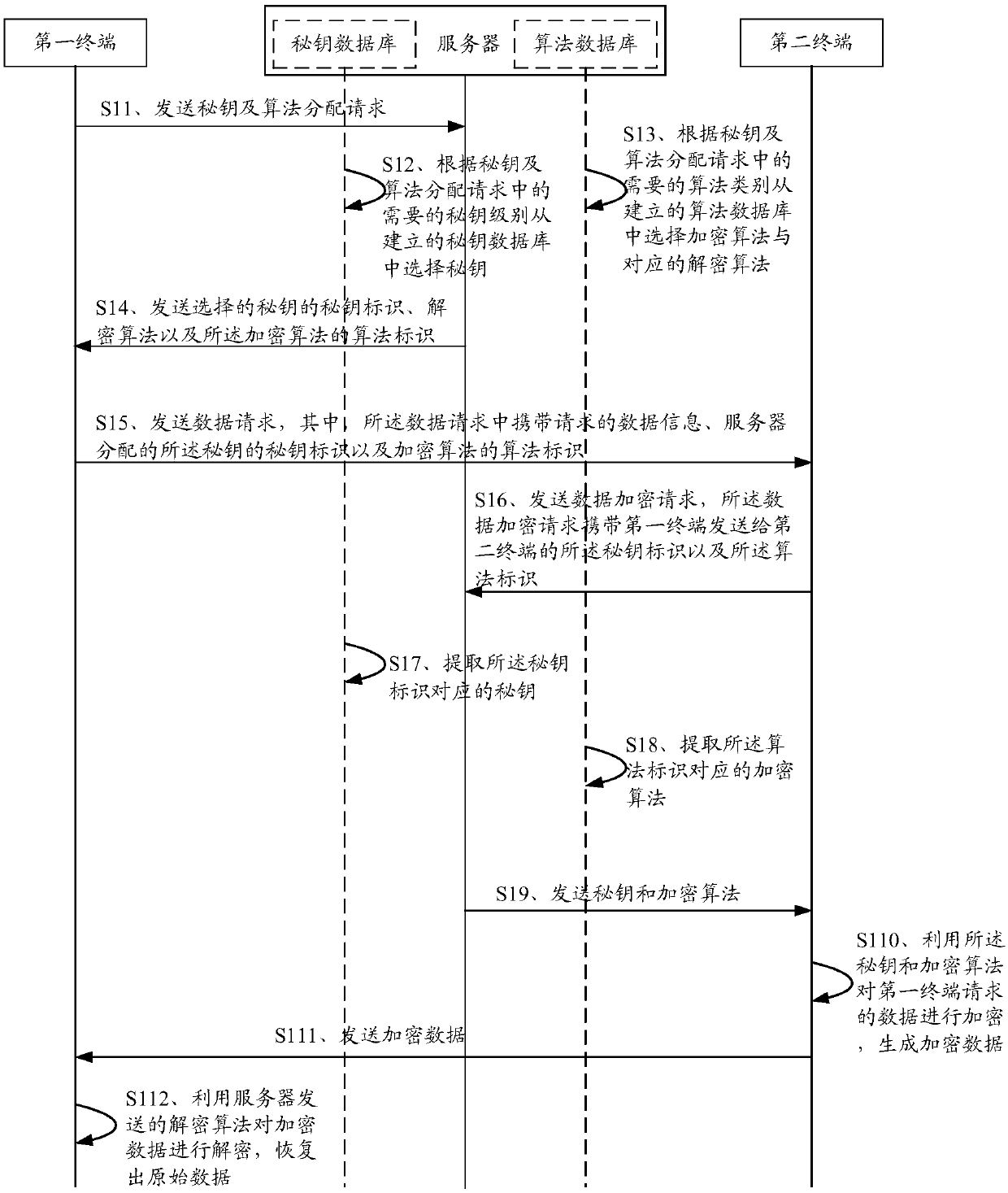
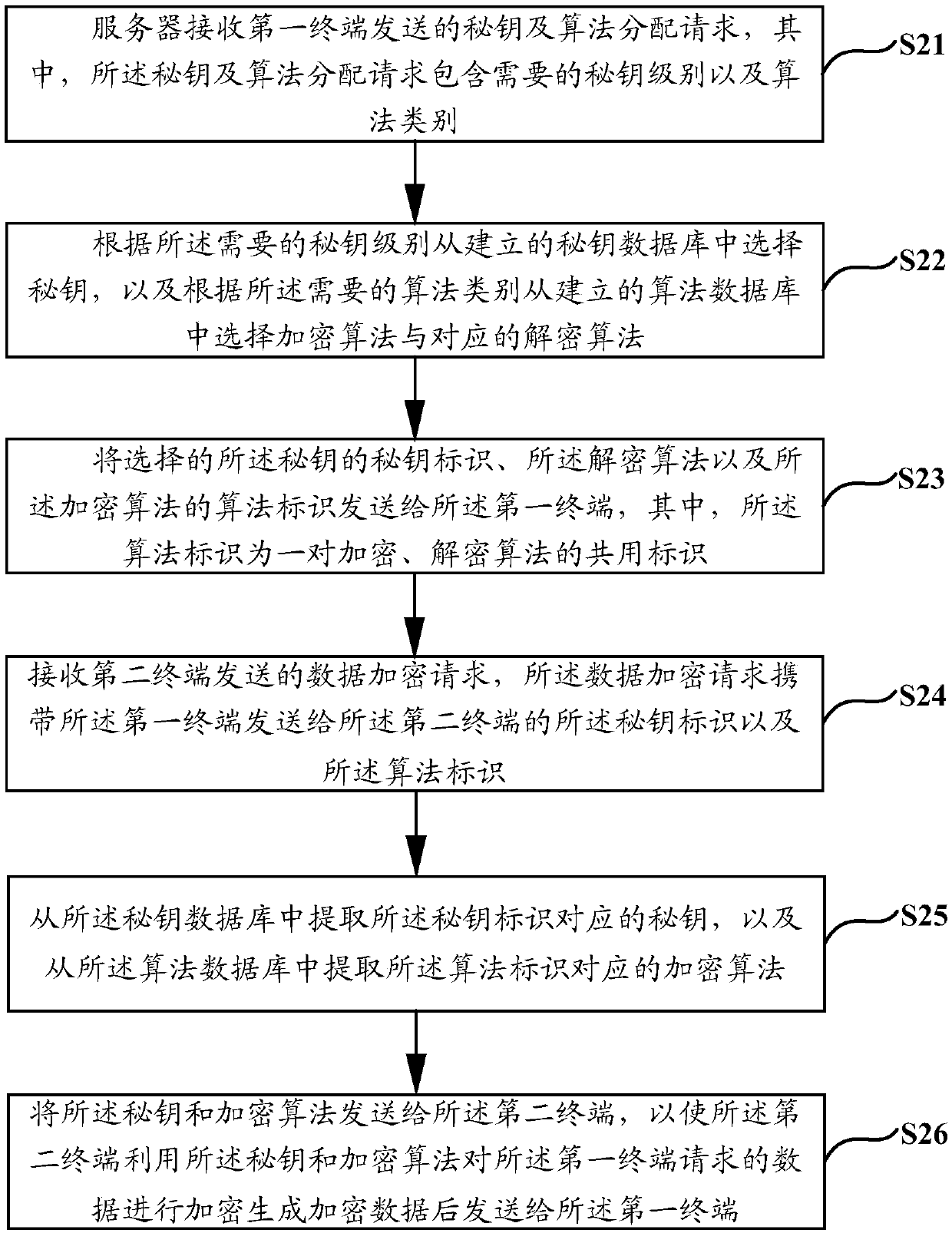
Data encryption and decryption method and device
ActiveCN110768787AFlexible allocationImprove encryption and decryption efficiencyKey distribution for secure communicationAlgorithmTheoretical computer science
The invention discloses a data encryption method and device and a data decryption method and device, and aims to solve the problems that a static secret key and an encryption algorithm in an existingdata encryption method are single, fixed for a long time and easy to crack. The method comprises the following steps: enabling a server to receive a secret key and algorithm allocation request sent bya first terminal, wherein the secret key and algorithm allocation request comprises a needed secret key level and an algorithm category; selecting a secret key, an encryption algorithm and a corresponding decryption algorithm from the established secret key database and algorithm database according to the required secret key level and algorithm category; sending the secret key identifier and thealgorithm identifier to the first terminal; receiving a data encryption request sent by a second terminal, wherein the data encryption request carries a secret key identifier and an algorithm identifier sent to the second terminal by the first terminal; extracting a secret key corresponding to the secret key identifier and an encryption algorithm corresponding to the algorithm identifier from thesecret key database and the algorithm database respectively; and enabling the second terminal to encrypt the data requested by the first terminal by using the secret key and the encryption algorithm.
Owner:CHINA MOBILE GROUP JILIN BRANCH +1
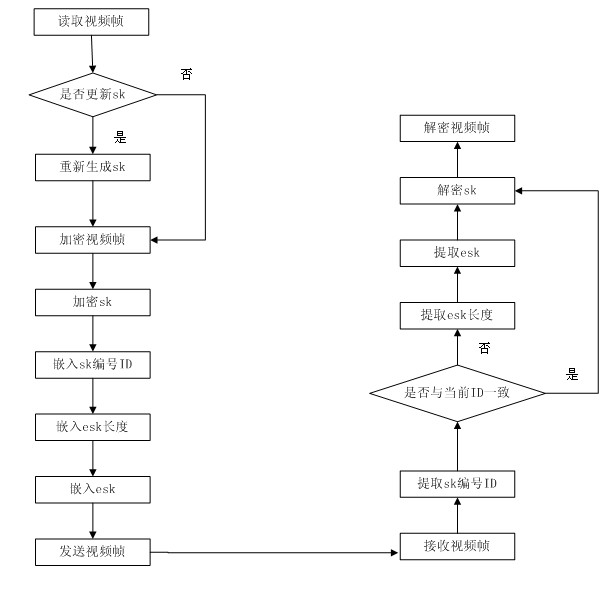
Digital watermarking-based high-definition video encrypted transmitting method and system
InactiveCN102014266AImplement secure encryptionEnsure safetyTelevision system detailsPulse modulation television signal transmissionComputer hardwareSecure transmission
The invention discloses a video watermarking-based high-definition video encrypted transmitting method. In the method, a random number generated by a random number generator is taken as a video scrambling key; the video scrambling key is encrypted by adopting an RSA algorithm to ensure that the video scrambling key cannot be captured in the transmitting process; and the encrypted video scrambling key is taken as a watermark to be embedded into the encrypted video by using a least significant bit (LSB) algorithm so as to realize secure encryption of the high definition video. The invention has higher security and lower computational complexity, and ensures the transmission quality of the high definition video content on the premise of secure transmission.
Owner:HUAZHONG UNIV OF SCI & TECH
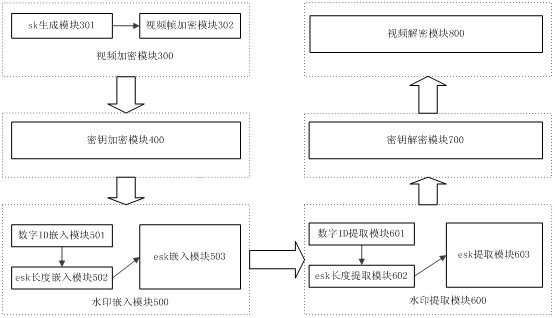
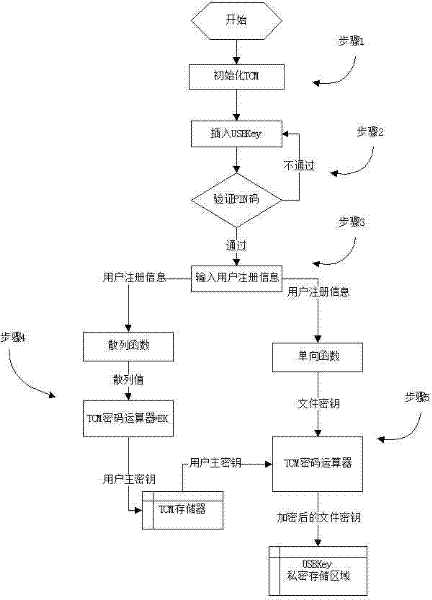
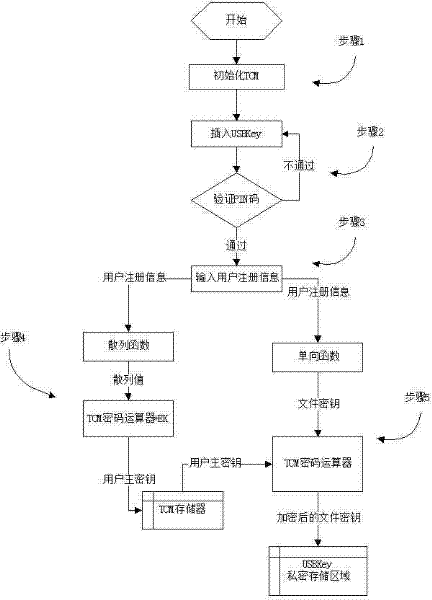
File encryption method based on TCM (trusted cryptography module) and USBkey
InactiveCN102236756AImprove securityImprove encryption and decryption efficiencyDigital data authenticationRecord carriers used with machinesSoftware modulesPrimary Key
The invention provides a file encryption method based on TCM (trusted cryptography module) and USBkey, which is implemented by a programmed software module. The software module comprises an initialization module, an encryption / decryption module and two hardware devices (TCM and USBkey); a user primary key is protected by the TCM, and the programmed software module is used for implementing file encryption; the initialization module activates and initializes the TCM, inputs the USBkey user logon information, and computes the user primary key and file key according to the user logon information; the user primary key is encrypted by EK and stored in the TCM; the file key is used for encrypting / decrypting the user file; and the file primary key is encrypted by the user primary key in the TCM and stored in a nonvolatile private storage region of the USBkey.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
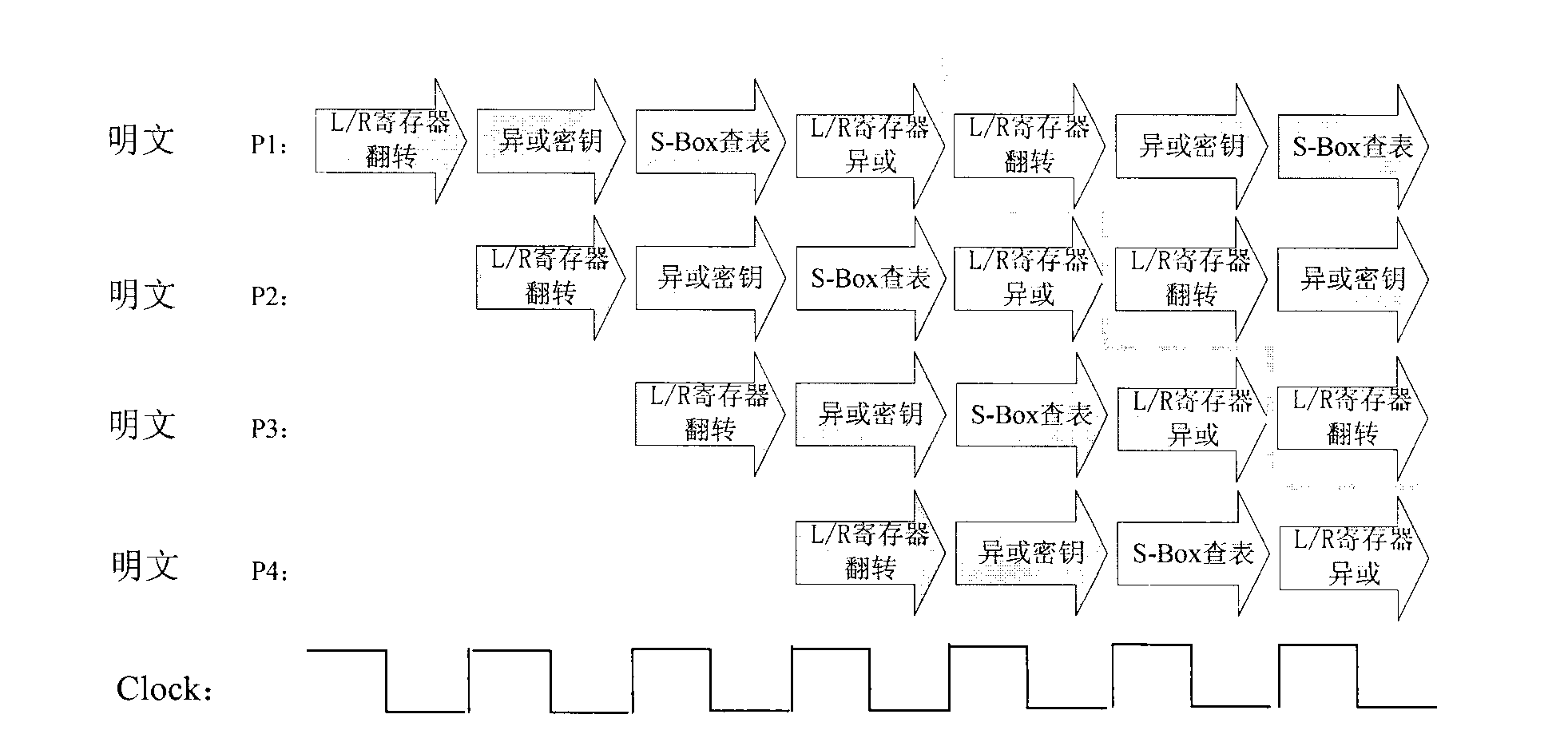
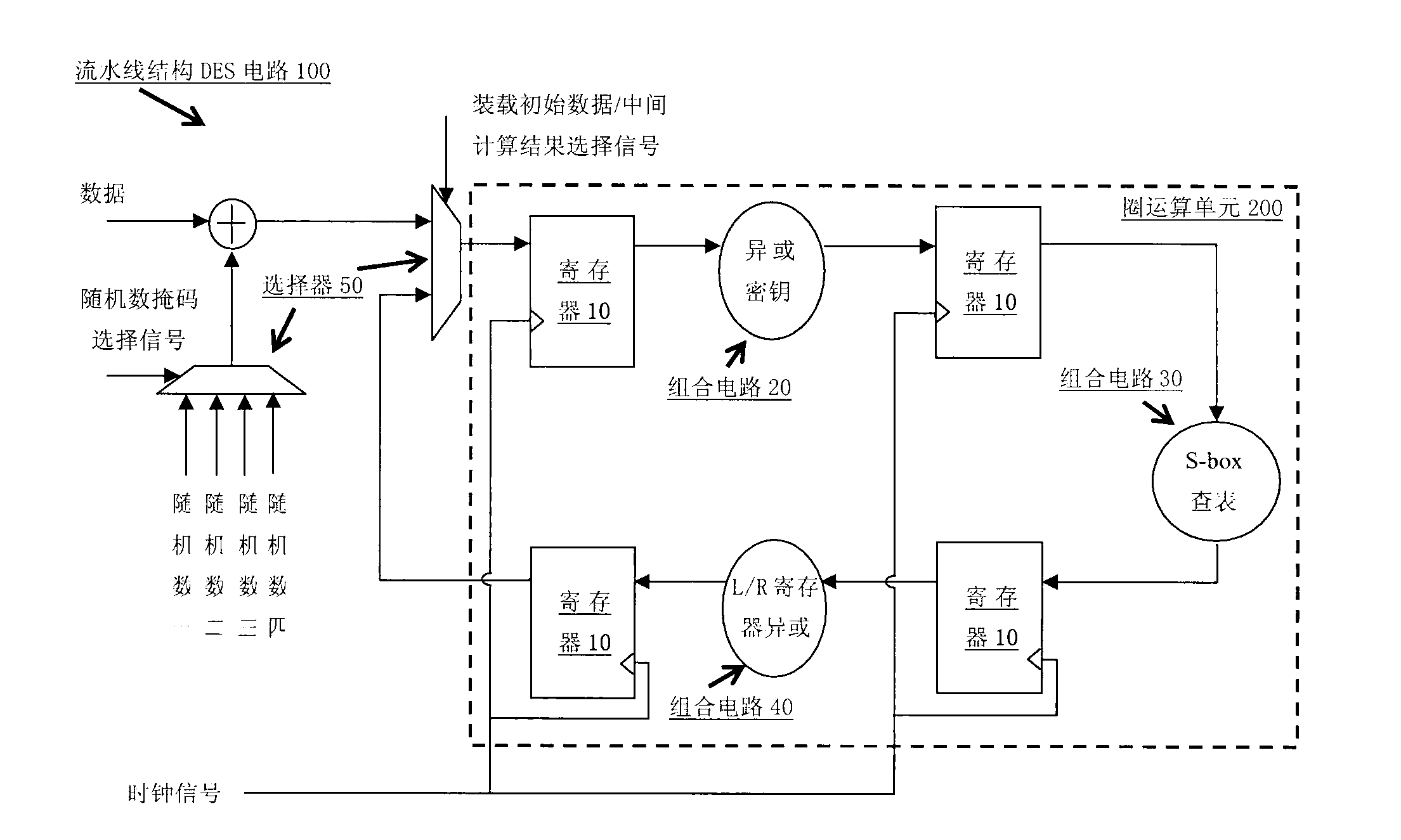
Circuit structure for preventing power attacks on grouping algorithm
InactiveCN102970131AGuaranteed defense effectGuaranteed protective effectEncryption apparatus with shift registers/memoriesElectronic identificationSmart card
The invention provides technology which can effectively resist to attacks on modules, chips, smart card bodies and the like adopting a grouping encryption and decryption algorithm through power analysis (simple power analysis (SPA) and difference power analysis (DPA)) or electromagnetic radiation analysis (DEMA) to obtain encryption and decryption operation secret keys and a circuit implementation structure of the technology. In application of a high-safety smart card, including but not limited to application areas such as electronic identification cards, debit cards and social security cards, the circuit structure can effectively protect the grouping encryption modules, the chips, the smart card bodies and the like and prevent the encryption and decryption operation secret keys from decoding and obtaining by the power analysis or the electromagnetic radiation analysis. The circuit structure can improve efficiency of encryption operation in continuous encryption operation, improves safety protection strength on the grouping encryption modules, the chips, the smart card bodies and the like, guarantees execution efficiency of the encryption operation, and has good innovation, practical applicability and effectiveness.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
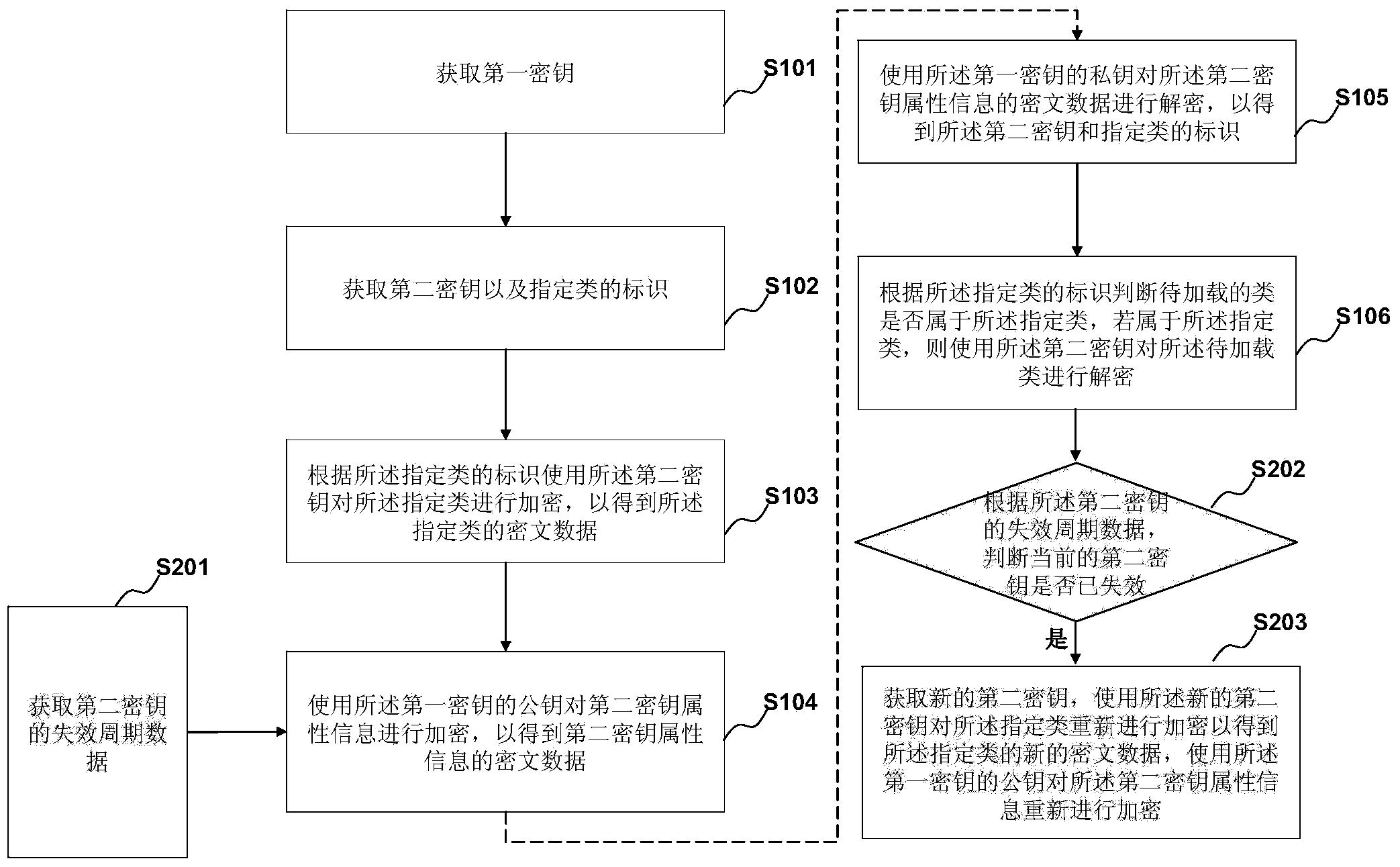
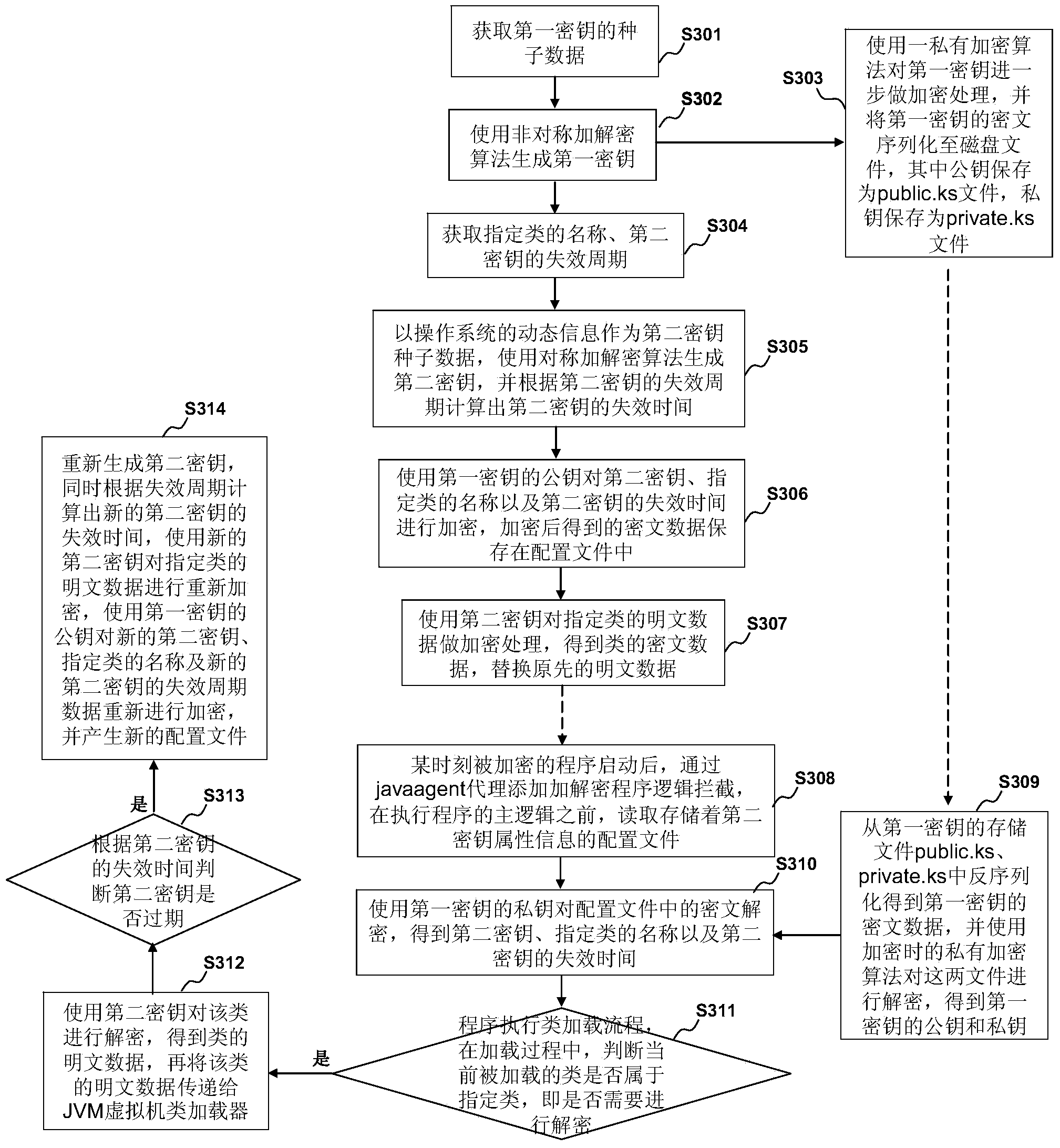
Program protection method and device
ActiveCN103853943AIncrease the difficulty of crackingProtect source codeDigital data authenticationProgram/content distribution protectionCiphertextSource code
The embodiment of the invention discloses a program protection method and device. The method comprises the following steps of encryption at a program generation stage: acquiring a first secrete key; acquiring a second secrete key and a mark of a designated category; encrypting the designated category by utilizing the second secrete key; encrypting the attribute information of the second secrete key by utilizing a public key of the first secrete key; decryption at a program running stage: decrypting encrypted data of the attribute information of the second secrete key by utilizing a private key of the first secrete key; judging whether the to-be-loaded category belongs to the designated category or not according to the mark of the designated category, and decrypting the to-be-loaded category by utilizing the second secrete key if the to-be-loaded category belongs to the designated category. The first secrete key and the second secrete key are used for doubly encrypting the program, so that the source code of the program can be effectively protected; meanwhile, the program is also distinguished, and only the designated category is encrypted, so that the encryption and decryption efficiency can be improved; moreover, the mark of the encrypted category is further encrypted and protected by the second secrete key, so that the safety of the program is further protected.
Owner:BEIJING AUTONAVI YUNMAP TECH CO LTD
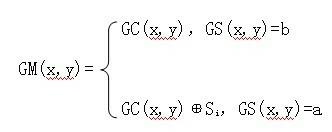
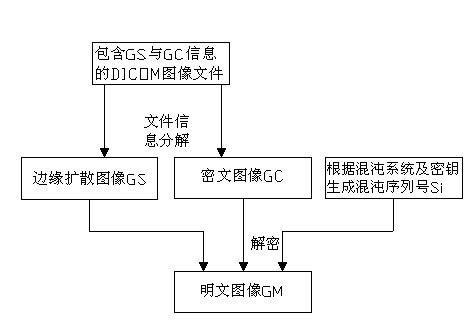
DICOM (Digital Imaging and Communications in Medicine) medical image encrypting and decrypting method based on edge detection
ActiveCN102184518AConform to the structural characteristicsReduce data volumeImage data processing detailsDICOMDigital imaging
The invention discloses a DICOM (Digital Imaging and Communications in Medicine) medical image encrypting and decrypting method based on edge detection, comprising an encrypting process and a decrypting process. Based on a selective encryption idea, the method comprises the following steps of: firstly using an edge detection technology to calculate edge information of a plaintext image; amplifying the edge range through an image morphological exchange operation; and then encrypting and decrypting the pixel of the plaintext image corresponding to the edge through a chaos system. Compared with a traditional medical image encrypting method, by application of the method of the invention, key information in the medical images is excellently encrypted; the encrypting data amount is greatly reduced; the encrypting efficiency is improved; and the method has strong practicability.
Owner:CHONGQING UNIV
Efficient encryption method and system of data
InactiveCN105809046AEncryption guaranteedGood encryptionDigital data protectionComputer hardwareOriginal data
The invention relates to an efficient encryption method and system of data. The encryption method of the data splits original data into at least two parts of data according to a preset rule, wherein the splitting is that the original data is split according to the preset rule according to a discontinuous way and is spliced again to obtain at least two parts of data. The invention also discloses a corresponding decryption method, an encryption and decryption storage system and the like. Since various combination ways are arranged, decryption difficulty is high after encryption is carried out, an original encryption index is enhanced manifold, and a data encryption effect is guaranteed. In addition, the data only needs to be split, and therefore, a good encryption effect can be performed. In addition, the encryption method is small in operation amount and high in encryption and decryption efficiency.
Owner:成都科创知识产权研究所
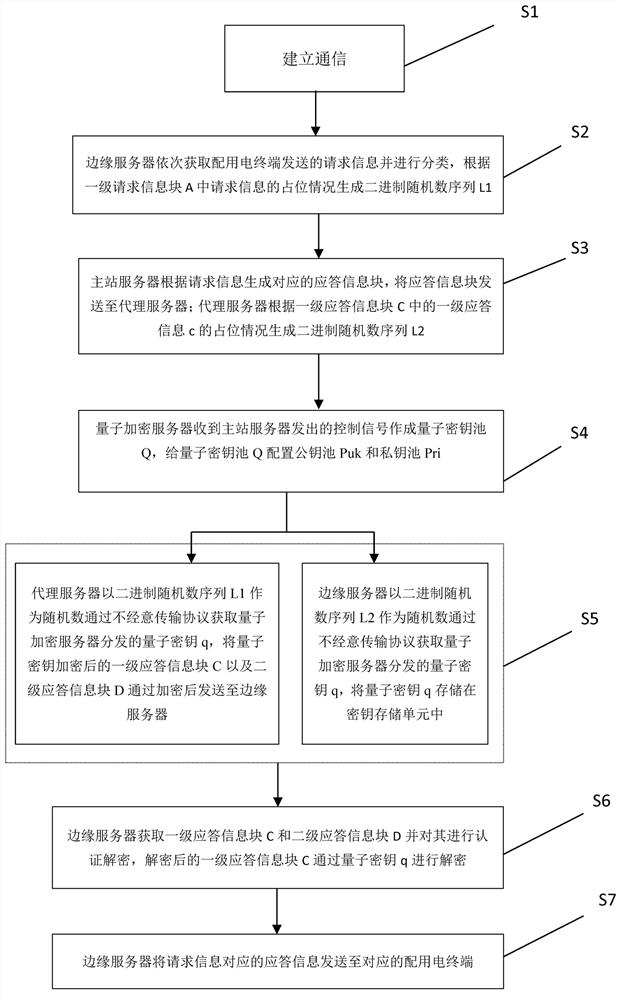
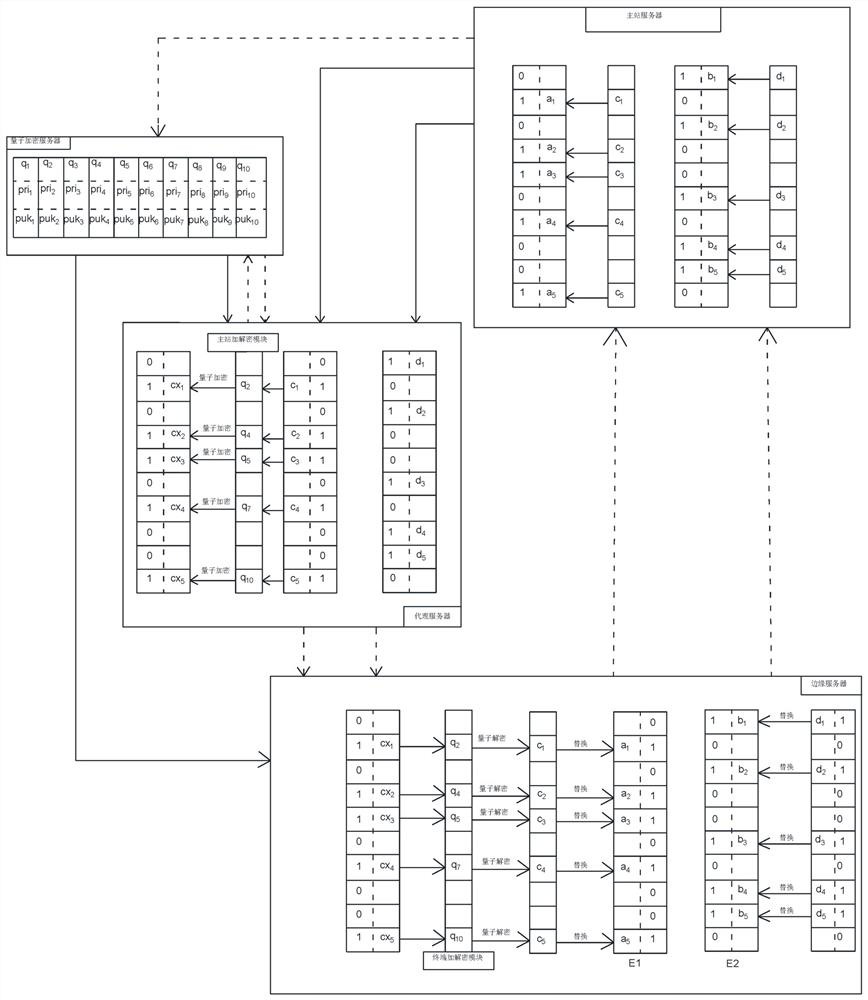
Power distribution network information secure transmission method based on quantum encryption
ActiveCN113114460AImprove safety and reliabilityImprove encryption and decryption efficiencyKey distribution for secure communicationEdge serverSecure transmission
The invention discloses a power distribution network information secure transmission method based on quantum encryption. The method comprises the following steps: S1, establishing communication; s2, the edge server obtains the request information of the power distribution and utilization terminal, and generates a binary random number sequence L1 according to the occupation condition of the request information in the first-level information block A; s3, the master station server generates response information blocks according to the request information, and generates a binary random number sequence L2 according to the occupation condition of the first-level response information blocks; s4, the quantum encryption server generates a key pool Q, and configures a public key pool Puk and a private key pool Pri for the quantum key pool Q; s5, respectively collecting quantum keys by taking the binary random number sequences L1 and L2 as random numbers; s6, the edge server carries out encryption by using the obtained quantum secret key, and carries out decryption by using the obtained quantum secret key; and S7, the power distribution and utilization terminal obtains corresponding response information. According to the scheme, positioning encryption and decryption of parallel data are realized, and the encryption and decryption efficiency based on the quantum key is improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO
Remote mirror image method and system based on iSCSI
The invention discloses a remote mirror image method and system based on iSCSI. The method comprises the steps that: a client stores critical application data in a local storage device, copies a copy of critical application data and sends a copy text of the critical application data to an encryption middleware; the encryption middleware encrypts the copy text to generate a data ciphertext and sends the data ciphertext to a remote server through an IP network; and the remote server stores the data ciphertext in an iSCSI disk array to serve as mirror image data. The method is used for guaranteeing the transmission and storage security of network data and improving the reading and writing performance of the system.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
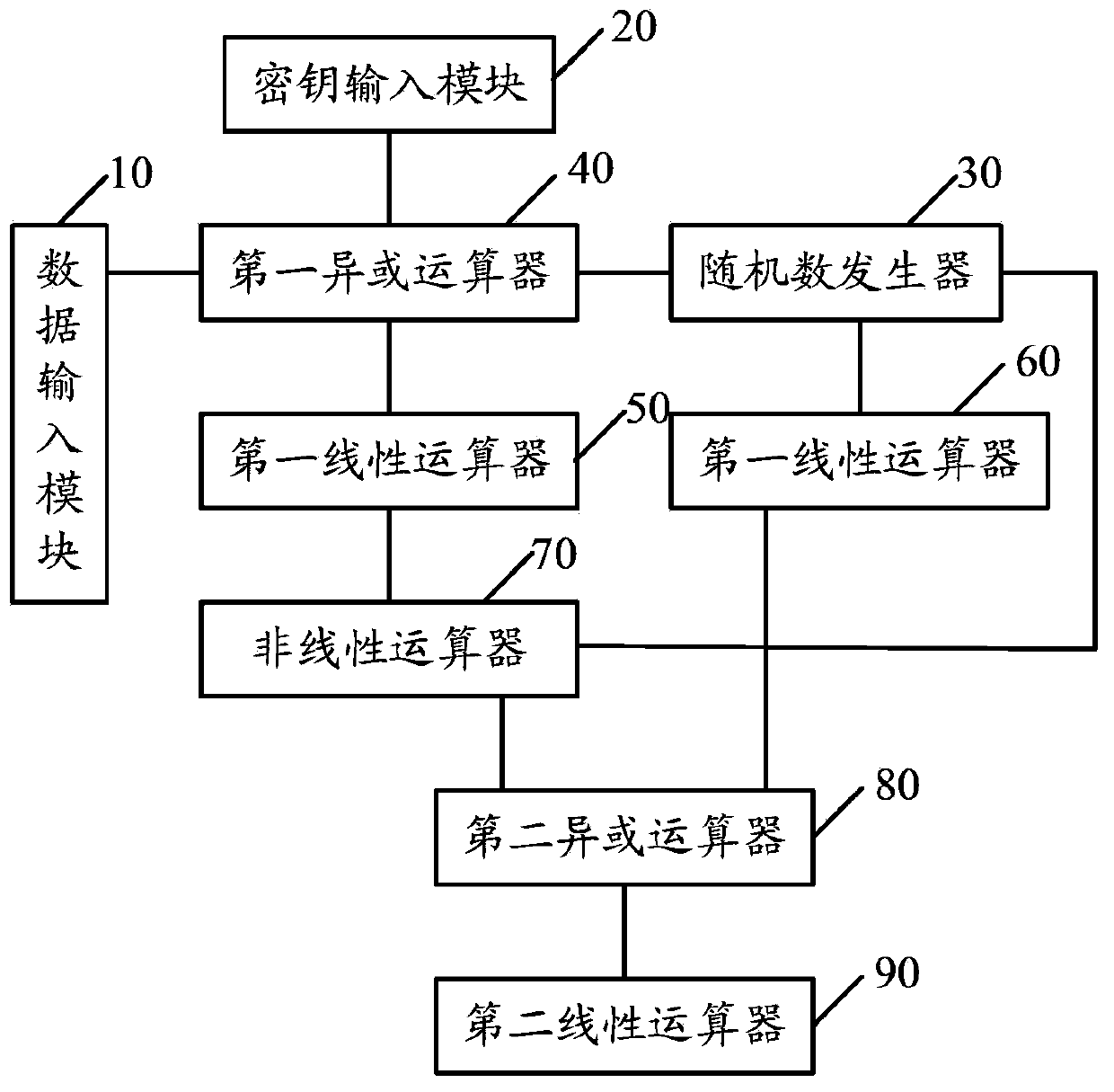
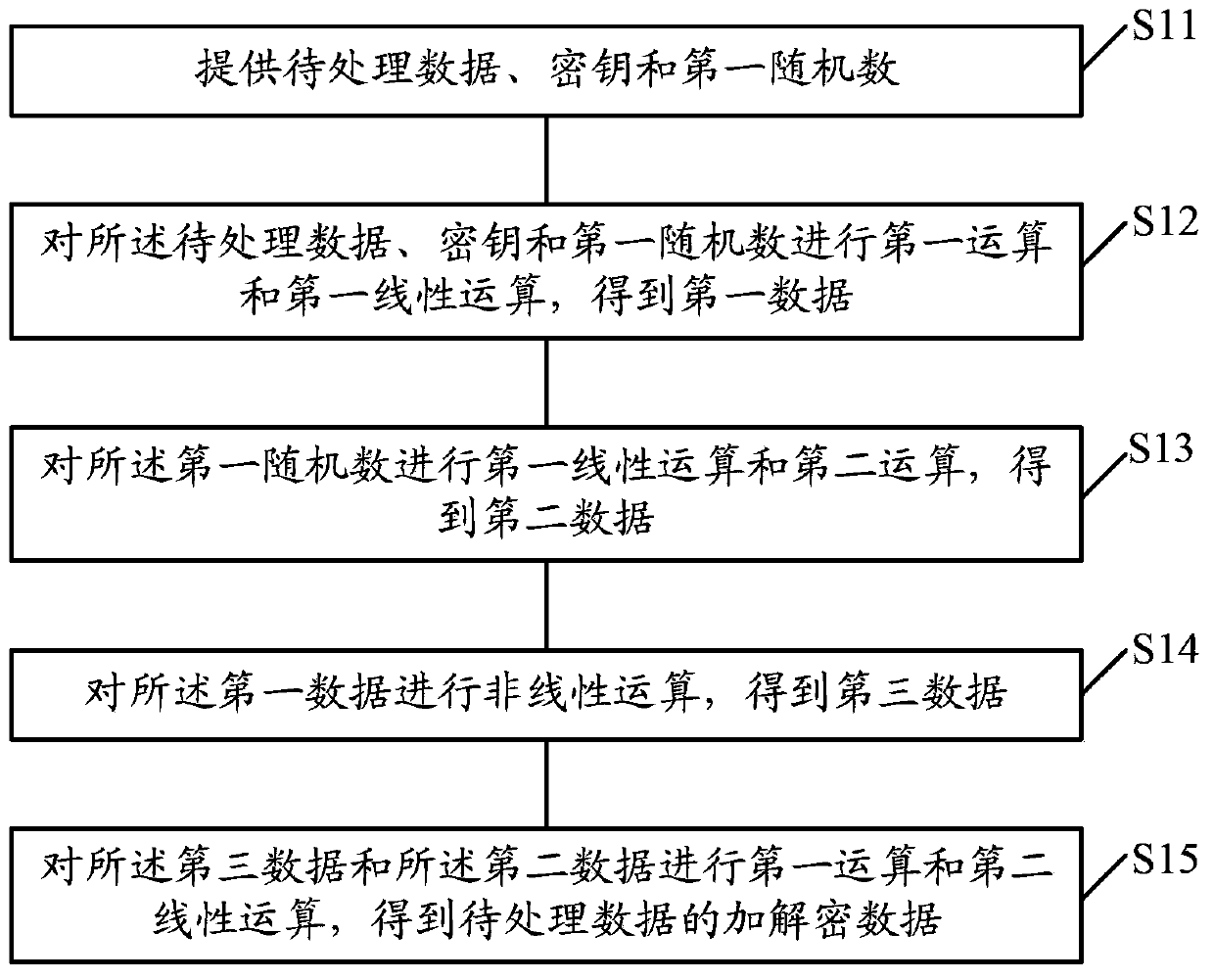
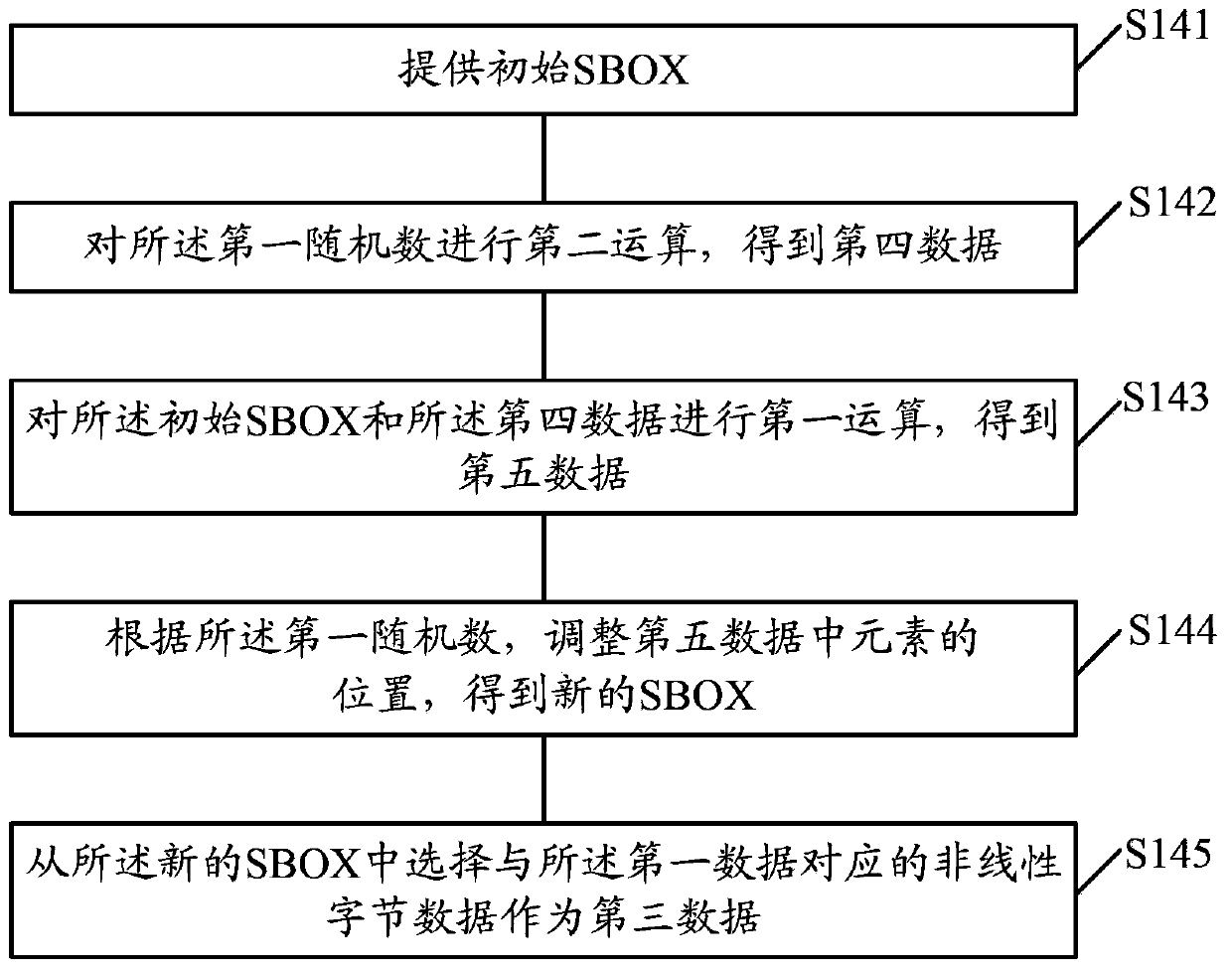
Symmetric encryption and decryption method, and symmetric encryption and decryption system
ActiveCN103684748AEnsure safetyImprove securityEncryption apparatus with shift registers/memoriesByteEncryption
A symmetric encryption and decryption method and a symmetric encryption and decryption system are provided. The symmetric encryption and decryption method includes the following steps that: data to be processed, keys and first random numbers are provided; first computation and first linear computation are performed on the data to be processed, the keys and the first random numbers, such that first data are obtained; the first linear computation and second computation are performed on the first random numbers, such that second data are obtained; nonlinear computation is performed on the first data, such that third data are obtained; the first computation and second linear computation are performed on the third data and the second data, such that encryption and decryption data are obtained; the nonlinear computation includes the step that initial SBOX is provided; the second computation is performed on the first random numbers, such that fourth data can be obtained; the first computation is performed on the initial SBOX and the fourth data, such that fifth data can be obtained; the locations of elements in the fifth data are adjusted according to the first random numbers, such that new SBOX is obtained; and nonlinear byte data corresponding to the first data are selected from the new SBOX and are adopted as the third data. With the symmetric encryption and decryption method and the symmetric encryption and decryption system of the invention adopted, the security and efficiency of encryption and decryption can be improved.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
Data encryption method based on password book
ActiveCN104518865AEnsure safetyImprove encryption and decryption efficiencyEncryption apparatus with shift registers/memoriesOriginal dataCiphertext
The invention discloses a data encryption method based on a password book and belongs to the technical field of computer data safety. The data encryption method includes that the password book self-defined by a user is utilized for date encryption, a sequence formed by stored data is utilized fully, and extraction of part of bit data or inserting of data among specific bits is not needed to disturb an original data storage sequence; the original data storage sequence is subjected to fixed-length cutting, and fixed length is generally not larger than 8 bit, so that more simplicity and conciseness in ciphertext display are realized, and difficulty in illegal decryption by the user is greatly increased. Compared with the prior art, the data encryption method has the advantages that length of ciphertext is compressed effectively, data encryption speed is increased, and difficulty in illegal decryption of data is increased greatly due to creating of the password book.
Owner:NANJING UNIV OF POSTS & TELECOMM
Data encryption and decryption method, device and system
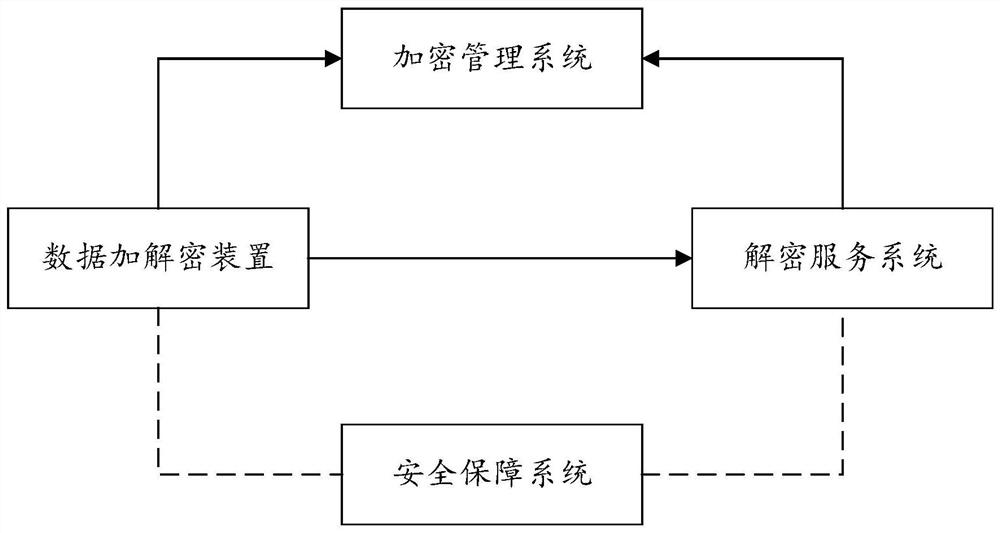
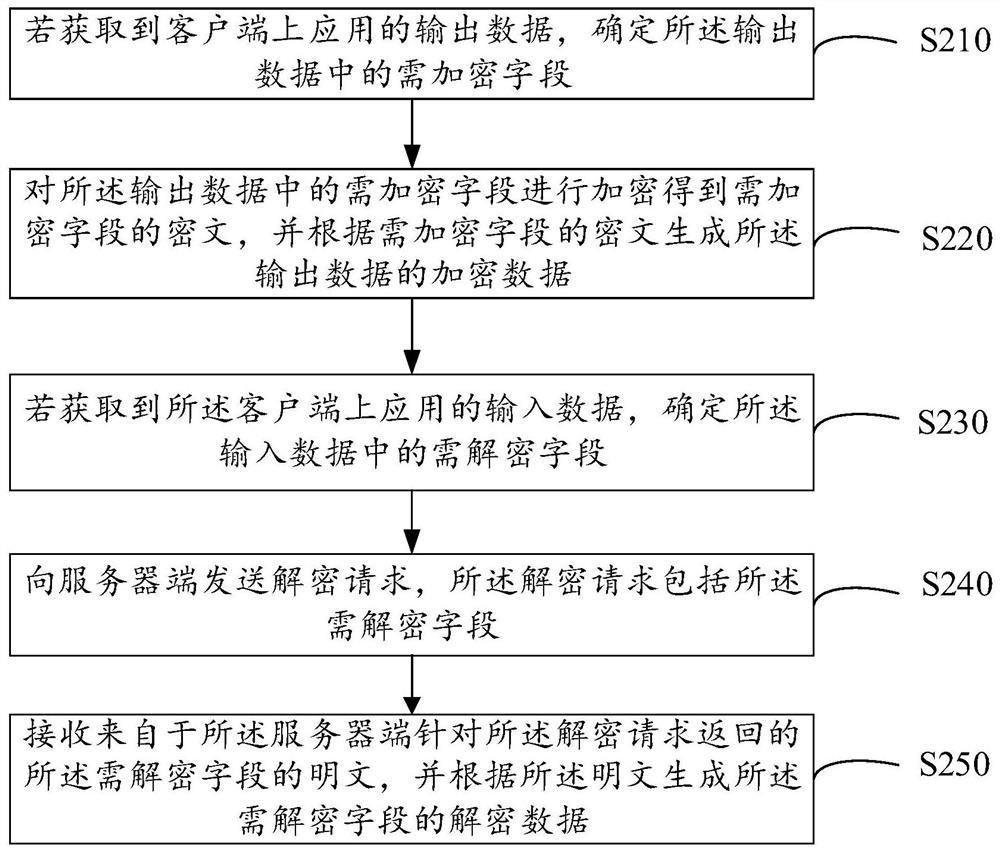
PendingCN112016113AEnsure safetyImprove encryption and decryption efficiencyDigital data protectionPlaintextCiphertext
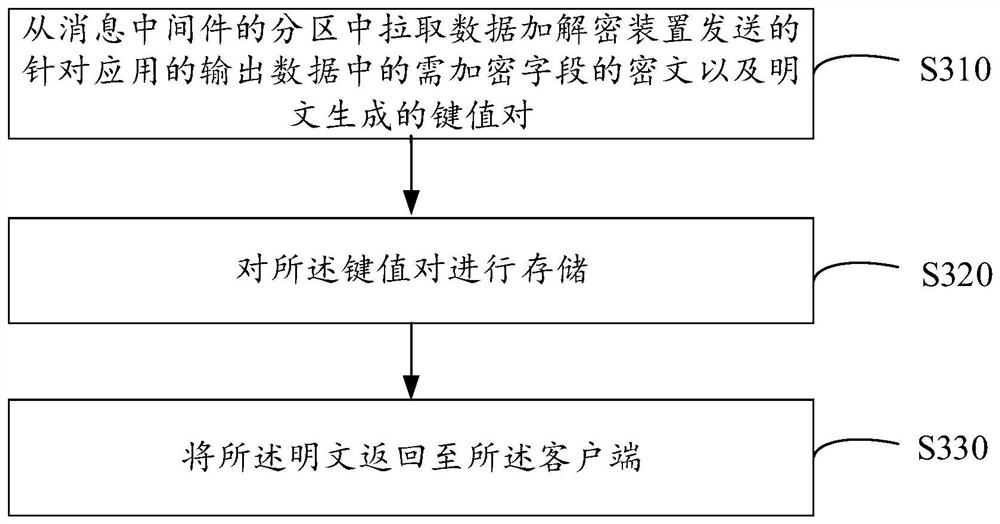
The embodiment of the invention provides a data encryption and decryption method, device and system, and the method comprises the steps of determining a to-be-encrypted field in output data if the output data of an application on a client is obtained; encrypting a to-be-encrypted field in the output data to obtain a ciphertext of the to-be-encrypted field, and generating encrypted data of the output data according to the ciphertext of the to-be-encrypted field; if the input data of the application on the client is obtained, determining a to-be-decrypted field in the input data; sending a decryption request to a server, wherein the decryption request comprises a to-be-decrypted field; receiving a plaintext of a to-be-decrypted field returned by the server for the decryption request, and generating decryption data of the to-be-decrypted field according to the plaintext, wherein the plaintext of the to-be-decrypted field is obtained by the server according to the to-be-decrypted field query key value pair in the decryption request. According to the invention, sensitive information of data can be prevented from being leaked, the data security is ensured, the data encryption and decryption efficiency is improved, and the influence of data encryption and decryption on service processing is reduced.
Owner:TONGDUN HLDG CO LTD
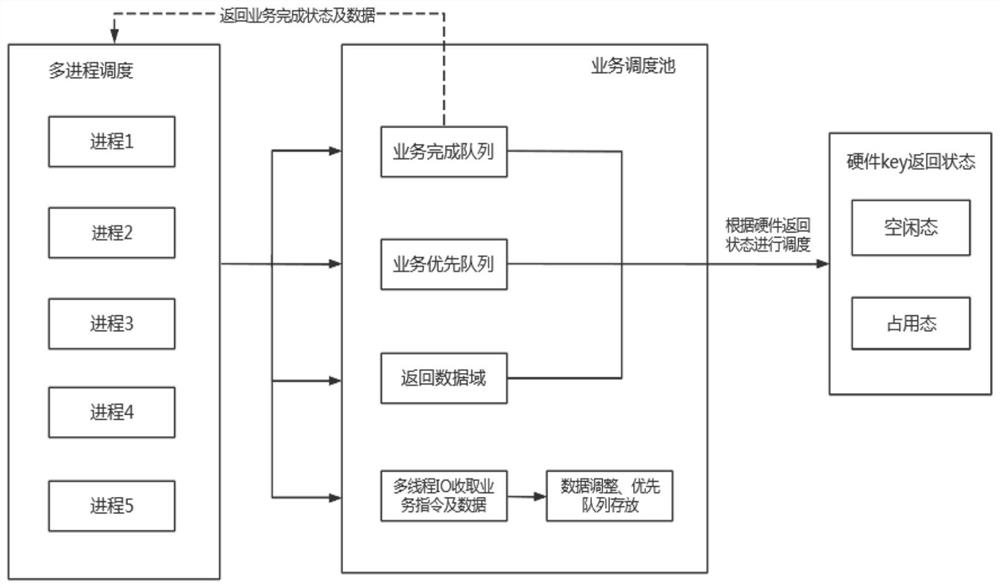
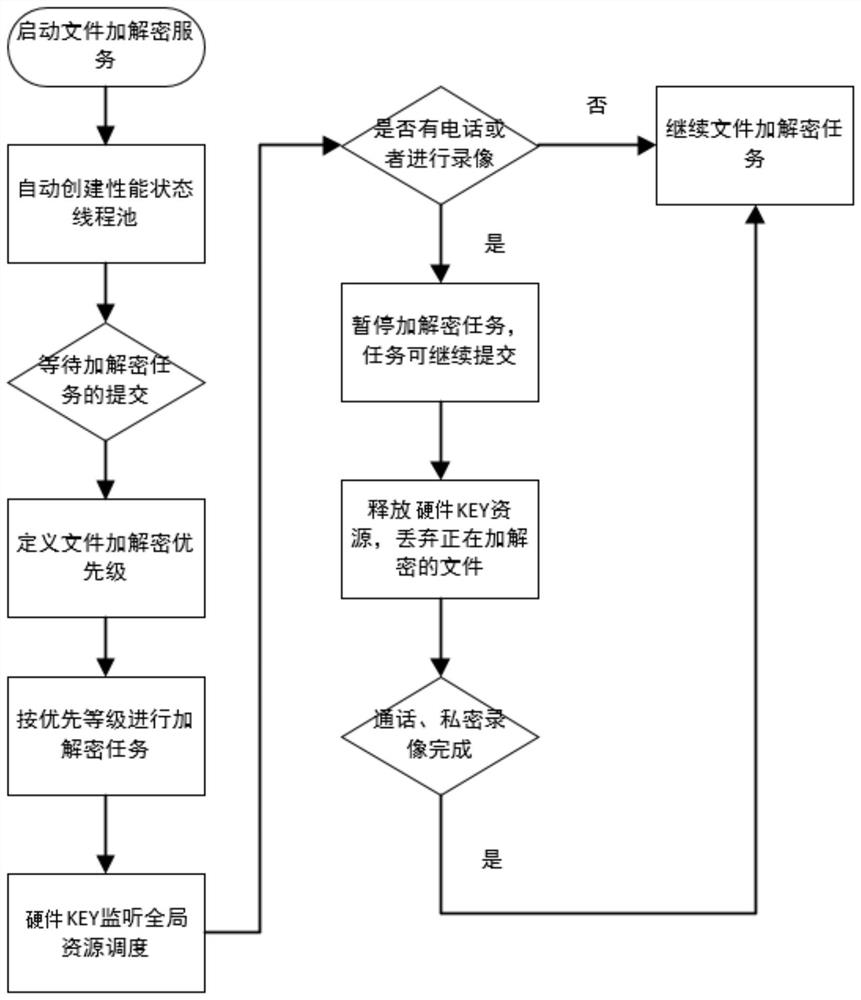
Scheduling method for multiple processes to preempt hardware key encryption and decryption resources
PendingCN114840318AImprove encryption and decryption efficiencyGuaranteed uptimeProgram initiation/switchingResource allocationComputer hardwareBatch processing
The invention provides a scheduling method for multiple processes to preempt hardware key encryption and decryption resources, which comprises the following steps of: 1, starting a file encryption and decryption service, and automatically creating a performance state thread pool; 2, the hardware key waits for submission of encryption and decryption tasks, file encryption and decryption priorities are defined, and the encryption and decryption tasks are carried out according to the priorities; step 3, detecting whether there is a call or recording, pausing the encryption and decryption task, and continuing to submit the task; 4, releasing hardware key resources, and discarding a file which is being encrypted and decrypted; and step 5, after calling or video recording is completed, continuing the file encryption and decryption task. The method has the advantages that it is guaranteed that other tasks can be carried out in the file encryption and decryption process, the file encryption and decryption efficiency is improved, and normal operation of a system is guaranteed; a thread pool is created for a batch processing file encryption and decryption task, and hardware resources are allocated according to task priorities, so that on one hand, memory consumption is reduced, and on the other hand, system resource management is facilitated.
Owner:中易通科技股份有限公司
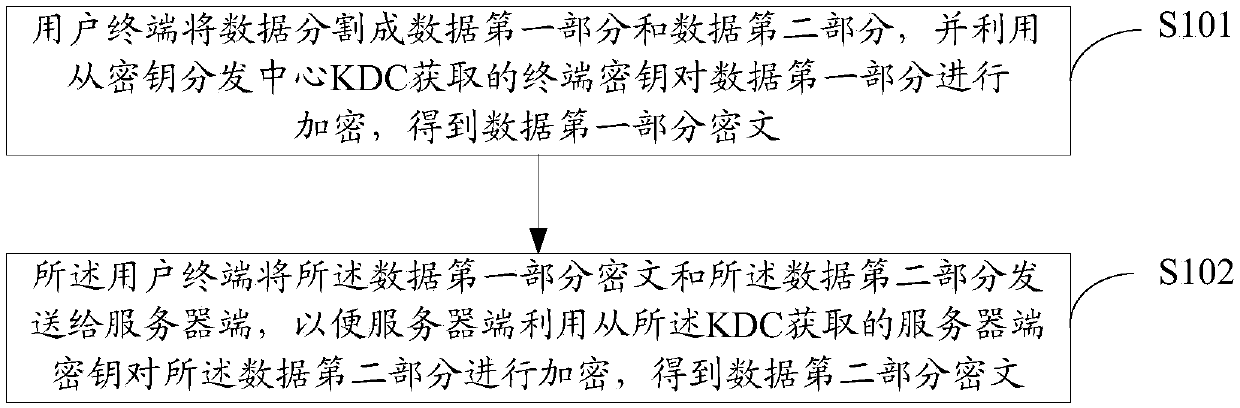
Key separation combined encryption method and system
ActiveCN109525388AReduce storage capacityImprove encryption and decryption efficiencyKey distribution for secure communicationComputer network technologyCiphertext
The invention discloses a key separation combined encryption method and system, and relates to the field of data security and computer network technology. The method comprises the following steps: dividing data into a first part of the data and a second part of the data by a user terminal; encrypting the first part of the data to obtain a first partial ciphertext of the data by utilizing the terminal key obtained from a key distribution center (KDC); sending the first partial ciphertext of the data and the second part of the data to a server end by the user terminal, so that the server end utilizes a server end key obtained from the KDC to encrypt the second part of the data to obtain a second partial ciphertext of the data.
Owner:ZTE CORP
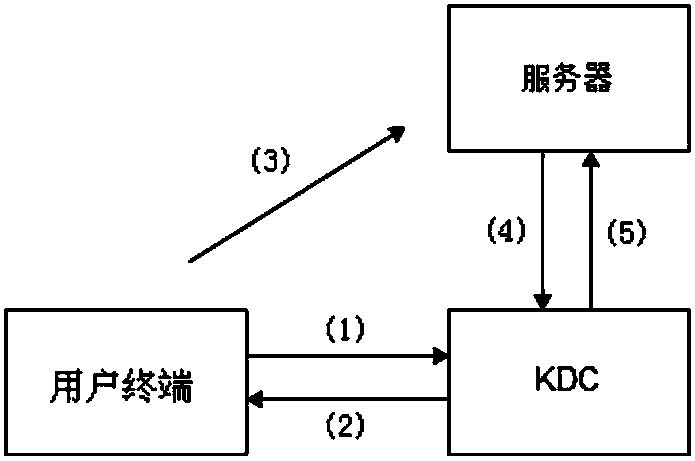
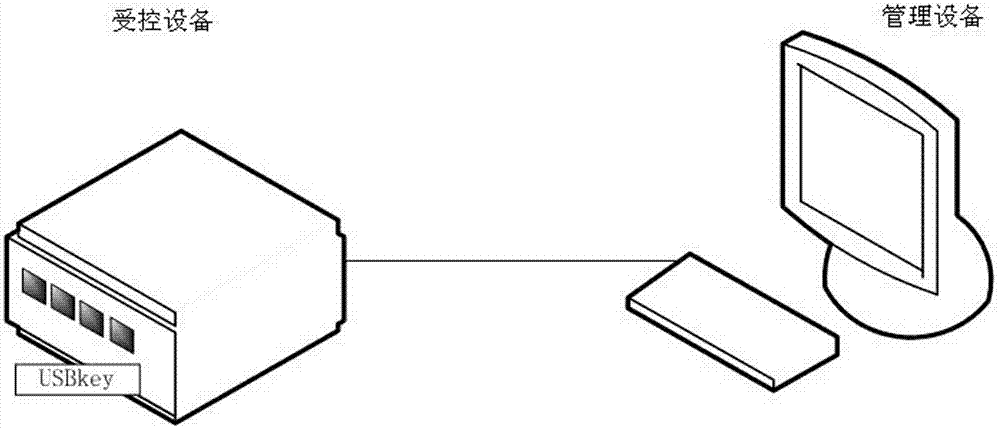
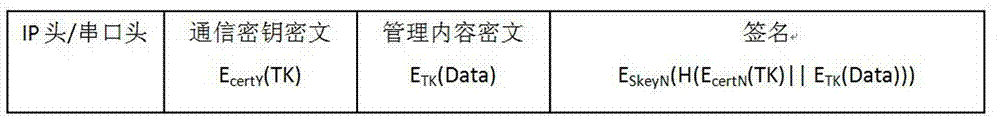
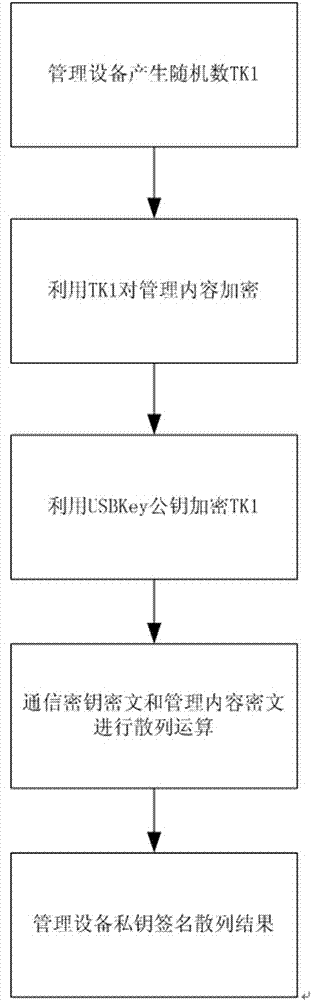
Communication content encryption and decryption method and encryption management method based on CS mode
ActiveCN103795549AImprove encryption and decryption efficiencyReduce computing power requirementsUser identity/authority verificationComputer hardwareEncryption decryption
The invention discloses a communication content encryption and decryption method and an encryption management method based on a CS mode, and relates to the information security technology. The novel encryption management method can improve encryption speed through hardware encryption. The encryption management method is characterized by comprising the steps of preparation, management device message packaging, controlled device message unpackaging, controlled device message packaging and management device message unpackaging.
Owner:中电科网络安全科技股份有限公司
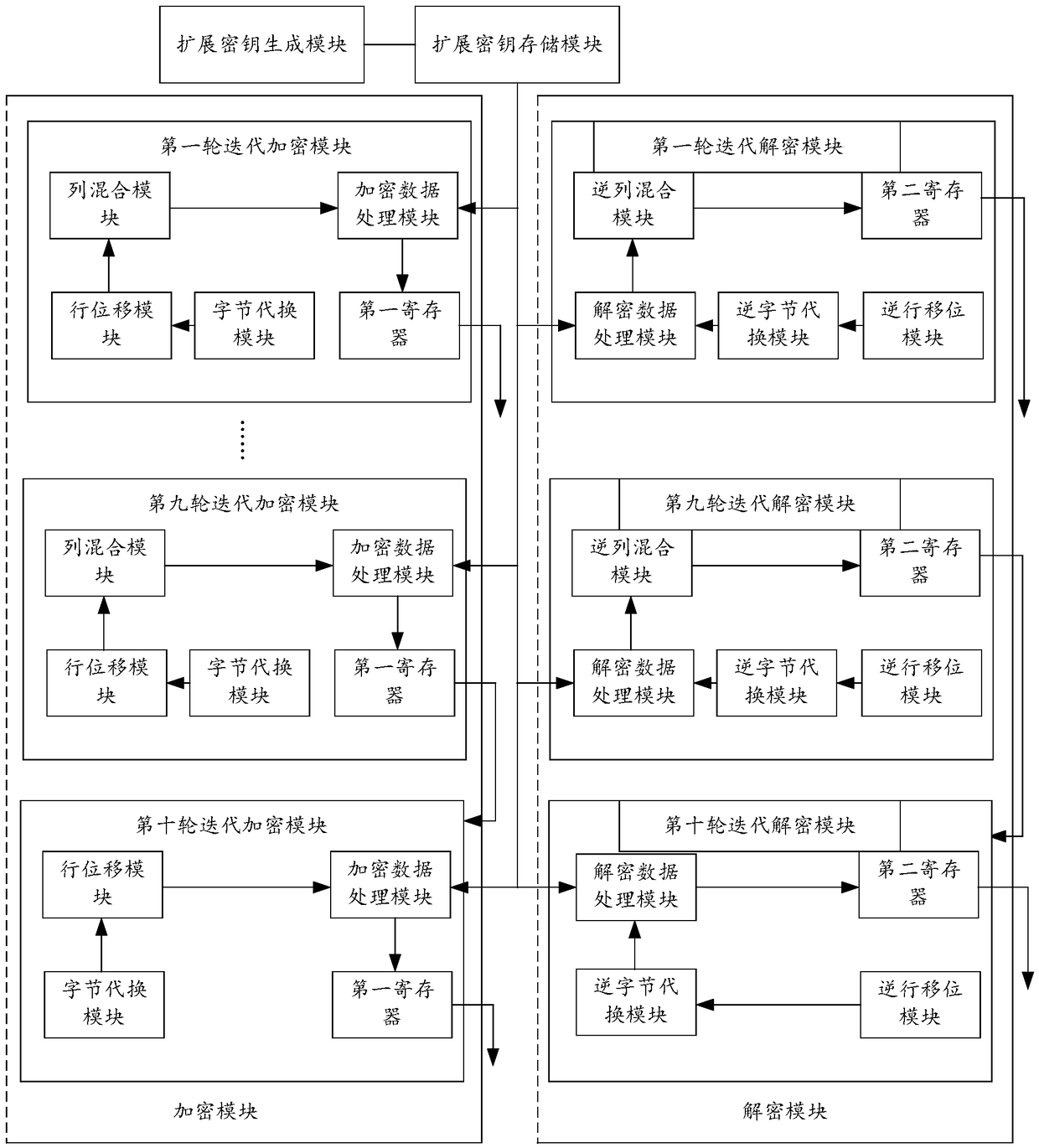
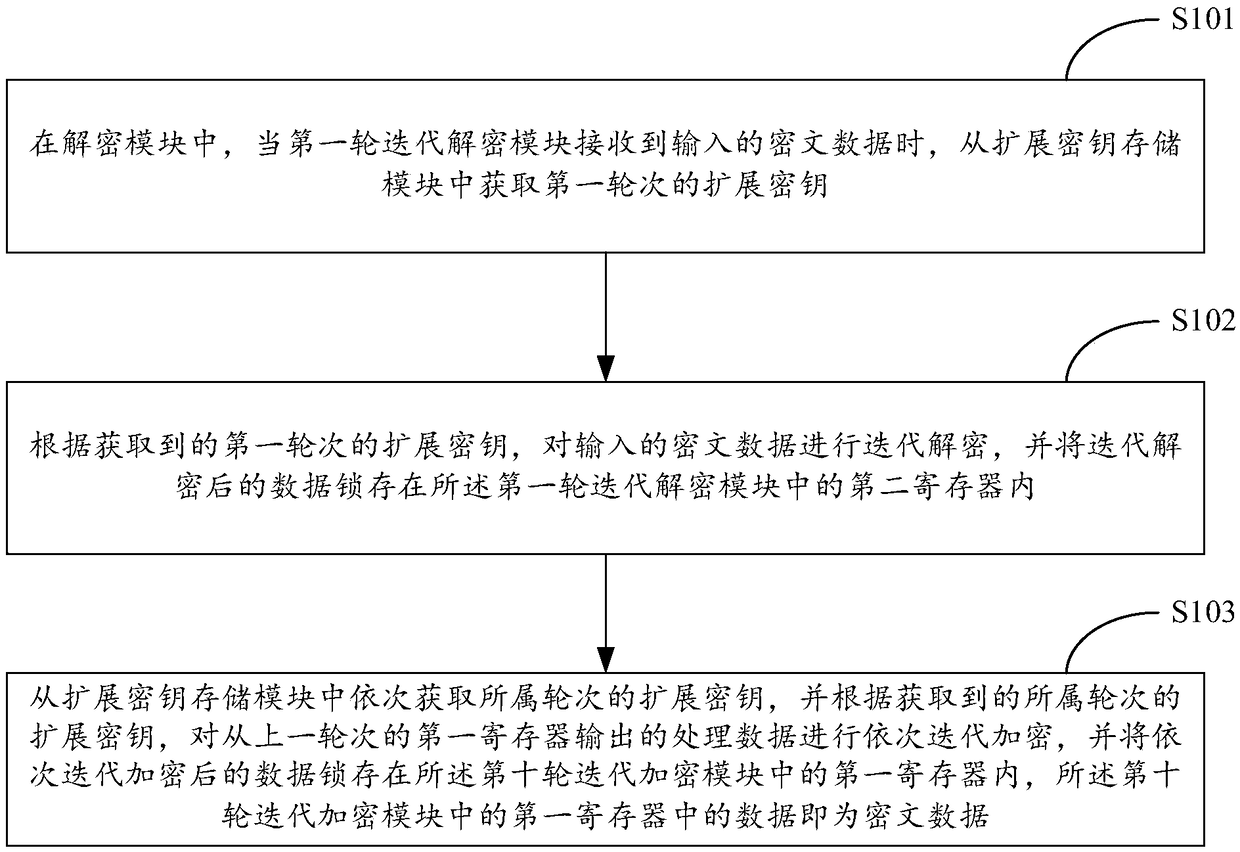
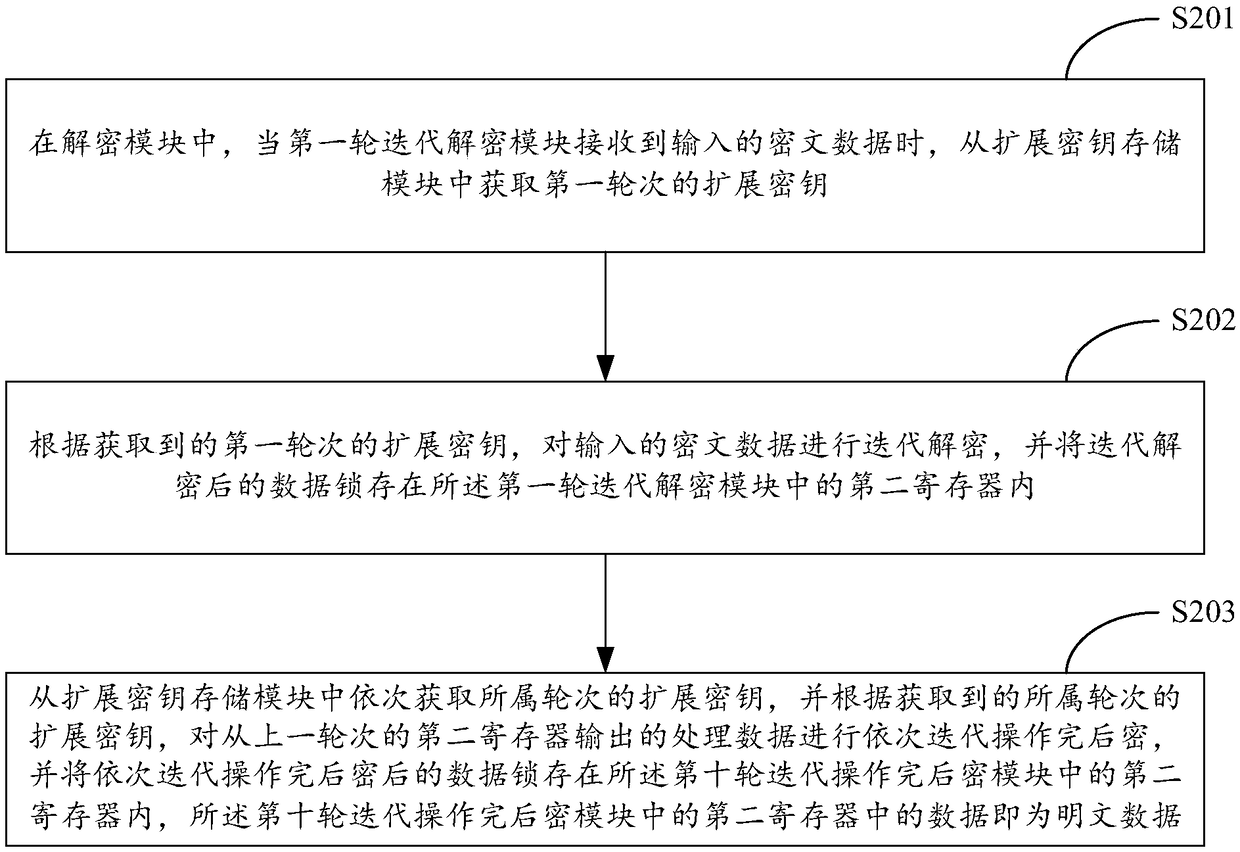
AES encryption and decryption system and method based on large-scale data
InactiveCN108933653AAchieve independent settingsShorten the expansion cycleEncryption apparatus with shift registers/memoriesDigital data protectionPlaintextCiphertext
The invention relates to the technical field of data encryption and decryption, and provides an AES encryption and decryption system and method based on large-scale data. The system comprises an encryption module, a decryption module and an extended key storage module, wherein the extended key storage module is used for storing 10 pre-generated extended keys required by 10 turns of iterations; theencryption module obtains the extended key of the corresponding turn of iteration from the extended key storage module, performs iteration encryption on an input plaintext and generates a ciphertext;and the decryption module obtains the extended key of the corresponding turn of iteration from the extended key storage module, performs iteration decryption on the inputted ciphertext and generatesa plaintext, thereby realizing independent setting for a key extension module, and shortening the key extension period. Meanwhile, the AES encryption and decryption system also shortens the depth of an encryption and decryption assembly line and improves the encryption and decryption efficiency of an AES algorithm.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
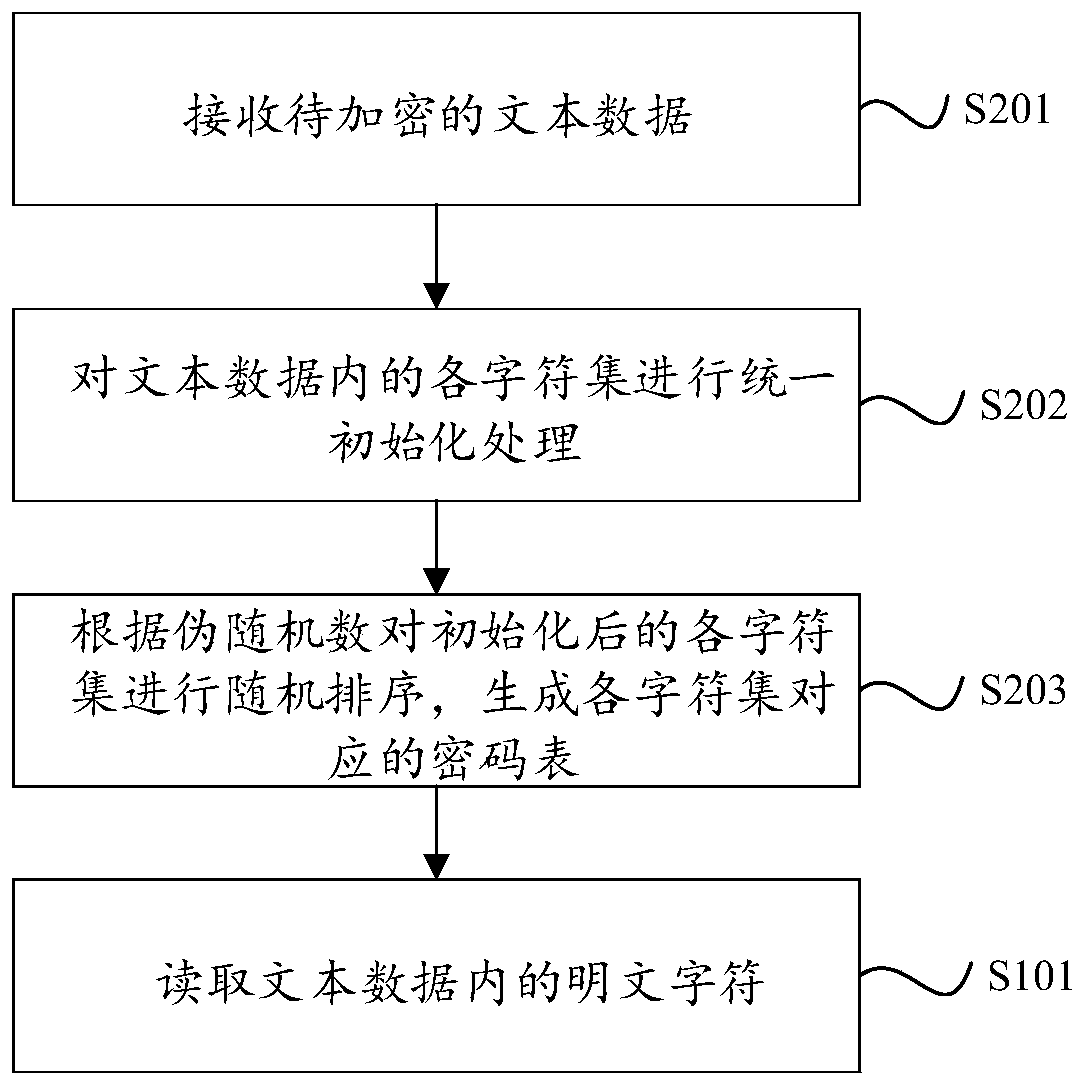
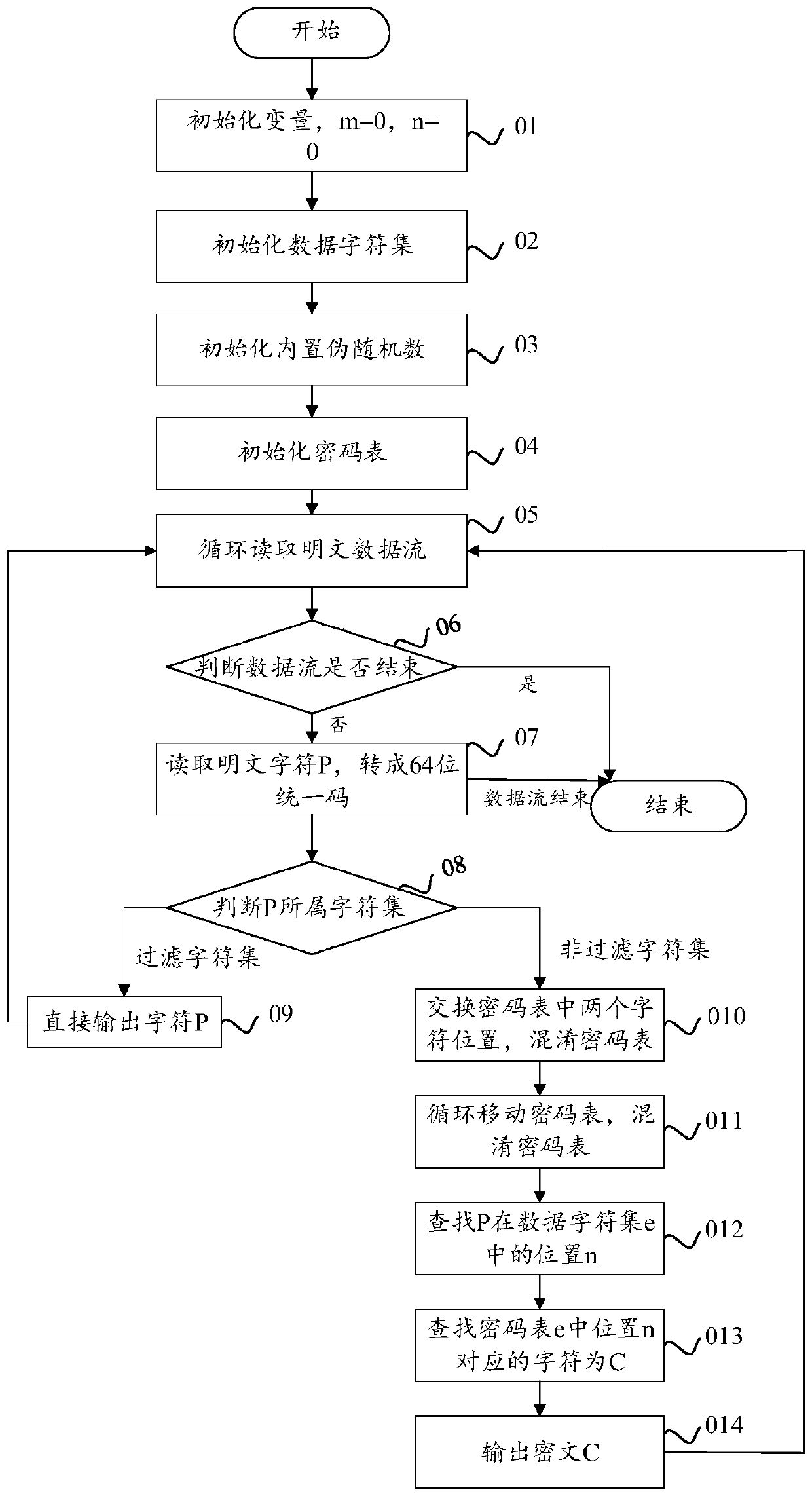
Streaming encryption method for text data reservation format
ActiveCN110704854AImprove encryption and decryption efficiencyKey distribution for secure communicationRandom number generatorsControl characterPassword
The invention provides a streaming encryption method and device for a text data reservation format. The method comprises the following steps: reading plaintext characters in text data; converting theplaintext character into a uniform code; judging whether a character set to which the plaintext character converted into the uniform code belongs is a filtered character set or not; if the character set is the filtering character set, directly outputting the current plaintext character; if the character set is a non-filtering character set, performing format-reserved obfuscation processing on thecharacters in the password table corresponding to the plaintext characters to obtain an updated password table; searching an encrypted character corresponding to the plaintext character in the updatedpassword table; and taking the plaintext character and the encrypted character which are directly output as final encrypted text data. According to the method, the filtering characters and the non-filtering characters are used, so that the plaintext characters are encrypted in a targeted manner, the consistency of character formats is controlled in a finer and richer manner. The method is more suitable for encryption on network transmission through one-by-one character encryption, and the encryption and decryption efficiency is improved.
Owner:车轮互联科技(上海)股份有限公司
Method and system for encrypting and decrypting data
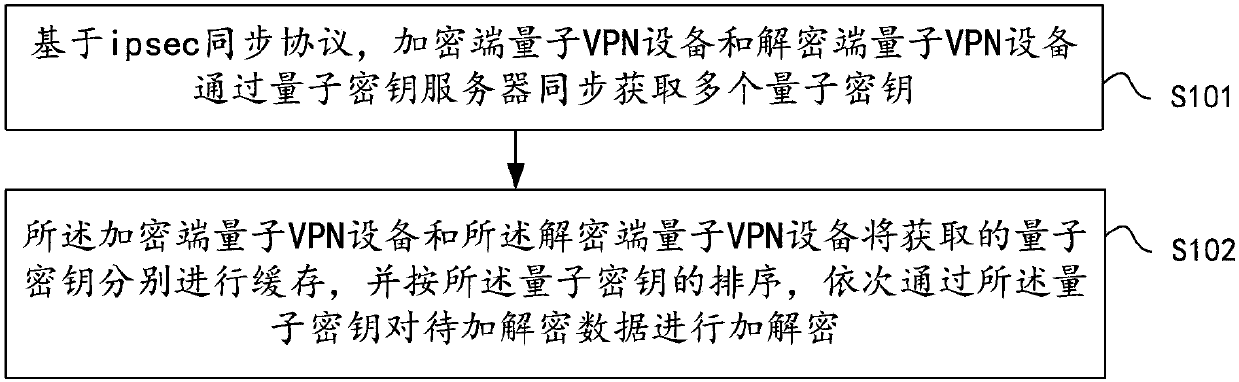
InactiveCN107896148AImprove encryption and decryption efficiencyQuick changeKey distribution for secure communicationQuantumEncryption
The invention discloses a method and system for encrypting and decrypting data. The method disclosed by the invention includes the following steps: synchronously acquiring multiple quantum keys through encryption-end quantum VPN equipment and decryption-end quantum VPN equipment, storing the acquired quantum keys in a buffer area, and subsequently performing encryption and decryption on data to beencrypted and decrypted by using each quantum key sequentially. In other words, according to the scheme of the invention, through the steps of synchronously acquiring the multiple quantum keys and establishing a quantum key buffer area, the rapid transformation of the quantum keys in an ipsec encryption and decryption process can be realized, and the efficiency of encryption and decryption of thequantum VPN equipment during communication can be greatly improved.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Medical image file segmentation encryption and decryption system and method based on greenplum
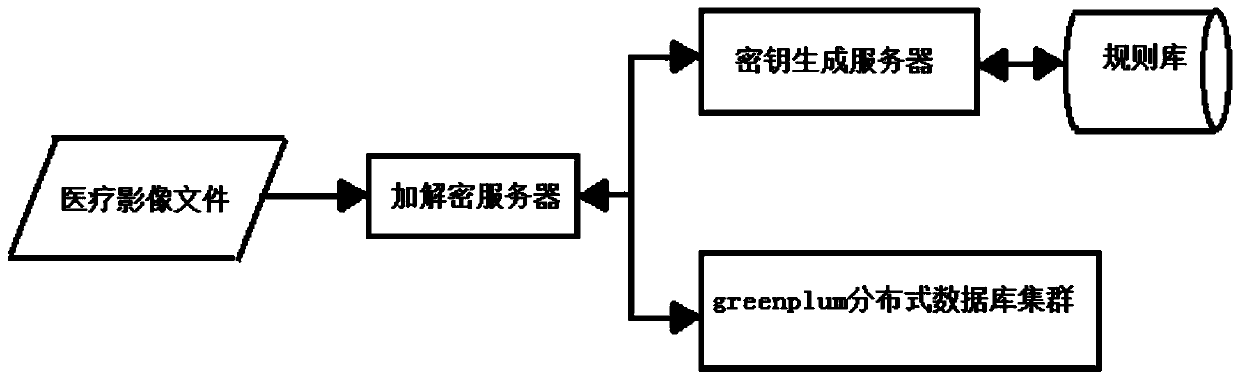
InactiveCN110990877AImprove reliabilityImprove encryption securityDigital data protectionMedical imagesKey storageKey generation
The invention discloses a medical image file segmentation encryption and decryption system and method based on greenplum and relates to the technical field of computers. The medical image file segmentation encryption and decryption system comprises an encryption and decryption server used for encrypting or decrypting a received medical image file; a rule base used for storing a secret key generation rule and a segmentation ID generation rule; a key generation server used for generating a key and a segment ID according to metadata information given by the encryption and decryption server and the key generation rule and the segment ID generation rule obtained from the rule base and returning the key and the segment ID to the encryption and decryption server; a greenplum distributed databasecluster used for storing the generated secret key and the segment ID. According to the invention, sensitive information in the medical image file is encrypted in a segmented manner by utilizing a datasegmented encryption means based on the segmented ID, and only the sensitive information in the medical image file is encrypted instead of the whole file, so that the encryption and decryption efficiency can be improved, and meanwhile, the encryption security of the medical image file and the reliability of key storage are improved.
Owner:中电健康云科技有限公司
Interceptor-based data encryption method and apparatus, and computer equipment
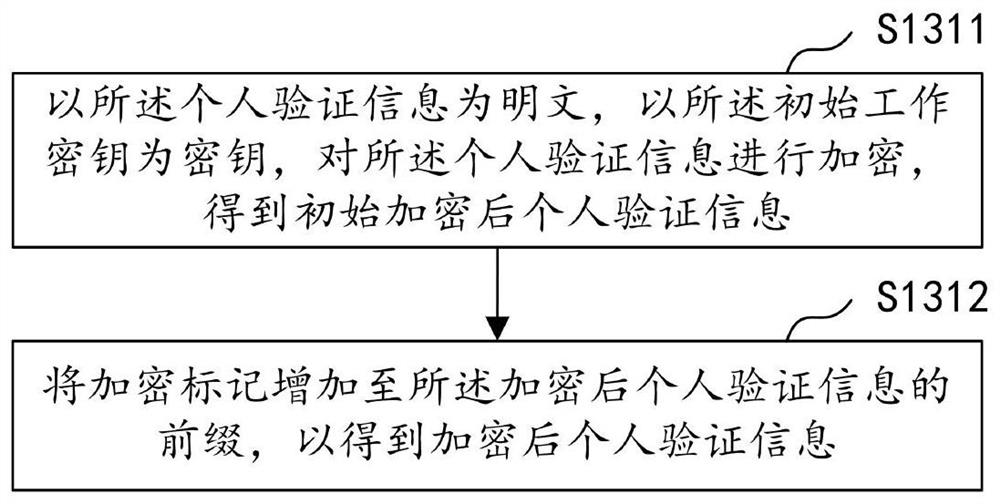
PendingCN111753320AImprove securityImprove encryption and decryption efficiencyKey distribution for secure communicationDigital data information retrievalDatasheetSoftware engineering
The invention discloses an interceptor-based data encryption method and apparatus, computer equipment and a storage medium, and relates to the big data and blockchain technology. The method comprisesthe steps: obtaining personal verification information through a reflection mechanism if a first pre-compiled SQL statement is intercepted through a Mybatis interceptor; obtaining an initial master key and an initial working key which are randomly generated, and encrypting the personal verification information by using the initial working key to obtain encrypted personal verification information;storing the personal verification information into a current data table to obtain an updated data table; if a second pre-compiled SQL statement is intercepted through the Mybatis interceptor, obtaining a corresponding result set in the updated data table of the database; and decrypting to obtain a decrypted result set. According to the method, the personal verification information is automaticallyencrypted before entering the database and is automatically decrypted when coming out, so that the data security is improved, the encryption and decryption processes are fully automatically carried out, and the encryption and decryption efficiency is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
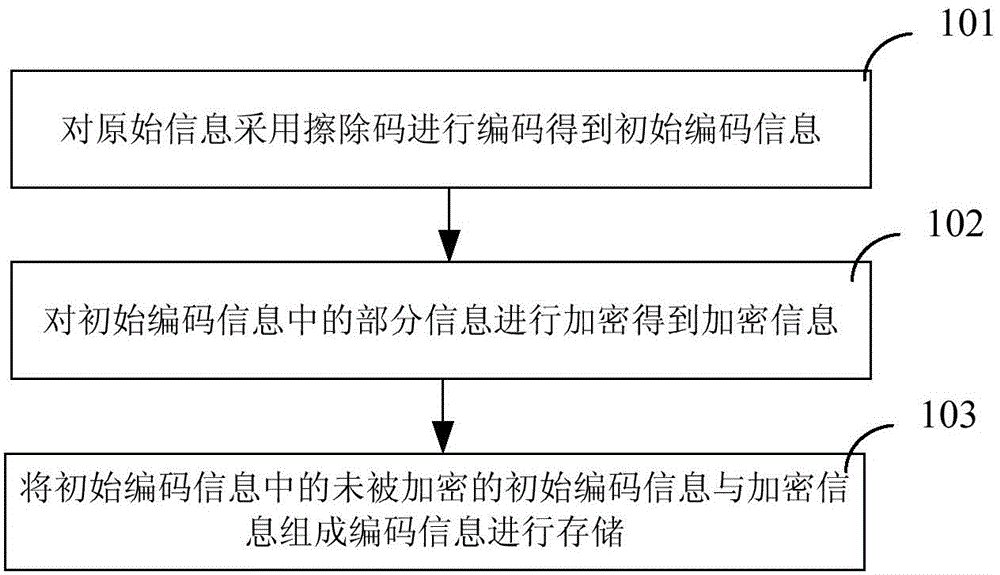
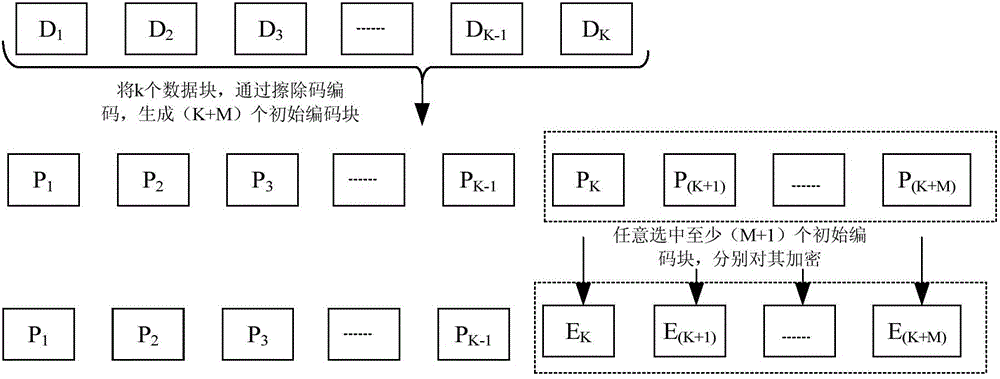
Method and device for encrypting and decrypting data processed by erasure code
The invention discloses a method and device for encrypting and decrypting data processed by erasure code. The method comprises steps of performing encryption on part of information in original coding information to obtain encrypted information after adopting an erasure code to perform coding on original information to obtain the original coding information, and constituting unencrypted original coding information which is not encrypted in the original coding information and encrypted information into coding information for storing. When decryption and decoding are performed on coding information of the original information, coding information having a same data quantity as the original information is extracted and decrypted and is constituted with other coding information into original coding information of the original information; an erasure code is adopted on the original coding information of the original information to perform decoding to obtain original data. The method and device can either prevent loss of data or guarantee safety of data, reduce the decrypted data quantity and improve encryption efficiency.
Owner:HANGZHOU HIKVISION SYST TECH
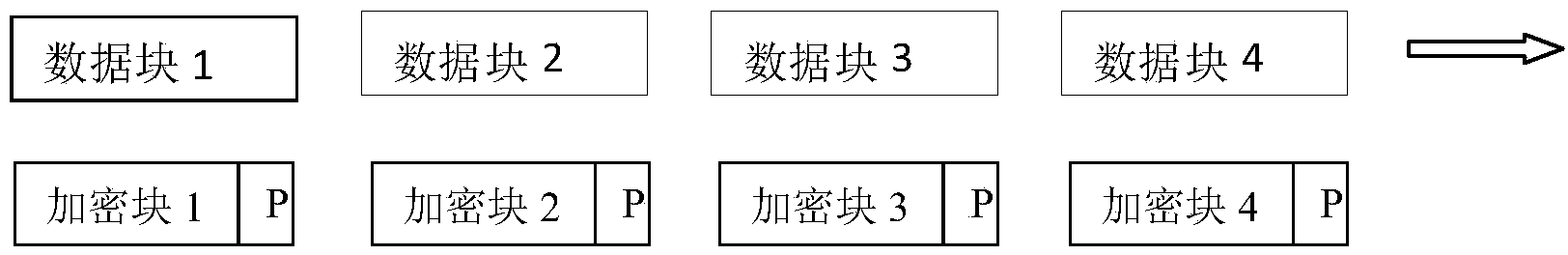
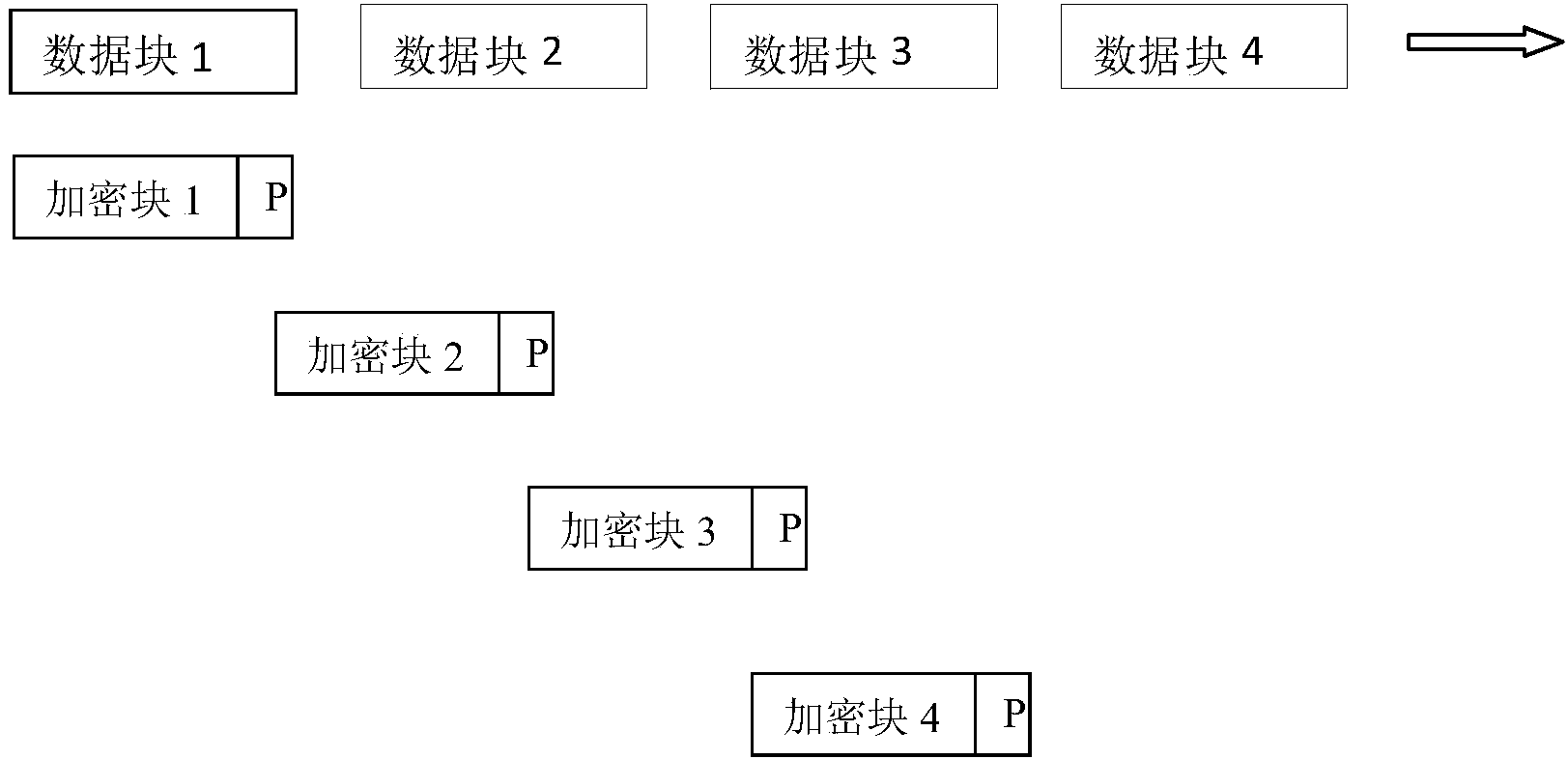
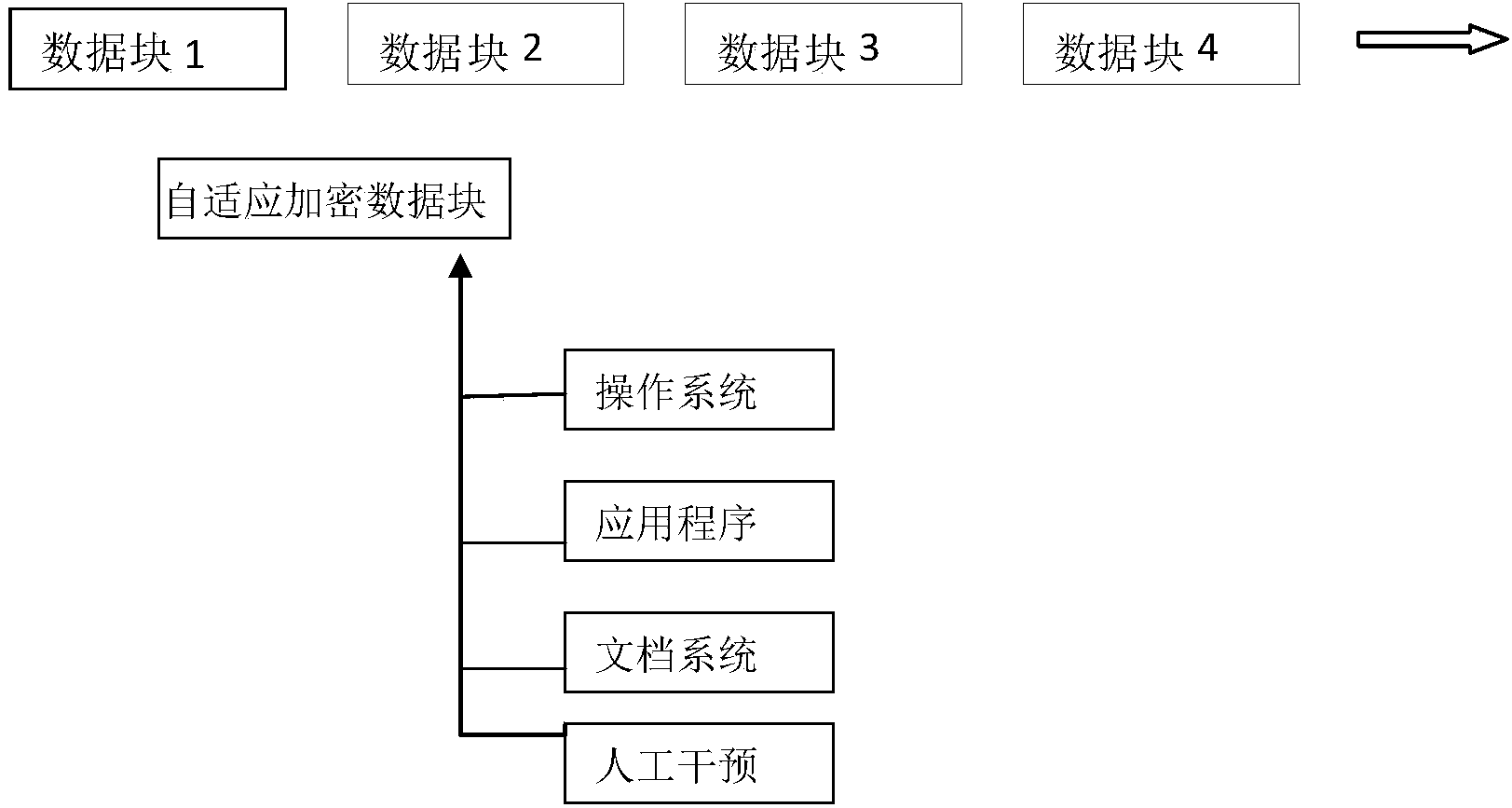
High-efficiency adaptive modular data encrypting method and high-efficiency adaptive modular data encrypting system
ActiveCN103488914AImprove encryption and decryption efficiencyShorten the timeDigital data protectionCoding/ciphering apparatusComputer hardwareOperational system
The invention discloses a high-efficiency adaptive modular data encrypting method. The method comprises a step of adjusting the size of adaptive encrypted data blocks, a step of partitioning data and a step of encrypting. The invention also discloses a high-efficiency adaptive modular data encrypting system. Division of the data blocks is directly relevant to data processing speed and data processing efficiency in computer encrypting and decrypting processes. An adaptive system is established to divide the data blocks, and the size of an encrypted block is automatically adjusted and matched according to different operation systems, different application programs and different file system environments, so that the processing speed and the processing efficiency of the data encrypting and decrypting processes are greatly increased.
Owner:BLOOMBASE TECH LTD
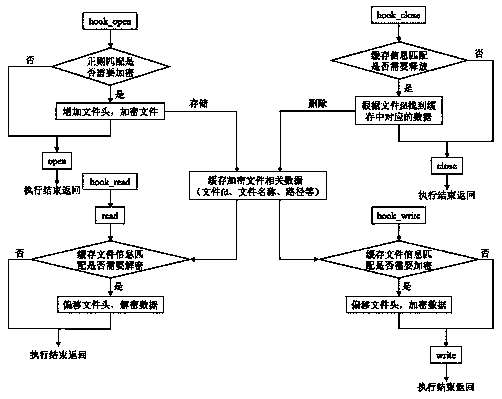
An Android file transparent encryption and decryption method based on a hook
InactiveCN109697366ASolve the real problemResist attackDigital data protectionFile/folder operationsComputer hardwareBlock cipher
The invention provides an Android file transparent encryption and decryption method based on a hook. Security protection such as checking prevention, scanning prevention and leakage prevention is carried out on a sensitive file. Inline-is used in the invention. According to the hook technology, a code instruction in a memory is directly modified to skip a hook function, so that the problem of a PLT hook is well solved; Combination inline The hook technology is used for re-packaging the file operation interface; and the file is encrypted in combination with the national cryptographic block symmetric cryptographic algorithm SM4, so that various attacks for the block cryptographic algorithm can be effectively resisted, and meanwhile, the whole platform architecture of Android can be well supported.
Owner:SUNINFO INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com