Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
45results about How to "Guaranteed recoverability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
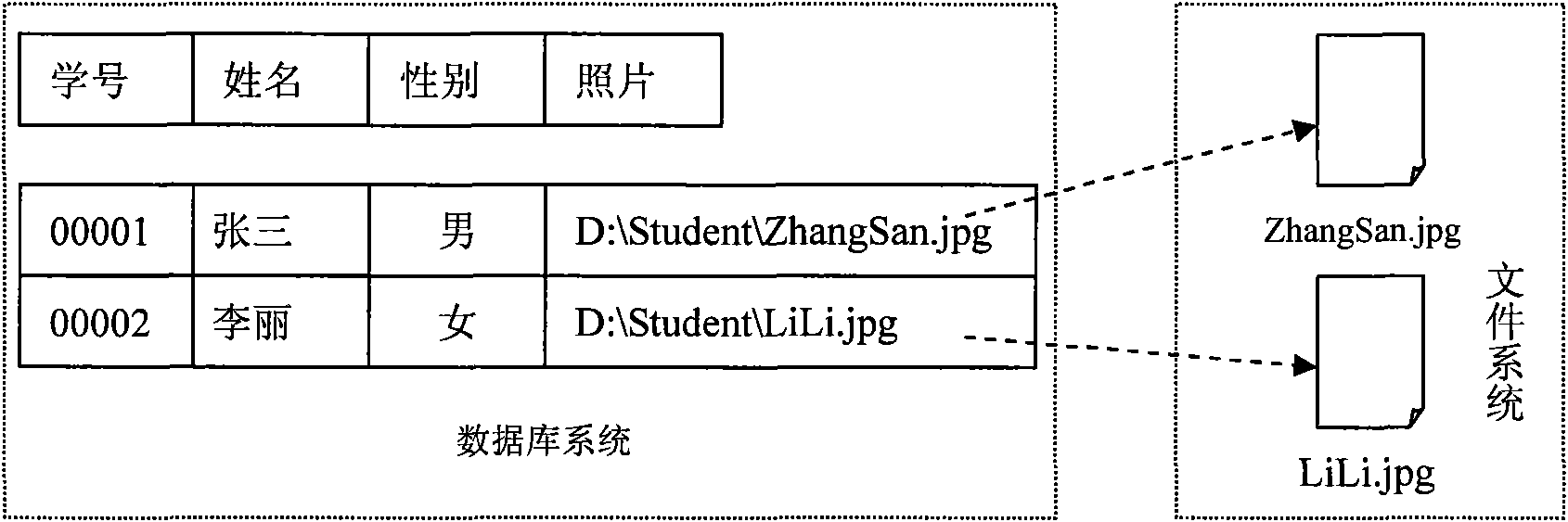
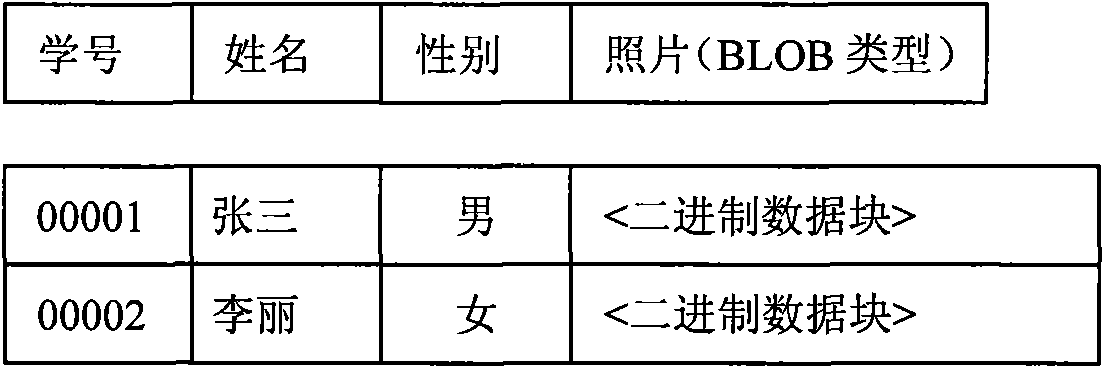
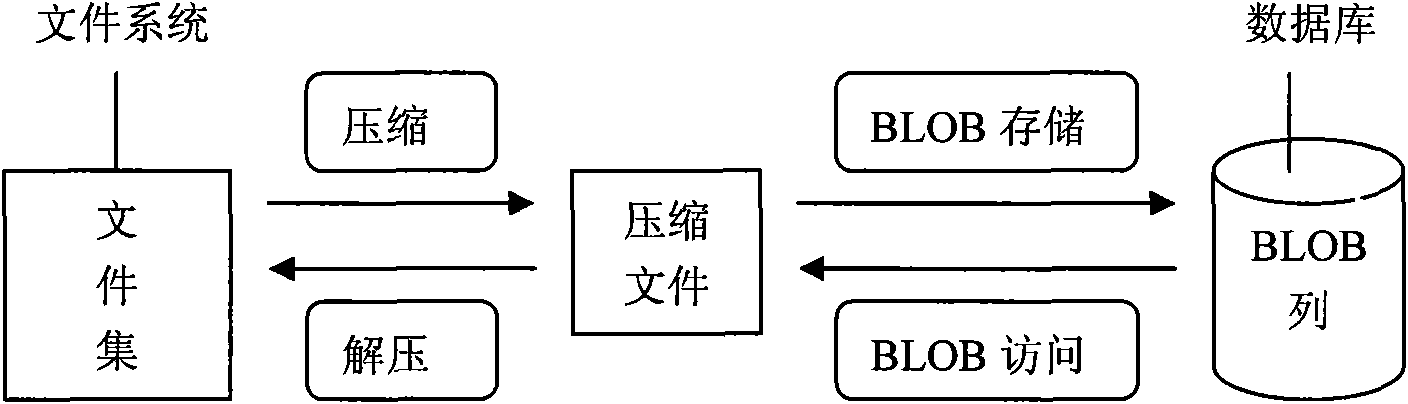
Method for storing and accessing file set under tree directory structure in database
InactiveCN101630322ASolve storage problemsIntegrity guaranteedSpecial data processing applicationsSocial benefitsAccess method
The invention relates to a method for storing and accessing file sets under a tree directory structure in a database, which can effectively solve the problems of overall storage and random access when file sets are stored in and extracted from a database system. The technical scheme is as follows: the overall storage extracts the directory structure, file data and attributes of the file sets from a file system to a local memory; organization structure object is serialized; data blocks are stored in the database; the random access recovers the directory structure of the file sets; corresponding files in the database are accessed according to user selection to read out the directory structure data blocks stored in the database; the directory structure data blocks are recovered to data structure objects by reverse serialization; and the information of the directory structure objects are shown to users in the forms of visible file node data structure, directory node data structure and file set directory structure objects. The invention solves the difficult technical problem that files are not supported to be directly stored and randomly accessed in the database in the prior art, thereby having enormous economic and social benefits.
Owner:THE PLA INFORMATION ENG UNIV
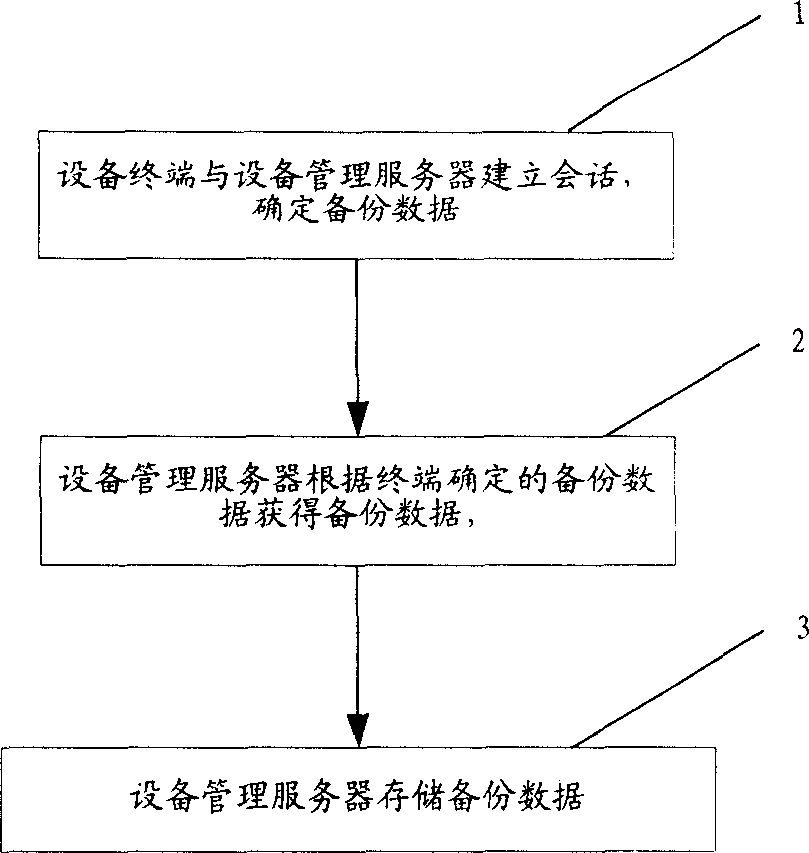
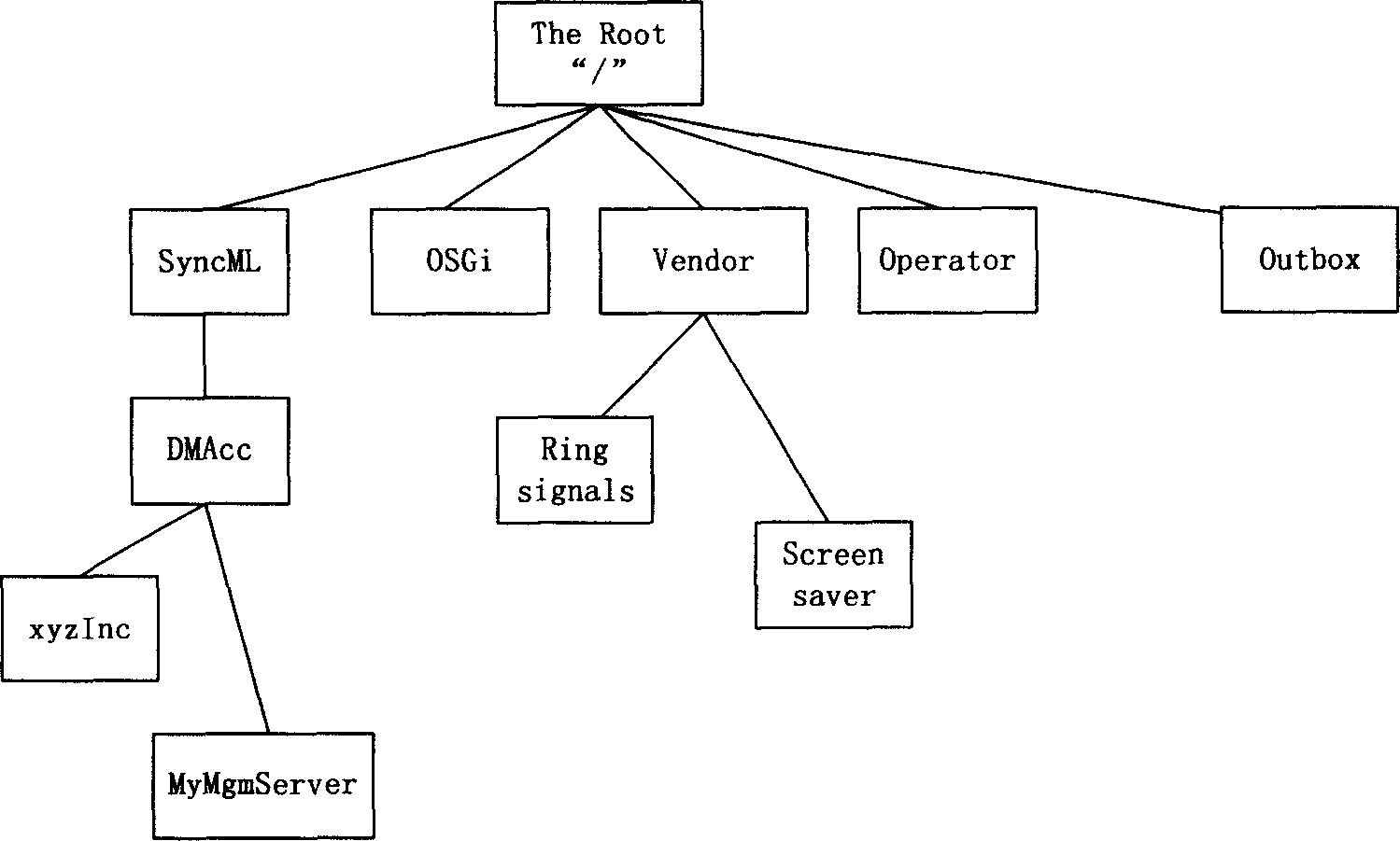
Data backing-up and recovering method and system
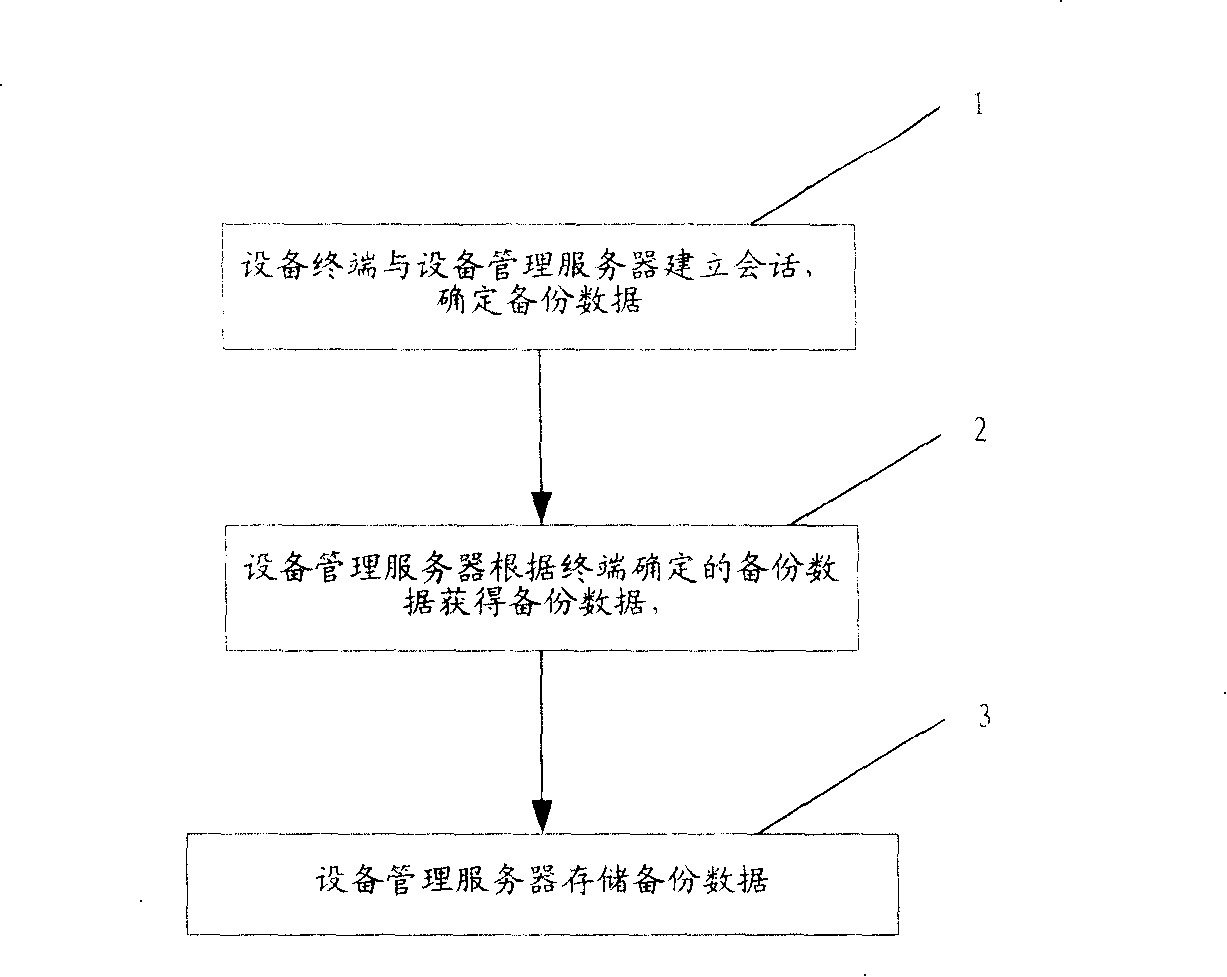
ActiveCN1852534AGuaranteed recoverabilityUser-friendlyWireless communicationProcedure errorPersonalization
First, the method backs up data of device terminal to device management (DM) server. The said data includes individualization data of software program and device terminal. When data of device terminal are lost or in error, the method can restore the backed data to terminal. When software program at terminal is in error, the method can down load the backed software, as well as installs and configures software in order to recover data and software of device terminal. Storing terminal data in DM server, the invention guarantees recoverability of device terminal data especially private data.
Owner:HUAWEI TECH CO LTD
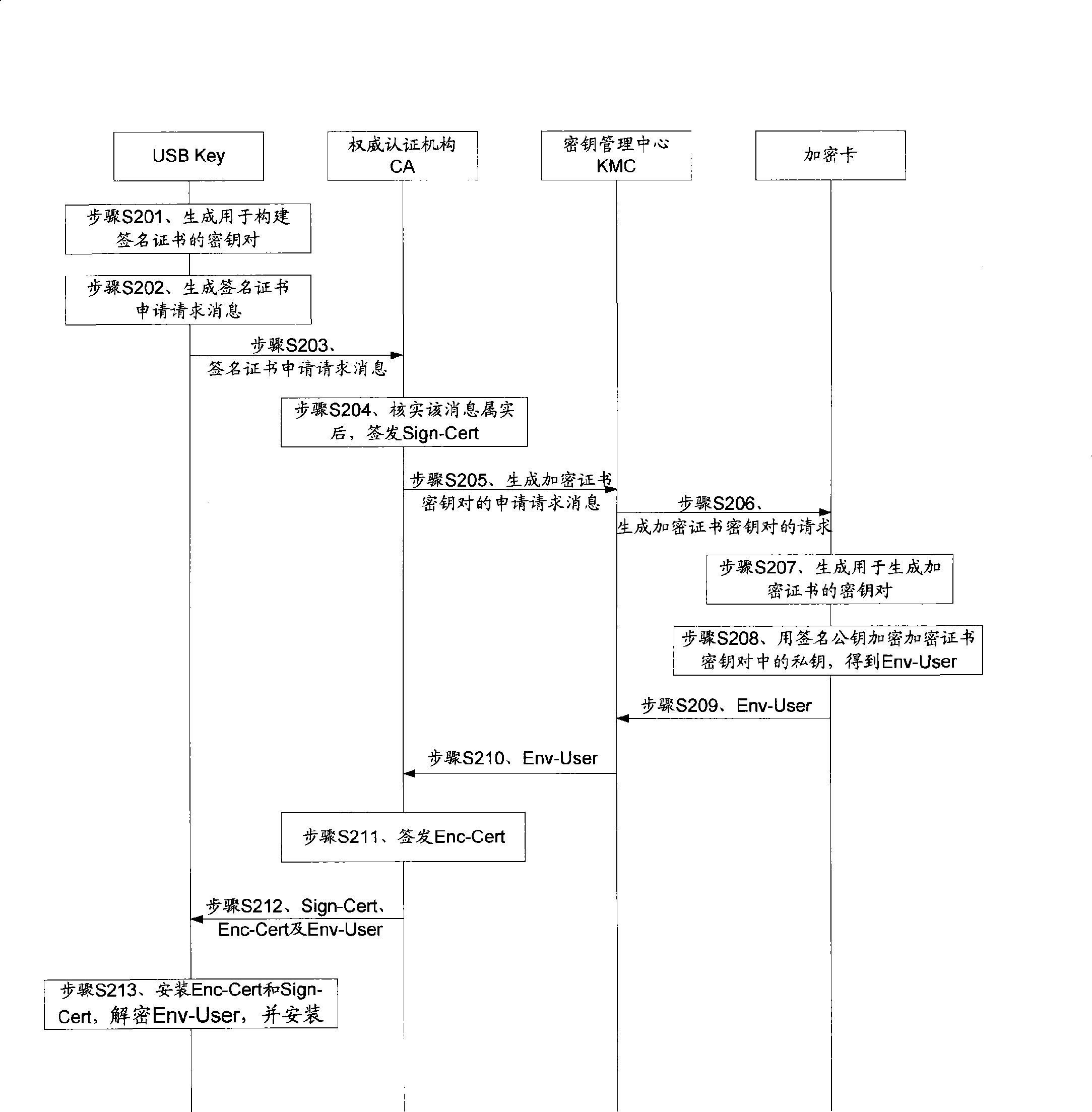
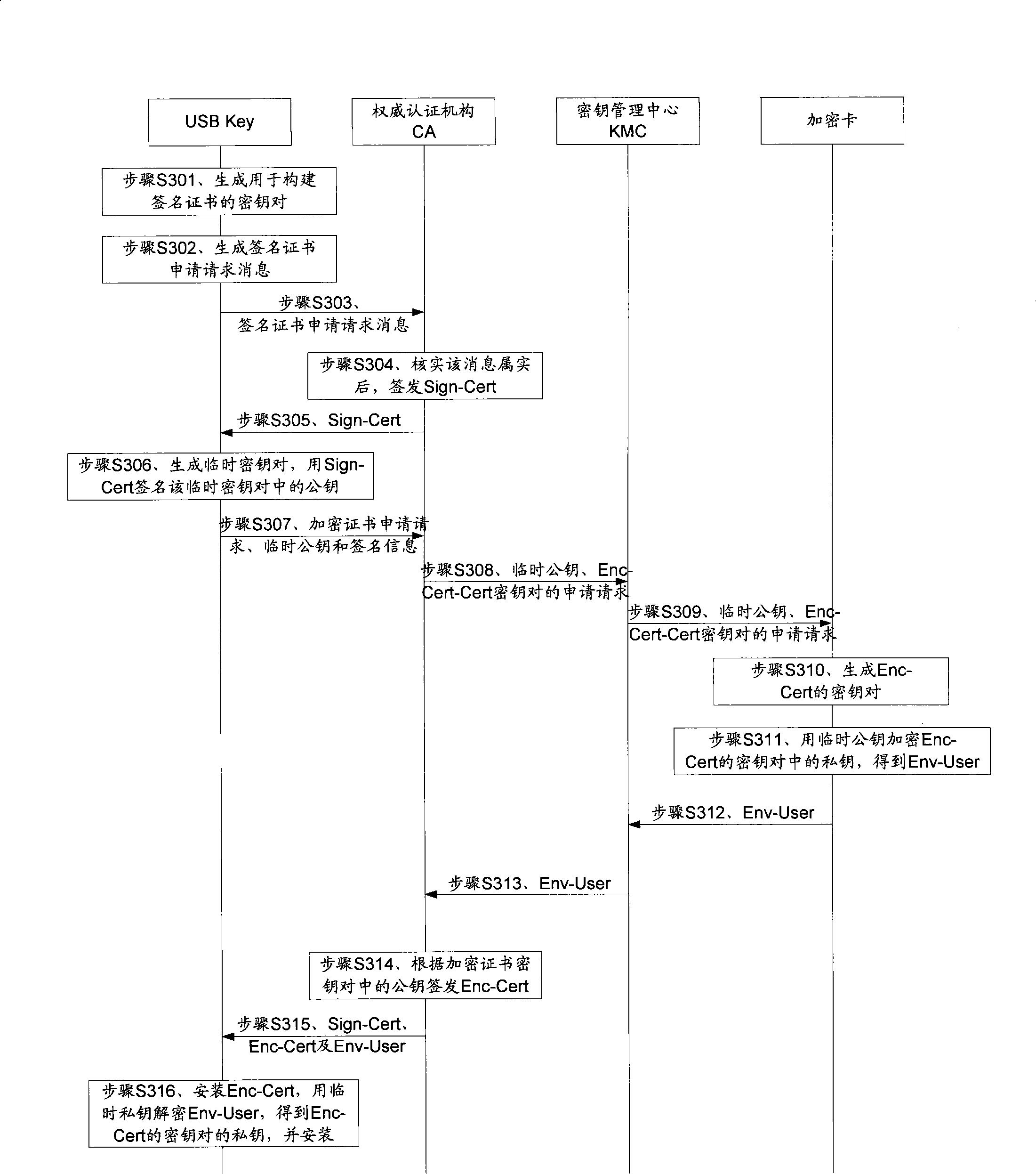
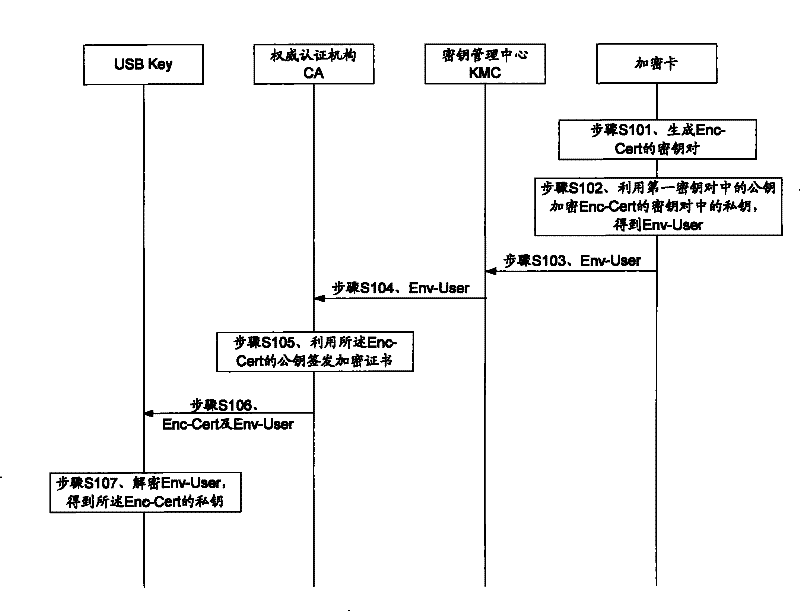
Customer digital certificate private key management method and system
ActiveCN101483518AEnsure safetyGuaranteed installation safetyKey distribution for secure communicationPublic key for secure communicationTransfer procedureUSB
An embodiment of the invention discloses a method for managing private key of user digital certificate, wherein the method comprises the following steps: generating the key pair of ciphered certificate; ciphering the private key in the key pair of ciphered certificate by the ciphering card with the common key in the preset key pair for obtaining digital envelop; authorizing the enciphered certificate by CA, and providing the enciphered certificate and digital envelop to the USB Key of user end; and deciphering the digital envelope according to the private key in the preset key pair for obtaining the private key of ciphered certificate. The embodiment of the invention simultaneously discloses a system for realizing the method. The embodiment of the invention ensures the security of private key of ciphered key in the transmission process. The embodiment of the invention also use KMC common key and KMC administrator common key for enciphering and backing up the private key of ciphered certificate, furthermore backs up the KMC private key and KMC administrator private key, and ensures the backup security and recoverability of private key of enciphered certificate.
Owner:北京天诚安信科技有限公司
Switch clock synchronization controller and control method for time-triggered network
ActiveCN107147465ARestore the truthSolve the lag problem of clock synchronizationTime-division multiplexThree levelMachine control
The invention discloses a switch clock synchronization controller and a control method for a time-triggered network. The switch clock synchronization controller comprises a curing module used for restoring a PCF frame sending sequence, a compression module used for calculating an SM clock deviation average value, an optimal compression point selection module, a local clock module used for correcting a local clock and generating a new PCF frame, a cluster detection module used for detecting a network state and a state machine control module used for coordinating the work of the modules. The curing module imports a transparent clock for identifying the transmission delay and a maximum transmission delay for restoring the sending sequence and moments of the PCF frames for solving the problem of lagged clock synchronization; the compression module adopts a hardware mode to realize a three-level streamline dynamic compression algorithm for improving the calculation precision and efficiency of clock synchronization; and a compression point having the largest member number and closest to a receiving window end moment is used as the optimal compression point to ensure that all nodes in a synchronization state in the network can be detected.
Owner:XIAN MICROELECTRONICS TECH INST
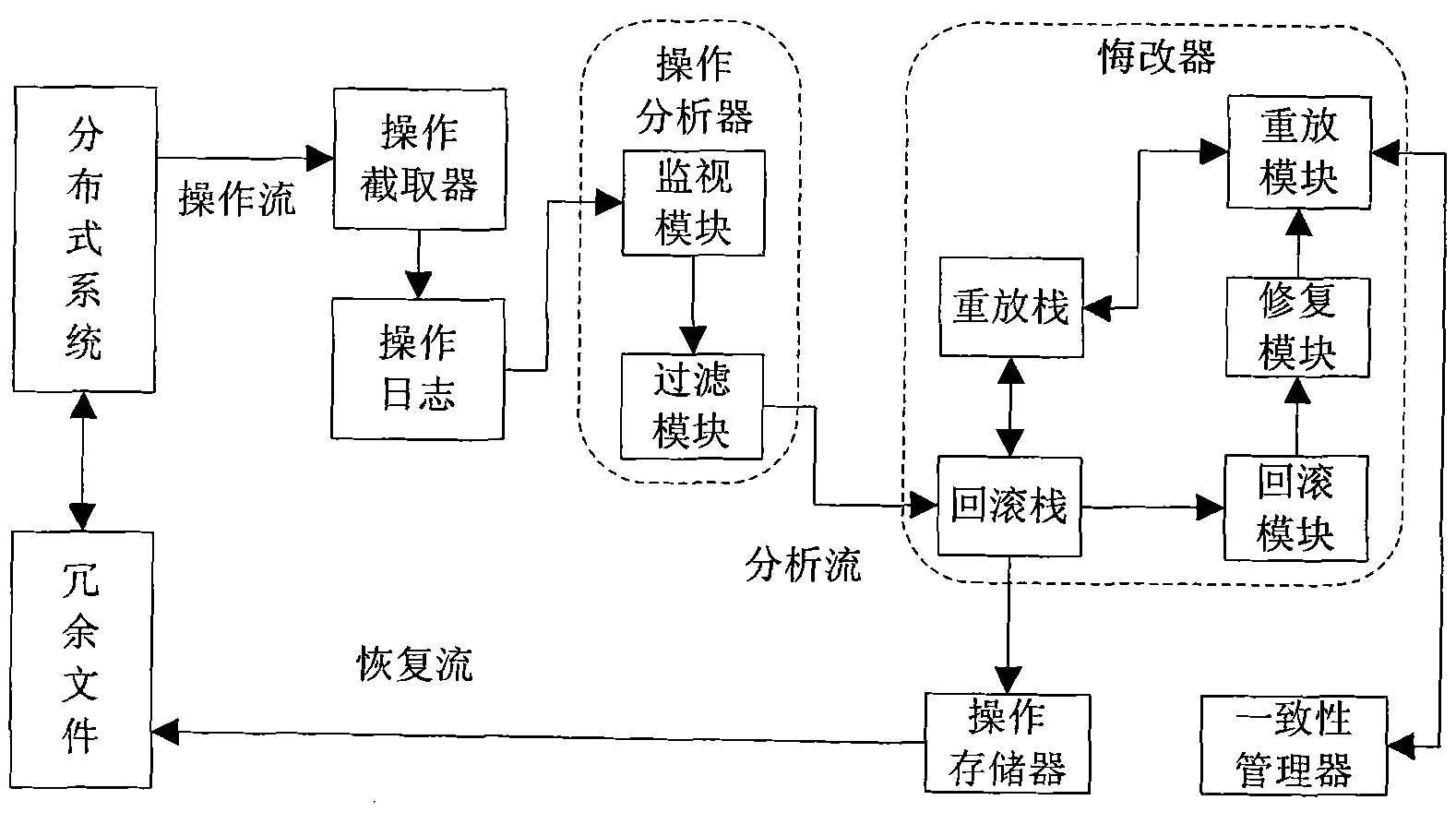
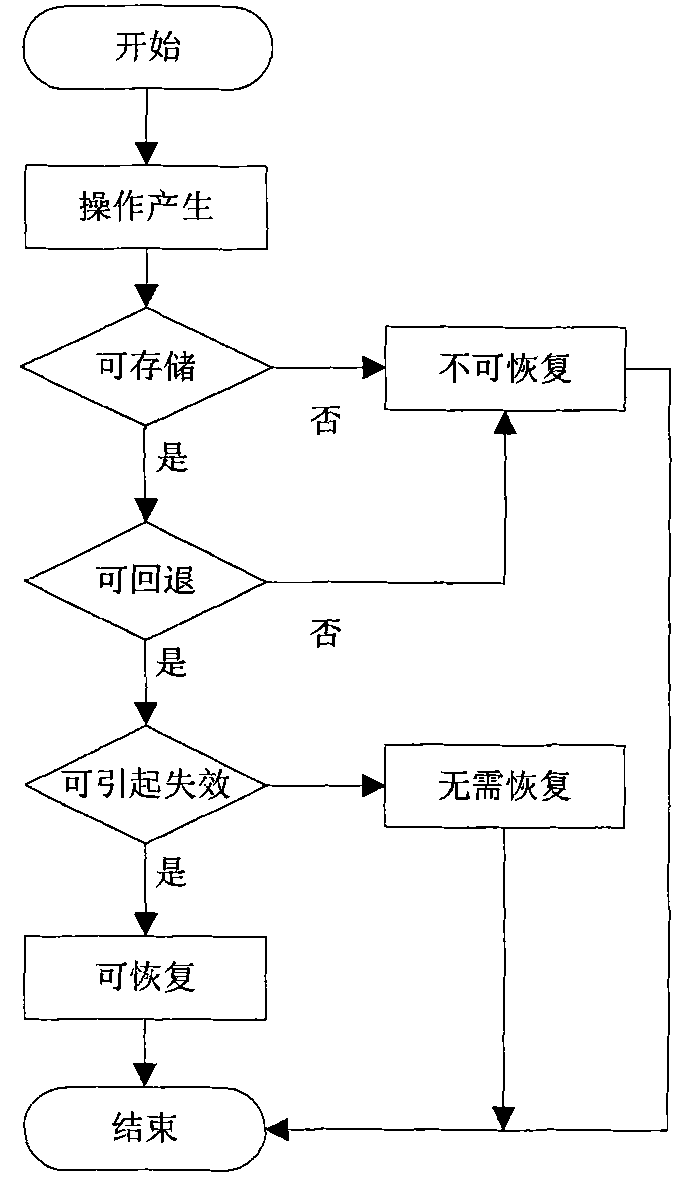
Operation intercept based repentance method of distributed critical task system
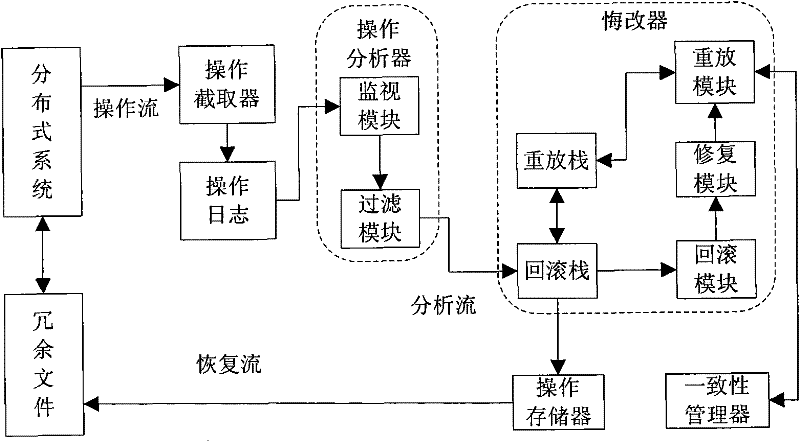
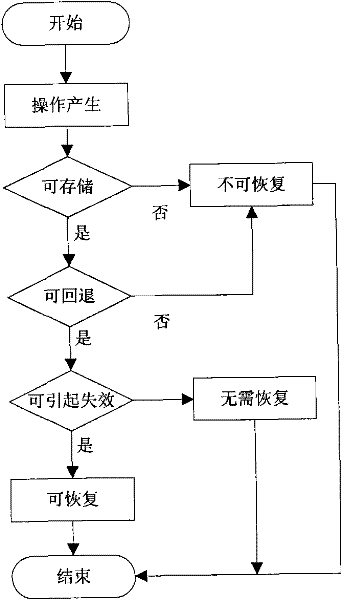
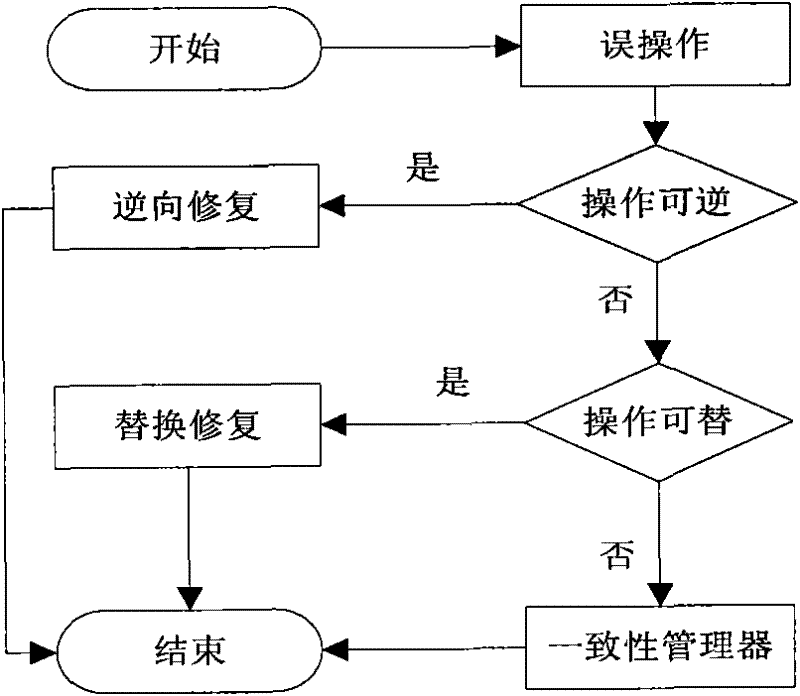
InactiveCN101916215AGuaranteed recoverabilityResolve inconsistenciesRedundant operation error correctionData informationMission critical systems
The invention provides an operation intercept based repentance method of a distributed critical task system, comprising the following steps of: firstly carrying out redundancy backup on important files of the system to ensure the recoverability of data information; secondly intercepting the operation information of the system by an operation intercepter in real time and writing into an operation log; and analyzing captured operation records by an operation analyzer and writing unrecoverable operation or operation which does not need to be recovered into redundant files by an operation storage and processing the operation which needs to be recovered by a repenter. When the system is faulty, the repenter carries out repentance recovery on the system through three continuous steps of operation rollback, operation restoration, operation resetting and solves the problem of inconsistency possibly generated in the repenting process through a consistency manager according to a graded compensation strategy.
Owner:HARBIN ENG UNIV
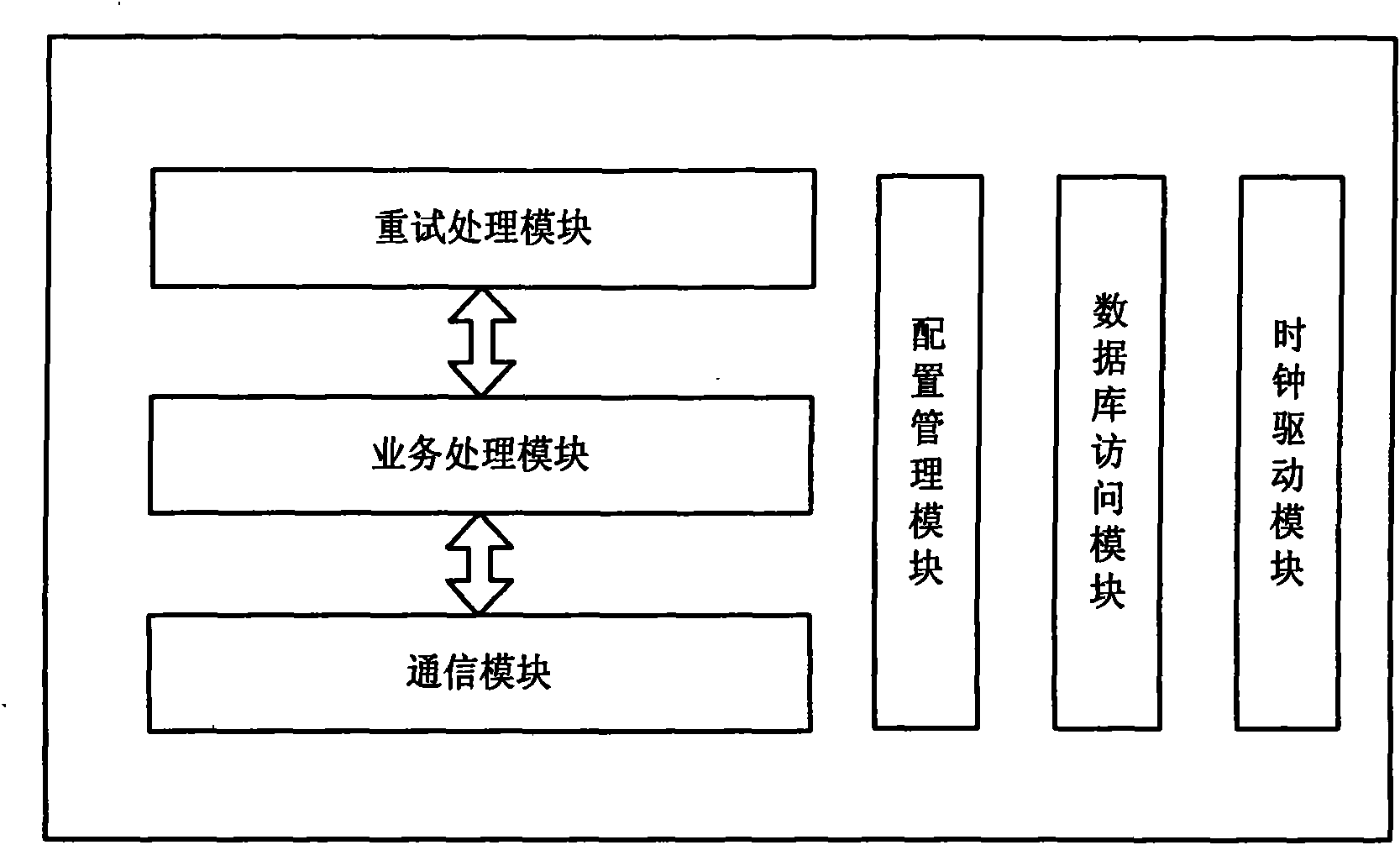
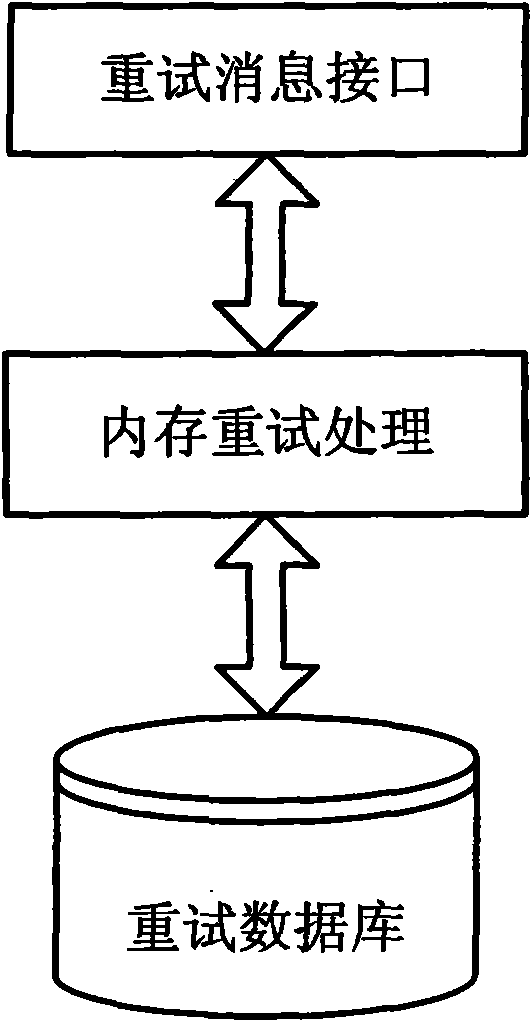
System and method for short message retry based on parallel queues
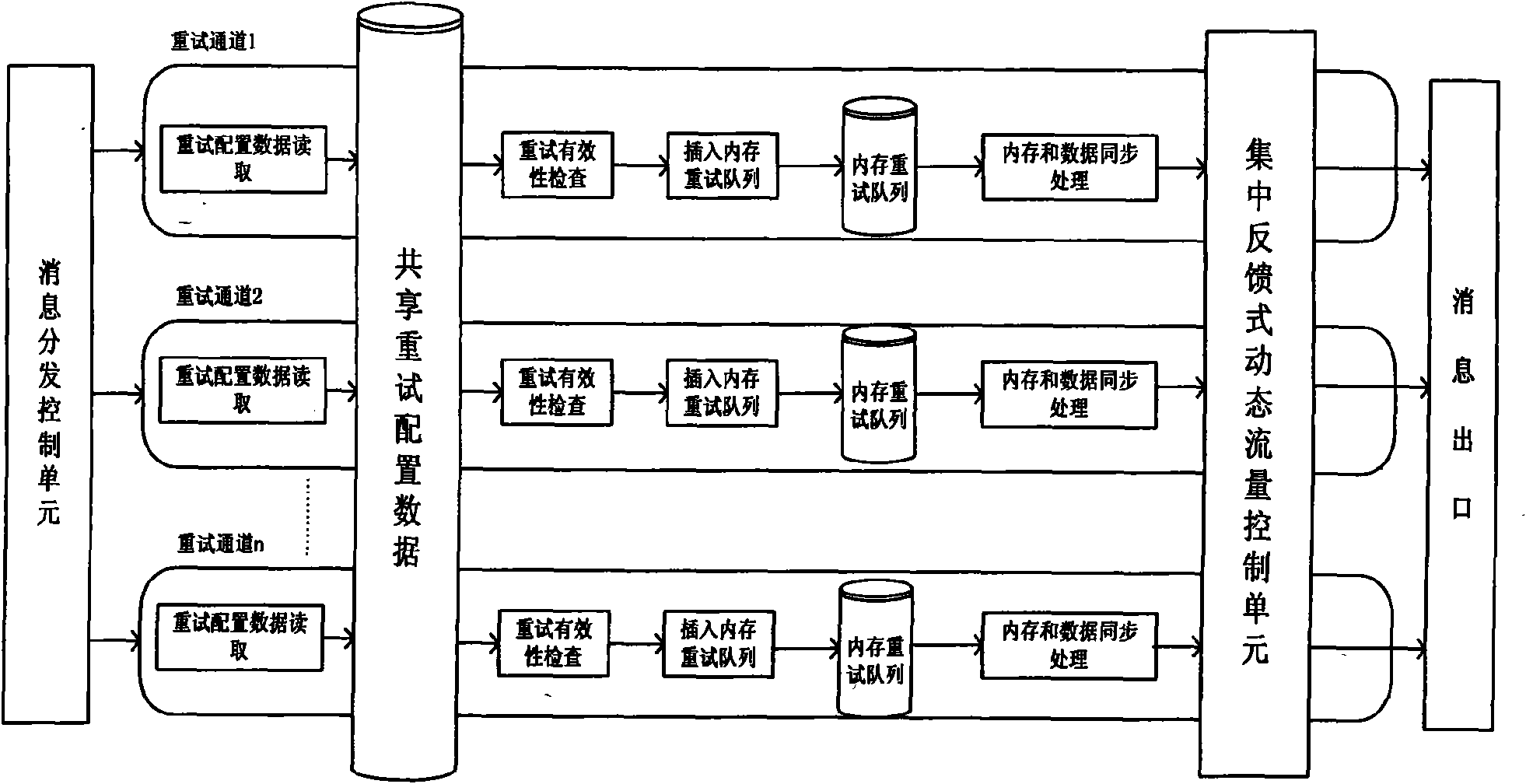
InactiveCN101616365AImprove retry handling capabilitiesReduce system costMessaging/mailboxes/announcementsData switching networksTraffic volumeTraffic capacity
The invention discloses a system and a method for short message retry based on parallel queues. The system comprises a retry processing module, a service processing module and a communication module; the retry processing module comprises a message distribution control unit, a plurality of retry channels, a shared retry configuration data unit, a centralized feedback dynamic flow control unit and a message export unit, wherein the message distribution control unit is used for receiving a message which needs retry, and distributing a retry message to the plurality of retry channels according toa distribution strategy; each retry channel forms a processing logical machine for integrally processing the retry message; the shared retry configuration data unit is used for configuring basic parameters of parallel retry processing; the centralized feedback dynamic flow control unit is used for controlling retry flow of a current target network element; and the message export unit sends the retry message to the communication module and then to the target network element. By adopting the flow of the current system to trigger the flow control, the system and the method remarkably improve theretry processing capacity of a short message gateway, effectively reduce the cost of the system, and realize efficient short message retry function.
Owner:ZTE CORP
Credit link automatic tracking platform and method thereof
PendingCN111782620AGuarantee disaster tolerance and recoverabilityAvoid performance impactDatabase updatingResource allocationInformation systemTime information
The invention discloses a credit link automatic tracking platform and a method thereof. The platform comprises a client, a log access layer, a log center, a log processing layer and a log storage layer, wherein the log information comprises login user information, user operation log information (addition / deletion / modification / login), time information, a system log and a database Bin log; the wholeoperation action and operation range of the user are collected, the complete information is calculated and processed in a distributed environment through a calculation model, and the platform can completely describe the movement track of the whole user; in a link system, a user is used as a search unit, all information data used by the user on a platform are searched rapidly and efficiently through a search engine and indexes according to a certain time range, and then a credit link track of the user on the platform in the period can be completely described through a platform track fixed-point algorithm and a tool.
Owner:庞茂林
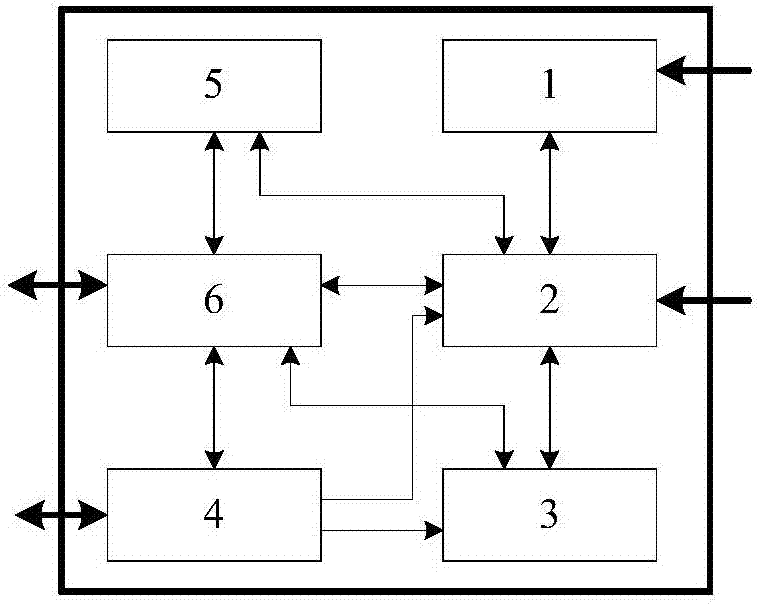
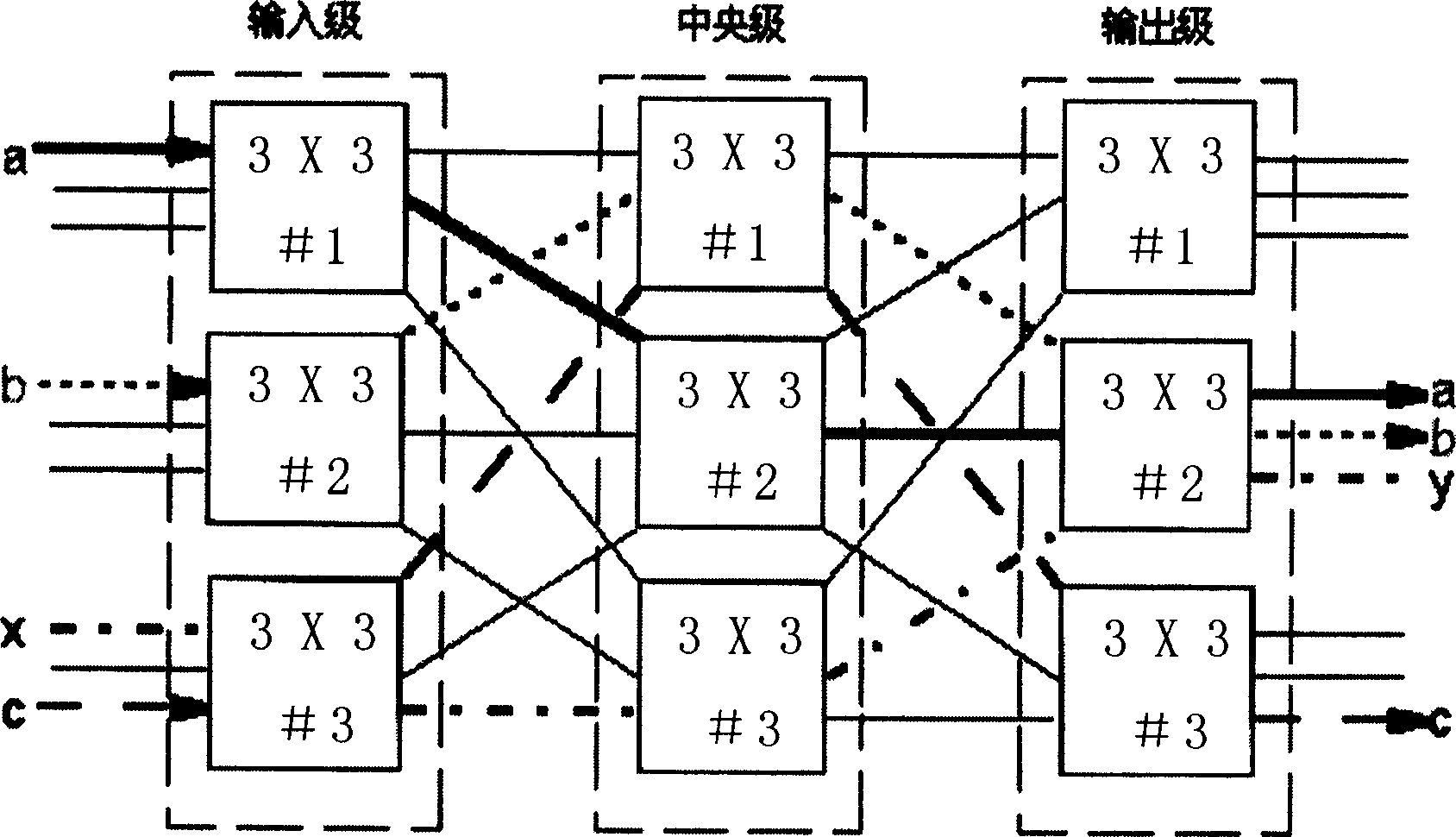
Method and device of realizing synchronous switchover of CLDS crosslink matrix
InactiveCN1602078ASimple structureRealize synchronous switching functionTime-division multiplexing selectionSynchronising arrangementCross connectionControl line
The method includes following steps: after receiving request for changing cross connections, configuration controller calculates request so as to obtain new CLOS matrix; configuration controller issues new CLOS matrix to group of cross node; waiting for ready signal returned from all cross nodes in group of cross node; after ready for preparing switching, each cross node returns ready signal to configuration controller; after all ready signals are returned, configuration controller sends out synchronous switching signal to inform each cross node to carry out switching operation for the cross matrix; after receiving 'synchronous switching signal' from configuration controller, each synchronous node switches to new matrix instantly. Configuration controller is composed of communication circuit, control line and state line.
Owner:HUAWEI TECH CO LTD
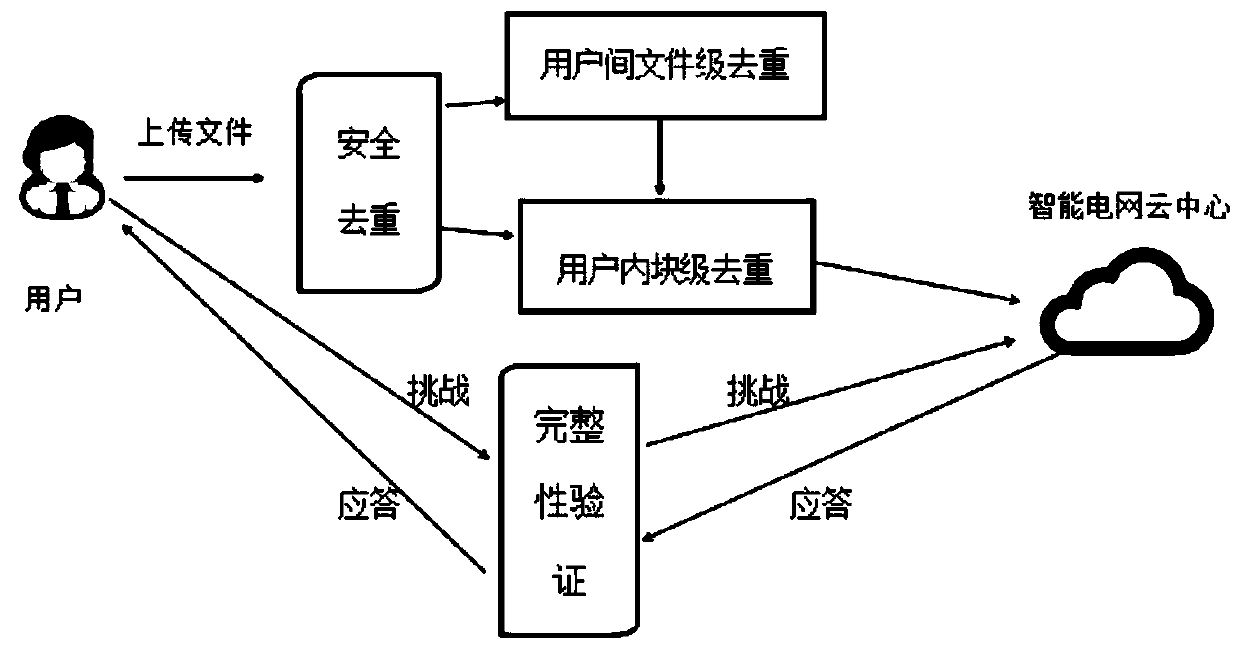
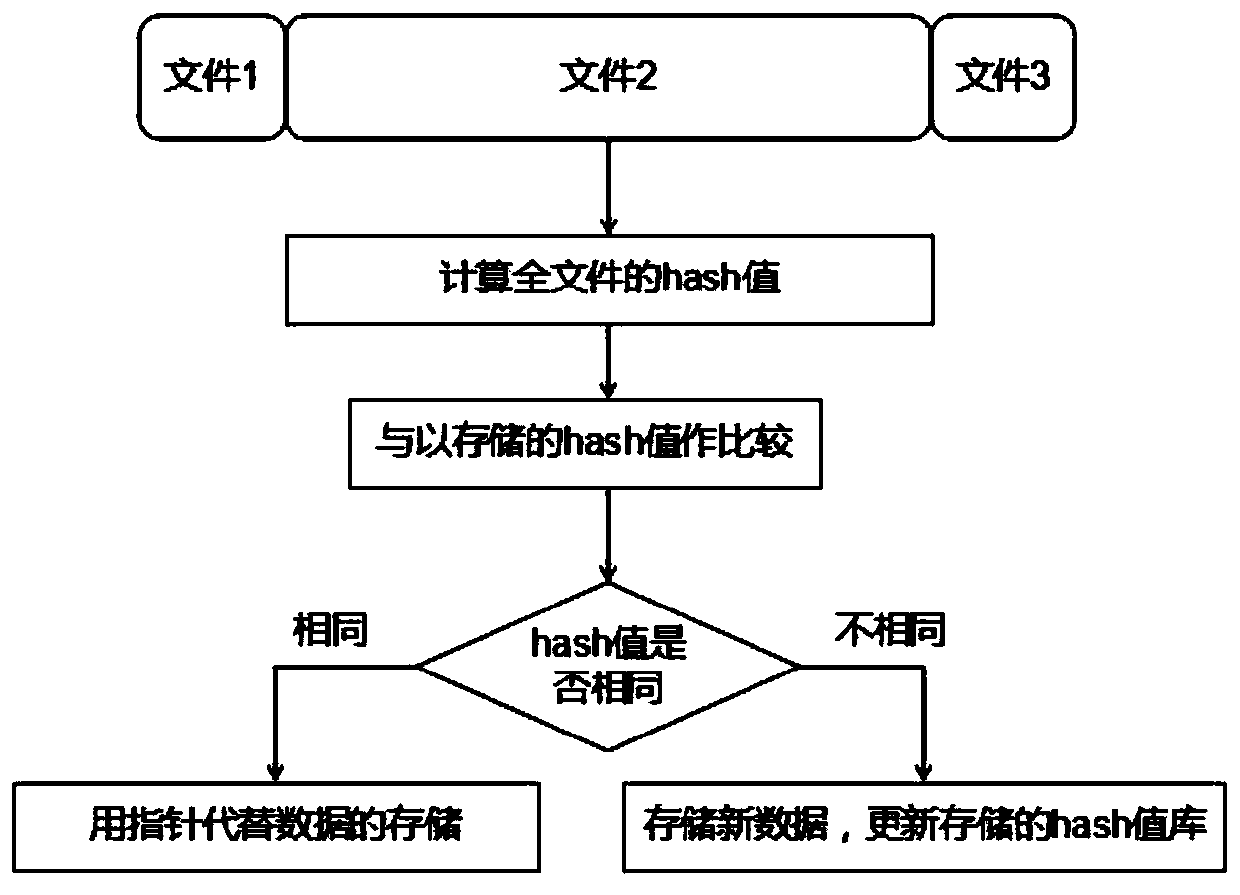
Data integrity verification method capable of safely removing duplication in cloud storage of smart power grid
PendingCN110968452APrivacy protectionEnsure safetyDigital data protectionFile access structuresData integrityUser privacy
The invention discloses a data integrity verification method capable of safely removing duplication in cloud storage of a smart power grid. The method comprises the following steps: firstly, performing erasure code encoding on a file; calculating a mark of the erasure code encodingfile and uploading the fileto a cloud server; enabling the cloud server to adopt a file-level deduplication strategy to perform deduplication and storage on the file; for files without duplication, adopting a data block level deduplication strategy for deduplication in the storage process, enabling the cloud server to verify the file ownership of a user through a Bloom filter, enabling the user to verify the integrity of stored data through an S-PDP mechanism to restore damaged data through erasure codes. An erasure code mechanism, a two-leveldeduplication strategy, the Bloom filter and the S-PDP mechanism are combined together, redundant power data can be effectively eliminated, the storage space and bandwidth are saved, ownership certification can be supported, data restorability is ensured, user privacy is protected, and therefore the safety and integrity of cloud storage data of the smart power grid are ensured.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
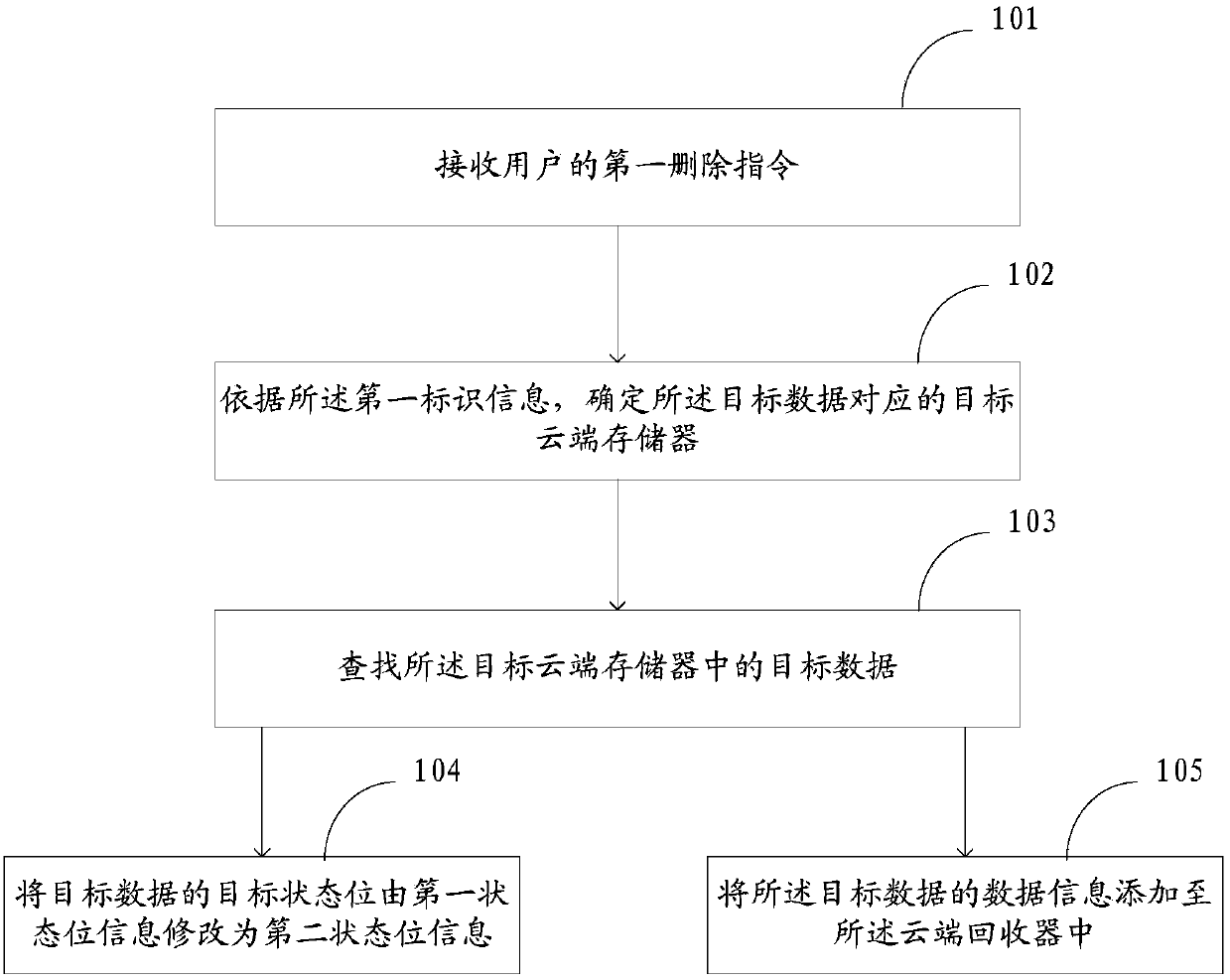
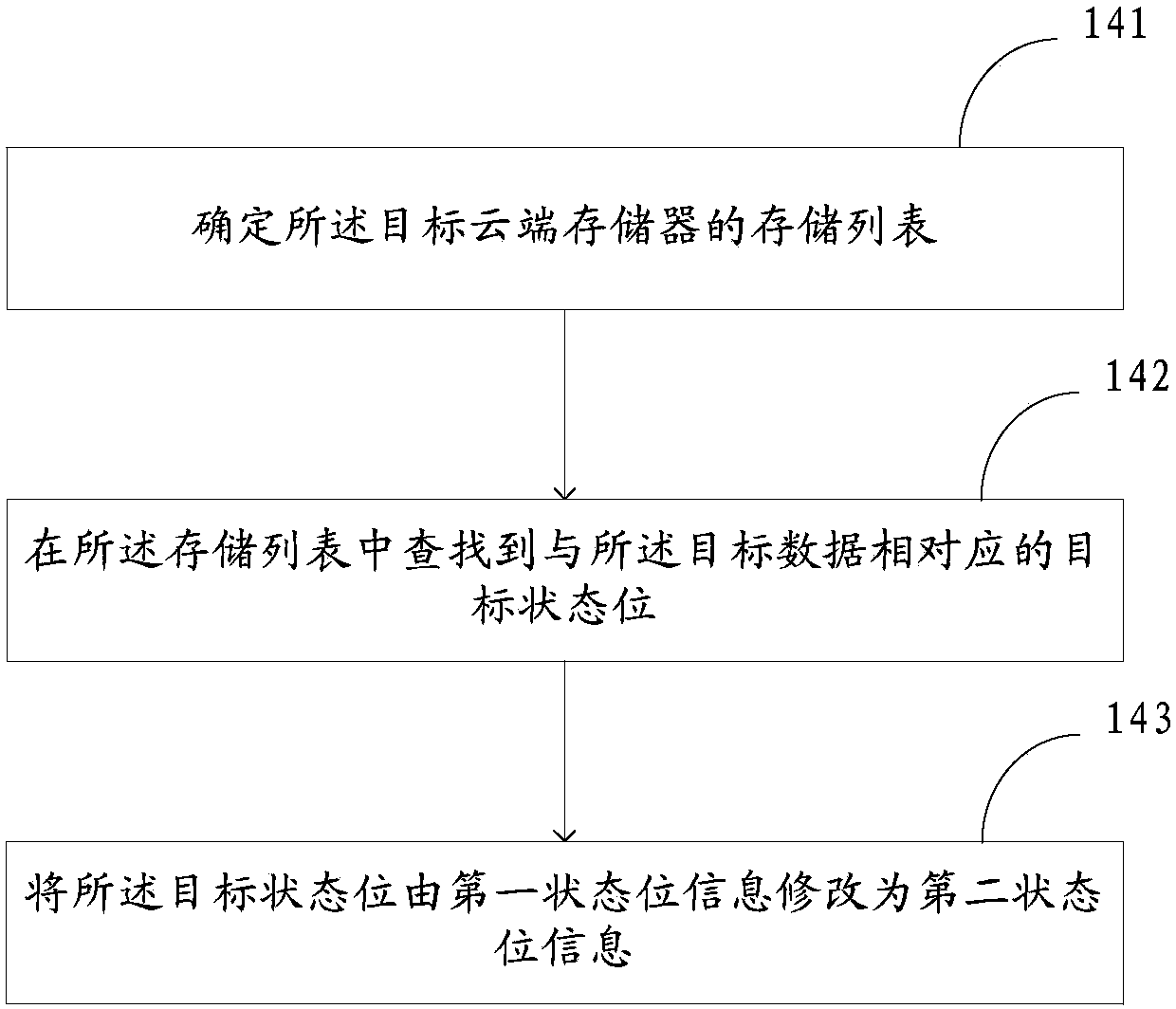
Data processing method and device based on cloud storage system
InactiveCN103747103AGuaranteed recoverabilityGood application effectInput/output to record carriersTransmissionData informationCloud storage system
The invention discloses a data processing method and a data processing device based on a cloud storage system. The cloud storage system at least comprises a cloud recover and a plurality of cloud storages. The method comprises the steps of receiving a first deleting instruction of a user, wherein the first deleting instruction comprises first identification information of target data; determining a target cloud storage corresponding to the target data according to the first identification information; searching target data in the target cloud storage; modifying a target status bit of the target data in the target cloud storage into second status bit information from first status bit information, and adding data information in the target data to the cloud recover. According to the embodiment of the invention, through the mode of modifying the status bit of the target data, target data in the cloud storage which are seemingly deleted by a user can still be recovered through the cloud recover in the subsequent operation, so that recoverability of data is ensured, the applicability of the data is improved, and further the user experience is improved.
Owner:沈文策
Method and system for realizing two paths of voice communication based on webpage
InactiveCN102130921AGuaranteed clarityReduce occupancyInterconnection arrangementsTransmissionVoice communicationMedia server
The invention discloses a method for realizing two paths of voice communication based on a webpage. The method comprises the following steps: a streaming media server authenticates the rights of received audio information commands sent by two communication parties; and after the authentication is passed, the two communication parties upload audio streams to the streaming media server respectively and communicate with each other through two paths established through the two communication parties. The invention also discloses a system for realizing two paths of voice communication based on a webpage. By adopting the method and the system, two paths of safe voice communication can be realized without downloading any software.
Owner:SUZHOU CODYY NETWORK SCI & TECH
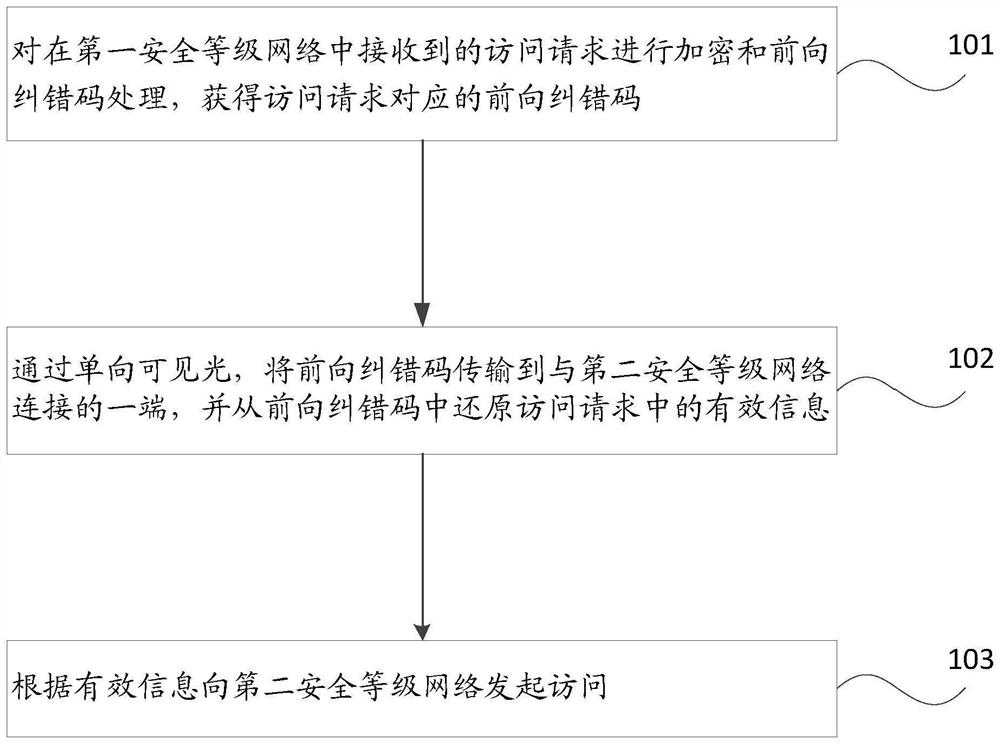
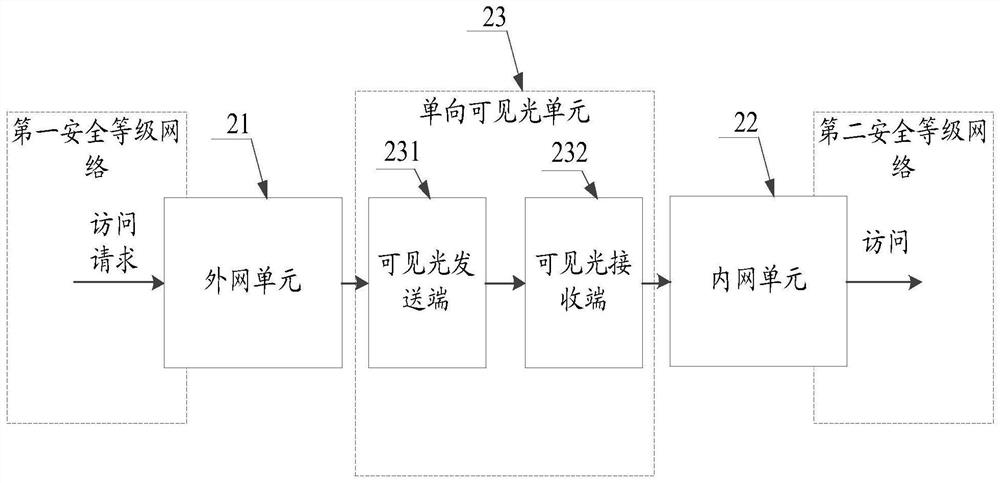
Visible light-based data transmission method and system, and storage medium
PendingCN114422173AGuaranteed absolute one-way transmissionGuaranteed recoverabilityUser identity/authority verificationClose-range type systemsSecure transmissionEngineering
The invention relates to the technical field of information security, provides a data transmission method and system based on visible light and a storage medium, and is used for solving the technical problem that high-security transmission of data between networks with different security levels cannot be realized in an absolute physical unidirectional isolation network environment in the prior art. The method comprises the following steps: performing encryption and forward error correction code processing on an access request received in a first security level network to obtain a forward error correction code corresponding to the access request; transmitting the forward error correction code to one end connected with the second security level network through one-way visible light, and restoring effective information in the access request from the forward error correction code; and initiating access to the second security level network according to the effective information.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Data degradation storage method and device
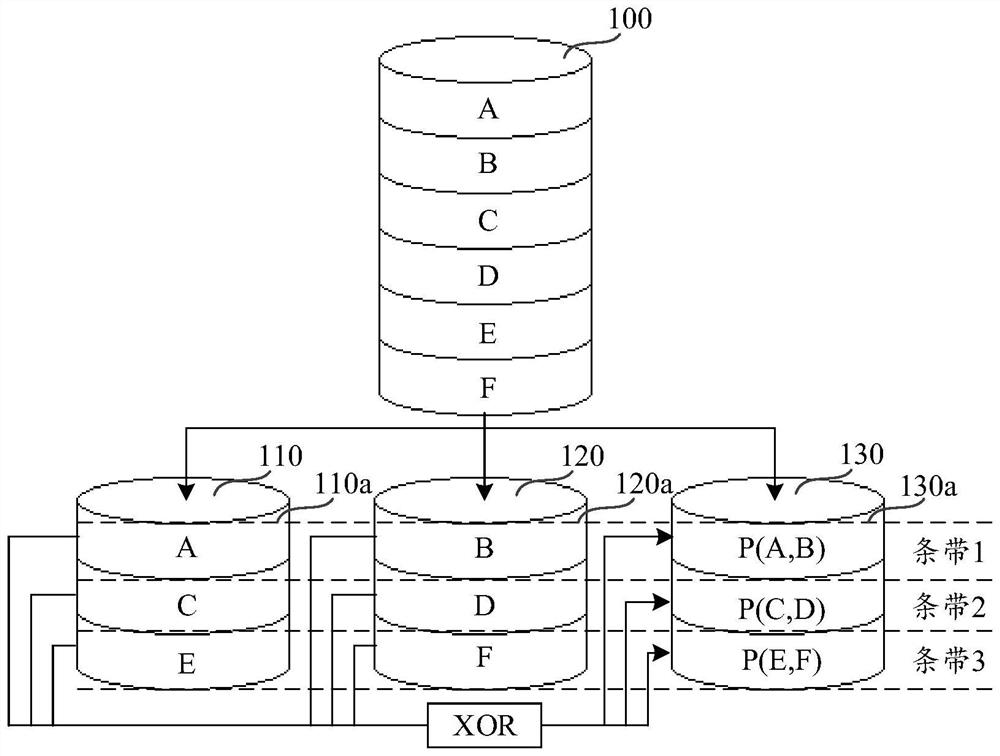
ActiveCN108932176AGuaranteed recoverabilitySolve the lossRedundant data error correctionRAIDData degradation
The embodiment of the invention discloses a data degradation storage method and device and belongs to the technical field of data storage. The method includes a step of obtaining data to be stored, detecting whether an online strip exists or not, and assigning an offline strip to the data if not, a step of reallocating data blocks and check blocks in online blocks of the offline strip if the number of the online blocks in the offline strip is larger than a sum of a preset number of check blocks in each strip and 1, wherein the number of the check blocks is the preset number of the check blocksin each strip, and a step of storing the data into the offline strip. In the prior art, a RAID in a degraded state only continues to distribute and store subsequently stored data and no longer calculates and stores verification data, and once a data block has reading and writing failures, all data stored in a disk are lost and unrecoverable, according to the method and the device, the above problem is solved, and an effect that the data stored by the RAID in the degraded state can be recovered is ensured.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Data backing-up and recovering method and system
ActiveCN100391291CGuaranteed recoverabilityImprove experienceRadio/inductive link selection arrangementsWireless communicationPersonalizationRestoration method
First, the method backs up data of device terminal to device management (DM) server. The said data includes individualization data of software program and device terminal. When data of device terminal are lost or in error, the method can restore the backed data to terminal. When software program at terminal is in error, the method can down load the backed software, as well as installs and configures software in order to recover data and software of device terminal. Storing terminal data in DM server, the invention guarantees recoverability of device terminal data especially private data.
Owner:HUAWEI TECH CO LTD
Operation intercept based repentance method of distributed critical task system
InactiveCN101916215BGuaranteed recoverabilityResolve inconsistenciesRedundant operation error correctionData informationMission critical systems
The invention provides an operation intercept based repentance method of a distributed critical task system, comprising the following steps of: firstly carrying out redundancy backup on important files of the system to ensure the recoverability of data information; secondly intercepting the operation information of the system by an operation intercepter in real time and writing into an operation log; and analyzing captured operation records by an operation analyzer and writing unrecoverable operation or operation which does not need to be recovered into redundant files by an operation storageand processing the operation which needs to be recovered by a repenter. When the system is faulty, the repenter carries out repentance recovery on the system through three continuous steps of operation rollback, operation restoration, operation resetting and solves the problem of inconsistency possibly generated in the repenting process through a consistency manager according to a graded compensation strategy.
Owner:HARBIN ENG UNIV
Method for storing and accessing file set under tree directory structure in database
InactiveCN101630322BSolve storage problemsIntegrity guaranteedSpecial data processing applicationsFile systemTree (data structure)
The invention relates to a method for storing and accessing file sets under a tree directory structure in a database, which can effectively solve the problems of overall storage and random access when file sets are stored in and extracted from a database system. The technical scheme is as follows: the overall storage extracts the directory structure, file data and attributes of the file sets froma file system to a local memory; organization structure object is serialized; data blocks are stored in the database; the random access recovers the directory structure of the file sets; corresponding files in the database are accessed according to user selection to read out the directory structure data blocks stored in the database; the directory structure data blocks are recovered to data structure objects by reverse serialization; and the information of the directory structure objects are shown to users in the forms of visible file node data structure, directory node data structure and file set directory structure objects. The invention solves the difficult technical problem that files are not supported to be directly stored and randomly accessed in the database in the prior art, thereby having enormous economic and social benefits.
Owner:THE PLA INFORMATION ENG UNIV
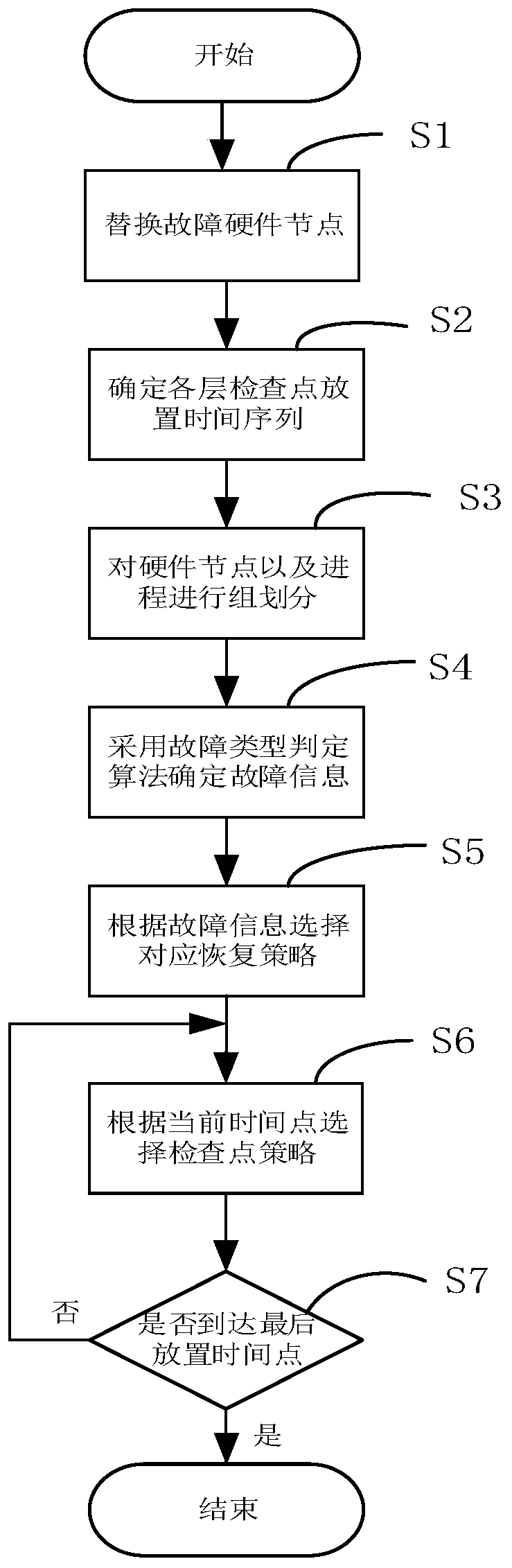
Optimization method of application-level multilayer check points based on super computer
ActiveCN110990197AGuaranteed recoverabilityAchieve isolationInterprogram communicationEnergy efficient computingPERQCheck point
The invention discloses a method for optimizing application-level multilayer check points based on a super computer, and belongs to the field of computer system structures and high-performance computing. The invention discloses an optimization method for application-level multilayer check points based on a super computer. The optimization method comprises the following steps: 1) replacing fault nodes; 2) determining a placement time sequence of each layer of check points; 3) performing group division on hardware nodes and processes running on the nodes; 4) determining the type of the fault occurring in the process group by adopting a fault type judgment algorithm; 5) for the fault type, adopting a corresponding recovery strategy in the process group; 6) when a corresponding time point in each layer of check point placement time sequence is reached, adopting a corresponding check point strategy to complete the storage of the intermediate state data; and (8) continuing to operate, if theoperation is not finished, returning to the step (6), otherwise, finishing the placement of the check points. The defect that the existing multi-layer check point optimization method depends on the hardware characteristics of the super computer, so that the super computer often does not have universality is overcome.
Owner:XI AN JIAOTONG UNIV
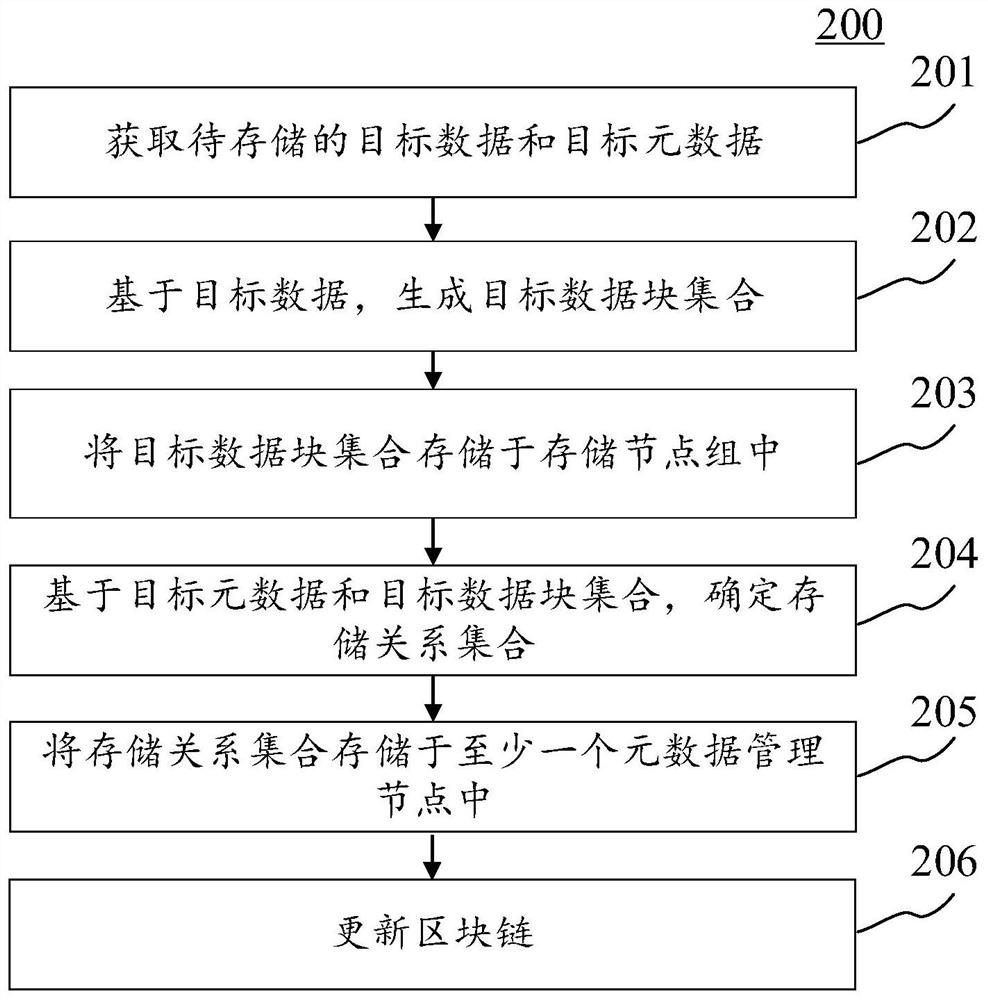
Distributed data dynamic storage method based on block chain and electronic equipment
InactiveCN112182112AMeet dynamic storage needsEnsure safetyDatabase updatingInput/output to record carriersMetadata managementEngineering
The embodiment of the invention discloses a distributed data dynamic storage method based on a block chain and electronic equipment. A specific embodiment of the method comprises the steps of obtaining to-be-stored target data and target metadata; generating a target data block set based on the target data; storing the target data block set in a storage node group; determining a storage relationship set based on the target metadata and the target data block set; storing the storage relationship set in at least one metadata management node; updating the block chain. According to the method, a target data block set is generated after a target data block to be stored is segmented and copied. The multi-copy target data block set ensures the security and restorability of the distributed storagedata. And the target data block set is stored in the storage node group, and the storage node with the highest current comprehensive performance index is dynamically selected for storage according tothe comprehensive performance index of each storage node in the storage node group, so that the storage efficiency and performance are improved.
Owner:宁波金狮科技有限公司
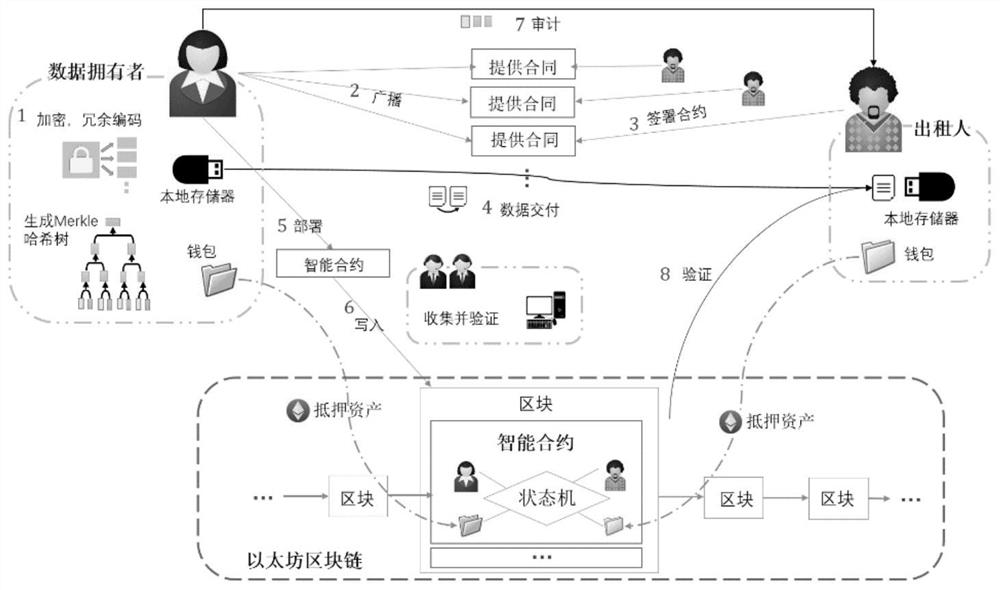
A distributed cloud storage system based on smart contracts
ActiveCN109245894BGuaranteed recoverabilityGuaranteed confidentialityUser identity/authority verificationConfidentialityCloud storage system
The invention discloses a distributed cloud storage system based on an intelligent contract, which belongs to the technical field of information security. The method of the present invention includes six modules including initialization, generating blocks, signing, storing, deploying contracts and auditing. Compared with the existing cloud storage solution, the present invention can prevent single-point storage failure; can guarantee the confidentiality, availability and user control of outsourced data at a lower cost; can guarantee the anonymity of the identity of the data owner and lessor ; It can ensure that after the lessor stores the outsourced data according to the contract, the data owner cannot deny the storage service enjoyed, and it can also ensure that the mortgaged assets are automatically transferred to the lessor's account after each integrity audit.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
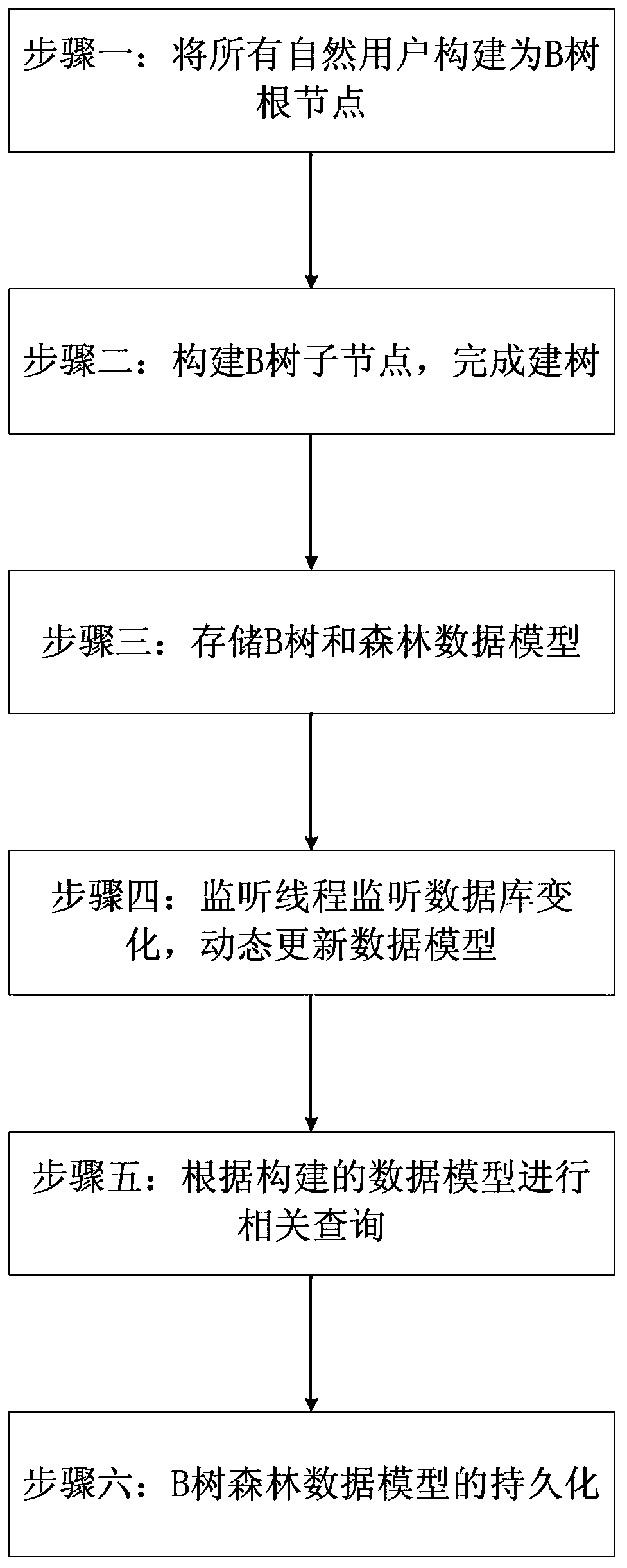
Invitation code promotion level query system based on B tree and forest
InactiveCN110851439AGuaranteed recoverabilityGuaranteed accuracySpecial data processing applicationsDatabase indexingData modelData science
The invention discloses an invitation code promotion level query system based on a B tree and a forest. The method comprises the following specific steps: 1, constructing all natural users as root nodes of a tree B in a forest, 2, constructing child nodes of the tree B and completing tree construction, 3, storing the B tree and a forest data model, 4, monitoring changes of database users by a monitoring thread and dynamically updating the tree and the forest, 5, carrying out related query according to the constructed B tree and forest model, and 6, performing persistence of the tree B and theforest data model. Through the query system, the farm game users are ranked, so that the problem of low efficiency in a massive data environment in hierarchical query is effectively solved, meanwhile,a model based on a B tree and a forest is provided, and tree nodes are self-defined, so that the system not only meets the requirement of improving the efficiency of common hierarchical query, but also can realize more conditional queries.
Owner:江苏一乙网络信息科技有限公司
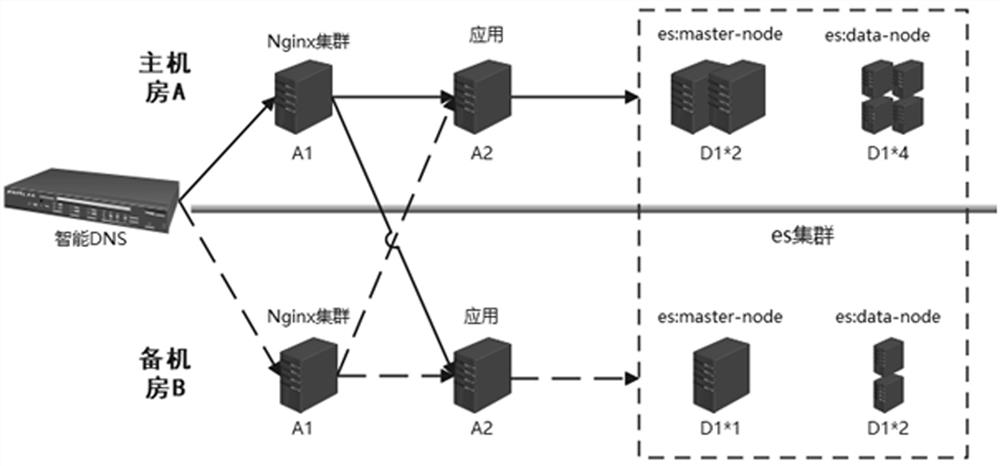
Es cluster double-computer-room high-availability deployment method
ActiveCN112905308AIntegrity guaranteedEnsure safetySoftware simulation/interpretation/emulationRedundant hardware error correctionComputer engineeringSystems engineering
The invention discloses an es cluster double-computer-room high-availability deployment method, belongs to the field of computer business application research and development, and solves the problem that cluster deployment in the prior art cannot ensure cluster data security, application availability and uninterrupted application service. Es clusters are installed and deployed in a main machine room A and a standby machine room B, after installation and deployment are completed, parameters are set that copies of the same fragment are distributed in the main machine room A and the standby machine room B respectively, and the fragment and the copies of the fragment are located in different areas; the Nginx cluster is installed and deployed in a primary machine room A and a standby machine room B, and routing configuration is carried out; and high-availability logic calling is realized based on the configured primary machine room A and standby machine room B. The invention is used for realizing the es cluster double-computer-room deployment.
Owner:武汉众邦银行股份有限公司
Truffle lagoon recovery and tree inoculation method
InactiveCN108713448AGuaranteed recoverabilityCultivating equipmentsMushroom cultivationSlurryInoculation methods
The invention relates to the field of truffle artificial cultivation, and discloses a truffle lagoon recovery and tree inoculation method. The method comprises the steps of selecting mature truffle, cleaning mature truffle and pulping the truffle into juice, adding purified water into the truffle juice, manufacturing the juice into a juice suitable for being sprayed, adopting a manual sprayer forspraying the truffle juice to a lagoon needing to be recovered and a region suitable for inoculation, performing timely earthing on the place obtained after the truffle juice is sprayed, insolation isavoided, the phenomenon that the concentration is diluted by rainwater is avoided, and the operation region is observed and detected periodically. The truffle lagoon obtained after picking is completed or cultivation fails can be recovered, growth picking and cultivation recovery of the truffle lagoon are ensured, meanwhile, the recovery means can be used for truffle cultivation and planting, andthe wide application is achieved in the field of artificial truffle cultivation and planting.
Owner:会东县生产力促进中心
Processing method and device for database
ActiveCN111367836ASolve the problem of low memory processing performanceGuaranteed recoverabilityMemory loss protectionEnergy efficient computingMemory processingIn-Memory Processing
The invention discloses a processing method and device for a database. The method comprises the steps of obtaining a first instruction used for recovering a database; obtaining first database entry identification information of a first page in a first storage medium according to the first instruction; according to the first database entry identification information, a first data storage structureused for managing the first storage medium is obtained, the first data storage structure comprises a second page, and the second page comprises second database entry identification information; and performing recovery processing on the database according to the first instruction and the first data storage structure. By adopting the method provided by the invention, the problem of low memory processing performance of the database in the nonvolatile memory in the prior art is solved.
Owner:ALIBABA GRP HLDG LTD
Customer digital certificate private key management method and system
ActiveCN101483518BEnsure safetyGuaranteed installation safetyKey distribution for secure communicationPublic key for secure communicationUSBKey management
An embodiment of the invention discloses a method for managing private key of user digital certificate, wherein the method comprises the following steps: generating the key pair of ciphered certificate; ciphering the private key in the key pair of ciphered certificate by the ciphering card with the common key in the preset key pair for obtaining digital envelop; authorizing the enciphered certificate by CA, and providing the enciphered certificate and digital envelop to the USB Key of user end; and deciphering the digital envelope according to the private key in the preset key pair for obtaining the private key of ciphered certificate. The embodiment of the invention simultaneously discloses a system for realizing the method. The embodiment of the invention ensures the security of privatekey of ciphered key in the transmission process. The embodiment of the invention also use KMC common key and KMC administrator common key for enciphering and backing up the private key of ciphered certificate, furthermore backs up the KMC private key and KMC administrator private key, and ensures the backup security and recoverability of private key of enciphered certificate.
Owner:北京天诚安信科技有限公司
Method, system, device and medium for data backup under private cloud architecture
ActiveCN111176904BReduce operation and maintenance costsReduce R&D costsRedundant operation error correctionData transportEngineering
The invention discloses a data backup method, system, device and storage medium under a private cloud architecture. The method includes the following steps: backing up the data of the management node every predetermined time, and backing up the data with the same name in chronological order Cyclic coverage; in response to the completion of the backup, start the backup receiving service; transfer the backup data to the local disk based on the backup receiving service, and transfer the backup data to the first and last reachable nodes in the private cloud based on the IP rule; and respond to When the management node fails, it sends data recovery requests to the local disk, the first and last reachable nodes, and receives backup data. The method, system, equipment and medium for data backup under the private cloud architecture proposed by the present invention transmit the backup data to the local, first and last reachable nodes respectively in the private cloud architecture to ensure data security to the greatest extent .
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
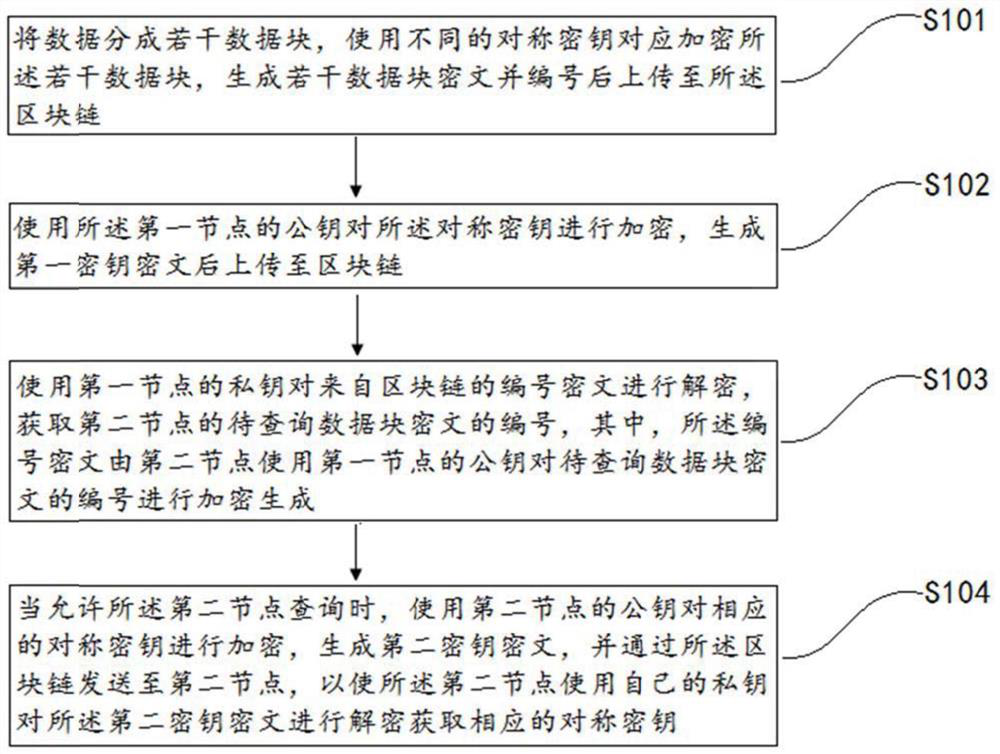
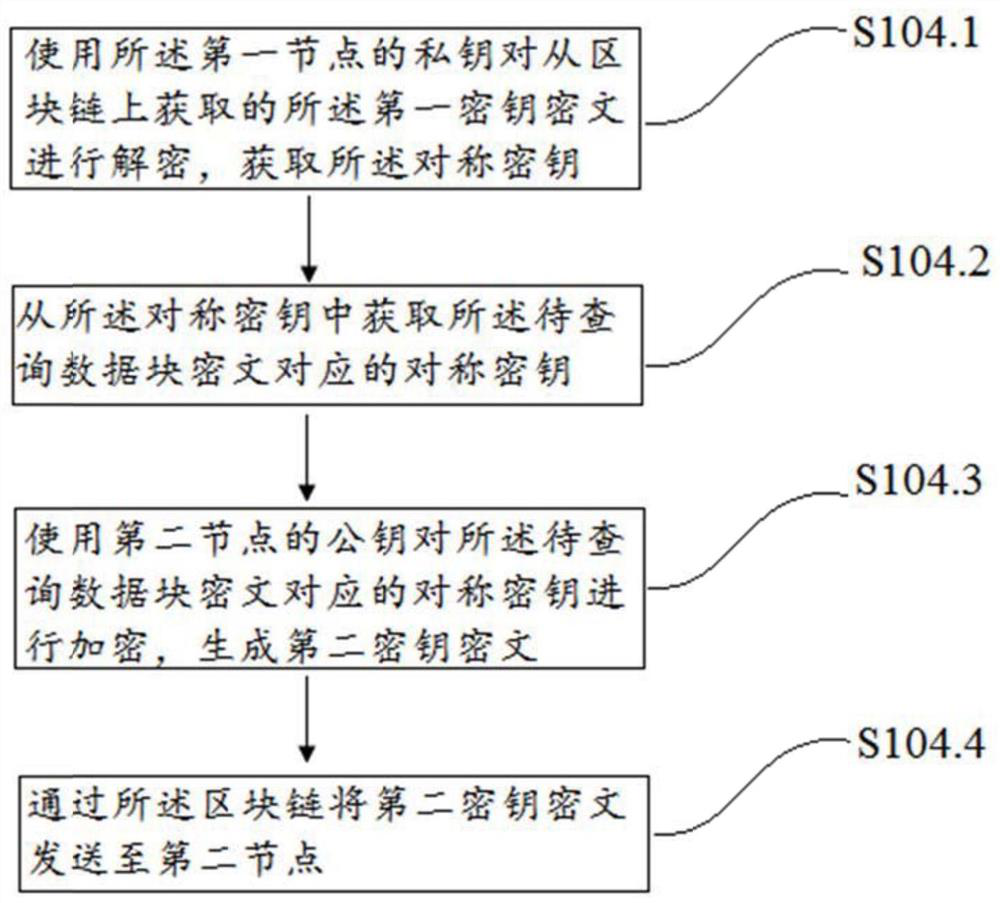
A data transmission method and device based on alliance chain
ActiveCN109587132BEnsure controllabilityControl access policyKey distribution for secure communicationMultiple keys/algorithms usageCiphertextEngineering
The invention discloses a data transmission method and device based on alliance chain, the method includes: dividing data into several data blocks, using different symmetric keys to encrypt data blocks correspondingly, generating and numbering ciphertexts of several data blocks and uploading them to the blocks chain; use the public key of the first node to encrypt the symmetric key, generate the first key ciphertext and upload it to the blockchain; use the private key of the first node to decrypt the numbered ciphertext from the blockchain, and obtain The number of the ciphertext of the data block to be queried by the second node; when the second node is allowed to query, use the public key of the second node to encrypt the corresponding symmetric key, generate the second key ciphertext, and pass the block chain Send to the second node, so that the second node uses its own private key to decrypt the second key ciphertext to obtain the corresponding symmetric key. The invention ensures the safety, controllability and recoverability of data, and simultaneously improves the efficiency of encryption and decryption.
Owner:NANJING SUNING SOFTWARE TECH CO LTD
IP (Internet Protocol) centralized dictation system and method
ActiveCN101834931BImprove reliabilityGuaranteed availabilityInterconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingInformation processingIp address
Owner:帝信科技股份有限公司
A construction method of a composite support structure positioning device
ActiveCN114319387BGuaranteed positioningGuaranteed StrengthExcavationsBulkheads/pilesArchitectural engineeringUltimate tensile strength
The invention discloses a positioning device and a construction method for a composite supporting structure, comprising a water-stop curtain located around the bottom of a foundation pit, a core pile connected in the water-stop curtain, and a hoisting assembly connected to the core pile; The bottom end of the core pile is higher than the bottom end of the water-stop curtain, and an anchor cable is also connected between the core pile and the surrounding soil; the water-stop curtain is located at the toe of the slope protection slope, and its inner side is close to the edge line of the toe of the slope. Through the three-dimensional modeling in the early stage, the invention is conducive to deepening and controlling the construction of the composite supporting structure and the positioning components, and the positioning components can effectively ensure the positioning of the core piles in the later stage; by inserting the core piles in the stirring piles, it is beneficial to strengthen the water-stop curtain, In addition, the length of the core pile is less than the height of the water-stop curtain, which saves the construction cost while ensuring the strength. The slope protection is used to connect the positioning components for the bearing system, and combined with the setting of the pile positioning frame and its connected sliding components, it is possible to carry out the construction of small sites. The hoisting positioning on the upper part further ensures the convenience and accuracy of construction.
Owner:BEIJING CONSTR ENG GRP CO LTD +1
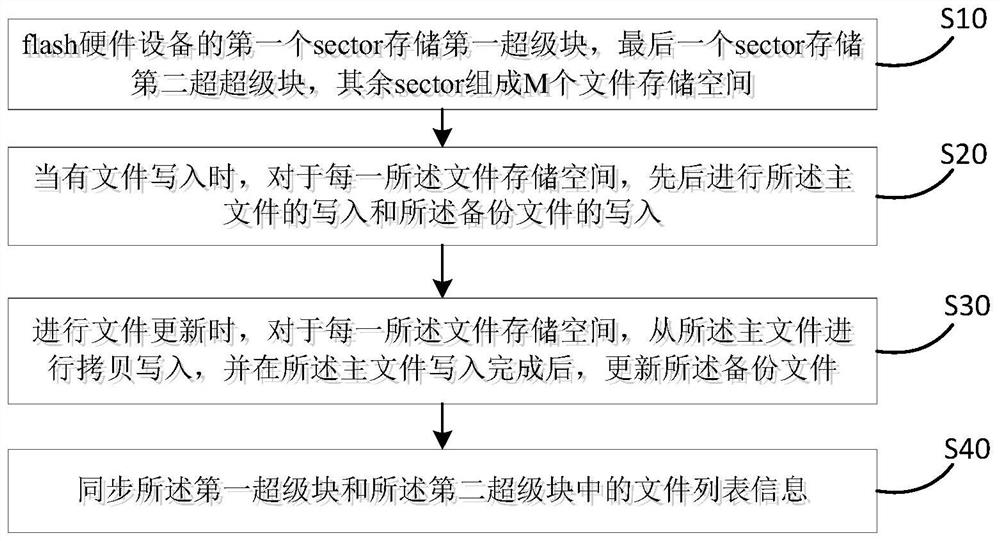
File system implementation method and device
PendingCN114238221AHigh speedImprove reliabilityFile access structuresRedundant data error correctionFile systemEngineering
The invention discloses a file system implementation method and device, and the method comprises the steps that a first section of flash hardware equipment stores a first super block, a last section stores a second super block, the rest sections form M file storage spaces, each file storage space comprises a main file and a backup file, the first super block stores the file list information of the main file, the second super block stores the file list information of the backup file, and the first super block stores the file list information of the backup file; the second super block stores file list information of backup files; when a file is written, writing of a main file and writing of a backup file are carried out in sequence for each file storage space; during file updating, copying and writing from the main file in each file storage space, and updating the backup file after the writing of the main file is completed; and synchronizing file list information in the first super block and the second super block. The whole file management speed and reliability can be improved, and the recoverability of the written file is ensured.
Owner:NANJING FENGDAO POWER TECH
Data degradation storage method and device
ActiveCN108932176BGuaranteed recoverabilitySolve the lossRedundant data error correctionRAIDCheck point
The embodiment of the invention discloses a data downgrade storage method and device, belonging to the technical field of data storage. The method includes: obtaining the data to be stored, detecting whether there is an online stripe, and if there is no online stripe, assigning an offline stripe to the data; if the number of online blocks in the offline stripe is greater than the preset number in each stripe If the number of verification blocks is increased by 1, the data blocks and verification blocks will be redistributed in the online blocks of the offline stripes, where the number of verification blocks is the preset verification points in each stripe. Number of blocks; store data in offline stripes. It solves the problem that the RAID in the degraded state in the prior art will only continue to disperse and store the subsequently stored data, and no longer calculate and store the verification data. Once a data block fails to read and write, all data stored on the disk will The problem of data loss and irrecoverability achieves the effect of ensuring the recoverability of the data stored in the degraded RAID.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com