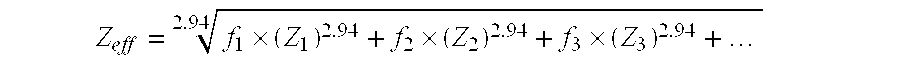Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37results about How to "Cost of energy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
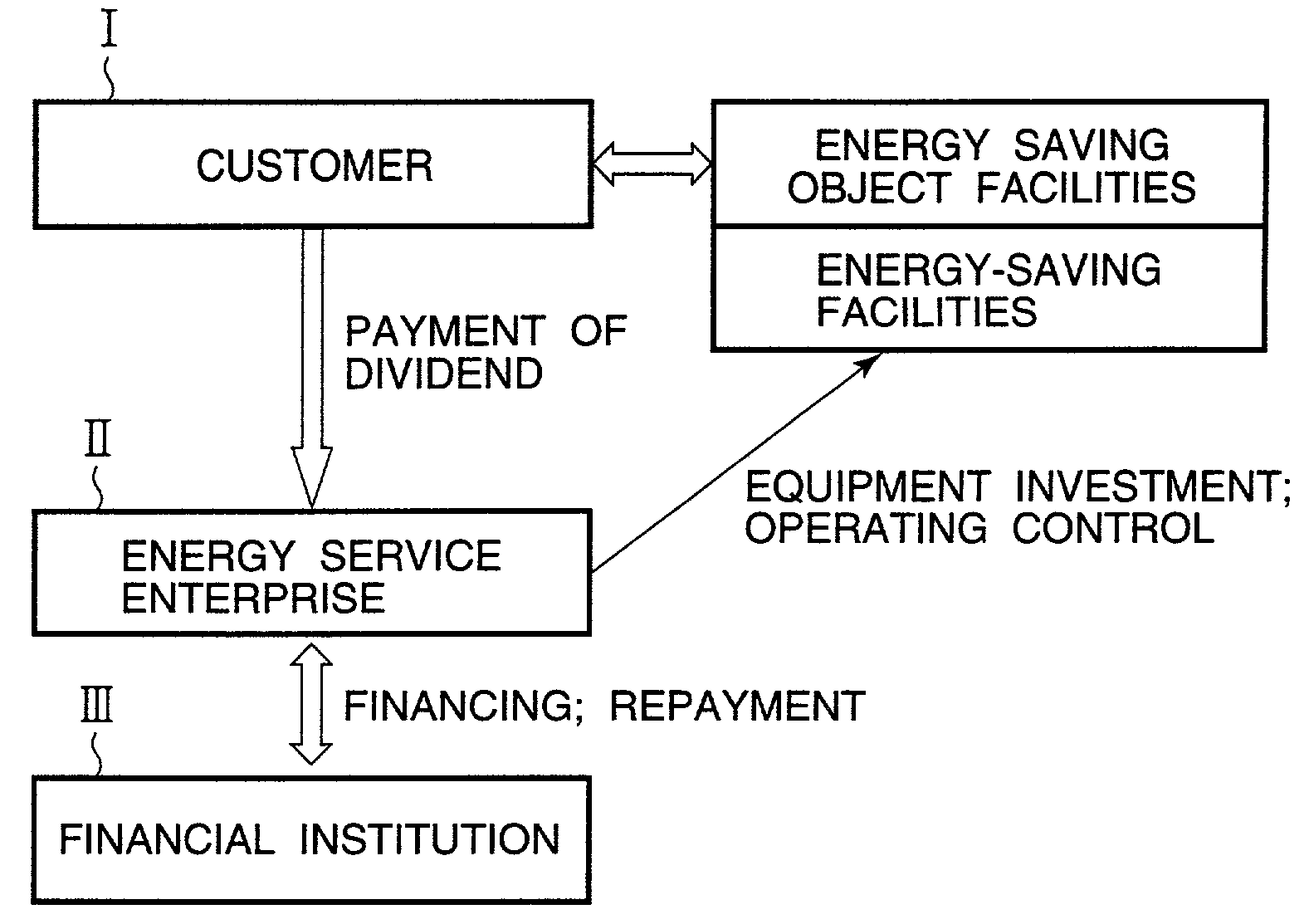
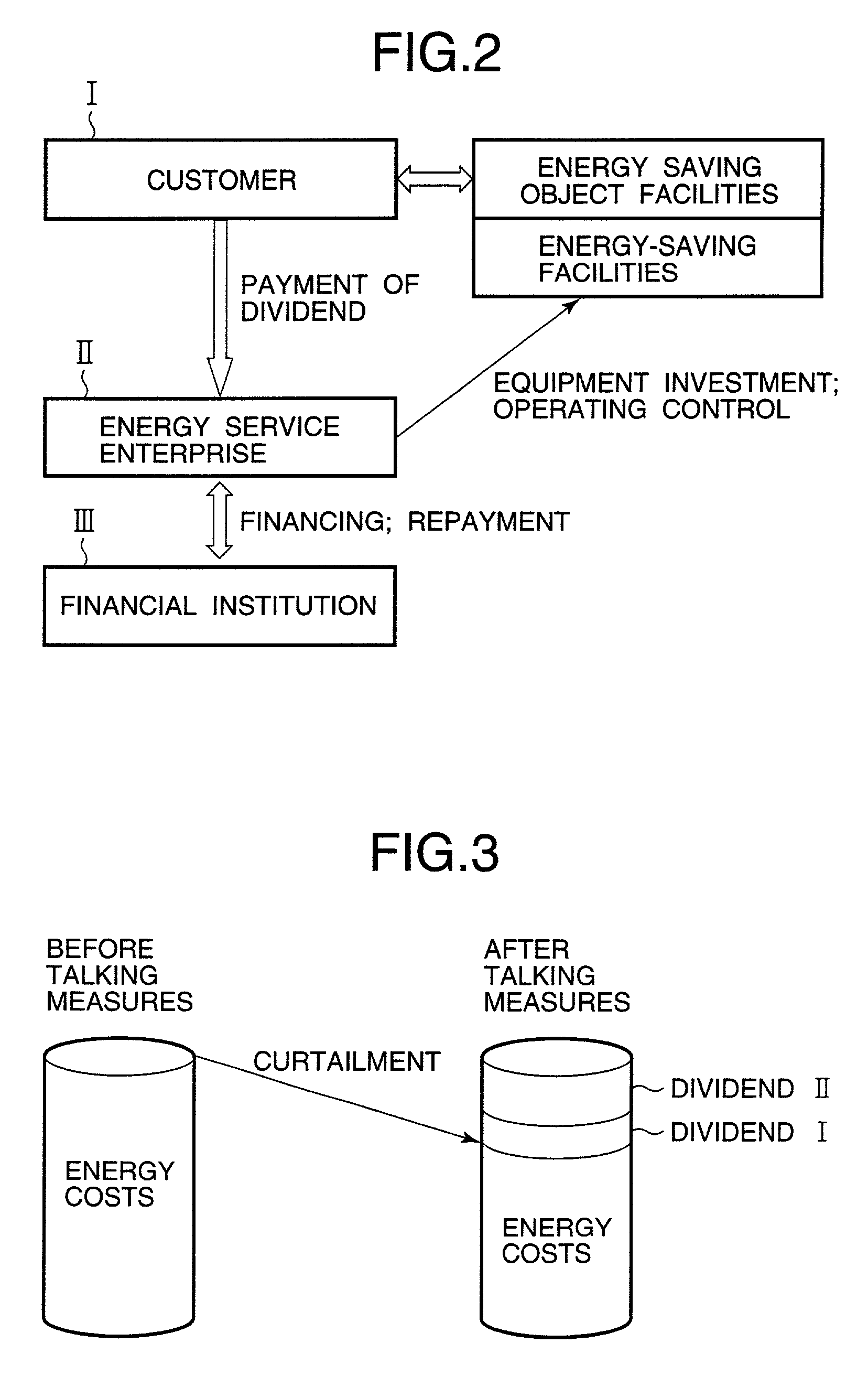
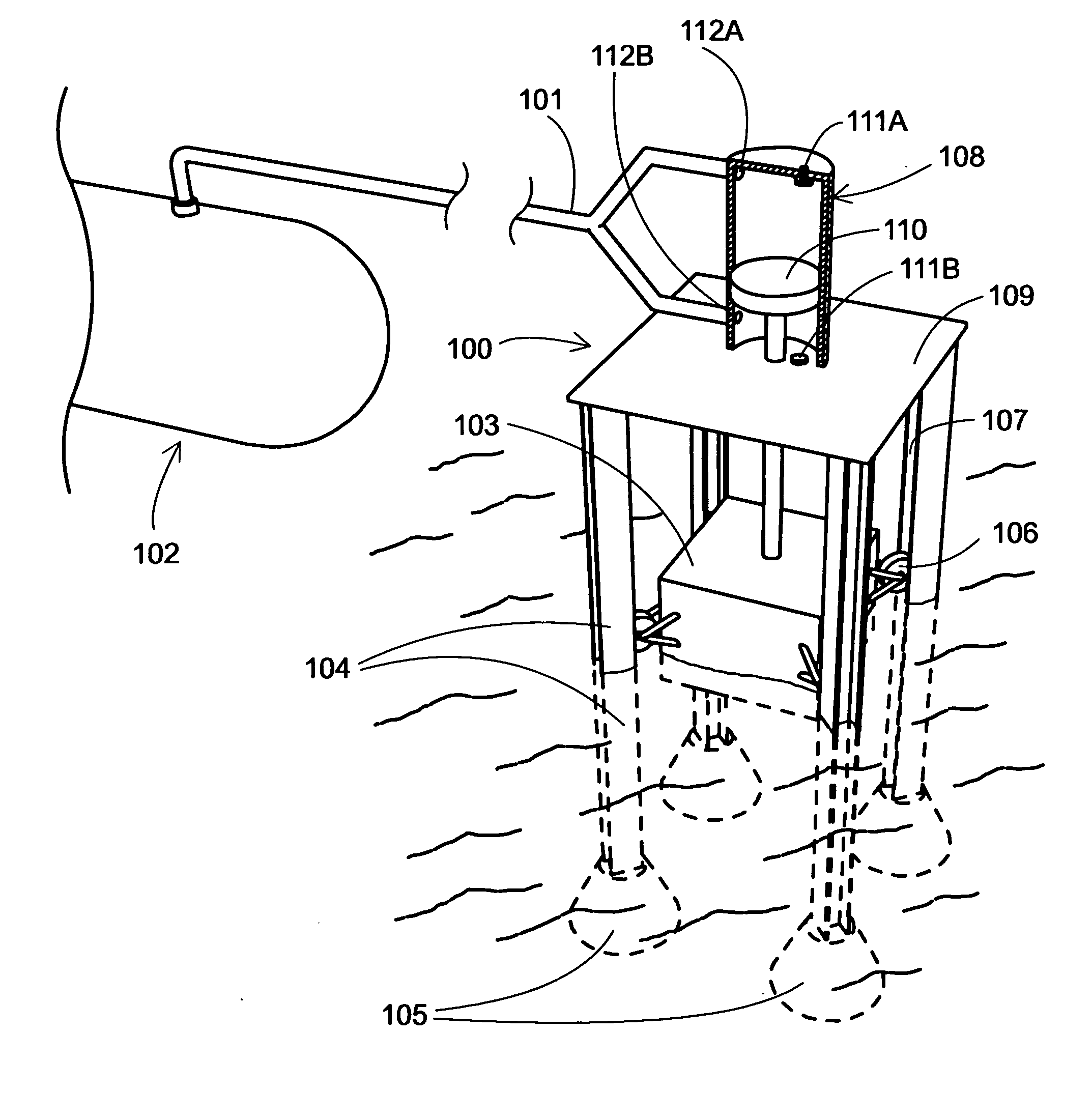
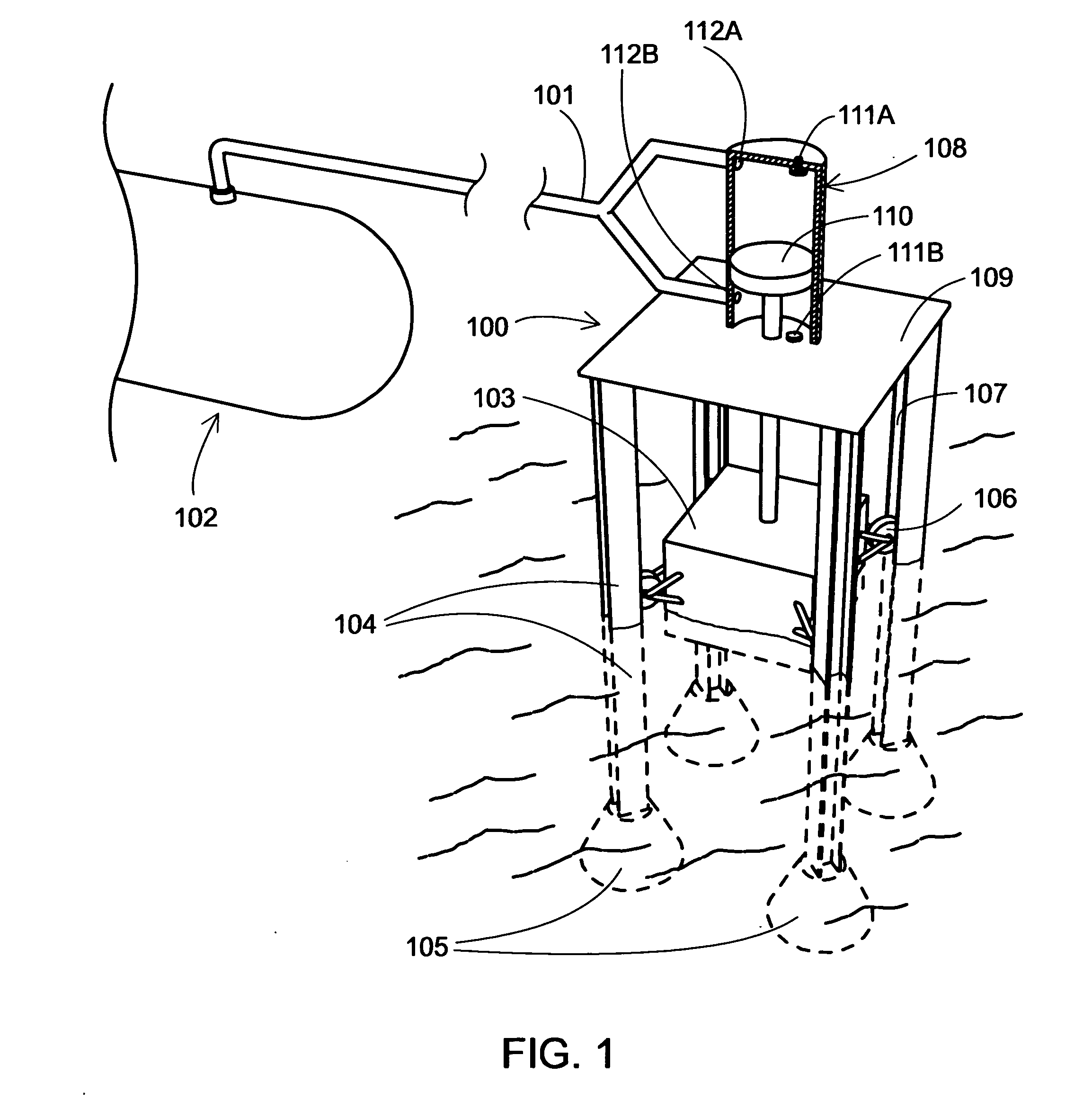
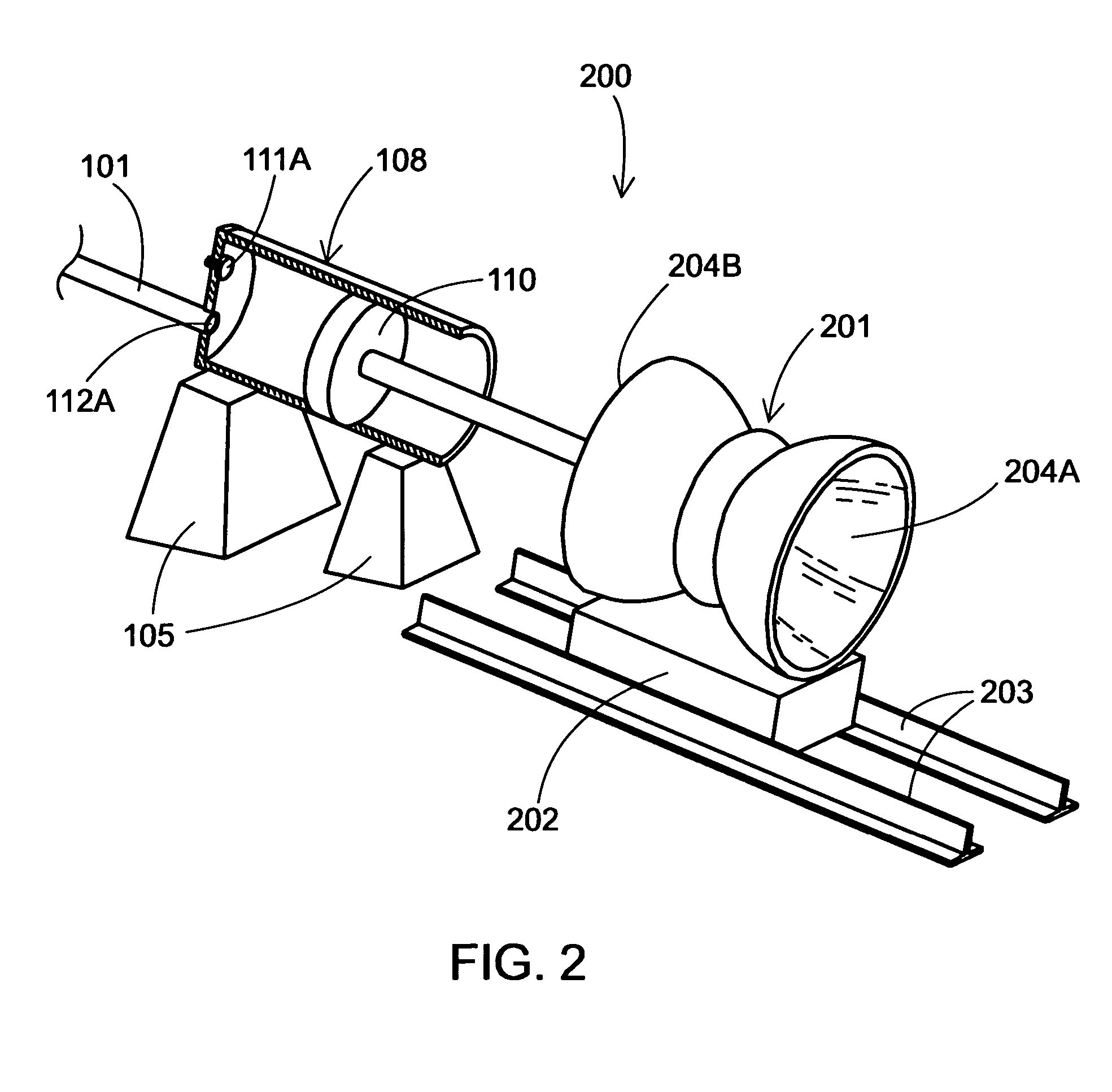
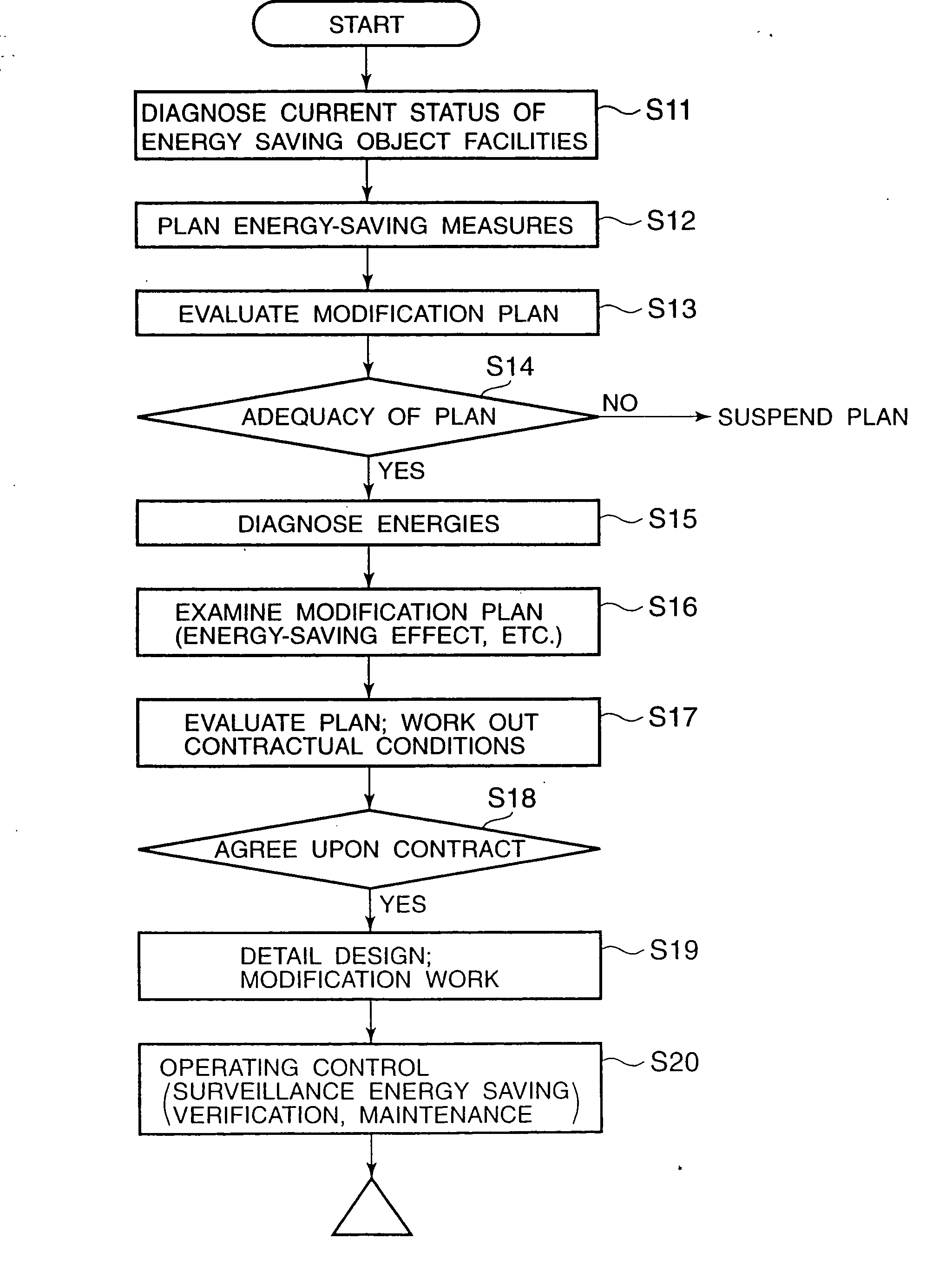
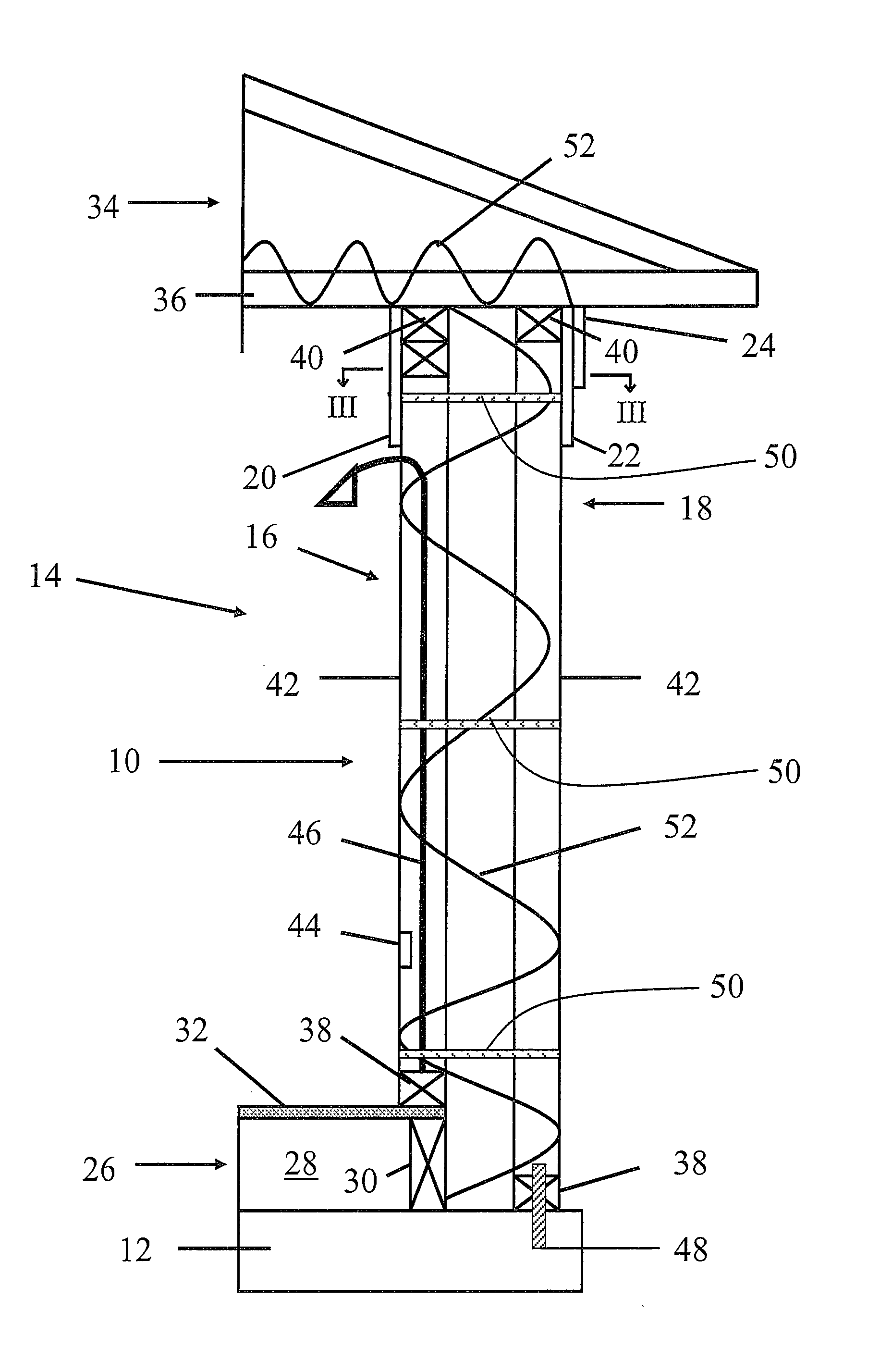
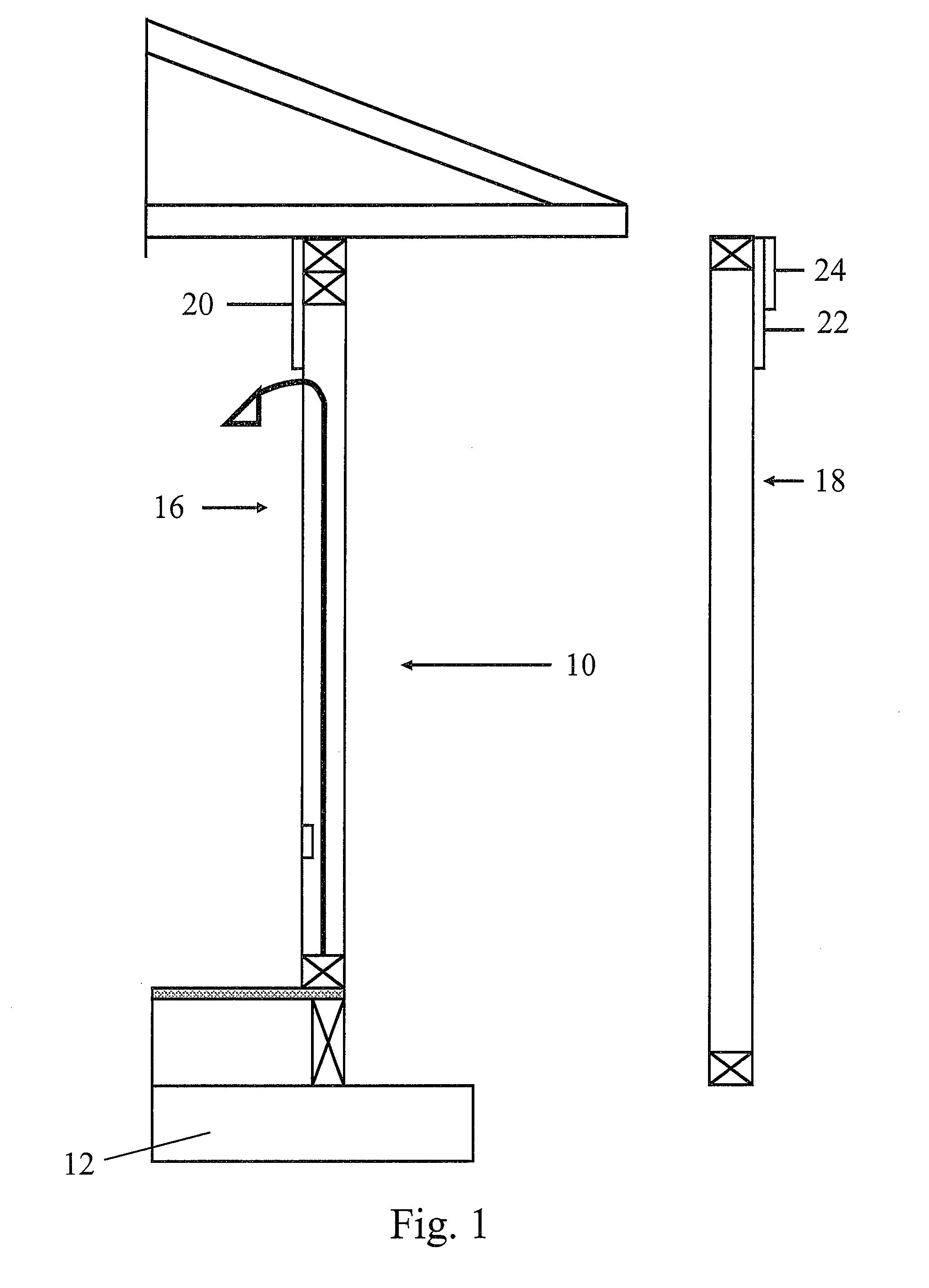
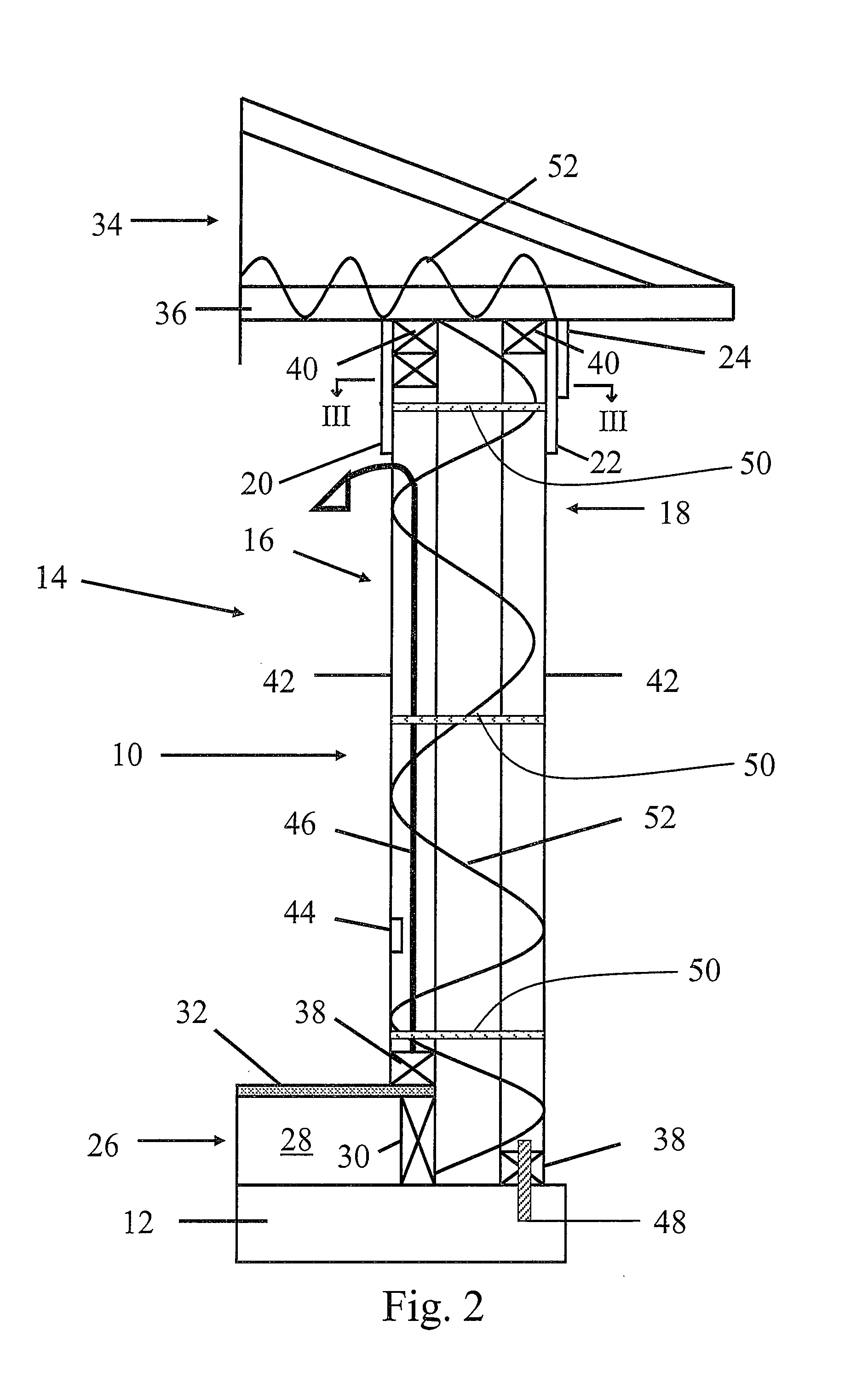
Energy service business method and system
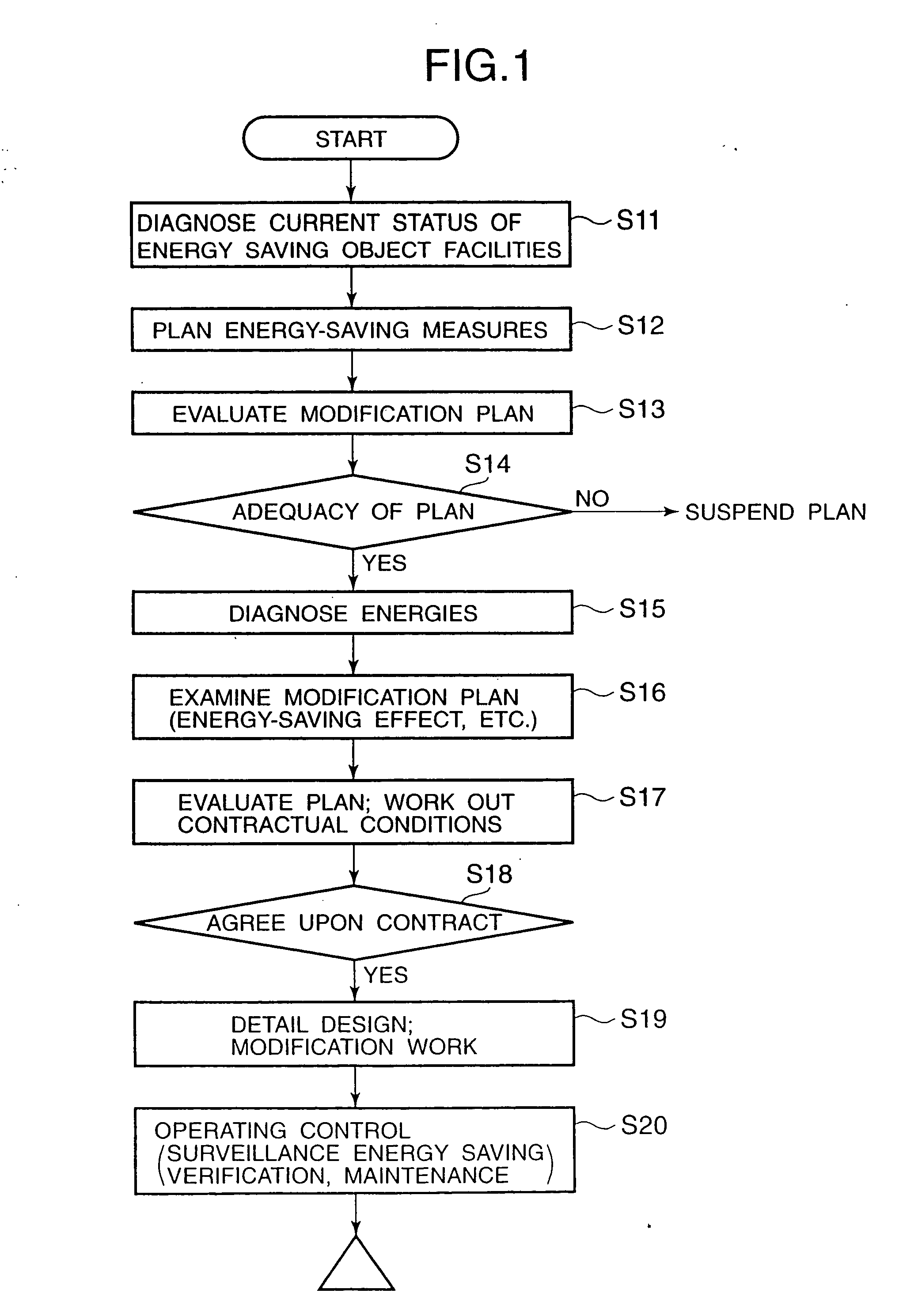
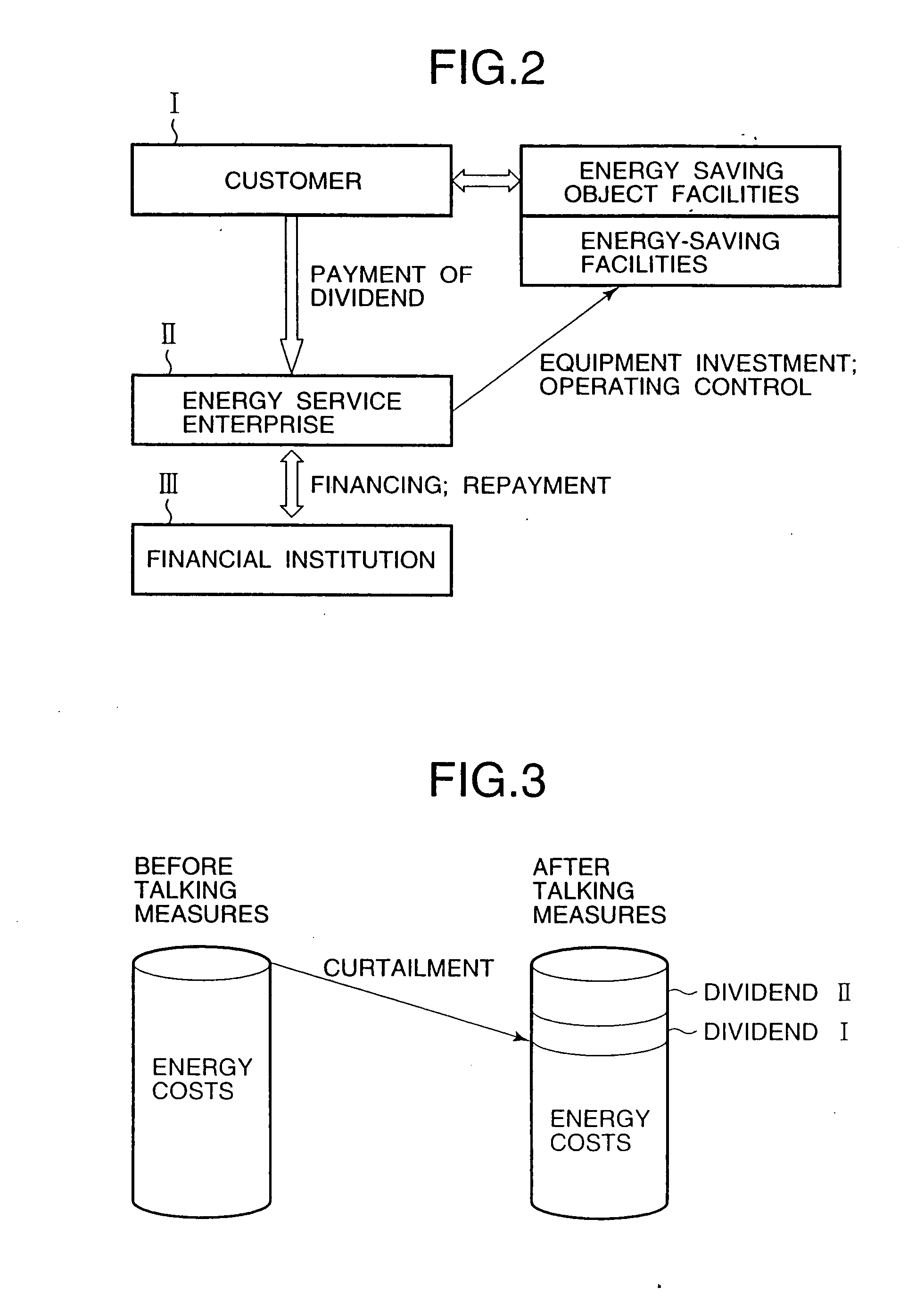
InactiveUS7130832B2Efficient use ofEasily introducedSpecial tariff metersTechnology managementEnergy serviceEnergy conservation measure
If the energy service enterprise is responsible for paying costs for applying energy-saving measures to the object facilities, measures the energy consumption after taking the energy-saving measures, calculates the amount of curtailed energy cost by comparing the measured value with the energy consumption before taking the energy-saving measures previously stored in the database, and receives at least a part of the curtailed amount, the customer is not required to plan equipment investment in energy-saving measures and collection thereof. Introduction of the energy-saving measures is thus made easier.
Owner:HITACHI LTD
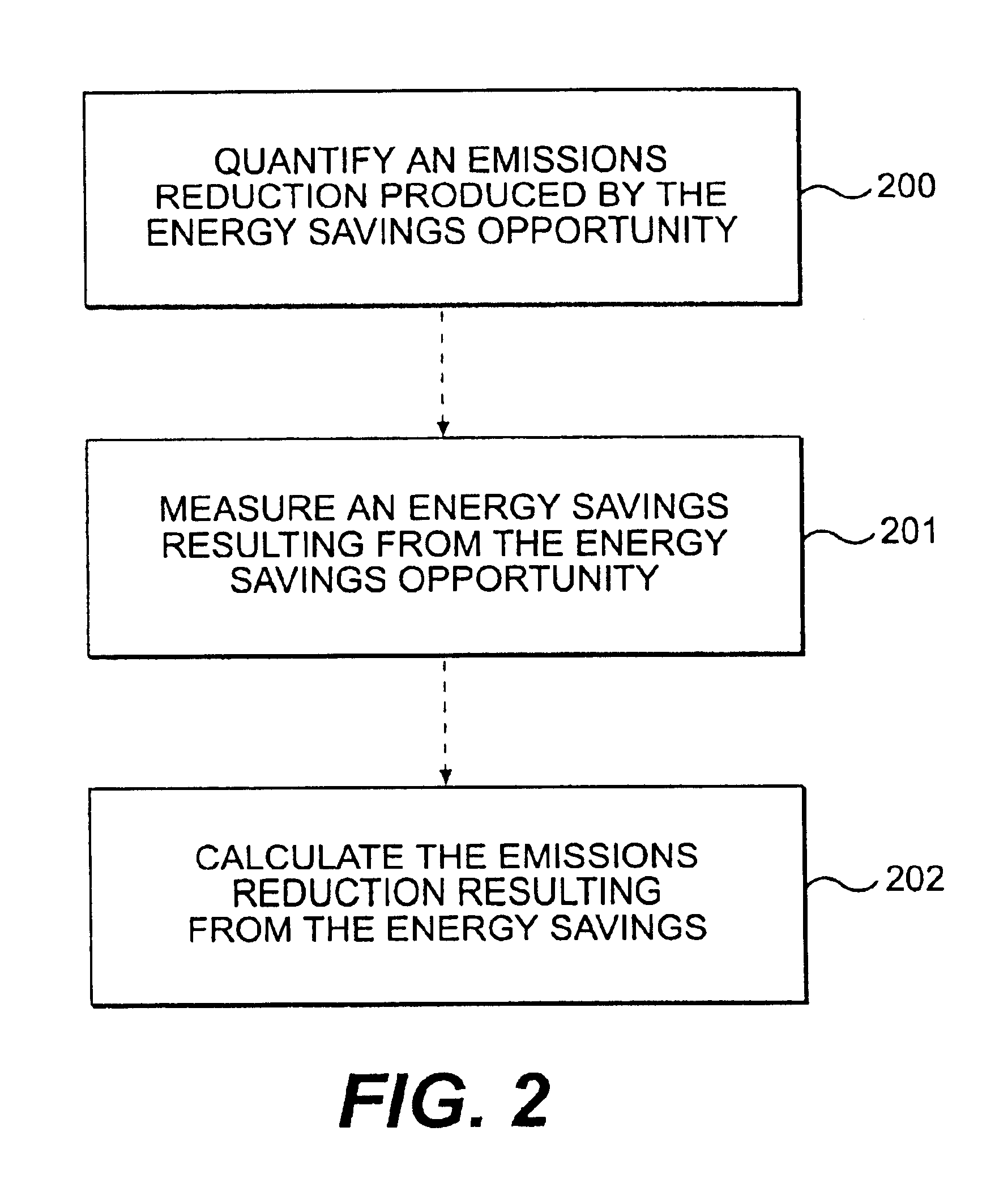
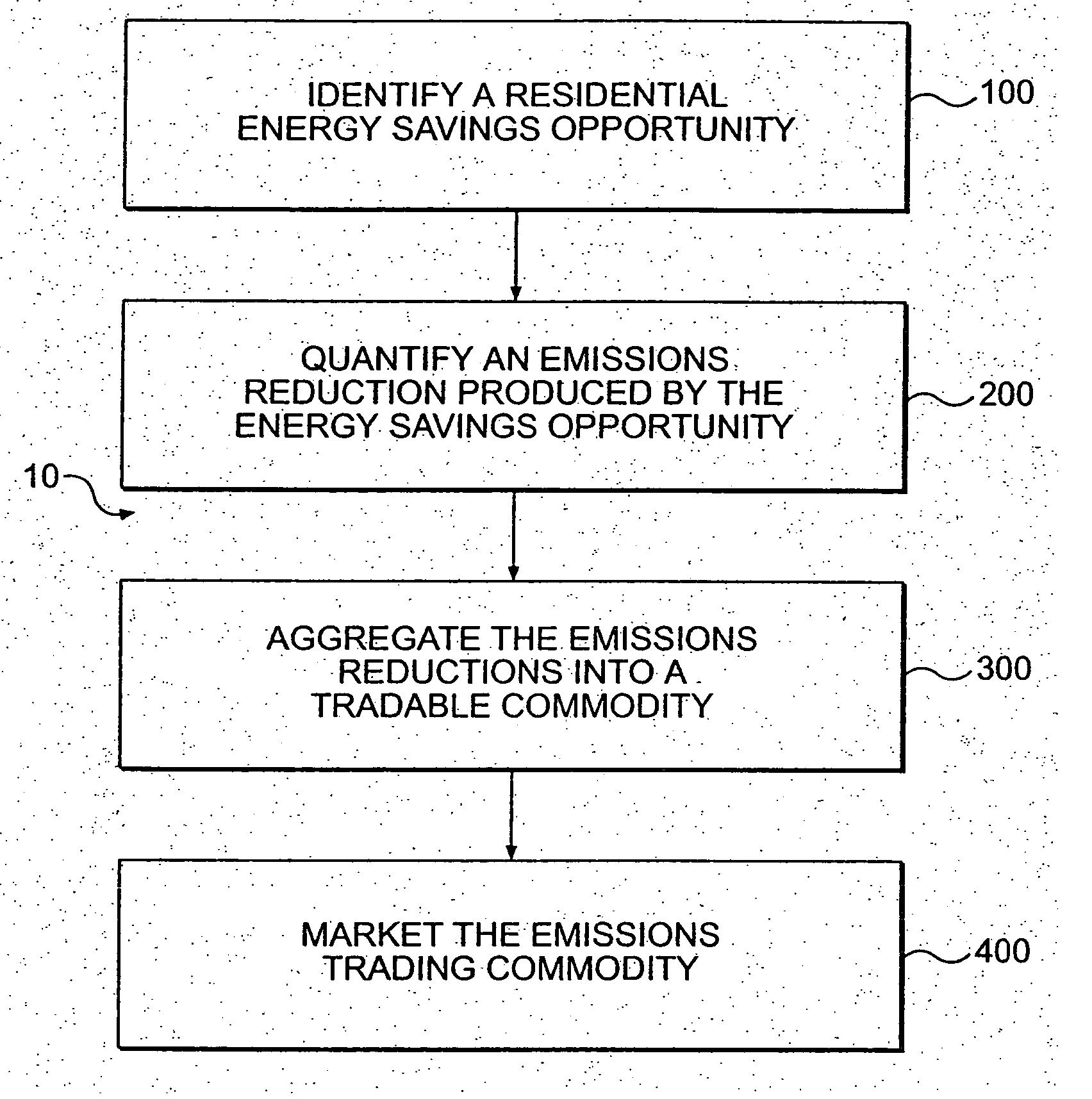
System and method for residential emissions trading
The present invention is directed to a method of residential emissions trading and a residential emissions trading commodity. In particular, an embodiment of the present invention is a method for identifying, quantifying, and aggregating reductions in residential emissions into a tradable commodity. The step of quantifying the emissions reduction may further comprise the steps of measuring an energy savings resulting from the energy savings opportunity and calculating the emissions reduction resulting from the energy savings. The method may further comprise the steps of verifying the quantification of the emissions reduction and monitoring the residential energy savings opportunities and the quantification of the emissions reduction.
Owner:COE COM +2
System and method for residential emissions trading
InactiveUS20050192711A1Save moneyLow costMechanical power/torque controlLevel controlEmissions tradingEngineering
The present invention is directed to a method of residential emissions trading and a residential emissions trading commodity. In particular, an embodiment of the present invention is a method for identifying, quantifying, and aggregating reductions in residential emissions into a tradable commodity. The step of quantifying the emissions reduction may further comprise the steps of measuring an energy savings resulting from the energy savings opportunity and calculating the emissions reduction resulting from the energy savings. The method may further comprise the steps of verifying the quantification of the emissions reduction and monitoring the residential energy savings opportunities and the quantification of the emissions reduction.
Owner:FANNIE MAE +1
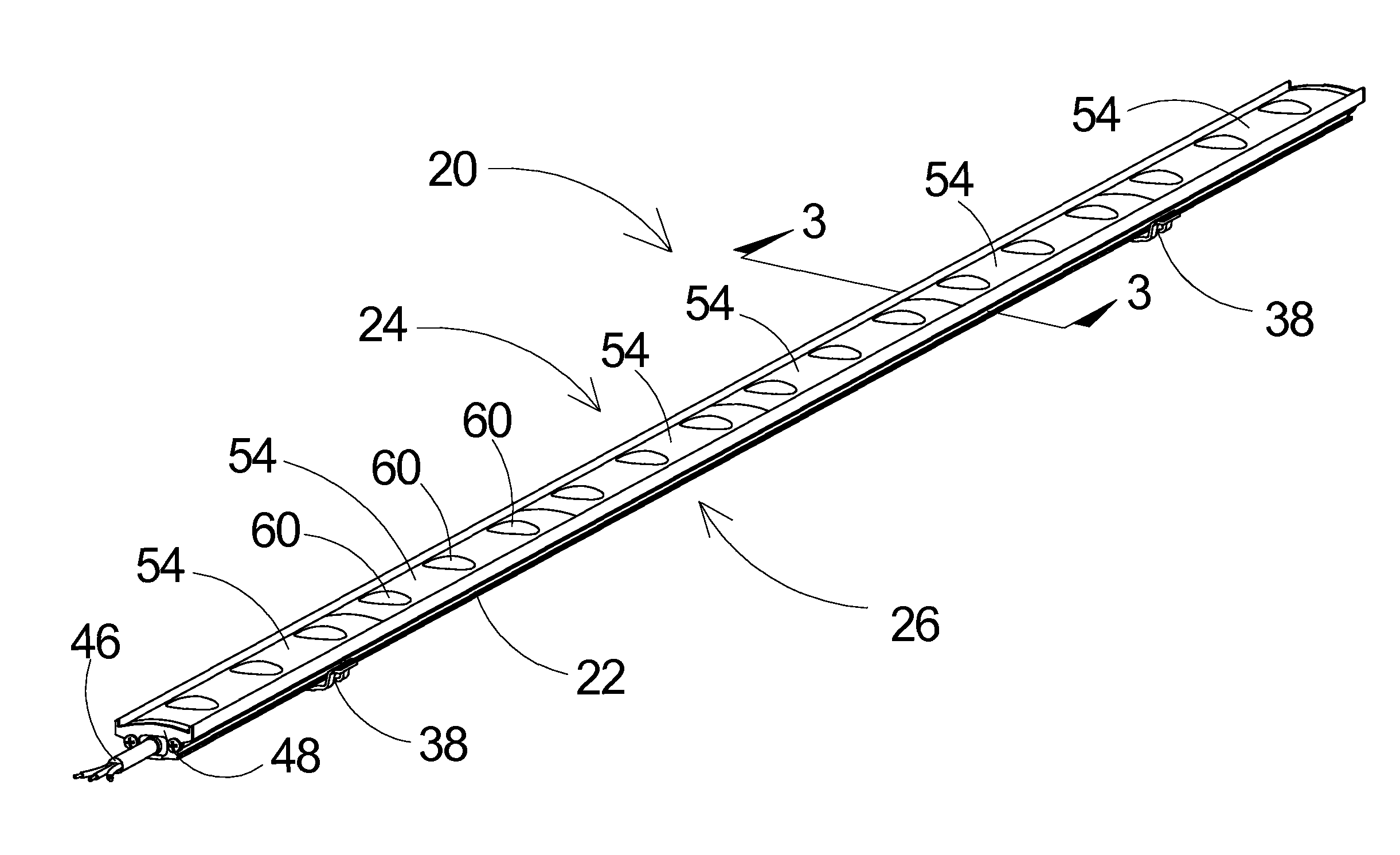
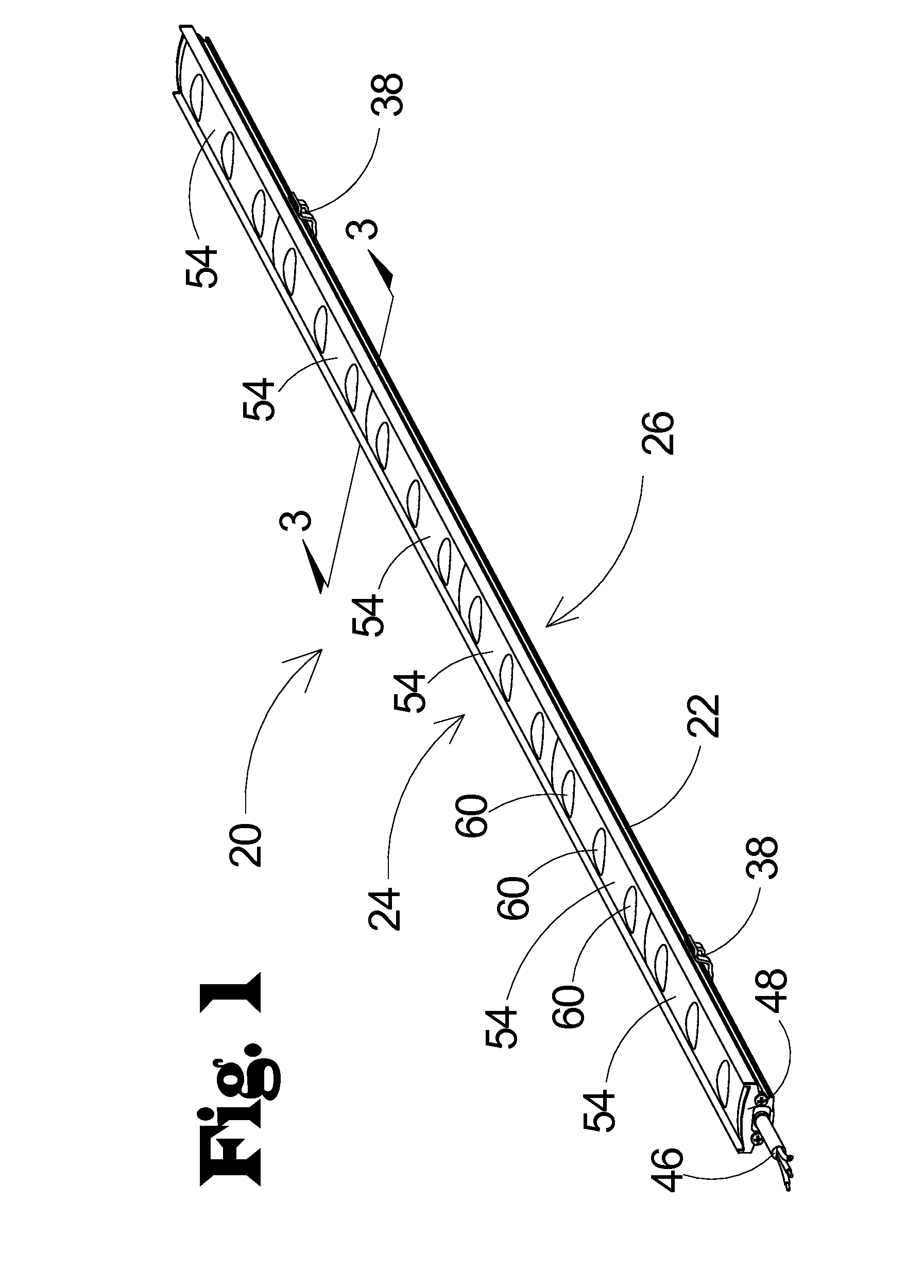
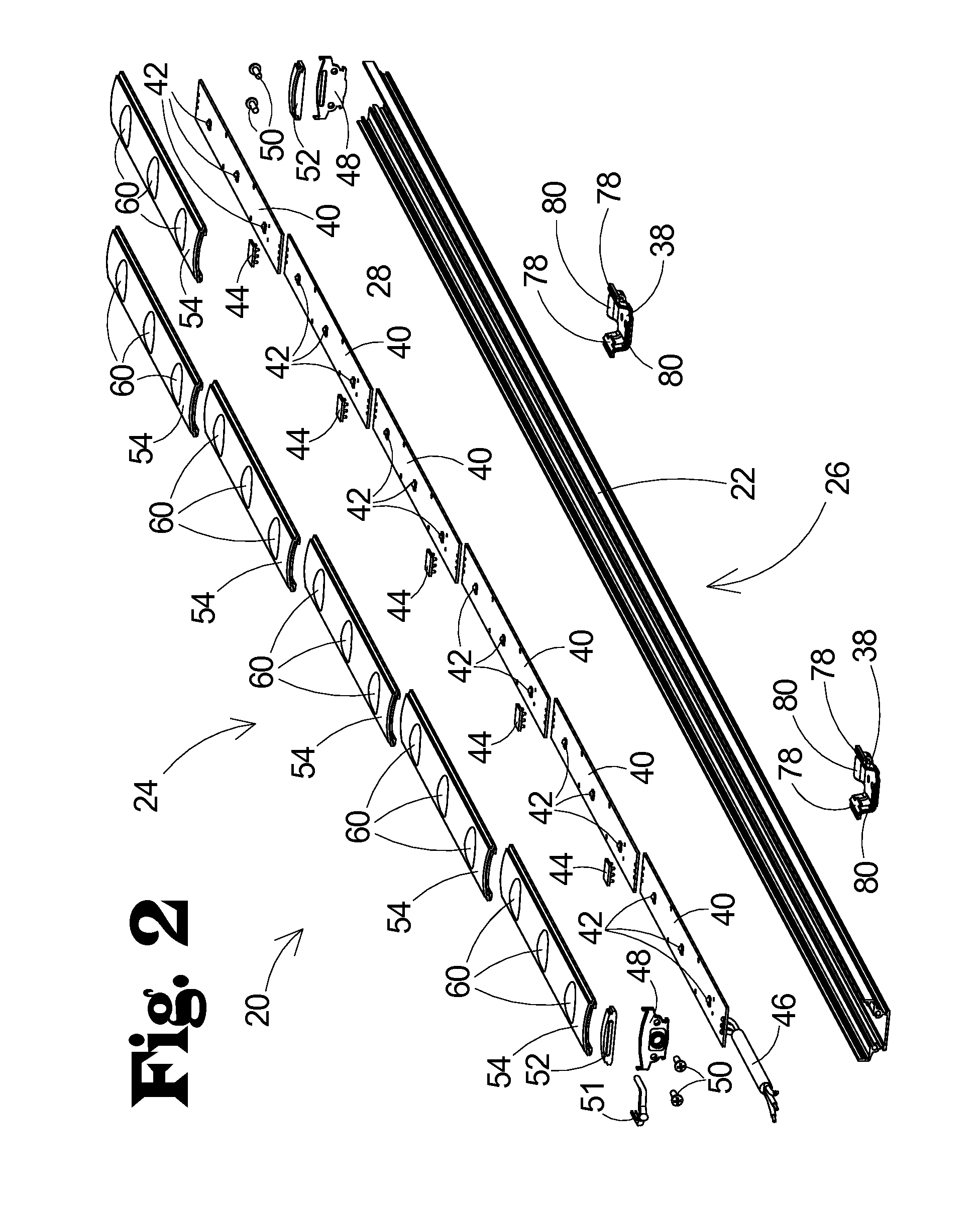
LED Lighting Fixture with Reconfigurable Light Distribution Pattern
ActiveUS20120250309A1Efficiency of energy consumptionGuaranteed effective sizeLight source combinationsLighting support devicesDistribution patternEffect light
Owner:INNOVATIVE LIGHTING LLC
Wave power generator
A machine and a process to produce compressed air by sea waves, using the weight of the floating platform with its fixture using its up and down movement to compress air in both directions to absorb the maximum energy of that wave in a direct drive bidirectional pump with a single piston wherein the kinetic energy and wave bouncy force is used to compress ambient air as stored energy. This unique arrangement doubles air volume for compression in both directions in any single wave curve, doubles the energy production in both upper and lower chambers of the pump and multiplies the “psi” based on the float thrust area against the size of the piston in the pump. The preferred embodiment can be used as a stand alone unit as well as in array formation for the desired output 24 / 7.
Owner:KHAN GHAZI +1
Shingle system
InactiveUS20050144870A1Reduce the temperatureImprove efficiencyPhotovoltaic supportsSolar heating energyInsulation layerEngineering
A barrier, such as a PV module, is secured to a base by a support to create a shingle assembly with a venting region defined between the barrier and base for temperature regulation. Water resistant junctions may be formed between the bases of adjacent shingle assemblies of an array of shingle assemblies. The base may include an insulation layer underlying a water barrier. The base may also include a waterproofing element; the width and height of the barrier may be shorter than the width and height of the waterproofing element.
Owner:SUNPOWER CORPORATION
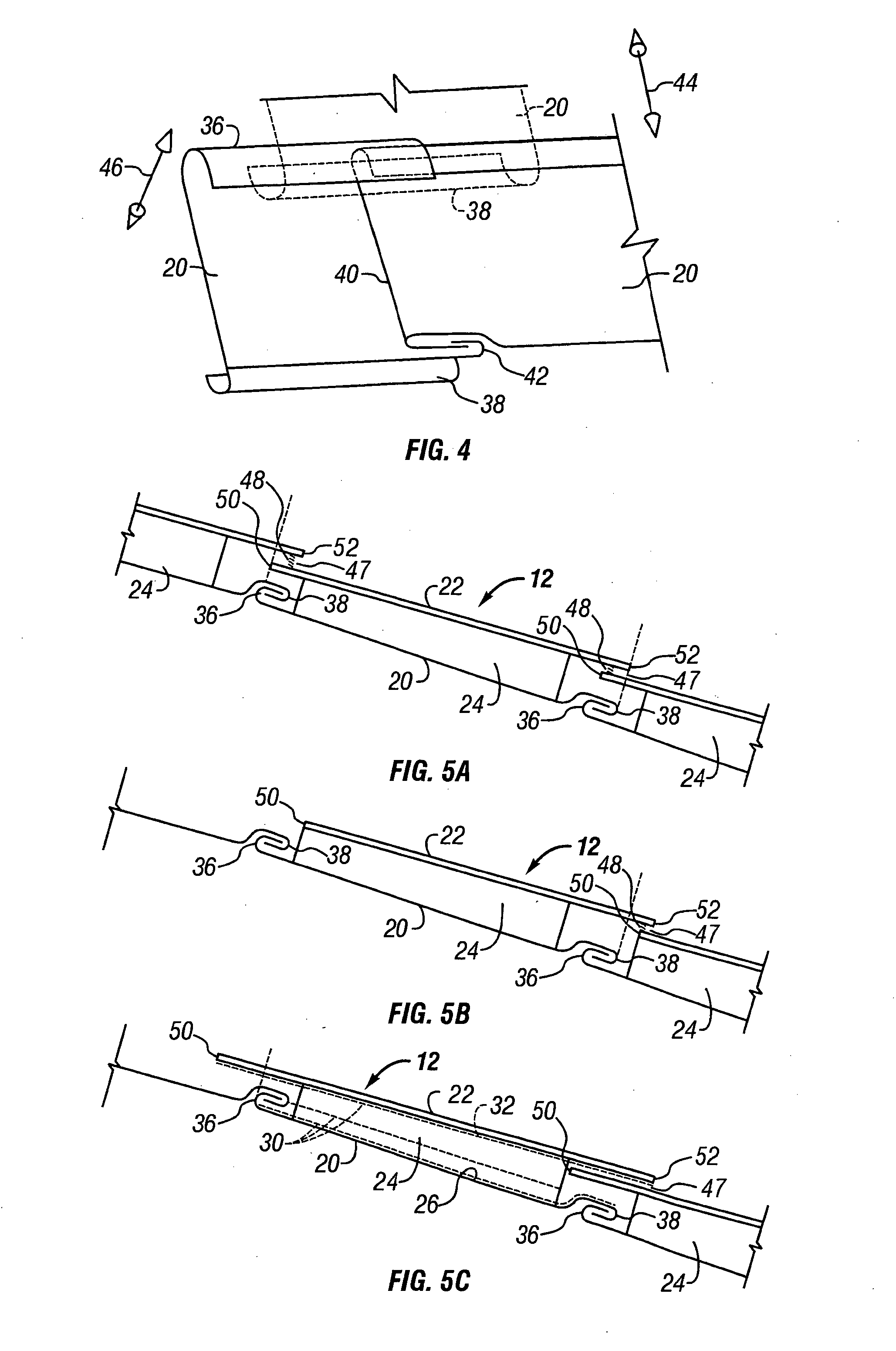
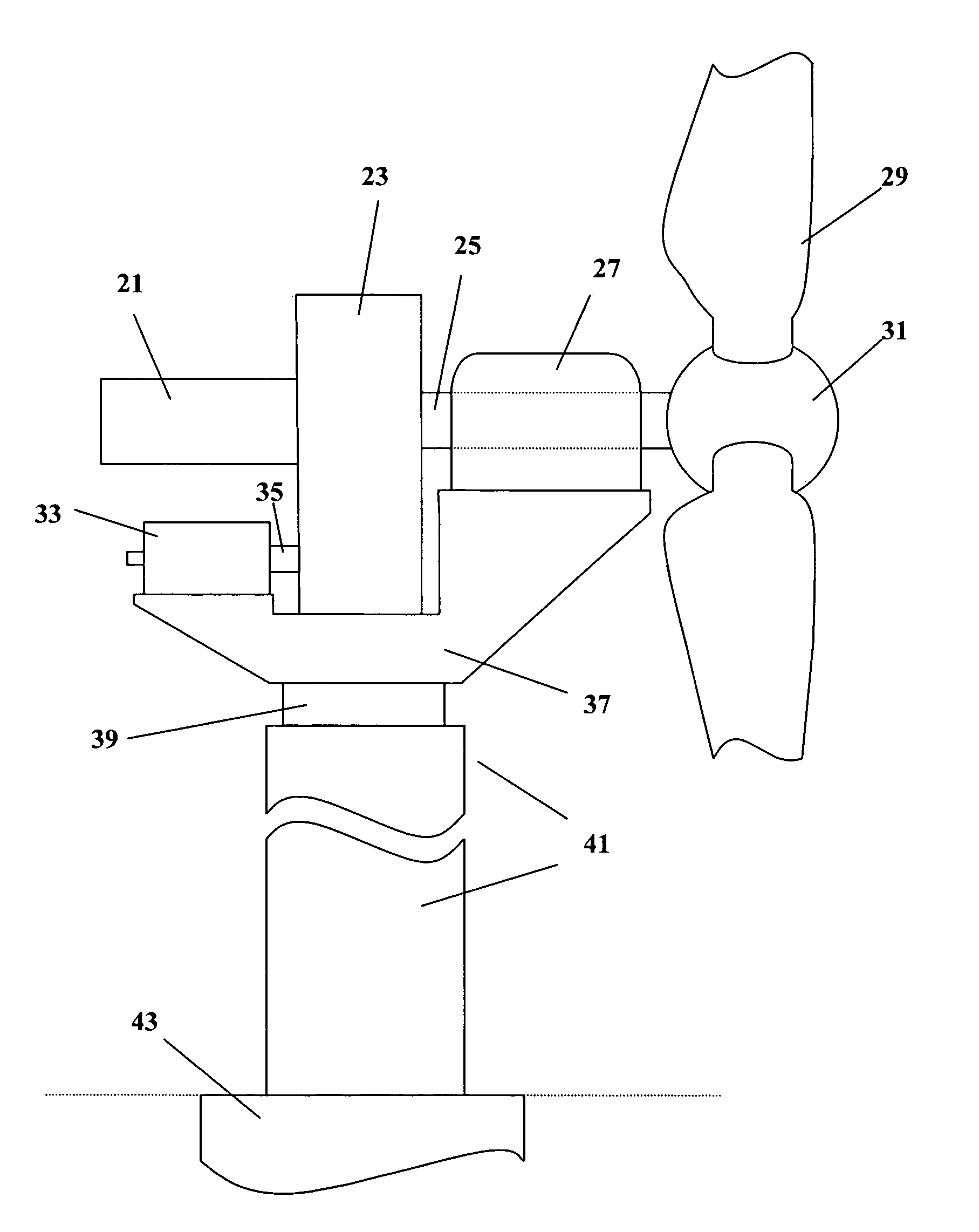
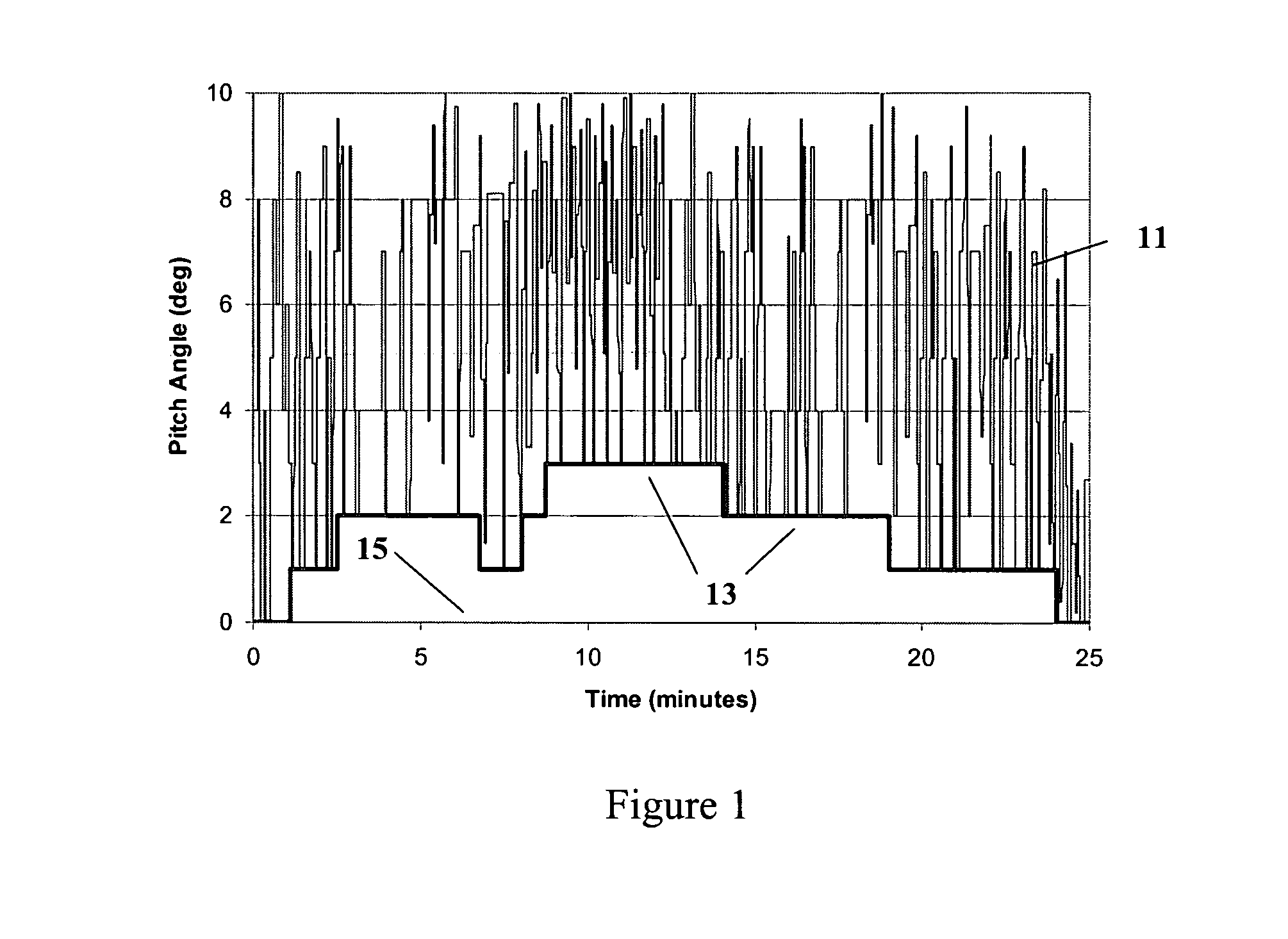
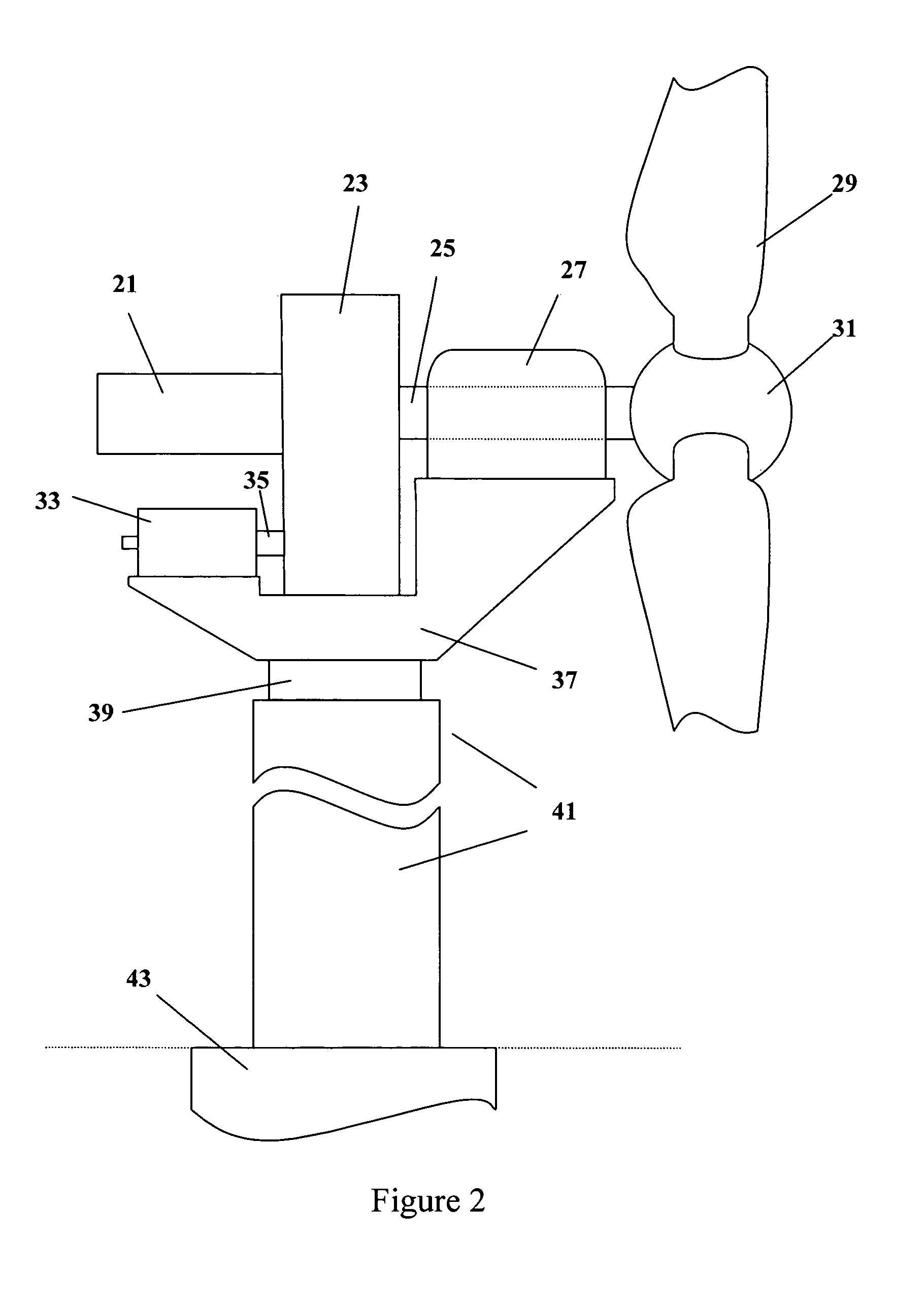
Wind turbine load control method
InactiveUS7351033B2Sufficient flexibilityReduce operating loadPropellersPump componentsTime segmentEngineering
A method for limiting loads in a wind turbine by using measured loads or wind speed to increase the minimum pitch angle for extended periods. The minimum pitch angle will be allowed to relax down to the default when load excursions diminish. The method will allow turbines to capture more energy by operating in higher wind speeds and / or utilizing larger rotors without additional loss of fatigue life.
Owner:MCNERNEY GERALD
LED lighting fixture with reconfigurable light distribution pattern
ActiveUS9016895B2Energy efficiencyGuaranteed effective sizeNon-electric lightingLight source combinationsDistribution patternEffect light
Owner:INNOVATIVE LIGHTING LLC
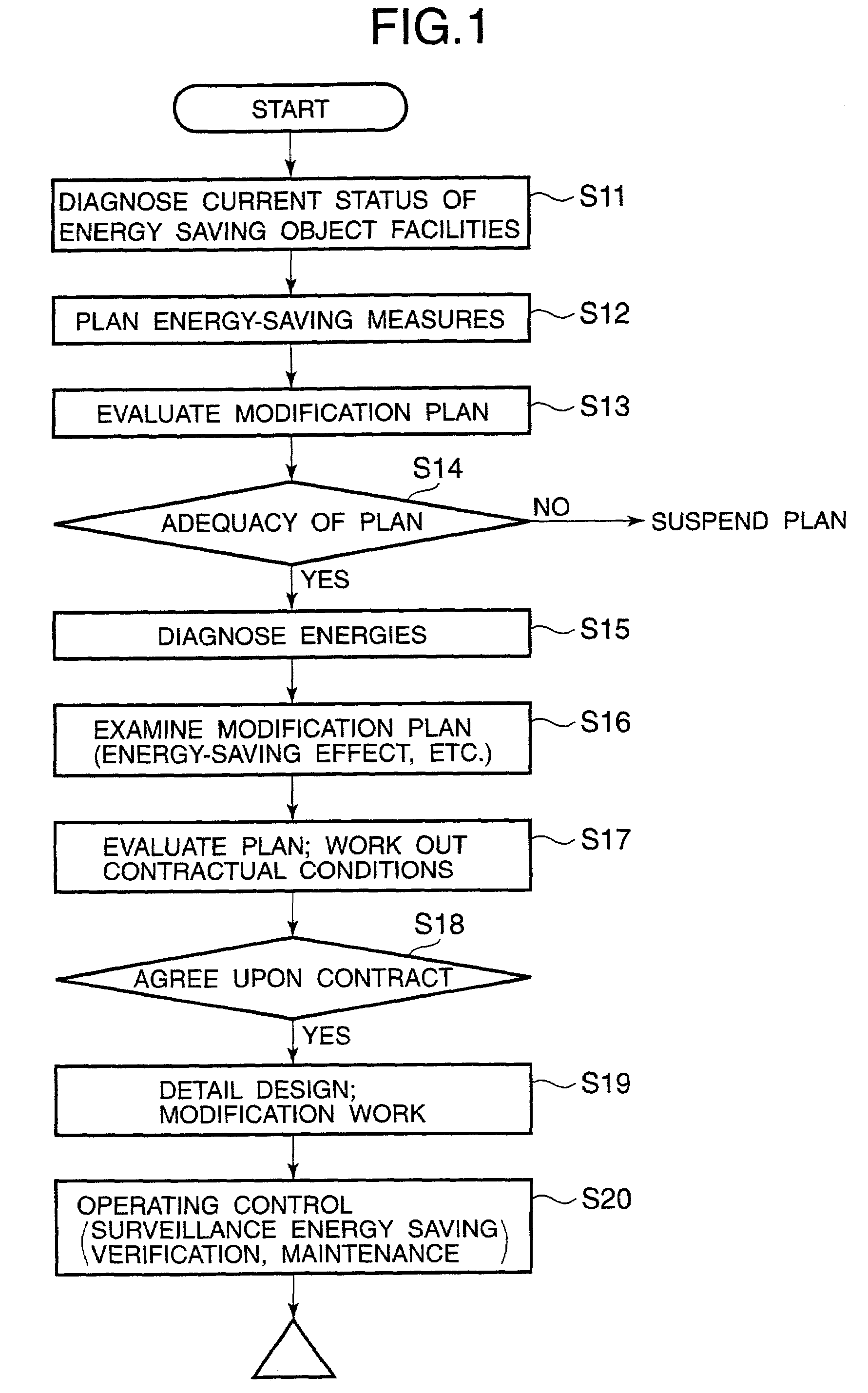
Energy service business method and system
InactiveUS20070094043A1Efficient use ofEasily introducedElectric devicesSpecial tariff metersProcess engineeringEnergy service
An energy service business system includes a database which stores past data about an energy consumption of a facility before taking energy-saving measures, a measurer which measures present data of the energy consumption after taking the energy-saving measures, and a calculator which calculates energy curtailment quantities facility before and after taking the energy-saving measures. The past data in the database are stored in a form correlated with data of a production quantity, and the measurer measures the present data of the energy consumption together with data of the production quantity after taking the energy-saving measures. The calculator retrieves the past data having production quantity data within a set allowable range corresponding to the measured present data having production quantity data, and calculates the energy curtailment quantities by comparing the retrieved past data having production quantity data and the measured present data having the production quantity data.
Owner:HITACHI LTD
Apparatus for converting gravitational energy to electrical energy
The present invention discloses an apparatus of converting gravitational energy to electrical energy. The apparatus includes a reciprocating drive mechanism for lifting liquid from a bottom reservoir to an upper reservoir and turbines between the upper and lower reservoirs which are turned by liquid falling down a flow path from the top reservoir through the turbines to the bottom reservoir. The reciprocating drive mechanism includes a large circular ring or wheel pivotally attached at its hub or center to a support frame and a cable over the upper periphery of the ring with two pipes attached one at each end of the cable. The ring pivots back and forth lifting one pipe and lowering the other pipe and vice versa. As a pipe moves down liquid enters the bottom of the pipe while liquid drains out the top of the pipe into the upper reservoir. One of the turbines is connected to the reciprocating drive mechanism and the other to a generator for producing electricity.
Owner:DUTTA ALOK
Door control system with obstacle detection
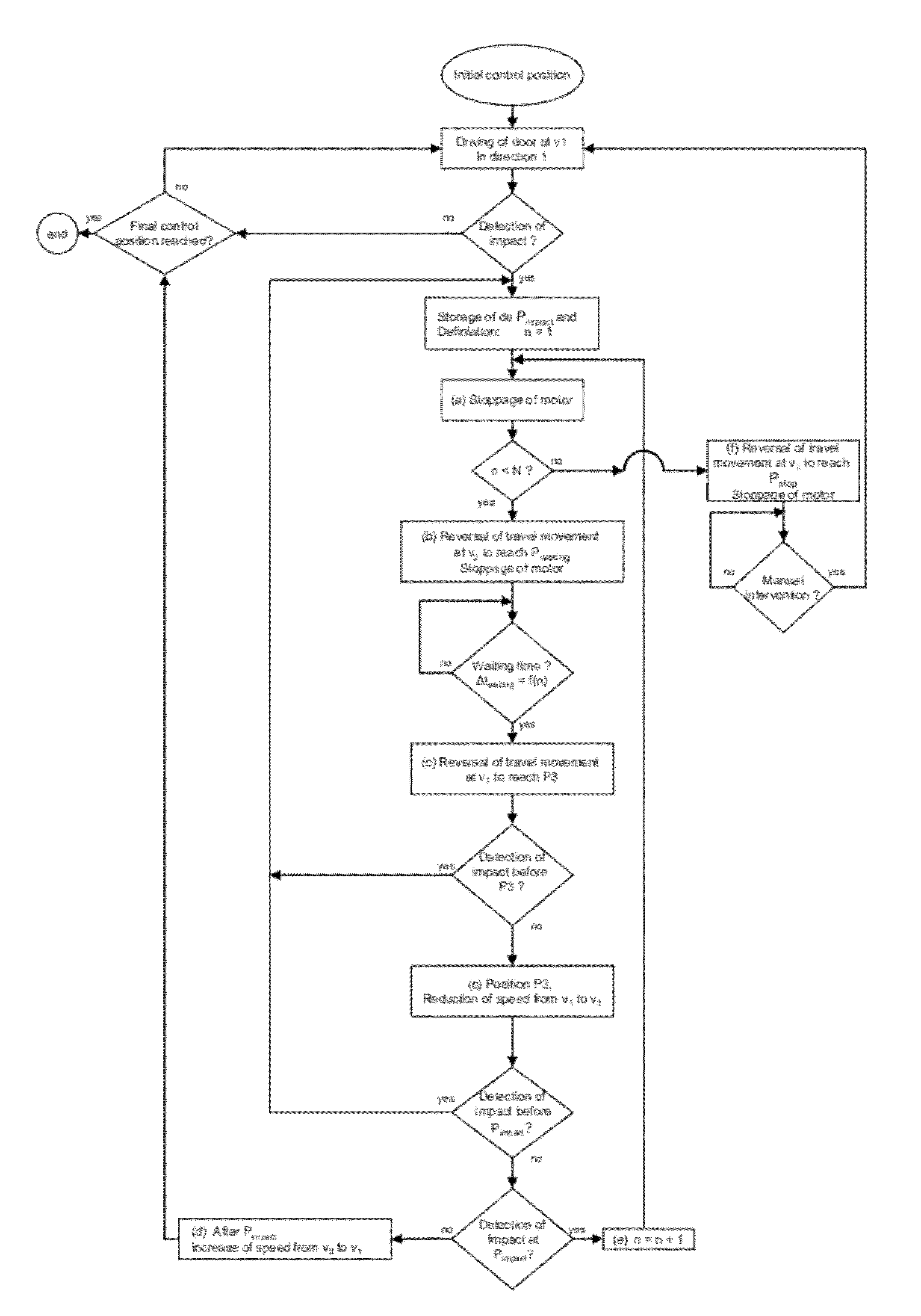
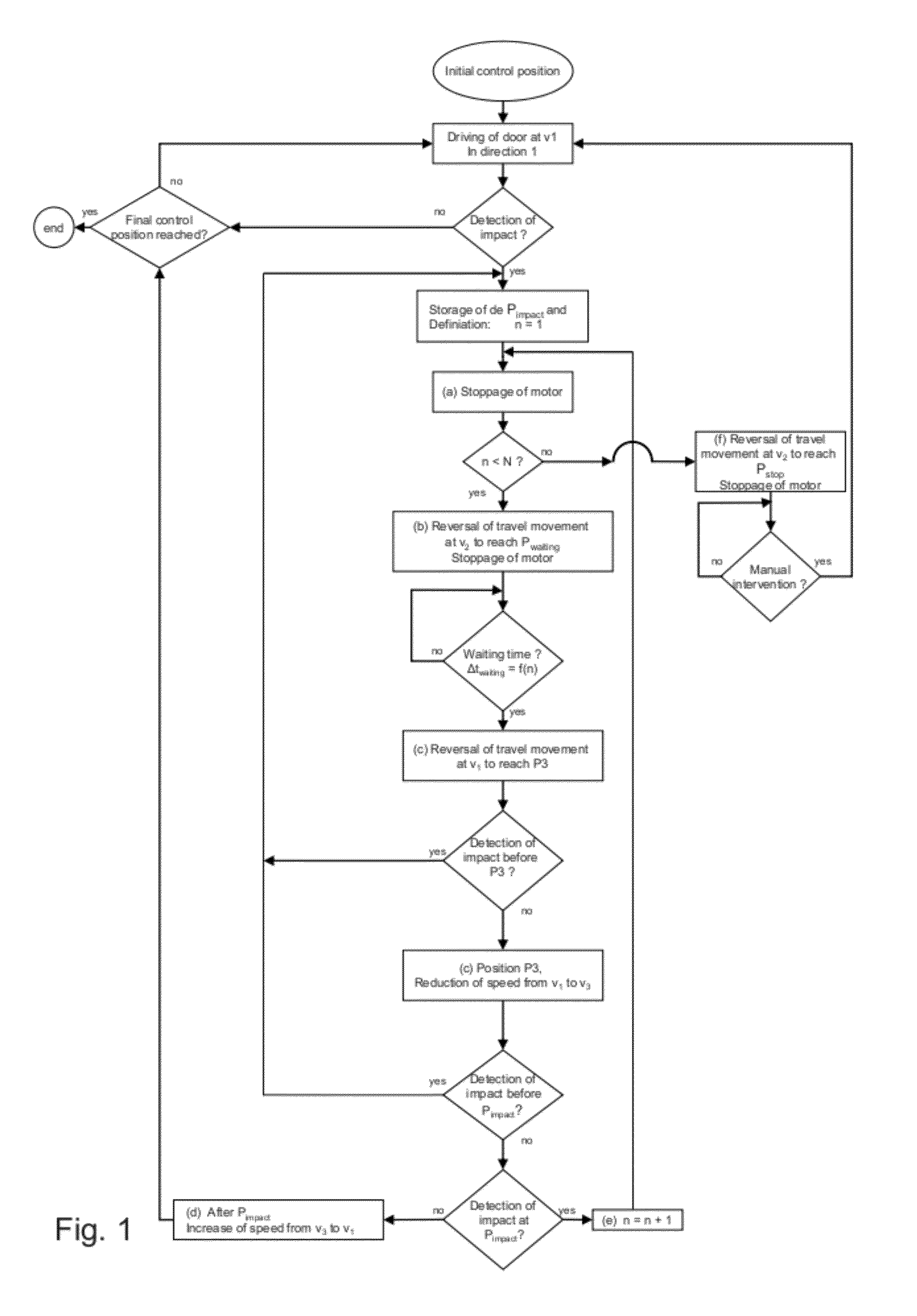
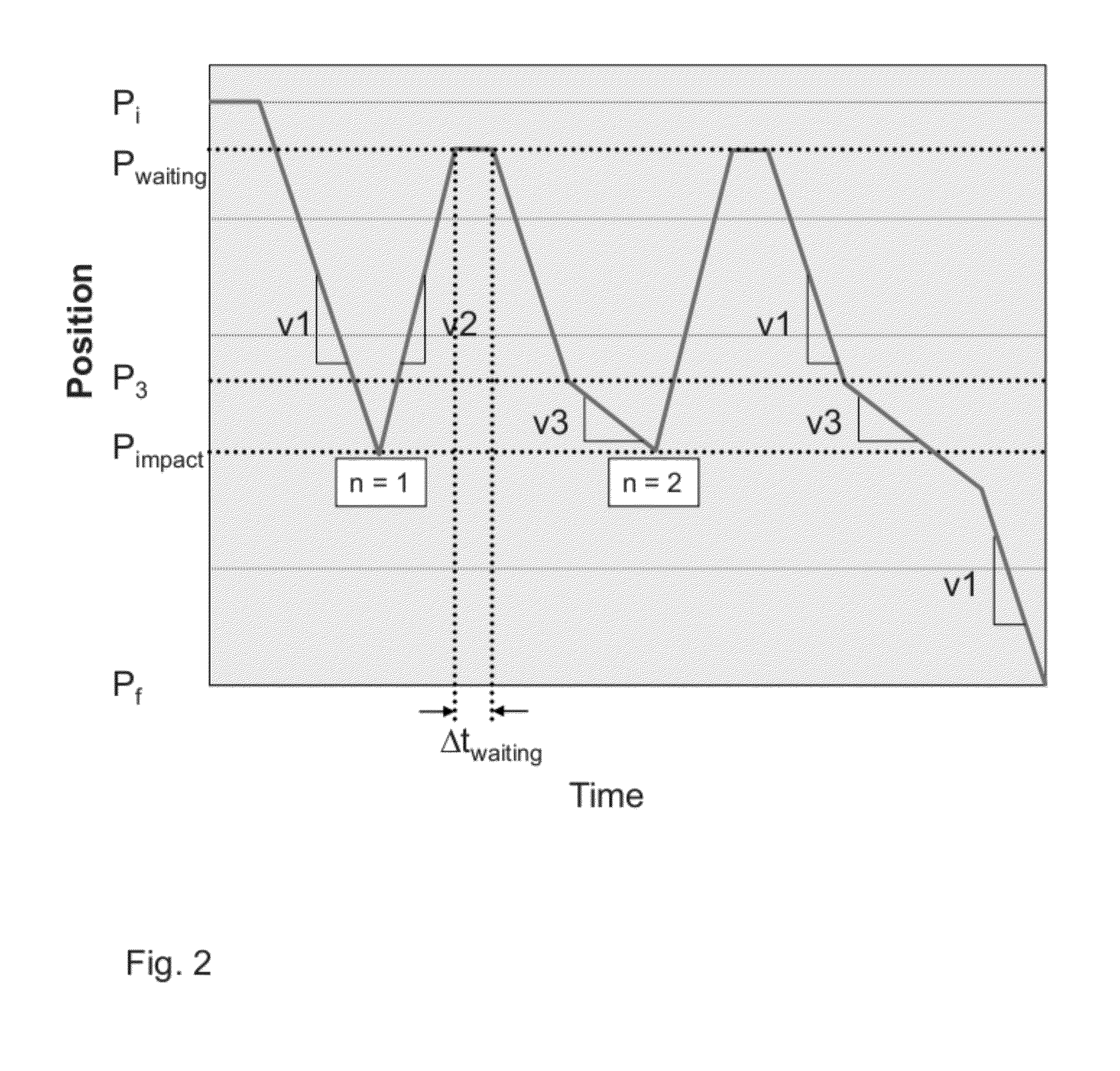
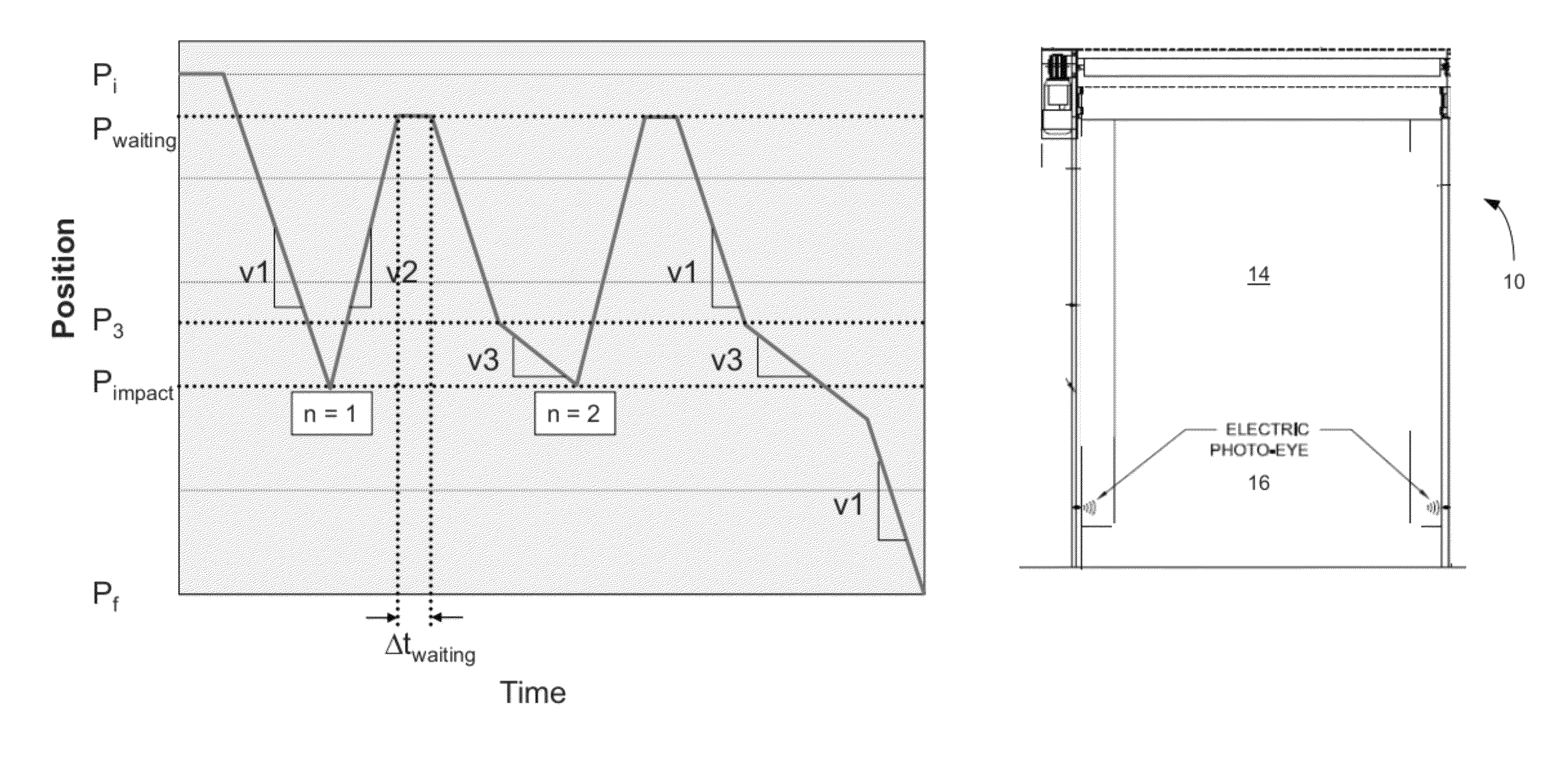
ActiveUS20120073200A1Avoid damageIncrease movement speedShutters/ movable grillesPower-operated mechanismControl systemImpact
System for controlling a door enabling driving from an initial position of its travel in a first direction at a speed v1 as far as a final position, said control system comprising a safety function comprising means for keeping a door in operation despite its having suffered an impact against an obstacle situated on its travel and enabling it to continue its initial movement automatically as soon as said obstacle is removed, through a design reconciling a sufficiently high normal speed of movement v1 of the door with the intention to prevent damage both to the obstacle and to the door by reducing the speed to v3<v1 close to the stored position of the impact.
Owner:DYNACO EURO
Oxygen-based biomass combustion system and method
InactiveUS7007616B2Heat loss from heating unnecessary oxidant is minimizedReduce heat lossSolidificationLiquefactionCombustion chamberOxygen
An oxygen-based biomass solid fuel combustion system and method has an air separator for separating oxygen from air providing a supply of oxygen for feeding oxygen to a solid fuel combustion chamber. An airlock feeds a metered amount of solid fuel to the solid fuel combustion chamber. A burner stage having a firetube for collecting fuel gases from the solid fuel combustion chamber combusts the collected fuel gases with further oxygen from the separator and heats a boiler to generate steam. A heat utilization device (e.g. an electrical generator) may be connected to the steam boiler. Nitrogen-free diluent gases (e.g. argon and carbon dioxide) are used to control combustion process temperatures. The usable heat energy and useful byproducts are extracted from the different stages of the process.
Owner:MUNIZ CESAR A
Oxygen-based biomass combustion system and method
InactiveUS20050022553A1Minimize heat lossHeat loss from heating unnecessary oxidant is minimizedSolidificationLiquefactionAutomotive engineeringCarbon dioxide
An oxygen-based biomass solid fuel combustion system and method has an air separator for separating oxygen from air providing a supply of oxygen for feeding oxygen to a solid fuel combustion chamber. An airlock feeds a metered amount of solid fuel to the solid fuel combustion chamber. A burner stage having a firetube for collecting fuel gases from the solid fuel combustion chamber combusts the collected fuel gases with further oxygen from the separator and heats a boiler to generate steam. A heat utilization device (e.g. an electrical generator) may be connected to the steam boiler. Nitrogen-free diluent gases (e.g. argon and carbon dioxide) are used to control combustion process temperatures. The usable heat energy and useful byproducts are extracted from the different stages of the process.
Owner:MUNIZ CESAR A
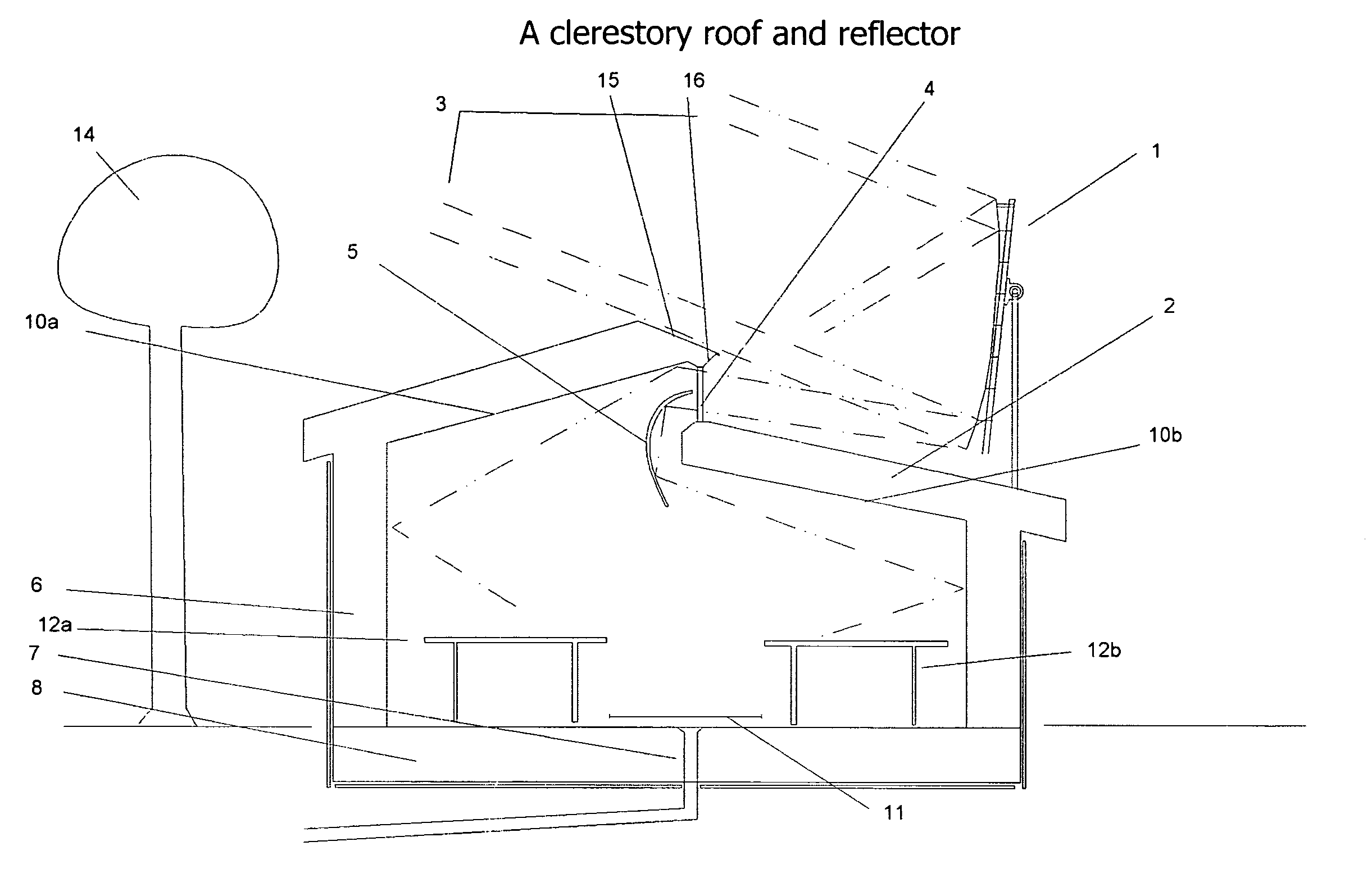
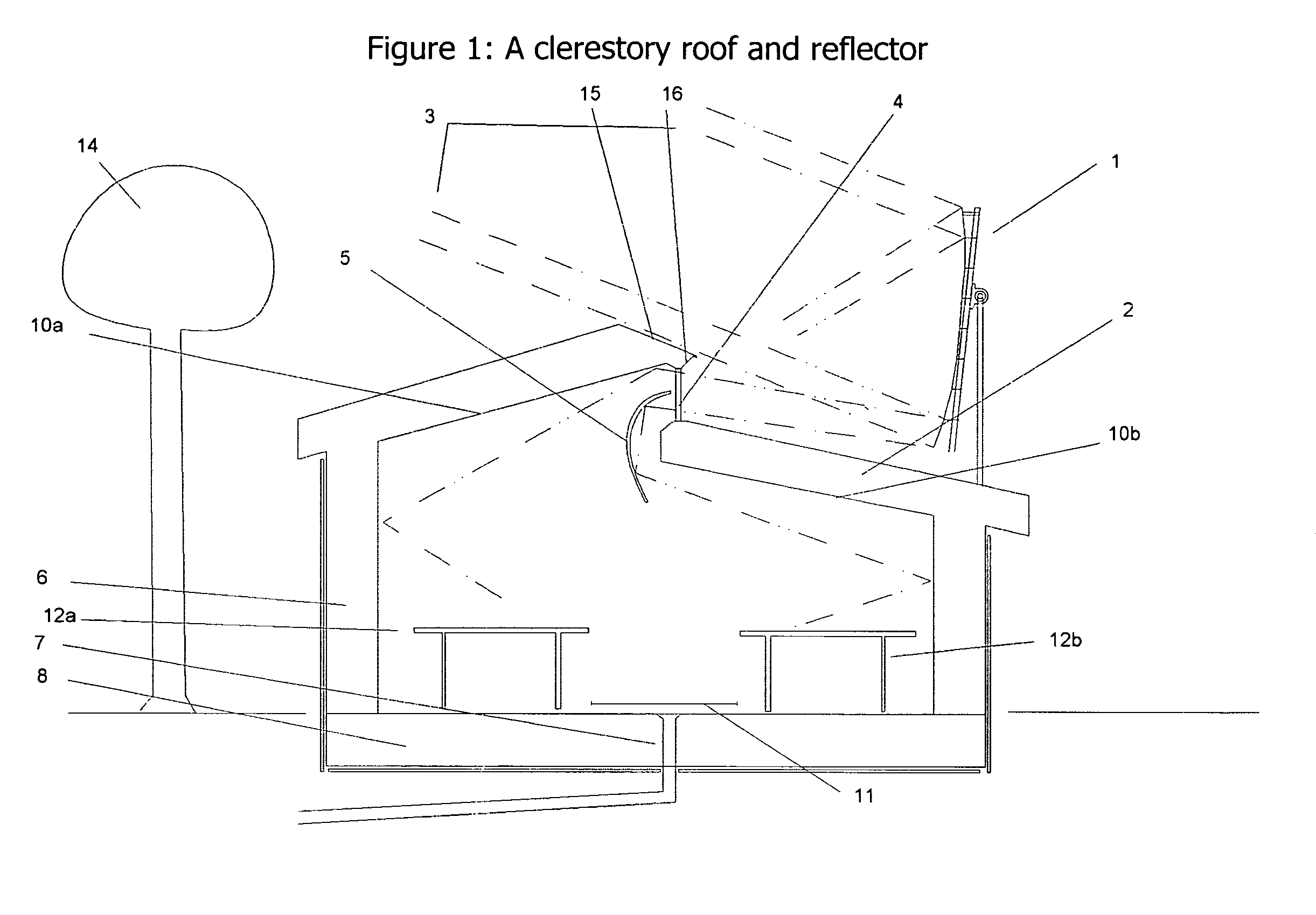
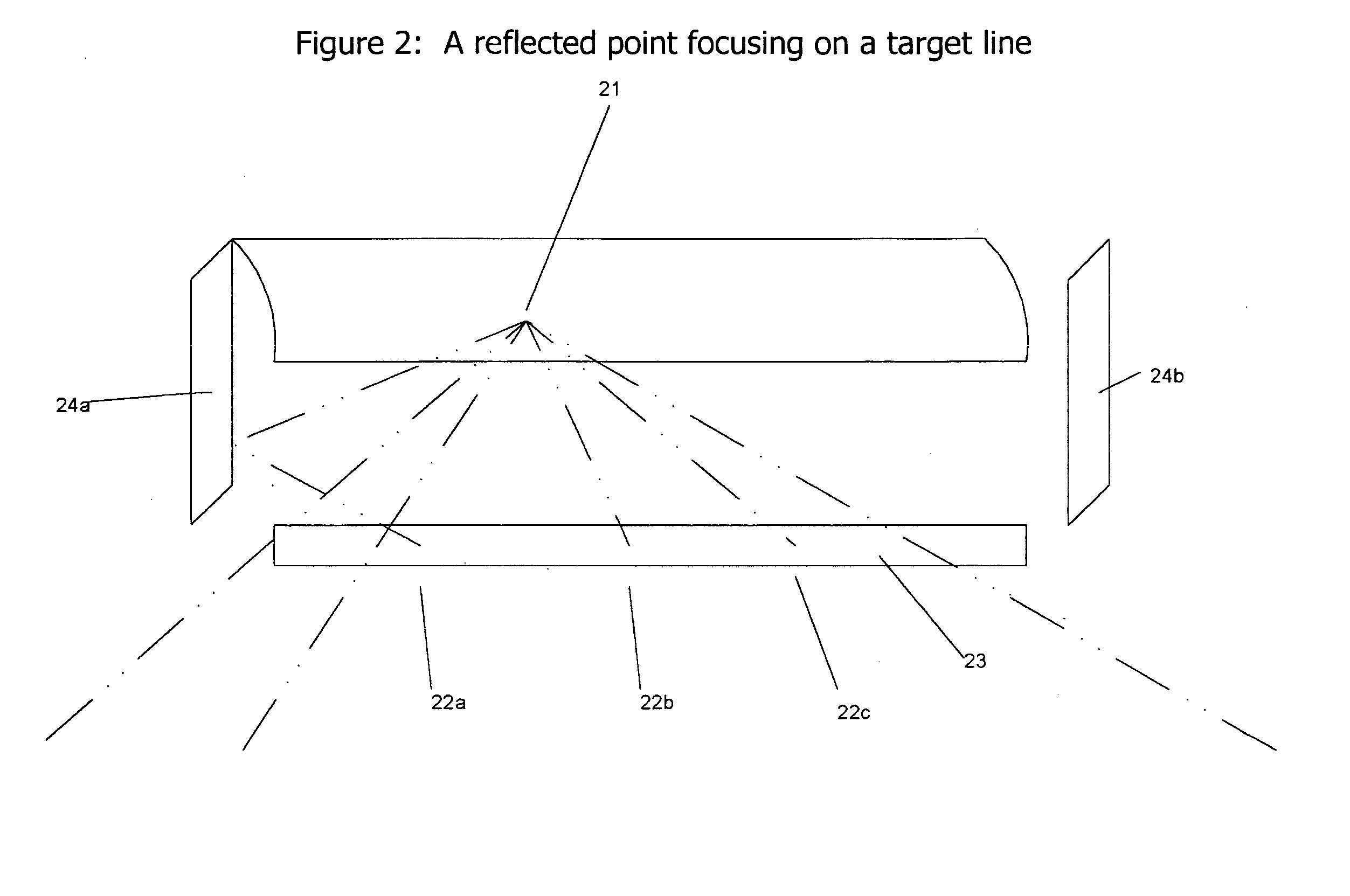
Solar reflector, collecting window and heat storage
InactiveUS8408199B1Little heatReduce heat lossSolar heating energyRoof covering using slabs/sheetsGreenhouseEngineering
A linear trough concentrates sunlight through a long target window in a greenhouse's roof or north wall. Heat is stored in a geothermal heat bank below the greenhouse's center, where a thermal skirt around the greenhouse reduces heat loss.
Owner:KLINKMON PAUL M
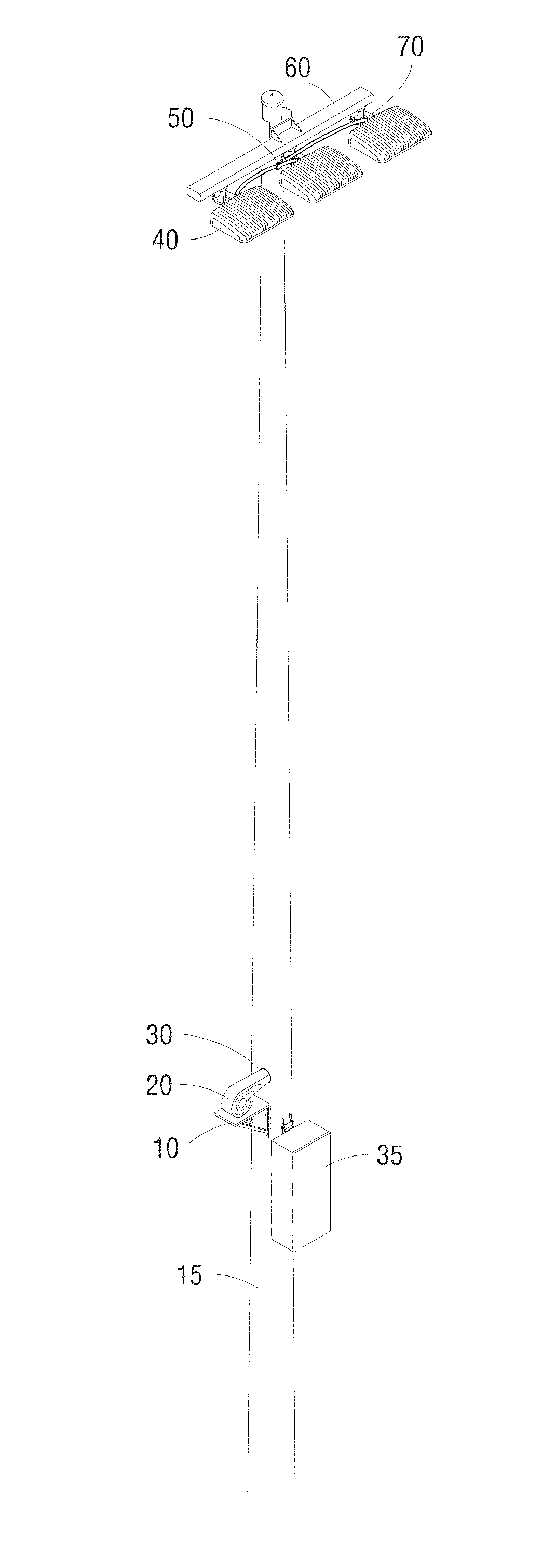
Apparatus, method, and system for lighting fixture cooling
ActiveUS9028115B1Good curative effectJustify costMechanical apparatusLighting support devicesEffect lightHigh intensity
A high-intensity LED lighting system is presented whereby one or more LED lighting fixtures are affixed to an elevating structure, the elevating structure having a substantially continuous internal pathway. Said pathway can be used as a conduit or duct for pressurized air which is introduced at or near the bottom of the elevating structure and forced upwardly toward the lighting fixtures so to provide cooling of one or more components of the lighting fixtures so to, ultimately, improve the efficacy of the LEDs contained therein. A method of designing lighting systems, including analysis of whether or not to add air cooling to increase light source efficiency is also disclosed.
Owner:MUSCO
Door control system with obstacle detection
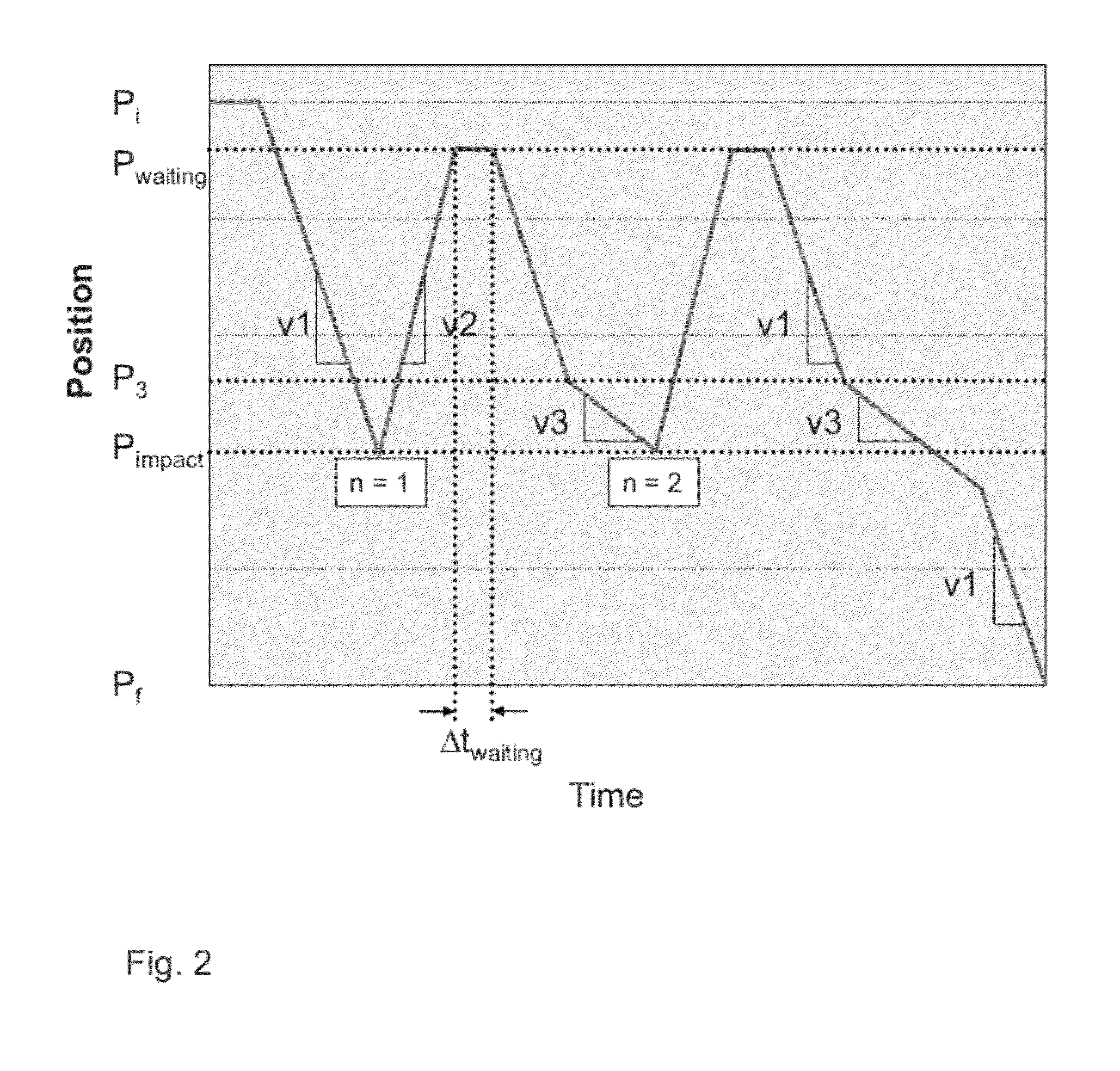
ActiveUS8341885B2Simple and reliable processAvoid damageProgramme controlShutters/ movable grillesControl systemSecurity function
System for controlling a door enabling driving from an initial position of its travel in a first direction at a speed v1 as far as a final position, said control system comprising a safety function comprising means for keeping a door in operation despite its having suffered an impact against an obstacle situated on its travel and enabling it to continue its initial movement automatically as soon as said obstacle is removed, through a design reconciling a sufficiently high normal speed of movement v1 of the door with the intention to prevent damage both to the obstacle and to the door by reducing the speed to v3<v1 close to the stored position of the impact.
Owner:DYNACO EURO
Energy efficient building construction
InactiveUS8590262B1Cost-effectiveEnergy efficiencyWallsPublic buildingsDouble wallArchitectural engineering
A cost-effective and energy-efficient system and method for building construction, such as for residential dwellings and the like, uses dual-wall building envelope system having outer walls and corresponding partition walls spaced outwardly from the outer walls. The envelope system provides ample space for insulation to enhance the thermal efficiently of the house or building, while permitting construction at reduced cost using pre-fabrication methods.
Owner:ENERGYSMART BUILDING METHOD
Active optoceramics with cubic crystal structure, method of production of the optoceramics, and uses thereof
InactiveUS20100193738A1High transparencyQuality improvementMaterial nanotechnologyCeramic shaping apparatusPowder mixtureCrystal structure
The transparent polycrystalline optoceramic has single grains with a symmetric cubic crystal structure and at least one optically active center. The optoceramic has the following formula: A2+xByDzE7, wherein −1.15≦x≦0, 0≦y≦3, 0≦z≦1.6, and 3x+4y+5z=8, and wherein A is at least one trivalent rare earth cation, B is at least one tetravalent cation, D is at least one pentavalent cation, and E is at least one divalent anion. The method of making the optoceramic includes preparing a powder mixture from starting materials, pre-sintering, sintering and then compressing to form the optoceramic. Scintillator media made from the optoceramic are also described.
Owner:SCHOTT AG
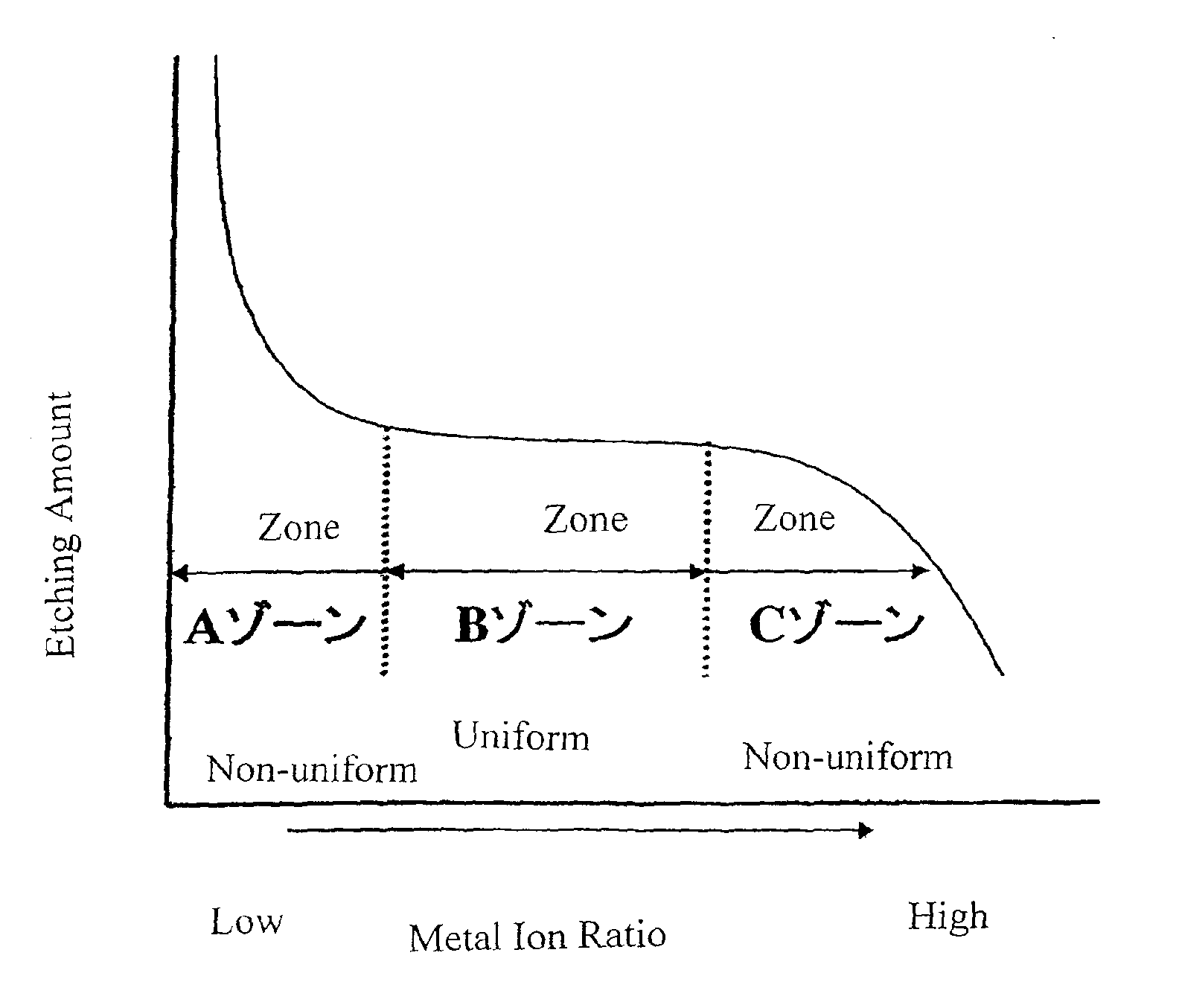
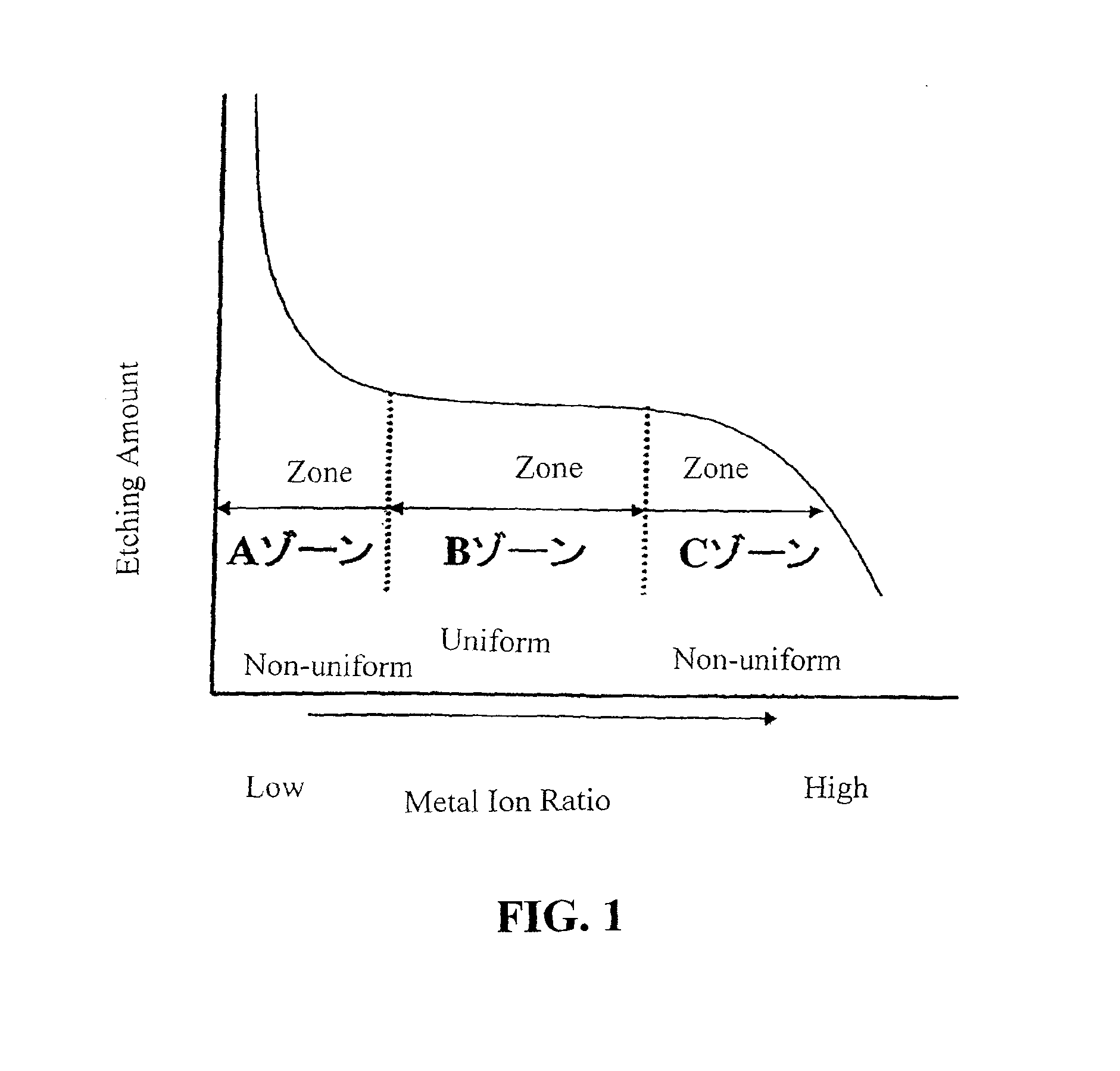
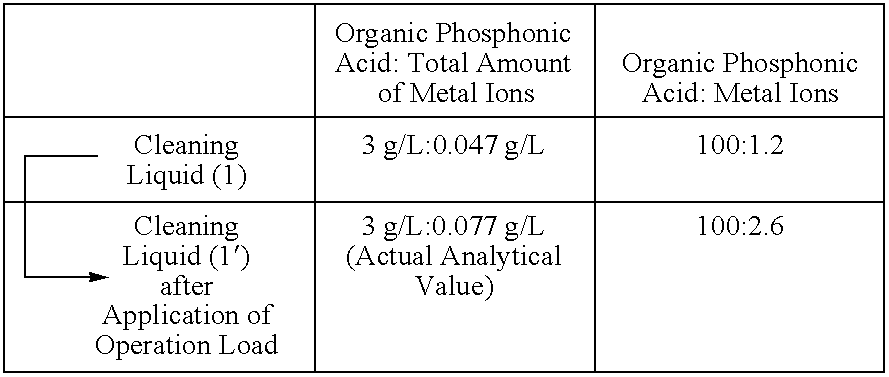
Alkaline cleaning liquid comprising metallic ions for aluminum or aluminum alloys and method of cleaning
ActiveUS7709435B2Mitigate such drawbackCost of energyInorganic/elemental detergent compounding agentsOrganic detergent compounding agentsPhosphateCleaning methods
There is provided an alkaline cleaning of aluminum alloy, in which the attained corrosion resistance is equal or superior to the acidic cleaning agent, and which mitigates the disadvantages of the acidic cleaning agent, such as corrosion of plant, processing of the waste liquid, and energy cost, and which attains improved productivity.The cleaning liquid from 0.5 to 40 g / L in total of one or more alkali builders selected from alkali metal hydroxide, alkali metal carbonate, inorganic alkali metal phosphate and alkali metal silicate, from 0.2 to 10 g / L of one or more of organic phosphonic acid and its salt (A), from 0.001 to 2 g / L of one or more metallic ions (B) selected from metallic ions having from 5.0 to 14.0 of stability constant with the organic phosphonic acid and its salt, and from 0.1 to 10 g / L of surfactant. Particularly, the weight ratio of (A):(B) is in a range of from 100:0.05˜20.
Owner:TOYO SEIKAN KAISHA LTD +1
Method for preparation of magnetic spinel ferrites from layered double hydroxide precursors
InactiveUS20050129609A1High activityLow mixture uniformityLiquid applicationFerroso-ferric oxidesDispersityMagnetization
The invention describes a method of preparing magnetic ferrites from layered precursors in which Fe2+ is first introduced into the layers of layered double hydroxides (LDHs) in order to prepare Me-Fe2+—Fe3+ LDHs, and then by utilizing the easily oxidized nature of Fe2+, binary or multi-component ferrite materials containing Fe3+ in a single crystalline phase can be prepared. Values of the saturation magnetization of ferrites prepared by the method are significantly increased compared with ferrites prepared by traditional methods. Because the metal elements in the layered precursor have the characteristics of a high degree of dispersion, high activity and small particle size (average particle size 40-200 nm), no milling is required before calcination, thus simplifying the production process, shortening the production period, reducing capital investment in equipment and economizing on energy costs. In addition, the method does not corrode production equipment and does not pollute the environment.
Owner:BEIJING UNIV OF CHEM TECH
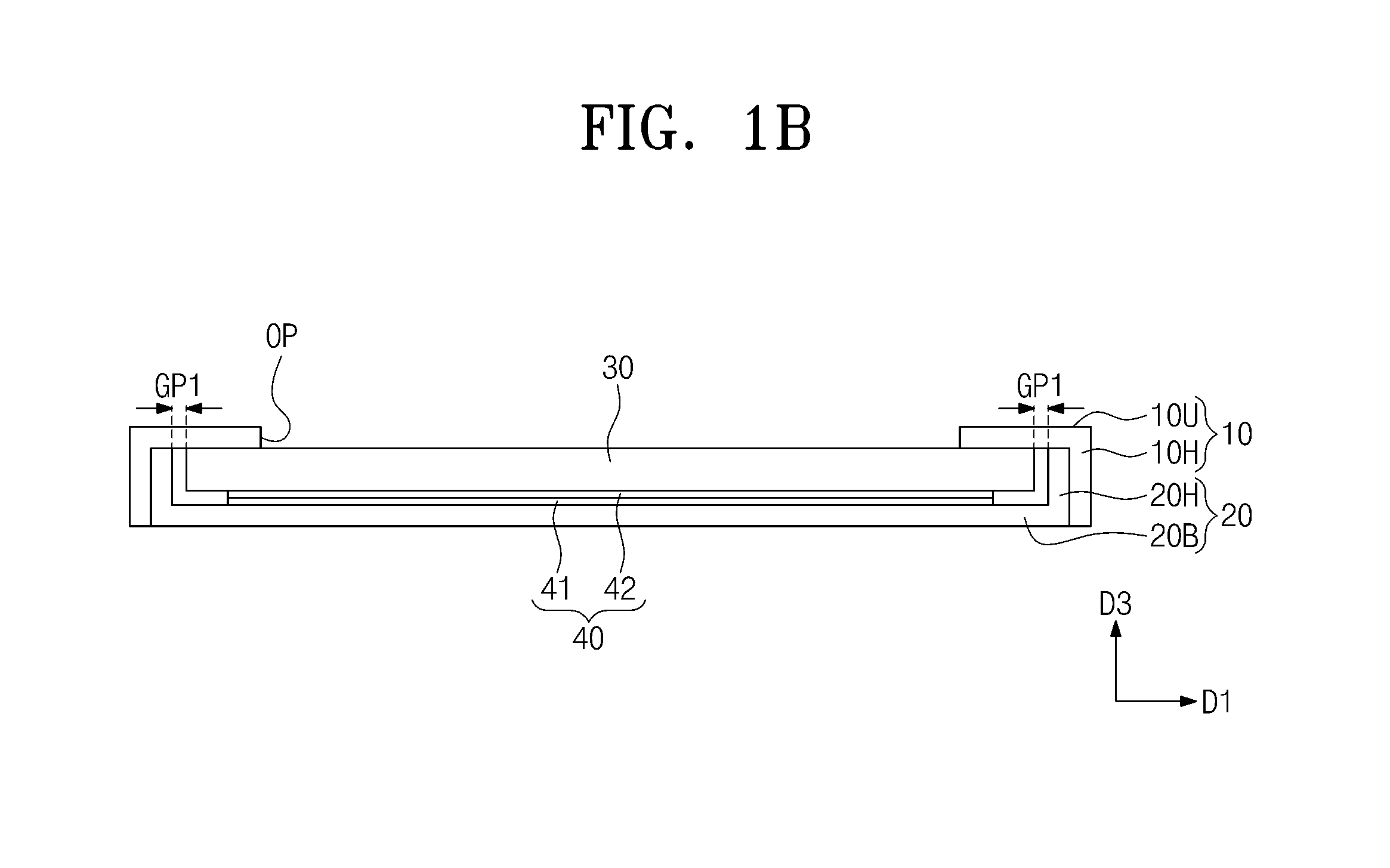
Display device
ActiveUS9490306B2Reduce power consumptionCost of energyStatic indicating devicesSolid-state devicesComputer moduleDisplay device
A display device includes an accommodating member in which an inner space is defined, a display panel accommodated in the inner space in the accommodating member, and an energy generating module disposed between the accommodating member and the display panel and which produces a triboelectricity, where the energy generating module includes a first electrified substrate fixed to the accommodating member and a second electrified substrate disposed on the first electrified substrate, the second electrified substrate moves relative to the first electrified substrate by a frictional event, and the triboelectricity is produced by the relative movement between the first and second electrified substrates.
Owner:SAMSUNG DISPLAY CO LTD
Active optoceramics with cubic crystal structure, method of production of the optoceramics, and uses thereof
ActiveUS20100193739A1High transparencyCost-effectivelyCeramic shaping apparatusLuminescent compositionsPowder mixtureRare earth
The transparent polycrystalline optoceramic has single grains with a symmetric cubic crystal structure and at least one optically active center. The optoceramic has the following formula: A2+xByDzE7, wherein 0≦x≦1.1, 0≦y≦3, 0≦z≦1.6, and 3x+4y+5z=8, and wherein A is at least one trivalent rare earth cation, B is at least one tetravalent cation, D is at least one pentavalent cation, and E is at least one divalent anion. The method of making the optoceramic includes preparing a powder mixture from starting materials, pre-sintering, sintering and then compressing to form the optoceramic. Scintillator media made from the optoceramic are also described.
Owner:SCHOTT AG
Active optoceramics with cubic crystal structure, method of production of the optoceramics, and uses thereof
ActiveUS8197711B2High transparencyCost-effectivelyMaterial analysis by optical meansCeramic shaping apparatusPowder mixtureCrystal structure
The transparent polycrystalline optoceramic has single grains with a symmetric cubic crystal structure and at least one optically active center. The optoceramic has the following formula: A2+xByDzE7, wherein 0≦x≦1.1, 0≦y≦3, 0≦z≦1.6, and 3x+4y+5z=8, and wherein A is at least one trivalent rare earth cation, B is at least one tetravalent cation, D is at least one pentavalent cation, and E is at least one divalent anion. The method of making the optoceramic includes preparing a powder mixture from starting materials, pre-sintering, sintering and then compressing to form the optoceramic. Scintillator media made from the optoceramic are also described.
Owner:SCHOTT AG
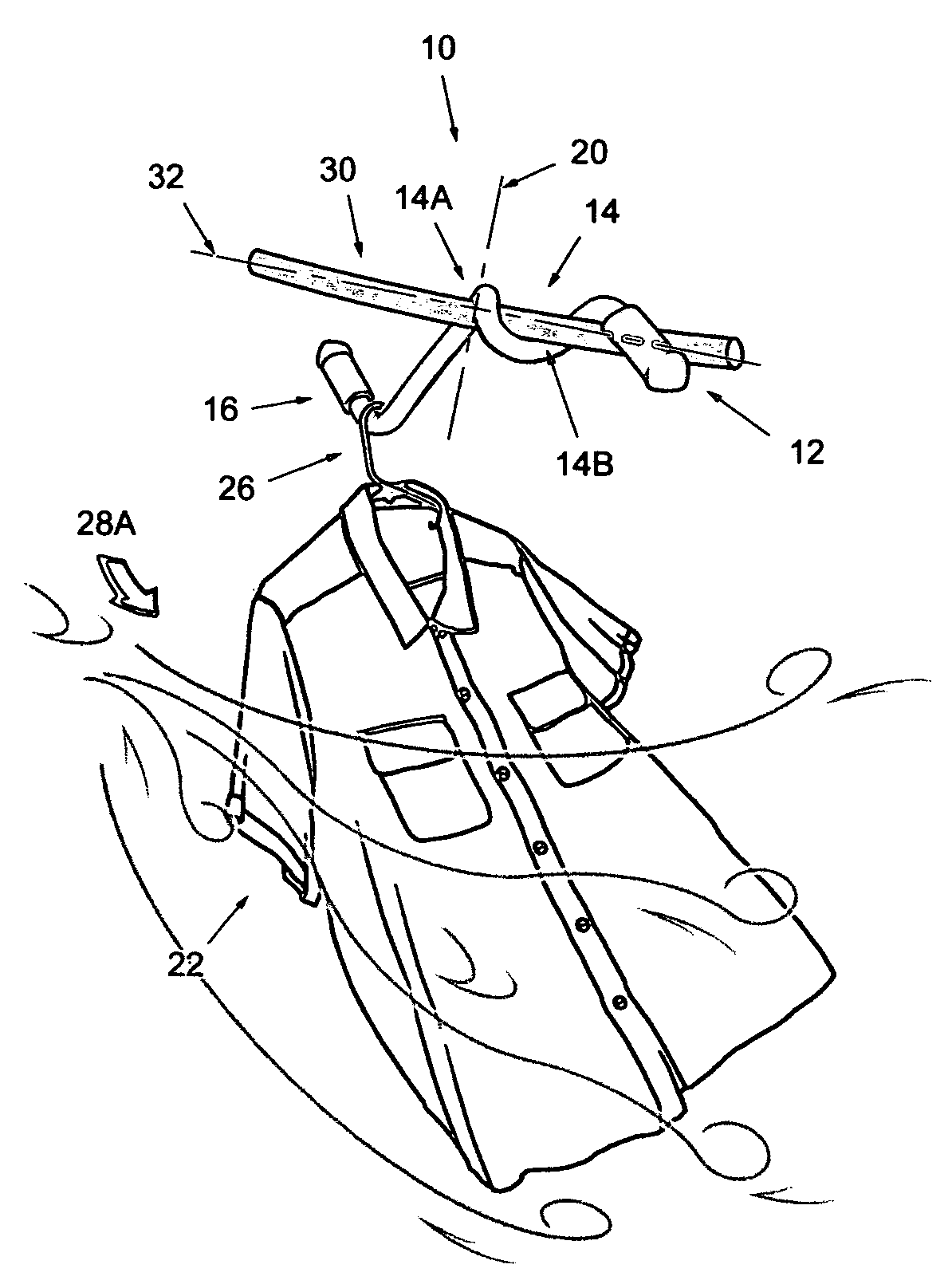
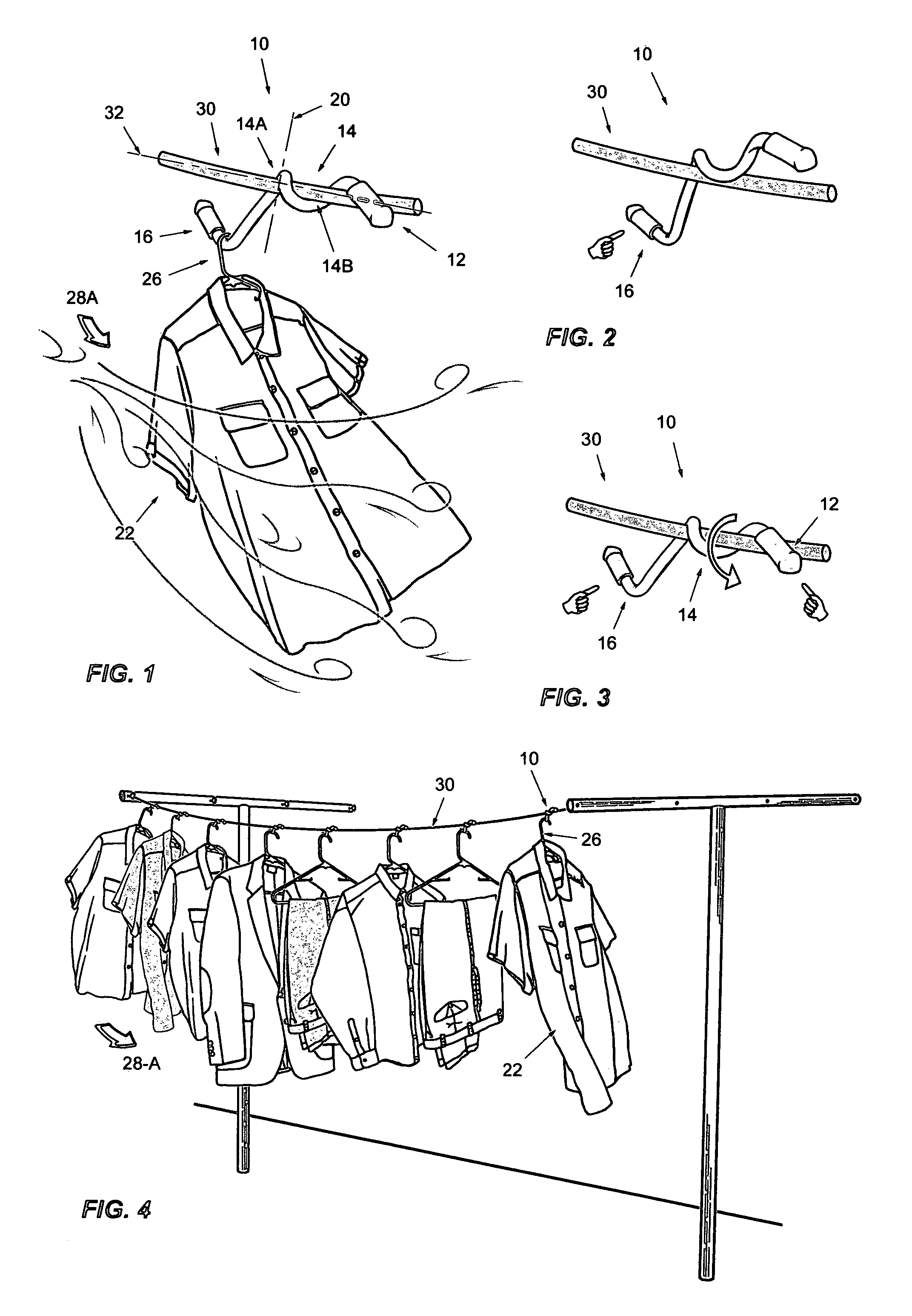
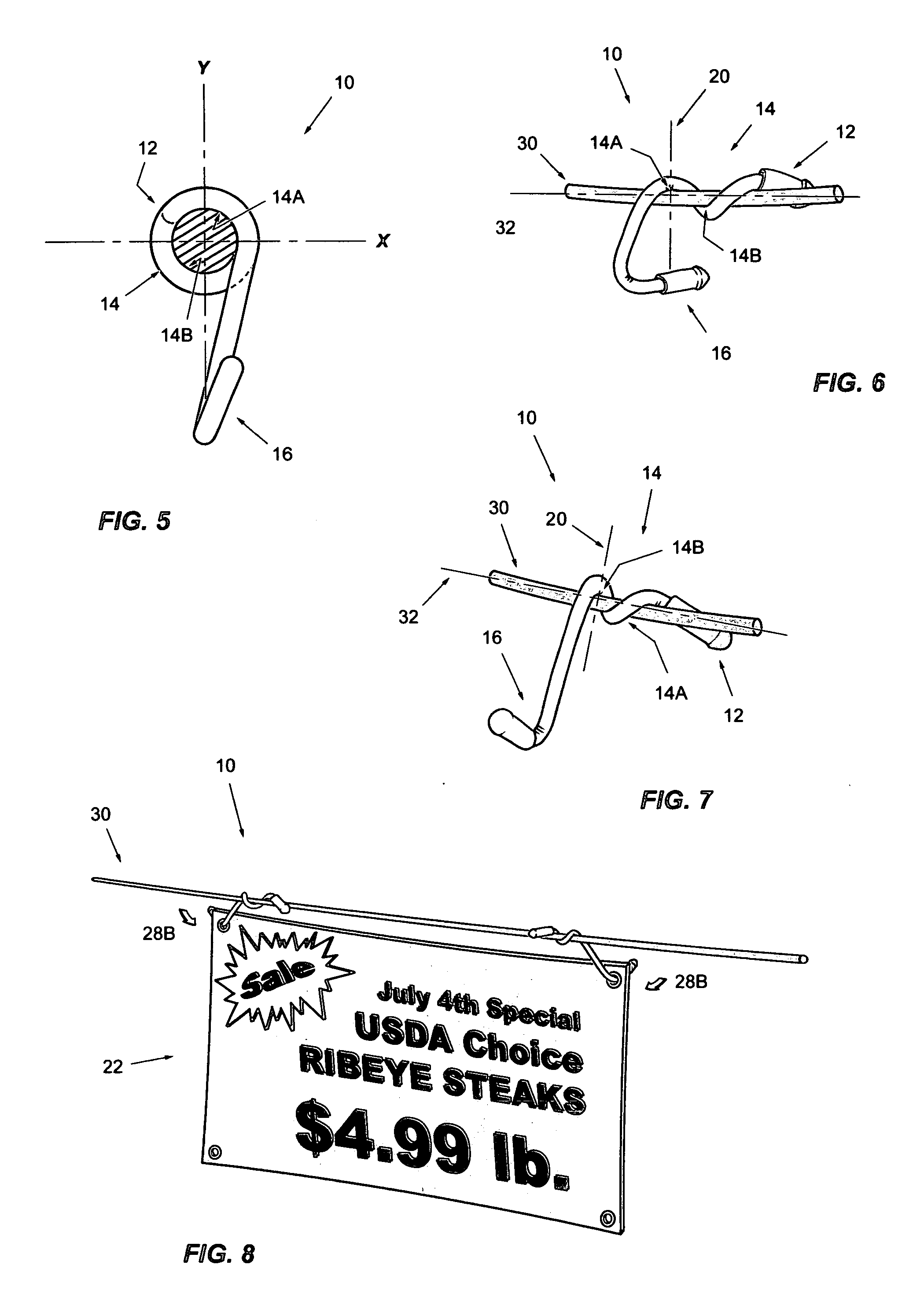
Non-symmetrical wire clip for clotheslines
InactiveUS20070290111A1Convenient ArrangementShorten drying timeApparel holdersPicture framesEngineeringIncrease pressure
An improved wire clip 10 to better keep hung garments 22 separated when suspending onto clotheslines 30. Also useful for hanging banners 22, the clip 10 offers a non-symmetrically centered axis 20 which is perpendicular to the line 30. A friction body 14 provides a pressure means by a fulcrum locus 14-A opposing a counter locus 14-B; a catch tail 16 is provided for suspending the garment 22. The weight of the suspended garment 22 leverages the body 14 at the non-symmetrical axis 20 which disposes the fulcrum 14-A, and opposes the counter 14-B to create increased pressure onto the line 30.
Owner:ALONSO RICARDO
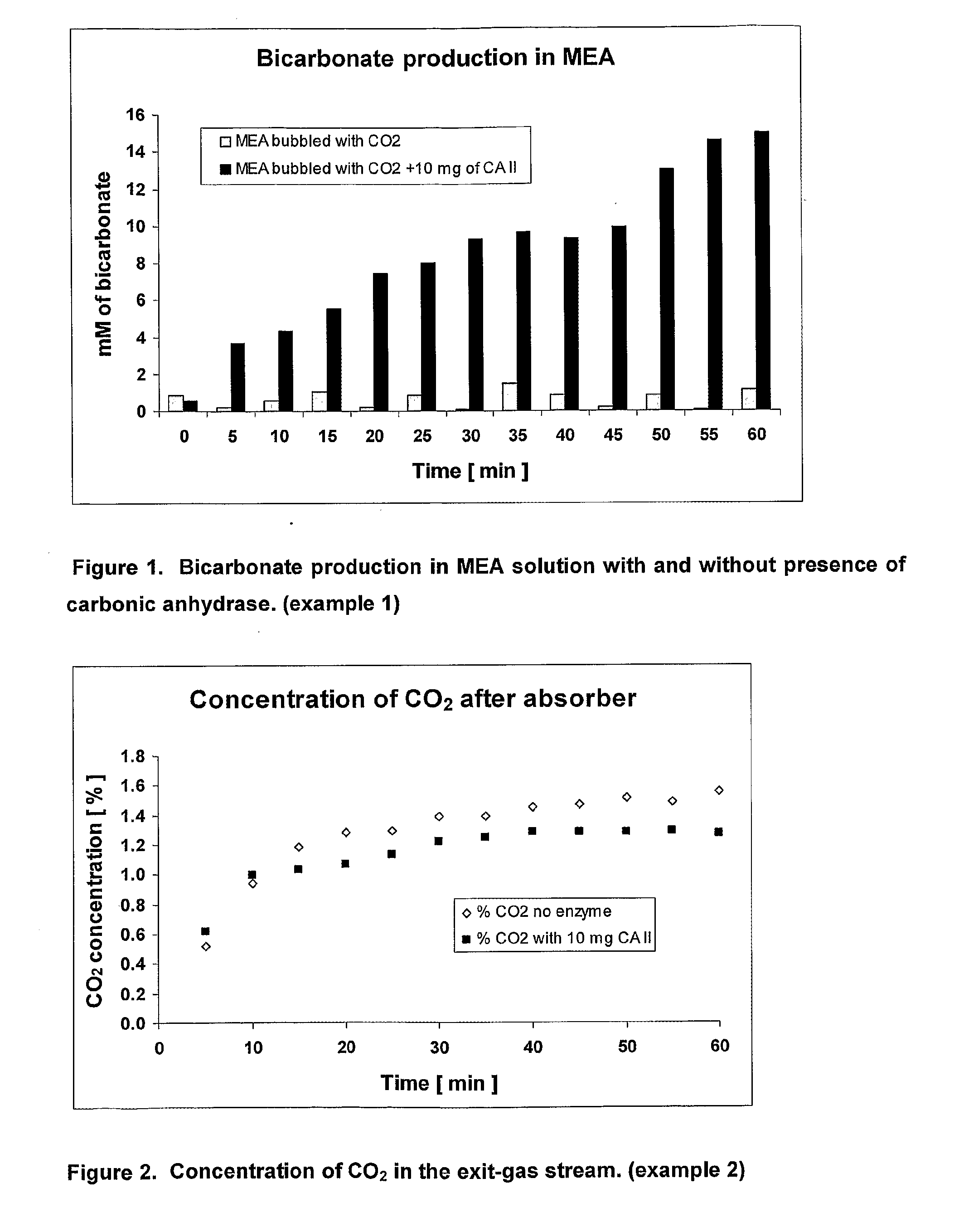
Use of enzyme catalysts in co2 pcc processes
A method for processing a stream enriched in CO2 from a gas by the action of an absorbent in the stream includes desorbing CO2 from the stream by application of heat to the stream to desorb the CO2 and regenerate the absorbent in a reaction system that includes reconstitution of carbon dioxide and an alkanolamine from carbamate and ammonium ion solution. The energy requirement is materially reduced by the presence of a biocatalyst. In another aspect, a gas stream is contacted with a sorbent system to effect absorption of CO2 from the gas stream, the sorbent and absorbed CO2 are separated from the gas stream to form a CO2-rich stream, and the sorbent system contains a primary or secondary alkanolamine and a catalyst selected to modify the reaction kinetics of the absorption process so as to materially increase the proportion of bicarbonate in the CO2-rich stream relative to carbamate.
Owner:COMMONWEALTH SCI & IND RES ORG
Resource Tower
InactiveUS20170033381A1Maximize its propertyGood energyEnergy based wastewater treatmentFlash steam boilersNuclear engineeringElectrochemistry
Invented is a Resource Tower that uses water electrolysis to separate out its elemental and purified H2 hydrogen gas and O2 oxygen gas. These gases form a pressurized flow for electricity generation for distribution and transport to heights atop the Resource Tower. Core advancements of this invention are the use of fuel cells at the top of the Resource Tower to electrochemically combine hydrogen gas and oxygen gas to produce electricity, heat, and water. The Resource Tower distributes the electricity, converts heat and water to steam to generate additional electricity for distribution, and ultimately coalesces the steam back to water at a height. The water that falls under acceleration of gravity from atop the Resource Tower is used to generate additional electricity for distribution. In addition to multiple sites of electricity generation for distribution, the purity of hydrogen gas and oxygen gas from water electrolysis is retained and the water resulting from the Resource Tower is purified and potable for distribution.
Owner:REILLY THOMAS MICHAEL
Method for preparation of magnetic spinel ferrites from layered double hydroxide precursors
InactiveUS7232557B2High activityLow mixture uniformityLiquid applicationFerroso-ferric oxidesMagnetizationSingle crystal
The invention describes a method of preparing magnetic ferrites from layered precursors in which Fe2+ is first introduced into the layers of layered double hydroxides (LDHs) in order to prepare Me-Fe2+—Fe3+ LDHs, and then by utilizing the easily oxidized nature of Fe2+, binary or multi-component ferrite materials containing Fe3+ in a single crystalline phase can be prepared. Values of the saturation magnetization of ferrites prepared by the method are significantly increased compared with ferrites prepared by traditional methods. Because the metal elements in the layered precursor have the characteristics of a high degree of dispersion, high activity and small particle size (average particle size 40-200 nm), no milling is required before calcination, thus simplifying the production process, shortening the production period, reducing capital investment in equipment and economizing on energy costs. In addition, the method does not corrode production equipment and does not pollute the environment.
Owner:BEIJING UNIV OF CHEM TECH
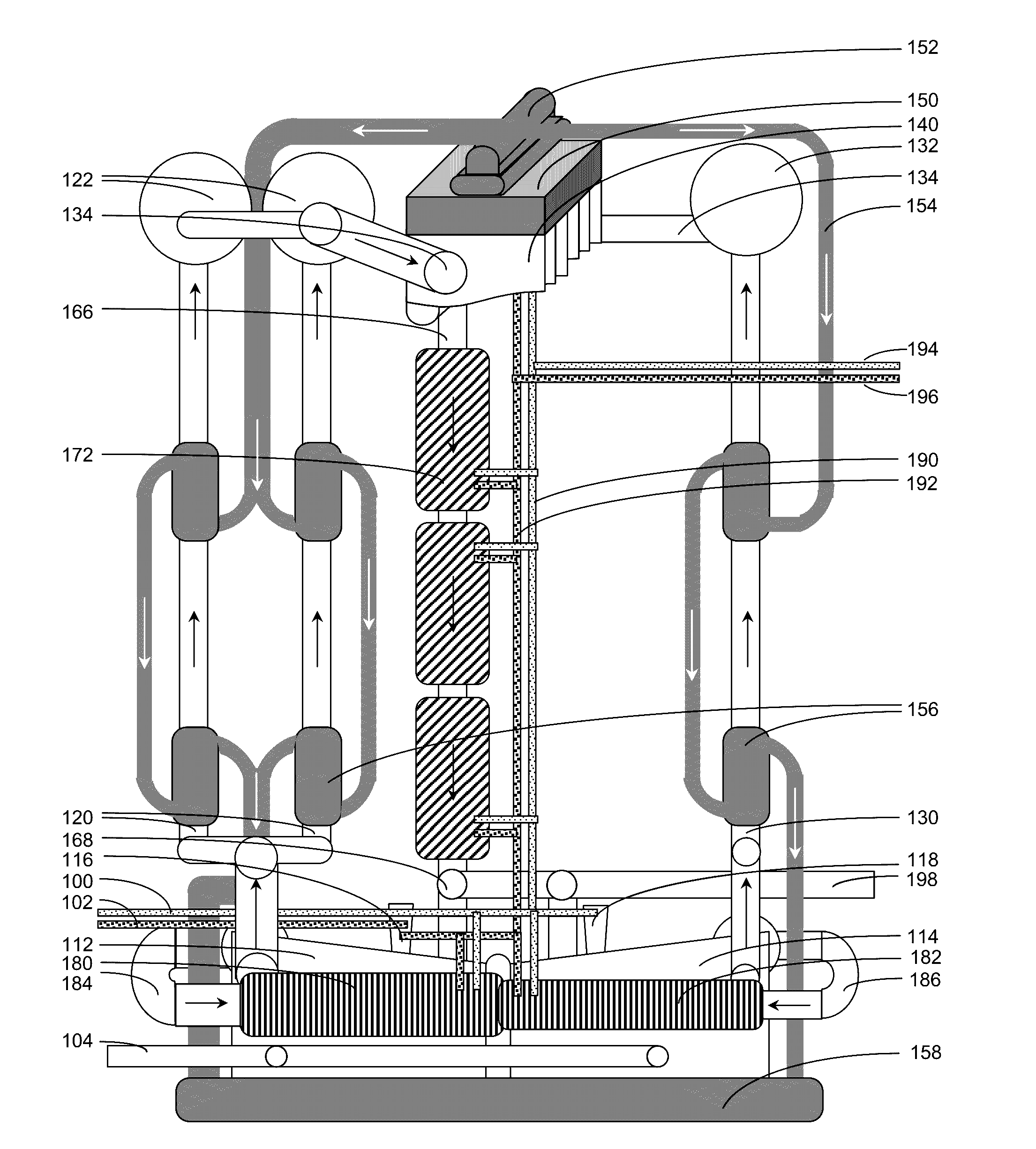
Apparatus, method, and system for lighting fixture cooling
InactiveUS9970645B1Reduce the temperatureCost of energyMechanical apparatusPoint-like light sourceEffect lightHigh intensity
A high-intensity LED lighting system is presented whereby one or more LED lighting fixtures are affixed to an elevating structure, the elevating structure having a substantially continuous internal pathway. Said pathway can be used as a conduit or duct for pressurized air which is introduced at or near the bottom of the elevating structure and forced upwardly toward the lighting fixtures so to provide cooling of one or more components of the lighting fixtures so to, ultimately, improve the efficacy of the LEDs contained therein. A method of designing lighting systems, including analysis of whether or not to add air cooling to increase light source efficiency is also disclosed.
Owner:MUSCO
Method for preventing a risk of freezing in a reducing-agent feeding device of a selective catalytic reduction system
ActiveUS20200284178A1Cost of energyIncrease volumeInternal combustion piston enginesExhaust apparatusInternal combustion engineExhaust pipe
Disclosed is a method for preventing a risk of freezing in a device for supplying reducing agent to a selective catalytic reduction system in an exhaust line, a freezing temperature specific to the agent being stored in memory, the system including a controller operating the system and emitting pulses to an injector, the controller being inactive when the engine is switched off. With the combustion engine switched off, the controller is woken up at predetermined intervals to initiate an emission of a specific electric pulse to the injector with measurements of a current-strength and voltage of the electric pulse providing a value of the electrical resistance of the injector. A temperature of the reducing agent at the injector is estimated as a function of the measured resistance and, when at least the temperature thus estimated is below the freezing temperature, a purge of the device is initiated.
Owner:VITESCO TECH GERMANY GMBH
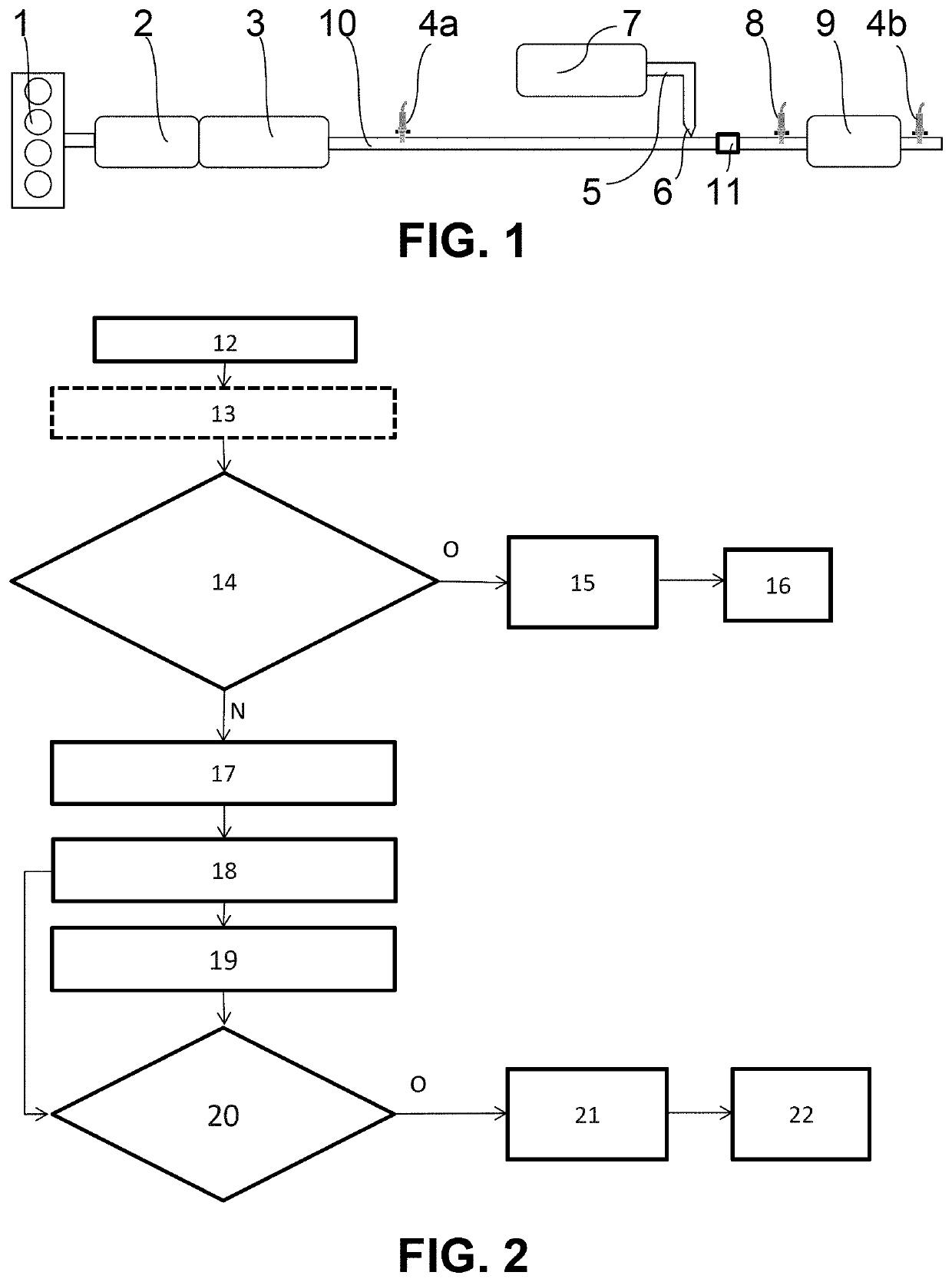
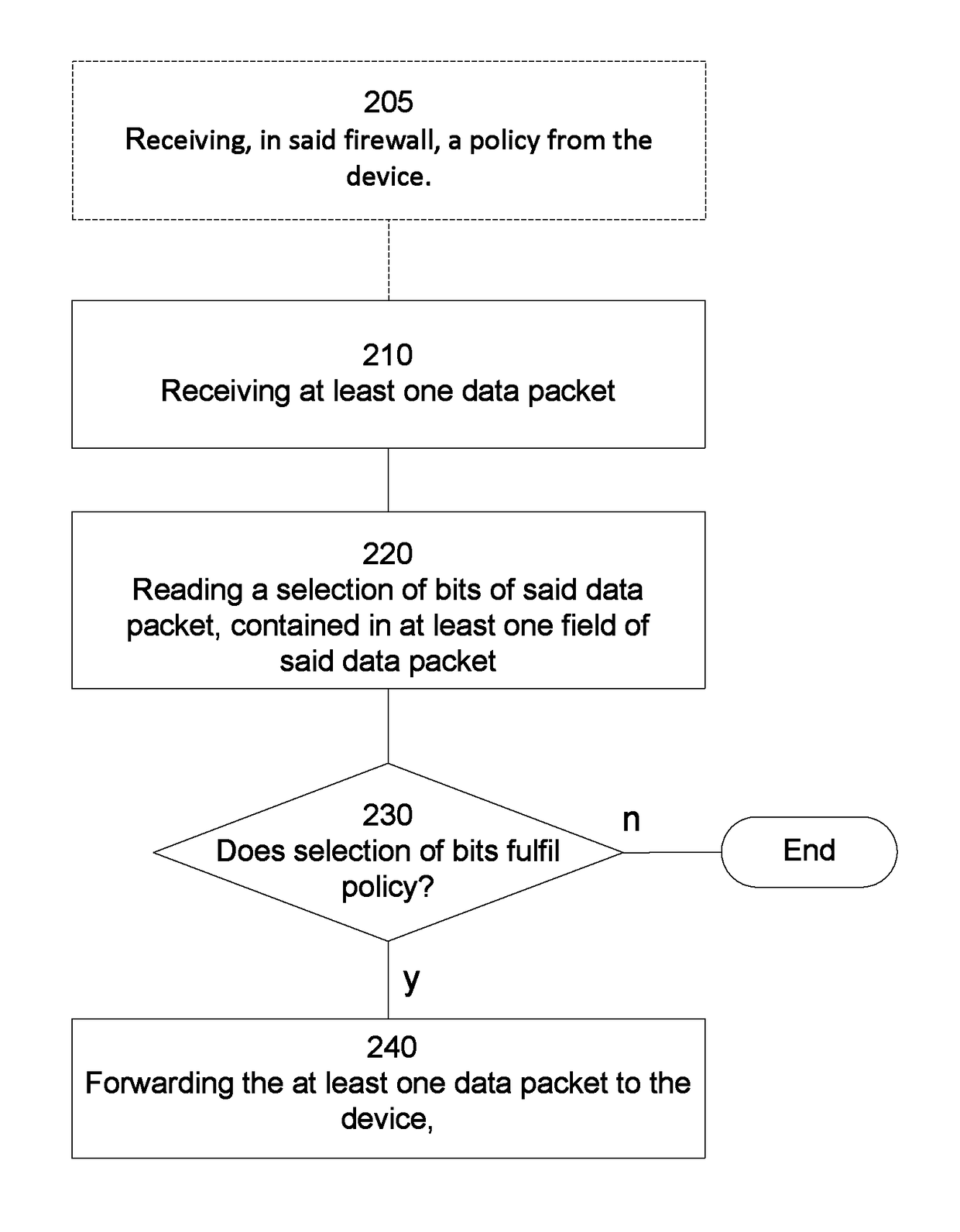
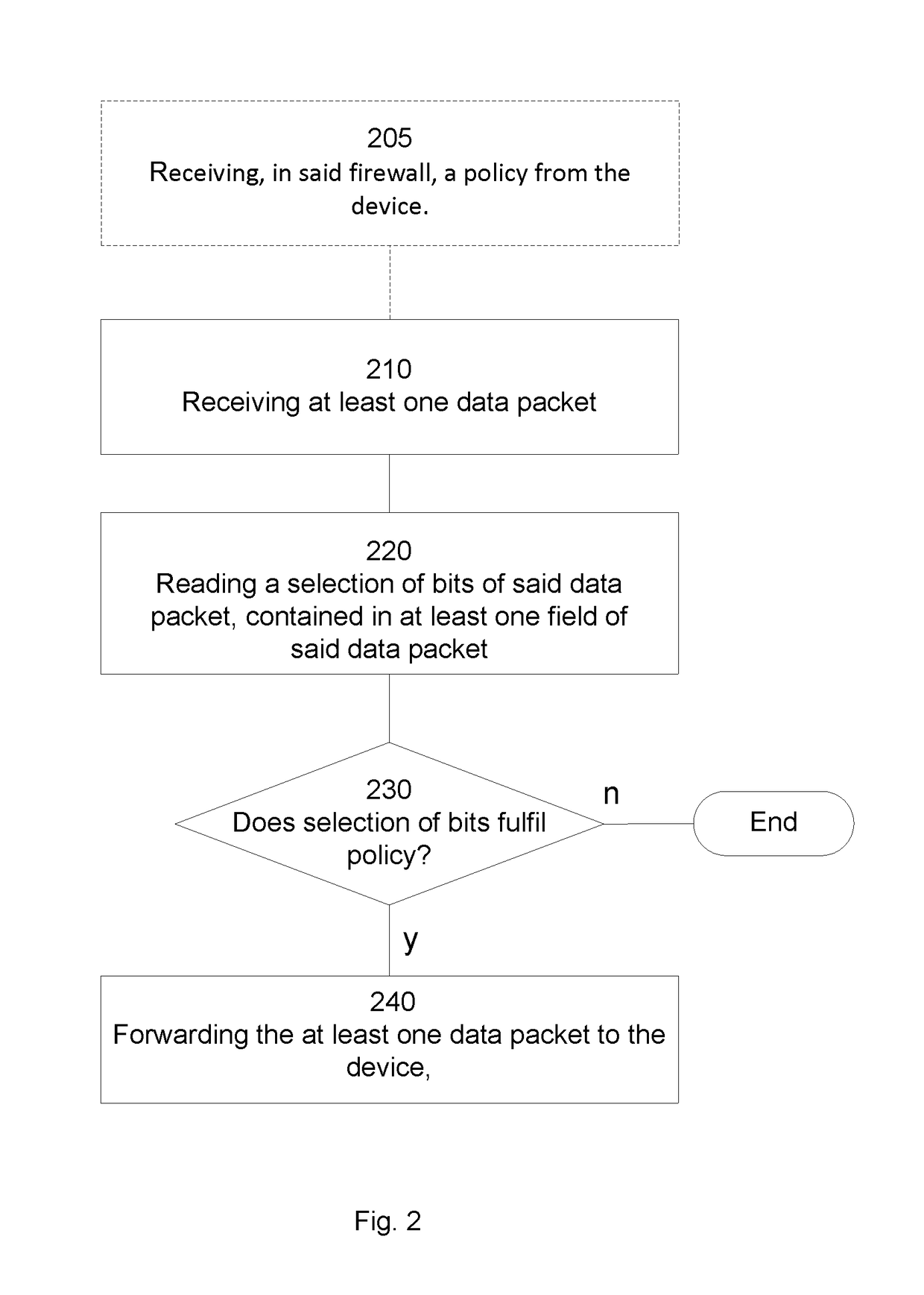
Method and firewall for soliciting incoming packets
ActiveUS10015136B2Minimization requirementsCost of energyTransmissionSecurity arrangementData streamNetwork packet
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com