Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Convenient for dynamic expansion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
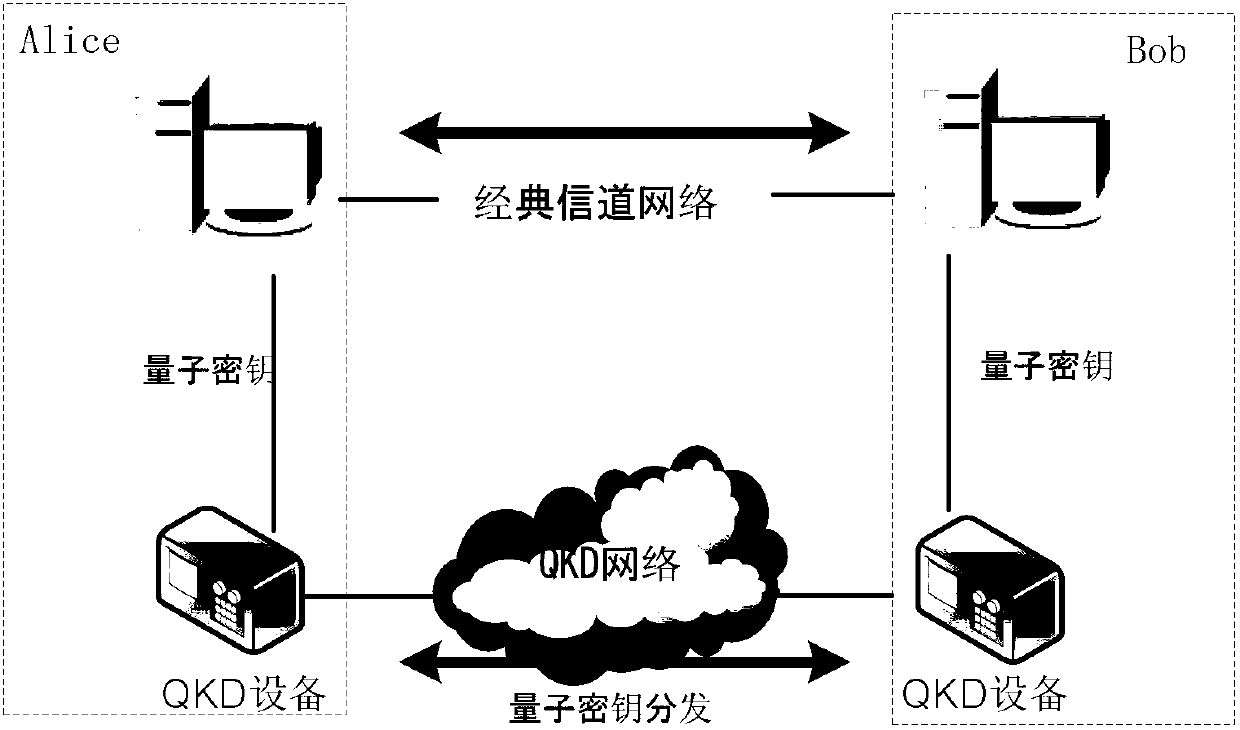
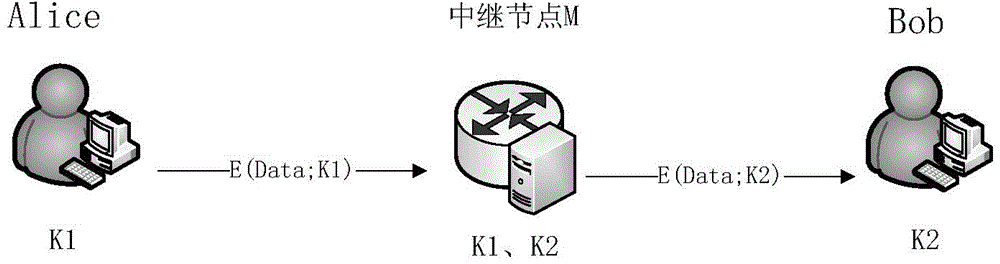
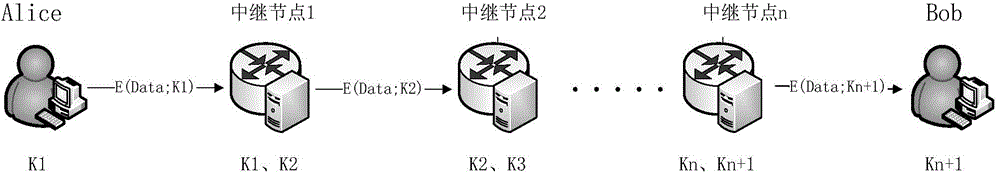
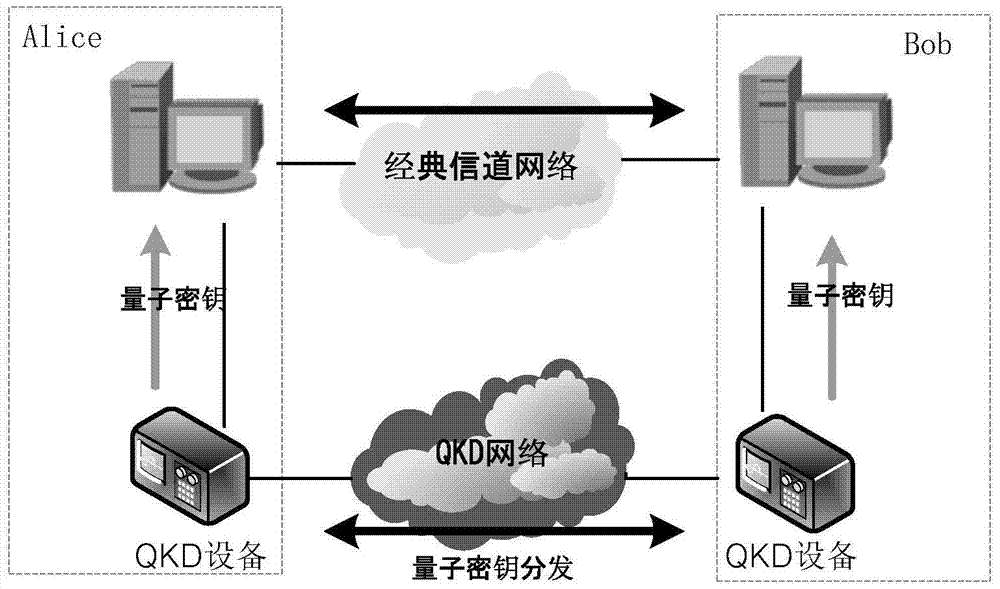
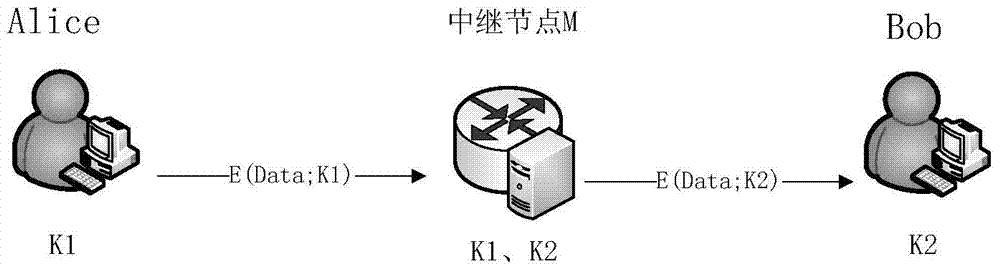
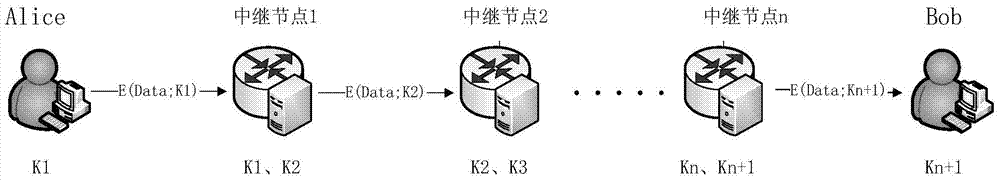
Quantum cryptography network dynamic routing method
ActiveCN103001875AConvenient for dynamic expansionFast convergenceKey distribution for secure communicationData switching networksRefresh cycleRoute server
The invention discloses a quantum cryptography network dynamic routing method. According to the method, dynamic routing selection of encryption communication is performed by utilizing quantum cryptography according to changes of the quantum key quantity between relay nodes of a quantum cryptography network. According to the method, a route server is arranged for the relay nodes of the whole quantum cryptography network, and topology refresh cycles of the quantum cryptography network are set; in each topology refresh cycle, each relay node collects and processes state information of the relay node and reports results to the route server. After the route server collects the topology state information of each relay node, quantum cryptography network topology state information of a next topology refresh cycle is generated and sent to all the relay nodes of the quantum cryptography network. According to the quantum cryptography network topology state information obtained from the route server, a target relay node is calculated and determined to be a next skip route of communication data of a random other relay node according to a shortest path law through each relay node.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +2
Dynamic route architecture system for quantum cryptography network
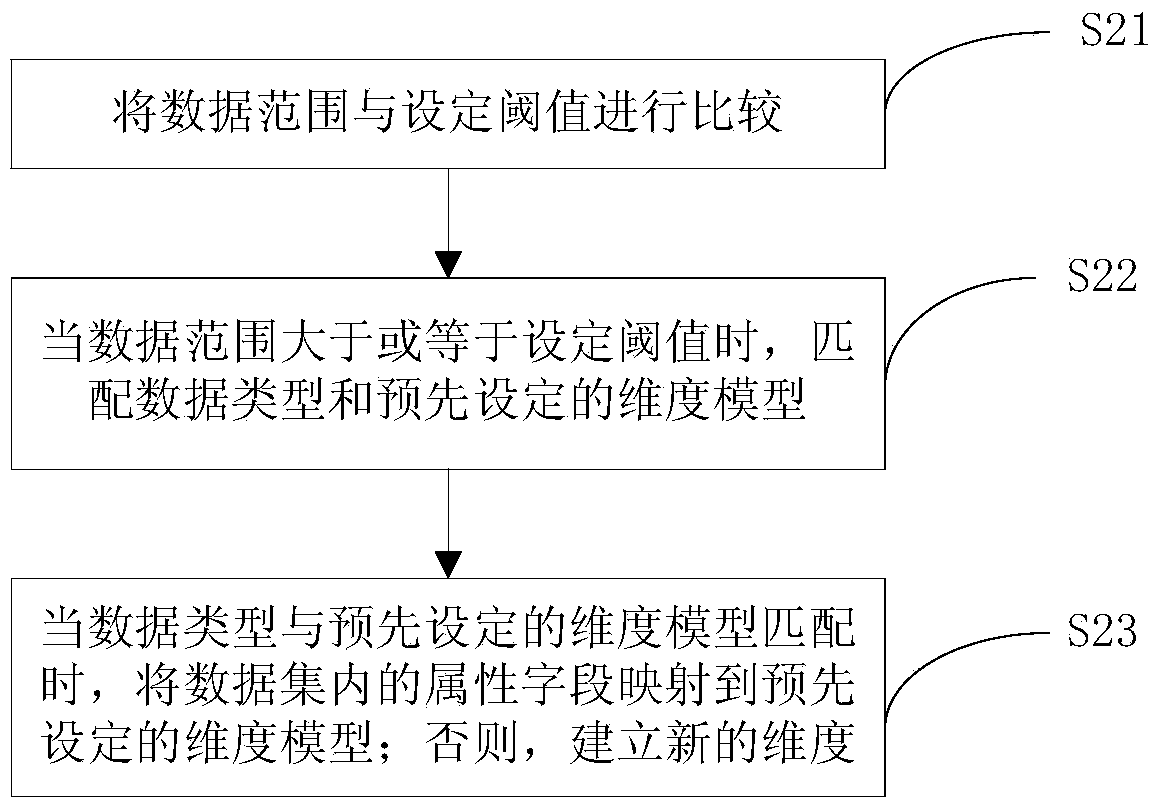
ActiveCN104579964AConvenient for dynamic expansionFast convergenceKey distribution for secure communicationData switching networksRoute serverProcess state
The invention discloses a dynamic route architecture system for a quantum cryptography network. The system performs dynamic route selection for cryptographic communication by the aid of quantum cryptography according to changes of quantum key quantities among relay nodes of the quantum cryptography network. Specifically, a route server is arranged for the relay nodes of the whole quantum cryptography network, and topology updating cycles of the quantum cryptography network are set; each relay node gathers and processes state information of each relay node and reports each result to the route server in each topology updating cycle. The route server generates topology state information of the quantum cryptography network in the next topology updating cycle after gathering the topology state information of all the relay nodes and sends the topology state information to all the relay nodes of the quantum cryptography network. Each relay node calculates and determines a target relay node as a next-hop route of communication data of any other relay node on the basis of a shortest path rule according to the topology state information of the quantum cryptography network acquired from the route server.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
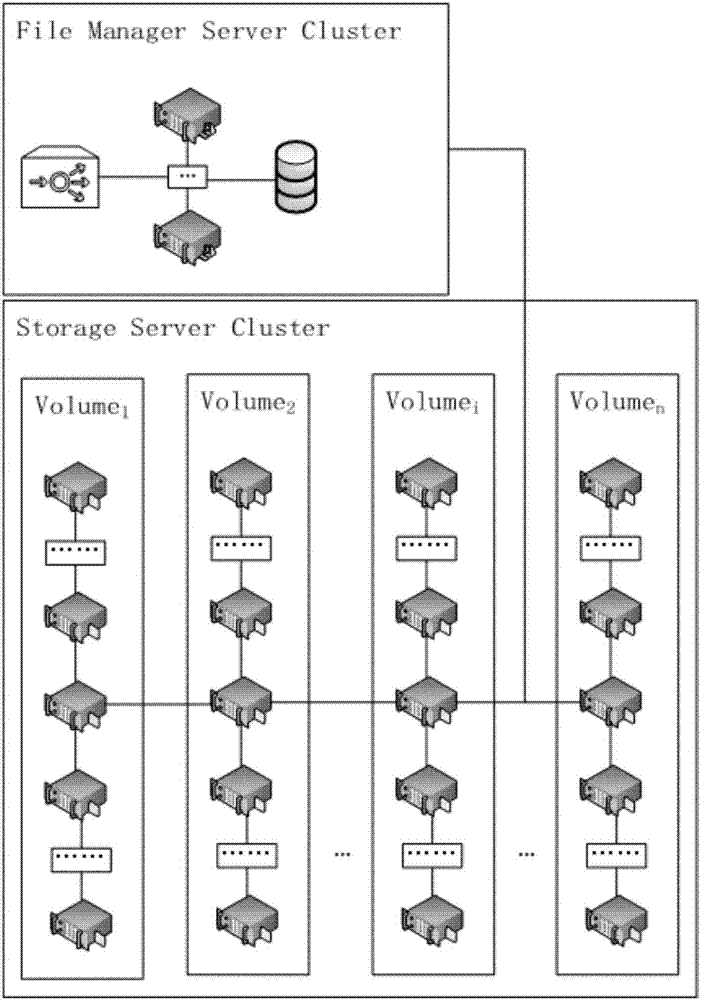
Distributed file storage system
ActiveCN107547653AImprove access performanceSupport real-time playbackTransmissionData fileMirror image
The invention provides a distributed file storage system, which comprises a data storage server cluster subsystem and a file management server cluster subsystem, wherein the file management server cluster subsystem comprises at least two storage volumes; each storage volume at least comprises two storage node servers, the storage node servers in each volume are backups and mirror images of each other, and a difference of storage capacities of the storage node servers in each volume is smaller than a first set value; and the file management server cluster subsystem is used for customer file uploading, storage management and storage server cluster synchronization. The invention provides a large number of super-large scale extensible and loosely-coupled distributed file systems, the performance is greatly improved, the dynamic expansion is greatly improved, the system supports file second pass, streaming media real-time playing, oversized data file storage and multi-user file sharing andprotection, and the basic services are provided for a data storage technology of the present era of big data.
Owner:NORTH CHINA UNIV OF WATER RESOURCES & ELECTRIC POWER
Dynamic server dilatation system and method
ActiveCN105162859AAvoid running out of disk capacityReduce security risksTransmissionLoad regulationOperating system
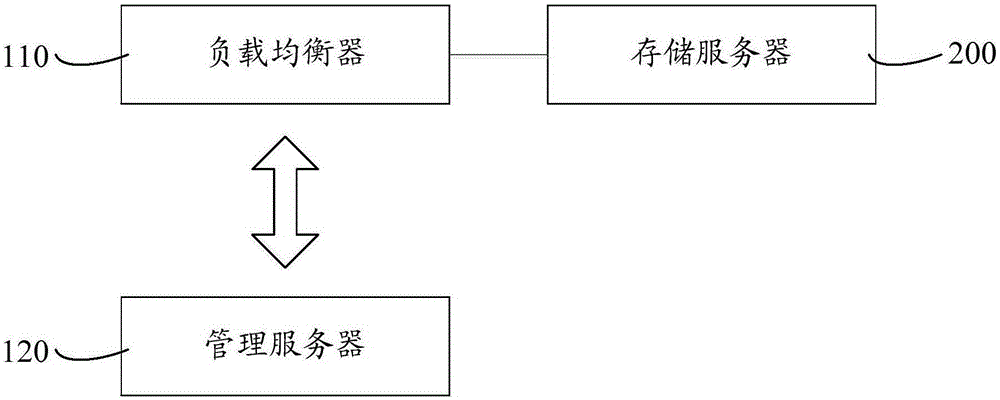
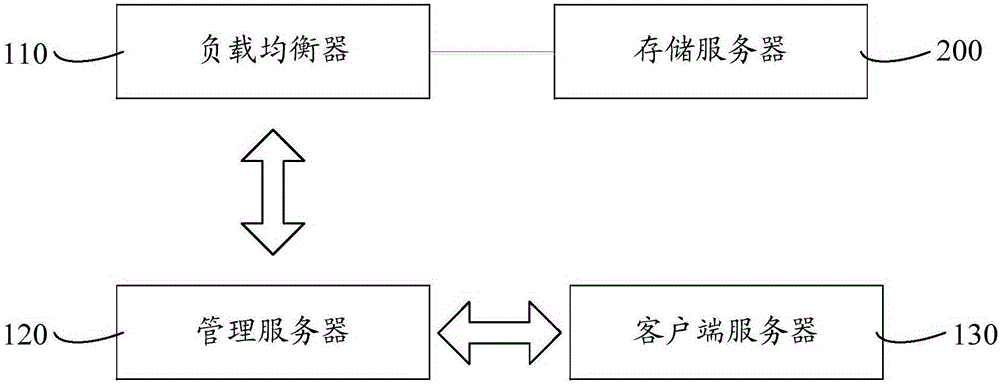
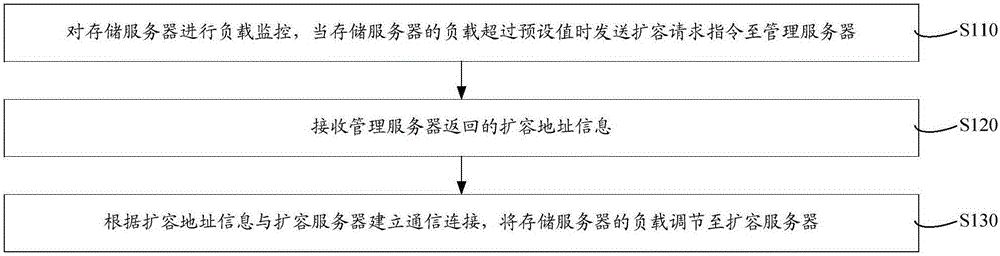
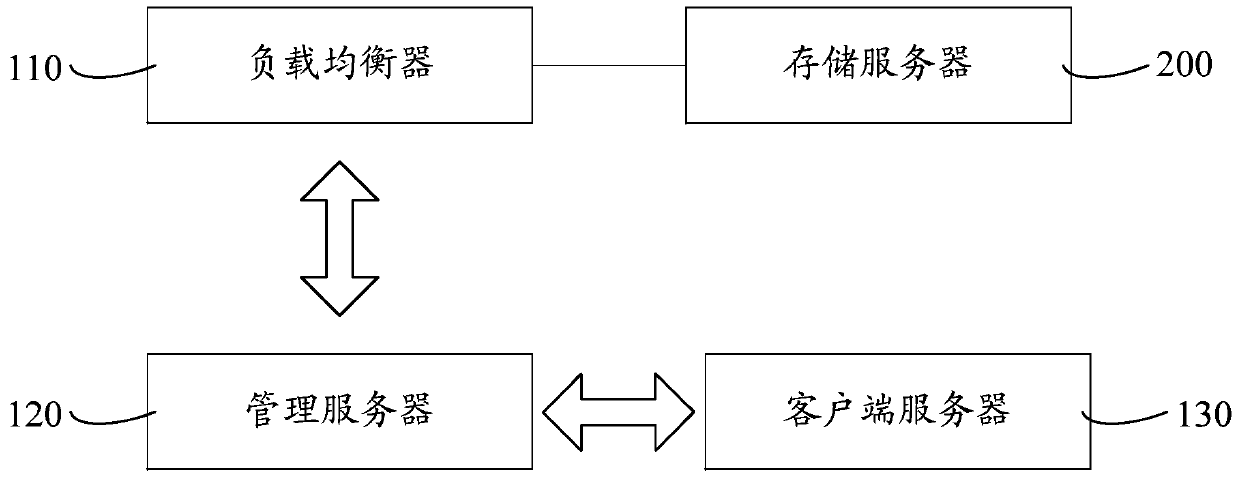
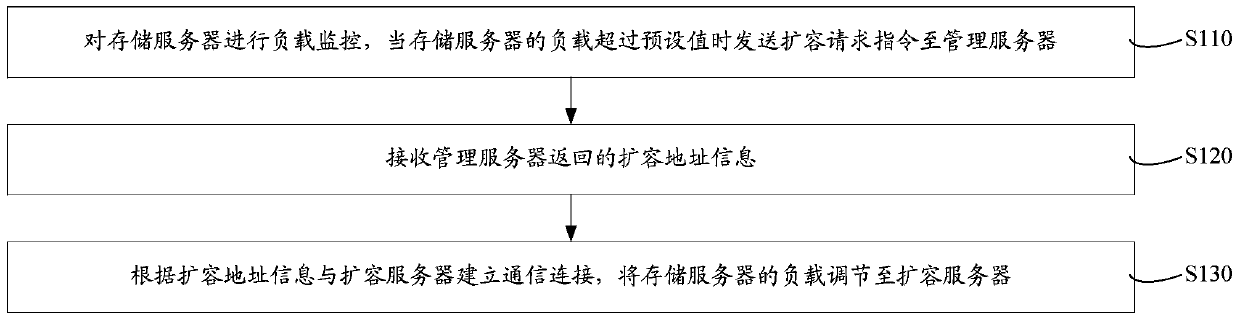
The invention relates to a dynamic server dilatation system and method. A load equalizer monitors the load of a storage server and sends a dilatation request instruction to a management server when the load of the storage server exceeds a preset value. The management server sends dilatation address information to the load equalizer after receiving the dilatation request instruction. The load equalizer establishes a communication connection with a dilatation server according to the dilatation address information and adjusts the load of the storage server to the dilatation server. After the overload of the storage server is detected, the load of the overload server is adjusted to the dilatation server to avoid an undercapacity of the disk of the server. During dilatation of the server, influence on normal operation of a website and normal access of a user can be avoided, and limitations to the model and the capacity of the disk of the server also can be reduced; as a result, potential safety hazards caused to the data of the server in the dilatation process are effectively relieved, and the operation reliability is high; besides, the dilatation method is simple and easy to implement, and convenient for dynamic expansion of a platform.
Owner:HUNAN YIGU TECH DEV
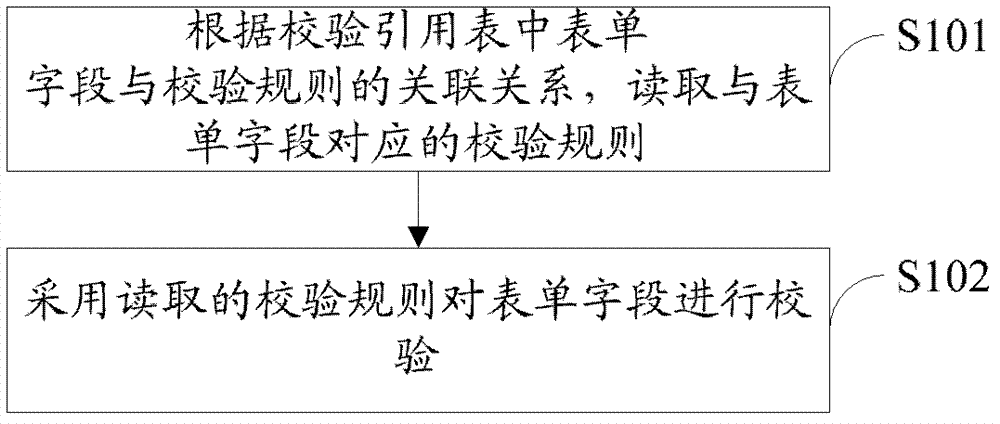
Method, device and enterprise system for checking forms
InactiveCN102819766AAchieve reuseConvenient for dynamic expansionInstrumentsReusabilityComputer software
The invention is suitable for the field of computer software and provides a method, a device and an enterprise system for checking forms. The method includes: reading checking rules corresponding to form fields according to correlation between the form fields in a checking reference list and the checking rules; and checking the form fields according to the read checking rules. By storing predefined checking rules into a database and building reference relationship between related form fields and the checking rules, the checking rules can be dynamically read from the database. When adding of the form fields or deleting of the form fields is needed, adding or deleting of the checking rules can be directly performed in the database, and accordingly dynamic expansion of checking is facilitated. The same form fields can read a same checking rule, so that reusability of the checking rules is achieved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
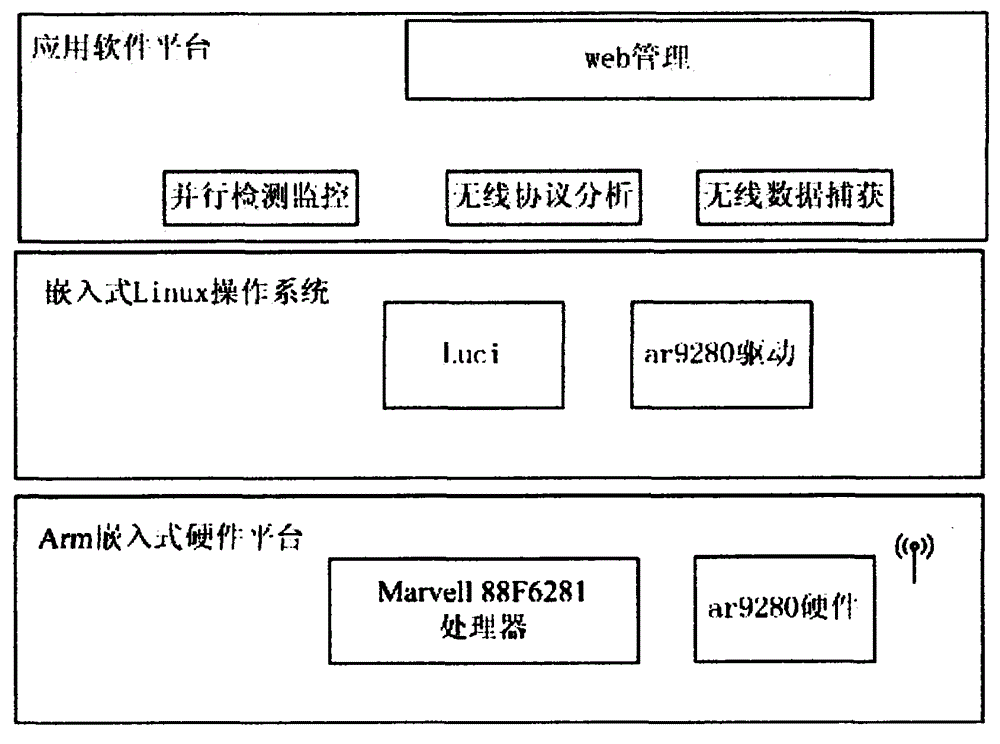
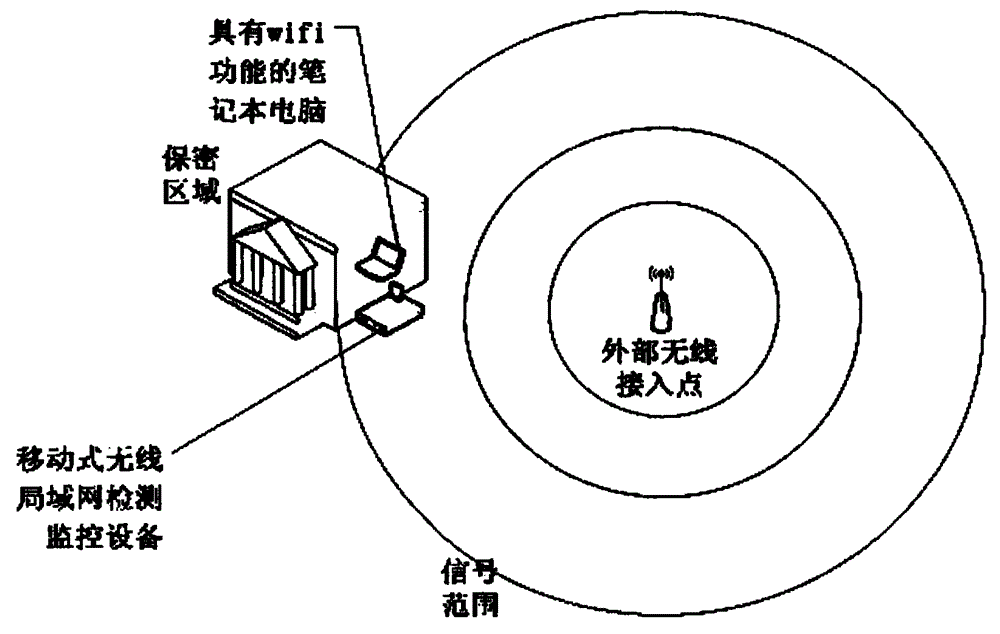
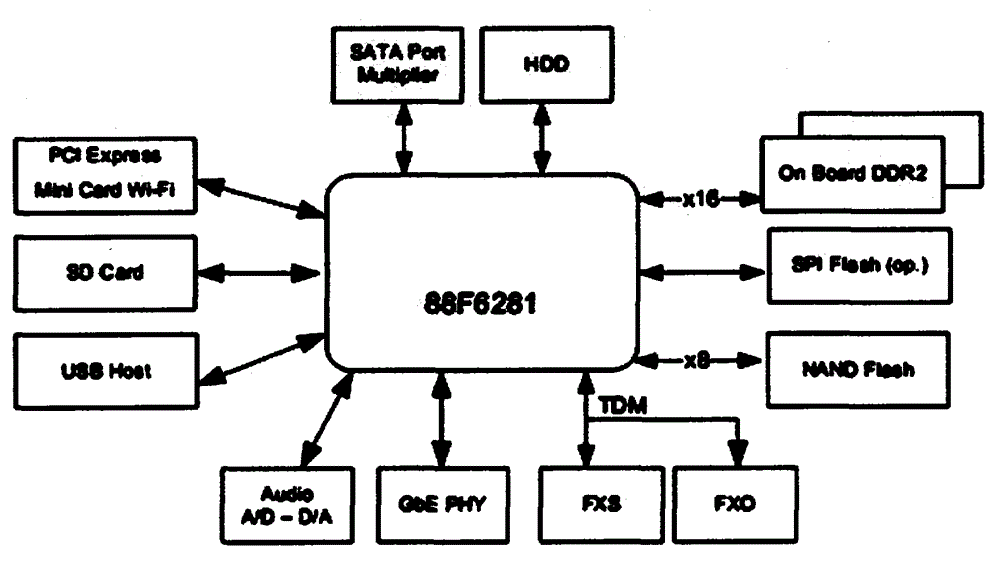
Portable wireless network detection evidence-obtaining system
InactiveCN104159244AConvenient for dynamic expansionReduce power consumptionHigh level techniquesWireless communicationOperational systemEmbedded operating system
The invention discloses a portable wireless network detection evidence-obtaining system which comprises an embedded hardware platform, as well as an embedded operating system module and an application platform module based on the embedded hardware platform, wherein the embedded hardware platform comprises an embedded mainboard and a wireless network card module; the wireless network card module specifically comprises a network interface controller, a baseband processor, a medium frequency processing unit, a radio frequency processing unit, a transmitting-receiving module and an antenna sequentially connected. According to the invention, a system framework taking a modularization architecture as a main body, the hardware platform based on a low-power and high-performance arm embedded platform, and a software platform taking a customized safe embedded Linux operating system as a backbone are realized, and the technologies such as wireless network drive optimization, concurrence multithreading real-time monitoring and multimode wireless security detection are combined and adopted, so that the problems about miniaturization, mobility and low energy consumption of equipment are effectively solved, and the perfect wireless detection function is realized through multiple innovative technologies.
Owner:王强
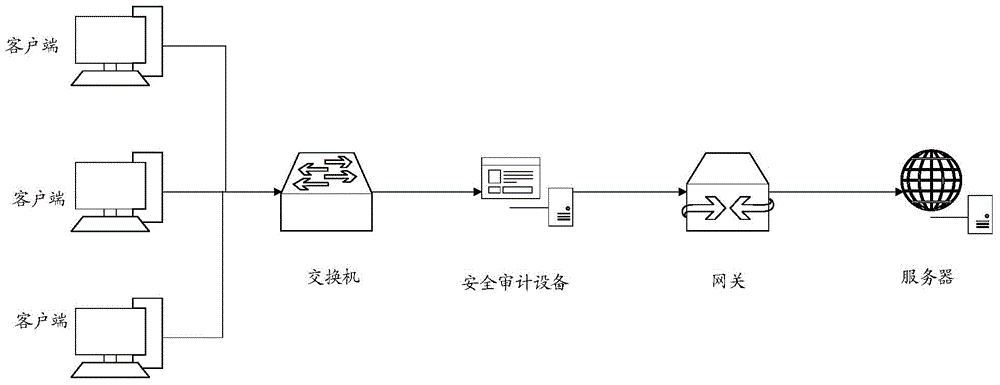
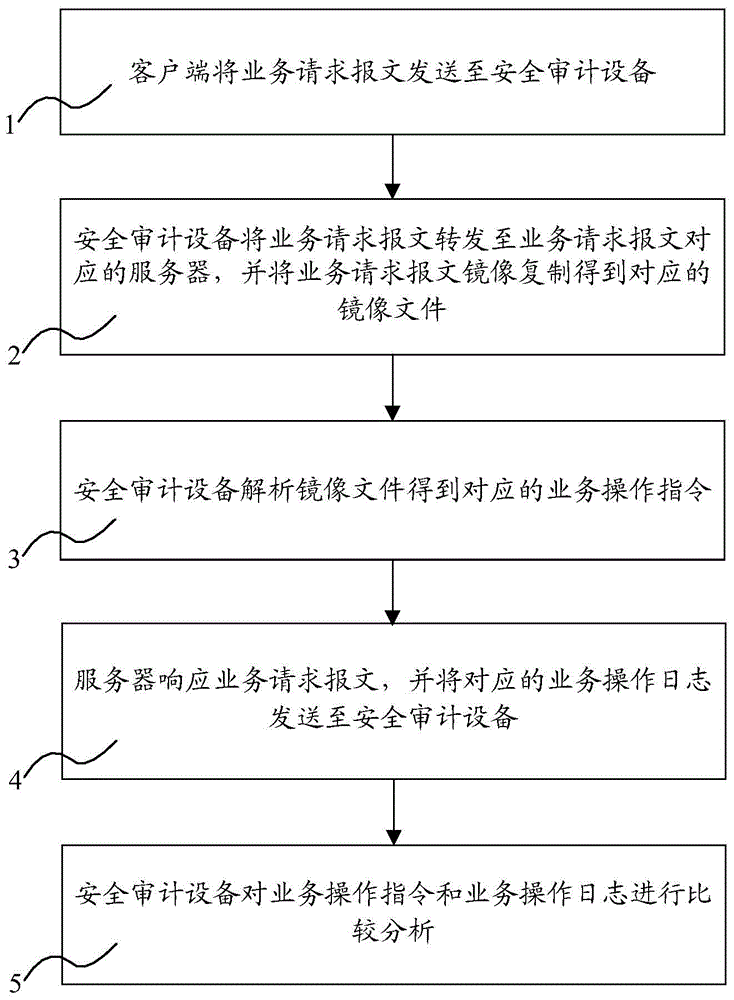
System and method for achieving safety audit
InactiveCN104468537AImprove scalabilityConvenient for dynamic expansionData switching networksClient-sideMirror image
The invention relates to a system for achieving a safety audit. The system comprises a plurality of clients, a plurality of servers and a safety audit device. The invention further relates to a safety audit method. The method includes the steps that service request messages are sent to the safety audit device by the clients; the safety audit device forwards the service request messages to the servers corresponding to the service request messages, and a service request message mirror image is copied so that a corresponding mirror image file can be obtained; the safety audit device analyzes the mirror image file so that corresponding service operation instructions can be obtained; the servers respond to the service request messages and send corresponding service operation logs to the safety audit device; the safety audit device compares and analyzes the service operation instructions and the service operation logs. The system for achieving the safety audit has the functions of double-machine hot standby and cluster deployment, is easy to popularize, stable and reliable, supports dynamic expansion and has a wider application range.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
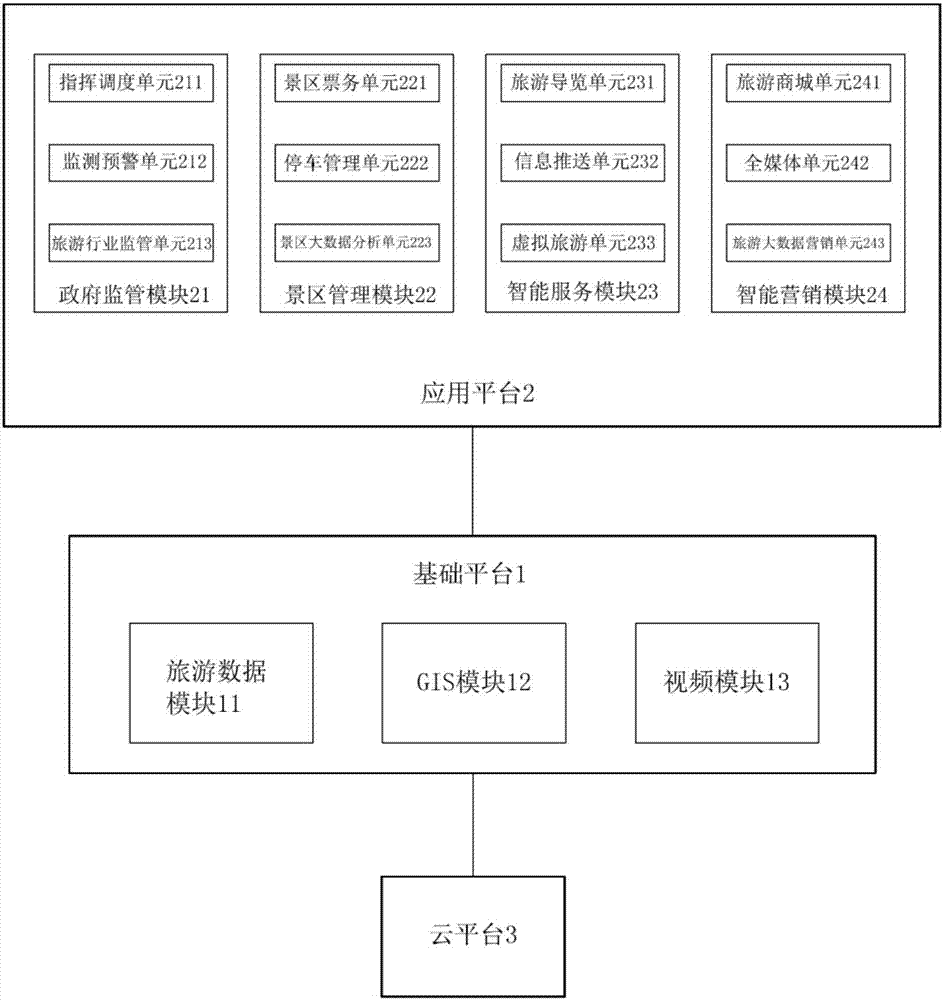
Travelling information management system
InactiveCN107491883AImprove data utilizationReduce operating costsResourcesData acquisitionManagement system
The invention relates to a travelling information management system which comprises a cloud platform, a basic platform and an application platform. The cloud platform utilizes cloud computing technology for constructing a basic operation environment for supporting operation of the basic platform and the application platform. The basic platform is used for performing data acquisition, processing an interface calling request which is transmitted from the application platform and performing comprehensive analysis processing. The application platform is used for transmitting the interface calling request for acquiring an analysis processing result of the basic platform. The application platform is further used for determining a corresponding management plan and supplying a traveling information service according to an analysis processing result which is fed back from the basic platform. Management plans in different angles are supplied according to different requirements. The travelling information management system has advantages of reducing system operation cost, facilitating dynamic expansion, simplifying maintenance, improving data utilization rate, etc.
Owner:中国东盟信息港股份有限公司
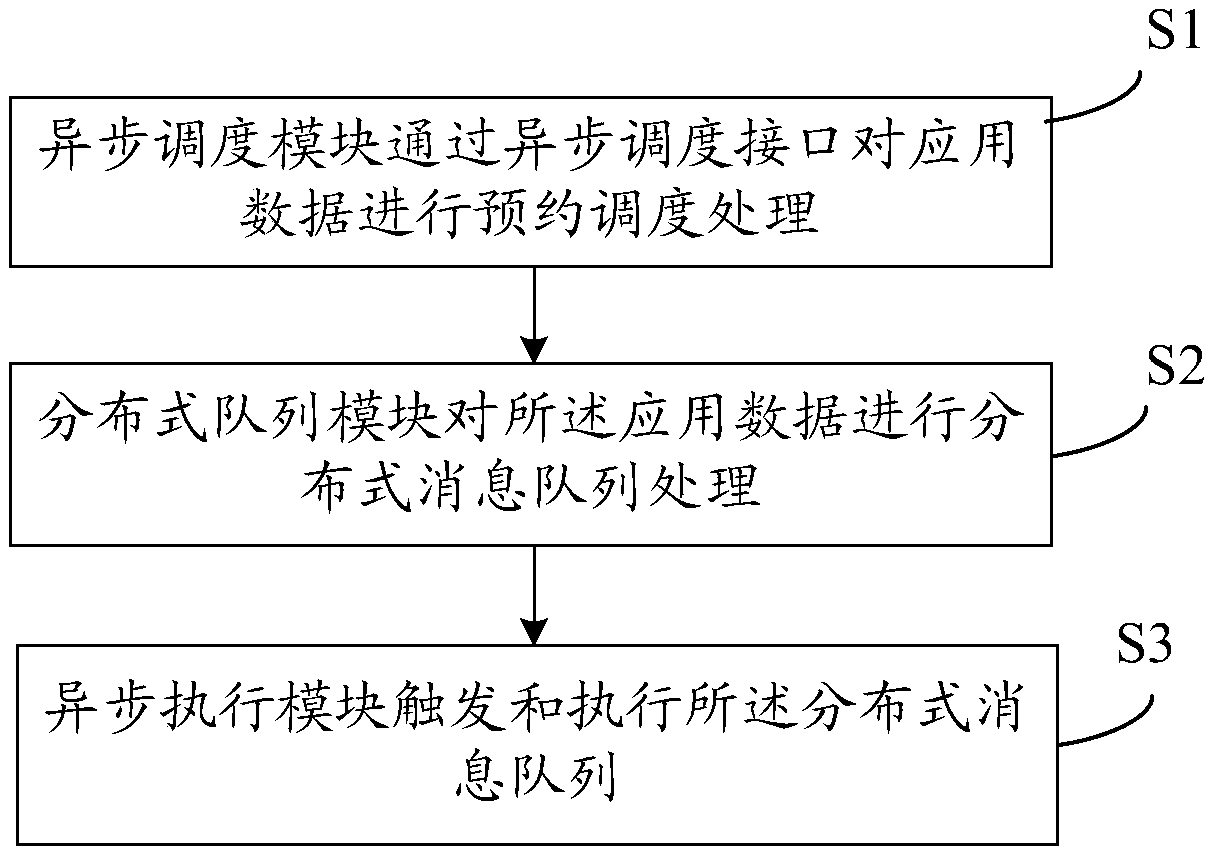
Quasi-real-time asynchronous batch processing system, method and device and storage medium
PendingCN109582446AFully decoupledStrong horizontal expansion capabilityProgram initiation/switchingInterprogram communicationExtensibilityMessage queue
The invention provides a quasi-real-time asynchronous batch processing system, and the system comprises an asynchronous scheduling module which is used for carrying out reservation scheduling processing on application data through an asynchronous scheduling interface; The distributed queue module is used for performing distributed message queue processing on the application data; And the asynchronous execution module is used for triggering and executing the distributed message queue. According to the method, the existing framework is transformed by using technologies such as sub-library and sub-table, distributed cache, distributed queue and streaming processing technologies, so that the problems of low efficiency and poor expandability in current scheduling processing are solved.
Owner:CHINA CONSTRUCTION BANK
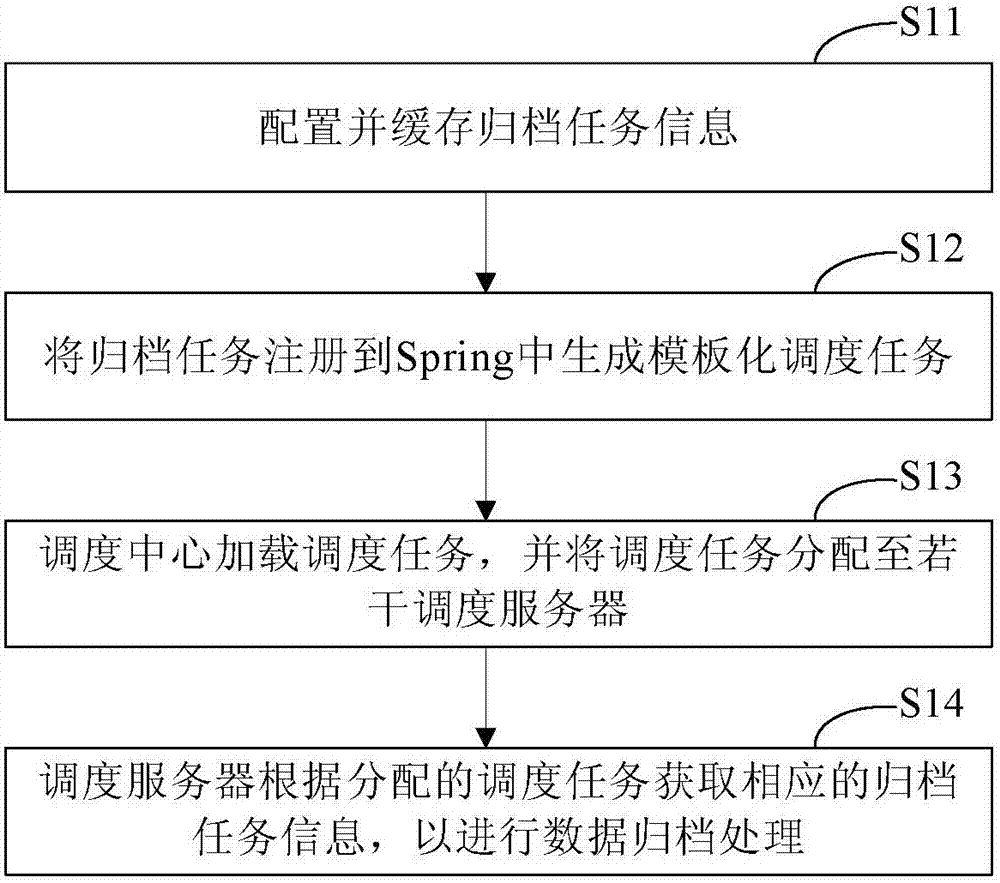
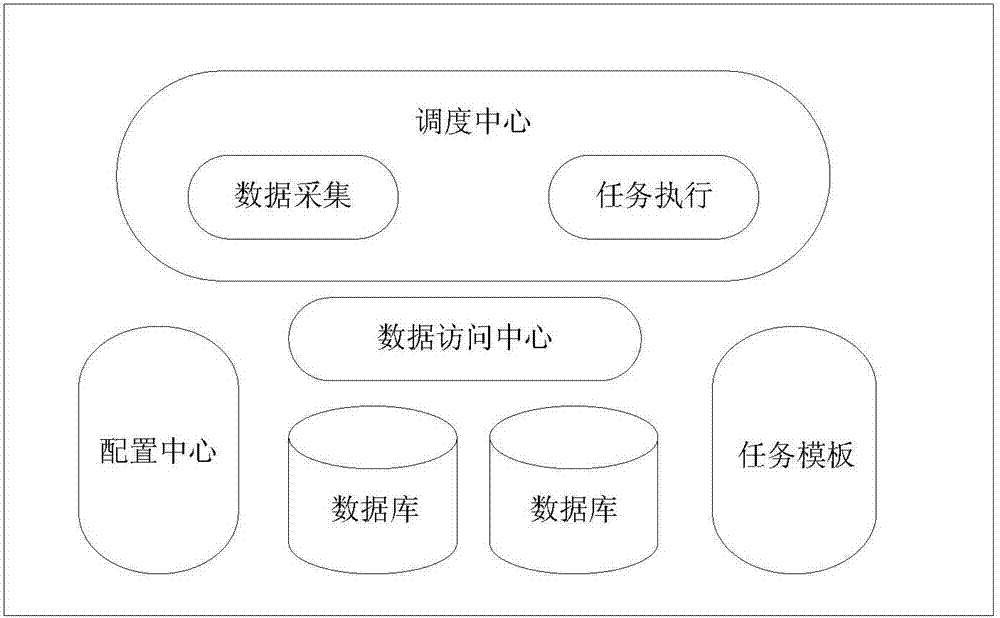
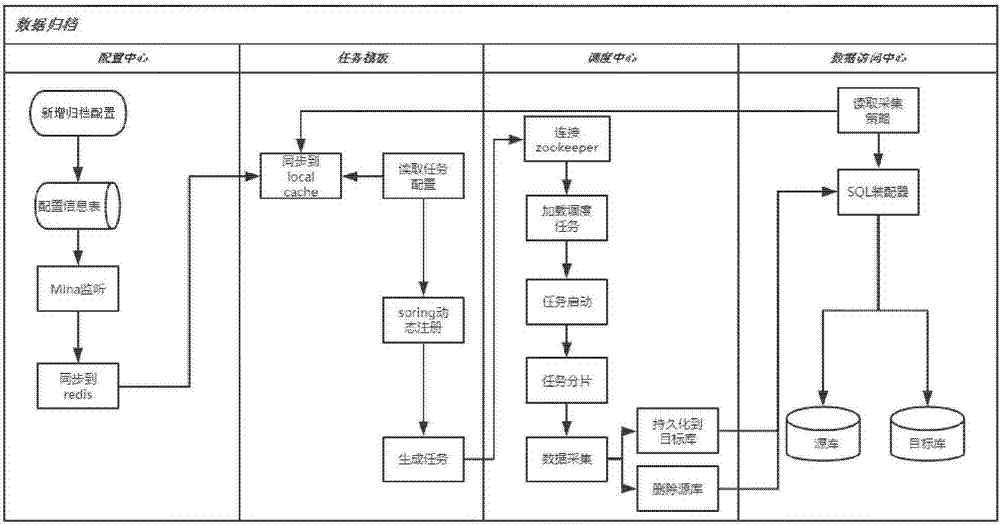
Highly available and scalable distributed data archiving method and system
InactiveCN107370773AFlexible configurationThe configuration table is flexibleTransmissionSpecial data processing applicationsData acquisitionScalable distributed
The invention provides a highly available and scalable distributed data archiving method and system, which can realize archiving algorithm configuration and schedule task templating, and the flexible configuration of data collection algorithms; and can also realize the dynamic expansion of scheduling servers and the stable performance. The method includes the steps of configuring and caching archiving task information, wherein, the caching of the archiving task information includes centralized cache of the archiving task information and local cache in schedule servers; registering an archiving task into the Spring to generate templated schedule tasks; loading the schedule tasks by a scheduling center, and allocating the schedule tasks to the plurality of schedule servers; and obtaining, by the schedule servers, the corresponding archiving task information according to the allocated schedule tasks for data archiving.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
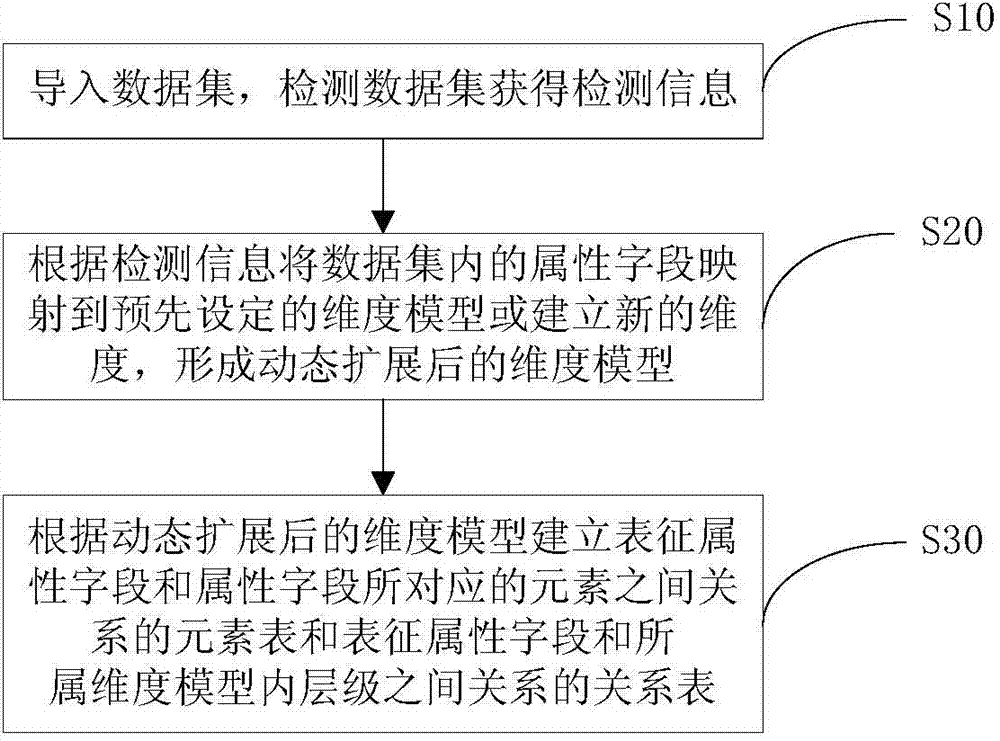
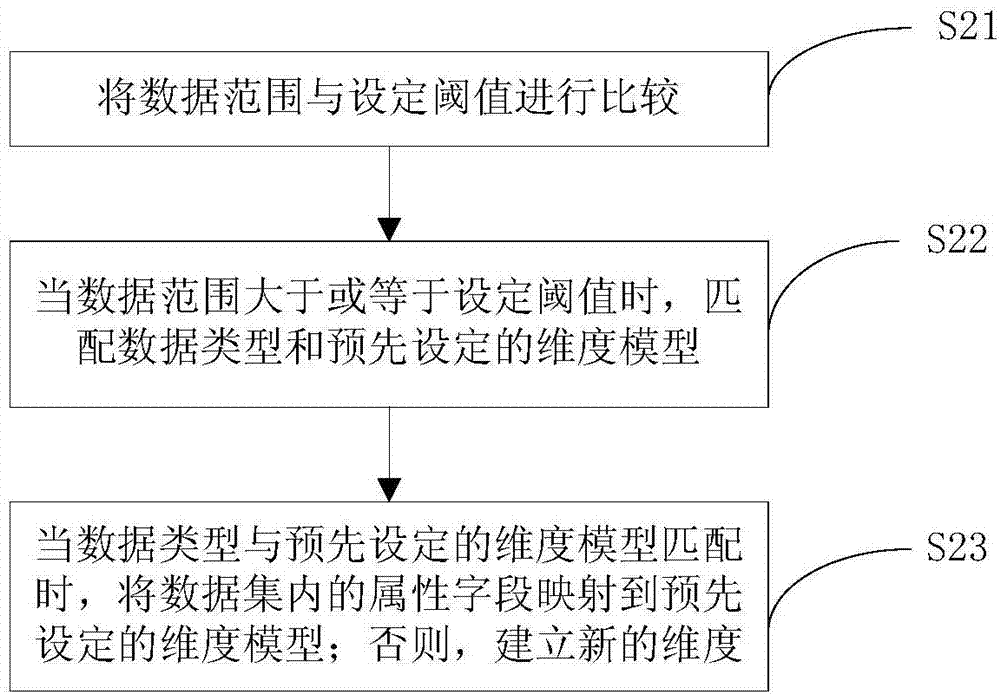
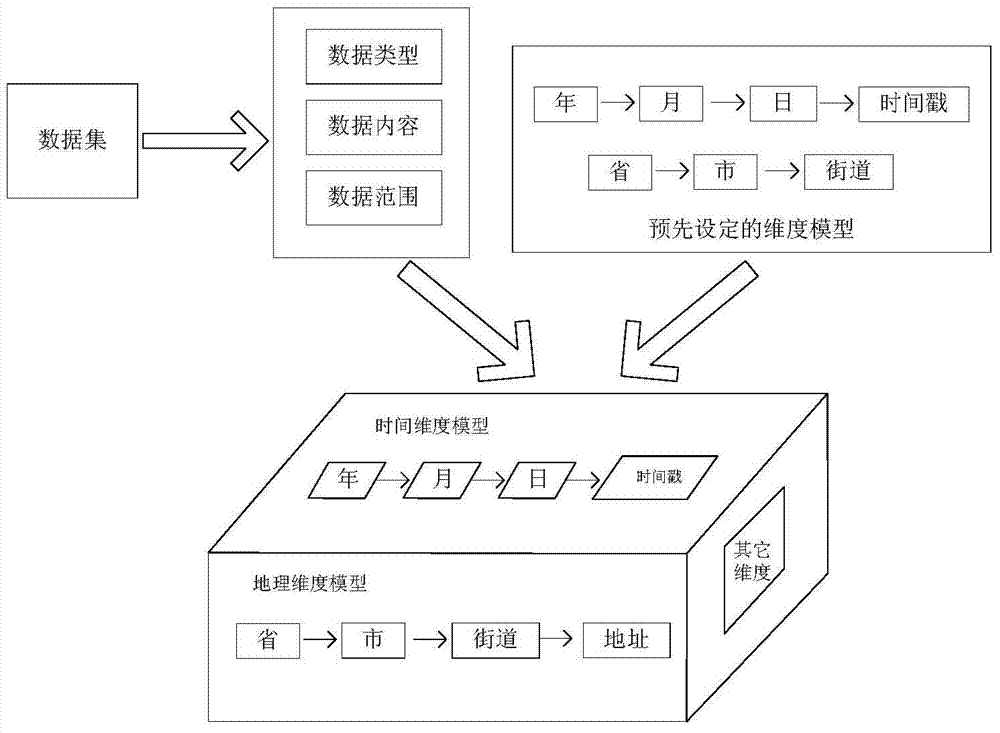
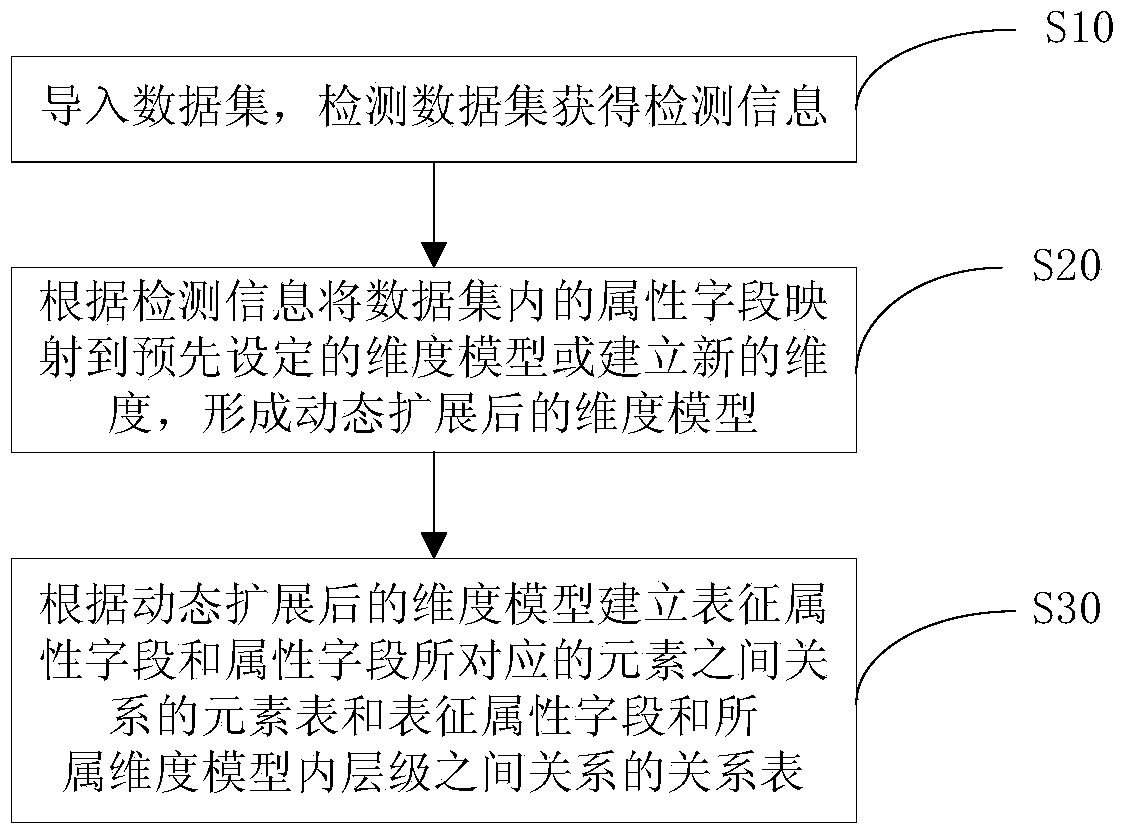
Dynamic extension method and system for multidimensional data analysis model
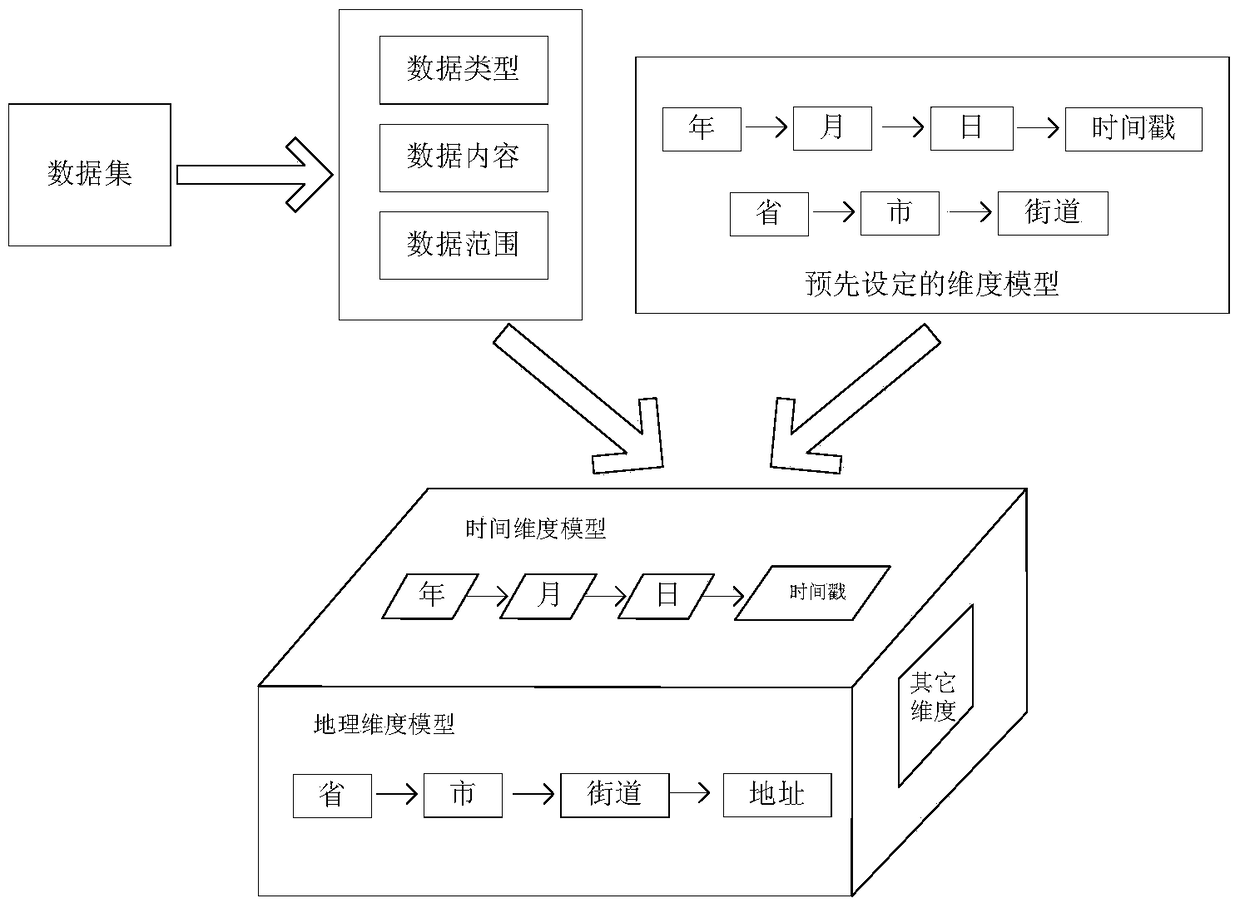
ActiveCN104850623AFlexible expansionMeet the needs of the big data eraSpecial data processing applicationsDynamic ExtensionExtension method
The present invention provides a dynamic extension method and system for a multidimensional data analysis model. The extension method comprises: importing a data set, and detecting the data set to obtain detection information; mapping attribute fields in the data set to a preset dimensional model according to the detection information or establishing new dimensions to form a dimensional model obtained after dynamic extension; and establishing an element table representing a relationship between the attribute fields and elements corresponding to the attribute fields, and a relation table representing the relationship between the attribute fields and the internal levels of the attribute fields in the dimensional model according to the dimensional model obtained after dynamic extension. According to the dynamic extension method and system for a multidimensional data analysis model provided by the present invention, the dynamic extension of dimensions is supported, the extension is very flexible, the extensions among different users cannot cause mutual interference, the extension cost is very low, and dynamic and various data can be processed, so that the dynamic extension method and system conform to the demands of the big data era.
Owner:HANGZHOU XUNHAN TECH CO LTD
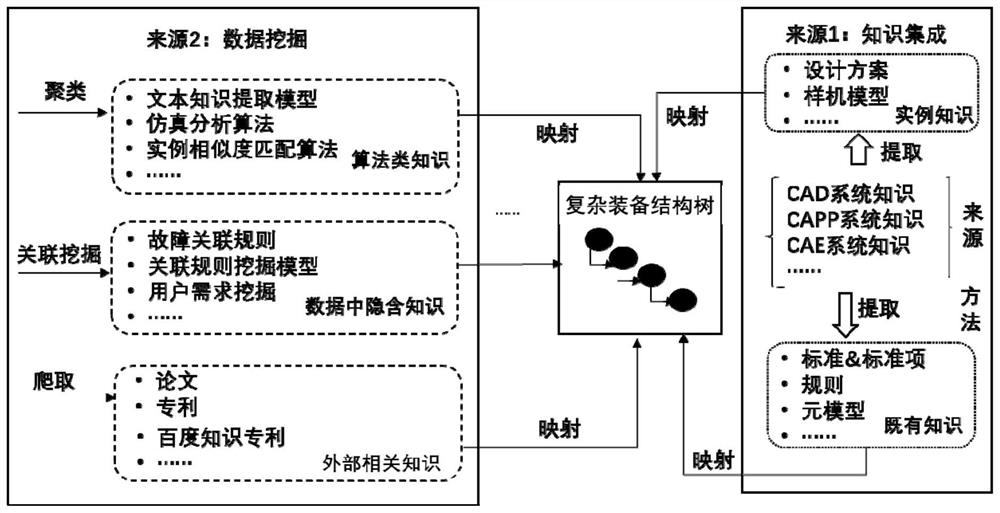
Knowledge service method for digital twin model of complex equipment
PendingCN114638160AAchieve loose couplingEasy to expand dynamicallyCharacter and pattern recognitionDesign optimisation/simulationKnowledge classificationKnowledge engineering
The invention provides a knowledge service method for a complex equipment digital twin model, and belongs to the technical field of complex equipment knowledge engineering. The invention discloses a knowledge service mechanism method for construction of a knowledge classification ontology model of complex equipment, knowledge mapping based on a meta-structure tree of the complex equipment and dynamic calling of a twinborn model according to a knowledge application requirement in digital twinborn of the complex equipment and a loose coupling and extensible reference principle of the knowledge and the digital twinborn model. A knowledge service algorithm oriented to dynamic calling of a digital twin model is designed and realized, dynamic requests of real-time physical information data of equipment nodes for knowledge are realized, and support is provided for equipment anomaly prediction, fault diagnosis, performance prediction and the like.
Owner:SOUTHWEST JIAOTONG UNIV
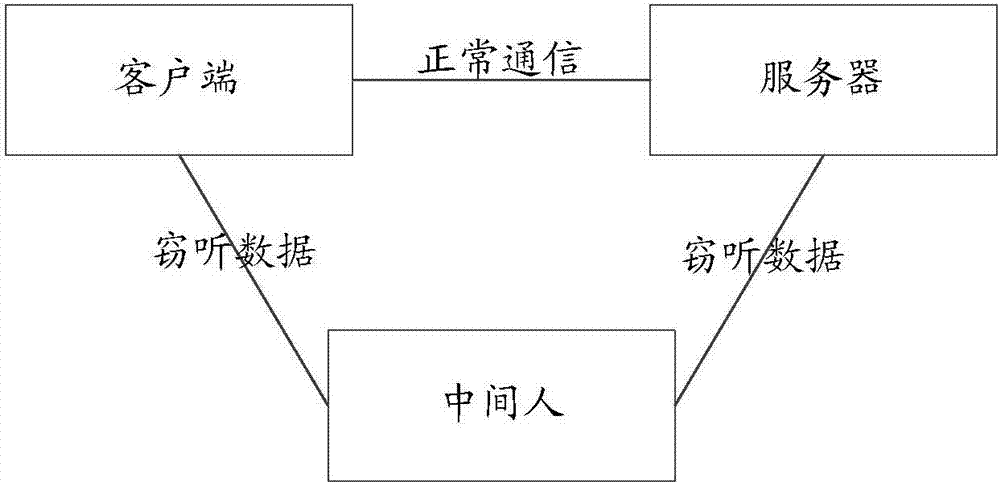
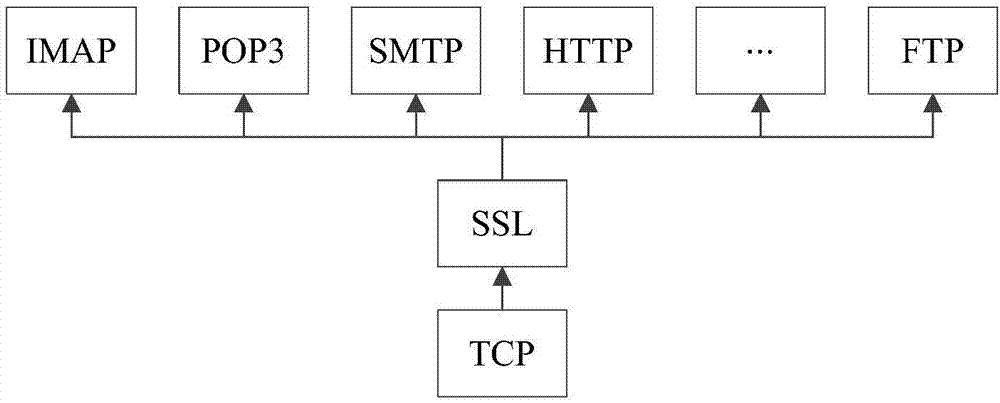
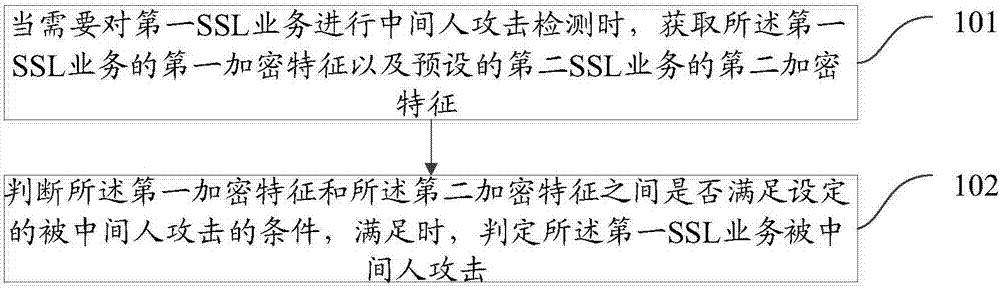
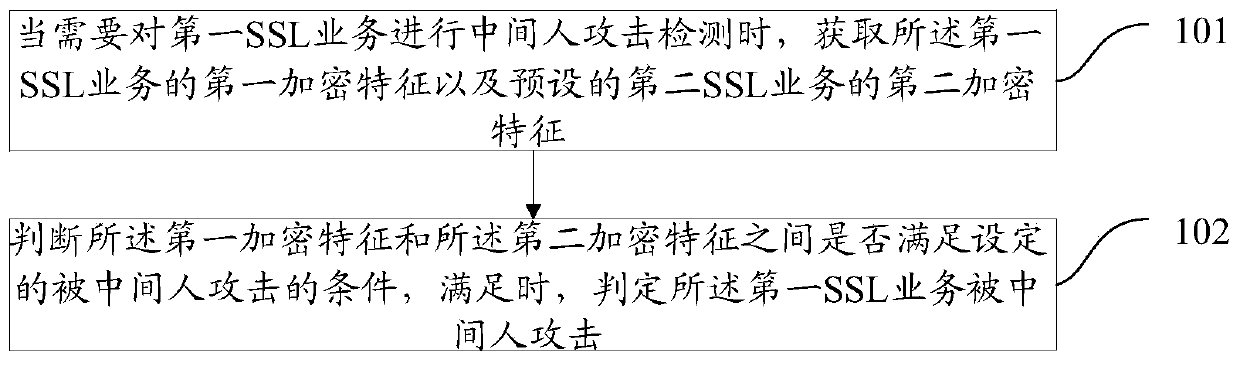
Method and device for detecting man-in-the-middle attack
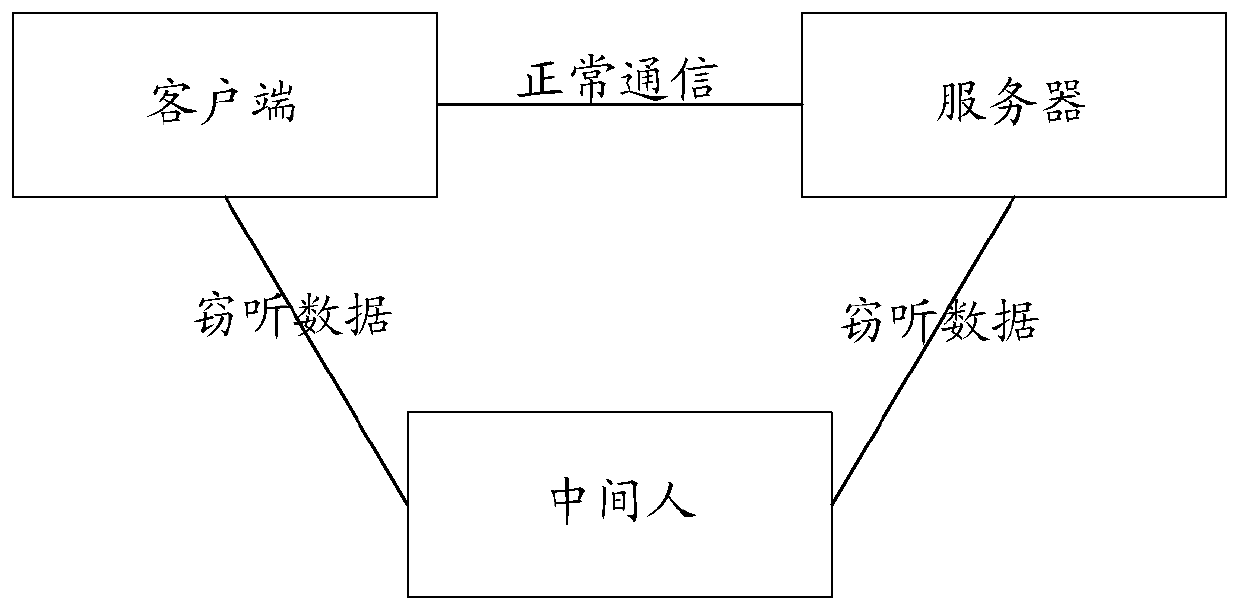
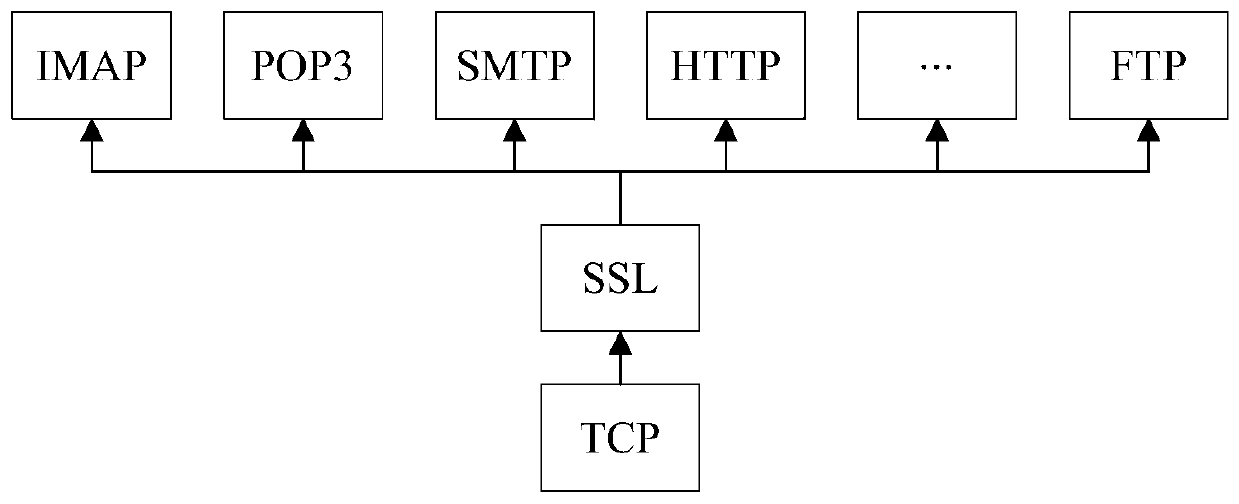
ActiveCN106899579AQuick checkConvenient for dynamic expansionUser identity/authority verificationMan-in-the-middle attackEncryption
The invention discloses a method for detecting a man-in-the-middle attack, which comprises the steps of: when a first SSL (Secure Socket Layer) service needs to be subjected to the man-in-the-middle attack, acquiring a first encryption feature of the first SSL service and a second encryption feature of a preset second SSL service; and judging whether the first encryption feature and the second encryption feature meet a set condition of being attacked by a man in the middle, and if yes, determining that the first SSL service is attacked by the man in the middle. The invention simultaneously further discloses a device for detecting the man-in-the-middle attack.
Owner:BEIJINGNETENTSEC
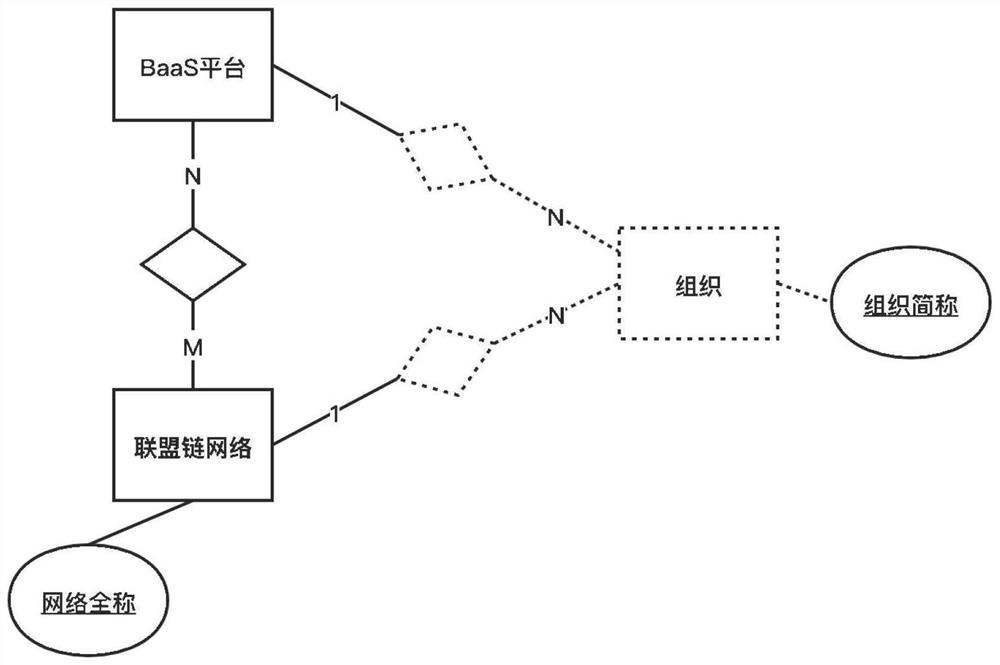
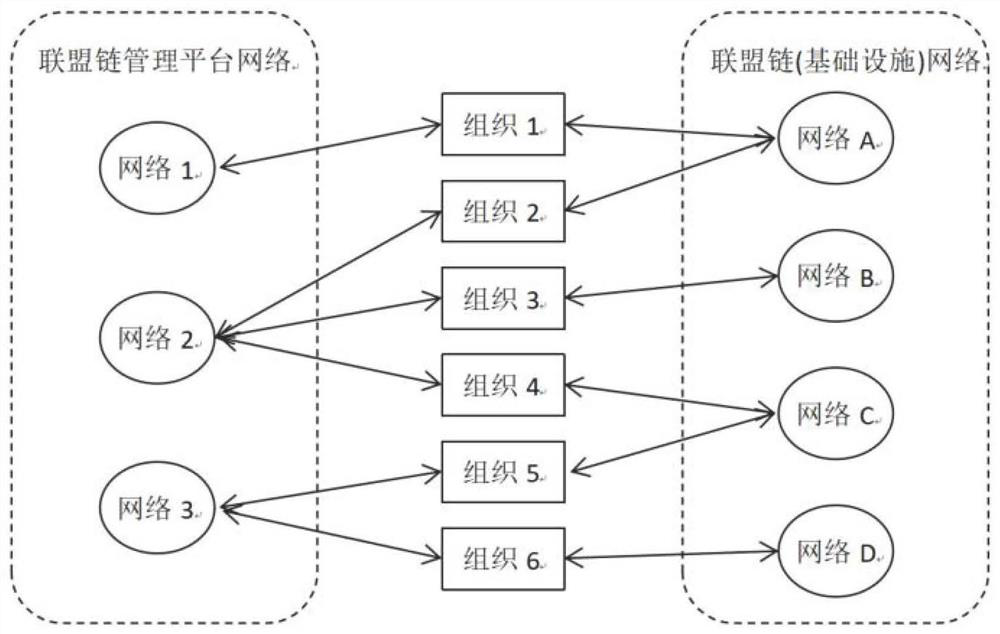
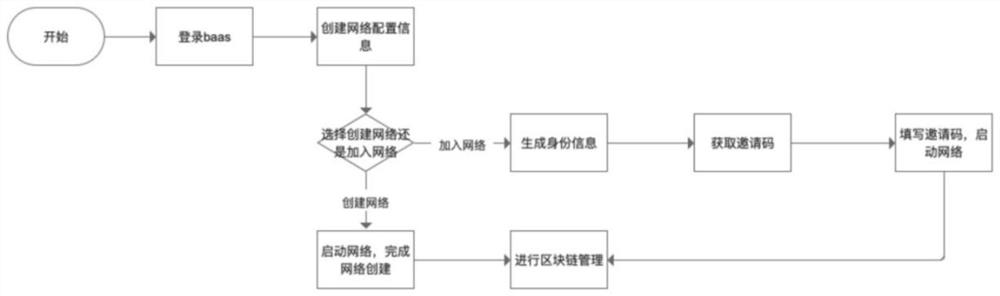
Alliance chain infrastructure and management platform many-to-many mapping method and system
PendingCN113542033AConvenient for dynamic expansionAchieve independent governanceData switching networksInformation networksChain network
The invention provides an alliance chain infrastructure and management platform many-to-many mapping method and system, and the method comprises the steps: obtaining configuration information on an alliance chain management platform, and splitting the configuration information into resource configuration information, network configuration information and node configuration information; performing availability check on the configuration information and creating an alliance chain management platform network according to the network configuration information; building an alliance chain network according to the alliance chain infrastructure network configuration information; respectively adding a plurality of organizations into different alliance chain management platform networks and alliance chain networks, and distributing different organization identity information, user permissions and network permissions to each node; according to different alliance chain management platform networks, selecting different organization identities to manage the alliance chain network, managing different alliance chain management platforms according to different organization identities in the alliance chain network corresponding to the alliance chain infrastructure, and achieving the many-to-many mapping relation between the alliance chain management platforms and the alliance chain infrastructure.
Owner:HANGZHOU YUNXIANG NETWORK TECH
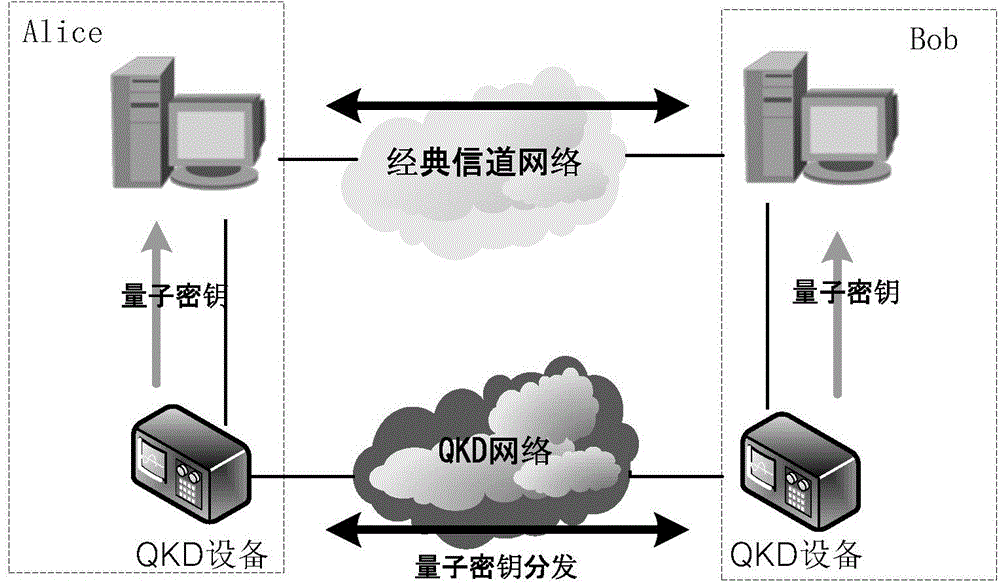
Quantum cryptography network dynamic routing method
ActiveCN103001875BConvenient for dynamic expansionFast convergenceKey distribution for secure communicationData switching networksRefresh cycleRoute server
The invention discloses a quantum cryptography network dynamic routing method. According to the method, dynamic routing selection of encryption communication is performed by utilizing quantum cryptography according to changes of the quantum key quantity between relay nodes of a quantum cryptography network. According to the method, a route server is arranged for the relay nodes of the whole quantum cryptography network, and topology refresh cycles of the quantum cryptography network are set; in each topology refresh cycle, each relay node collects and processes state information of the relay node and reports results to the route server. After the route server collects the topology state information of each relay node, quantum cryptography network topology state information of a next topology refresh cycle is generated and sent to all the relay nodes of the quantum cryptography network. According to the quantum cryptography network topology state information obtained from the route server, a target relay node is calculated and determined to be a next skip route of communication data of a random other relay node according to a shortest path law through each relay node.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +2
A quantum cryptography network dynamic routing architecture system
ActiveCN104579964BConvenient for dynamic expansionFast convergenceKey distribution for secure communicationData switching networksPasswordNetwork architecture
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
Identifier generation method and device based on Redis
PendingCN111694845AUniqueness guaranteedImprove usabilitySpecial data processing applicationsDatabase design/maintainanceSign bitHigh availability
The invention discloses an identifier generation method and device based on Redis, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of receivingan identifier generation request, and detecting whether a current main database runs normally or not; if so, setting the main / standby switching flag bit as a first numerical value, and generating anidentifier by utilizing the main database based on the sign bit, the first numerical value and the serial number; and if soothe current main database runs abnormally, setting the main / standby switching flag bit as a second numerical value, carrying out main / standby switching on the main database and a normally running standby database, and further generating an identifier by utilizing the standbydatabase based on the sign bit, the second numerical value and the serial number. According to the embodiment, the values of the main and standby switching flag bits are different when the main database or the standby database is used, so that the uniqueness and high availability of identifier generation are ensured, the disaster tolerance capability is high, and a single-point fault is avoided. By setting the idle bits, the ID length can be shortened, the occupation amount of the storage space is reduced, and subsequent dynamic expansion of other identification bits is facilitated.
Owner:CHINA CONSTRUCTION BANK
Public cloud-based computing system, method, computer device, and storage medium
ActiveCN113037856BConvenient for dynamic expansionComplete logical isolationTransmissionEnergy efficient computingDynamic resourceComputational simulation
Owner:苏州云霄电子科技有限公司
A Key Management Method for Wireless Sensor Networks Based on Integer Modulo
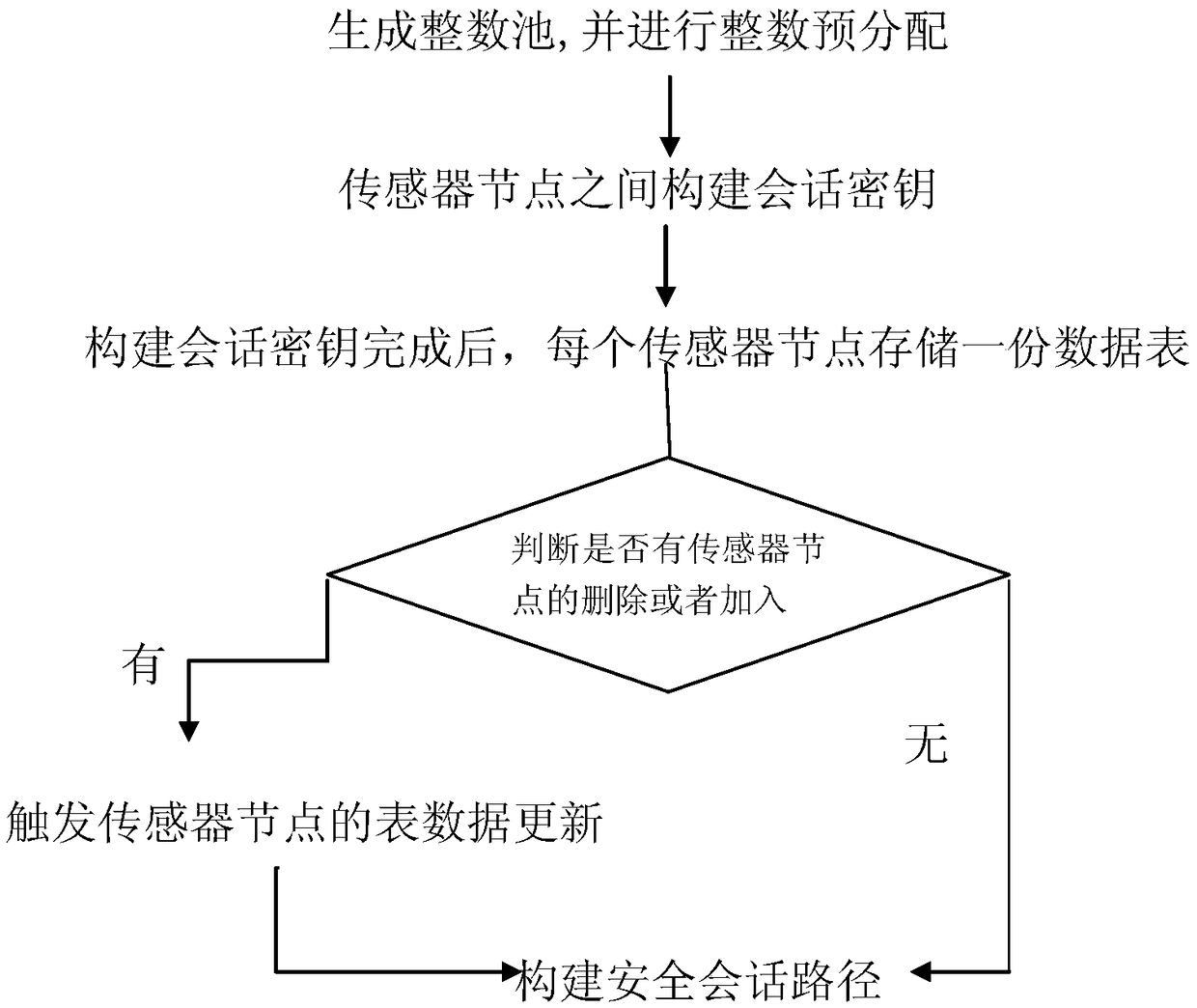
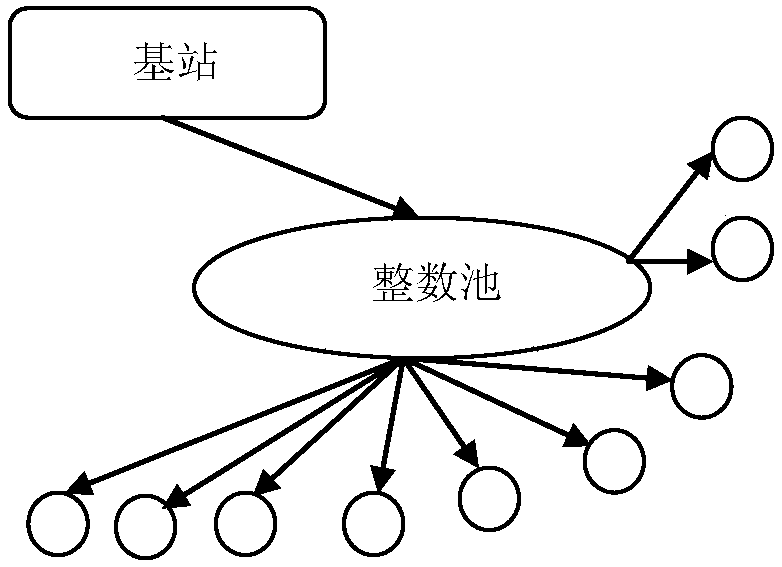
ActiveCN105657704BConvenient for dynamic expansionGuaranteed reliabilityNetwork topologiesSecurity arrangementPathPingWireless sensor networking
The invention relates to a wireless sensor network key management method based on integer modulo, and belongs to the field of network communication security. It includes the following steps: generate an integer pool and pre-allocate integers; construct a session key between sensor nodes; after the session key is constructed, each sensor node stores a table data, and the table data mainly records other information that the sensor node can communicate with. Sensor nodes and corresponding session keys; determine whether there is a deletion or addition of sensor nodes, and if so, update the table data of the sensor nodes to build a secure remittance path. The invention reduces the session key that each sensor node needs to store, and is beneficial to the dynamic expansion of the entire network; at the same time, it greatly reduces the storage requirement and communication load in the session key construction stage.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
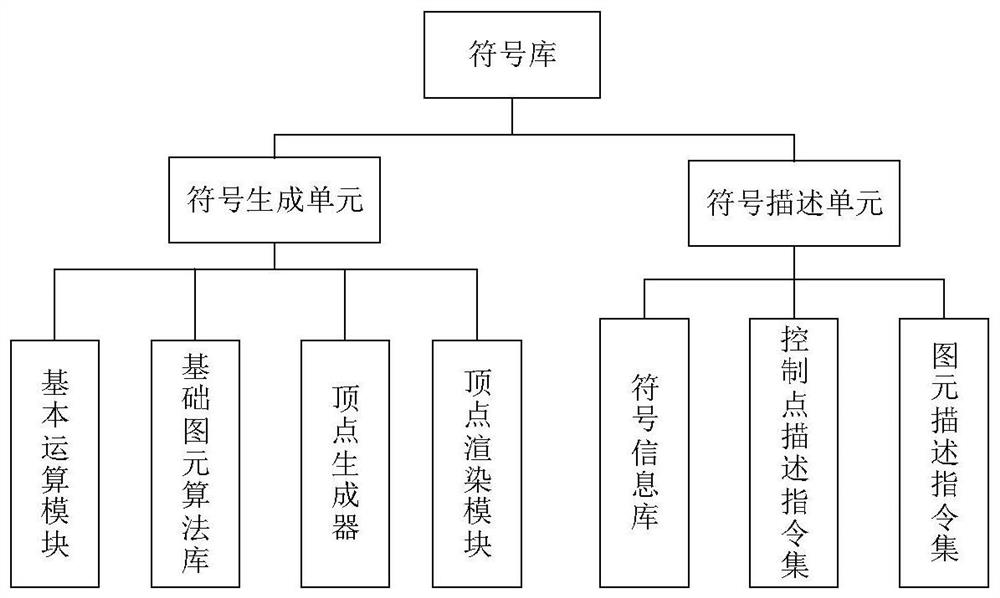
Symbol library based on three-dimensional plotting system
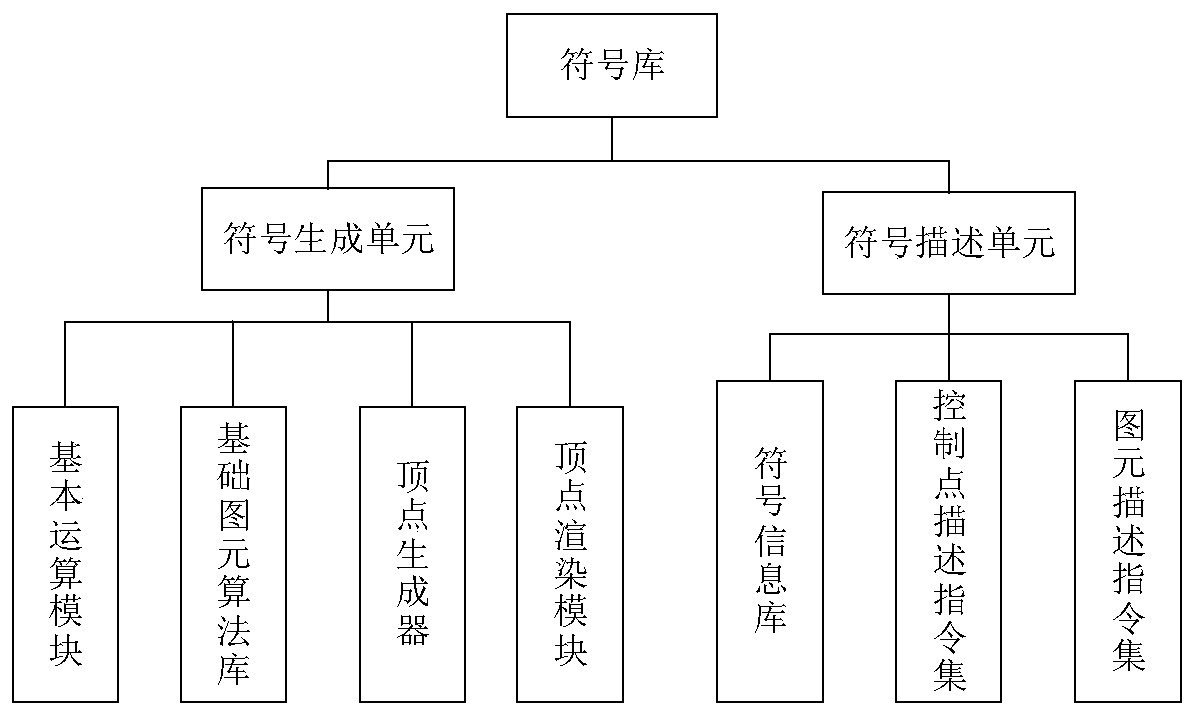
ActiveCN110781324AEasy constructionConvenient for dynamic expansionStill image data indexingSpecial data processing applicationsInformation repositoryEngineering
The invention discloses a symbol library based on a three-dimensional plotting system. The symbol library comprises a symbol description unit and a symbol generation unit, and is characterized in thatthe symbol description unit comprises a symbol information library, a control point description instruction set and a primitive description instruction set; and the symbol generation unit comprises abasic operation module, a basic primitive algorithm library, a vertex generator and a vertex rendering module. According to the symbol library, the symbol generation algorithm and the symbol description are separated, and the custom symbol can be conveniently constructed according to the symbol description specification, and the complexity of creating the custom symbol is reduced.
Owner:中国科学院电子学研究所苏州研究院
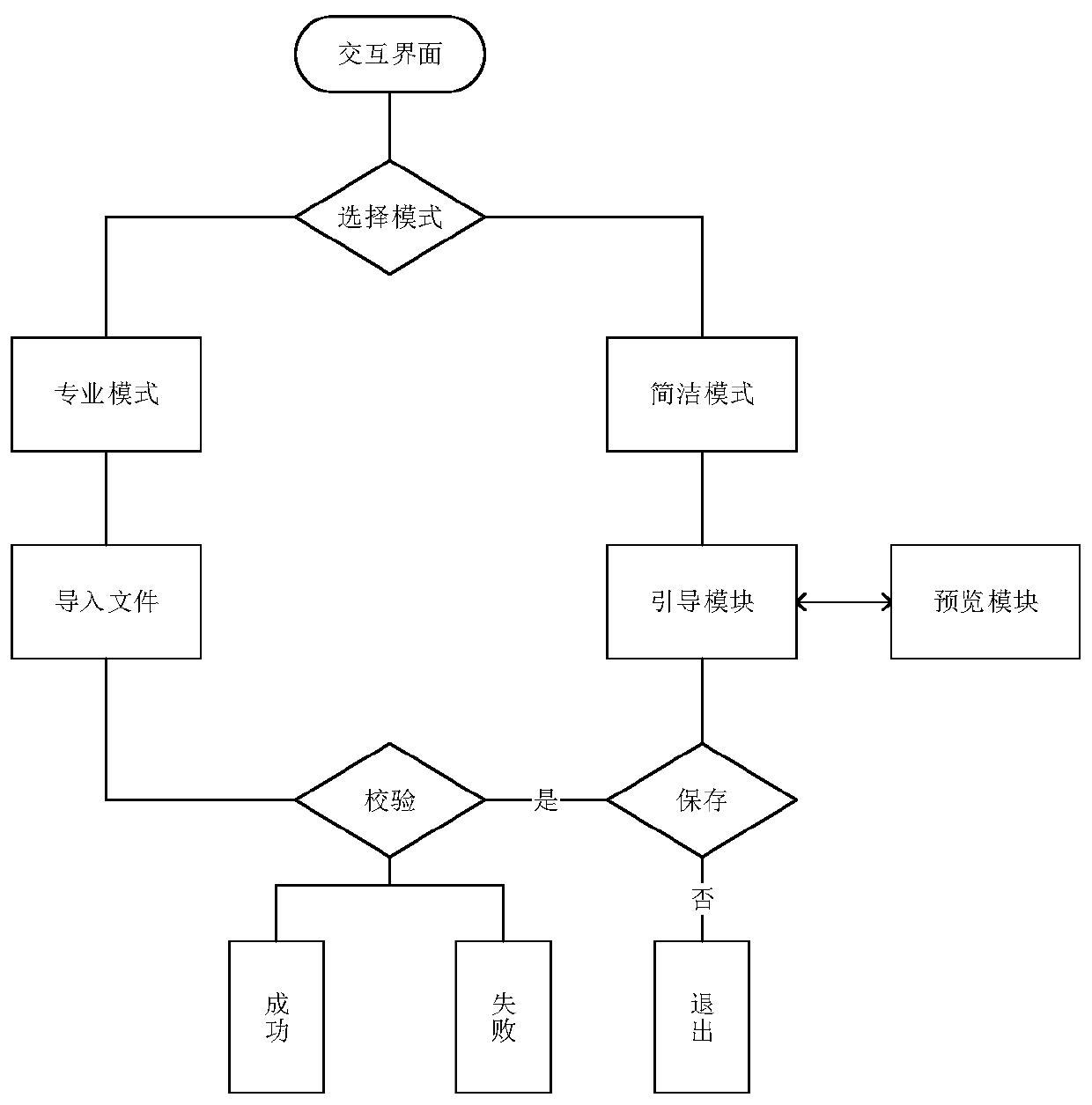
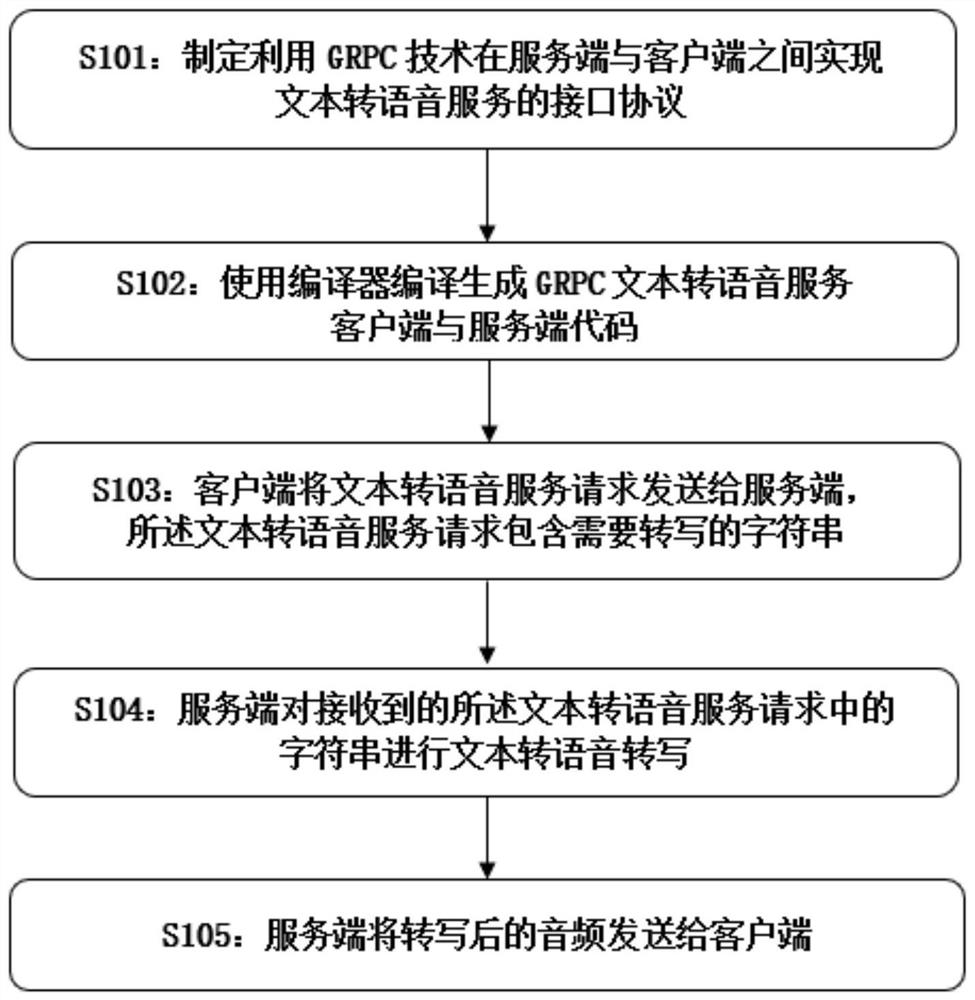
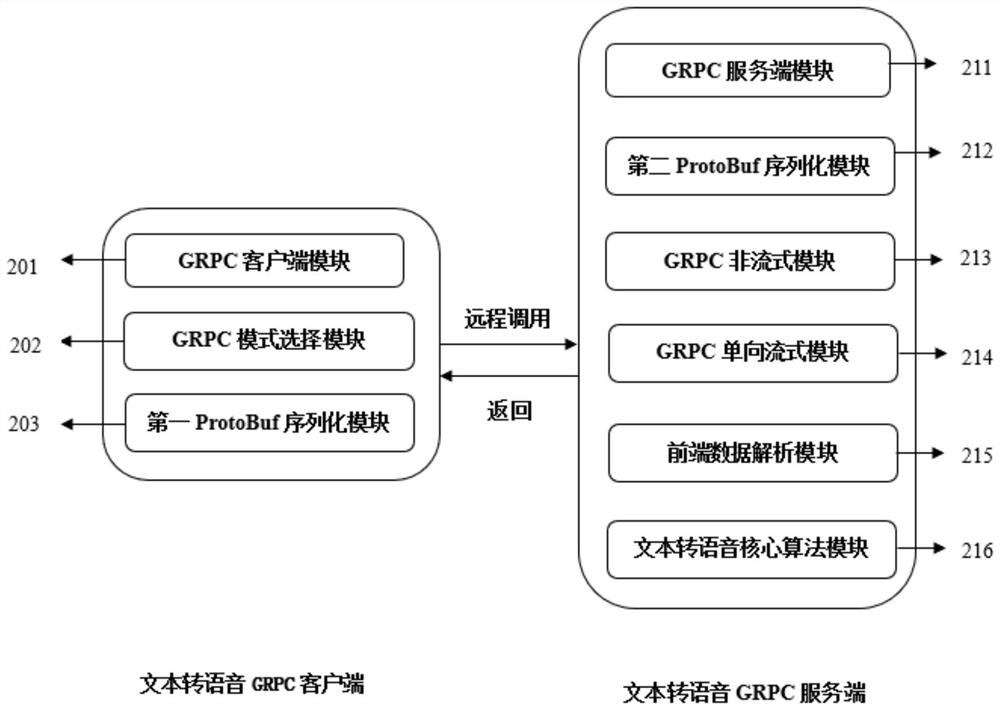
Method, system, medium and device for realizing text-to-voice service based on GRPC
InactiveCN113450763ASolve the problem that is not easy to packageImprove resource utilizationNatural language data processingTransmissionInterface protocolTimed text
The invention relates to natural language processing, particularly provides a method, a system, a medium and a device for realizing text-to-voice service based on GRPC, and aims to solve the problems of poor flexibility and poor expansibility of an existing text-to-voice method. In order to achieve the purpose, the method comprises the steps that an interface protocol for achieving the text-to-voice service is formulated in advance, a ProtoBuf compiler is used for compiling and generating a client side code and a server side code, ProtoBuf is used for serializing or de-serializing data, a conversion request sent by the client side is processed at the server side, and a processed result is returned to the client side. According to the method, the voice and audio data are serialized by using the ProtoBuf, the network transmission efficiency of a large audio file is greatly improved, a text-to-voice core algorithm is realized based on a GRPC remote procedure call lightweight framework, the deployment problem of real-time online text-to-voice and non-real-time text-to-voice is solved based on GRPC one-way streaming and non-streaming transmission, and the method has relatively high flexibility, expandability and concurrency capability.
Owner:四川云从天府人工智能科技有限公司
Method and system for dynamic expansion of multi-dimensional data analysis model
ActiveCN104850623BFlexible expansionMeet the needs of the big data eraSpecial data processing applicationsData setMultidimensional data
The present invention provides a dynamic extension method and system for a multidimensional data analysis model. The extension method comprises: importing a data set, and detecting the data set to obtain detection information; mapping attribute fields in the data set to a preset dimensional model according to the detection information or establishing new dimensions to form a dimensional model obtained after dynamic extension; and establishing an element table representing a relationship between the attribute fields and elements corresponding to the attribute fields, and a relation table representing the relationship between the attribute fields and the internal levels of the attribute fields in the dimensional model according to the dimensional model obtained after dynamic extension. According to the dynamic extension method and system for a multidimensional data analysis model provided by the present invention, the dynamic extension of dimensions is supported, the extension is very flexible, the extensions among different users cannot cause mutual interference, the extension cost is very low, and dynamic and various data can be processed, so that the dynamic extension method and system conform to the demands of the big data era.
Owner:HANGZHOU XUNHAN TECH CO LTD
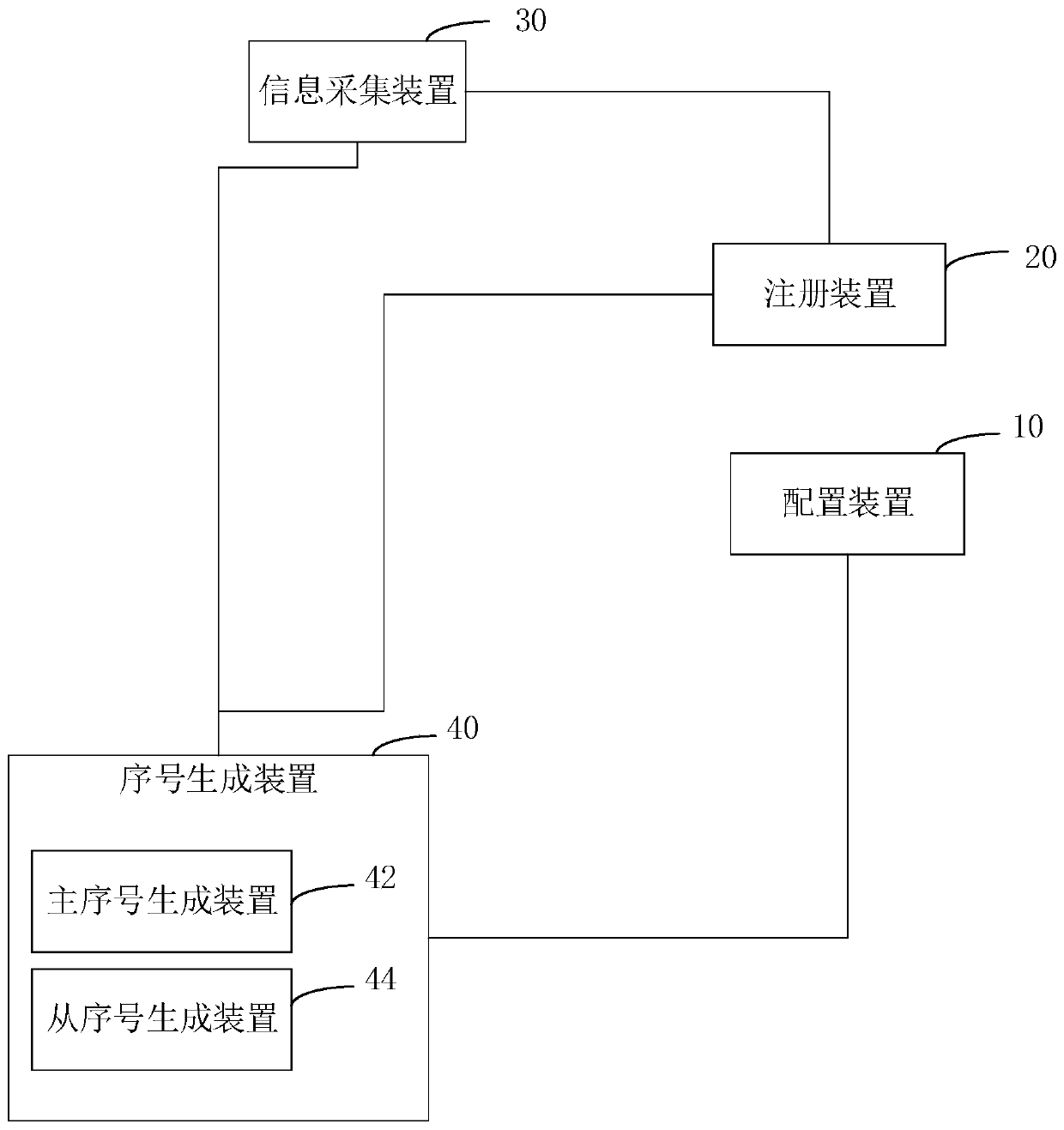
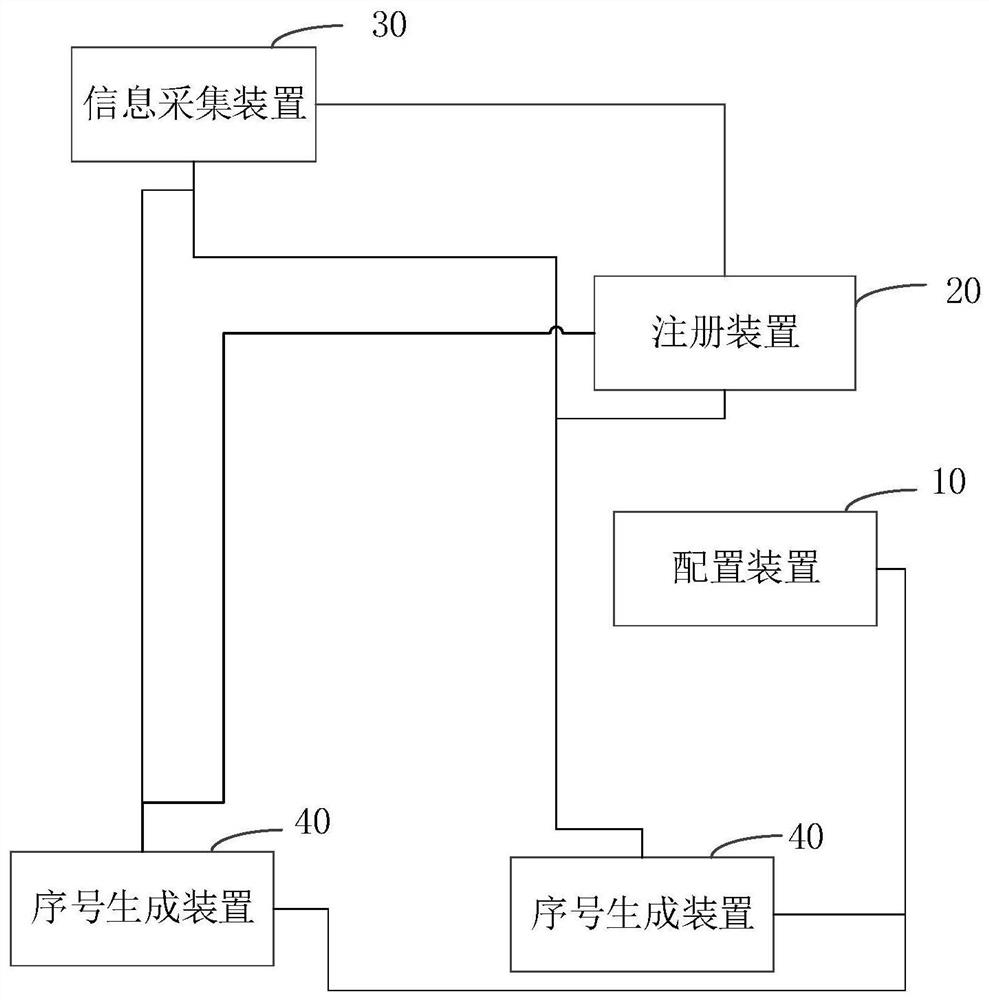
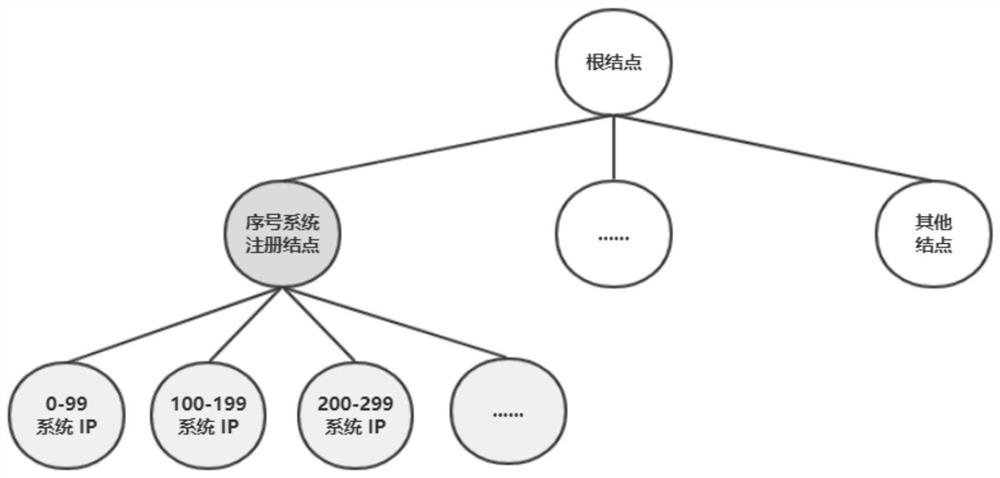
Request information serial number generation system and method
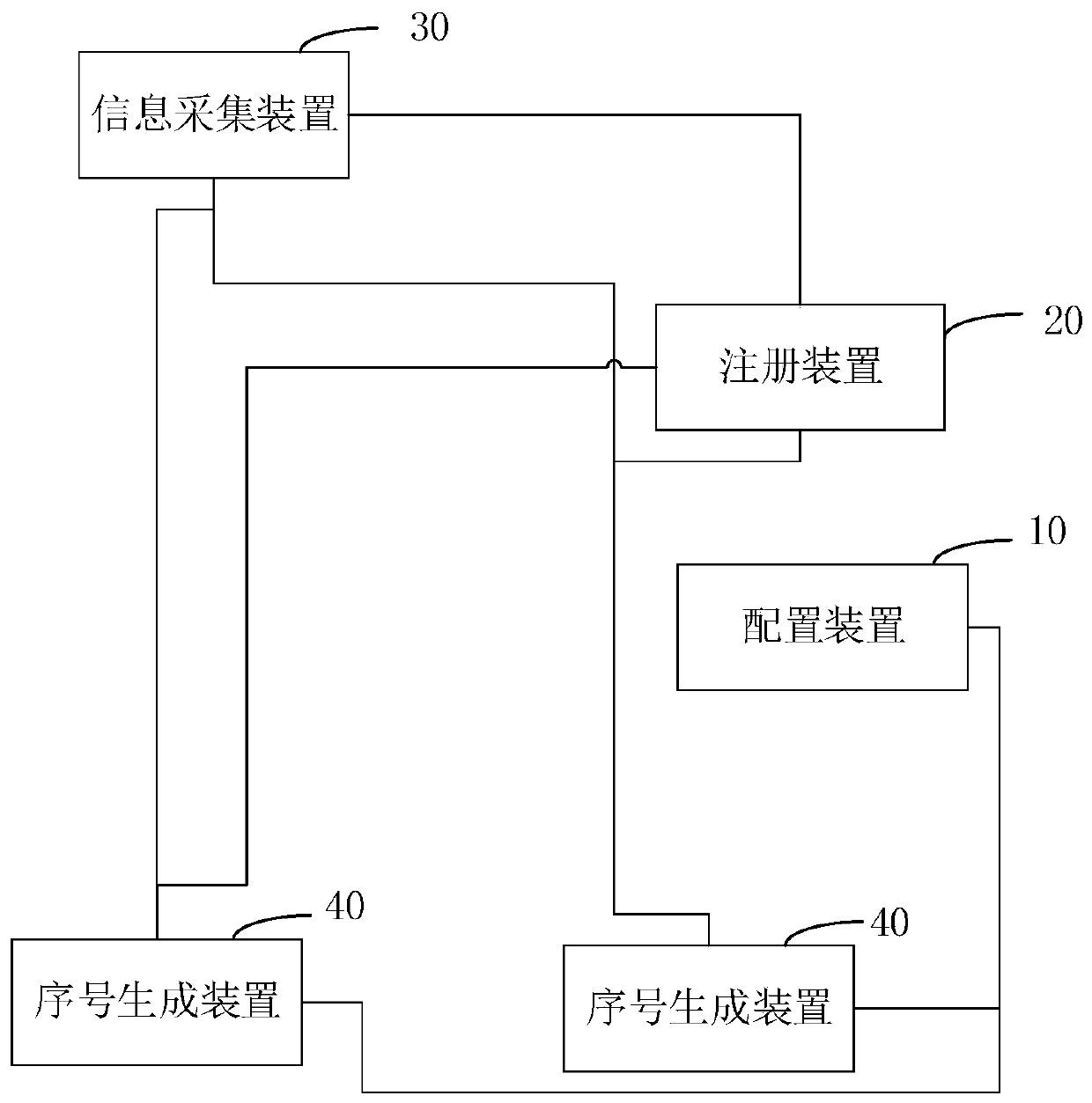
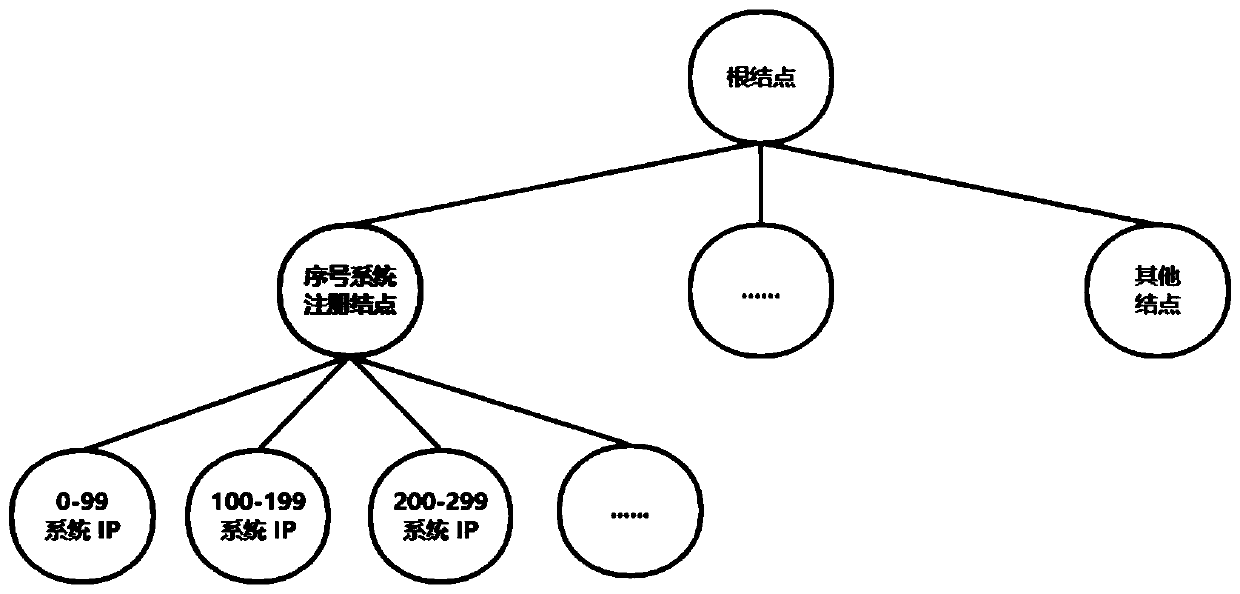
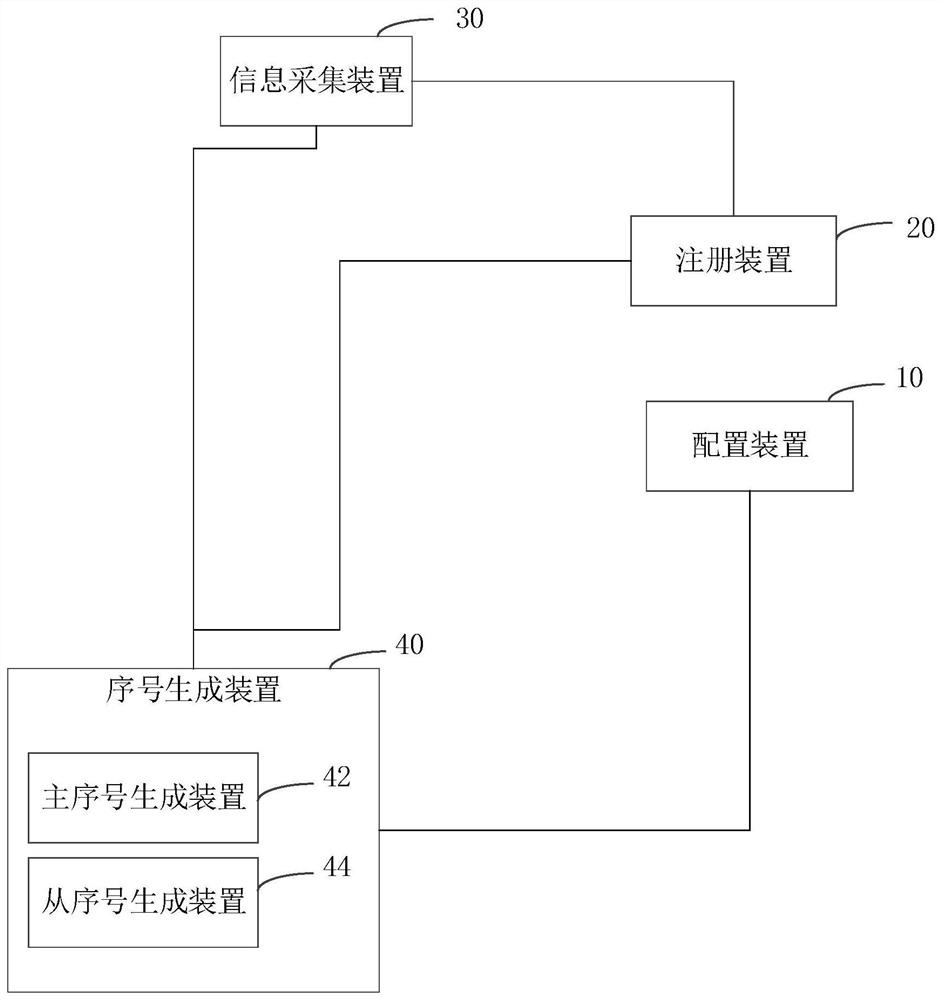
ActiveCN110046192ALower latencyProcessing speedDatabase management systemsNatural language data processingInformation processingSerial code
The invention relates to a request information serial number generation system and method. The system comprises a configuration device, a registration device, an information acquisition device and atleast one serial number generation device. Each serial number generation device is used for obtaining the corresponding configuration information from the configuration device and sending a registration request to the registration device, and the registration device is used for registering each serial number generation device according to the configuration information to generate the correspondingregistration information, wherein the registration information comprises an address of the serial number generation device and a number interval corresponding to the address; the information acquisition device is used for acquiring the request information and extracting the number of the request information, acquiring the registration information, determining the address of the serial number generation device, and sending the request information and the serial number generation request to the serial number generation device corresponding to the address; the serial number generation device isused for obtaining the serial number of the request information according to the serial number generation request and the serial number of the previous request information. According to the above system, the information processing delay can be reduced, and the information processing speed is greatly increased.
Owner:GUANGZHOU LIZHI NETWORK TECH CO LTD
Information service security evaluation method and device
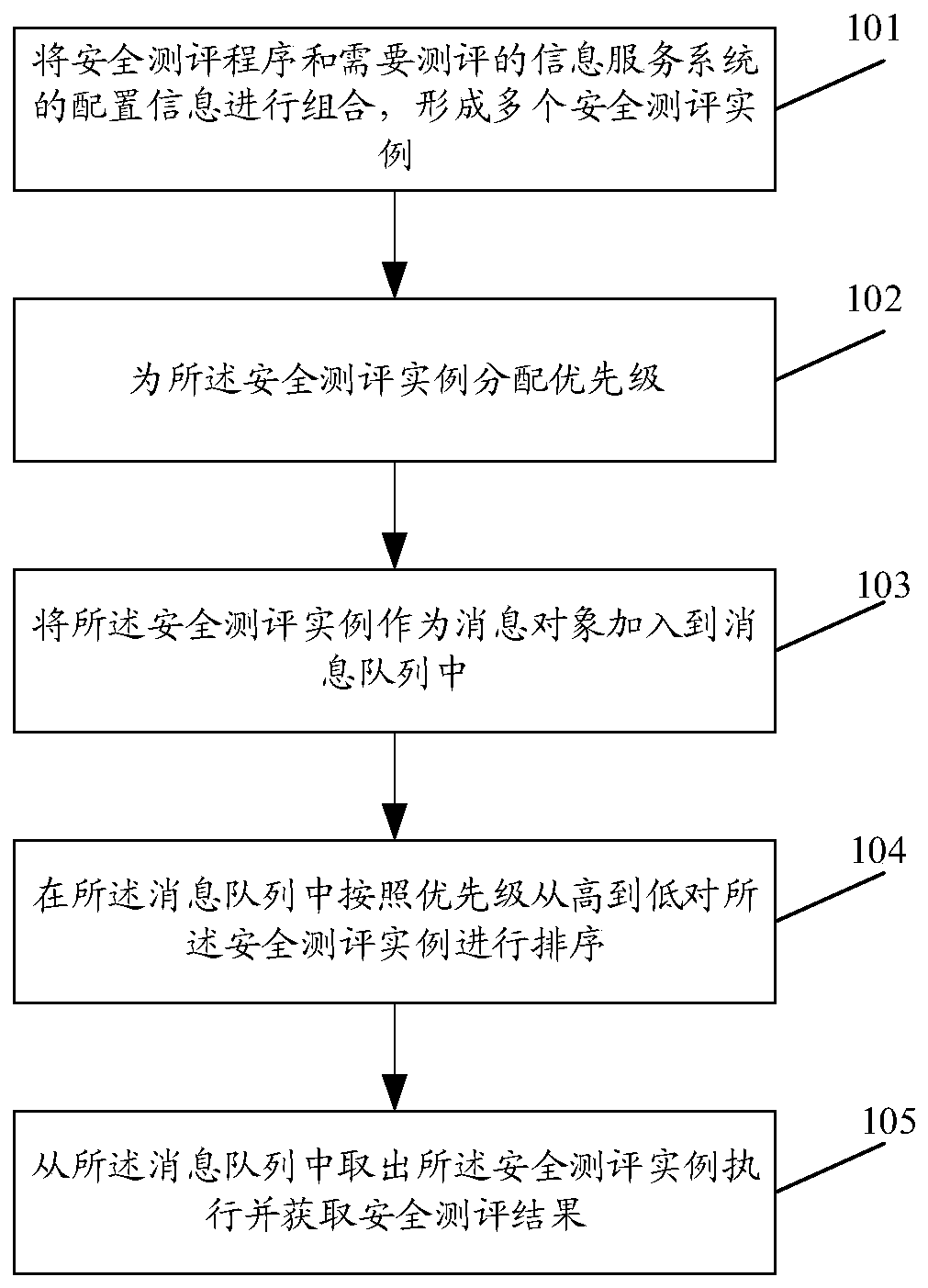
PendingCN111506898AConvenient for dynamic expansionRealize evaluationPlatform integrity maintainanceMessage queueEvaluation result
The invention provides an information service security evaluation method and device, and the method comprises the steps: combining a security evaluation program with the configuration information of an information service system needing to be evaluated, and forming a plurality of security evaluation examples; assigning a priority to each security evaluation instance; adding the security evaluationinstance into a message queue as a message object; sorting the security evaluation instances in the message queue according to priorities from high to low; and taking out the security evaluation instance from the message queue for execution and obtaining a security evaluation result. According to the method, information service security evaluation can be realized on the premise of easiness in use, high efficiency and low cost.
Owner:CHINA ACADEMY OF INFORMATION & COMM
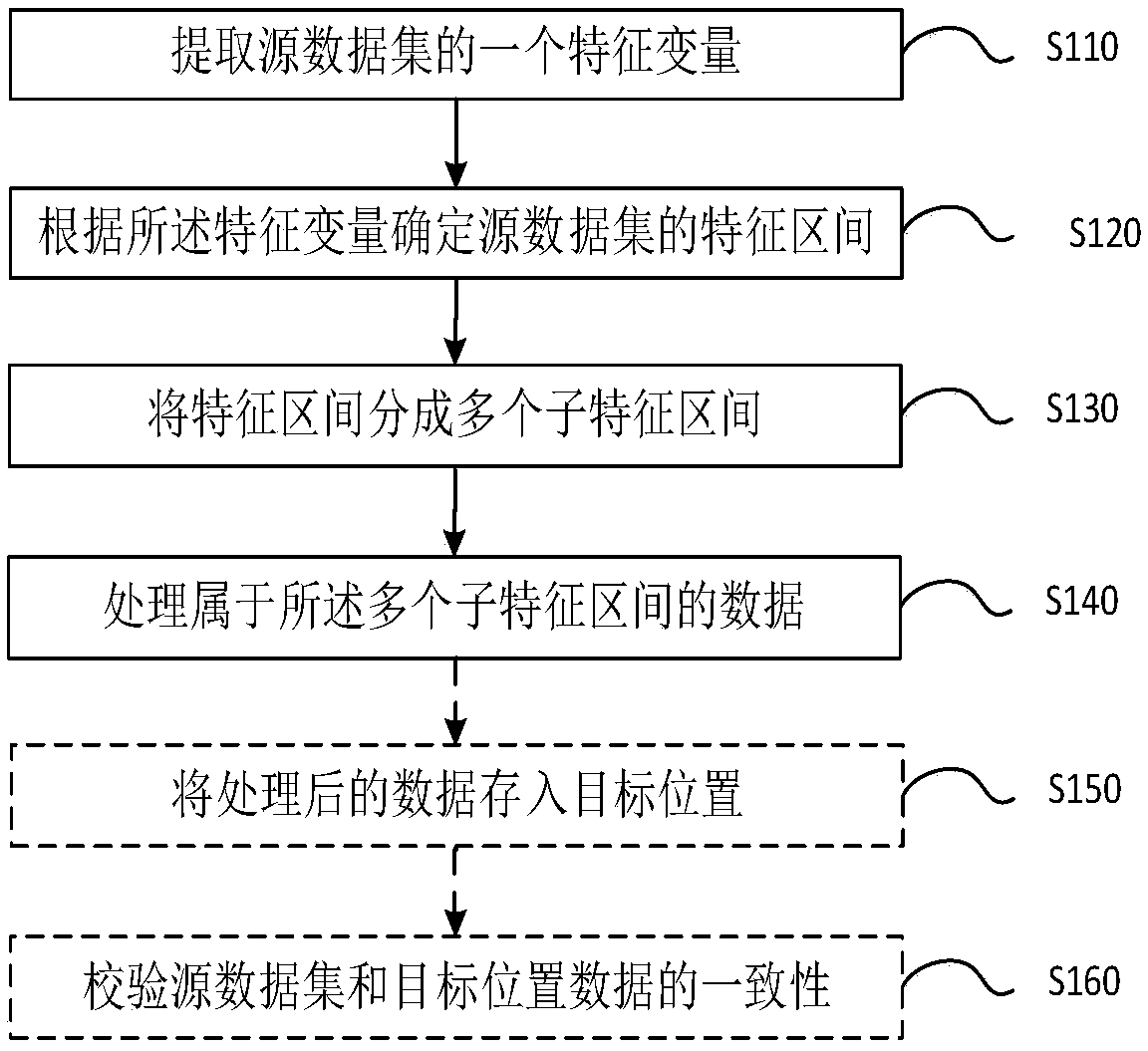
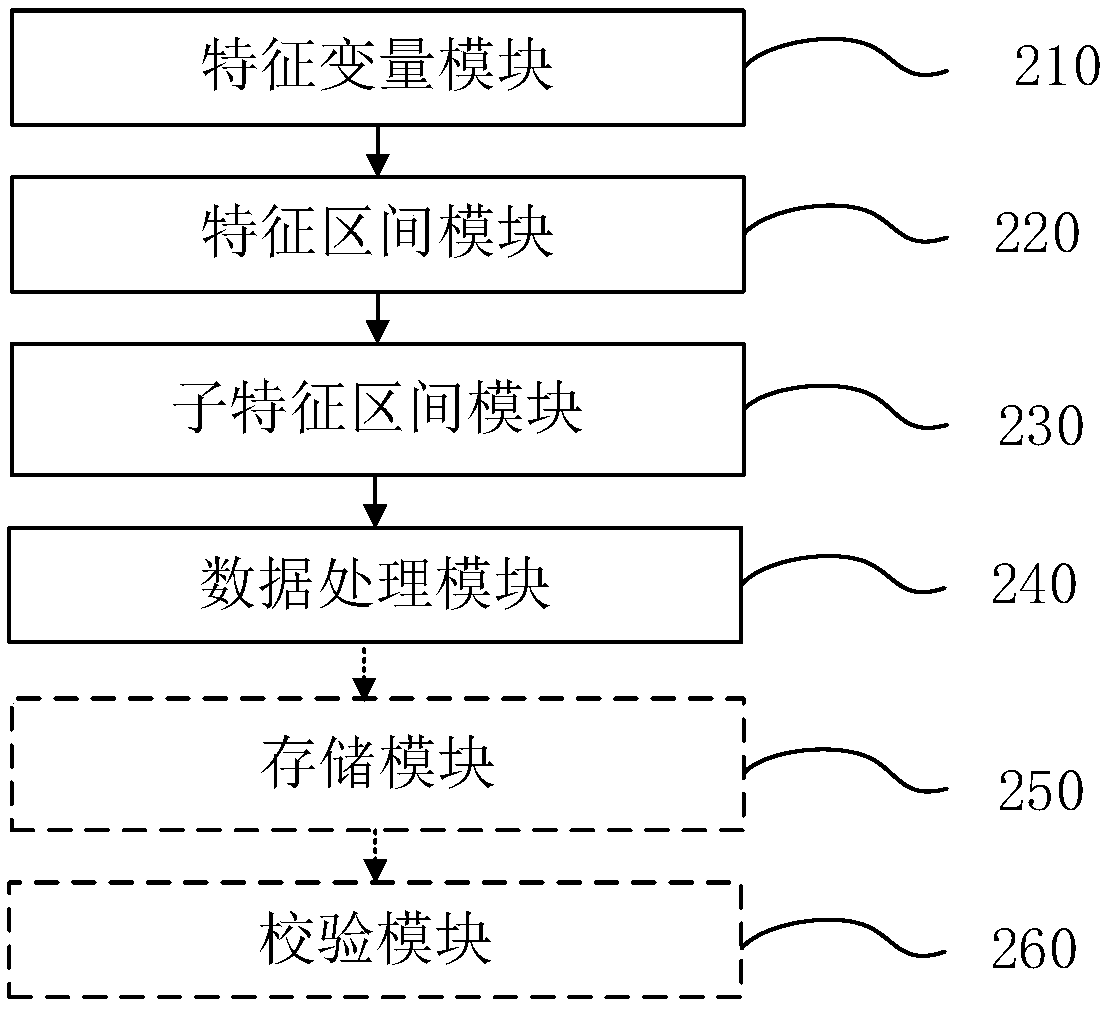
A method and apparatus for preprocessing data
InactiveCN109241045AImprove efficiencyConvenient for dynamic expansionDigital data information retrievalSpecial data processing applicationsSource dataData science
Embodiments of the present invention provide a method of preprocessing data. The method comprises the following steps of: extracting a characteristic variable of a source data set; Determining a feature interval of a source data set according to the feature variable; Dividing the feature interval into a plurality of sub-feature intervals; Processing data belonging to the plurality of sub-feature intervals. The invention improves the efficiency of data preprocessing and enhances the expandability of the data preprocessing module without increasing the operation and maintenance cost. In addition, embodiments of the present invention also provide an apparatus for preprocessing data, a piece of equipment, and a computer-readable storage medium.
Owner:优赛恒创科技发展(北京)有限公司 +1
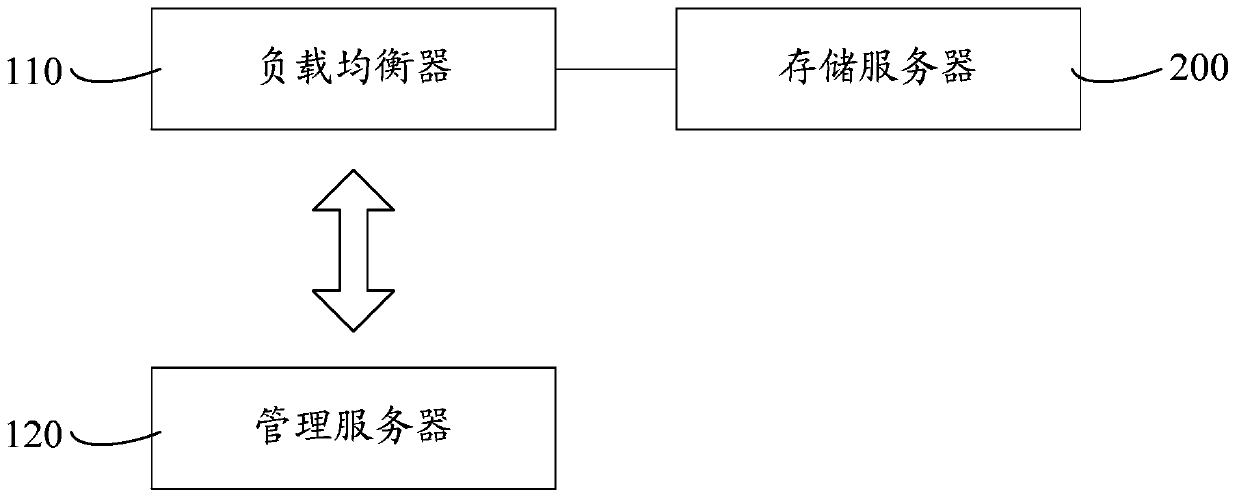
Server dynamic expansion system and method
ActiveCN105162859BAvoid running out of disk capacityReduce security risksTransmissionLoad regulationOperating system
The invention relates to a server dynamic expansion system and method. A load balancer monitors the load of a storage server, and sends an expansion request command to a management server when the load of the storage server exceeds a preset value. After receiving the expansion request instruction, the management server sends the expansion address information to the load balancer. The load balancer establishes a communication connection with the expansion server according to the expansion address information, and adjusts the load of the storage server to the expansion server. When it is detected that the storage server is overloaded, the load of the overloaded server is adjusted to the expansion server to avoid insufficient disk capacity of the server. When the server is expanded, it can avoid the impact on the normal operation and access of the website and users, and it can also reduce the restrictions on the server disk model and capacity, effectively alleviating the security risks brought by the server data during the expansion process. Operation The reliability is high, and the expansion method is simple and easy, which facilitates the dynamic expansion of the platform.
Owner:HUNAN YIGU TECH DEV
A detection method and device for a man-in-the-middle attack
ActiveCN106899579BQuick checkConvenient for dynamic expansionUser identity/authority verificationMan-in-the-middle attackEncryption
The invention discloses a method for detecting a man-in-the-middle attack, which comprises the steps of: when a first SSL (Secure Socket Layer) service needs to be subjected to the man-in-the-middle attack, acquiring a first encryption feature of the first SSL service and a second encryption feature of a preset second SSL service; and judging whether the first encryption feature and the second encryption feature meet a set condition of being attacked by a man in the middle, and if yes, determining that the first SSL service is attacked by the man in the middle. The invention simultaneously further discloses a device for detecting the man-in-the-middle attack.
Owner:BEIJINGNETENTSEC
A Symbol Library Based on 3D Plotting System
ActiveCN110781324BEasy constructionConvenient for dynamic expansionStill image data indexingSpecial data processing applicationsInformation repositoryInstruction set
Owner:中国科学院电子学研究所苏州研究院
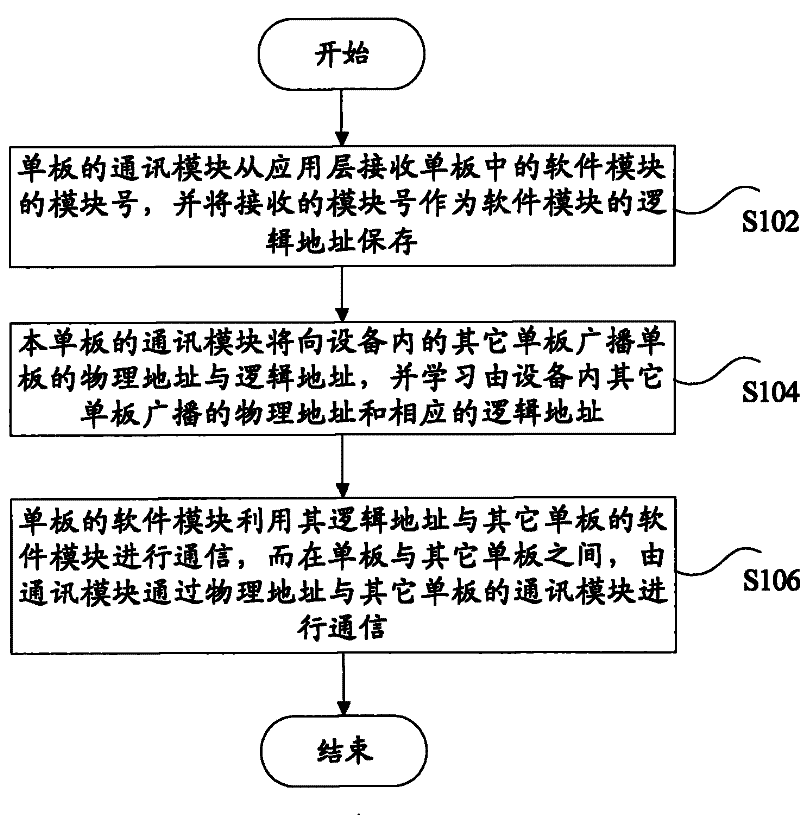
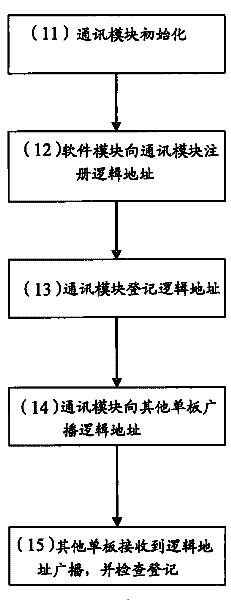
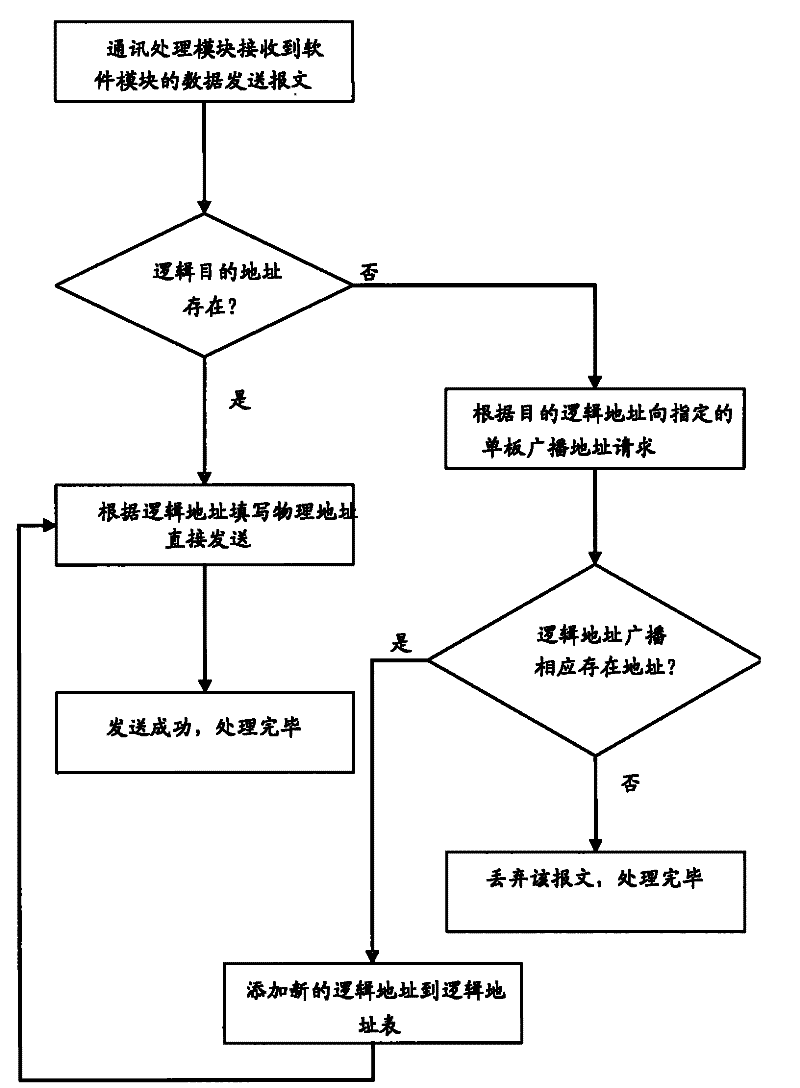
Communication method of a plurality of modules among single boards, single board with a plurality of software modules and communication device
InactiveCN101599852BSolve communication problemsConvenient for dynamic expansionProgram loading/initiatingData switching networksComputer moduleMonoboard
Owner:GLOBAL INNOVATION AGGREGATORS LLC
System and method for generating serial number of requested information
ActiveCN110046192BLower latencyProcessing speedDatabase management systemsNatural language data processingInformation processingEngineering
The present invention relates to a serial number generation system and method for requesting information, wherein the system includes a configuration device, a registration device, an information collection device and at least one serial number generation device; each serial number generation device is used to obtain corresponding configuration information from the configuration device, and Send a registration request to the registration device; the registration device is used to register each serial number generating device according to the configuration information, and generate corresponding registration information; the registration information includes the address of the serial number generating device and the number interval corresponding to the address; the information collection device uses To collect request information, extract the number of the request information; obtain registration information, determine the address of the serial number generating device, and send the request information and the serial number generating request to the serial number generating device corresponding to the address; the serial number generating device is used to generate the request according to the serial number and the sequence number of the previous request information to obtain the sequence number of the requested information. The above system can reduce the delay of information processing and greatly improve the speed of information processing.
Owner:GUANGZHOU LIZHI NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com