Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
129 results about "System Generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System Generation (SysGen) is a two-stage process for installing or updating OS/360, OS/VS1, OS/VS2 (SVS), OS/VS2 (MVS) and chargeable systems derived from them. There are similar processes for, e.g., DOS/360, which this article does not cover. Also, some of the details have changed between releases of OS/360 and many details do not carry over to later systems.
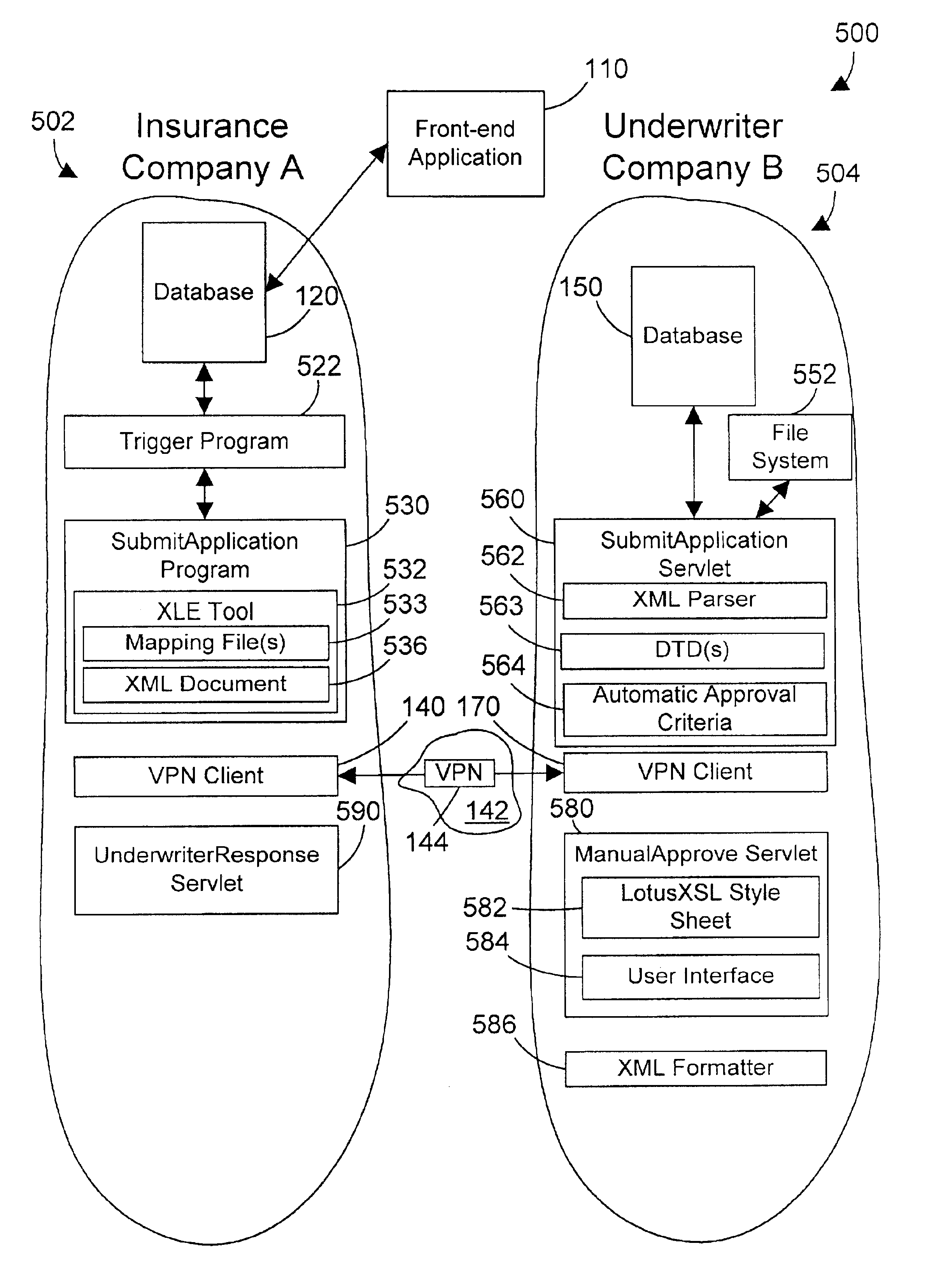
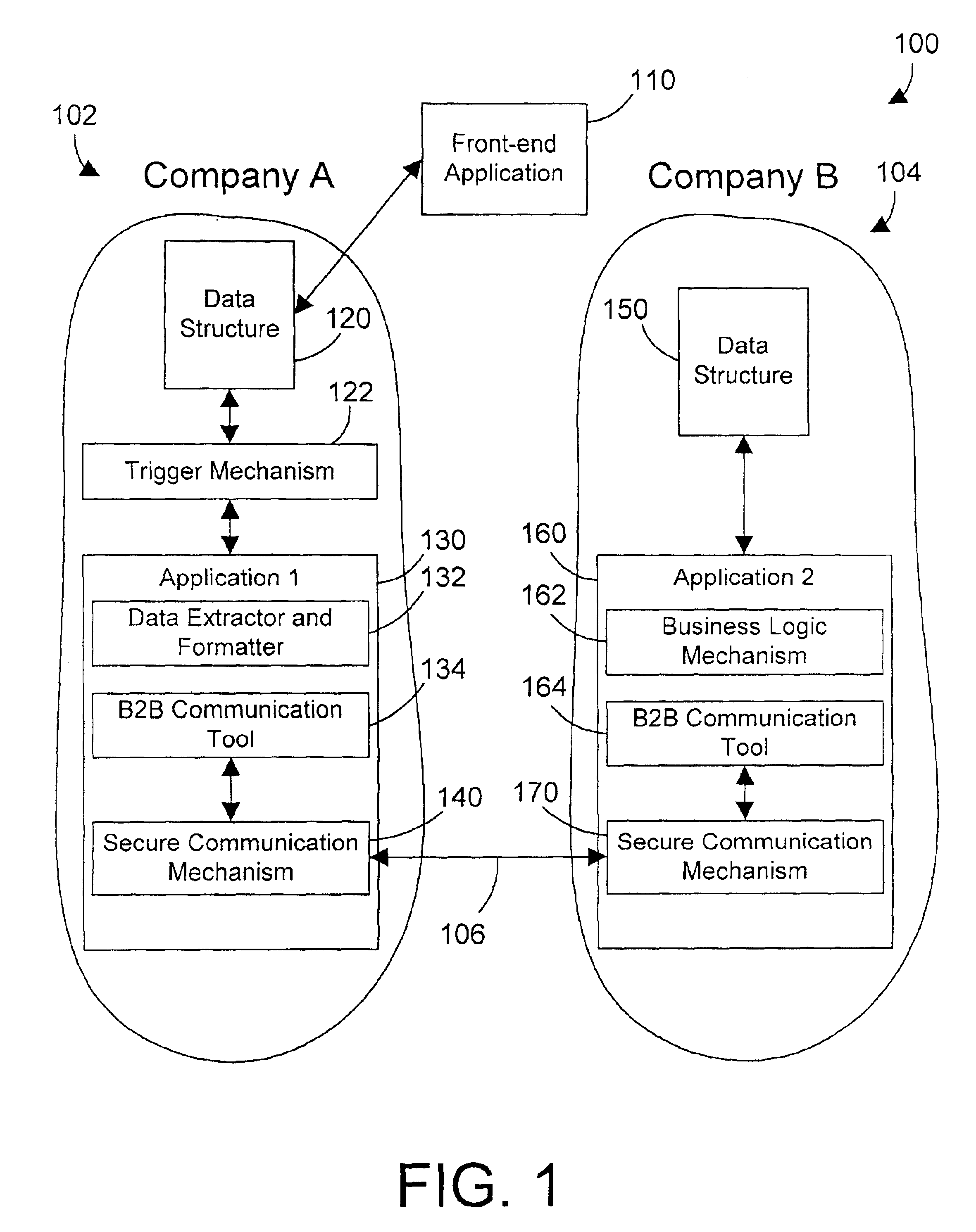
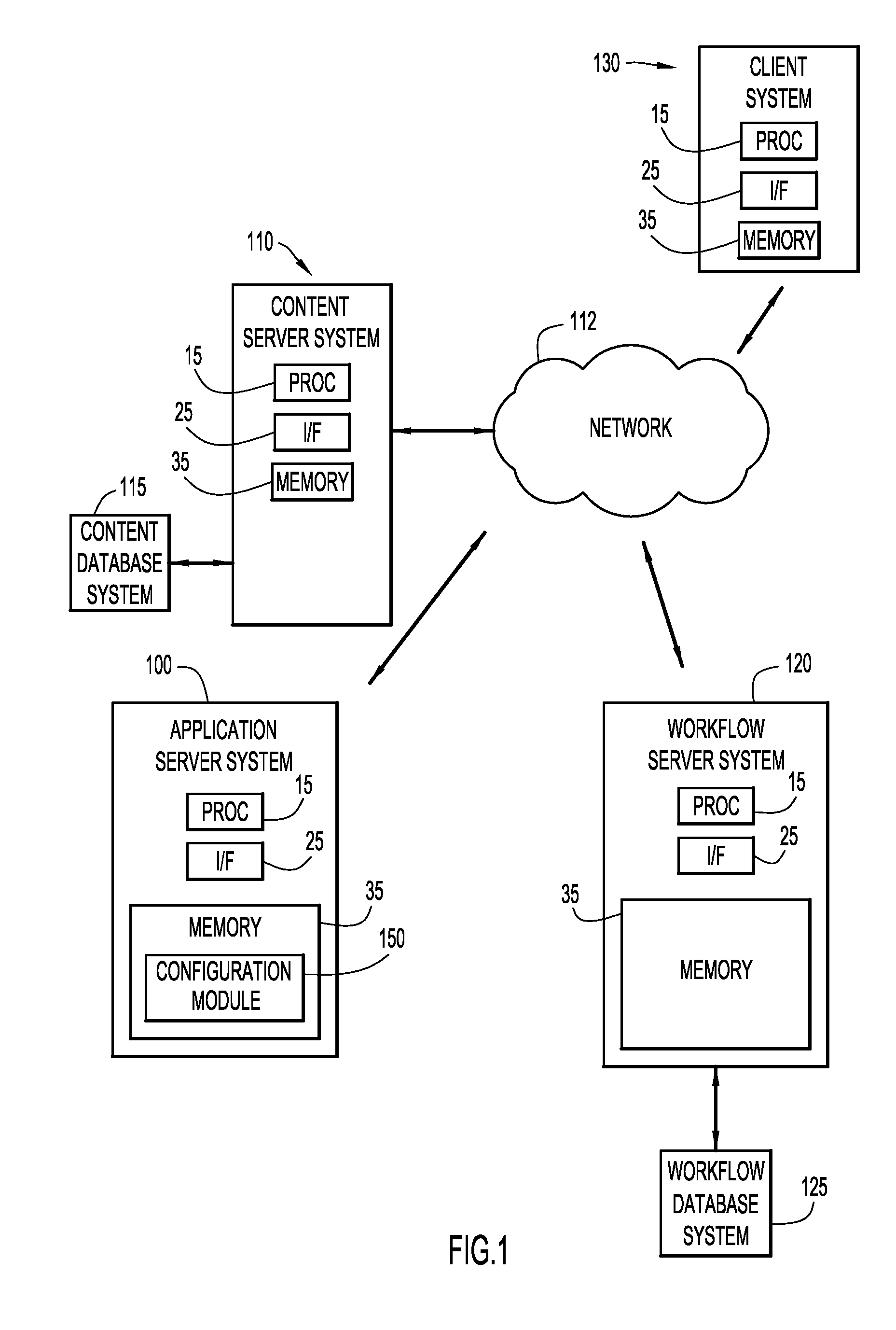
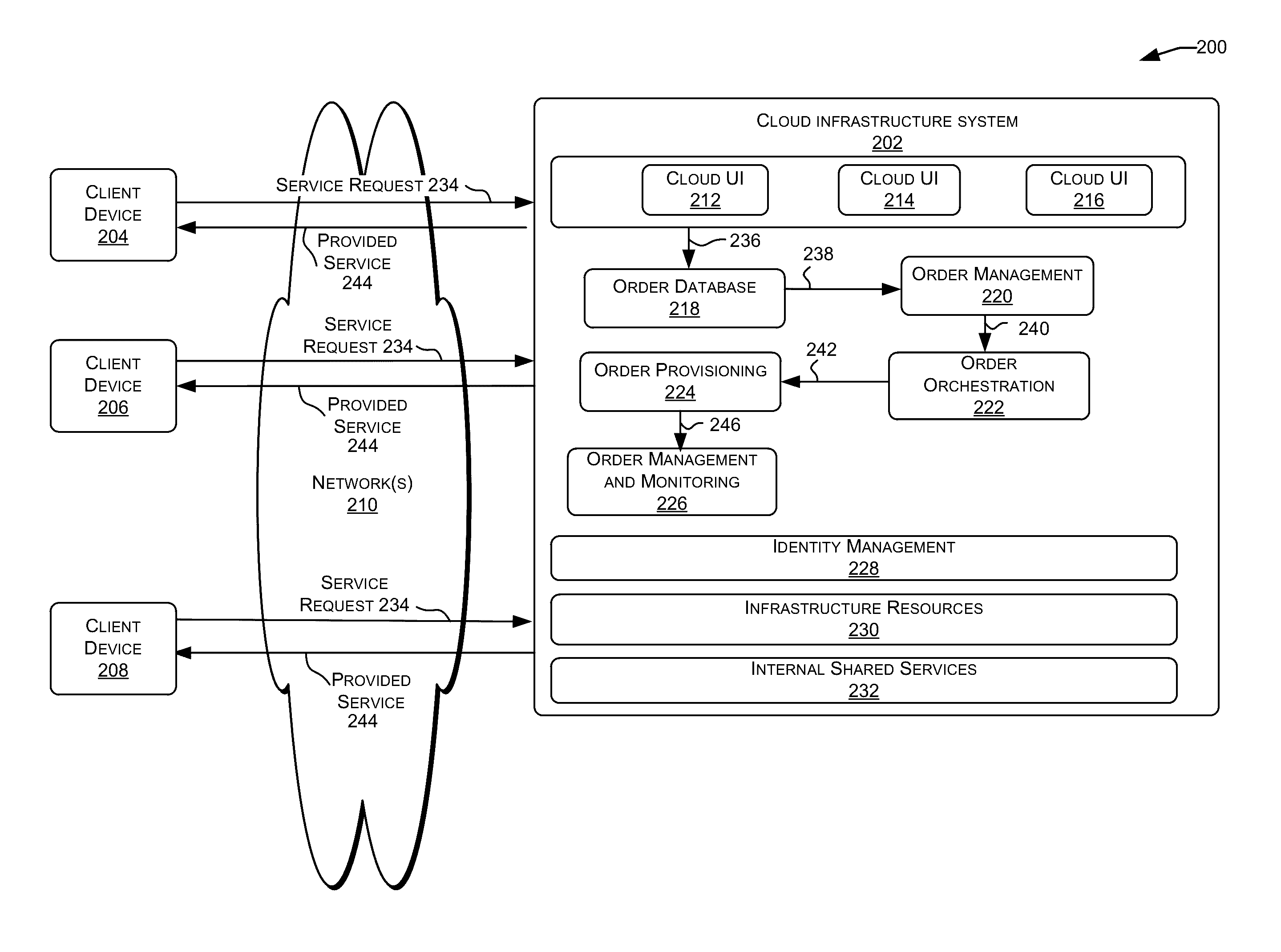
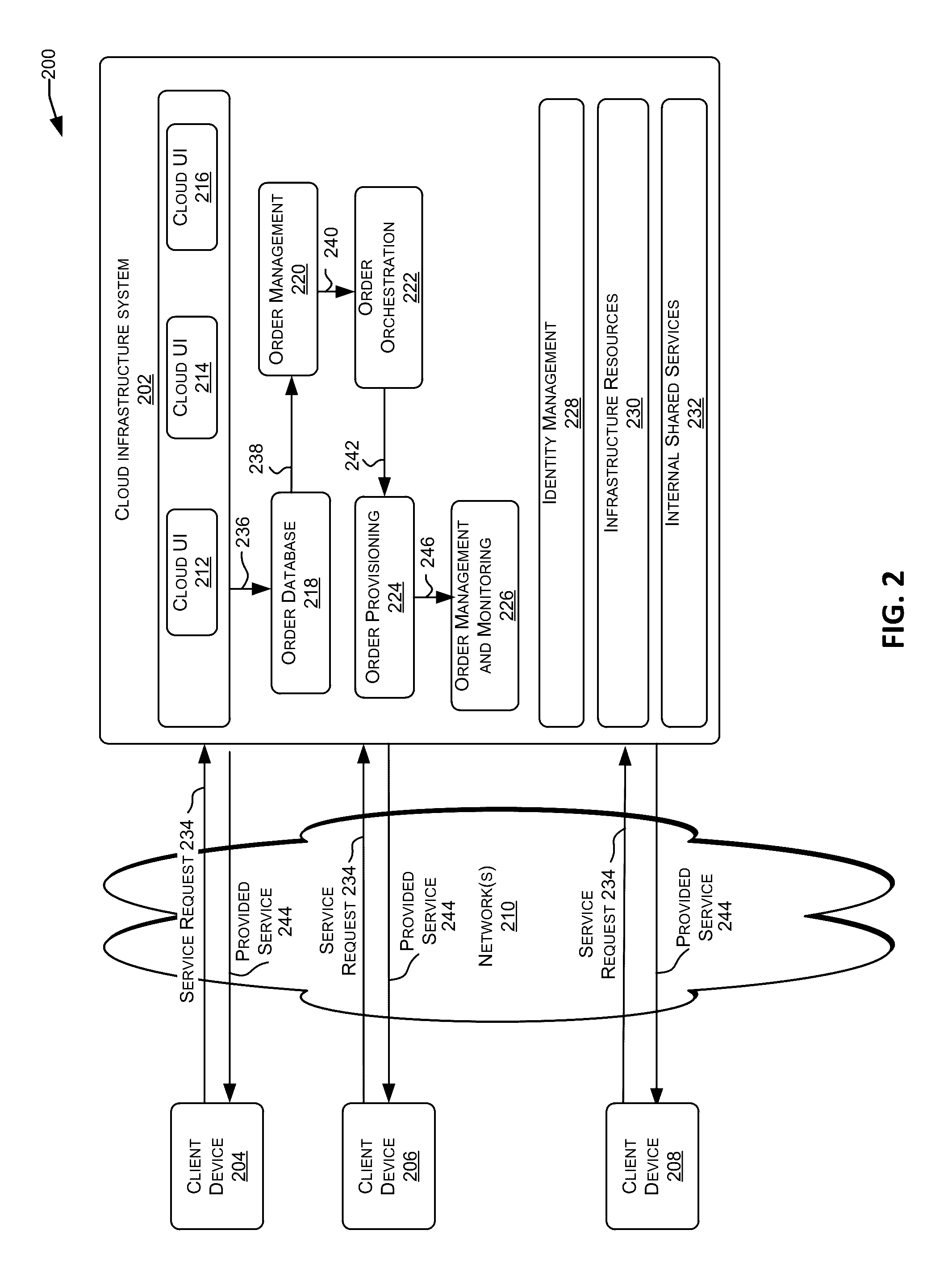
Computer system, method, and business method for automating business-to-business communications
InactiveUS6928487B2Database distribution/replicationMultiple digital computer combinationsSecure communicationPrivate network
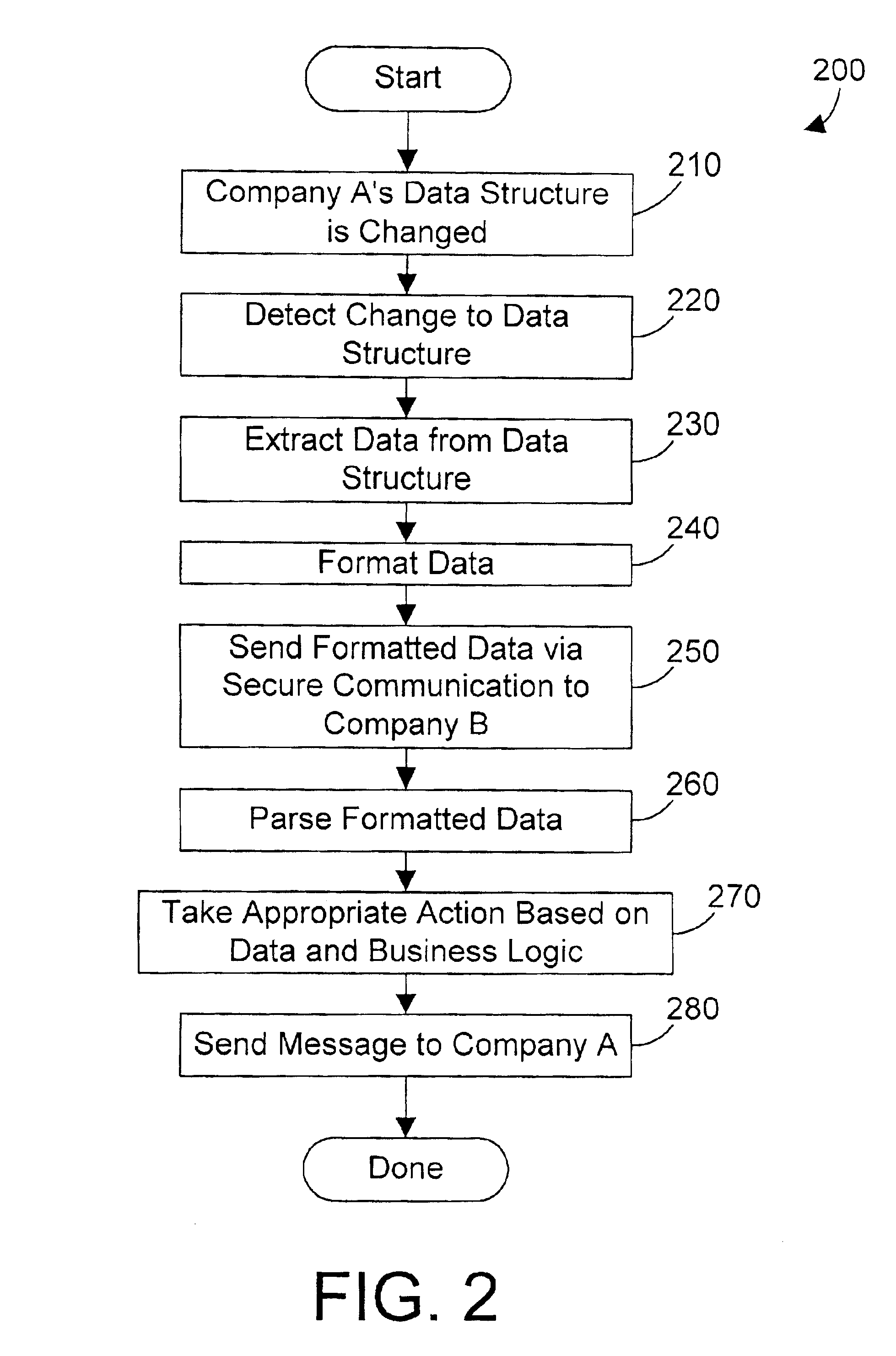
An apparatus, method, and method for doing business allows two business partners to communicate with each other in an architected manner. A first company monitors for changes to its internal data structure that indicate that communication with a second company may be required. A trigger mechanism monitors the data structure for changes, and invokes a software application when the data structure is changed in a defined manner. The software application extracts the new or changed data from the data structure, formats the data into an XML document, and sends the XML document to the second company via a secure communication mechanism, such as a virtual private network (VPN). The second computer system receives the information from the first computer system, parses the information, and processes the information. The second computer system then generates an appropriate response to the first computer system. In this manner, the first and second computer systems can communicate in an architected manner using XML documents, thereby allowing automation of processes between the two companies.
Owner:IBM CORP
Generating runtime components
Owner:ORACLE INT CORP
Method and system for simplifying the structure of dynamic execution profiles
InactiveUS7096499B2Reduce dimensionalityReduce in quantityMemory loss protectionDigital data processing detailsSoftware systemTheoretical computer science
A real-time approach to detecting aberrant modes of system behavior induced by abnormal and unauthorized system activities indicative of abnormal activity of a software system is based on behavioral information obtained from a suitably instrumented computer program as it is executing. The theoretical foundation is founded on a study of the internal behavior of the software system. As a software system is executing, it expresses a set of its many functionalities as sequential events. Each of these functionalities has a characteristic set of modules that is executed to implement the functionality. These module sets execute with defined and measurable execution profiles among the program modules and within the execution paths of the individual modules, which change as the executed functionalities change. Over time, the normal behavior of the system will be defined by the boundary of the profiles. Abnormal activity of the system will result in behavior that is outside the normal activity of the system and thus result in a perturbation of the system in a manner outside the scope of the normal profiles. Such anomalies are detected by analysis and comparison of the profiles generated from an instrumented software system against a set of nominal execution profiles. Moreover, a method for reducing the amount of information necessary to understand the functional characteristics of an executing software system identifies the common sources of variation among the program instrumentation point frequencies and builds execution profiles based on a reduced set of virtual execution domains.
Owner:STRATACLOUD
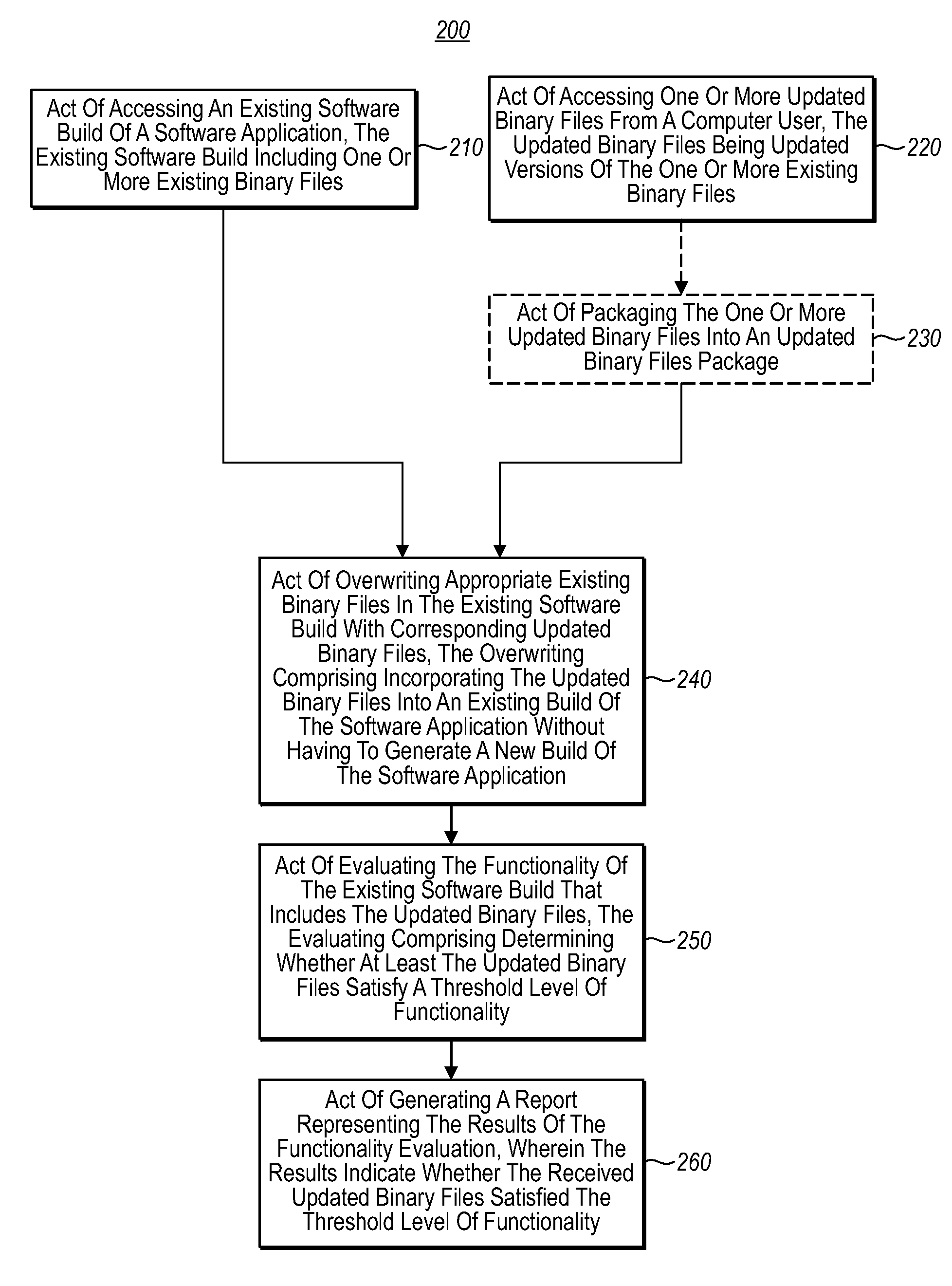
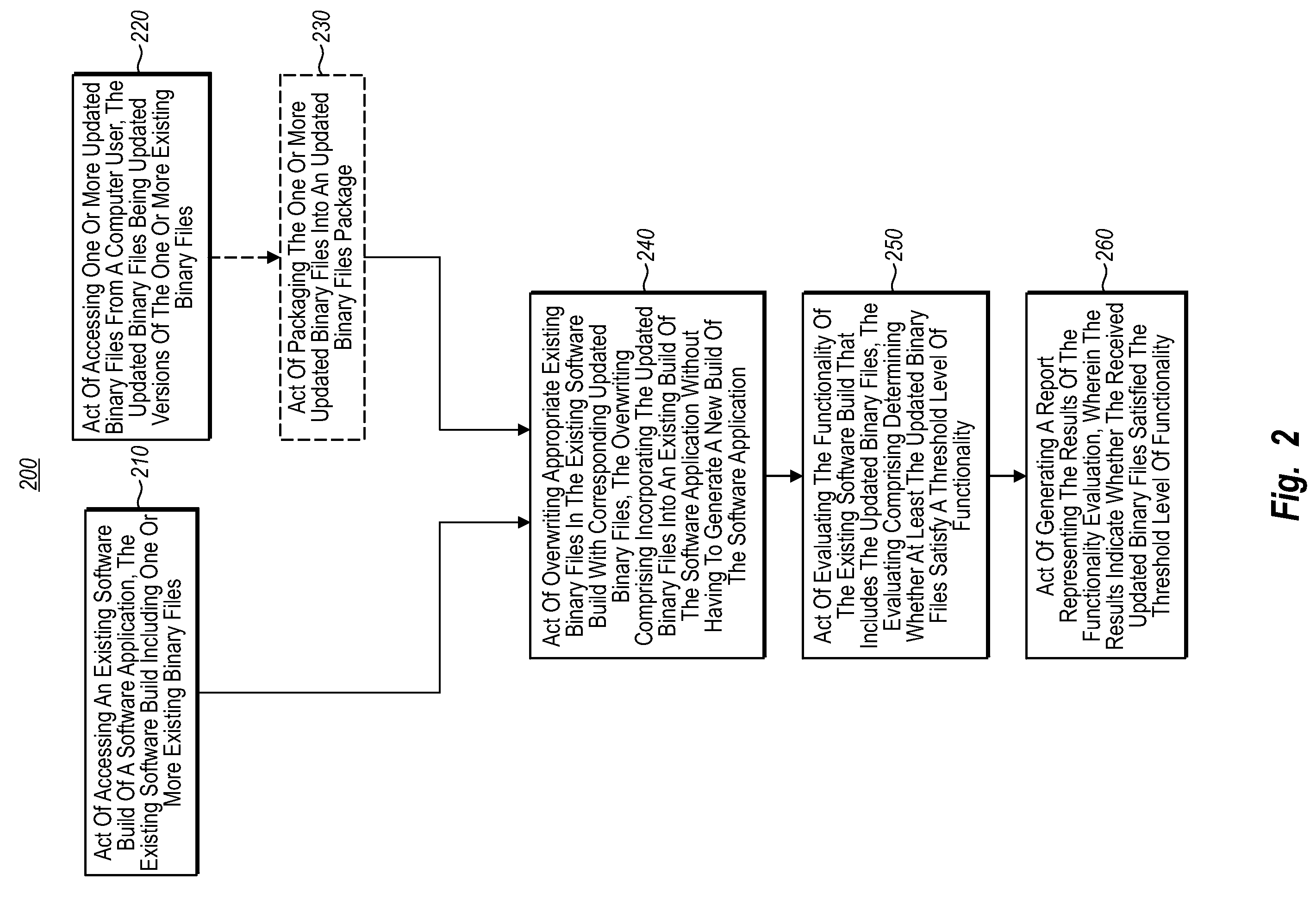
Software build validation before check-in
InactiveUS20080104573A1Satisfy functionalityWell formedError detection/correctionVersion controlComputer usersComputerized system
In one embodiment of this invention, a computer system performs a method for validating a software build before check-in. A computer system accesses an existing software build of a software application that includes one or more existing binary files. The computer system accesses one or more updated binary files from a computer user. The computer system overwrites appropriate existing binary files in the existing software build with corresponding updated binary files for the updated binary files package. The overwriting included incorporating the updated binary files into the existing build of the software application without having to generate a new build of the software application. The computer system evaluates the functionality of the updated existing software build, wherein evaluating includes determining whether at least the updated binary files satisfy a threshold level of functionality. The computer system generates a report representing the results of the functionality evaluation.
Owner:MICROSOFT TECH LICENSING LLC
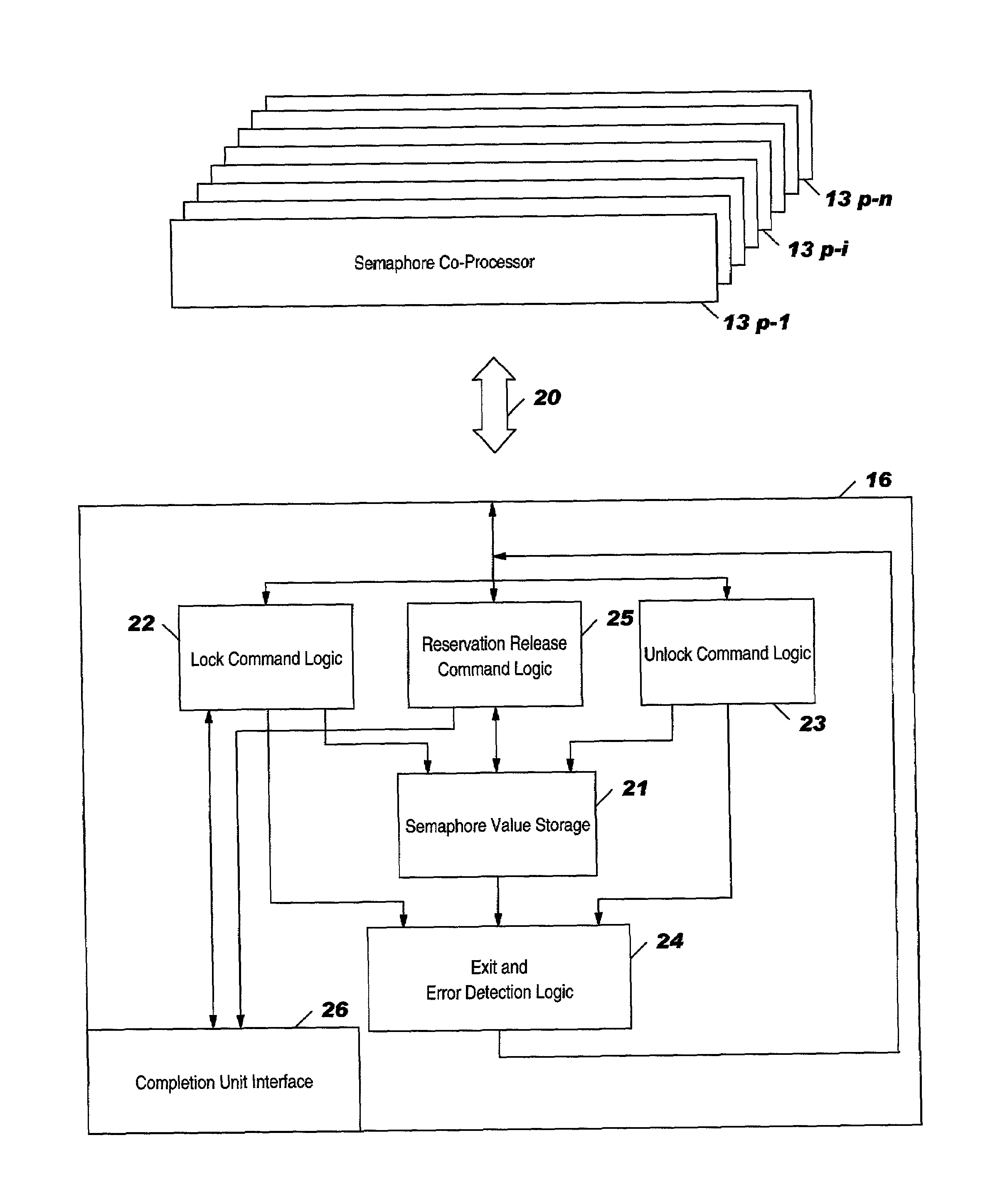
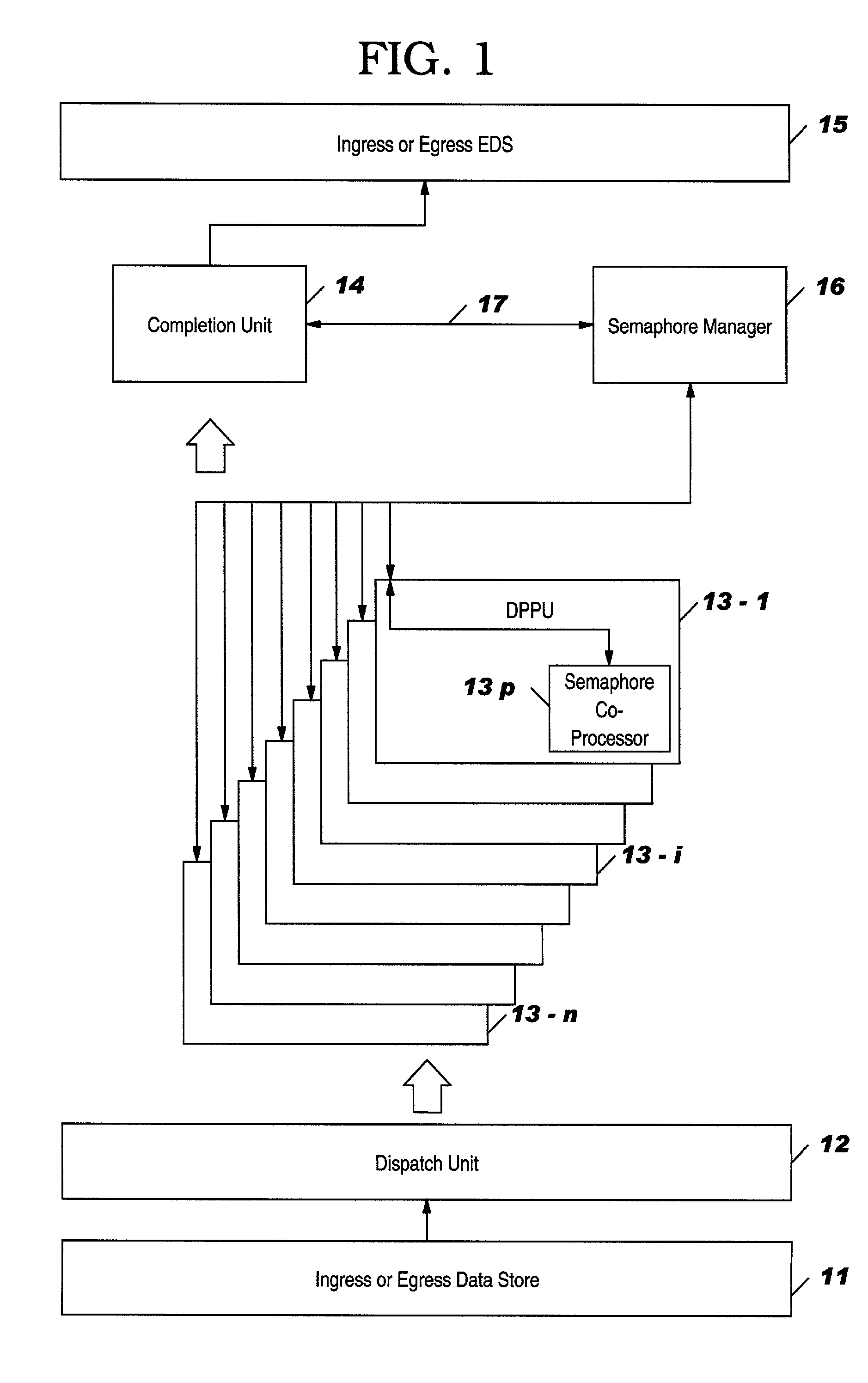
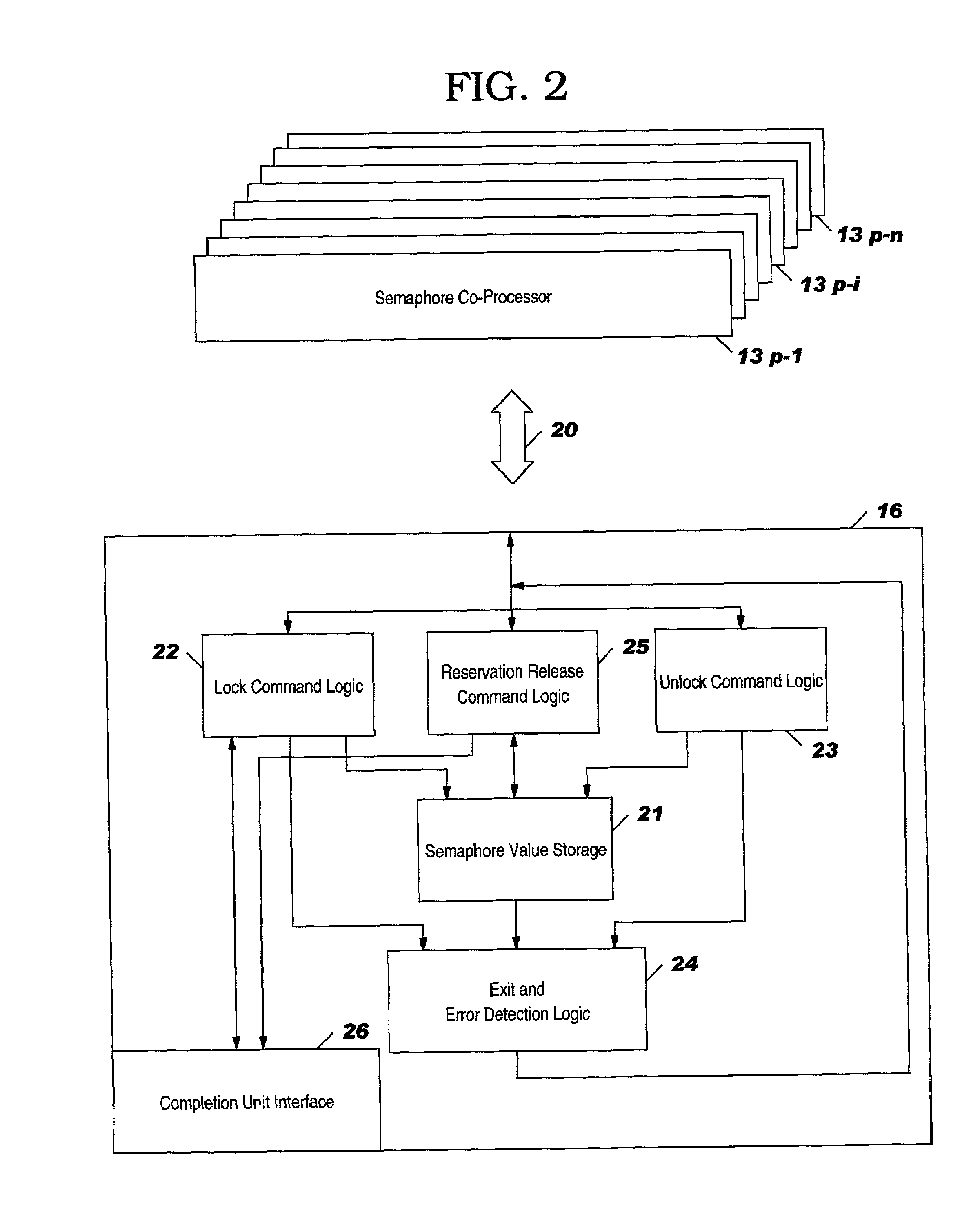
Ordered semaphore management subsystem
An ordered semaphore management subsystem and method for use in an application system which includes a plurality of processors competing for shared resources each of which is controlled by a unique semaphore. The subsystem generates an ordered semaphore field (OSF) corresponding to each processor in a linked list of processors and assigns one of four statuses to the OSF depending on the position the processor occupies in the linked list of processors competing for the shared resources. The four states are (1) semaphore head (SH); (2) behind semaphore head (BSH); (3) semaphore head behind (SHB); and (4) skip (Skip). Only the SH processor is allocated the semaphore when requested. A processor not in the SH state will be denied the semaphore even if is available to assure sequential access.
Owner:IBM CORP
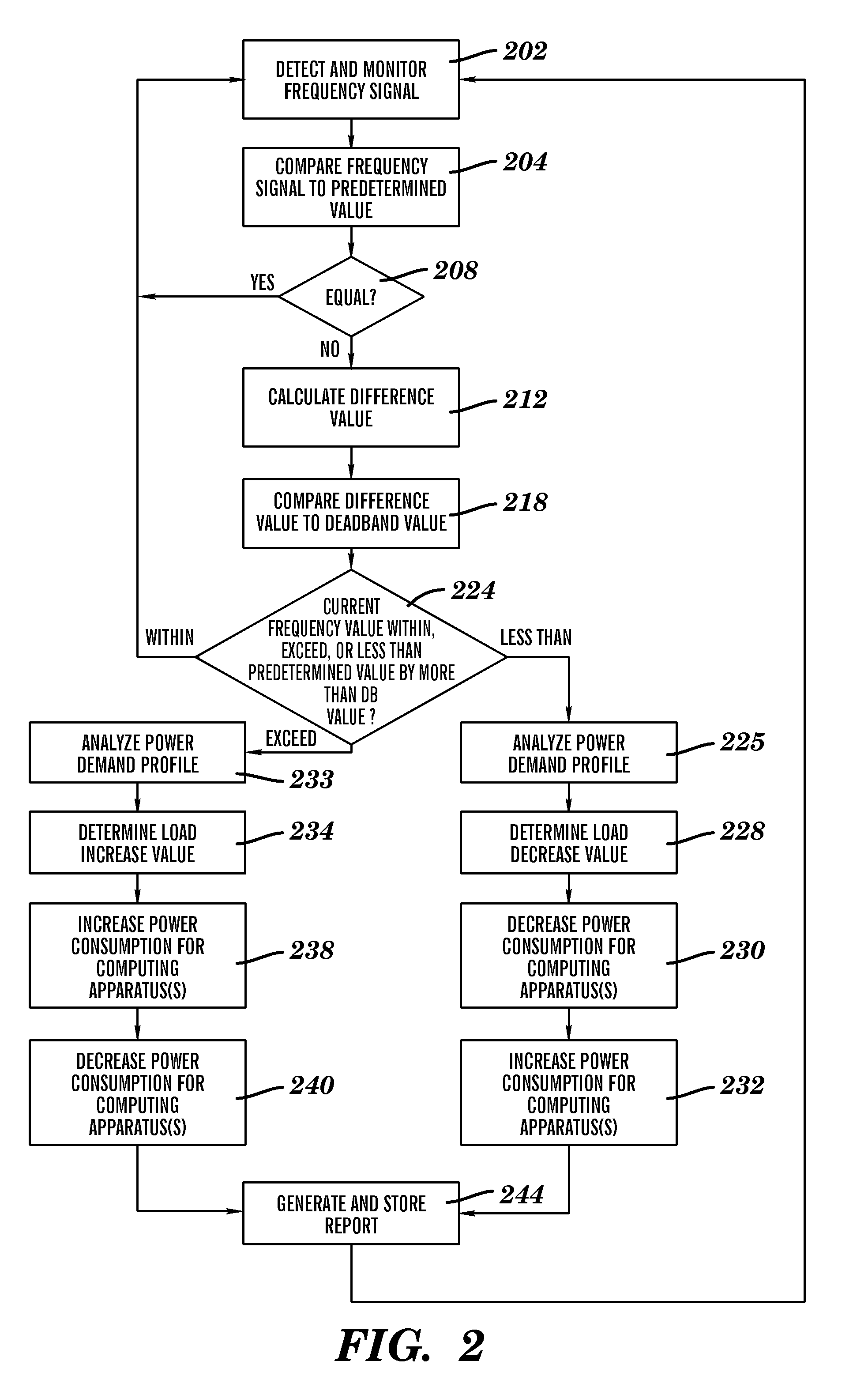
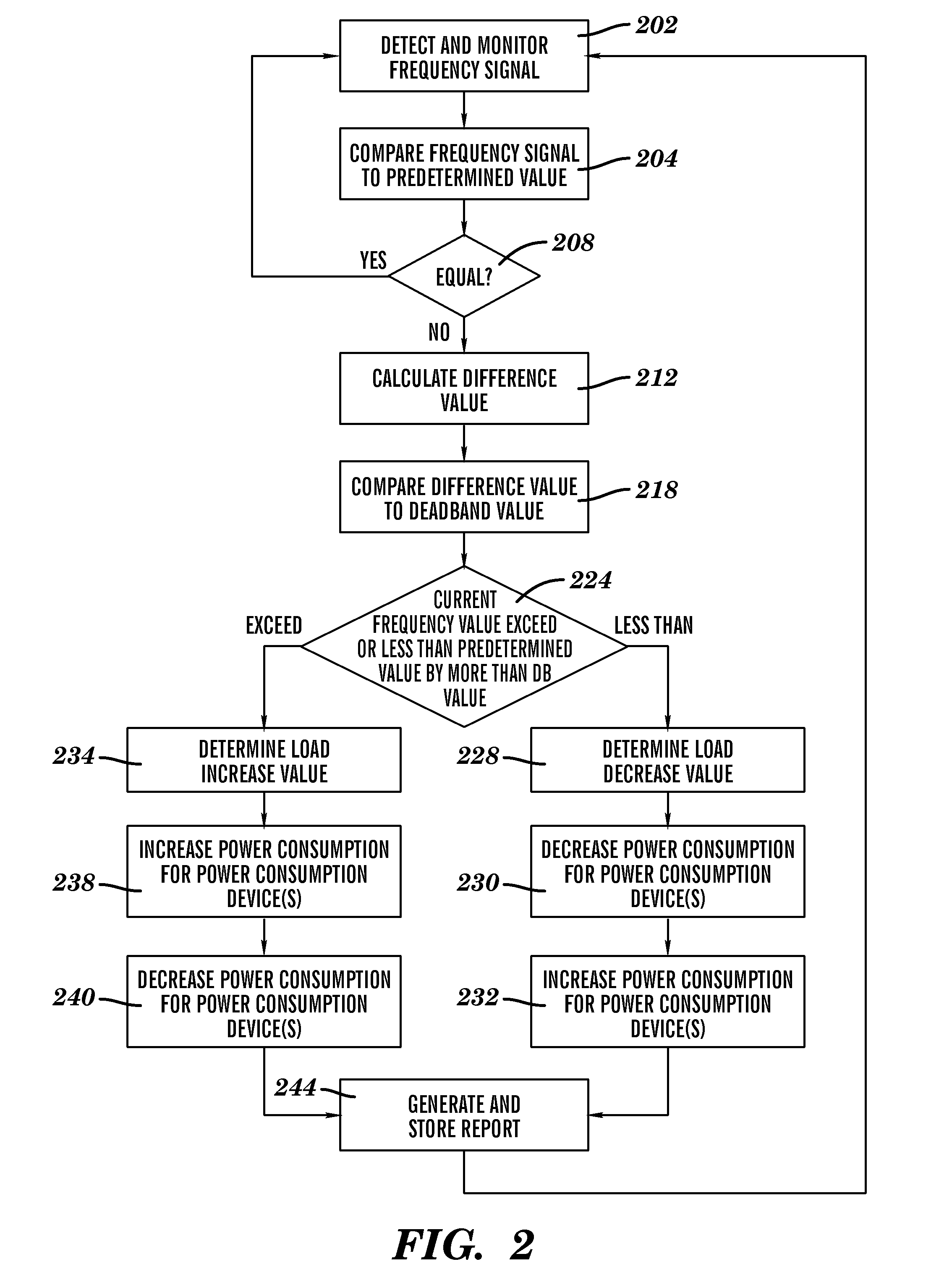
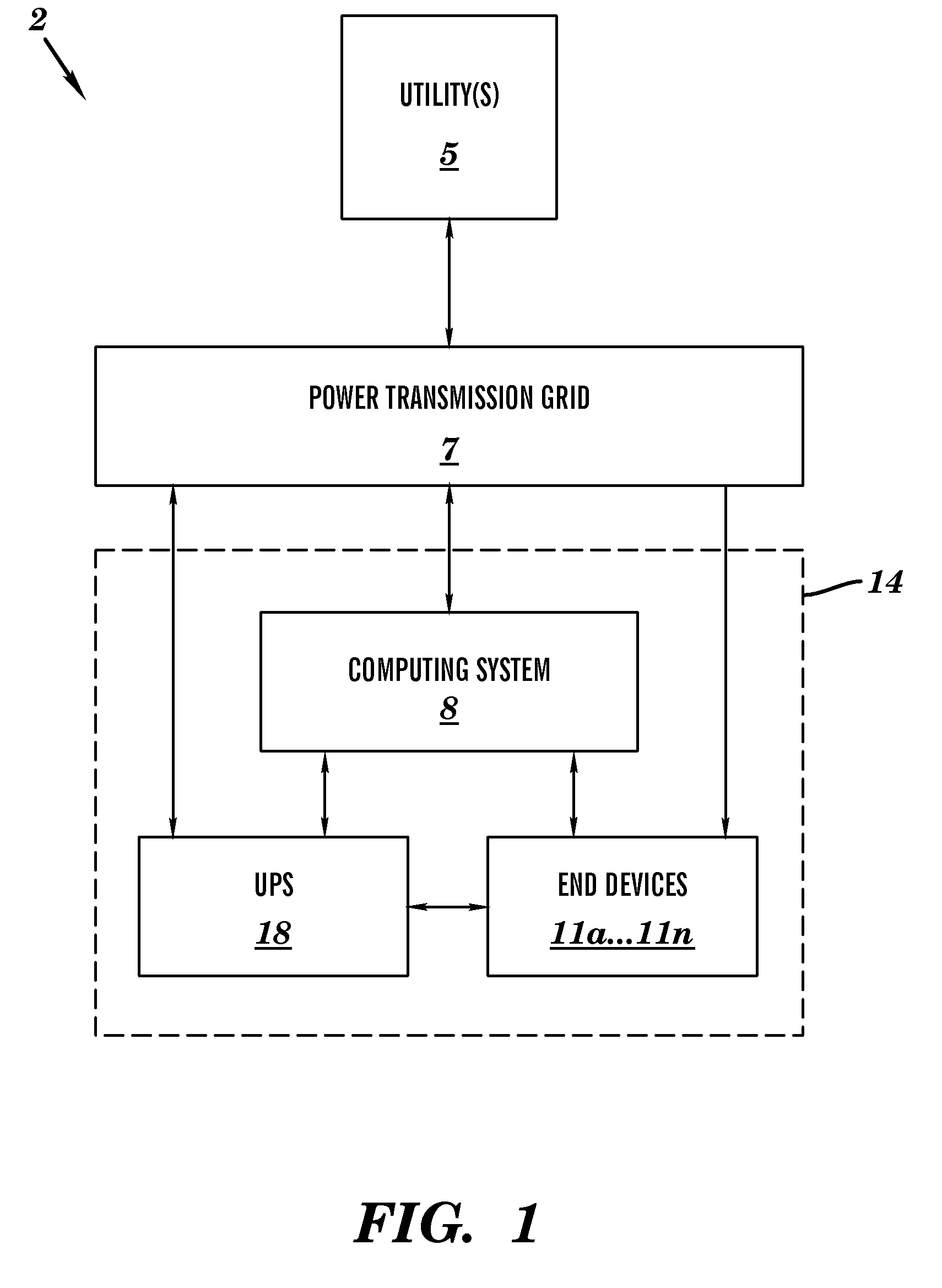
Computing load management method and system
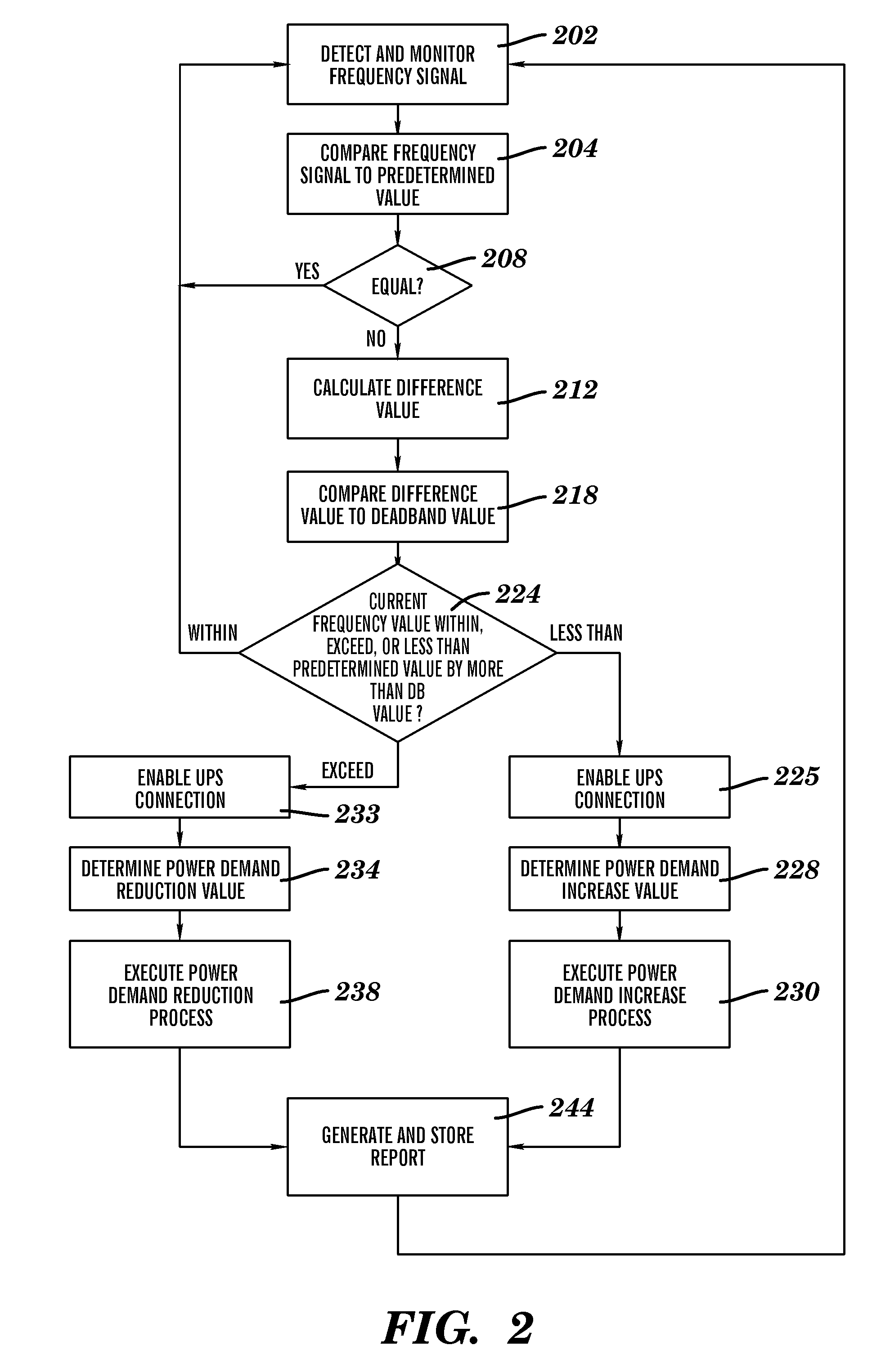
A load management method and system. The method includes detecting and monitoring by a computing system, a frequency signal associated with an input voltage signal used for powering computing apparatuses at a specified location. The computing system compares the frequency signal to a predetermined frequency value. The computing system determines that the frequency signal comprises a first value that is not equal to the predetermined frequency value. The computing system calculates a difference value between the first value and the predetermined frequency value. The computing system compares the difference value to a second value and analyzes a power demand profile. The computing system enables a load adjustment modification process associated with the plurality of power consumption devices based on the difference value and the power demand profile. The computing system generates and stores a report associated with the load adjustment modification process.
Owner:IBM CORP
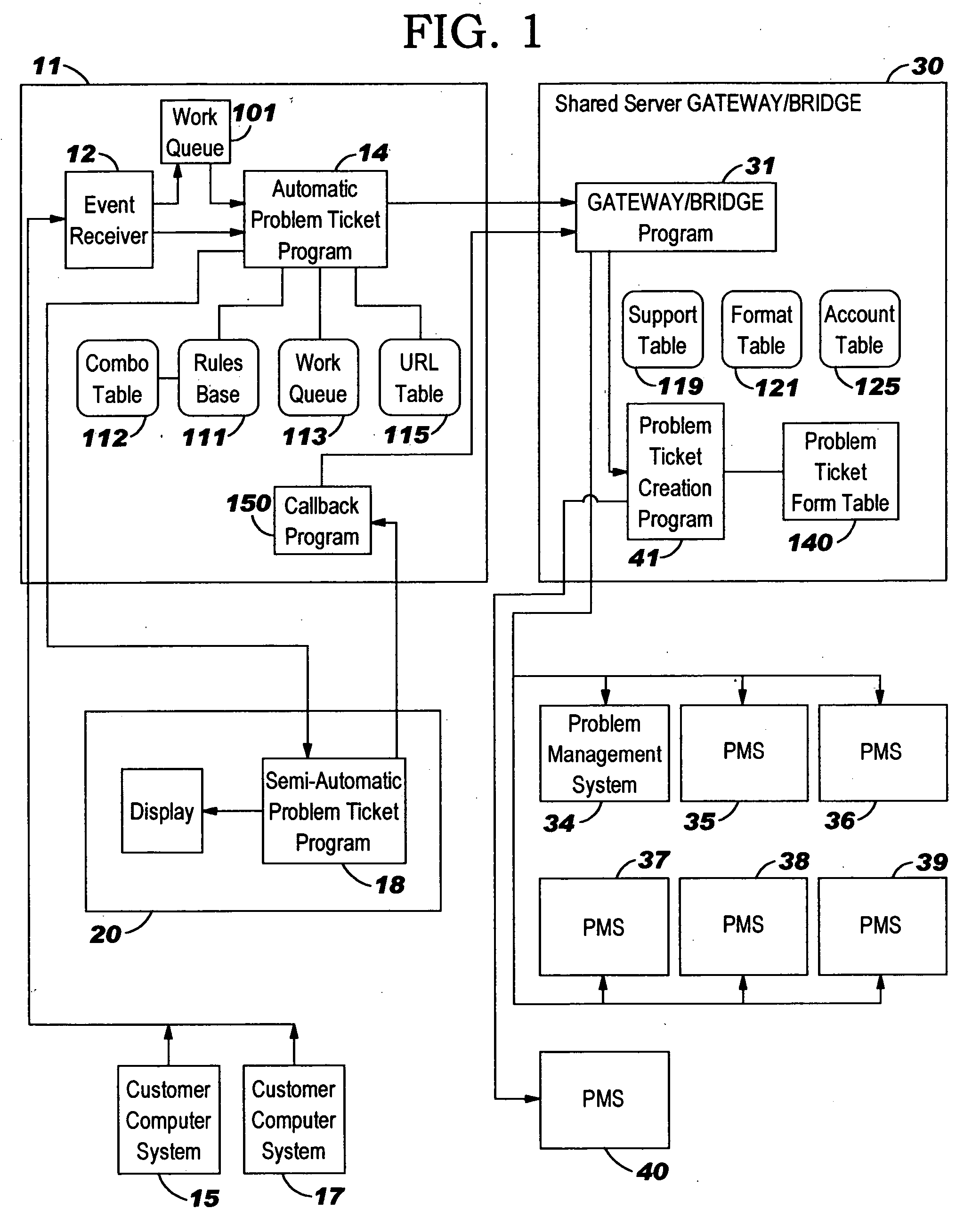
Generation of problem tickets for a computer system
ActiveUS20050039192A1Power supply for data processingNon-redundant fault processingProgram instructionEvent type
A computer system and program product for managing events. Program instructions, respond to notification of an event, by determining if a problem ticket can be automatically generated for the event. If so, the program instructions make a request to generate the problem ticket. The program instructions determine if the problem ticket can be automatically generated based in whole or in part on (a) a type of the event and a customer who owns or uses a computer system in which the event occurred, (b) a type of the event, a customer who owns or uses a computer system in which the event occurred, and a severity of the event, (c) a type of the event, a customer who owns or uses a computer system in which the event occurred, and a magnitude of the event, or (d) a type of the event and whether other events of a same type occur at approximately a same time. If a determination is made that a problem ticket cannot be automatically generated, other program instructions notify or initiate notification of an operator and supply event information for the operator so that the operator can determine whether to generate a problem ticket.
Owner:KYNDRYL INC
Method and system for automated metamodel system file generation
InactiveUS20050071750A1Improve productivityShorten the lead timeDigital computer detailsOffice automationProgramming languageElectronic form
An automated metamodel system file generation method and system (146) generates a plurality of metamodel files (148) using a set of metamodel requirements (144) derived for a metamodel system (180). The invention includes the steps of and instructions for (180, 182) capturing for a metamodel system (80) a set of metamodel requirements (144). The system (146) saves the captured set of metamodel requirements in at least one requirements spreadsheet (152) and then opens (146) the spreadsheet (152) to make accessible the captured set of metamodel requirements. The system (146) further generates at least one each of an object type spreadsheet (192), a relationship type spreadsheet (198), and a symbol type spreadsheet (188) by applying a predetermined set of generation instructions to said at least one requirements spreadsheet (152). From the specified object type spreadsheet (192), relationship type spreadsheet (198), and symbol type spreadsheet (188) the system (146) generates a plurality of metamodel files (148) for use in a metamodel system (80).
Owner:ELECTRONICS DATA SYST CORP
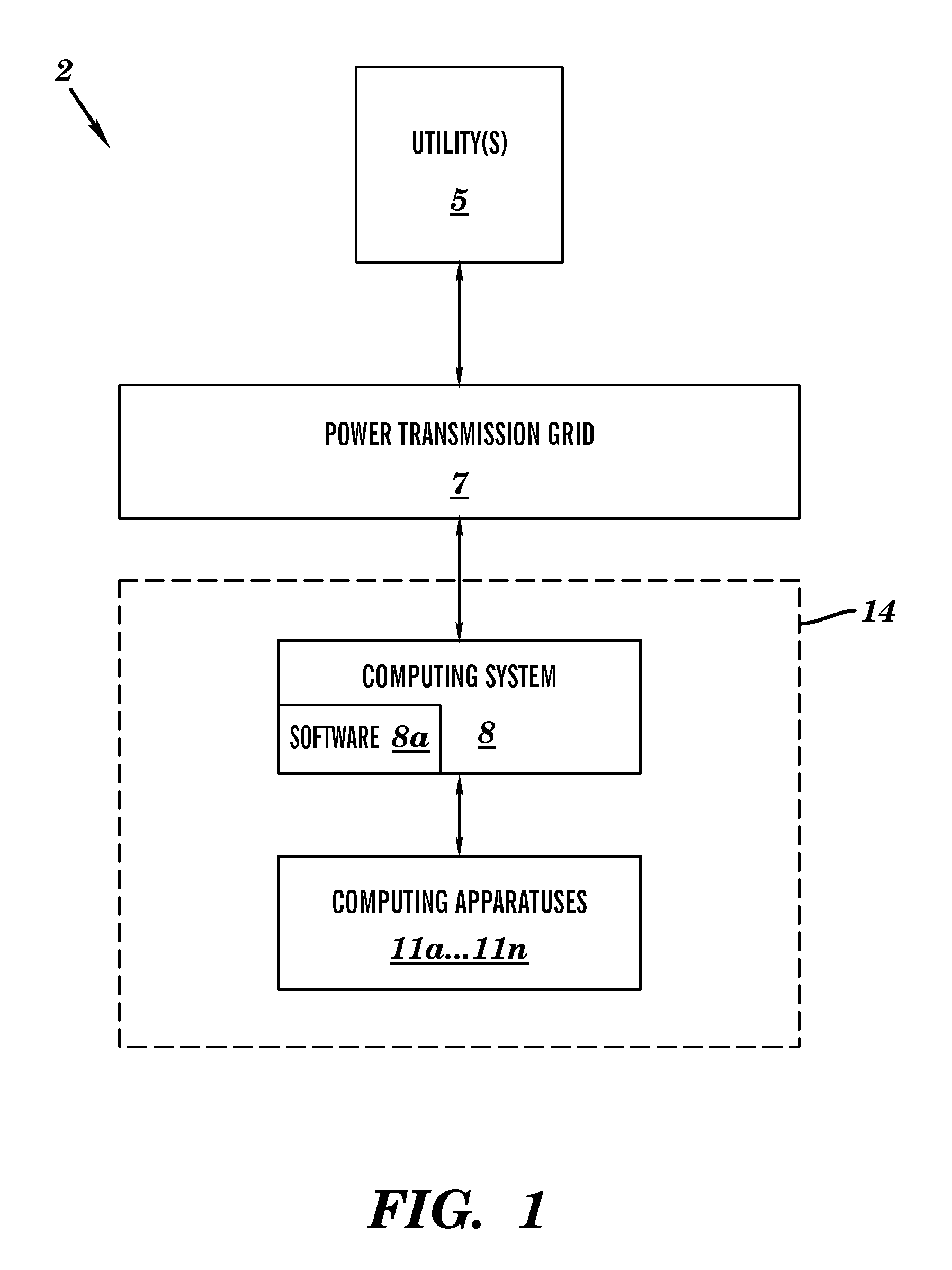
Energy load management method and system
A modification method and system. The method includes detecting and monitoring by a computing system, a frequency signal associated with an input voltage signal used for powering a plurality of power consumption devices at a specified location. The computing system compares the frequency signal to a predetermined frequency value. The computing system determines that the frequency signal comprises a first value that is not equal to the predetermined frequency value. The computing system calculates a difference value between the first value and the predetermined frequency value. The computing system compares the difference value to a second value. The computing system enables a load adjustment modification process associated with the plurality of power consumption devices. The computing system generates and stores a report associated with the load adjustment modification process.
Owner:IBM CORP
Power demand management method and system
InactiveUS20100213763A1Electric devicesPower network operation systems integrationControl theoryUninterruptible power supply
A power demand modification method and system. The method includes detecting and monitoring by a computing system, a frequency signal associated with an input voltage signal used for powering a plurality of power consumption devices at a specified location. The computing system compares the frequency signal to a predetermined frequency value. The computing system determines that the frequency signal comprises a first value that is not equal to the predetermined frequency value. The computing system calculates a difference value between the first value and the predetermined frequency value. The computing system compares the difference value to a second value. The computing system enables a connection to an uninterruptable power supply (UPS) and performs a power demand modification process associated with the UPS. The computing system generates and stores a report associated with the load adjustment modification process.
Owner:IBM CORP
Configuring a System with Various System Components Utilizing a Configuration Profile
InactiveUS20140047228A1Program control using stored programsDigital computer detailsComputerized systemComputer science
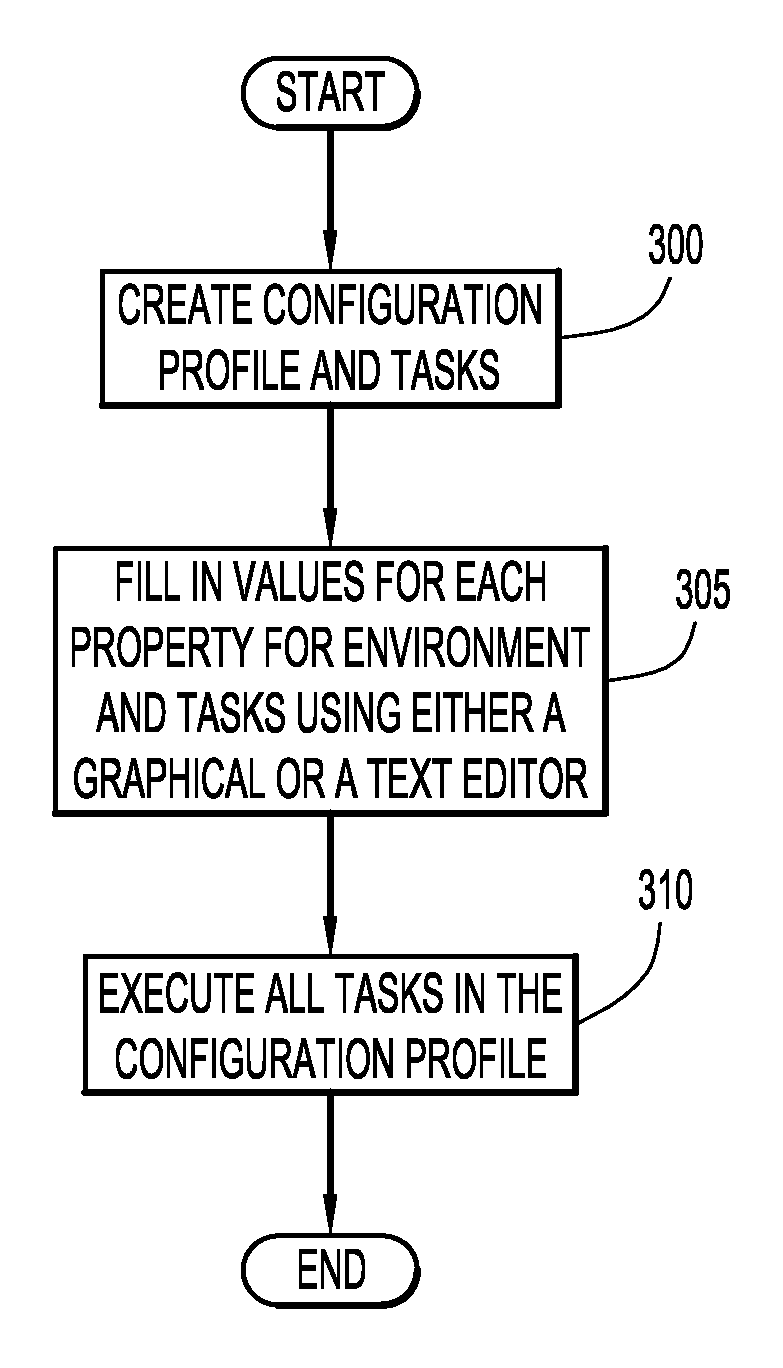
According to an embodiment of the present invention, a computer system for configuring a system with at least two different system components based on a target computing environment includes at least one processor. The computer system generates a profile to configure each of the different system components for the target computing environment. The profile identifies the corresponding tasks to be performed and properties to configure each of the different system components for the target computing environment. The computer system processes the profile and performs the tasks in the order listed in the profile and in accordance with the properties to configure the system for the target computing environment. Embodiments of the present invention further include a method and computer program product for configuring a system with at least two different system components based on a target computing environment in substantially the same manner described above.
Owner:IBM CORP
Generating a vibration profile for a rotating cooling device in a computer system
ActiveUS20100217543A1Eliminate the effects ofFlow propertiesDigital computer detailsTime domainFrequency spectrum
One embodiment of the present invention provides a system that generates a vibration profile for a rotational device in a computer system. During operation, the system sequentially sweeps a rotation speed of a rotational device over a range of rotation speeds. While driving the rotational device at each rotation speed, the system collects a time-domain vibration signal produced by the rotational device and subsequently computes a frequency spectrum of the time-domain vibration signal. In this way, the system generates a set of frequency spectra associated with the range of rotation speeds. Next, the system combines the set of frequency spectra to generate a composite vibration profile for the rotational device.
Owner:ORACLE INT CORP
Method and computer system for monitoring an HVAC system
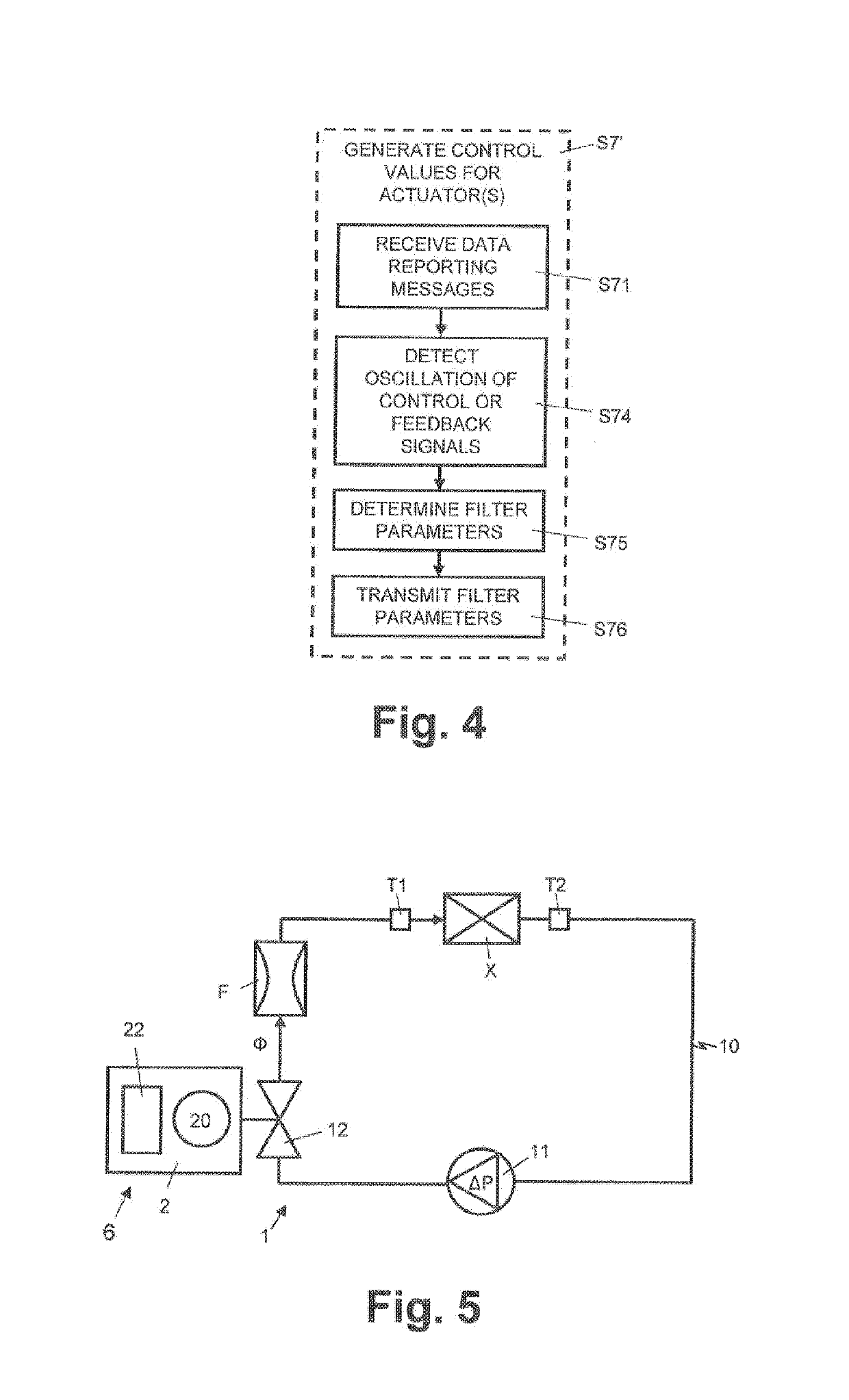
ActiveUS20190212022A1Increased system hysteresisProgramme controlMechanical apparatusCloud baseComputerized system
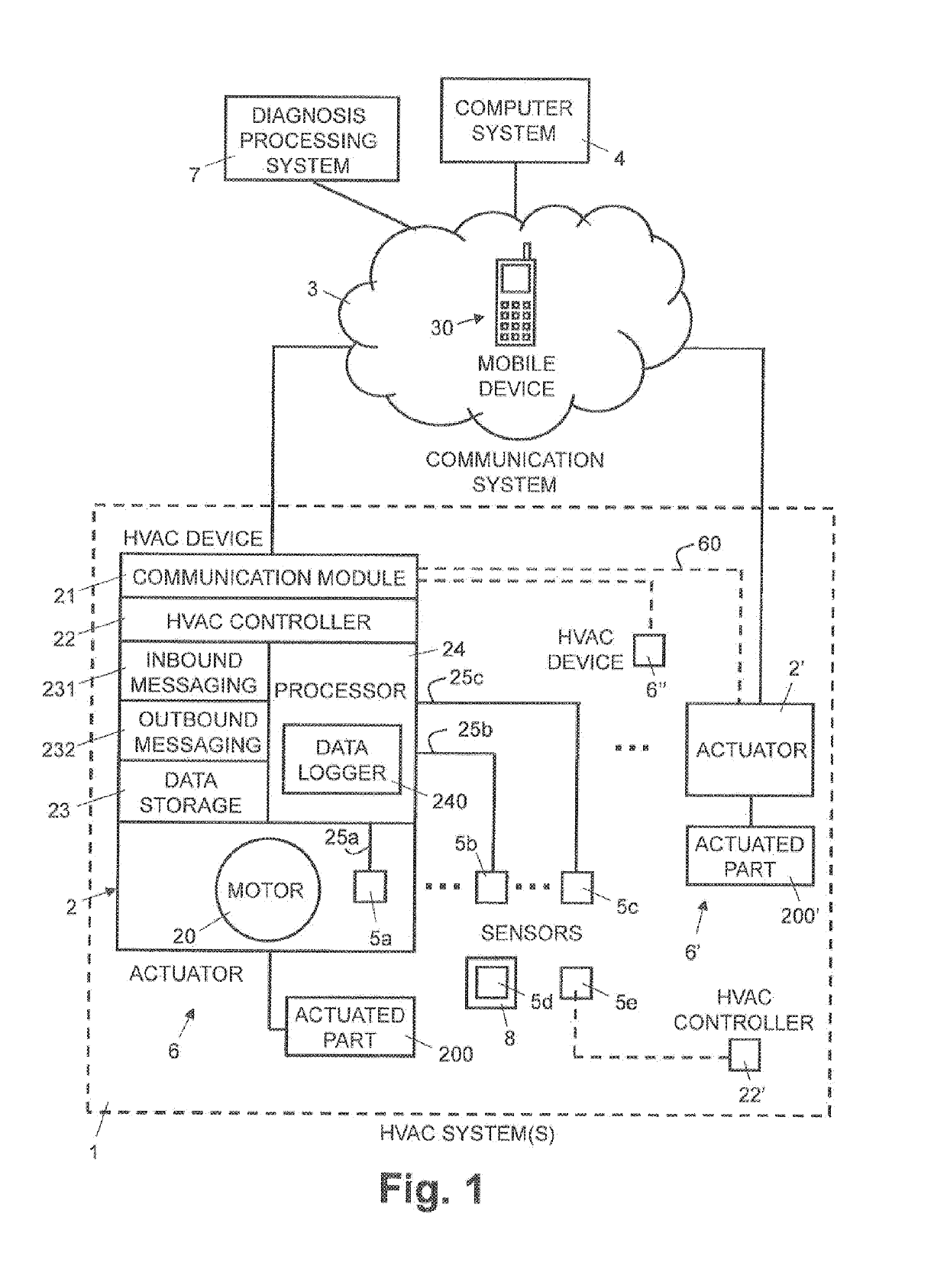
For monitoring an HVAC system (1), HVAC data reporting messages are received and stored in a cloud-based computer system (4). Each HVAC data reporting message includes one or more operation data values included by an HVAC controller (22) of the HVAC system (1). The cloud-based computer system (4) generates (S73) remote diagnoses for a particular HVAC device, using a plurality of HVAC reporting messages received from a plurality of the HVAC controllers (22) from one or more HVAC systems (1). Each remote diagnosis is generated (S73) by using more than one operational data value, included in HVAC reporting messages received (S71) received from HVAC controllers (22) of more than one HVAC systems (1) and / or from at least two different types of operational data values. A diagnosis message which includes a remote diagnosis is transmitted to a diagnosis processing system for the particular HVAC device.
Owner:BELIMO HOLDING AG
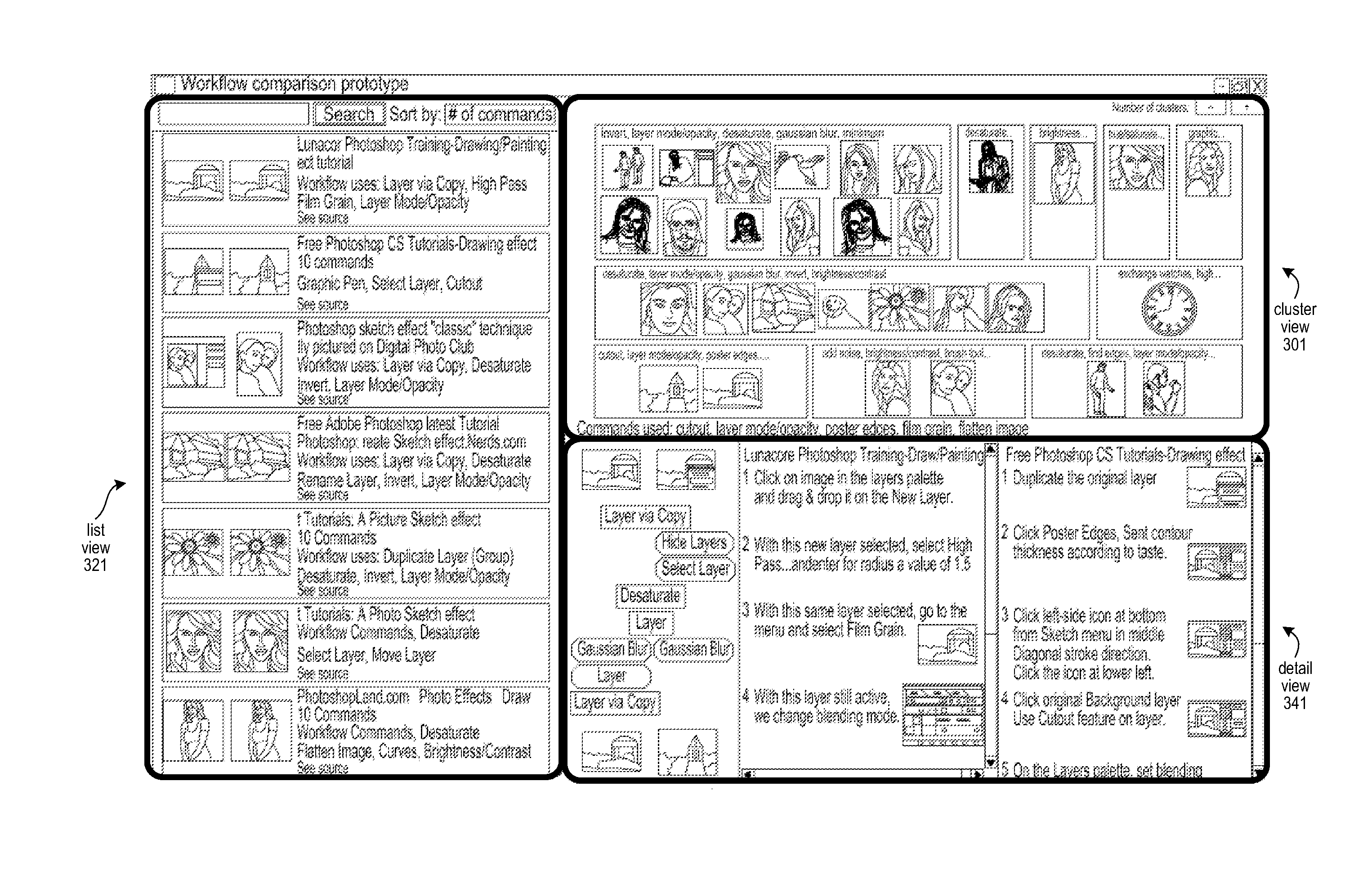
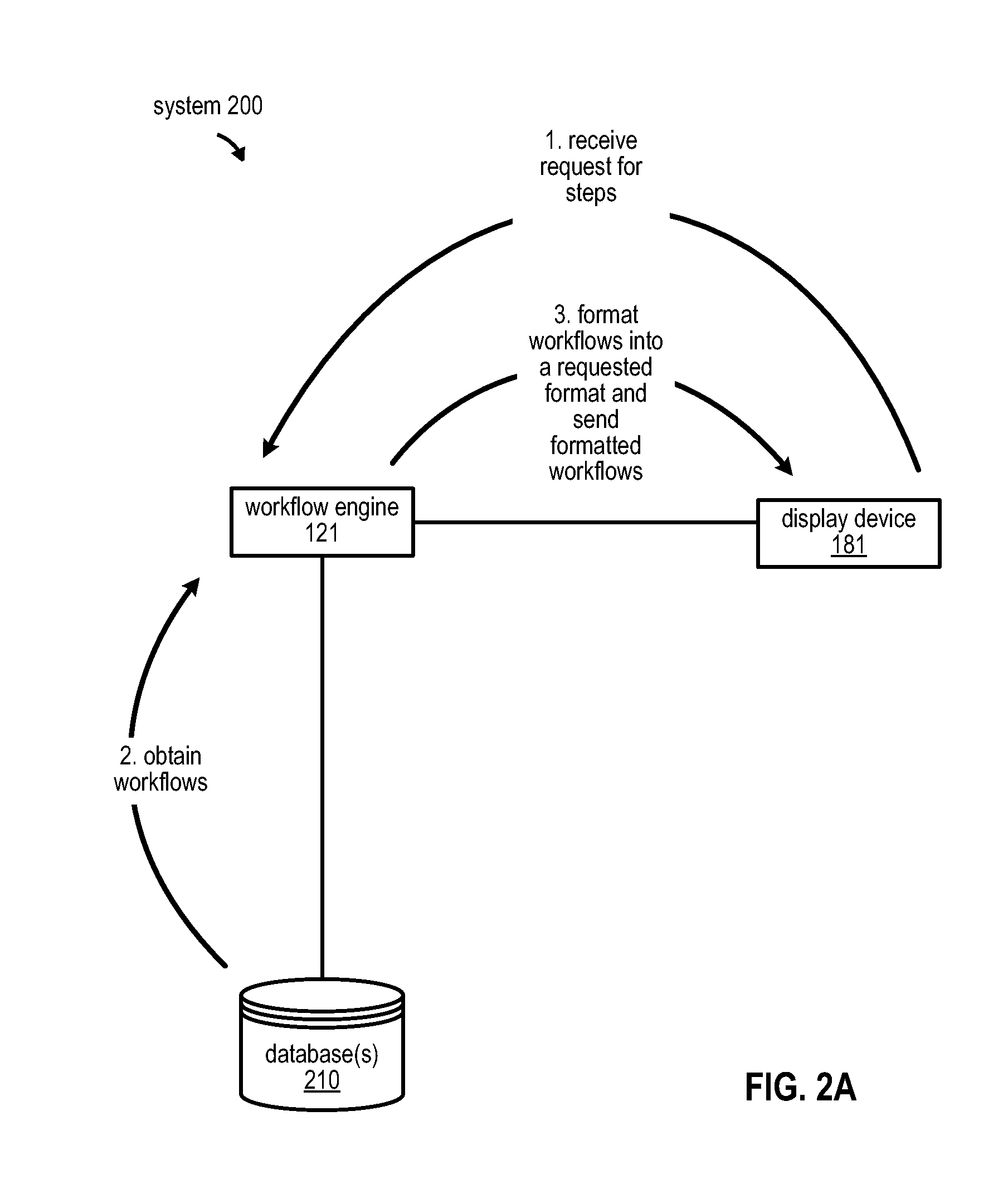
Techniques for representing and comparing workflows
An approach is provided for sending pre-defined workflows to a display device of a user device. In one example, the approach includes receiving a request for steps to complete a task associated with a software application. In response to receiving the request for steps, the system obtains at least a first workflow and a second workflow, each workflow including one or more steps that the user device can execute to complete the task. The system receives a request to format the first workflow and the second workflow into one or more view formats. The system generates a summary of the first workflow and a summary of the second workflow. Each summary includes one or more salient attributes of the each workflow. The system sends to the display device at least the first workflow and the second workflow in the one or more view formats.
Owner:AUTODESK INC
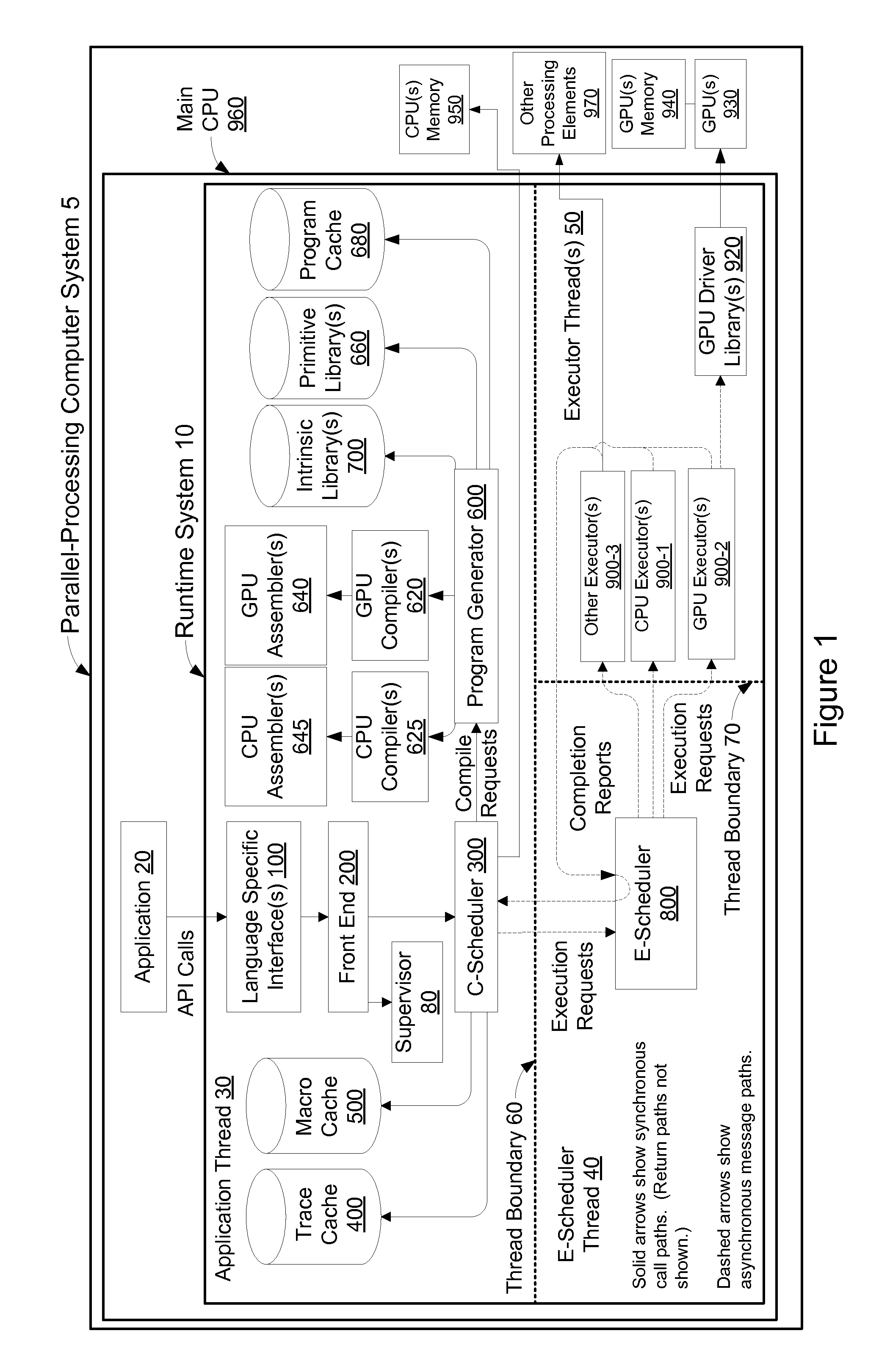
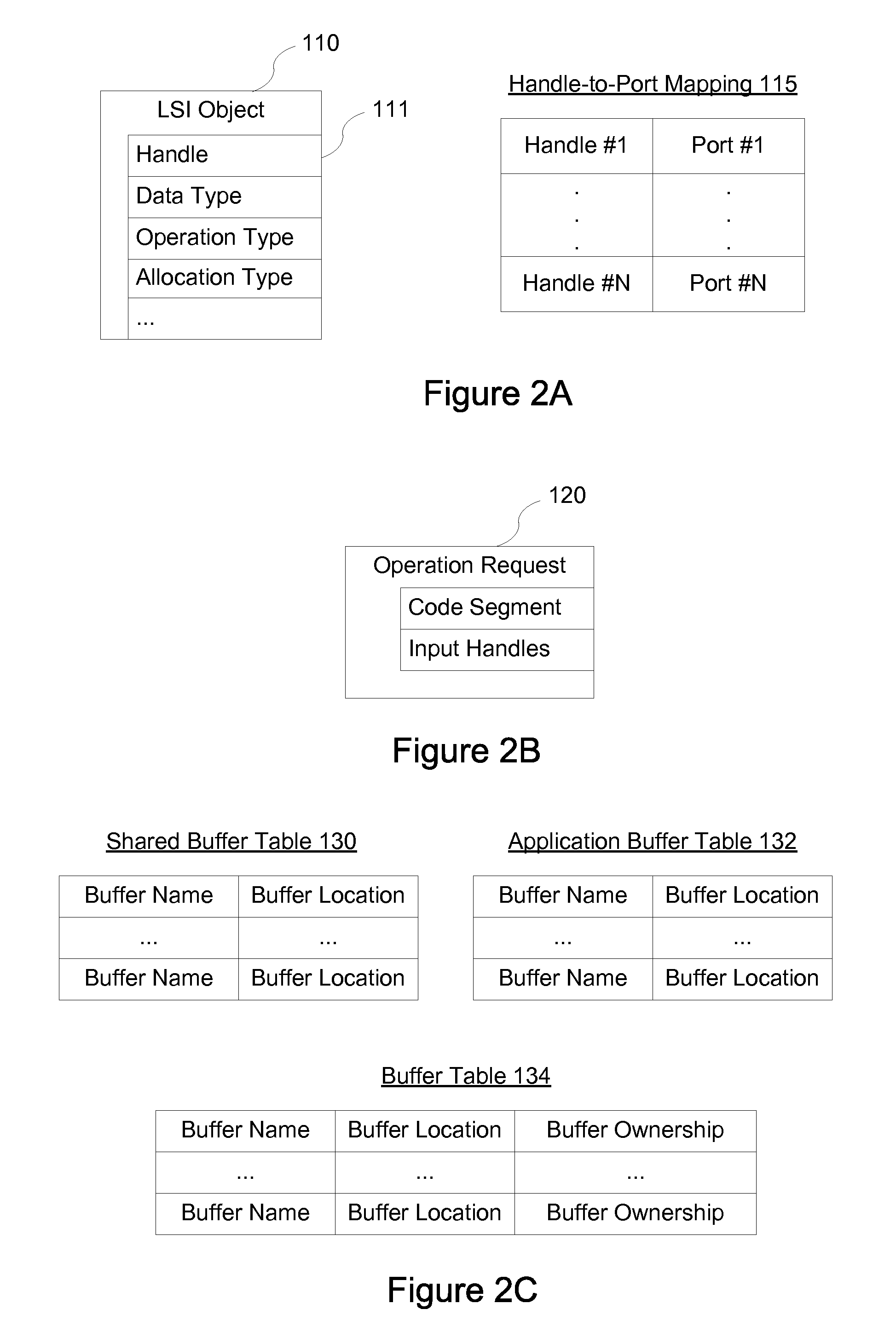
Systems and methods for generating reference results using parallel-processing computer system
ActiveUS20130061230A1Multiprogramming arrangementsMemory systemsTheoretical computer scienceParallel processing
Owner:GOOGLE LLC
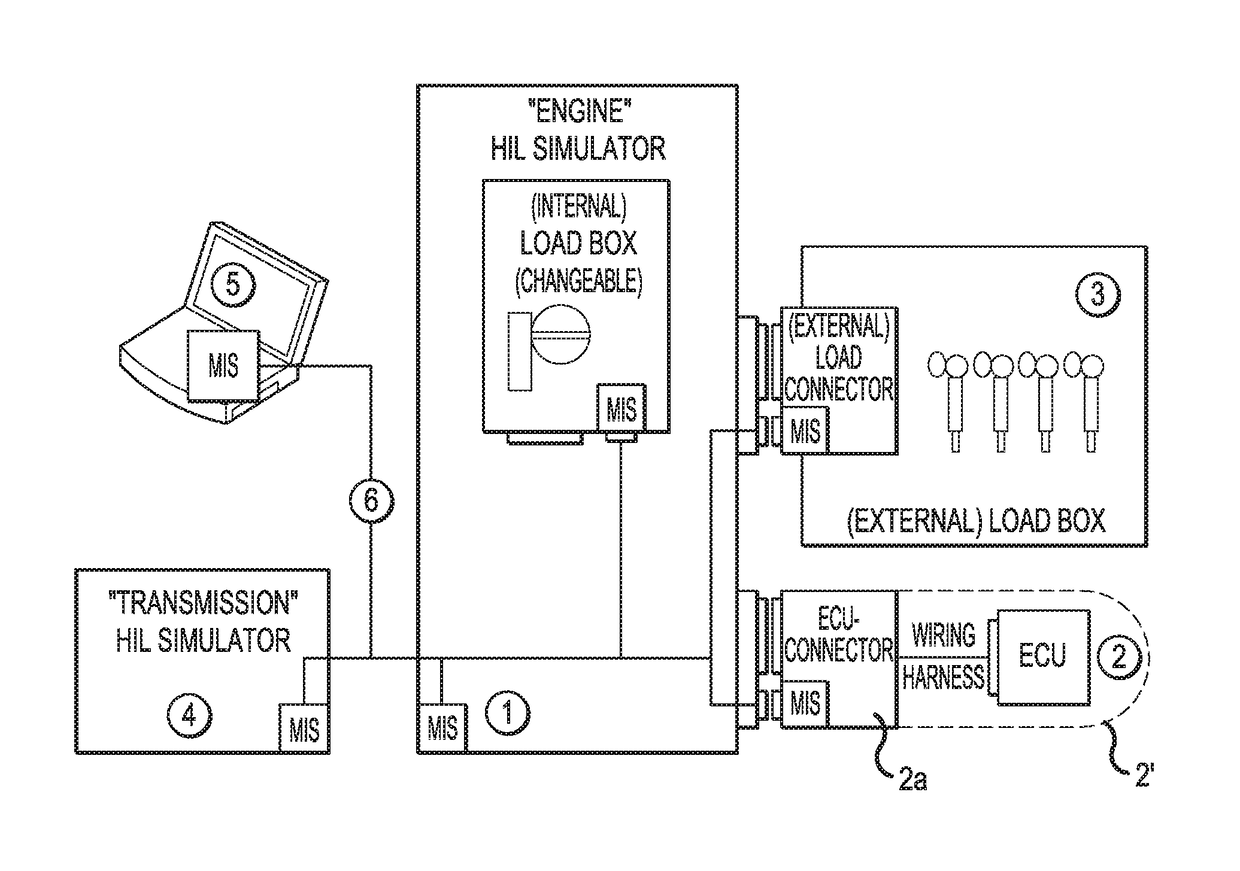
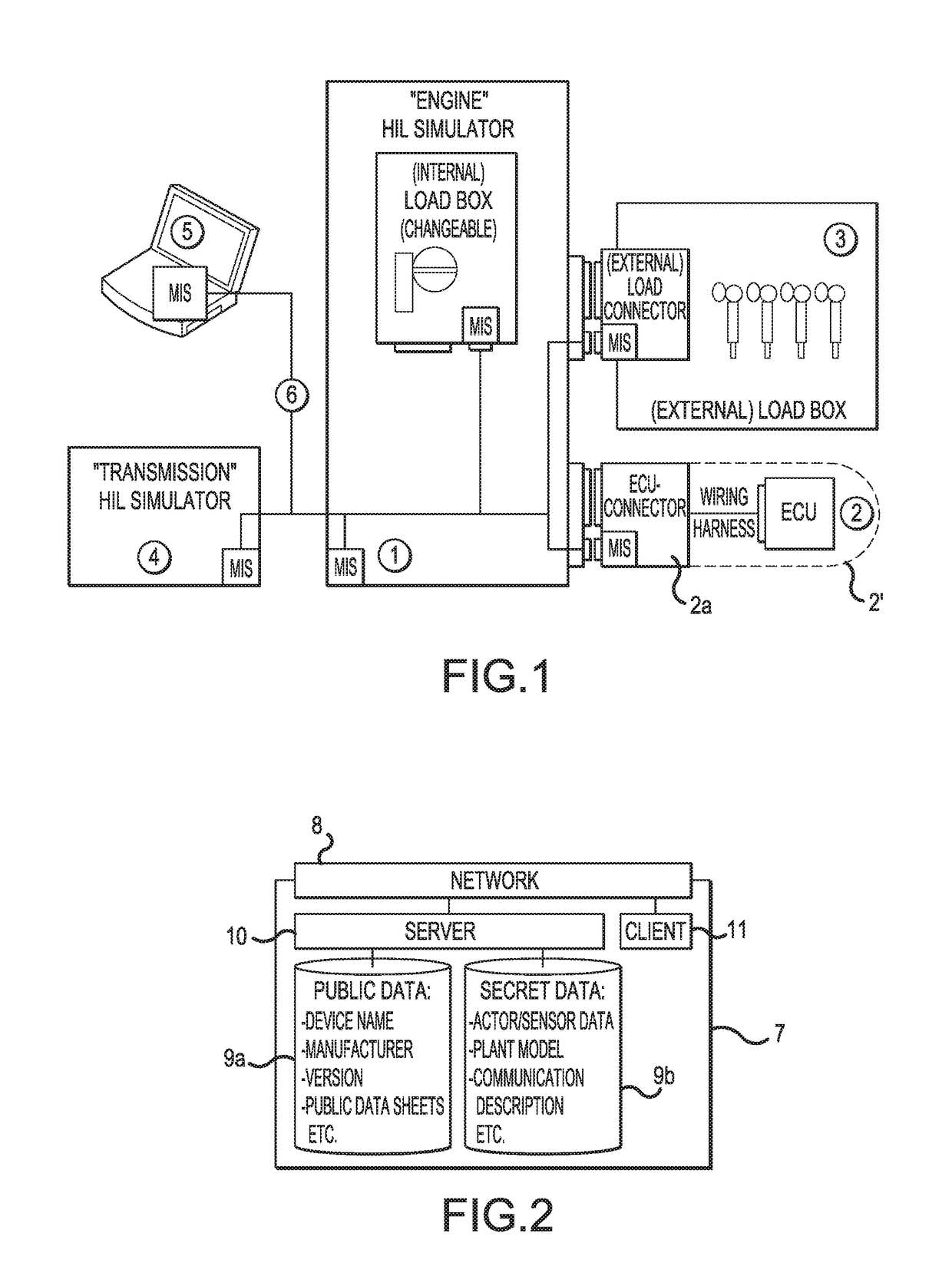
Method for generating a configuration for a control unit test system
ActiveUS10025883B2Improve reliabilityProgramme controlElectric testing/monitoringExecution controlUnit testing
A method for performing configuration of a control unit test system with hardware components connected thereto, wherein control units can be tested with the test system in an environment simulated by the test system by means of a model, and wherein the test system comprises at least one computer, in particular a computer executing the model, as well as hardware components, connected to one another by means of at least one network, in which at least a portion of the hardware components comprises a dedicated server (MIS) that, by means of communication, provides access to the configuration data associated with the hardware component, in particular stored in the hardware component, and the model and / or the hardware component is adapted, in particular configured, as a function of the configuration data that are made accessible.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
Automated feature engineering for machine learning models
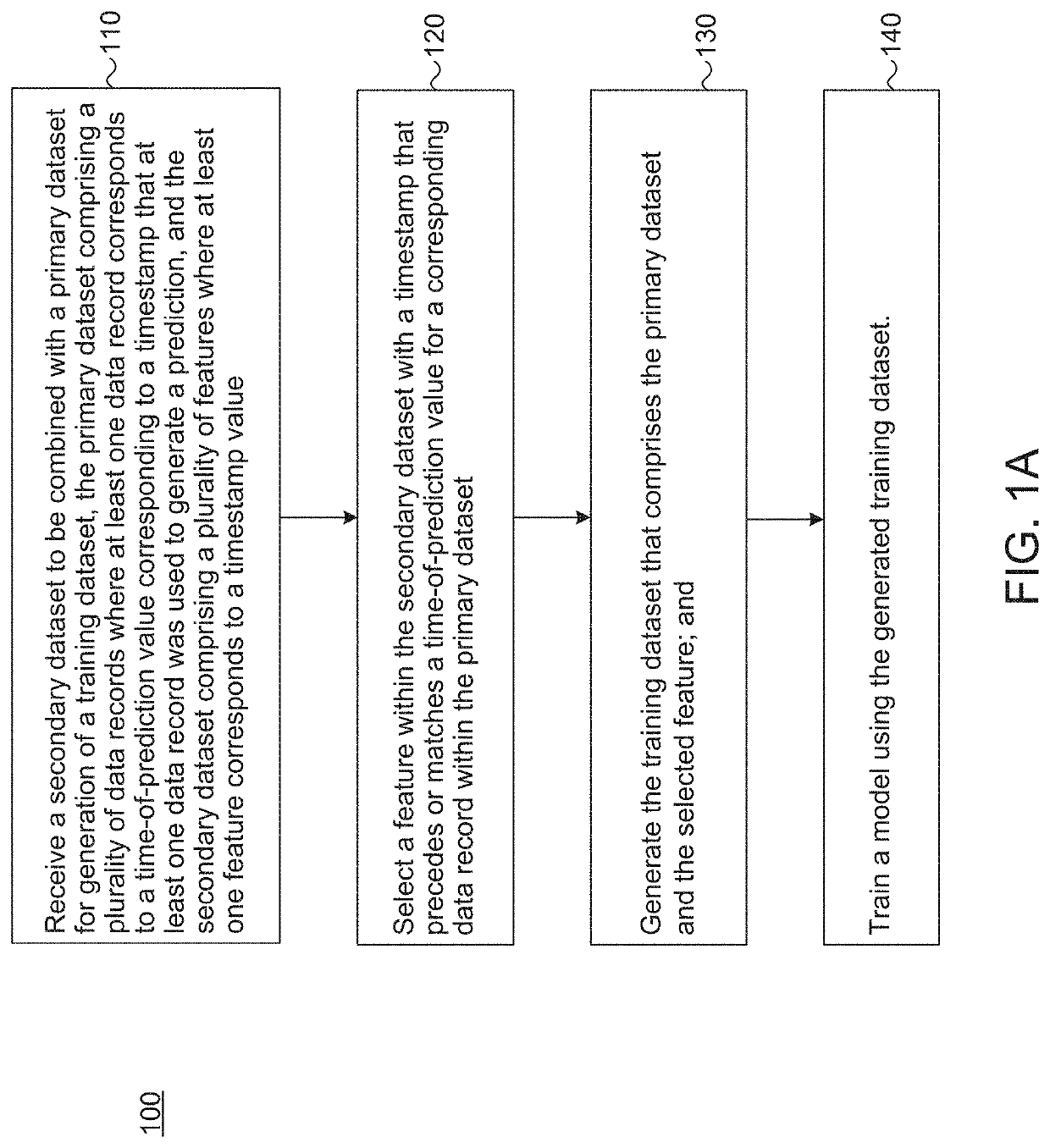
Training computer models by generating time-aware training datasets is provided. A system receives a secondary dataset to be combined with a primary dataset for generation of a training dataset. The primary dataset includes a plurality of data records where at least one data record corresponds to a time-of-prediction value corresponding to a timestamp at which at least one data record was used to generate a prediction. The secondary dataset includes a plurality of features where at least one feature corresponds to a timestamp value. The system selects a feature within the secondary dataset with a timestamp that precedes or matches a time-of-prediction value for a corresponding data record within the primary dataset. The system generates the training dataset that includes the primary dataset and the selected feature. The system trains a model using the generated training dataset.
Owner:DATAROBOT INC
Planning and Engineering Method, Software Tool and Simulation Tool for an Automation Solution
ActiveUS20160300001A1Determinacy of the plant behavior can be guaranteedGeometric CADProgramme controlComputer scienceSecurity information
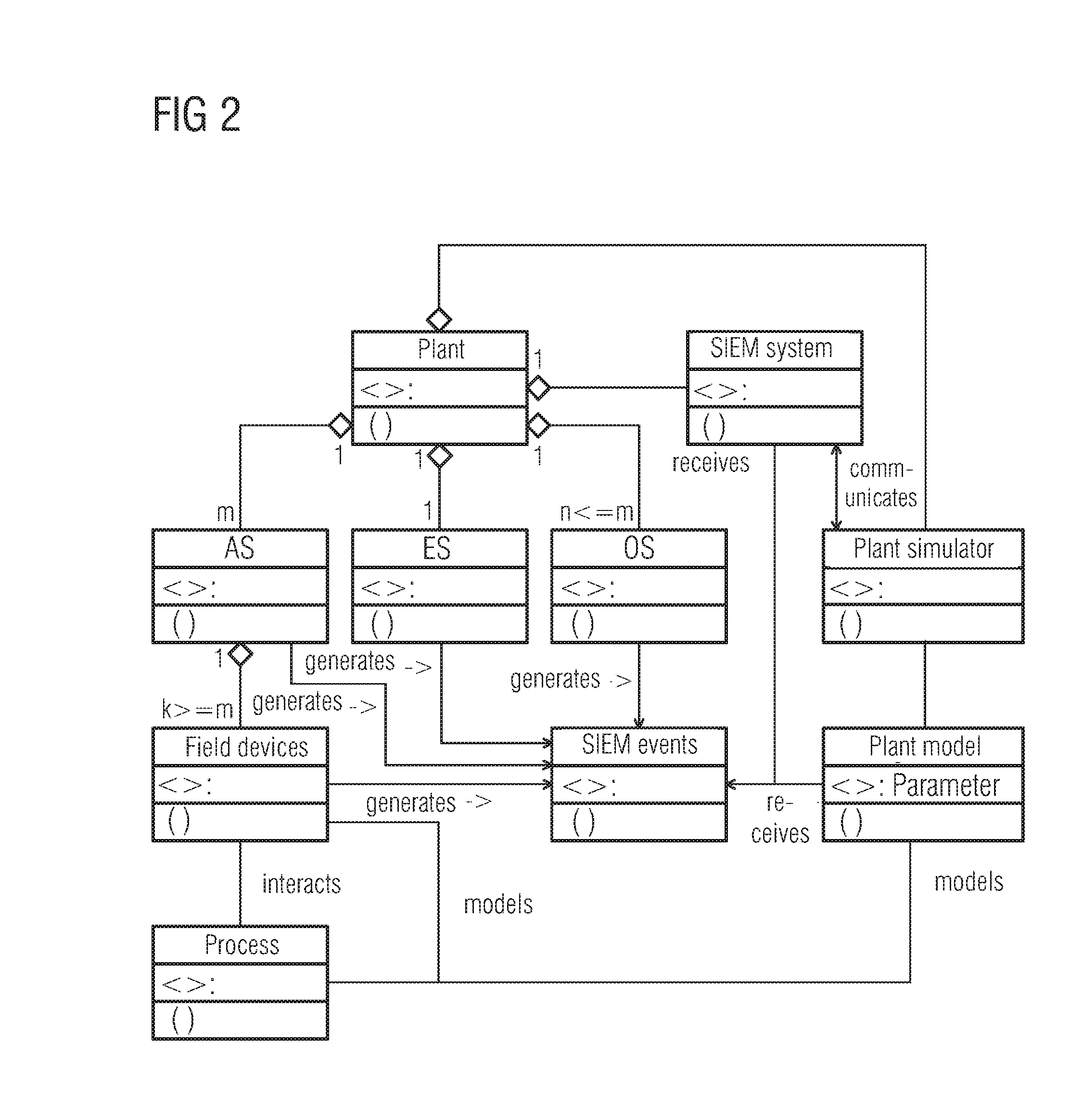
In planning and engineering an automation solution which comprises an automation system and a process engineering plant, objects that represent the components of the configured automation solution are imported by means of a simulation tool to simulate the automation solution on the basis of simulation models associated with the imported objects. Attributes contained in objects which represent the hardware components of the automation system and which describe IT security events that may be generated by the components are entered into the associated simulation models for simulatively generating security events in a simulation of the automation solution, for transferring the simulatively generated security events to a Security Information Event Management (SIEM) system for evaluation, and for using the results of the evaluation generated by the SIEM system to simulate the automation solution.
Owner:SIEMENS AG
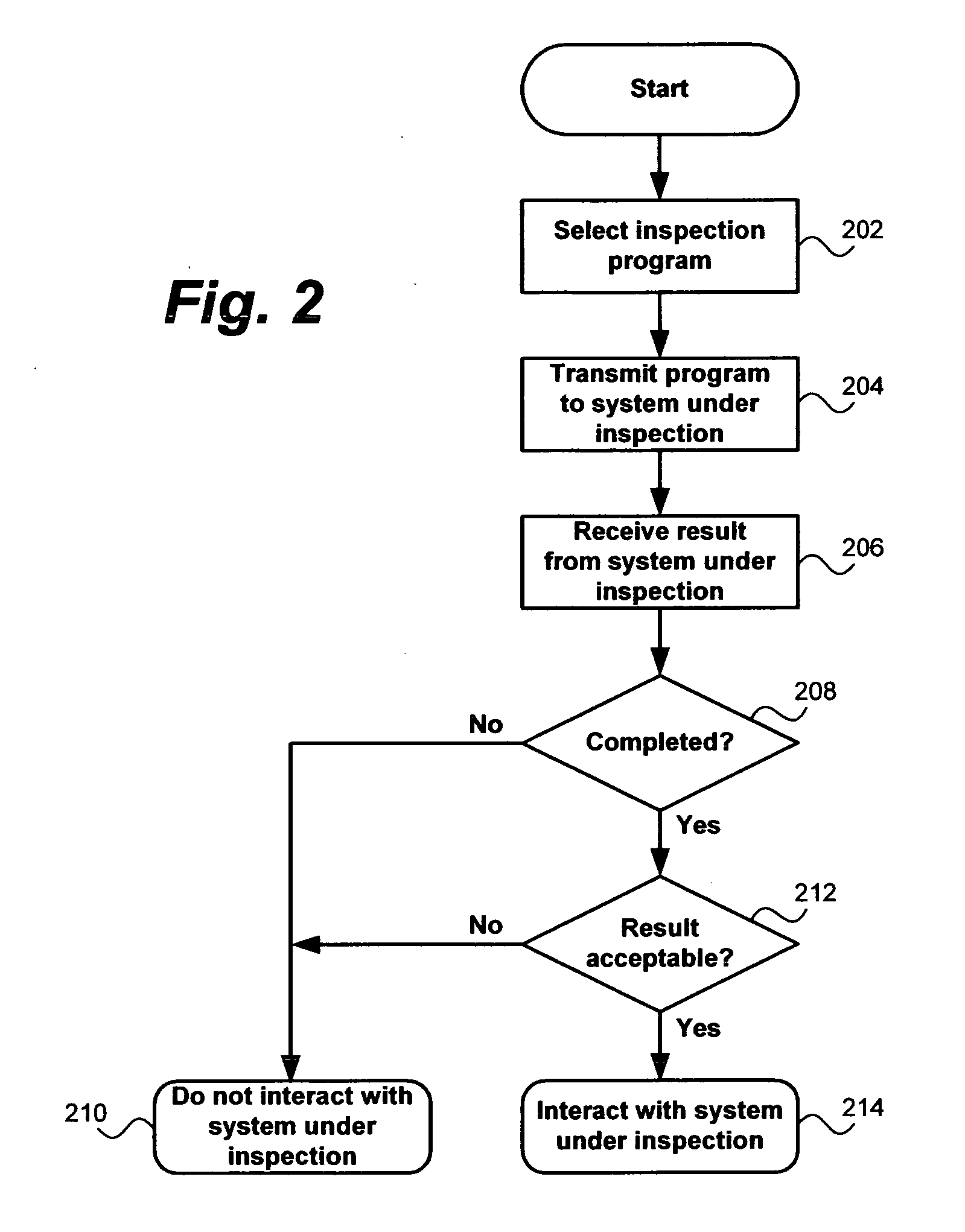
Computer system evaluation
InactiveUS20070220137A1Minimizing amount of informationMemory loss protectionError detection/correctionComputer hardwareComputerized system
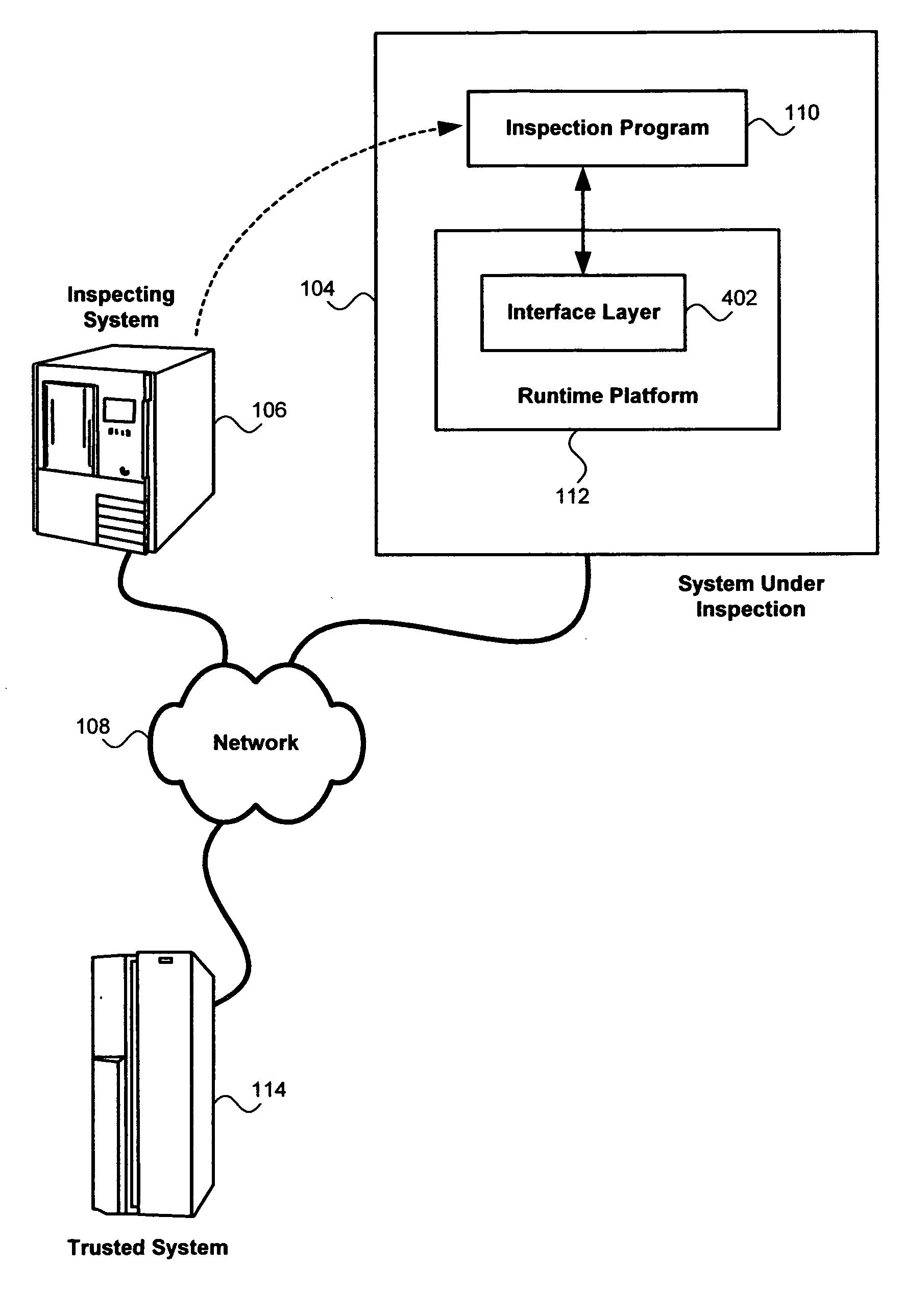
A system, computer program and method for inspection of a system under inspection. The system may include an inspection program configured to access information available at the system under inspection and generate inspection data for the system under inspection. A runtime platform independent from the inspection program at the system under inspection is configured to limit the limit the contents of the inspection data to a maximum information content. A trusted third-party computer system may assist in selecting the inspection program and transferring the resulting inspection data.
Owner:IBM CORP
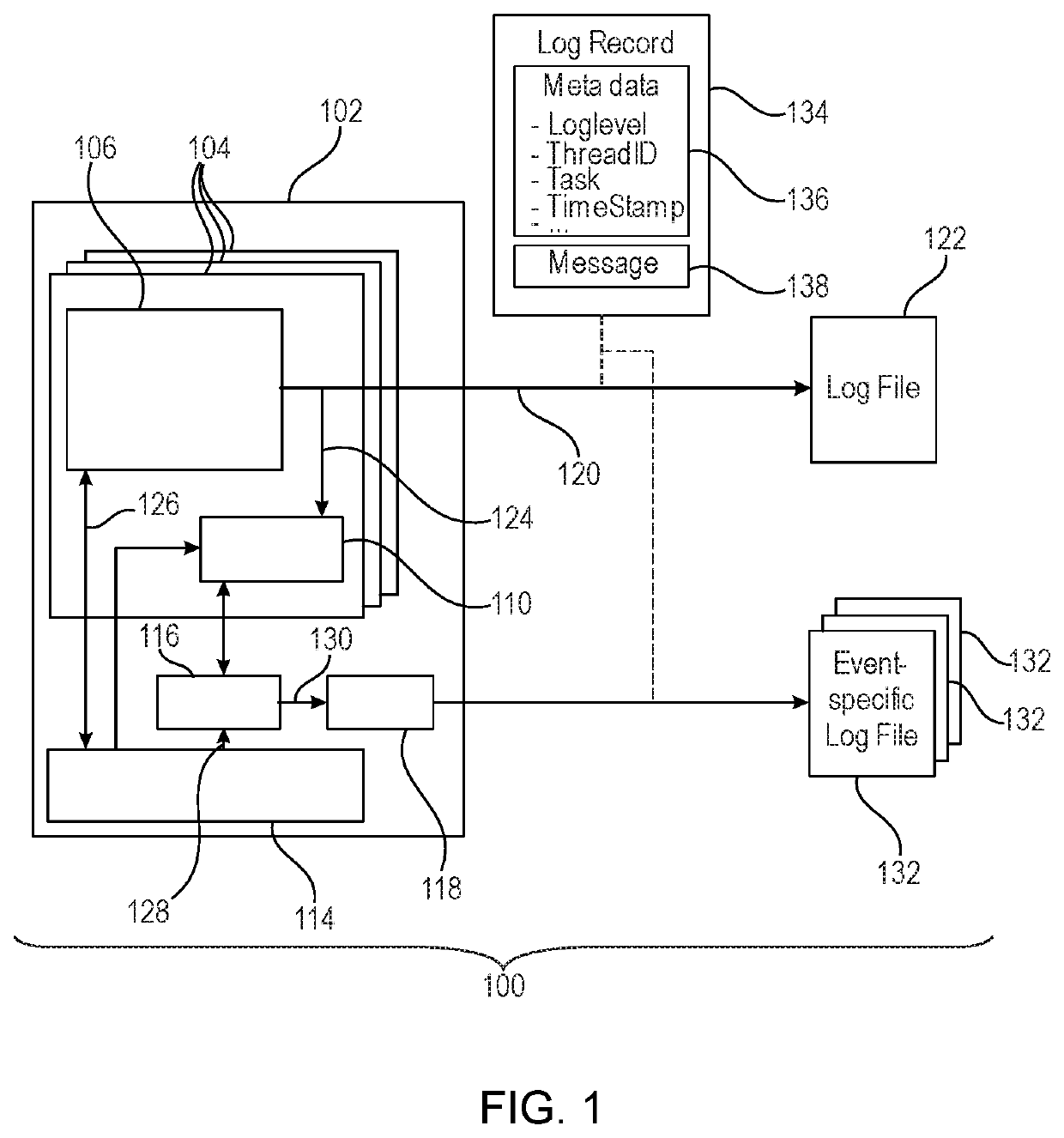
Event specific log file generation
ActiveUS20210149790A1Software testing/debuggingFile system administrationParallel computingComputer engineering
The present disclosure relates to generating an event specific log file for a computer system. The generation comprises storing buffered log data in at least one memory buffer during an execution of one or more threads in real time. The generation further comprises receiving thread execution data. The generation further comprises inputting the thread execution data into an anomalous program event detector module configured to generate an anomalous program event signal in response to detecting an anomalous program execution event. The generation further comprises searching the buffered log data for event specific log data in the at least one memory buffer with a log dependency analyzer module in response to the anomalous program event signal. The method further comprises writing the event specific log data to an event specific log file using a log archive writer module.
Owner:IBM CORP
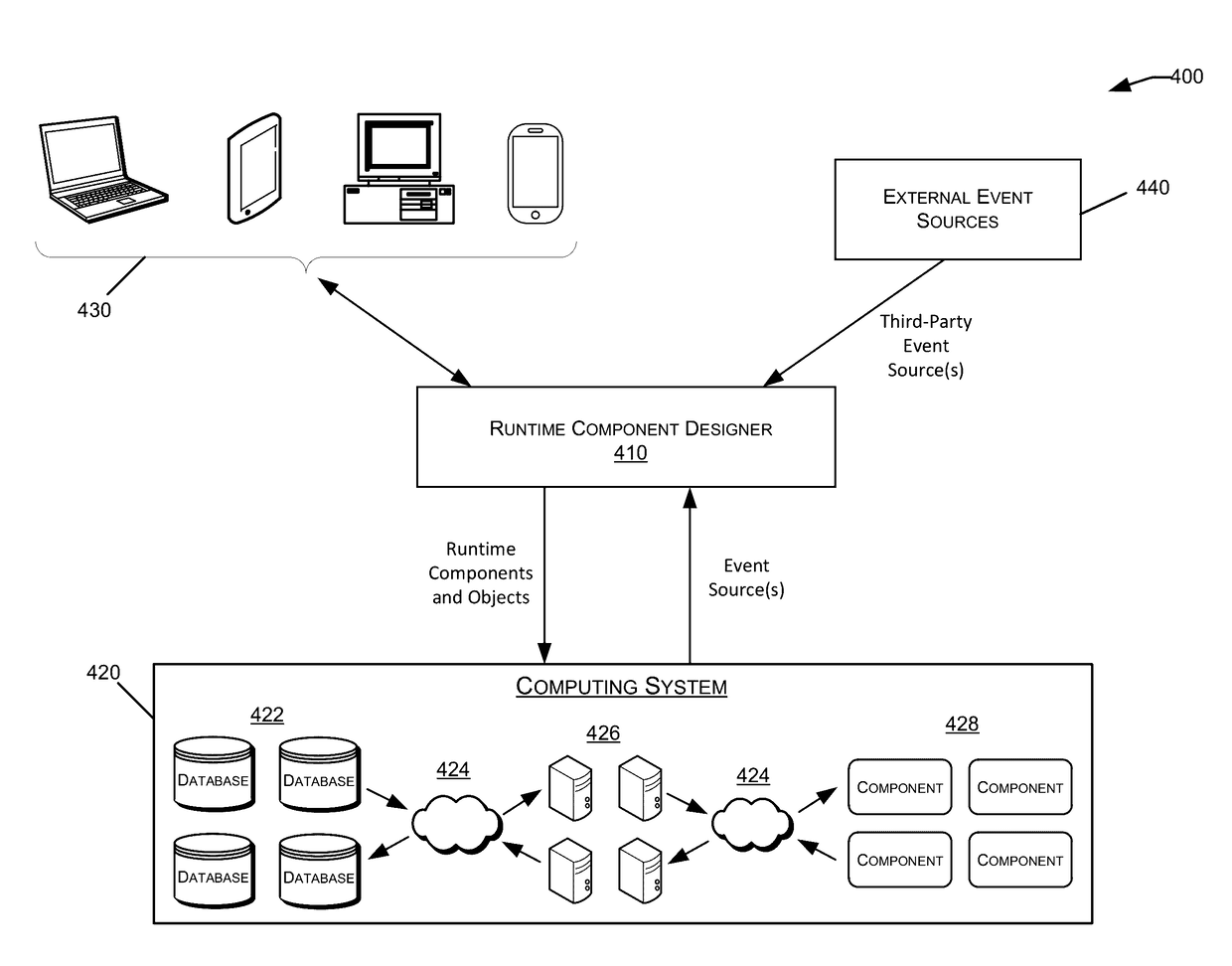
Generating runtime components
Embodiments of the invention provide systems and methods for generating runtime components in various hardware and software computer systems. More specifically, certain embodiments of the present invention describe a design-time interface by which applications may be designed, generated, and deployed in accordance within the underlying source systems of a computer system. Components may be selected, customized, and linked together to form a functional end-to-end application based on a multitude of underlying technologies within a system. Upon completion of the application design, application metadata and / or runtime components may be generated and deployed within the computer system. During execution, such the runtime components deployed within the system may collaborate to receive and process event streams from various event sources, analyze incoming data, and generate logical transaction objects, alerts, and other responses using various source systems.
Owner:ORACLE INT CORP
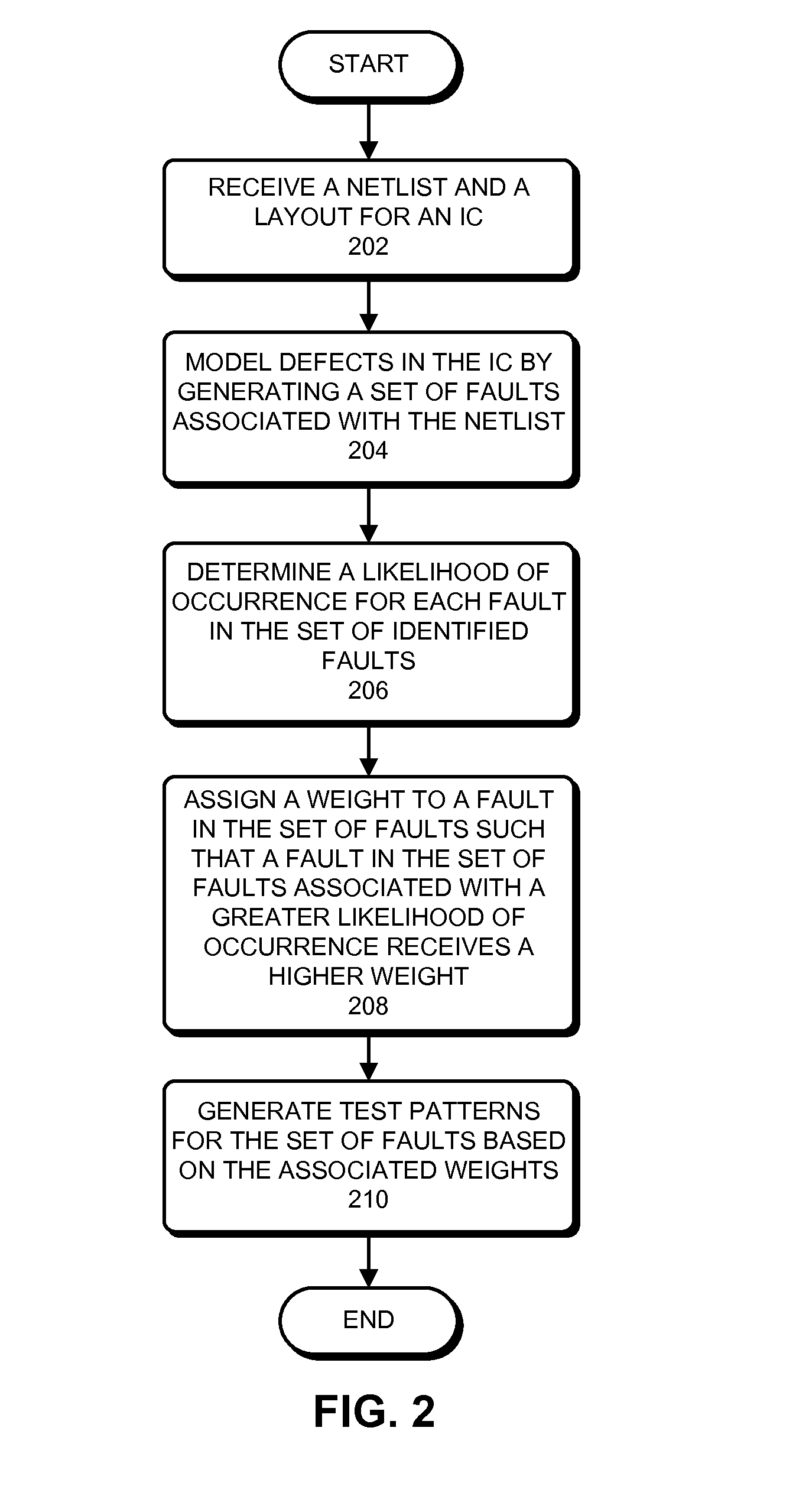
Layout-aware test pattern generation and fault detection
ActiveUS20140032156A1Increase weightReduce weightResistance/reactance/impedenceSpecial data processing applicationsIntegrated circuitNetlist
Methods and apparatuses to generate test patterns for detecting faults in an integrated circuit (IC) are described. During operation, the system receives a netlist and a layout for the IC. The system then generates a set of faults associated with the netlist to model a set of defects associated with the IC. Next, the system determines a set of likelihoods of occurrence for the set of faults based at least on a portion of the layout associated with each fault in the set of faults. The system subsequently generates a set of test patterns to target the set of faults, wherein the set of test patterns are generated based at least on the set of likelihoods of occurrence associated with the set of faults.
Owner:SYNOPSYS INC
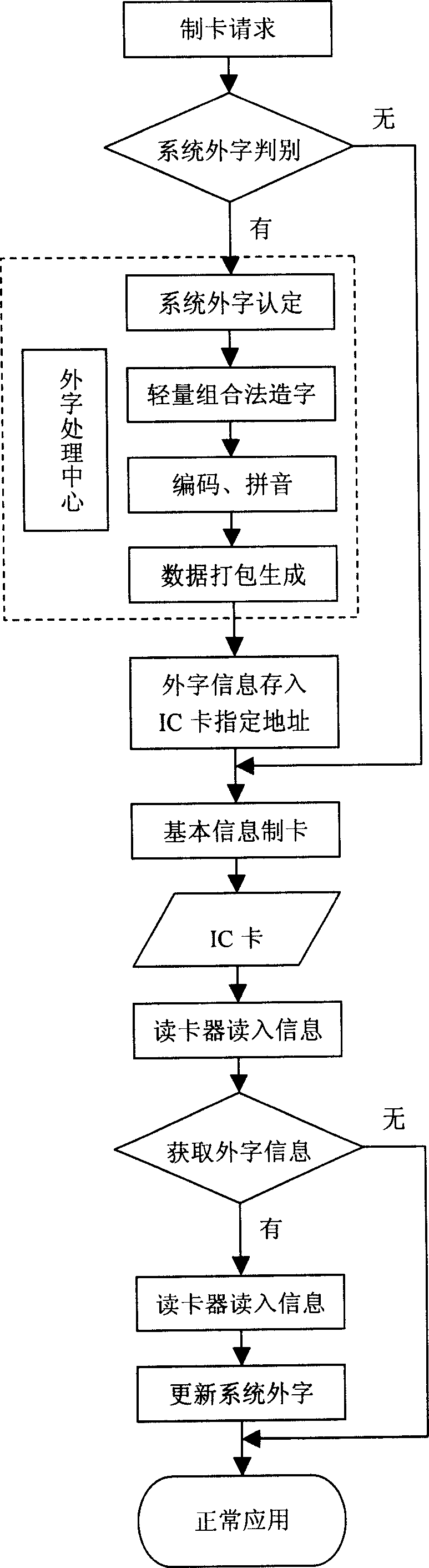
Technique for automatically accessing system exterior words from different places
The invention relates to a computer system outer character. It has the following characters: content supplier uses the' Chinese character word-formation system' technique and device of the invention to generate outer character information with 'Chinese system outer character format' and transmits it to user's computer by one of the two transmission modes. First transmission mode is adding the outer characters into the handled file or media such as IC card and transmitting it into user's computer. Second transmission mode is transmitting the outer character into the assigned Internet server and then transmitting it into user's computer. At user end, 'Chinese system outer character operator' can automatically convert outer character information and add it into computer system.
Owner:BEIJING CHINA E CHINA S ELECTRONICS
Method and system for smart address classification
ActiveUS20200058042A1Improve productivityHigh precisionMachine learningMarketingGeographic regionsClassification methods
The present disclosure provides computer-implemented method and a system for classification and sorting of one or more addresses to increase productivity of classification and sorting process of the one or more addresses. The system logically partitions a geographical region into one or more zones in real-time. The system fetches an address data from an entity of the one or more entities containing destination address. Further, the system extracts one or more points of interests from the fetched address data based on hardware-run machine learning algorithms. Furthermore, the system generates a signal to determine a zone of the one or more zones associated with the entity of the one or more entities. The system logically updates the one or more zones based on the extracted one or more points of interests in real-time.
Owner:NTEX TRANSPORTATION SERVICES PVT LTD
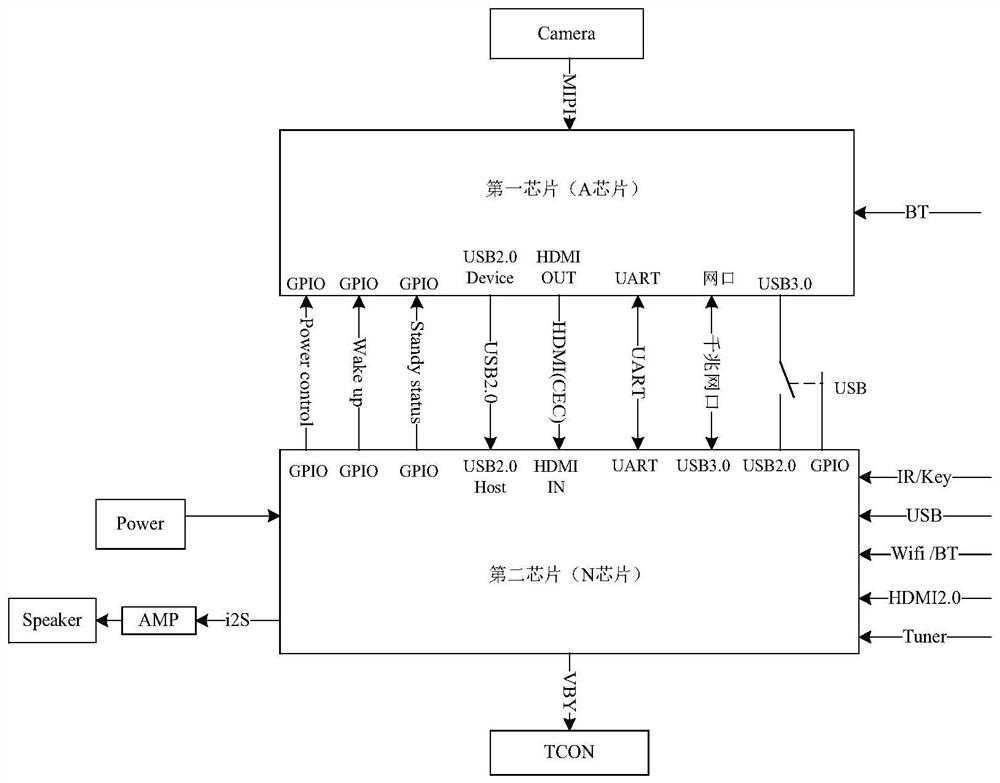
Dual-system OTA parallel upgrading method and system
ActiveCN112073446AImprove experienceImprove upgrade efficiencyTransmissionSoftware deploymentVerificationComputer engineering
The invention discloses a dual-system OTA parallel upgrading method and system. The method comprises the steps: enabling a first hardware system and a second hardware system to enter a recovery mode at the same time, and then synchronously entering a verification mode, i.e., enabling the second hardware system to verify a second OTA upgrading package while the first hardware system verifies a first OTA upgrading package; after verification is completed, enabling the second hardware system to generate an installation instruction and send the installation instruction to the first hardware system, wherein the first hardware system and the second hardware system synchronously enter an installation mode, and the second hardware system also installs a second OTA upgrade package while the first OTA upgrade package is installed in the first hardware system; when the installation is completed, synchronously restarting the first hardware system and the second hardware system. Therefore, according to the method and the system provided by the embodiment of the invention, OTA parallel upgrading of the dual systems can be realized, the dual systems can simultaneously enter a verification mode, synchronously enter an installation mode and simultaneously restart, the upgrading efficiency of the dual systems is improved, the upgrading duration cannot be prolonged, and the user experience is improved.
Owner:HISENSE VISUAL TECH CO LTD
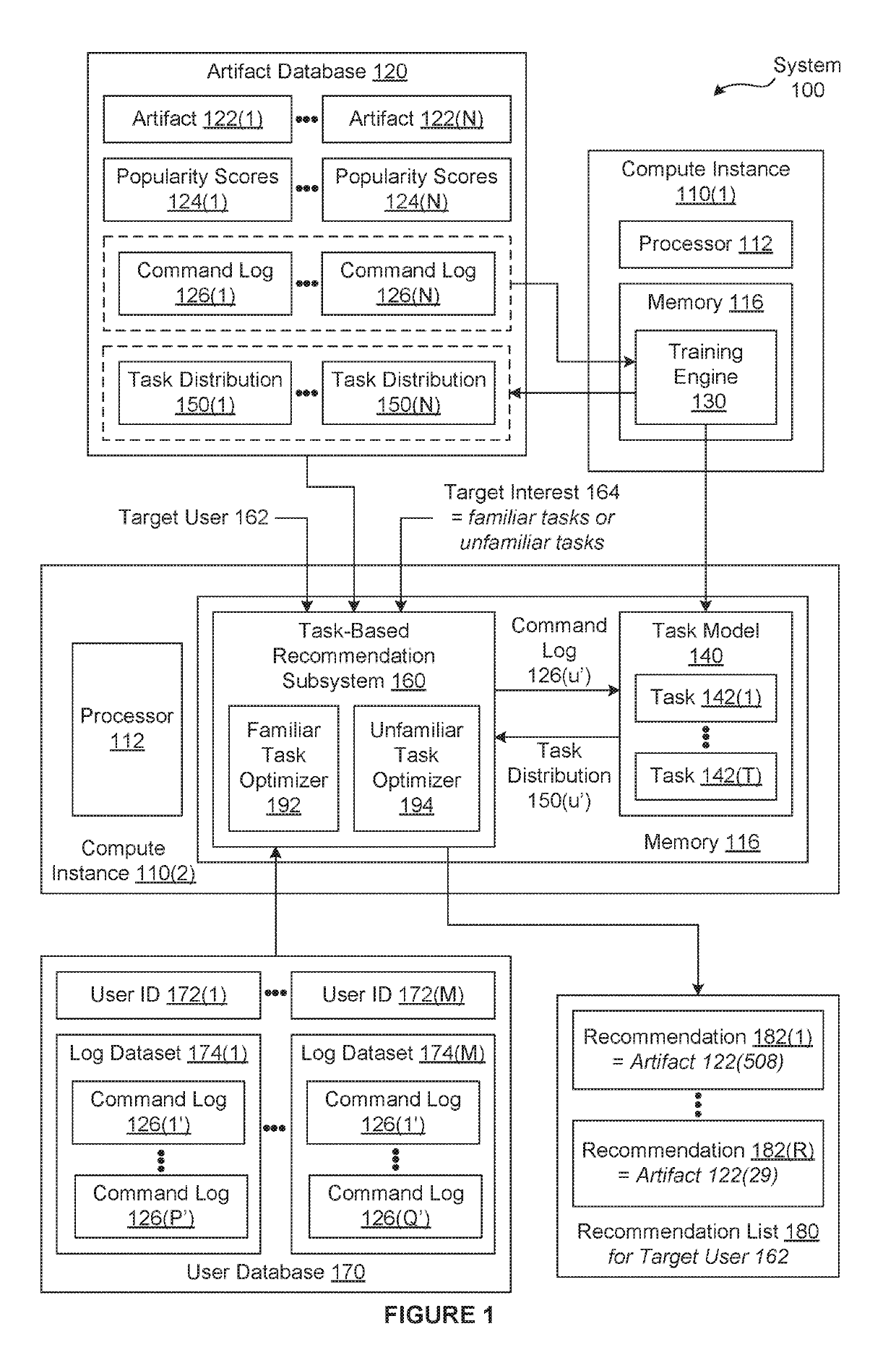
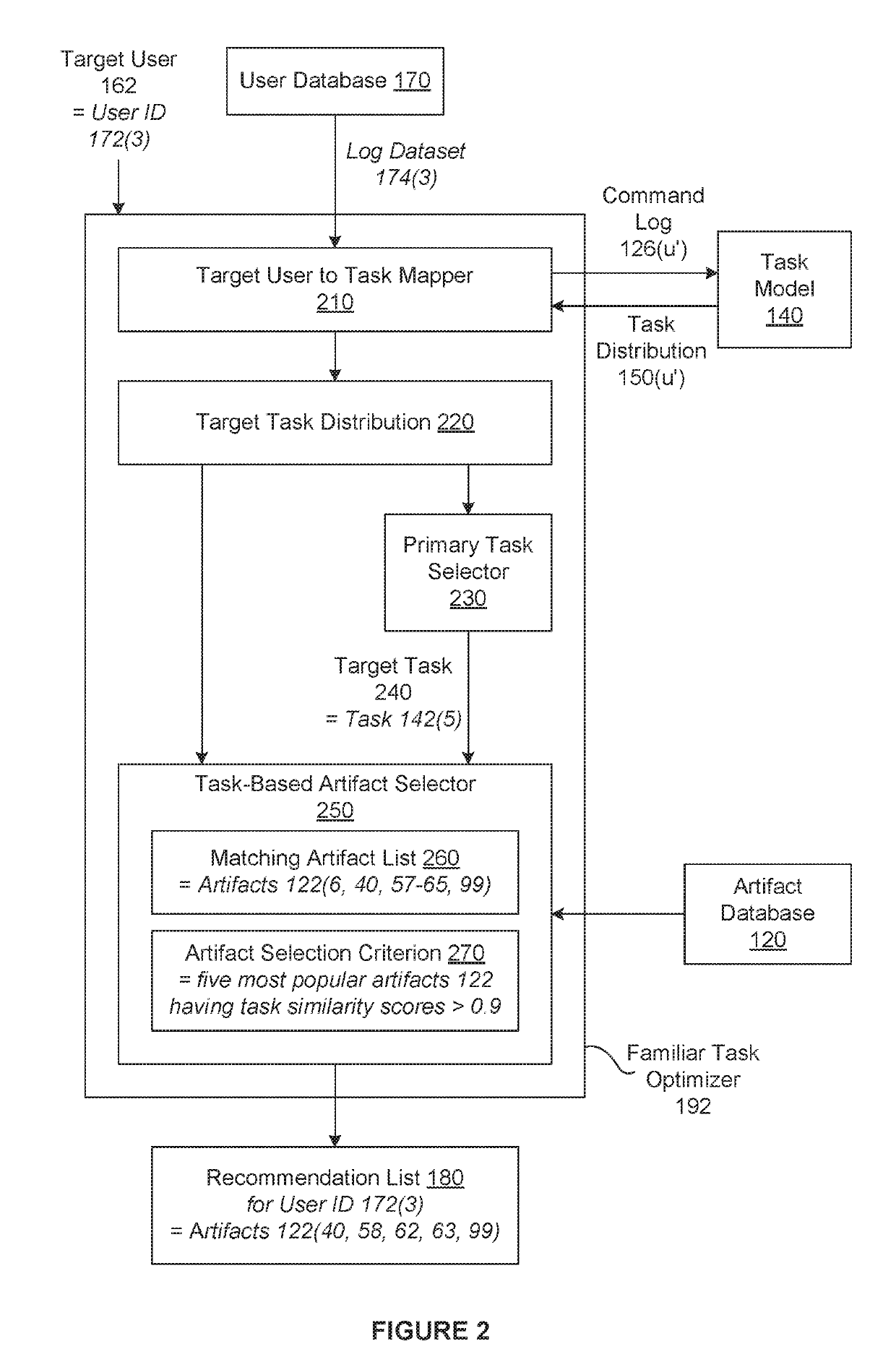
Techniques for classifying and recommending software workflows
PendingUS20190294993A1Raise the possibilityEfficient automationMathematical modelsDigital data information retrievalTarget distributionMachine learning
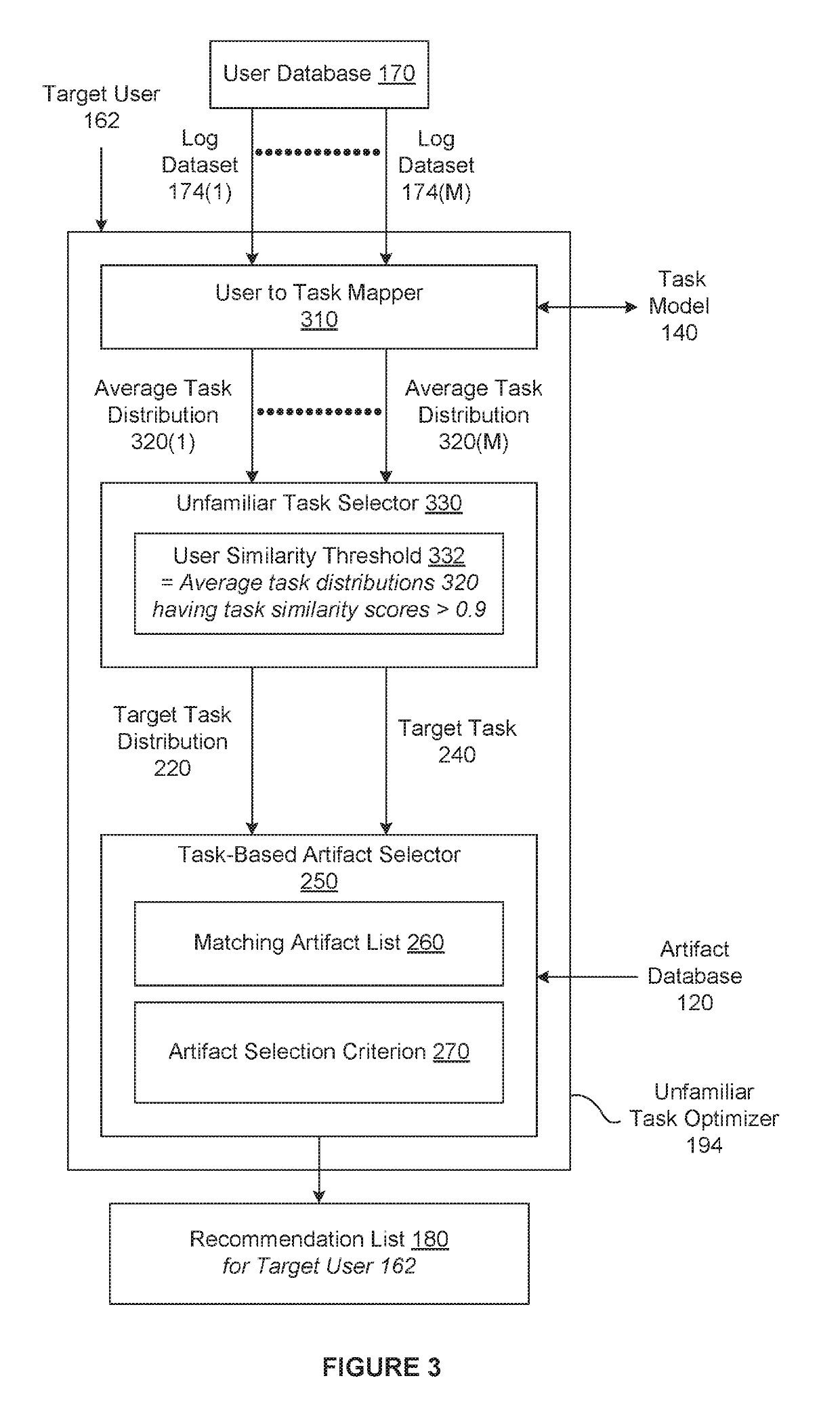
In various embodiments, a task-based recommendation subsystem automatically recommends workflows for software-based tasks based on a trained machine-learning model that maps different sets of commands to different distributions of weights applied to a set of tasks. In operation, the task-based recommendation subsystem applies a first set of commands associated with a target user to the trained machine-learning model to determine a target distribution of weights applied to the set of tasks. The task-based recommendation subsystem then performs processing operation(s) based on at least two different distributions of weights applied to the set of tasks and the target distribution to determine a training item. Subsequently, the task-based recommendation subsystem generates a recommendation that specifies the training item. Finally, the task-based recommendation subsystem transmits the recommendation to a user to assist the user in performing a particular task.
Owner:AUTODESK INC
System and method for regression testing of an application programming interface
ActiveUS10824549B1Database updatingEncryption apparatus with shift registers/memoriesRegression testingApplication programming interface
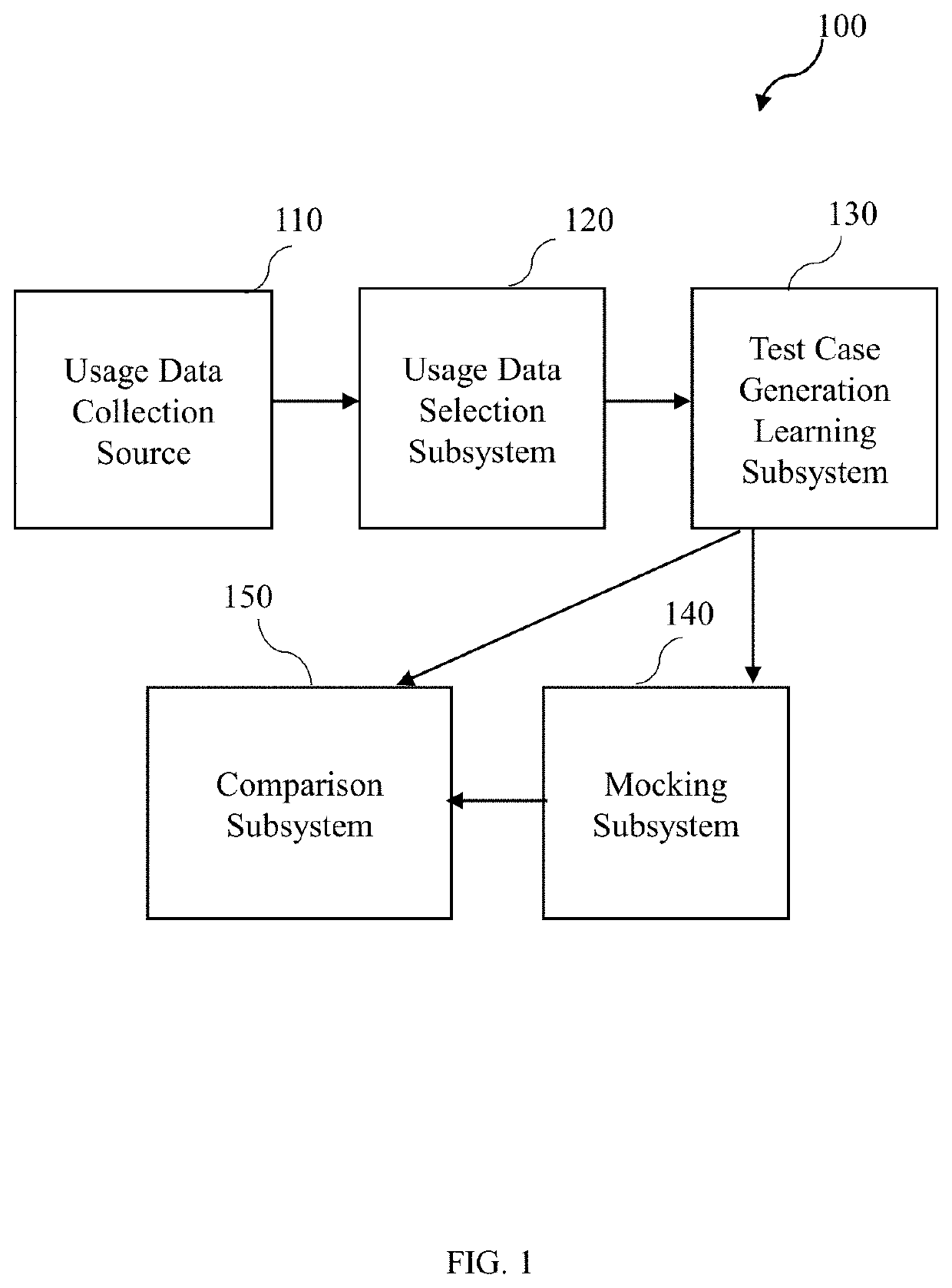
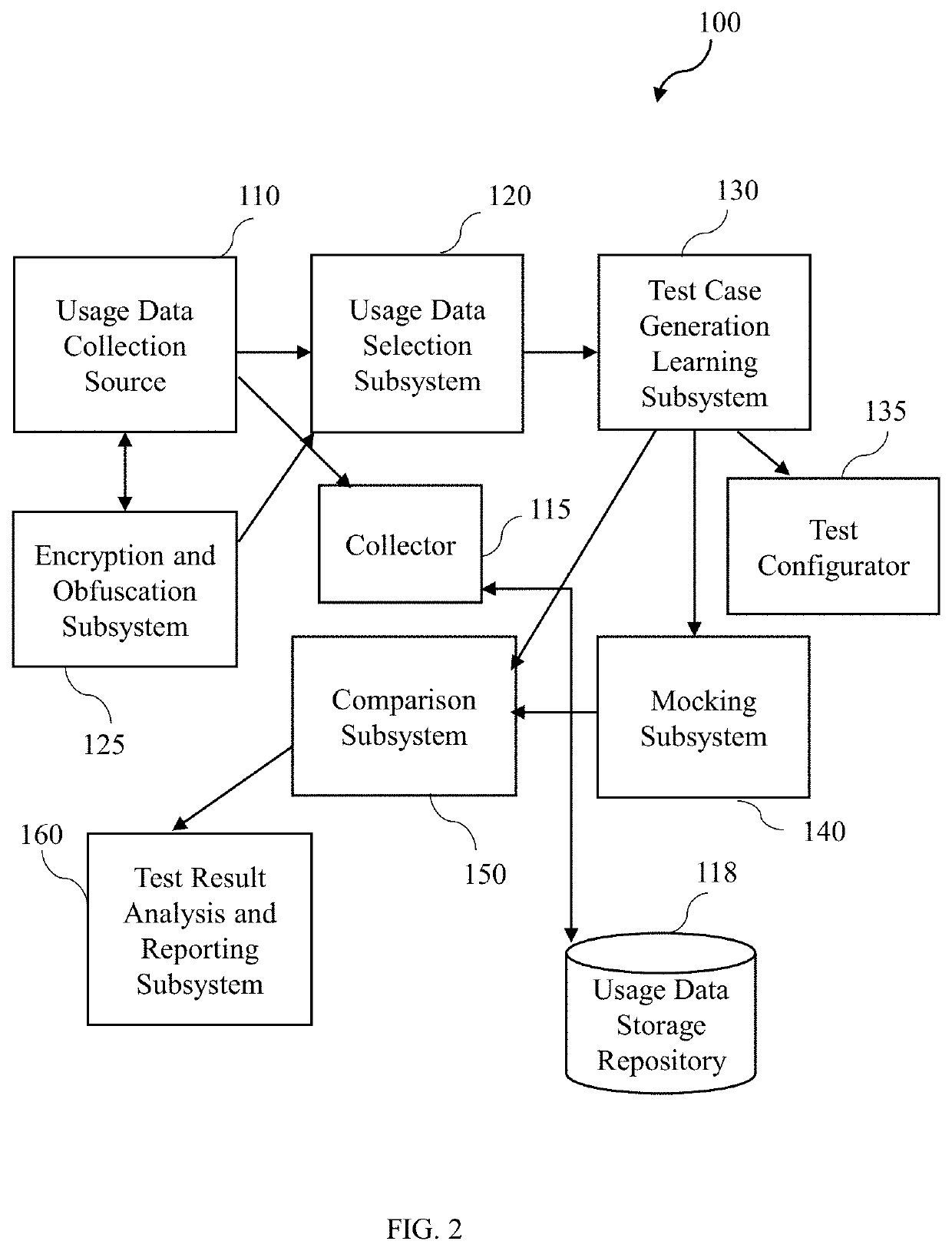
A system for testing of an application programming interface (API) is disclosed. The system includes a usage data collection source to track a trace identity associated with at least one message exchange pattern of the API using an end to end tracing (E2E) technique, captures usage data of an application in one or more modes, wherein the usage data corresponds to the trace identity. A usage data selection subsystem selects a predefined strata of usage data. A test case generation learning subsystem generates multiple test cases. A mocking subsystem use the trace identity to simulate the at least one message pattern associated with the usage data from a current version of the application against an updated version of the application. A comparison subsystem records an actual result, compares the actual result with an expected result and generates a test result upon comparison of the actual result with the expected result.
Owner:MESH DYNAMICS
Validation data structure for decentralized identity claim
ActiveUS20200403810A1Reduce riskCommunication securityRandom number generatorsUser identity/authority verificationEngineeringIdenticon
Use of a validation data structure in order to securely communicate an encrypted claim that has a decentralized identifier as a subject. The sending system generates the validation data structure and presents the validation data structure to a user that owns the decentralized identifier. The sending system encrypts the claim using at least the validation data structure, and constructs a message that includes the encrypted claim, but which does not include the validation data structure. The relying party receives the message. However, without separately receiving the validation data structure from the user, the relying party computing system cannot decrypt the encrypted claim. If the user wishes the relying party computing system to have access to the claim, the user may communicate the validation data structure to the relying party computing system.
Owner:MICROSOFT TECH LICENSING LLC
System-generated resource management profiles
InactiveUS8271988B2Multiprogramming arrangementsMultiple digital computer combinationsGraphicsGraphical user interface
A method for computer control of collaborating devices enables automatic generation of resource management profiles to coordinate resource allocation within the collaborating device. The method includes utilization of a graphical user interface to select an initial resource management profile and instruct the device to automatically generate a resource profile. Timing is specified for creation of the automatically generated optimized resource profile. The optimized resource profile is developed from statistics maintained, collected, and interpreted about the demand for resources within each component of the collaborating device. An operator may elect to automatically invoke the most recently generated optimized profile after a specified period of collaborating device idleness or to invoke it upon an instruction from the operator. The optimized resource profile may be saved for future use or discarded.
Owner:XEROX CORP
System and method for generating evidence for the superiority of a distributed system configuration
ActiveUS20210014283A1Reduce the numberPlatform integrity maintainanceKnowledge representationUser deviceDistributed computing
The system generates evidence of a recommended configuration for a distributed system based on a plurality of configuration parameters. The system displays, on a screen of a user device, the evidence, which includes a list of configuration parameters, including a name, a current value, and a recommended value for a respective configuration parameter. The recommended value is obtained based on a strategy for optimizing security, functionality, or both. The system further displays interactive elements which allow the user to: view a resolution of a pair of mutually incompatible constraints resulting in the recommended value for the respective configuration parameter, wherein the resolution includes a name of the configuration parameter removed from the list and a reason for the removal; and view information associated with each of the pair of mutually incompatible constraints, wherein the information includes a name, a goal, a security impact, and a description of the constraint.
Owner:XEROX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com