Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32 results about "Software inspection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Inspection in software engineering, refers to peer review of any work product by trained individuals who look for defects using a well defined process. An inspection might also be referred to as a Fagan inspection after Michael Fagan, the creator of a very popular software inspection process.
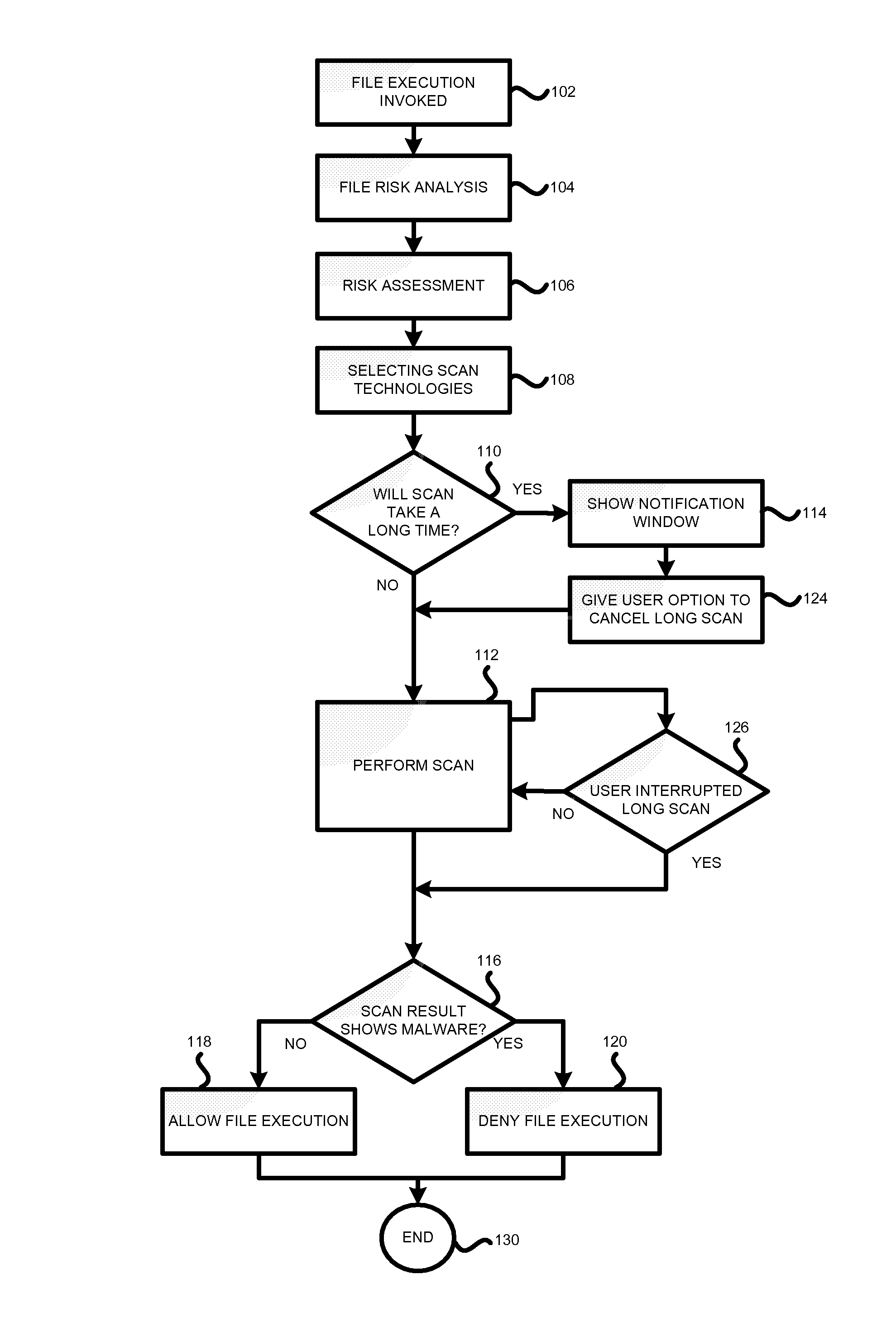
Method and system for anti-malware scanning with variable scan settings
A system, method and computer program product for scanning an executable file for malware presence, the method comprising: (a) detecting an attempt to execute a file on a computer; (b) identifying whether the file is known or unknown; (c) if the file is a known file, performing a signature malware check; (d) if the file is an unknown file, performing risk analysis and risk assessment for the file; (e) based on the risk analysis and the risk assessment, identifying which malware detection algorithms need to be used for the file, in addition to signature detection; (f) performing the malware detection algorithms on the file; and (g) if no malware is detected, permitting execution of the file. The risk analysis is based on file source, file origin, file path, file size, whether the file is digitally signed, whether the file is a download utility, whether the file is packed, whether the file was received from a CDROM.
Owner:AO KASPERSKY LAB
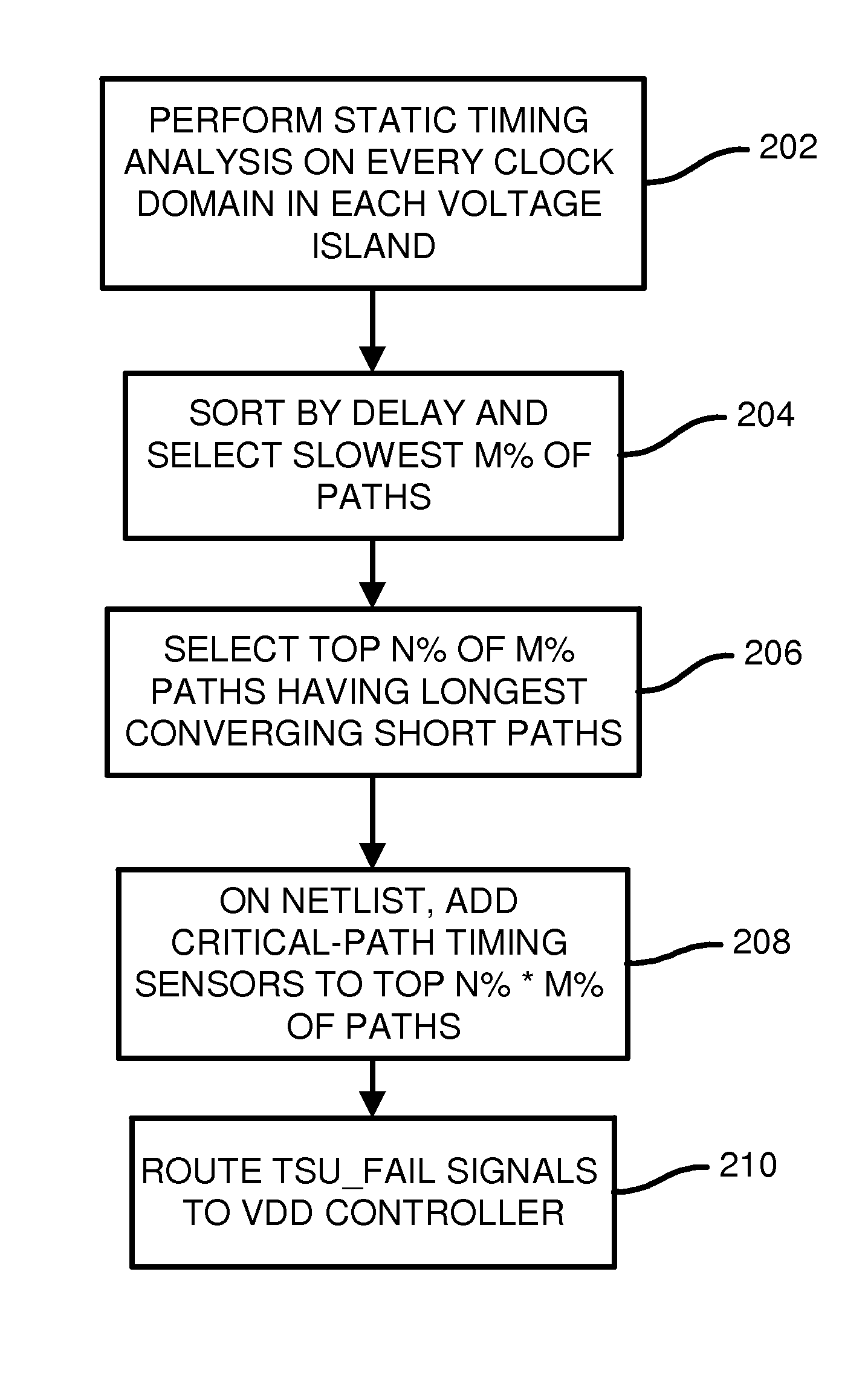
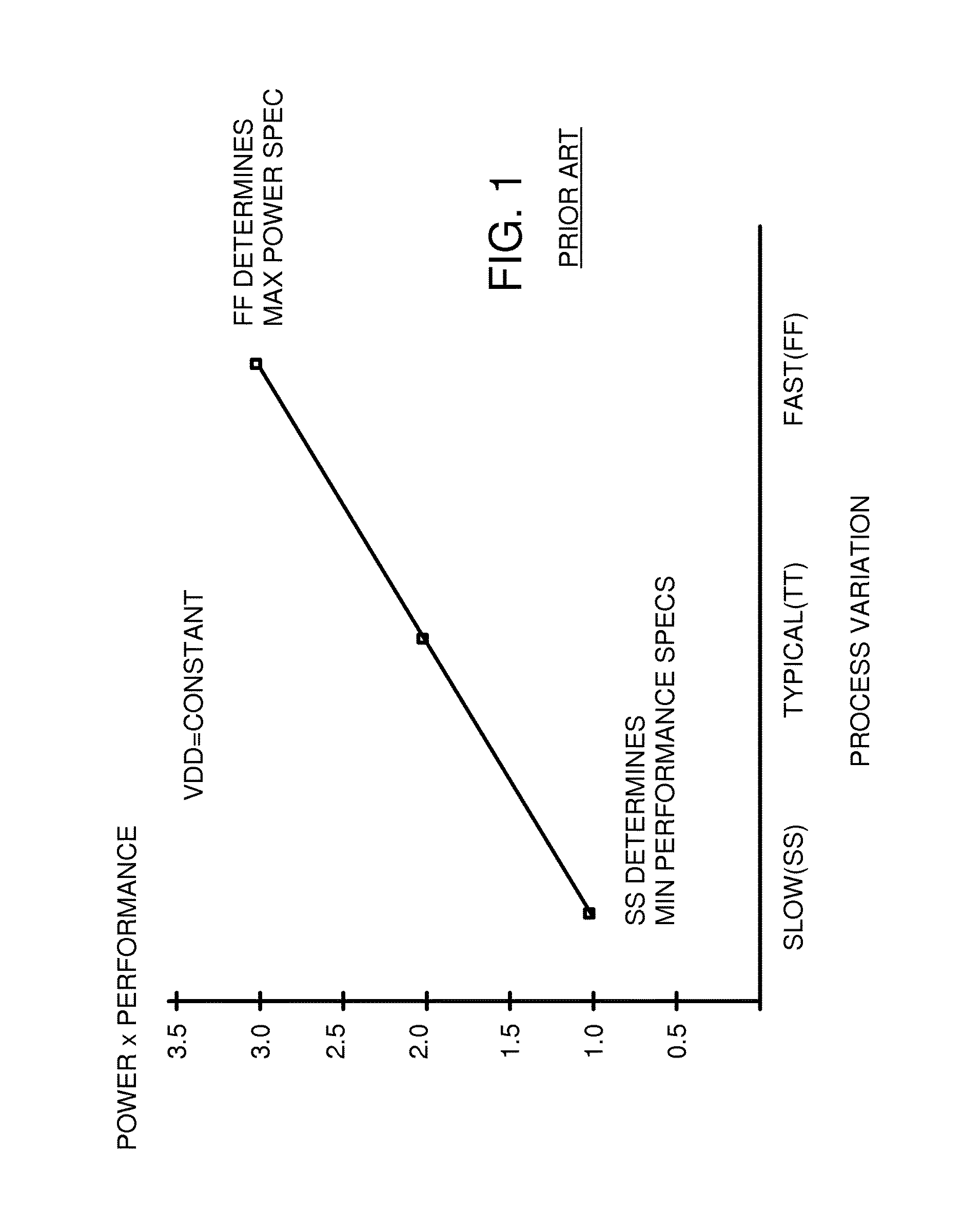
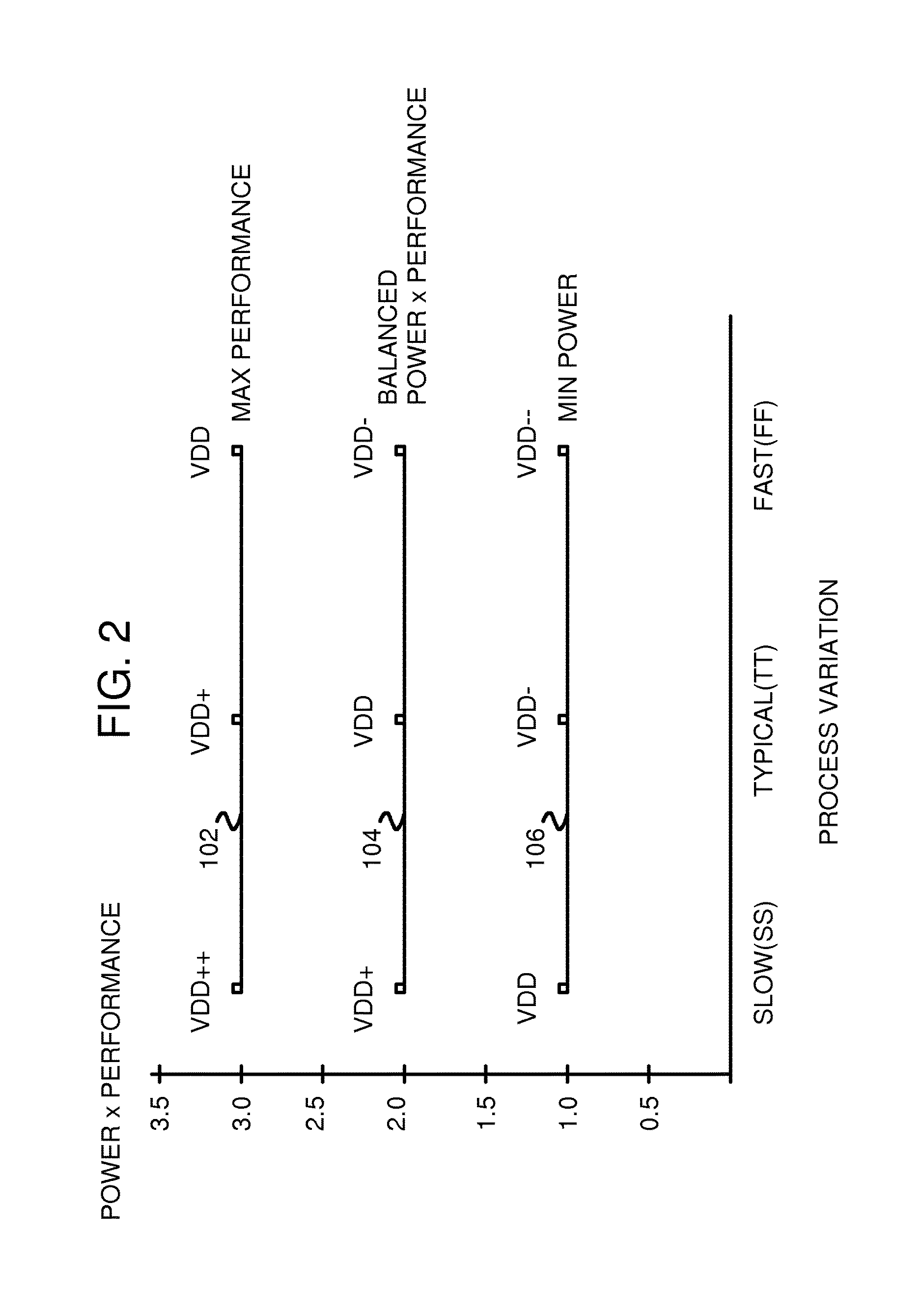
Method and algorithm for functional critical paths selection and critical path sensors and controller insertion
InactiveUS9536038B1CAD circuit designSpecial data processing applicationsDesign engineerCritical path method
CAD software examines delays of paths in a design from design engineers and first selects the longest paths. Then all paths that converge with these longest paths are examined for delays, and a fastest converging path is selected for each of the longest paths. The longest paths are again sorted by the fastest converging delay, and paths with slower converging paths are selected to be Functional Critical Paths (FCP's). Functional critical path timing sensors are added to each FCP to test setup time with an added margin delay. When the margined path delays fail to meet setup requirements, the functional critical path timing sensors signal a controller to increase VDD. When no failures occur over a period of time, the controller decreases VDD. The CAD software can replicate some of the FCP's and add toggle pattern generators and timing sensors and a margin controller to adjust the margin delay.
Owner:QUALCOMM INC
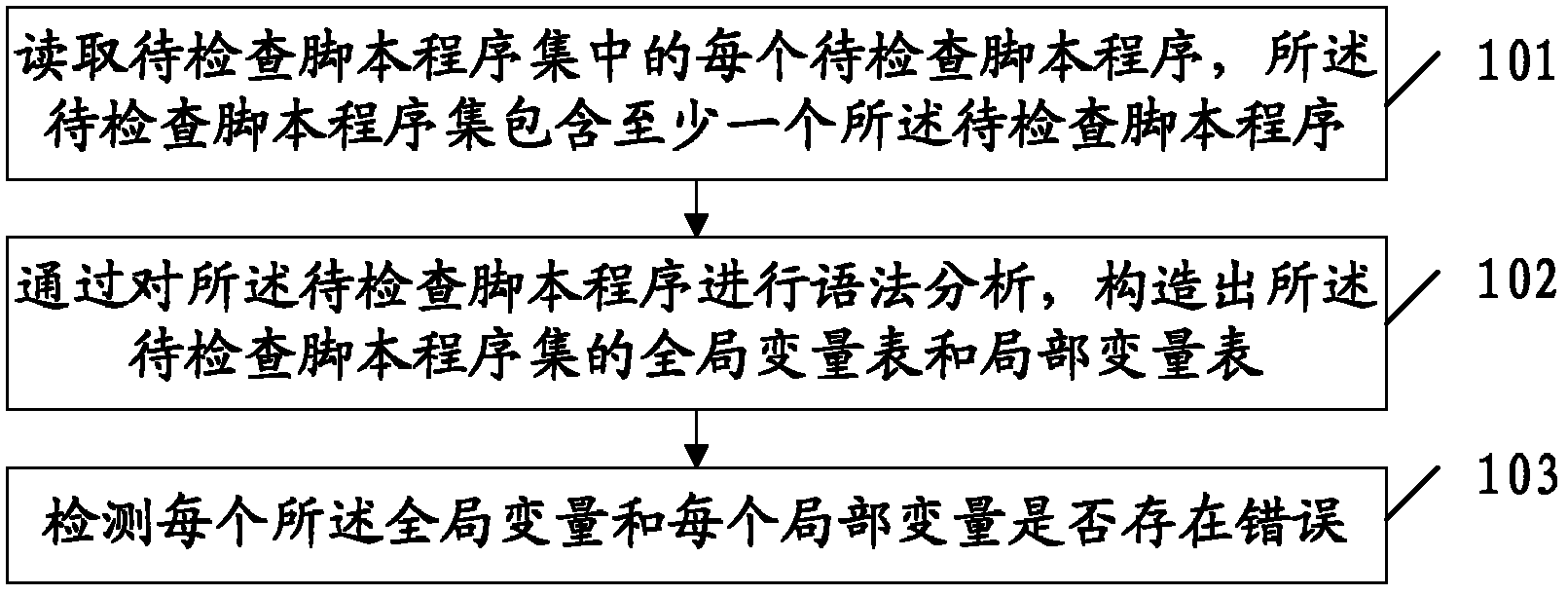
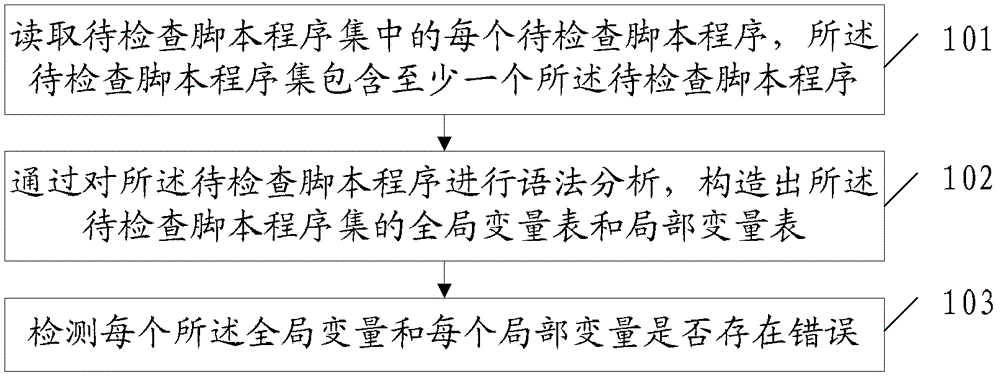
Inspection method and device for script programs
An embodiment of the invention discloses an inspection method and device for script programs and relates to the technical field of software inspection. According to the inspection method and device, variables can be inspected before a script program set is executed, and probabilities of errors of script programs during operation are reduced. The method comprises reading each script program to be inspected in the script program set to be inspected, wherein the script program set to be inspected contains at least one of the script program to be inspected; performing grammatical analysis on the script programs to be inspected and constructing a global variable table and a local variable table of the script program set to be inspected; and inspecting whether each global variable and each local variable has errors. The inspection method and device are mainly used for inspecting variables in script programs.
Owner:TENCENT TECH (SHENZHEN) CO LTD
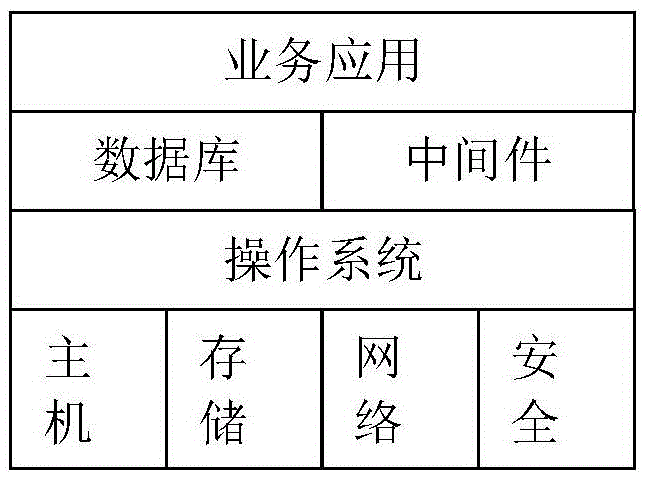
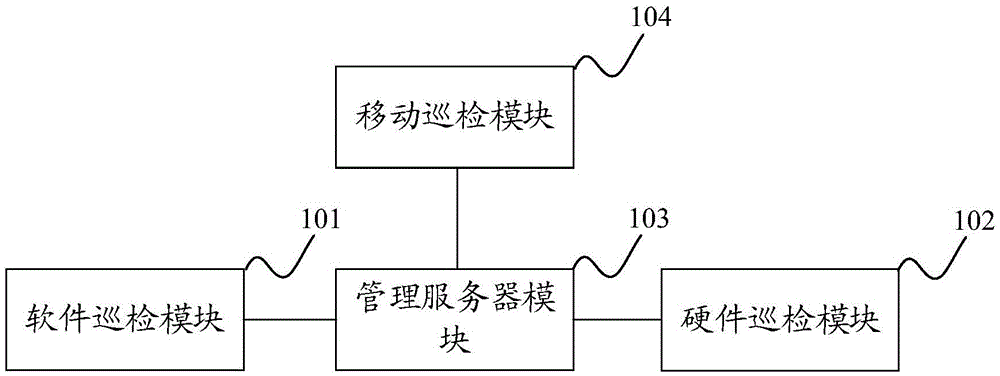
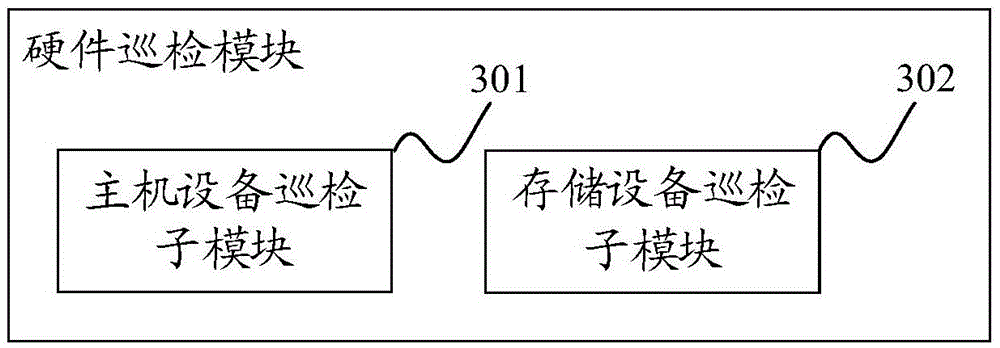
Inspection system and method of information system
The invention discloses an inspection system and method of an information system. The system comprises a software inspection module, a hardware inspection module, a management server module and a mobile inspection module; the software inspection module carries out software inspection to an operation system, a database and a middleware according to preset inspection indexes and collects and records software inspection data; the hardware inspection module carries out hardware inspection to host equipment and a storage device according to preset hardware inspection indexes and collects and records hardware inspection data; the mobile inspection module interacts the inspection data with the management server module through a mobile terminal and records the operation environment data conditions of the information system; the management server module manages and analyzes the inspection tasks of the software inspection module and the hardware inspection module and interacts the inspection data with the mobile terminal. The invention has data storage and analysis functions, can realize high precise inspection, can inspect the information system in high efficiency, immediately finds and eliminates potential failure and realizes preventive maintenance.
Owner:STATE GRID CORP OF CHINA +1
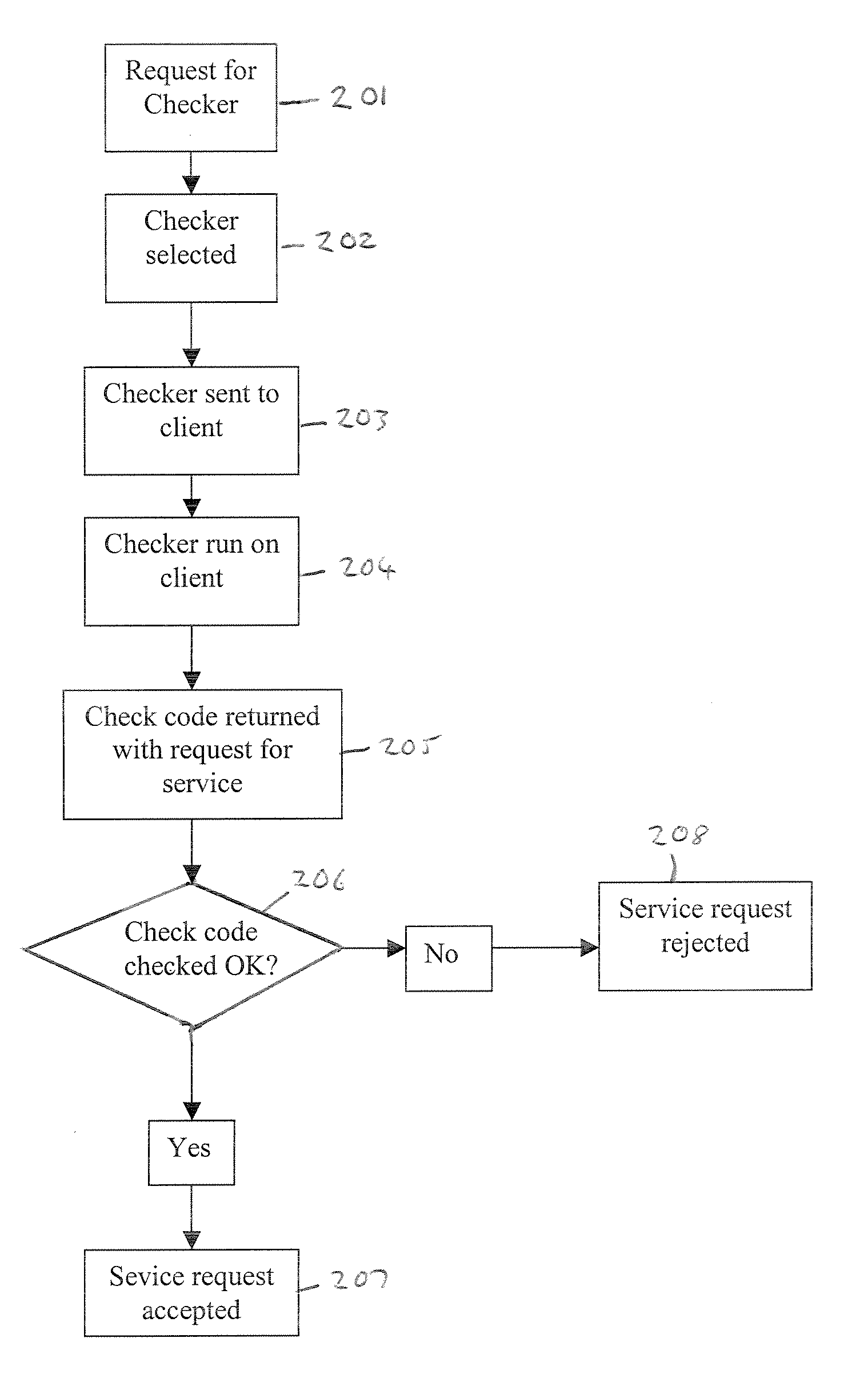
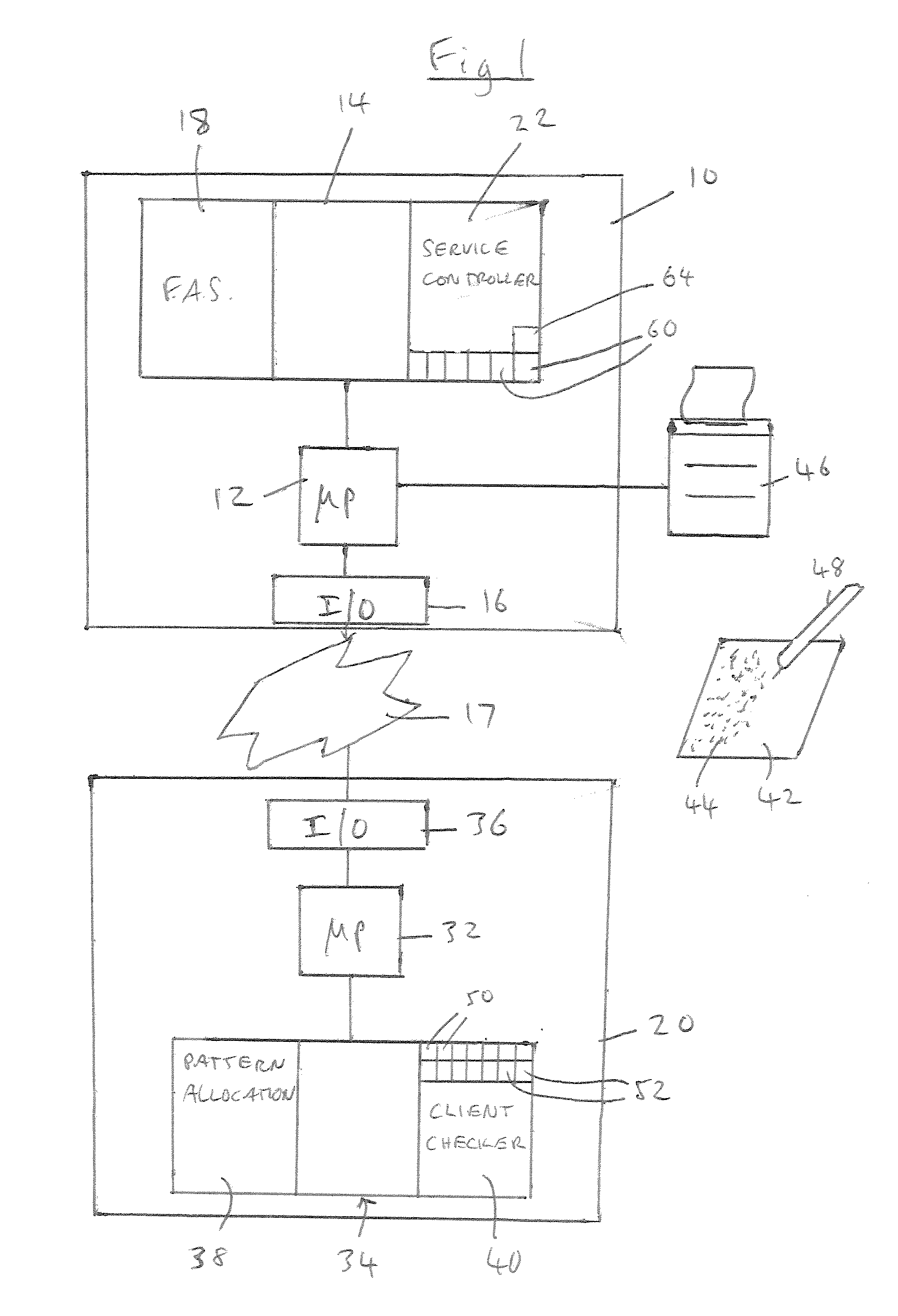
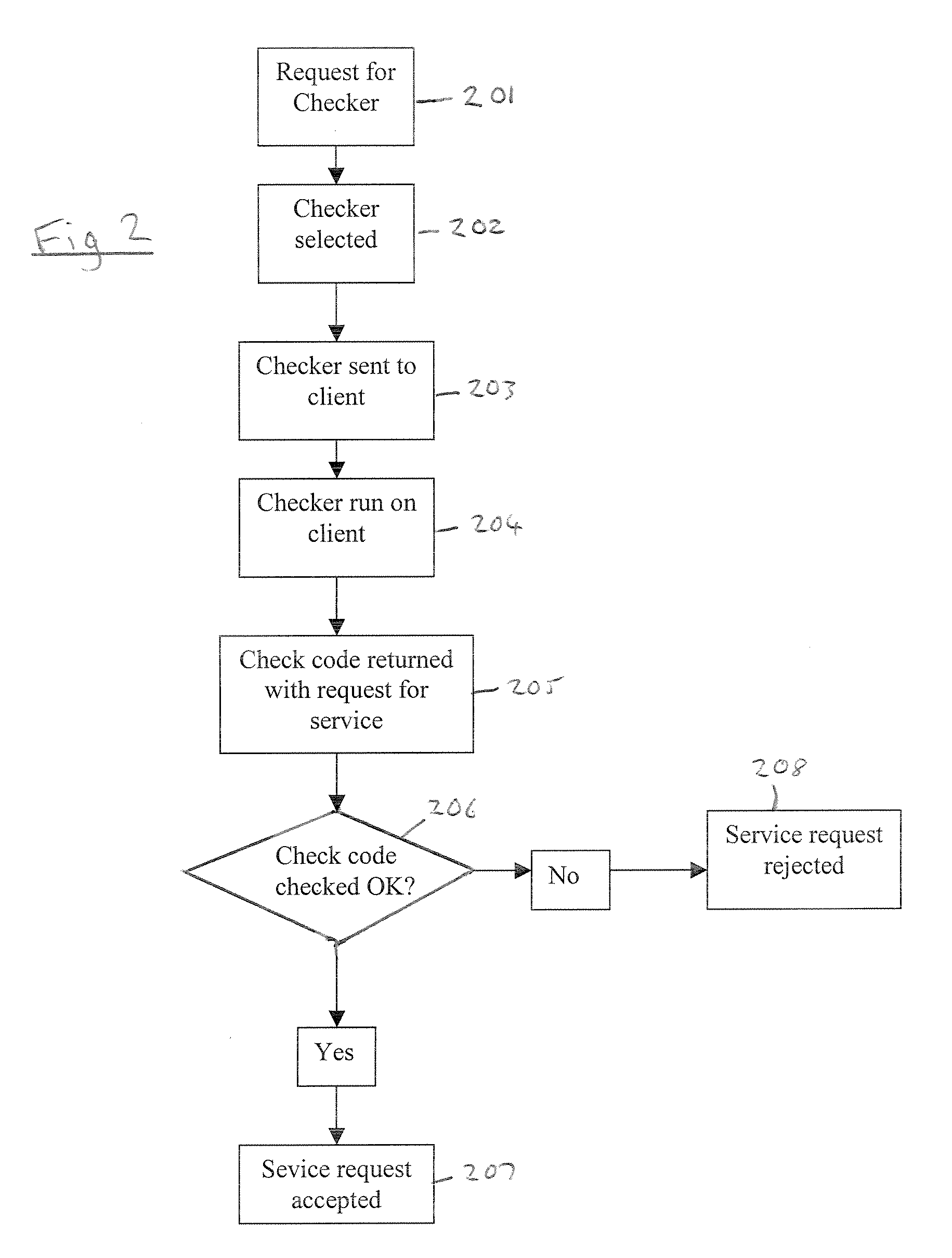
Software Checking
A method of checking the integrity of a software component comprises: selecting a checking algorithm 50 from a plurality of checking algorithms in a pseudo-random manner; performing the algorithm on the component 22 to produce a checking code that is dependent on the integrity of the component and the algorithm selected; and comparing the checking code with a reference code 52 to check the integrity of the component.
Owner:HEWLETT PACKARD DEV CO LP
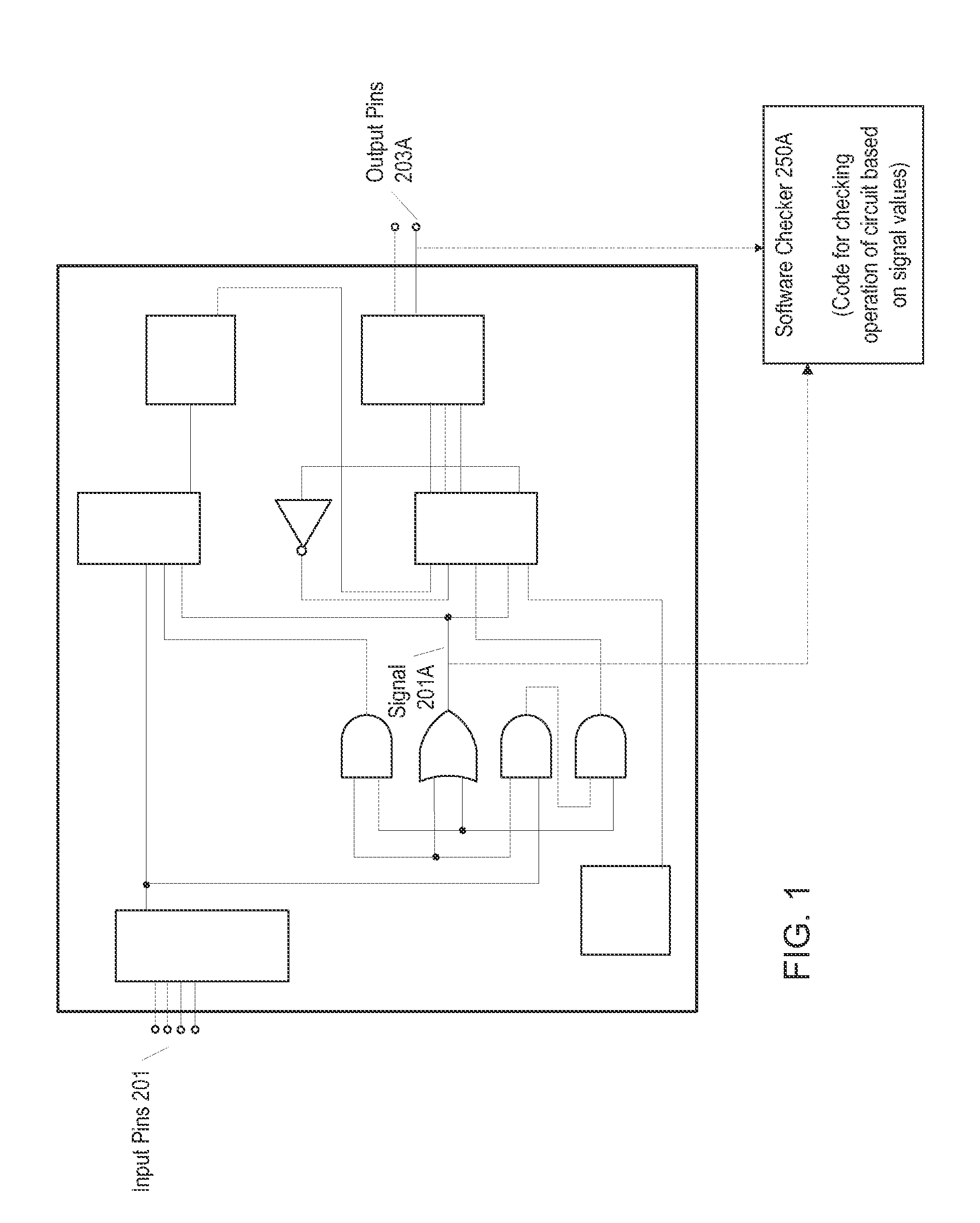
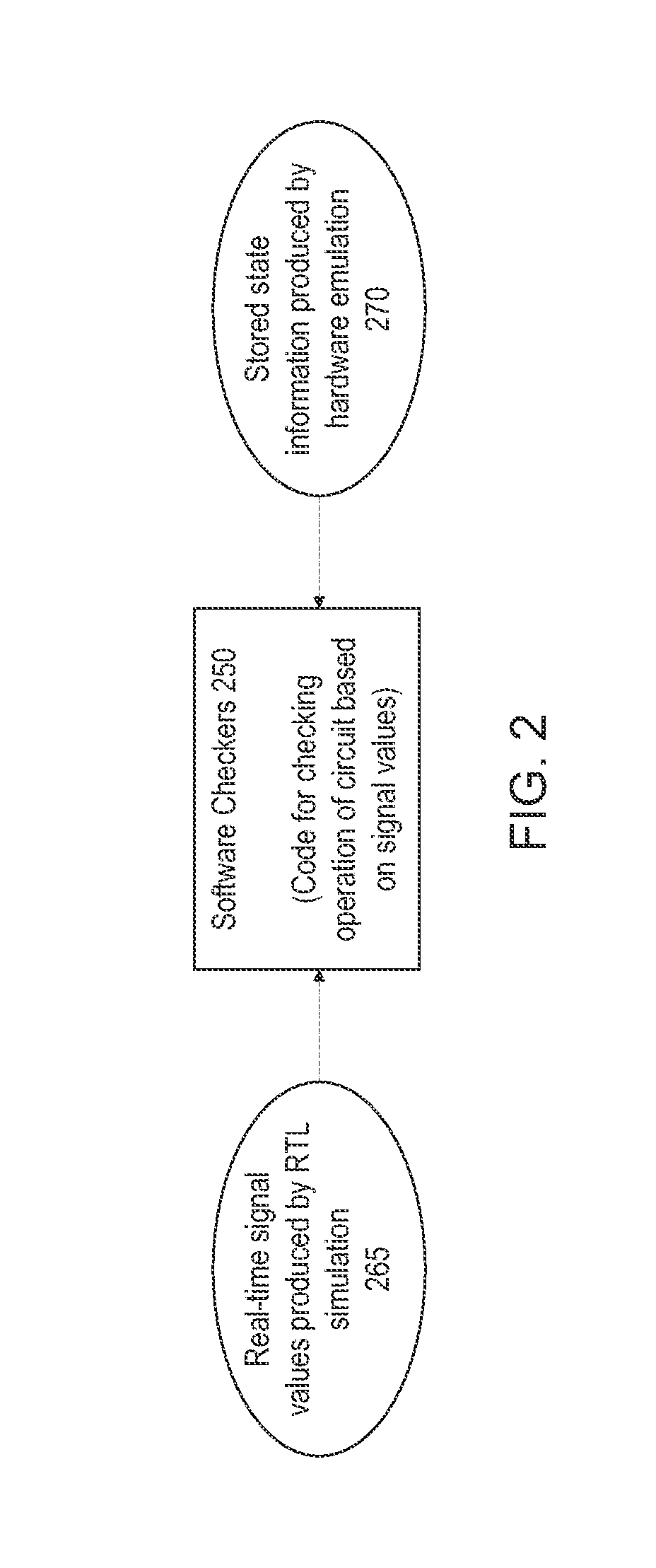
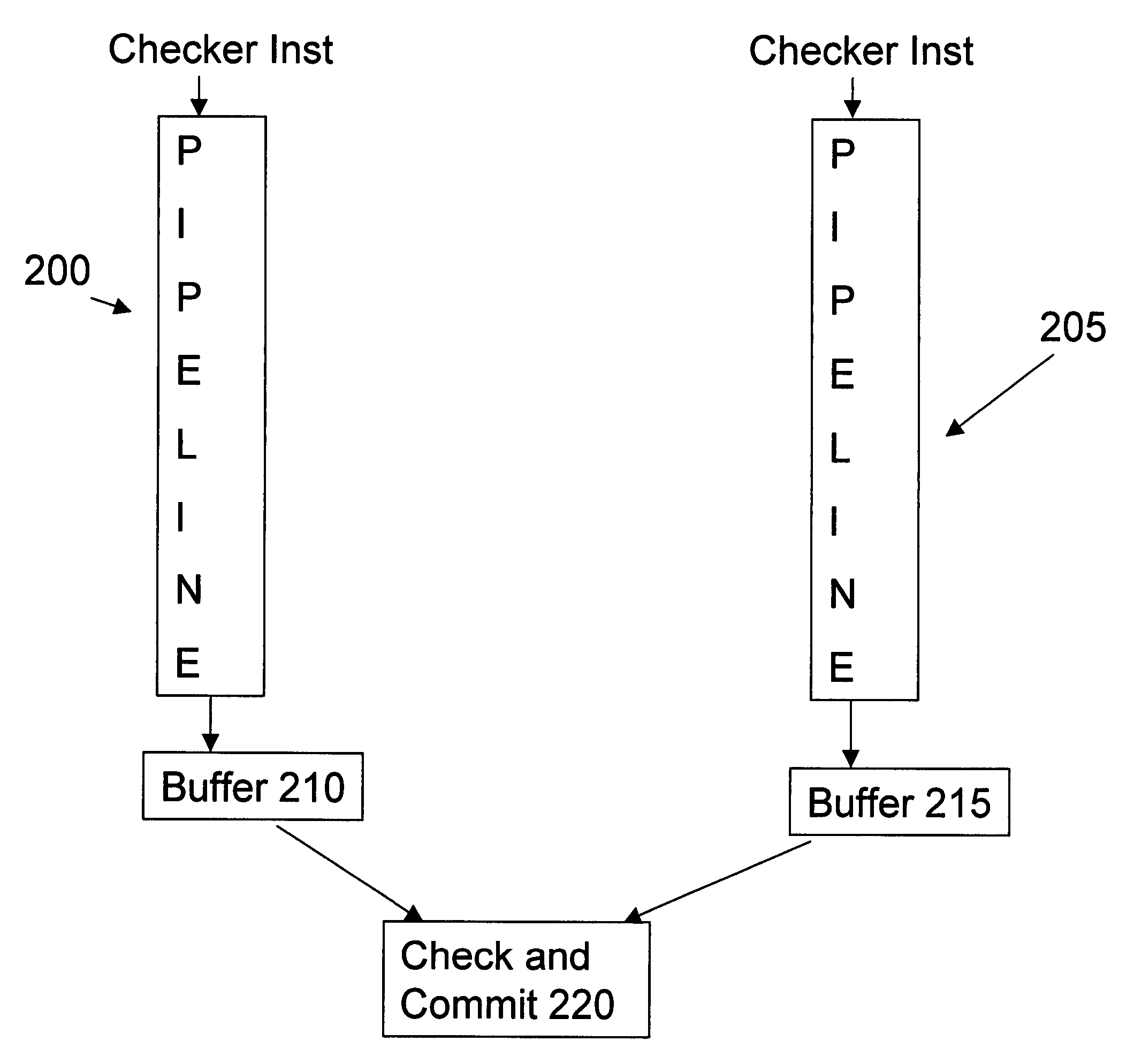
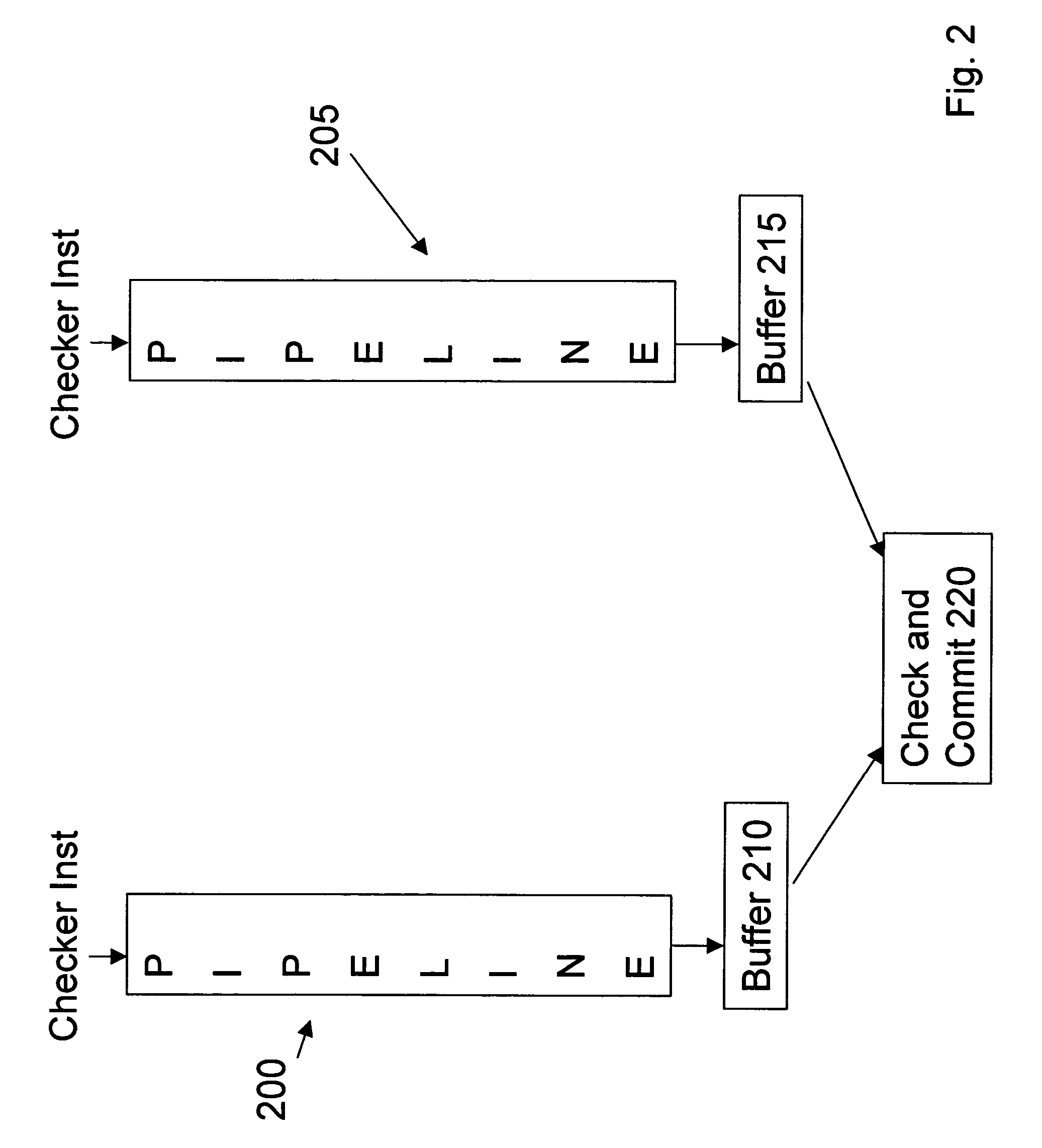
Testing a Hardware Emulation Model of a Circuit with Software Checker Routines Designed for an RTL Model of the Circuit
InactiveUS20140100841A1Software simulation/interpretation/emulationSpecial data processing applicationsComputer hardwareComputerized system
A hardware emulation system may emulate a plurality of cycles of a circuit, and may store state information at each cycle which specifies signal values for one or more signals of the circuit. After the hardware emulation has finished, the state information may be streamed from the memory of the hardware emulation system to a different storage device that is accessible by a computer system that executes one or more software checker routines. The computer system may execute the software checker routines, which may include passing the signal values specified in the state information to the software checker routines on a cycle-by-cycle basis similarly as if the software checker routines were receiving them in real time directly from the hardware emulation system.
Owner:APPLE INC
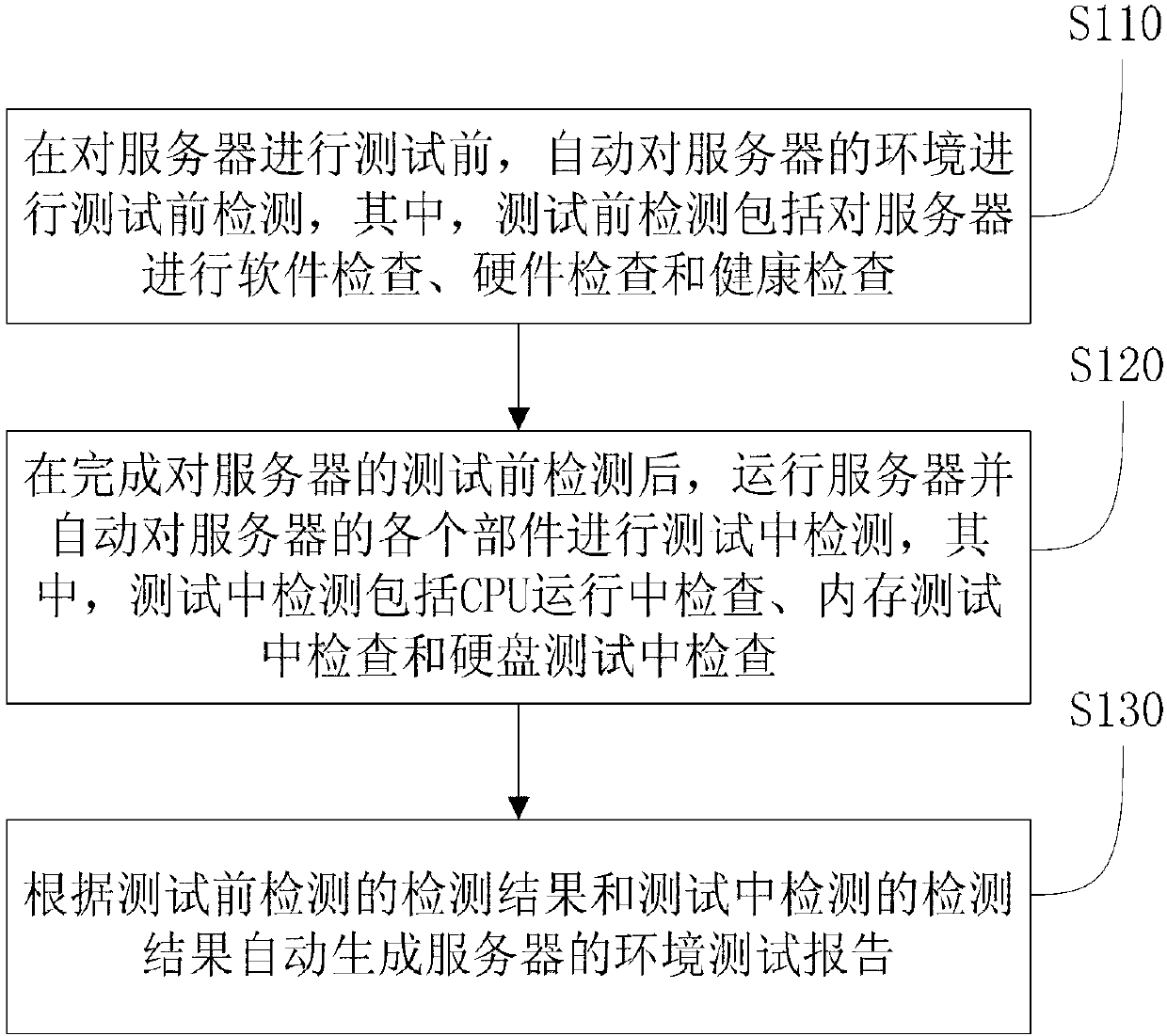
Automatic detection method and device for server environment
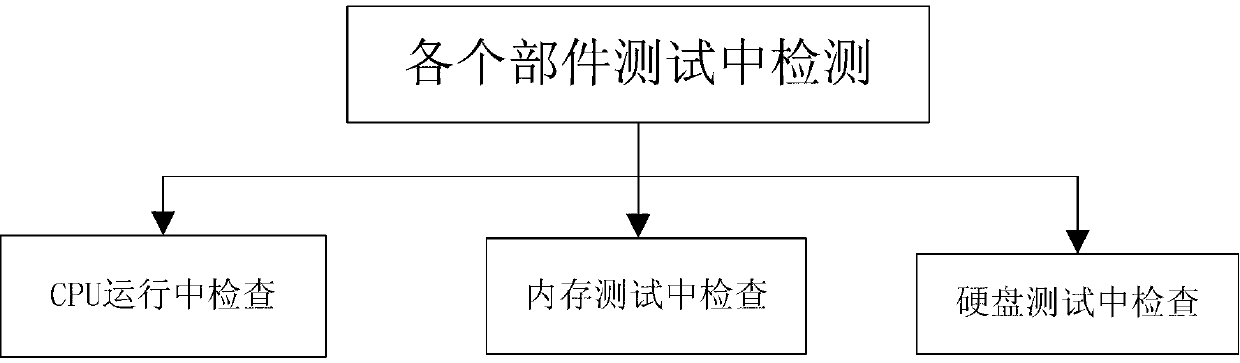
InactiveCN103218277AGuaranteed to be normalKeep healthyDetecting faulty computer hardwareHardware monitoringInternal memorySoftware
The invention provides an automatic detection method for a server environment. The automatic detection method comprises the following steps of automatically performing before-test detection on the environment of a server before the server is detected, wherein the before-test detection comprises software inspection, hardware inspection and health inspection on the server; after the server is subjected to the before-test detection, running the server and automatically performing in-test detection on each part of the server, wherein the in-test detection comprises central processing unit (CPU) in-running inspection, internal memory in-test inspection and hard disk in-test inspection; and automatically generating an environment test report of the server according to a detection result of the before-test detection and a detection result of the in-test detection. The server is automatically subjected to the before-test detection and the in-test detection, and the test report is generated according to the acquired test data and data of the running server, so that the manual inspection cost is saved, the efficiency is improved, and guidance is provided for repeated tests and server performance analysis. The invention also discloses an automatic detection device for the server environment.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Fault free store data path for software implementation of redundant multithreading environments
A method for a fault free store data path in a software implementation of redundant multithreading environments is described. In one embodiment, after a check is performed by a hardware / software checker, the processor still needs to ensure that the data just checked reaches protected memory without any faults. The present implementation provides sufficient redundant information along the path of a store from register read to commit, such that it may detect any single bit upset error in the path.
Owner:INTEL CORP
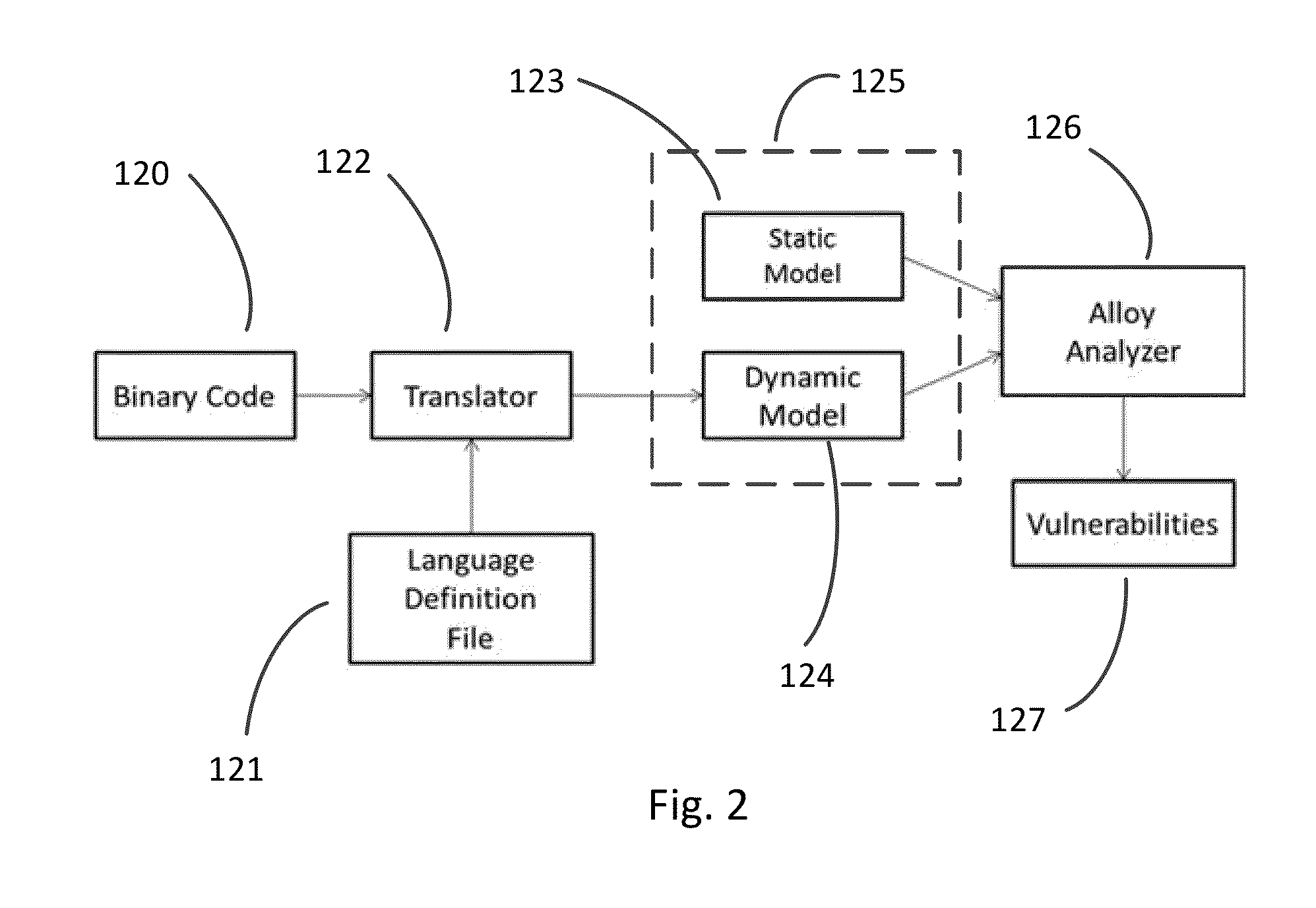
Software Inspection System
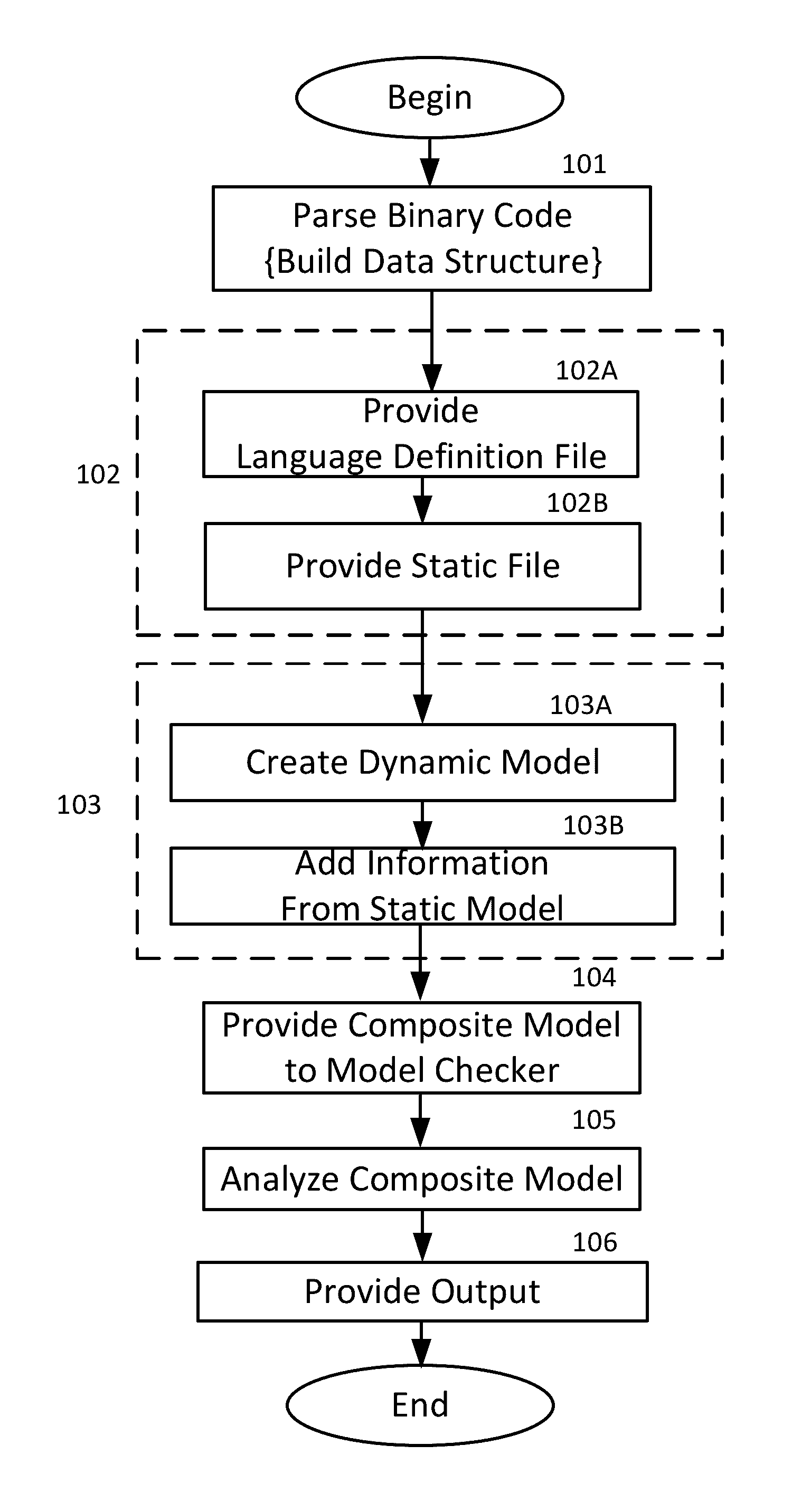
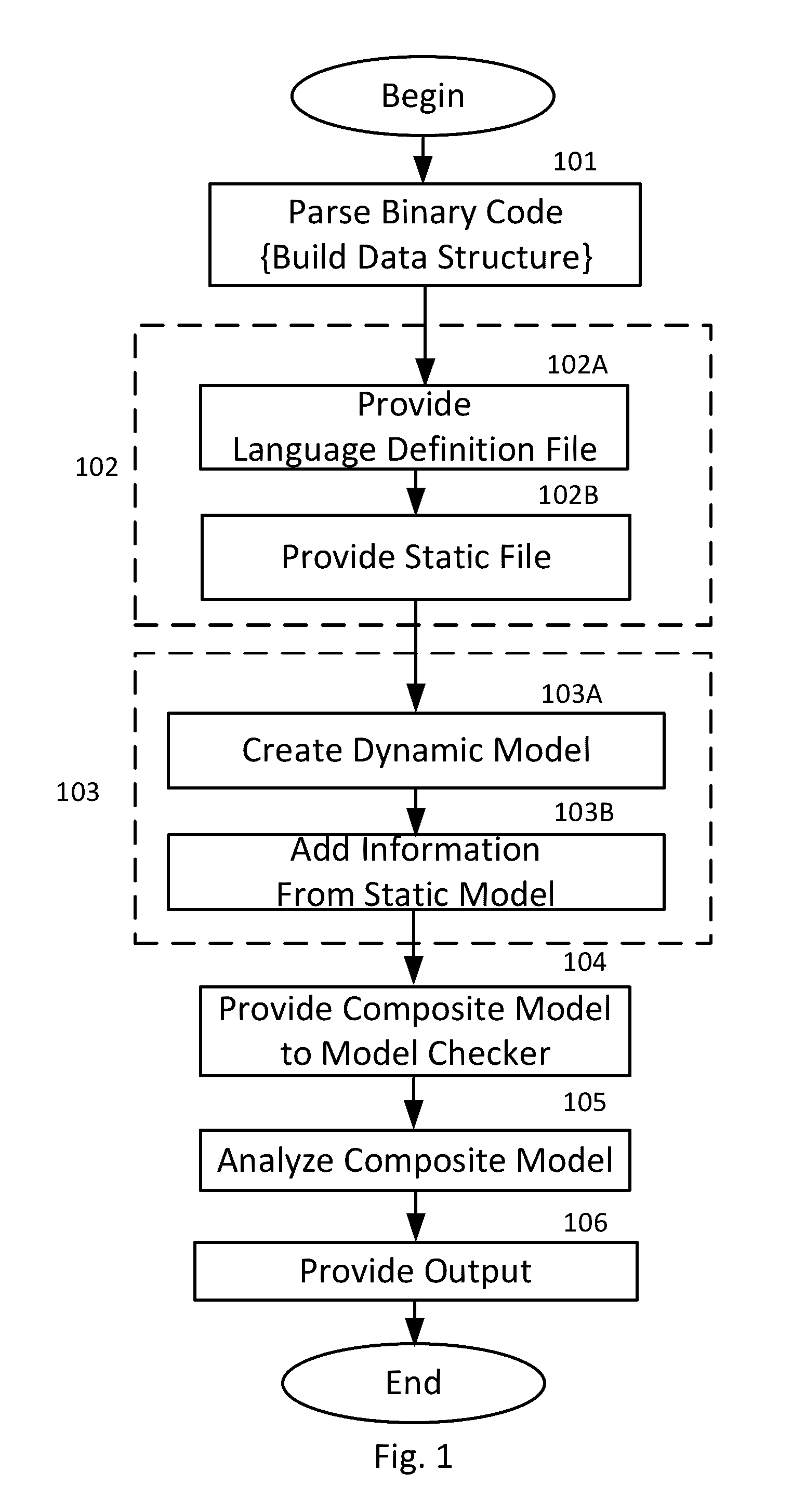
A method for software inspection analyzes a body of computer code to assess whether the body of computer code contains malware. Various embodiments extract the executable elements of the body of computer code and modify those elements using rules defining the format of instructions for the programming language in which the computer code was written, and using rules defined from the security specification of that programming language, to produce a model of the body of computer code. The method then analyzes the model using a model checking system, which determines whether any of the language rules have been violated, in which case the method flags the computer code as potentially including malware.
Owner:TRUSTEES OF BOSTON UNIV
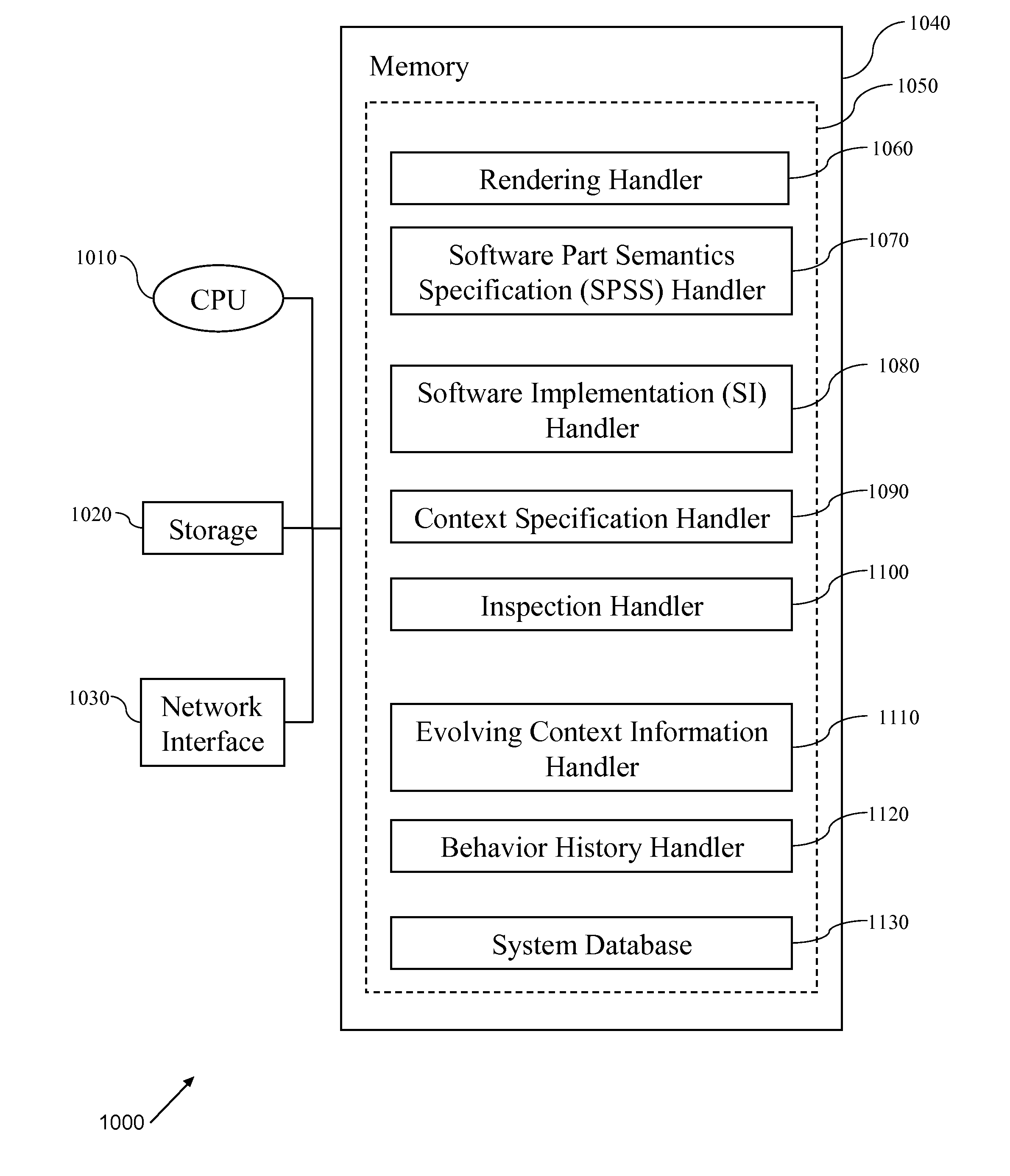
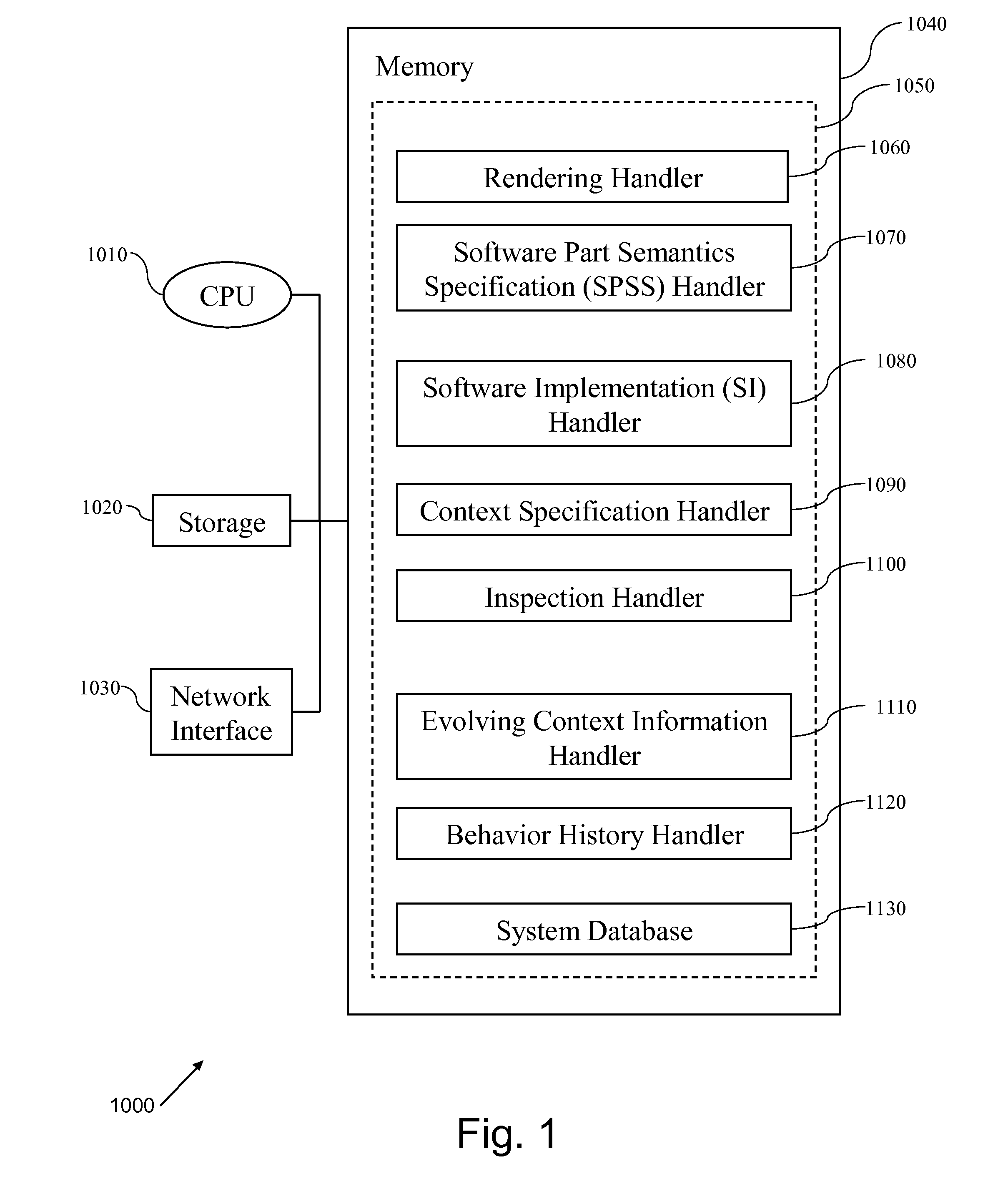
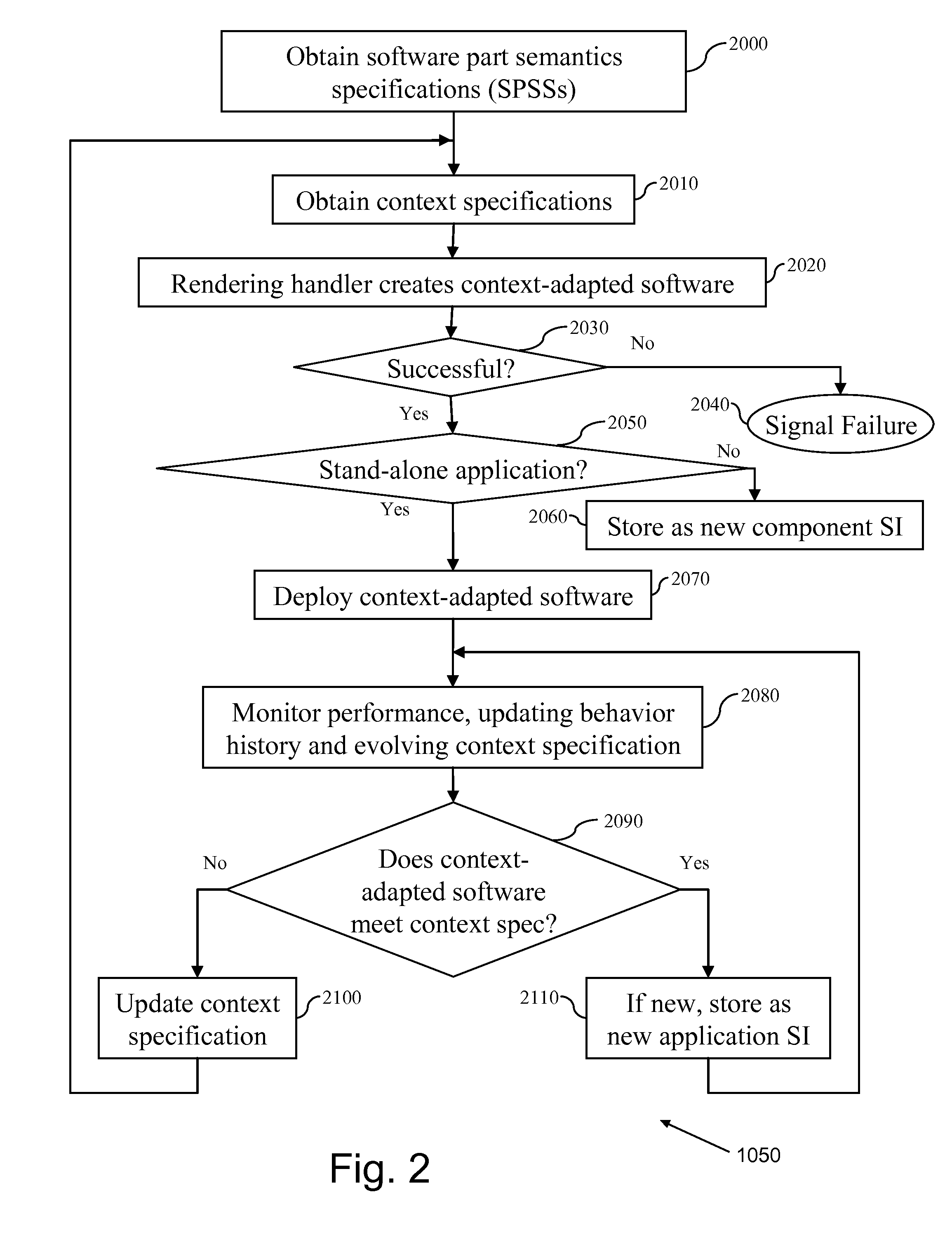
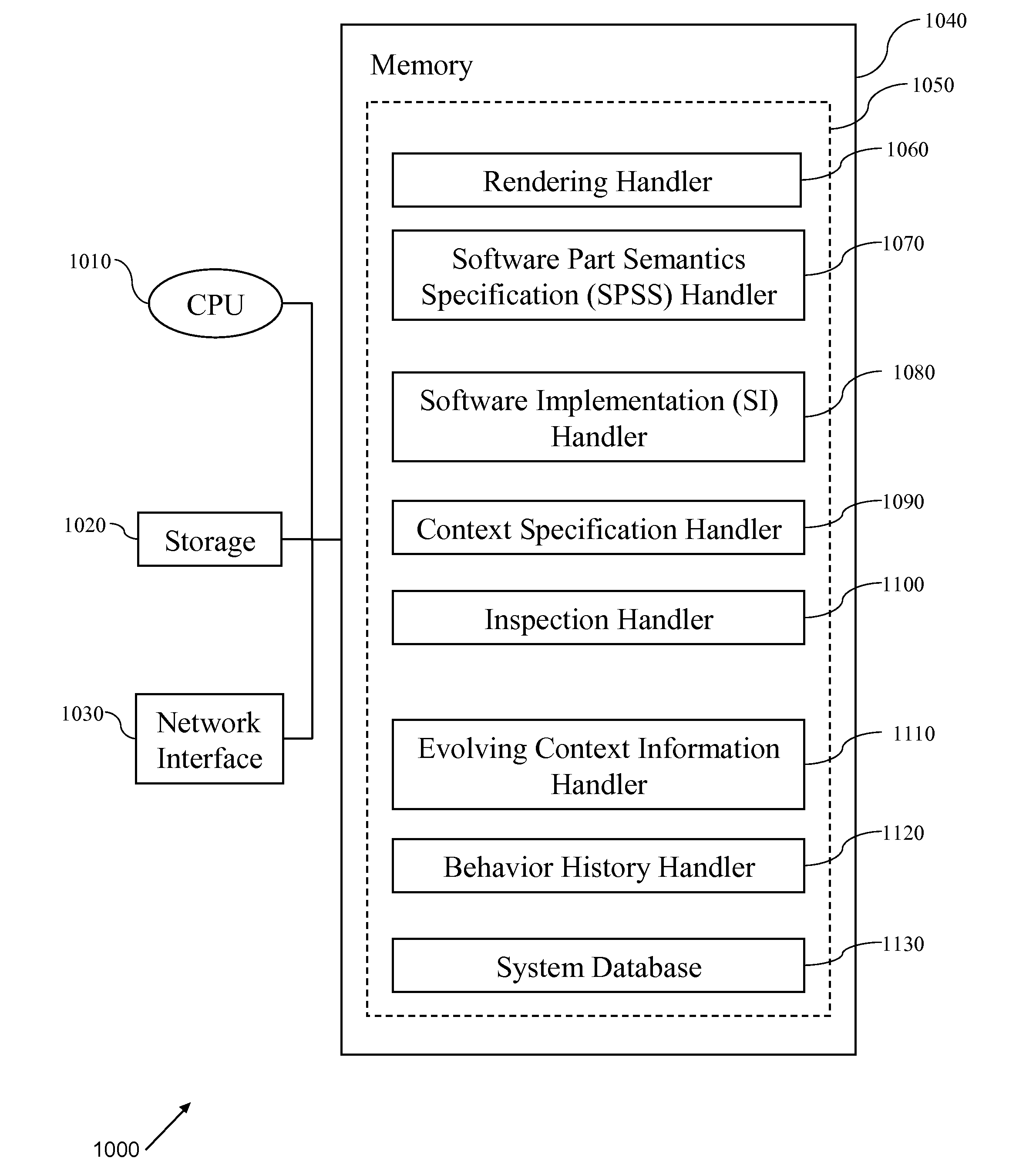
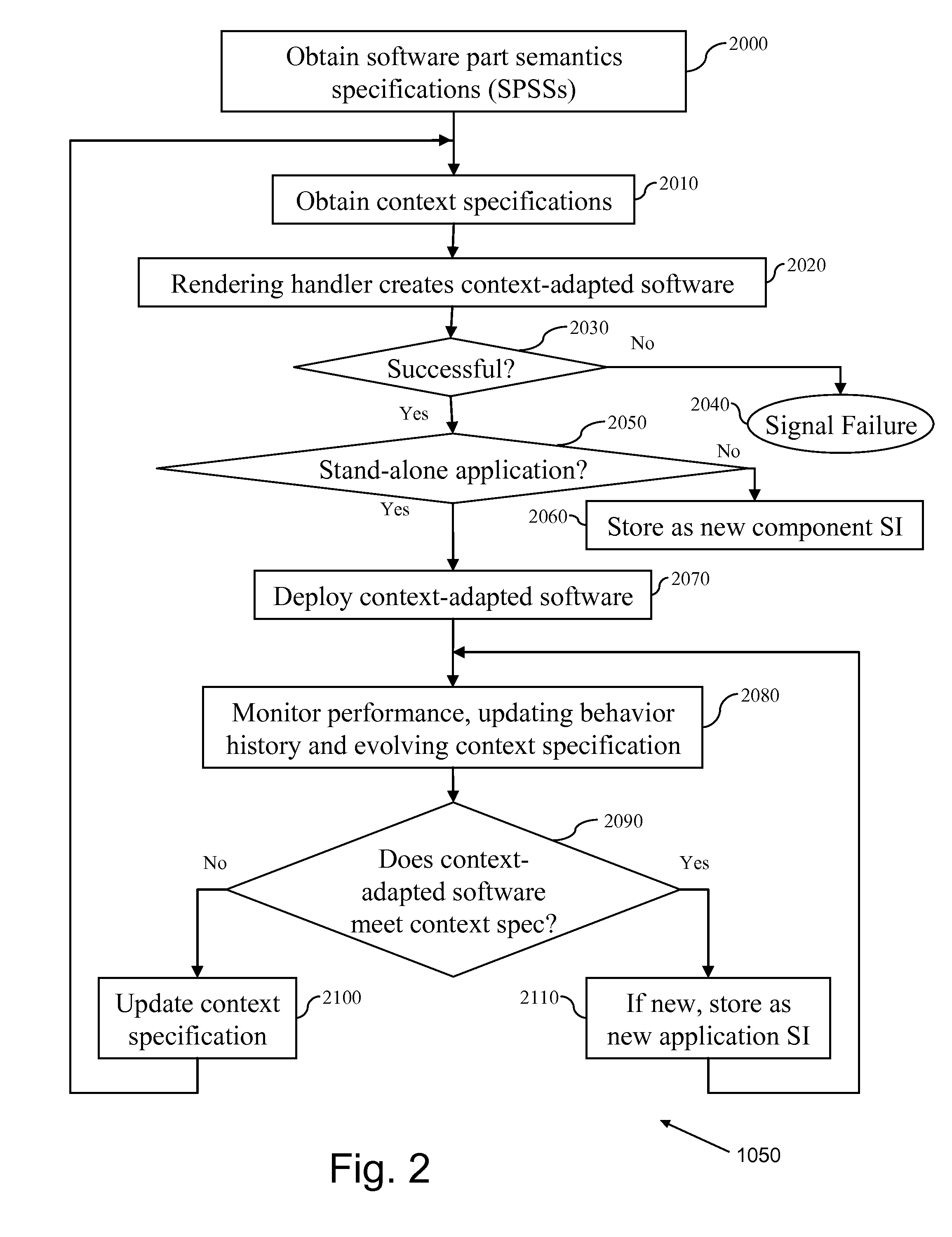
Software development, deployment and evolution system, method and program product
InactiveUS8448133B2Reduce maintenance costsLow costSoftware maintainance/managementSoftware reuseSoftware development processBehavioral analytics
A method of software evolution, software evolution system and program product therefor. A context specification handler stores context specifications describing requirements on context-adapted software. A Software Part Semantics Specification (SPSS) handler stores software part semantics specifications. A Software Implementation (SI) handler stores SIs. Behavior History handler stores a history of active software behavior analysis results of monitoring previous versions. A software rendering handler combines software behavior history with context specification, software part semantics specifications and SIs and distributes (and optionally deploys) context-adapted software. A software inspector continuously monitors context behavior of deployed versions and selectively identifies active context-adapted software failing to satisfy context specification for reassembly of a new version(s).
Owner:INT BUSINESS MASCH CORP
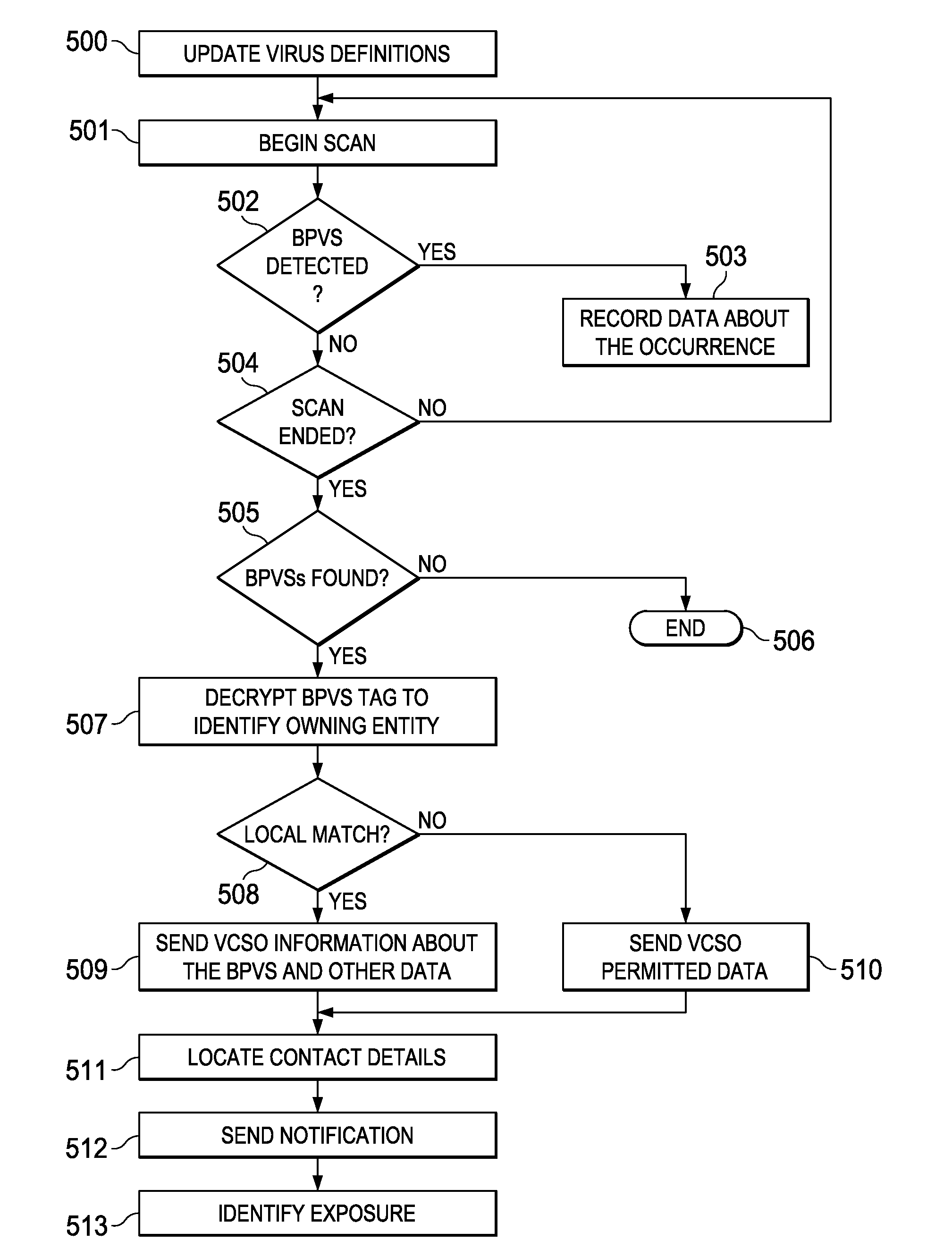
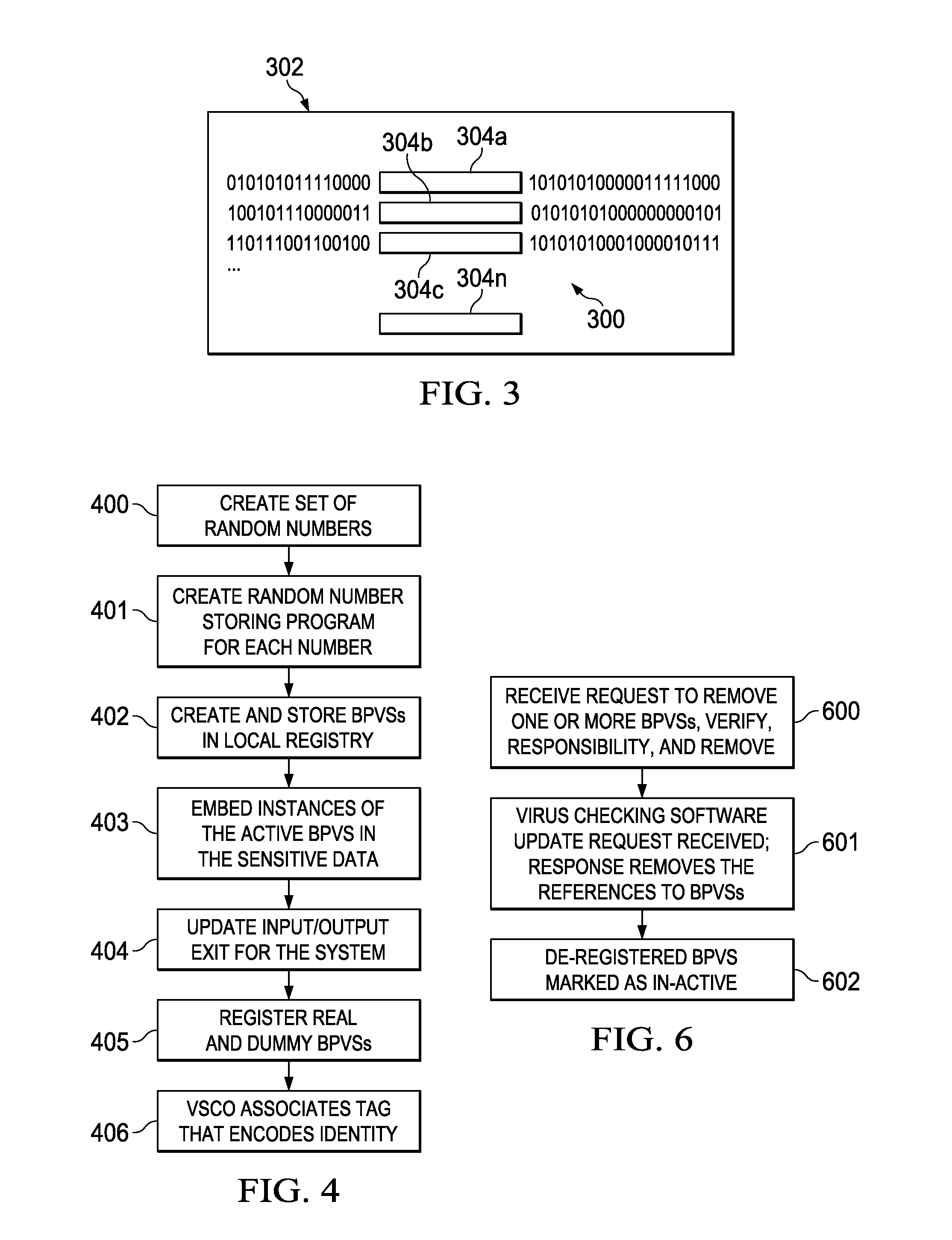
Detecting sensitive data access by reporting presence of benign pseudo virus signatures
InactiveUS20140359772A1Memory loss protectionError detection/correctionInternet privacyRemedial action
An owner of sensitive data is provided with a notification that the sensitive data has been located. To achieve this, the sensitive data is first modified to include one or more data strings that may appear to be suspect but are otherwise benign. These data strings, which are referred to herein as benign pseudo virus signatures (BPVSs), preferably are embedded throughout a piece of sensitive data according to a frequency distribution. When the sensitive data is examined by virus checking software, the benign pseudo virus signatures are detected as potential computer viruses. By using information associated with the signatures, the owner is identified, preferably using the assistance of an intermediary entity that acts as a registry for the BPVSs. Once the owner is identified, a notification is provided to the owner that the sensitive data has been located. Appropriate remedial action can then be taken.
Owner:GLOBALFOUNDRIES INC
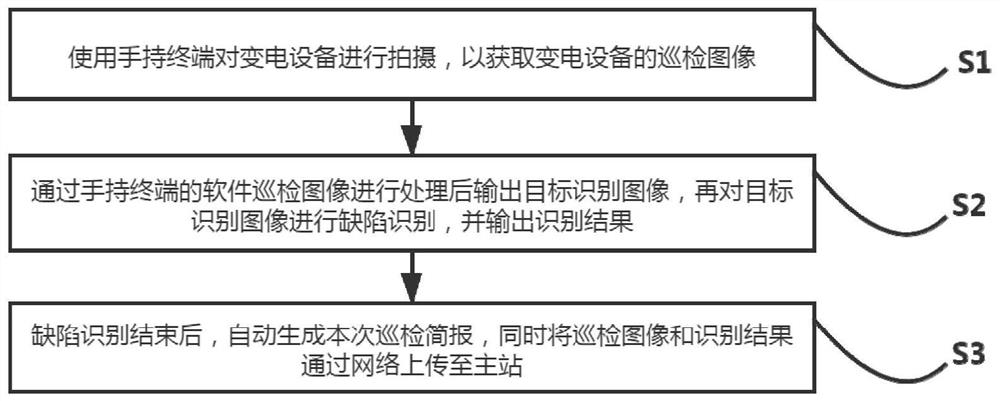
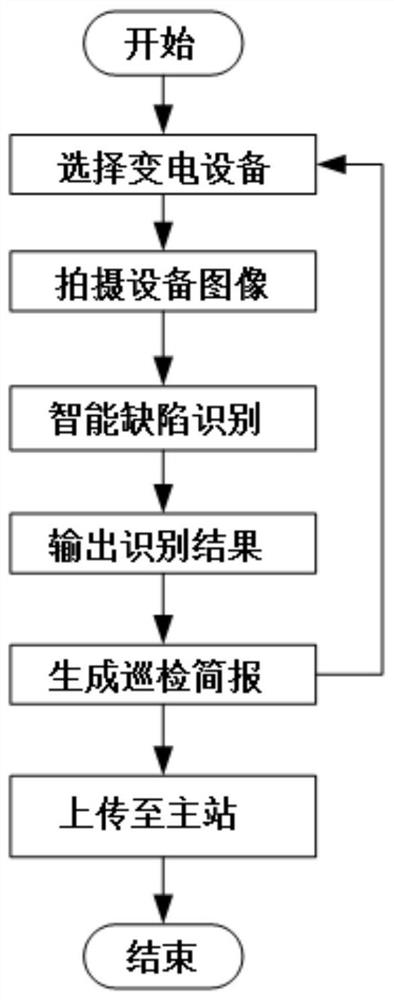
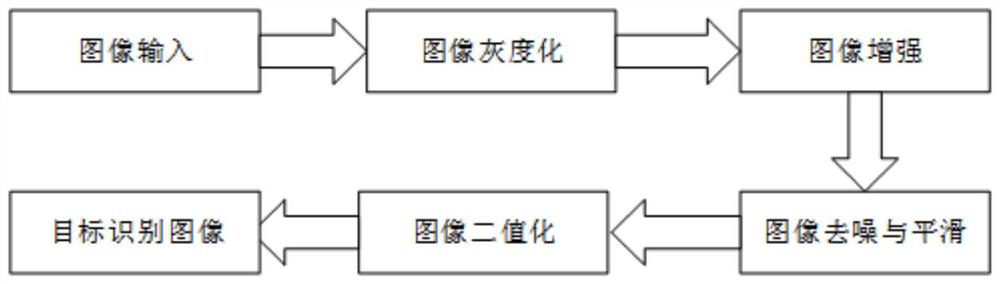
Substation equipment defect intelligent image recognition method and management system thereof
PendingCN112380907ARealize fault traceabilityRealize regulationData processing applicationsRelational databasesNetwork connectionEmbedded system
The invention firstly discloses a substation equipment defect intelligent image identification method, which comprises the following steps of S1, shooting substation equipment by using a handheld terminal so as to acquire an inspection image of the substation equipment; S2, processing the software inspection image of the handheld terminal, outputting a target identification image, performing defect identification on the target identification image, and outputting an identification result; and S3, after defect identification is finished, automatically generating a current inspection brief report, and uploading an inspection image and an identification result to a main station through a network. The invention further discloses a substation equipment defect intelligent image recognition and management system thereof. The system comprises a main station, a database server and the handheld terminal, the main station is in network connection with the database server; and the main station isin communication connection with the handheld terminal. According to the invention, defects of power transformation equipment can be discovered and eliminated in time, equipment accidents are prevented, and the equipment state is effectively supervised.
Owner:ZHONGSHAN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID
Determining Reviewers for Software Inspection
InactiveUS20200226054A1Reduce the amount of calculationImprove rendering capabilitiesSoftware testing/debuggingSoftware designSoftware engineeringSubject matter
Provided are techniques for an objective determination of the most appropriate person to conduct a software inspection in a large software development project with multiple components, packages and micro-services in which individuals or small groups are each assigned specific modules. Historical information from testing of software commits is stored. An automated and objective analysis of an entire project, including the historical information is performed, revealing connections that would otherwise not be apparent between specific potential reviewers and the commit to be reviewed. Based upon the analysis, the system suggests one or more reviewers for the commit to be reviewed. An appropriate code reviewer may be a person with subject matter expertise (SME) in a related are or have more knowledge of a bigger picture and more context of the project, including knowledge of other components.
Owner:IBM CORP
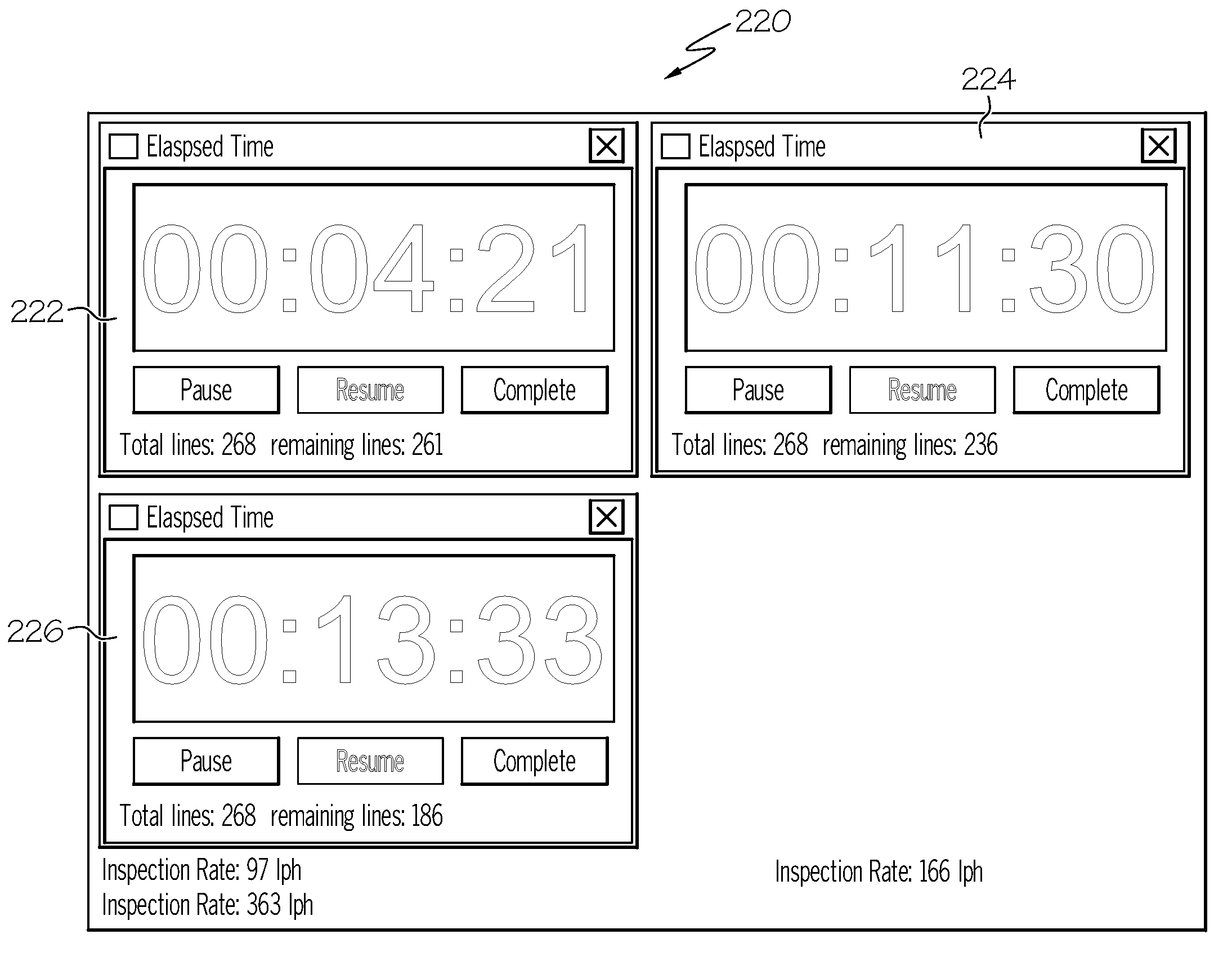
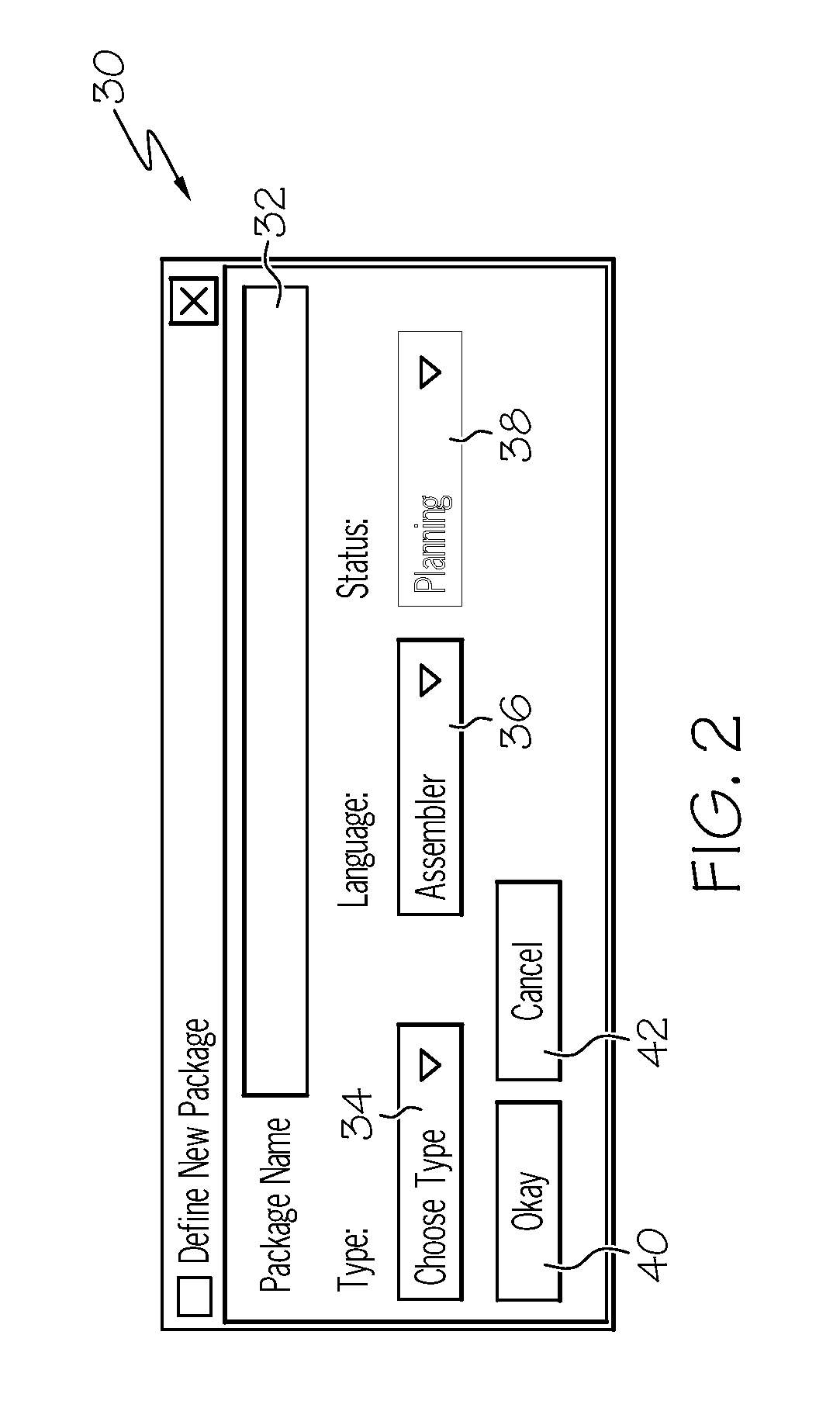
Software inspection management tool
InactiveUS20080098344A1Error detection/correctionSpecific program execution arrangementsManagement toolDisplay device
A software inspection management tool for monitoring inspection rates of code, the tool including: a display device for displaying a primary window having a plurality of functions; a first function being used for defining a new package by; a second function being used for opening an existing package; an inspection rate monitor for displaying elapsed time of inspection by a user; and a viewer window having two panes for examining the code, the first pane including a table view of items being inspected and the second pane including a table of comments to be made concerning the items being inspected; wherein the elapsed time is compared to a predetermined minimum and maximum range of permitted inspection time predefined in a preference dialog window; and wherein color modifications of the elapsed time occur in accordance with the user's inspection rate progress.
Owner:IBM CORP
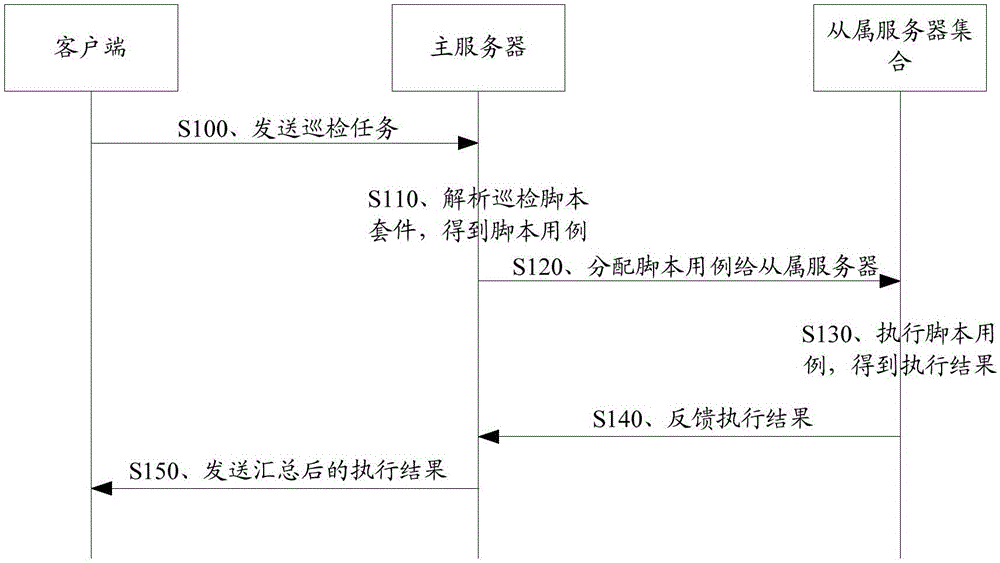
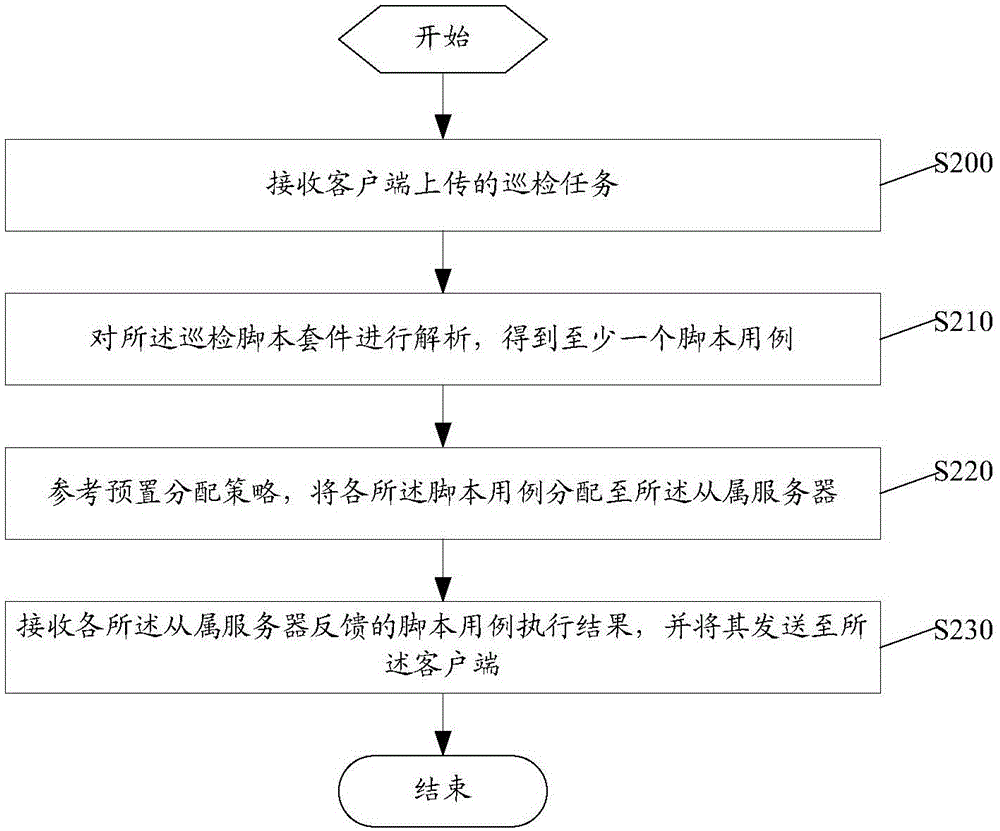
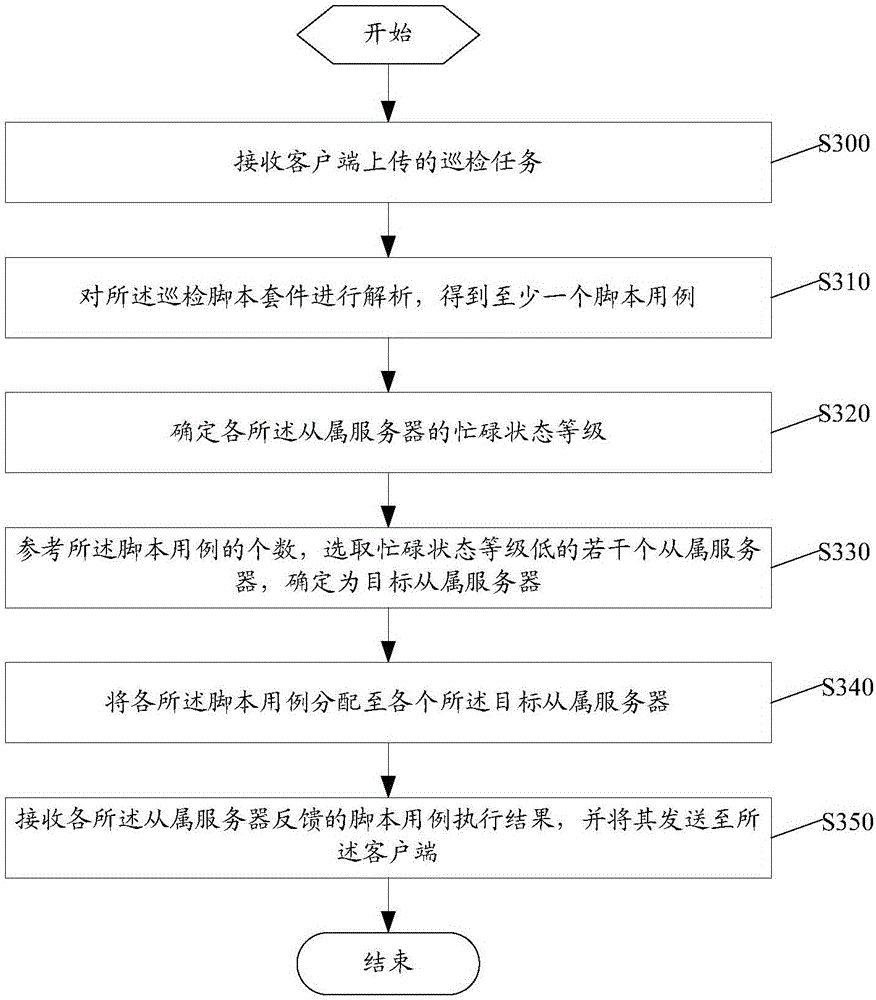
Software inspection method, device and system
InactiveCN105100277AImprove inspection efficiencyThere is no missed detectionData switching networksClient-sideParallel processing
The invention discloses a software inspection method, device and system. The method is based on a cloud platform in which a plurality of master server and a plurality of slave servers are arranged; a user can upload an inspection task via a client, wherein the task comprises an inspection script suite composed of at least one script use case; the master server obtains at least one script use case by analyzing after receiving the inspection task, and distributes each script use case to the slave servers with reference to a preset distribution policy; the slave servers execute the script use cases and feed back execution results to the master server; furthermore, the master server collects all the execution results and sends the collected execution results to the client. According to the software inspection method, automatic inspection can be realized by virtue of the cloud platform; the master server distributes the script use cases to the corresponding slave servers, and all the slave servers are capable of processing concurrently, and therefore, the inspection efficiency is improved. In addition, the user only needs to upload the script use cases needed by inspection and the cloud platform will traverse and execute all the script use cases, and therefore, the problems of missing inspection and wrong inspection can be avoided.
Owner:STATE GRID CORP OF CHINA +1
Software development, deployment and evolution system, method and program product
InactiveUS20100333063A1Reduce maintenance costsLow costSoftware maintainance/managementSoftware reuseBehavioral analyticsSoftware engineering
A method of software evolution, software evolution system and program product therefor. A context specification handler stores context specifications describing requirements on context-adapted software. A Software Part Semantics Specification (SPSS) handler stores software part semantics specifications. A Software Implementation (SI) handler stores SIs. Behavior History handler stores a history of active software behavior analysis results of monitoring previous versions. A software rendering handler combines software behavior history with context specification, software part semantics specifications and SIs and distributes (and optionally deploys) context-adapted software. A software inspector continuously monitors context behavior of deployed versions and selectively identifies active context-adapted software failing to satisfy context specification for reassembly of a new version(s).
Owner:IBM CORP
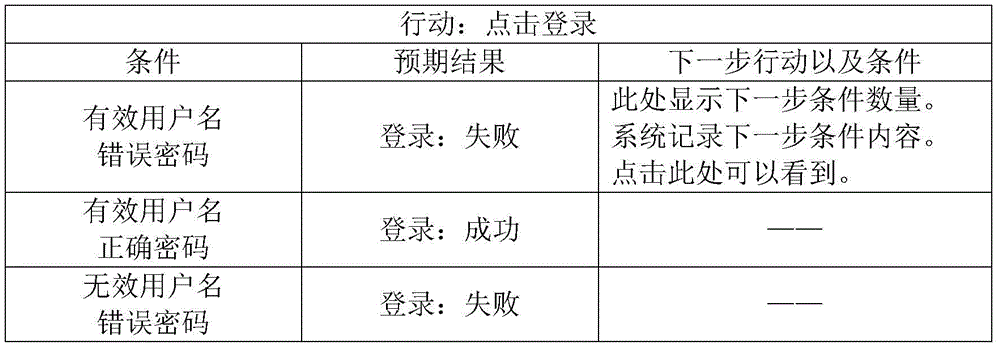
Automatic generation method for software graphic user man-machine interface test case
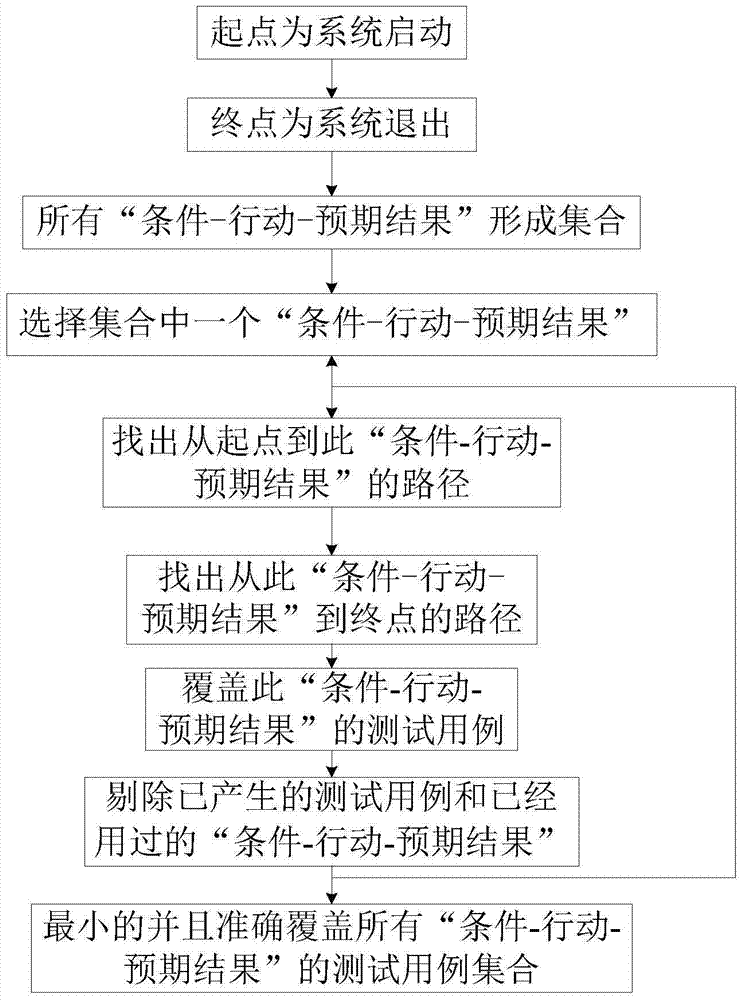
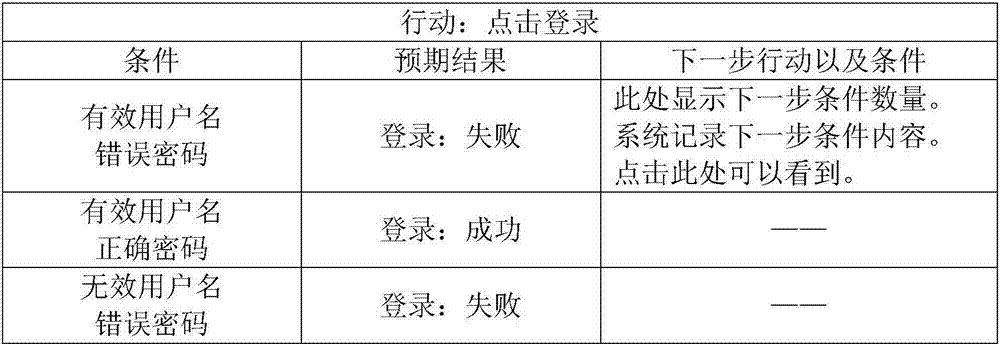
ActiveCN105550110ALow costStrong ability to avoid risksSoftware testing/debuggingAutomatic Generation ControlGraphics
The invention relates to an automatic generation method for a software graphic user man-machine interface test case, belongs to the technical field of software inspection and detection, and solves the problems of time, labor and money waste of an existing test case writing method. The invention proposes a concept of ''condition-action-expected result''. The method comprises the following steps: defining that defining that a starting point of a calculation path is system start and an ending point of the calculation path is system exit; collecting to-be-tested software behavior specifications and defining that all ''condition-action-expected result'' units form a set; selecting one ''condition-action-expected result'' unit in the set; finding out a path from the starting point to a current position; finding out a path from the current position to the ending point; connecting calculation results to obtain a test case covering the ''condition-action-expected result'' unit; and deleting generated test cases and used ''condition-action-expected result'' units until a minimum test case set accurately covering all the ''condition-action-expected result'' units is obtained. The method has the advantages of low maintenance and updating costs, low personnel cost, good risk avoidance capability and the like, and can be widely applied to software inspection and detection occasions.
Owner:艾瑞克李
Determining Reviewers for Software Inspection
InactiveUS20200226055A1Reduce the amount of calculationImprove rendering capabilitiesSoftware testing/debuggingSoftware designSoftware engineeringSubject matter
Provided are techniques for an objective determination of the most appropriate person to conduct a software inspection in a large software development project with multiple components, packages and at in which individuals or small groups are each assigned specific modules. Historical information from testing of software commits is stored. An automated and objective analysis of an entire project including the historical information is performed, revealing connections that would otherwise not be apparent between specific potential reviewers and the commit to be reviewed. Based upon the analysis, the system suggests one or more reviewers for the commit to be reviewed. An appropriate code reviewer may he a person with subject matter expertise (SME) in a related are or have more knowledge of a bigger picture and more context of the project, including knowledge of other components.
Owner:IBM CORP
Inspection method and device for script programs
An embodiment of the invention discloses an inspection method and device for script programs and relates to the technical field of software inspection. According to the inspection method and device, variables can be inspected before a script program set is executed, and probabilities of errors of script programs during operation are reduced. The method comprises reading each script program to be inspected in the script program set to be inspected, wherein the script program set to be inspected contains at least one of the script program to be inspected; performing grammatical analysis on the script programs to be inspected and constructing a global variable table and a local variable table of the script program set to be inspected; and inspecting whether each global variable and each local variable has errors. The inspection method and device are mainly used for inspecting variables in script programs.
Owner:TENCENT TECH (SHENZHEN) CO LTD
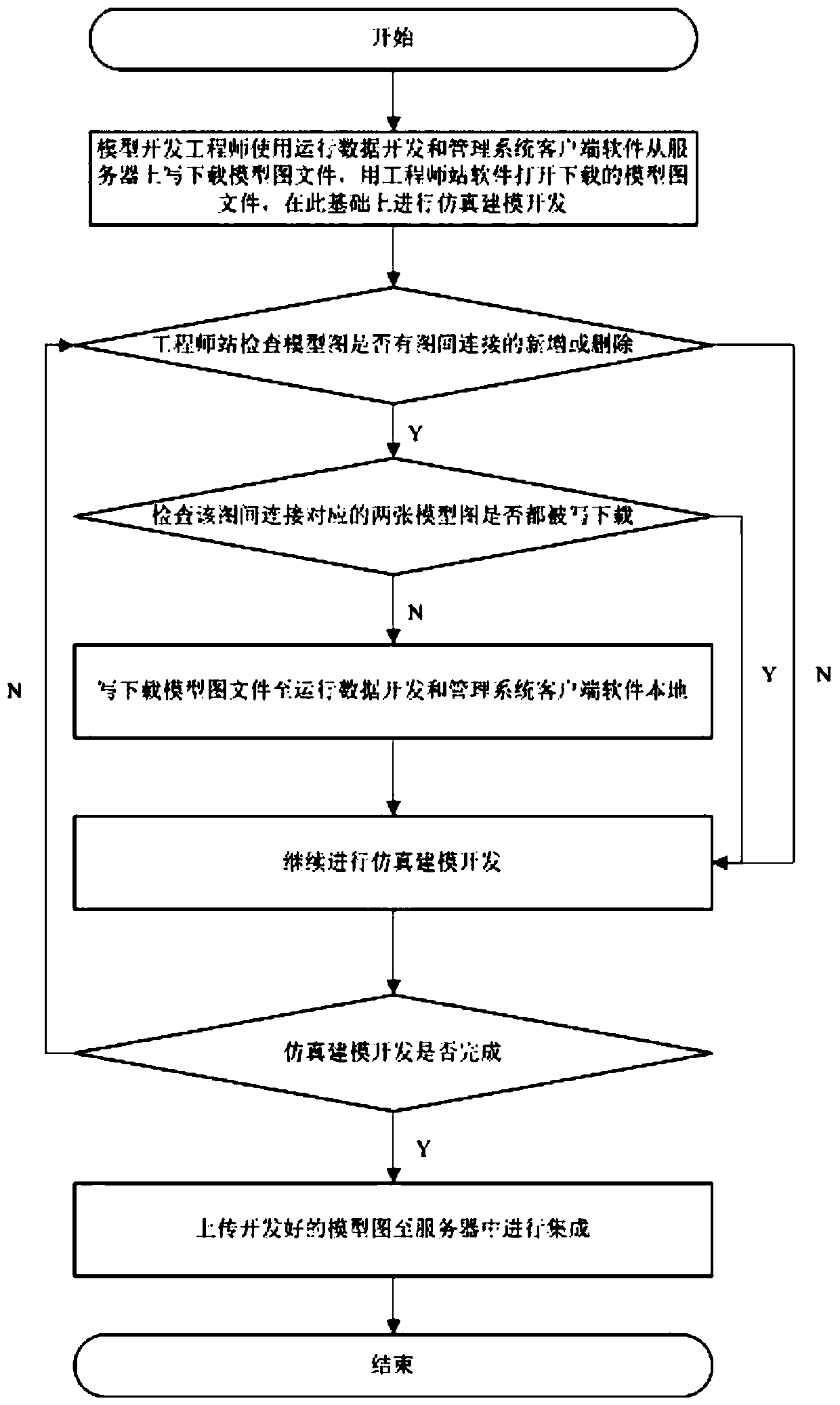
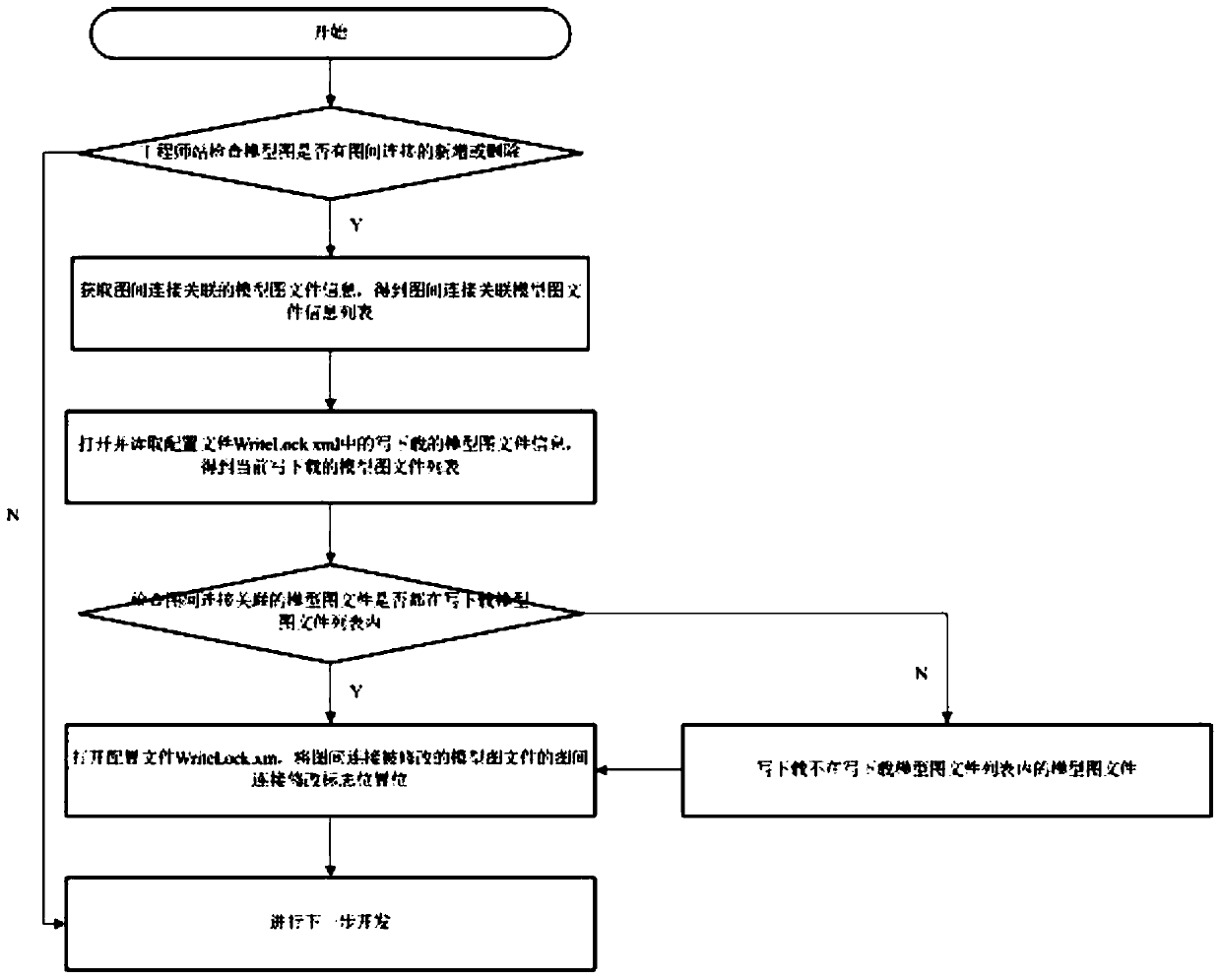
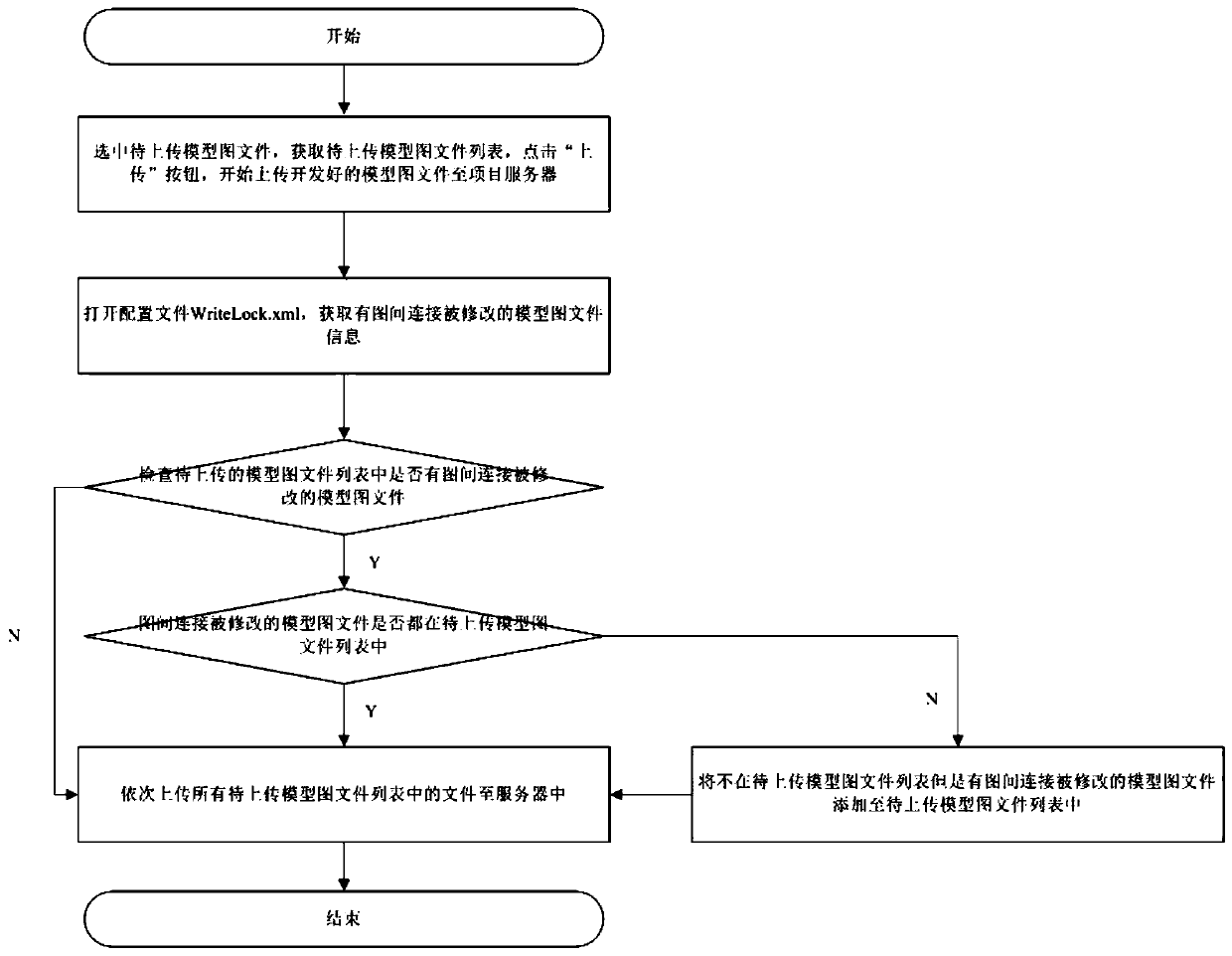
Method for guaranteeing inter-graph connection consistency of nuclear power station analog machine simulation system
ActiveCN111428379AEnsure consistencyGuaranteed correctnessDesign optimisation/simulationNuclear powerModelSim
The invention relates to a nuclear power station analog machine simulation system, in particular to an inter-graph connection consistency guaranteeing method in a nuclear power station analog machinesimulation technological process. Existing engineer station software does not have a guarantee mechanism for inter-graph connection consistency, so that the situation of inter-graph connection loss orinter-graph connection mismatching on a certain model graph occurs sometimes. The quality of nuclear power analog machine products is ensured. The method comprises the specific steps of 1, data downloading, 2, simulation modeling, 3, software inspection and 4, uploading integration. The invention can provide a method capable of guaranteeing the consistency of connection between graphs, and the quality of nuclear power analog machine products is guaranteed.
Owner:CHINA NUCLEAR POWER OPERATION TECH
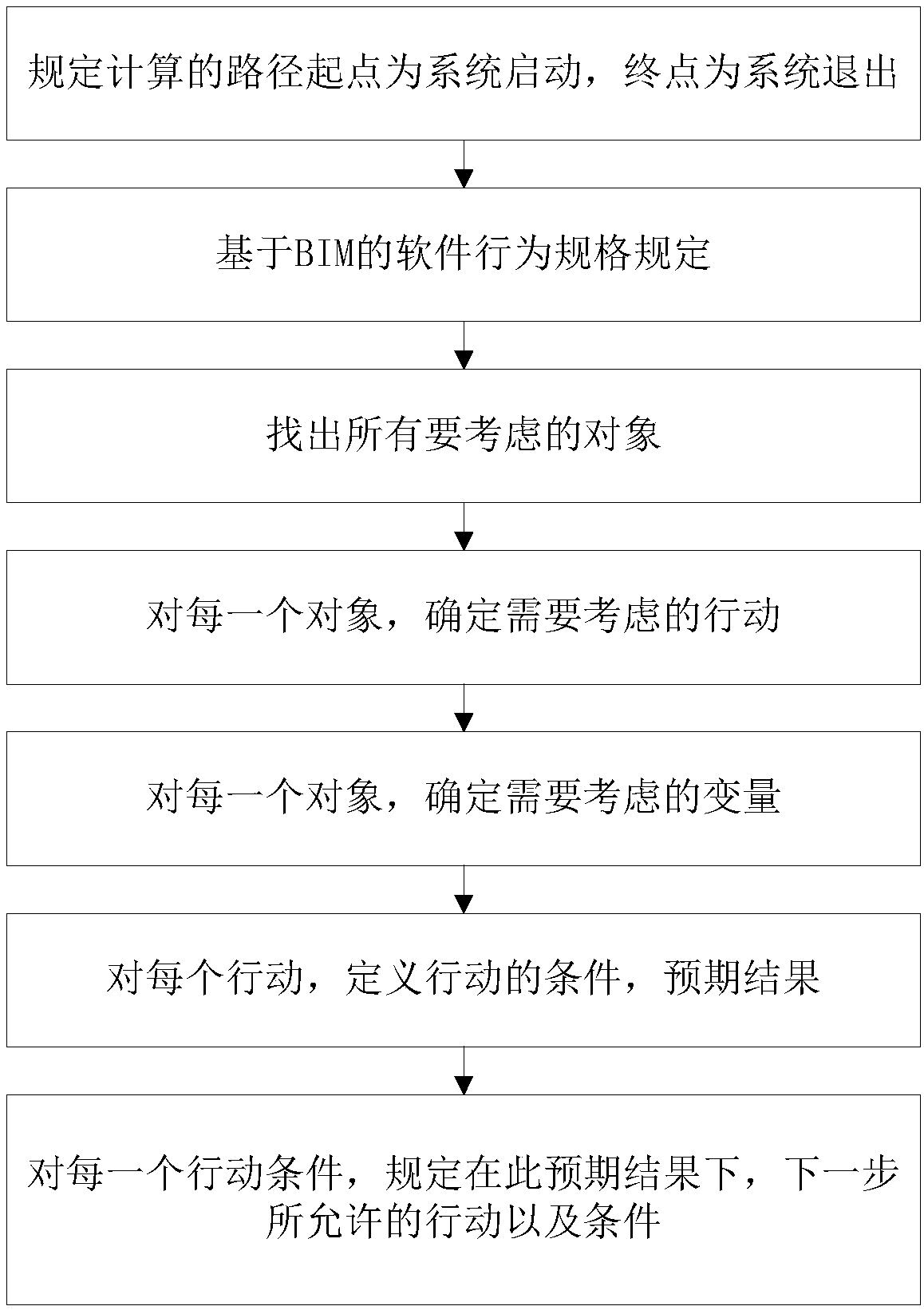
Software test case building method based on BIM
The invention relates to a method for establishing a software test case based on BIM, belonging to the technical field of software inspection and detection. The invention comprises the following steps: the first step: the starting point of the prescribed calculated path is system start, and the end point is system exit; Step 2: Software behavior specification based on BIM; Step 3: Find out what you want to consider. Step 4: Identify actions to be considered for each target; Step 5: Determine the variables to be considered for each object; Step 6: For each action, define the conditions of the action and the expected results; 7, for each action condition, specify that next allowed action and condition under the expected result: the invention realizes the establishment of the BIM t case through the combination of the software test case and the specific parameters of the BIM, and improves the establishment efficiency and the evaluation quality of the test case.
Owner:誉光工程咨询有限公司 +2
Action-Oriented analytics-driven electronic data identification and labeling
InactiveUS20130339277A1Digital computer detailsComputer security arrangementsDocumentationElectronic data
A corporate compliance / document retrieval system and method for enabling automated software inspection of textual documents based upon seeding the software with examples of categories of interest. The system enables resultant actions such as breach dismissals, breach escalations, closer inspection of an offender's communications, and iterative machine learning when specific content is detected that is representative of a category of interest. The alerting breaches occur in near real time and can alleviate further breaches from occurring.
Owner:FASTLINE TECH
Method for searching for non-standard requirements of locking rail temperature data of seamless track
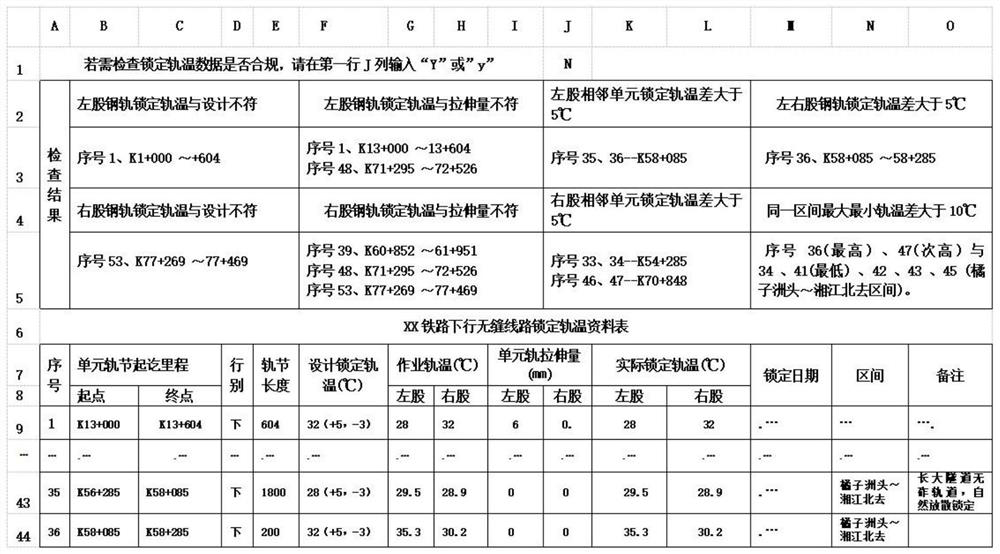
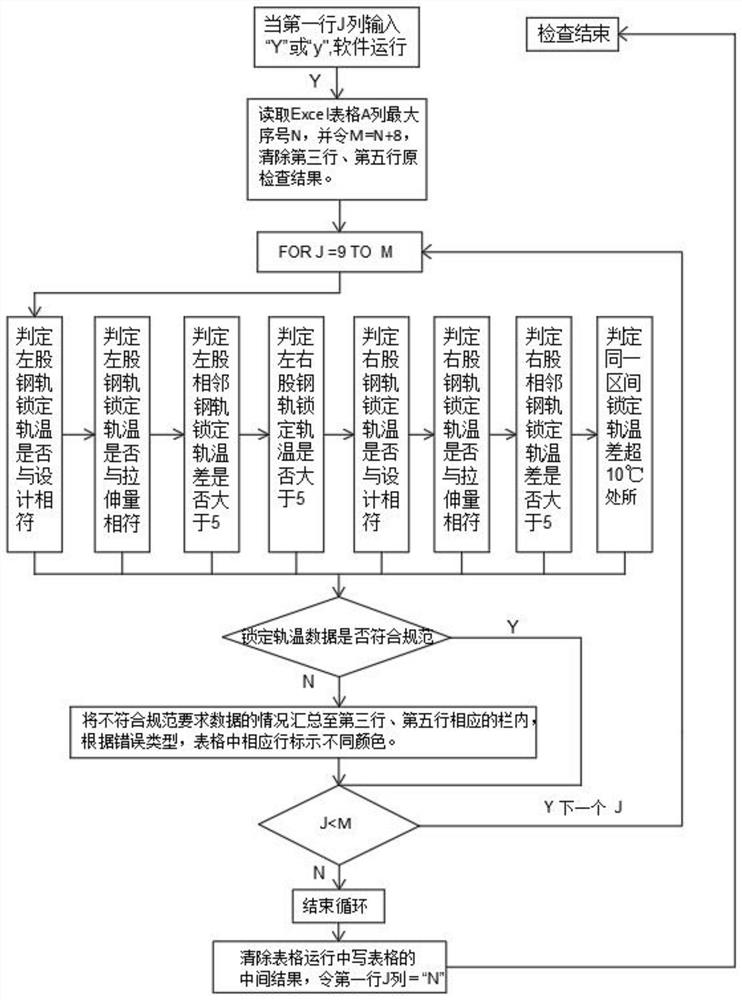
InactiveCN111881122AEasy to findQuick discoveryRelational databasesSpecial data processing applicationsDatasheetAlgorithm
The invention discloses a method for searching for non-standard requirements of locking rail temperature data of a seamless track, and the method comprises the following steps: 1, performing the following processing on a common seamless track locking rail temperature data EXCEL table: 1) inserting a header into five blank rows, wherein the first row is used for starting a software row; 2) making title bars of error types in the second row and the fourth row; 3) employing the third row and the fifth row for summarizing error data to a corresponding title bar after software inspection; 2, programming: 1) setting corresponding program starting conditions; 2) after the program is started, firstly reading the maximum serial number in the column A serial number column of the EXCEL table, and taking the serial number as a termination condition of program cycle operation; 3) performing programming according to the modules set in the previous step, determining whether the seamless track lockingrail temperature data meet the standard requirements or not through operation, and summarizing the non-compliant data into corresponding columns of the third row and the fifth row according to the error categories.
Owner:梁致源
Automatic Generation Method of Software Graphical User Interface Test Cases
ActiveCN105550110BLow costStrong ability to avoid risksSoftware testing/debuggingGraphicsMan machine
Owner:艾瑞克李
Software inspection system
A method for software inspection analyzes a body of computer code to assess whether the body of computer code contains malware. Various embodiments extract the executable elements of the body of computer code and modify those elements using rules defining the format of instructions for the programming language in which the computer code was written, and using rules defined from the security specification of that programming language, to produce a model of the body of computer code. The method then analyzes the model using a model checking system, which determines whether any of the language rules have been violated, in which case the method flags the computer code as potentially including malware.
Owner:TRUSTEES OF BOSTON UNIV
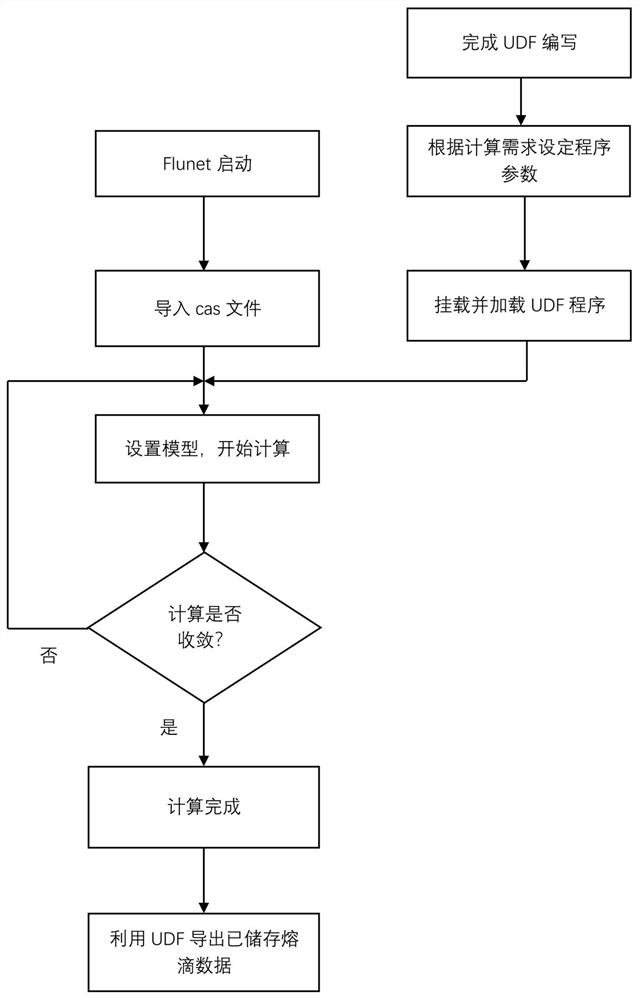
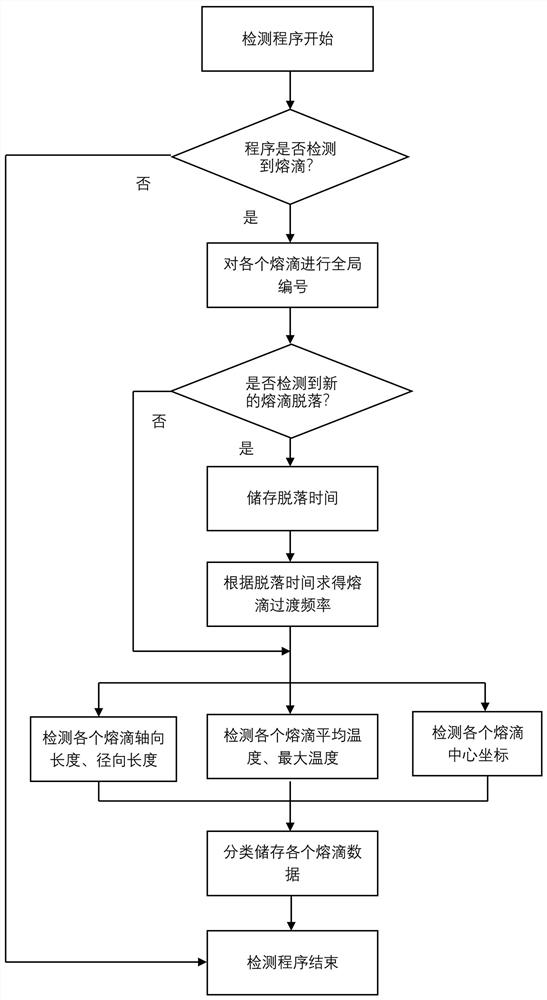
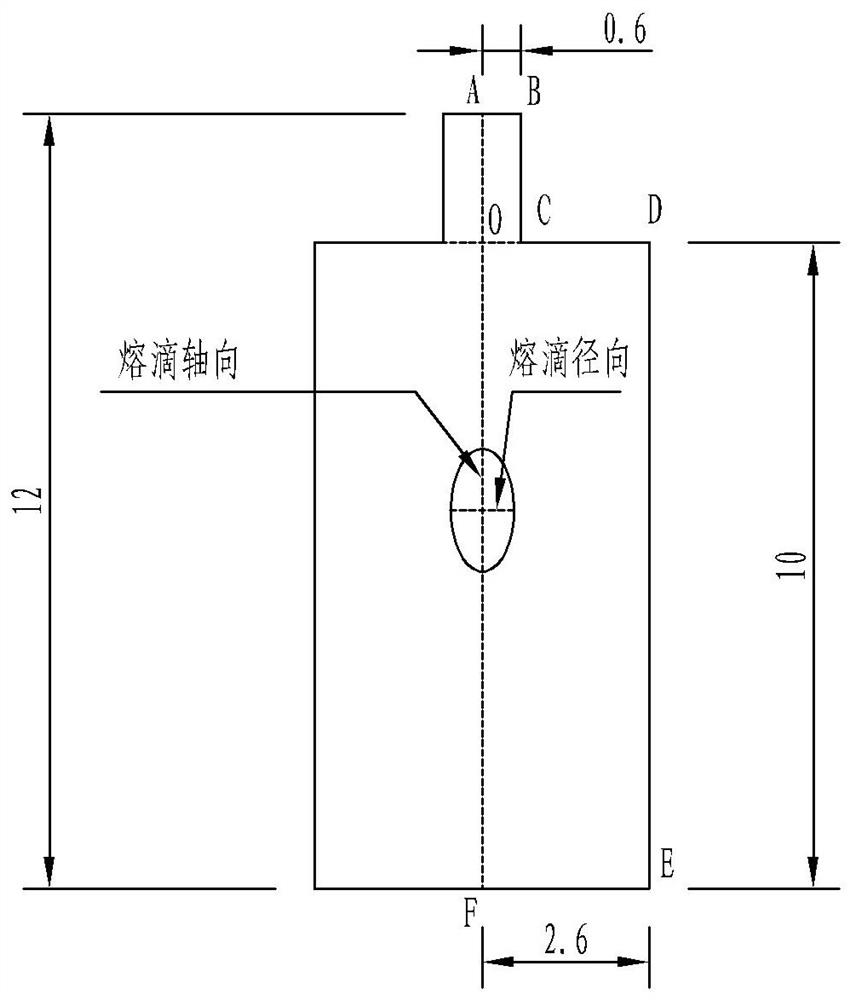
Automatic detection and storage method for welding droplet data based on Fluent UDF
ActiveCN113297806AImprove efficiencyImprove accuracyGeometric CADDesign optimisation/simulationComputational scienceError check
The invention relates to an automatic detection and storage method for welding droplet data based on Fluent UDF, and the method comprises the following steps: S1, building a droplet transition geometric model, and dividing a grid; S2, importing Fluent software, checking whether the grid volume has an error or not, and checking the grid proportion and quality; S3, adopting a multiphase flow VOF model as a simulation model; s4, acquiring material parameters of a gas phase and a liquid phase, and presetting boundary conditions; s5, based on a PISO solver, obtaining a control equation of each physical field; s6, according to program parameters such as the operation cycle and the detection precision of the droplet data automatic detection storage program, mounting the droplet data automatic detection storage program; s7, initializing the model, then starting calculation, and carrying out automatic detection and storage of molten drop data by utilizing a droplet data automatic detection and storage UDF (User Defined Function) program; and S8, finishing the calculation and carrying out convergence, and exporting all droplet data by using a DEFINE_ON_DEMAND macro function pre-packaged by software. According to the invention, droplet data can be effectively and accurately detected.
Owner:FUZHOU UNIV
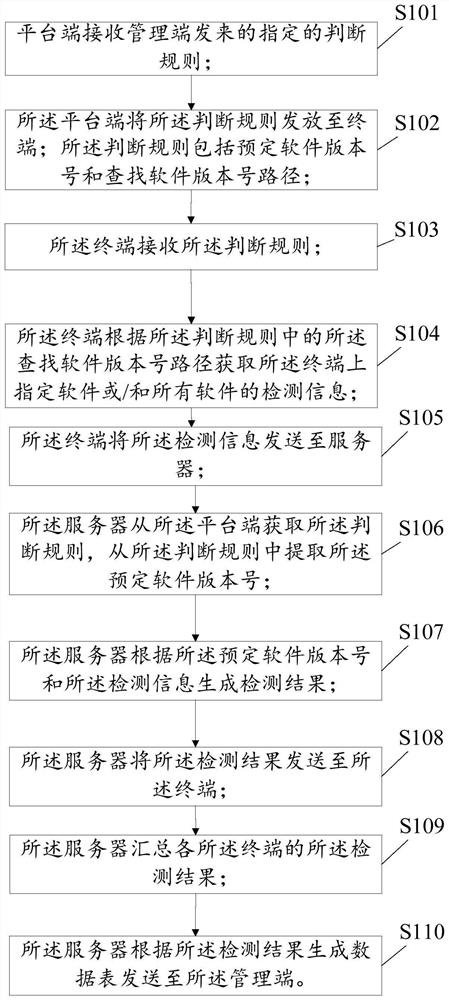
Method for checking genuine software, electronic equipment and storage medium
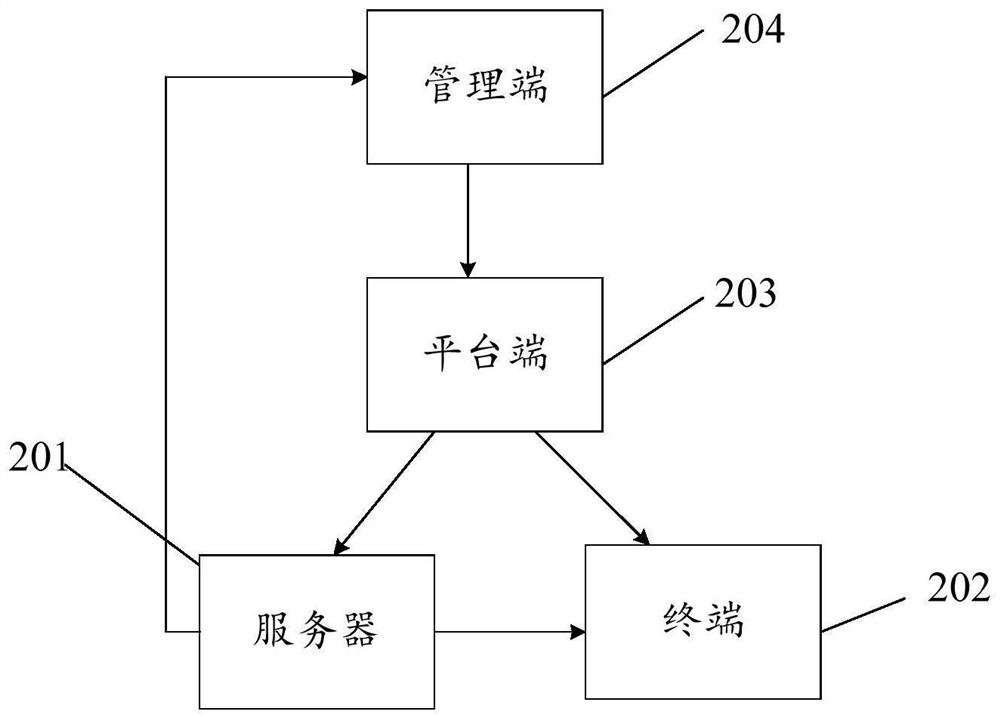
PendingCN114416465AQuick checkAccurate checkHardware monitoringProgram/content distribution protectionProgramming languagePathPing
The invention provides a genuine software checking method, electronic equipment and a storage medium. The genuine software checking method comprises the steps that a platform end receives a specified judgment rule sent by a management end and sends the judgment rule to a terminal, and the judgment rule comprises a preset software version number and a software version number searching path; the terminal obtains detection information of specified software on the terminal according to the software version number searching path in the judgment rule, and sends the detection information to the server; the server obtains the judgment rule from the platform end, extracts a preset software version number from the judgment rule, and generates a detection result according to the preset software version number and the detection information; the server sends a detection result to the terminal; and the server summarizes the detection results of the terminals, generates a data table and sends the data table to the management end. And the computer checks the software state and the violation condition in the computer according to the self software version number, so that the software in the computer can be quickly, accurately and comprehensively checked.
Owner:FIBRLINK NETWORKS
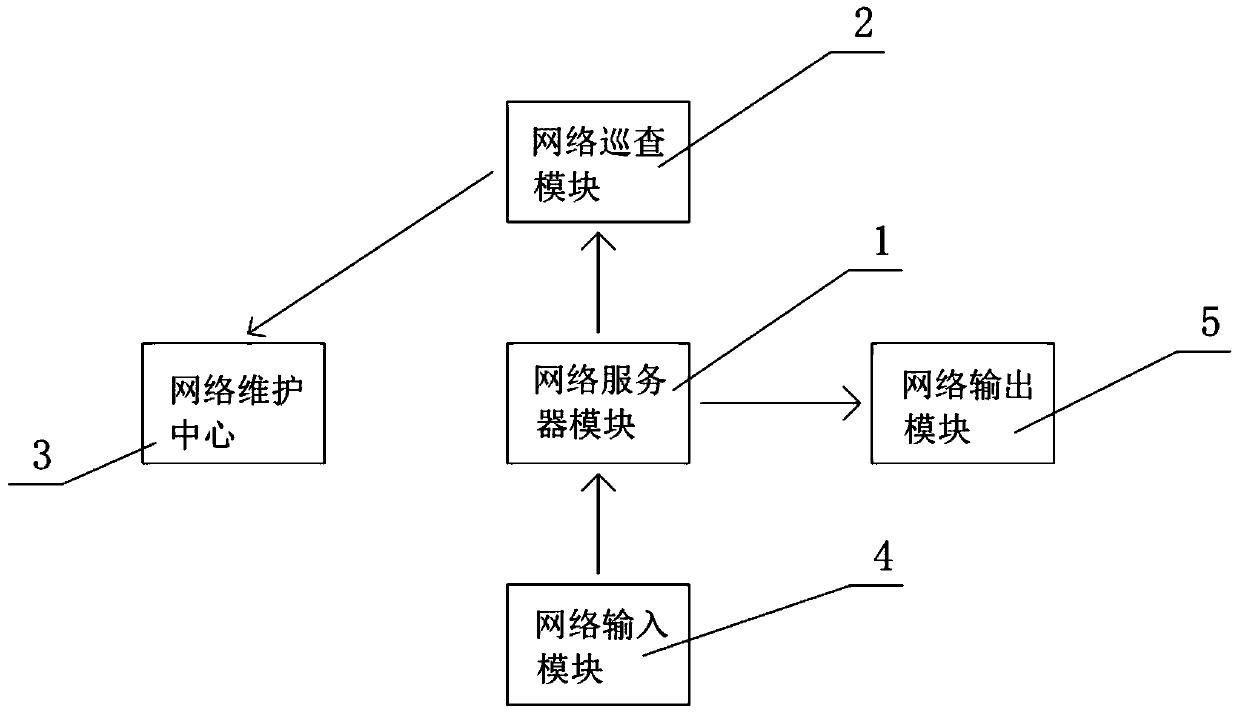
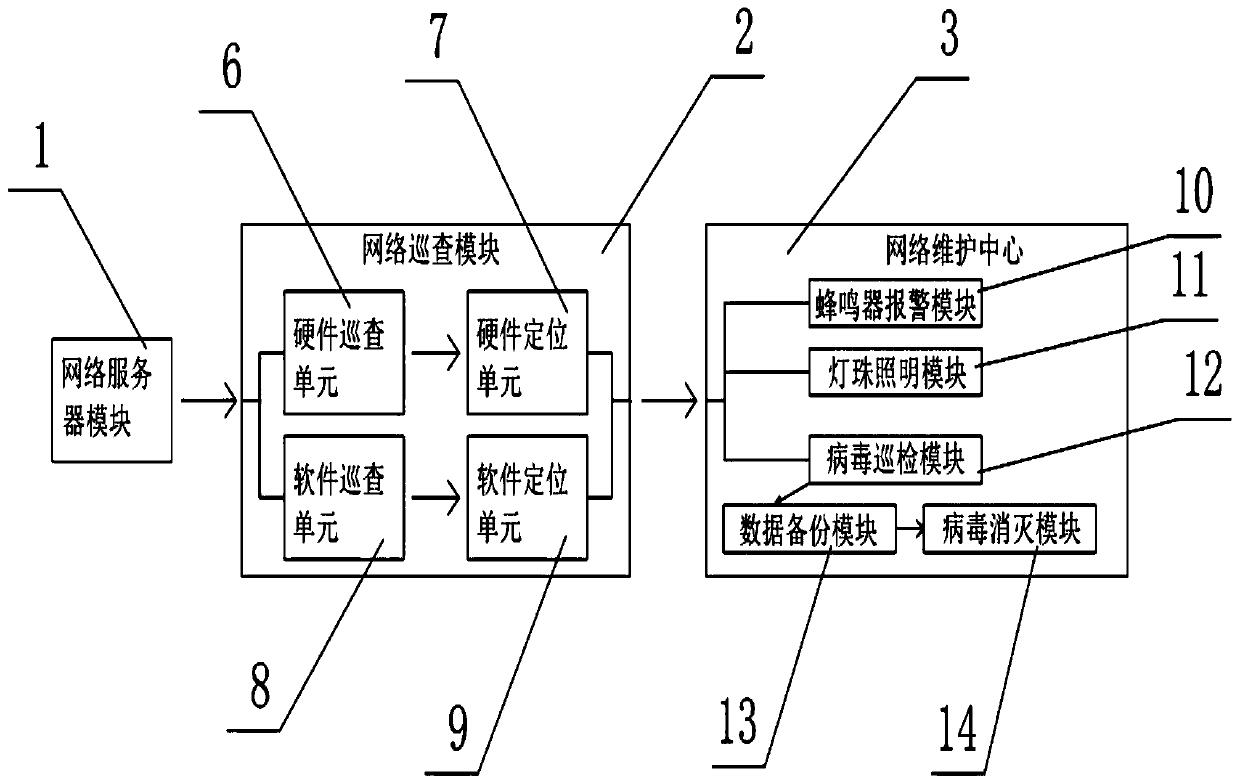
Maintenance system for communication network
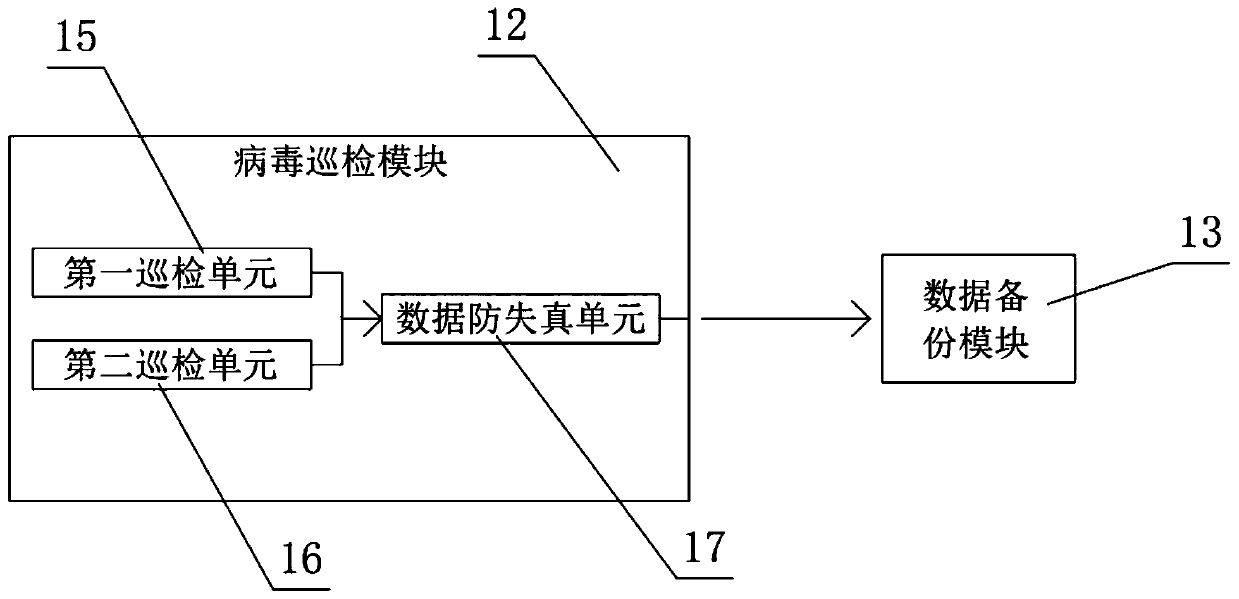
The invention relates to a maintenance system, in particular to a maintenance system for a communication network. The system comprises a network server module, a network inspection module, a network maintenance center, a network input module and a network output module, through a hardware inspection unit and a hardware positioning unit, inspection work can be timely carried out on normal operationconditions of a network influenced by phenomena of short circuit, disconnection and the like of hardware, and inspection work can be timely carried out on normal operation conditions of the network influenced by existence of virus invasion of software through a software inspection unit and a software positioning unit. The specific category of the virus is checked and analyzed again through a virus inspection module, so that the working speed of the maintenance system on network maintenance is increased; under the effect that the data backup module has multiple backup modes, multi-path data backup work is carried out on the terminal using the communication network, and the phenomenon of data loss is effectively prevented.
Owner:HLJ E LINK NETWORK CORP LTD
Assistant PCB design software system and method
ActiveCN105938507ASave on errors and omissionsImprove design efficiencySpecial data processing applicationsData inputDesign software
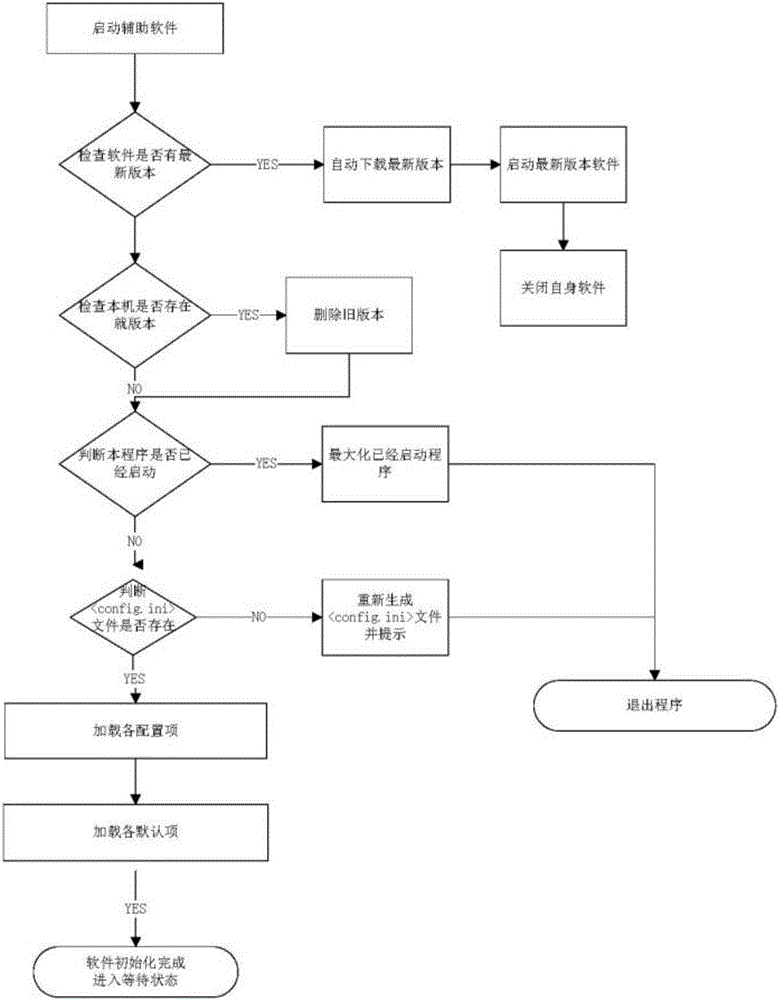
The present invention relates to an assistant PCB design software system. The method comprises the following steps of starting assistant software, detecting whether the software has a latest version, if so, automatically downloading the latest version, starting the latest version software, and closing the self software; detecting whether a native machine has an older version, and if so, deleting the older version; determining whether program is already started, if so, maximizing the already started program, and finally existing the program; determining whether a file exists; loading configuration items; and completing software initialization and entering a waiting state. According to AD9 software, by adoption of a simulation keyboard mode, entry data and software are automatically input into coordinates and network, so that required test points and network are arranged, and errors and omissions caused by manual data input are prevented. According to the software, the coordinate test points can be automatically arranged according to the given data, a corresponding schematic library can also be generated, network connection relation is automatically disposed, automatic contrasting of the network relation in the later period is supported, design efficiency is largely improved, and design quality is ensured.
Owner:深圳市明信测试设备股份有限公司
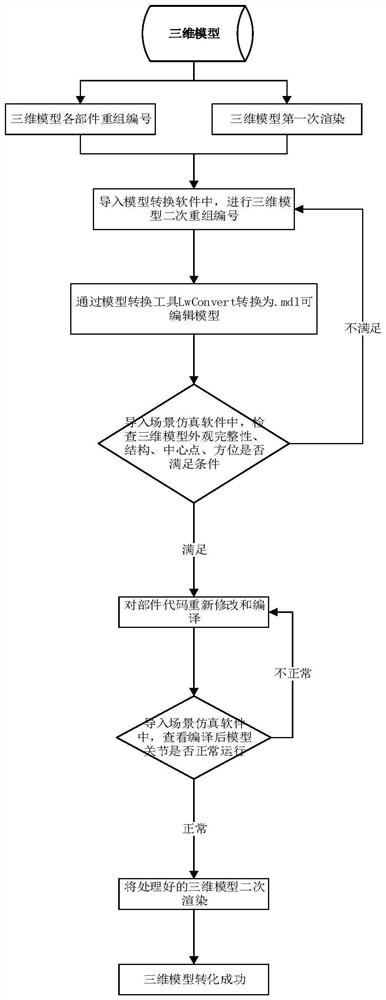
Three-dimensional model conversion method
PendingCN114187430APreserve authenticityPreserve integrityGeometric CADDesign optimisation/simulationAlgorithmModel transformation
The invention provides a three-dimensional model conversion method, which comprises the following steps of: performing first rendering on a first helicopter complete machine model to obtain a second helicopter complete machine model; importing the second helicopter complete machine model into model conversion software to obtain a third helicopter complete machine model; importing the third helicopter complete machine model into a model conversion tool to form a fourth helicopter complete machine model; importing the fourth helicopter complete machine model into scene simulation software; if the preset condition is met, code re-modification and compiling are carried out on components of the fourth helicopter complete machine model, and a fifth helicopter complete machine model is obtained; the fifth helicopter complete machine model is imported into AGI STK software, and whether parts of the fifth helicopter complete machine model operate normally or not is checked; and if the parts of the fifth helicopter complete machine model operate normally, performing second rendering on the second helicopter complete machine model to complete conversion.
Owner:CHINA HELICOPTER RES & DEV INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com