Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54 results about "Email security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
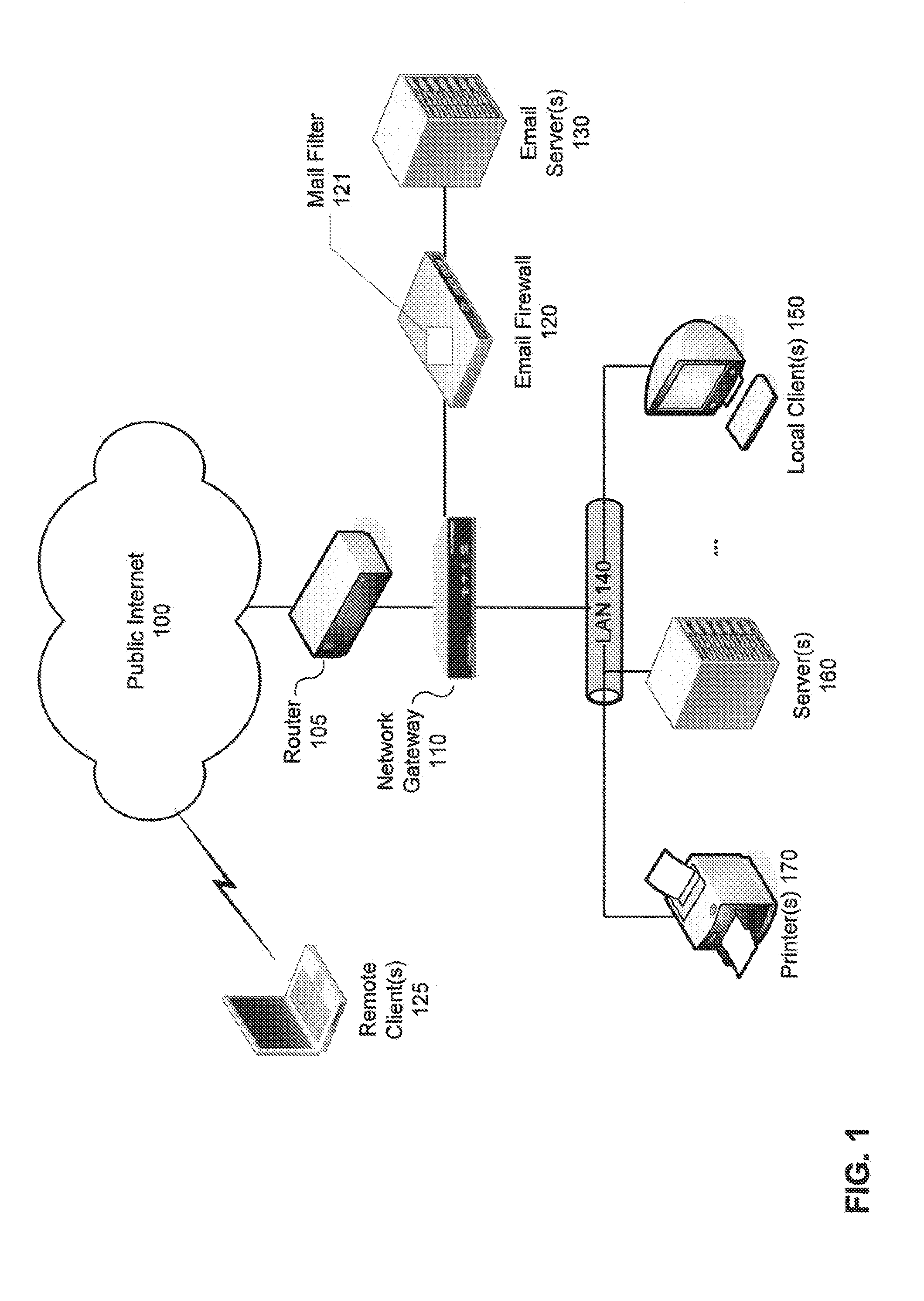
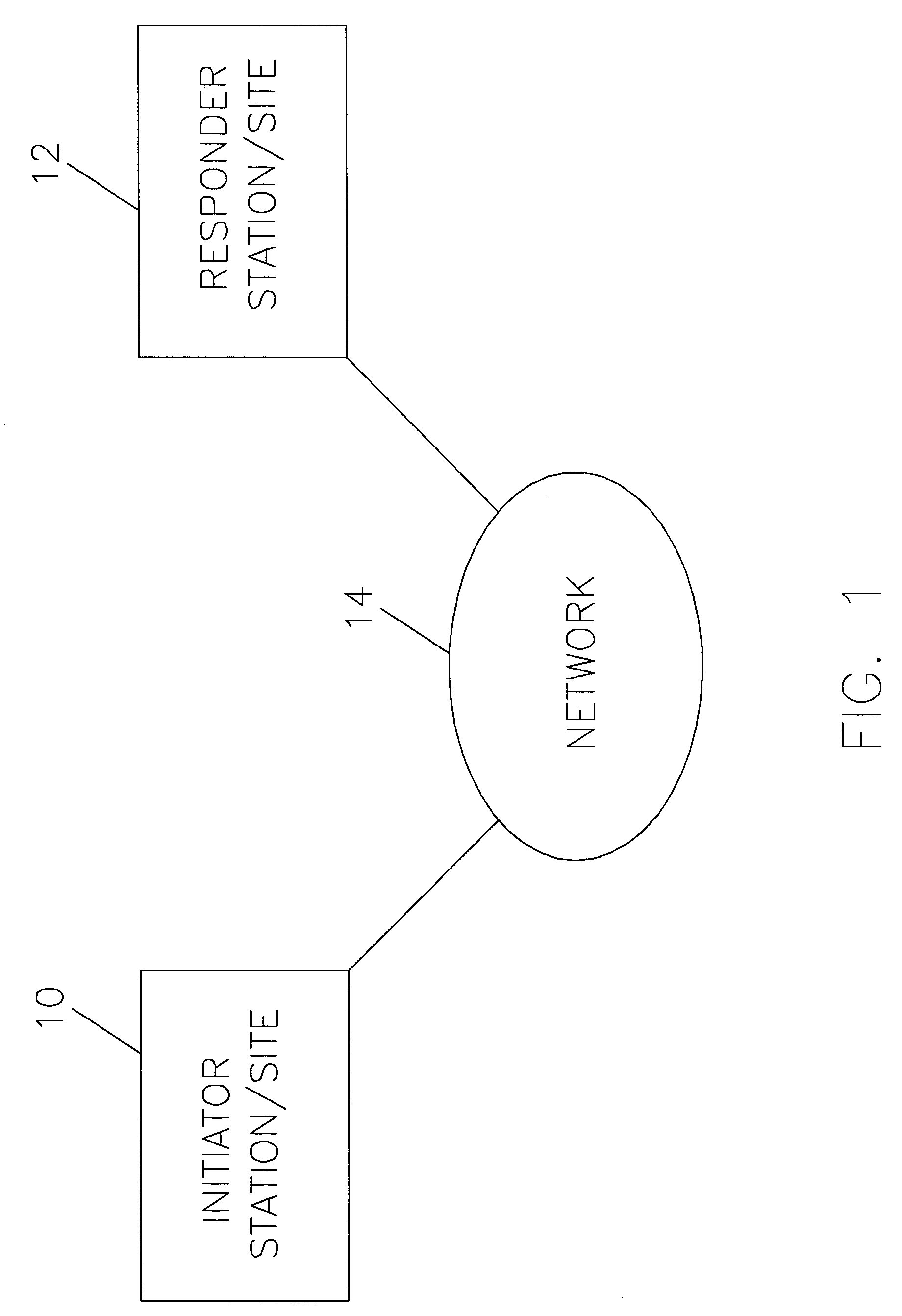
Universal recallable, erasable, secure and timed delivery email
ActiveUS20050267937A1Easy to acceptMultiple digital computer combinationsData switching networksWeb siteWorld Wide Web
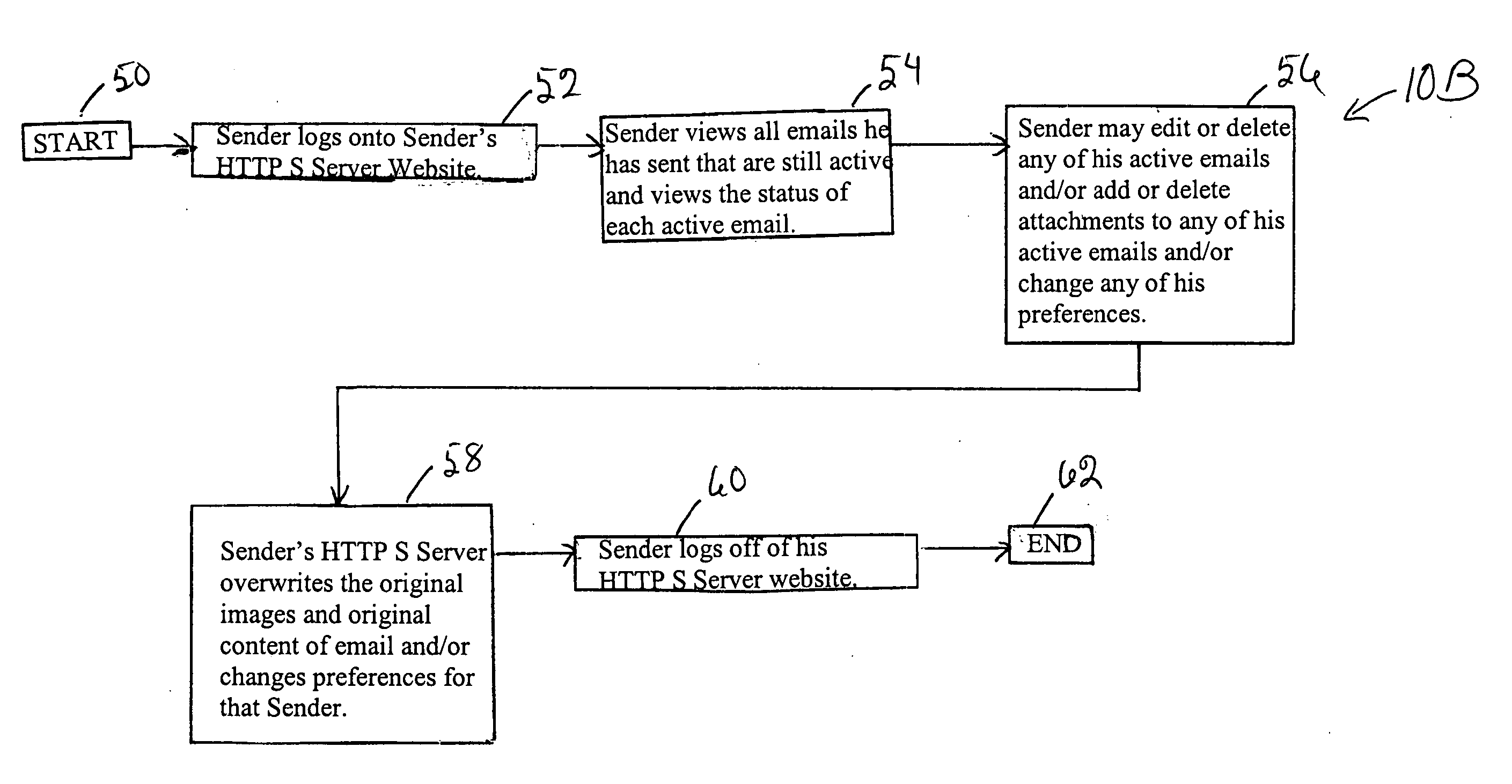
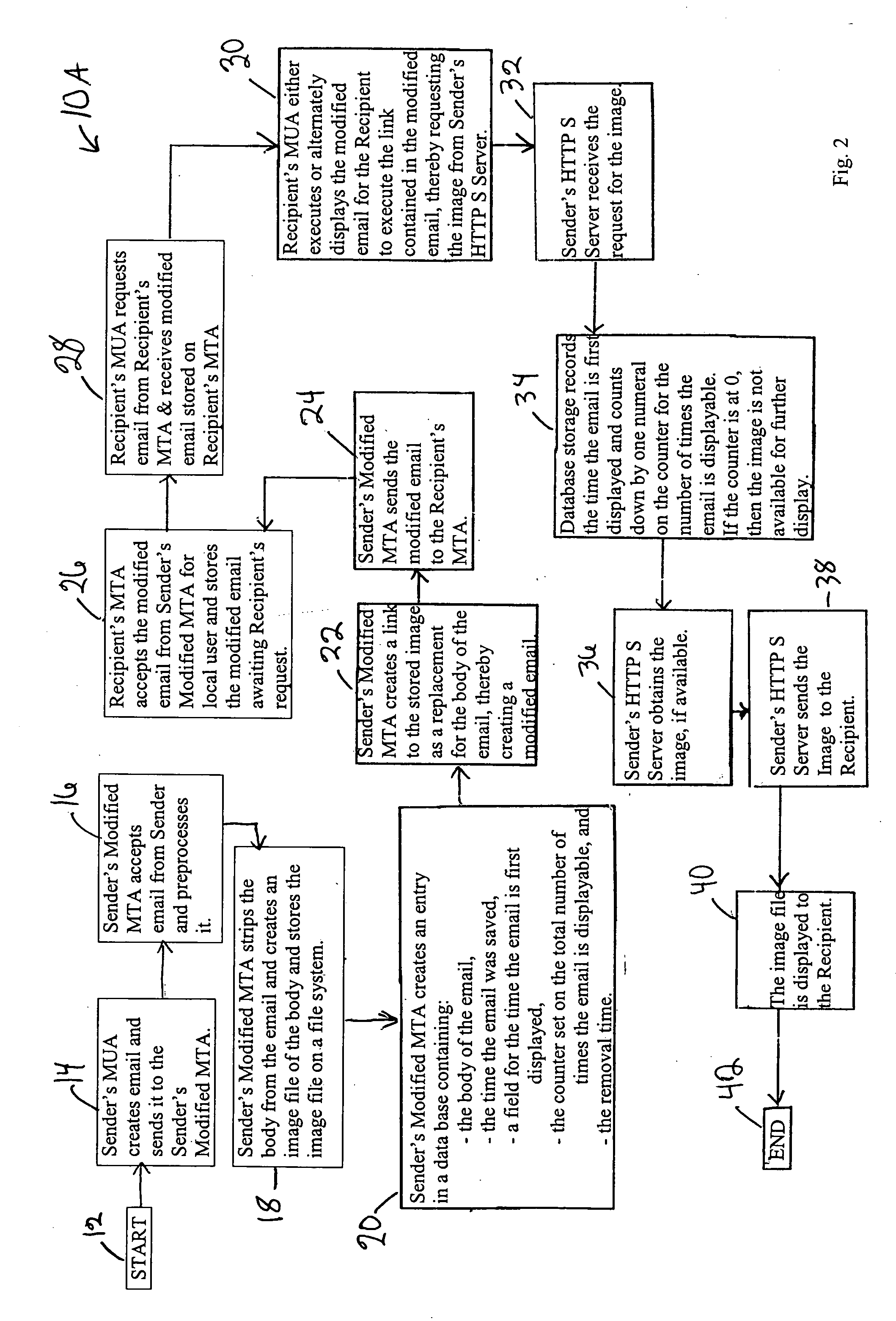
A process for secure, recallable and erasable delivery of email employing a modified sender's MTA that preprocesses email prior to sending a substituted modified email to the recipient's MTA. The sender's MTA preprocesses the email by first stripping the body from the email and creating an image file of the body and a separate image file for each attachment, then creating an entry into a data base containing the body of the email, time saved, destroy time, a field for logging time first displayed, and optionally a counter for total number of times displayable, and finally creating a link to the stored image and substituting the link for the body in the email. The recipient views the email or attachments when the link is executed. The sender can edit or delete any active email and attachments he has sent by logging onto the website of sender's HTTP S server.
Owner:TAMIRAS PER PTE LTD LLC
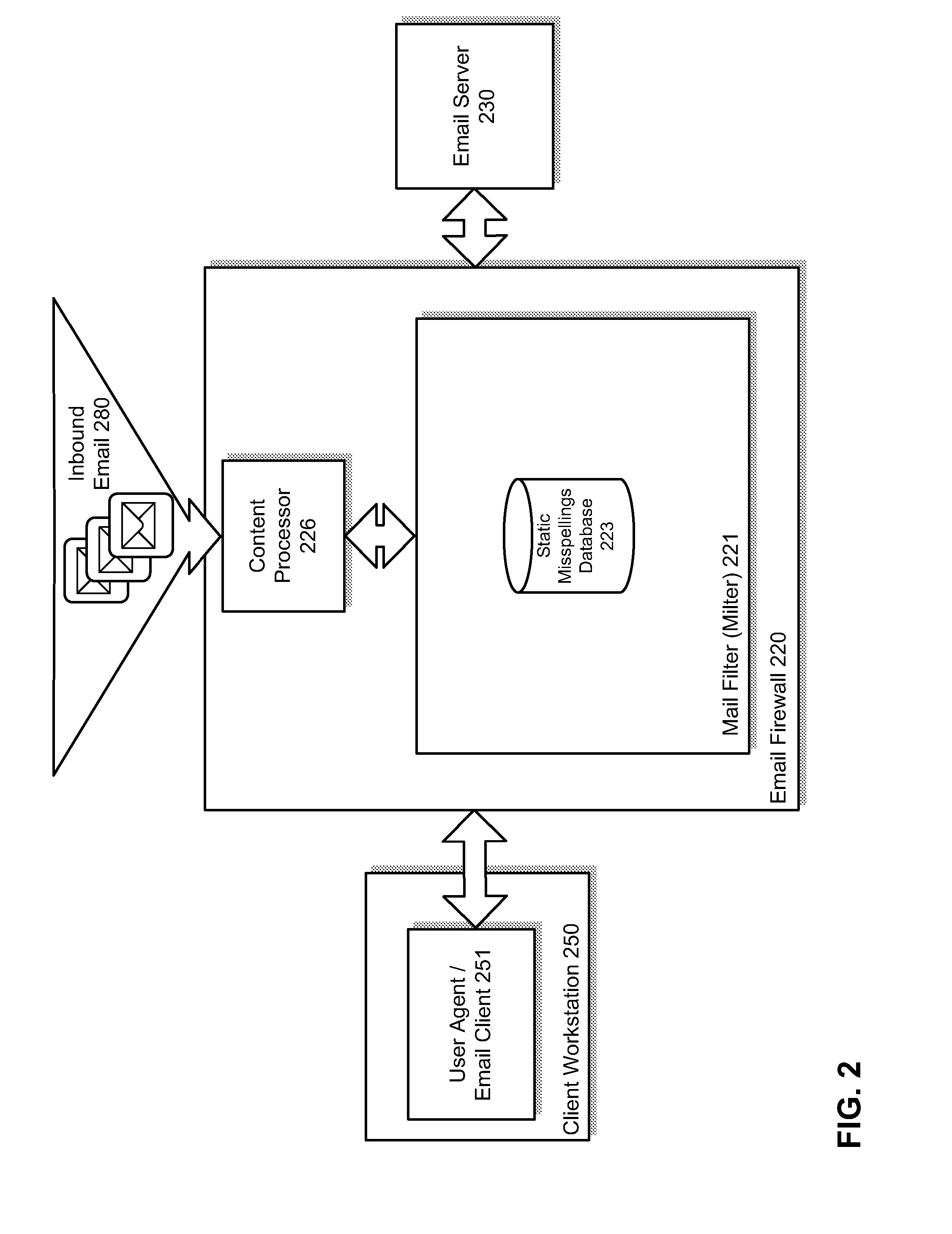
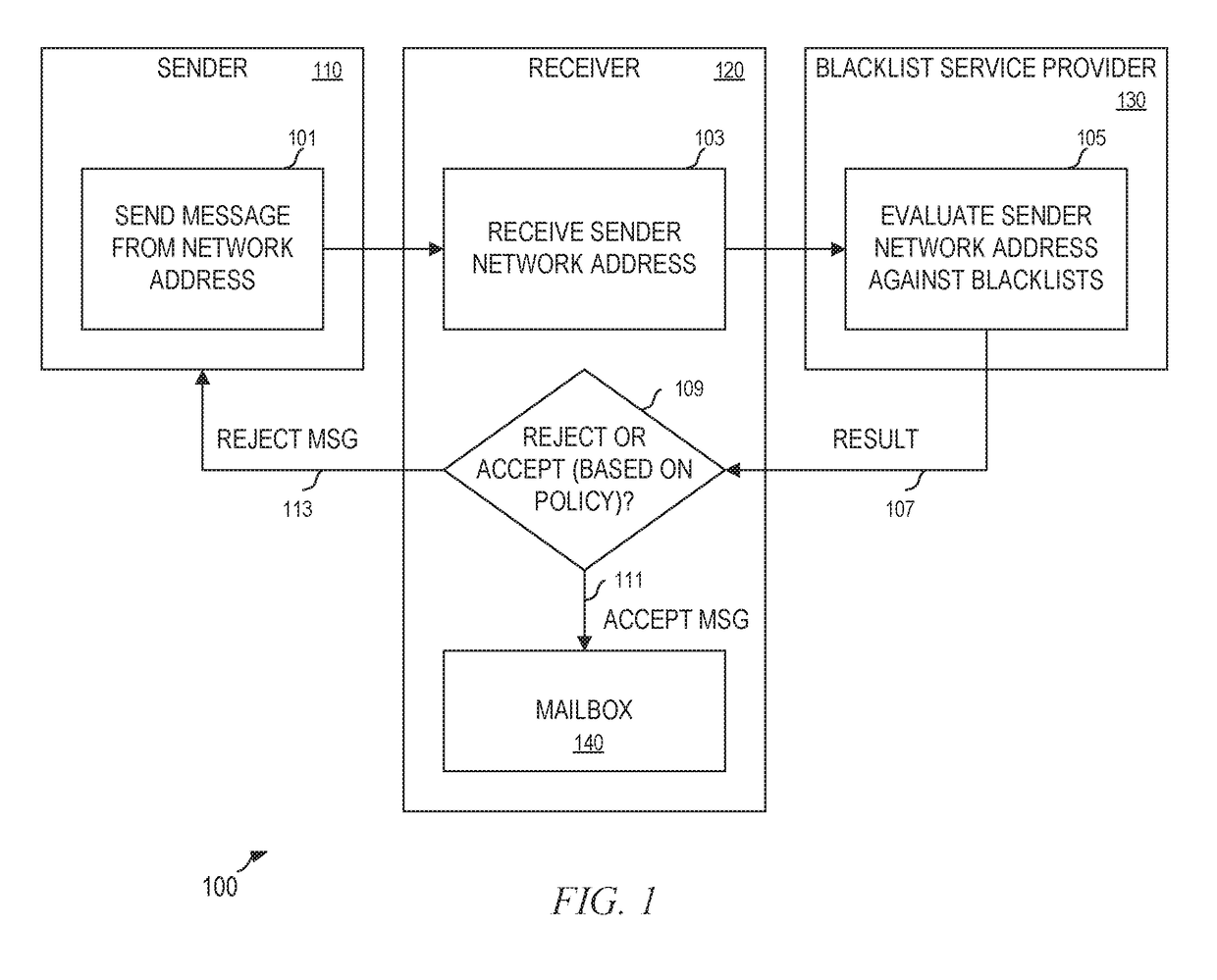
Detection of suspicious traffic patterns in electronic communications
InactiveUS20100095377A1Memory loss protectionError detection/correctionTraffic capacityInternet privacy
Methods and systems for detecting suspicious traffic patterns in electronic communications are provided. According to one embodiment, an electronic mail (email) message is received by a mail filter (milter), which evaluates a traffic pattern represented by the email message by scanning information associated with the email message and comparing it to information associated with one or more traffic analysis profiles. If the email message is identified by the milter as being inconsistent with normal email traffic patterns as represented by the one or more traffic analysis profiles, then the milter causes the email message to be handled in accordance with an email security policy associated with suspicious traffic patterns. For example, in the context of an outbound message, the originator may be alerted to a factor contributing to the identification and the originator may be provided with an opportunity to address the factor.
Owner:FORTINET
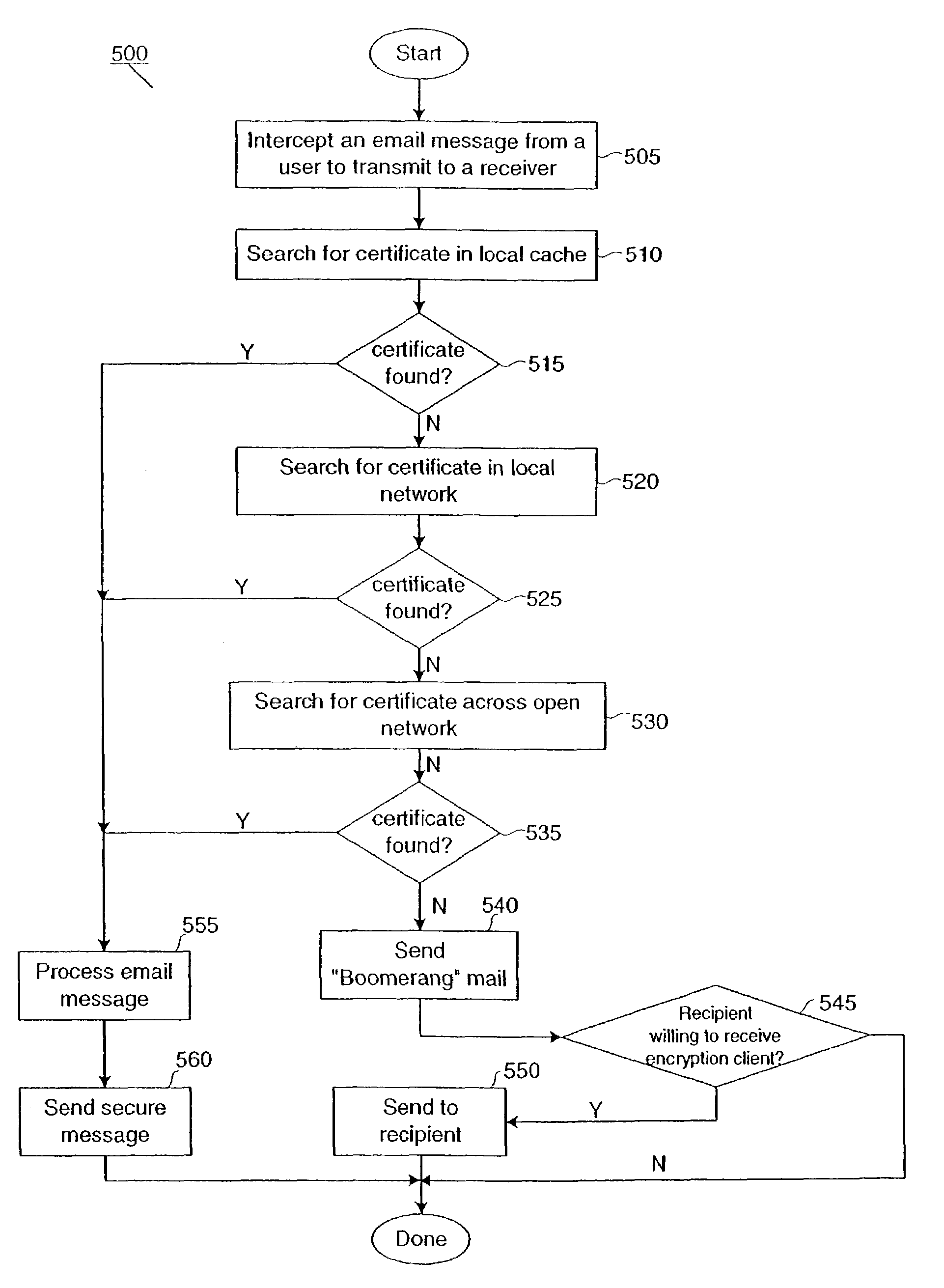
System and method for secure electronic communication in a partially keyless environment
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
Method and system for email privacy, security, and information theft detection
Owner:MIRAGE DATA INC
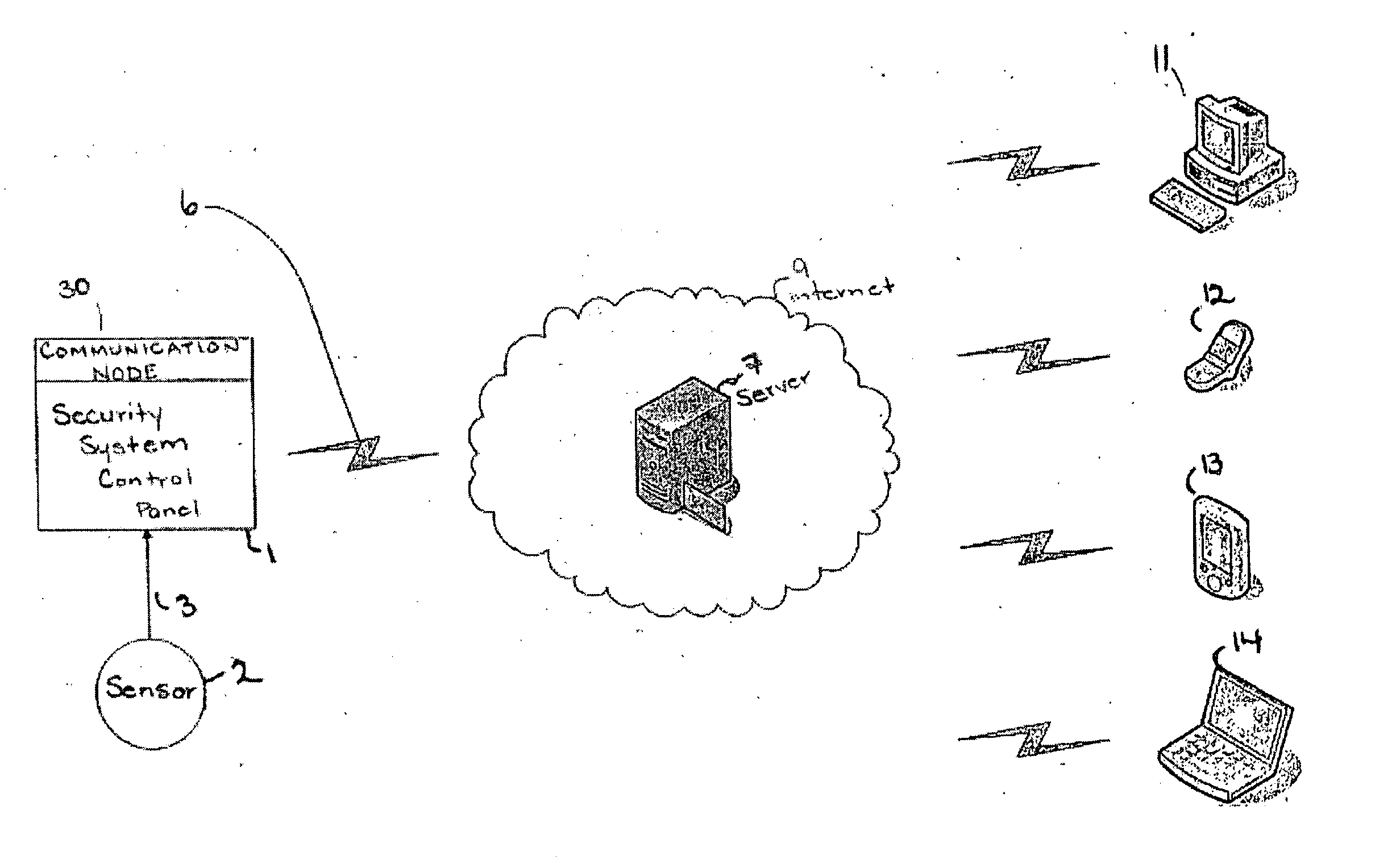
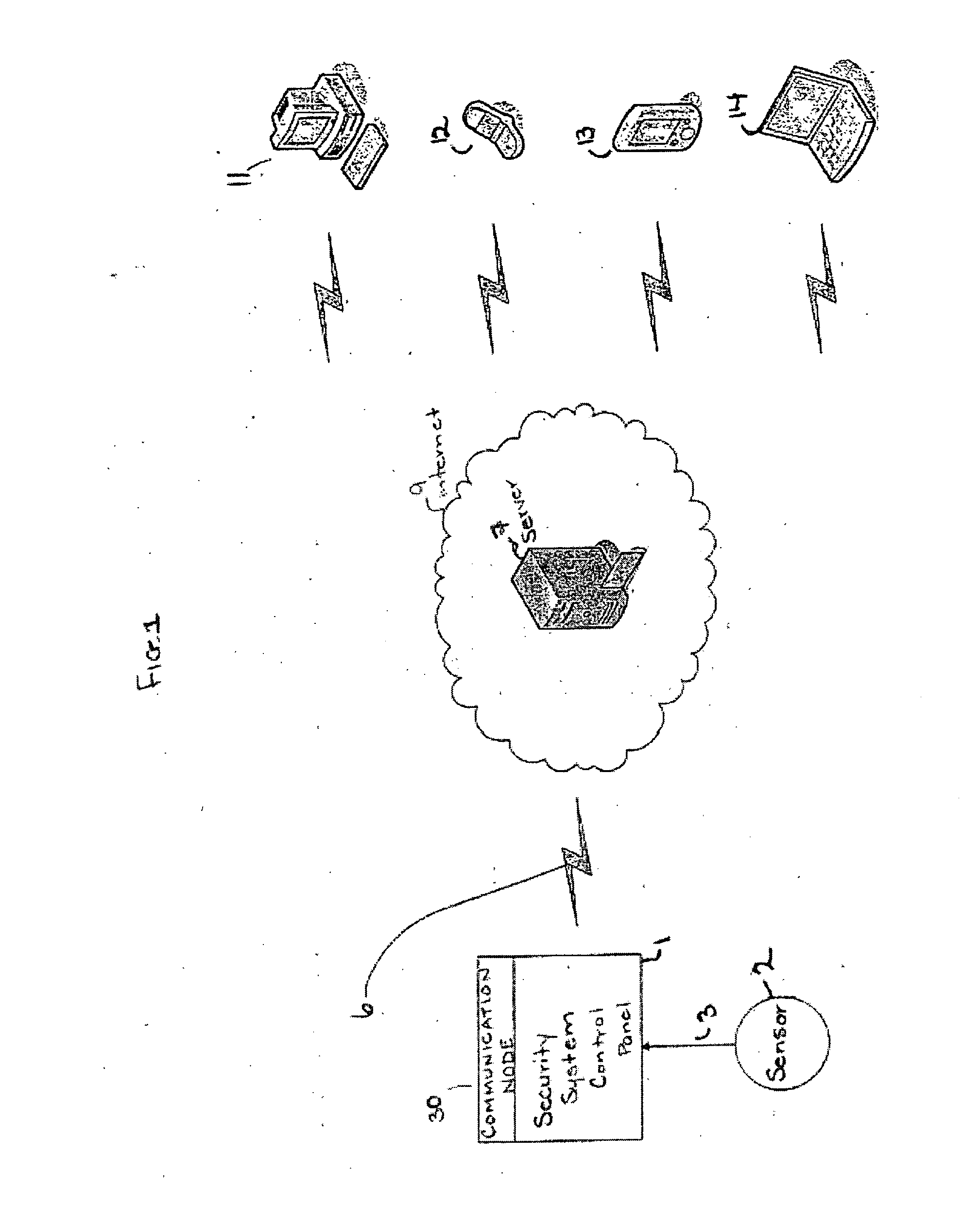
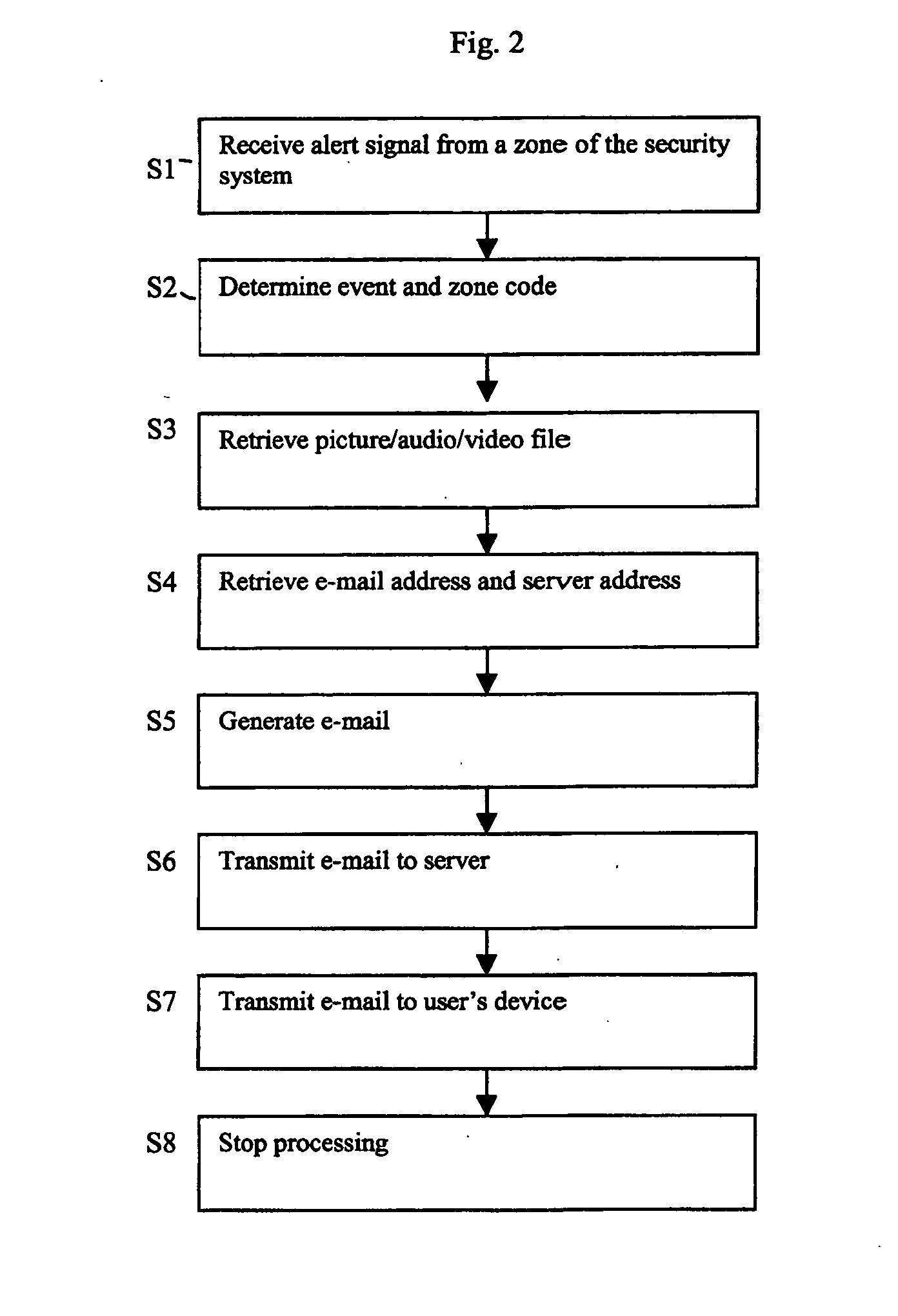
Security system reporting events through e-mail massages
ActiveUS20070085676A1Frequency-division multiplex detailsTime-division multiplexUser deviceInternet privacy
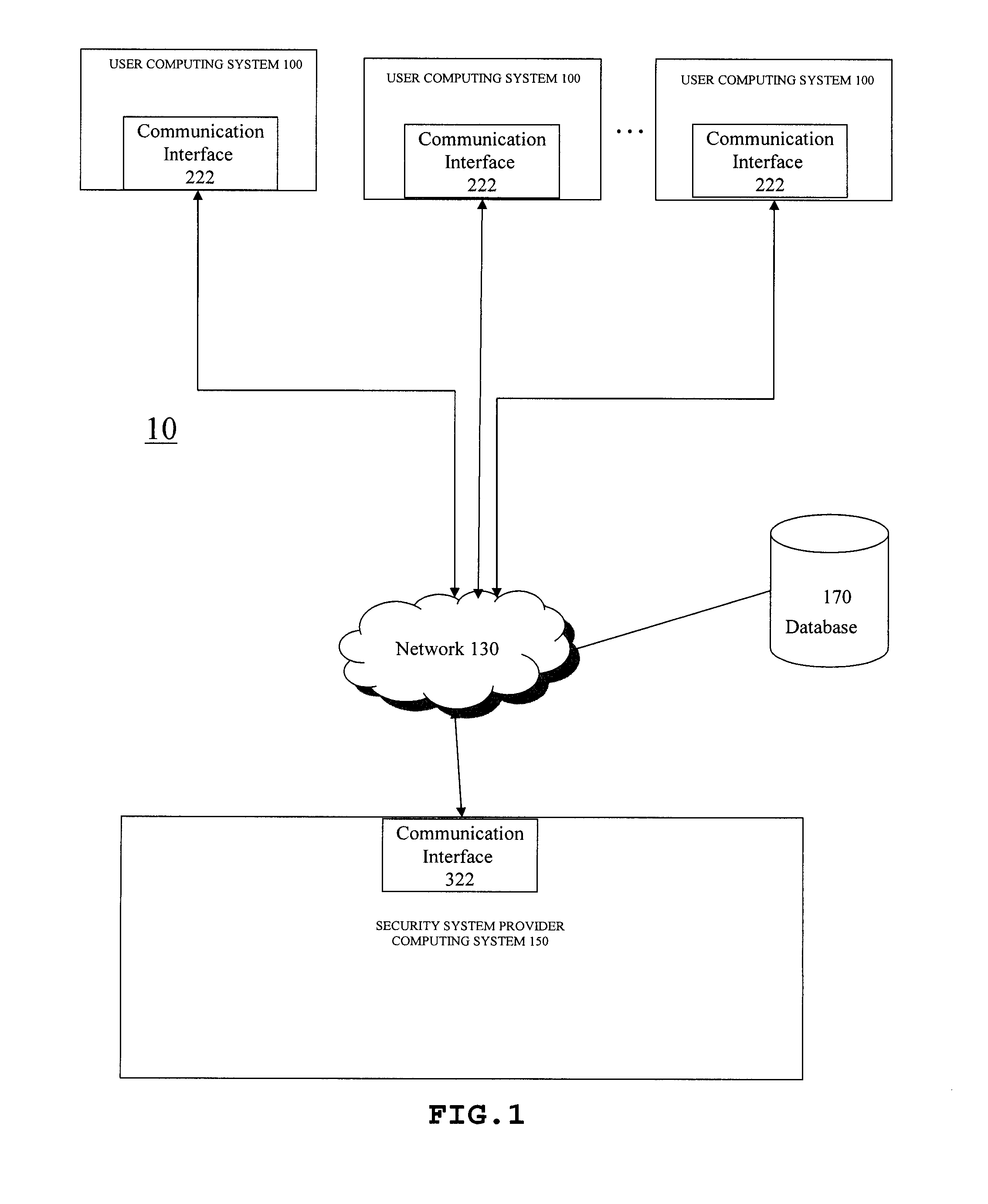
Security system communication with a user device via electronic means, including via e-mail transmitted over the internet are provided. A security system interface receives a signal indicating an occurrence of an event, such as a fault or alarm condition, in a zone of the security system; a memory stores a user e-mail address associated with the security system and the address of a server for providing internet service, such as an ISP server; and an e-mail generator transmits to the server an e-mail message based on the event. The communication node in such a system may be integrated with the control panel of the security system. The e-mail generator can transmit the e-mail using SMTP or other TCP / IP. An attachment of the e-mail, such as a picture or an audio or video file relevant to the event or the zone may be transmitted.
Owner:ADEMCO INC
Method and system for email privacy, security, and information theft detection
ActiveUS20160094566A1Provide privacyProvide securityDigital data authenticationData switching networksEmail privacyEmail address
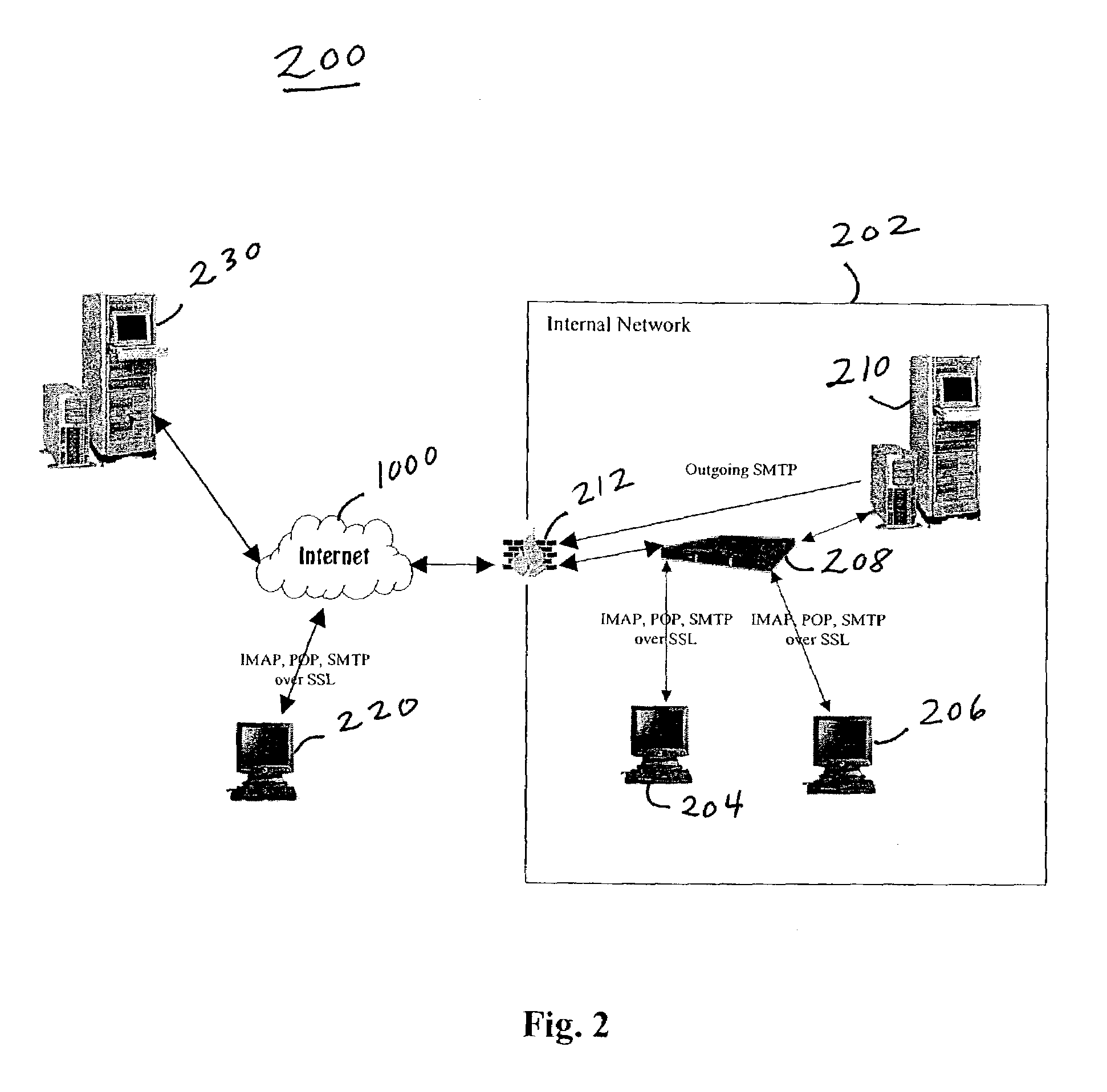
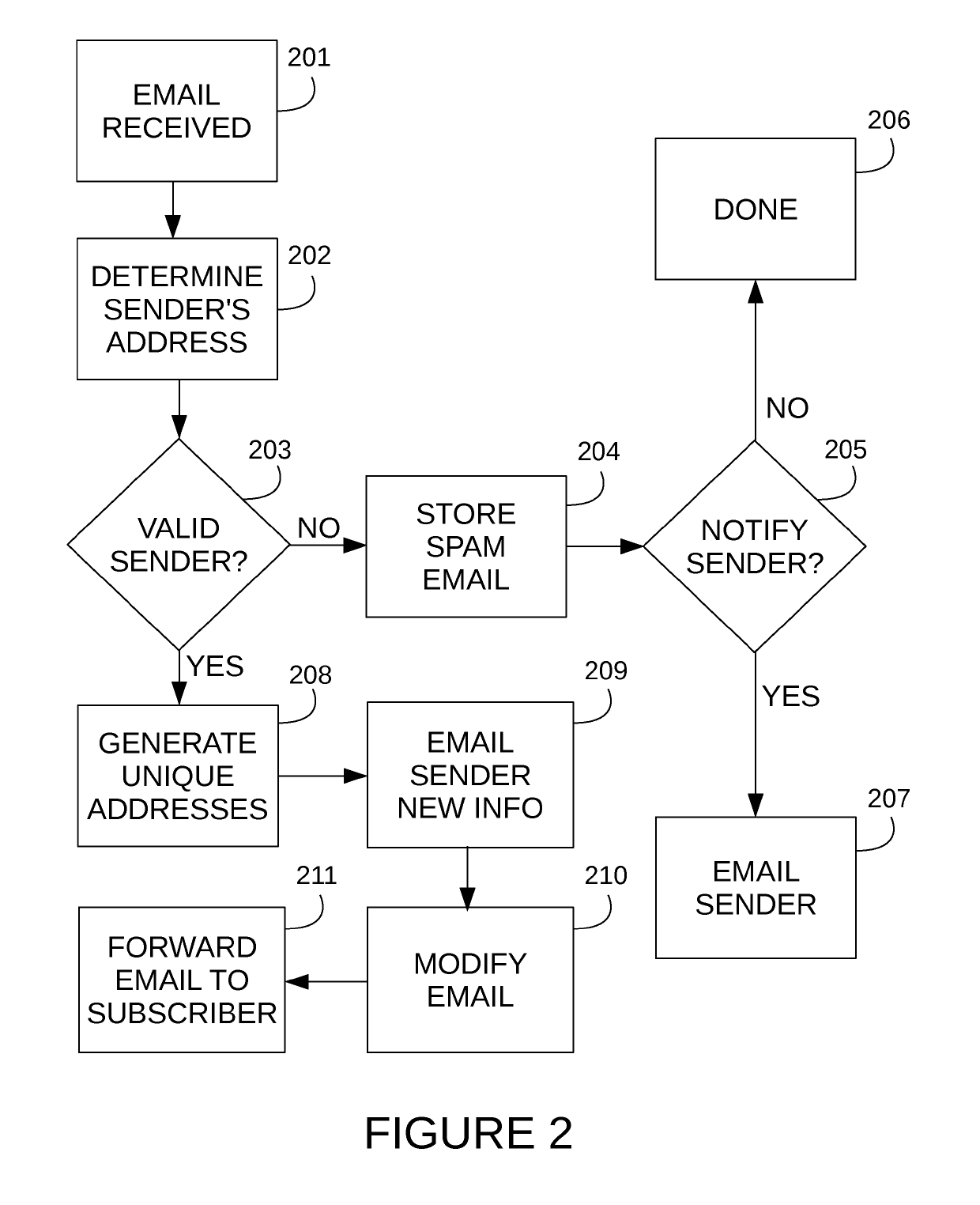
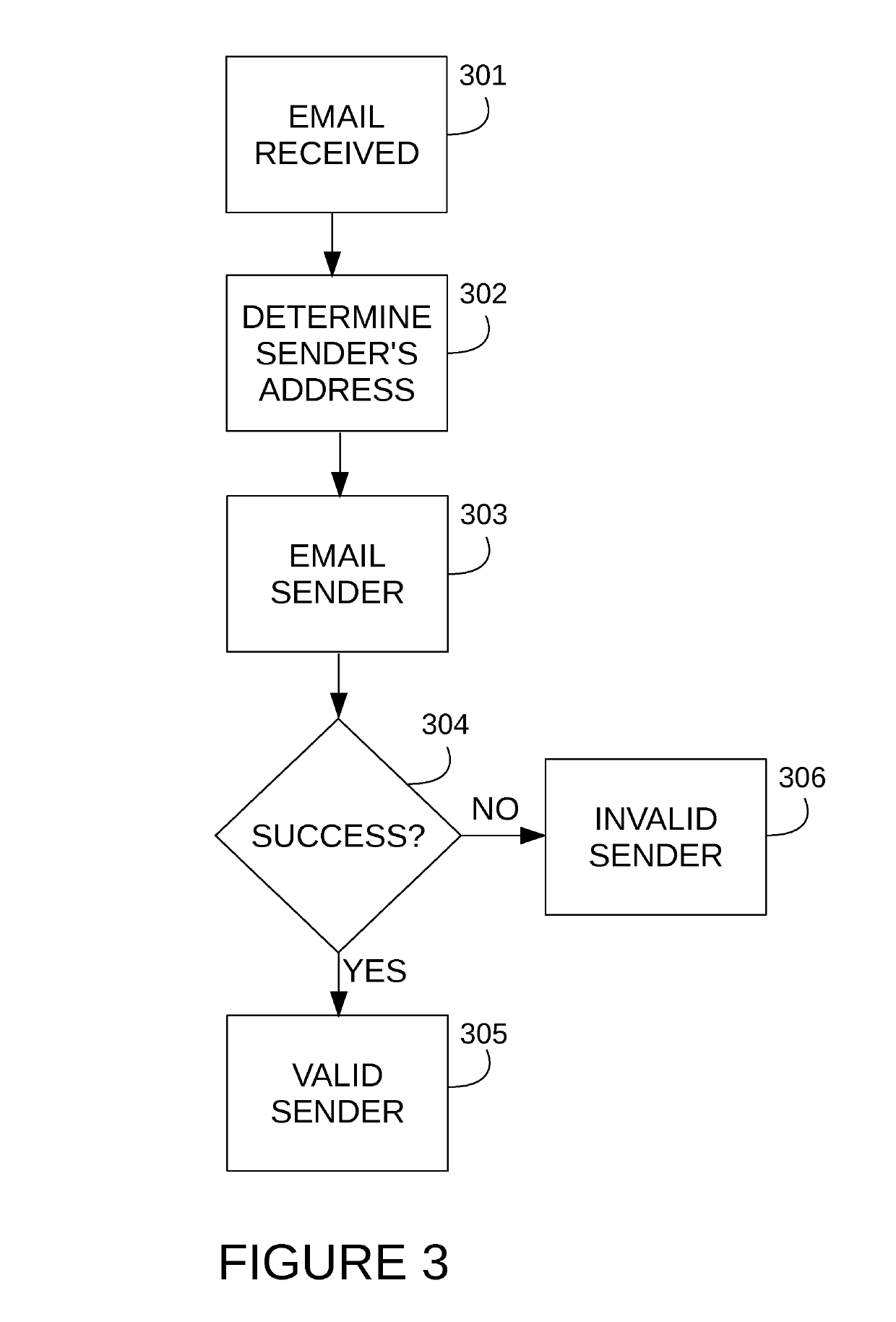
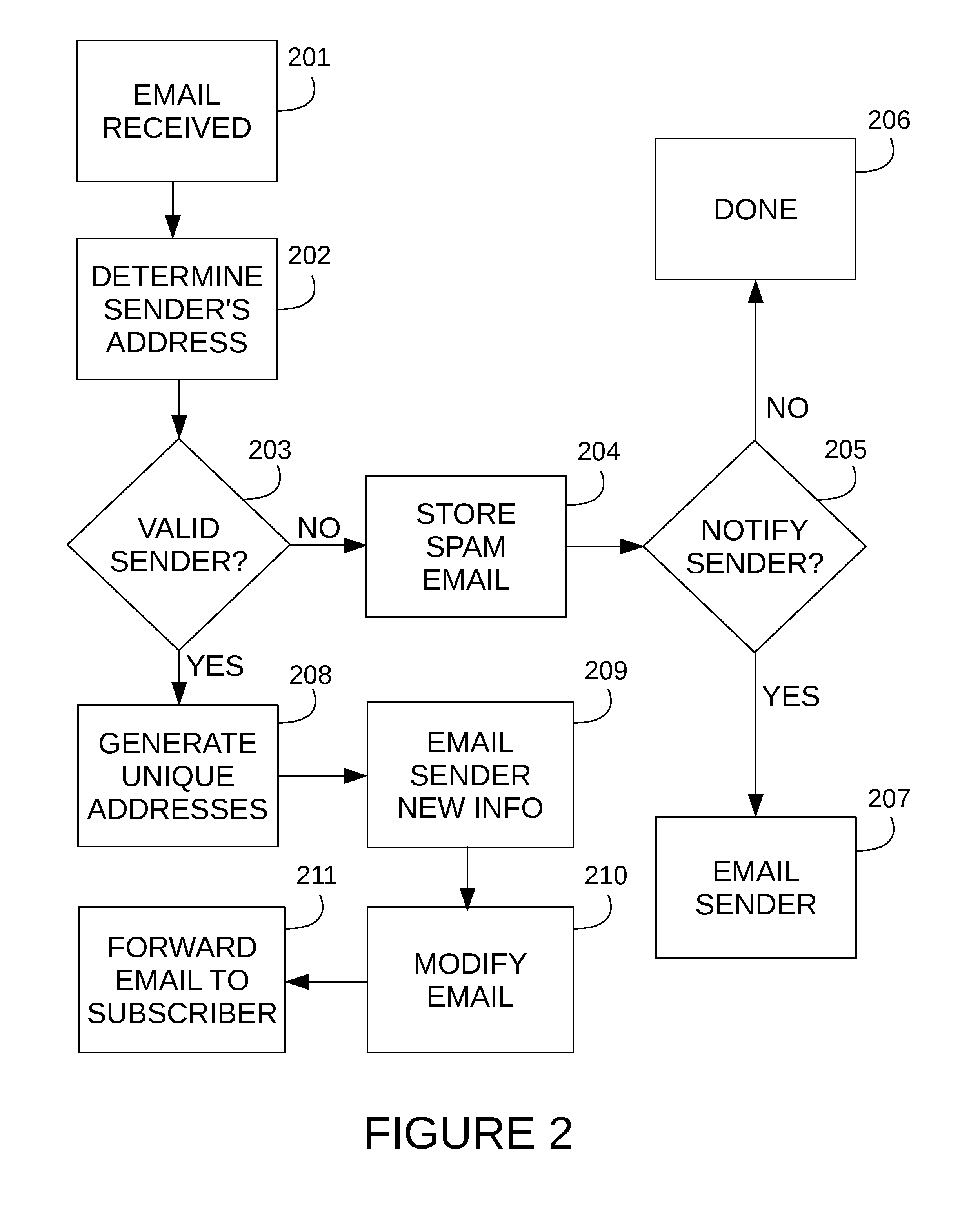
A system and method is proposed for managing email messages across a network. The system provides multiple means of verifying an originating sender of email. In addition, the system automatically generates unique email addresses as a means mask the email address of an original sender and shield users from unwanted email. The system may also be configured to block email security threats (e.g. phishing, spear phishing, etc.). Further, the system provides means of processing email messages to enable encryption, spam detection, geographical location identification of users, and social networking
Owner:MIRAGE DATA INC
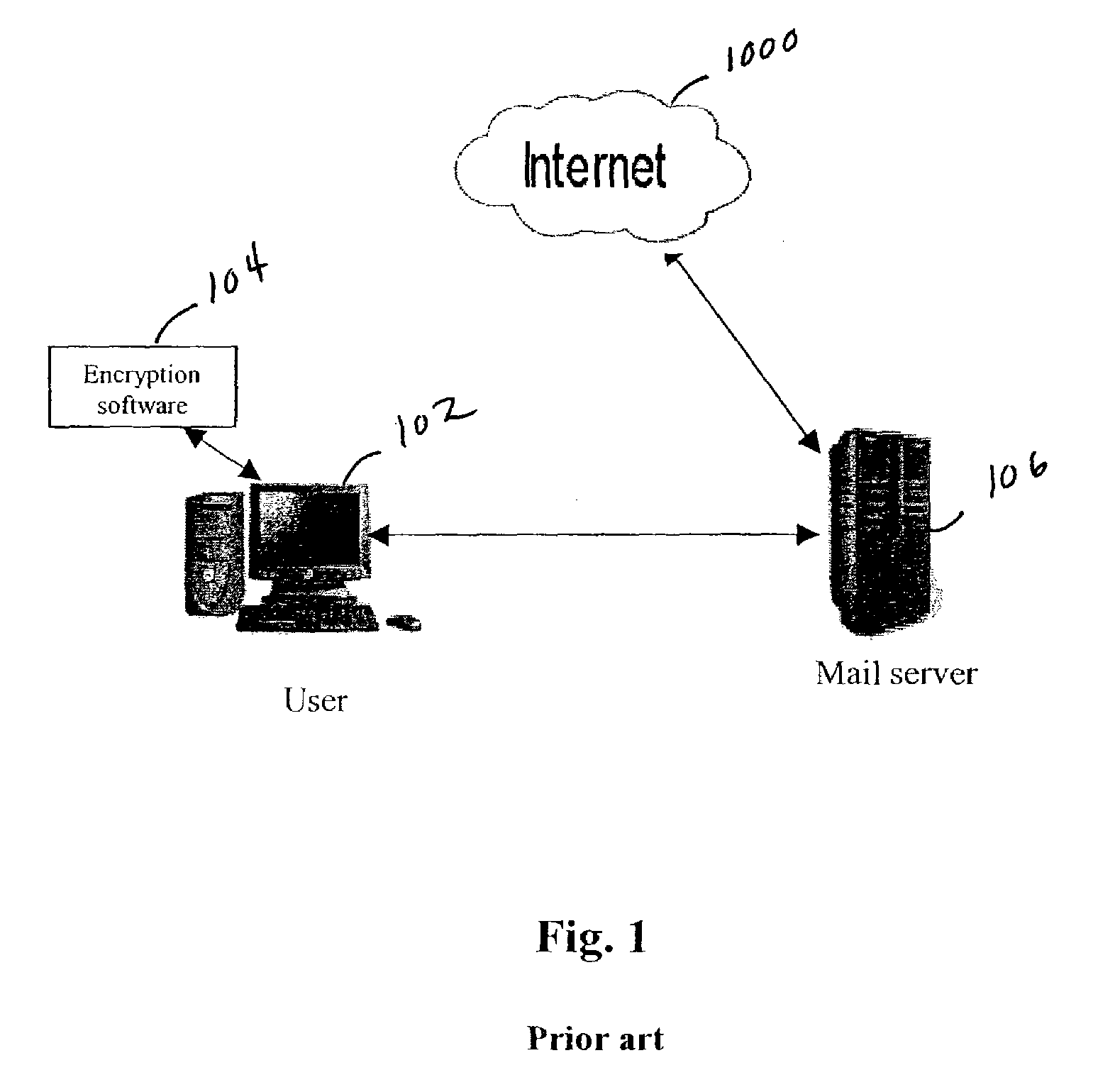
Enhanced electronic mail security system and method
InactiveUS20050268327A1Data switching networksSpecial data processing applicationsPatent searchClient-side
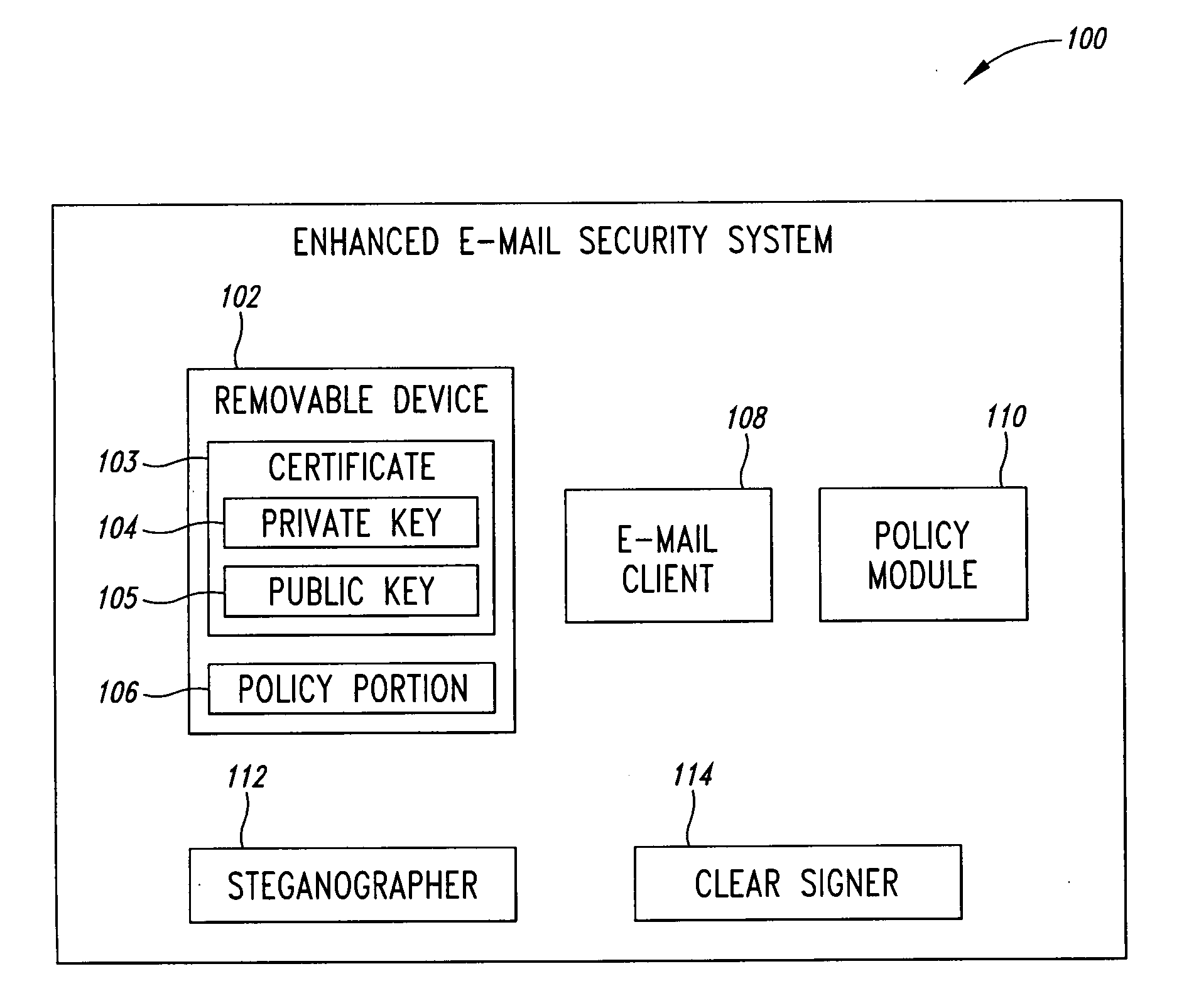
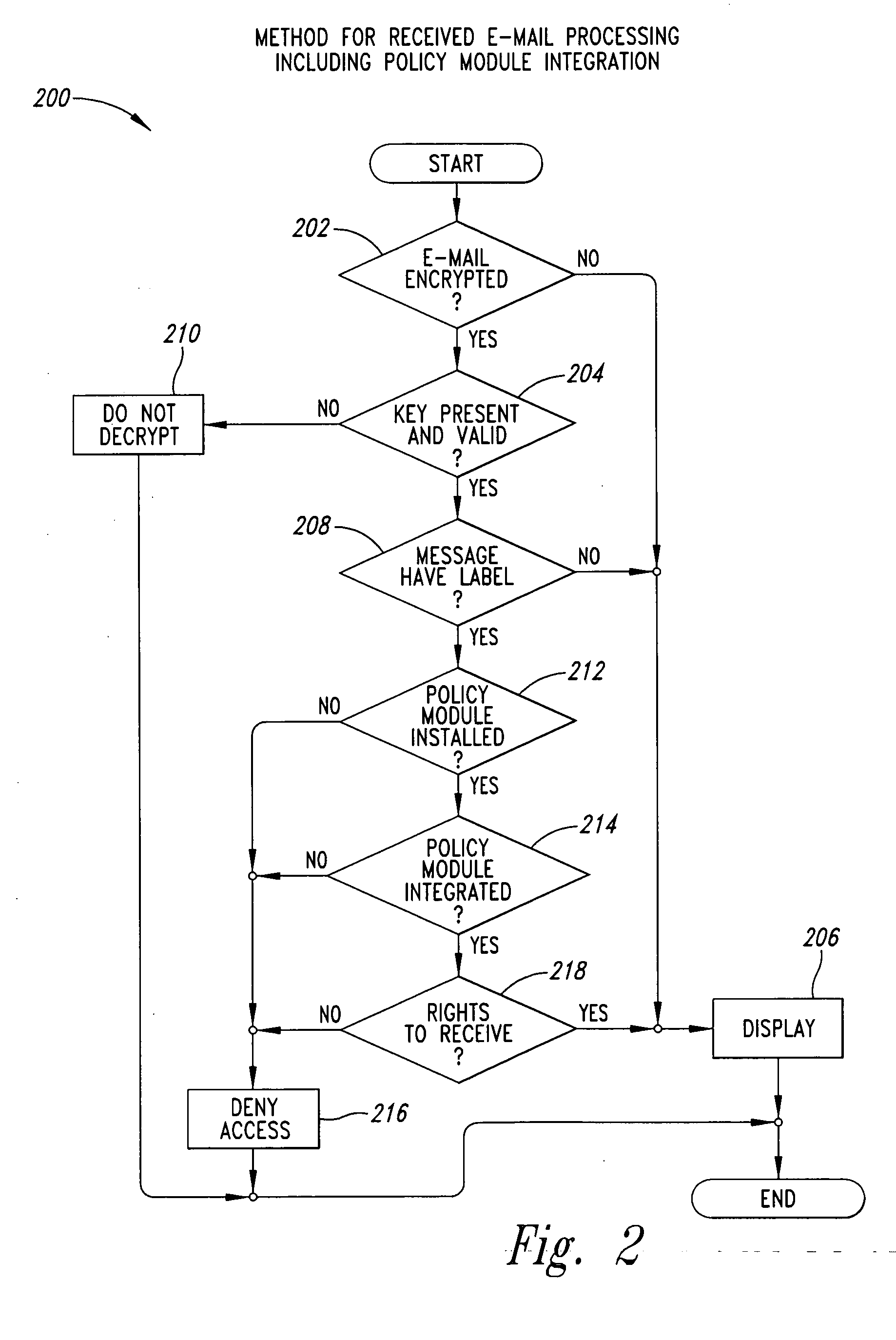
For purposes of patent searching the following description involves an enhanced system that has an e-mail client, policy module, a clear signer and a steganographer. A removable device includes a public key, a private key, and a policy portion. The policy module requires the policy portion for operation such as in decrypting e-mails. The e-mail client encrypts using the private key in conjunction with clear signing with the public key and / or using steganography to mask e-mails. Other validation features are described that can be used before decryption of e-mails occurs.
Owner:SECURE COMM TECH
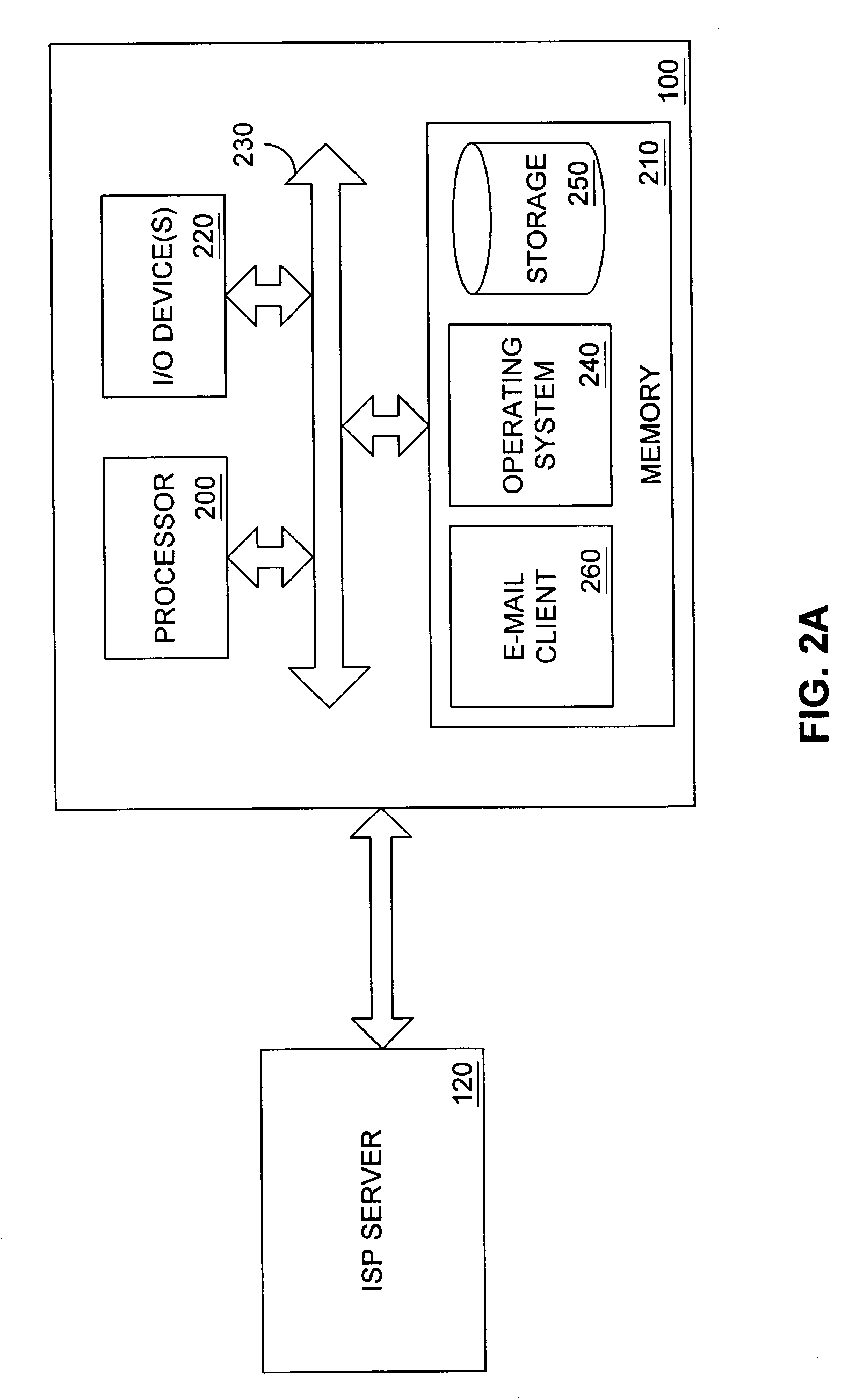
Method of establishing a secure e-mail transmission link
InactiveUS7660987B2Key distribution for secure communicationDigital data processing detailsKey exchangeSecure transmission
Owner:BAYLIS STEPHEN W +1
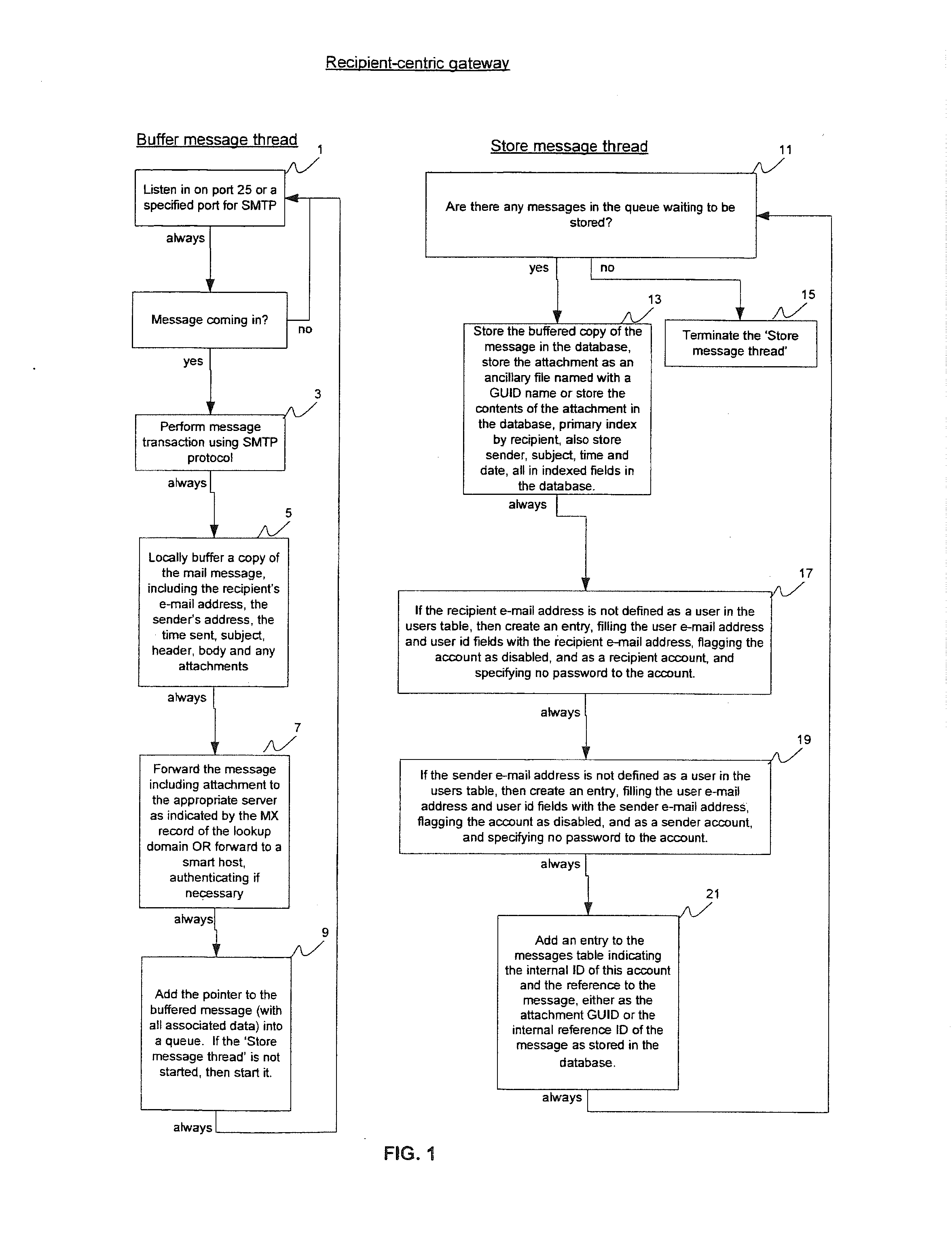
System and method for managing email and email security
InactiveUS20160269440A1Maximizing responsiveness of systemPassword reset costMultiple keys/algorithms usagePublic key for secure communicationThird partyDomain name
A recipient-centric gateway sits at the corporate network perimeter, retaining all outgoing e-mail, organizing the e-mail by recipient so that senders or other designated individuals can view the retained mail from the perspective of the recipient. A login retry limit is based on password strength. A system that guarantees the sender that the recipient is not phished with e-mail fraudulently purported to be from the sender's domain. A system that, without communicating certificates or publishing certificates to third parties and without requiring any workflow changes, enables the transparent two way sending of secure e-mail. A system that, based on feedback and usage, optimizes mailbox responsiveness across the network.
Owner:HARTMAN ROBERT
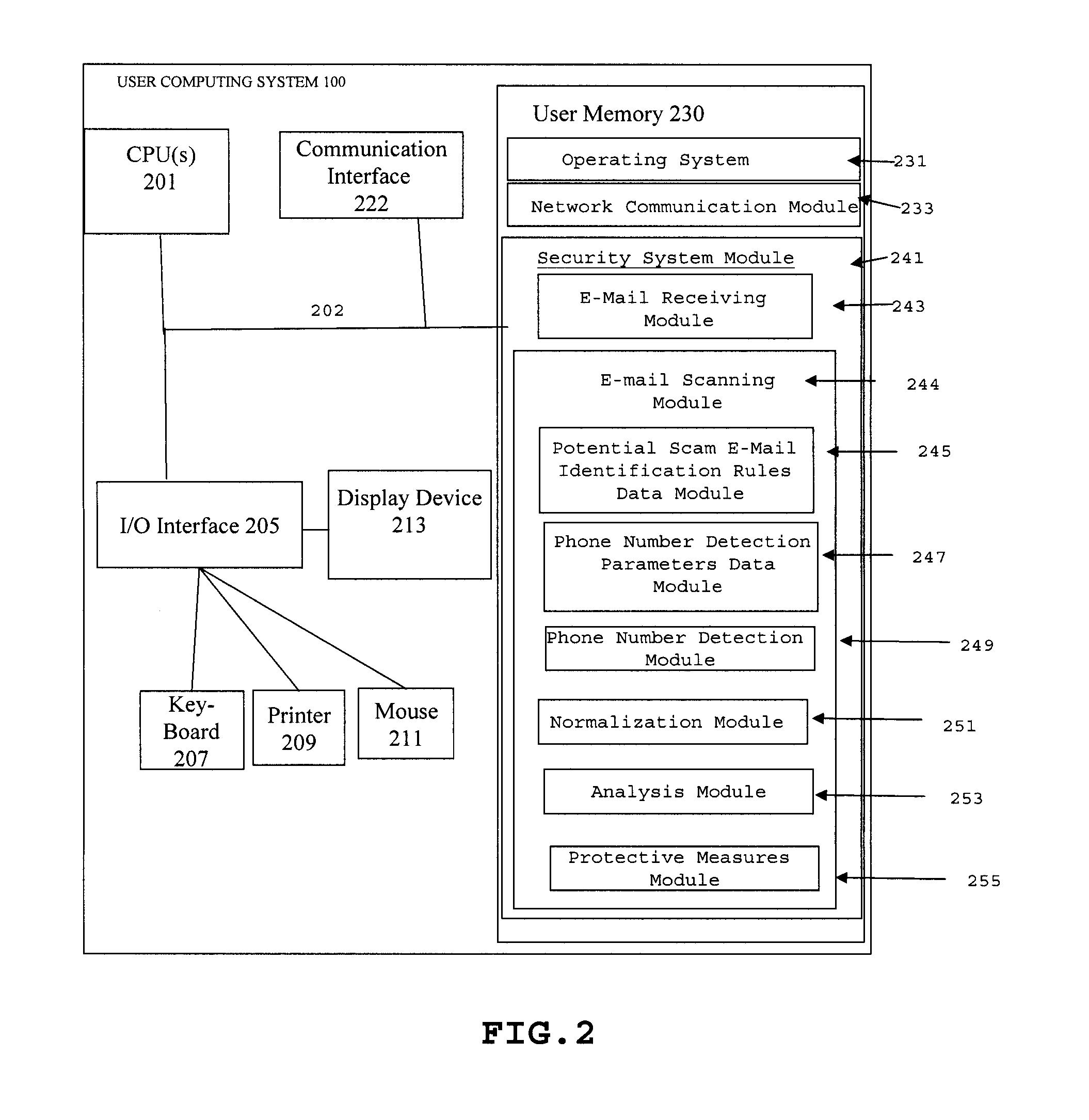
Method and system for employing phone number analysis to detect and prevent spam and e-mail scams
InactiveUS7917655B1Avoid of unnecessary delayReliable identificationMemory loss protectionDigital data processing detailsData miningSecurity system
Owner:GEN DIGITAL INC
E-mail security audit system for company security
InactiveUS20030188196A1Avoid spreadingMemory loss protectionError detection/correctionInternet privacyEngineering
An email security system for company security is disclosed. The email security system has a transmission server and a reception server. The transmission server has a mail code assigning and mail separating unit, a database, a security violation checking unit, a virus checking and curing unit, and a mail sending unit; and the reception server has a CGI operating unit. The security violation checking unit checks whether or not the email written and sent by a mail sender violates security, and sets a flag to prevent a mail receiver from reading the email if the email violates the security. The virus checking and curing unit checks whether the main body and the attached file are infected with computer viruses, and sets the flag to prevent the mail receiver from reading the email if the main body and the attached file are infected with the computer viruses.
Owner:CHOI JEONG HWAN
E-mail security system
InactiveUS20050039028A1User identity/authority verificationUnauthorized memory use protectionElectronic mailSecurity system
E-mail security systems are provided. A representative system, among others, includes an e-mail client. A representative e-mail client, among others, includes a message composition logic and a write protect logic. The message composition logic is operable to compose a message to at least one recipient, and the write protect logic is operable to protect the message against subsequent alteration by said at least one recipient. Methods and other systems for e-mail security are also provided.
Owner:AT&T INTPROP I L P
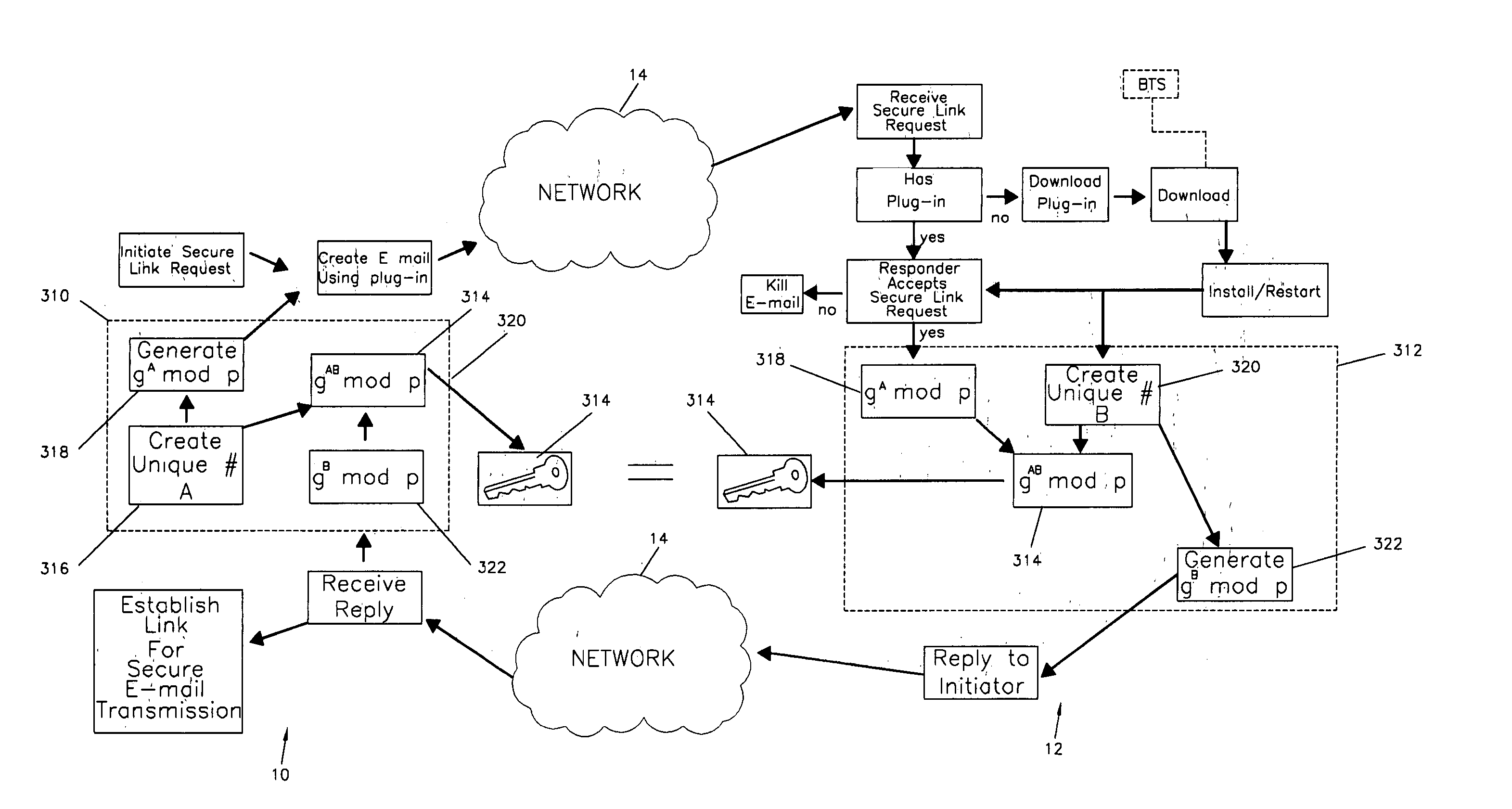
Method of establishing a secure e-mail transmission link
InactiveUS20060095770A1User identity/authority verificationPayment architectureSecure transmissionElectronic mail
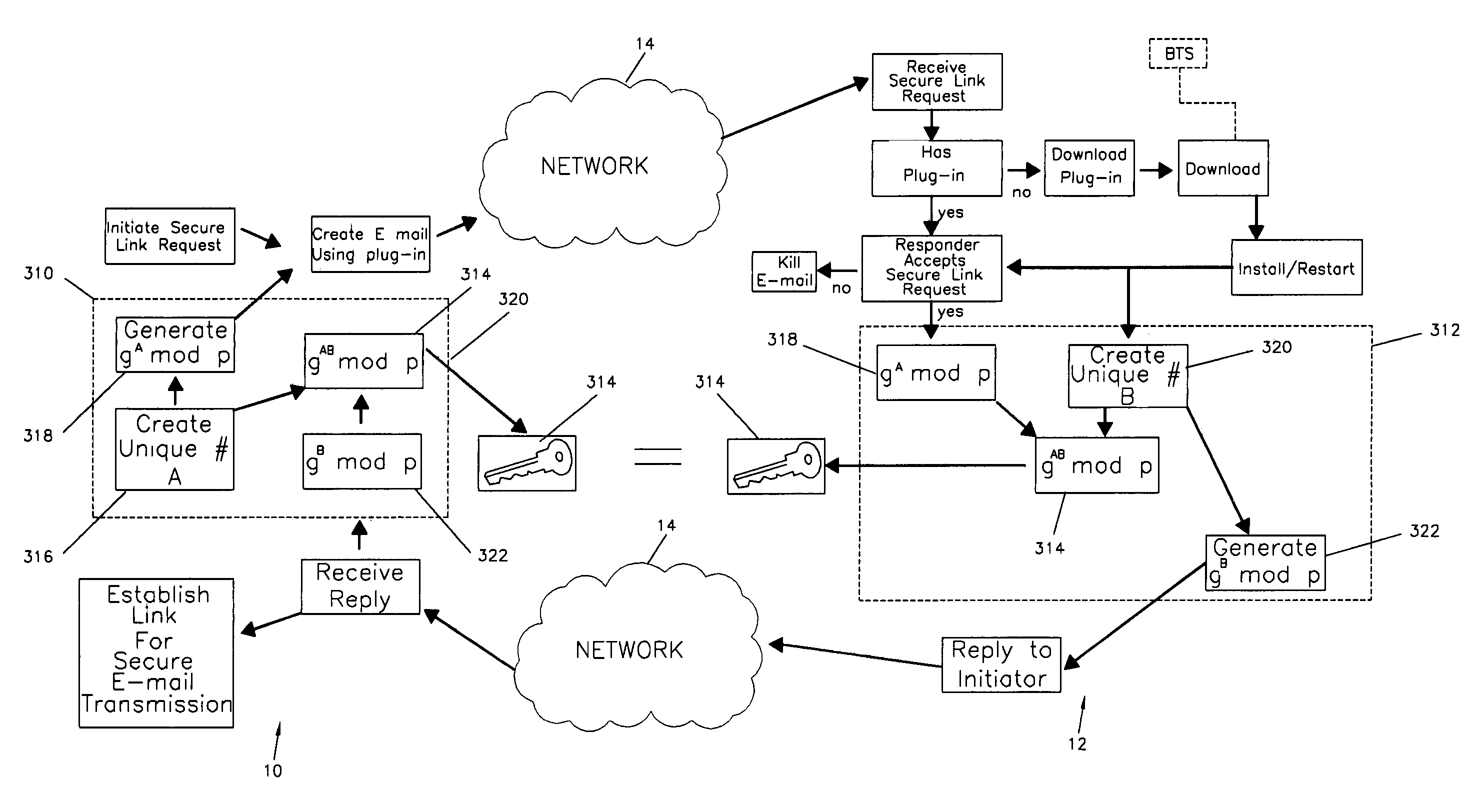
A method of establishing an e-mail secure transmission link between an initiator and a responder for the transmission of secure e-mail messages over a network comprising creation of a unique initiator designator or number, generation of a unique initiator exchange key component including the unique initiator designator or number, transmission of a request from the initiator to the responder to establish the e-mail secure transmission link and the unique initiator exchange key component, acceptance of the request by the responder to establish the e-mail secure transmission link, creation of a unique responder designator or number, combining of the unique responder designator and the unique initiator exchange key component to create a unique initiator / responder exchange key at the responder site, generation of a unique responder exchange key component including the unique responder designation, transmission of the unique responder exchange key component from the responder to the initiator, combining the unique initiator designator with the unique responder exchange key component to create the unique initiator / responder exchange key at the initiator site and to establish the e-mail secure transmission link to send and receive e-mail between the initiator and the responder exchange with the unique initiator / responder exchange key.
Owner:BAYLIS STEPHEN W +1
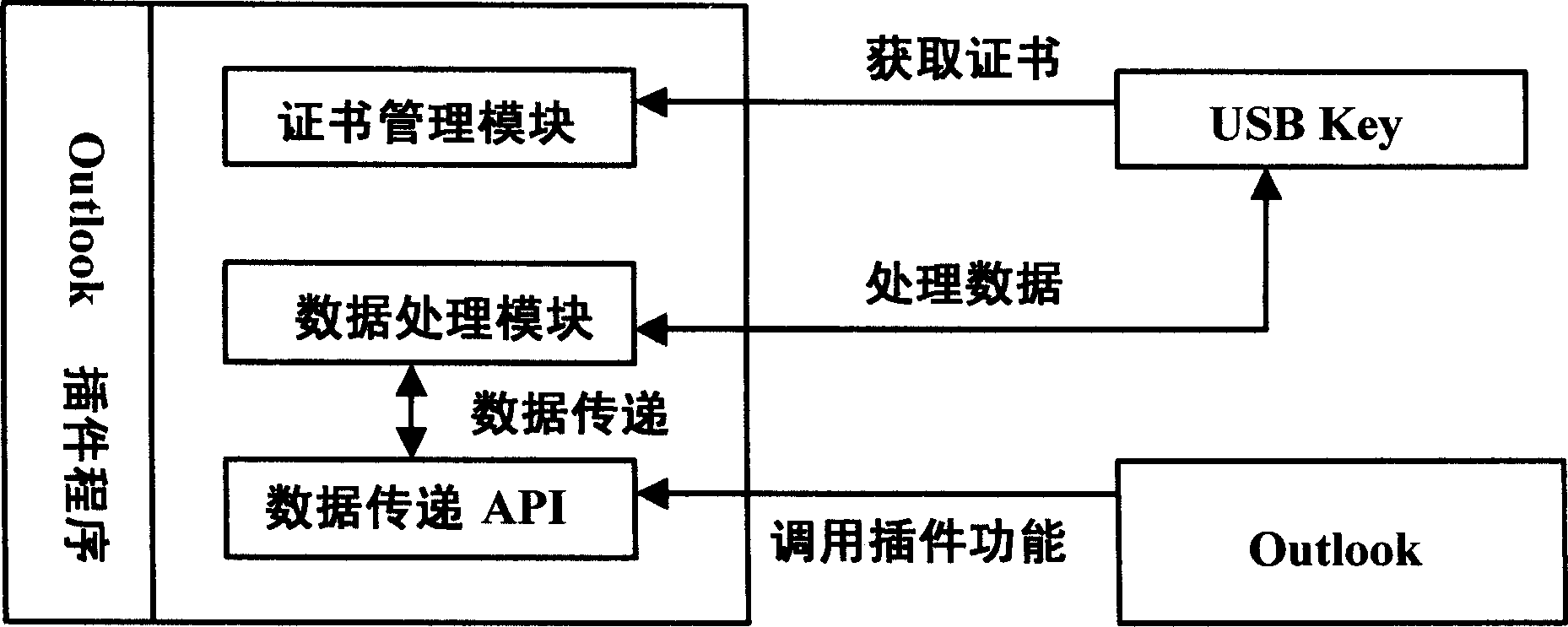
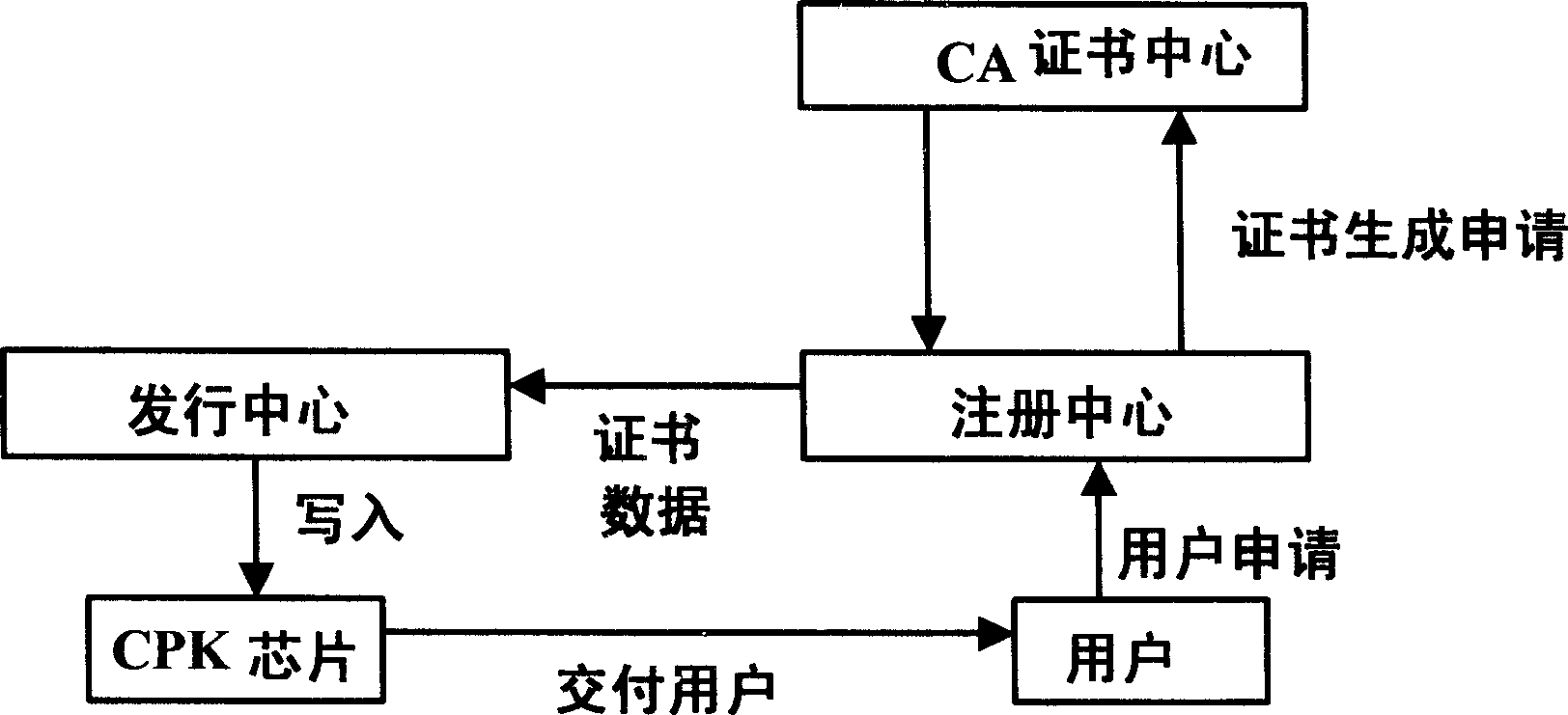
Electronic mail system and method based on CPK safety authentication
InactiveCN1835434AReduce the amount of informationImprove operational efficiencyData switching networksSecuring communicationSecure authenticationElectronic mail
The system includes ID certificate module and protocol module. ID certificate module is in use as ID for encrypting, authenticating, and signing E-mail when transmission of E-mail, and CPK private key. In procedure of transferring E-mail, protocol module uses ID provided by ID certificate module and CPK private key to encrypt, authenticate, and validate, and sign E-mail as well as validate validity of signature. The invention also discloses method of safety certification based on CPK E-mail. Features are: making E-mail safer, higher efficiency, and more economy.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
Systems, methods and computer program products for ingress email security
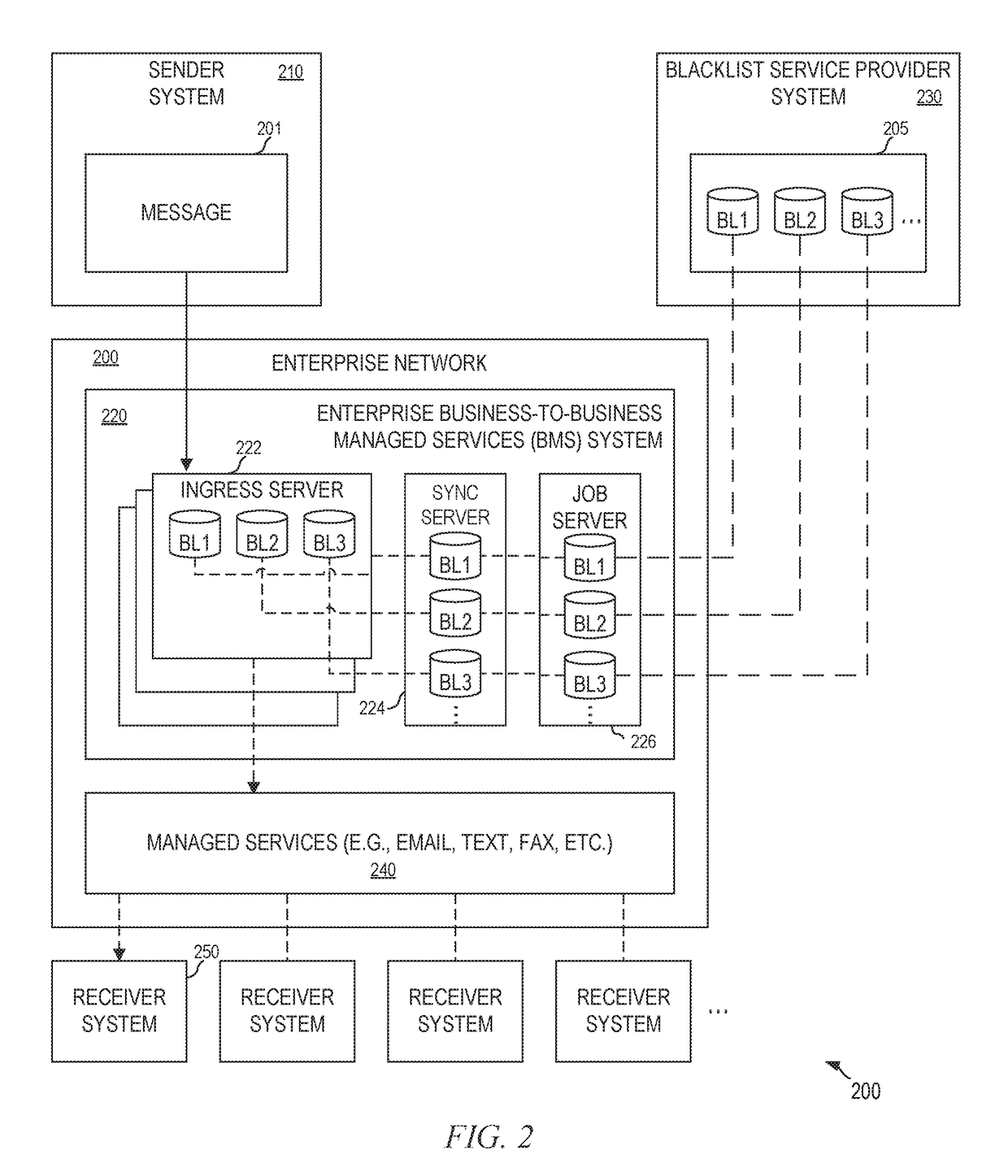
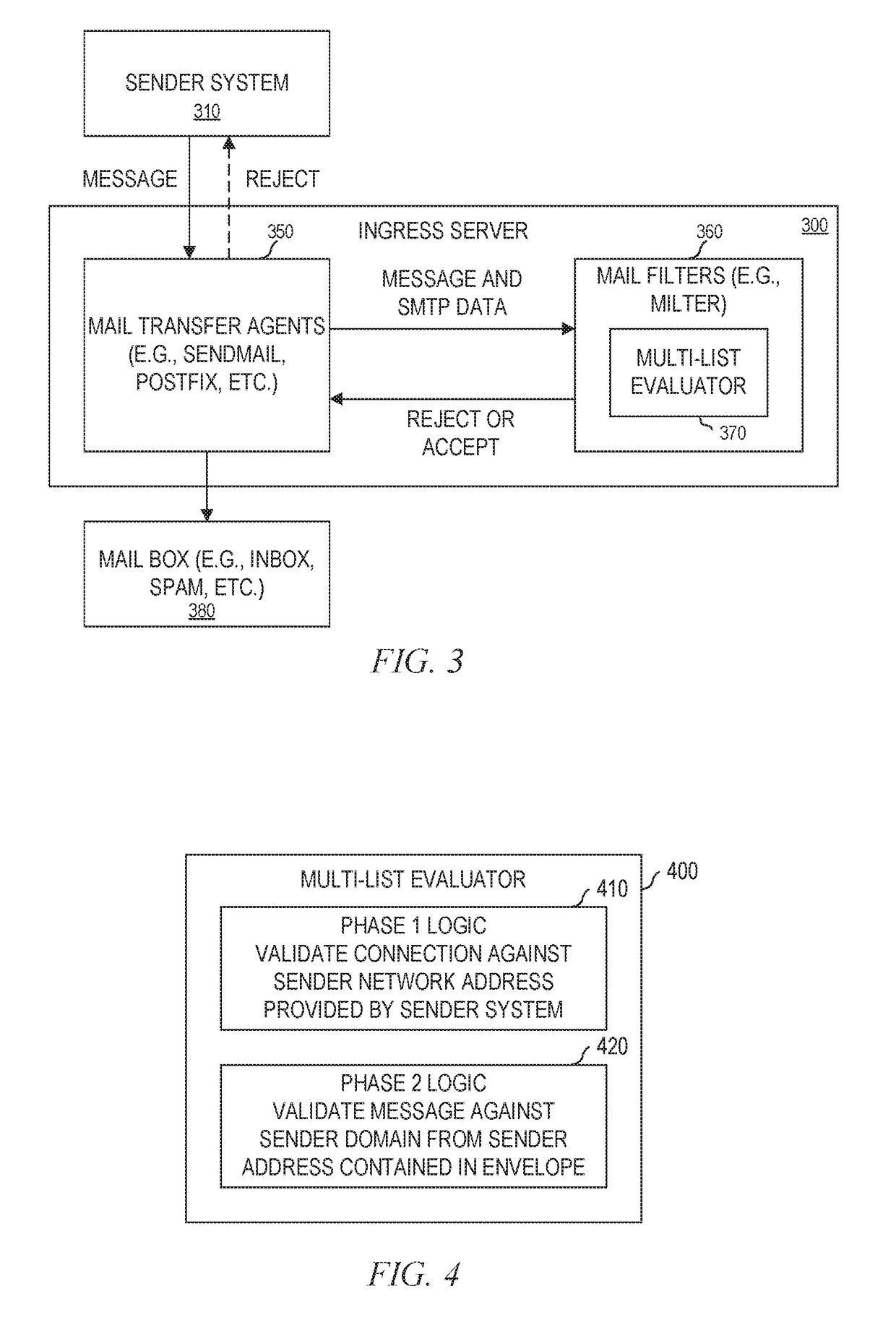
ActiveUS20190075121A1Mitigate and avoid such disruptionImproved ingress email securityData switching networksSingle sessionEmail address
An ingress server is operable to perform, through a multi-list evaluator, two different validations: one utilizes a sender network address of a sender's server to determine whether to trust, accept, or reject a connection and one utilizes a domain of a sender email address from an envelope to determine whether to accept or reject a message. The multi-list evaluator may perform the validations in two phases. If a connection can be trusted, the connection is accepted and any message over the connection (in a single session) is accepted and no further validation is necessary. Further, in the both phases, the multi-list evaluator can utilize a whitelist maintained by the ingress server to override a blacklist provided by a blacklist supplier. This override can reduce false-positives and drastically reduce delays usually associated with correcting false-positives and improve system throughput.
Owner:OPEN TEXT HLDG INC
E-mail safety management system and method based on content filtering
InactiveCN105635080AAccurate judgmentAccurate analysisData switching networksSpecial data processing applicationsSafety management systemsFiltering rules
The invention discloses an e-mail safety management system and method based on content filtering. The system is characterized by comprising: a main program module, a content filtering function module, a spam preventing module, an information record module, etc.; an e-mail safety management method based on content filtering is characterized by comprising following steps: starting a rule base; generating a filtering word stock according to the filtering rule base; matching the e-mail content with the words in the filtering word stock; performing statistics on the presence number of times of each key word and the spacing distance among the key words; performing relevance analysis of the key words according to the presence number of times of each key word and the spacing distance among the key words; distinguishing the danger grades of e-mails according to the relevance; and returning the danger grades of e-mails to the main program. According to the invention, by use of intelligent technology of content filtering, accurate determination and analysis for e-mail filtering are realized, and then the danger grades of e-mails are confirmed. Managerial personnel can adjust and change the filtering rules in real time according to audit information.
Owner:江苏华御威盾网络科技有限公司
Method, device and system for safe communication of email based on cell phone mailbox
ActiveCN102404699AImprove securityImprove reliabilityMessaging/mailboxes/announcementsTransmissionCurrent technologyOn cells
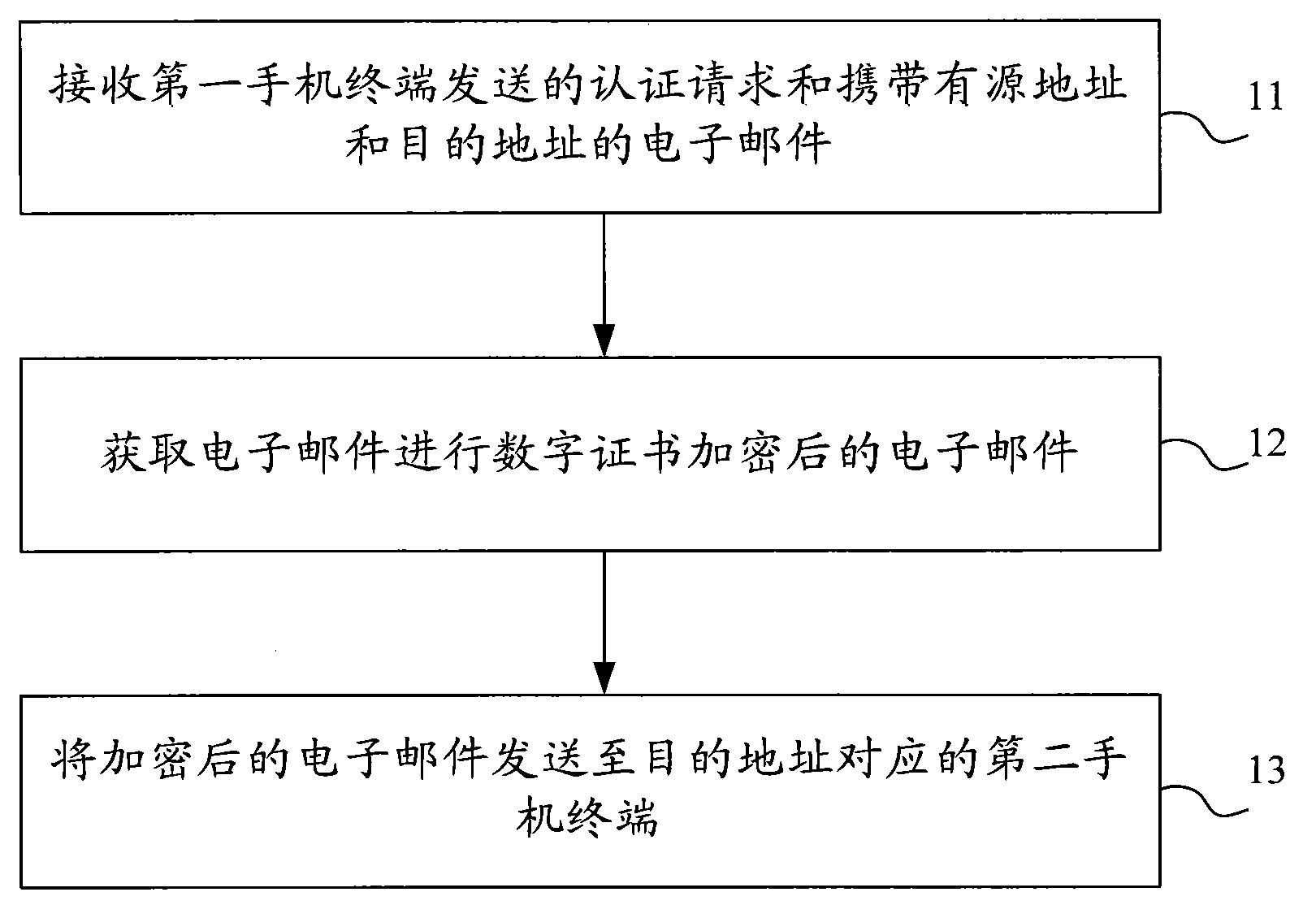
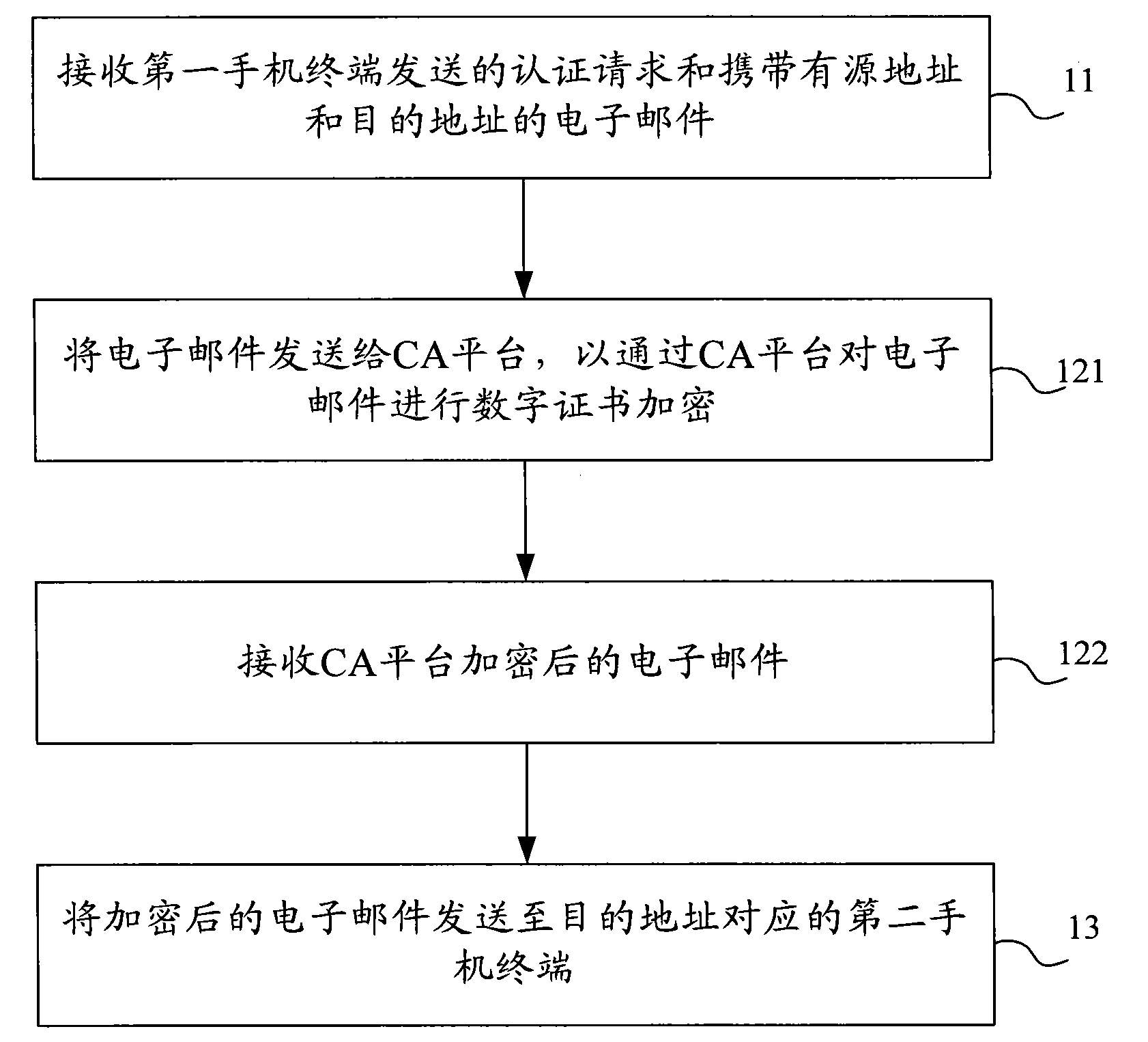
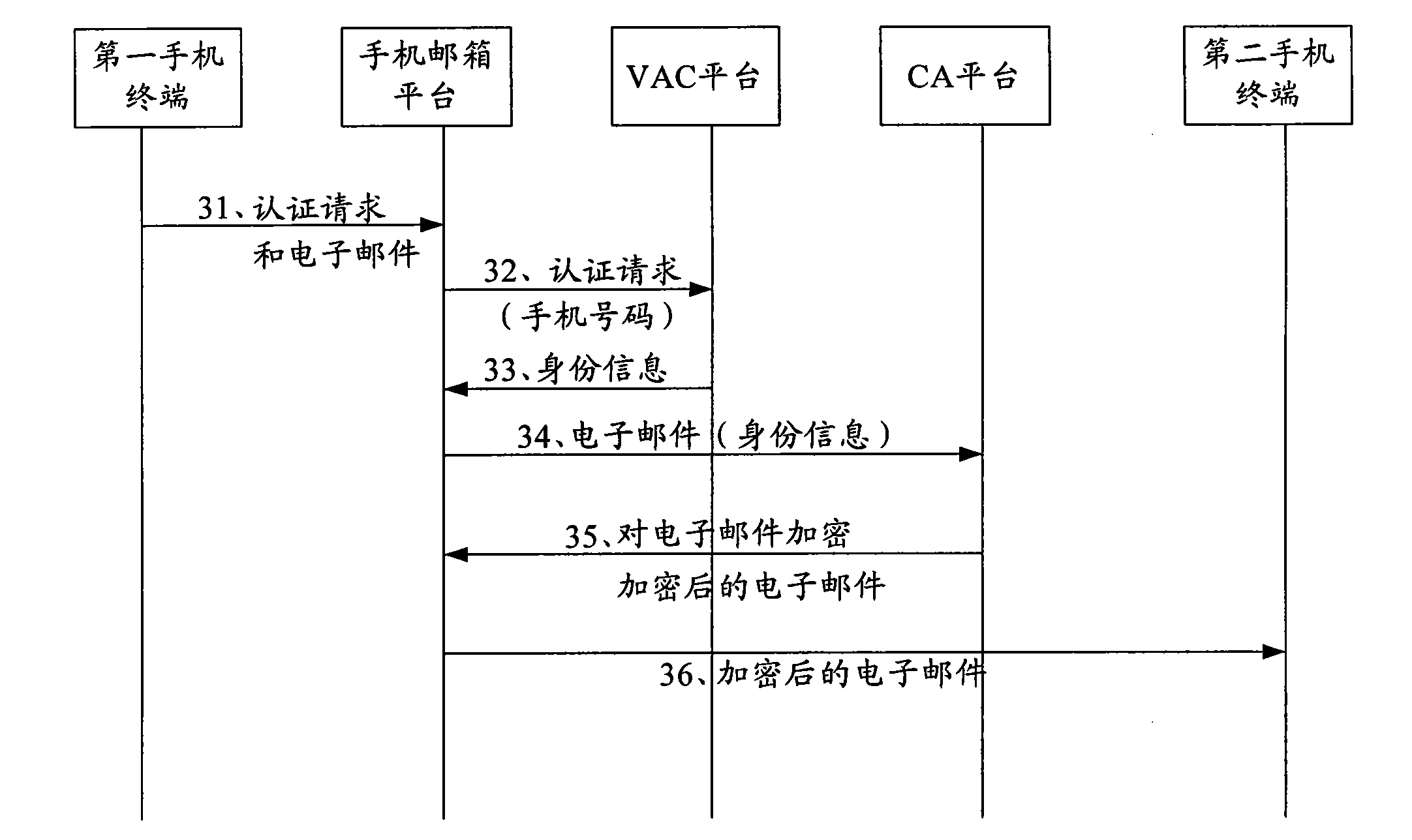
The invention provides a method, a device and a system for safe communication of an email based on a cell phone mailbox; the method comprises receiving an authentication request sent by a first cell phone terminal and an email containing a source address and a destination address, obtaining an email which is encrypted with a digital certificate, and sending the encrypted email to a second cell phone terminal corresponding to the destination address. With the adoption of the method, the device and the system for safe communication of the email based on the cell phone mailbox, the problem of the current technology, that the cell phone mailbox fails to further satisfy higher requirements of business users on security and reliability of the email, is solved, thus effectively improving the security and the reliability of the email.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Apparatus for setting an email security and method thereof
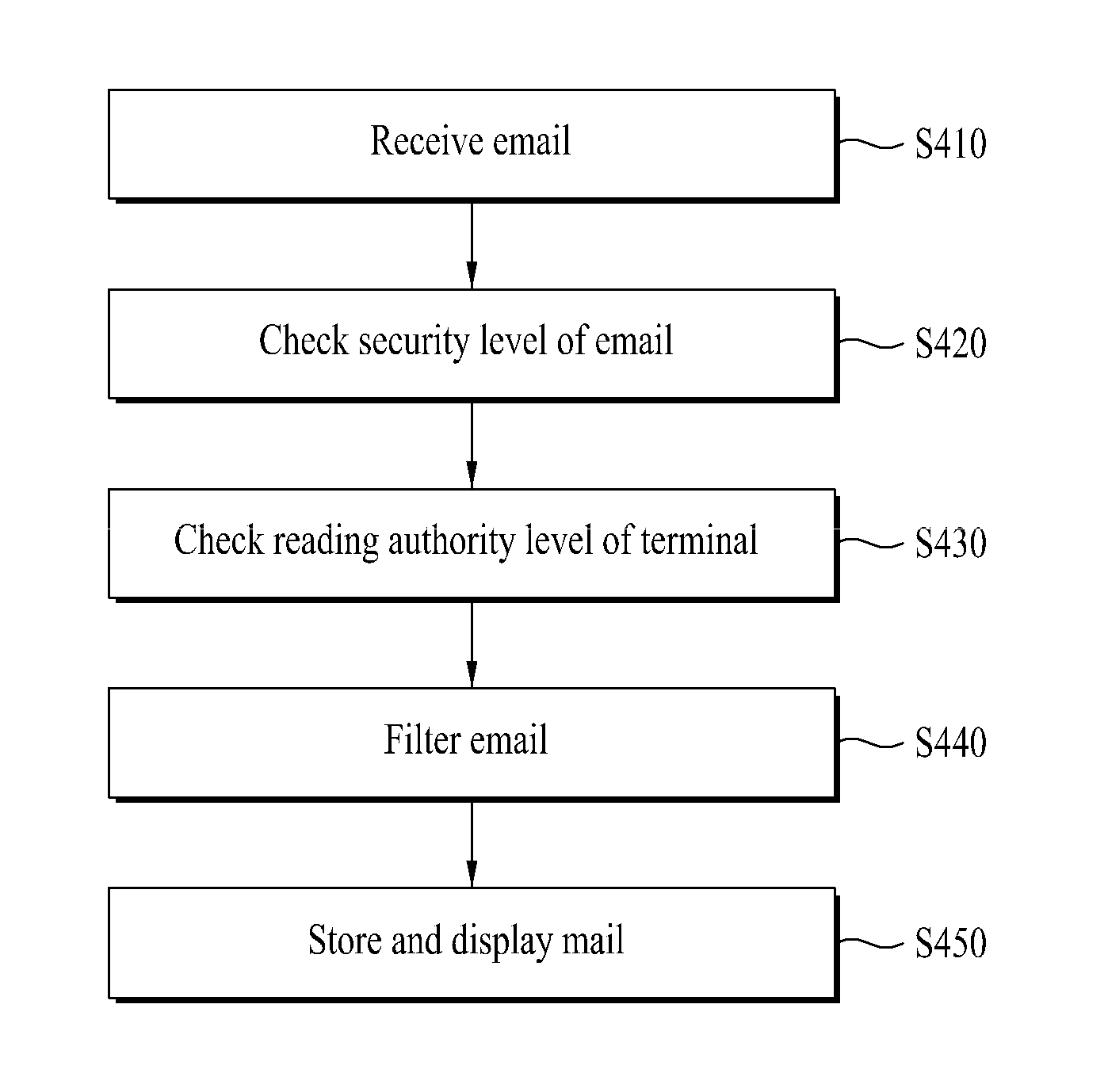
InactiveUS20110030063A1Process safetyData processing applicationsDigital data processing detailsInternet privacySecurity level
An apparatus for setting an email security and method thereof are displayed. The present invention includes receiving an email from a email server, deleting partial information of the email according to a security level of the email, and displaying the partial information deleted email.
Owner:LG ELECTRONICS INC
E-mail security control method, client and system
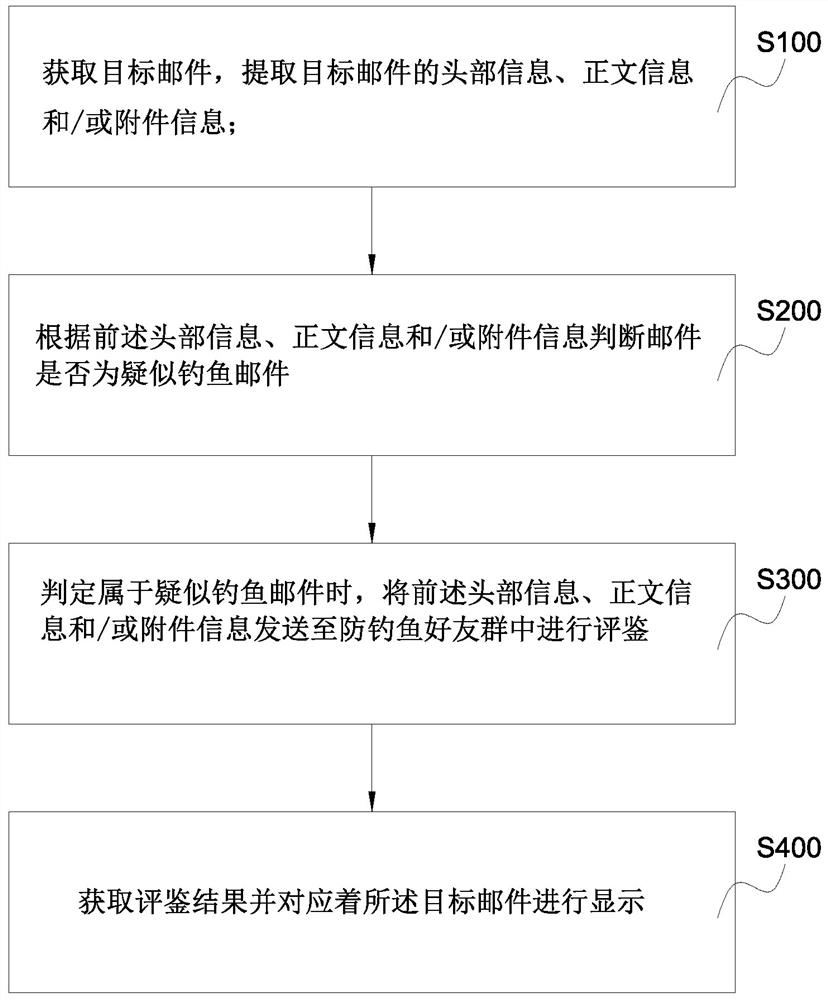
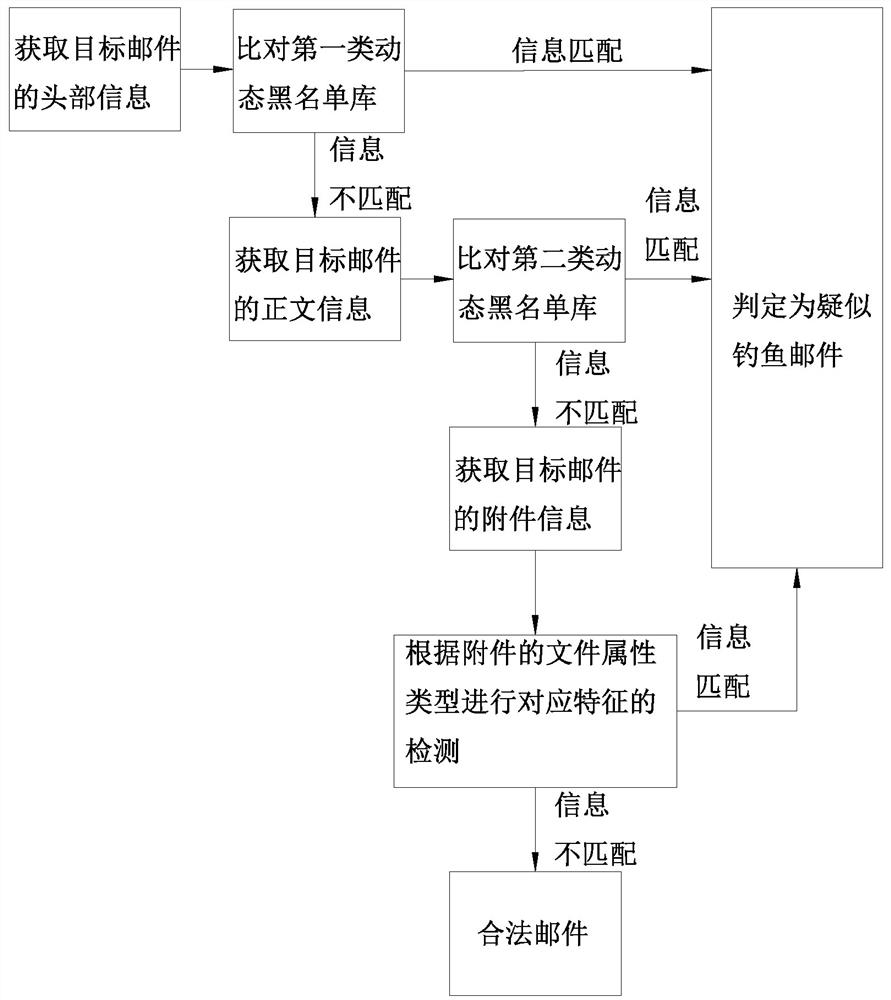
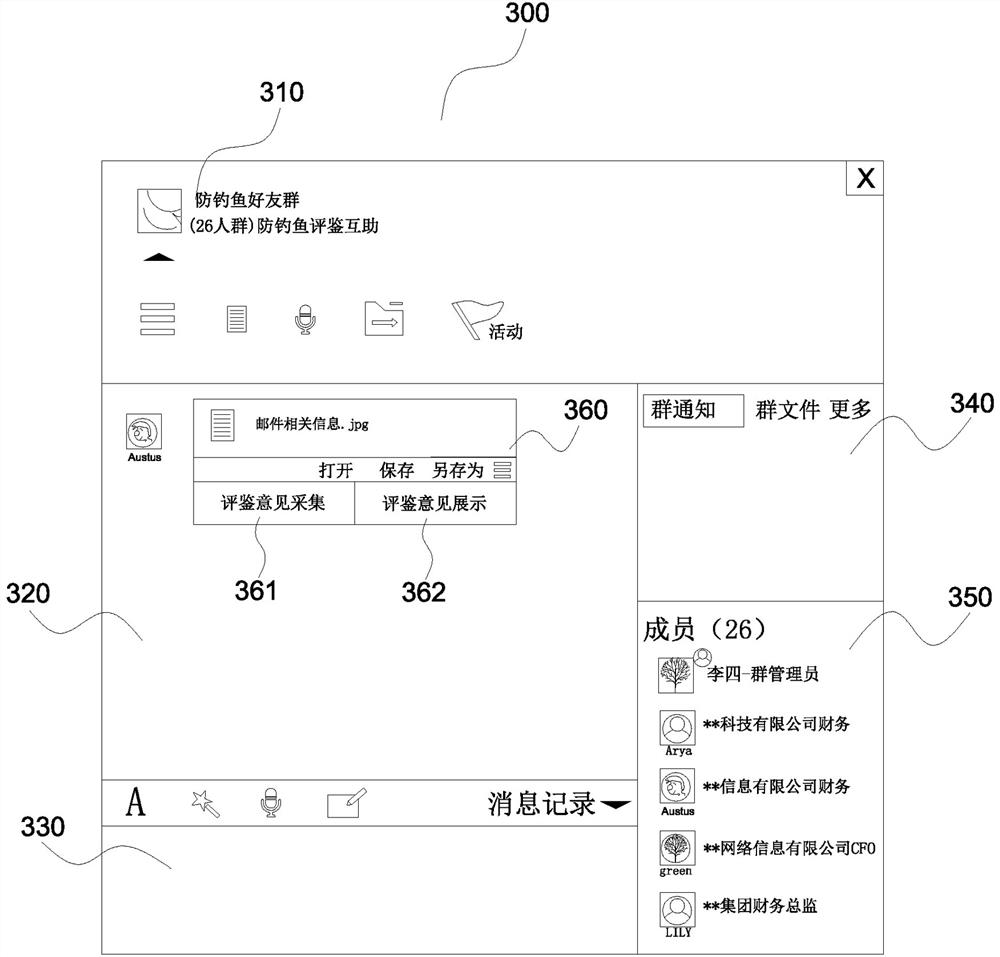
ActiveCN113630397AEffective detection and confirmationImprove detection reliabilityData switching networksEvaluation resultEngineering
The invention discloses an E-mail security control method, a client and a system, and relates to the technical field of network security. The method comprises the following steps: acquiring a target mail, and extracting header information, text information and / or attachment information of the target mail; judging whether the mail is a suspected phishing mail according to the header information, the text information and / or the attachment information; when judging that the mail belongs to the suspected phishing mail, sending the header information, the text information and / or the attachment information to an anti-phishing friend group for evaluation; and obtaining an evaluation result and displaying the evaluation result corresponding to the target mail. According to the invention, the detection reliability of the phishing mail is improved, and the detection and confirmation of the suspected phishing mail can be more effectively completed.
Owner:上海纽盾网安科技有限公司
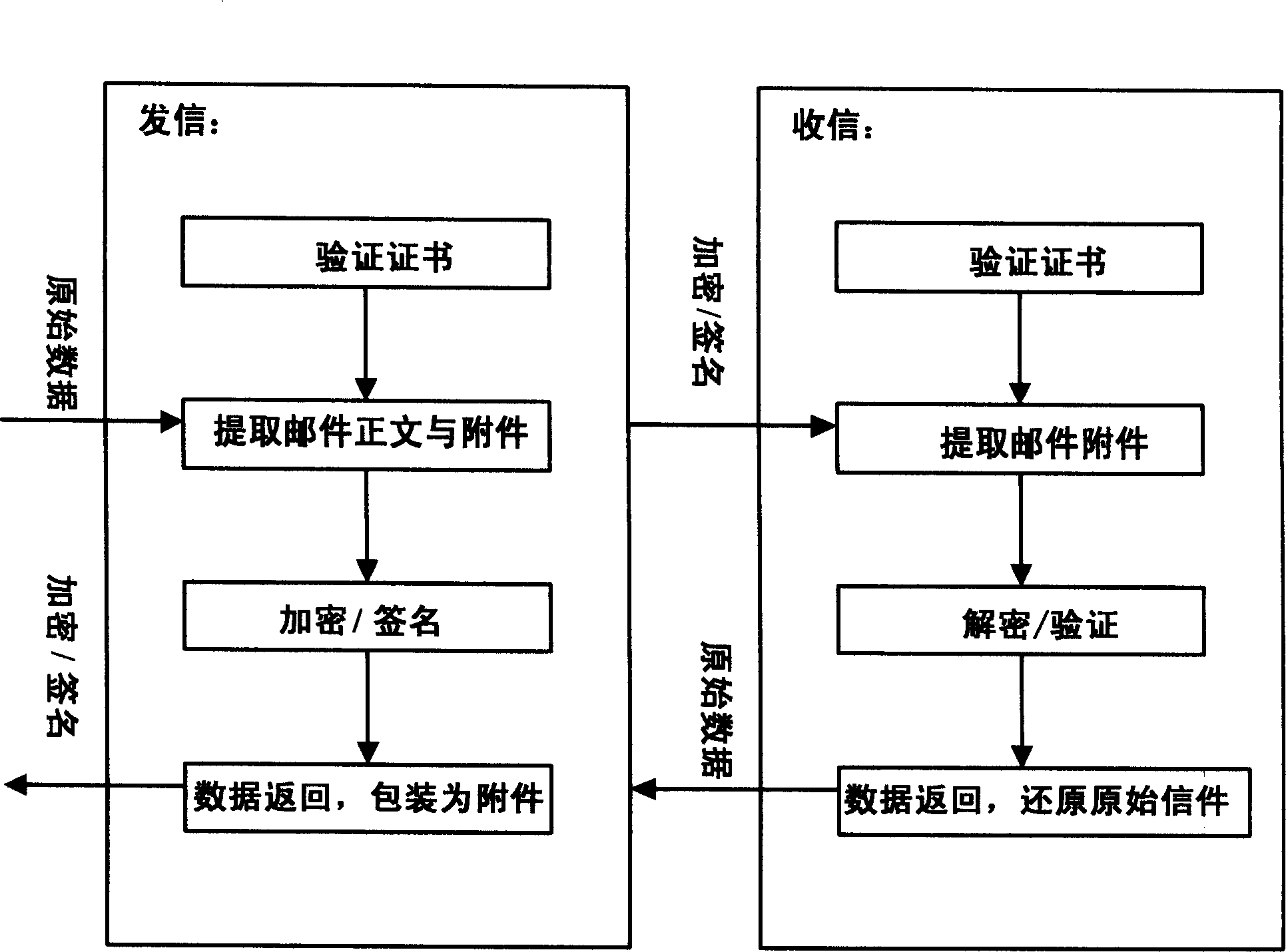
Secure receiving and transmitting system and method for email
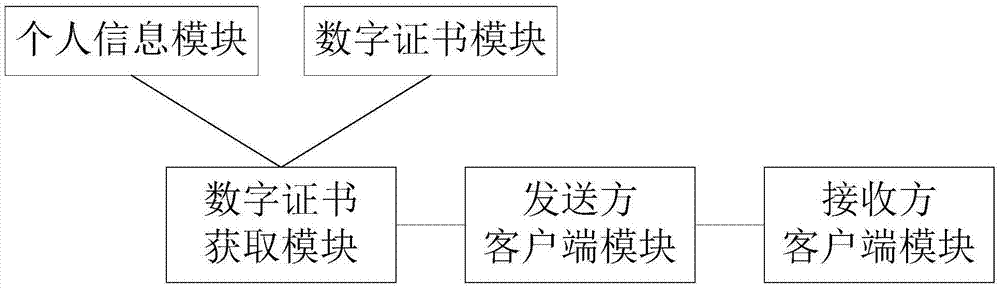
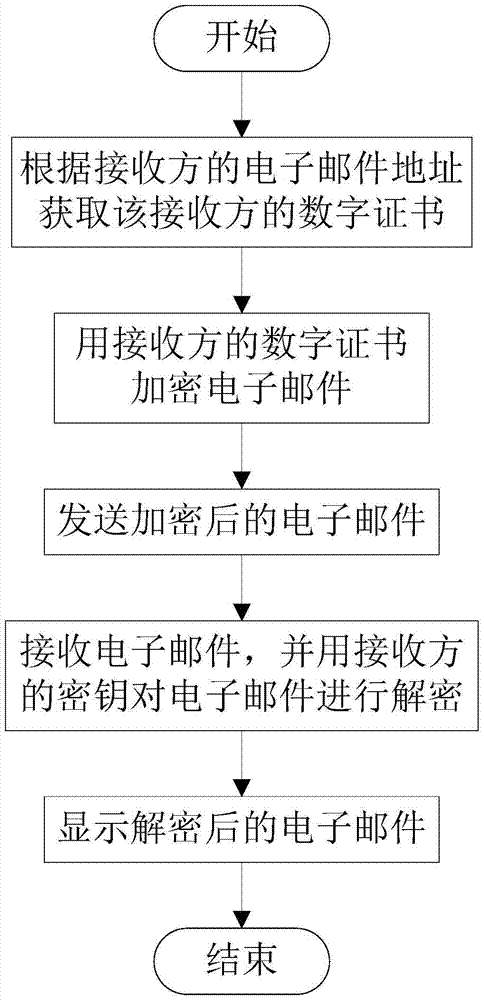
InactiveCN106921558APrevent counterfeitingData switching networksNetworked Transport of RTCM via Internet ProtocolEmail address
The invention relates to the field of secure email receiving and transmitting technologies, and discloses a secure receiving and transmitting system and a secure receiving and transmitting method for an email. The system comprises a digital certificate acquisition module, a sender client module and a receiver client module, wherein the digital certificate acquisition module is used for acquiring a digital certificate of a receiver according to an email address of the receiver; the sender client module is used for encrypting the email by using the digital certificate of the receiver, and sending the encrypted email; and the receiver client module is used for receiving the email, decrypting the email by using a secret key of the receiver and displaying the decrypted email. According to the system and the method provided by the invention, the digital certificate of the receiver is automatically acquired, so that the corresponding digital certificate is automatically searched for encryption and decryption, security protection of email data is automatically performed, the email data in local, network transmission and email servers are all strictly protected in an encrypted manner, and thus behaviors of forging or modifying the email under the name of the receiver can be well completely eradicated.
Owner:AEROSPACE INFORMATION
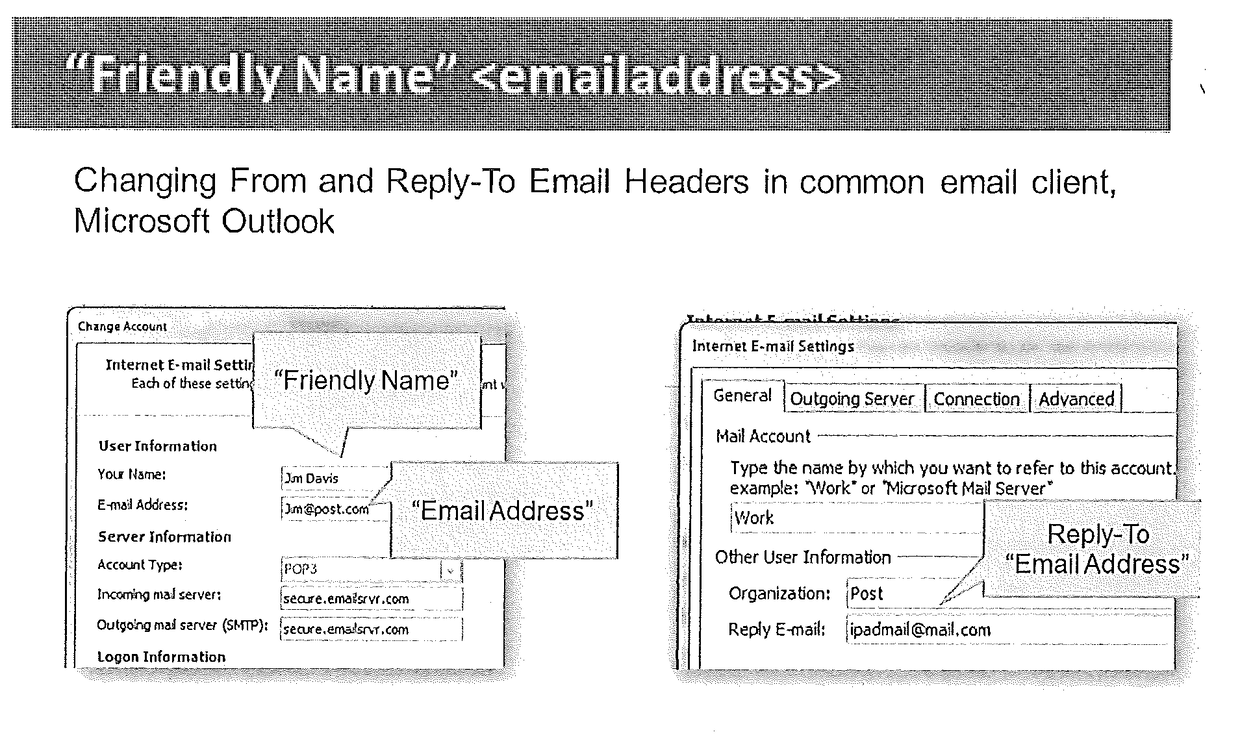
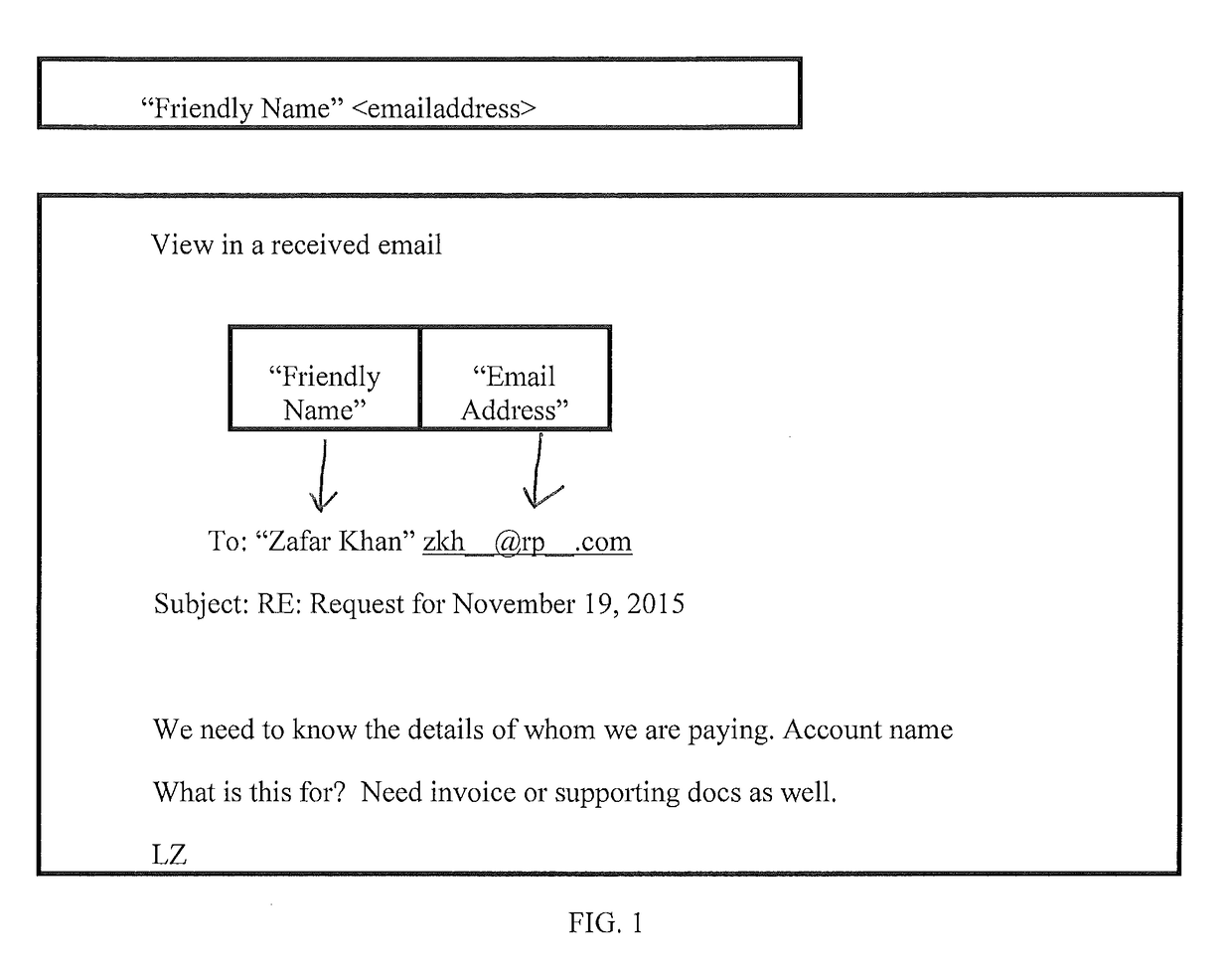
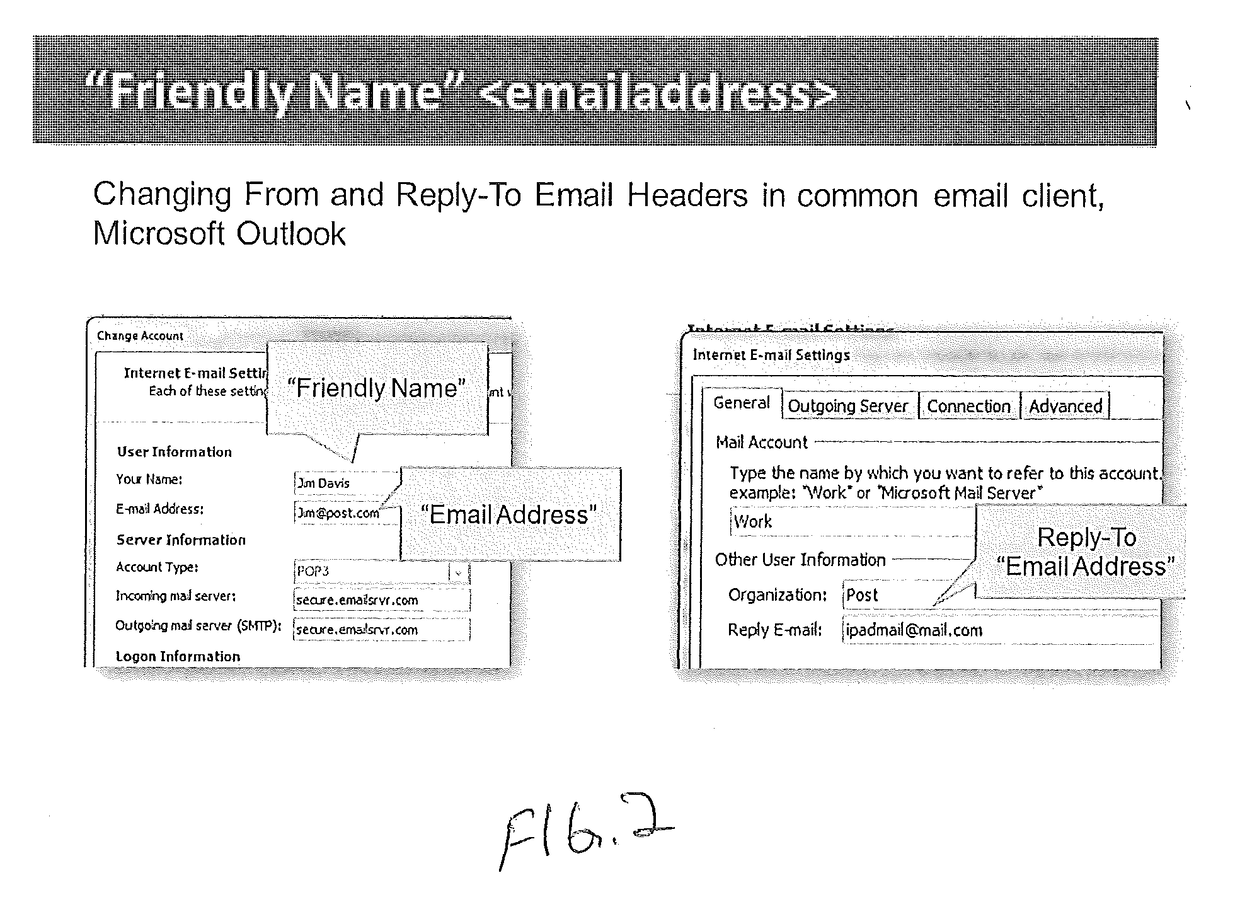
Email Sender and Reply-To Authentication to Prevent Interception of Email Replies
An electronic messaging system that reviews content of inbound messages, verifies elements of header fields, and initiates an action if Name (N) and Address (A) of From (F) and Reply-To (R) elements of header fields match or do not match, those elements being NF=NR and AF≠AR, to protect recipients against inadvertent routing of their reply email to an imposter of the named From sender, thereby mitigating risk of recipients falling prey to what is referred to herein as “Reply-To Whaling” attacks, within the email security category of anti-phishing.
Owner:KHAN ZAFAR
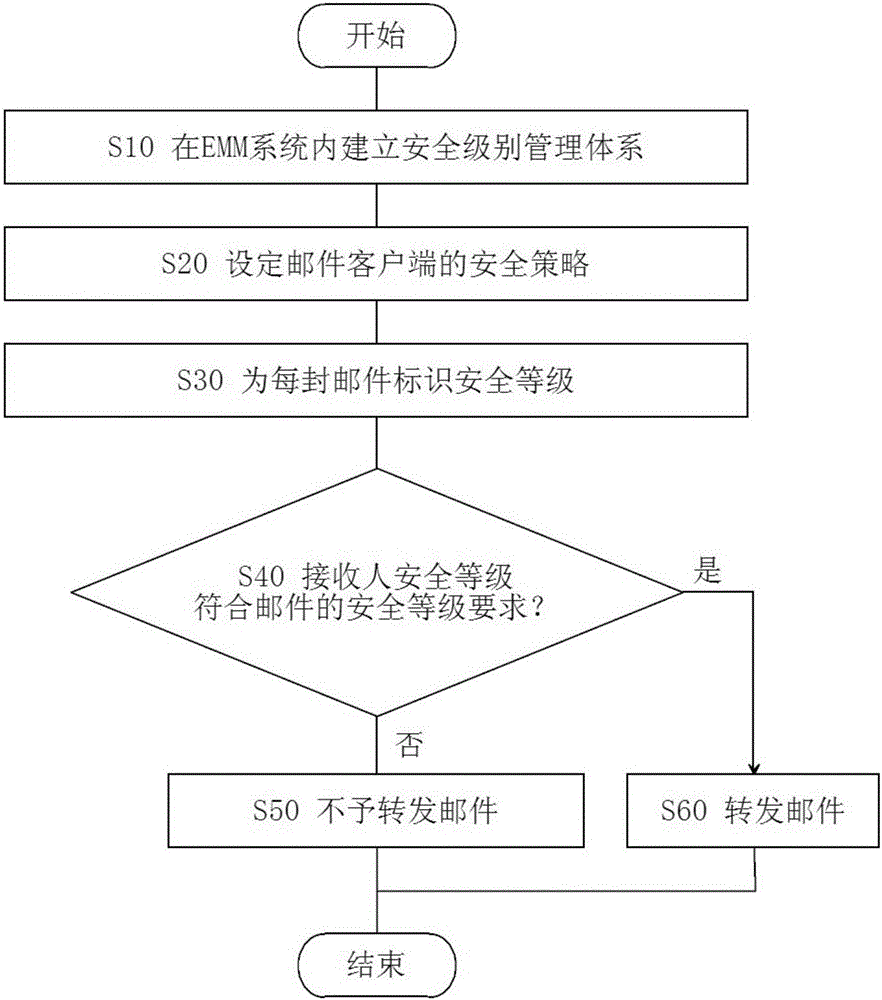
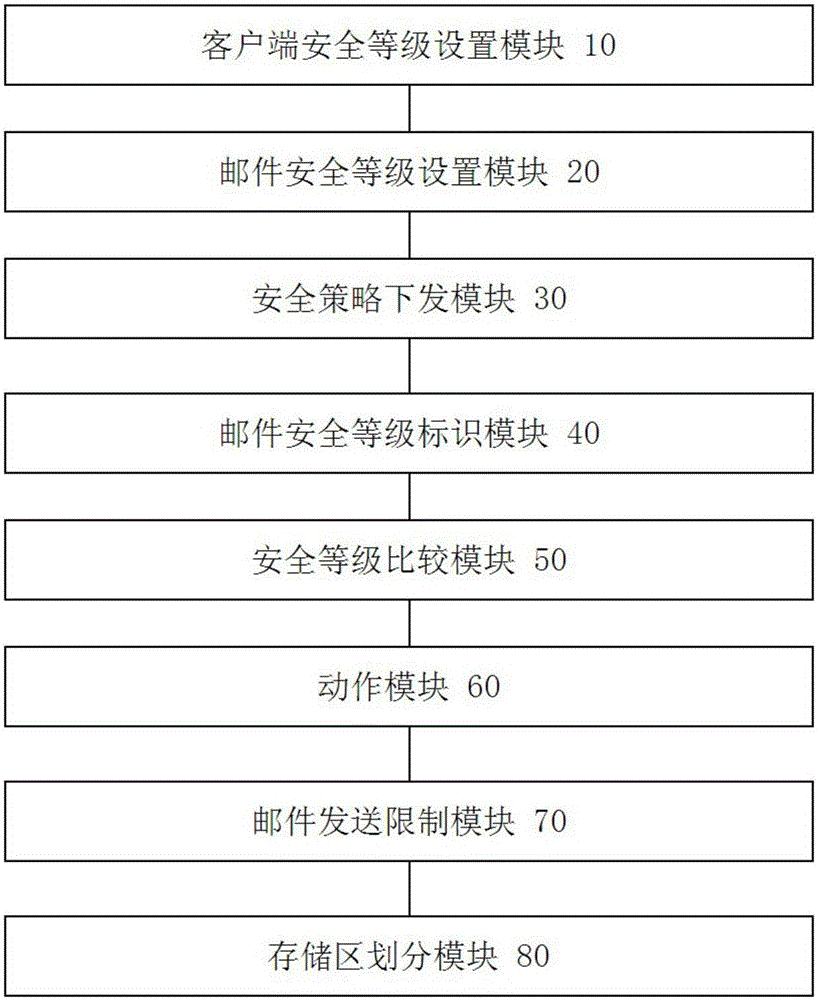
Method and device for improving email security of enterprise mobile management (EMM) system
The application discloses a method and a device for improving email security of an enterprise mobile management (EMM) system. The method comprises the following steps: setting client security levels for email clients in the EMM system; setting email security grading and security strategies which corresponds to the email security levels in the EMM system; issuing the security strategies to an email server and the email clients; marking the email security levels of emails in response to sending of the emails; checking whether the security levels of the email clients to receive the emails are lower than the security levels of the emails or not before the email server forwards the emails; and making the email server not forward the emails in response to that the security levels of the email clients are lower than the security levels of the emails to be forwarded. Through adoption of the method and the device, the overall security of the EMM system can be improved.
Owner:BEIJING YUANXIN SCI & TECH
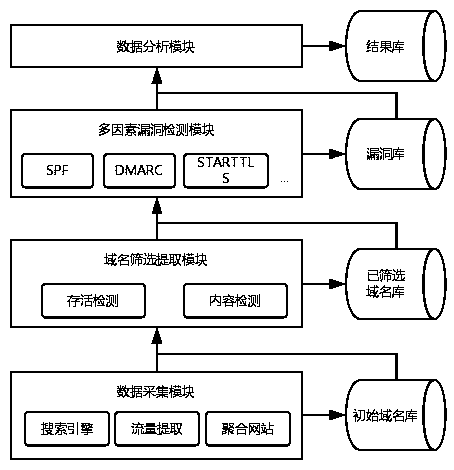
Email security protection detection technology based on multiple factors
InactiveCN109474611ASolve the defect of relay transmissionGuaranteed confidentialityData switching networksDomain nameInternet privacy
The invention relates to an email security protection detection technology based on multiple factors, and designs an email security detection model based on the multiple factors aiming at the problemthat the email with a Chinese domain name is lack of security detection. The technology comprises the steps of extracting different types of true and effective domain name data based on a data collection and domain name screening module; and then, detecting implementation conditions of email security extension protocols such as SFP, DMARC and STARTTLS based on a multi-factor vulnerability detection and data analysis module.
Owner:SICHUAN UNIV
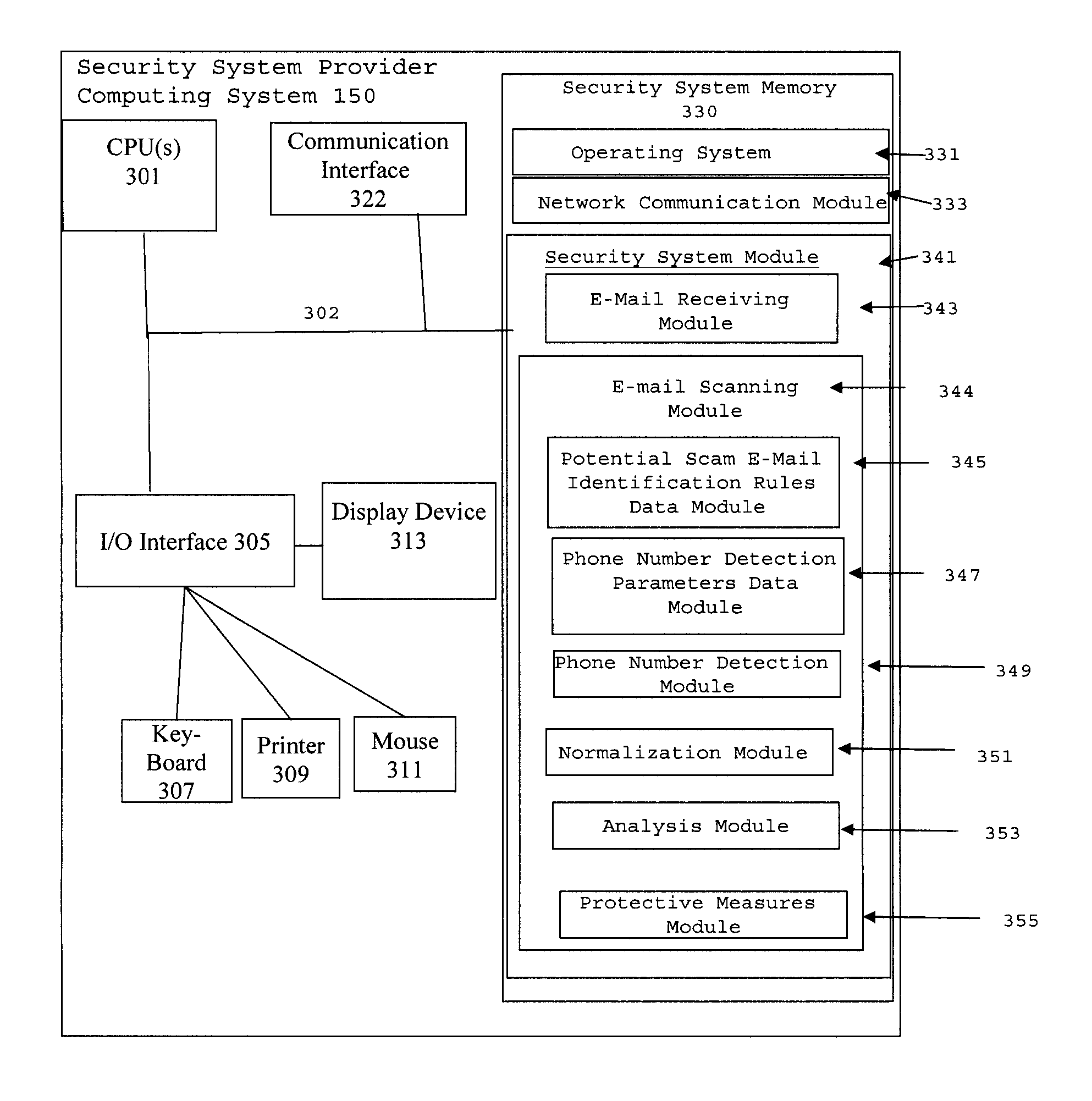
Electronic mail security system
ActiveUS10693891B2Office automationPlatform integrity maintainanceGraphical user interfaceDisplay device
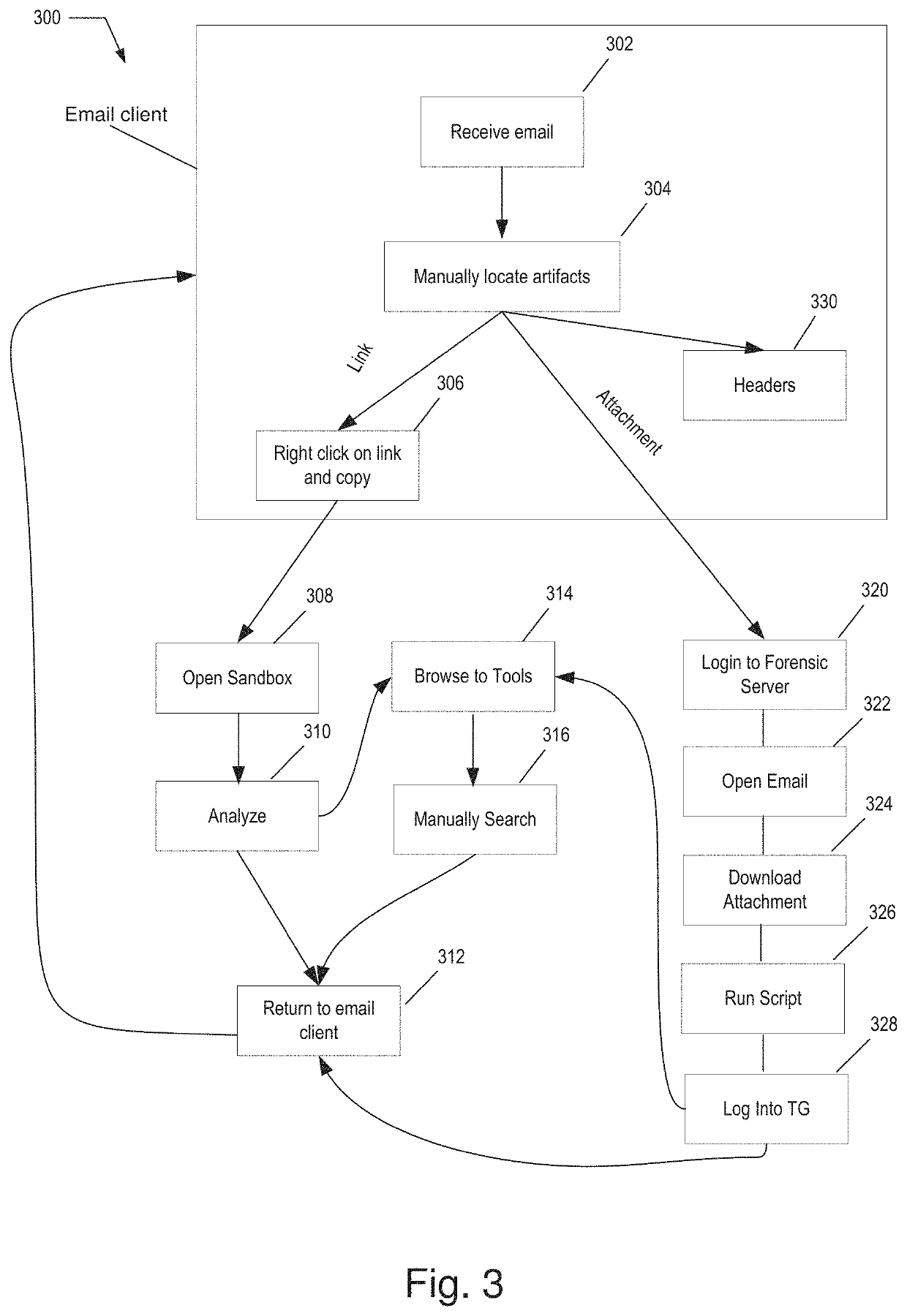
A method includes, in response to receiving an email message, detecting one or more artifacts within an email message, wherein each of the artifacts is associated with a payload; for each artifact, generating, a descriptor object representing the artifact that does not include the payload, so that the processor is prevented from accessing the payload via the descriptor object; and at least one payload button based on the payload associated with the artifact for causing the payload to be transmitted to an external system for analysis of the payload; and presenting an artifact dashboard in a graphical user interface (GUI) rendered on a display of the email security system, the artifact dashboard displaying, for each artifact, the descriptor object representing the artifact and the at least one payload button based on the payload associated with the artifact.
Owner:CHICAGO MERCANTILE EXCHANGE INC
Interactive email
Owner:MICROSOFT TECH LICENSING LLC
Electronic mail security system
A method comprises, in response to receiving an email message, detecting one or more artifacts within an email message, wherein each of the artifacts is associated with a payload; for each artifact, generating, a descriptor object representing the artifact that does not include the payload, so that the processor is prevented from accessing the payload via the descriptor object; and at least one payload button based on the payload associated with the artifact for causing the payload to be transmitted to an external system for analysis of the payload; and presenting an artifact dashboard in a graphical user interface (GUI) rendered on a display of the email security system, the artifact dashboard displaying, for each artifact, the descriptor object representing the artifact and the at least one payload button based on the payload associated with the artifact.
Owner:CHICAGO MERCANTILE EXCHANGE
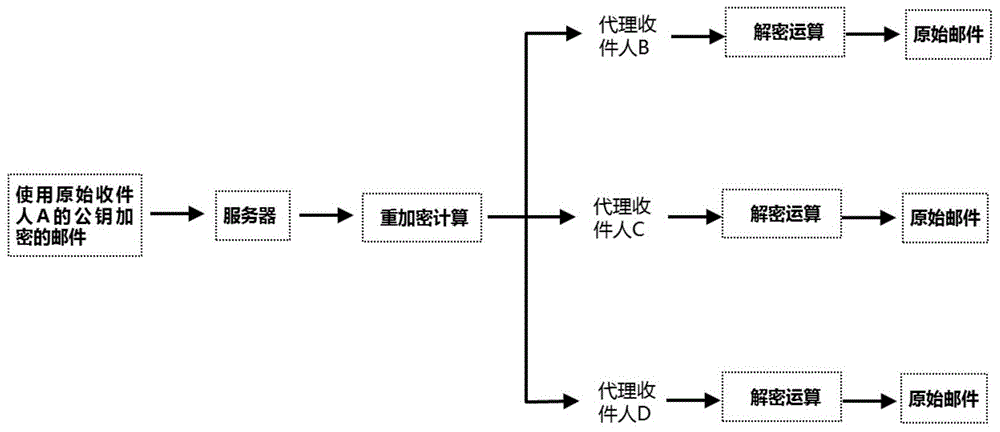
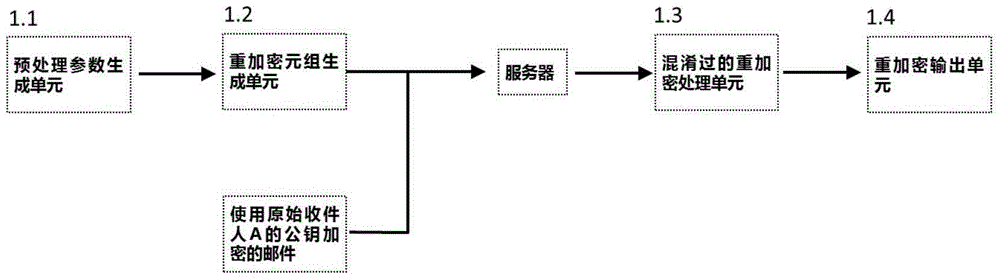
Reverse-engineering-resistant safe E-mail forwarding system and method
The invention discloses a reverse-engineering-resistant safe E-mail forwarding system and method. The system comprises a secret mail re-encryption module and a re-encrypted mail recovery module, wherein the secret mail re-encryption module comprises a preprocessed parameter generating unit, a re-encryption tuple generating unit, a confused re-encryption processing unit and a re-encryption output unit; and the re-encrypted mail recovery module comprises a re-encrypted mail receiving unit, a re-encrypted mail decryption unit and an original mail searching unit. The method comprises an E-mail re-encryption method and an E-mail re-encryption recovery method. The reverse-engineering-resistant safe E-mail forwarding system and method have the characteristics of low realization complexity, high safety, recovery simplicity and the like and are suitable for re-encrypting and forwarding a mail through a third-party mail service provider under the conditions that the private keys of the original mail receiver and the mail agent receiver are not leaked, and any information of the mail is not leaked.
Owner:HUBEI UNIV OF TECH
Intelligent terminal enterprise Email security office method and system
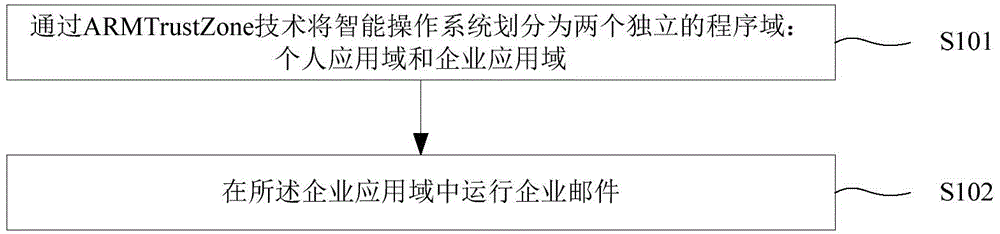
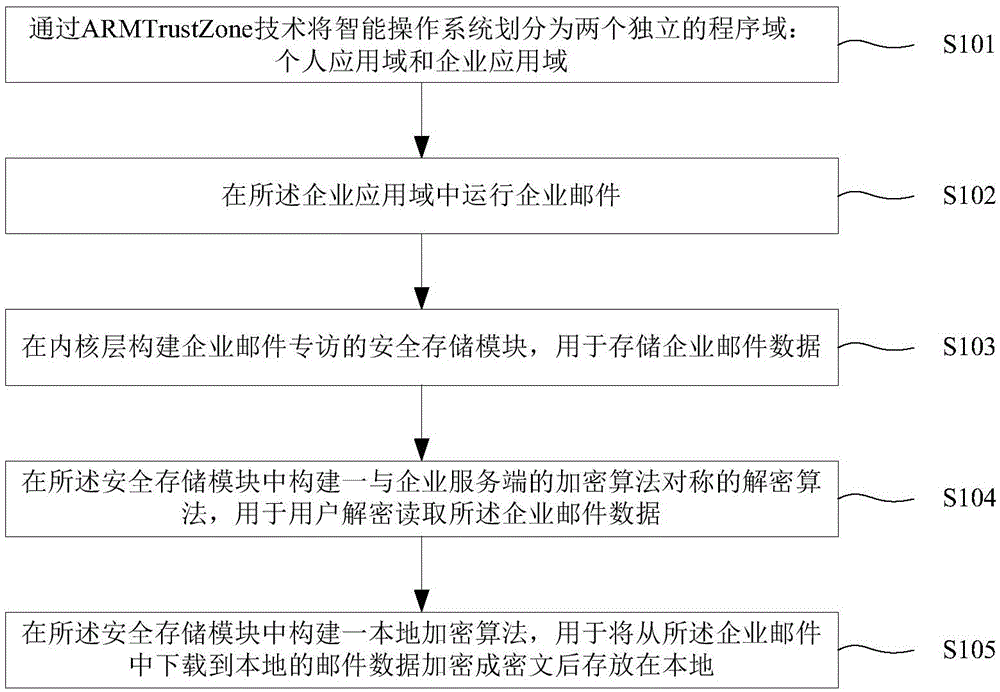
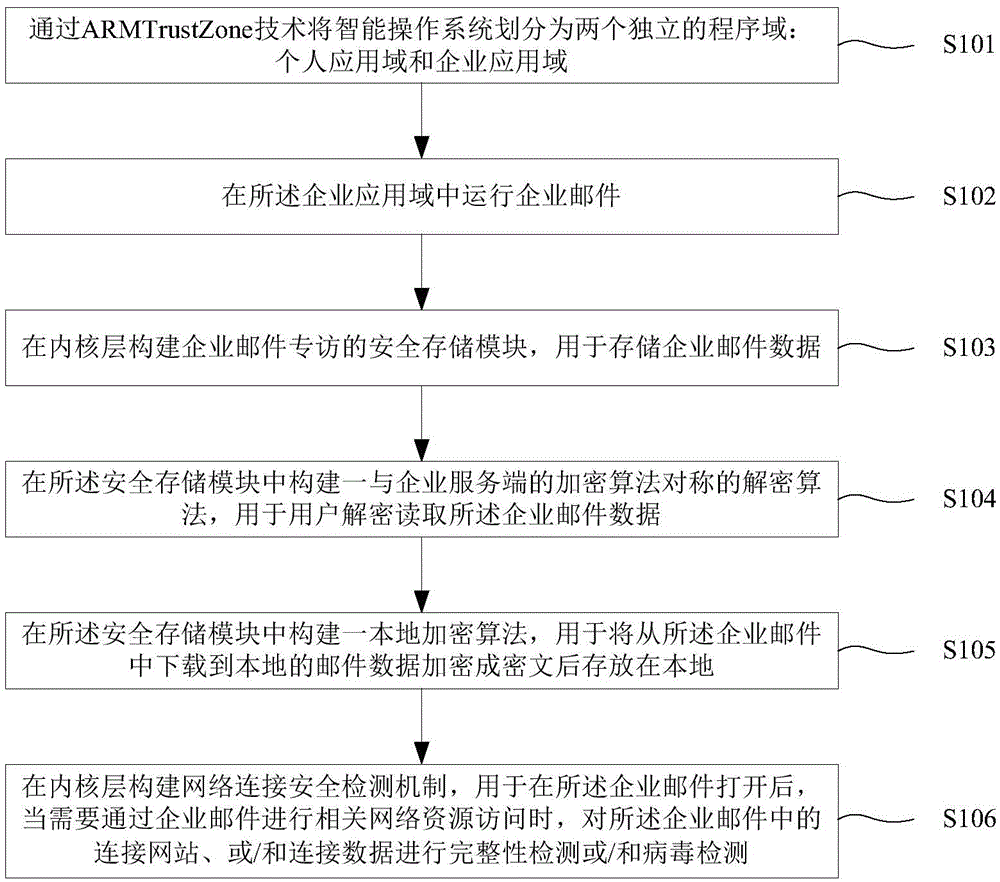
InactiveCN104378381APrevent leakageAvoid visitingOffice automationTransmissionThird partyOperational system
The invention provides an intelligent terminal enterprise Email security office method and system. The method includes: an intelligent operating system is divided into a personal application domain and an enterprise application domain which are independent through the ARMTrustZone technology; the personal application domain operates third-party software downloaded by a user; the enterprise application domain operates safe application software authenticated by an enterprise; enterprise Emails are operated in the enterprise application domain. The method has the advantages that the intelligent operating system is divided into the personal application domain and the enterprise application domain which are independent through the ARMTrustZone technology, data accessing and interaction between the two domains are avoided, and the enterprise Emails of the enterprise application domain are protected from being interfered or invaded by the applications of the personal application domain.
Owner:PHICOMM (SHANGHAI) CO LTD
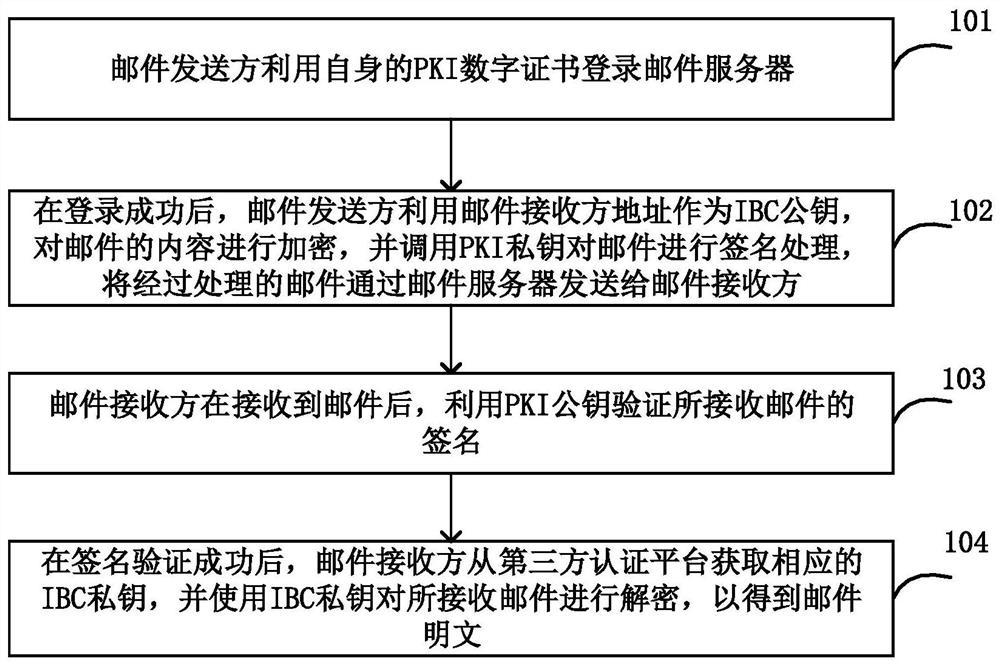
E-mail secure transmission method and system
InactiveCN113381852ASolve the problem of authenticityFix security issuesKey distribution for secure communicationUser identity/authority verificationPlaintextEngineering
The invention provides an E-mail secure transmission method and system. The mail sender logs in the mail server by using the own PKI digital certificate, encrypts the content of the mail by using the mail receiver address of the mail as an IBC public key after successful login, calls the PKI private key to perform signature processing on the mail, and sends the processed mail to the mail receiver through the mail server; after receiving the mail, the mail receiver verifies the signature of the received mail by using the PKI public key; and after the signature verification succeeds, the mail receiver obtains the corresponding IBC private key from the third-party authentication platform, and decrypts the received mail by using the IBC private key to obtain a mail plaintext. According to the invention, the authenticity of the user is verified by using the PKI certificate, and the secure transmission of the secret key is realized by using the IBC password system, so that the secure transmission of the mail can be effectively realized.
Owner:CHINA TELECOM CORP LTD
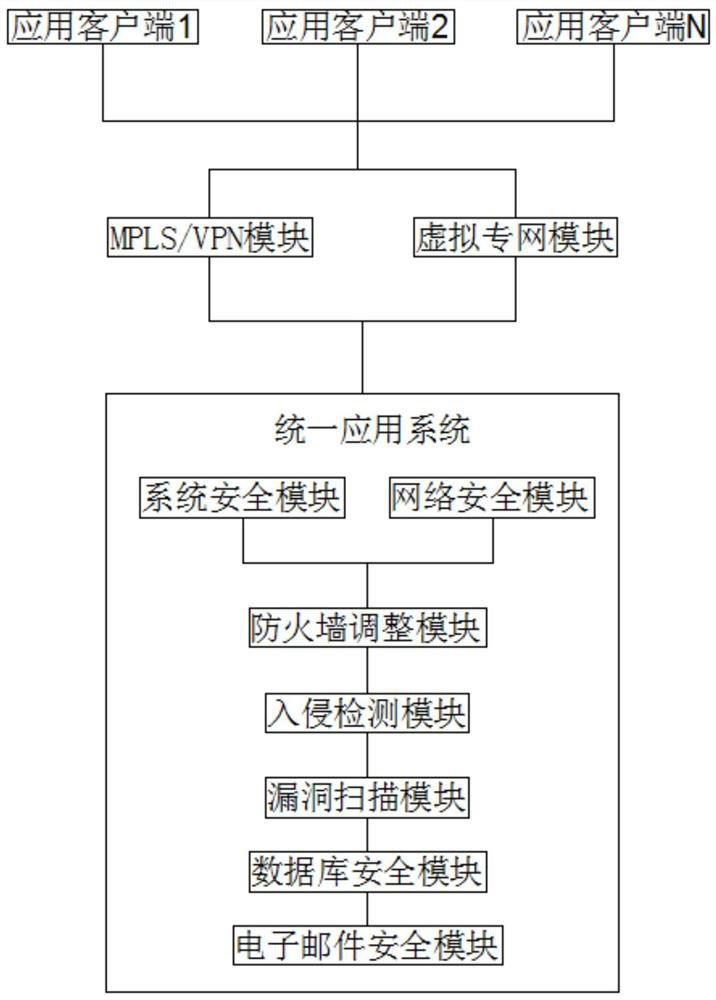
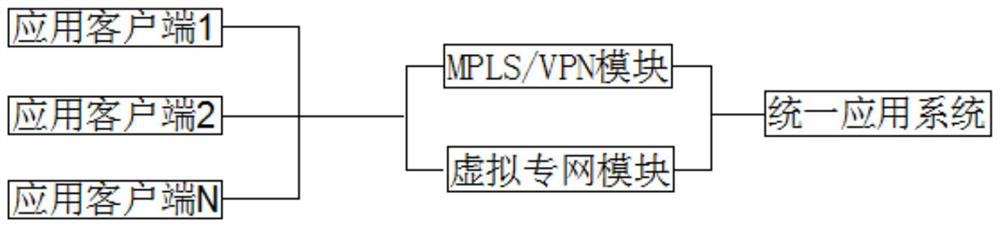
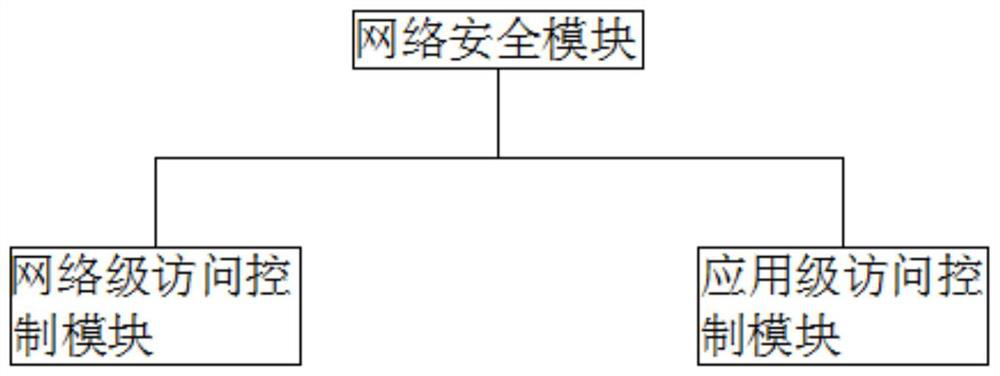
Internet-based company security network implementation system
InactiveCN112738017AConvenient encrypted transmissionEasy to viewTransmissionPrivate networkNetwork connection
The invention discloses an Internet-based company security network implementation system, which comprises an application client 1, an application client 2, an application client N, a virtual private network module and a unified application system, the unified application system comprises a system security module, a network security module, a firewall adjustment module, an intrusion detection module, a vulnerability scanning module, a database security module and an e-mail security module. The application client 1, the application client 2 and the application client N are connected to the MPLS / VPN module and the virtual private network module through a network and are connected to a system security module, a network security module, a firewall adjustment module, an intrusion detection module, a vulnerability scanning module, a database security module and an e-mail security module in the unified application system in series; the method has the advantages that the system information encryption transmission is high, the information security in the system is high, the cross-region encryption transmission and viewing are convenient, and the system loopholes and dangerous factors are discovered in time, so that the effective protection is carried out.
Owner:南京英诺森软件科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com