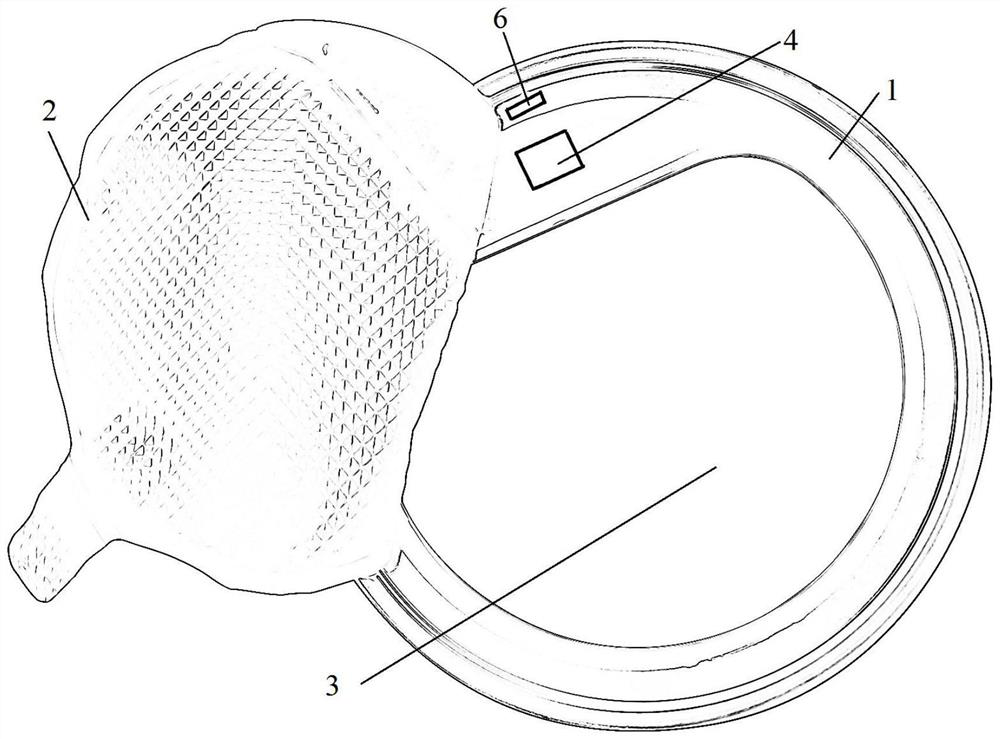
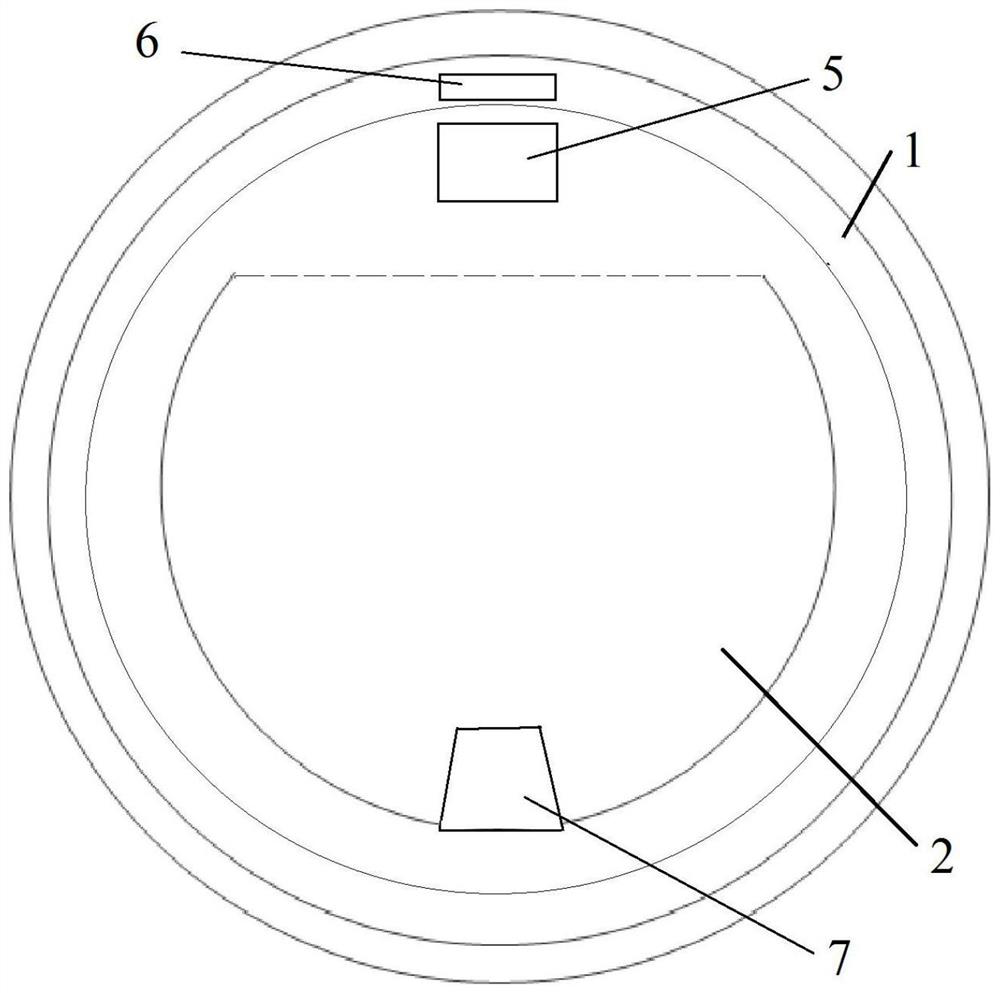
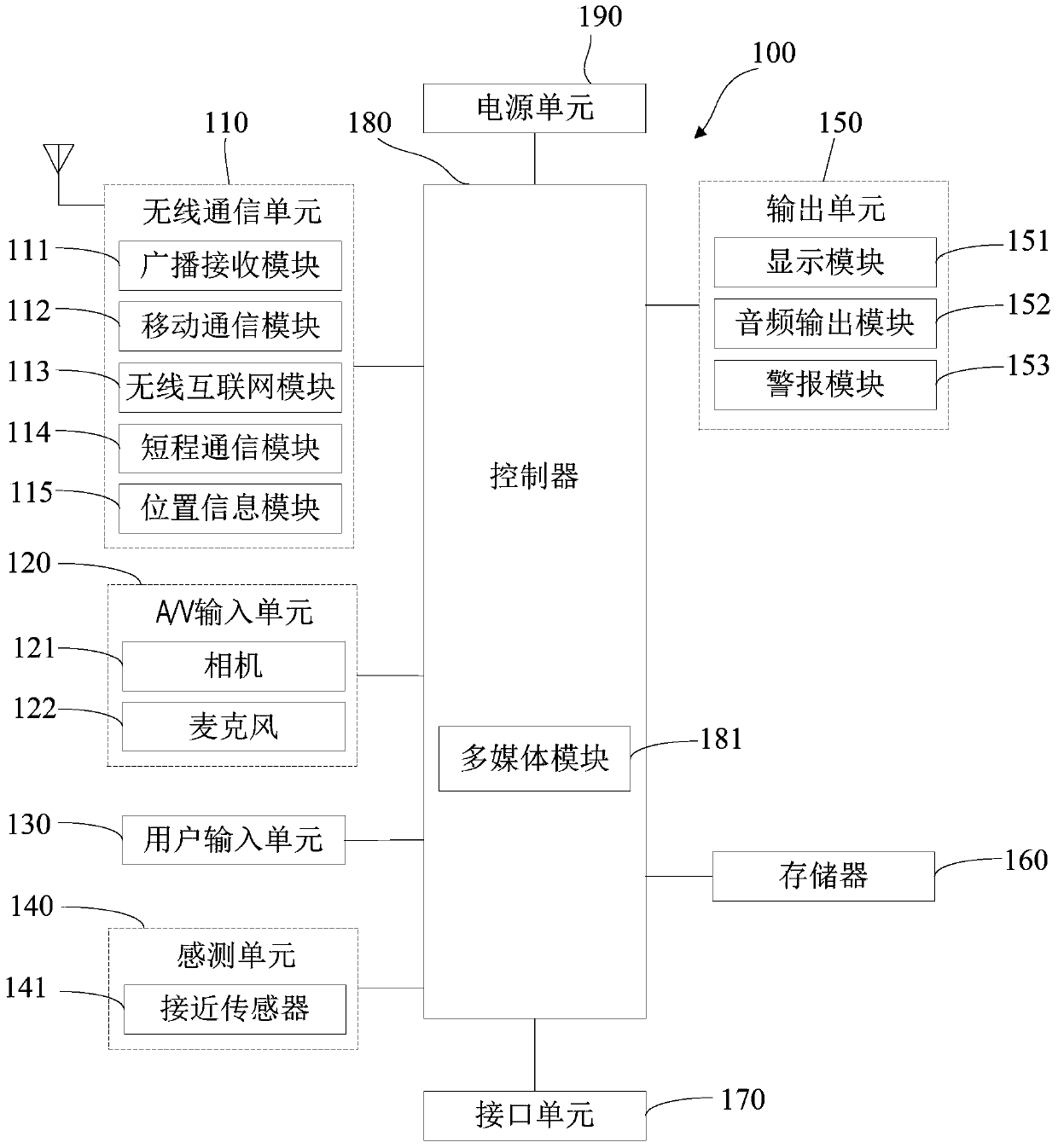
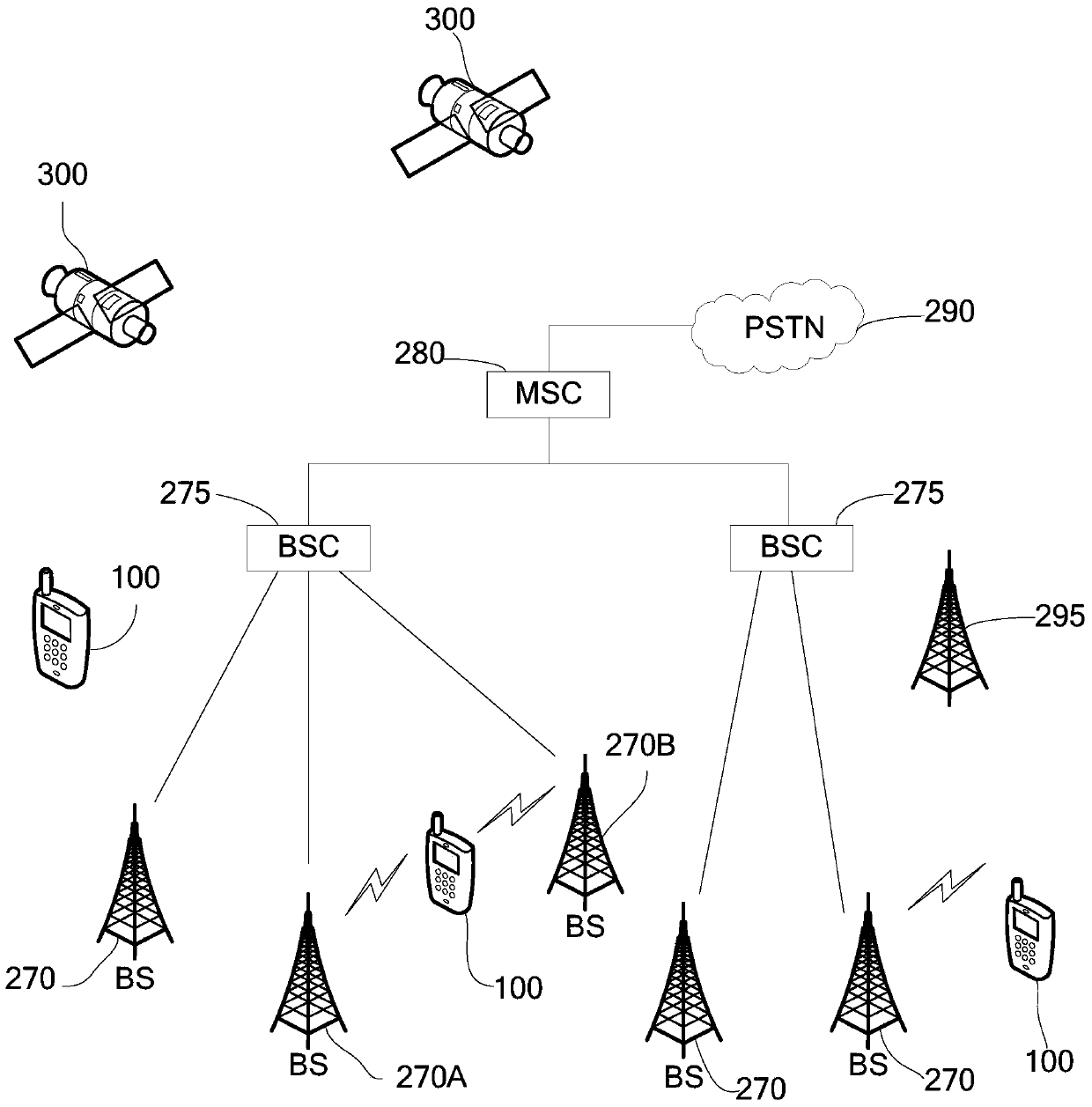
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49results about How to "Reduce the Risk of Misappropriation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Abnormity monitoring method and device for user registration
ActiveCN103532797AReduce complexityReduce the Risk of MisappropriationData switching networksInternet privacy
Owner:NETEASE INFORMATION TECH(BEIJING) CO LTD
Account login method and system
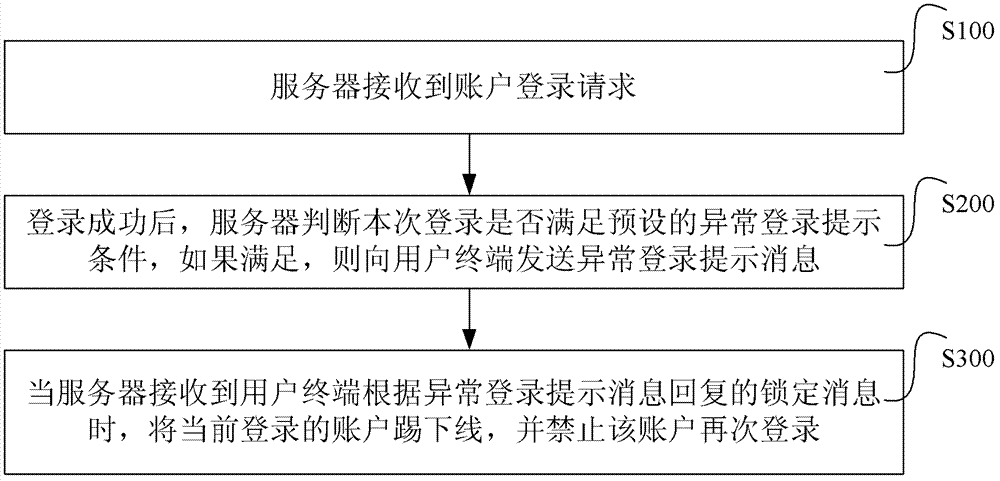
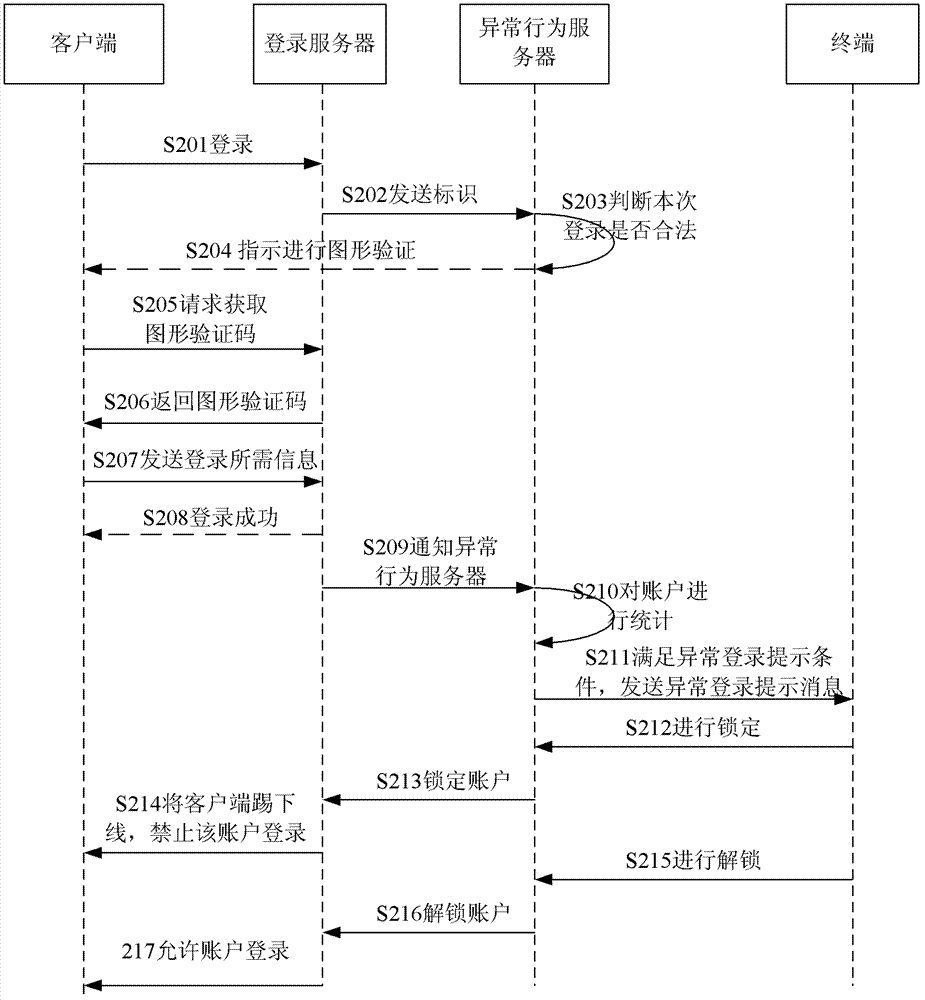
The invention discloses an account login method and a system. The method comprises: step 1, an account login request is received by a server; step 2, the server judges whether the login meets pre-set unusual login prompt conditions or not after success of login, and if the login meets the pre-set unusual login prompt conditions, unusual login prompt information is sent to a user terminal; and step 3, when the server receives lock information replied according to unusual login prompt information through the user terminal, a current registered account is forced to log off, and the account is forbidden to log in again. The account login method and the system can inform a user timely after the account of the user is stolen, and meanwhile usage of the account is limited so as to prevent loss of the user.
Owner:ULTRAPOWER SOFTWARE
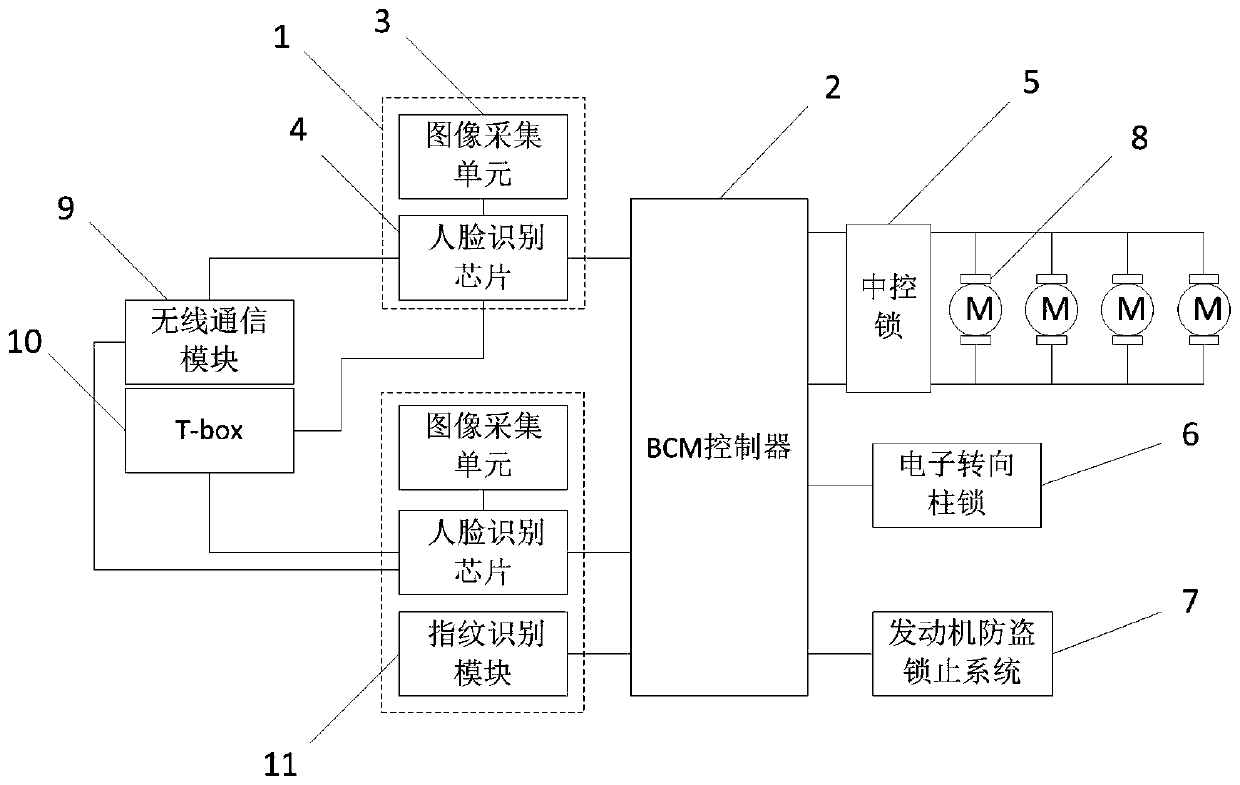
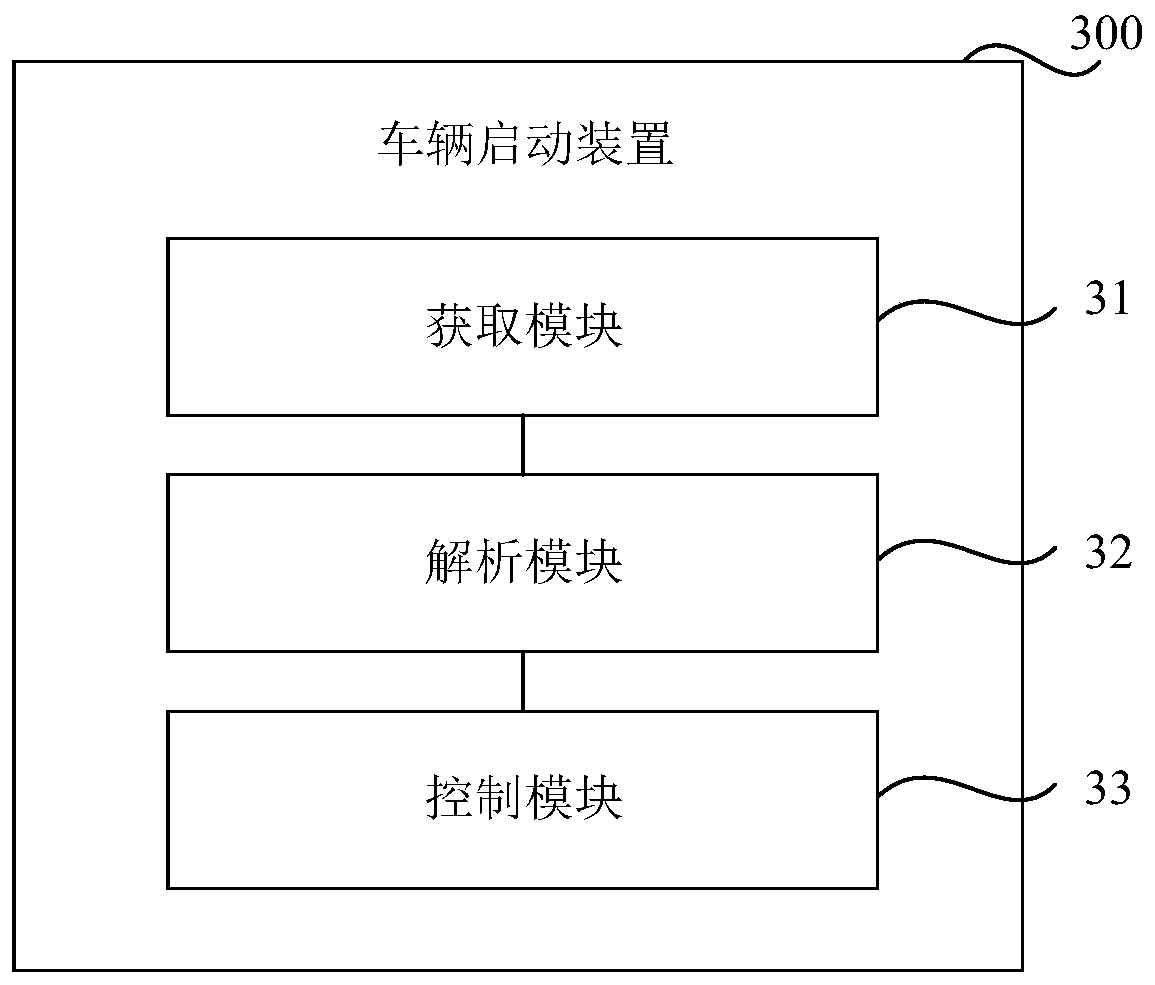
Automobile keyless entry and starting system based on face recognition
InactiveCN110182174AReduce the Risk of MisappropriationAchieve normal startupAnti-theft devicesSteering columnComputer science
The invention relates to an automotive electronic technology, and discloses an automobile keyless entry and starting system based on face recognition. The automobile keyless entry and starting systemcomprises an image collecting unit, a face recognition chip and a BCM controller; and through the face recognition chip, a face image, obtained by the image collecting unit, of a current automobile user and a pre-saved face image of a legal automobile user are subjected to feature comparison to conduct identity verification on the current automobile user, a corresponding triggering instruction issent to the BCM controller after verification is passed to unlock a central lock, an electronic steering column lock and an engine anti-theft locking system of an automobile through the BCM controller, and thus keyless entry and starting of the automobile are achieved. Through the technical scheme, an automobile owner can enter and start the automobile without relying on an intelligent key, and thus the convenient and worriless effects are achieved; and meanwhile through the technical scheme, the purpose of conducting identity verification on the current automobile user is also achieved, and thus the risk that the automobile is embezzled is lowered.
Owner:深圳市赛格车圣科技有限公司
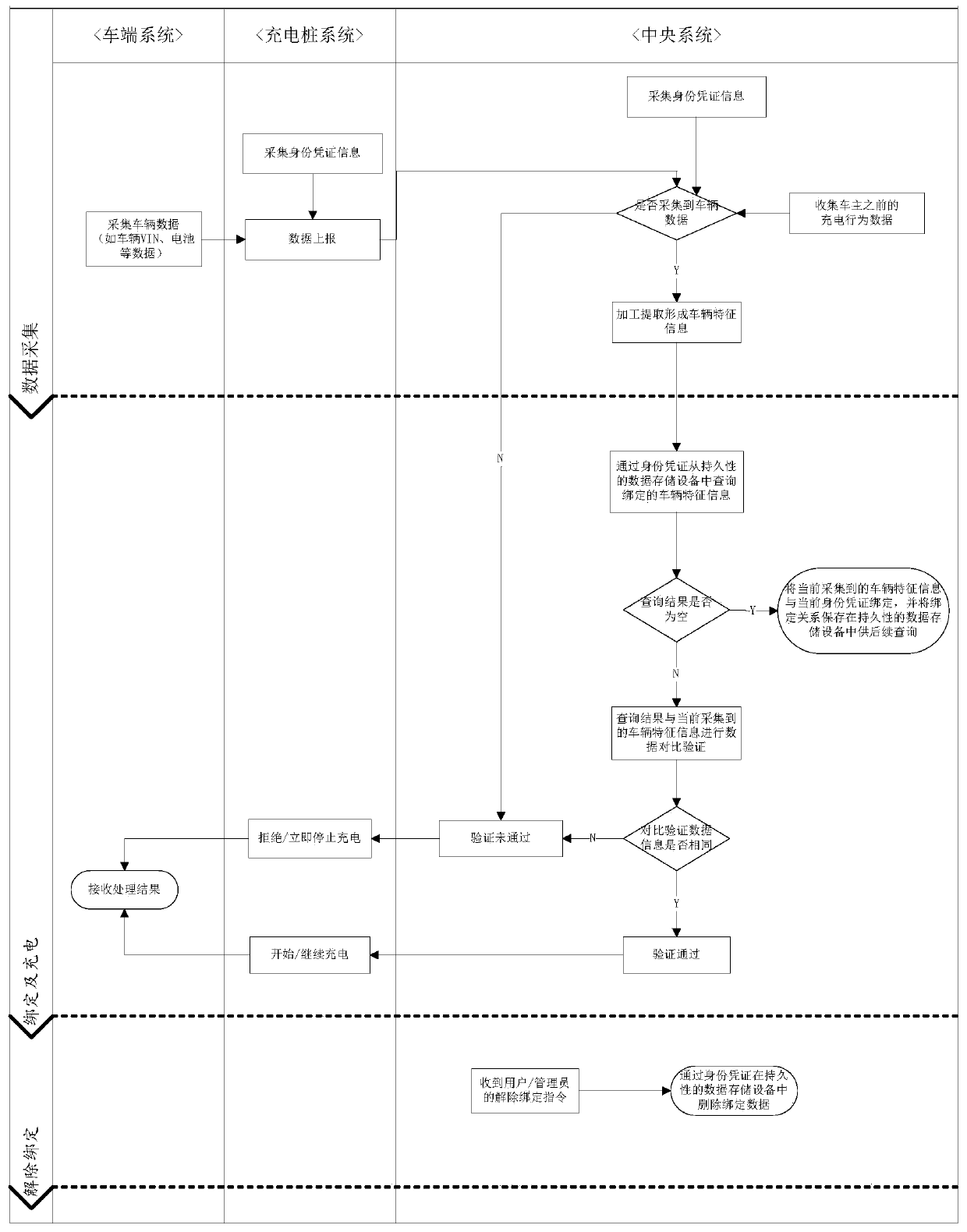
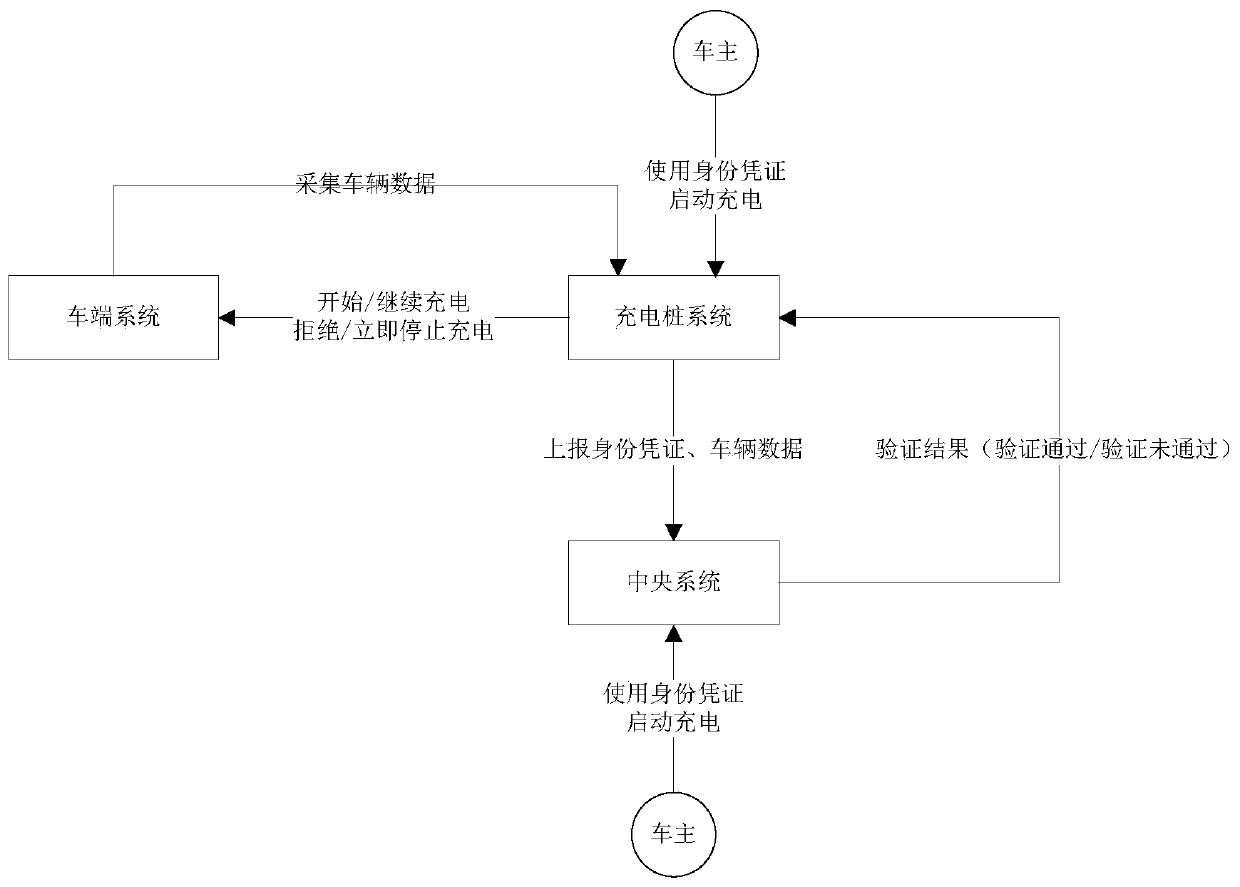
Method and system for reducing stealing risk of electric vehicle charging identity certificate
InactiveCN110143151AReduce the Risk of MisappropriationAvoid economic lossCharging stationsElectric vehicle charging technologyData acquisitionBattery electric vehicle
The invention discloses a method and a system for reducing the stealing risk of an electric vehicle charging identity certificate. The method comprises the following steps: (1) data acquisition: acquiring the charging identity certificate and vehicle data, processing the charging identity certificate and the vehicle data by a central system, and processing and extracting to form vehicle characteristic information; (2) binding and charging: enabling the central system to inquire vehicle characteristic information bound with the charging identity certificate from a persistent data storage device, if the vehicle characteristic information is empty, binding the currently collected vehicle characteristic information with the current charging identity certificate, and storing the binding relationship in the persistent data storage device for subsequent inquiry; if the vehicle characteristic information bound with the charging identity certificate is inquired, comparing the inquired vehicle characteristic information with the currently collected vehicle characteristic information for verification, if the verification passes, enabling the central system to indicate a charging pile system to start / continue charging, otherwise, the charging is refused / the charging is stopped immediately / an electric vehicle owner is notified to confirm whether to continue the charging or not.
Owner:BEIJING X CHARGE TECH CO LTD
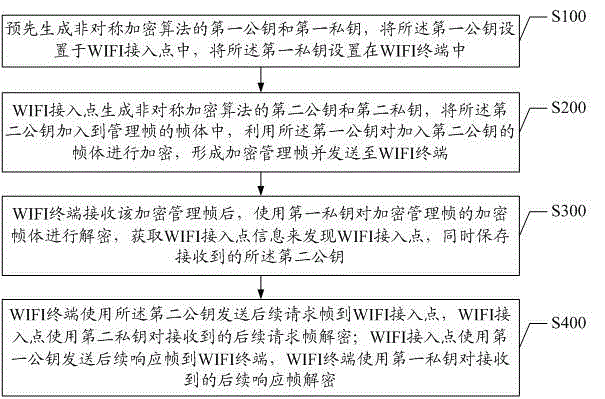
Method and system for encrypting, hiding and discovering of WIFI access point
ActiveCN105025472ANormal visibilityReduce the Risk of MisappropriationSecurity arrangementVisibilityEncryption
The invention discloses a method and a system for encrypting, hiding and discovering of a WIFI access point. The method comprises steps of generating a first public key and a first private key, wherein the first public key is positioned in an AP, and placing the first private key in an STA, B generating a second public key and a second private key, wherein the second public key is added into a management frame, and utilizing the first public key to encrypt the frame body which is transmitted to the STA, C using the first private key to decrypt the encryption to find the AP by the STA and storing the second public key, D using the second public key to transmit the following-up management frame to the AP by the STA, using the second private key to perform decryption on the following-up management frame by the AP, using the first public key to transmit the following- up management frame to the STA by the AP, and using the first private key to perform decryption on the received following-up management frame by the STA. The invention utilizes the asymmetric encryption algorithm to perform encryption on the STA and the AP management frame, only the STA has the correct private key to decrypt the management frame and find the existence of the AP so as to hide the visibility of the AP toward the illegal user and thus reduce the risk that the AP can be stolen.
Owner:TCL CORPORATION
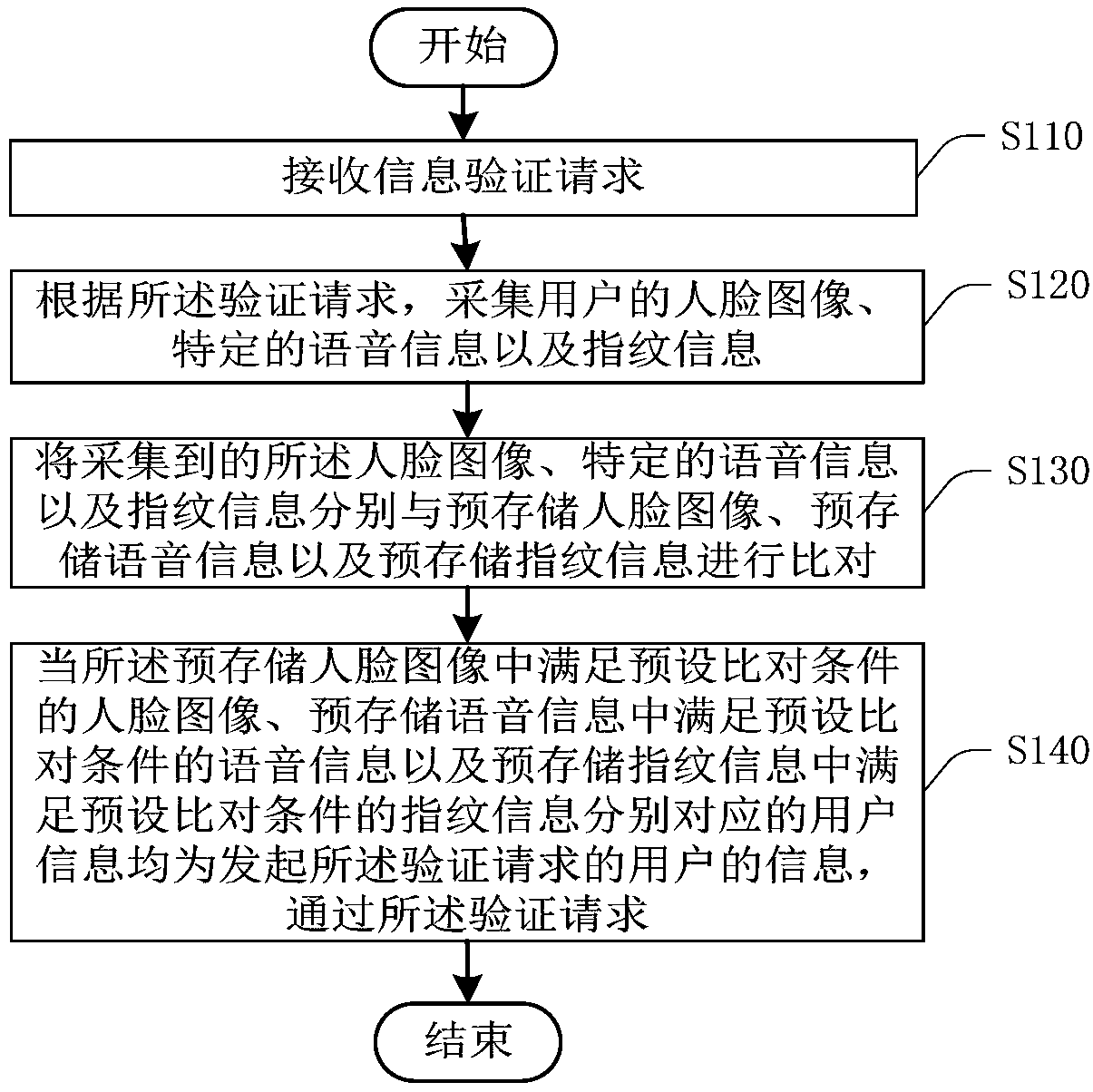
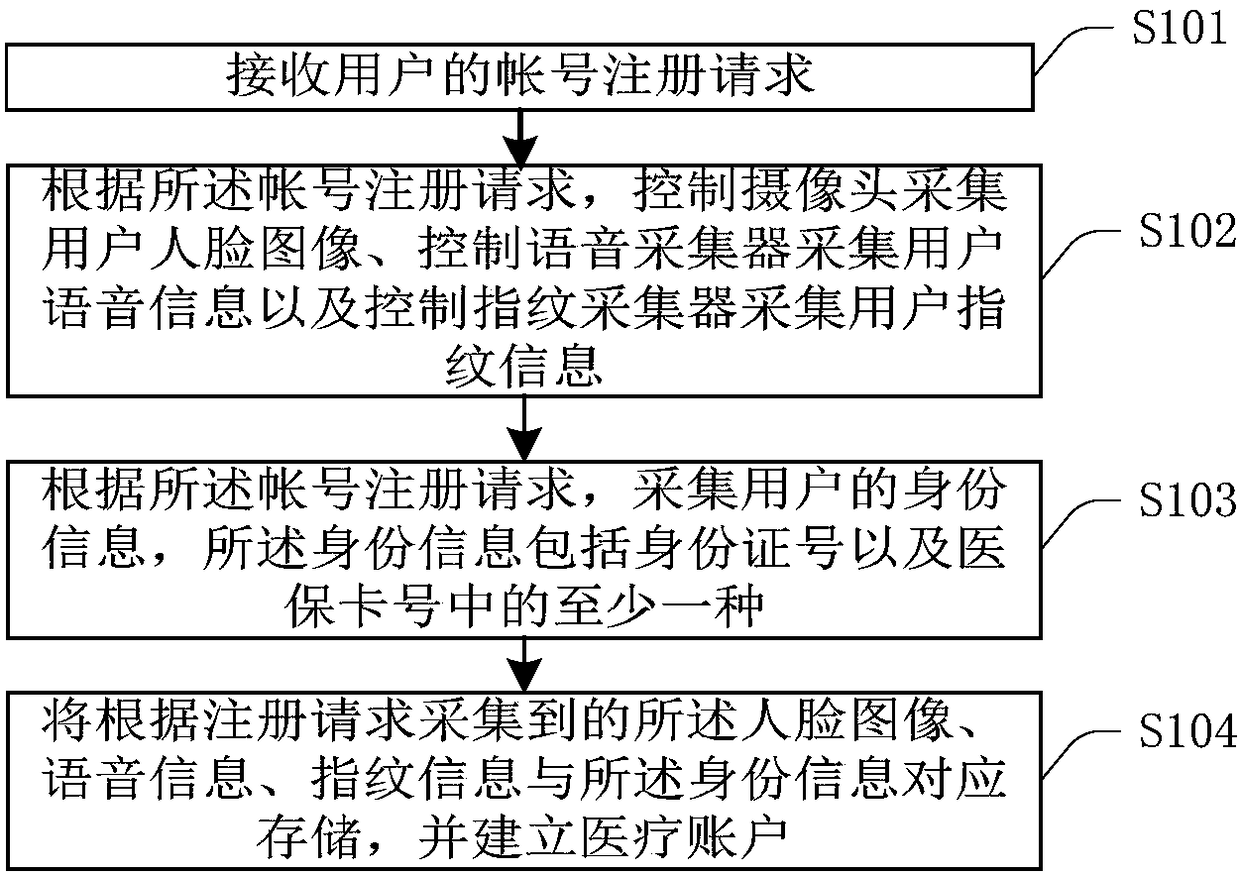
Information verification method and device
InactiveCN108959874AImprove securityReduce the Risk of MisappropriationDigital data authenticationPattern recognitionComputer terminal
The invention provides an information verification method and device, relates to the medical field, and is applied to information verification of the medical terminal. The method comprises the following steps: receiving an information verification request; collecting a user's face image, specific voice information and fingerprint information according to the verification request; comparing the collected face image, the specific voice information and the fingerprint information with the pre-stored face image, the pre-stored voice information and the pre-stored fingerprint information respectively; and when the user information respectively corresponding to the face image meeting the preset comparison condition of the pre-stored face image, the voice information meeting the preset comparisoncondition of the pre-stored voice information and the fingerprint information meeting the preset comparison condition of the pre-stored fingerprint information is the information of the user initiating the verification request, the verification request is passed. According to the scheme, multi-verification is performed through the face image, the voice information and the fingerprint informationso that the security of the account number can be enhanced.
Owner:WUHAN MEDICAL UNION
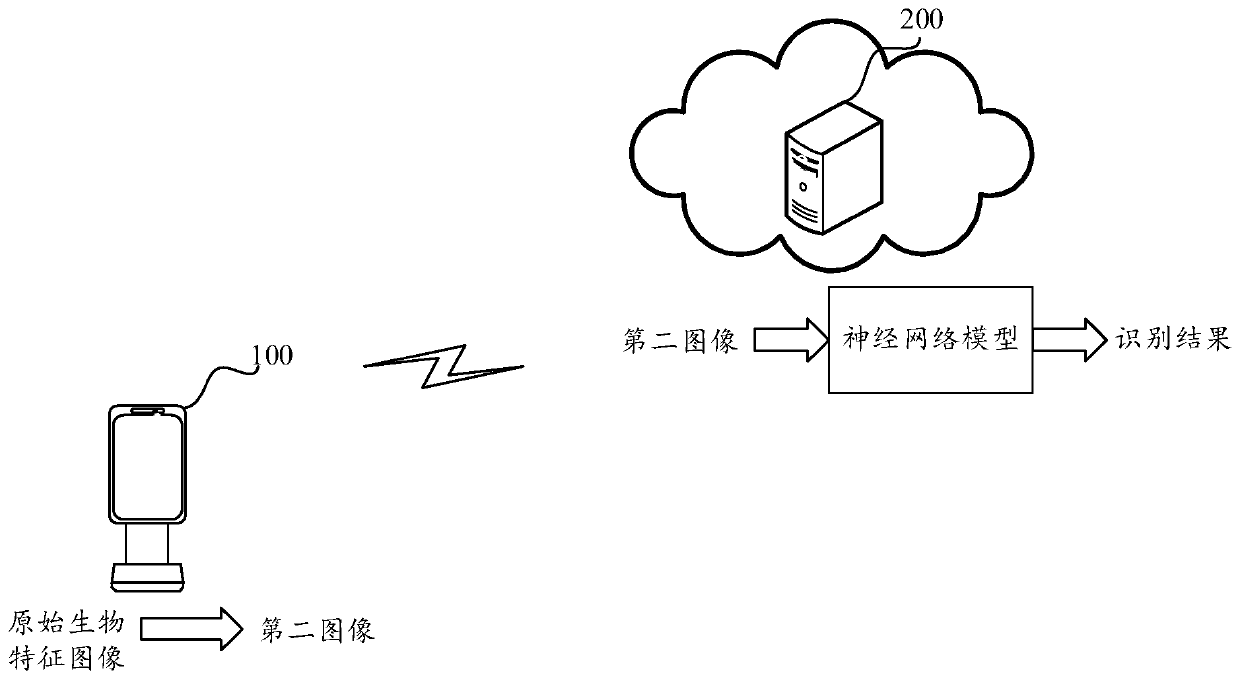
Privacy-protecting biological characteristic image processing method and device
ActiveCN111401320AAccurate identificationImprove securityDigital data protectionNeural architecturesImaging processingImage manipulation
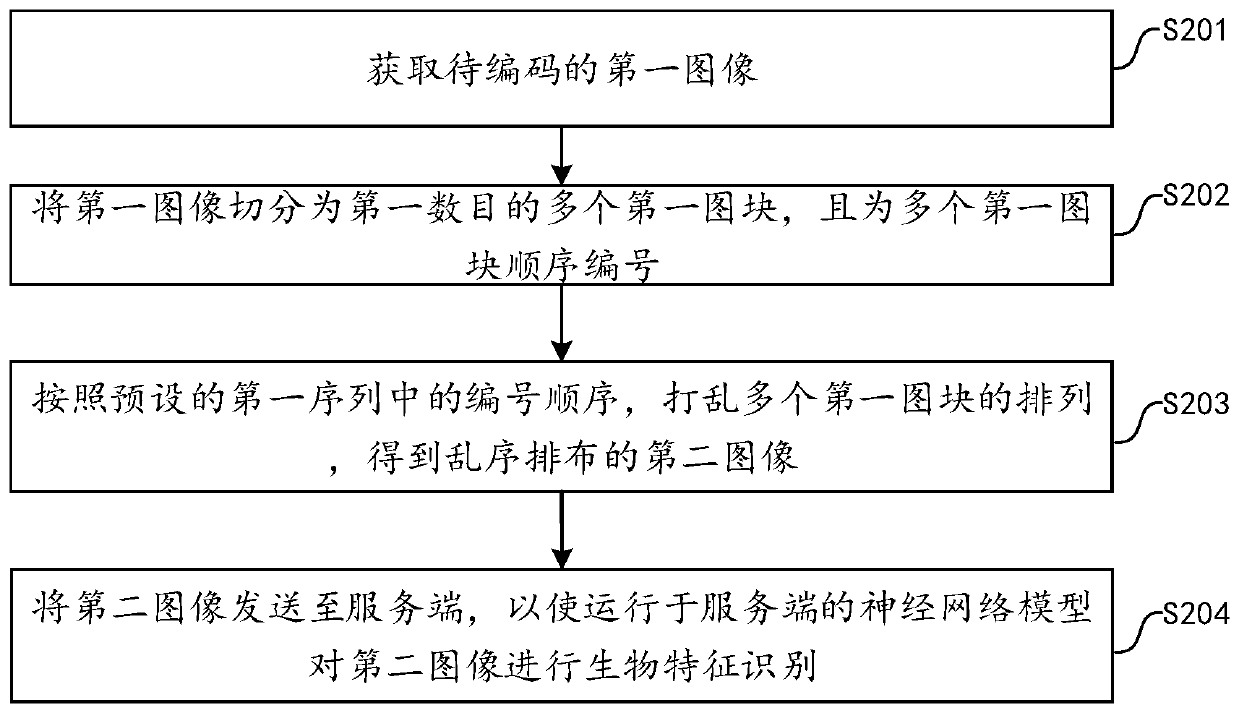
The embodiment of the invention provides a biometric image processing method and device, and the method comprises the steps: firstly obtaining a to-be-coded first image, segmenting the first image into a first number of first image blocks, and sequentially numbering the first image blocks; according to a number sequence in a preset first sequence, and disrupting the arrangement of the plurality offirst image blocks to obtain a second image which is arranged out of order; enabling the neural network model running on the server to perform biological feature recognition on the second image, wherein the neural network model is obtained by training specified training samples in advance, and each training sample in the specified training samples is arranged out of order according to a first sequence. The method can effectively improve the security of the private data of the user.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
User and terminal binding system and method applied to electrical stimulation physiotherapy system
PendingCN106934227AEasy retrievalClear processElectrotherapyData processing applicationsPhysical medicine and rehabilitationPhysical therapy
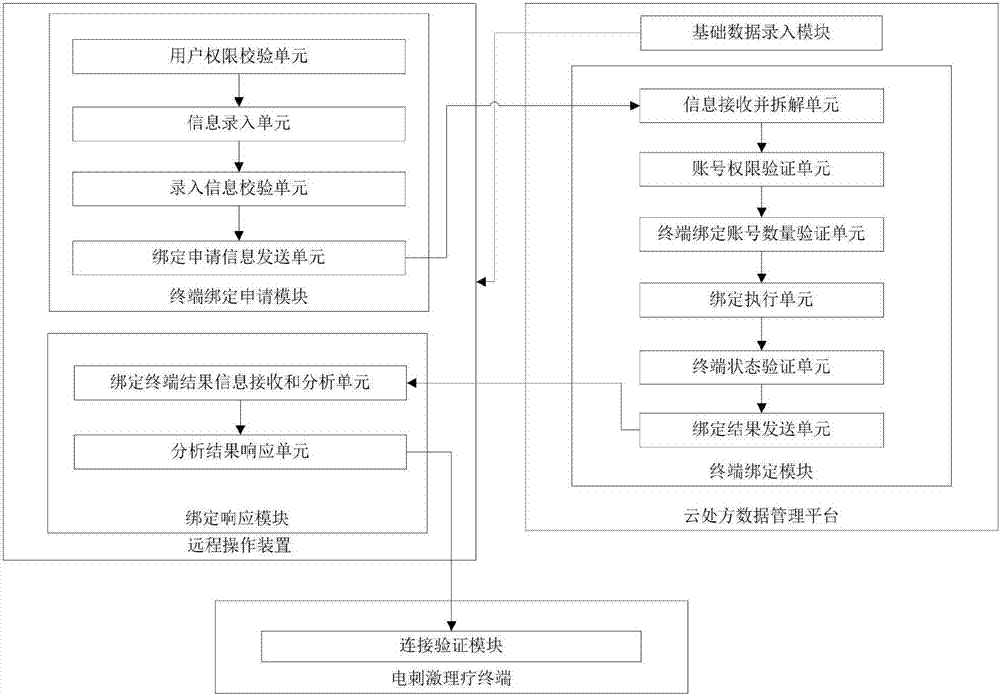
The invention relates to a user and terminal binding system and method applied to an electrical stimulation physiotherapy system. The system comprises an electrical stimulation physiotherapy terminal, a remote operation apparatus and a cloud prescription data management platform which are connected mutually, wherein the electrical stimulation physiotherapy terminal comprises a connection verification module; the remote operation apparatus comprises a terminal binding application module and a binding response module; and the cloud prescription data management platform comprises a terminal binding module and a basic data input module used for inputting basic information of the electrical stimulation physiotherapy terminal. According to the system and the method, user information is bound with the electrical stimulation physiotherapy terminal; prescription data is easier to manage; the security of the electrical stimulation physiotherapy terminal is guaranteed; the permission of a remote operation terminal is higher; and the operation error rate is better prevented.
Owner:成都华信高科医疗器械有限责任公司
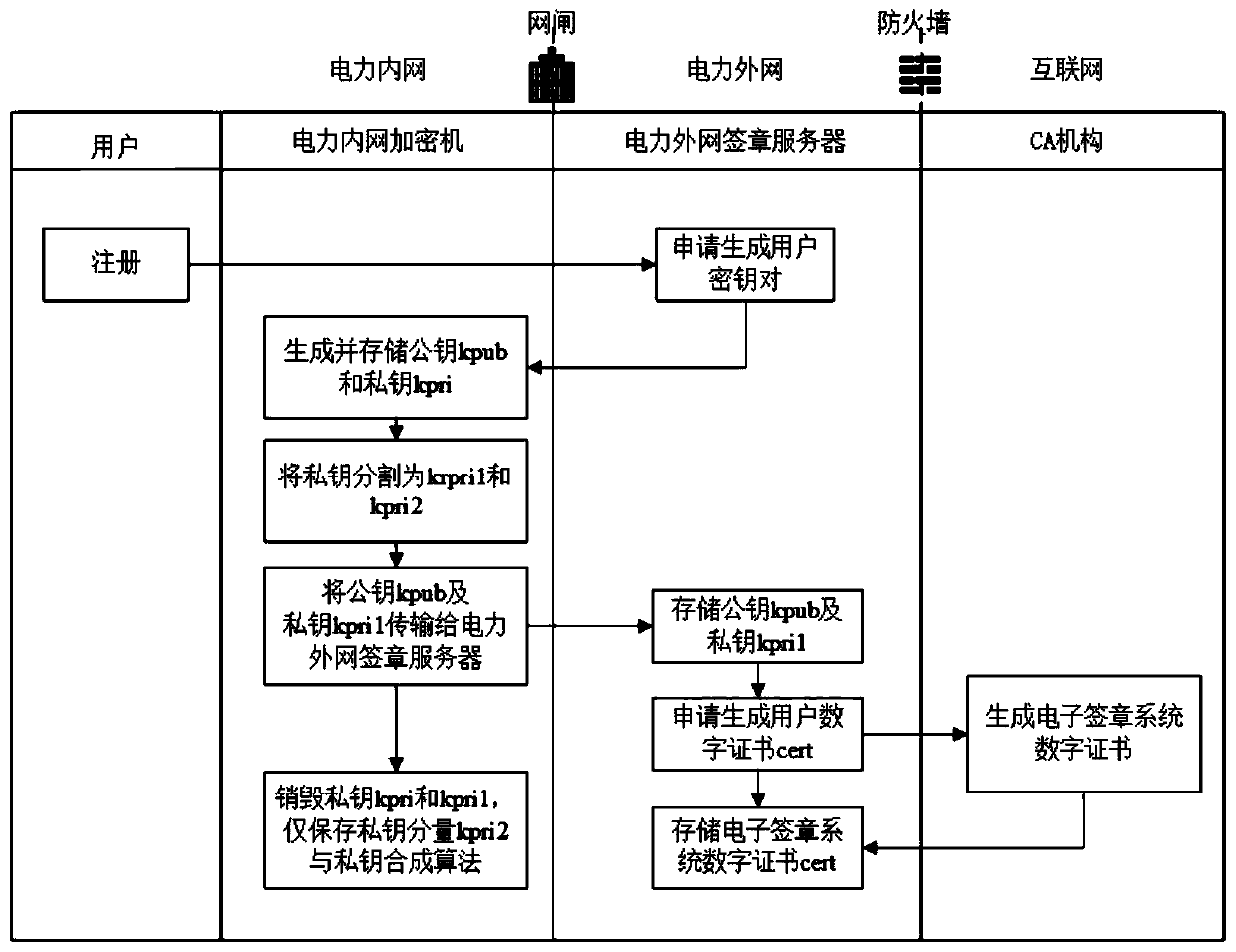
Electronic signature implementation method based on state grid security technology architecture
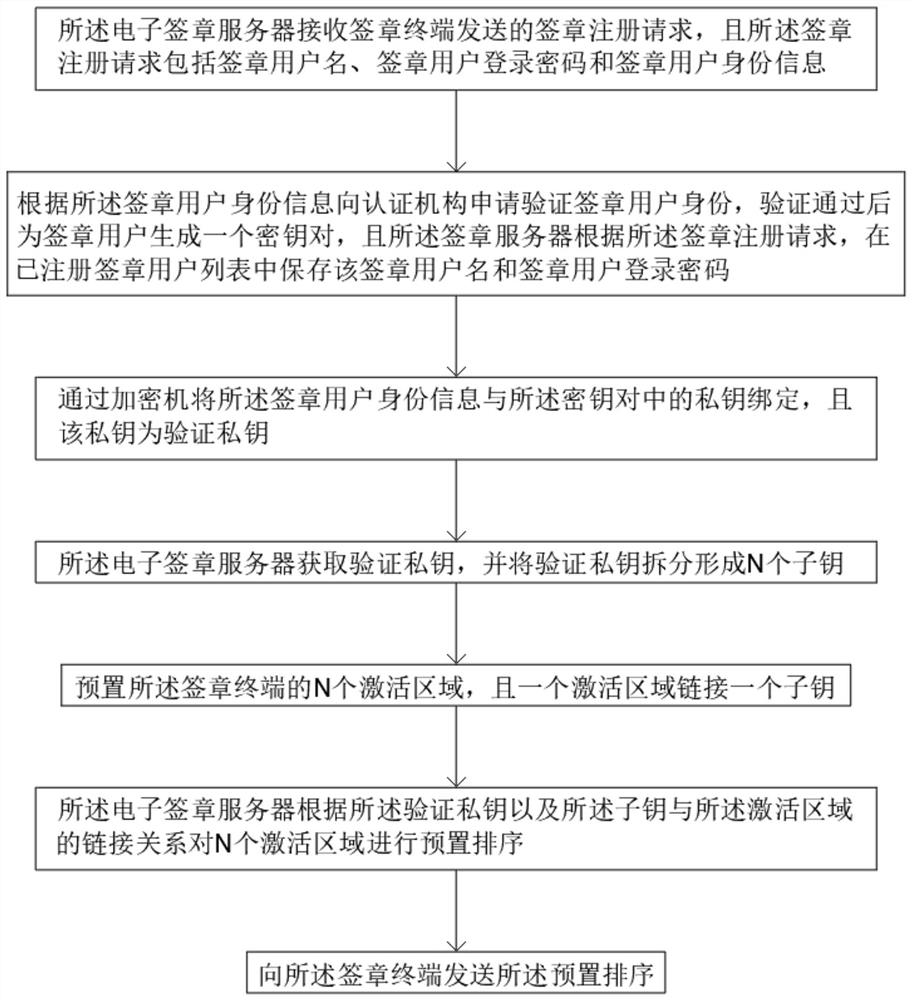
PendingCN111277417AImprove securityReduce the Risk of MisappropriationKey distribution for secure communicationUser identity/authority verificationDigital signatureEngineering
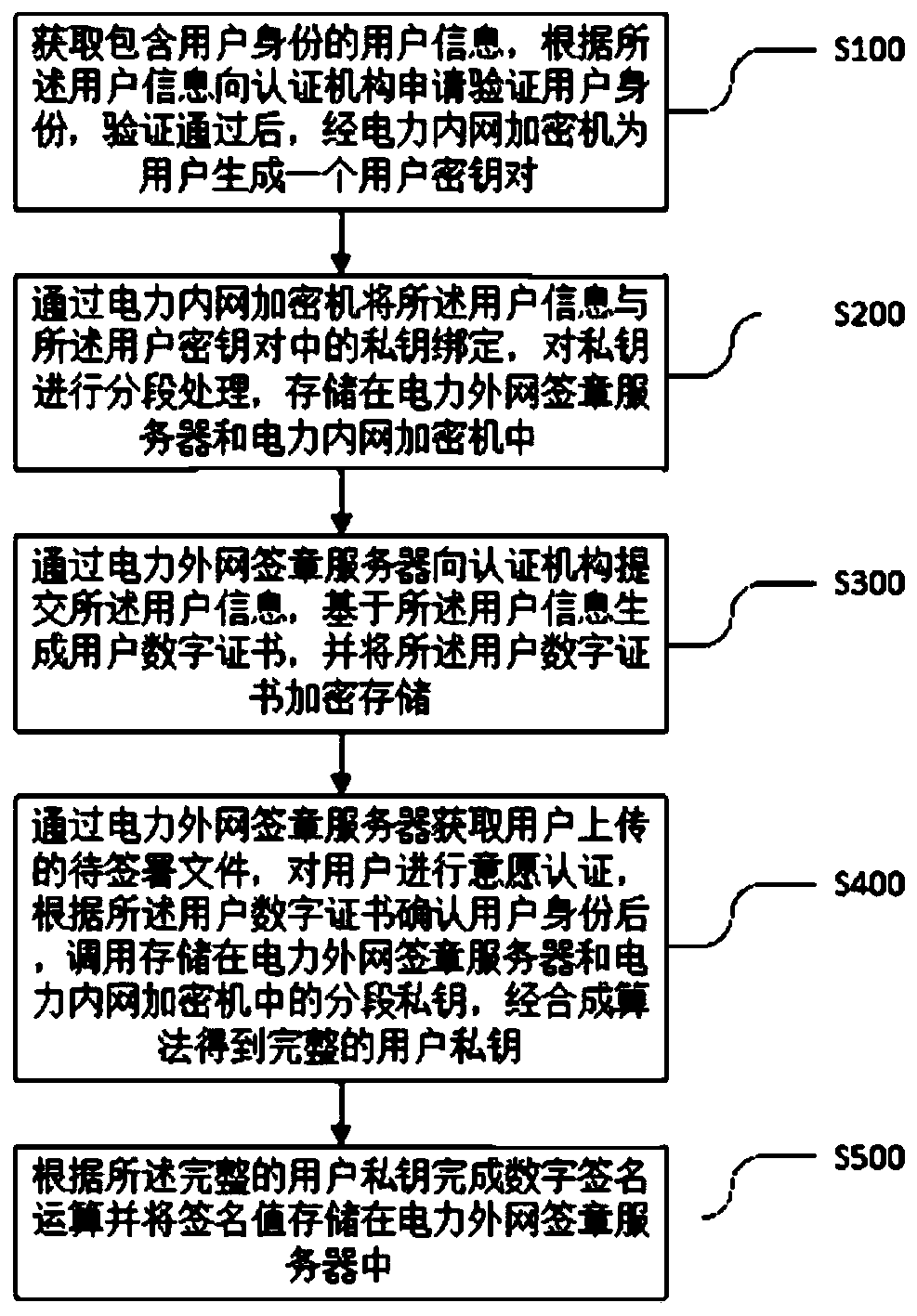
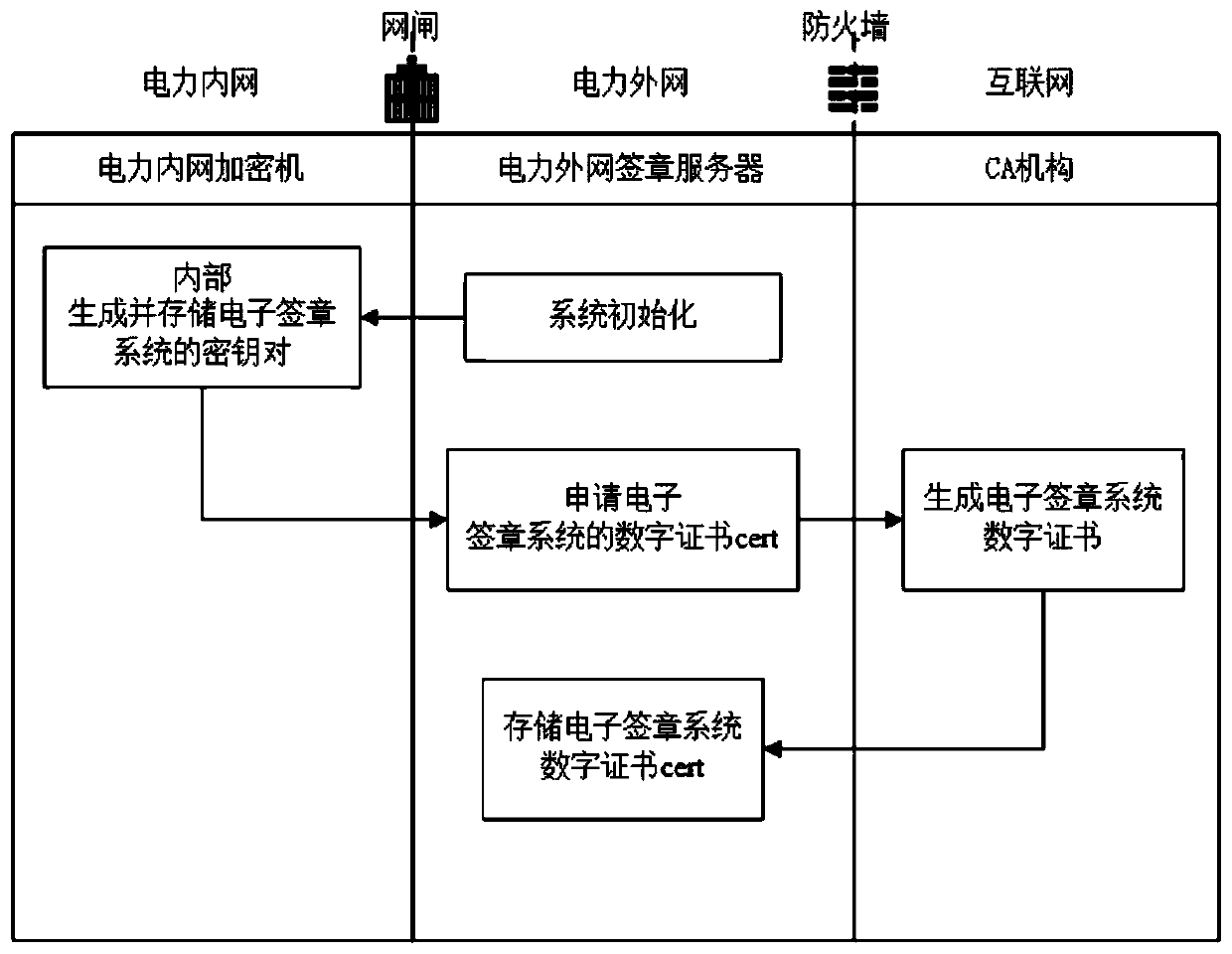
The invention discloses an electronic signature implementation method based on state grid security technology architecture, which comprises the following steps: acquiring user information containing auser identity, applying to an authentication institution for verifying the user identity according to the user information, and generating a user key pair for a user through a power intranet encryption machine; binding the user information with a private key in the user key pair, and carrying out segmentation processing on the private key; submitting user information to an authentication institution through a power extranet signature server, generating a user digital certificate based on the user information, and encrypting and storing the user digital certificate; a to-be-signed file uploaded by a user is obtained through a power extranet signature server, after the identity of the user is confirmed according to a user digital certificate, a segmented private key is called, and a complete user private key is obtained through a synthesis algorithm; and digital signature operation is completed according to the complete user private key. And the security and reliability of the electronic signature system are improved by encrypting and storing the user private key segment by segment, and the risk of stealing the private key is reduced.
Owner:ZHEJIANG HUAYUN INFORMATION TECH CO LTD
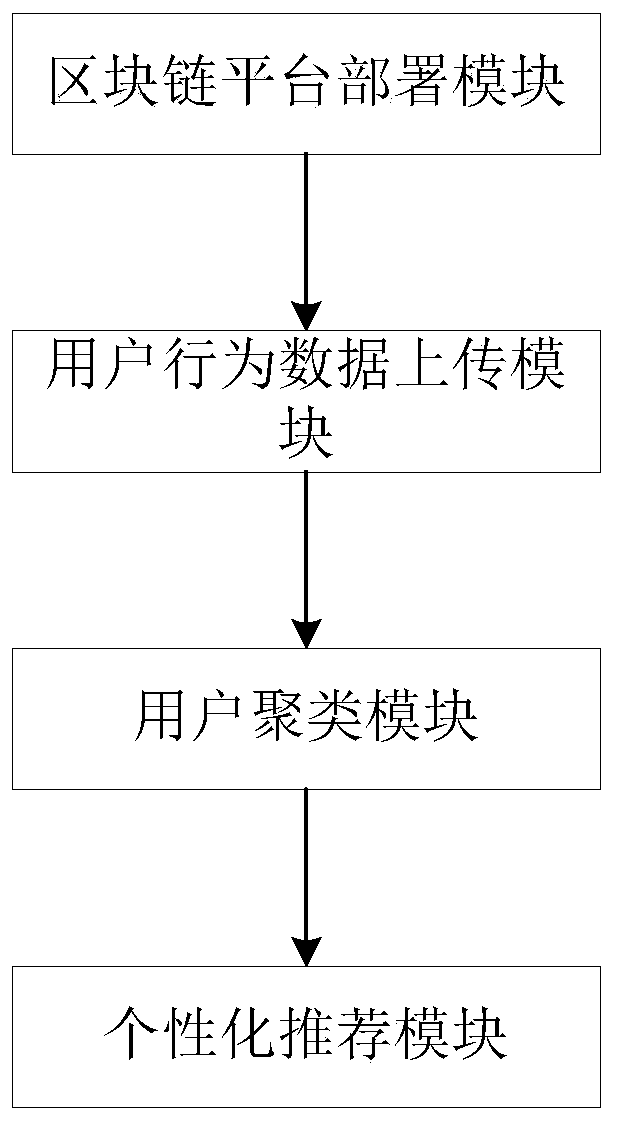
Personalized recommendation system and method based on block chain
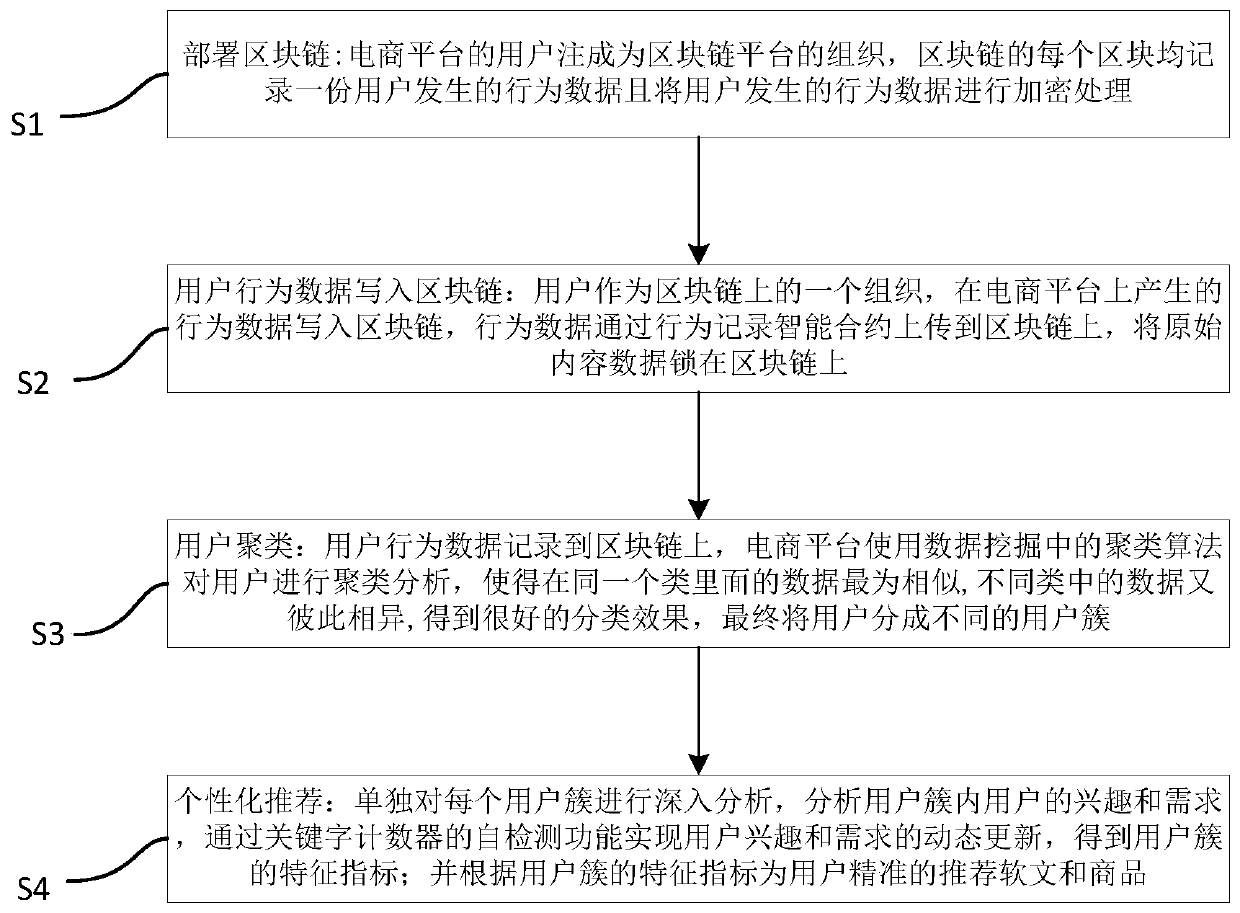
InactiveCN110598111AGuaranteed availabilityImprove securityDigital data information retrievalBuying/selling/leasing transactionsPersonalizationE-commerce
The invention discloses a personalized recommendation system and method based on a block chain, and belongs to personalized recommendation based on a block chain. In order to solve the technical problem of how to realize accurate recommendation of information on the premise of improving the security of user behavior data and reducing the data maintenance cost, the adopted technical scheme is as follows: the system comprises a block chain platform deployment module, a user behavior data uploading module, a user clustering module and a personalized recommendation module. The method specificallycomprises the following steps: deploying a block chain, wherein users of an e-commerce platform are noted as an organization of the block chain platform, and each block of the block chain records behavior data of the user and encrypts the behavior data of the user; writing the user behavior data into a block chain; clustering the users; and performing personalized recommendation, wherein feature indexes of the user cluster are extracted, and the advertorial and the commodity are accurately recommended to the user according to the feature indexes of the user cluster.
Owner:山东爱城市网信息技术有限公司
Marking inkjet printing method
ActiveCN103823648AAvoid gettingImprove data securityDuplicating/marking methodsDigital output to print unitsSoftware engineeringData file
The invention relates to a marking inkjet printing method. By adding marker data files during marking inkjet printing, security of printing operational data files is improved; meanwhile, printing original documents can be more recognizable.
Owner:SHENZHEN JUDING MEDICAL DEVICE
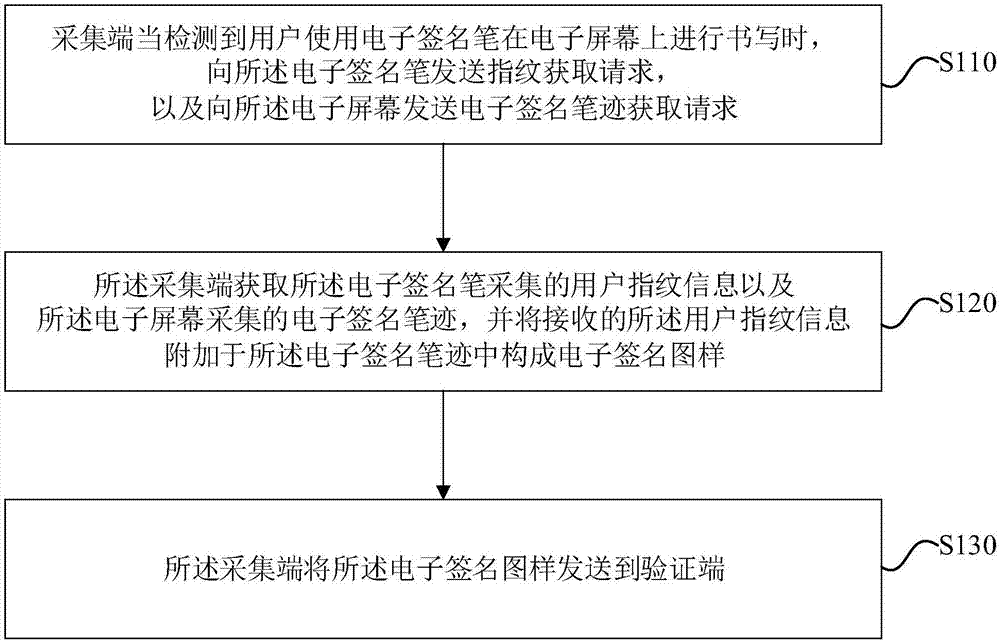
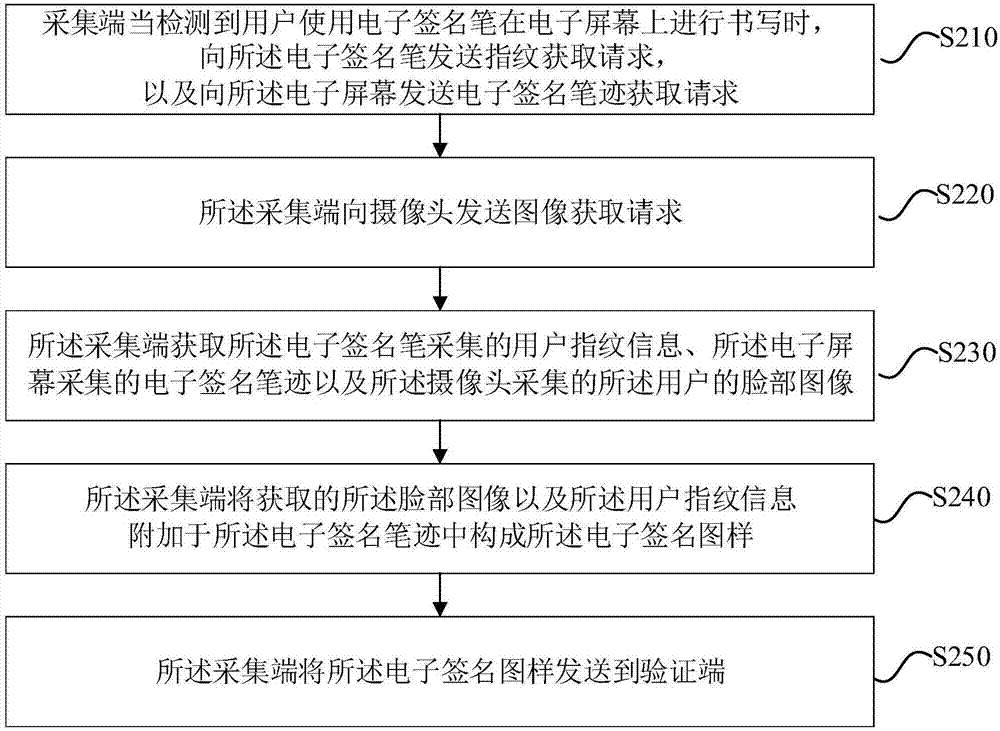
Signature information collection method, signature verification method and electronic signature system
InactiveCN107885989AReduce the Risk of MisappropriationEasy to be stolenDigital data authenticationHandwritingCollection methods
The present invention discloses a signature information collection method, a signature verification method and an electronic signature system. The signature information collection method comprises that: when detecting that a user writes on an electronic screen by using an electronic signature pen, a collection end sends a fingerprint acquisition request to the electronic signature pen, and sends an electronic signature handwriting acquisition request to the electronic screen; the collection end obtains fingerprint information collected by the electronic signature pen and the electronic signature handwriting collected by the electronic screen, and attaches the received fingerprint information to the electronic signature handwriting to form an electronic signature pattern; and the collectionend sends the electronic signature pattern to a verification end. According to embodiments of the present invention, an effective electronic signature can be obtained, and the risk of the electronicsignature being stolen can be reduced.
Owner:SHENZHEN YIHUA COMP +2
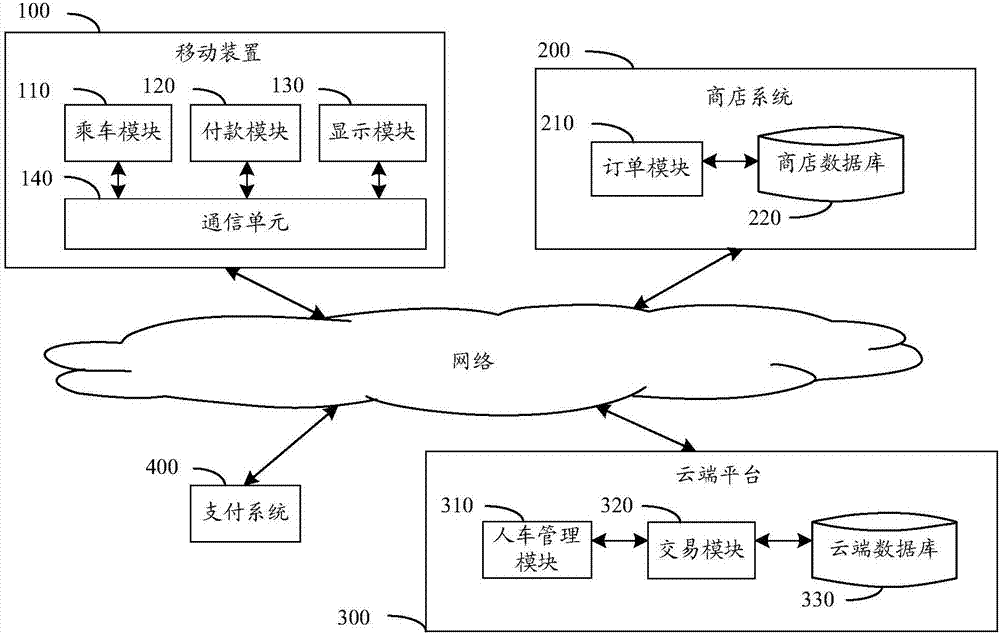
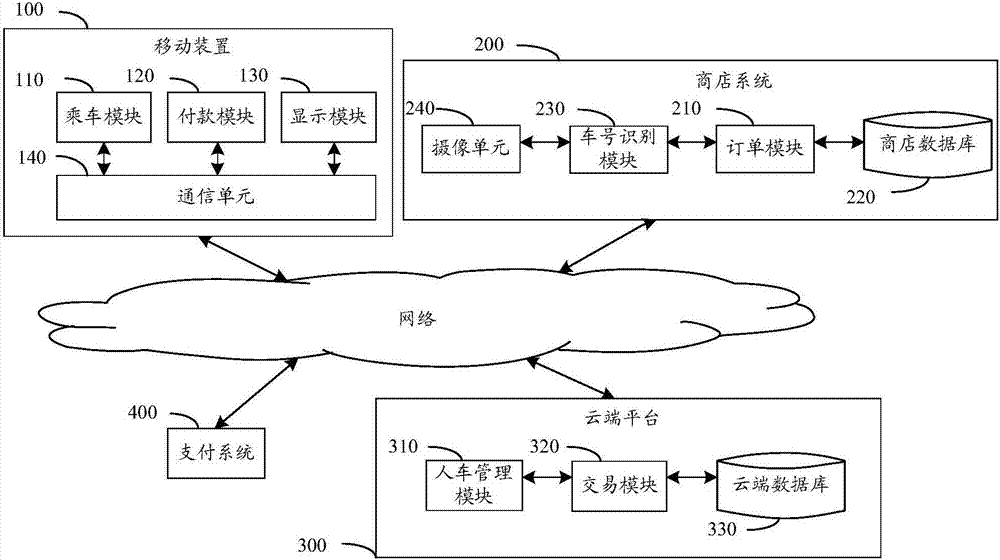
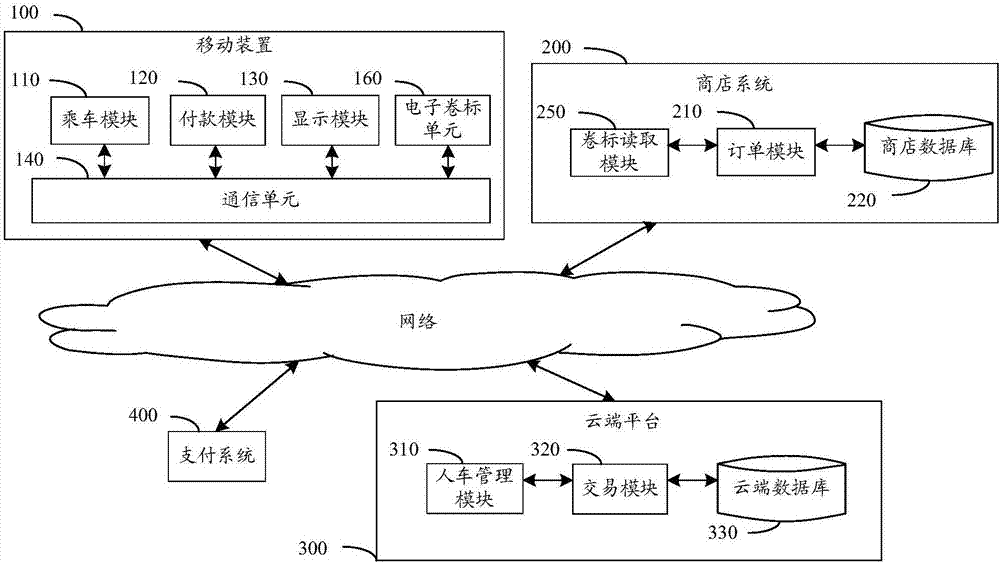
In-vehicle payment system and device
InactiveCN106952086ASkip the drop-off queueEliminate the inconvenience of changePayment architectureUser needsIn vehicle
The embodiment of the invention provides an in-vehicle payment system and device. The system comprises a mobile device, a shop system, a cloud platform and a payment system; the mobile device receives user load data containing vehicle identification information and user identification information and transmits to the cloud platform; the shop system identifies a consumer vehicle and generates order data, when the shop confirms that the user uses in-vehicle payment, the shop system transmits the vehicle identification information and order data to the cloud platform and asks the user to pay the order; the existence of the user load data corresponding to the vehicle identification information is confirmed through the cloud platform, the to-be-paid order data asked by the shop is informed the user to perform payment confirmation, the cloud platform receives user payment data and performs authentication and authorization on the payment system, and a payment result is returned to the shop system and the mobile device; and the shop system receives a paid notification and provides service for the user. The inconvenient that the user needs to get off the vehicle to queue and change in consumption can be avoided, and the risk of embezzlement can be reduced.
Owner:CHUNGHWA TELECOM CO LTD
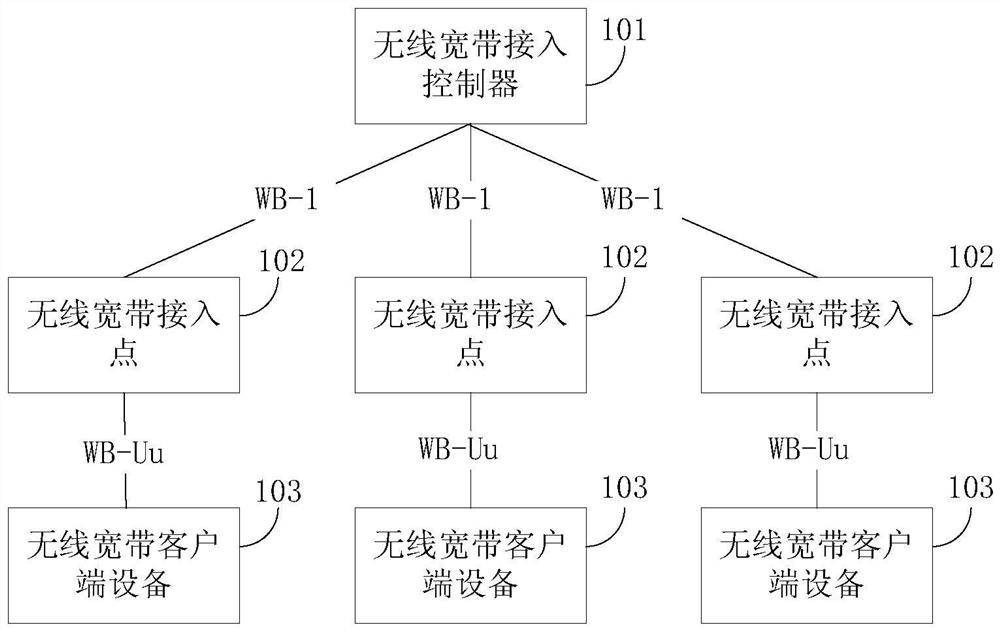
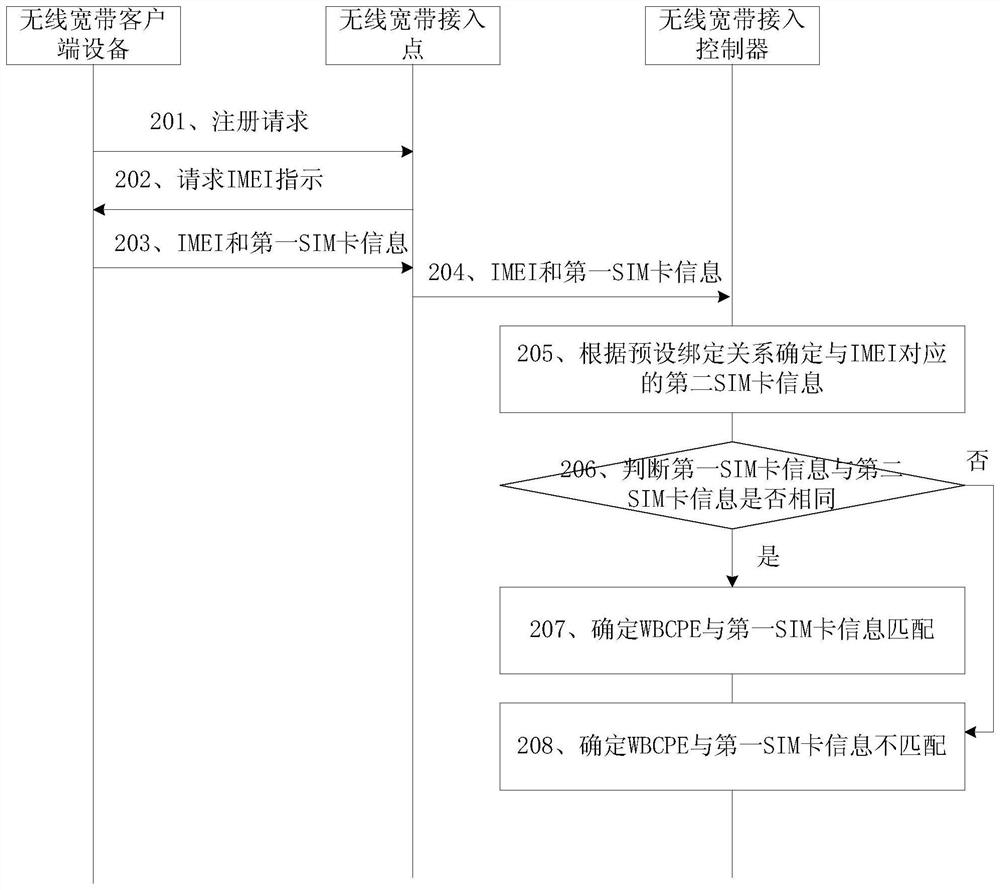
Machine card verification method applied to extremely simple network and related equipment
PendingCN112929881AReduce the Risk of MisappropriationImprove securitySecurity arrangementComputer networkInternational mobile subscriber identity
The invention provides a machine card verification method applied to an extremely simple network. The method comprises the steps that after a WBCPE sends a registration request to a WBAP, the WBAP generates a request IMEI indication according to the registration request, the WBAP sends the request IMEI indication to the WBCPE, the WBCPE responds to the request IMEI indication and sends the IMEI and first SIM card information to a WBAC through the WBAP, and the first SIM card information comprises at least one of the following information: an international mobile subscriber identity (IMSI), a network access identifier (NAI) and a certificate name; and the WBAC verifies the IMEI and the first SIM card information according to the preset binding information. According to the machine card verification method, the IMEI and SIM card information is verified, so that the risk that the SIM card is stolen is reduced, and the safety of a very simple network is improved. The invention further provides related equipment capable of realizing the method.
Owner:HUAWEI TECH CO LTD
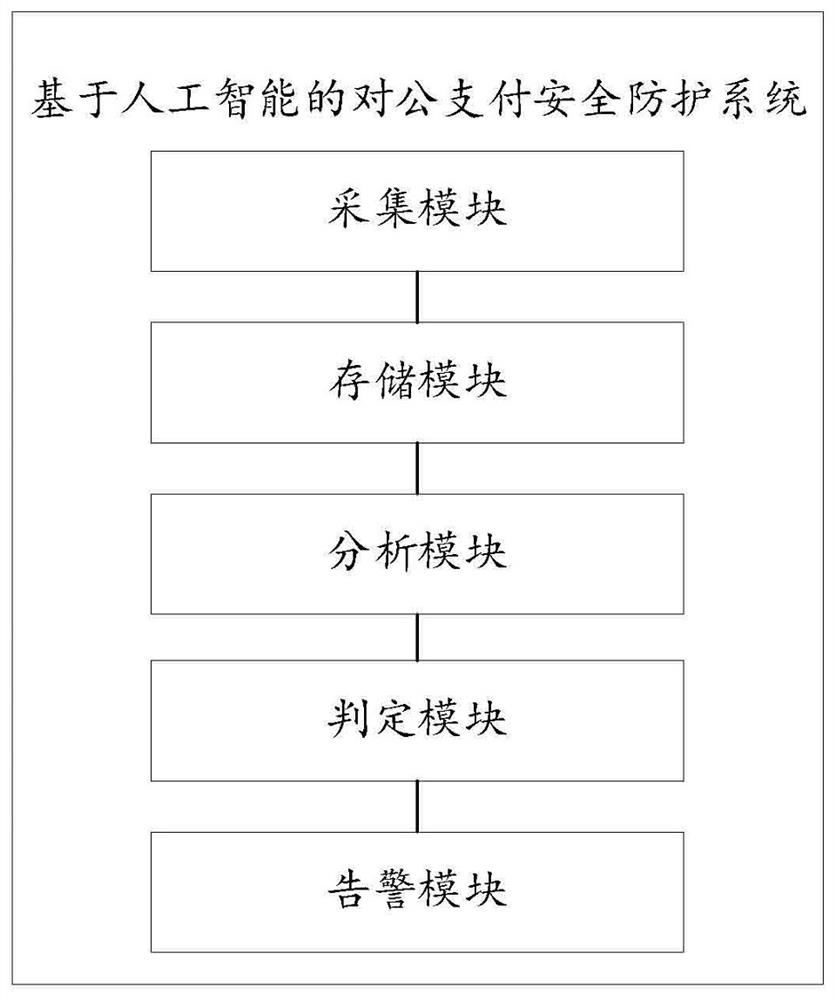
Public payment security protection system based on artificial intelligence
ActiveCN114612108AImprove transaction securityImprove securityProtocol authorisationPaymentFinancial transaction
The invention relates to a public payment security protection system based on artificial intelligence, in particular to the technical field of payment security, and the system comprises a collection module which is used for collecting the transaction information and transaction environment information of a first interaction body and the credit information of a second interaction body in real time; the storage module is used for storing transaction records of the first interaction main body and is connected with the acquisition module; the analysis module is used for analyzing the transaction security of the first interaction main body and the second interaction main body, is connected with the acquisition module, and is also used for judging the security of the transaction environment of the first interaction main body according to the transaction position of the first interaction main body; the judgment module is used for carrying out transaction safety judgment according to the safety analysis result and is connected with the analysis module; and the alarm module is used for carrying out corresponding transaction early warning according to the transaction security judgment result and is connected with the judgment module. According to the invention, the transaction security of public payment is effectively improved.
Owner:湖南三湘银行股份有限公司
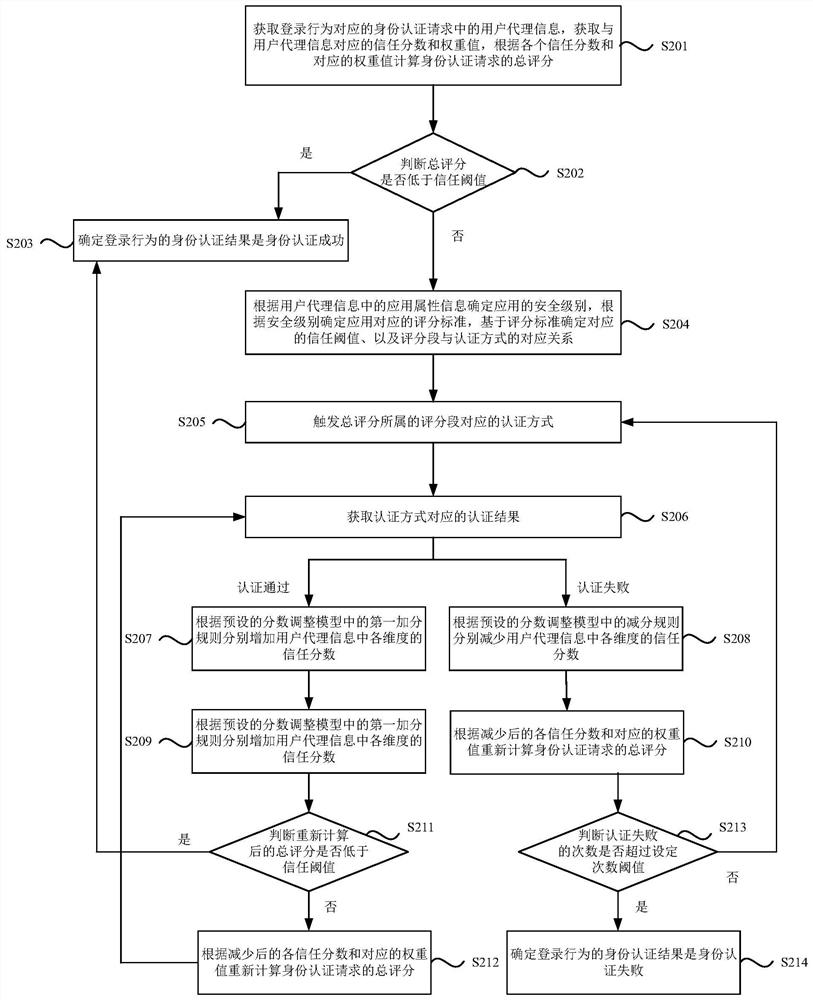
Dynamic identity authentication method and device, server and storage medium
ActiveCN112653679AImprove securityReduce convenienceMessaging/mailboxes/announcementsTransmissionInternet privacyTrust score
The embodiment of the invention discloses a dynamic identity authentication method and device, a server and a storage medium. The method comprises the steps of obtaining user agent information in an identity authentication request corresponding to a login behavior, obtaining corresponding trust scores and weight values, and calculating a total score of the identity authentication request; if the total score is lower than a trust threshold, triggering an authentication mode corresponding to a score segment to which the total score belongs; updating the trust score of each dimension in the user agent information according to the authentication result and a preset score adjustment model, and recalculating the total score according to each adjusted trust score and the corresponding weight value, wherein the score adjustment model is used for indicating configuration information for adjusting the trust score of each dimension in the user agent information according to the authentication result; and determining an identity authentication result of the login behavior according to a comparison result of the recalculated total score and the trust threshold and the authentication result. According to the embodiment of the invention, dynamic identity authentication is carried out on the login behavior, so that the security of identity authentication is improved.
Owner:北京指掌易科技有限公司
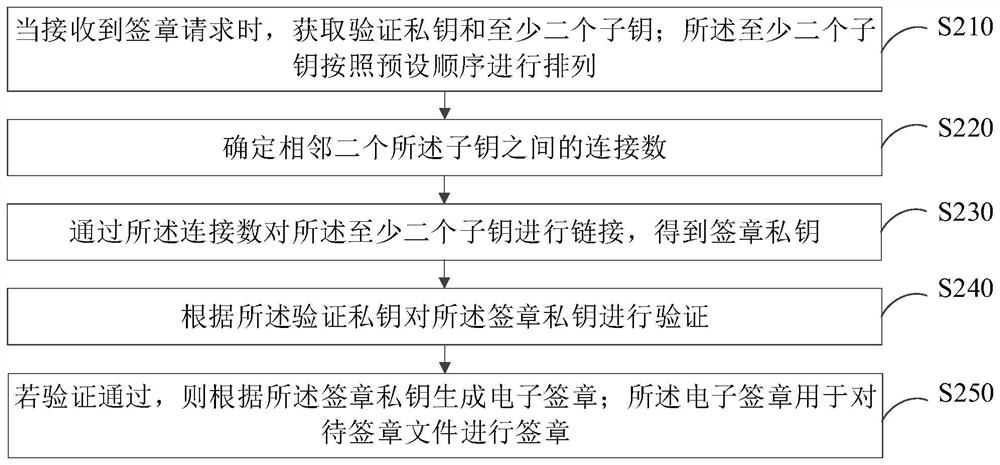
Electronic signature generation method and device, computer equipment and storage medium
PendingCN114239004AImprove securityReduce the Risk of MisappropriationDigital data protectionEngineeringConnection number
The invention relates to an electronic signature generation method and device, computer equipment and a storage medium. The method comprises the following steps: when a signature request is received, acquiring a verification private key and at least two sub-keys; the at least two sub-keys are arranged according to a preset sequence; determining a connection number between two adjacent sub-keys; linking the at least two sub-keys through the connection number to obtain a signature private key; verifying the signature private key according to the verification private key; if the verification is passed, generating an electronic signature according to the signature private key; the electronic signature is used for signing a to-be-signed file. By adopting the method, the risk that the private key is stolen can be reduced, and the security of the electronic signature is improved.
Owner:CHINA SOUTHERN POWER GRID COMPANY
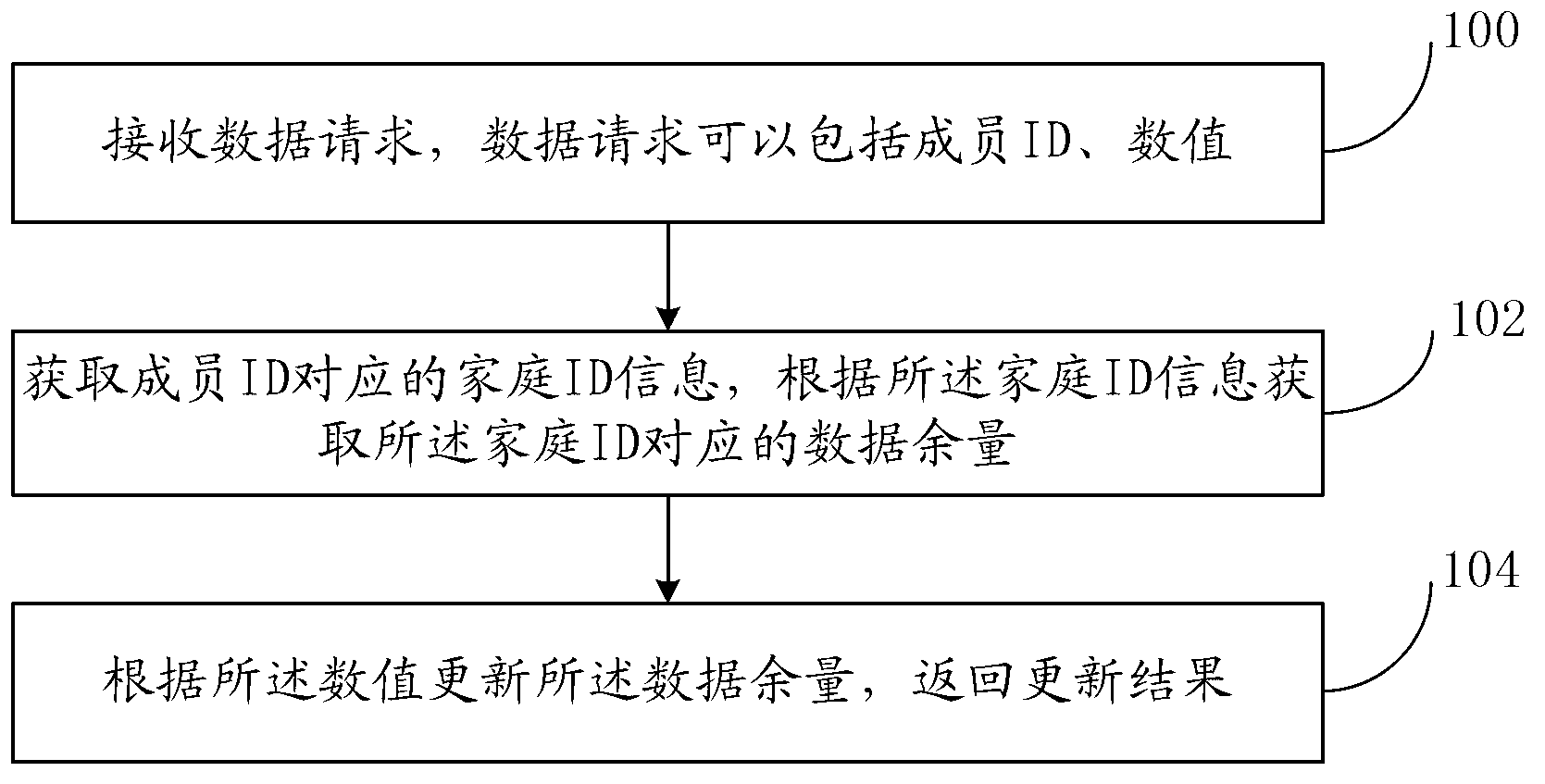
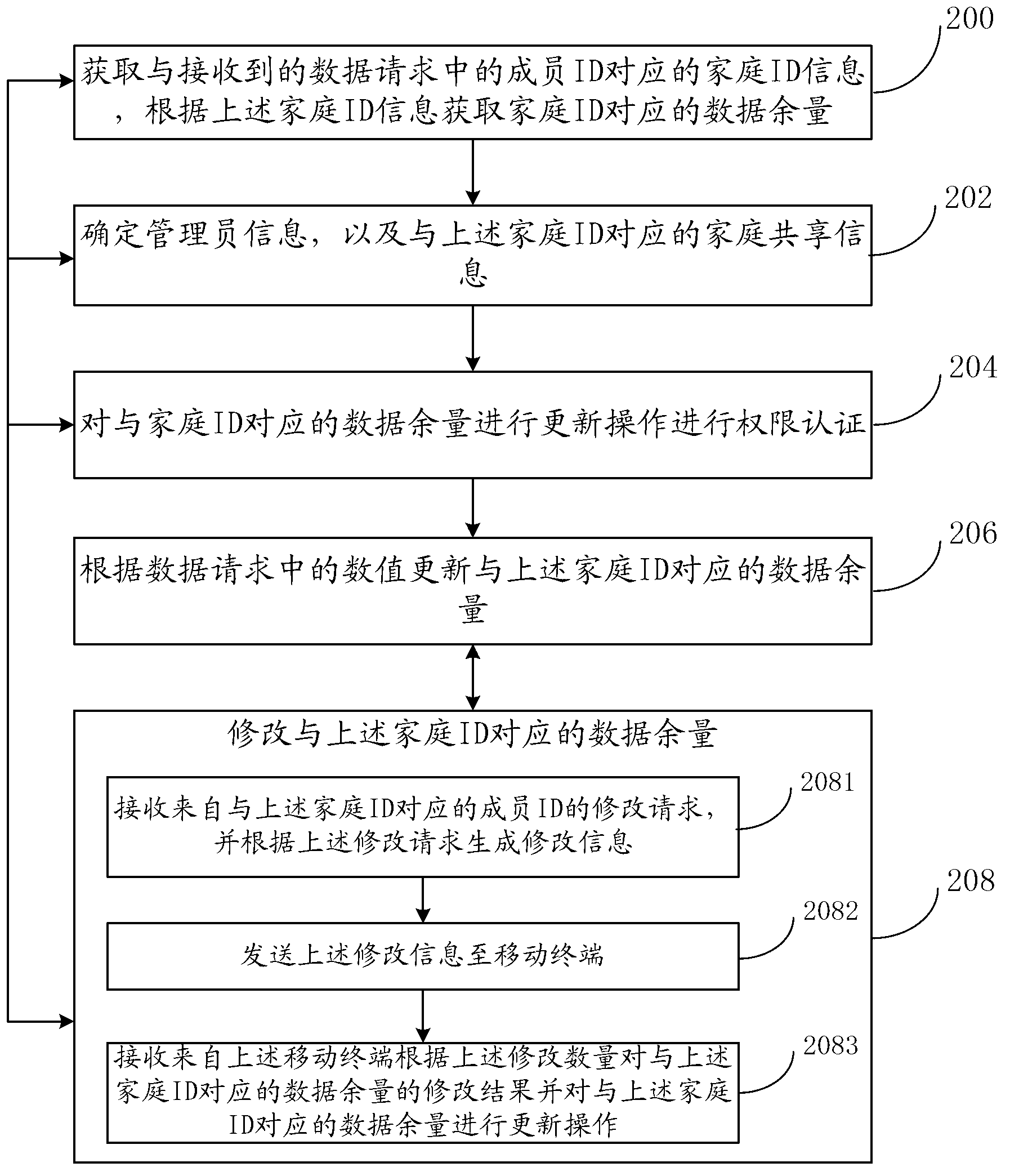
Method and system for processing data
InactiveCN103268552AReduce the Risk of MisappropriationPayment architectureSpecial data processing applicationsPaymentData mining
The embodiment of the invention discloses a method and a system for processing data, which are used for solving problems that payment operations of a plurality of users in a family environment are inconvenient and poor in safety. The method comprises steps of obtaining a family ID (identity) corresponding to member IDs and redundant data corresponding to the family ID according to the member IDs in a received data request and a preset mapping relationship, wherein the family ID corresponds to a plurality of member IDs; and updating the redundant data corresponding to the family ID according to values in the received data request. By utilizing the method of the embodiment of the invention, when a plurality of members in the family environment need to process data, members are not required to have data processing accounts or the redundant data, and each member only needs to submit the member ID corresponding to the family ID, so that risks that the data processing accounts are stolen are reduced.
Owner:XIAOMI INC
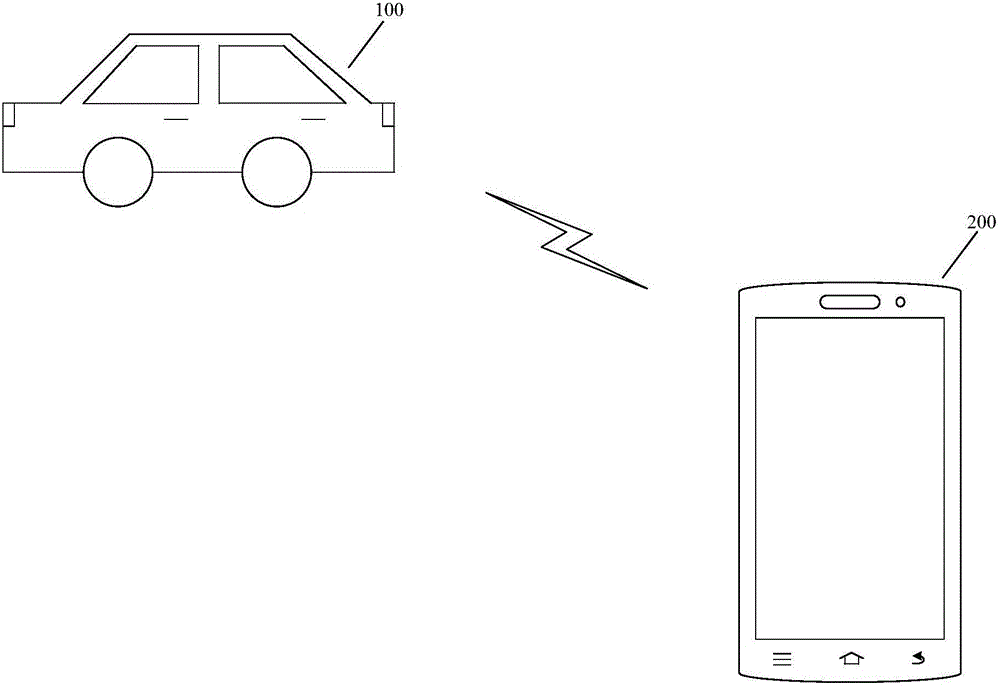
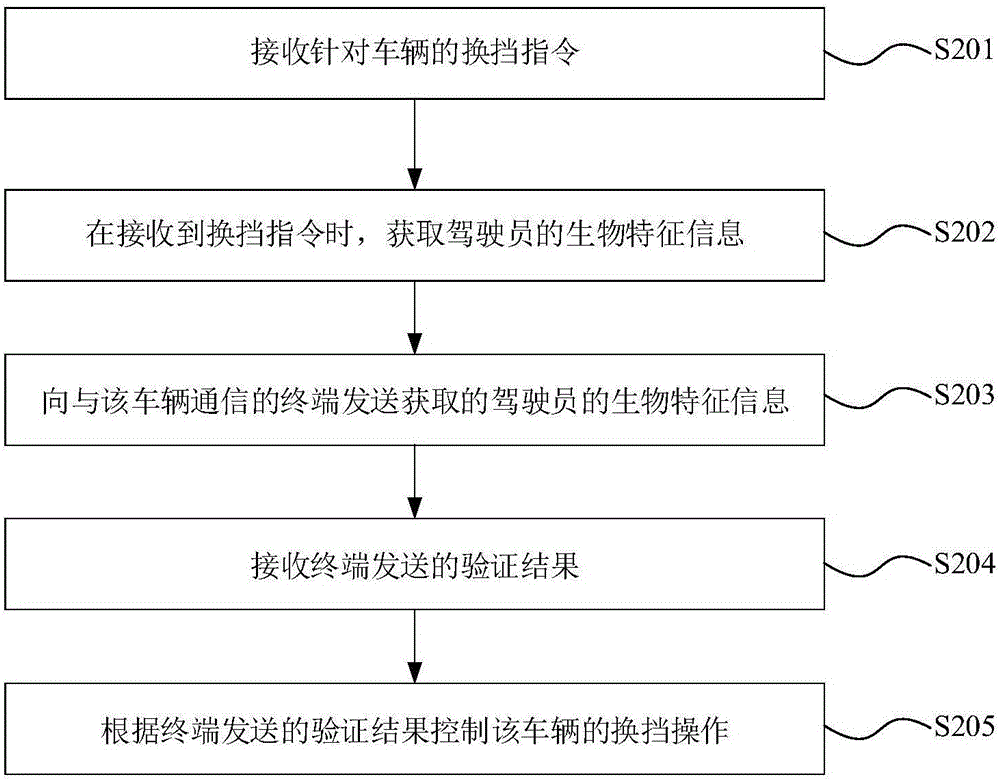
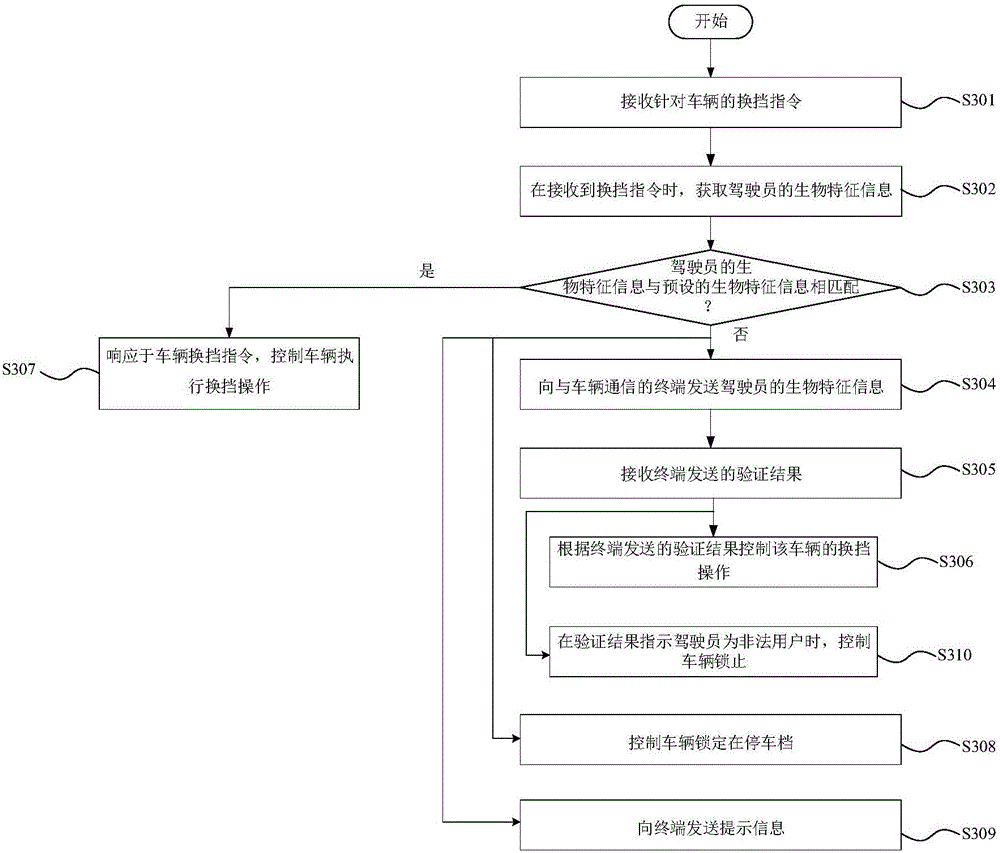
Control method and device for vehicle gear shifting and vehicle
ActiveCN105936256AImprove the anti-theft indexImprove accuracyAnti-theft devicesIdentity recognitionComputer terminal
The invention discloses a control method and device for vehicle gear shifting and a vehicle. The control method includes the steps of receiving a gear shifting instruction for the vehicle; obtaining biological characteristic information of a driver when receiving the gear shifting instruction; sending the biological characteristic information to a terminal communicated with the vehicle, wherein the biological characteristic information is used for verifying whether the driver is a legal user or not through the terminal; receiving a verification result sent by the terminal; controlling he gear shifting opening of the vehicle according to the verification result. Thus, the risk that the vehicle is stolen by an illegal user for use can be reduced, it is ensured that only a legal user can operate the vehicle and conduct gear shifting operation, and therefore the antitheft index of the vehicle is increased. In the technical scheme, the biological characteristic information serves as the basis for driver identity recognition, the biological characteristic information can be uniquely used for identifying the user identity and can not be easily faked, and therefore the accuracy of identity recognition can be further improved, and vehicle safety is improved.
Owner:BEIQI FOTON MOTOR CO LTD
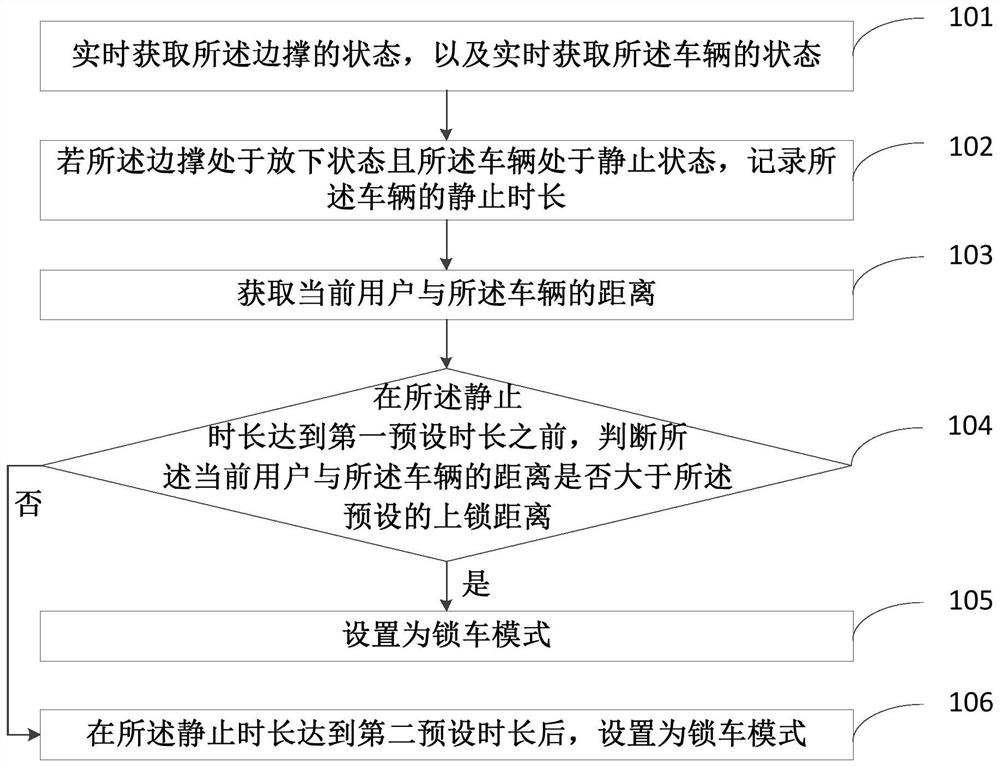
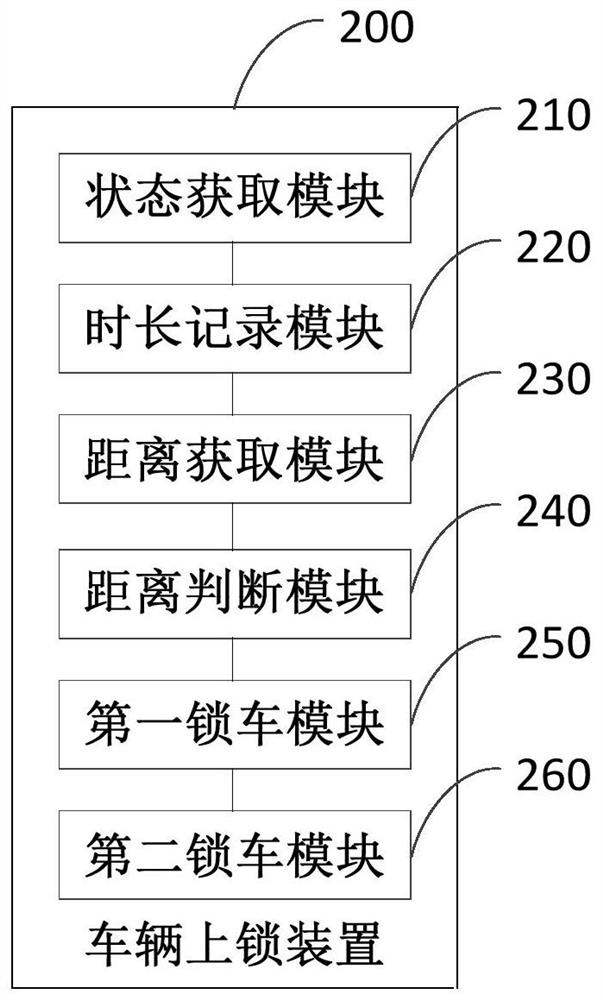
Vehicle locking method and device and vehicle
InactiveCN113096282AReduce the Risk of MisappropriationAnti-theft cycle devicesIndividual entry/exit registersReal-time computingAutomotive engineering
The invention discloses a vehicle locking method and device and a vehicle, which are applied to the vehicle comprising a temple. The state of the temple is acquired in real time, the state of the vehicle is acquired in real time, if the temple is in a put-down state and the vehicle is in a static state, the static duration of the vehicle is recorded, and the distance between a current user and the vehicle is acquired. Before the static duration reaches a first preset duration, whether the distance between the current user and the vehicle is larger than a preset locking distance or not is judged; if the distance is larger than the preset locking distance, a vehicle locking mode is set; and if the distance is not greater than the preset locking distance, after the static duration reaches a second preset duration, the vehicle locking mode is set. According to the method provided by the invention, the vehicle can be locked after the user forgets to lock the vehicle, so that the risk that the vehicle is stolen is reduced.
Owner:浙江小遛信息科技有限公司
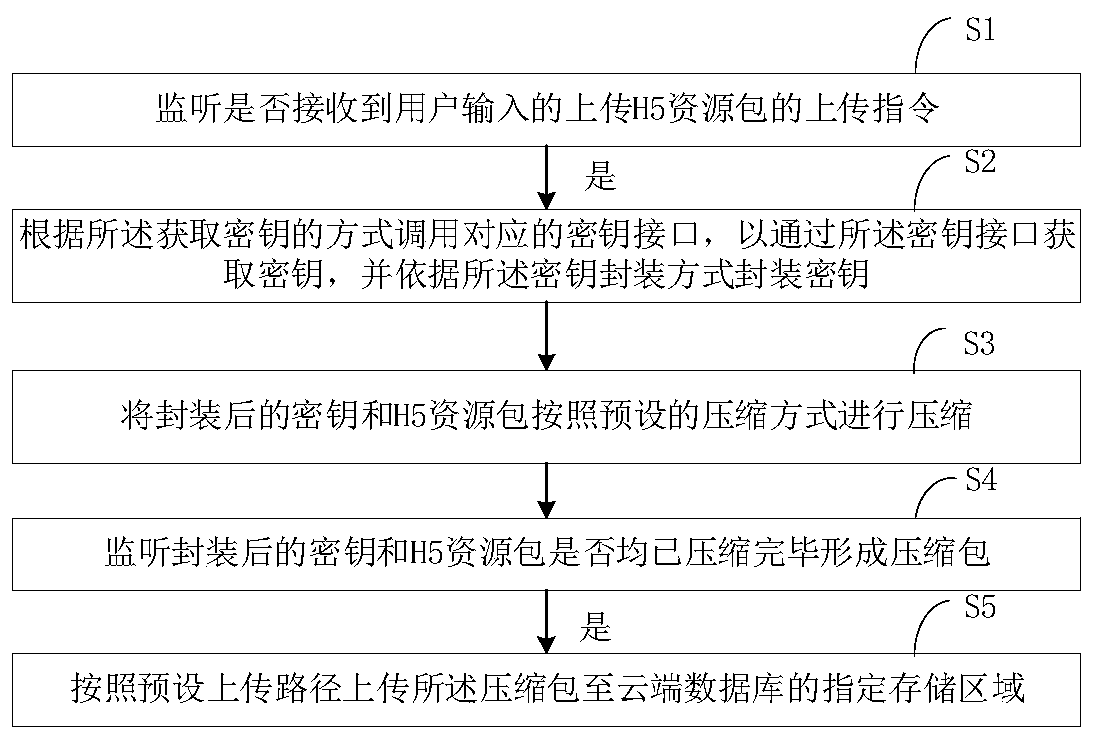
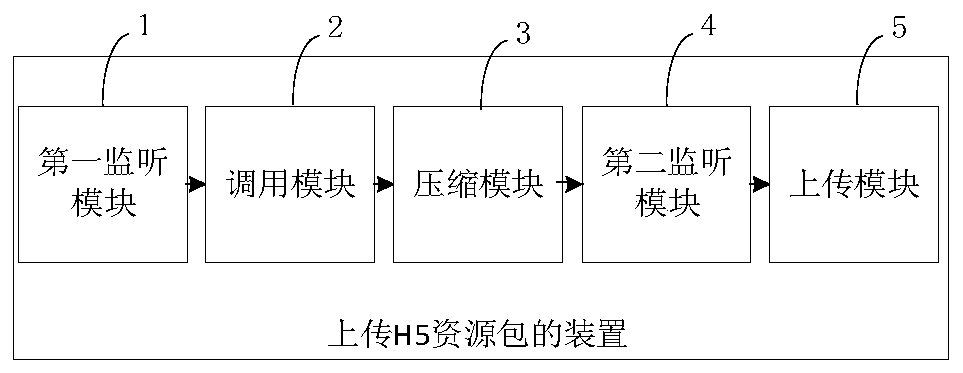
H5 resource packet uploading method, H5 resource packet downloading method and related equipment
PendingCN110069904AImprove securityReduce the Risk of MisappropriationDigital data protectionProgram/content distribution protectionPathPingEngineering
The invention discloses an H5 resource packet uploading method, an H5 resource packet downloading method and related equipment. The H5 resource packet uploading method comprises the following steps: monitoring whether an uploading instruction for uploading an H5 resource packet input by a user is received or not; if yes, calling a corresponding secret key interface according to the secret key obtaining mode to obtain a secret key through the secret key interface, and packaging the secret key according to the secret key packaging mode; compressing the packaged secret key and the H5 resource package according to a preset compression mode to form a compressed package; and uploading the compressed packet to an appointed storage area of a cloud database according to a preset uploading path. Theserver encrypts the uploaded H5 resource packet and encapsulates the secret key, so that the security of the secret key is enhanced, and the risk that the H5 resource packet is stolen is reduced.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Method, system and server for hosting data access of static website
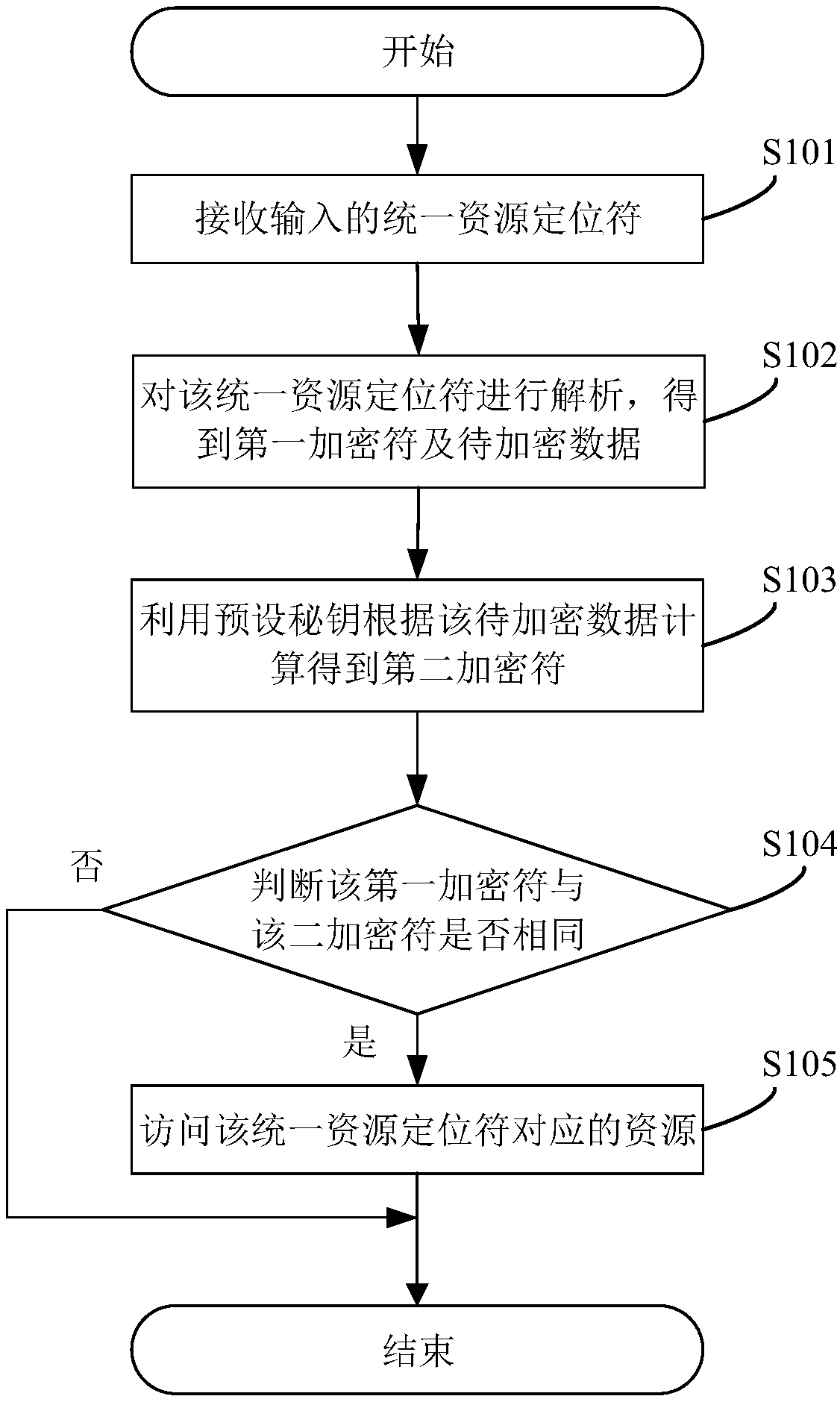
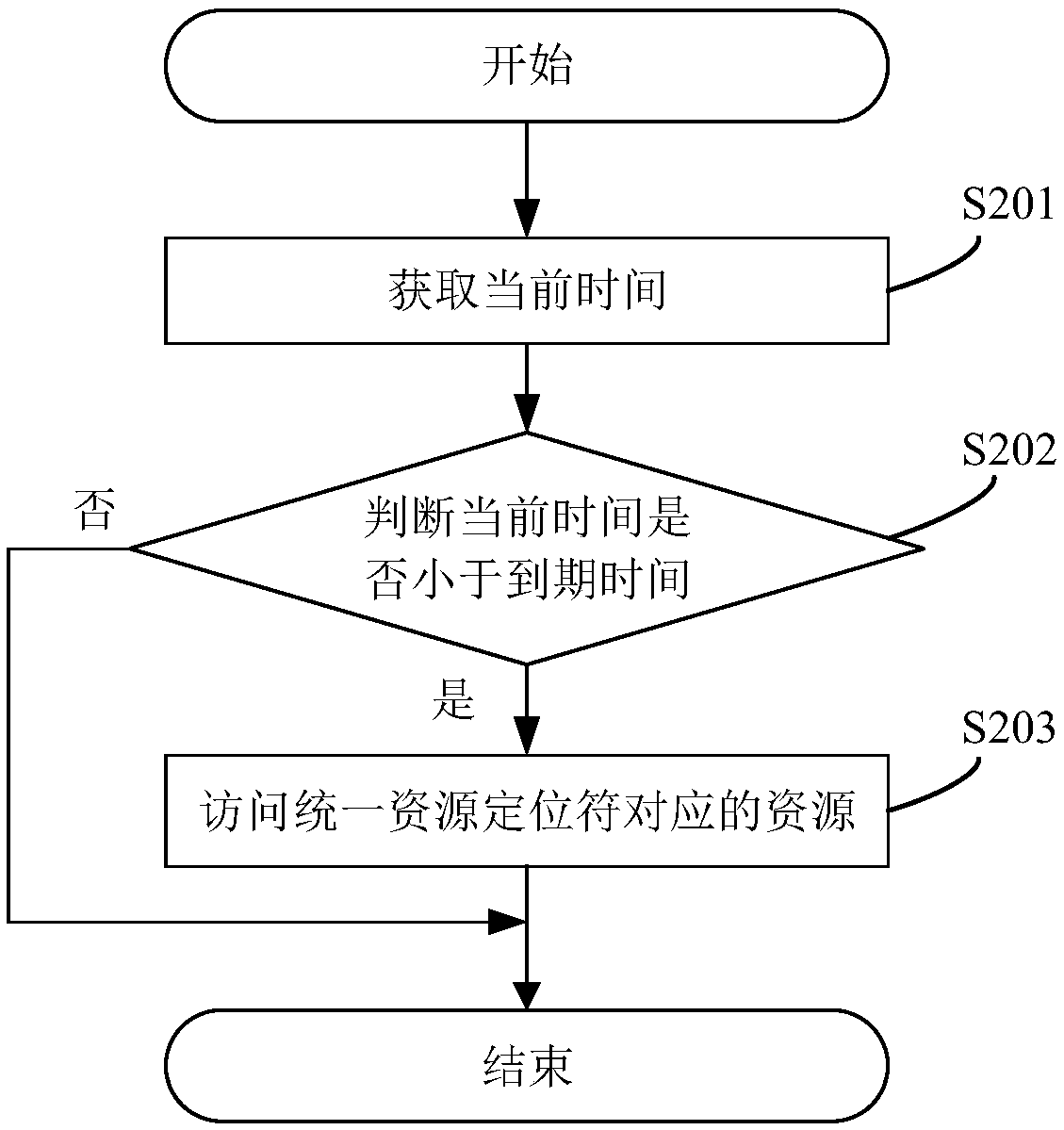
InactiveCN108897898AImplement permission controlReduce the Risk of MisappropriationDigital data protectionSpecial data processing applicationsWeb siteData access
A method for hos data access to a static web site includes receive an input uniform resource locator; Parsing the uniform resource locator to obtain a first encryption character and data to be encrypted; Calculating a second encryption character according to the data to be encrypted by using a preset secret key; Judging whether the first encryption symbol and the second encryption symbol are identical; If so, the resource corresponding to the uniform resource locator is accessed. The present application determines whether the second encryption symbol calculated by the system according to the preset secret key and the data to be encrypted is the same as the received first encryption symbol, If the resource corresponding to the uniform resource locator is accessed again, if the resource corresponding to the uniform resource locator is not accessed again, the access is not allowed, the permission control of the hosted data access of the static website is realized, and the risk of the dataembezzlement of the static website is reduced. At that same time, the application also provide a system, a server and a computer-readable storage medium for hos data access to a static web site, which has the above beneficial effects.
Owner:GUANGDONG INSPUR BIG DATA RES CO LTD
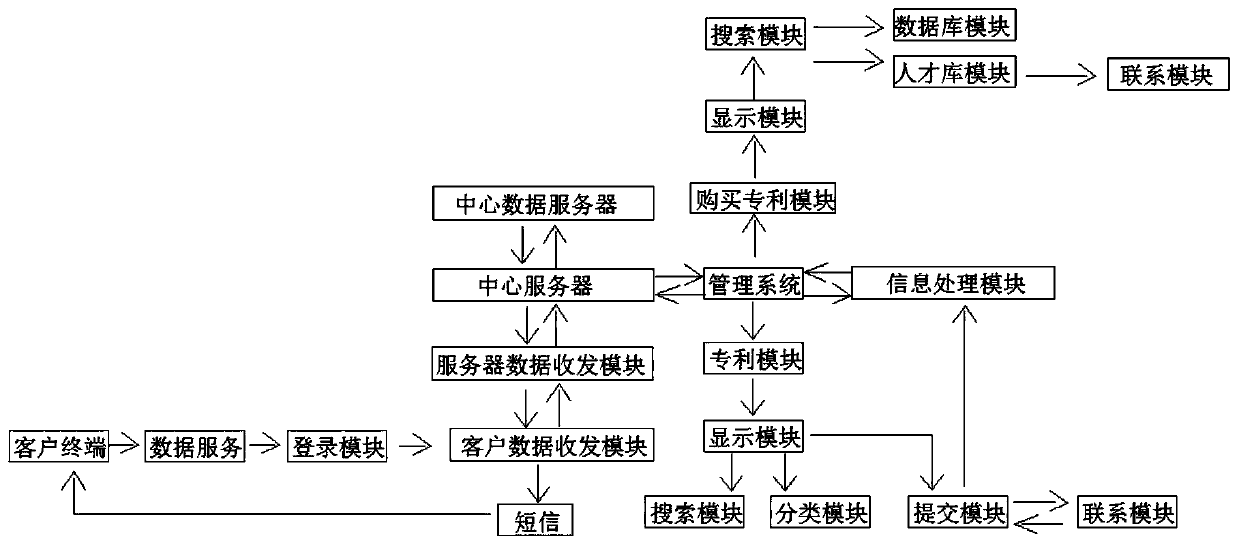
New material technology transfer service management system
InactiveCN109993630AReduce the Risk of MisappropriationAvoid Illegal TradingBuying/selling/leasing transactionsPasswordComputer terminal
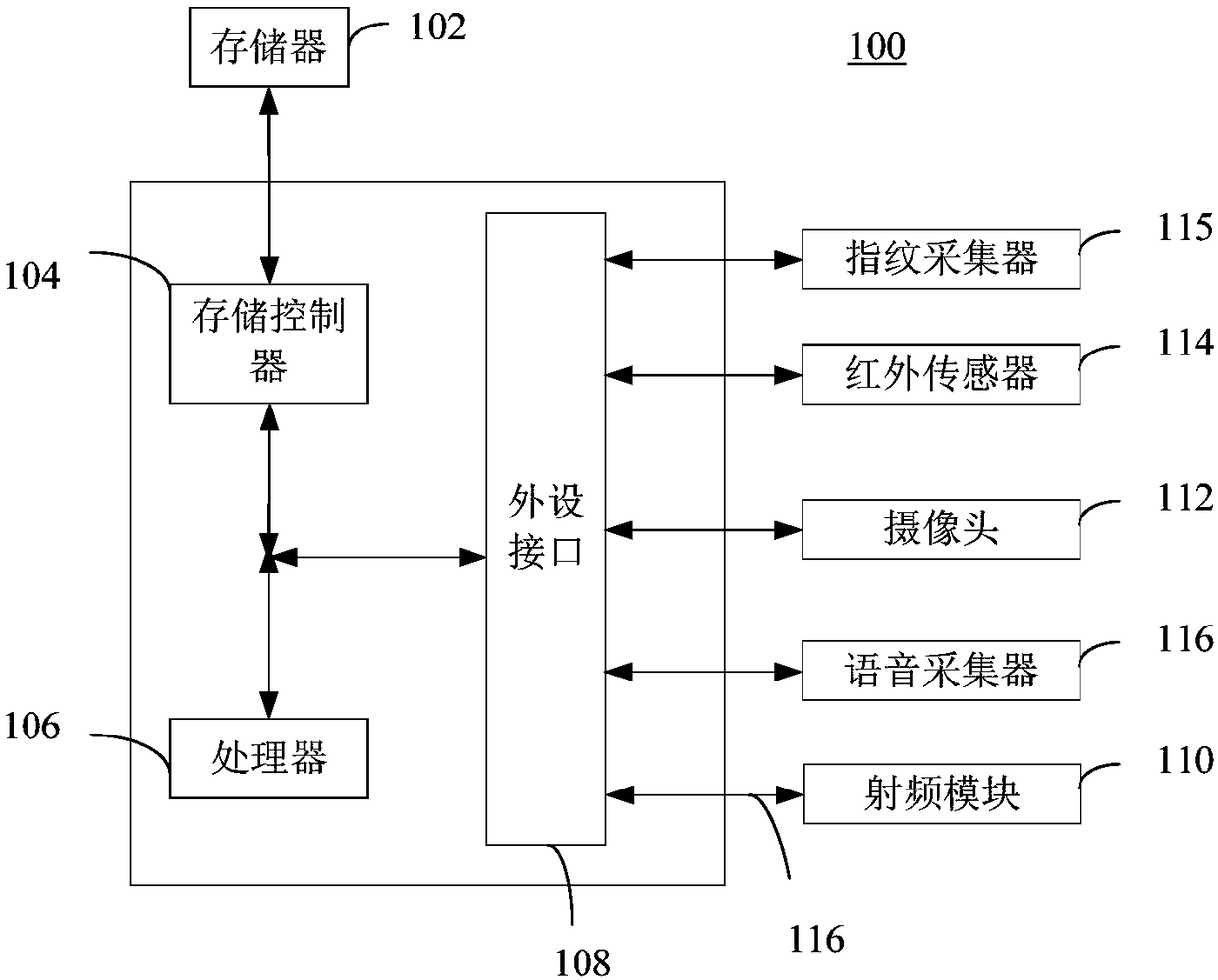
The invention discloses a new material technology transfer service management system. The system comprises a client terminal, the output end of the client terminal is electrically connected with a data service; wherein the output end of the data service is electrically connected with a login module, the output end of the login module is electrically connected with a client data receiving module, the output end of the client data receiving and transmitting module is electrically connected with a server data receiving and transmitting module, and the output end of the server data receiving and transmitting module is electrically connected with a central server. According to the invention, the client data receiving and transmitting module, the server data receiving and transmitting module andthe short message are arranged; an account number and a password can be sent to the central server when a client logs in; and then the central data server sends a short message of a verification codeto the client terminal to prove that the logger is the owner, so that the risk of client information theft is reduced, the patent security of the client is higher, and the client patent is preventedfrom being illegally purchased and sold by a theft crime.
Owner:河南仙于山环保科技有限公司
Vehicle starting method and device, storage medium and vehicle
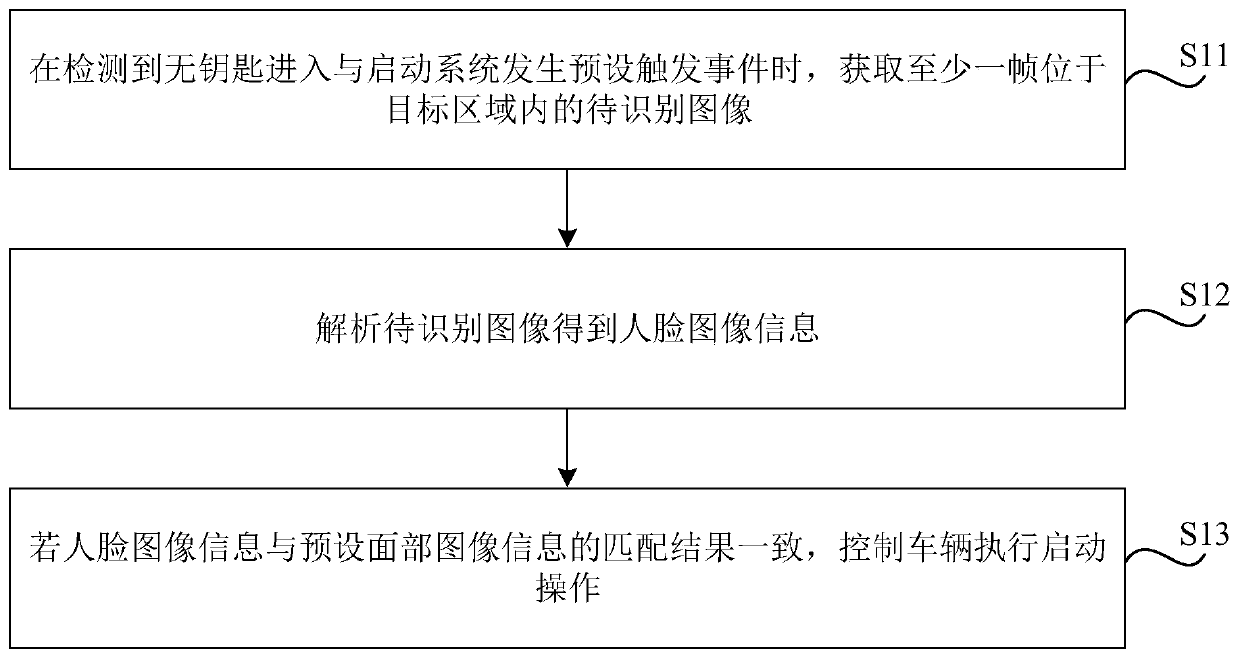
InactiveCN111368277AImprove securityReduce the Risk of MisappropriationAnti-theft devicesCharacter and pattern recognitionImage parsingReal-time computing
The invention relates to a vehicle starting method and device, a storage medium and a vehicle, and aims at solving the technical problem that an existing vehicle anti-theft coefficient is not high. The method comprises the steps of obtaining at least one frame of to-be-identified image located in a target area when it is detected that a preset trigger event occurs in a keyless entry and startup system; analyzing the to-be-recognized image to obtain face image information; and if the matching result of the face image information and the preset face image information is consistent, controlling the vehicle to execute a starting operation.
Owner:BEIQI FOTON MOTOR CO LTD
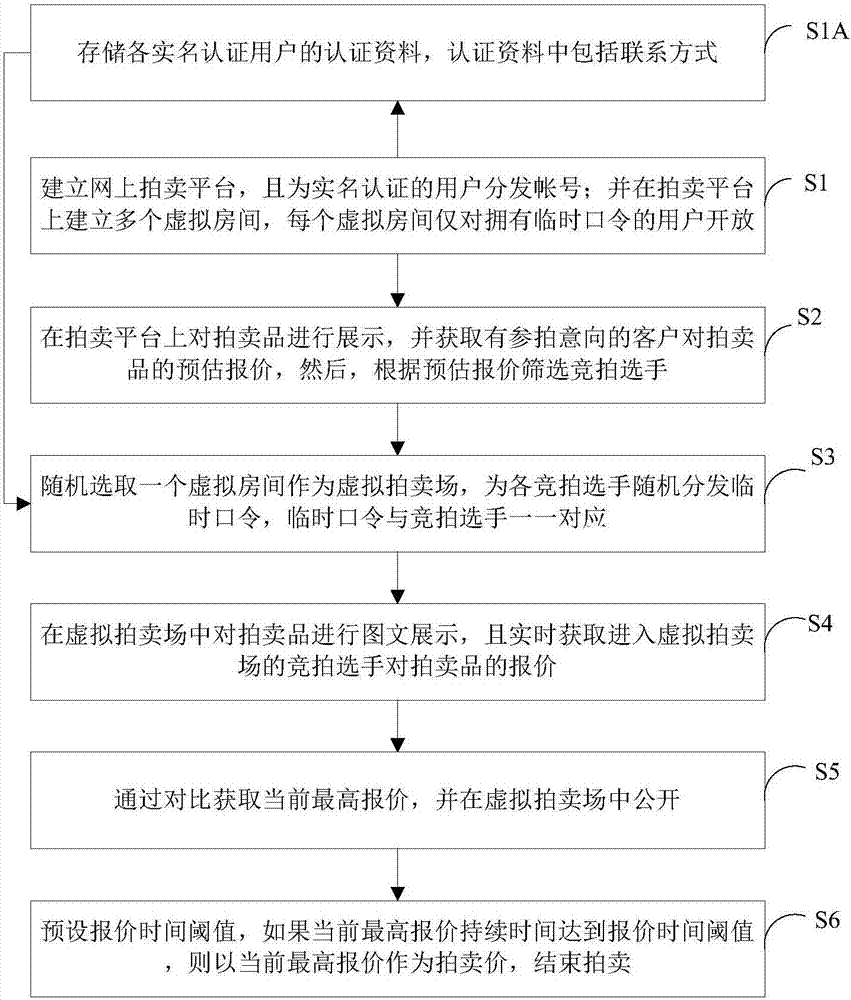
Remote auction method
A remote auction method disclosed by the present invention comprises the following steps of S1 establishing an online auction platform, and distributing the accounts to the users of the real name authentication; establishing a plurality of virtual rooms on the auction platform, wherein each virtual room is only opened to the users having the temporary passwords; S2 displaying the auction items on the auction platform, obtaining the estimated quotations to the auction items of the customers intending to participate in the auction, and then screening the bidders according to the estimated quotations; S3 randomly selecting one virtual room as a virtual auction place, and distributing the temporary passwords to the bidders randomly, wherein the temporary passwords are in one-to-one correspondence with the bidders. According to the present invention, by establishing the online auction platform, the place is provided for the remote auction; the real name authentication guarantees the safe usage of the online auction platform; by establishing the virtual rooms, and by the temporary passwords, more guarantee is provided for the identity verification of the participants, and the auction safety is conducive to being guaranteed further.
Owner:安徽云软信息科技有限公司
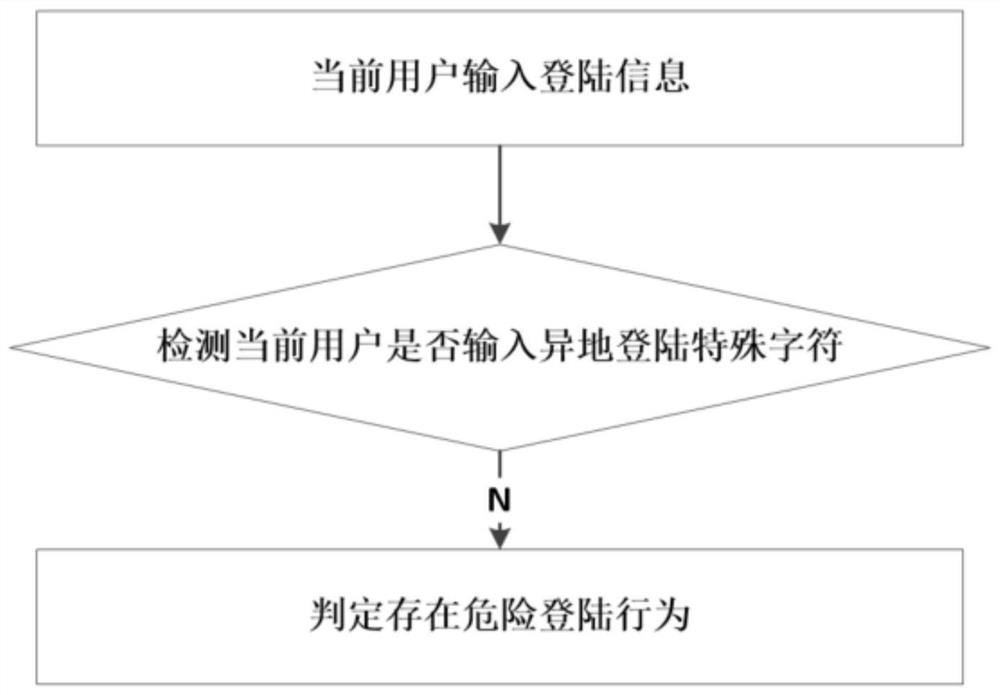
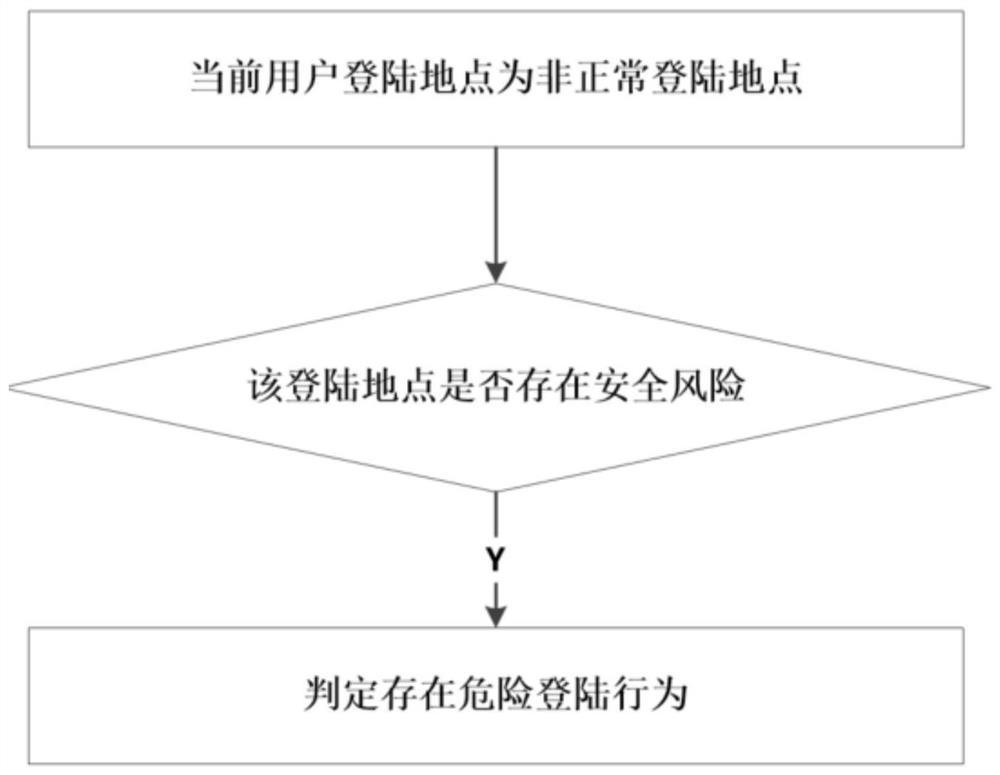
A security detection method and system for remote login risk control
ActiveCN109660566BReduce the Risk of MisappropriationPrevent exitTransmissionOperating systemReliability engineering
The invention relates to a safety detection method and system for remote login risk control. The method comprises the following steps of acquiring a login site of a current user, and verifying whetherthe current login site is a common login site of the user or not; if the current login site is not the common login site of the user, detecting whether user login equipment is the common equipment ornot; if the user login equipment is not the common equipment, acquiring the current position of the common equipment of the user; if the common equipment of the user does not exist in the preset range of the current equipment, judging that a dangerous login behavior exists at present; if the current user inputs login information, detecting whether the current user inputs a remote login special character or not; if the current user does not enter the remote login special character, judging that the dangerous login behavior exists at present; if the preset number of dangerous login behaviors exist in the single login, judging that the login is the abnormal login, recording the login behavior and exiting the login.
Owner:陕西绝顶人峰网络科技有限公司
Ink-jet printing method with mark
ActiveCN103809926AImprove data securityReduce the Risk of MisappropriationDuplicating/marking methodsDigital output to print unitsData fileInkjet printing
Owner:SHENZHEN JUDING MEDICAL DEVICE
Two-dimensional code anti-theft metal cover, preparation method and two-dimensional code anti-theft pot
PendingCN113682641AReduce the Risk of MisappropriationFlexible coversWrappersEngineeringStructural engineering
The invention relates to a two-dimensional code anti-theft metal cover, a preparation method and a two-dimensional code anti-theft pot, the two-dimensional code anti-theft metal cover comprises a basic cover, wherein the basic cover is provided with an opening, and the opening is sealed through an aluminum film seal adhered to the outer surface of the basic cover; a first two-dimensional code is endowed on the surface, pasted with the aluminum film seal, of the basic cover, one face of the aluminum film seal is pasted with the basic cover, a second two-dimensional code is endowed on the other face of the aluminum film seal, and first data obtained according to the first two-dimensional code and second data obtained through the second two-dimensional code have a data association relationship; and the first data obtained by scanning the first two-dimensional code comprises an auxiliary identifier. The two two-dimensional codes are arranged inside and outside, so that the risk that the two-dimensional codes are stolen is reduced.
Owner:HANGZHOU CPMC
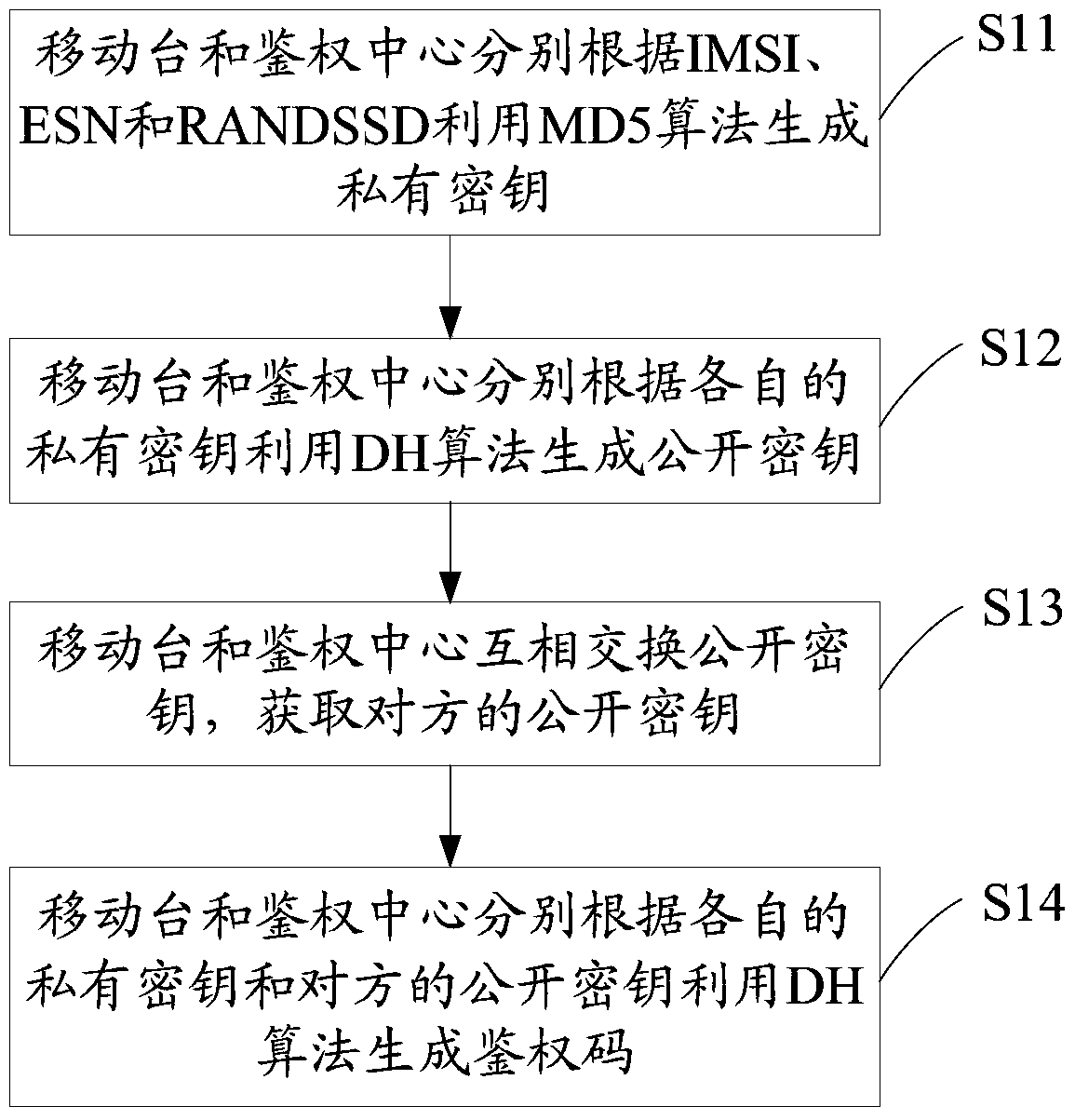
Method, system and device for dynamically generating authentication code based on cdma
ActiveCN104967993BImprove securityReduce the Risk of MisappropriationSecurity arrangementEngineeringMobile station
Owner:高新兴物联科技股份有限公司
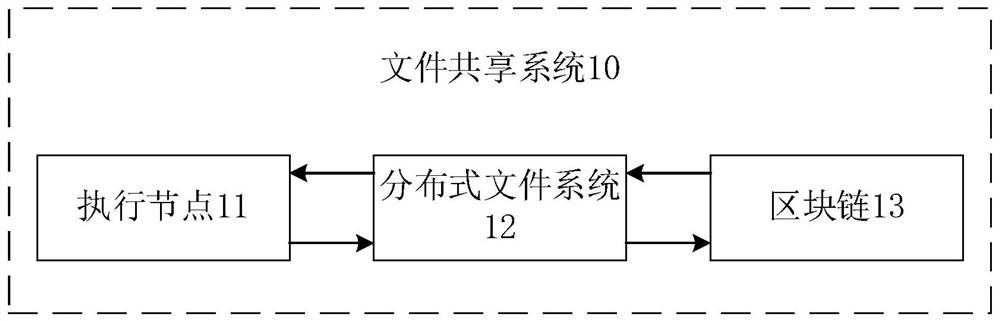
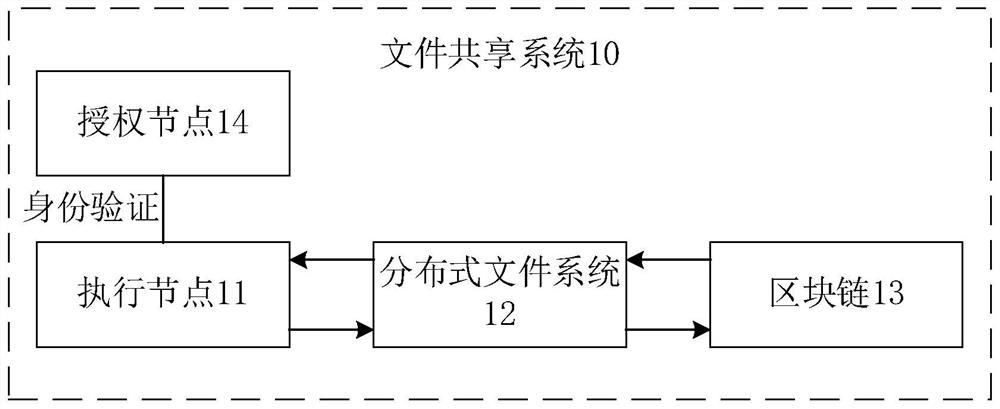
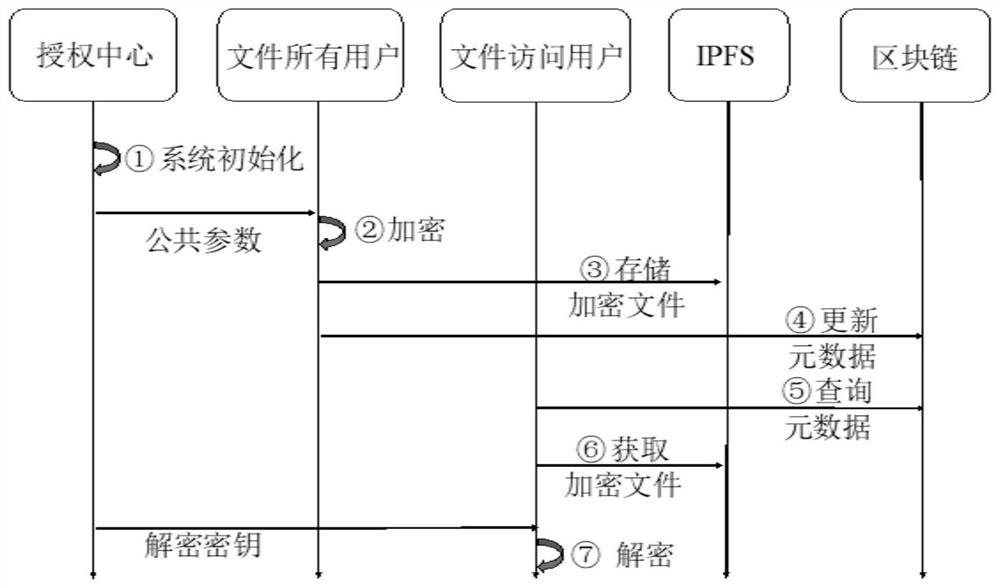
File sharing system, method and storage medium
PendingCN113505098AReduce the Risk of MisappropriationAvoid frequent occurrenceDatabase distribution/replicationFile access structuresDistributed File SystemBlockchain
The embodiment of the invention provides a file sharing system, a method and a storage medium. The file sharing system comprises an execution node, a distributed file system and a block chain, wherein the distributed file system is used for storing a shared file; the execution node is used for encrypting the shared file and uploading the encrypted shared file to the distributed file system, and / or the execution node is used for downloading the encrypted shared file from the distributed file system and decrypting the encrypted shared file; the block chain is used for storing file metadata of the shared file, the file metadata comprises a hash index value of the shared file, and the hash index value is used for searching a corresponding file in the distributed file system. The file can be encrypted through the execution node when the file is uploaded, the risk that the file is stolen is reduced, and meanwhile, the file metadata used for searching the shared file is stored through the block chain, so that traceability and tamper-proof management are performed on the file in the system, and frequent occurrence of pirated files and malicious files is avoided.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com