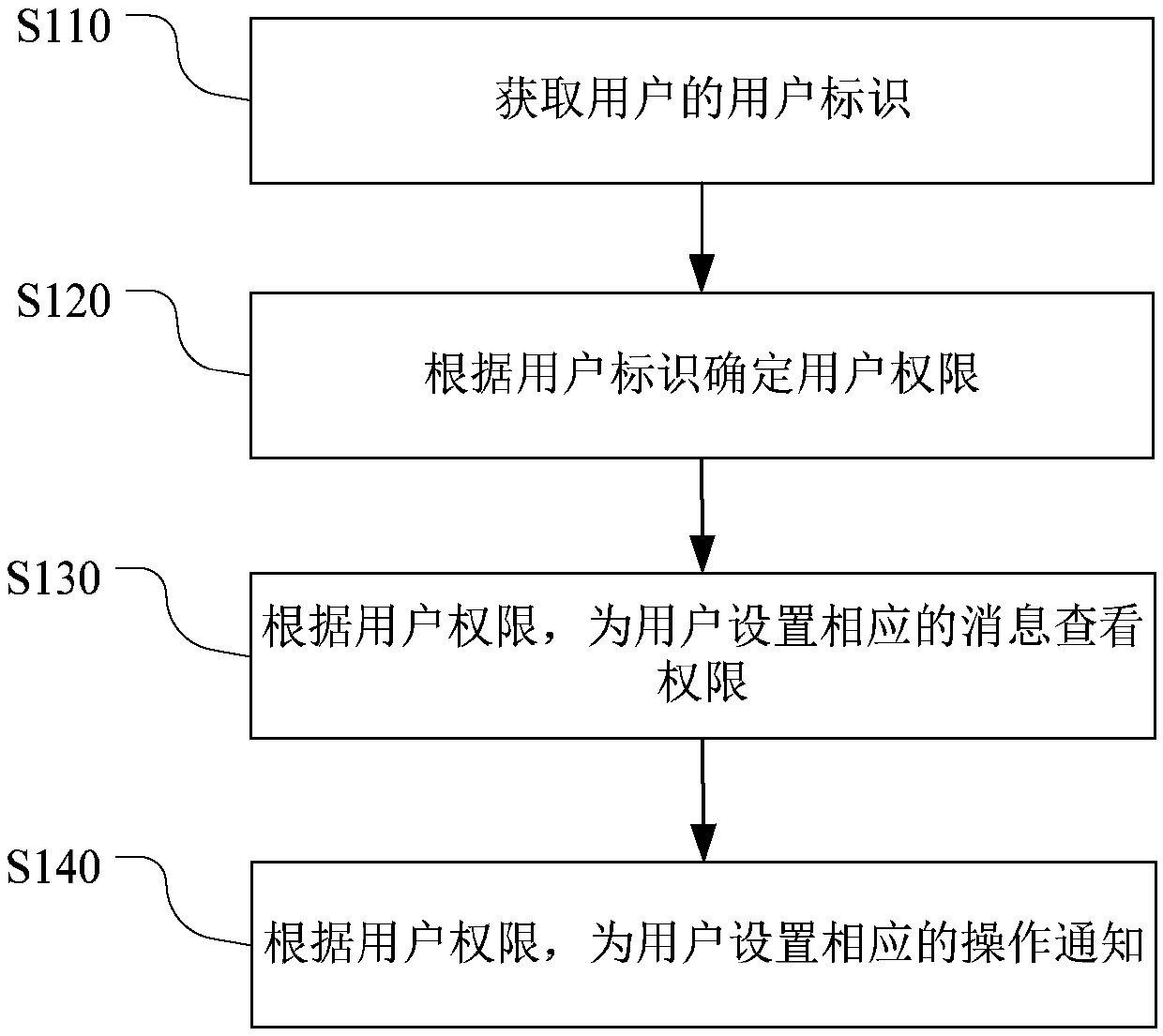
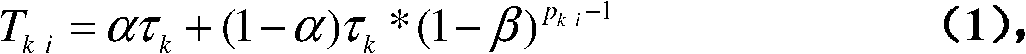Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
78results about How to "Increase permissions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
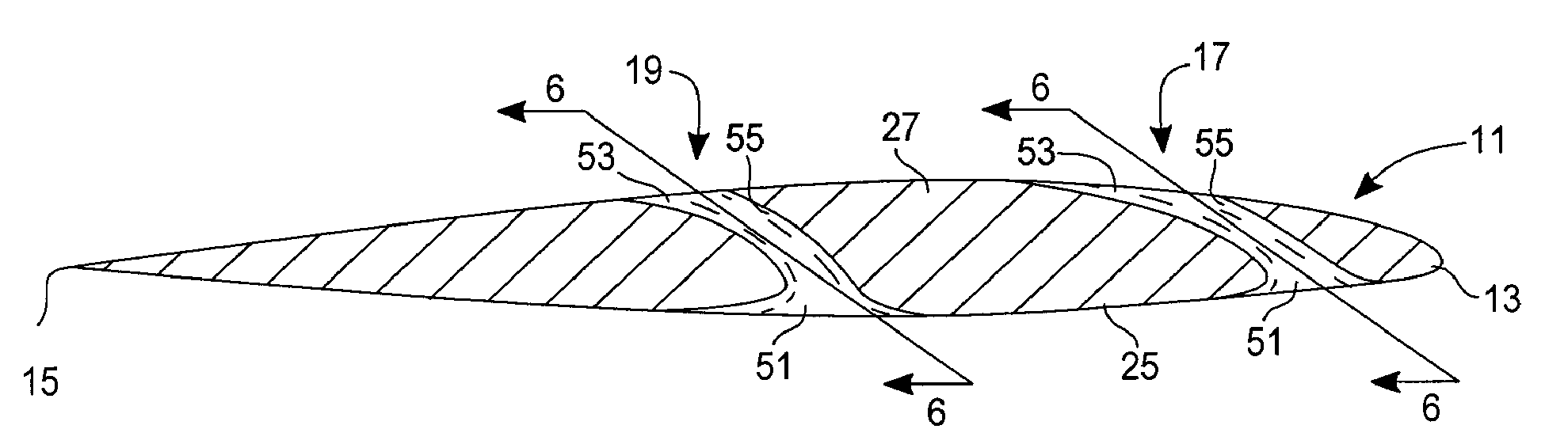
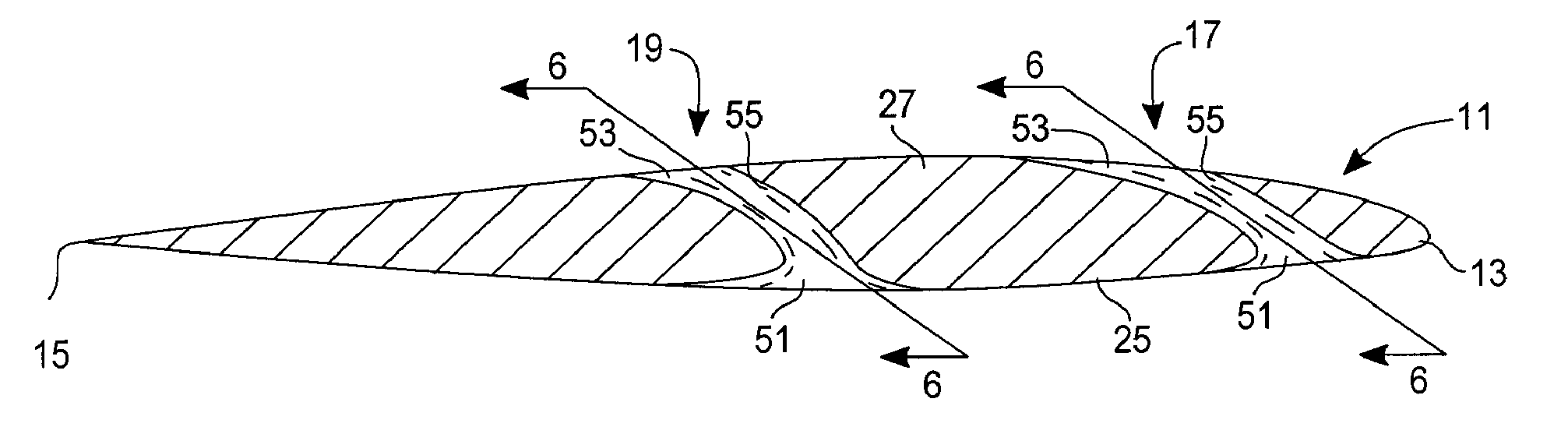
Fluid dynamic section having escapelet openings for reducing induced and interference drag, and energizing stagnant flow
InactiveUS20100303634A1Reduce trail vortex and wake turbulenceReduce dragPropellersWater sport boardsWire frameAirplane
A fluid dynamic section provides one or more fixed size escapelets through a foil body to reduce the induced and interference drag caused by trailing vortices and similar wake turbulence. The escapelets, which can be provided in both aerodynamic and hydrodynamic structures, such as wings, tail sections; rotary blades, guy wire frames, wing sails, and various underwater keels and wing keels. The escapelets transfer energy from an inlet located in the high-pressure surface of the foil or foil body to an outlet located in the lower-pressure surface, allowing energy that would normally form a vortex at the tip of the foil to be redirected and dissipated in a beneficial way. As a result, drag is reduced and fuel economy is increased, while at the same time increasing the authority of ailerons and similar flight control surfaces, allowing aircraft that were not previously spin recovery rated to become spin recoverable.
Owner:LONG DONALD JAMES
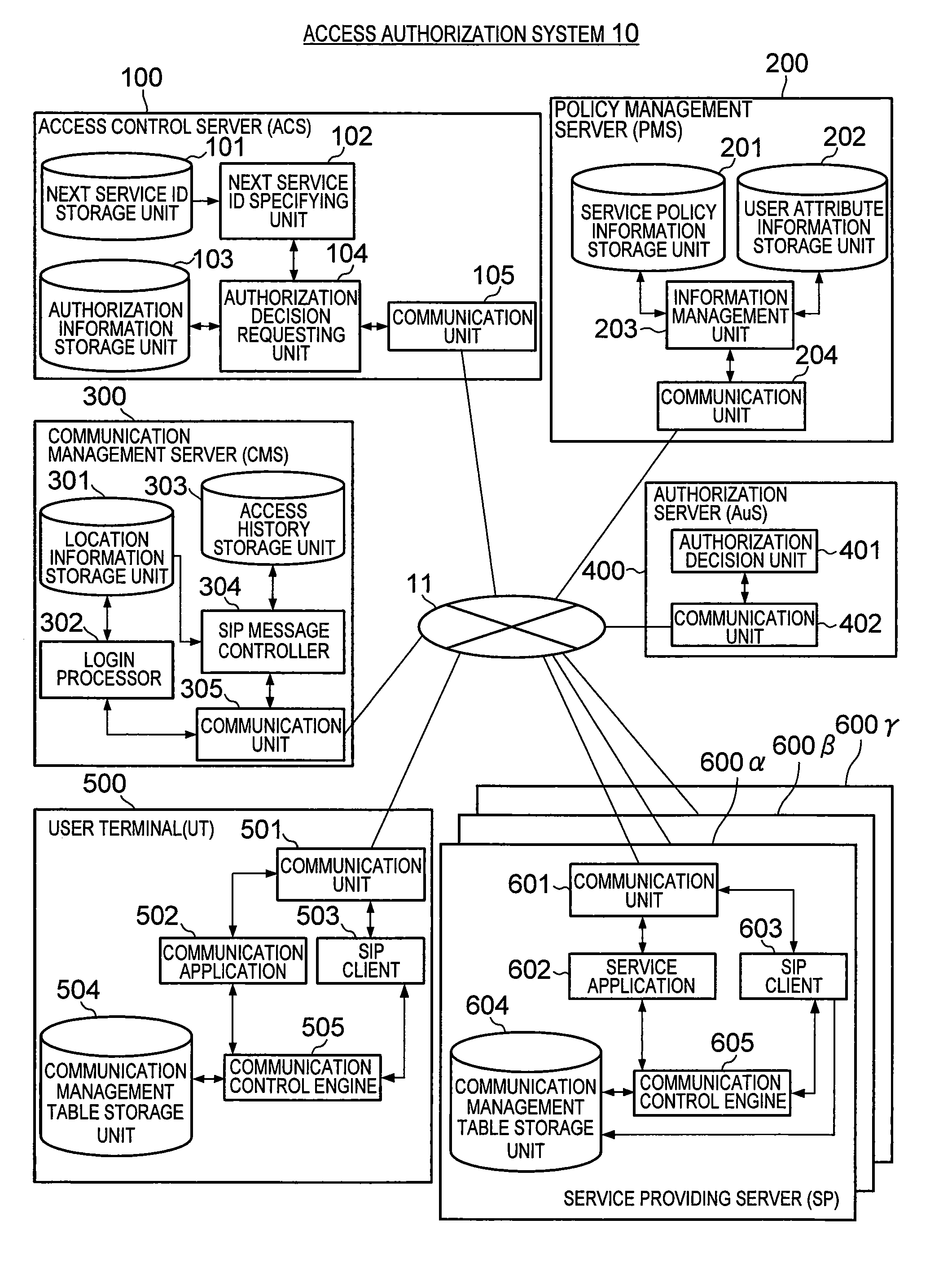
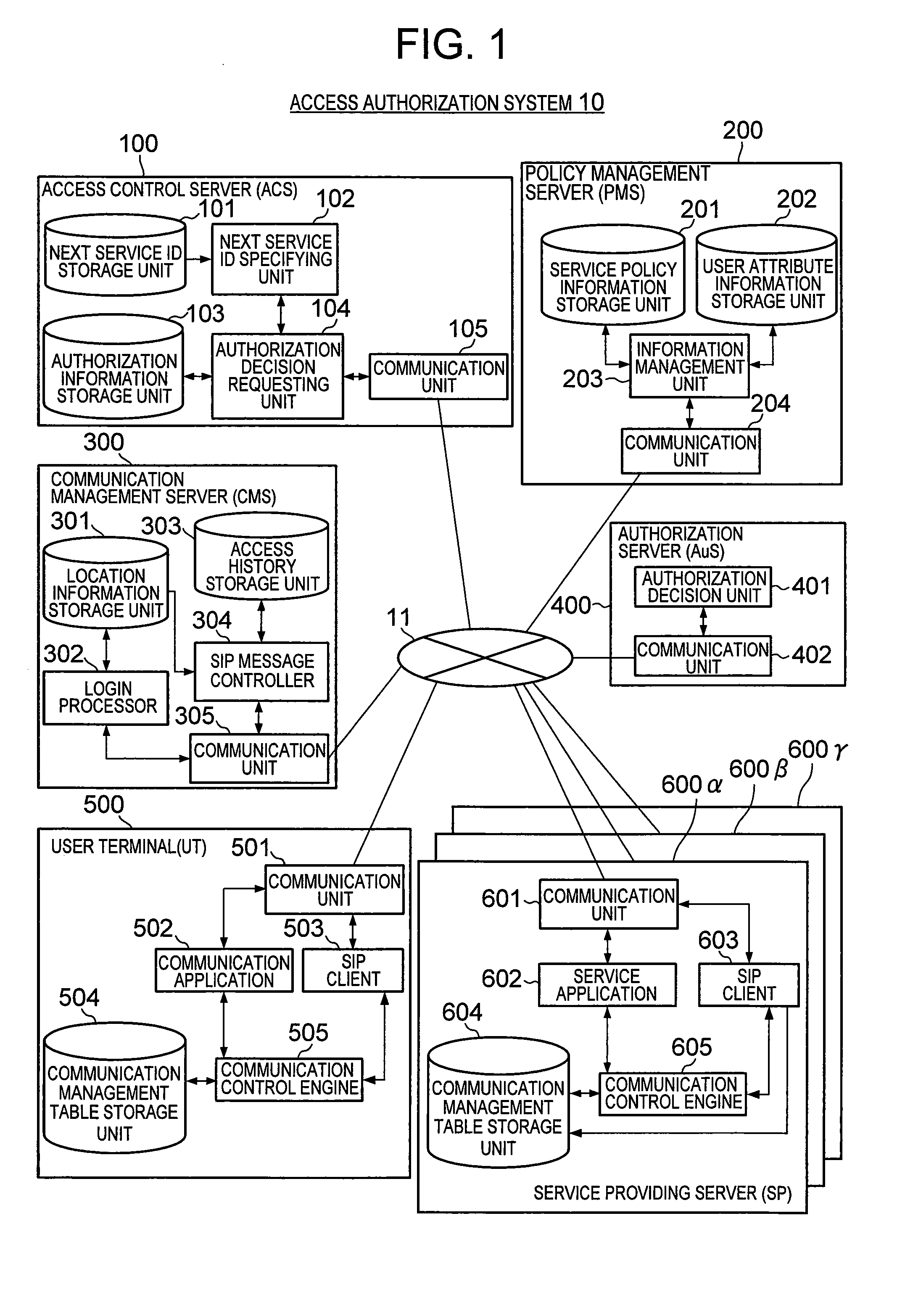
Access authorization system, access control server, and business process execution system
InactiveUS20090089866A1Short timeProcessing loadDigital data processing detailsUser identity/authority verificationClient-sideBusiness process
An access authorization system is provided, which can reduce the user wait time until the provision of a user-requested service. The access authorization system of the present invention specifies the next service to be provided to a UT (a client-side communication device) after the service currently being provided to the UT, and then executes process to make an authorization decision in advance regarding the next service with respect to the user of the UT, before the UT requests the next service.
Owner:HITACHI LTD
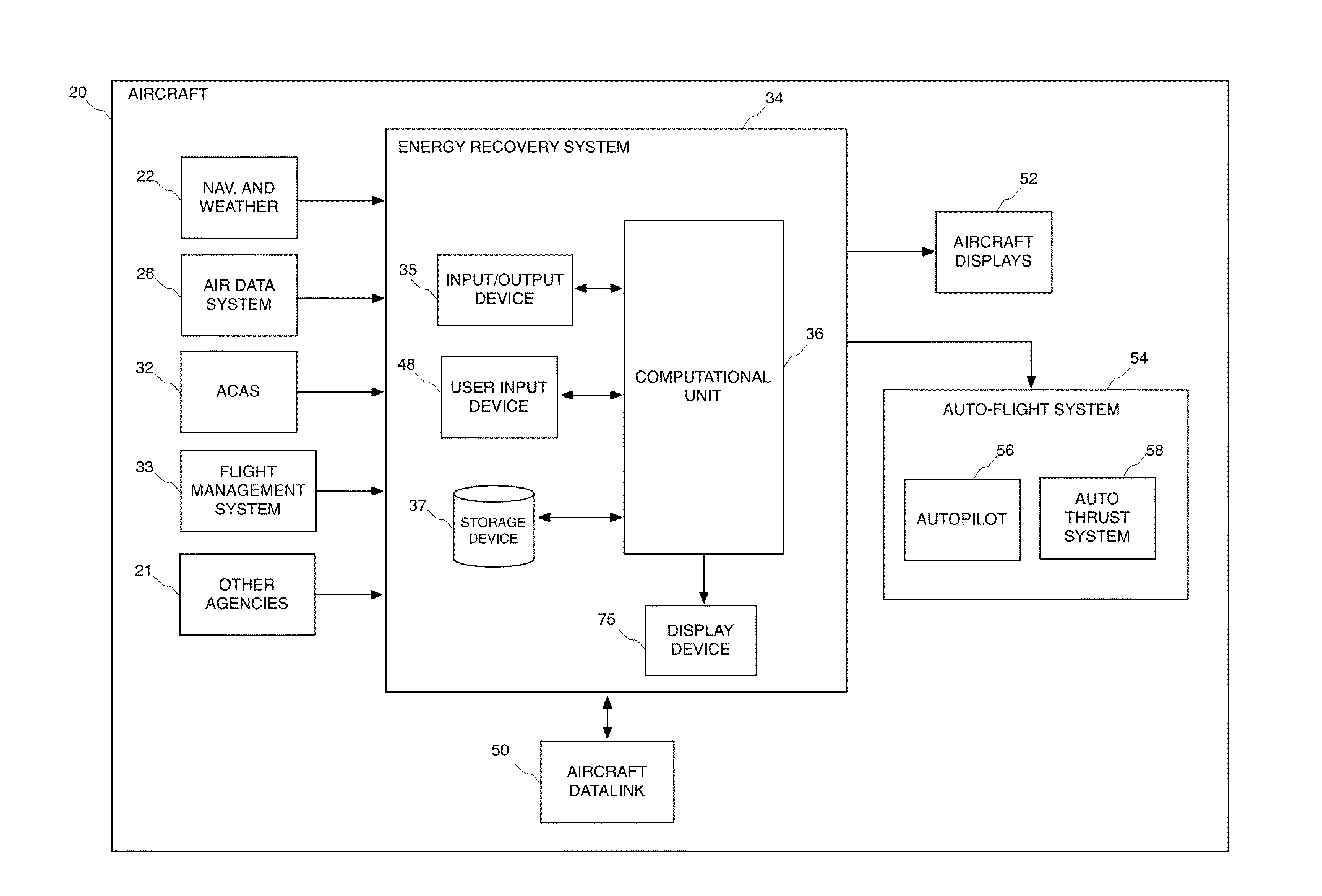
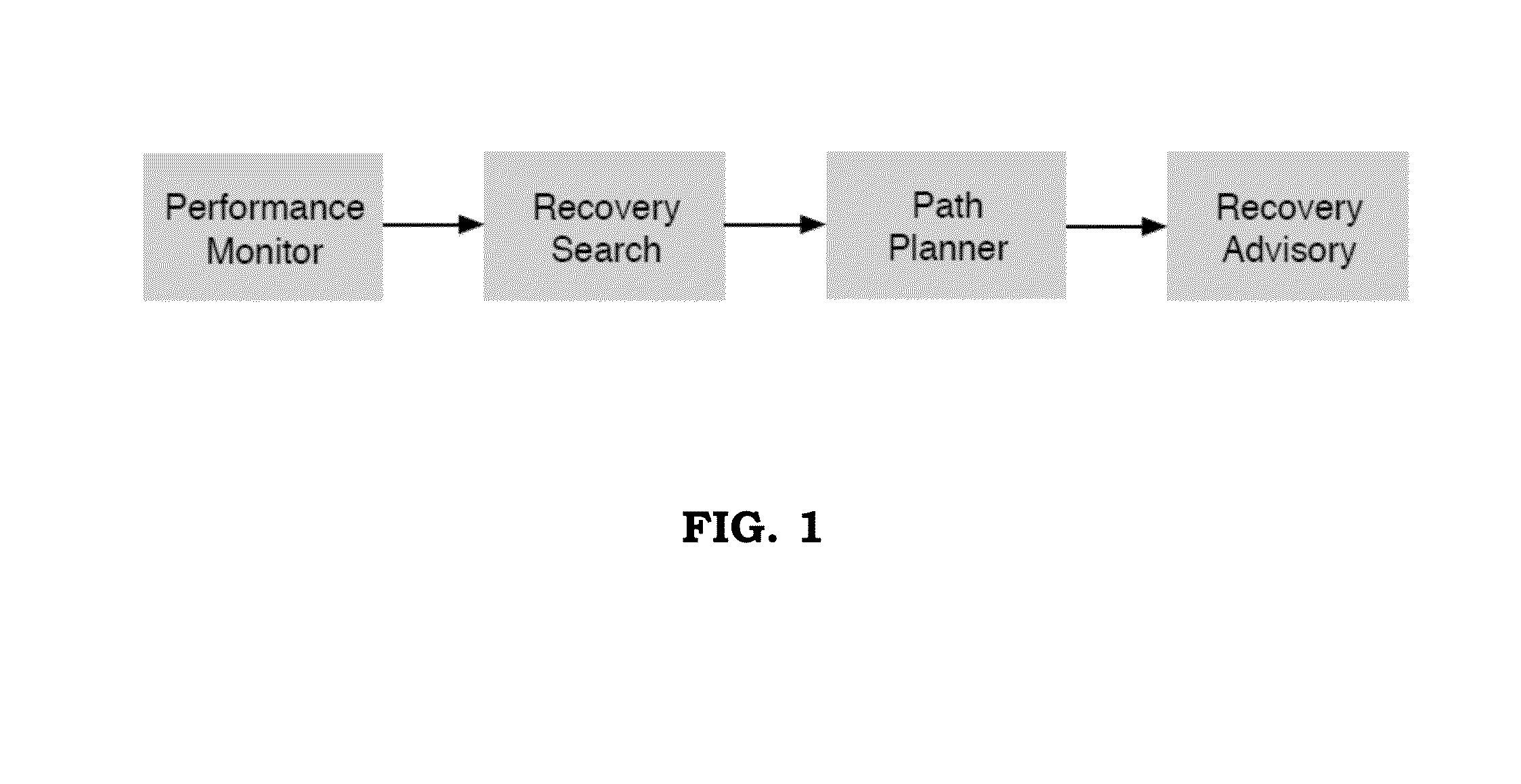
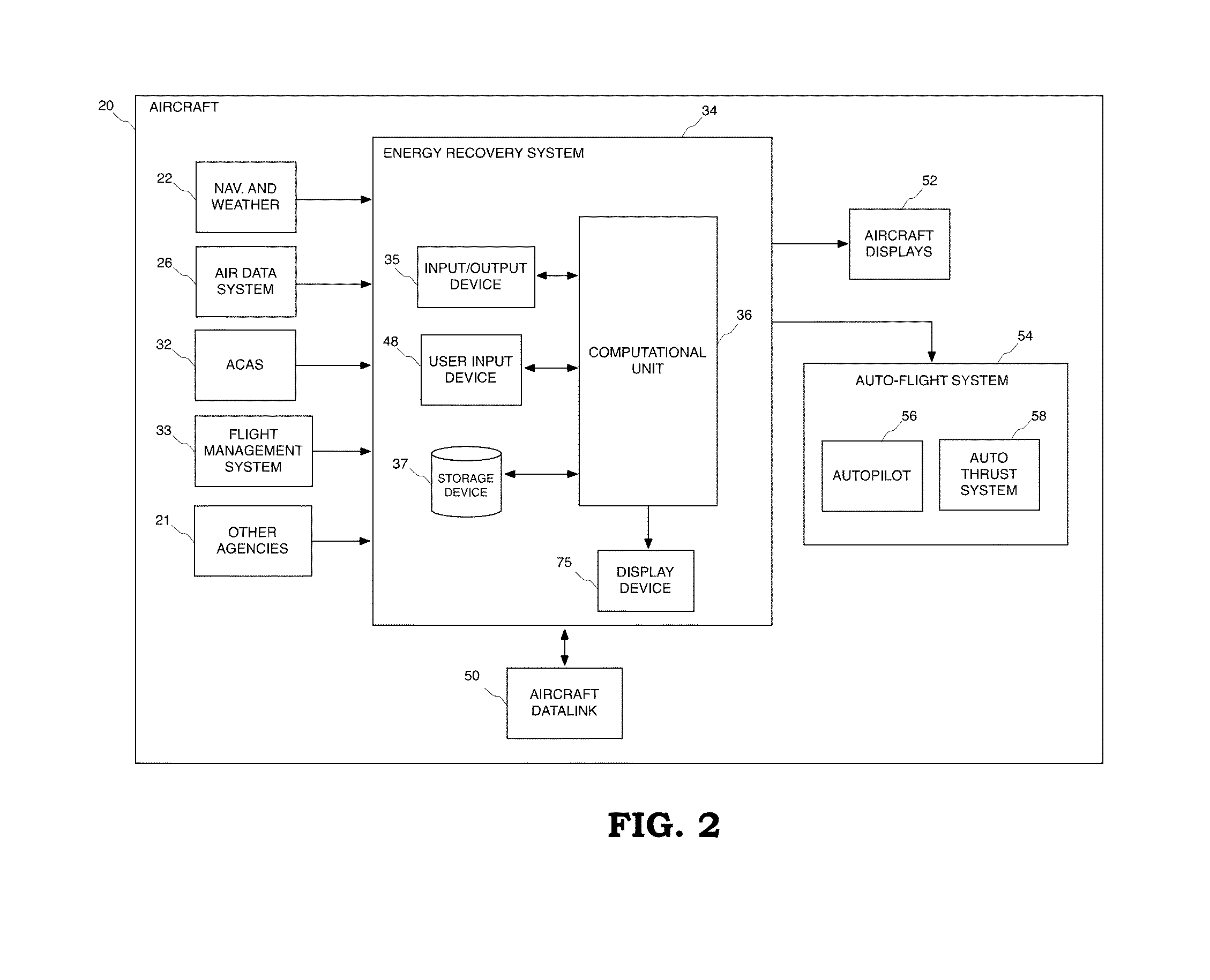
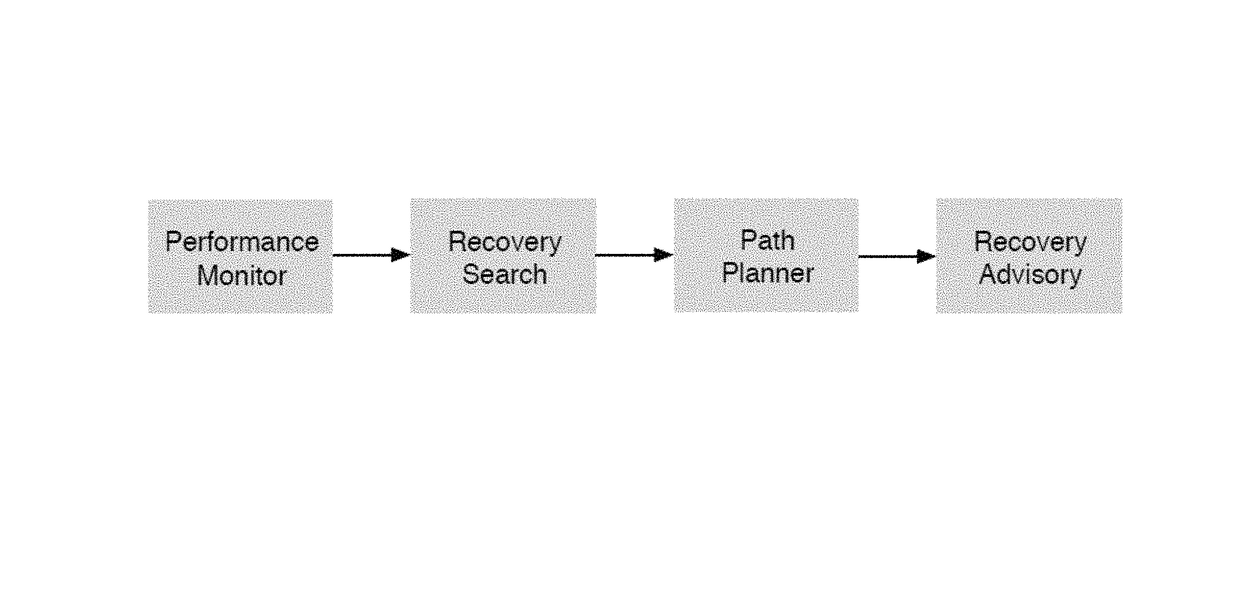
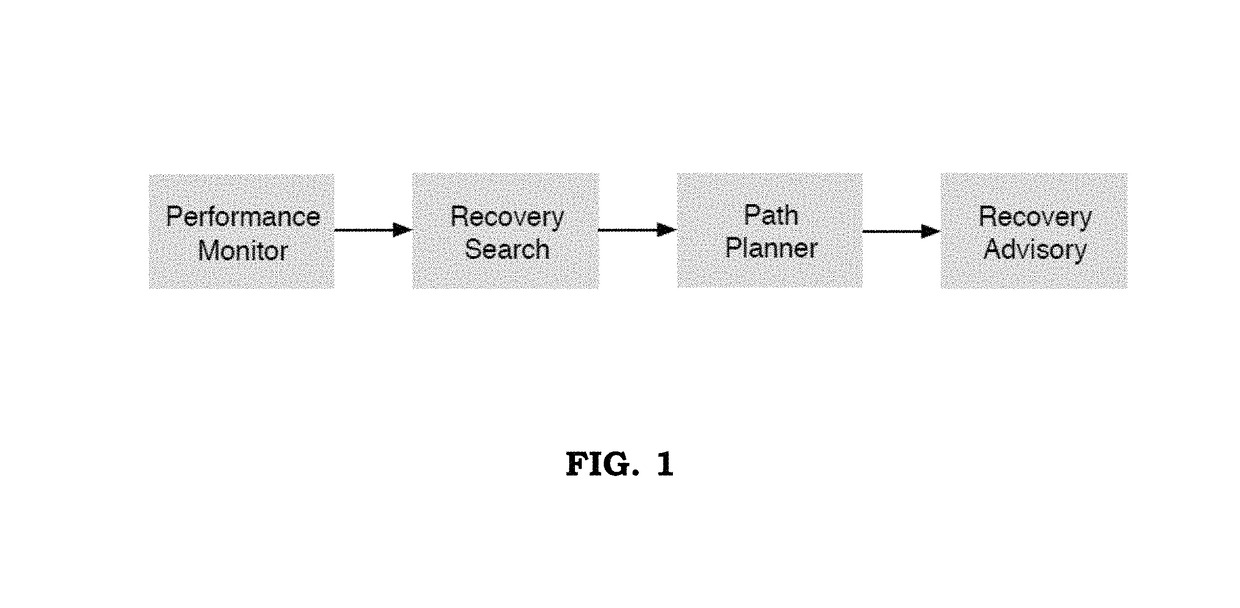
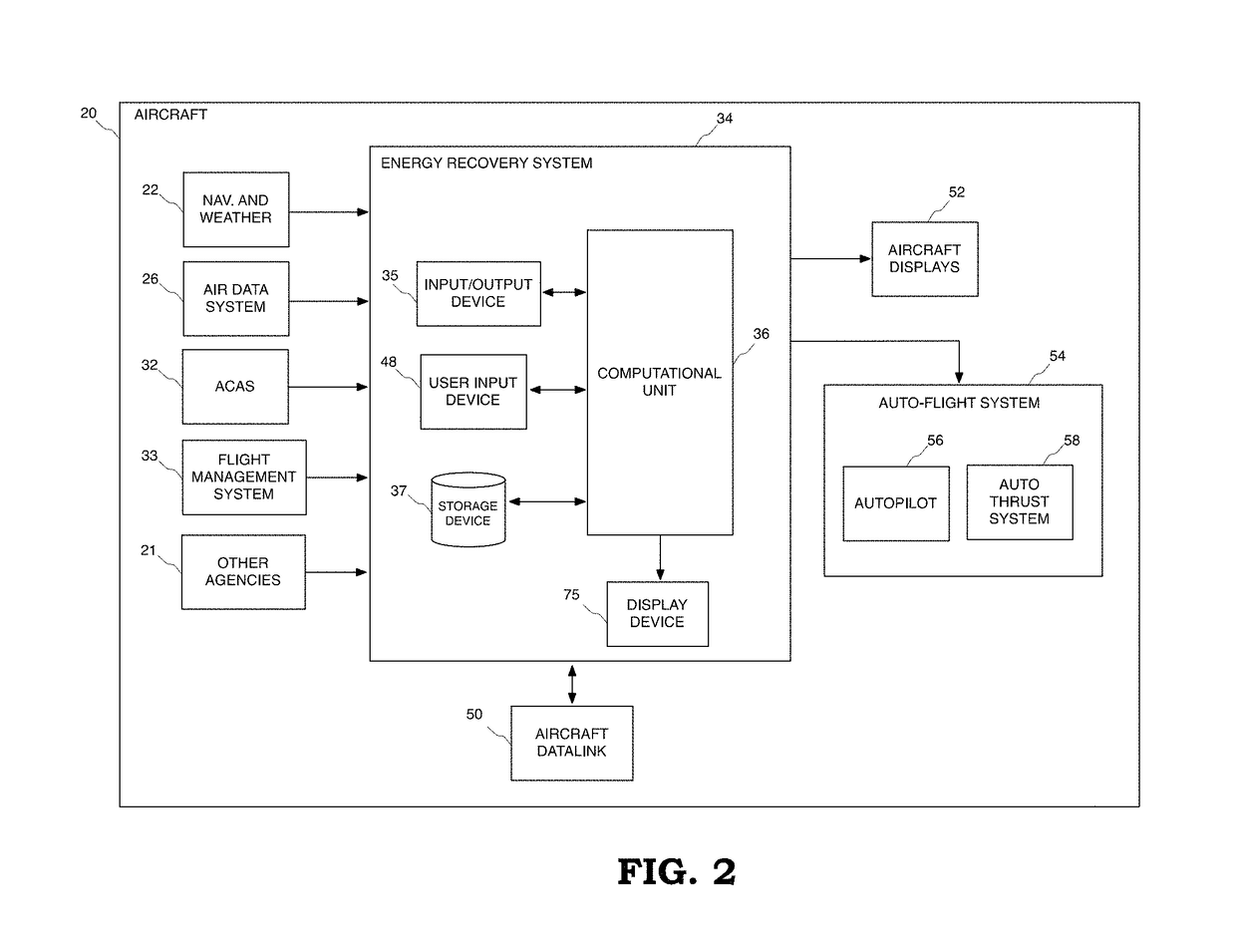
Method and system for recovering the energy state of an aircraft during descent
ActiveUS20160063867A1Easy to followImprove recovery authorityAnalogue computers for vehiclesEnergy efficient operational measuresAirplaneTime constrained
A method and system is provided for the recovery of an aircraft energy upset in a time-constrained descent. The system includes a computational unit to assess a number of adjustments involving a combination of speed changes, aerodynamic brake deployment and track miles adjustments that alter the energy dissipation profile whilst allowing the aircraft to maintain a pre-determined time-of-arrival over an incoming waypoint along the original descent path.
Owner:UNIVERSITY OF MALTA
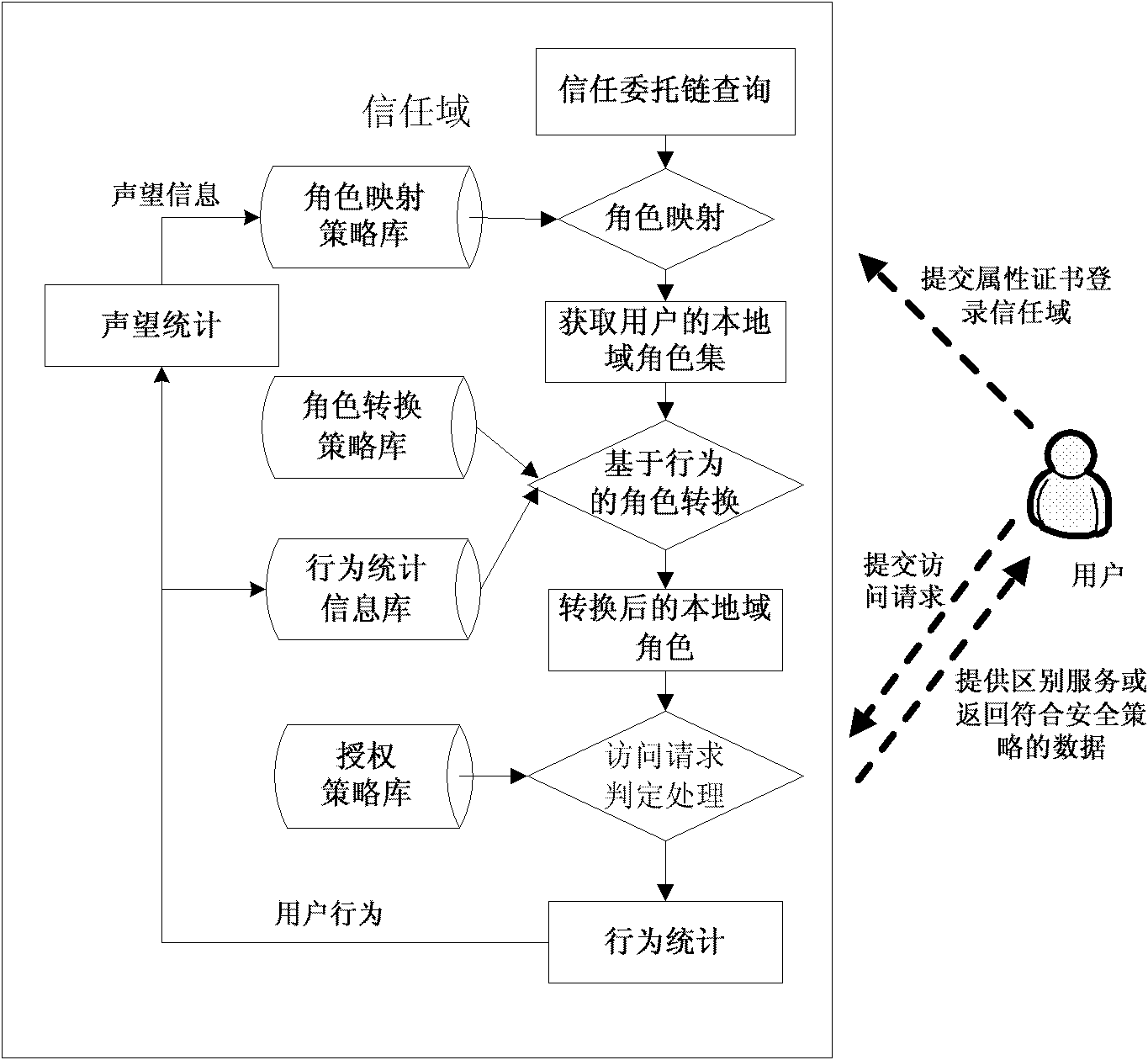
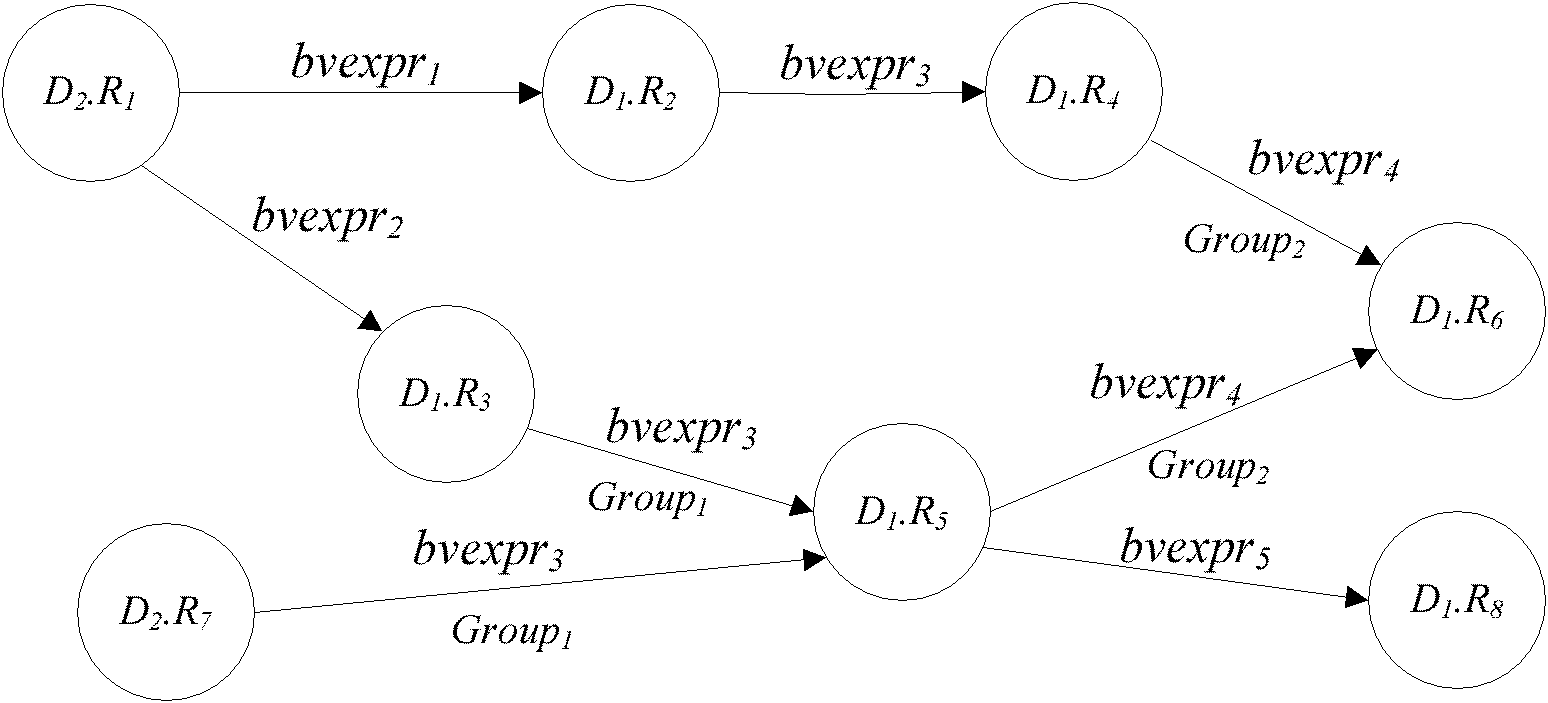
Calculable creditworthiness-based access control method under distributed environment of multiple trusting domains
InactiveCN101888341AIncrease permissionsImprove the trust management mechanismDigital data protectionData switching networksResource informationNetworked system
The invention relates to a calculable creditworthiness-based access control method under the distributed environment of multiple trusting domains in the technical field of network. The method comprises the following steps of: logging in a target trusting domain by a user, and giving the trusting domain a role set of the user by role mapping and role changing; trying acquiring resource informationin the target domain by the user; inquiring a delegated strategy database; updating user behavior variable values in an accumulation behavior library, and updating the times of executing user behaviors corresponding to outland roles in a behavior evaluating library; changing the role on the basis of the behavior; generating behavior evaluation vectors, and calculating a fame value of the role; and regulating a role mapping strategy related to the role. The method realizes dynamic trust management of role mapping, role changing and fame feedback, improves interaction capacity between the trusting domains and the user, improves flexibility, security and reliability of access control in the trusting domains, and effectively solves the problems of user authorization and resource management inservice of network systems by taking the user behavior as trusted evaluation objects.
Owner:SHANGHAI JIAO TONG UNIV
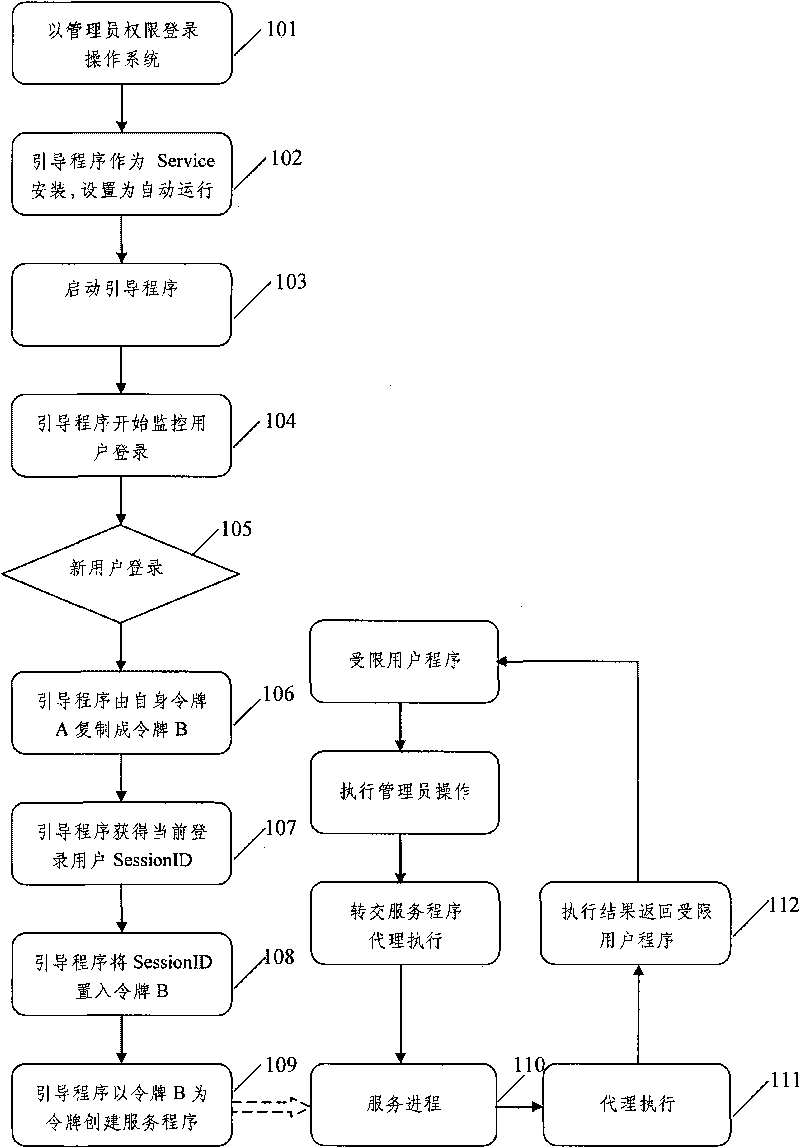
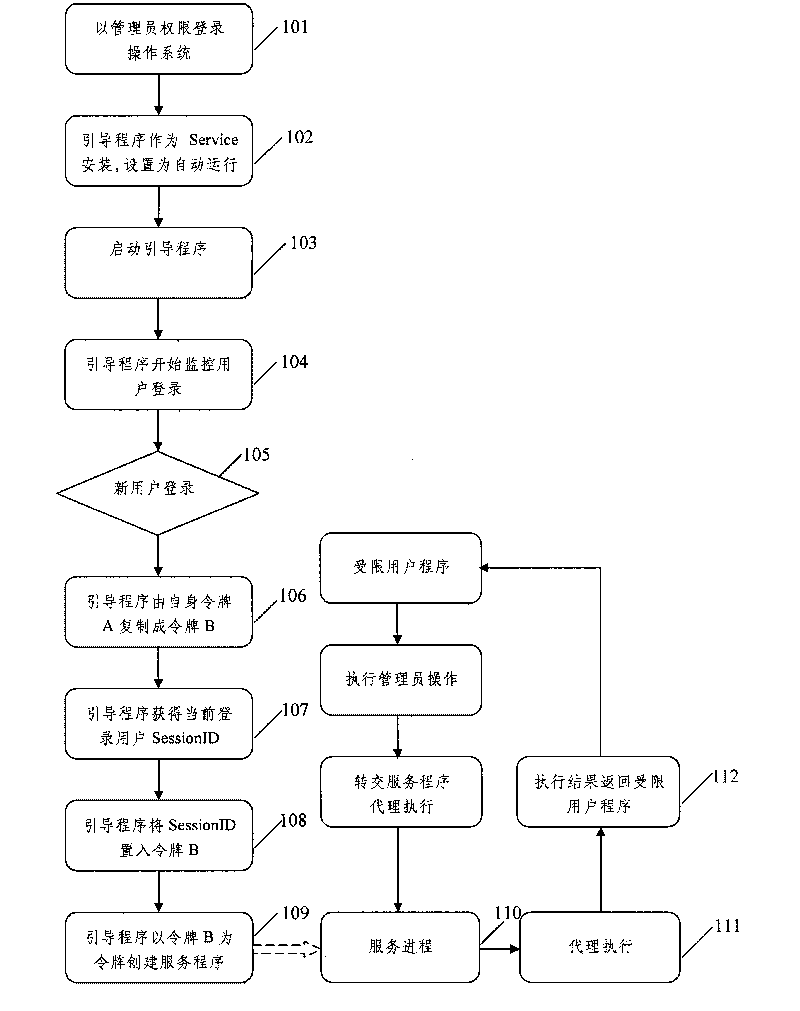
Method for executing operation under Windows without limitation of user right
ActiveCN101751287APrivilege not elevatedIncrease permissionsMultiprogramming arrangementsInternal/peripheral component protectionBootingUser environment
The invention discloses a method for executing operation under Windows without limitation of user right. The method includes the steps: installing a boot program in a Windows operating system in the way of service program; creating a service program running in the dialogue of a newly logged user at current when the new user is monitored to successfully log in the operating system after starting the boot program; handing over the operations needing to be operated to the service program to complete through agent executing when a limited user program needs operating, and obtaining an agent executing result thereof from the service program; the method for executing operation under Windows without limitation of user right realizes to execute the operating demand of an administrator through theuser program under limited user environment, and does not improve the right of the limited user during the process, thereby guaranteeing the safety of operating systems.
Owner:BEIJING TOPSEC TECH
Fluid dynamic body having escapelet openings for reducing induced and interference drag, and energizing stagnant flow
A fluid dynamic body provides one or more fixed size escapelets through a foil body to reduce the induced and interference drag caused by trailing vortices and similar wake turbulence. The escapelets, which can be provided in both aerodynamic and hydrodynamic structures, such as wings, tail sections; rotary blades, guy wire frames, wing sails, and various underwater keels and wing keels. The escapelets transfer energy from an inlet located in the high-pressure surface of the foil or foil body to an outlet located in the lower-pressure surface, allowing energy that would normally form a vortex at the tip of the foil to be redirected and dissipated in a beneficial way. As a result, drag is reduced and fuel economy is increased. For example, in aircraft, escapelets can increase the authority of ailerons and similar flight control surfaces, allowing aircraft that were not previously spin recovery rated to become spin recoverable.
Owner:LONG DONALD JAMES
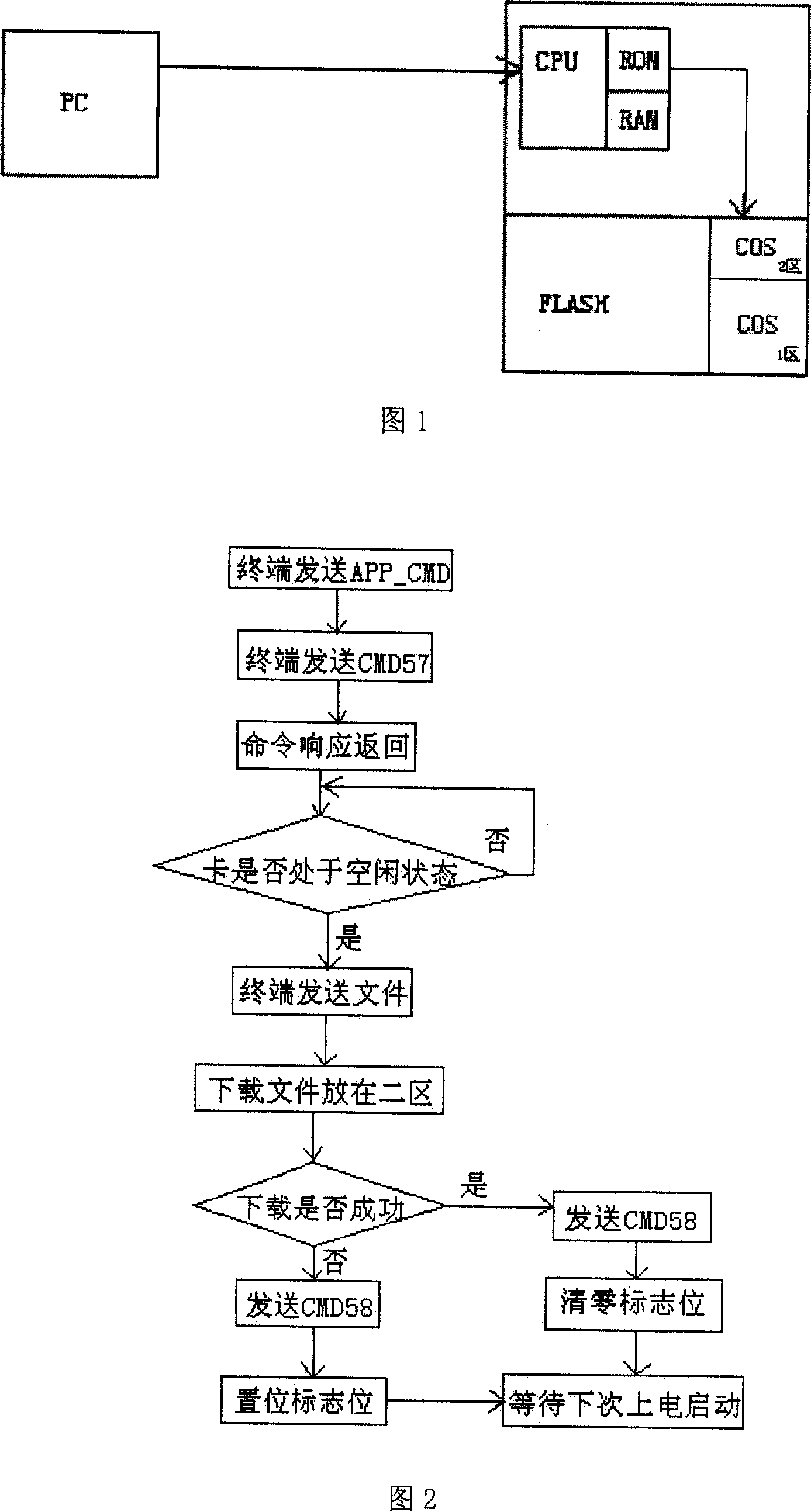
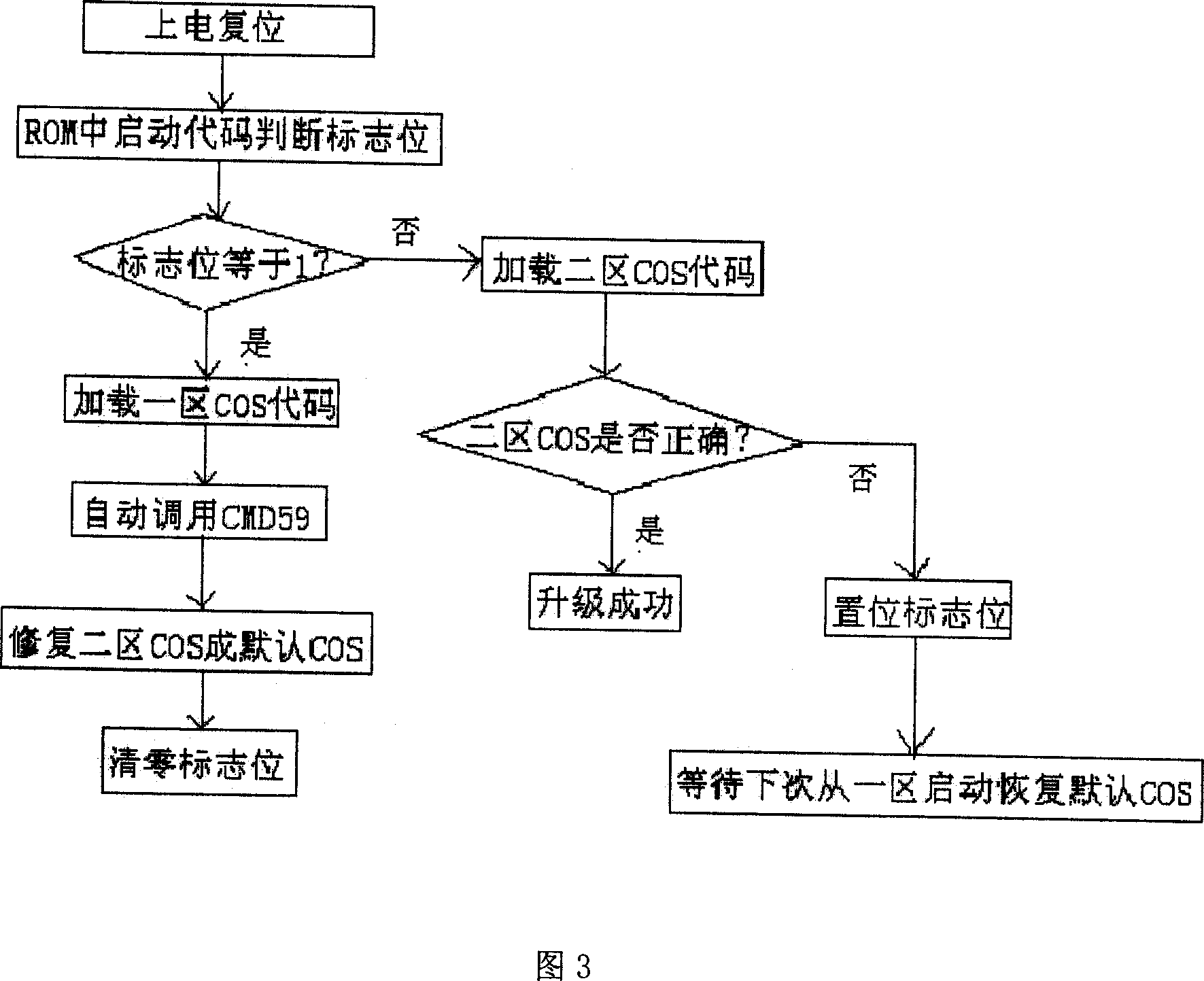
Method for upgrading operation system for memory card
InactiveCN101086701AIncrease permissionsFlexible upgradeProgram loading/initiatingRead-only memoryStart up
The invention relates to memory card operation system updating method that sets a code area on the removable memory into two parts, with one being the default operation system code, the other the current operation system code with marks on them. On the ROM start up code, inner core order of the operation system is loaded based on the marking status to load the operation system for different areas. Add operation system updating order CMD57, writes the update system file to the operation system code of two areas, and add order CMD58. When the update file is transmitted or making a mistake in transmission, the terminal will send CMD58 order to the memory card and write the marking position. It expands the feature of the memory card with intensified safety of it.
Owner:CHINA POTEVIO INFORMATION IND
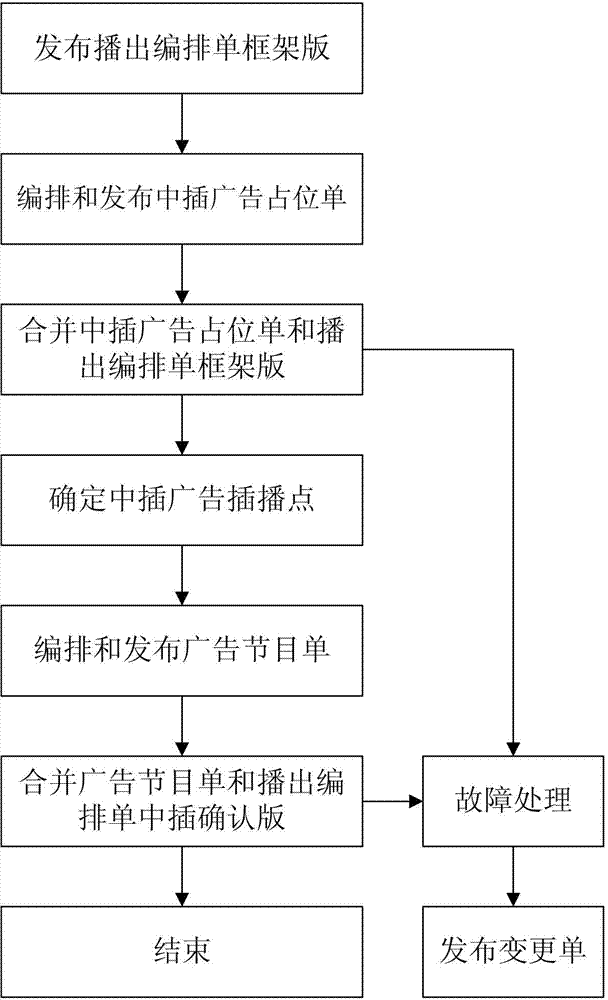
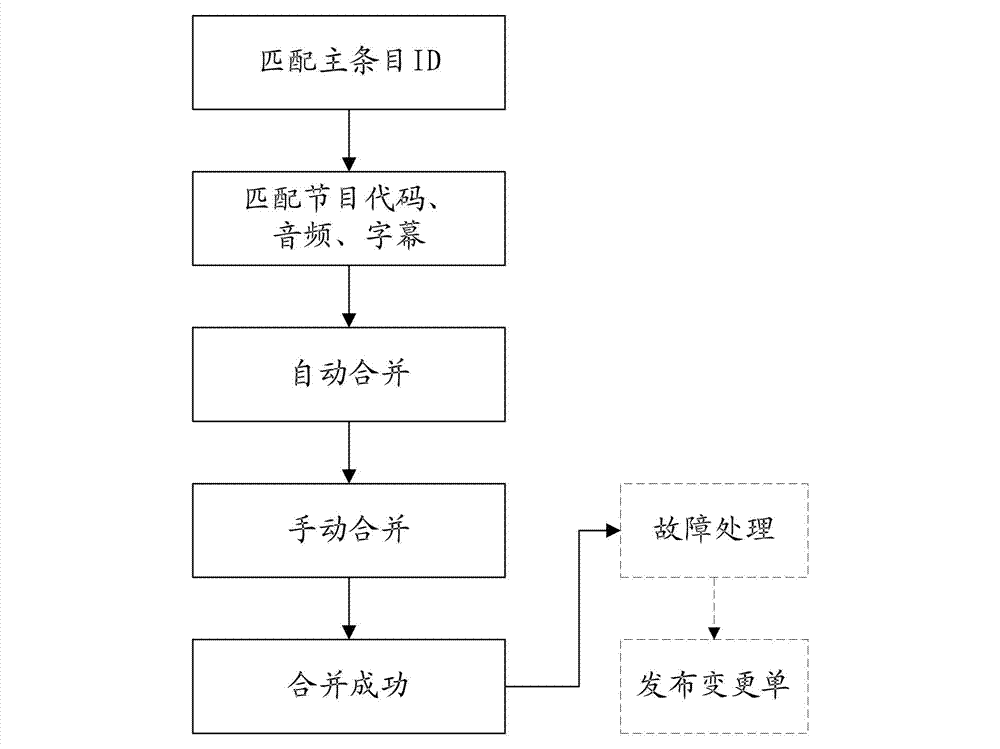
Method for arrangement processing of inserting advertisement
ActiveCN103051939AReduce modificationIncrease permissionsSelective content distributionBroadcastingFault handling
The invention relates to a method for the arrangement processing of inserting advertisement, which comprises the following steps of: issuing a broadcasting arranging-bill framework version; arranging and issuing an inserting advertisement space-occupying bill; merging the inserting advertisement space-occupying bill and the broadcasting arranging-bill framework version; determining the inserting point of the inserting advertisement; merging an advertisement program bill and a broadcasting arranging bill; ending; processing faults; and issuing a modifying bill. In the method disclosed by the invention, an inserting-advertisement program bill is added on the basis of an original broadcasting arranging bill, an original program-modifying bill and an original advertisement program bill, so that the original mode of fixed advertisement insertion is changed, and the inserting time point, the inserting duration and the inserting form of the advertisement are more flexible through secondary merging.
Owner:CHINA CENTRAL TELEVISION +1
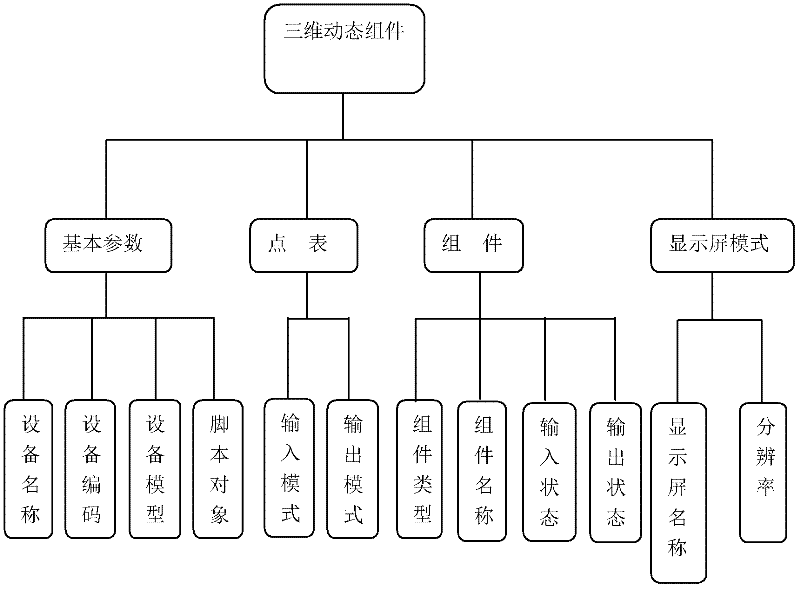
Dynamic model building method based on three-dimensional (3D) engine
ActiveCN102509331AConvenient for dynamic adjustmentIncrease permissionsAnimationDynamic models3D rendering
The invention provides a dynamic model building method based on a three-dimensional (3D) engine, which is used for building a 3D dynamic model of equipment. The method comprises the following steps of dividing equipment into components, respectively encoding the divided components, building a 3D dynamic model of equipment by a user as required, and modifying the parameters of the components as required. According to the method, the model is encoded, and based on a 3D rendering engine, the model can be updated through writing the background codes, and moreover, the user can change the information of equipment parameters, components and the like in the model list through simply operating the information list of simulation equipment; and the authority of the user is improved, the operation is simple and safe, and the user can perform updating operation on the existing model, so that the troublesome code operation is eliminated.
Owner:江苏南大先腾信息产业股份有限公司
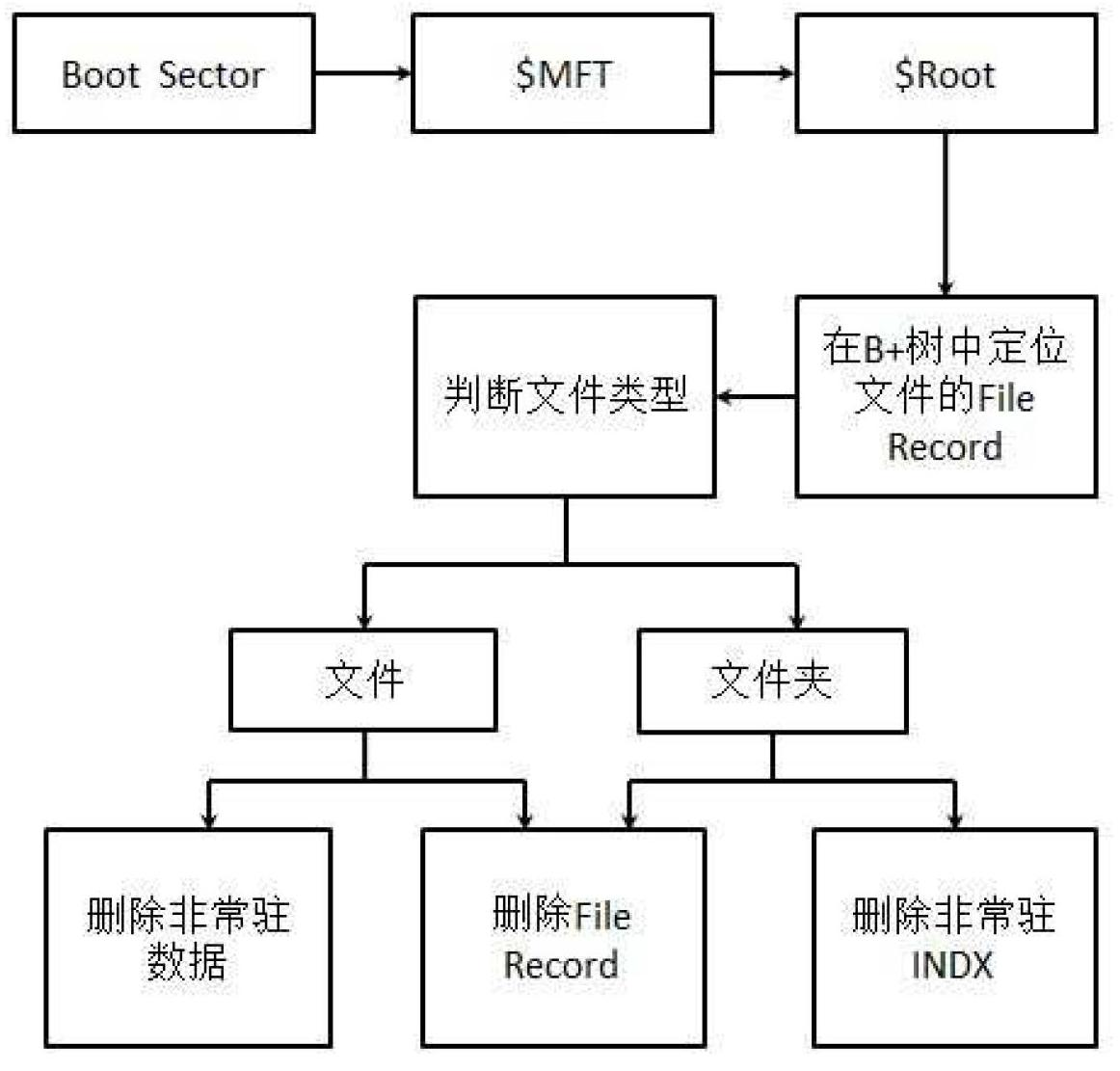
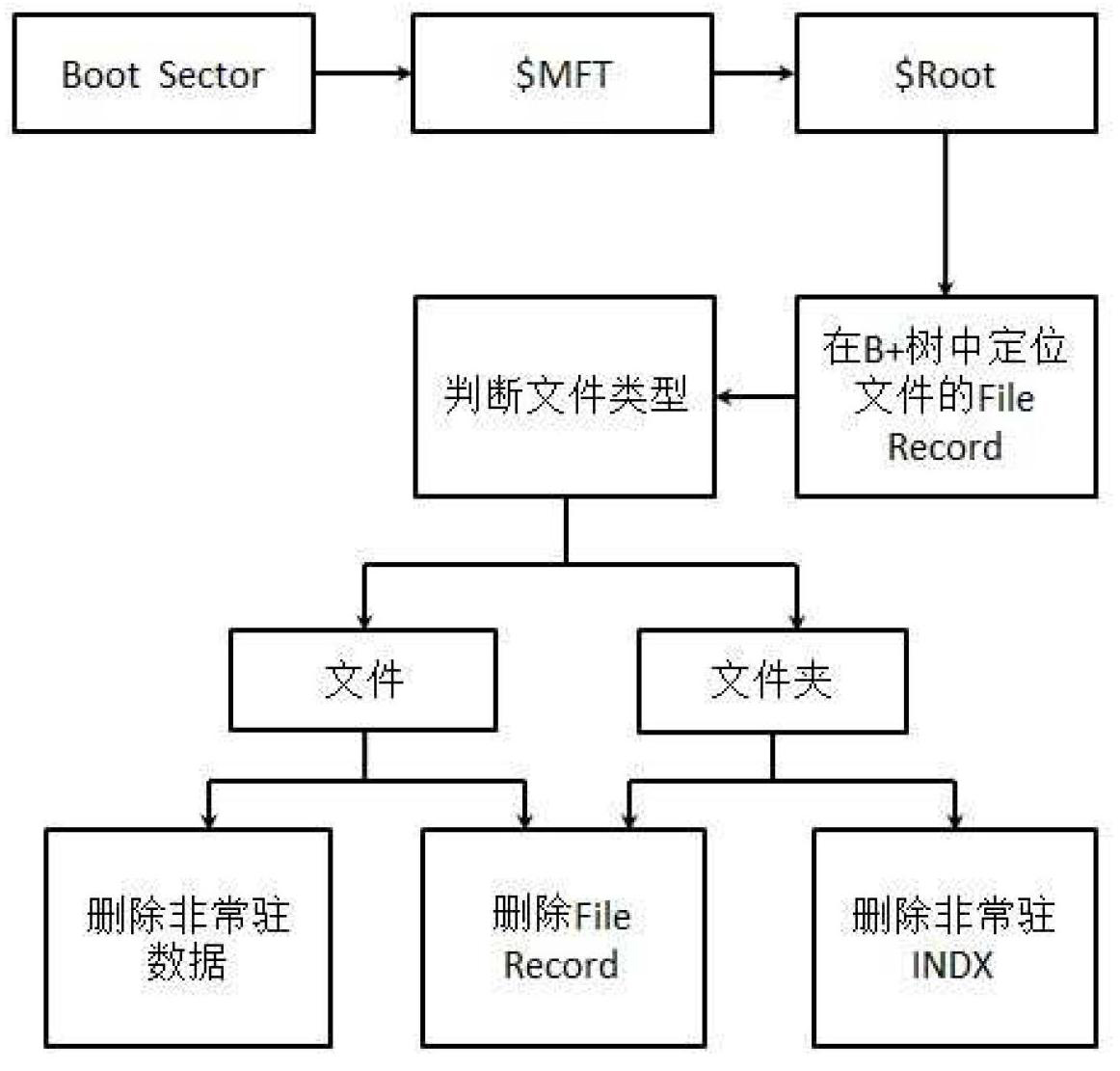
Data wiping method for NTFS (new technology file system)
InactiveCN102693387AGuaranteed to deleteGuaranteed recoveryDigital data protectionSpecial data processing applicationsOperational systemFile system
The invention relates to a data wiping method for an NTFS (new technology file system). The method includes the following steps of firstly, opening an X disk, namely a volume of the NTFS, in the Windows, and reading front 512 bytes of the volume, namely a starting sector; secondly, searching the ID (identity) of a file according to the path of the file to be deleted; and thirdly, wiping related information of the file. A system of the file is analyzed directly from disk data at the bottom, all file data on the disk can be accessed directly, and influence of an operation system is avoided, so that the highest authority is acquired for the file data on the disk, and deletion of the file data is guaranteed and cannot be recovered.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Vehicle maintenance information system based on blockchain technology
ActiveCN108154243AGuaranteed to be true and cannot be tampered withIncrease permissionsDatabase management systemsRegistering/indicating working of vehiclesComputer scienceInformation system
The invention relates to a vehicle maintenance information system based on a blockchain technology. The system comprises an association module, a maintenance module, a health management module and a query module; participants comprise a vehicle owner node, a relative and friend node, a vendor node, a repairer node and a query node. By means of the vehicle maintenance information system based on the blockchain technology, vehicle maintenance information is added to a distributed account book in the form of blocks, and it is ensured that data is true and cannot be tampered; an association mechanism of the nodes is established, and permissions of the nodes are expanded; the health management function is added, an owner is timely reminded to maintain a vehicle, and the health state of the vehicle is monitored in real time; two kinds of query permissions are designed, not only can vehicle maintenance records be queried, but also the health state of the vehicle can be queried, and differentneeds are met.
Owner:SHANGHAI WEILIAN INFORMATION TECH CO LTD
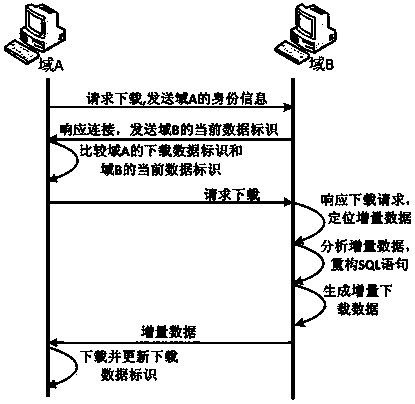
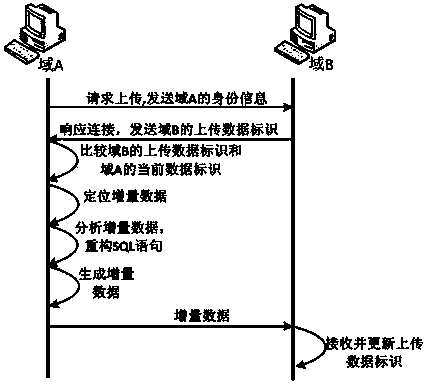
Cross-domain incremental data exchange model and method based on exchange identification
InactiveCN103595727ARapid positioningIncrease permissionsData switching networksData needsData exchange
The invention provides a cross-domain incremental data exchange model and a method based on exchange identification, and belongs to the field of data exchange in cross-domain environment. The model comprises a data layer, an exchange layer and a data transmission layer, wherein the exchange layer comprises an exchange identification module and an exchange strategy generation module. The data layer comprises a log analyzing module, an SQL statement reconstitution module, an XSD standard template, an XML file import and export module and a data calibration module. All the data are deleted or modified logically instead of physically when deleted or modified; even if one datum is modified or deleted, a new datum needs to be added behind the end data, the log analyzing module in the data layer analyzes SQL statements in a log to obtain a DML statement for operating a database, and therefore a target database executes the same statement to achieve date synchronization. Due to the fact that the model is used for incremental data exchange, the data exchange quantity each time is much smaller than that of a traditional method, and incremental data exchange is safer.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
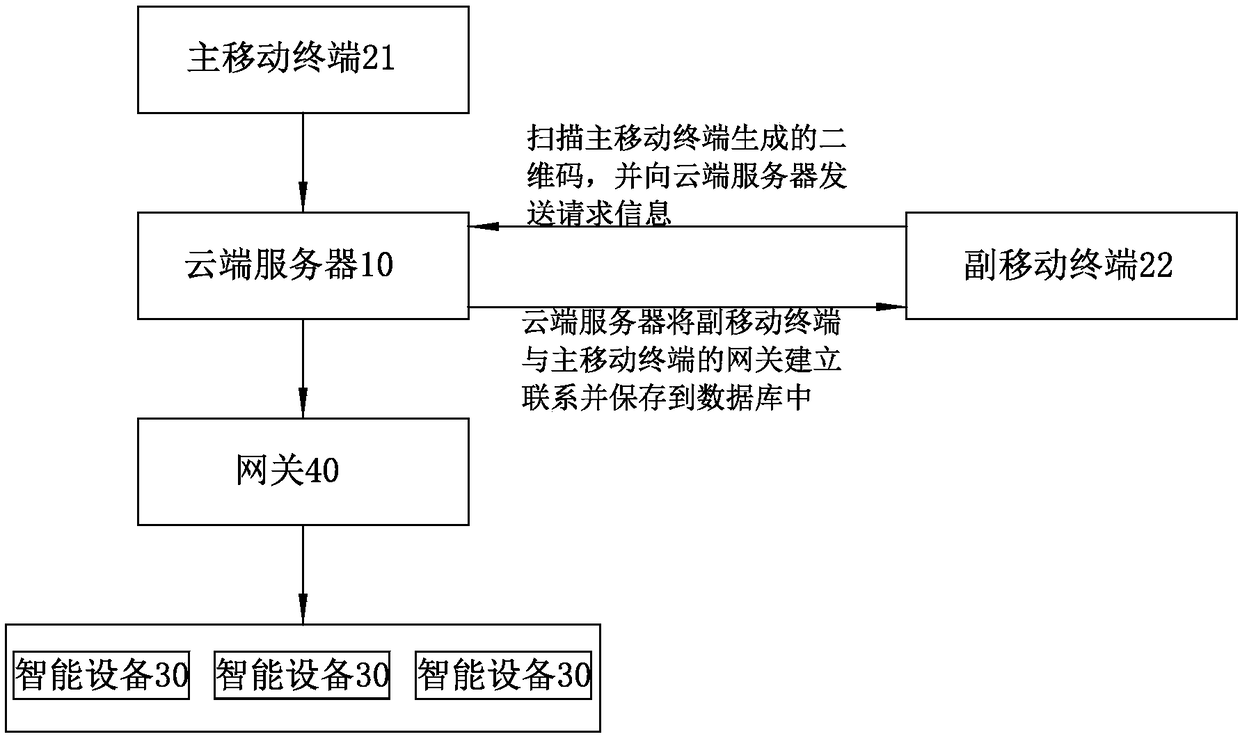
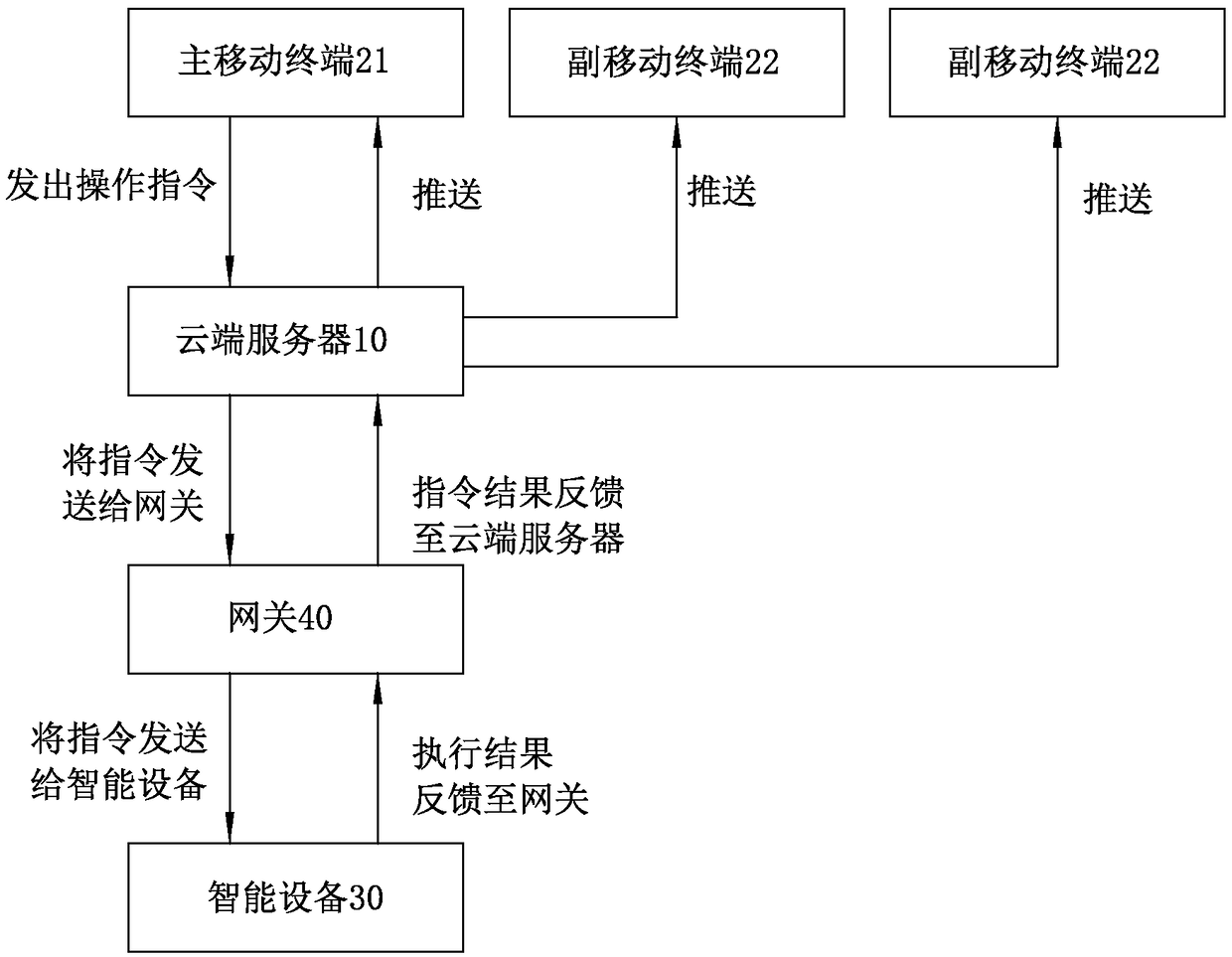
Sharing method of intelligent home equipment based on mobile terminal
InactiveCN108173724AShorten the timeImprove experienceCo-operative working arrangementsSubstation equipmentComputer terminalTerminal operation
The invention discloses a sharing method of intelligent home equipment based on a mobile terminal. The method comprises the following steps that: I, a main mobile terminal is bound with a gateway through a cloud server, and establishes a communication connection with intelligent equipment through the gateway; II, the main mobile terminal generates a shared two-dimensional code; III, a secondary mobile terminal scans the two-dimensional code, parses information of the two-dimensional code, and generates request information requiring sharing for the cloud server; IV, the cloud server establishesa temporary binding relationship between the secondary mobile terminal and the gateway bound with the main mobile terminal after receiving the request information in the step III, and saves the binding relationship in a database of the cloud server; and V, the secondary mobile terminal also implementation a communication connection with the intelligent equipment through the gateway. An intelligent home equipment control function can be shared with other secondary mobile terminals through the main mobile terminal, and all mobile terminals having control permission on the intelligent equipmentare synchronized when any intelligent mobile terminal operates the intelligent equipment.
Owner:陈占辉
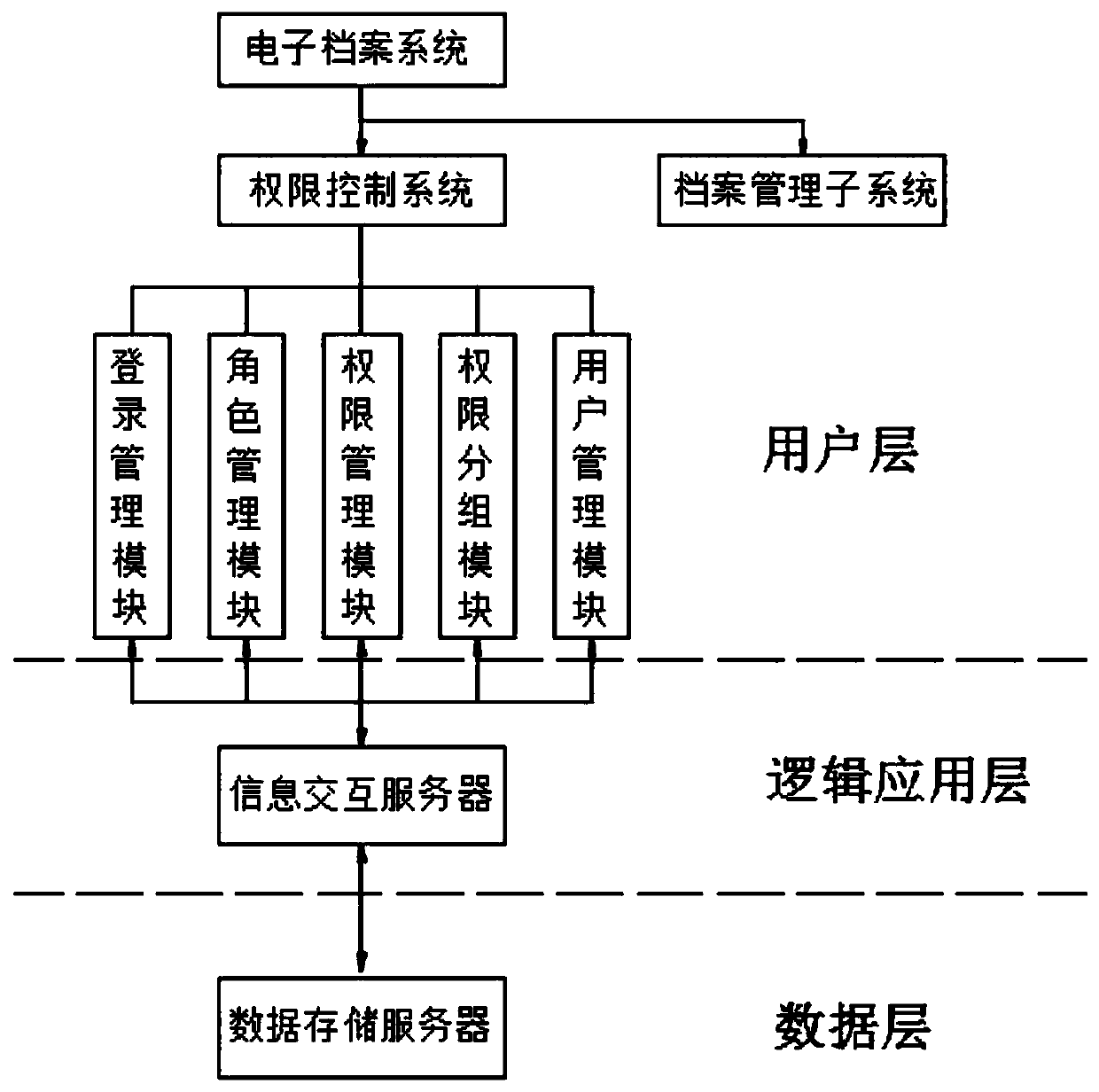
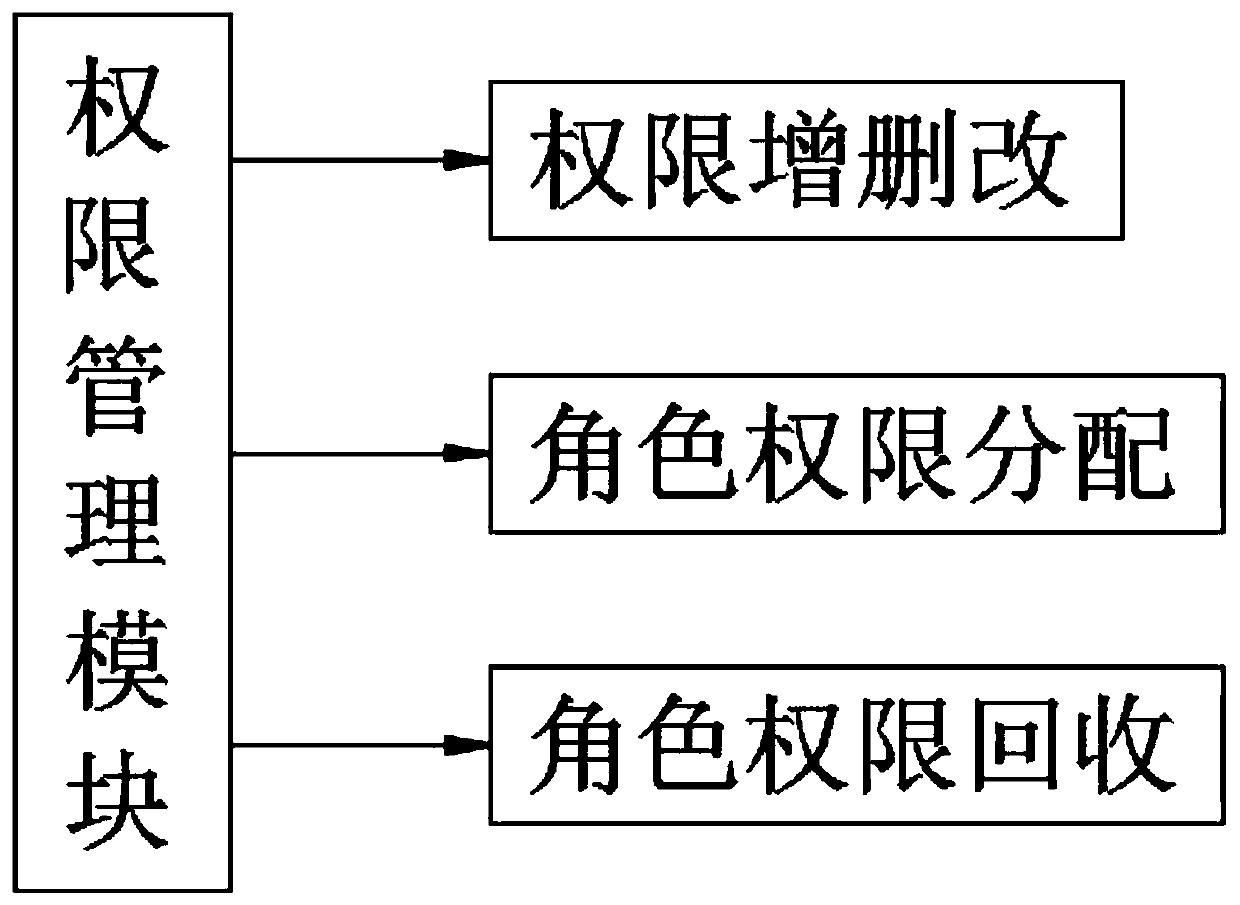
Archive permission management system
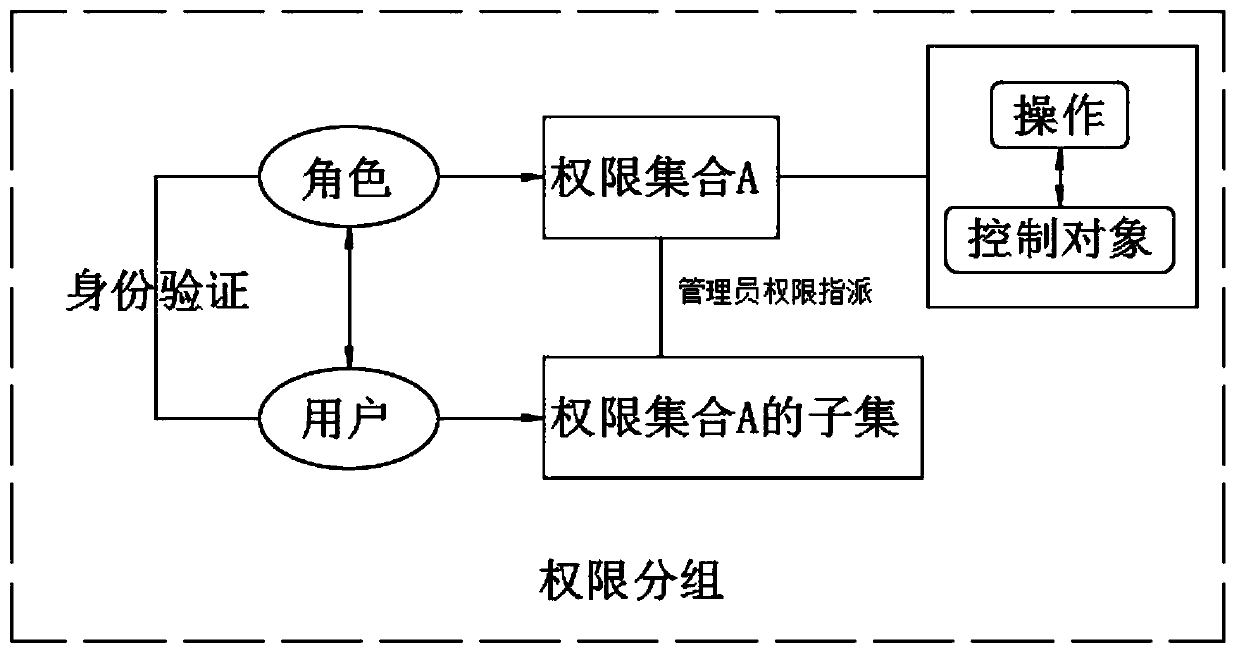
InactiveCN110474897AIncrease permissionsOptimize allocationDigital data authenticationFile system administrationUser needsRole management
The invention discloses an archive permission management system, which belongs to the technical field of permission management, and comprises a user layer, a logic application layer and a data layer,the user layer comprises an electronic archive system and an authority control system based on the interior of the electronic archive system, the authority control system is used for controlling the authority of a user and a role to access the electronic archive system, and the electronic archive system realizes operations of adding, deleting, modifying, calling and reading data through the authority; the authority control system comprises a login management module, a role management module, an authority management module, an authority grouping module and a user management module. The authority grouping module is used for grouping roles and authorities of users, a plurality of access authorities owned by the roles are called authority sets, and a plurality of access authorities owned by the users are subsets of the authority sets. Permissions are distributed to users and roles, and the permissions of the users are directly modified when the permissions of the users need to be modified,so that the permissions in a role permission set are not influenced.
Owner:合肥泓泉档案信息科技有限公司
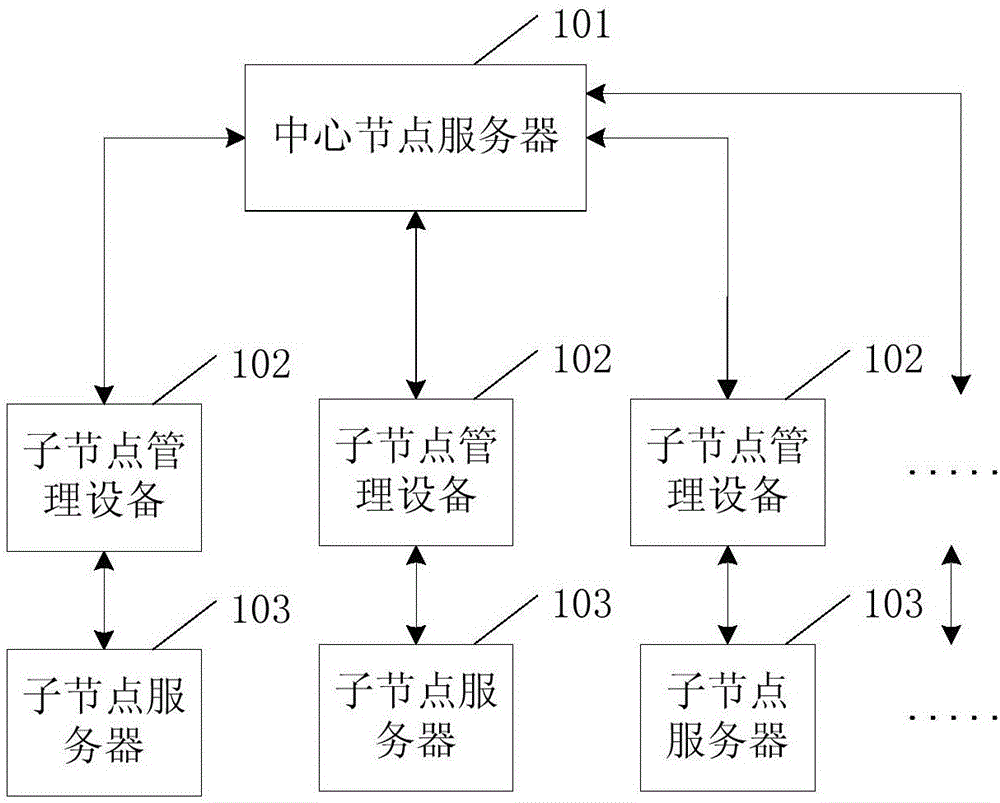
Method and system for synchronizing metadata under mass network data environment
ActiveCN106599195AEnsure safetyEnsure consistencyDatabase updatingDatabase distribution/replicationNetwork dataDatabase
The embodiment of the invention provides a method and a system for synchronizing metadata under a mass network data environment. The method comprises the following steps: after the metadata inside a metadata base list in a center node server are updated to a second stable version number from a first stable version number, sending a notification message to sub-node administration equipment, wherein the second stable version number is greater than the first stable version number; after the notification message is received by the sub-node administration equipment, obtaining the metadata base list from the center node server, wherein the version number of the metadata inside the metadata table list is the second stable version number; and sending the obtained metadata table list to the sub-node server by the sub-node administration equipment so that the metadata inside the center node server and the metadata inside the sub-node server are synchronized. According to the method and the system, the metadata inside the metadata table list in the system for synchronizing the metadata are synchronized in time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
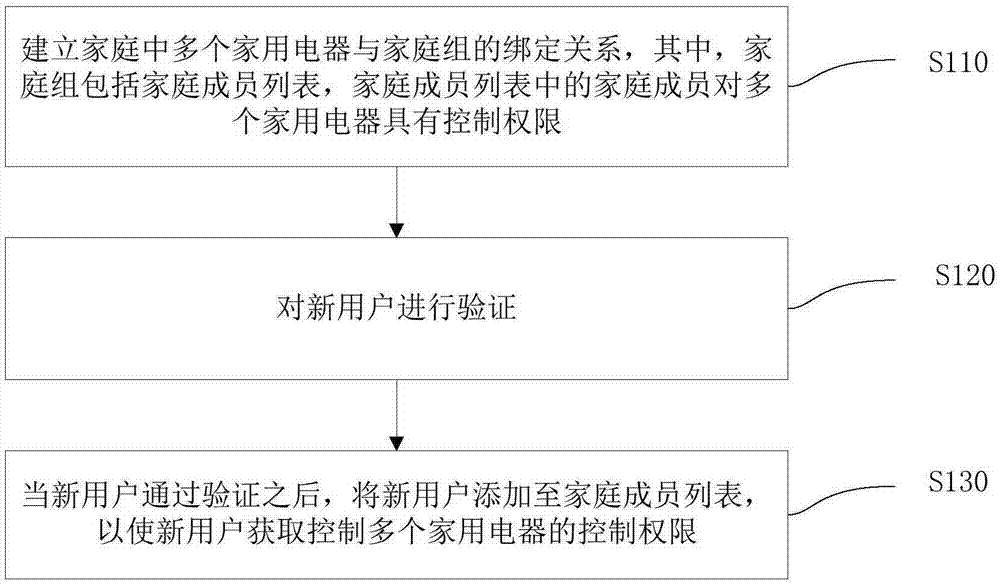
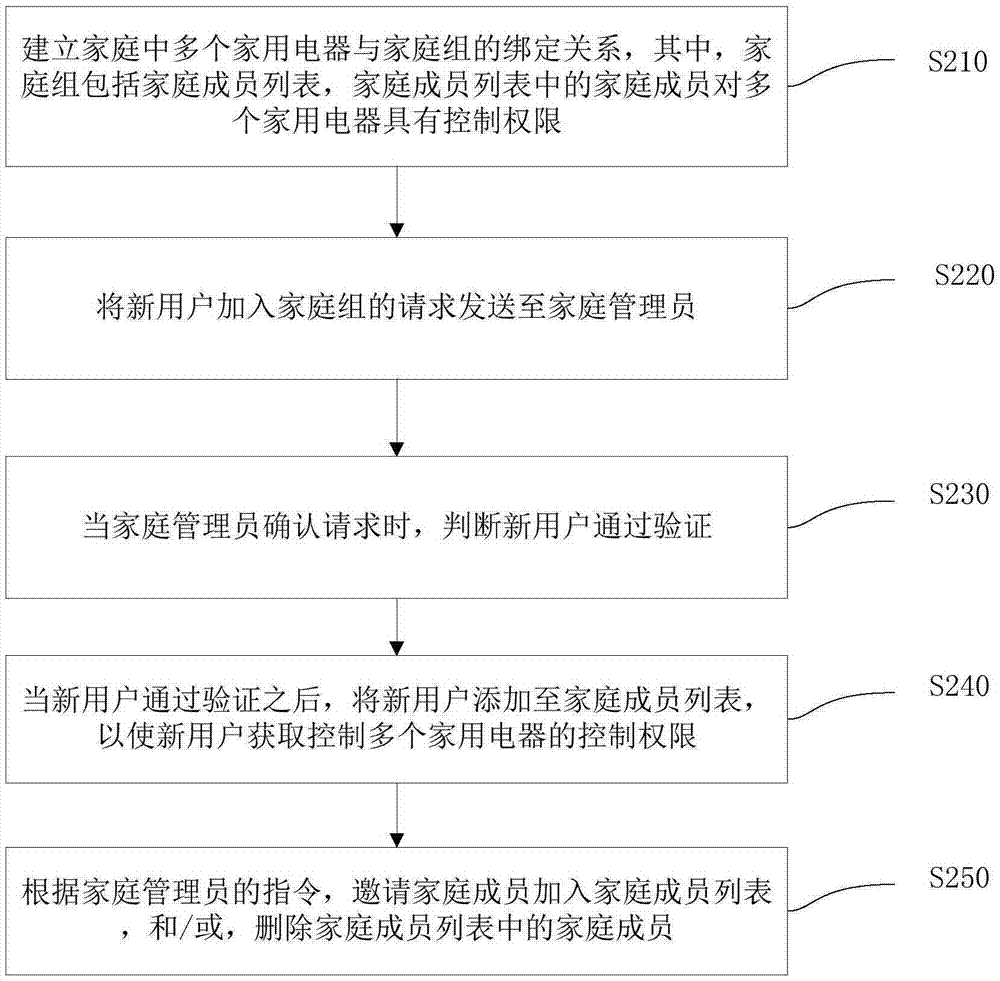
Method, device and system for managing family group household appliances
InactiveCN106896729AEasy to operateImprove experienceComputer controlProgramme total factory controlComputer engineering
The invention discloses a method, a device and a system for managing family group household appliances. The method comprises steps: a binding relationship between multiple household appliances and a family group in a family is built, wherein the family group comprises a family member list, and family members in the family member list have control privileges over the multiple household appliances; a new user is verified; and after the new user passes verification, the new user is added to the family member list to enable the new user to acquire the control privileges over the multiple household appliances. The method simplifies the operation of the user, and the experience of the user is enhanced.
Owner:MIDEA GRP CO LTD
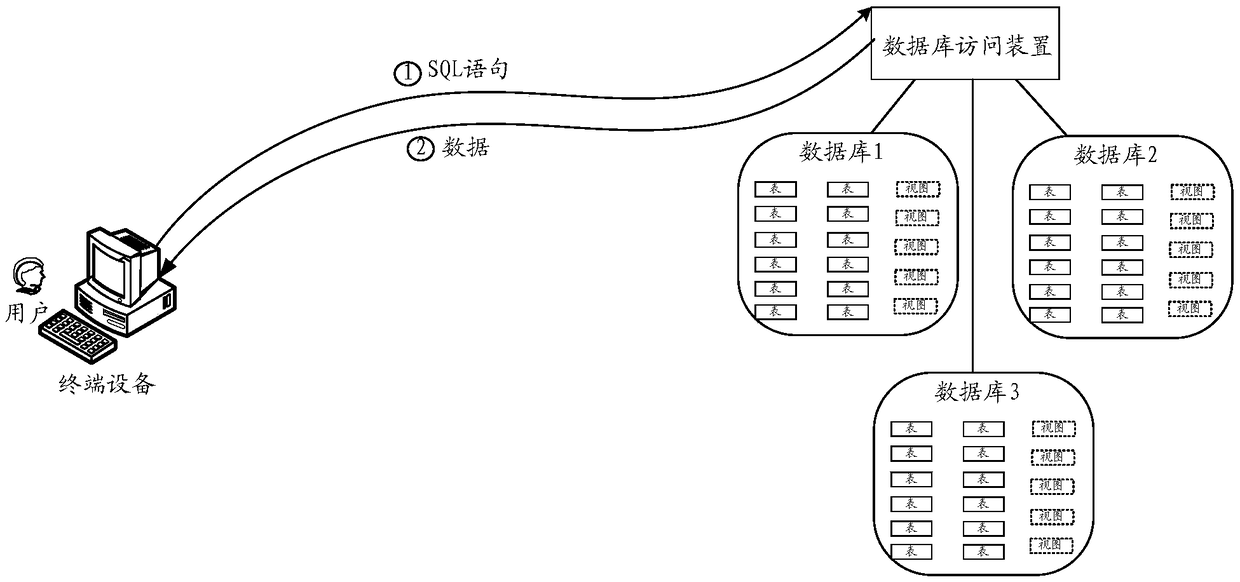
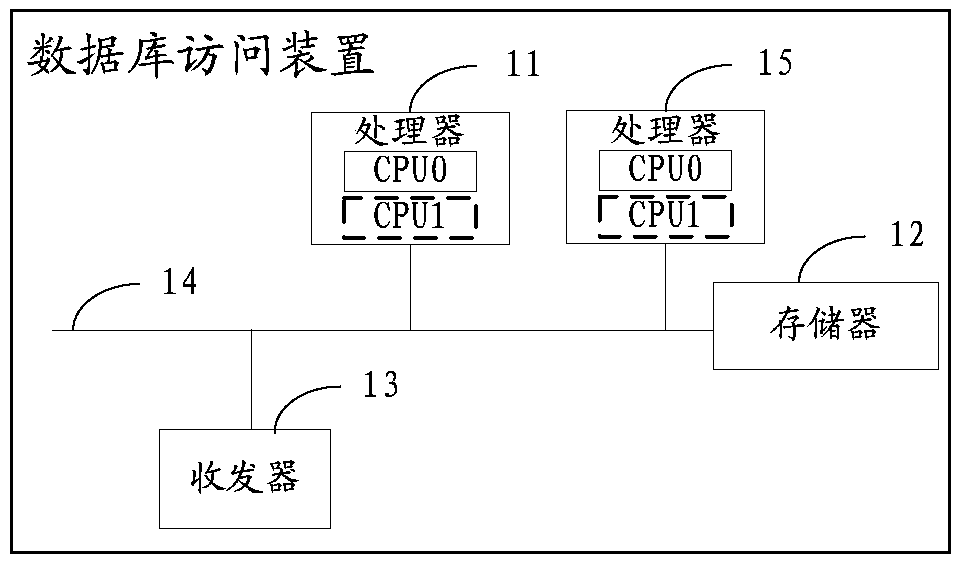
Data access control method and database access device
ActiveCN108874863AAvoid risk of leakageAdd execution conditionsInternal/peripheral component protectionDigital data authenticationData operationsData access control
The embodiment of the invention discloses a data access control method and a database access device, relates to the field of data storage, can provide a safety guarantee for data access, and avoids aninformation leakage risk to a certain degree. The method comprises the following steps that: obtaining a first data operation instruction (which carries the identification of a target data volume), wherein the instruction is triggered by a first user; according to the identification of the target data volume, inquiring permission setting information, and determining the permission of the first user to operate the target data volume, wherein the permission setting information comprises the identification of at least one data volume and permission for at least one user (which comprises the target data volume) to operate at least one data volume (including the first user); according to the permission for the first user to operate the target data volume and the first data operation instruction, generating a second data operation instruction; and executing the second data operation instruction, and operating the data of the target data volume in a target range, wherein the target range isa range permitted by the permission that the first user operates the target data volume.
Owner:HUAWEI TECH CO LTD
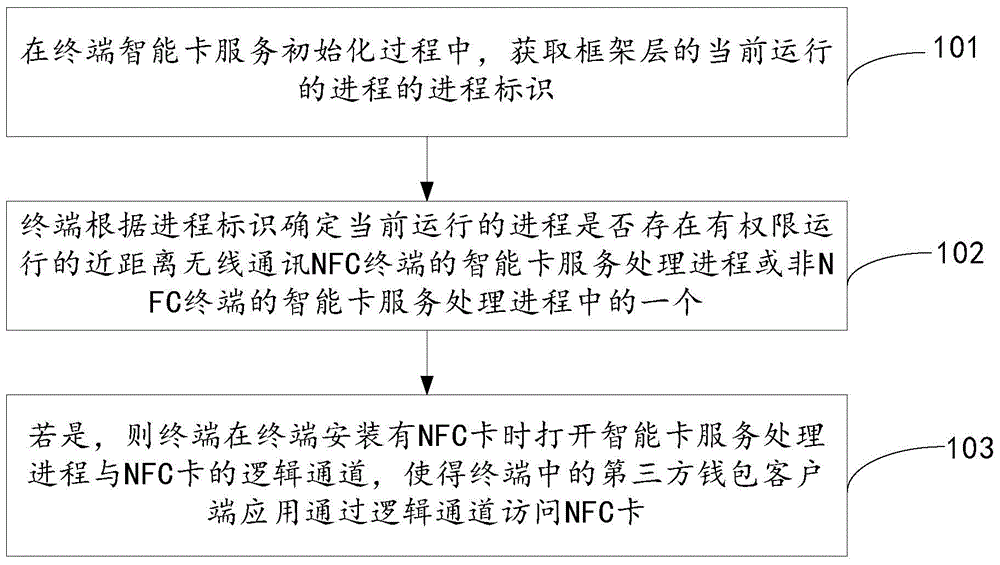
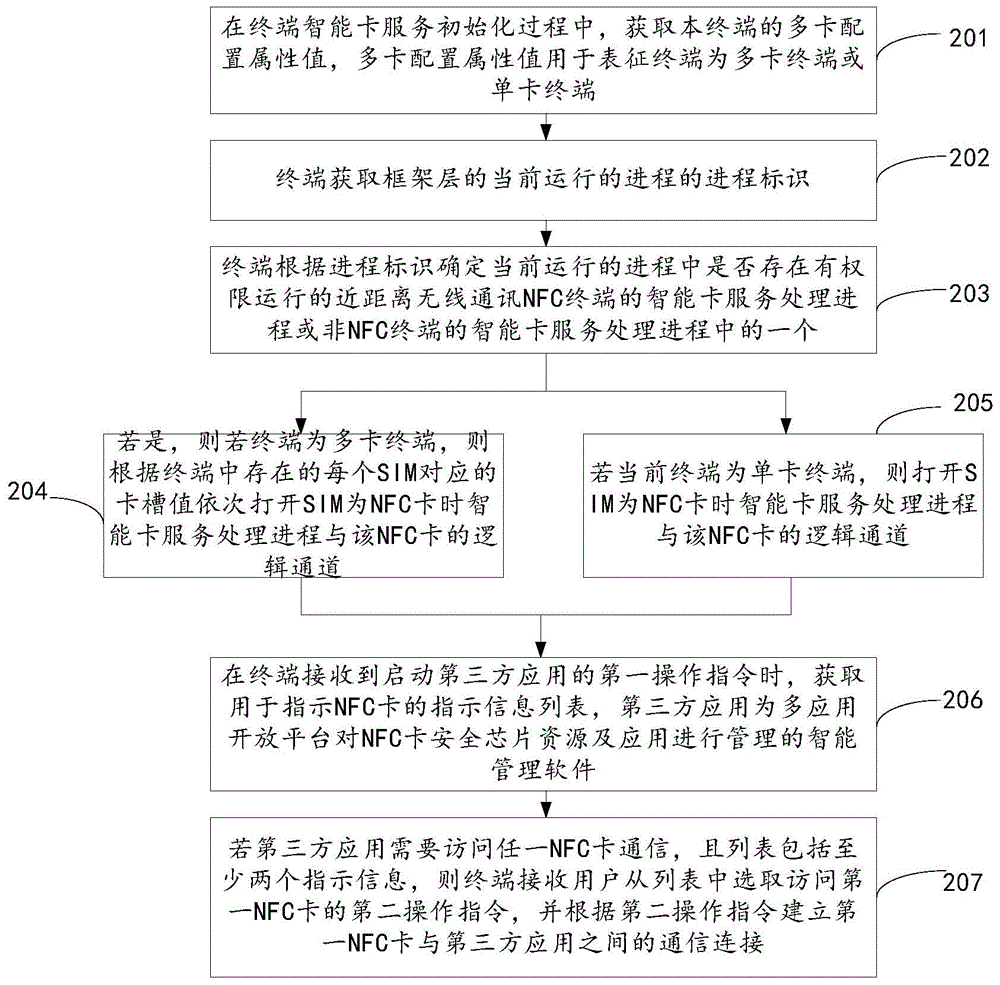
NFC card access method and terminal
ActiveCN106529942ASolve the problem of not being able to access the NFC cardIncrease permissionsPayment architectureThird partyAccess method
An embodiment of the invention provides an NFC card access method and a terminal, which relate to the field of communication, and can solve the problem that a third-party wallet client application of a non-NFC terminal cannot access the NFC card. The NFC card access method comprises the steps of: acquiring process identifiers of currently running processes of a framework layer during the service initialization process of an intelligent card of the terminal; determining whether one of an intelligent card service processing process of a near field communication (NFC) terminal or an intelligent card service processing process of a non-NFC terminal with authority to run exists in the currently running processes according to the process identifiers; if so, opening a logical channel of the intelligent card service processing process and an NFC card when the terminal is provided with the NFC card, so that a third-party wallet client application in the terminal can access the NFC card via the logical channel. When the NFC card access method is applied to the multi-card terminal, free switching of card slots and OMAPI support are realized.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Method and system for recovering the energy state of an aircraft during descent
ActiveUS9734724B2Easy to followIncrease permissionsEnergy efficient operational measuresAutomatic aircraft landing aidsAirplaneState of energy
A method and system is provided for the recovery of an aircraft energy upset in a time-constrained descent. The system includes a computational unit to assess a number of adjustments involving a combination of speed changes, aerodynamic brake deployment and track miles adjustments that alter the energy dissipation profile whilst allowing the aircraft to maintain a pre-determined time-of-arrival over an incoming waypoint along the original descent path.
Owner:UNIVERSITY OF MALTA
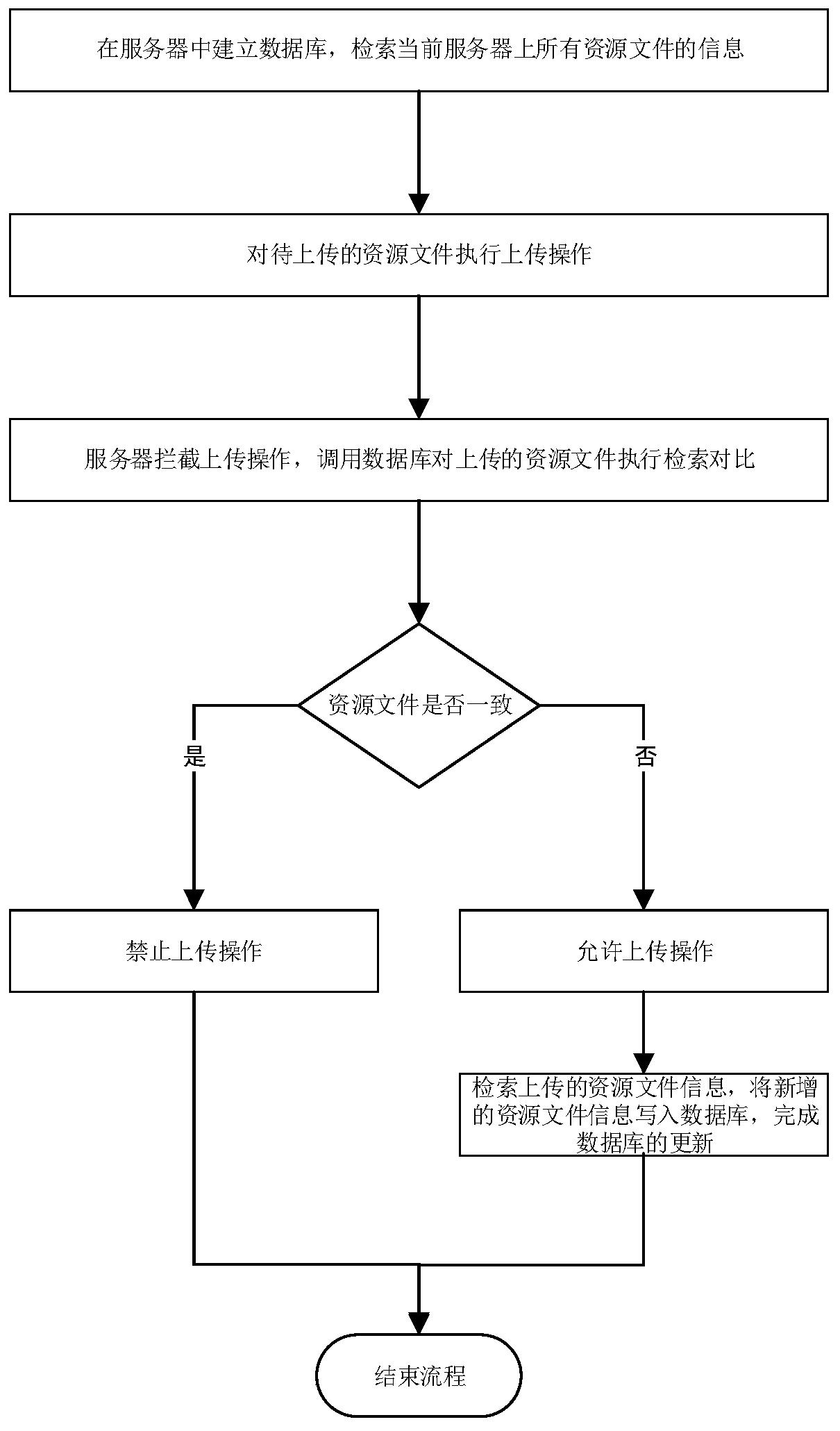
Server data management method and system
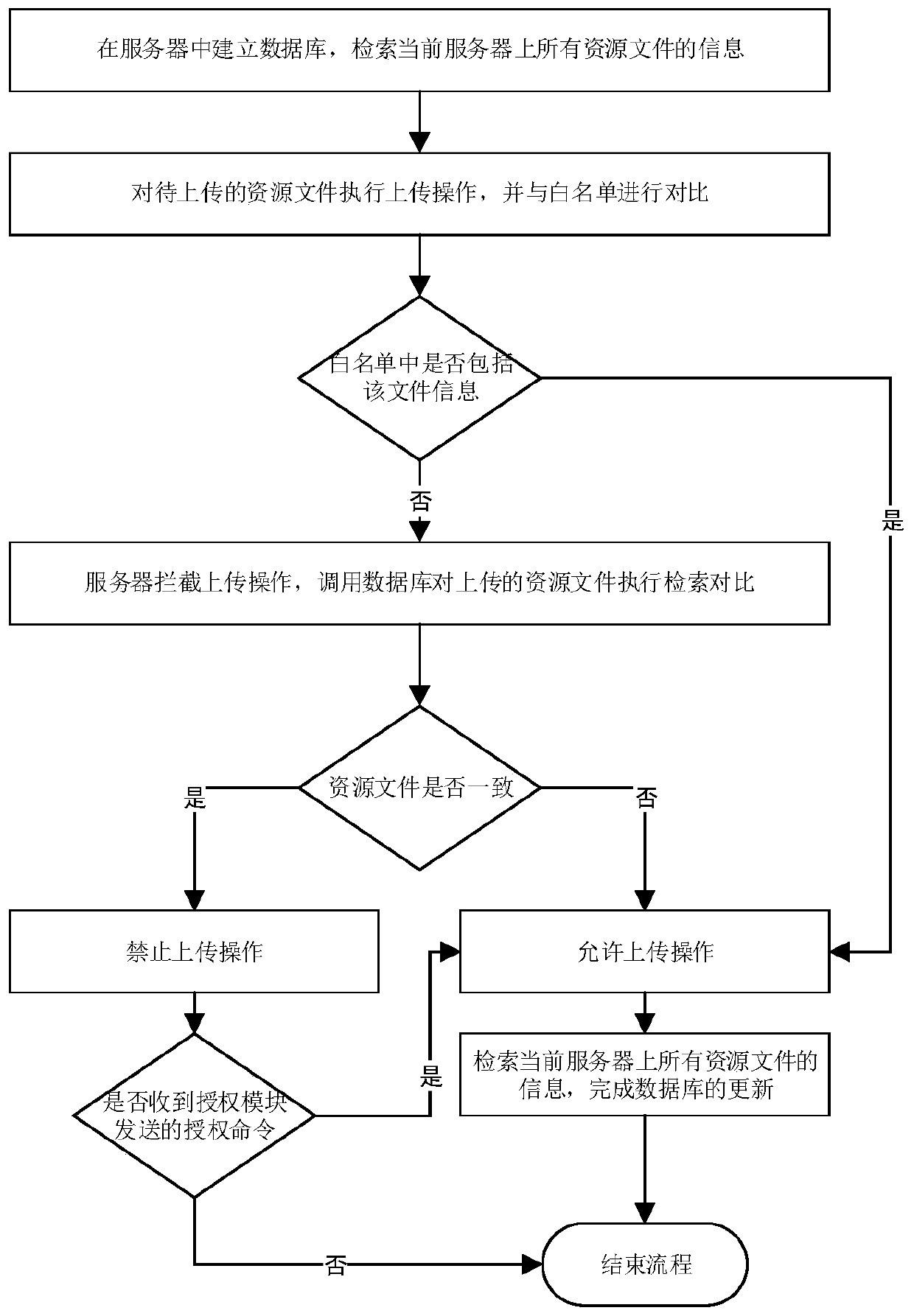
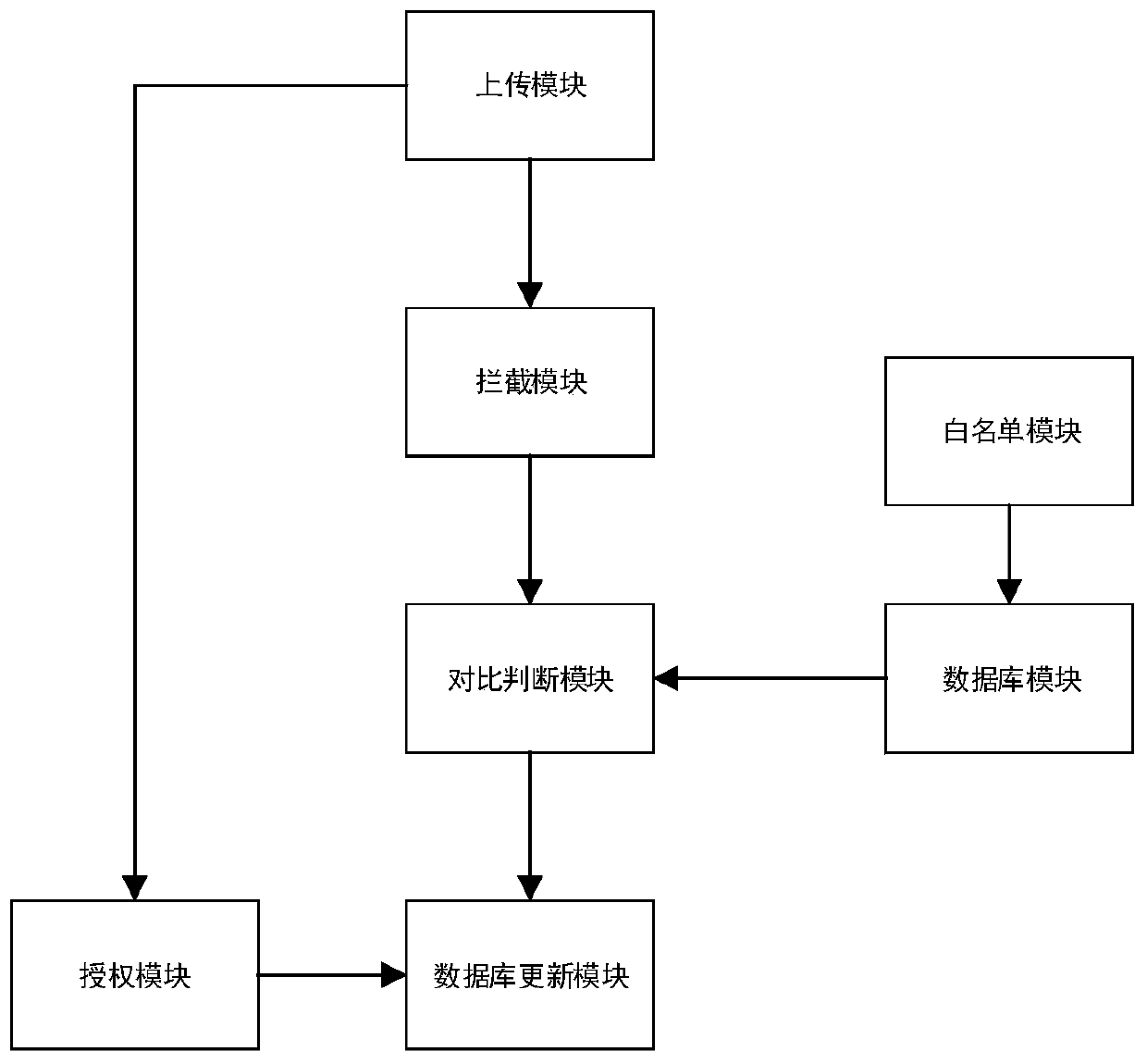
ActiveCN109893854AIncrease permissionsReduce storage pressureOther databases queryingVideo gamesEngineeringResource management
The invention relates to a server data management method and system. According to the technical scheme, the method includes: building a database in a server, retrieving the information of all resourcefiles on the current server, and uploading to-be-uploaded resource files, wherein the uploading operation comprises but is not limited to uploading import, file locking and new directory creating; bythe server or a client, intercepting the uploading operation, calling the database to perform retrieving and comparison on the uploaded resource files to judge whether the resource files are duplicated or not, if so, forbidding the uploading operation and ending the process, or else, allowing the uploading operation; retrieving the information of the uploaded resource files, and writing the newlyadded resource file information into the database to update the database. The server data management method has the advantages that the generation of duplicated resources is reduced from the source,server storage pressure is reduced greatly, unnecessary resource waste is reduced, game development efficiency is increased, later maintenance cost is lowered, and the standardized game resource management is helpful to game quality increasing.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD +1
User and terminal binding system and method applied to electrical stimulation physiotherapy system
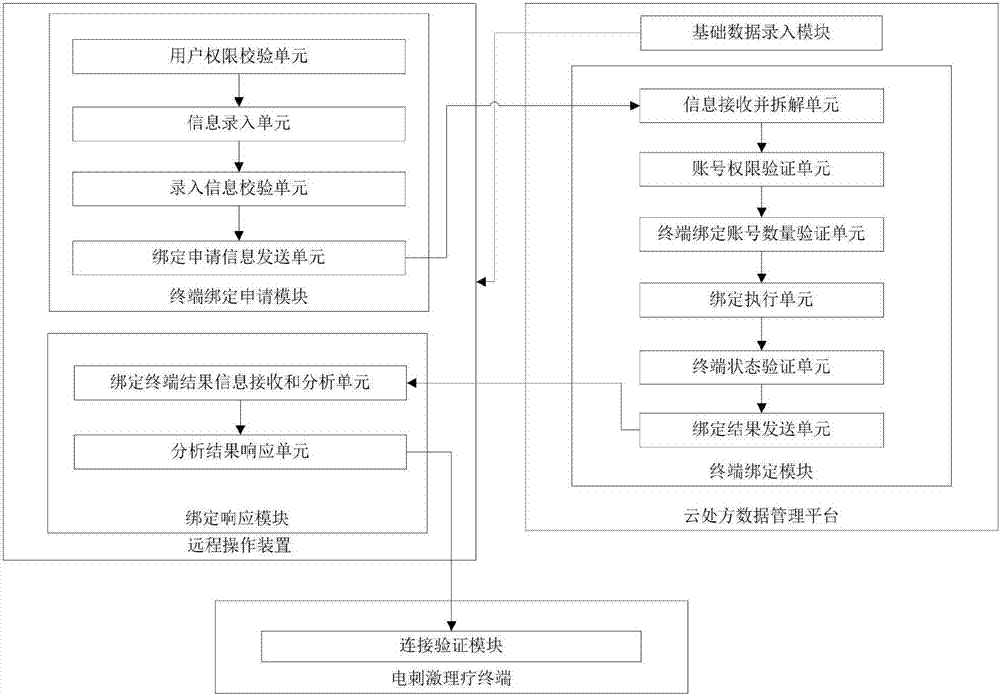
PendingCN106934227AEasy retrievalClear processElectrotherapyData processing applicationsPhysical medicine and rehabilitationPhysical therapy
The invention relates to a user and terminal binding system and method applied to an electrical stimulation physiotherapy system. The system comprises an electrical stimulation physiotherapy terminal, a remote operation apparatus and a cloud prescription data management platform which are connected mutually, wherein the electrical stimulation physiotherapy terminal comprises a connection verification module; the remote operation apparatus comprises a terminal binding application module and a binding response module; and the cloud prescription data management platform comprises a terminal binding module and a basic data input module used for inputting basic information of the electrical stimulation physiotherapy terminal. According to the system and the method, user information is bound with the electrical stimulation physiotherapy terminal; prescription data is easier to manage; the security of the electrical stimulation physiotherapy terminal is guaranteed; the permission of a remote operation terminal is higher; and the operation error rate is better prevented.
Owner:成都华信高科医疗器械有限责任公司
Electronic doorbell interception and break-in management apparatus and method
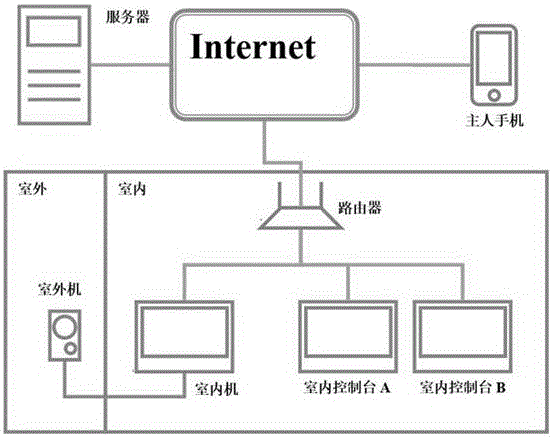
PendingCN106603994AHome App SecurityAchieve modularityClosed circuit television systemsDoorbellSoftware
The present invention provides an electronic doorbell interception and break-in management apparatus and method. The apparatus comprises an indoor machine, an outdoor machine and a plurality of indoor consoles. The outdoor machine is connected to the indoor machine. The indoor machine and the outdoor machine are accessed to a router together. The router is connected to a server and the mobile phone of an owner through a network. After analyzing the authority and level of a software exchange system, the functions of interception and break-in between a mobile phone and an electronic doorbell can be realized.
Owner:江苏启泰物联网科技有限公司
Instant messaging management method and device
InactiveCN109561013AIncrease permissionsEasy to controlSpecial service provision for substationUser PrivilegeTelecommunications equipment
The invention relates to an instant messaging management method, an instant messaging device, electronic equipment and a non-temporary computer readable storage medium. The management method comprisesthe steps of obtaining user identification of a user; determining a user authority according to the user identification; and setting a corresponding message checking authority for the user accordingto the user authority, wherein a message supervision function is provided when the user has a supervision authority. The supervision for chat information of the user is realized through improving themessage checking authority of the supervision personnel in instant messaging.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
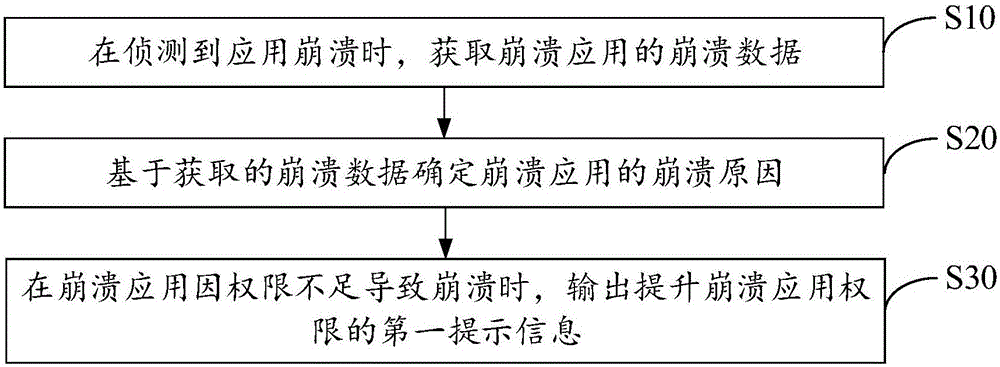
Application crashing processing method and mobile terminal
InactiveCN106681853AImprove stabilityIncrease permissionsDigital data authenticationNon-redundant fault processingCrash dataComputer engineering
The invention discloses an application crashing processing method. The application crashing processing method comprises the steps of obtaining crashing data of a crashing application when the application is detected to be crashing; determining the crashing reason of the crashing application based on the obtained crashing data; outputting first prompting information of jurisdiction of the crashing application when insufficient jurisdiction results in crashing of the application. The invention further discloses a mobile terminal. According to the application crashing processing method and the mobile terminal, the stability of running the application through the mobile terminal can be promoted.
Owner:SHENZHEN TINNO WIRELESS TECH
Website authentication method and apparatus, and website credit giving method and apparatus
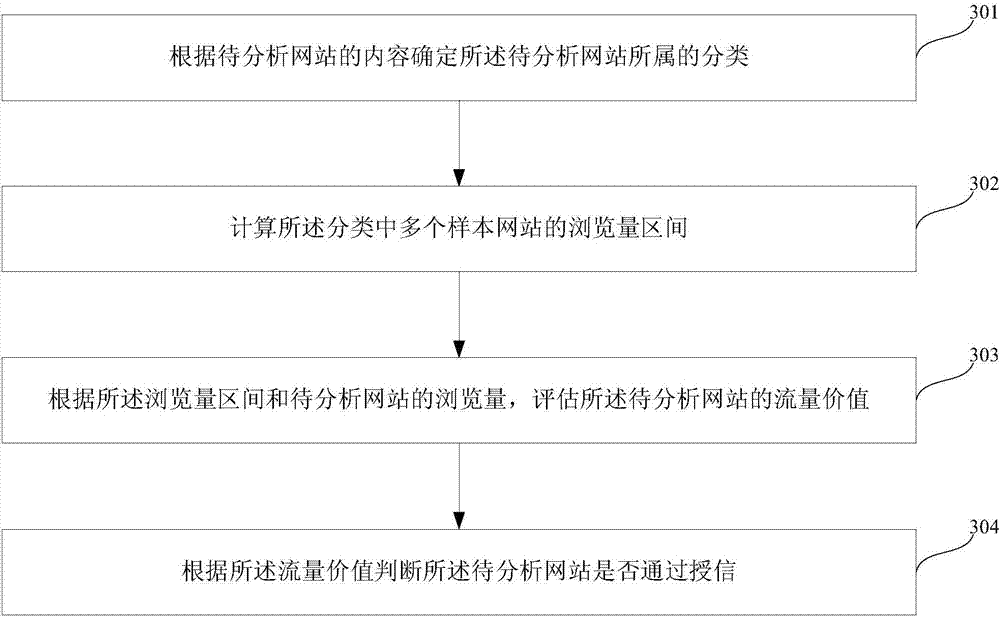
ActiveCN107038377AImprove accuracyIncrease permissionsPlatform integrity maintainanceTraffic volumeInternet privacy
The invention relates to the technical field of information security, in particular to a website authentication method and apparatus, and a website credit giving method and apparatus. The website authentication method comprises the steps of determining a category which a to-be-analyzed website belongs to according to contents of the to-be-analyzed website; calculating a page view interval of a plurality of sample websites in the category; according to the page view interval and a page view of the to-be-analyzed website, assessing an initial level of the to-be-analyzed website; and judging whether the to-be-analyzed website passes authentication or not according to the initial level. The website can be authenticated according to the flow and revisit quality of the website, so that the website passing the authentication can have a higher permission to perform certain operations such as expansion, operation of obtaining a higher priority to perform certain businesses and the like; and the website authentication accuracy can be further enhanced by analyzing a behavior of a website manager.
Owner:ADVANCED NEW TECH CO LTD
Refrigerating pump regeneration control method and system
ActiveCN104279149APrevent backflowAutomate managementVacuum evaporation coatingSputtering coatingEmbedded systemAND gate
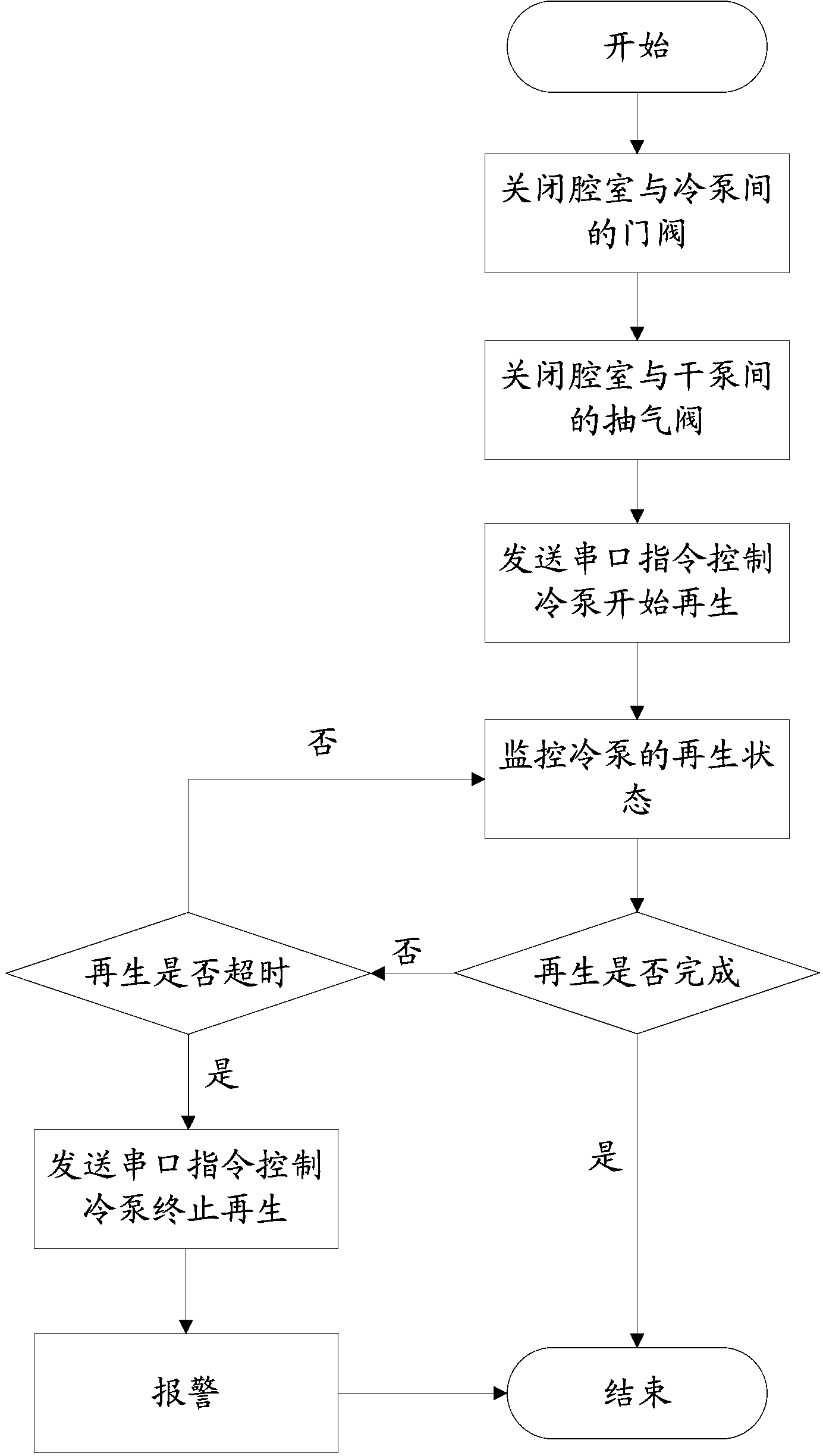
The embodiment of the invention provides a refrigerating pump regeneration control method. A refrigerating pump is connected with a system dry pump. The method includes the following steps that a regeneration execution request submitted by the refrigerating pump to regenerated is received, and the right to the use of the system dry pump is applied for according to the request; when the right to the use of the system dry pump is obtained, all air pumping valves associated with the system dry pump are closed; the refrigerating pump to be regenerated and gate valves of corresponding cavities of the refrigerating pump are closed; a regeneration start command is sent to the refrigerating pump to be regenerated; the refrigerating pump to be regenerated is used for executing regeneration according to the regeneration command; when the refrigerating pump to be regenerated finishes regeneration, the right to the use of the dry system is released. According to the method, the system dry pump is set as the shared resources to manage and coordinate the refrigerating pump to execute regeneration, automated management and coordination of devices are achieved in the regeneration process of the refrigerating pump, and the problem of gas backward flowing caused by misoperation is avoided.
Owner:BEIJING NAURA MICROELECTRONICS EQUIP CO LTD
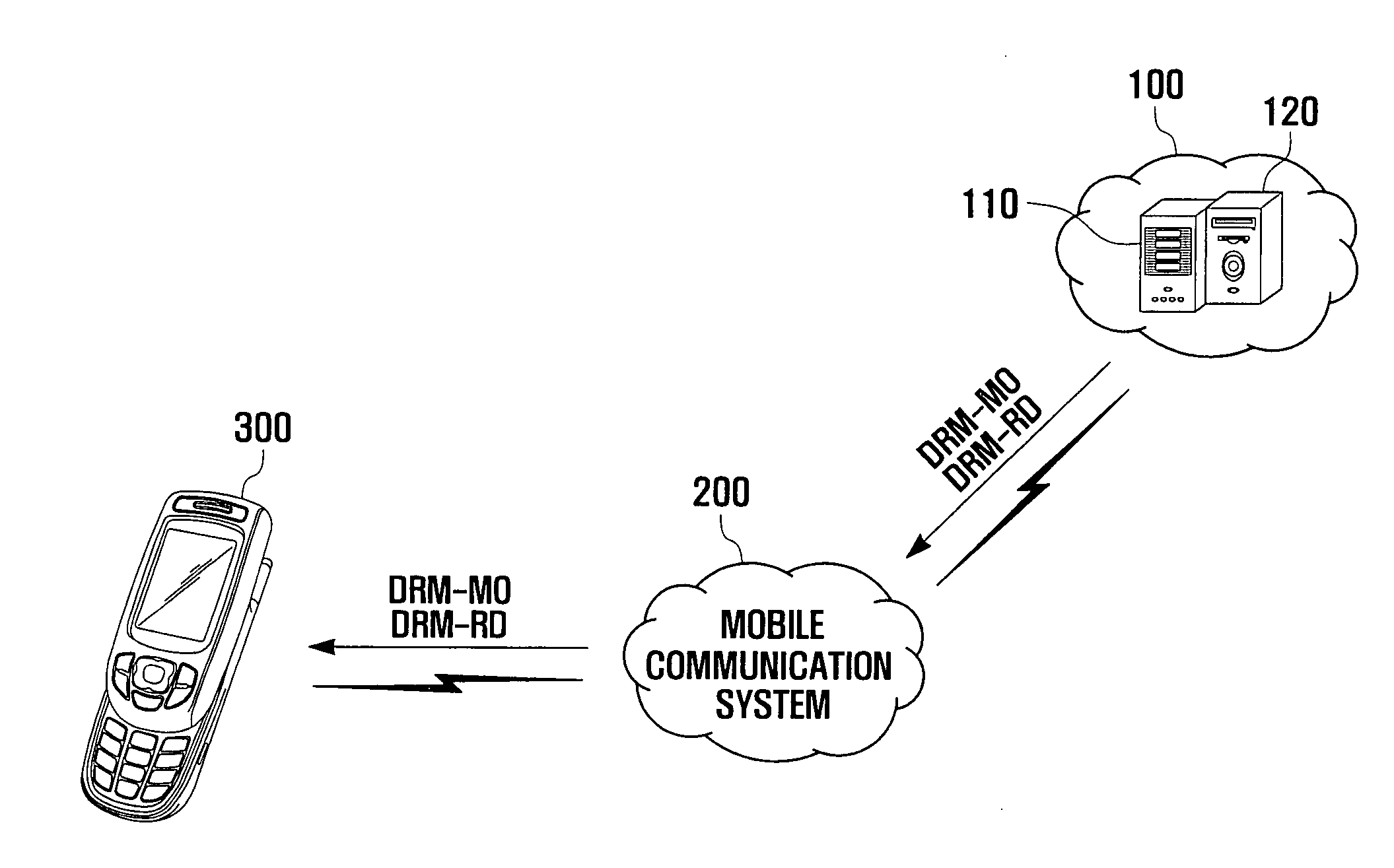
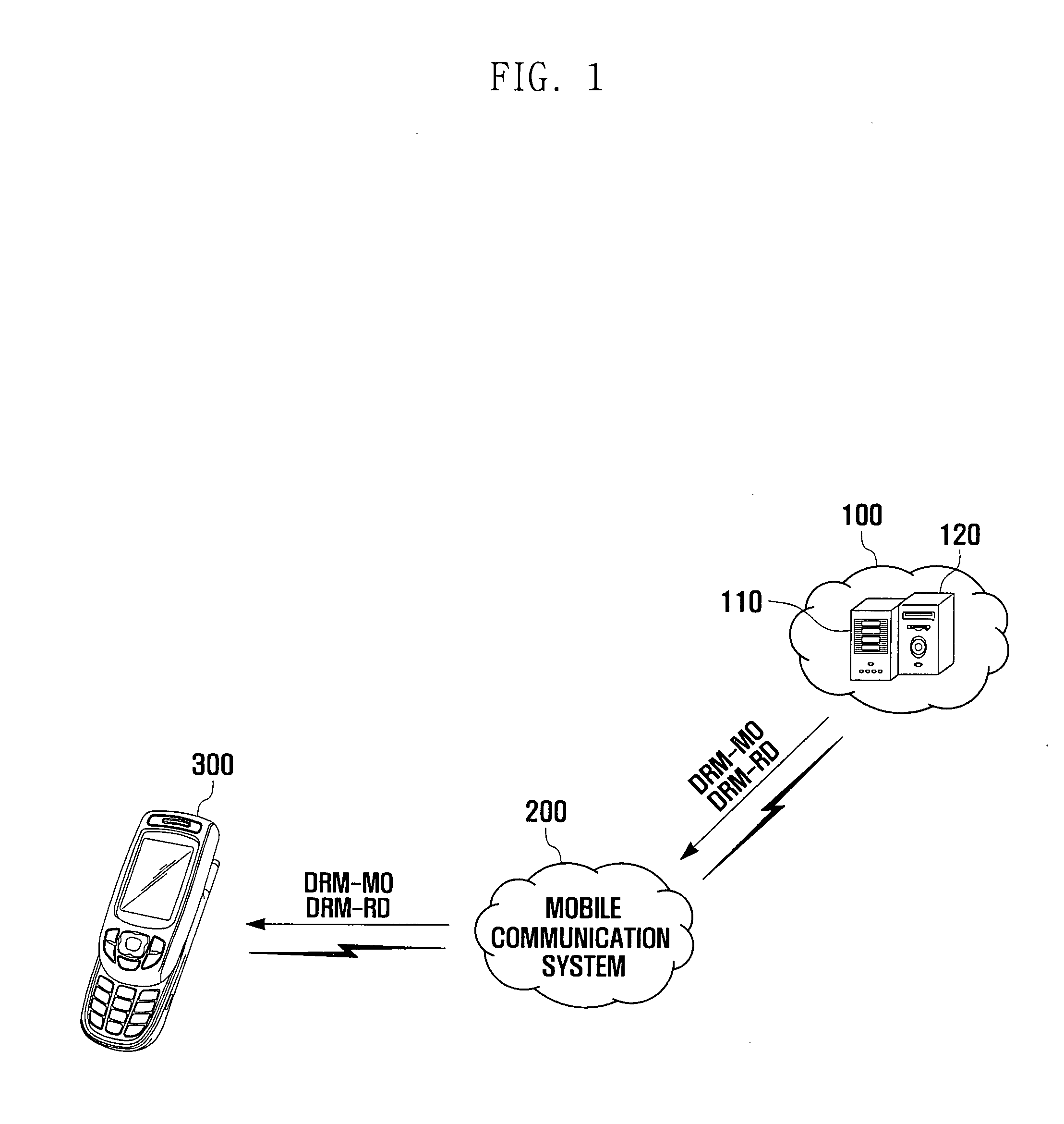
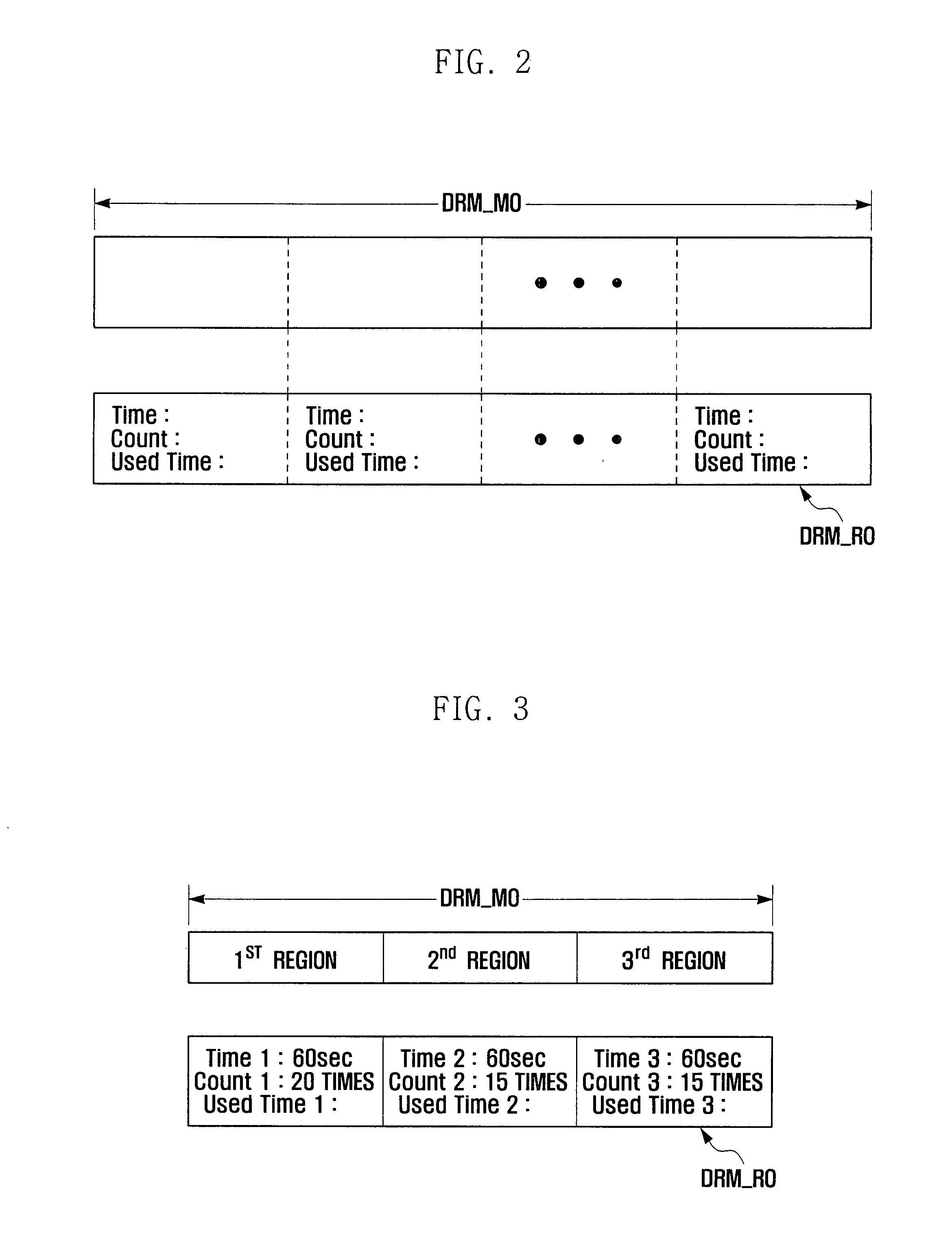
Method for enhancing DRM authority, enhanced DRM authority content, and portable terminal using the same
InactiveUS20080109364A1Enhancing DRM authorityTime remainingProgram/content distribution protectionSecuring communicationComputer hardwareDigital rights management
A method for enhancing a Digital Rights Management (DRM) authority, a content having an enhanced DRM authority and a portable terminal using the same. Reproduction of divisional regions of the content is prevented when a corresponding count value is equal to a permitted maximum number of reproductions. The DRM authority includes: reproducing DRM content having a first division region to an nth division region, where n is a natural number; and changing a first count value to an nth count value according to reproduction of the DRM content, wherein the count value limits a number of reproduction times of the DRM content for the corresponding division region. A variety of parameters can be set for each individual region to change the count value.
Owner:SAMSUNG ELECTRONICS CO LTD
Access control for short-lived resource principals
ActiveUS20210409218A1Reduce in quantityLess complex to implementMultiple keys/algorithms usageUser identity/authority verificationEngineeringComputing systems
Techniques are described for enabling resources within a cloud computing system to interact with each other. In certain embodiments, a resource is assigned a digital token that provides certain access privileges for the duration in which the digital token is valid. The digital token permits the resource to have access for a duration sufficient to perform some operation (e.g., run one-time code or the same code periodically on a scheduled basis), but without extending the level of access for significantly longer than necessary to complete the operation. Each time the resource principal is to perform the operation, the token can be reissued to the resource to provide the resource with time-limited access privileges. The use of this short-lived token avoids having to create permanent credentials for the resource.
Owner:ORACLE INT CORP
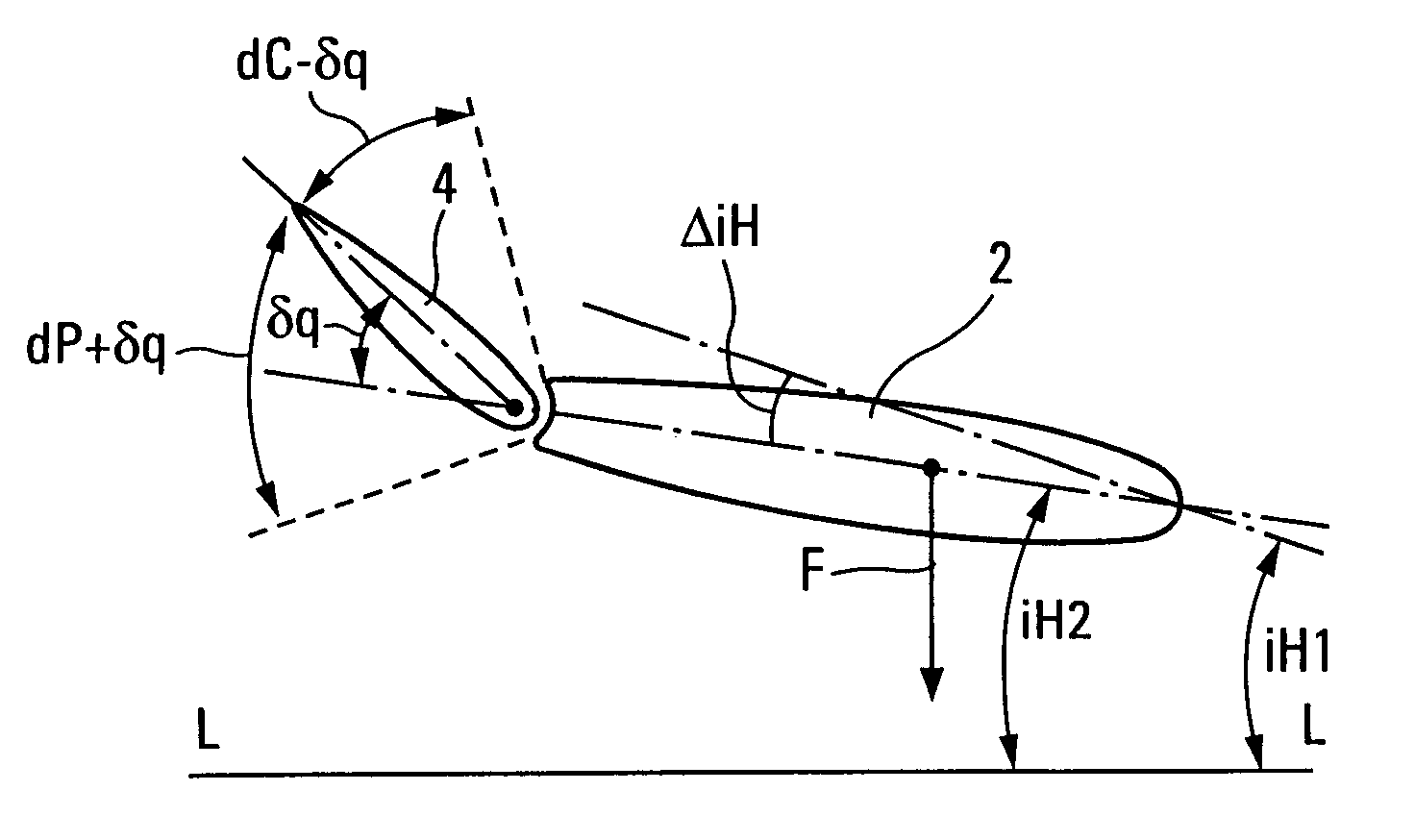
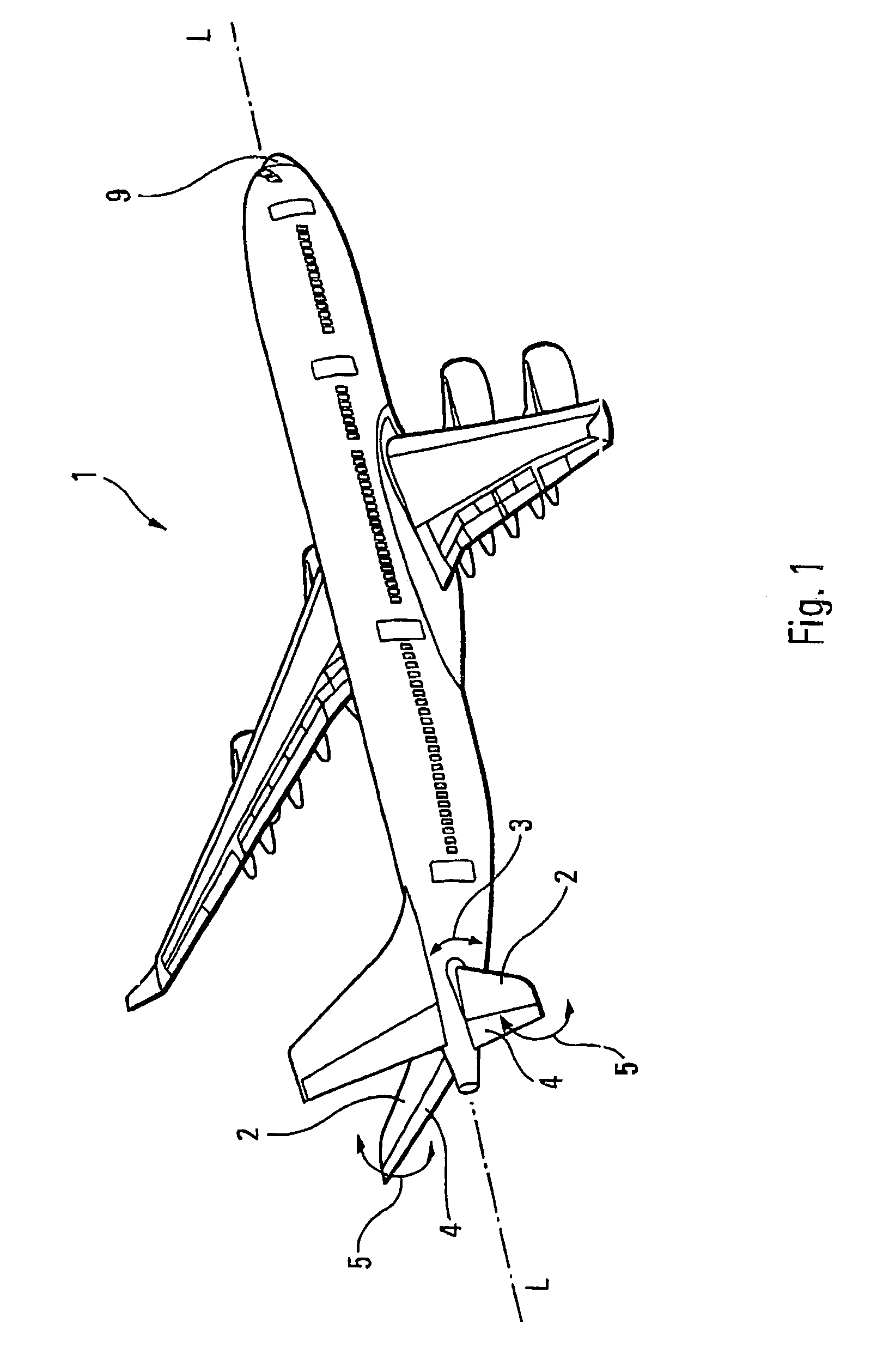
Process for improving the landing of an aircraft
ActiveUS7201347B2Increase permissionsIncrease the itineraryAircraft stabilisationWith power amplificationHead-Down TiltAirplane
A process for improving the landing of an aircraft may include, prior to the aircraft contacting the ground, nose-up under-deflecting the aircraft's adjustable horizontal tail plane and nose-up deflecting the elevators. This arrangement increases the maximum nosedown swing of the elevators to increase the ability of the elevators to make the nose of the aircraft tilt downwards.
Owner:AIRBUS OPERATIONS (SAS)
Module of Internet of vehicles
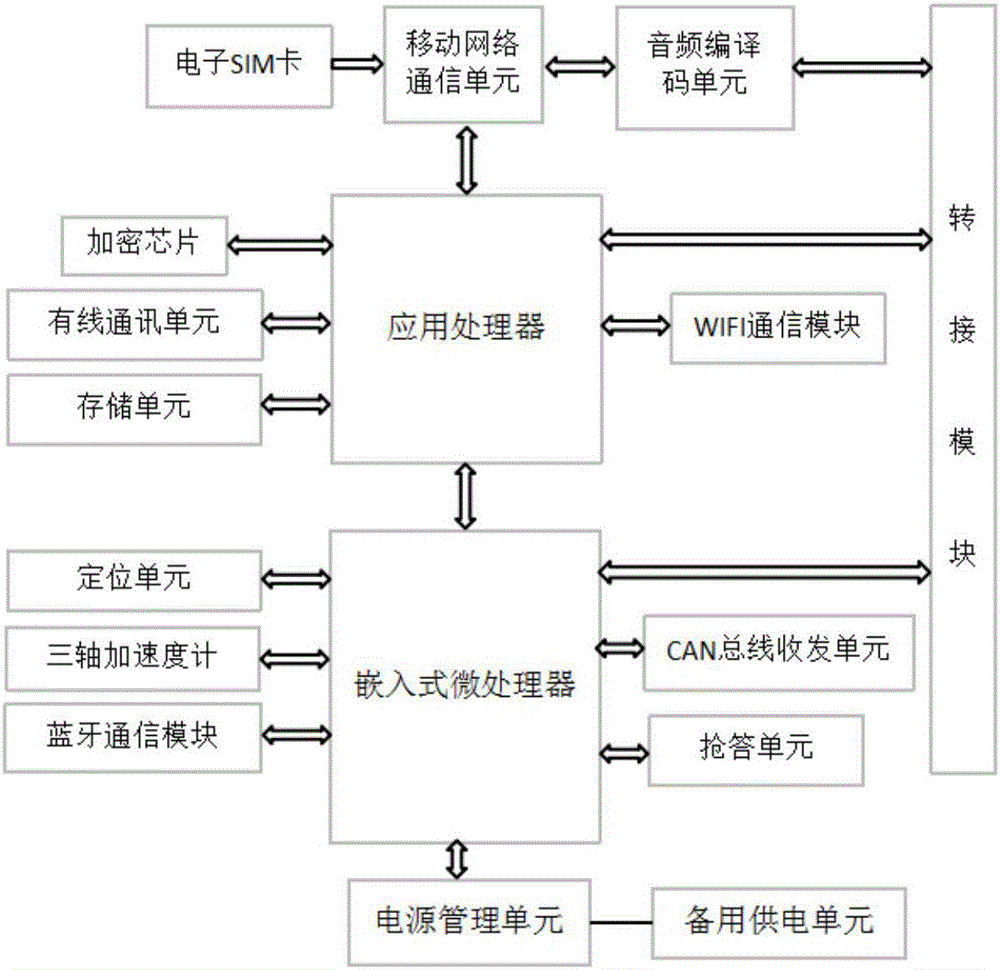
PendingCN106647541AEasy to monitor vehiclesDiscover and track in timeProgramme controlComputer controlVoice communicationThe Internet
The invention provides a module of Internet of vehicles. The module of Internet of vehicles comprises a CAN bus transceiving unit, a mobile network communication unit, an electronic SIM card, an audio coding and decoding unit, a connecting and switching module, a power supply management unit, a standby power supply unit and a switching module. The module further comprises a control unit which comprises a communication protocol uniformly predefined by a vehicle electronic control unit of a monitored vehicle and is separately and correspondingly connected to the CAN bus transceiving unit, the mobile network communication unit and the power supply management unit. The standby power supply unit is connected to the power supply management unit and supplements a vehicle power supply unit to supply power required for the module of Internet of vehicles. Compared with the prior art, the module of the Internet of vehicles, provided by the invention, is convenient to monitor the vehicle, and can immediately find and track the abnormal vehicle; under the circumstance that the vehicle power supply unit is cut off, a battery in the module of Internet of vehicles continuously provides electric energy and supports dialing rescue calls; and personnel in the same vehicle can perform voice communication nearby or dial the rescue calls through the module of Internet of vehicles.
Owner:桑德科技(重庆)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com