Account login method and system
An account and abnormal login technology, applied in the field of information security, can solve the problems of random misappropriation of communication software accounts, inability to take further precautions, account theft, etc., and achieve the effect of reducing the risk of account theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
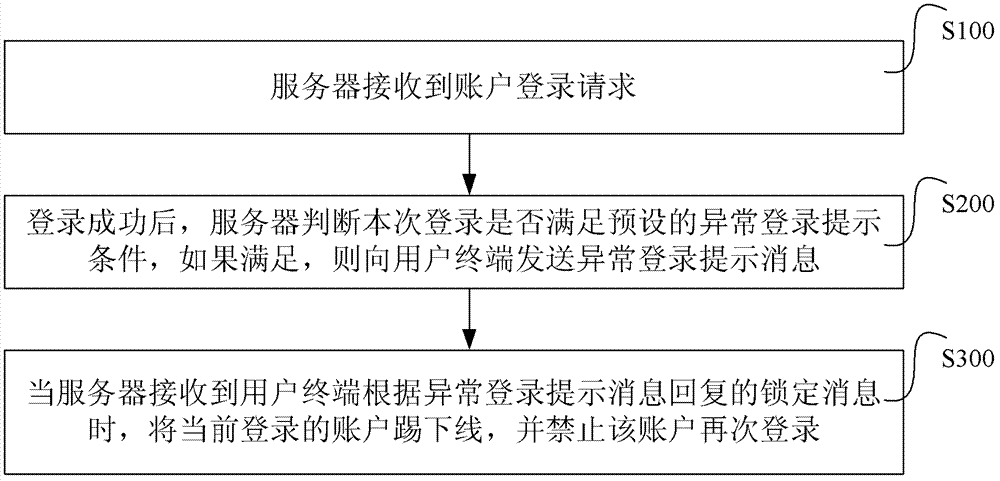
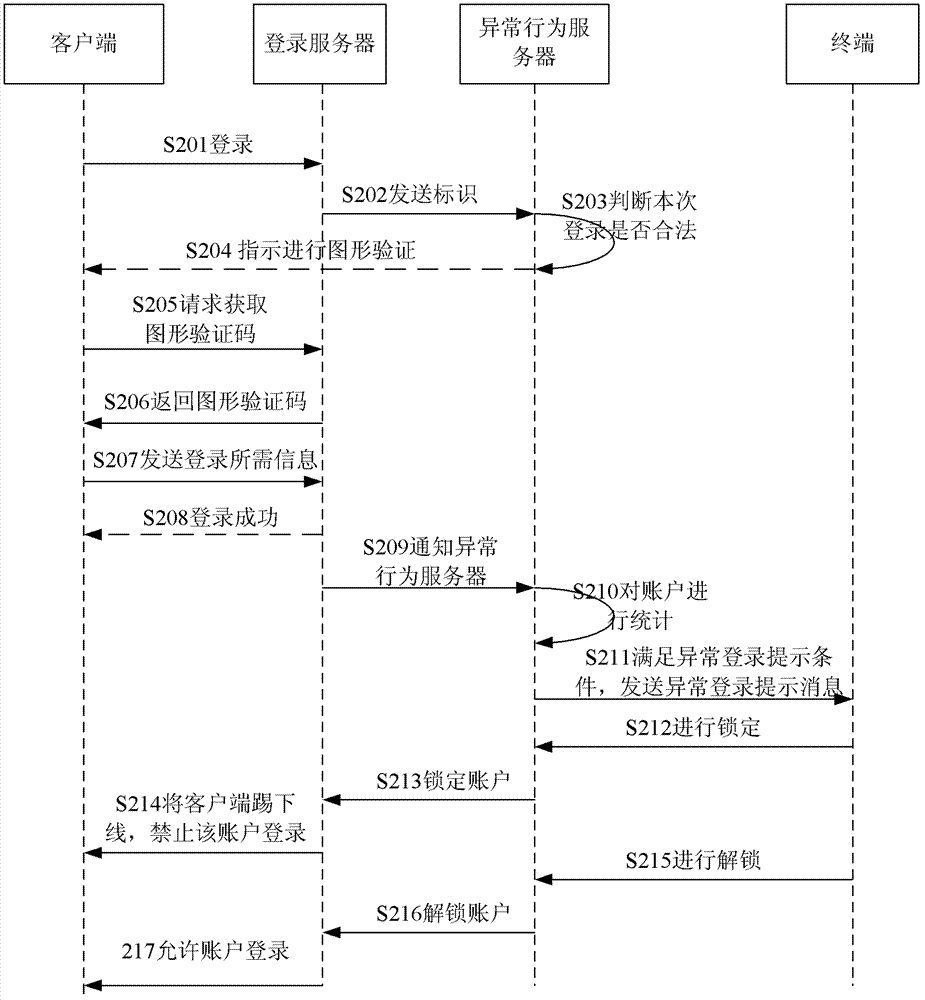
[0046] A method for account login of the present invention is as follows: figure 1 shown.
[0047] Step S100, the server receives an account login request.
[0048] Wherein, the step S100 includes:
[0049] In step S110A, the server receives an account login request carrying the identifier of the currently used machine.
[0050] In step S120A, the server verifies the legality of the identification, if it is not legal, it returns an instruction to perform graphic verification to the account, and then executes step S130A; if it is legal, executes step S200.
[0051] In step S130A, the server receives the graphic verification code submitted by the account, and verifies the legitimacy of the graphic verification code. If it is valid, step S200 is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com