Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
258results about How to "Restricted access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
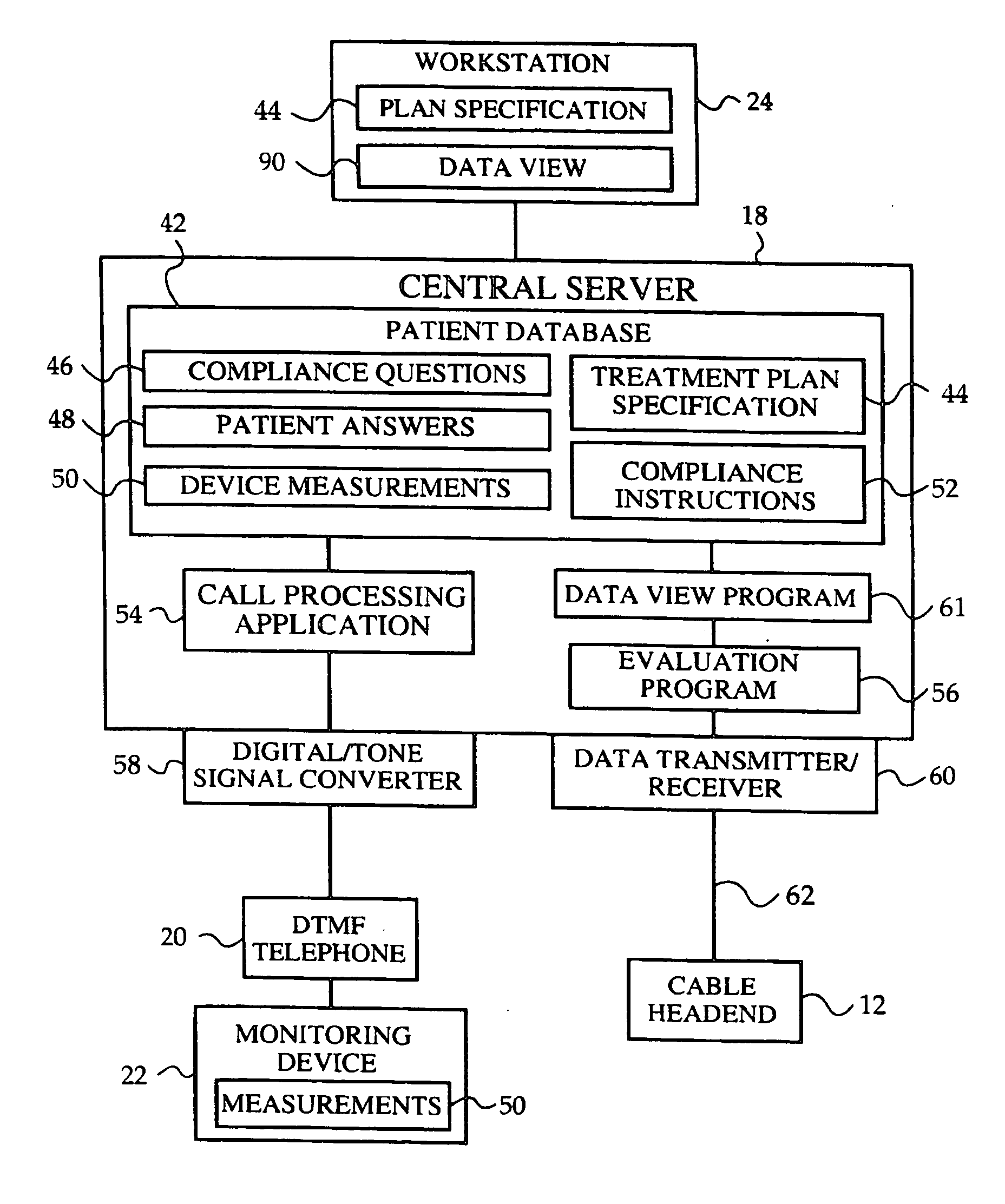
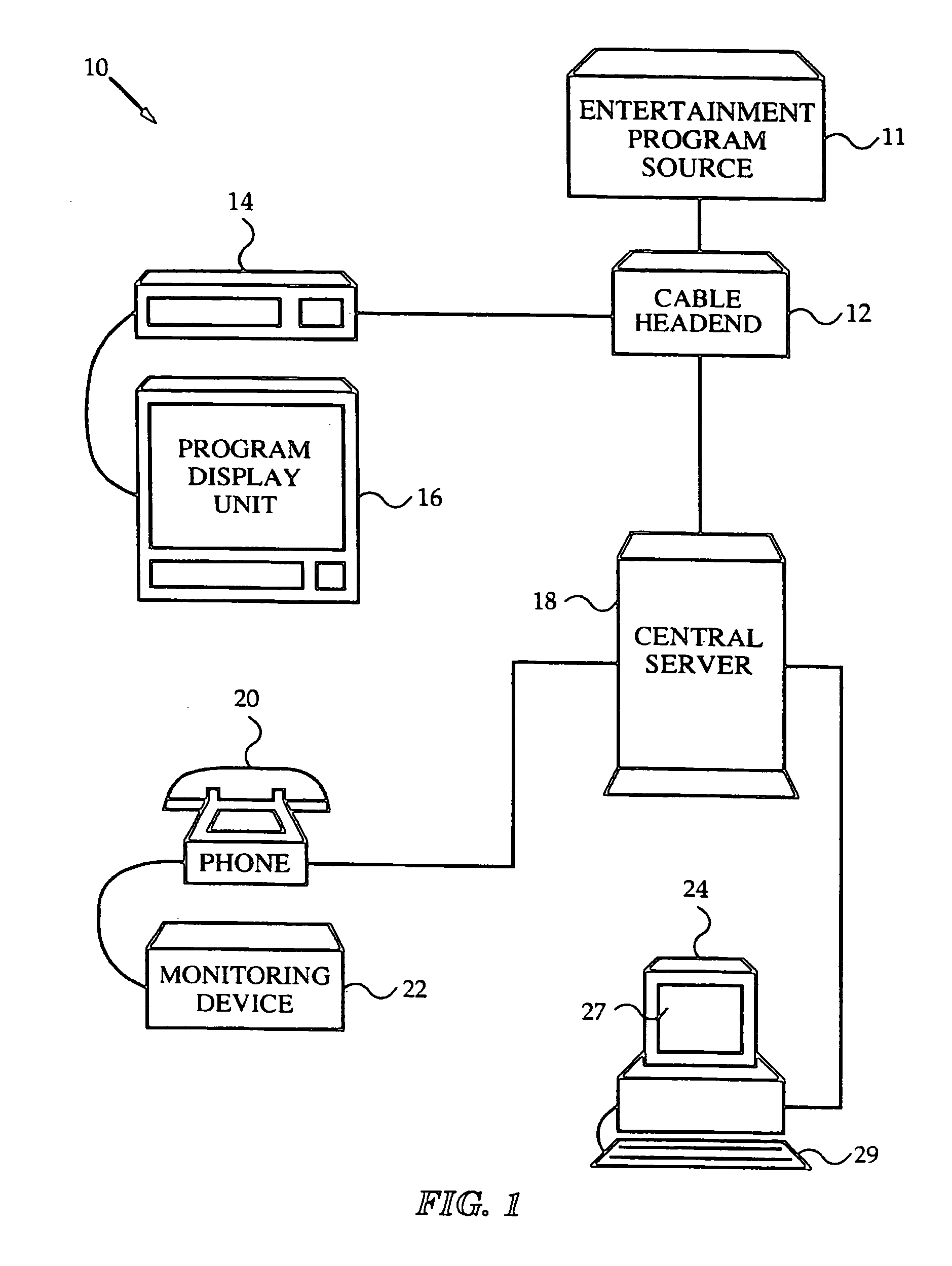
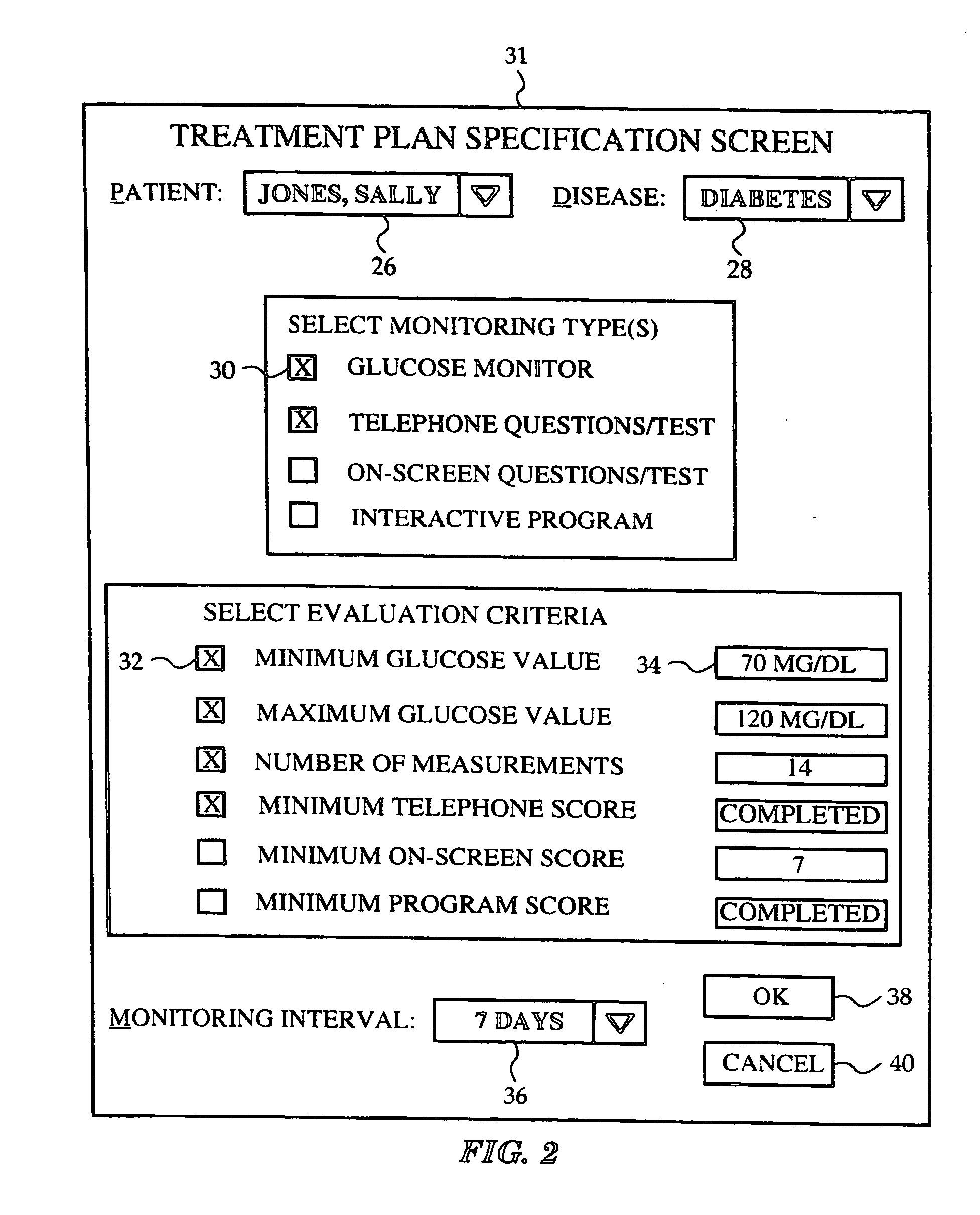
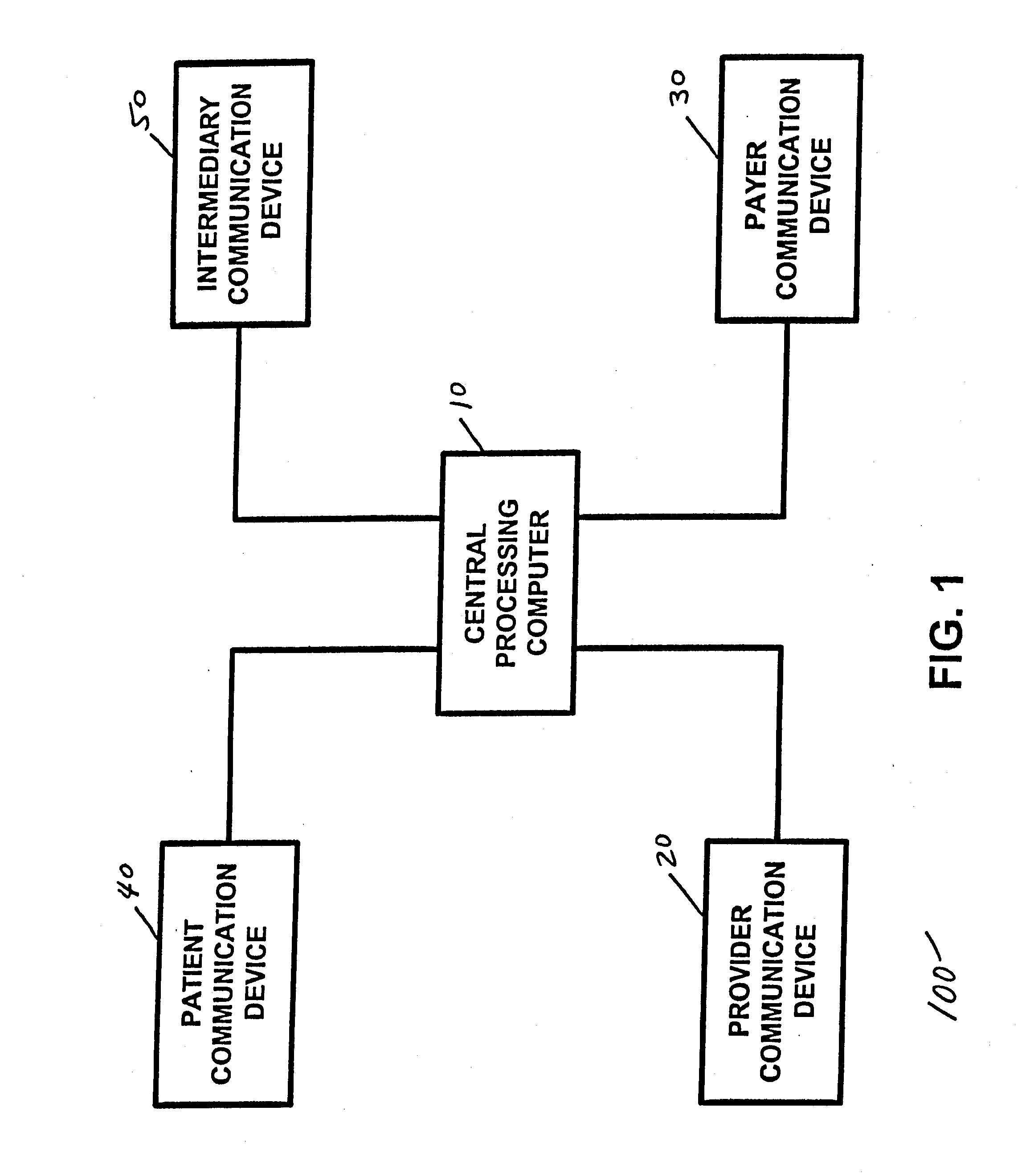
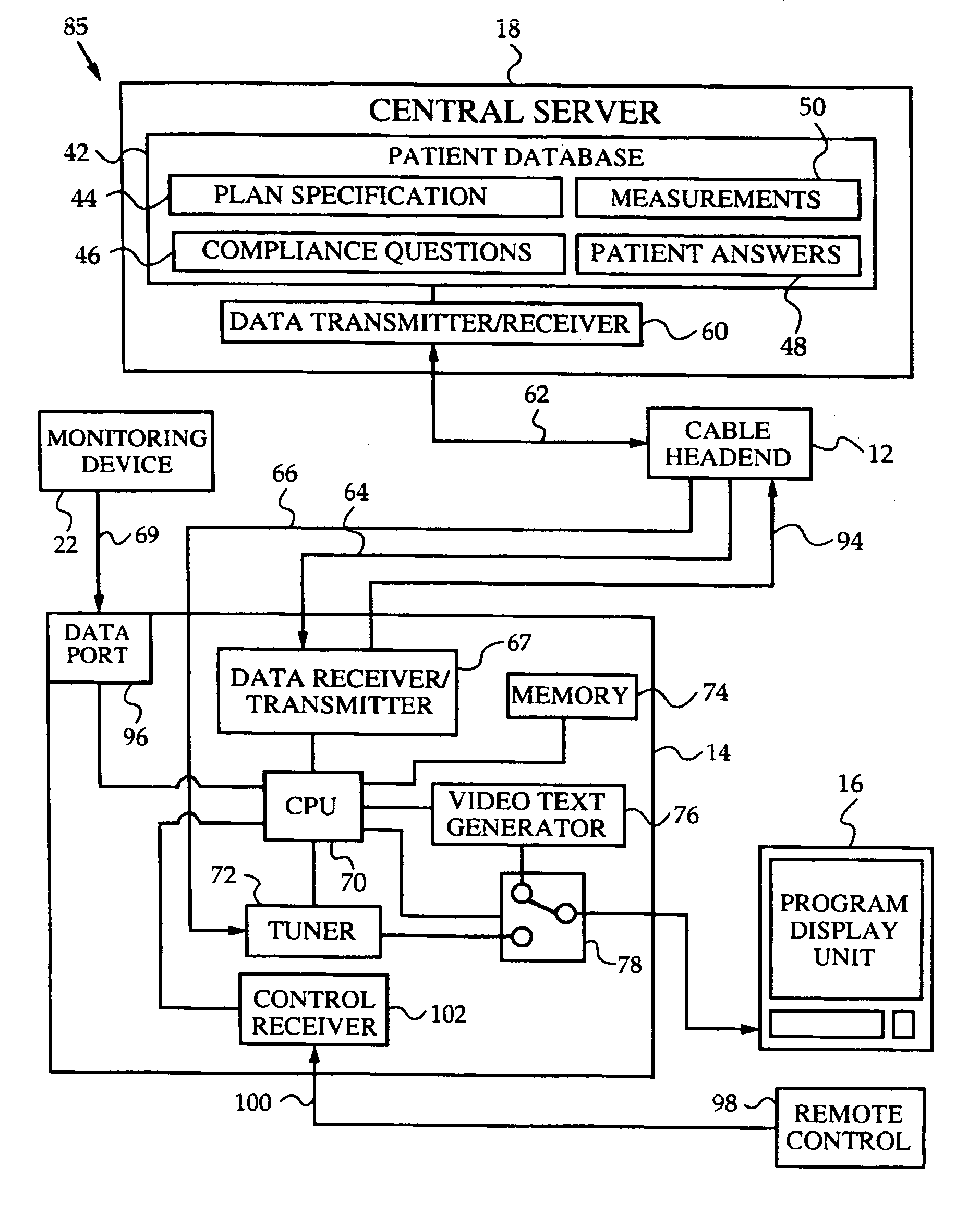
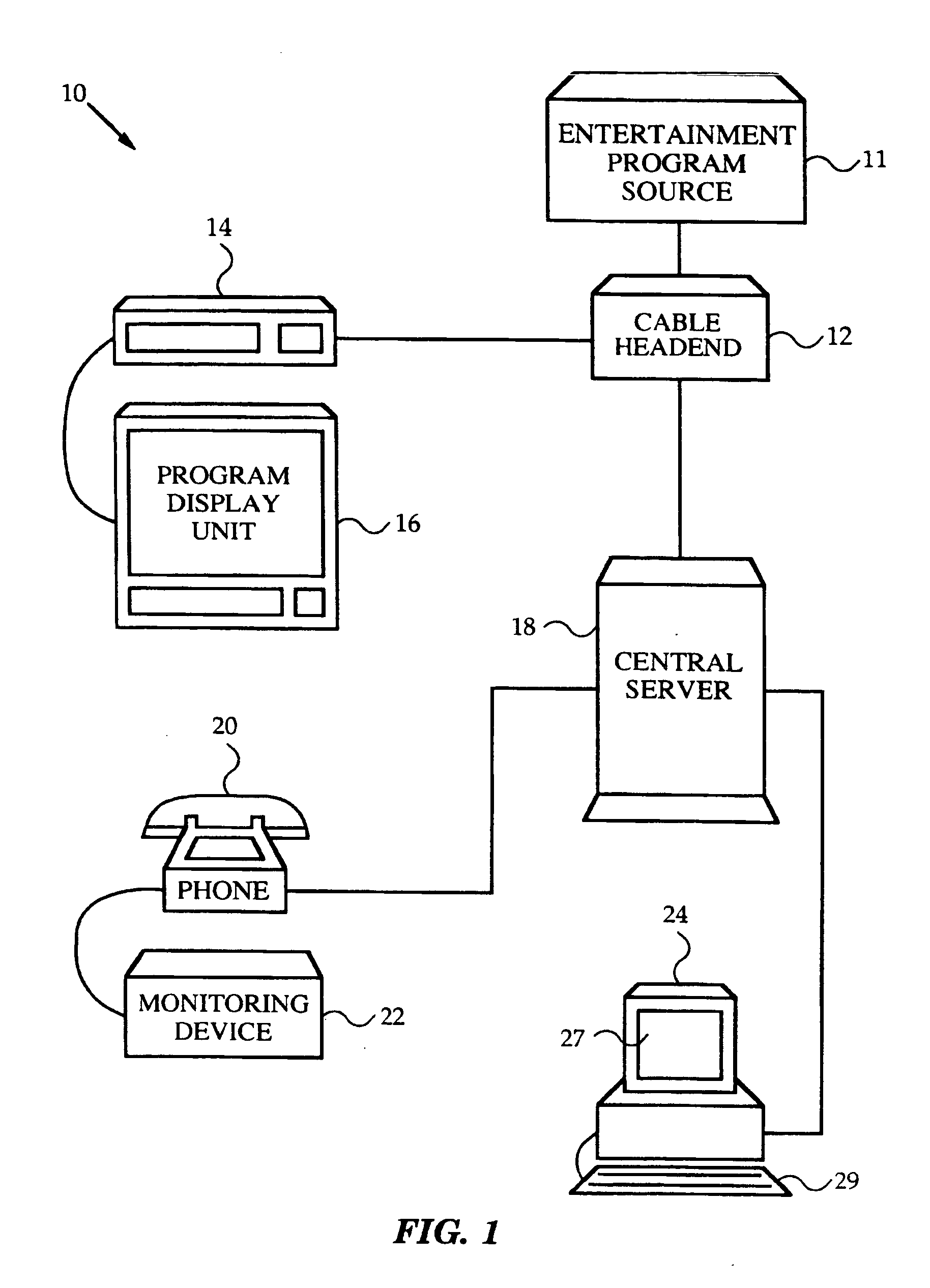
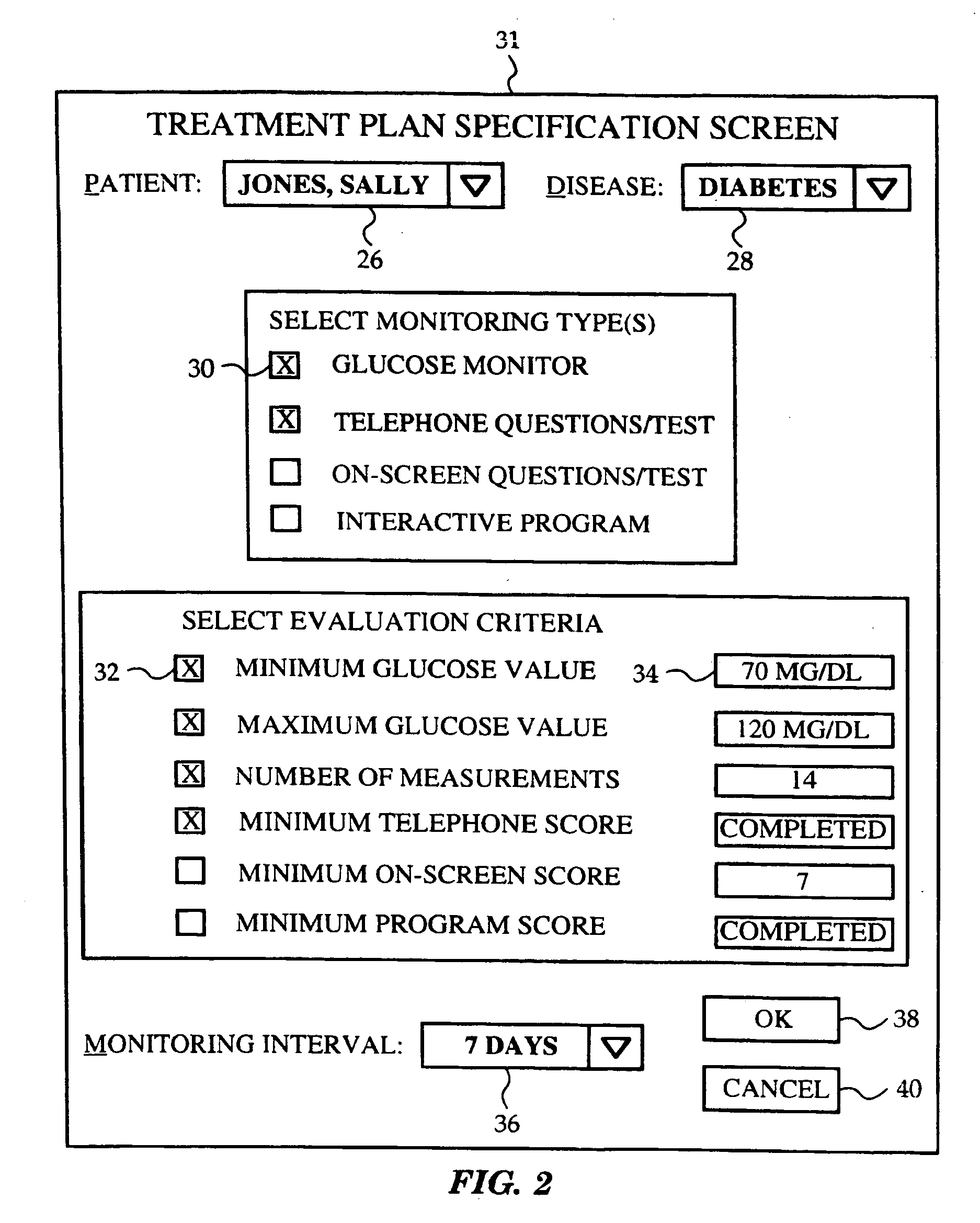
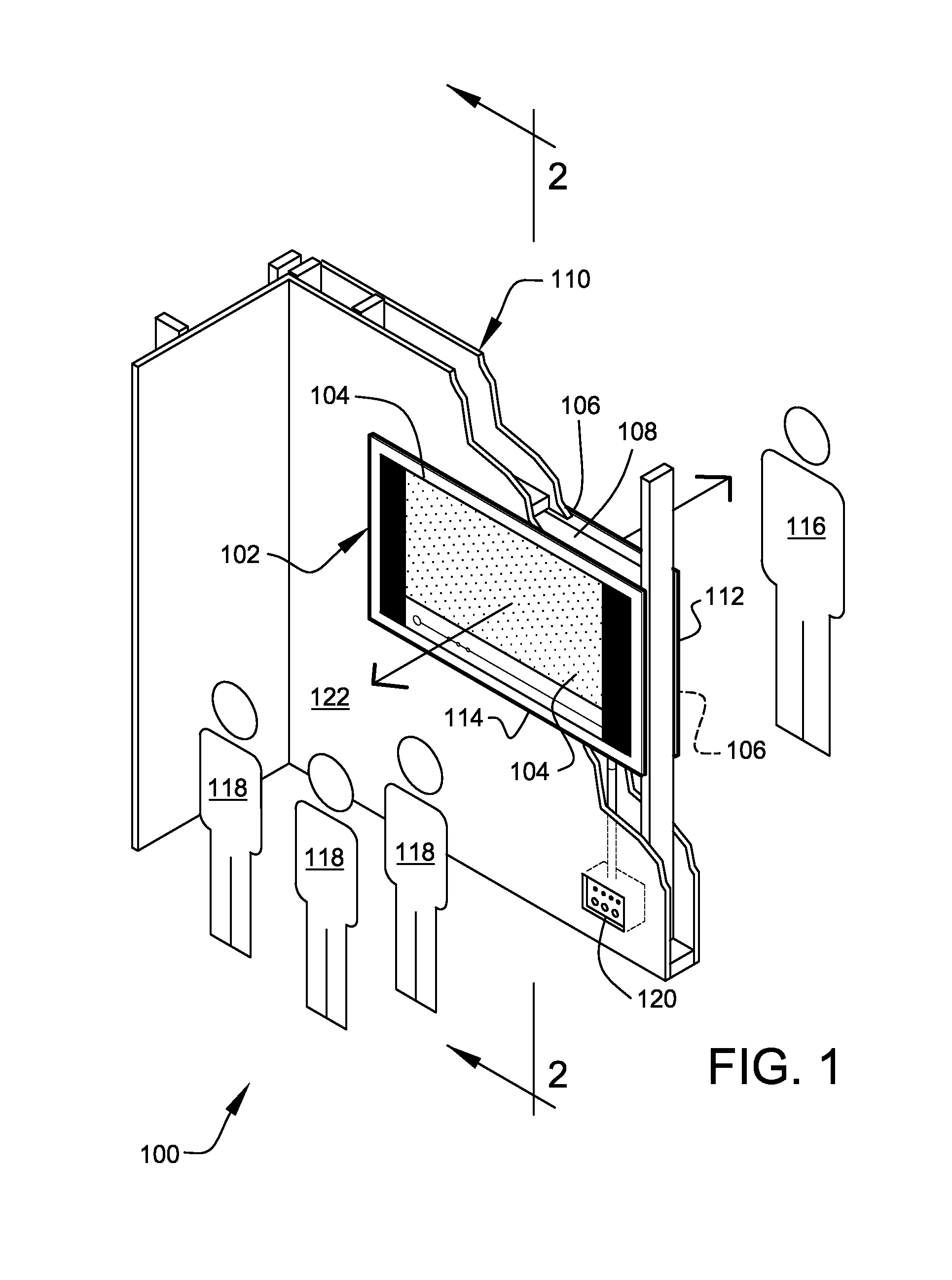
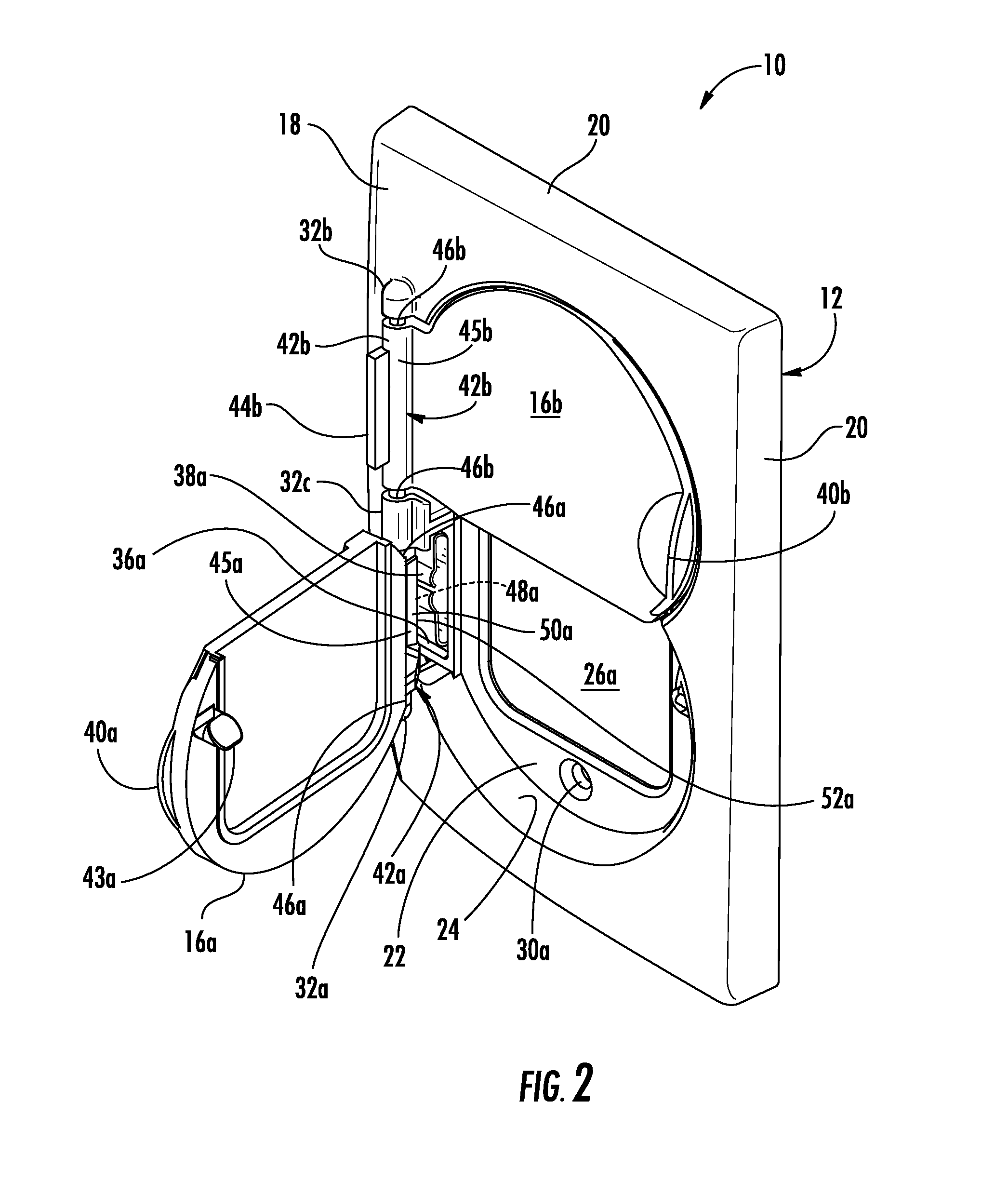
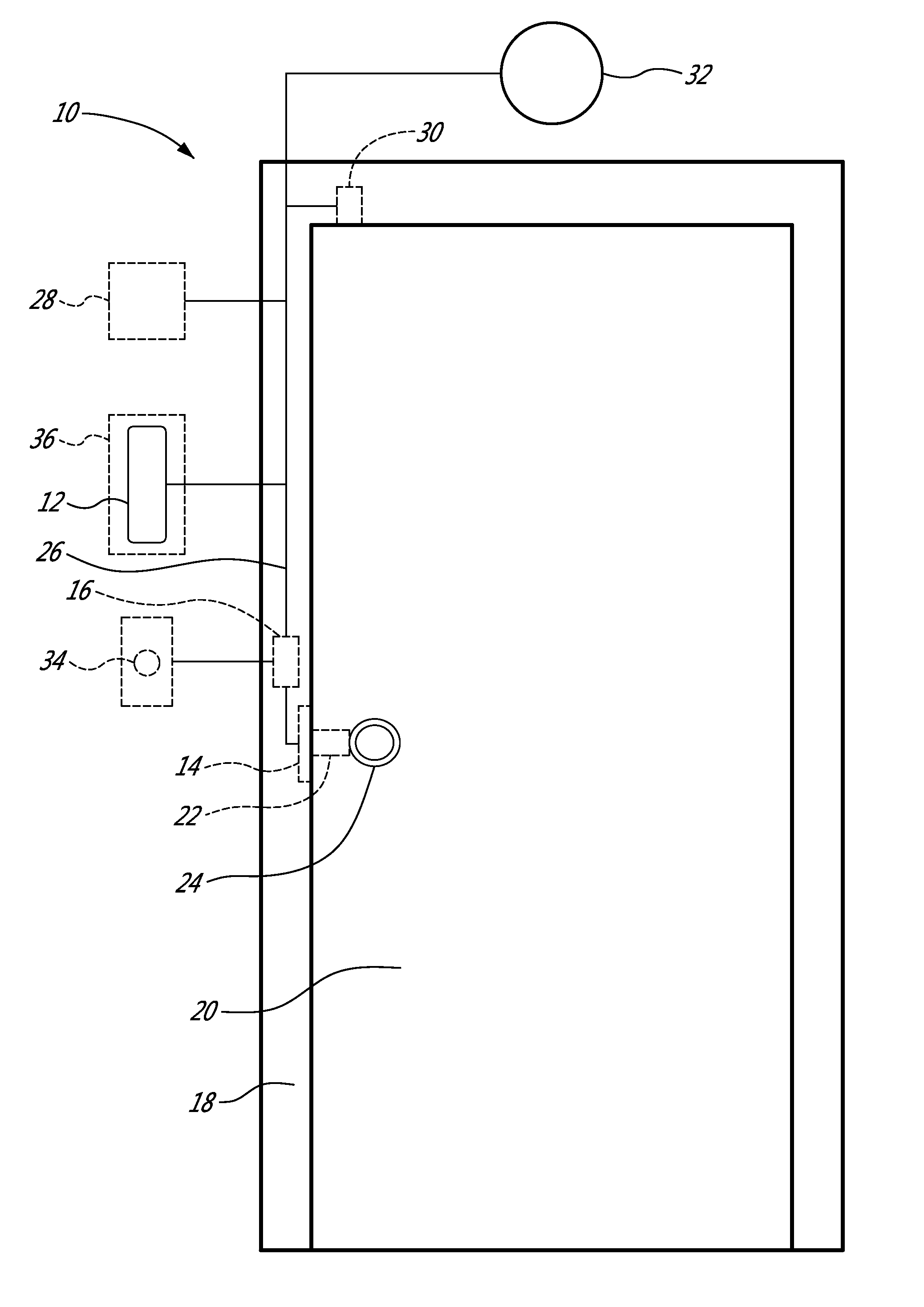
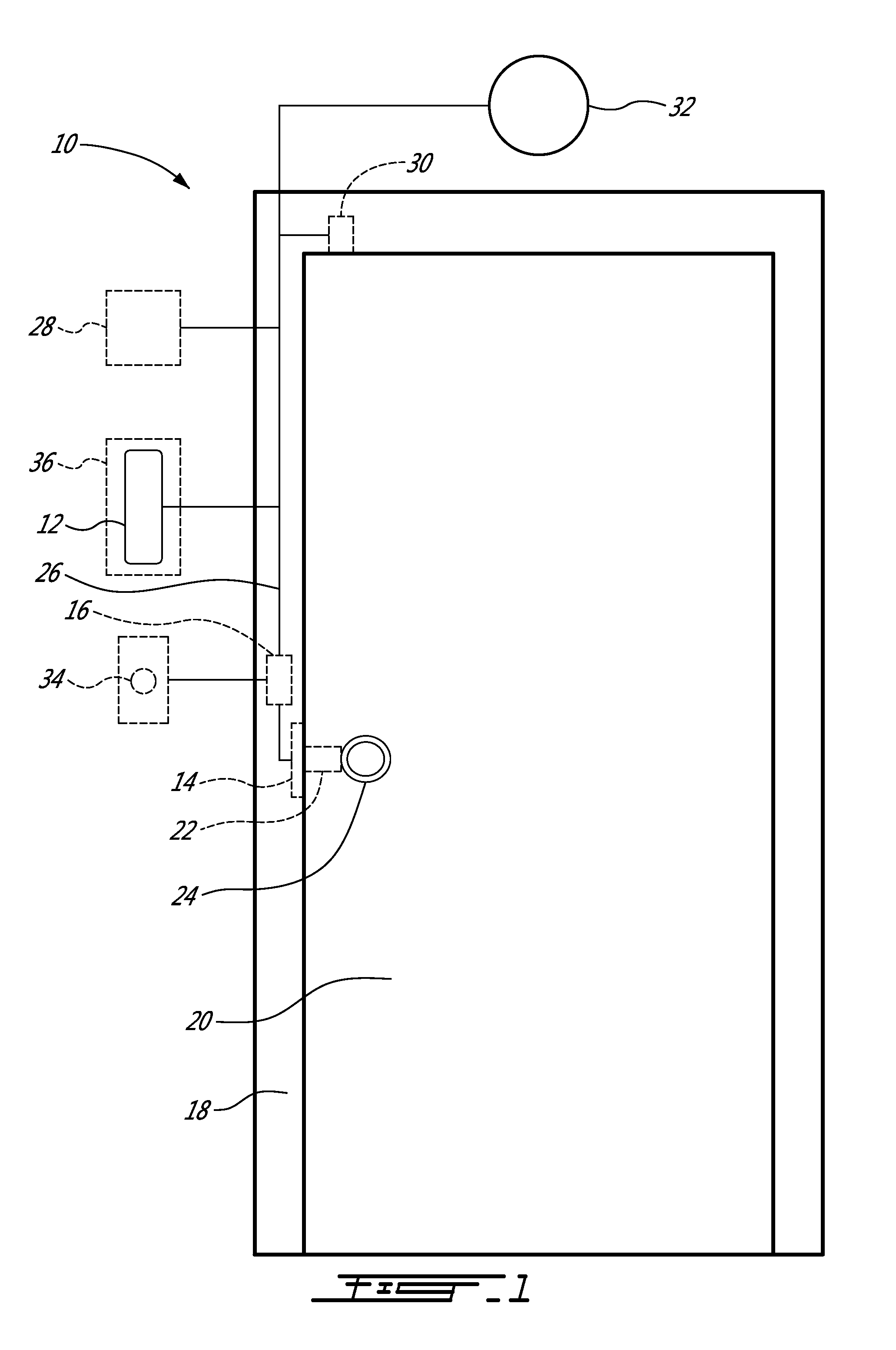
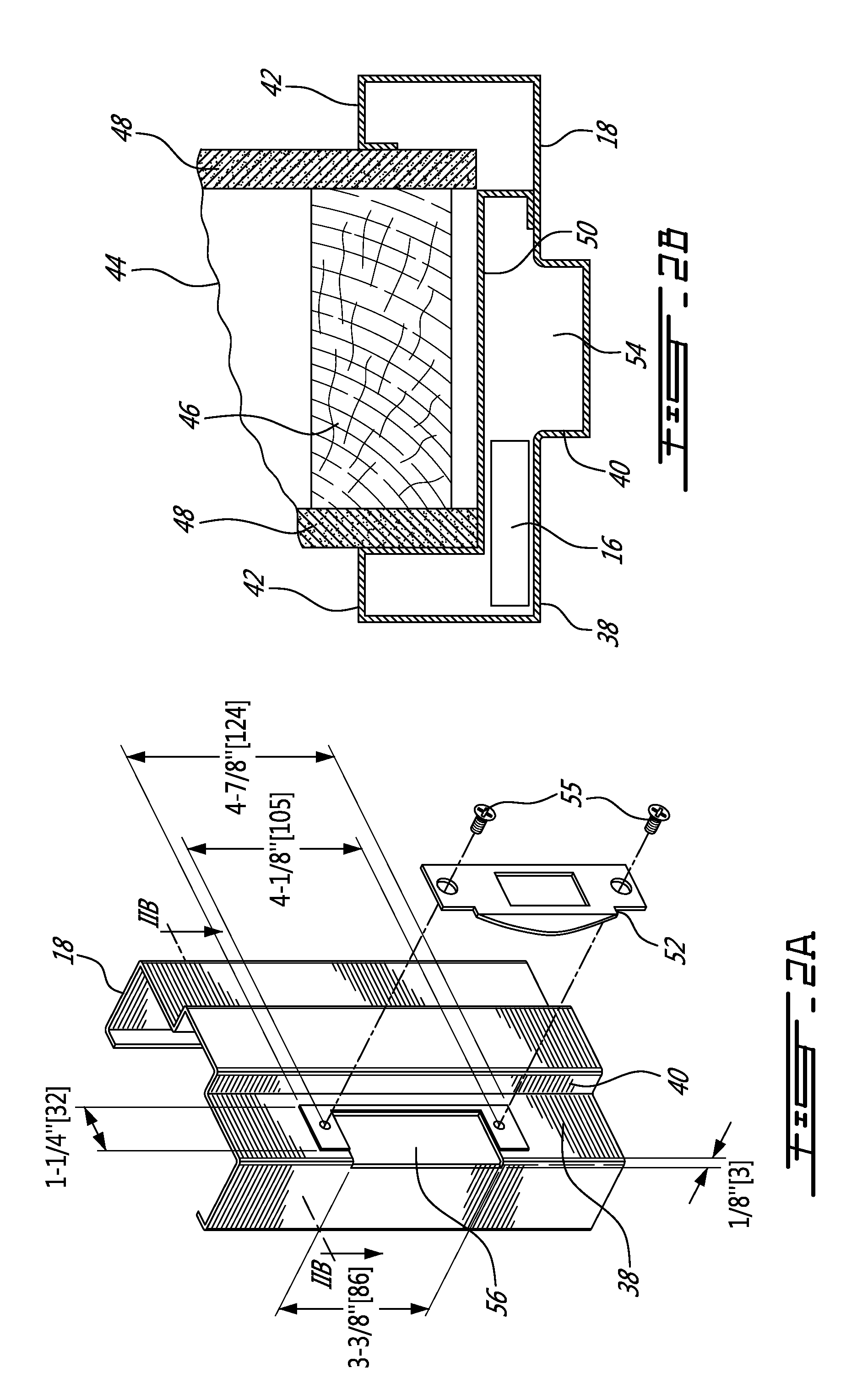
Network media access control system for encouraging patient compliance with a treatment plan
InactiveUS20070016446A1Restricted accessTelemedicineDiagnostic recording/measuringNetwork mediaPatient compliance
Owner:HEALTH HERO NETWORK
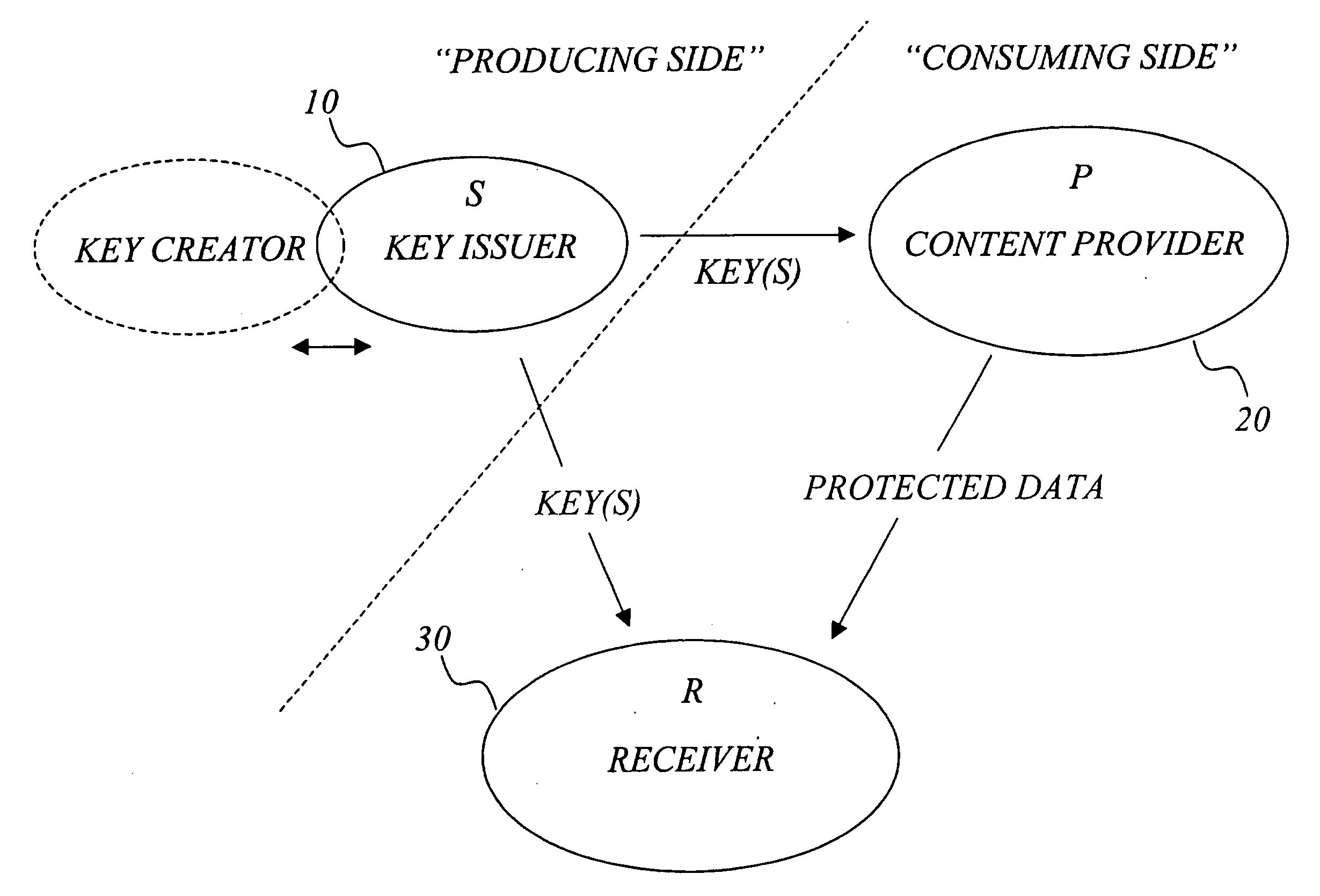
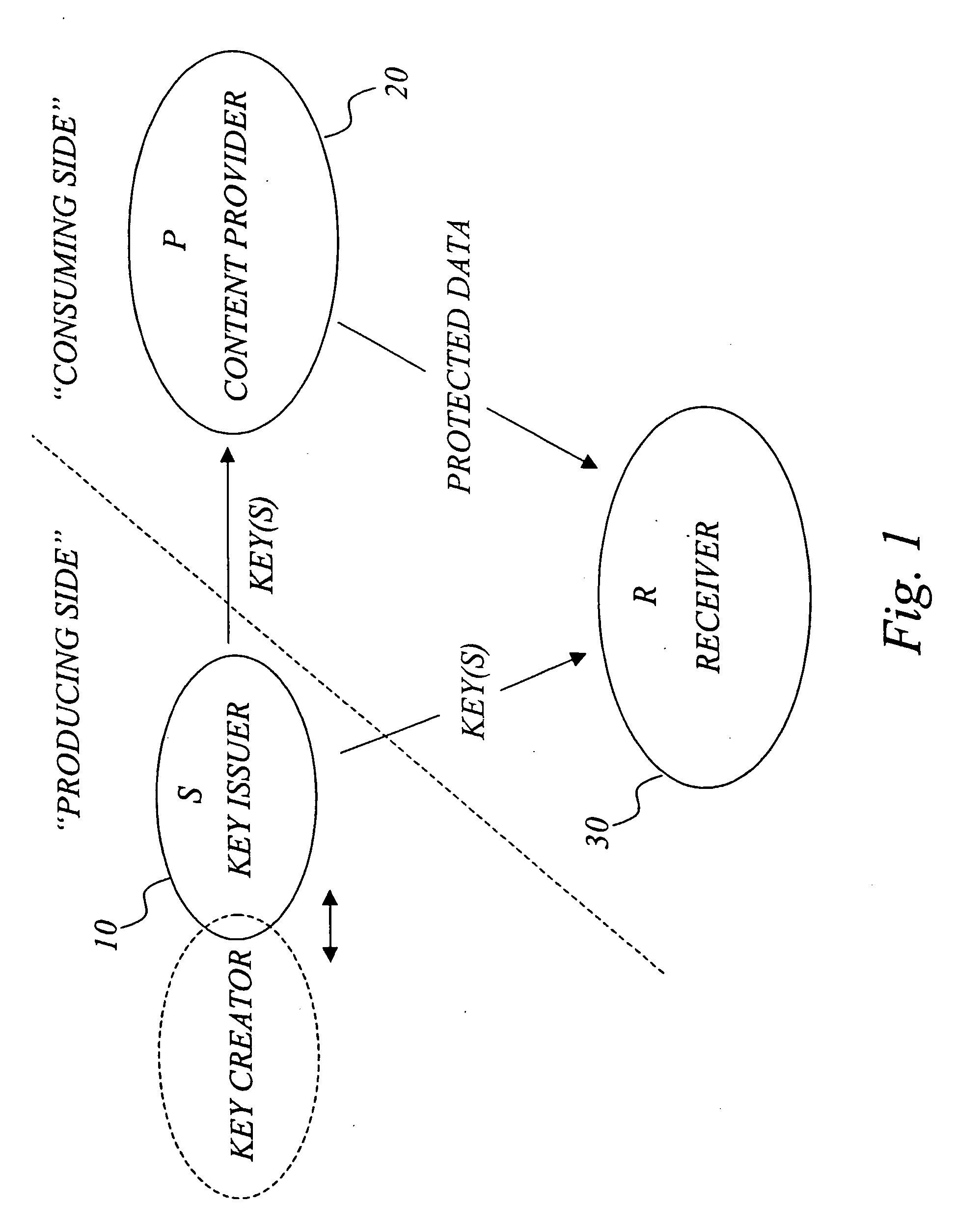
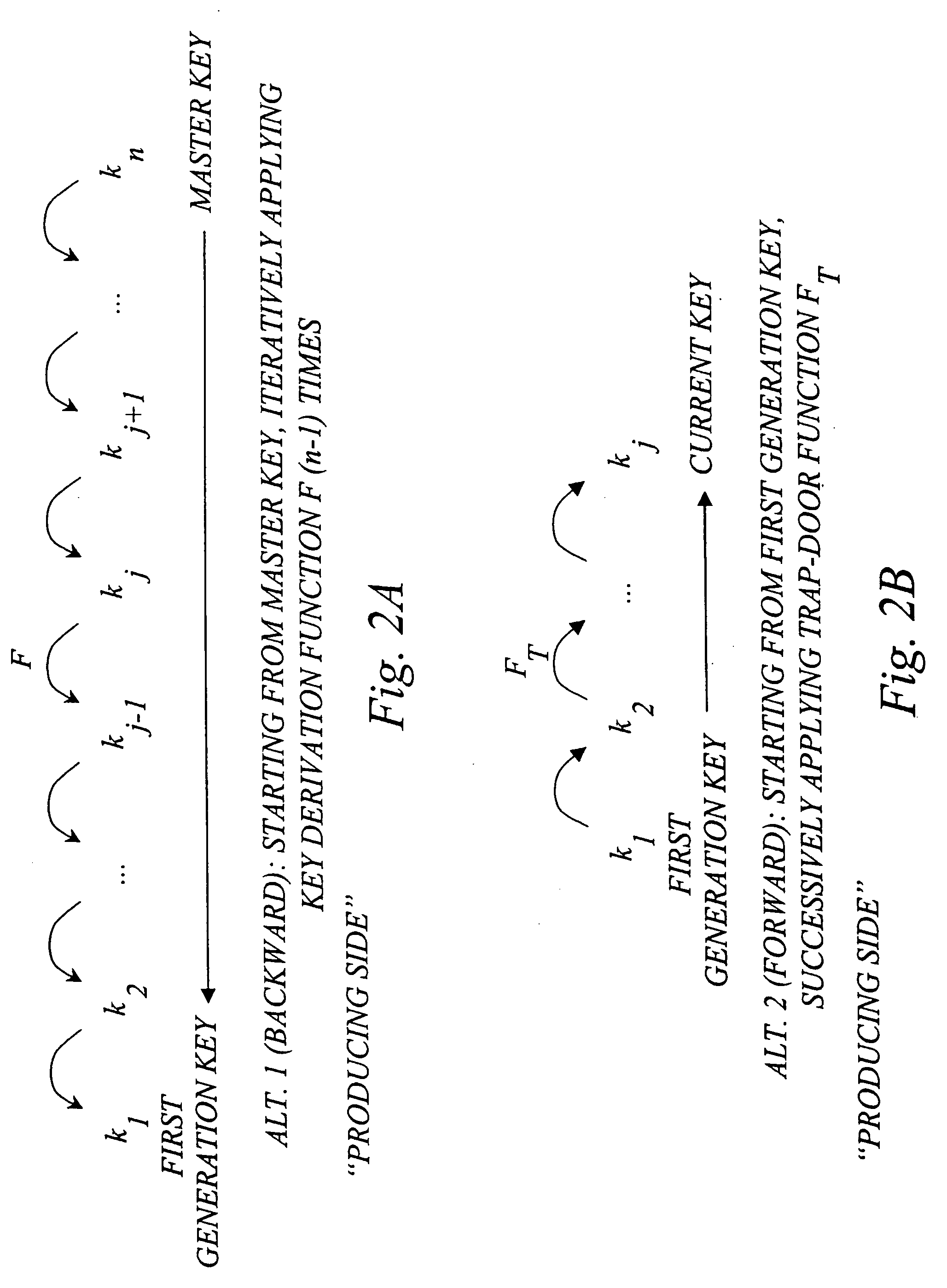
Efficient management of cryptographic key generations
InactiveUS20070127719A1Restricted accessEfficient storageKey distribution for secure communicationPublic key for secure communicationCryptographic key generationEarly generation
The invention generally relates to management of cryptographic key generations in an information environment comprising a key-producing side generating and distributing key information to a key-consuming side. A basic concept of the invention is to define, by means of a predetermined one-way key derivation function, a relationship between generations of keys such that earlier generations of keys efficiently may be derived from later ones but not the other way around. A basic idea according to the invention is therefore to replace, at key update, key information of an older key generation by the key information of the new key generation on the key-consuming side. Whenever necessary, the key-consuming side iteratively applies the predetermined one-way key derivation function to derive key information of at least one older key generation from the key information of the new key generation. In this way, storage requirements on the key-consuming side can be significantly reduced.
Owner:EMC CORP +1
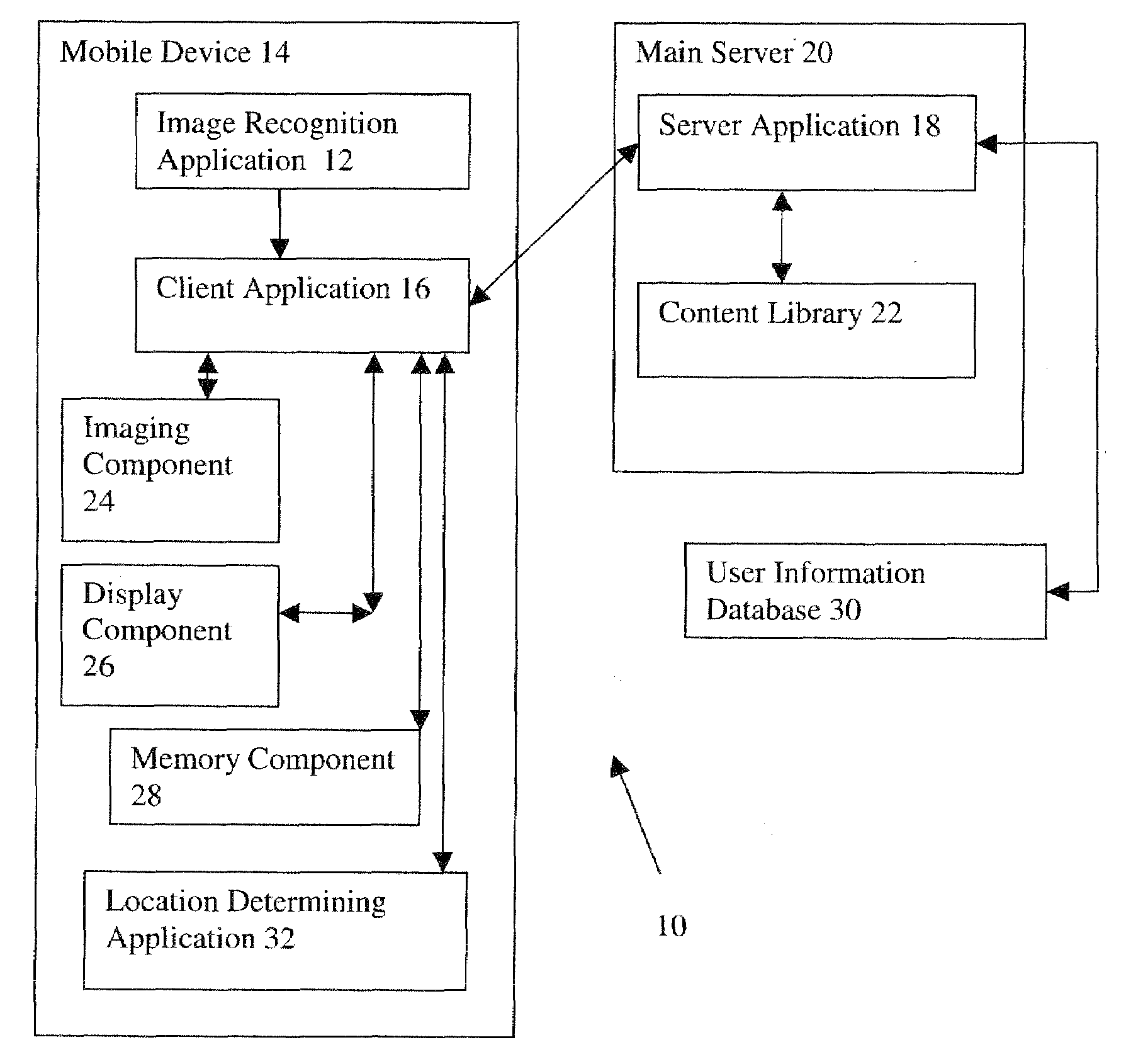
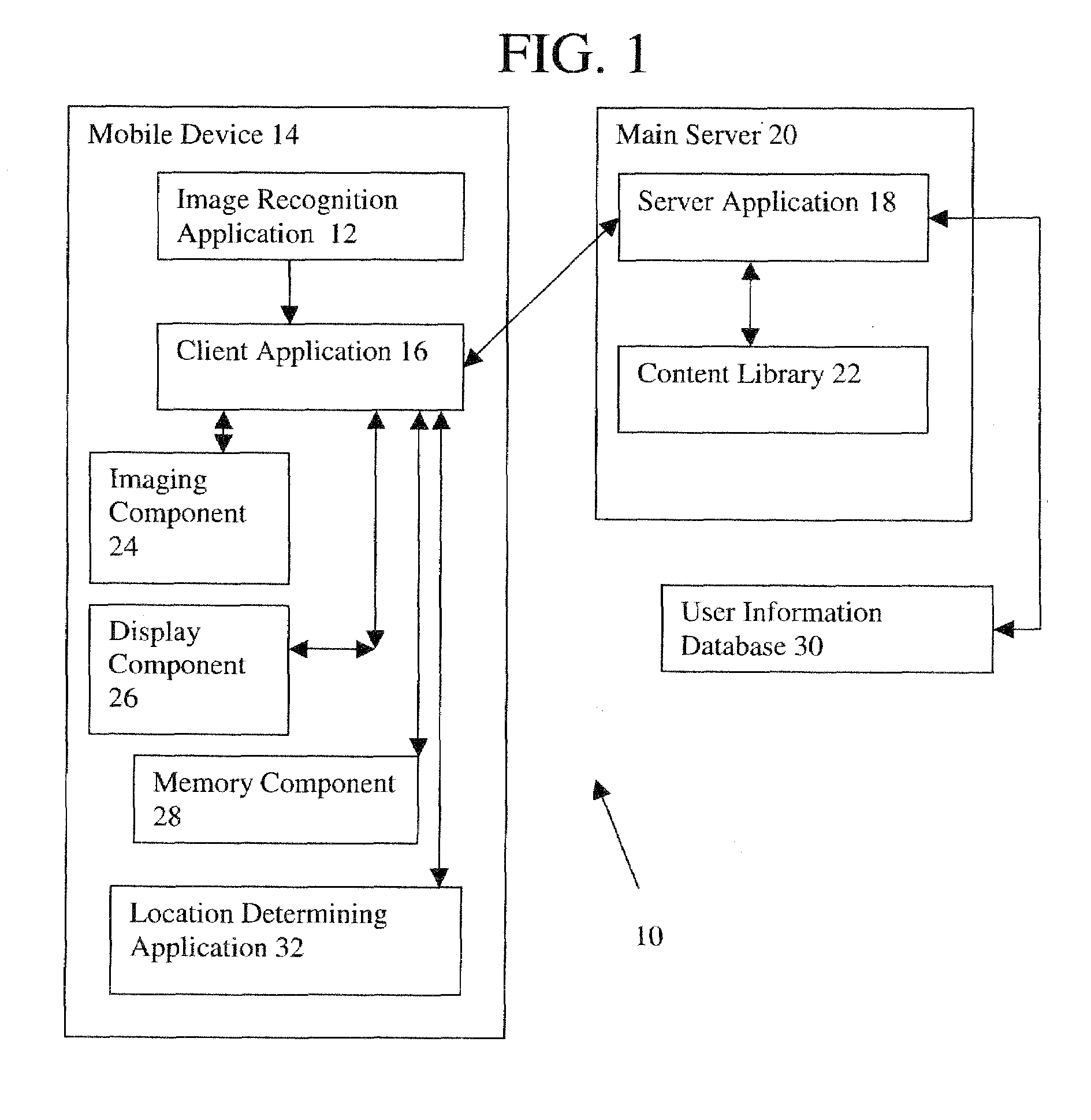
Augmented reality collaborative messaging system
InactiveUS20090300122A1Restricted accessEffective pointingCharacter and pattern recognitionMultiple digital computer combinationsPrivacy ruleMessage passing
An augmented reality messaging platform is provided which interacts between one or more mobile device and a server via a communication network. The augmented reality platform includes an image recognition application located on the mobile device which receives a live, real-time image and identifies objects, such as markers or logos, within the environment to determine the pose (position and orientation) of the camera. The data, in combination with user information, is used to send, retrieve and display digital, spatialized (those registered with the physical world) multimedia messages, including audio, video, text and virtual object. A server application provided on the server may receive and store the messages from the client application or may deliver appropriate messages to a receiving mobile device, based on a set of privacy rules. The client application on the mobile device processes and renders this content thereto and forms an augmented reality image on a display of the mobile device based on the live, real-time image and the content. The client application is further capable of uploading new message content to be stored on a centralized server through methods which are specific to the medium of the message.
Owner:FREER CARL JOHAN
Outlet covering system
InactiveUS6457843B1Restricted accessEasily and efficiently manufactured and marketedLighting support devicesElectric discharge tubesEngineeringMechanical engineering
An outlet covering system for restricting access to an outlet mounted on a wall surface. The outlet covering system includes an enclosure mountable to a wall surface for covering an outlet. The enclosure comprises a plate member that includes an opening for receiving the outlet and a cover member pivotally coupled to the plate member for selectively blocking access to the outlet. The cover member includes a front wall, a top wall, a bottom wall, and a pair of side walls. A securing member is provided for releasably securing the cover member to the plate member. A locking means is provided for selectively locking said cover member in a closed position.
Owner:KESTER BILLIE JO M +1
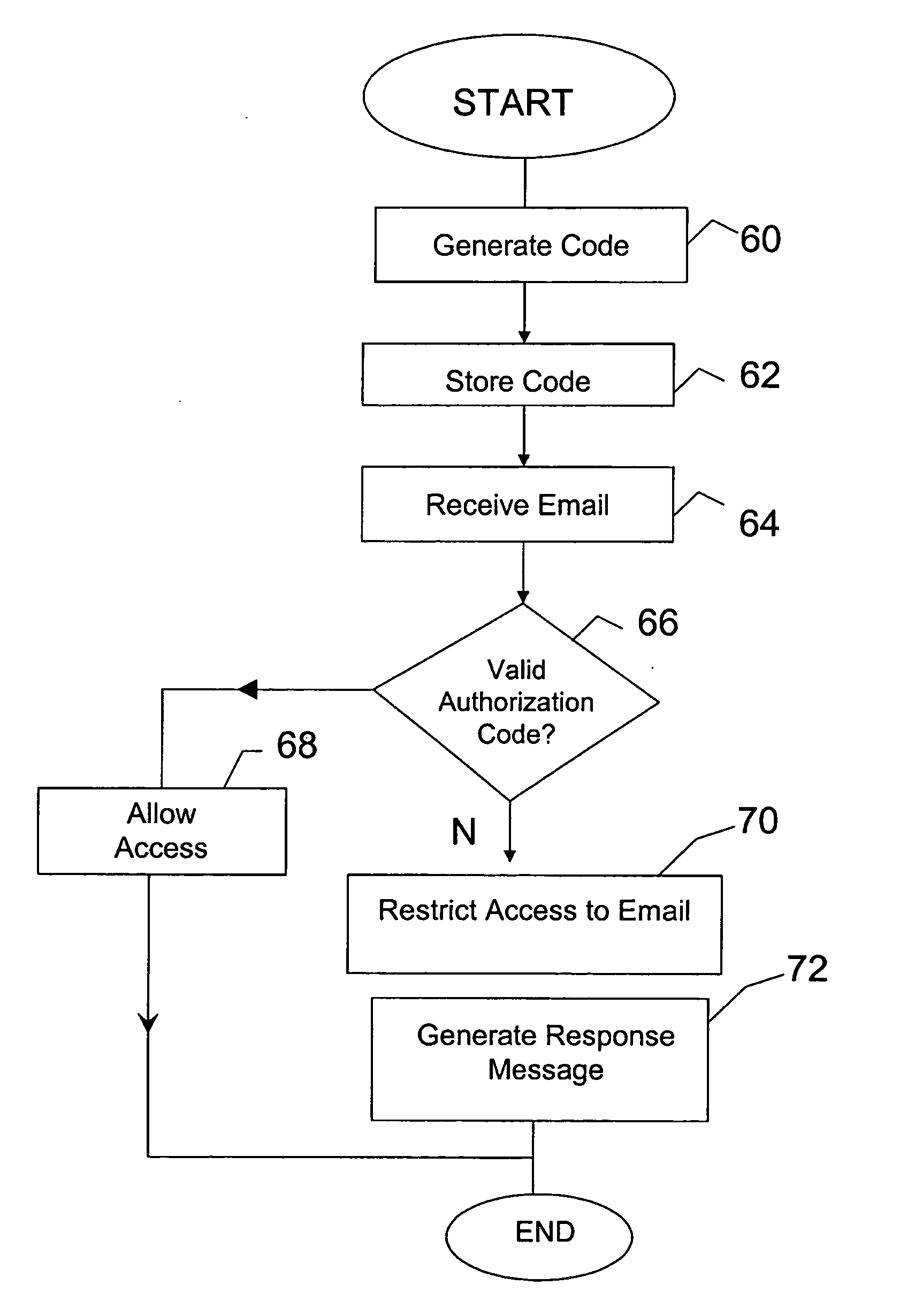
System and method for restricting access to email and attachments
ActiveUS20050289221A1Restricted accessLimited accessMultiple digital computer combinationsDigital data authenticationAuthorizationInternet privacy
One aspect of the invention is a method for restricting access to one or more email attachments includes receiving an email addressed to a first recipient and including at least a first attachment. The email is processed to determine whether a valid authorization code is associated with the email (and / or the attachment (s)). The valid authorization code identifies the email (and / or the attachment(s)) as an authorized communication. Access by the recipient to the first attachment is prevented if the processing of the email determined that no valid authorization code is associated with the email (and / or the attachment(s)).
Owner:ENT SERVICES DEV CORP LP
Apparatus and Method for Processing and/or Providing Healthcare Information and/or Healthcare-Related Information
InactiveUS20090313049A1Restricted accessFacilitates creation and managementMedical communicationFinanceDatabaseTransmitter
An apparatus, including a processor which processes a request to access, obtain, change, alter, or modify, information contained in a provider's or payer's record or file, wherein the processor determines whether a requesting individual or entity is authorized to access, obtain, change, alter, or modify, information contained in the provider's or payer's record or file, wherein the processor either allows the accessing, obtaining, changing, altering, or modifying, of the information contained in the record or file, or the processor denies the accessing, obtaining, changing, altering, or modifying, of the information contained in the record or file, and further wherein the processor generates a notification report containing information regarding the allowance or the denial of the accessing, obtaining, changing, altering, or modifying, of the information contained in the record or file, and a transmitter, wherein the transmitter transmits the notification report to a communication device associated with the provider or payer.
Owner:JOAO RAYMOND ANTHONY +1
Network media access control system for encouraging patient compliance with a treatment plan
InactiveUS20070016447A1Restricted accessTelemedicineDiagnostic recording/measuringNetwork mediaPatient compliance
Owner:HEALTH HERO NETWORK
Networking method of wireless electricity consumption information acquisition ad hoc network
InactiveCN103906044ALarge capacityGuaranteed stabilityTransmission systemsNetwork topologiesElectricityComputer network
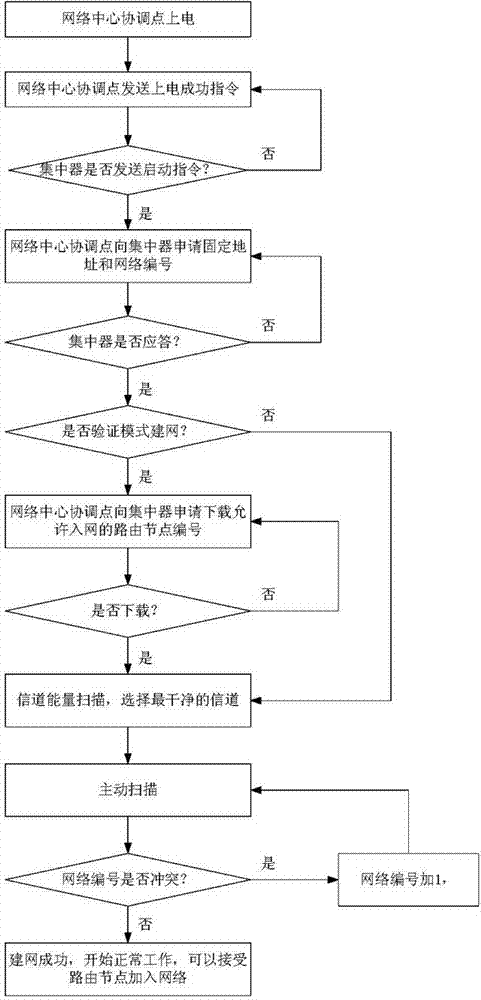
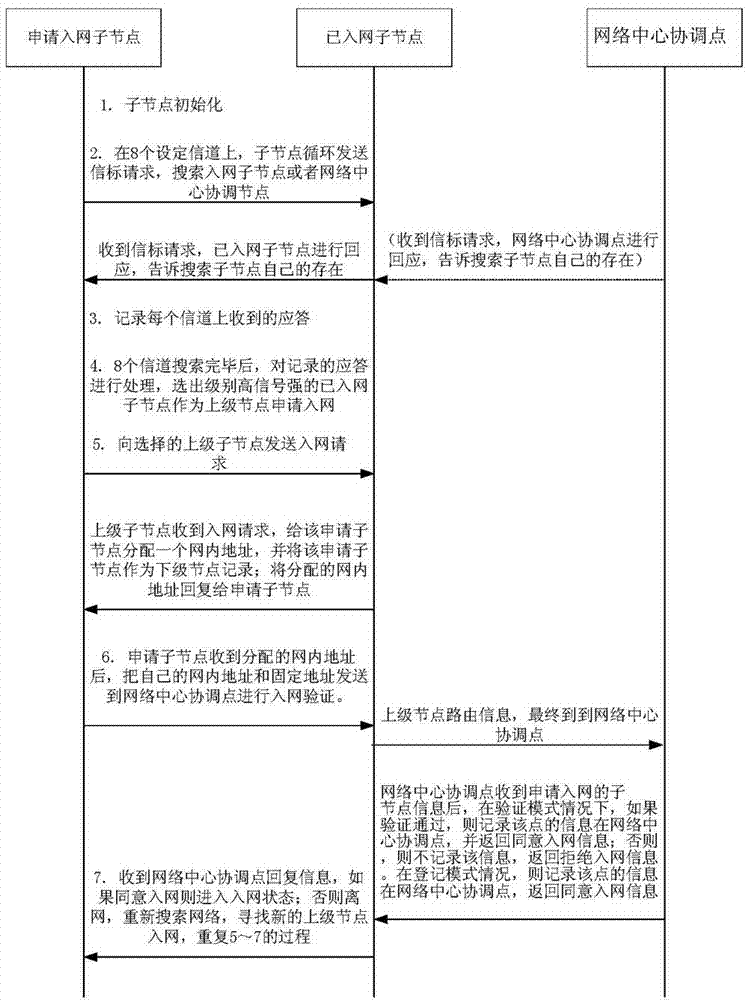
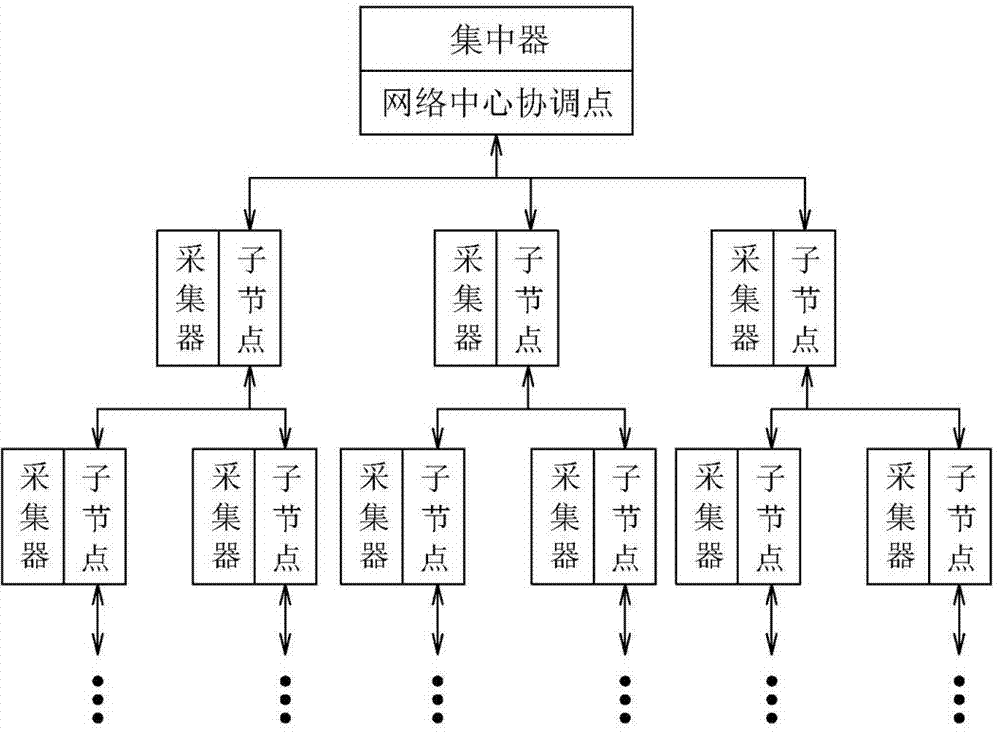
The invention relates to a networking method of a wireless electricity consumption information acquisition ad hoc network. According to the technical scheme, the networking method of the wireless electricity consumption information acquisition ad hoc network includes the steps that first, the network is established; second, child nodes without access to the network search for a network center coordinator or child nodes with access to the network; third, the child nodes without access to the network which are searching for the network select the network center coordinator or the child nodes with access to the network as ancestor nodes and send network access requests to the ancestor nodes; fourth, after the ancestor nodes receive the network access requests, network access addresses are allocated to the child nodes applying for access to the network; fifth, the child nodes applying for access to the network send the network access addresses and fixed addresses to the network center coordinator; sixth, if the network center coordinator agrees with that the child nodes applying for access to the network have access to the network, the child nodes applying for access to the network successfully get access to the network, if the network center coordinator does not agree with that, reject information is returned to the child nodes applying for access to the network, and after receiving the information, the child nodes applying for access to the network execute the second step to the sixth step till successfully getting access to the network. The networking method of the wireless electricity consumption information acquisition ad hoc network is used in the field of wireless acquisition of electricity consumption information.
Owner:HANGZHOU XUNLONG TECH
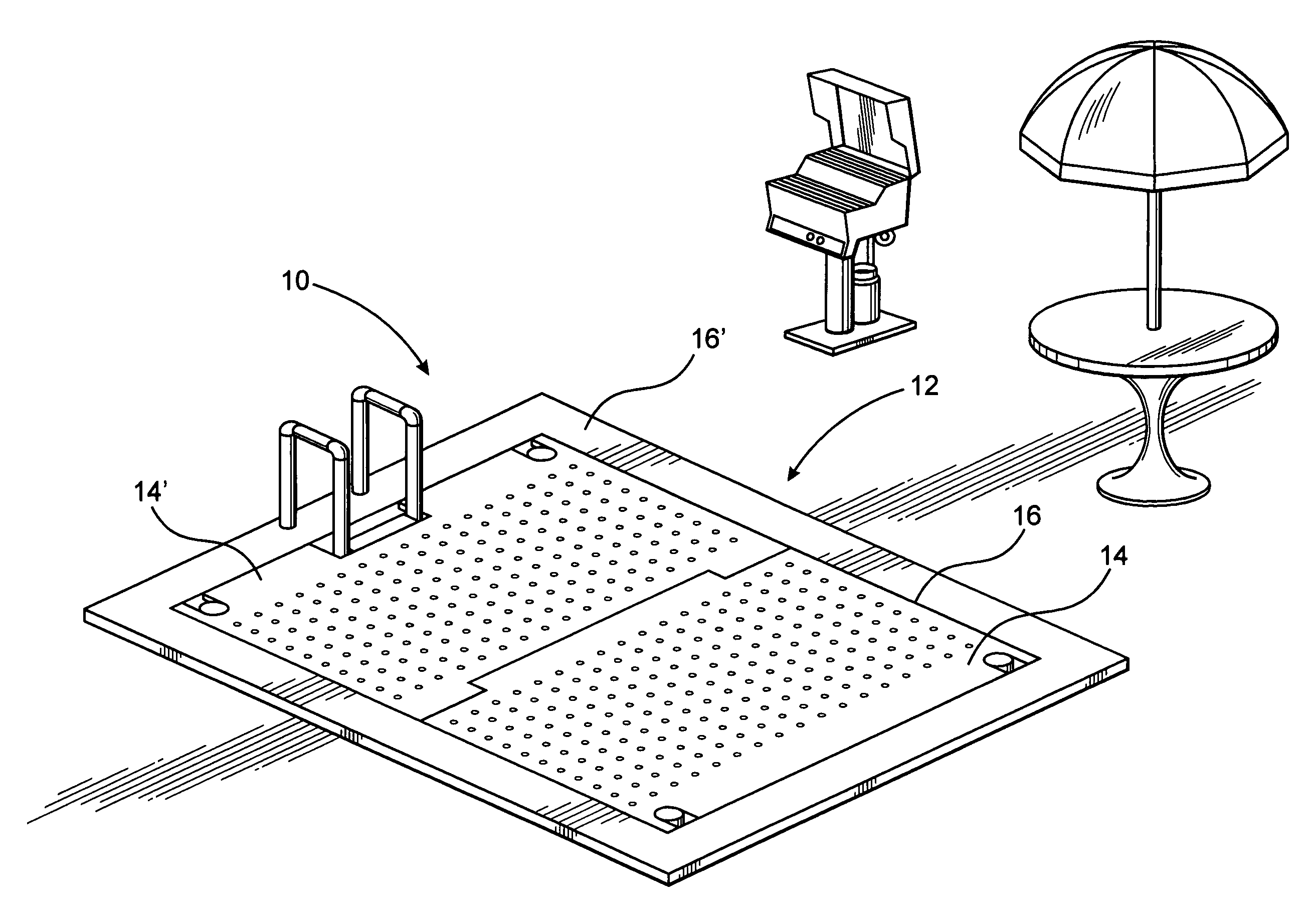
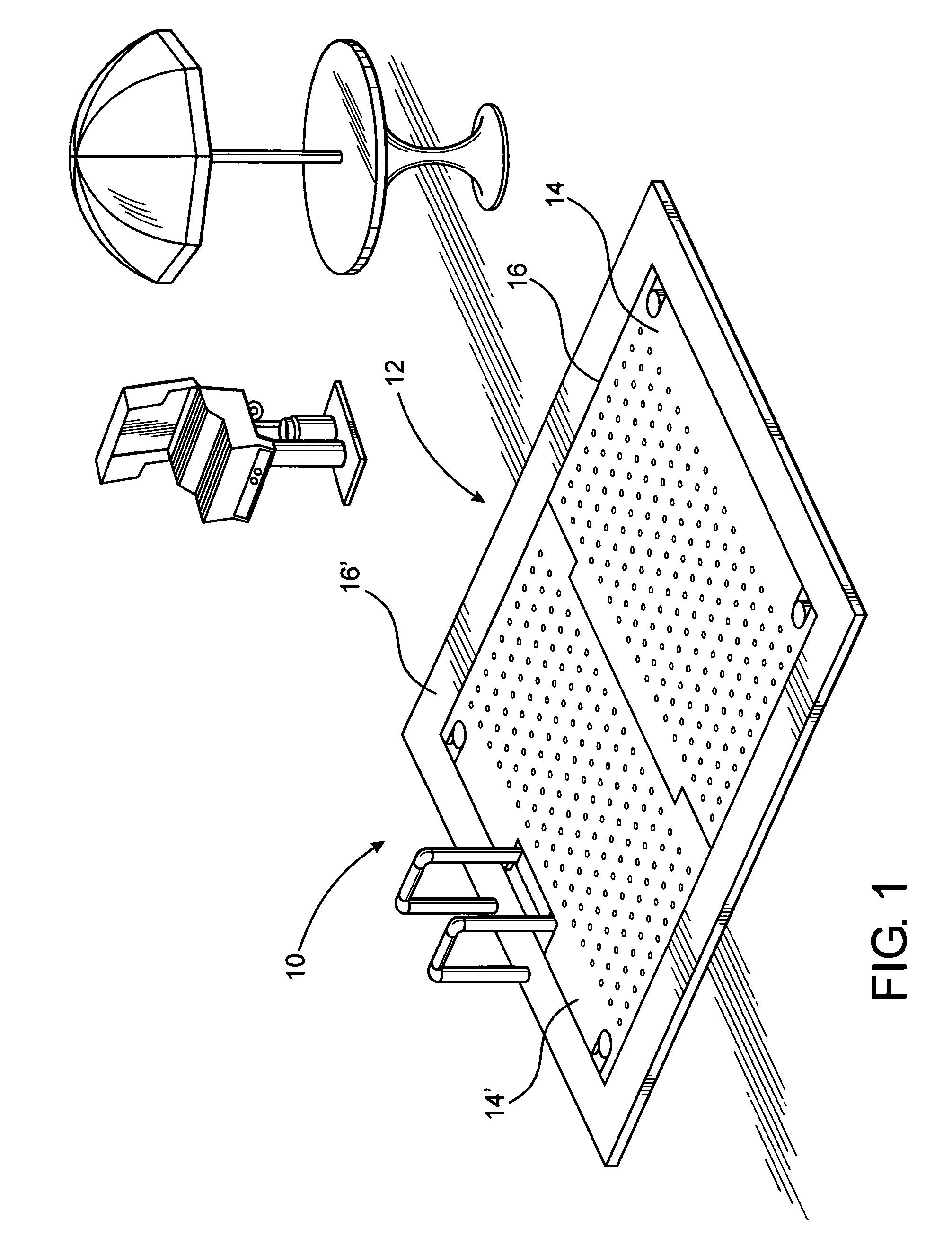
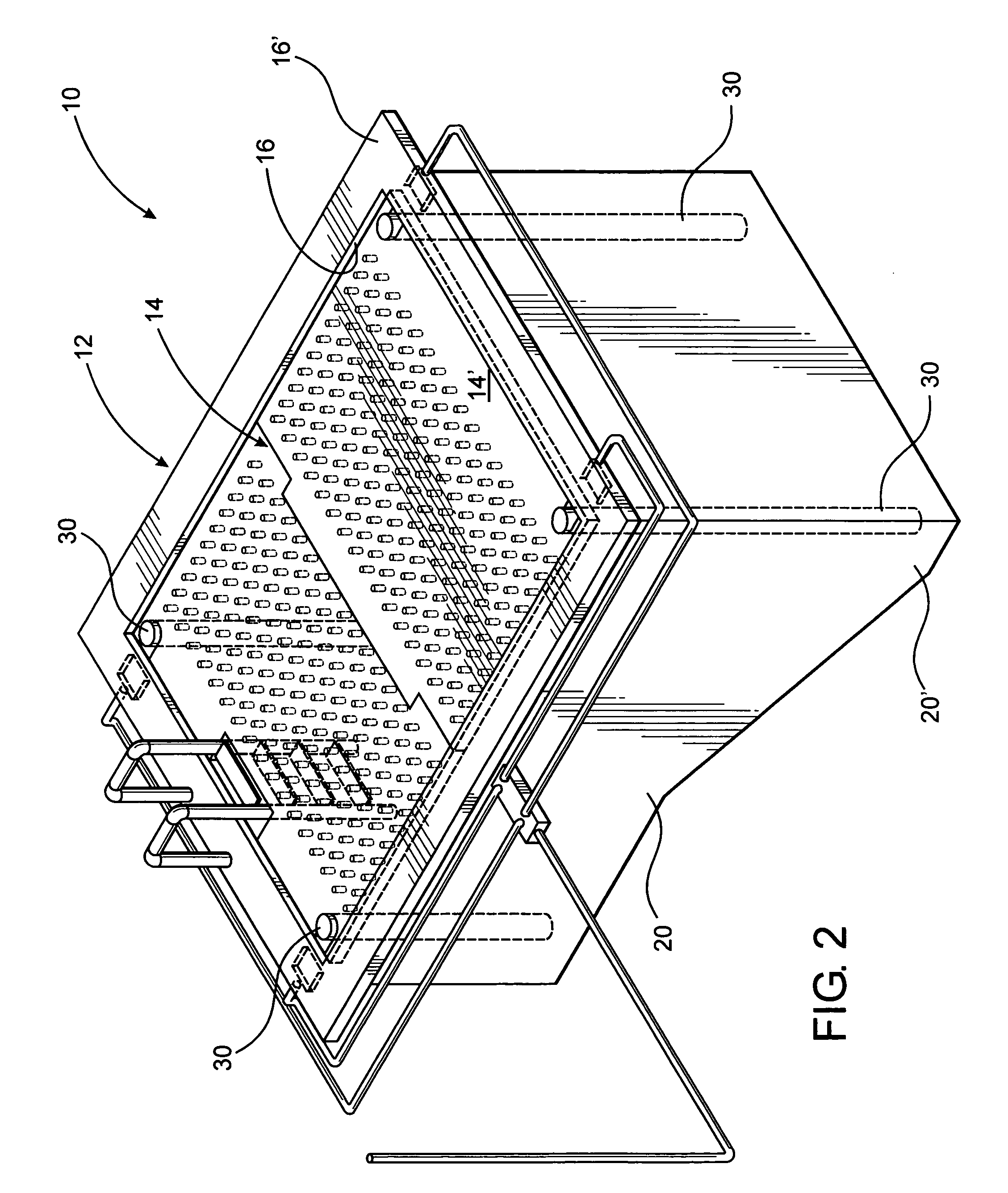
Elevator assembly for swimming pool
InactiveUS20090126096A1Restricted accessEasy to moveGymnasiumSwimming poolsMarine engineeringWater flow
An elevator assembly structured to regulate the accessible depth of a swimming pool including a platform selectively and automatically moveable between lowered, intermediate and raised positions thereby regulating the depth of the pool as well as providing a stable barrier and support area adjacent the open top of the pool when in a raised position. A support assembly and drive assembly are operatively associated to move and maintain the platform in any of the aforementioned positions. The platform includes a passage assembly comprising an apertured construction including a plurality of openings disposed and dimensioned to facilitate water flow therethrough as the platform moves within the pool. A sensor assembly is disposed to monitor predetermined vicinity adjacent the pool and functions to automatically dispose the platform in the raised position, thereby preventing drowning of individuals who cannot swim.
Owner:BOCOS JUAN CARLOS
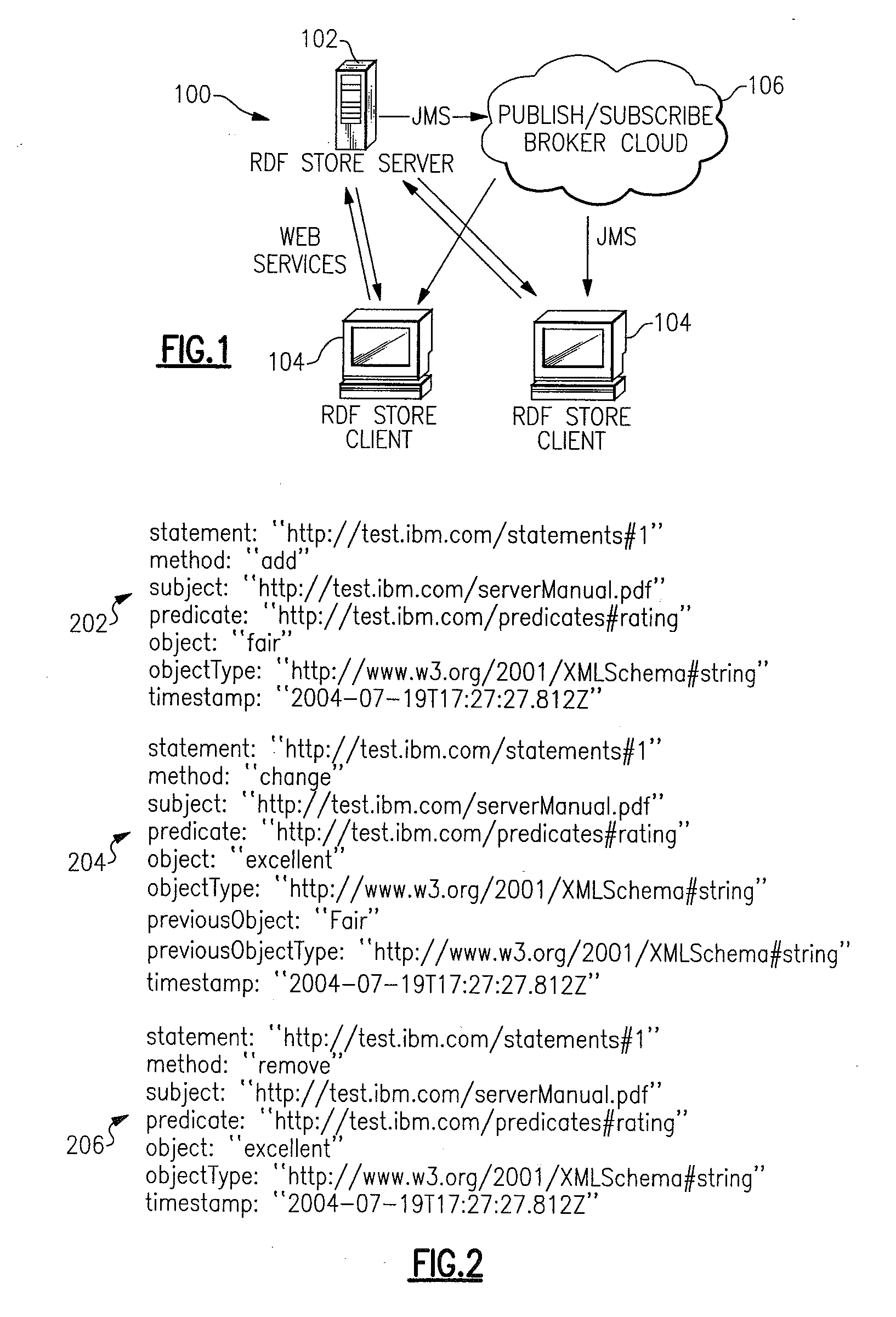
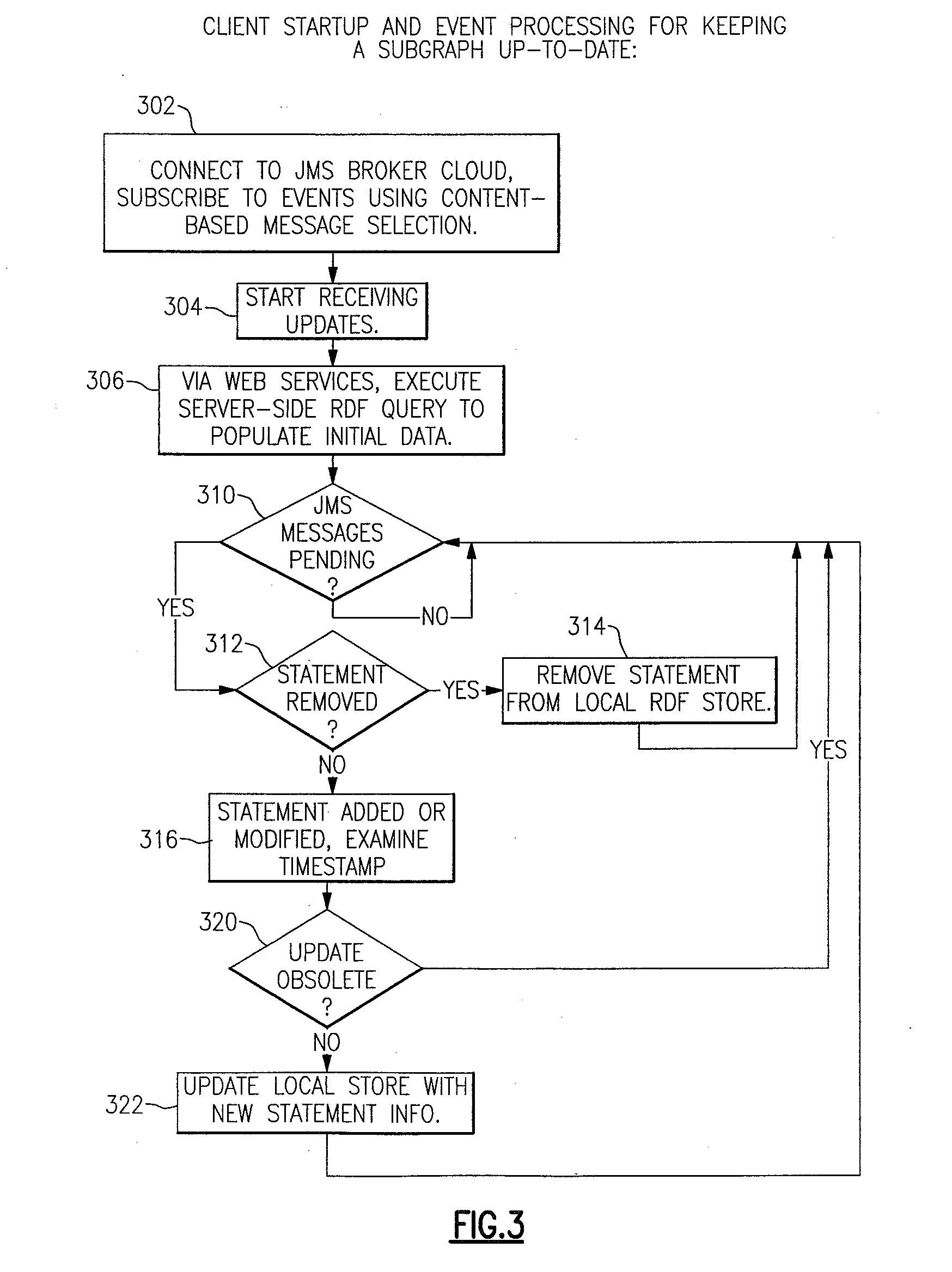
System and Method for Scalable Distribution of Semantic Web Updates
InactiveUS20080005278A1Restricted accessData processing applicationsComputer security arrangementsPublish–subscribe patternRDF
Disclosed are a method and system for scalable distribution of semantic web updates. A first embodiment of the invention leverages publish / subscribe technology to distribute those updates such that clients receive only the information they require. A second embodiment of the invention uses an access control feature to limit the statements clients are allowed to read. Optionally in this second embodiment, the same publish / subscribe messaging infrastructure may be used both to distribute updated semantic web data and also to distribute relevant changes to the access control information. The invention is particularly well suited for use with the Resource Description Framework (RDF) language.
Owner:IBM CORP
Data management device, stored data management method and computer program
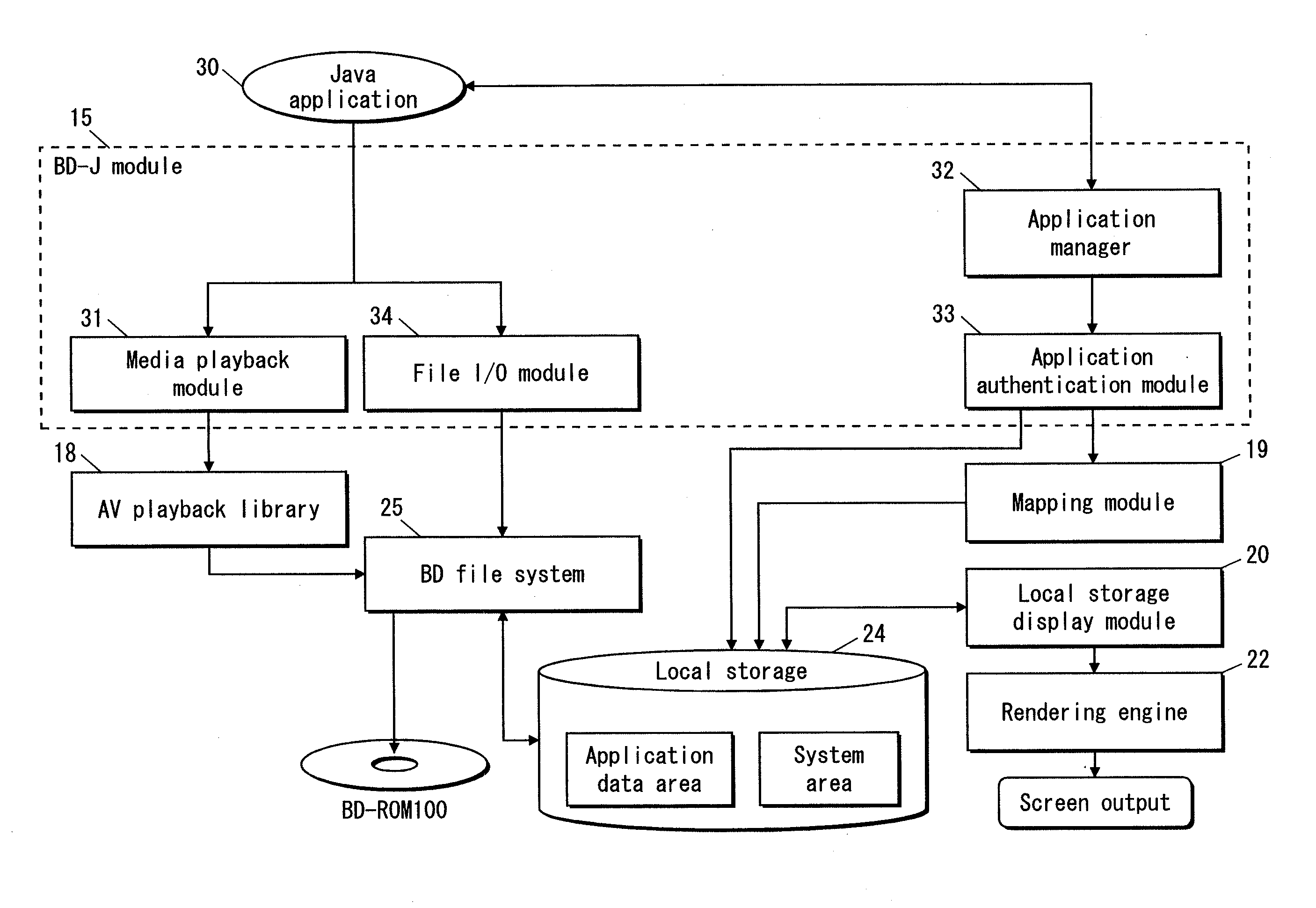
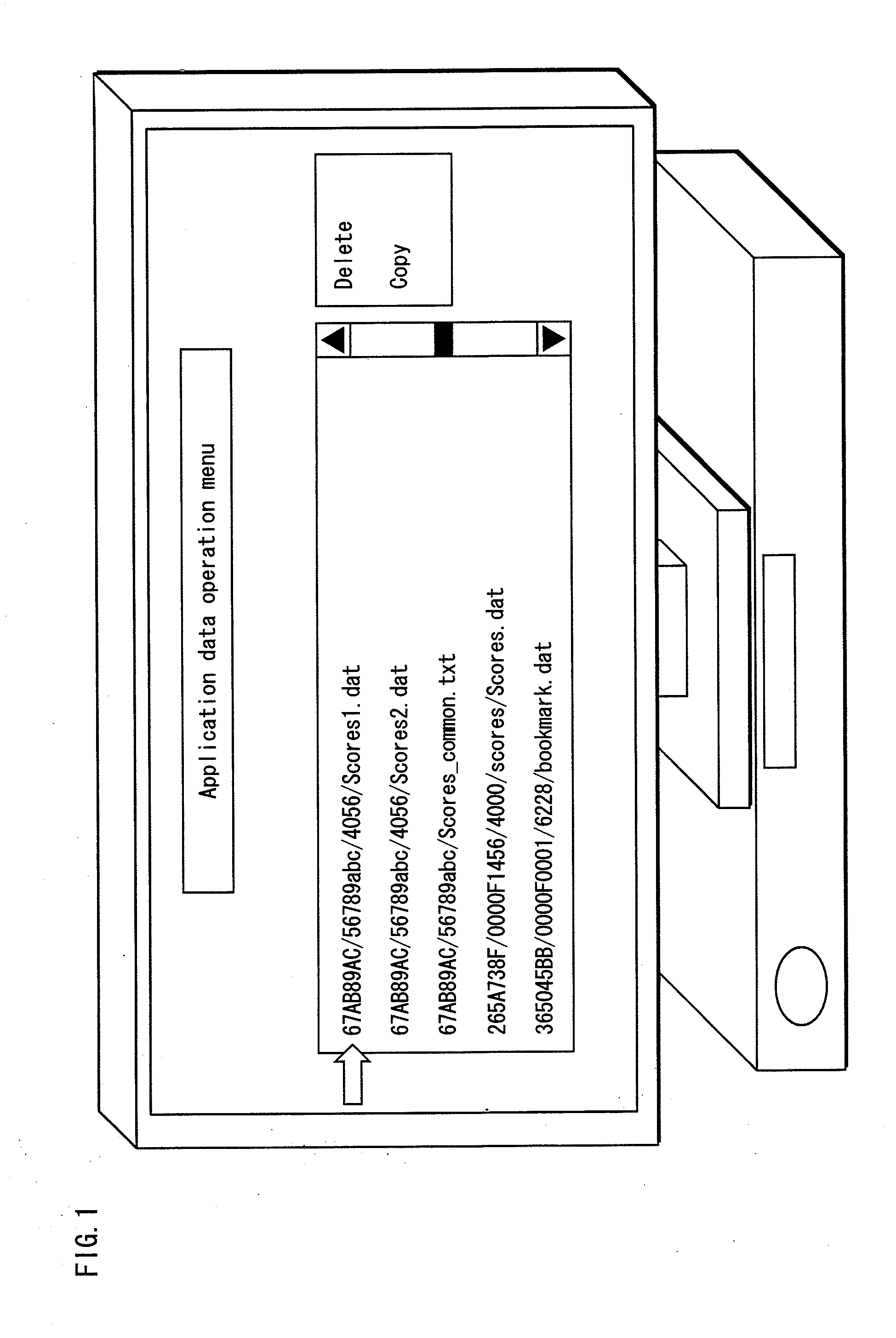
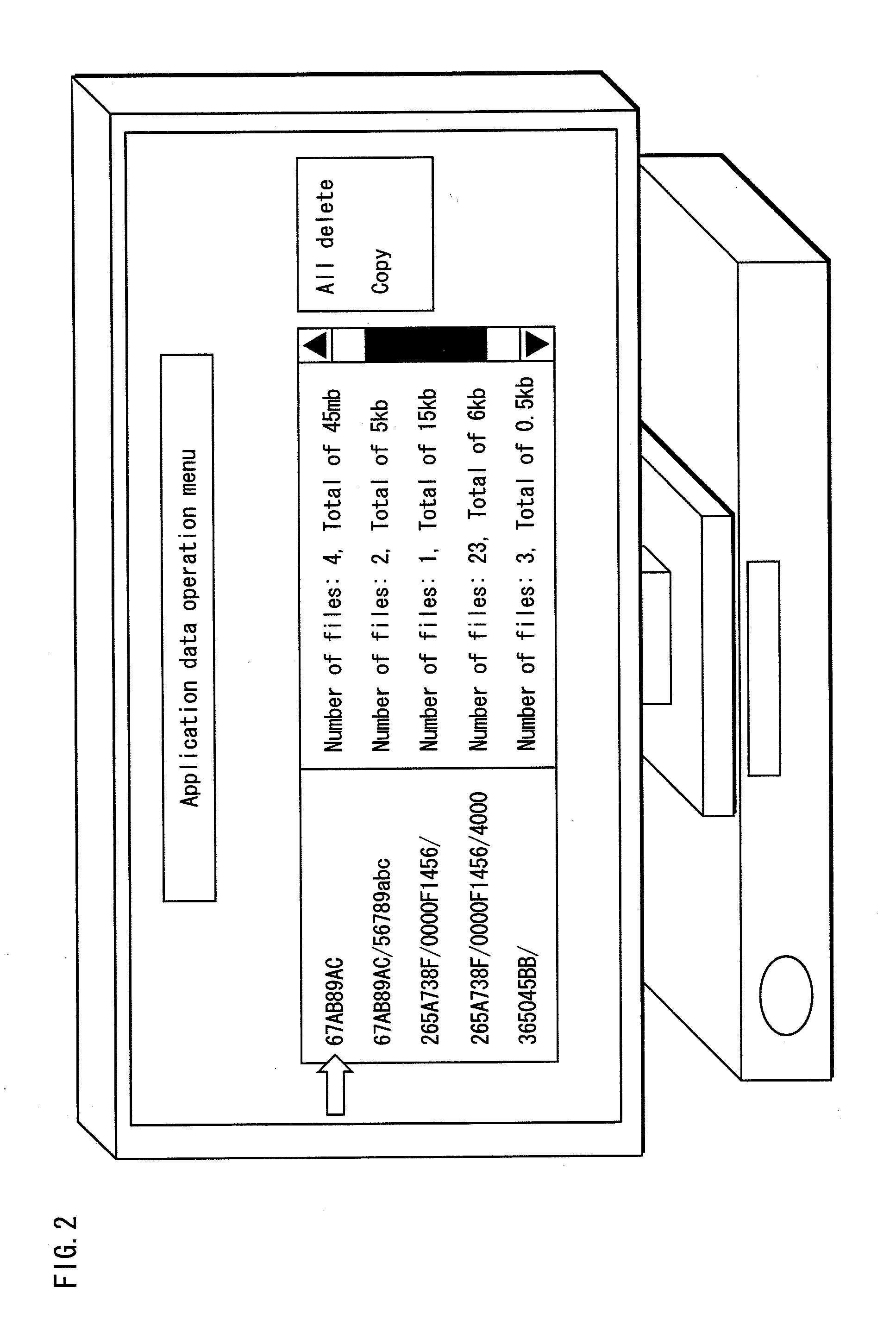
InactiveUS20100138933A1Restricted accessAccurate informationDigital data processing detailsUser identity/authority verificationApplication softwareSubject Name
Provided is a data management device for managing data recorded onto a readable and writable recording medium by an application that is verified based on a digital certificate. The recording medium has a plurality of areas and access to each area is restricted to a different application. The data management device includes an application authentication module, a mapping module, and a local storage display module. The application authentication module verifies that an application is an authentic application based on a digital certificate attached to the application. The mapping module associates, if the application is verified, an area accessible by the application with a subject name described in the digital certificate used for the verification. The local storage display module displays information regarding the area accessible by the application, with the use of the subject name associated with the area.
Owner:SOVEREIGN PEAK VENTURES LLC
Protective elastic sleeve
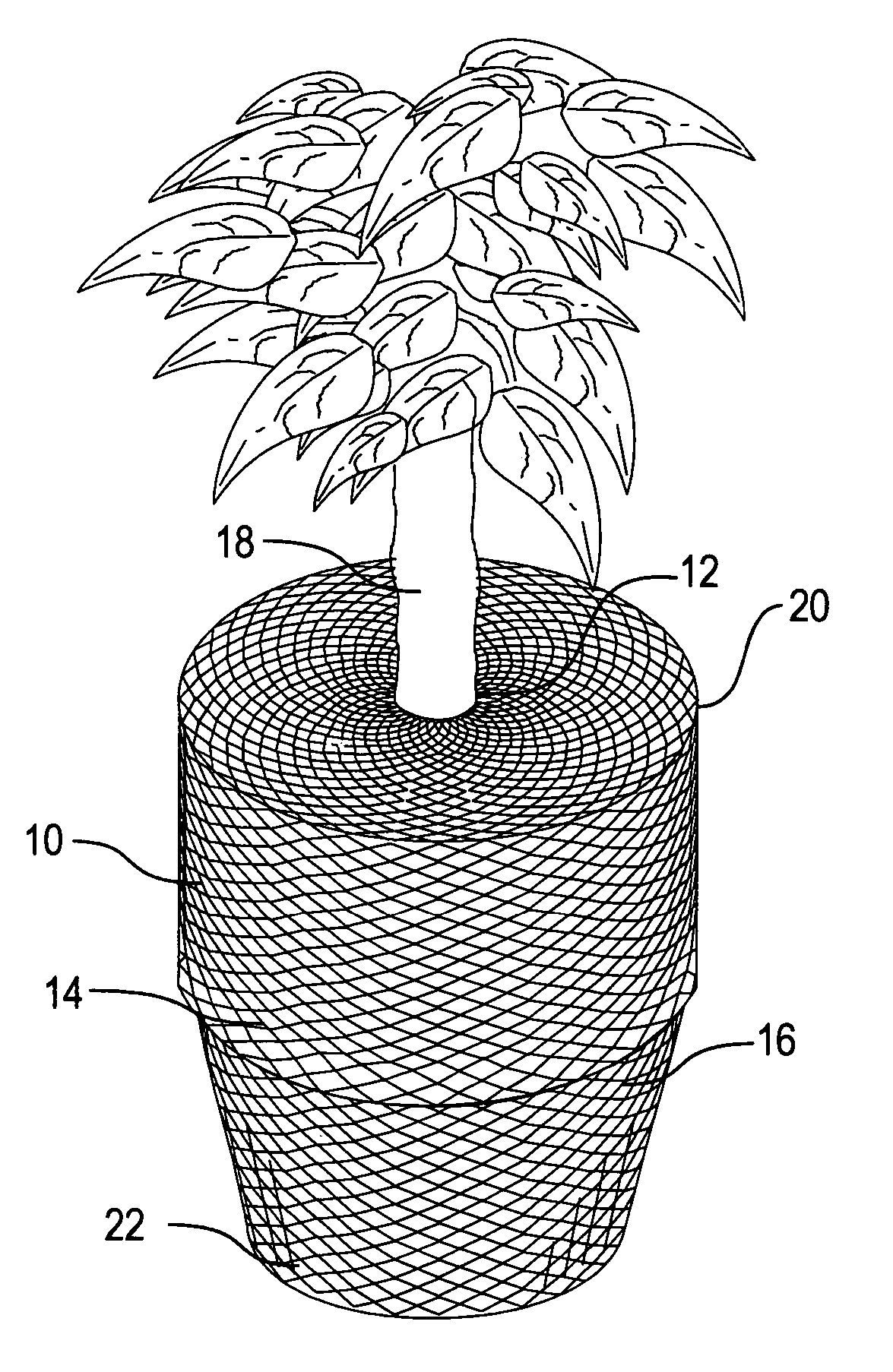
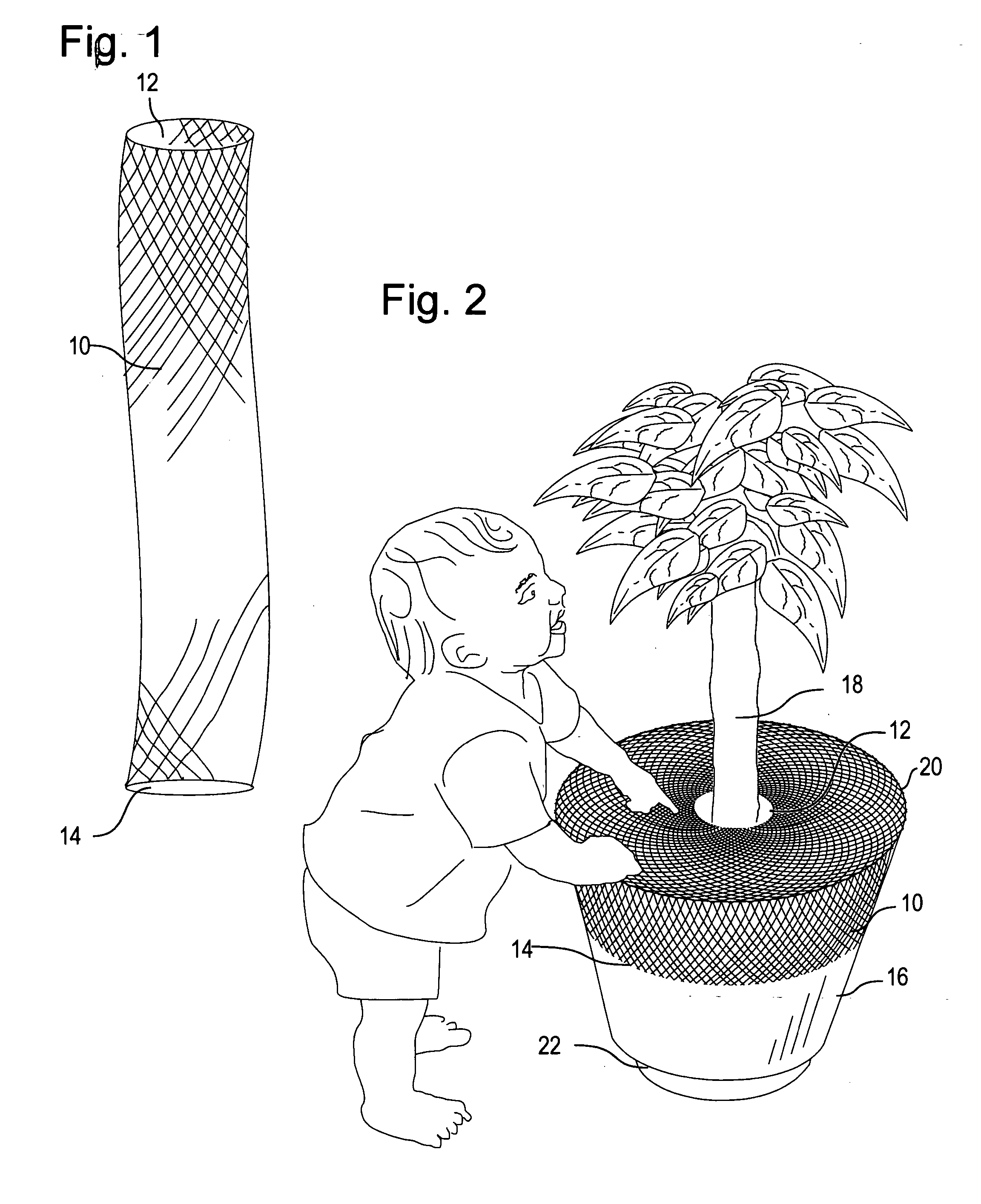
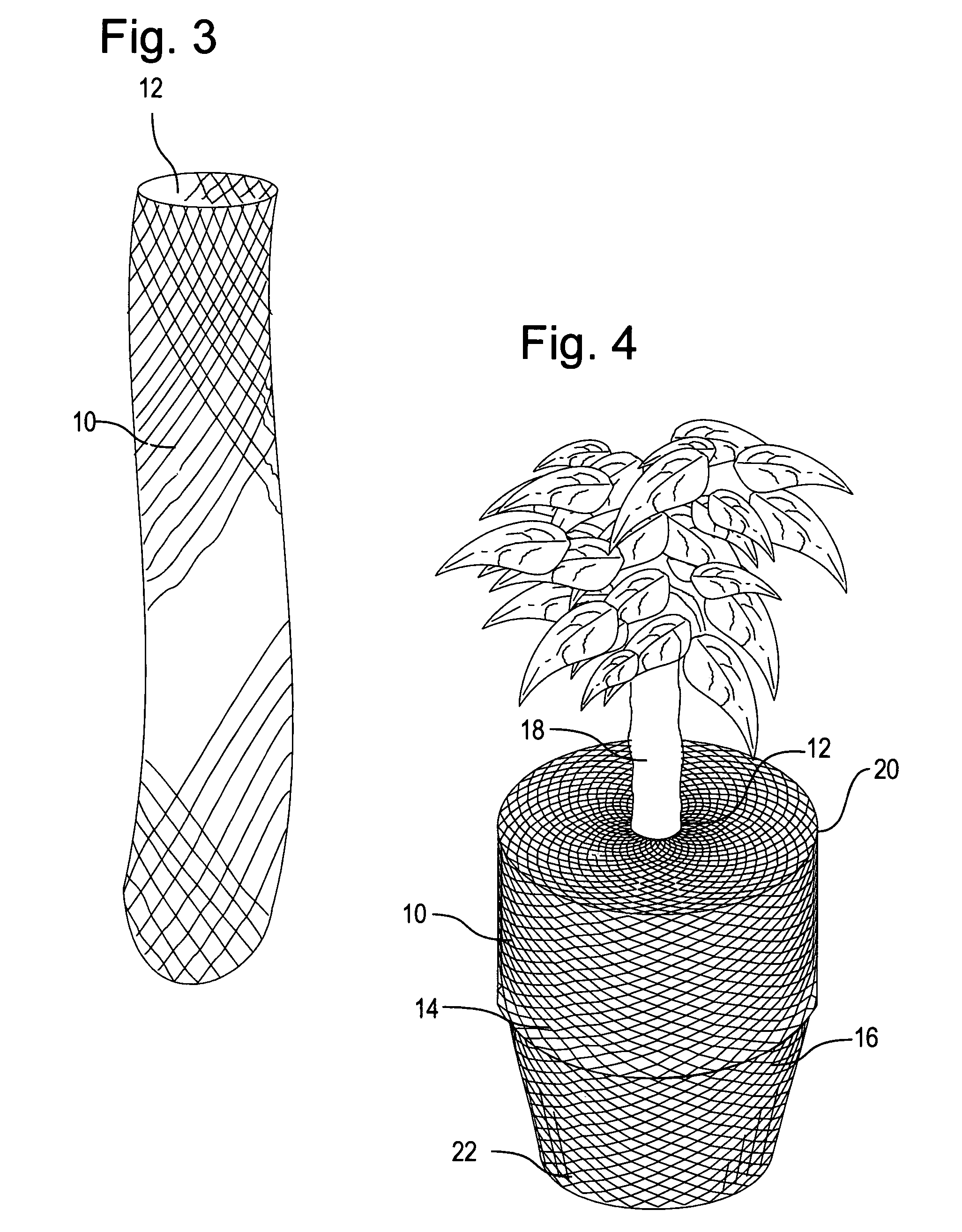
InactiveUS20060032133A1Restricted accessLimited accessFlower holdersCultivating equipmentsEngineering
A method of isolating plant potting material from humans and animals, comprising: Having a pot with a bottom and a wall extending vertically upwards from the bottom, and an open top. The pot is containing soil and a plant which extends vertically upwards from the soil. A porous elastic sleeve having an opening on at least one end of the sleeve is stretchied over the wall of the pot. The sleeve is extending along the wall until a partial length of the sleeve, including said opening, extends above an upper edge of the pot. The above-the-upper-edge-extending sleeve is released over the top of the pot, so that a perimeter of opening recovers towards an unstretched perimeter of said opening, to thereby at least partially cover said open top of the pot and restricts access to the potting material.
Owner:TUORINIEMI VEIJO MATIAS +1
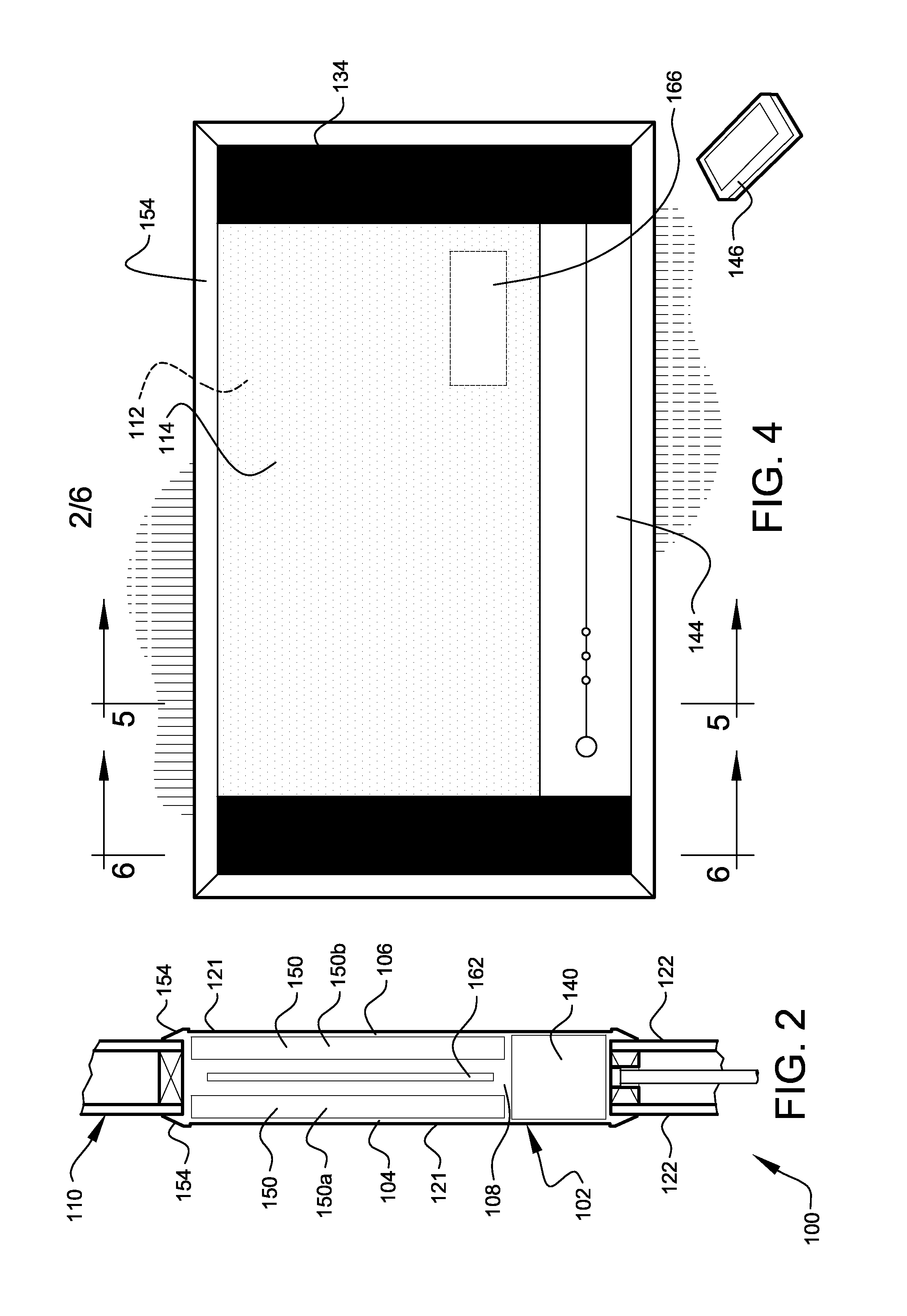
Electronic image display systems
InactiveUS8593578B1Restricted accessTelevision system detailsProjectorsComputer graphics (images)Image display
Owner:GERONIMI HEATHER A
Electrical Outlet Cover with Safety Lock
An outlet cover for an electrical outlet. The outlet cover includes a plate having at least one opening sized and positioned to receive an electrical outlet, a lid hingedly attached to the plate so that the lid can be moved between an open position that allows access to the electrical outlet and a closed position wherein the lid is in a locked position covering the electrical outlet, and a locking assembly having a locking pin. The lid includes a latch which cooperates with the locking pin in order to lock the lid in a closed position or release the lid for opening it for access to the electrical outlet.
Owner:STAYCONNECT
Compound profile modifying/water plugging agent
ActiveCN103911134ALittle external influenceHigh viscosityDrilling compositionTemperature resistanceOrganic chemistry
The invention provides a compound profile modifying / water plugging agent. The compound profile modifying / water plugging agent comprises the following components in percentage by mass: 0.5-5% of pre-crosslinked particles, 0.1-0.3% of polyacrylamide, 0.1-0.4% of crosslinking agent, 0.04-0.5% of regulator and the balance of water. A preparation method of the compound profile modifying / water plugging agent comprises the following steps of adding a certain quantity of polyacrylamide into water by using a jet mixing hopper, and dissolving polyacrylamide for 30min; then, adding a certain quantity of pre-crosslinked particles, crosslinking agent and regulator, and uniformly stirring. The profile modifying / water plugging agent is good in profile modifying effect, capable of increasing the oil yield and reducing the water content, excellent in salt and temperature resistance, low in cost and simple in preparation method.
Owner:BEIJING ENRUIDA TECH
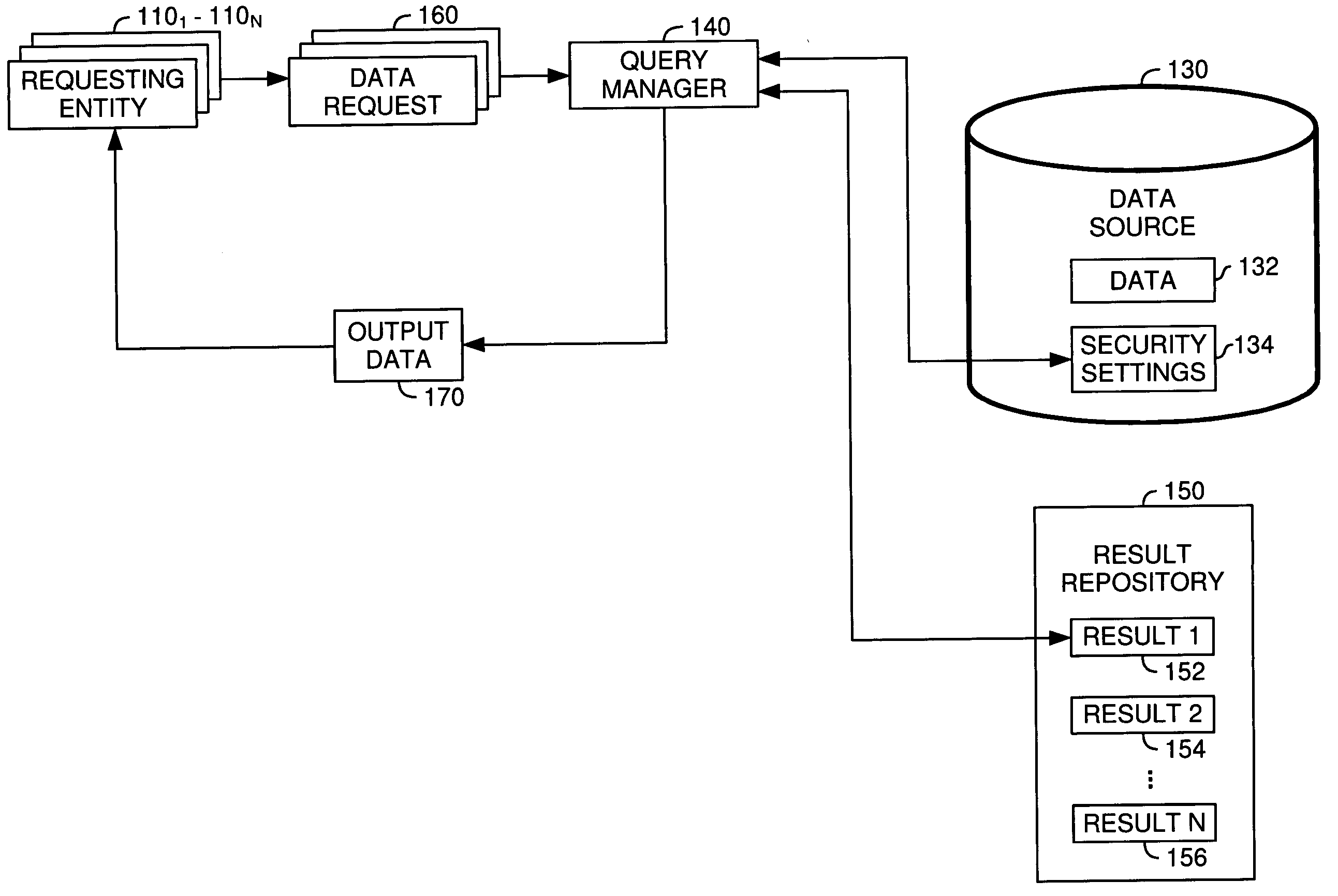
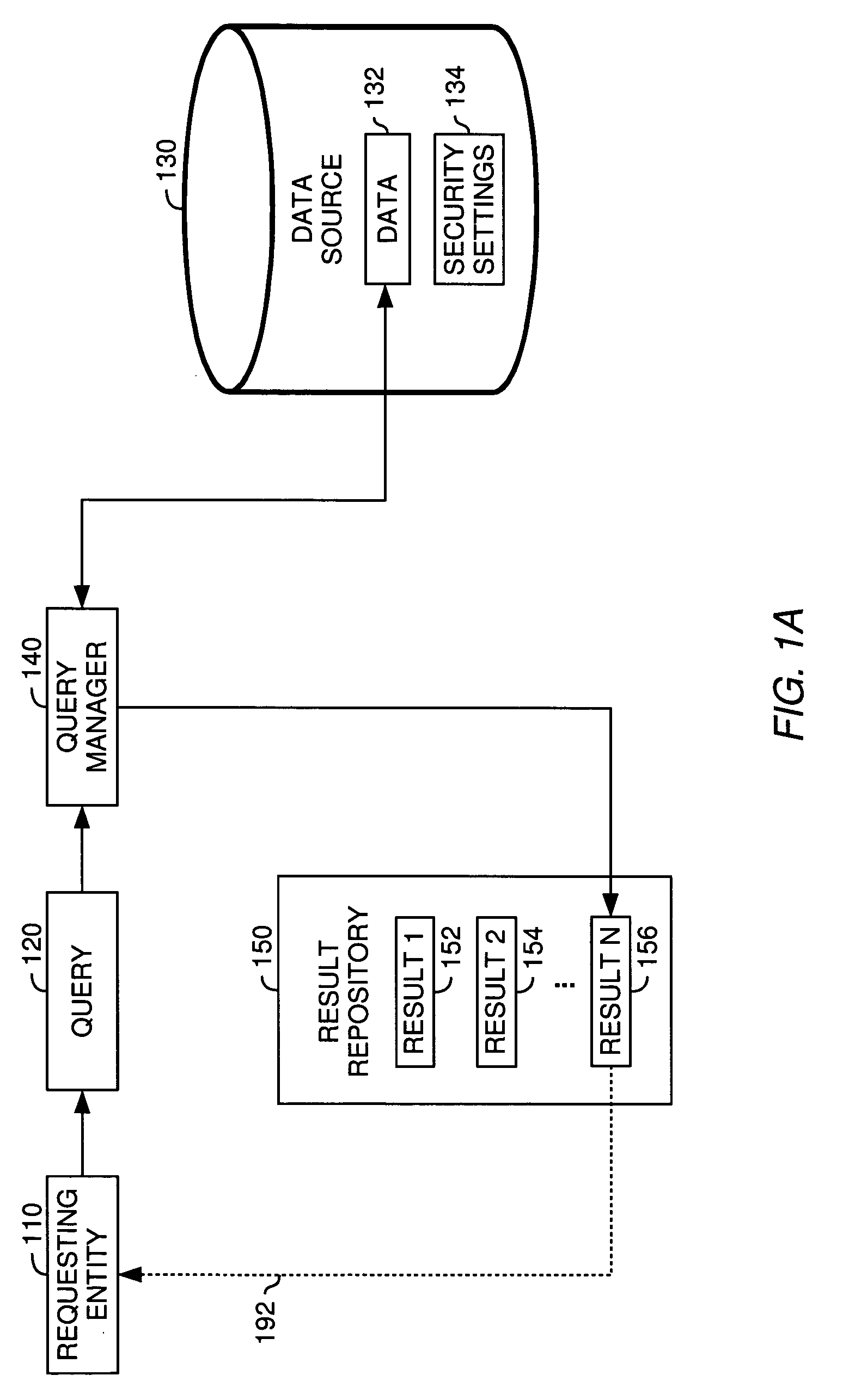
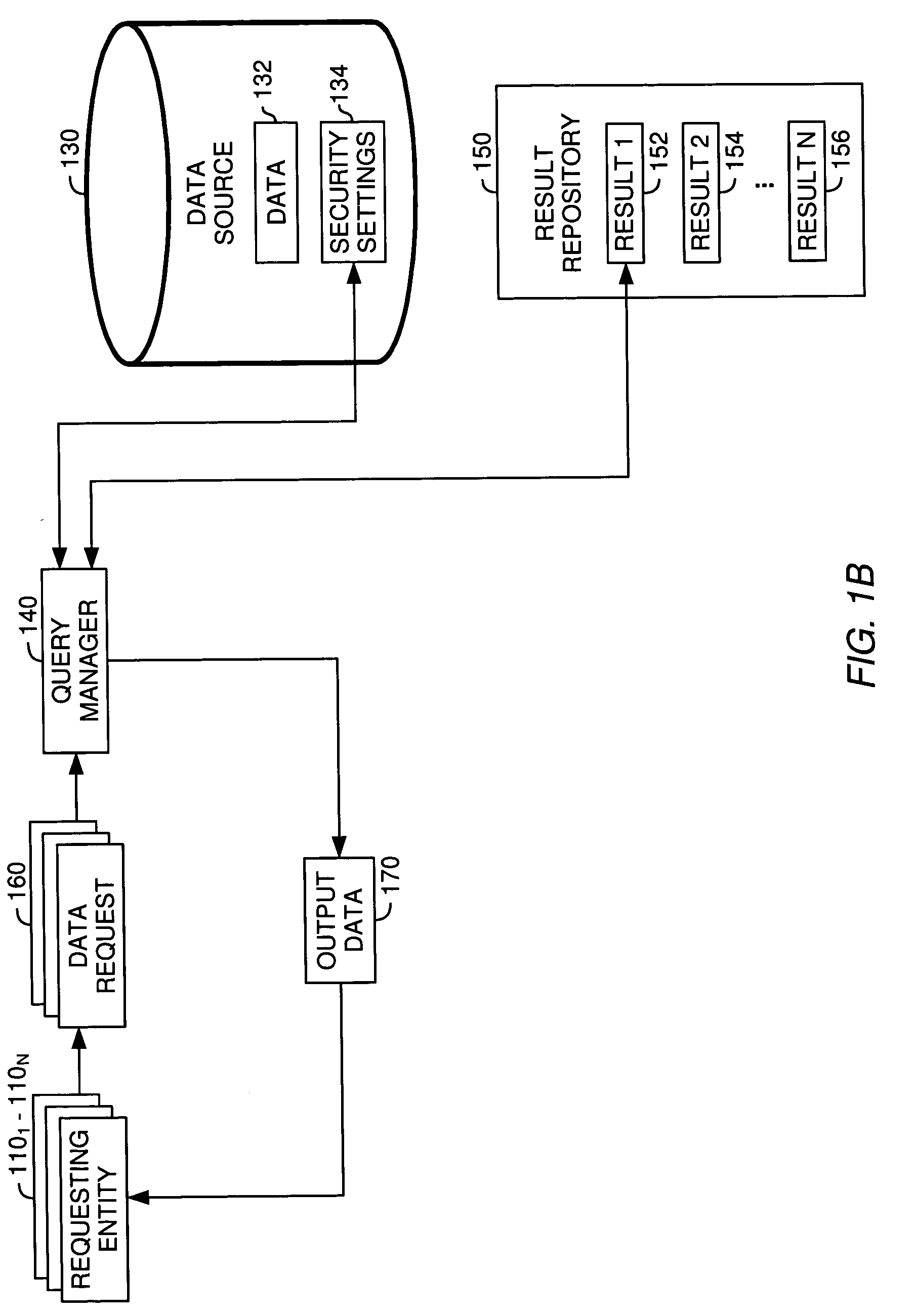
Techniques for sharing persistently stored query results between multiple users
InactiveUS20050289144A1Managing accessRestricted accessComputer security arrangementsSpecial data processing applicationsSecurity informationDatabase
A method, system and article of manufacture for managing access to query results and, more particularly, for managing access by multiple users to persistently stored query results, whereby at least some of the users may have different access rights. One embodiment provides a method of managing access to a query result obtained upon execution of a query against one or more databases. The method comprises creating security information configured for restricting access to the query result. The security information is associated with the query result. Access to some or all of the query result is granted to a requesting entity on the basis of the security information and an attribute of the requesting entity.
Owner:SERVICENOW INC
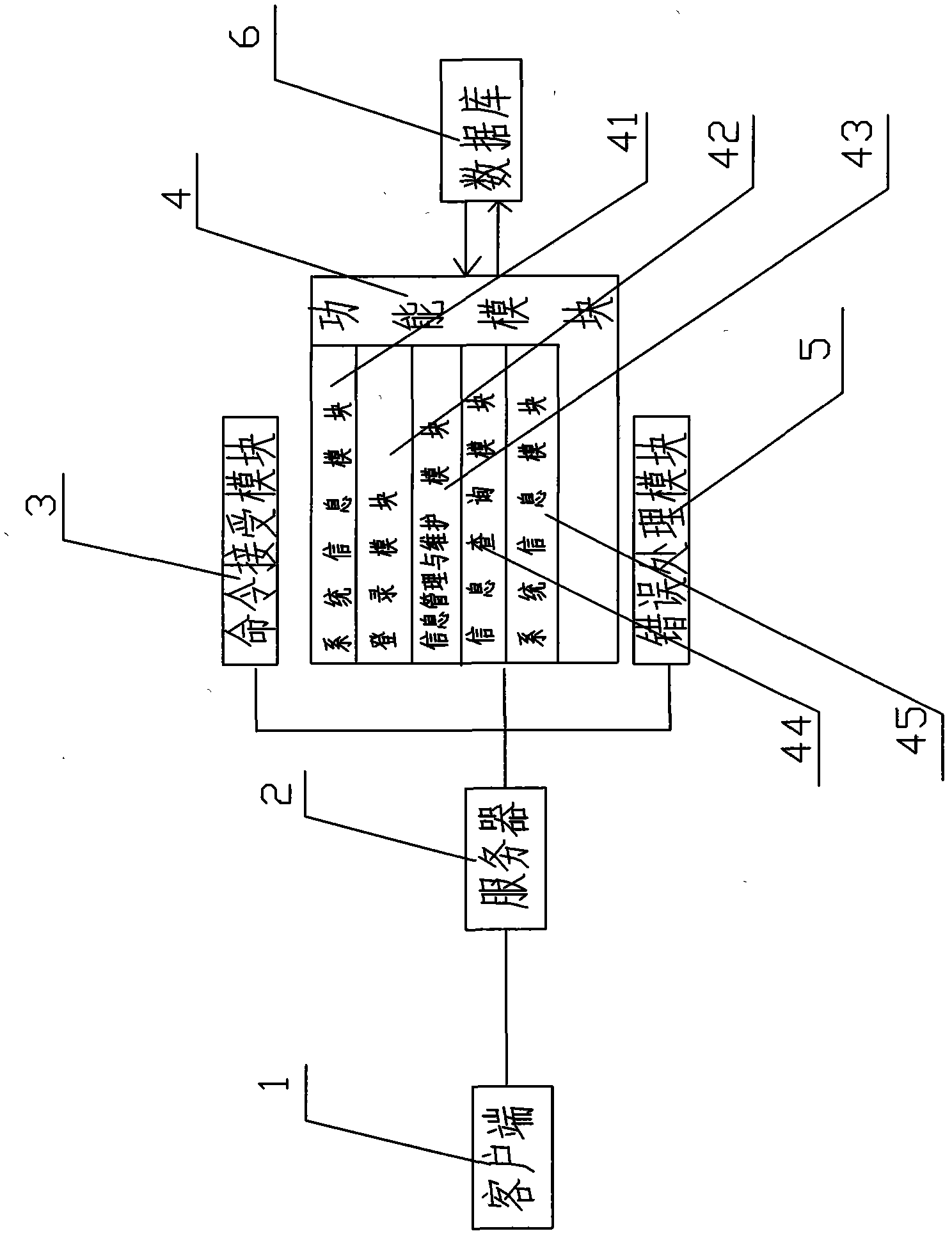
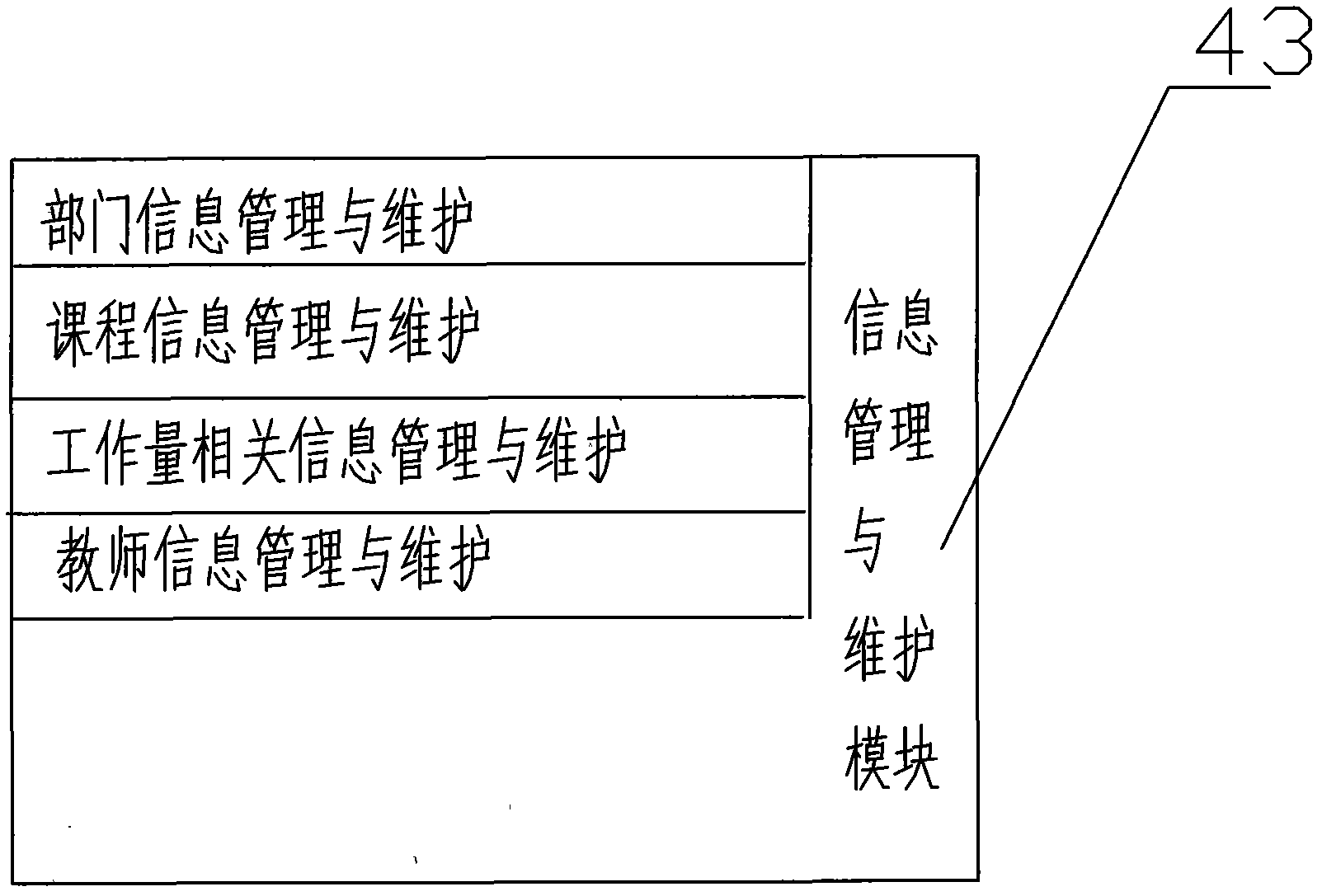
Computer automatic management system for teaching load
InactiveCN102103735AAutomate managementStrong distributionData processing applicationsClient-sideData information
The invention discloses a computer automatic management system for teaching load, which relates to the field of design of a computer automatic system. The system adopts a B / S structure and comprises a plurality of clients (1) and a server (2). A user can realize entering, storage, edition, accurate inquiry and fuzzy inquiry of basic data in combination with different rights, can directly print a report according to inquired data and can update various data information related to work load calculation in time, the requirement on statistics and management of teaching load in a school is well met, and computer automatic management on the teaching load is realized.
Owner:SHANDONG ELECTRIC POWER SCHOOL
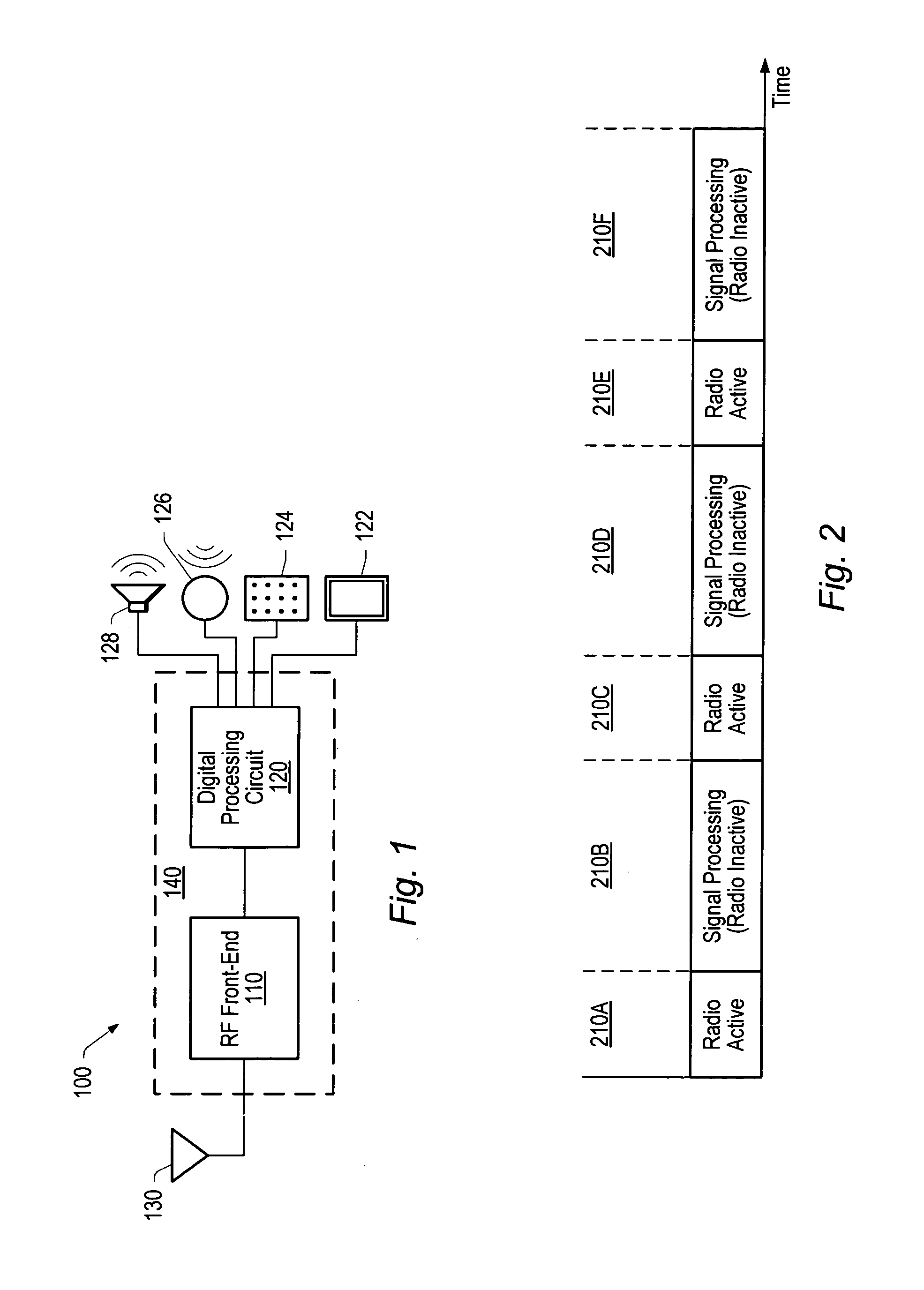
Communication apparatus implementing time domain isolation with restricted bus access
ActiveUS20050228913A1Restricted accessPower managementTwo-way working systemsTime domainRadio frequency signal
A communication apparatus includes a radio frequency circuit that operates on a radio frequency signal and a digital processing circuit coupled to the radio frequency circuit. The digital processing circuit includes a plurality of bus masters coupled to a shared bus. A bus arbiter is provided for arbitrating between requests to access the bus by a first bus master and one or more other bus masters. Accesses by the one or more other bus masters to the bus are restricted in response to a signal indicative of a change in a mode of operation of the RF circuit. In one particular implementation, a communication apparatus employs time domain isolation wherein the digital processing circuit may be placed in a shutdown mode when the radio frequency circuit is active.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method for running bridge plug sitting tool by means of differential pressure and bridge plug sitting tool utilized by same
ActiveCN102635328ARestricted accessThe sealing process is stableSealing/packingUpper jointDifferential pressure
The invention relates to a method for running a bridge plug sitting tool by means of differential pressure and a bridge plug sitting tool used by the same. When a bridge plug is sit, the bridge plug is electrified from the ground through a cable, an electromagnetic valve is turned on or a rupture disk is ruptured, a liquid inlet hole is opened, or a clock is turned on to drive an upper mandrel to move, annulus fluid enters into the tool to drive a piston to move upwards due to the differential pressure with an air chamber, the bridge plug is sit, and the piston moves continuously and upwards so as to be released from the bridge plug. The bridge plug sitting tool has three types such as an electromagnetic valve control type, a rupture disk control type and a clock control type, and consists of a cable connecting joint, an upper joint, an upper outer cylinder, a middle outer cylinder, a lower outer cylinder, an adjusting nut, a push rod, one bridge plug connecting joint, an internally-arranged electromagnetic valve, an internally-arranged contact switch, an upper mandrel, a piston, an upper piston rod, a lower piston rod, another bridge plug connecting joint and the like which are in threaded connection with one another. According to the invention, the bridge plug is stable in sitting process, and small in vibration, and when the bridge plug is connected with a perforation hole in parallel, a perforation apparatus can not be vibrated to be broken; and when the bridge plug is released, the contact switch can be touched, so that a conducting wire is disconnected, and the tool provided by the invention is obvious in ground display.
Owner:CHINA PETROLEUM & CHEM CORP +1
Method and apparatus for resisting hardware hacking through internal register interface
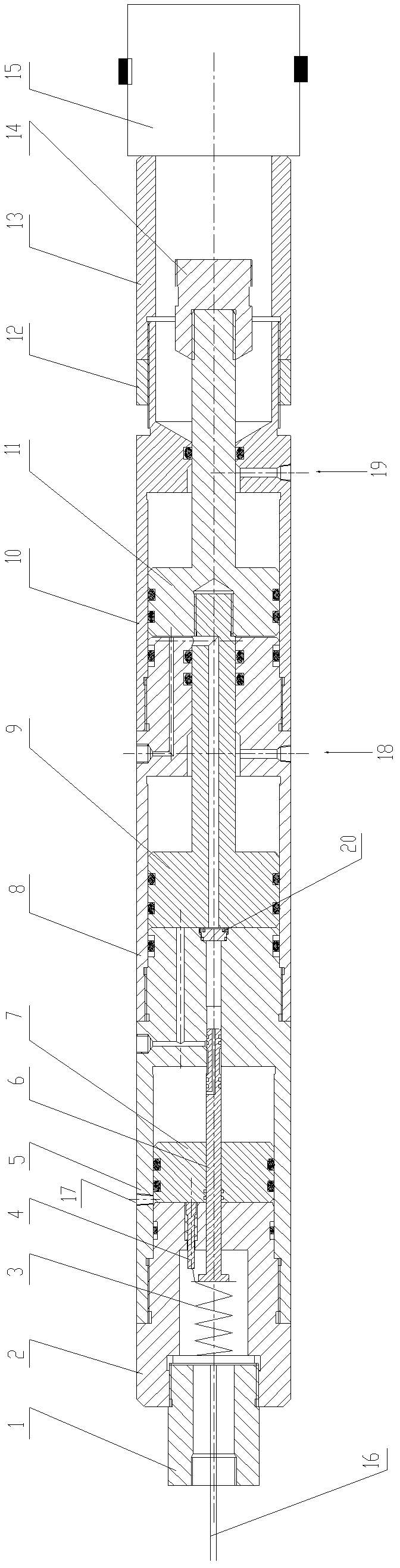
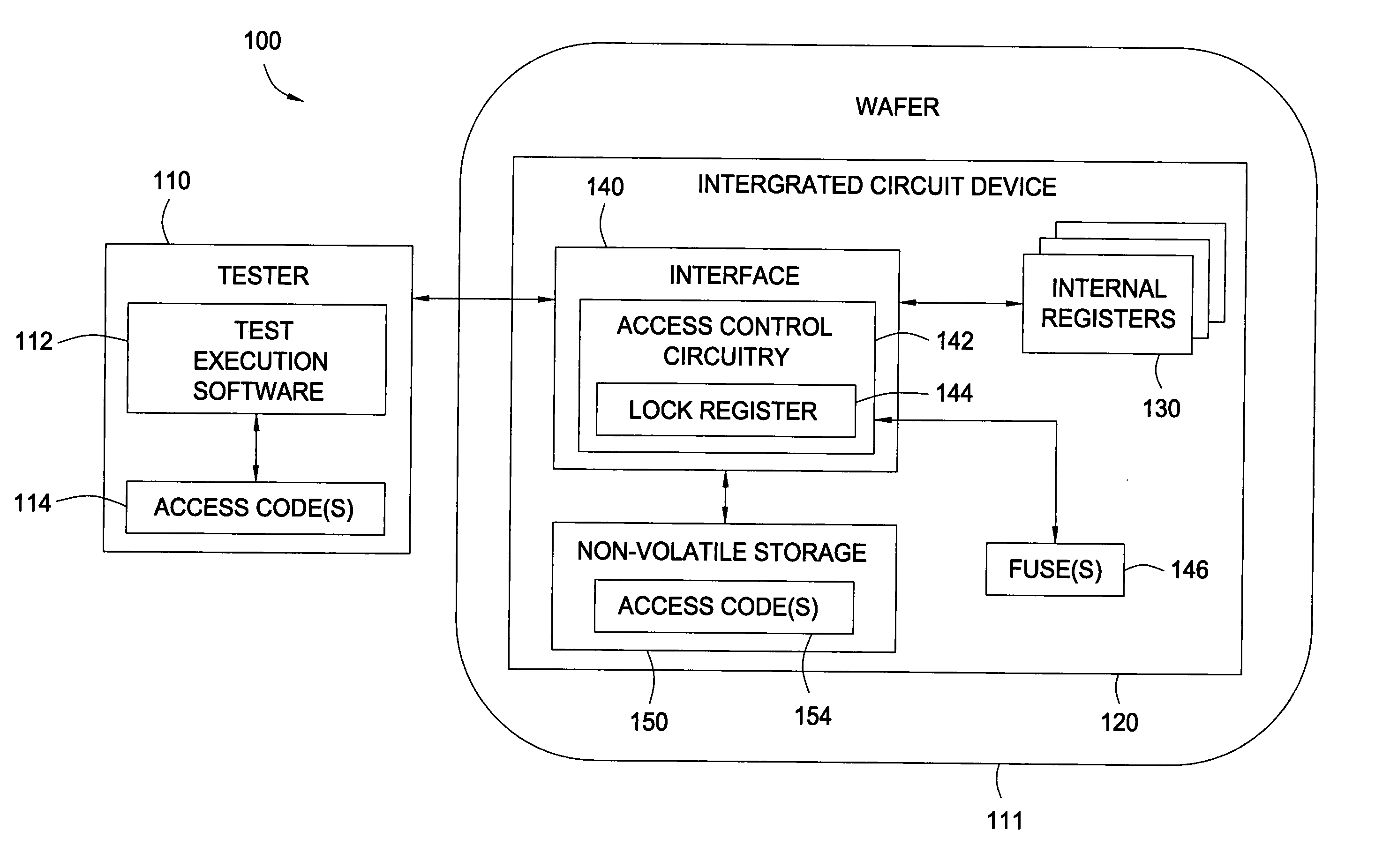
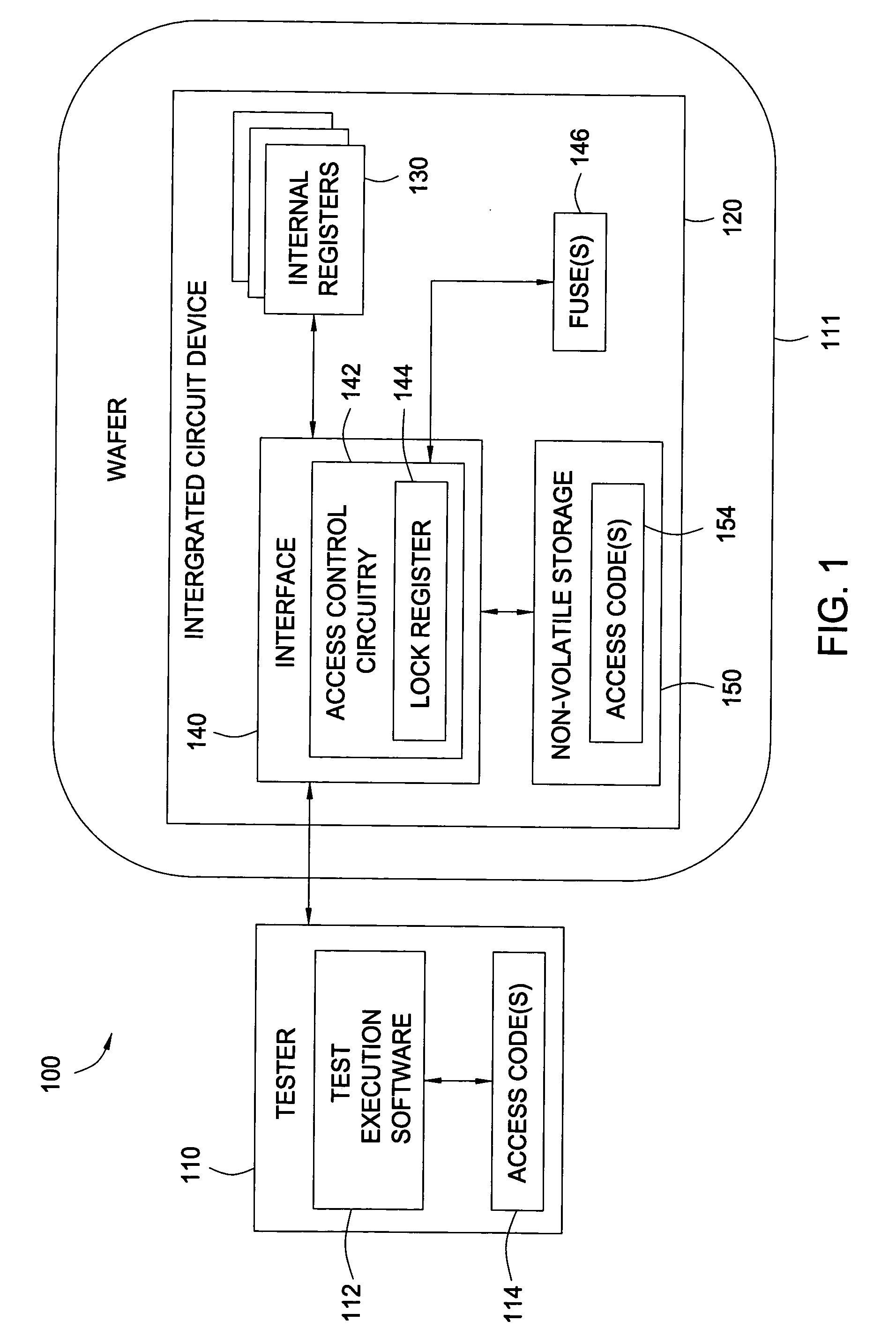
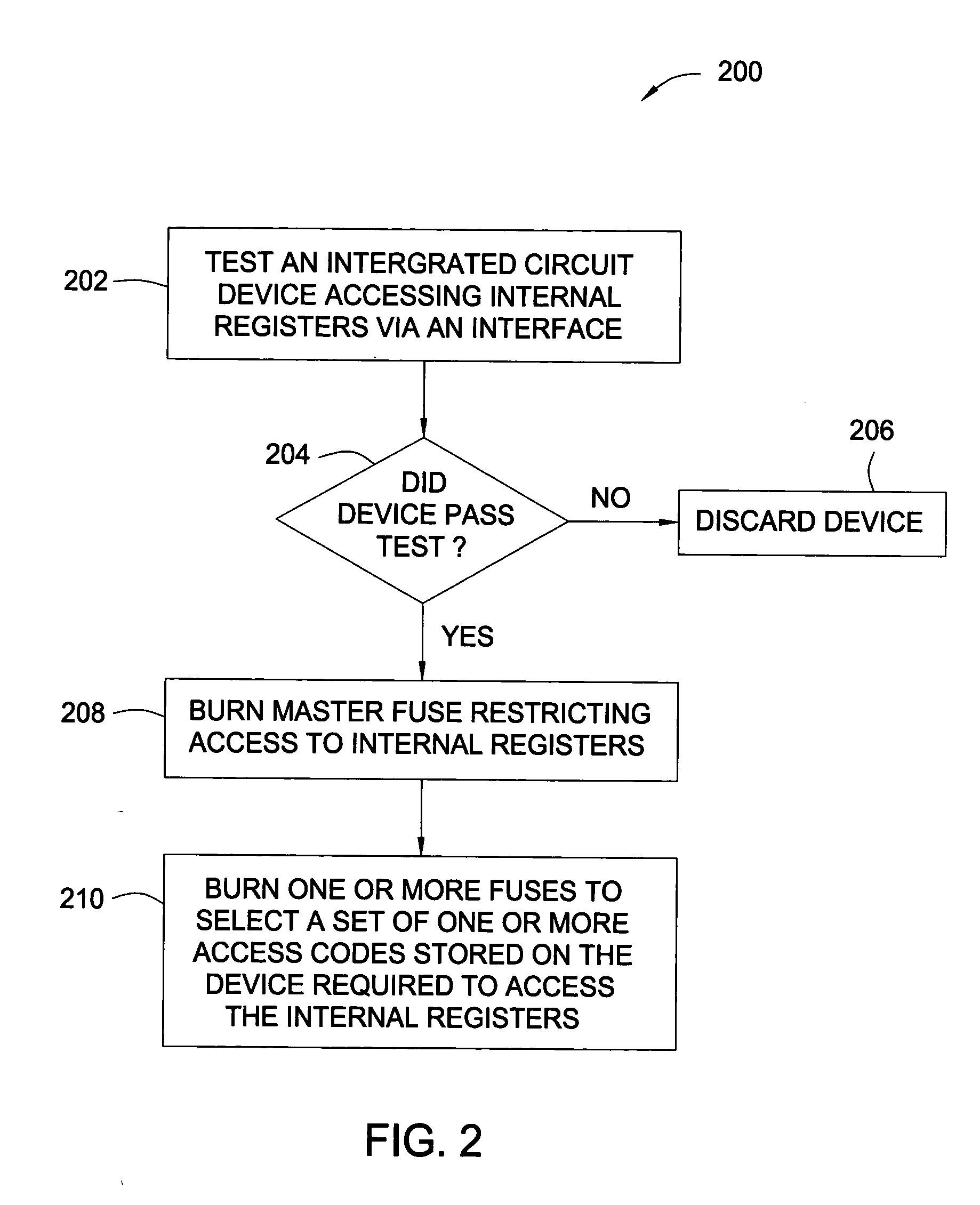
ActiveUS20050242924A1Restricted accessElectric signal transmission systemsMultiple keys/algorithms usageIntegrated circuitComputer hardware
Methods and apparatus that allow restricted access to internal registers of an integrated circuit (IC) device via an interface are provided. Unrestricted access to internal registers via the interface may be allowed during a manufacturing process to allow device testing. After such testing is complete, the device may be placed in a restricted access mode, for example, by blowing a master “lock” fuse, to prevent unrestricted access to one or more of the internal registers via the interface. However, full or partial access to the internal registers may still be provided via an access code or “combination lock” allowing the master fuse lock, in effect, to be bypassed.
Owner:IBM CORP
Mobile terminal webpage display control method and device
InactiveCN102054030ARestricted accessImprove experienceSubstation equipmentSpecial data processing applicationsUser inputWeb page
Owner:HUIZHOU TCL MOBILE COMM CO LTD
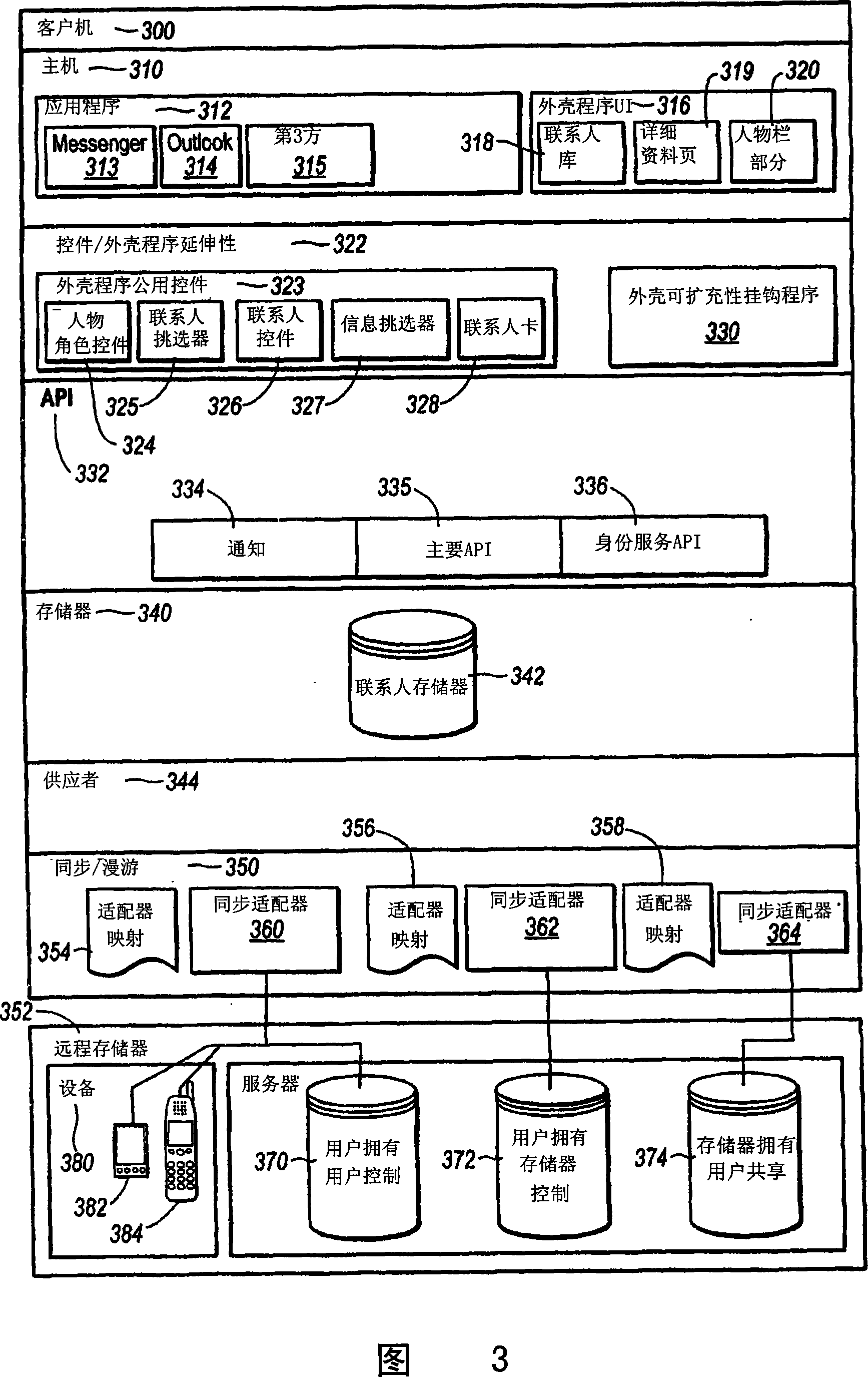
Contact management
InactiveCN101095161ARestricted accessDigital data processing detailsSubstation equipmentSoftware engineeringMechanical engineering
Owner:MICROSOFT CORP
Nano silicon dioxide modified polyurethane composite material
The invention discloses a nano silicon dioxide modified polyurethane composite material comprising the raw materials: polytetrahydrofuran glycol, hydroxyl-terminated polyepichlorohydrin, isocyanate, epoxy resin, a chain extender, 1H,1H,8H,8H-dodecafluoro-1,8-octanediol, a catalyst, polypropylene, a maleic anhydride grafted ethylene-octene copolymer, an acrylonitrile-styrene-butadiene copolymer, ethylene-propylene-diene rubber, organic modified nano silicon dioxide, tetrapod-like zinc oxide whiskers, graphene oxide, carbon nanotubes, expanded graphite, tris(2-chloroethyl) phosphate, triphenyl phosphite, tris(2,4-di-tert-butylphenyl)phosphite, di(octane phenol polyoxyethylene)phosphate, polythiazole, and a silane coupling agent. The nano silicon dioxide modified polyurethane composite material provided by the invention has the advantages of excellent heat resistance, good flame retardancy, good water resistance, and high strength.
Owner:CHUZHOU GLOBAL POLYURETHANE TECH CO LTD
Process and system for treating ethylene tar
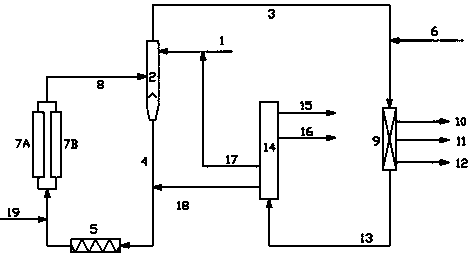
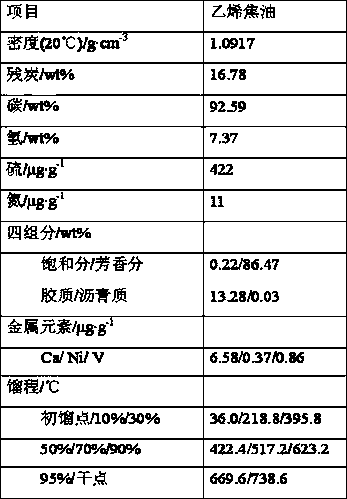
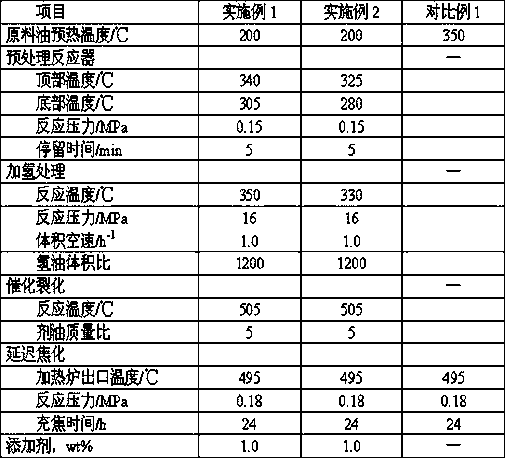
ActiveCN109929592APlay a role in strippingRestricted accessTreatment with hydrotreatment processesCracking reactionTreatment system
The invention discloses a process and a system for treating ethylene tar. According to the process, preheated ethylene tar contacts a coking reaction effluent from a delayed coking reaction system ina pretreatment reactor, and a light component and a heavy component are obtained after separation; the heavy component enters the delayed coking reaction system, and the generated coking reaction effluent enters the pretreatment reactor; the light component and hydrogen enter a hydrogenation reaction system, and the reaction effluent is separated to obtain gas, gasoline distillate, diesel oil distillate and heavy oil distillate; and the heavy oil distillate enters a catalytic cracking reaction system, and the catalytic diesel oil obtained after separation enters the pretreatment reaction. Thetreatment system comprises the pretreatment reactor, the coking reaction system, the hydrogenation reaction system, and the catalytic cracking reaction system. With the process and the system of the present invention, the stable long-cycle operation of the whole treatment system can be ensured, and the yield of the light oil product is high.
Owner:CHINA PETROLEUM & CHEM CORP +1
Intelligent entrance guard system
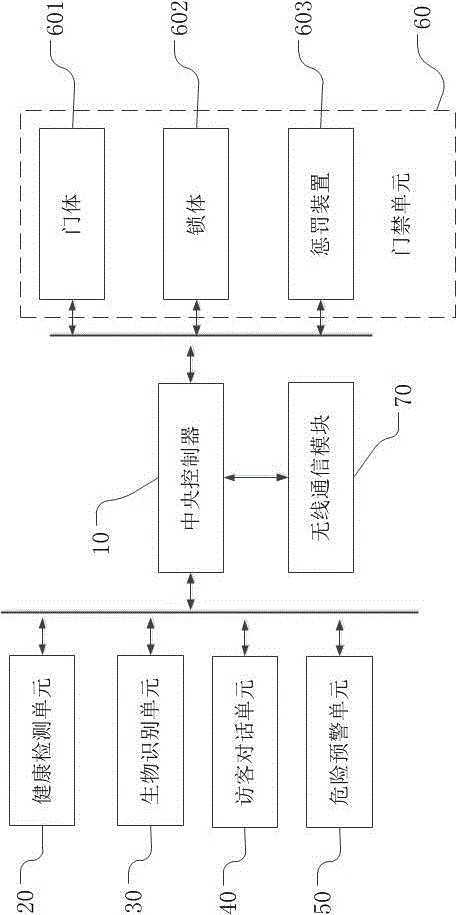
InactiveCN105488888ARestricted accessDefending and defending the safety of persons and propertyIndividual entry/exit registersComputer moduleComputer science
The invention provides an intelligent entrance guard system. The intelligent entrance guard system comprises a central controller, an entrance guard unit, a wireless communication module, a risk prewarning unit, a health detection unit, a biological recognition unit and a visitor conversation unit, wherein the entrance guard unit is a carrier of all functional modules; the risk prewarning unit, the health detection unit, the biological recognition unit and the visitor conversation unit are connected with the central controller. The intelligent entrance guard system can not only restrict in and out by passages but also guard and protect the personal and property security of residents in rooms; the risk prewarning unit is provided to alarm in case of indoor harmful gases, earthquakes, fire hazards and the like and to automatically open the room doors to enable outside air to flow in; the health detection unit is provided to conduct health scanning detection on persons in and out of the passages, so that the self-health attention of people is improved; the biological recognition and visiting functions are also provided, so that the functions are powerful and the use is convenient.
Owner:NINGBO LIKETEK INFORMATION TECH
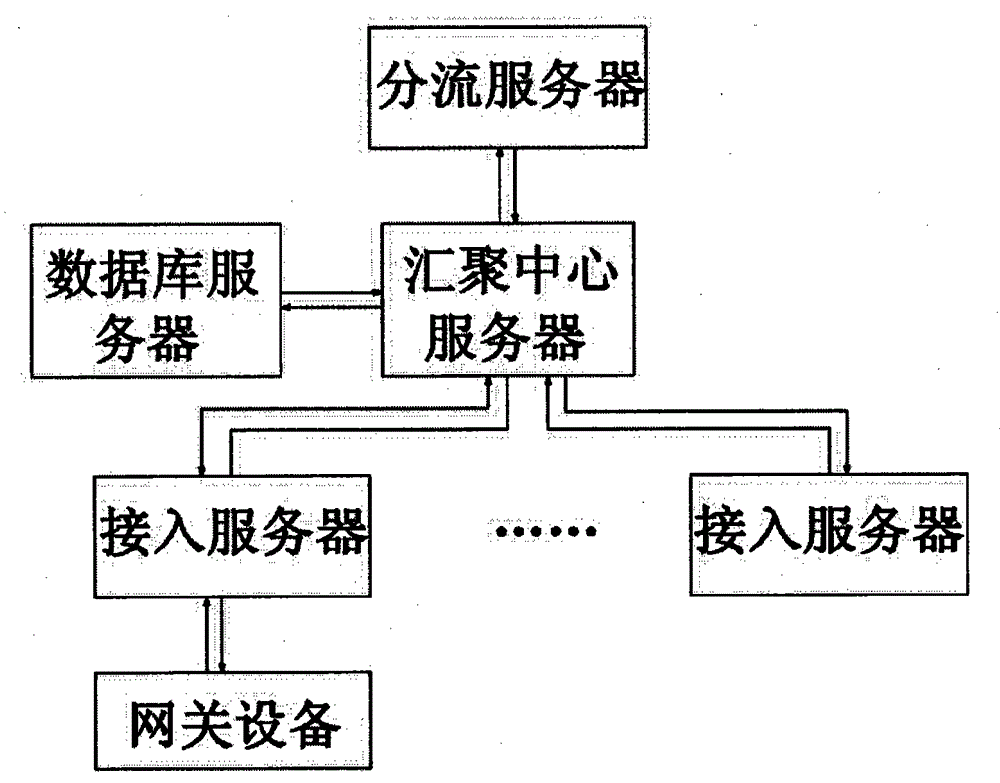
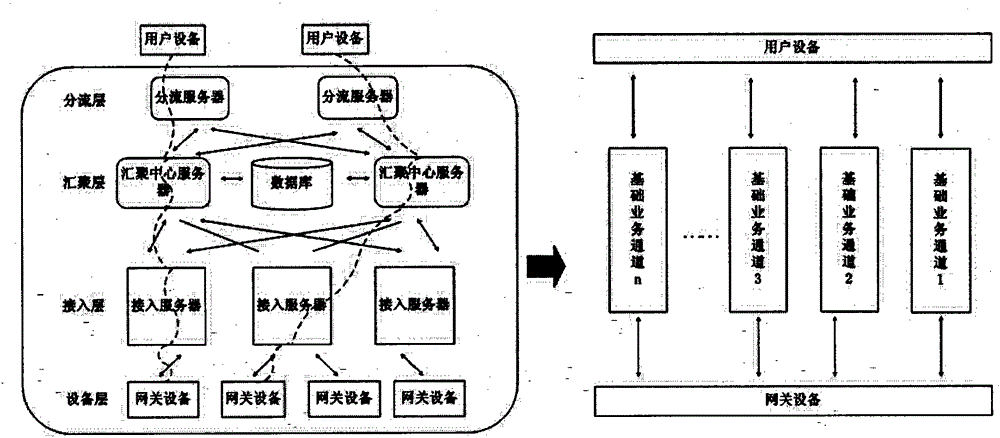
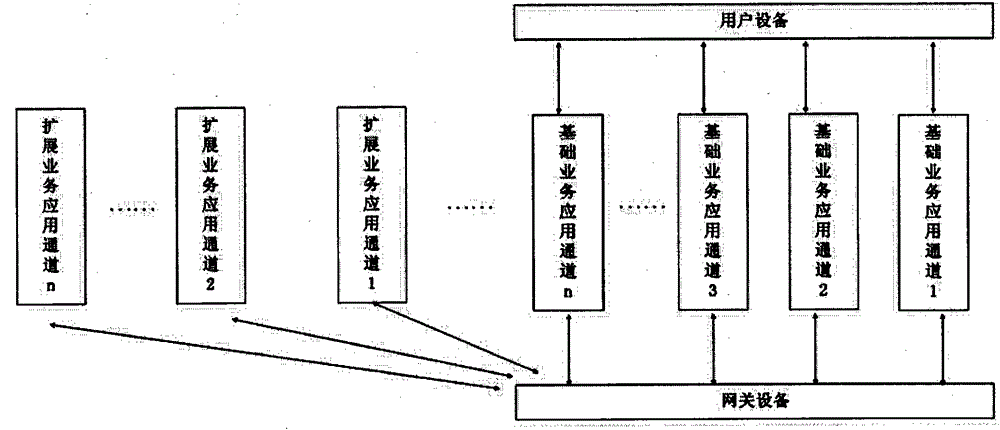
Automatic switchover method of service application channel based on open intelligent gateway platform
InactiveCN104158710AEasy to deployRealize automatic switchingData switching by path configurationComputer networkBasic service
The invention discloses an automatic switchover method of a service application channel based on an open intelligent gateway platform. The automatic switchover method comprises the following steps: S1, a user logs in to an intelligent gateway platform system; S2, user equipment and gateway equipment are bound; S3, a convergent central server transmits user account information to the gateway equipment; S4, the user equipment transmits a command for connection to an extended service application channel to the gateway equipment; S5, the gateway equipment is connected to an access server; S6, the gateway equipment issues a command request to the access server to execute configuration and installation of an extended service application plug-in and a timer is started; and S7, the gateway equipment judges whether the no-operation time between the gateway equipment and the access server exceeds a set time. If so, the gateway equipment and the access server are disconnected, and the gateway equipment automatically switches to a basic service application channel; if not, the step S6 is continued to process until configuration and installation are completed. According to the automatic switchover method, quick and flexible deployment of a new service application of the intelligent gateway platform is implemented, and the automatic switchover method has the advantage of good industrial application prospect.
Owner:SHENZHEN FENGLIAN TECH
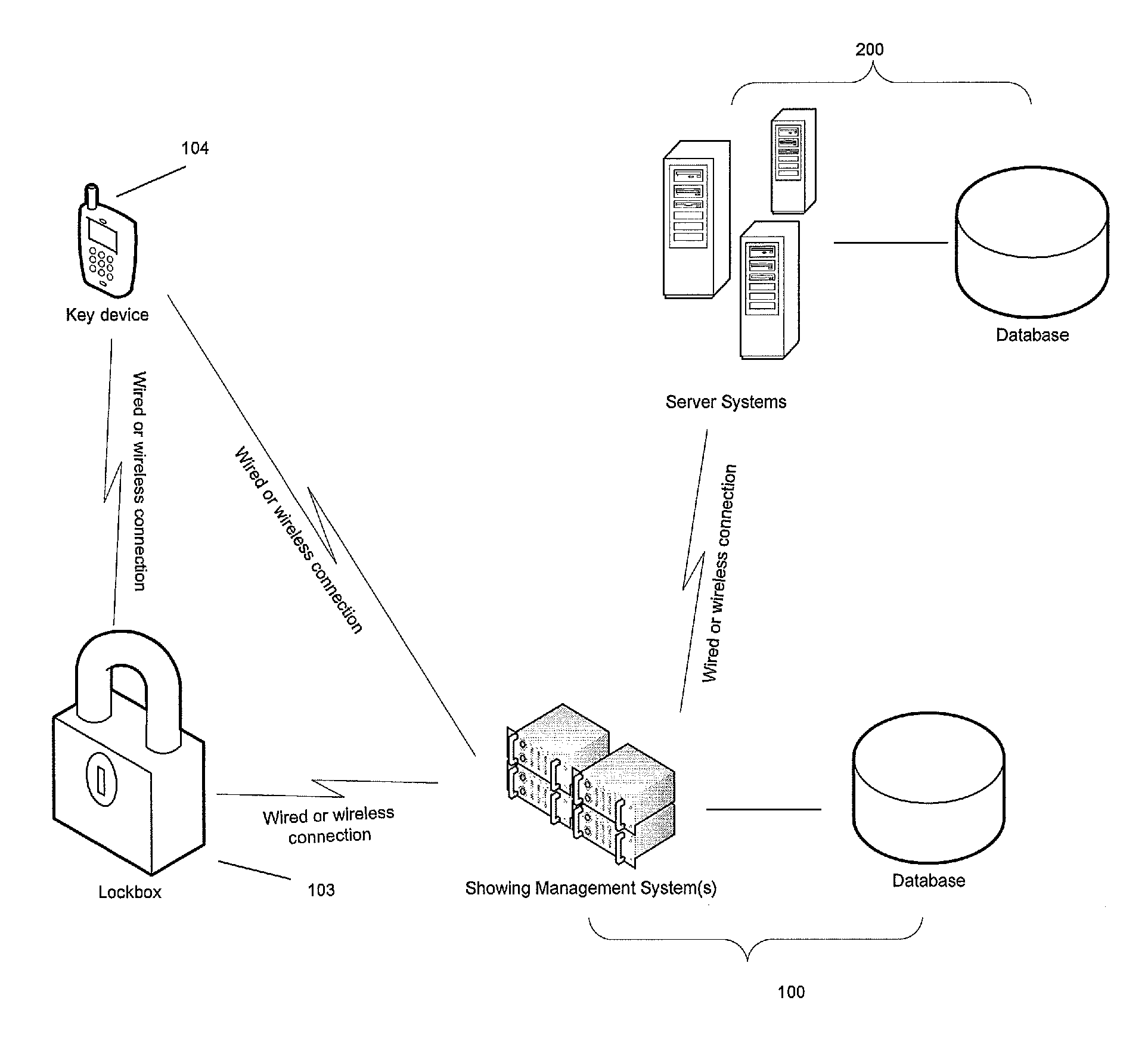
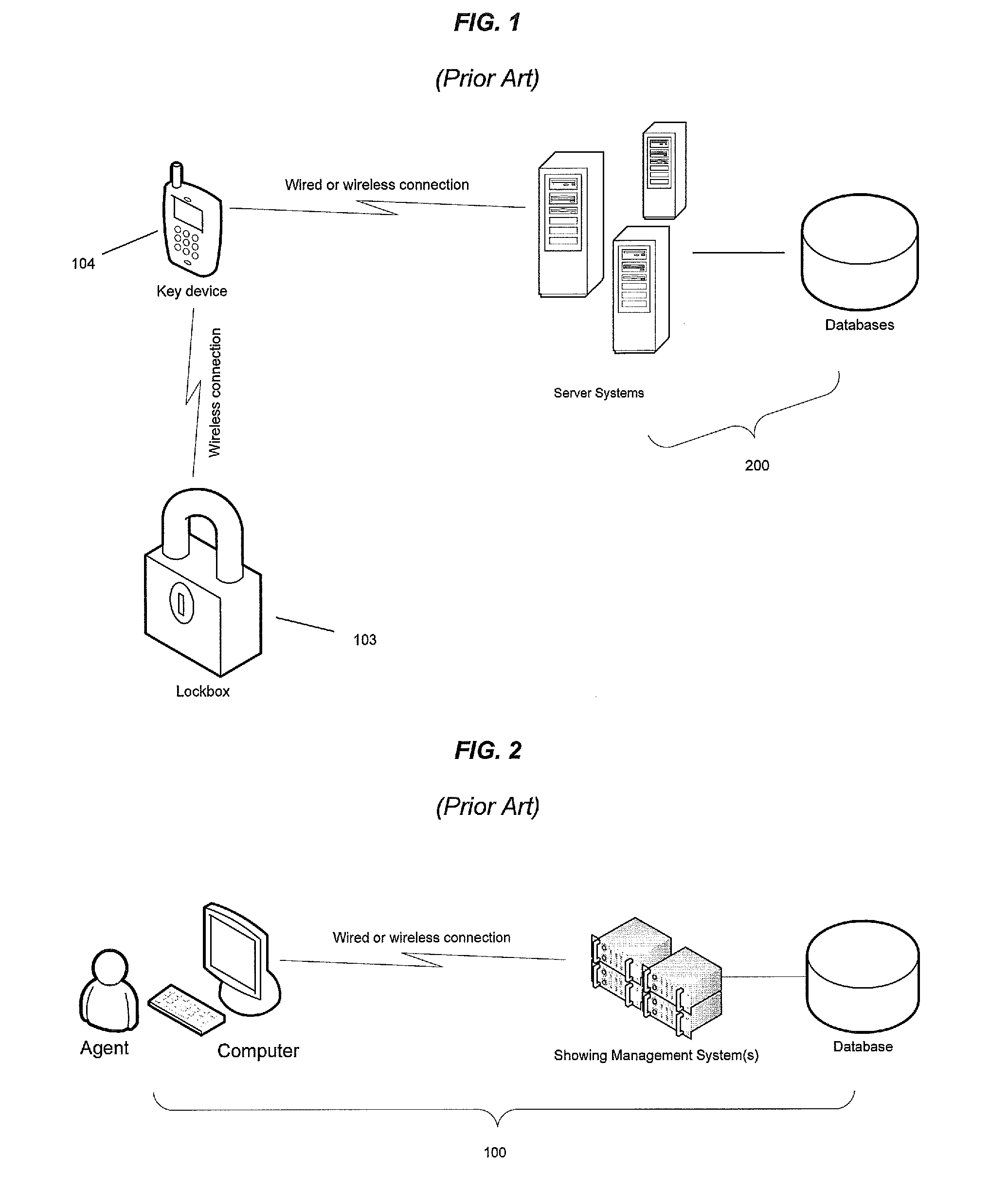
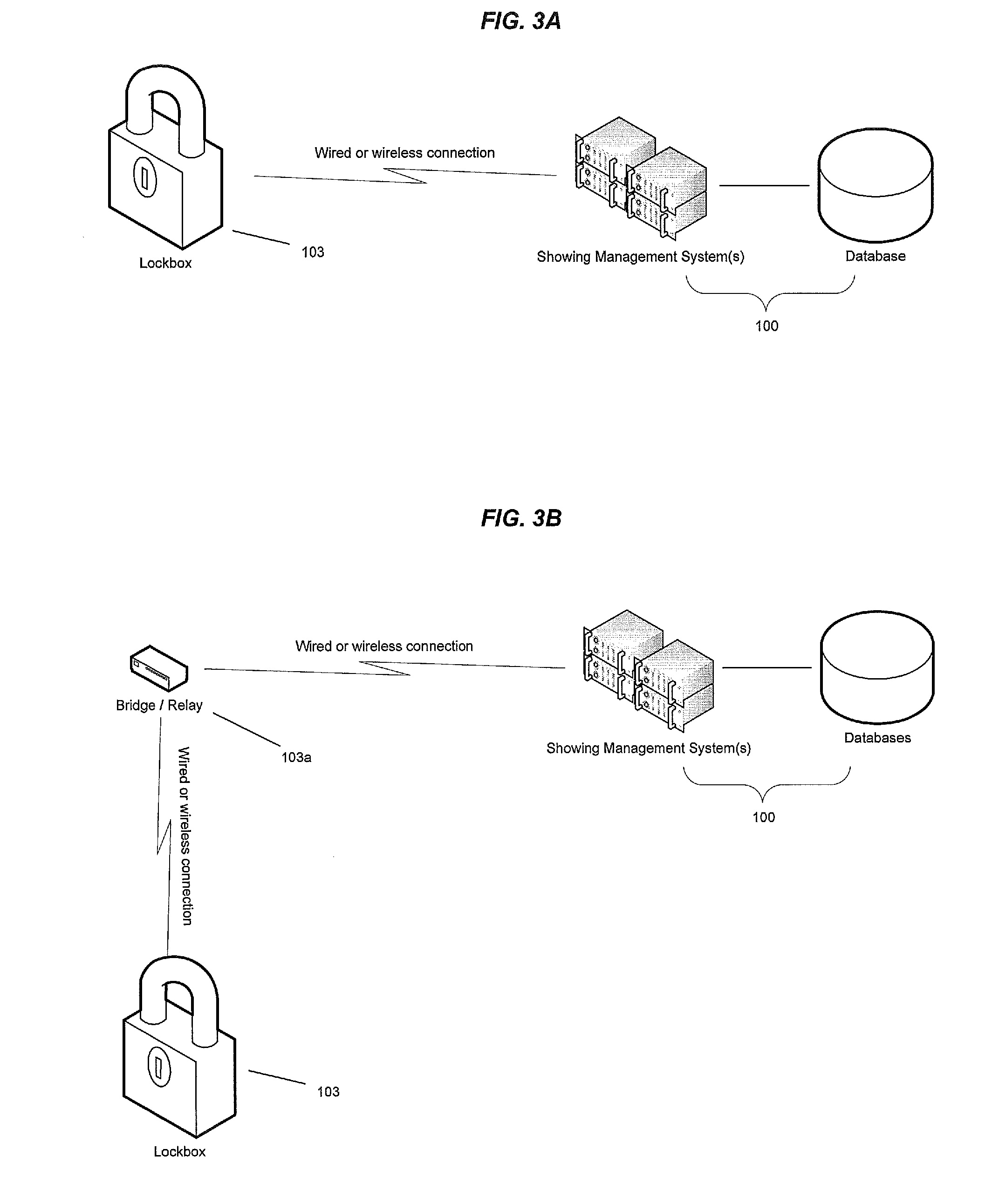
Showing management system to automatically match and control electronic lockboxes
ActiveUS20090219133A1Restricted accessLimited accessProgramme controlElectric signal transmission systemsAutomatic controlAccess time
A showing management system for automatically controlling access to an electronic lockbox utilizing showing appointment data maintained by the showing management system, whereby the showing appointment data is transmitted to the electronic lockbox and / or electronic key device. The electronic lockbox will open only when the actual access time is within the scheduled showing appointment time. The showing management system further programmatically matching a specific electronic lockbox with a specific Listing ID, whereby lockbox access data from an electronic lockbox are matched with showing appointment records maintained in the showing management system to complete the lockbox access records when the Listing ID for a particular showing appointment is missing from the lockbox access record.
Owner:MFTB HOLDCO INC
Electronic door access control system
InactiveUS20140247113A1Restricted accessProgramme controlElectric signal transmission systemsEmbedded systemControl unit
An electronic door lock system comprising a door control unit, a key reader and an encrypted binding between the key reader and the door control unit. When tampering is detected the encrypted binding is terminated thereby preventing the door from being opened. There is also disclosed a method for retrofitting a door comprising a key reader with a door control unit. The door control unit, key reader and the latch release mechanism may also be powered by a key comprising a power supply, the key also supplying a coded sequence to the door control unit.
Owner:PAQUIN YVES
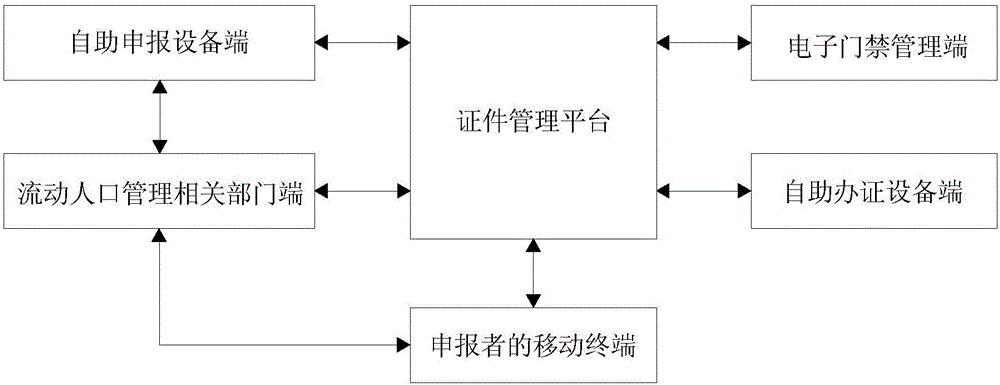
Certificate declaration management system and certificate declaration management method
ActiveCN106097223AEasy to useGuarantee safe and effectiveData processing applicationsIndividual entry/exit registersElectronic accessElectronic identification
The invention discloses a certificate declaration management system and a certificate declaration management method. The system comprises a certificate management platform, a declarant's mobile terminal, an electronic access management side, a self-service declaration equipment side, a self-service certificate handling equipment side, and a floating population management relevant department side. The method comprises the steps of getting declarant information from the floating population management relevant department side, judging whether the declarant information is approved by the floating population management relevant department side, generating a QR code according to the approved declarant information when judging that the declarant information is approved, and pushing the generated QR code and the declarant information to the declarant's mobile terminal, the electronic access management side, the self-service declaration equipment side, the self-service certificate handling equipment side and the floating population management relevant department side. According to the invention, a QR code used as the unique electronic identifier of a declarant can be generated according to the approved declarant information, use of certificates on the Internet is facilitated, and convenience in management and use is increased.
Owner:广州市华标科技发展有限公司
Method for matching and comparing user ID and ID matching system
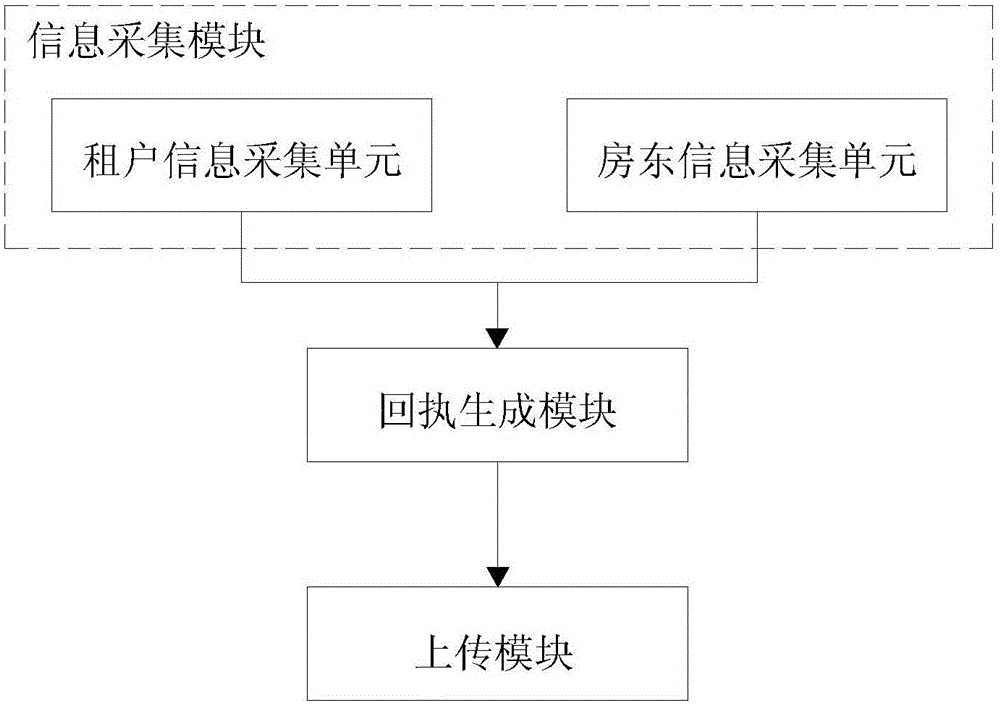
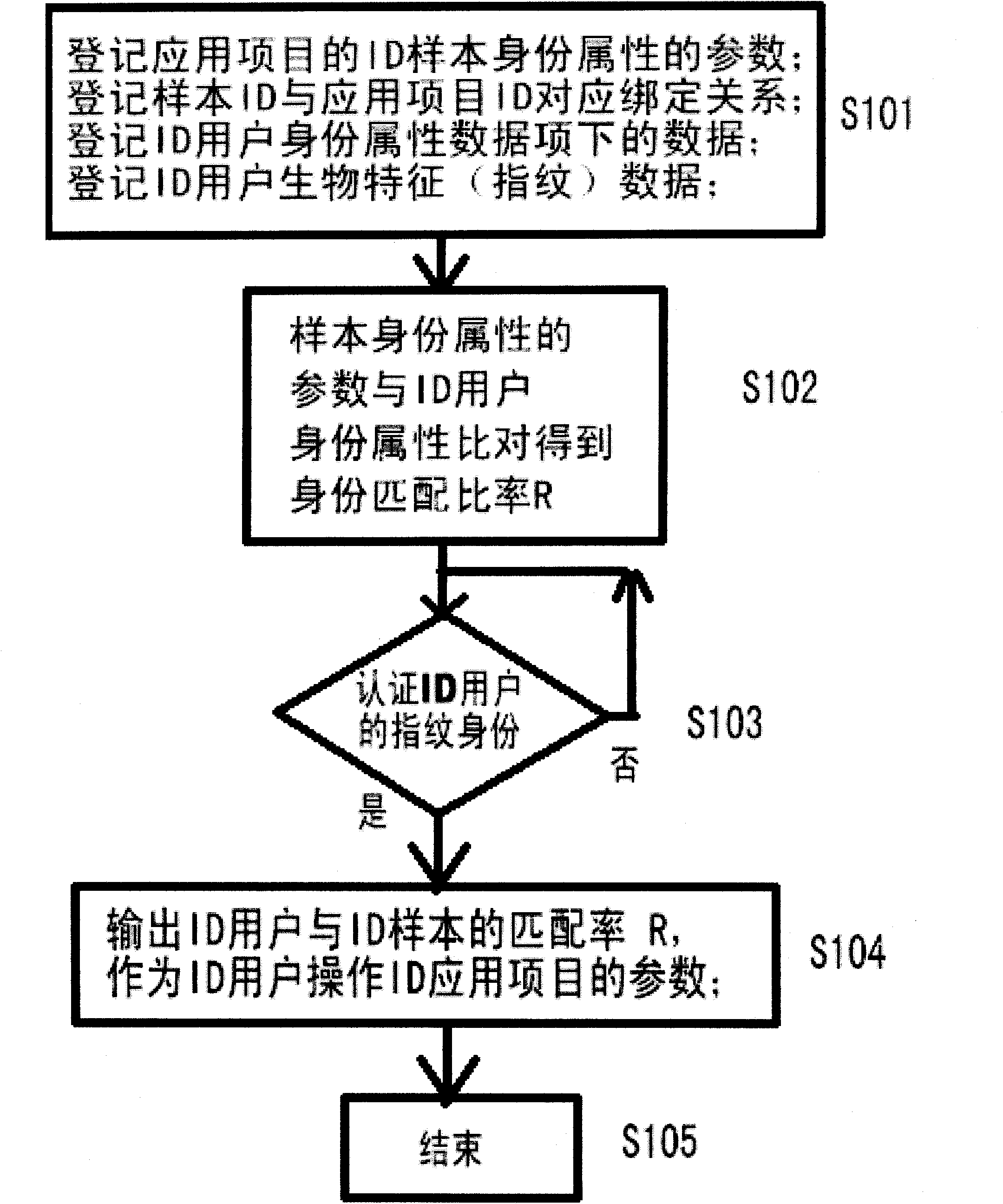
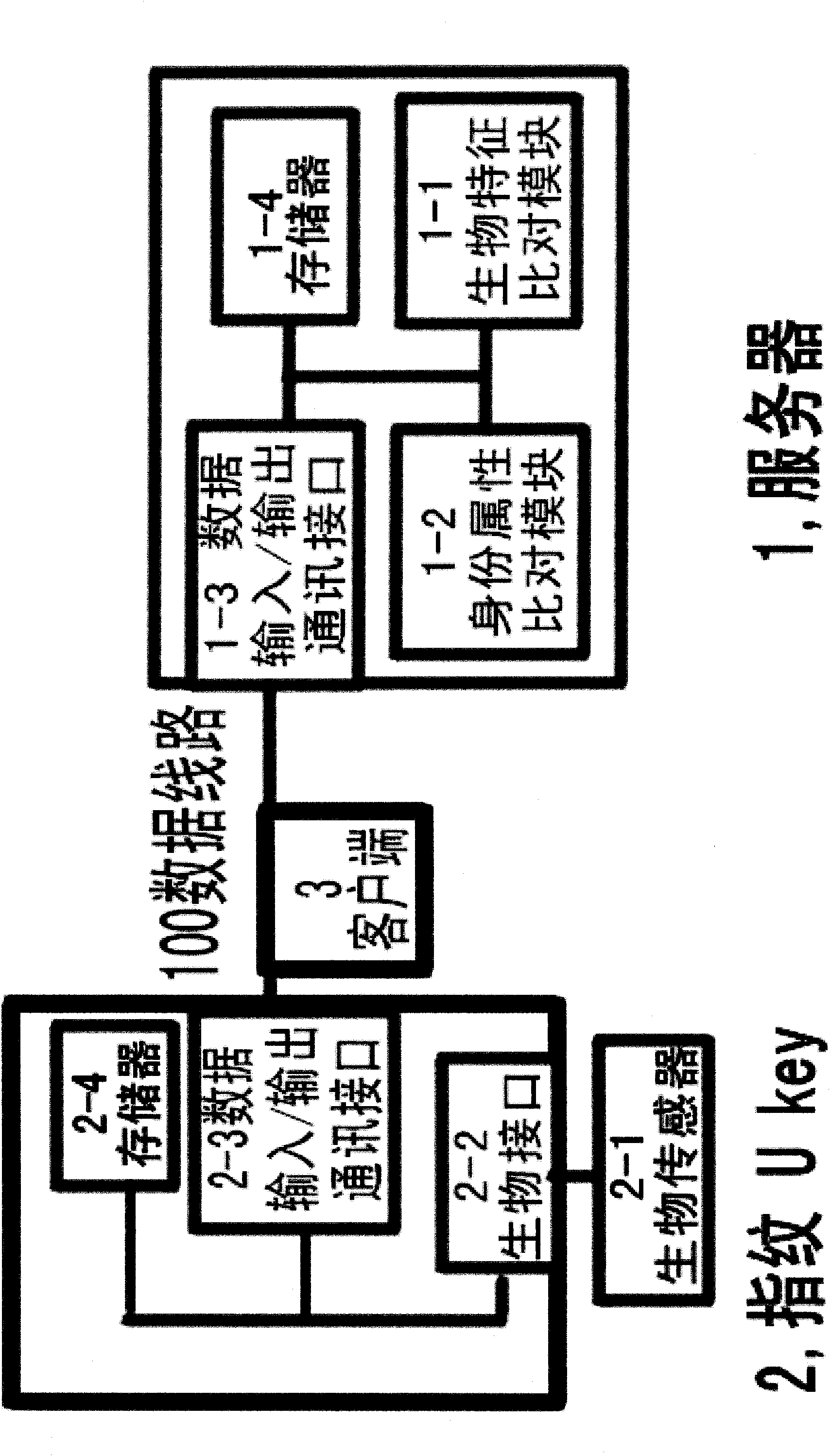
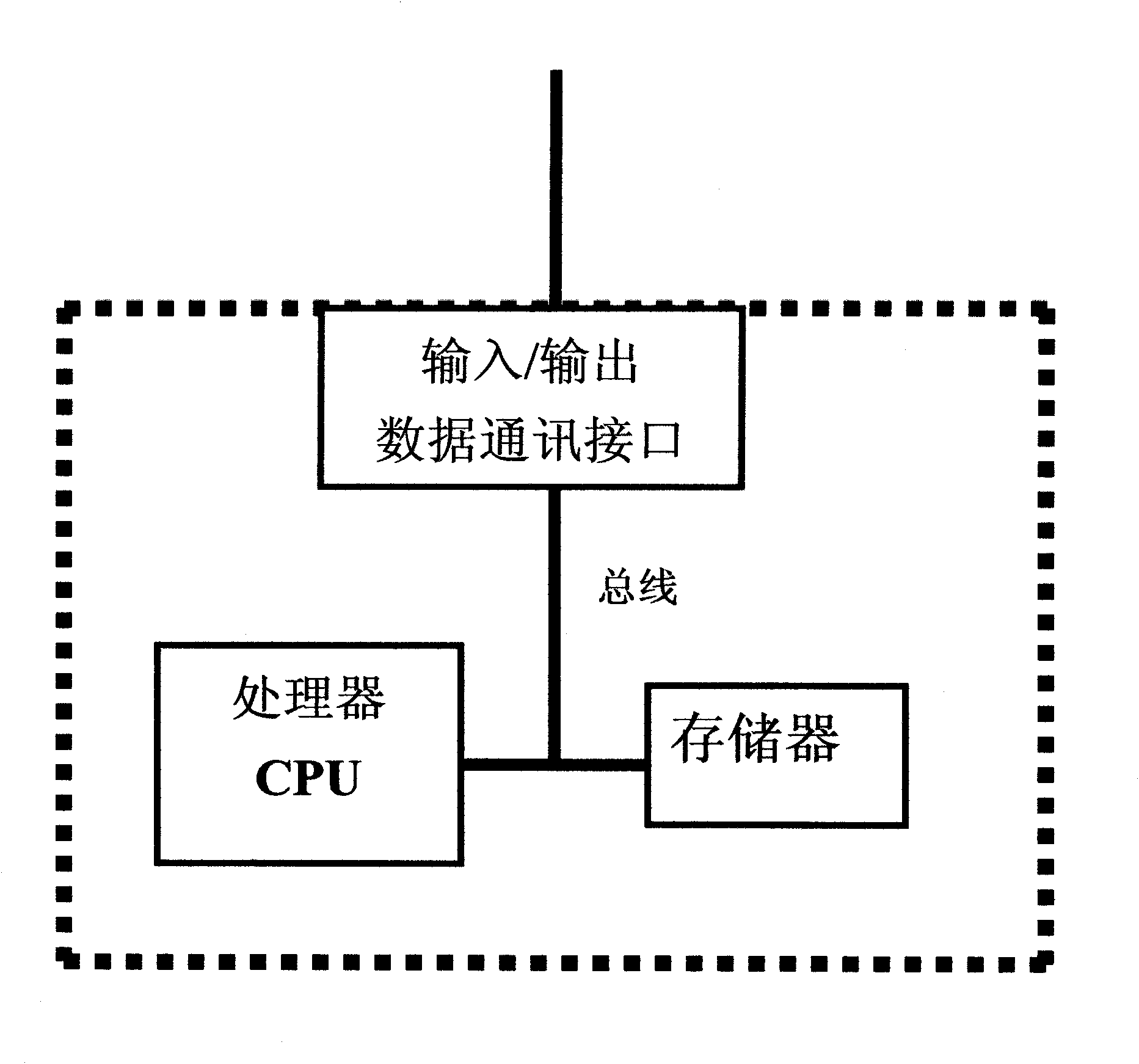
InactiveCN101833725AWaste of time and energySave processing resourcesCharacter and pattern recognitionCommerceExternal applicationBiometric data
The invention relates to a method for matching and comparing user ID and an ID matching system. The method for matching and comparing user ID comprises the following steps of: registering the parameters of user sample ID attribute data items of application projects; registering a unique corresponding bonding relation between sample ID identifiers and external application project ID identifiers; registering a data group which contains the same ID attribute data items of ID identifier users and corresponds to the sample ID attribute data items by using the sample ID attribute data items as a template; registering the biological specificity data of an ID user; and respectively comparing the data of the user ID attribute data items with the parameters in the same ID attribute data items corresponding to a sample ID attribute table to acquire an ID attribute comparison matching ratio R of the ID user. Only by the biological specificity ID authentication of an ID user, a matching ratio R between an ID identifier user and an ID identifier sample can be output as a parameter for the ID identifier user to operate an external application project of the ID identifier.
Owner:刘洪利
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com