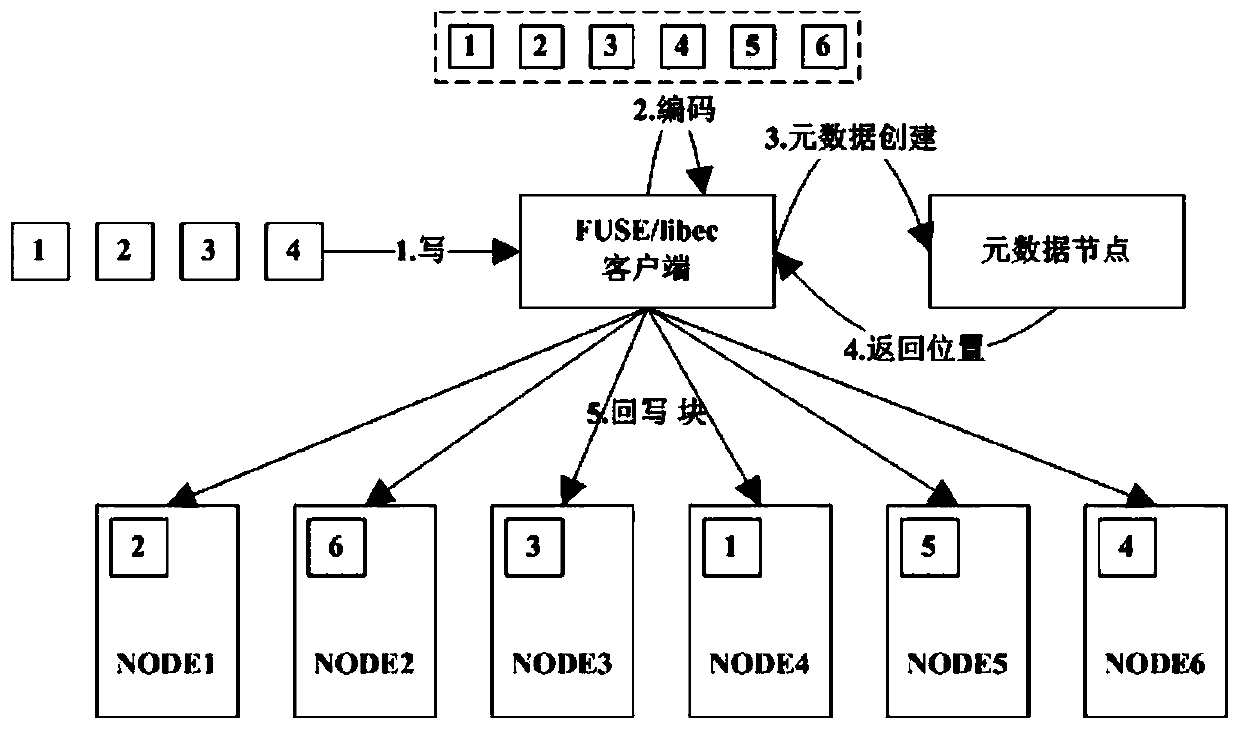
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
81results about How to "Reduce network overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
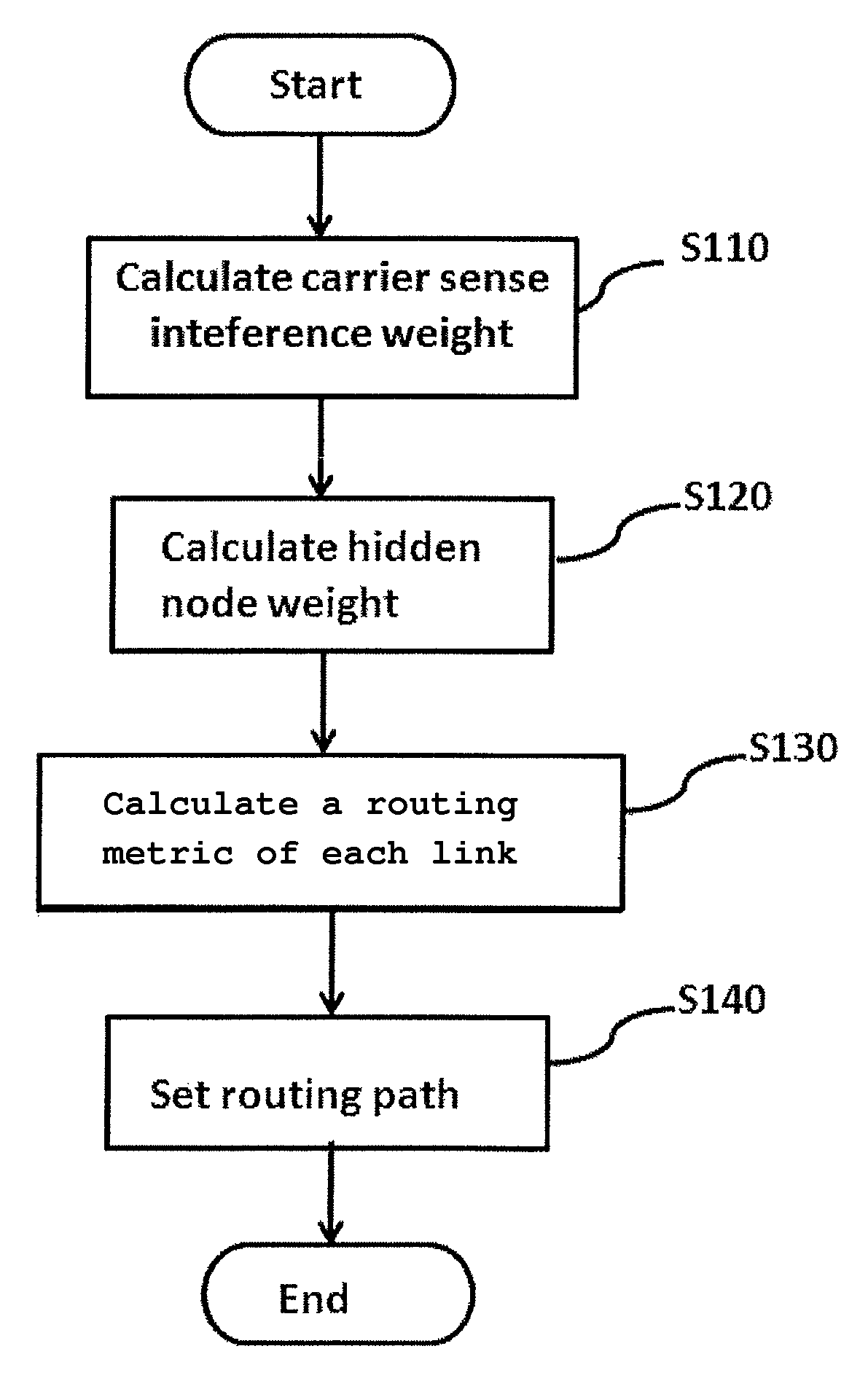
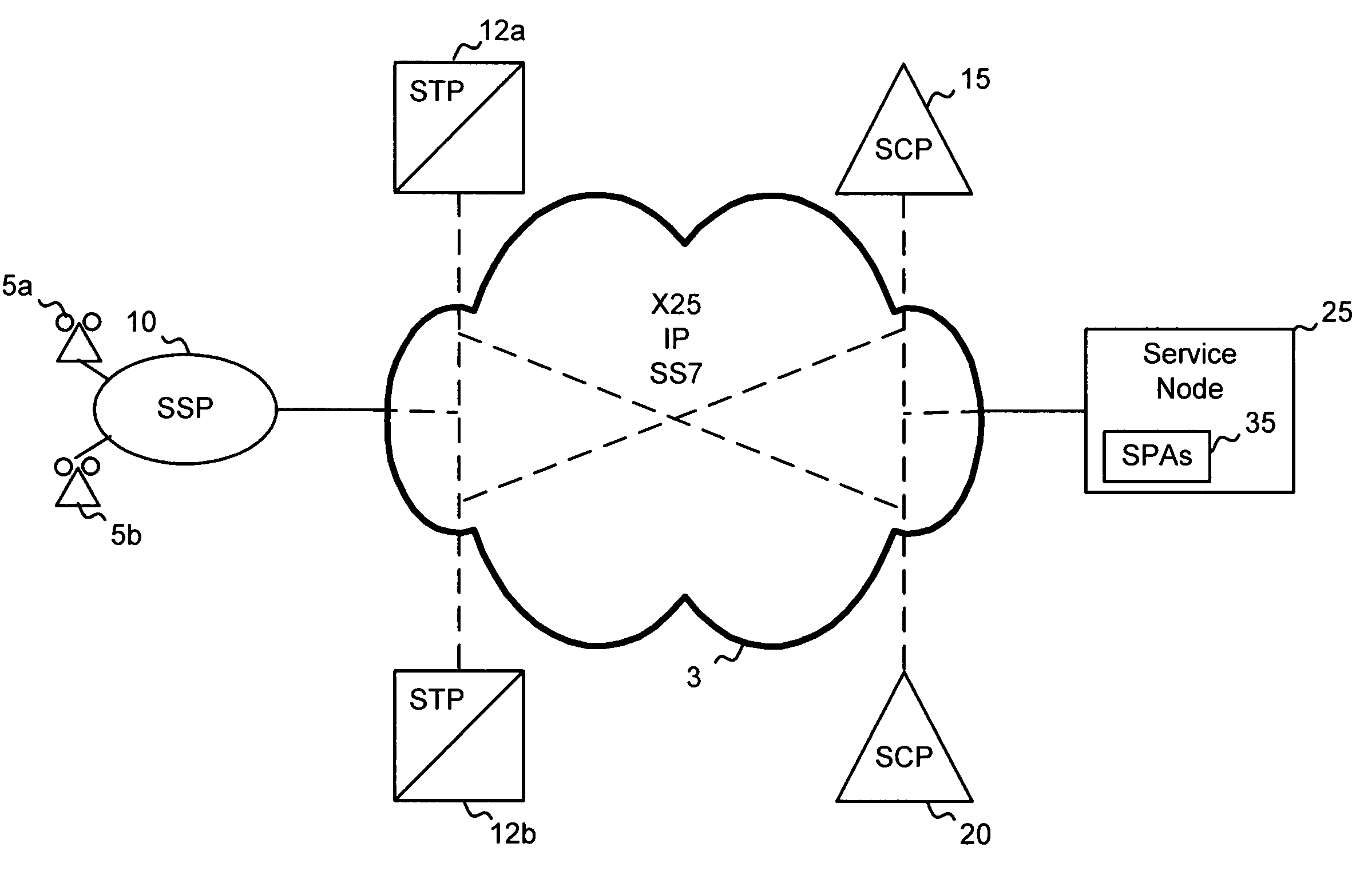
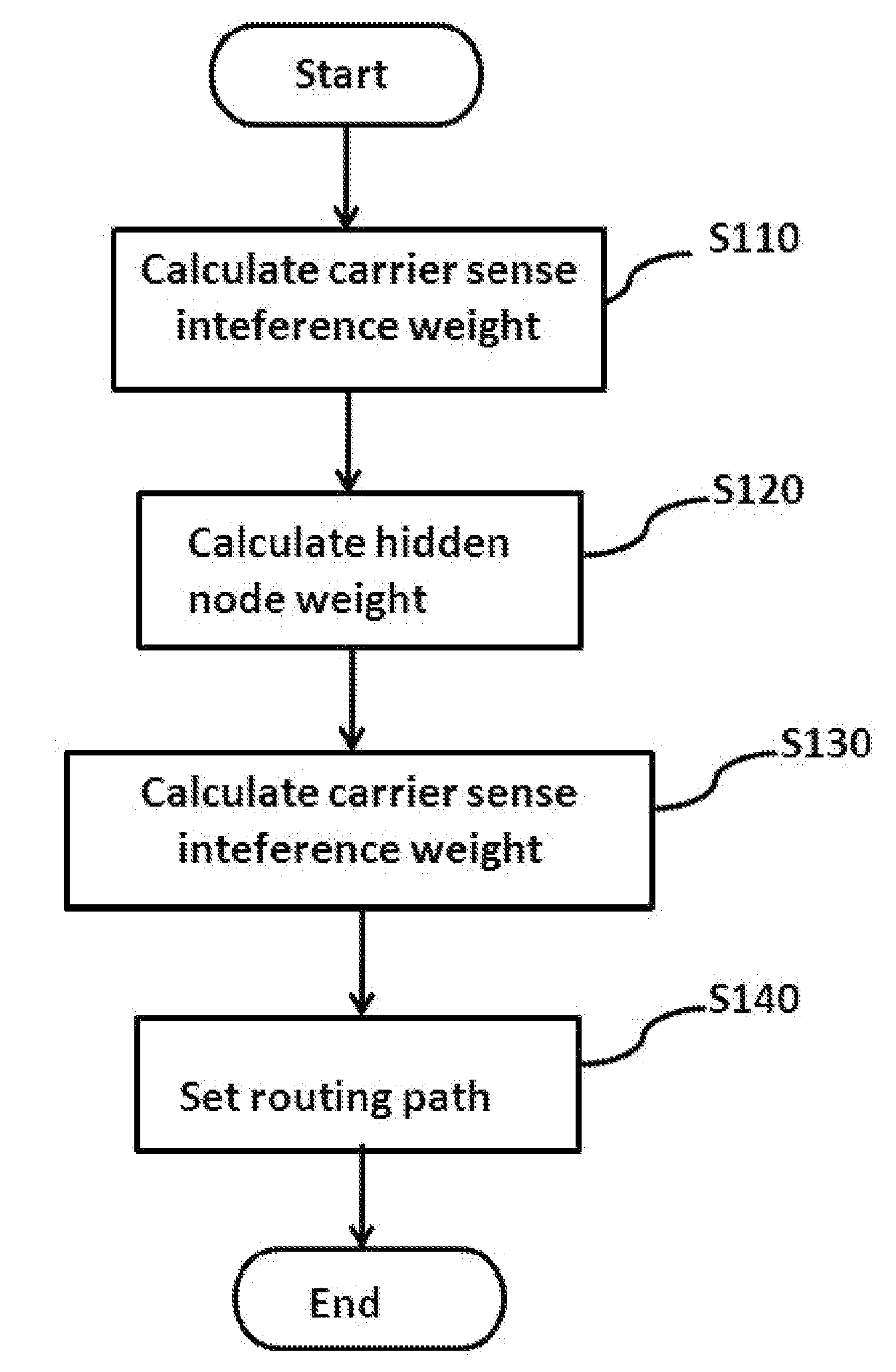
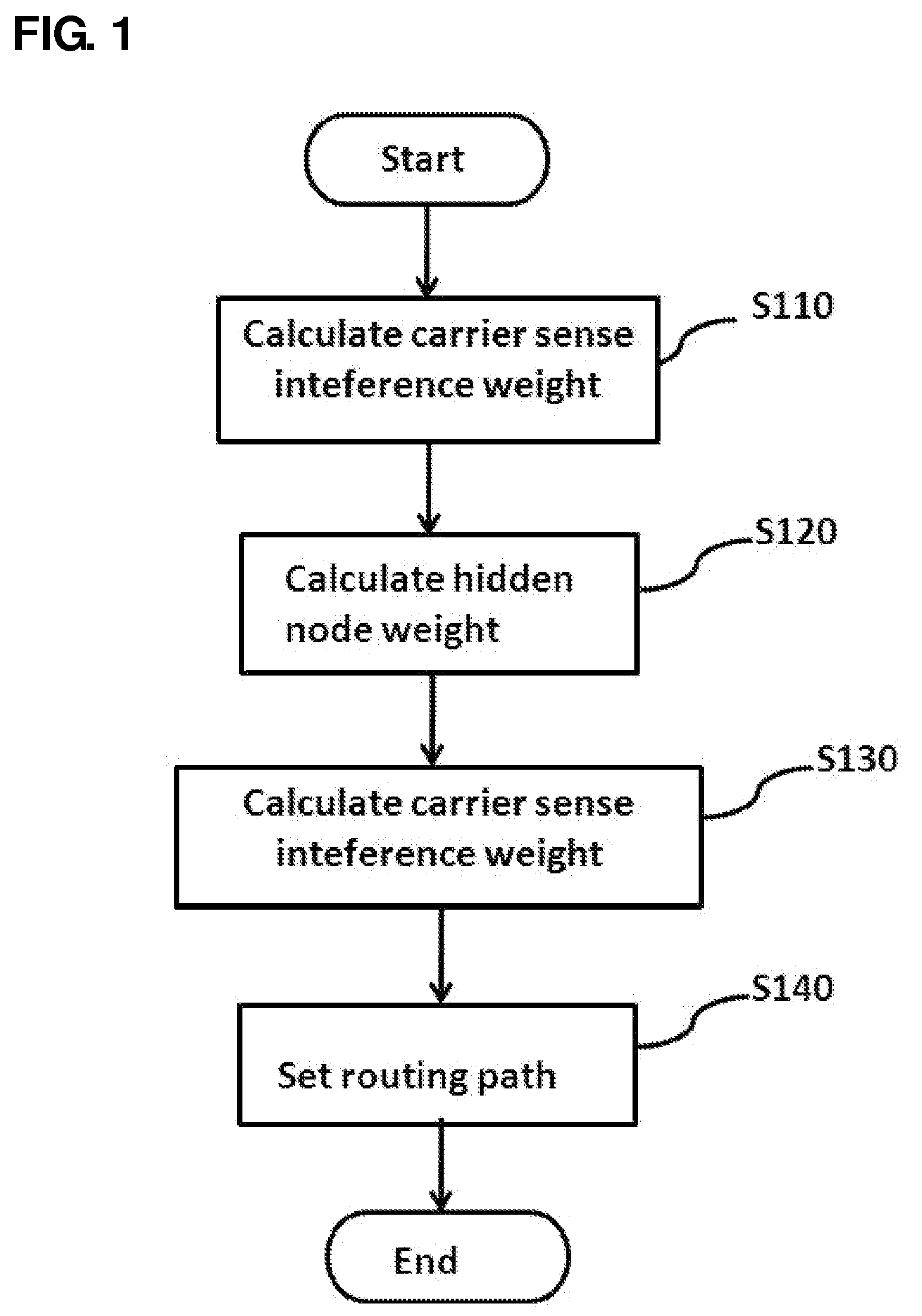
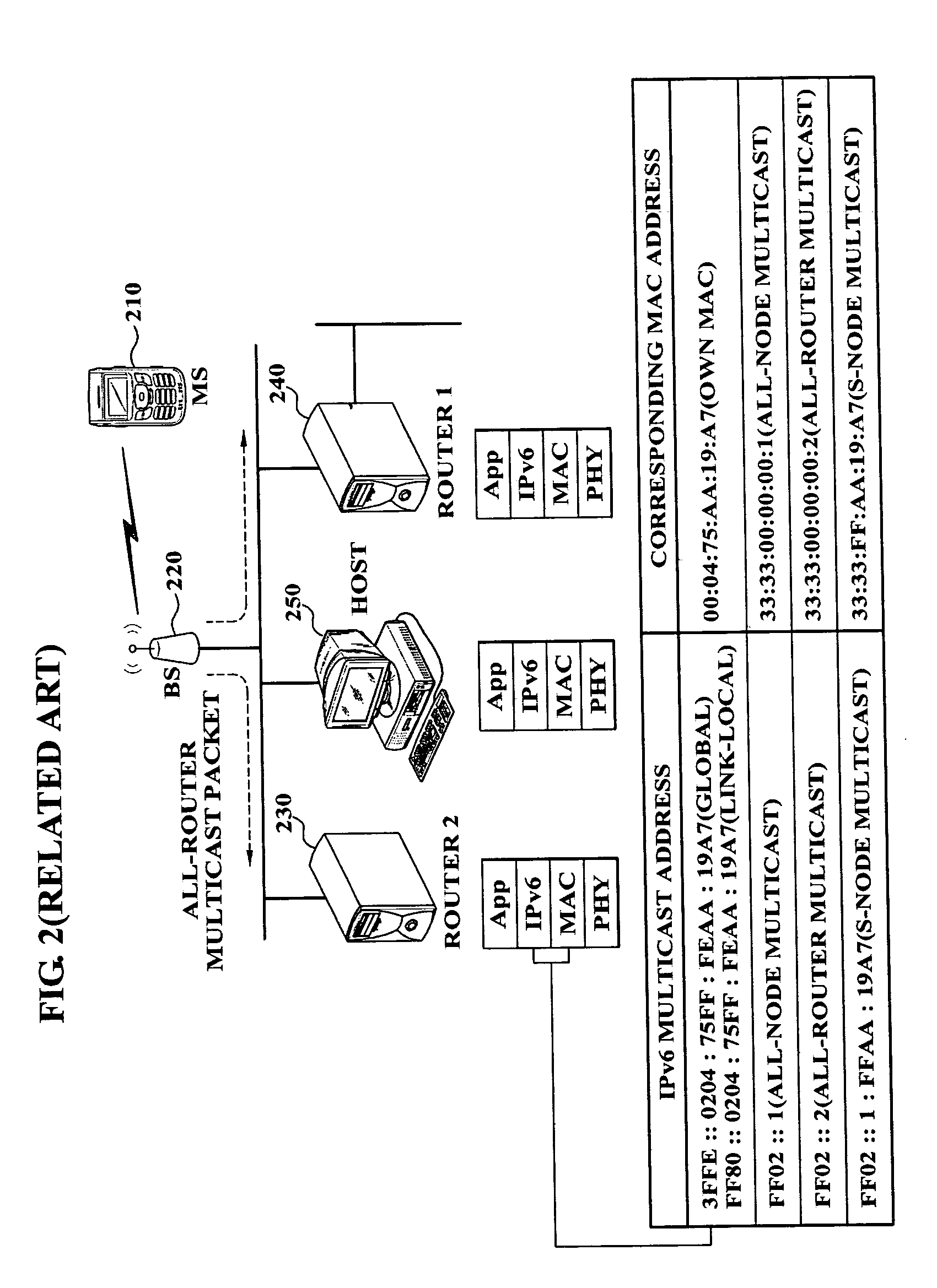
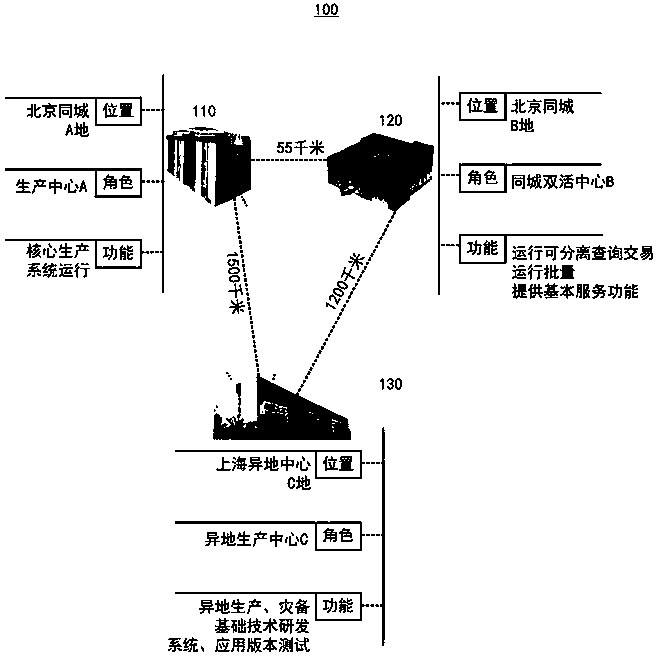
Method and system for setting routing path considering hidden node and carrier sense interference, and recording medium thereof
ActiveUS8300538B2Improve routing performanceImprove network performanceError preventionFrequency-division multiplex detailsHidden node problemCarrier signal
A method of setting a routing path for transmitting a packet from a source node to a destination node in a wireless multi-hop network including plural nodes and plural links for connecting two nodes with each other. The method includes calculating carrier sense interference weights representing carrier sense interference related to the respective links and combining the carrier sense interference weights of the links included in at least one specific path connecting the source node with the destination node. The method further includes calculating hidden node weights representing hidden node problems related to the respective links and accumulating the hidden node weights of the links included in the path. The method further includes calculating a metric value for the specific path by combining the carrier sense interference weights and the hidden node weights, and determining the specific path with the least metric value as the routing path.
Owner:KOREA ADVANCED INST OF SCI & TECH
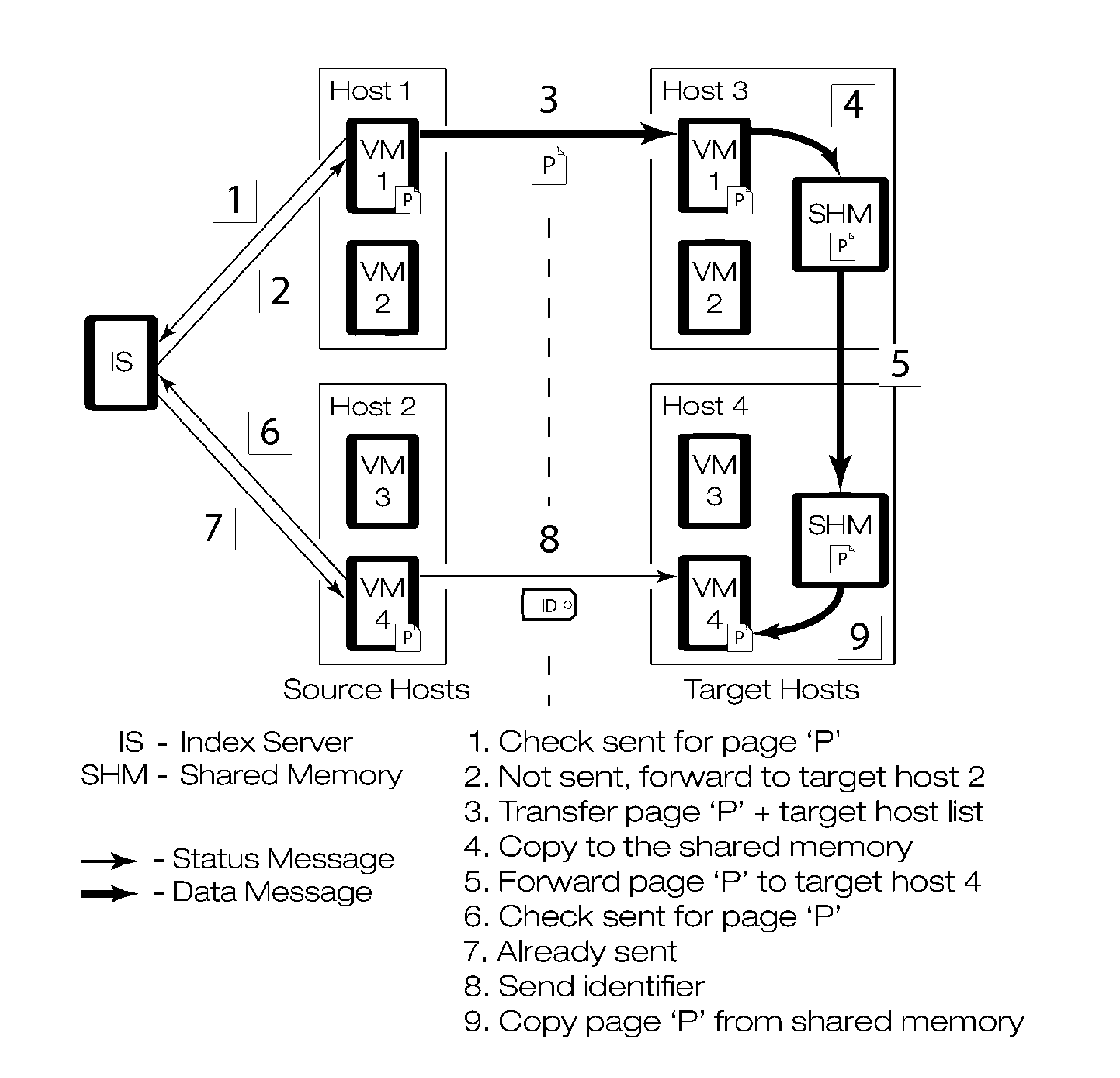
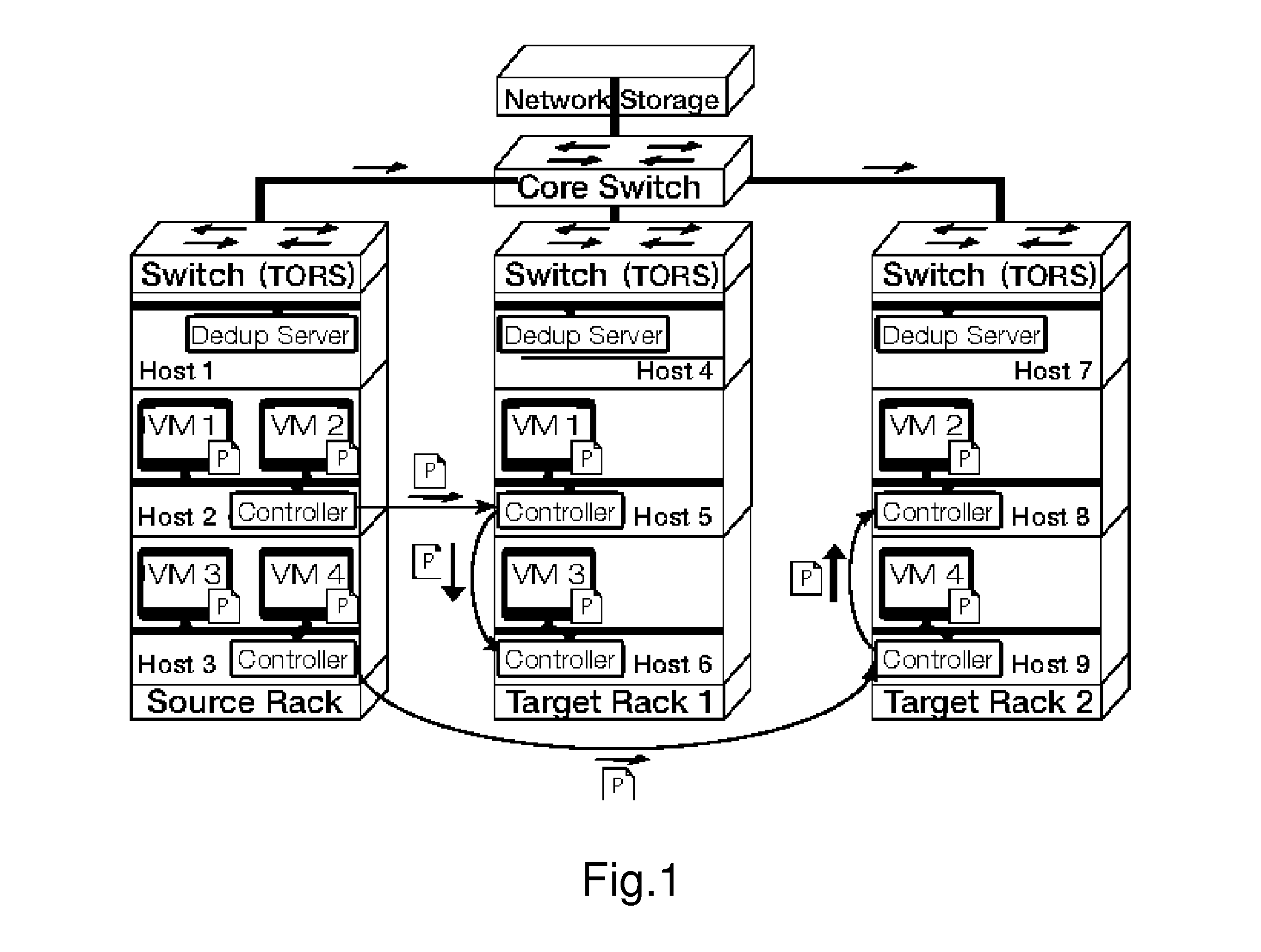
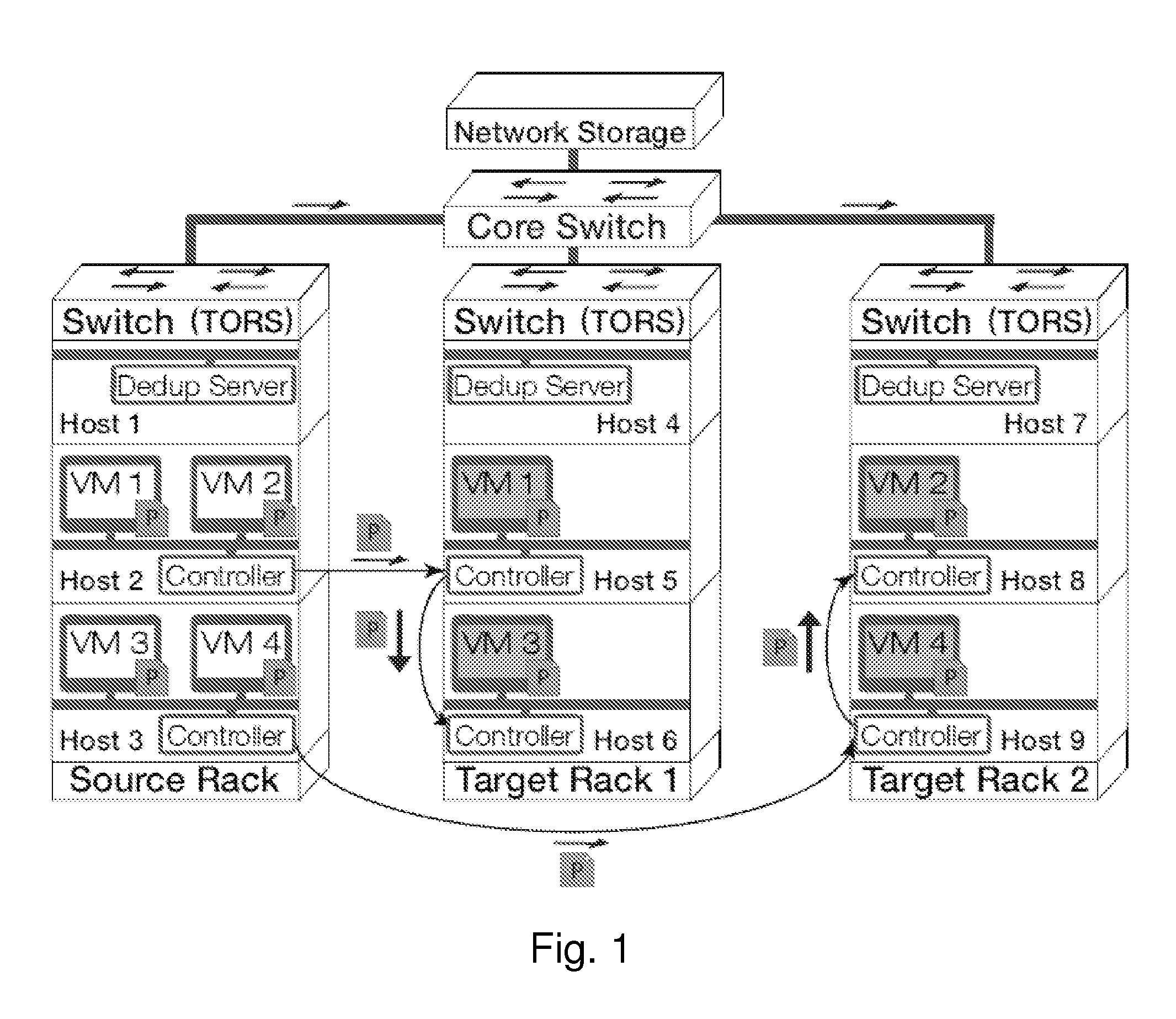
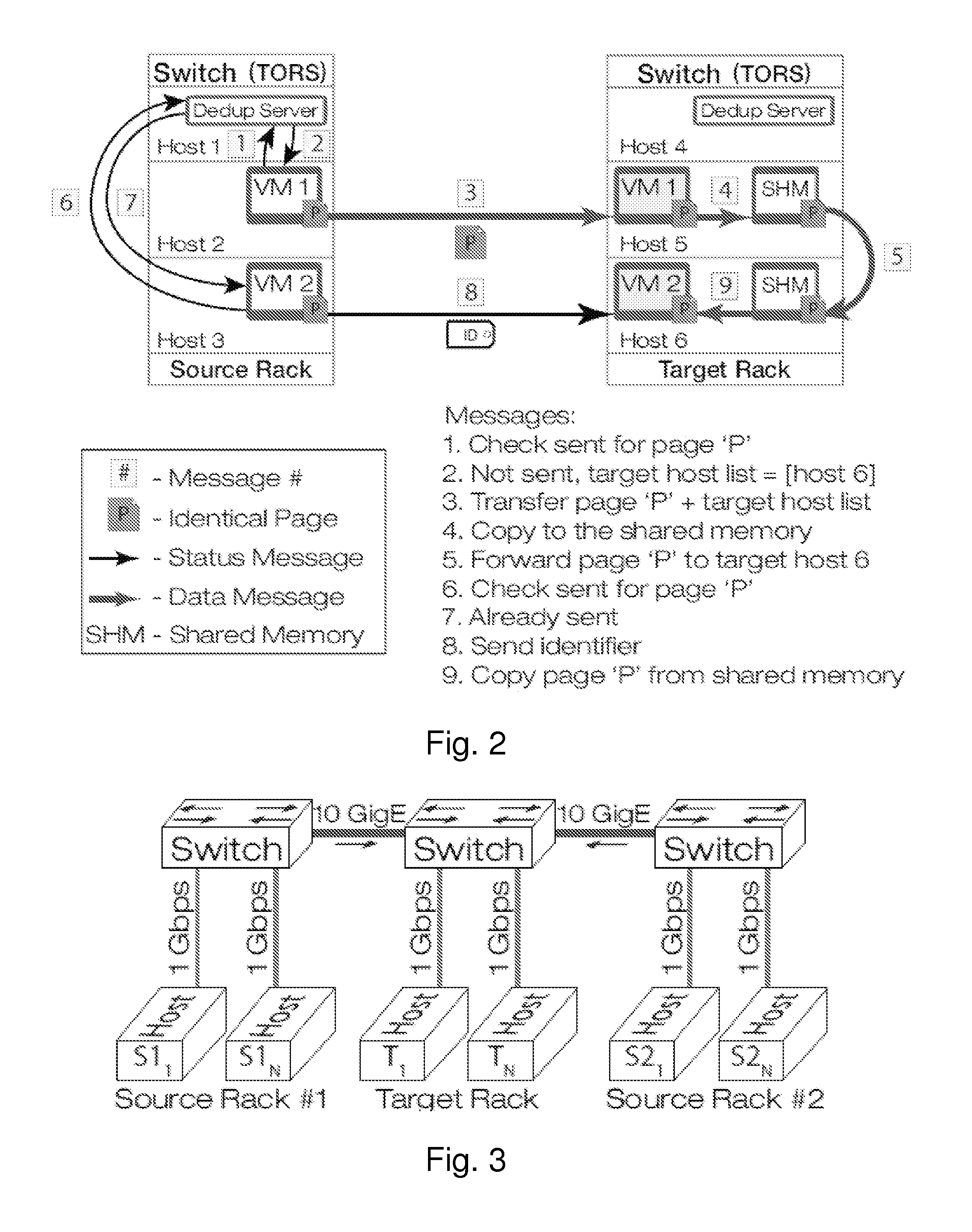
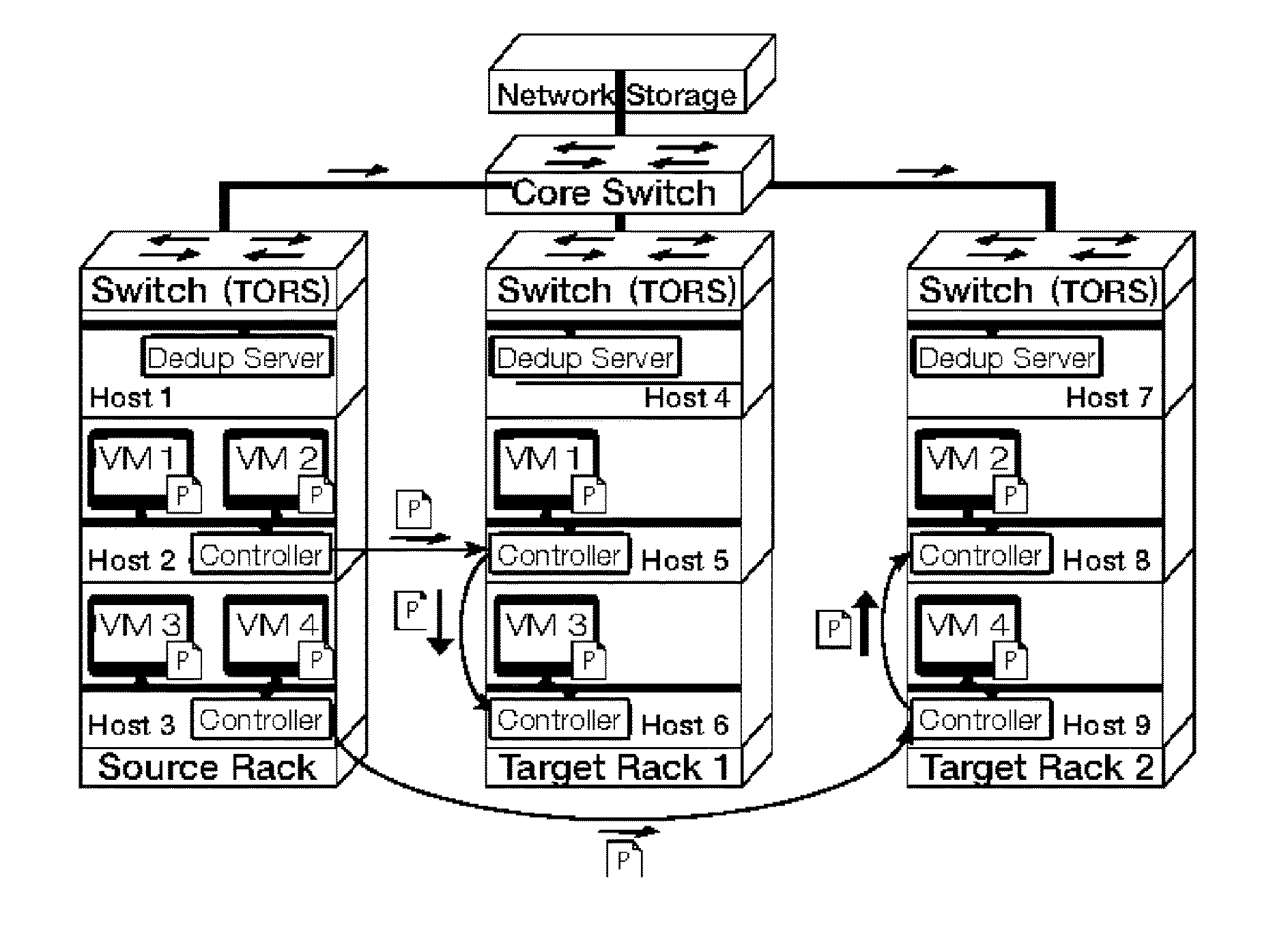
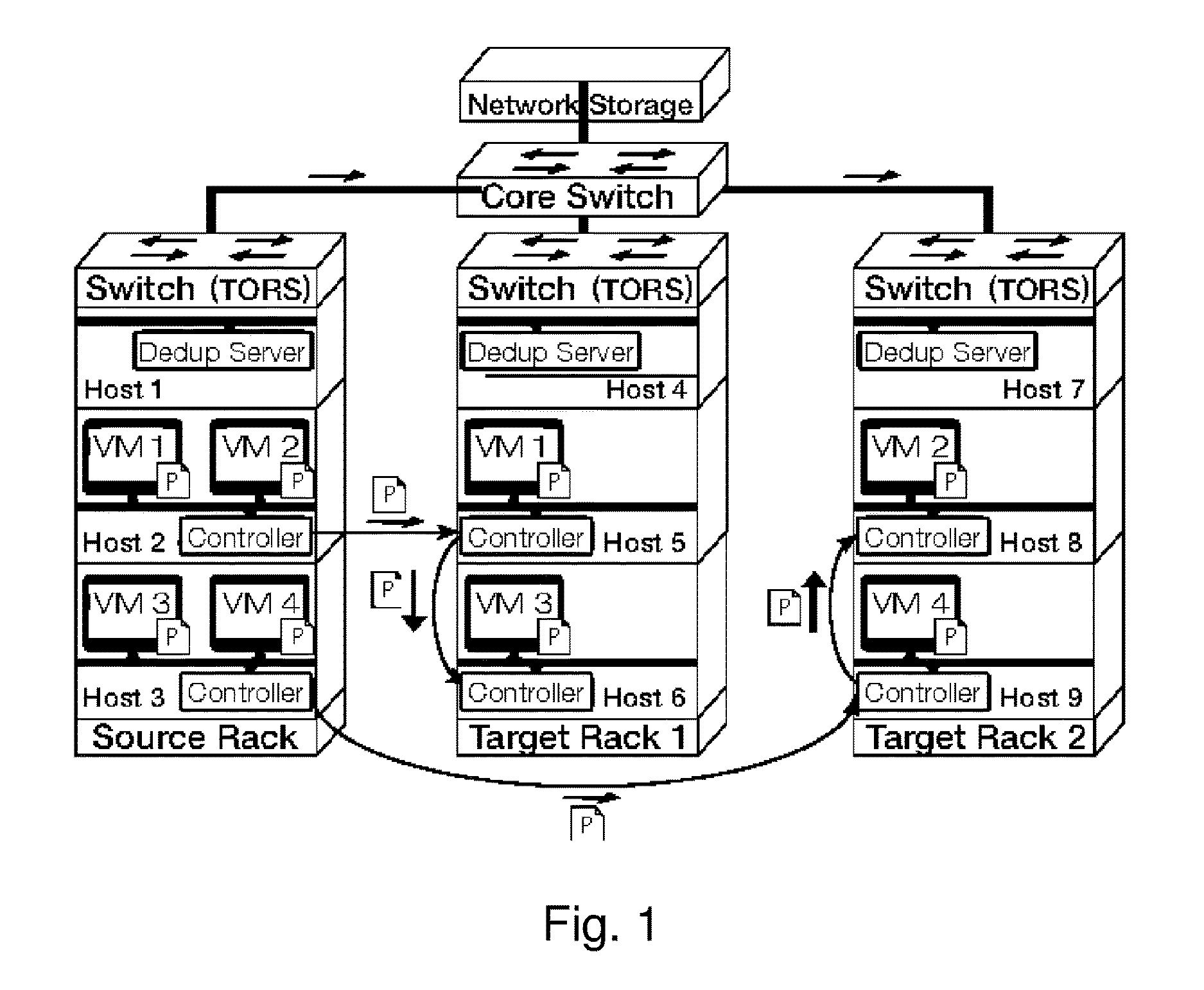
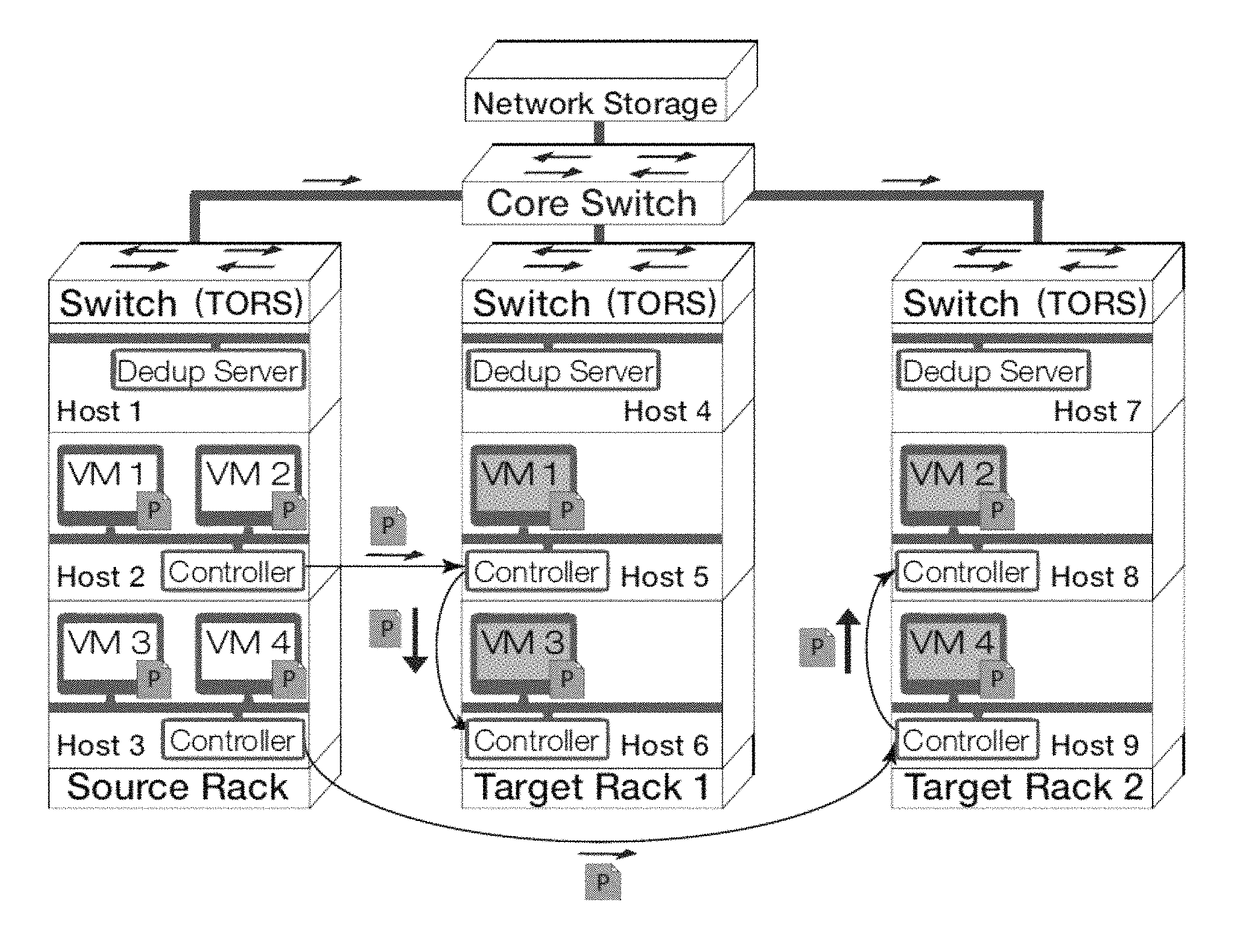
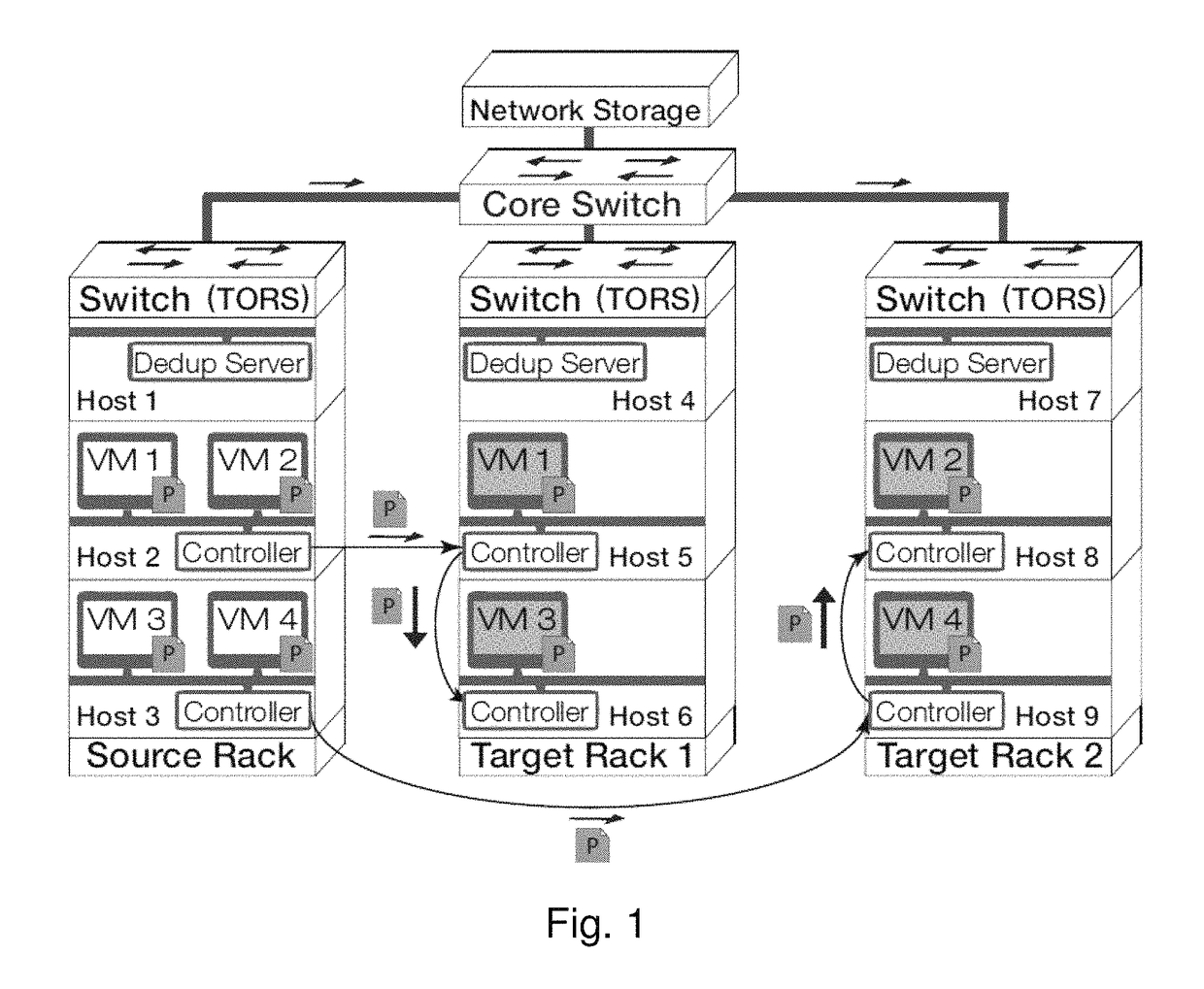
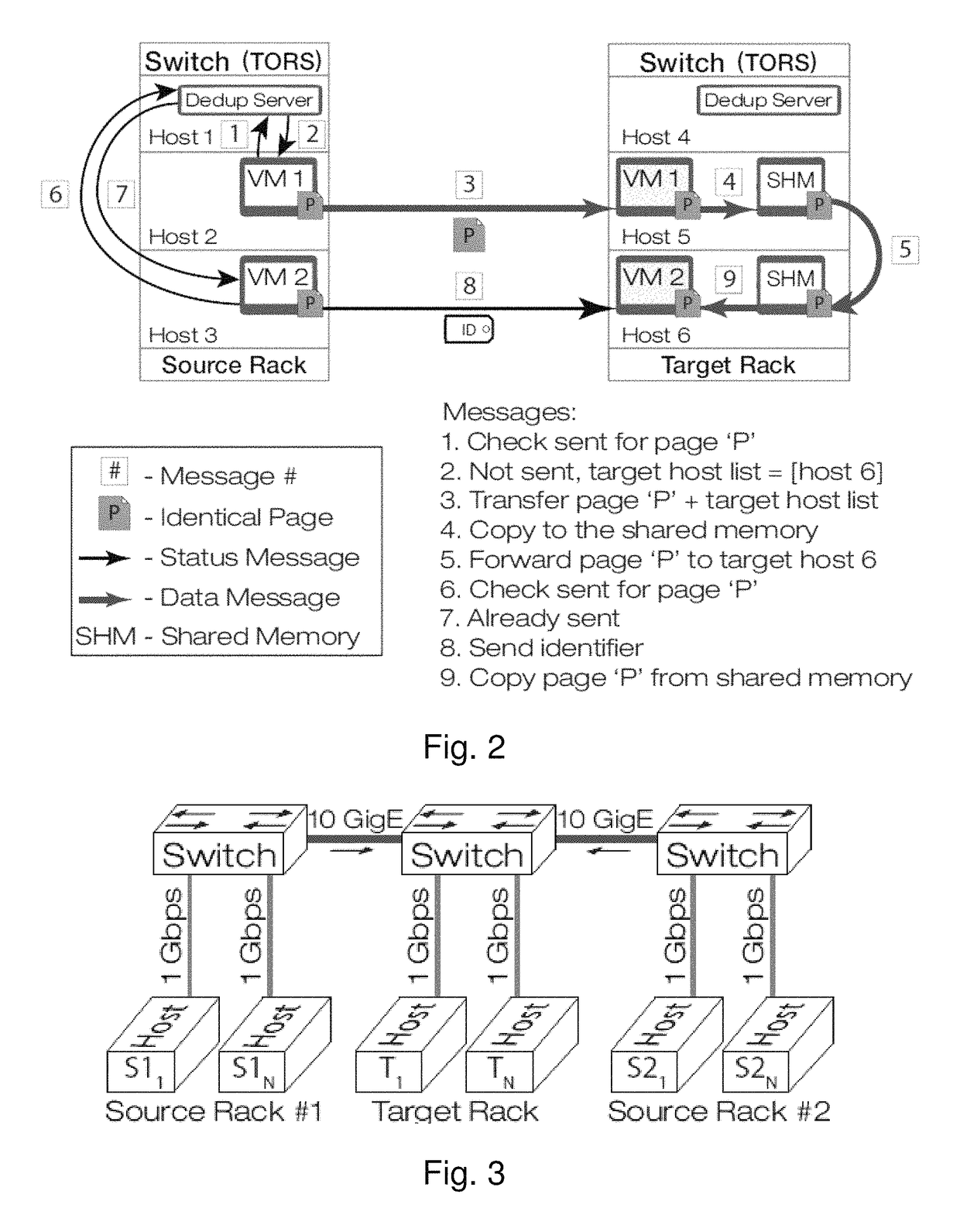
Gang migration of virtual machines using cluster-wide deduplication
ActiveUS20140196037A1Reduce throughputIncrease delayMemory architecture accessing/allocationProgram initiation/switchingTraffic capacityData center
Datacenter clusters often employ live virtual machine (VM) migration to efficiently utilize cluster-wide resources. Gang migration refers to the simultaneous live migration of multiple VMs from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a data center. The present technology reduces the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. A prototype GMGD reduces the network traffic on core links by up to 51% and the total migration time of VMs by up to 39% when compared to the default migration technique in QEMU / KVM, with reduced adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Downhole data transmission system
InactiveUS20040104797A1Reduce overheadHighly reliable communicationElectric signal transmission systemsSurveyTransmission systemData transmission systems
A system for transmitting data through a string of downhole components. In one aspect, the system includes first and second magnetically conductive, electrically insulating elements at both ends of the component. Each element includes a first U-shaped trough with a bottom, first and second sides and an opening between the two sides. Electrically conducting coils are located in each trough. An electrical conductor connects the coils in each component. In operation, a varying current applied to a first coil in one component generates a varying magnetic field in the first magnetically conductive, electrically insulating element, which varying magnetic field is conducted to and thereby produces a varying magnetic field in the second magnetically conductive, electrically insulating element of a connected component, which magnetic field thereby generates a varying electrical current in the second coil in the connected component.
Owner:INTELLISERV
Systems and methods for efficient hand-off in wireless networks
InactiveUS20060268756A1Freeing network capacityReduce eliminateAssess restrictionNetwork topologiesWireless mesh networkFrequency spectrum
Embodiments of systems and methods for efficient hand-off in a wireless network employ a neighbor report which may include, in addition to more convention information about neighboring access point, search thresholds, target beacon transmission time of neighboring access points, and execution thresholds. The present systems and methods also provide a mechanism of updating neighbor report and its elements. A faster and lower spectrum cost active search scheme based on sending a null packet may also be used by the systems and methods.
Owner:HONG KONG APPLIED SCI & TECH RES INST
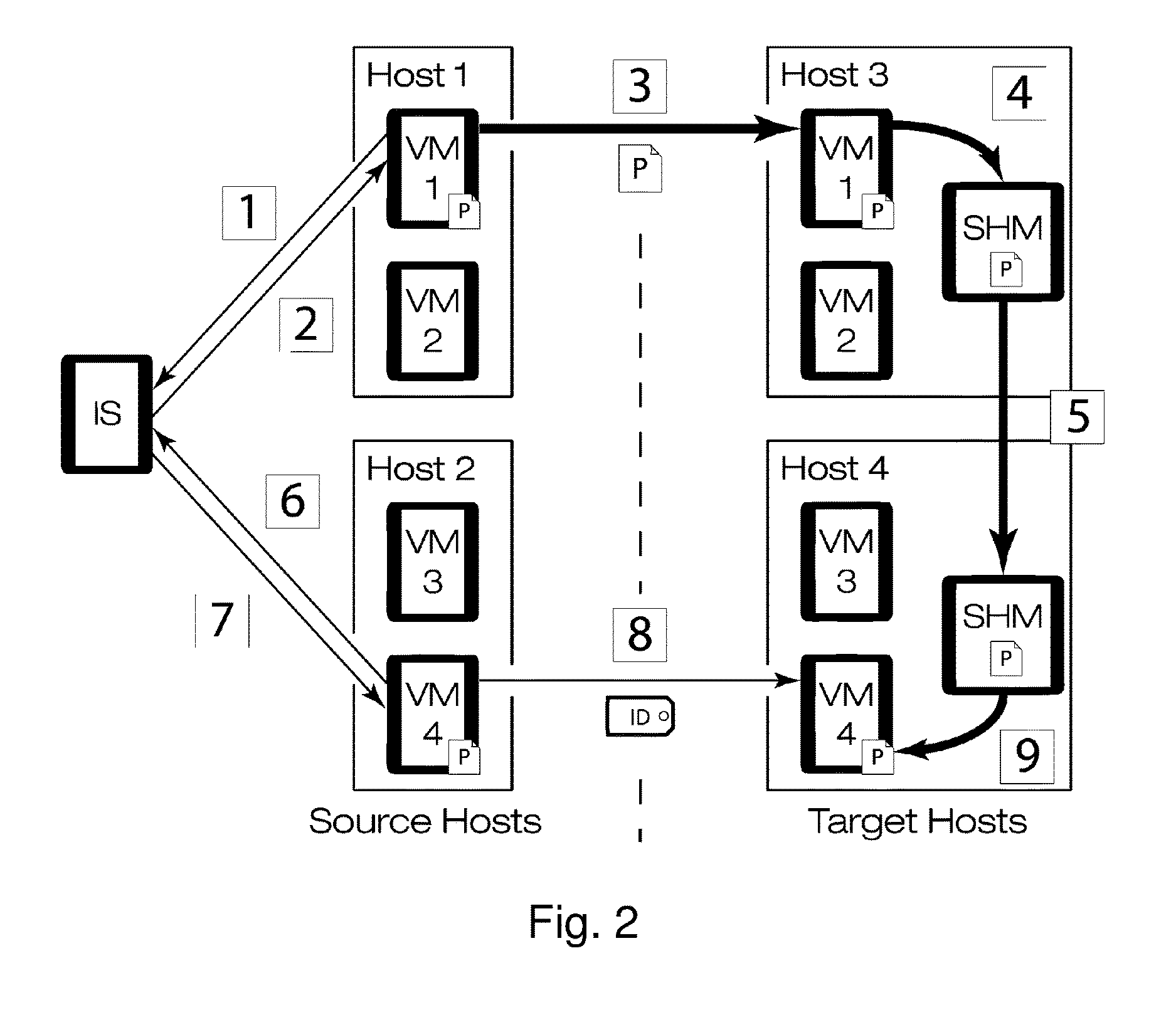
Gang migration of virtual machines using cluster-wide deduplication
ActiveUS20150324236A1Prevent race conditionReduce network overheadInput/output to record carriersResource allocationInternet trafficEngineering
Gang migration refers to the simultaneous live migration of multiple Virtual Machines (VMs) from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a datacenter. In this paper, we present an approach to reduce the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. The design, implementation and evaluation of a GMGD prototype is described using QEMU / KVM VMs. Evaluations on a 30-node Gigabit Ethernet cluster having 10 GigE core links shows that GMGD can reduce the network traffic on core links by up to 65% and the total migration time of VMs by up to 42% when compared to the default migration technique in QEMU / KVM. Furthermore, GMGD has a smaller adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
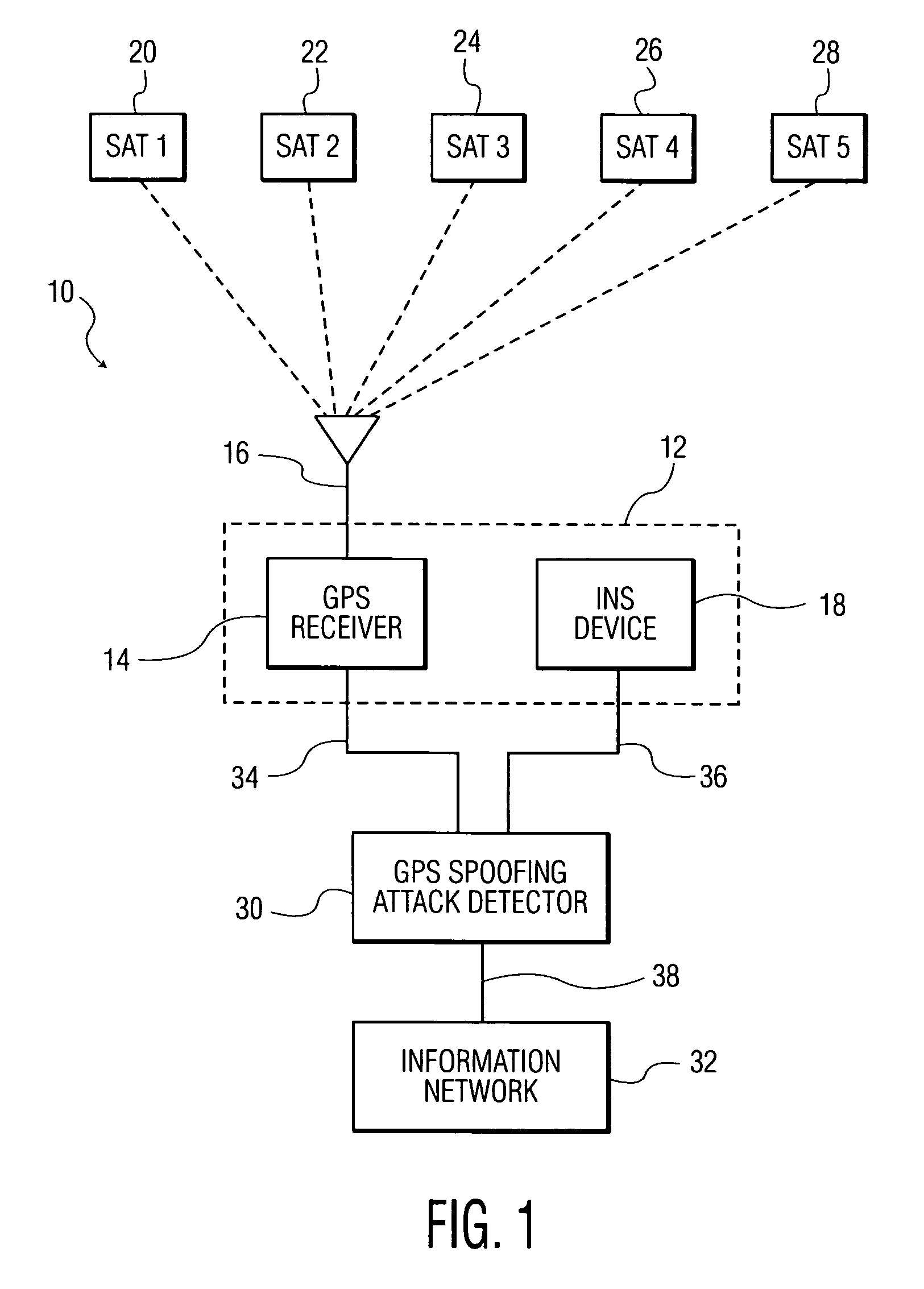
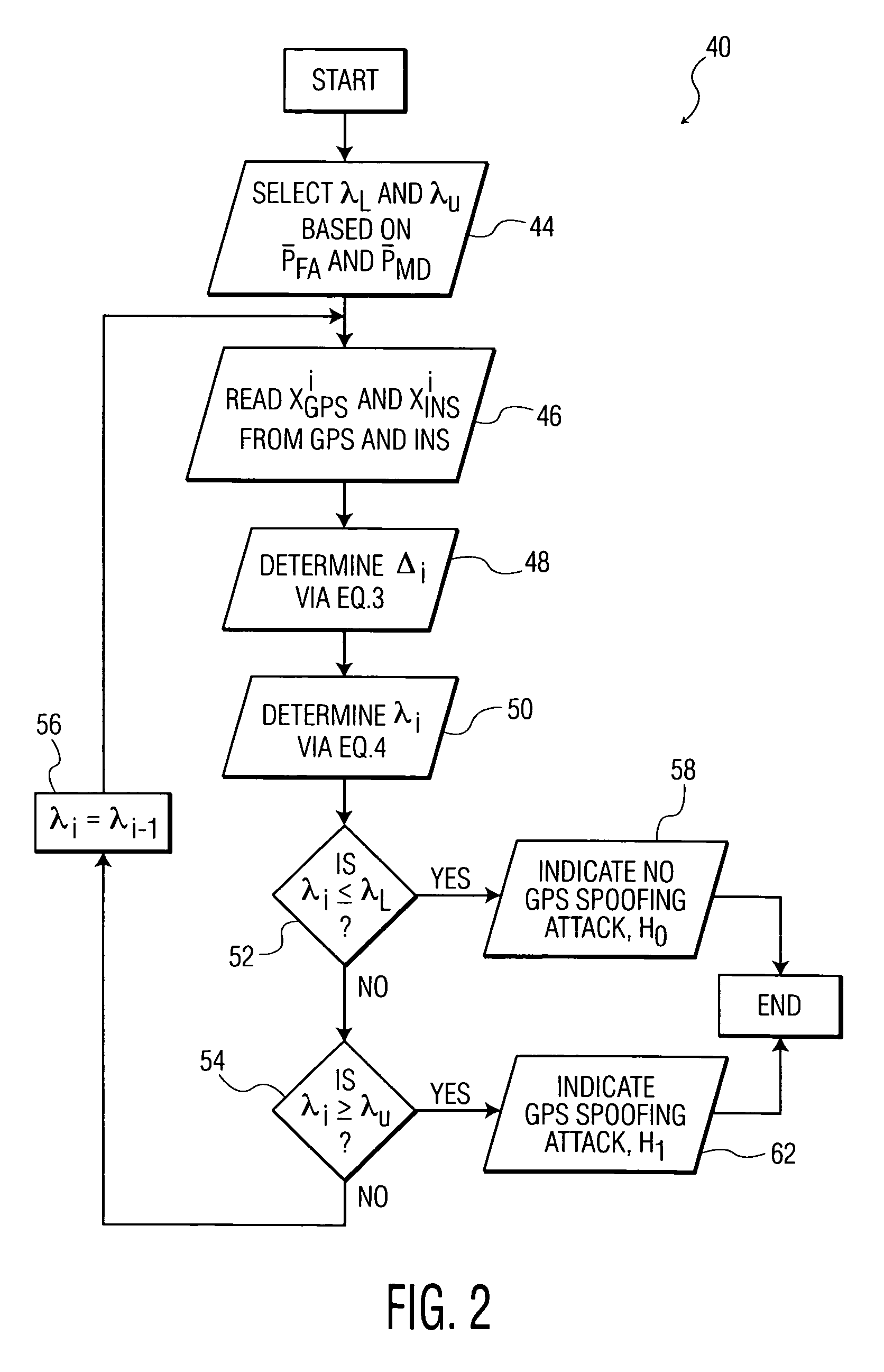
Methods and systems for detecting GPS spoofing attacks
ActiveUS8922427B2Improve efficiencyDetect identifyNavigation by speed/acceleration measurementsSatellite radio beaconingGround truthNavigation system
A system and method for detecting global positioning system (GPS) spoofing attacks includes collecting GPS readings along with inertial navigational system (INS) readings as a ground truth, and sequentially testing the GPS readings and INS readings through the use of a sequential probability ratio testing (SPRT) process.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTEGRATION INC
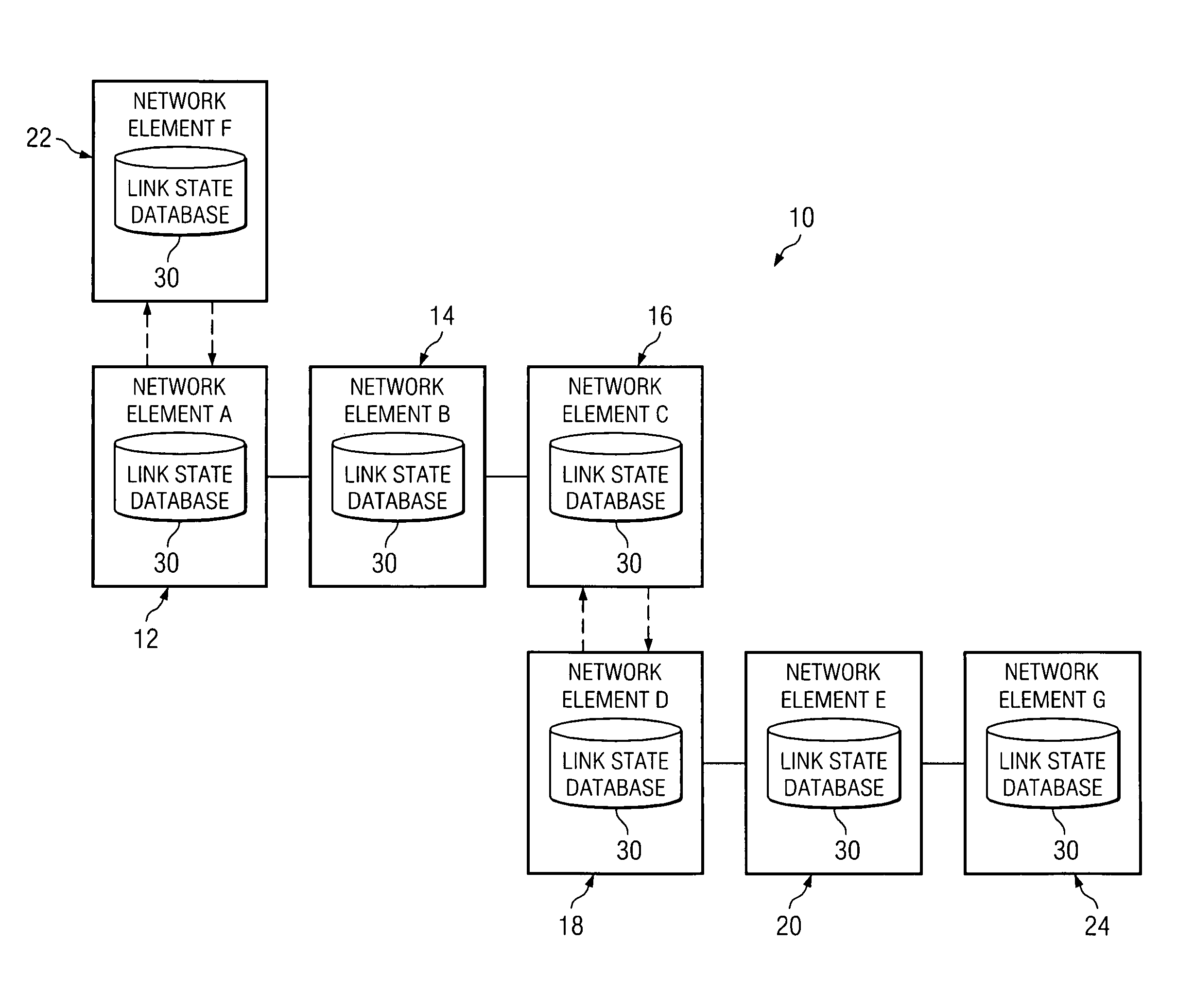
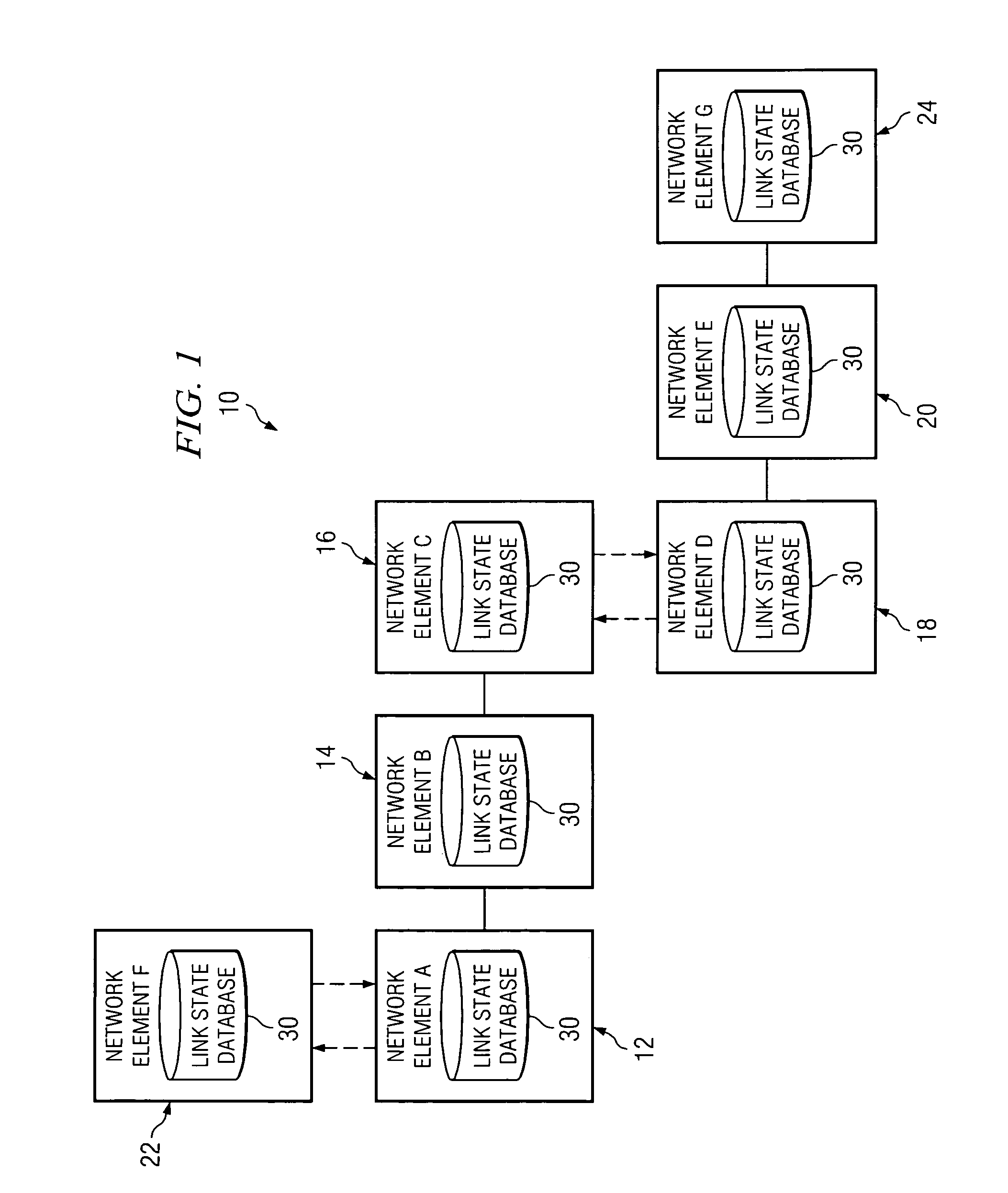
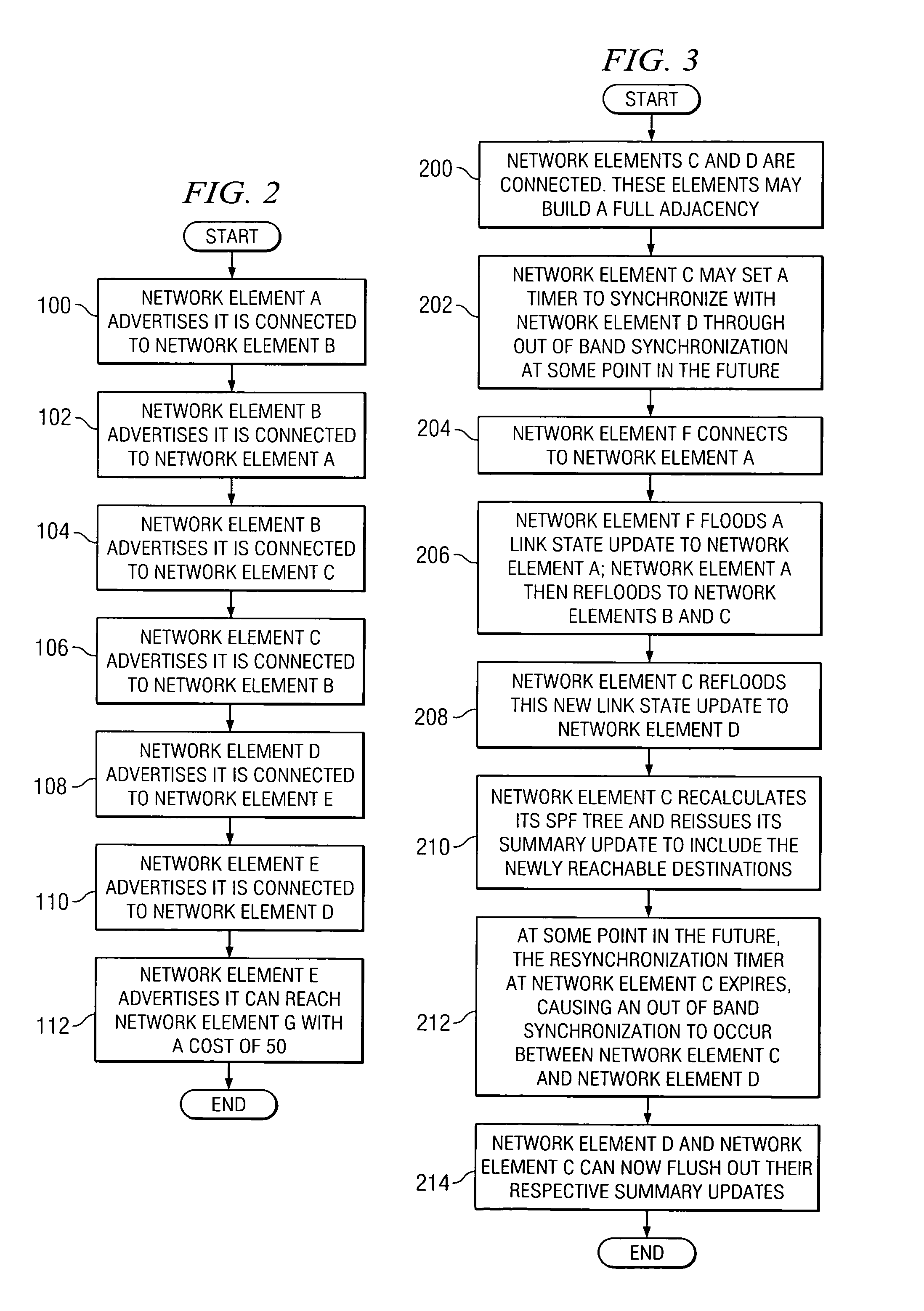
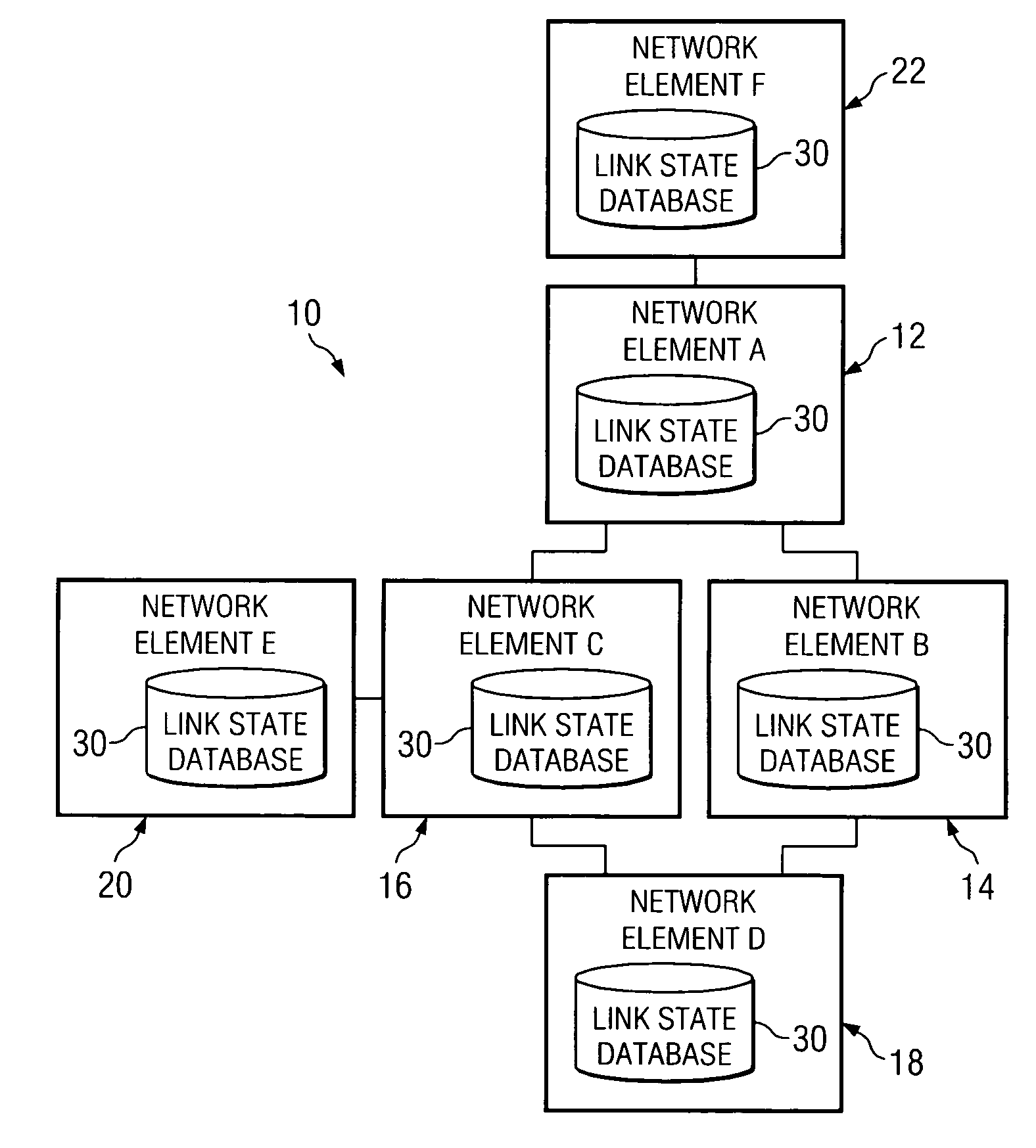
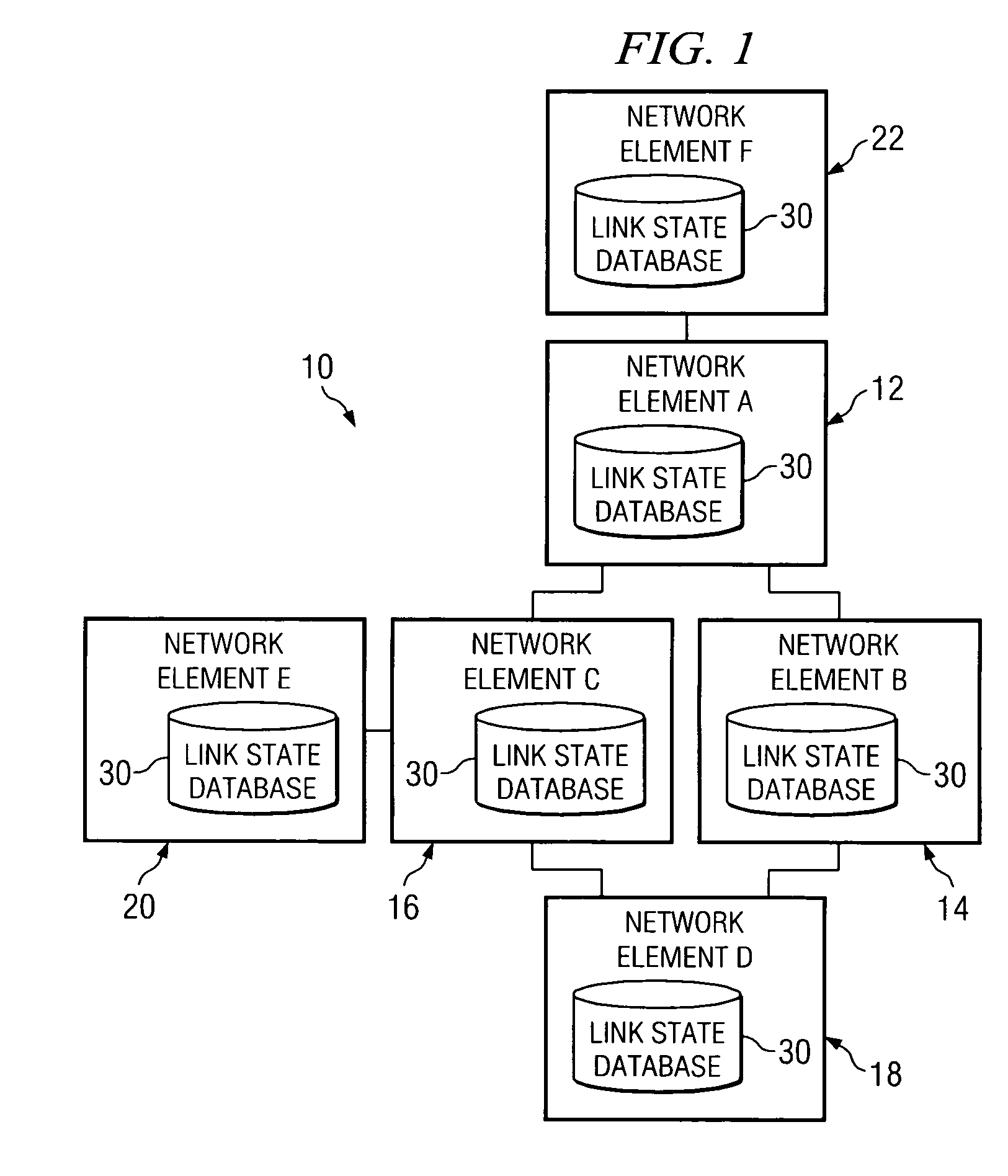
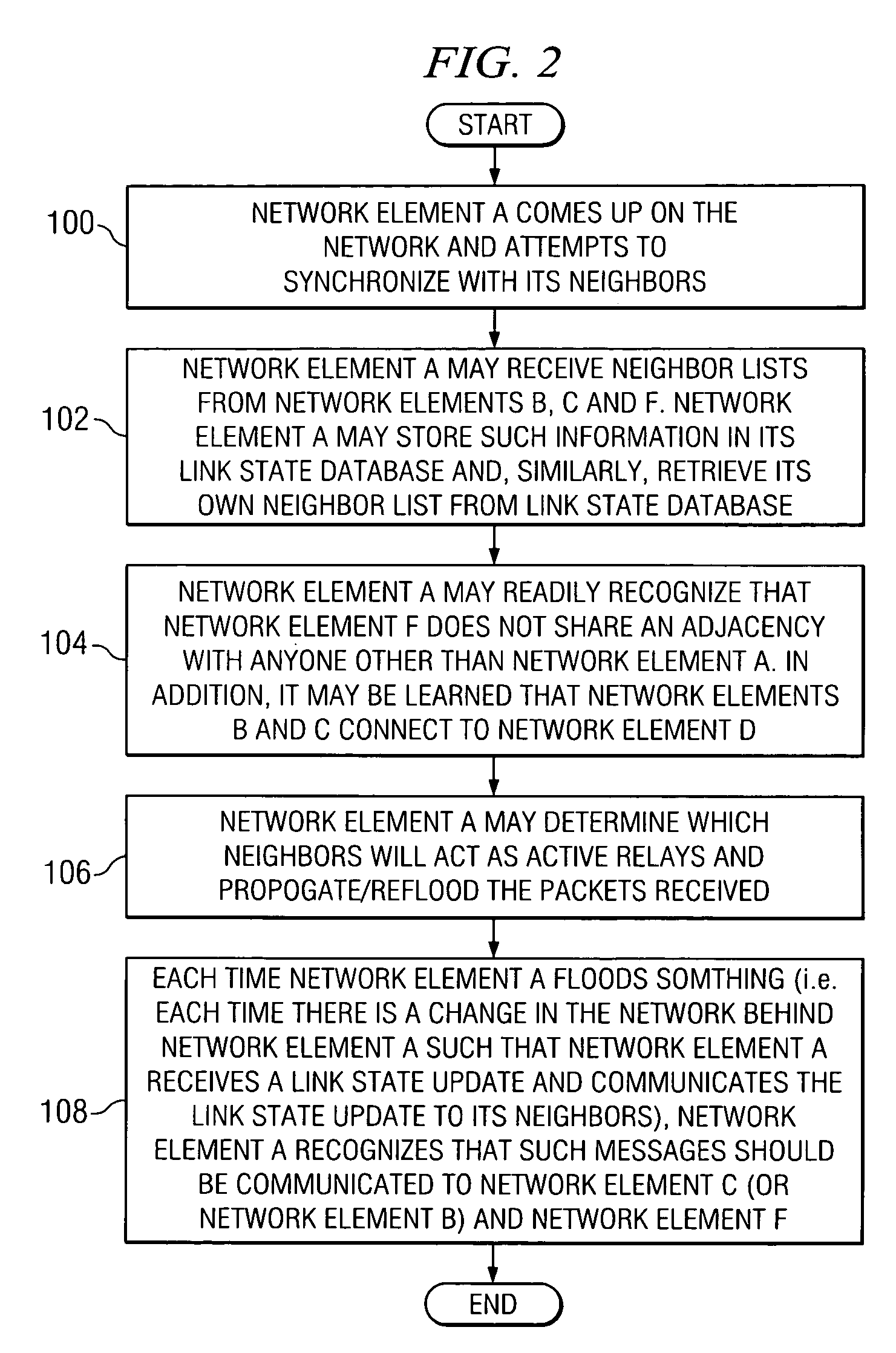
System and method for synchronizing link state databases in a network environment
ActiveUS7391730B1Avoid modificationRealize the operationError preventionTransmission systemsDistributed computingWeb environment
A method for communicating packets in a network environment is provided that includes communicating, by a first network element, a first summary update to a second network element. The method further includes receiving a second summary update from the second network element. The exchange of the first and second summary updates achieves adjacency between the first and second network elements. The first and second summary updates include, at least, locally generated state information and a single link state.
Owner:CISCO TECH INC
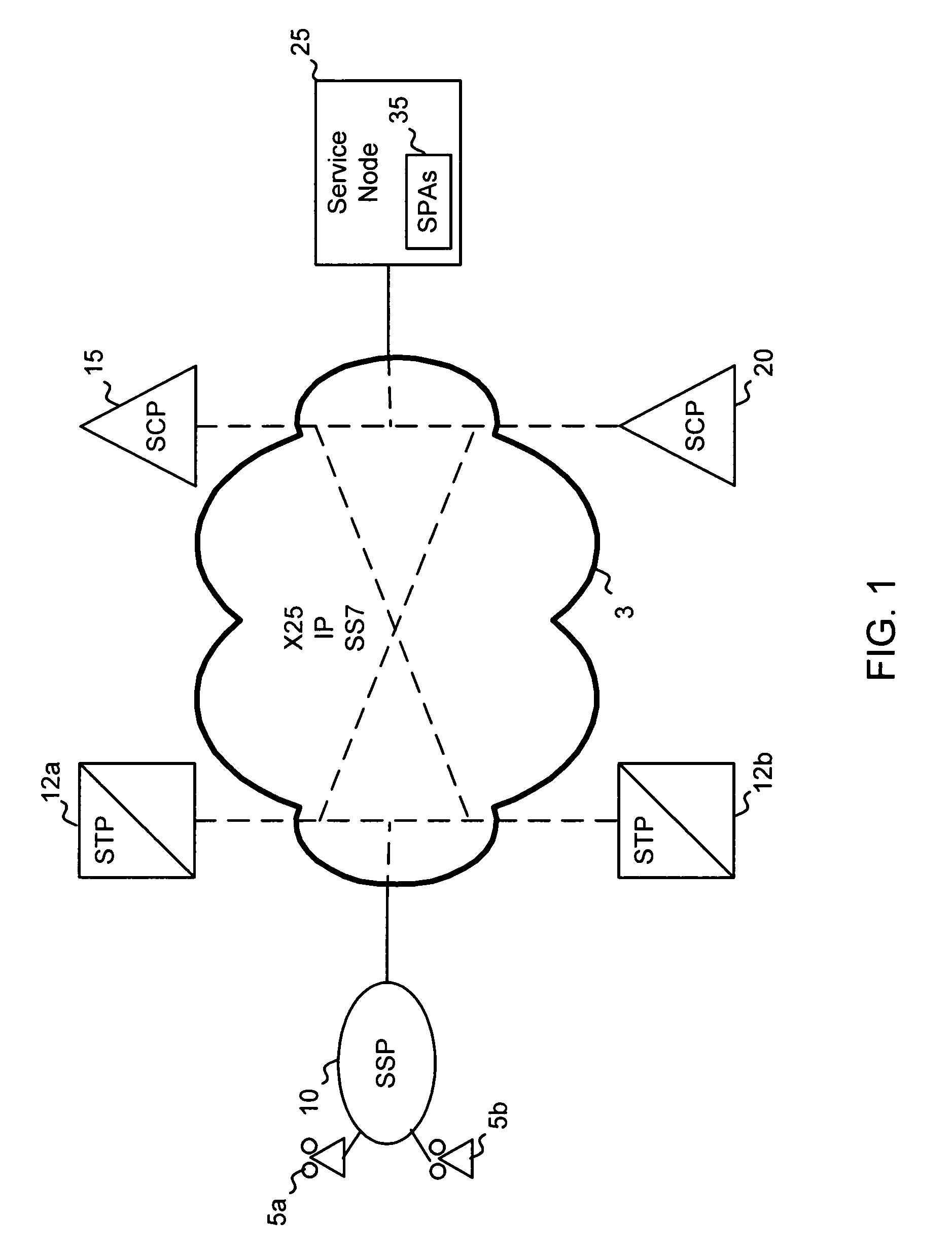
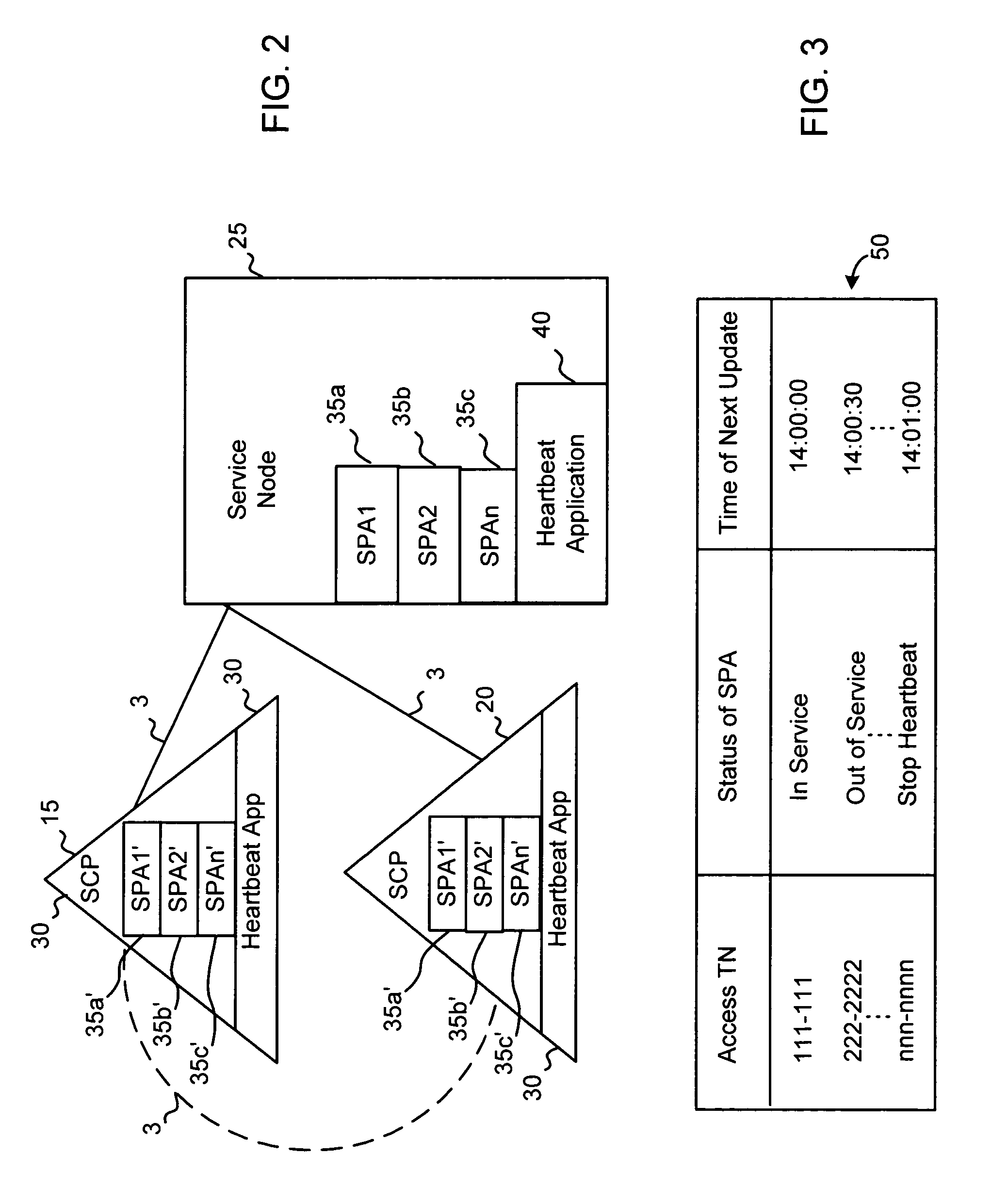
Systems and methods for an infrastructure centralized heartbeat
InactiveUS7120688B1Reduce expensesReduce network overheadDigital computer detailsTransmissionTelecommunications networkService control
A system for monitoring the status of a plurality of service package applications operating on a service node of a telecommunications network. A heartbeat message generating application is stored on the service node and includes a shared database that is accessible by at least two of the plurality of service package applications. A heartbeat message receiving application is stored on a service control point (SCP) that is in communication with the service node, the heartbeat message receiving application including a status database that includes records for monitoring the status of the at least two of the plurality of service package applications. The heartbeat message generating application generates a heartbeat message containing information retrieved from the shared database and sends the heartbeat message to the heartbeat message receiving application where the information is extracted and used to update the status database. Calls are routed to the service package applications based on the status stored in status database.
Owner:BELLSOUTH INTPROP COR
Method and system for setting routing path considering hidden node and carrier sense interference, and recording medium thereof
ActiveUS20110075578A1Improve network performanceReduce network overheadError preventionFrequency-division multiplex detailsHidden node problemWireless mesh network
Disclosed are a method and a system for setting a routing path in consideration of hidden nodes and carrier sense interference.The method of setting a routing path for transmitting a packet from a source node to a destination node in a wireless multi-hop network consisting of plural nodes and plural links for connecting two nodes with each other, comprises: calculating carrier sense interference weights representing carrier sense interference related to the respective links and combining the carrier sense interference weights of the links included in at least one specific path connecting the source node with the destination node; calculating hidden node weights representing hidden node problems related to the respective links and accumulating the hidden node weights of the links included in the path; and calculating a metric value for the specific path by combining the carrier sense interference weights and the hidden node weights, and determining the specific path with the least metric value as the routing path.Accordingly, in the multi-channel multi-radio wireless mesh network, the path with minimized hidden node problem and carrier sense interference can be selected to improve network performance
Owner:KOREA ADVANCED INST OF SCI & TECH
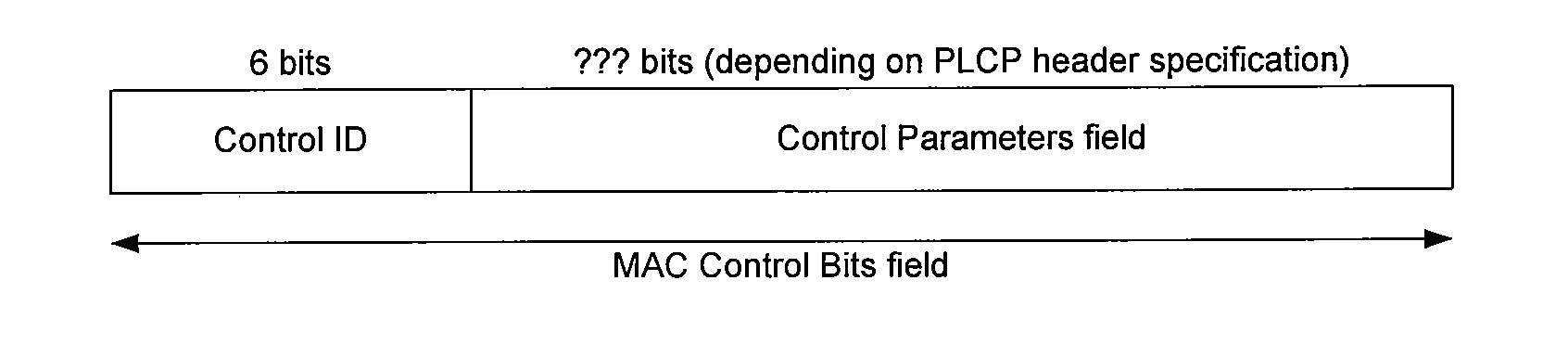
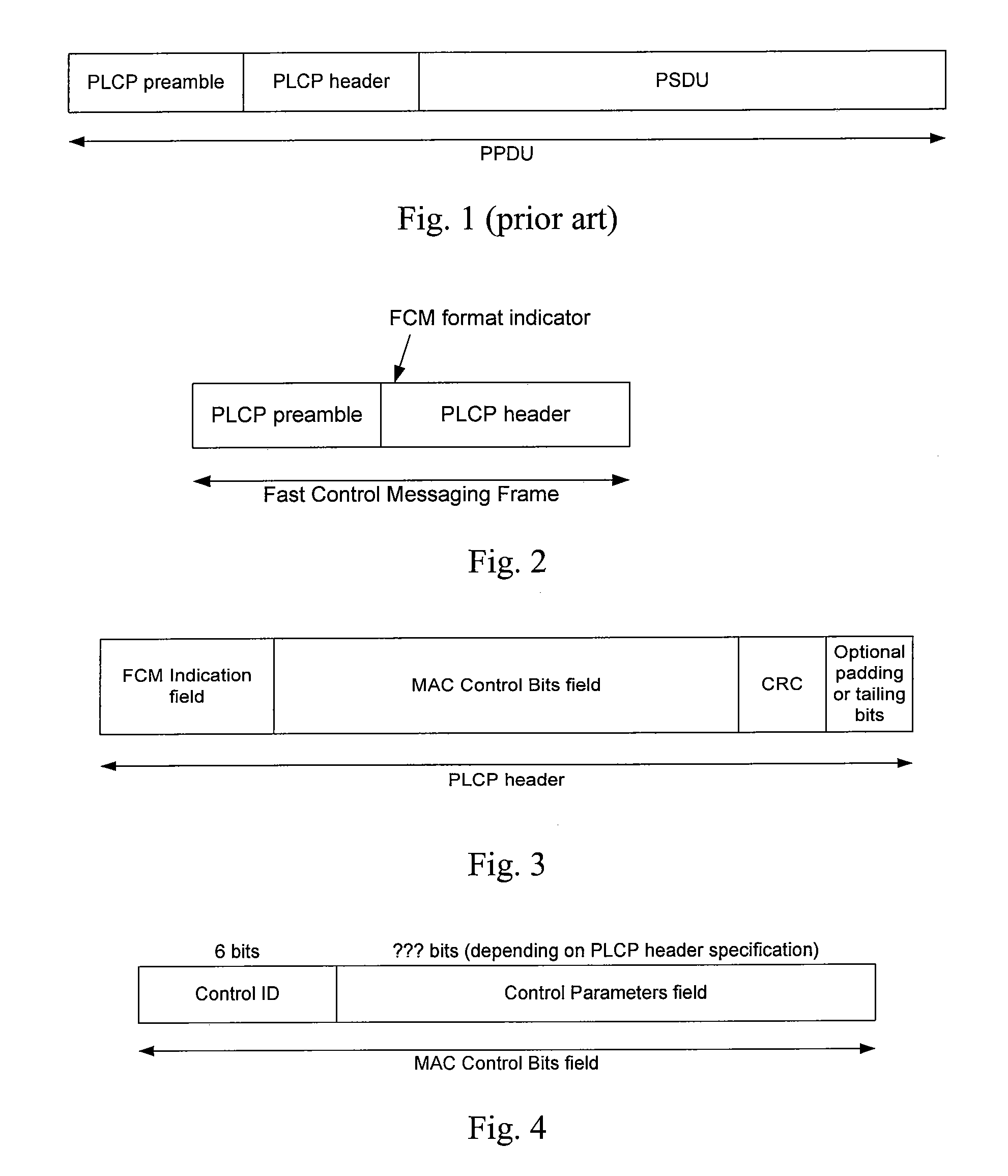
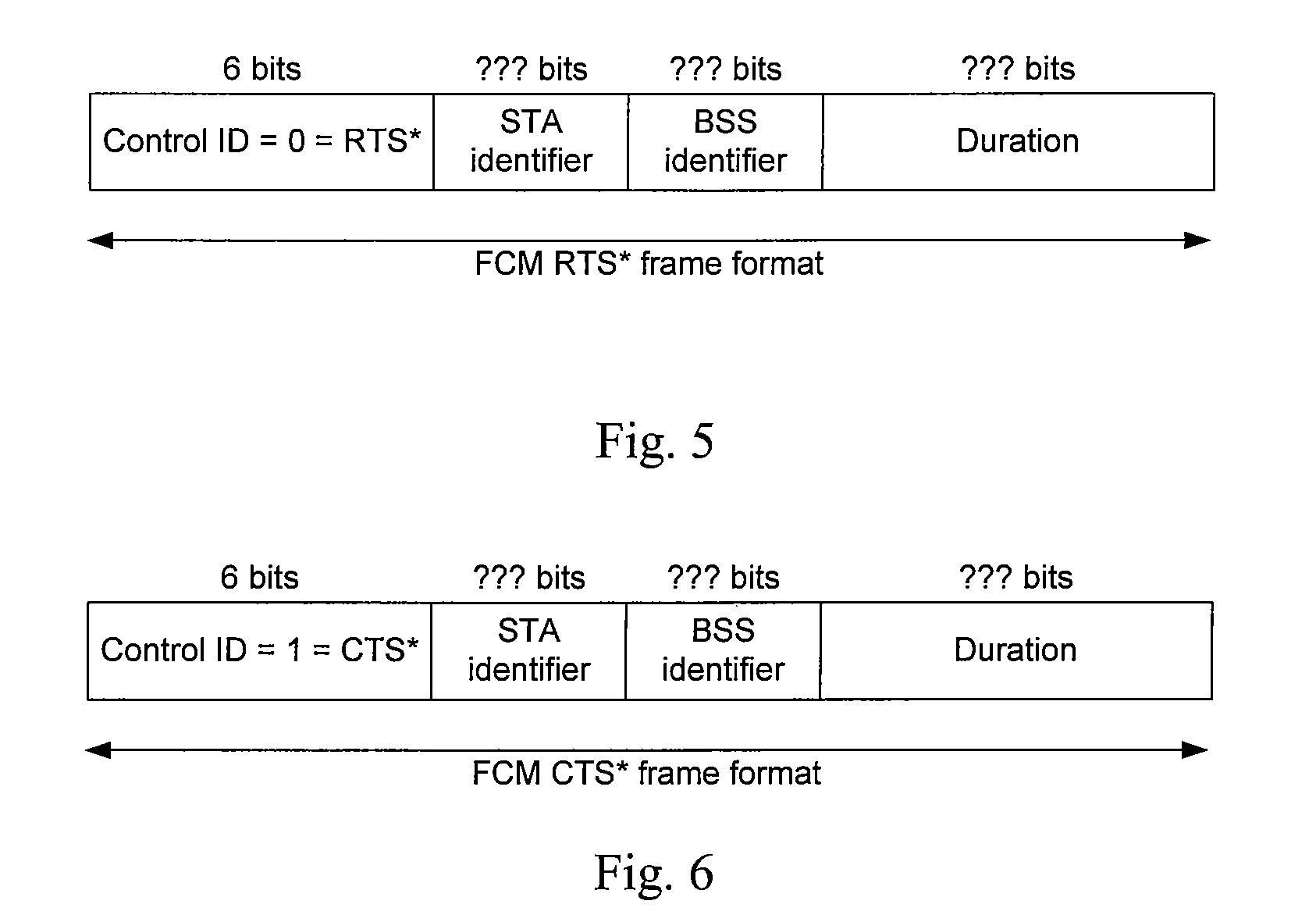
Fast Control Messaging Mechanism For Use In Wireless Network Communications
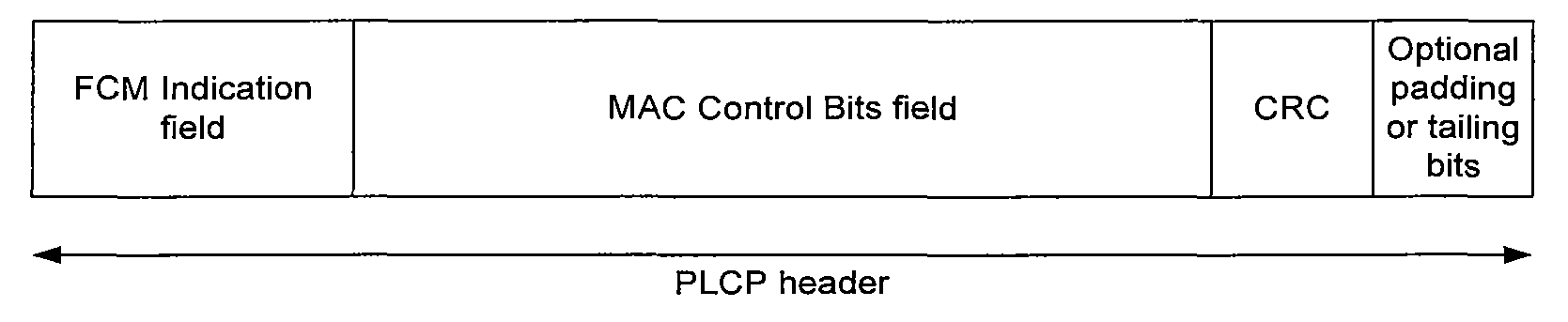
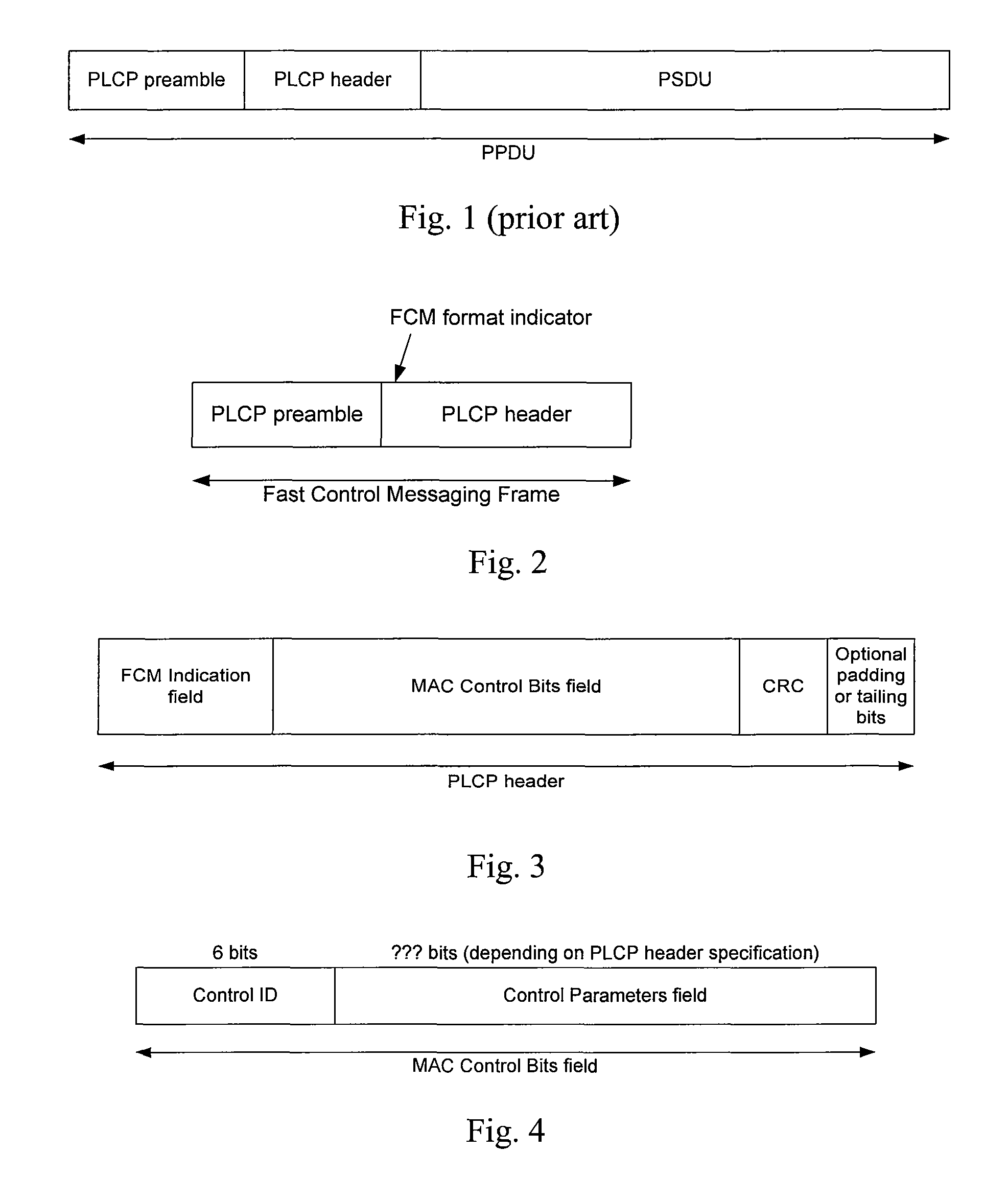
ActiveUS20070058566A1Reduce network overheadBroadcast with distributionTransmission systemsMessage passingReal-time computing
In a wireless network according to embodiments of the present invention, fast control messaging frames are used to signal control information. A fast control messaging (“FCM”) frame includes MAC layer control bits in a PLCP header, obviating the need for a PSDU. These frames can be used in 802.11n wireless networks as well as in other suitable 802.11x networks as well as non-802.11x networks to exchange control information while significantly reducing network overhead. In some embodiments, some information that might have been conveyed to a receiver's MAC layer in a PSDU is conveyed by including that information is a PLCP header and having logic within the receiver's PHY layer processing to process that information and convey that information up to the receiver's MAC layer in a simulated PSDU or other method. The indicator of an FCM frame can be a bit in a PLCP header, a modification of a CRC field of the PLCP header, or other indicator. The medication of the CRC field of the PLCP header can be an inversion of the CRC field, a translation of the CRC field by a constant value, or both, or some other variation.
Owner:QUALCOMM INC
Cross-layer self-healing in a wireless ad-hoc network
ActiveUS20060239216A1Improve self-healing abilityEnhanced network operationPower managementNetwork topologiesSuccessful transmissionWireless ad hoc network
Disclosed is a method and apparatus for improved self-healing in a mobile ad-hoc wireless network in which network communication functions are divided into a plurality of functional layers. The system utilizes cross-layer self-healing techniques. Network data from at least one of the functional layers is stored, for example in a storage unit of the network node. The stored network data is then used to modify the functioning of at least one of the other layers. In one embodiment, a management module manages the storage and use of the network data. In particular embodiments, the stored network data relates to successful transmission rates and / or clear channel rates, and this stored data is used to adjust the transmission power of the network node. In another embodiment, the stored data may be used to generate a table of interchangeable network nodes, which may then be used to reroute a data packet to a network node other than an originally specified destination node. In yet another embodiment, the stored data may be used to generate a list of recent neighbor nodes, which data may be used to reroute data packets to intermediate network nodes.
Owner:TELCORDIA TECHNOLOGIES INC
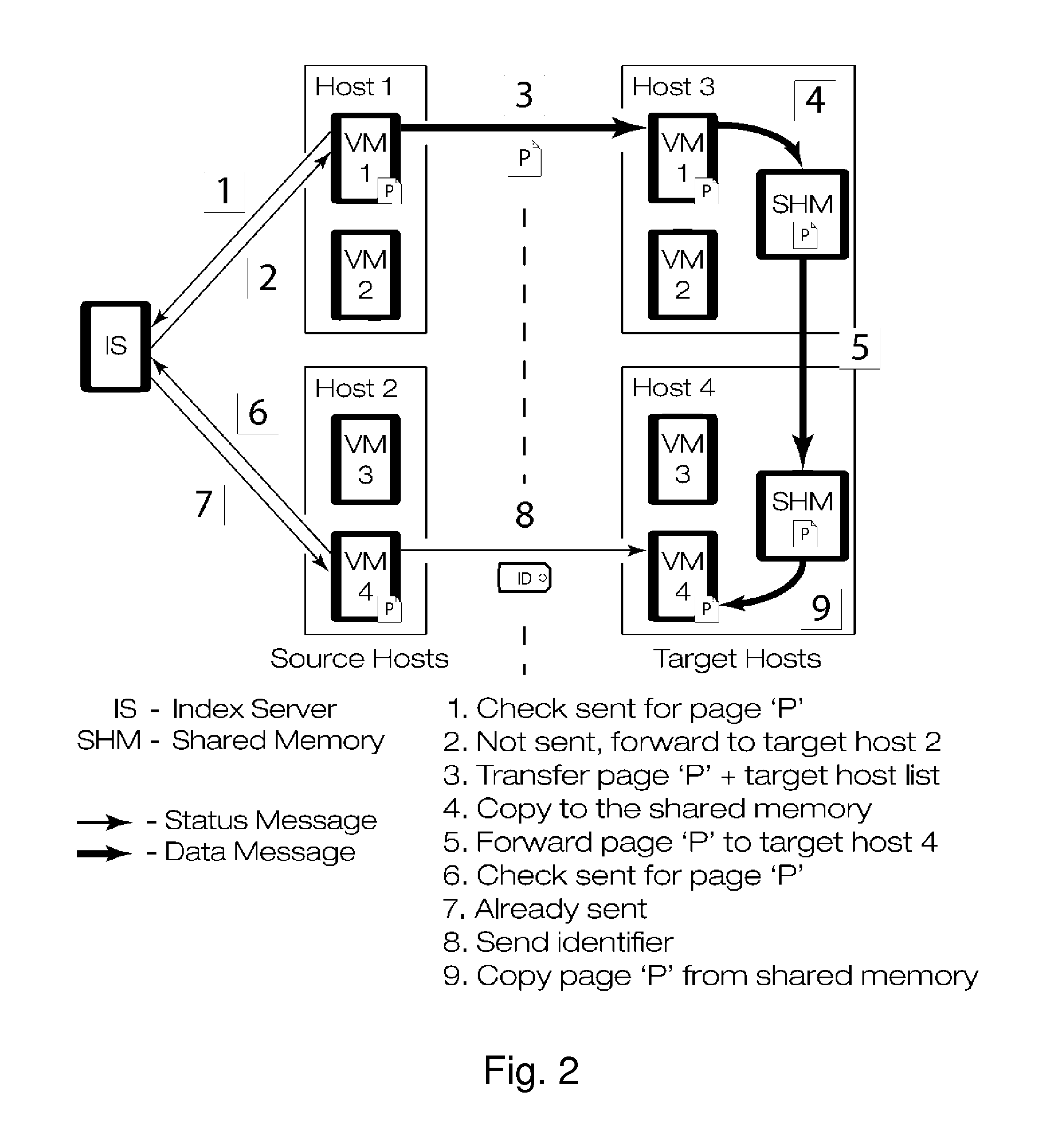
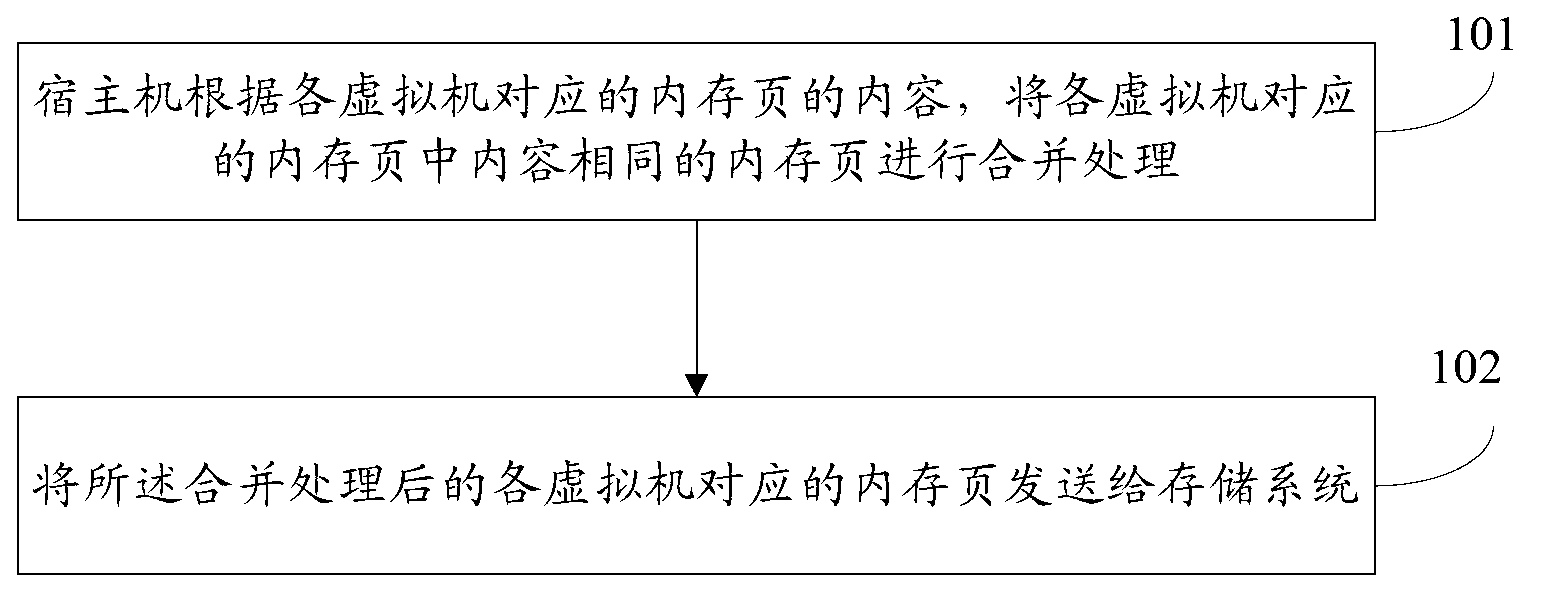
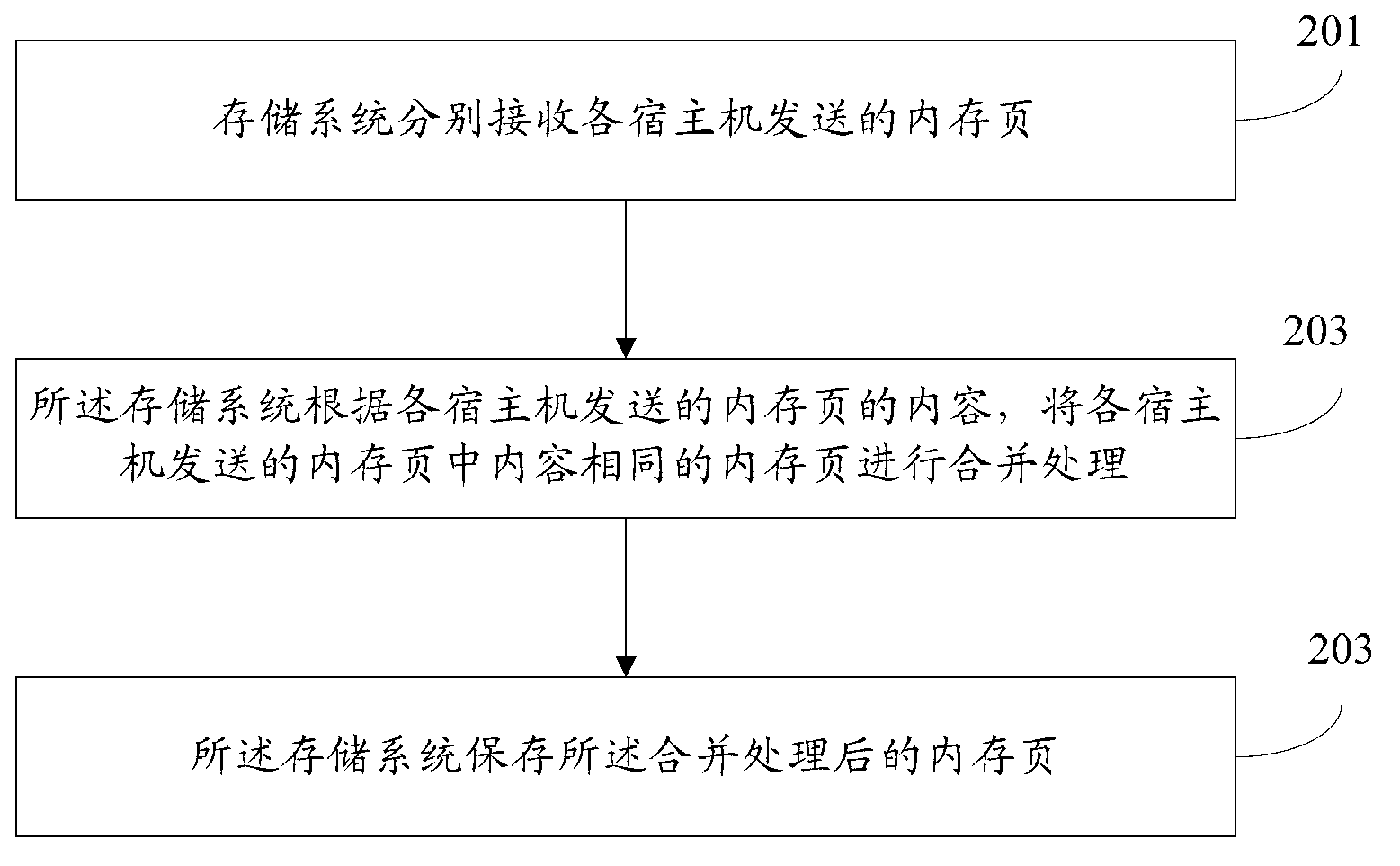
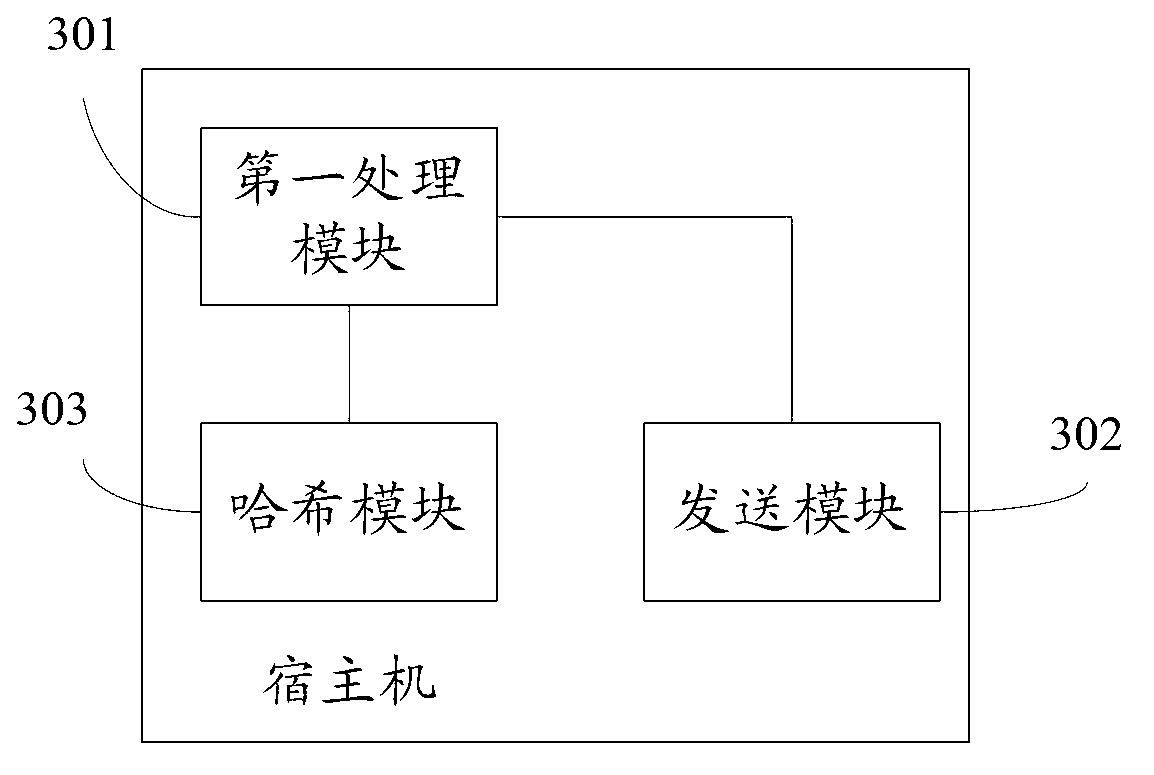
Memory page de-weight method and memory page de-weight device based on virtual machine snapshot
ActiveCN103019884AImprovements take up a lot of disk spaceReduce network overheadMemory adressing/allocation/relocationRedundant operation error correctionVirtual machineDisc space
The invention provides a memory page de-weight method and memory page de-weight device based on virtual machine snapshot, which are applied to a virtual machine snapshot system. The method comprises the following steps: a host computer carries out combination processing on memory pages (of the same content) of memory pages corresponding to each virtual machine according to the content of the memory pages corresponding to each virtual machine; and the memory pages (subjected to combination processing) corresponding to each virtual machine are transmitted to a storage system. Problems that snapshot backup data occupy a large quantity of disc space in a virtual machine snapshot technique are modified; and meanwhile the time for backing up the snapshot is reduced.
Owner:BEIHANG UNIV
System and method for controlling the flooding of information in a network environment
ActiveUS7298707B2Minimize floodingReduce disadvantagesError preventionTransmission systemsWeb environmentNetwork element
Owner:CISCO TECH INC
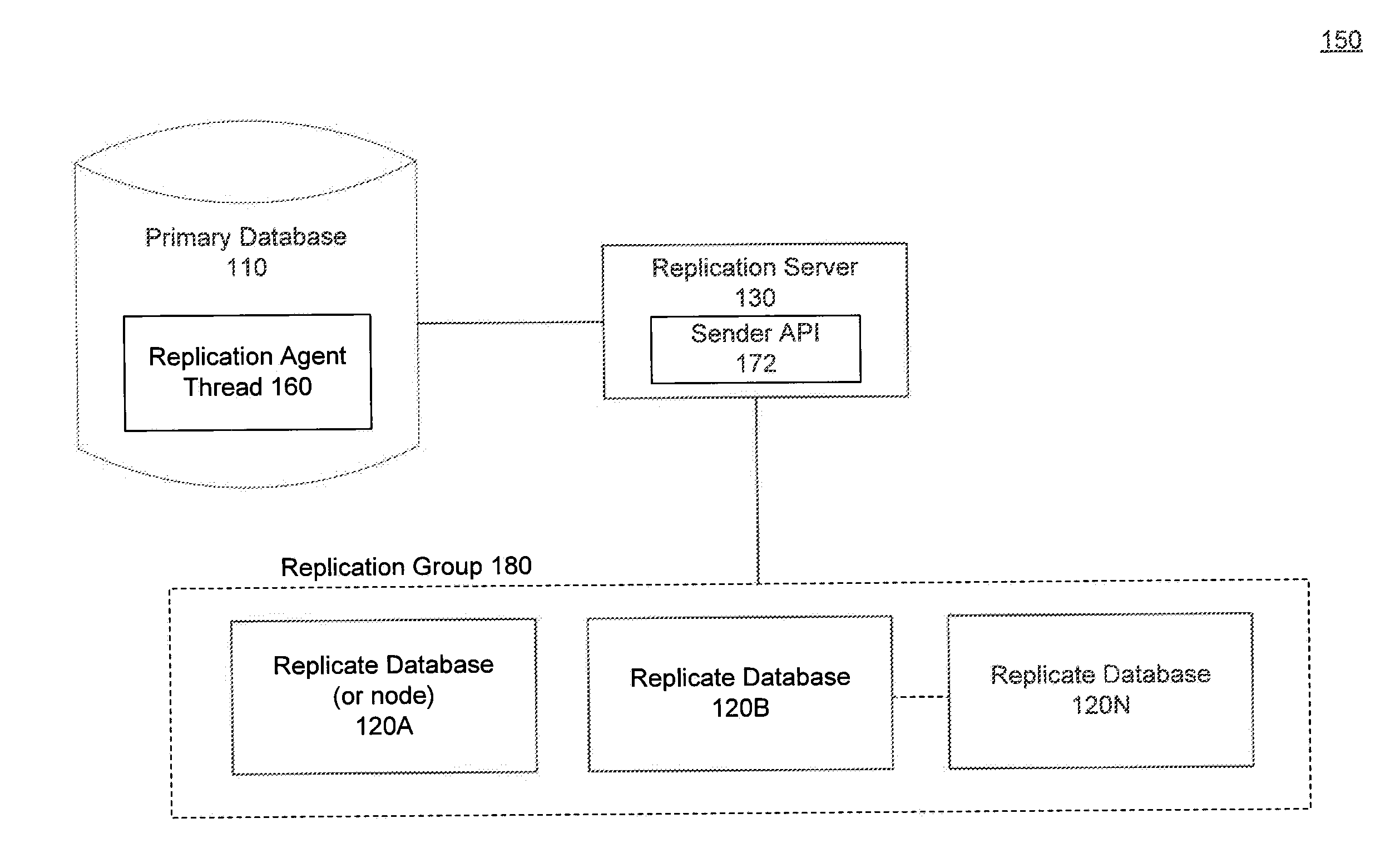
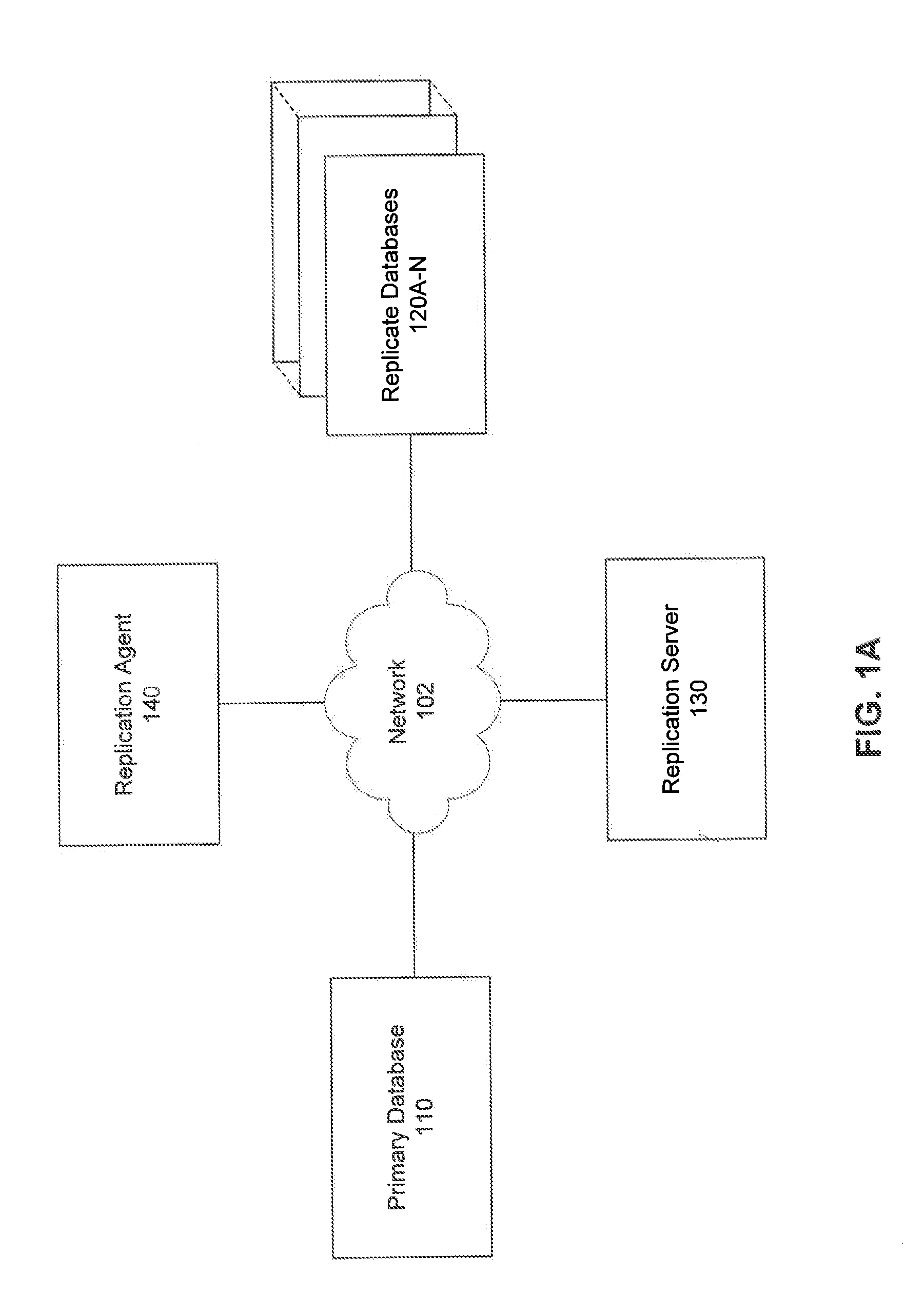
Multicast database replication
ActiveUS20130054526A1Attenuation bandwidthReduce network overheadDigital data processing detailsDatabase distribution/replicationMulticast addressComputer program
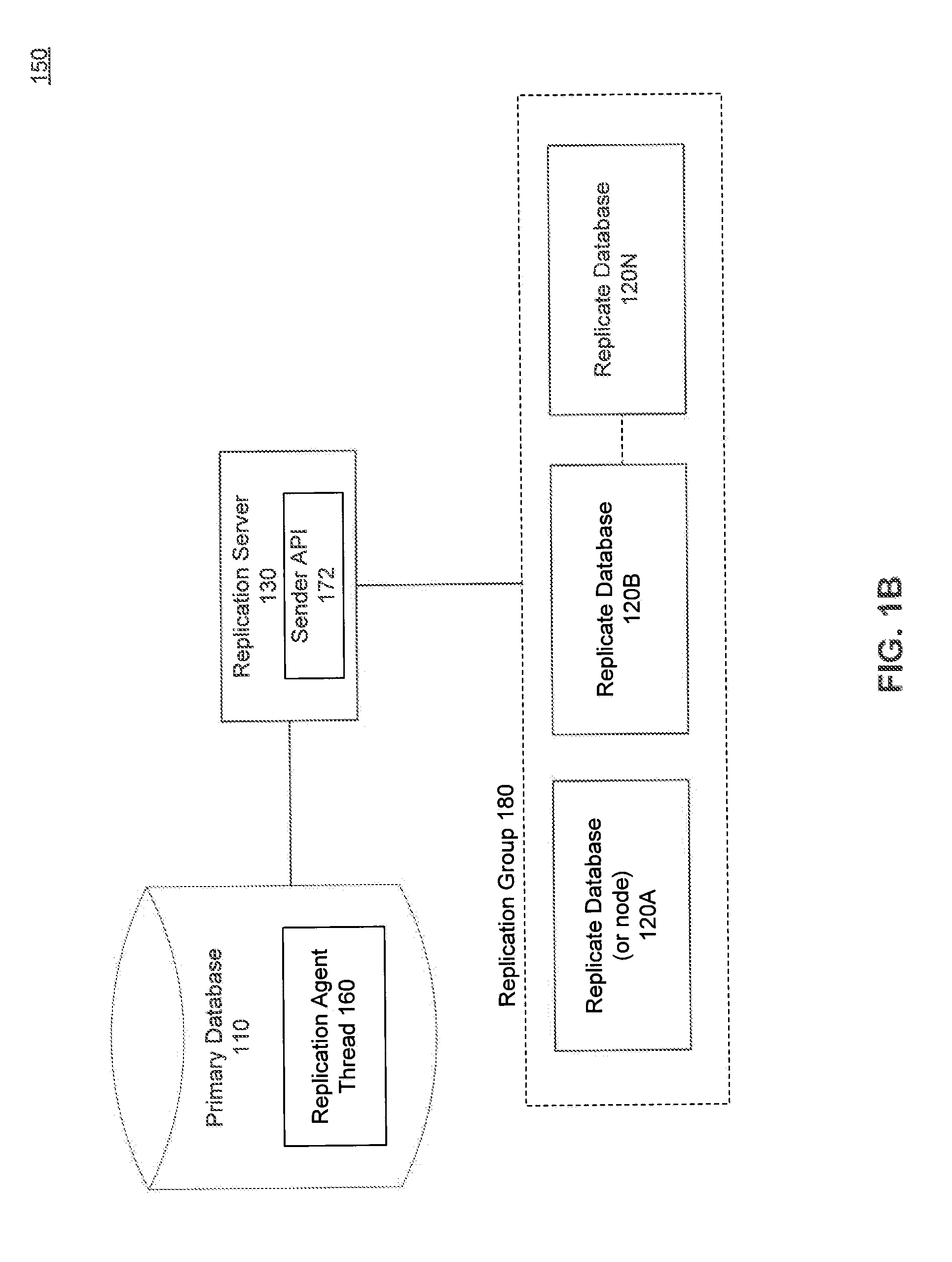
Systems, methods and computer program products for multicast database replication are described herein. An embodiment includes creating a replication group for replication of data. One or more replicate (or target) databases are subscribed to the replication group and the replication group may include one or more subscribed replicate databases. The replication group is associated with a replication group address. Embodiments send (or publish) data that is to be replicated to the replication group multicast address causing automatic replication of the data to the subscribed replicate databases. In this way, by sending data to be replicated once to a replication group address, the data is automatically replicated to several subscribed replicate databases and a replication server need not establish distinct point-to-point connections with each replicate database.
Owner:SYBASE INC
System and method for exchanging awareness information in a network environment
InactiveUS7319674B2Increased awareness feature and characteristicReduce disadvantagesError preventionTransmission systemsSerial codeAwareness information
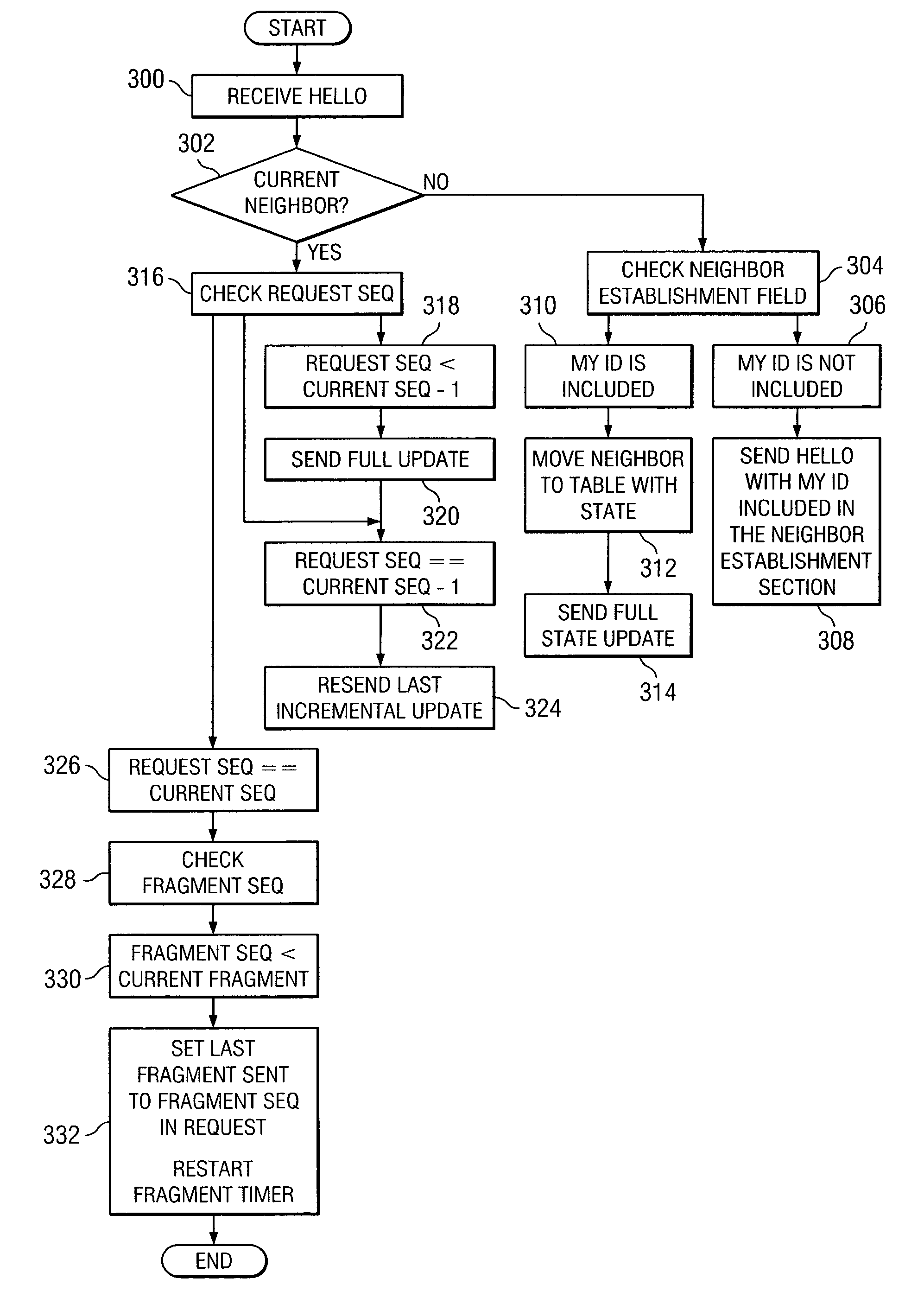
A method for communicating packets in a network environment is provided that includes receiving a packet at a network element and identifying a sequence number included in the packet that correlates to awareness information associated with one or more adjacent network elements. A table included in the network element may be updated in order to account for the awareness information included within the packet that has not been accounted for by the network element. In cases where the awareness information included in the packet has already been accounted for, the packet may be ignored.
Owner:CISCO TECH INC
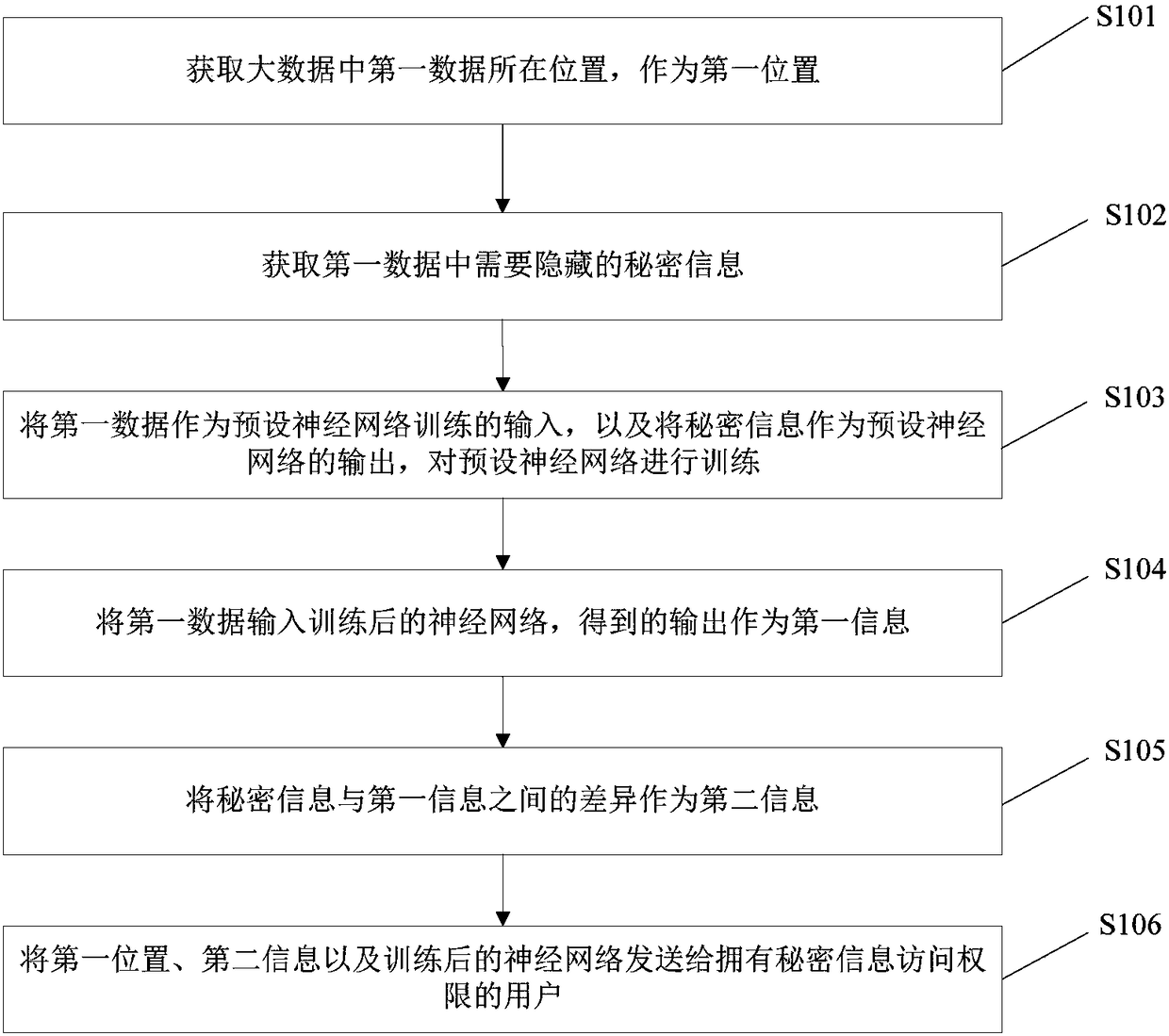
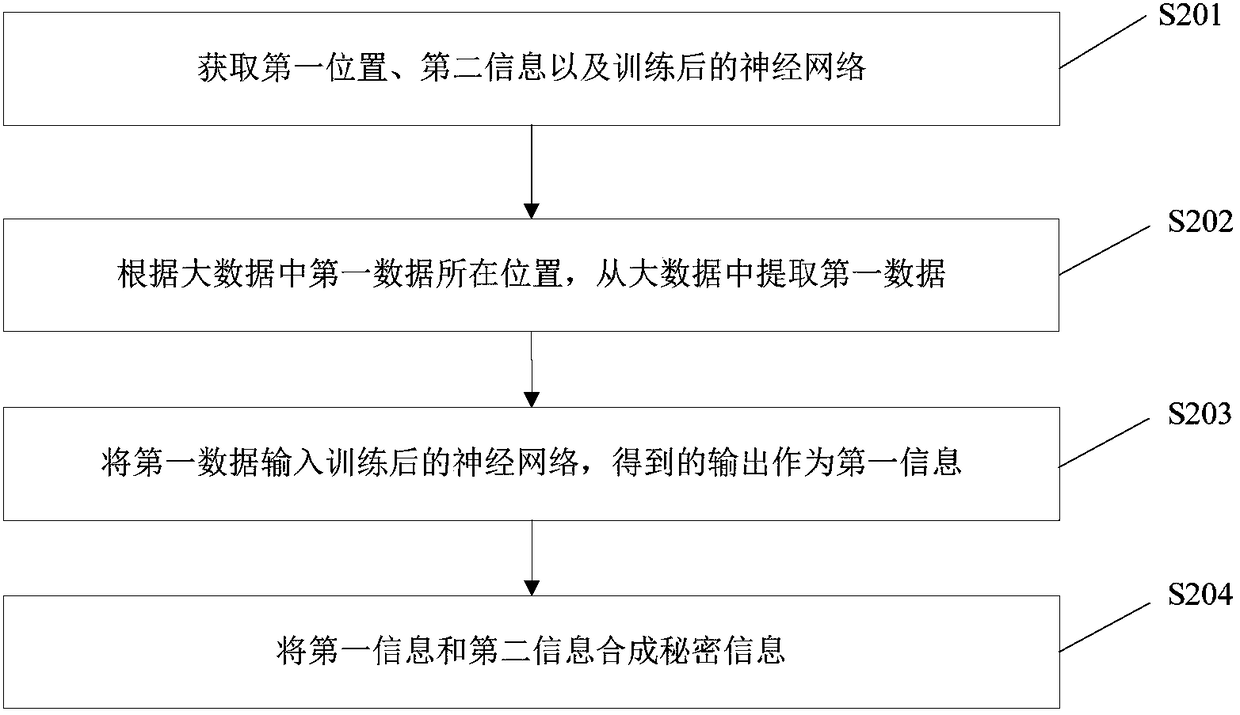
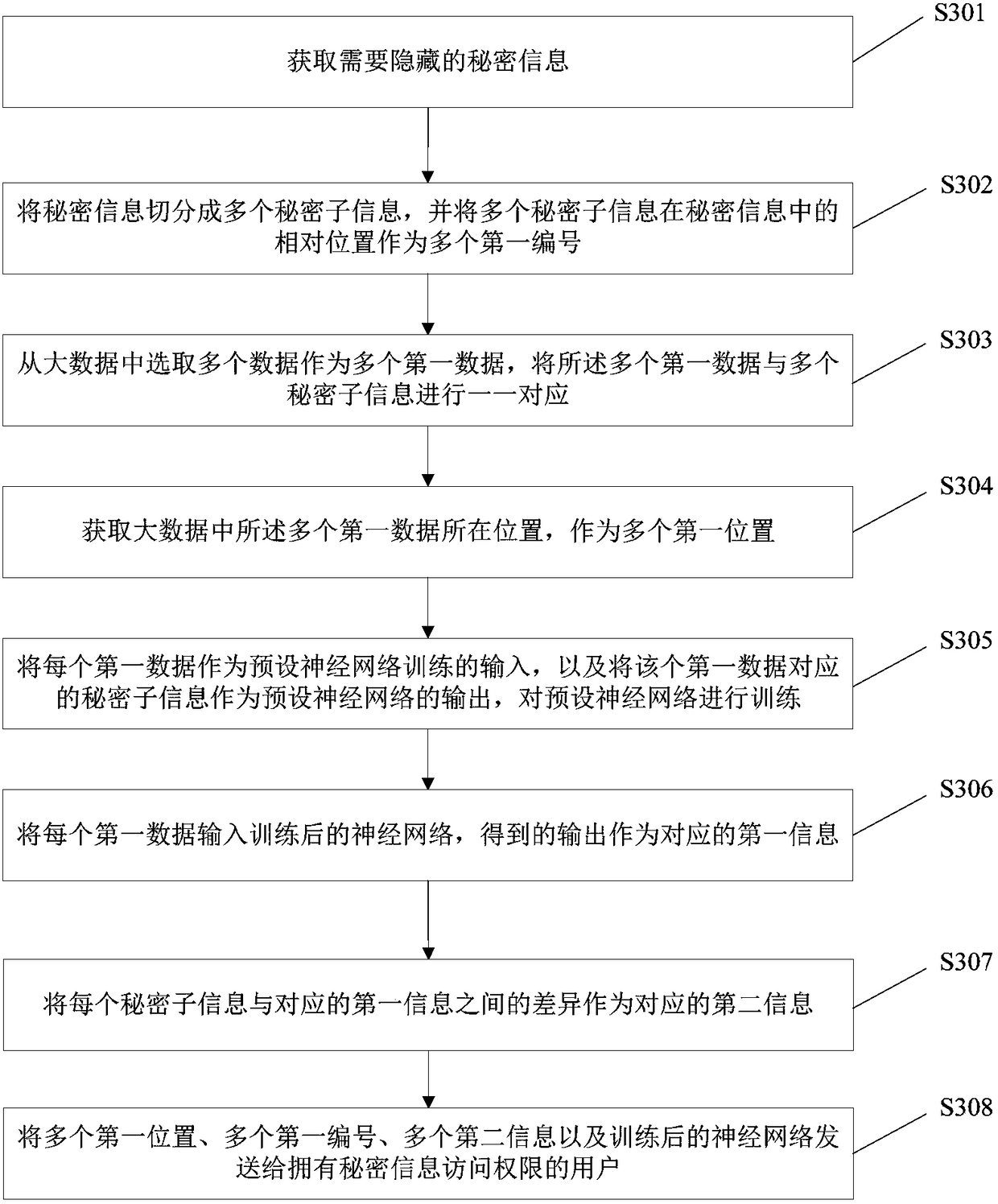
Information hiding methods and systems and extraction methods and systems based on big data and neural network
ActiveCN108197488AEnsure safetyImprove concealmentDigital data protectionNeural learning methodsNerve networkInformation access
The invention discloses information hiding methods and systems and extraction methods and systems based on big data and a neural network. One of the information hiding methods includes: acquiring a location of first data in the big data; acquiring secret information which is in the first data and needs to be hidden; respectively using the first data and the secret information as input and output of the preset neural network to train the preset neural network; inputting the first data into the trained neural network, and using obtained output as first information; using differences between thesecret information and the first information as second information; and sending the location of the first data in the big data, the second information and the trained neural network to the user with secret-information access authority. According to the method, the information can be hidden in the big data, security of the secret information is ensured through training of the neural network, the user with the secret-information access authority can extract the secret information from the big data through synthesis, and network overheads, storage overheads and computational overheads are all extremely low.
Owner:SUPERPOWER INNOVATION INTELLIGENT TECH DONGGUAN CO LTD
Gang migration of virtual machines using cluster-wide deduplication
InactiveUS20170024246A1Reduce network overheadAvoid spreadingMemory architecture accessing/allocationInput/output to record carriersData centerNetwork overhead
Datacenter clusters often employ live virtual machine (VM) migration to efficiently utilize cluster-wide resources. Gang migration refers to the simultaneous live migration of multiple VMs from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a data center. The present technology reduces the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. A prototype GMGD reduces the network traffic on core links by up to 51% and the total migration time of VMs by up to 39% when compared to the default migration technique in QEMU / KVM, with reduced adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
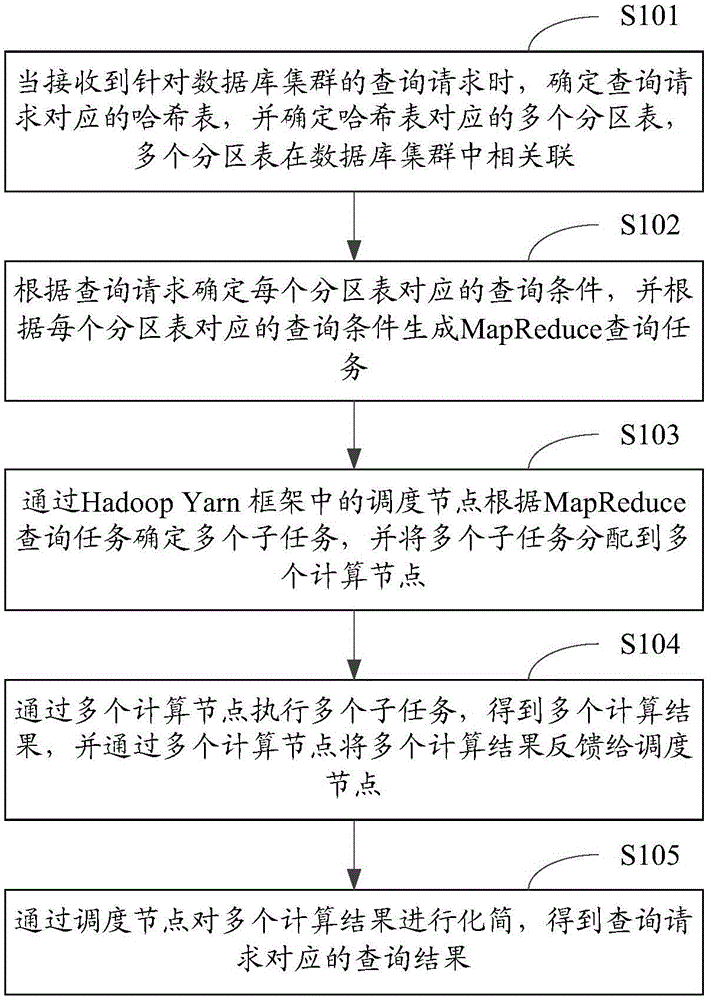
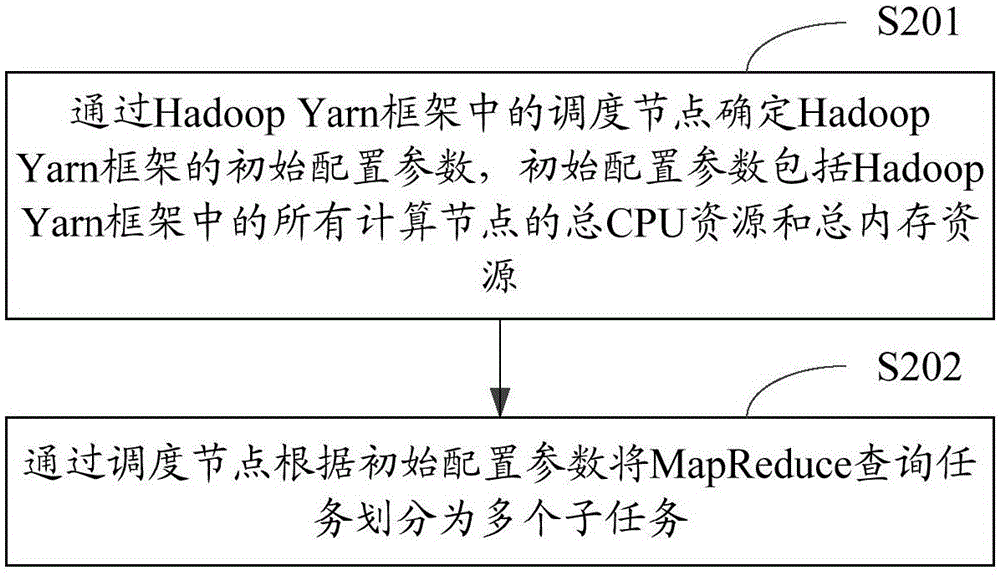
Data aggregation query method and apparatus
ActiveCN105045871AReduce network overheadImprove efficiencySpecial data processing applicationsData aggregatorYarn
The invention is suitable for the technical field of large-scale data processing and particularly relates to a data aggregation query method and apparatus. The method comprises: when receiving a query request for a database cluster, determining a hash table corresponding to the query request, determining a plurality of partition tables corresponding to the hash table, and generating a MapReduce query task; through scheduling nodes in an Hadoop Yarn framework, according to the MapReduce query task, determining a plurality of subtasks, and distributing the subtasks to a plurality of computing nodes; through the computing nodes, performing the subtasks, obtaining a plurality of computing results, and through the computing nodes, feeding the computing results back to the scheduling nodes; and through the scheduling nodes, simplifying the computing results, and obtaining a query result corresponding to the query request. The method and the apparatus realize relational query and statistics of the relevant partition tables in the database cluster, reduce network overhead, and improve data aggregation query efficiency.
Owner:国家超级计算深圳中心(深圳云计算中心) +1
Fast control messaging mechanism for use in wireless network communications
ActiveUS7760700B2Reduce network overheadBroadcast with distributionTransmission systemsNetwork overheadMessage passing
In a wireless network according to embodiments of the present invention, fast control messaging frames are used to signal control information. A fast control messaging (“FCM”) frame includes MAC layer control bits in a PLCP header, obviating the need for a PSDU. These frames can be used in 802.11n wireless networks as well as in other suitable 802.11x networks as well as non-802.11x networks to exchange control information while significantly reducing network overhead. In some embodiments, some information that might have been conveyed to a receiver's MAC layer in a PSDU is conveyed by including that information is a PLCP header and having logic within the receiver's PHY layer processing to process that information and convey that information up to the receiver's MAC layer in a simulated PSDU or other method. The indicator of an FCM frame can be a bit in a PLCP header, a modification of a CRC field of the PLCP header, or other indicator. The medication of the CRC field of the PLCP header can be an inversion of the CRC field, a translation of the CRC field by a constant value, or both, or some other variation.
Owner:QUALCOMM INC
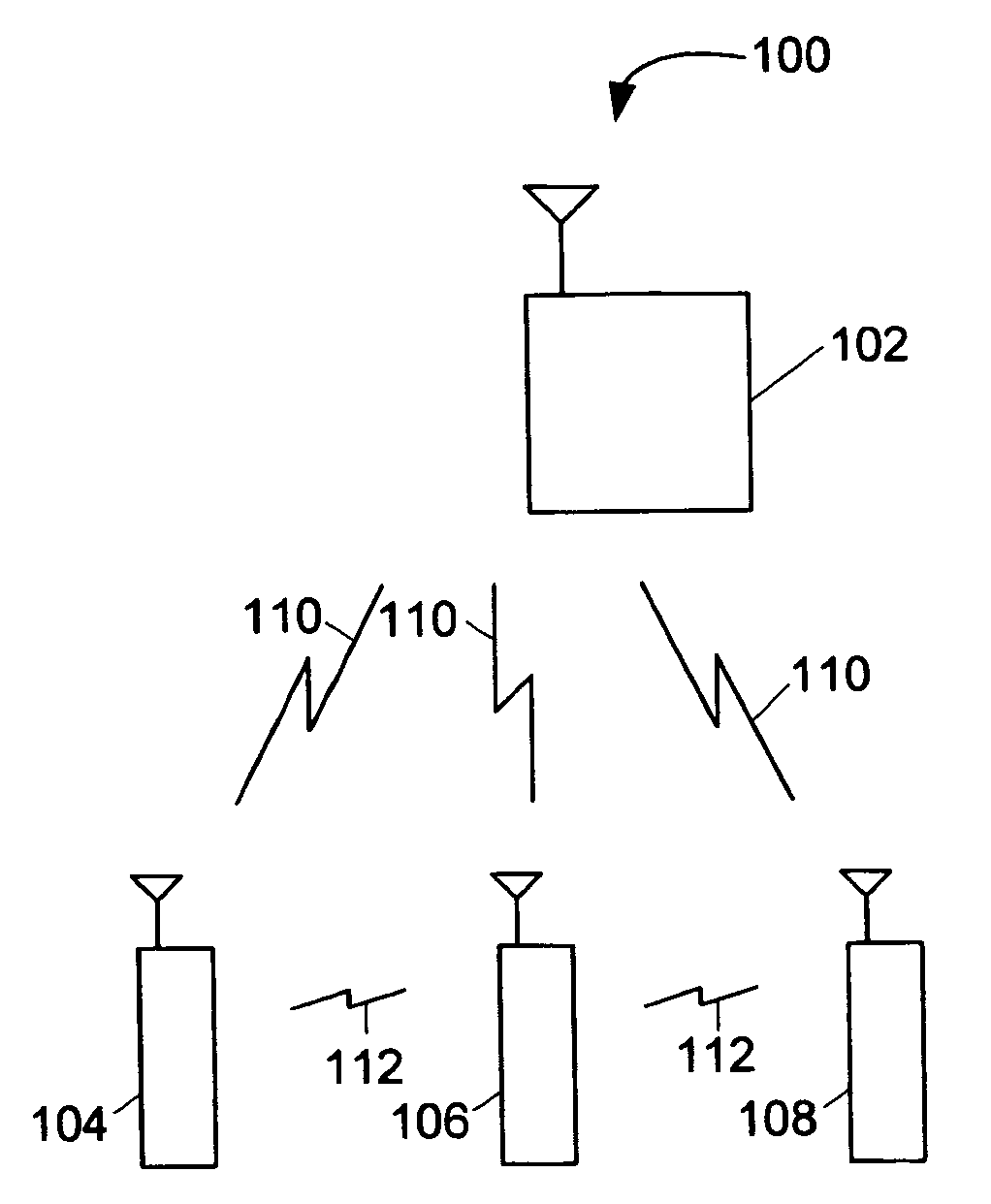
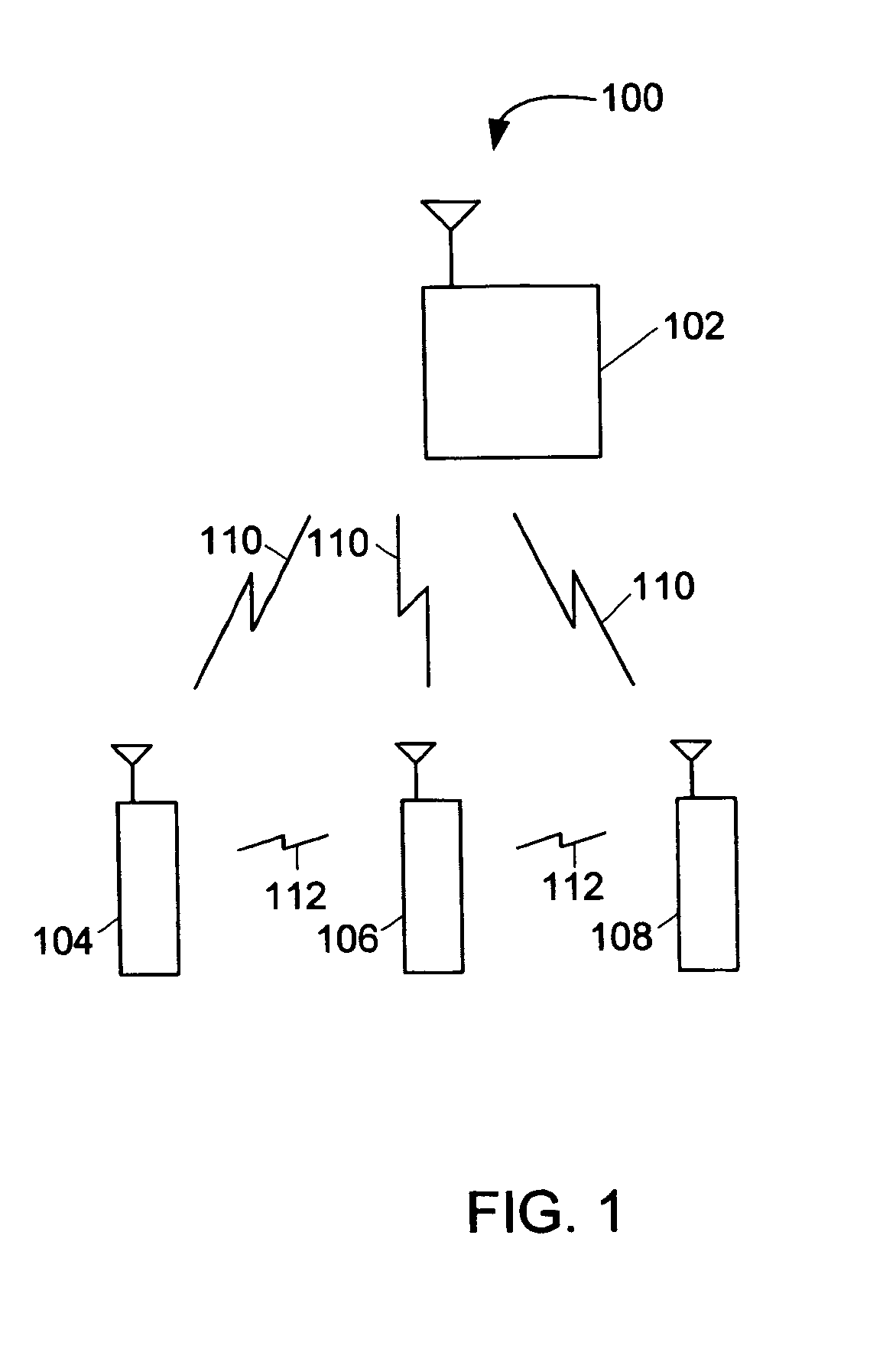
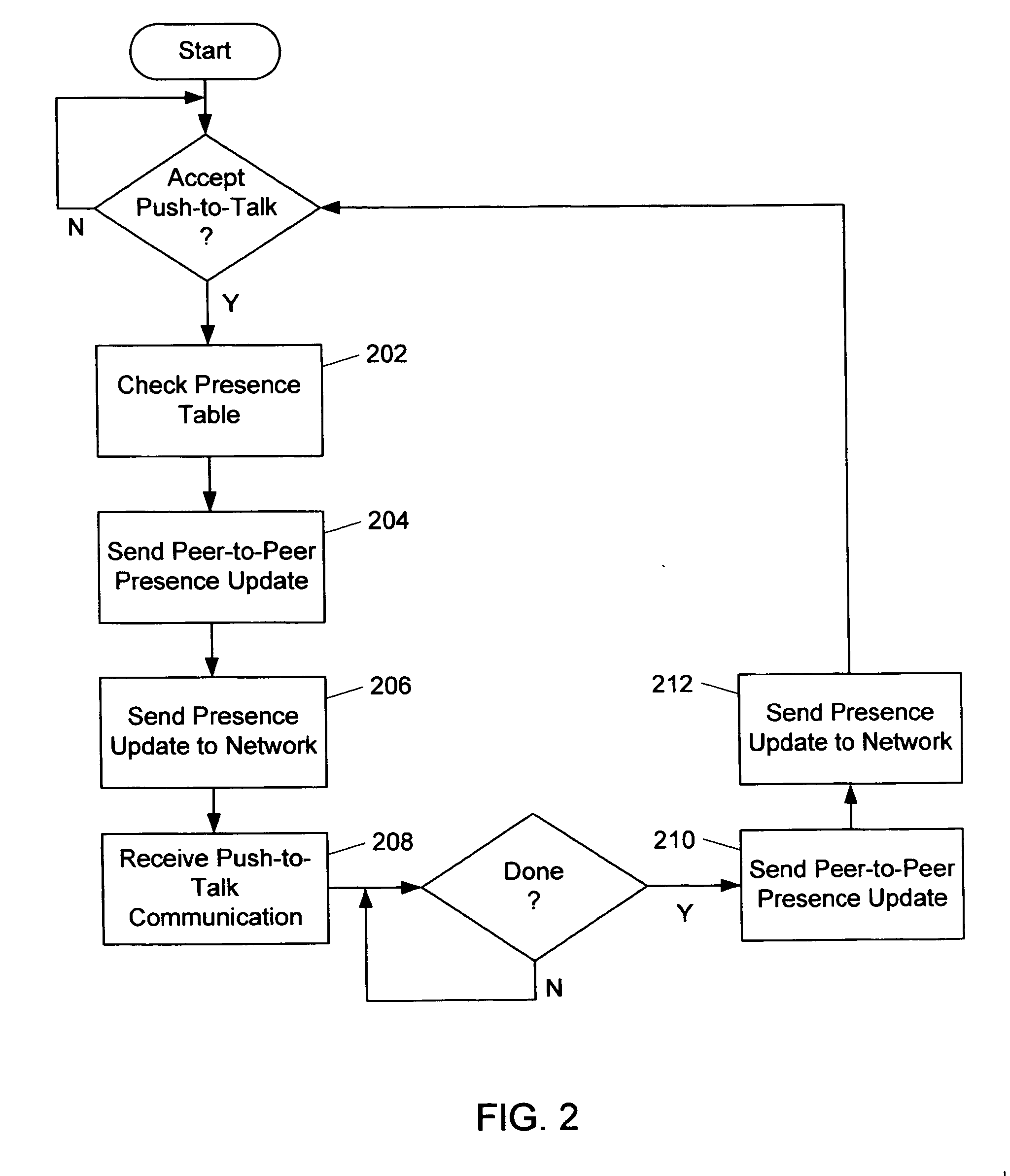
Systems and methods for updating presence in a mobile communication network
InactiveUS20060240855A1Reduce bandwidth consumptionReduce network overheadNetwork topologiesRadio/inductive link selection arrangementsNetwork overheadCommunication device
A mobile communication device is configured to use peer-to-peer communication to update presence information for the associated subscriber. Peer-to-peer communication bypass the network and reduce network overhead and reduce bandwidth consumption. The mobile communication device can also be configured to provide updated presence information to the network, whenever there is a change in presence.
Owner:KYOCERA CORP
Service communication method, service communication device and service communication system
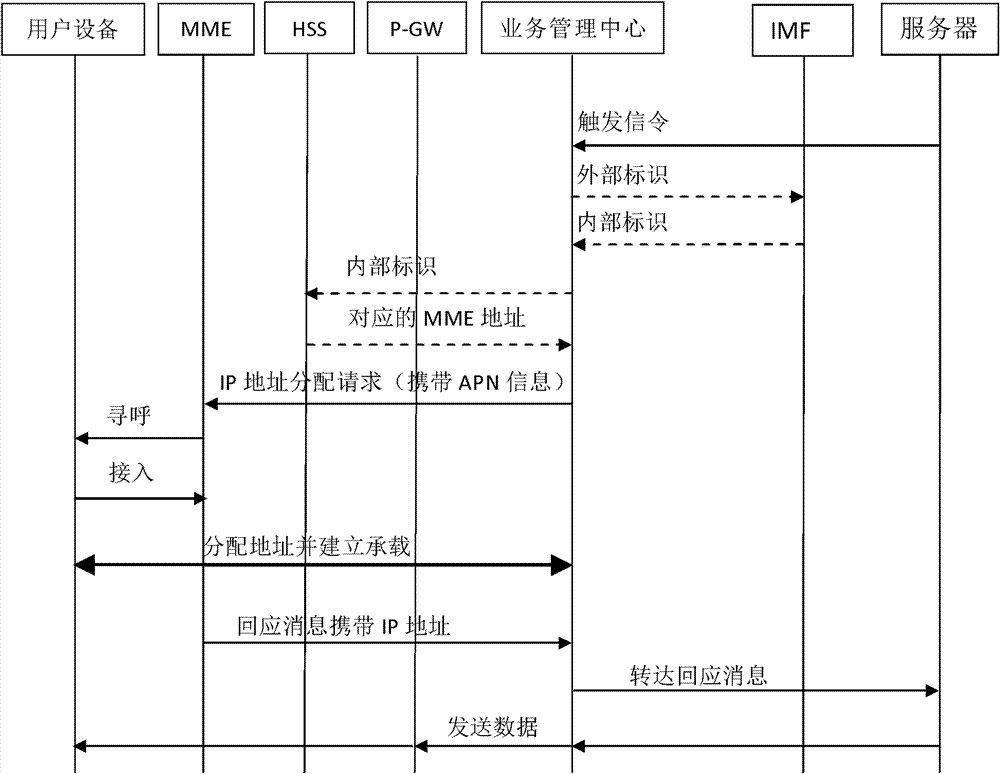
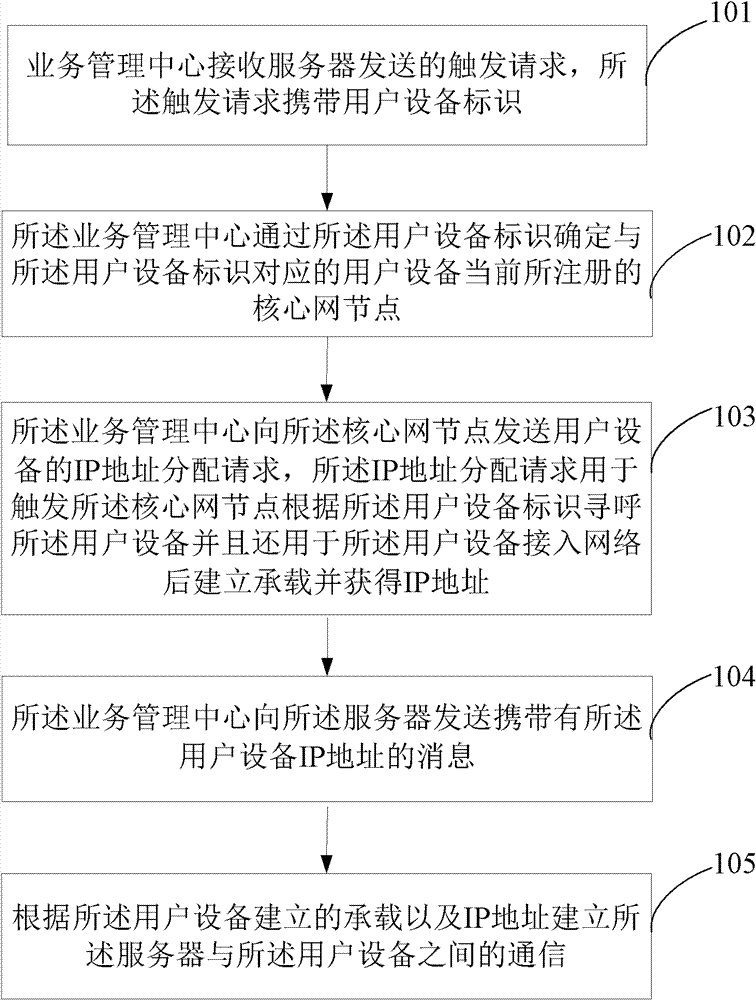
InactiveCN102780999AReduce network overheadReduce overheadConnection managementTransmissionIp addressNetwork overhead
The invention discloses a service communication method, a service communication device and a service communication system. When needing to communicate with the user equipment, the server sends a trigger request to the target user equipment again in order to trigger temporary IP (Internet Protocol) assignment for the user equipment and the establishment of temporary bearing or other data connection between the user equipment and the server, and thereby can temporarily communicate with the user equipment, and however, within most of the time when the server and the user equipment do not communicate, the user equipment does not have an exclusive IP address, bearing or other data connection, so that the network overhead can be effectively saved.
Owner:HUAWEI TECH CO LTD
Method for capturing computer application diagnostics
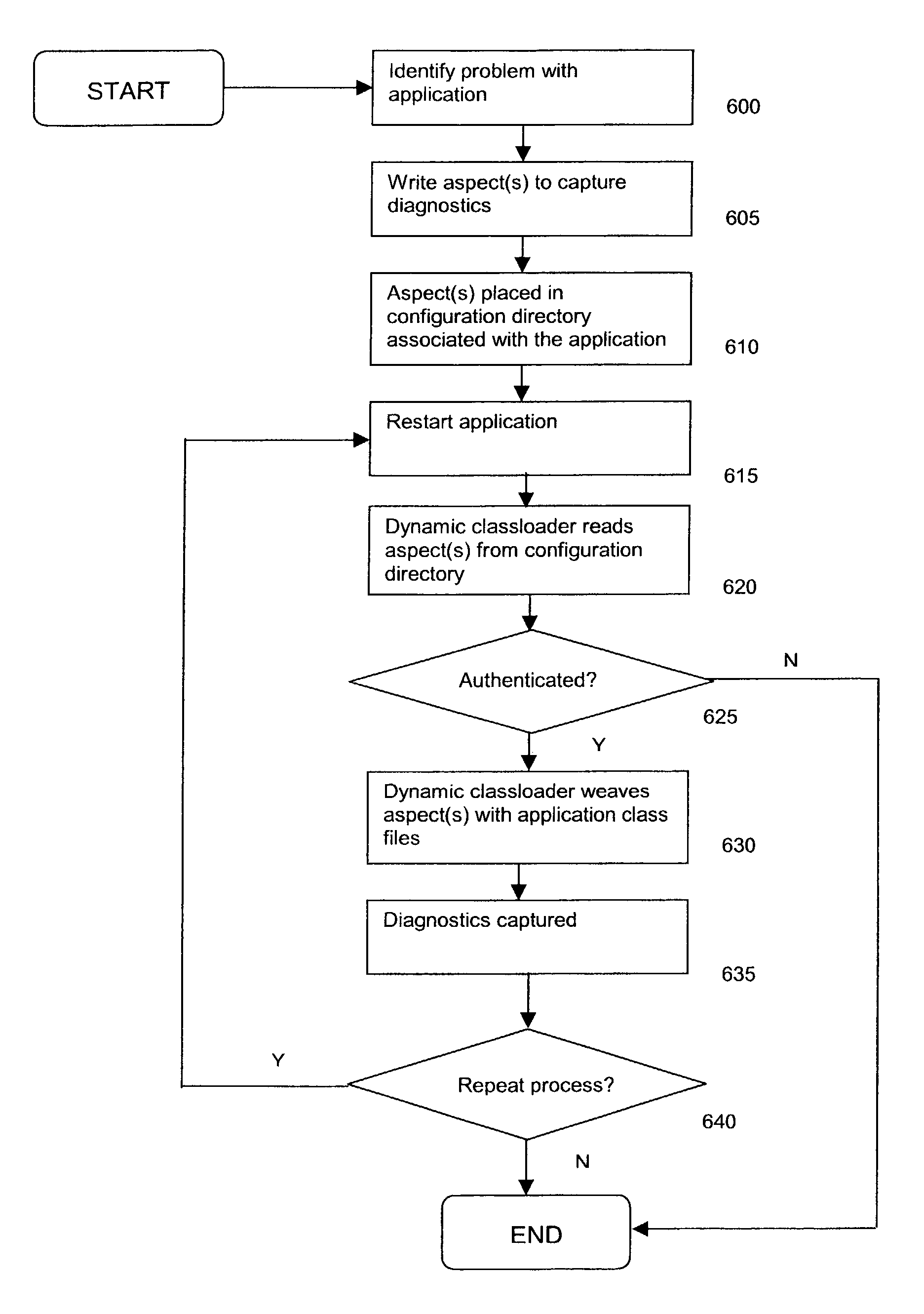
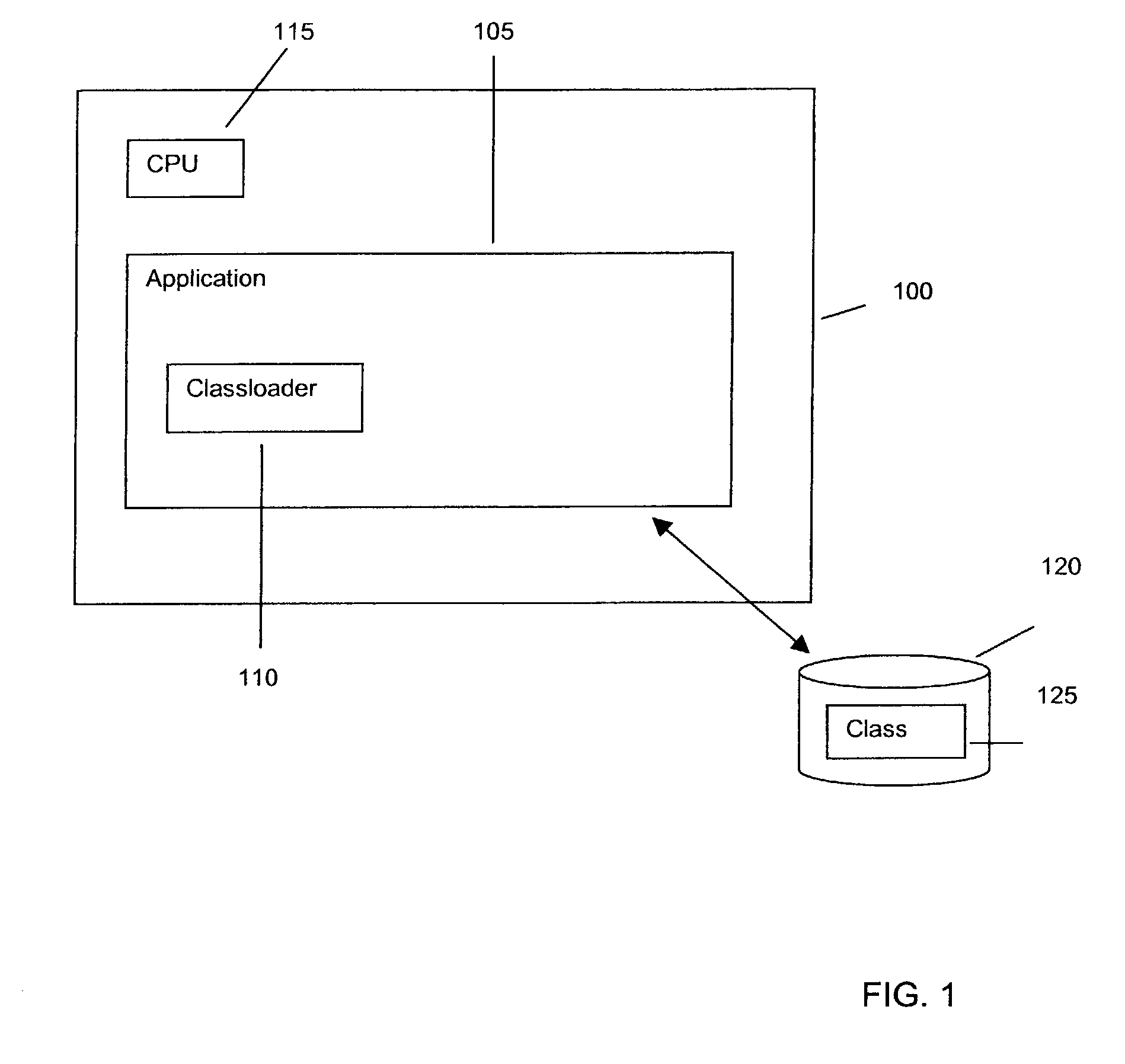
InactiveUS7398426B2Enhance applicationAdvantageous performanceSoftware engineeringSoftware testing/debuggingObject ClassApplication software
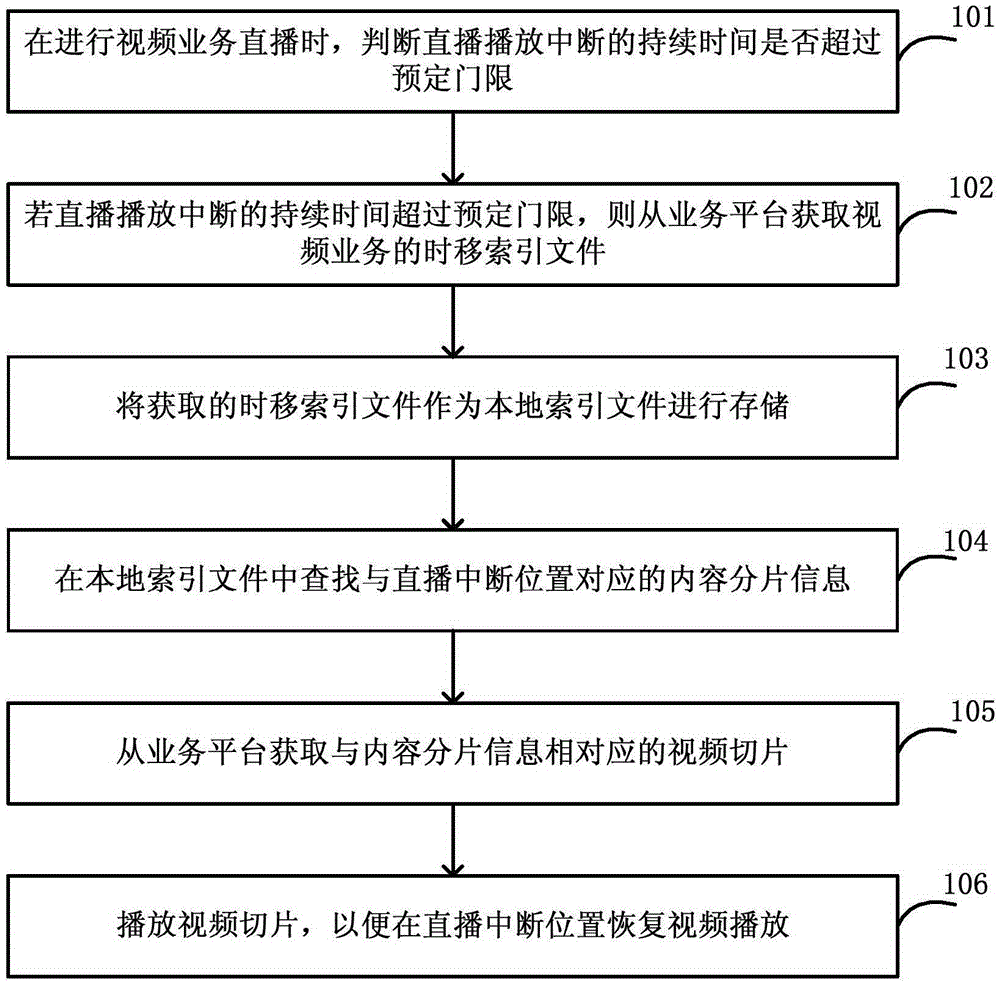
A diagnostic method in an aspect-oriented data processing environment is provided. The environment comprises a data processing system having an operating system for executing an application, wherein the application comprises an object class. The environment also comprises means for loading the object class at runtime and storage means for storing a diagnostic aspect. An aspect implements concerns (e.g. logging, security) that cross-cut the application. The object class of the application is loaded at runtime and the diagnostic aspect is read from the storage means. The means for loading now combines the object class with the diagnostic aspect, so that for example, diagnostics can be captured and repairs on the application can be carried out.
Owner:IBM CORP
Erasure code updating method and system based on copy data logs
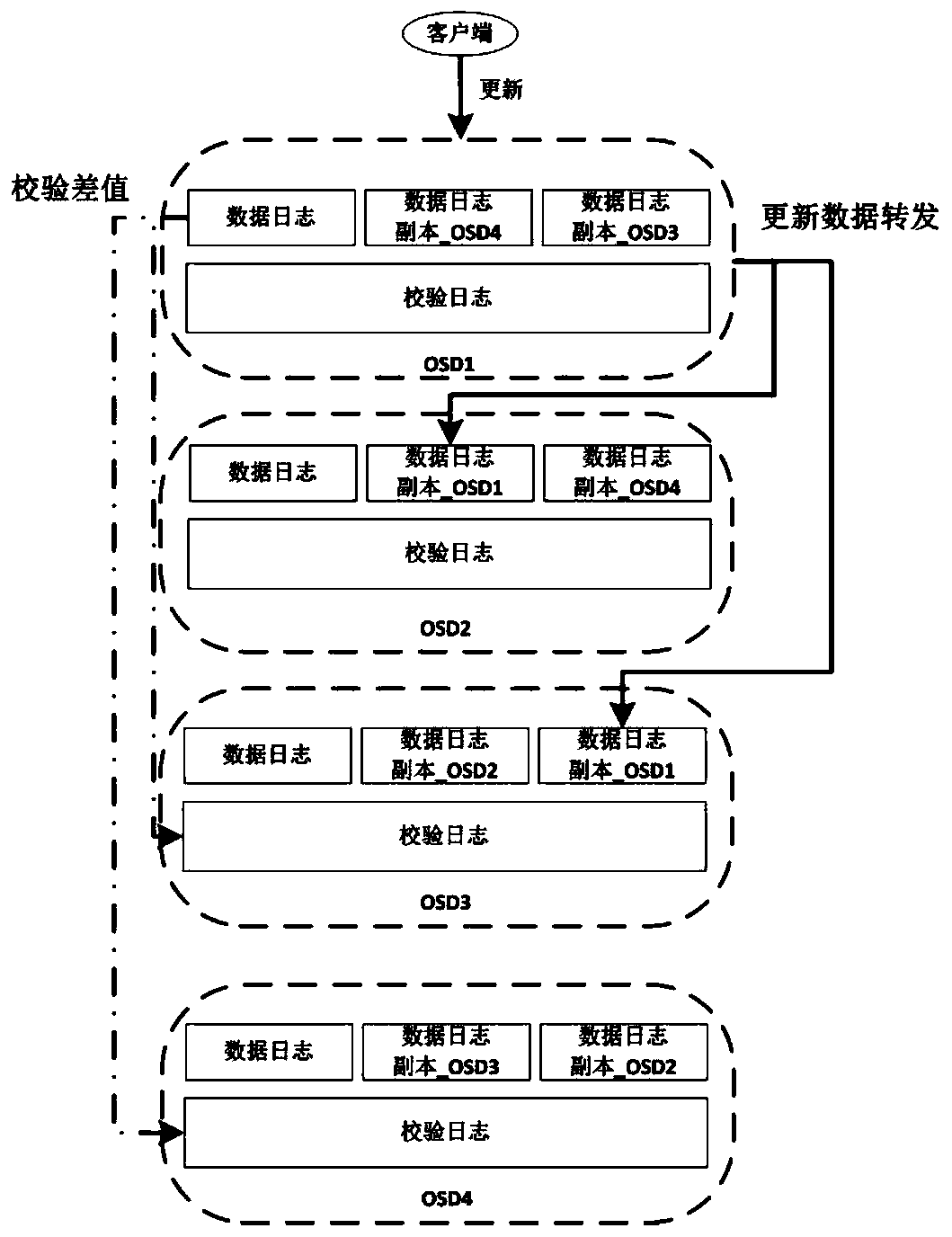
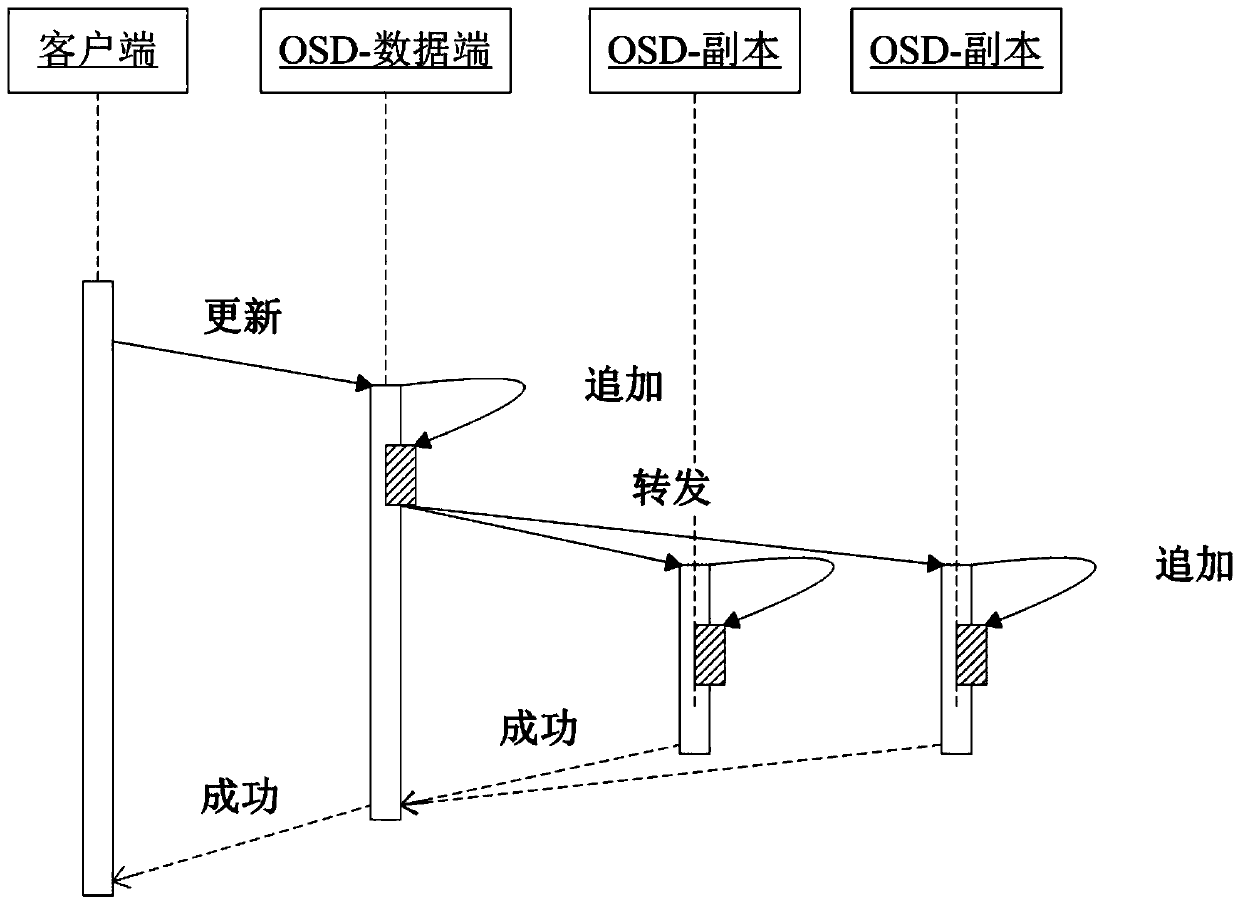
ActiveCN110262922AImprove update efficiencyEnsure consistencyResource allocationRedundant data error correctionComputer architectureNetwork overhead
The invention relates to an erasure code updating method based on copy data logsreplica data log-based erasure code updating method, which comprises the following steps of: receiving updated data, and storing the updated data to a replica data log of a data end; when the copy data log is full, obtaining a verification difference value by using the updated data and the data block, updating the corresponding data block by using the verification difference value, and forwarding the verification difference value to a verification end for storing the verification block; and storing the verification difference value to a verification log of the verification end, generating verification data through the verification difference value when the verification log is full, and updating a verification block by using the verification data. According to the erasure code updating method provided by the invention, on the premise that the consistency is ensured, the calculation overhead, the network overhead and the disk channel finding overhead generated in the updating process are reduced, the updating efficiency of the erasure codes is improved, and the performance improvement of one order of magnitude is achieved in some application scenarios compared with other updating methods.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
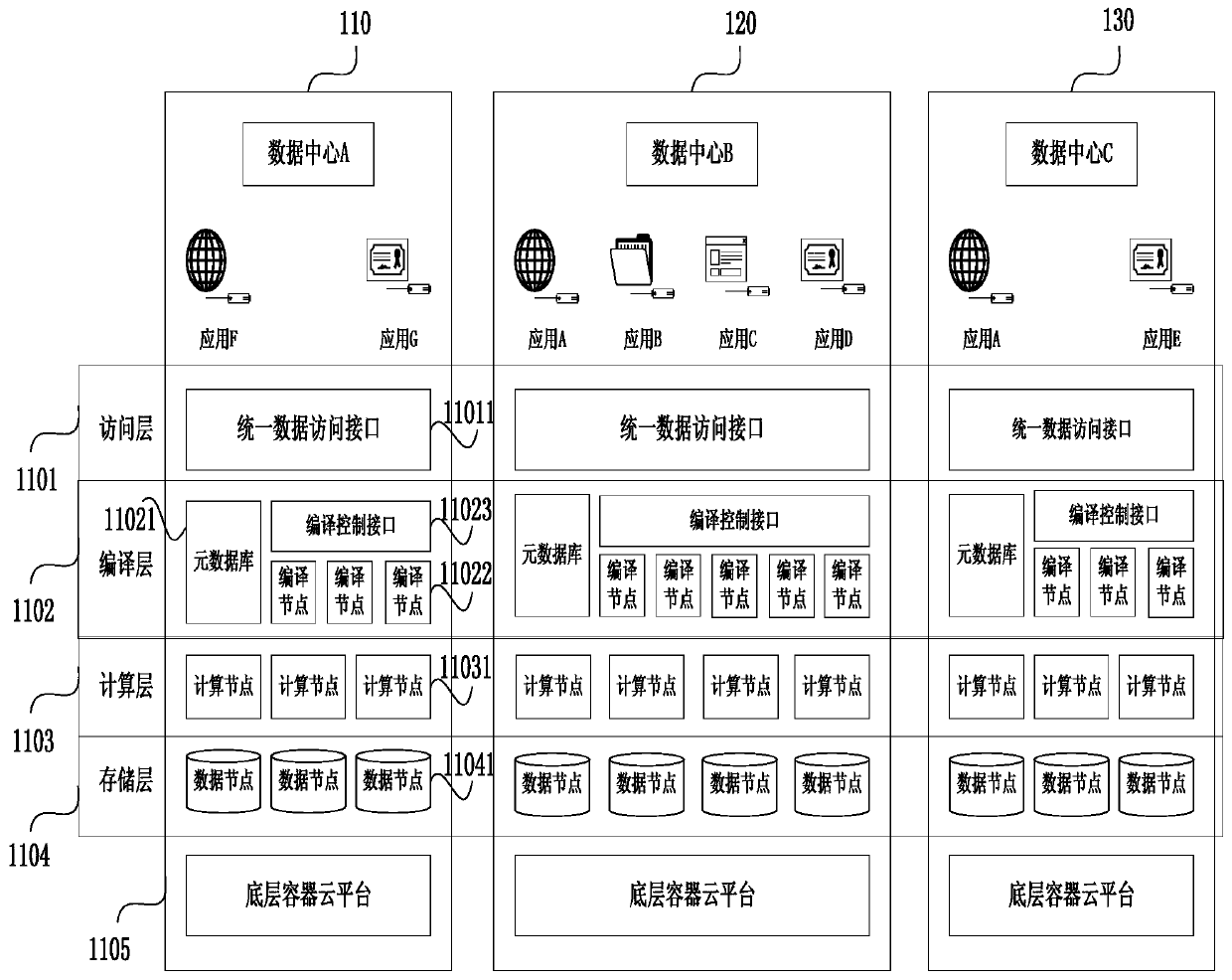
Data storage system, metadatabase synchronization method and data cross-domain calculation method
ActiveCN109726250AImprove performanceReduce network overheadDatabase management systemsDatabase distribution/replicationExecution planSQL
The invention discloses a data storage system, a metadatabase synchronization method and a data cross-domain calculation method. The data storage system comprises at least two data centers, wherein each data center comprises an access layer, a compiling layer, a computing layer, a storage layer and a bottom container cloud platform; The access layer is used for providing a unified data access interface; The compiling node is used for inquiring the metadatabase according to the received SQL statement, generating a matched execution plan and distributing the job task to the computing node for execution according to the execution plan; The computing nodes are used for acquiring data from data nodes of a data center where the computing nodes are located for computing according to the operationtasks and sending computing results to the computing nodes serving as summarizing nodes; The data node is used for storing data; And the bottom container cloud platform is used for carrying out containerization management on all services of the same data center. According to the technical scheme provided by the embodiment of the invention, the input cost is saved while the cross-domain computingservice is provided with high quality, and the data compliance requirement is met.
Owner:TRANSWARP INFORMATION TECH SHANGHAI
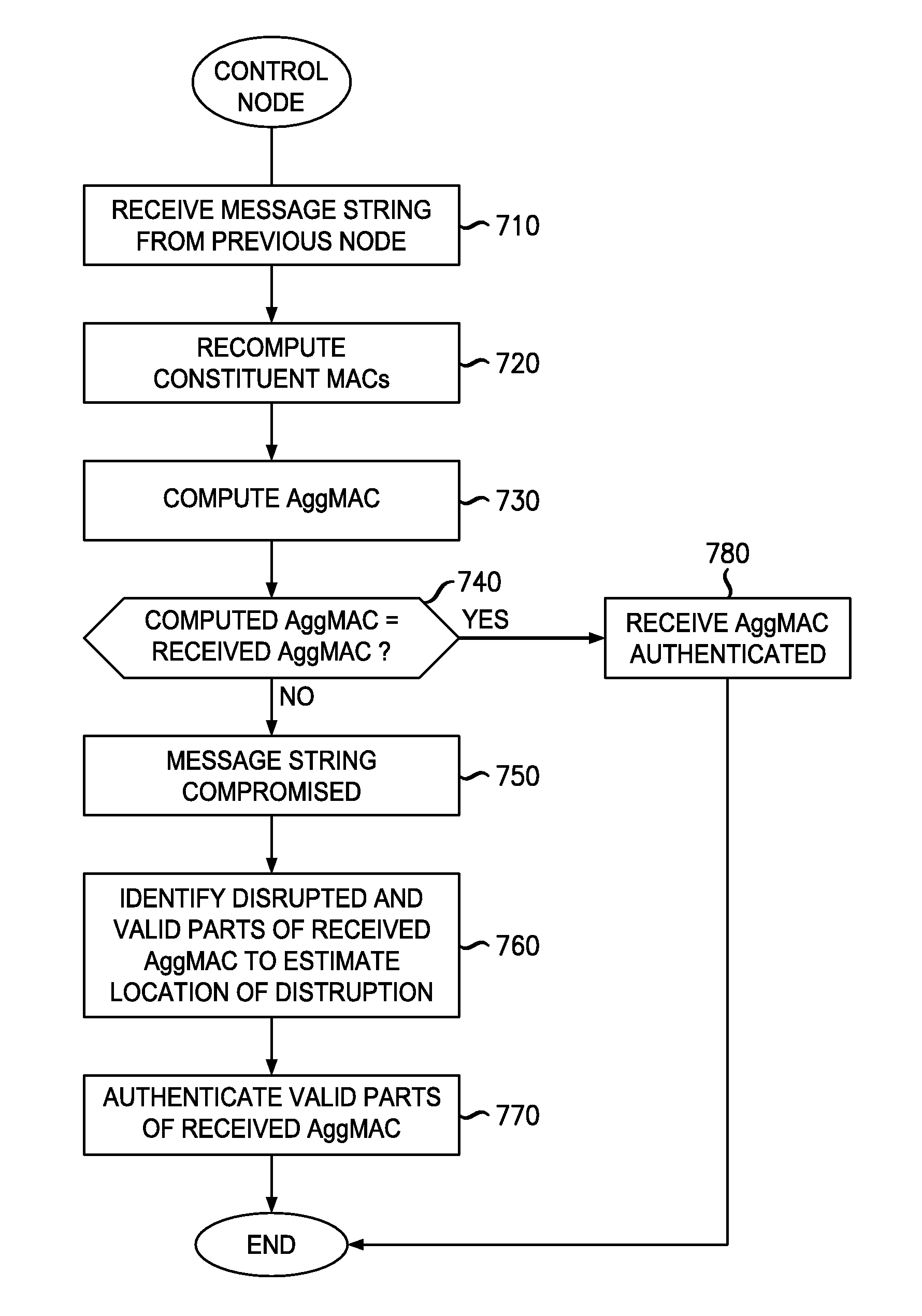
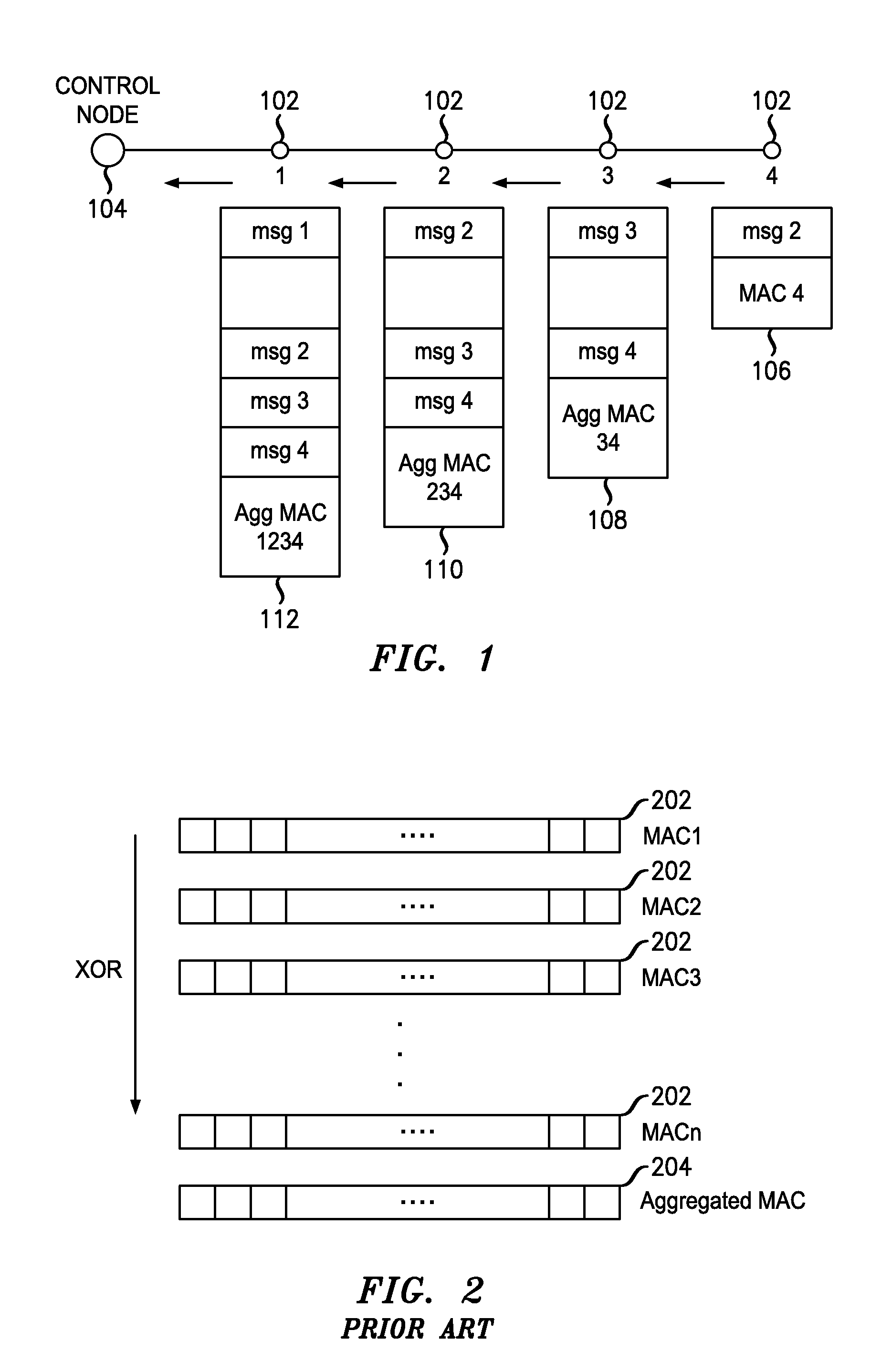
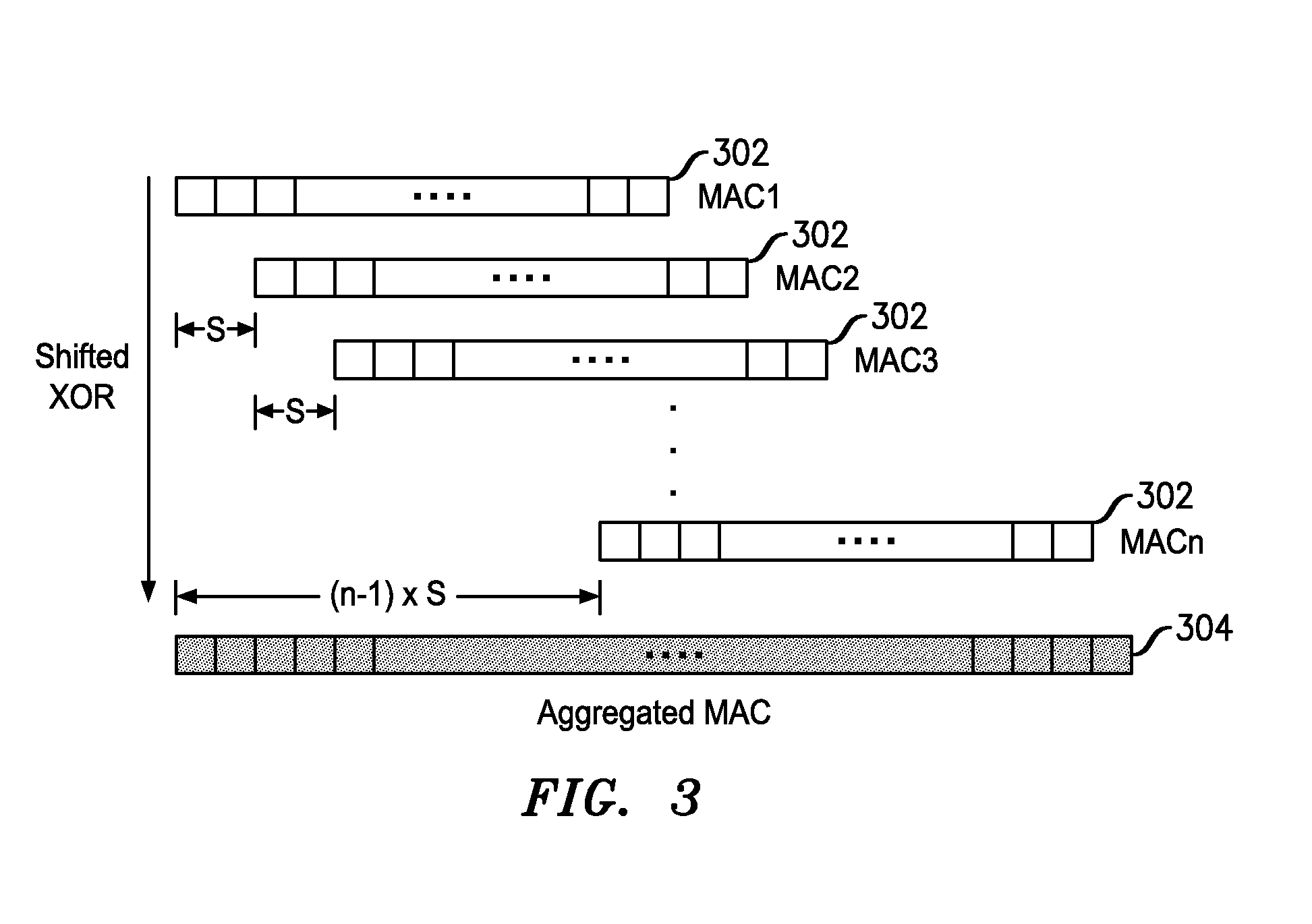
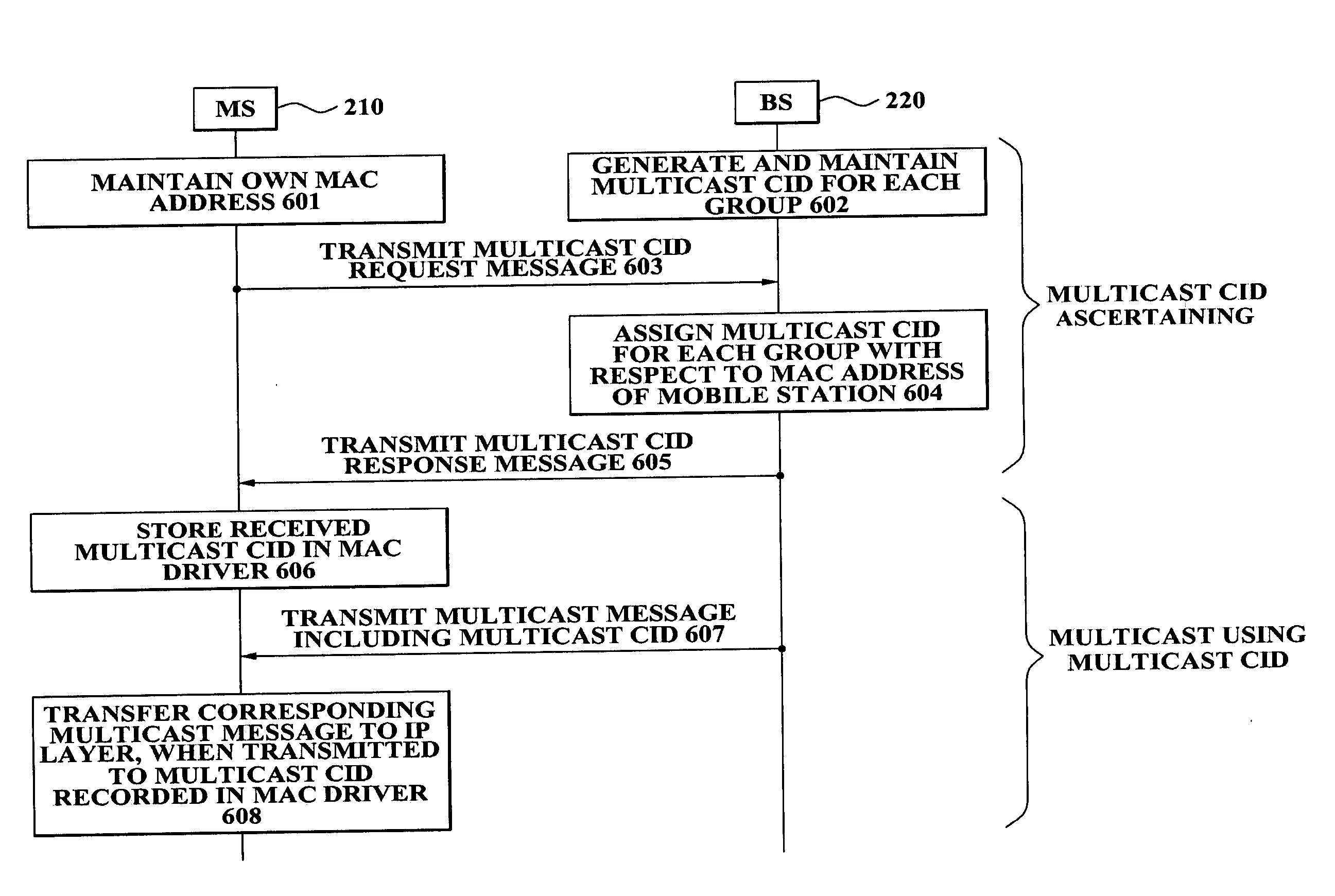
MAC Aggregation Resilient To Denial-Of-Service Attacks For Use In A Multi-Node Data Network
InactiveUS20120284523A1Strong toughnessReduce network overheadDigital data processing detailsUser identity/authority verificationMan-in-the-middle attackChannel impairments
An improved MAC aggregation technique is disclosed that yields an aggregate MAC much shorter than the concatenation of constituent MACs while achieving improved resilience to denial-of-service (DoS) attacks. The aggregate MAC is constructed in a manner wherein upon instance of channel impairments or malicious attack (e.g., from a rogue node or man-in-the-middle attacker), only a portion of the aggregate MAC will include corrupted data, at least a portion of the aggregate MAC thereby including valid verifiable data. A source of corruption of the aggregate MAC may be ascertained based on indicia of which constituent MACs are included in the valid portion; and constituent MACs that are wholly included in the valid portion may be declared valid.
Owner:ALCATEL LUCENT SAS
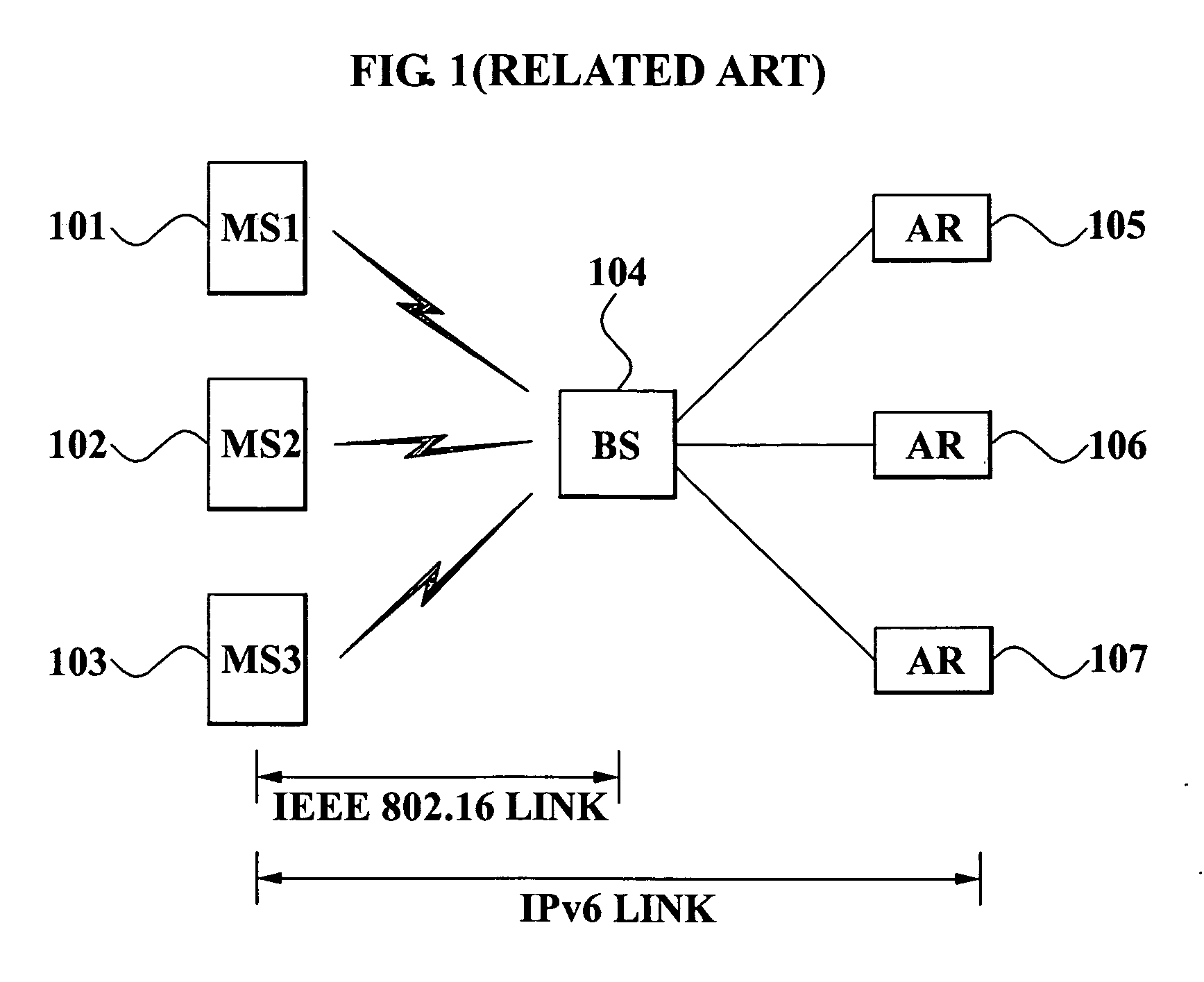
Method of generating and managing connection identifiers for supporting multicast for each group in IPv6-based wireless network and network interface using the method
InactiveUS20070097971A1Reduce network overheadBroadcast transmission systemsTime-division multiplexIp layerMulticast message
Provided is a method of generating and managing a connection identifier (CID) for supporting an IPv6 multicast in a wireless network based on IEEE 802.16 and a network interface using the method. Further provided is a network interface included in a node of IPv6-based wireless network, the network interface includes a MAC driver for storing at least one multicast CID and a MAC address of the node which is mapped in the at least one multicast CID, and a control unit for receiving a multicast message which is transmitted from a base station, and transferring the multicast message to an IP layer, when the multicast message includes the multicast CID which is stored in the MAC driver.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and client for realizing network video live broadcast
InactiveCN106686471AImprove viewingReduce network overheadSelective content distributionClient-sideWeb environment
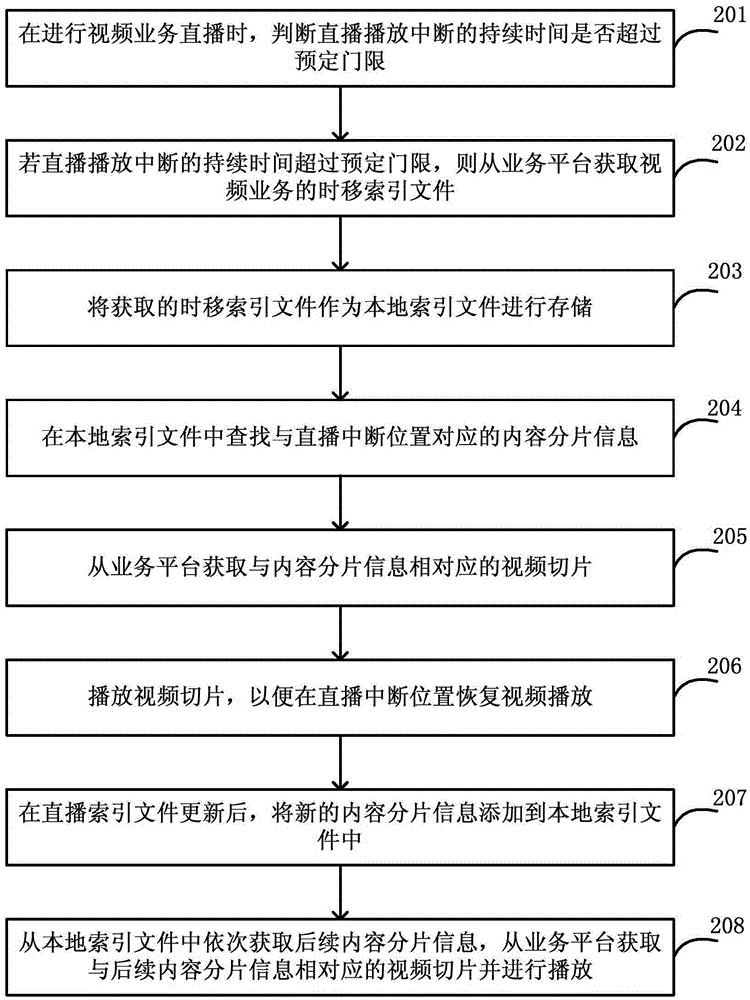
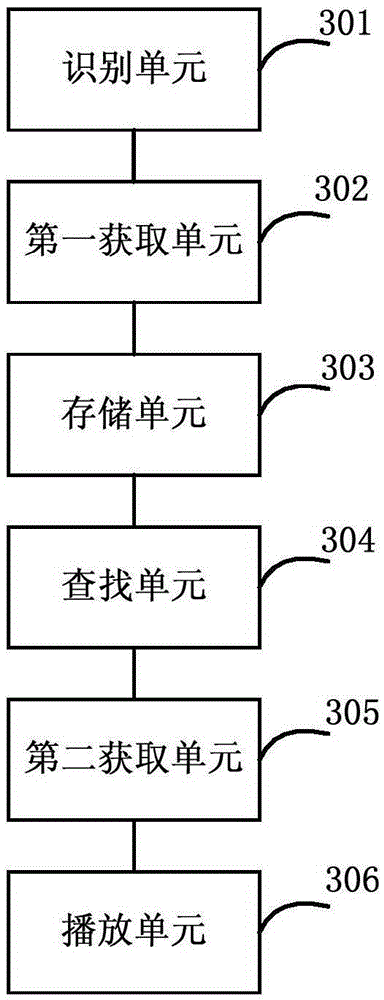
The invention discloses a method and a client for realizing network video live broadcast, wherein the client determines whether an interruption duration time period in live broadcast playing exceeds a preset threshold; if yes, the client acquires a time shift index file of a video service from a service platform. The acquired time shift index file is used as a local index file for being stored. Content fragment information which corresponds with a live broadcast interruption position is searched from the local index file. A video fragment which corresponds with the content fragment information is acquired from the service platform. The video fragment is played for restoring video playing at a live broadcast interruption position. According to the method and the client, through automatically switching between the live broadcast index file and the time shift index file on the condition of low network quality, user experience in viewing a live broadcast program is improved on the condition of low network quality, and furthermore relatively low network expenditure can be kept.
Owner:CHINA TELECOM CORP LTD
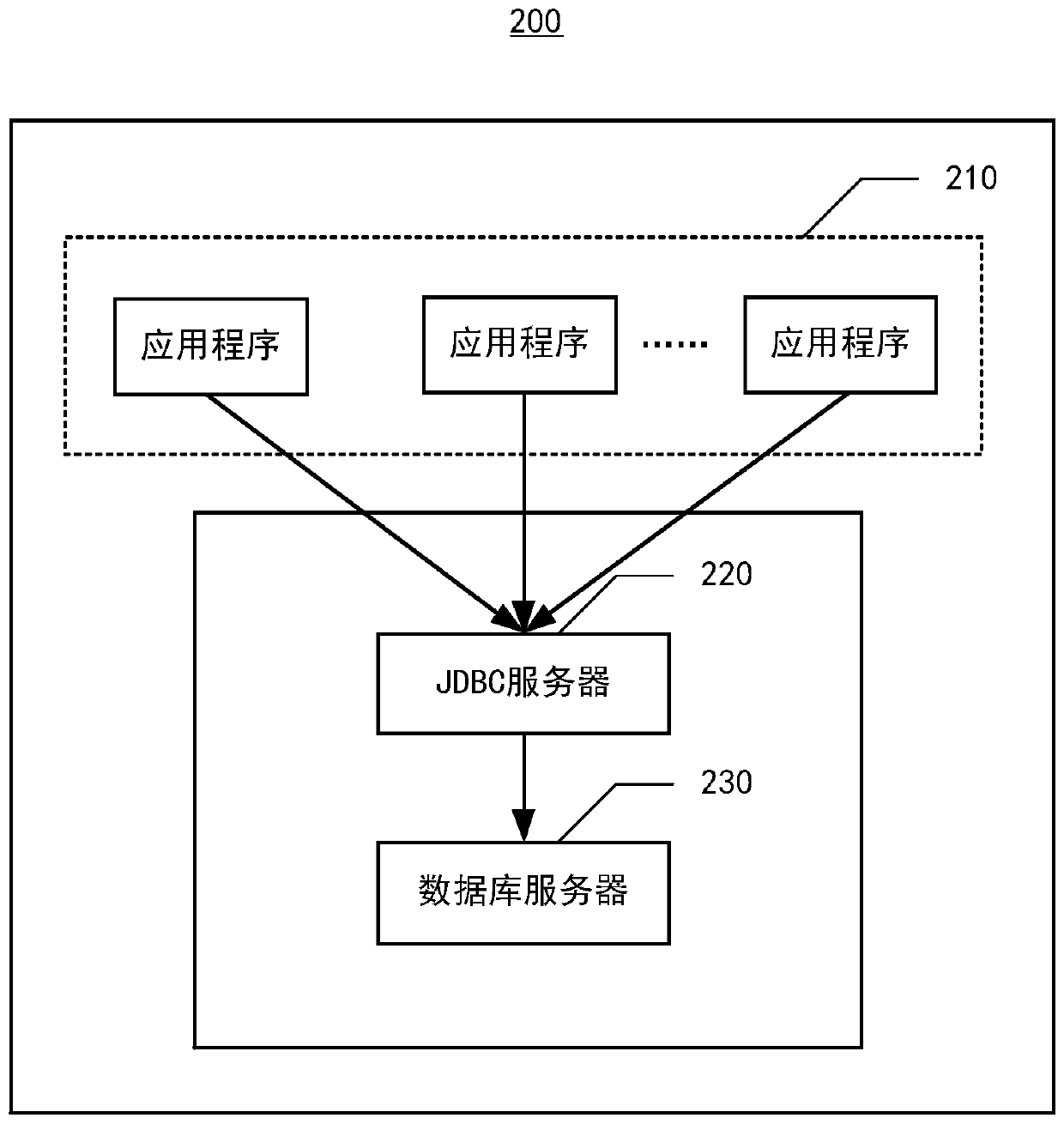
Database access method and device, electronic equipment and medium
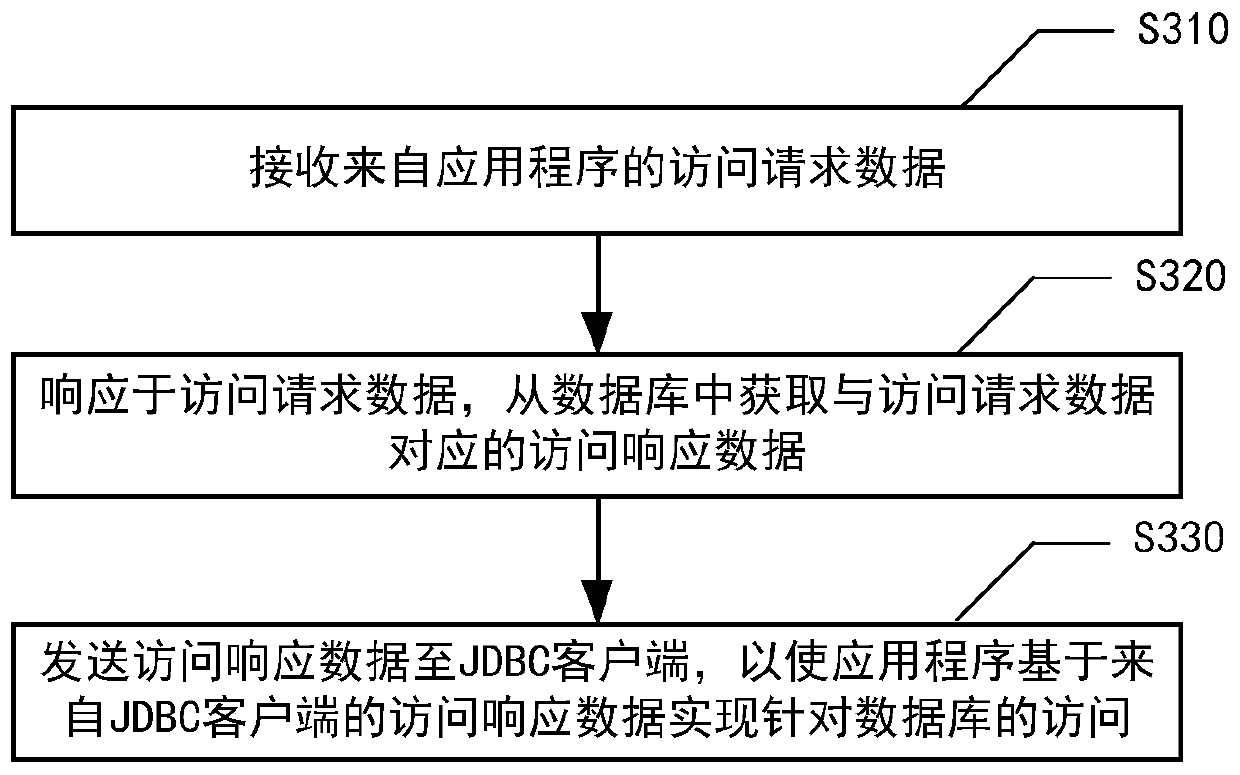
ActiveCN110413676AOvercome Performance Loss and Security HazardsReduce network overheadDatabase management systemsSpecial data processing applicationsClient-sideApplication software
The invention provides a database access method. The method is executed by a Java database connection (JDBC) server. The JDBC server and the database are deployed in the same network area; the methodcomprises the following steps: receiving access request data from an application program, wherein the access request data is sent by the JDBC client in response to an access request of an applicationprogram for a database, and the access request data is obtained by encrypting and / or compressing a structured query statement and an access parameter carried in the access request by the JDBC client;in response to the access request data, obtaining access response data corresponding to the access request data from a database; and sending the access response data to the JDBC client, so that the application program realizes access to the database based on the access response data from the JDBC client. The invention further provides a database access device which is applied to the JDBC server, electronic equipment and a computer readable storage medium.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Gang migration of virtual machines using cluster-wide deduplication
ActiveUS9823842B2Reduce network overheadAvoid spreadingInput/output to record carriersResource allocationData centerInternet traffic
Gang migration refers to the simultaneous live migration of multiple Virtual Machines (VMs) from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a datacenter. In this paper, we present an approach to reduce the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. The design, implementation and evaluation of a GMGD prototype is described using QEMU / KVM VMs. Evaluations on a 30-node Gigabit Ethernet cluster having 10 GigE core links shows that GMGD can reduce the network traffic on core links by up to 65% and the total migration time of VMs by up to 42% when compared to the default migration technique in QEMU / KVM. Furthermore, GMGD has a smaller adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
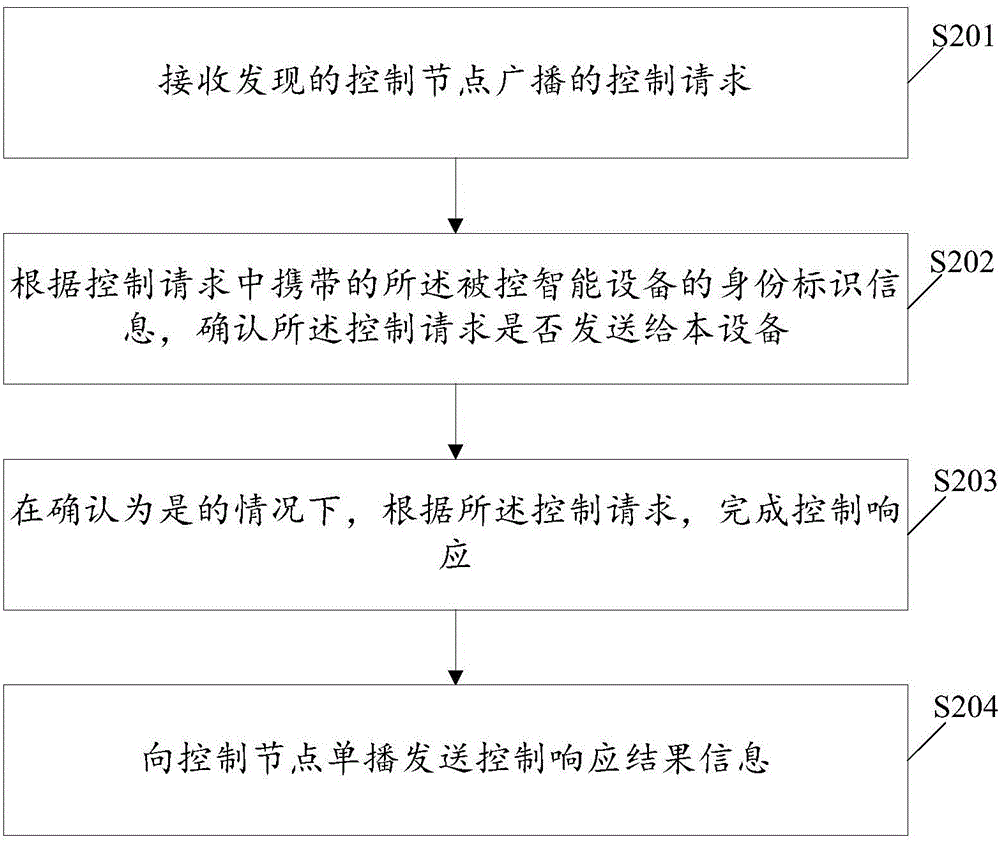
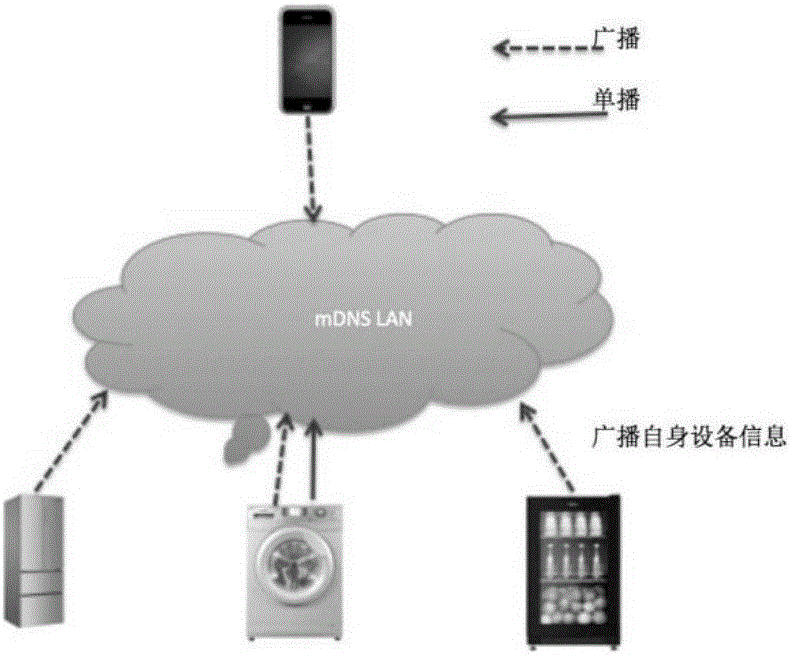
Intelligent equipment control method, control node and intelligent equipment
InactiveCN105847019AReduce software development costs and low learning costsReduce network overheadSpecial service provision for substationData switching by path configurationSoftware developmentUnicast
The invention discloses an intelligent equipment control method, a control node and intelligent equipment. The intelligent equipment control method applied to the control node side comprises the steps of: selecting the controlled intelligent equipment from the discovered intelligent equipment; broadcasting a control request to the discovered intelligent equipment, so that that the controlled intelligent equipment completes control response, wherein the control request carries identity identification information of the controlled intelligent equipment; and receiving control response result information send by the controlled intelligent equipment in a unicast manner. The intelligent equipment control method, the control node and the intelligent equipment realize the unicity of a discovery protocol and a control protocol, reduce software development cost, are low in learning cost, reduce network overhead and enhance the user experience.
Owner:HAIER YOUJIA INTELLIGENT TECH BEIJING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com