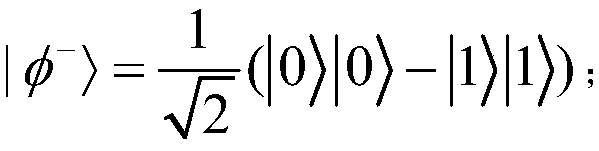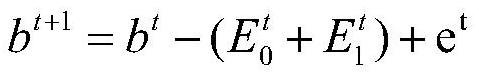Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
44results about How to "In line with the actual scene" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Six-axes robot kinetic parameter identification method based on neural network
ActiveCN109773794AFast convergenceSuppress random disturbanceProgramme-controlled manipulatorJointsAverage filterObservation matrix
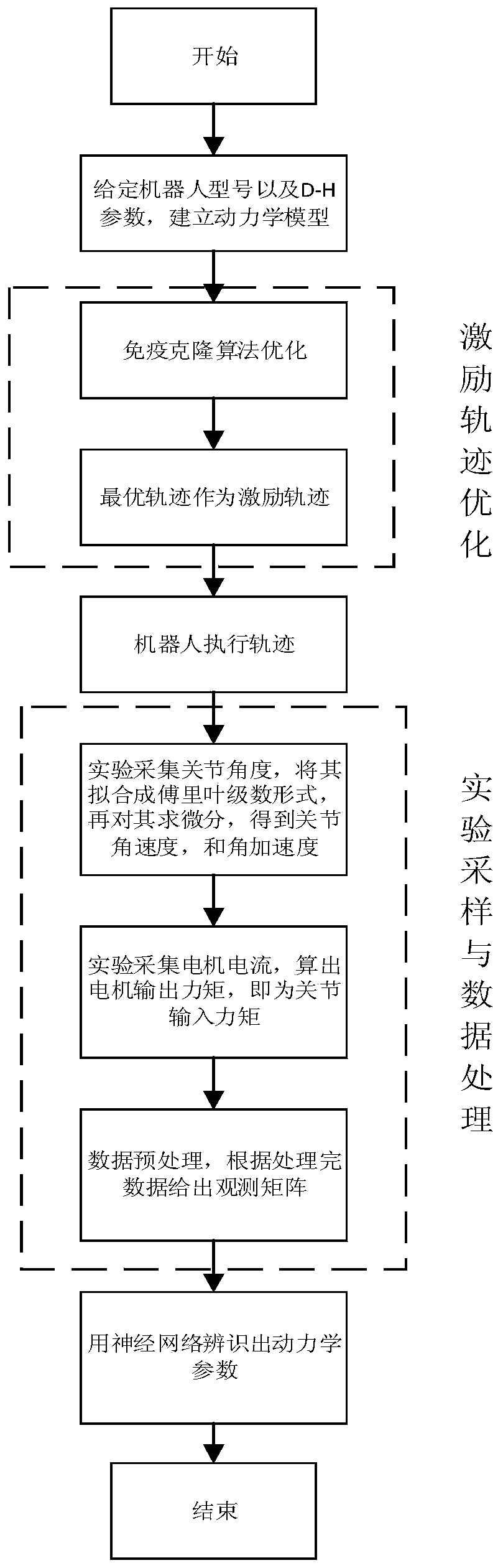
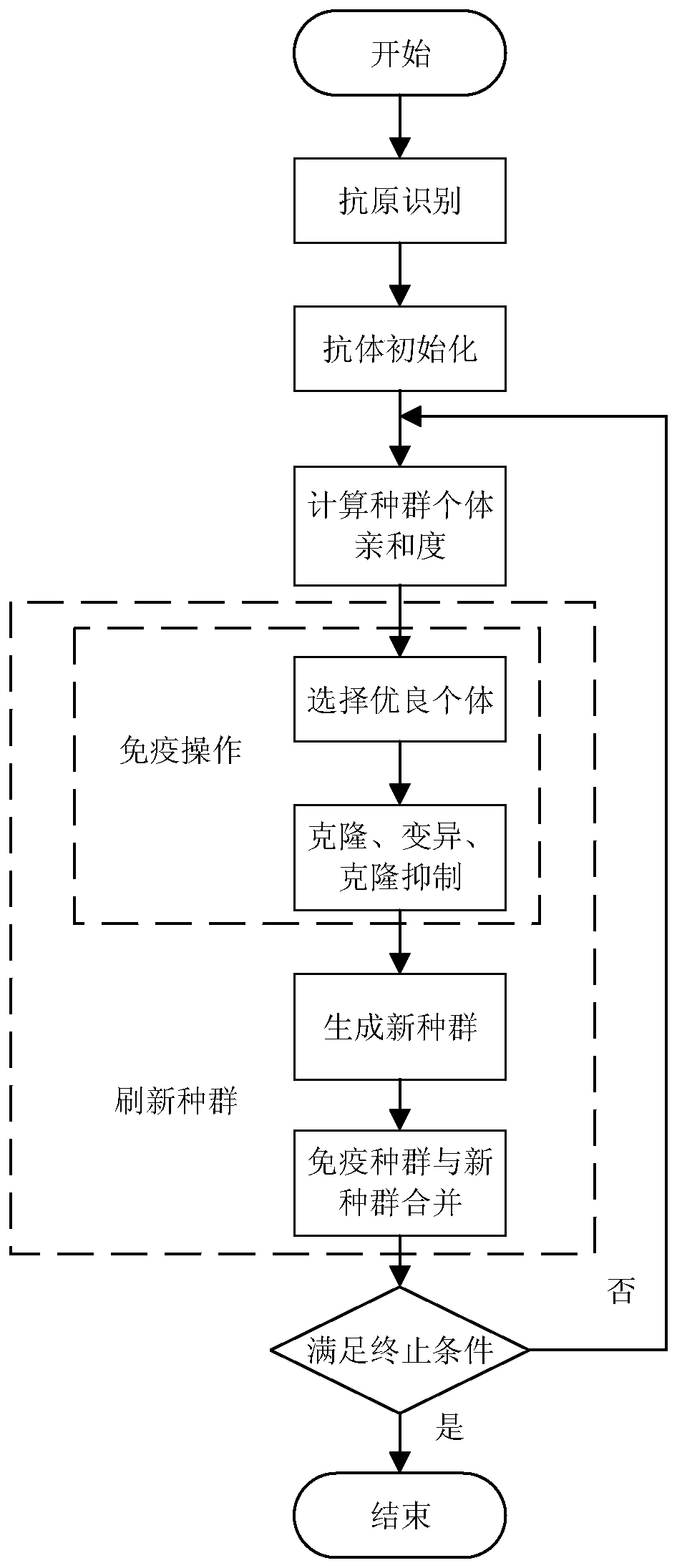
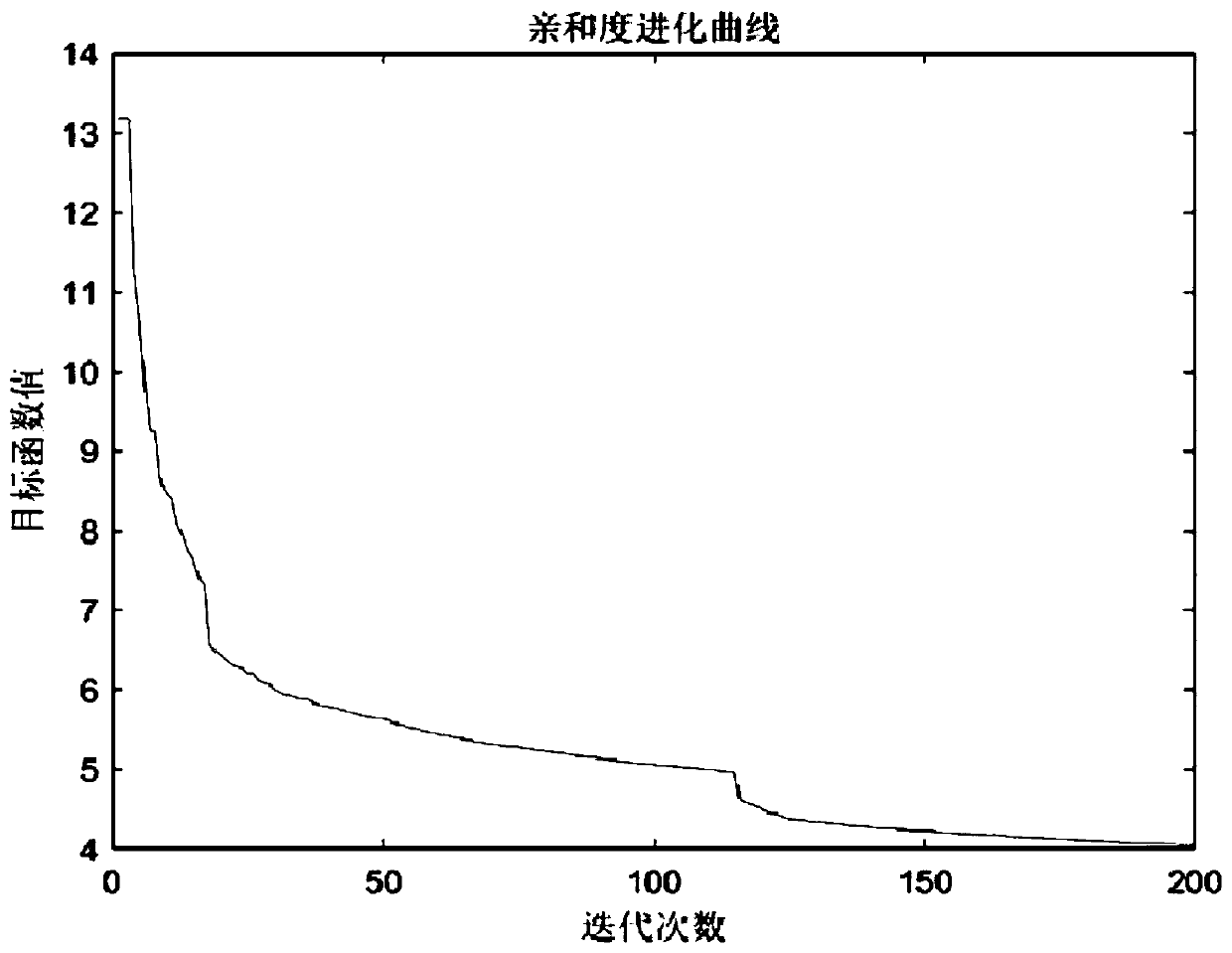
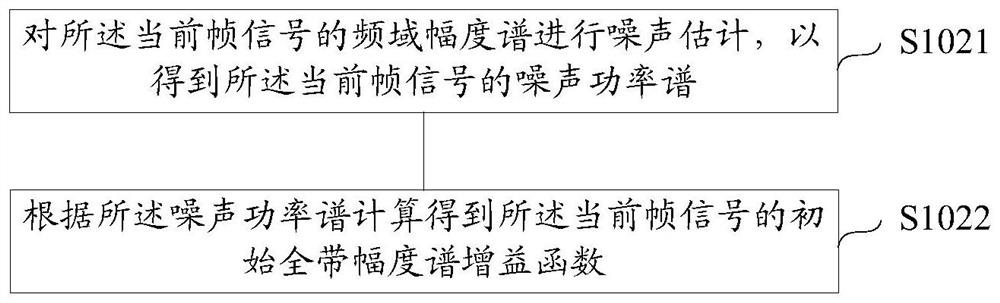
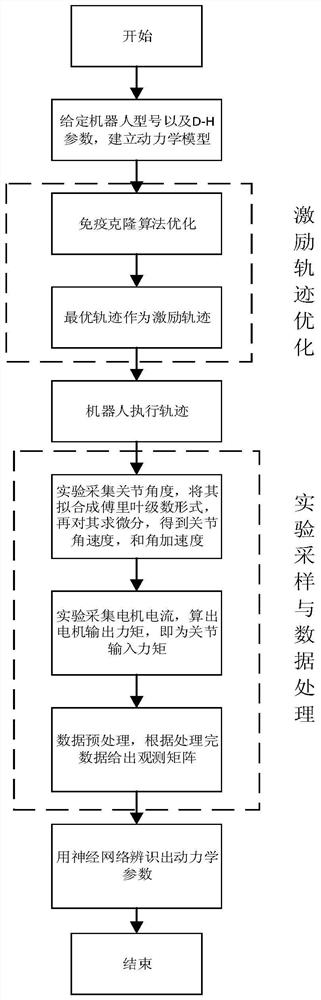
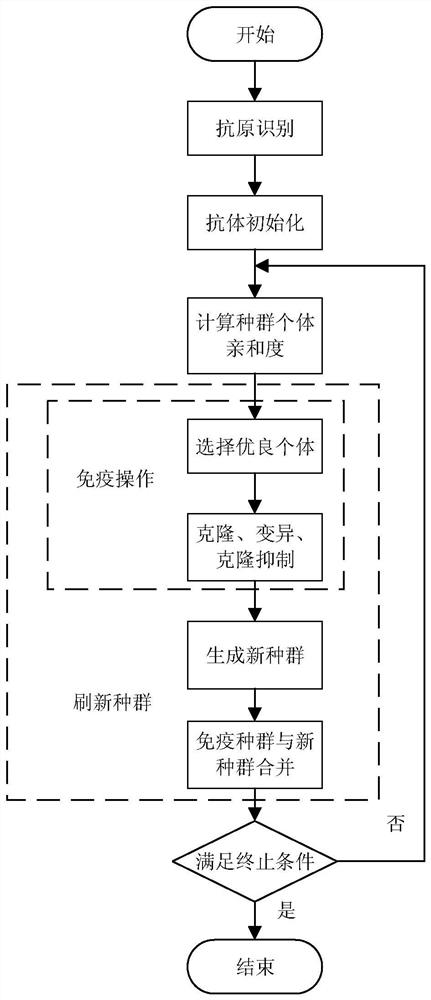
The invention discloses a six-axes robot kinetic parameter identification method based on a neural network. The six-axes robot kinetic parameter identification method comprises the following steps that firstly, robot kinetic modeling and linearization are conducted; secondly, motivation trajectory optimization is conducted, and specifically a motivation trajectory is optimized through an artificial immune algorithm; thirdly, experiment sampling is conducted, specifically a robot moves along the motivation trajectory, and multiple sets of observation matrices and joint torque are obtained as experiment data; fourthly, data processing is conducted, the data collected in an experiment are preprocessed through a three standard deviation norm and a median average filter method, and the influence brought by data noise is lowered; fifthly, kinetic parameter estimation is conducted, and kinetic parameters are estimated through the neural network; and sixthly, parameter verification is conducted, the robot follows an executable trajectory different from the motivation trajectory, experiment data are sampled again, theoretical joint torque is predicted according to kinetic parameters obtained by identification, and reliability of the identified kinetic parameters is evaluated with the torque residual root.
Owner:ZHEJIANG UNIV
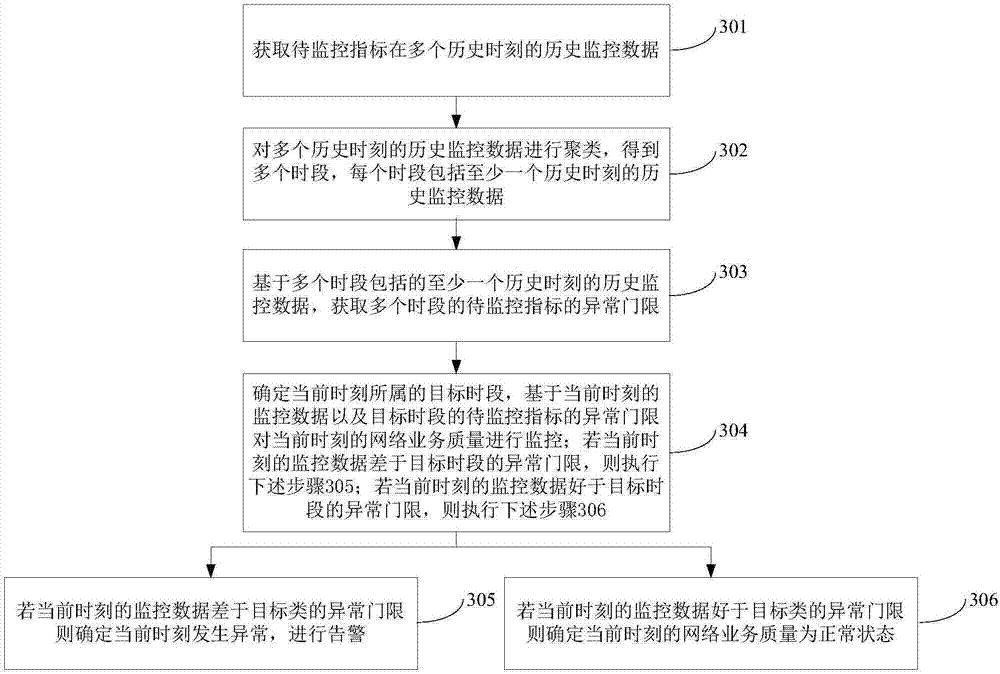
Network service quality monitoring method and device
ActiveCN107204894AAvoid errors of judgmentIn line with the actual sceneData switching networksNetwork serviceTime frame
The invention provides a network service quality monitoring method and device and belongs to the technical field of network operation and maintenance. The method comprises steps as follows: historical monitoring data of to-be-monitored indexes in multiple historical moments are acquired, the historical monitoring data at multiple historical moments are clustered, multiple time frames are obtained, and each time frame comprises historical monitoring data in at least one historical moment; abnormal thresholds of the to-be-monitored indexes at multiple time frames are acquired on the basis of the historical monitoring data in at least one historical moment contained in multiple historical moments; the network service quality is monitored on the basis of abnormal thresholds of the to-be-monitored indexes at multiple time frames. The multiple historical moments are clustered, the multiple time frames are clustered, and the abnormal thresholds of the to-be-monitored indexes at the time frames are determined, so that the abnormal thresholds at the time frames are generated according to historical monitored data, following monitoring of the network service quality according to the abnormal thresholds better accords to the actual scene, misjudgment of the network service quality is avoided, and the monitoring accuracy is higher.
Owner:HUAWEI TECH CO LTD
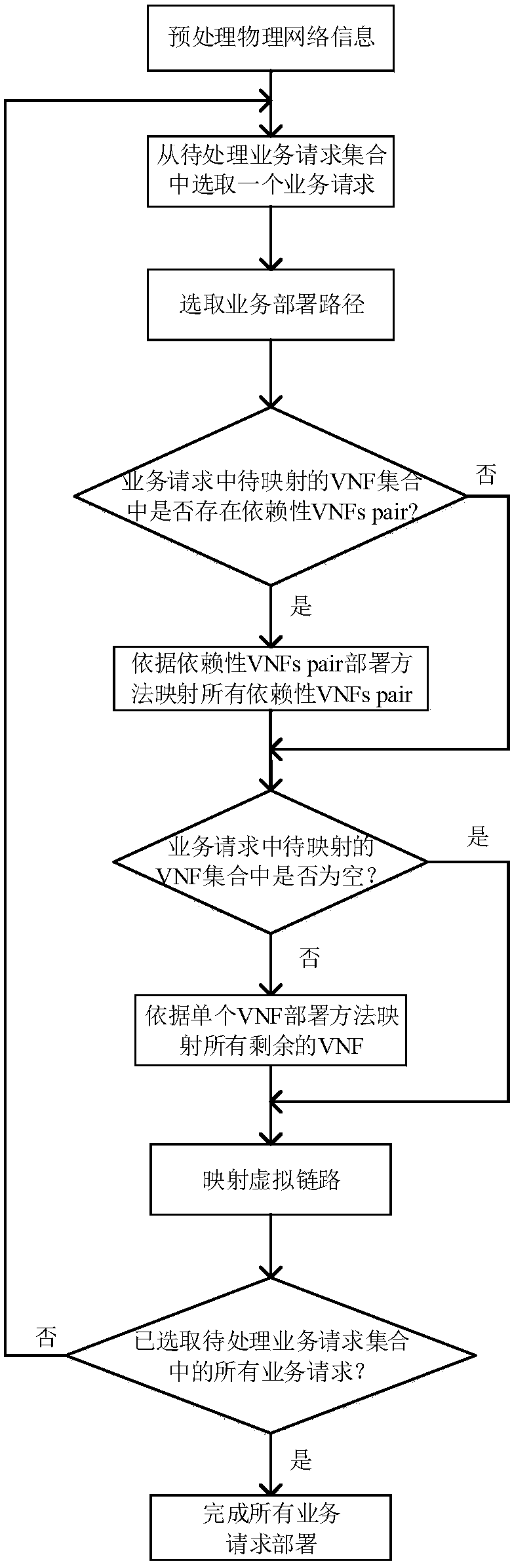
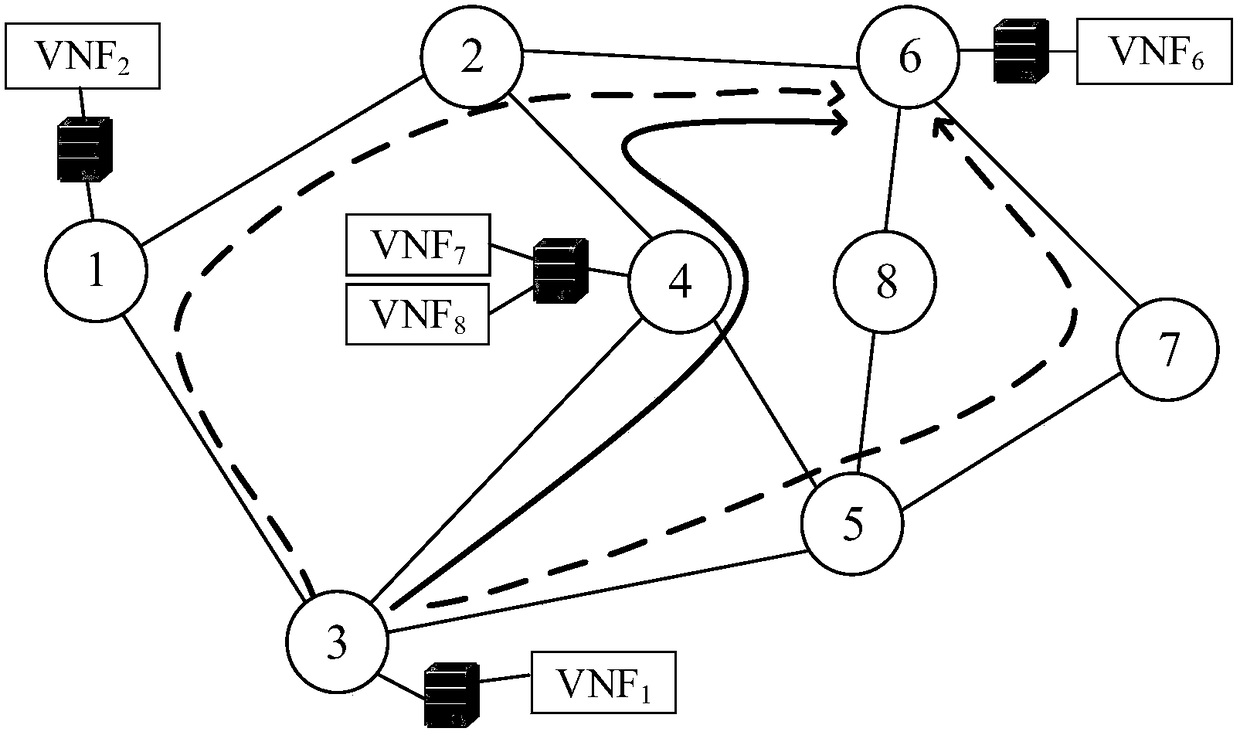
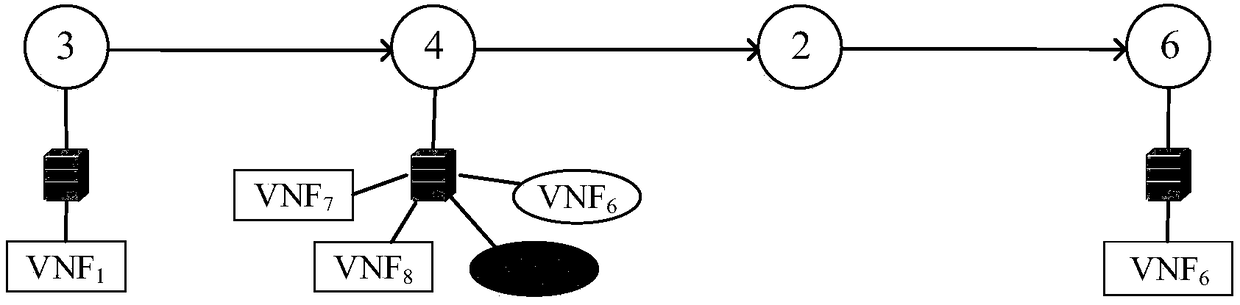
Cooperative construction and mapping SFC (Service Function Chain) method for dependence among multiple VNF (Virtualized Network Function)
ActiveCN108494596AIn line with the actual sceneLower deployment costsService provisioningData switching networksFrequency spectrumAllocation method
The invention discloses a cooperative construction and mapping SFC (Service Function Chain) method for dependence among multiple VNF (Virtualized Network Function). Specific steps for implementing themethod are as follows: first of all, according to the number of VNFs capable of being reused, selecting a deployment path between source and destination nodes of a service request; then, on the premise of meeting a dependence relationship among the VNFs, mapping the VNFs and constructing an SFC; and at last, mapping virtual links by using a route and spectrum allocation method, thereby finishingthe deployment of a user service. According to the cooperative construction and mapping SFC method, a deployment scheme can be provided for a service request having the dependence among the VNFs, andthe application scope is wider; the maximum frequency slot number and the number of deployed VNFs in a bottom elastic optical network are reduced, and the service deployment cost is saved.
Owner:XIDIAN UNIV
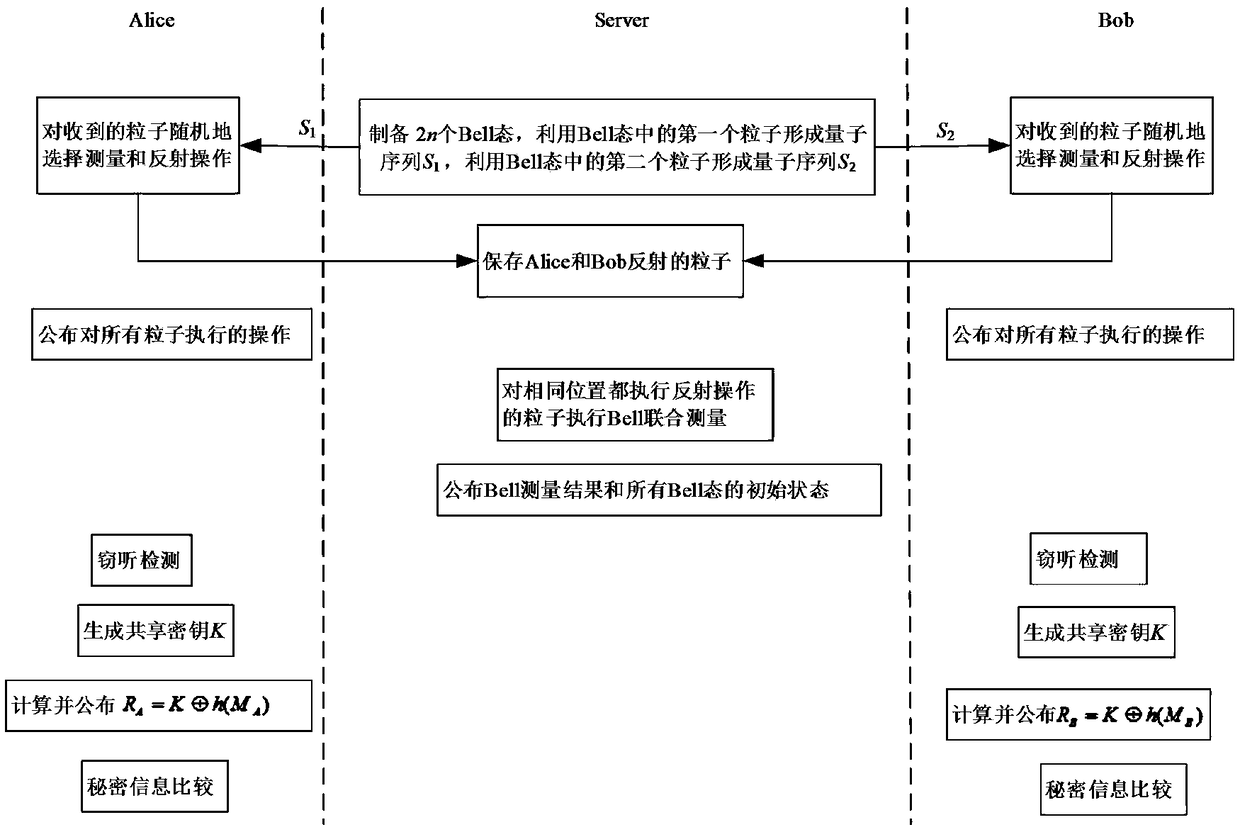
Efficient quantum privacy comparison method and system
ActiveCN109474417AIn line with the actual sceneEasy to implementKey distribution for secure communicationEncryption apparatus with shift registers/memoriesBell stateInternet privacy
The invention belongs to the technical field of communication networks, and discloses an efficient quantum privacy comparison method and system. In a quantum privacy comparison protocol, only a semi-trusted server needs to be configured with a quantum memory, a Bell-state preparation device and Bell-state joint measuring equipment; in secrete information comparison, both parties only need to configure quantum equipment for measuring and reflecting a |0>,|1> state of a quantum, so that the comparison of secrete information can be realized; in the operation process of the protocol, the semi-trusted server can be provided by a special quantum server provider, and the provider only needs to strictly comply with the requirements of the protocol, even if the provider records data in the protocolcommunication process, the provider cannot obtain the secret information of a user. The application scene of the efficient quantum privacy comparison method provided by the invention is easy to be implemented compared with an existing protocol and accords with an actual scene of a future quantum network application, and the efficient quantum privacy comparison method has a promoting effect on theapplication development of a quantum communication network.
Owner:CHENGDU UNIV OF INFORMATION TECH
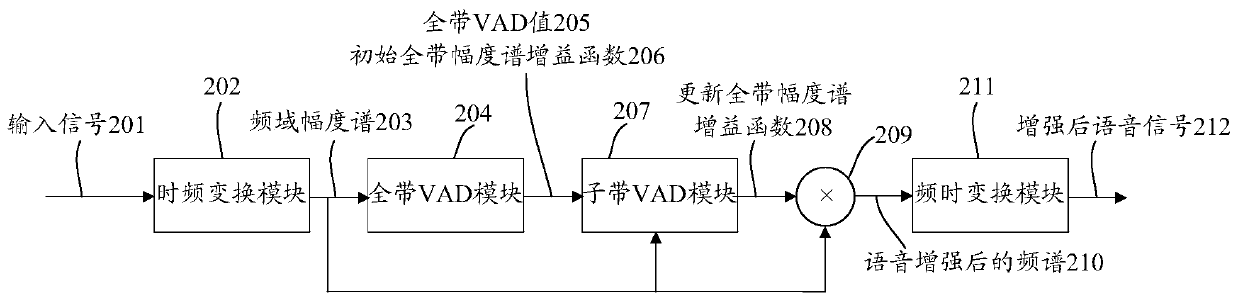
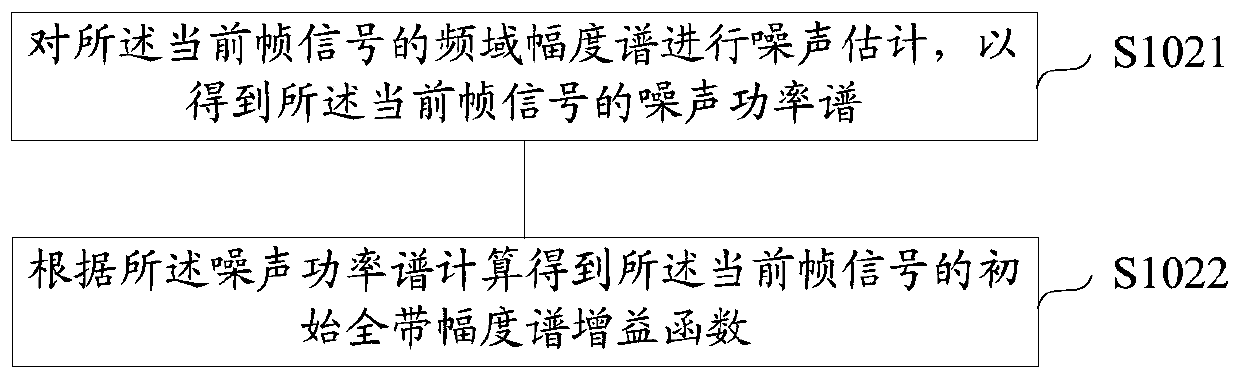
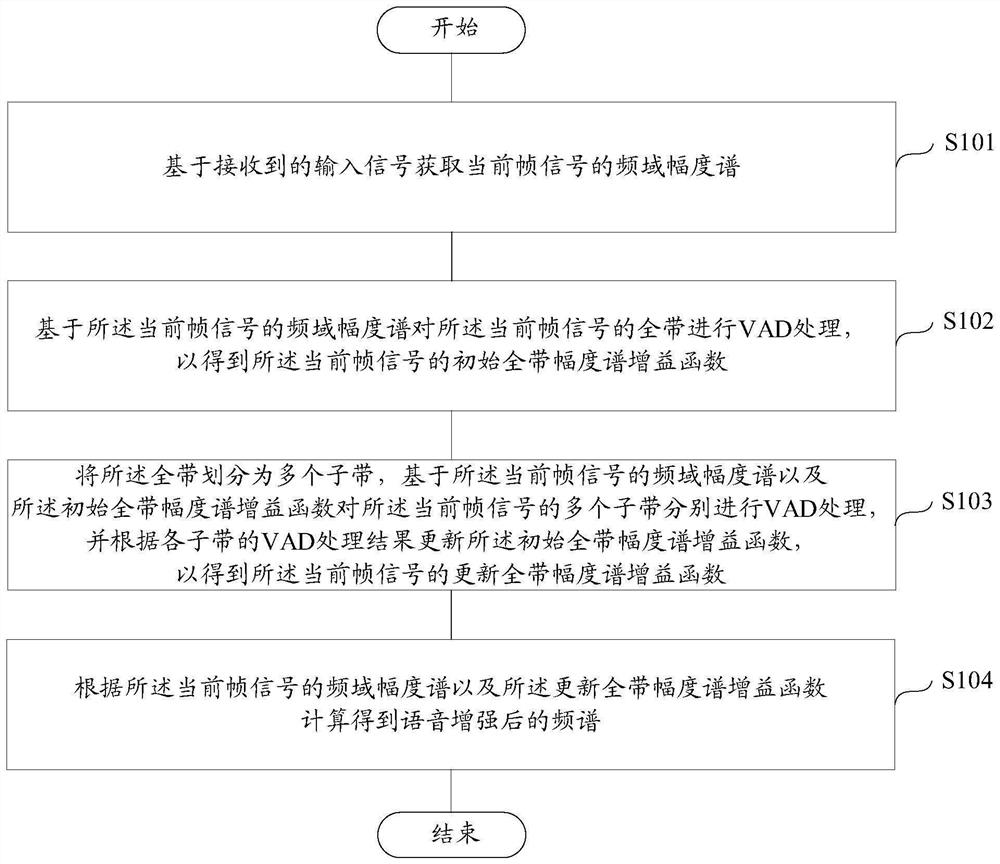
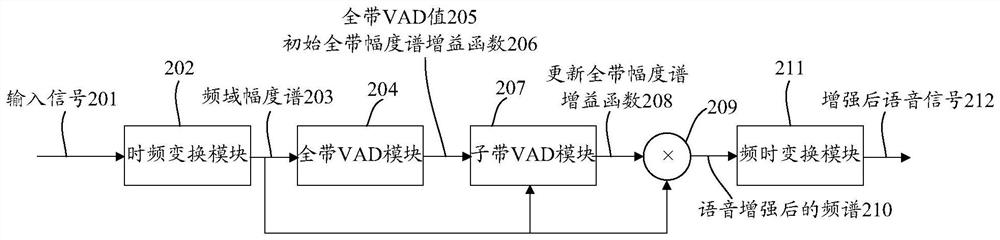
Single-channel voice enhancement method and device, storage medium and terminal
ActiveCN111554315AImprove voice call qualitySuppress non-stationary noiseSpeech analysisStationary noiseFrequency spectrum
The invention discloses a single-channel voice enhancement method and device, a storage medium and a terminal. The method comprises the steps of obtaining a frequency domain amplitude spectrum of a current frame signal based on a received input signal; performing VAD processing on the full band of the current frame signal based on the frequency domain amplitude spectrum of the current frame signalto obtain an initial full band amplitude spectrum gain function of the current frame signal; dividing the whole band into a plurality of sub-bands; performing VAD processing on the plurality of sub-bands of the current signal frame based on the frequency domain amplitude spectrum of the current frame signal and the initial full-band amplitude spectrum gain function, and updating the initial full-band amplitude spectrum gain function according to the VAD processing result of each sub-band to obtain an updated full-band amplitude spectrum gain function of the current frame signal; and calculating according to the frequency domain amplitude spectrum of the current frame signal and the updated full-band amplitude spectrum gain function to obtain a frequency spectrum after speech enhancement.Through the scheme of the invention, non-stationary noise can be effectively suppressed, the voice quality is protected from being lost, and the voice call quality of mobile equipment such as a mobilephone is favorably improved.
Owner:SPREADTRUM COMM (TIANJIN) INC
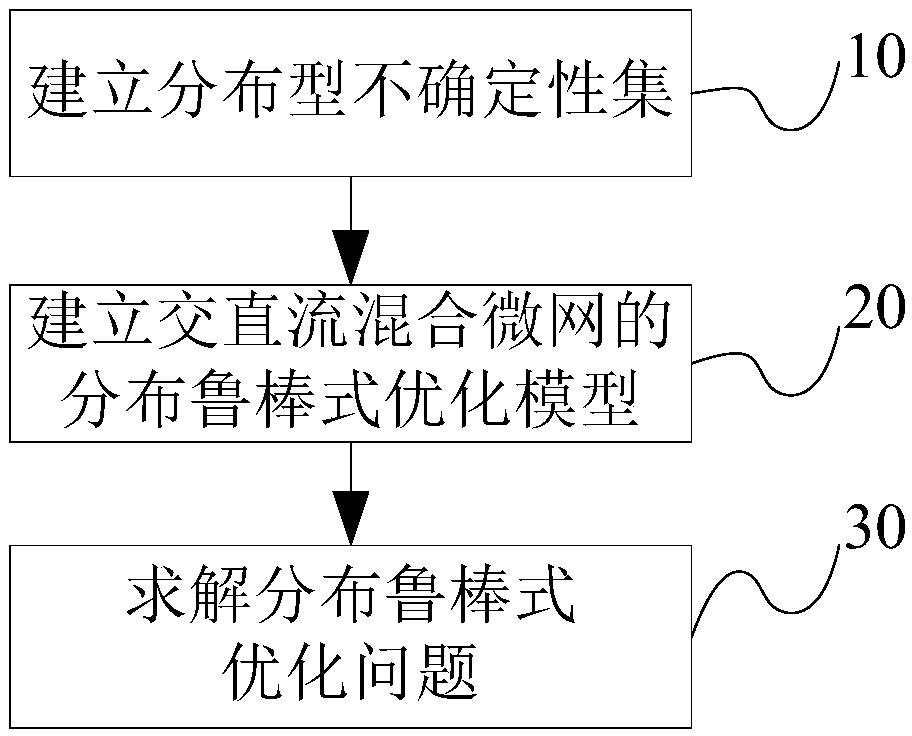
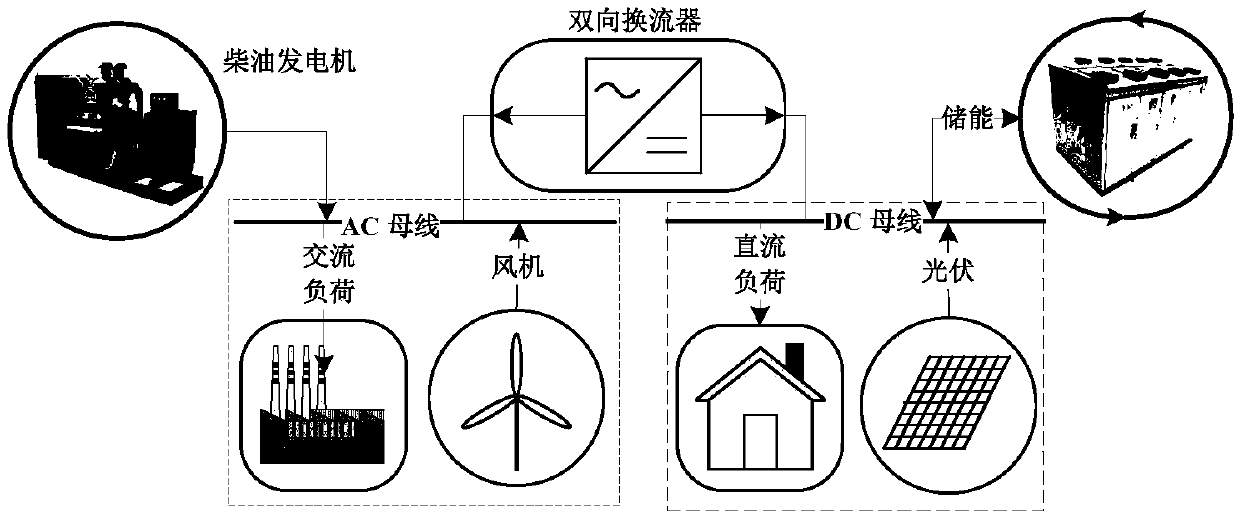
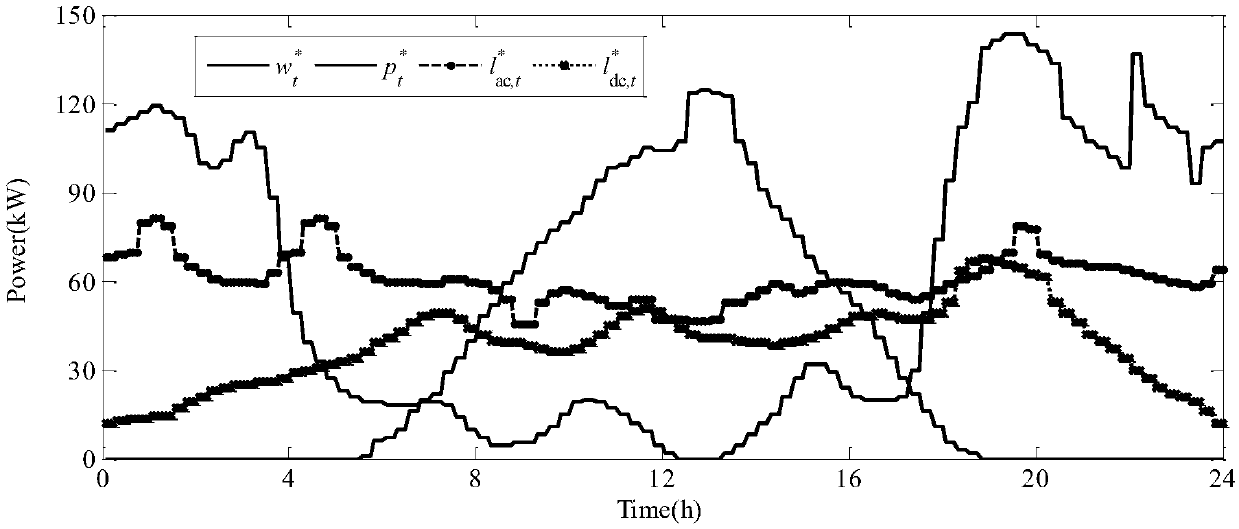
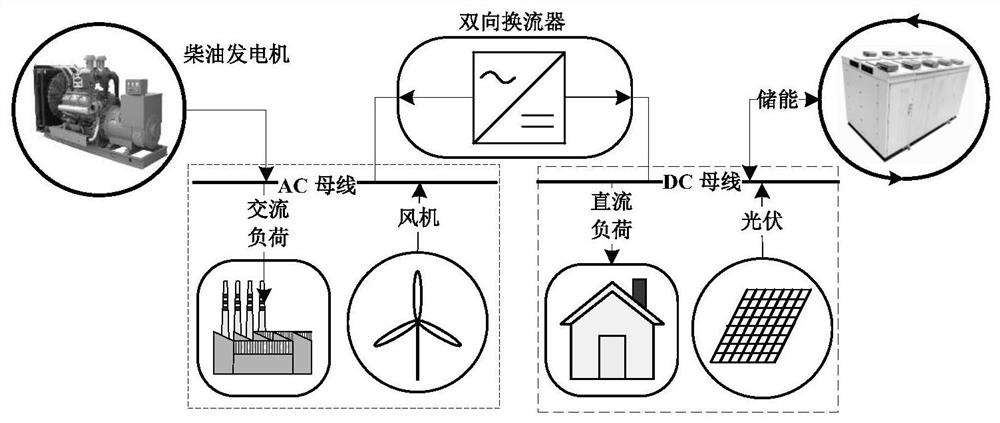
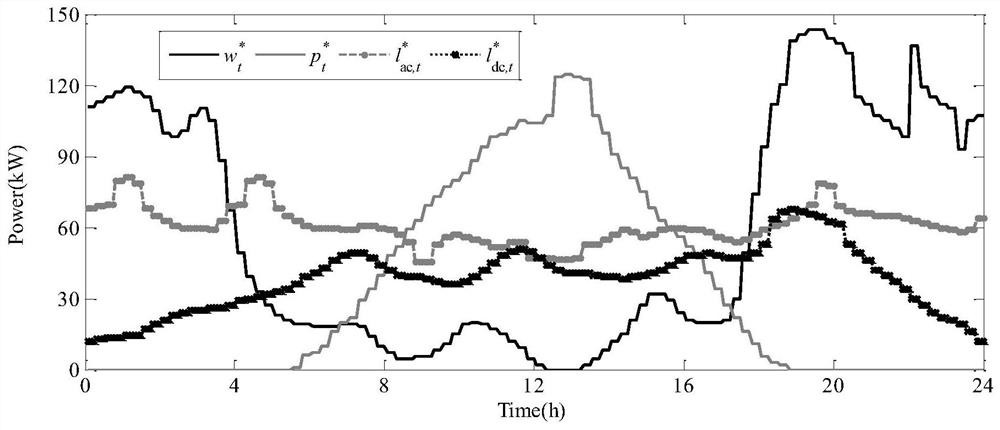
Distributed robust optimization scheduling method for AC/DC hybrid micro grid
ActiveCN108629449AReduce conservatismIn line with the actual sceneElectrical apparatusForecastingProgram planningDistribution characteristic
The invention discloses a distributed robust optimization scheduling method for an AC / DC hybrid micro grid. The method comprises steps that Step 10), a source load uncertainty prediction parameter isobtained, and a distributed uncertainty set is established; Step 20), an operating cost coefficient and operating limit values of each device in the AC / DC hybrid micro grid are obtained, based on theuncertainty set of Step 10), a distributed robust optimization scheduling model of the AC / DC hybrid micro grid is established; and Step 30), a problem of the distributed robust optimization schedulingmodel is solved, the distributed robust problem is iteratively solved through the dual decomposition method, and a robust operation plan of the AC / DC hybrid micro grid is obtained. The method is advantaged in that distribution characteristics of source load uncertainty in the AC / DC hybrid micro grid are considered, the probability distribution function is utilized to describe the source load uncertainty set, conservativeness of traditional robust optimization scheduling is improved, and a reasonable operating and scheduling plan for the AC / DC hybrid micro grid is made.
Owner:LIYANG RES INST OF SOUTHEAST UNIV +1
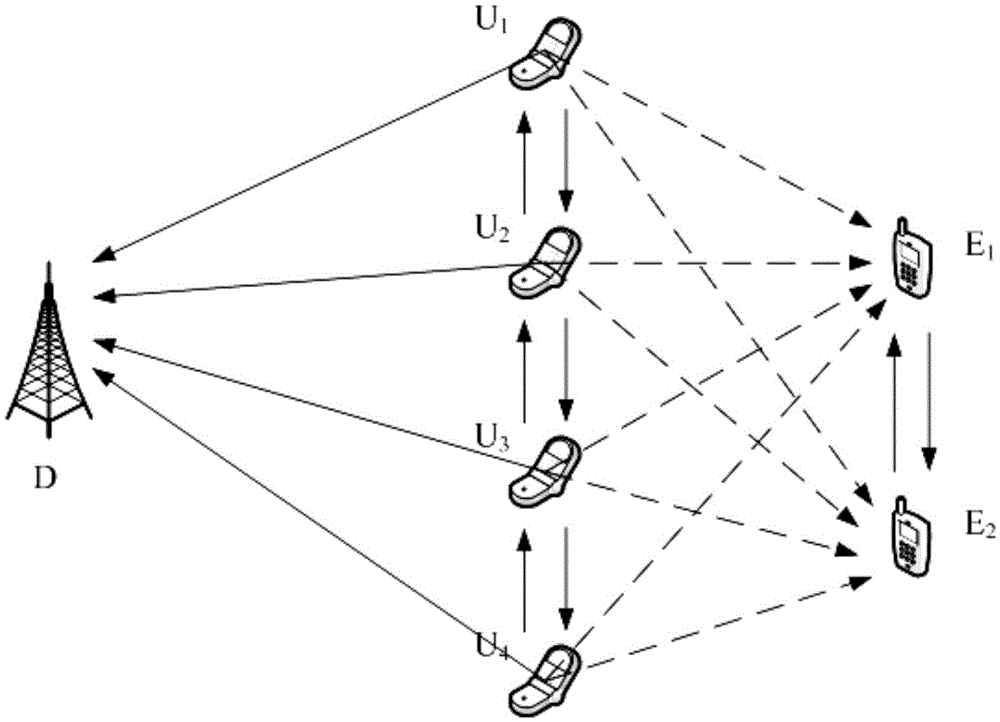
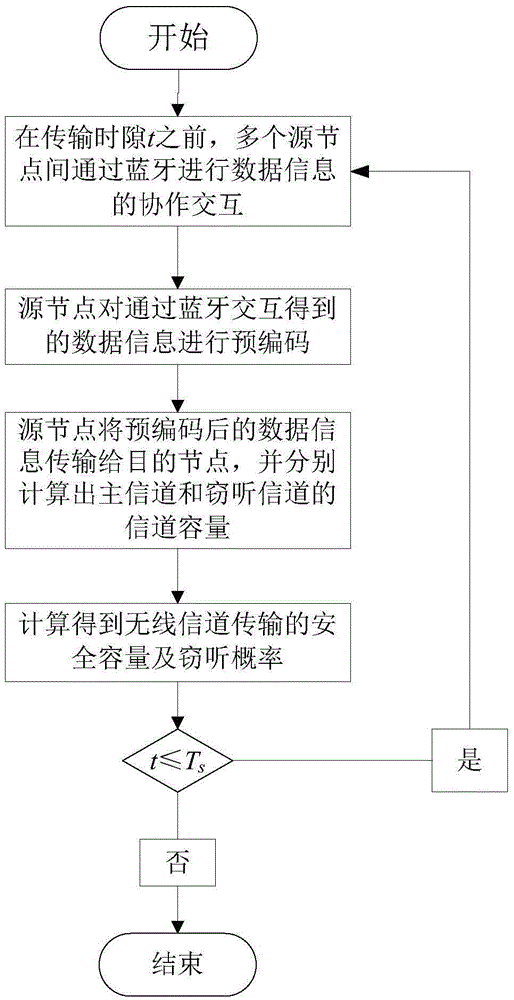
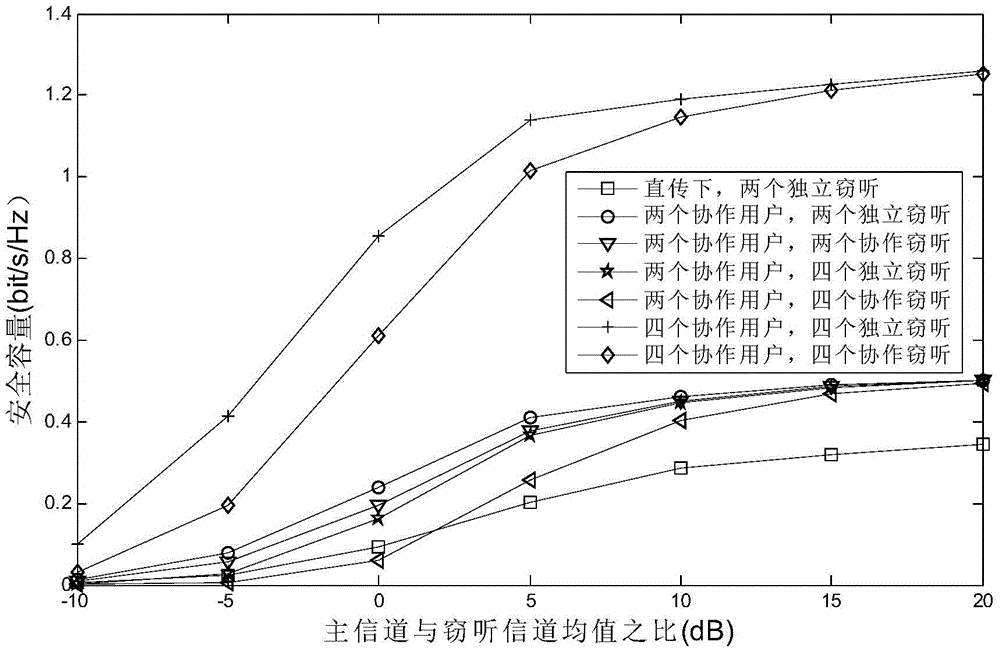
Wireless anti-eavesdropping communication method based on cooperation of multiple source nodes
ActiveCN105657700AAvoid illegal acquisitionIncrease safety capacityWireless commuication servicesTransmissionPrecodingTelecommunications
The invention discloses a wireless anti-eavesdropping communication method based on cooperation of multiple source nodes. The method includes the steps that data interaction is conducted on all the source modes in a Bluetooth mode, so that all the source nodes synchronously transmit the same data information to a target node; according to main channel state information, all the source nodes conduct precoding on the data information to be transmitted; all the source nodes synchronously transmit respective precoded information to the target node, then the target node and an eavesdropping node calculate capacity of the main channel and capacity of an eavesdropping channel respectively, and safety capacity and eavesdropping probability of wireless channel transmission are obtained further. In the mode of cooperation and precoding of the source nodes, the safety capacity of wireless transmission is remarkably improved, and the eavesdropping probability of wireless transmission is effectively reduced, which is beneficial for solving the safety problem caused by multiple eavesdropping nodes existing in an actual wireless communication scene.
Owner:NANJING UNIV OF POSTS & TELECOMM
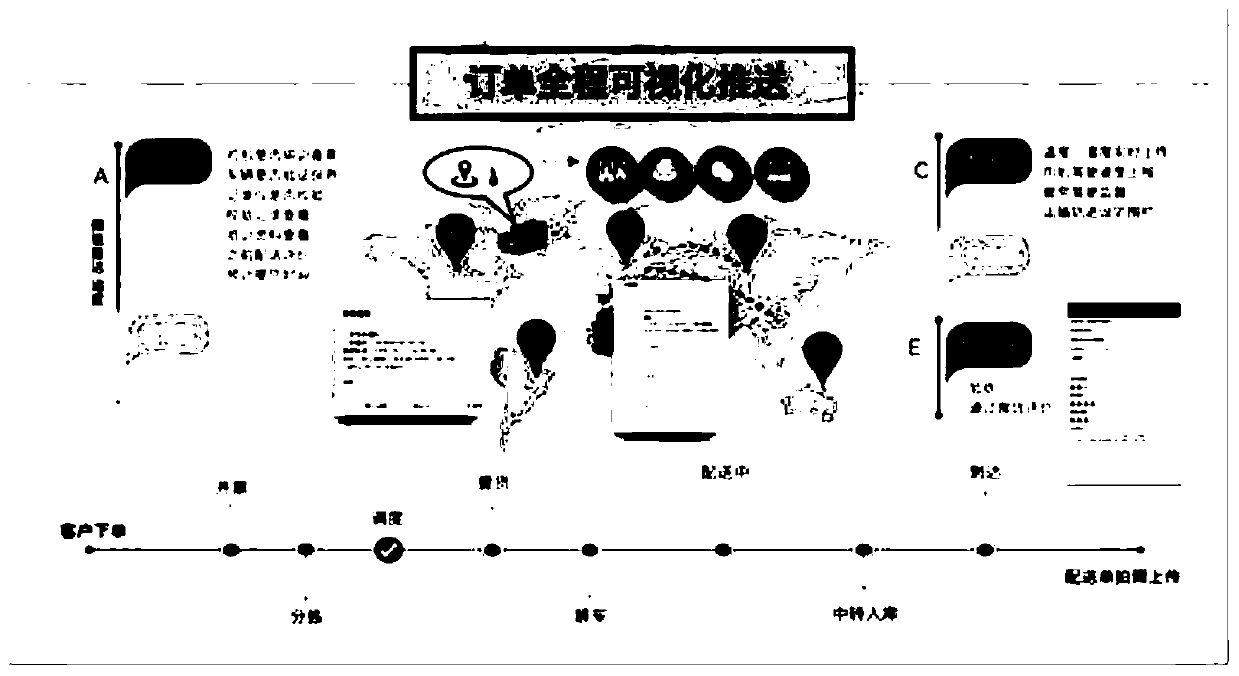
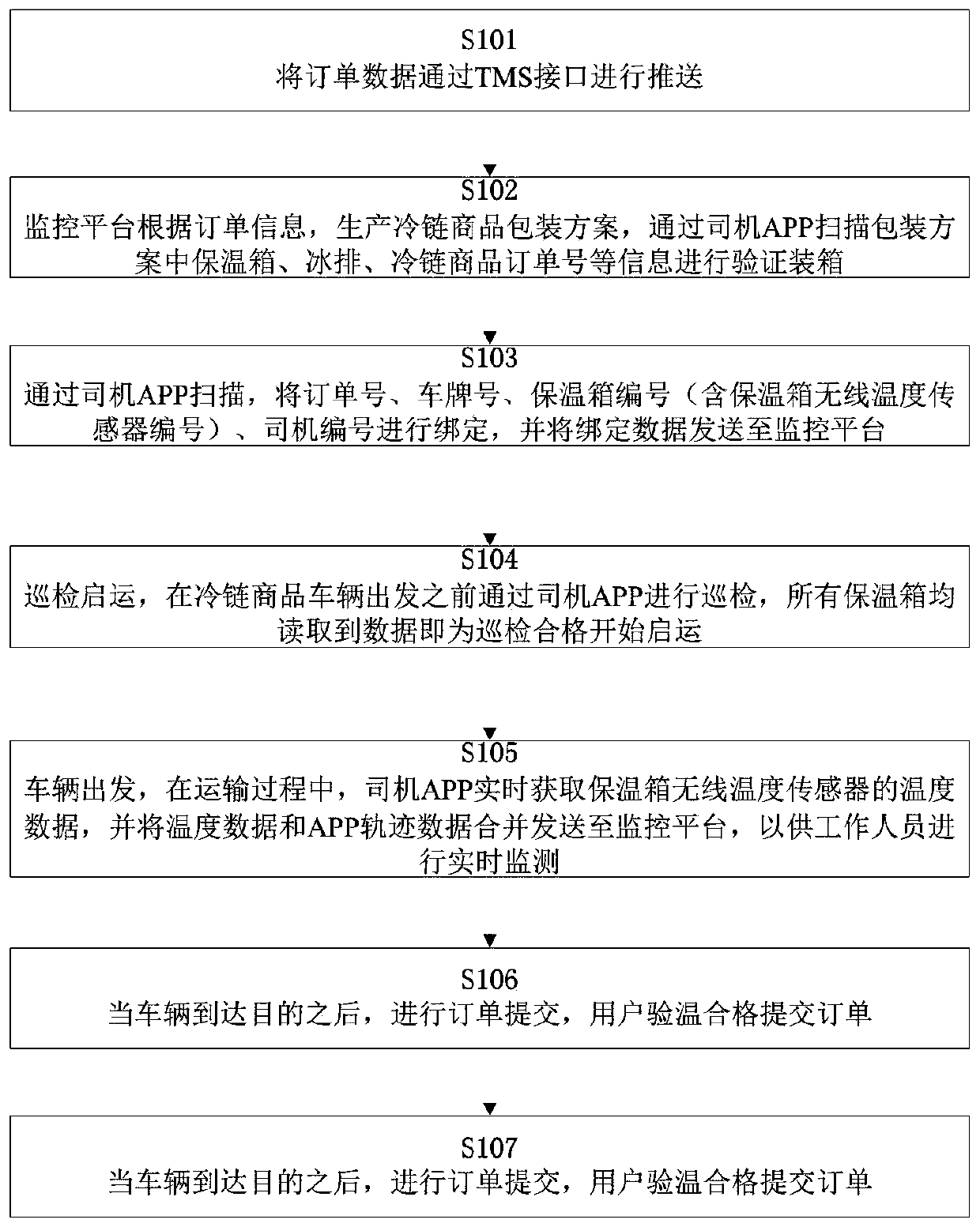
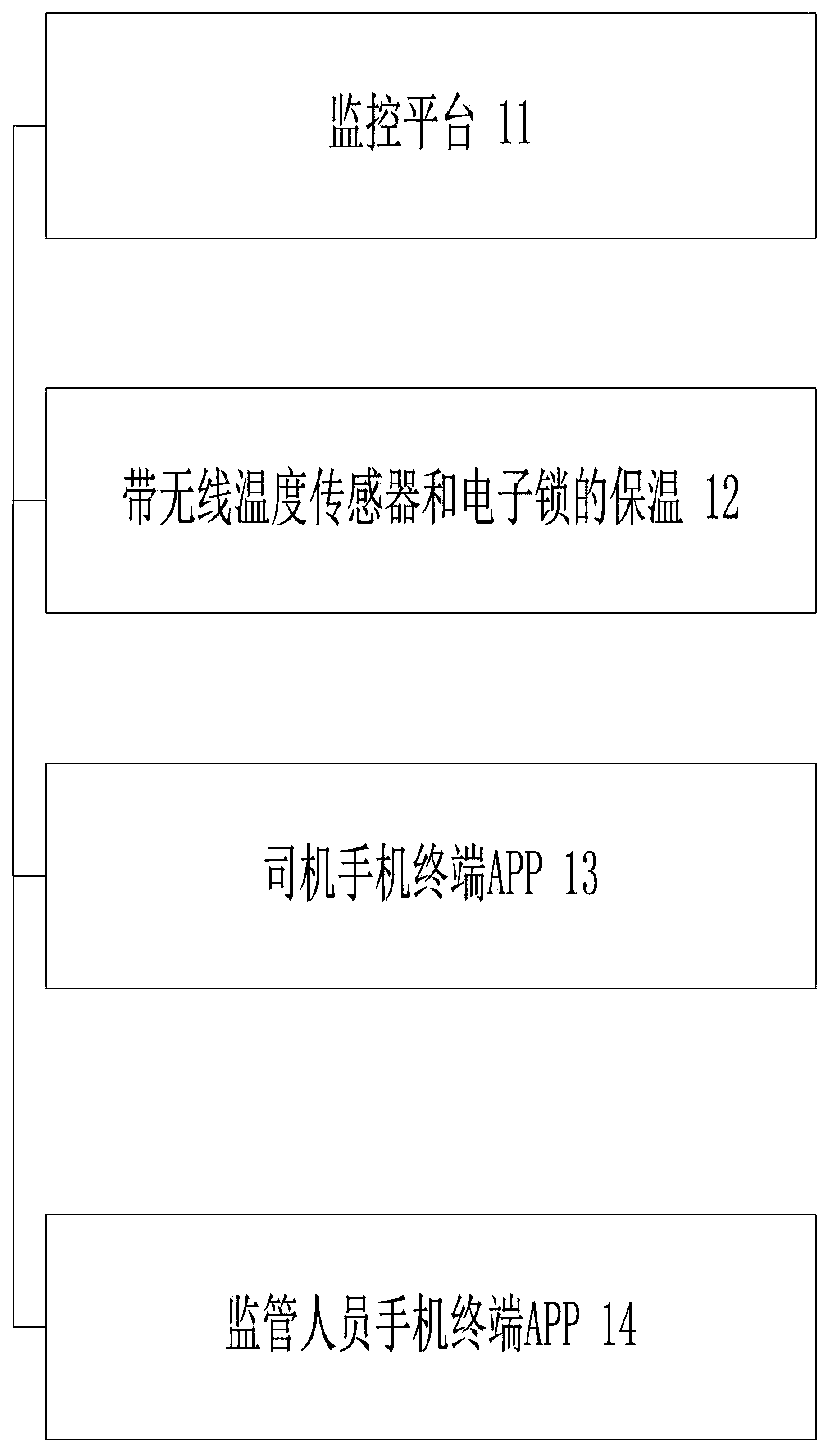
Temperature monitoring and control method and system in cold-chain commodity transportation process
PendingCN110568877AReduce lossesAvoid wastingTemperatue controlSubstation equipmentCold chainTemperature control
The invention provides a temperature monitoring and control method and system in a cold-chain commodity transportation process. An AI intelligent calculation module of a monitoring platform obtains atransportation heat preservation packaging scheme of cold-chain commodities; a heat preservation box and matched materials are configured according to the transportation heat preservation packaging scheme, and the heat preservation box is internally provided with a wireless temperature sensor, an irreversible cold charging interface and an electronic lock; before cold-chain transportation, a transportation driver terminal APP matches transportation materials according to the packaging scheme and scans a code of material parameters for verification and boxing; in the transportation process, thewireless temperature sensor transmits temperature data of cold-chain commodities in the box to the driver mobile phone APP in real time and uploads tracks to the monitoring platform in real time forbackground display, and if the temperature obtained by the driver APP is about to exceed the preset cold-chain commodity temperature zone range, the APP constantly gives a sound-light alarm to remindthe transportation driver while the APP starts a vehicle-mounted air conditioner through Bluetooth to realize temperature control; and when the commodities reach a destination at qualified temperature, a consignee user scans the number of the heat preservation box to authenticate unlocking and submit an order.
Owner:管海兵
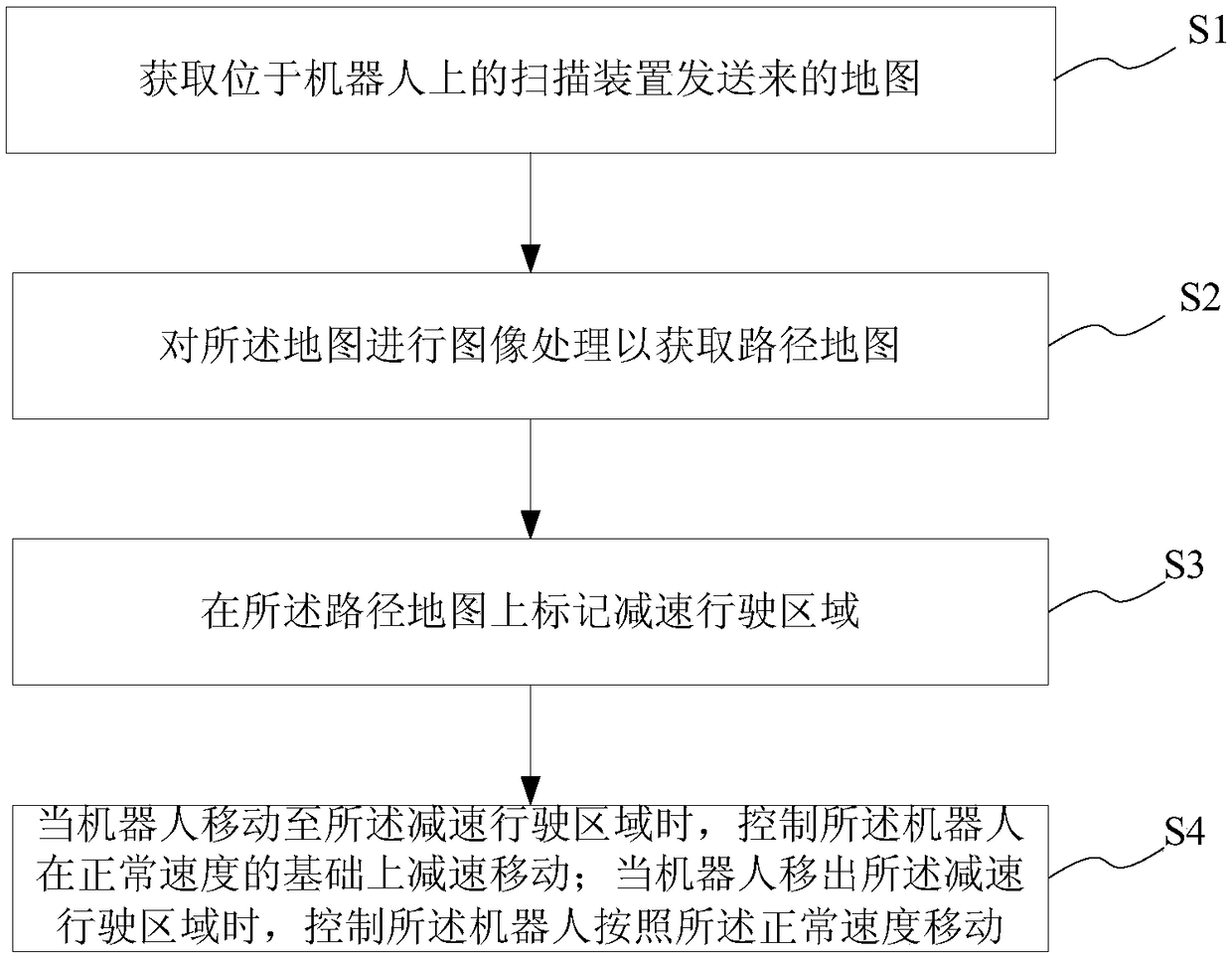
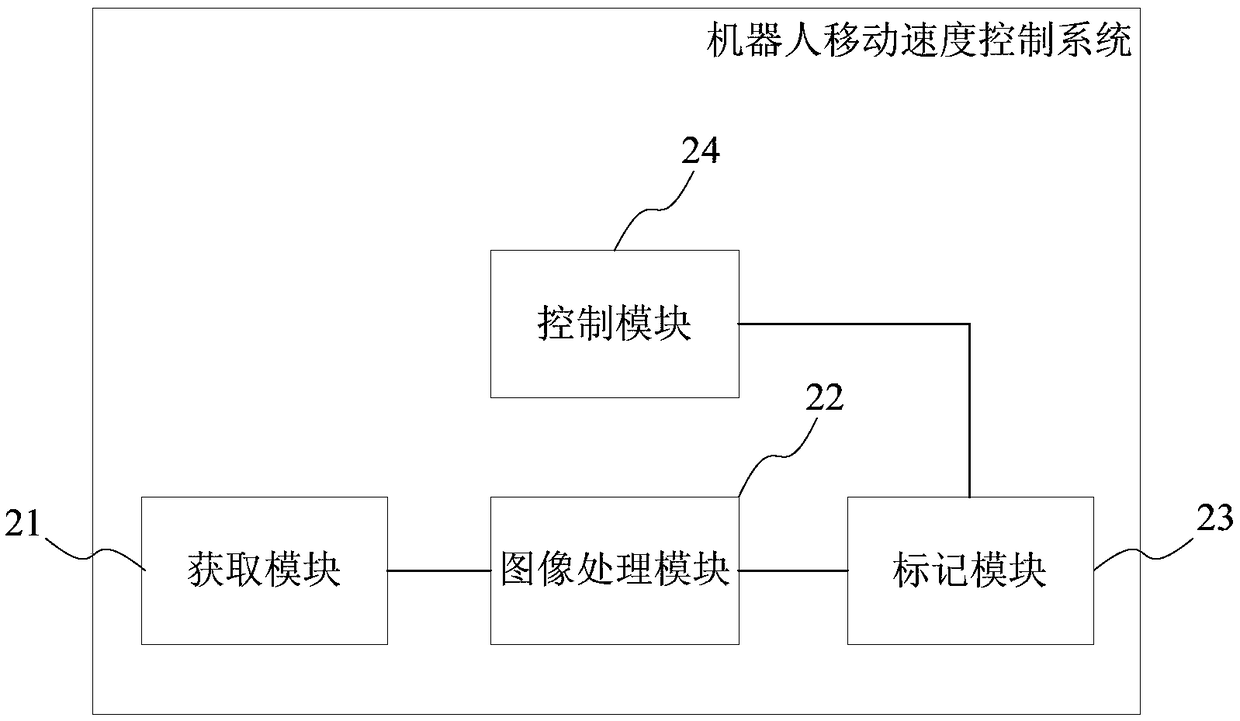
Method and system for controlling moving speed of robot, storage medium and terminal
InactiveCN108983783ASports intelligenceIn line with the actual scenePosition/course control in two dimensionsImaging processingComputer terminal
The present invention provides a method and system for controlling the moving speed of a robot, a storage medium and a terminal. The method comprises a step of acquiring a map sent by a scanning device in the robot, a step of performing image processing on the map to obtain a path map, a step of marking a decelerating traveling area on the path map, a step of controlling the robot to decelerate ona normal speed basis when the robot moves to the decelerating traveling area, and a step of controlling the robot to move in a normal speed when the robot moves out of the decelerating traveling area. According to the method and system for controlling the moving speed of a robot, the storage medium and the terminal, by identifying a driving scene of the robot, the robot decelerates in a preset decelerating driving area, and therefore, the a condition that the movement of the robot is more intelligent and conforms to an actual scene is ensured.
Owner:SHANGHAI YOGO ROBOTICS CO LTD
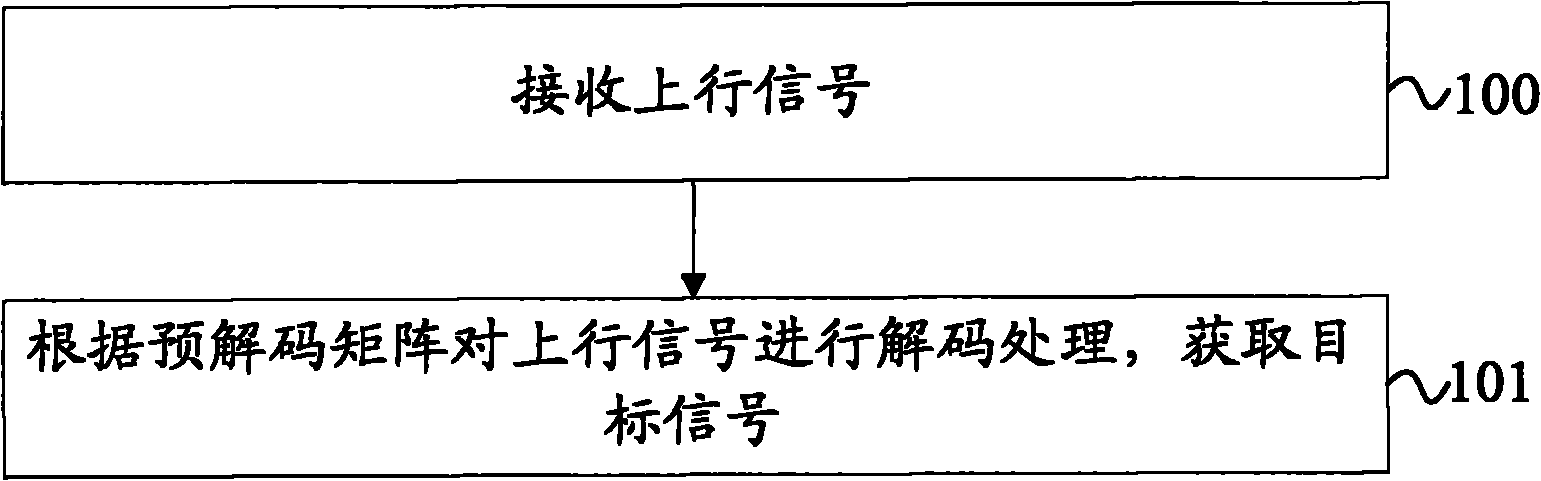
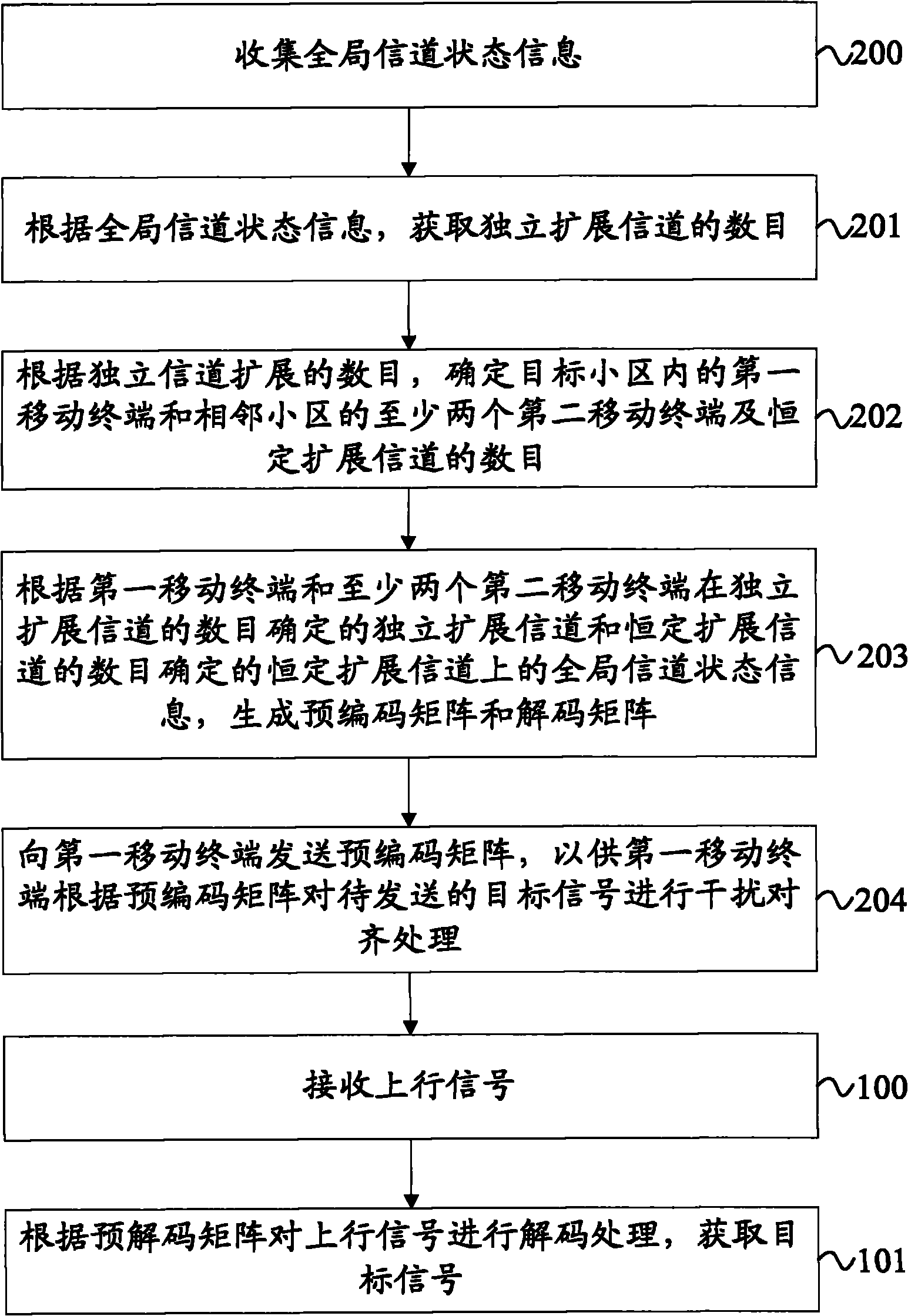
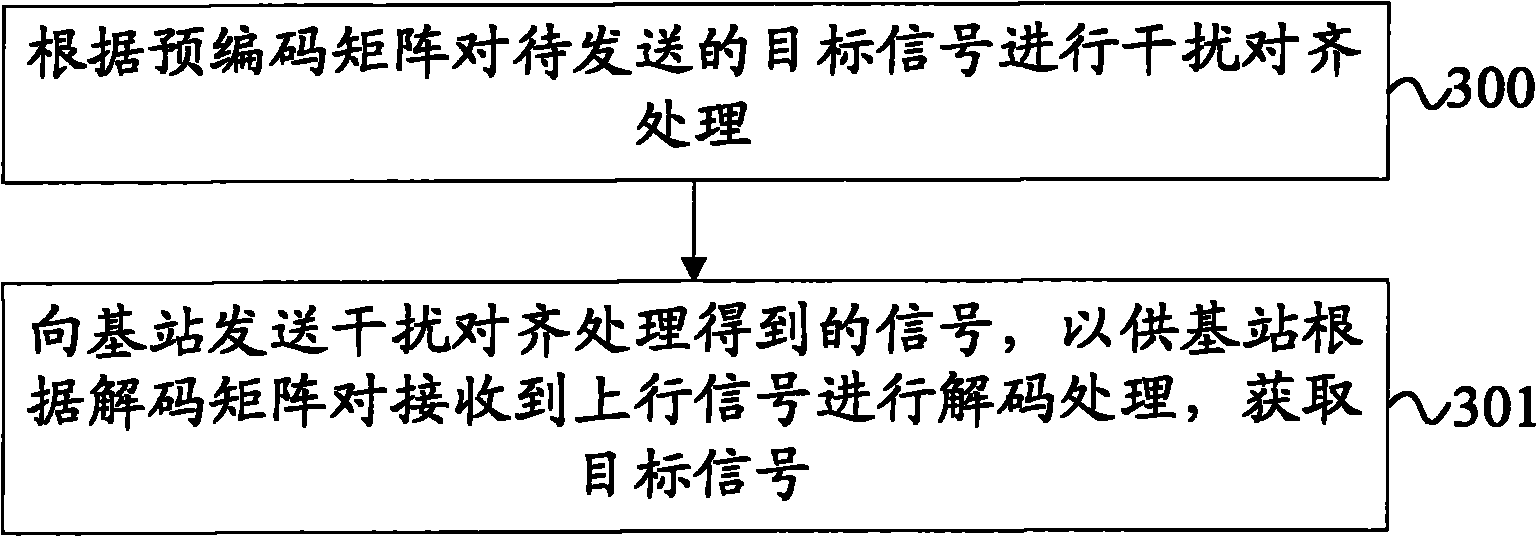
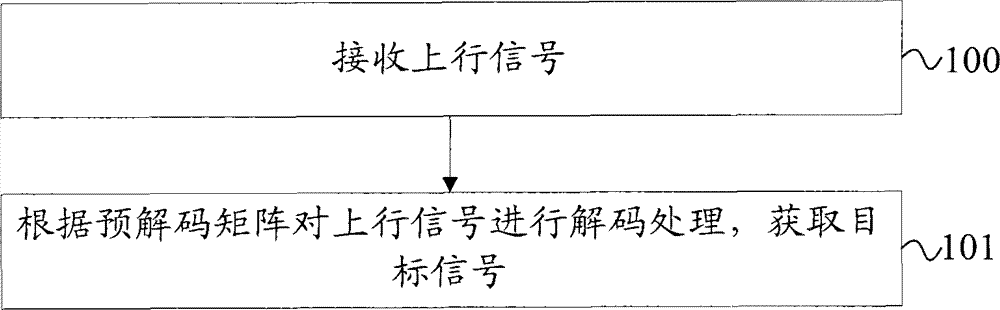
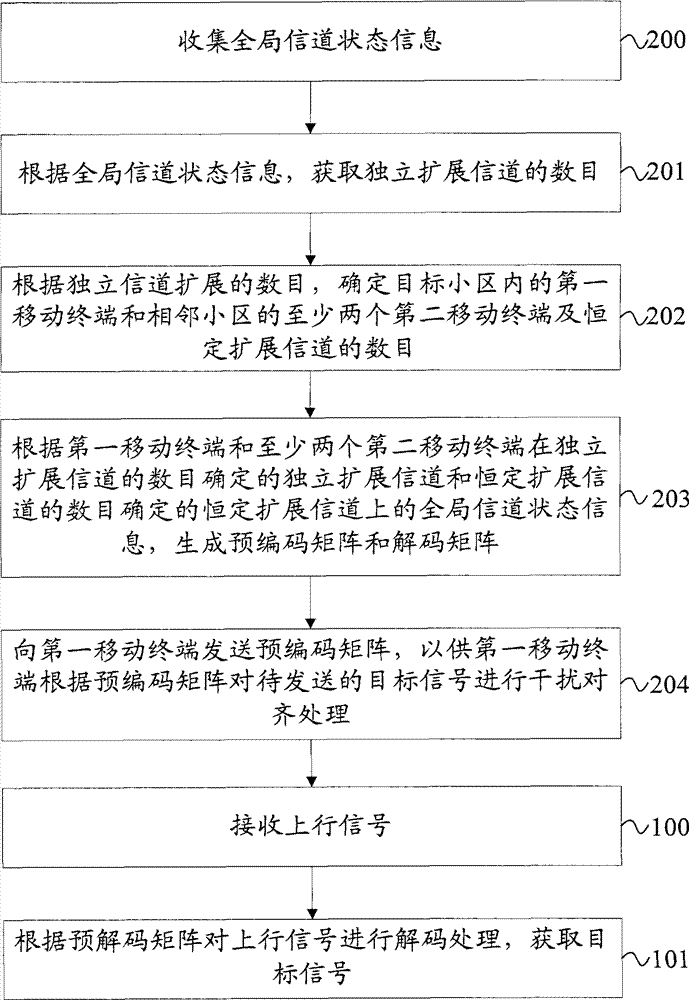
Signal processing method, equipment and system
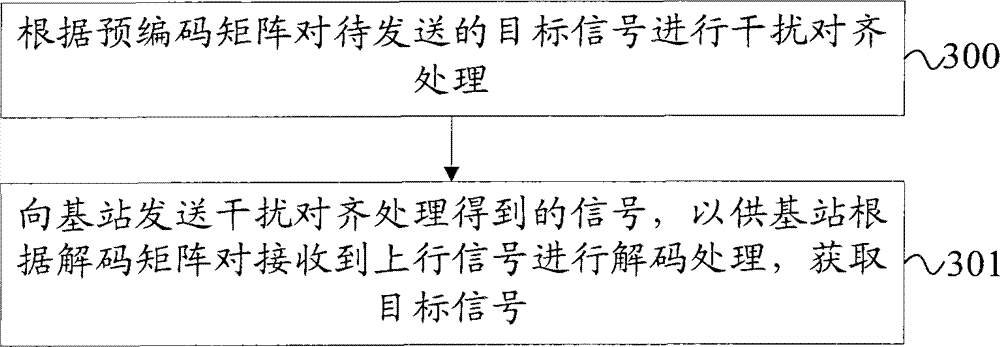
ActiveCN102468916AIn line with the actual sceneEfficient use ofError preventionChannel state informationCommunications system
The invention provides a signal processing method, equipment and system. The signal processing method comprises the following steps: receiving uplink signals which comprises the signals obtained by interfering and aligning target signals to be sent by a first mobile terminal according to a precoding matrix and interference signals sent by at least two mobile terminals of an neighboring cell, decoding the uplink signals according to a decoding matrix and obtaining the target signals, wherein the precoding matrix and the decoding matrix are obtained according to the global channel state information of the first mobile terminal and the at least two mobile terminals on an independent expansion channel and a constant expansion channel, and the interference signals and the target signals on the constant expansion channel utilize the dimensionality which is not utilized by the independent expansion channel. The technical scheme of the embodiment of the invention is in line with the actual scene of an actual communication system and is highly practical.
Owner:深圳市信方达科技发展股份有限公司
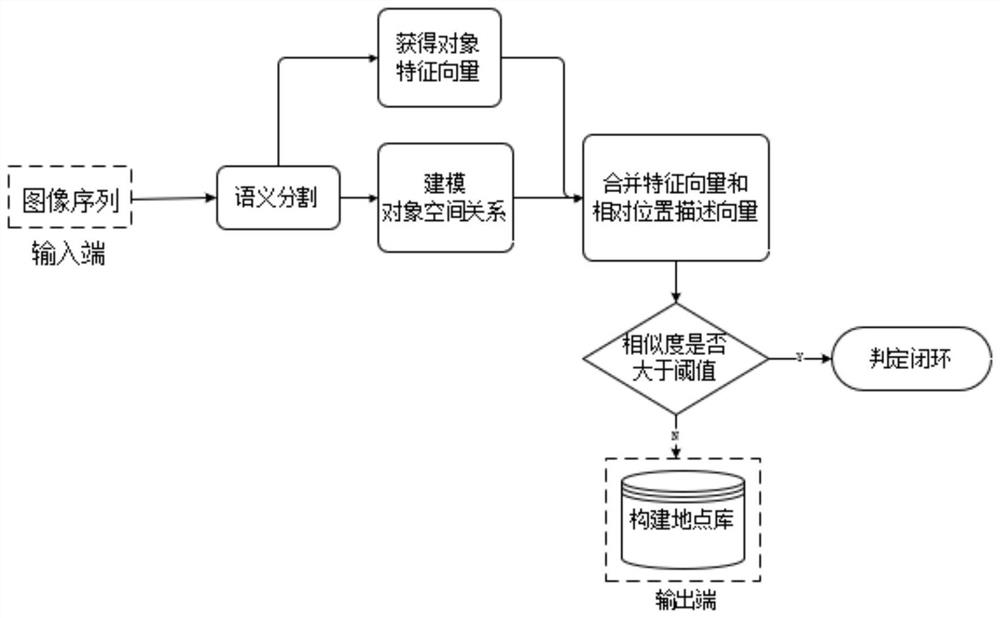
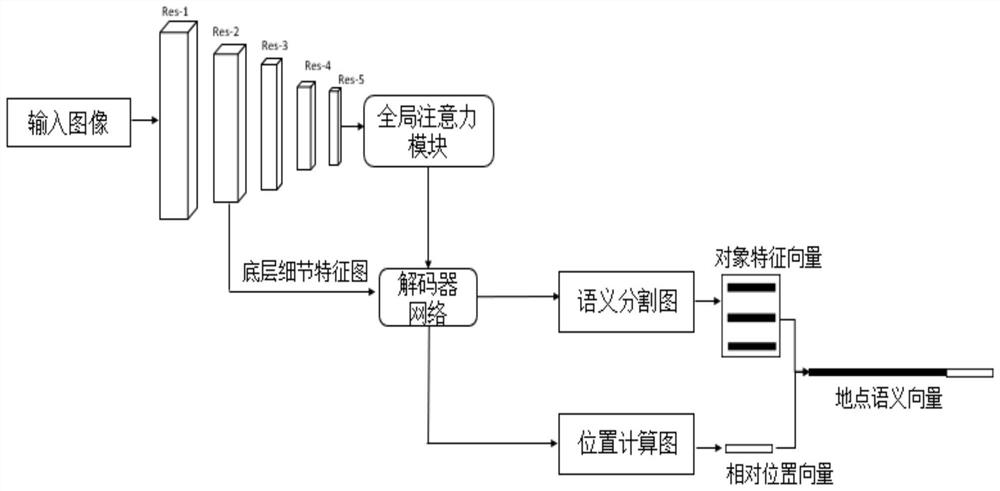
SLAM loopback detection improvement method based on semantic segmentation
ActiveCN112508985AAvoid the problem of closed-loop detection failureAccurate Data SourceDigital data information retrievalImage analysisFeature vectorData set
The invention discloses a SLAM loopback detection improvement method based on semantic segmentation. The method comprises the following steps of 1, obtaining a general data set of road scene semanticsegmentation; 2, acquiring an environment image by using an RGB camera, and acquiring a road environment image under different environment conditions; 3, obtaining a classification result of each pixel predicted by semantic segmentation; 4, according to a classification result, obtaining an object feature vector containing a corresponding category in the semantic segmentation graph; 5, constructing a place model containing semantic information; 6, analyzing the images in the general data set through a place model to obtain a semantic place vector, creating an image library of places, and storing the semantic place vector into a vector containing place semantic information; 7, matching the similarity between the images to be detected and the images in the image library; and 8, carrying outclosed-loop detection, if a vector of which the similarity exceeds a threshold value is found, representing that the current image is a closed-loop node, and otherwise, adding the current image into an existing image library.
Owner:SOUTH CHINA UNIV OF TECH
Classification method, computer equipment and storage medium
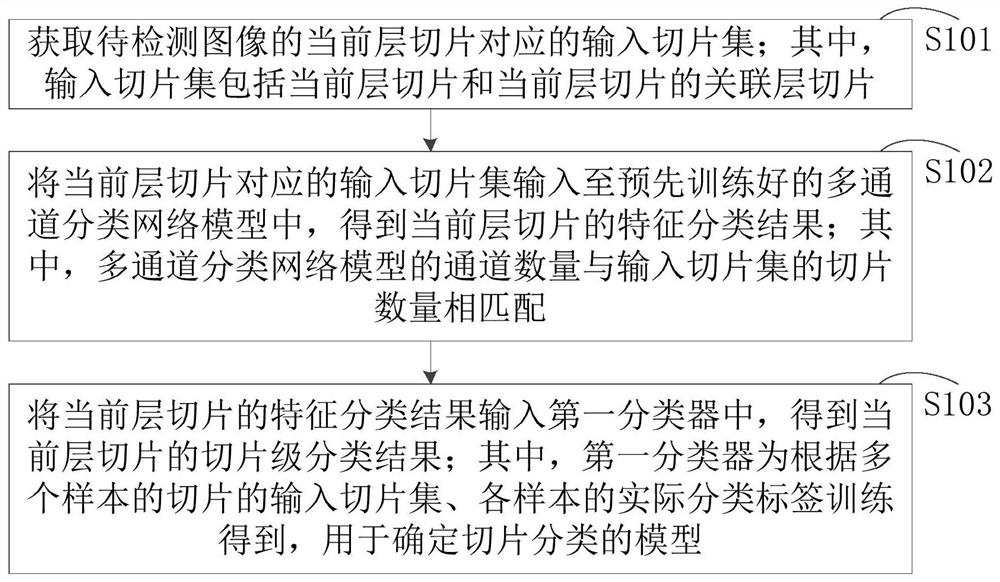
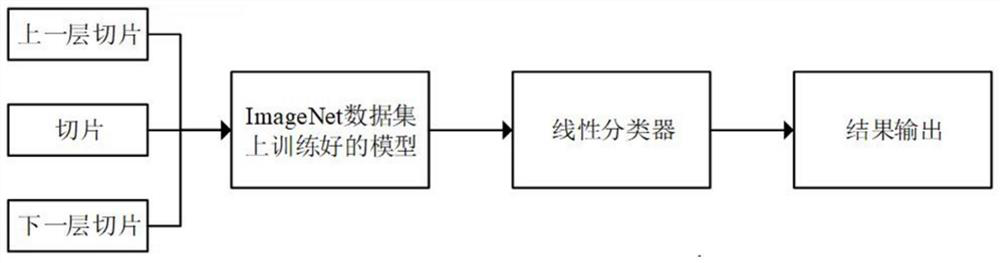
ActiveCN110210519AClassification results are specificIn line with the actual sceneImage analysisMedical automated diagnosisClassification methodsNetwork model
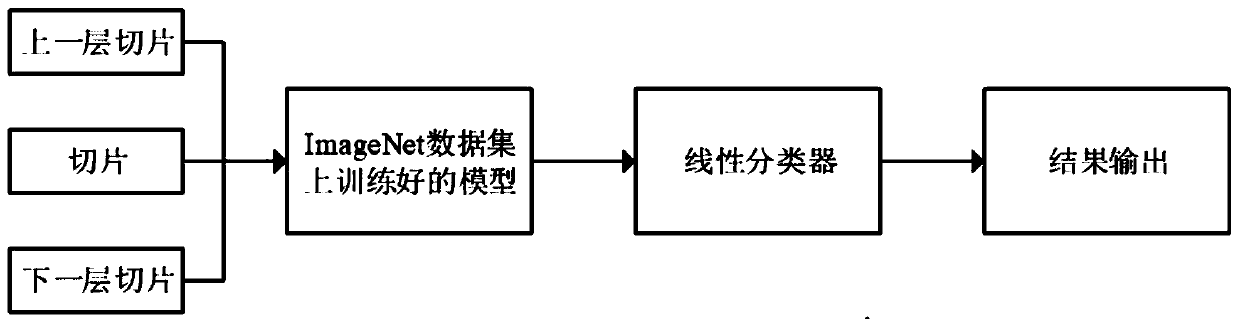
The invention relates to a classification method, computer equipment and a storage medium. The computer equipment inputs an input slice set corresponding to a current layer slice of a to-be-detected image into a pre-trained multi-channel classification network model to obtain a feature classification result of the current layer of slices, and inputs the feature classification result of the current-layer slice into a first classifier to obtain a slice level classification result of the current slice. As in the classification method, the input slice set corresponding to the current layer slice comprises the current layer slice and an associated layer slice of the current layer slice, the slices related to the current-layer slice are classified as input at the same time, and the data completestructure information of the current layer of slices is reserved, and the first classifier is obtained by training according to the slices of the plurality of samples and the actual classification labels, so that the classification result is more specific and more conforms to the actual scene, and the reliability and accuracy of the classification result are greatly ensured.
Owner:SHANGHAI UNITED IMAGING INTELLIGENT MEDICAL TECH CO LTD
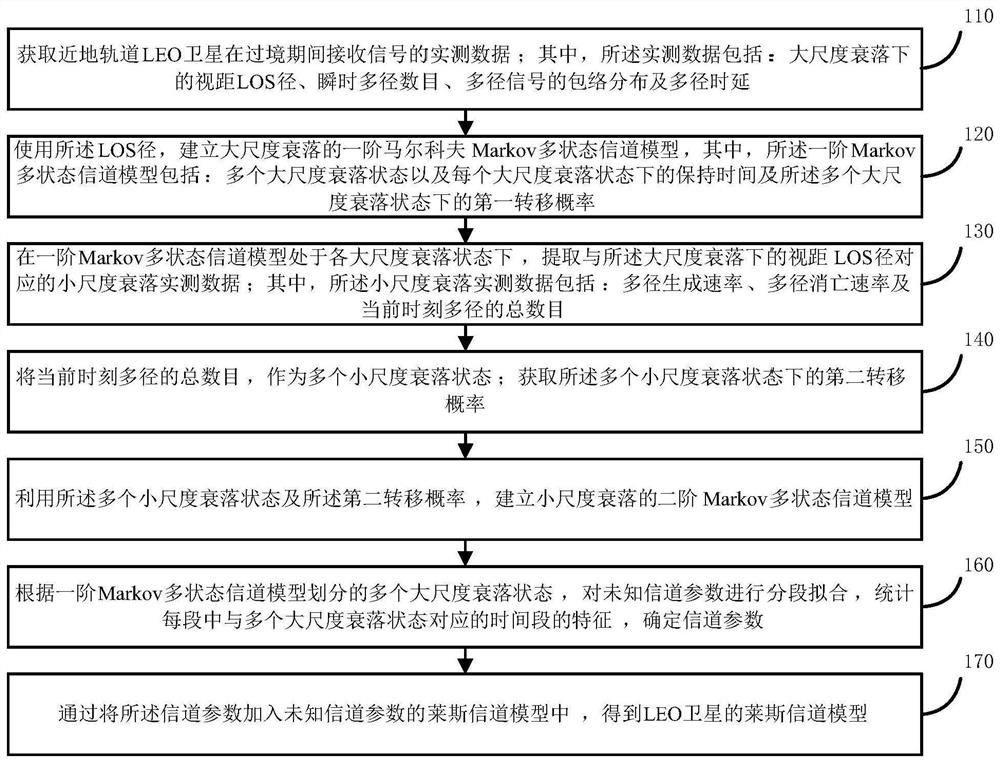
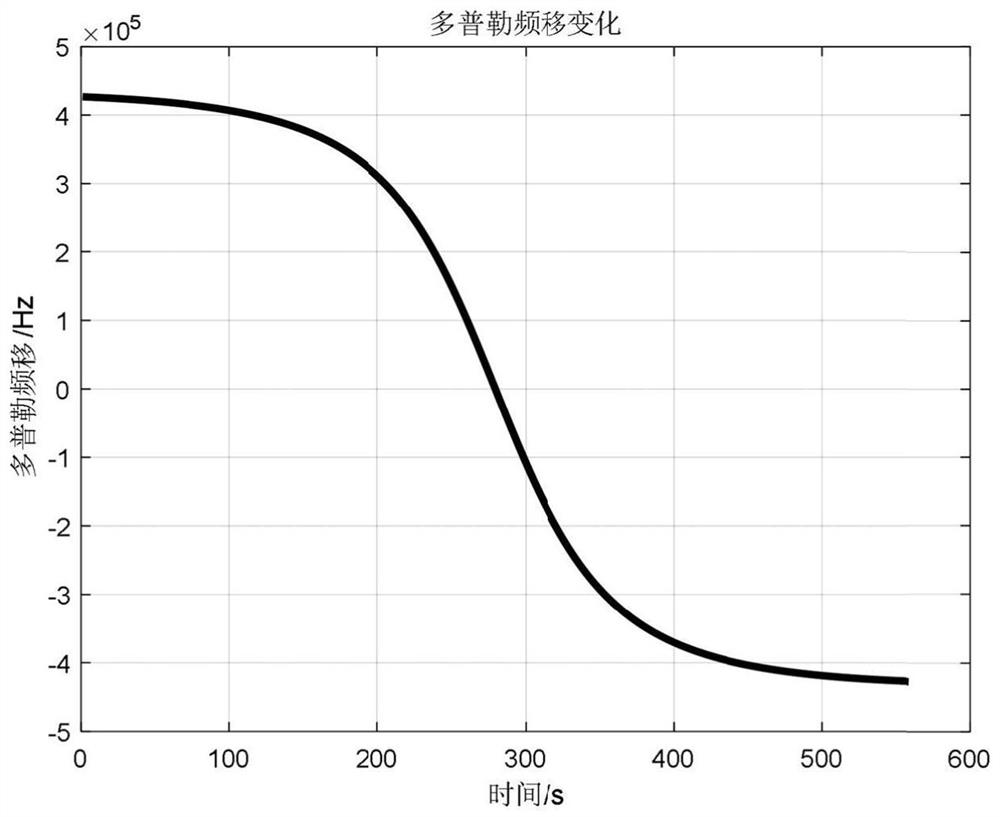
LEO satellite channel modeling method and device based on double Markov models
ActiveCN112436882ADynamic conformityMeet the requirements of dynamic time-varyingTransmission monitoringRadio transmissionEngineeringLow earth orbit
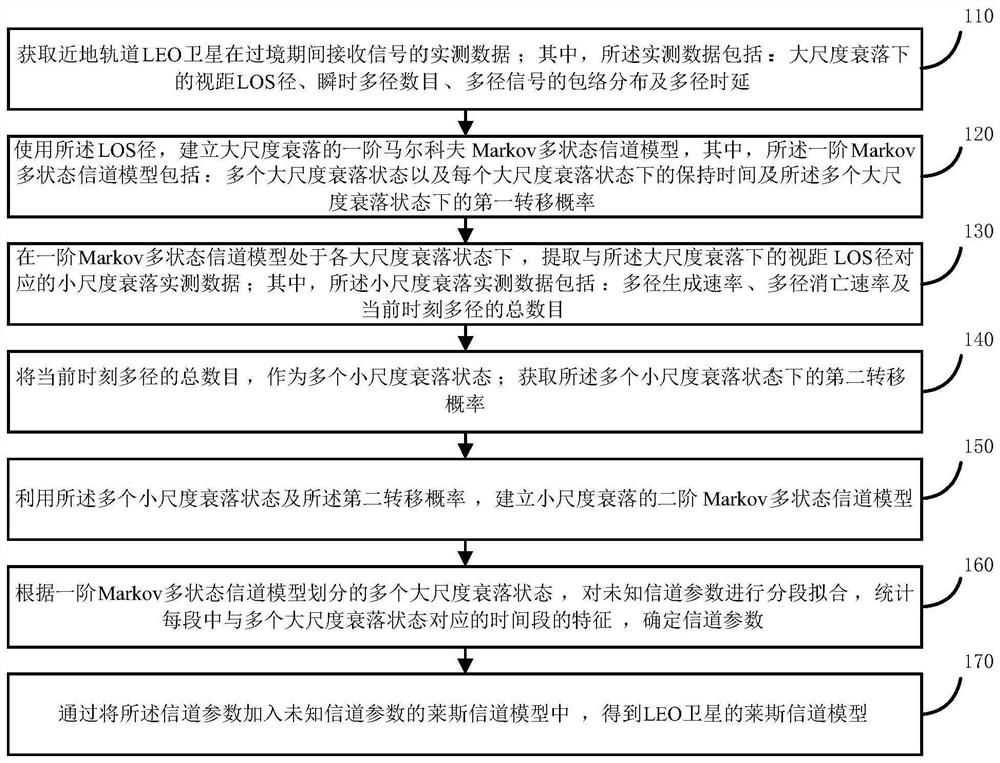
According to the LEO satellite channel modeling method and device based on the double Markov models, the influence of shadow fading on LOS paths under large-scale fading can be reflected through the first-order Markov multi-state channel model; moreover, when the first-order Markov multi-state channel model is in each large-scale fading state, small-scale fading actual measurement data corresponding to a sight distance LOS path under large-scale fading is extracted, and a multi-path dynamic generation and deactivation process under small-scale fading can be reflected, so that the dynamic time-varying requirement of the LEO satellite channel model on a time axis is met, and the dynamics of LEO satellite channel characteristics is met; and moreover, by determining the channel parameters andestablishing the channel parameters required by the complete Rician channel model, the Rician channel model of the LEO satellite is obtained, so that the Rician channel model of the LEO satellite better conforms to the actual scene of the low earth orbit satellite channel.
Owner:BEIJING UNIV OF POSTS & TELECOMM
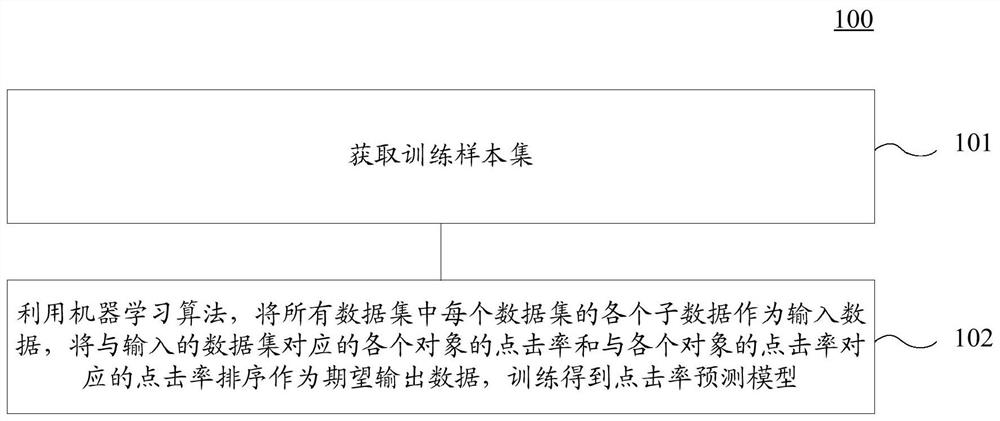
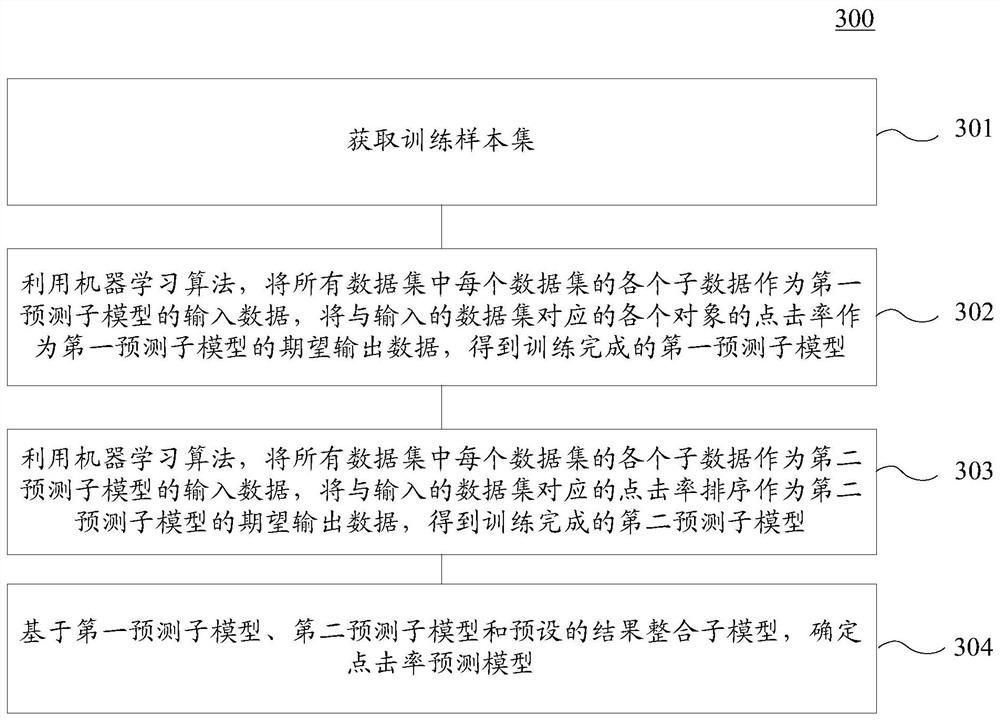
Method and device for training model, equipment and storage medium
PendingCN113780548ASolve the problem of not being able to perceive the actual ranking ability of the model during the training processGuaranteed Fitting AccuracyForecastingCharacter and pattern recognitionData setEngineering
The invention discloses a method and device for training a model. The specific implementation scheme comprises the steps: obtaining a training sample set, wherein a training sample in the training sample set comprises the sub-data of each data set in all data sets of one batch, the click rate of each object, and the click rate order; by utilizing a machine learning algorithm, taking each sub-data of each data set in all the data sets as input data, taking the click rate and click rate sequence of each object corresponding to the input data set as expected output data, and training to obtain a click rate prediction model, wherein a loss function of the click rate prediction model is constructed by using a first loss function and a second loss function, the first loss function is used for calculating the accuracy of the click rate of each object, and the second loss function is used for calculating the sorting capability of the click rate sorting. According to the scheme, the problem that an existing click rate prediction model cannot perceive the actual sorting capability of the model in the training process is solved.
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD
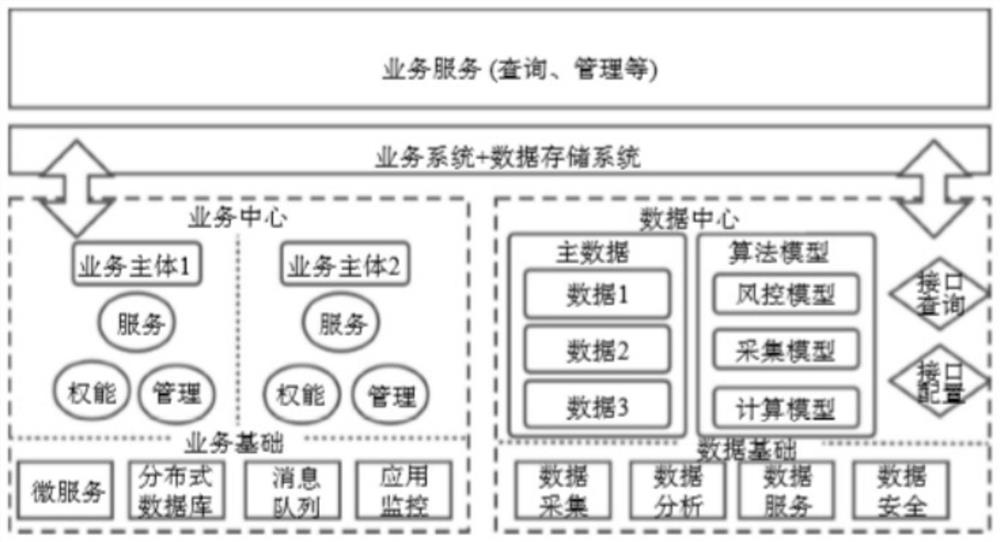
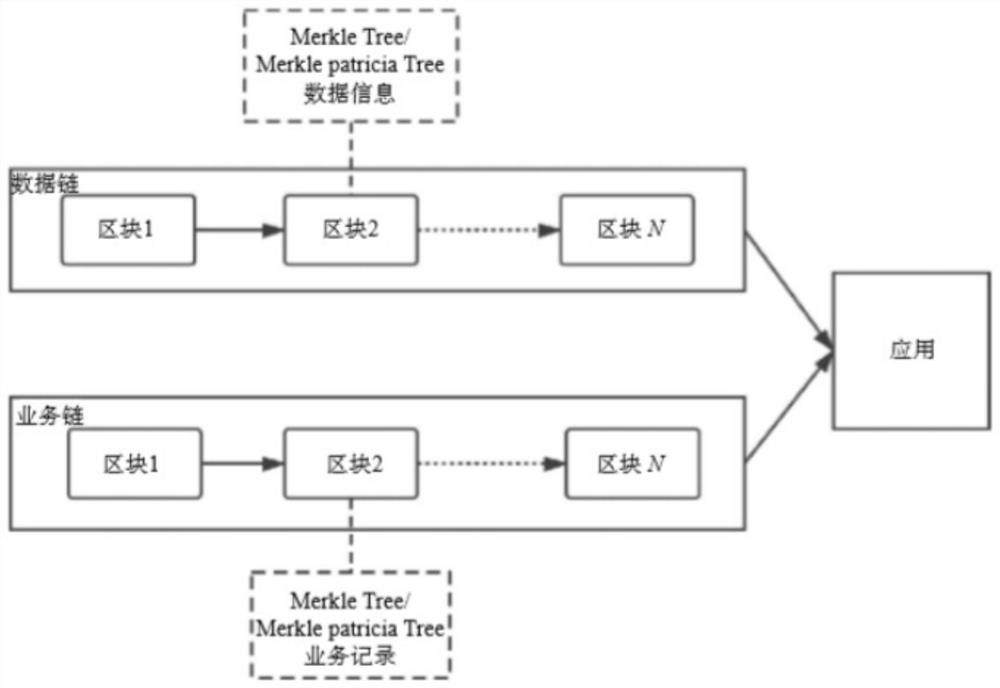
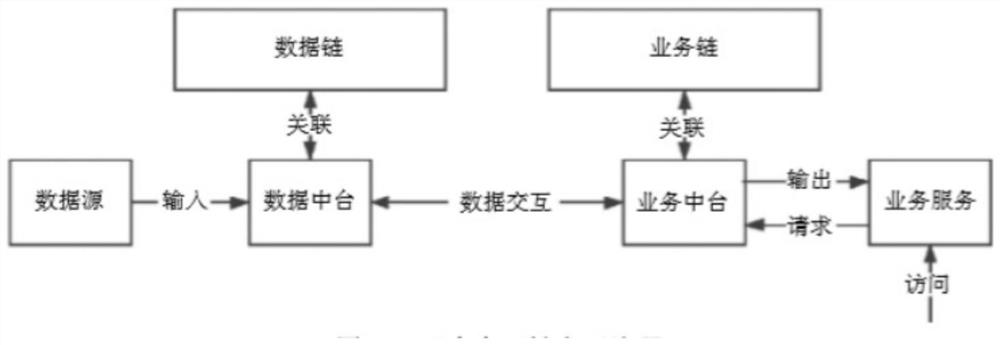
An endogenous data security interaction method for a double-middle-station double-chain architecture
ActiveCN112347491AIn line with the actual sceneEnsure safetyKey distribution for secure communicationUser identity/authority verificationStationDouble chain
The invention discloses an endogenous data security interaction method for a double-middle-station double-chain architecture, and the invention employs the double-middle-station architecture and the double-chain architecture, and the double-middle-station architecture comprises a business service, a business system, a business center, a data center, a business foundation and a data foundation; thedouble-chain architecture comprises data information, a data chain, a service chain and a service record. According to the endogenous data security interaction method of the double-middle-station double-chain architecture, the interaction security of endogenous data is improved by importing a block chain technology into a middle station, the credibility of the middle platform data before the middle platform data is linked is ensured, and an improved Shoup threshold endogenous data interaction protocol is constructed to ensure the security of the data before the data is linked. On the basis ofthe above work, an interaction mechanism integrating the under-chain signature and the on-chain signature verification is designed, so that the data interaction efficiency of the double middle stations and the double chains is improved, the service middle stations can extract the related information of the data middle stations more efficiently, and the service processing capability is enhanced.
Owner:SHANGHAI UNIVERSITY OF INTERNATIONAL BUSINESS AND ECONOMICS +1
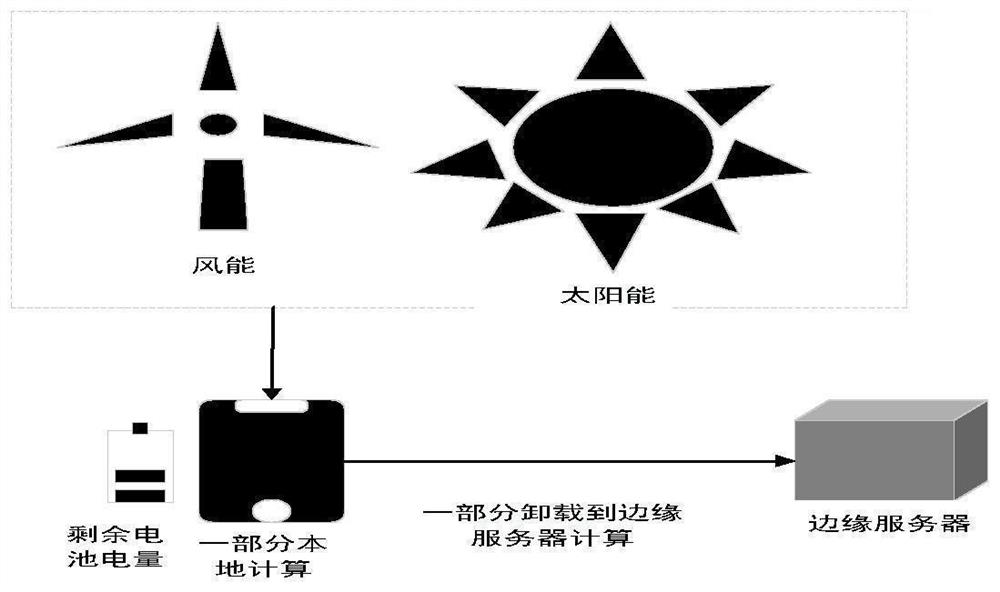
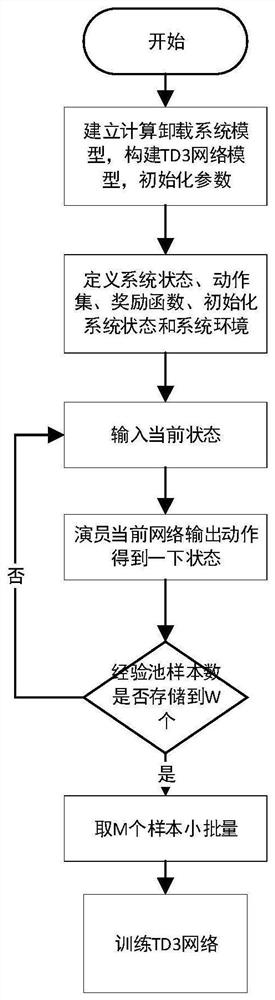
TD3 algorithm-based calculation unloading distribution method and device
ActiveCN112600869AReduce consumptionAddressing the downside of overestimationMachine learningTransmissionAlgorithmThe Internet
The invention discloses a TD3 algorithm-based calculation unloading distribution method and device, and the method comprises the steps: obtaining the state of a calculation unloading system, inputtingthe state of the calculation unloading system into a pre-trained actor current network of a calculation unloading TD3 network, and obtaining a calculation unloading proportion and calculation unloading transmitting power, wherein the computing unloading system state comprises a channel gain from the Internet-of-Things device to the edge server, a battery capacity of the Internet-of-Things deviceand collectable renewable energy. Through a deep reinforcement learning method, the optimal unloading strategy of the equipment is determined, and the energy consumption of the intelligent equipment is reduced by utilizing energy collection.
Owner:NANJING UNIV OF POSTS & TELECOMM
Leo satellite channel modeling method and device based on double Markov model
ActiveCN112436882BDynamic conformityMeet the requirements of dynamic time-varyingTransmission monitoringRadio transmissionEngineeringRemote sensing
Owner:BEIJING UNIV OF POSTS & TELECOMM
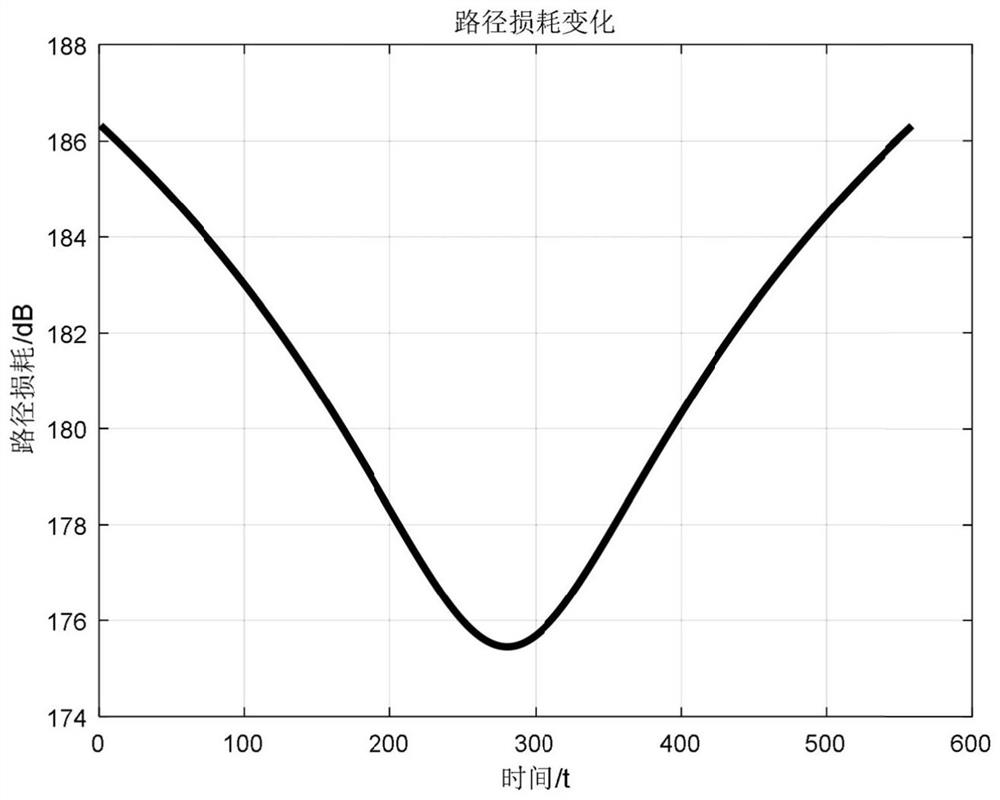
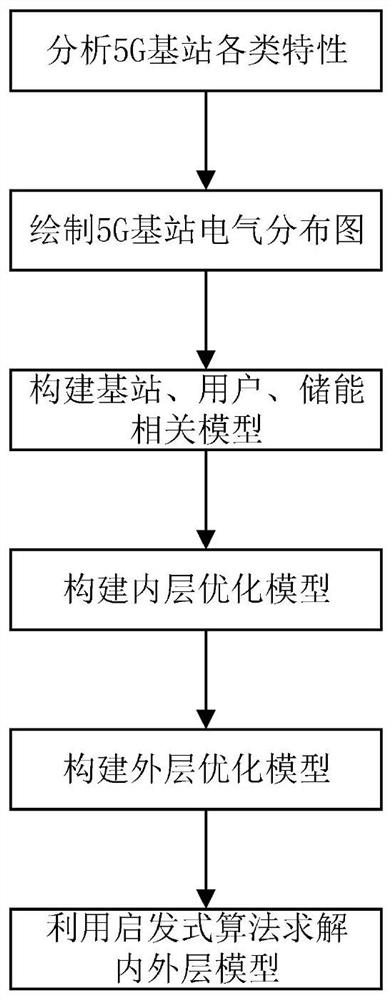
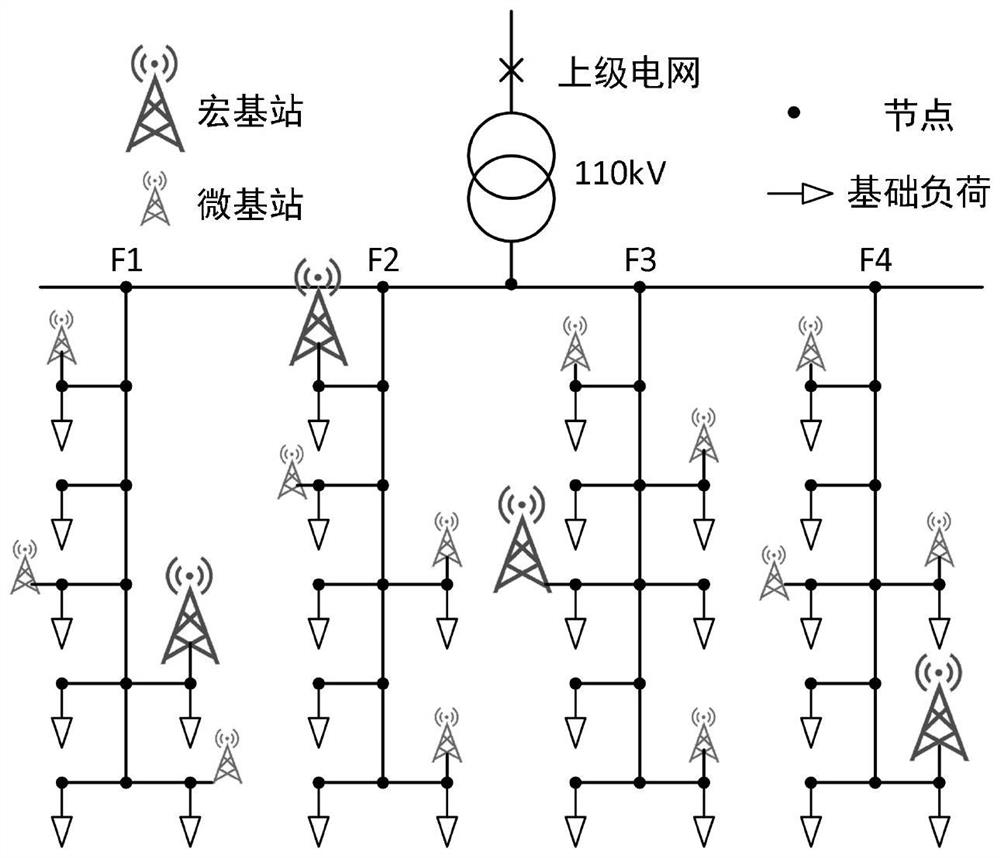
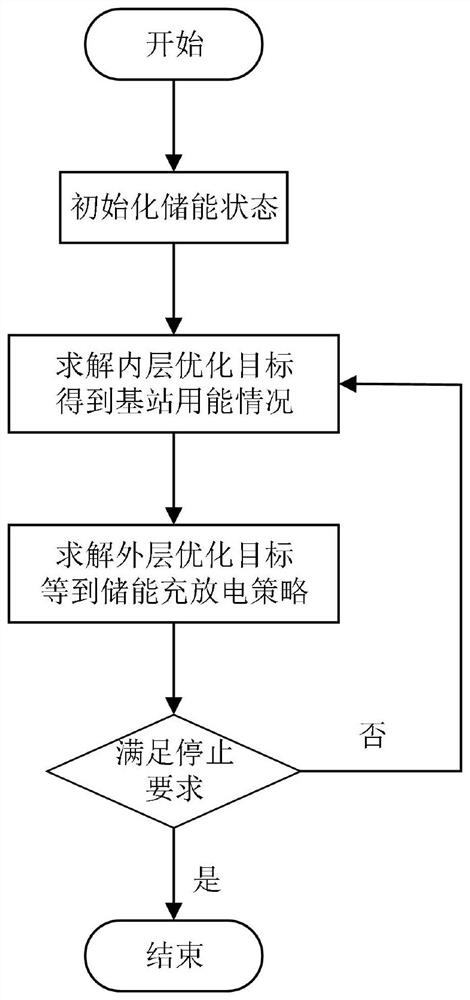
Base station regulation and control method considering 5G communication base station power network topology distribution
PendingCN114254506ADefects that solve blocking problemsIn line with the actual sceneData processing applicationsCircuit arrangementsMacro base stationsEngineering
The invention discloses a base station regulation and control method considering 5G communication base station power network topology distribution, comprising the following steps: S1, analyzing geographical distribution and electrical distribution characteristics of 5G macro base stations and micro base stations, and drawing a 5G macro base station and micro base station distribution diagram considering network topology; s2, analyzing power supply and consumption characteristics of the 5G base station, and constructing a base station power consumption model, a user distribution and demand model and a base station energy storage and power supply reliability model; s3, constructing an inner-layer optimization model, considering the requirements of a mobile communication service provider, and taking the minimum total electricity utilization cost of the 5G base station as an optimization target; s4, constructing an outer-layer optimization model, and taking the minimum topological node peak-valley difference as an optimization target by considering the power grid demand; and S5, solving the emission power consumption of the active antenna unit of the 5G base station, the internal energy storage charging and discharging strategy and the mobile user connection scheme by comprehensively considering the requirements of the service provider and the power grid through internal and external nesting iteration by using a heuristic algorithm. Requirements of a communication service provider and a power grid are comprehensively considered, and a base station regulation and control strategy is optimized.
Owner:ECONOMIC TECH RES INST OF STATE GRID HENAN ELECTRIC POWER +1
Remote multi-target efficient detection and identification method
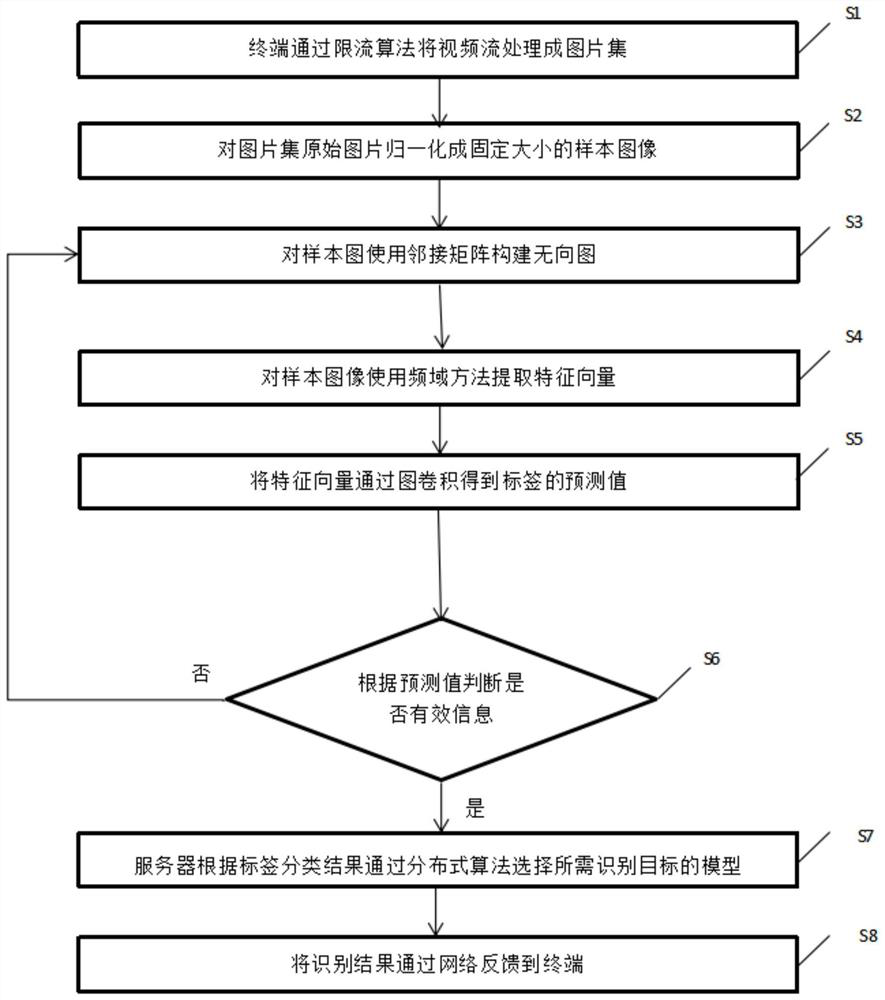
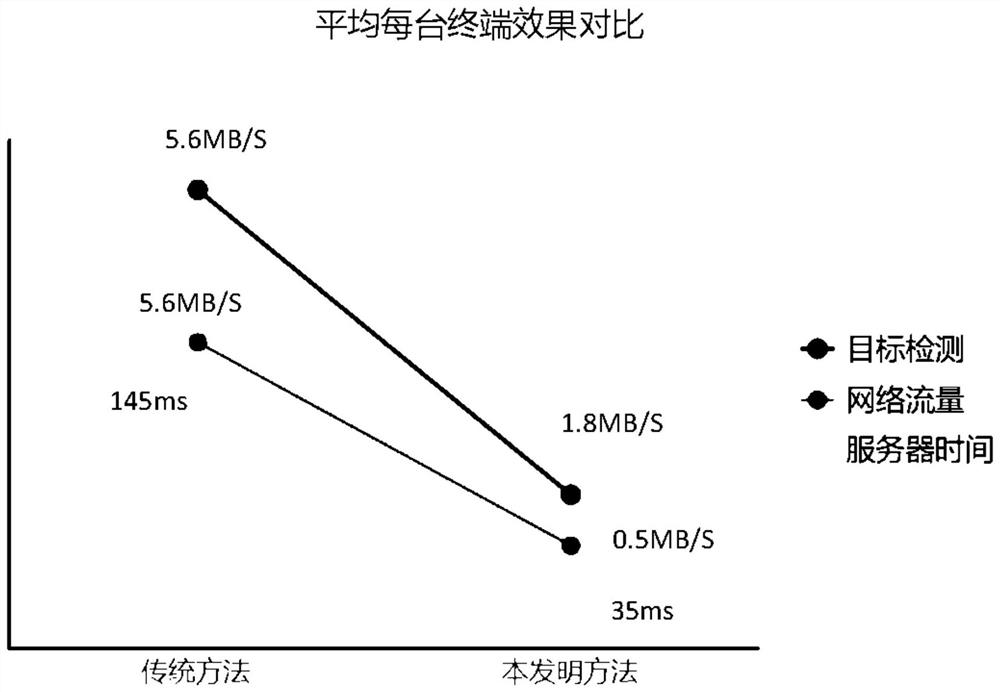
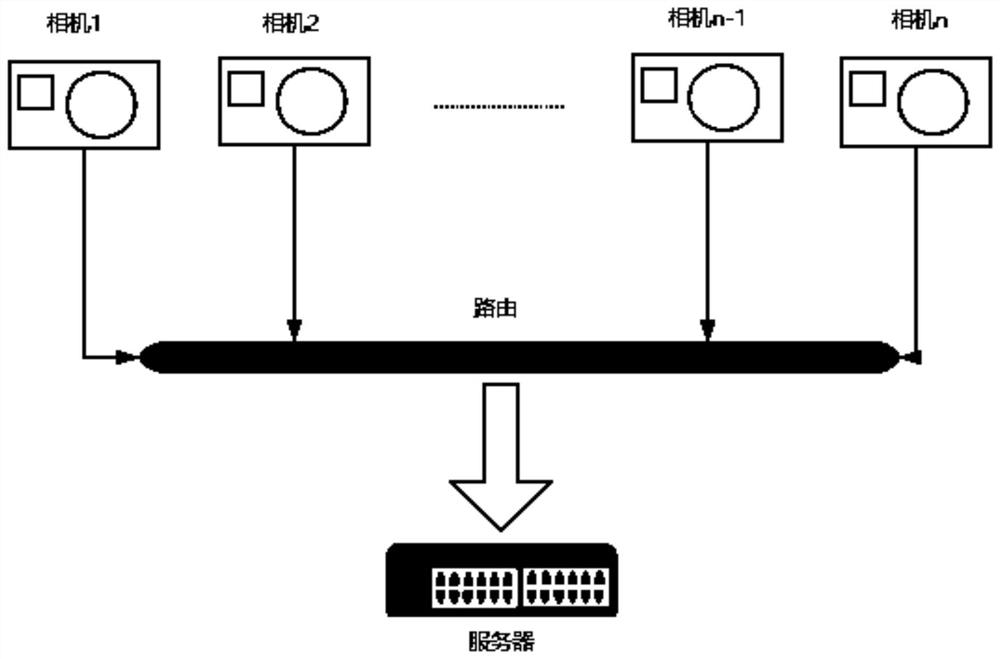
ActiveCN112784709AReduce trafficAvoid congestionScene recognitionEnergy efficient computingSample graphGoal recognition
The invention discloses a remote multi-target efficient detection and identification method. The method comprises the following steps that S1, a terminal processes a video stream into a picture set through a current limiting algorithm; S2, original pictures of the picture set are normalized into sample images with fixed sizes; S3, with pixel points of the sample images as nodes, the state of an undirected graph is depicted by using an adjacent matrix of all the nodes; S4, an s latitude feature vector of each node is obtained; S5, a complete vectorized tag dictionary is pre-constructed, and predicted values of tags are obtained from the output feature matrix through the dictionary; S6, the terminal carries out threshold screening on the predicted values of the tags; S7, a server generates a corresponding hash code according to a tag result, and enters different target recognition model channels through the hash code; and S8, the server recognizes all known targets in advance and then stores the recognized targets into a feature vector library, effective pictures enter corresponding model channels and then are analyzed into feature vectors, a result is obtained after the feature vectors are compared with the feature vector library, and the result is fed back to the terminal.
Owner:SOUTH CHINA UNIV OF TECH
Scenario-based bluetooth sign-in method and system
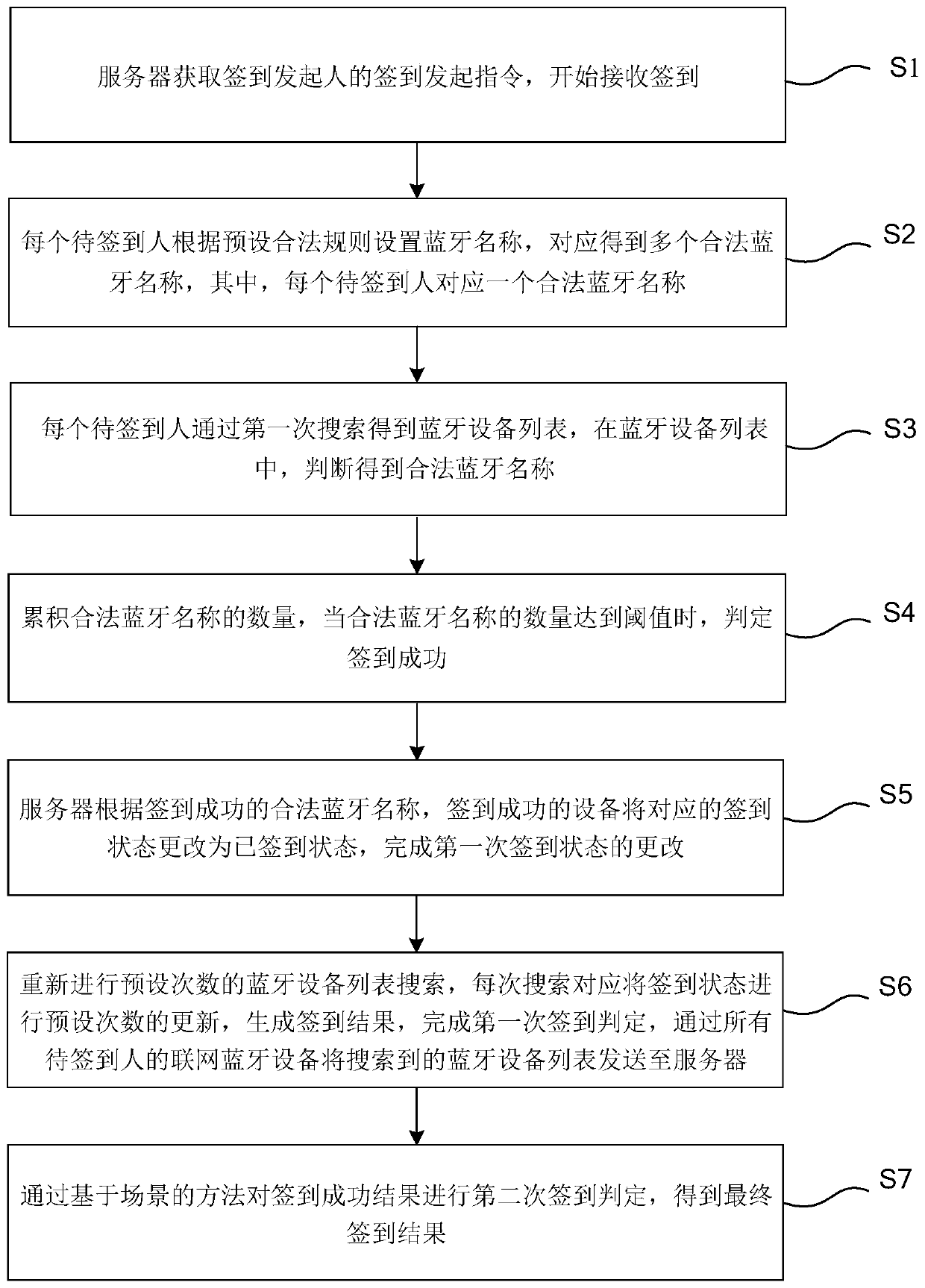
InactiveCN107195007BLow costIn line with the actual sceneRegistering/indicating time of eventsShort range communication serviceBluetoothService condition
The invention provides a scene-based Bluetooth sign-in method and system. The method comprises the following steps: setting Bluetooth names for all to-be-signed persons according to a preset legal rule to correspondingly obtain a plurality of legal Bluetooth names; carrying out first search by all the o-be-signed persons to obtain a Bluetooth equipment list, and judging to obtain legal Bluetooth names; when the quantity of the legal Bluetooth names reaches a threshold, judging the sign-in to be successful; changing corresponding sign-in states into signed states according to the successfully-signed legal Bluetooth names, researching the Bluetooth equipment list for preset times to generate sign-in results, finishing first sign-in judgment and transmitting the sign-in results to a server; carrying out second sign-in judgment by the scene-based method to obtain a final sign-in result. According to the scene-based Bluetooth sign-in method and system, provided by the invention, a scene-based Bluetooth sign-in mode is adopted, and no extra hardware equipment is needed, so investments are saved; by adopting parallel operation, sign-in time is saved; the mode that all people are in network is not needed, so actual service conditions are better met, and the cheating phenomenon is avoided.
Owner:何雨航 +3
Intelligent seating training method and system based on machine learning and data mining
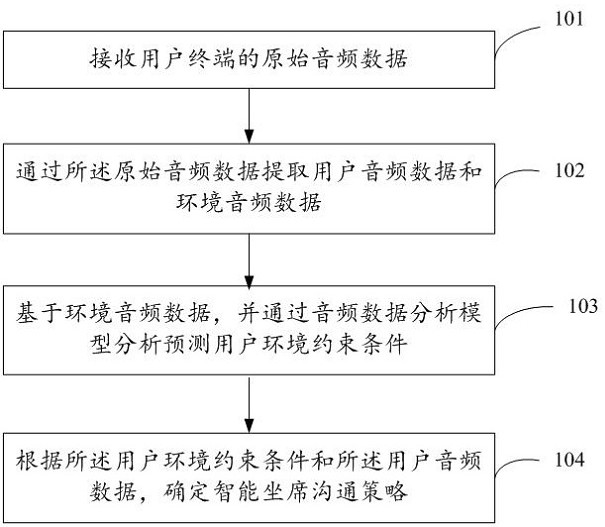
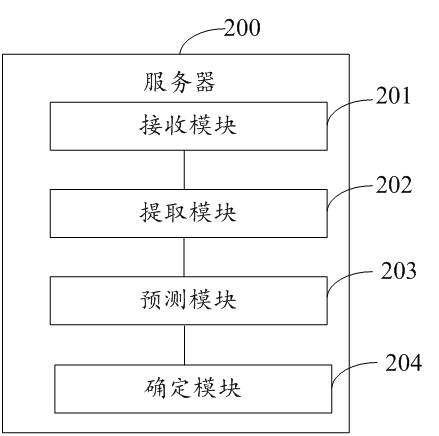
ActiveCN112687293AImprove efficiency and accuracyReduce ineffective useSpeech analysisNeural learning methodsMachine learningEngineering
The invention discloses an intelligent seating training method and system based on machine learning and data mining. The method comprises the following steps: receiving original audio data of a user terminal; extracting user audio data and environment audio data through the original audio data; analyzing and predicting a user environment constraint condition through an audio data analysis model based on the environment audio data; and determining an intelligent seating communication strategy according to the user environment constraint condition and the user audio data. Thus, the intelligent seating communication strategy can be determined according to the user audio data and the environment audio data, analysis of the environment audio data is added when the intelligent seating communication strategy is determined, the accuracy and efficiency during intelligent communication can be improved, and the formulated seating communication strategy better conforms to the actual scene of the user; and the problem that the authenticity of the information acquired according to the audio data cannot be judged due to single dependence on the audio data of the user is avoided, so that computing and communication resources are fully utilized or manual invalid use is reduced.
Owner:BEIJING DEXI TIANDI TECH TRADE CO LTD
A modular chemical control honeypot system
ActiveCN113162948BDifficult to distinguishImprove realismSecuring communicationChemical controlSoftware engineering
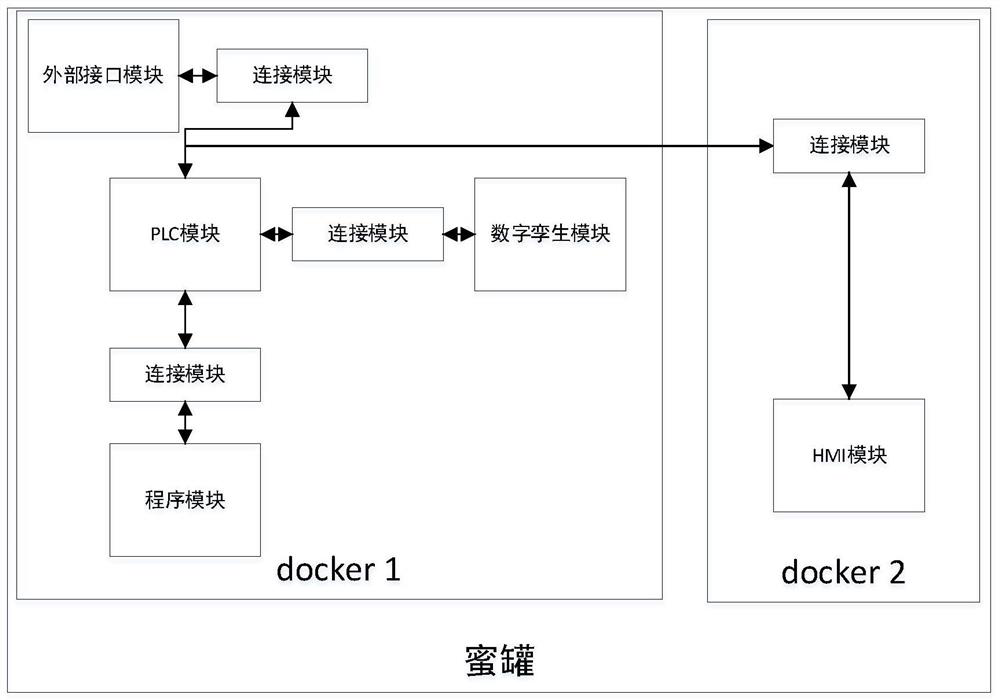
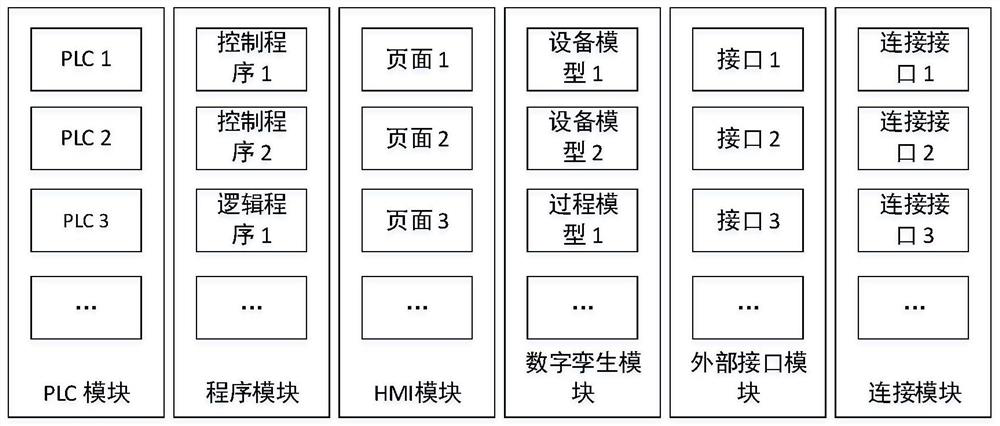
The invention discloses a modular chemical control honeypot system, which relates to the security field of industrial control systems. The honeypot system builds a module library through a modular method, and the module library includes: a PLC module, a program module, a digital twin module, HMI module, external interface module and connection module, wherein: the PLC module simulates the actual PLC and is the controller in the honeypot system; the PLC module is connected to the program module, the The digital twin module, the HMI module and the external interface module are connected. The present invention builds a corresponding digital twin model according to the actual physical model, supports deep interaction, has high fidelity, and is not easy to be identified by an attacker. The invention realizes the modularization of the structure and function of the honeypot, so that the user can easily configure the honeypot individually, and build an industrial control honeypot more in line with the actual scene. The present invention can conveniently realize large-scale deployment by encapsulating the honeypot as a docker container.
Owner:上海交通大学宁波人工智能研究院
A task collaborative planning method and system for smart factories
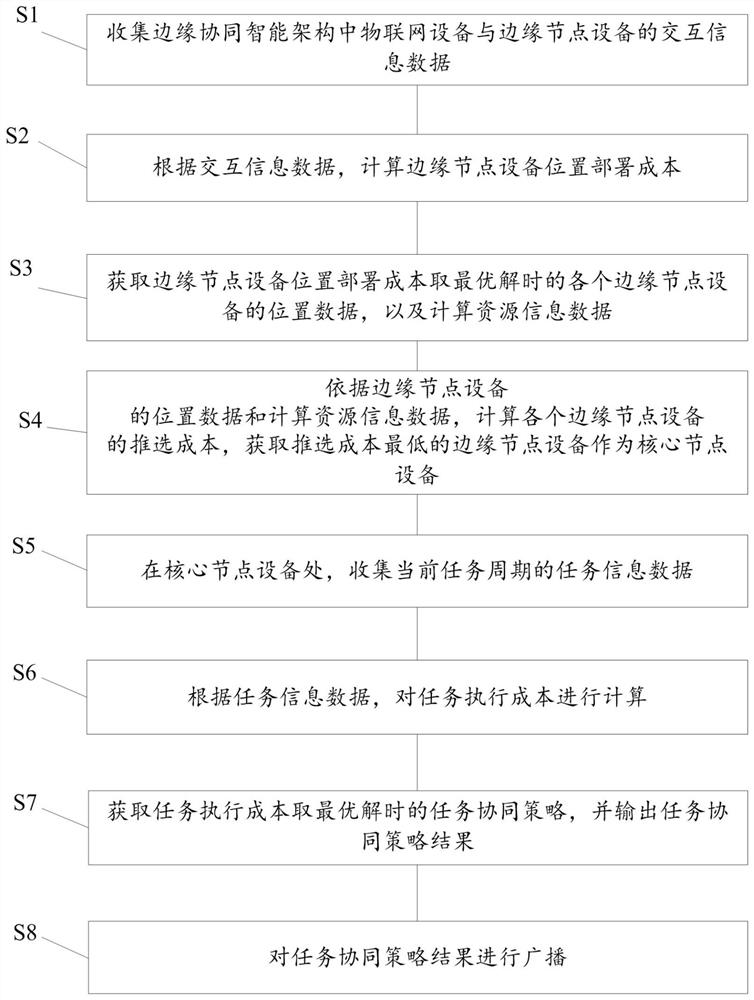
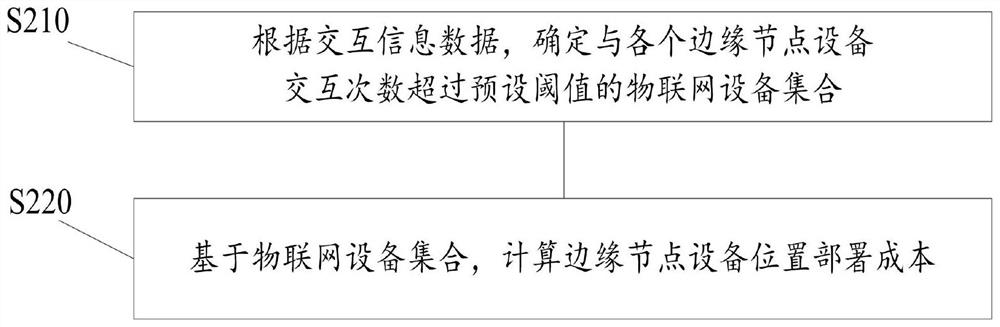
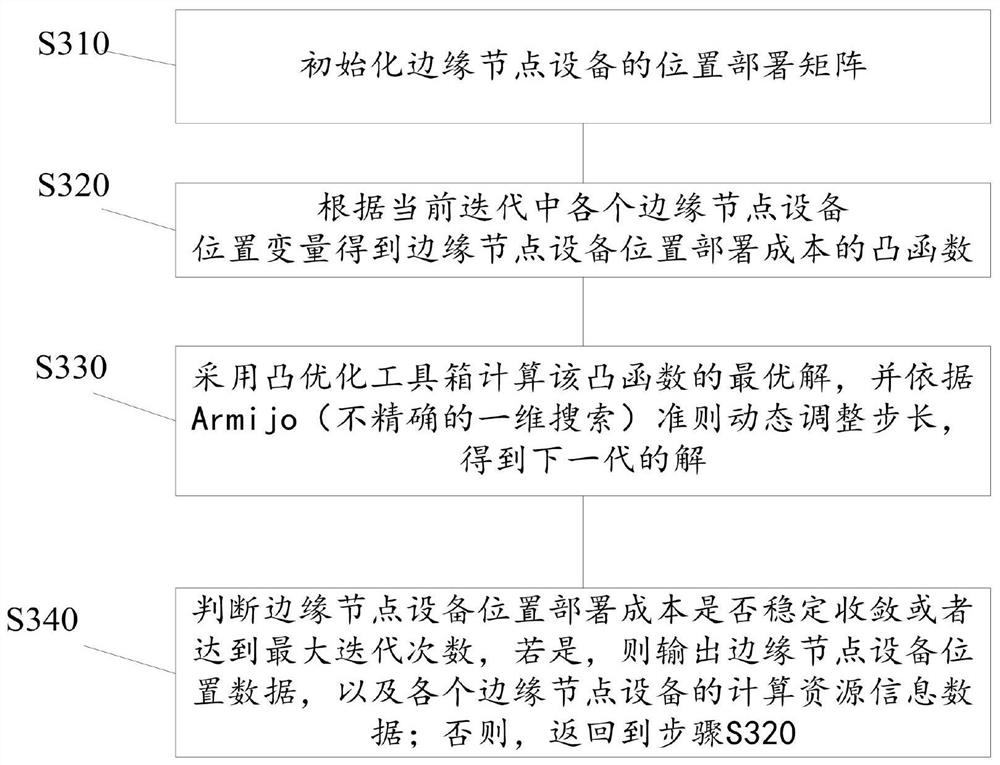
ActiveCN113315659BReduce latencyReduce energy consumptionTransmissionInstrumentsSmart factoryResource information
The present application provides a task collaborative planning method and system for smart factories. The method includes the following steps: collecting interactive information data between IoT devices and edge node devices in the edge collaborative intelligent architecture; calculating the cost of edge node location deployment; obtaining edge nodes The location data of each edge node when the location deployment cost is the optimal solution; calculate the selection cost of each edge node based on the location data of the edge node and computing resource information data, and obtain the edge node with the lowest selection cost as the core node device; At the node device, collect the task information data of the current task cycle; calculate the task execution cost according to the task information data; obtain the task collaboration strategy when the task execution cost is optimal. The application reduces the selection cost of core node equipment and edge node location deployment costs in artificial intelligence production tasks, and makes task execution cost less loss and task processing delay smaller.
Owner:JIANGXI XINBORUI TECH CO LTD
Single-channel voice enhancement method and device, storage medium and terminal
ActiveCN111554315BImprove voice call qualitySuppress non-stationary noiseSpeech analysisStationary noiseFrequency spectrum
A single-channel voice enhancement method and device, storage medium, and terminal, the method comprising: acquiring a frequency domain amplitude spectrum of a current frame signal based on a received input signal; VAD processing is performed on the entire band to obtain the initial full-band amplitude spectrum gain function of the current frame signal; the full-band is divided into multiple sub-bands, and the current frame signal is based on the frequency domain amplitude spectrum of the current frame signal and the initial full-band amplitude spectrum gain function. The multiple sub-bands of the sub-bands are respectively subjected to VAD processing, and the initial full-band amplitude spectrum gain function is updated according to the VAD processing results of each sub-band to obtain the updated full-band amplitude spectrum gain function of the current frame signal; According to the frequency domain amplitude spectrum of the current frame signal And update the full-band amplitude spectrum gain function to calculate the spectrum after speech enhancement. The solution of the invention can effectively suppress non-stationary noise and protect the voice quality from loss, which is beneficial to improve the voice call quality of mobile devices such as mobile phones.
Owner:SPREADTRUM COMM (TIANJIN) INC
A Neural Network-Based Identification Method for Dynamic Parameters of a 6-axis Robot
ActiveCN109773794BIn line with the actual sceneThe identification result is close toProgramme-controlled manipulatorJointsAlgorithmSimulation
Owner:ZHEJIANG UNIV
Game-based network resource allocation method and device
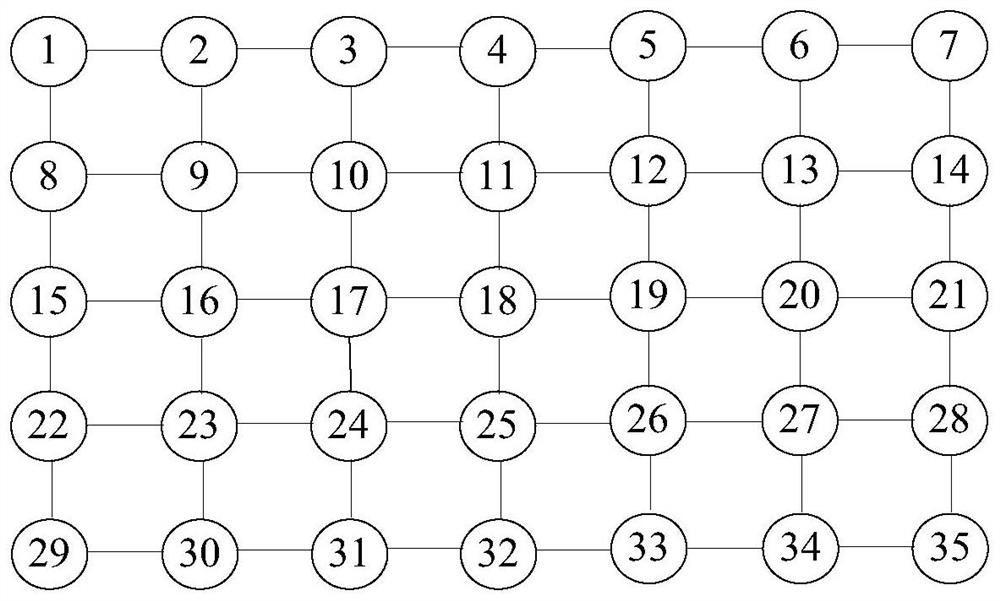
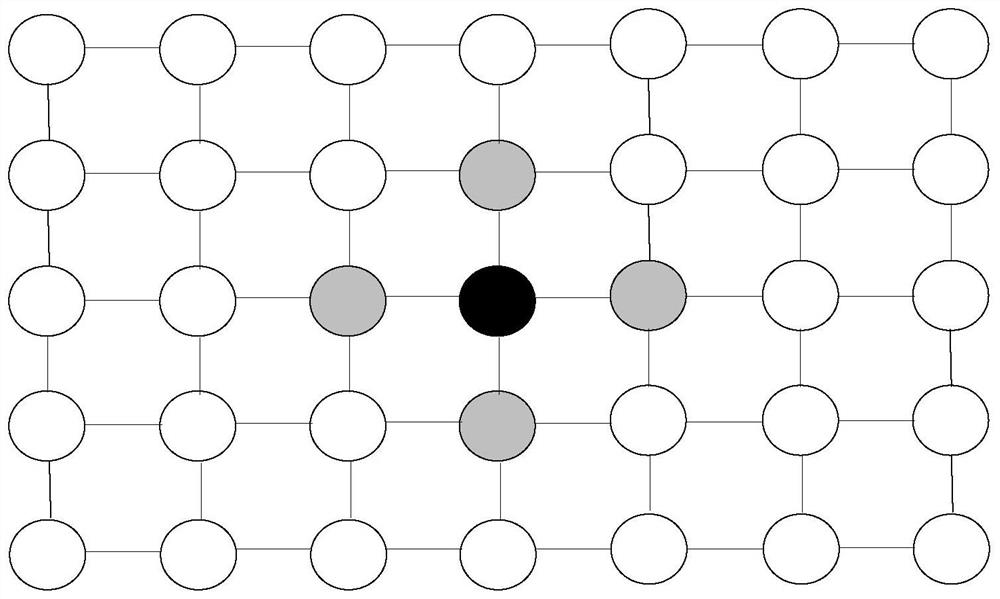
The invention discloses a game-based network resource allocation method and device, and the method comprises the steps: determining the number of game nodes in a public article game model based on the number of devices for processing target resources in a network, and dividing the game nodes in the public article game model into at least two types of game nodes, and selecting a target node from game nodes of the public item game model, performing game playing, adjusting the state of the target node to the state of the target neighbor node based on the adjustment probability, and repeatedly executing the game playing process until the public item game model is stable. And determining the number of devices sharing the target resource in the network based on the public item gaming model. According to the technical scheme, the public article game model comprising various types of game nodes is established, the diversity of the nodes in the game model can be met, the obtained game result is more in line with the actual scene condition, and therefore the network resources distributed based on the game result meet the requirement of resource distribution.
Owner:AGRICULTURAL BANK OF CHINA
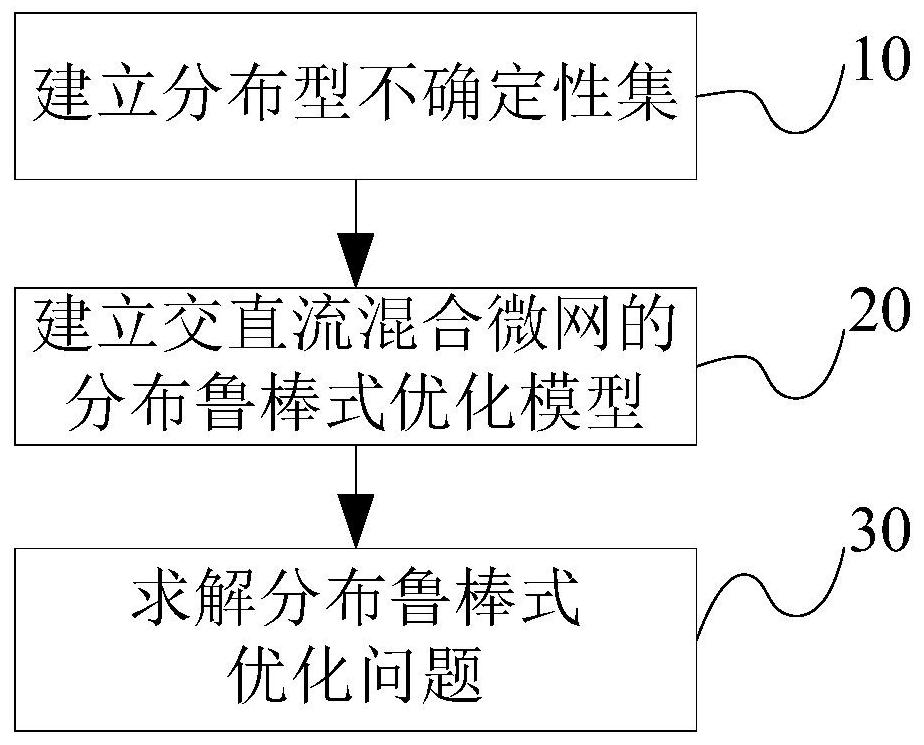
A Distributed Robust Optimal Scheduling Method for AC-DC Hybrid Microgrid
ActiveCN108629449BReduce conservatismIn line with the actual sceneElectrical apparatusForecastingMicrogridOptimal scheduling
The invention discloses a distributed robust optimal scheduling method for AC / DC hybrid microgrids, comprising the following steps: step 10) obtaining source-load uncertainty prediction parameters, and establishing a distributed uncertainty set; step 20) obtaining The operating cost coefficient and operating limit of each device in the AC-DC hybrid microgrid, based on the uncertainty set in step 10), establishes a distributed robust optimization scheduling model for the AC-DC hybrid microgrid; step 30) solves the distributed robust optimization Scheduling model problem: The dual decomposition method is used to iteratively solve the distributed robust problem, and the robust operation plan of the AC-DC hybrid microgrid is obtained. This method takes into account the distribution characteristics of the source-load uncertainty in the AC-DC hybrid microgrid, uses the probability distribution function to describe the source-load uncertainty set, improves the conservatism of the traditional robust optimal scheduling, and formulates a reasonable AC-DC hybrid microgrid of the running schedule.
Owner:LIYANG RES INST OF SOUTHEAST UNIV +1
Signal processing method, equipment and system
InactiveCN102468916BIn line with the actual sceneEfficient use ofError preventionChannel state informationCommunications system
The invention provides a signal processing method, equipment and system. The signal processing method comprises the following steps: receiving uplink signals which comprises the signals obtained by interfering and aligning target signals to be sent by a first mobile terminal according to a precoding matrix and interference signals sent by at least two mobile terminals of an neighboring cell, decoding the uplink signals according to a decoding matrix and obtaining the target signals, wherein the precoding matrix and the decoding matrix are obtained according to the global channel state information of the first mobile terminal and the at least two mobile terminals on an independent expansion channel and a constant expansion channel, and the interference signals and the target signals on the constant expansion channel utilize the dimensionality which is not utilized by the independent expansion channel. The technical scheme of the embodiment of the invention is in line with the actual scene of an actual communication system and is highly practical.
Owner:深圳市信方达科技发展股份有限公司
Classification methods, computer equipment and storage media
ActiveCN110210519BClassification results are specificIn line with the actual sceneImage analysisMedical automated diagnosisData integrityAlgorithm
Owner:SHANGHAI UNITED IMAGING INTELLIGENT MEDICAL TECH CO LTD
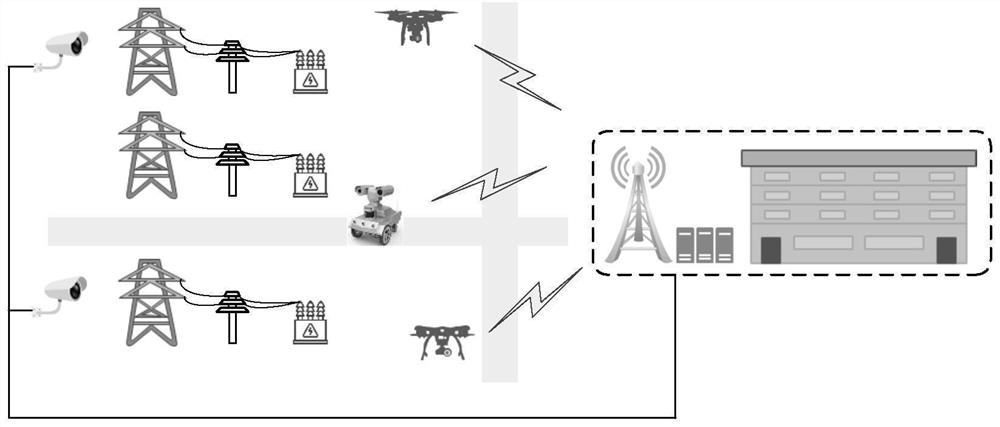
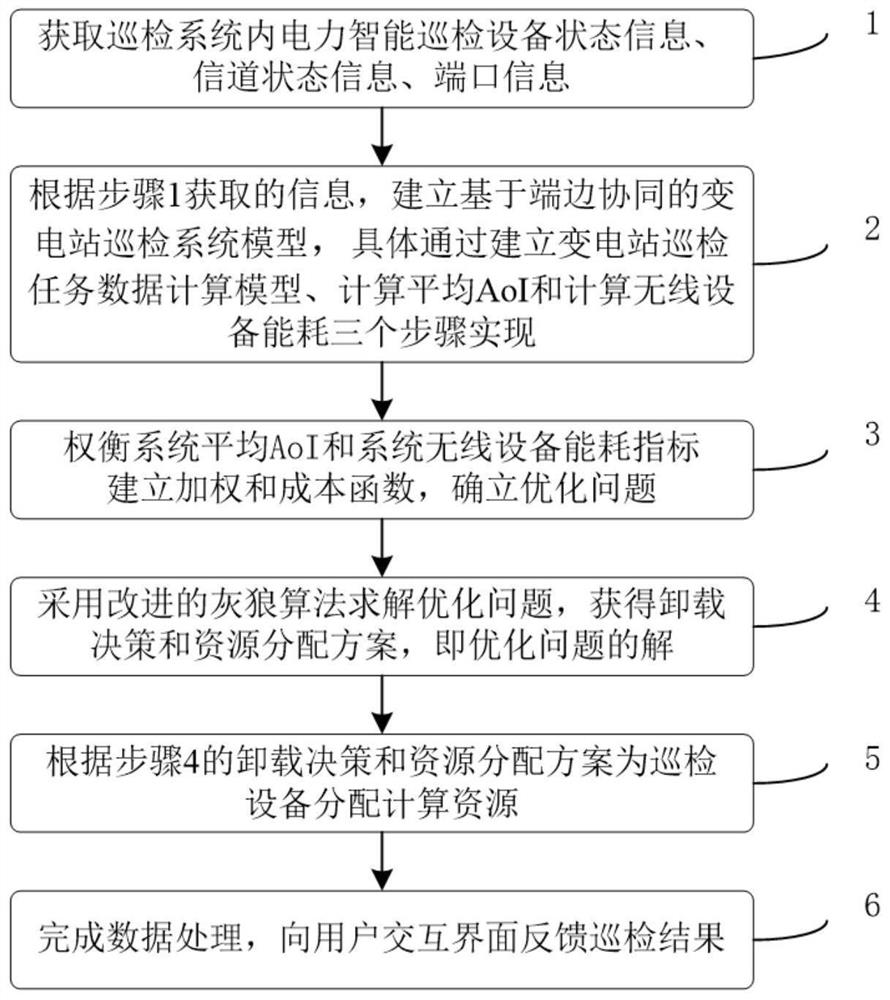
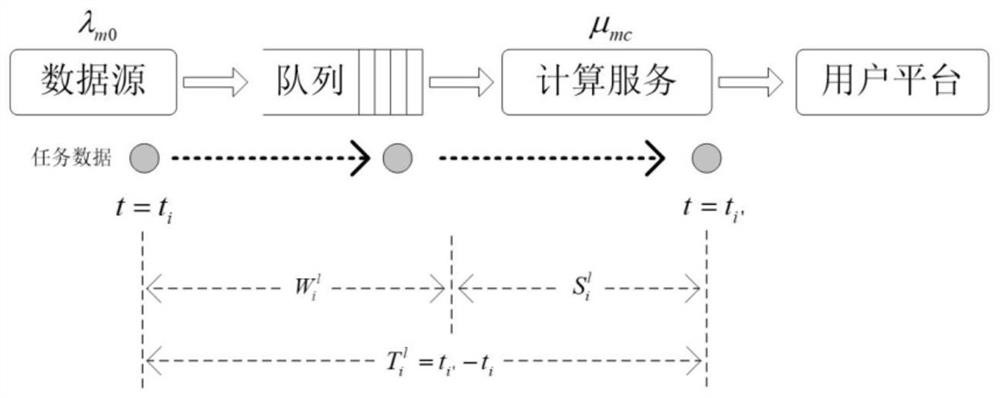
Transformer substation inspection method based on end-side cooperation
ActiveCN114693141AImprove processing efficiencySave bandwidth resourcesChecking time patrolsResource allocationEngineeringResource management
The invention discloses a transformer substation inspection method based on end-side cooperation, relates to the technical field of electric power Internet of Things, establishes a transformer substation inspection system model based on end-side cooperation, and provides a task unloading and resource management scheme for balancing the average information age of the system and the energy consumption index of wireless equipment. According to the method, the processing of the inspection task data comprises local calculation and unloading calculation, and the end-side equipment cooperates to complete the inspection work of the transformer substation. Compared with an existing method that data analysis is conducted manually after data are collected by equipment, labor input is saved, the data processing efficiency is obviously improved, and the data processing process does not depend on experience of inspection personnel excessively and is more scientific. Compared with an existing method for returning the inspection task data to the cloud center for processing, the method has the advantages that network bandwidth resources are saved, the computing pressure of the cloud center is relieved, and the problem of low data processing timeliness caused by an overlong return link is solved.
Owner:CHANGCHUN UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com