Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42results about How to "Avoid illegal attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for protecting privacy of vehicle ad hoc network based on signcryption
InactiveCN107682149AEffective calculationProtect identity privacyKey distribution for secure communicationParticular environment based servicesDigital signatureSigncryption
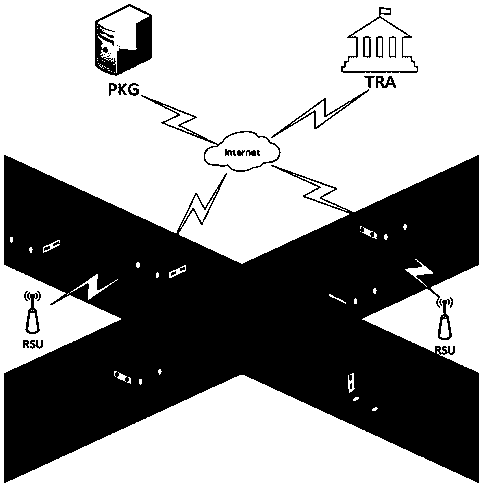
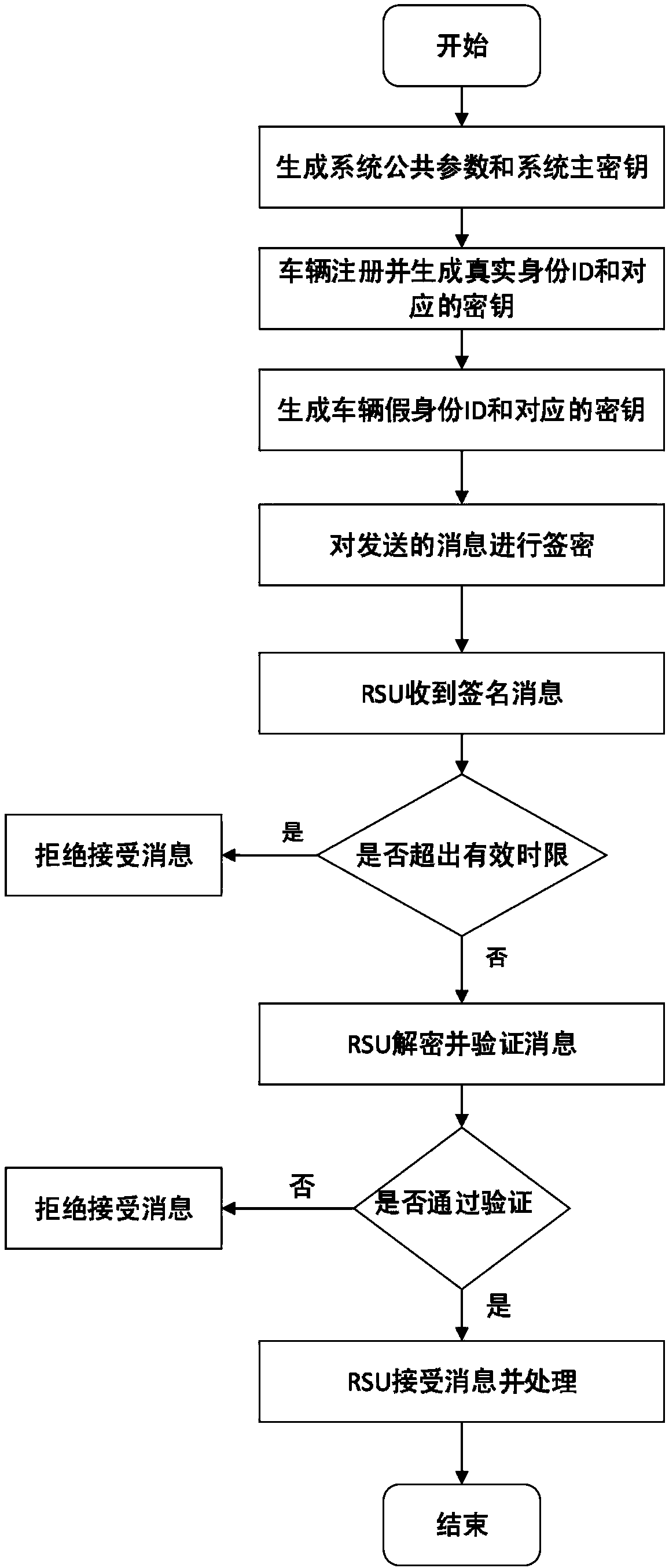
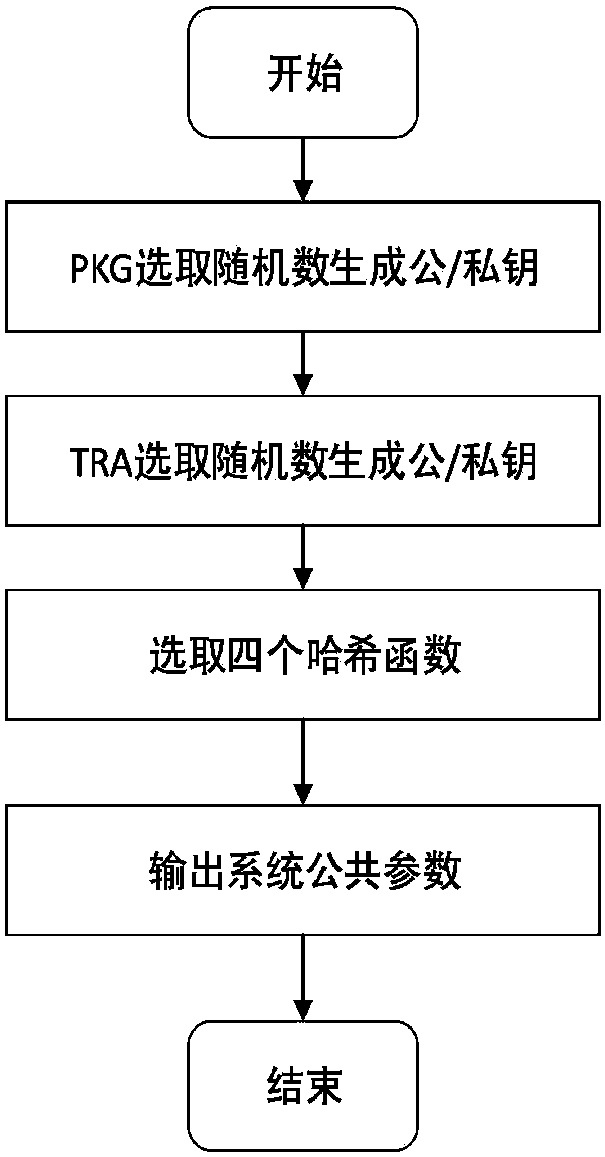
The invention request to protect a method for protecting privacy of a vehicle ad hoc network based on signcryption. The method is used for solving a privacy protection problem when a vehicle node (OBU) under an environment of the Internet of vehicles communicates with a road side unit (RSU). On the basis of a digital signature mechanism and a pseudonym mechanism, the invention provides a signcryption mechanism which is an integrated scheme synthesizing encryption and signature; in the method, privacy protection on the vehicle node is achieved via the pseudonym mechanism. Under the environmentof the Internet of vehicles, the vehicle node sends own identity information to a TRA to generate a pseudonym, a secret key generation center generates a secret key corresponding to a private key of the pseudonym, the vehicle node uses the generated pseudonym and the secrete key to perform signcryption on a message and sends the message to the road side unit, after receiving the message, the roadside unit uses the private key to decrypt the message and verify the same, and the message is accepted if the verification is passed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
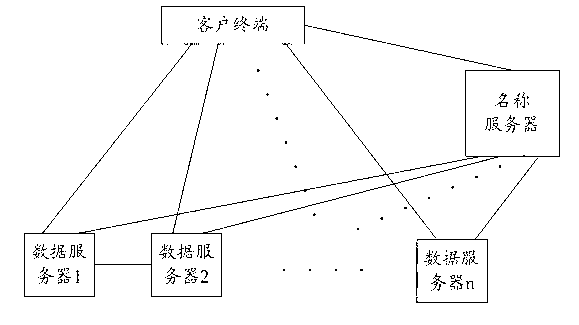
Method for realizing file reading and/or writing and data server
InactiveCN102073741AAchieve readAchieve writeTransmissionSpecial data processing applicationsName serverDistributed File System
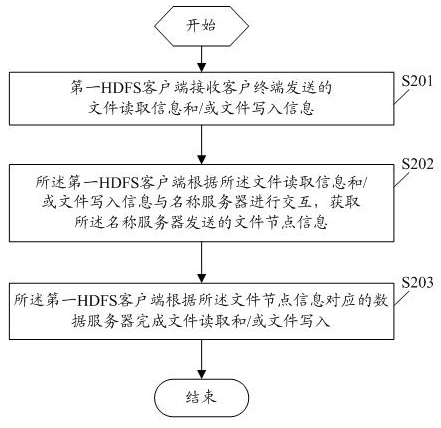
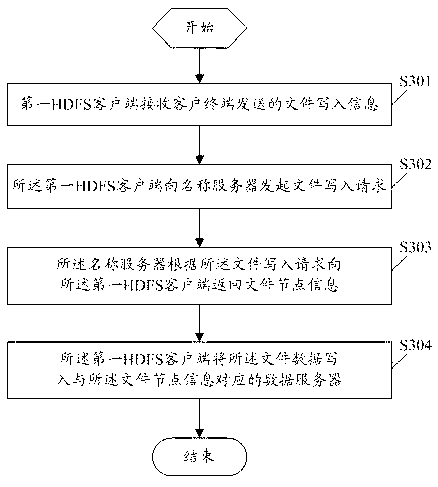
The embodiment of the invention discloses a method for realizing file reading and / or writing, comprising the following steps: a first hadoop distributed file system (HDFS) client receives file reading information and / or file writing information sent by a client terminal, wherein the first HDFS client is the preset HDFS client corresponding to the client terminal in default; the first HDFS client interacts with a name server according to the file reading information and / or file writing information and acquires file node information sent by the name server; and the first HDFS client finishes the file reading and / or writing according to a data server corresponding to the file node information. The embodiment of the invention further discloses the data server. According to the invention, the file reading and writing based on HDFS can be simply and quickly realized, and the storage of huge data amount is finished; and the method can be conveniently operated on common computers, thereby greatly improving the system compatibility.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
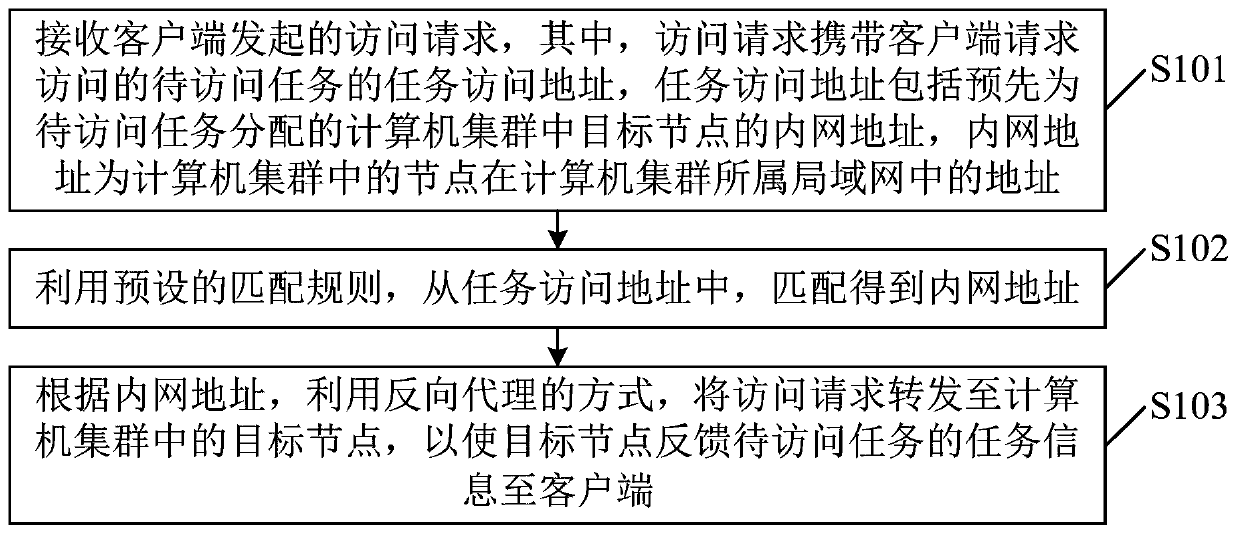
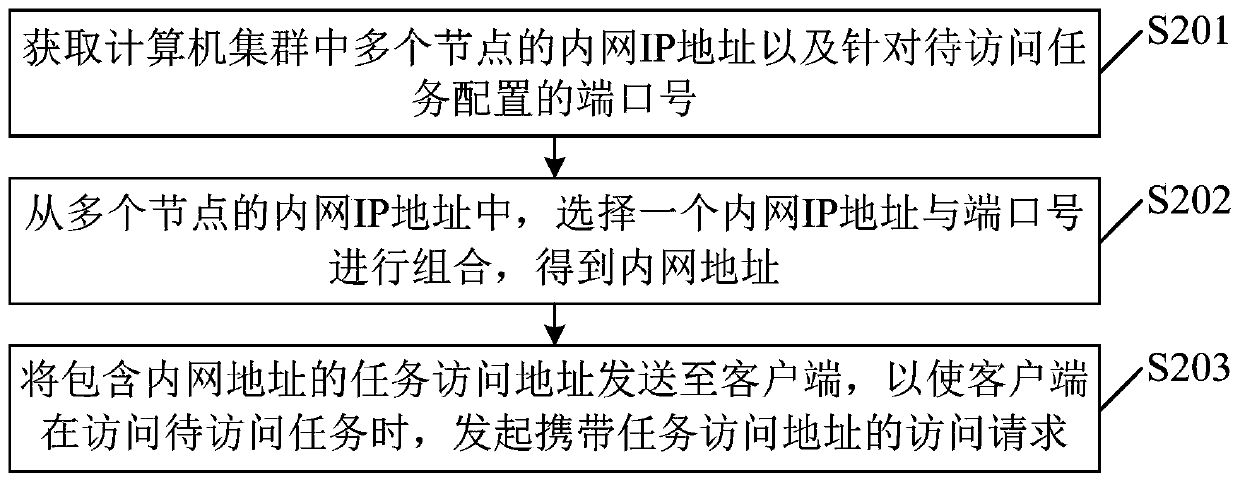
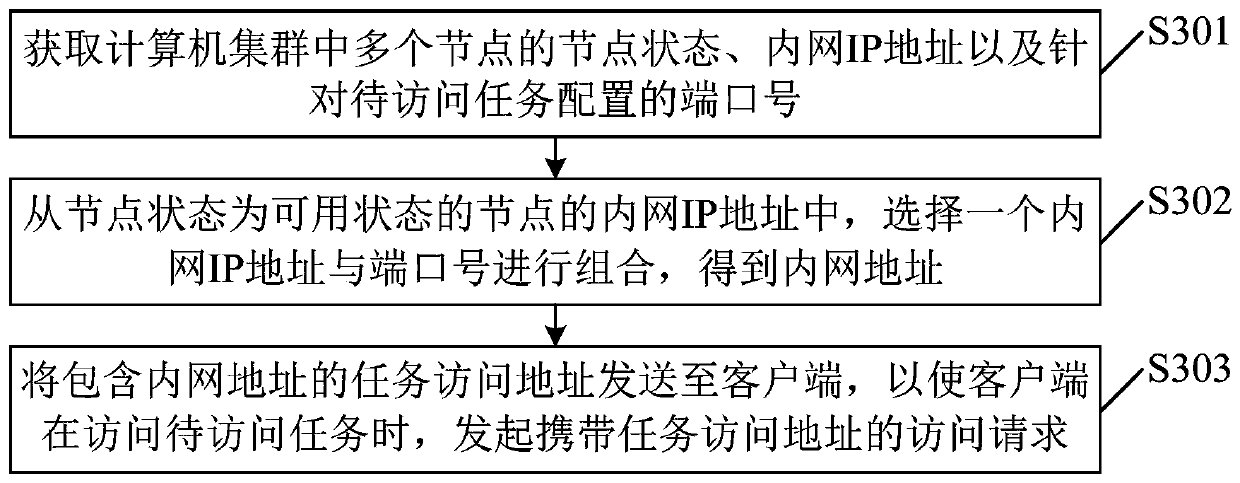
Task access method and device, proxy server and machine readable storage medium
PendingCN111460460AAvoid illegal attacksImprove securityPlatform integrity maintainanceSpecial data processing applicationsComputer clusterAccess method
The embodiment of the invention provides a task access method and device, a proxy server and a machine readable storage medium, and relates to the field of cloud calculation. According to the embodiment, the proxy server is used as intermediate equipment; receiving an access request initiated by a client, and matching the task access address carried by the access request by using a preset matchingrule to obtain an intranet address, forwarding the access request to a target node in the computer cluster by using a reverse proxy mode according to the intranet address, and feeding back task information of the to-be-accessed task to the client after the target node receives the access request. A client obtains an intranet address allocated to a task to be accessed in advance; the client cannotdirectly access the computer cluster, but can access the target node in the computer cluster through the proxy server, so that an illegal client can be prevented from obtaining the public network address of the computer cluster, the computer cluster is prevented from being illegally attacked, and the safety of the computer cluster is improved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD
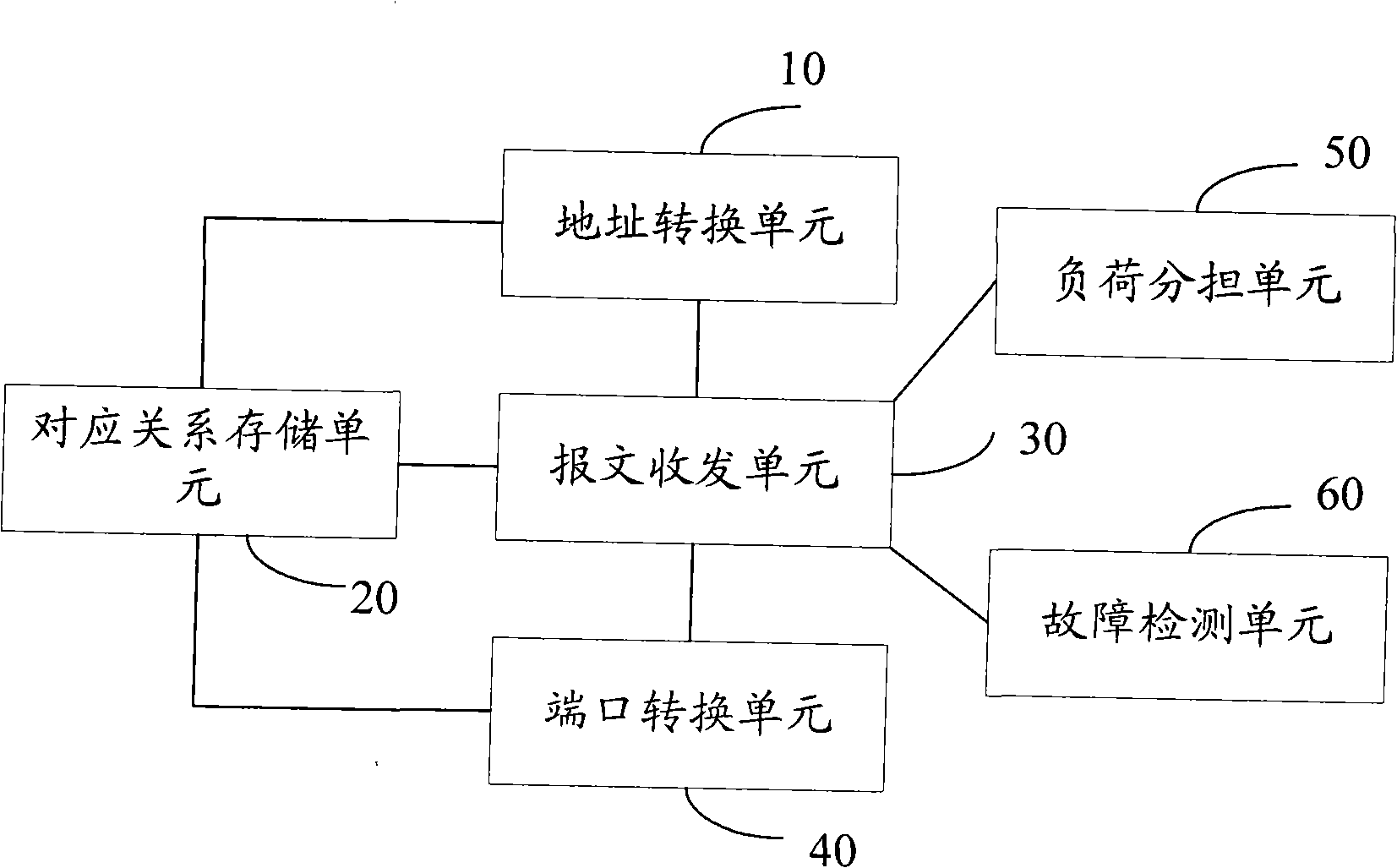
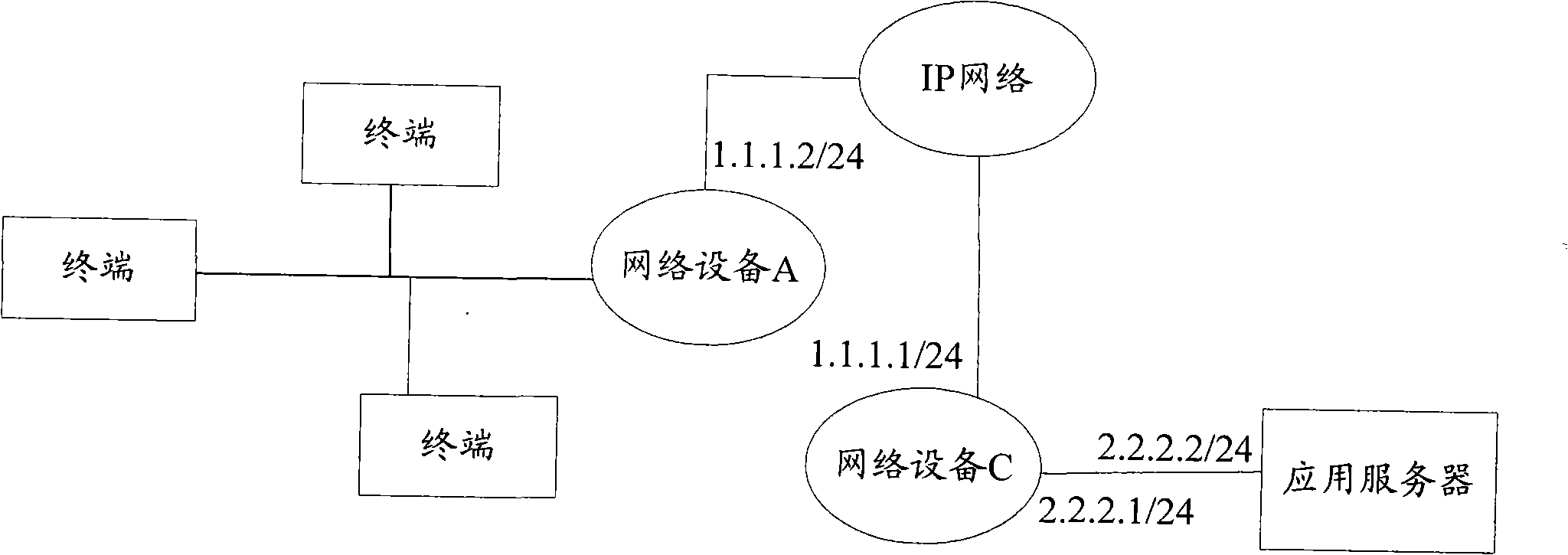
A method, device and system for source and destination IP address translation
InactiveCN101262504AImprove securityAvoid illegal attacksNetwork connectionsApplication serverIp address
The invention discloses a method for converting a source IP address and a destination IP address, which comprises the steps that: terminal network equipment configures the source IP address of sending a message into the IP address of the terminal network equipment, configures the destination IP address of sending a message into the IP address of IP address conversion equipment and sends the message to the IP address conversion equipment; the IP address conversion equipment configures the source IP address of the obtained message as the IP address of the IP address conversion equipment, configures the destination IP address of the message as the IP address of an application server and sends the message to the application server; the IP address conversion equipment stores corresponding relationship between the IP address of the terminal network equipment and the IP address of the application server and transmits the message from the application server to the corresponding terminal network equipment according to the corresponding relationship.
Owner:NEW H3C TECH CO LTD
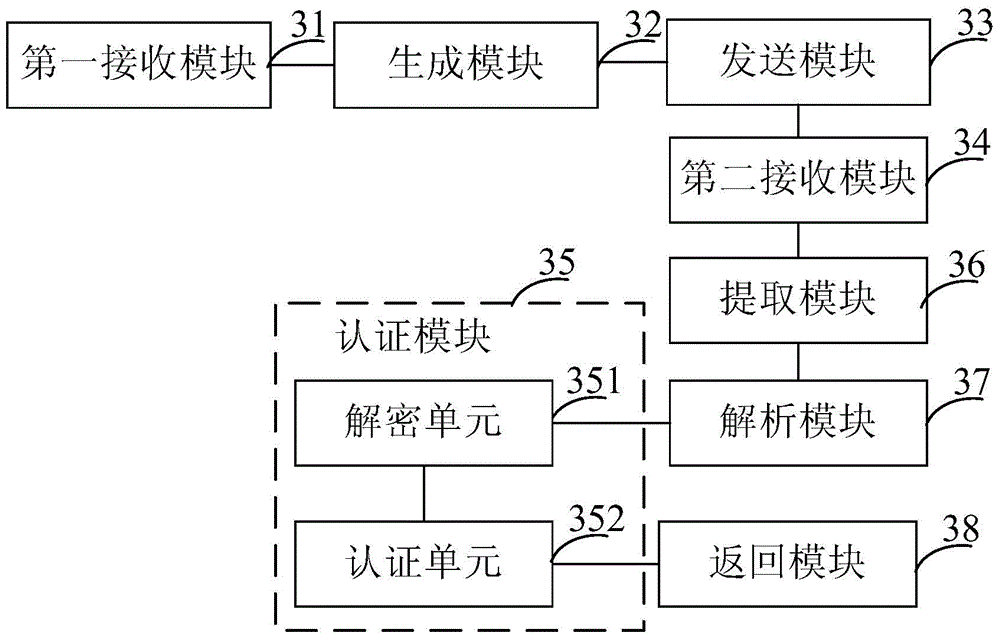
Method and device for identity authentication
InactiveCN104579657AAvoid multiple information exchangesAvoid illegal attacksUser identity/authority verificationSoftware developmentAuthentication information
The invention provides a method and a device for identity authentication. The method comprises the following steps of receiving a download request sent by a user through a terminal, wherein the download request carries an identification of the user; generating a private key file corresponding to the user according to the download request; sending an SDK (Software Development Kit) and the private key file to the terminal s to enable the terminal to use the SDK and the private key to encrypt identity information of the user so as to obtain authentication information; receiving a service call request carrying the authentication information; and authenticating the identity of the user according to the authentication information. According to the method and the device, the identity information of the user is written into the service call request, the identity information of the user is sent to the server while the service call request is sent to a server, so that the server can directly obtain the identity information from the service call request to verify the identity of the user, and thus the efficiency for service call in a system with the light-weight identity authentication need is improved and the waste of resources is reduced.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
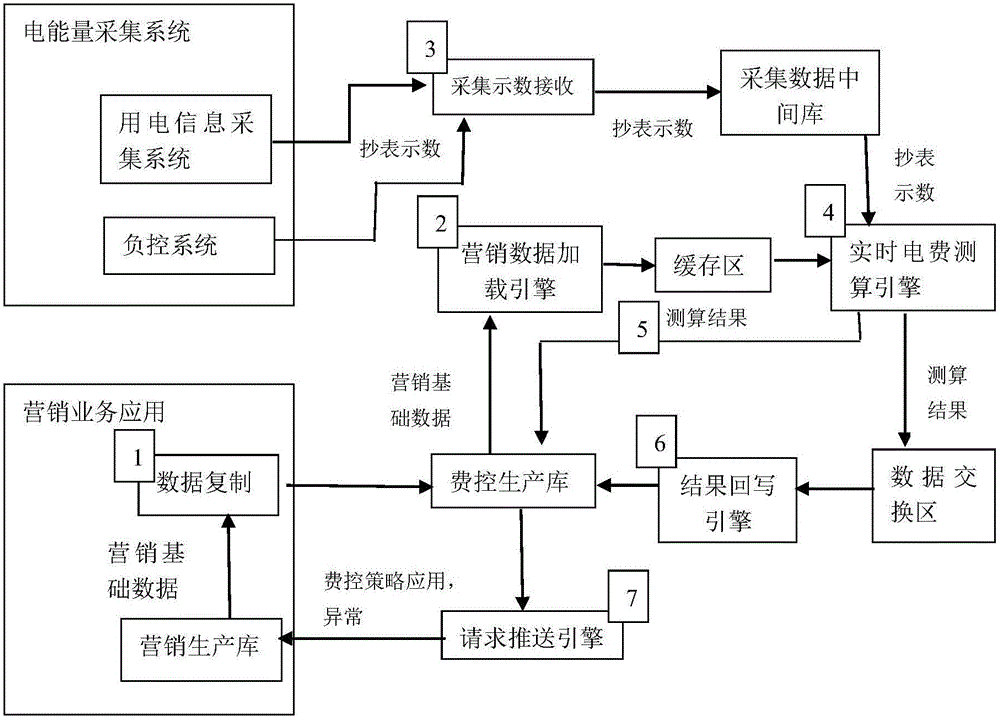
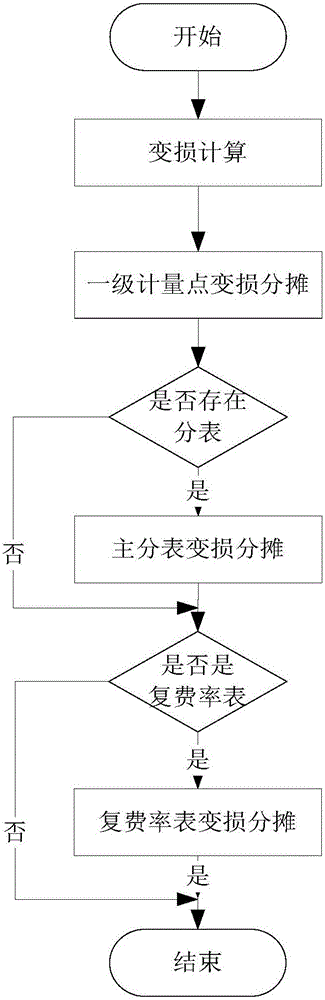
Marketing remote real-time cost control application operation analysis and monitoring method
InactiveCN105976088AImprove service levelInnovation management toolsResourcesMarket data gatheringData synchronizationElectricity
A marketing remote real-time cost control application operation analysis and monitoring method is disclosed. The method comprises the following steps of step1, marketing data synchronization; step2, marketing data loading; step3, marketing data loading; step4, collected reading receiving; step5, measurement and calculation result writing back; and step6, cost control request pushing. Through carrying out integral analysis on an operation condition of a cost control service, according to development conditions of a month and a daily, services of cost control prompting, early warning, power failure, a telegram in reply and the like are analyzed and displayed so that a trend of user electricity charge development can be grasped, a development prospect is pre-estimated and a service decision is assisted; and finally, a service accomplishment is guaranteed to obtain a high economic benefit.
Owner:BEIJING KEDONG ELECTRIC POWER CONTROL SYST
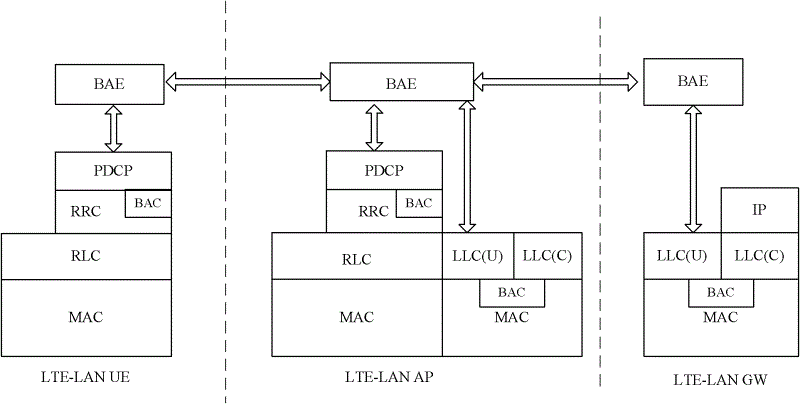
Wireless network access system
ActiveCN102625307AAvoid illegal attacksAchieve accessWireless network protocolsSecurity arrangementNetwork architectureAuthorization
Disclosed in the invention is a wireless network access system, comprising at least a piece of user equipment (UE), at least one access point (AP) and a gateway (GW). The UE is used for carrying out mutual authentication and authorization between the UE itself and the AP and making communication with an external network and UE in the system by the AP and the GW after the success of the authorization. The AP is used for carrying out mutual authentication and authorization with the UE and the GW and providing network coverage and a wireless access service for the UE after the success of the authorization; and the GW is used for carrying out mutual authentication and authorization with the AP and making interaction with the AP, core network equipment and the external network after the success of the authorization, thereby realizing access to the external network by the UE and communication between the UE in the system. According to the invention, a flattening network architecture is employed with consideration of indoor and hotspot data service characteristics, thereby simply realizing access to other UE in the system and access to the external network by the UE with low cost; meanwhile, security of two-way communication between a user and a network can also be guaranteed.
Owner:DATANG MOBILE COMM EQUIP CO LTD
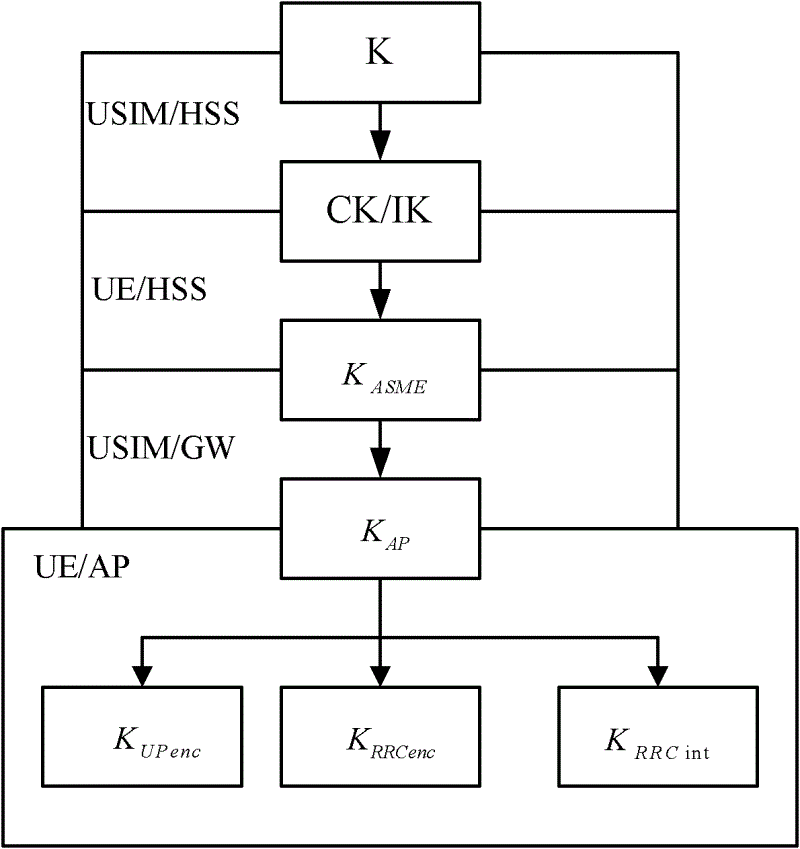
Communication method and device
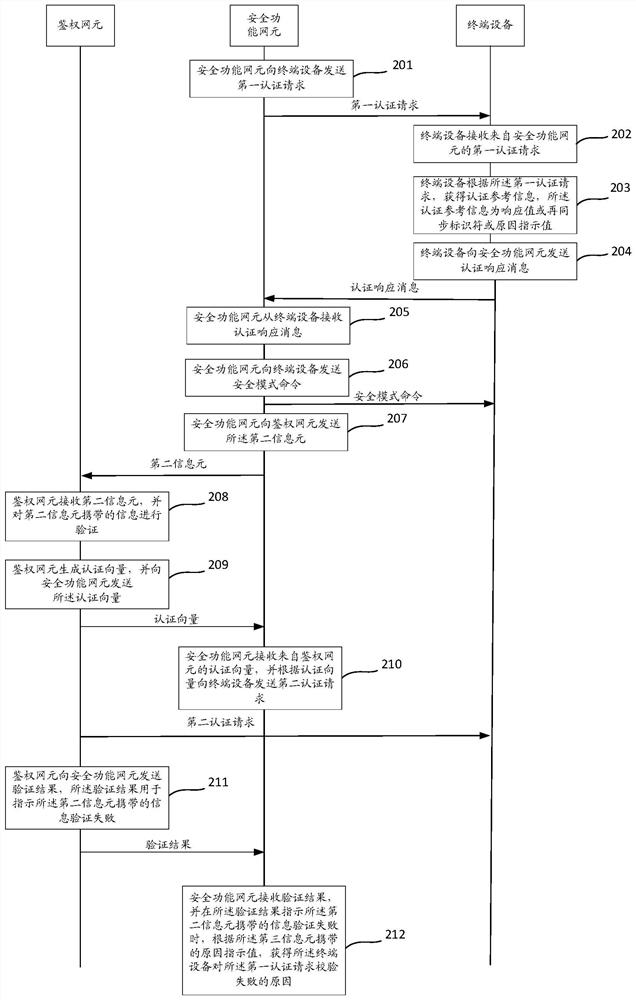
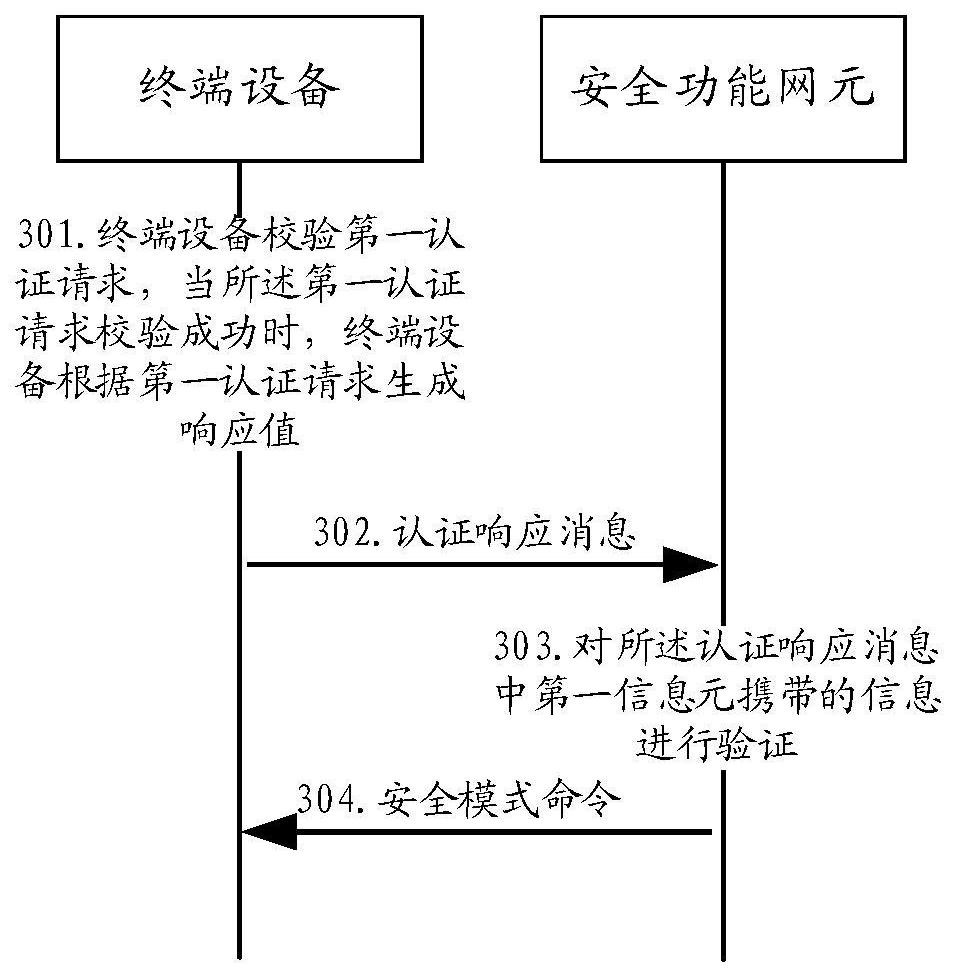
ActiveCN109788480AAvoid illegal attacksImprove securityUser identity/authority verificationSecurity arrangementTerminal equipmentComputer terminal
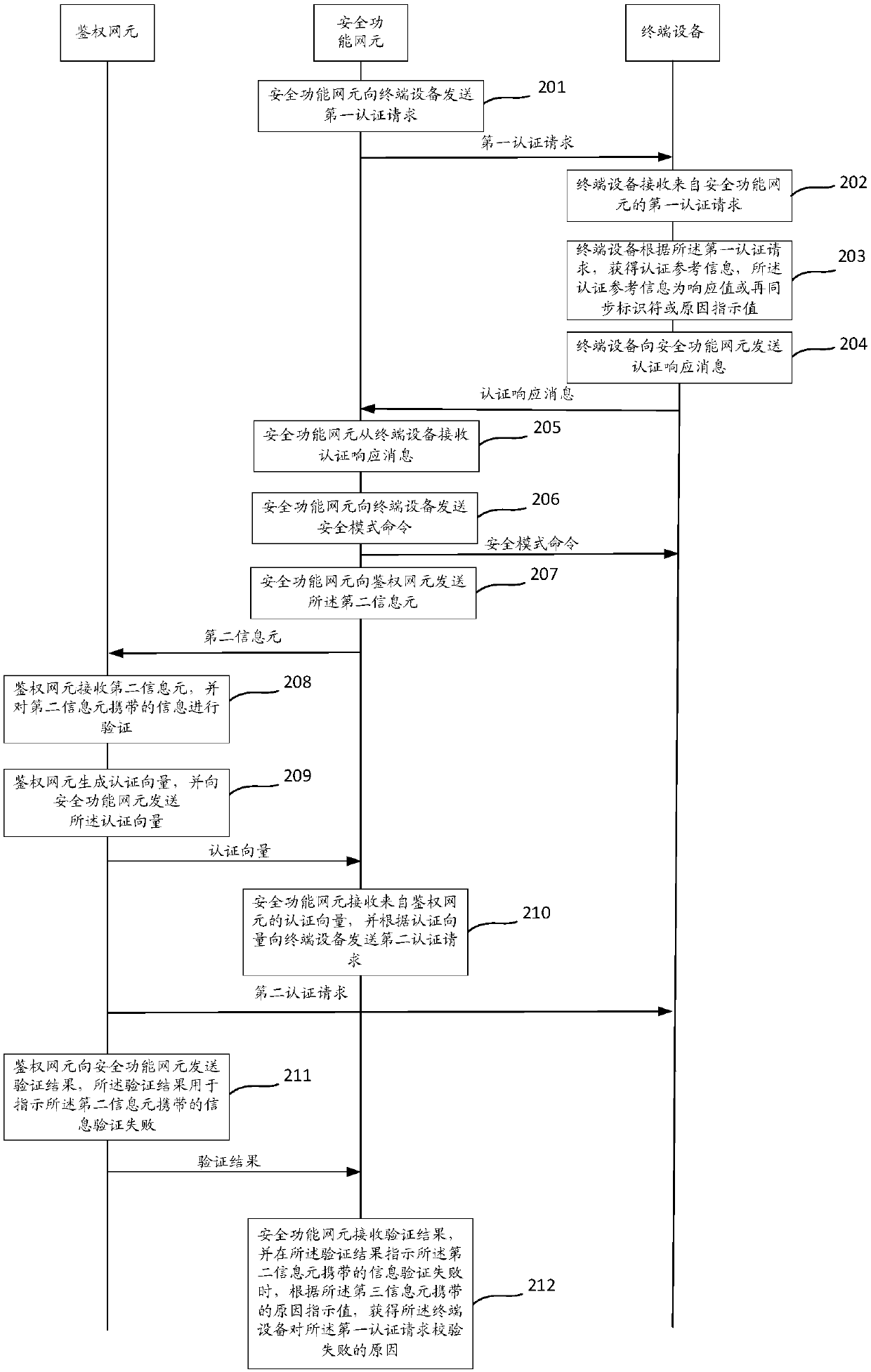
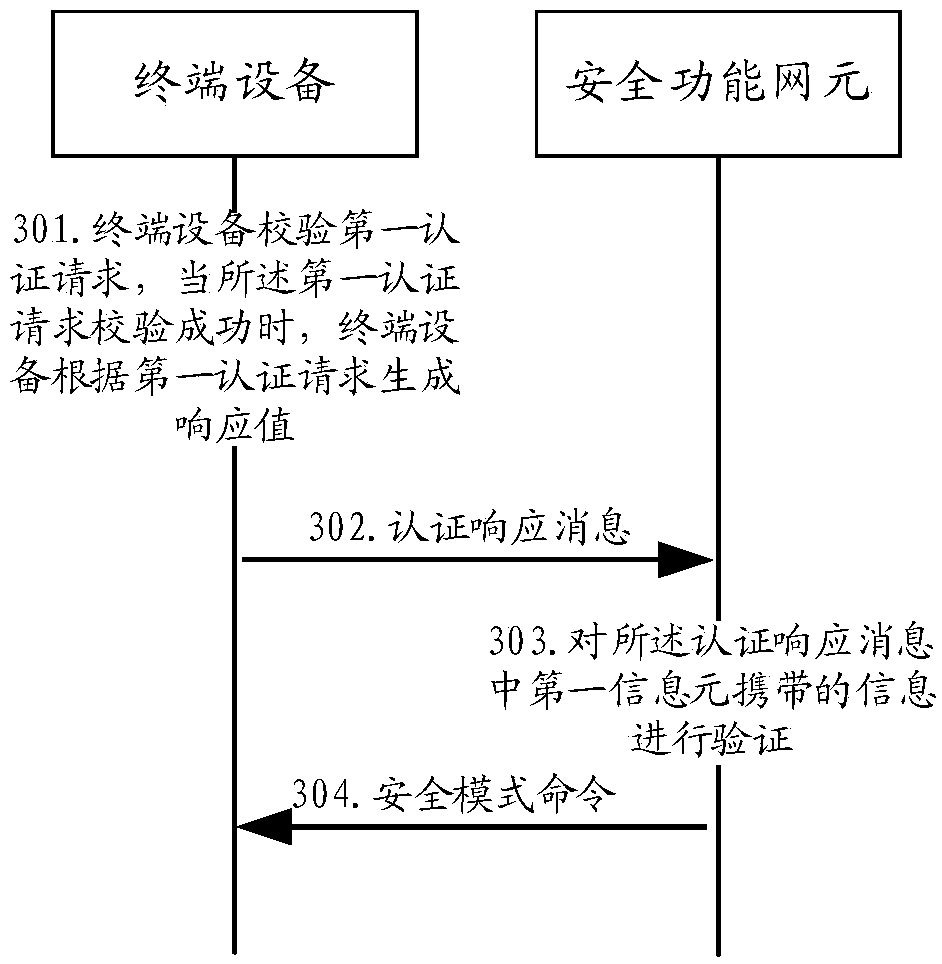
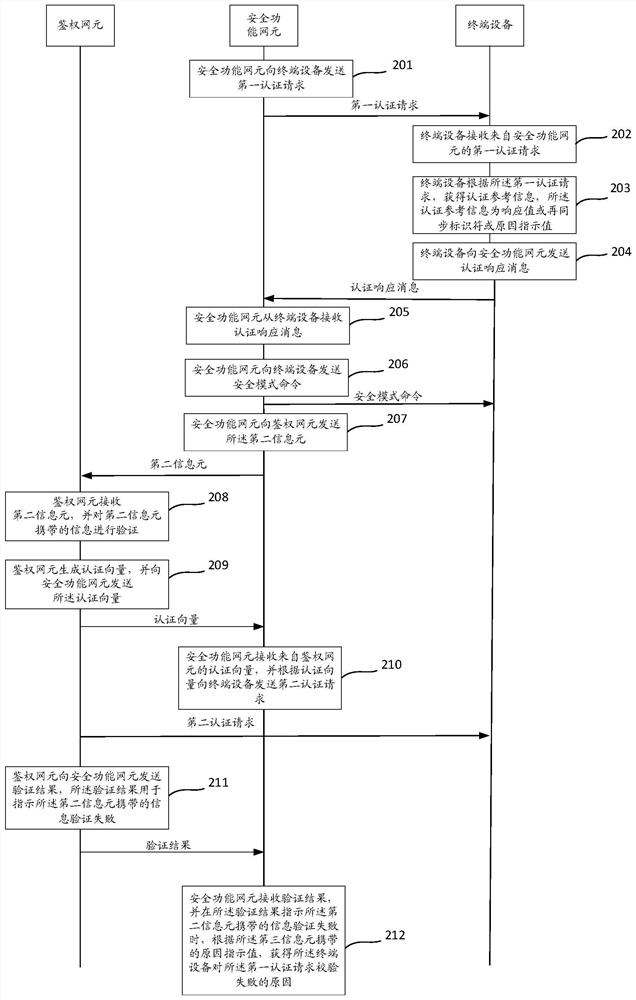
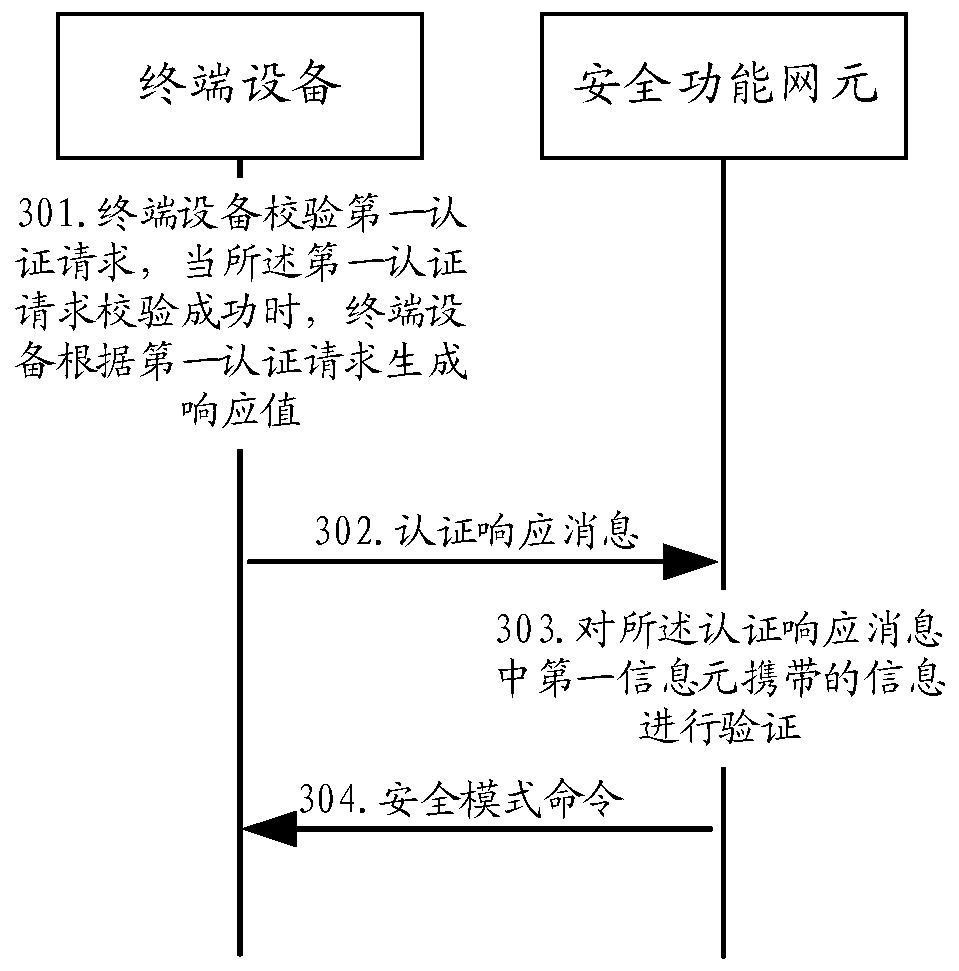
The invention discloses a communication method and device. The method comprises the steps that terminal equipment receives a first authentication request from a security function network element; Theterminal device obtains authentication reference information according to the first authentication request, and the authentication reference information is a response value or a resynchronization identifier or a reason indication value; And the terminal device sends an authentication response message to the security function network element, wherein the authentication response message comprises afirst information element used for carrying a response value, a second information element used for carrying a resynchronization identifier and a third information element used for carrying a reason indication value, and the authentication reference information is carried in the information element corresponding to the authentication reference information.
Owner:HUAWEI TECH CO LTD
Coding convention control transformation type information authentication method, and coding convention control transformation type information encryption/decryption method
ActiveCN104868995AEasy to operateEasy to implementUser identity/authority verificationComputer hardwareCoding conventions
The present invention relates to an information technology and an electronic technology, and mainly provides a coding convention control transformation type information authentication method, and a coding convention control transformation type information encryption / decryption method. According to the present invention, the coding convention control transformation is a technology core, defines a series of different transformation modes in a coding format and according to the artificial convention, and divides the to-be-transformed data into the control codes and the basic codes. The control codes transform the basic codes according to a coding defined control mode to generate a new data result, so that the information authentication or the information encryption / decryption is carried out according to the coding convention control transformation and the generated result. The coding convention control transformation type information authentication method, and the coding convention control transformation type information encryption / decryption method of the present invention are simple, easy, safe and reliable, are low in cost, are very suitable for the software program processing, and can be widely used in the fields, such as the daily life, the economy, the military, etc.
Owner:陈麟华
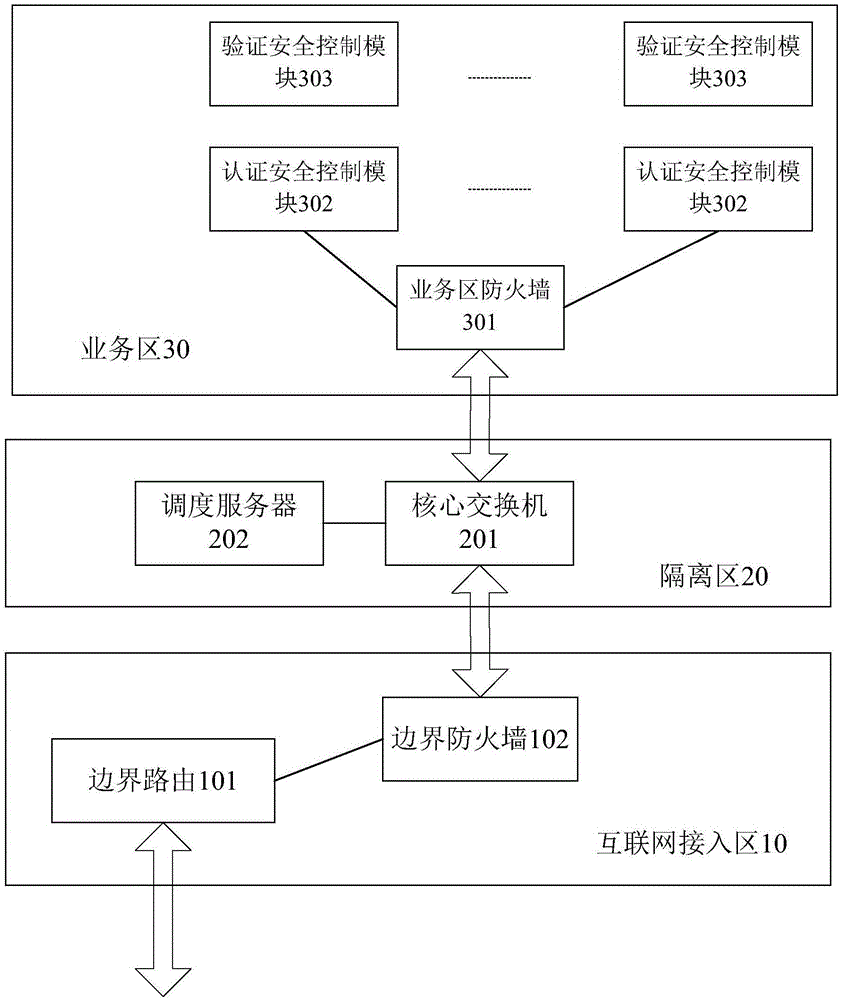
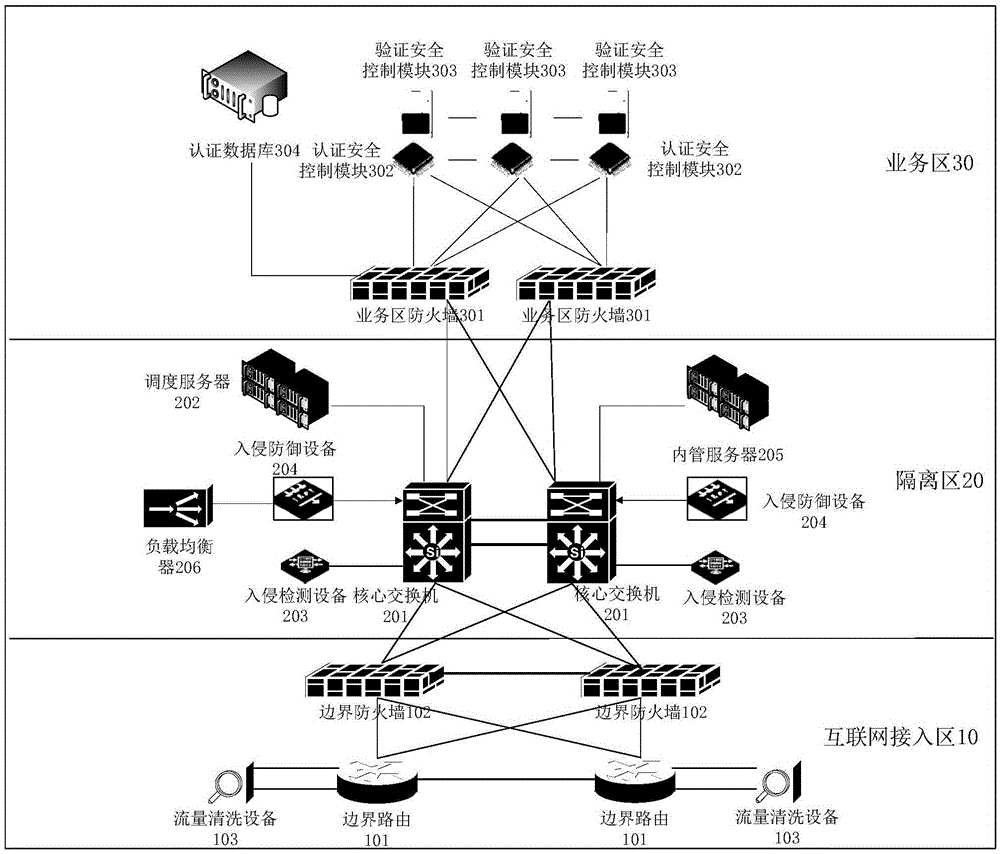
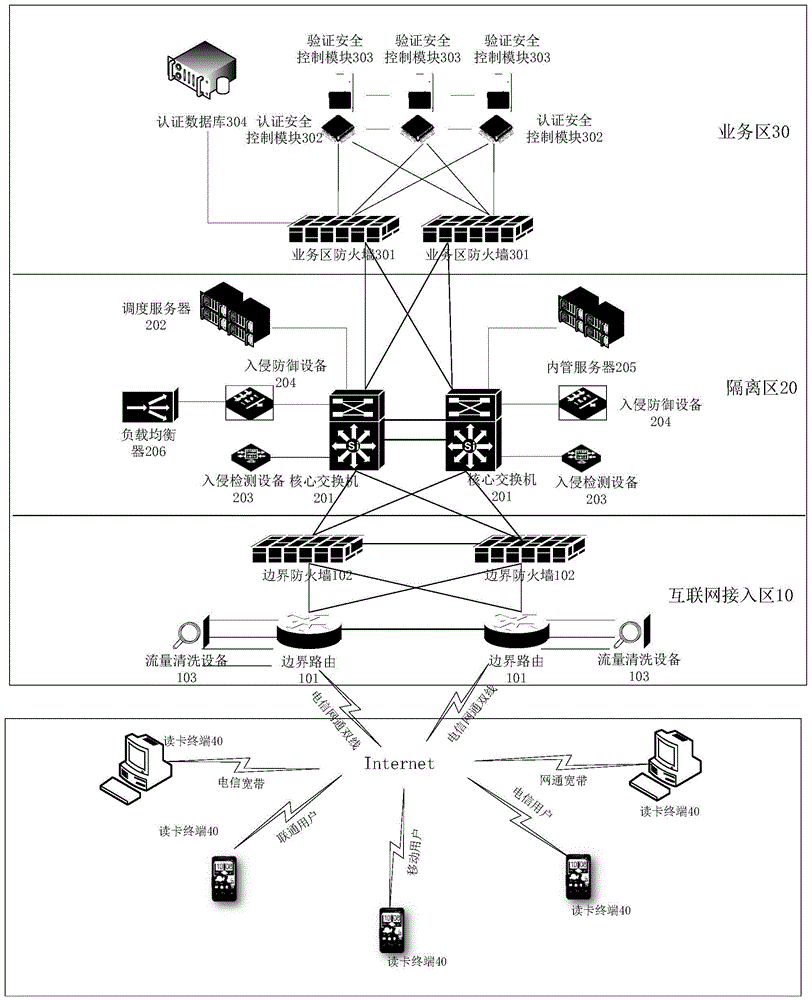
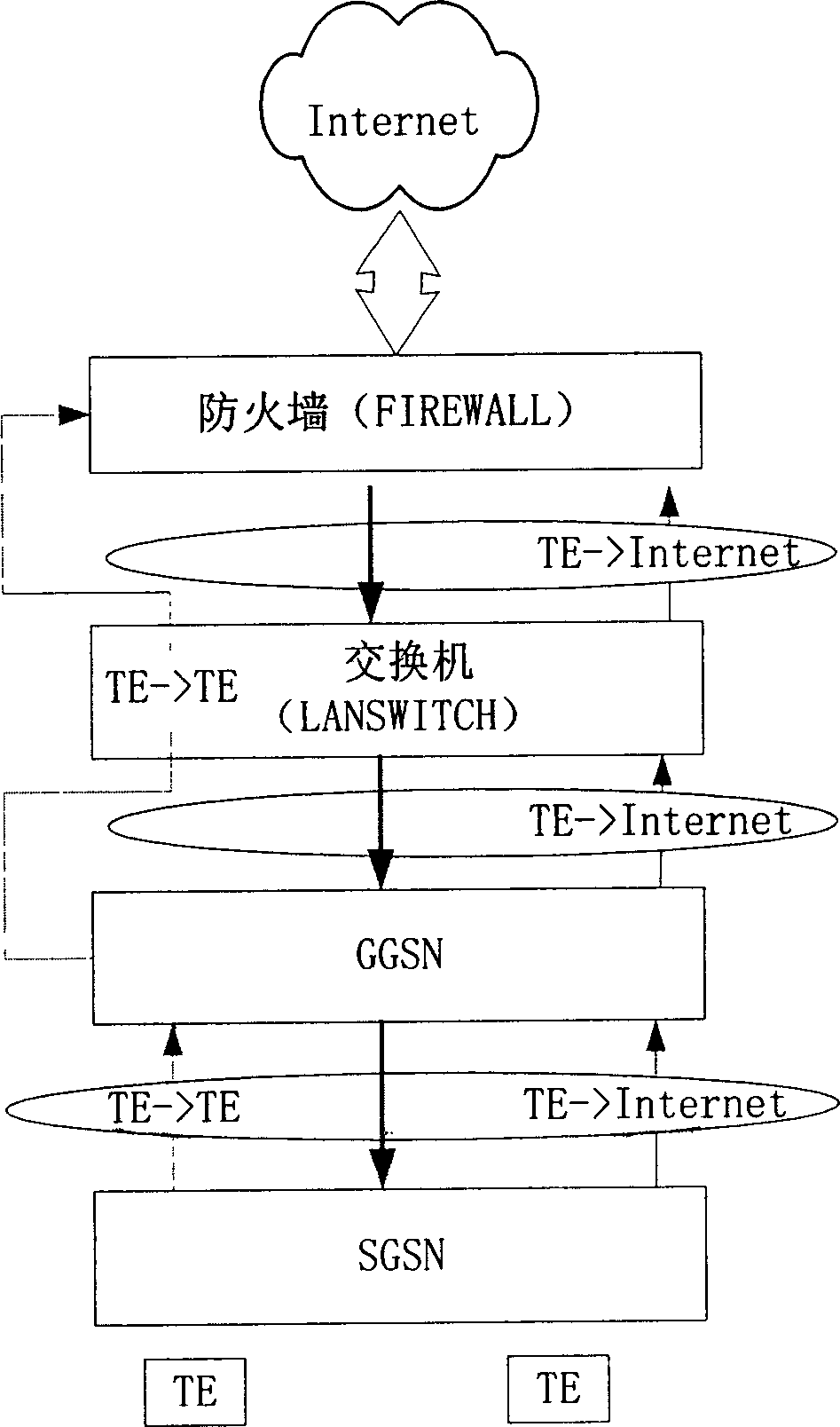
Identity card cloud authentication system and card reading system
The invention provides an identity card cloud authentication system and a card reading system. The identity card cloud authentication system comprises an edge router, an edge firewall, a core switcher, a dispatch server, a business region firewall, an authentication safety control module and a verification safety control module, wherein the edge router is used for transmitting a data package transmitted by a card reading terminal to the core switcher through the selected edge firewall. The core switcher transmits the data package to the dispatch server or the business region firewall. After the dispatch server receives the data package, the dispatch server selects an idle authentication safety control module, and transmits a corresponding identification to the card reading terminal. After the business region firewall receives the data package, the business region firewall transmits the data package to a first authentication safety module. A first authentication safety control module transmits a decrypted data package to a first verification safety control module. The first verification safety control module returns a corresponding first data package to the first authentication safety control module. The first authentication safety control module encrypts the first data package, and transmits the encrypted first data package to the card reading terminal.
Owner:TENDYRON CORP
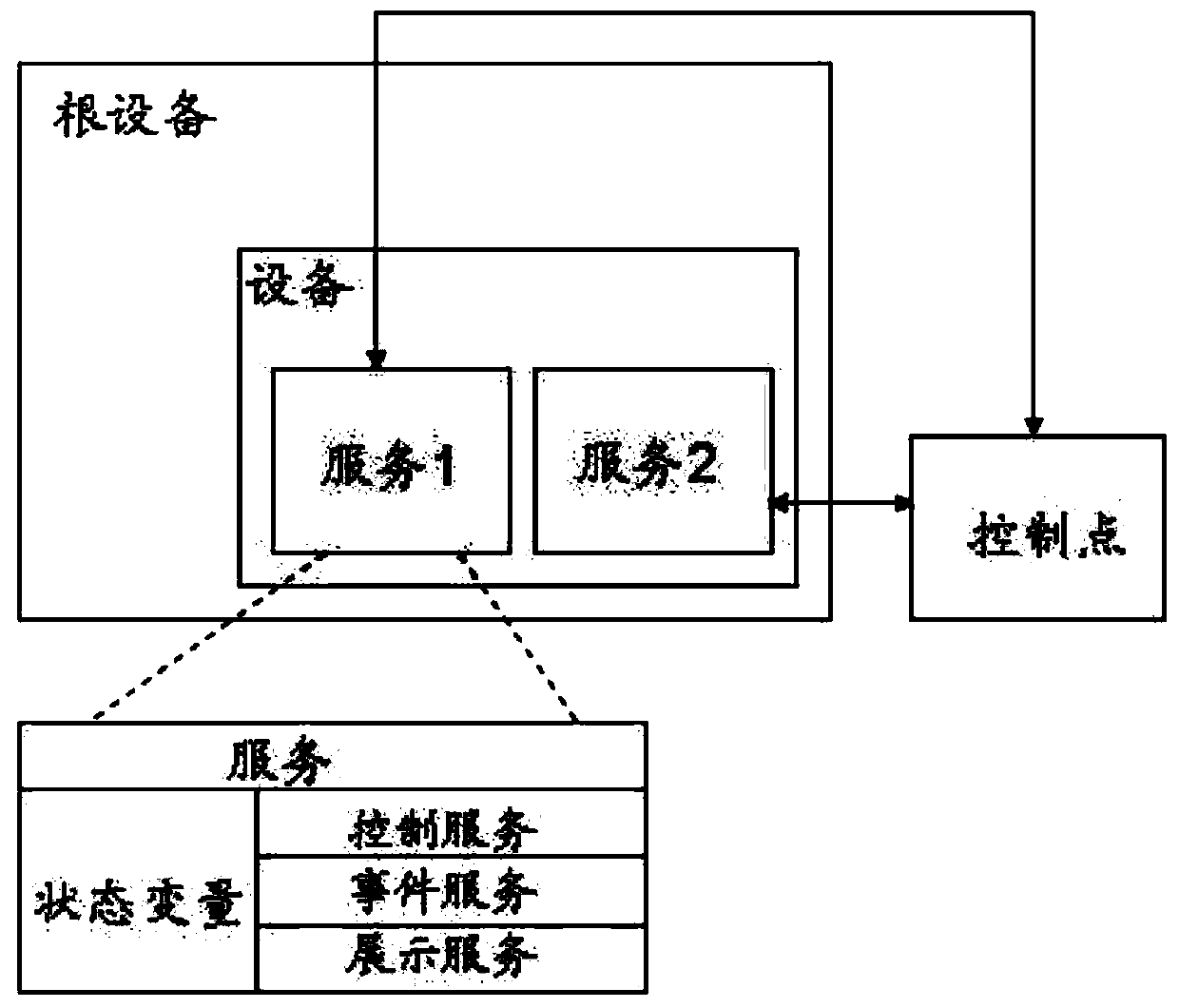
Equipment control method and related equipment
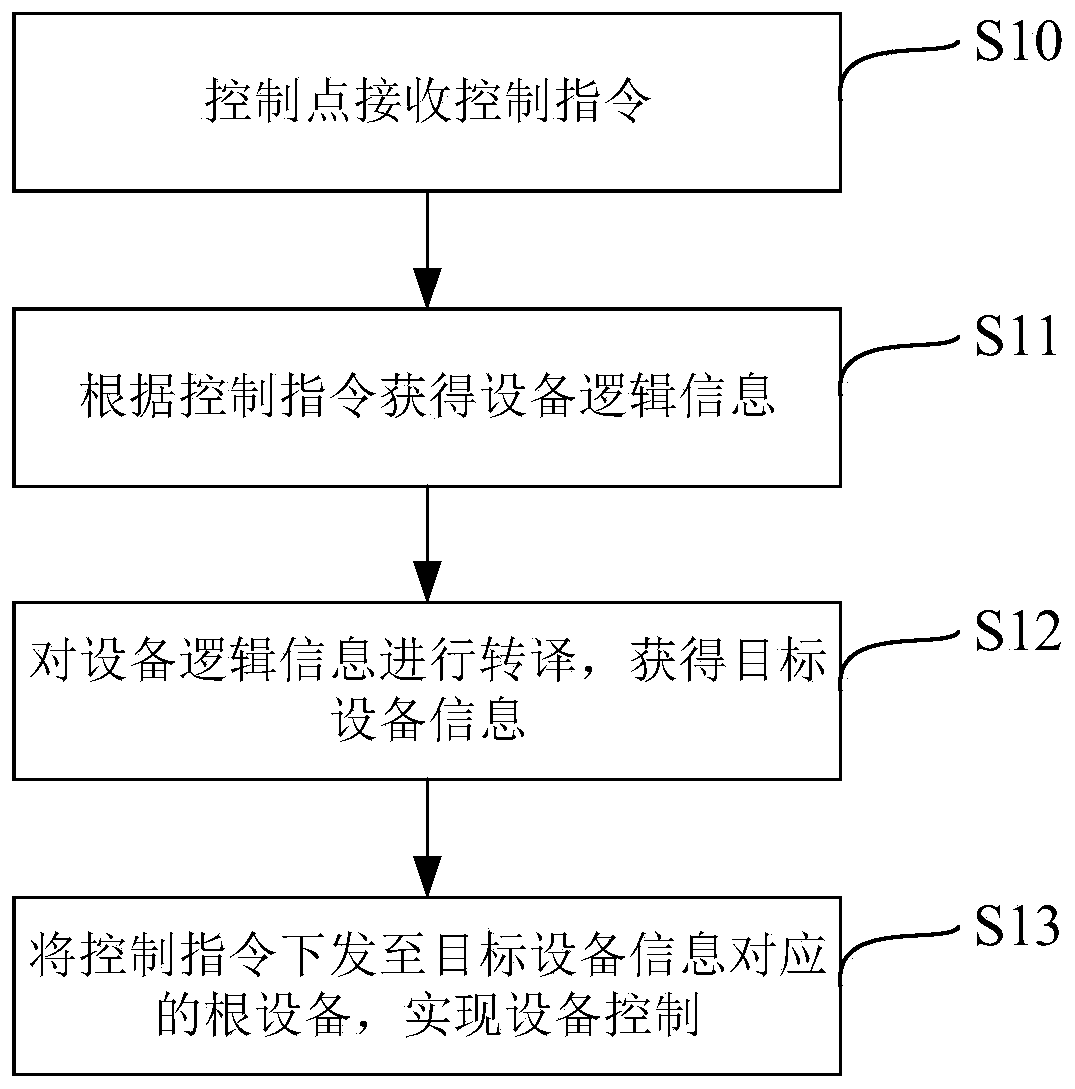
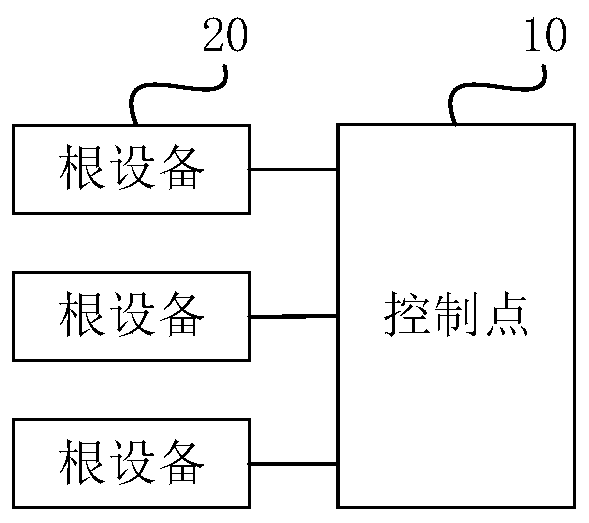
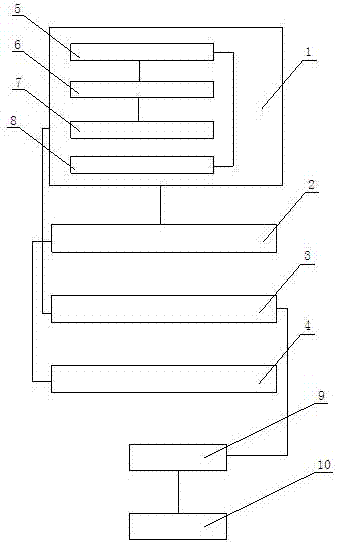
InactiveCN110673537AAchieve unified controlRealize managementProgramme controlComputer controlControl systemSoftware engineering
The invention discloses an equipment control method. The method comprises the following steps that: a control point receives a control instruction; equipment logic information is obtained according tothe control instruction; the equipment logic information is translated, so that target equipment information can be obtained; and the control instruction is issued to root equipment corresponding tothe target equipment information, so that equipment control can be realized. The invention further discloses an equipment control system, an equipment control device, a computer readable storage medium, a computer program product and control point equipment. According to the equipment control method, the equipment control system, the equipment control device, the computer readable storage medium,the computer program product and the control point equipment provided by the technical schemes of the invention adopted, the safety of intranet equipment is effectively ensured, and at the same time,the unified management and control of the equipment can be realized.
Owner:SHENZHEN ONETHING TECH CO LTD
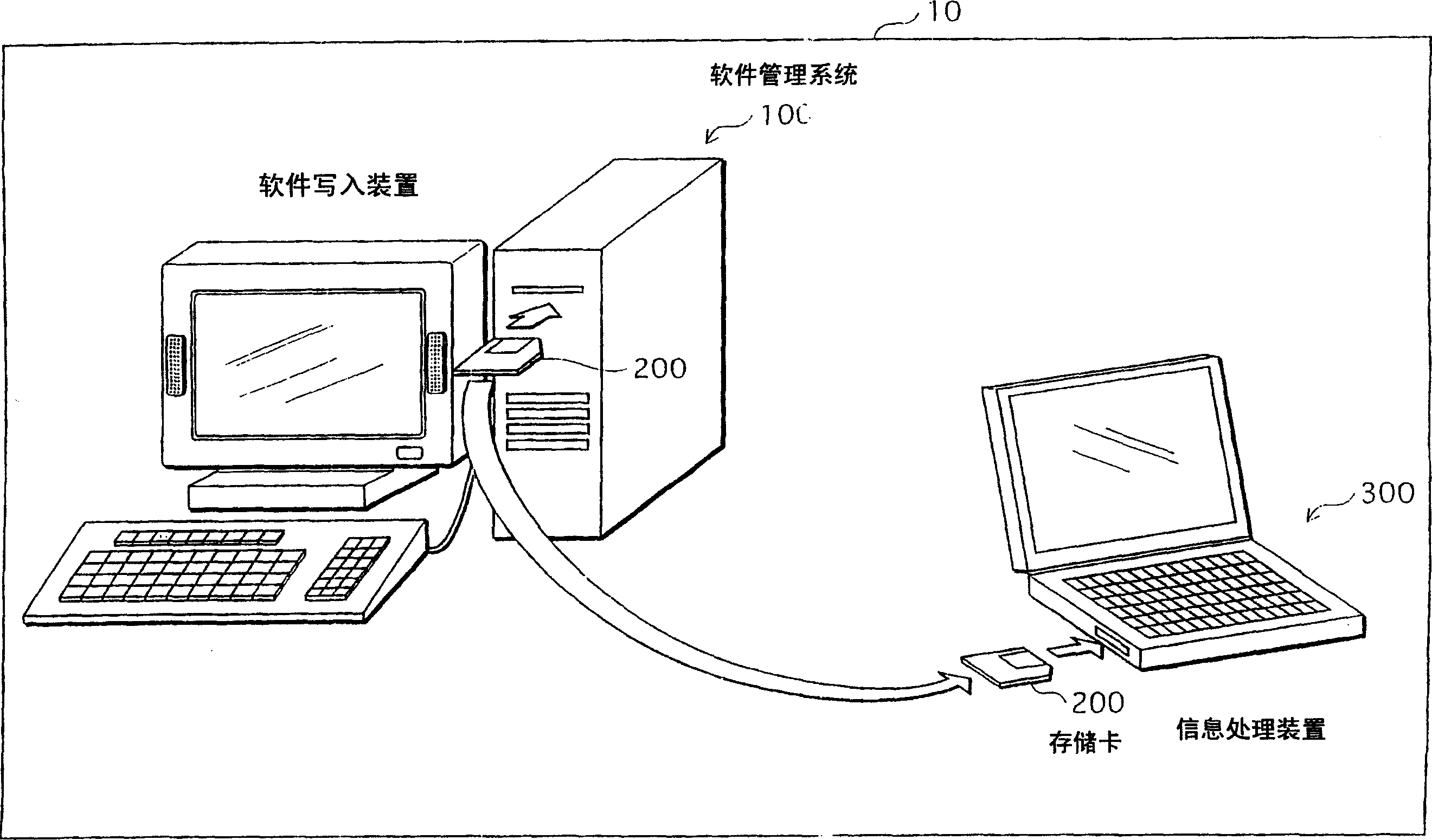
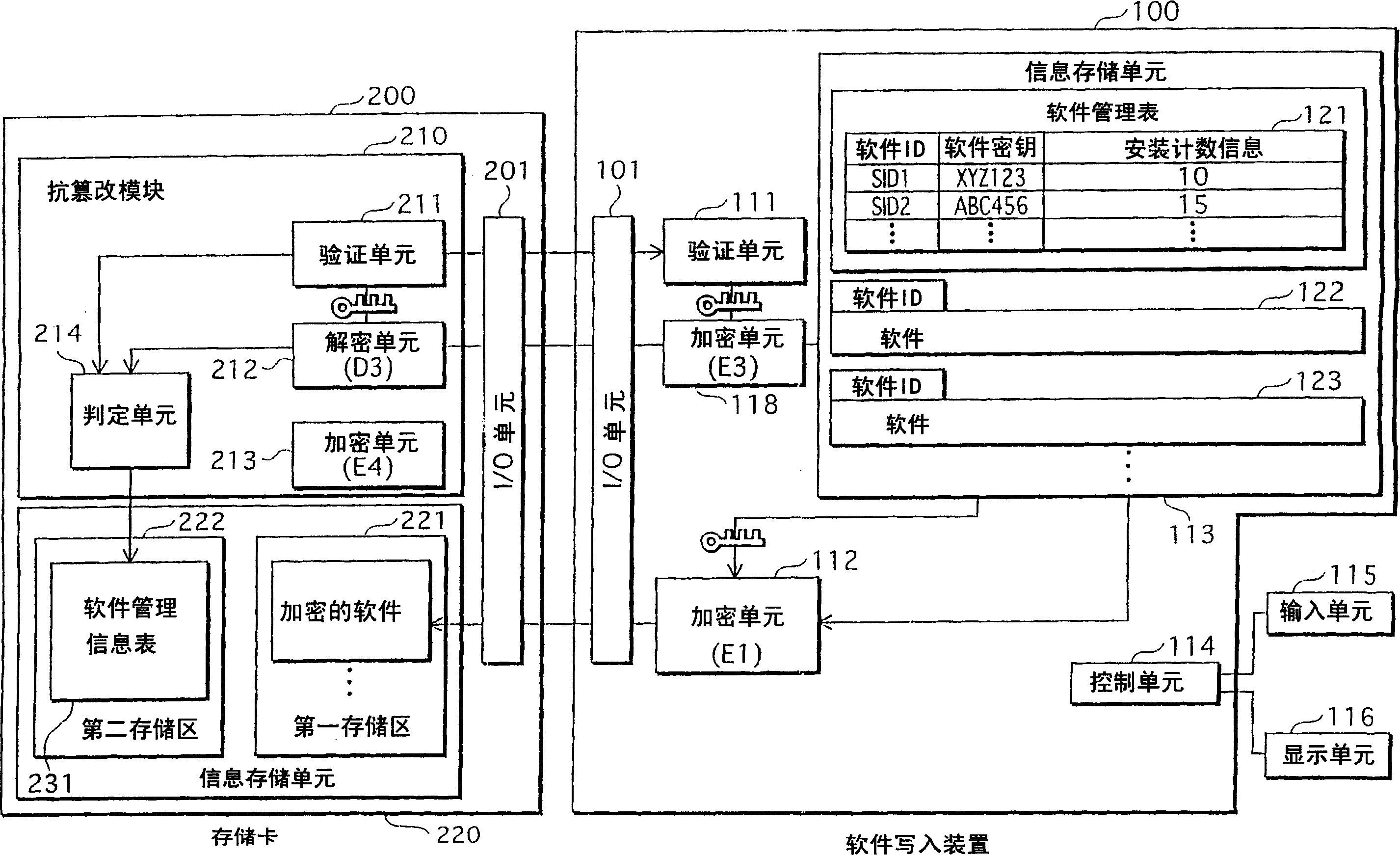
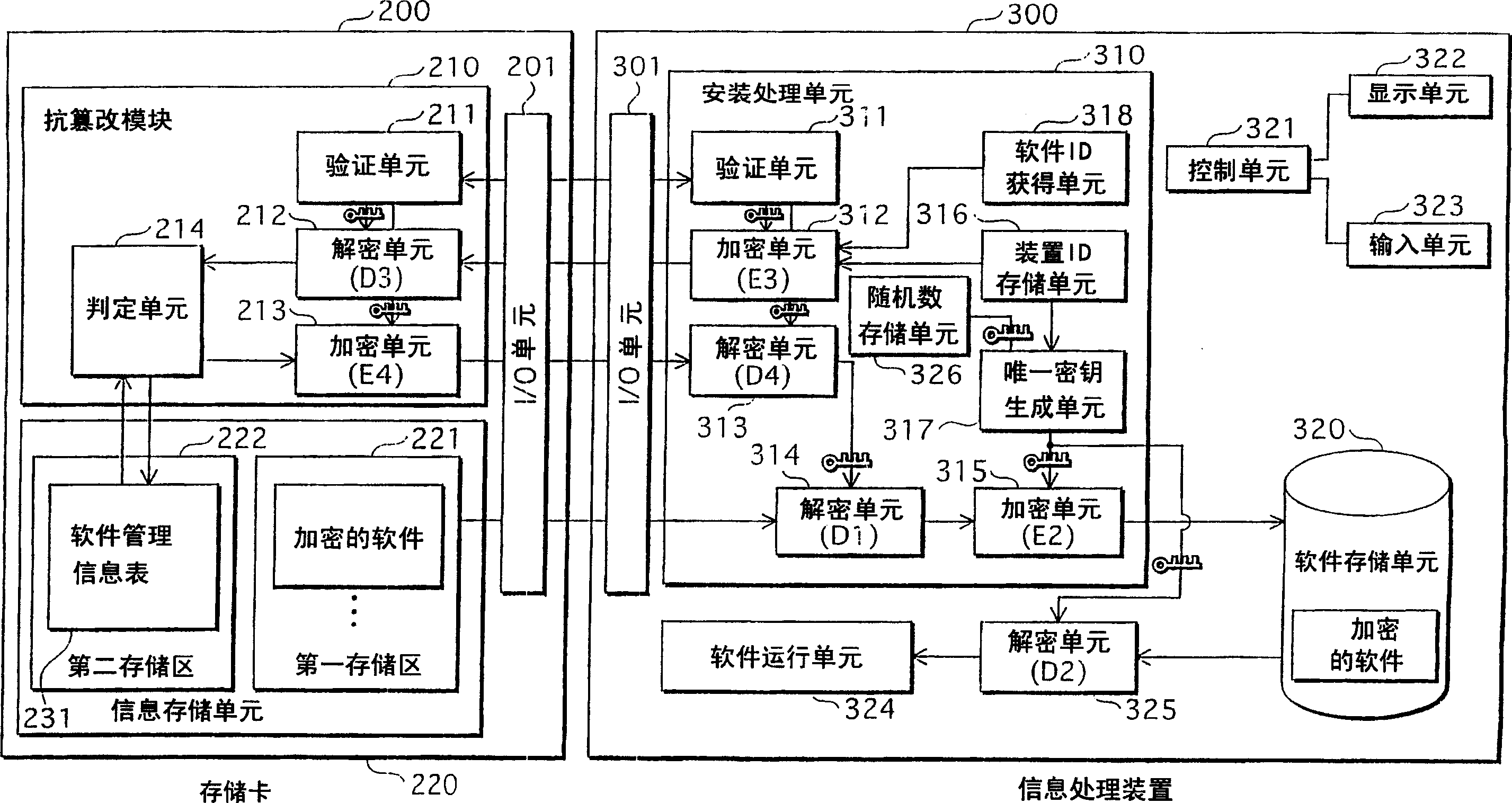
Software-management system, recording medium, and information-processing device
InactiveCN1754173APrevent unauthorized updatesAvoid illegal attacksDigital data processing detailsDigital computer detailsInformation processingManagement system
Owner:PANASONIC CORP
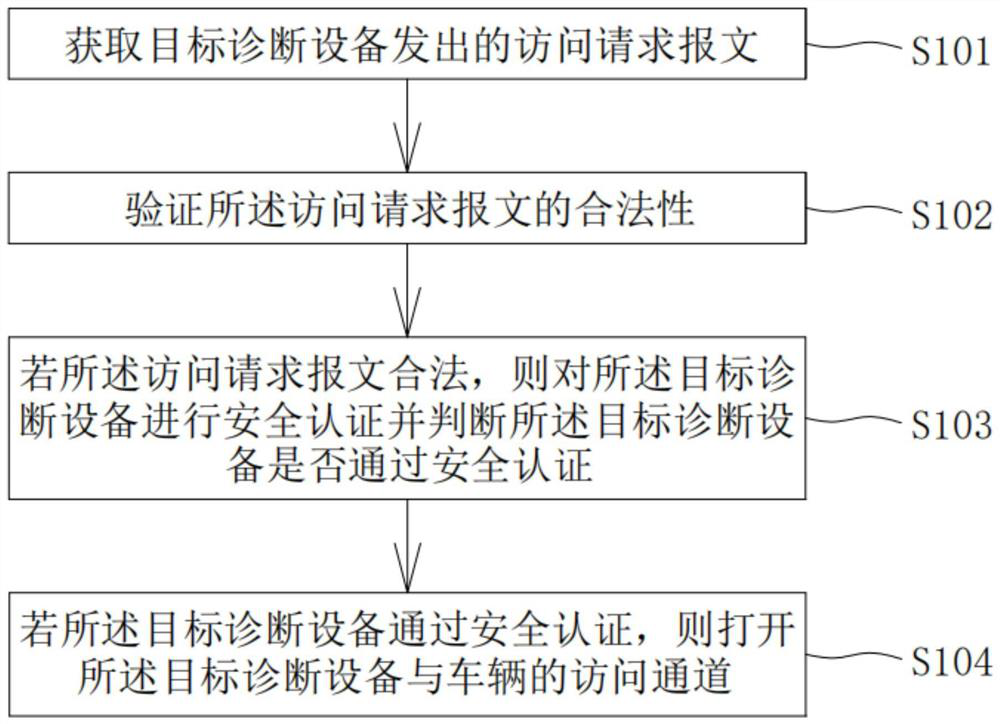
Vehicle-mounted network protection method and system, storage medium and equipment
PendingCN114338073AEnsure safetyTo achieve the purpose of double protectionRegistering/indicating working of vehiclesSecuring communicationCommunication interfaceIn vehicle
The invention provides a vehicle-mounted network protection method and system, a storage medium and equipment, and is applied to a diagnosis CAN line, the diagnosis CAN line is connected with external diagnosis equipment and a communication interface of a vehicle, the method comprises the following steps: obtaining an access request message sent by target diagnosis equipment, verifying the legality of the access request message, and if the access request message is legal, sending the access request message to the target diagnosis equipment; if yes, performing security authentication on the target diagnosis equipment and judging whether the target diagnosis equipment passes the security authentication or not, and if yes, opening an access channel between the target diagnosis equipment and the vehicle. According to the diagnosis CAN line, the legality of the access request message of the target diagnosis equipment is verified, and the security authentication is carried out on the target diagnosis equipment, so that the purpose of dual protection on the vehicle-mounted network can be achieved, the security of the vehicle-mounted network is effectively guaranteed, and the vehicle-mounted network is prevented from being illegally attacked.
Owner:JIANGLING MOTORS
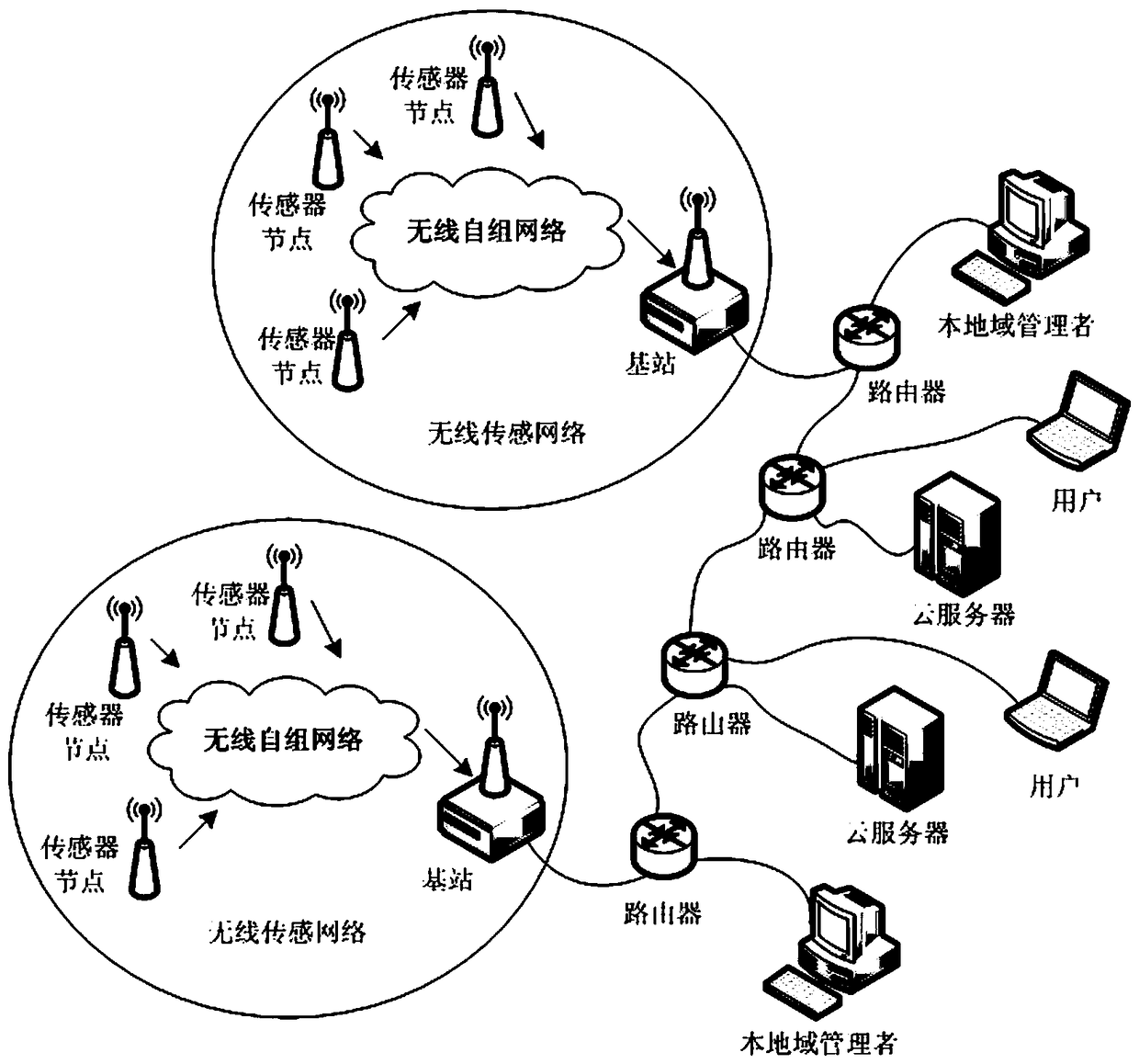
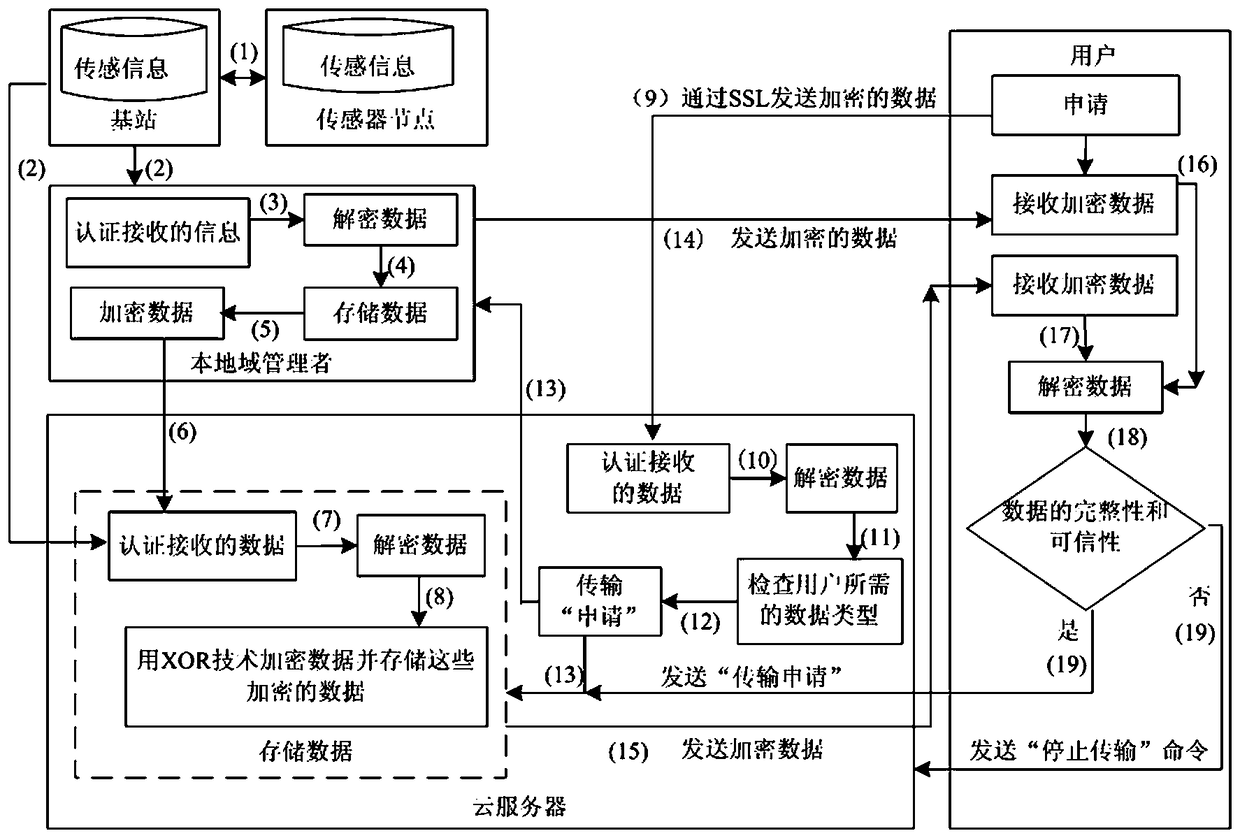
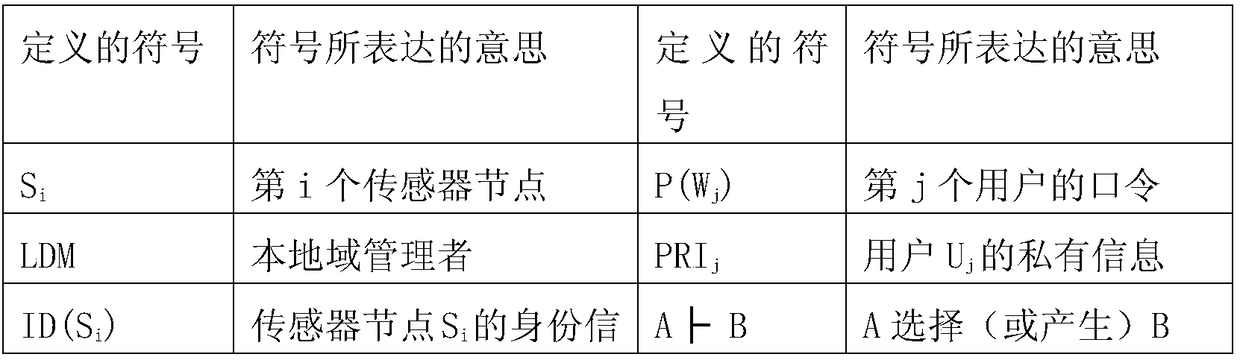
Privacy protection method of sensing information virtual service in Internet of Things
InactiveCN108512856AImprove adaptabilityImprove versatilityNetwork topologiesTransmissionSensing dataData privacy protection
The invention discloses a privacy protection method of sensing information virtual service in Internet of Things. Sensor sensing data, a cloud server, a local domain manager, and a user are provided.By aiming at generating of sensing information in a wireless sensing network and during a virtual service process in cloud computation, the data privacy protection strategy of the cloud computation virtual service is divided into two parts: (1) the sensing information is transmitted in the network, and is stored in the cloud server; (2) the sensing data stored in the cloud server is used to provide service for a user. By aiming at each of the safety problems faced by the abovementioned two parts, a safety protection algorithm is provided, and therefore the safety storage algorithm of the sensing information and the safety access algorithm of the data stored in the cloud server are provided.
Owner:HANGZHOU DIANZI UNIV
Method for preventing offence between inserted users
InactiveCN1832450AHigh security requirementsAvoid illegal attacksData switching networksComputer network
Owner:HUAWEI TECH CO LTD
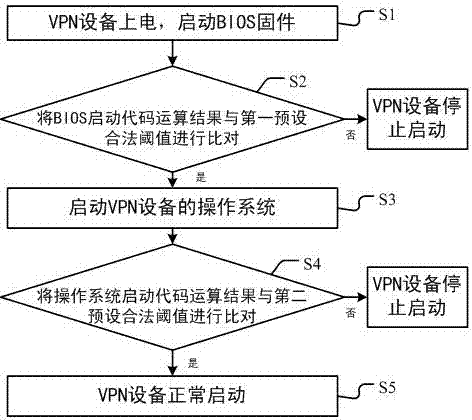
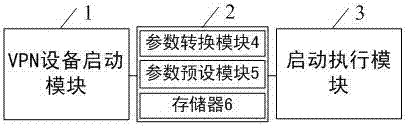
VPN (Virtual Private Network) device safe starting method and VPN device safe starting system
InactiveCN107196755AGuarantee legality and reliabilityEnsure information securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesBIOSPrivate network
The invention provides a VPN (Virtual Private Network) device safe starting method and a VPN device safe starting system. The VPN device is power-on, and BIOS firmware is started; a trusted cryptography module carries out HASH operation on the starting code of the BIOS firmware, and the BIOS starting code operation result is compared with a first preset legal threshold; when the BIOS starting code operation result meets the first preset legal threshold, the VPN device operation system is started; the trusted cryptography module carries out HASH operation on the starting code of the operation system, and the operation system starting code operation result is compared with a second preset legal threshold; and when the operation system starting code operation result meets the second preset legal threshold, the VPN device is started normally. The VPN device can be protected from being illegally attacked in the case of starting, the legality and the reliability of private network access can be ensured, and the information safety is ensured.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
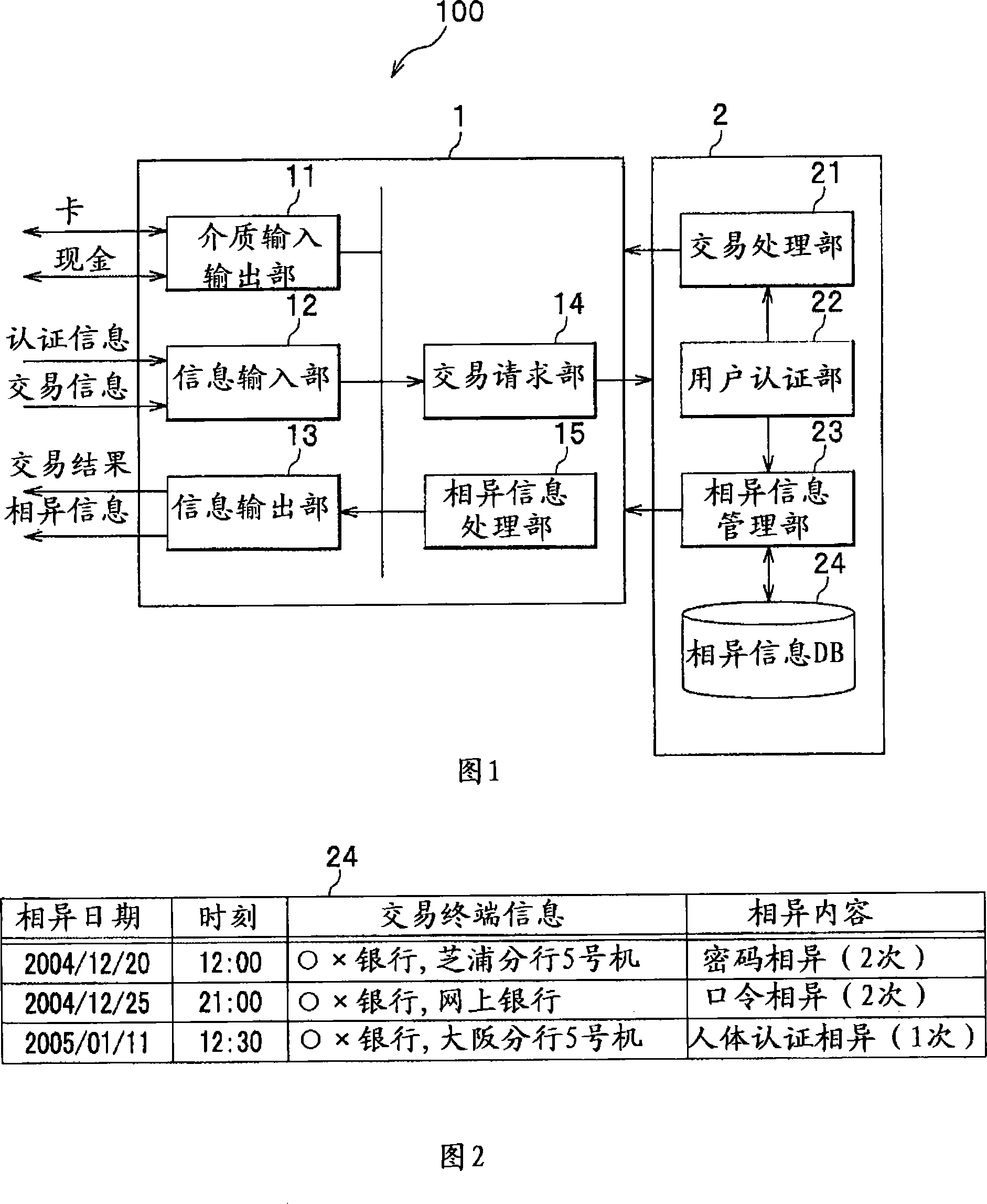
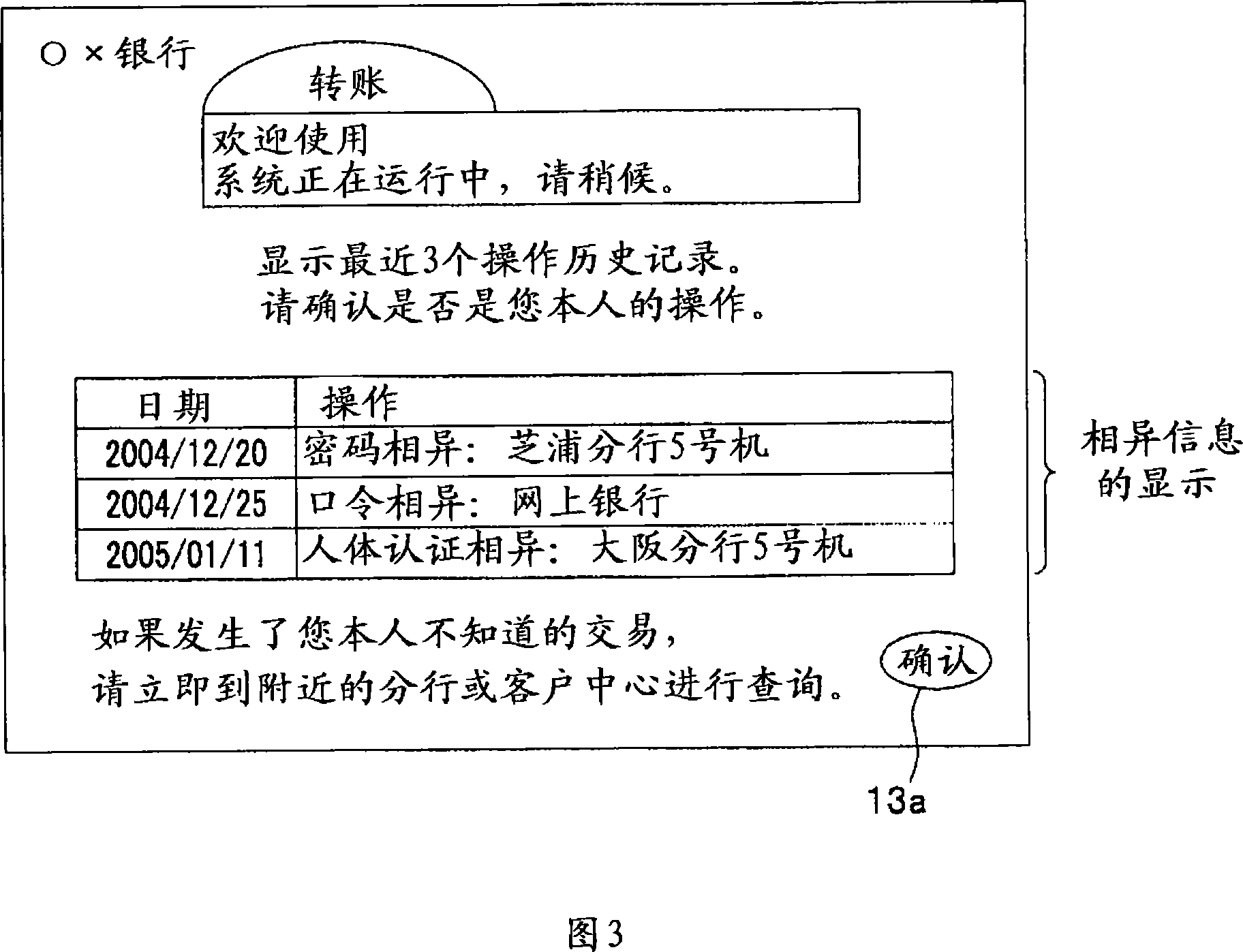
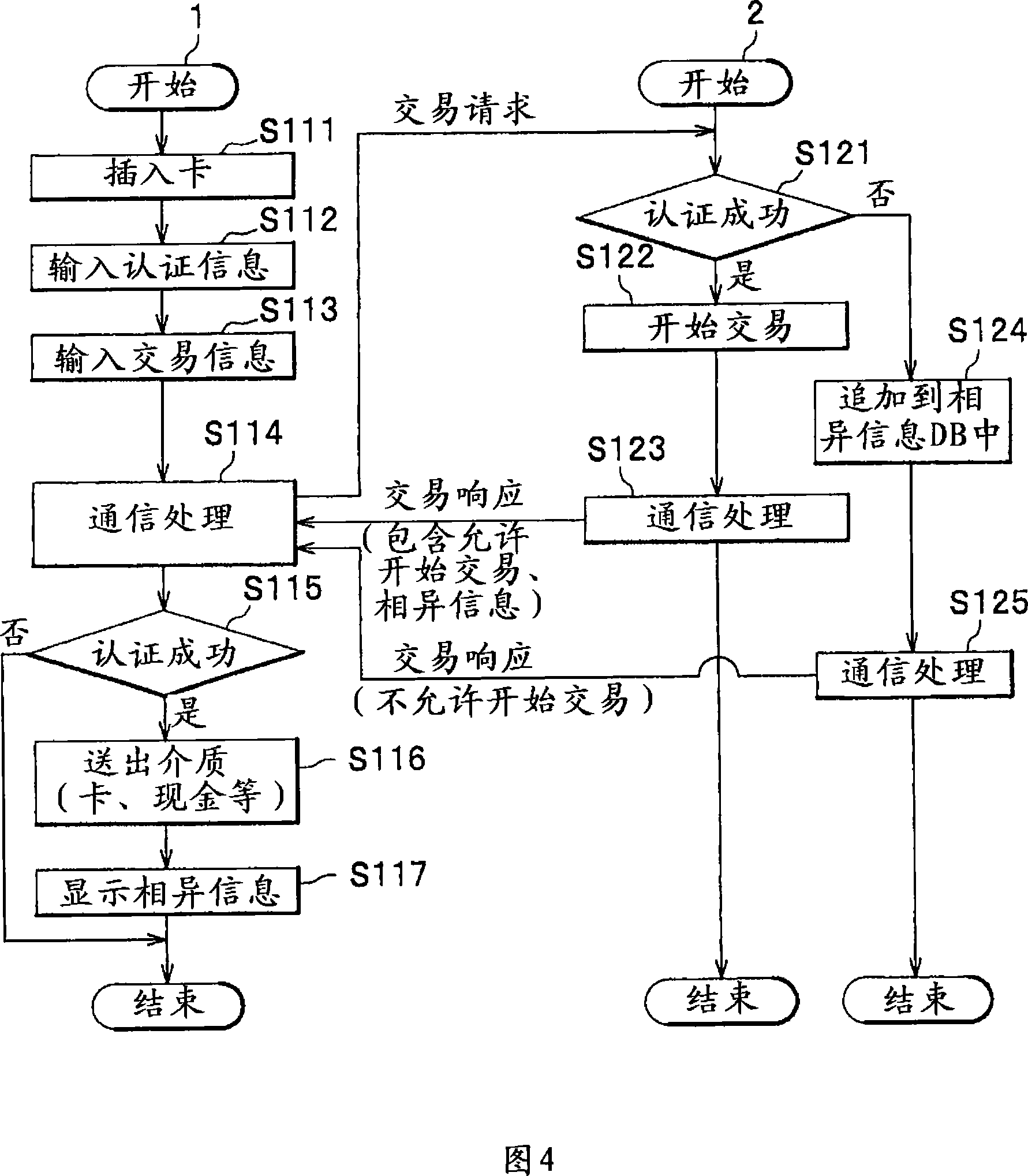
Trading system, trading method and trading server
InactiveCN101154309AAvoid illegal attacksComplete banking machinesFinanceInformation processingCountermeasure
The invention provides a trade system, a trade method and a trade server, which enables the legal user of the account to prevent the illegal attack to the account. The trade system comprises an operational trade terminal, a trade server accepting the trade requirement from the trade terminal, which is characterized in that the trade server has: a user identification portion for identifying the user at the trade terminal, who proposes the trade requirement to the operation, a dissimilarity information management portion for storing the dissimilarity information in the storage device and transmitting to the dissimilarity information management portion at the trade terminal, wherein the dissimilarity information shows the identification results that the user is not allowed to trade by the user identification portion; the trade terminal has a dissimilarity information processing portion outputting the dissimilarity information received from the trade server.
Owner:OKI ELECTRIC IND CO LTD
Communication method and device
PendingCN112492590AAvoid illegal attacksImprove securityUser identity/authority verificationSecurity arrangementTerminal equipmentEngineering
The invention discloses a communication method and device. The method comprises the steps that terminal equipment receives a first authentication request from a security function network element; theterminal equipment obtains authentication reference information according to the first authentication request, wherein the authentication reference information is a response value or a resynchronization identifier or a reason indication value; the terminal equipment sends an authentication response message to the security function network element, wherein the authentication response message comprises a first information element used for carrying a response value, a second information element used for carrying a resynchronization identifier and a third information element used for carrying a reason indication value, and the authentication reference information is carried in an information element corresponding to the authentication reference information.
Owner:HUAWEI TECH CO LTD
Kernel access method and device and medium
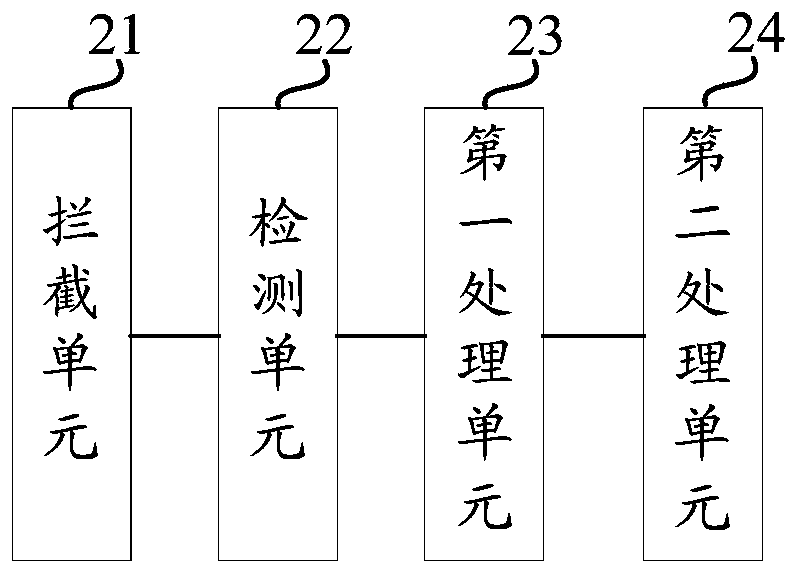
PendingCN111079135AAvoid illegal attacksEnsure safetyPlatform integrity maintainanceAccess methodData access
Embodiments of the invention disclose a kernel access method and device, and a medium. The method comprises: intercepting data access requests of all applications for a system kernel; detecting whether each data access request belongs to a preset interception range or not; for the first data access request belonging to the preset interception range, calling a corresponding preset process to process the first data access request according to the service type corresponding to the first data access request; and for the second data access request which does not belong to the preset interception range, transmitting the second data access request to the system kernel for processing. Operation corresponding to the data access request may have a security hole, and if the access to the system kernel is directly executed, the security of the system kernel is threatened. According to the technical scheme, the data access request belonging to the preset interception range is processed by the independent preset process by intercepting the data access request, so that the system kernel is effectively prevented from being illegally attacked, and the security of the container system is ensured.
Owner:INSPUR BUSINESS MACHINE CO LTD
Electronic commerce information processing system
InactiveCN107248104AEasy to receiveEasy to storeBuying/selling/leasing transactionsInformation processingCentral database
The invention discloses an electronic commerce information processing system, which comprises a central database system, a central server, a memory, a CA authentication center and an information processing module, wherein the central database system is connected with the central server; the central server is connected with the CA authentication center; the information in the central database system is stored in the memory; the information processing module is connected with the memory; and the information processing module is connected with a management module. The electronic commerce information processing system has the beneficial effects that the system is safe and reliable; easy popularization is realized; an illegal attack can be effectively prevented; data can be received, stored and processed conveniently; the safety performance is improved; the data can be analyzed through the information processing module and management module; the processing efficiency is ensured; and needs can be met.
Owner:太仓市华安企业管理有限公司
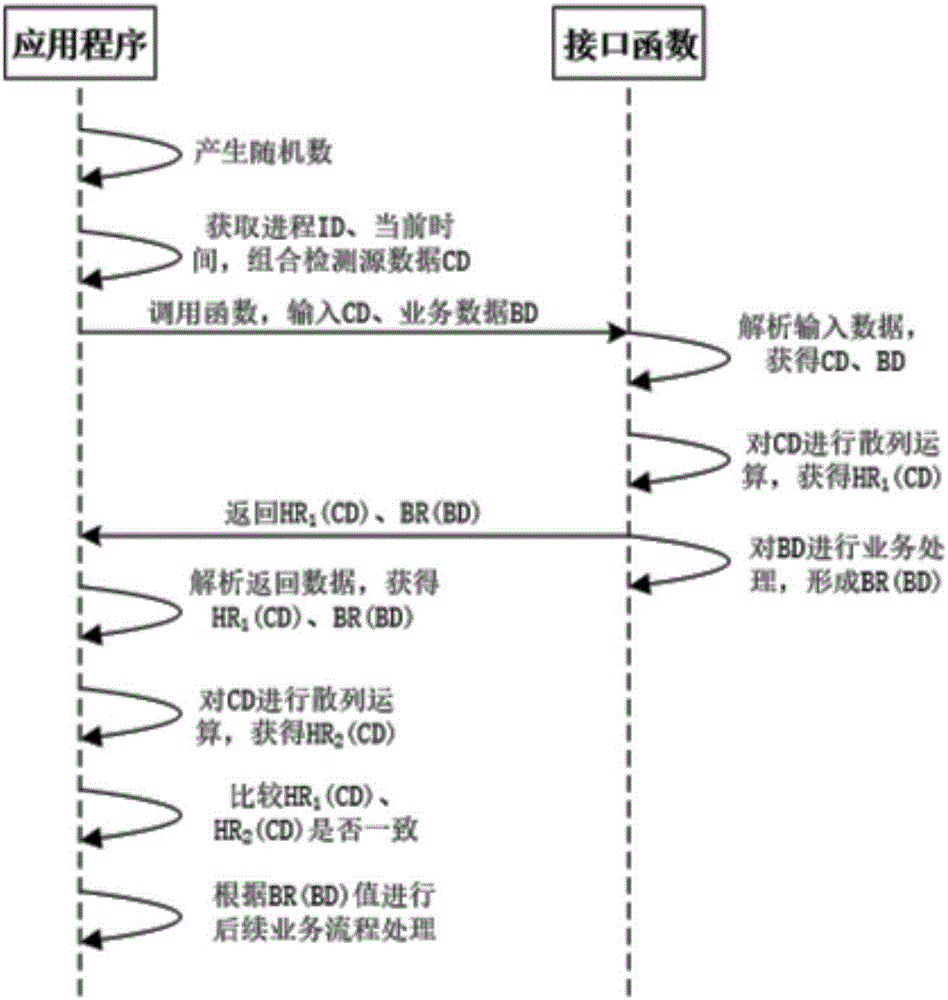
Method for performing dynamic safety detection on calling function
InactiveCN106778272AGuaranteed legal and credibleImprove securityPlatform integrity maintainanceProgramming languageTime information
The invention discloses a method for performing dynamic safety detection on a calling function. The method comprises the steps that in the processes of directly inputting function calling safety detection into an interface function of a function library and calling and processing an application program, the real-time operation processing process for calling information is added when the function library is realized, and an operation result is returned back outwards. The process of inputting current real-time data is added when the application program calls the function, meanwhile, the application program performs operation on the real-time information, the operation result is compared with a detection operation result returned back by the function, and if the operation results are consistent, the application program party considers that the function calling is real and effective. The method can accurately recognize whether the current function calling is safe and credible or not, and safety risks that the function library is replaced in the midway, and the function calling is intercepts illegally due to the currently-adopted one-time detection and long-term effectiveness mode are effectively avoided.
Owner:成都三零瑞通移动通信有限公司
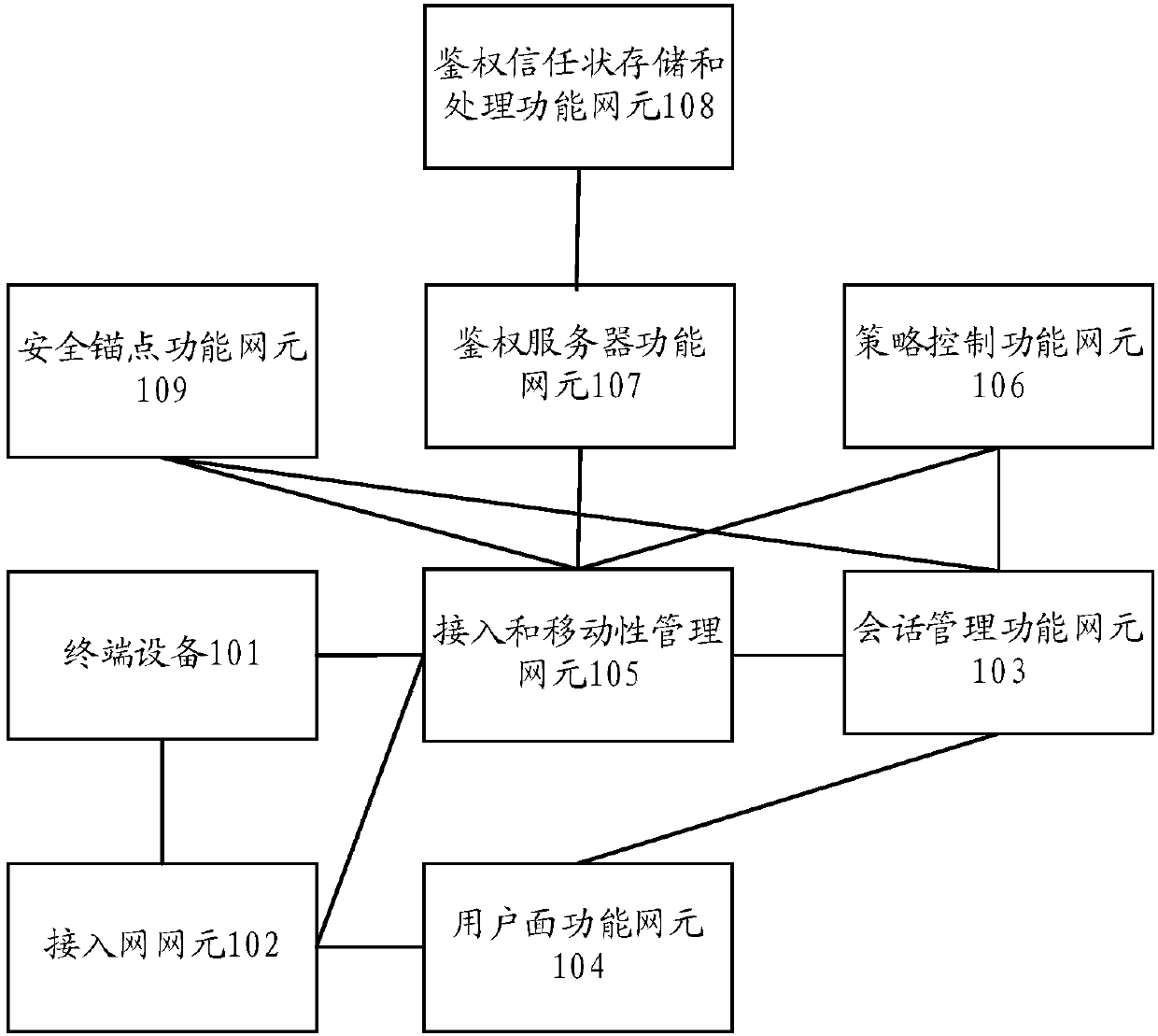
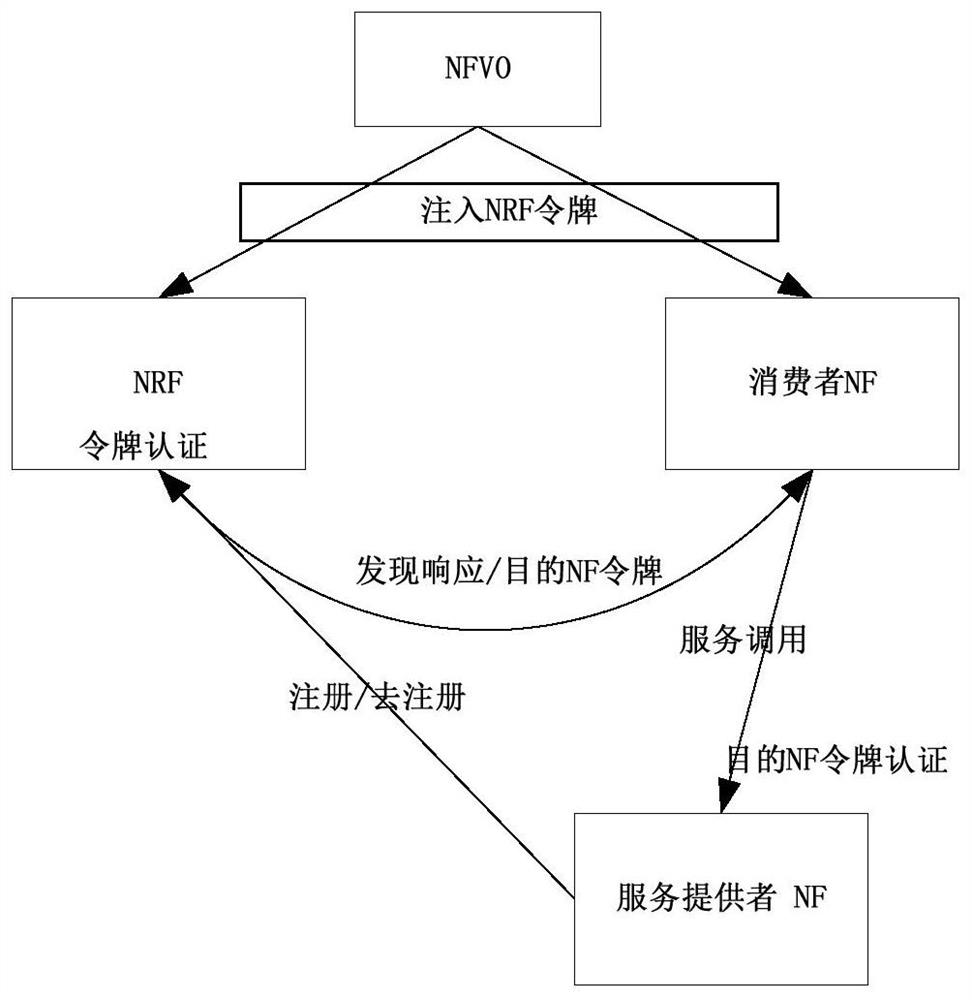
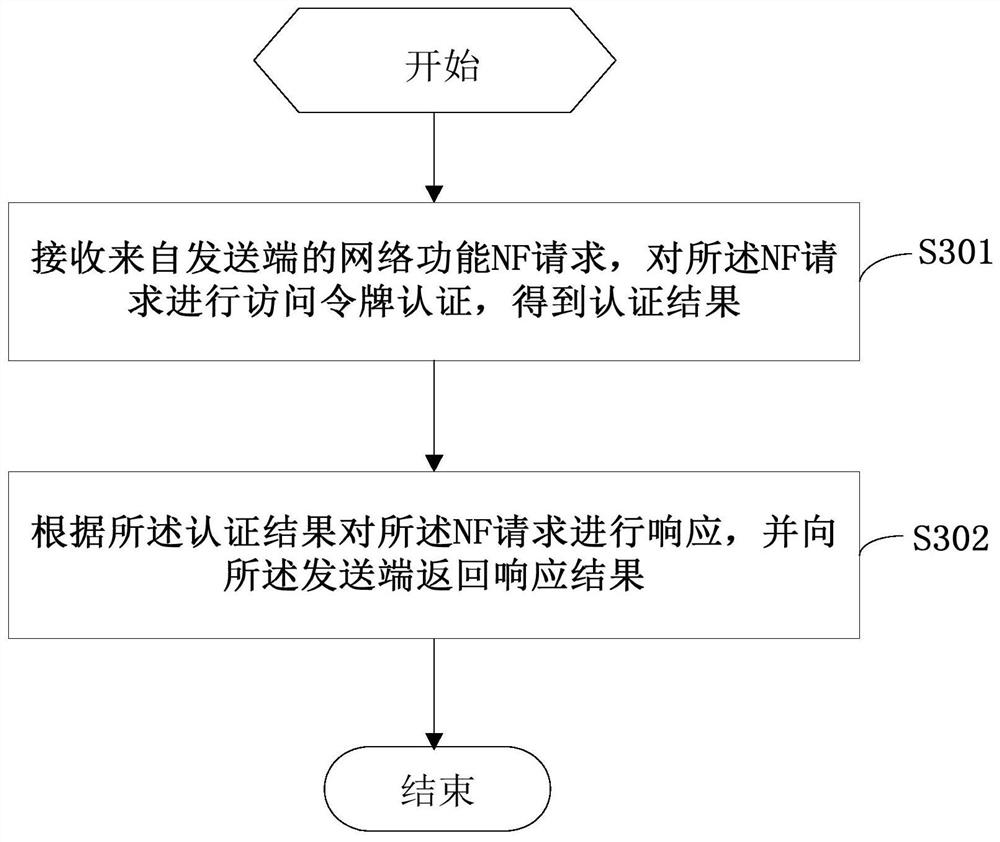
Method, device and computer-readable storage medium for network function authentication
Embodiments of the present invention provide a network function authentication method, device, and computer-readable storage medium. The network function authentication method includes: receiving a network function NF request from a sender, performing access token authentication on the NF request, and obtaining Authentication result; respond to the NF request according to the authentication result, and return the response result to the sending end, the method of network function authentication uses NRF to authenticate the request NF during registration, discovery and other processes to improve the system At the same time, when the NF automatically registers, it provides its own token for the NF to discover, and the NRF provides it to the service requesting NF, so that the service provider NF can authenticate the NF service call, which improves the security of the system and avoids system illegally attacked.
Owner:ZTE CORP
A communication method and device
ActiveCN109788480BAvoid illegal attacksImprove securityUser identity/authority verificationSecurity arrangementInternet privacyTerminal equipment
The present application discloses a communication method and device, wherein the method includes: a terminal device receives a first authentication request from a safety function network element; the terminal device obtains authentication reference information according to the first authentication request, and the authentication reference The information is a response value or a resynchronization identifier or a cause indication value; the terminal device sends an authentication response message to the security function network element, and the authentication response message includes a first information element for carrying the response value, for carrying The second information element of the resynchronization identifier and the third information element used to carry a cause indication value, the authentication reference information is carried in the information element corresponding to the authentication reference information.
Owner:HUAWEI TECH CO LTD
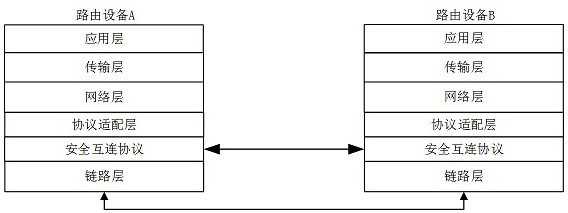
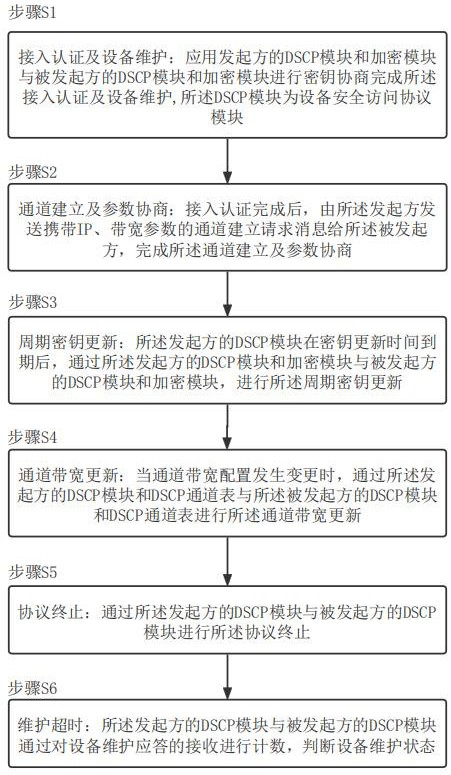
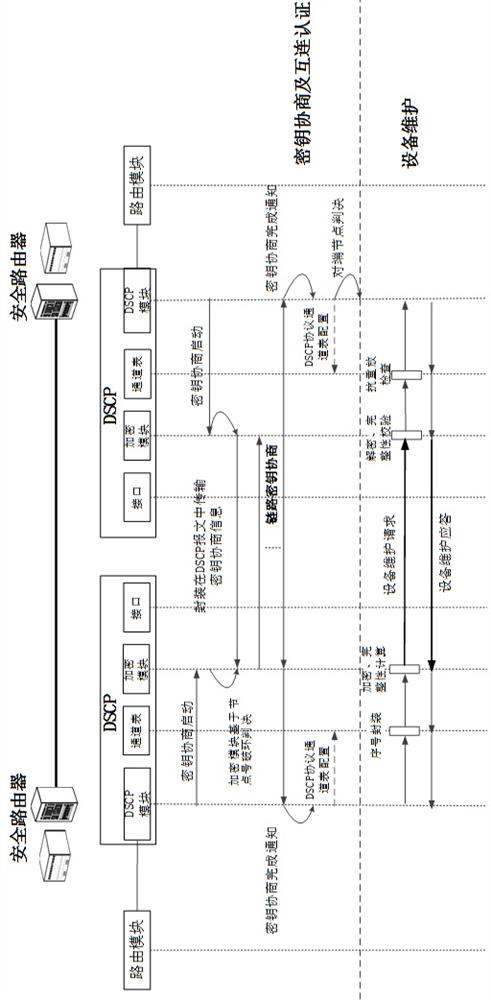
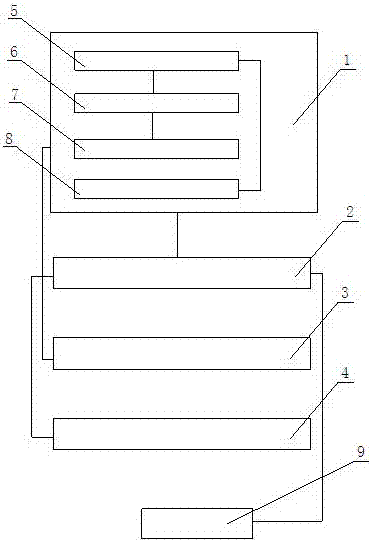
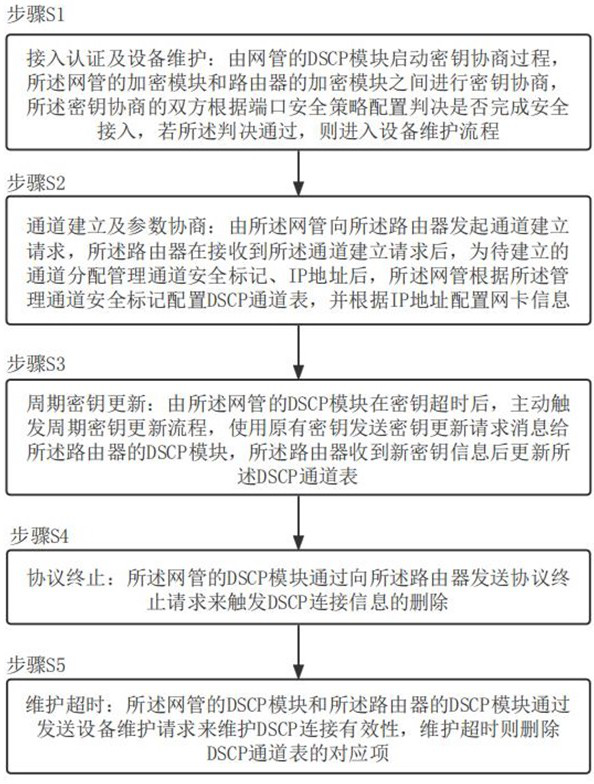
A secure interconnection protocol method and system for router equipment
ActiveCN113839777BAvoid accessAvoid illegal attacksKey distribution for secure communicationCiphertextAttack
The invention proposes a method and system for a secure interconnection protocol for router equipment. The method includes: step S1, access authentication and equipment maintenance; step S2, channel establishment and parameter negotiation; step S3, periodic key update; step S4, channel bandwidth update; step S5, protocol termination; step S6, maintenance timeout . The above method can realize functions such as router device automatic discovery, secure access authentication, data encapsulation, anti-replay, and ciphertext transmission, effectively preventing illegal device access, and preventing devices from being subjected to multi-level illegal attacks from access control to message forwarding , and provide functions such as device identity security identification, and provide safe exchange means for control and service messages between routers.
Owner:军事科学院系统工程研究院网络信息研究所
Method for realizing file reading and/or writing and data server
InactiveCN102073741BAchieve readGuaranteed uptimeTransmissionSpecial data processing applicationsName serverDistributed File System
The embodiment of the invention discloses a method for realizing file reading and / or writing, comprising the following steps: a first hadoop distributed file system (HDFS) client receives file reading information and / or file writing information sent by a client terminal, wherein the first HDFS client is the preset HDFS client corresponding to the client terminal in default; the first HDFS client interacts with a name server according to the file reading information and / or file writing information and acquires file node information sent by the name server; and the first HDFS client finishes the file reading and / or writing according to a data server corresponding to the file node information. The embodiment of the invention further discloses the data server. According to the invention, the file reading and writing based on HDFS can be simply and quickly realized, and the storage of huge data amount is finished; and the method can be conveniently operated on common computers, thereby greatly improving the system compatibility.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Embedded partition image security authentication and kernel trusted boot method and device thereof
ActiveCN104794393BAvoid hijackingPrevent tamperingComputer security arrangementsKernel methodFile system
The invention discloses an embedded type partition image security certification and kernel trusted boot method. Based on an embedded type equipment platform of the Android system, on the premise that the system power, the system Bootloader guide and kernel loading and starting are secure and trusted, security reinforcement is conducted to the system in a mode that system partition and kernel verification are combined. According to the method, the system power, the Bootloader, the kernel partition Layout and part of loading areas are subjected to the security reinforcement and reconstitution according to specific rules. The invention provides a set of novel embedded type system partition image security certification and operation system kernel trusted boot method based on security hardware, multi-layer reinforcement is conducted to the starting process of the embedded type system, the BOOTLOADER, the operation system kernel, the file system data or application program data of the system are prevented from malicious hijack or tamper, and the using security of the embedded type equipment is protected.
Owner:HANGZHOU BYTE INFORMATION TECH CO LTD
Enterprise business information processing system
InactiveCN107294973AEasy to promoteAvoid illegal attacksUser identity/authority verificationSystem safetyInformation handling system
The invention discloses an enterprise business information processing system. The enterprise business information processing system includes a center data base system, a center server, a memory and a CA authentication center, wherein the center data base system is connected with the center server; the center server is connected with the CA authentication center; the information in the center data base system is stored in the memory; and a business pairing module is connected with the center server. The enterprise business information processing system has the advantages of being safe and reliable, being easy to popularize, effectively preventing illegal attacking, being convenient for receiving, storing and processing data, improving safety performance, setting of the pairing module, being able to quickly perform data pairing, improving work efficiency, and satisfying the demand.
Owner:太仓市华安企业管理有限公司
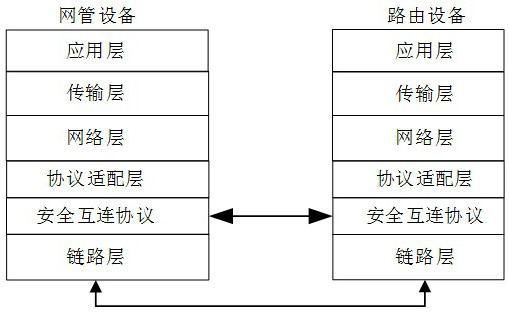
Secure interconnection protocol method and system used between network manager and router
ActiveCN113839776APrevent unauthorized device accessEnsure safetyKey distribution for secure communicationData switching networksProtocol for Carrying Authentication for Network AccessNetwork management
The invention provides a secure interconnection protocol method and system between a network manager and a router. The method comprises the following steps: S1, access authentication; S2, channel establishment and parameter negotiation; S3, updating of the periodic key; S4, protoco terminating; and S5, maintaining overtime. The functions of automatic discovery, secure access authentication, data encapsulation, anti-replay, ciphertext transmission and the like of network management and router equipment are realized, illegal equipment access is effectively prevented, the equipment is prevented from being subjected to multi-level illegal attacks from access control to message forwarding, the functions of equipment identity security identification and the like are provided, and a secure interaction means between the network management equipment and the managed equipment is provided.
Owner:军事科学院系统工程研究院网络信息研究所
Method and system for multicast and broadcast service authentication and authorization
ActiveCN101150405BAuthentication time shortenedReduce occupancySpecial service provision for substationUser identity/authority verificationThird partyBroadcast service
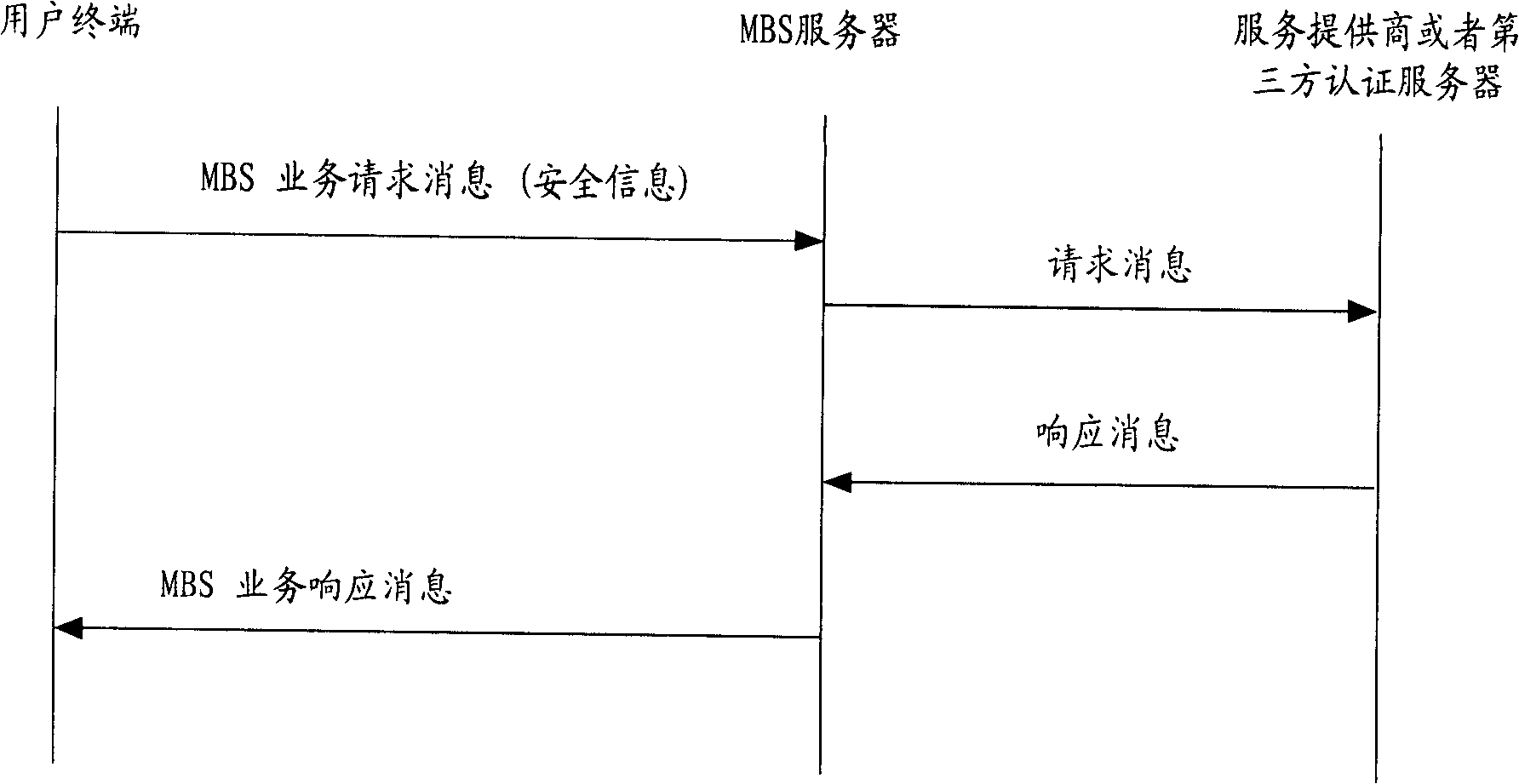
This invention provides a method and a system for realizing authentication authorization of MBS service including: a user terminal sends a MBS service authentication request to the MBS server including safety information used in verifying validity of user terminal identity, MBS enquires if it holds the safety information, if so, it judges if it is legal, if not, the MBS sends an authentication request to AAA server or a server of a third party to ask for verifying if the user terminal is a signed user and if the authentication request information to the AAA server or the third party server bythe MBS is legal, which reduces time of authority authentication of MBS service and prevents illegal attack effectively.
Owner:XFUSION DIGITAL TECH CO LTD
Enterprise business security processing system
InactiveCN107341661AEasy to promoteAvoid illegal attacksPayment protocolsSystem safetyInformation storage
The invention discloses an enterprise business security processing system. The enterprise business security processing system includes a central database system, a center server, a storage device, a CA certification center and a background service module. The central database system is connected with the central server. The central server is connected with the CA certification center. Information in the central database system is stored in the storage device. The central server is connected with the background service module. The enterprise business security processing system has the advantages that the system is secure, reliable and easy to promote, illegal attacks can be effectively prevented, data is conveniently received, stored and processed, the background service module is connected with the central server, the security of the system during an operation process is guaranteed, the speed of processing is increased, and demands are met.
Owner:太仓市华安企业管理有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com