Embedded partition image security authentication and kernel trusted boot method and device thereof
An embedded device and security certification technology, which is applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as inability to verify security, and achieve the effect of ensuring the uniqueness of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be described in further detail below in conjunction with the accompanying drawings, but it is not intended to limit the protection scope of the present invention.
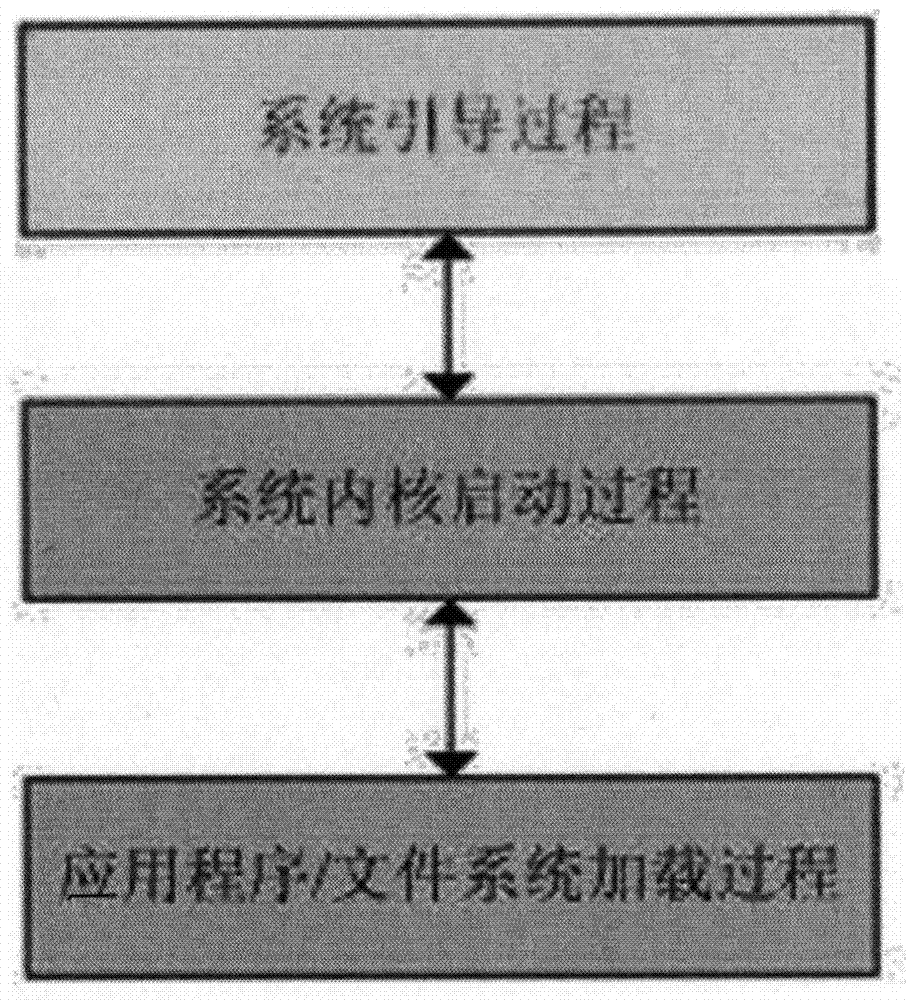
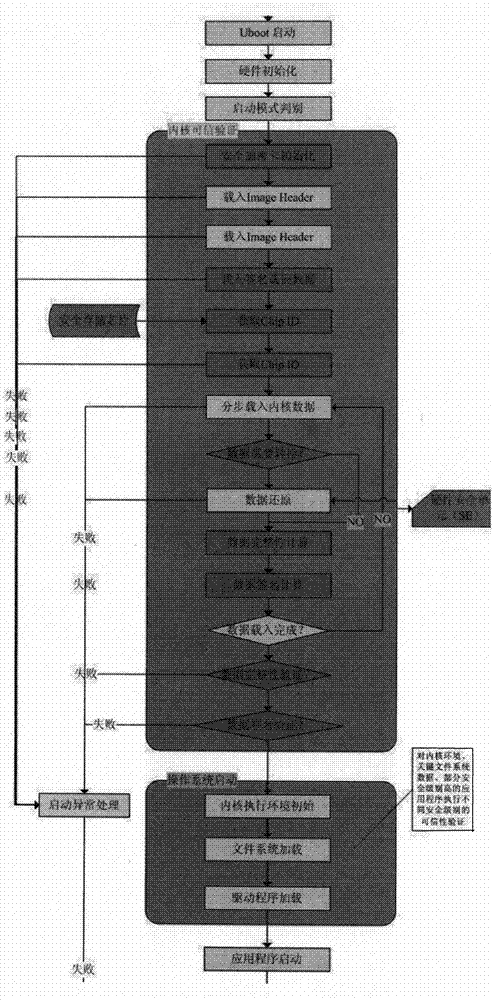
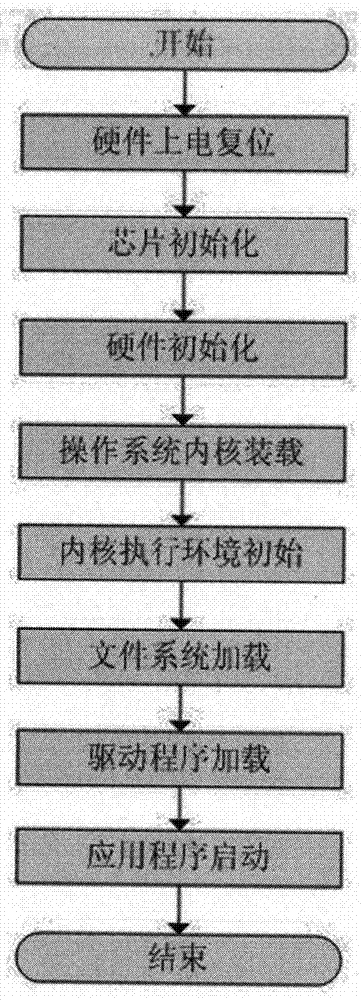
[0050] The present invention provides a set of new embedded system partition image security authentication, operating system kernel trustworthy guidance mechanism, this technical scheme is designed based on the embedded device platform of Android system; The loading domain has been security reinforced and reconstructed according to specific rules, including: realizing the system power-on and initialization phase, ensuring DMA / MMU / MPU / CACHE (I-CACHE / D-CACHE) / DDR / JTAG and other system storage, Physical isolation of processor cache and on-chip debugging system, system access control, etc., to prevent intruders from "bypass attacks" at this stage through physical technology, bus detection, etc., to ensure that the U-Boot partition is not maliciously tampered with; realize U-Boot The im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com