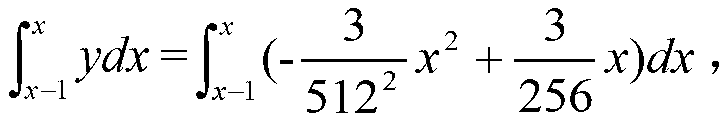Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
44results about How to "Achieve data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
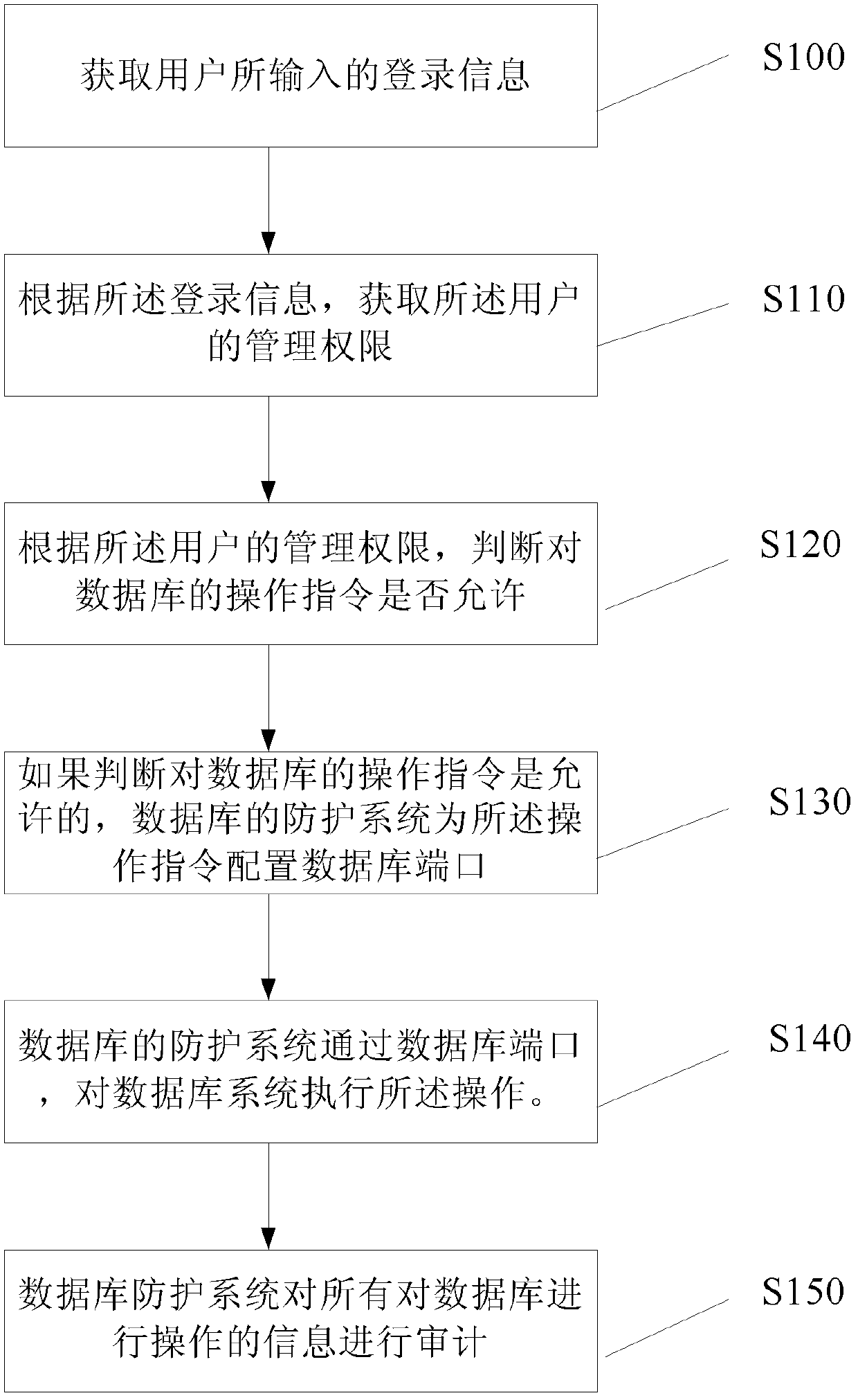
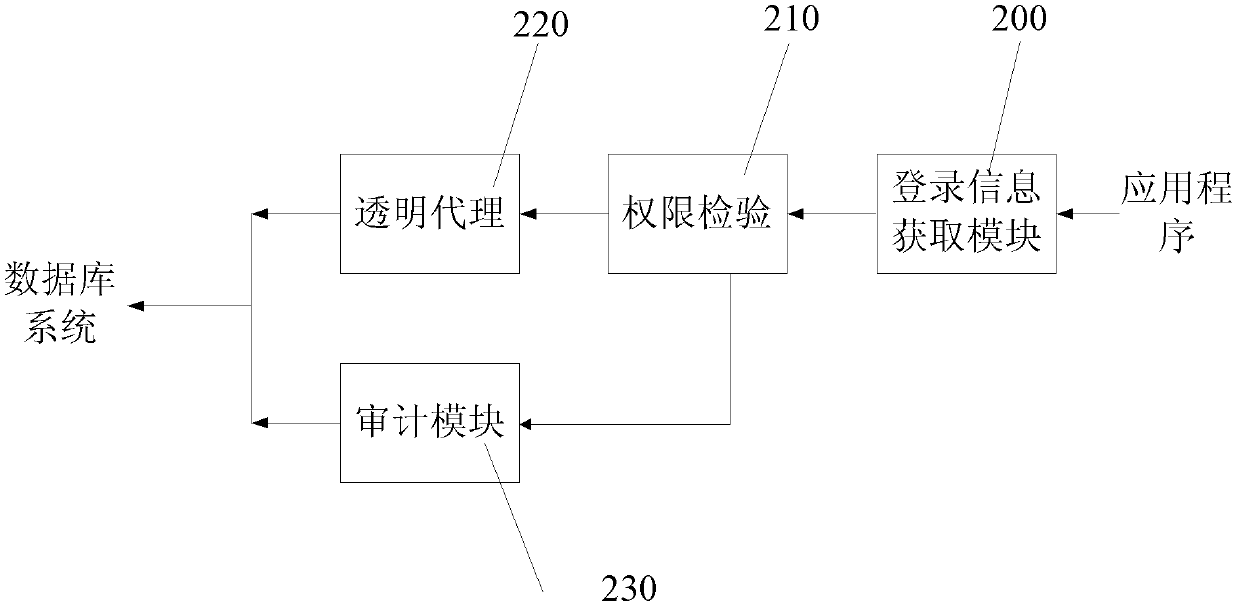
Protection method and system for database system
ActiveCN103310161ADeter unauthorized accessNo need to worry about password leakageDigital data protectionDatabase serverApplication software
The embodiment of the invention provides a protection method for a database system, comprising the steps that A, login information inputted by a user is obtained; B, whether an operational instruction is allowed for the database or not is judged according to the login information; C, if the judgment that the operational instruction is allowed for the database is made, a database protection system configures a database port for the operational instruction; D, the database protection system executes the operation to the database system through the database port. The embodiment of the invention also provides a protection system for the database system. With the database protection system, the database server and applications are isolated. All accesses to the database have to access the database protection system, so that a data transmission channel is shielded and cannot be directly utilized by an attacker.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Protection method for confidential files
InactiveCN102708326AAchieve data securityImprove reliabilityInput/output to record carriersDigital data protectionClient-sideData security
The invention discloses a protection method for confidential files and uses the sandbox principle for reference. When downloading files through a client program of a file management software, a user redirects the downloaded files into a virtual disk of a client computer and conducts all operations of scanning and editing files in the virtual disk; the modified and newly-created files during the file operation process are controlled to be redirected into the virtual disk and the courses not performed the redirected control are forbidden to access to the virtual disk; and finally, the edited files are uploaded to a server from the virtual disk to complete a process of file modification. The user can normally use the files in the virtual disk, but cannot copy or dump the files out, and the virtual disk is like a sandbox only importing but not exporting. The security software developed by using the method can be integrated with the file management software of a third party, so as to realize secure use and anti-disclosure of the confidential files on the client computer and improve the level of data security management of the user.
Owner:南京赛孚科技有限公司
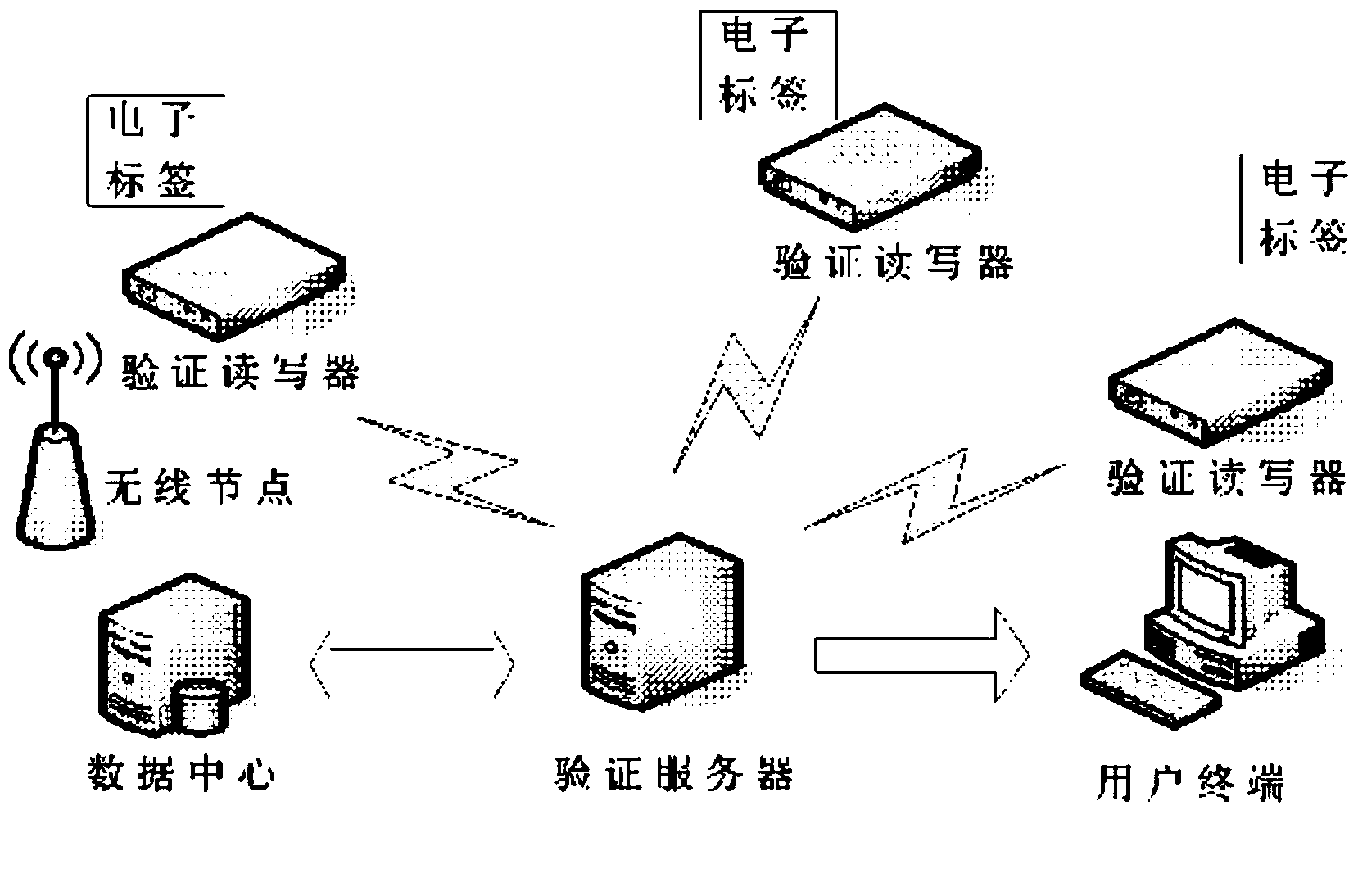
RFID (Radio Frequency Identification Device) data transmission and authentication system and method
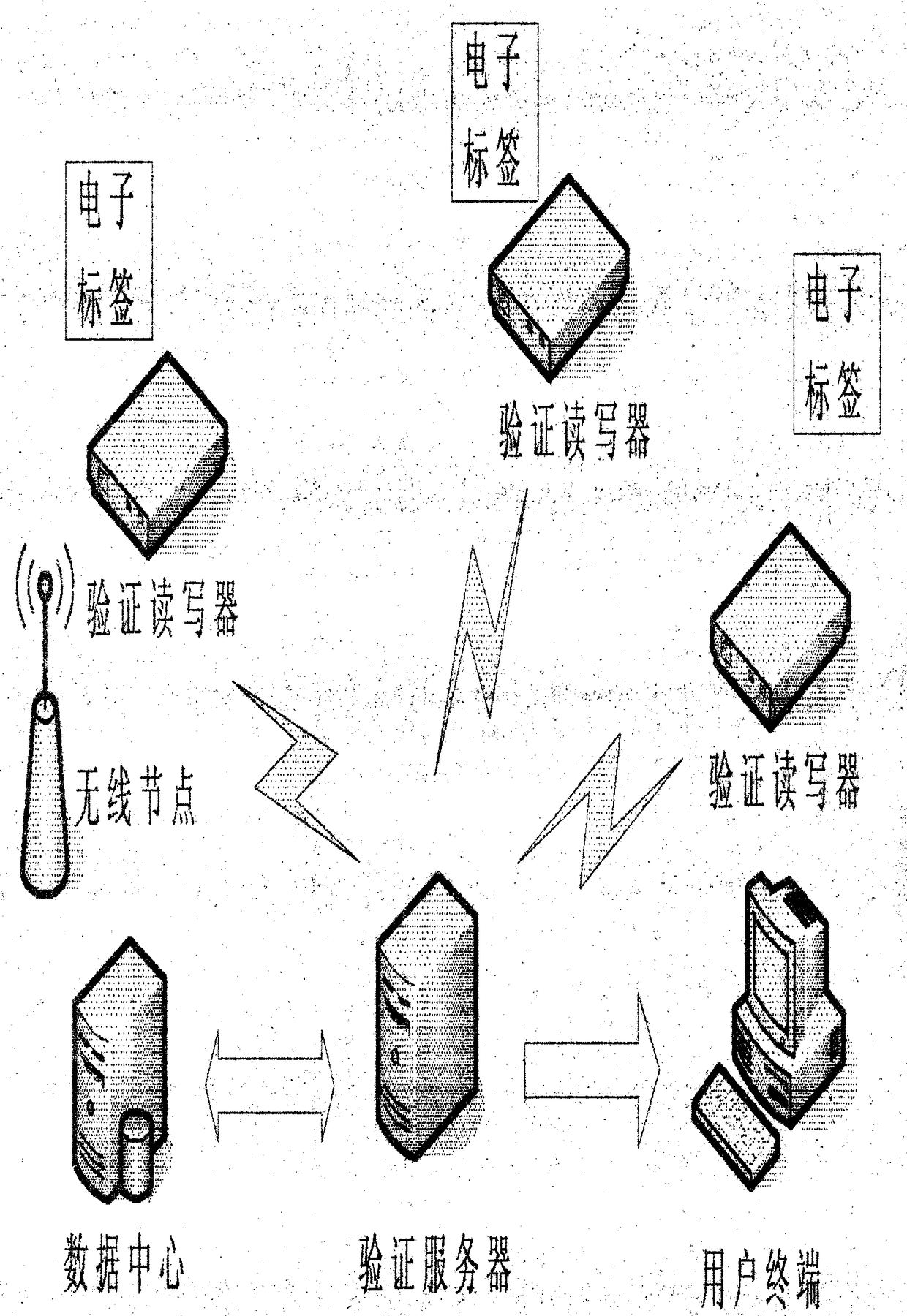
ActiveCN102646203AProtection securityAchieve data securityUser identity/authority verificationCo-operative working arrangementsComputer hardwareData center
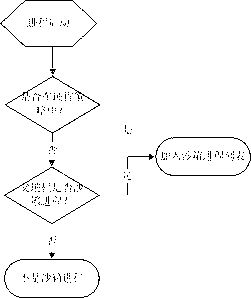
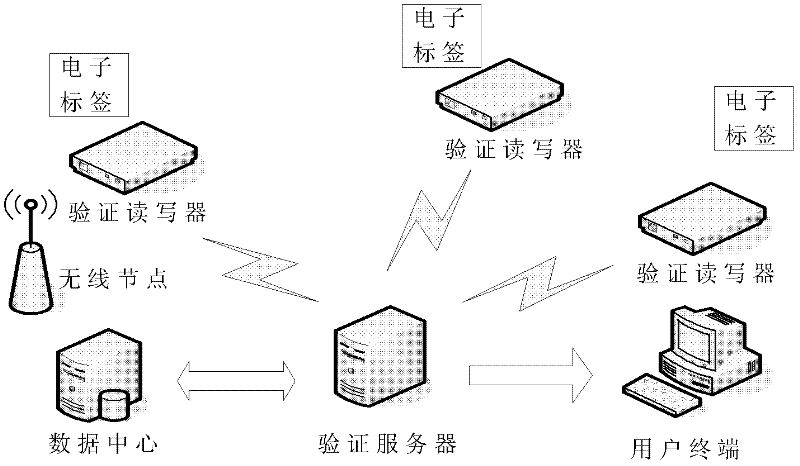
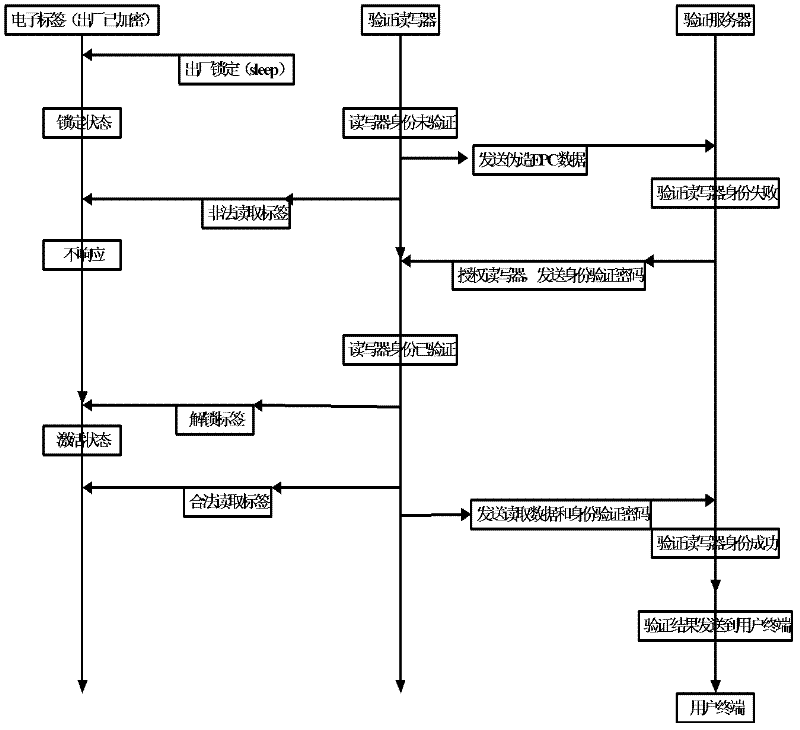
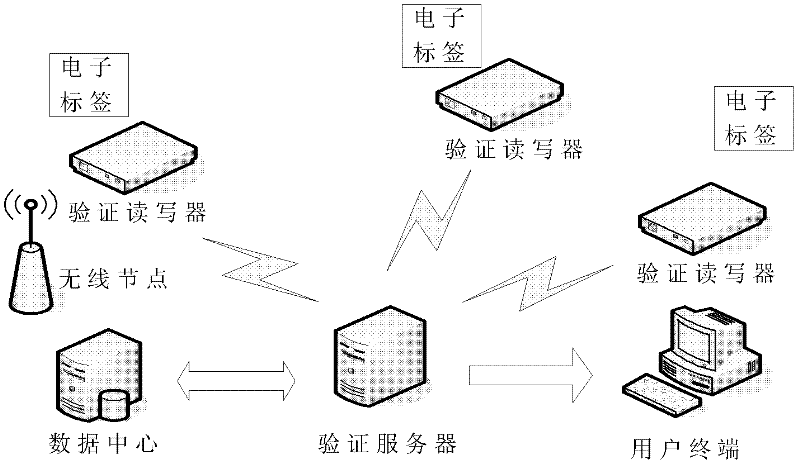
The invention discloses an RFID (Radio Frequency Identification Device) data transmission and authentication system and method. The RFID data transmission and authentication system comprises a checking reader-writer system at a user terminal and a background checking server system, wherein the checking reader-writer system at the user terminal comprises a checking reader-writer and an electronic tag; and the background checking server system comprises a checking server and a data center. Based on the data transmission and authentication system, the RFID data safe transmission and authentication method comprises the steps of a preparation stage of the electronic tag and a radio frequency identification field stage of the electronic tag. According to the RFID data transmission and authentication system and method, by using an electronic tag sleeping technology and combining with a private key encrypted EPC (Electronic Product Code), checking reader-writer identification and background server authentication as well as matching with a passive ultra-high frequency electronic tag, practicability for various kinds of special application occasions is enhanced, the security of target information is effectively protected, application cost is lowered, and RFID data security and a function of anti-counterfeiting identification are realized.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
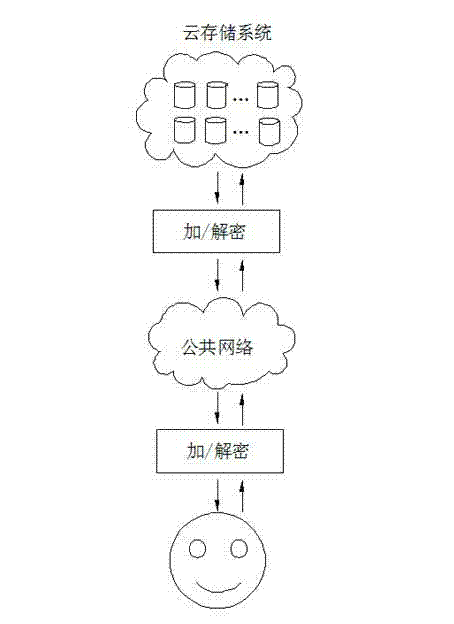
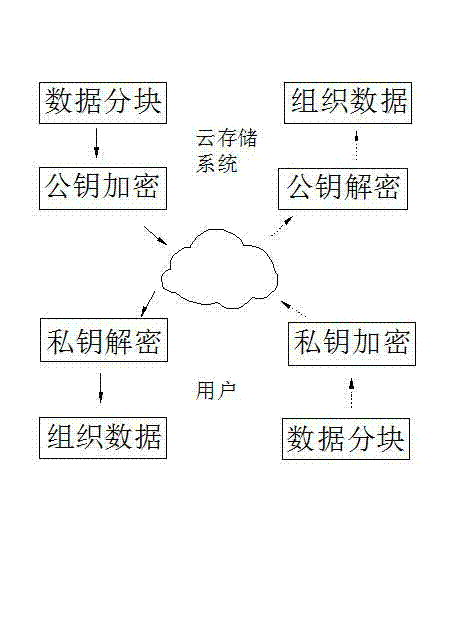
Method for realizing secure transmission of data in cloud storage system
InactiveCN102857338AGuaranteed privacyEnsure data securityKey distribution for secure communicationService systemData transmission
The invention provides a method for realizing the secure transmission of data in a cloud storage system. According to the method, when in the actual data transmission, the data are subjected to encryption through a symmetric algorithm or an asymmetric algorithm according to the size of the transmitted data volume; when mass data are transmitted, the data are subjected to encryption and decryption through the symmetric algorithm in order to ensure the throughput; and when a small amount of data are transmitted, the data are subjected to encryption and decryption through the asymmetric algorithm. The method is applied in the cloud storage system, so as to ensure the security of the data when the data are transmitted between a user and a cloud storage service system, thereby ensuring the privacy of the data of the user and realizing the real data security.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
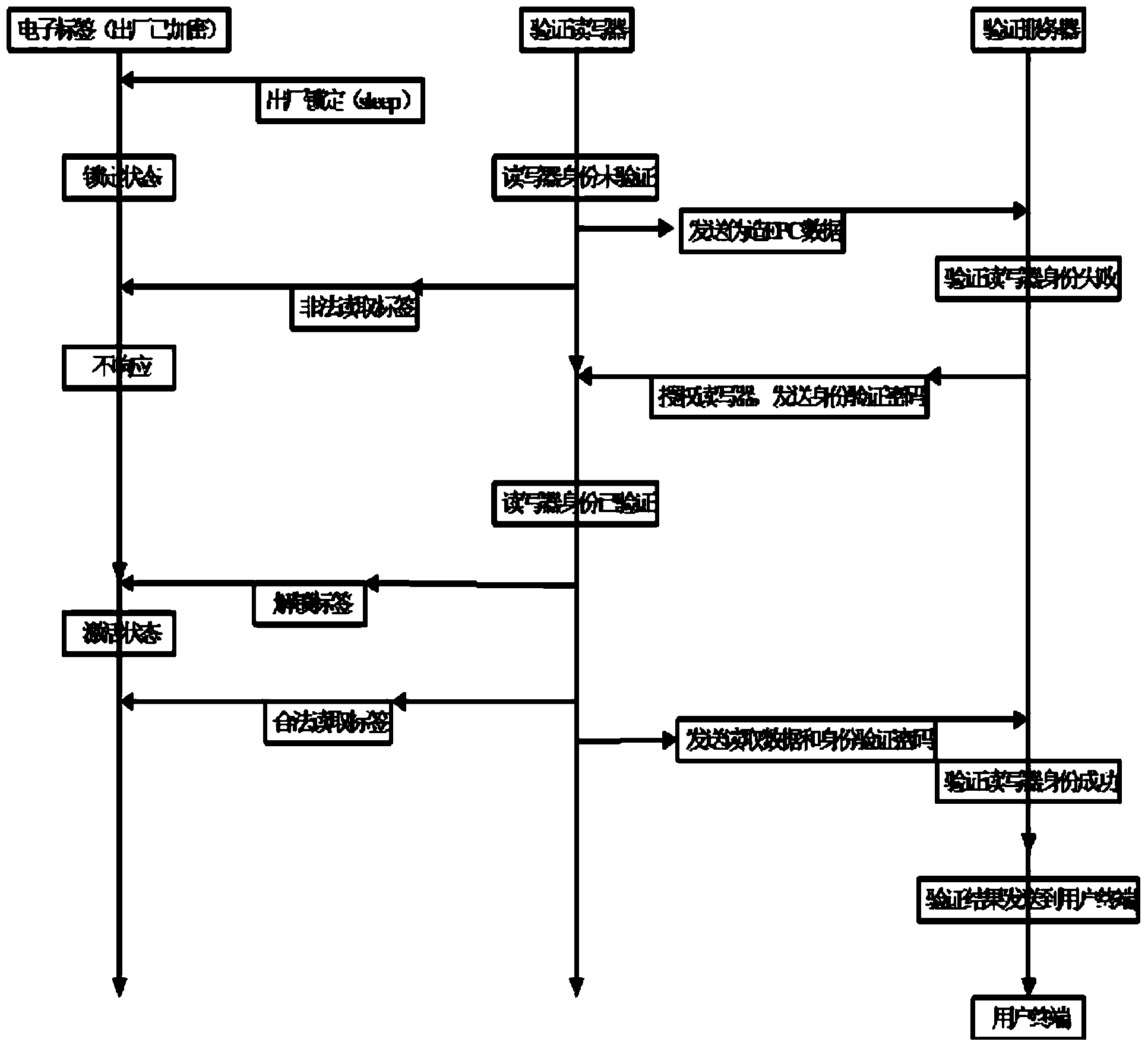
Data safe transmission system and method based on electronic tag
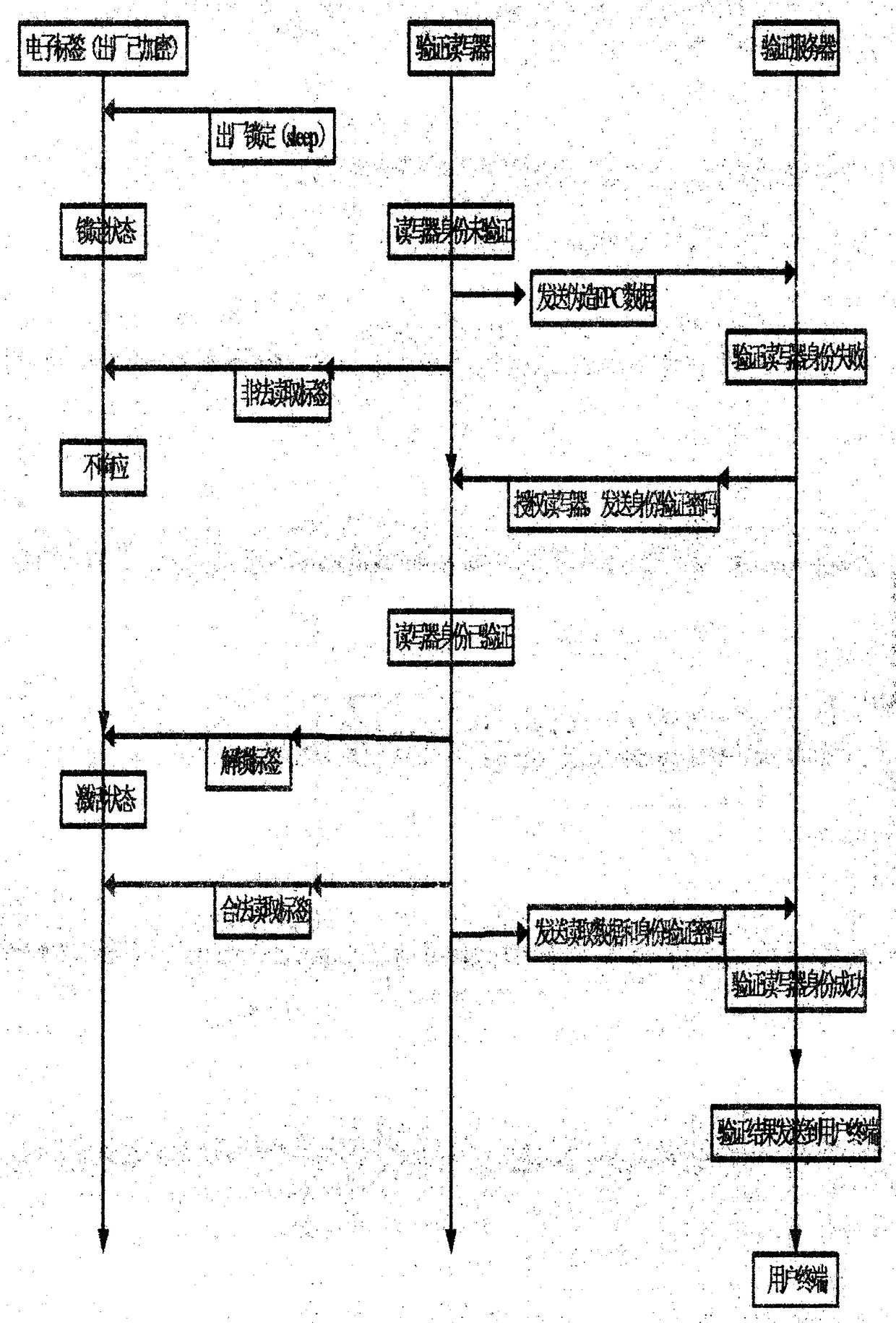
InactiveCN103516520AImprove practicalityProtection securityUser identity/authority verificationSensing record carriersRadio frequencyData transmission
The invention provides a data safe transmission system and method based on an electronic tag. The method comprises the steps of electronic tag generation and electronic tag identification. The generation step of the electronic tag is used for generating the electronic tag. Under the sleep condition of the electronic tag, requirements of any readers can not be responded, information of the electronic tag is prevented from being pried upon by illegal readers, a legal reader sends a sleep release code to a radio frequency electronic tag to attempt to activate the sleep tag to read tag data, after the tag data are successfully read, and the tag data and an identify identification code are together uploaded to a verification server. The identification step of the electronic tag is mainly used for reading encryption information of the electronic tag, and identifying the electronic tag through the encryption information. Through identification and verification of the electronic tag, safety of data transmission is effectively protected.
Owner:张家港市速达电子商务有限公司
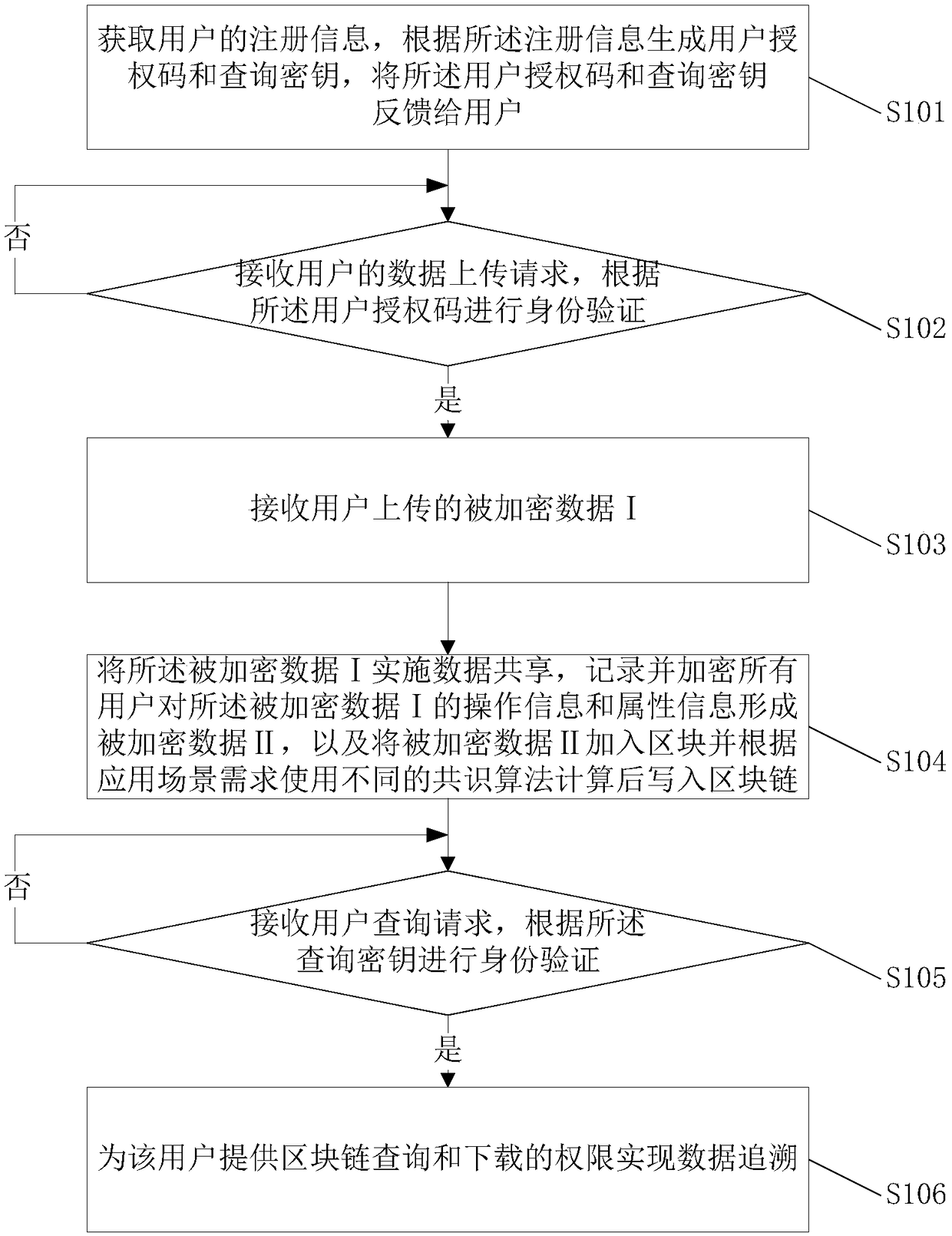
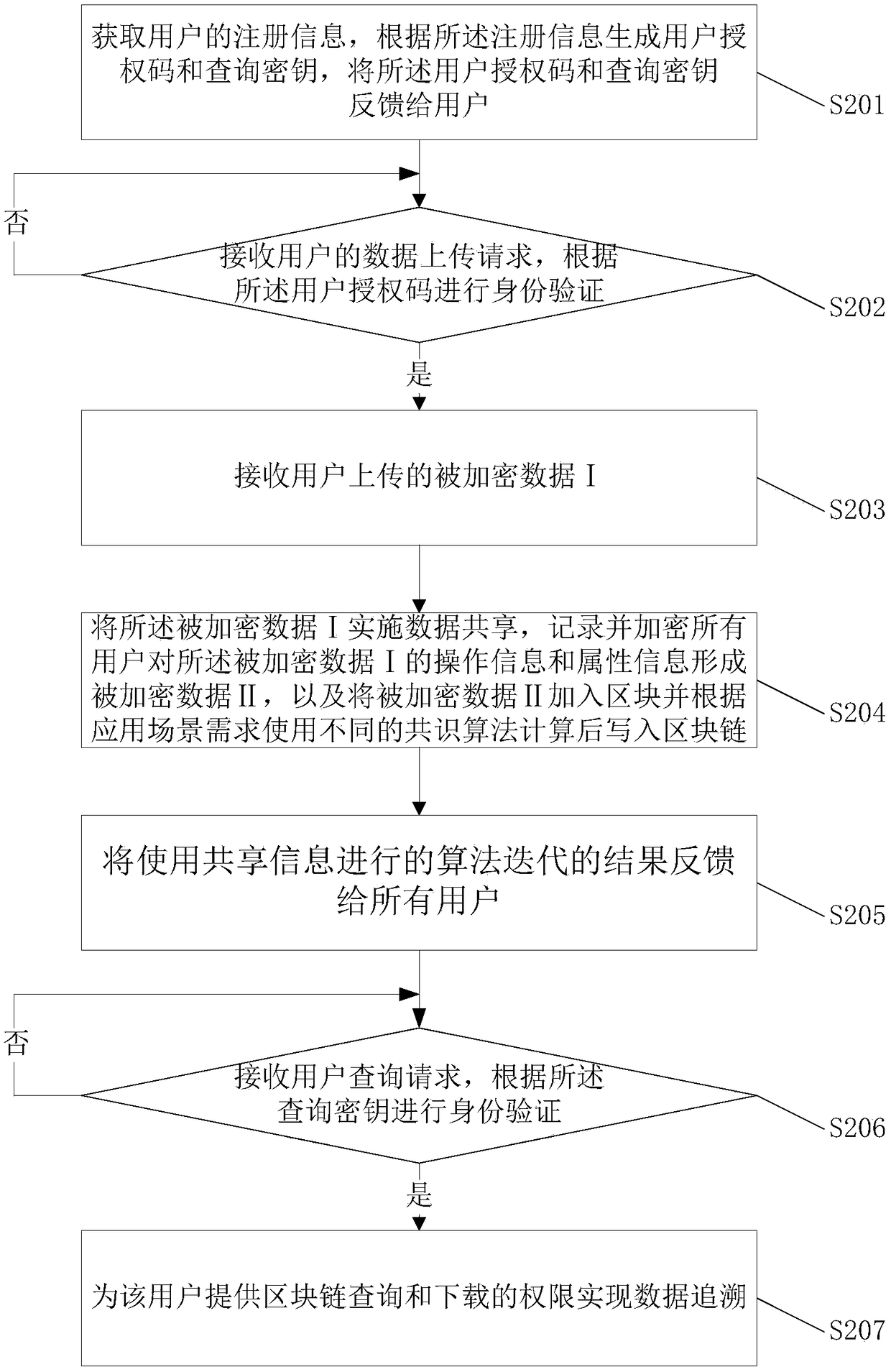
Blockchain-based data traceability and strong encryption method, device, medium and system
InactiveCN108449336AGuarantee data privacy and securityStrong Encryption ImplementationTransmissionBlockchainData security
The invention relates to the field of blockchain technology applications, and discloses a blockchain-based data traceability and strong encryption method and device, a medium and a system. The methodincludes the following steps: acquiring user registration information, generating a user authorization code and a query key according to the registration information, and returning the data back to users; receiving data upload requests of the users, and then receiving encrypted data I uploaded by the users who pass the verification; performing data sharing on the encrypted data I, recording and encrypting operation information and attribute information of all users on the encrypted data I to form encrypted data II, adding the encrypted data II to a block, calculating the encrypted data II by using different consensus algorithms according to application scenario requirements, and then writing the calculated encrypted data II to a blockchain; and receiving a user query request, performing identity authentication according to the query key, and providing blockchain query and download permissions for the users who pass the authentication to achieve data traceability. According to the scheme of the invention, the users can benefit from added values brought by shared data, and can also enjoy complete data privacy and data security.
Owner:ZHEJIANG CHUANGLIN TECH CO LTD
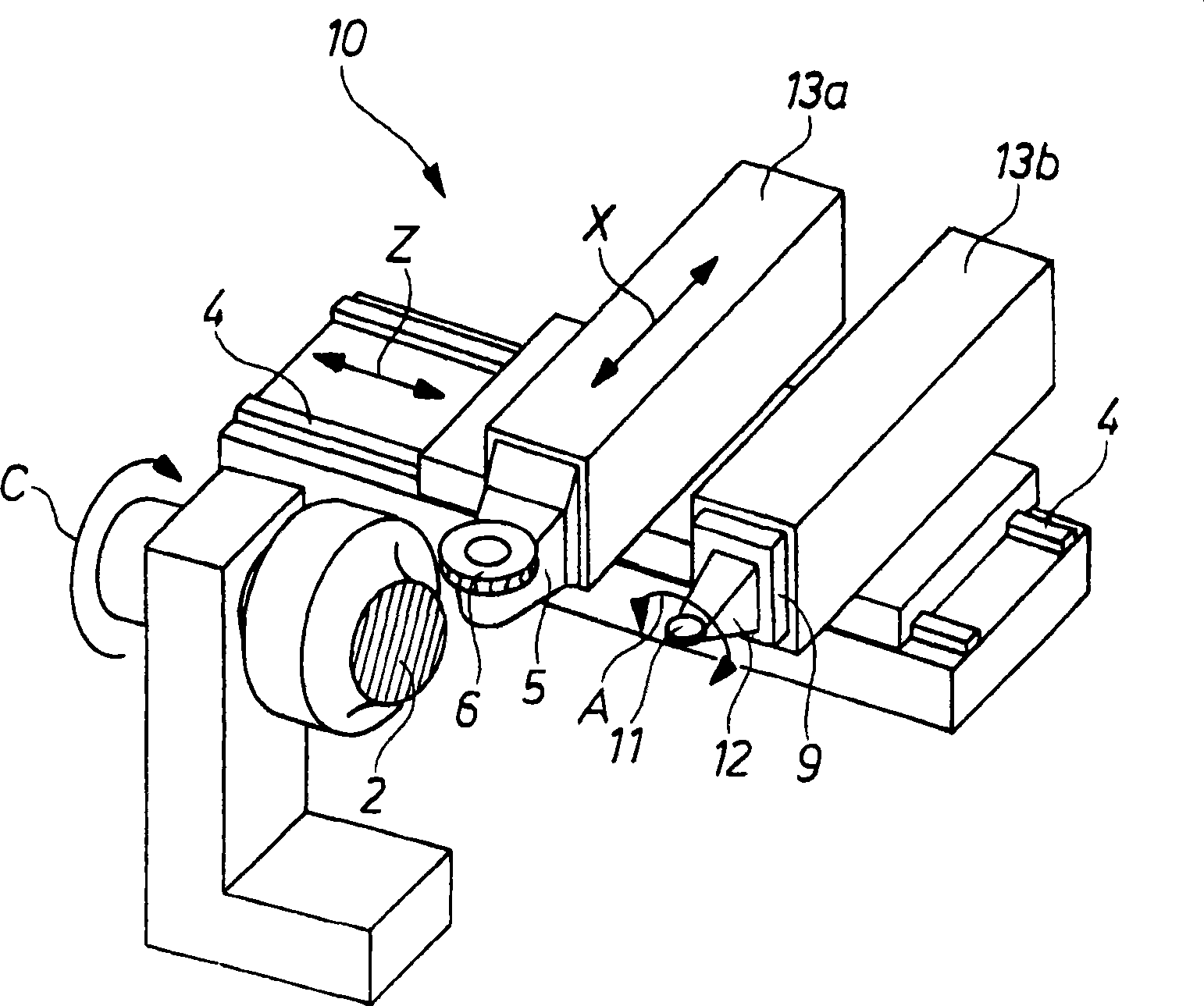
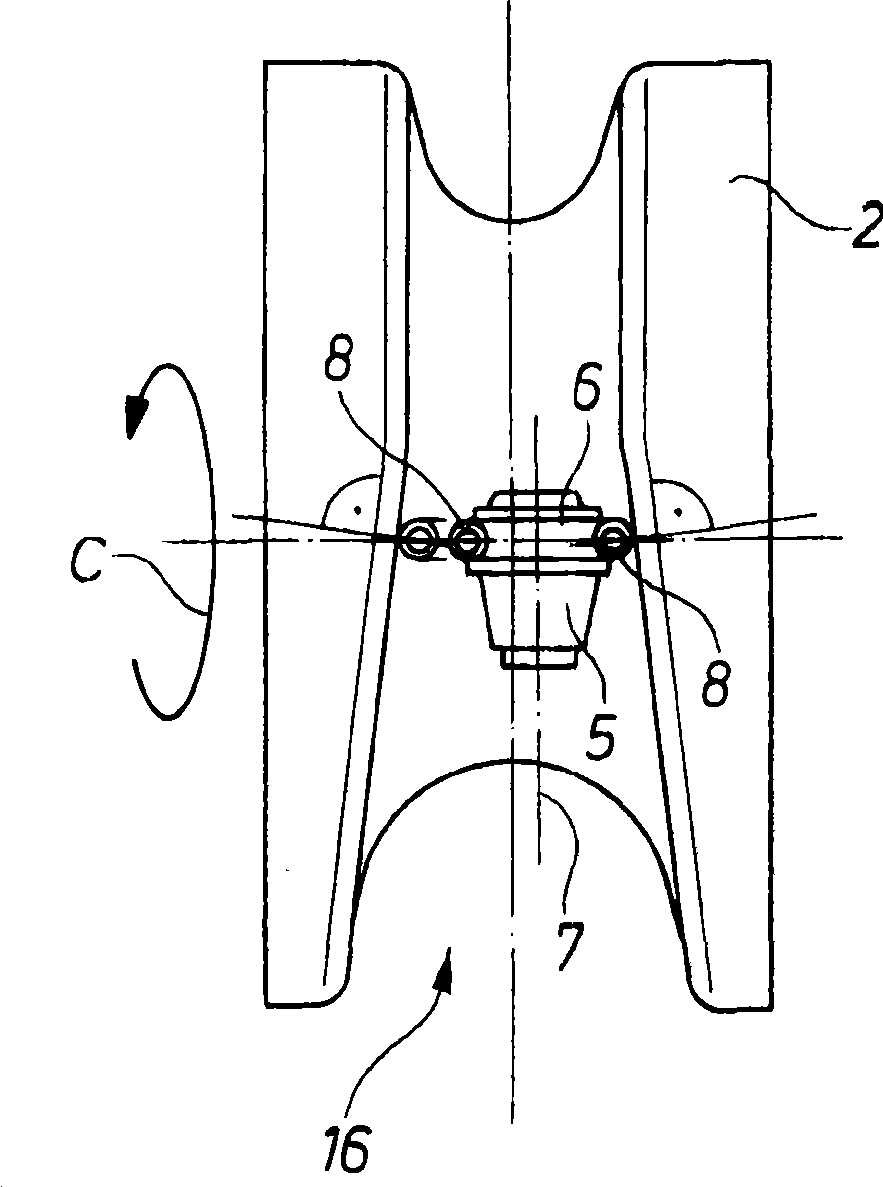
Method and processing machine for tensioned processing of complex contours of asymmetric workpieces
InactiveCN101502925ALow costAchieve data securityAttachable milling devicesMilling equipment detailsEngineeringSymmetrical contour
The invention relates to a method and a processing machine for tensioned processing of complex contours of asymmetric work pieces, specially relates to a method and a processing machine for tensioned processing complex contours of asymmetric work pieces such as pilger rolling on a computer-controlled processing machine. In prior machinery design, complex contour can be obtained by the same cutting speed of cutters and relatively low acceleration force. According to the invention, the method involves machining a work piece by turning and milling with circular plates (11) as a cutting tool on amachine, wherein a tuning is carried out for rotationally symmetrical contour areas of the work piece, and a milling is carried out for asymmetrical contour areas of the work piece.
Owner:SMS MEER
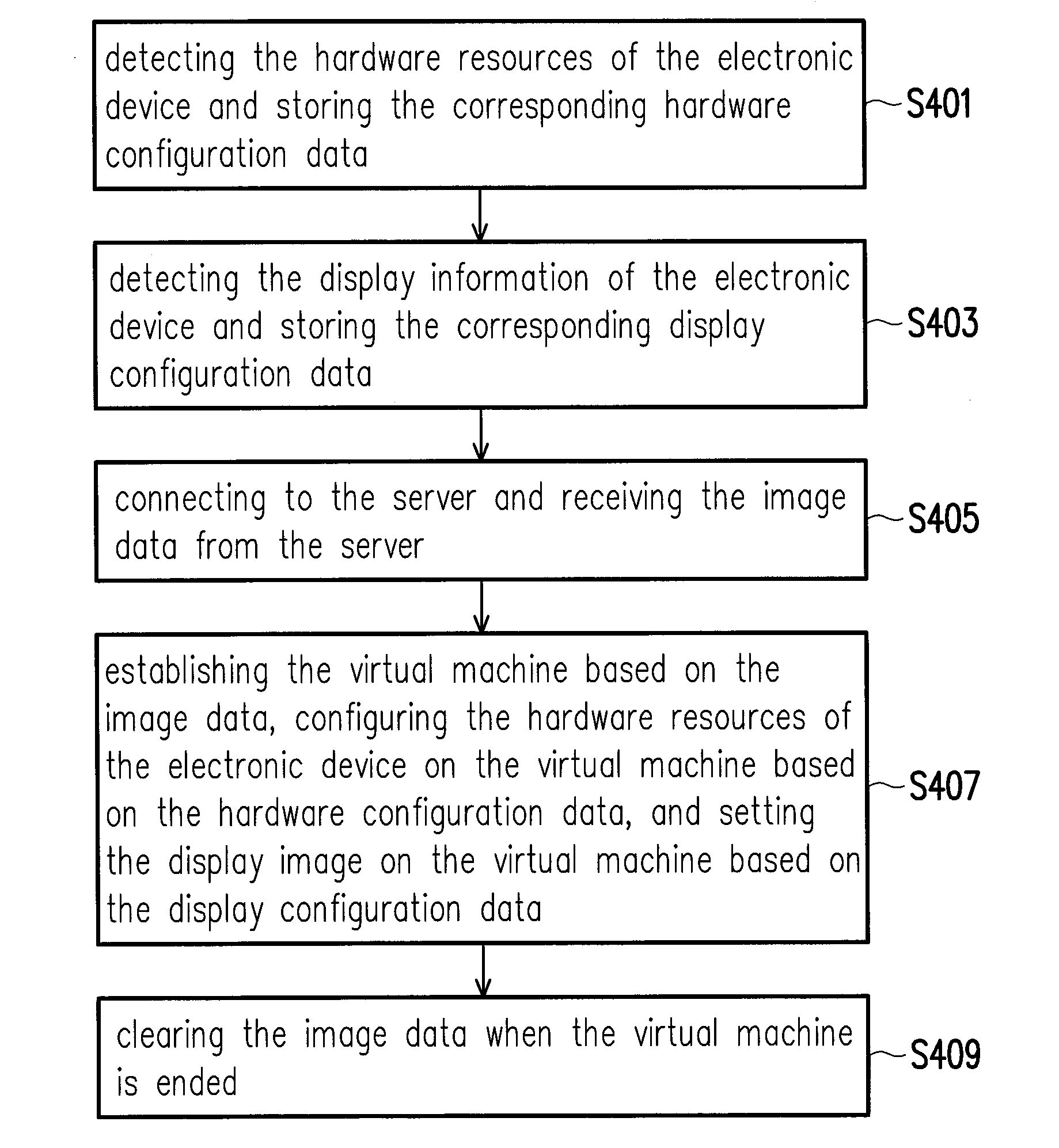
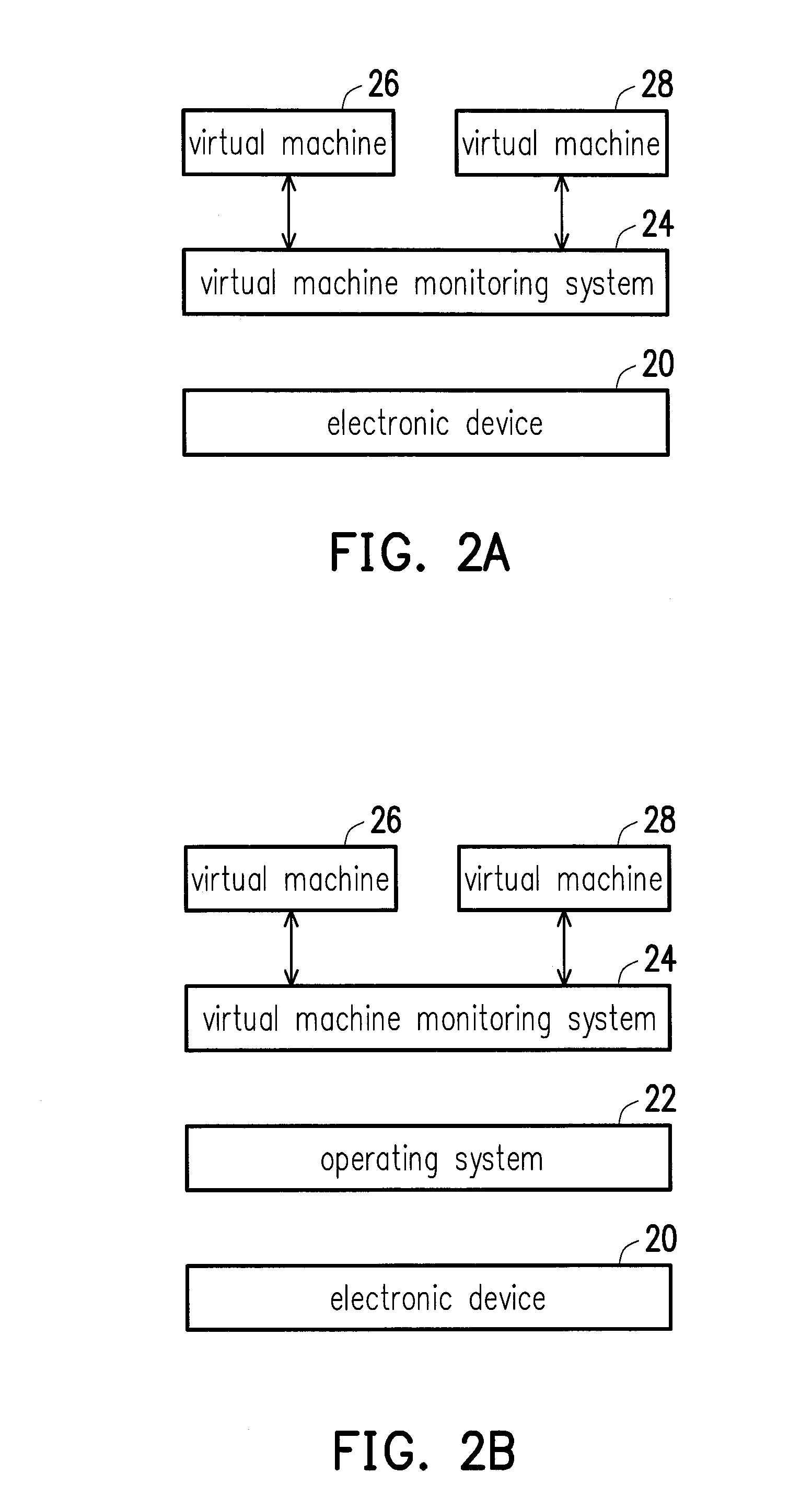
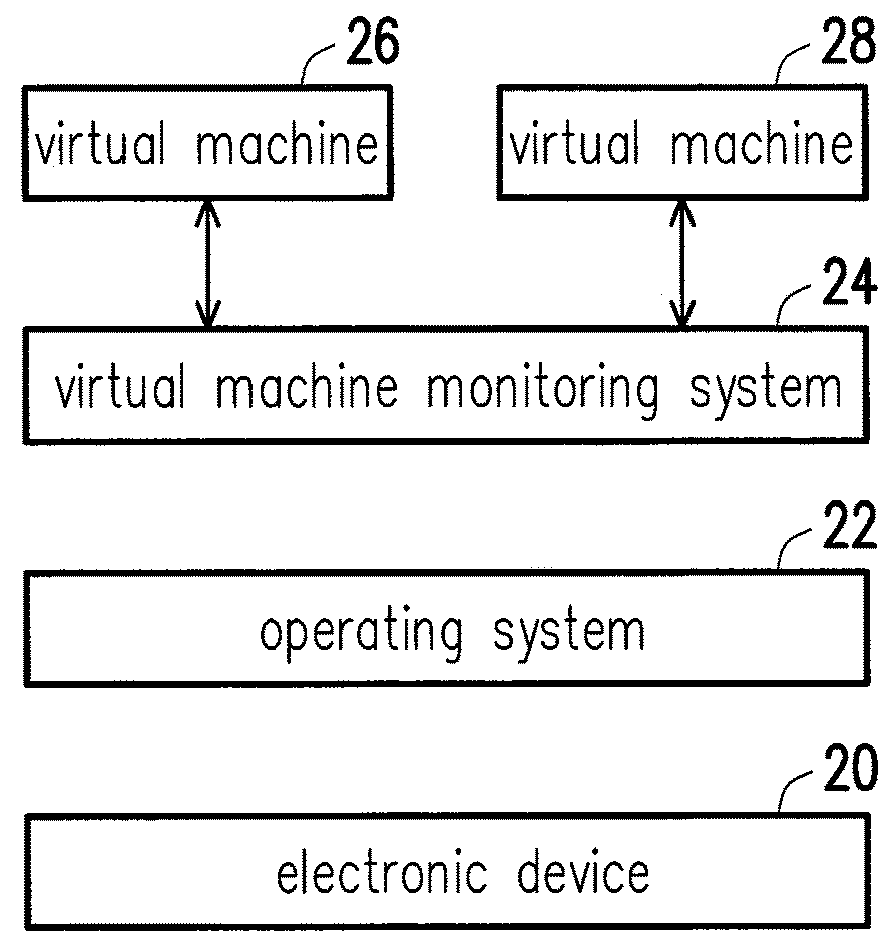
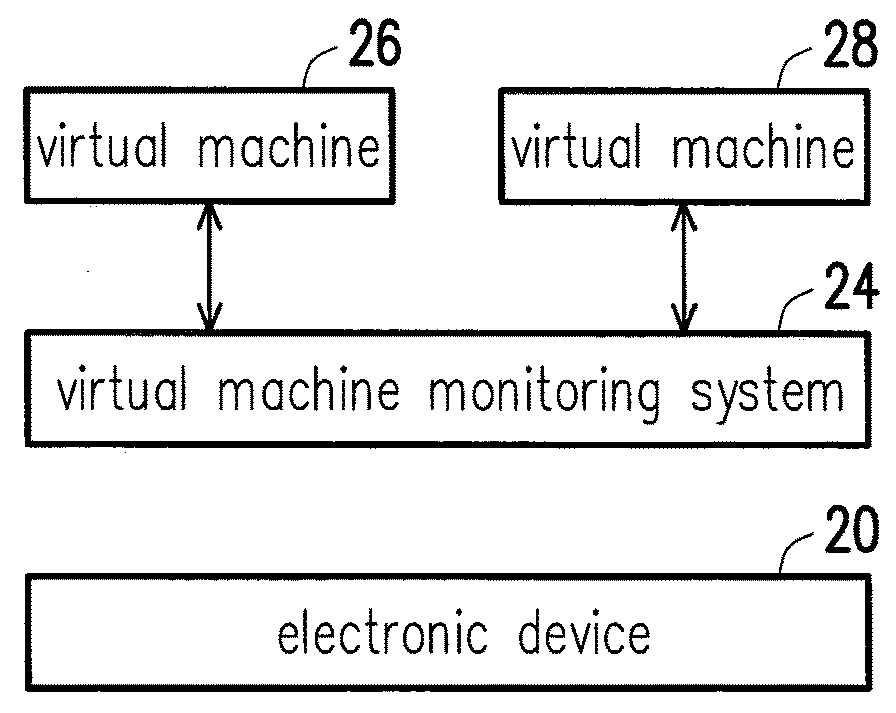
Virtual machine monitoring method and system thereof
ActiveUS20160110213A1Achieve data securityEasy to manageTransmissionSoftware simulation/interpretation/emulationUser FriendlyImaging data
A virtual machine monitoring method and a system thereof are provided. The virtual machine monitoring method includes: detecting at least one hardware resource of an electronic device and storing corresponding hardware configuration data, detecting display information of the electronic device and storing corresponding display configuration data, connecting a server and receiving image data therefrom, establishing a virtual machine based on the image data, configuring the at least one hardware resource on the virtual machine based on the hardware configuration data, setting a display image on the virtual machine based on the display configuration data, and clearing the image data to end the virtual machine, so as to provide a user-friendly interface and achieve corporate data security.
Owner:WISTRON CORP
Data producing method and electronic device thereof
ActiveUS20110141127A1Avoid confusionCharacteristic is differentCathode-ray tube indicatorsNon-linear opticsElectricityData display
Owner:WISTRON CORP
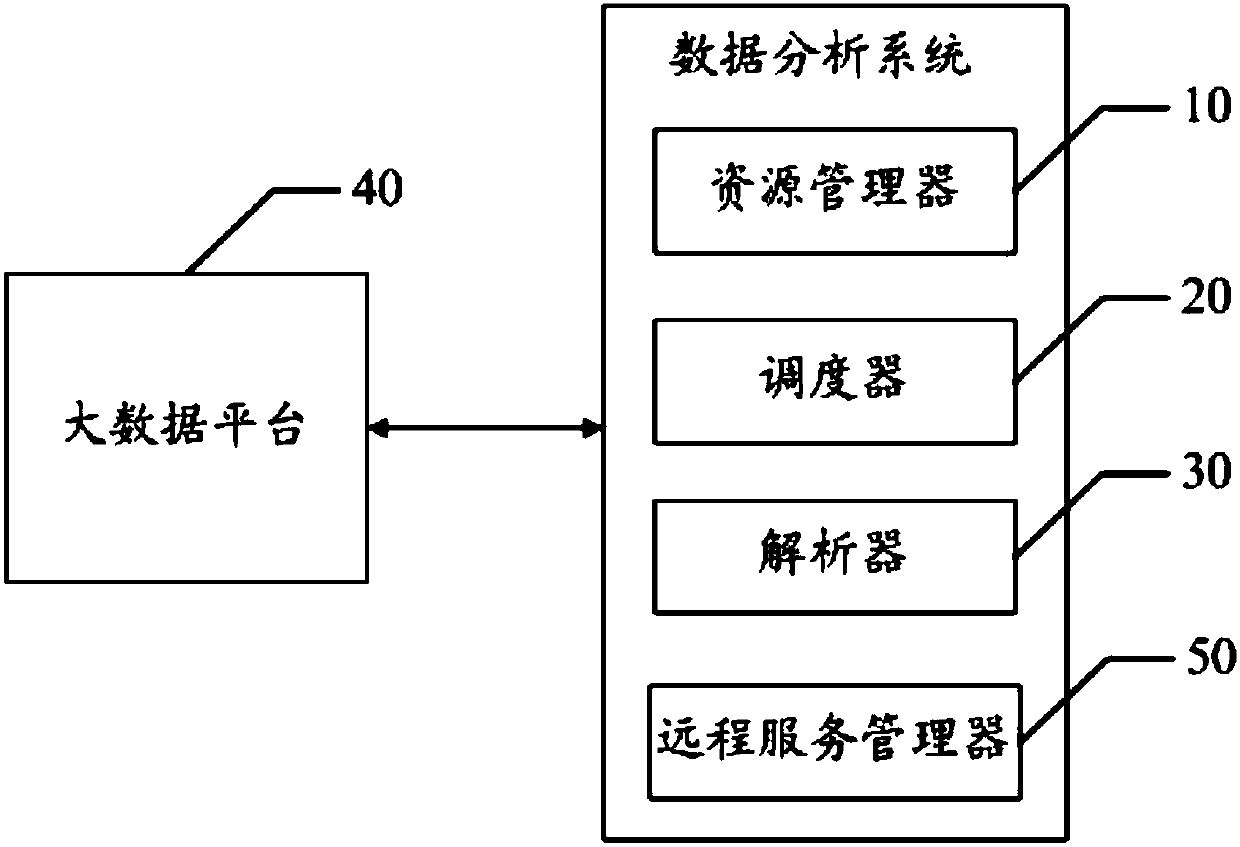
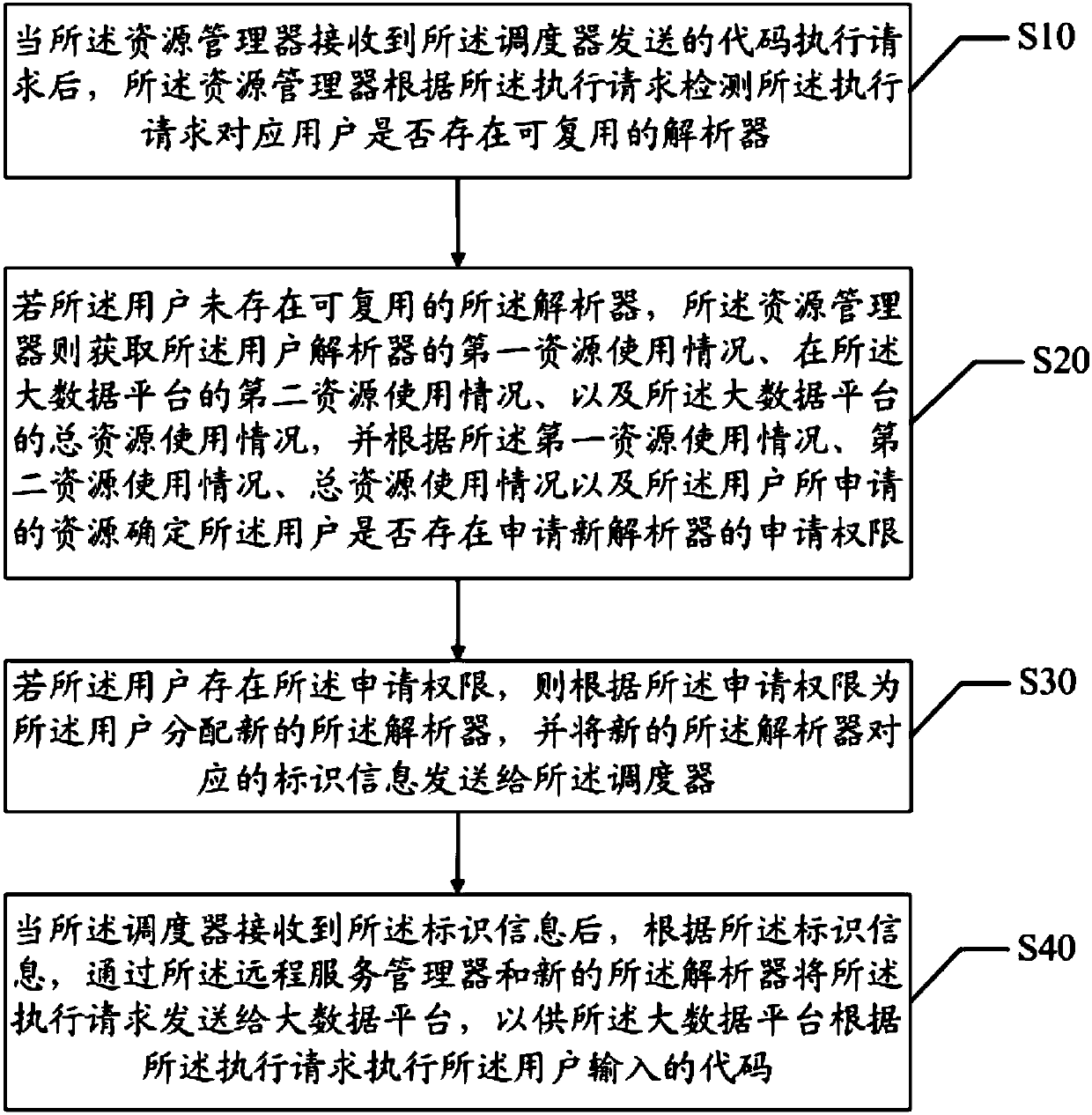
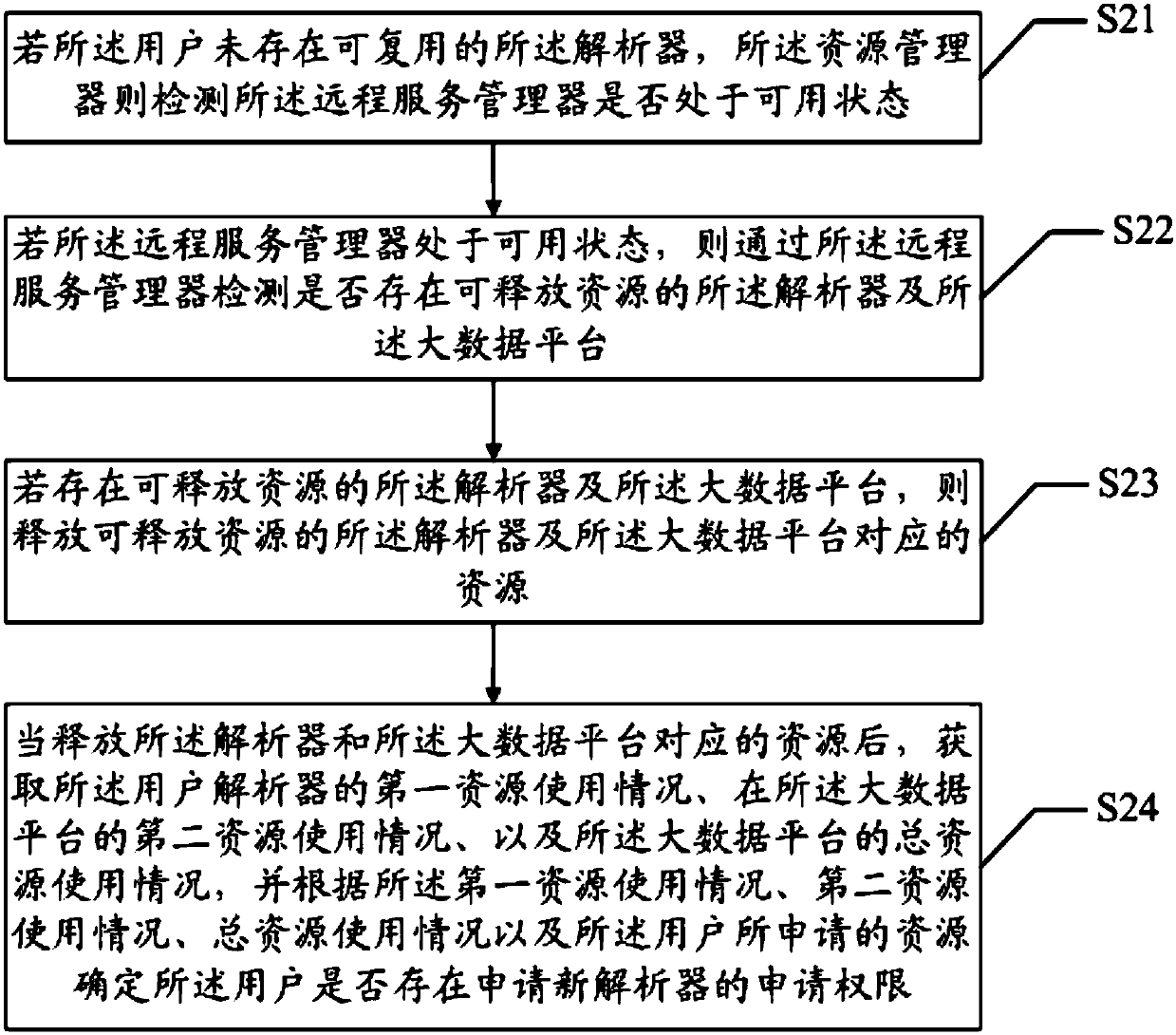
Resource management method and system for data analysis and readable storage medium
ActiveCN108037984AReduce complexityAchieve data securityProgram initiation/switchingData platformUser input
The invention discloses a resource management method and system for data analysis and a readable storage medium. The method comprises the steps that a resource manager detects that corresponding usershave no reusable parser according to a code execution request which is sent by a scheduler, the resource use condition of the users and the total resource use condition of a big data platform are acquired, and according to the resource use condition of the users, the total resource use condition and resources which are applied by the users, whether or not the users have application permissions for applying new parsers is determined; if yes, the new parsers are distributed to the users according to the application permissions, and identification information of the new parsers is sent to the scheduler; the scheduler sends an execution request to the big data platform through a remote service manager and the new parsers according to the received identification information, so that the big data platform executes codes which are input by the users according to the execution request. According to the resource management method for data analysis, the resources among different users are separated through the parsers, and the resources are dynamically distributed for the users.
Owner:WEBANK (CHINA)
Business data processing method based on block chain, related system and node
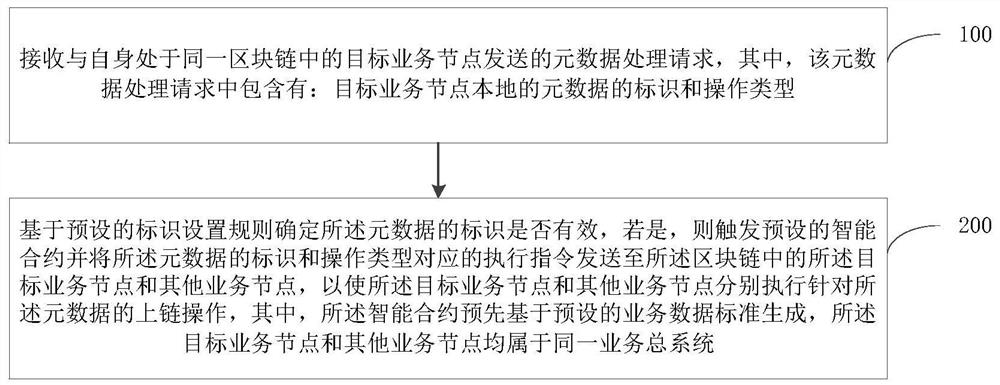
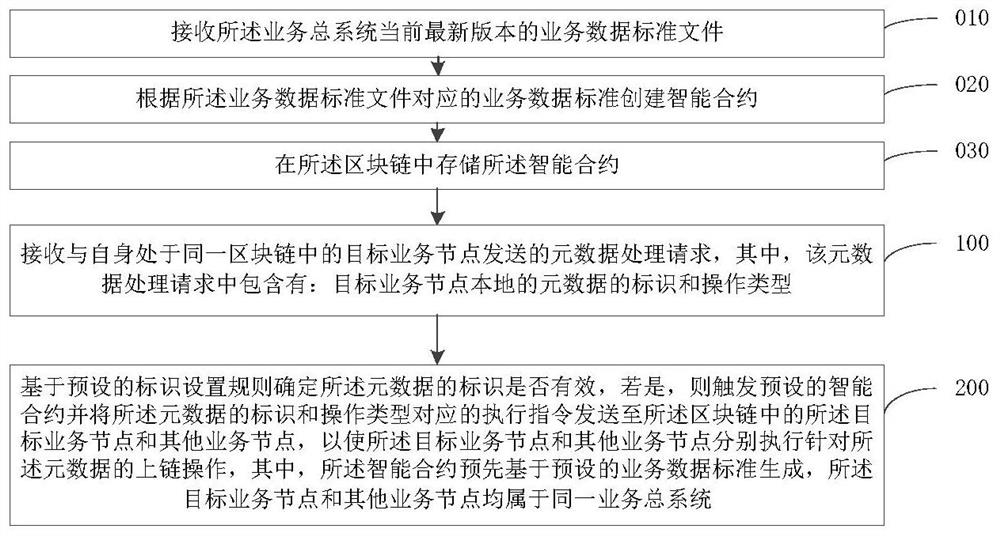
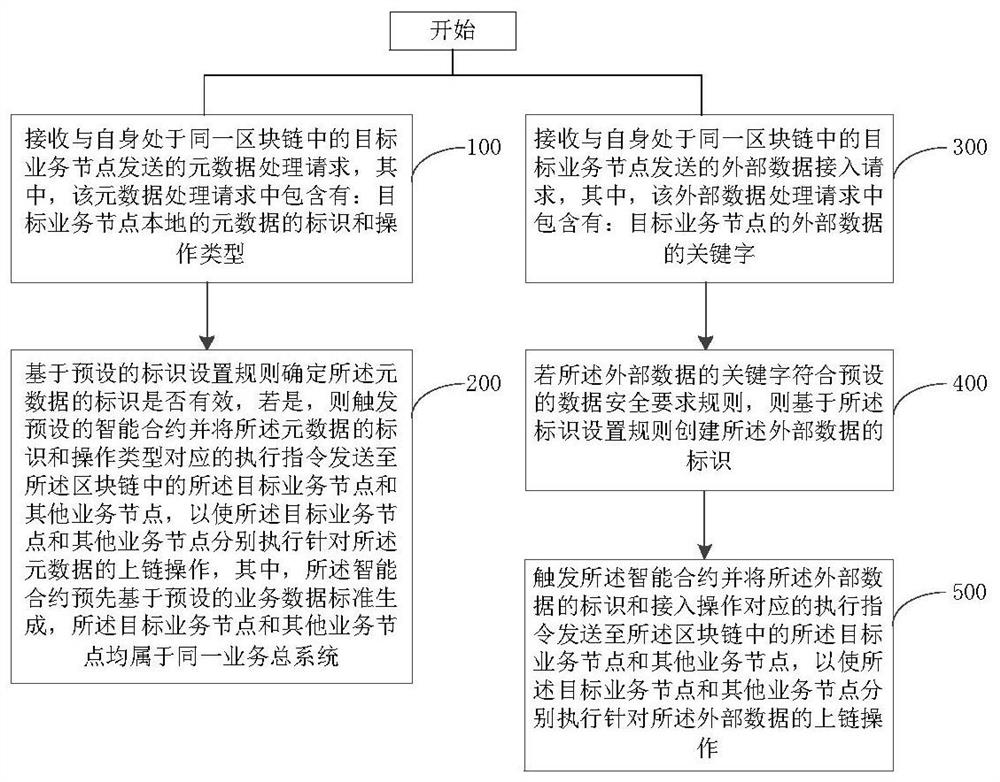
PendingCN113034281AImprove securityImprove data standardizationFinanceDigital data protectionData criteriaComputer network
The embodiment of the invention provides a business data processing method based on a block chain, a related system and a node, which can be applied to the technical field of block chains, and the method comprises the following steps: receiving a metadata processing request sent by a target business node in the same block chain with the target business node; and determining whether the identifier of the metadata is valid based on a preset identifier setting rule, if so, triggering a preset smart contract, and sending an execution instruction corresponding to the identifier of the metadata and the operation type to a target service node and other service nodes in the block chain, the target business node and the other business nodes are enabled to execute the uplink operation for the metadata, and the smart contract is generated in advance based on a preset business data standard. According to the application, the security of business data processing, the reliability, the efficiency and the effectiveness of data processing standardization and business metadata management can be effectively improved, so that collaborative governance of the data security, the data standardization and the metadata management can be realized.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
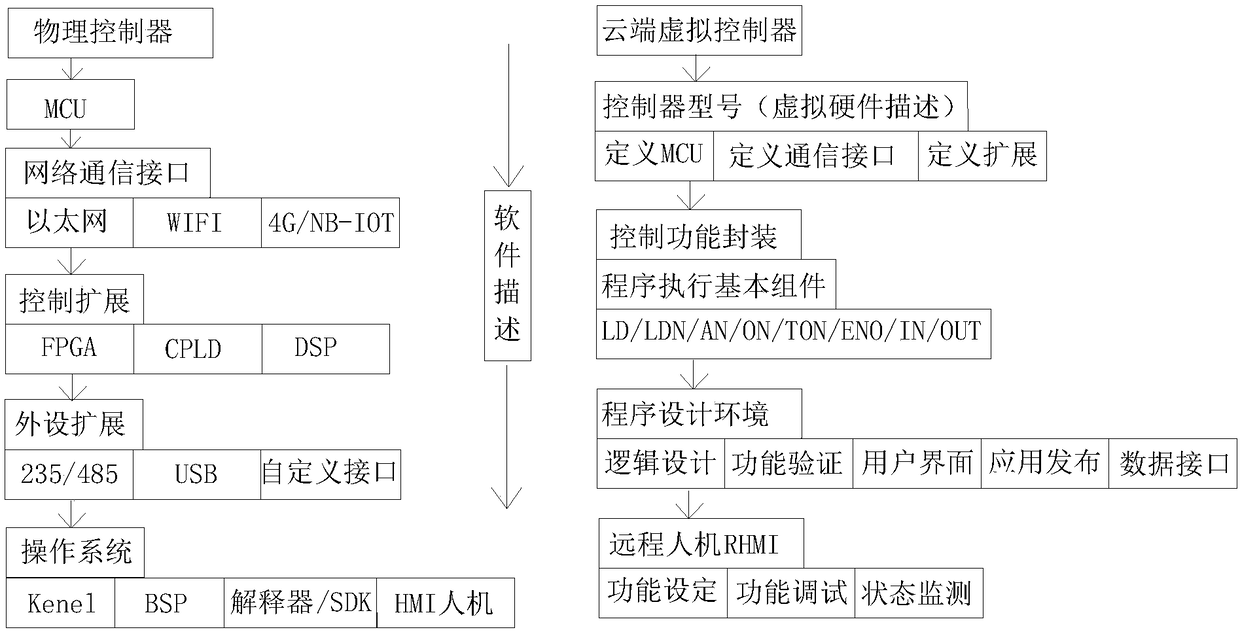
Software-defined network type industrial controller
InactiveCN108241304AConvenient networking needsRealize data collectionSimulator controlControl layerControl system
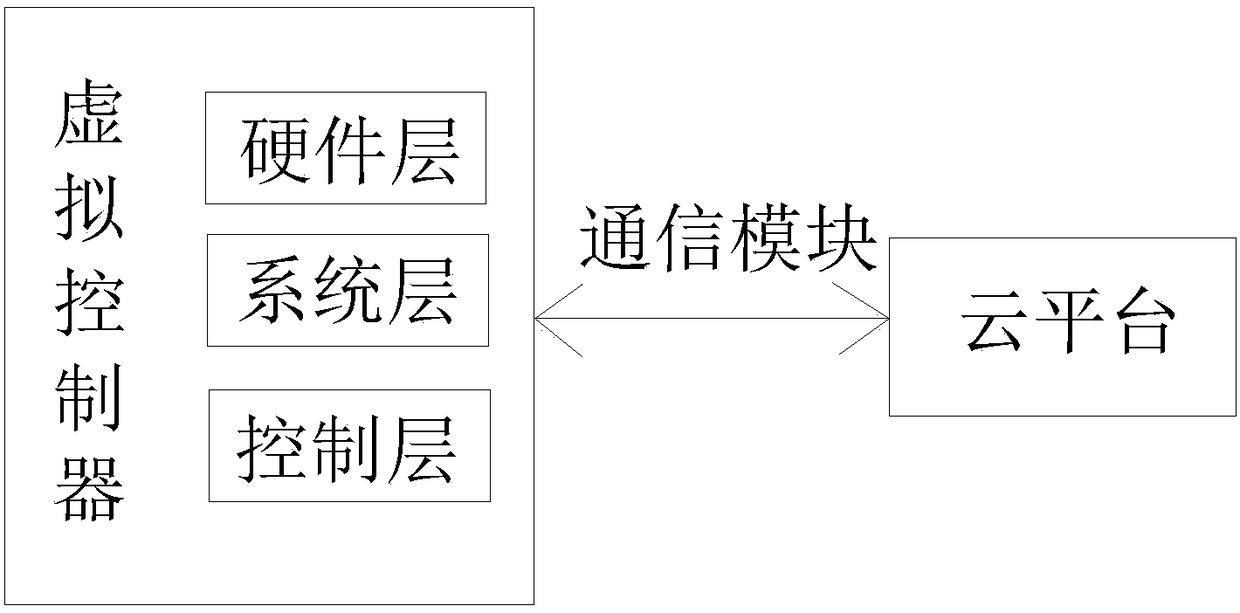
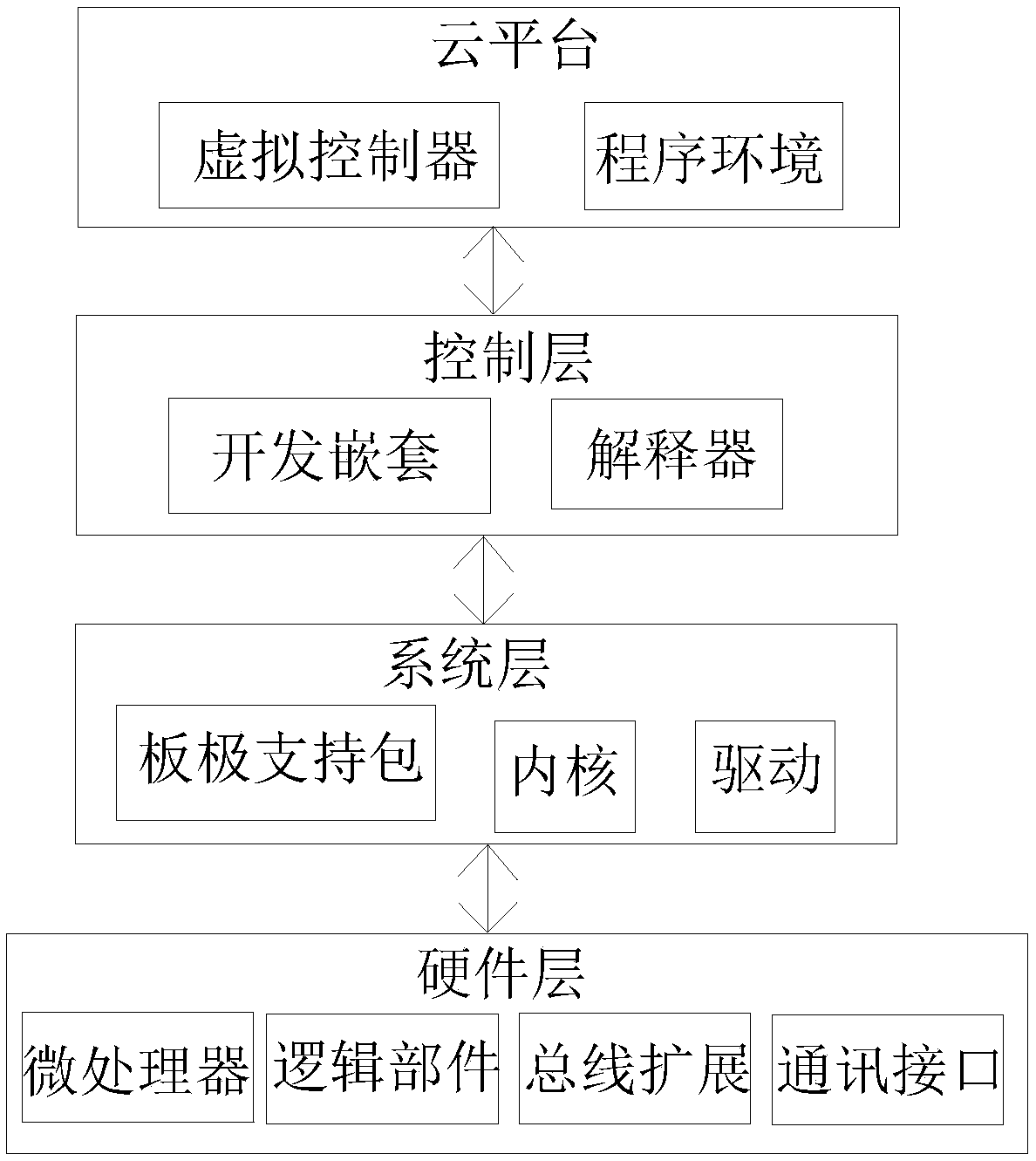
The invention discloses a software-defined network type industrial controller, which comprises a system layer, a control layer, a cloud platform with a virtual controller, a hardware layer and a communication module; the virtual controller is in signal connection with the hardware layer and the cloud platform through the communication module. By modularizing the hardware design, it is convenient to use the software method to describe the control functions, interface components, peripheral modules, etc. implemented by the controller, and form the virtual controller. The user uses the developerenvironment provided by the cloud platform to perform function development for a to-be-implemented control system. In the development process, the virtual controller is used as the object to completethe program design, interface configuration, and virtual simulation function. After the function development is completed, the result is pushed to the device end of the physical controller, and the controller receives the result and then submits it to the controller. A program interpreter performs responding and execution. Development and verification are carried out on the cloud platform, and theInternet is implanted at the beginning of equipment design. Obvious advantages are realized in the later use process.
Owner:广东青璃智造科技有限公司
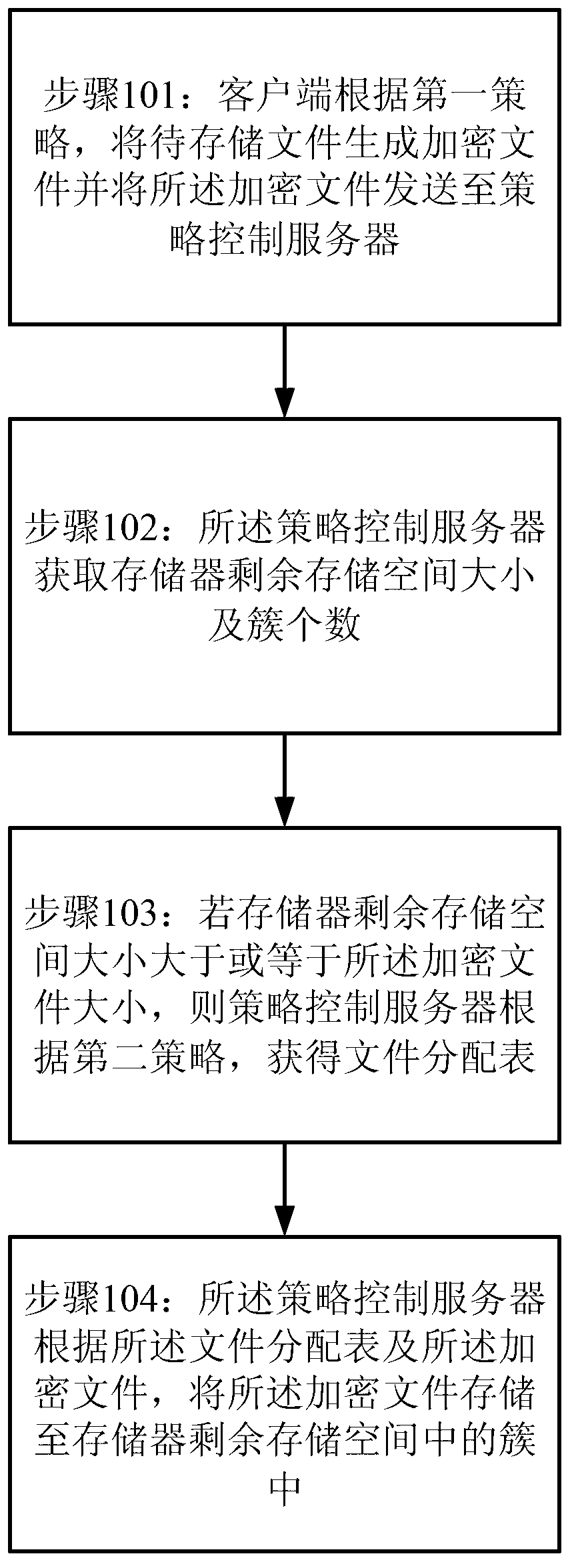
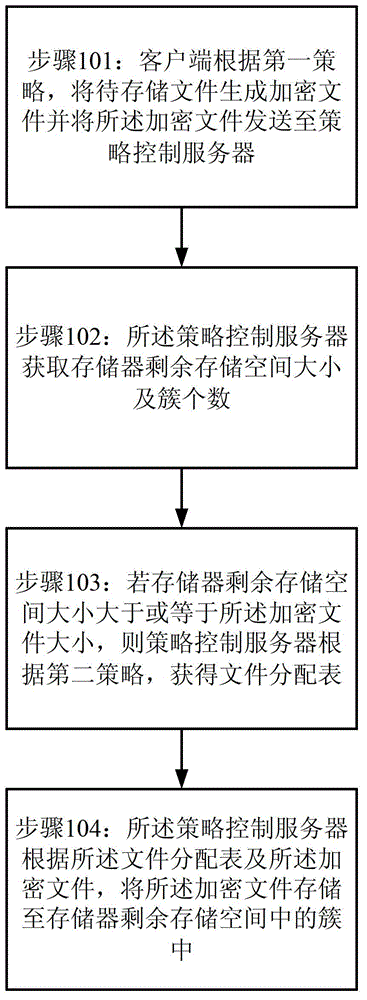
Method and system for storing enciphered data
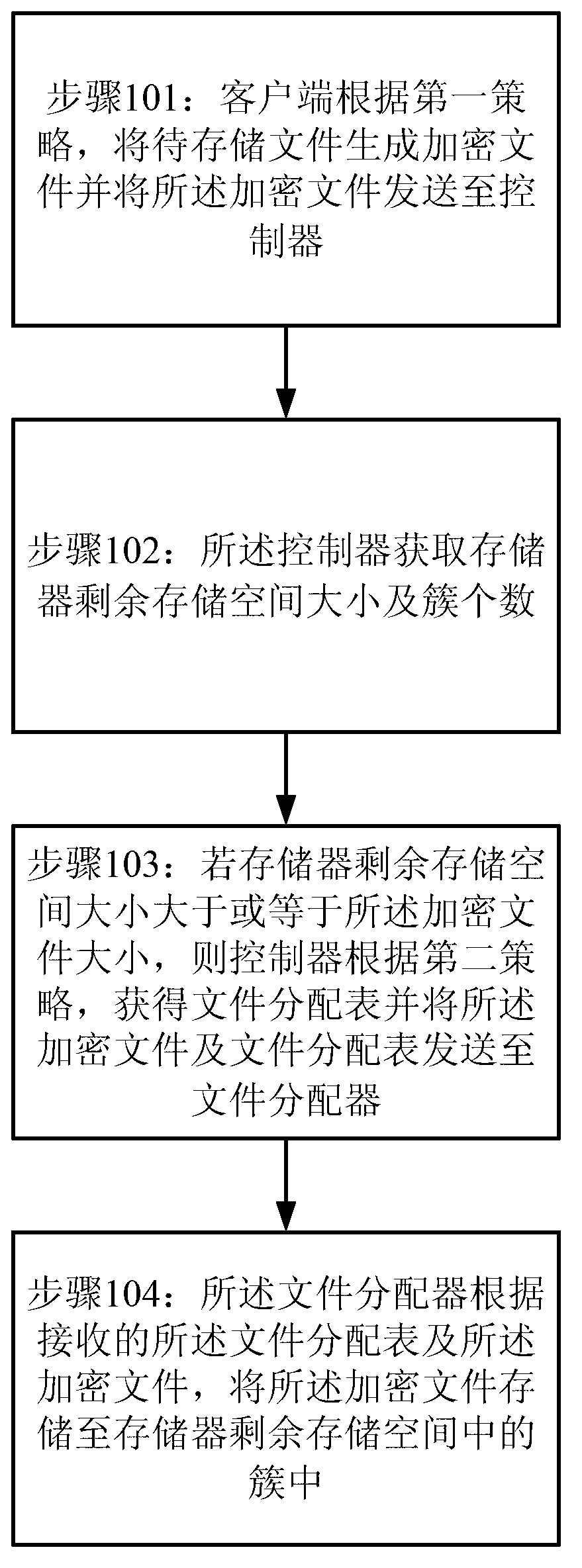
The invention provides a method and system for storing enciphered data. The method for storing the enciphered data comprises the steps that according to a first strategy, a file to be stored is generated to be an encrypted file by a client side, and the encrypted file is sent to a strategy control server. The strategy control server acquires the size of remaining storing space of memorizer and the number of clusters. If the size of the remaining storing space of the memorizer is larger than or equal to the size of the encrypted file, the strategy control server acquires a file distribution table according to a second strategy. The strategy control server stores the encrypted file in clusters of remaining storing space of the memorizer according to the file distribution table and the encrypted file.
Owner:SUZHOU CODYY NETWORK SCI & TECH
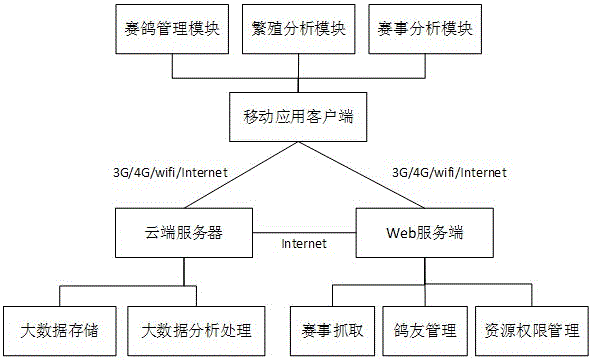
Carrier pigeon competition management and competition analysis system based on mobile terminal
InactiveCN105046411ARaise the level of competitionEfficient managementResourcesWeb serviceClient-side
The present invention provides a technical scheme of a carrier pigeon competition management and competition analysis system based on a mobile terminal. The scheme is that the carrier pigeon competition management and competition analysis system based on the mobile terminal comprises a mobile application client, a cloud server and a web server; the mobile application client is interacted with the cloud server and the web server via a wireless network, the web server real-timely obtains the information in the network and stores the information in the cloud server, and the mobile application client can obtain the information from the cloud server and the web server, display the information, record the carrier pigeon information and upload the recorded information to the cloud sever to store. According to the scheme, the system can manage the carrier pigeon information effectively, promotes to improve the carrier pigeon species, analyzes the competition data, provides forceful foundation for the pigeon friend competition, and enables the carrier pigeon competition level of our country to be improved.
Owner:SICHUAN ZHIHUA SOFTWARE TECH CO LTD
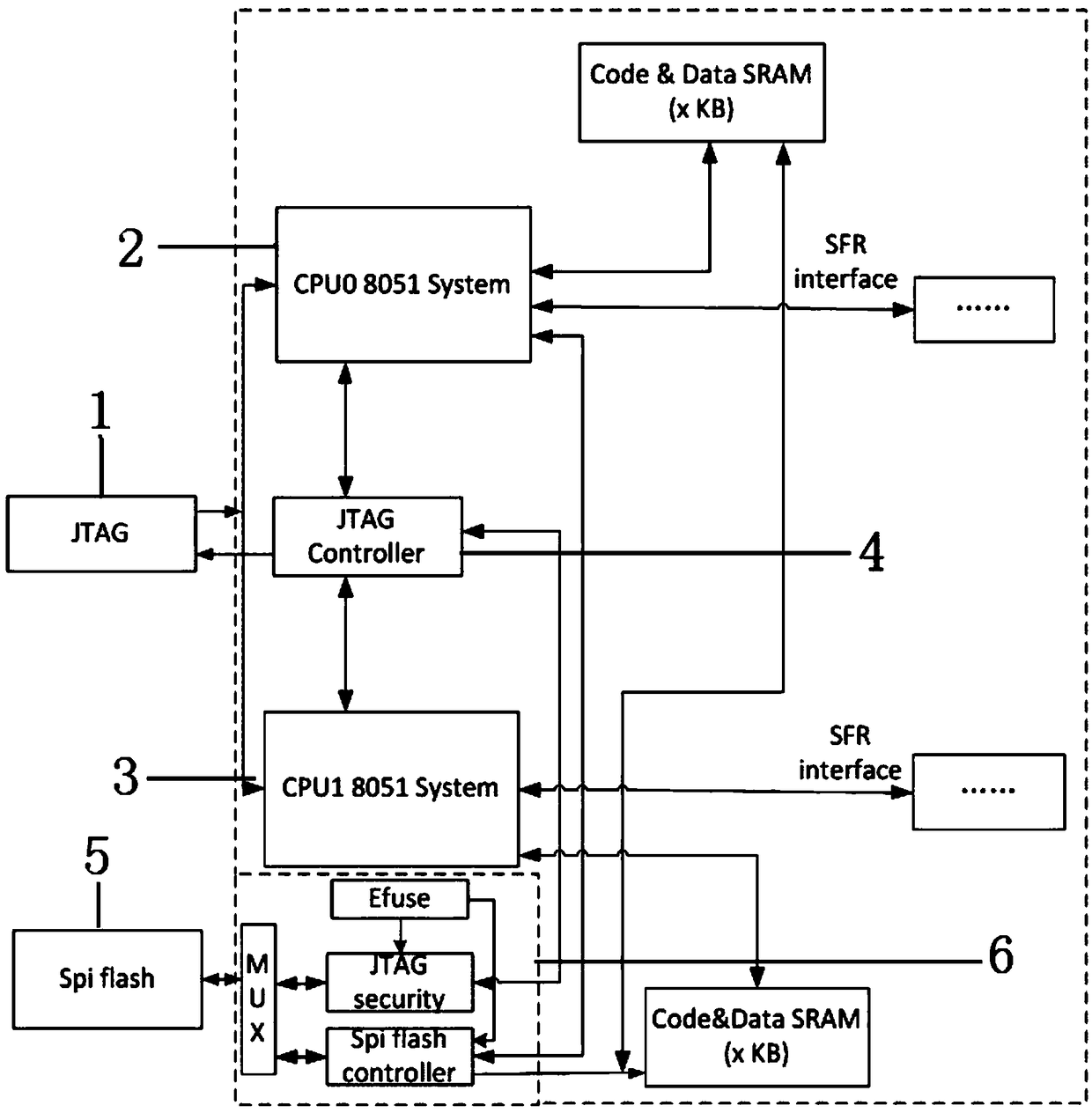
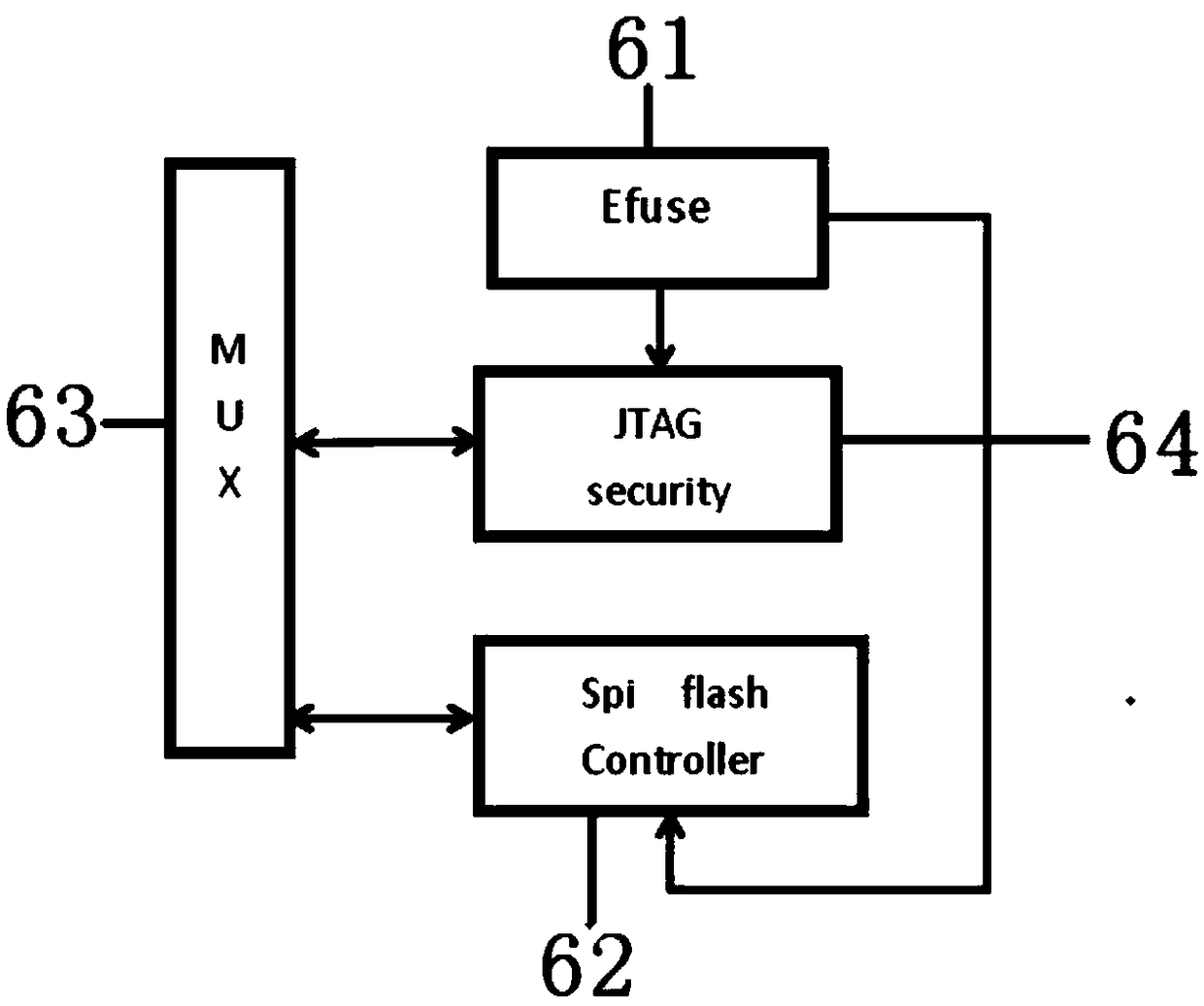
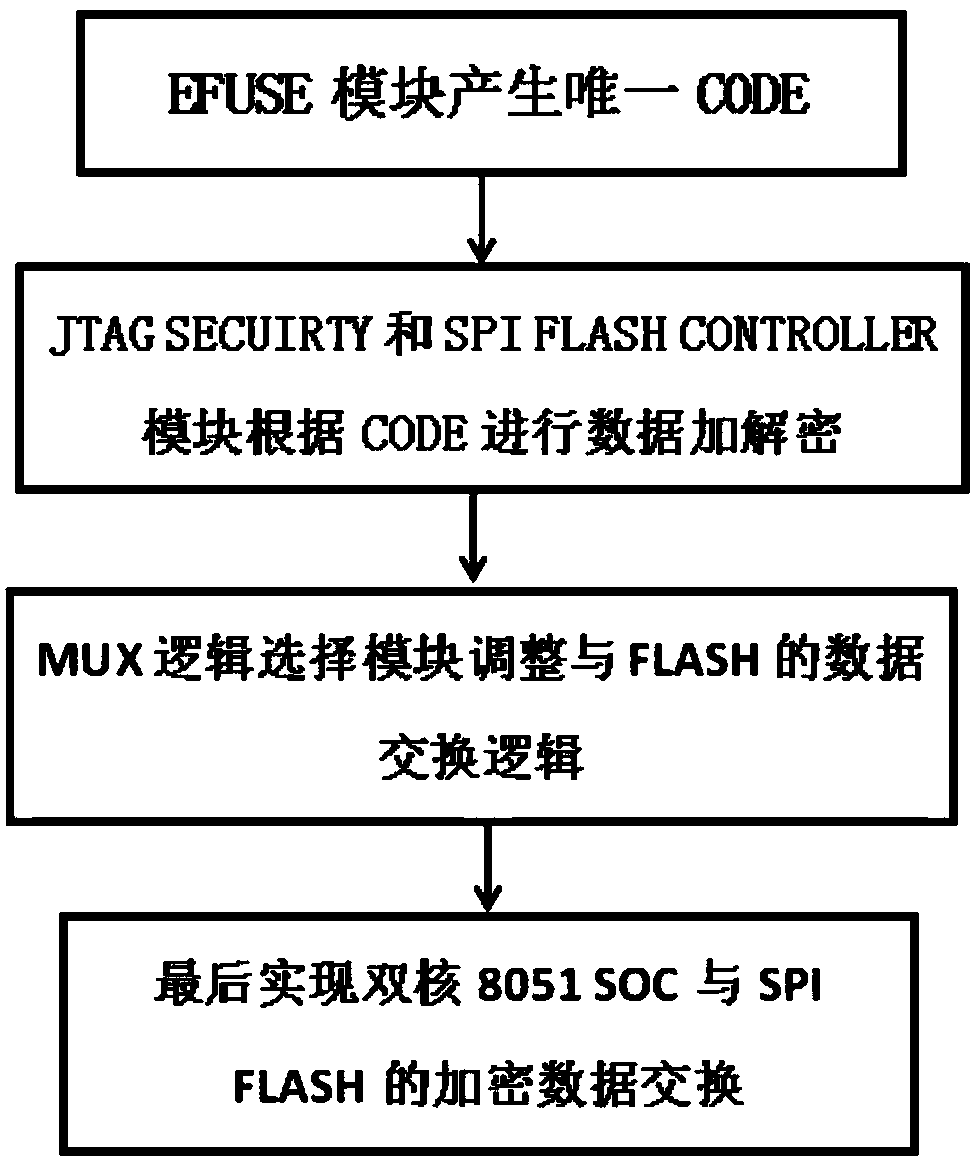
Secure realization device and method for multi-core 8051 processor SOC
ActiveCN108228525AImprove reliabilityDestroy correctnessDigital data protectionArchitecture with single central processing unitComputer hardwareJoint Test Action Group
The invention relates to an encryption method and device for data exchange between a multi-core 8051 processor SOC and an off-chip FLASH. A secure realization device system comprises multiple 8051 processors, a JTAG Controller, a Code&Data SRAM and an encryption / decryption processing module; an encryption module comprises an MUX module, an Efuse module, a JTAG security module and a Spi flash controller module; and the processors perform external read-write on an SPI FLASH based on a unique CODE generated by the EFUSE module through the Spi flash controller module; a JTAG interface of the double-core 8051 SOC performs communication with the JTAG security module through the JTAG Controller, the JTAG security module performs encryption / decryption processing through the unique CODE generated by the EFUSE module, and finally data read-write exchange with the SPI FLASH is performed.
Owner:BEIJING DWIN TECH
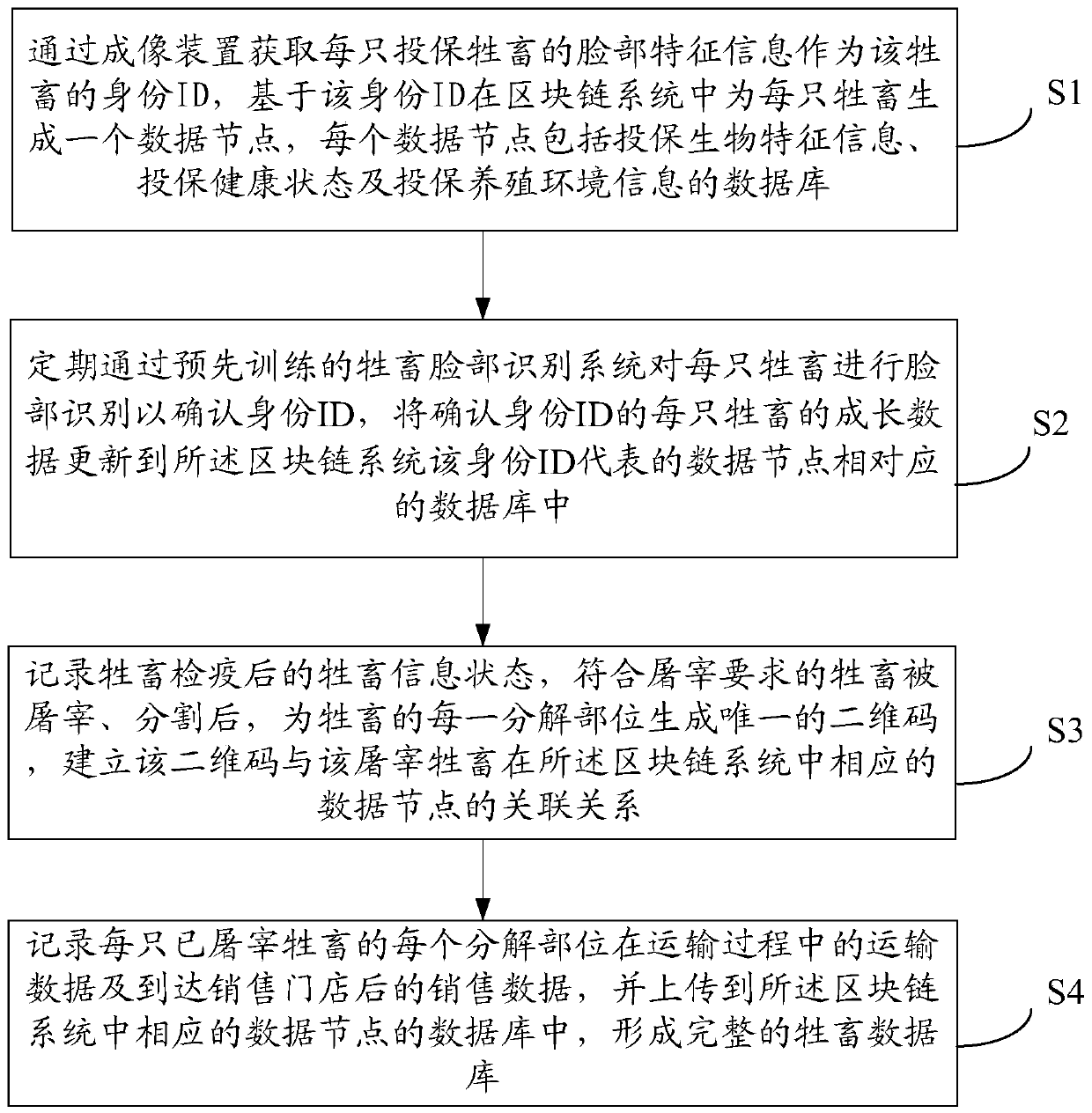
Livestock breeding circulation tracking method based on block chain, electronic device and storage medium
The invention relates to a livestock breeding circulation tracking method based on a block chain, an electronic device and a storage medium. The method comprises the following steps of acquiring the face feature information of each insured livestock through the imaging device to serve as the identity ID of the livestock; generating a data node for each livestock in the block chain system, whereineach data node comprises the insuring biological characteristic information, the insuring the health state and the insuring the breeding environment information; periodically updating growth data of livestock into a block chain system, slaughtering the livestock meeting a slaughtering requirement, segmenting the slaughtered livestock to generate a unique two-dimensional code, establishing an association relationship with a data node corresponding to the livestock, and uploading livestock related data which are transported and sold in a store to the block chain system to form a complete livestock database. The insured livestock life cycle is tracked by using the block chain technology, and the livestock information symmetry and the safety are realized.
Owner:PING AN TECH (SHENZHEN) CO LTD
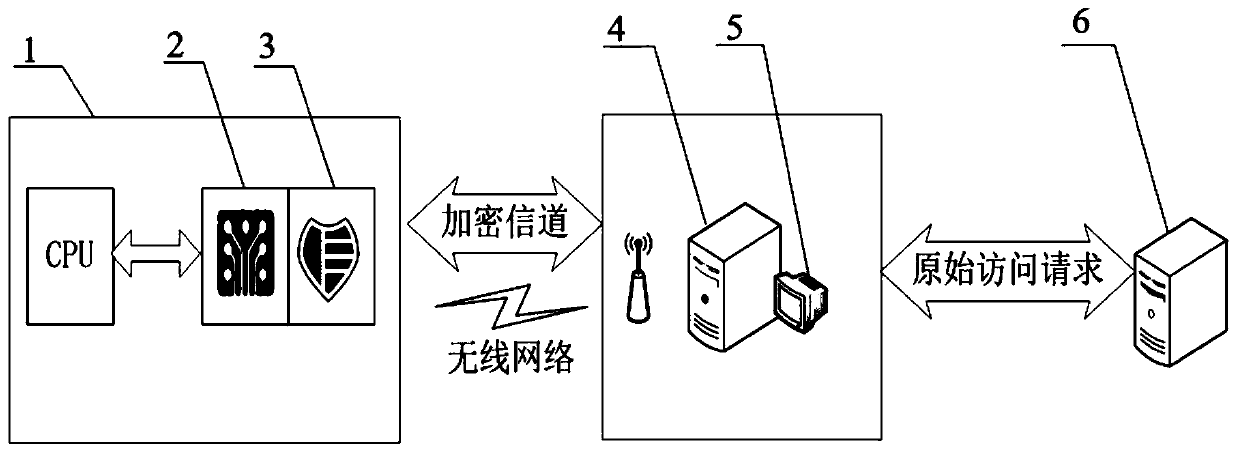
Wearable equipment authentication device and authentication encryption method
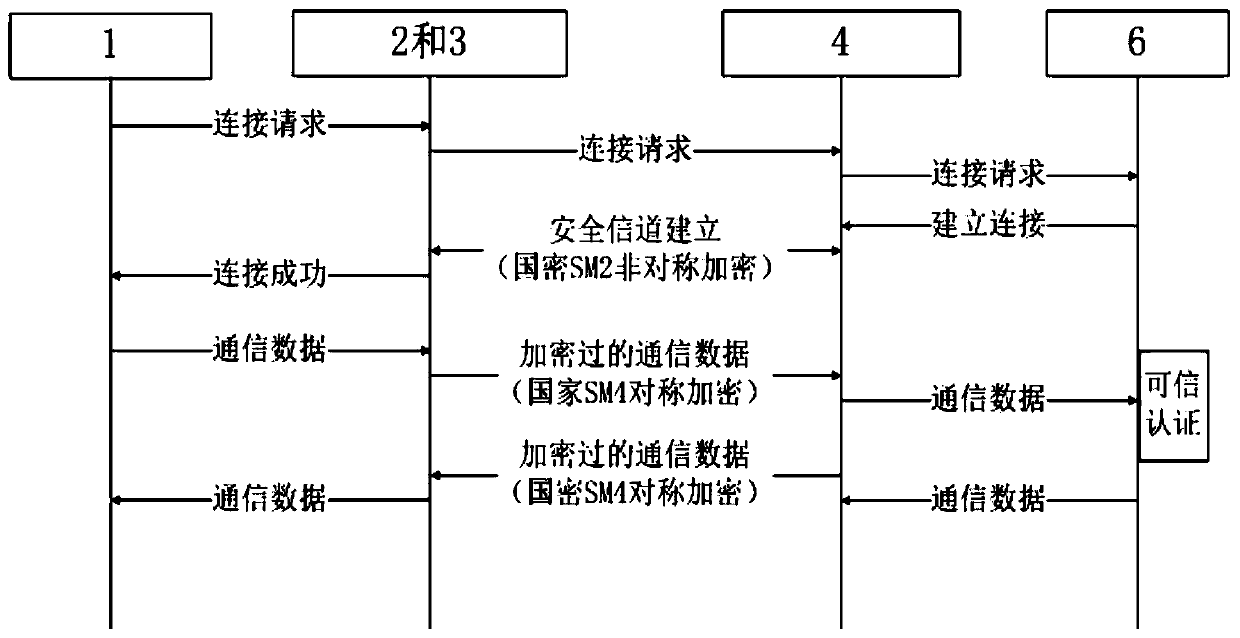
PendingCN110572825AAchieving communication securityAchieve data securityPublic key for secure communicationSecurity arrangementCommunications securityPassword
The invention discloses a wearable equipment authentication device and an authentication encryption method. The authentication encryption method comprises a security support platform. The security support platform comprises wearable equipment, a cryptographic chip, a security agent module, a security agent server, a security management console and a server. The method comprises the steps that wearable equipment sends a network request to a cryptographic chip through an application program; the cryptographic chip receives the network request, encrypts the received network request and sends theencrypted network request to the security agent module; the security agent module transmits the received encrypted network request to a security agent server through an encryption channel; and the security proxy server decrypts the received network request and transmits the decrypted network request to a background server to complete security channel establishment, communication data encryption and credible authentication operation of the equipment. Security support and password service are provided for the wearable device, and communication security, data security and device trusted authentication of the wearable device are realized.
Owner:GUANGDONG IND TECHN COLLEGE
RFID data transmission and authentication system and method
InactiveCN109309916AProtection securityAchieve data securitySecurity arrangementData centerUltrahigh frequency
The invention discloses an RFID data transmission and authentication system and method. The system comprises: a verification reader-writer system at a user terminal, and a background verification server system, wherein the verification reader-writer system at the user terminal comprises a verification reader-writer and an electronic tag; and the background verification server system comprises an authentication server and a data center. Based on the above data transmission and authentication system, the RFID data transmission and authentication method proposed by the invention comprises a preparation stage of the electronic tag and an a radio frequency identification field stage of the electronic tag. According to the method and system disclosed by the invention, by adopting the sleep technology of the electronic tag in combination with the private key encryption EPC, the identity identification of the verification reader-writer and the background server authentication, and in cooperation with the passive ultrahigh frequency electronic tag, the practicality for various special application occasions is enhanced, the security of target information is effectively protected, the application cost is reduced, and RFID data security and anti-counterfeiting authentication functions are achieved.
Owner:颜馨
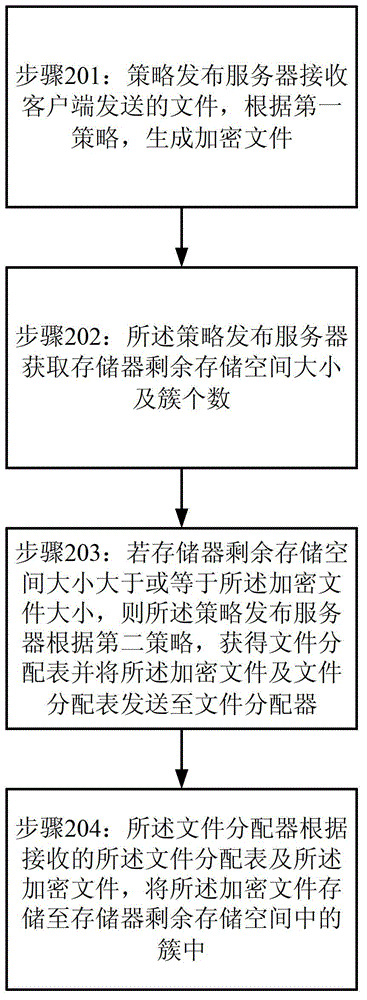
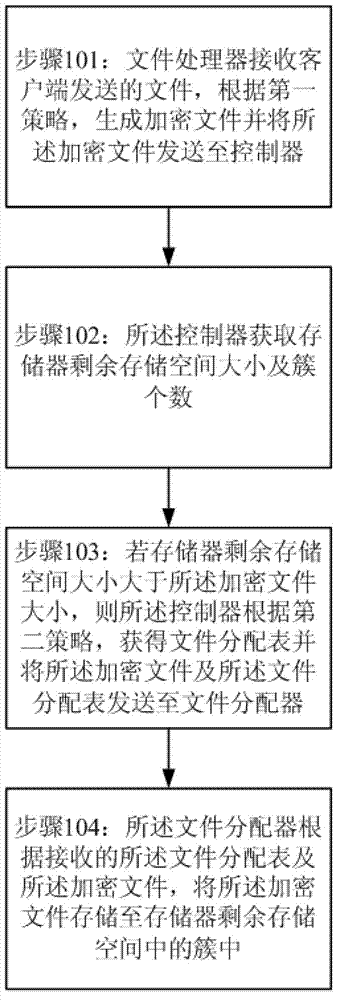
Method and system of data hidden storage
InactiveCN103220209AAchieve data securityDigital data protectionData acquisition and loggingFile allocationParallel computing
The invention provides a method and a system of data hidden storage. The method comprises the following steps: a client end enables a file to be stored to generate an encryption file and sends the encryption file to a controller according to a first strategy; the controller acquires the size of the remaining memory space of a memorizer and the number of clusters; if the size of the remaining memory space of the memorizer is larger than or equal to the size of the encryption file, the controller obtains a file allocation table and sends the encryption file and the file allocation table to a file allocator according to a second strategy; and the file allocator stores the encode file to the clusters in the remaining memory space of the memorizer according to the received file allocation table and the encryption file.
Owner:SUZHOU CODYY NETWORK SCI & TECH
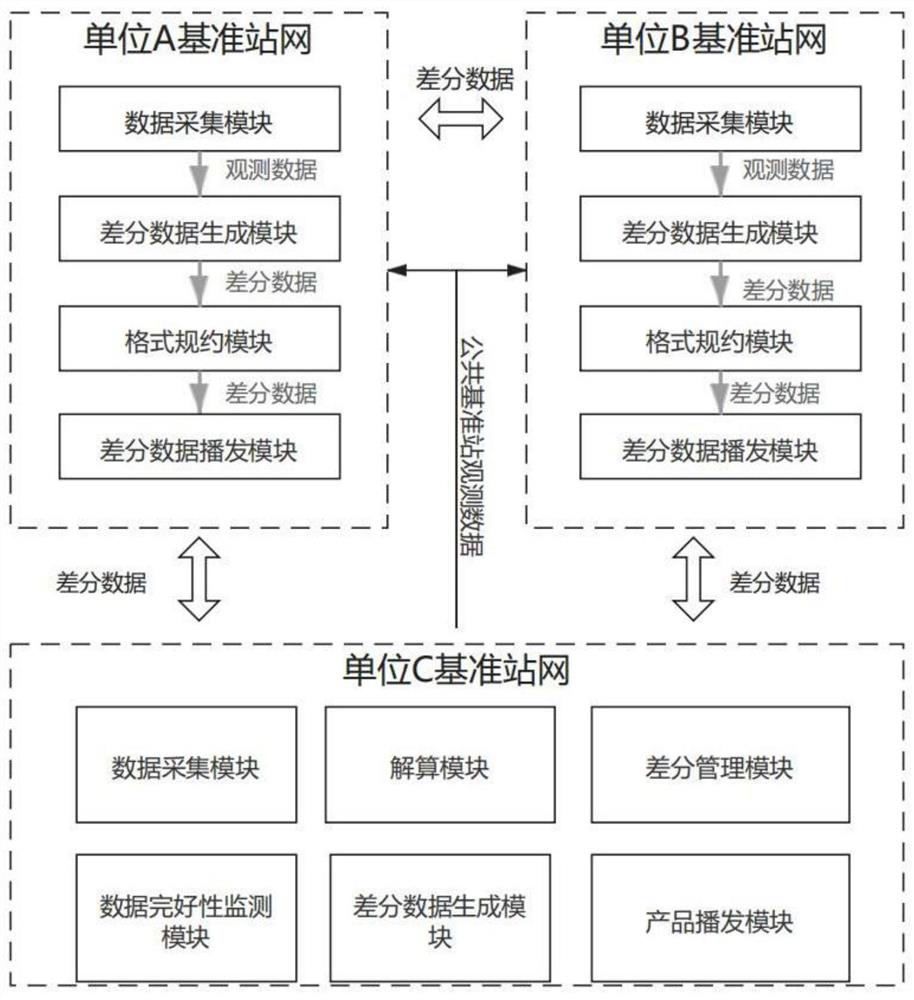
Peer-to-peer security satellite high-precision enhanced network method constructed based on P2P technology
ActiveCN113791431ASolve bottlenecks that cannot be sharedSolve the "joining edge problem"Satellite radio beaconingTransmissionStationService mode
The invention discloses a peer-to-peer security satellite high-precision enhanced network method constructed based on a P2P technology. The method comprises the following schemes of (1) a single-difference scheme in an NRTK service mode, (2) a non-difference scheme in an NRTK service mode, and (3) a technical scheme in a PPP-RTK service mode. The bottleneck problem that data of each unit reference station cannot be shared is solved, the'edge matching problem 'of location services of different units is solved, and high-precision location services with unified reference and consistent precision of a nationwide'network' are realized; high-precision positioning integrated service of the whole society is realized, data security of grid-connected service is realized, data benchmark unification of various families is realized, the problem of base station construction redundancy is solved, and great economic and social significance is achieved.
Owner:国汽大有时空科技(安庆)有限公司
Virtual machine monitoring method and system thereof
ActiveUS9996376B2Achieve data securityEasy to manageComputer security arrangementsTransmissionUser FriendlyImaging data
A virtual machine monitoring method and a system thereof are provided. The virtual machine monitoring method includes: detecting at least one hardware resource of an electronic device and storing corresponding hardware configuration data, detecting display information of the electronic device and storing corresponding display configuration data, connecting a server and receiving image data therefrom, establishing a virtual machine based on the image data, configuring the at least one hardware resource on the virtual machine based on the hardware configuration data, setting a display image on the virtual machine based on the display configuration data, and clearing the image data to end the virtual machine, so as to provide a user-friendly interface and achieve corporate data security.
Owner:WISTRON CORP
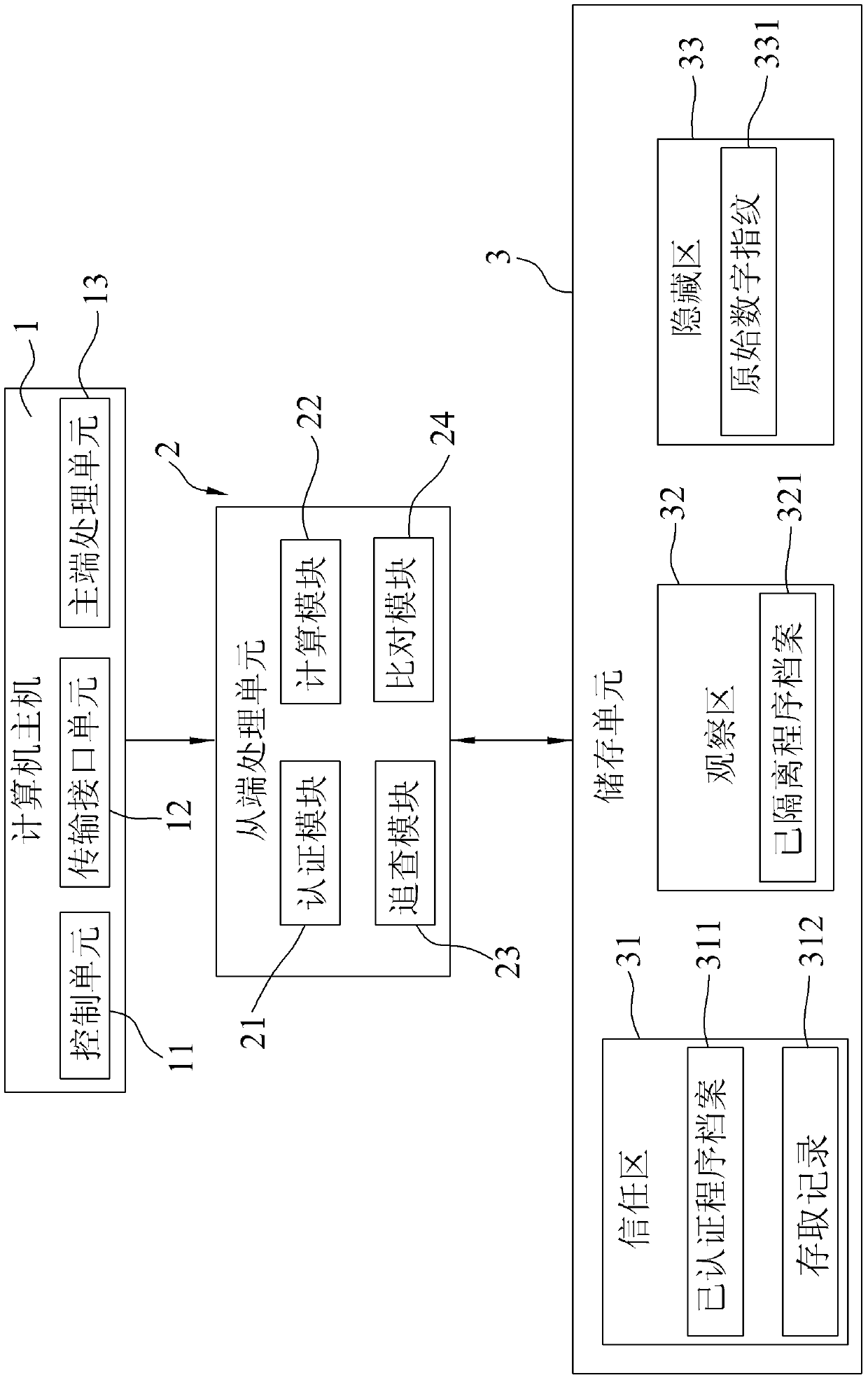
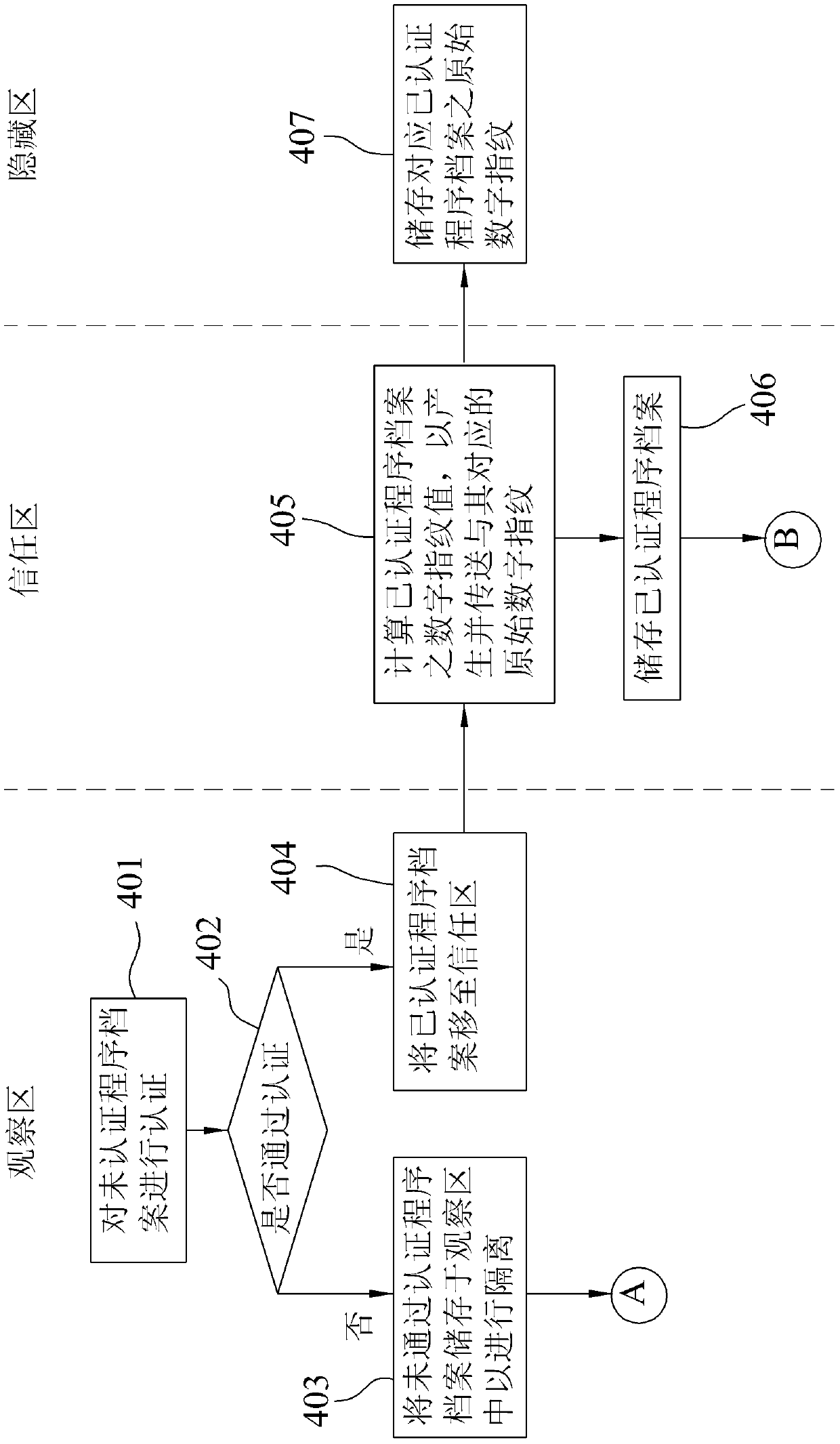
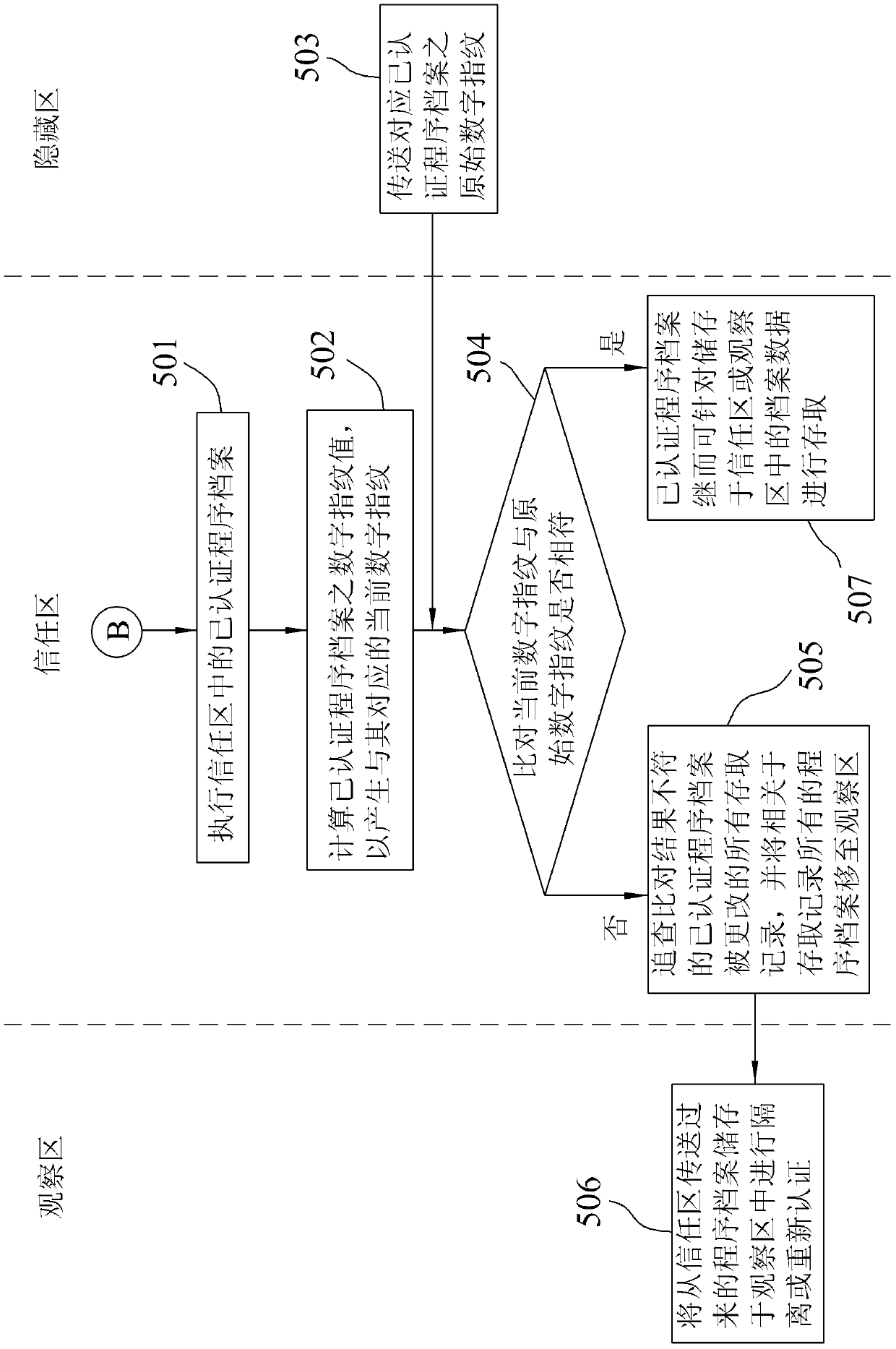
Data security access method and system thereof
InactiveCN104751069BAvoid random accessAvoid destructionDigital data protectionInternal/peripheral component protectionAccess methodData access
A data security access method and system thereof, comprising: when executing an authenticated program file stored in a trust zone of a storage unit, calculating the digital fingerprint value of the authenticated program file to generate a corresponding current Digital fingerprint; load an original digital fingerprint corresponding to the certified program file stored in the hidden area of the storage unit in advance, and compare whether the current digital fingerprint matches the original digital fingerprint; if so, the certified program file for The file data stored in the trusted zone or the observed zone is accessed; if not, the access record related to the certified program file is traced from the trusted zone, and the related program file in the access record Move to observation area for storage for subsequent quarantine actions or recertification.
Owner:周宏建
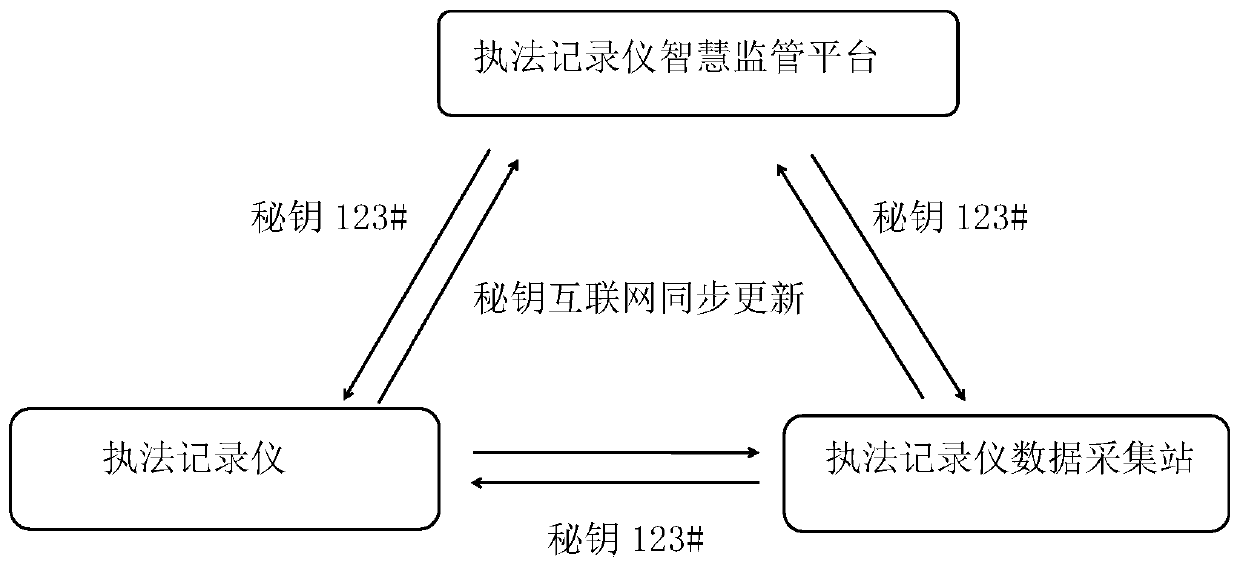
Law enforcement recorder intelligent supervision platform and system and law enforcement recorder
InactiveCN111050052ARealization of smart supervisionRealize real-time status monitoringTelevision system detailsColor television detailsFile systemVideo record
The invention discloses a law enforcement recorder intelligent supervision platform, a supervision system and a law enforcement recorder. An NB-IOT narrowband Internet of Things module is embedded inthe law enforcement recorder, and a platform is used for receiving real-time state information sent by the law enforcement recorder in real time, and the real-time state information comprises electricquantity, storage space, police officer information, a video recording state, a use unit, a GPS position and / or a video recording resolution; and when the electric quantity or the storage space is insufficient, the platform can automatically dial the telephone number of the corresponding police officer to carry out notification prompt. According to the invention, the current situations that an existing common law enforcement recorder cannot perform real-time supervision and a 4G law enforcement recorder cannot be practically applied are broken through; real-time state supervision of the law enforcement recorder can be realized, the situations of police officer negligence, police officer making excuses and the like in file system supervision are avoided from the technical perspective, caseascertainment is facilitated, and intelligent law enforcement of the law enforcement recorder is realized; moreover, when the law enforcement recorder deletes the copied video and audio data in an unauthorized manner, the intelligent supervision platform can give an alarm and lock the operation in time, so that the data security is realized.
Owner:周莲萍
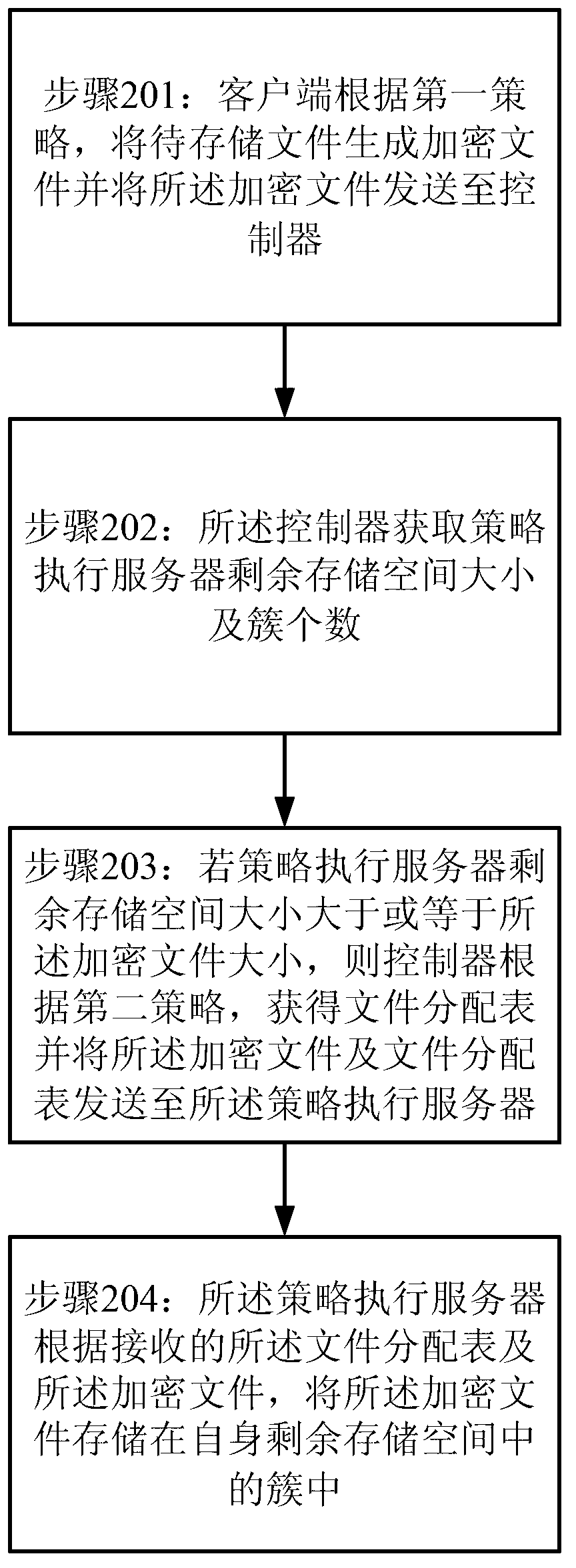
A method and system for stealth processing of files
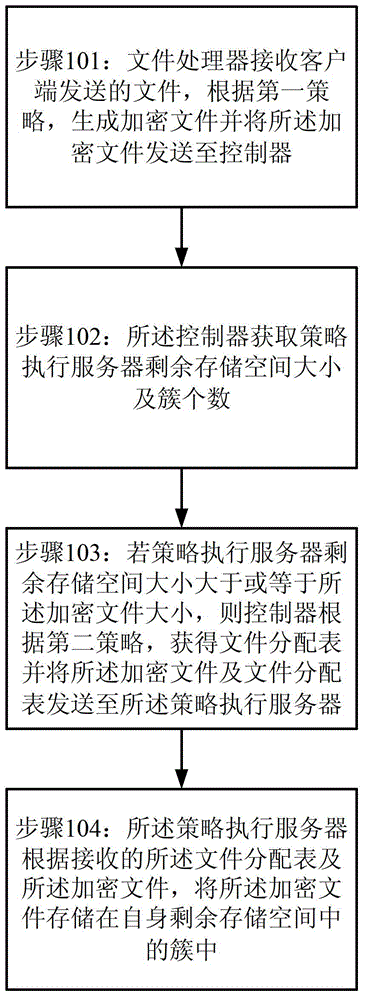
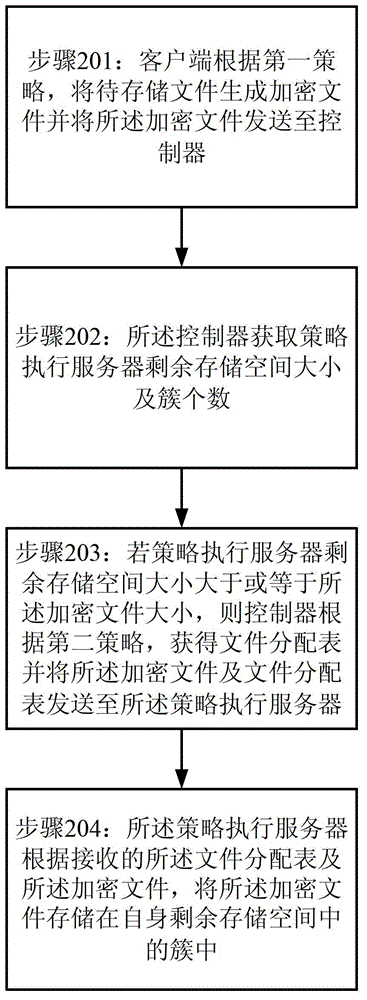
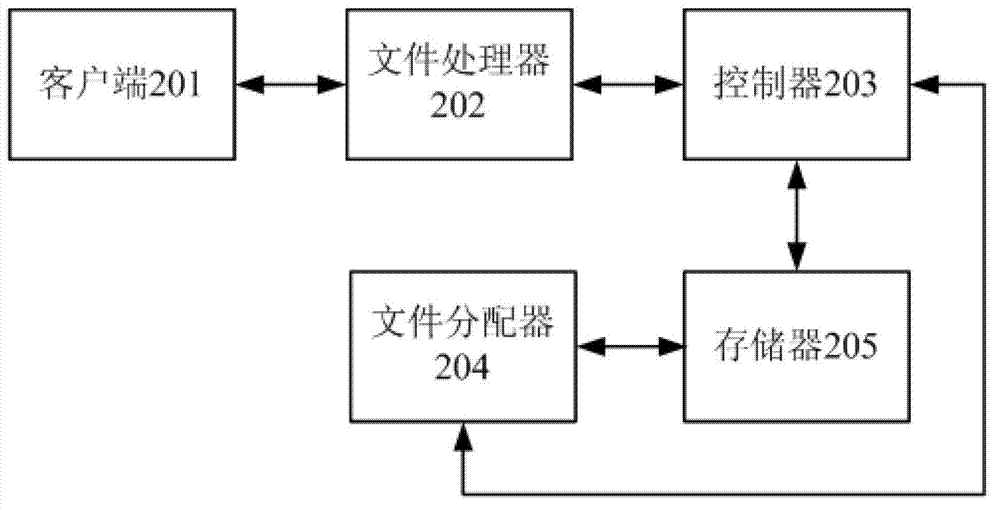
InactiveCN103259779BAchieve data securityDigital data protectionData switching networksStrategy executionDocument handling
The invention provides a method for file invisibility processing and a system for the file invisibility processing. The method comprises the following steps: a file sent by a client terminal is received by a file processor; according to a first strategy, an encrypted file is generated and sent to a controller. The size of free storage space of a strategy execution server and the number of clusters are obtained by the controller. If the size of the free storage space of the strategy execution server is larger than or equal to the size of the encrypted file, a file allocation table is obtained and the encrypted file and the file allocation table are sent to the strategy execution server by the controller according to a second strategy. The encrypted file is stored in the clusters in the free storage space of the strategy execution server according to the received file allocation table and the received encrypted file through the strategy execution server.
Owner:SUZHOU CODYY NETWORK SCI & TECH
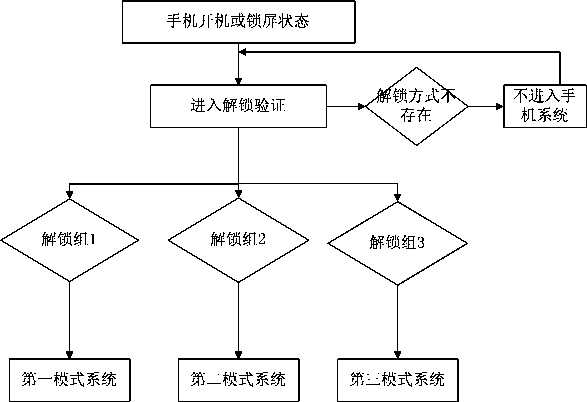
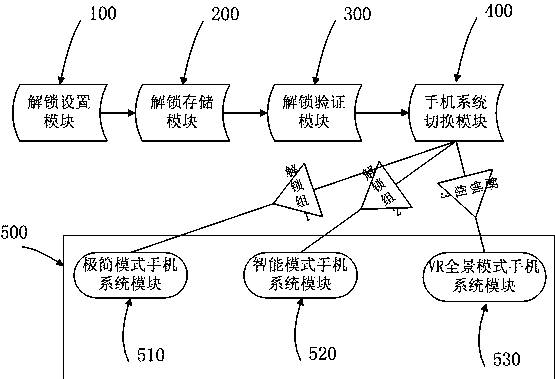
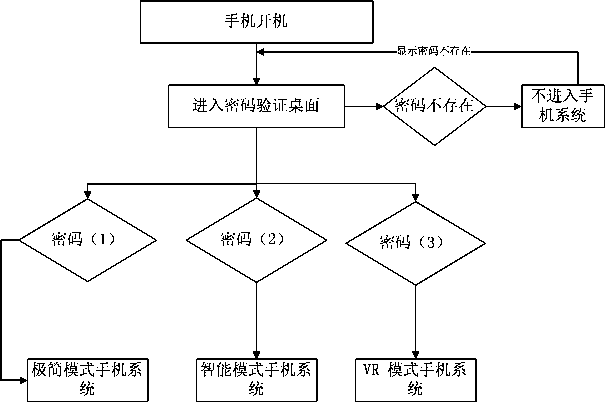
Multi-system mobile phone and switching method thereof
InactiveCN110855831AEasy to usePrevent leakageUnauthorised/fraudulent call preventionComputer hardwareMobile phone
The invention discloses a multi-system mobile phone and a switching method thereof, the mobile phone comprises a plurality of different mobile phone systems, the mobile phone is provided with a plurality of different unlocking groups, the unlocking groups comprise more than one unlocking mode, each unlocking group corresponds to a corresponding mobile phone system, and each unlocking mode starts the corresponding mobile phone system; the method comprises the following steps: (1) entering an unlocking desktop: inserting a power supply into the mobile phone, and pressing a power button to enterthe unlocking desktop, or pressing an unlocking button to enter the unlocking desktop in a mobile phone screensaver state; (2) inputting an unlocking mode to carry out unlocking verification: when theunlocking mode is verified as a first unlocking group, starting a first mode system, when the unlocking mode is verified as a second unlocking group, starting a second mode system, and when the unlocking mode is verified as a third unlocking group, starting a third mode system; and when the unlocking mode does not exist, not entering the system, prompting an error, and returning to unlock the desktop.
Owner:触信(厦门)智能科技有限公司
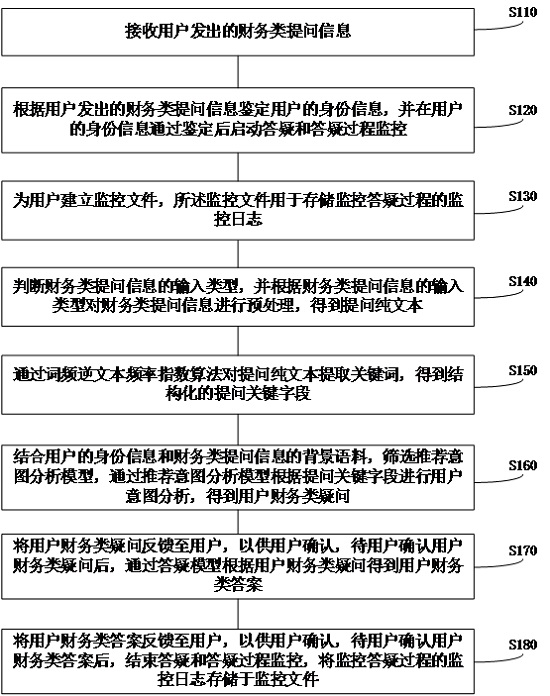
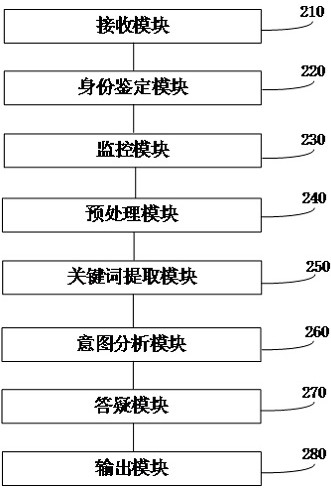
Intelligent customer service method and system based on power grid business
InactiveCN114881675AImprove the efficiency of centralized financial processingPrevent theftCustomer relationshipDigital data information retrievalPower gridEngineering
The invention provides an intelligent customer service method and system based on power grid business. The method comprises the following steps: after user identity authentication, starting question answering and question answering process monitoring; obtaining a question plain text according to the input type of the financial question information; extracting keywords from the question plain text to obtain structured question key fields; in combination with the identity information of the user and the background corpus of the financial question information, screening a recommendation intention analysis model and carrying out user intention analysis to obtain a user financial question; after the user confirms the financial questions of the user, obtaining financial answers of the user according to the financial questions of the user through a question answering model; after the user confirms the financial answer of the user, question answering and question answering process monitoring are ended. According to the intelligent customer service method and system based on the power grid business provided by the embodiment of the invention, the efficiency of financial centralized processing and the data security through a power grid financial sharing center can be improved.
Owner:GUANGDONG POWER GRID CO LTD
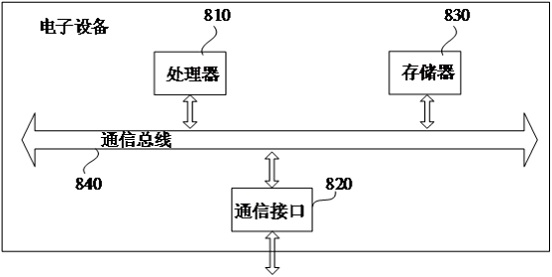
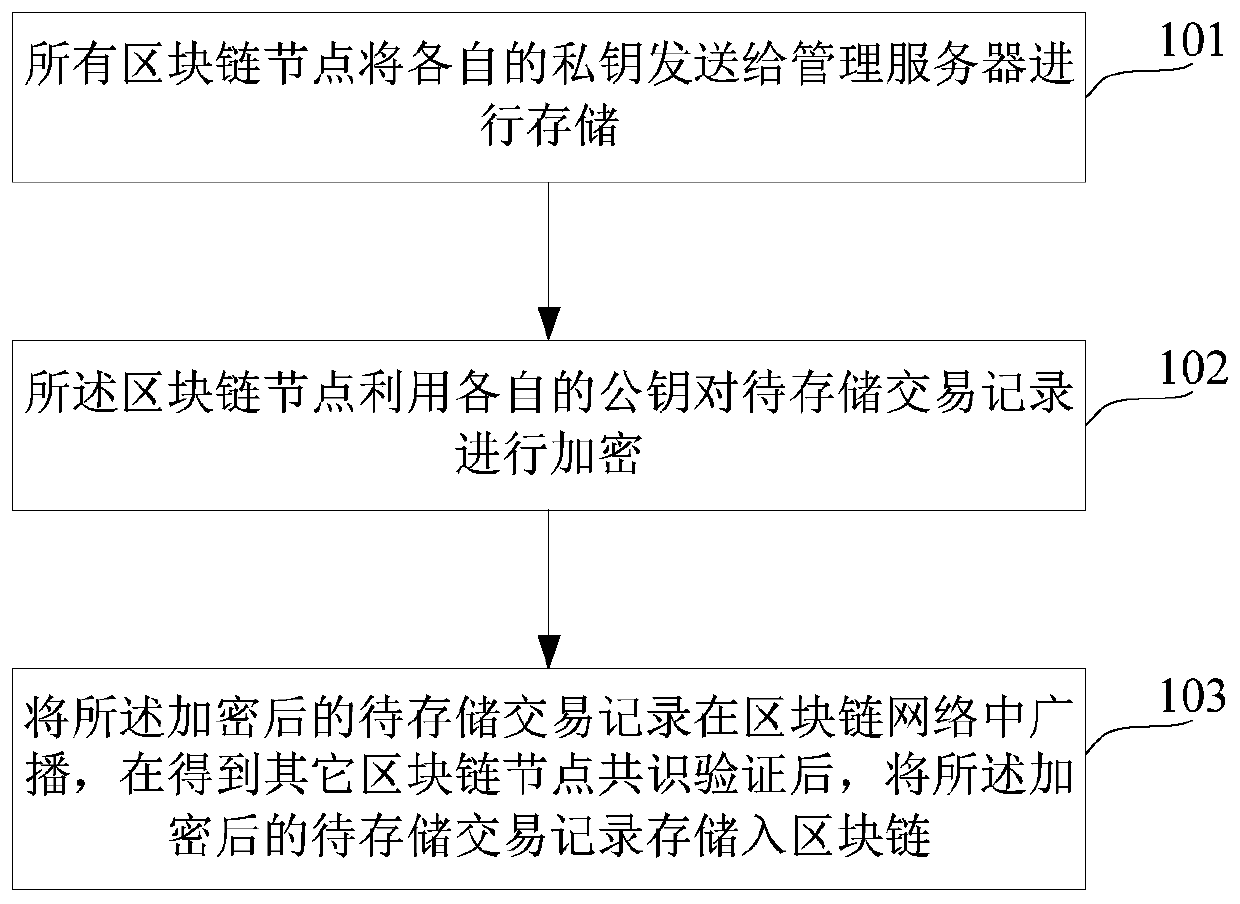
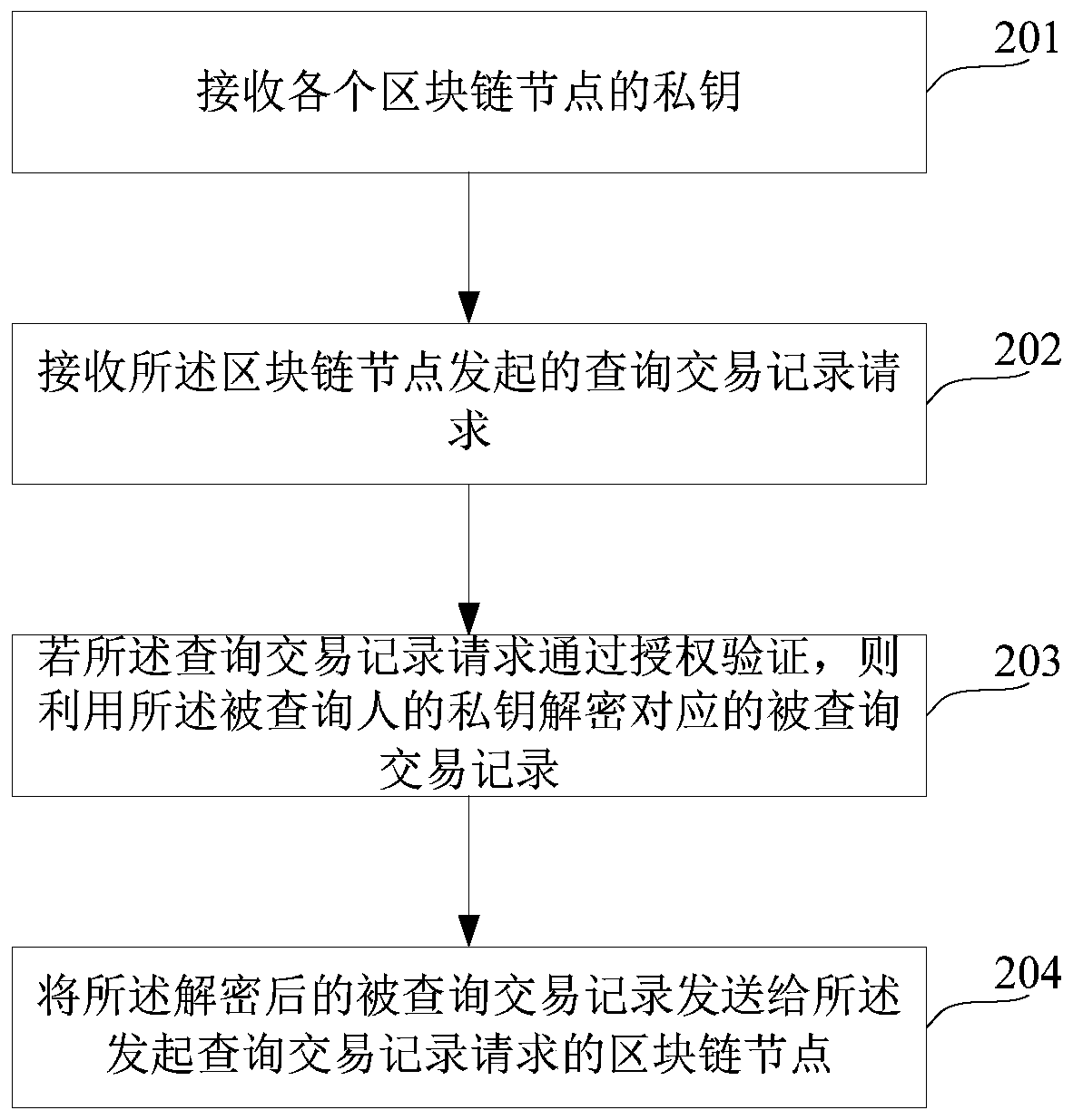
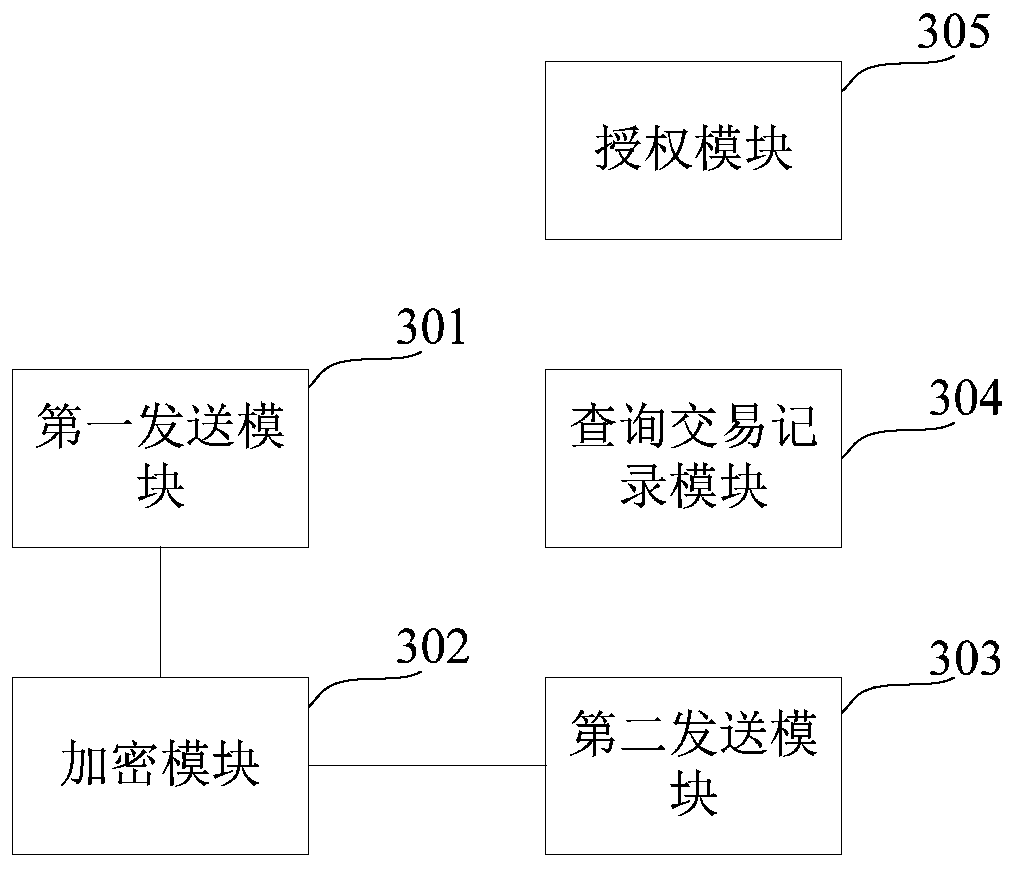
A method and system for accessing blockchain transaction records
Owner:东莞市恒邦企业服务有限公司
Method and system for encrypting data storage
Owner:SUZHOU CODYY NETWORK SCI & TECH
Method and system for invisibly storing file in encrypted manner
InactiveCN103207973AImprove data securityAchieve data securityDigital data protectionData switching networksFile sizeDocument processing
The invention provides a method and a system for invisibly storing a file in an encrypted manner. The method includes the steps: receiving the file transmitted by a client by a file processor, generating an encrypted file according to a first strategy and transmitting the encrypted file to a controller; acquiring the size of residual storage space and the number of clusters of a memory by the controller; acquiring a file assignment table according to a second strategy and transmitting the encrypted file and the file assignment table to a file distributor by the controller if the residual storage space of the memory is larger than or equal to the size of the encrypted file; and storing the encrypted file in the clusters in the residual storage space by the file distributor according to the received file assignment table and the received encrypted file.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Data processing method and device, equipment and storage medium
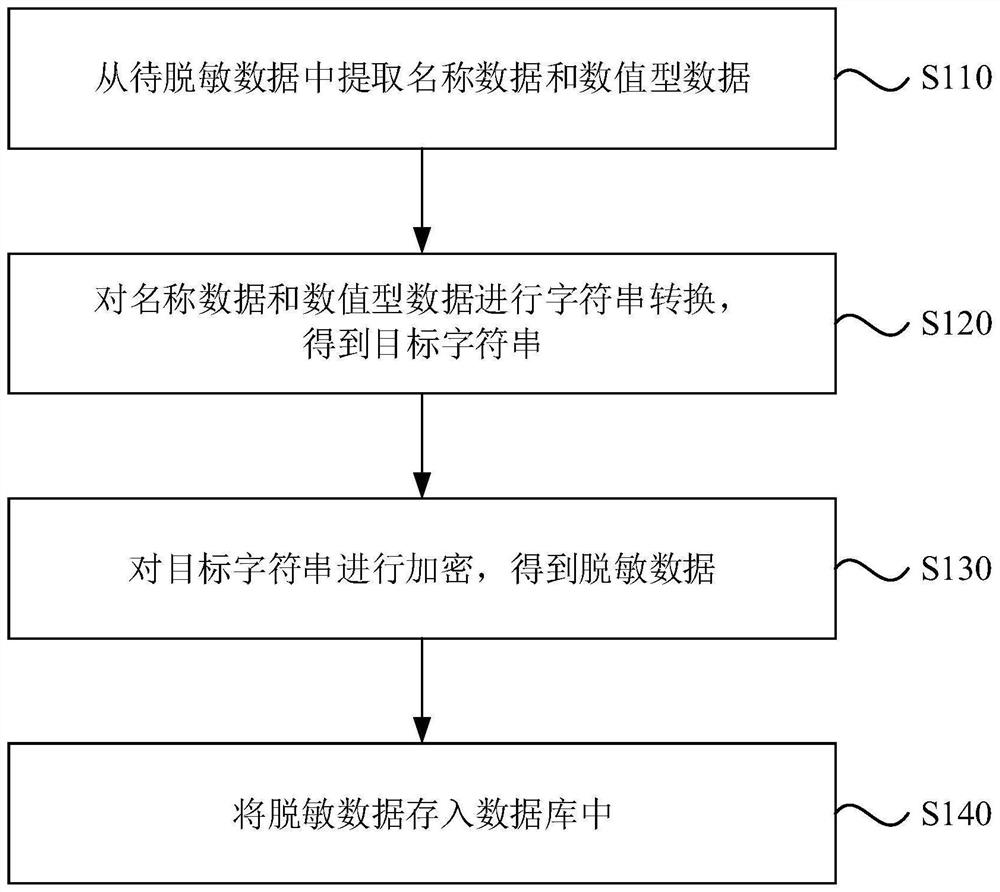
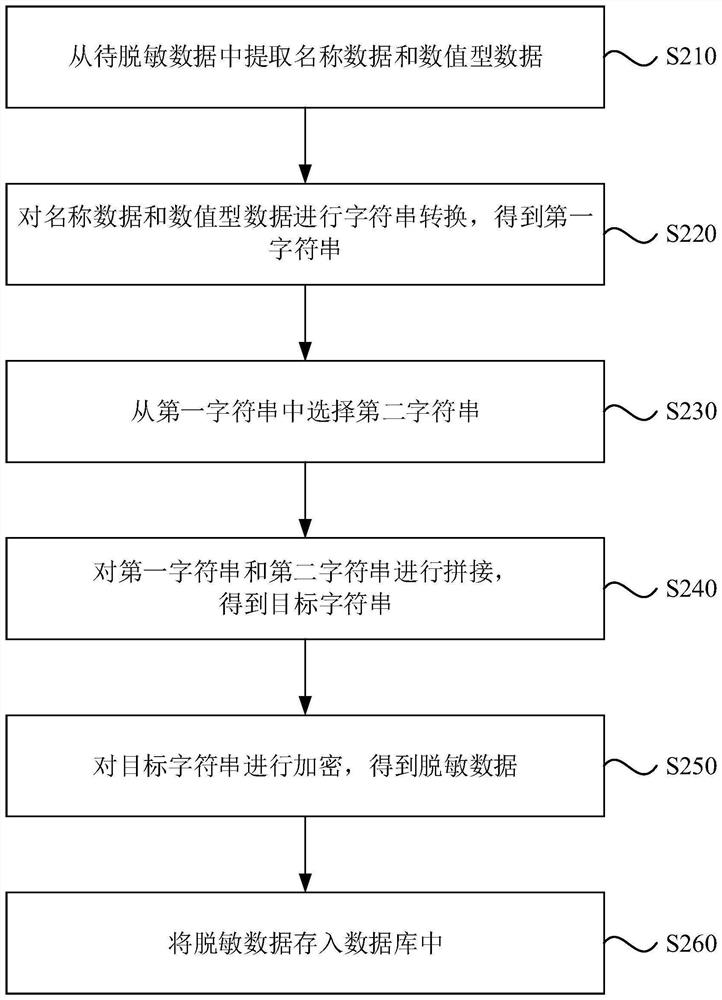
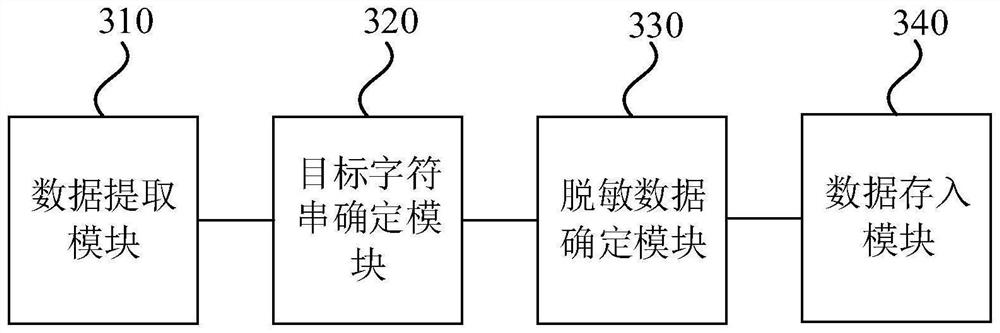
PendingCN114186261AIncrease desensitization speedImprove securityDigital data protectionSoftware engineeringNumeric data
The invention discloses a data processing method and device, equipment and a storage medium, and belongs to the technical field of distributed database data desensitization and encryption. The method comprises the following steps: extracting name data and numeric data from to-be-desensitized data; performing character string conversion on the name data and the numeric data to obtain a target character string; encrypting the target character string to obtain desensitized data; and storing the desensitized data into a database. By means of the technical scheme, the data desensitization speed is increased, the data safety is enhanced, and therefore the data safety and autonomous controllability of the financial institution are achieved.
Owner:CHINA ZHESHANG BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com