Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
173 results about "Data scatter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
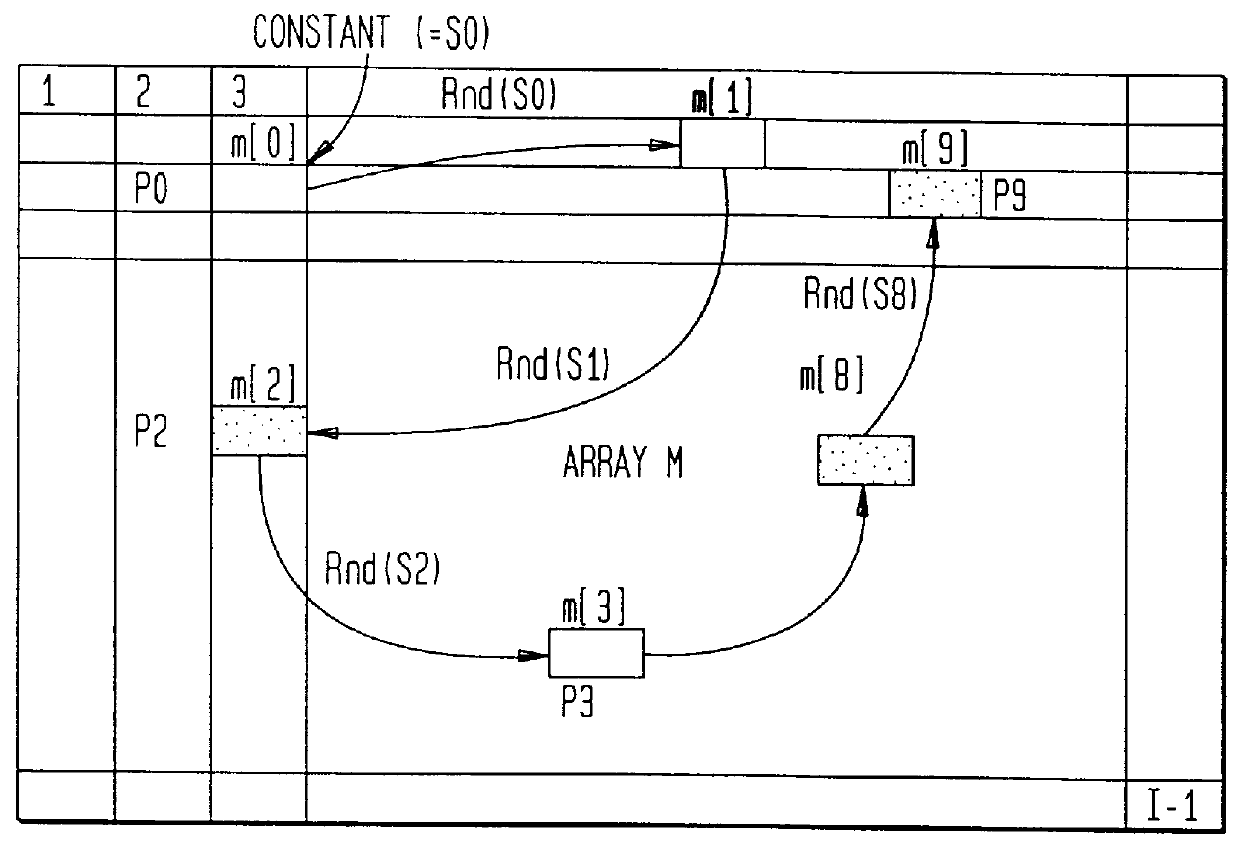
System and method for hiding and extracting message data in multimedia data
The present invention provides a data hiding method of hiding media data in message data and a data extraction method of extracting the hidden data wherein message data is dispersively hidden in media data such as an image or sound to prevent a third person from modifying the message data easily. More specifically, the present invention relates to a data hiding method in which media data is expressed as a media array while message data is expressed as a message array so that the array elements of the message array can be dispersively hidden in the message array based on a state values specifying a particular array element of the media array, comprising the steps of: (a) determining the j-th (j> / =0) state value Sj; (b) determining (j+1)-th state value Sj+1 based on the j-th state value, the array element of the media array indicated by the j-th state value, and the array element of the message array; and (c) hiding data with respect to the array element of the media array indicated by the (j+1)-th state value Sj+1.
Owner:IBM CORP
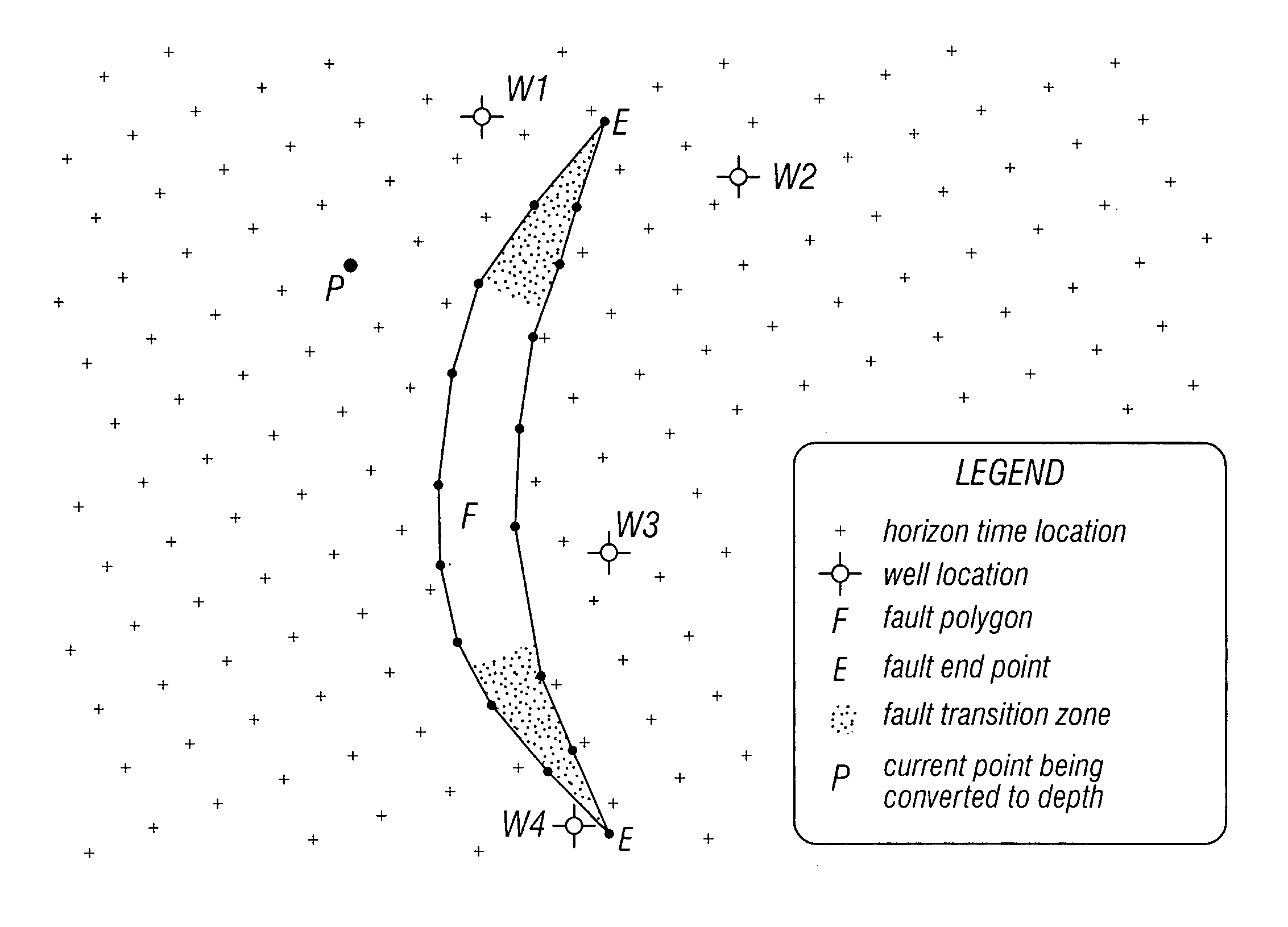
Method of estimating geological formation depths by converting interpreted seismic horizons from the time domain to the depth domain
InactiveUS20060047429A1Electric/magnetic detection for well-loggingSeismic signal processingHorizonData set
According to one aspect of the invention, a method of estimating geological location depths by converting horizon data from the time domain to the depth domain is provided, wherein the method comprises at least a data accumulation step and a data evaluation step, wherein the data evaluation step further comprises assignment of greater statistical weight to data derived from closer data acquisition points than to data derived from further data acquisition points using a weighted regression analysis, with distance being one of several weighting criteria. According to a further aspect of the invention, a method of estimating geological location depths is provided, wherein the method comprises a continuous, layer-by-layer computation of geological formation depths achieved by extracting values from horizon time data set at an exact geographic location of the next deeper horizon, thereby allowing interval computations to be carried out without the need for gridding. According to a still further aspect of the invention, a method of estimating geological formation depths is provided, wherein the method comprises estimating an expected error based on data scatter, and then allowing an alternative solution to be either partially or fully employed in areas where the accumulated data is insufficient to determine an acceptably reliable geophysical model.
Owner:ADAMS STEVEN L
Adjusting data dispersal in a dispersed storage network
A method begins by a processing module determining a performance based indication regarding storage of a data segment as a set of encoded data slices and comparing the performance based indication with a performance threshold. When the performance based indication compares unfavorably with the performance threshold, the method continues with the processing module decoding the set of encoded data slices to reproduce the data segment, adjusting error coding dispersal storage function parameters based on the unfavorable comparison of the performance based indication with the performance threshold to produce performance adjusted error coding dispersal storage function parameters, encoding the reproduced data segment in accordance with the performance adjusted error coding dispersal storage function parameters to produce a second set of encoded data slices, and selecting a storage set of encoded data slices from the set of encoded data slices and the second set of encoded data slices.
Owner:PURE STORAGE
Target recognition method based on millimeter-wave radar data
ActiveCN109061600AImprove robustnessImprove effectivenessWave based measurement systemsAlgorithmRadar
The invention provides a target recognition method based on millimeter-wave radar data, comprising the following steps: S100, performing single-frame radar data scatter information extraction and de-noising processing; S200, performing multi-frame radar data overlay processing; S300, performing radar target segmentation and determining positions; and S400, based on target recognition of a classifier, forming a characteristic sample space for millimeter-wave radar target recognition by one-dimensional range profile of each segmented target along radial direction, randomly dividing the characteristic sample space into a training sample subspace and a detection sample subspace, and performing sample training and detection by adopting the classifier, thus radar data of each target is extractedby segmenting the target; and performing the target recognition on basis of the data, so that correct radar target recognition rate is effectively improved, multi-target recognition is also realized,and important reference data can be provided for a radar target recognition method.
Owner:SHANGHAI CRIMINAL SCI TECH RES INST +1
Cloud computing system for data scatter storage
The invention discloses a cloud computing system for data scatter storage. The cloud computing system comprises a cloud computing server group; a middleware server further comprises a data partitioning module and a distributing module; after a user uploads a to-be-computed data packet to the middleware server, the data partitioning module is used for partitioning the to-be-computed data packet into n data blocks to generate a file including partitioning information and binding the file including the partitioning information with one data block, and the distributing module is used for respectively storing the n data blocks to n governable cloud computing servers; a load detecting module is used for detecting load, the governable server with the smallest load is the current server, the distributing module is used for copying (n-1) data blocks onto the current server, and the current server is used for combining the n data blocks into the data packet according to the partitioning information, and computing the combined data packet to obtain a computed result. Even if other users try to visit the data of the user, only a part of the data rather than all data can be visited, so that the security of the user data is ensured.
Owner:天聚地合(苏州)科技股份有限公司
State monitoring and fault diagnosing method for rotating mechanical equipment
ActiveCN105204493AQuality improvementFully verifiable separabilityElectric testing/monitoringFeature vectorDecomposition
The invention discloses a state monitoring and fault diagnosing method for rotating mechanical equipment based on systematic cluster analysis and Fisher discriminant analysis. The method includes the steps that empirical mode decomposition is carried out on obtained monitoring data in a normal state and various fault states to extract energy feature vectors; based on systematic cluster analysis, the separability among samples is verified, and the influence on the dispersibility of sample data is eliminated; on the basis, discriminant analysis functions are extracted, a discrimination totality is built, and faults are diagnosed according to the real-time state monitoring data of the rotating mechanical equipment. Hot problems of online fault diagnosis for rotating mechanical equipment are solved, and intelligent fault diagnosis for the rotating mechanical equipment is achieved. A state monitoring and fault diagnosing model can be set up without the fault state data of a plenty of samples or full-life state monitoring data, dependency on the data is reduced, operability is improved, and the state monitoring and fault diagnosing method has high engineering applicability.
Owner:BEIJING INST OF ELECTRONICS SYST ENG
HTTP streaming media live broadcasting method and system based on multiple TCP links
ActiveCN103457956AImprove experienceFaster and more stable transmissionTransmissionClient-sideBroadcasting
The invention discloses an HTTP streaming media live broadcasting method and system based on multiple TCP links. According to the method and system, the transmission speed can be obviously increased, the problem of playing lagging caused by network congestion or packet dropout is solved, the live broadcasting with a higher code rate can be supported, and the user experience can be improved. According to the technical scheme, through the linking and binding technology, the multiple TCP links are related with one another on the service side, and streaming type data are dispersed to all the links to be transmitted. A client side splices the segmentation streaming type data received by all the links and can then conduct playing.
Owner:CHINANETCENT TECH
Data interaction method, system and device based on multiple data platforms and storage medium
PendingCN112148679AImprove utilization efficiencyImprove sharing efficiencyFile access structuresTransmissionData platformEngineering
The invention relates to a data interaction method, system and device based on multiple data platforms and a storage medium, and aims to solve the technical problems that data is dispersed in different departments, and the working efficiency is reduced because the departments often lack cooperation and cannot use the data of the opposite side. The method includes: registering a resource source andtaking the resource source as a resource providing platform; editing the resource fields needing to be shared or displayed to form a resource directory; submitting the resource directory to big datamanagement department equipment for approval; publishing the resource directory according to the obtained approval information; enabling the resource subscription equipment to determine a subscriptionprocess of the resource directory according to the sharing attribute of the resource providing platform; enabling the resource subscription device to subscribe to the resource data from the resourcesharing platform according to the subscription process; and enabling the resource subscription equipment to call the resource data from the resource providing platform according to the resource catalogue to perform data exchange. The method, system and device have the effect of achieving sharing of data resources among different departments so as to improve the working efficiency.
Owner:江苏锐创软件技术有限公司
Big data application method and system for environmental supervision law enforcement decision
ActiveCN110852601AImprove work performanceImprove decision makingDigital data information retrievalOffice automationInformation processingMulti source data
The invention discloses a big data application method for environmental supervision law enforcement decision. The method comprises the following steps: data acquisition and integration: cleaning and integrating government affair data resources of internal and external pollution sources, and converging and integrating multi-source data; data mining analysis: analyzing the aggregated and integratedmulti-source data; generating an information clue: generating the information clue for environmental supervision and law enforcement according to the data analysis result, and managing the informationaccording to the weight; generating an intelligence portrait: labeling the enterprise problem according to the generated intelligence clue to generate an enterprise intelligence portrait; informationclosed-loop application: carrying out information research and judgment, information dispatching, information processing and result feedback closed-loop application management according to the information clues; and evaluating the efficiency of the information: evaluating the research and judgment, order dispatching and settlement conditions of the information according to the information processing conditions. By adopting the method provided by the invention, the problems that the environmental protection data dispersion data cannot be effectively applied and the like are solved, and the timeliness and accuracy of law enforcement can be improved.
Owner:佛山市南海区环境技术中心
Biological feature template saving and verification method and biological feature identification device and terminal
ActiveCN107113170AReduce the probability of attackReduce leak rateKey distribution for secure communicationUser identity/authority verificationIdentification deviceBiometric encryption
The embodiments of the present invention provides a biological feature template saving and verification method and a biological feature identification device and terminal, and belongs to the biological identification technology field. The biological feature template saving method comprises the steps of processing a biological feature encryption template encrypted and generated according to a biological feature template to obtain M sets of biological feature encryption template data, wherein M >=2; storing the M sets of biological feature encryption template data in N storage areas, at least one set of biological feature encryption template data is saved in each storage area, wherein 1<N<=M. According to the embodiments of the present invention, the biological feature encryption template is processed into multiple sets of biological feature encryption template data, and then the biological feature encryption template data is saved in at least two storage areas dispersedly, so that the multiple sets of biological feature encryption template data is saved in the plurality of storage areas dispersedly, is not easy to leak overall, and accordingly the larger potential safety hazards brought by the prior art to the application of the biological feature template can be eliminated effectively.
Owner:SHENZHEN GOODIX TECH CO LTD
Cross-partition calls in partitioned, tamper-evident data stores
ActiveUS20210165890A1Input/output to record carriersEncryption apparatus with shift registers/memoriesTamper resistanceComputer network
Provided is a process that includes: obtaining a first request by a first program associated with a first sub-partition of a first partition of a tamper-evident data store of a decentralized computing platform to read data stored in either (i) a second sub-partition of the first partition of the tamper-evident data store of the decentralized computing platform, or (ii) a second partition of the tamper-evident data store of the decentralized computing platform; determining with a subset of peer computing nodes of a set of peer computing nodes that the first program is authorized to read from the second sub-partition or the second partition; and in response to the determination, causing the requested data to be read from the second sub-partition or the second partition.
Owner:SCHVEY INC D B A AXONI
Blockchain cloud storage user data security solution
PendingCN111428271AAchieve decentralizationRealize decentralized storageDigital data protectionComplete dataSoftware engineering
A blockchain cloud storage user data security solution includes four steps: step A, a client constructs a blockchain client operation environment and downloads an operation framework through an application construction unit in a PC; b, the client performs multi-signature by adopting a multi-signature technology based on zero knowledge consensus through an application unit in the client; c, the client cuts, fragments and encrypts the to-be-uploaded data through an application fragment cutting unit in the client; and step D, when the client downloads the file in the cloud storage system, whetherthe data stored in the blockchain by the client is complete and available or not is verified by adopting a Merkle tree verification method. Based on the fact that the blockchain technology has natural decentralization characteristics, the method totally adopts four steps, achieves scattered storage of data, reduces risks of data loss and complete data stealing, prevents data from being maliciously tampered by a center node, and effectively achieves the effect that cloud storage data of users is safer. Based on the above, the method has a good application prospect.
Owner:上海坤仪金科信息技术有限公司
Network linkage management method and digital police linkage management method
InactiveCN107277470ASolving Dispersion ProblemsSolve the coexistence of centralized storageClosed circuit television systemsVideo monitoringData source
The invention discloses a network linkage management method and a digital police linkage management method. Video information is acquired by using a data source layer. The video information of the data source layer is captured and stored by using a video access layer configured at a client front end. An application layer performs information interaction with a big data computing layer and is configured for providing at least one functional requirement. The big data computing layer performs intelligent analysis and data mining on the video information transmitted by the video access layer according to the requirement. The problems of dispersed and concentrated storage and coexistence and multistage distribution of the massive video data can be solved through fusion of the big data technology and the video monitoring service so that the read-write efficiency of the unstructured video data can be enhanced, and the end-to-end solution can be provided for quick retrieval and intelligent analysis of video monitoring.
Owner:四川天翼网络股份有限公司
Method of sharing data in WEB page flow and client apparatus
The invention provides a method for sharing data in WEB page flow and the client end devices thereof, making the client end devices identify shared data in WEB pages to disperse the course that server identifies shared data in the WEB pages to all client ends so as to save processor resources of the server; storing the shared data into the client ends to disperse the shared data stored in the server to all client ends so as to storage resources of the server; storing the shared data into the client ends to make a browser need not to firstly send data to the server and then make the server return the shared data to the browser in the course that the browser submits the shared data from one page to another page for display, so as to avoid shared data transmission between client end and server, thus saving network transmission resources and improving server performance.
Owner:JIANGSU HENGBO PNEUMATIC CONVEYING EQUIP MFG CO LTD
Distributed cloud storage method and system
InactiveCN108494826AAvoid Overburdening ProblemsPrevent crashTransmissionStructure of Management InformationData transmission
The invention discloses a distributed cloud storage method and system. A central server receives a file transfer request sent by a user side, searches for a node server closest to the user side, and forwards the file transfer request to the node server; and when the file transfer request is a file upload request, the node server stores the file uploaded by the user side and synchronizes the file to the central server. The method and the system have the beneficial effects that a distributed storage structure is constructed by utilizing the central server and the node server, and data is dispersedly stored on a plurality of node servers, so that the breakdown of the whole storage system caused by single-point faults is avoided, and the stability and the safety are higher; the central serverdistributes the tasks of data transmission to all node servers, adapts to high-concurrency data interaction scenes, and forwards the file transfer request to the node server closest to the user side,so that a communication distance between the node server and the user side is as small as possible, and the communication efficiency is higher.
Owner:HEART TOUCH WUHAN CULTURE MEDIA
Data scatter storage method, data recovery method and data card
InactiveCN103312494AAchieve restorationSolve defects that cannot be restored normallyKey distribution for secure communicationRAIDOriginal data
The invention discloses a data scatter storage method, a data recovery method and a data card which has the functions of data scatter storage and cross recovery. According to the technical scheme provided by the invention, original data can be stored in a scattered manner in a plurality of data cards according to a predetermined rule, so that each data card automatically stores corresponding part of data according to the serial number index of the card and stores part of data in other data cards in a cross mode. Therefore, original data stored in all data cards can be recovered just by the any more than half of data cards. Efficient, convenient and raid data reduction is realized while data is safely protected.
Owner:SECURITY PRINTING INST OF PEOPLES BANK OF CHINA +1
Anti-money laundering suspicious transaction monitoring method and device
PendingCN111127200AImprove monitoring efficiencyImprove monitoring accuracyFinanceProtocol authorisationData packDatasheet
The invention provides an anti-money laundering suspicious transaction monitoring method and device. The method comprises the following steps: obtaining anti-money laundering data, wherein the anti-money laundering data comprises client data, transaction data and account data; standardizing the anti-money laundering data to generate a basic data table; calling an anti-money laundering suspicious model to perform data screening on the basic data table to generate a screening result; and determining a suspicious transaction by using the screening result. According to the invention, the anti-money laundering suspicious model is used for screening the anti-money laundering data; suspicious transactions are determined through screening results, the problems of data dispersion, insufficient dataanalysis early warning capability and the like in the anti-money laundering work field are solved, and meanwhile, the monitoring efficiency and the monitoring accuracy of anti-money laundering monitoring are improved, so that the detection quality is greatly improved in an enterprise range.
Owner:CHINA CONSTRUCTION BANK
Storage capacity sharing method and device, service server, user terminal and system
The invention discloses a storage capacity sharing method. The storage capacity sharing method comprises: enabling a service server to receive a data processing request sent by a first user terminal,Wherein the data processing request comprises a data backup request; Determining a second user terminal according to the data processing request; Obtaining request permission information of a second user terminal; And establishing a data transmission channel between the first user terminal and the second user terminal according to the request permission information, so that the first user terminaland the second user terminal execute corresponding operation on the to-be-processed data corresponding to the data processing request. Therefore, the cost is saved, the data is dispersed in other user terminals, the safety of data storage is enhanced, the storage memory of the user client is reasonably utilized, and the situation that the storage space of the user terminal is wasted is solved. The invention further provides a storage capacity sharing device, a service server, a user terminal and a system which all have the above beneficial effects.
Owner:SHENZHEN ONETHING TECH CO LTD
Data communication system, data transmitting apparatus, data receiving apparatus, data communication method and data communication program
InactiveCN101027851AImprove communication qualitySuitable for real-time applicationsFrequency-division multiplex detailsPower distribution line transmissionCommunication qualityCommunications system
There is provided a data communication system that performs power line communication having satisfactory communication quality by disposing data in channels where notches or noises do not exist in a distributed manner. There is included a step S01 of transmitting a pilot tone from a data transmitting device to a data receiving device, a step S03 of detecting a frequency band where a notch exists, among frequency bands used for the power line communication, on the basis of the pilot tone by means of the data receiving device, a step S05 of transmitting information on the frequency band where the notch exists, as channel information, to the data transmitting device by means of the data receiving device, a step S07 of setting a channel, which is located within a frequency band where a notch does not exist, as a channel used for the power line communication, by means of the data transmitting device, and a step S09 of disposing data, which is to be transmitted, in each channel and then transmitting the data to the data receiving device, by means of the data transmitting device.
Owner:MITSUBISHI MATERIALS CORP
Video cloud storage system based storage and extraction performance balancing method and device
ActiveCN104702654ADecentralized storage function is preferredEnsure safetyProgram controlTransmissionCloud storage systemDistributed computing
The invention relates to video cloud storage and discloses a video cloud storage system based storage and extraction performance balancing method and device. The method includes: dividing acquired data into data blocks according to capacity and storing the data into different storage equipment of at least one storage server in a scattered manner; when extracting the data, acquiring information of the storage servers where the to-be-extracted data are located, wherein the information includes the size of the data blocks and the level of system loads; under the premise that scattered storage priority is guaranteed, formulating extraction strategies with user defined priority according to the information of the storage servers; concurrently extracting the data from the storage servers according to the extraction strategies. The data are stored in the different stored servers in a scattered manner, so that system resources are effectively utilized; under the premises that the scattered storage priority is guaranteed, the data are concurrently extracted from the different storage servers according to the extraction strategies, data security is guaranteed, the data can be extracted effectively, and confliction in preemption of the system resources in data storage and extraction is reduced.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Method for monitoring operation performance of large-scale wind turbine generator
ActiveCN112032003APerformance Abnormal State SensitivityImprove monitoring accuracyMachines/enginesWind motor monitoringControl engineeringTurbine
The invention discloses a method for monitoring the operation performance of a large-scale wind turbine generator. The method comprises the following steps: 1, acquiring operation data and preprocessing data; 2, dividing wind speed intervals; 3, dividing an operation area; and 4, carrying out performance anomaly determination. According to the technical scheme, operation area division is conductedon a data scatter diagram shape of the wind speed interval where low-efficiency data points are prone to accumulation, the whole operation space is divided into a normal operation area and a low-efficiency operation area, and the abnormal state of the operation performance of a unit is judged based on two quantitative indexes of a low-efficiency regional area and the low-efficiency data proportion.
Owner:ZHEJIANG WINDEY
Comprehensive energy system parameter determination method based on distributed optimization and related device
PendingCN112380681AGuaranteed co-optimizationAchieve independent controlForecastingTechnology managementIntegrated energy systemEngineering
The invention provides a comprehensive energy system parameter determination method based on distributed optimization and a related device, a comprehensive energy system represented by an electric power natural gas comprehensive energy system comprises at least one processor, and the processors correspond to different energy analysis areas respectively. In other words, different energy analysis areas are processed by using different processors, so that a regional management mode can be adopted during management, and when the processors perform area regulation and control, the conditions of equipment in the areas and the conditions of line equipment connected with the different areas are considered, cooperative optimization of the whole comprehensive energy system can still be guaranteed while independent control over the energy analysis area is achieved. Compared with a unified control mode of all areas, only boundary data needs to be shared among different areas, the data sharing content is small, data dispersion processing is achieved, the probability of data leakage of the whole comprehensive energy system can be reduced, and the equipment operation safety of the whole comprehensive energy system is improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Adverse drug reaction monitoring method and device, computer equipment and storage medium
PendingCN111223571AReduce resource consumptionDoes not affect running speedMedical data miningDrug and medicationsOriginal dataEngineering
The invention discloses an adverse drug reaction monitoring method and device, computer equipment and a storage medium. The method comprises the following steps: acquiring diagnosis and treatment dataof a patient, wherein the diagnosis and treatment data is dispersed in a multi-item information table; arranging the diagnosis and treatment data according to the ID number of the patient and storingthe diagnosis and treatment data in a layered directory file form to form directory file data; and reading the directory file data, and retrieving and comparing the directory file data according to apreset monitoring model to obtain a monitoring result conforming to the monitoring model. According to the technical scheme, when monitoring is executed, original data does not need to be requested any more, the performance is improved by 10 times or above while the HIS running speed is not affected, and due to the fact that diagnosis and treatment data of a patient is very small (less than 10 M), the data less than 10M can be called into the memory only by 1% of the CPU, and no pressure is applied to the hard disk, so that the resource consumption of the CPU, the memory and the hard disk isgreatly saved.
Owner:GENERAL HOSPITAL OF PLA
Parameter identifying method for airplane trial flight data
ActiveCN106114876AImprove the efficiency of design improvementsImprove versatilityAircraft indicatorsJet aeroplaneIndependent function
The invention discloses a parameter identifying method for airplane trial flight data. The method comprises: acquiring trial flight data; selecting a dependent variable as dependent variable data, selecting a plurality of independent variables as independent variable data and generating data scatters; carrying out geometric topology operation on all data scatters and mapping the data scatters into a multi-dimensional space; calculating the linear independent base function of each dimension in the multi-dimensional space; utilizing a linear independent function to fit all of the data scatters into a multi-dimensional curved surface; and based on the multi-dimensional curved surface, carrying out curve fitting on the dependent variable data and single independent variable data in the independent variable data so as to obtain a function relationship of the dependent variable data and single independent variable data. By calculating and fitting the multi-dimensional curved surface and decoupling the variables, the parameter identifying method does not need to carry out physical modeling and simplification according to the physical backgrounds of flight states. The parameter identifying method has excellent universality, and at the same time, is relatively lower in calculation amount, has high calculation efficiency and accuracy and is favorable to the efficient estimation of airplane performance.
Owner:COMAC +1
Metallurgical industry data management system and method
InactiveCN111784170AAchieve aggregationAchieve sharingInterprogram communicationCharacter and pattern recognitionData aggregatorData acquisition
The invention provides a metallurgical industry data management system and method, and the system comprises a data definition module which defines static data and dynamic data, and carries out the classification of the data at the same time, and the classification comprises the steps: carrying out the preliminary classification of the data according to the flow of a production line, and carrying out the secondary classification of a preliminary classification result according to the flow and the equipment type; a data acquisition module which is used for acquiring the dynamic data; a data distribution module which is used for caching the acquired data and pushing the data; a data processing module which comprises an event triggering unit, a data statistics unit and a data filtering unit used for filtering data. According to the invention, data standardization is taken as a core, and functions of data acquisition, storage and the like are performed on the basis of specification definition according to data characteristics of the iron and steel industry, so that data aggregation and sharing are realized, an island phenomenon of data dispersion is avoided, and data capitalization becomes simple.
Owner:CISDI INFORMATION TECH CO LTD
Bridge dynamic characteristic abnormity early warning method considering environment temperature variation
InactiveCN113175987AGuaranteed correctnessSimple processVibration measurement in solidsAlarmsLinear correlationSimulation
Owner:SOUTHEAST UNIV
Data decentralized access method
InactiveCN101067826AImprove securityFast accessSpecial data processing applicationsAccess methodData scatter
This invention relates to a method for accessing data separately used in between a file and a user host including the following steps: segmenting said file into multiple data blocks, storing them in the host of the data separately, in which, a data host in it responds a file read instruction sent by the user host to finish information exchange with other data hosts, and the user host responds the exchange result to take back the data blocks scattered in the data host to compose said file.
Owner:VIA TECH INC
GNSS (Global Navigation Satellite System) forwarding deception jamming detection method based on C/N0-MV
ActiveCN113406671ASatellite elevation affects shieldingImprove detection efficiencySatellite radio beaconingData setEngineering
The invention discloses a GNSS forwarding deception jamming detection method based on C / N0-MV. According to the method, a deception signal is detected by capturing the fluctuation degree of the carrier-to-noise ratio of a satellite during a deception attack by utilizing the characteristic that variance represents data dispersity. In the process, firstly, GNSS signals are preprocessed, a software receiver receives and captures signals and estimates a receiver noise floor, then the carrier-to-noise ratio C / N0 is calculated according to the signal-to-noise ratio SNR, then a fixed-length sliding window is set, a data set variance MV is calculated, a variance sequence is created, finally, a detection threshold is set, the variance sequence is detected, and through a semi-physical simulation experiment, whether deception interference occurs is detected. The method has the advantage of shielding the influence of the satellite elevation angle and is high in detection efficiency.
Owner:SOUTHEAST UNIV
Remote health monitoring management system and method
PendingCN111447288AAccurate analysis and processingAnalytical Processing QuantificationHealth-index calculationTransmissionThe InternetEmergency medicine
The invention discloses a remote health monitoring management system and method. According to the invention, sign data is monitored through each sign health data monitoring device at a field monitoring point; the physical sign data is transmitted to the remote monitoring center through the Internet, then the physical sign data is analyzed and processed by the remote monitoring center and the system server platform, and health monitoring data analysis and processing result feedback, health early warning and health management are carried out. The problems that data monitored by an existing physical sign monitoring device is scattered, pathological condition analysis and condition evaluation cannot be comprehensively carried out, a reasonable health management scheme is given in combination with the actual condition of a patient, and certain limitation exists are solved. And secondly, the analysis and processing of the health monitoring data are more accurate and quantitative, and a powerful guarantee is provided for further health evaluation and evaluation, health early warning and health management of the system. Finally, rich health management schemes are provided.
Owner:SHANGHAI UNIV OF MEDICINE & HEALTH SCI
Method and device for data entry based on block chain network, and computer equipment
PendingCN111177754AAvoid splittingAvoid distractionFinanceDigital data protectionCiphertextEngineering
The invention provides a method and a device for data entry based on a block chain network, computer equipment and a computer readable storage medium, and relates to the technical field of block chainencryption. The block chain network is composed of block chain nodes corresponding to a plurality of participants. When a user uploads service data, the service data is encrypted at second-level encryption nodes of the block chain node, an encryption private key is stored in the second-level encryption nodes, and then the encrypted ciphertext data is uploaded to first-level data nodes for chain entry to generate a service block, so that data consensus synchronization with block chain nodes corresponding to other participants is realized. The block chain nodes corresponding to the participantsare located in the same block chain network, and the service data in the first-level data nodes of the block chain nodes are synchronized with each other, so that information splitting and data dispersion among the participants can be avoided, and the registration efficiency is effectively improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com