Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
209 results about "Counter measures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Counter Measures: Bringing balance to the process. A Counter Measure is an action that corrects or “counter acts” the Root Cause creating the problem. Counter Measures bring balance to an out of balance process, but they are not solutions.
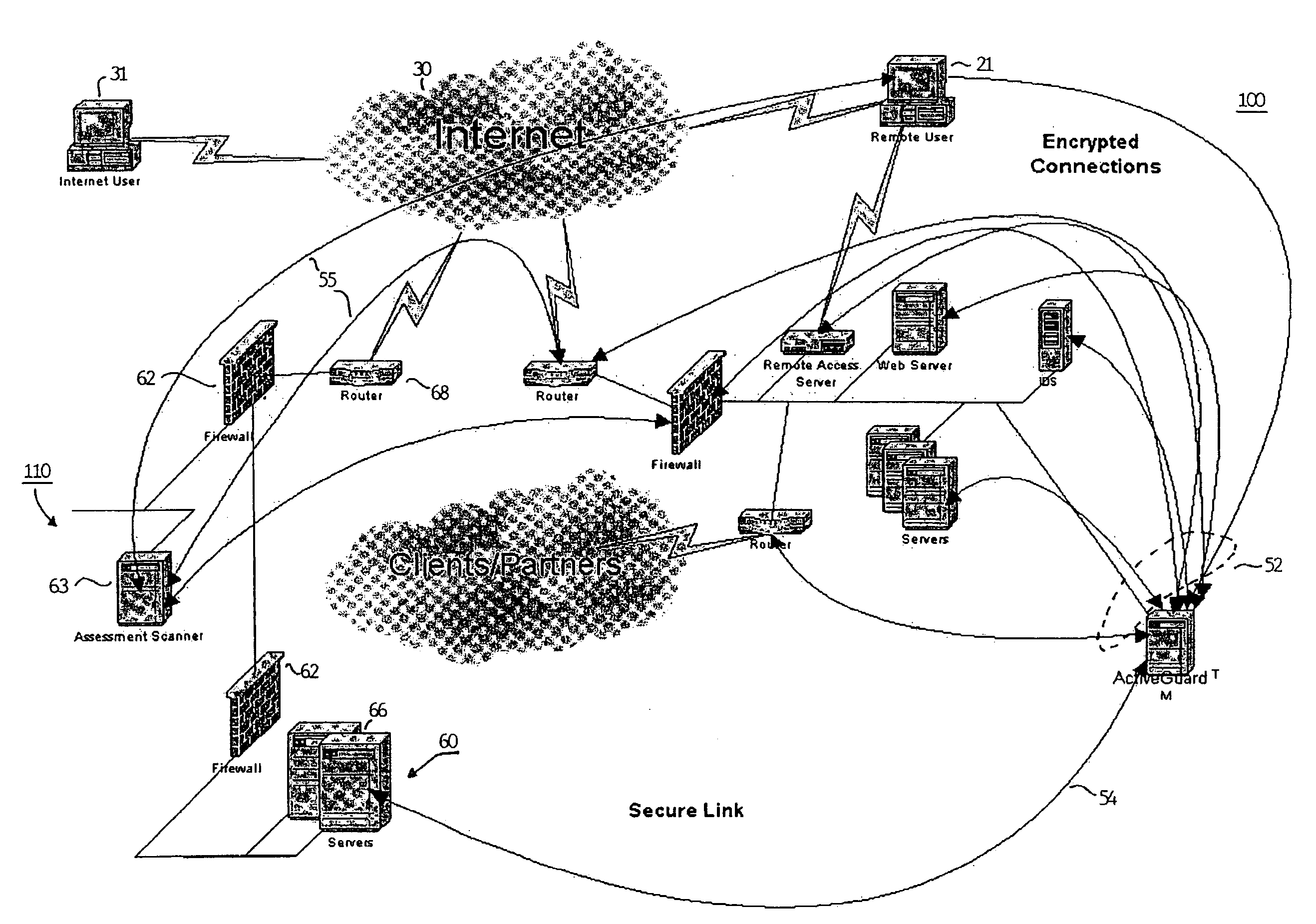
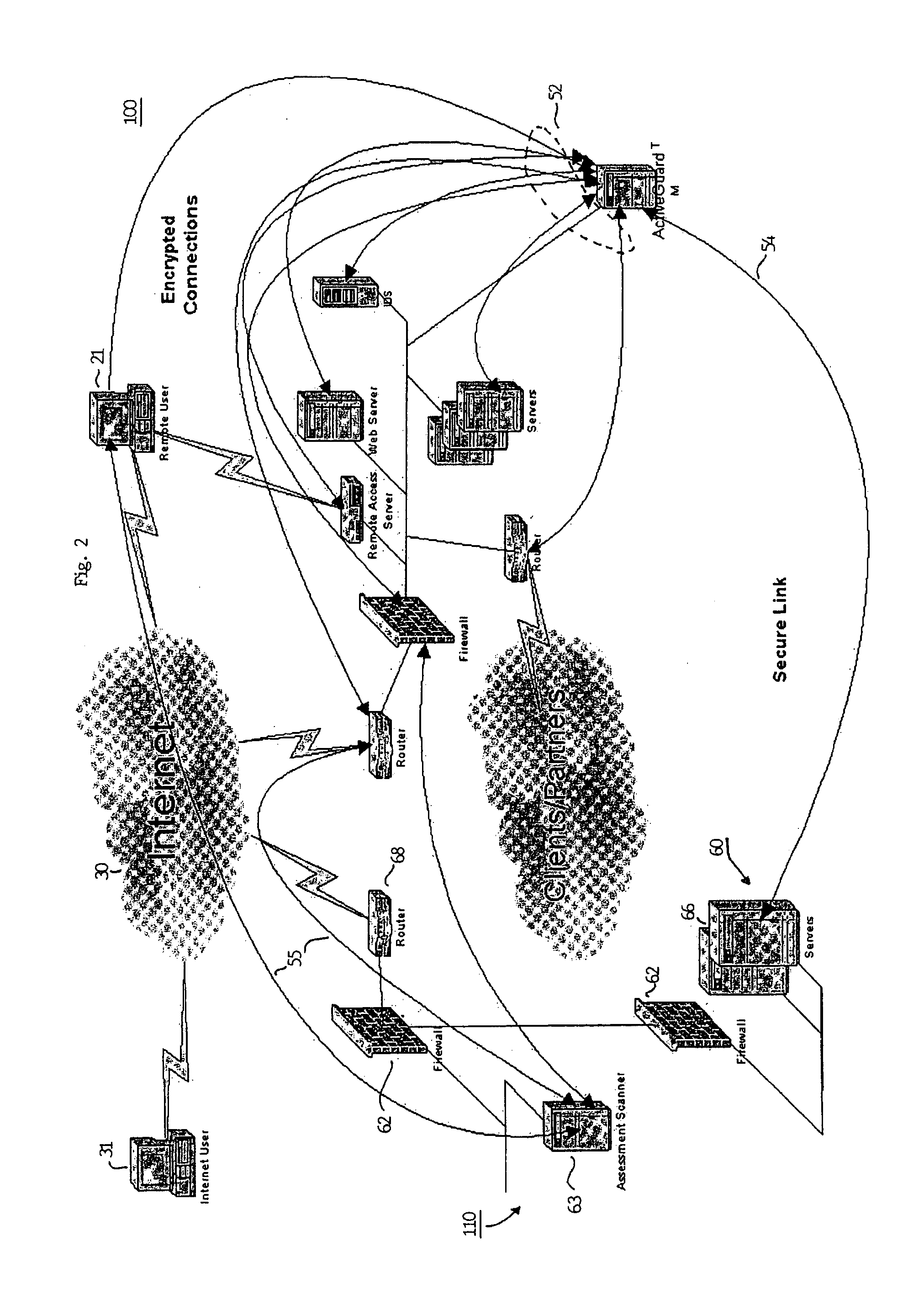
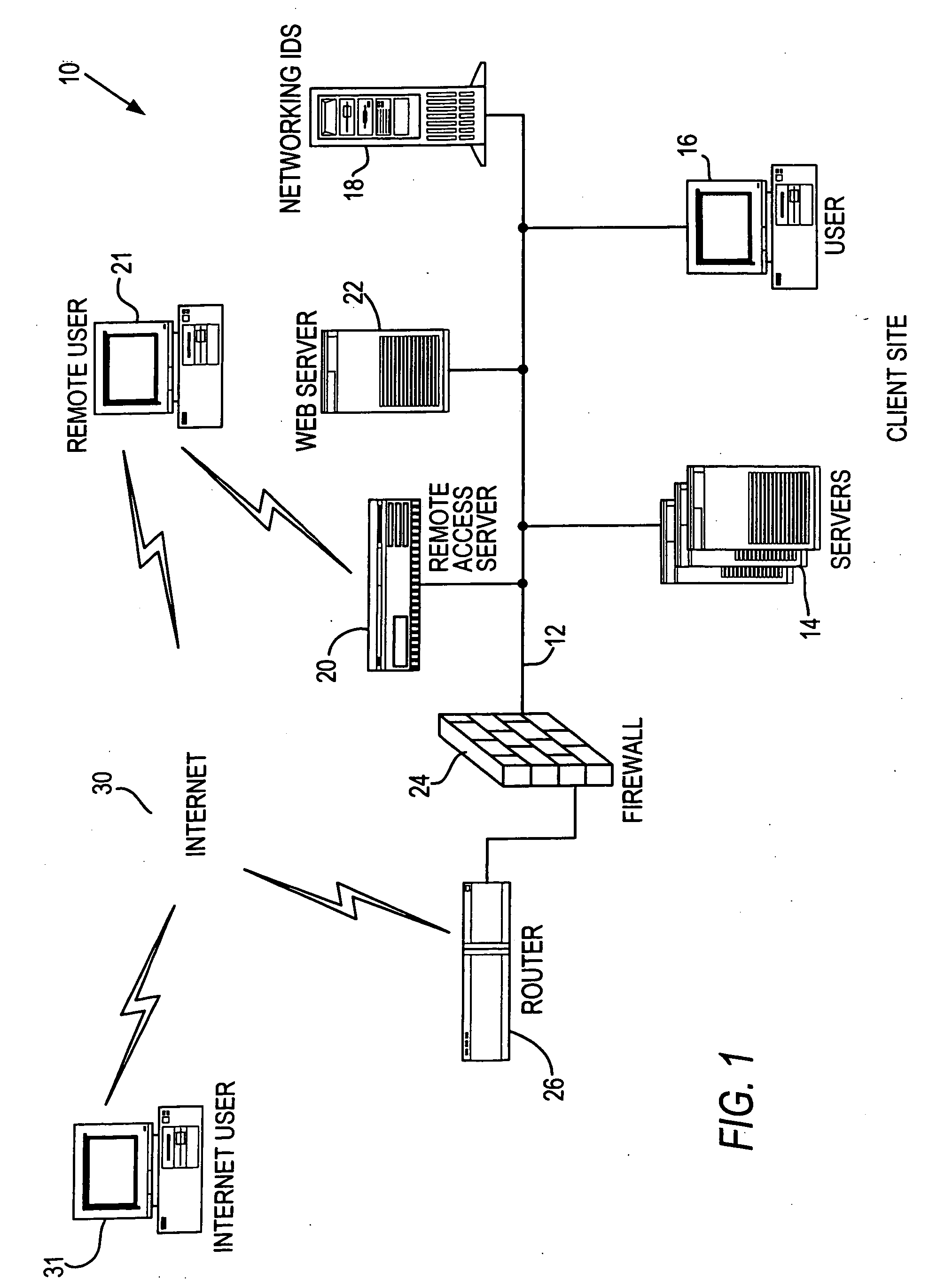
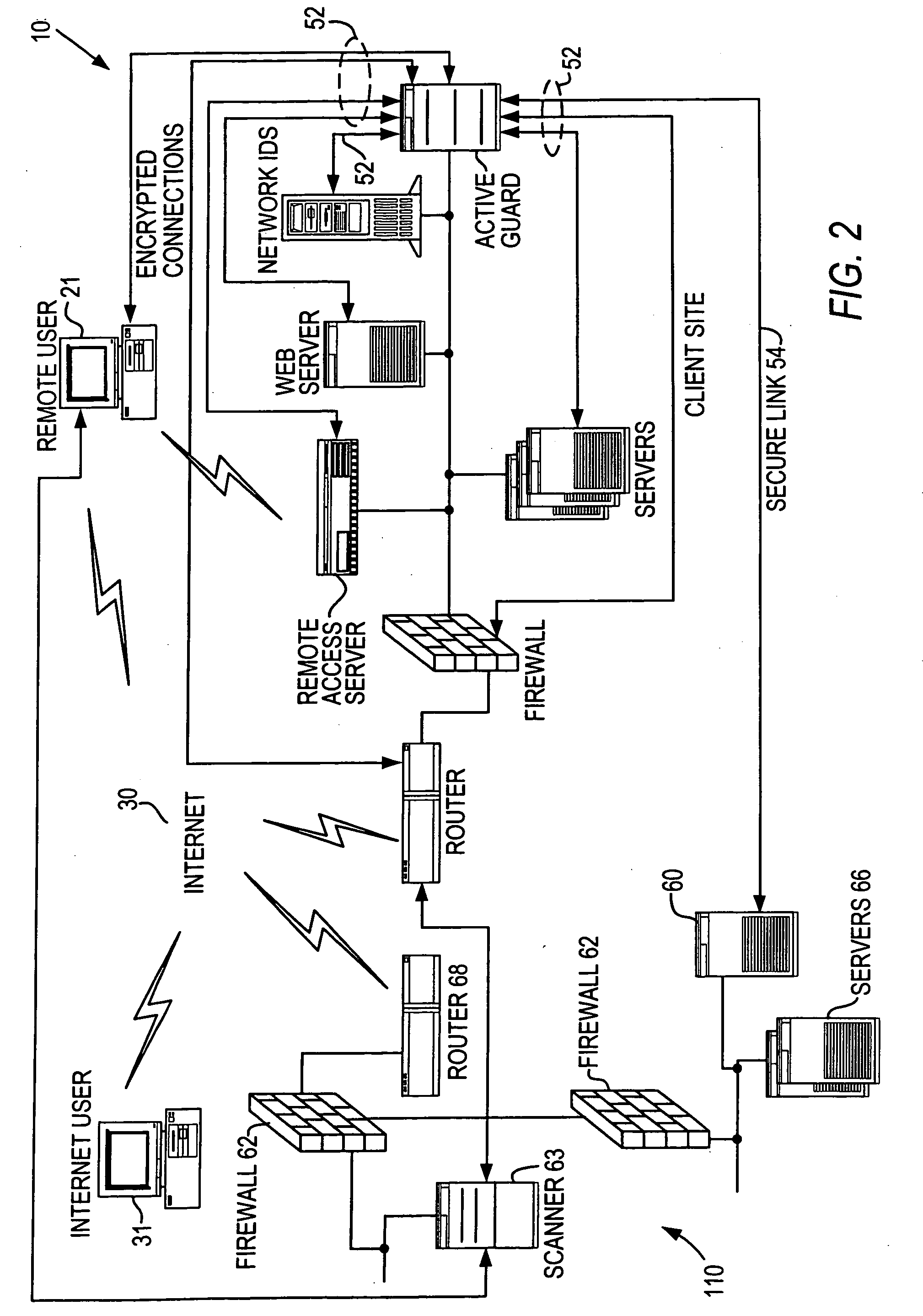
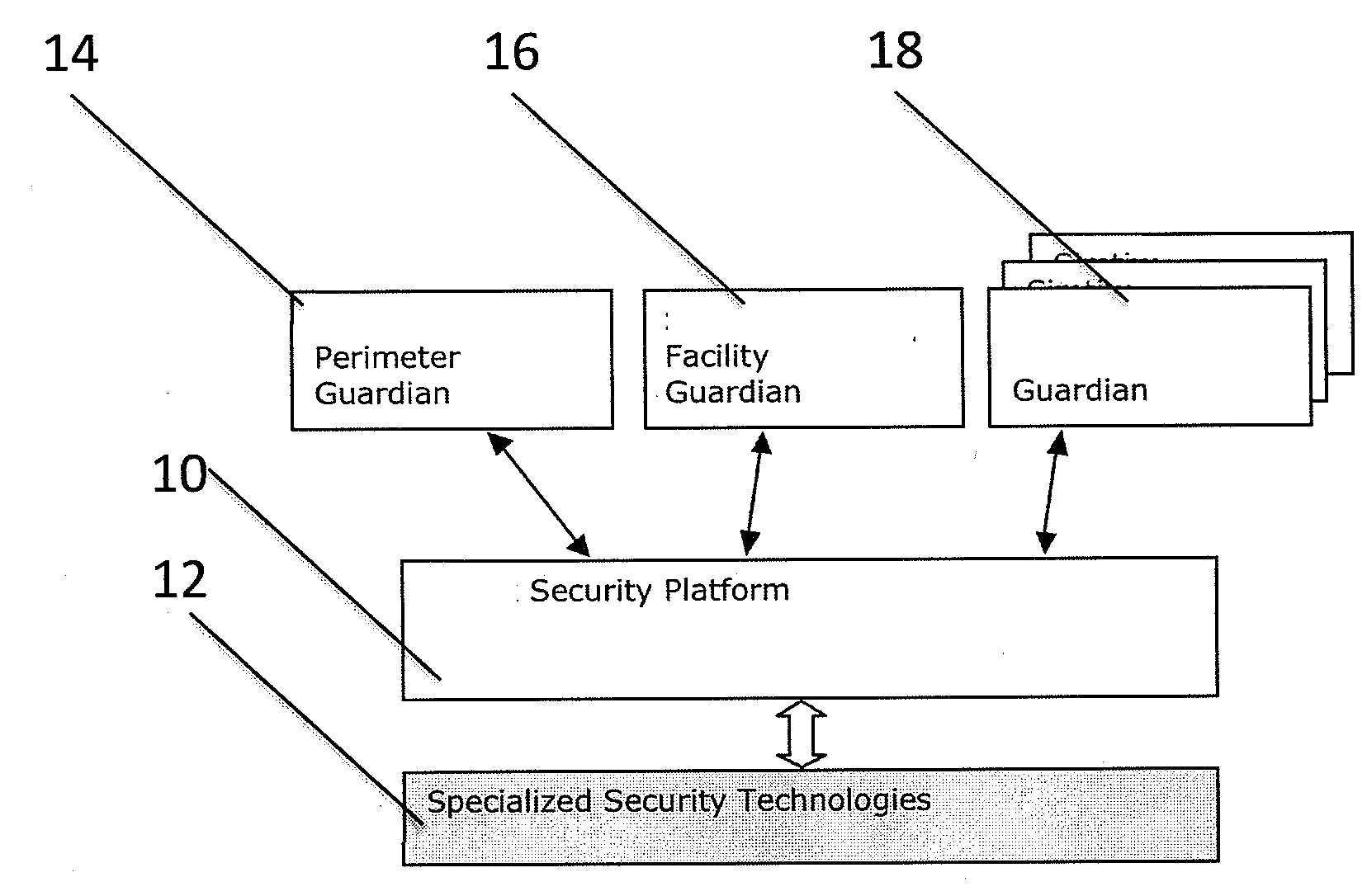
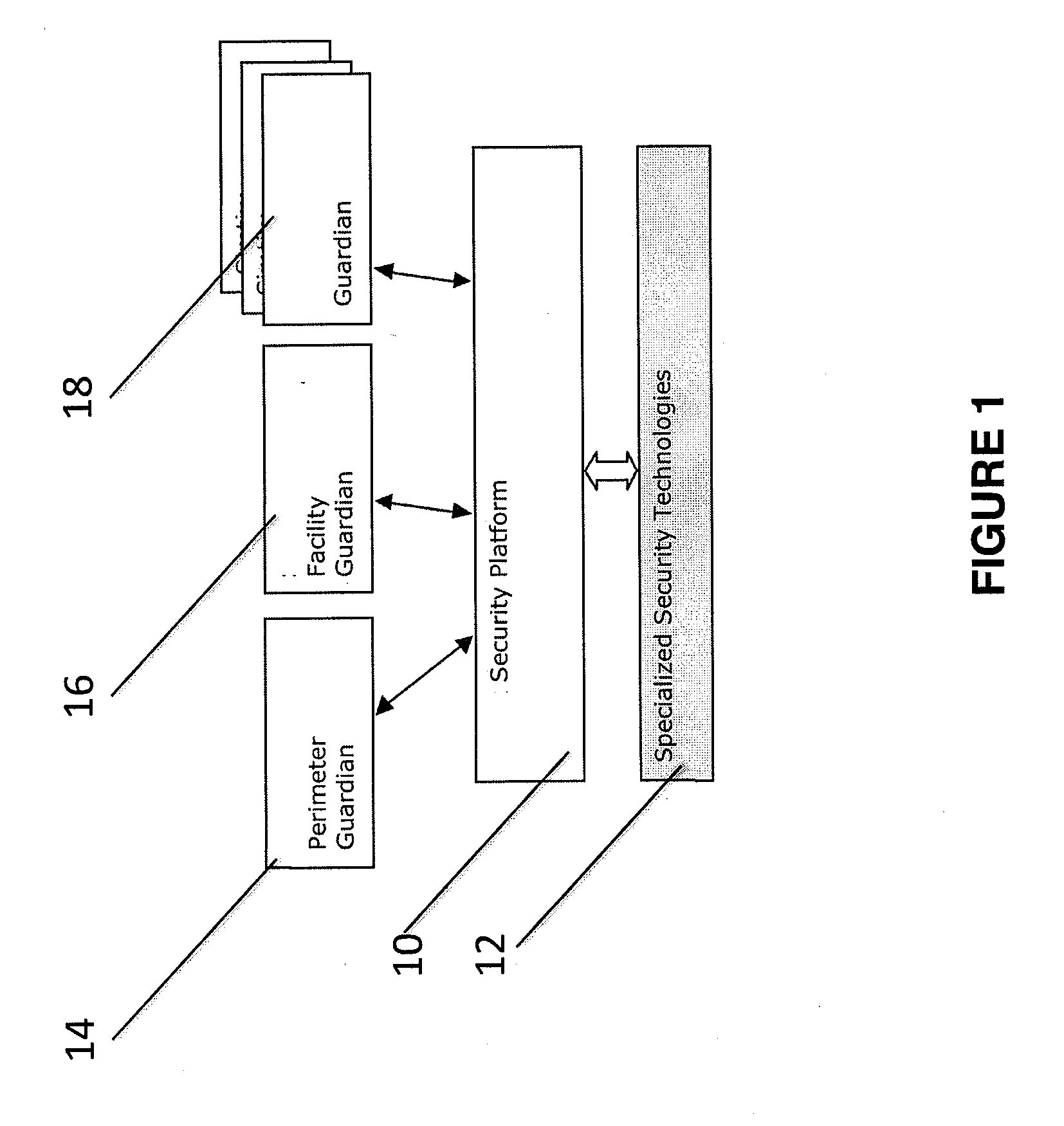
Method and apparatus for verifying the integrity and security of computer networks and implementing counter measures
InactiveUS6988208B2Mitigate or thwart suspected intruder attacks on the target networkMemory loss protectionDigital data processing detailsCountermeasureSecurity system
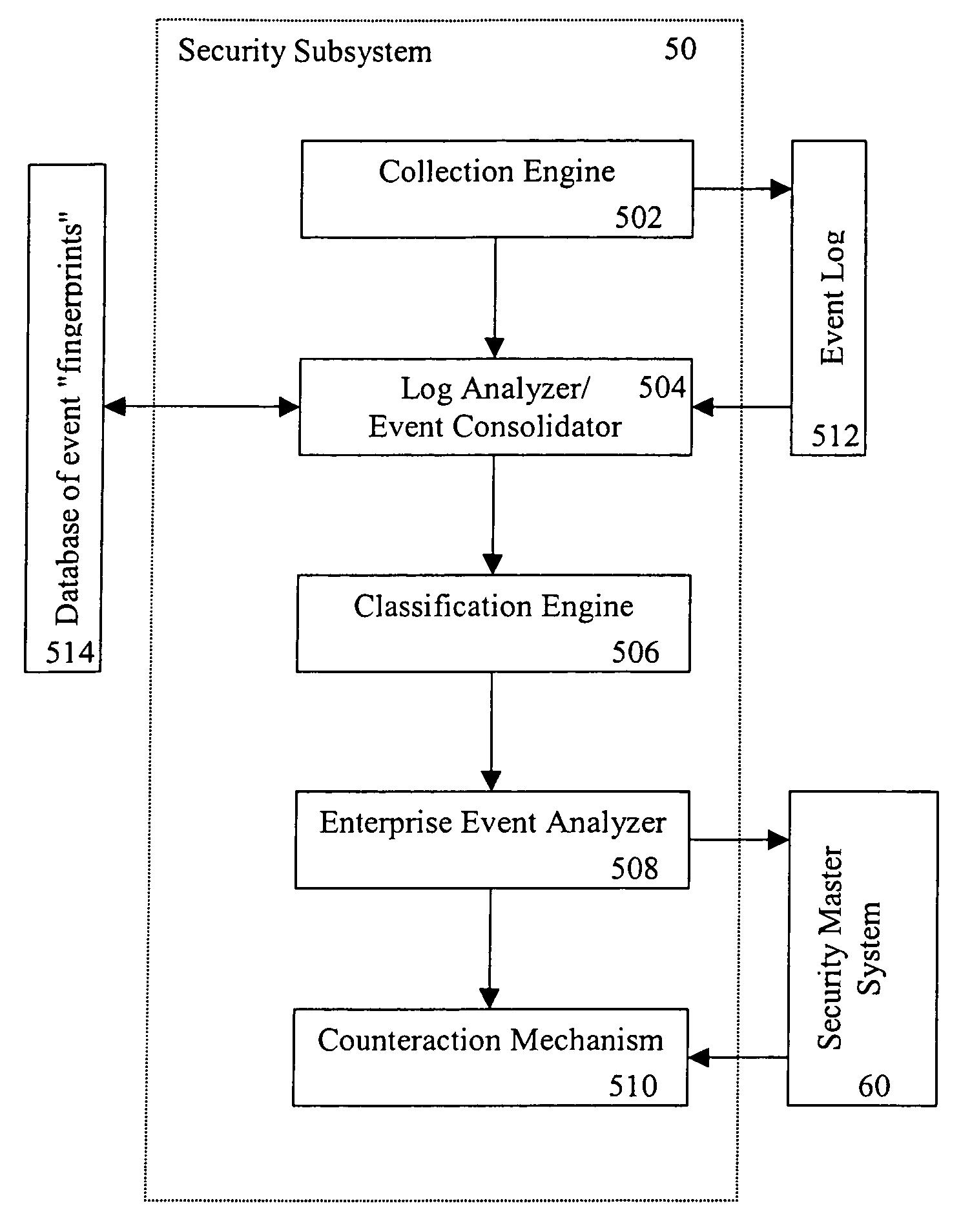
A method and apparatus for verifying the integrity of devices on a target network. The apparatus has security subsystems and a master security system hierarchically connected to the security subsystems via a secure link. The target network includes various intrusion detection devices, which may be part of the security subsystem. Each intrusion detection device generates a plurality of event messages when an attack on the network is detected. The security subsystem collects these event messages, correlates, and analyzes them, and performs network scanning processes. If certain events warrant additional scrutiny, they are uploaded to the master security system for review.
Owner:SICORTEX
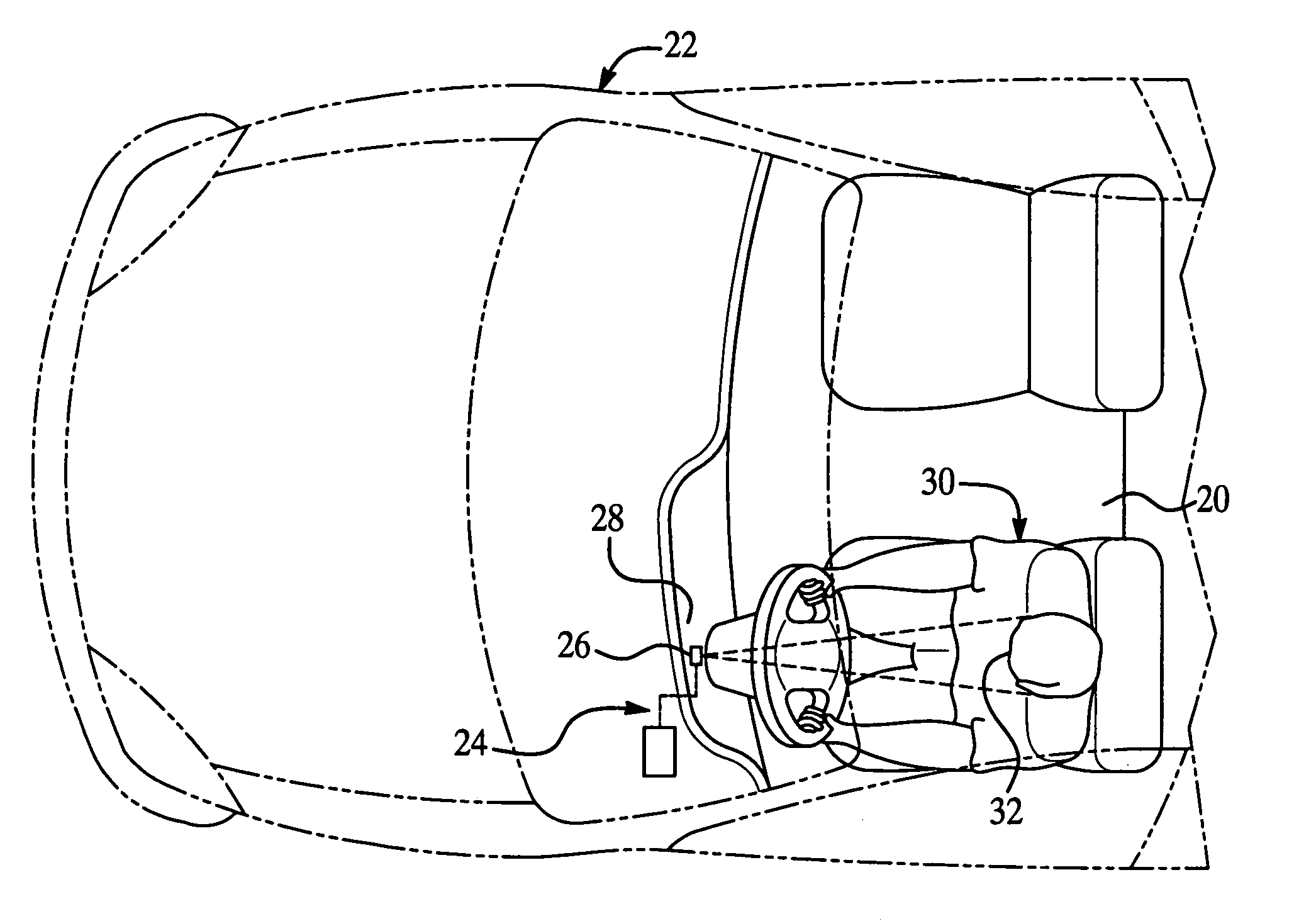
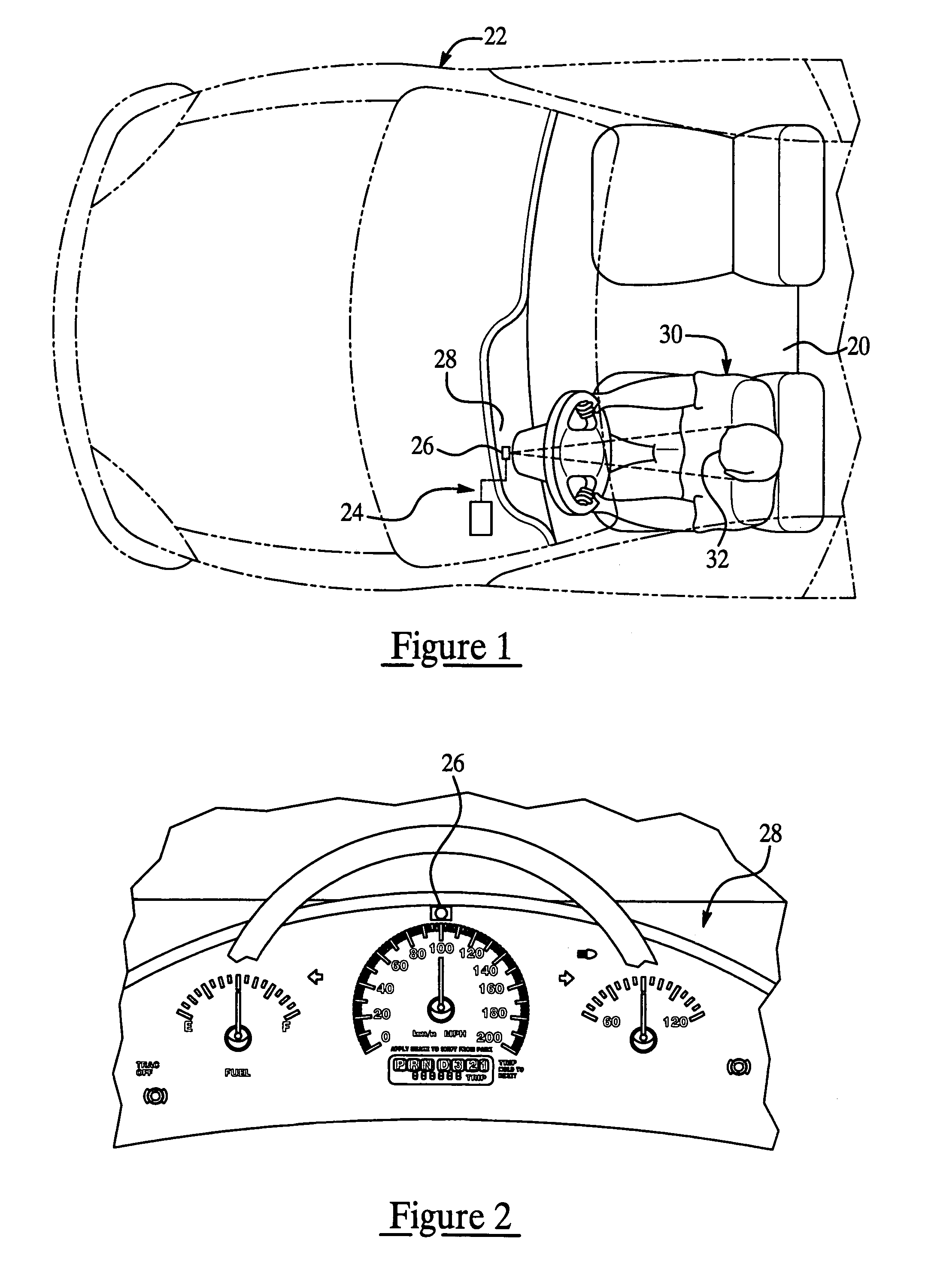
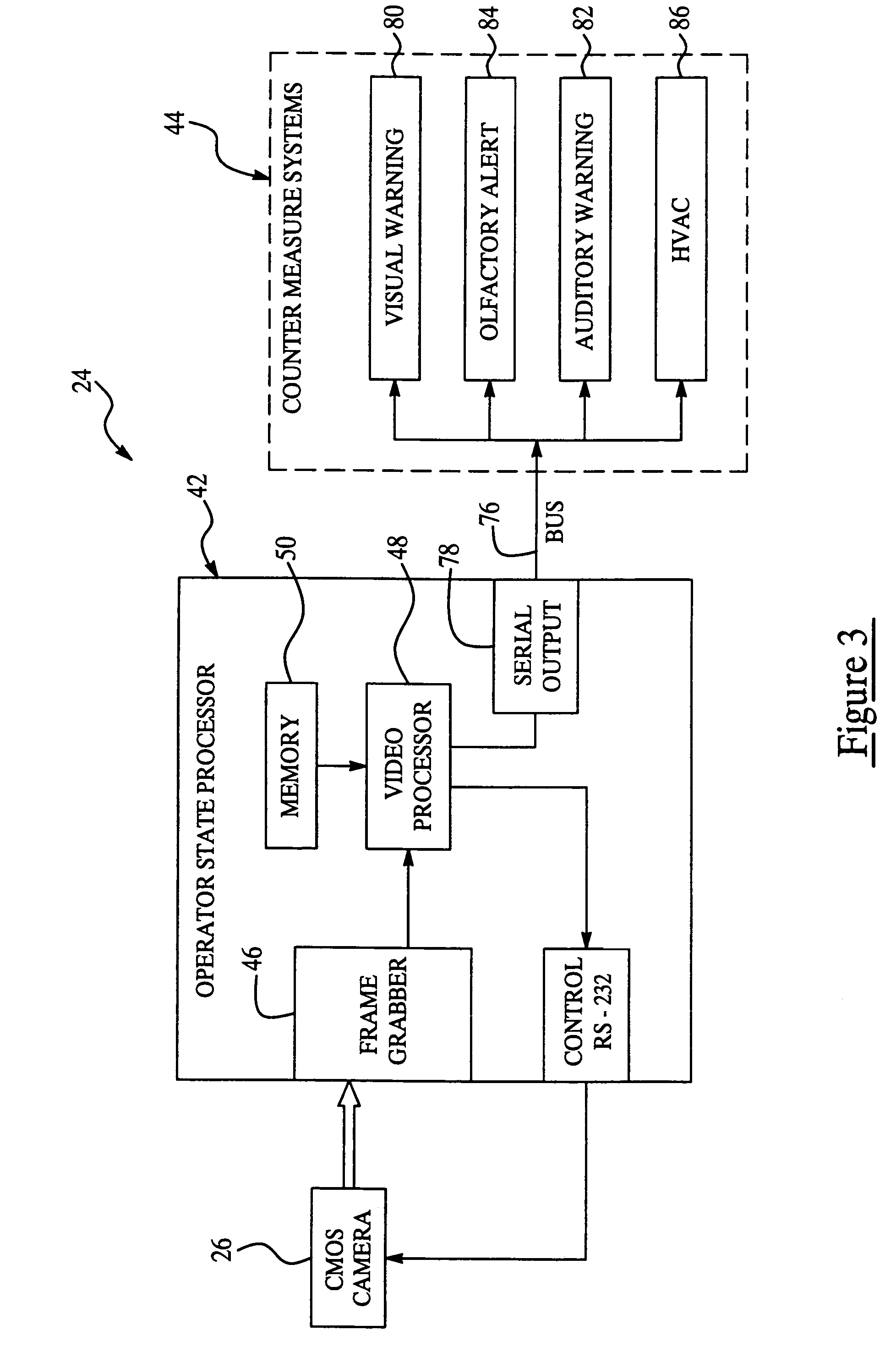
Method of detecting vehicle-operator state
ActiveUS7423540B2Less componentsShort response timeImage enhancementImage analysisDriver/operatorCounter measures
A method of detecting the state of an operator of a vehicle utilizes a low-cost operator state detection system having no more than one camera located preferably in the vehicle and directed toward a driver. A processor of the detection system processes preferably three points of the facial feature of the driver to calculate head pose and thus determine driver state (i.e. distracted, drowsy, etc.). The head pose is generally a three dimensional vector that includes the two angular components of yaw and pitch, but preferably not roll. Preferably, an output signal of the processor is sent to a counter measure system to alert the driver and / or accentuate vehicle safety response.
Owner:APTIV TECH LTD
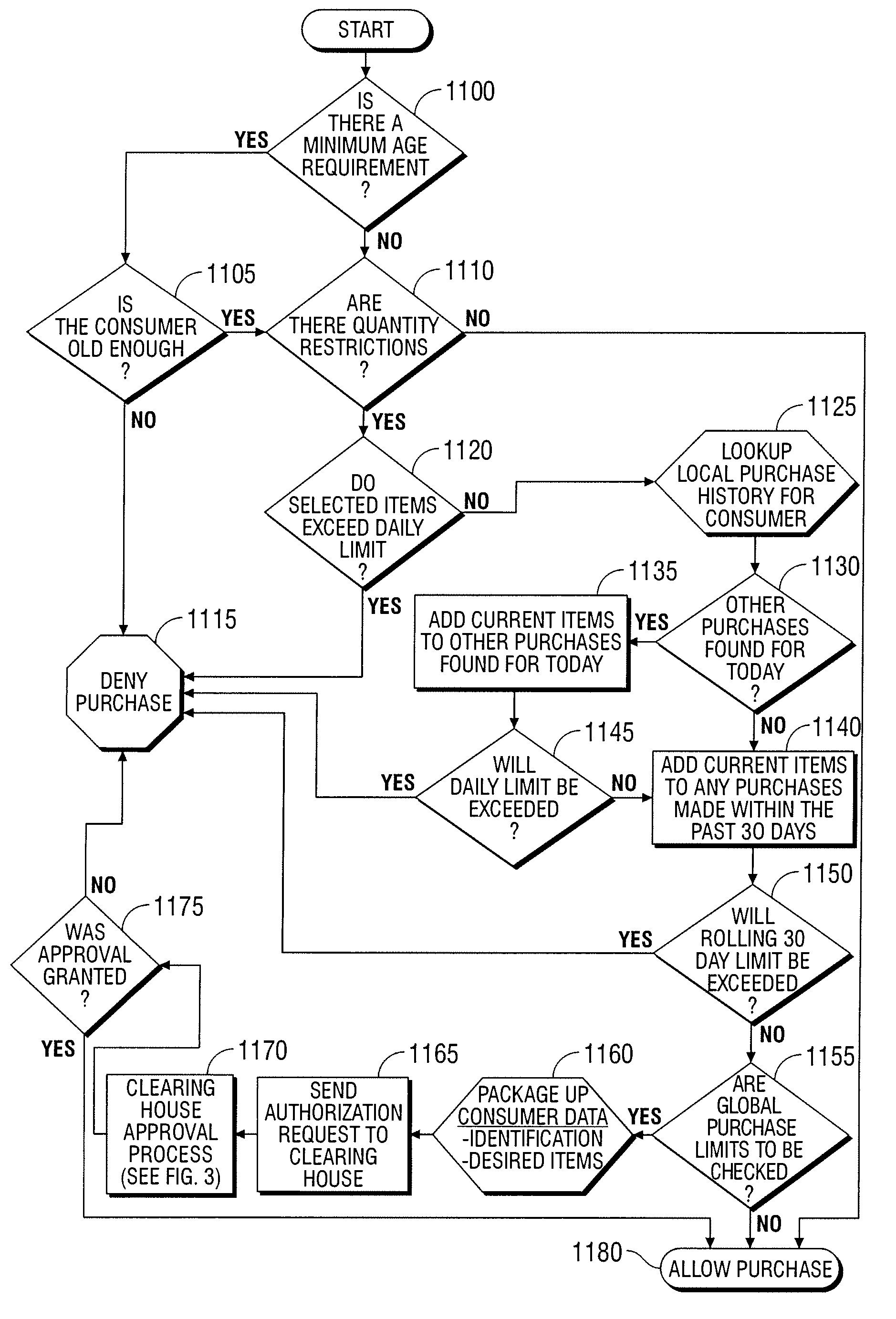
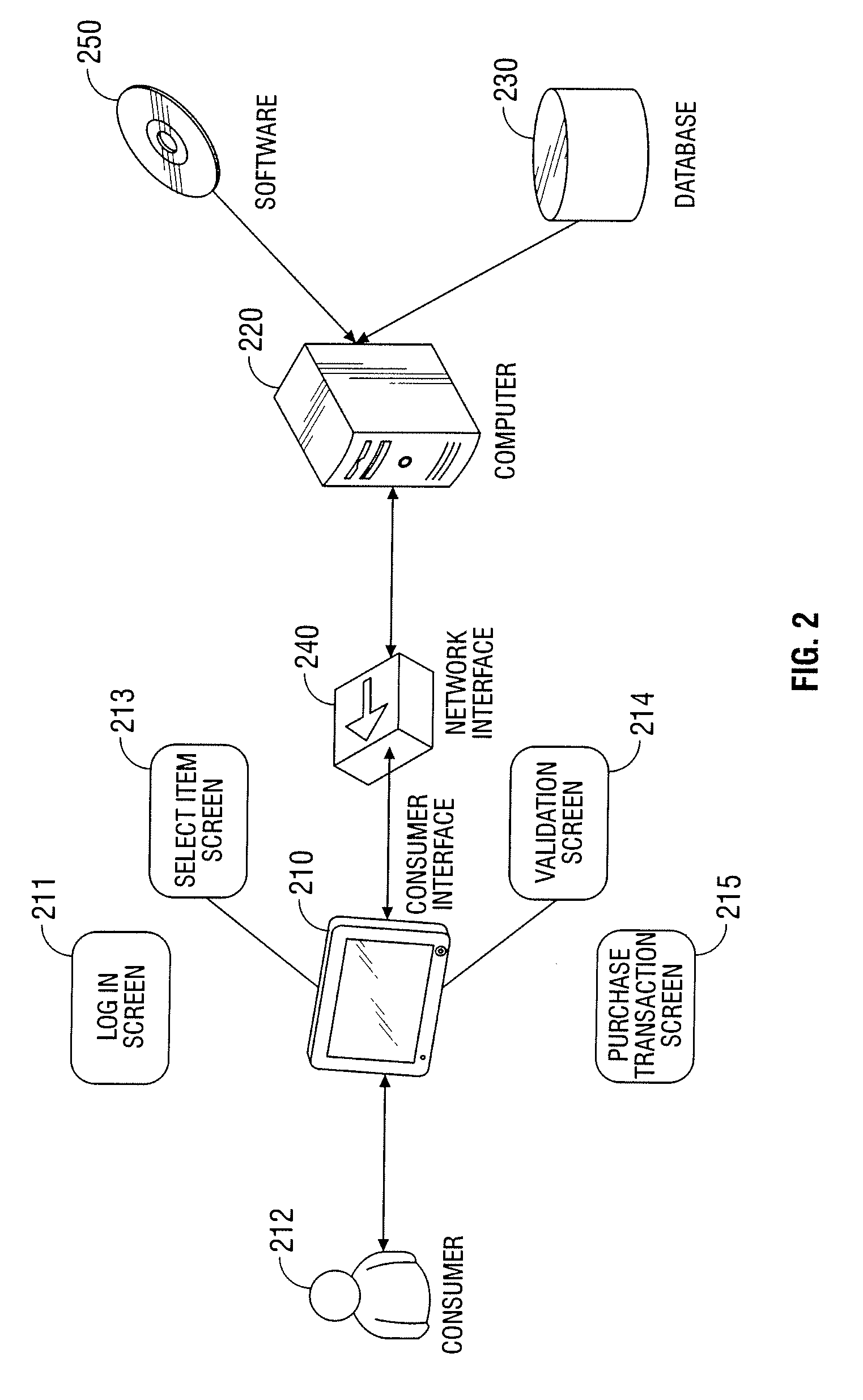
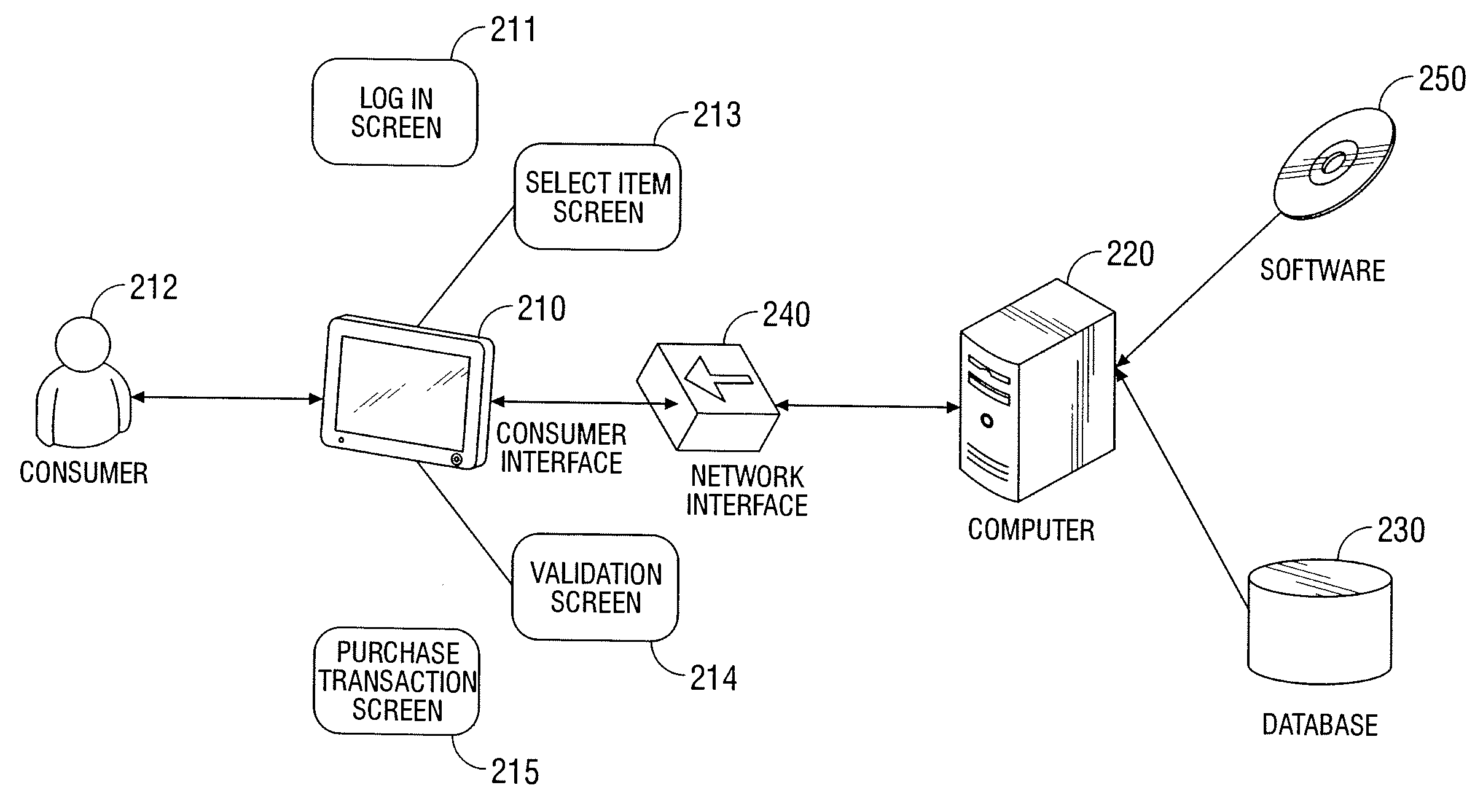
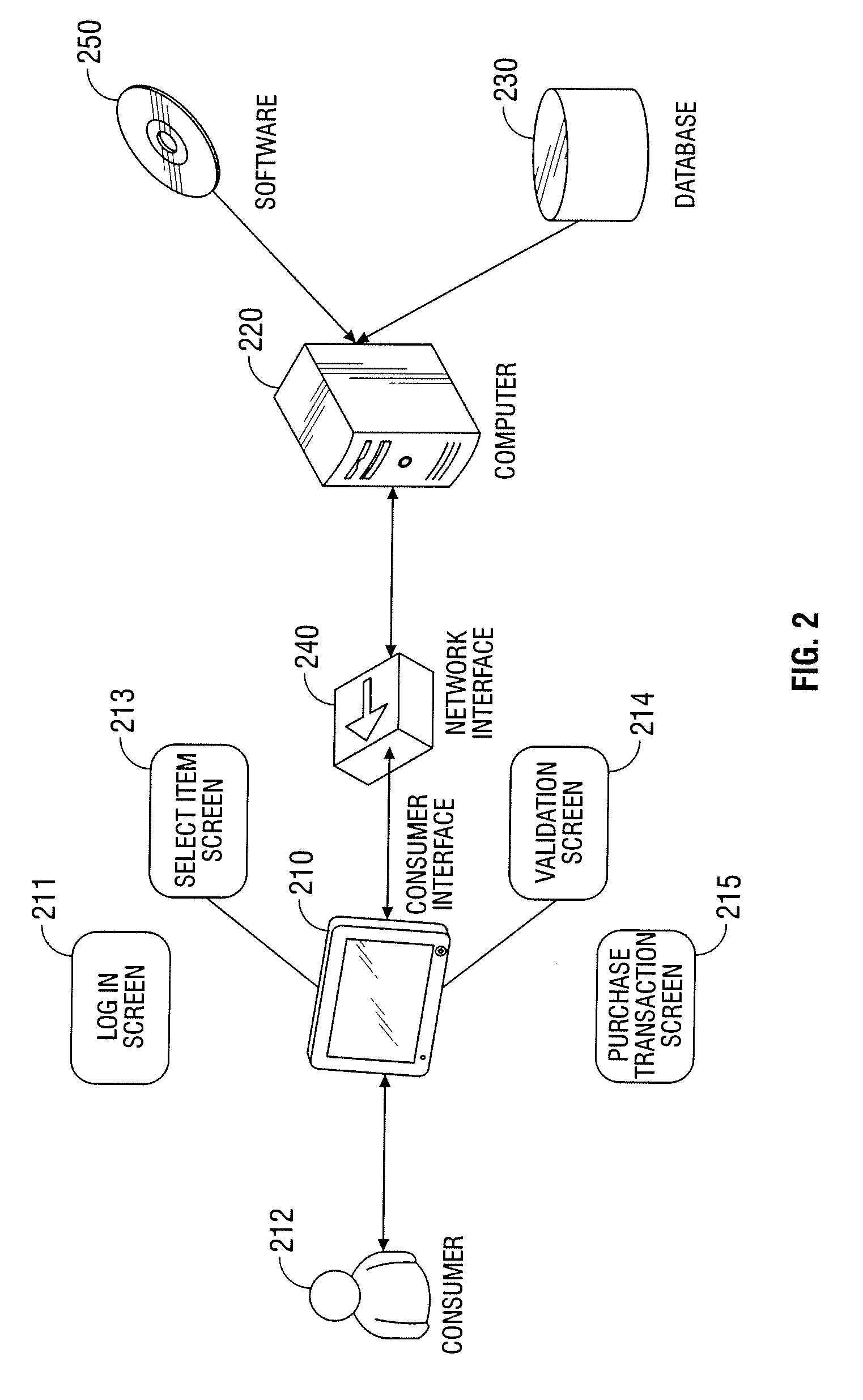
Automated vending of products containing controlled substances
ActiveUS7783379B2Efficient and widespread enforcementReduced resourceCoin-freed apparatus detailsCommercePseudoephedrineControl substances
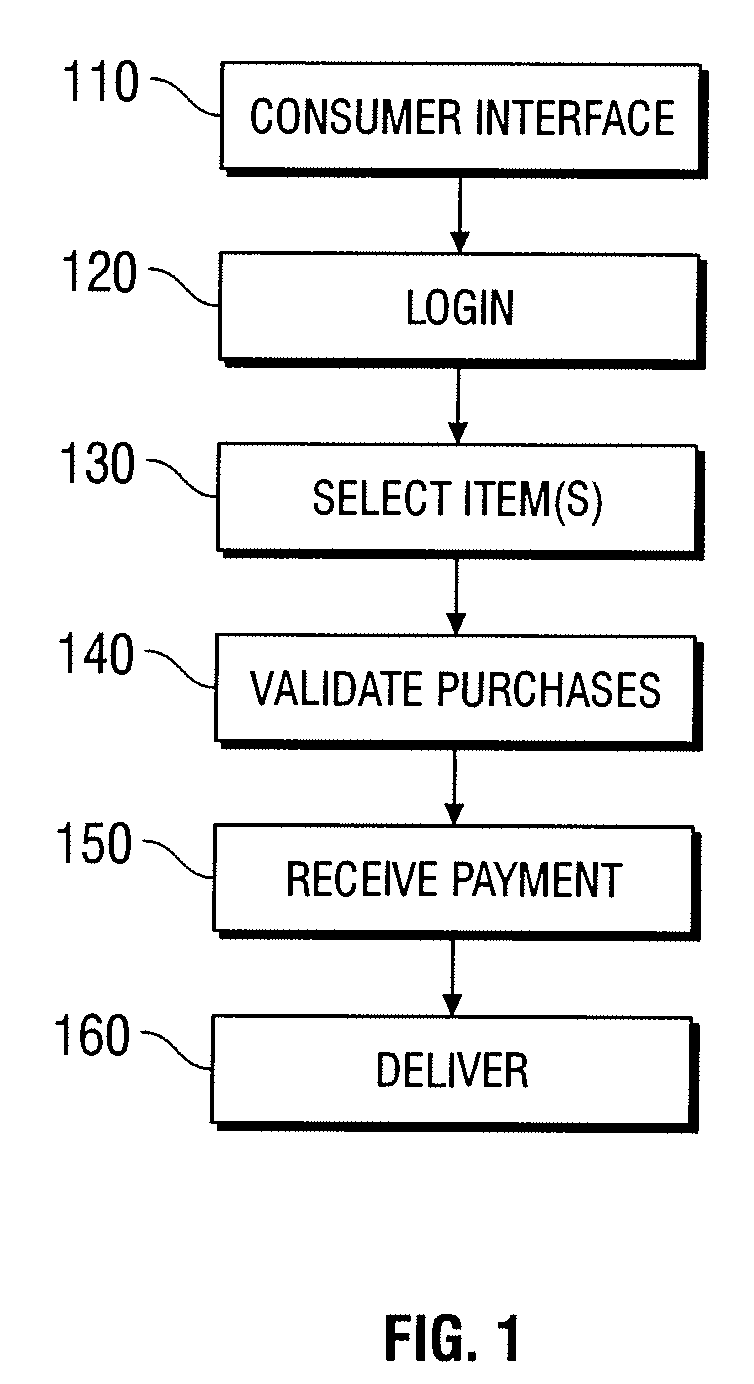
The present invention provides for devices and methods for vending regulated products, particularly controlled substances, including those containing pseudoephedrine. The present invention allows for the identification of consumers through reliable log-in-procedures, allows the consumer to select items, validates whether the purchase request complies with regulations, to facilitate the delivery of the requested product to a consumer. Other embodiments include a vending machine that is placed into a retail environment in which software enforces validation of the purchasers' identities, limits the amount of pseudoephedrine for each purchaser within the regulations of local, state and federal agencies.This invention reduces the resources which must be expended in retail locations to comply with regulatory agencies, to implement effective counter measures against illegal purchases of regulated and controlled substances, and to ensure the effective limitation of these substances within reasonable limits required for normal consumption.
Owner:ASTERES
System and method for optimized task scheduling in a heterogeneous data processing system
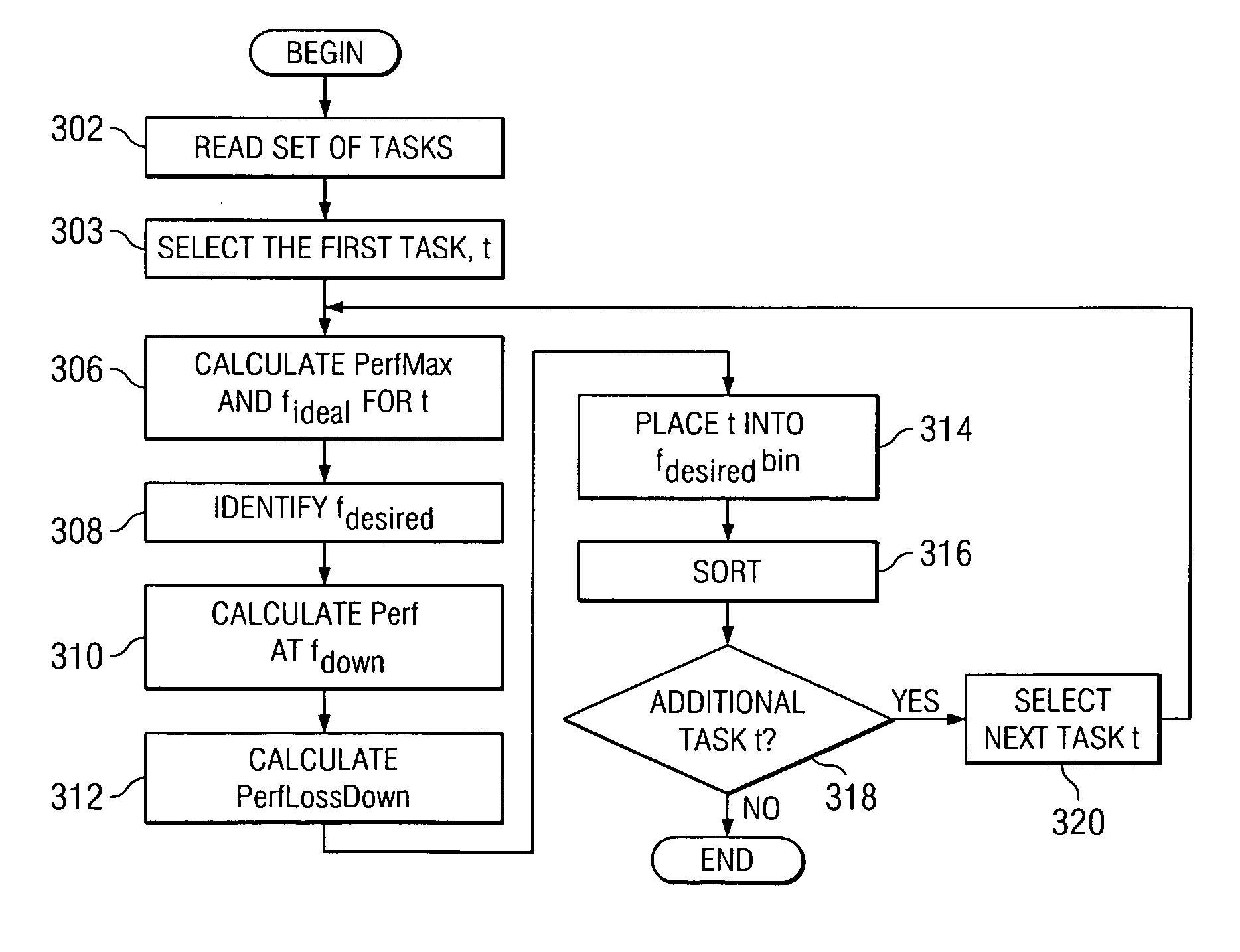
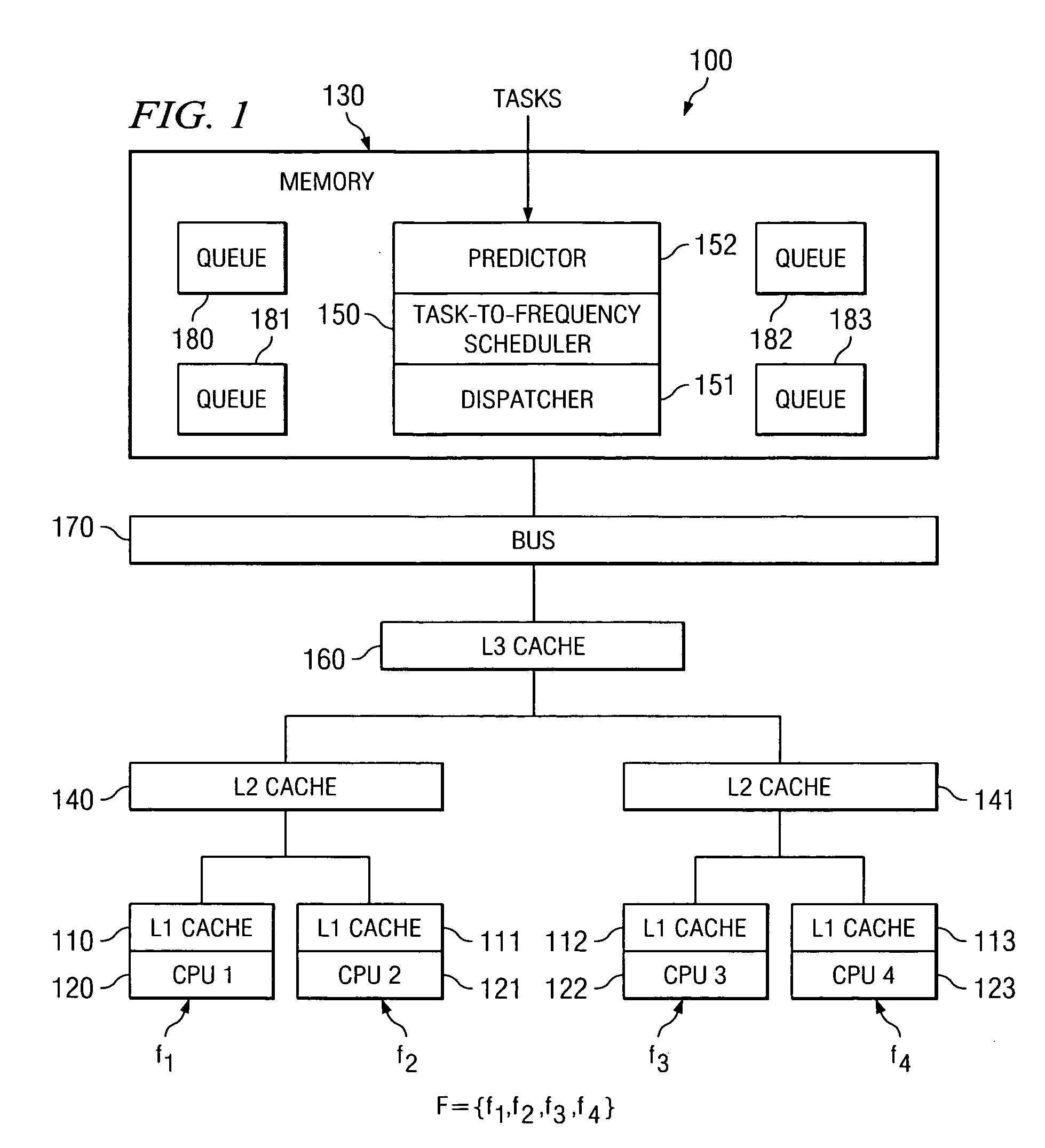
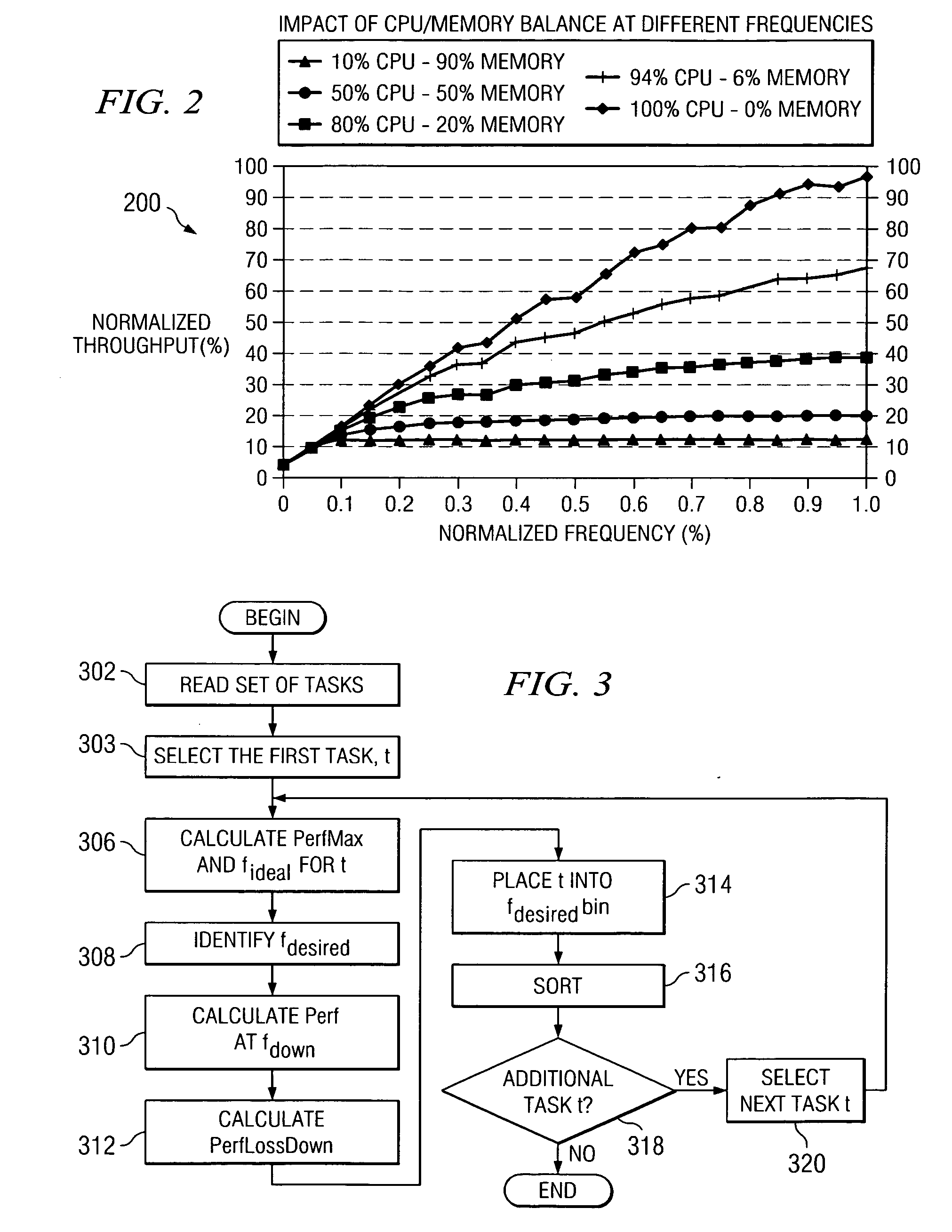
InactiveUS20060168571A1Optimizing task throughputPerformance of was minimizedEnergy efficient ICTEnergy efficient computingData processing systemLoad Shedding
A method, computer program product, and a data processing system for optimizing task throughput in a multi-processor system. A performance metric is calculated based on performance counters measuring characteristics of a task executed at one of a plurality of processor frequencies available in the multi-processor system. The characteristics measured by the performance counters indicate activity in the processor as well as memory activity. A performance metric provides a means using measured data at one available frequency to predict performance at another processor frequency available in the multi-processing system. Performance loss minimization is used to assign a particular task to a particular frequency. Additionally, the present invention provides a mechanism for priority load balancing of tasks in a manner that minimizes cumulative performance loss incurred by execution of all tasks in the system.
Owner:IBM CORP
Method and apparatus for verifying the integrity and security of computer networks and implementing counter measures
InactiveUS20050204404A1Mitigate or thwart suspected intruder attacks on the target networkMemory loss protectionUnauthorized memory use protectionCountermeasureSecurity system
A method and apparatus for verifying the integrity of devices on a target network. The apparatus has security subsystems and a master security system hierarchically connected to the security subsystems via a secure link. The target network includes various intrusion detection devices, which may be part of the security subsystem. Each intrusion detection device generates a plurality of event messages when an attack on the network is detected. The security subsystem collects these event messages, correlates, and analyzes them, and performs network scanning processes. If certain events warrant additional scrutiny, they are uploaded to the master security system for review.
Owner:NTT SECURITY US INC
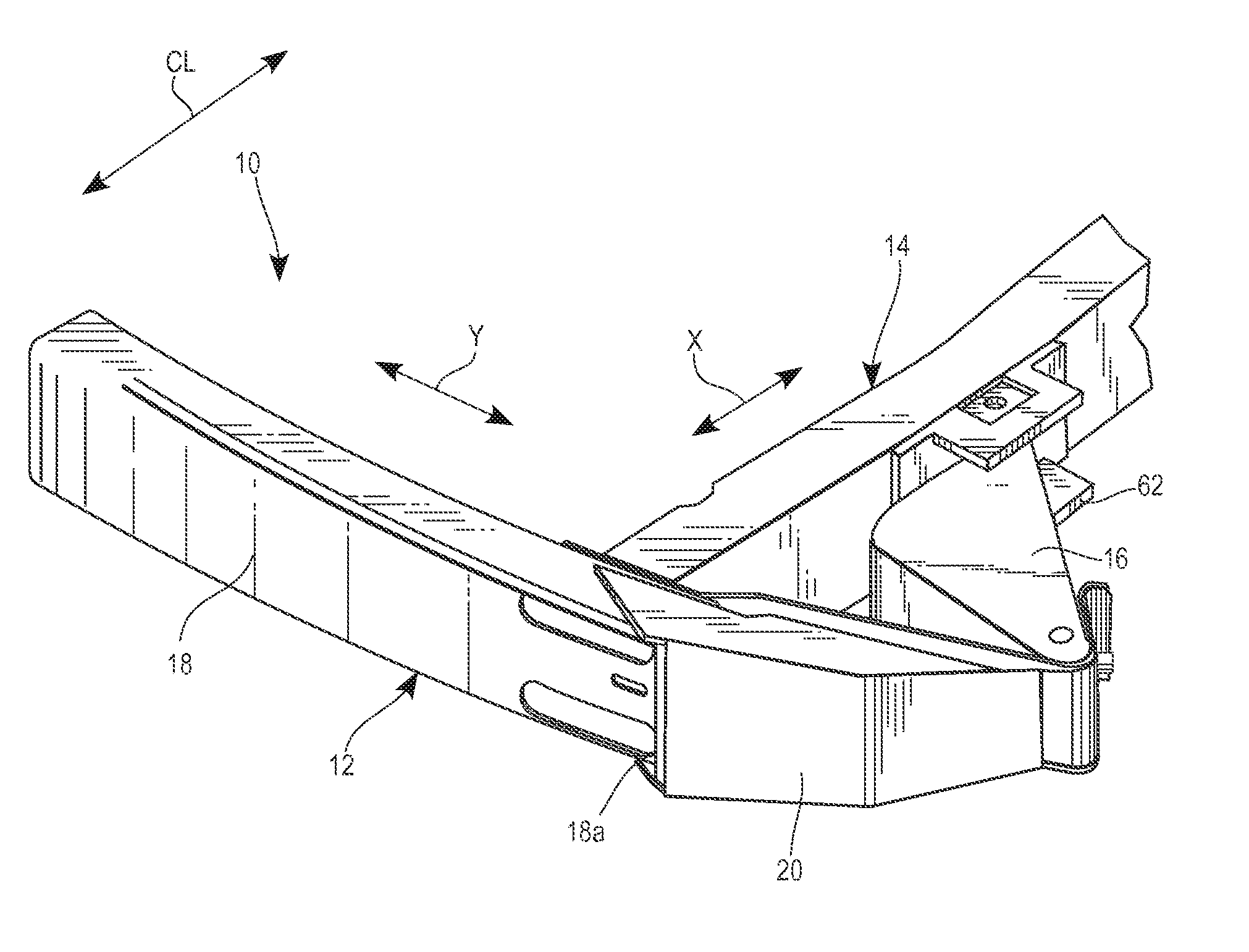
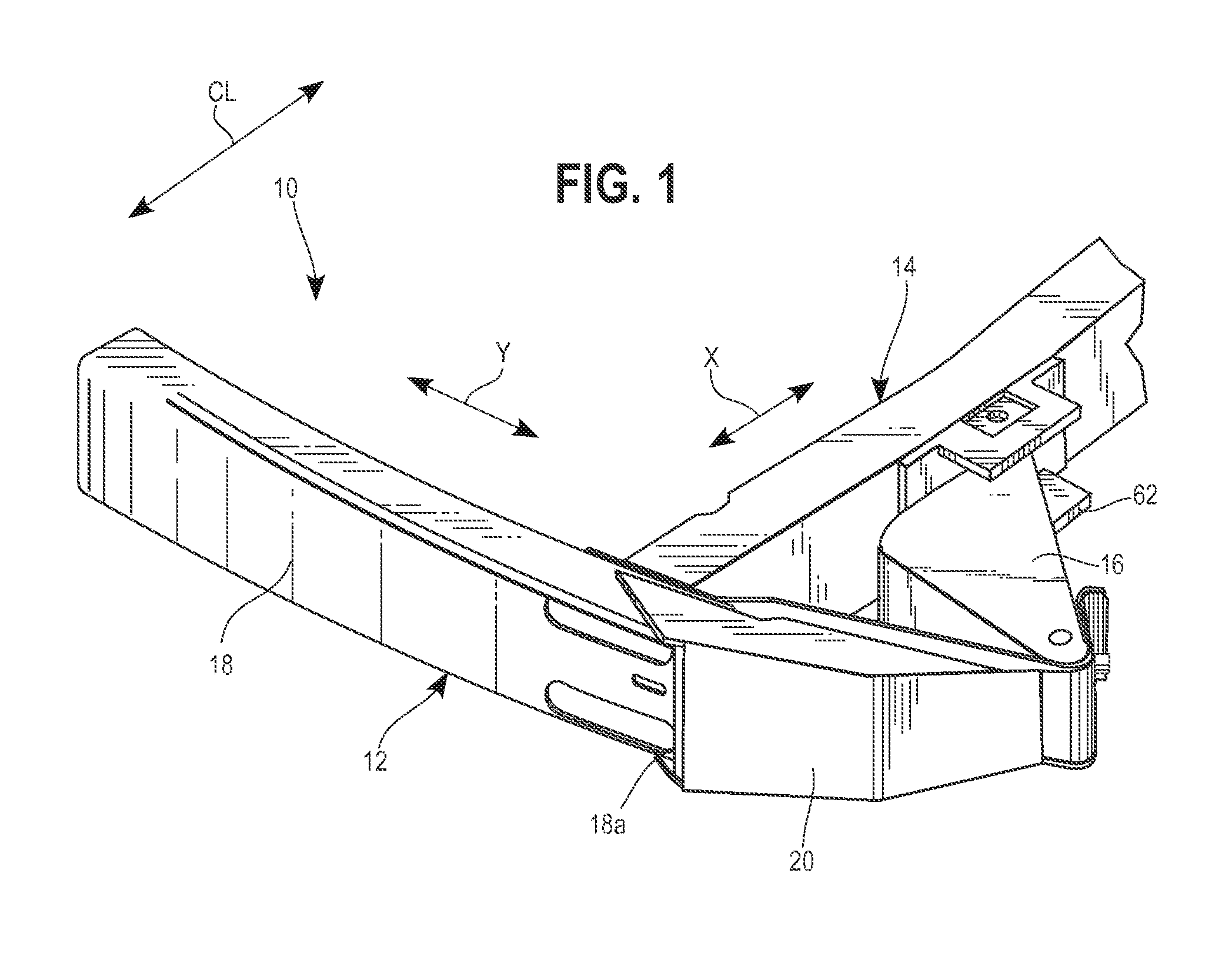
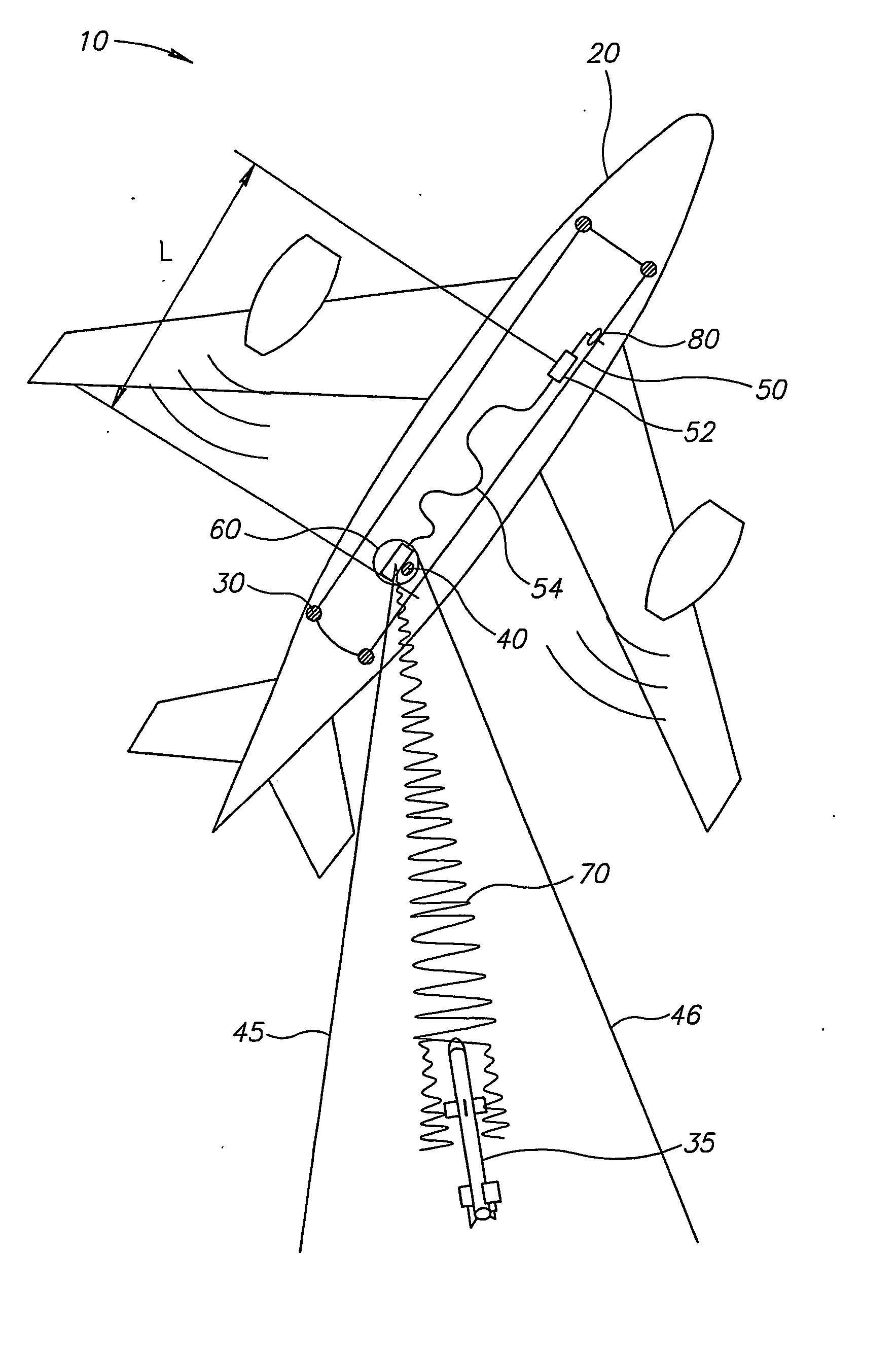
Small overlap frontal impact counter-measure
An automotive vehicle support structure assembly includes a bumper extending across the front of the vehicle, a longitudinal side member extending rearwardly from the bumper, and a link member extending between the end of the bumper and the side member. The link member is mounted to the side member and bumper via a pair of hinged connections. In the event of a small overlap collision, the link member is configured to contact a colliding barrier and pivot rearwardly in response while maintaining contact with the barrier to transfer the force of the collision inwardly toward the side member.
Owner:TOYOTA MOTOR ENGINEERING & MANUFACTURING NORTH AMERICA
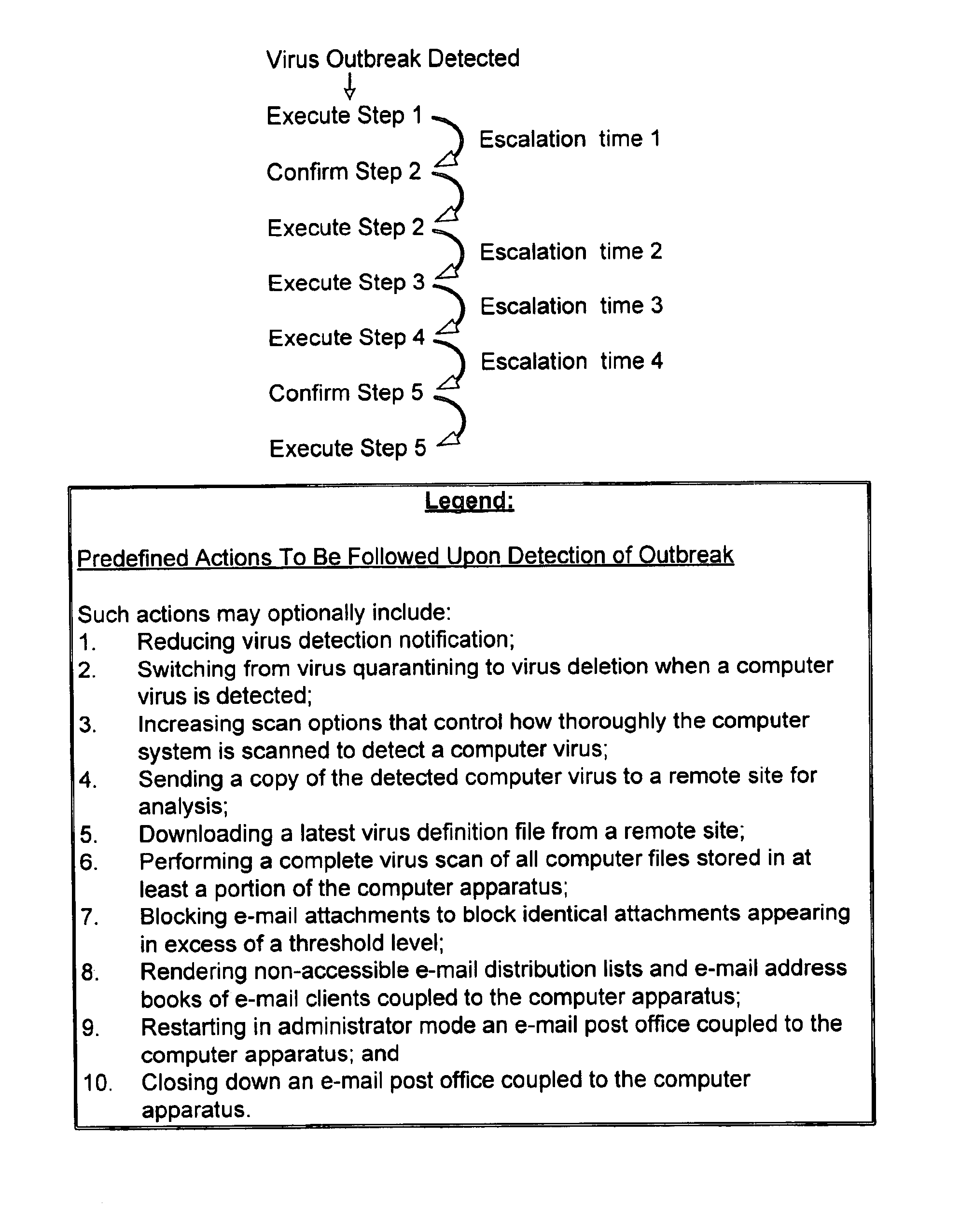
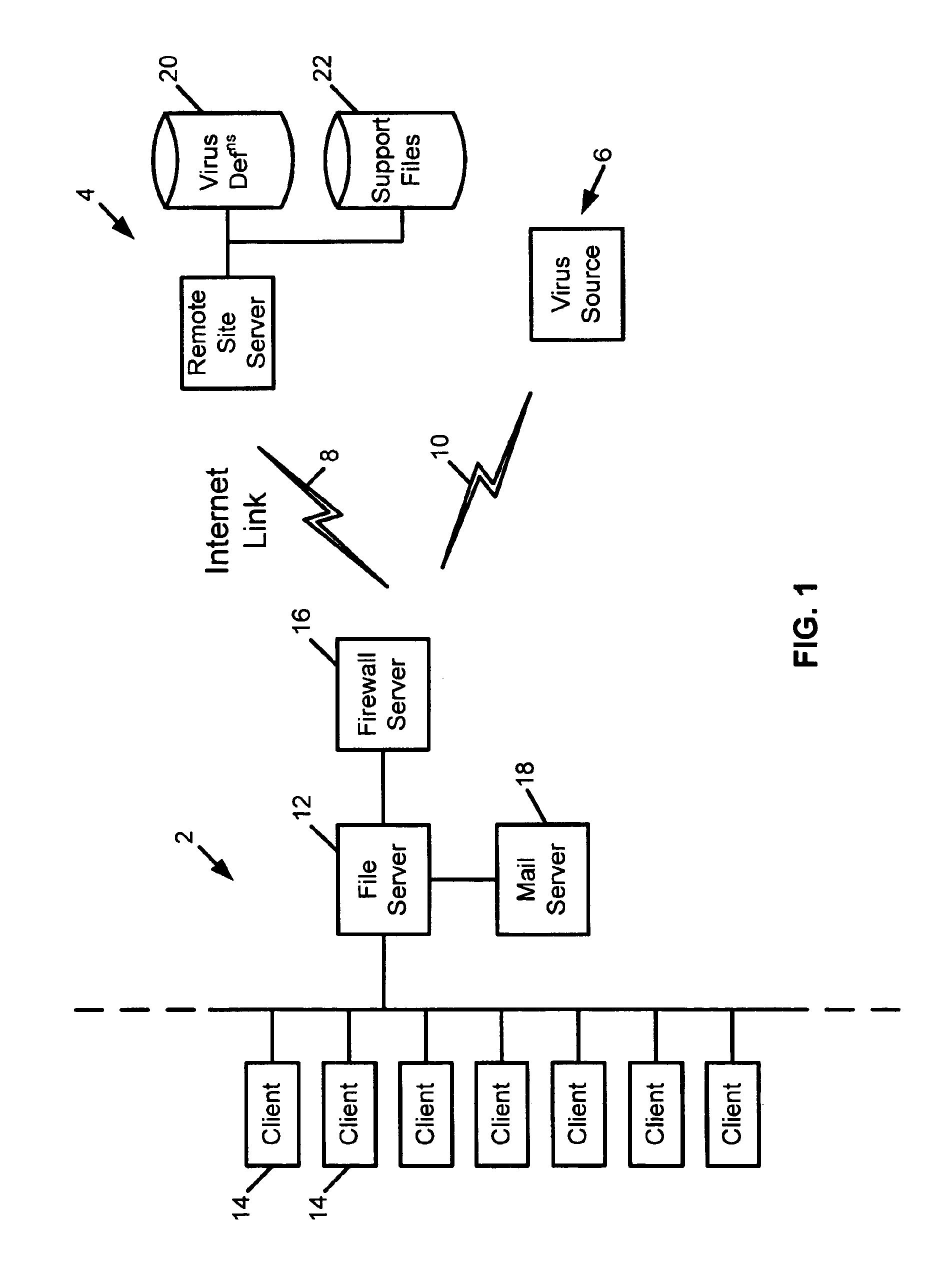
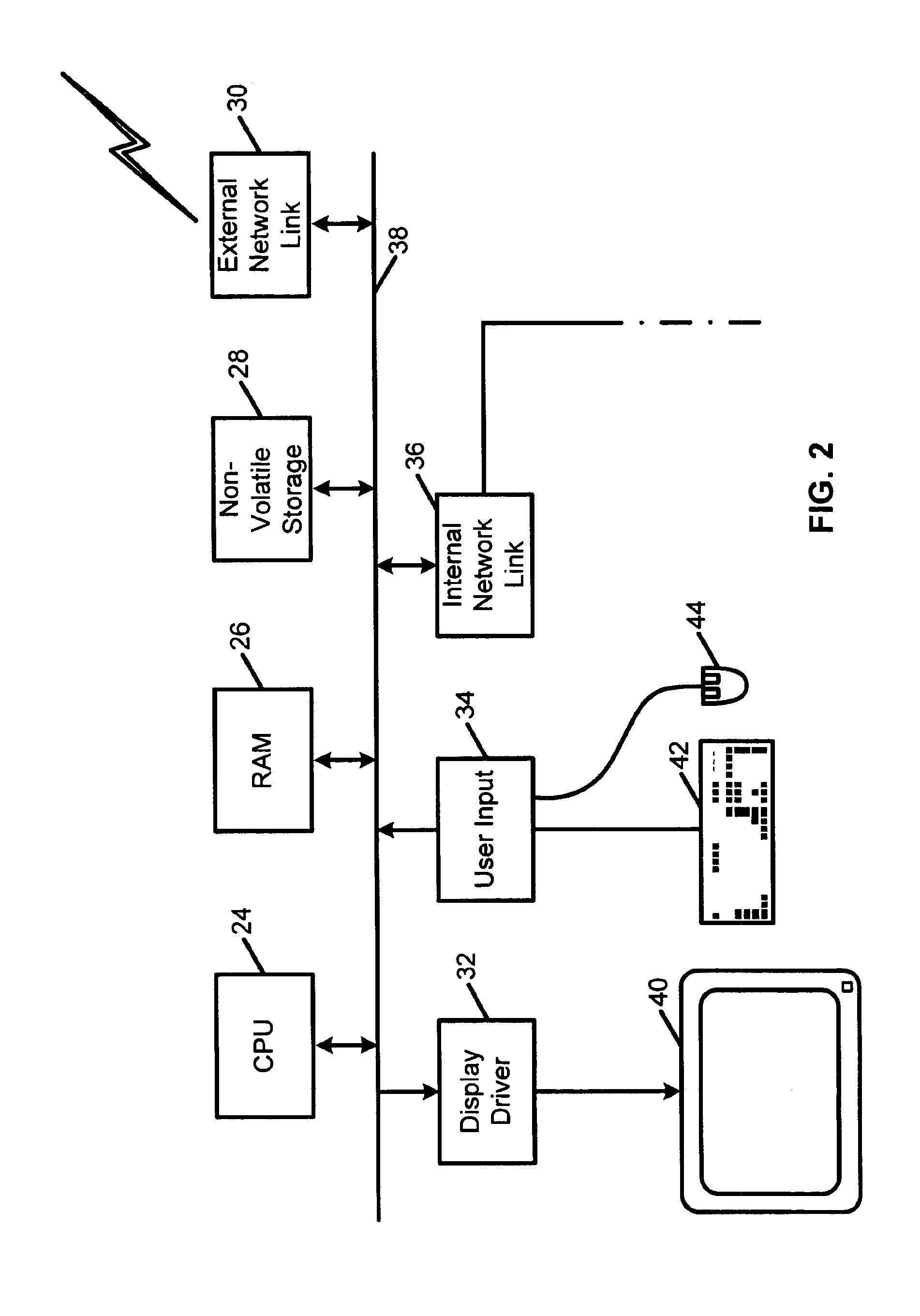
Response to a computer virus outbreak
InactiveUS6898715B1Light loadInhibit computer virus propagationMemory loss protectionUnauthorized memory use protectionAnti virusAddress book
When a computer virus outbreak is detected, a predefined sequence of steps are automatically or manually followed using rule definitions, that may include office hours, to invoke anti-virus counter-measures. The counter-measures can include reducing virus notification, increasing scanning options, blocking E-mail attachments, hiding E-mail address books and the like. The predetermined sequence of actions may be varied with the time of day and day of week.
Owner:MCAFEE LLC
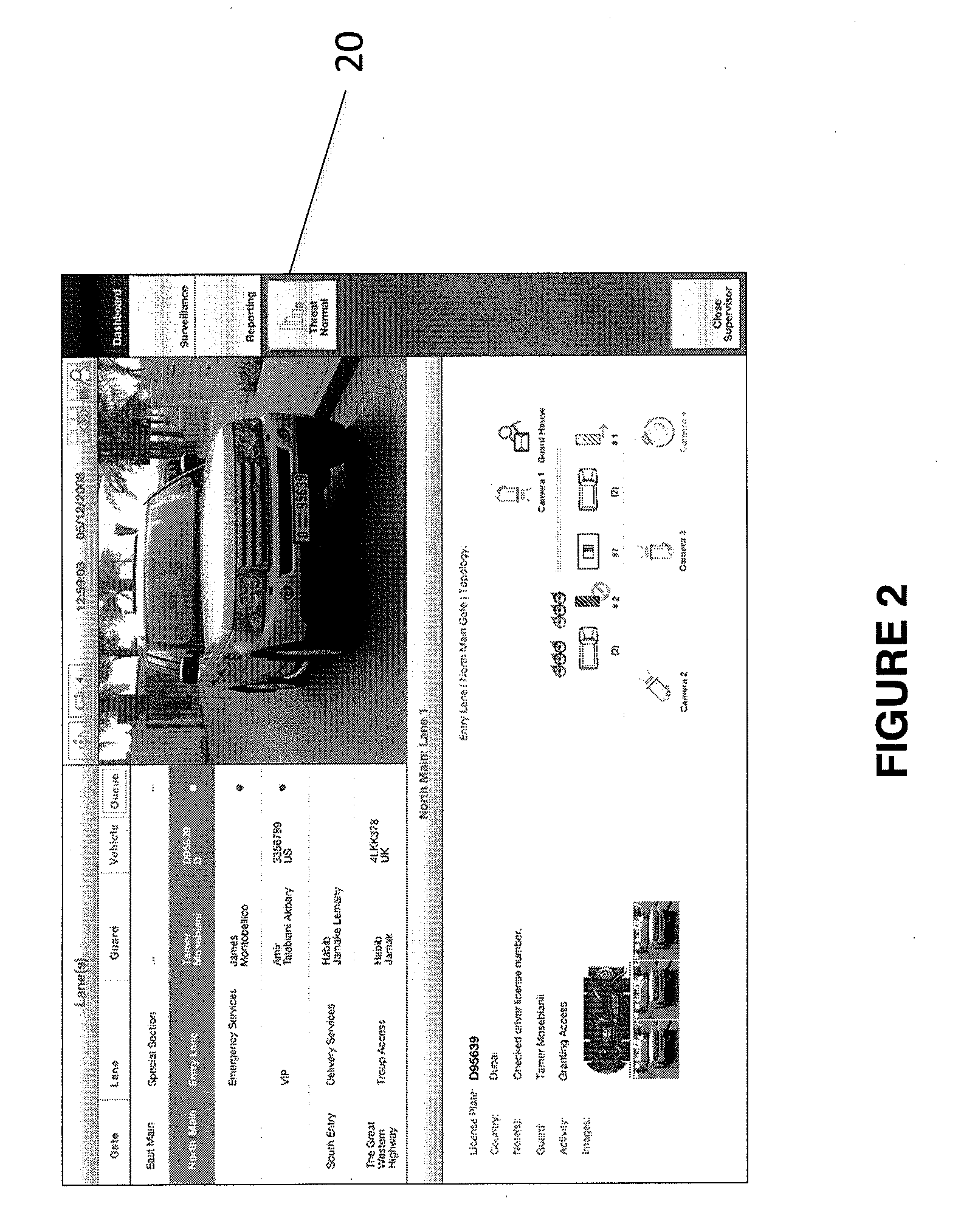
Contextual Risk Indicators in Connection with Threat Level Management
InactiveUS20100156630A1Easy to adjustHigh riskIndication of parksing free spacesIndividual entry/exit registersCountermeasureInternet privacy
A system is provided that that allows users to define factors that uniquely affect the security risk of certain events at a certain locale. The system can then change its behavior based on these custom risks and invoke various counter measures when threats are more likely. Accordingly, one embodiment of the invention provides for the use of contextual risk indicators in connection with threat level management.
Owner:TITAN HLDG
Electronic device
InactiveUS20090011197A1Avoid dippingCellulosic plastic layered productsThin material handlingAdhesiveDisplay device
Provided is an electronic device in which a display panel fixed by a metal bezel is entirely bonded to a touch panel or a transparent plate for protection with a liquid adhesive so that the liquid adhesive is prevented from permeating a gap between the metal bezel and the display panel. In other words, the display panel is adhered to the metal bezel by providing an adhesive or the like there between. The display device of the aforementioned structure is bonded to the touch panel or the transparent plate for protection by filling an entire surface of the gap there between with a liquid transparent adhesive. Further, the adhesive or the like is made to have conductivity, and a transparent conductive film is formed on a surface of the display panel, whereby the transparent conductive film is electrically connected to the metal bezel, which provides counter-measures against static electricity.
Owner:SEIKO INSTR INC
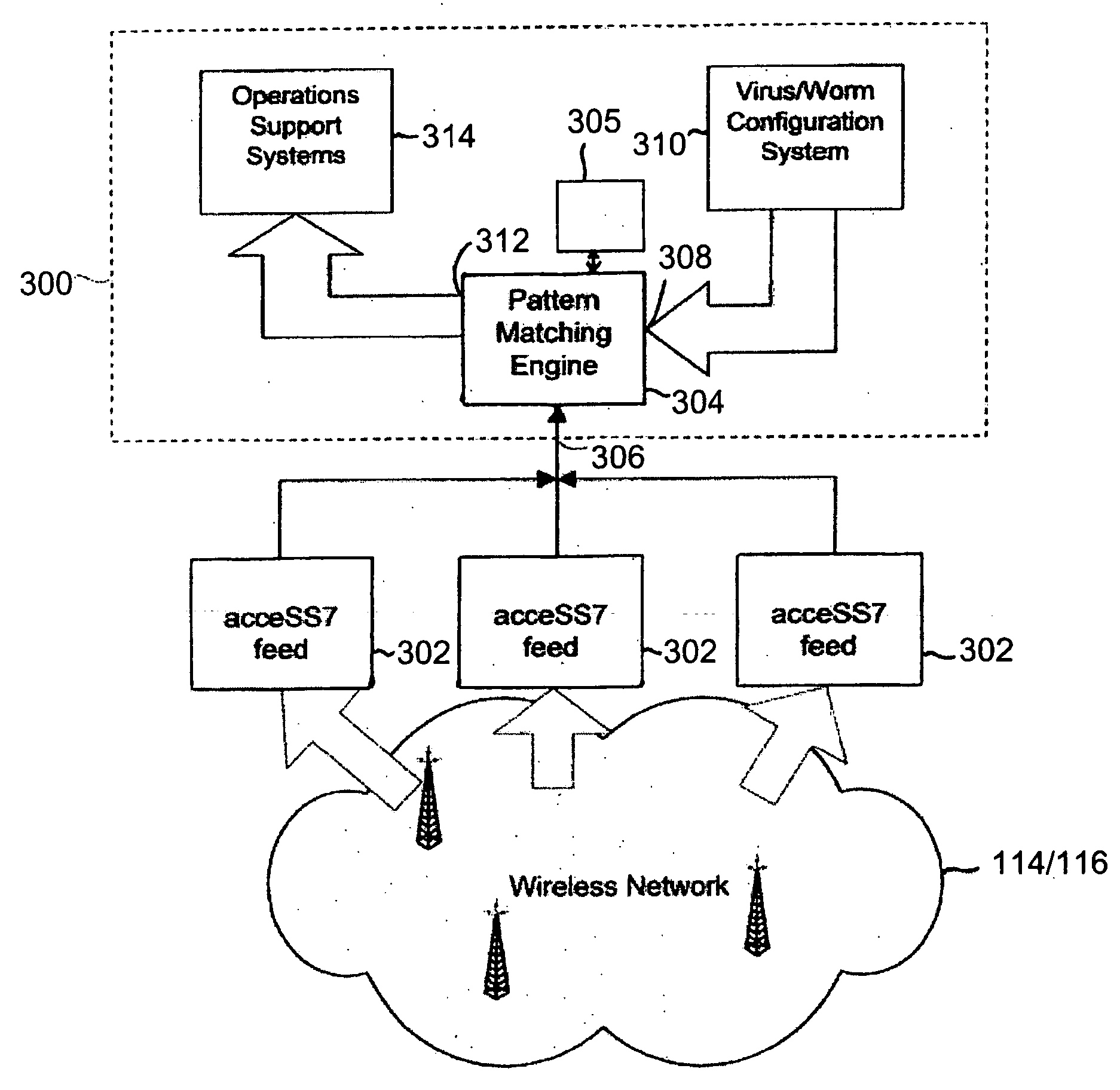
System, apparatus and method for detecting malicious traffic in a communications network
InactiveUS20060128406A1Reduce malicious attacksBattery life is therefore not consumedRadio/inductive link selection arrangementsWireless commuication servicesPattern matchingUse of services
Monitoring apparatus has a pattern matching engine that analyses service usage in a network in order to identify traffic relating to malicious attacks. Optionally, the monitoring apparatus can also arrange for a counter-measure to be deployed upon detection of the malicious traffic.
Owner:JDS UNIPHASE CORP
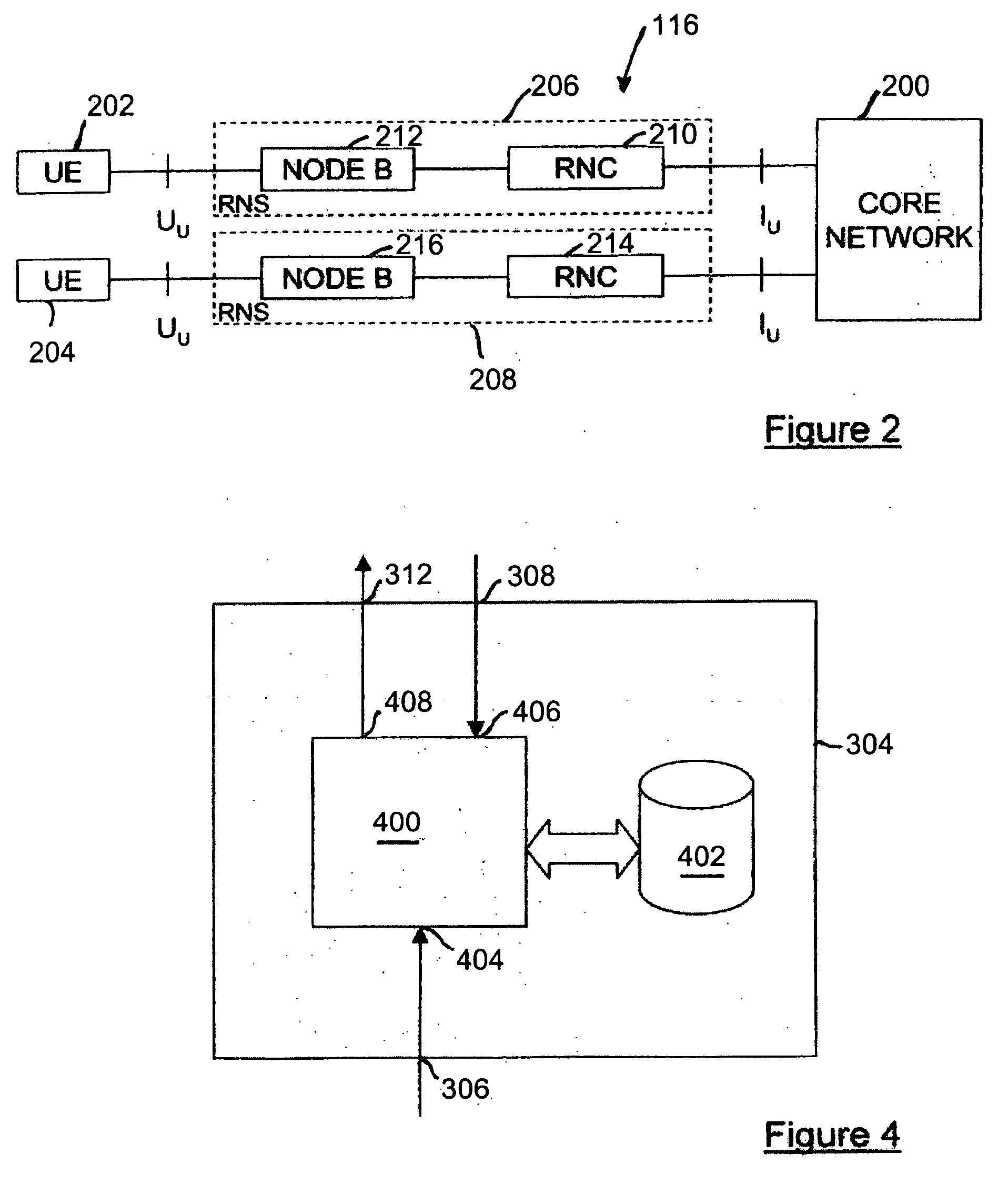
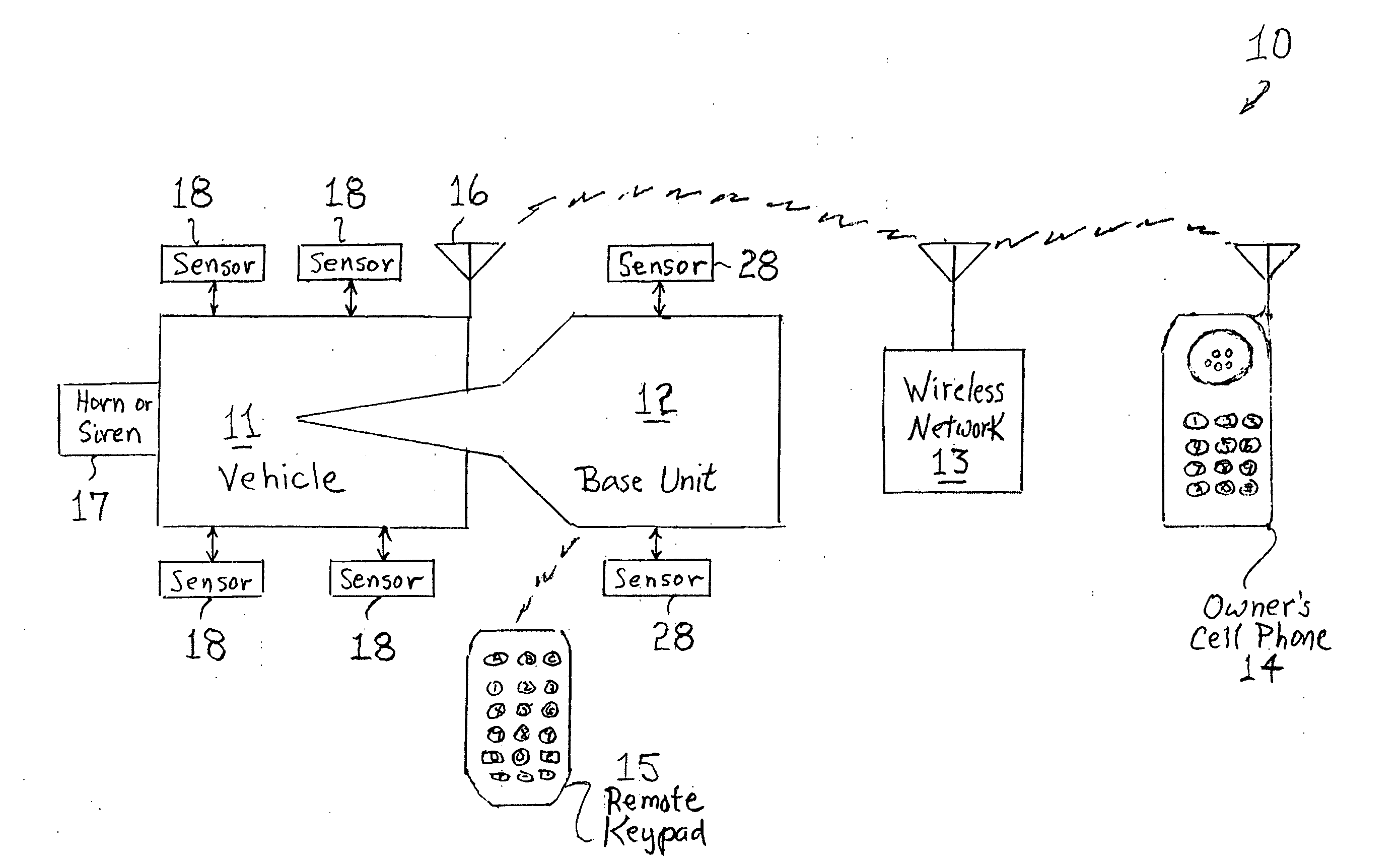
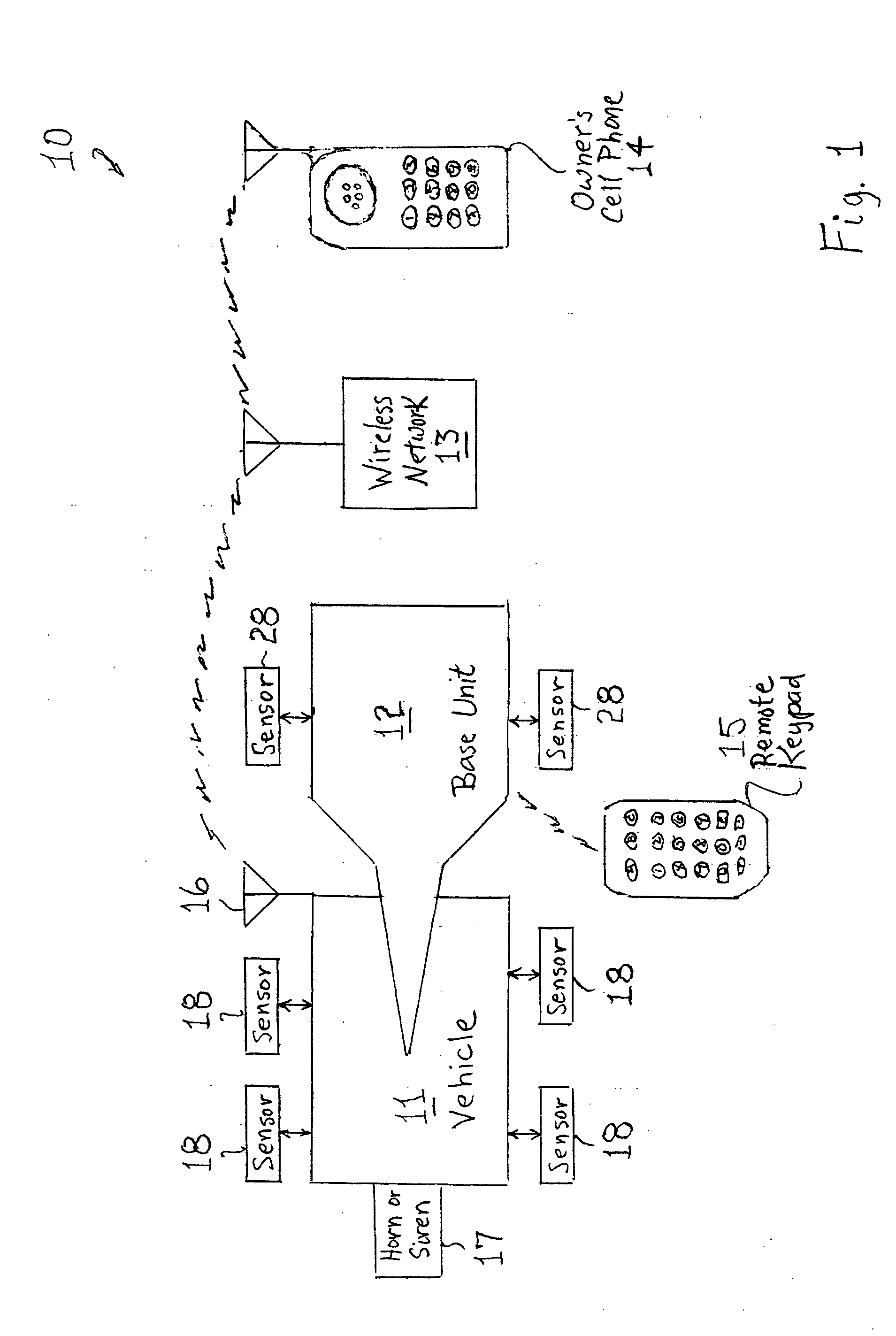
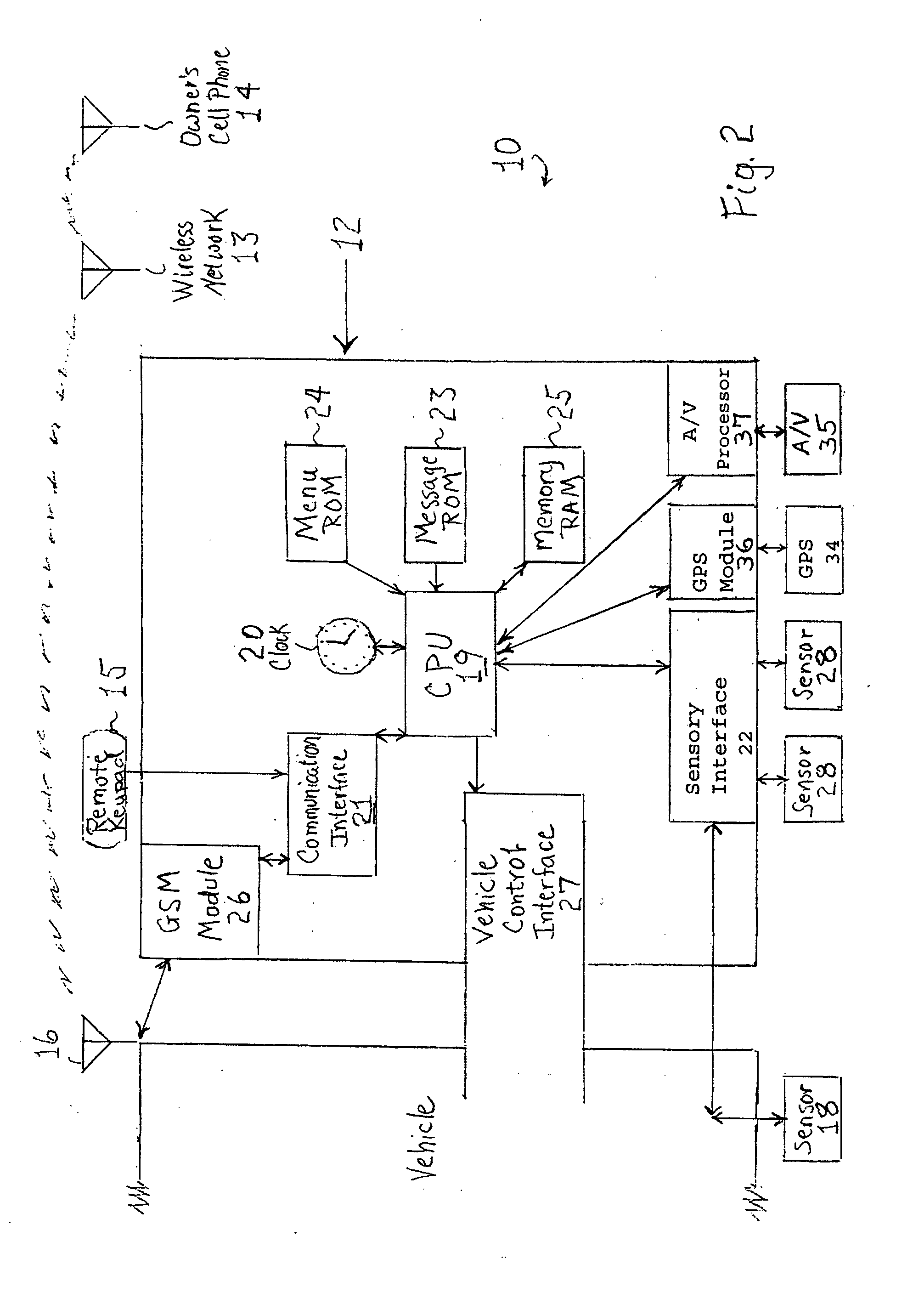
Interactive wireless vehicle security system
InactiveUS20090066488A1Easy to integrateImprove abilitiesAnti-theft devicesTelephonic communicationCountermeasureWireless mesh network
A security system detects intrusive activities in and around a vehicle and transmits warnings specifically describing the intrusions through a wireless telephone network to the owner's designated contacts. In response to the intrusion warnings, the vehicle owner or designees can establish remote wireless communication with the security system and obtain further information on the intrusion or initiate counter-measures to thwart an incipient theft.
Owner:SHEN ZHEN AMWELL SCI & TECH DEV +1
Intelligent backup system
In one embodiment, a method for ransomware-aware file backup is implemented on a computing device and includes: backing up a target population of files from a target file location in a backup transaction, computing a backup delta score for the backup transaction, where the computing comprises comparing backup data from the backup transaction with backup data from a previous backup transaction, determining whether the computer backup delta score exceeds a pre-defined threshold, and upon the computed backup delta score exceeding the pre-defined threshold: determining that the backup transaction is indicative of a ransomware infection, and performing at least one counter-measure in response to the ransomware infection.
Owner:CISCO TECH INC
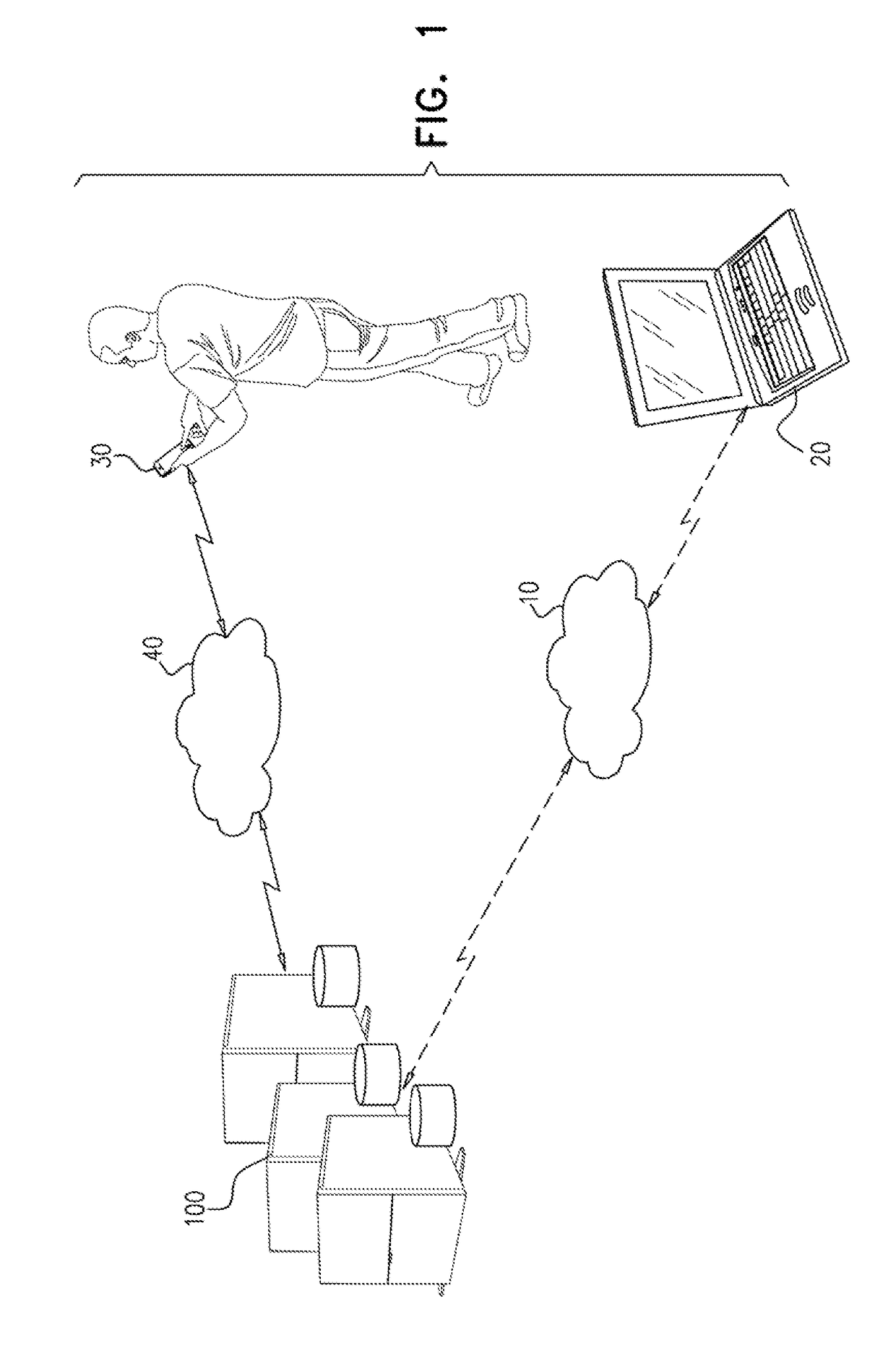
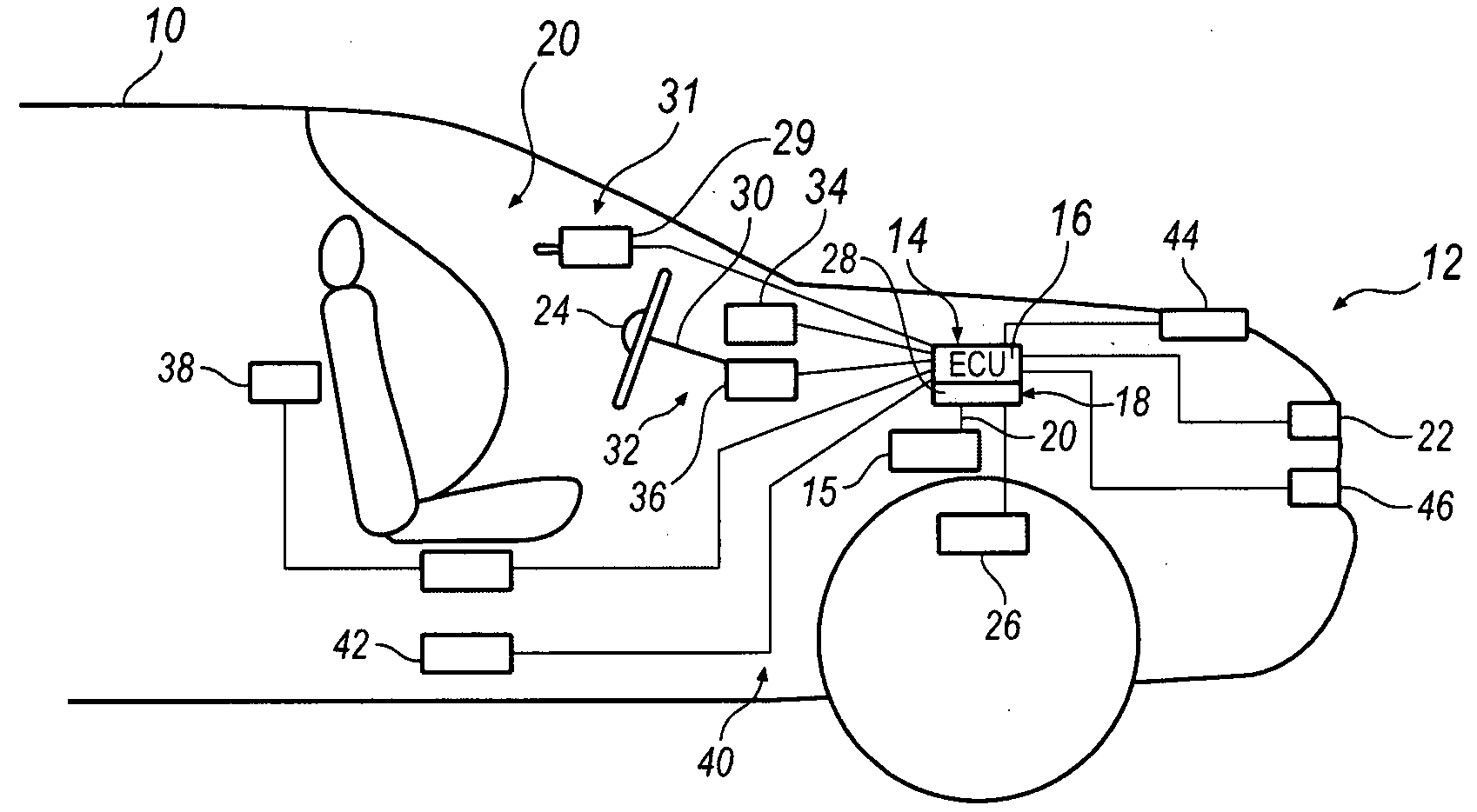
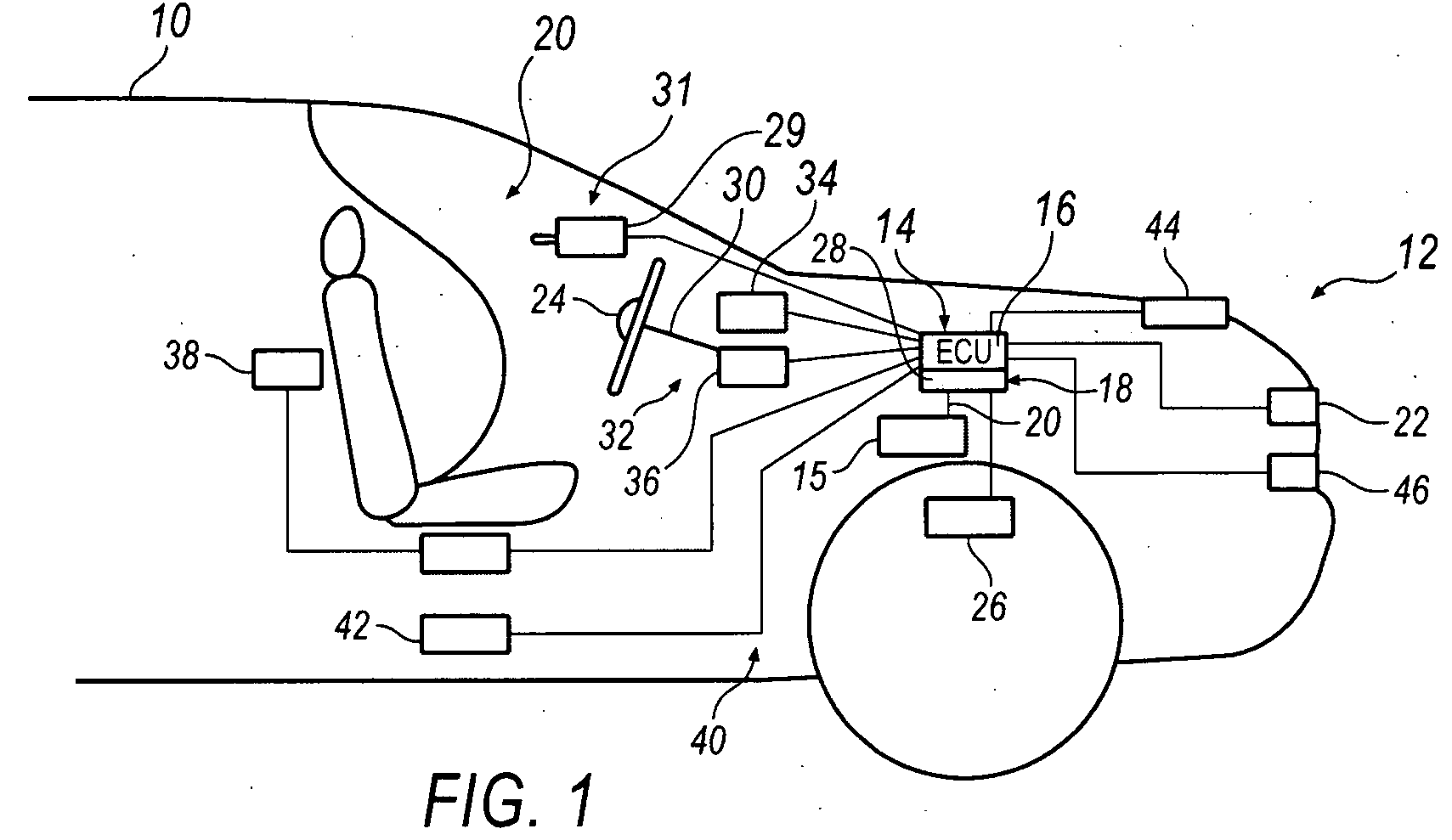
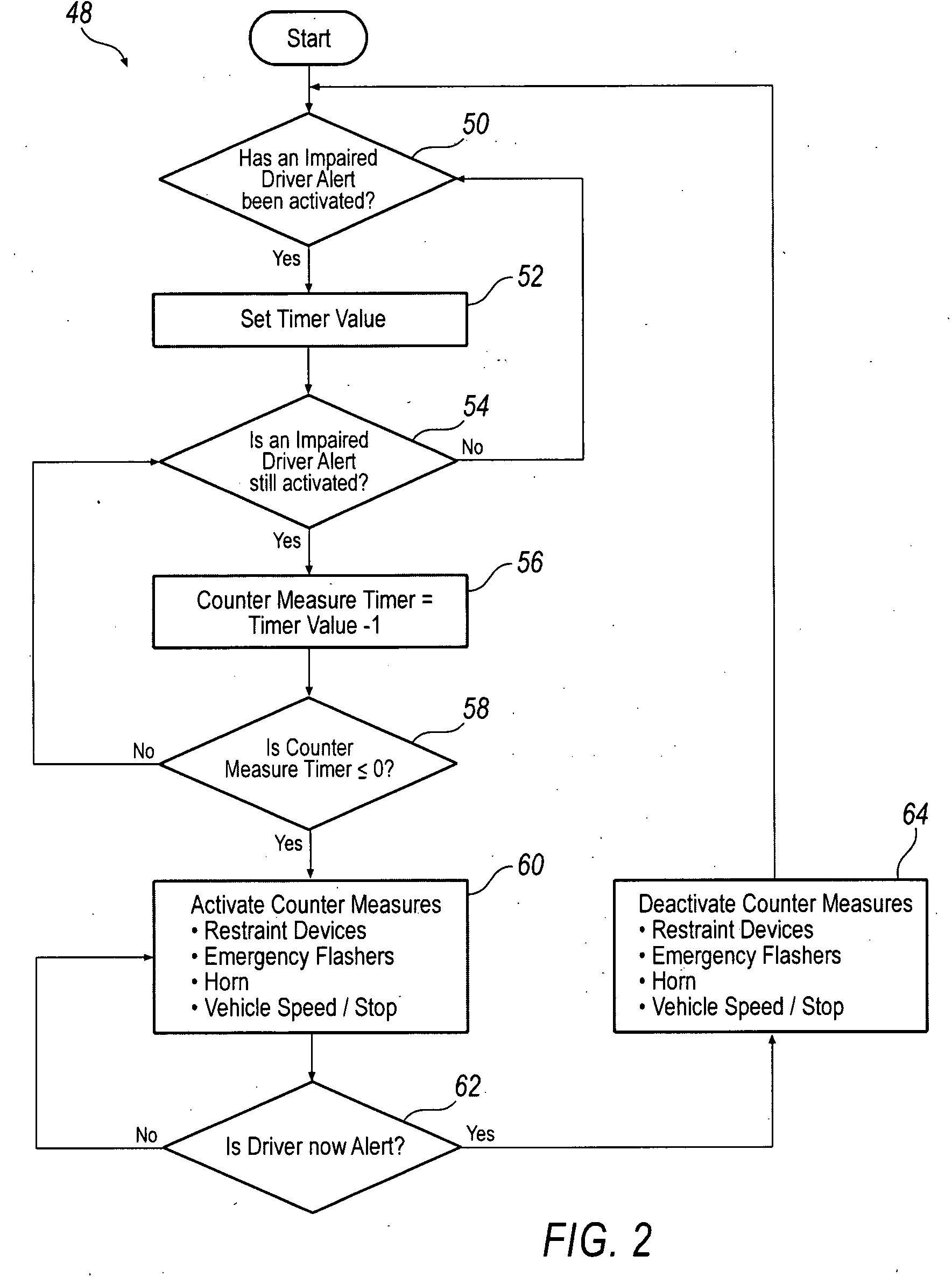
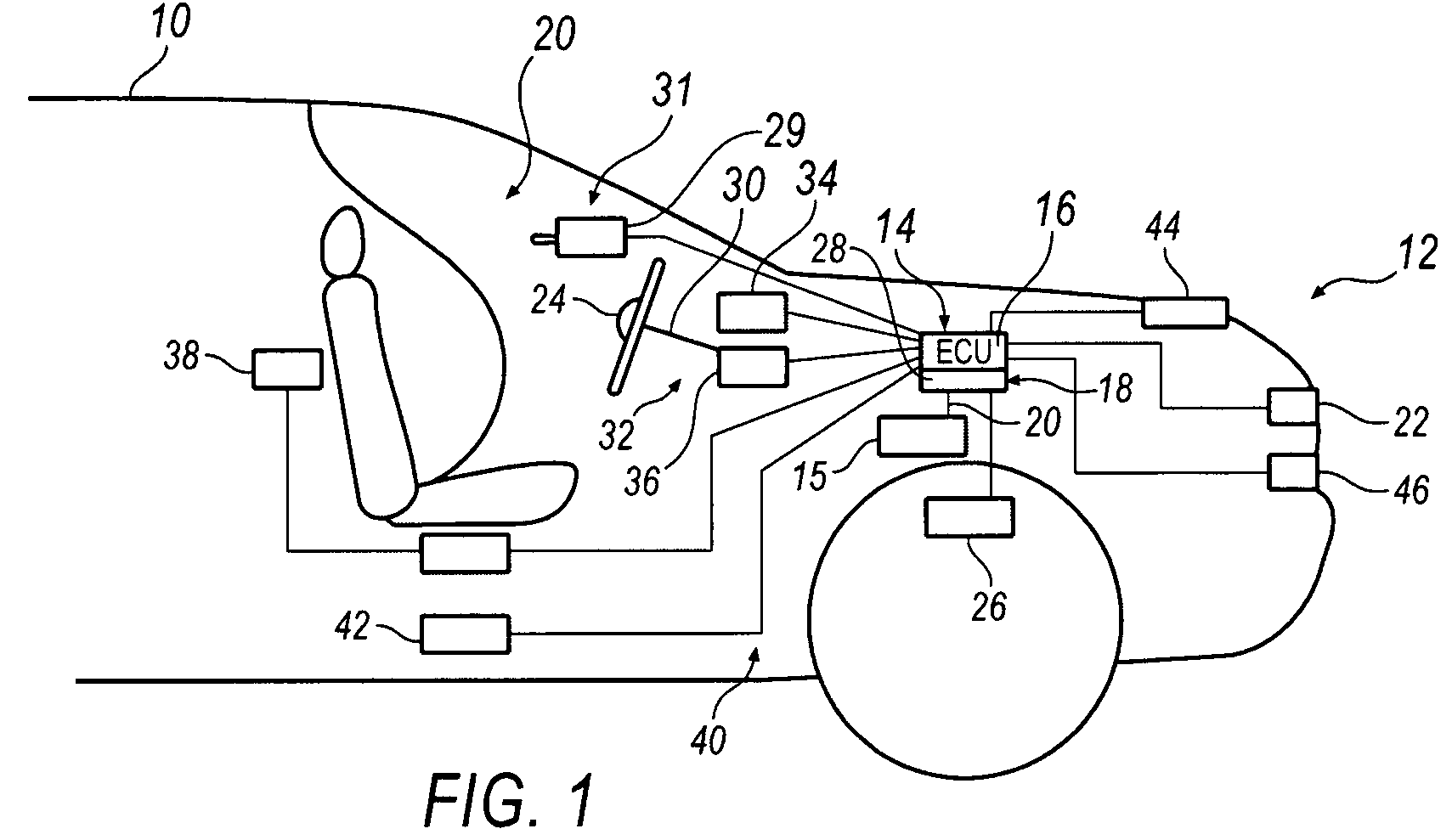
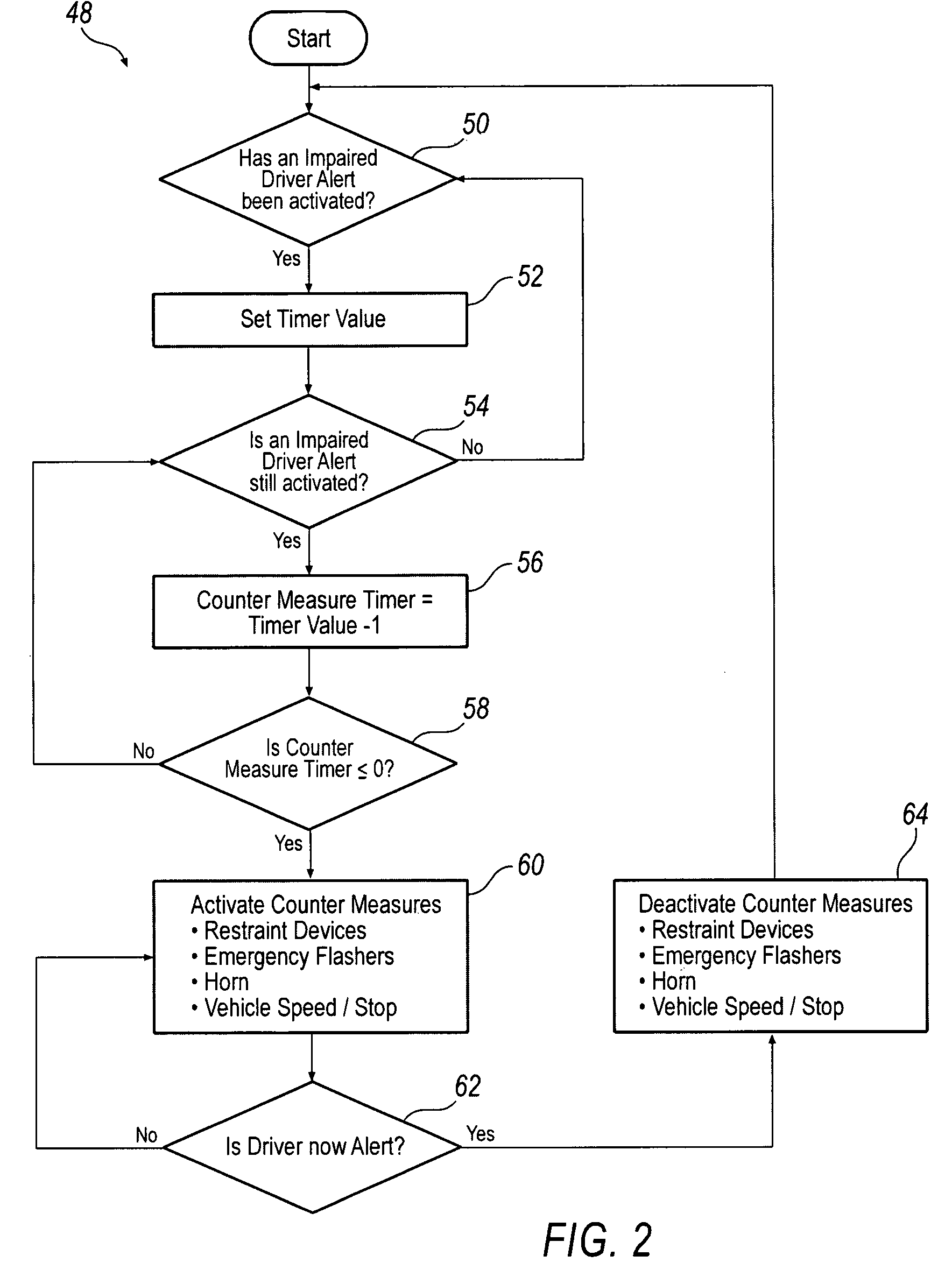
System and method for implementing active safety counter measures for an impaired driver
Various methods and systems are disclosed for implementing active safety countermeasures in vehicles when it is determined that the driver is impaired.
Owner:FORD GLOBAL TECH LLC
Automated Vending of Products Containing Controlled Substances
ActiveUS20080269947A1Efficient and widespread enforcementReduced resourceAcutation objectsCoin-freed apparatus detailsPseudoephedrineControl substances
The present invention provides for devices and methods for vending regulated products, particularly controlled substances, including those containing pseudoephedrine. The present invention allows for the identification of consumers through reliable log-in-procedures, allows the consumer to select items, validates whether the purchase request complies with regulations, to facilitate the delivery of the requested product to a consumer. Other embodiments include a vending machine that is placed into a retail environment in which software enforces validation of the purchasers' identities, limits the amount of pseudoephedrine for each purchaser within the regulations of local, state and federal agencies.This invention reduces the resources which must be expended in retail locations to comply with regulatory agencies, to implement effective counter measures against illegal purchases of regulated and controlled substances, and to ensure the effective limitation of these substances within reasonable limits required for normal consumption.
Owner:ASTERES
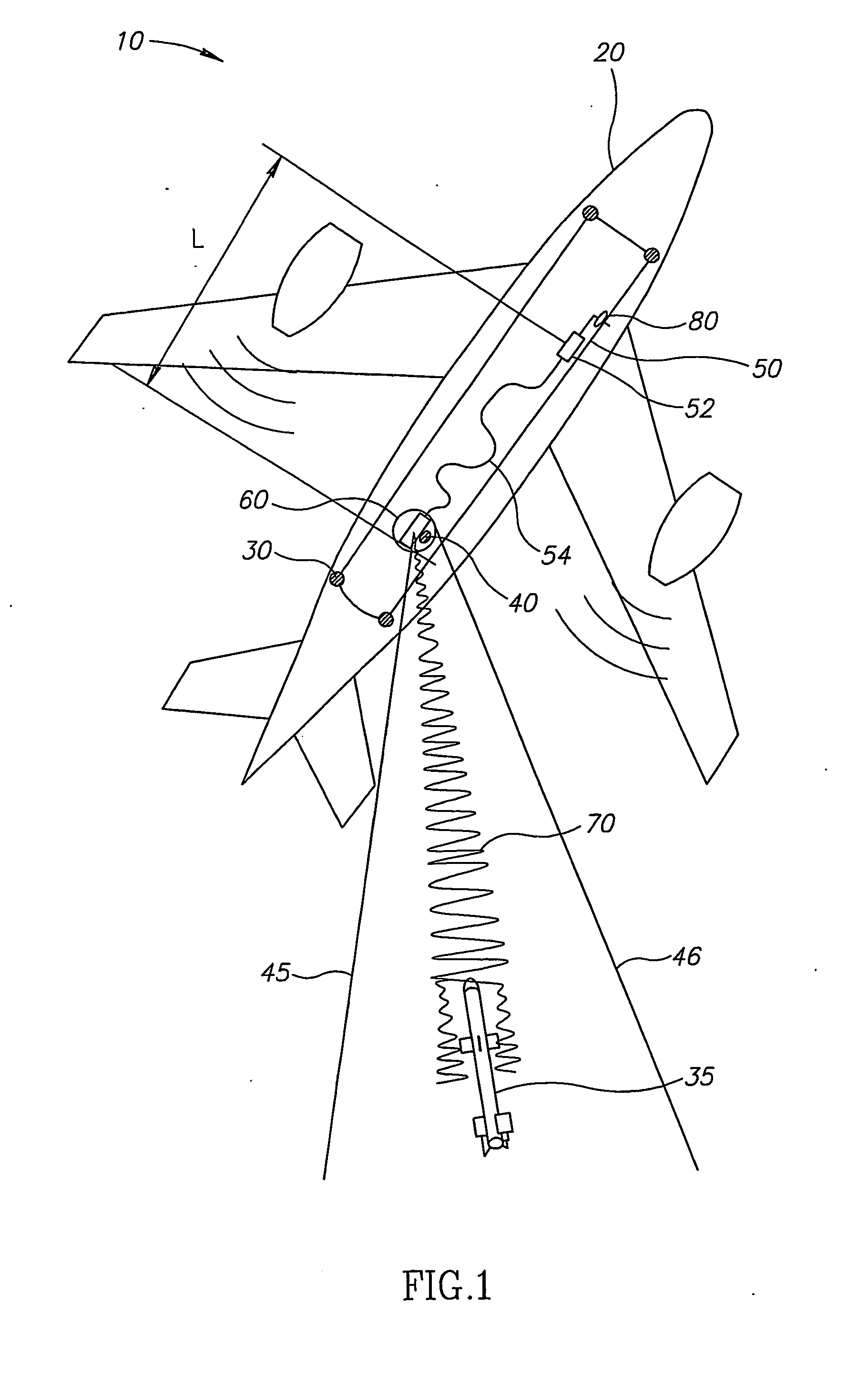
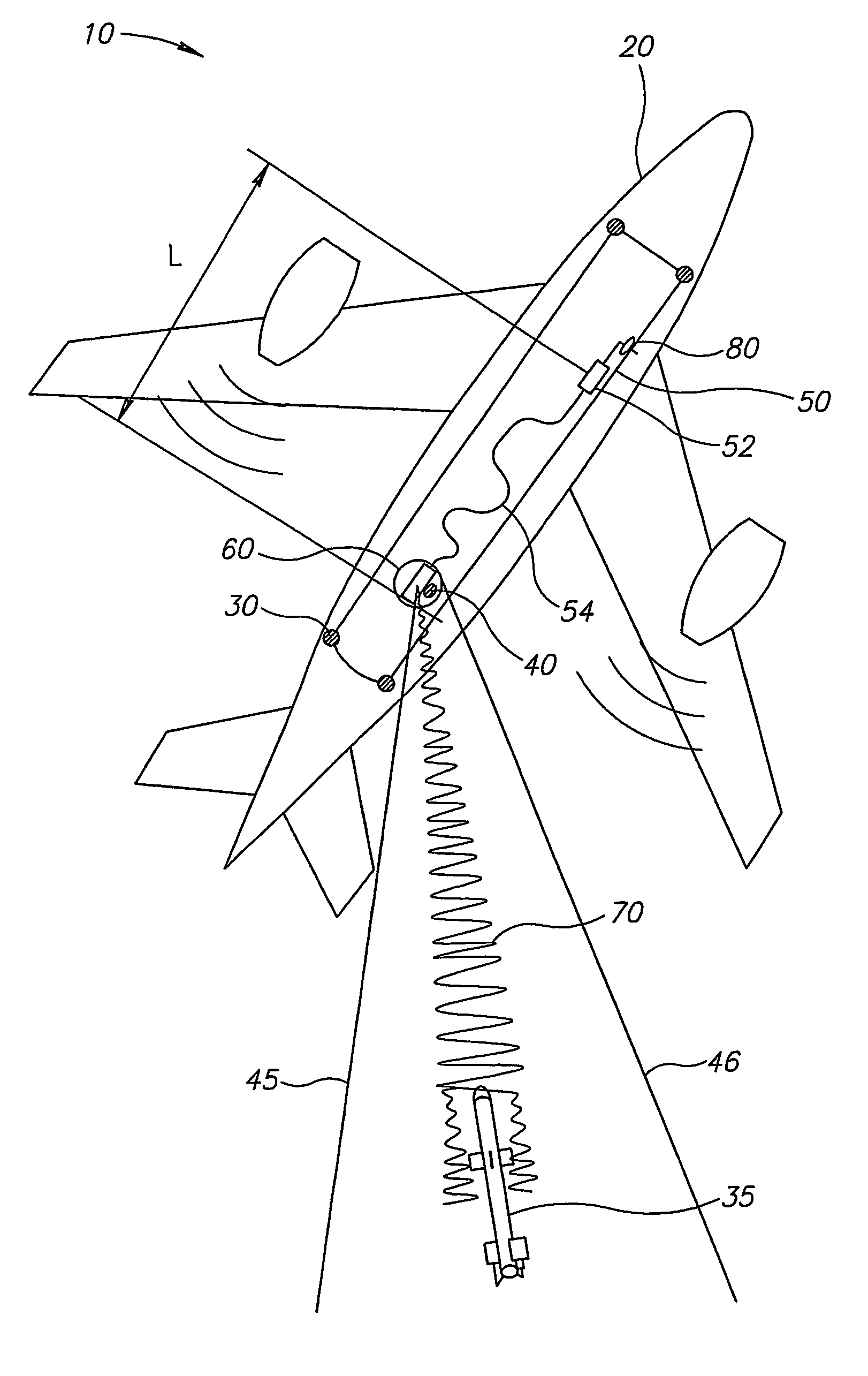
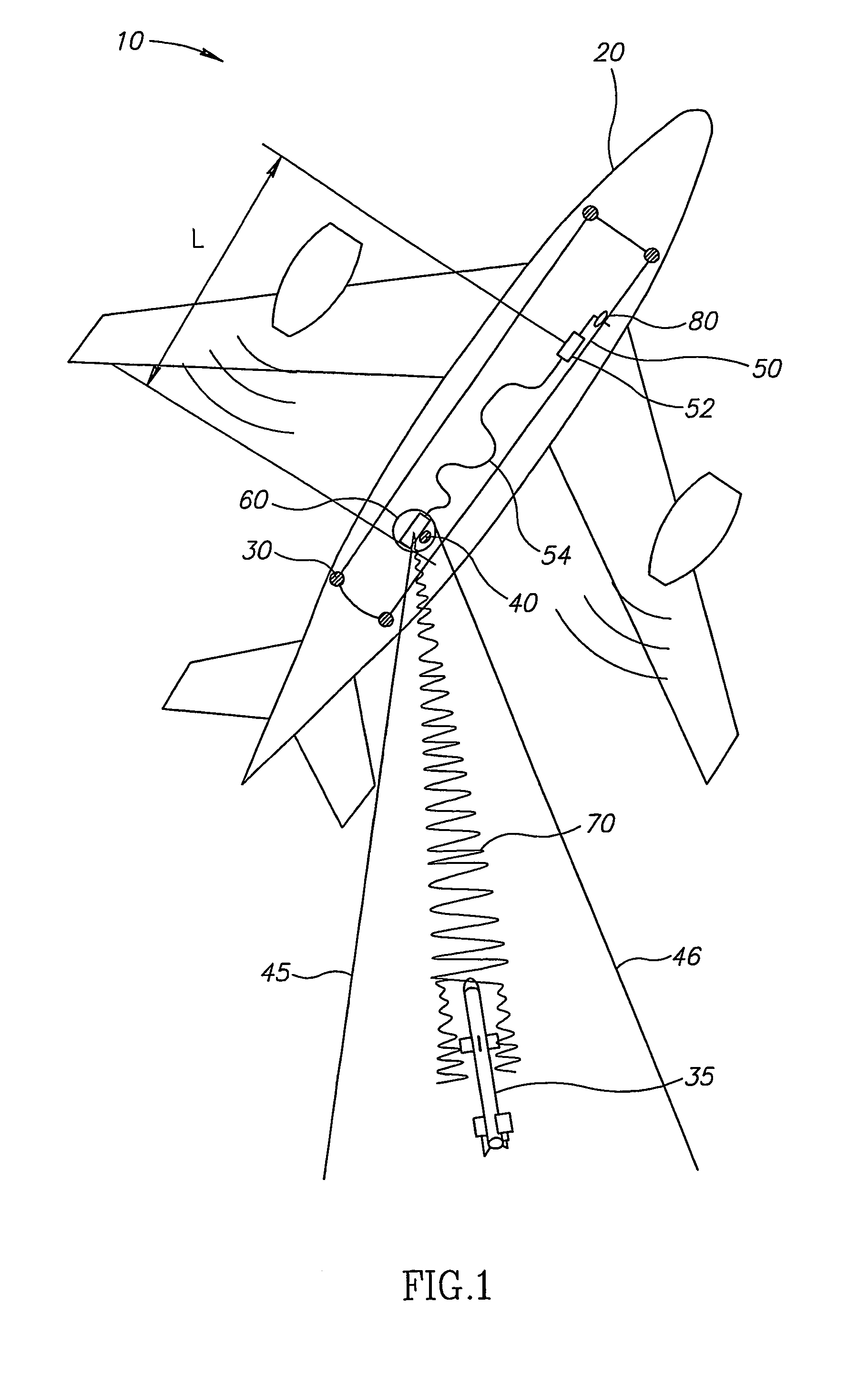
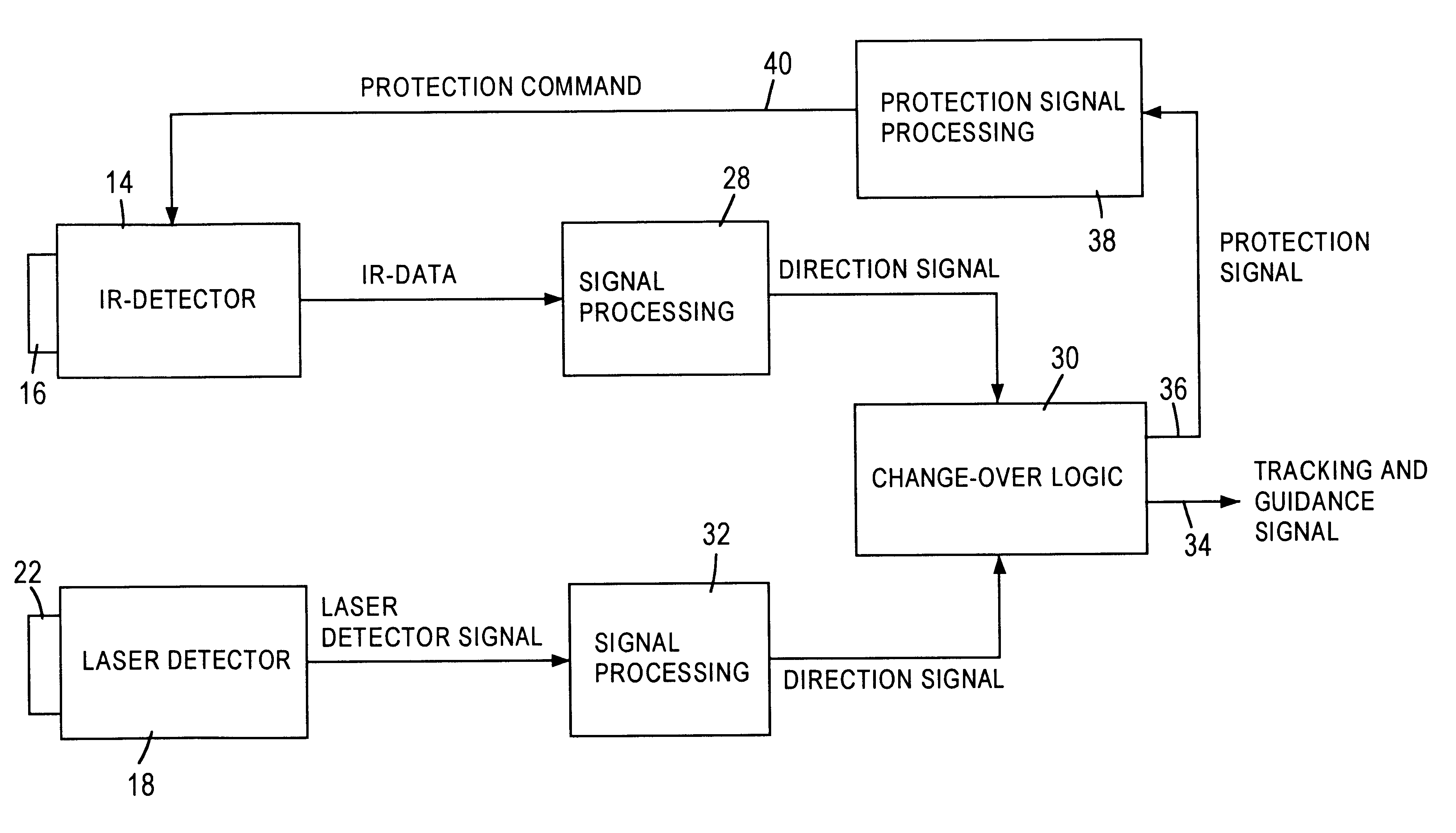
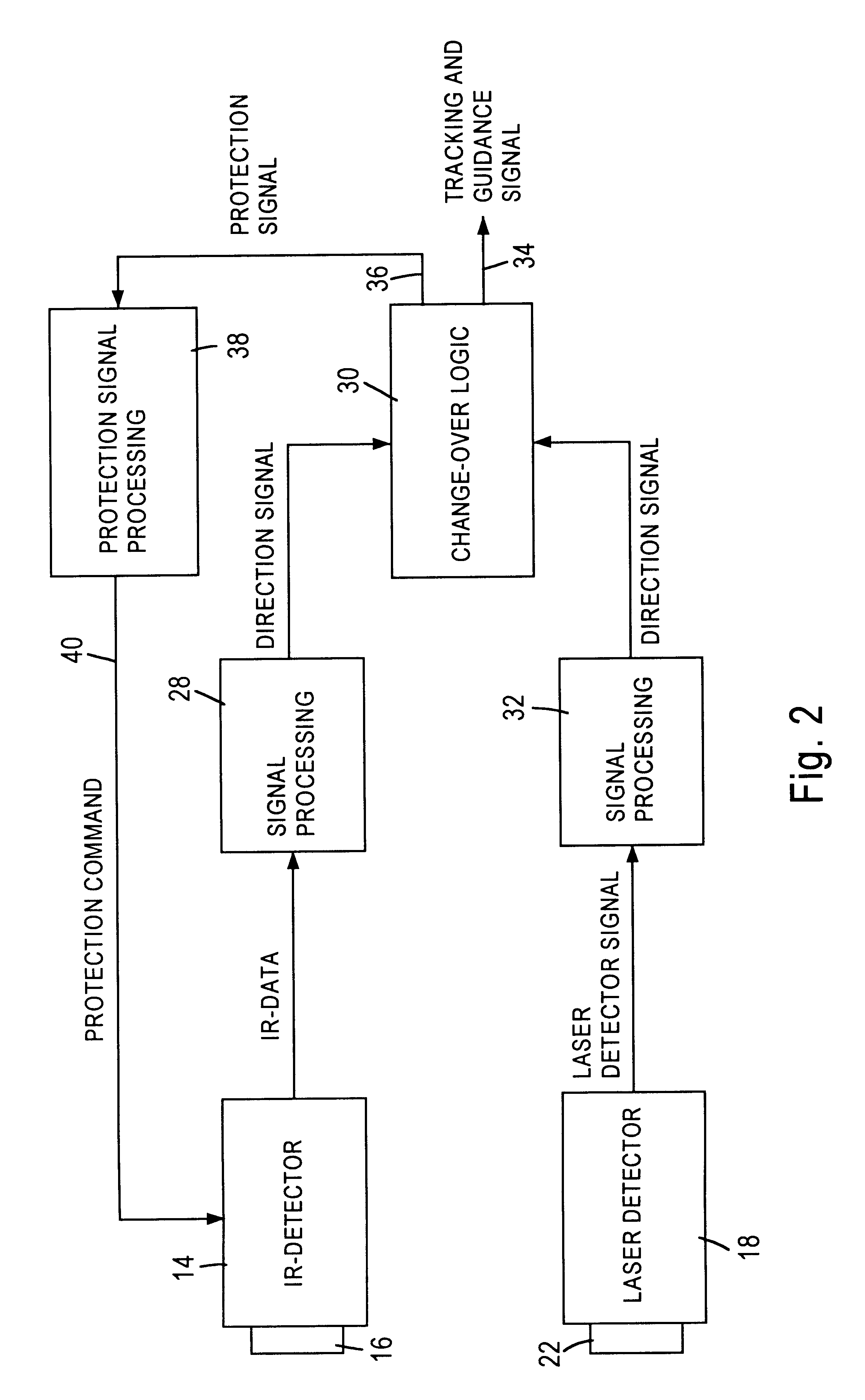
Fiber laser based directional infrared countermeasure (dircm) system
ActiveUS20070206177A1Improve operating characteristicsImprove efficiencyDefence devicesAmmunition projectilesCountermeasureData system
A DIRCM (Direct IR Counter Measures) system includes a detection and warning apparatus for detecting a missile that might pose a threat on the platform to which said system is allocated, and for generating a warning of its existence. The warning may include data that enable the calculation of the expected direction from which the missile is approaching. The DIRCM system may also include an acquisition device for performing acquisition of the approaching missile in accordance with the data provided by the detection and warning apparatus, and issuing data that may enable the calculation in real time of the updated position of the missile, a fiber laser for generating a laser beam, and a motion and aiming enabled turret, coupled with the laser, for directing the laser beam onto the approaching missile. The laser beam may be generated in accordance with the missile's updated position as calculated based on data received from the acquisition device, and processing means, linked to the detection and warning apparatus and also to the acquisition device, the laser and the turret.
Owner:EL OP ELECTRO OPTICS INDS
Fiber laser based directional infrared countermeasure (DIRCM) system
ActiveUS7688247B2Improve operating characteristicsImprove efficiencyDefence devicesAmmunition projectilesCountermeasureLight beam
A DIRCM (Direct IR Counter Measures) system includes a detection and warning apparatus for detecting a missile that might pose a threat on the platform to which said system is allocated, and for generating a warning of its existence. The warning may include data that enable the calculation of the expected direction from which the missile is approaching. The DIRCM system may also include an acquisition device for performing acquisition of the approaching missile in accordance with the data provided by the detection and warning apparatus, and issuing data that may enable the calculation in real time of the updated position of the missile, a fiber laser for generating a laser beam, and a motion and aiming enabled turret, coupled with the laser, for directing the laser beam onto the approaching missile. The laser beam may be generated in accordance with the missile's updated position as calculated based on data received from the acquisition device, and processing means, linked to the detection and warning apparatus and also to the acquisition device, the laser and the turret.
Owner:EL OP ELECTRO OPTICS INDS
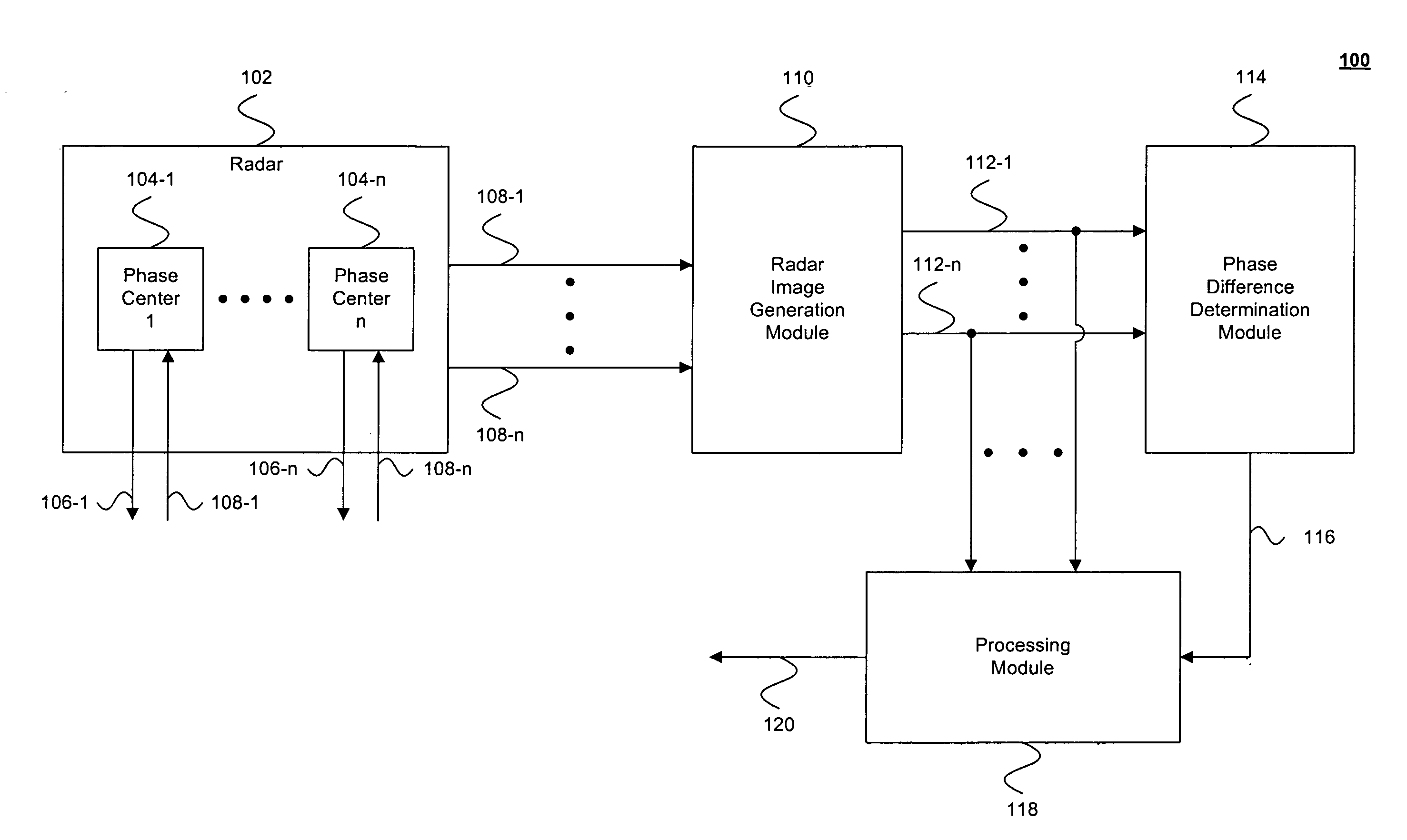
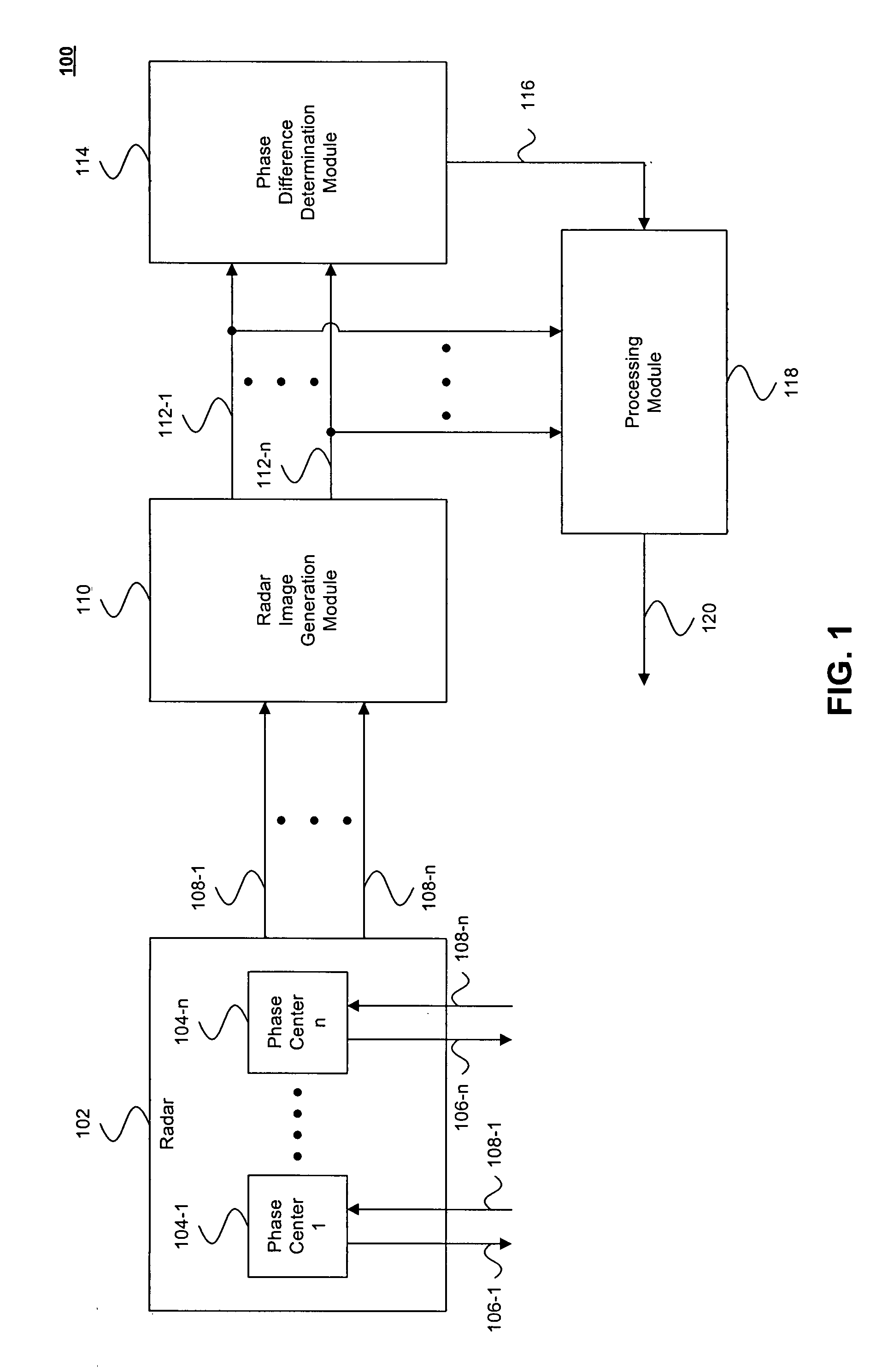
Radar systems and methods
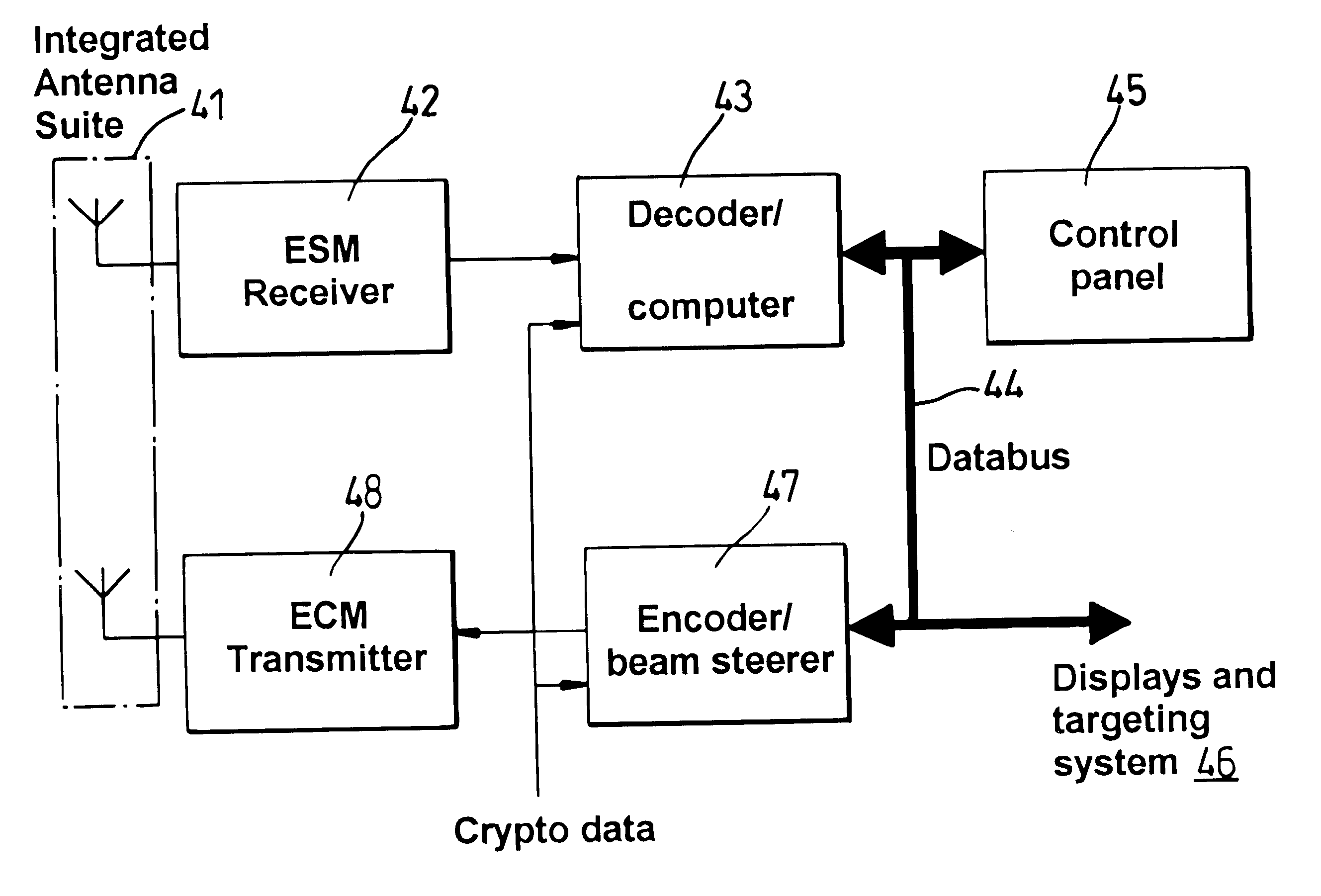
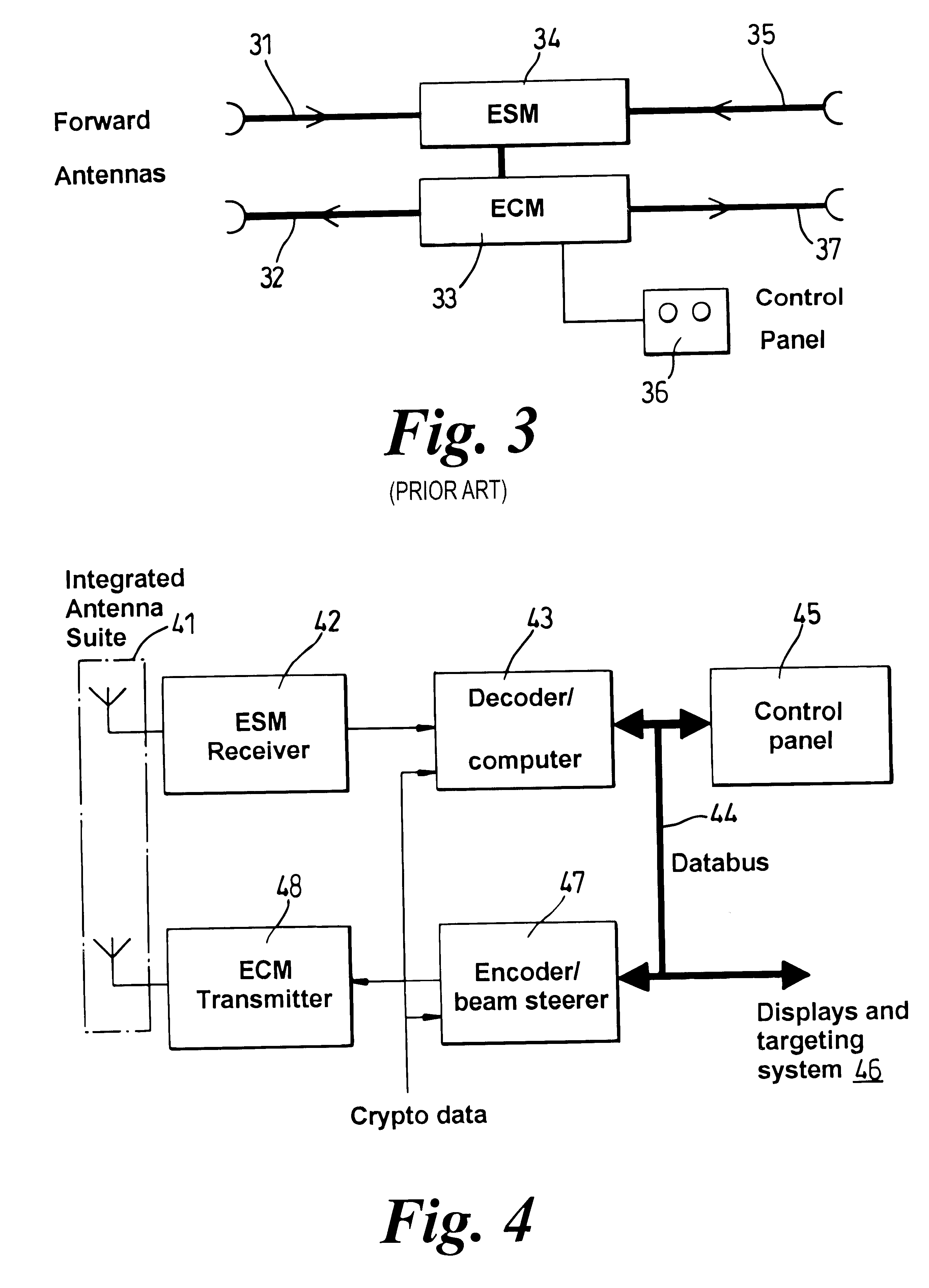
A mobile radar system including Electronic Support Measures (ESM) which is adapted to detect and decode Identify Friend or Foe (IFF) signals. The system includes means for decoding or decrypting received IFF signals. The system uses an Electronic Counter Measure (ECM) transmitter which is adapted to transmit IFF response and interrogation signals. The IFF signals to be transmitted can be encrypted. Integrating IFF means into the ESM and ECM components results in mass and volume savings due to shared use of the transmitting and receiving resources. As the IFF signals are transmitted using ESM antennas, they can be directed towards a particular aircraft, thereby reducing spurious transmissions.
Owner:BAE SYSTEMS PLC
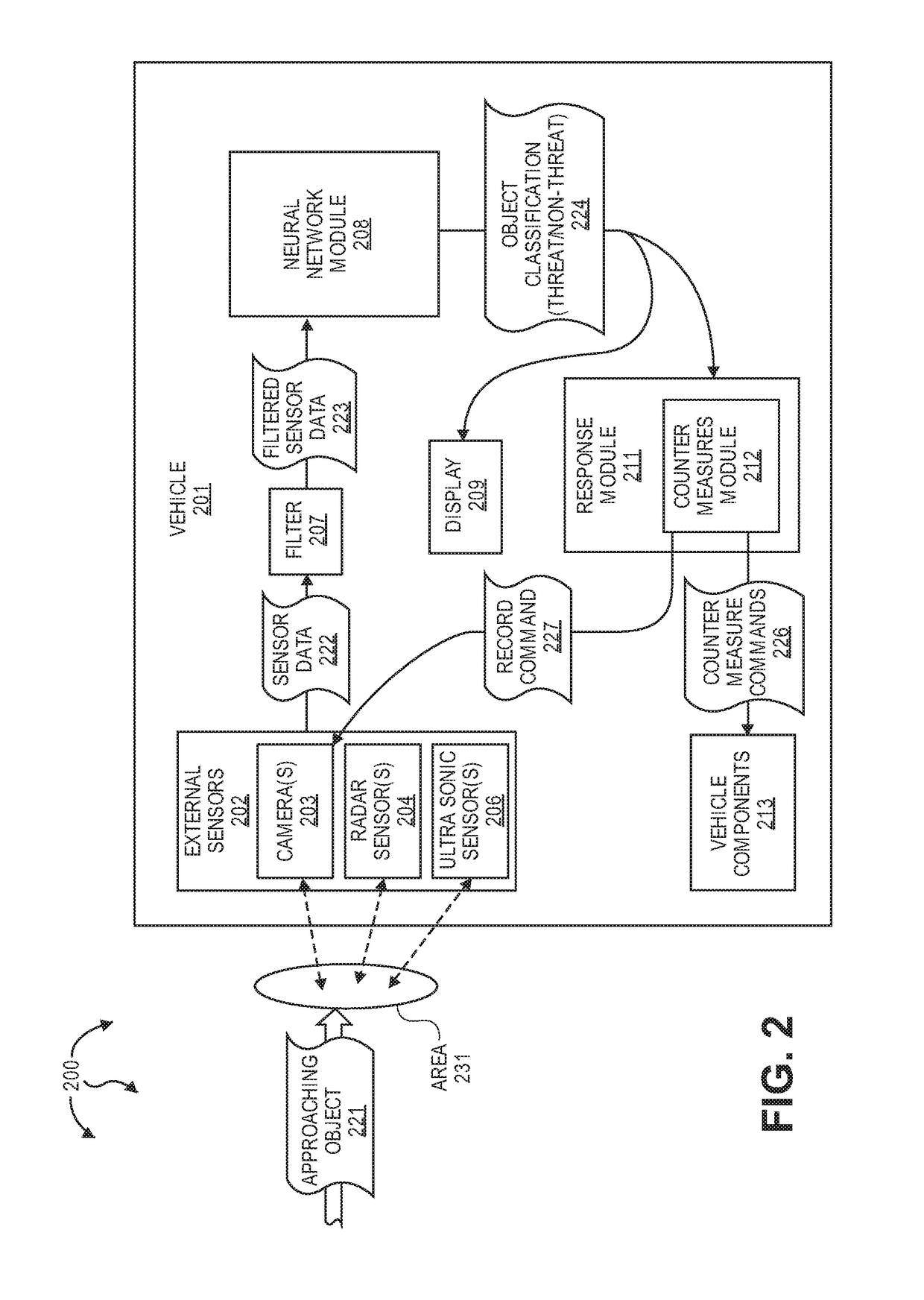
Detecting Physical Threats Approaching A Vehicle
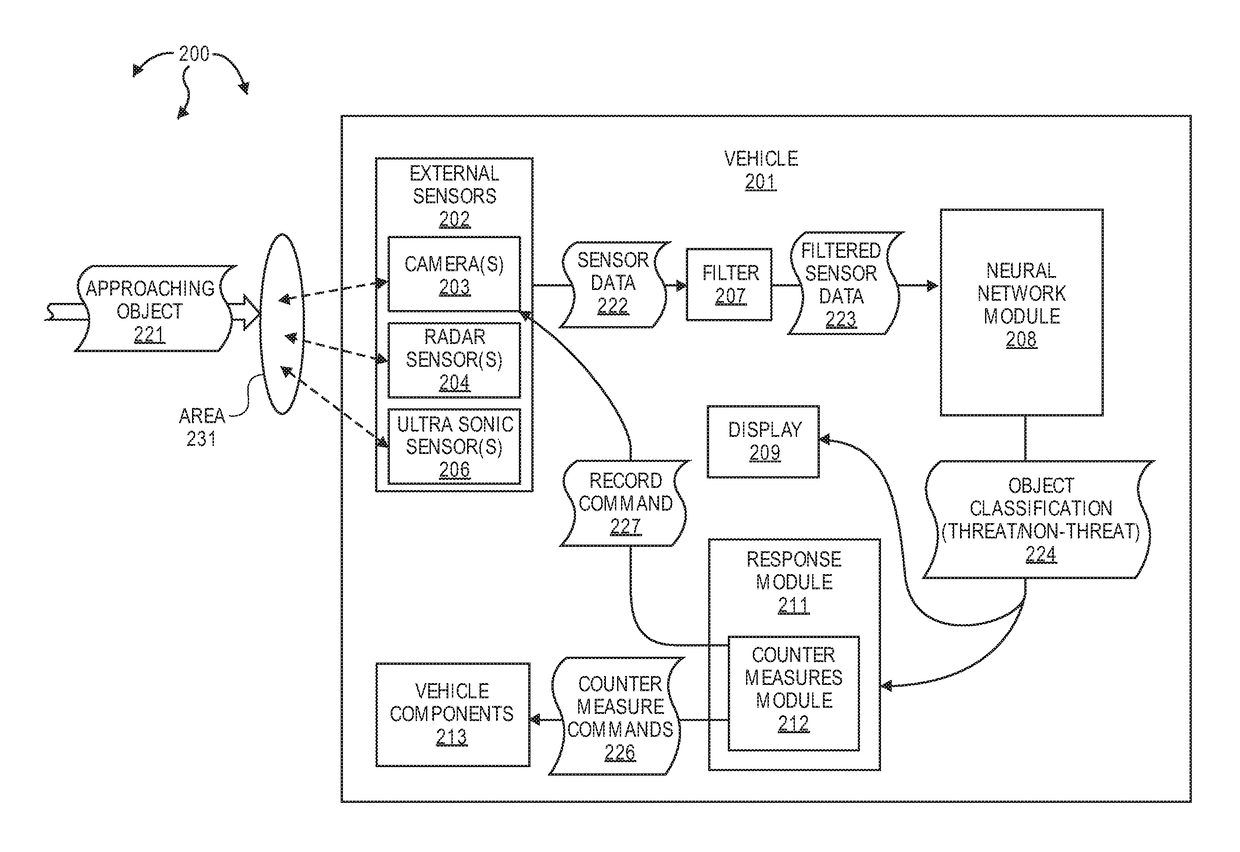
ActiveUS20170371339A1Simple methodAutonomous decision making processPedestrian/occupant safety arrangementTemporal informationKaiman filter
The present invention extends to methods, systems, and computer program products for detecting physical threats approaching a vehicle. External sensors on a vehicle capture the environment around the vehicle. Approaching targets detected by the external sensors can be fed into a neural network to recognize and / or classify approaching targets as potential threats. Tracking mechanisms (e.g., Kalman filters, Particle filters, etc.) can leverage temporal information to determine if a threat is approaching a vehicle. When an approaching threat is detected, a vehicle can activate one or more counter measures to deter the threat. When a vehicle includes autonomous driving capabilities, counter measures can include automatically attempting to drive away from an approaching threat.
Owner:FORD GLOBAL TECH LLC
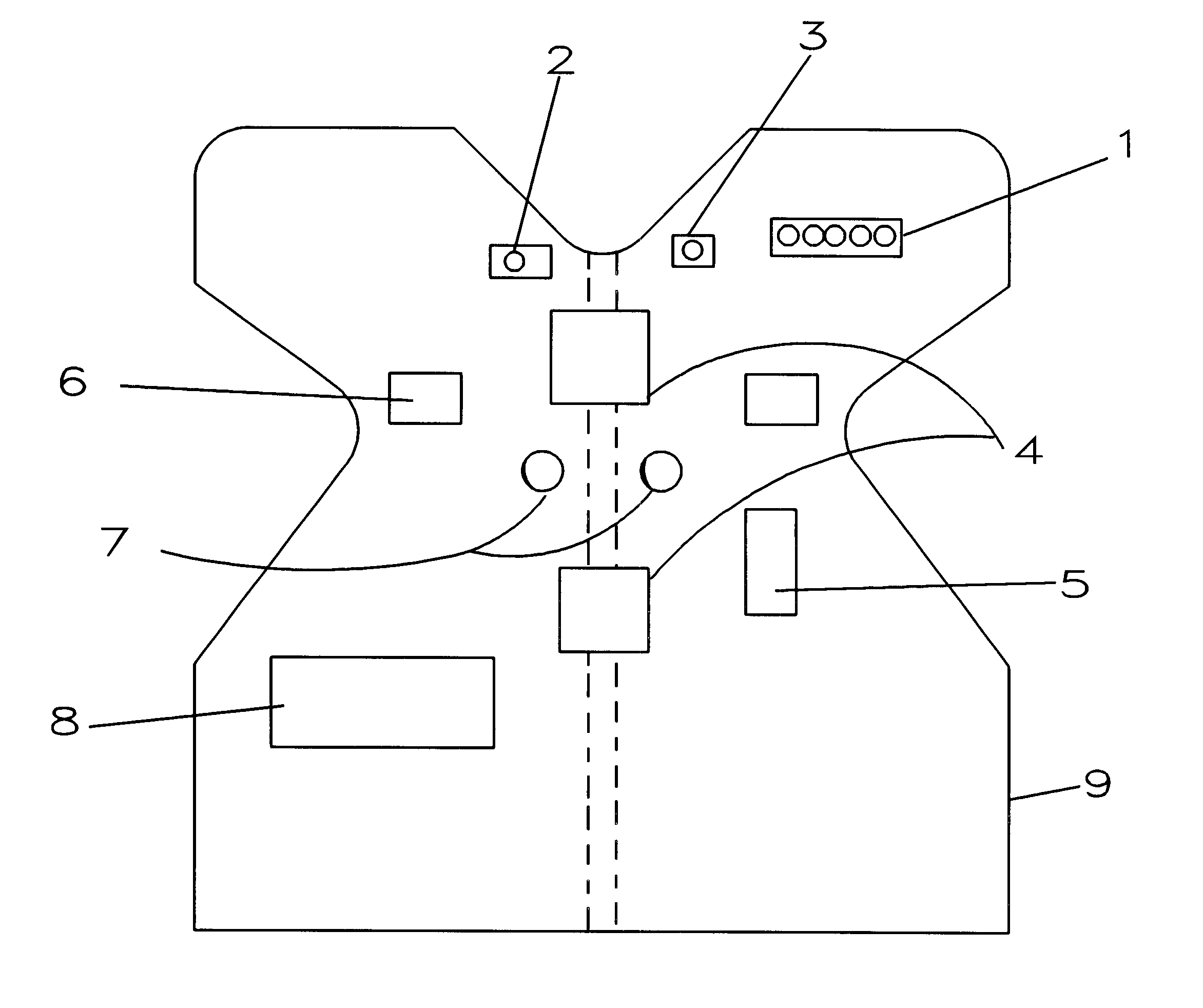
Close-contact counter-measure garment and method
A garment equipped with emitter, said emitter positioned on the garment such that the emitter can be a weapon, where said emitter can be fired by the wearer of the garment or fired remotely by a second person, an observer, or a third person, a monitor, an observer who is monitoring, where said emitter emits a means to mark an attacker by marking means, the position, identification of, and, alternatively, to immobilize or interfere with an attacker of the wearer of the garment. A method of defending an individual, including wearing by the individual a garment having contained upon, in, or proximal thereto a lethal, non-lethal, or less-than lethal weapon, and discharging or firing the weapon from the garment in the direction of an attacker.
Owner:RESNICK JOSEPH ANTHONY
Techniques for avoiding and remedying DC bias buildup on a flat panel variable refresh rate display
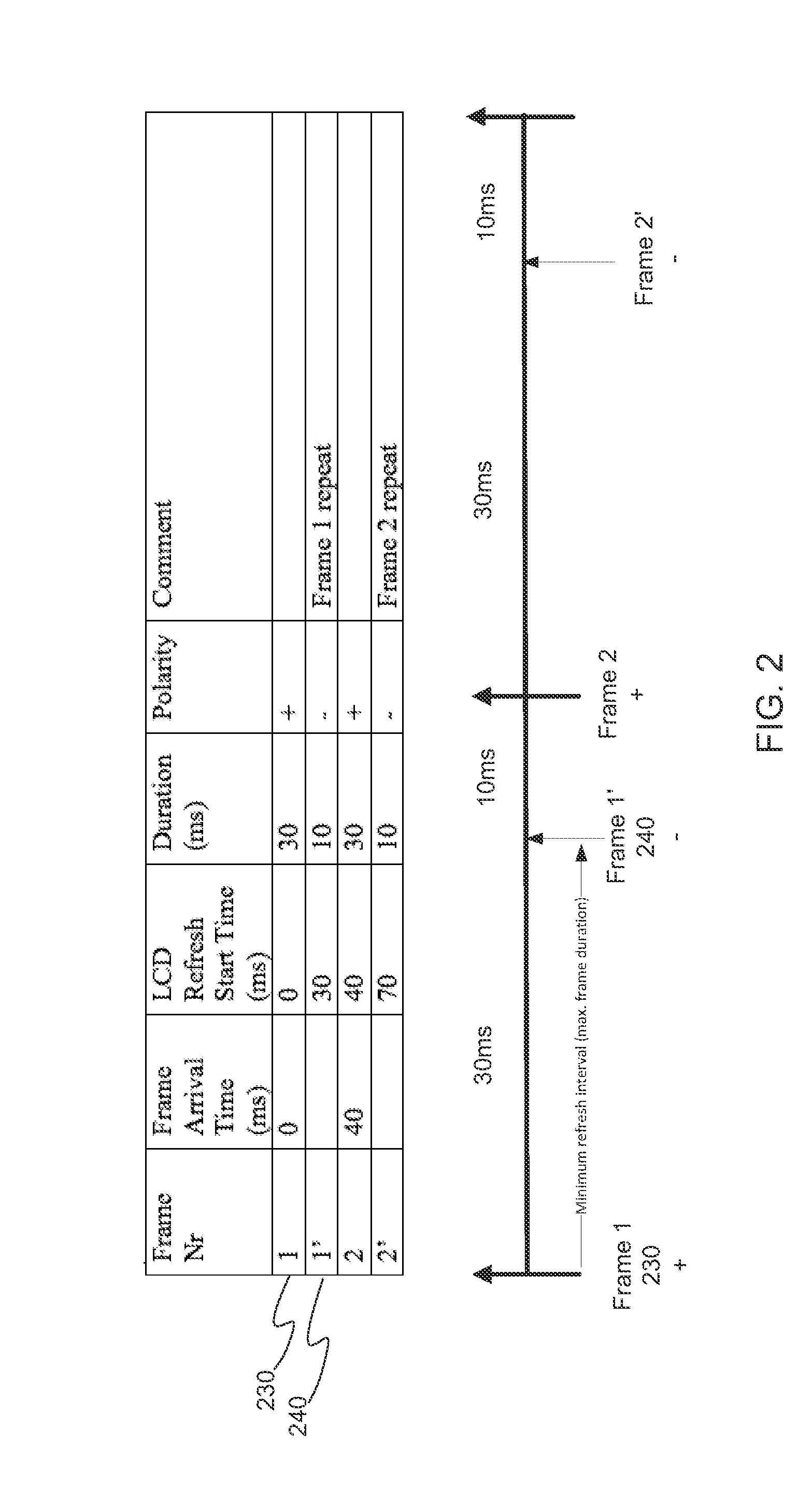
ActiveUS20150243233A1Avoid charge accumulationAvoiding resultant visual artifactStatic indicating devicesCountermeasureDisplay device
A method for driving a display panel having a variable refresh rate is disclosed. The method comprises receiving a current input frame from an image source. Next, it comprises determining a number of re-scanned frames to insert between the current input frame and a subsequent input frame, wherein the re-scanned frames repeat the input frame, and wherein the number of re-scanned frames depends on the minimum refresh interval (MRI) of the display panel. Further, it comprises calculating respective intervals at which to insert the re-scanned frames between the current input frame and the subsequent input frame. Subsequently, it comprises determining if a charge accumulation in pixels of the display panel has crossed over a predetermined threshold value. Finally, responsive to a determination that the charge accumulation has crossed over a predetermined threshold value, it comprises performing a counter-measure to remediate the charge accumulation.
Owner:NVIDIA CORP
Electronic countermeasures transponder system
A system is provided that has an ECM (electronic counter measures) system and a transponder monitor connected to or forming part of the ECM system. The system monitors for a transponder signal from a remote transponder. The system determines information, such as transponder location, based on the transponder signal and makes use of the information in the ECM system and / or the system extracts encoded information contained in the transponder signal, such as information about a transponder owner, such as status of consumables, medical status. The ECM system may have a reactive jammer that is used both for a reactive jamming function, and as the transponder monitor function.
Owner:SKY IND
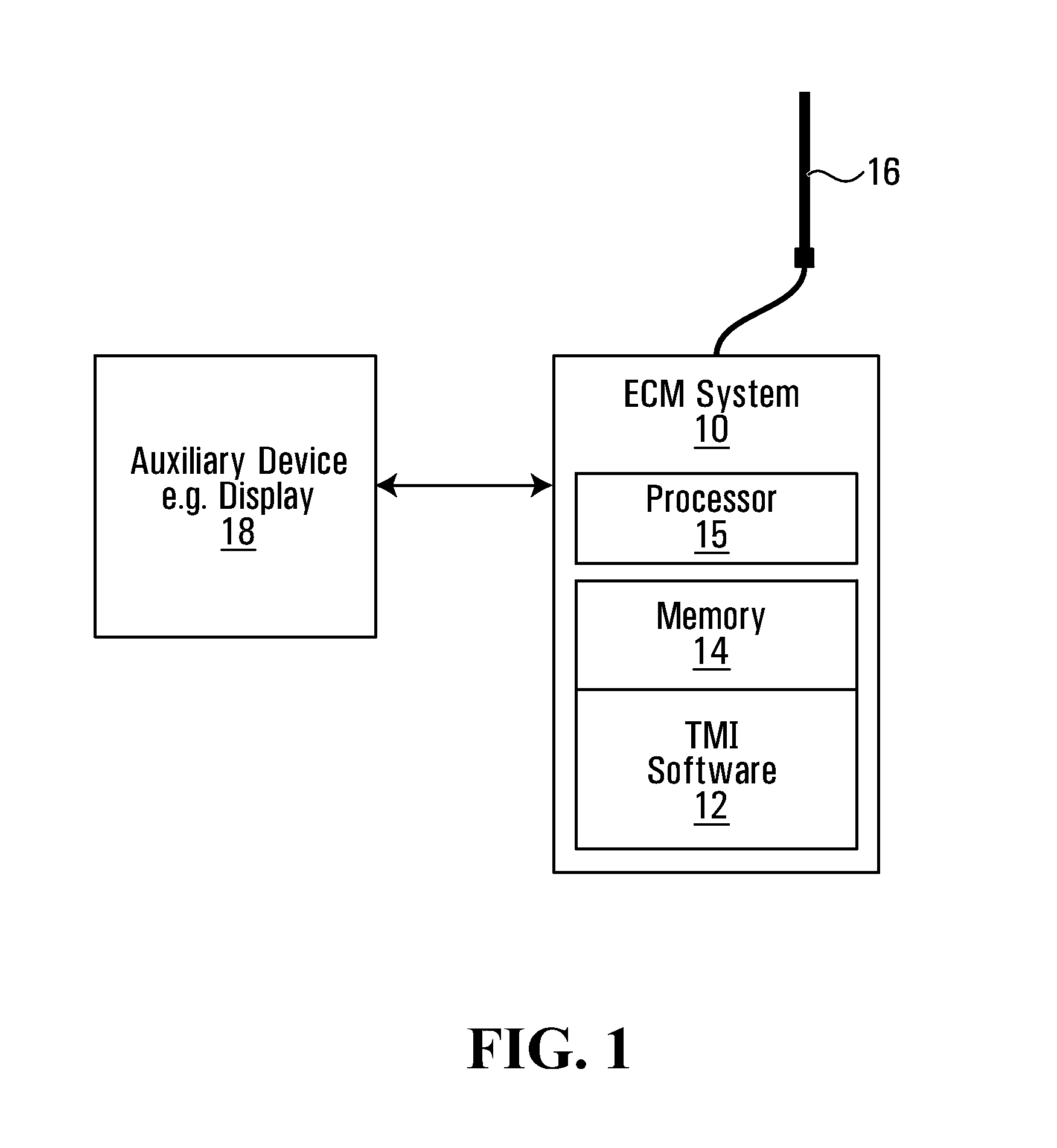
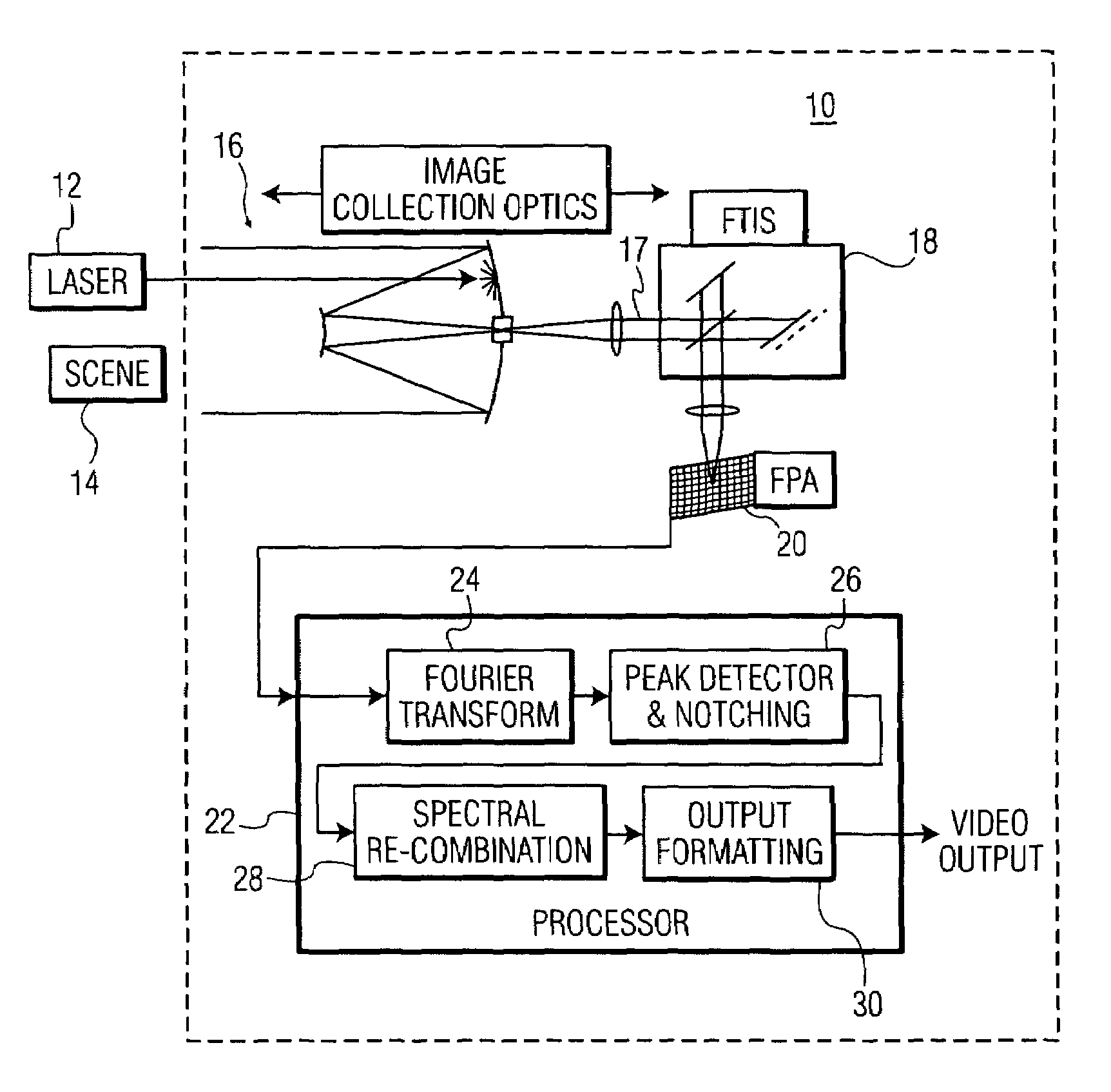
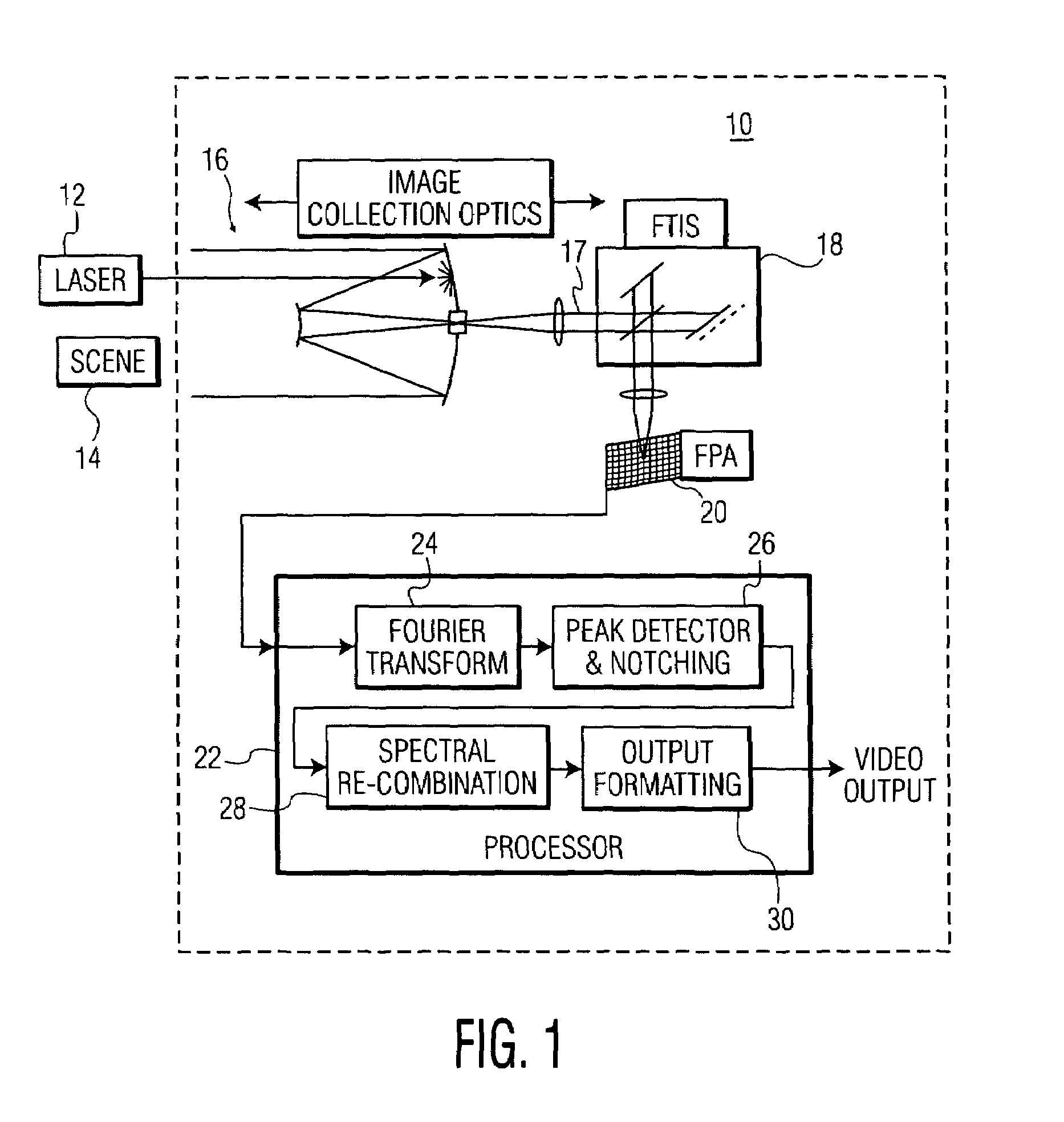
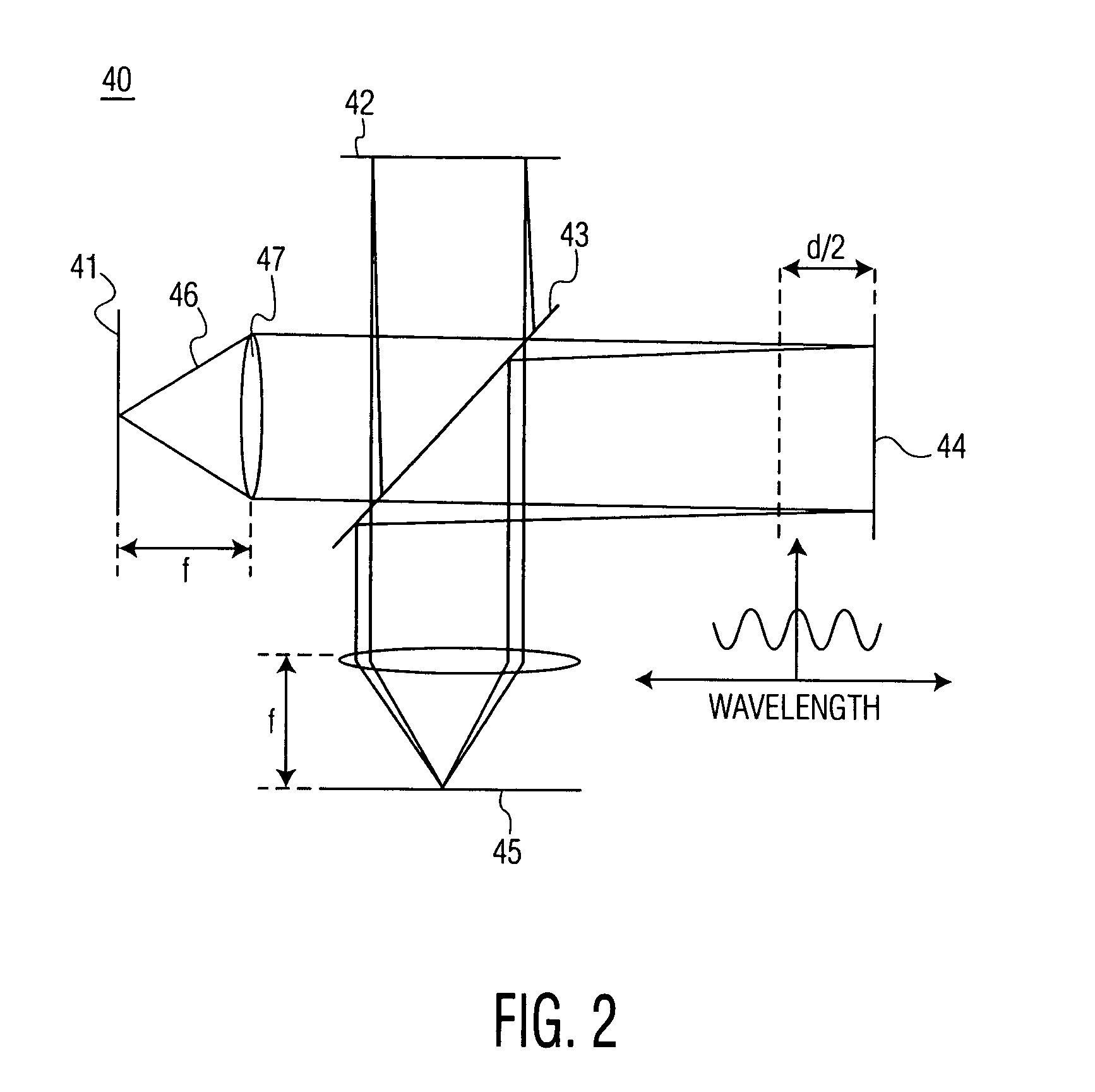
Laser counter-measure using fourier transform imaging spectrometers
ActiveUS6963405B1Lower Level RequirementsRadiation pyrometryWave based measurement systemsSpectral bandsOptical energy
In an imaging system providing an image of a target of interest, a method of reducing interference from a laser beam includes the steps of: (a) receiving optical energy from the target of interest and the laser beam; (b) forming an interferogram of spectral energy, at each spatial position of an image, based on the optical energy received in step (a); (c) detecting the interferogram of spectral energy, at each of the spatial positions, to provide a corresponding spectral band of intensity values; (d) selecting an intensity level in the spectral band, detected in step (c), that is greater than a predetermined value, and reducing the selected intensity level; and (e) forming an image of the target of interest, after reducing the selected intensity level of step (d).
Owner:HARRIS CORP
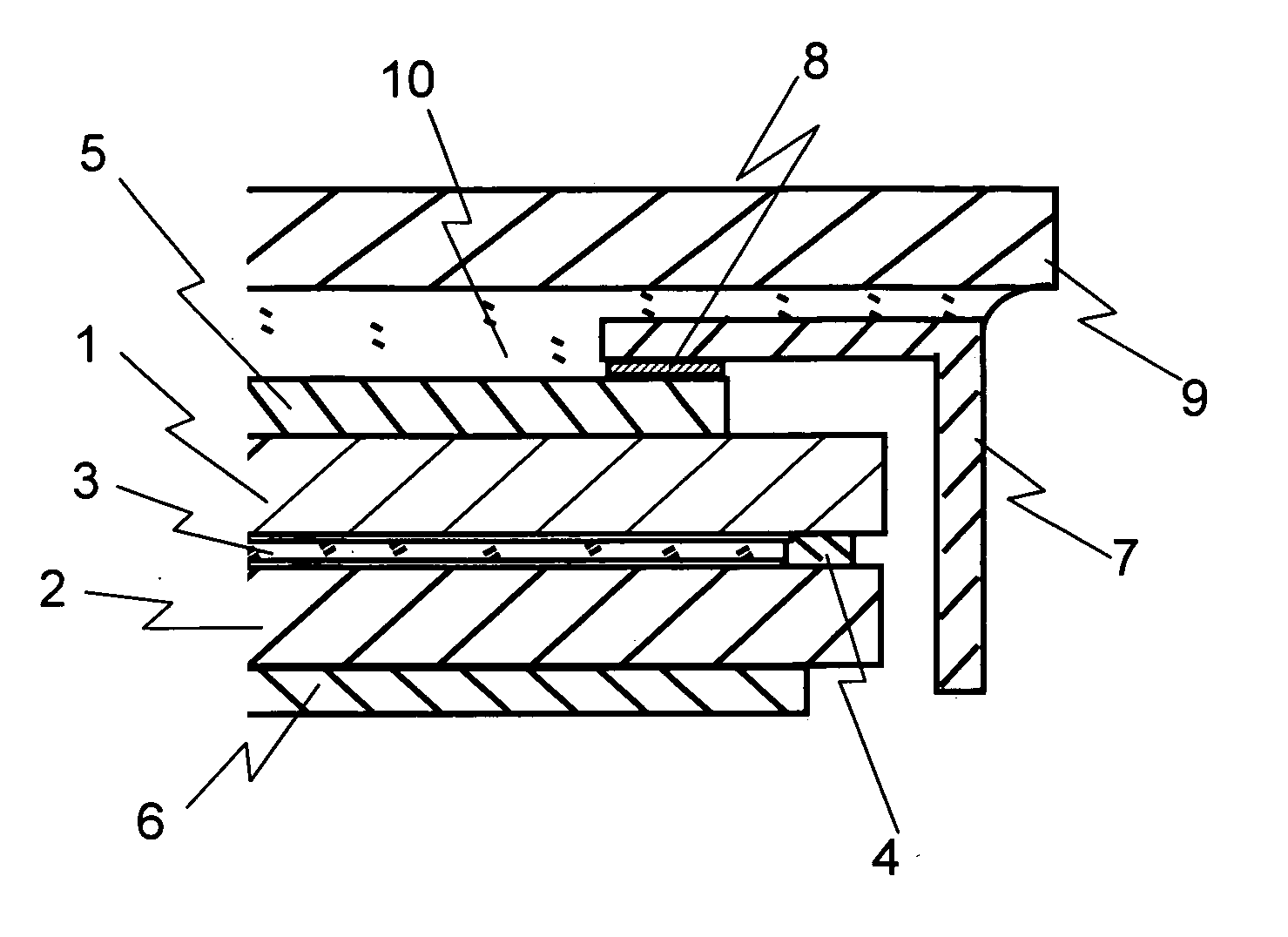
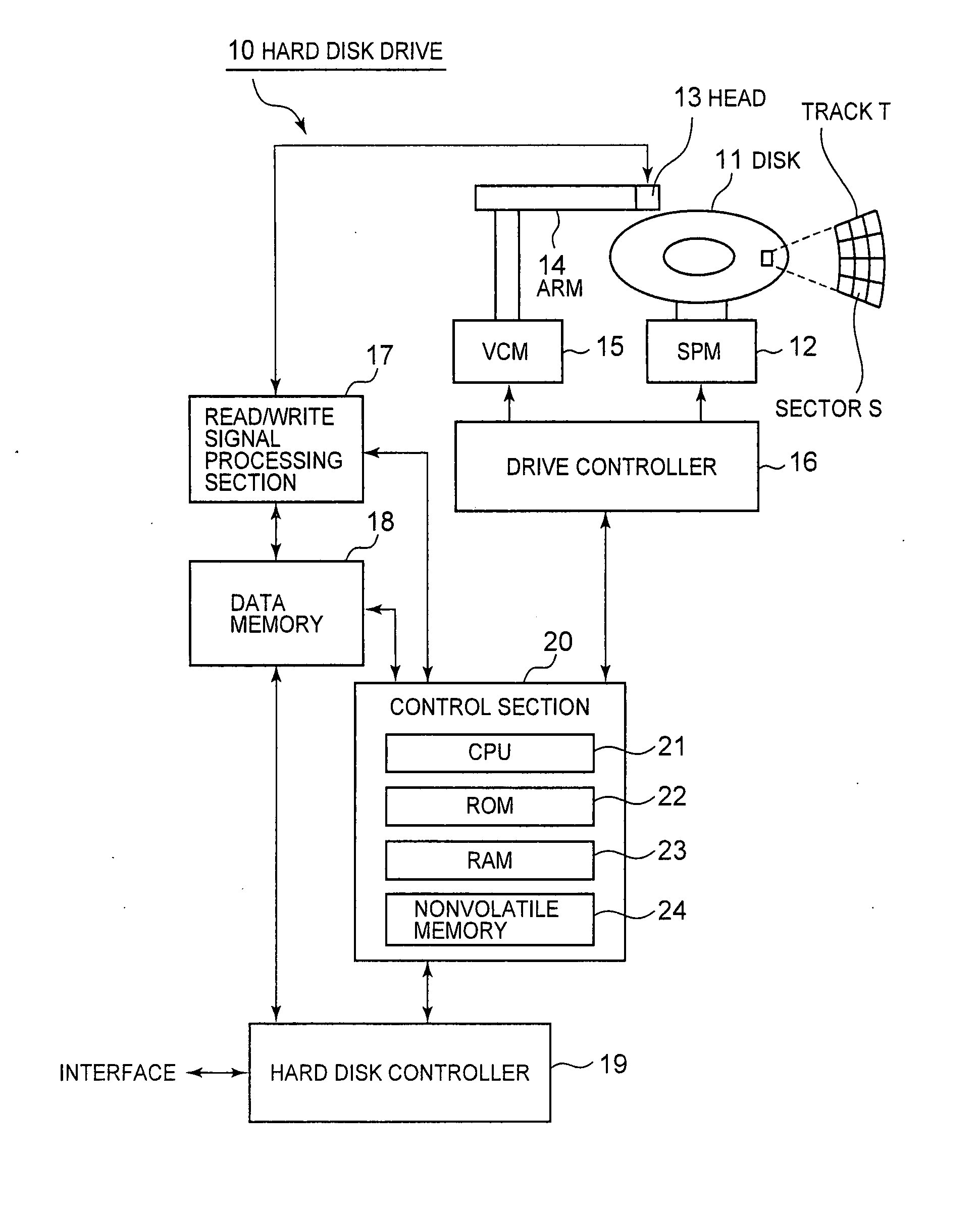
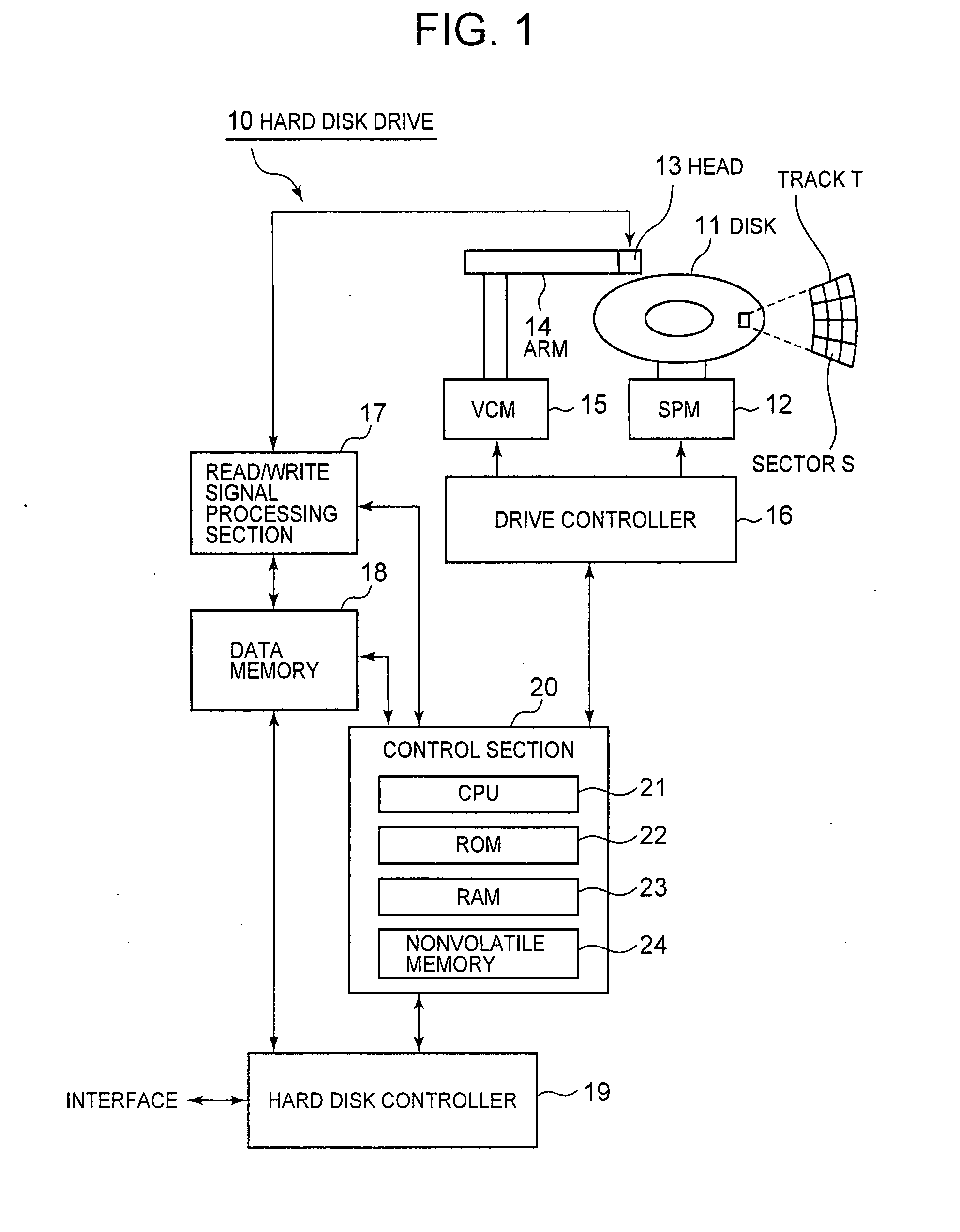
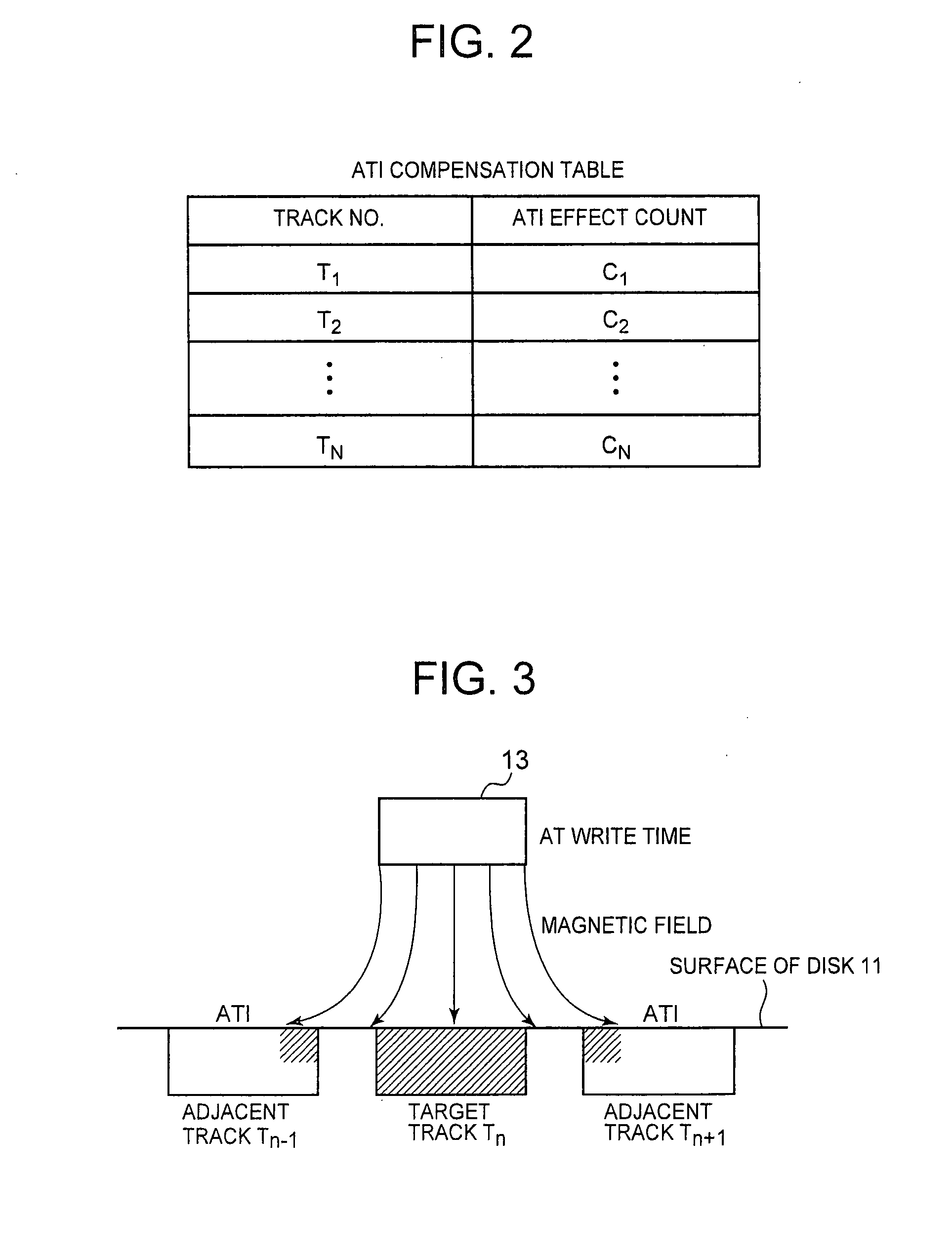
Method and apparatus for recording data on a magnetic recording medium
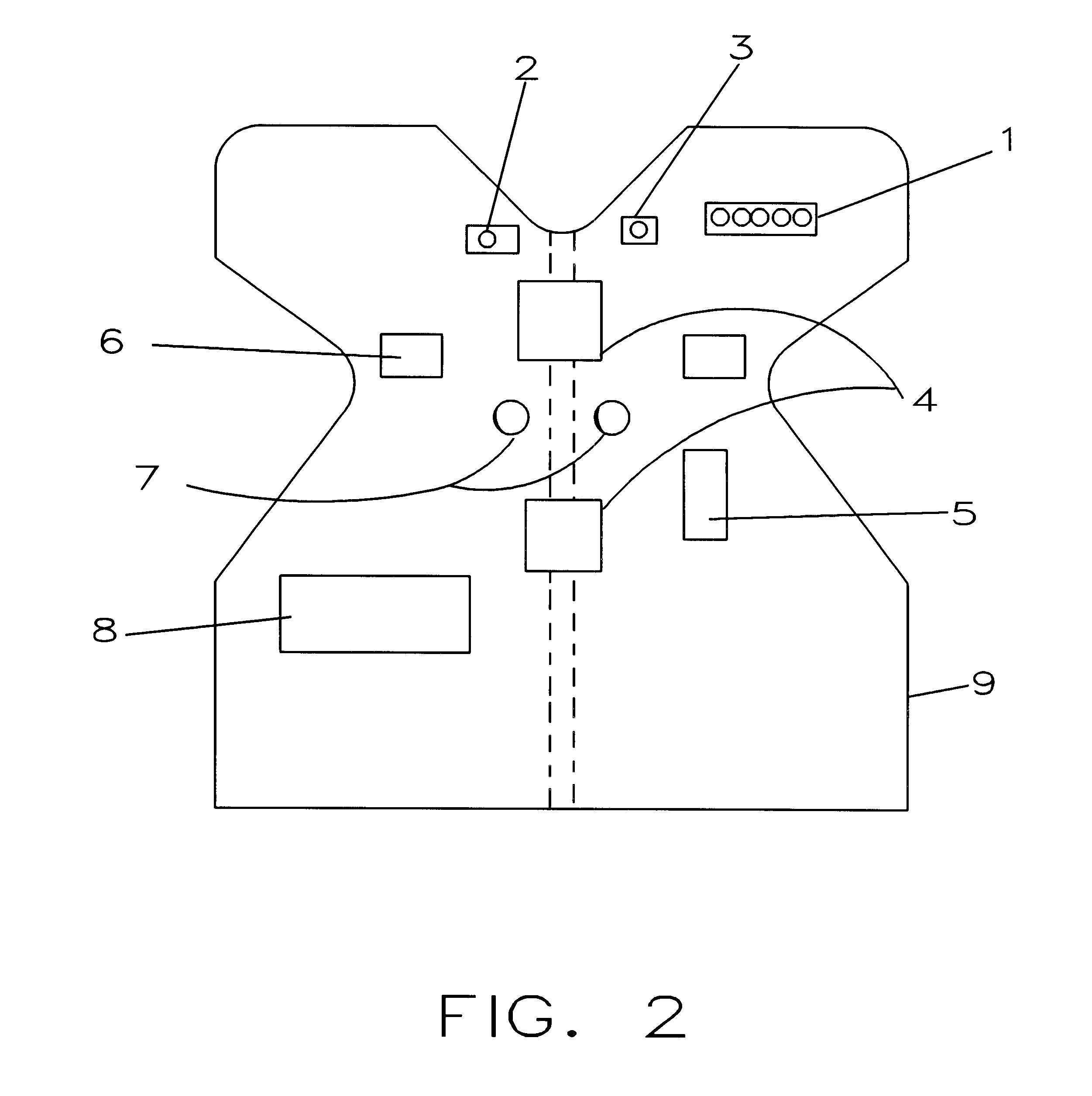
InactiveUS20080174905A1Record information storageAlignment for track following on disksComputer hardwareCounter measures
A method for recording data on a magnetic recording medium is disclosed. When data are written to a target track Tn, the numbers of effects on tracks Tn−1 and Tn+1 adjacent to a target track are counted as Adjacent Track Interference (ATI) effect counts Cn−1 and Cn+1, respectively, to determine whether or not the ATI effect counts Cn−1 and Cn+1 are greater than a permissible ATI count Np. If the ATI effect counts Cn−1 and Cn+1 are greater than the permissible ATI count Np, ATI error preventive processing is performed on the tracks Tn−1 and Tn+1. All sectors on the Tn−1 and Tn+1 are determined as to whether or not they are affected by ATI, and ATI error counter-measure processing is performed on all affected sectors to recover data.
Owner:LENOVO (SINGAPORE) PTE LTD
System and method for implementing active safety counter measures for an impaired driver
Various methods and systems are disclosed for implementing active safety countermeasures in vehicles when it is determined that the driver is impaired.
Owner:FORD GLOBAL TECH LLC
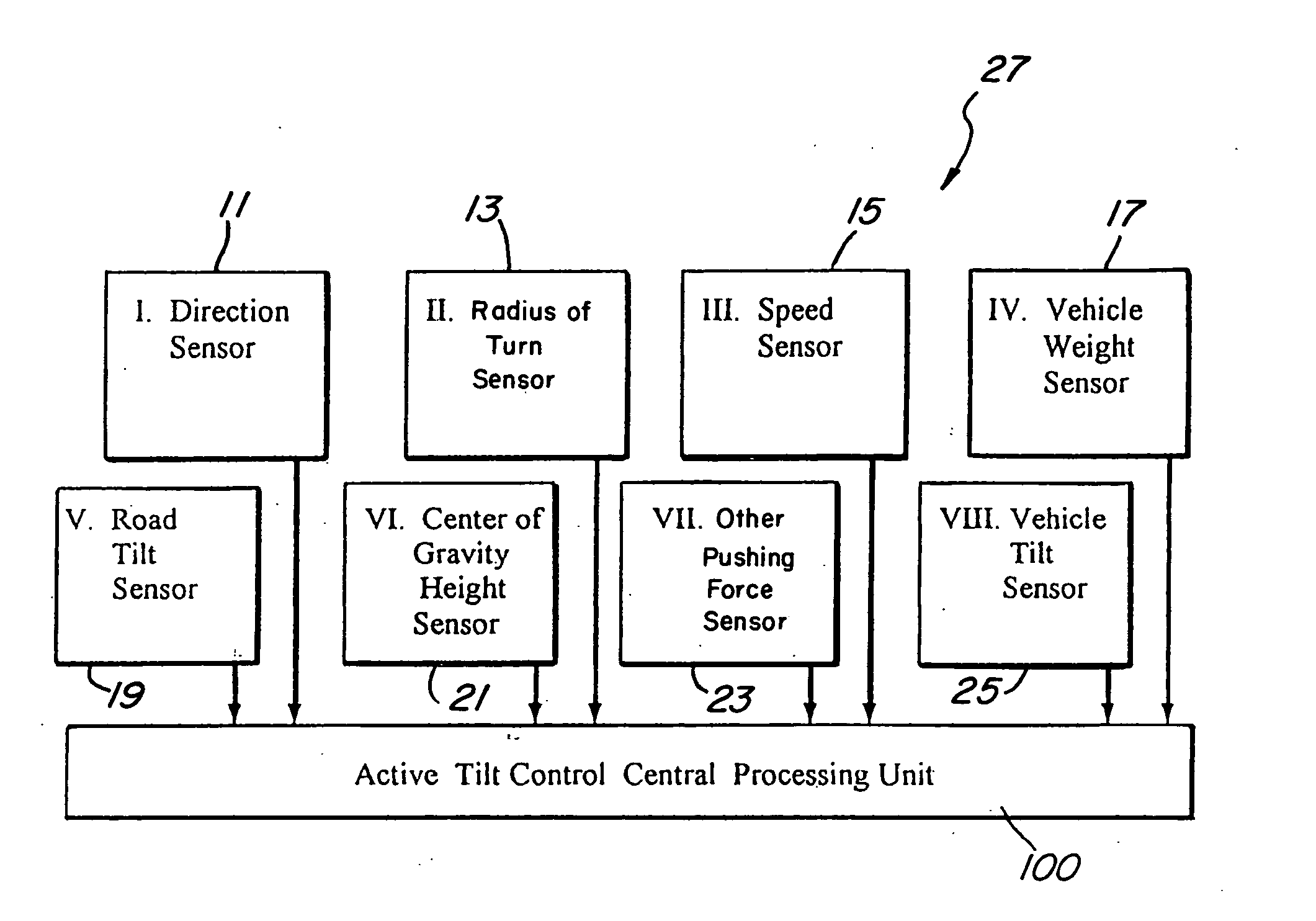
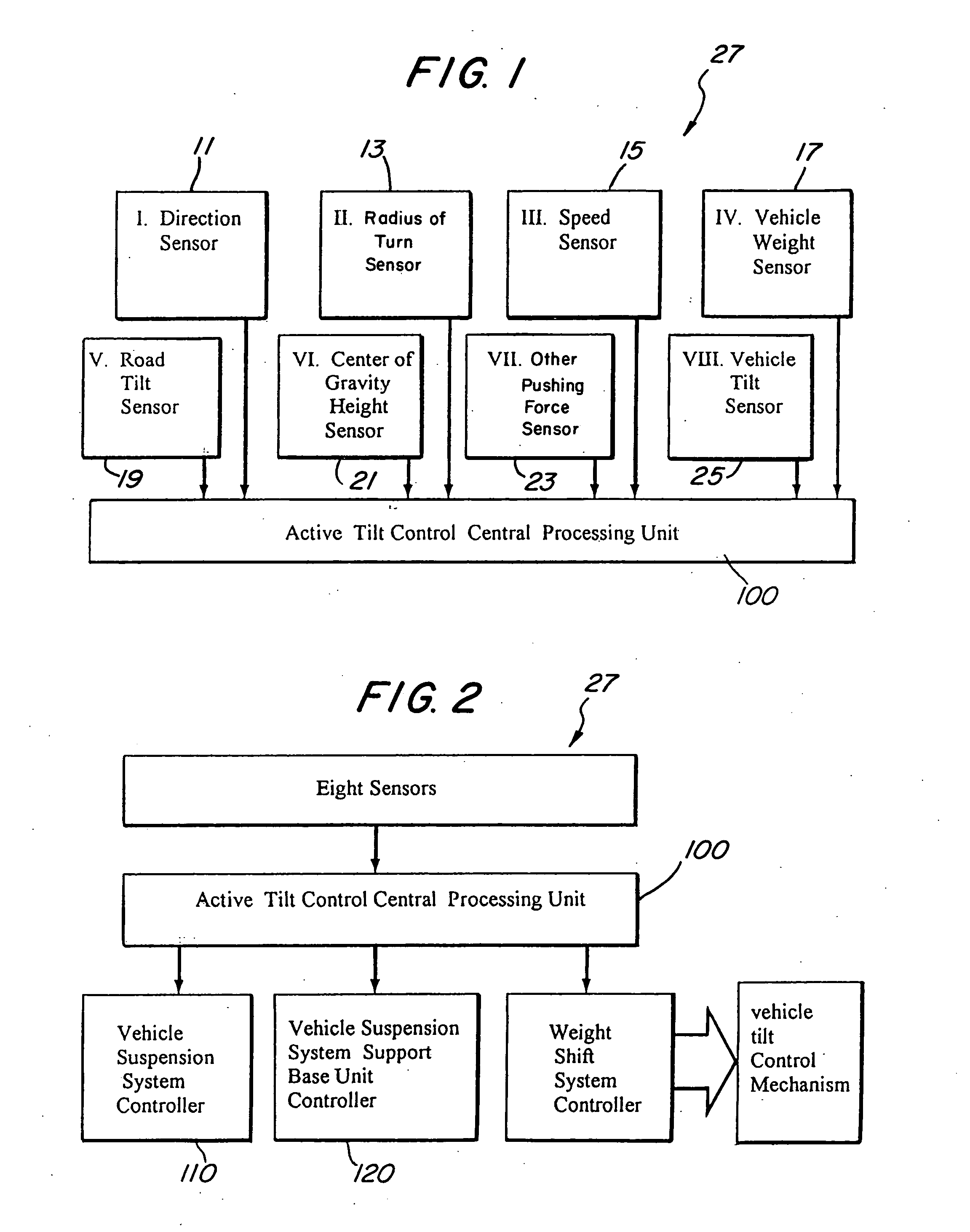
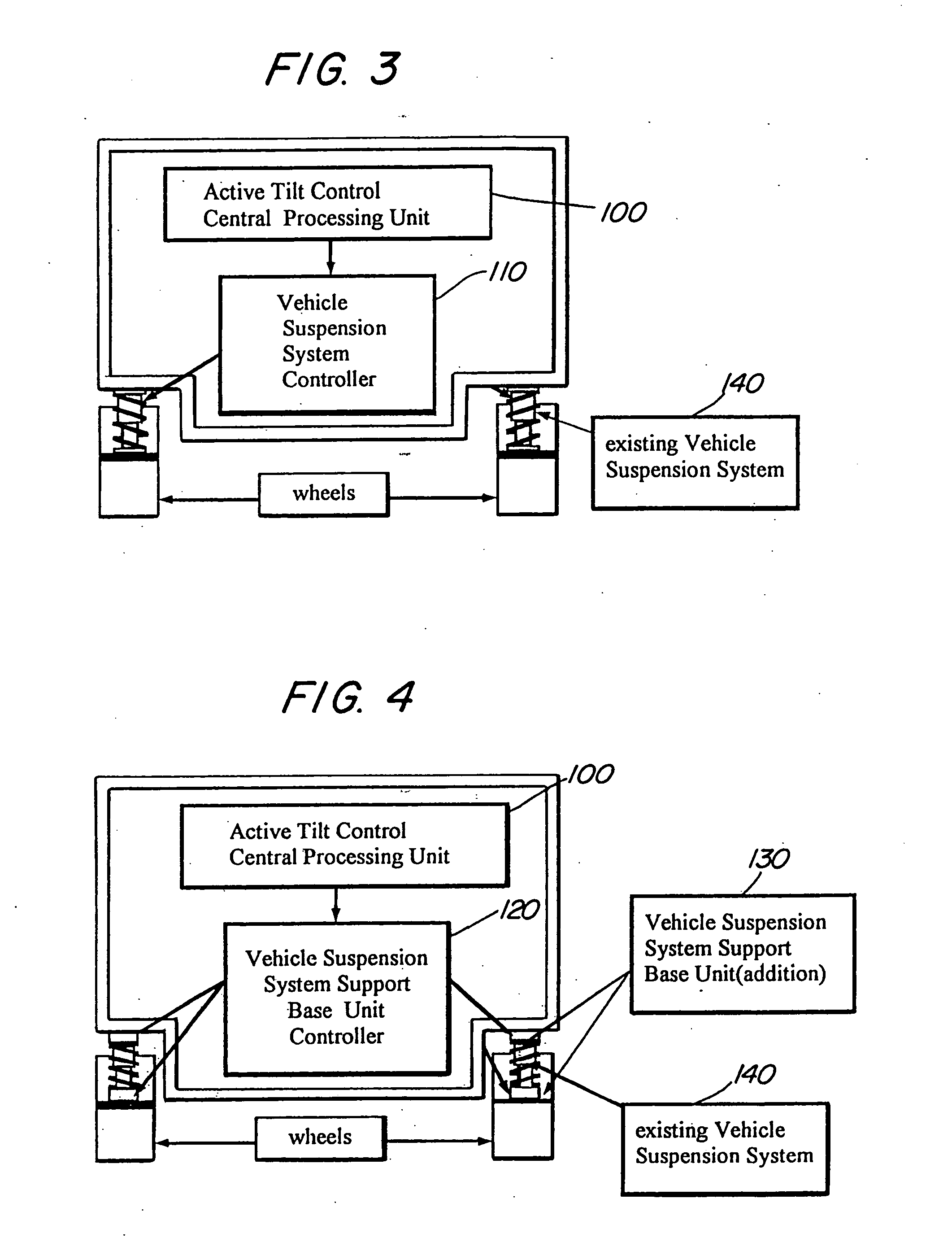
Vehicle stability system: using active tilting mechanism as a counter measure to natural tilt
InactiveUS20060076741A1Brake system interactionsInterconnection systemsCountermeasureMarine engineering
The present invention is a vehicle stability system that affords safe turn with higher speed as well as maximum brake performance and resists rollover by using one or more electrical and mechanical modes to shift the center of gravity of the vehicle into a more stable position in the event of a turn condition. A preferred embodiment of the present invention utilizes an active tilt control to tilt the vehicle in the opposite direction to the vehicle's natural inclination to tilt. A second preferred embodiment utilizes a shifting weight, that is a ballast or any heavy part of the vehicle to move the center of gravity toward to side of the vehicle tending to lift up during a tilt condition. The first and second preferred embodiments can be used alone or in a combination to create a more dynamic stable condition for the vehicle in turn mode.
Owner:LIM HOWARD TAK SU
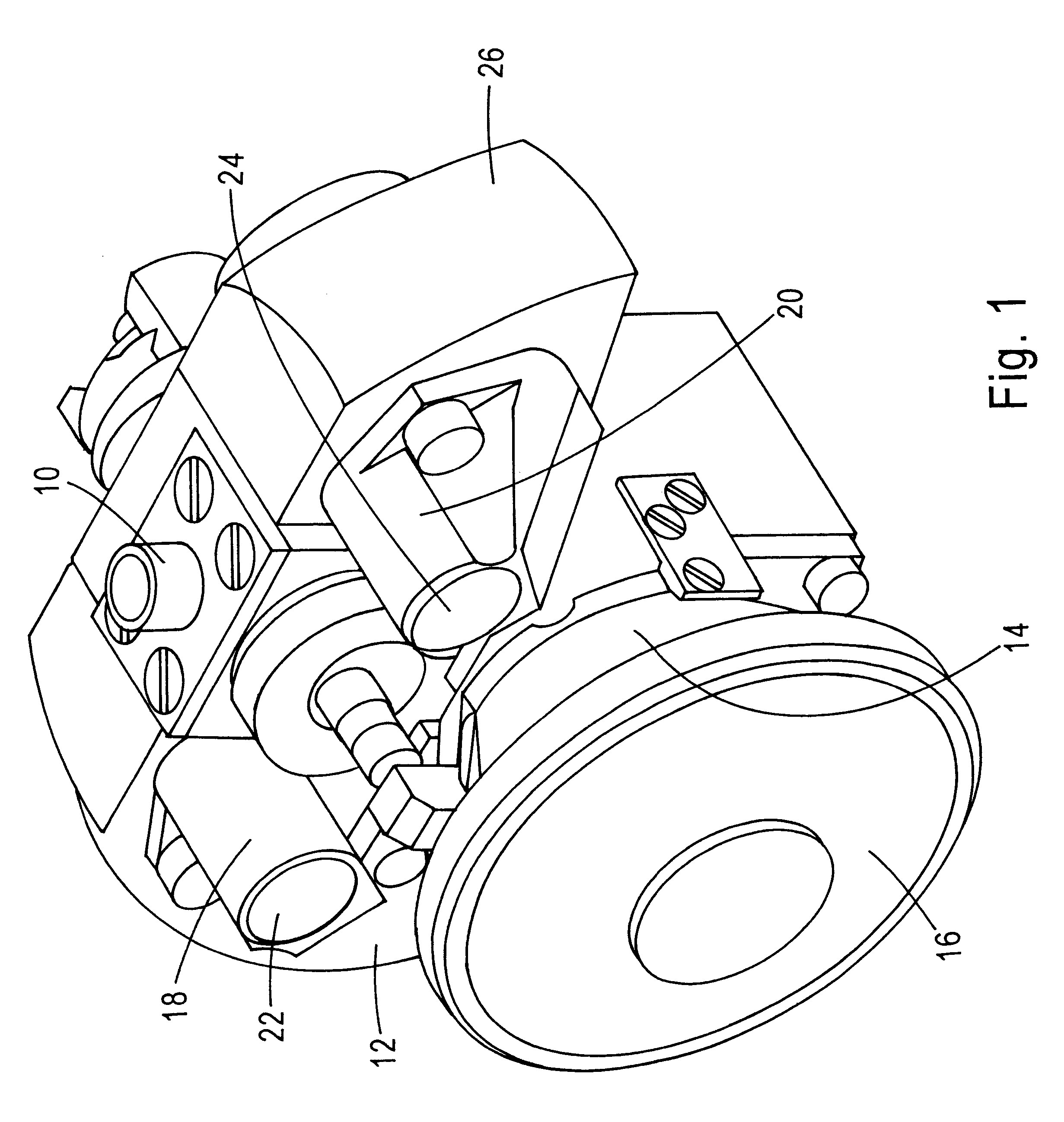
Infrared seeker head for target seeking missile
An infrared seeker head for target tracking missiles has a main detector and an imaging optical system generating an image of a field of view on the main detector. The field of view contains a target such as an enemy aircraft. The missile is guided to the target in accordance with signals from the main detector. The target, if attacked by the missile, emits high-intensity laser radiation towards the missile as a counter-measure. This is to disturb the operation of the seeker head by dazzling or even destroying the main detector. The seeker head contains a device for defending against such disturbances. Various types of such defending devices are described. Incident light is deviated from the main detector. A second-quadrant-detector of reduced sensitivity guides the missile along the disturbing laser beam. Another embodiment uses attenuating optical elements in front of the main detector under the control of one or more second detectors.
Owner:BODENSEEWERK GERATETECHNIK GMBH
Treatment method against side-effects of chemotherapy
InactiveUS6979688B2Preserving anti-cancer systemic efficacyAdverse side effectBiocideKetone active ingredientsSide effectWhole body
A method and composition is provided for organ rescue wherein a specific counter-measure is applied locally to a tissue at risk for or exhibiting an adverse side effect of a cancer treatment. More particularly, the method and composition is directed at controlling Hand-Foot Syndrome, a painful redness and cracking of the skin of the hands and feet which can occur with systemic treatment with 5-fluorouracil or a precursor thereof. Uracil ointment is applied to the skin of the hands and feet to prevent Hand-Foot Syndrome which can occur from systemic administration of 5-fluorouracil (or precursor thereof) as cancer treatment.
Owner:ASYMMETRIC THERAPEUTICS
ECM techniques to counter pulse compression radar
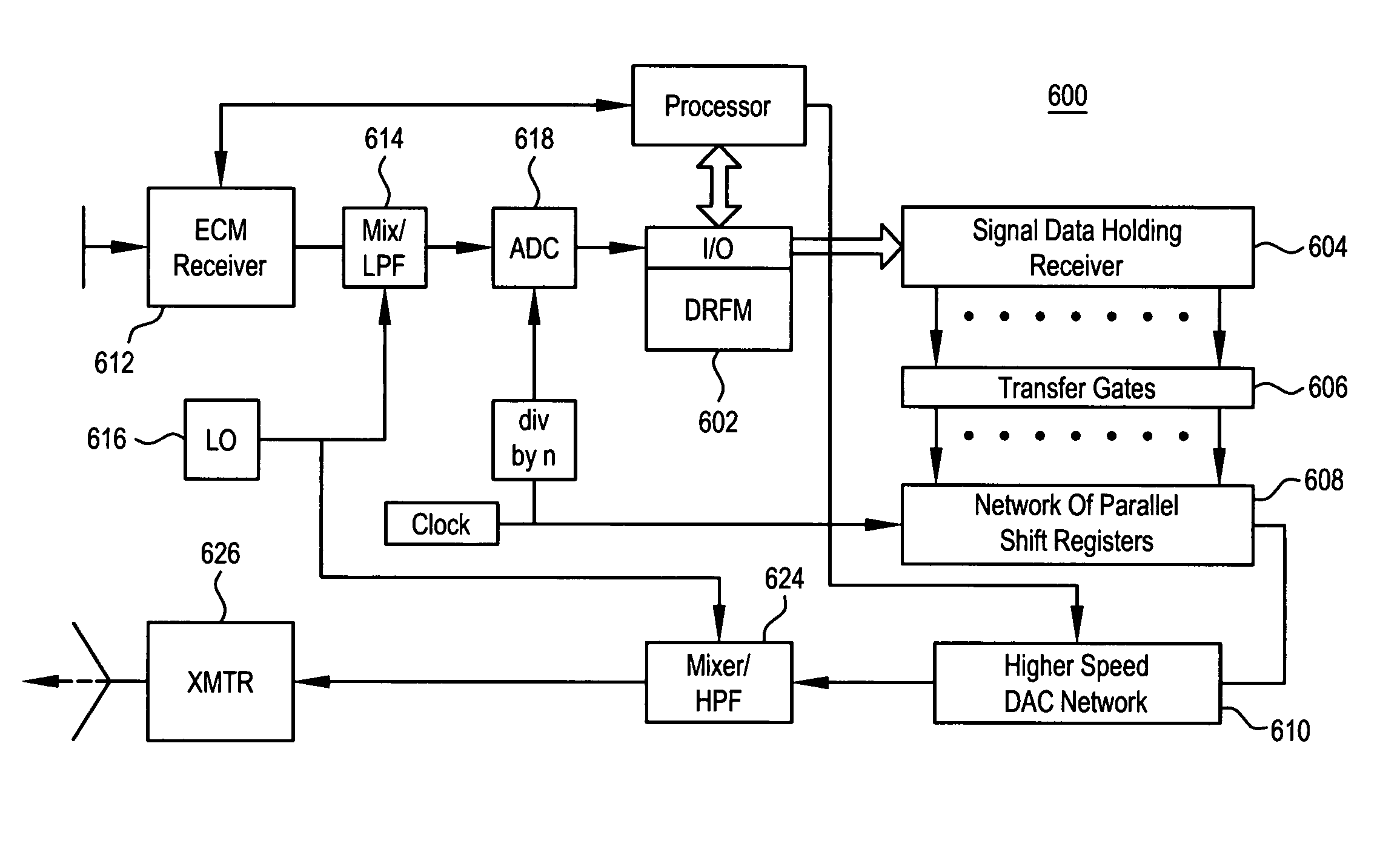
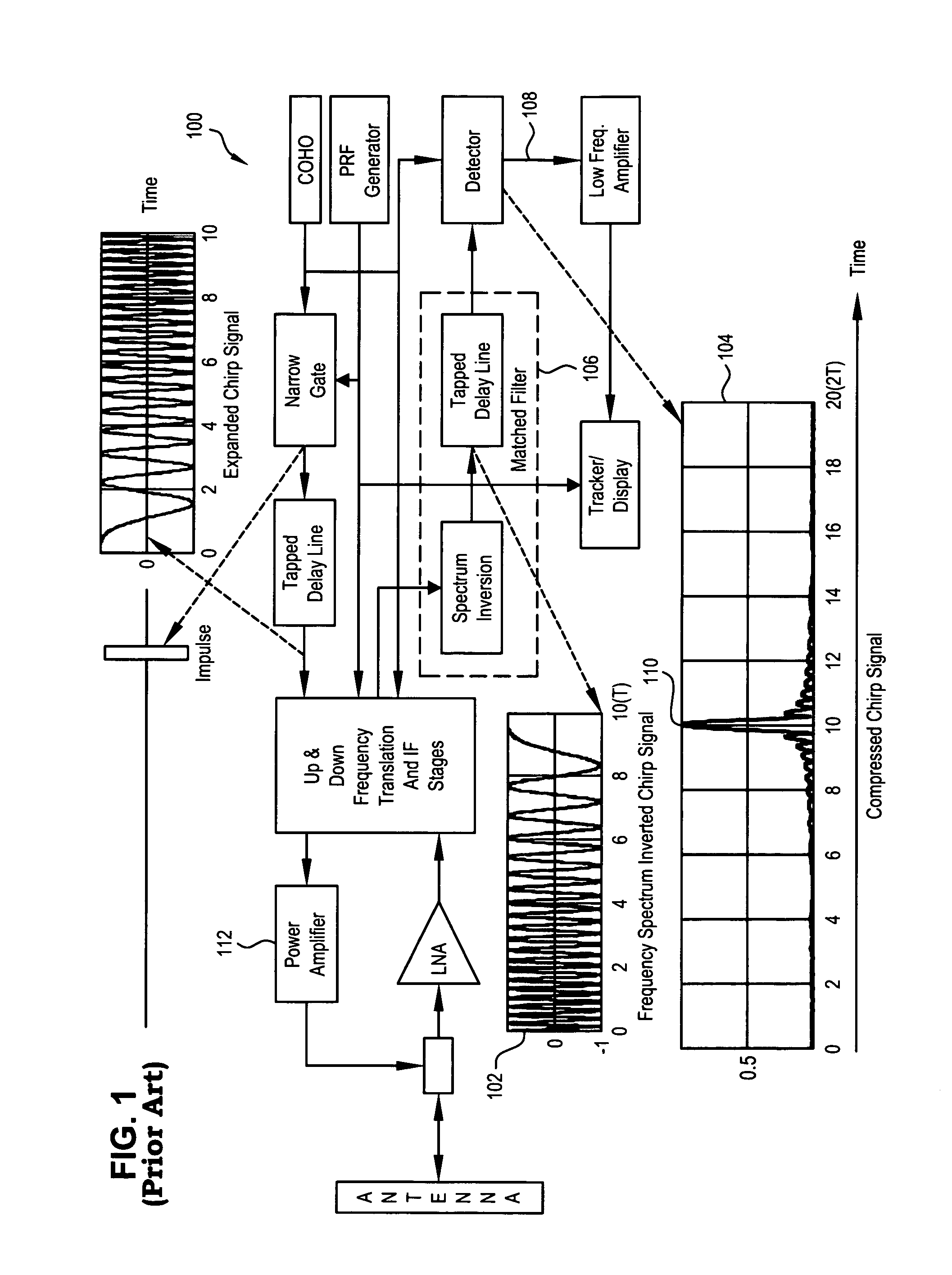
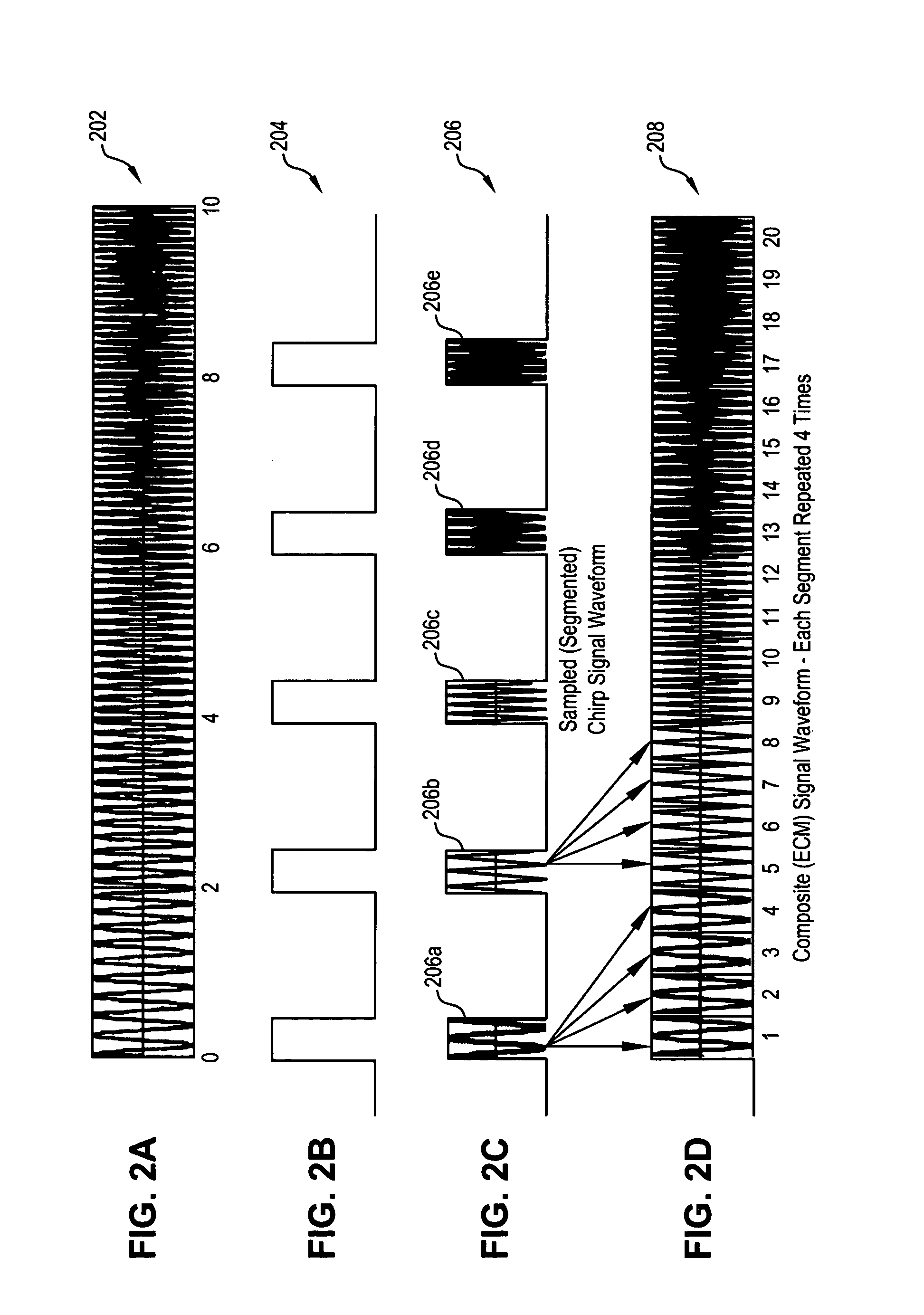
ActiveUS7081846B1Increase Jamming to Signal (J/S) power ratioEnhanced signalWave based measurement systemsCommunication jammingRadar systemsRadar signals
A system and method for generating a counter-measure signal in response to an incoming radar signal from a remote linear frequency modulated (LFM) pulse compression radar system. One method comprises the steps of receiving an incoming radar signal having a time period T; storing at least a portion of the radar signal in a memory; extracting predetermined segments of the radar signal from the memory; replicating the predetermined segments to create a predetermined plurality of each of the predetermined segments; concatenating the plurality of predetermined segments into a further signal, like ones of the plurality of predetermined segments adjacent one another; and transmitting the further signal to the remote radar system.
Owner:HARRIS CORP
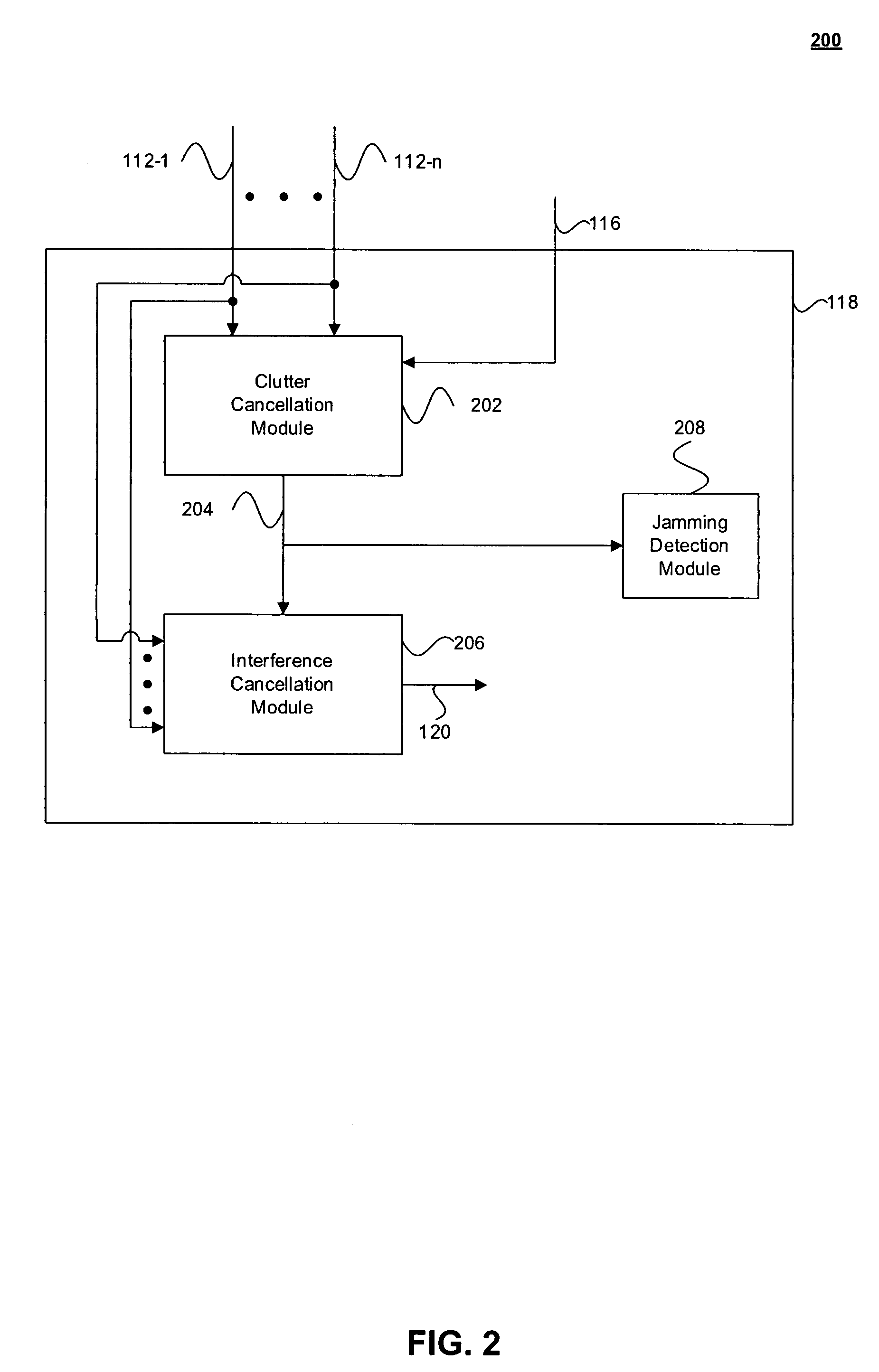
Detection and mitigation radio frequency memory (DRFM)-based interference in synthetic aperture radar (SAR) images
InactiveUS20090091492A1Reduced effectivenessRadio wave reradiation/reflectionPattern recognitionSynthetic aperture sonar
Methods and systems for detecting and mitigating DRFM-based interference in SAR images are provided. Embodiments include methods and systems for detecting and removing DRFM-based interference from SAR images by exploiting multi-channel SAR data. Embodiments provide an Electronic Counter Counter Measure (ECCM) technique that is effective against, among others, SAR DRFM-based repeater jamming, false target images, noise jamming, and vector multiplier jamming for false scene generation. When used, embodiments of the present invention reduce jammer effectiveness to a small range strip (a strip parallel to the range dimension) in the direction of the jammer. In addition, jammer mitigation is performed without losing SAR image data at the affected SAR pixels. Furthermore, embodiments of are compatible with time variable ECCM techniques, including orthogonal waveforms or pulse jitter techniques, for example.
Owner:MITRE SPORTS INT LTD
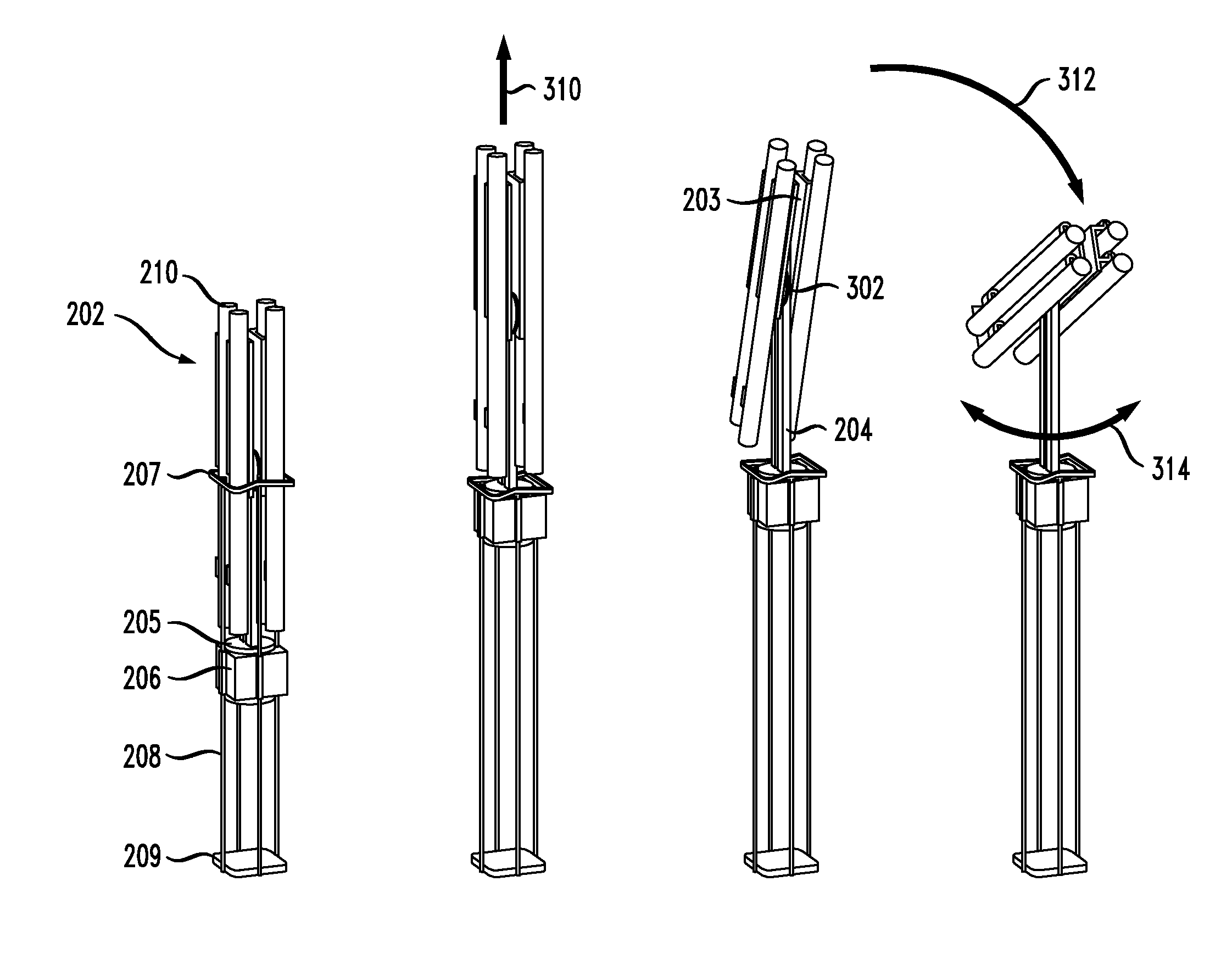
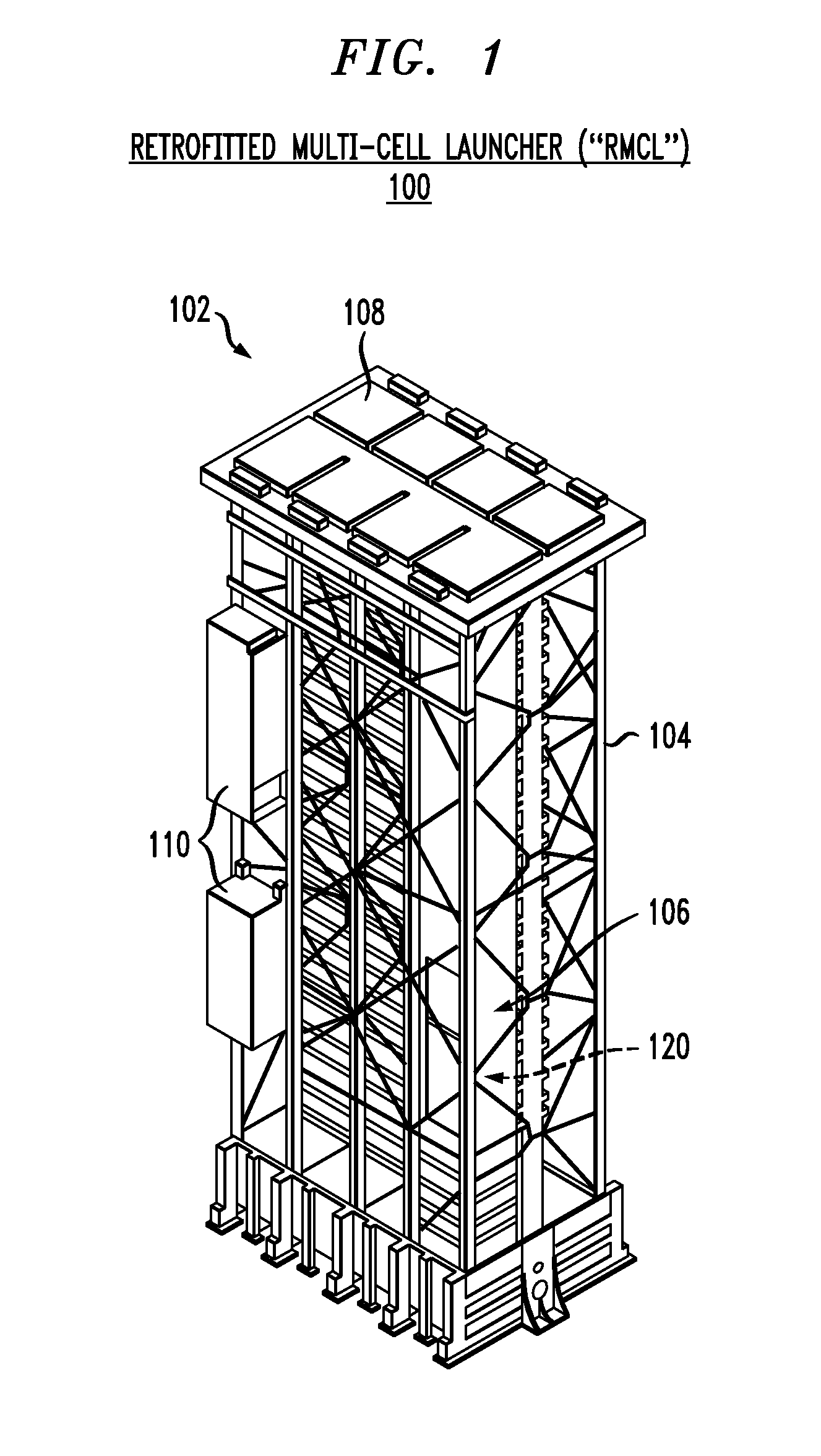
Stowable Elevating Trainable Launcher (SETL)
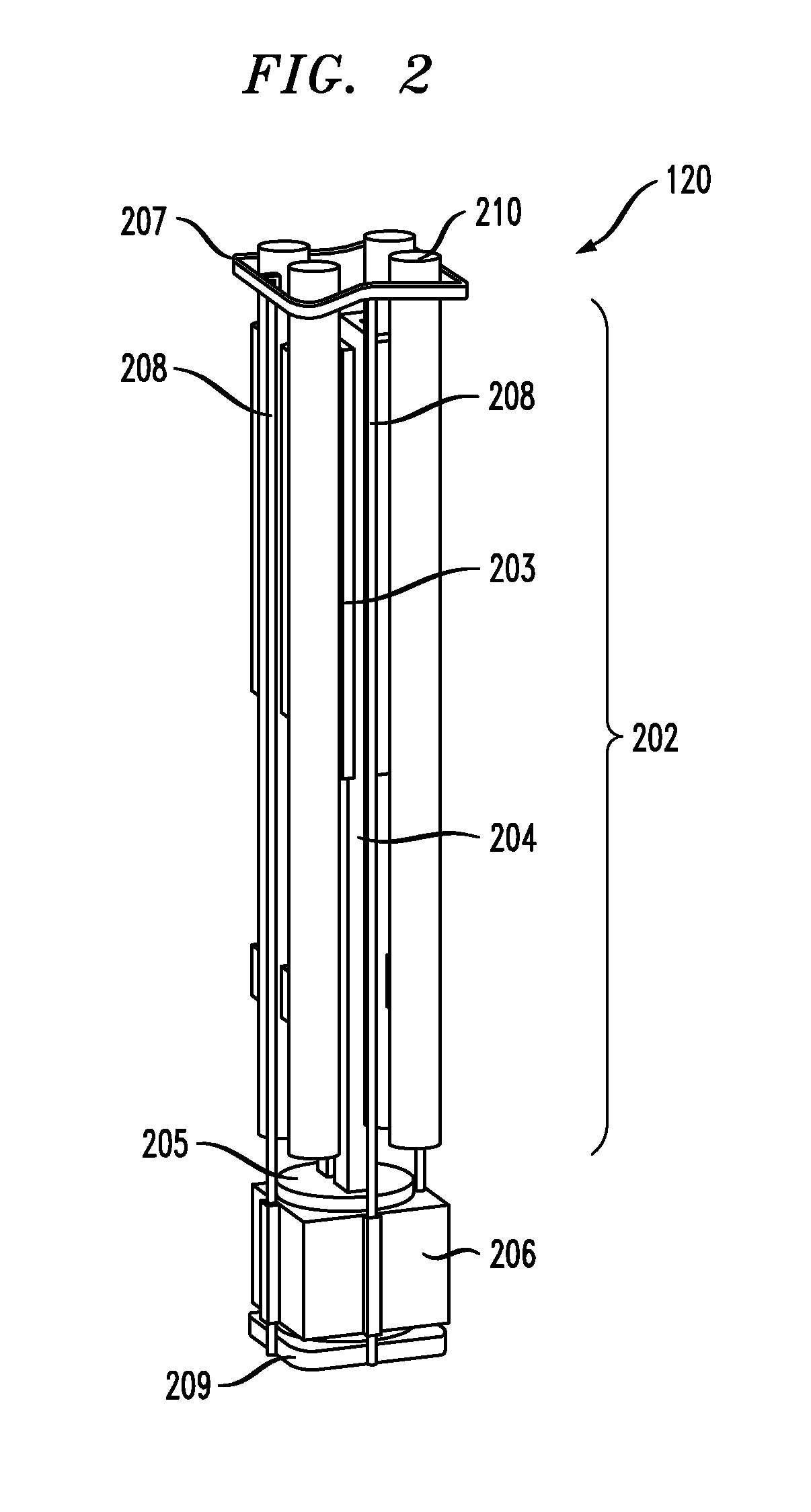
A system and method for launching non-vertical launch munitions with a non-vertical launch trajectory from a launcher that is operationally coupled to a vertical launching system (VLS). The inventors of the present invention recognized that munitions that are unsuitable for vertical launches were unavailable for use with vertical launching systems, thus foreclosing important defense, attack, and cost-savings opportunities for VLS-equipped platforms. A VLS could be substantially more versatile if it accommodated munitions such as torpedoes, counter-measures, direct-fire munitions, point-and-shoot munitions, and a variety of other missiles and equipment. The launcher according to the present invention is also stowable in an upward orientation within a cell of the host vertical launching system.
Owner:LOCKHEED MARTIN CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com