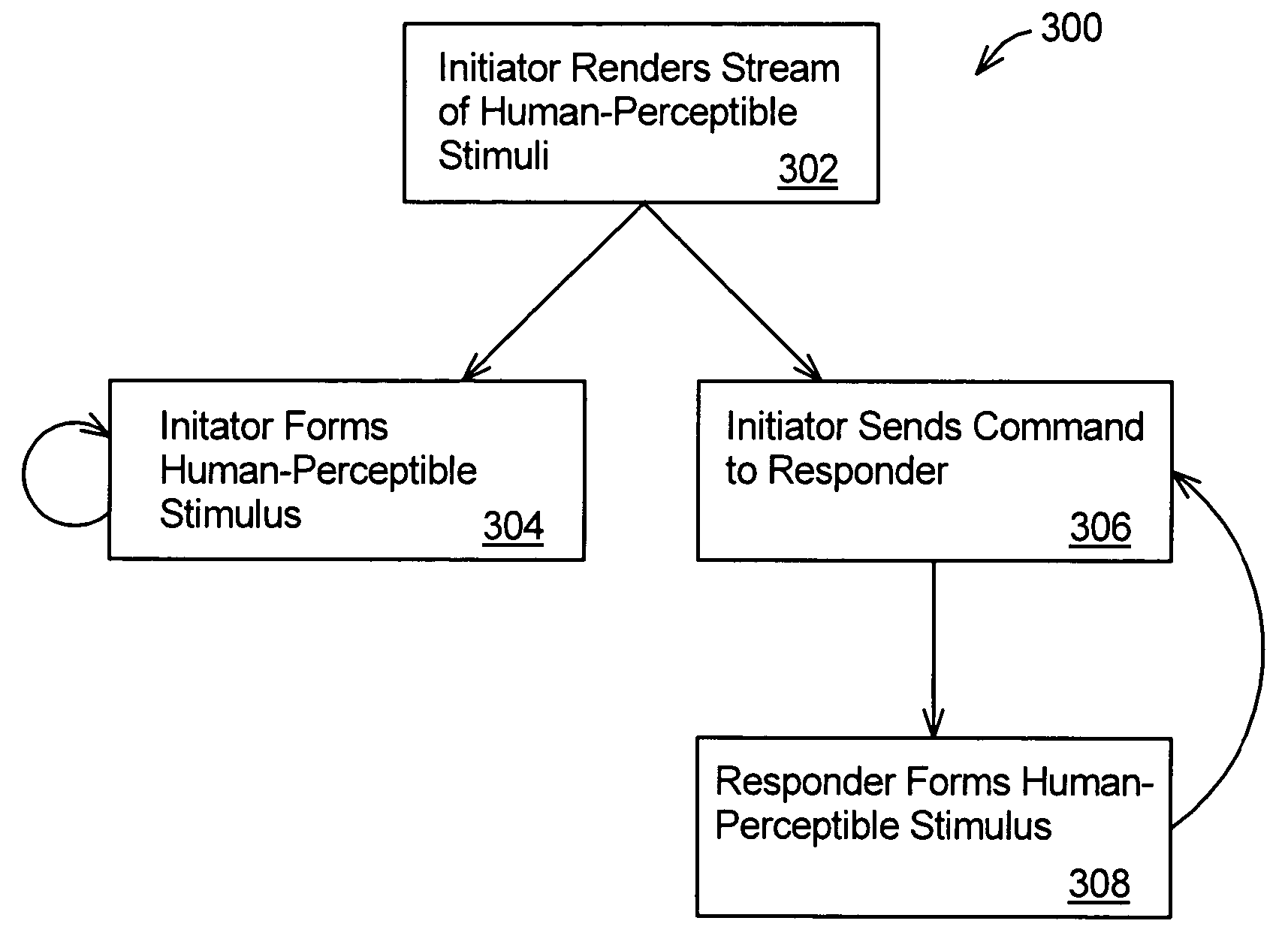
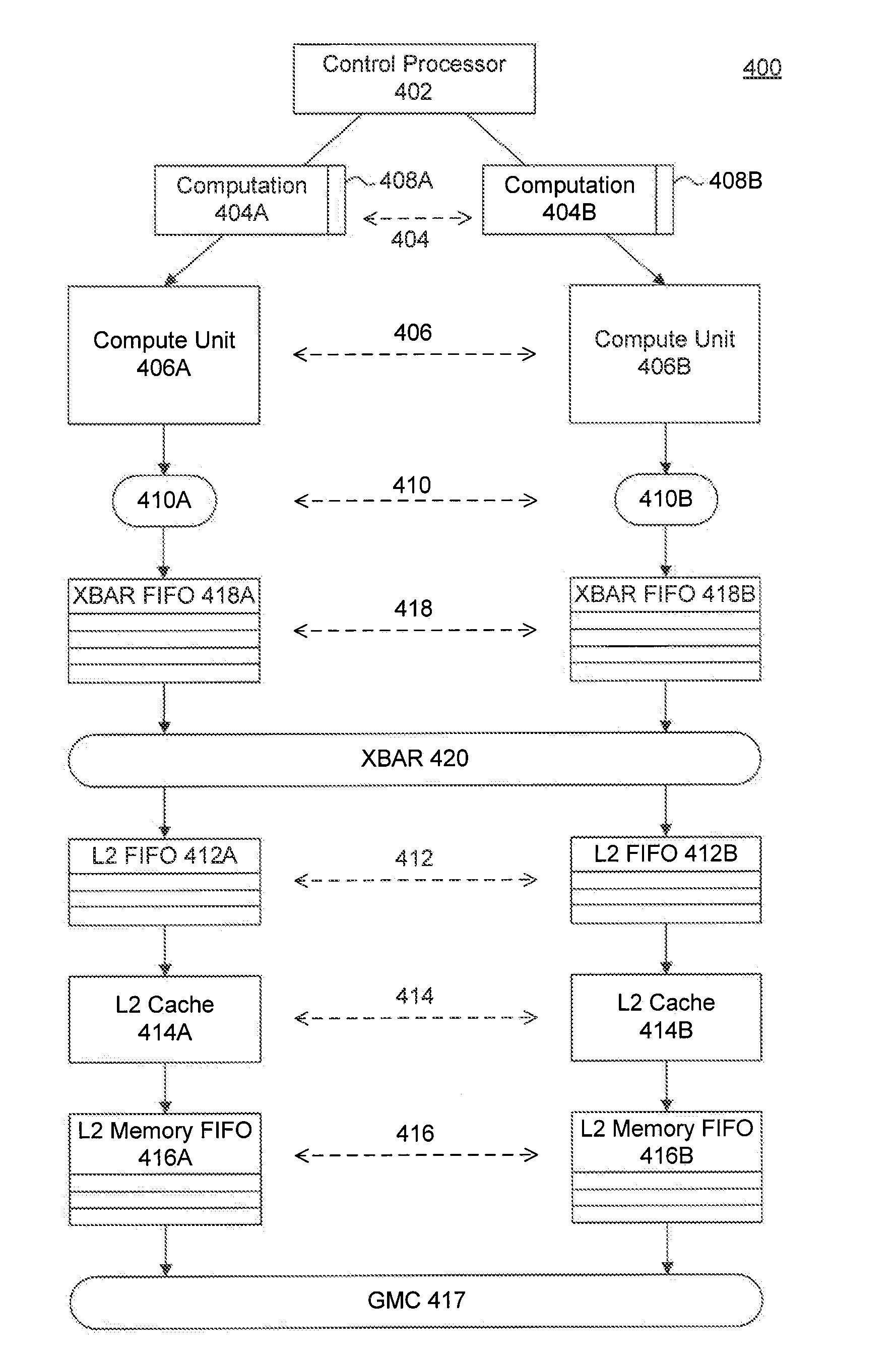
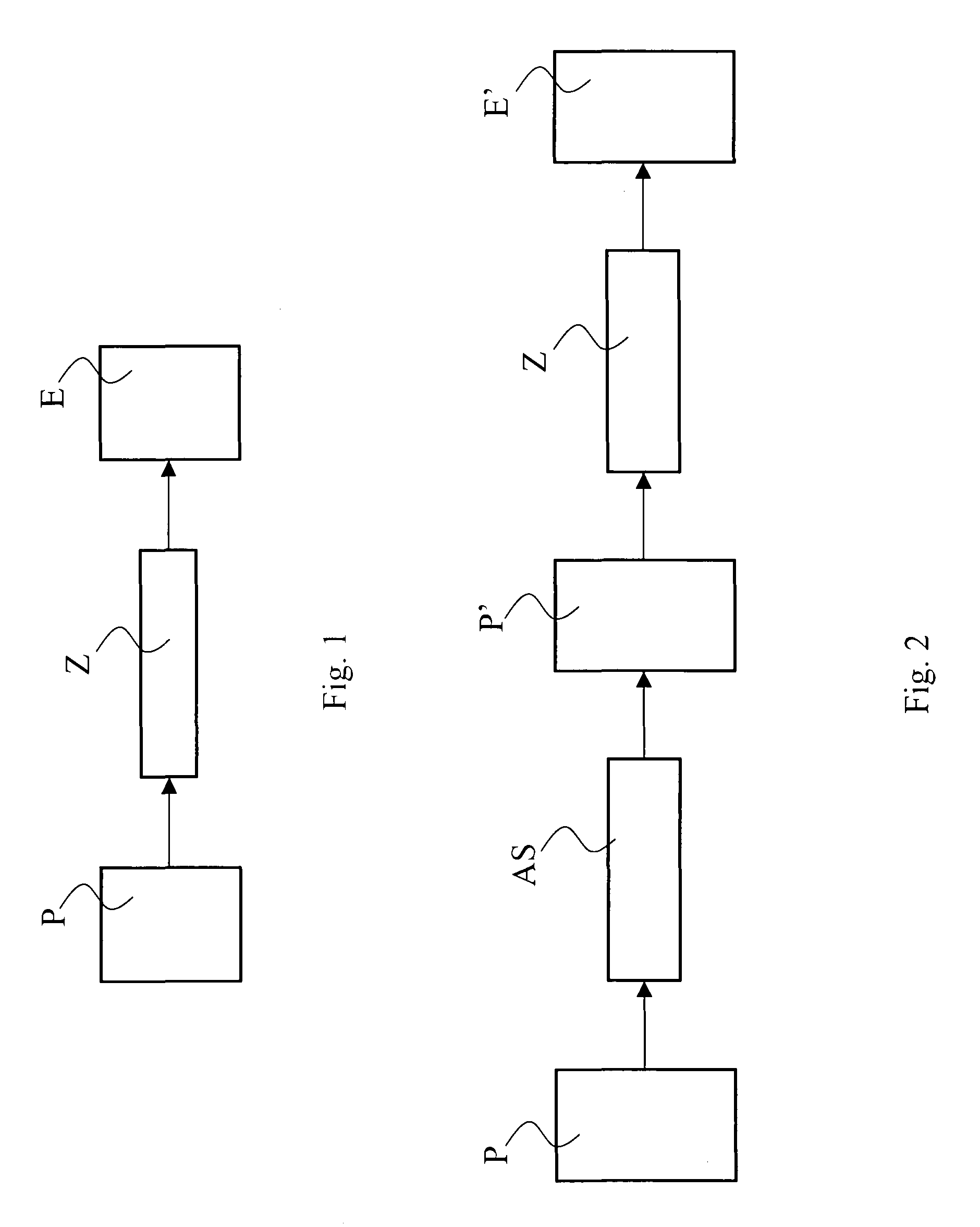Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
74 results about "Verified computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
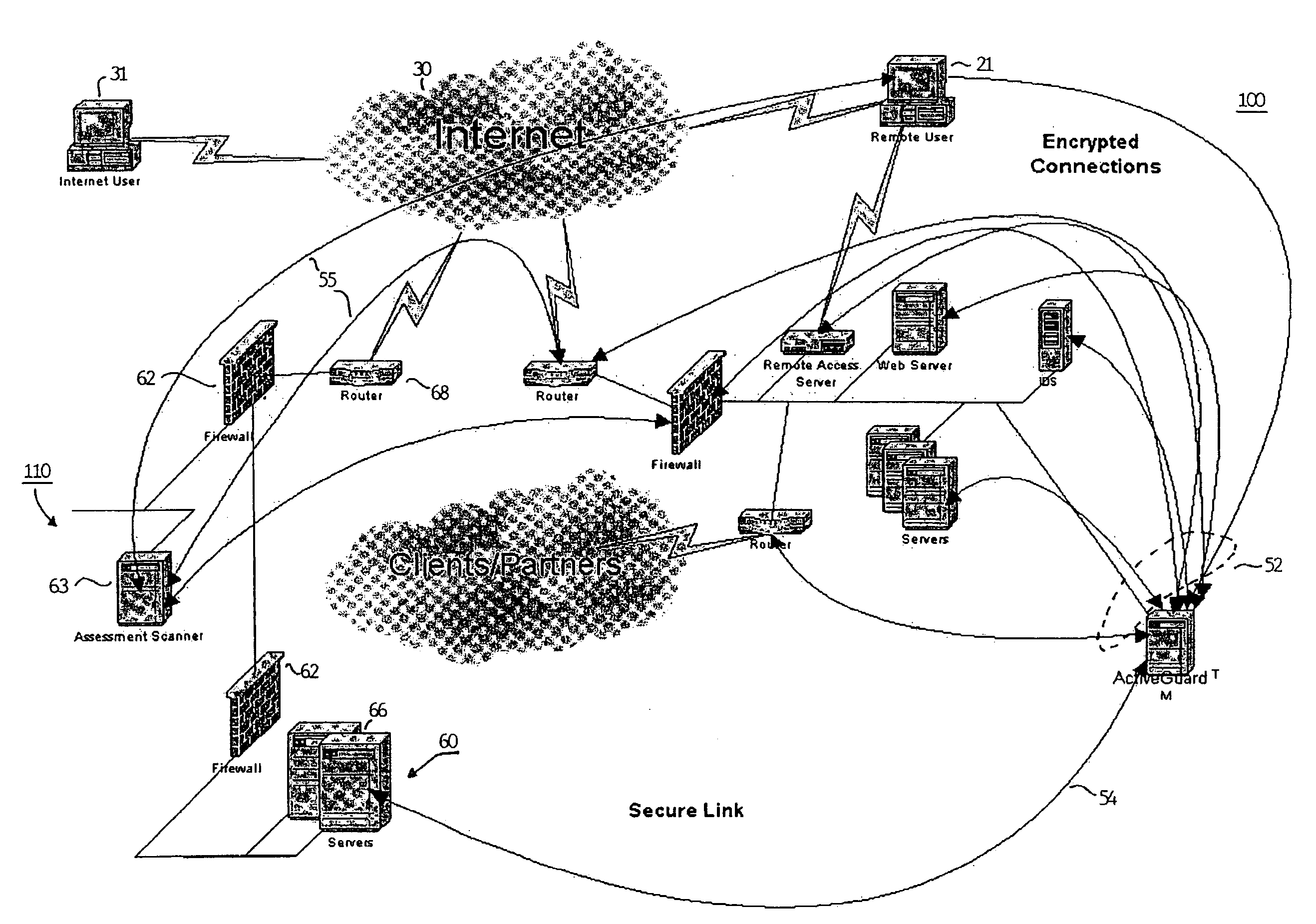
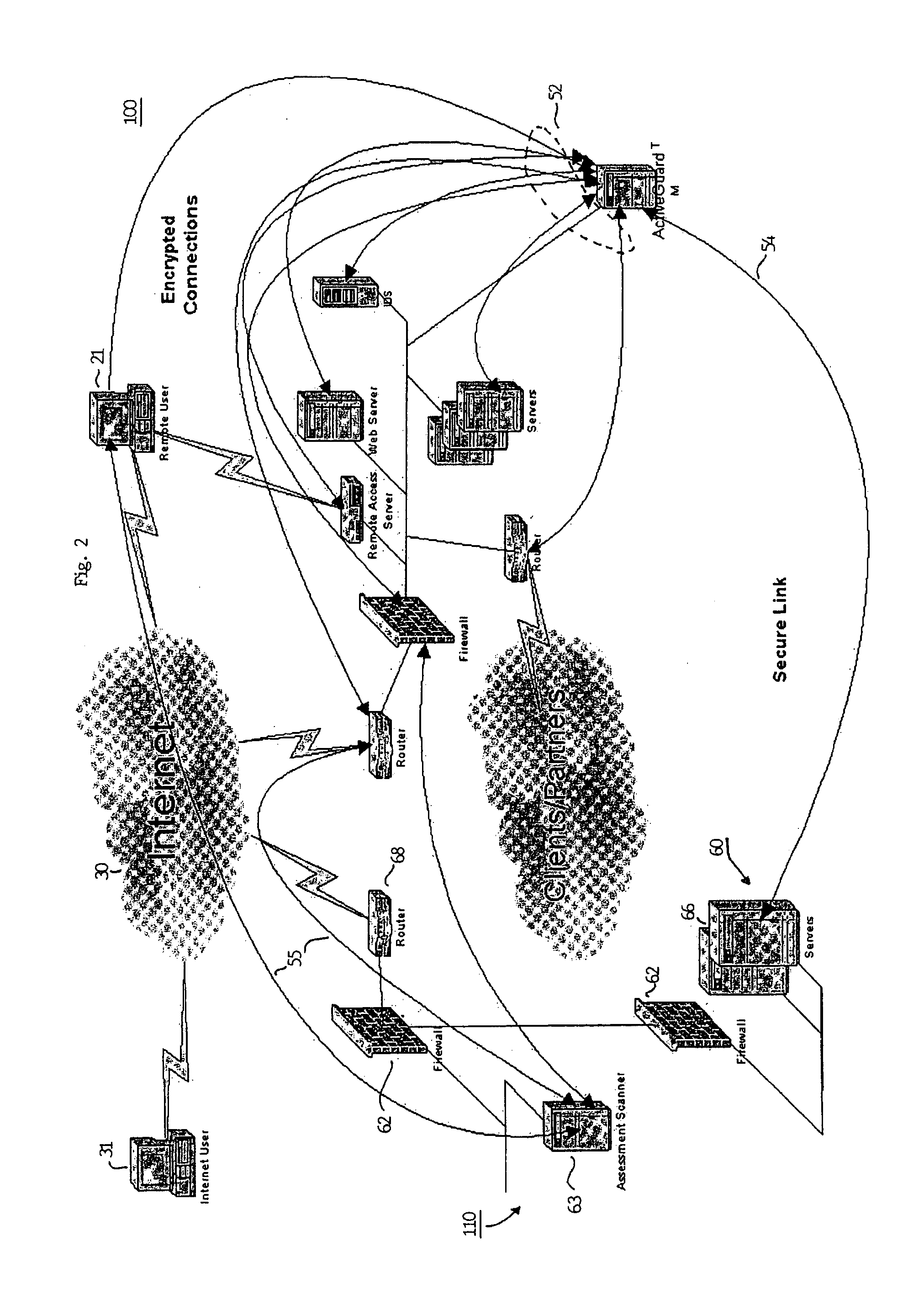
Method and apparatus for verifying the integrity and security of computer networks and implementing counter measures
InactiveUS6988208B2Mitigate or thwart suspected intruder attacks on the target networkMemory loss protectionDigital data processing detailsCountermeasureSecurity system
A method and apparatus for verifying the integrity of devices on a target network. The apparatus has security subsystems and a master security system hierarchically connected to the security subsystems via a secure link. The target network includes various intrusion detection devices, which may be part of the security subsystem. Each intrusion detection device generates a plurality of event messages when an attack on the network is detected. The security subsystem collects these event messages, correlates, and analyzes them, and performs network scanning processes. If certain events warrant additional scrutiny, they are uploaded to the master security system for review.
Owner:SICORTEX
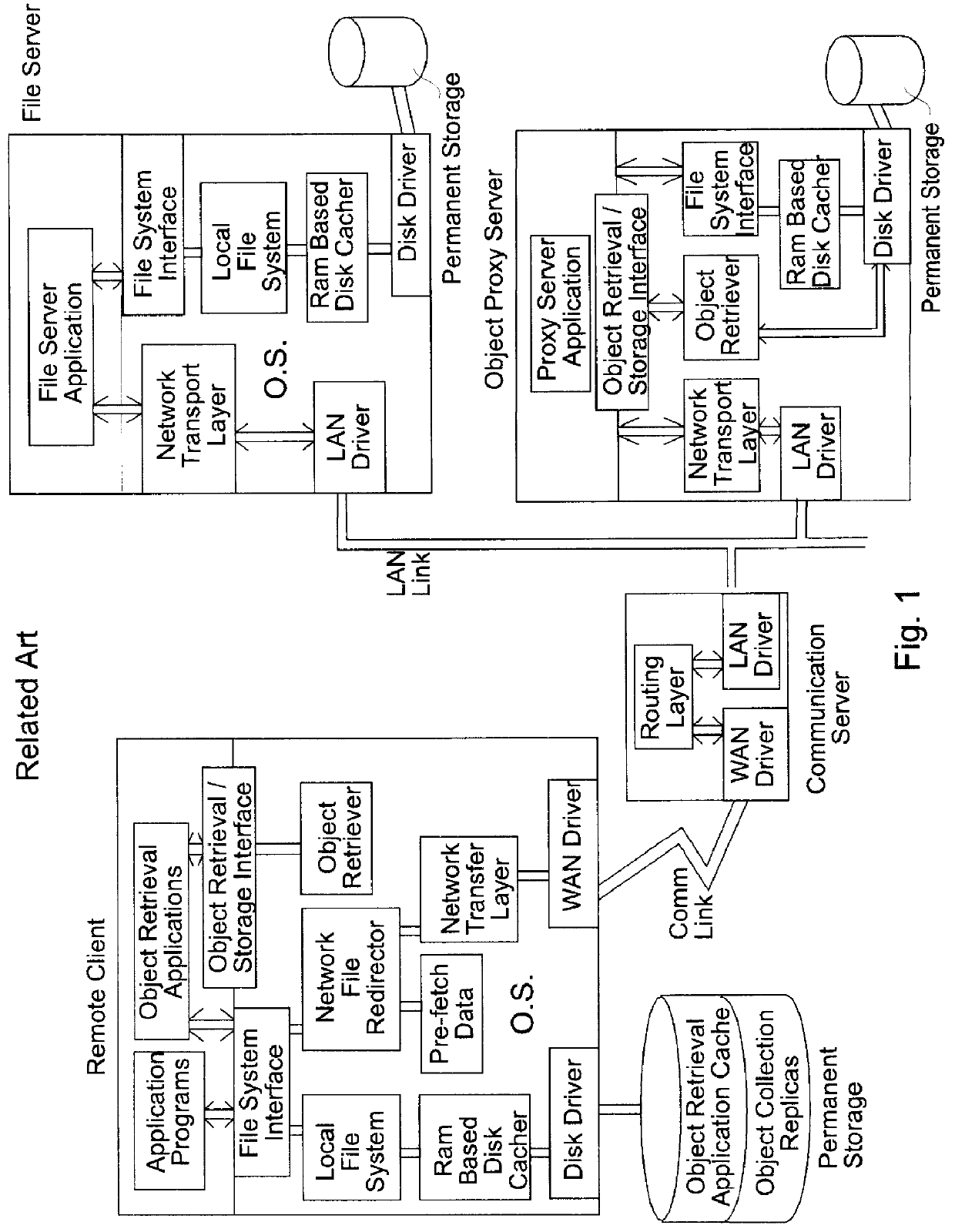
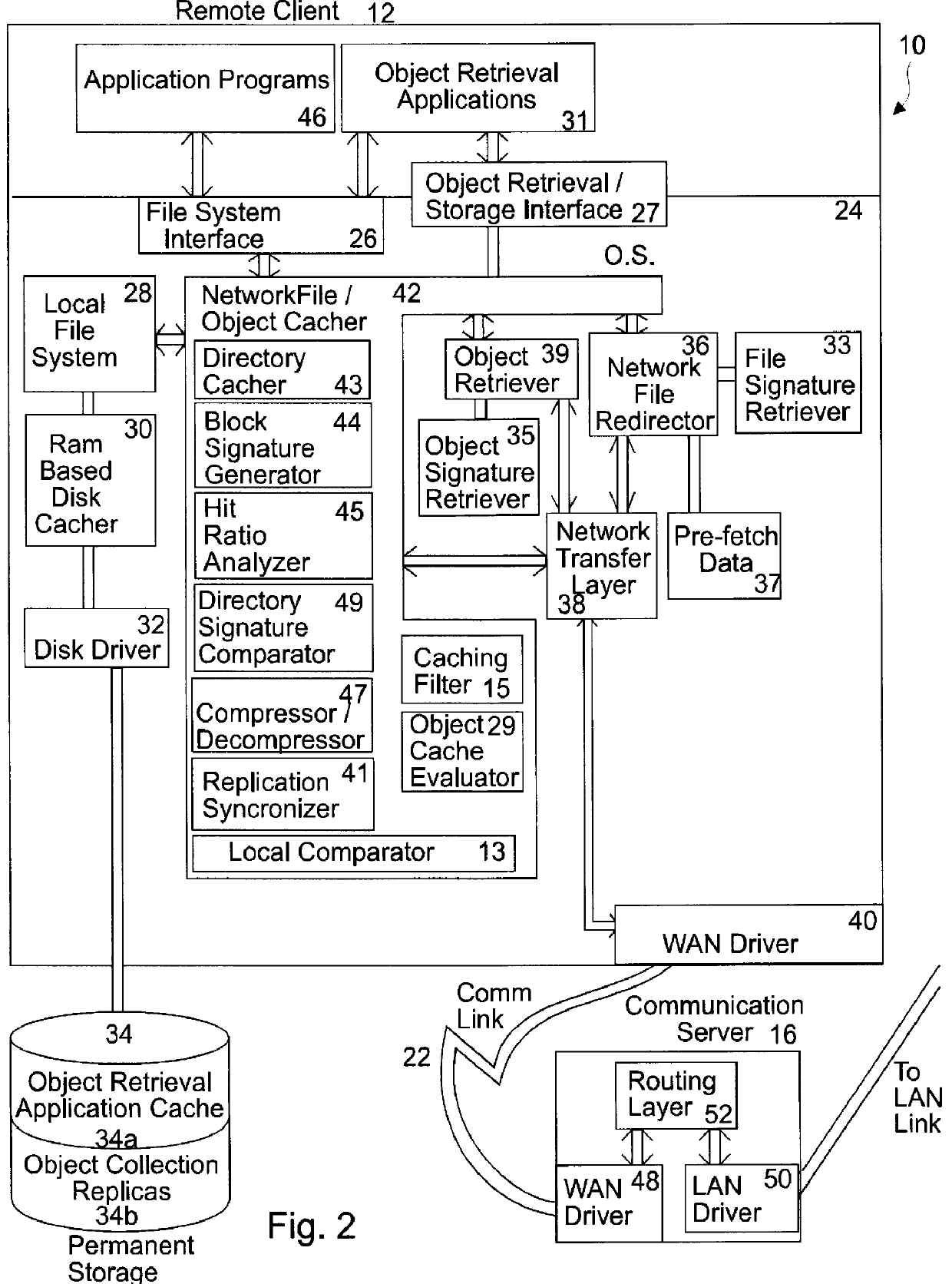
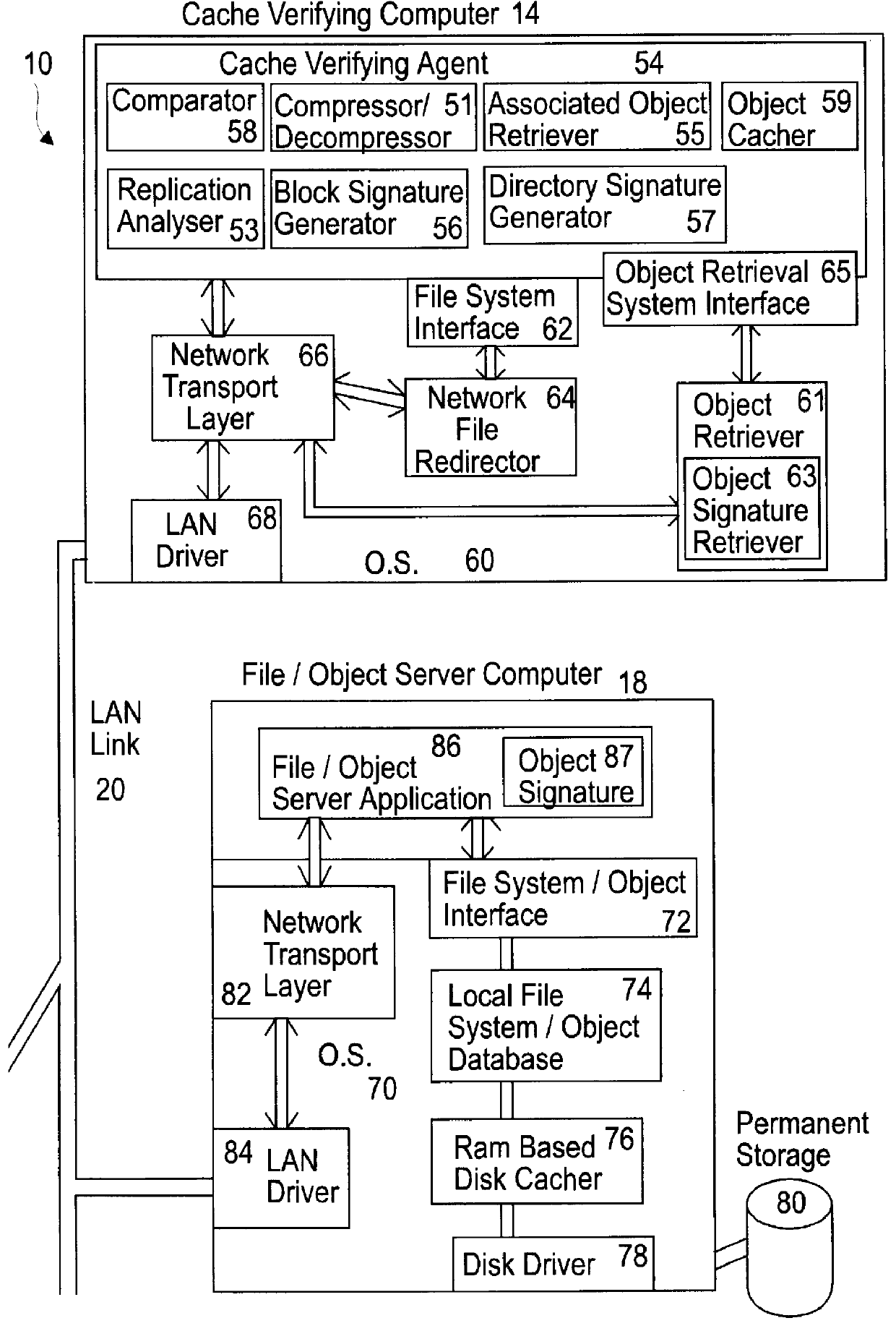
Apparatus and method for increased data access in a network file object oriented caching system
An apparatus for increased data access in a network includes a file / object server computer having a permanent storage memory, a cache verifying computer operably connected to the file / object server computer in a manner to form a network for rapidly transferring data, the cache verifying computer having an operating system, a first memory and a processor capable of performing an operation on data stored in the permanent storage memory of the file / object server computer to produce a signature of the data characteristic of one of a file, an object and a directory, a remote client computer having an operating system, a first memory, a cache memory and a processor capable of performing an operation on data stored in the cache memory to produce a signature of the data, a communication server operably connected to the remote client computer to the cache verifying computer and the file / object server computer and comparators operably associated with the cache verifying computer and remote client computer for comparing the signatures of data with one another to determine whether the signature of data of the remote client is valid.
Owner:COMTECH EF DATA
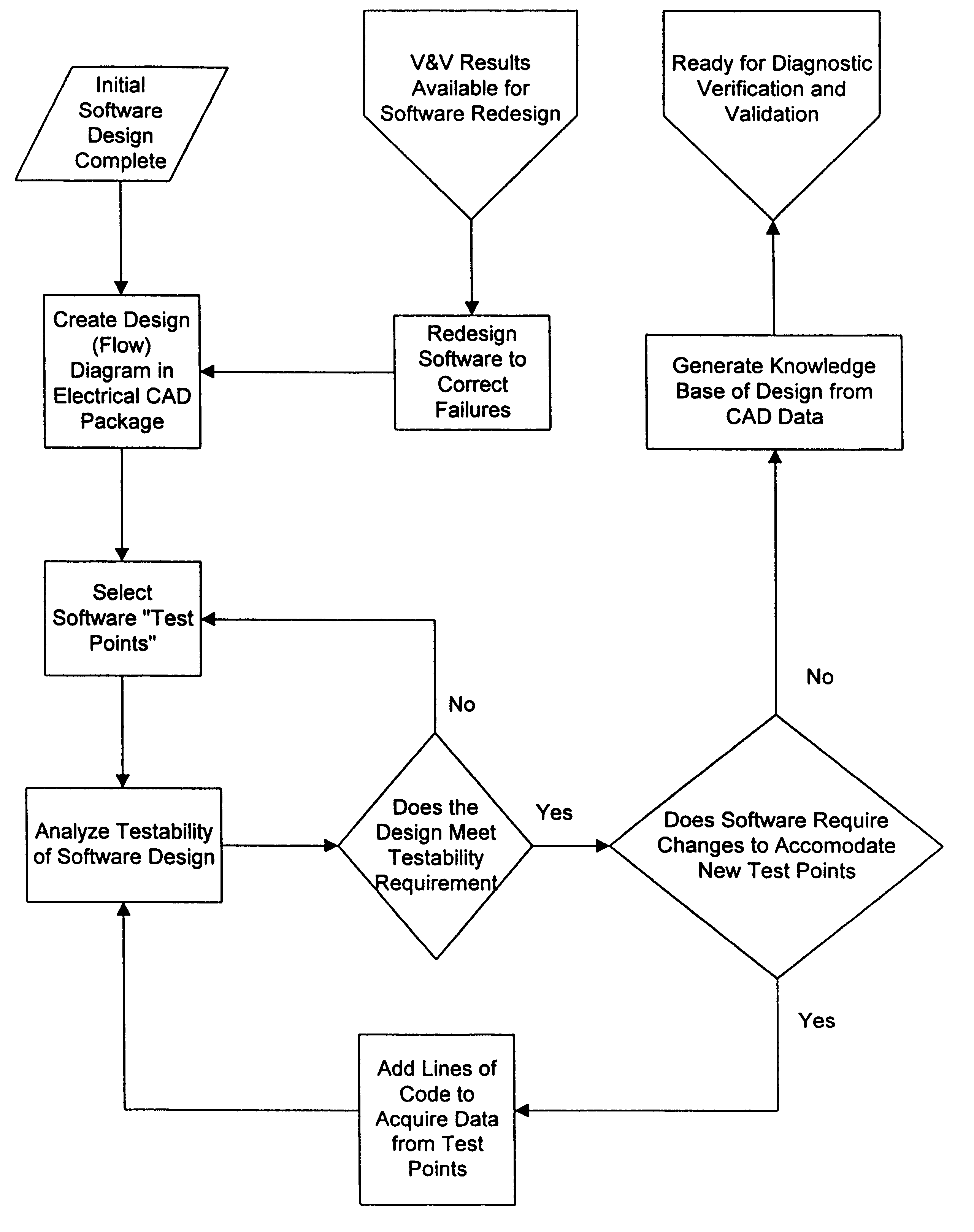
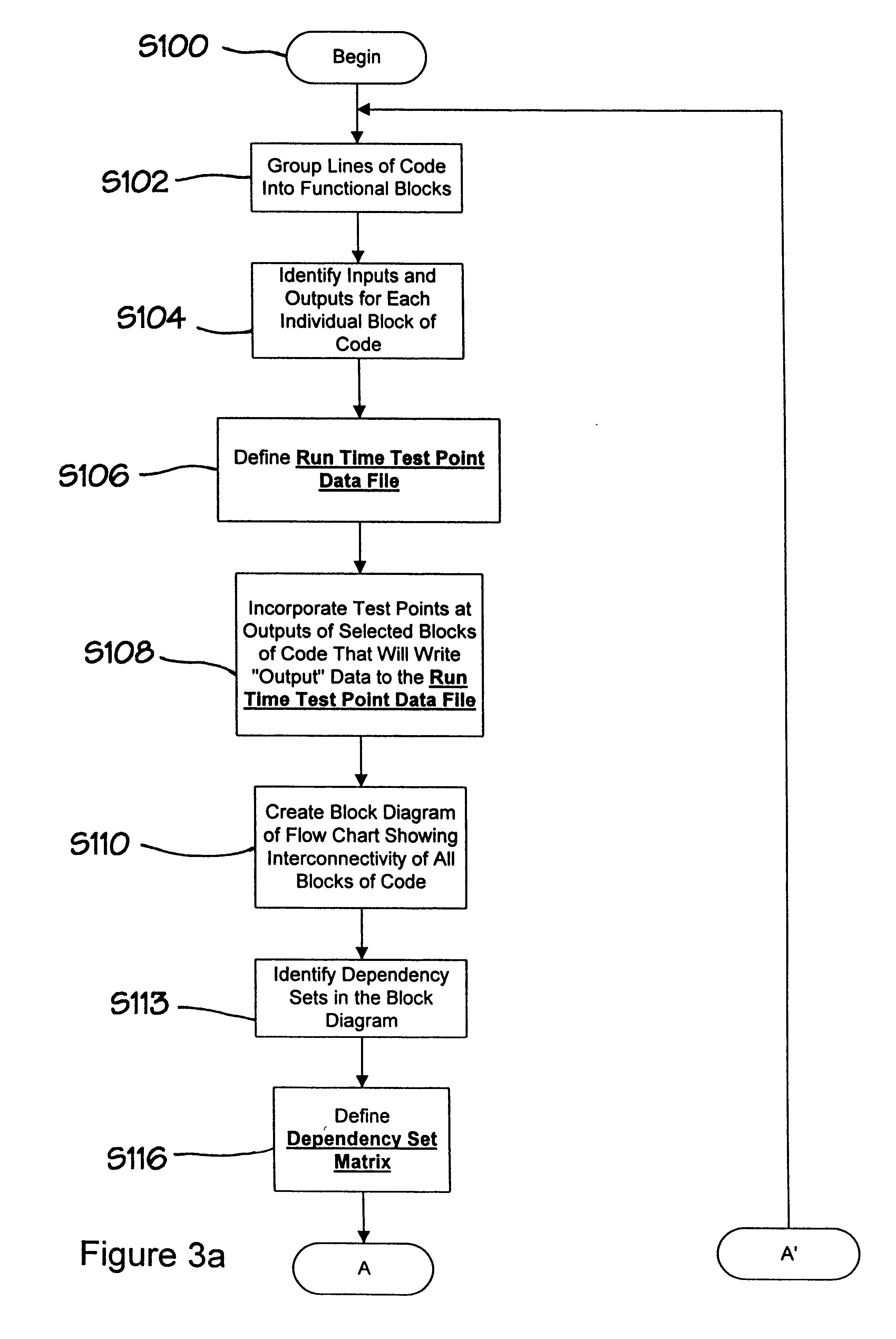
Method and apparatus for debugging, verifying and validating computer software
InactiveUS6173440B1Software testing/debuggingProgram loading/initiatingSoftware designVerification procedure
A new approach for software debugging, verification and validation is disclosed. The present invention utilizes a knowledge-based reasoning approach to build a functional model of the software code for identifying and isolating failures in the software code. The knowledge-based reasoning approach of the present invention uses the software design, which is preferably based upon a flow chart or block diagram representation of the software functionality, to build the functional model. The software block diagram contributes to the functional model by defining the inputs and outputs of the various blocks of code, as well as defining data interconnections between the various blocks of code. In accordance with a method of the present invention, test points are strategically inserted throughout the code, and each test point is associated with a corresponding block of code. Expected values of the test points for an expected proper-operation execution of the computer program are generated. The computer program is then executed on a computer, and the actual values of the test points from the program execution are compared with the expected values of the test points. Failed test points which do not agree with corresponding expected values are determined. The functional model, which includes information functionally relating the various test points to one another, is then used to isolate the failed test points to one or more sources of failure in the code.
Owner:MCDONNELL DOUGLAS
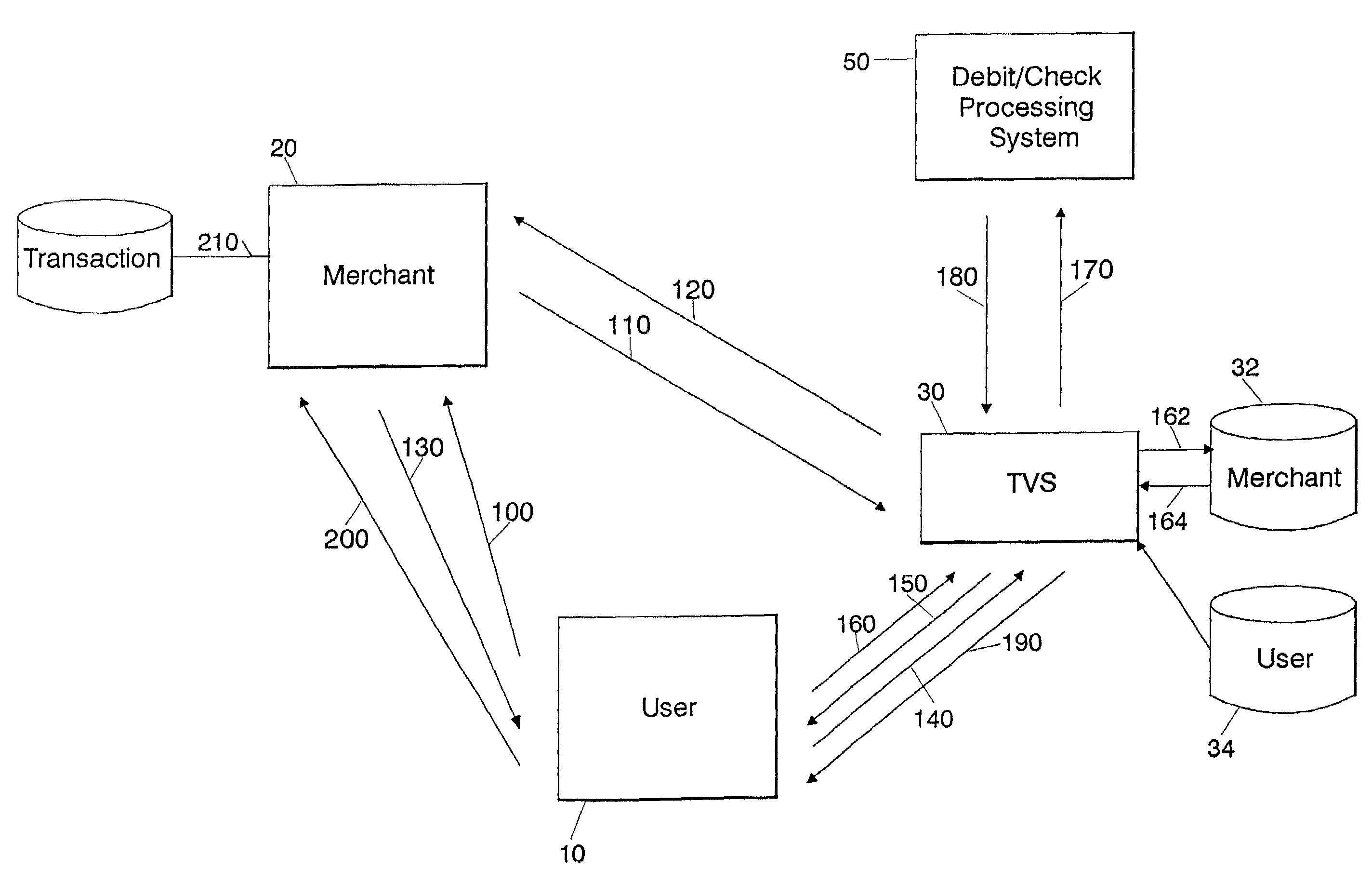
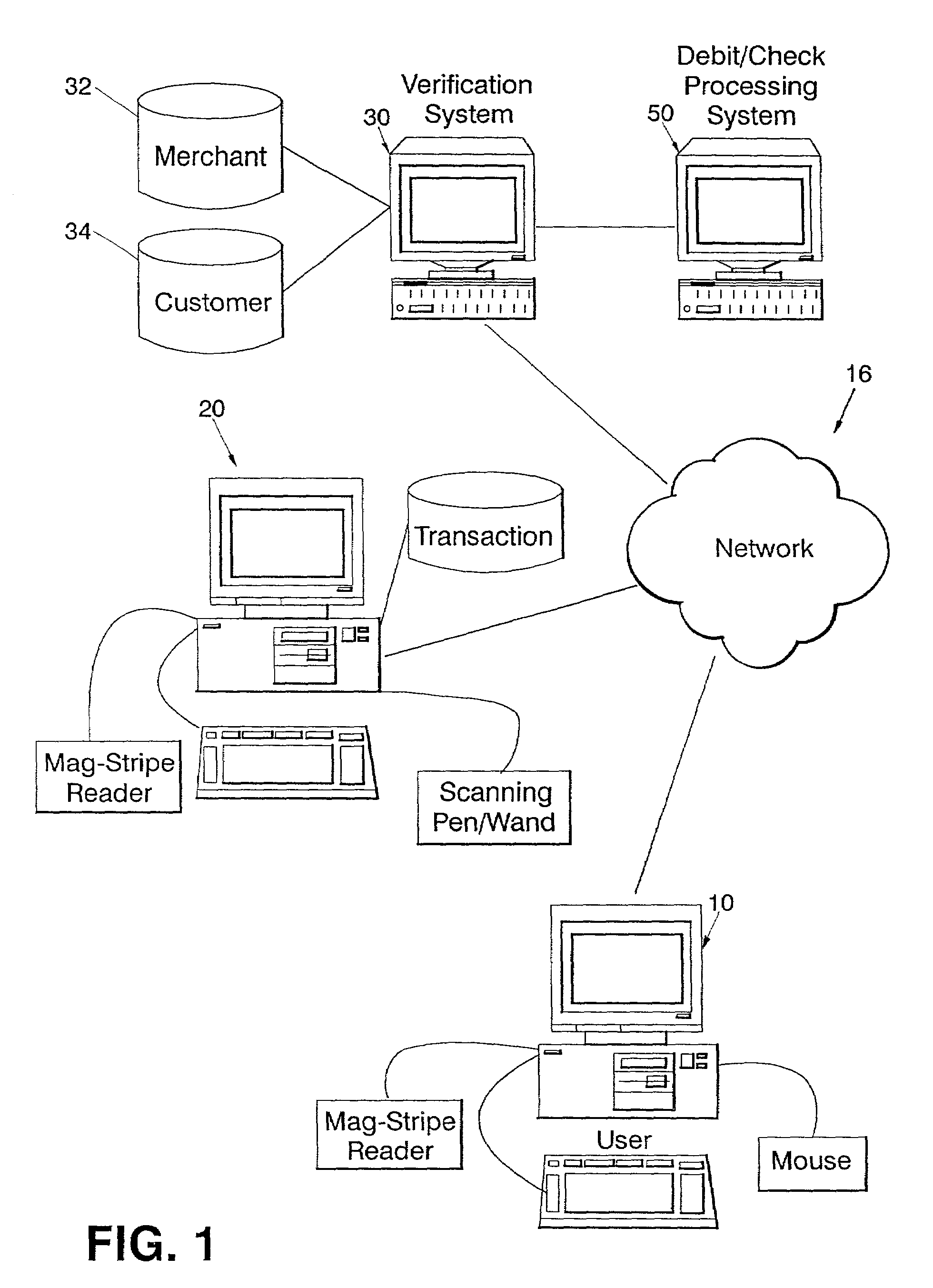
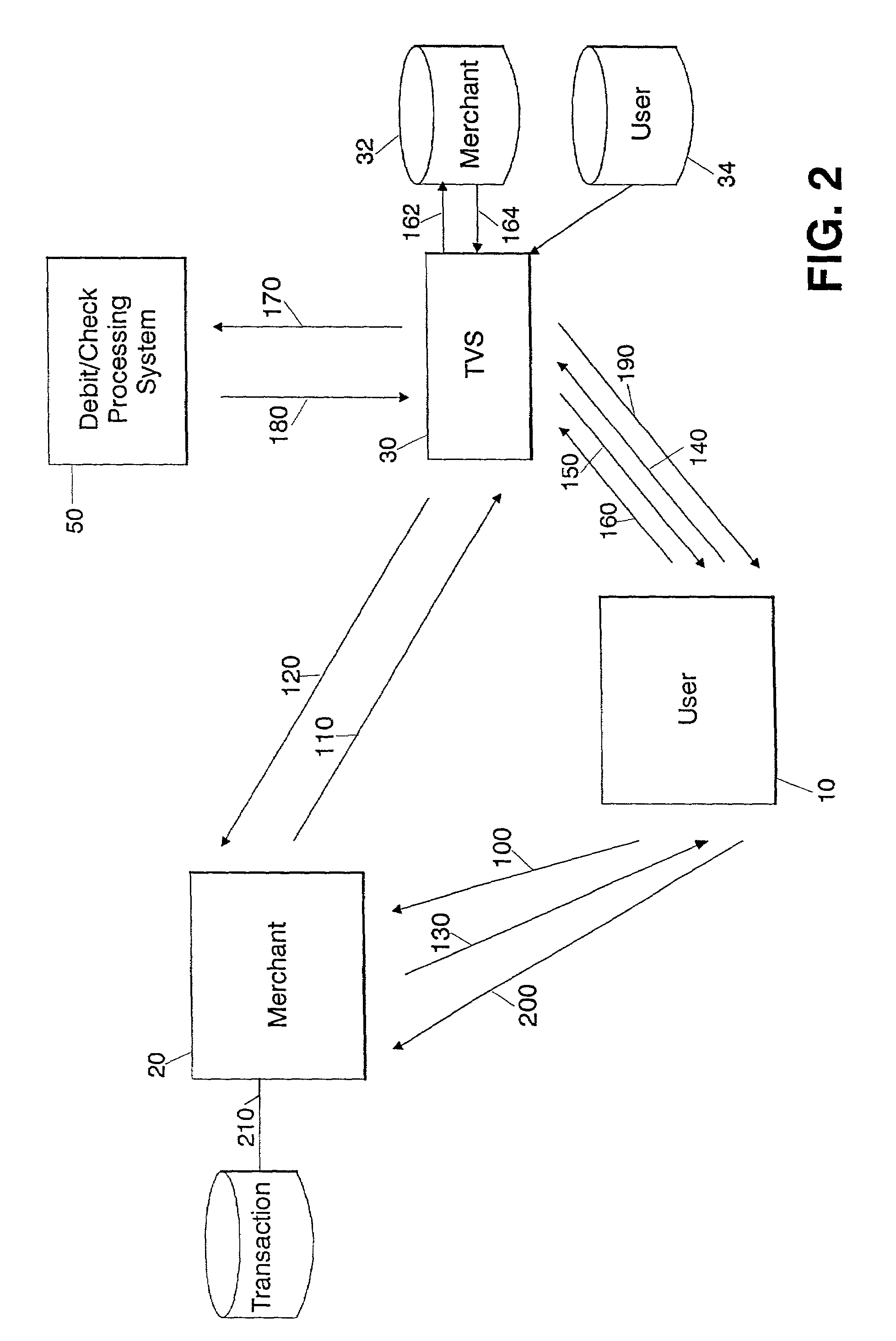
Secure networked transaction system
A method and system for approval by a verification computer of an online transaction between a user computer and a merchant computer over the Internet. The user computer transmits a transaction request to the merchant computer, which may include a product to be purchased and the payment amount. The merchant computer transmits to the verification computer a verification request including a first data string associated with the payment card (such as a debit card account number or a portion thereof) and the payment amount. The verification request is stored at the verification computer with a transaction identifier and a verification data string, which are also transmitted to the merchant computer. The merchant computer stores the verification data string as an expected verification data string and the transaction identifier, transmits the transaction identifier to the user computer, and the user computer transmits the transaction identifier to the verification computer. This may be accomplished by the merchant computer redirecting the web browser of the user computer to the verification computer. The user computer also transmits a second data string associated with the payment card (such as the PIN for the debit card) after being requested by the verification computer. The verification computer uses the transaction identifier received via the user computer to retrieve the verification request previously stored with that received transaction identifier, and then it performs a verification step by using the first data string associated with the payment card retrieved from storage and the second data string associated with the payment card received from the user computer to verify if the transaction should be approved, e.g. by determining if an account associated with the payment card is sufficient to cover the payment amount in the verification request. The verification computer will, upon successful verification that the transaction should be approved, transmit a verification approval message to the user computer, which includes the transaction identifier and the verification data string associated therewith as a confirmation verification data string, and the user computer transmits the verification approval message to the merchant computer. This may also be accomplished by the verification computer redirecting the web browser of the user computer to the merchant computer with the appropriate data. The merchant computer uses the transaction identifier in the verification approval message to retrieve an expected verification data string it had previously stored. The merchant computer then compares the expected verification data string with the confirmation verification data string from the verification approval message and indicates that the transaction has been approved if the comparison is positive.
Owner:KIOBA PROCESSING LLC
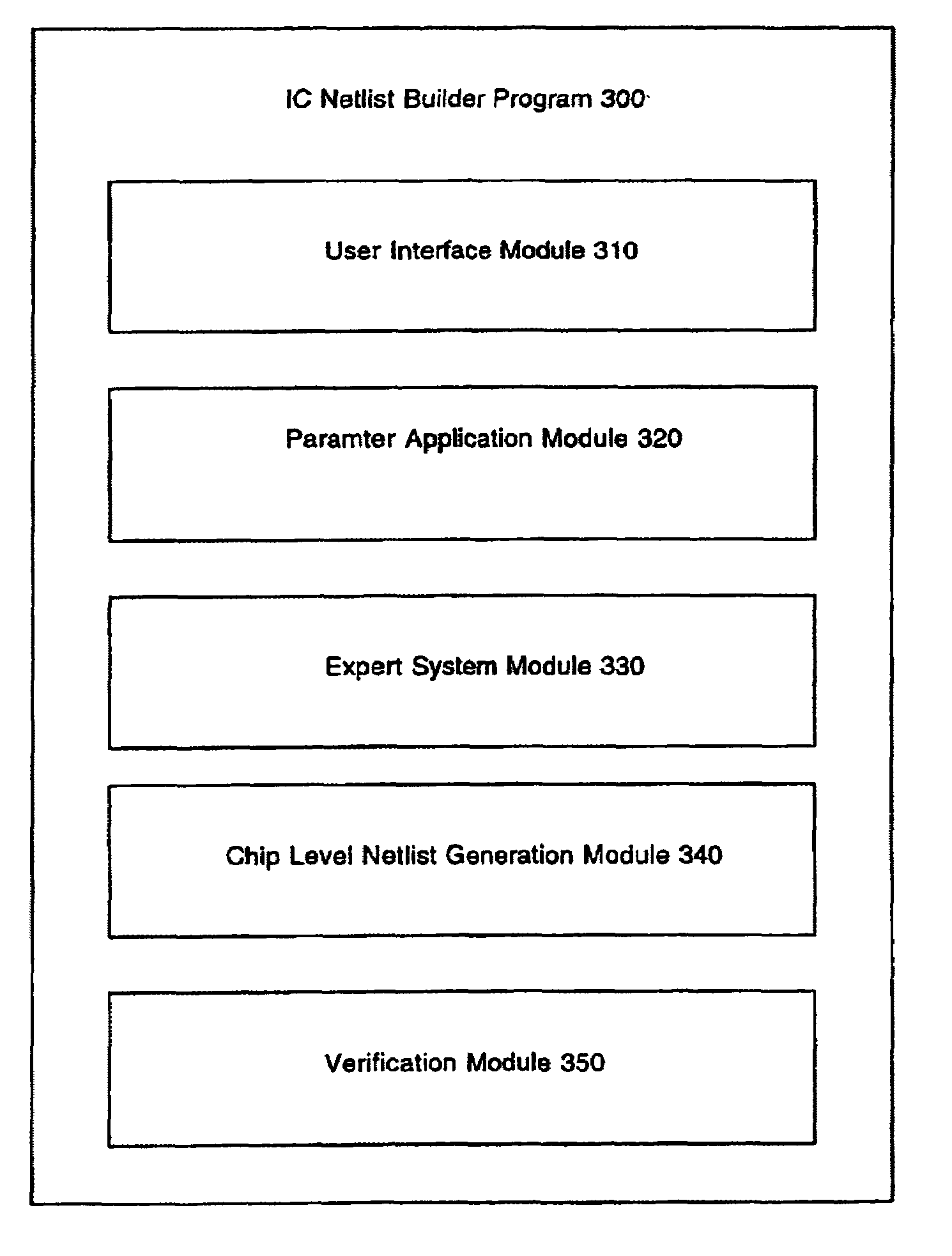
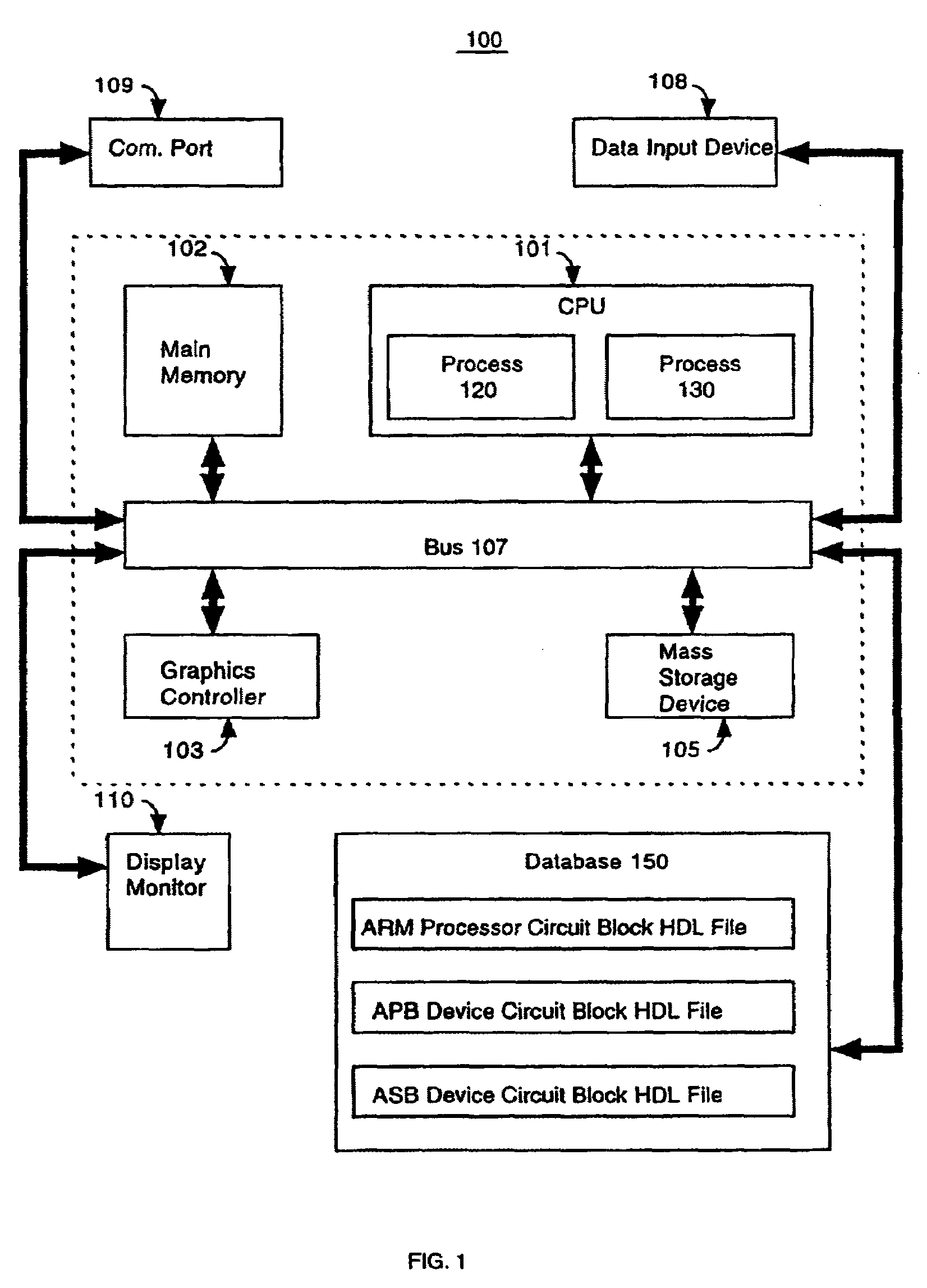
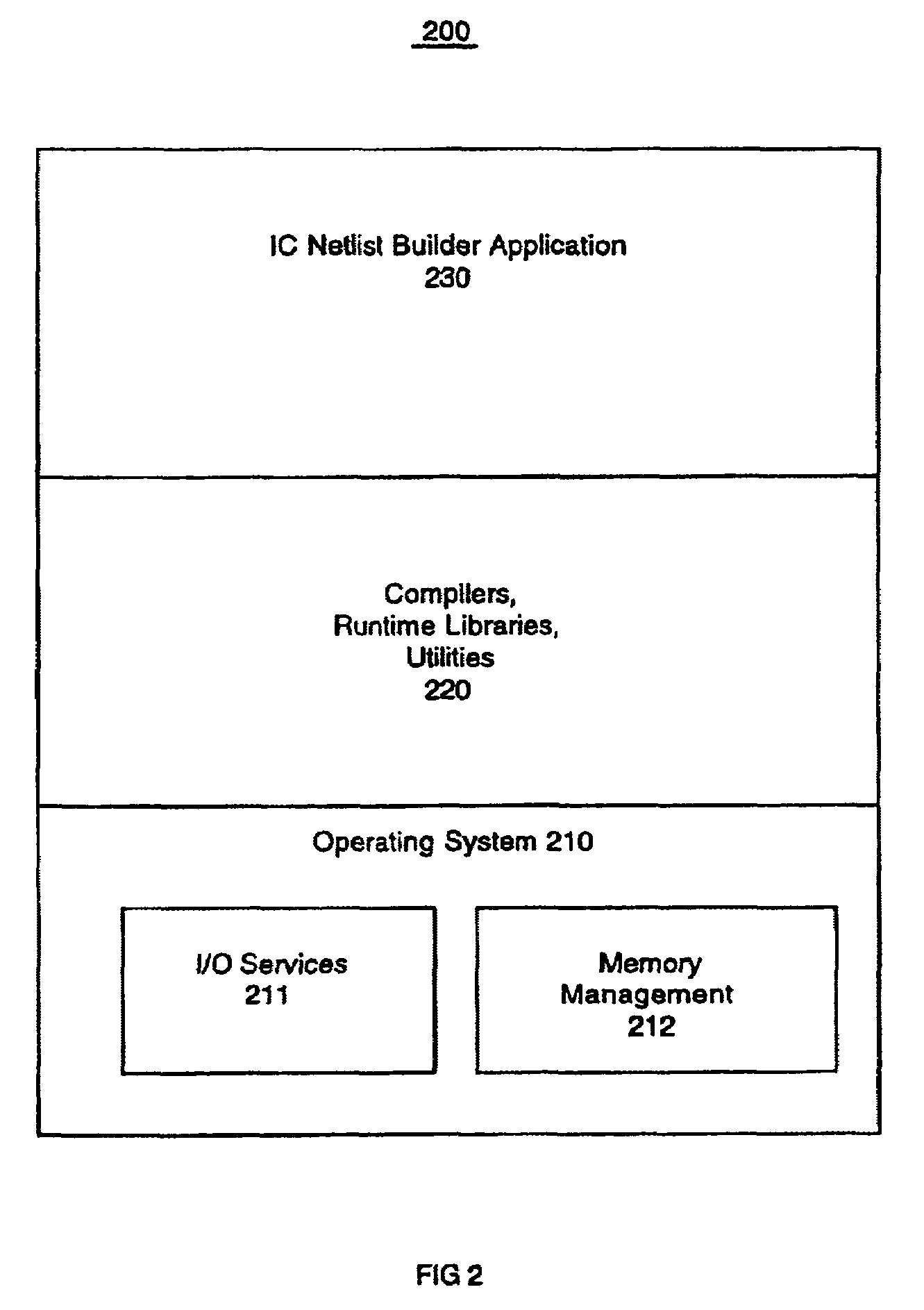
Computer system and method to dynamically generate system on a chip description files and verification information
InactiveUS7100133B1Facilitates efficient and effective creation and modification and verificationConvenience to mergeCAD circuit designSoftware simulation/interpretation/emulationComputer architectureTest platform
The present invention facilitates automation of system on a chip (SoC) design, manufacture and verification in a convenient and efficient manner. In one embodiment, a SoC netlist builder and verification computer system of the present invention includes a user interface module, a parameter application module, an expert system module and a chip level netlist generation module. The user interface module provides user friendly and convenient interfaces that facilitate easy entry and modification of user selections and parameters. The parameter application module interprets information supplied by the user module and the expert system module and creates directions (e.g., command lines) passed to other modules for execution. The expert system module analyzes information and automatically provides SoC building and verification data including automated addition of default architectural features, automated insertion of default parameters, and automated input of information to the verification module. The chip level netlist generation module automatically generates a chip level netlist, including the instantiation of internal IC devices and connections between the circuit blocks for internal signals. The verification module automatically generates a test bench and a logical verification environment including simulation models (e.g., a chip model and a system level model).
Owner:NXP BV
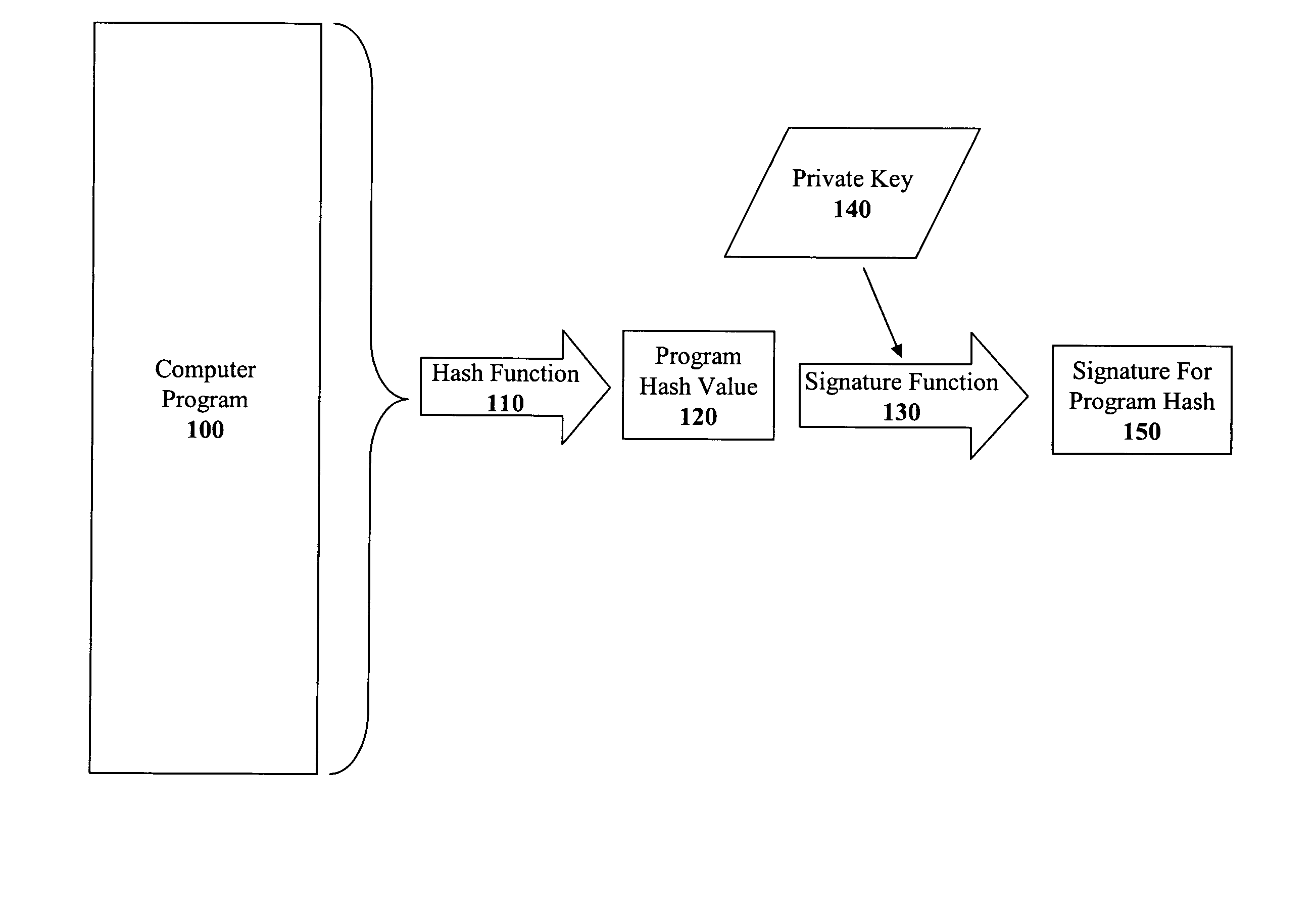
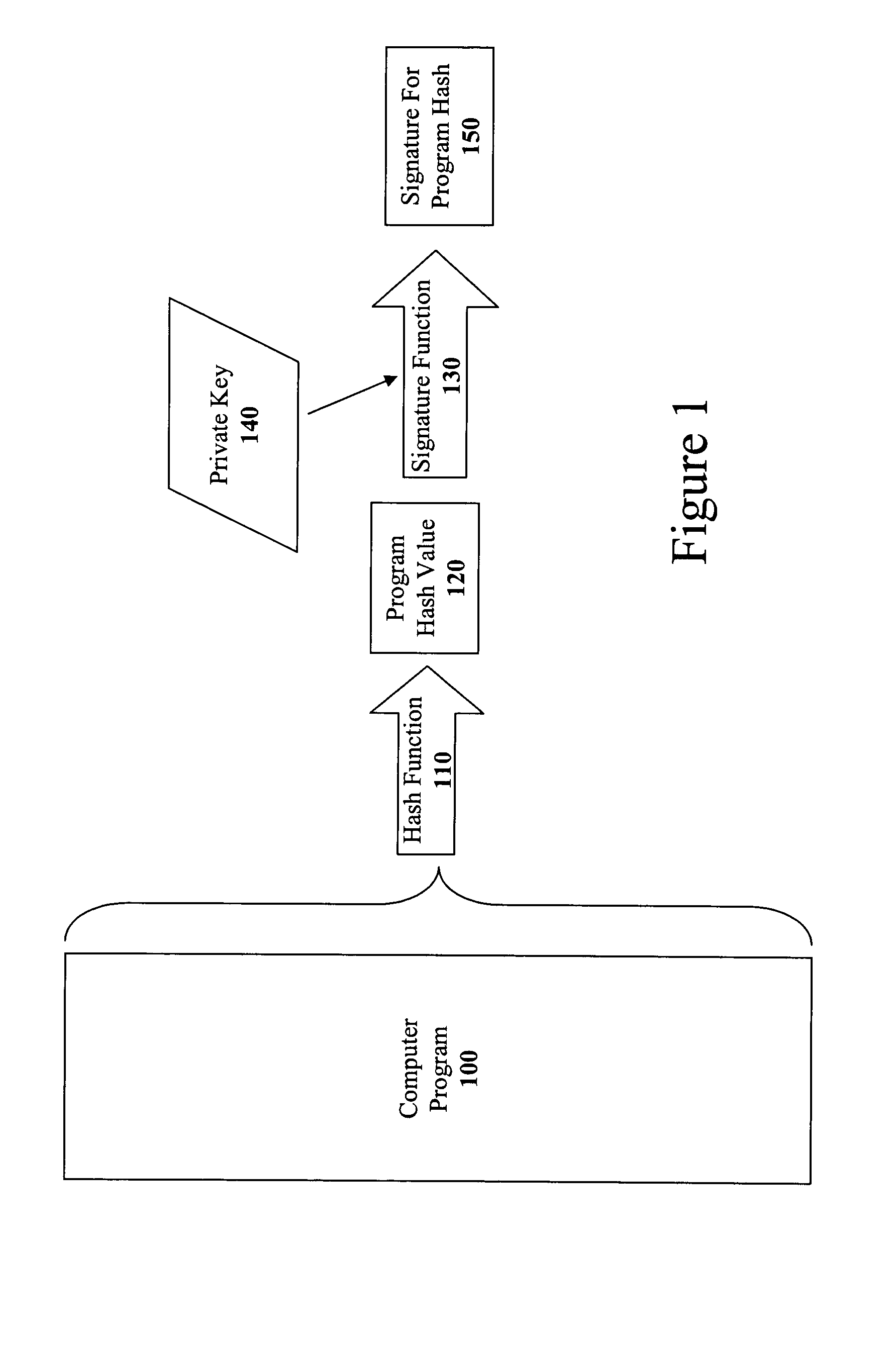
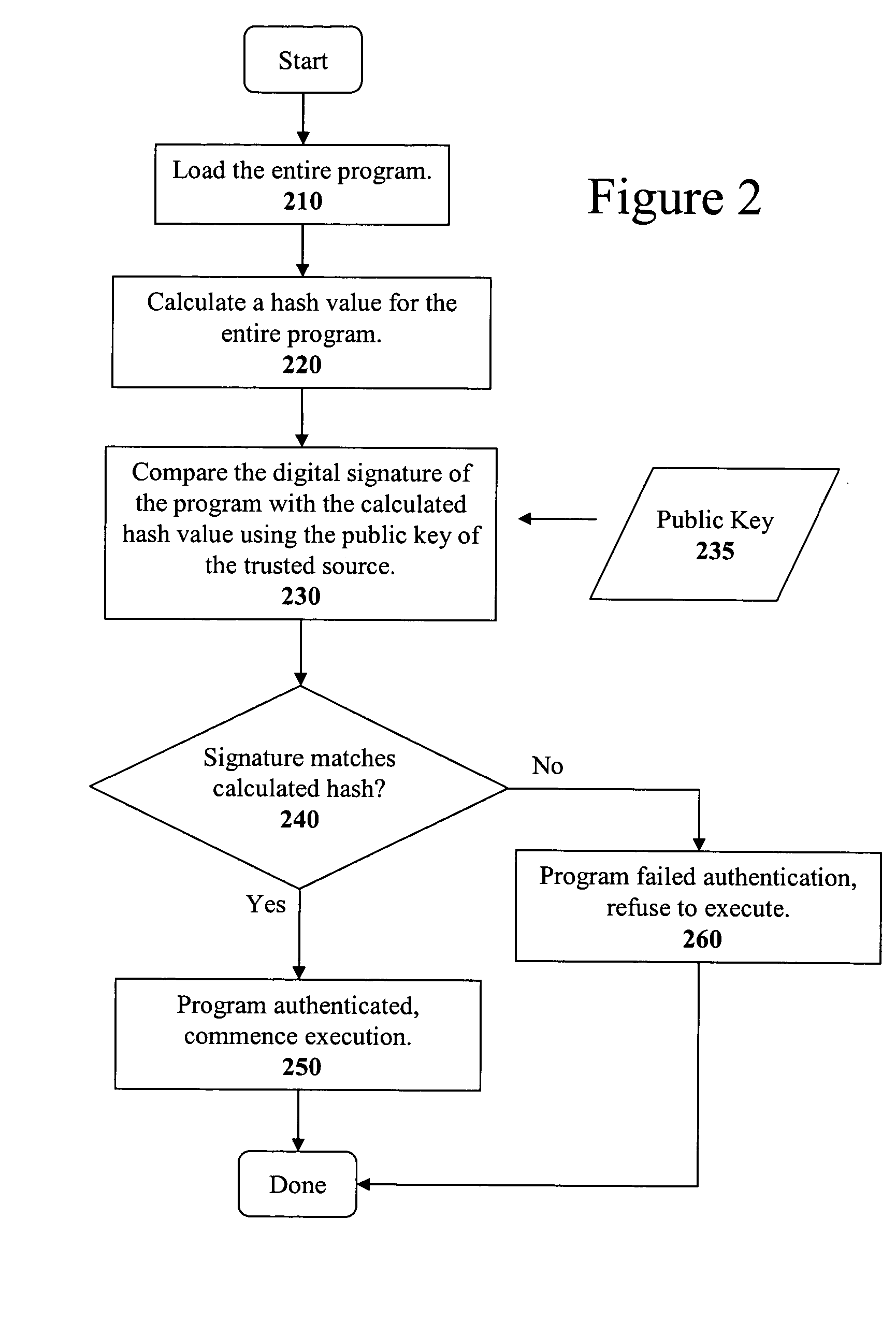
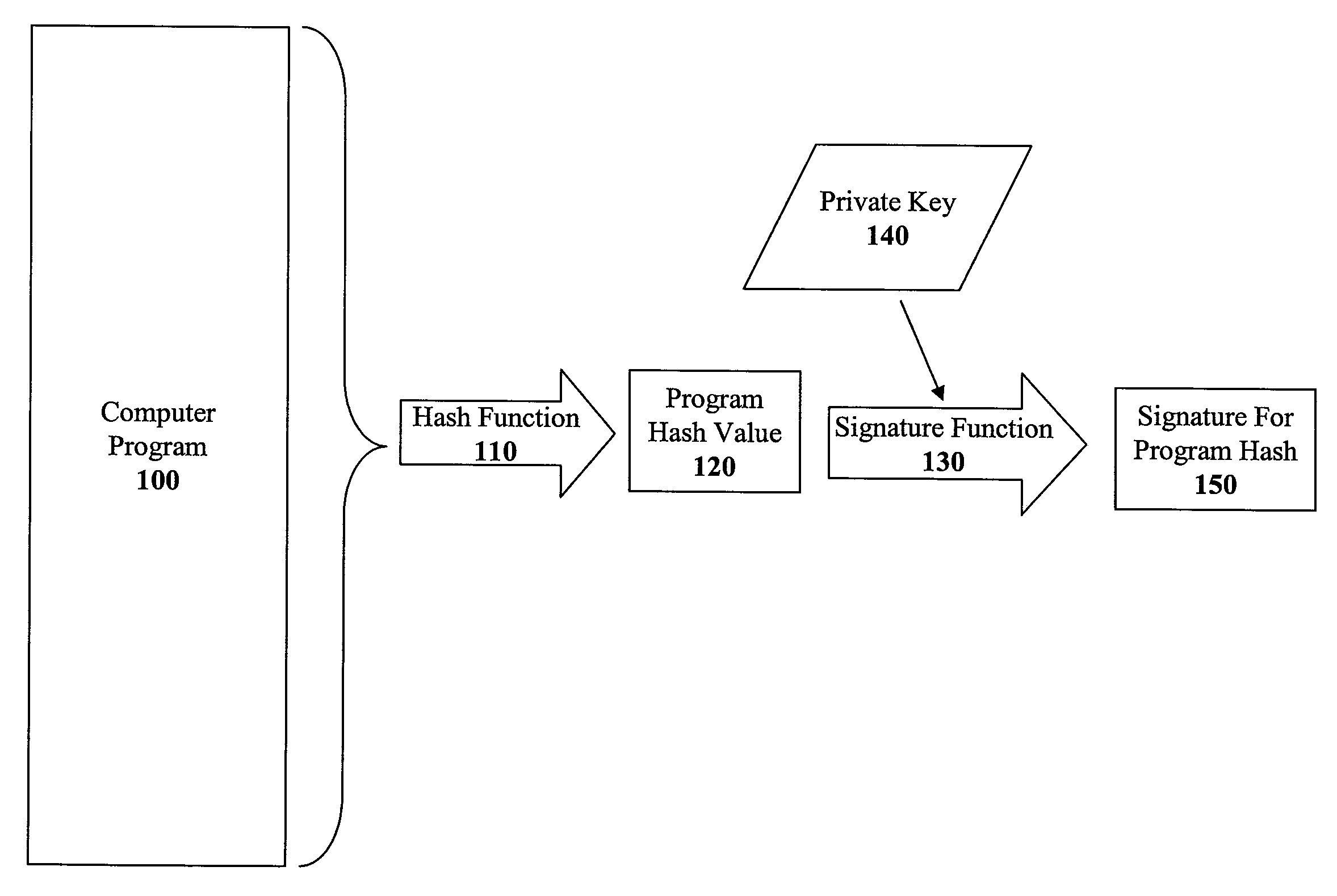
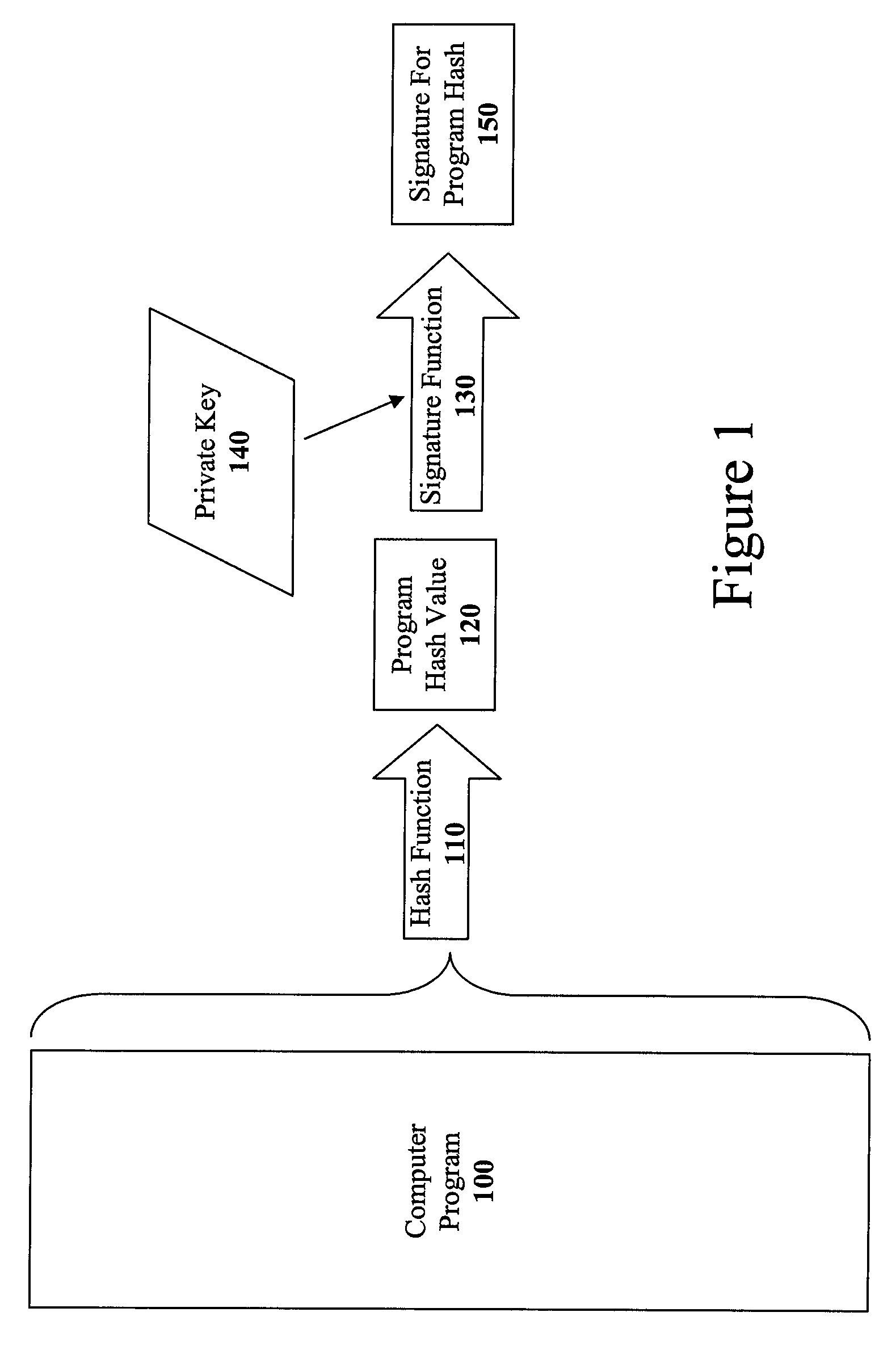
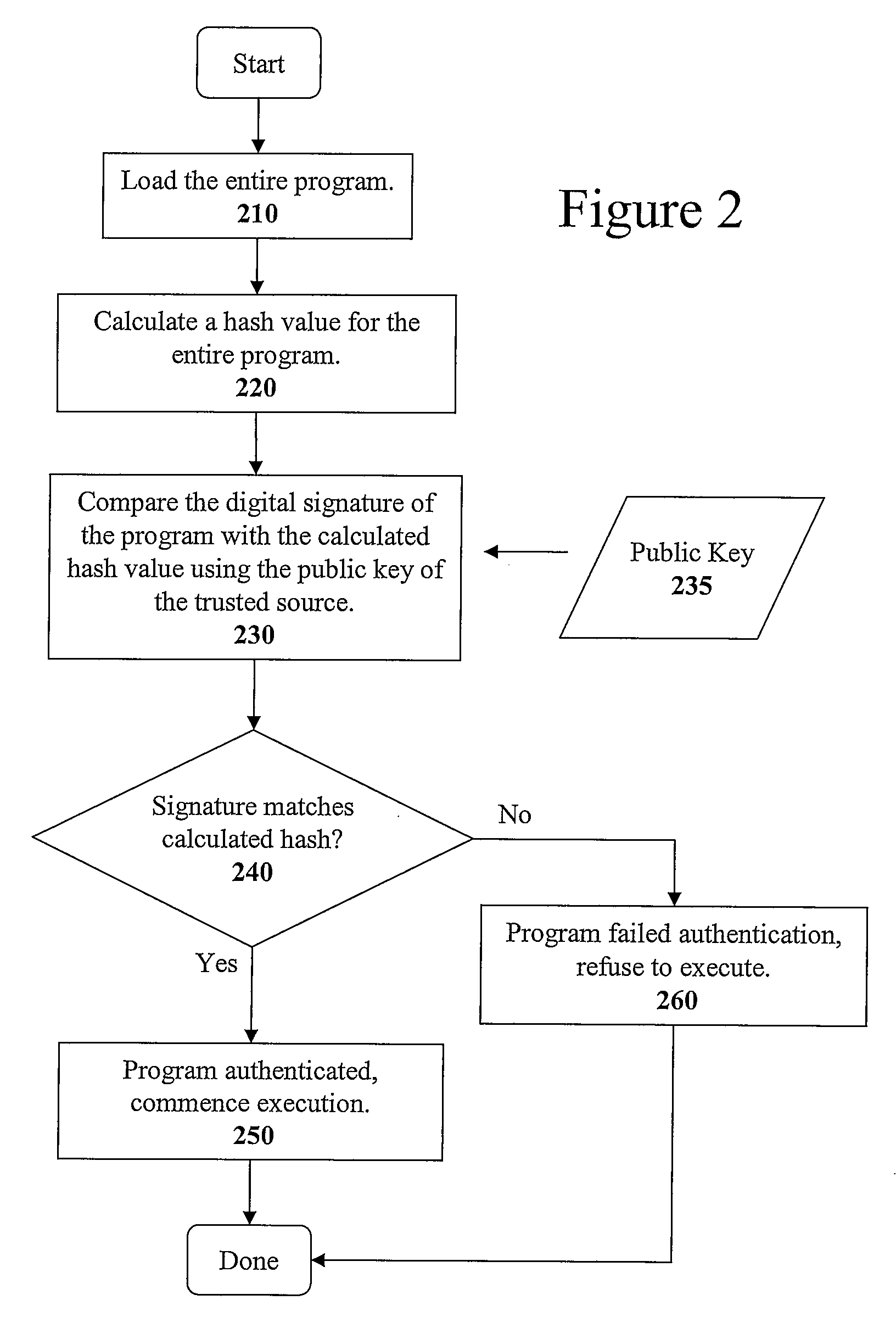
Method and apparatus for incremental code signing
ActiveUS20050066169A1Quickly and easily authenticatingMemory loss protectionUser identity/authority verificationArray data structureCode signing
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
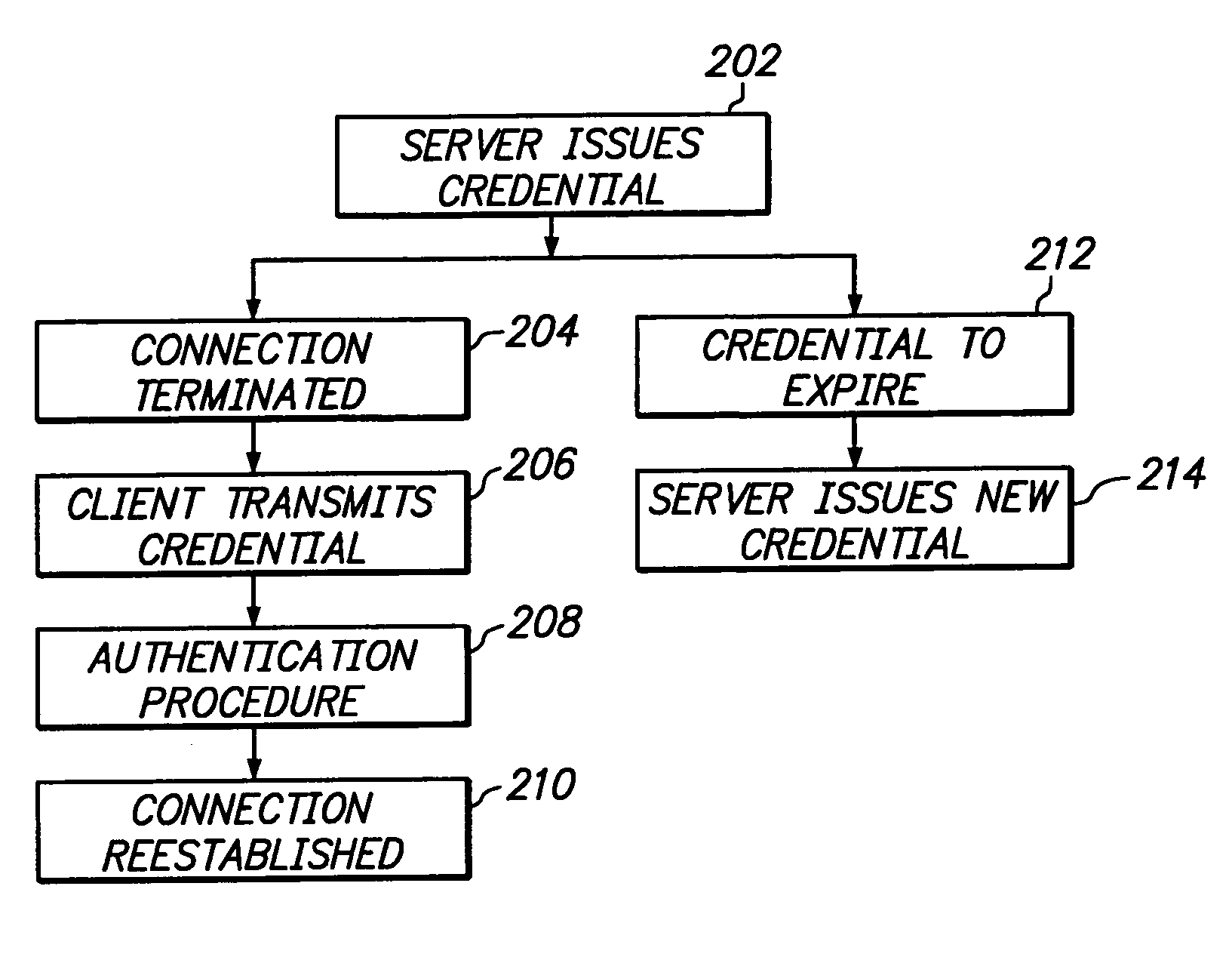
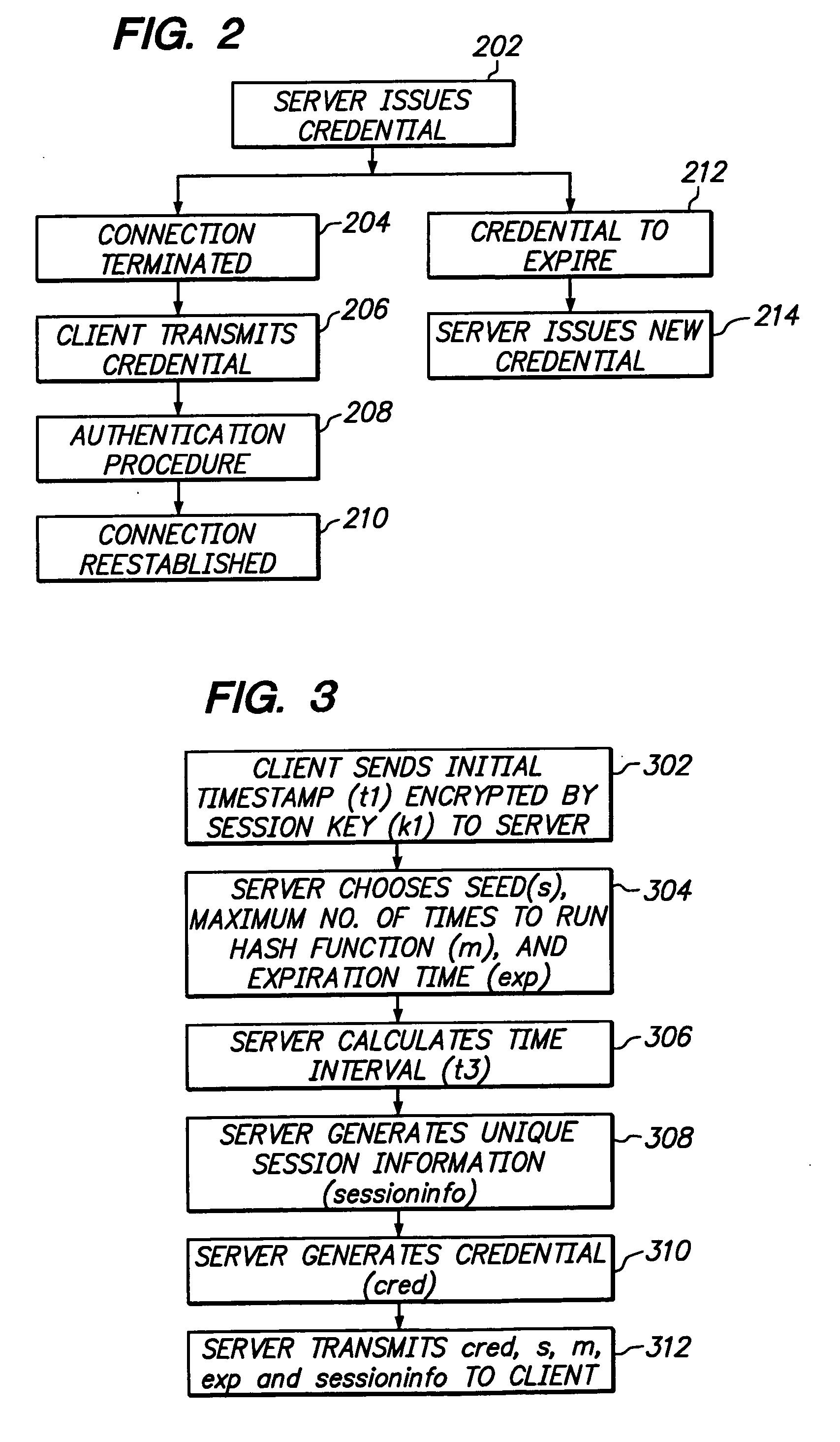
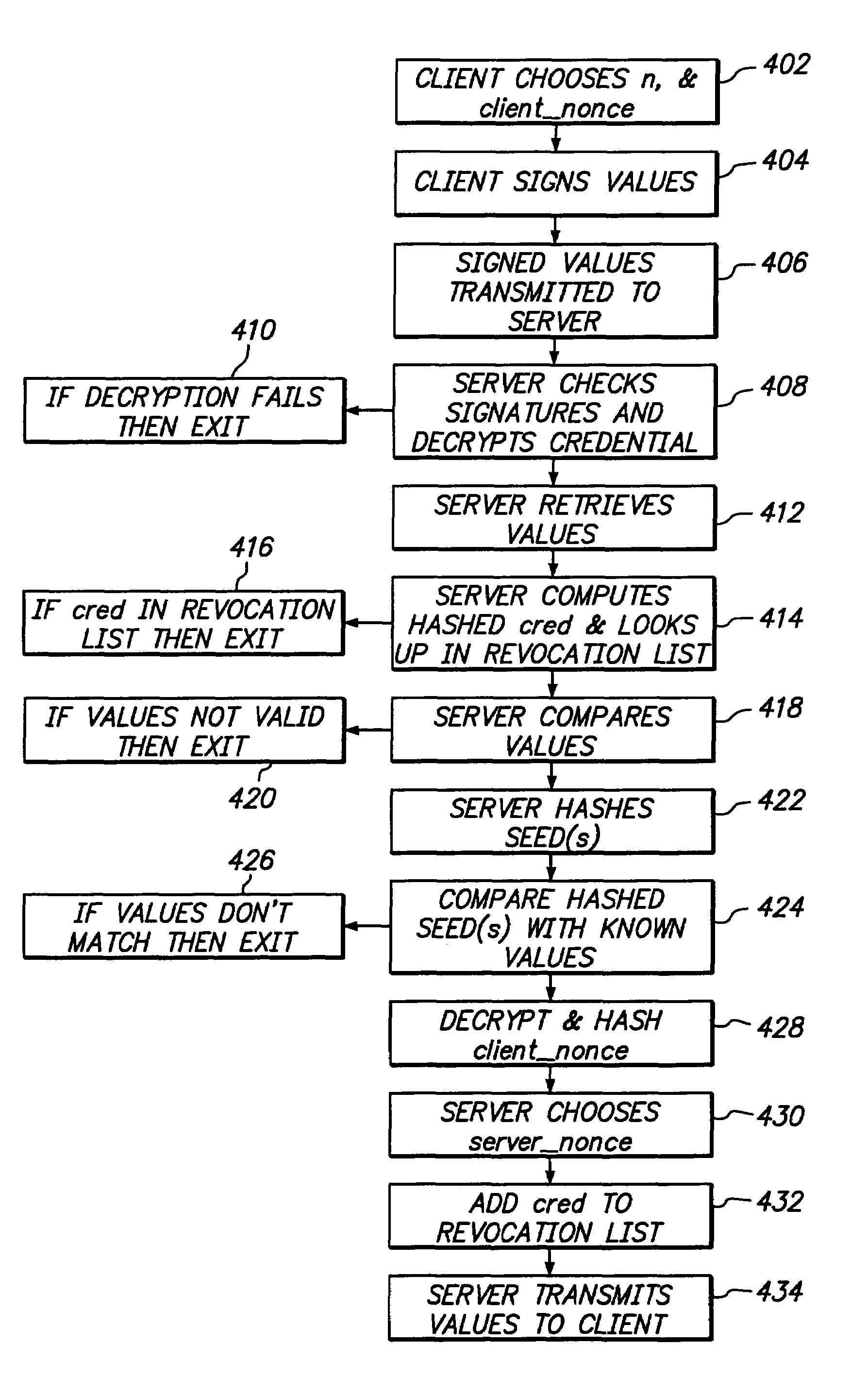
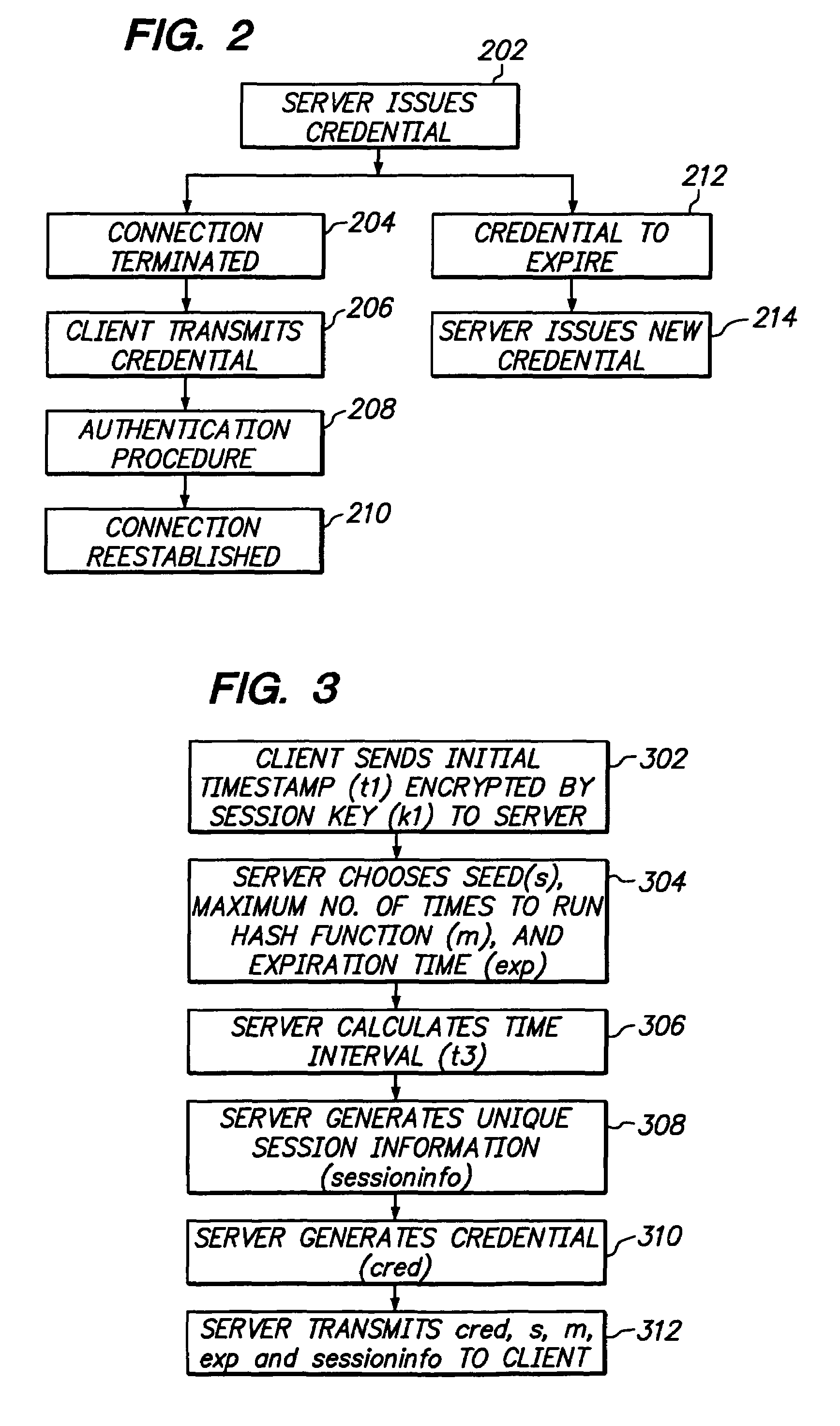
Server computer issued credential authentication
InactiveUS20050198489A1Digital data processing detailsUnauthorized memory use protectionServerAuthentication
Owner:APPLE INC
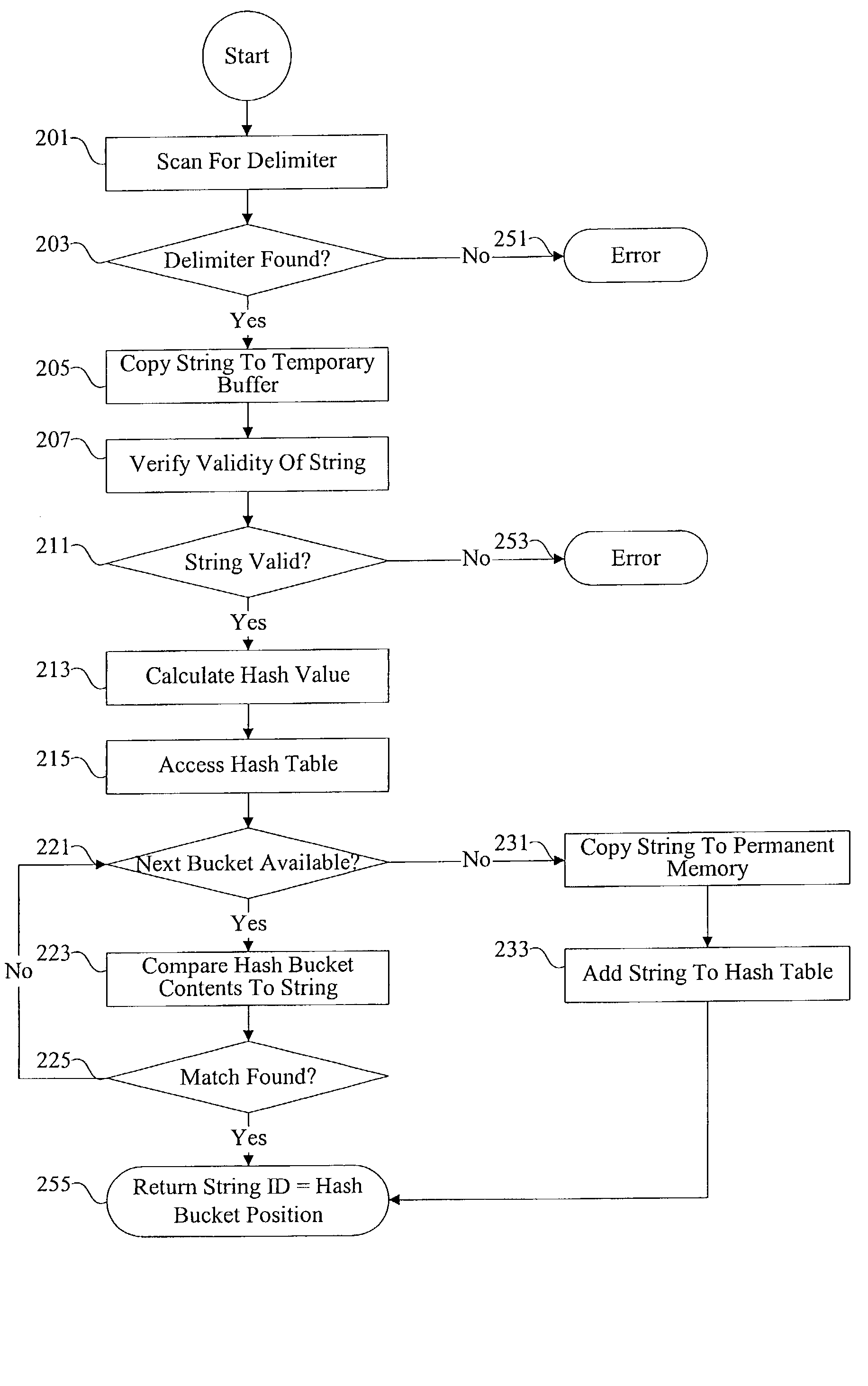
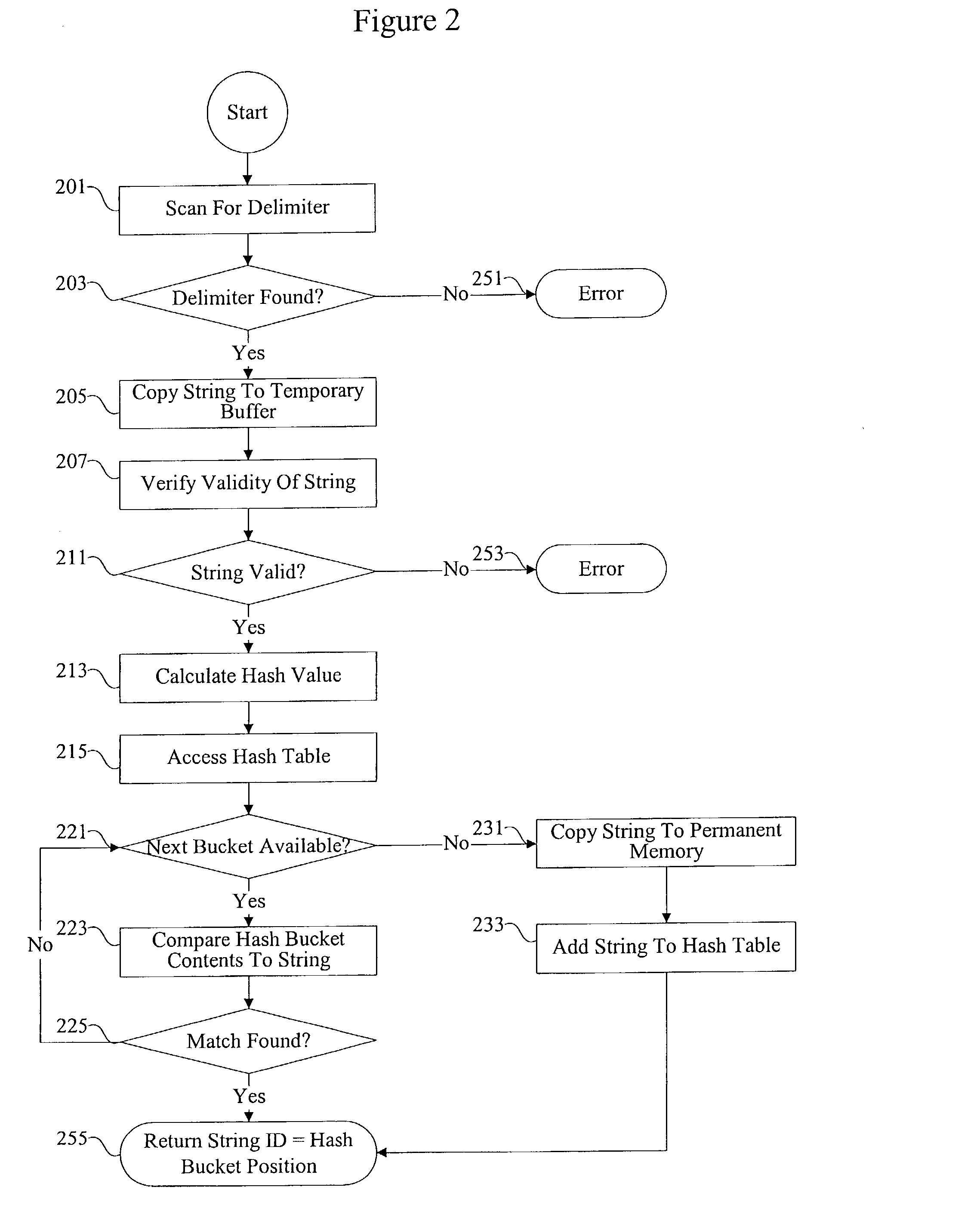
Methods and apparatus for accelerating data parsing
InactiveUS20030023633A1Natural language data processingSpecial data processing applicationsComputerized systemData mining
According to the present invention, methods and apparatus are provided for improving the efficiency of data parsing. Data parsing can be applied to a variety of different types of data in various computer systems and appliances. Some of the methods and apparatus provided include techniques for scanning, verifying, calculating hash values, copying, and white space handling.
Owner:ROSS RICHARD A
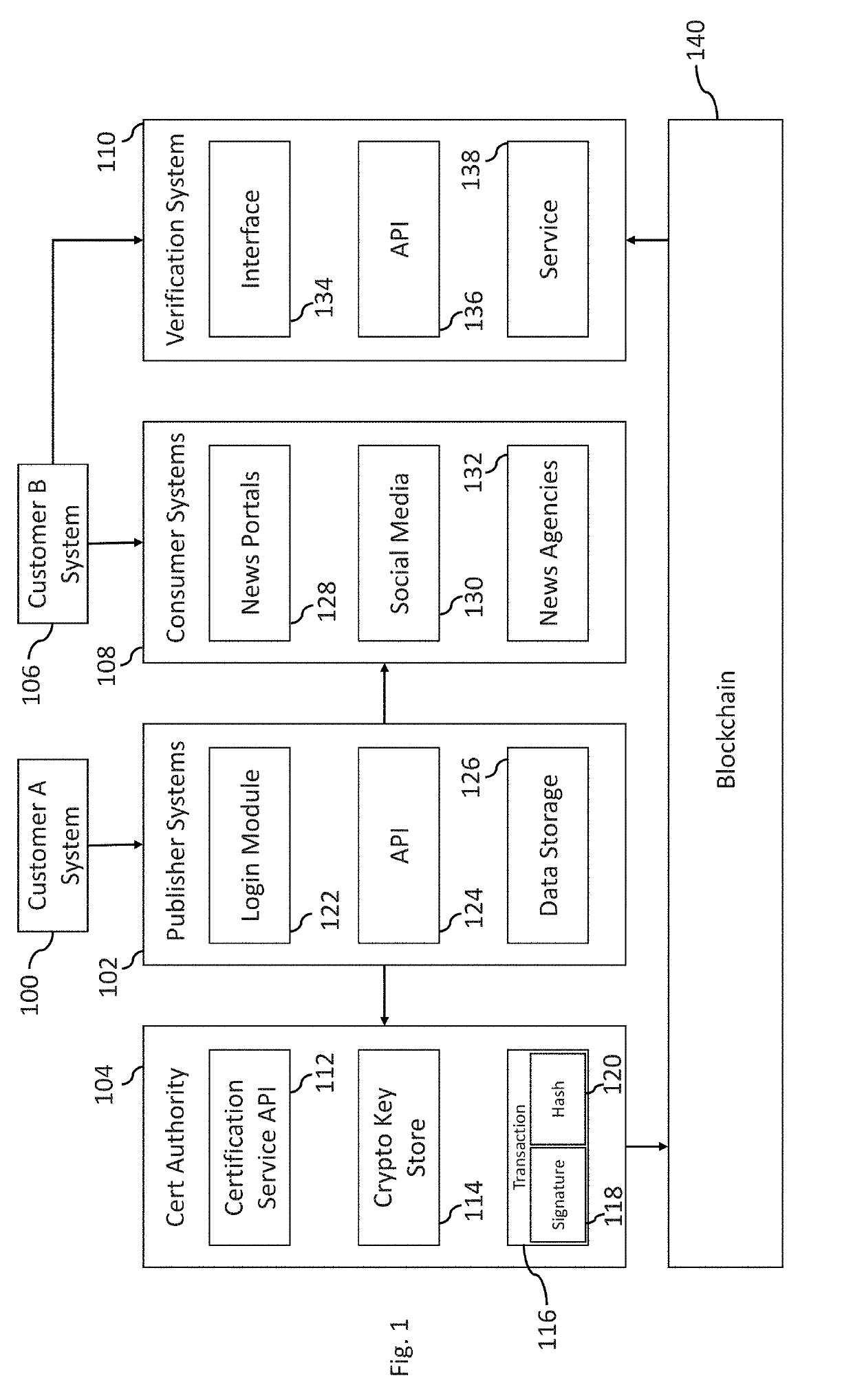
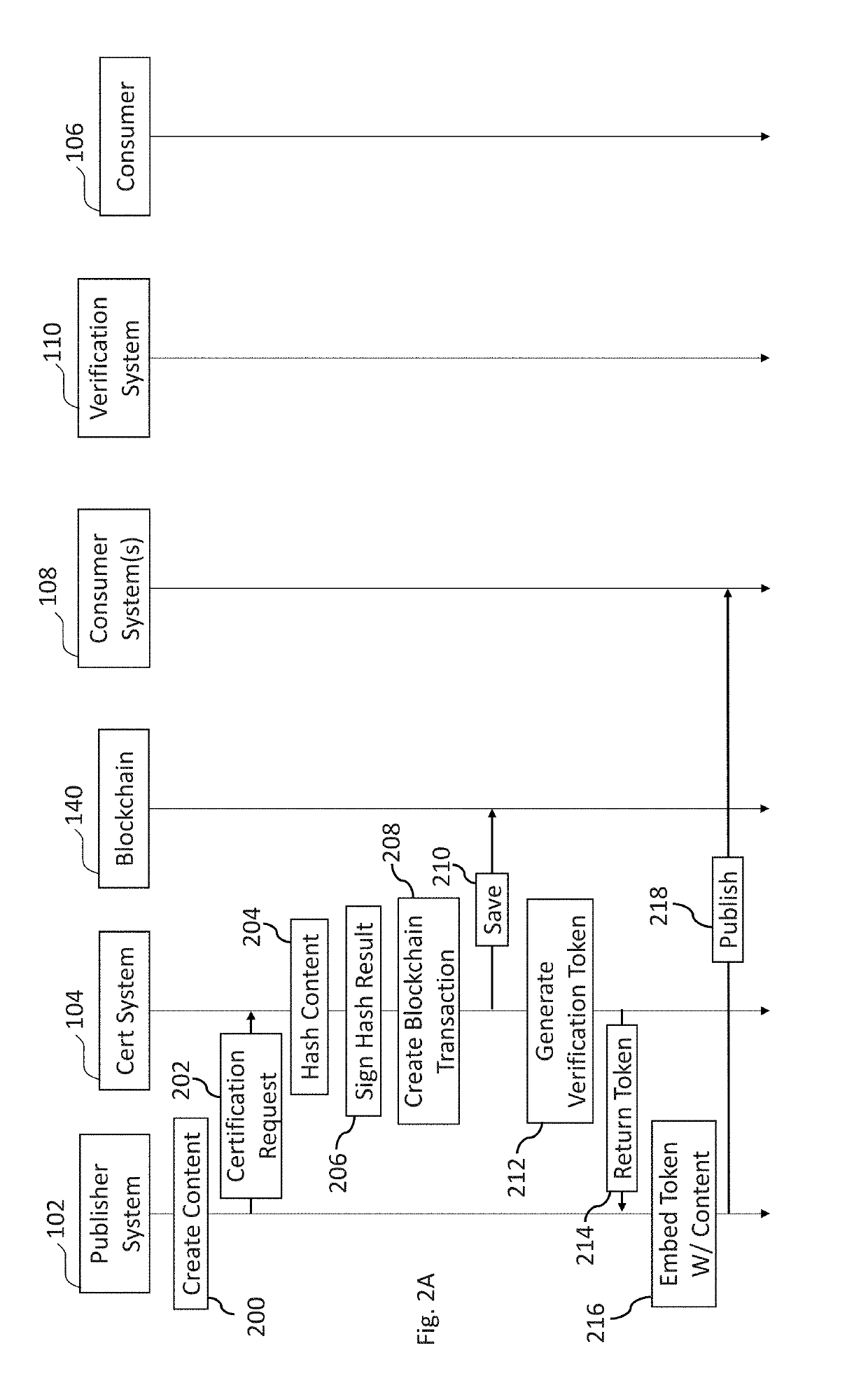
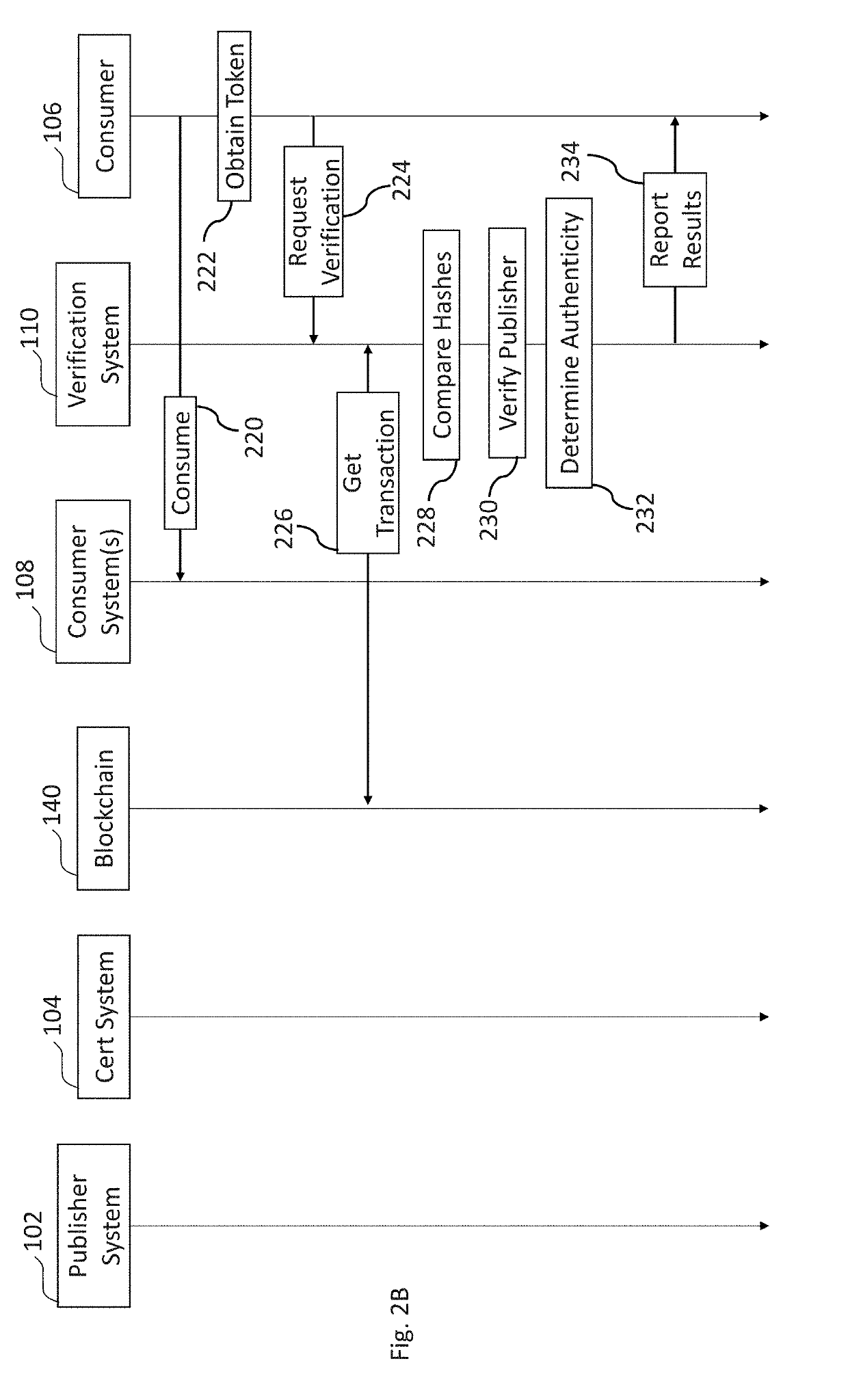
Systems and methods of digital content certification and verification using cryptography and blockchain
ActiveUS20190228133A1Encryption apparatus with shift registers/memoriesCryptography processingDigital contentNumber content
A verification computer system is provided that provides for content certification and verification using cryptography and a blockchain.
Owner:NASDAQ INC
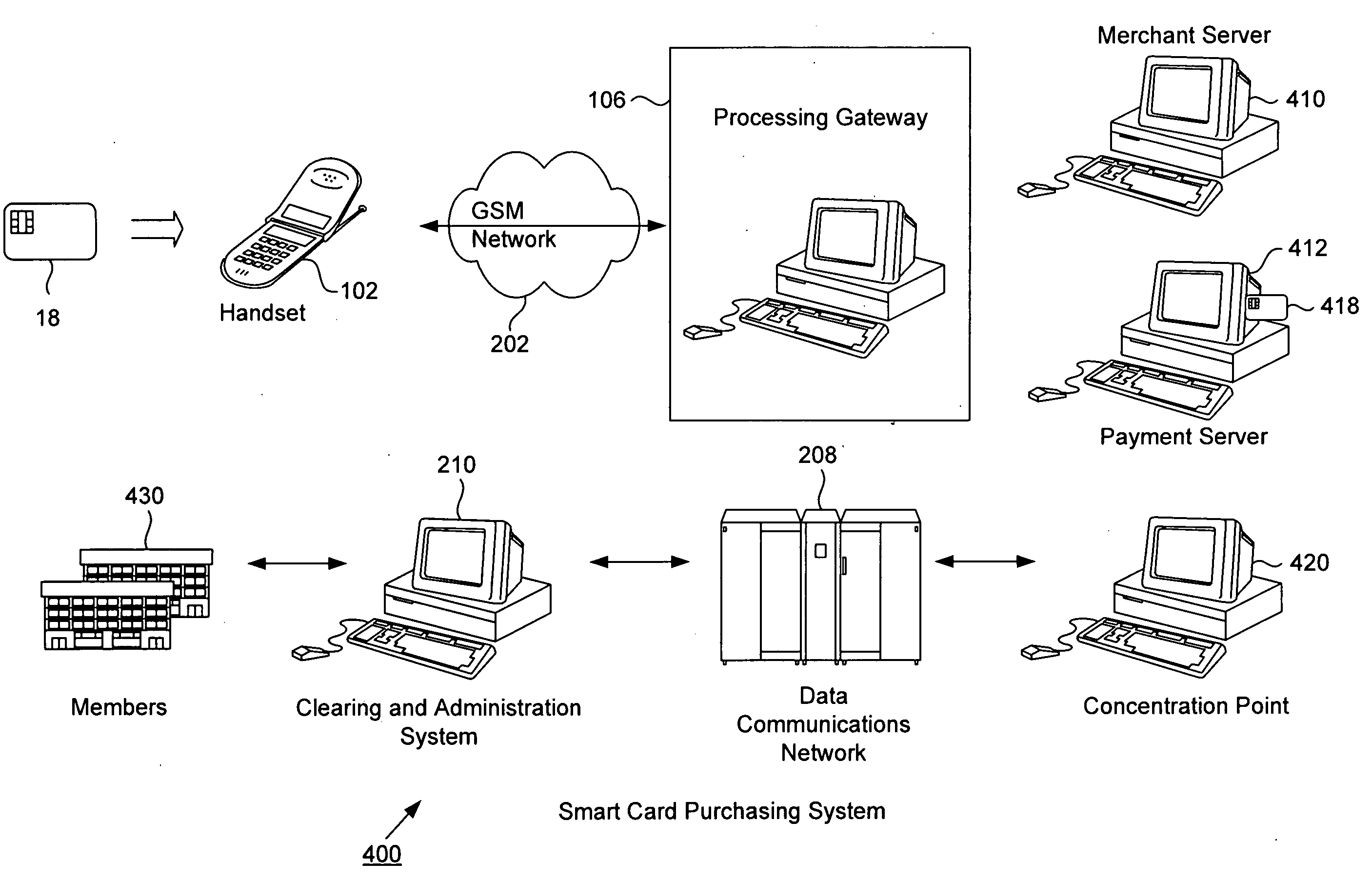
Smart card purchasing transactions using wireless telecommunications network
InactiveUS20090030842A1Enhanced anonymityPrivacy protectionCryptography processingUser identity/authority verificationMerchant servicesPayment
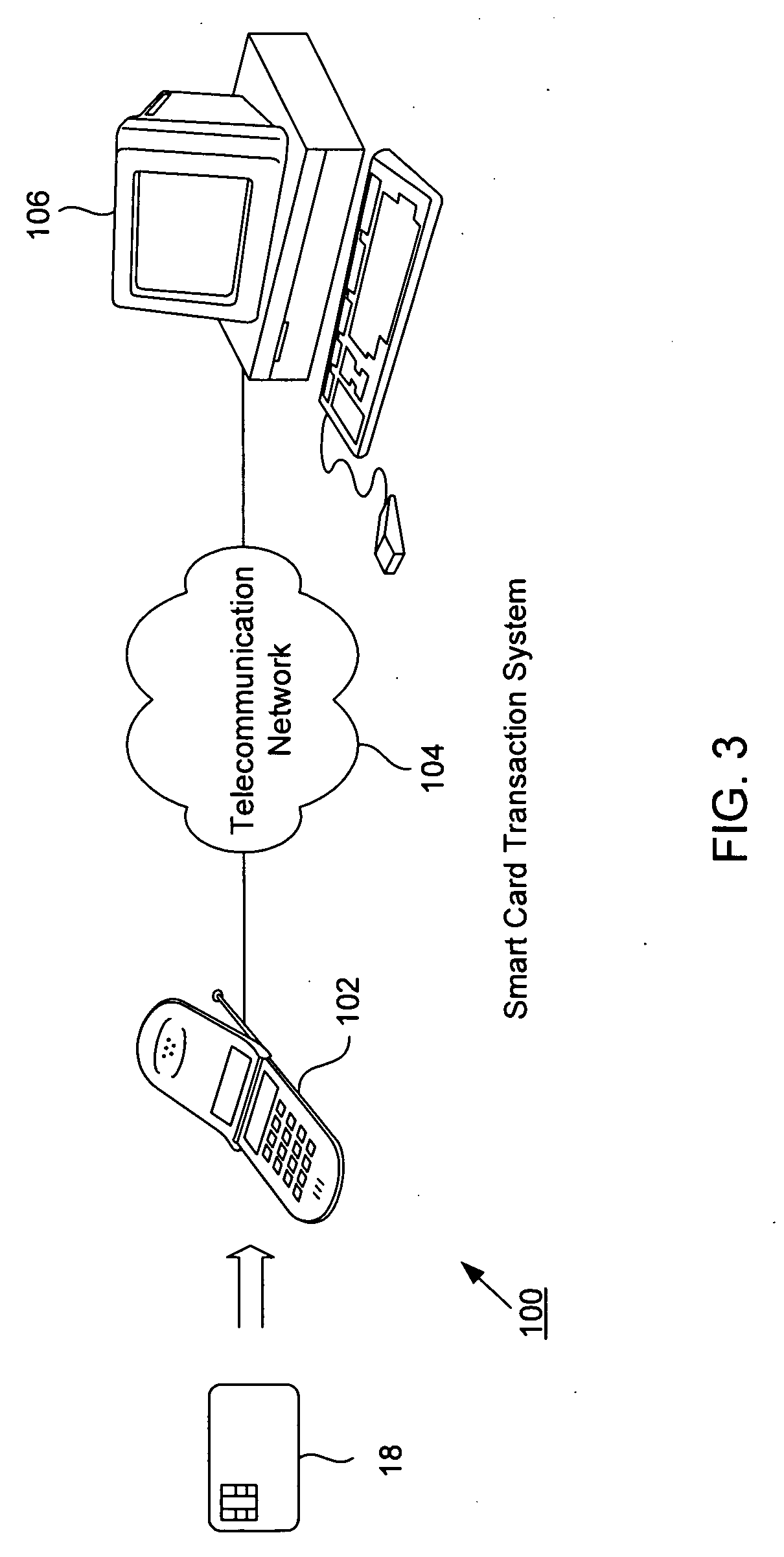
A smart card transaction allows a consumer to load value onto a smart card and to make purchases using a smart card with a mobile telephone handset over the telecommunications network. For loading, the system includes: a mobile telephone handset including a card reader; a gateway computer; a funds issuer computer; and an authentication computer. The mobile telephone handset receives a request from a user to load a value onto the smart card. The handset generates a funds request message which includes the value and sends the funds request message to a funds issuer computer. The funds issuer computer debits an account associated with the user. Next, the handset generates a load request message with a cryptographic signature and sends the load request message to an authentication computer which authenticates the smart card. The handset receives a response message which includes a cryptographic signature and an approval to load. Finally, the handset validates the second cryptographic signature and loads the value onto the smart card. For payment, the system includes a merchant server and a payment server. First, the handset sends an order request message to the merchant server computer, and in return receives a purchase instruction message. The handset processes the purchase instruction message locally, and then sends a draw request message to a payment server computer. The payment server computer sends a debit message which includes a cryptographic signature and an approval to debit the smart card. Finally, the handset validates the cryptographic signature and debits the smart card.
Owner:VISA USA INC (US)
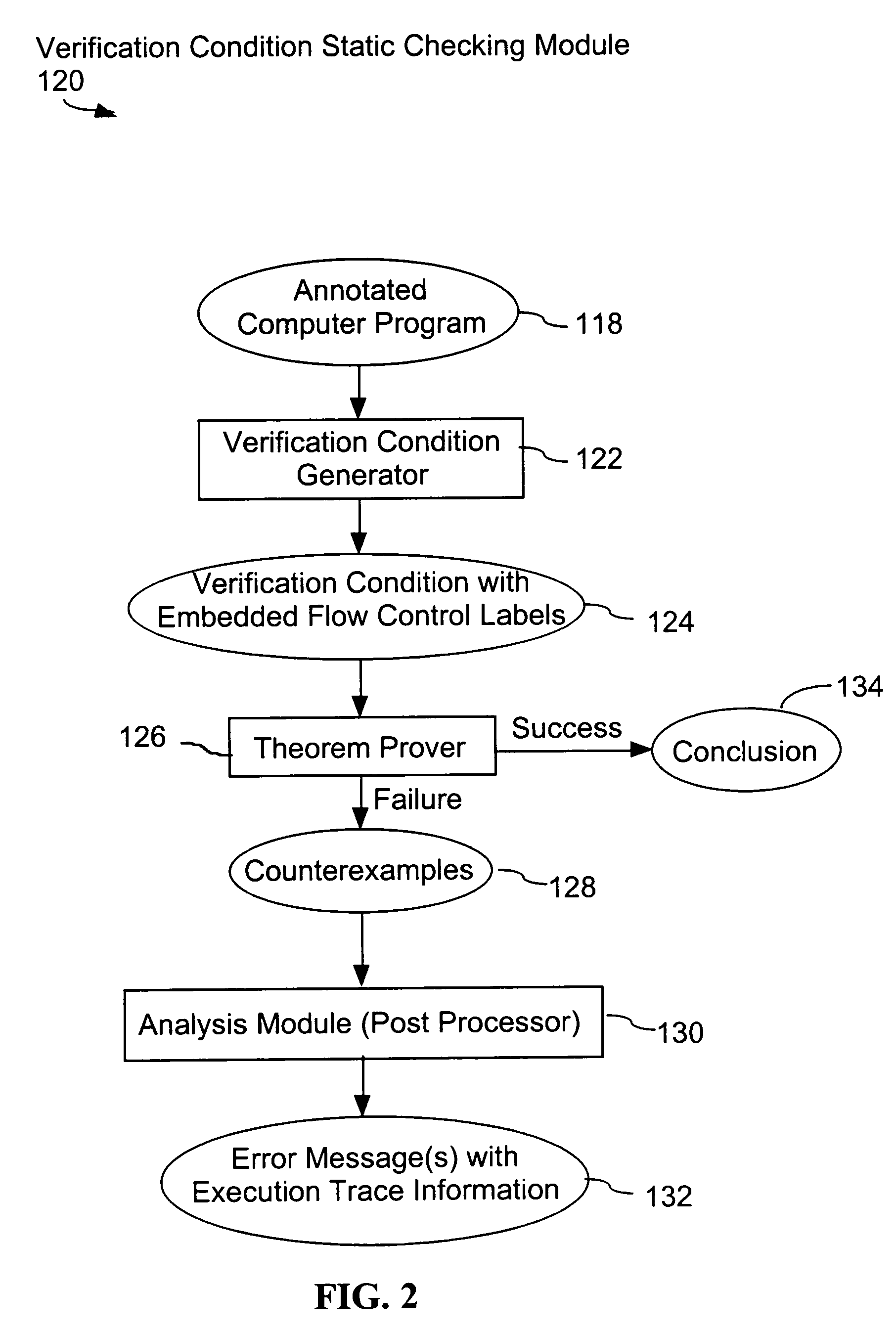
System and method for verifying computer program correctness and providing recoverable execution trace information
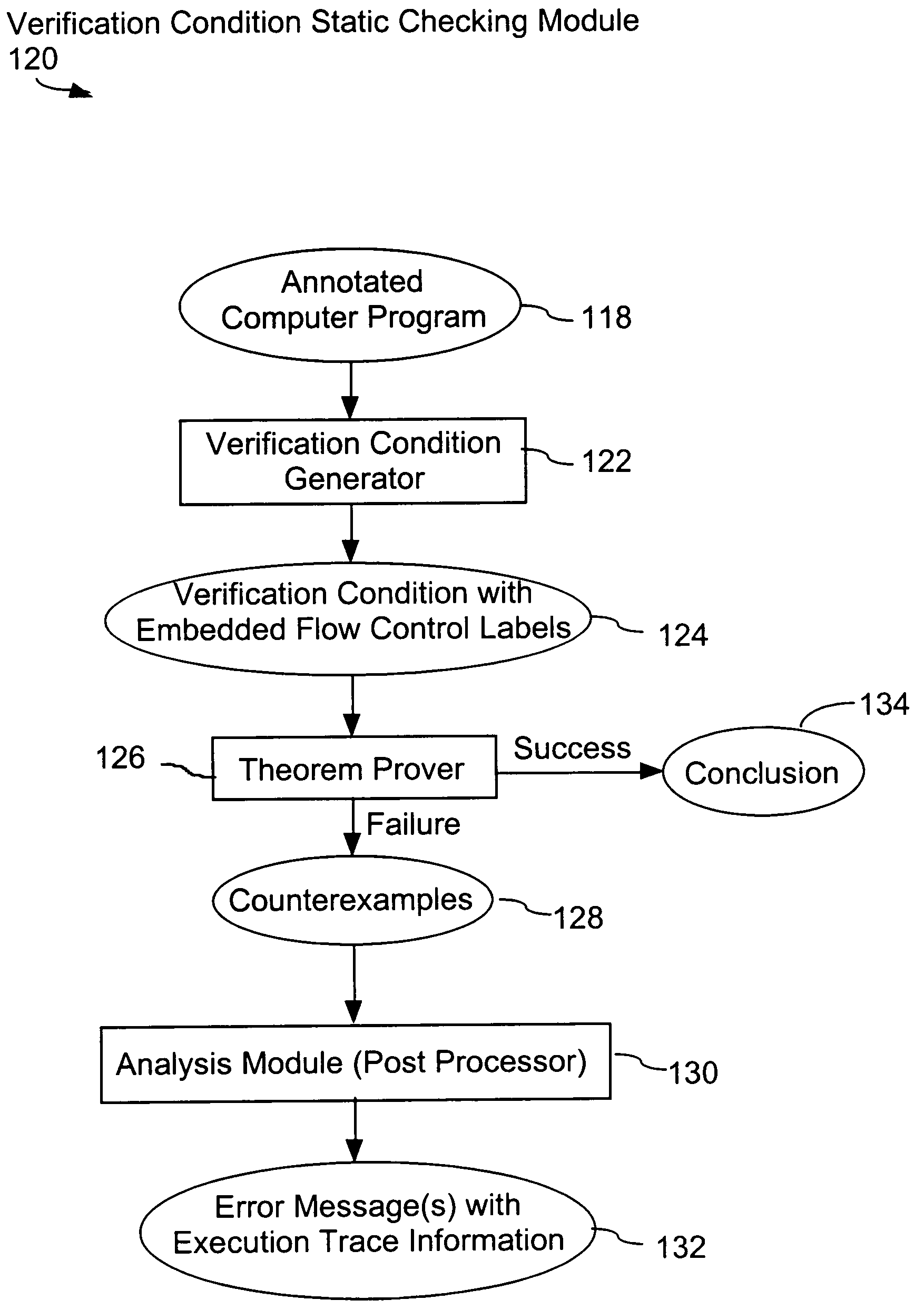
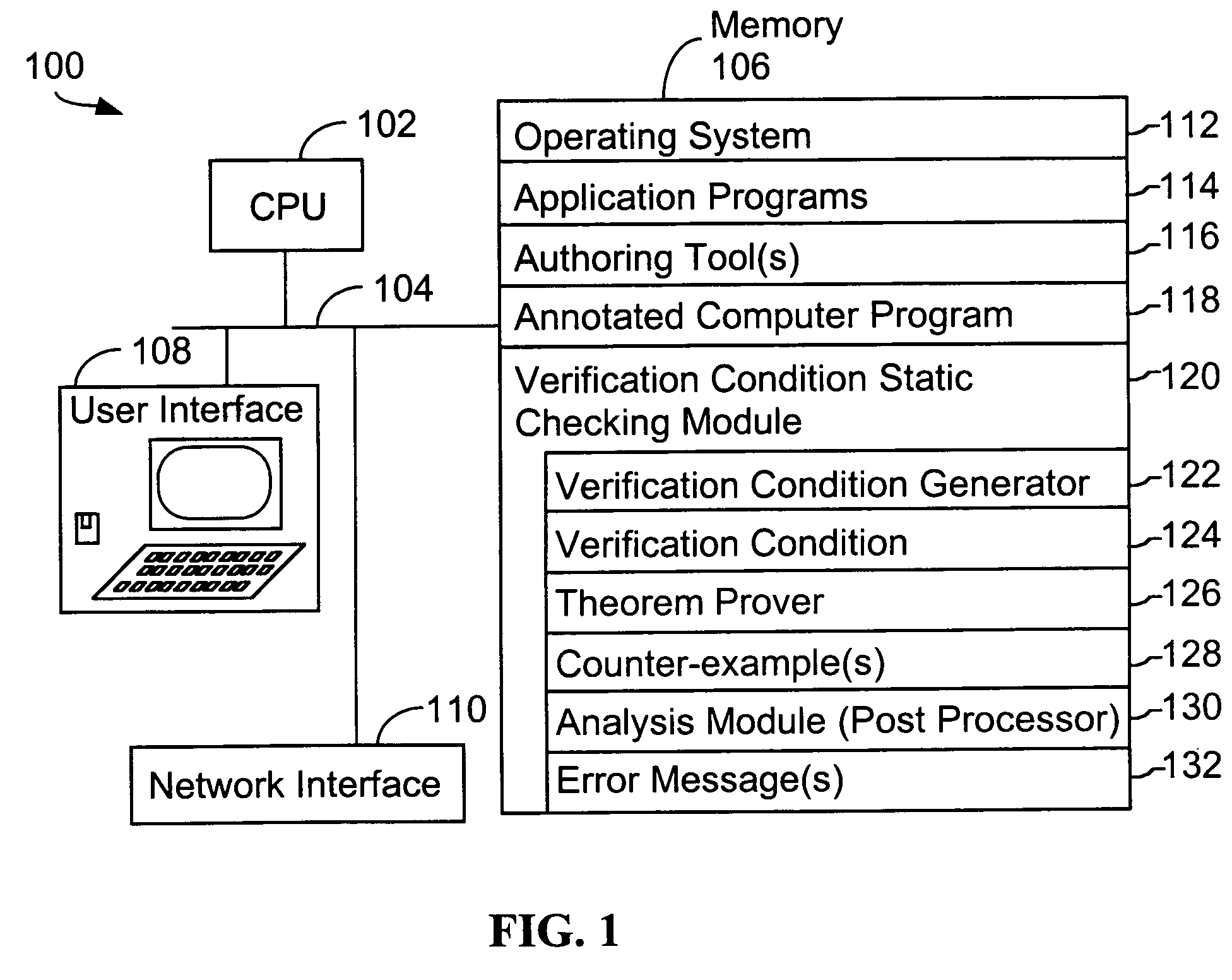
In a system for statically analyzing a specified computer, a verification condition generator converts the program into a logical equation, called a verification condition, and inserts program flow control labels into the sub-equations of the verification condition. The flow control labels identify conditional branch points in the specified computer program. A theorem prover is applied to the logical equation to determine truth of the logical equation, and when the truth of the logical equation cannot be proved, the theorem prover generates at least one counter-example identifying one of the conditions, one or more variable values inconsistent with that condition, and any of the flow control labels for conditional branch points of the program associated with the identified variable values. A post processing module converts each counter-example into an error message that includes a program trace when the counter-example identifies one or more of the flow control labels.
Owner:HEWLETT PACKARD DEV CO LP
Server computer issued credential authentication
InactiveUS7735120B2Digital data processing detailsUnauthorized memory use protectionAuthenticationServer
Owner:APPLE INC
Validation for secure device associations
InactiveUS7370200B2Memory loss protectionError detection/correctionComputer scienceVerified computing
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
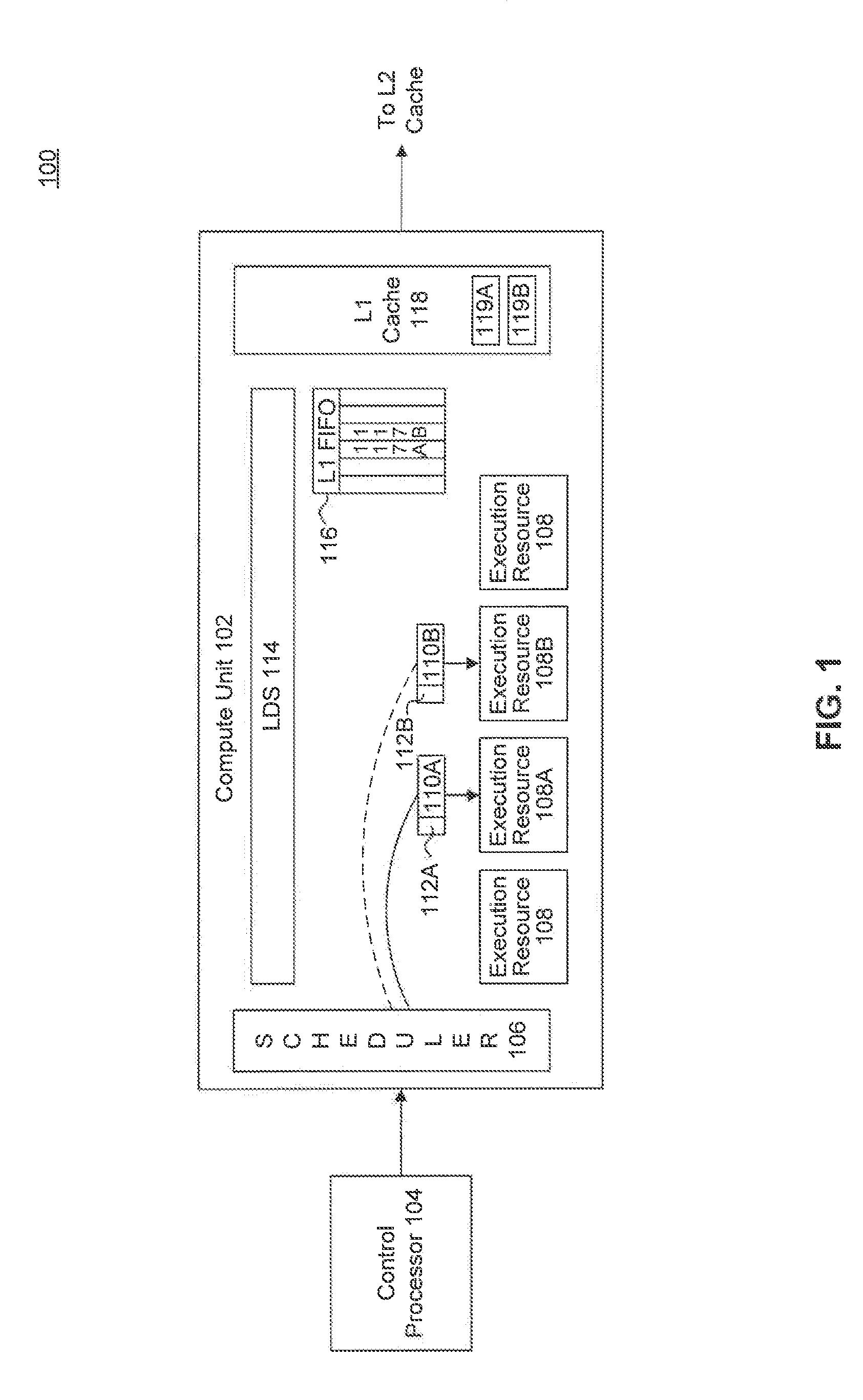
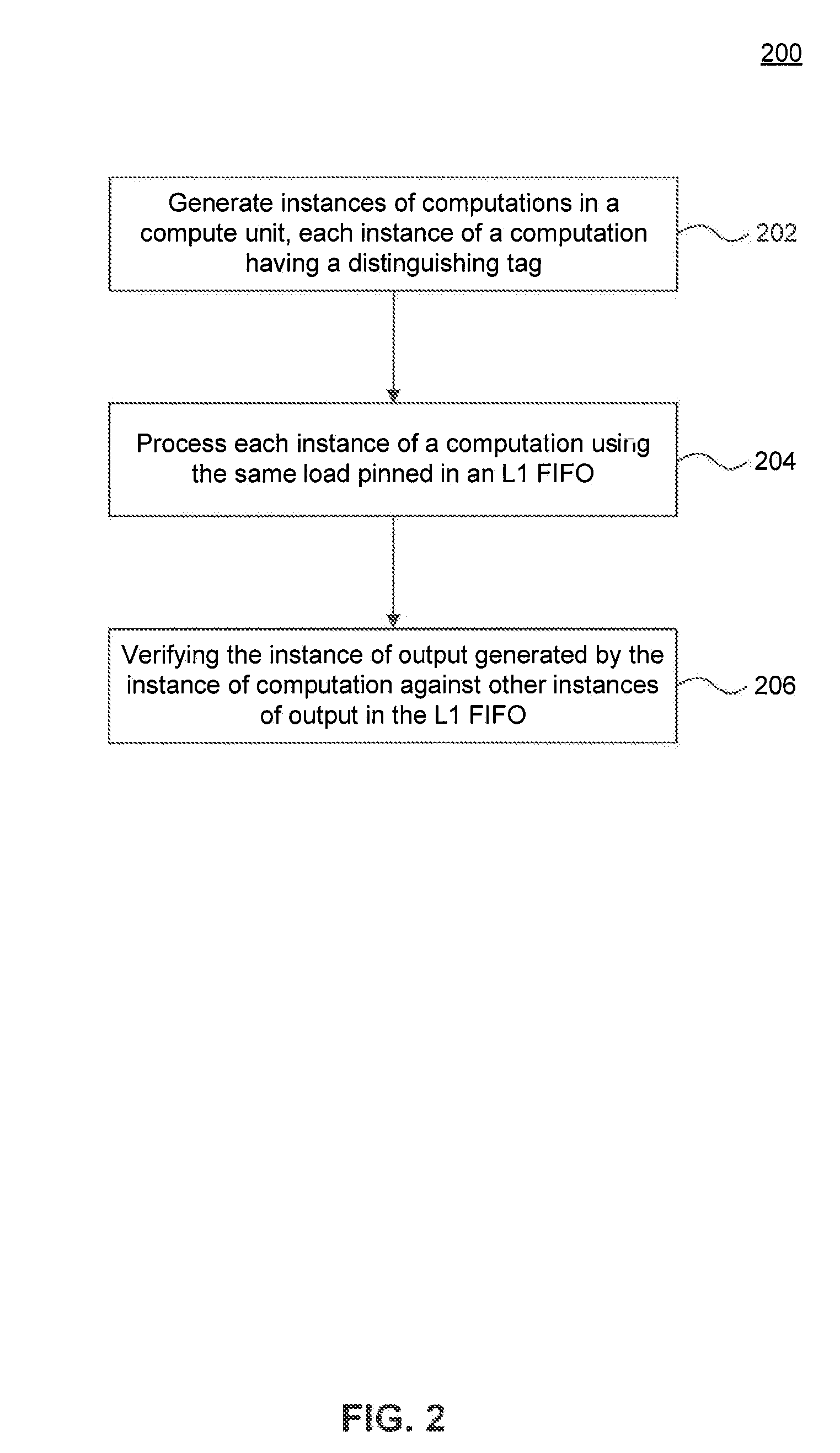
Hardware Based Redundant Multi-Threading Inside a GPU for Improved Reliability
A system and method for verifying computation output using computer hardware are provided. Instances of computation are generated and processed on hardware-based processors. As instances of computation are processed, each instance of computation receives a load accessible to other instances of computation. Instances of output are generated by processing the instances of computation. The instances of output are verified against each other in a hardware based processor to ensure accuracy of the output.
Owner:ADVANCED MICRO DEVICES INC
Method for verifying the execution of a software product
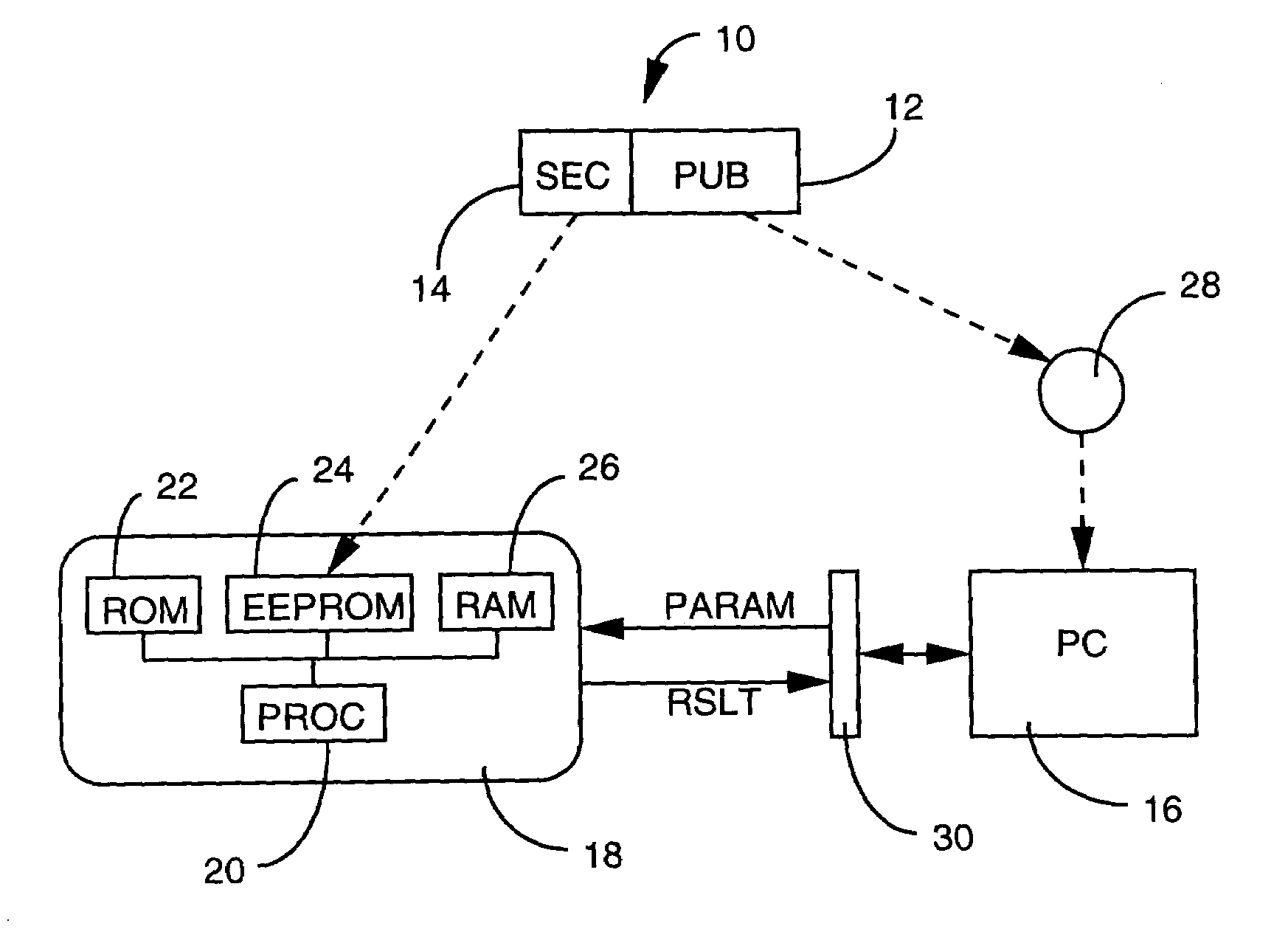
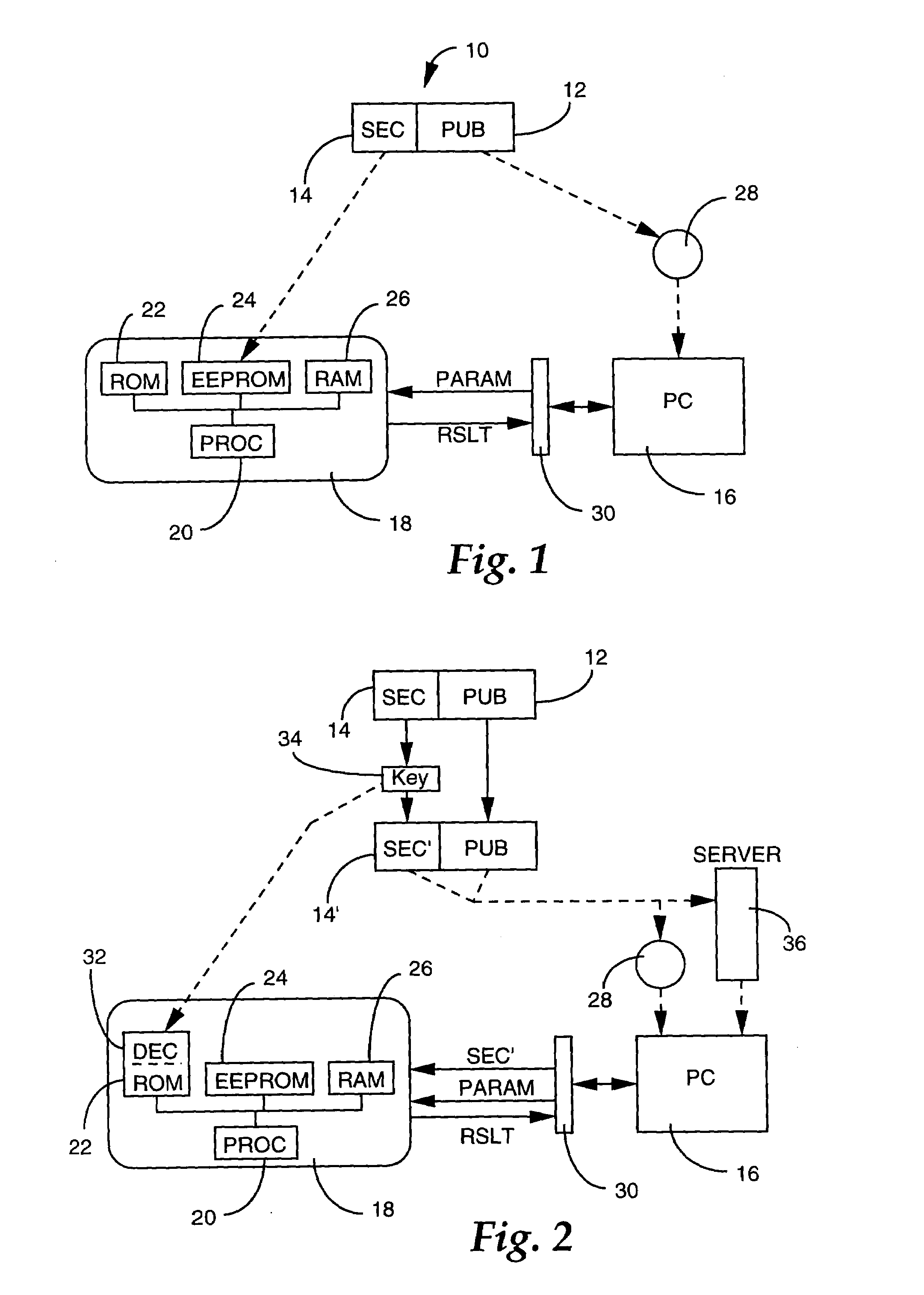
InactiveUS6931542B1Easy to operateSolve large capacityMemory loss protectionDigital data processing detailsVerified computingComputer program
The present invention relates to a method for verifying the execution of a computer program, comprising the following steps: 1) a program is split up into at least two parts, one public and one secret, whereby the public part is executed on a first processing means and the second part is executed on a second secure processing means; 2) the public part is placed in a memory pertaining to the first processing means; 3) the secret part is placed on a secure support pertaining to the second processing means in order to be connected to the first processing means; 4) the following operations are performed so that the program can be executed by the first processing means: a) the second processing means is connected to the first and parameters and variables that are a function of external signals triggered by a user are transmitted from the first processing means to the second, b) at least one part of the program is executed by the second processing means, implementing a certain number of received parameters / variables, c) the results of the execution as described in b) are transmitted from the second processing means to the first, d) a certain number of said results are used in the execution performed by the first means. The invention is characterized in that the second means is a portable and detachable auxiliary support which is provided with a chip.
Owner:GEMPLU
Method and Apparatus for Incremental Code Signing
ActiveUS20060288223A1Memory loss protectionUser identity/authority verificationArray data structureCode signing
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
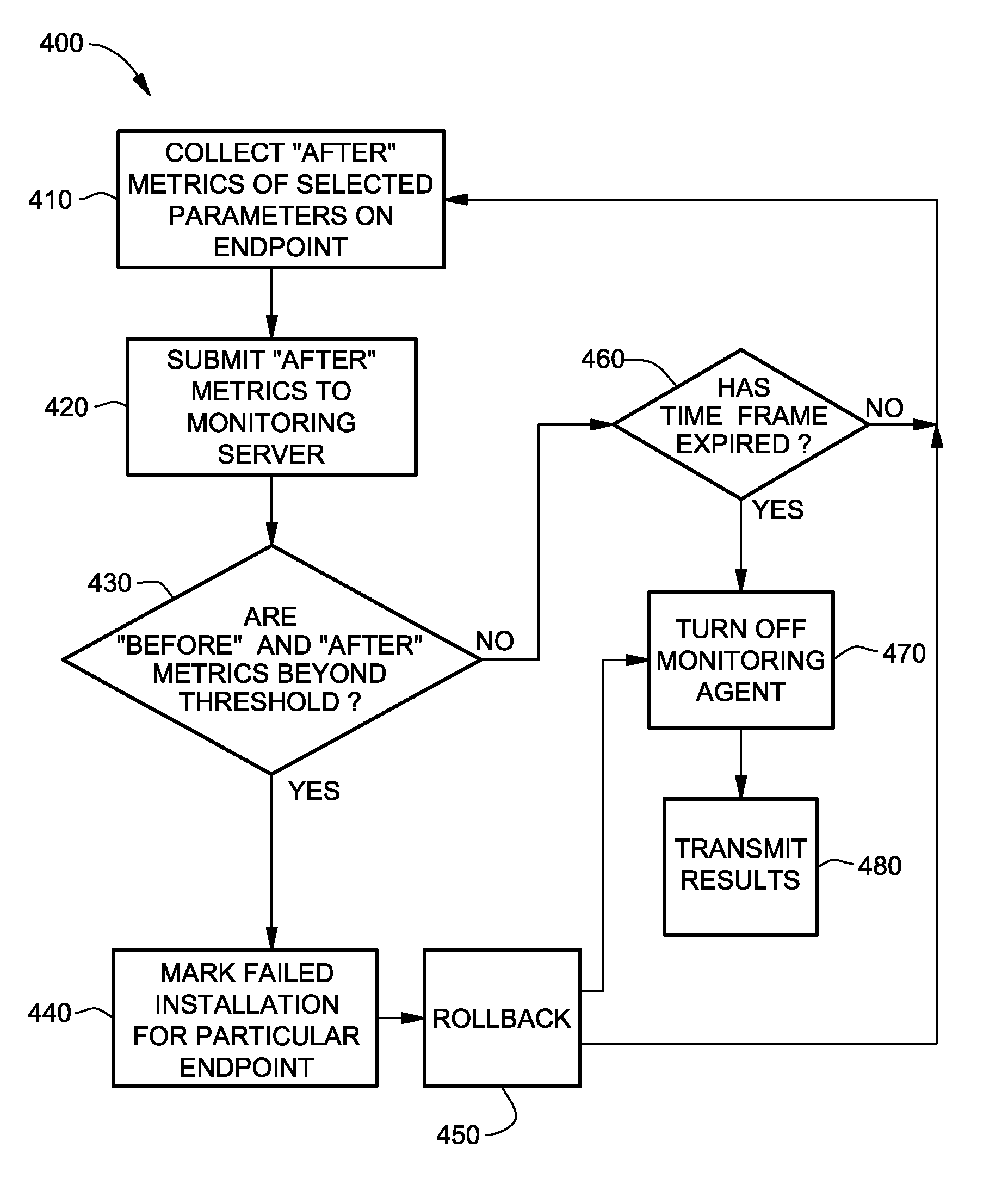
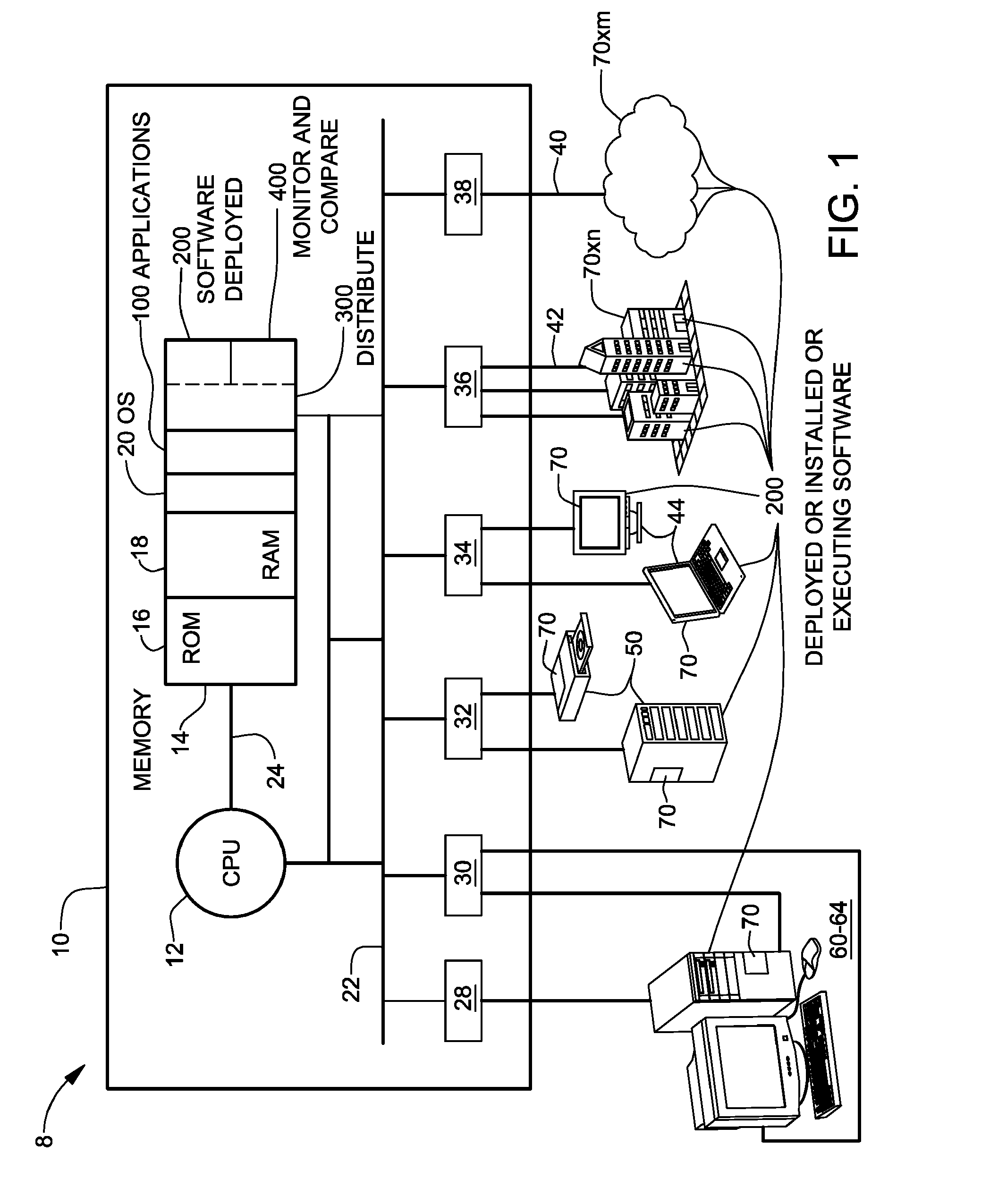
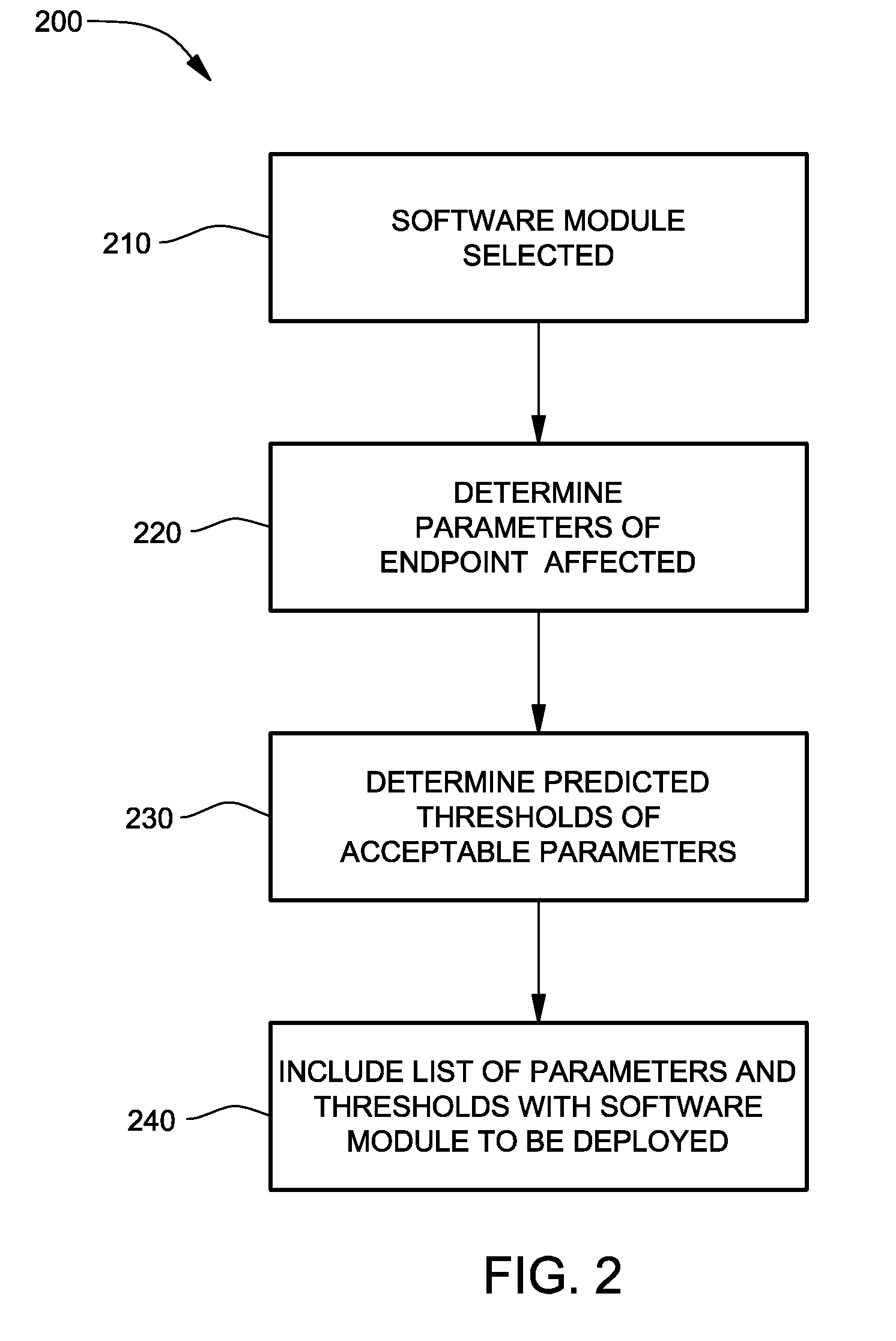
Verification of successful installation of computer software
A computerized method, program product, system, and service to verify installation of computer software onto an endpoint machine. The software to be installed is evaluated to determine what operating parameters of the endpoint machine may be affected by the software deployment, installation, and execution. Acceptable ranges of these operating parameters are included with the list of potentially affected parameters, distributed with the software module or sent as a separate script. Metrics are collected during the software installation, e.g., before deployment, after deployment but before installation, after installation, during execution, etc. How and when these operating parameters are monitored can be programmable. If and when the operating parameters extend beyond the acceptable ranges, a message that the software was not successfully installed is generated. The endpoint machine can be rolled back to a prior configuration.
Owner:KYNDRYL INC
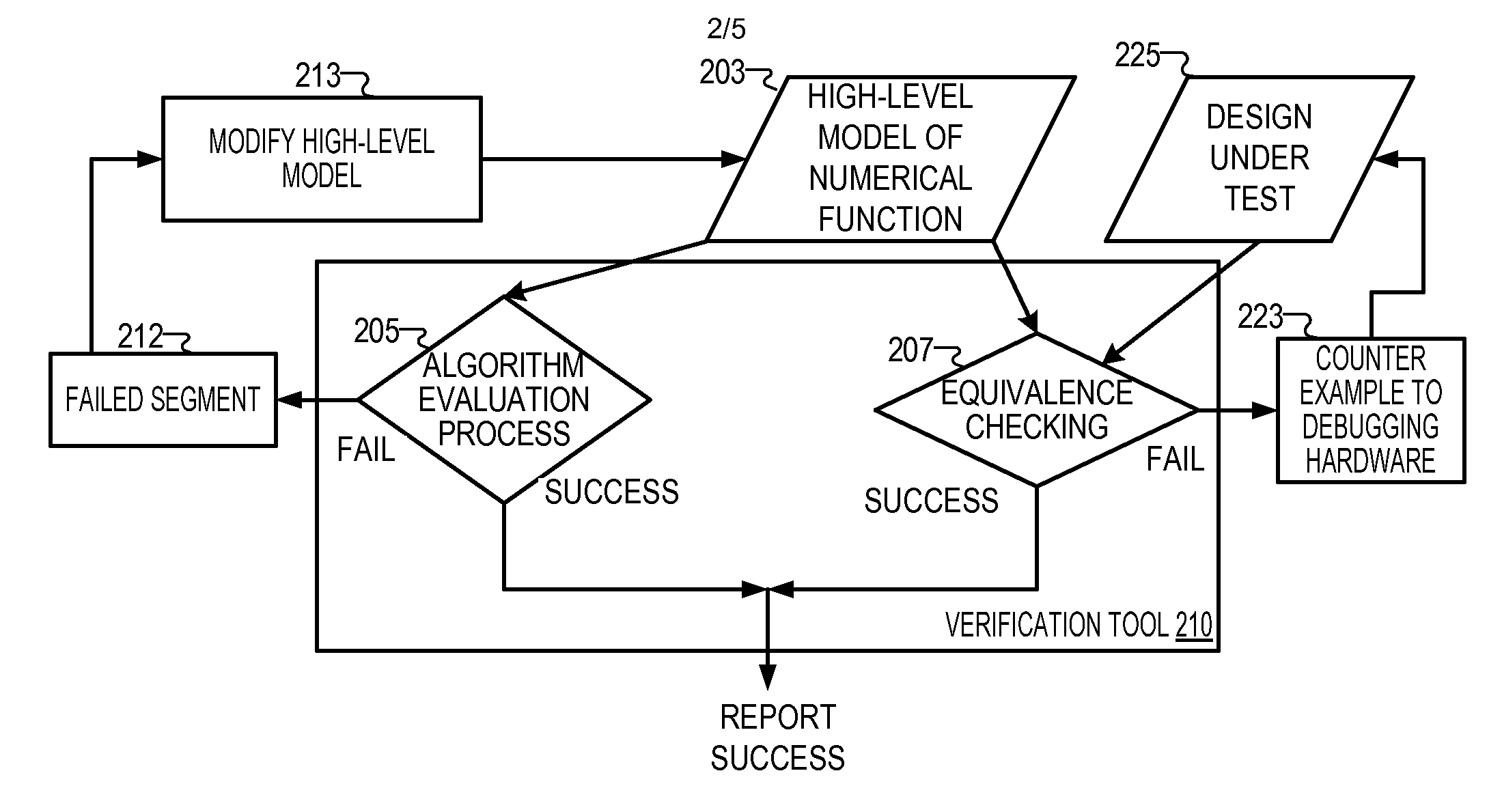
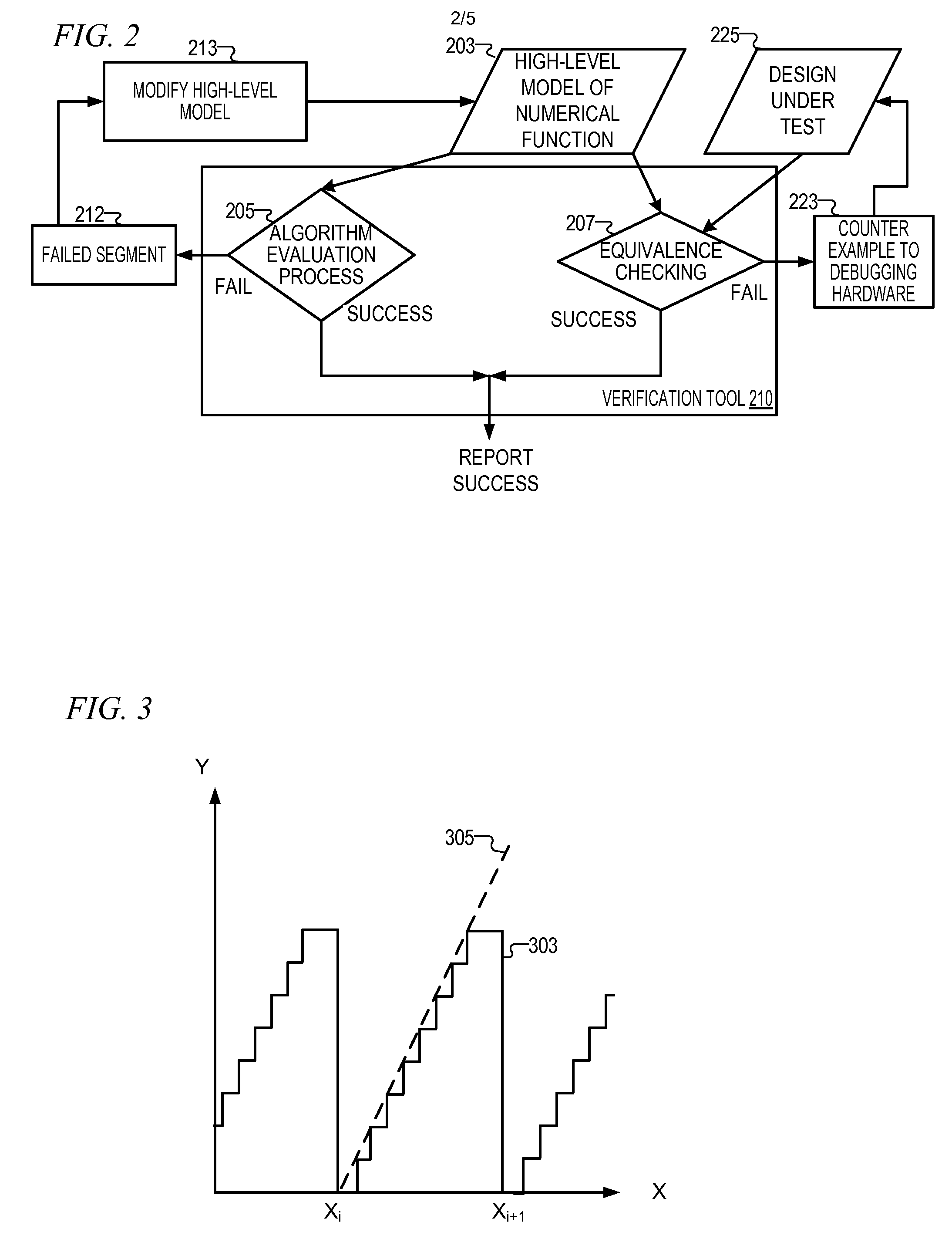
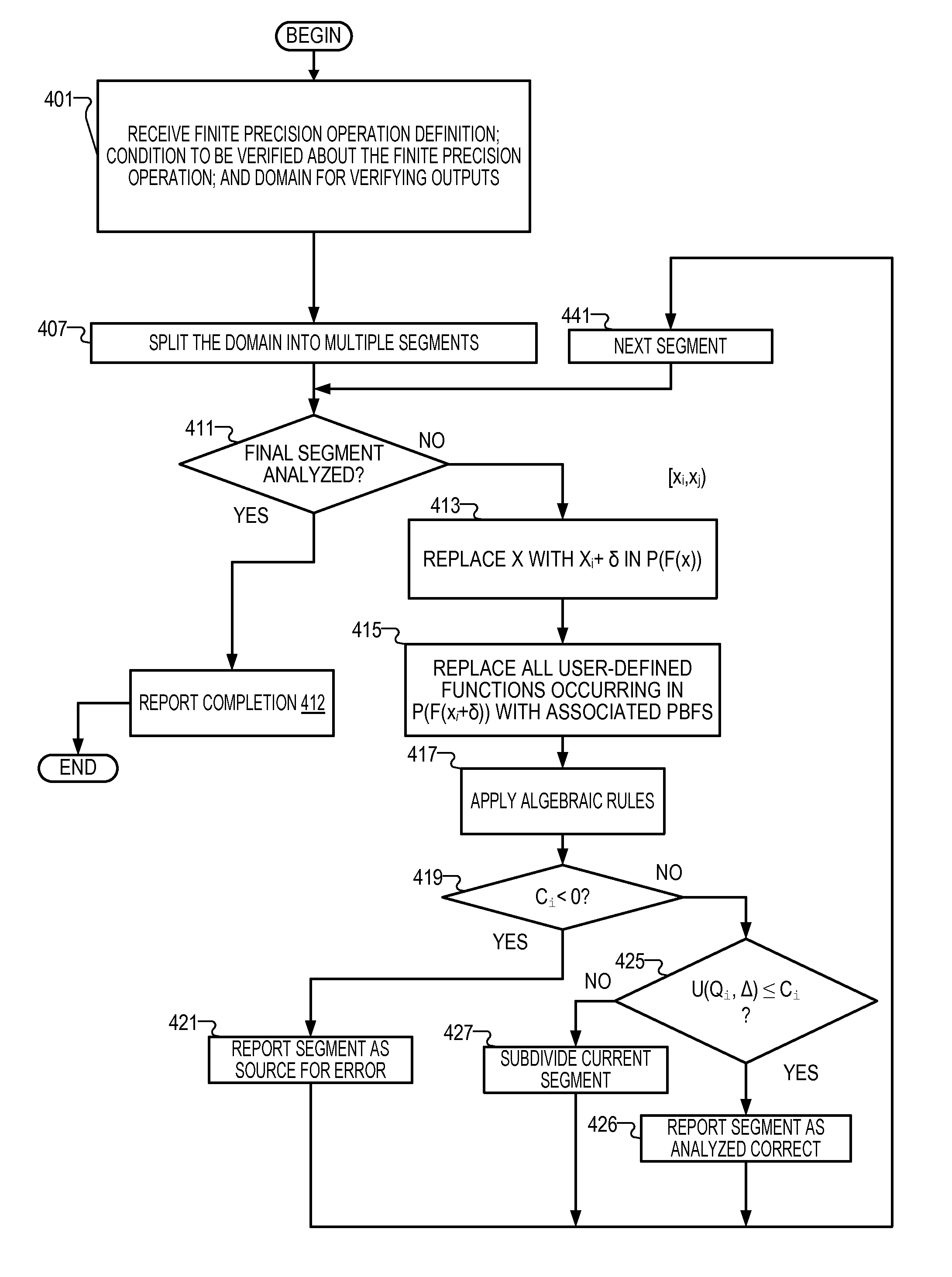
Verifying the error bound of numerical computation implemented in computer systems
InactiveUS20110264990A1Fault responseDetecting faulty computer hardwareTheoretical computer scienceA domain
A verification tool receives a finite precision definition for an approximation of an infinite precision numerical function implemented in a processor in the form of a polynomial of bounded functions. The verification tool receives a domain for verifying outputs of segments associated with the infinite precision numerical function. The verification tool splits the domain into at least two segments, wherein each segment is non-overlapping with any other segment and converts, for each segment, a polynomial of bounded functions for the segment to a simplified formula comprising a polynomial, an inequality, and a constant for a selected segment. The verification tool calculates upper bounds of the polynomial for the at least two segments, beginning with the selected segment and reports the segments that violate a bounding condition.
Owner:IBM CORP
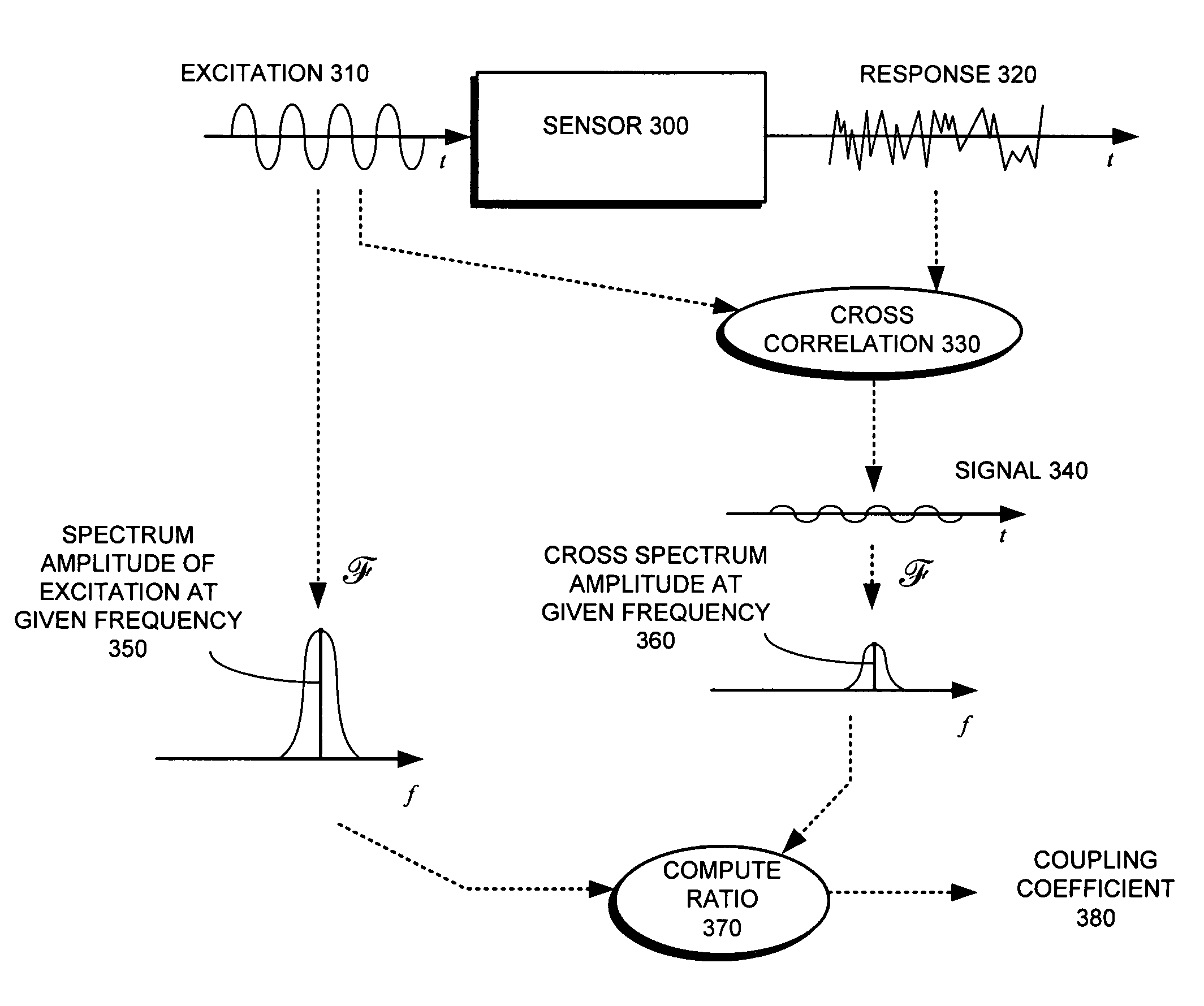
Method and apparatus for validating sensor operability in a computer system
One embodiment of the present invention provides a system that validates sensor operability in a computer system. During operation, the system perturbs the computer system with an excitation, wherein the excitation may be physical or software-based. The system then receives a number of responses to the excitation through sensors in the computer system, wherein each response is represented as a value of a variable which may vary with time. Next, the system compares the received responses with a set of reference responses gathered from properly functioning sensors in a reference computer system. The system then determines from the comparison whether the sensors in the computer system are operating properly.
Owner:ORACLE INT CORP
System and method of cryptographically provable zero knowledge social networking
ActiveUS20180019873A1Strong privacy guaranteeZero knowledge assuranceCryptography processingUser identity/authority verificationInternet privacyProtocol for Carrying Authentication for Network Access
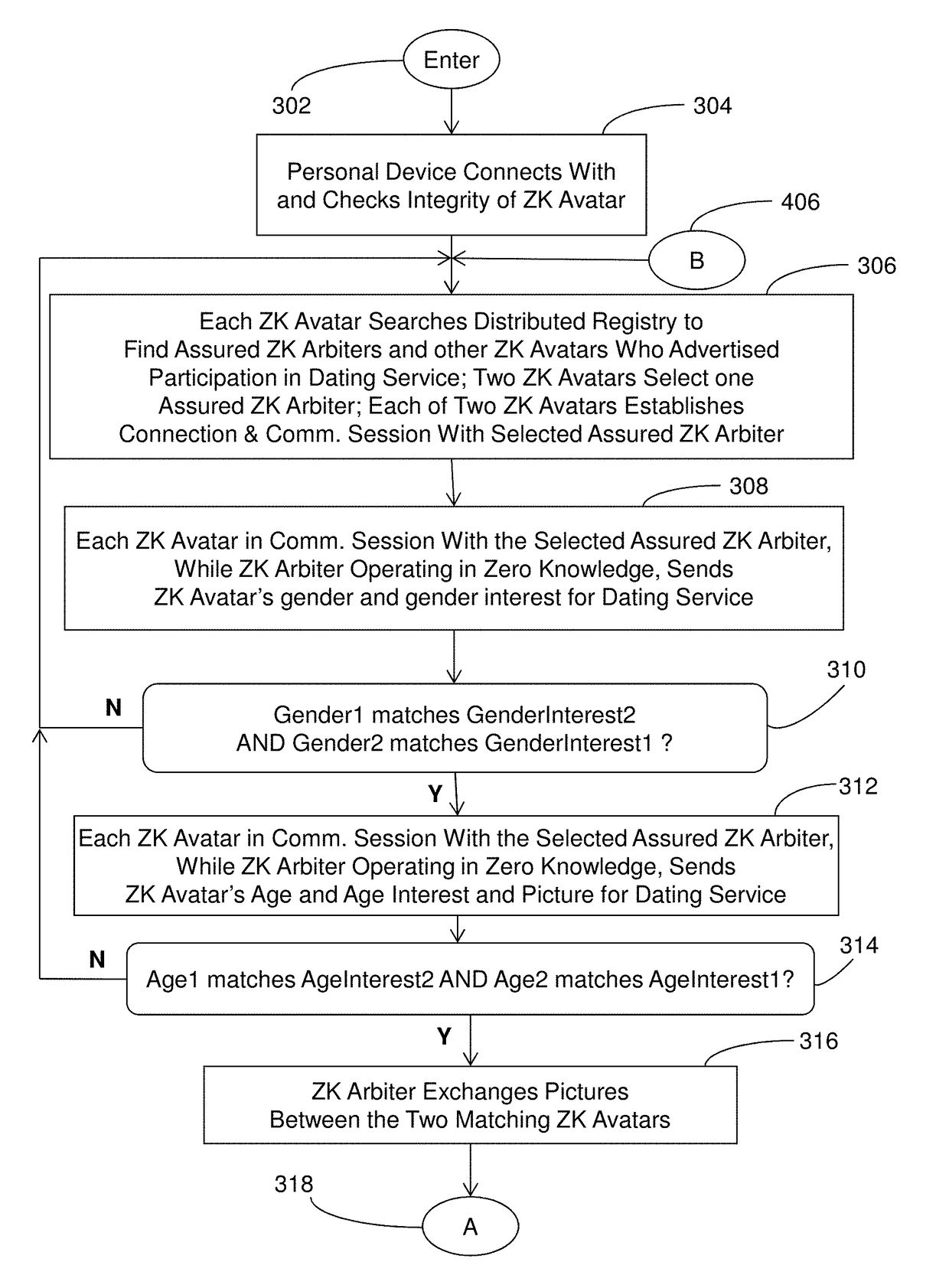
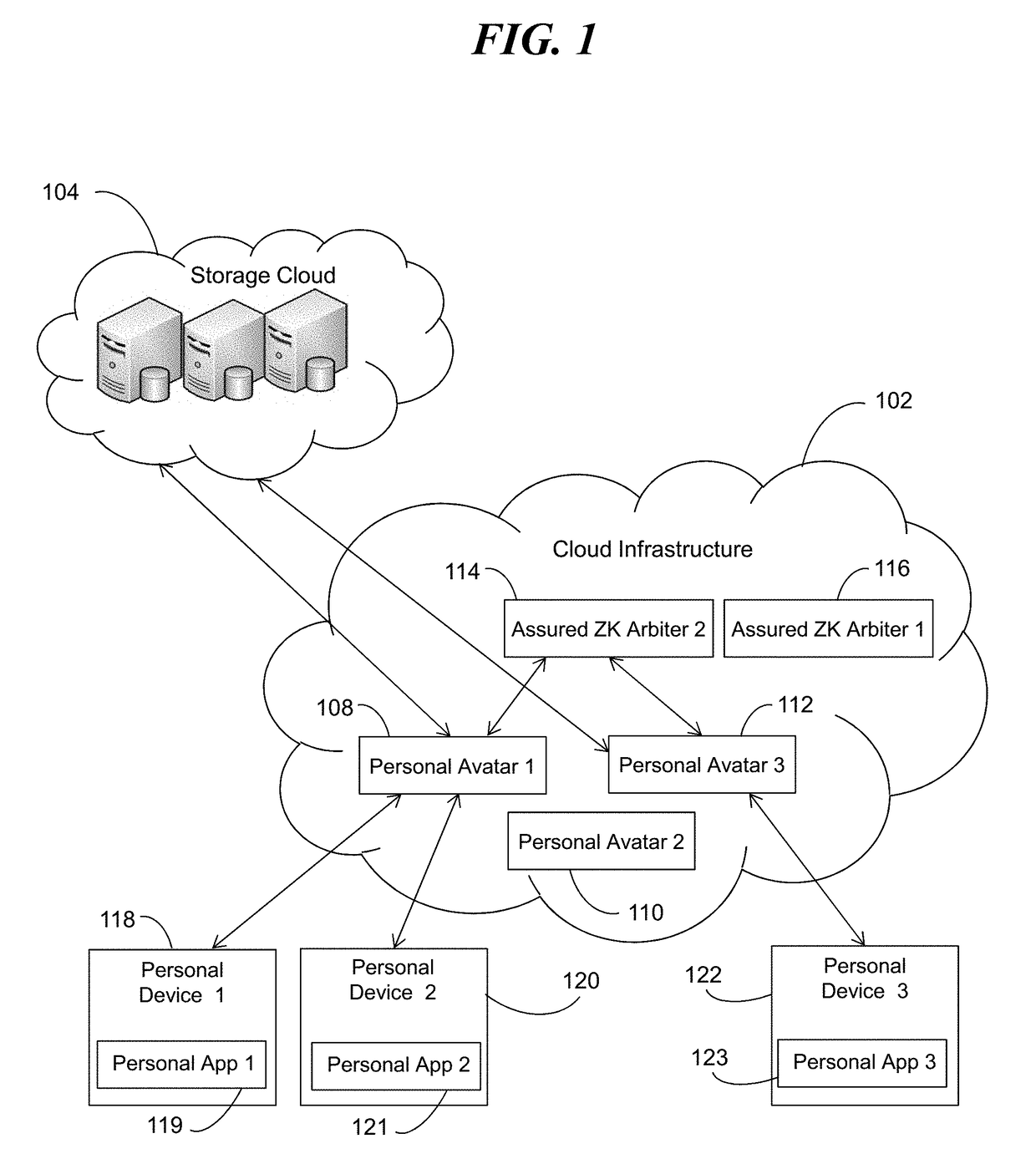
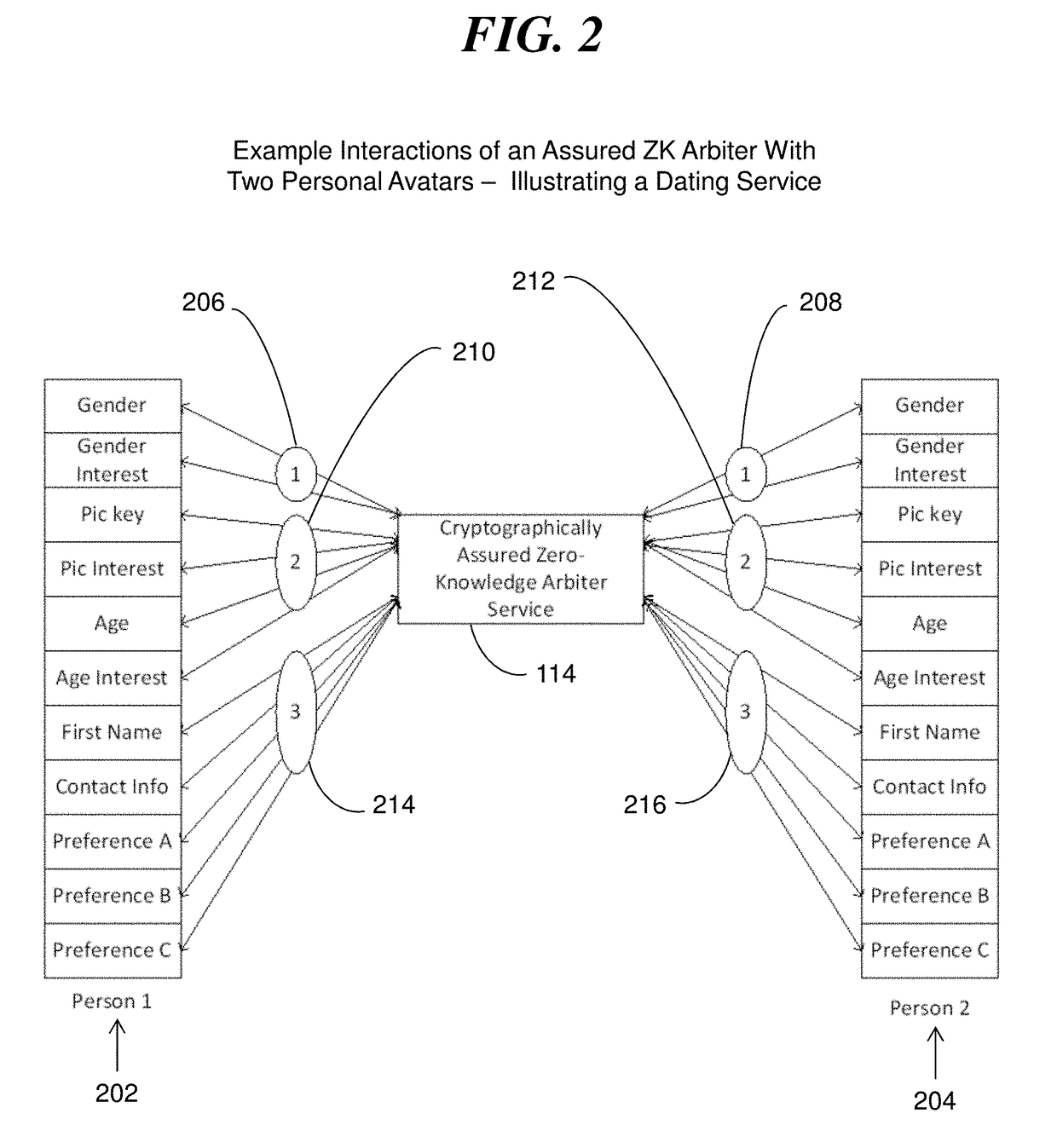
A social networking system, computer program product, and methods with a Personal Avatar executing on a first server node and a zero knowledge Arbiter executing on a second server node in a network of the social networking system. The Personal Avatar communicates social networking system messages in a communication session using a zero knowledge protocol with the zero knowledge Arbiter executing on the second server node operating in zero knowledge and using zero knowledge verifiable computing to enforce usage conditions on social networking system messages communicated in a communication session with the zero knowledge Arbiter. The zero knowledge Personal Avatar communicates social networking system messages in a communication session using a zero knowledge protocol with the zero knowledge Arbiter. The methods ensure privacy of an end user of the social networking system.
Owner:IBM CORP
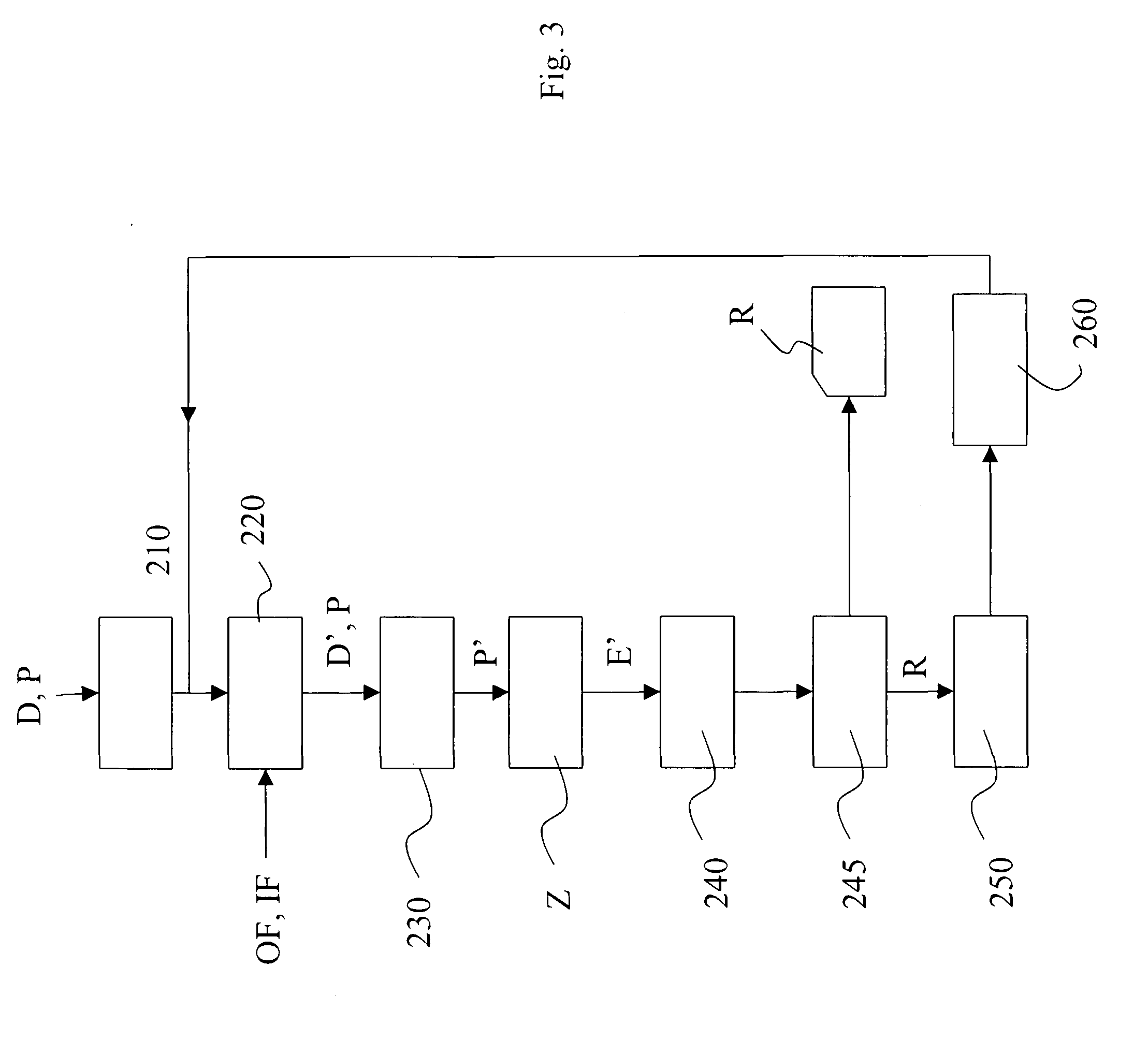
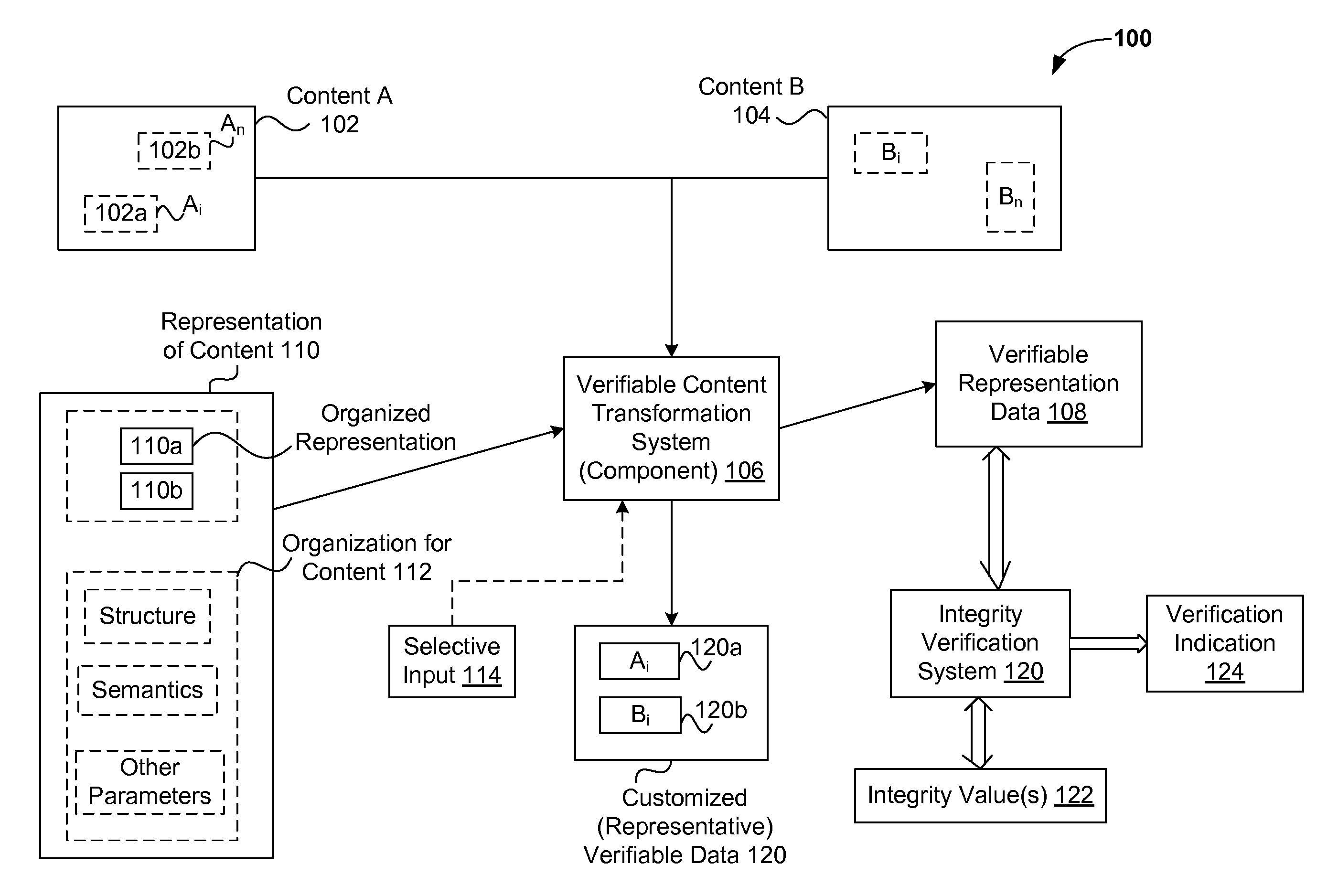
Process for verifying computer codes and corresponding verification system
ActiveUS20100281466A1Increase independenceError detection/correctionSpecific program execution arrangementsIdentifying VariableTheoretical computer science
A process for detecting errors in computer code in C / C++ language in a computer, which comprises the operations of:—making available in said computer a source computer program (P) containing computer codes in C / C++ language; compiling (Z) said source computer program (P) to obtain an executable program (E); and—executing (240) said executable program (E) to generate (245) an error report (R). According to the invention, said method comprises, prior to the operation of compilation (Z): executing an operation of syntactic analysis (AS) to identify variables (x) having a structure of vector or pointer; modifying said source computer program (P) via the application to said identified variables (x) of a test function (f ( . . . ); io_sper; io_sper2; io_sper3; io_sper4) that is able to veriCy, during the operation of execution, whether an index (y) supplied for said variable x is valid.
Owner:REMOLLINO ANTONIO
Verification of integrity of computing environments for safe computing
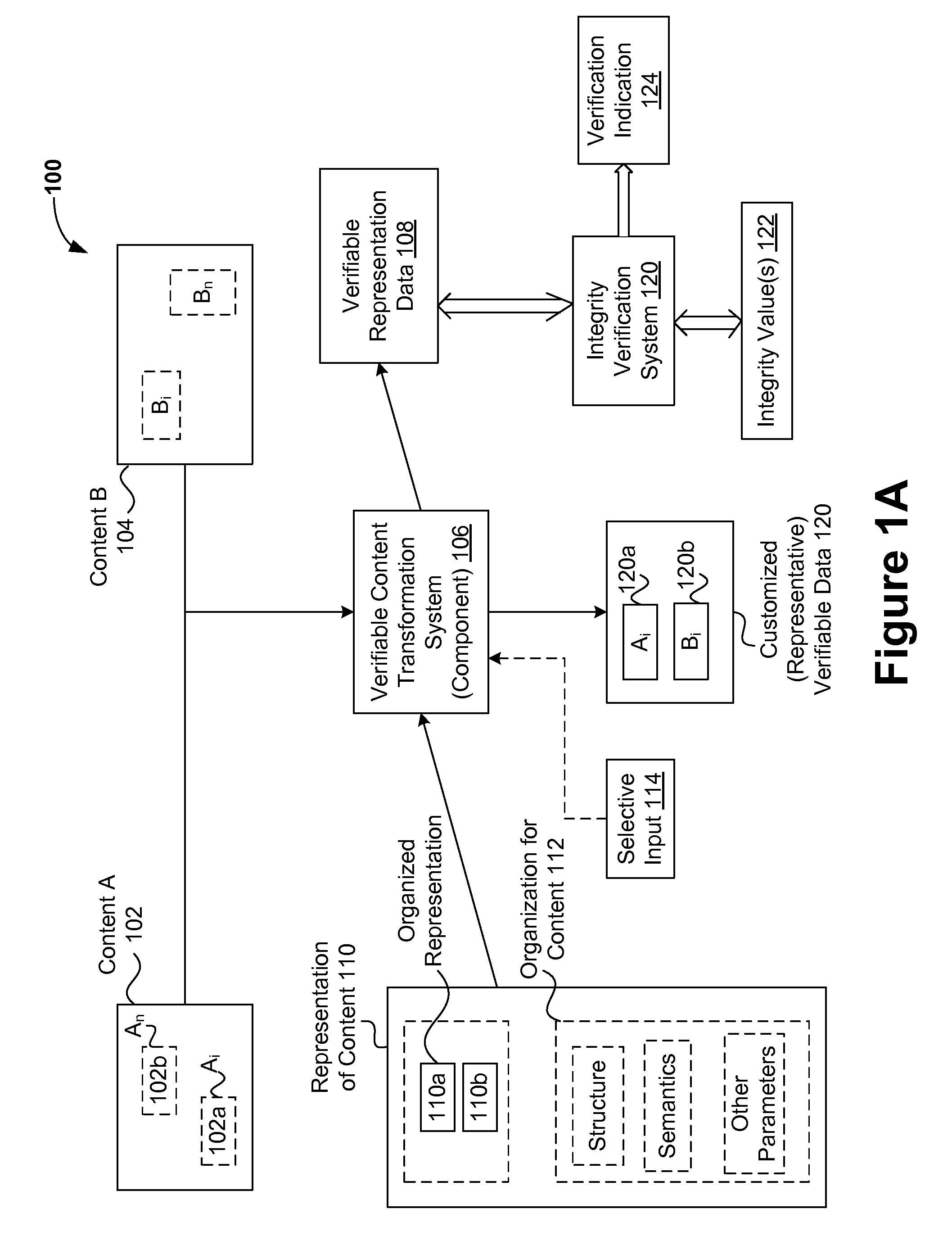
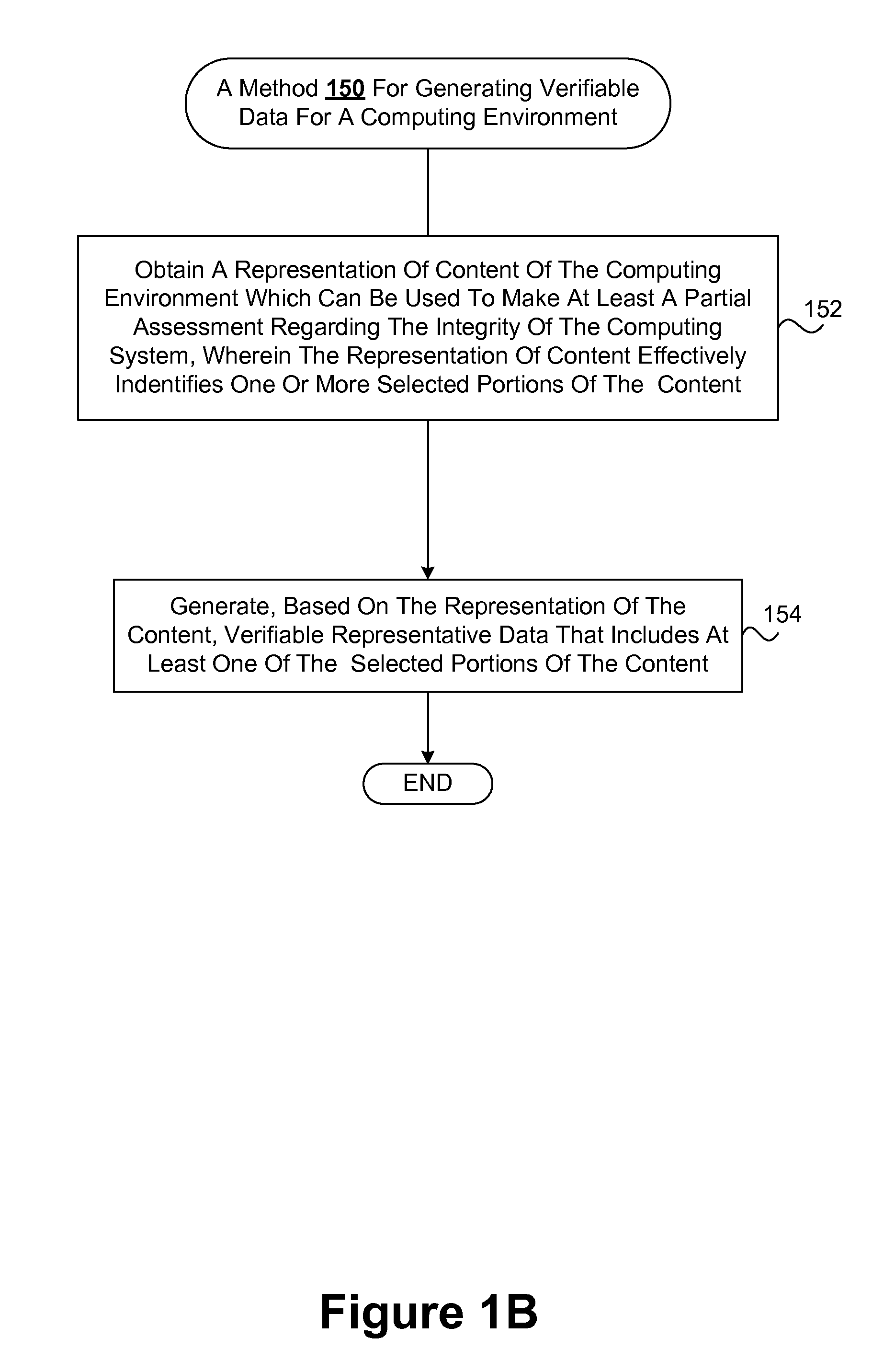
InactiveUS20090300049A1Reduce contentVerify integrityPlatform integrity maintainanceSpecial data processing applicationsXML schemaStructured content
Improved verification techniques for verification of the integrity of various computing environments and / or computing systems are disclosed. Verifiable representative data can effectively represent verifiable content of a computing environment, thereby allowing the integrity of the computing environment to be verified based on the verifiable representative data instead of the content being represented. Verifiable representative data can effectively include selected portions of the content (e.g., selected content which may be of general and / or specific security interest) and can be generally smaller than the verifiable content it represents. As such, it may generally be more efficient to use the verifiable representative data instead of the content it represents. Verifiable representative data can also be organized. By way of example, unstructured content (e.g., a configuration file written in text) can be effectively transformed based on a scheme (e.g., an XML schema) into a structured text-based content written in a structured language (e.g., XML). Verifiable organized representative data can be organized in accordance with various organizational aspects including, for example, structural, semantics, parameter verification, parameter simplification, and other organizational rules and / or preferences. Organization of verifiable organized representative data can be verified as an additional measure of its integrity, and by in large the integrity of a computing environment and / or system being effectively represented by the verifiable representative data.
Owner:SAMSUNG ELECTRONICS CO LTD
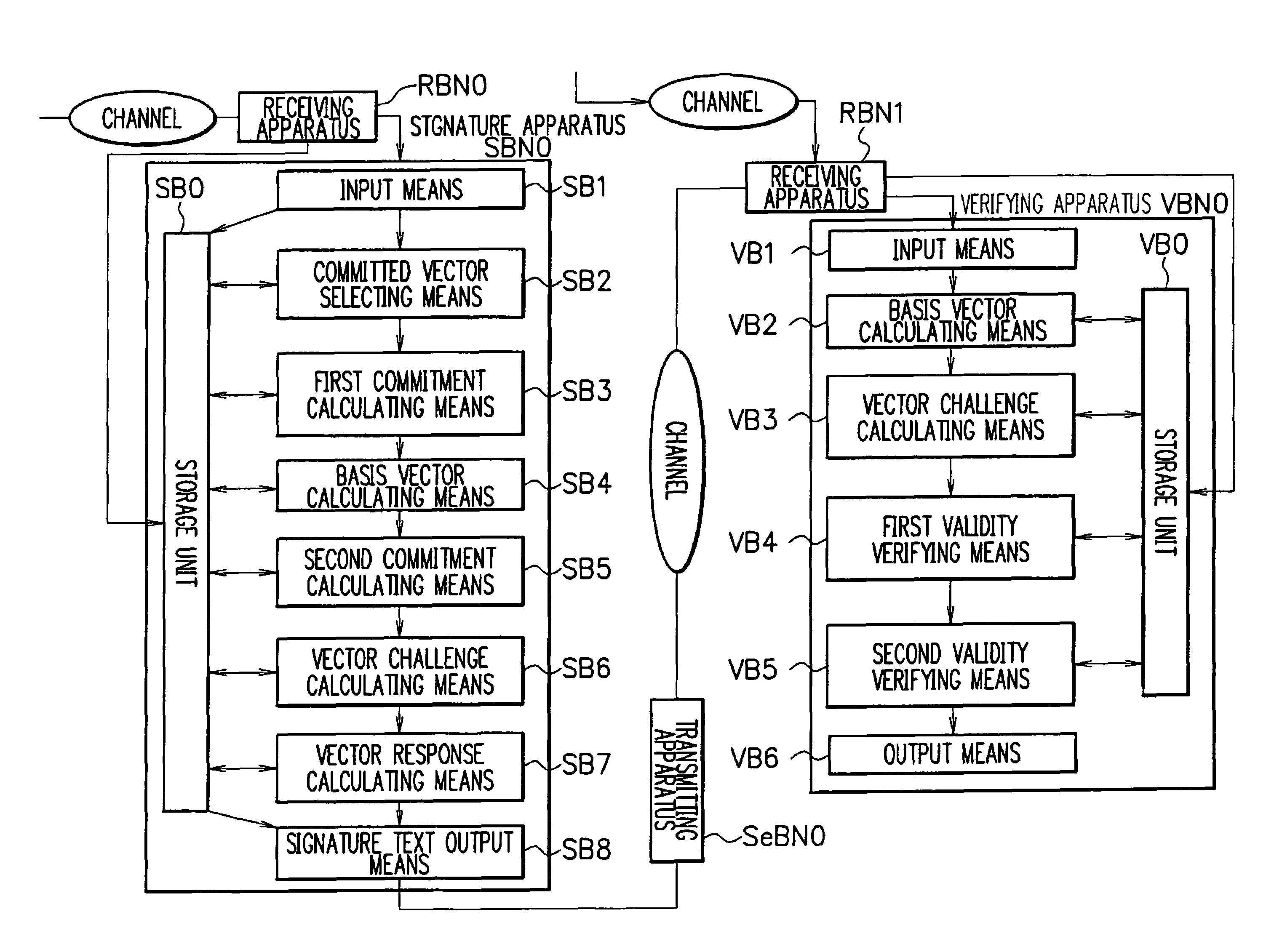
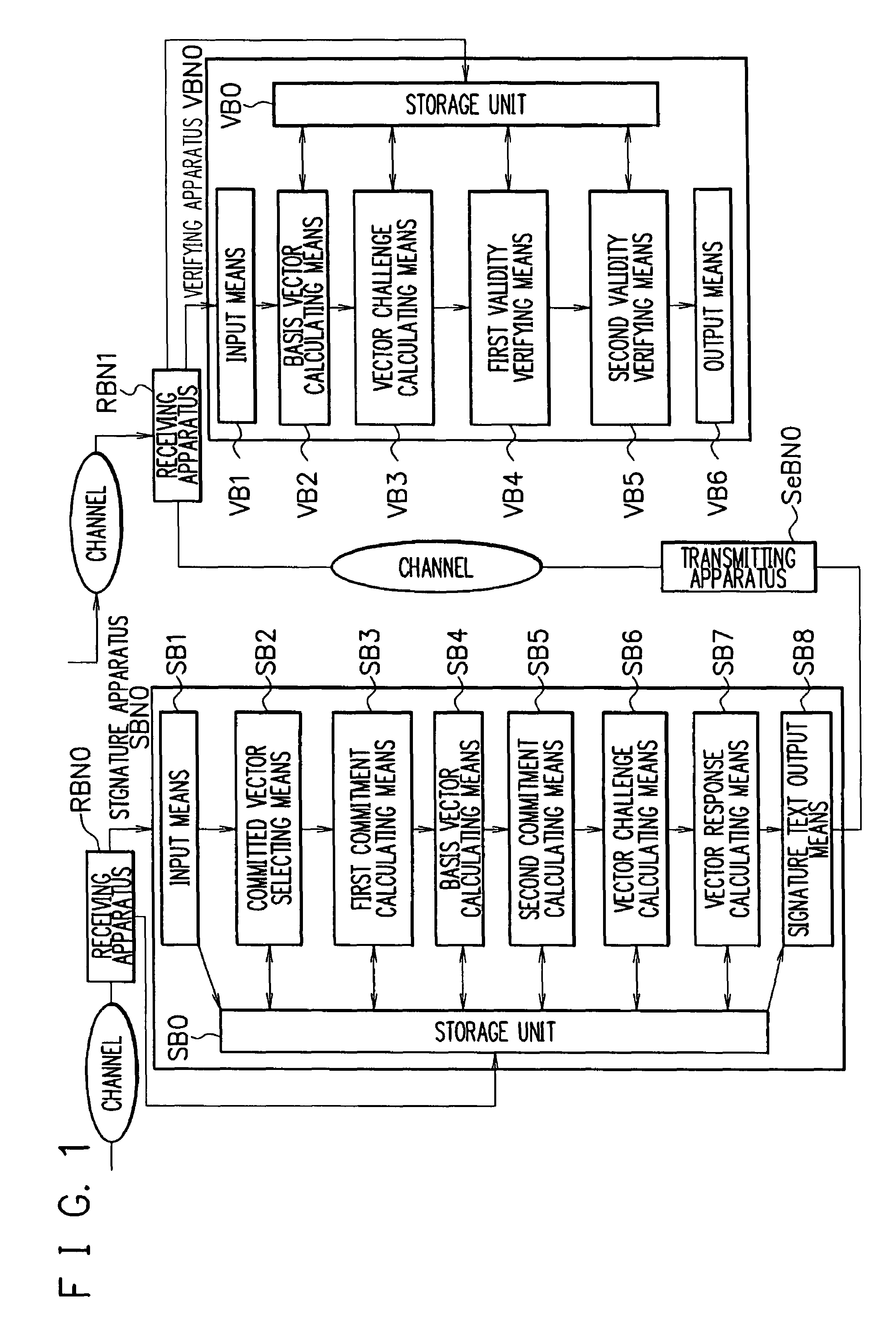
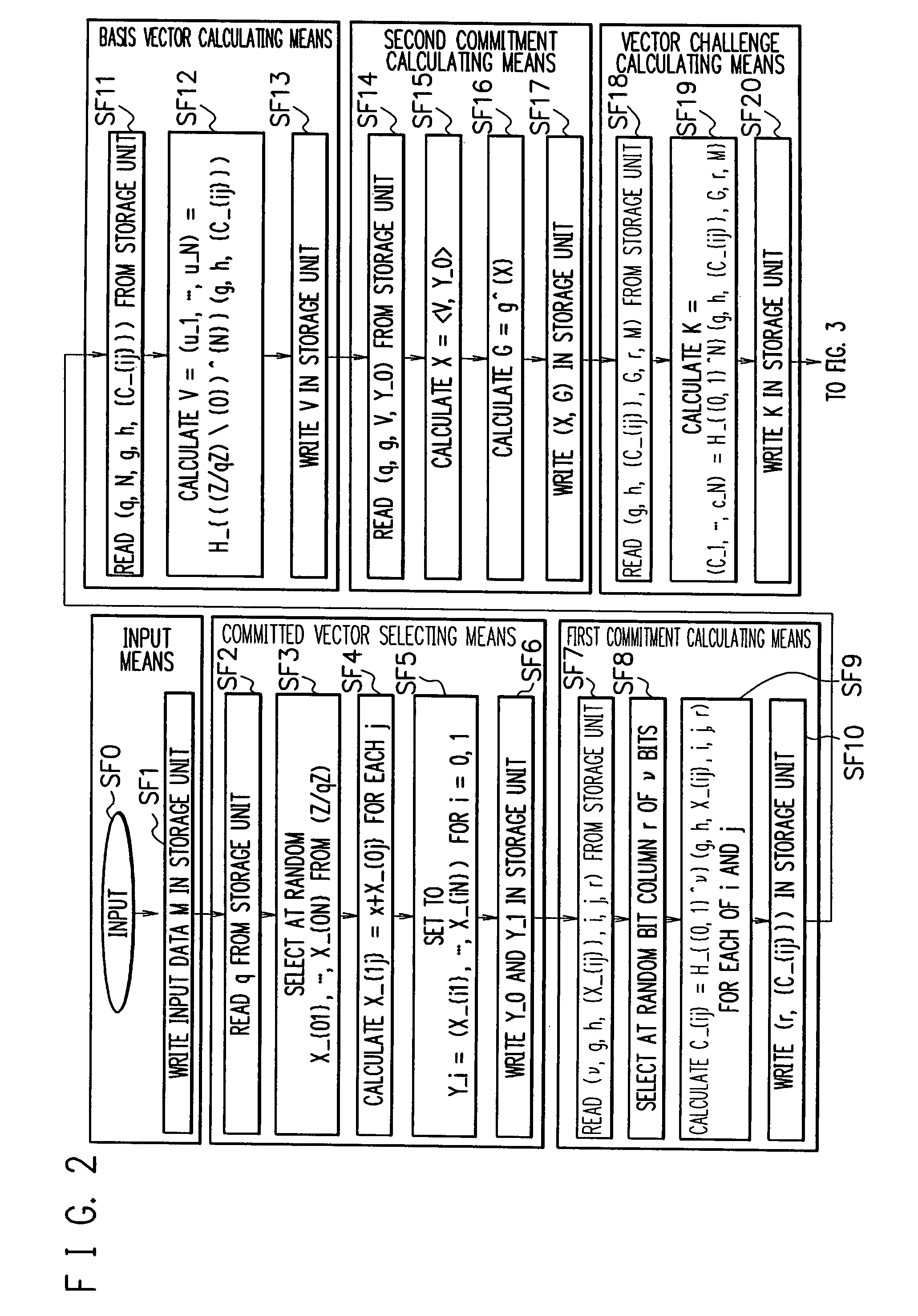
Signature apparatus, verifying apparatus, proving apparatus, encrypting apparatus, and decrypting apparatus
InactiveUS8028171B2Reduce the amount requiredImprove securityUser identity/authority verificationSecret communicationDiscrete logarithmSchnorr signature
Owner:NEC CORP
Secured computing
ActiveUS20200136797A1Public key for secure communicationCommunication with homomorphic encryptionProcessing coreAlgorithm
According to an example aspect of the present invention, there is provided an apparatus comprising at least one processing core, at least one memory including computer program code, the at least one memory and the computer program code configured to cause the apparatus to receive an identifier of a function, encrypted input data, an encrypted computation result, encrypted random data and an encrypted output of the function, when nm with the random data, obtain a homomorphic polynomial factorization of the function, comprising obtaining a decomposed representation of the function, the representation comprising a sum of polynomials, and verify that the computation result is correct by checking, whether a difference between the encrypted output and the encrypted computation result equals a value of the decomposed representation, wherein the encrypted random data and the encrypted input data are used as parameter values in the sum of polynomials.
Owner:NOKIA TECHNOLOGLES OY
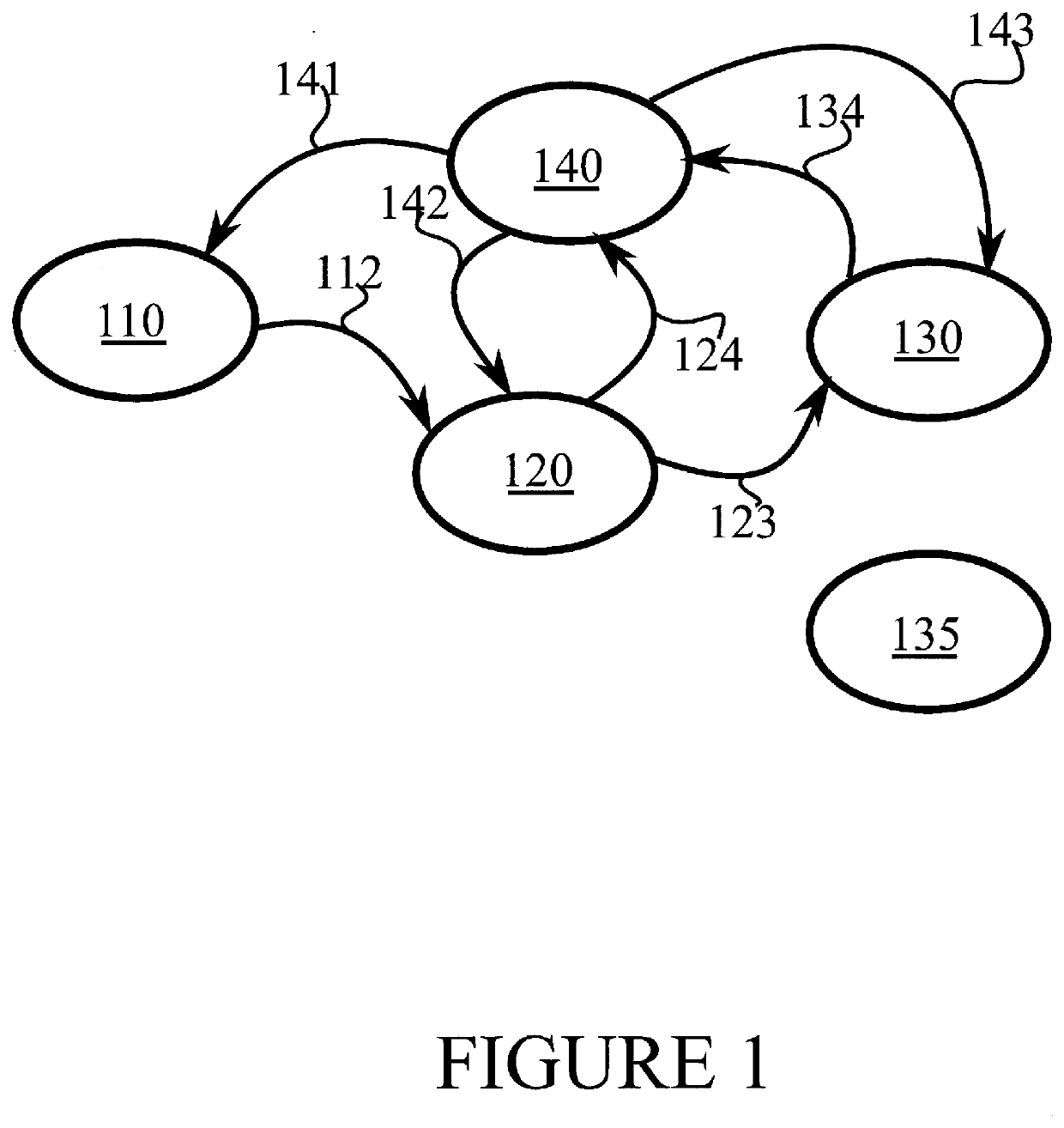
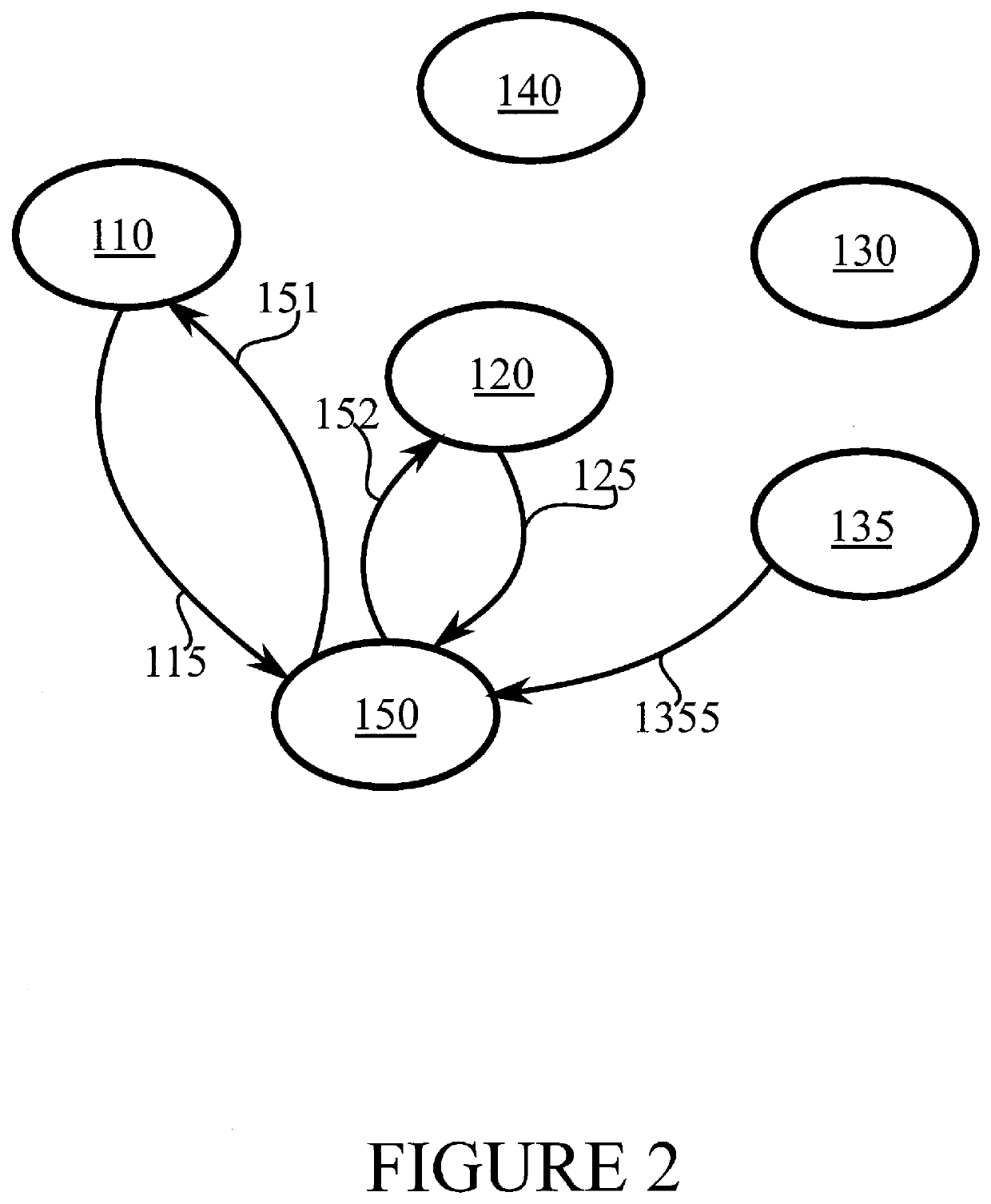
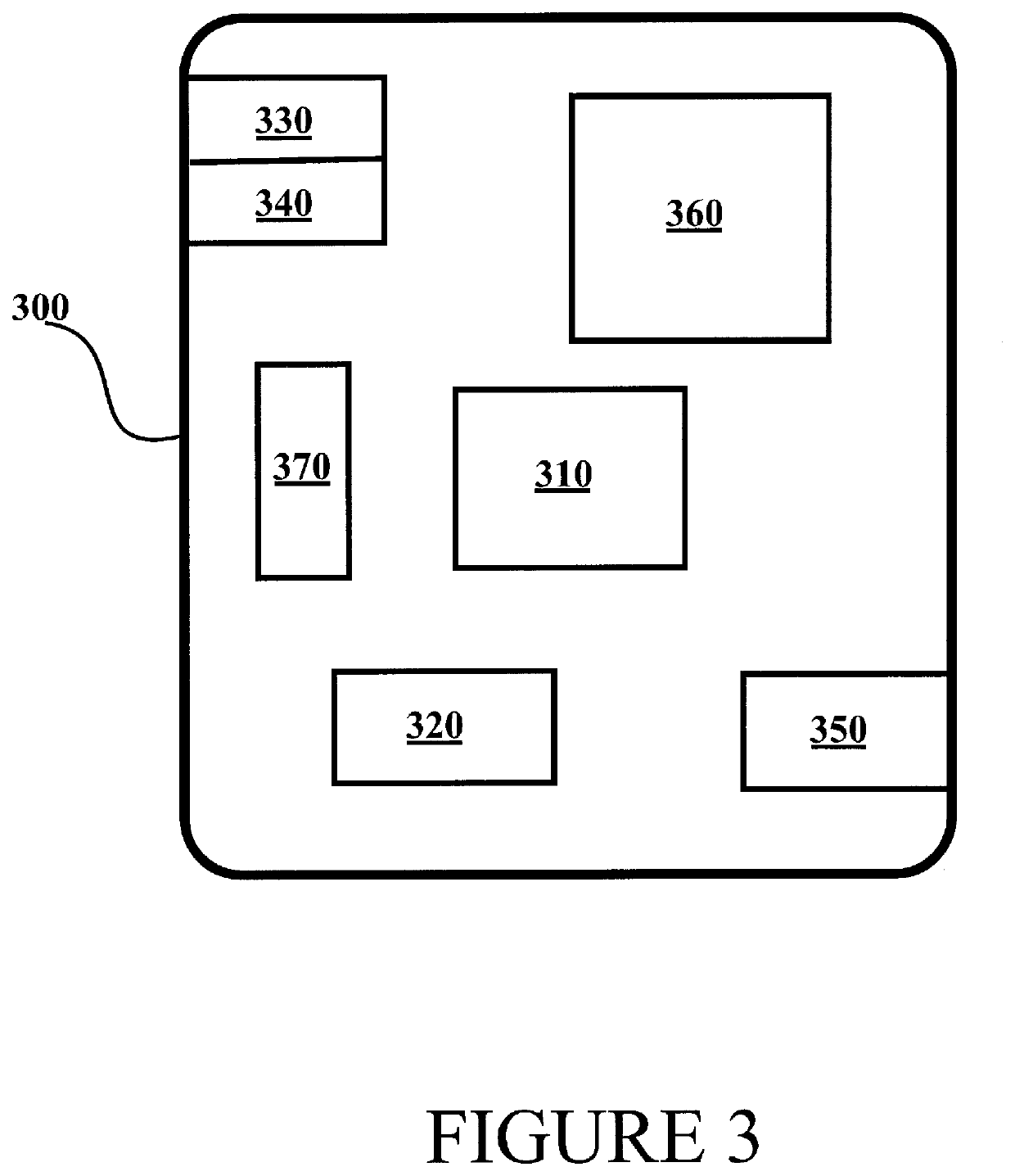
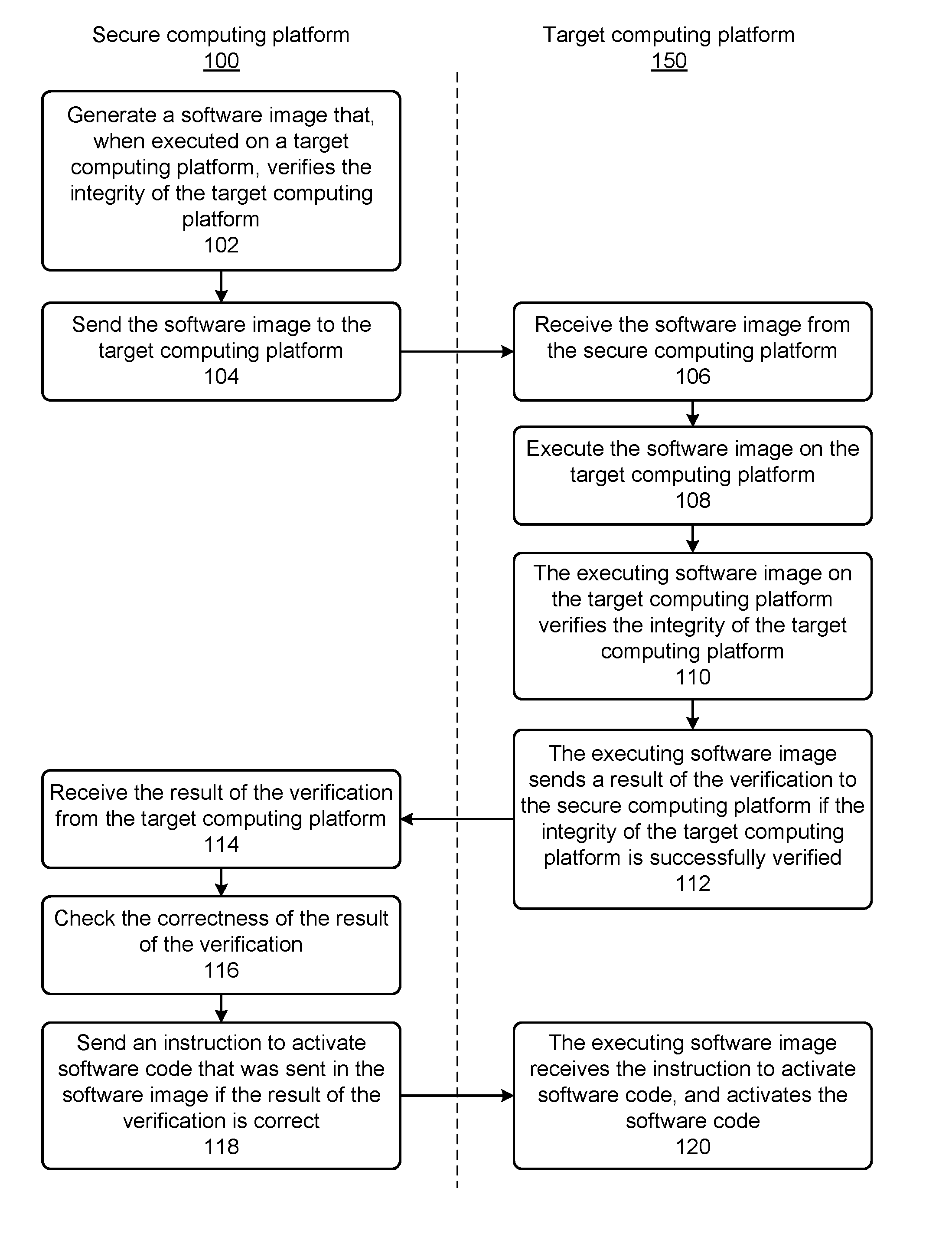
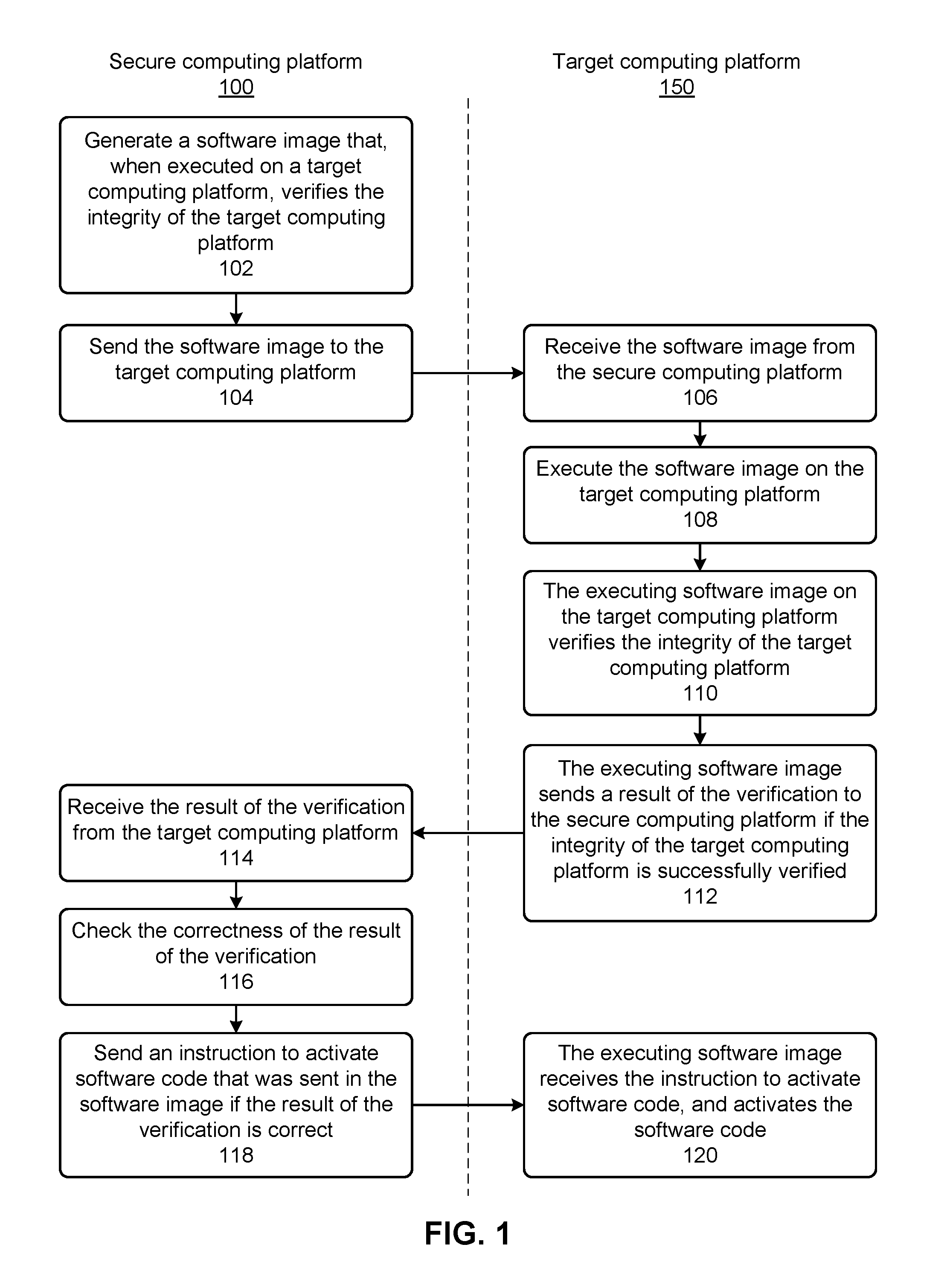
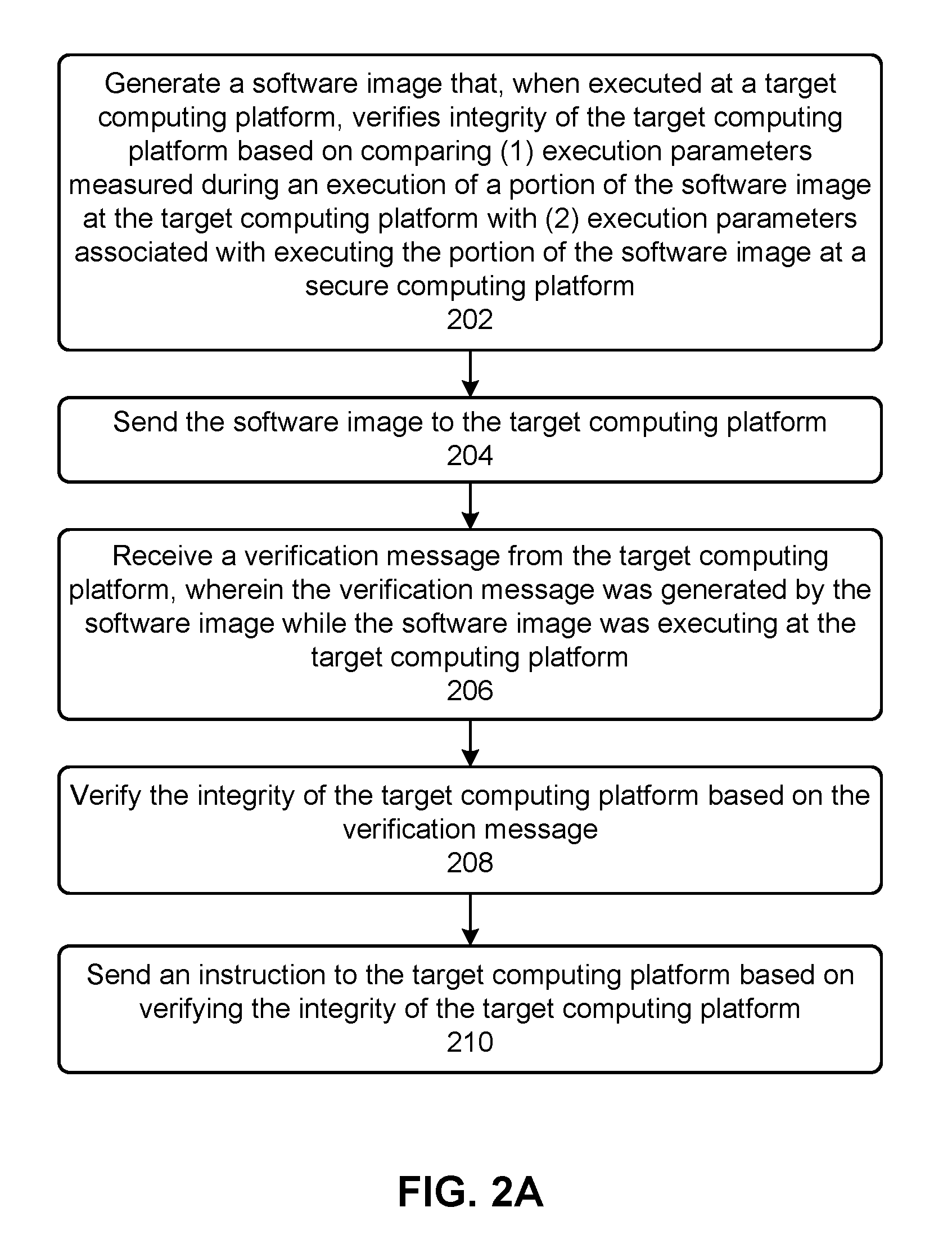
Verifying the integrity of a computing platform
Systems and techniques are described for verifying the integrity of a computing platform. Specifically, a software image can be generated that, when executed at a computing platform, verifies integrity of the computing platform. Next, the software image can be sent to the computing platform. The computing platform can execute the software image, thereby enabling the verification of the integrity of the computing platform.
Owner:HAMLIN CHRISTOPHER LUIS
Identity verification
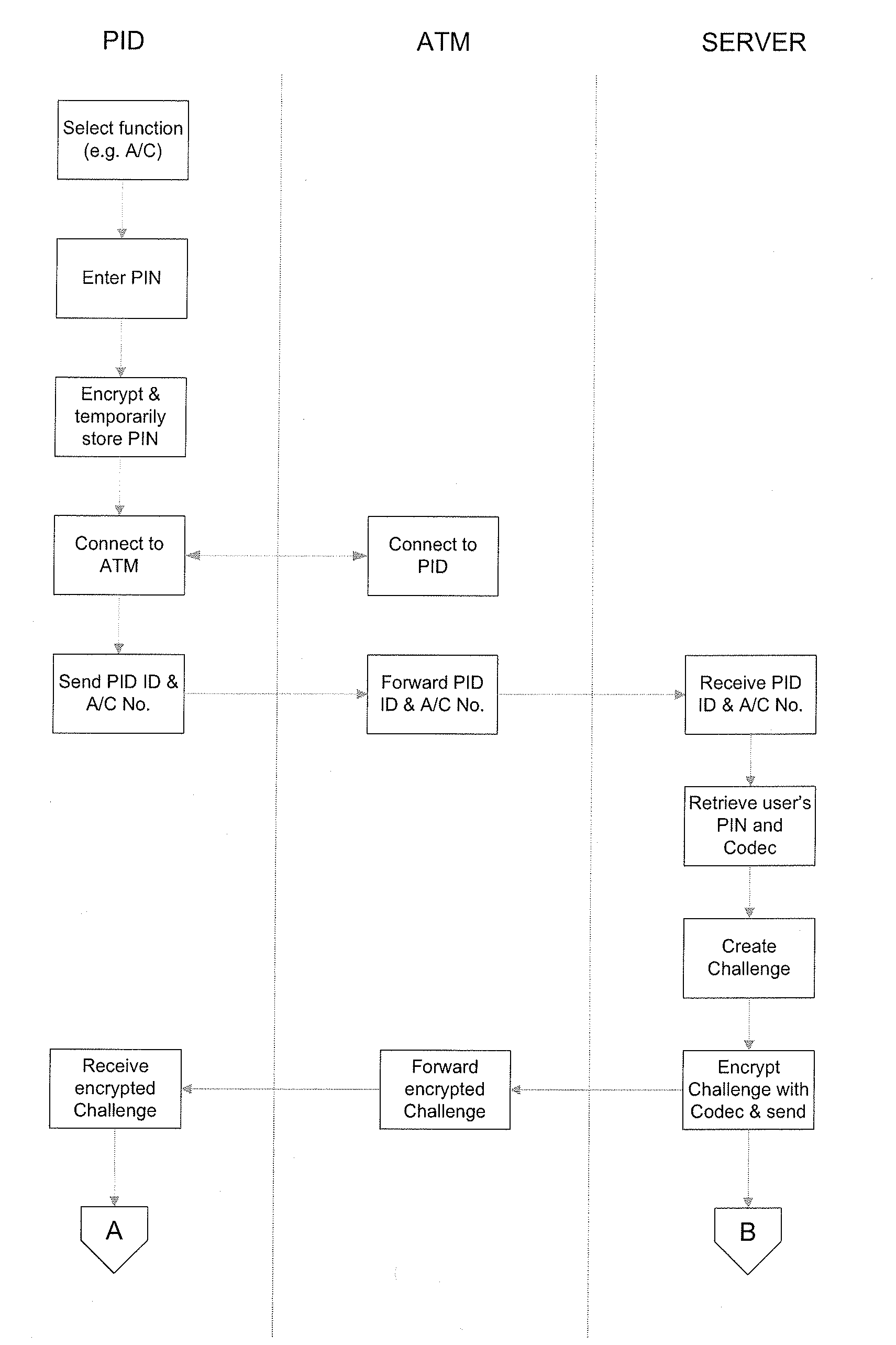
InactiveUS20090287937A1Avoid spreadingAcutation objectsUser identity/authority verificationPasswordUser input
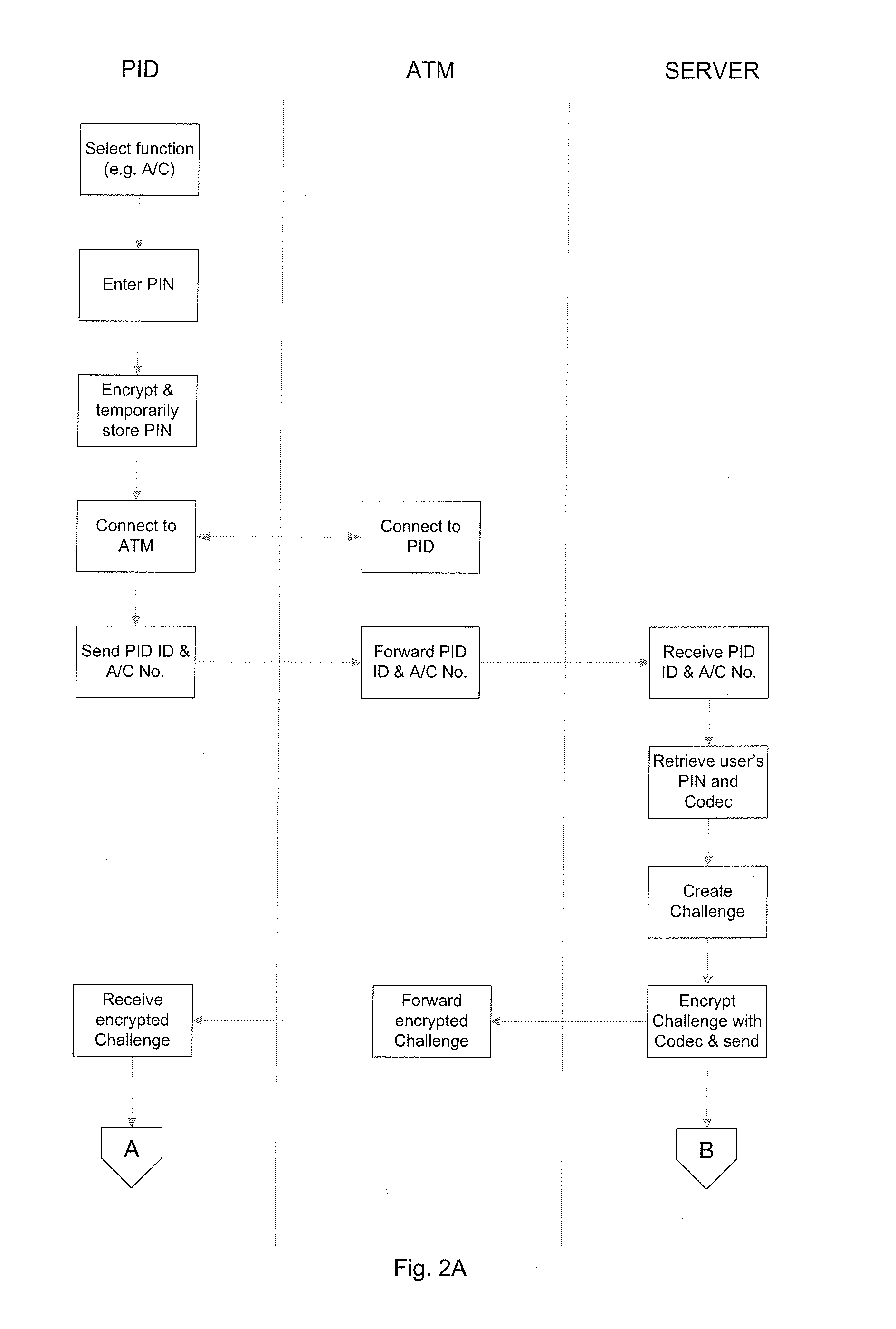
The invention provides a method for verifying the identity of an entity to a computerised system. The entity is in possession of a personal identification device (PID) having a PID ID and storing a Codec that can be used to encode and decode data. The computerised system holds data associated with the entity including the PID ID of the entity's PID, the Codec and a password associated with and known to the entity. The method involves transmitting an encoded Challenge from the computerised system to the PID, calculating a Reply using the Challenge and the password entered by the user, and transmitting the Reply from the PID to the computerised system. The transmitted Reply is compared with a reply calculated by the computerised system and the identity of the entity is verified if the comparison determines that Replies are the same.
Owner:BURDEN ROBERT W
Peer-to-peer geolocation system
ActiveUS20170188197A1Ensure integrityMultiple keys/algorithms usagePublic key for secure communicationLocation sharingGeolocation
A method and apparatus for location sharing, consisting of sending a location report by a location determining device to a plurality of network enabled devices over a peer-to-peer network, the location determining device being associated with a first digital key pair. A first of the plurality of network enabled devices, associated with a second digital key pair, performs a validation computation on the location report and submits a validation computation result and the location report to a remainder of the plurality of network enabled devices for inclusion in a shared ledger. Including the location report creates commercially-valued credits associated with the public key of the second digital key pair recorded in the shared ledger. A transfer of commercially-valued credits from association with the first public key of the first digital key pair to the public key of the second digital key pair is also recorded in the shared ledger.
Owner:PHILIPS NORTH AMERICA LLC
Verifying the error bound of numerical computation implemented in computer systems
InactiveUS8397187B2Detecting faulty computer hardwareCode conversionTheoretical computer scienceA domain
A verification tool receives a finite precision definition for an approximation of an infinite precision numerical function implemented in a processor in the form of a polynomial of bounded functions. The verification tool receives a domain for verifying outputs of segments associated with the infinite precision numerical function. The verification tool splits the domain into at least two segments, wherein each segment is non-overlapping with any other segment and converts, for each segment, a polynomial of bounded functions for the segment to a simplified formula comprising a polynomial, an inequality, and a constant for a selected segment. The verification tool calculates upper bounds of the polynomial for the at least two segments, beginning with the selected segment and reports the segments that violate a bounding condition.
Owner:IBM CORP
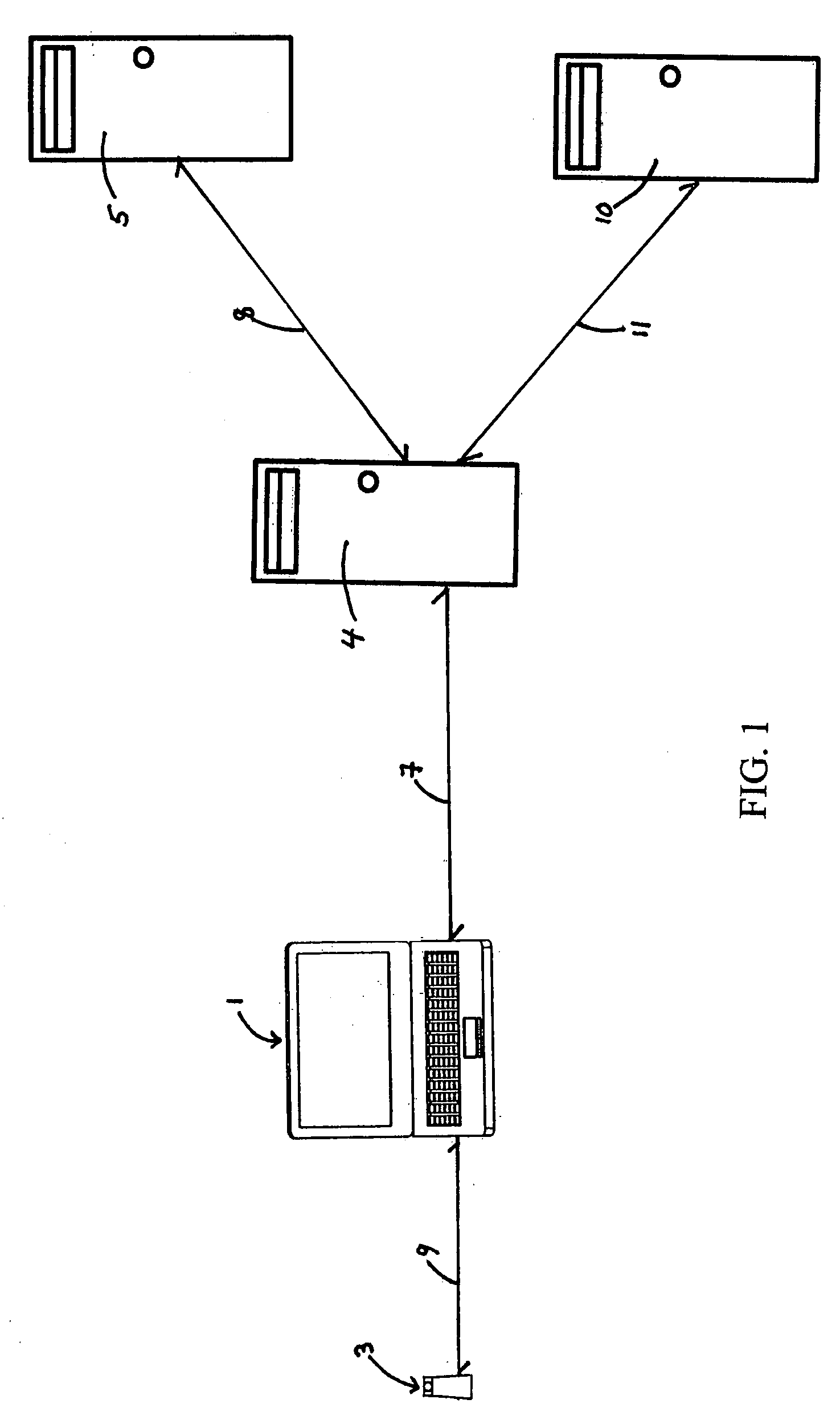
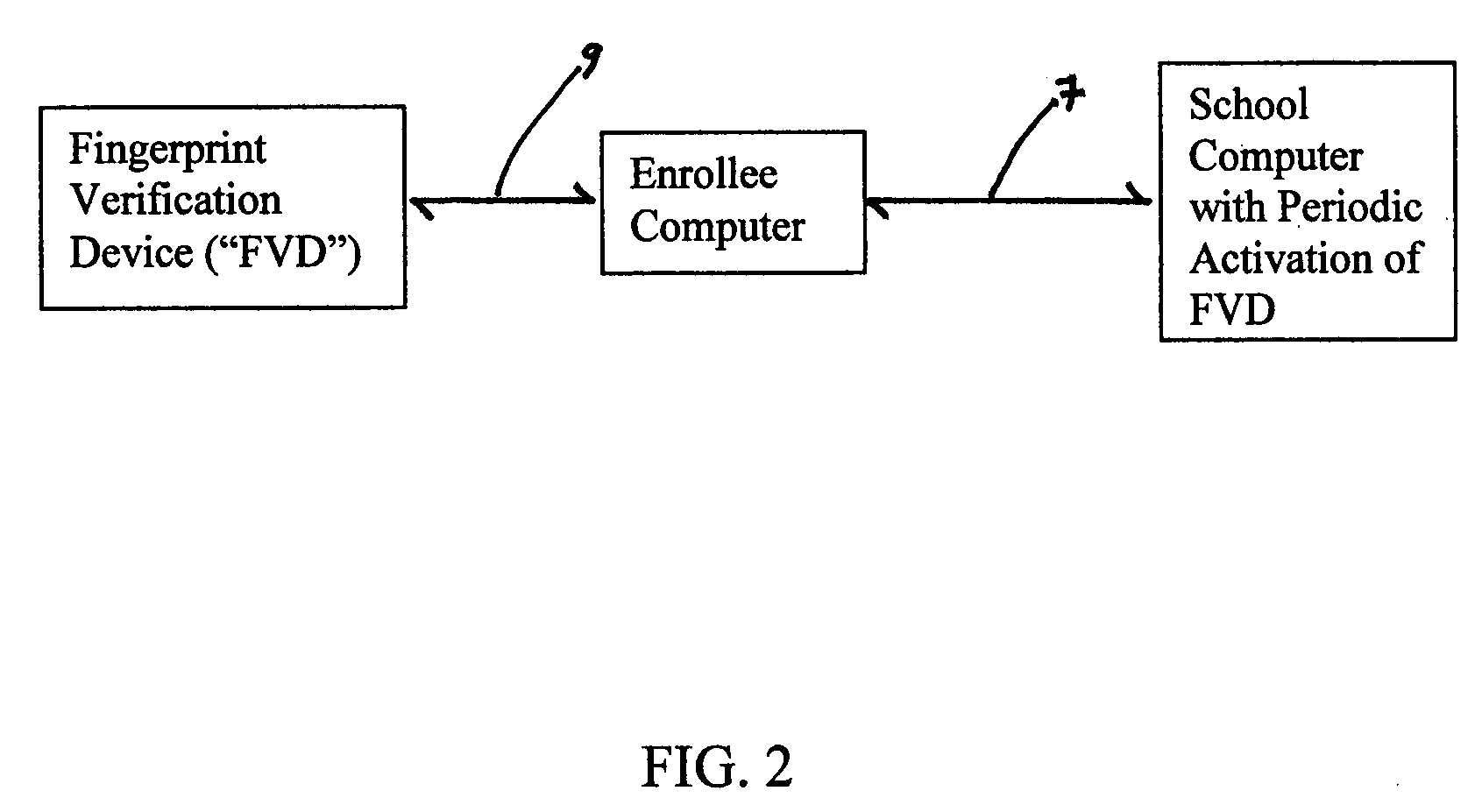
Fingerprint verification system for computerized course attendance and performance testing
InactiveUS20080285818A1Improve accessibilityCharacter and pattern recognitionElectrical appliancesVerification systemComputer science
This “Fingerprint Verification System for Computerized Course Attendance and Performance Testing”, relates to a new, useful, and significant means and method of verifying the identity of a computerized or computer-based course enrollee, and verifying said enrollee's attendance throughout the computer-based course, and the enrollee's identity during test taking throughout the course. Such a computer-based course may be online or off-line, but in both sets of embodiments, fingerprint identification of the enrollee is required, and at times, periodic, random, or a combination thereof, specifically designed to reliably verify the identity of the enrollee, and to overcome counter-measures an enrollee may attempt to enter a false positive fingerprint identification.
Owner:WARREN HARDY
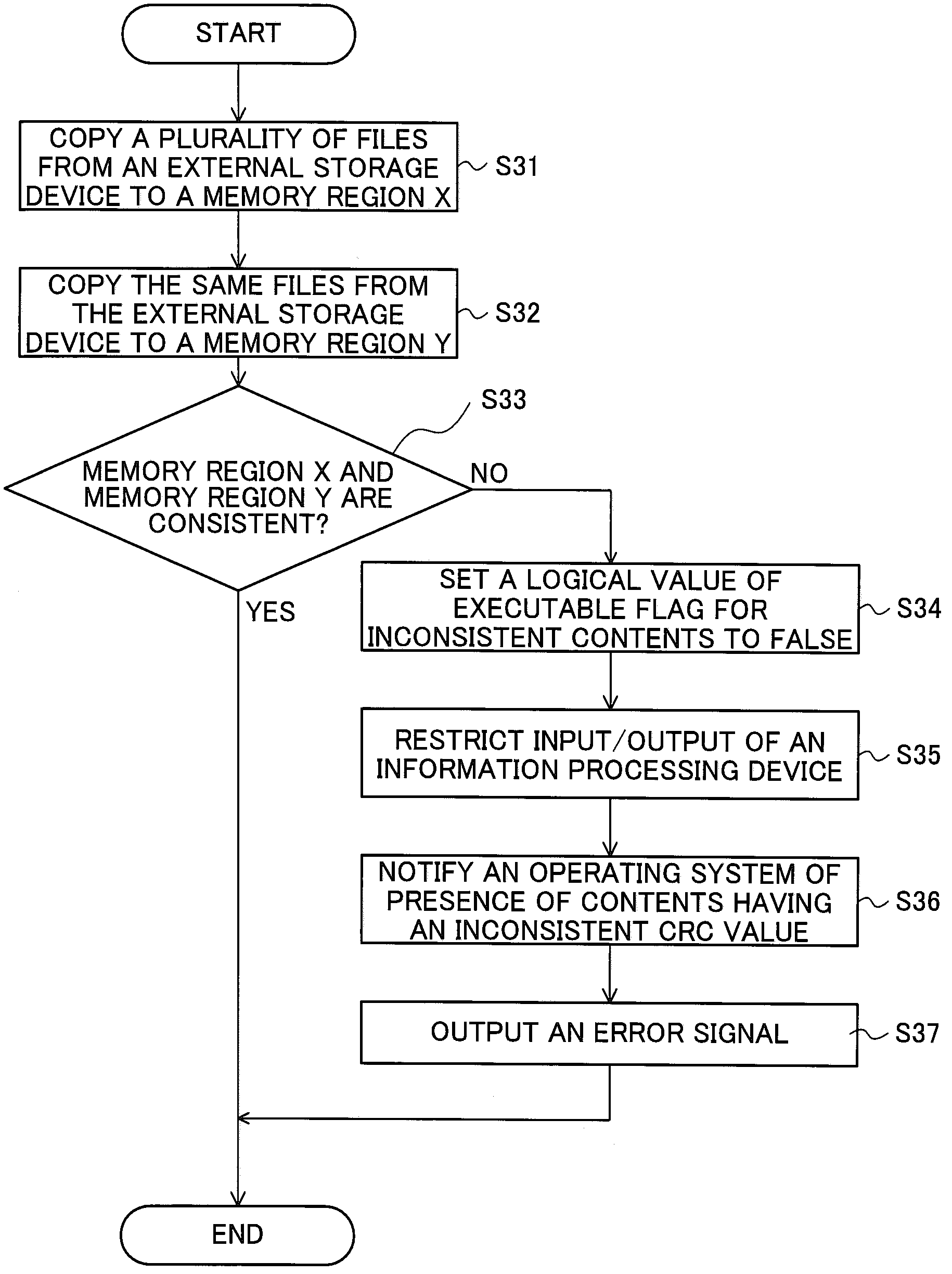
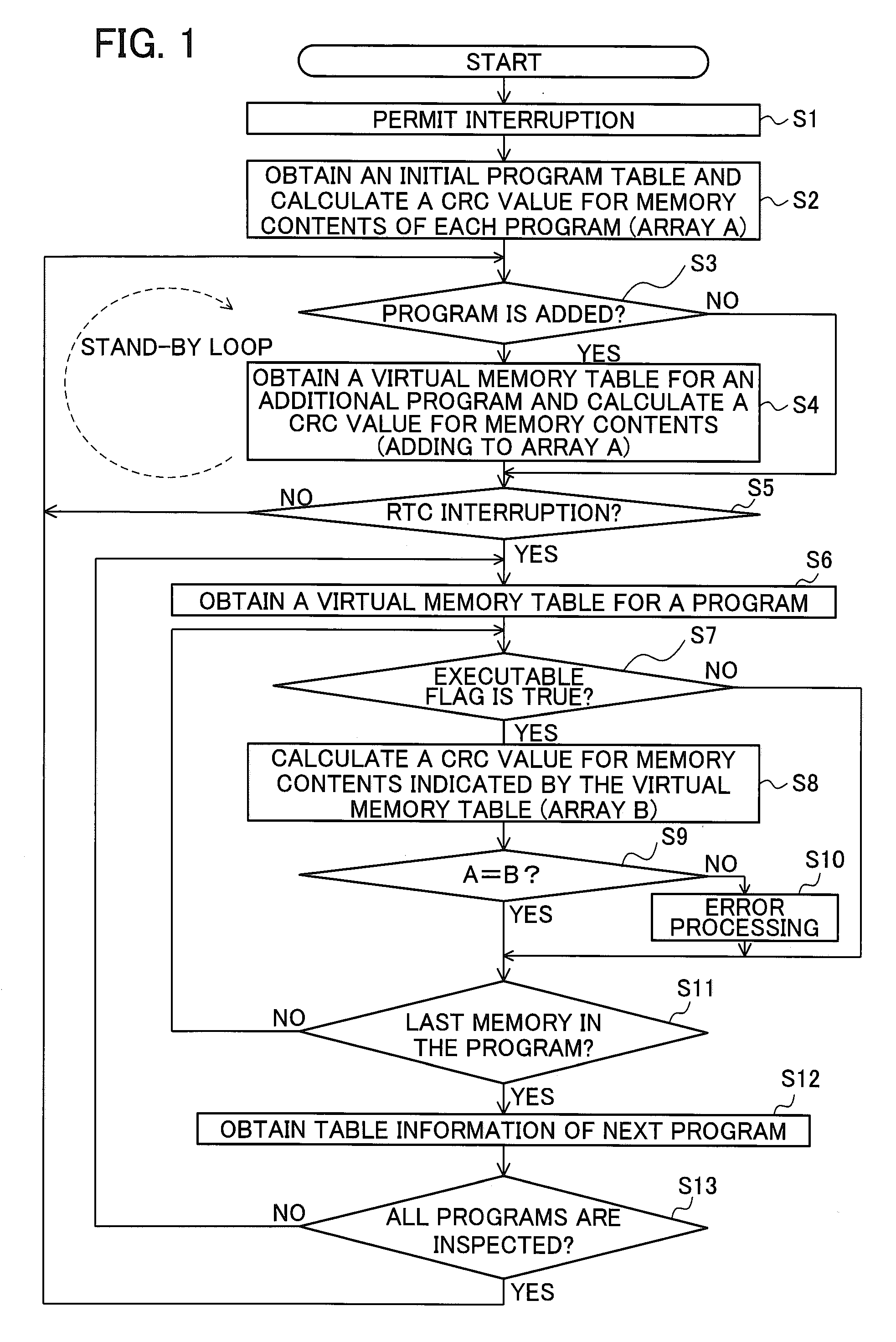
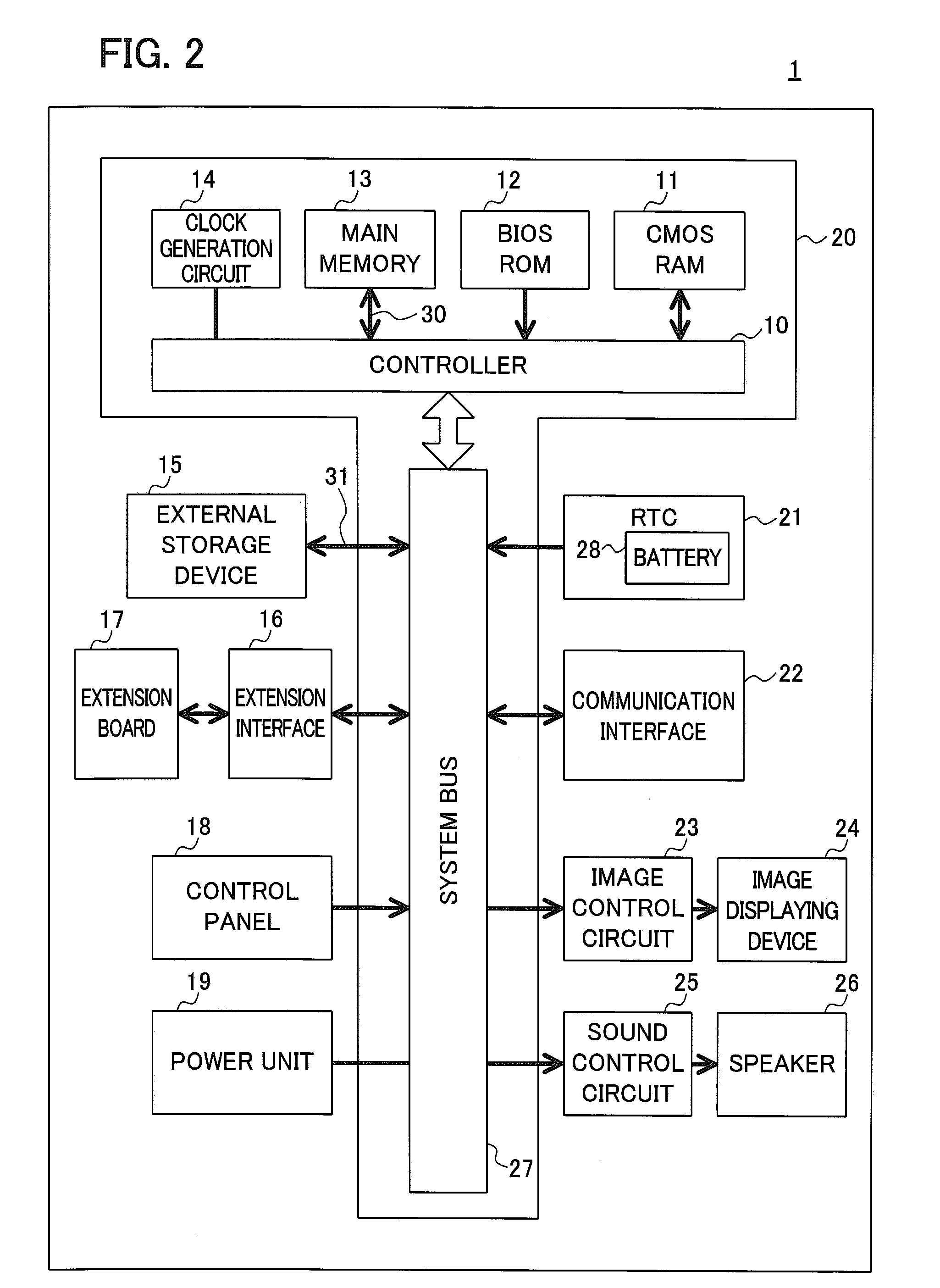
Information Processing Device That Verifies A Computer Program, And Gaming Machine
ActiveUS20090038009A1Memory loss protectionUnauthorized memory use protectionComputer hardwareInformation processing
An apparatus for processing information includes a memory device and a controller. The controller is configured to: access to a memory area in the memory device in which information related to a location of data including a computer program is stored; store contents of the memory area as a first inspection code into a first memory area of the memory device; at predetermined timing, access to a memory area in the memory device in which latest information is stored; store contents of the memory area as a second inspection code into a second memory area; compare the first and the second inspection codes; if the second inspection code does not agree with the first inspection code, output an error signal indicating inconsistency between the first and the second inspection codes; and if the second inspection code agrees with the first inspection code, perform verification of the computer program.
Owner:UNIVERSAL ENTERTAINMENT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com