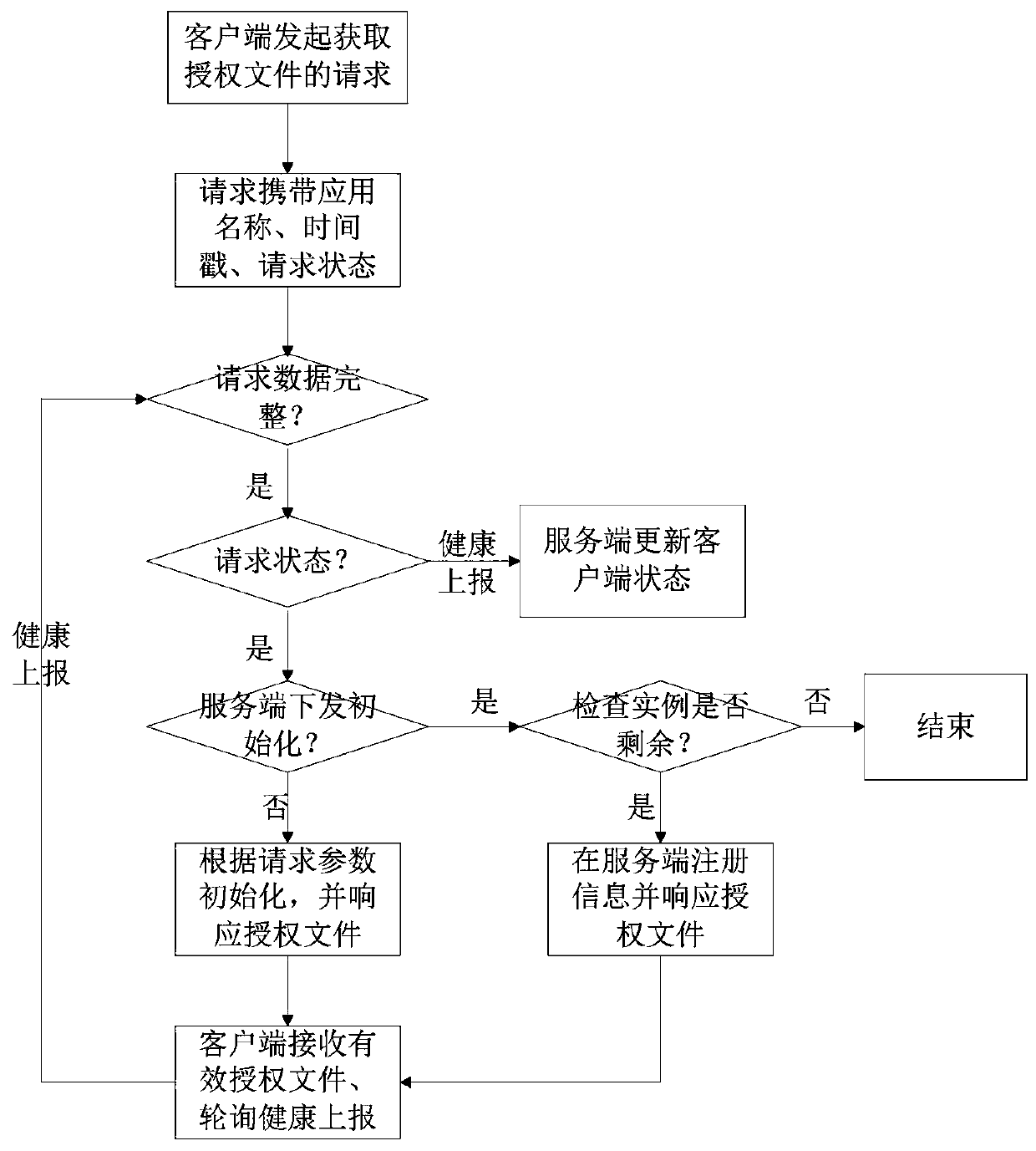
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
143 results about "Authorization documentation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
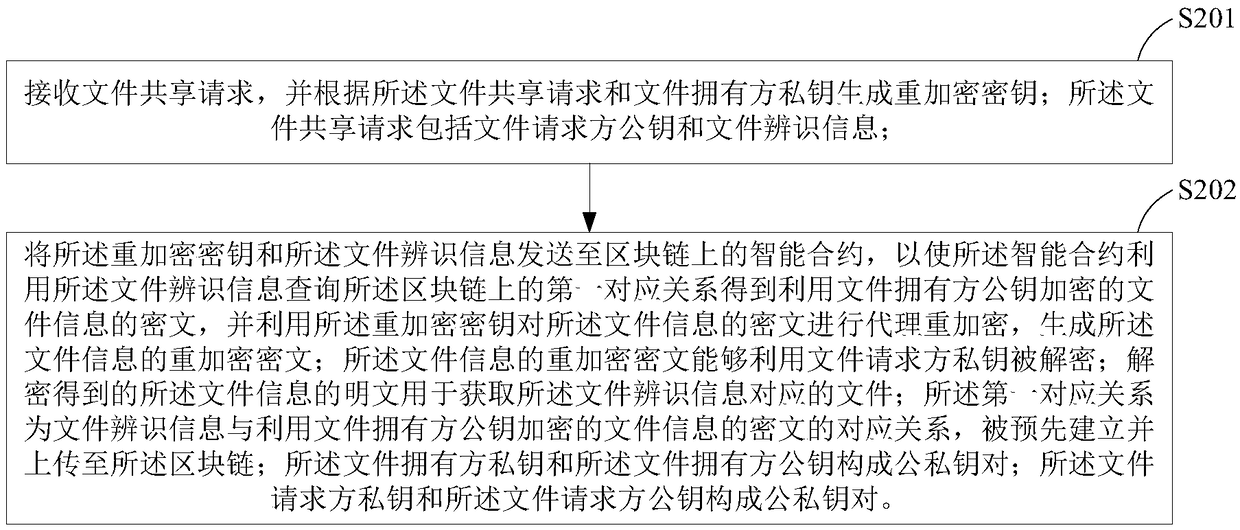
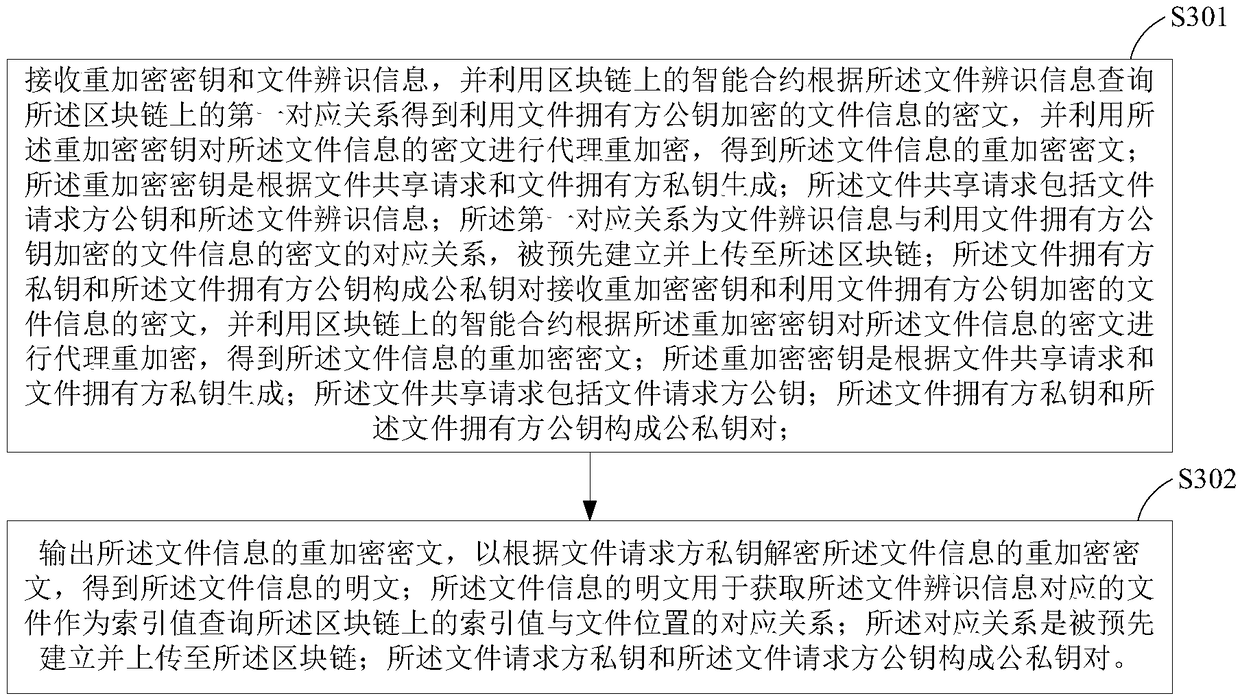
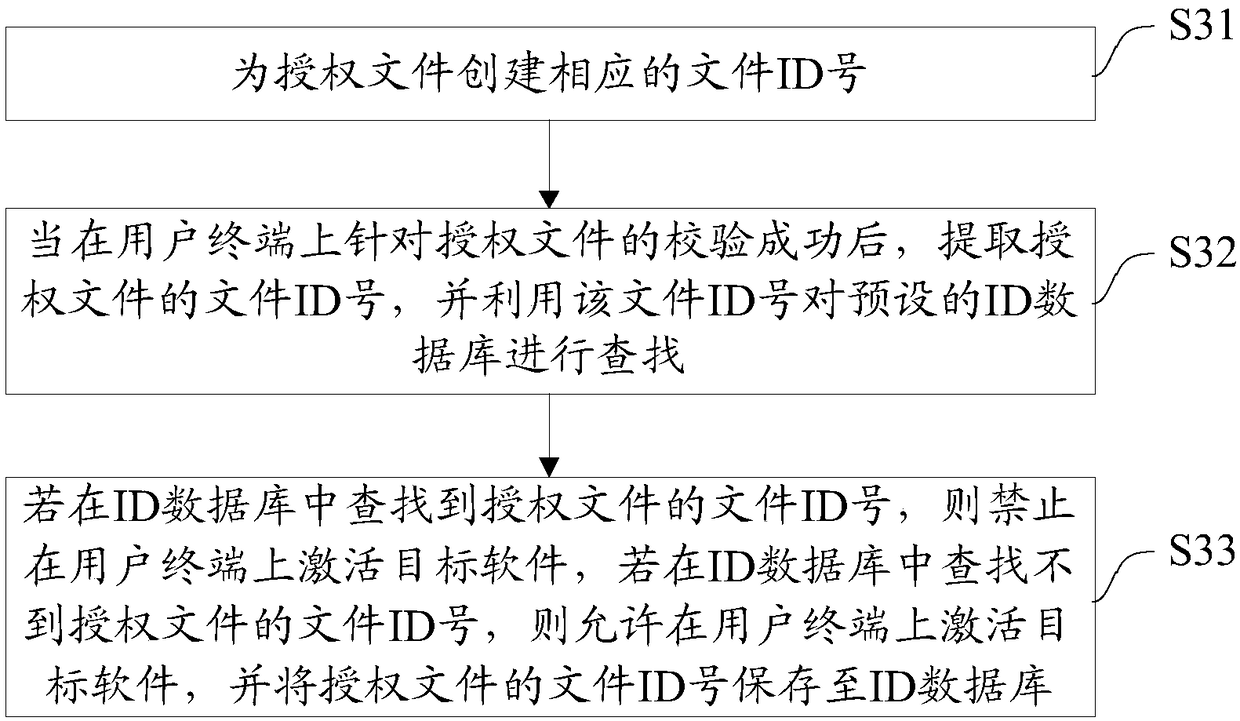
Authorized file share method and device
ActiveCN109144961AAchieve sharingTake advantage ofKey distribution for secure communicationDigital data information retrievalPlaintextSmart contract
The invention provides an authorized file sharing method and a device. The method comprises the following steps: generating a re-encryption key according to the file sharing request and the private key of the file owner, wherein the file sharing request includes a file requester public key and file identification information; sending the re-encryption key and the file identification information tothe smart contract on the block chain, so that the intelligent contract uses the file identification information to query the correspondence between the pre-established file identification information and the cipher text of the file information encrypted by the file owner's public key, obtaining the ciphertext of the file information encrypted by the public key of the file owner, and performing proxy re-encryption on the ciphertext of the file information by using the re-encryption key; the re-encrypted ciphertext being decrypted using the private key of the file requester. The plaintext of the decrypted file information is used for obtaining the file corresponding to the file identification information. The invention can protect data security and ensure data ownership by using block chain and proxy re-encryption.
Owner:JUZIX TECH SHENZHEN CO LTD
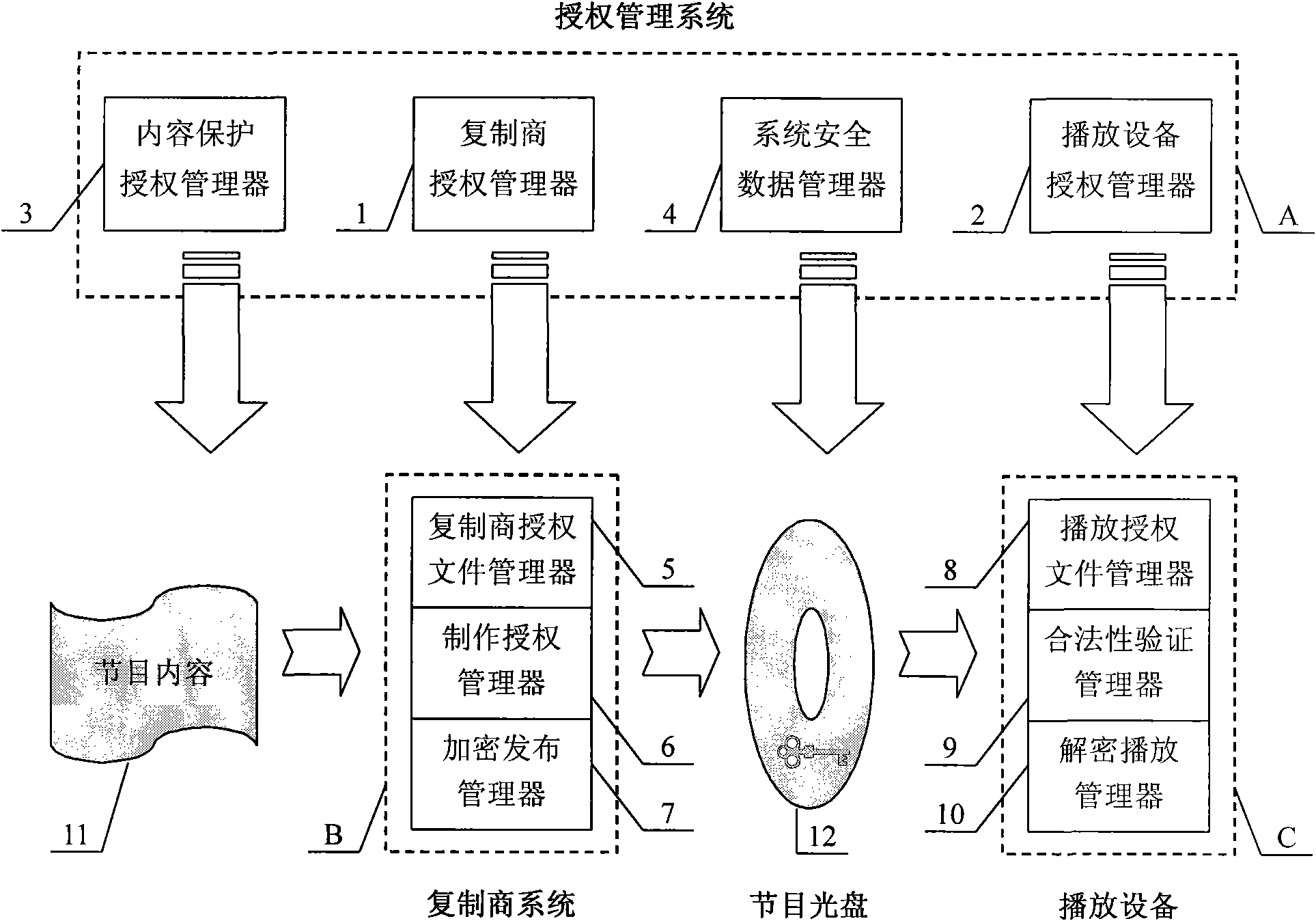
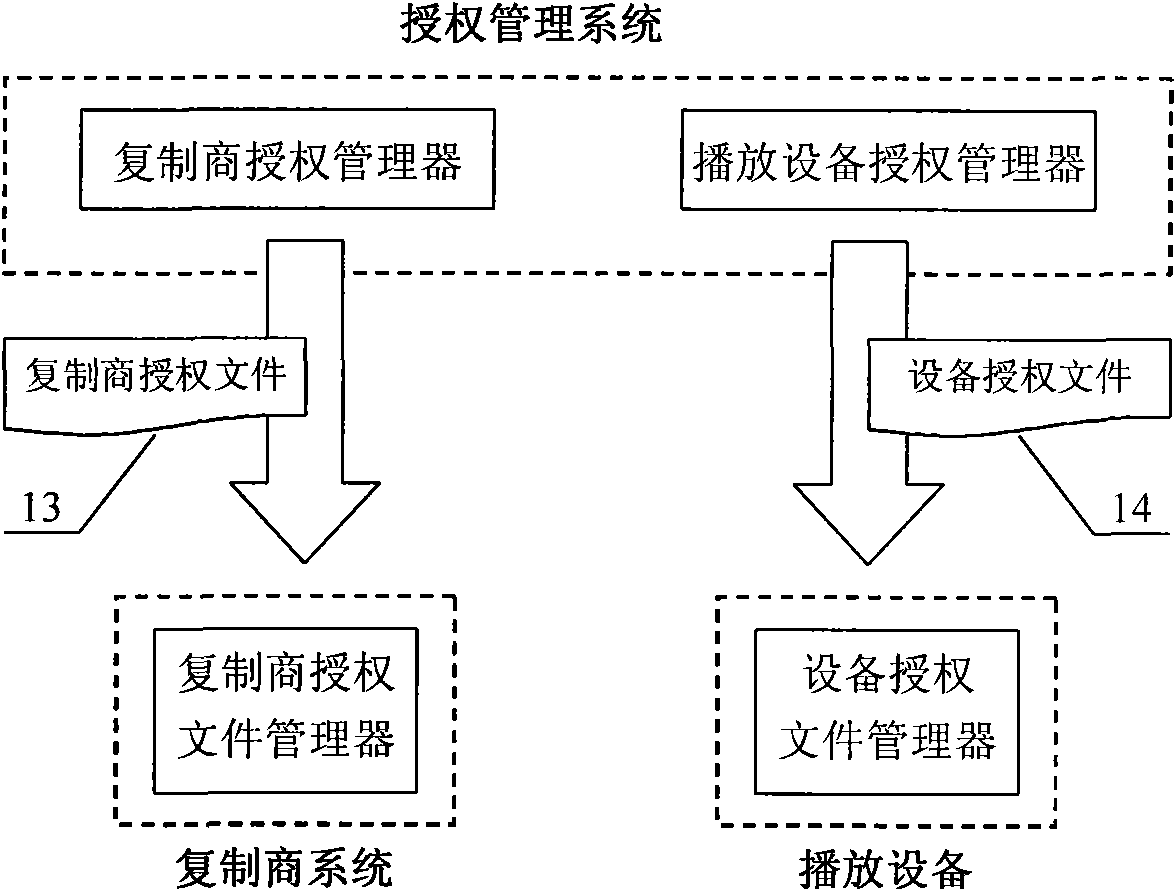
Digital copyright protection method and management device thereof for digital video disc system
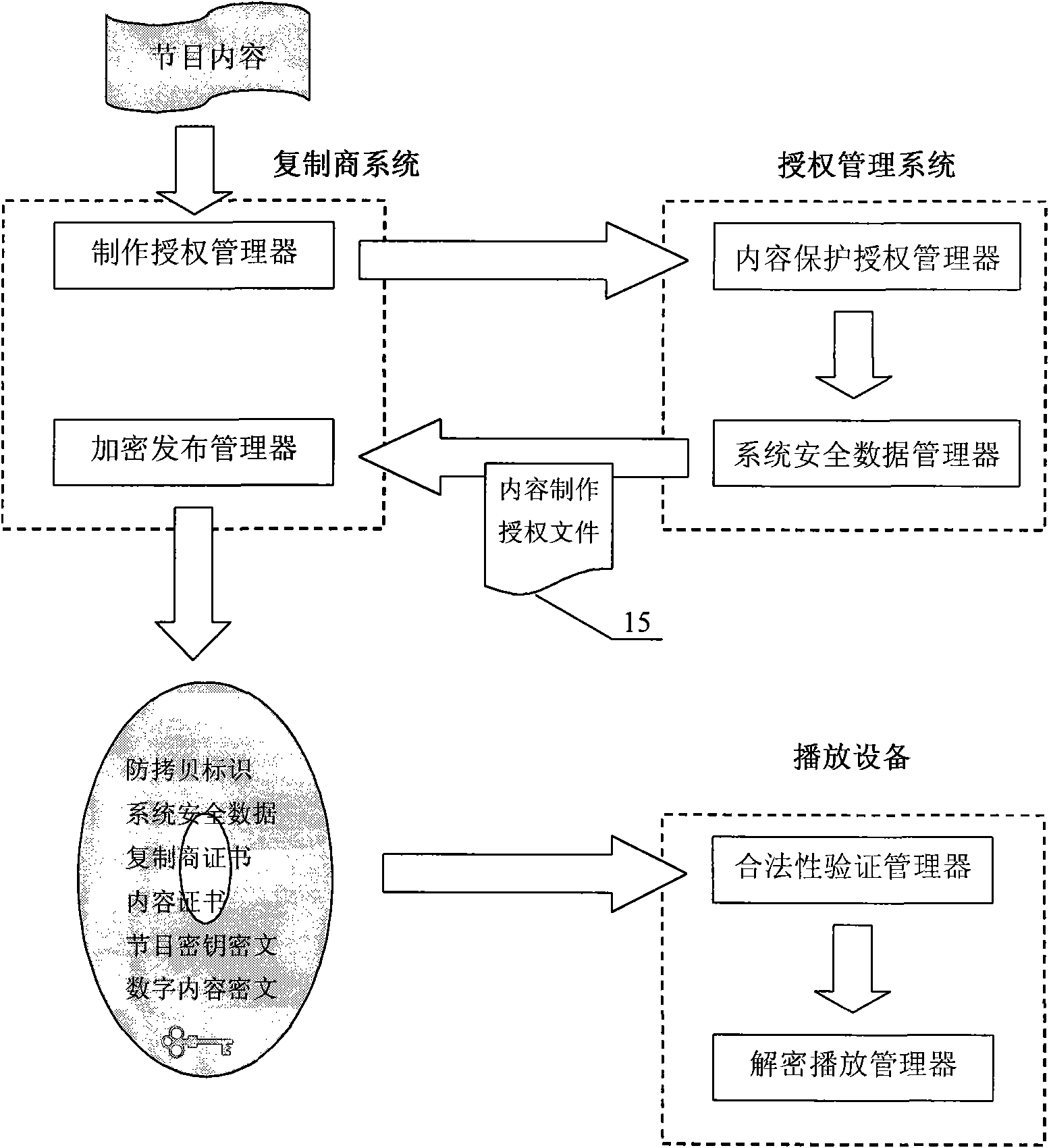
InactiveCN101770794AEnable safe propagationAchieve effectivenessRecord information storageRecording signal processingSoftware engineeringAuthorization
A digital copyright protection method and a management device thereof for a digital video disc system relate to multimedia field. The management device is composed of an authorization management system, a replication business system and authorized playing equipment. The authorization management system is composed of a content protection authorization manager, a replication business authorization manager, a system safety data manager and a playing equipment authorization manager; the replication business system is composed of an authorization file manager, a making authorization manager and an encryption distribution manager; the playing equipment is composed of a playing authorization file manager, a legality authentication manager and a decryption playing manager. The invention adopts dual-key asymmetric encryption technique to build the digital copyright protection safety system for the digital video disc system, realizes the authorization management of the replication business system and meets the domestic tremendous HD content publishing and consumption demands; besides, the invention also has the advantages of safety, reliability and low operation cost.
Owner:TSINGHUA TONGFANG CO LTD +2
Application file verification method and system
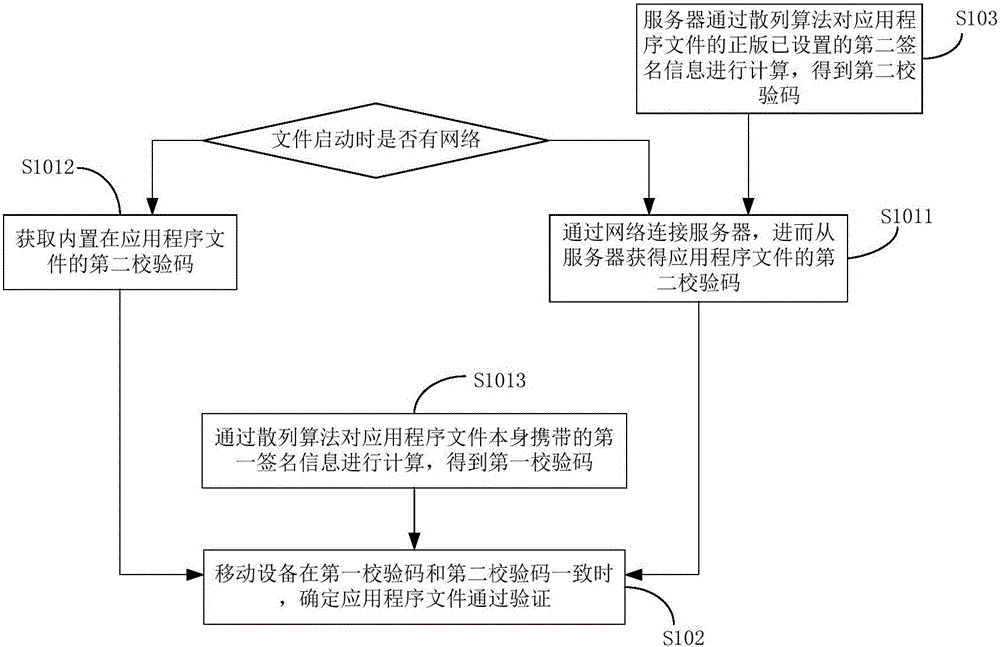
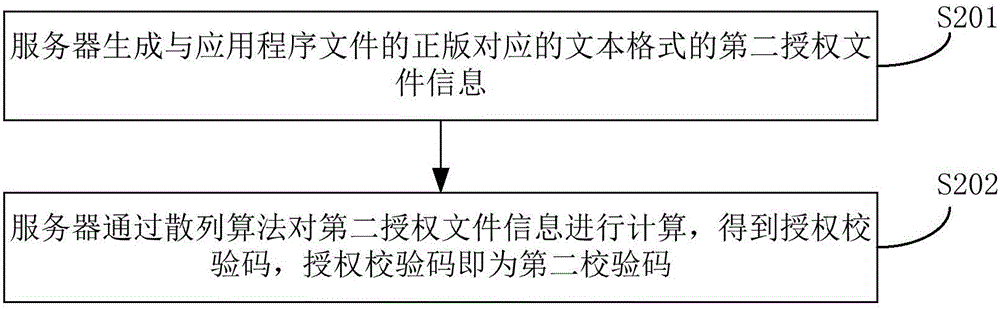
InactiveCN106096381ADetermine securityDigital data authenticationComputer hardwareApplication software
The invention discloses an application file verification method and system. The method comprises the steps that a mobile device obtains a first check code and a second check code of an application file, wherein the first check code is obtained according to first authorization file information carried by the application file, and the second check code is obtained according to second authorization file information carried by an authorized edition of the application file; and the mobile device determines that the application file passes the verification when the first check code is consistent with the second check code. Through the method and the system, the security of the application file can be determined at a mobile terminal and relatively long codes do not need to be input.
Owner:BEIJING ERENEBEN INFORMATION TECH
System for sharing and distributing reliable data in multiple internet of vehicles
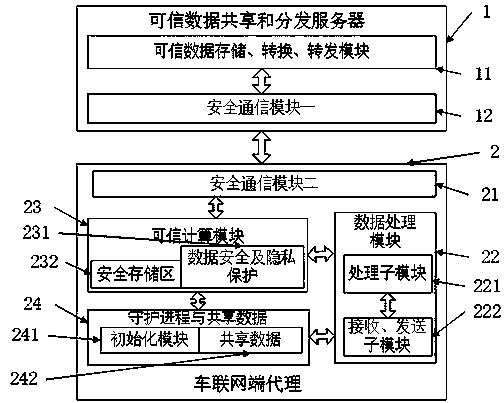
InactiveCN108322488AEnsure secure interconnectionAchieve sharingTransmissionPrivacy protectionThe Internet
The invention provides a system for sharing and distributing reliable data in multiple internet of vehicles and belongs to the field of internet of vehicles. The system comprises a reliable data sharing and distributing server, an internet of vehicles terminal agency, a certification and authentication system and a content management system, wherein the certification and authentication system is used for carrying out access control of the internet of vehicles and generating access authorization files; the content management system is used for defining processes, defining message and file interfaces and controlling data types and formats, forwarding rate, secure transfer protocols, privacy protection protocols and communication interface requirements; the internet of vehicles terminal agency is installed on an internet of vehicles terminal access gateway and is used for receiving data submitted by users or devices of a source internet of vehicles, generating forwarding data packets andsending the forwarding data packets to the reliable data sharing and distributing server; a reliable data counting server is used for checking, storing, converting and forwarding the received data toa target internet of vehicles. The system is capable of sharing and distributing the reliable data in multiple internet of vehicles as well as ensuring secure interconnection among the multiple internet of vehicles.
Owner:广州市联奥信息科技有限公司
Application usage policy enforcement
ActiveCN103180859AAvoid bypassingBuying/selling/leasing transactionsProgram/content distribution protectionReceiptAuthorization
Disclosed herein are systems, methods, and non-transitory computer-readable media for enforcing application usage policies. As part of an application purchase transaction, the application distributor creates a unique proof of purchase receipt. This receipt can be bundled with the application and delivered to the purchaser. Each machine can maintain an authorization file that lists the users authorized to use applications on that machine. A system configured to practice the method verifies that a user is authorized to use an application on a machine based on an application proof of purchase receipt and the authorization file. If the application proof of purchase receipt and the authorization file are both valid, the system checks if the user account identifier in the receipt is contained in the authorization file. If so, the user can be considered authorized to use the application on the machine.
Owner:APPLE INC
Verification method and system for software license under virtual airport scene
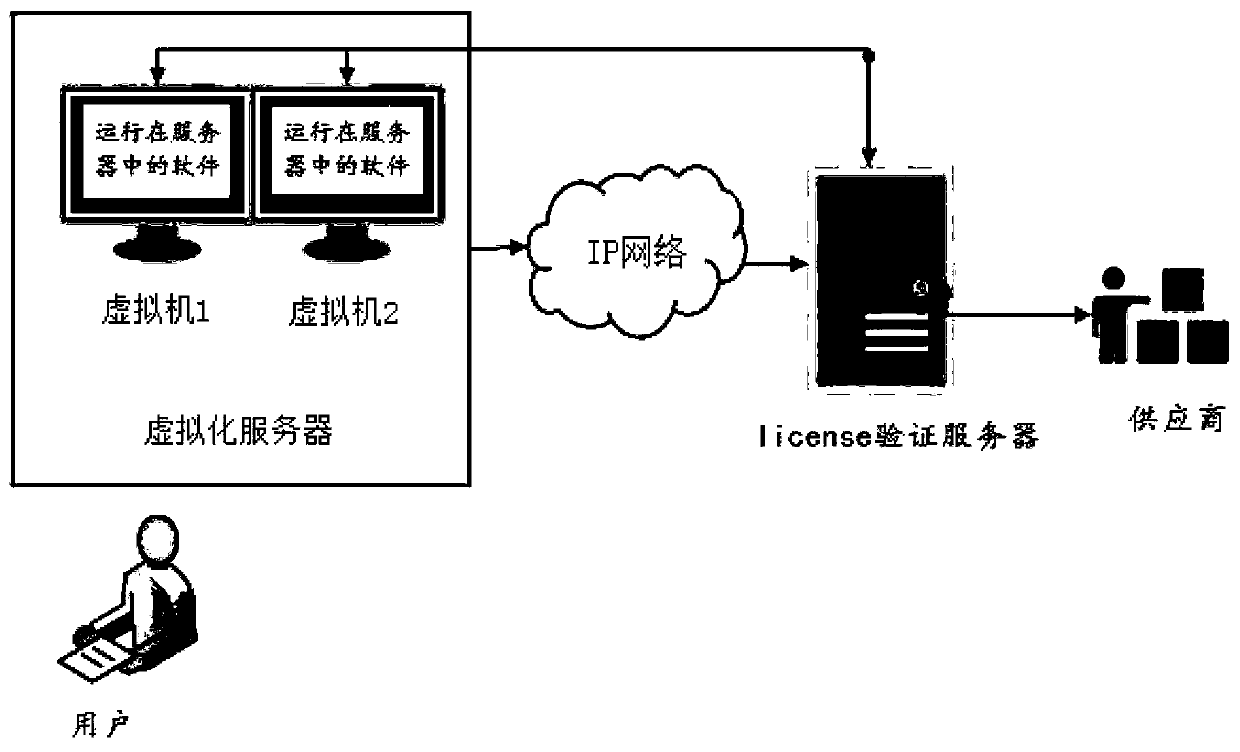
ActiveCN110798466APrevent illegal reuse of license functionsSave resourcesTransmissionSoftware simulation/interpretation/emulationVirtualizationSoftware license
The invention provides a verification method and system for a software license under virtual airport scene.. The method comprises the steps that S1, conducting network communication between a virtualmachine and a license verification server; S2, configuring a license verification server address for software; S3, acquiring the hardware information of the license verification server by the softwarethrough the network, and generating a license application file by using the acquired hardware information; S4, making a license authorization file by using the license application file; and S5, enabling the software to send the hardware information in the license authorization file and the process ID of the software to a license verification server together to verify the validity of the license.The license can be effectively prevented from being illegally reused due to virtual machine copying, and meanwhile, excessive physical hardware resources cannot be occupied.
Owner:西安雷风电子科技有限公司
Software authorization method, system and device
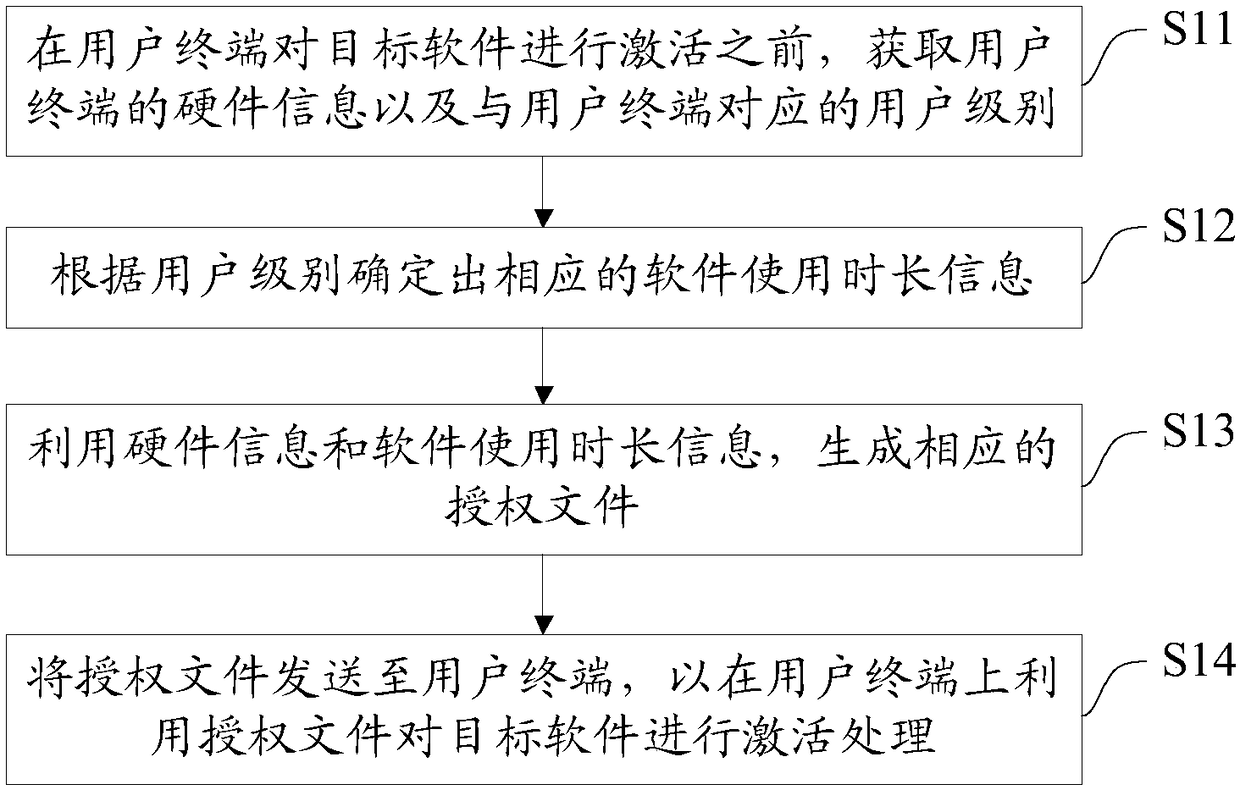
ActiveCN108124480AMeet the needs of on-demand softwareReduce use costProgram/content distribution protectionComputer terminalPurchasing
A software authorization method, system and device. The method comprises: before a user terminal activates target software, acquiring hardware information about the user terminal and a user level corresponding to the user terminal (S11); determining corresponding software usage duration information according to the user level (S12); generating a corresponding authorization file by using the hardware information and the software usage duration information (S13); and sending the authorization file to the user terminal so as to activate the target software on the user terminal by using the authorization file (S14). Authorization files with different software usage duration information can be generated according to different user levels, so that a software user can acquire an authorization file with corresponding software usage duration information by means of purchasing according to the actual requirements thereof, thereby avoiding unnecessary waste, that is, the user's demand for using software according to requirements can be satisfied, and the software usage cost of the user is reduced.
Owner:SHENZHEN A&E INTELLIGENT TECH INST CO LTD
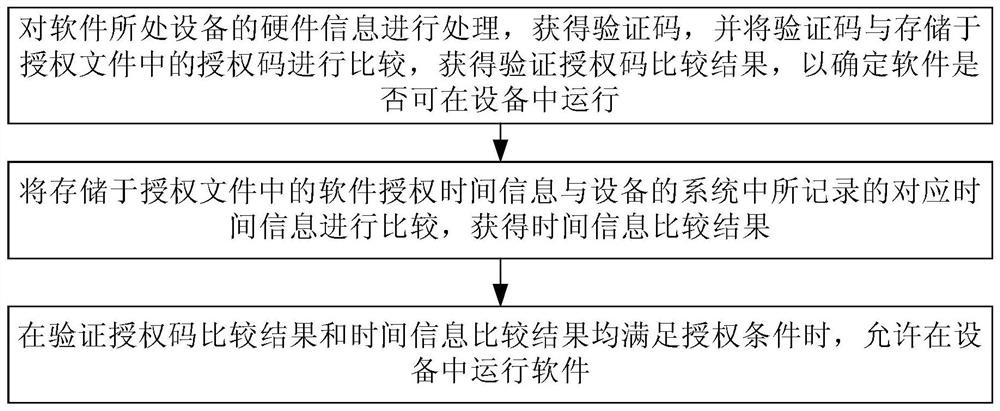
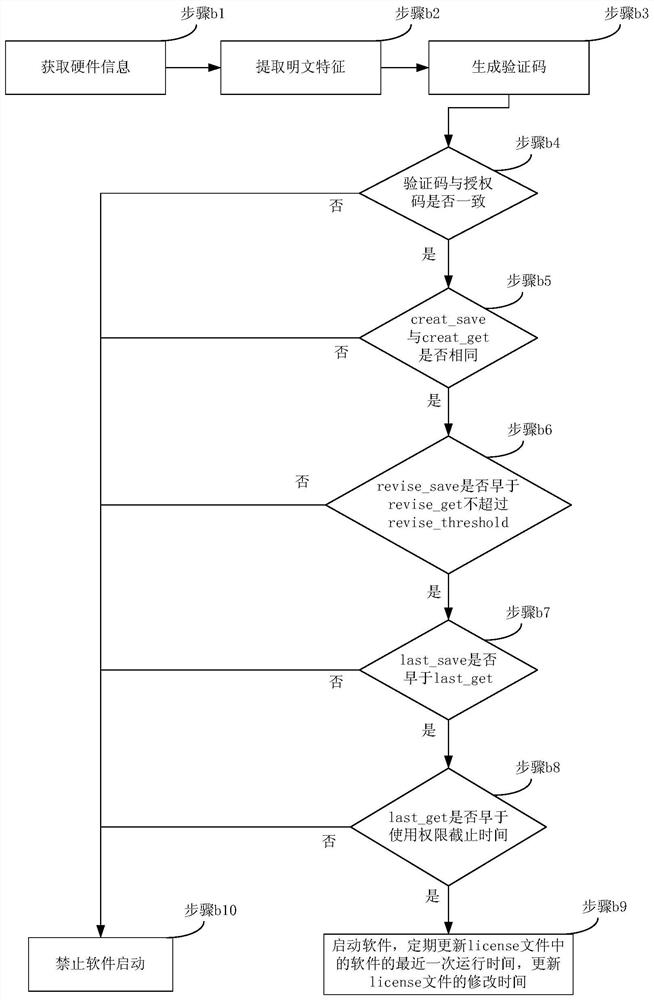
Software authorization verification method
InactiveCN112231647AControl expiration dateReduce investmentDigital data protectionProgram/content distribution protectionTime informationSoftware engineering
The invention discloses a software authorization verification method. The method comprises the following steps of before software is started each time, processing hardware information of equipment inwhich the software is positioned to obtain a verification code, and comparing the verification code with an authorization code stored in an authorization file to obtain a verification authorization code comparison result; comparing the software authorization time information stored in the authorization file with corresponding time information recorded in a system of the equipment to obtain a timeinformation comparison result; and when the verification authorization code comparison result and the time information comparison result both meet the authorization condition, allowing the software torun in the equipment. According to the method, the authorization verification of the software is realized without depending on external pluggable encryption hardware equipment, a far-end authorization server, the Internet and a satellite positioning time service system, the content of the authorization file can be effectively prevented from being modified by a user, and the service life of the software is effectively controlled.
Owner:POTEVIO INFORMATION TECH
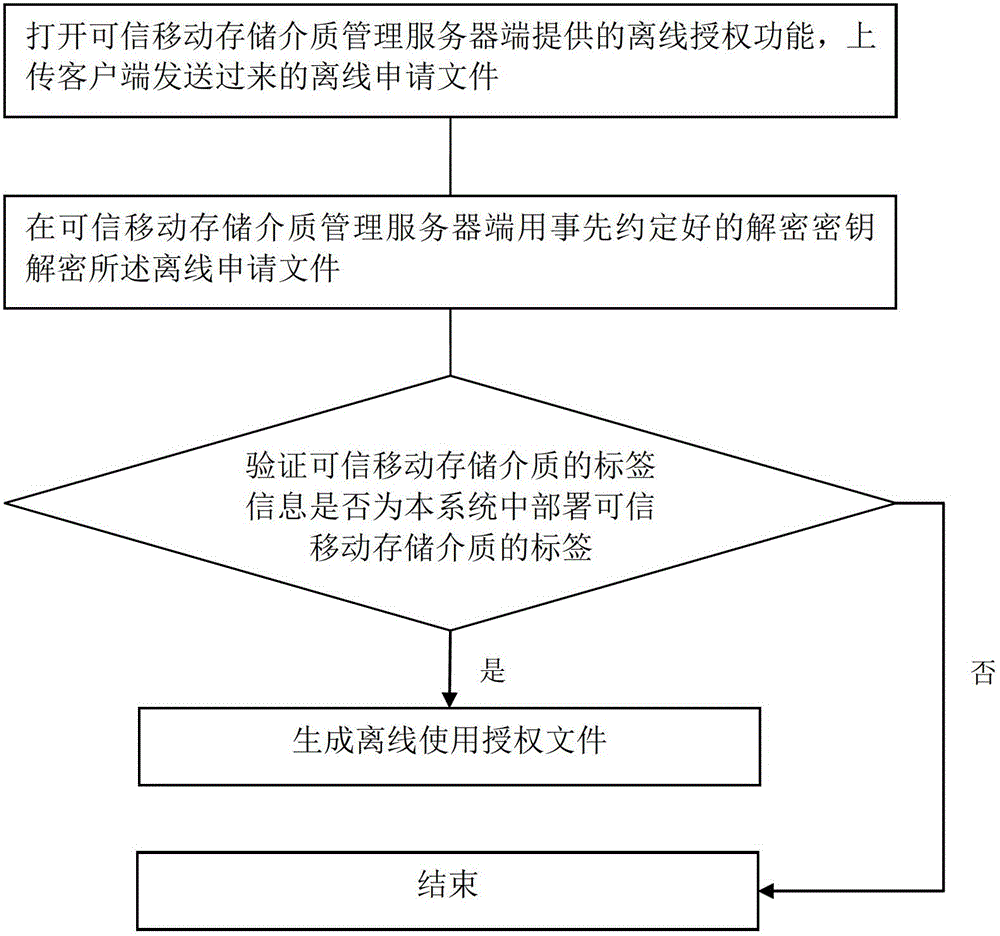
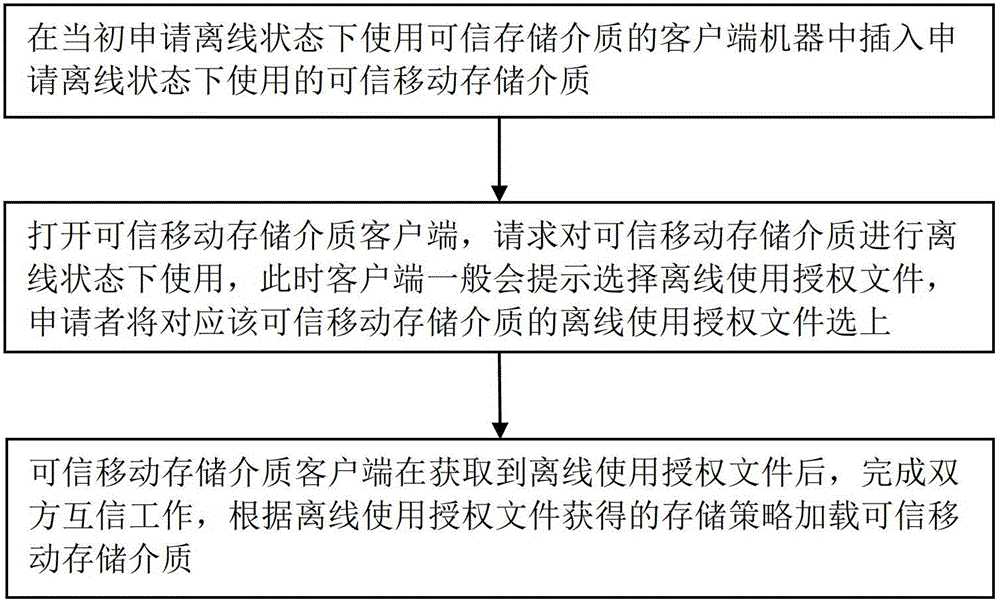
Method and system for safely using credible mobile storage medium in off-line state
ActiveCN102724137ASolve the problem that the trusted removable storage media cannot be used safely and needs to be verified onlineData switching networksRemovable mediaClient-side
The invention provides a method and a system for safely using a credible mobile storage medium in an off-line state. The method comprises the following steps: inserting a client side into the credible mobile storage medium in the off-line state and applying for using the credible mobile storage medium in the off-line state, and outputting an off-line application file of the mobile storage medium; sending the off-line application file to a credible mobile storage medium managing server by the client side, and after examining and verifying the off-line application file to be successful by the credible mobile storage medium managing server, sending the off-line authorization file to a credible mobile storage medium client side; and after the client side gets the off-line authorization file, loading the off-line authorization file in the off-line state, and loading the specified credible mobile storage medium according to a storage strategy after verification by both sides. According to the scheme of the invention, the problem of verification by both sides in the off-line state is solved, and the credible mobile storage medium is guaranteed to be safely used.
Owner:NEW H3C TECH CO LTD
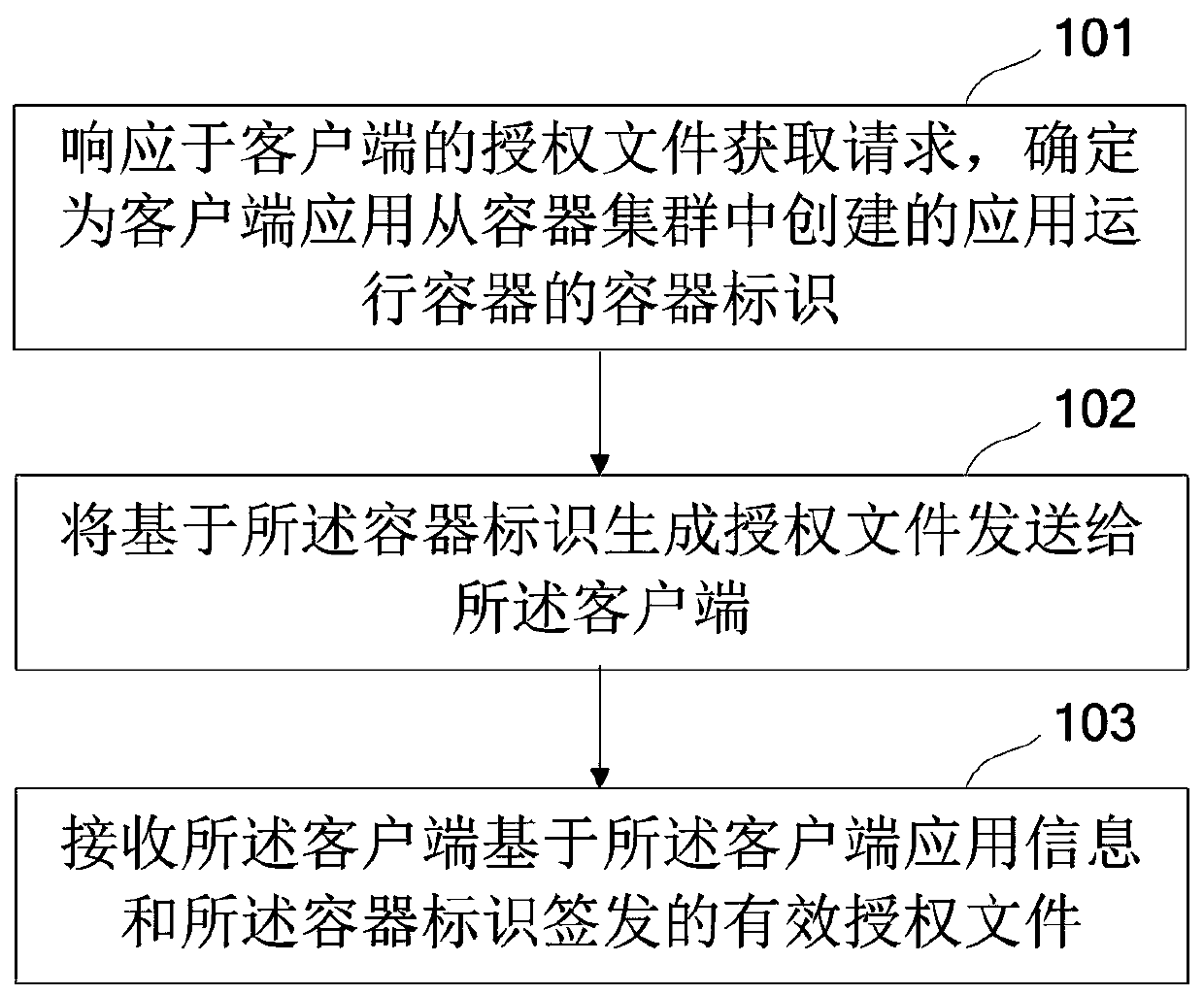
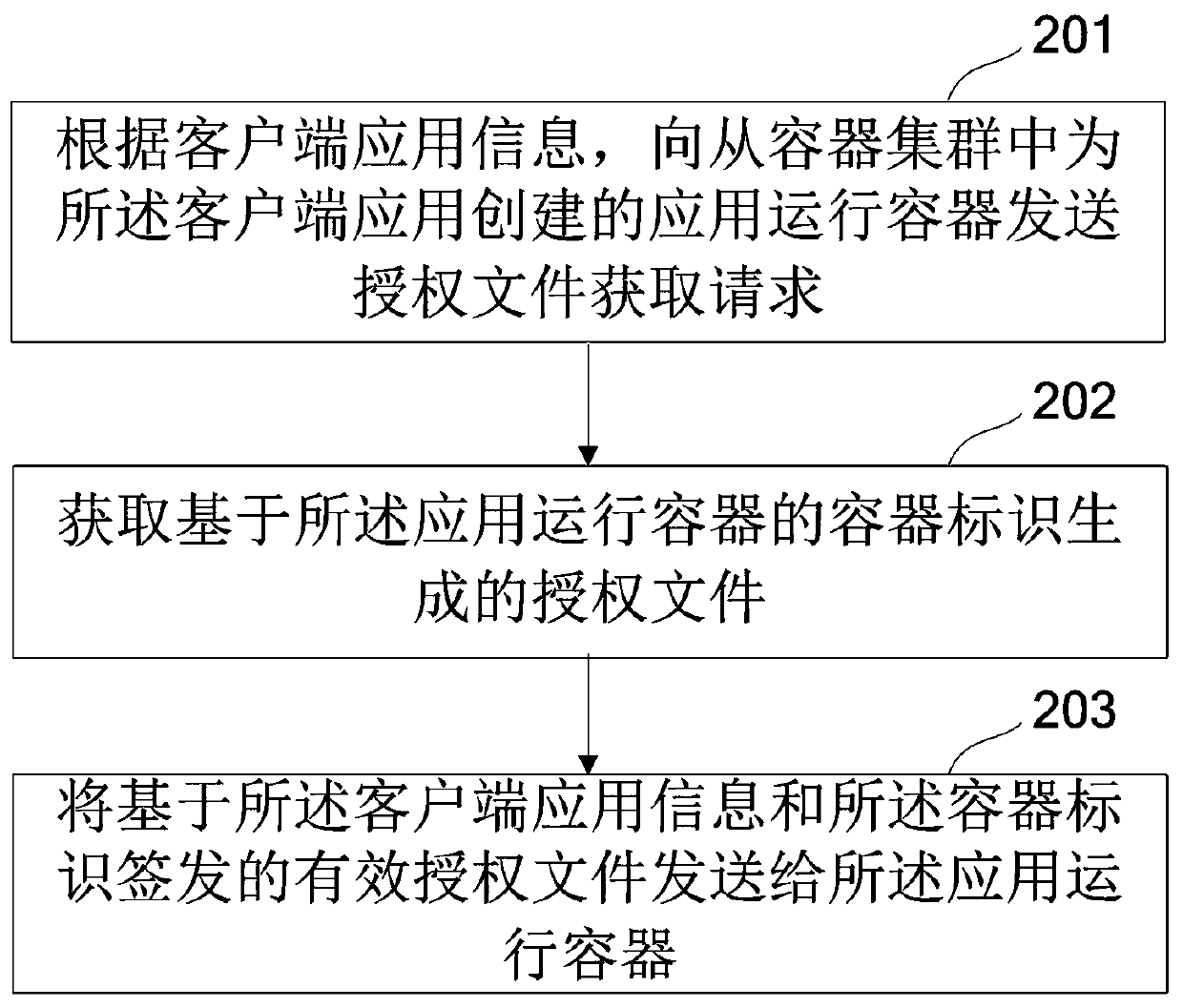
Application software authorization method and device and storage medium
ActiveCN111428208AProgram/content distribution protectionSoftware simulation/interpretation/emulationSoftware engineeringApplication software
The embodiment of the invention provides an application software authorization method and device and a storage medium. In some embodiments of the invention, in response to an authorization file acquisition request of a client, a container identifier of an application running container created for a client application from a container cluster is determined; an authorization file is generated basedon the container identifier and the authorization file is sent to the client; and an effective authorization file signed and issued by the client based on the client application information and the container identifier are received. A special application running container is independently created for a client application, and equipment information generation, authorization file issuing and the like are realized by utilizing the application running container and are not influenced by application software update and hardware information change, so that the effectiveness of an authorization fileis ensured, and the copyright of application software is better protected.
Owner:北京信安世纪科技股份有限公司
Software authorization method and device, authorization server and terminal equipment
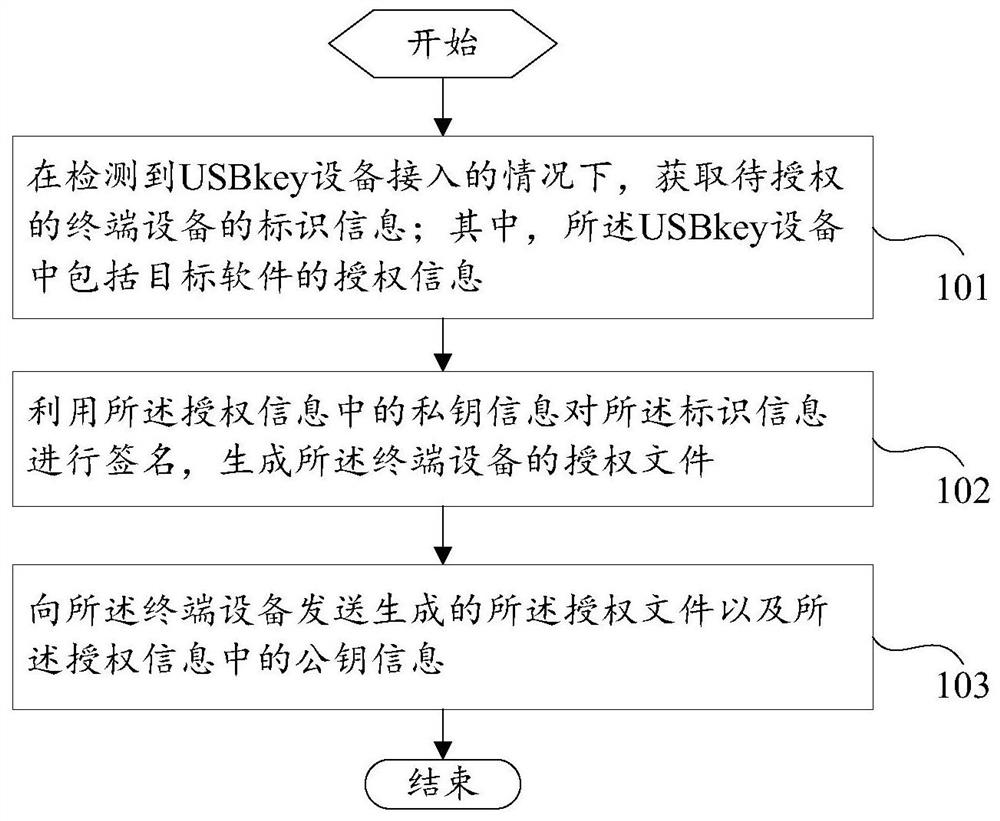
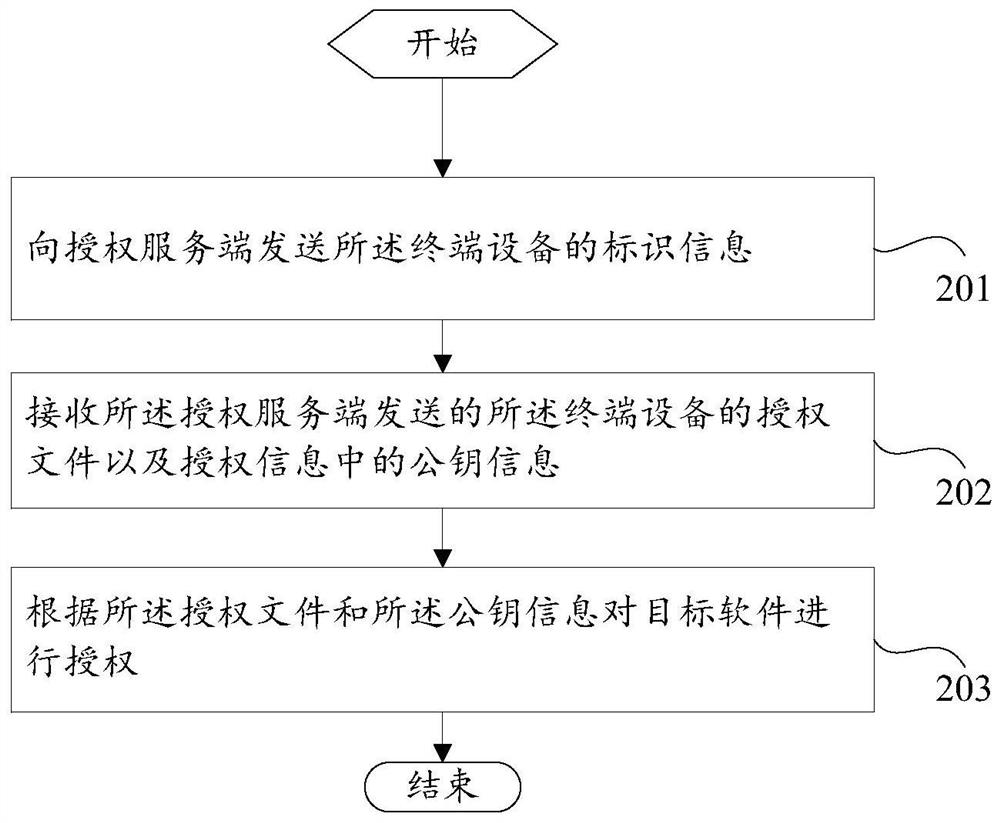
ActiveCN112165382AAvoid the problem of poor authorization flexibilityIncrease flexibilityKey distribution for secure communicationProgram/content distribution protectionAuthorization ModeSoftware engineering
The invention discloses a software authorization method and device, an authorization server and terminal equipment, and relates to the technical field of computers. The software authorization method comprises the steps that: under the condition that USBkey equipment access is detected, the authorization server acquires identification information of to-be-authorized terminal equipment; wherein theUSBkey equipment comprises authorization information of target software; signing the identification information by using private key information in the authorization information to generate an authorization file of the terminal equipment; and sending the generated authorization file and public key information in the authorization information to the terminal equipment. According to the scheme provided by the invention, the authorization of the authorization server to the target software of the plurality of terminal equipment is realized, and the problems that a local software authorization modeis poor in flexibility and an online authorization mode is not suitable for the terminal equipment which are not allowed to be networked are solved.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
Authorization control method and device, authorization method and device and computing equipment
ActiveCN112699342APrevent leakagePrevent reuseDigital data protectionProgram/content distribution protectionCiphertextApplication procedure
The invention discloses an authorization control method, which comprises the steps of receiving an authorization request sent by a client based on an application file, and obtaining an application ciphertext, first signature information and a first public key from the application file; verifying the first signature information based on the first public key; decrypting the application ciphertext based on the second private key to obtain a device identifier of the client, and generating corresponding device information based on the device identifier; establishing association between the authorization configuration information and the equipment information to generate an authorization file; sending the authorization file to the client, so that the client activates the application program based on the authorization file; and regularly obtaining the actual running duration of the client, and judging whether the actual running duration exceeds the preset running duration of the application program or not so as to determine whether the application program authorization expires or not. The invention also discloses a corresponding authorization method, an authorization device and computing equipment. The authorization scheme provided by the invention can be used for an intranet environment, and can prevent leakage and reuse of authorization information.
Owner:UNIONTECH SOFTWARE TECH CO LTD
File storage and access method and system based on block chain
ActiveCN110784463AControl operation authorityNot tampered withEncryption apparatus with shift registers/memoriesPublic key for secure communicationTamper resistanceSignature file
The invention discloses a file storage and access method and system based on a block chain, and the method comprises the steps: carrying out file partitioning, carrying out file encryption signature,carrying out file information chaining, carrying out file access authorization, carrying out file reconstruction and sharing, and finally transmitting a reconstruction target file to an access user inan encrypted manner for related reading or writing operation. Separated file storage and a file management mechanism based on a blockchain smart contract are adopted, the file access permission management module utilizes the main characteristics of openness, transparency, tamper resistance and the like of a blockchain, and the security and traceability of file access are effectively enhanced. Bydividing the file into a plurality of sub-files and encrypting the sub-files with different private keys, the file can be prevented from being operated unidirectionally. Meanwhile, the sub-file related information is encrypted and stored in the block chain and cannot be tampered, so that the security of the file information is greatly enhanced.
Owner:深圳市乾数科技有限公司
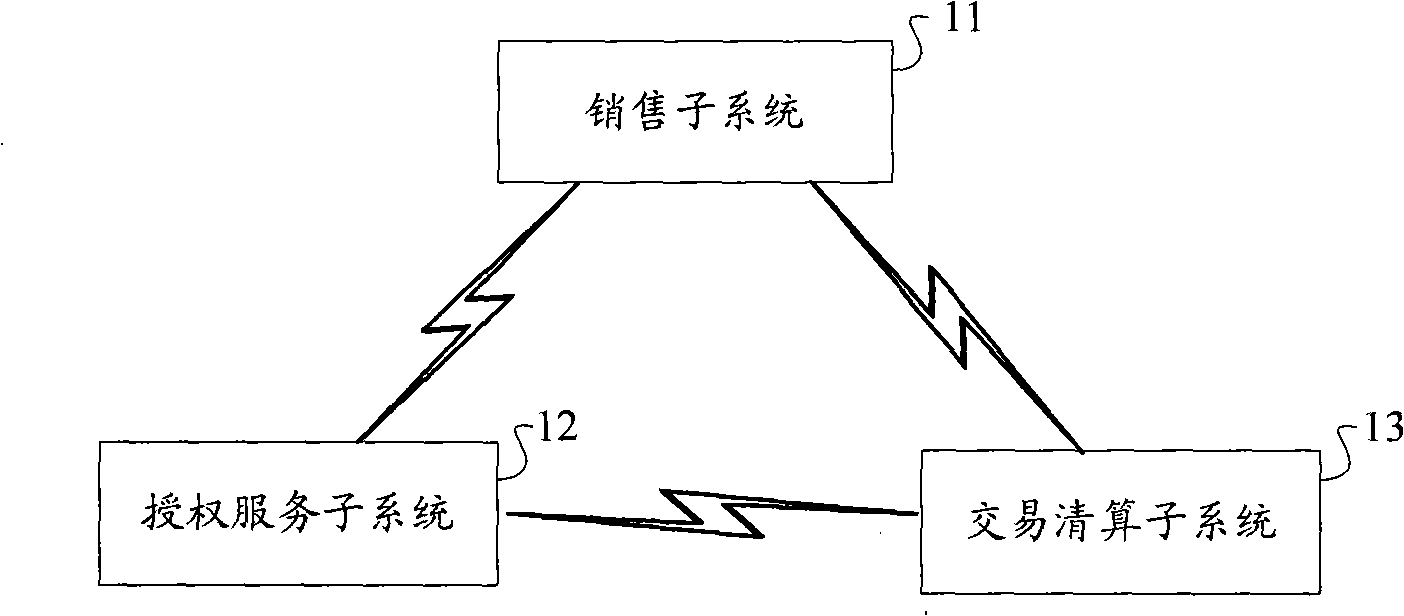
System and method for counting digital content
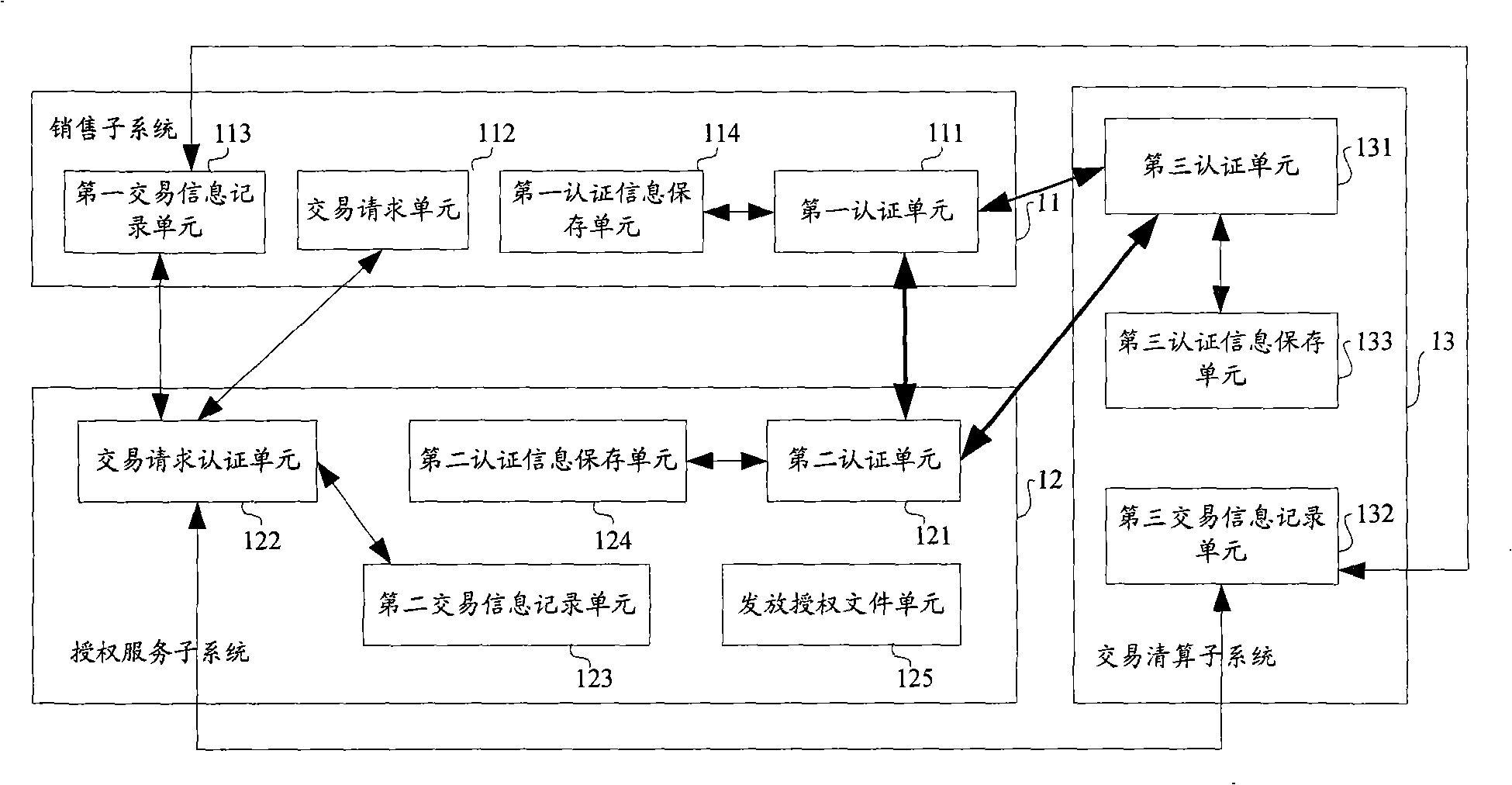
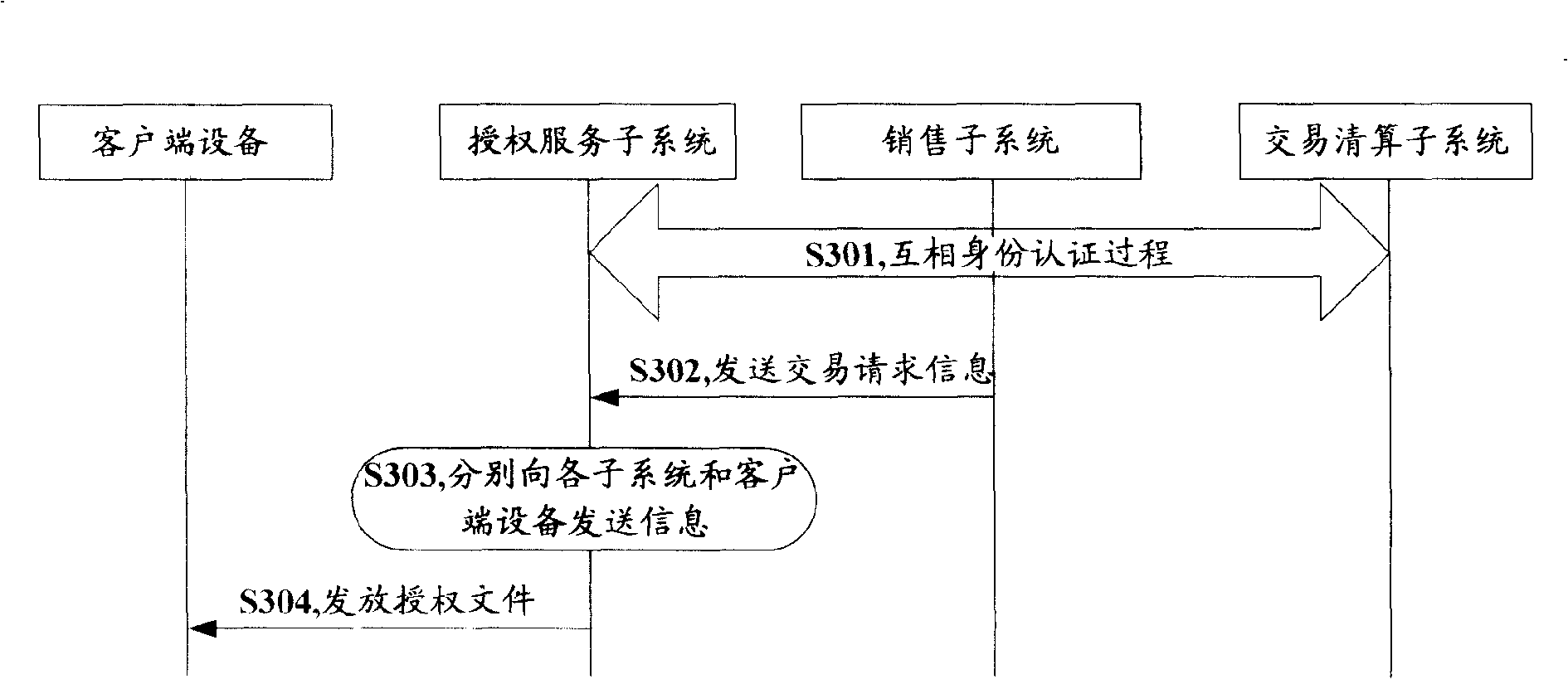
The invention discloses a digital content counting system and a method thereof for building the believable dealing counting mechanism between the copyright owner and the seller to make the two parties recognize the dealing information of the digital content. The system includes a selling subsystem, an authorization subsystem and a dealing reckoning subsystem, wherein the selling subsystem and the dealing reckoning subsystem are authenticated with the authorization subsystem each other; the dealing reckoning subsystem certificates the selling subsystem; the selling subsystem is used to generate the dealing request information and transmit to the authorization subsystem by authentication according to the purchase list, record the dealing success information; the authorization subsystem is used to receive and affirm the dealing request information to transmit the dealing success information to the client-end device, the selling subsystem and the dealing reckoning subsystem by authentication, and transmit the acquisition path of the authorization file to the client-end device, record the dealing request information, grant the authorization file; the dealing reckoning subsystem is used to record the dealing success information.
Owner:PEKING UNIV +2
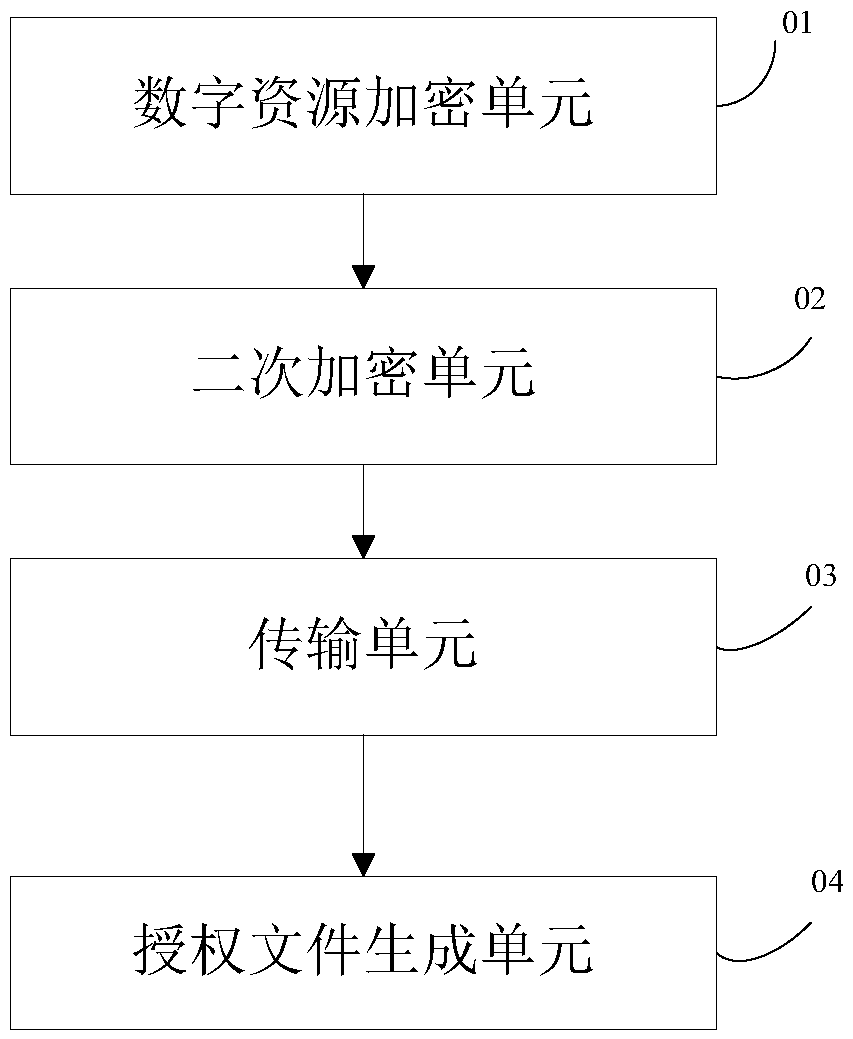
Digital resource copyright protection method, opening method and device, and hardware storage device
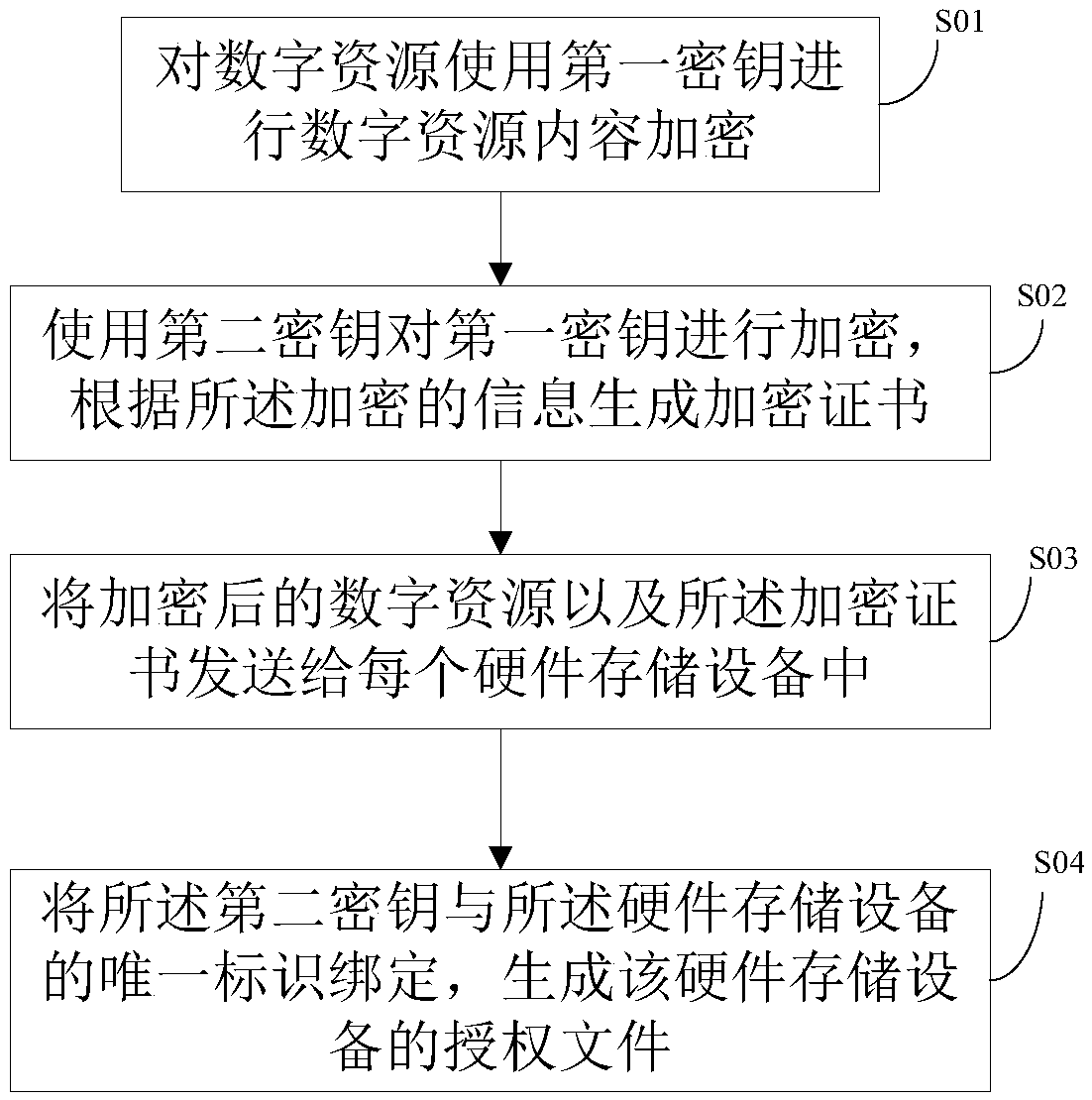
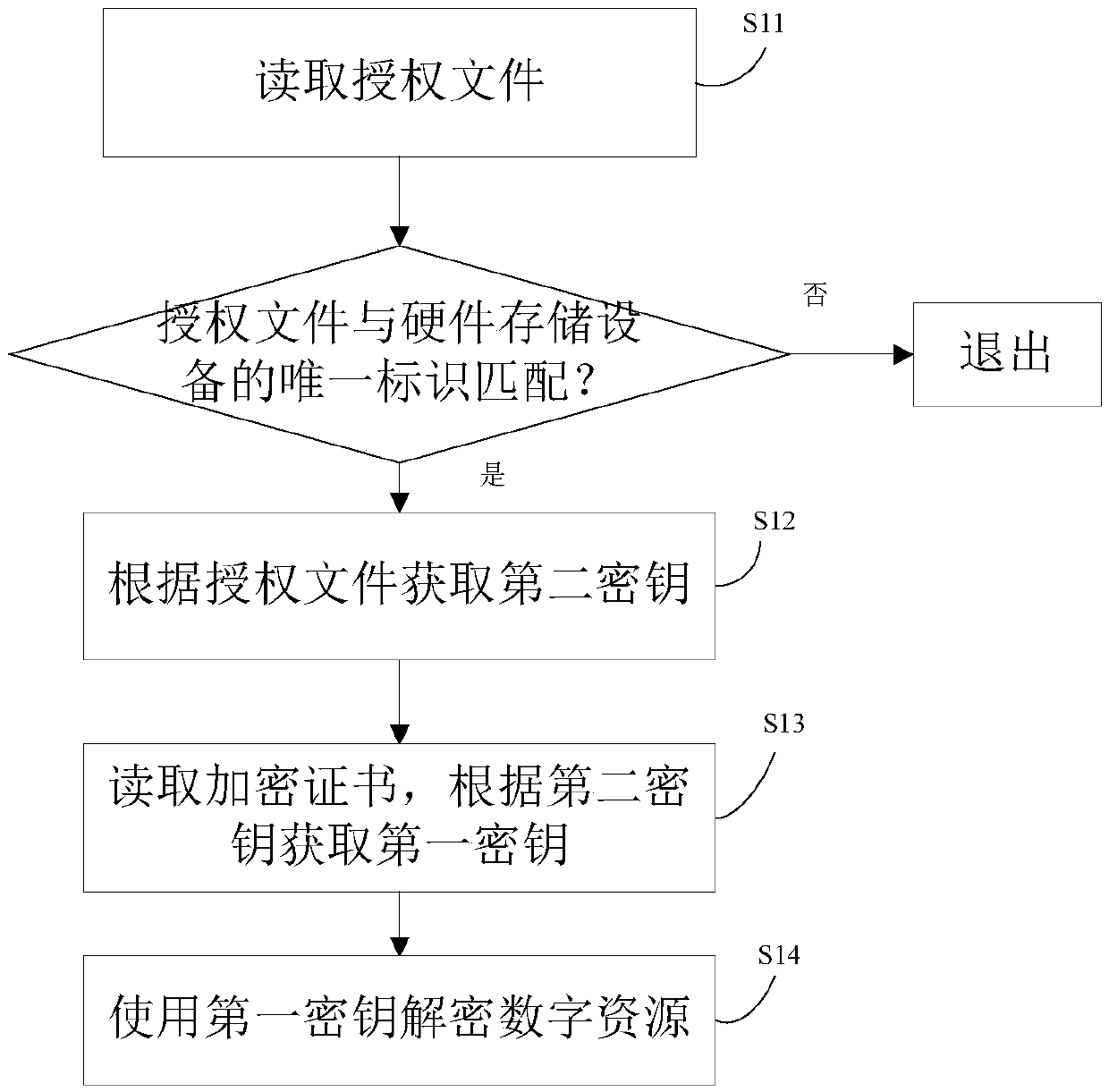
InactiveCN105512519APrevent being copied and stolenGet rid of dependenceProgram/content distribution protectionResource protectionAuthorization certificate
The invention provides a digital resource copyright protection method and device. Digital resource content encryption is carried out to a digital resource by means of a first secret key; the first secret key is encrypted by means of a second secret key, and an encryption certificate is generated in dependence on encrypted information; the encrypted digital resource and the encryption certificate are sent to each hardware storage device; the second secret key is bound with a unique identification of the hardware storage devices, and an authorization file of the hardware storage devices is generated. According to the scheme, when the digital resource is licensed to a plurality of mobile terminals in a batch manner, only two times of encryption work are needed, one authorization certificate is made for each hardware storage device, encryption in a batch manner is achieved, time spending on binding the hardware storage devices with the digital resource is greatly reduced, the production efficiency of massive copyright protection resources based on bound storage devices is improved, the production cost is reduced, at the same time, resource copyright protection is guaranteed, the resource is prevented from being copied and embezzled, and dependence of hardware resource protection on hardware equipment is avoided.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
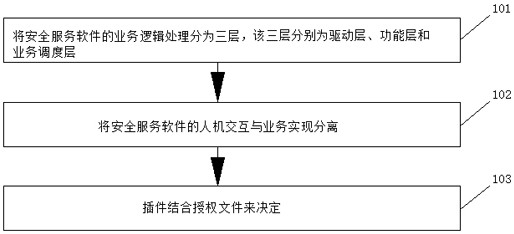
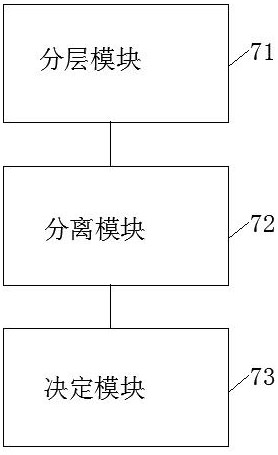
Cross-platform security service software construction method, device and equipment and storage medium
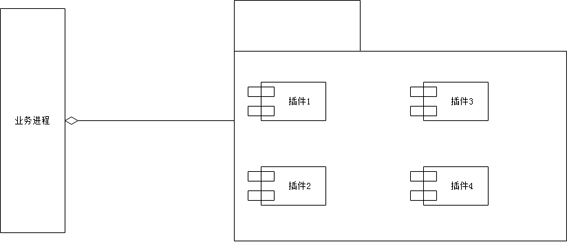
ActiveCN112394917AImprove scalabilityRealize reusabilityVersion controlInterprogram communicationOperational systemHot swapping
The embodiment of the invention discloses a cross-platform security service software construction method, device and equipment and a storage medium, and the cross-platform security service software construction method comprises the steps: dividing the business logic processing of security service software into three layers: a drive layer, a function layer and a business scheduling layer; separating human-computer interaction and business of the security service software; and determining the plug-in in combination with the authorization file. All the functional modules are used to be completelyindependent in a plug-in mode, transverse dependence does not exist among all the functional modules, and all the functional modules only depend on one public module. The functional module can realize a hot plug function in a software running process. All the functional modules only concern service logic codes and do not need to concern the difference of operating systems, and the effects of codereusability, service logic reusability, module reusability and software expandability in the true sense are achieved.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Method and device for preventing unauthorized use of software, equipment and storage medium
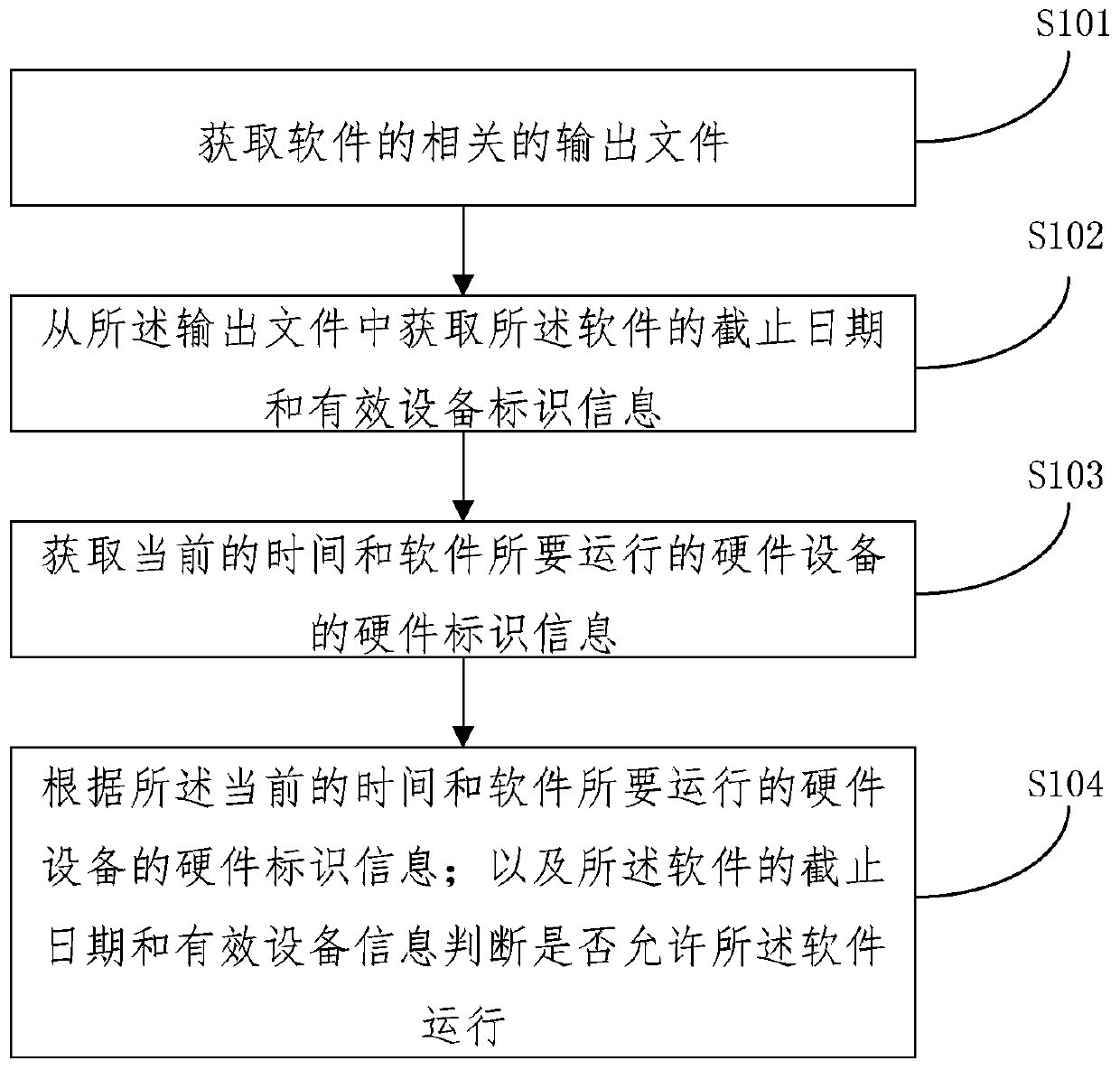
InactiveCN111159656AAuthorization verification implementationSolve the problem that the software cannot be verifiedProgram/content distribution protectionSoftware engineeringVerification
The embodiment of the invention relates to the technical field of information safety, in particular to a method and device for preventing software from being used in an unauthorized mode, equipment and a storage medium. The invention discloses a method capable of preventing unauthorized use of software. The method comprises the following steps: acquiring a related authorization file of the software; obtaining the deadline and the effective equipment recognition information of the software from the authorization file; acquiring current time and hardware recognition information of hardware equipment to be operated by software; identifying information according to the current time and hardware; and judging whether the software is allowed to run or not according to the deadline of the softwareand the effective equipment information. Whether the software is allowed to run or not can be judged according to the current time, the hardware recognition information of the hardware equipment to be run by the software, the deadline and the effective equipment information; according to the method and the device, networking is not needed, authorization verification of the software can be completed locally, and the problem that in the prior art, if equipment cannot be networked, the software cannot be authenticated is solved.
Owner:核芯互联科技(青岛)有限公司
Access system, access device and access method for accessing health information
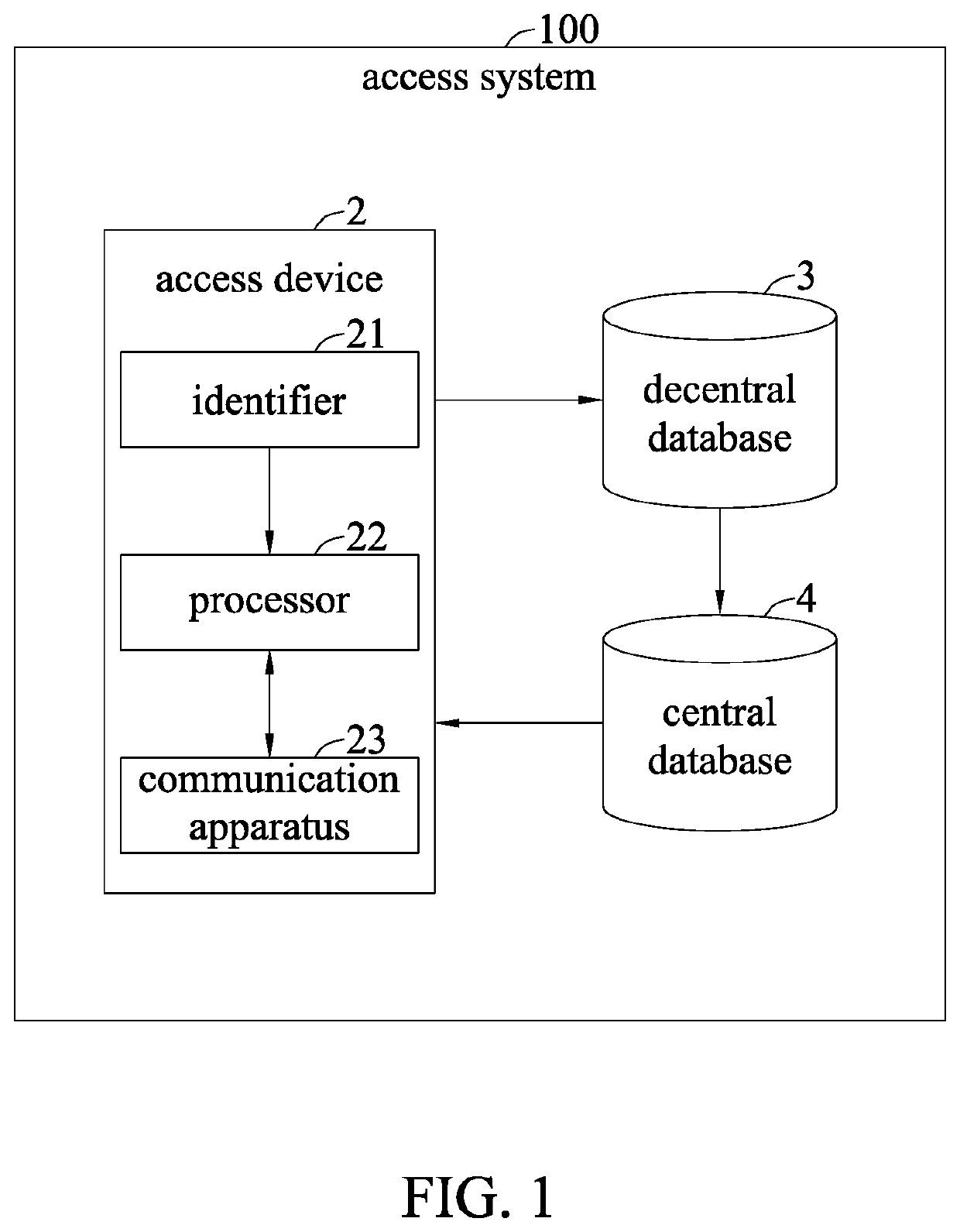
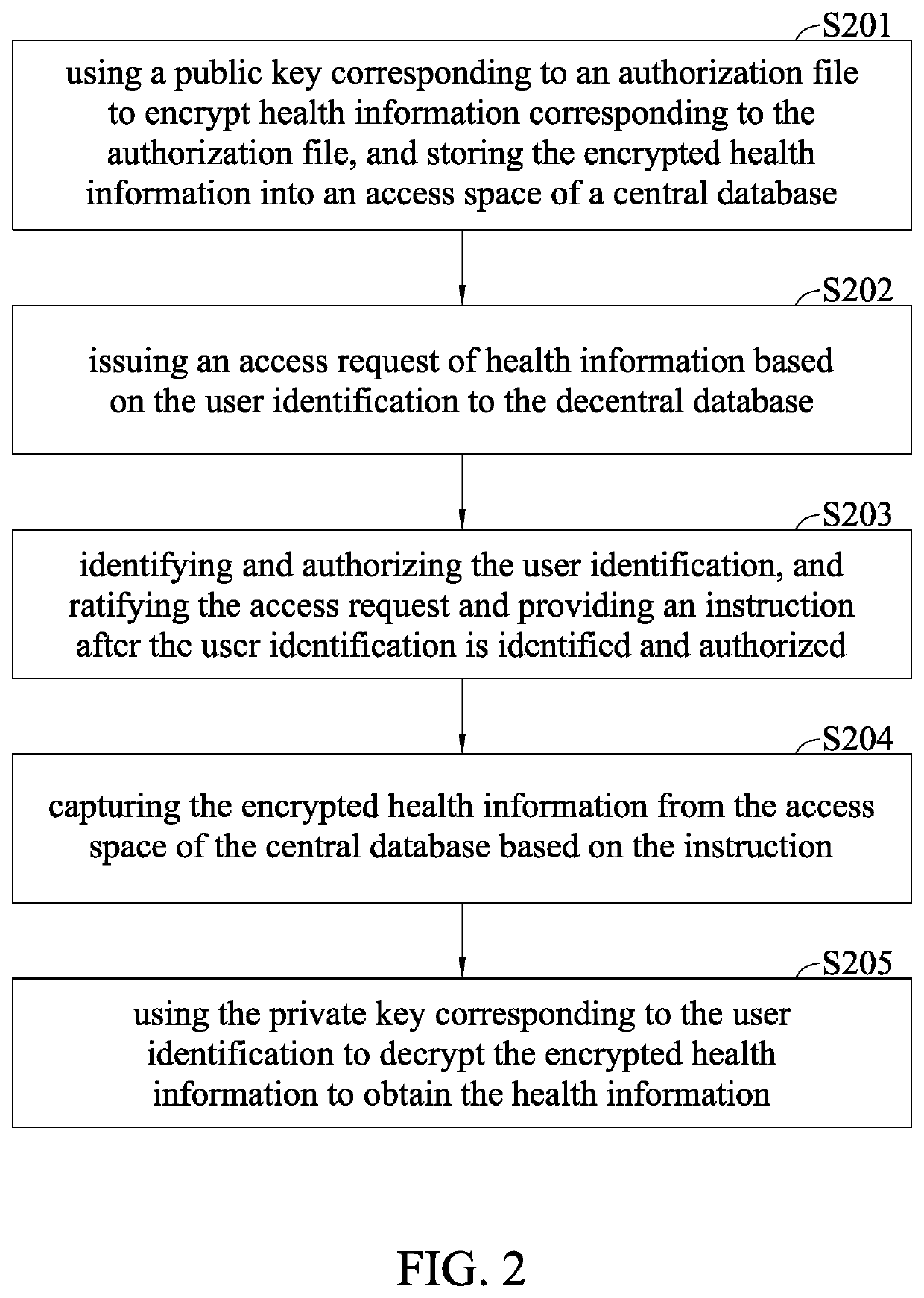
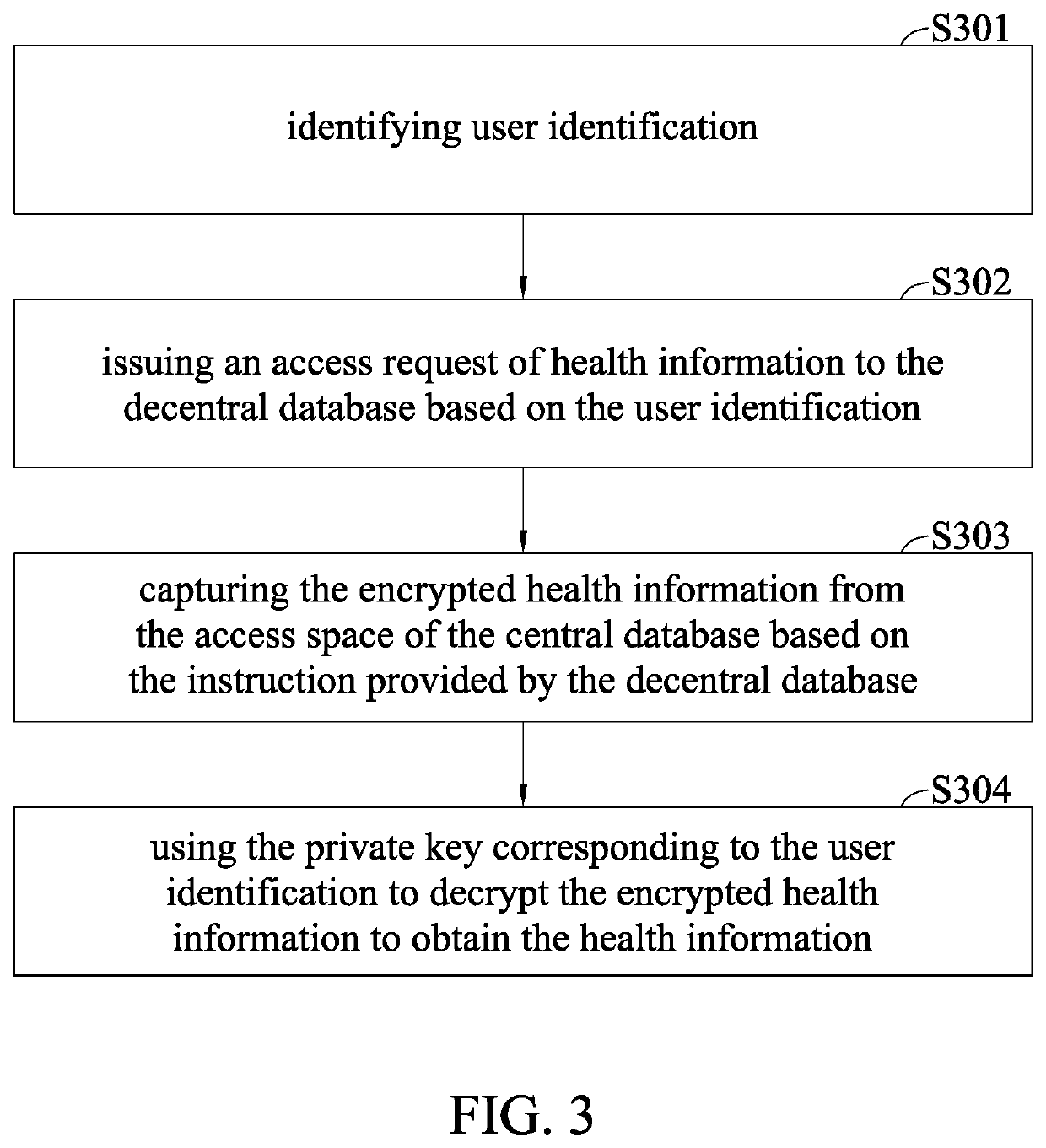
ActiveUS20200184099A1Encryption apparatus with shift registers/memoriesPublic key for secure communicationAccess methodInternet privacy
An access system, an access device and an access method for accessing health information are disclosed. The access system includes a decentralized database for recording an authorization file corresponding to health information and a public key corresponding to the authorization file, a centralized database for using the public key corresponding to the authorization file to encrypt and store the health information corresponding to the authorization file into an access space, and an access device for issuing an access request of health information to the decentralized database based on user identification, for the decentralized database to identify and authorize the user identification based on the authorization file corresponding to the health information and ratify the access request and provide an instruction after identifying and authorizing the user identification, and for acquiring the encrypted health information from the access space based on the instruction.
Owner:IND TECH RES INST
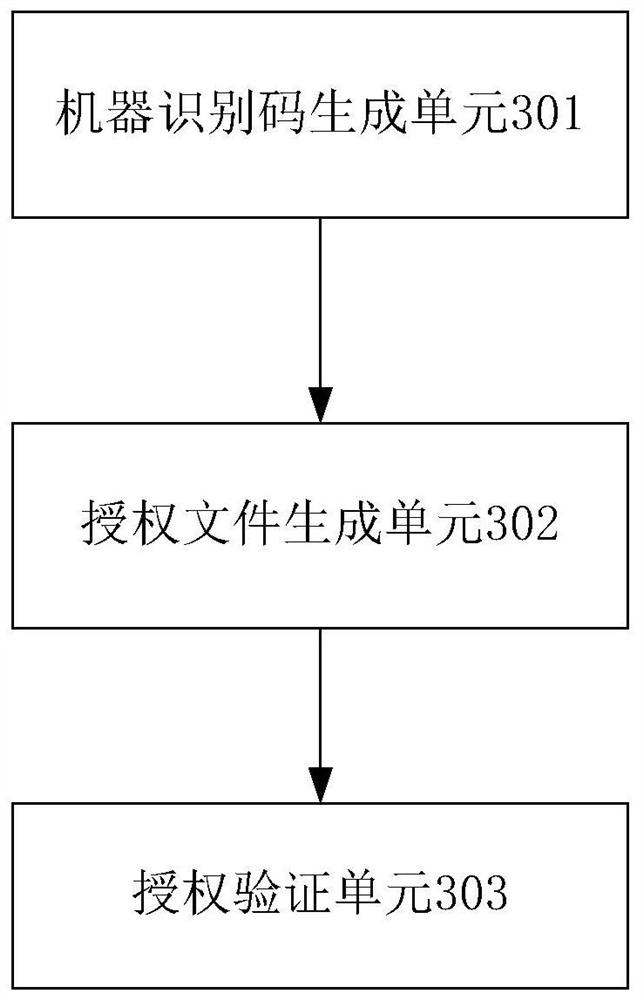
Permission authorization method and device based on machine identification code
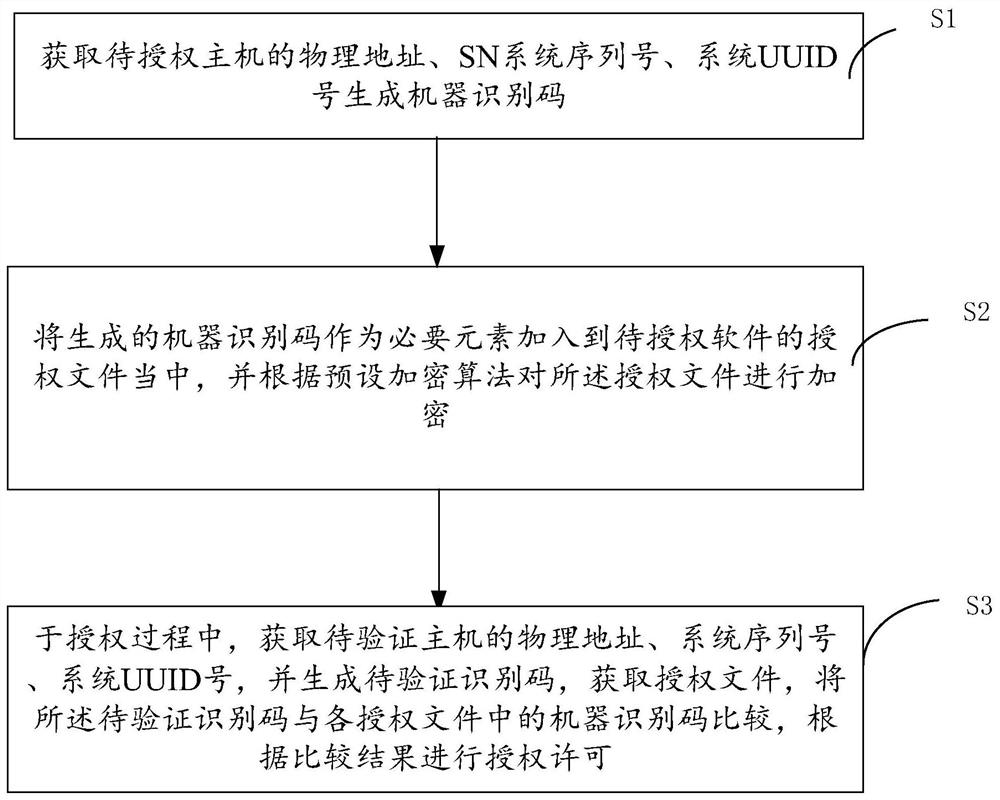
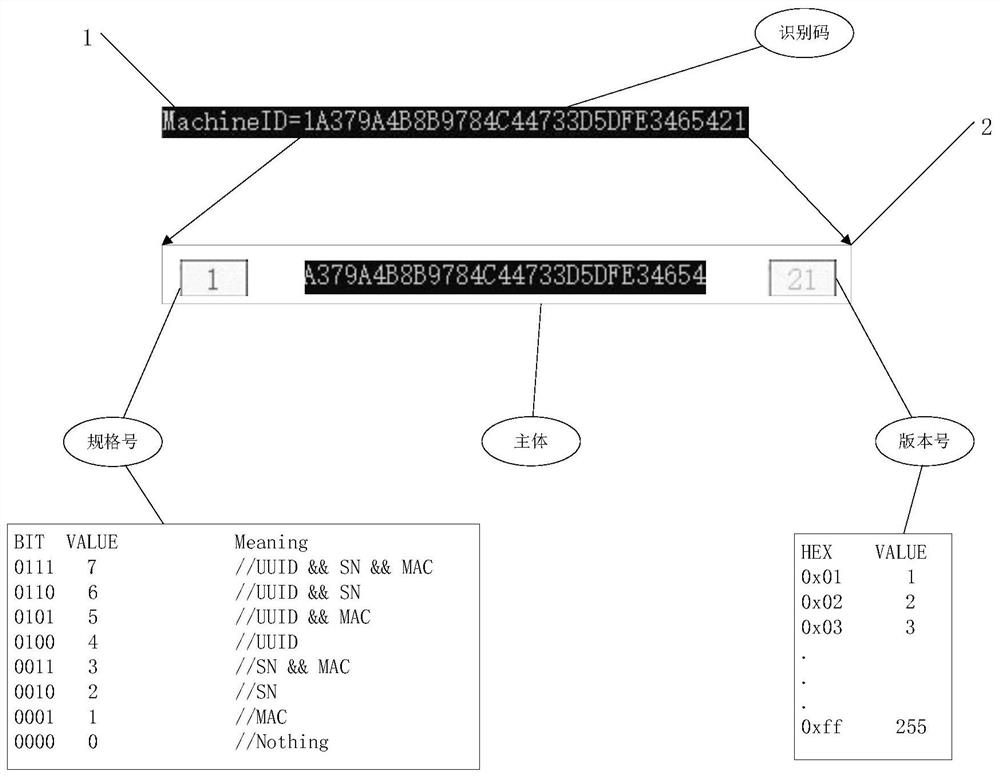
PendingCN111881424ATo achieve the purpose of authorization verificationProgram/content distribution protectionProgramming languagePhysical address
The invention discloses a permission authorization method and device based on a machine identification code, and the method comprises the following steps: S1, obtaining a physical address, a system serial number and a system UUID number of a to-be-authorized host, and generating the machine identification code; S2, adding the generated machine identification code as a necessary element into an authorization file of to-be-authorized software, and encrypting the authorization file according to a preset encryption algorithm; and S3, in the authorization process, obtaining a physical address, a system serial number and a system UUID number of the to-be-verified host, generating a to-be-verified identification code, obtaining an authorization file, comparing the to-be-verified identification code with the machine identification code in each authorization file, and performing authorization permission according to a comparison result.
Owner:INFORMATION2 SOFTWARE SHANGHAI
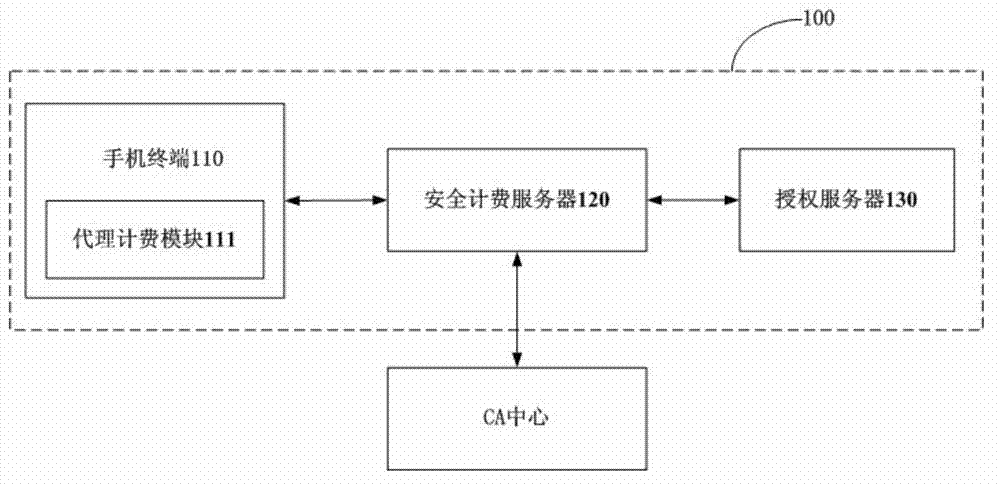
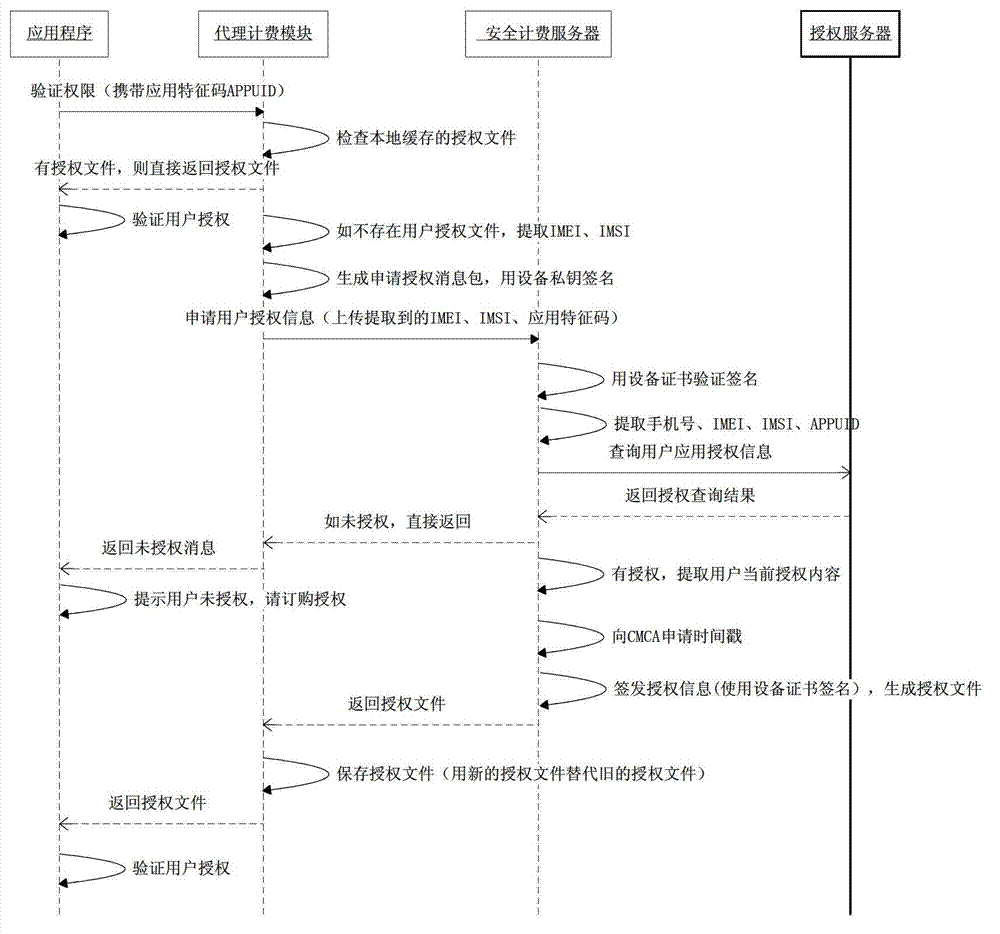
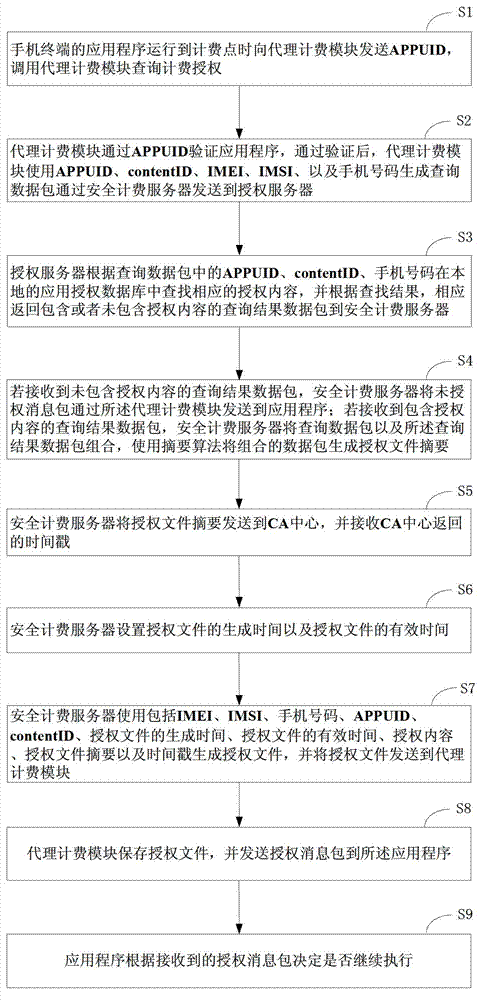
Billing point verification method and system
ActiveCN103716763AMeet billing needsNon-counterfeitAccounting/billing servicesSecurity arrangementTimestampNetwork packet
The invention discloses a billing point verification method and system. The system comprises a mobile phone terminal, a security billing server and an authorization server. The mobile phone terminal comprises an application and a proxy billing module. The method comprises the steps that S1, when the application runs to a billing point, the proxy billing module is called; S2, the proxy billing module generates a query data packet and sends the query data packet to the authorization server; S3, the authorization server returns a query result data packet; S4, the security billing server sends an unauthorized message packet to the application or generates an authorization document summary according to the query result data packet; S5, the security billing server acquires a timestamp; S6, the security billing server sets authorization document generation and effective time; S7, the security billing server generates an authorization document and sends the authorization document to the proxy billing module; and S8, the proxy billing module saves the authorization document. A user actively initiates service billing. The billing point of the application has the characteristics of faking prevention, repudiation prevention and the like.
Owner:卓望数码技术(深圳)有限公司
Safety control method and system
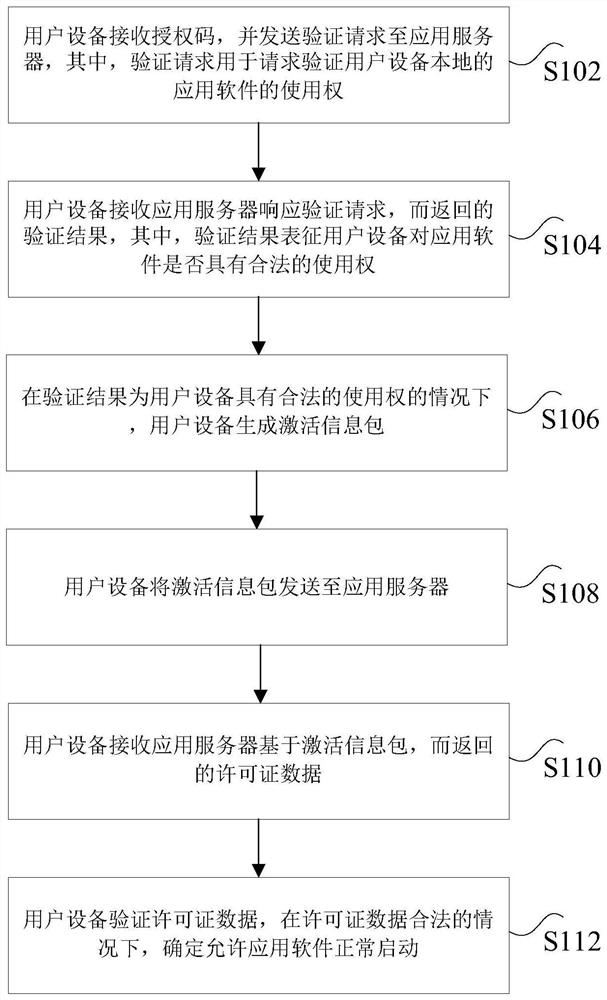
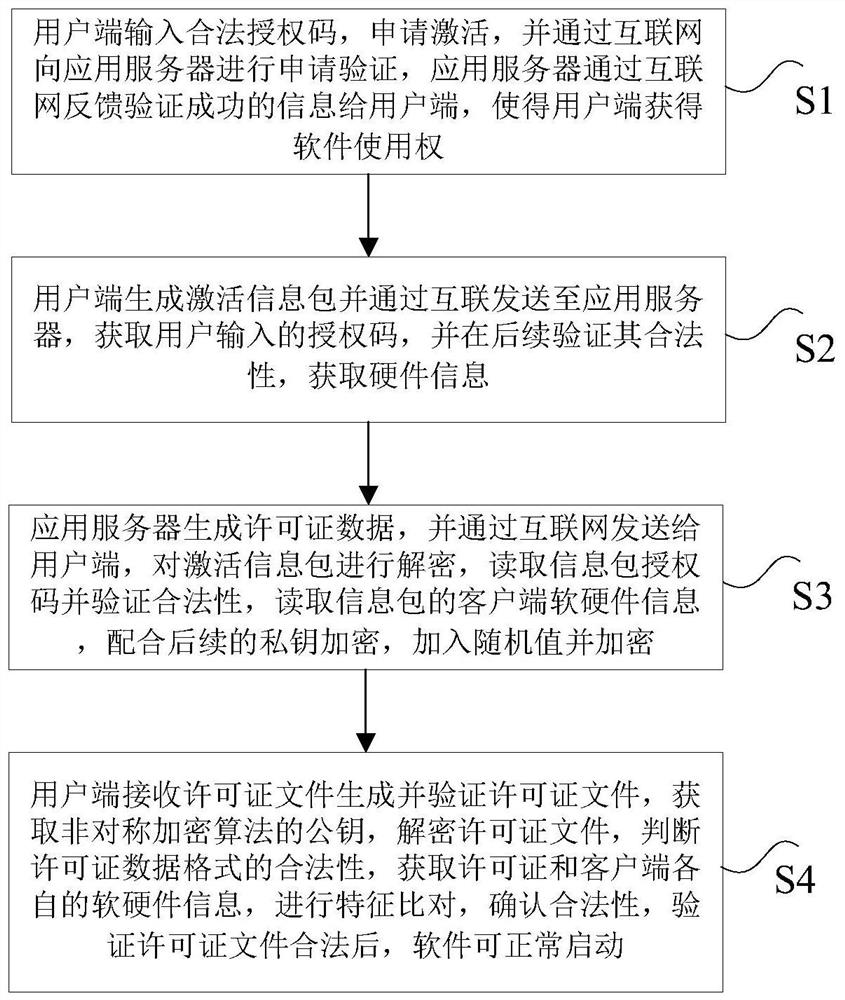
PendingCN112417385AImprove securityDigital data authenticationProgram/content distribution protectionApplication serverApplication software
The invention discloses a safety control method and system. The method comprises the steps that user equipment receives an authorization code and sends a verification request to an application server;the user equipment receives a verification result returned by the application server in response to the verification request; under the condition that the verification result shows that the user equipment has the legal right to use, the user equipment generates an activation information packet; the user equipment sends the activation information packet to an application server; the user equipmentreceives license data returned by the application server based on the activation information packet; and the user equipment verifies the license data, and determines that the application software isallowed to be normally started under the condition that the license data is legal. According to the method and the device, the technical problems that the use security of the software is threatened and the security is relatively low due to the fact that the software is easy to crack and the authorization file is intercepted in an authorization use process at present and the software is illegally used are solved.
Owner:STATE GRID BEIJING ELECTRIC POWER +1
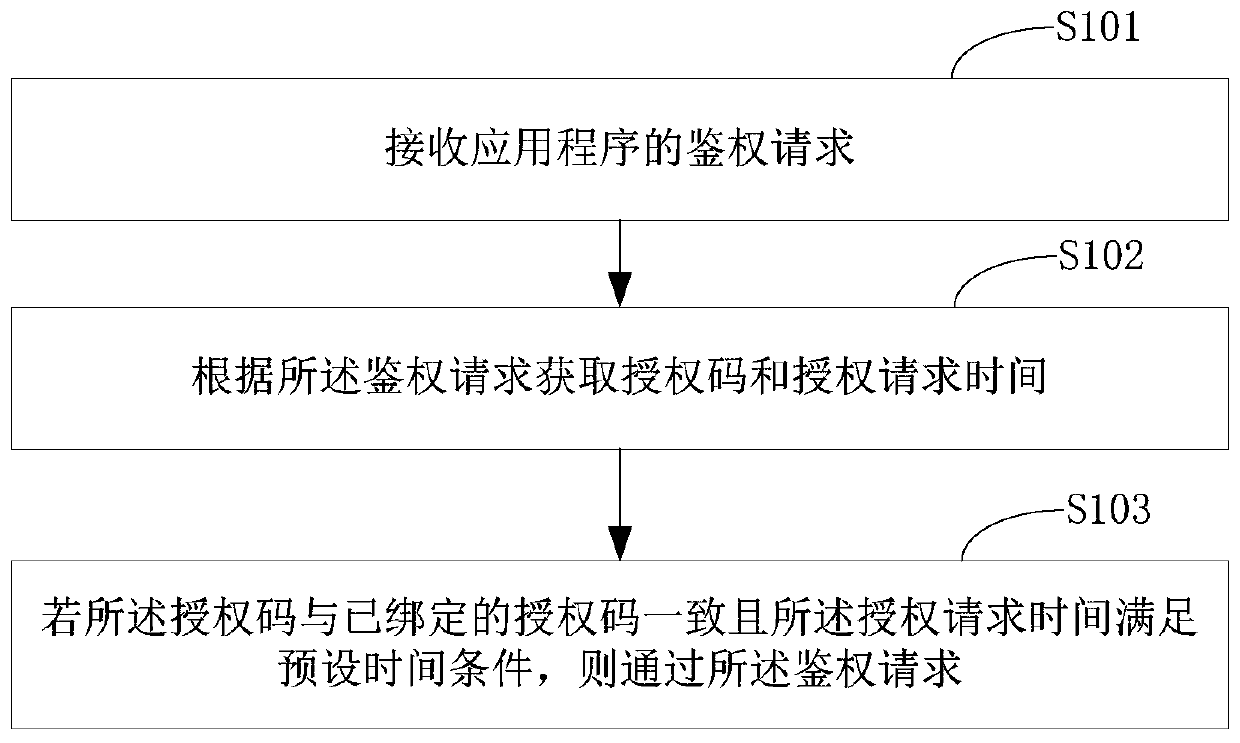
Application program authentication method and system
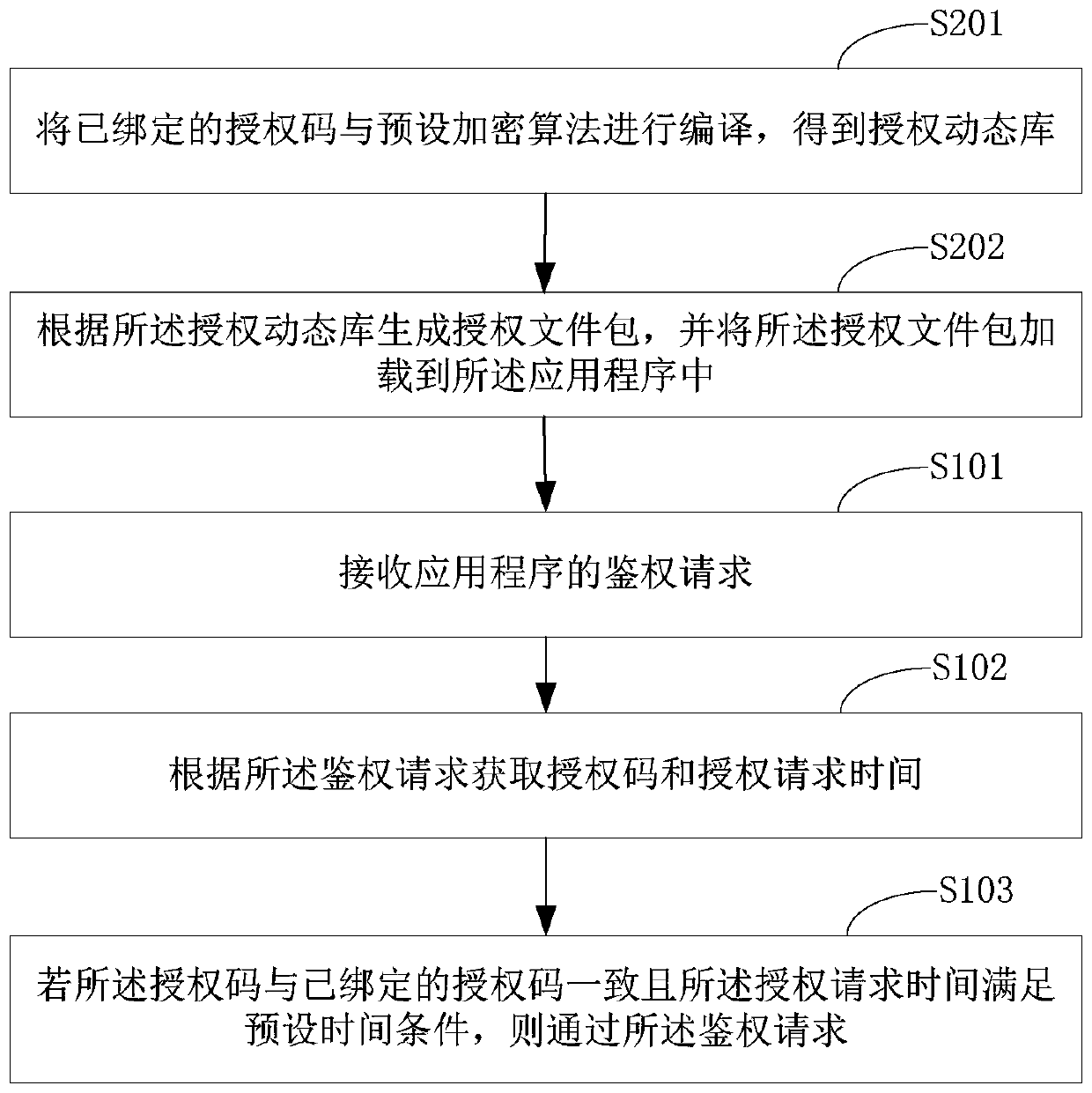
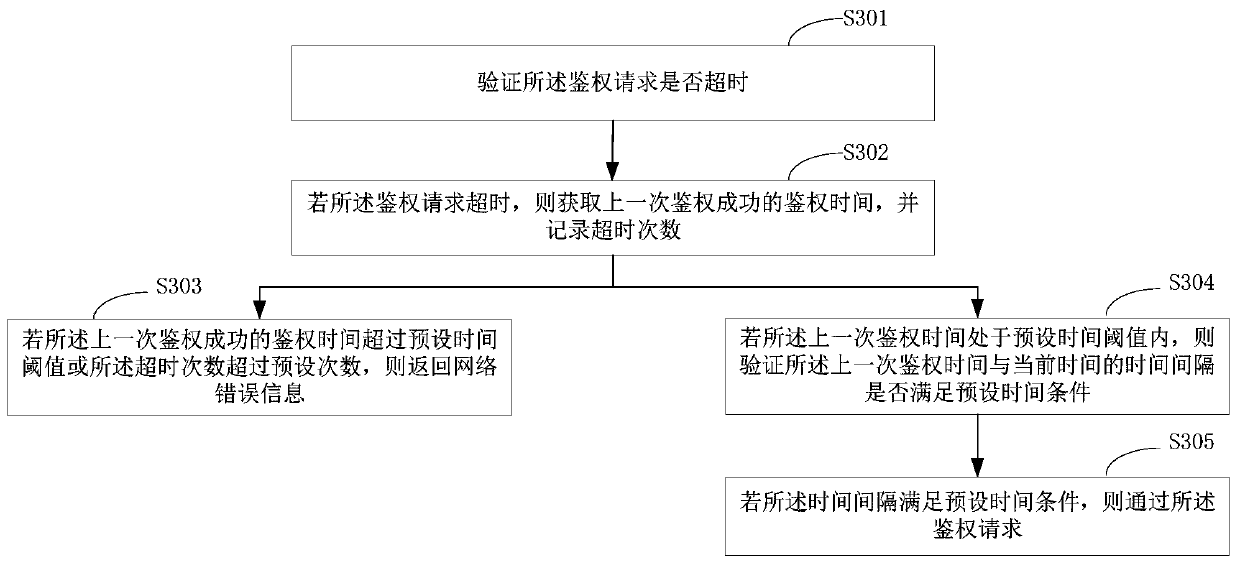
InactiveCN111159657AReach Authorization ManagementUsabilityProgram/content distribution protectionSoftware engineeringApplication procedure
The invention is suitable for the technical field of software, and provides an application program authentication method and system. The method comprises the steps: receiving an authentication requestof an application program; wherein the authentication request is generated by calling an authorization file package when the application program is started or operated; obtaining an authorization code and authorization request time according to the authentication request; if the authorization code is consistent with the bound authorization code and the authorization request time meets a preset time condition, sending the authorization request to a server; if so, passing the authentication request; centralized authorization management is provided for a large number of application programs; when an application program is started or operated, an assigned authorization file package is called to realize authorization verification when a service is started and timing authorization verificationwhen the service is operated; and verifying whether the application program is a service program in an authorization period or not based on the verification request, thereby realizing the purposes ofremotely performing authorization management and timed use management on the service program.
Owner:深圳智链物联科技有限公司
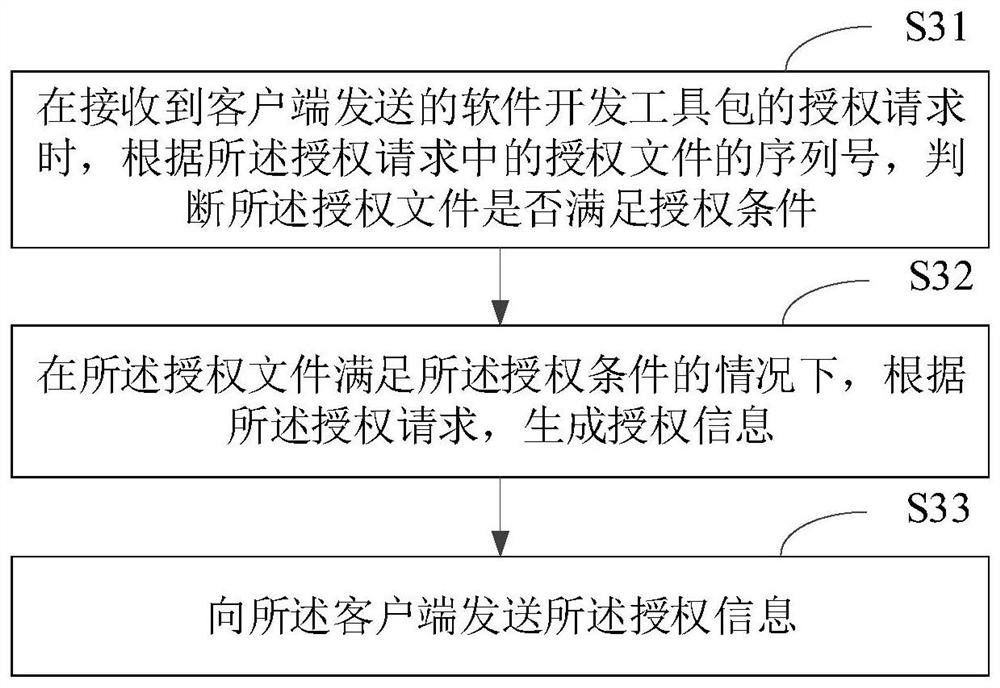
Authorization method and device, electronic equipment and storage medium
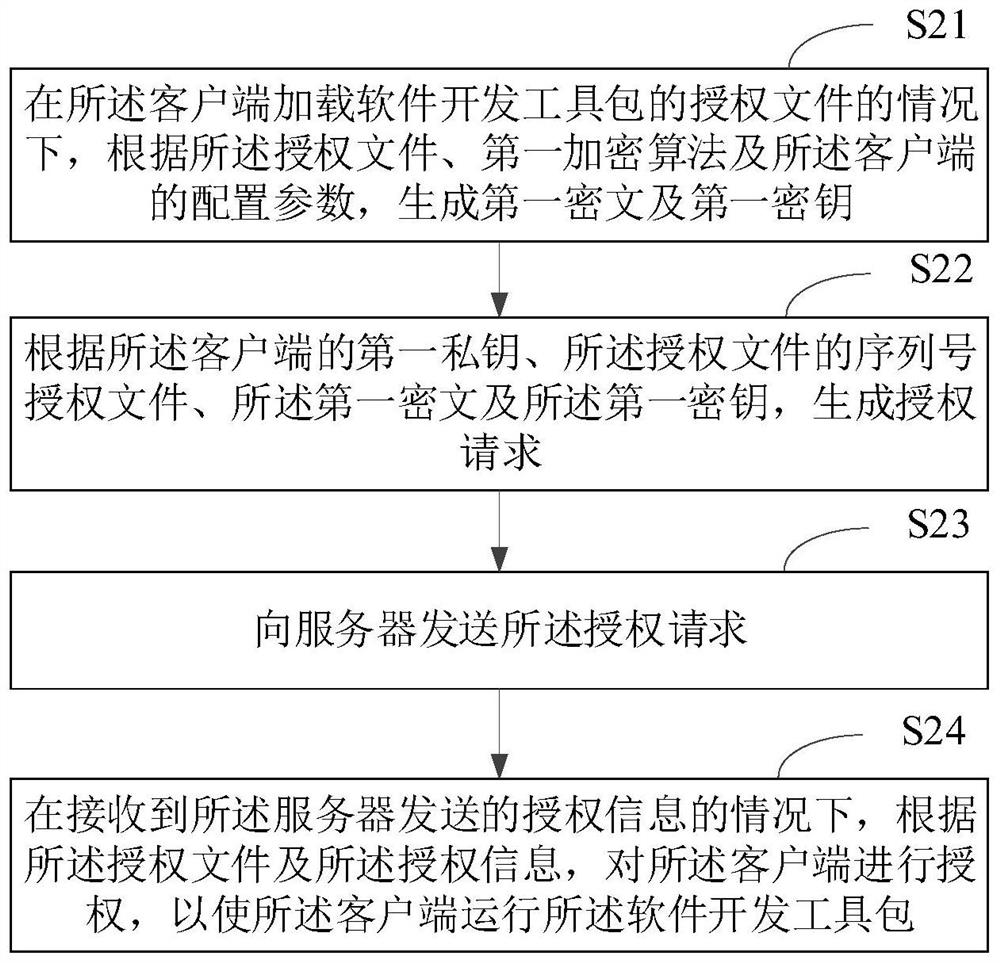
ActiveCN113242224AImprove securityReduce the number of interactionsUser identity/authority verificationCiphertextEngineering
The invention relates to an authorization method and device, electronic equipment and a storage medium, and the method is applied to a client, and comprises the steps: generating a first ciphertext and a first secret key according to an authorization file, a first encryption algorithm and a configuration parameter of the client under the condition that the client loads the authorization file of a software development kit; generating an authorization request according to the authorization file, the first ciphertext and the first key; sending the authorization request to a server; under the condition that authorization information sent by the server is received, authorizing the client according to the authorization file and the authorization information, so that the client runs the software development kit. According to the embodiment of the invention, one-time pad can be realized during data transmission, the data security is improved, the number of times of interaction between the client and the server can be reduced, and the data transmission efficiency is improved.
Owner:BEIJING SENSETIME TECH DEV CO LTD
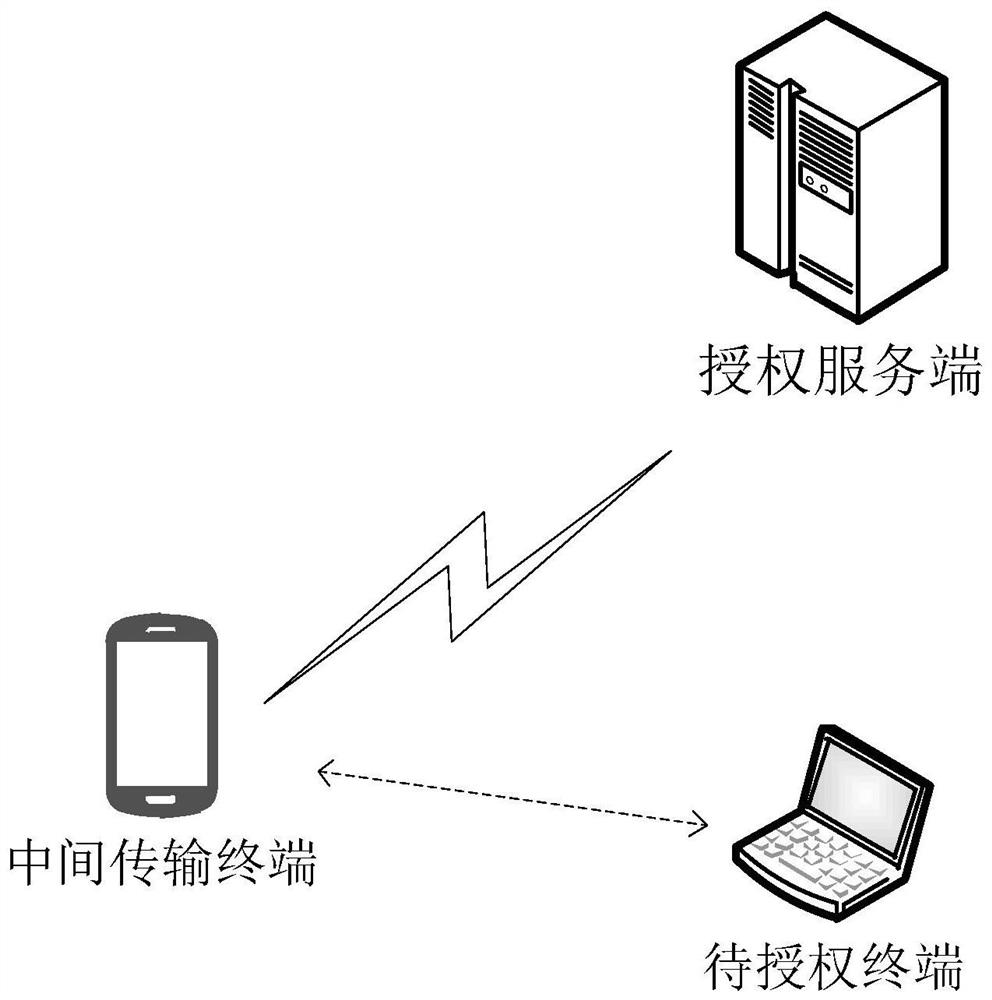
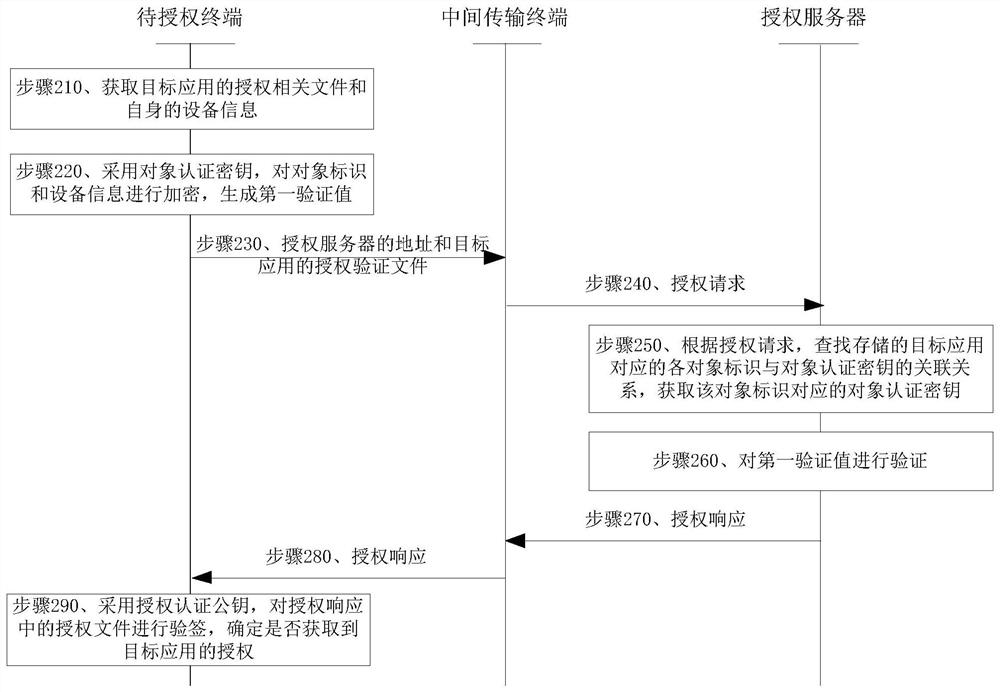
Authorization management method and device
The invention discloses an authorization management method and device. The method comprises the following steps: in a scene that no communication connection exists between a to-be-authorized terminaland an authorization server of a target application, after the to-be-authorized terminal acquires an authorization related file of the target application and equipment information of the to-be-authorized terminal, encrypting an object identifier and the equipment information by adopting an object authentication key to generate a first verification value; transmitting the address of the authorization server and the authorization verification file of the target application to an intermediate transmission terminal, so that the intermediate transmission terminal accesses the authorization server;if the authorization file sent by the authorization server and received by the intermediate transmission terminal is obtained, performing signature verification on the authorization file by adopting an authorization authentication public key; and when the signature verification succeeds, determining that the authorization of the target application is obtained. According to the method, data transmission between the to-be-authorized terminal and the authorization server is realized through the intermediate transmission terminal, so that the to-be-authorized terminal is authorized, and the user experience is improved.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Application software authority management method and device, server and storage medium
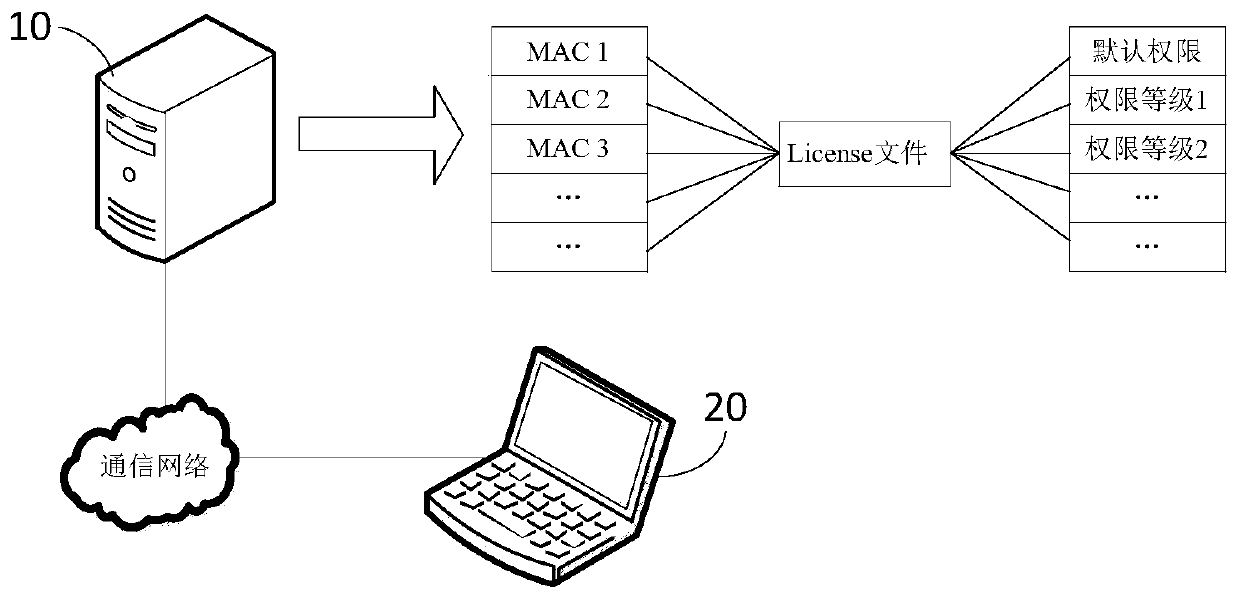
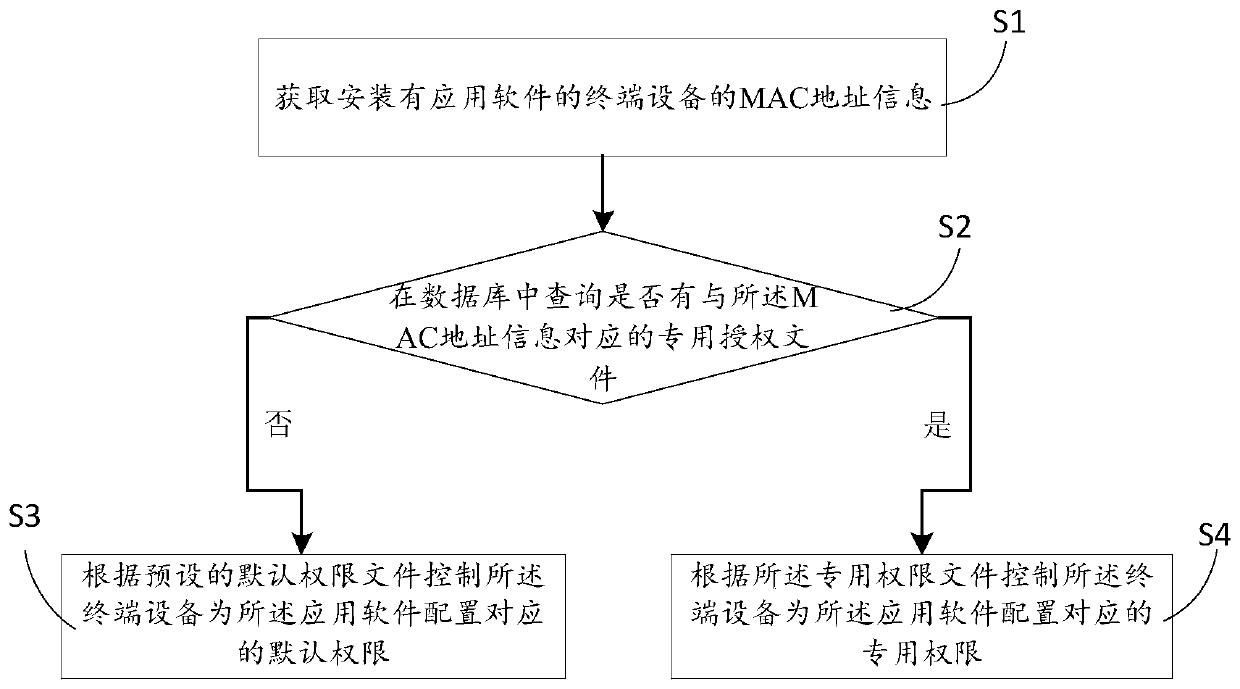
ActiveCN111143782ATransmissionProgram/content distribution protectionSoftware engineeringTerminal equipment
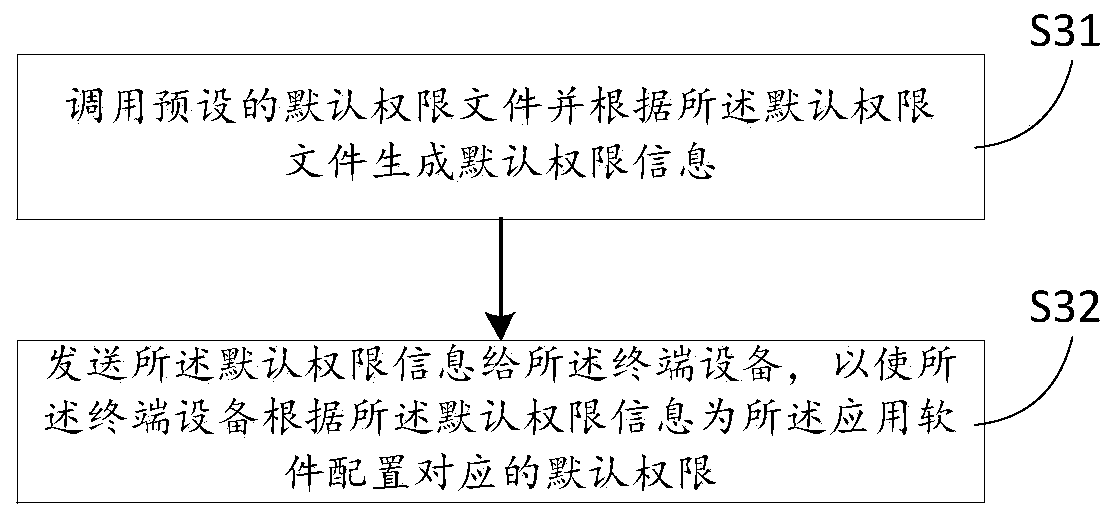
The invention discloses an authority management method and device for application software, a server and a storage medium, the method is applied to the server, and the method comprises the following steps: acquiring MAC address information of terminal equipment installed with the application software; inquiring whether a special permission file corresponding to the MAC address information exists or not in a database, wherein the special permission file is an authorization file corresponding to the application software and generated according to record information after the server receives therecord information of the application software; if the special permission file corresponding to the MAC address information does not exist in the database, controlling the terminal equipment to configure corresponding default permission for the application software according to a preset default permission file; and if the special permission file of the MAC address information exists in the database, controlling the terminal equipment to configure a corresponding special permission for the application software according to the special permission file.
Owner:LAUNCH TECH CO LTD
License authorization method and device
ActiveCN114186199ALow costImprove experienceProgram/content distribution protectionEngineeringProtection system
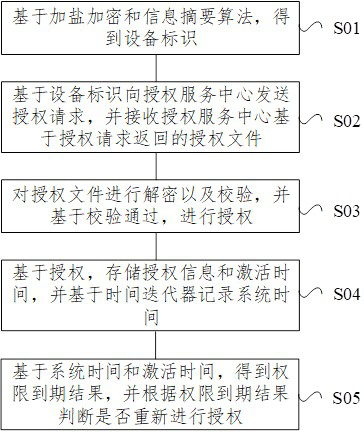
The invention provides a permission authorization method and device, and the method comprises the steps: obtaining an equipment identifier based on salting encryption and an information abstract algorithm; sending an authorization request to an authorization service center based on the equipment identifier, and receiving an authorization file returned by the authorization service center based on the authorization request; the authorization file is decrypted and verified, and authorization is carried out based on verification success; storing authorization information and activation time based on authorization, and recording system time based on a time iterator; and obtaining a permission expiration result based on the system time and the activation time, and judging whether to re-authorize according to the permission expiration result. According to the method and the device, the obtained equipment identifier is sent to the authorization service center to obtain the authorization file, so that the authorization file is used for authorizing the corresponding product, the leakage risk is further reduced, the safety is further improved, and the use copyright of the system and the rights and interests of developers are more effectively protected.
Owner:北京安帝科技有限公司
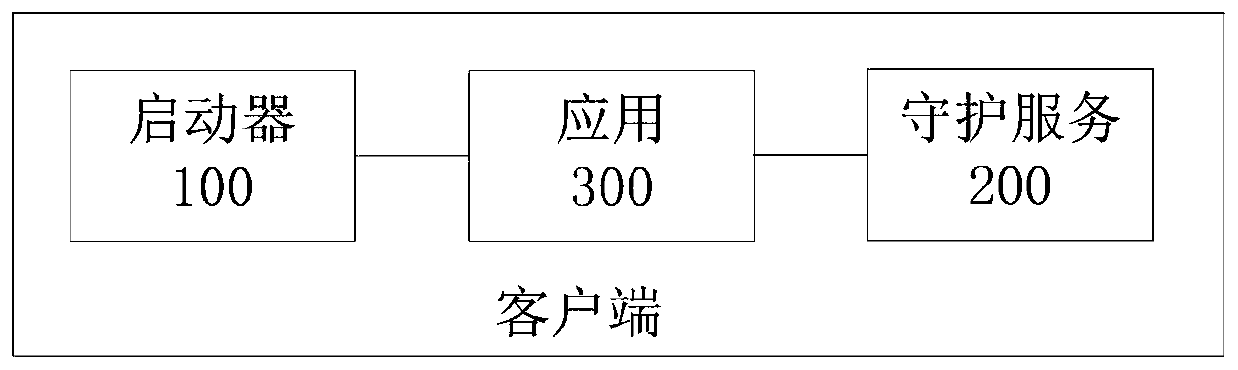
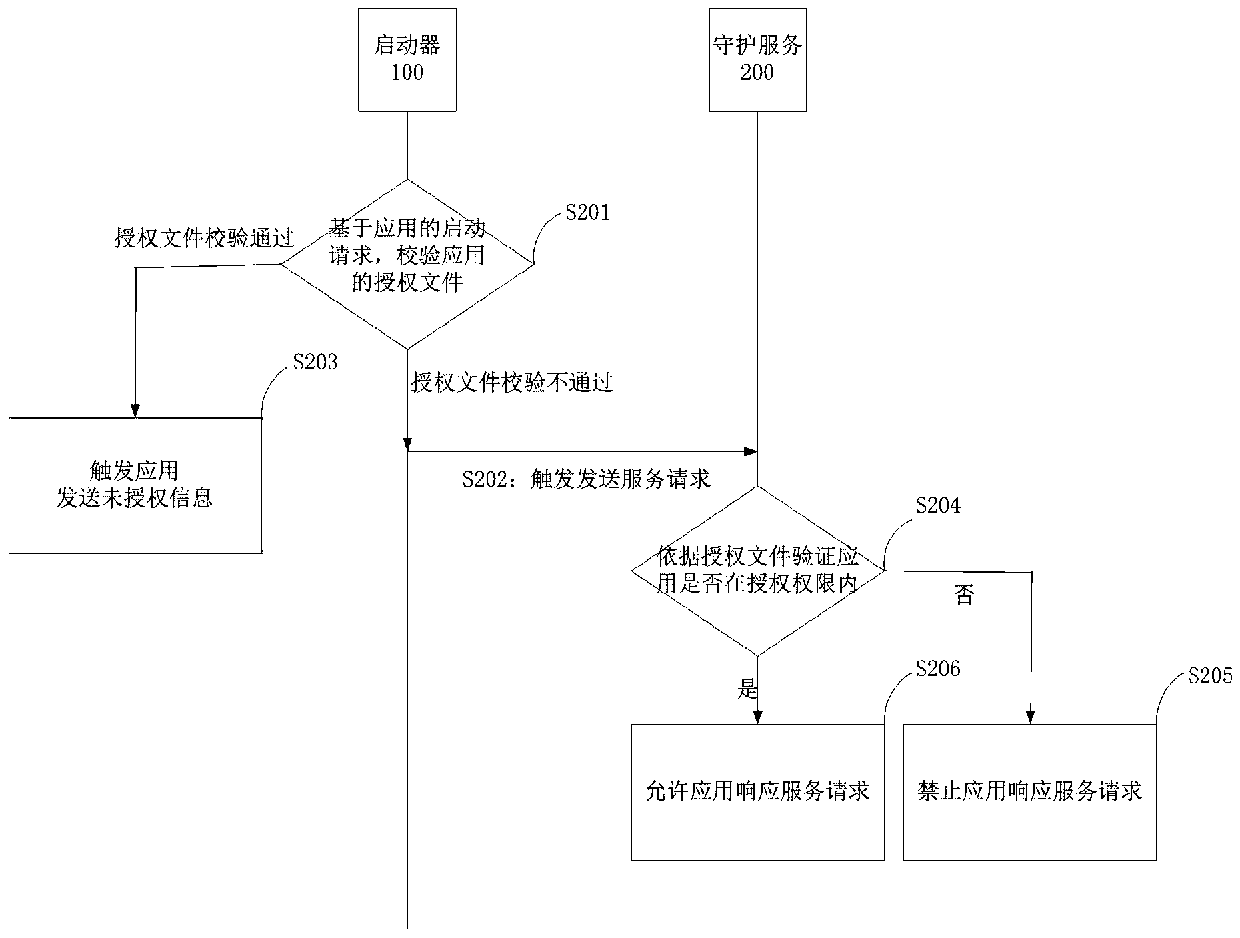
Application authorization verification method, device and system
ActiveCN110659457AAvoid issues with bypassing authorization verificationDigital data authenticationProgram/content distribution protectionEngineeringAuthorization
The invention provides an application authorization verification method, a device and a system. The method comprises the steps of verifying the authorization file of the application based on the starting request of the application, triggering the application to send a service request under the condition that the verification of the authorization file is passed, verifying whether the application iswithin the authorization authority or not according to the authorization file, and forbidding the application to respond to the service request if the application is determined not to be within the authorization authority. Since the service request is triggered according to the authorization file and then whether the application is within the authorization authority is further verified accordingto the authorization file, the application can respond to the service request only when the authorization file is legal and the application is within the authorization authority. Visibly, even if theapplication is started by means of a command line and the like based on the characteristics of the pseudo CS architecture, the service request sent by the application can be responded only after authority verification, so that the problem that the service request bypasses authorization verification can be effectively avoided, and the application of the pseudo CS architecture is subjected to authorization protection.
Owner:ANHUI IFLYREC TECH CO LTD
Card modification method and device of terminal equipment, storage medium and terminal equipment
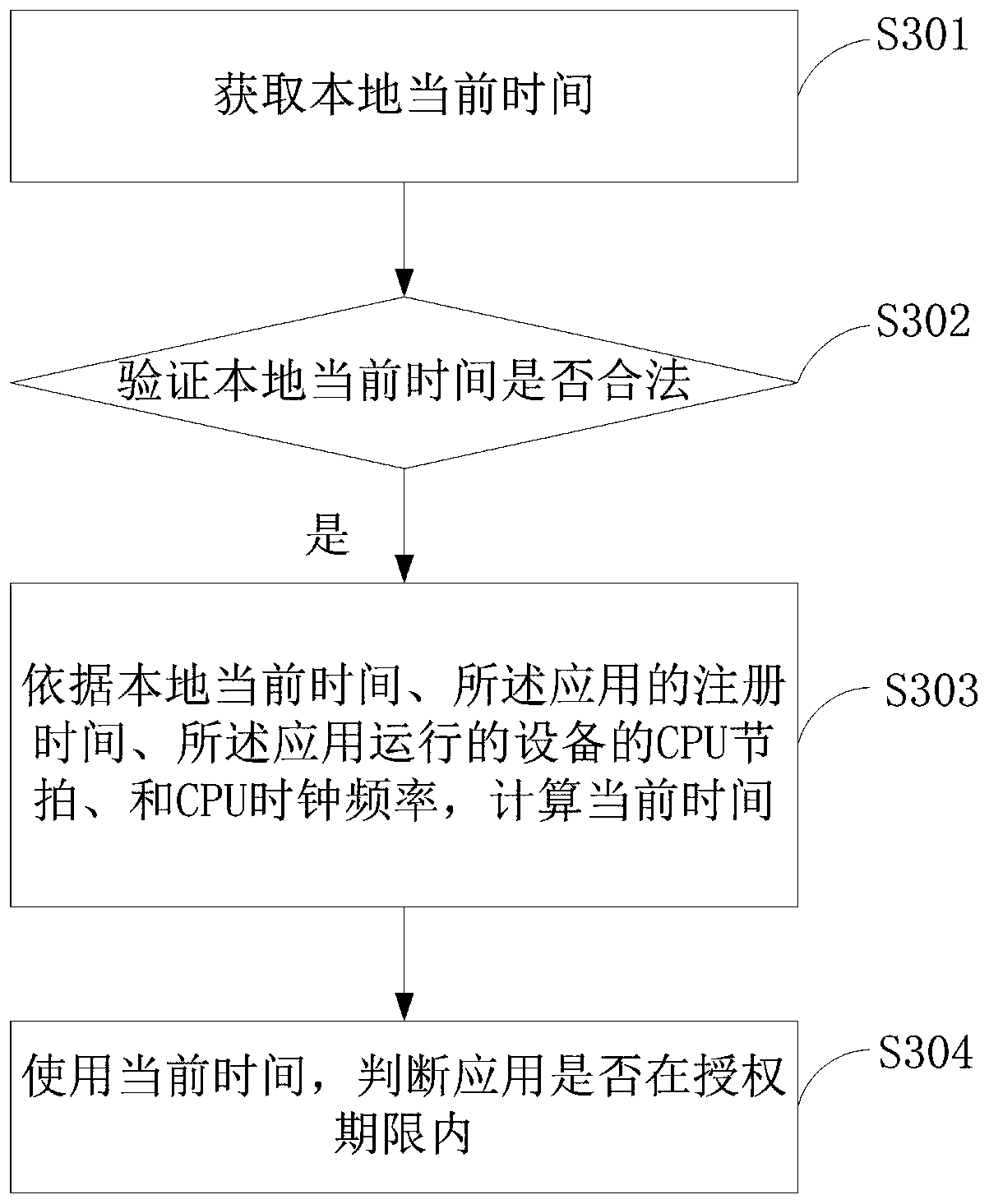
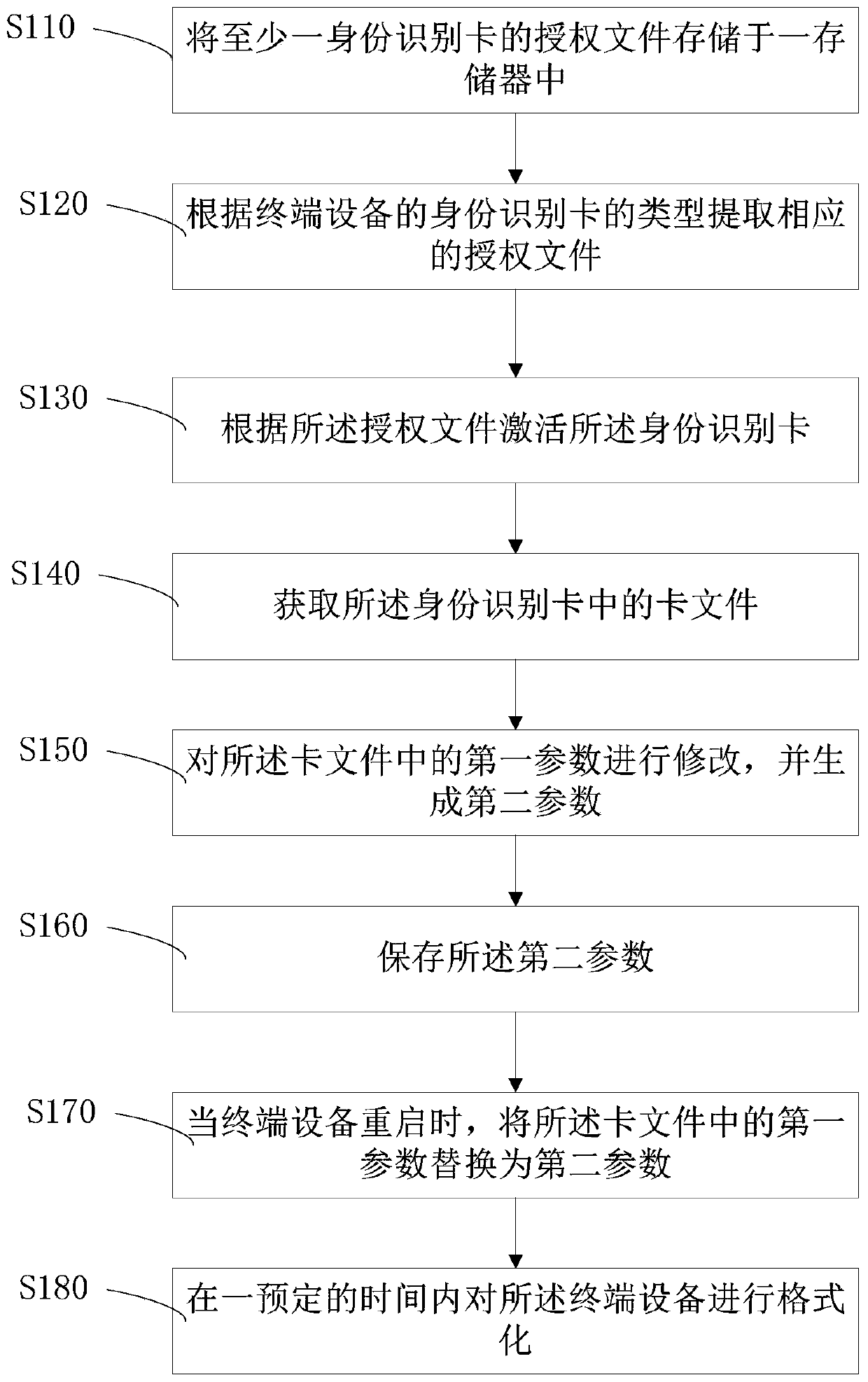
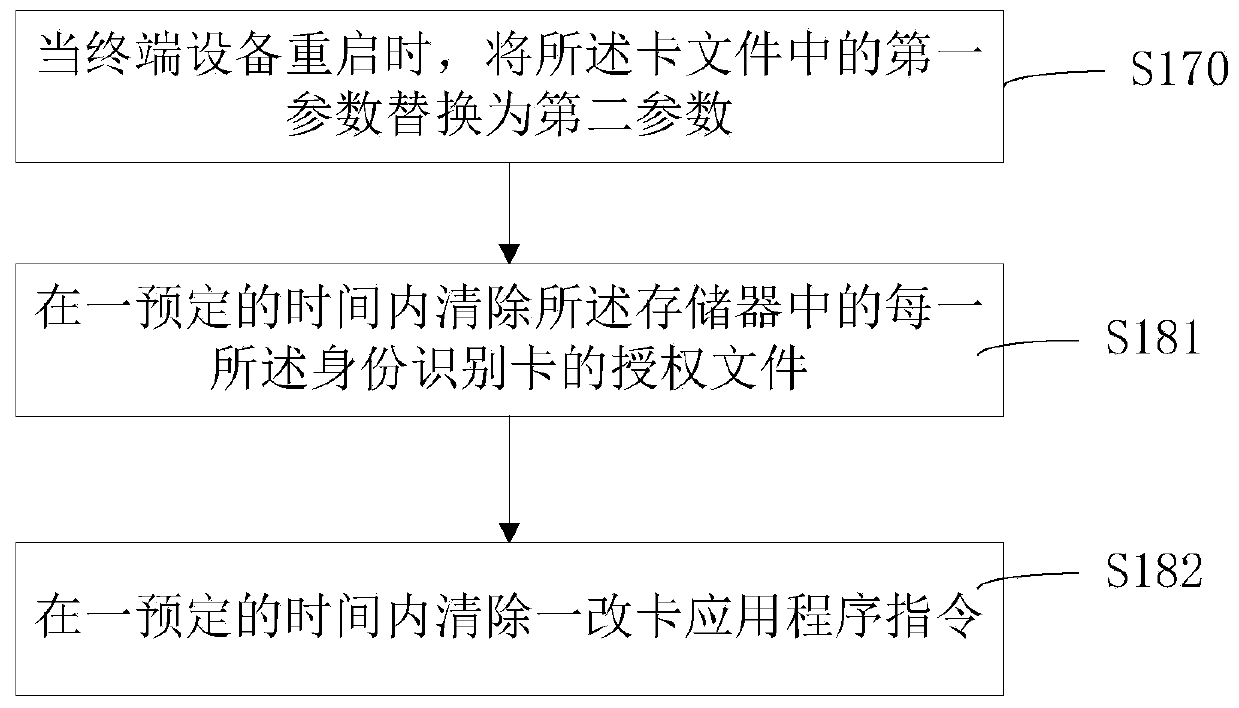
PendingCN111045742AAvoid repeated plugging and unpluggingReduce lossSoftware testing/debuggingBootstrappingIdentity recognitionTerminal equipment
The invention discloses a card modification method and device of terminal equipment, a storage medium and the terminal equipment. The card modification method of the terminal equipment comprises the following steps: storing an authorization file of at least one identity identification card in a memory; extracting a corresponding authorization file according to the type of an identity identification card of the terminal equipment; activating the identity identification card according to the authorization file; obtaining a card file in the identity identification card; and modifying the first parameter in the card file, and generating a second parameter. According to the invention, the card modification method is adopted in the terminal equipment, and parameter modification is directly carried out on the identity identification card in the terminal equipment.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
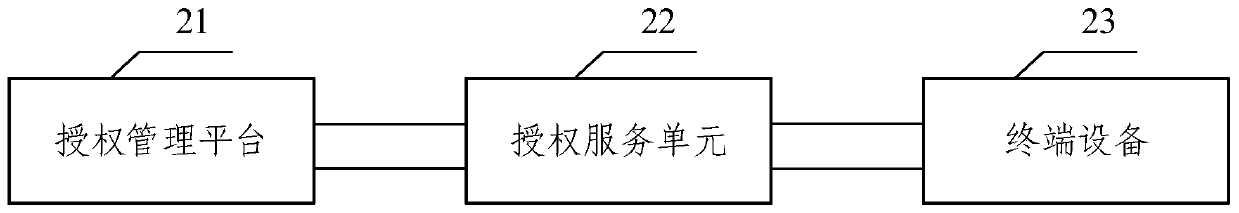
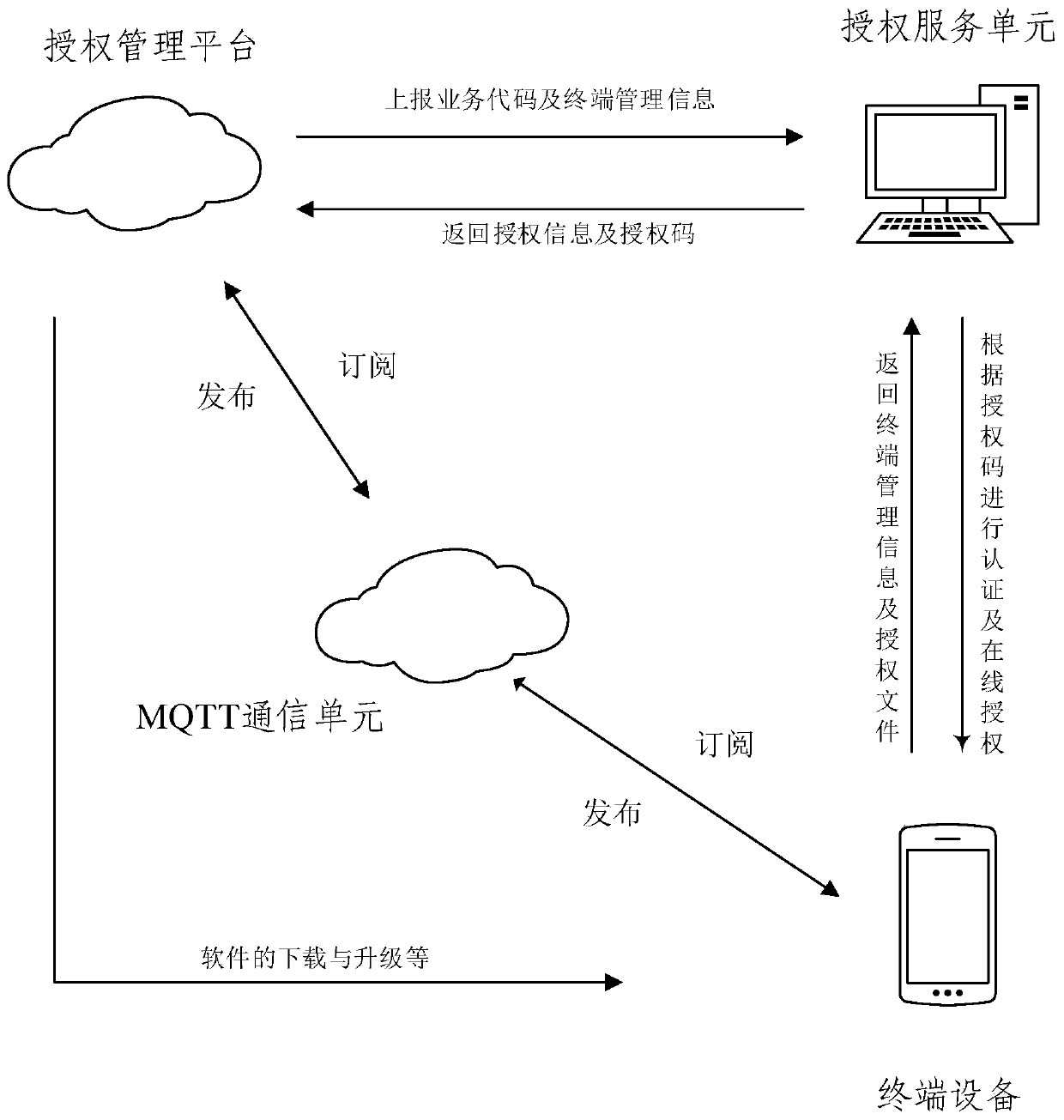
Cross-platform terminal authorization management method and system
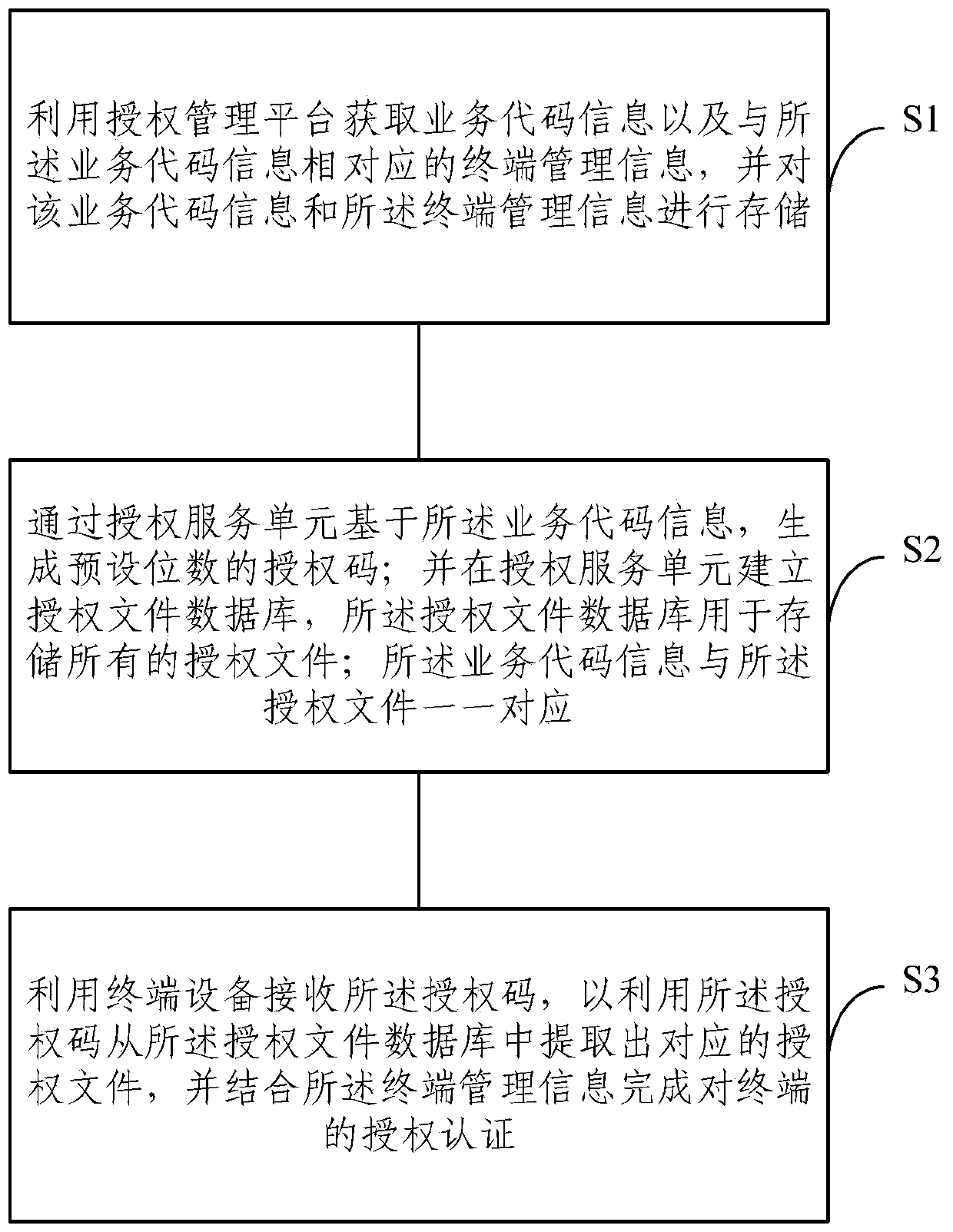
InactiveCN110737884AImprove securitySafe and efficient authorization issuanceDigital data authenticationTransmissionTerminal equipmentEngineering
The embodiment of the invention provides a cross-platform terminal authorization management method and a system, and the method comprises the steps: obtaining business code information and terminal management information through an authorization management platform, and storing the business code information and the terminal management information of terminal equipment; generating an authorizationcode with a preset digit through an authorization service unit based on the service code information; establishing an authorization file database in the authorization service unit, wherein the authorization file database is used for storing all authorization files; wherein the service code information is in one-to-one correspondence with the authorization files; and receiving the authorization code by using terminal equipment, extracting a corresponding authorization file from an authorization file database by using the authorization code, and finishing authorization authentication of the terminal in combination with the terminal management information. According to the method of the invention, safe and efficient authorization issuing and management are directly carried out on various terminals, so that unified management of terminal software authorization is achieved.
Owner:武汉普利商用机器有限公司 +1
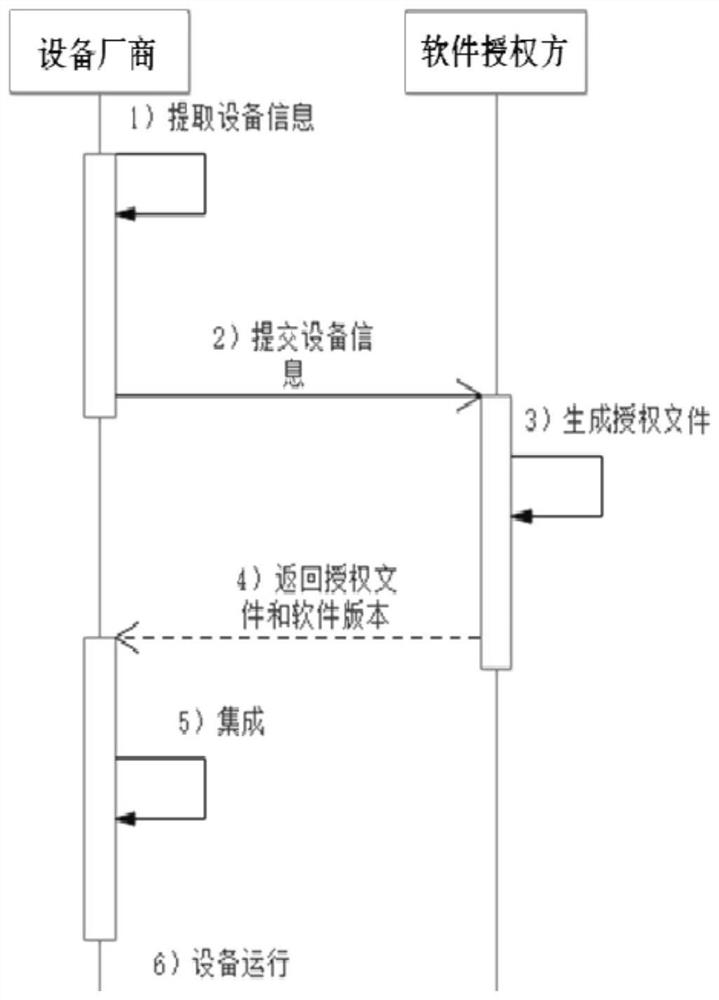
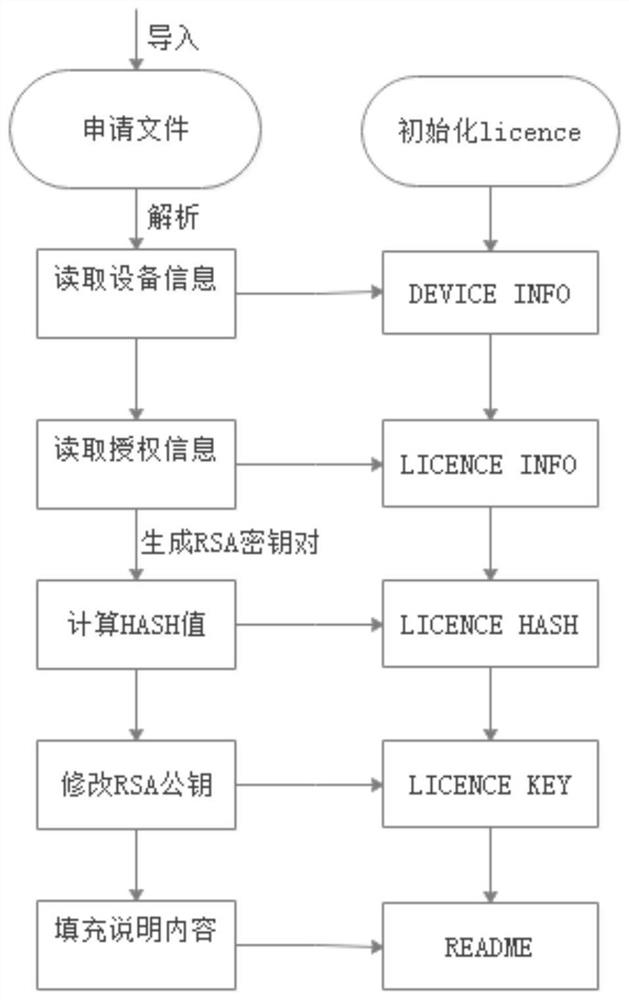
Software authorization method and system and storage medium
PendingCN113987421AImprove experienceReduce use costDigital data protectionProgram/content distribution protectionMultiple encryptionKey pressing
The embodiment of the invention discloses a software authorization method and system and a storage medium. The method comprises the steps that a software authorization party generates an authorization file according to received equipment information and corresponding authorization information; the software authorization party returns the authorization file and the software version to an equipment manufacturer; The equipment manufacturer integrates the software version and the authorization file according to requirements; and after the equipment runs, the software loads an authentication module and performs authorization verification, the equipment runs normally if the authorization verification succeeds, and otherwise, the equipment stops running. The authorization file can be preset, a user does not need to manually input an activation code, and the method is more suitable for equipment without key input or interface; off-line authorization simplifies the server authorization link and reduces the development and maintenance cost of the server. Batch authorization can be performed on equipment models, manufacturers, software versions and the like, and independent authorization can also be performed on a chip ID, a network card address and the like of single equipment; multiple signature verification and multiple encryption algorithms are used in authorization and authentication, and cracking is not prone to occurring.
Owner:北京朝歌数码科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com