Billing point verification method and system
A billing point, billing server technology, applied in accounting/billing services, electrical components, wireless communications, etc. The effect of solving the problem of billing counterfeiting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further explained below in conjunction with the accompanying drawings and embodiments.
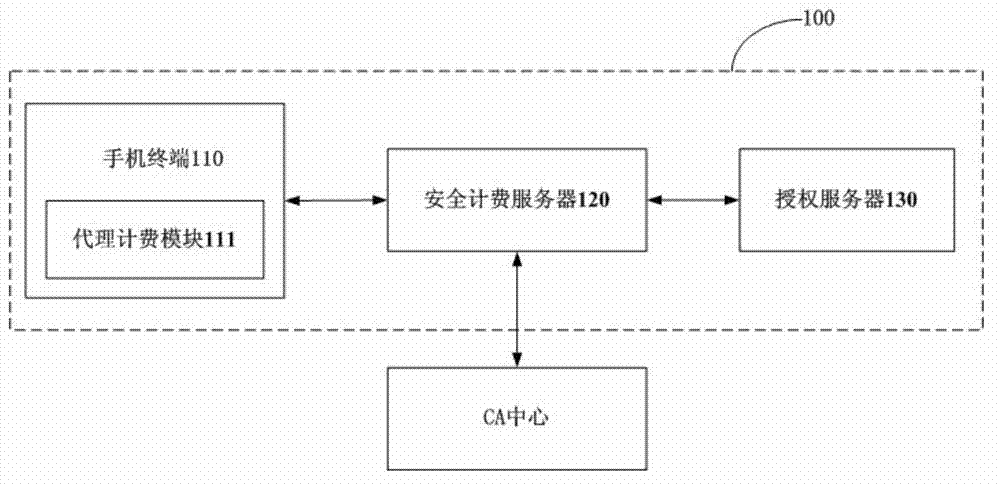
[0058] figure 1 It is a system block diagram of the first embodiment of the system 100 for verifying billing points of the present invention, as figure 1 As shown, the system 100 for verifying billing points of the present invention includes a mobile phone terminal 110 , a secure billing server 120 connected in communication with the mobile phone terminal 110 , and an authorization server 130 connected in communication with the secure billing server 120 . The mobile terminal 110 includes multiple application programs (not shown in the figure) and a proxy billing module 111 .
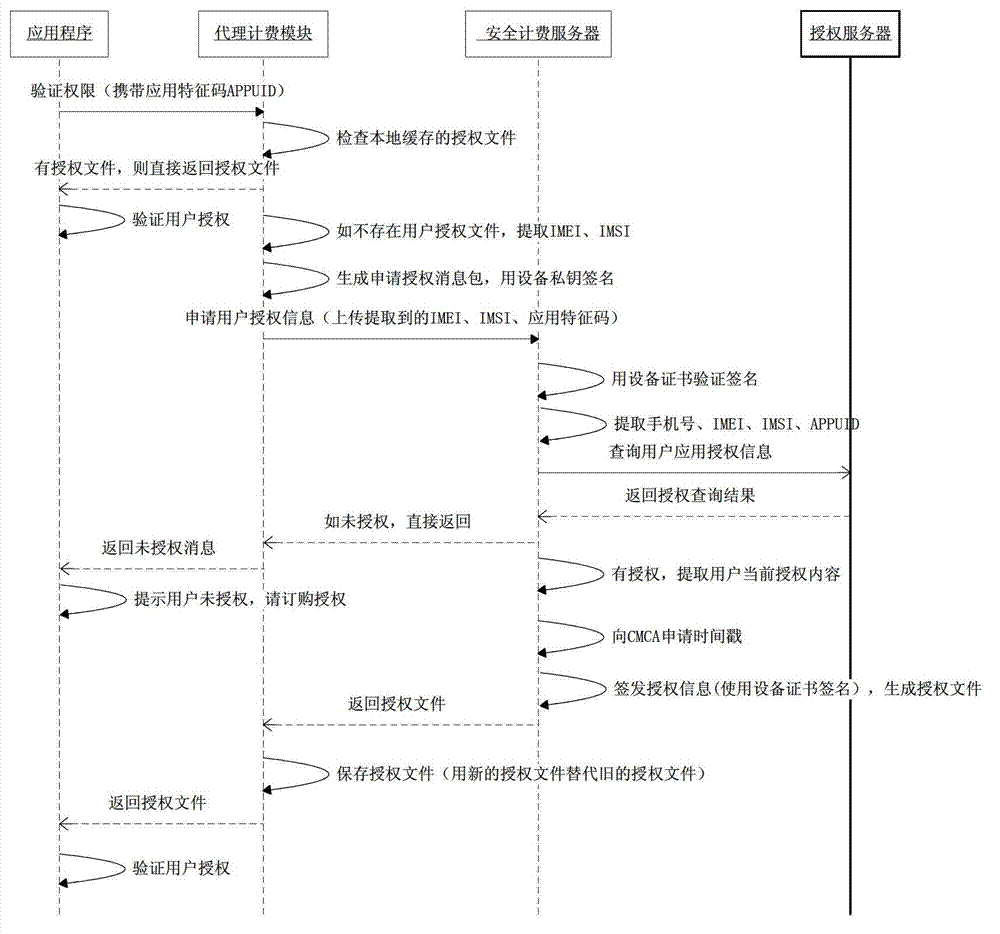
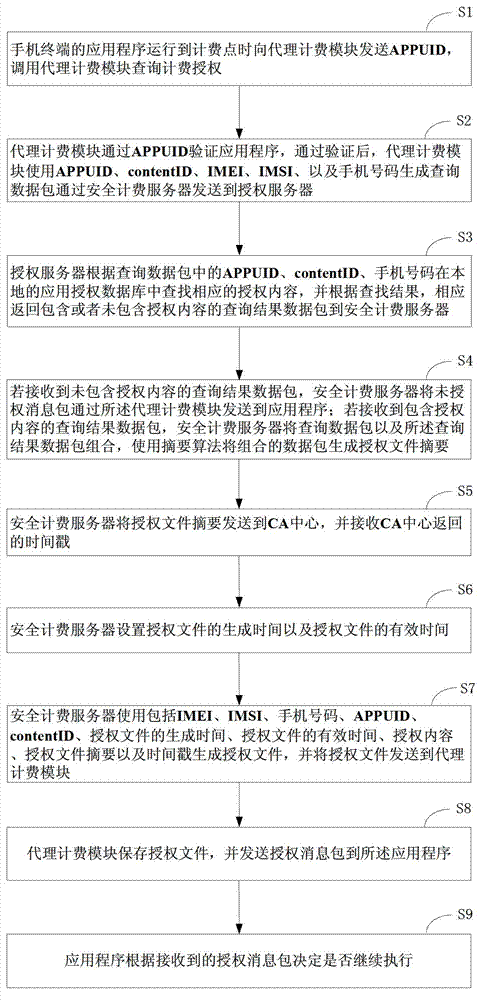
[0059] figure 2 It is the work flow diagram of the first embodiment of the system 100 for verifying charging points of the present invention, as figure 2 As shown, when an application runs to the charging point, it carries its application feature code APPUID to call the proxy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com