Application usage policy enforcement
An application package and application identifier technology, applied in the field of enforcing application usage policies, which can solve problems such as difficulty and trouble in user migration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Various embodiments of the present disclosure are discussed in detail below. While specific implementations are discussed, it should be understood that this is done for illustration purposes only. A person skilled in the relevant art will recognize that other components and configurations may be used without departing from the spirit and scope of the present disclosure. The present disclosure addresses the need in the art for an improved method of selecting targeted content for presentation to a user based on characteristics describing the user and / or the user's interaction with one or more items of targeted content.
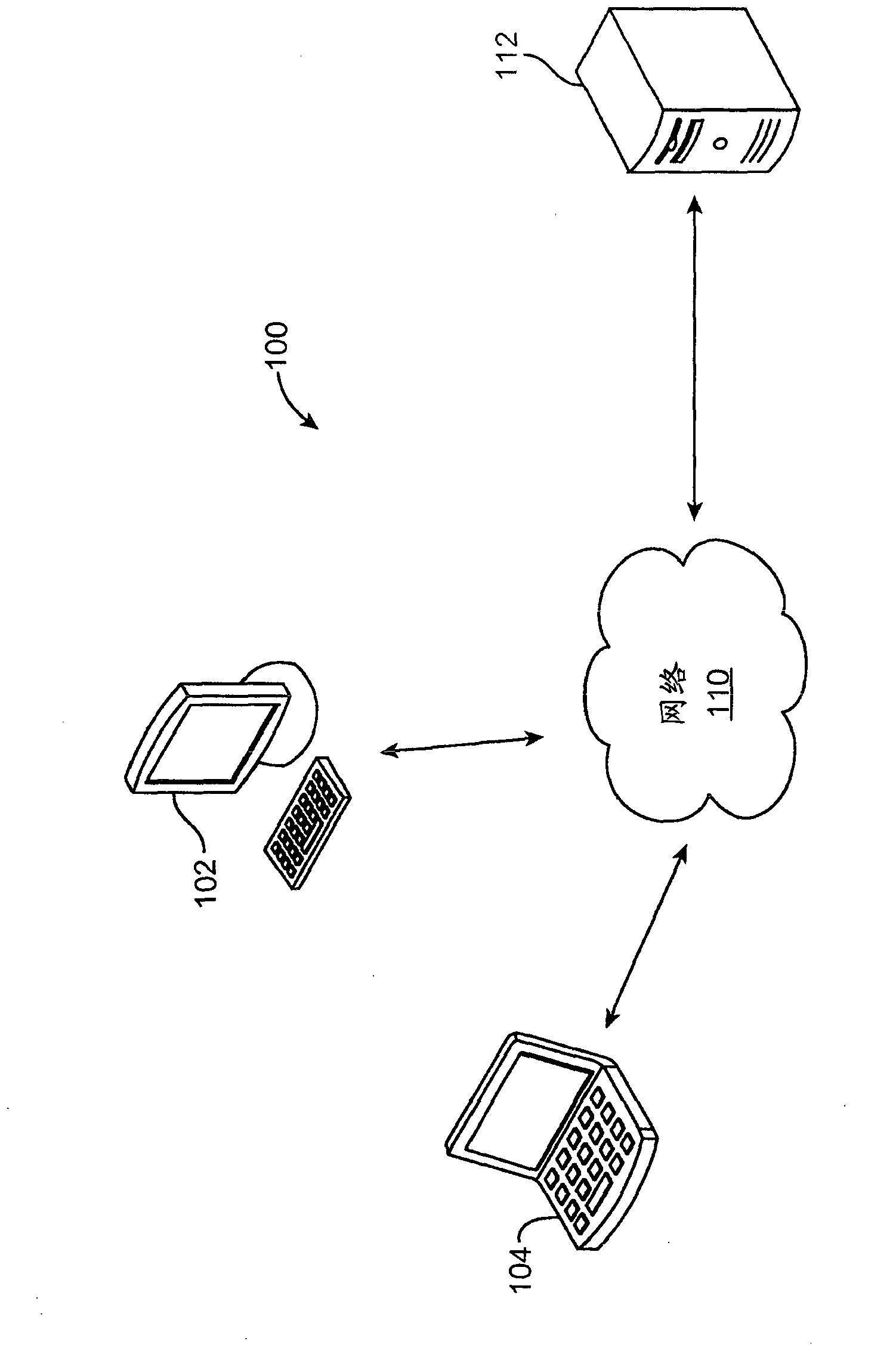
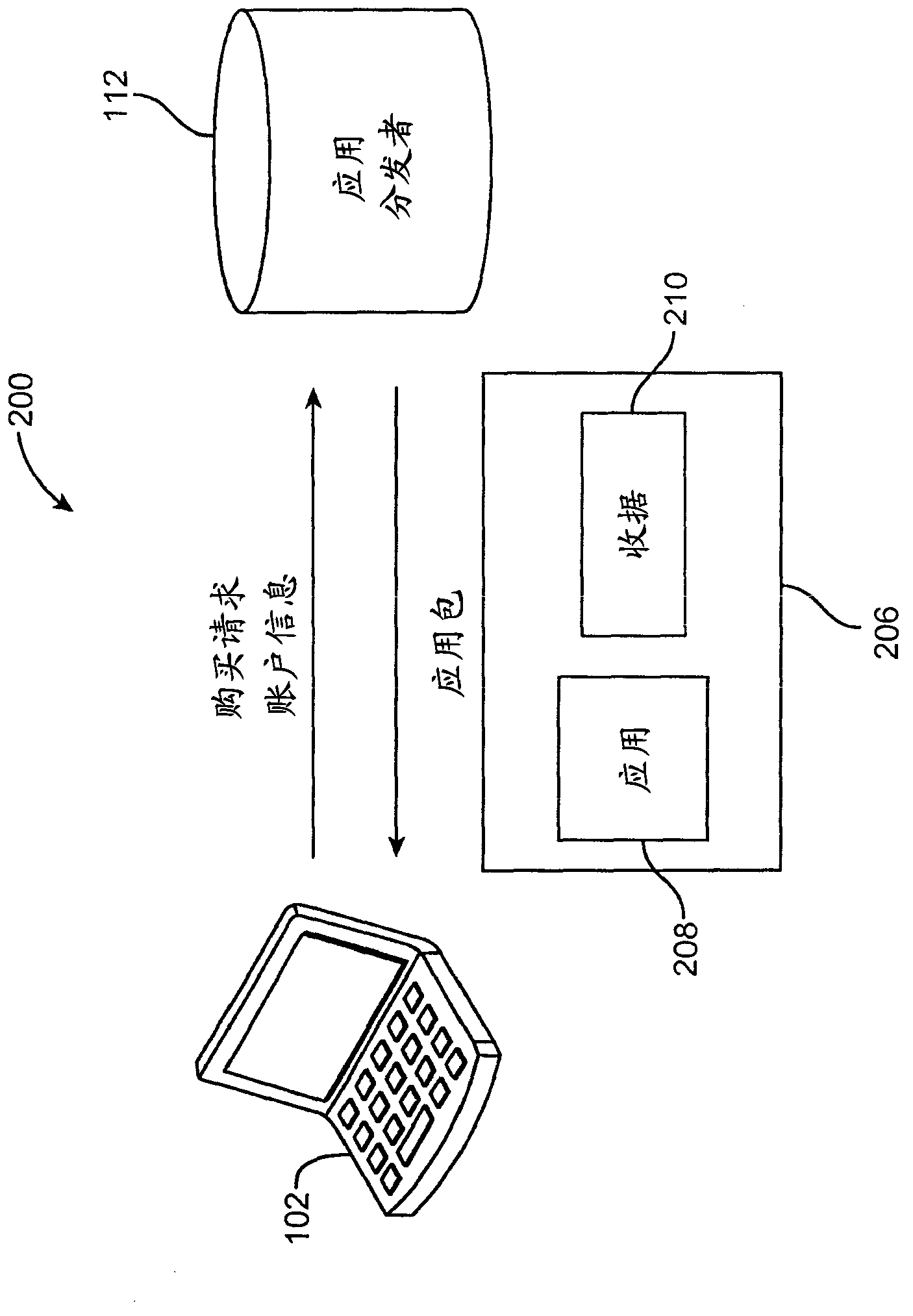
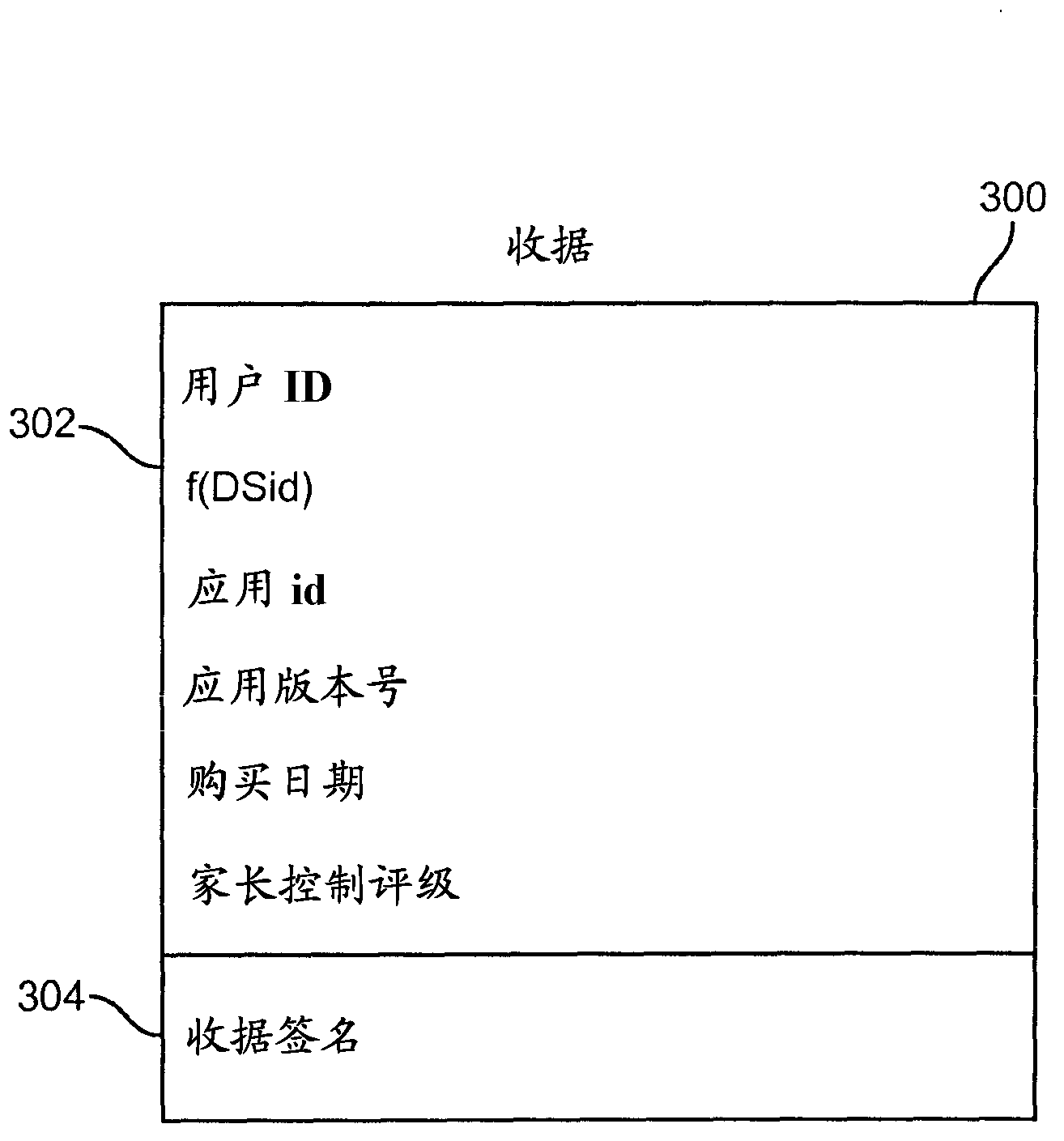
[0026] The systems and methods of the present disclosure are particularly useful for enforcing application usage policies on computers. figure 1 An exemplary system configuration 100 is shown for application distribution and usage, where electronic devices 102 , 104 communicate with an electronic application distributor 112 via a network 110 . The syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com