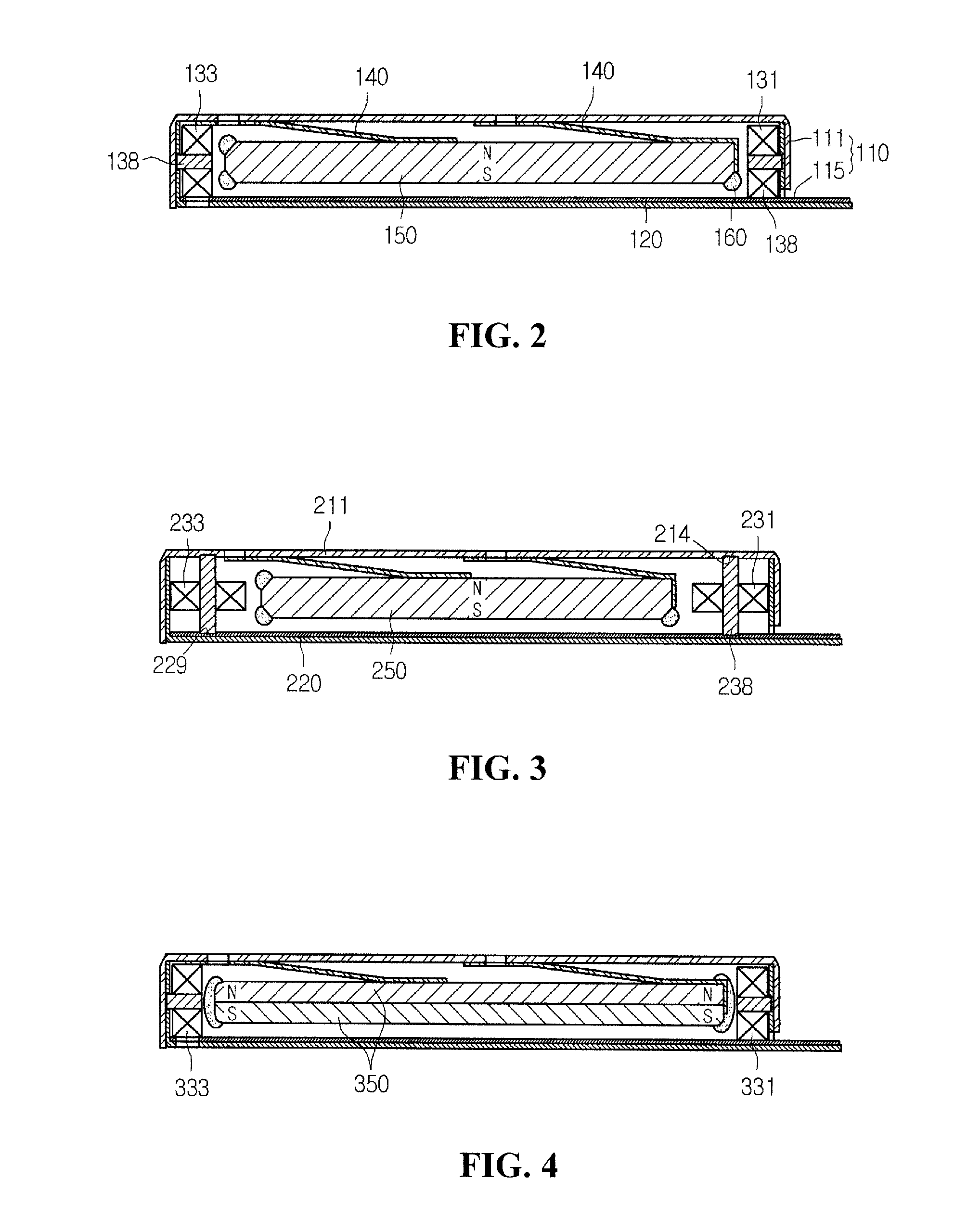
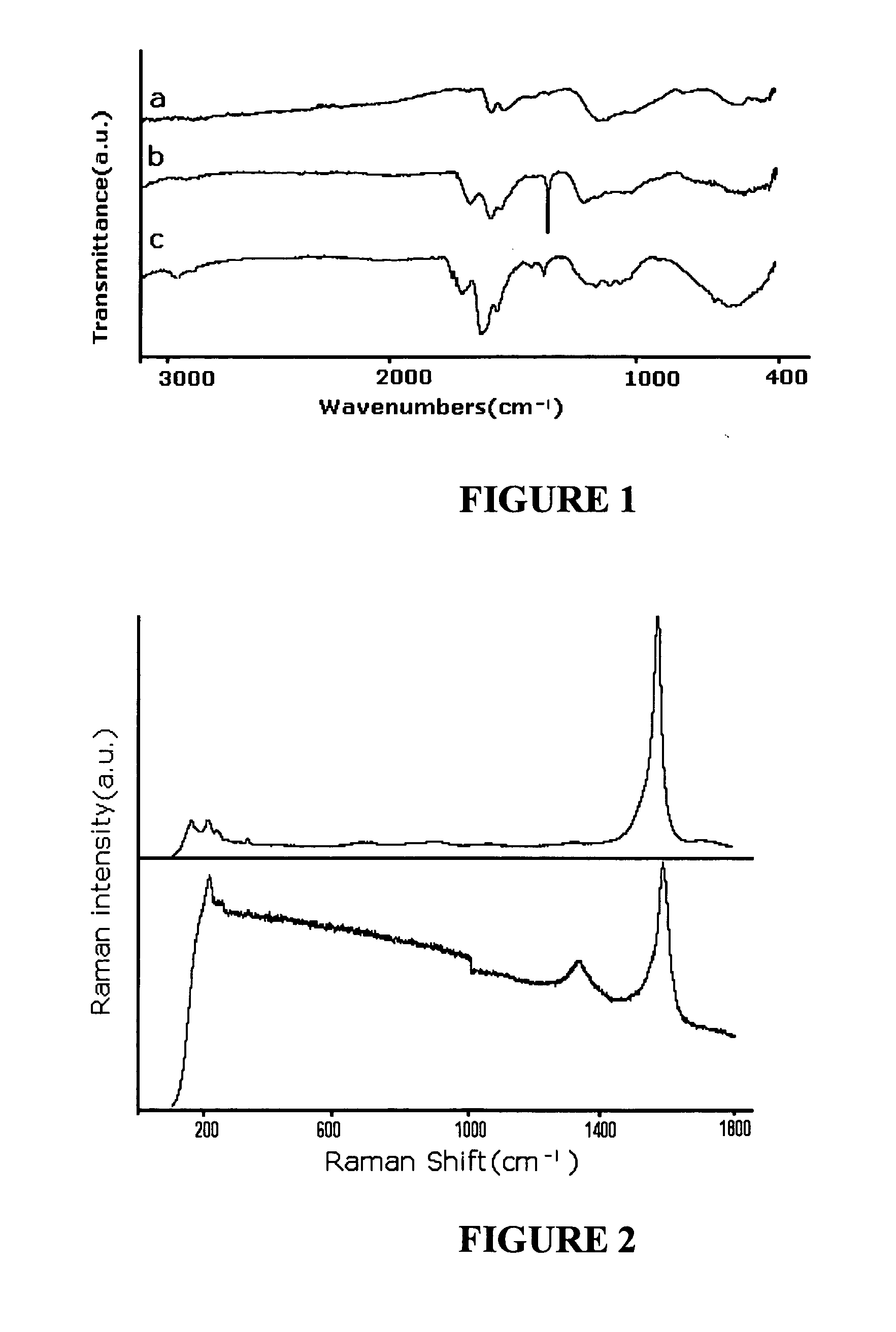
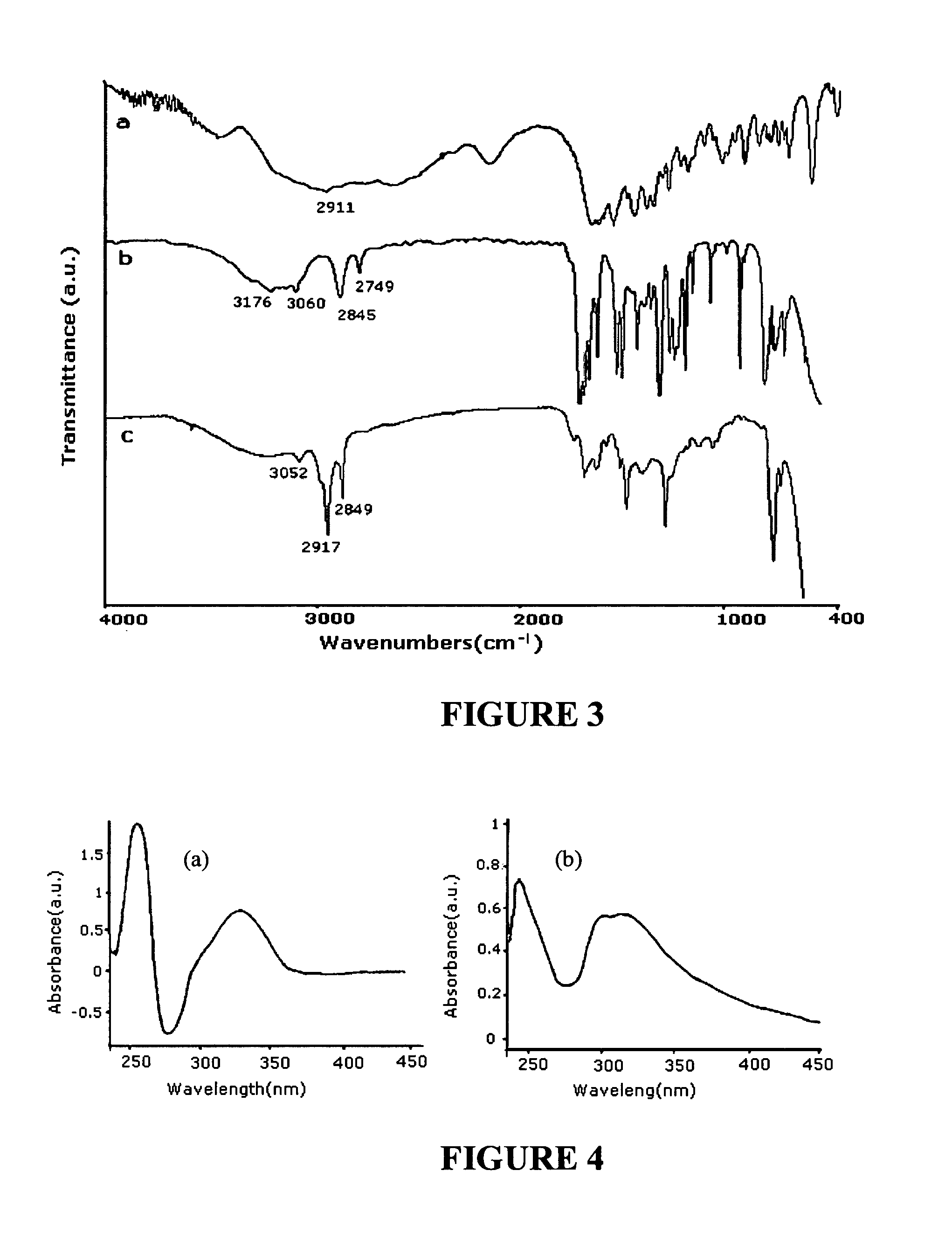
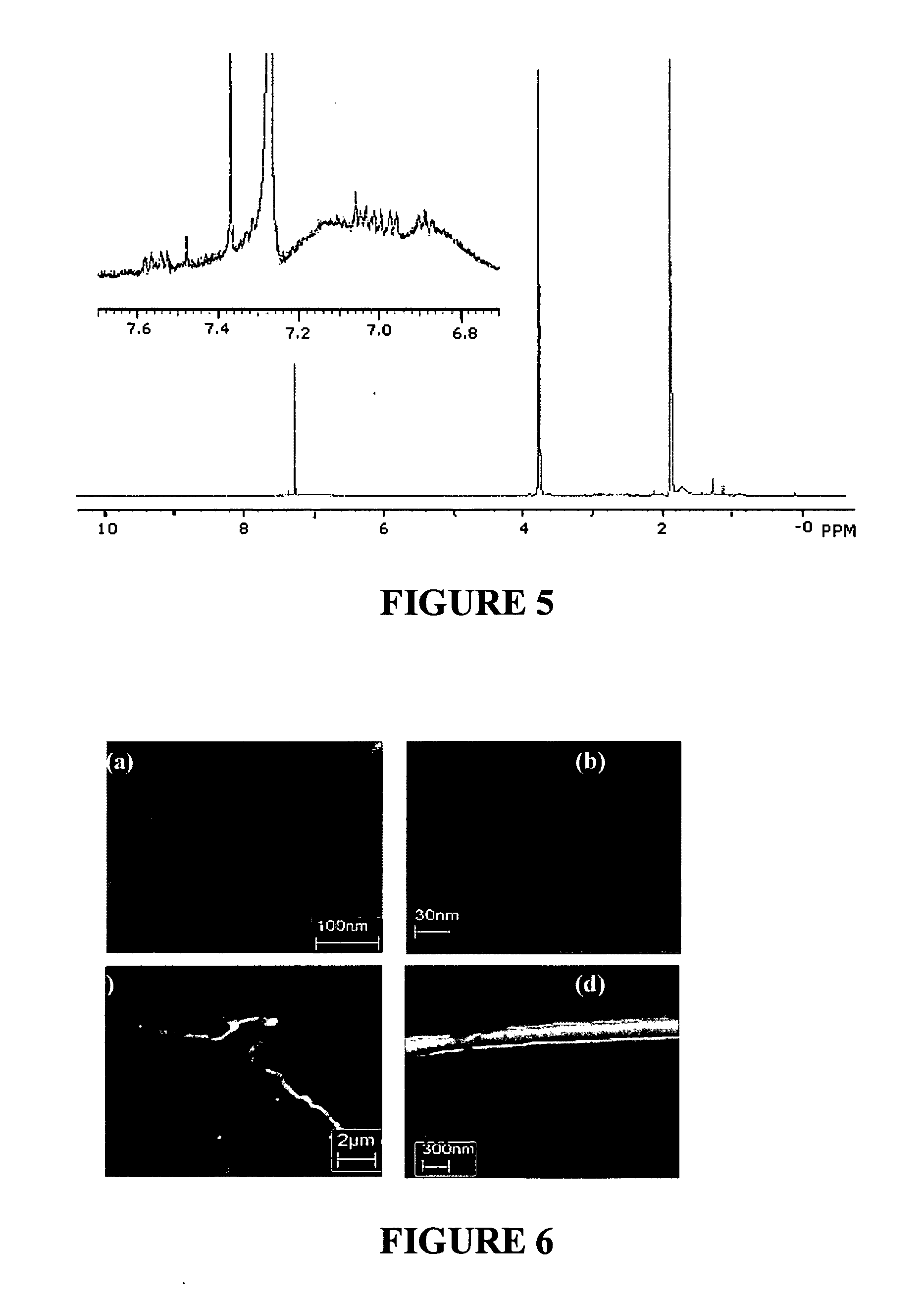
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
184results about How to "Cost effectiveness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
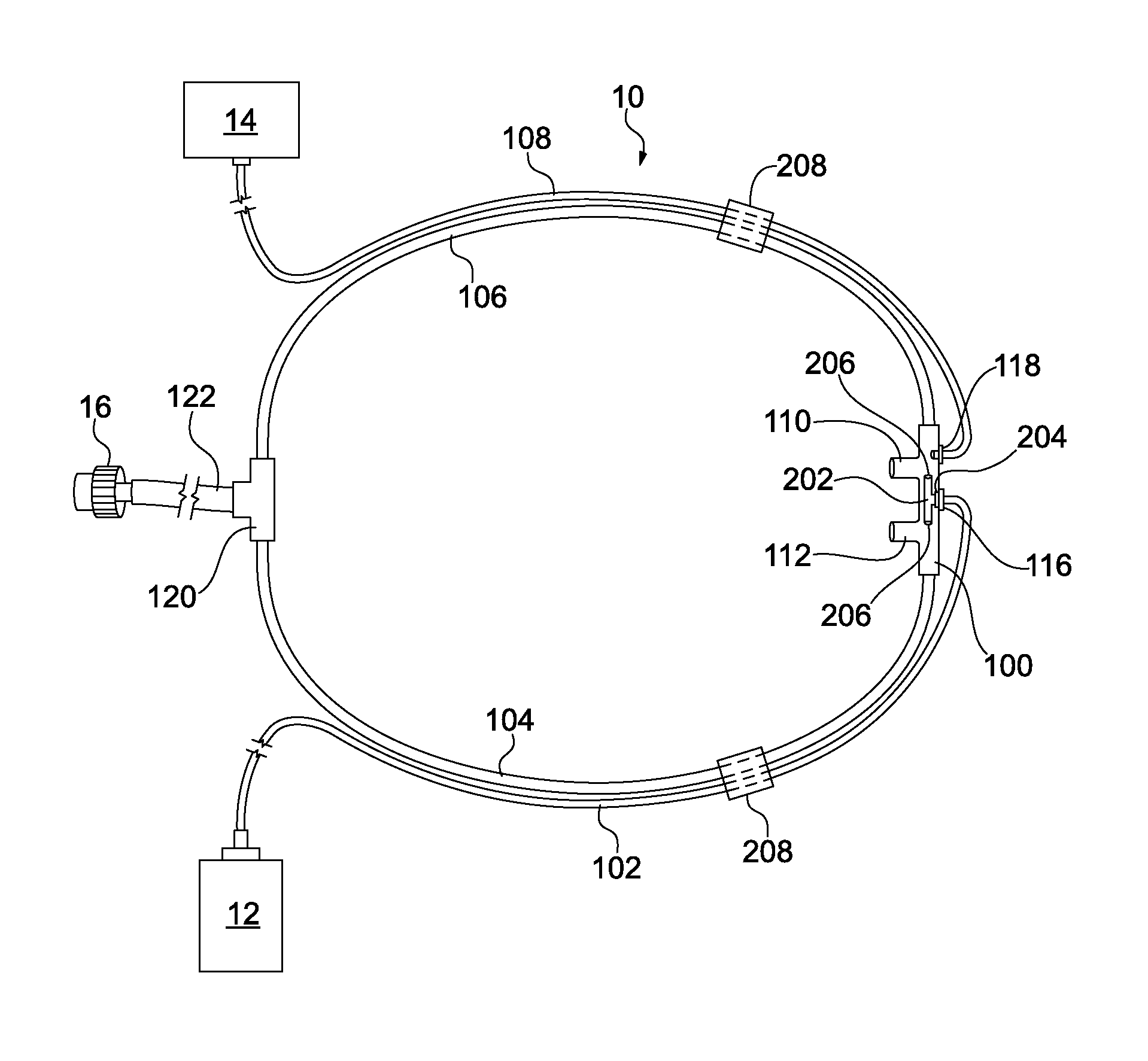
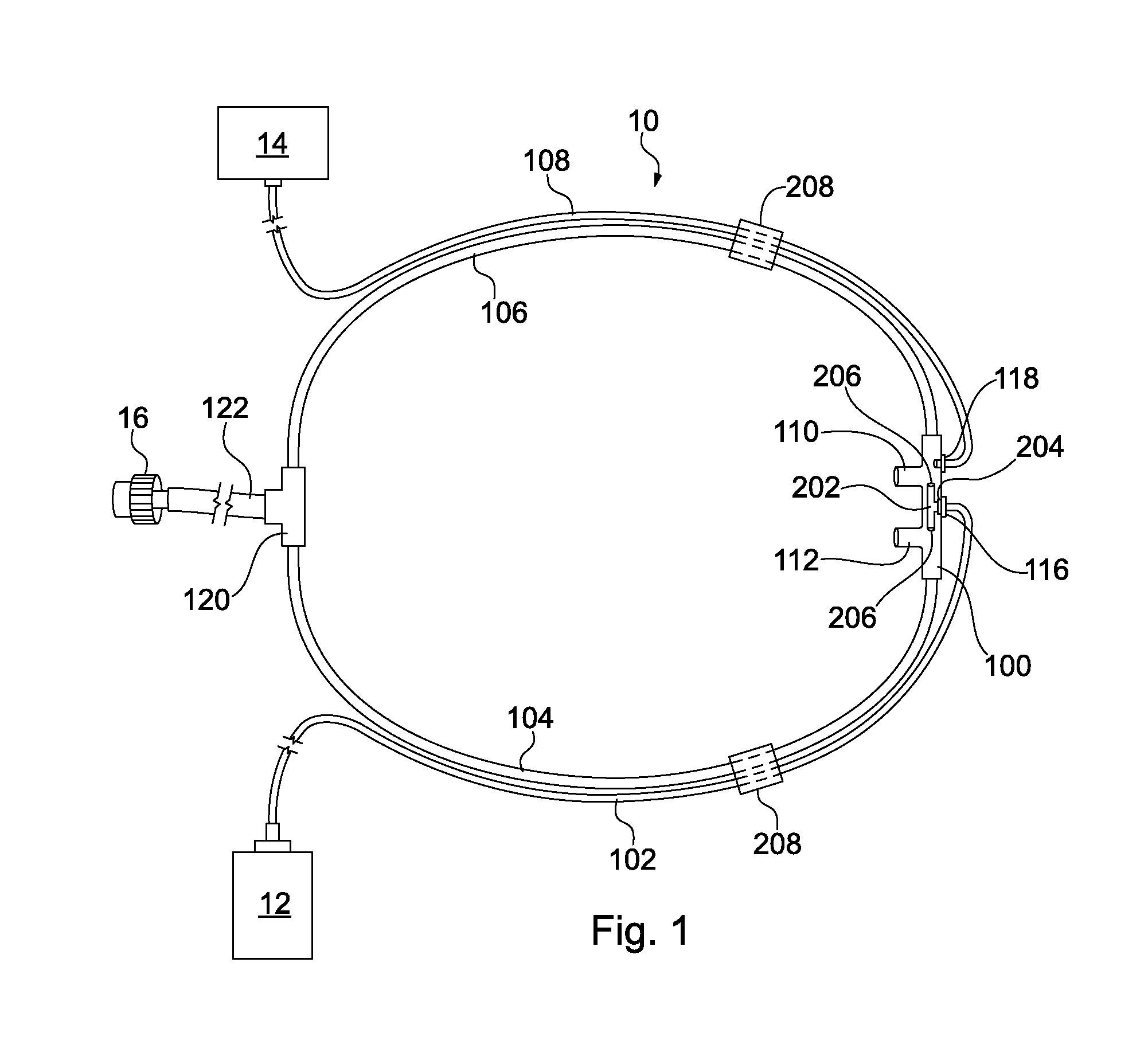
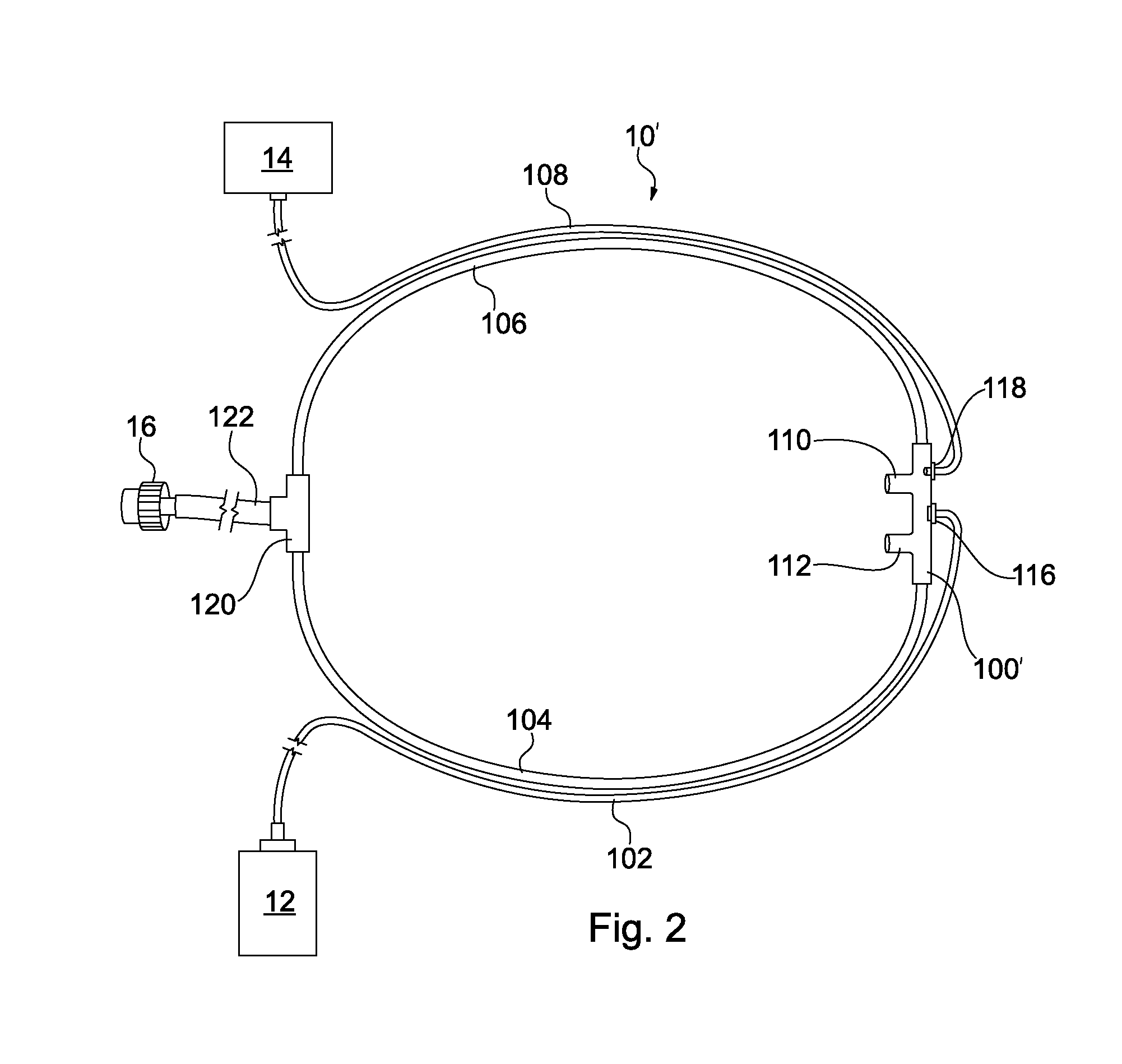
System and method for minimizing energy consumption in hybrid vehicles
ActiveUS7013205B1Reduce energy costsMinimizing consumable fuel consumptionAuxillary drivesInternal combustion piston enginesElectricityFuel cells
The present invention provides a system and method relating to the operation of plug-in hybrid electric vehicles powered both by electricity from rechargeable batteries and by consumable fuel powered means, such as an internal combustion engine or a fuel cell. More particularly, the system and method of the claimed invention enable optimization of the energy cost associated with the operation of such plug-in hybrid electric vehicles, especially when the cost of recharging batteries from external electric power sources may be less than the cost of recharging batteries from the onboard consumable fuel powered means. To this end, the invention enables maximization of the use of electricity from external electric power sources and minimization of the use of electricity produced by the plug-in hybrid electric vehicle's onboard consumable fuel powered means, when the cost of recharging batteries from external electric power sources is less than the cost of recharging batteries from the onboard consumable fuel powered means.
Owner:SLINGSHOT IOT LLC
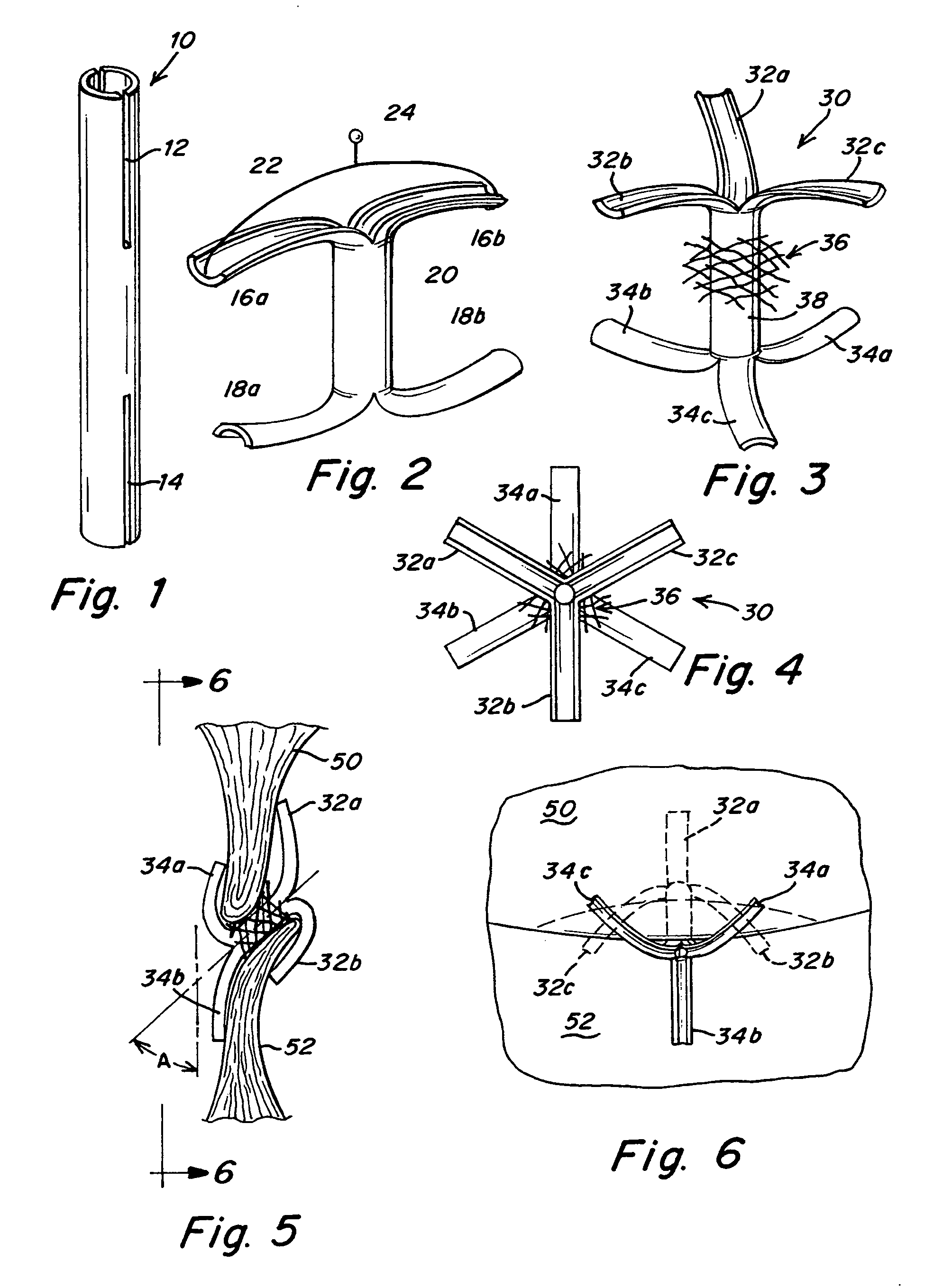
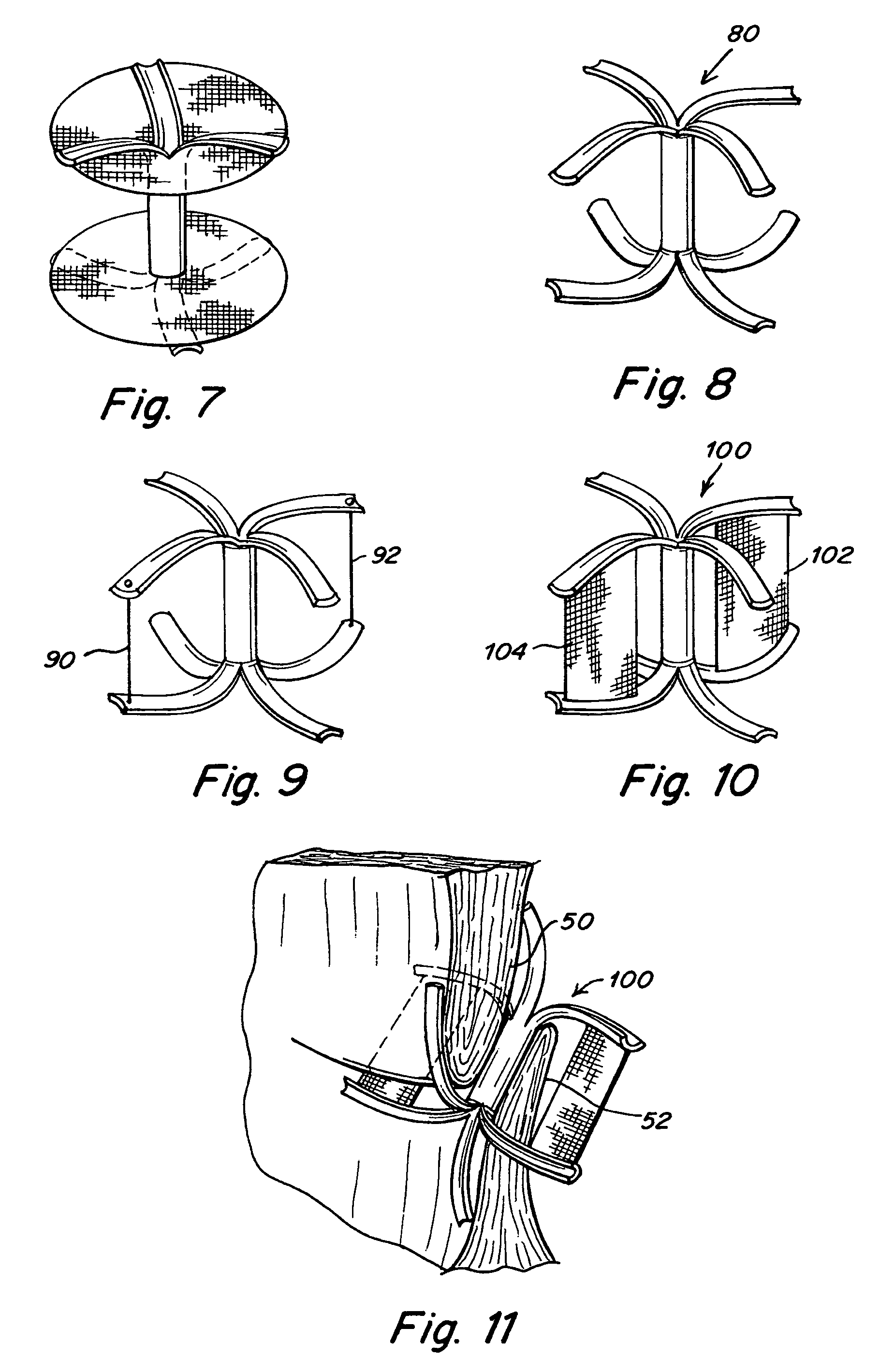
Split ends closure device
InactiveUS20050267524A1Improve conformitySmall diameter delivery sheathSurgical veterinaryWound clampsBlood flowEngineering
A device closes a patent foramen ovale (PFO), thus reducing or eliminating blood flow through the defect. The device is formed from a tubular structure having split ends, such that, after insertion, struts defined by the split ends pivot in a radial direction away from the tube, thereby securing the device within the septal defect.
Owner:NMT MEDICAL
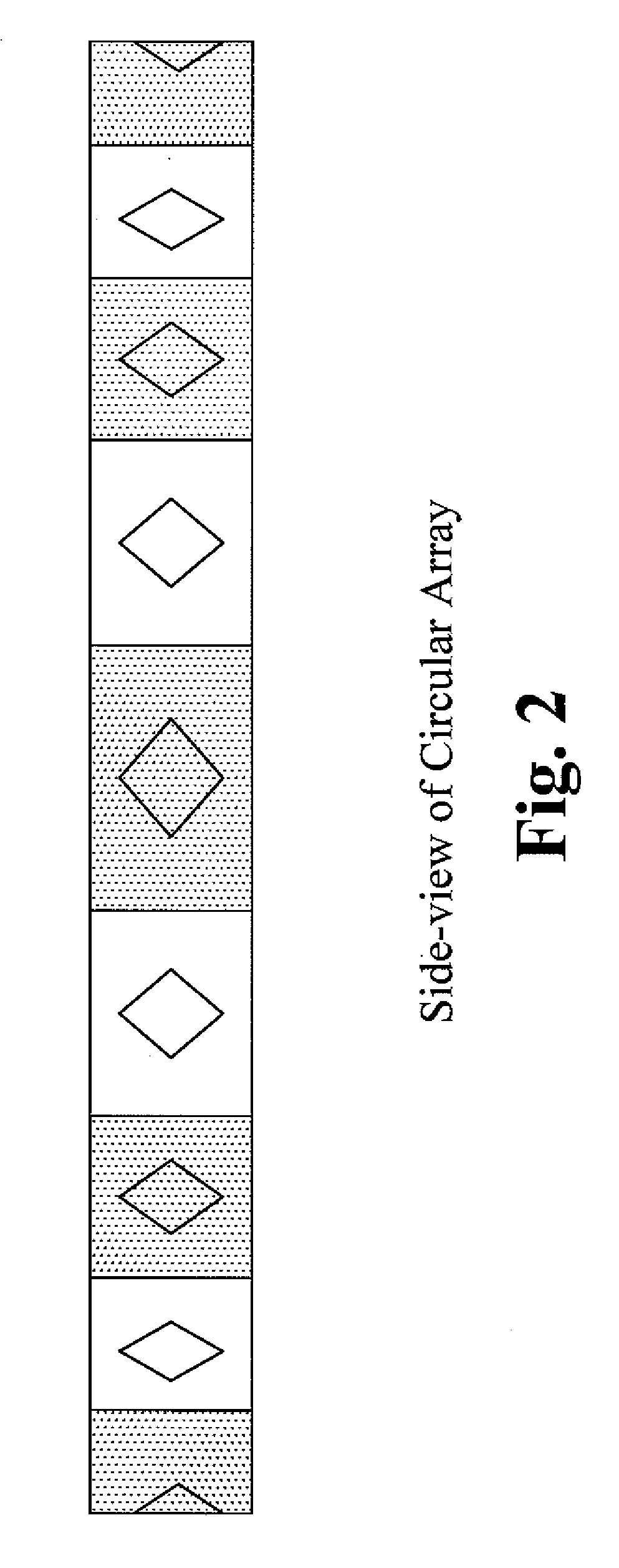
Array structure for the application to wireless switch of WLAN and wman
InactiveUS20070257858A1Improve efficiencyLow budgetIndoor communication adaptationIndividually energised antenna arraysArea networkArray data structure
The present invention provides an antenna array structure which includes multiple array elements, and the antenna array structure is using for the application of the WLAN (wireless local area network) or WMAN (wireless metro area network.) Furthermore, the array elements of the present invention are phased arrays or attenuated arrays, and when configuration with different type of the array element is used, the corresponding BFN (beam forming network) can also be implemented in various possibilities. With all the configuration of the present invention, the manufacturers can have a stable array structure for their applications.
Owner:ACCTON TECHNOLOGY CORPORATION
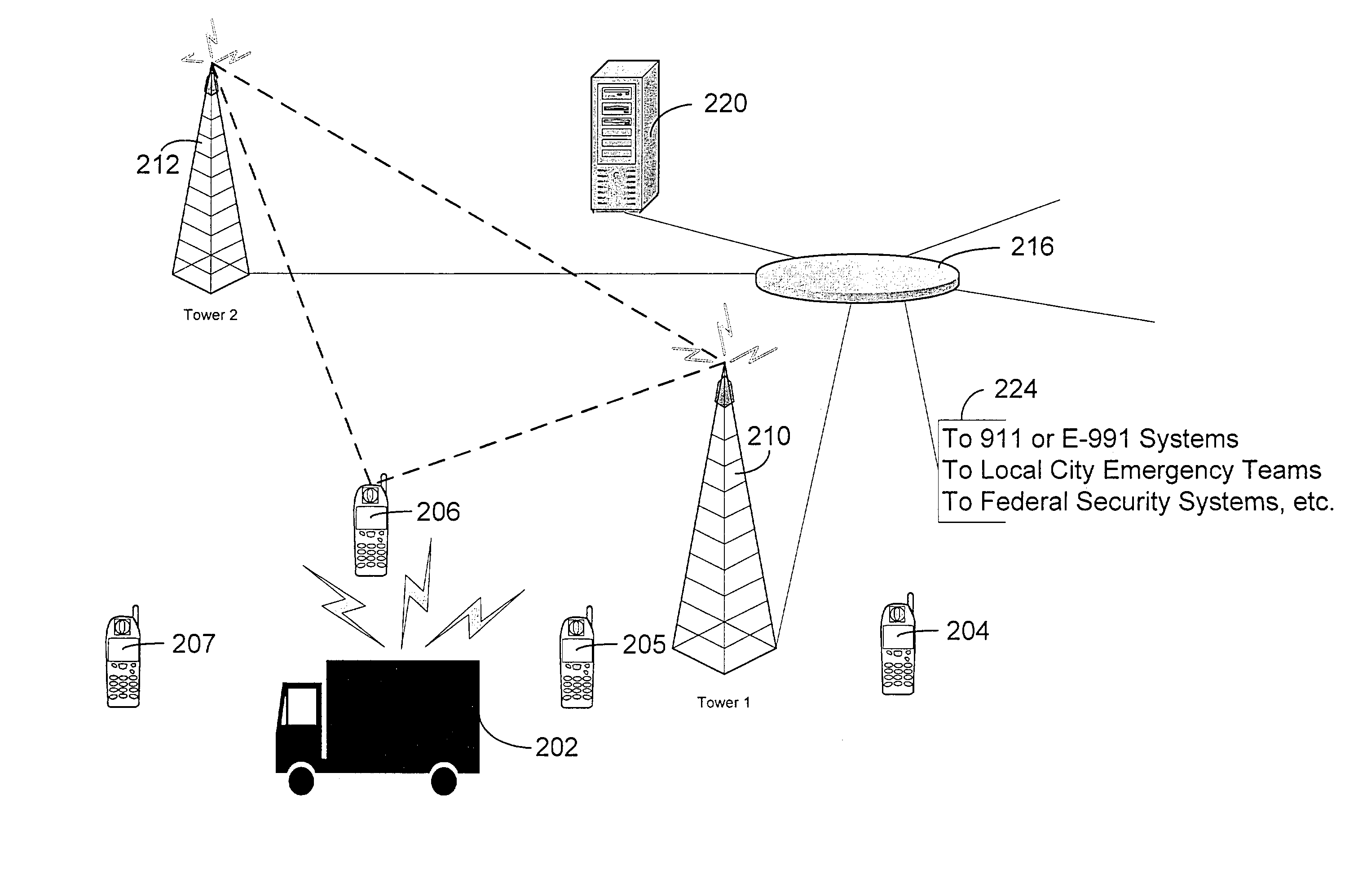
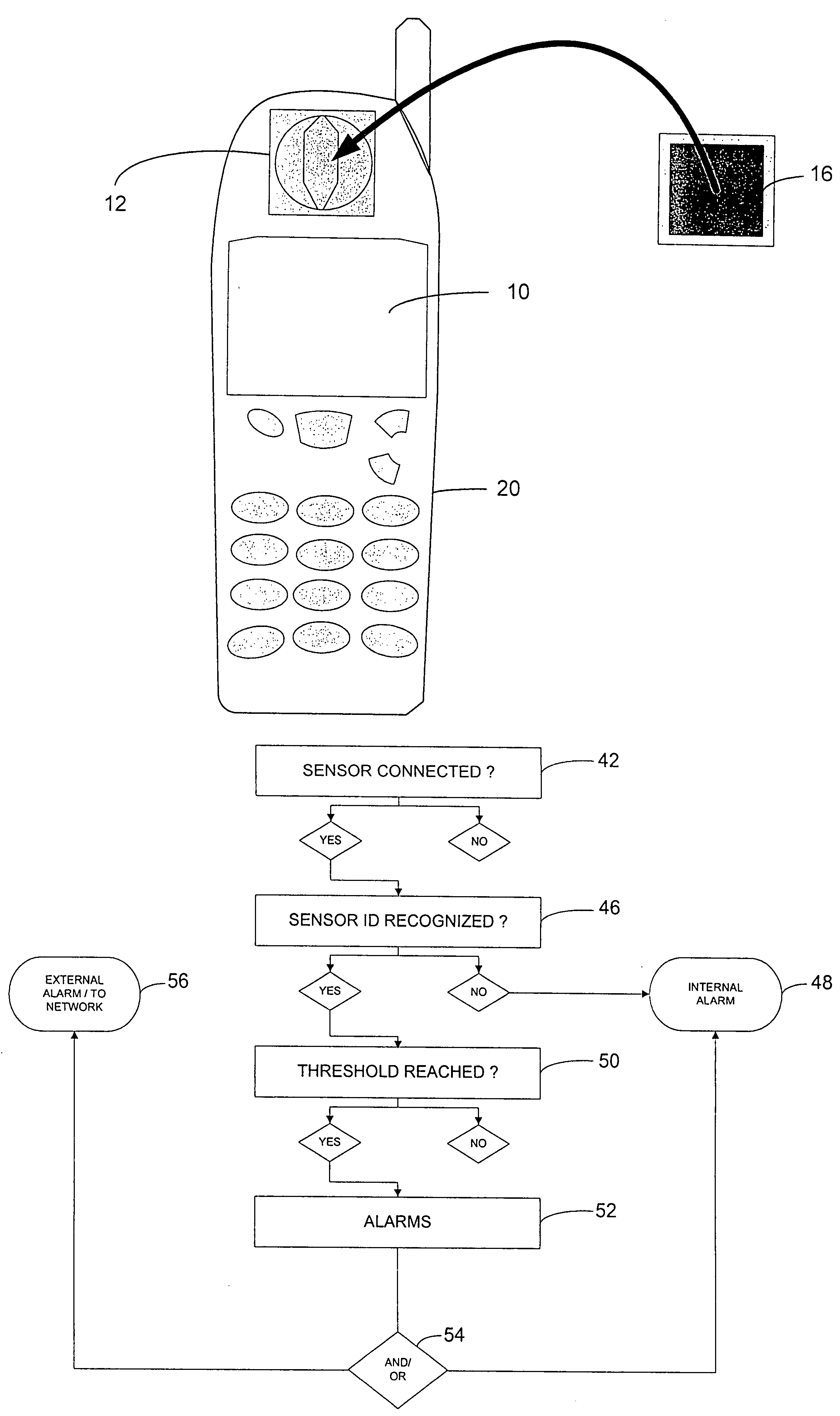
Method and apparatus for wide area surveillance of a terrorist or personal threat
ActiveUS7109859B2Low costEasy to useNetwork traffic/resource managementNanosensorsMobile telephonyWide area
The present invention is related to a means for detecting external threats by the use of methods and apparatuses for the wide area detection of chemical, radiological or biological threats using modified personal wireless devices combined with new advanced micro and nanosensor technologies. A cost effective method is provided for wide area surveillance of a potential terrorist or personal threat. Personal electronic devices such as mobile phones, PDAs or watches, in combination with new microsensor technologies described herein, can be used as a new type of platform detection technology for wide area surveillance of major threats. A “Homeland Security” chip is further provided which combines the elements of geo-location, remote wireless communication and sensing into a single chip. The personal electronic devices can be further equipped for detecting various medically related threats. Similarly modified personal devices can be used to detect external threats that are person-specific.
Owner:GENTAG
Method and apparatus for providing three axis magnetic bearing having permanent magnets mounted on radial pole stack
InactiveUS6727617B2Effective and inexpensive techniqueHighly linear magnetic biasMechanical energy handlingBearingsAxial displacementAudio power amplifier
An improved magnetic bearing that uses permanent magnets to provide the bias flux. The magnetic circuits generating the control flux and bias fluxes are substantially non-coincident but share the same path over some portions that include radial and axial airgaps allowing for a low reluctance and an efficient path for the electromagnetic flux. The flux paths of the permanent magnets are completely defined with minimized airgaps for achieving higher forces and efficiency and very low control currents that produce extremely large forces. A single coil and amplifier for the axial force control and two coils with one associated amplifier for each radial axis of control provides simplicity and cost effectiveness. A single thrust disk is provided that is reacted against for both radial and the axial displacement. The permanent magnets used in the present invention are first fabricated and axially magnetized as segments or as continuous rings prior to being mounted on the sides of the rotor pole, providing an effective and inexpensive technique of manufacturing magnetic bearings.
Owner:CALNETIX TECH +1
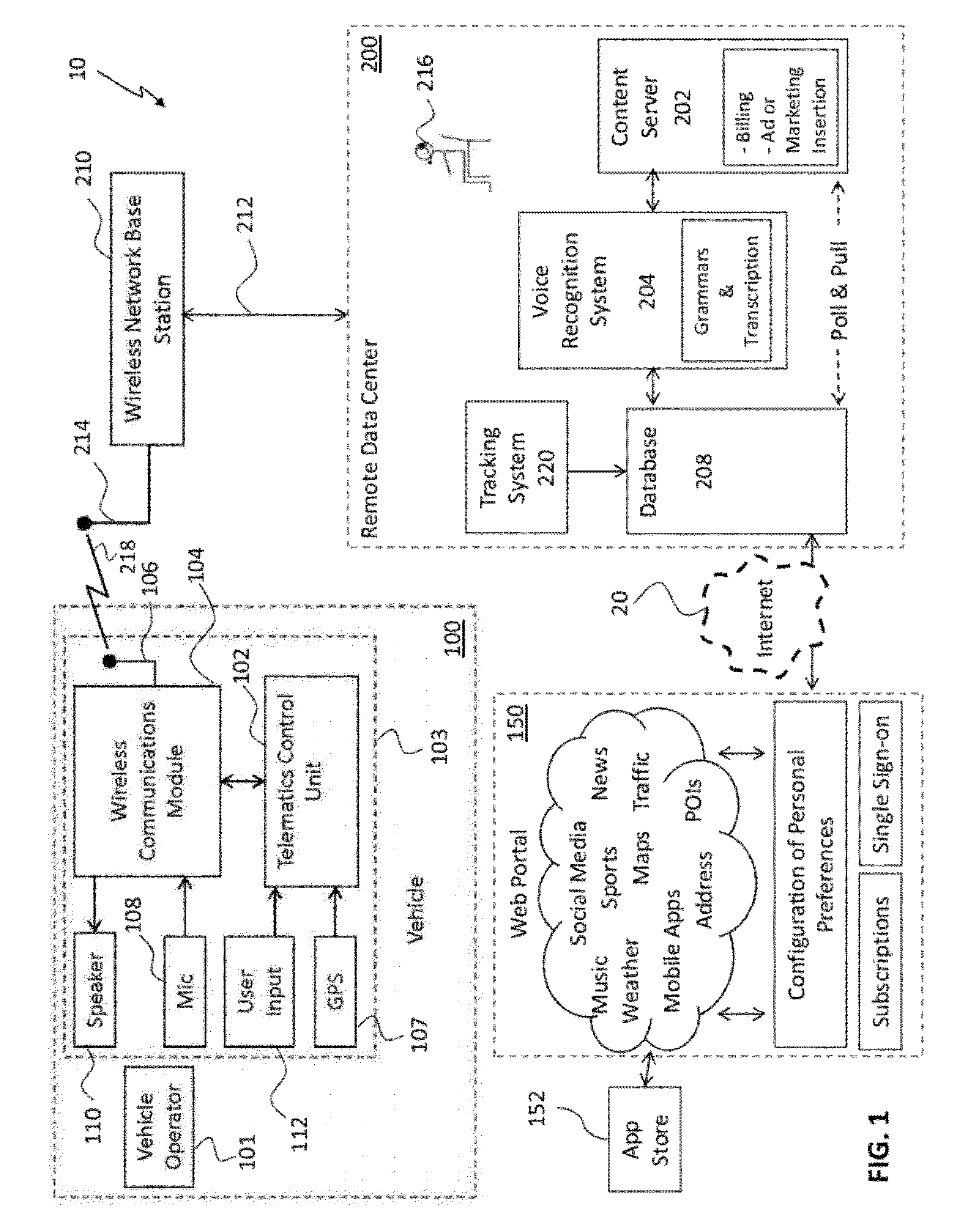
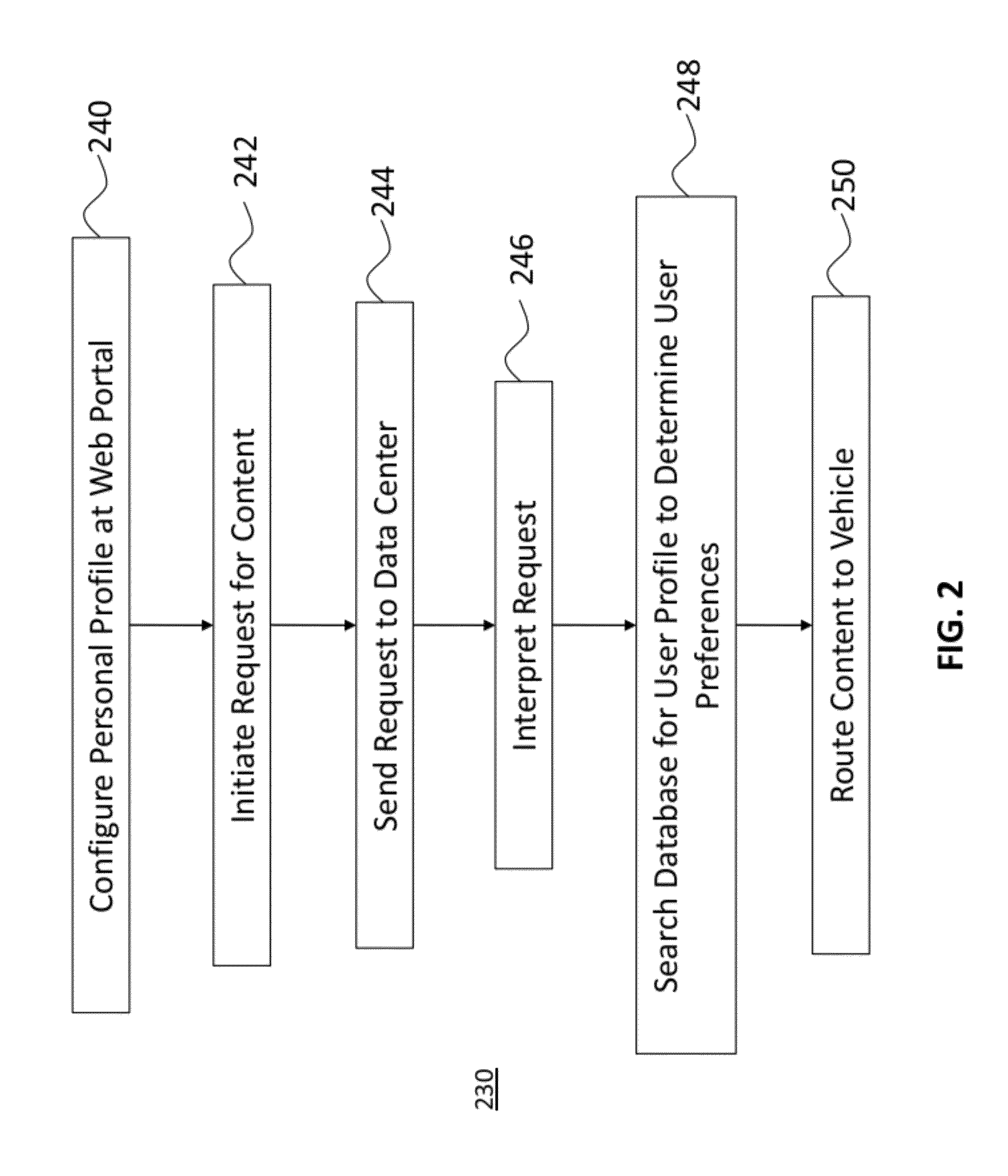
Systems and Methods for Delivering Content to Vehicles
InactiveUS20120259951A1MinimizeImprove reliabilityRegistering/indicating working of vehiclesRoad vehicles traffic controlData centerThe Internet
A content delivery system includes a remote data center in wireless communication with a vehicle telematics system. The remote data center includes a content server, an automated voice recognition system, and a database. The remote data center utilizes combinations of GPS information, voice automation technology, and preconfigured vehicle operator preferences to deliver content to vehicles over a wireless link. The content delivery system includes a web portal at which vehicle operators configure personal profiles, including information regarding personal preferences and / or information pertaining to application access. The web portal feeds the profile information to the remote data center over a remote Internet connection. The remote data center stores the preconfigured vehicle operator profiles in the database, which is later accessed in response to vehicle operator commands recognized by the voice recognition system.
Owner:SIRIUS XM CONNECTED VEHICLE SERVICES
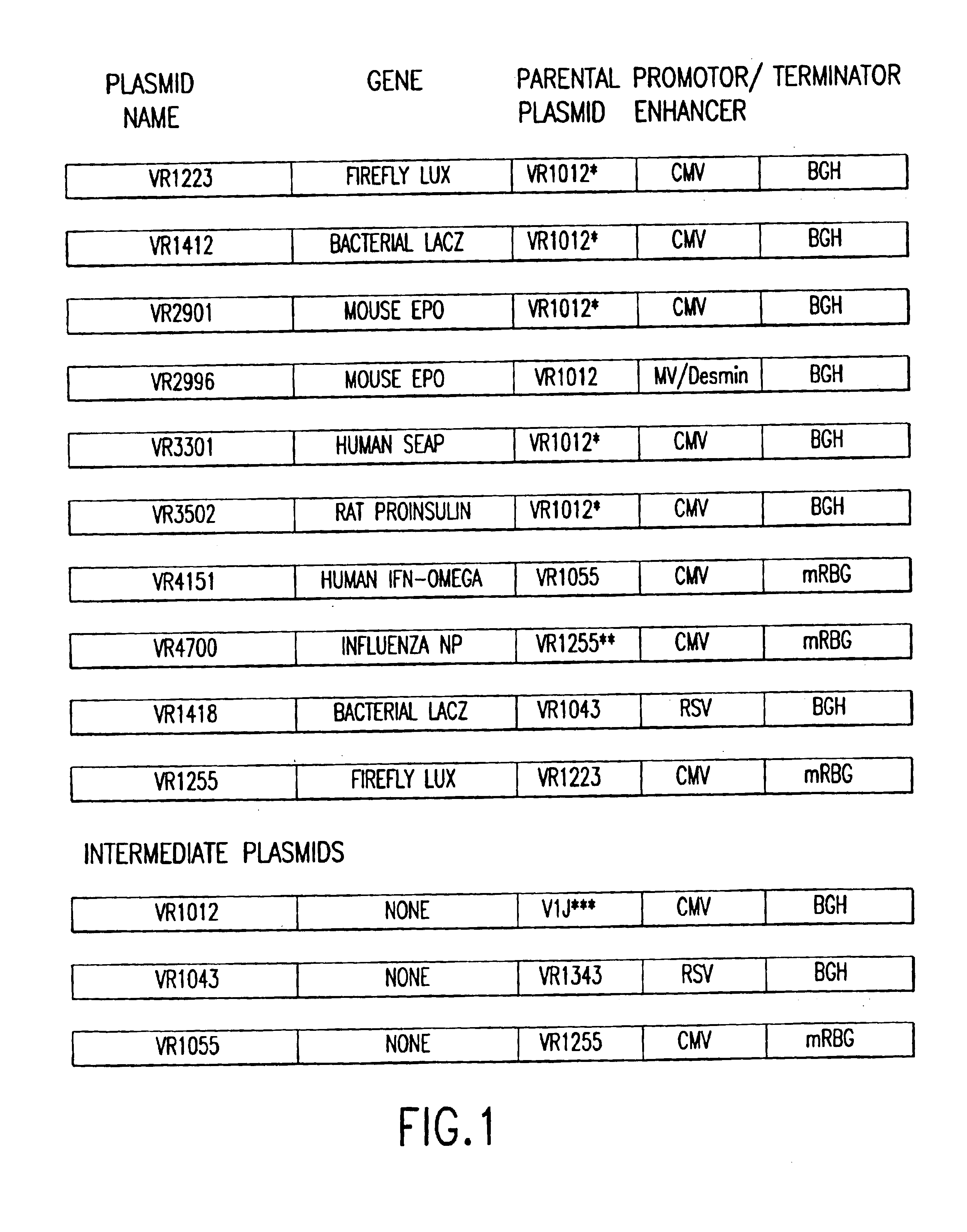
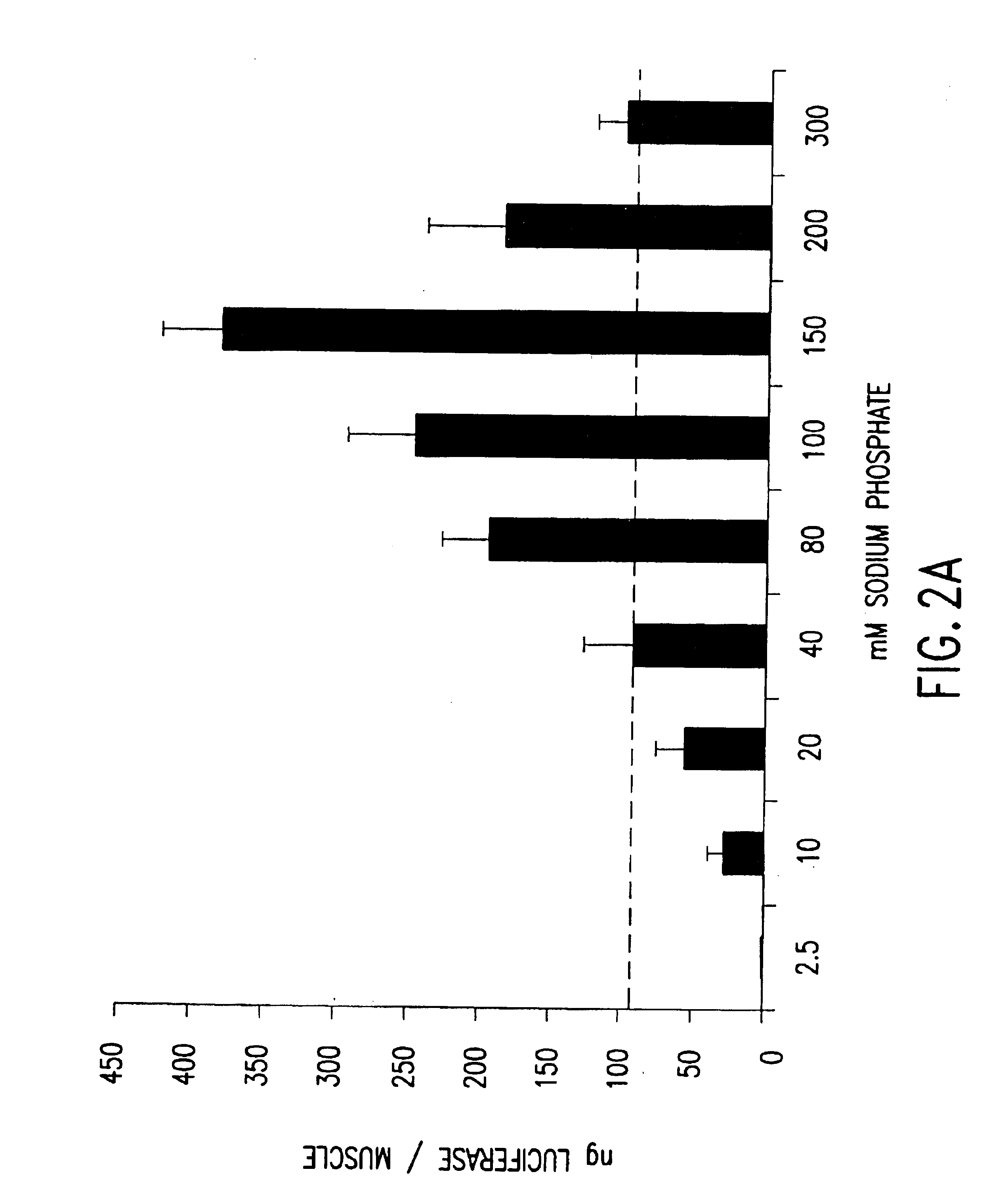
Compositions and methods for in vivo delivery of polynucleotide-based therapeutics
InactiveUS6875748B2High expressionCost effectivenessSsRNA viruses negative-sensePeptide/protein ingredientsPhosphateNucleotide
The present invention relates to pharmaceutical compositions and methods to improve expression of exogenous polypeptides into vertebrate cells in vivo, utilizing delivery of polynucleotides encoding such polypeptides. More particularly, the present invention provides the use of salts, in particular sodium and potassium salts of phosphate, in aqueous solution, and auxiliary agents, in particular detergents and surfactants, in pharmaceutical compositions and methods useful for direct polynucleotide-based polypeptide delivery into the cells of vertebrates.
Owner:VICAL INC
Method of producing micropulp and micropulp made therefrom
InactiveUS20030114641A1More cost-effectivelySmall sizeCellulose coatingsPaper/cardboardFiberSolid component
The present invention is directed to a process for producing micropulp. The process includes contacting organic fibers with a medium comprising a liquid component and a solid component, agitating the medium and the organic fibers to transform the organic fibers into the micropulp dispersed in the medium. If desired, the slurry of the micropulp in the liquid component can be used or the micropulp can be separated from the medium. The micropulp can be readily incorporated into coating compositions such as those used in automotive OEM or refinish applications. The micropulp can also be incorporated into powder coating applications or as a thixotrope or reinforcement in polymer formulations.
Owner:EI DU PONT DE NEMOURS & CO
Systems and methods for wound area management
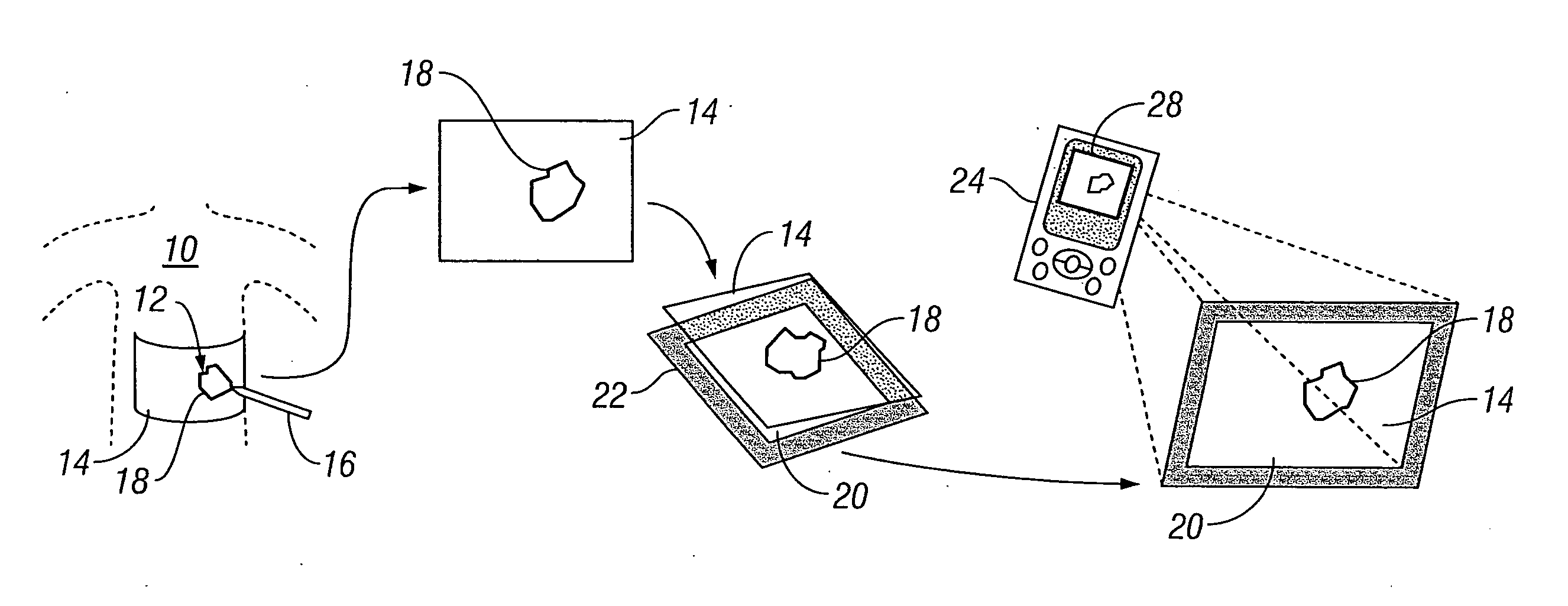
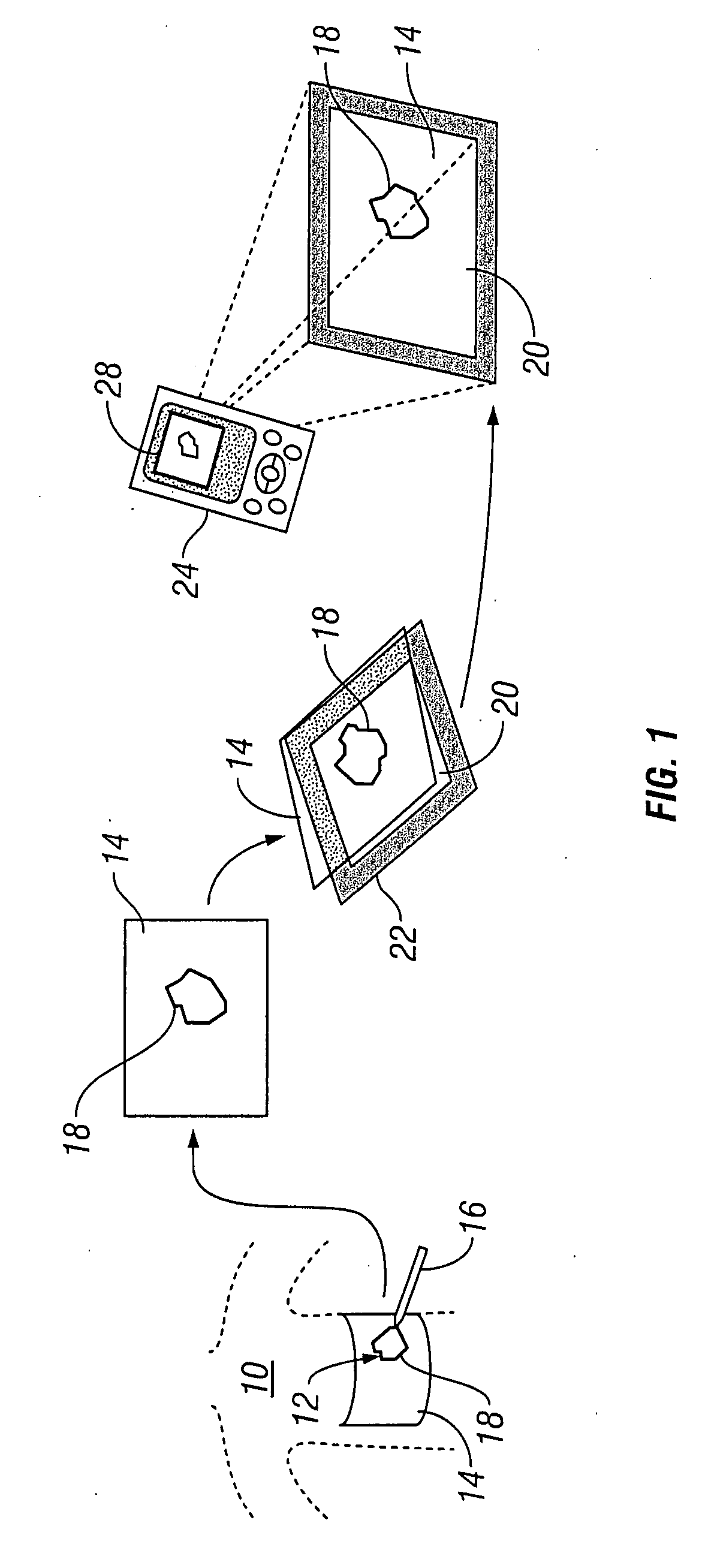
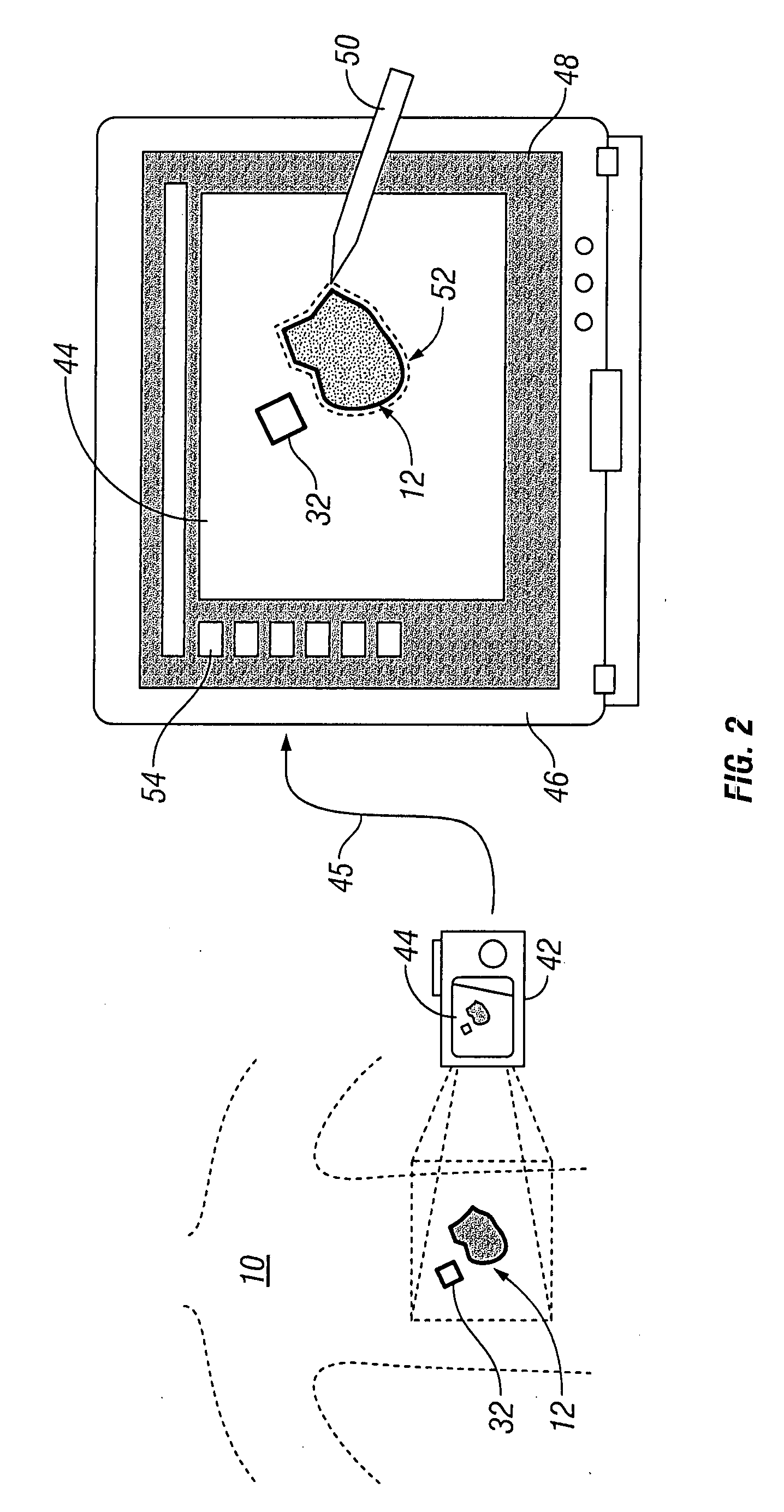
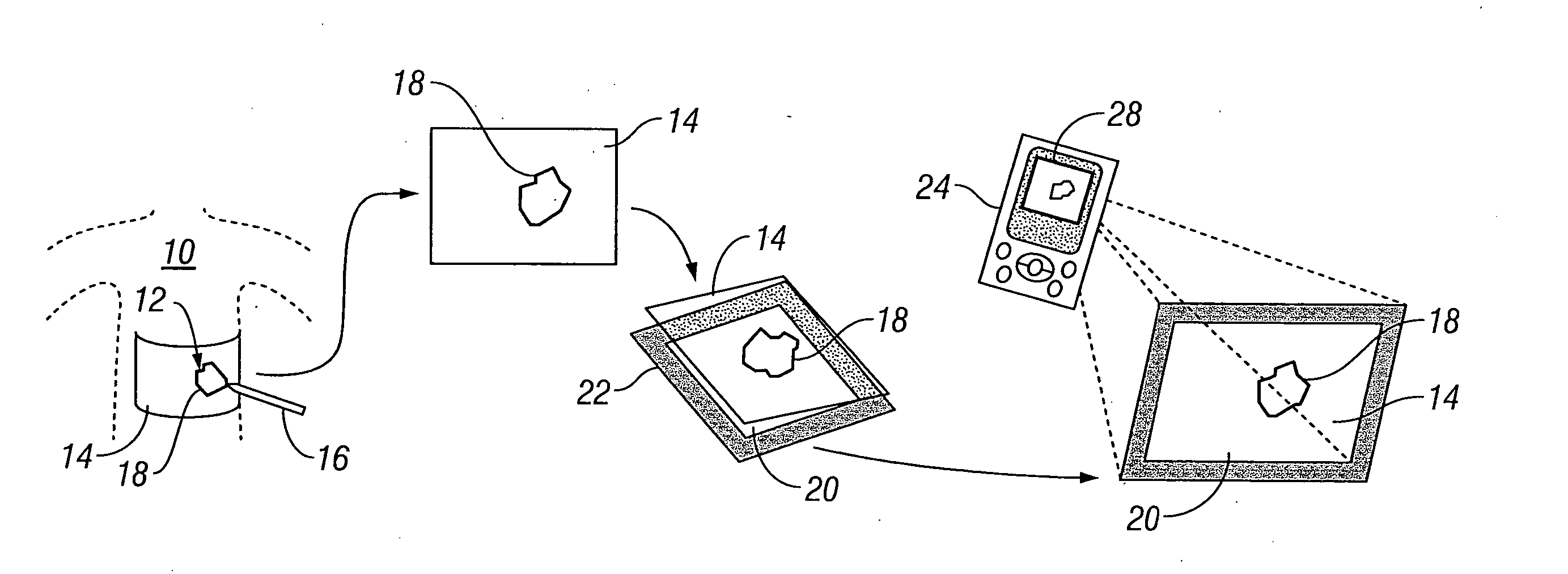
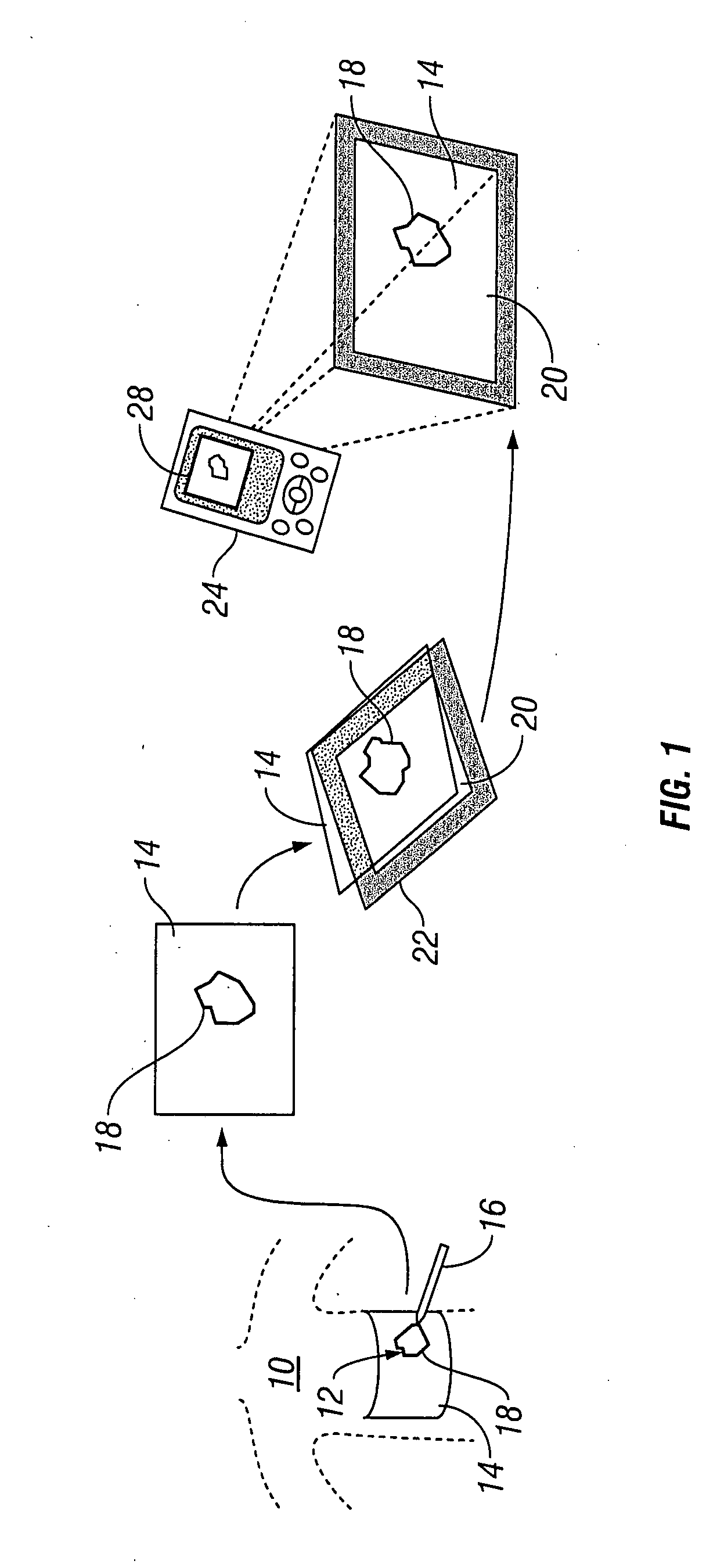
InactiveUS20070276309A1Repeatability, non-invasivenessCost effectivenessProjector film strip handlingCamera film strip handlingData setDigital imaging
Systems and methods for capturing and digitizing an image of a wound and / or a wound trace from a patient and determining there from a degree of change in the characteristics of the wound. A first embodiment includes a transparent / translucent film onto which a dark outline of the wound is traced. The film is fixed to a reference template that provides a geometrically defined reference area. The film / template assembly is imaged with a digital imaging device associated with a handheld digital processor (such as a PDA). The digital image of the template and the wound trace are analyzed to identify the wound tracing and quantify the area within the closed curve. A second embodiment includes imaging the wound site with a reference tag and viewing the image on a display with an associated graphical data input device. A trace of the wound perimeter is made on display with the graphical data input device to establish a data set for the wound perimeter. The data set for the wound trace and the reference tag are analyzed to identify and quantify the wound area. In each embodiment, the system includes a display for providing both a view of the wound trace and the calculated data associated with the wound area.
Owner:KCI LICENSING INC
Method and apparatus for providing three axis magnetic bearing having permanent magnets mounted on radial pole stack
InactiveUS20030155829A1Effective and inexpensive techniqueHighly linear magnetic biasMechanical energy handlingBearingsAxial displacementMagnetic bearing
An improved magnetic bearing that uses permanent magnets to provide the bias flux. The magnetic circuits generating the control flux and bias fluxes are substantially non-coincident but share the same path over some portions that include radial and axial airgaps allowing for a low reluctance and an efficient path for the electromagnetic flux. The flux paths of the permanent magnets are completely defined with minimized airgaps for achieving higher forces and efficiency and very low control currents that produce extremely large forces. A single coil and amplifier for the axial force control and two coils with one associated amplifier for each radial axis of control provides simplicity and cost effectiveness. A single thrust disk is provided that is reacted against for both radial and the axial displacement. The permanent magnets used in the present invention are first fabricated and axially magnetized as segments or as continuous rings prior to being mounted on the sides of the rotor pole, providing an effective and inexpensive technique of manufacturing magnetic bearings.
Owner:CALNETIX TECH +1
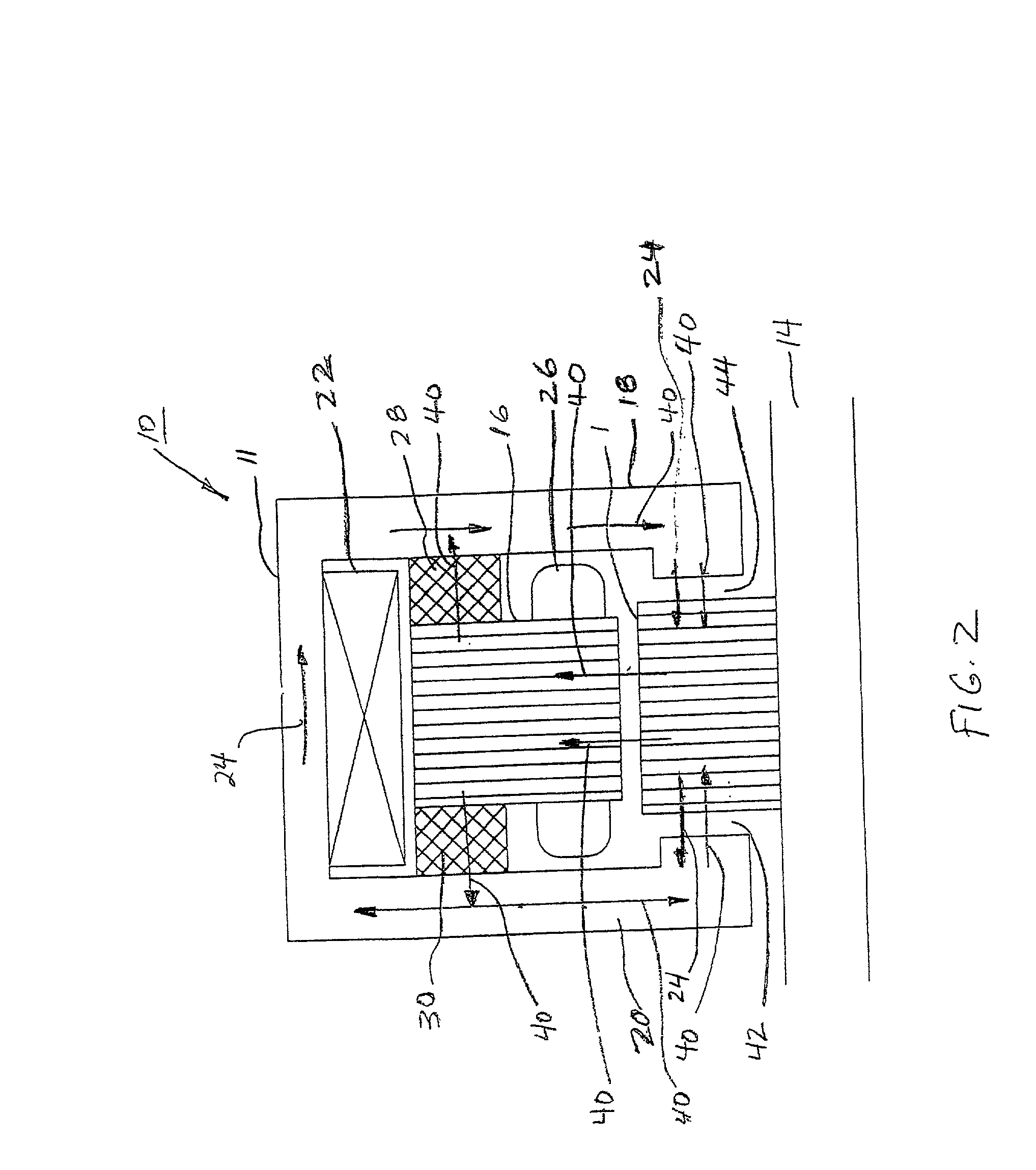
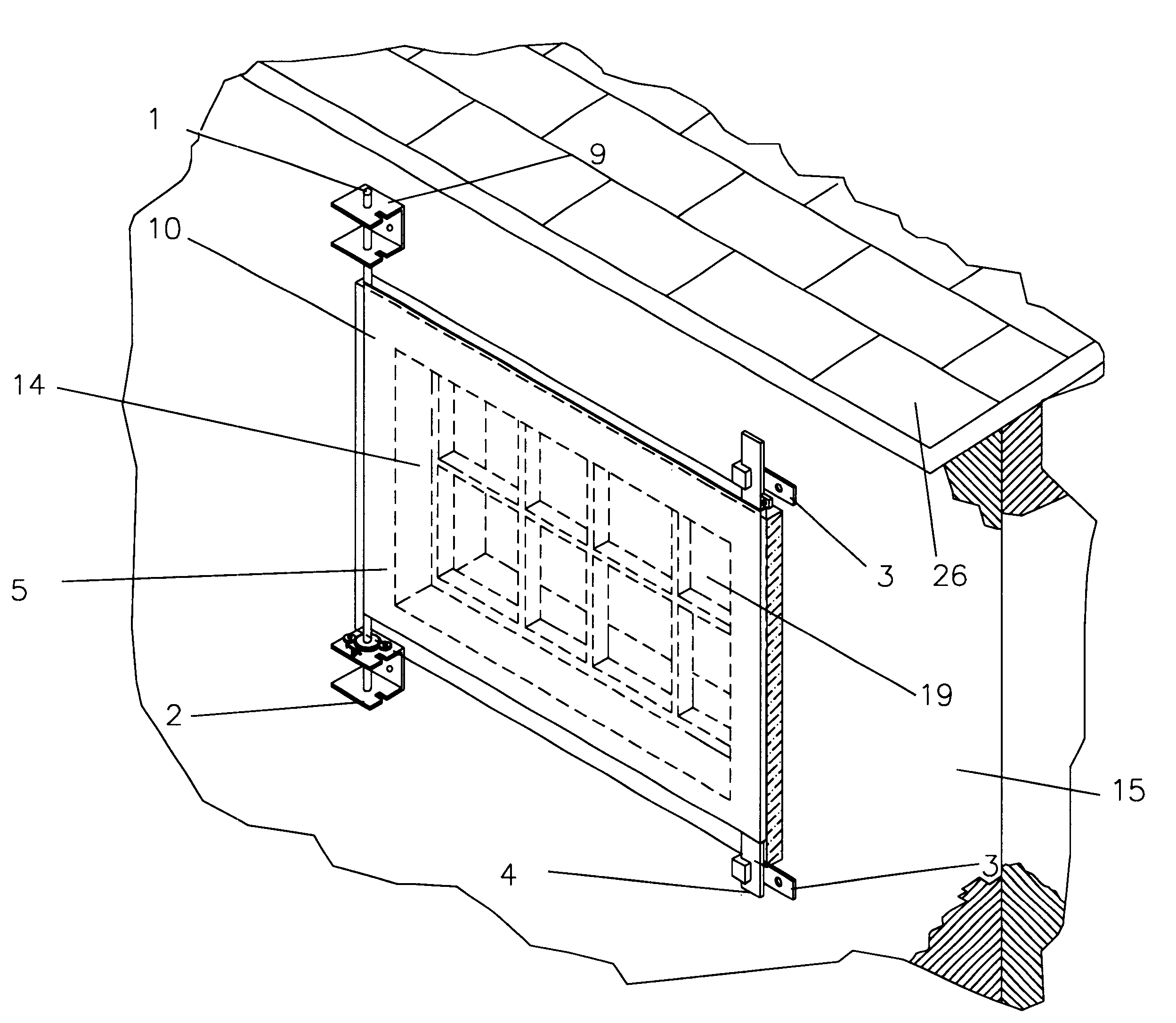
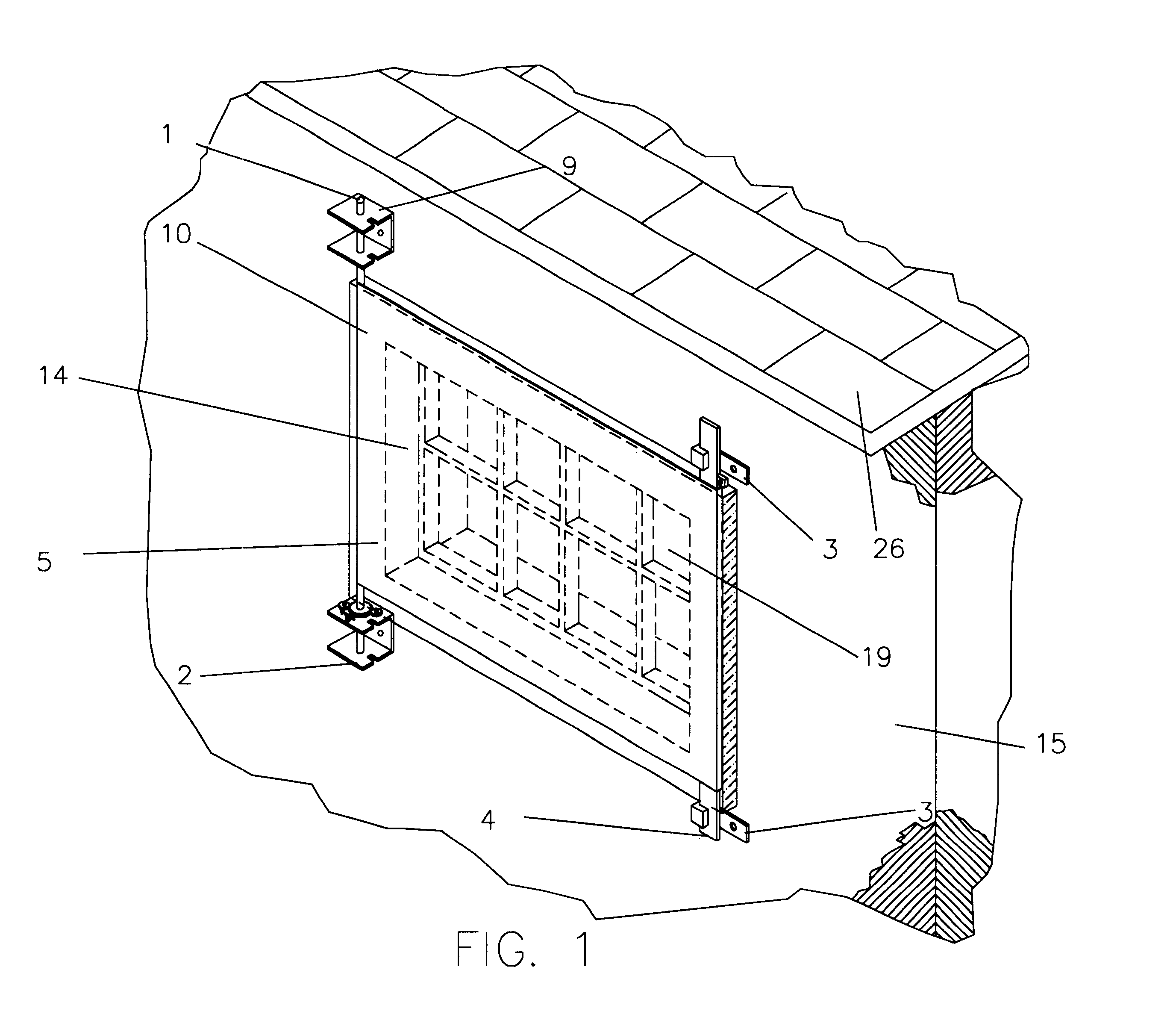
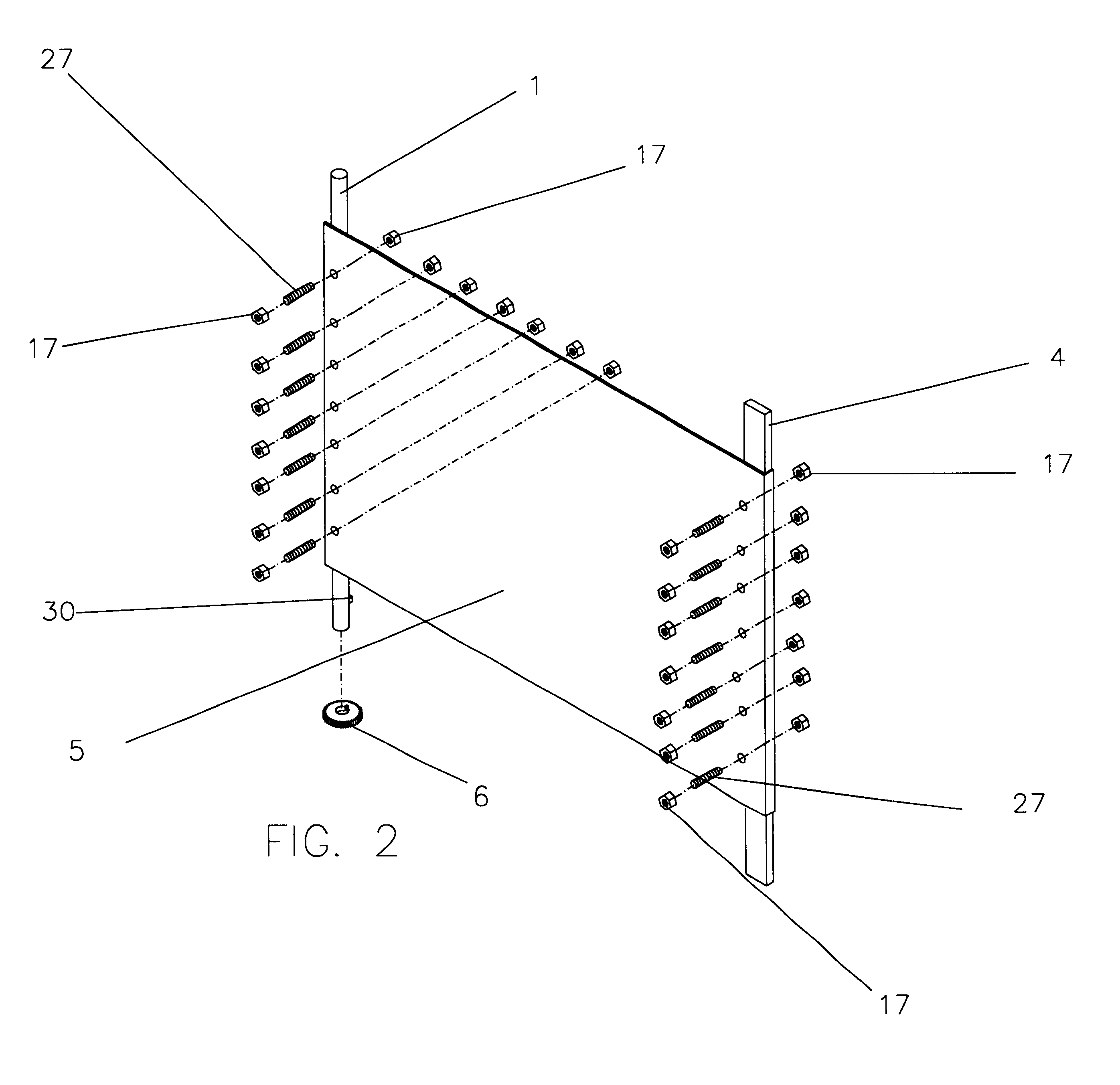
Protective cover assembly
A protective cover assembly used to cover and protect windows, doors or other wall openings for homes, office buildings, hotels, and other walled structures from the destructive forces of a high windstorm, such as a hurricane. The current form of the preferred embodiment consists of a high strength fabric covering an opening, such as a window and being supported by brackets, a rod and a bar. Once installed, the high strength fabric is stretched over the opening, through the use of a gears and ratchet assembly. The high strength fabric once stretched will provide protection from high winds and wind borne debris common in storms such as hurricanes. The protective cover assembly also prevents unlawful entries or break-ins of buildings. The high strength fabric is securely supported to the rod and steel bar that are firmly attached to the wall structure near the wall opening.
Owner:GUNN CAMERON T
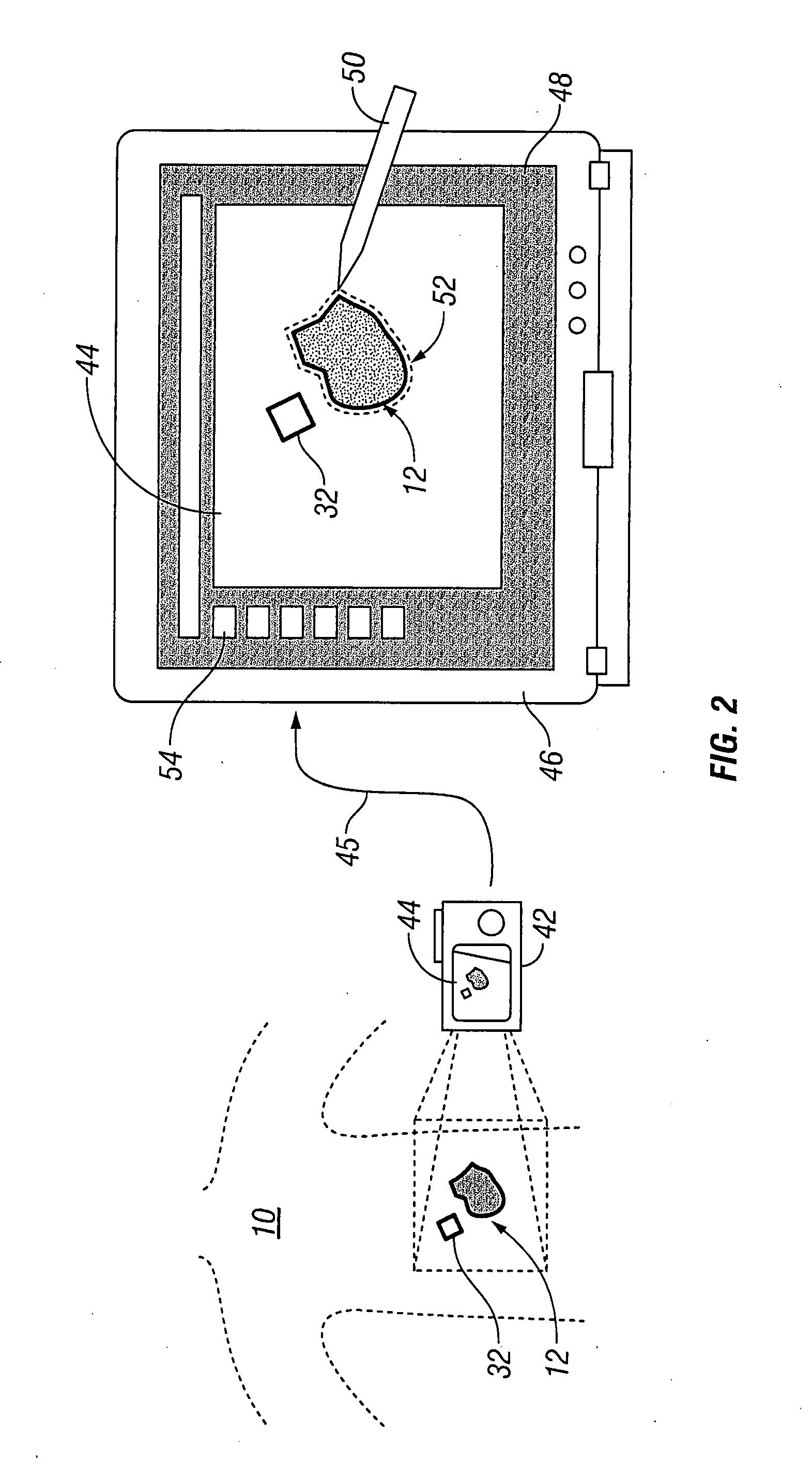
Systems and methods for wound area management
InactiveUS20070276195A1Repeatability, non-invasivenessCost effectivenessPrintersProjectorsData setDigital imaging
Systems and methods for capturing and digitizing an image of a wound and / or a wound trace from a patient and determining there from a degree of change in the characteristics of the wound. A first embodiment includes a transparent / translucent film onto which a dark outline of the wound is traced. The film is fixed to a reference template that provides a geometrically defined reference area. The film / template assembly is imaged with a digital imaging device associated with a handheld digital processor (such as a PDA). The digital image of the template and the wound trace are analyzed to identify the wound tracing and quantify the area within the closed curve. A second embodiment includes imaging the wound site with a reference tag and viewing the image on a display with an associated graphical data input device. A trace of the wound perimeter is made on display with the graphical data input device to establish a data set for the wound perimeter. The data set for the wound trace and the reference tag are analyzed to identify and quantify the wound area. In each embodiment, the system includes a display for providing both a view of the wound trace and the calculated data associated with the wound area.
Owner:KCI LICENSING INC
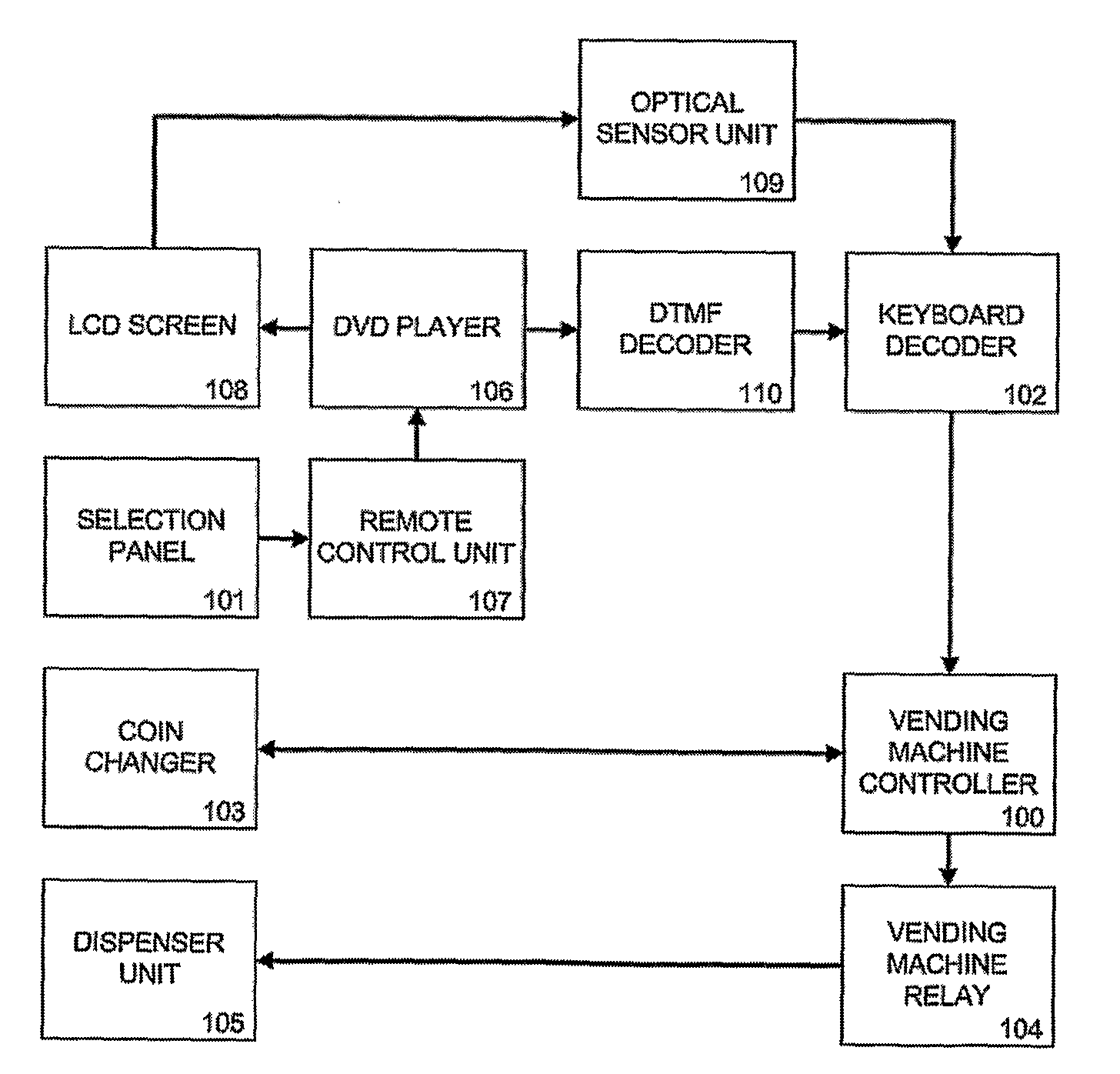
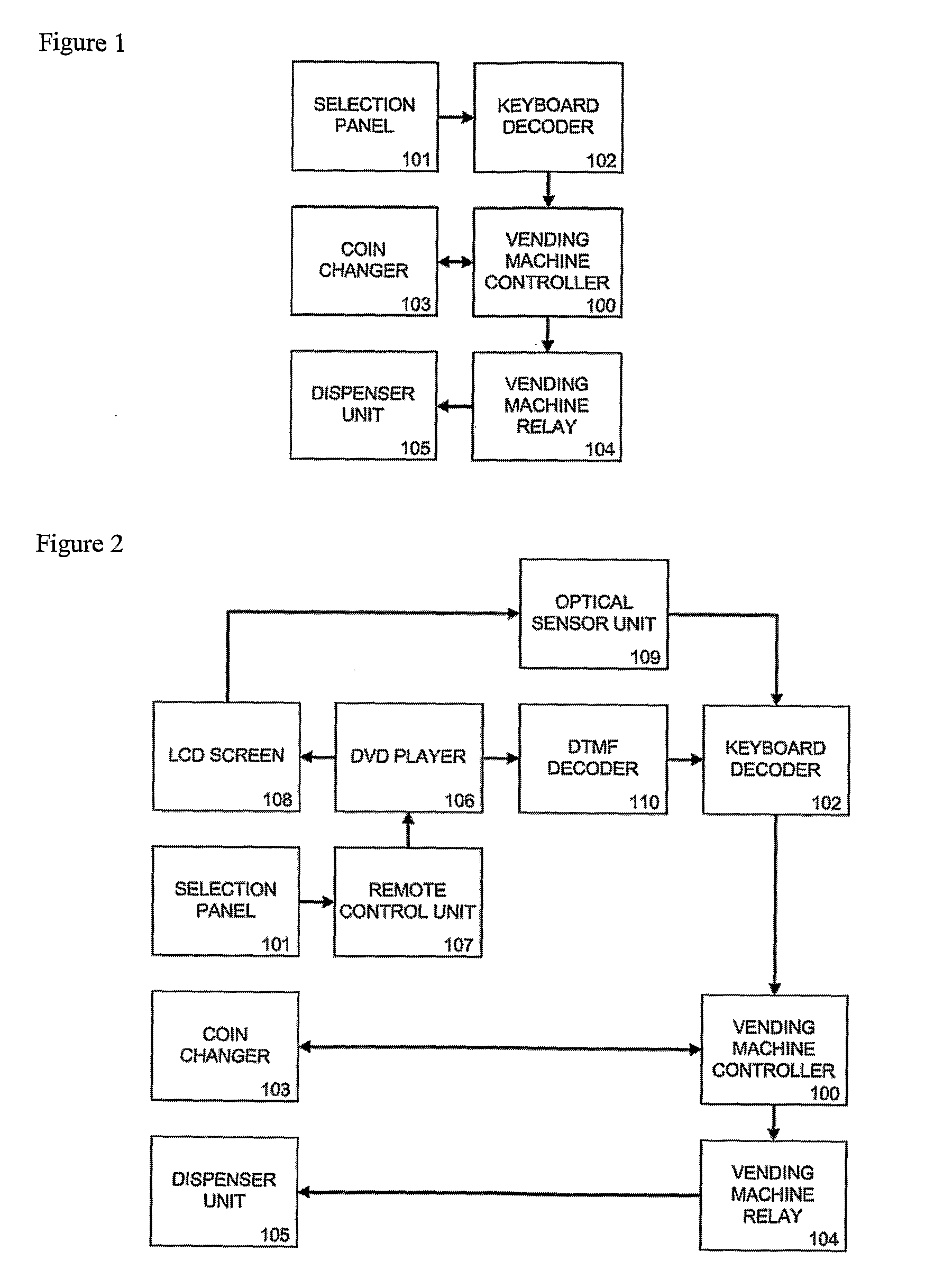
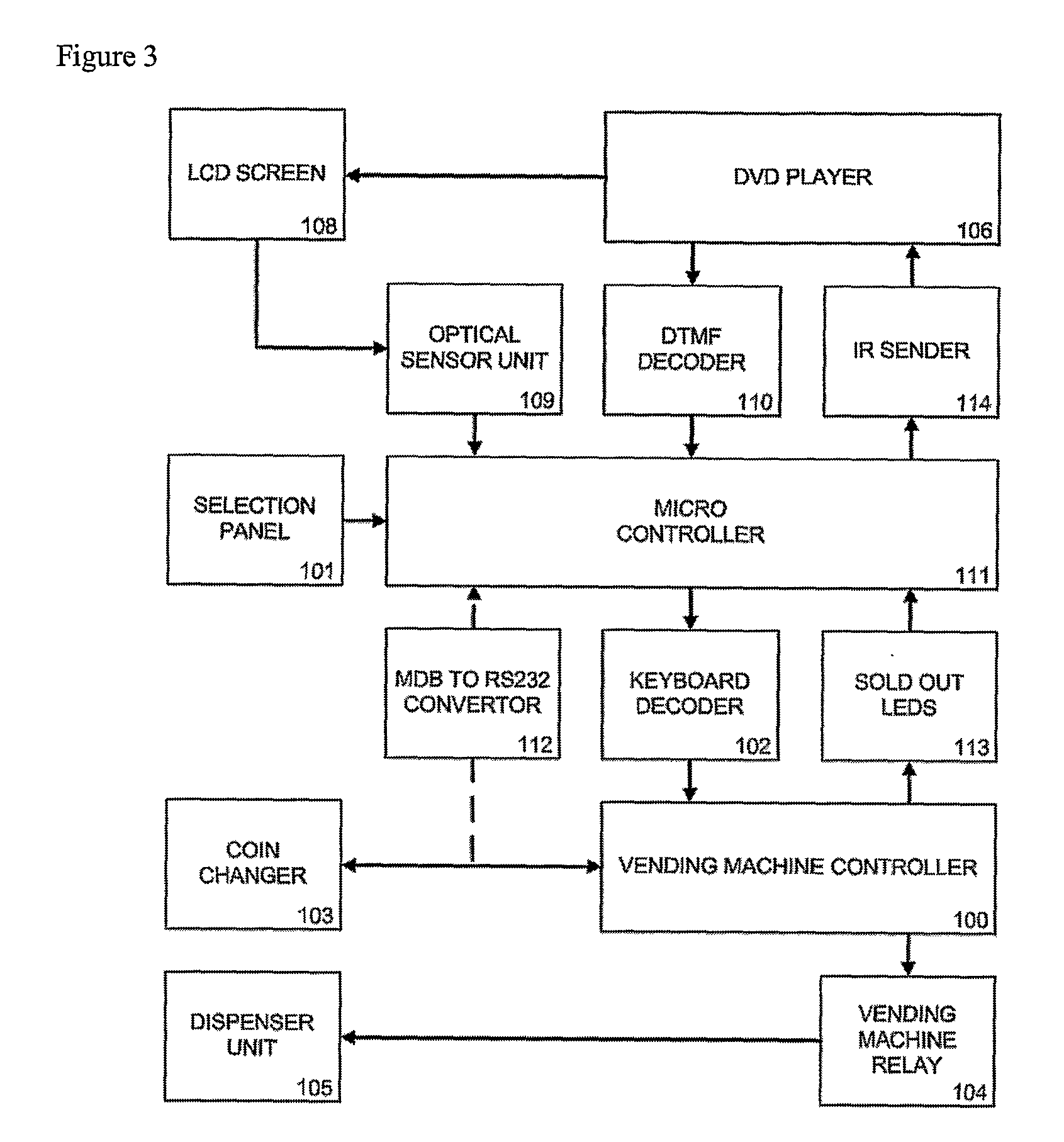
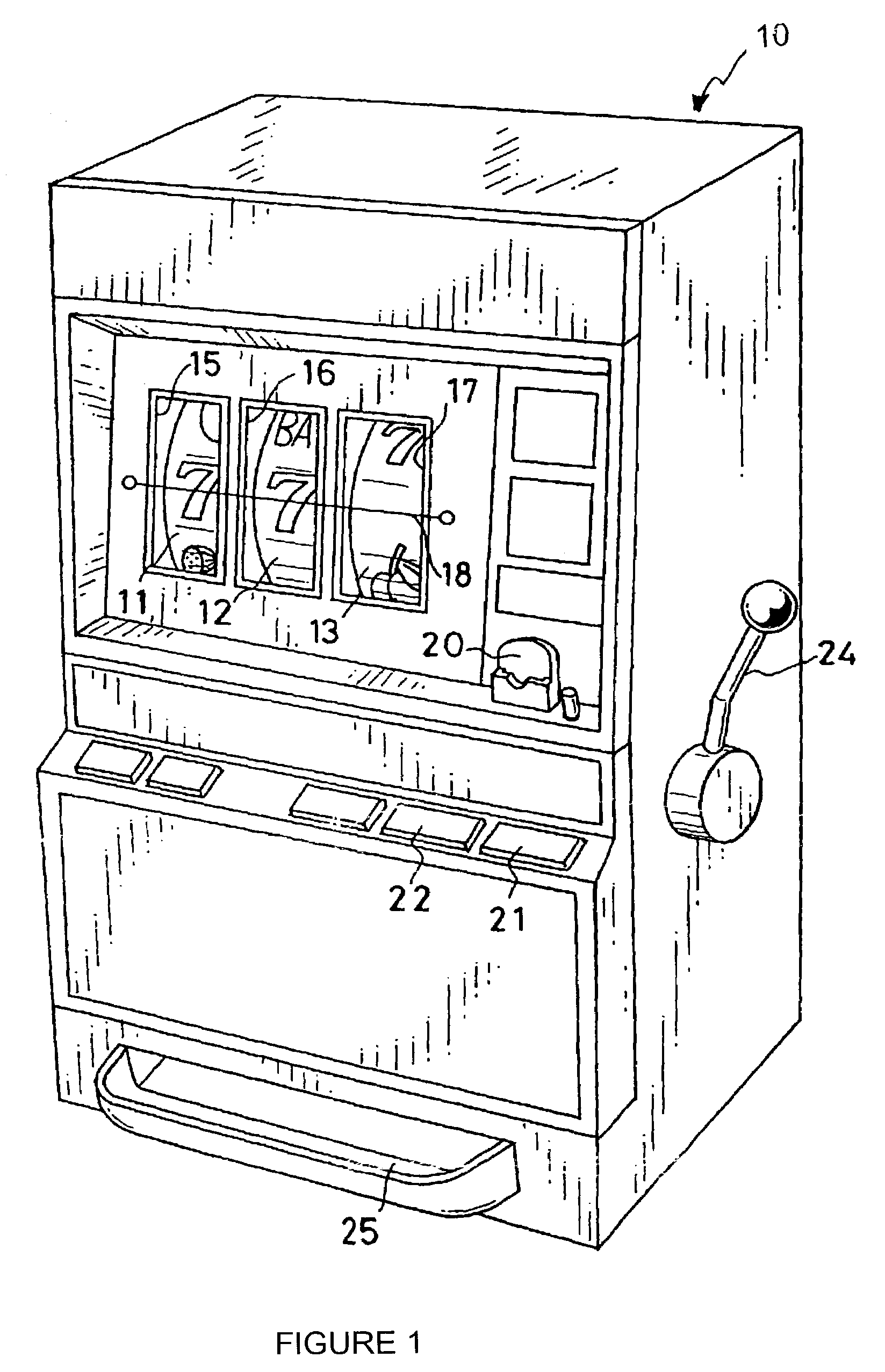
Method and Apparatus for Controlling a Vending Machine
ActiveUS20100198400A1Cost effectivenessEffective local commercialsFlat record carrier combinationsRecord information storageMicrocontrollerGraphics
A solution comprising cost-effective methods and techniques for converting a traditional vending machine into a vending machine with a graphical user interface, multimedia advertising and info kiosk capabilities. A key aspect of this invention is the integration of a consumer DVD player in a vending machine, in which the graphical user interface is implemented as DVD Menu structures stored on a DVD disc that also contains the video clips. Another aspect of this invention, is the changed logic of a traditional vending machine to delay item dispense until a video clip has been played. The present invention provides interfacing methods between a DVD player, a Vending Machine Controller and an optional microcontroller. These methods can be used to implement a communication protocol between a DVD player and a microcontroller. The methods and techniques of the invention can be integrated in an MDB peripheral device of a vending machine.
Owner:FELIQUE PASCAL +1
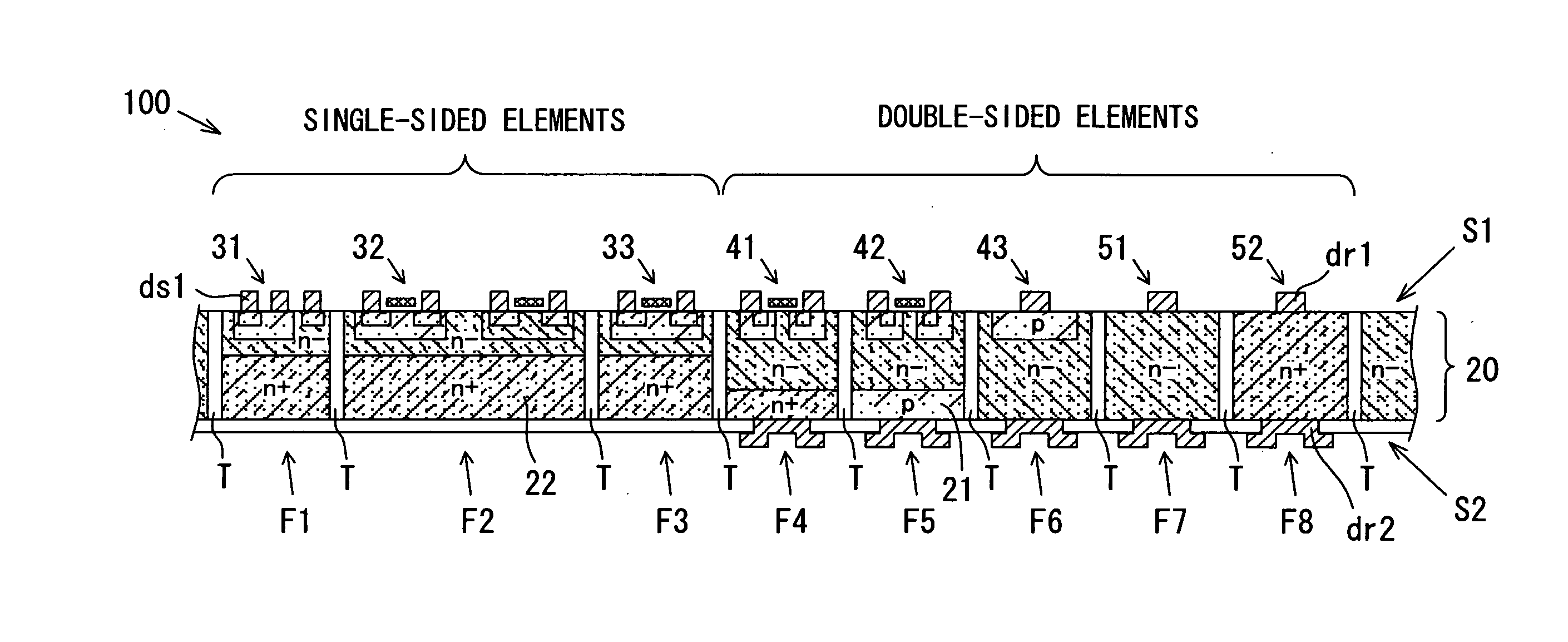
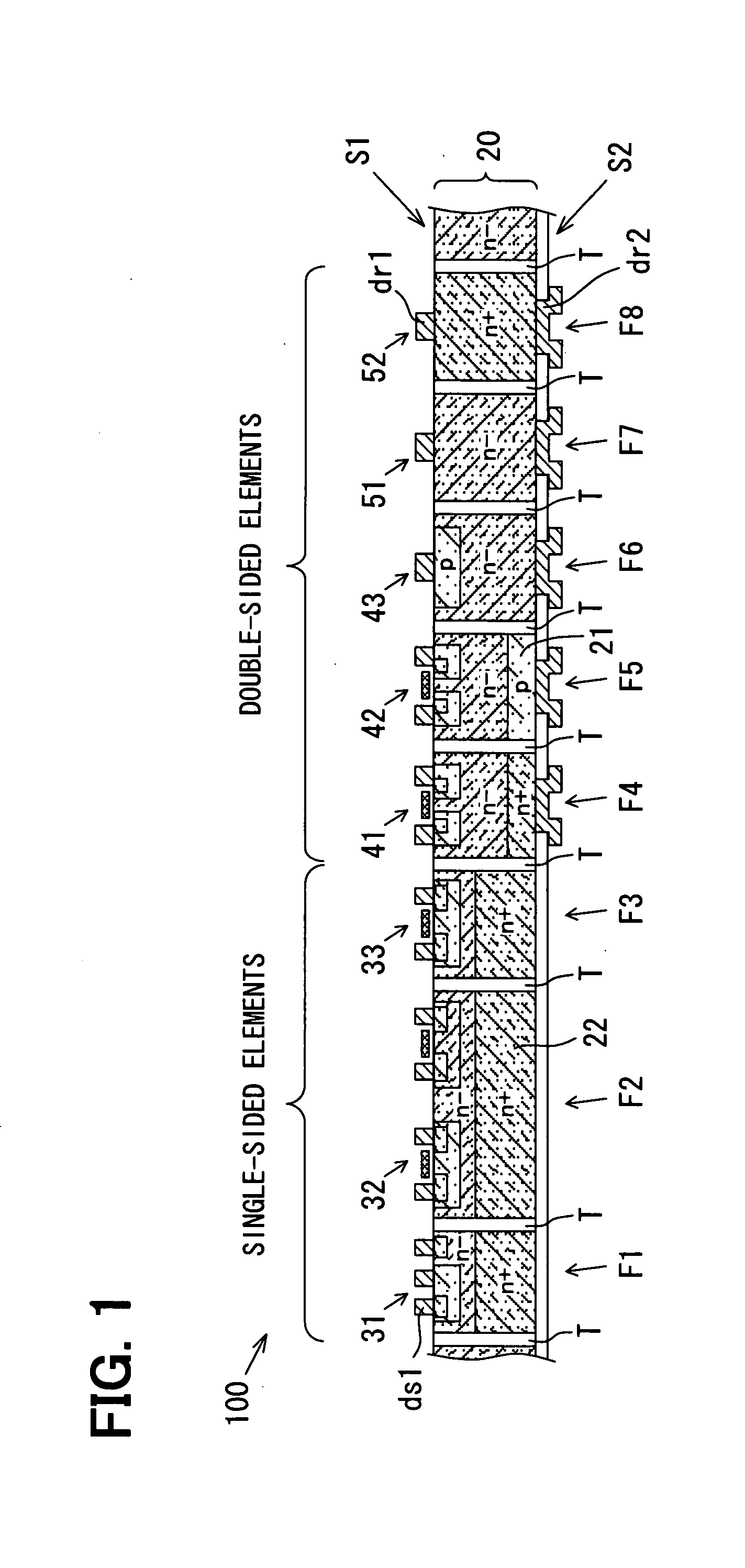
Semiconductor device and method for manufacturing same
ActiveUS20080135932A1Cost effectivenessCost-effectiveTransistorSemiconductor/solid-state device detailsSemiconductorSemiconductor device
A semiconductor device having plural active and passive elements on one semiconductor substrate is manufactured in the following cost effective manner even when the active and passive elements include double sided electrode elements. When the semiconductor substrate is divided into plural field areas, an insulation separation trench that penetrates the semiconductor substrate surrounds each of the field areas, and each of the either of the plural active elements or the plural passive elements. Further, each of the plural elements has a pair of power electrodes for power supply respectively disposed on each of both sides of the semiconductor substrate to serve as the double sided electrode elements.
Owner:DENSO CORP
Device and method for measuring compressive force of flexible linear body
InactiveUS7984659B2Easy to compressCost effectivenessForce measurement by measuring magnetic property varationForce measurement by measuring optical property variationMeasurement deviceCost effectiveness
Owner:NAGOYA INSTITUTE OF TECHNOLOGY +1
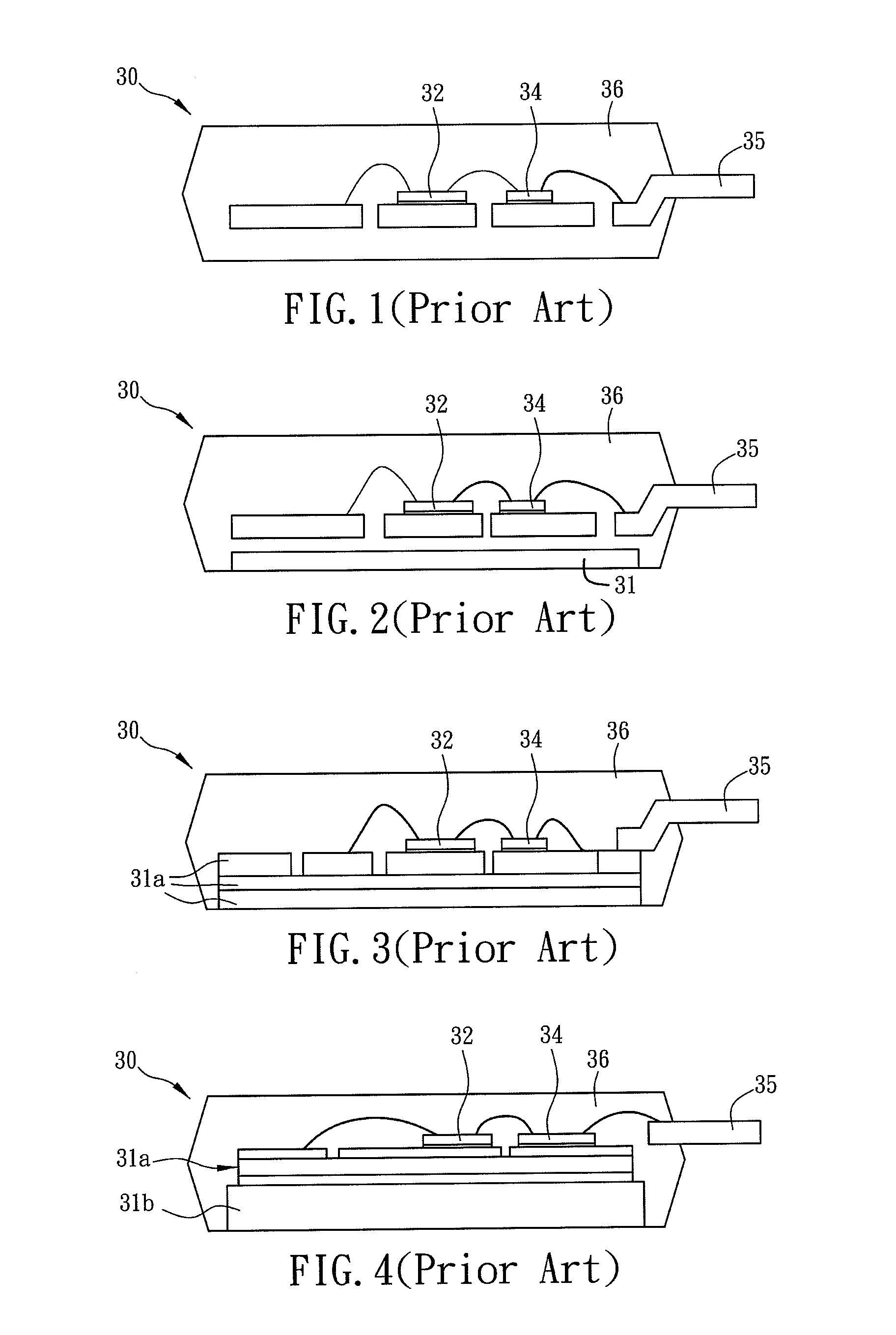
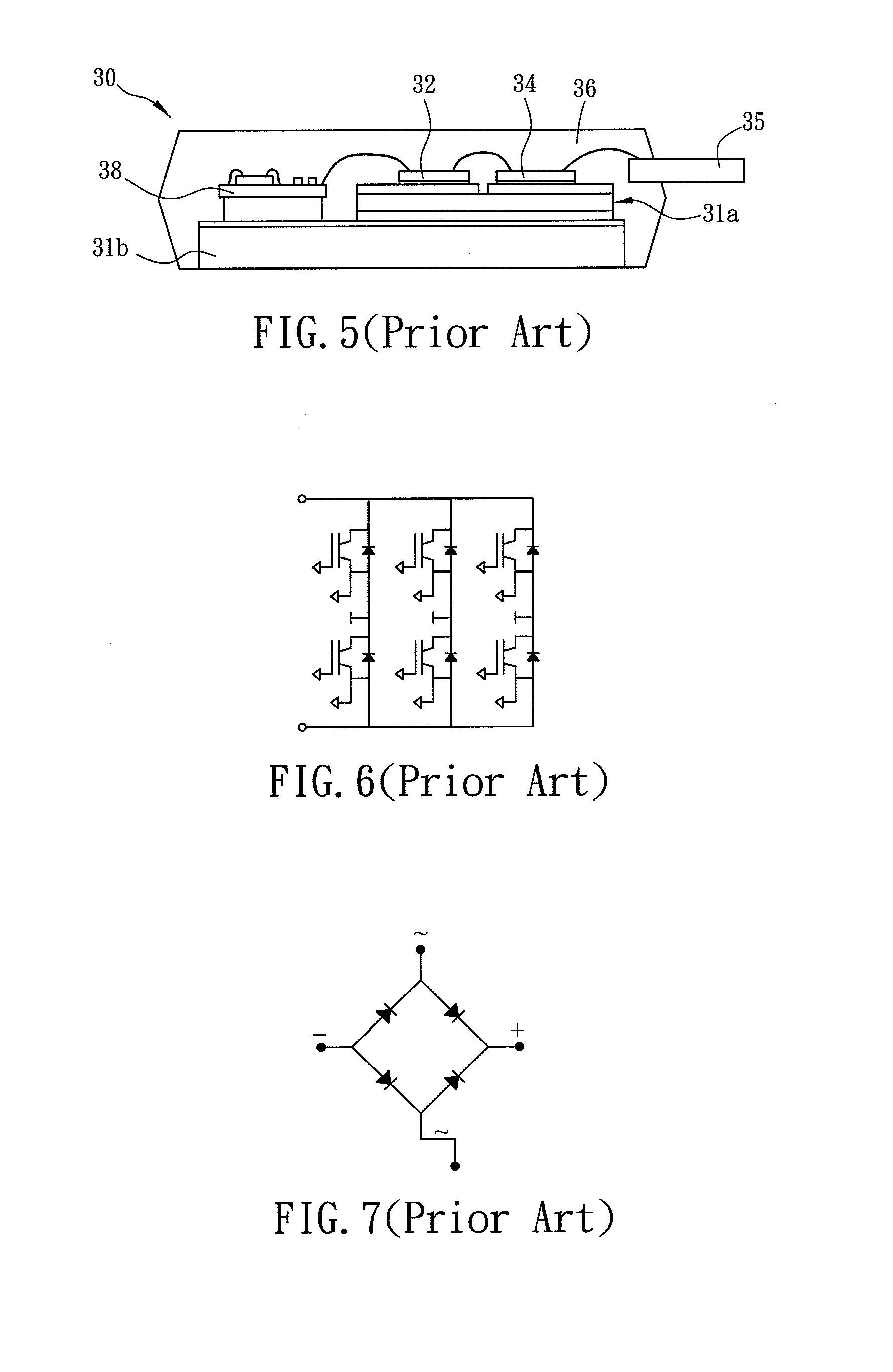
Power module
ActiveUS20120014069A1Improve efficiencyImprove power densityPrinted circuit assemblingConversion constructional detailsEngineeringLead frame
A power module includes a first heat sink, first and second power chips, a thermo-conductive insulating layer, a lead frame and a molding compound. The first heat sink has a first area and a second area. The first power chip is disposed in the first area. The thermo-conductive insulating layer is disposed in the second area. The second power chip is disposed on the heat sink through the thermo-conductive insulating layer. The lead frame is electrically connected to at least one of the first and second power chips. The molding compound covers the first and second power chips, the thermo-conductive insulating layer and a portion of the lead frame. The first heat sink is electrically connected to at least one of the first and second power chips. Because the first power chip is not disposed on the first heat sink through the thermo-conductive insulating layer, the cost can be reduced.
Owner:DELTA ELECTRONICS INC
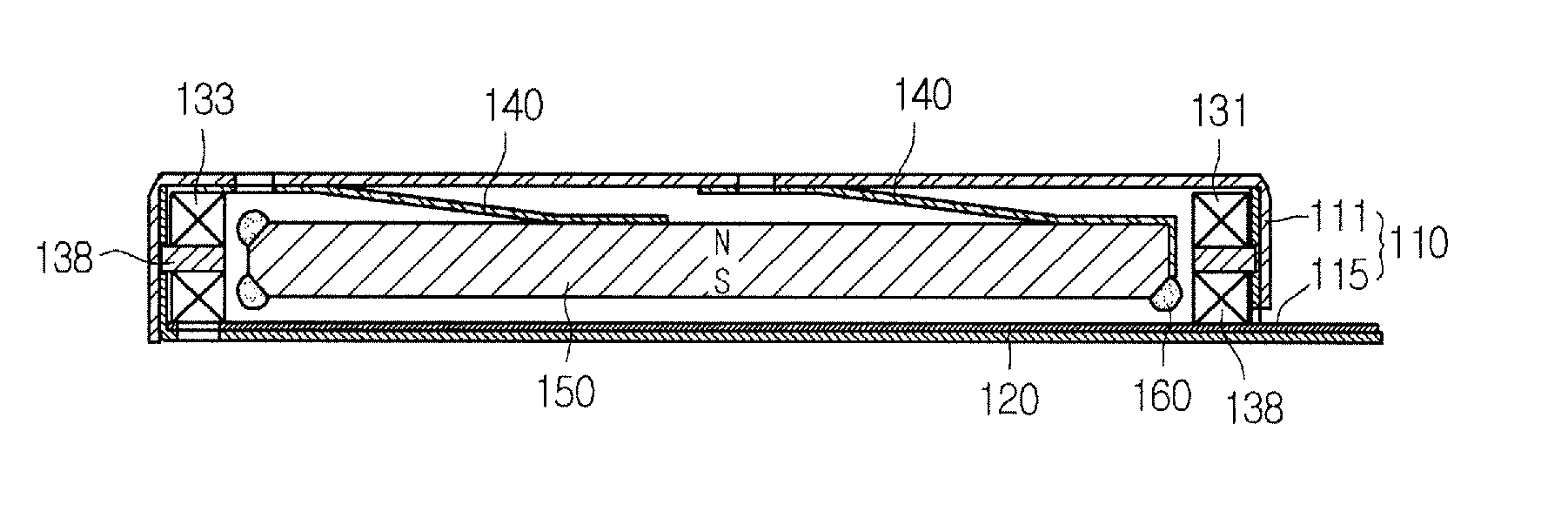
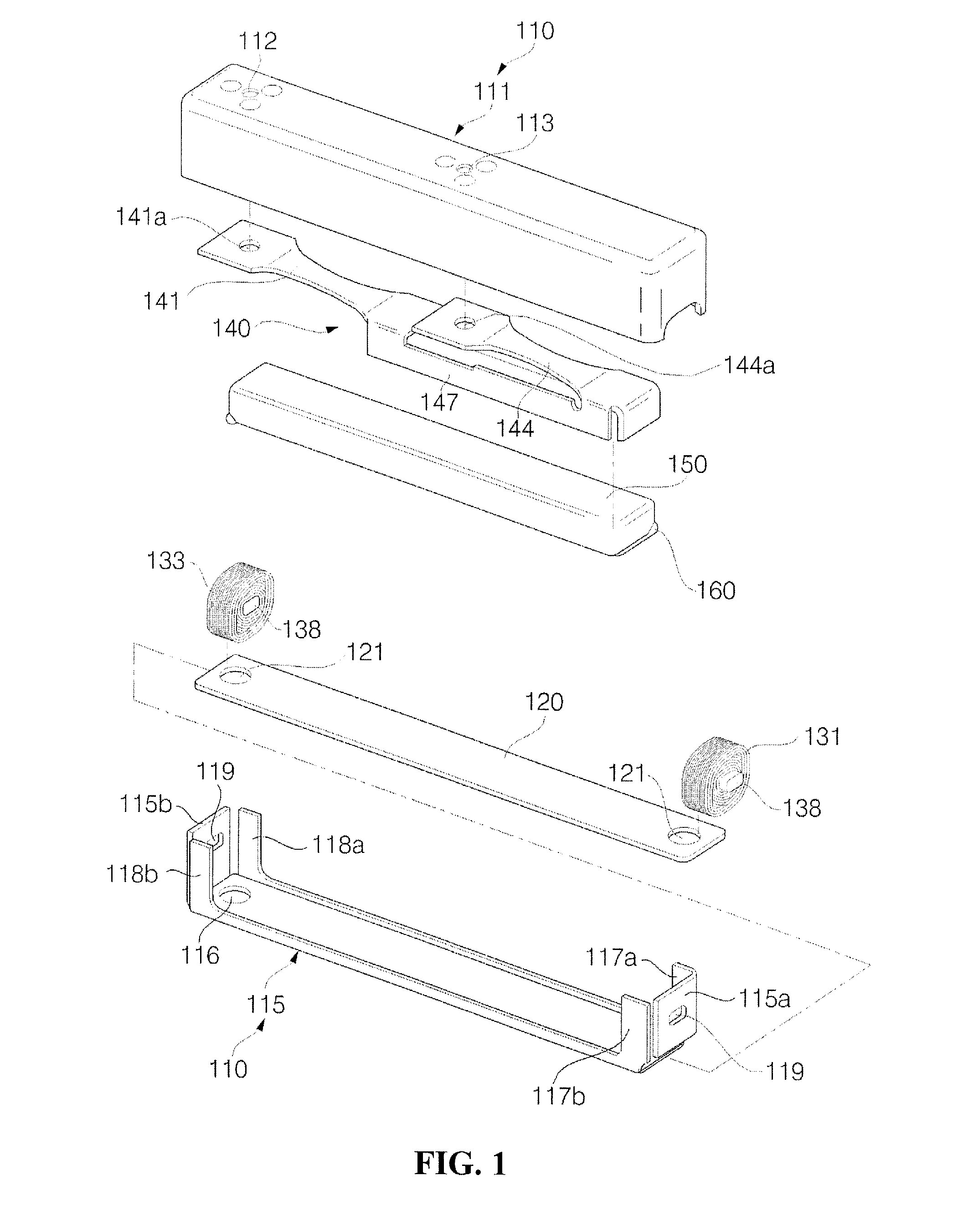
Linear Vibrator
InactiveUS20070216235A1Reduce manufacturing costImprove product reliabilityDynamo-electric machinesManufacturing cost reductionInterior space
Embodiments of a linear vibrator are provided that are capable of reducing the manufacturing cost, increasing the product reliability and increasing the vibrating quantity. An embodiment of a linear vibrator can include a case formed of an upper case portion and a lower case portion coupled to each other to provide a predetermined inner space; a substrate disposed on an upper surface of the lower case portion; a first coil and a second coil installed at both end parts inside of the case and connected to the substrate; a spring having one side fixed on at least one of the inside faces of the case; and a magnet fixed at another side of the spring and located between the first and second coils inside of the case, where the magnet can vertically vibrate through an interaction with the first and second coils.
Owner:EM TECHNOLOGY CO LTD
Microwave induced functionalization of single wall carbon nanotubes and composites prepared therefrom
InactiveUS20060210466A1Rapid funtionalizationHigh purityMaterial nanotechnologyGroup 1/11 element organic compoundsCarbon nanotubeMicrowave electromagnetic radiation
The invention is directed to a method of forming, producing or manufacturing functionalized nanomaterials, and, specifically, soluble functionalized nanomaterials. The presently described invention also relates to nanomaterial-based composites consisting of a target material, which can include ceramic, polymer, or metallic matrices incorporated into or grown on nanomaterials, as well as a method or synthesis technique for the formation, production, or manufacture of nanomaterial-based composites through microwave-induced reaction.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
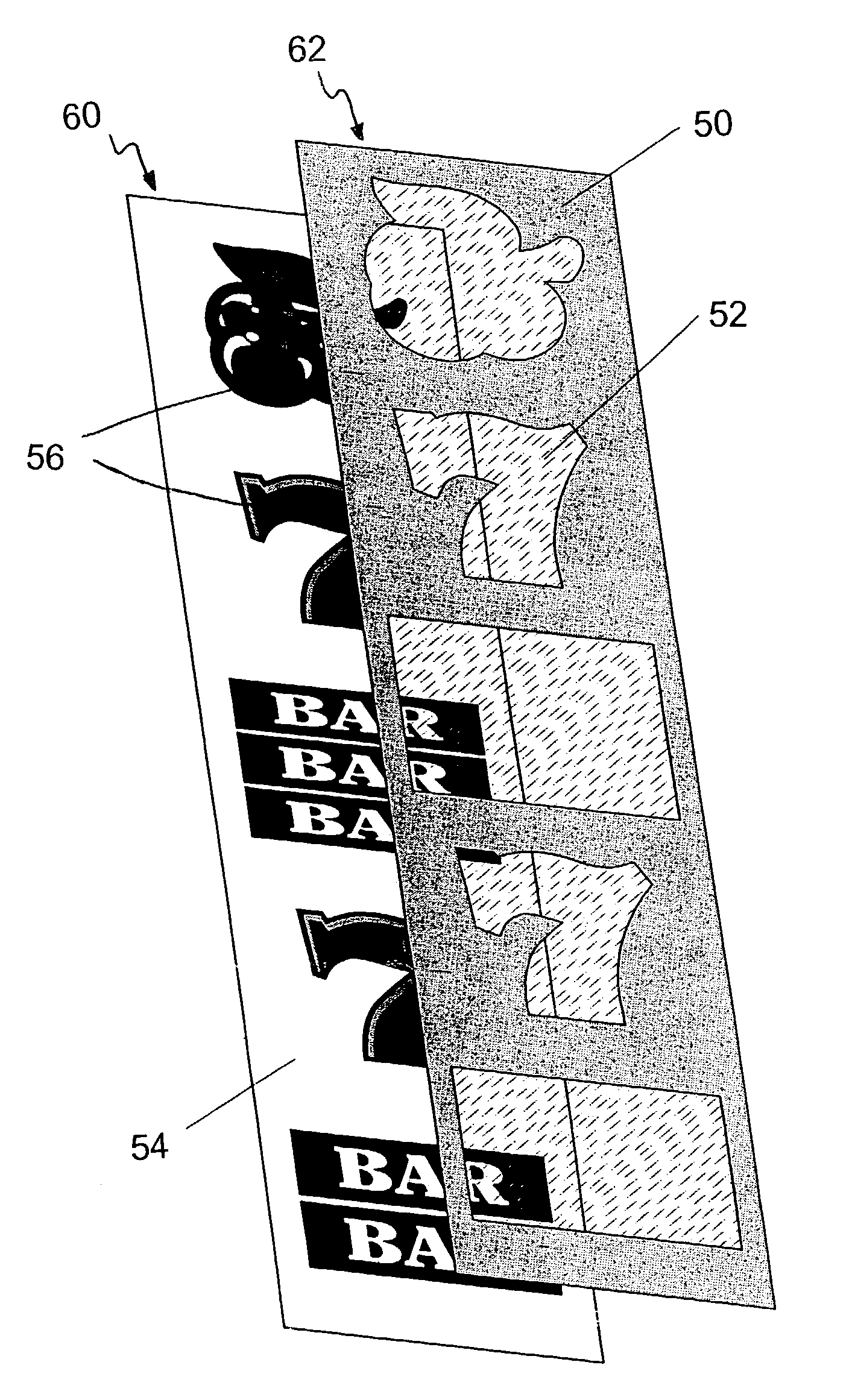
Enhanced reel strip and method for assembling same
InactiveUS7316395B1Increased attractiveness and excitementGood lookingCard gamesApparatus for meter-controlled dispensingCost effectivenessEngineering
An enhanced reel strip includes a base reel strip and an overlay strip, wherein the base reel strip has symbols applied thereto and the overlay strip has designated portions thereof removed to create cut-outs. The base reel strip and overlay strip are affixed in such a manner that the symbols of the base reel strip are visible through the cut-outs of the overlay strip. The joined strips produce an enhanced reel strip. Furthermore, these enhanced reel strip production methods dramatically improve the quality and appearance of reel strips while utilizing a relatively simple manufacturing process that maintains cost effectiveness.
Owner:BALLY GAMING INC
Method and apparatus for wide area surveillance of a terrorist or personal threat
InactiveUS20080169921A1Maximize chanceCost effectivenessNetwork traffic/resource managementNanosensorsWide areaCost effectiveness
The present invention is related to a means for detecting external threats by the use of methods and apparatuses for the wide area detection of chemical, radiological or biological threats using modified personal wireless devices combined with new advanced micro and nanosensor technologies. A cost effective method is provided for wide area surveillance of a potential terrorist or personal threat. Personal electronic devices such as mobile phones, PDAs or watches, in combination with new microsensor technologies described herein, can be used as a new type of platform detection technology for wide area surveillance of major threats. A “Homeland Security” chip is further provided which combines the elements of geo-location, remote wireless communication and sensing into a single chip. The personal electronic devices can be further equipped for detecting various medically related threats. Similarly modified personal devices can be used to detect external threats that are person-specific.
Owner:GENTAG
Array structure for the application to wireless switch of WLAN and WMAN
InactiveUS7567213B2Improve efficiencyLow budgetIndoor communication adaptationIndividually energised antenna arraysArea networkWireless metropolitan area network
The present invention provides an antenna array structure which includes multiple array elements, and the antenna array structure is using for the application of the WLAN (wireless local area network) or WMAN (wireless metro area network.) Furthermore, the array elements of the present invention are phased arrays or attenuated arrays, and when configuration with different type of the array element is used, the corresponding BFN (beam forming network) can also be implemented in various possibilities. With all the configuration of the present invention, the manufacturers can have a stable array structure for their applications.
Owner:ACCTON TECHNOLOGY CORPORATION
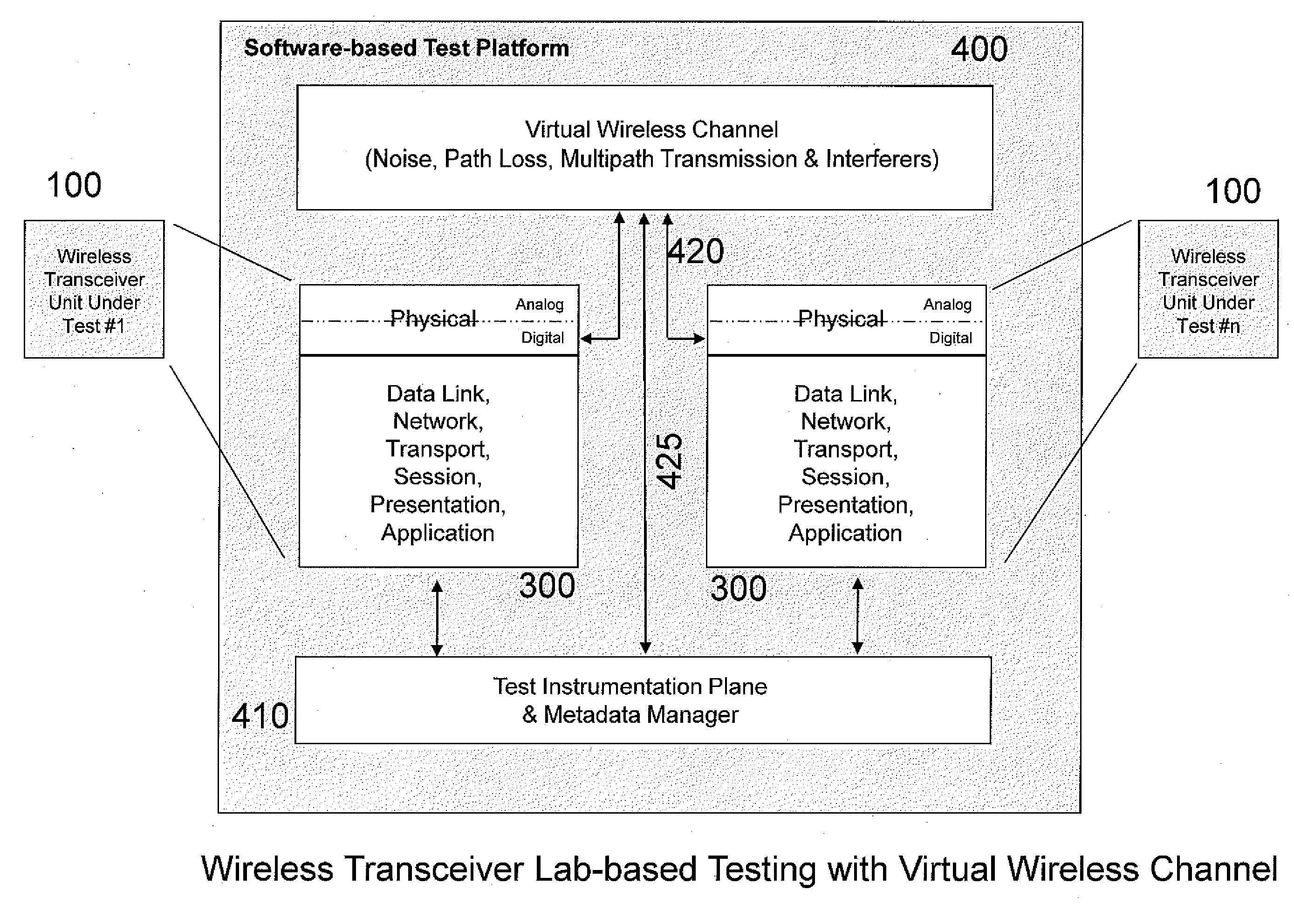
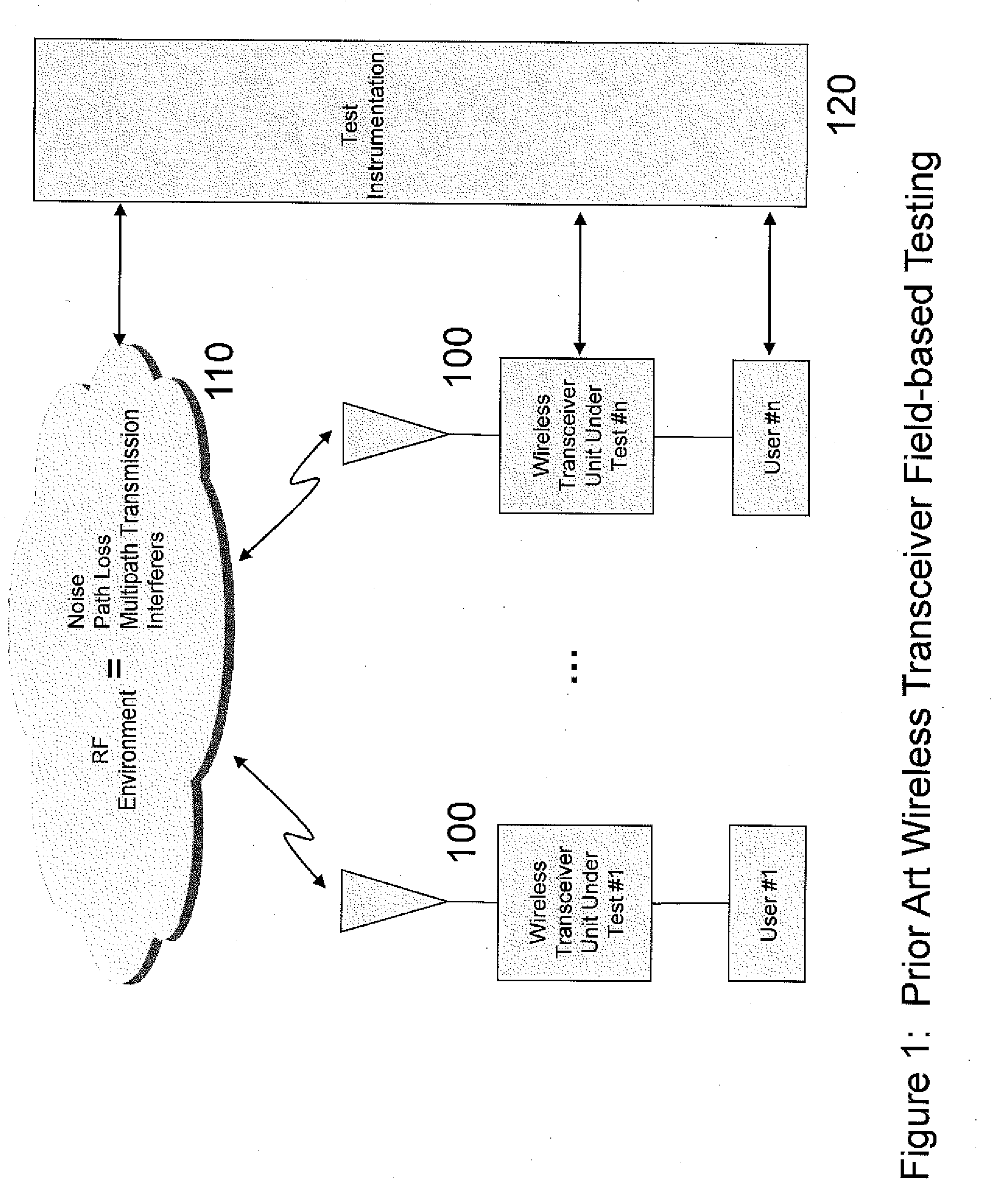
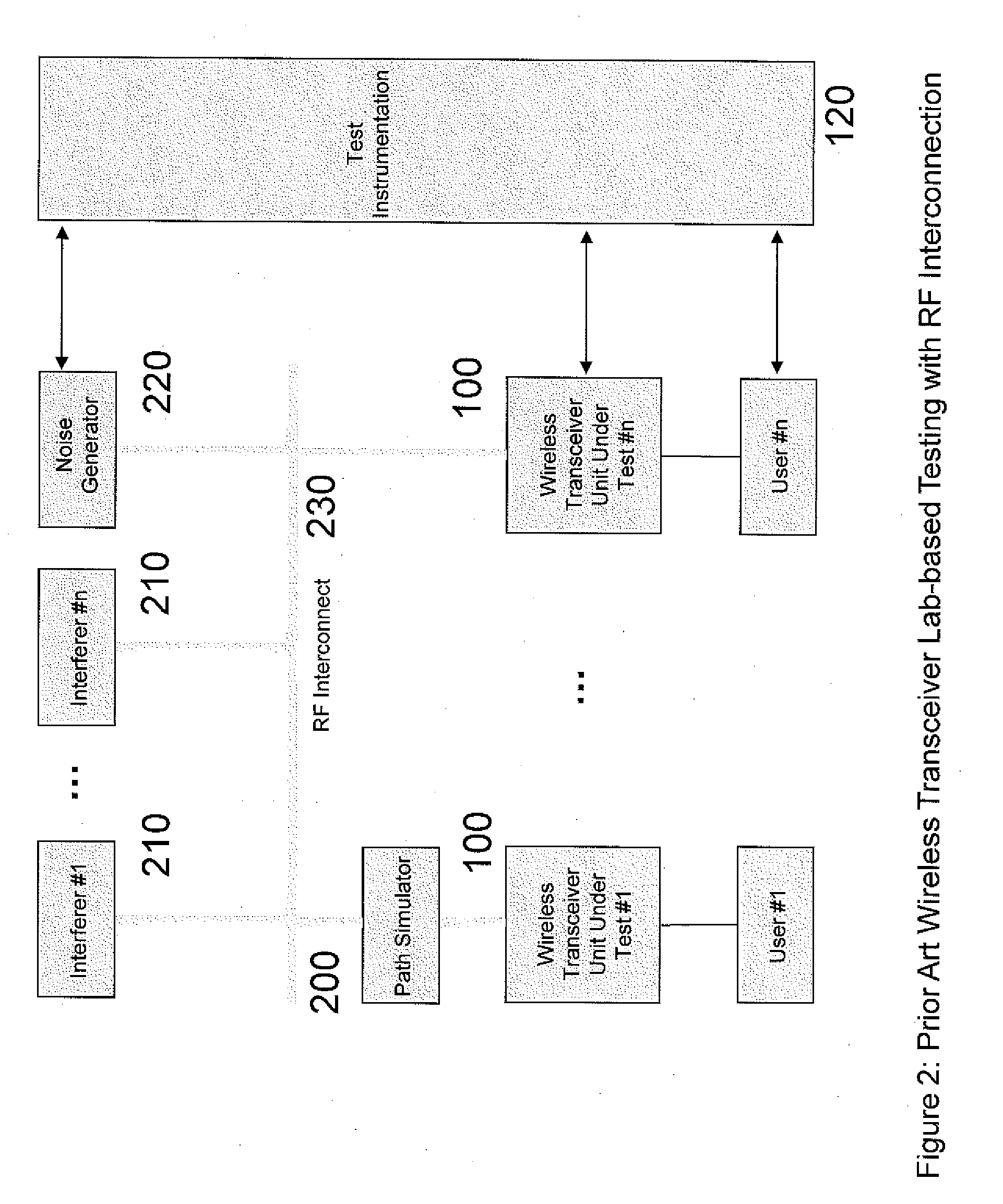
Wireless transceiver test bed system and method
ActiveUS20100304686A1Flexibility in numberCost effectivenessTransmitters monitoringReceivers monitoringFrequency spectrumTransceiver
A system and method for testing wireless transceivers in a virtual wireless environment including emulating an RF environment, creating virtual spectrum users having selectable transmission parameters and physical characteristics and evaluating the operation of the wireless transceiver in the virtual wireless environment.
Owner:PARSONS CORPROATION
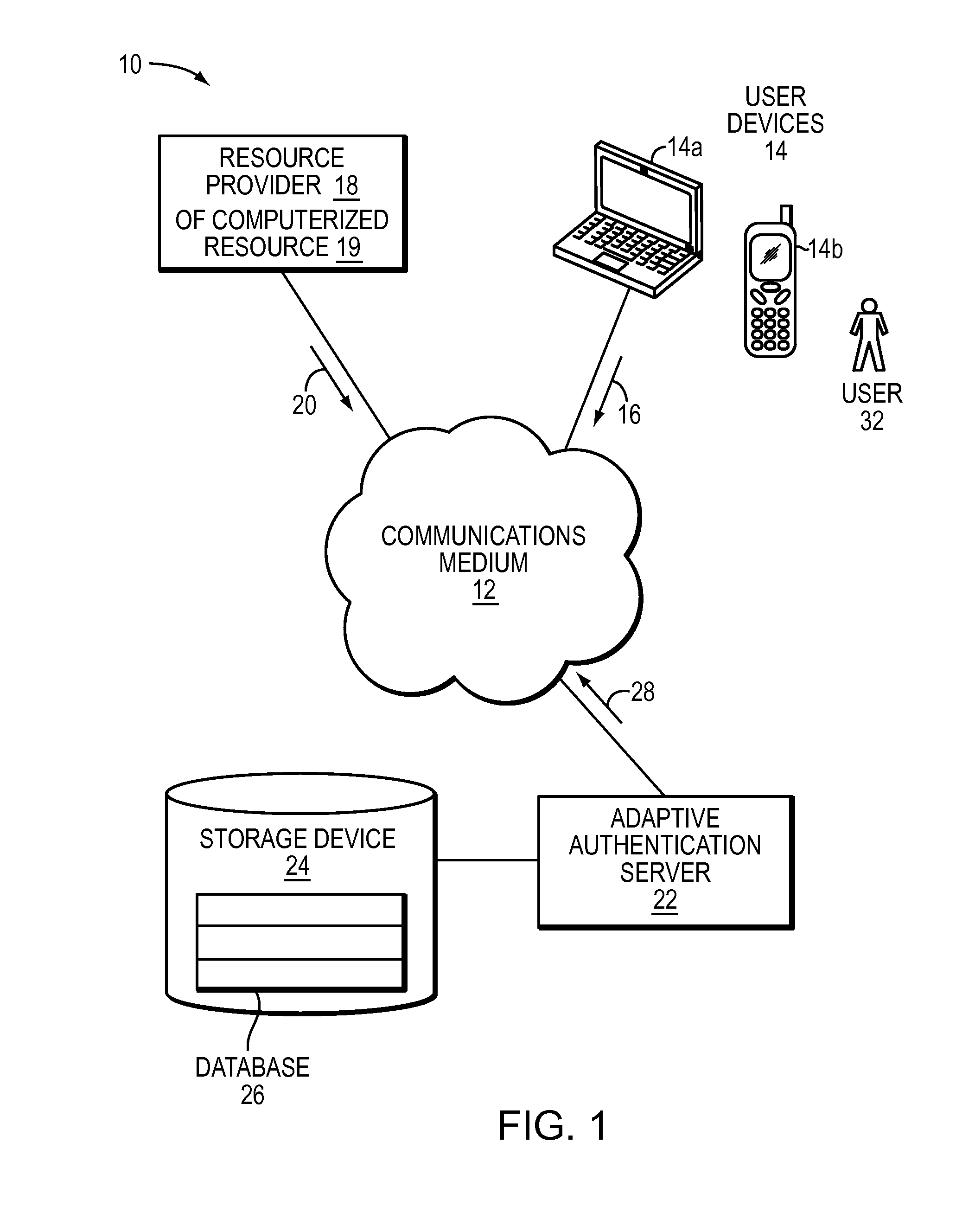
User authentication
ActiveUS9122866B1Cost effectivenessDigital data processing detailsDigital data authenticationUser authenticationInternet privacy
There is disclosed some techniques for selecting a user authentication challenge. In one example, the method comprises the steps of receiving an authentication request to authenticate a user and selecting a user authentication challenge to issue to the user in response to receiving the authentication request. The selection of the user authentication challenge comprises selecting a user authentication challenge among a plurality of user authentication challenges based on the cost effectiveness of the respective user authentication challenges and characteristics of the authentication request.
Owner:EMC IP HLDG CO LLC
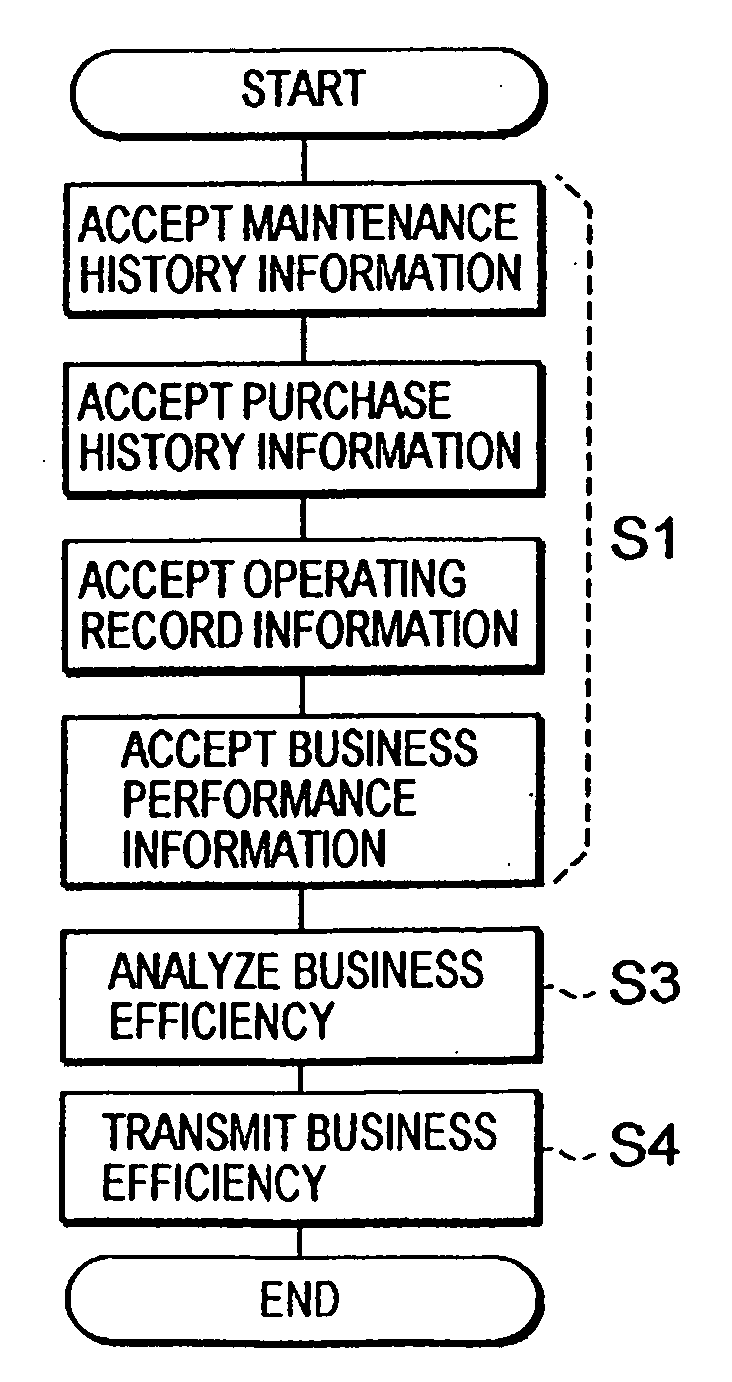
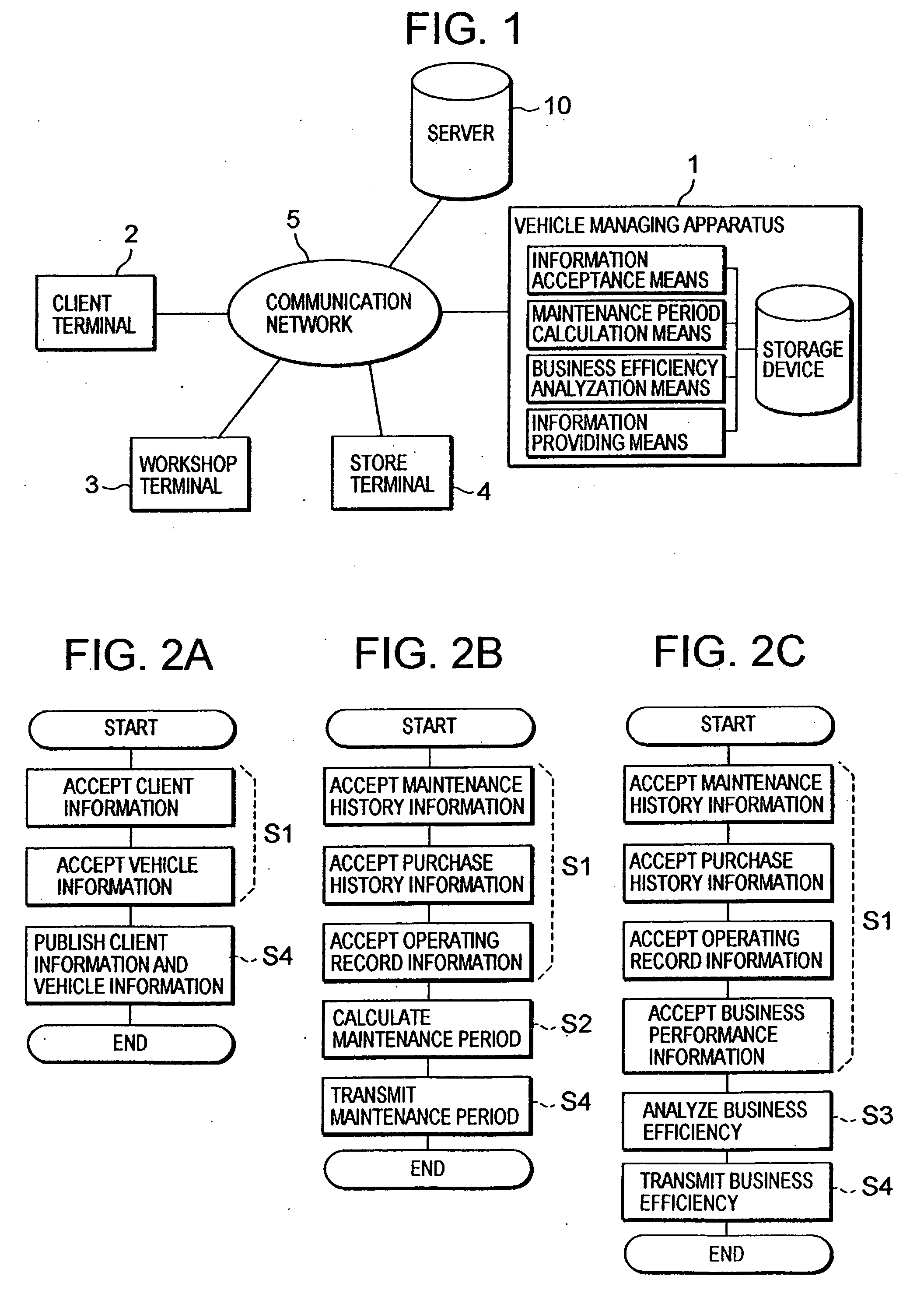
Vehicle managing method, vehicle managing apparatus and vehicle managing program
InactiveUS20080208656A1Cost effectivenessImprove management efficiencyResourcesBusiness efficiencyNetwork connection
A method is disclosed for performing comprehensive management for vehicles owned by clients, including an appropriate number of vehicles to be operated and appropriate operation methods, instead of simple maintenance and management of the vehicles, and according to this method, a vehicle managing apparatus, a client terminal, a workshop terminal and a store terminal are connected via a communication network, and the vehicle managing apparatus includes information acceptance means, maintenance period calculation means, business efficiency analyzation means and information providing means. First, the information acceptance means receives maintenance history information for a vehicle, automotive accessories purchase history information, vehicle operating record information and business performance information for a client, all of which are entered by the workshop terminal or the store terminal. Sequentially, the maintenance period calculation means calculates a maintenance period for the vehicle based on the maintenance history information, the purchase history information and the operating record information, and the business efficiency analyzation means analyzes business efficiency based on the maintenance history information, the purchase history information, the operating record information and the business performance information. Then, the information providing means transmits, to the client terminal, the maintenance period calculation results and the business efficiency analysis results.
Owner:PURE CO LTD
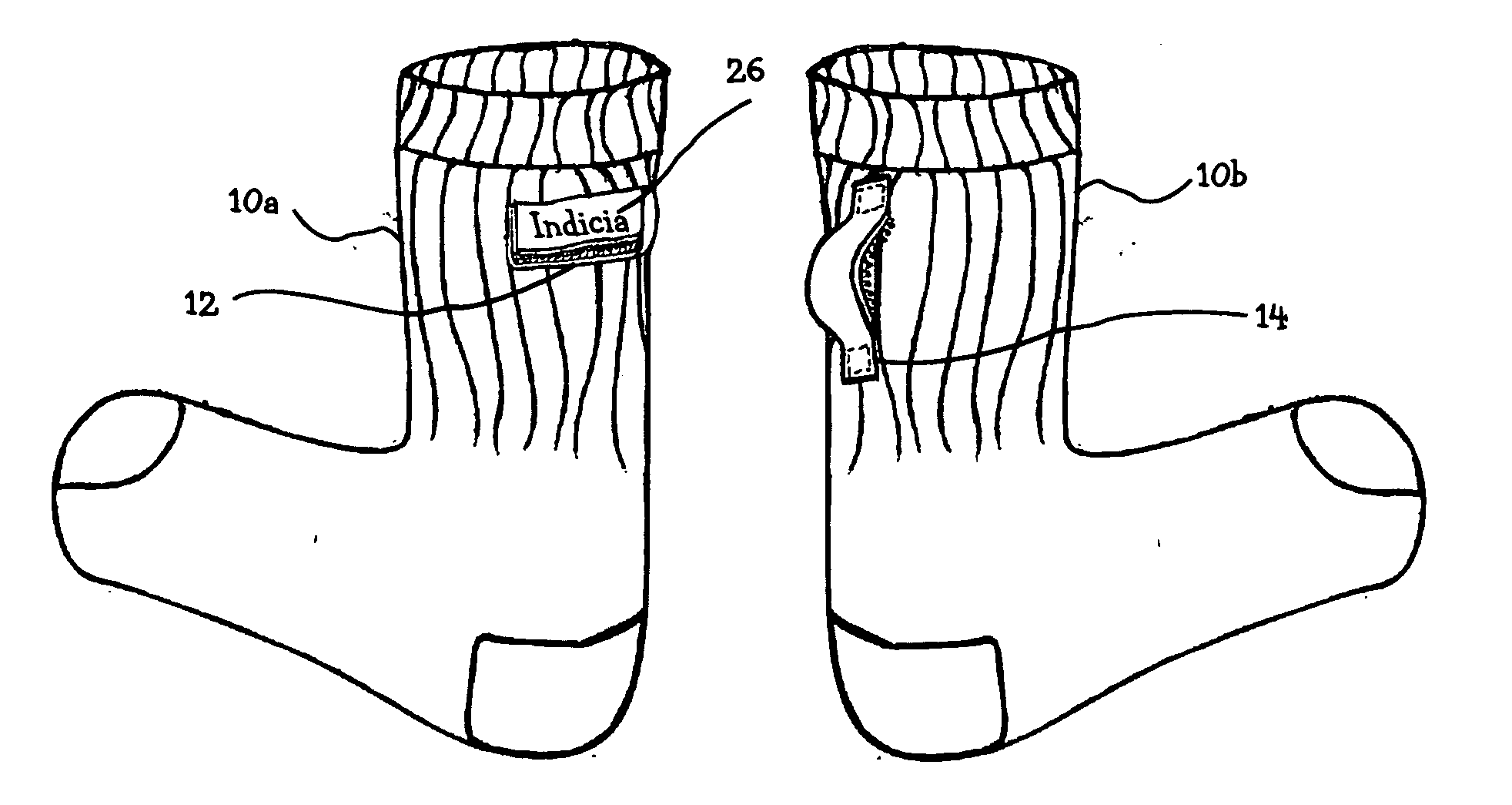
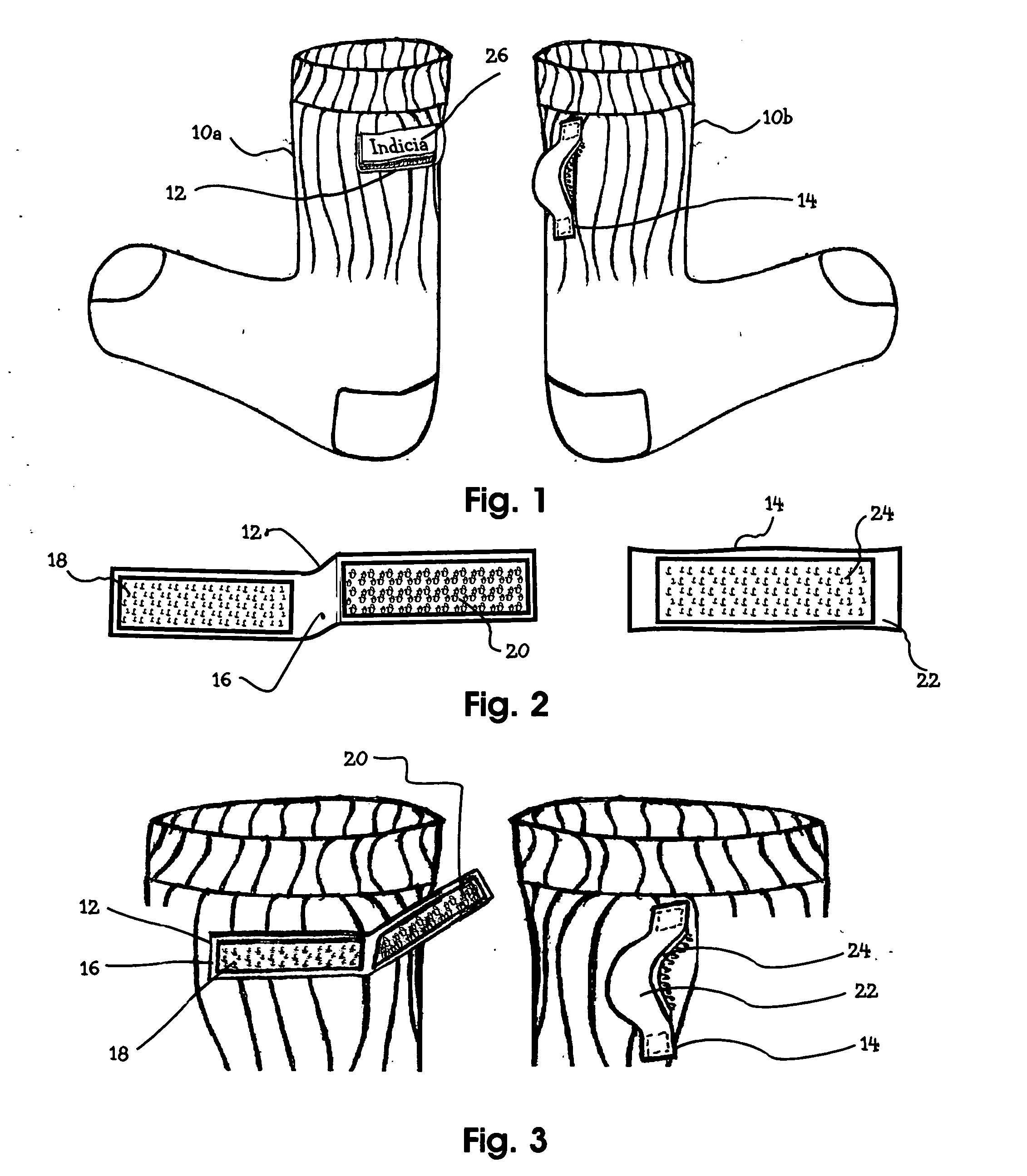
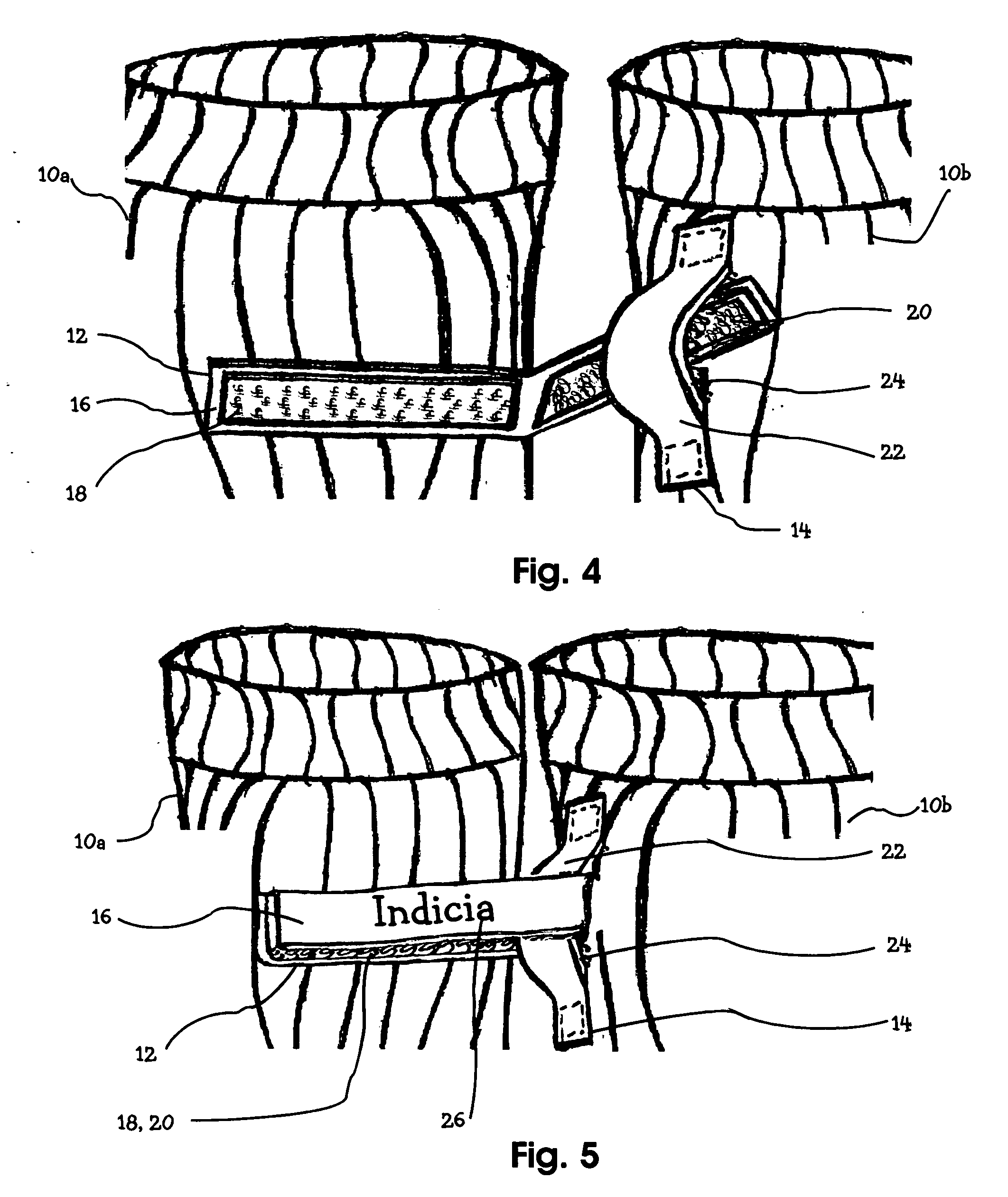
Tube wonder lock
InactiveUS20080034478A1Reduce manufacturing costPromotes long lifeInsolesPanty-hoseEngineeringMechanical engineering
An adjoining device for securing paired items of clothing, such as socks, or gloves comprises a releasable fastening tab strip embedded with velcro hook and loop fastening elements and a tab strip embedded with velcro hooks wherein first tab appended horizontally on one sock of a pair and the second tab appended vertically with a belt loop form on the other sock of same pair allows loop section of first tab to engage after being inserted through the opening of belt loop of second tab strip with hooks, and then, closed to interconnect with hooks of first tab strip appended horizontally providing a secure releasable attachment that resist forces that separate paired articles clothing during the laundry process.
Owner:PATTERSON MICHAEL I
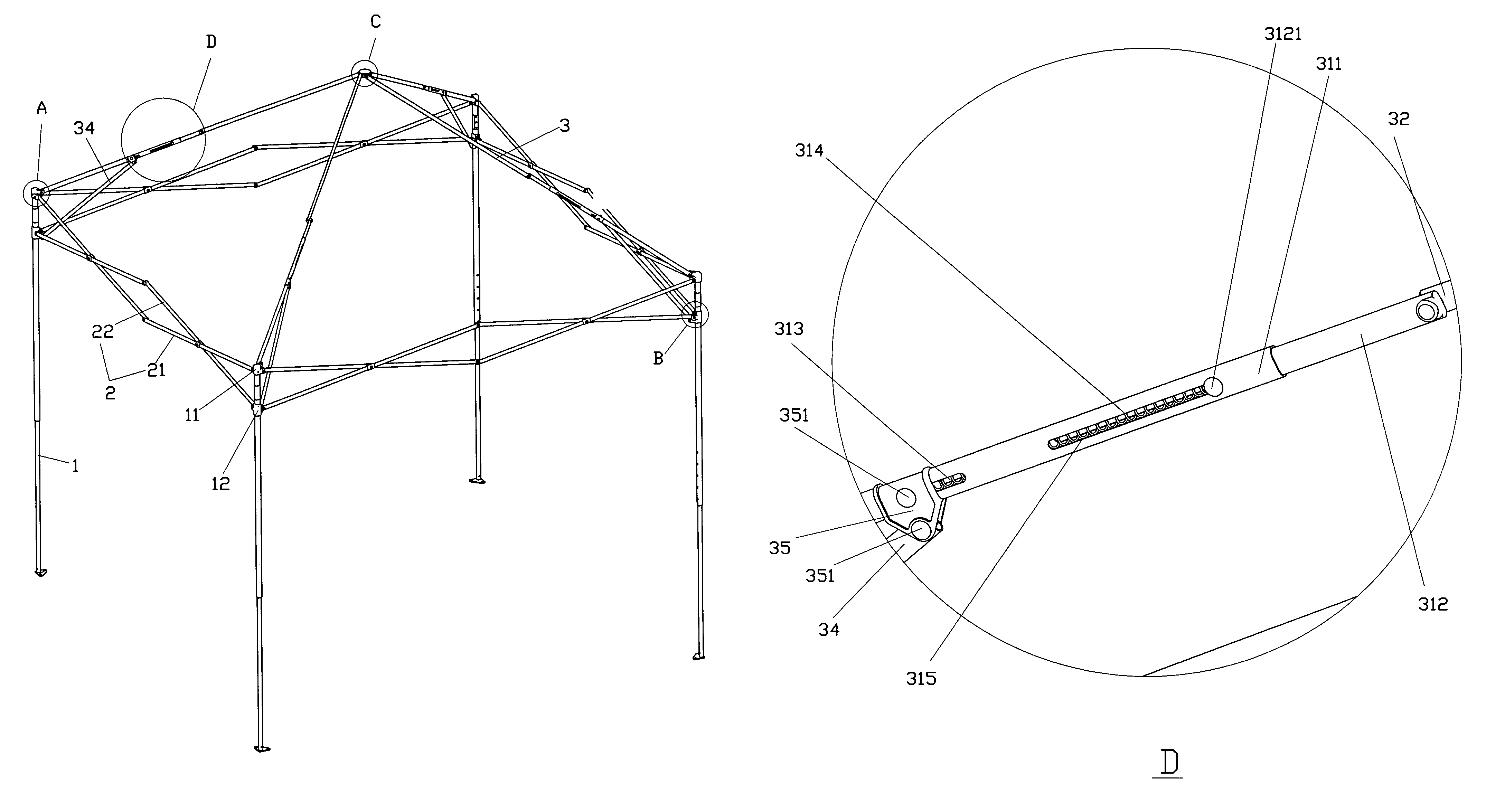
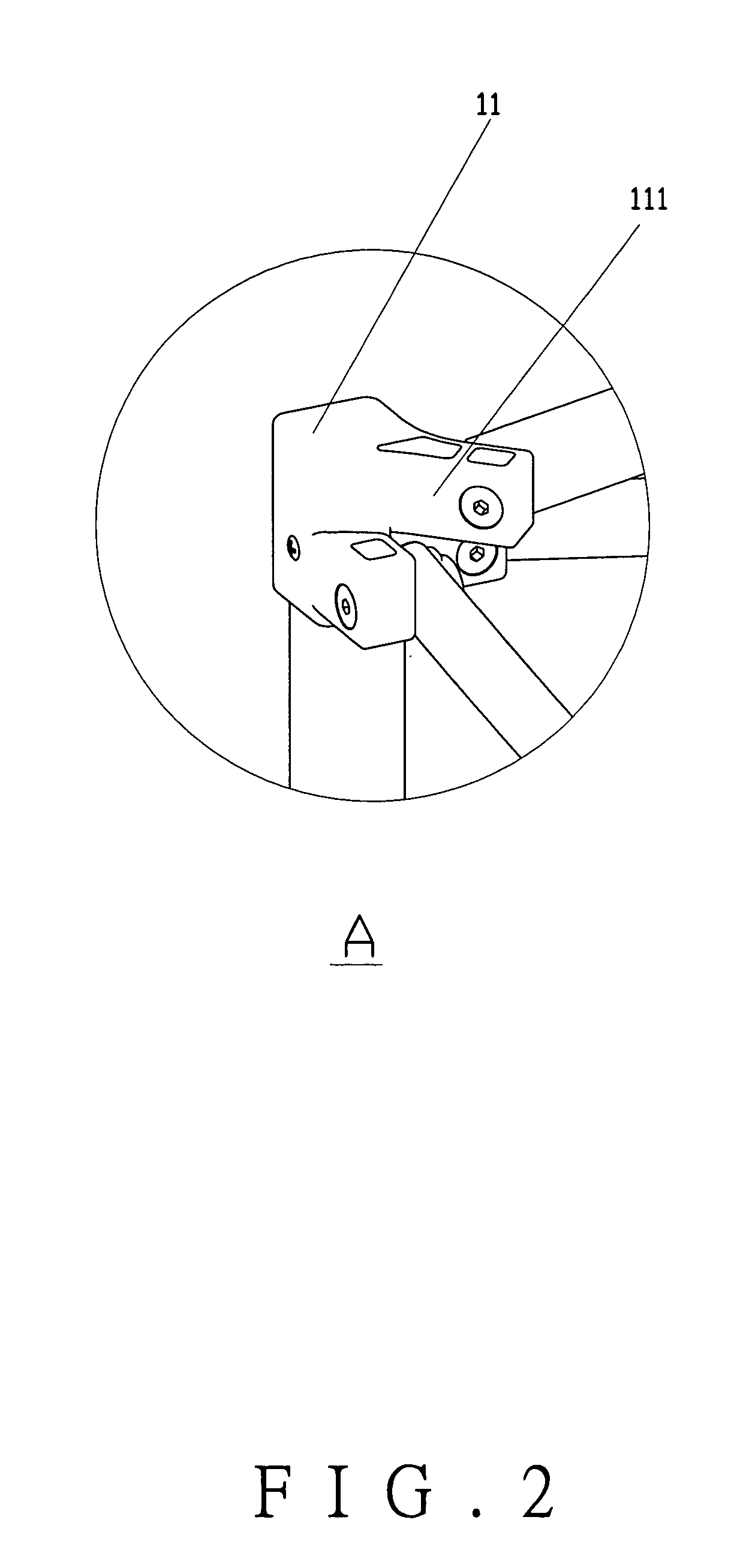
Tent structure
Owner:TSAI MING LIANG
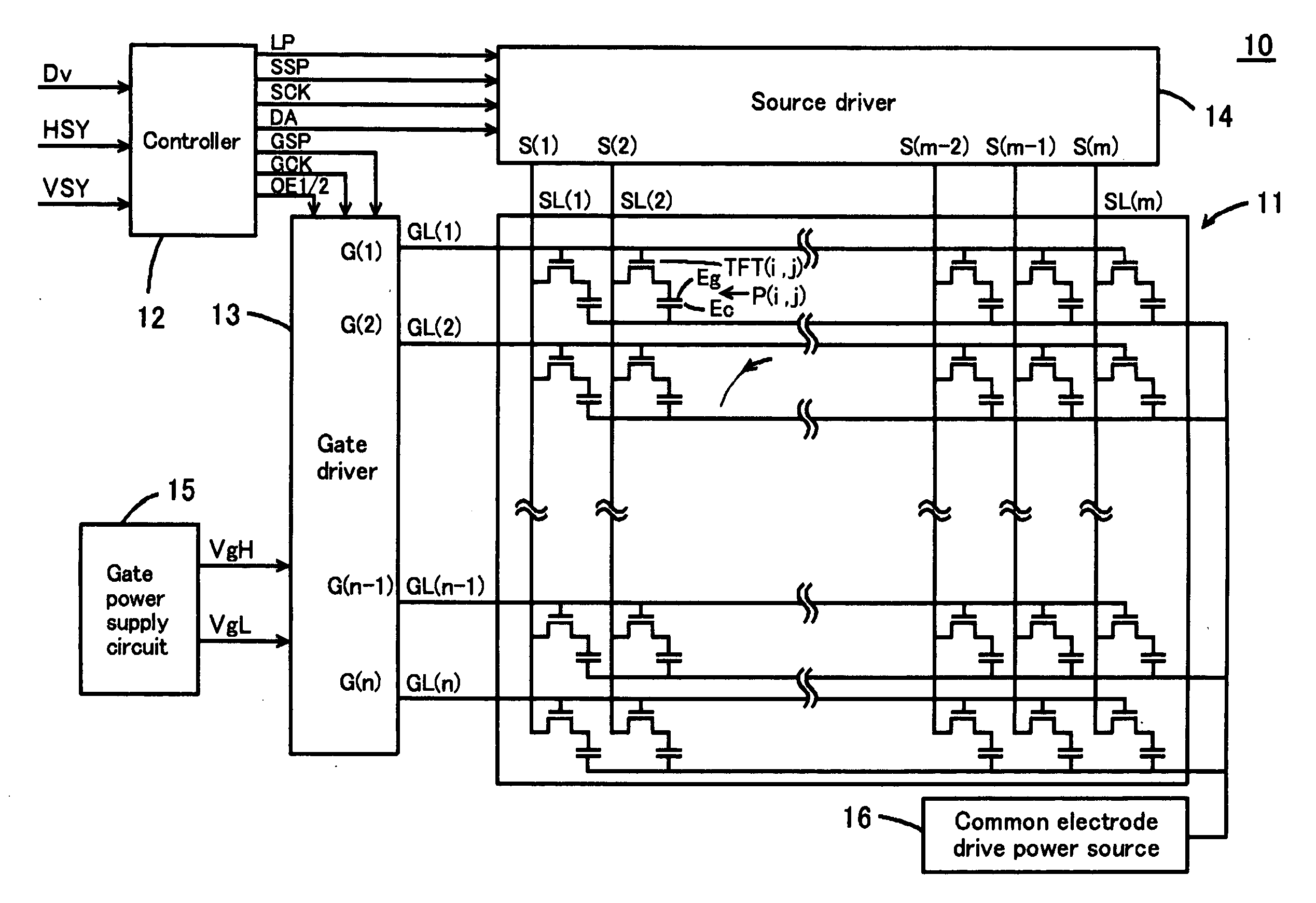
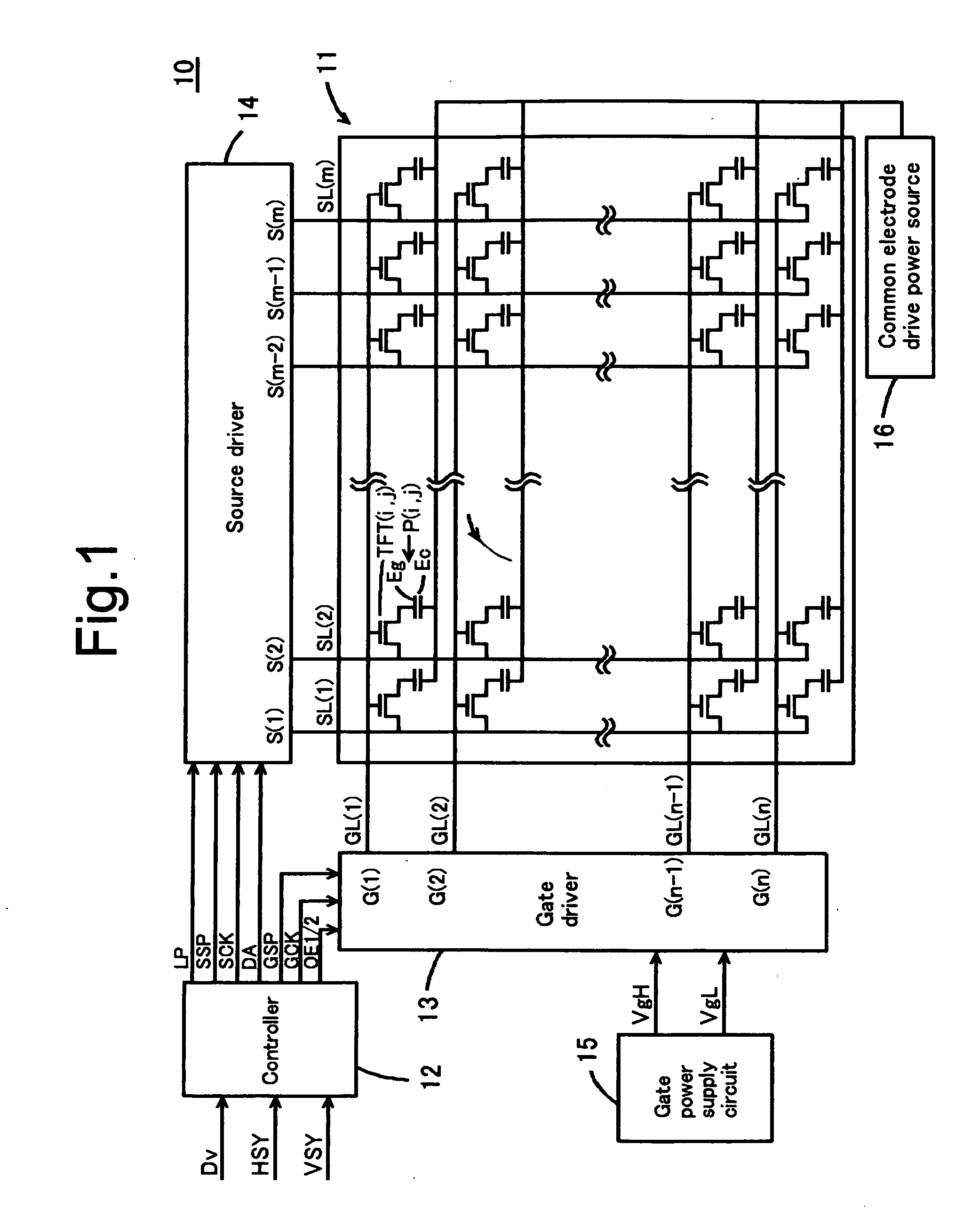
Liquid crystal display device and driving method thereof
InactiveUS20080303765A1Cost effectivenessProvides cost-effectivenessStatic indicating devicesLiquid-crystal displayData signal
In a liquid crystal display device, the TFT(i,j) is switched by a gate signal supplied from the gate driver 13 to supply the data signal to the pixels P(i,j). The gate driver 13 includes a charging waveform section with the electric charge lower than the threshold voltage to the TFT(i,j), a drive waveform section at the voltage higher than the threshold voltage, and a falling waveform section having the falling waveform modulated.
Owner:FUNAI ELECTRIC CO LTD
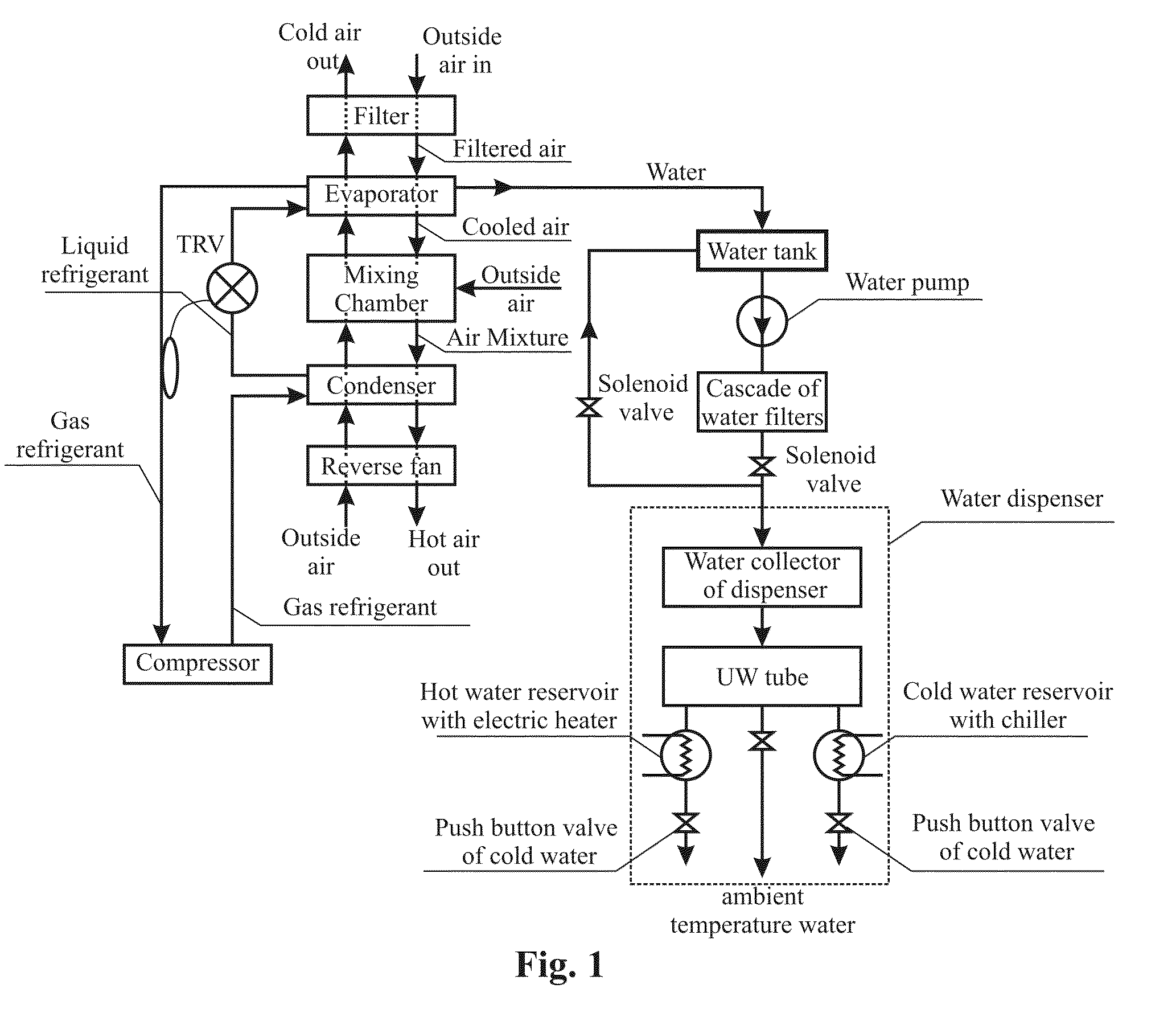
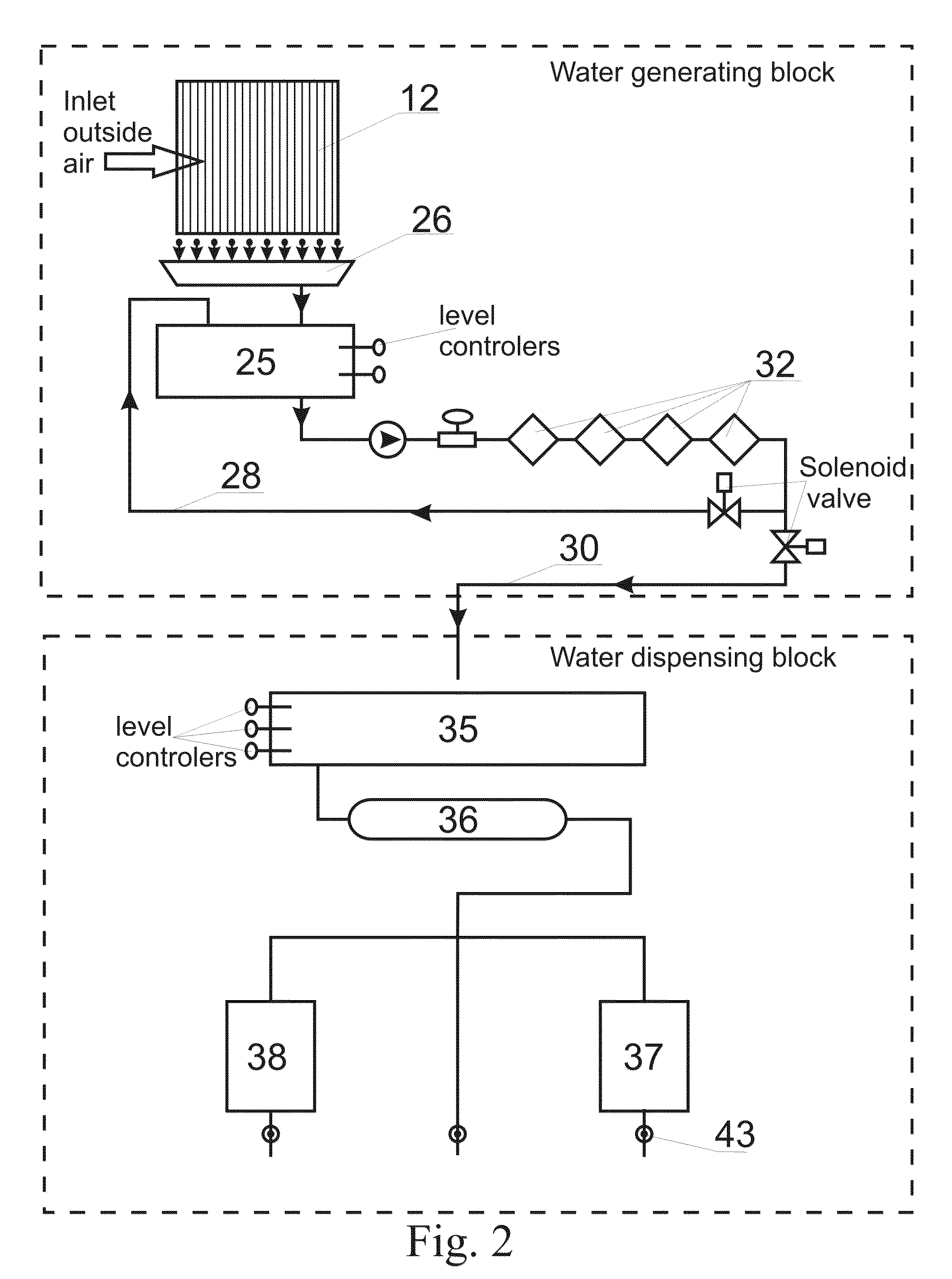
Apparatus and method for a split type water extractor and water dispenser
ActiveUS8075652B2Low costImprove energy efficiencyCombination devicesFunctional valve typesWater usePotable water
A split type potable water extractor from ambient air and water dispenser is invented, comprising separate water generating block located outside a water use area and water dispensing block located inside a water use area. The water generator block cycles refrigerant through a condenser and an evaporator to create condensation by heat exchange with ambient air circulated by an intake airflow system. The condensate water is collected and purified in a cascade of bactericidal loop to remove impurities. The purified water is pumped to a dispensing apparatus which can be installed in the home or other area of water use separate from the water generating block. If any one of the functional parts or units of water generator is disabled the water generator immediately stops operating to deliver water to the tank of the dispensing apparatus.
Owner:WATER TECH INST
Nasal Interface Device
ActiveUS20110284001A1Easily adjust CPAPEfficient use ofRespiratorsOperating means/releasing devices for valvesNasal cavityBreathing gas
A nasal interface device delivers a high flow rate of a gas having a pressure that is adjustable to a patient. The device includes a nasal insert that is adapted to deliver pressurized gas to a nasal cavity of the patient, and receive and direct expired air. The nasal insert has a pressurized breathing gas delivery port and an expired gas port. An expiratory limb pressure regulator is in fluid communication with the expired gas port.
Owner:TERO ROBERT
Shoe with shell portions
InactiveUS20060117608A1Improve bending performanceReduce weightSolesFasteningsEngineeringPlantar arch
A shoe includes a first shell portion, and a second shell portion complementing the first shell portion to form an upper. The second shell portion is more flexible than the first shell portion and is mechanically connected to the first shell portion. The first shell portion includes a surrounding wall of substantially U-shaped cross-section which is adapted to extend around the wearer's heel. The surrounding wall includes two opposite side wall sections that have frontmost ends posterior to the ball of the foot and anterior to the plantar arch of the foot.
Owner:CHEN EDDIE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com