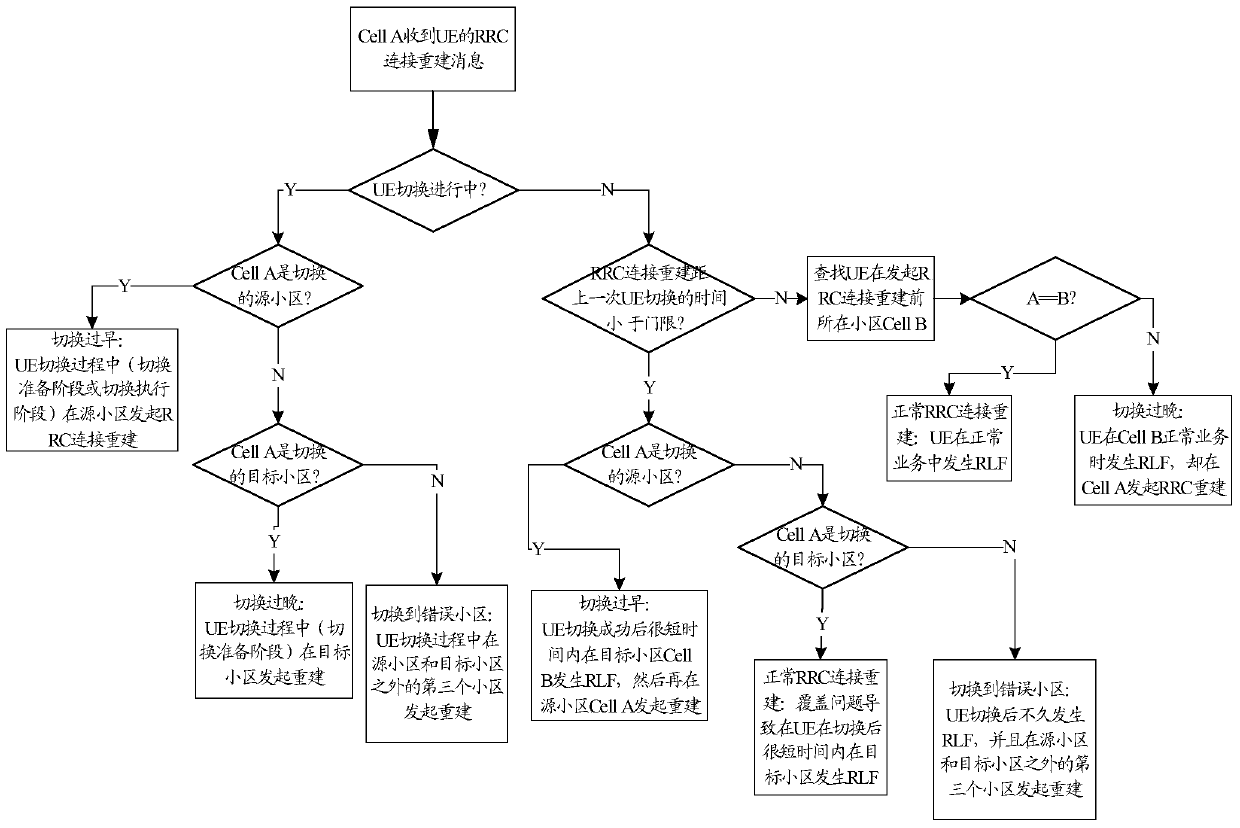
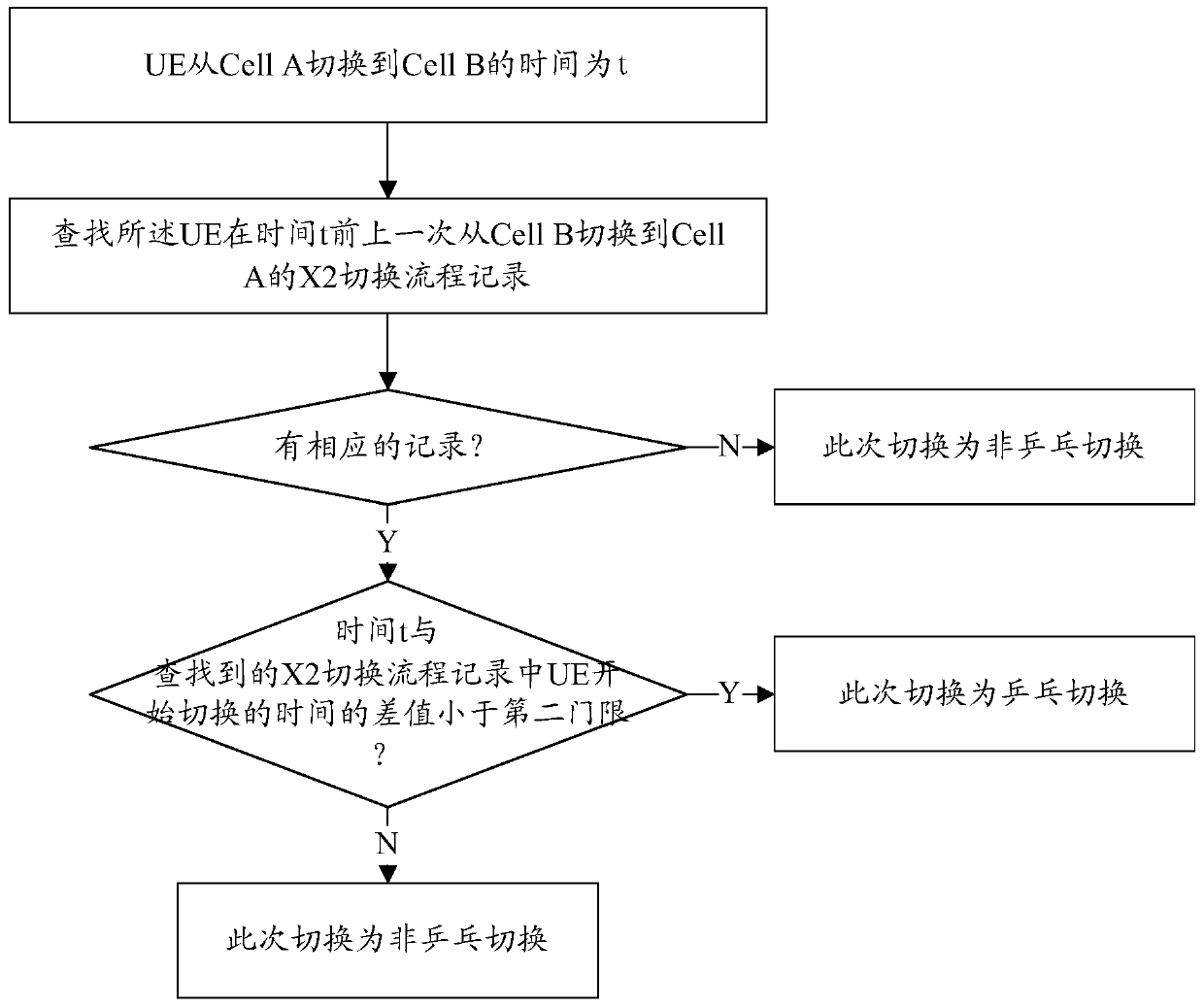
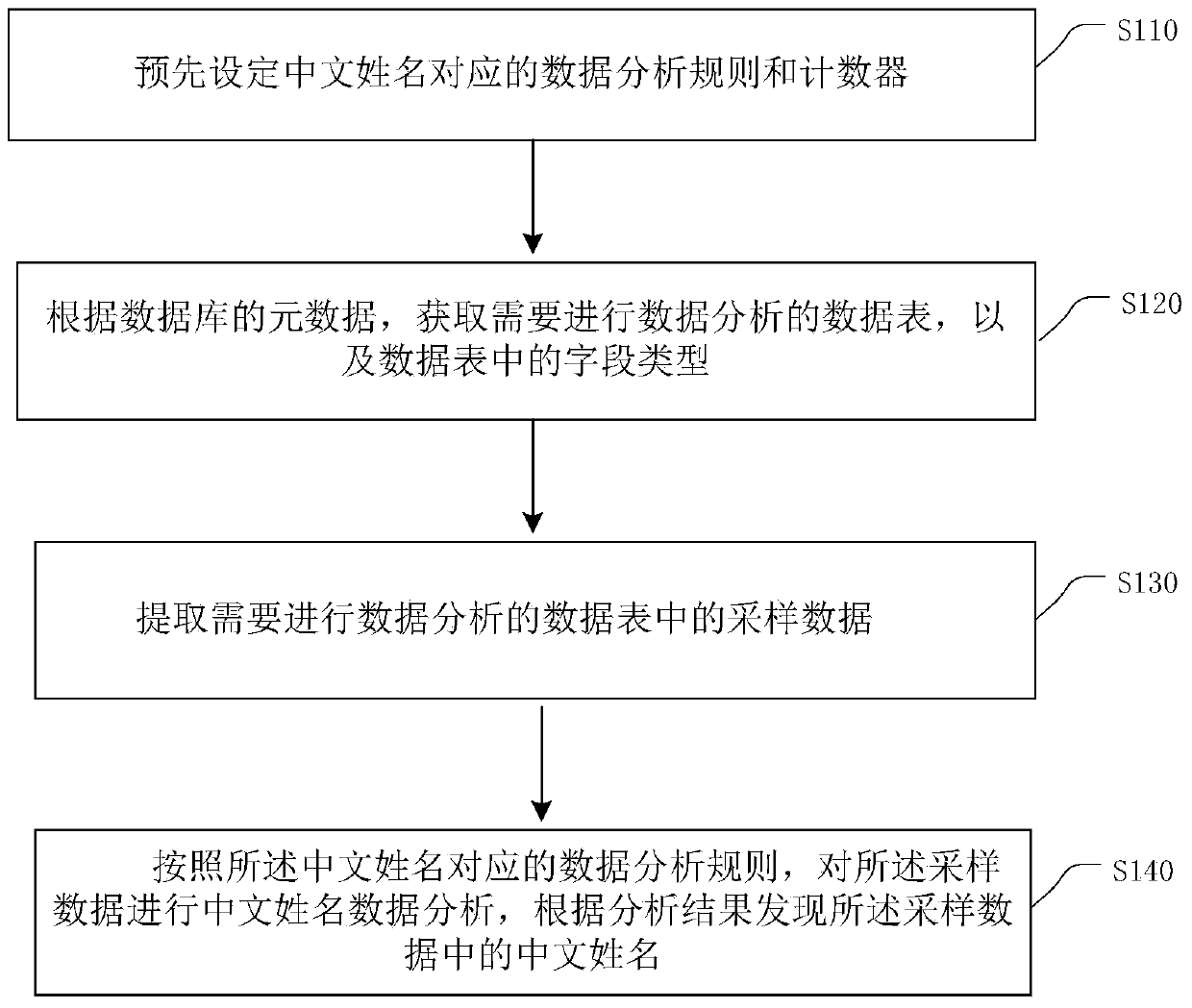
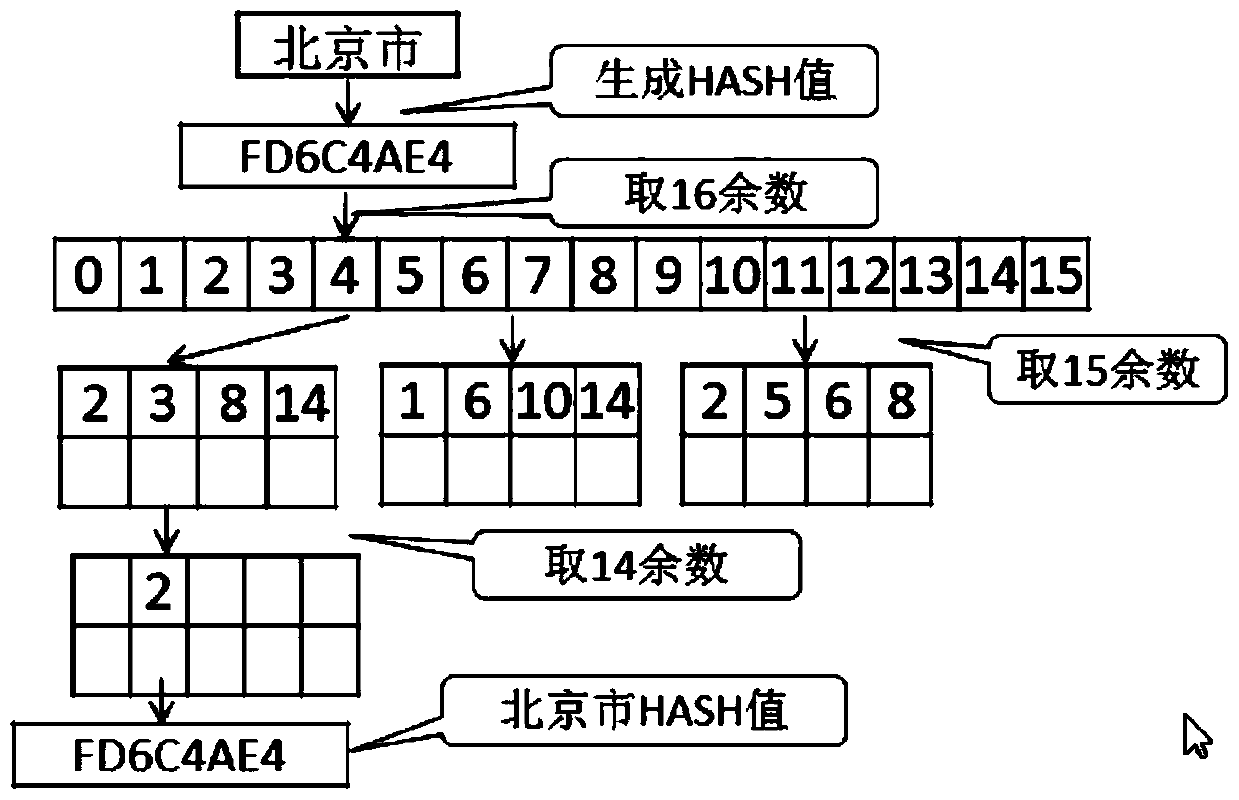
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32results about How to "Automatic discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
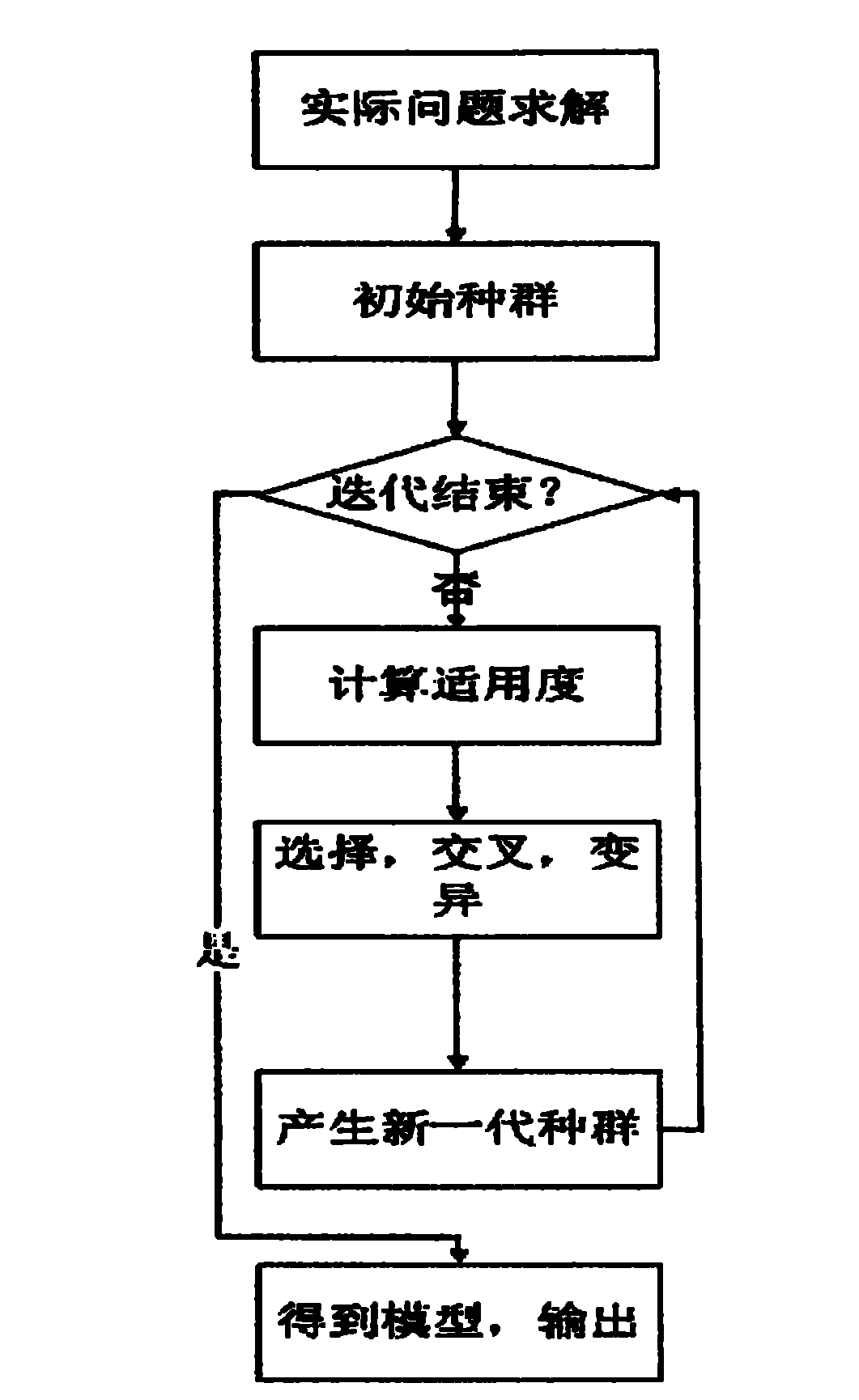
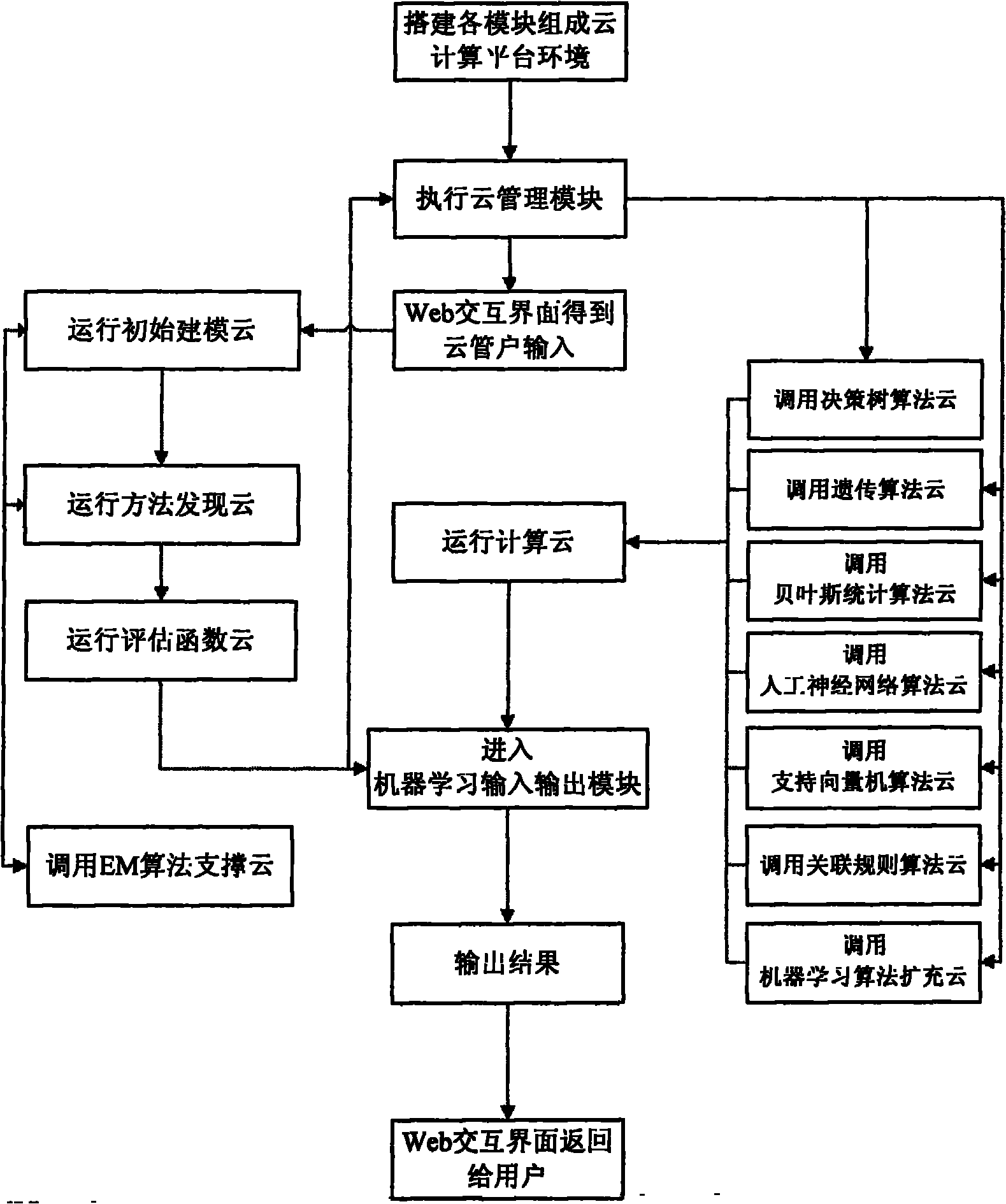
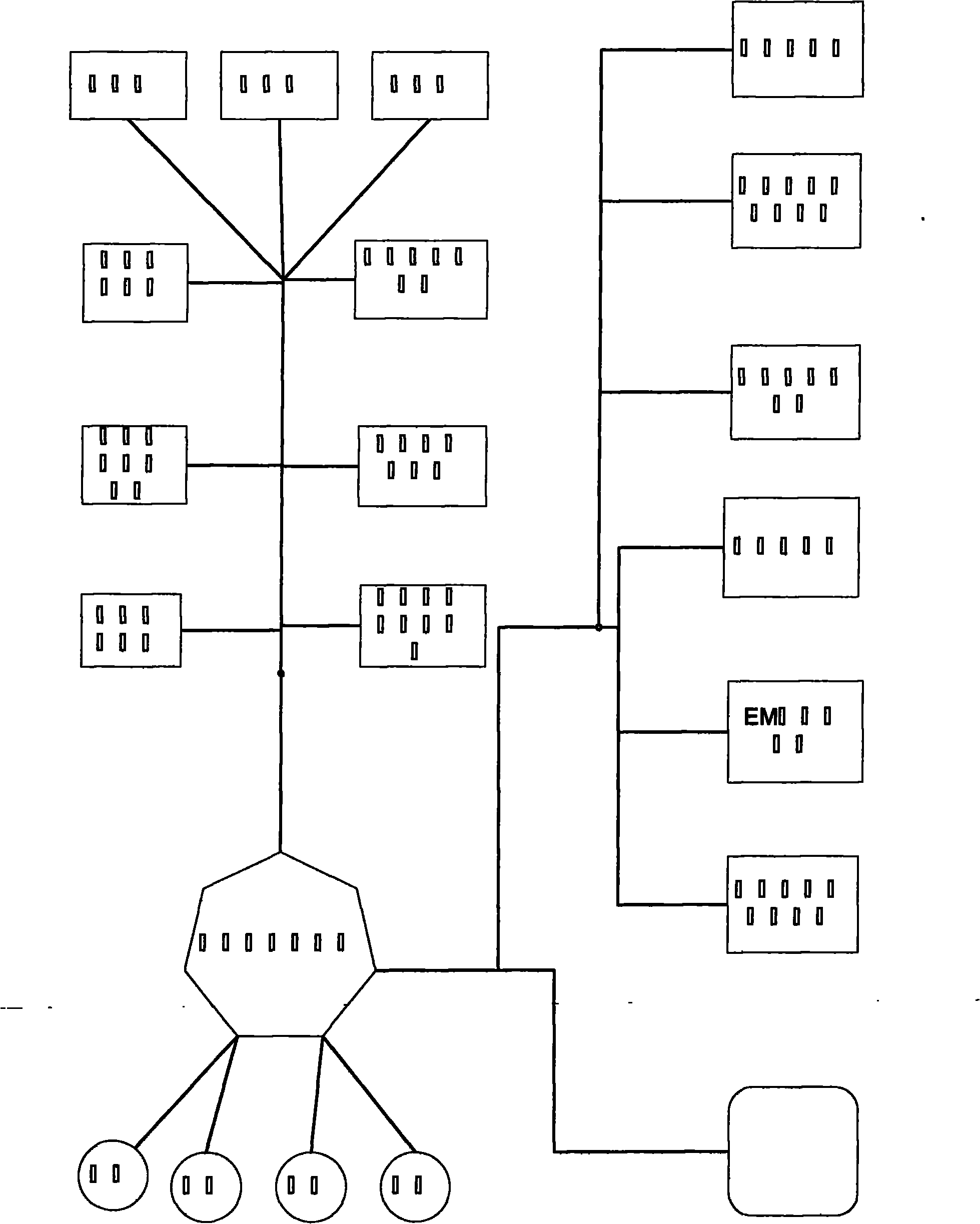
Automatic selection method for machine learning in cloud computing environment
ActiveCN101782976ALower barriers to useImprove computing performanceComputing modelsMathematical modelMachine learning
The invention relates to an automatic selection method for machine learning in cloud computer environment. By using a cloud computing platform, a user can automatically and intelligently build a machine learning mathematic model which meets actual problems without building the operation environment of machine learning, selecting a machine to learn algorithm and even adjusting complicated machine learning functions and accompanying parameters but only using a Web method to upload sample data. Through the method, the use of machine learning is free from the environmental constraints and displays the advantages of the cloud computing platform, so that the machine learning model building is transparent to the user, so as to best reduce the use threshold of machine learning. The automatic selection method for machine learning in cloud computing environment solves the disadvantages of the unpredictability of model building selection, the manual experience of parameter adjustment, the difficulties of common users and the like when machine learning is applied in actual life.
Owner:NANJING UNIV OF POSTS & TELECOMM
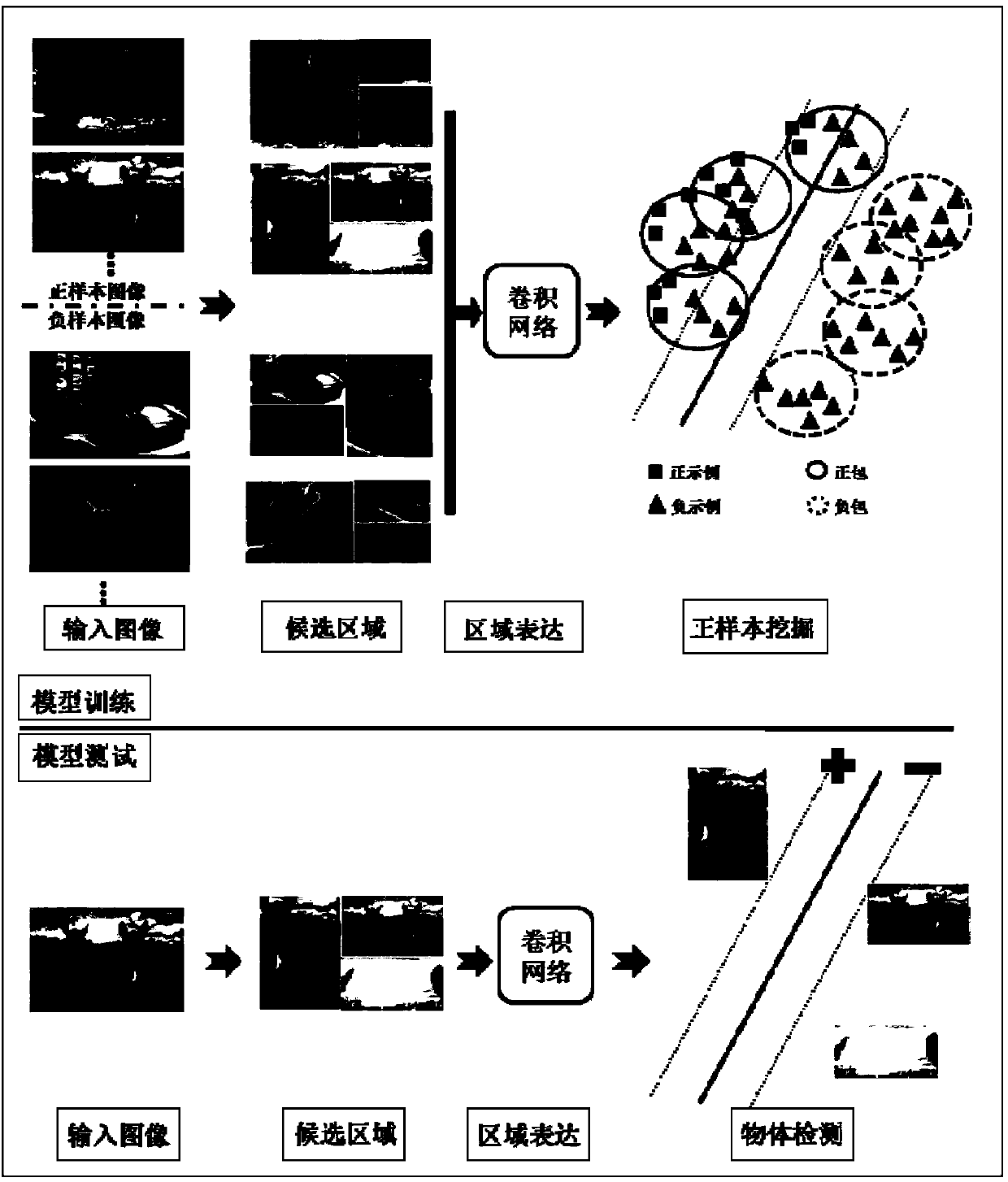
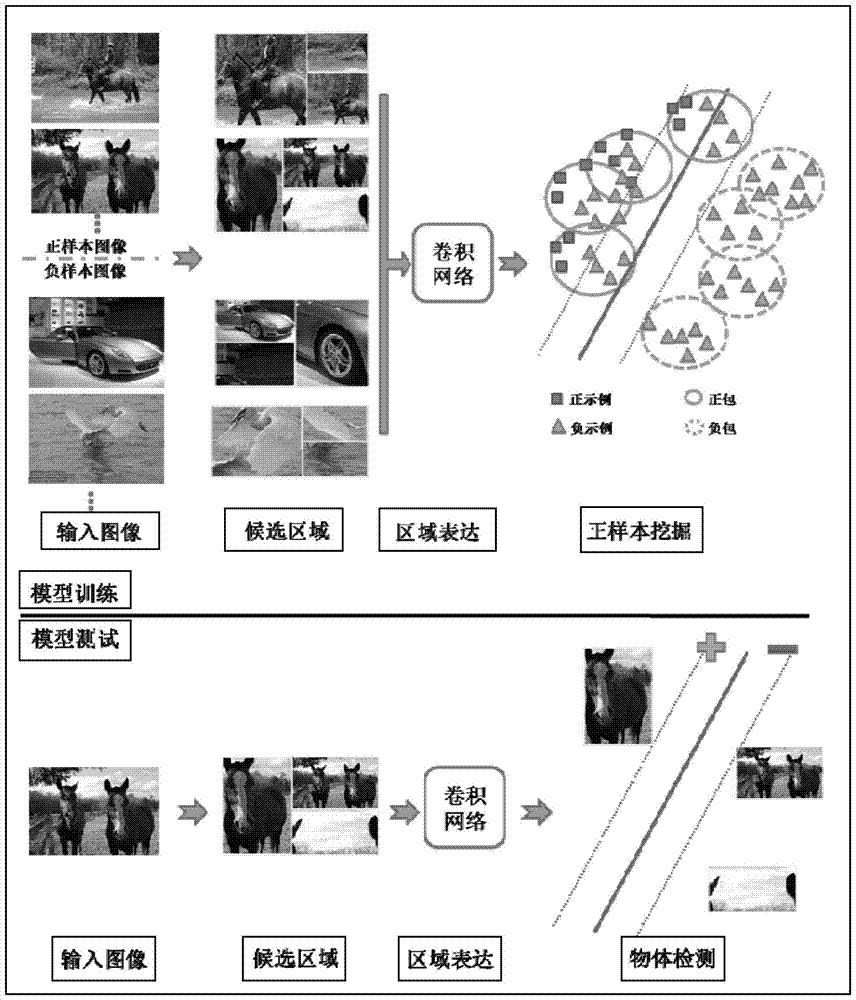
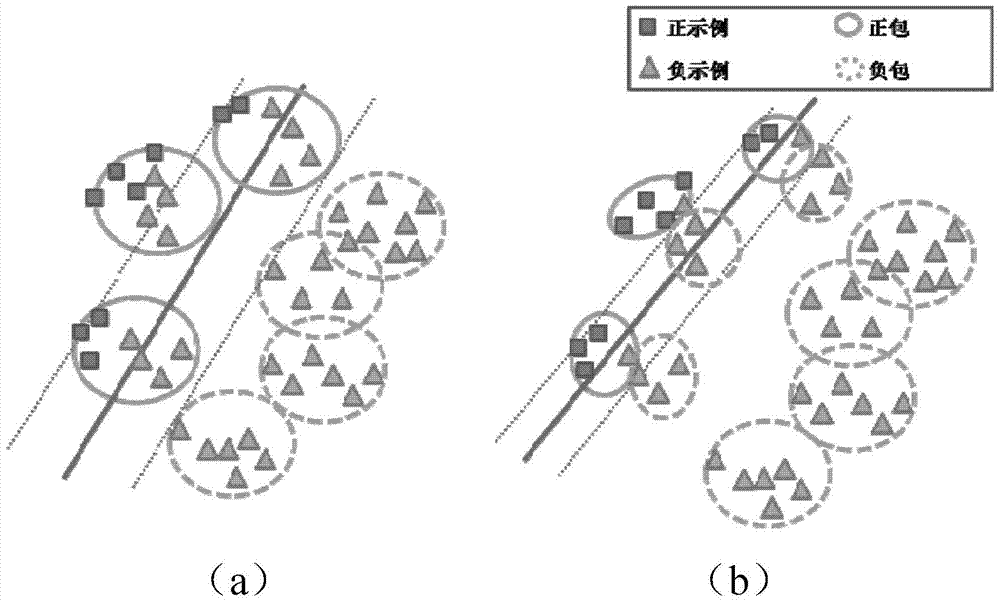
A visual target detection and labeling method
ActiveCN104217225AKeep boundariesHigh overlap rateCharacter and pattern recognitionPositive sampleData set
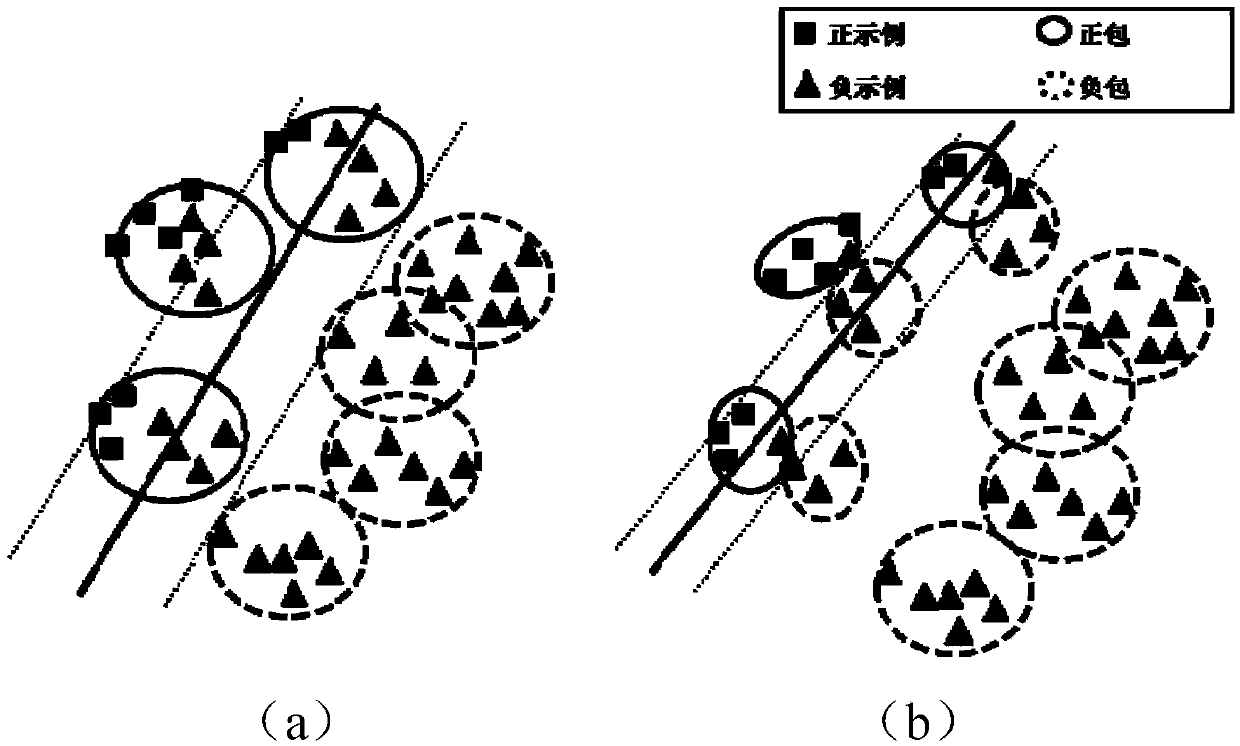
The present invention discloses a visual target detection and labeling method. The method includes: an image inputting step, to input an image to be detected; a candidate region extracting step, to extract a candidate window as the candidate region from the image to be detected using selectively search algorithm; a feature description extracting step, to perform feature description on the candidate region using a pre-trained large-scale convolutional neural network and output the feature description of the candidate region; a visual target predicting step, to predict the candidate region based on the feature description of the candidate region using a pre-trained object detection module, to estimate regions having the visual target; and a position labeling step, to labeling the position of the visual target according to the estimated result. Experiments show that, compared with the mainstream week supervision visual target detection and labeling method, the present invention has a stronger ability to excavate positive samples and a more general application prospect, and is suitable for visual target detection and automatic labeling tasks on the large-scale data set.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Method for finding and sorting private data in data table
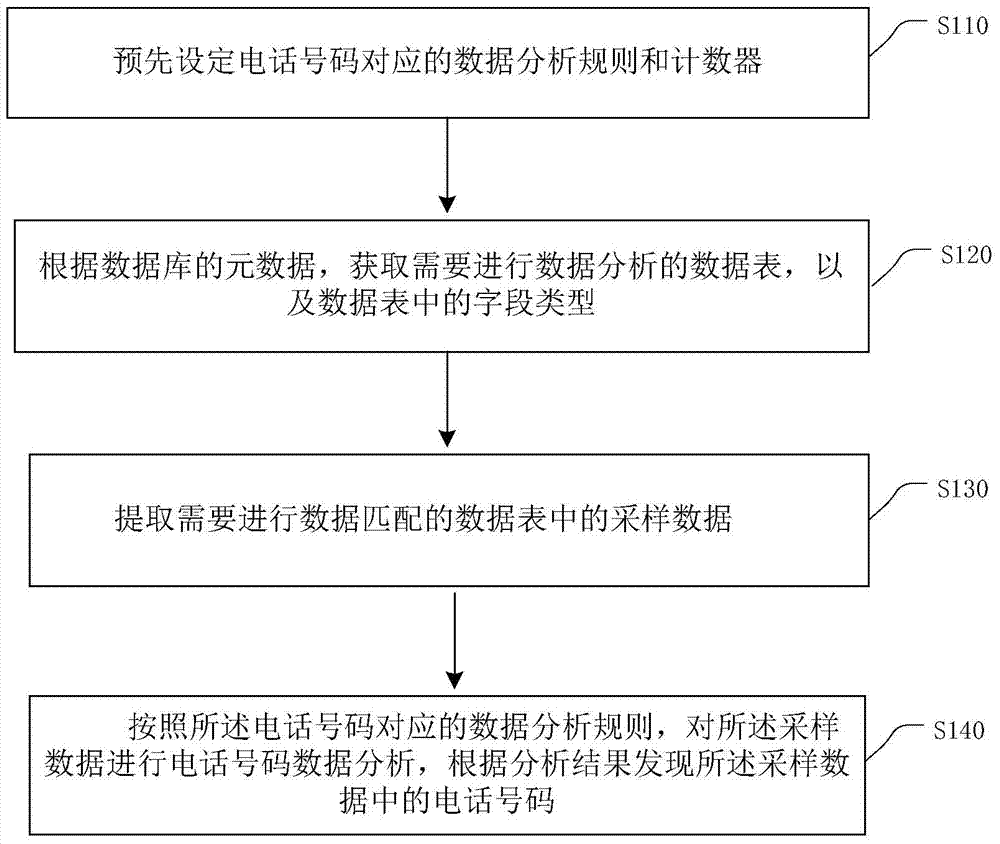
ActiveCN104731976AAutomatic discoveryEfficient discoverySpecial data processing applicationsLicense numberEmail address
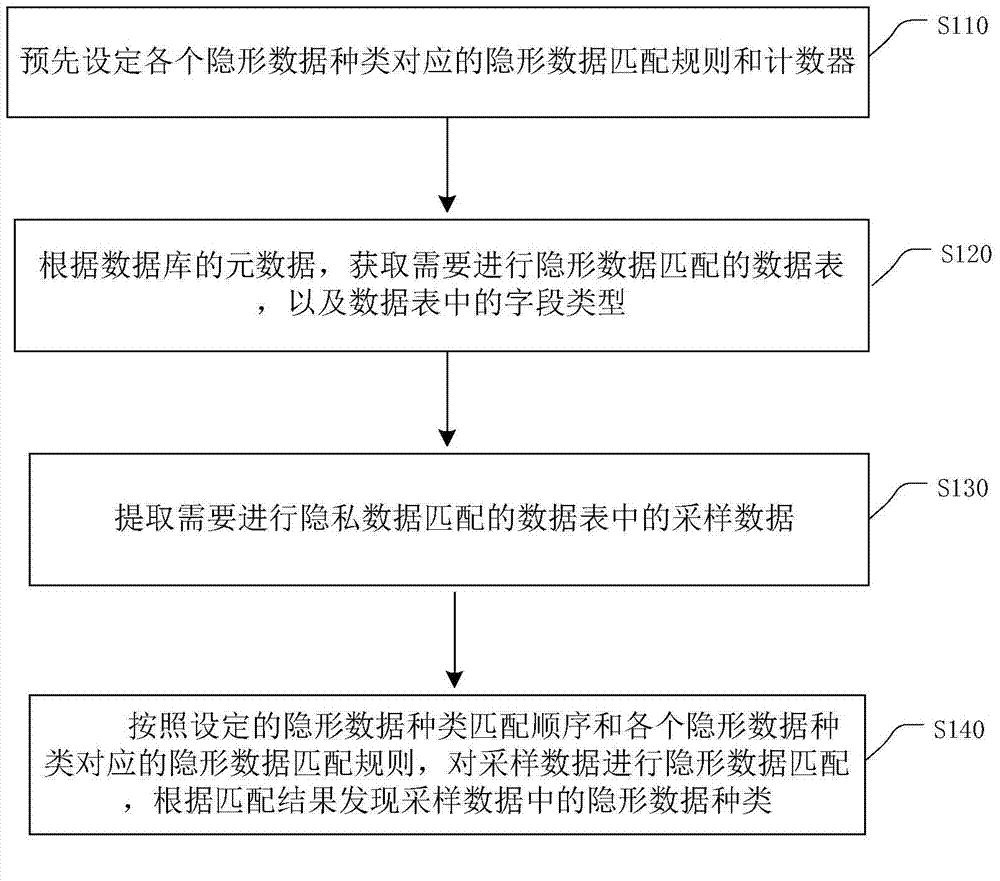
The embodiment of the invention provides a method for finding and sorting private data in a data table. The method mainly comprises the steps that private data analysis rules corresponding to all private data types are preset; sampling data are extracted from the data table; private data analysis is conducted on the sampling data according to the set analysis sequence of the private data types and the private data analysis rules corresponding to all the private data types, 10 kinds of private data types are found in the sampling data according to the analysis result, wherein the private data types include ID card numbers, zip codes, business license numbers, organization codes, identification numbers of taxpayers, e-mail addresses, company names, phone numbers, Chinese names and addresses. Key data in the data table of an enterprise application database are efficiently found out and sorted, workload can be greatly lightened, and work time can be greatly shortened.
Owner:MASSIVE CLOUD BEIJING DATA TECH
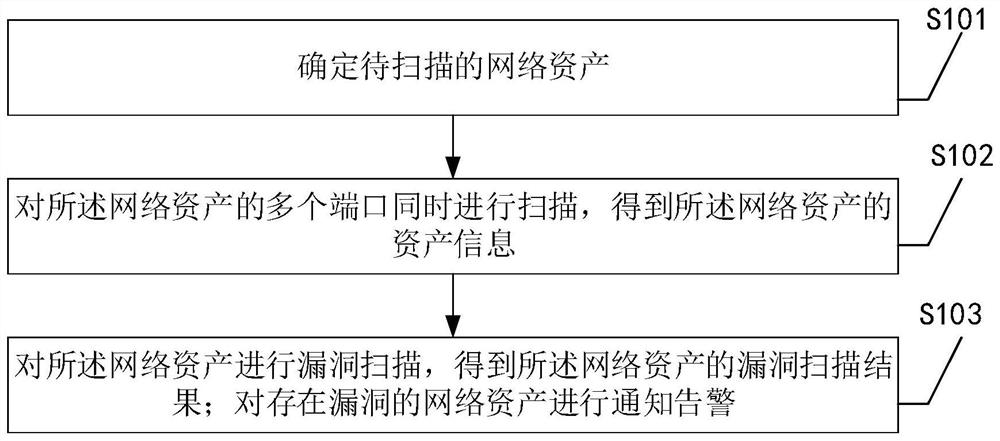
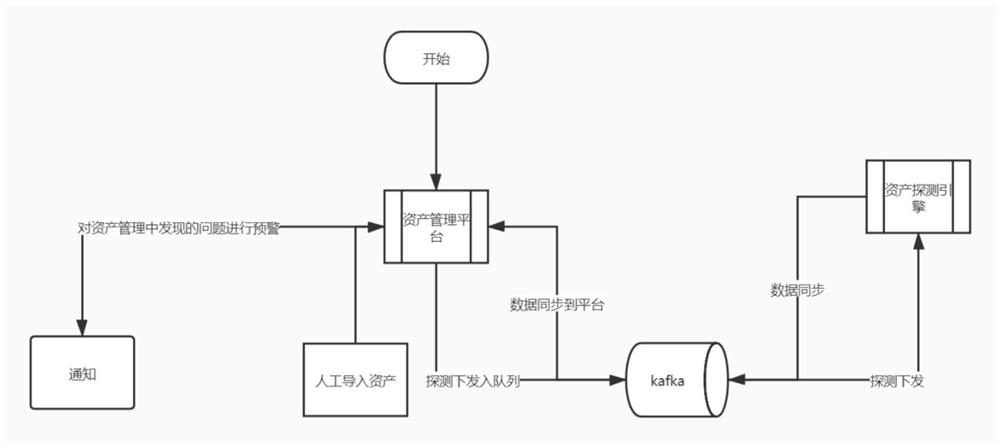
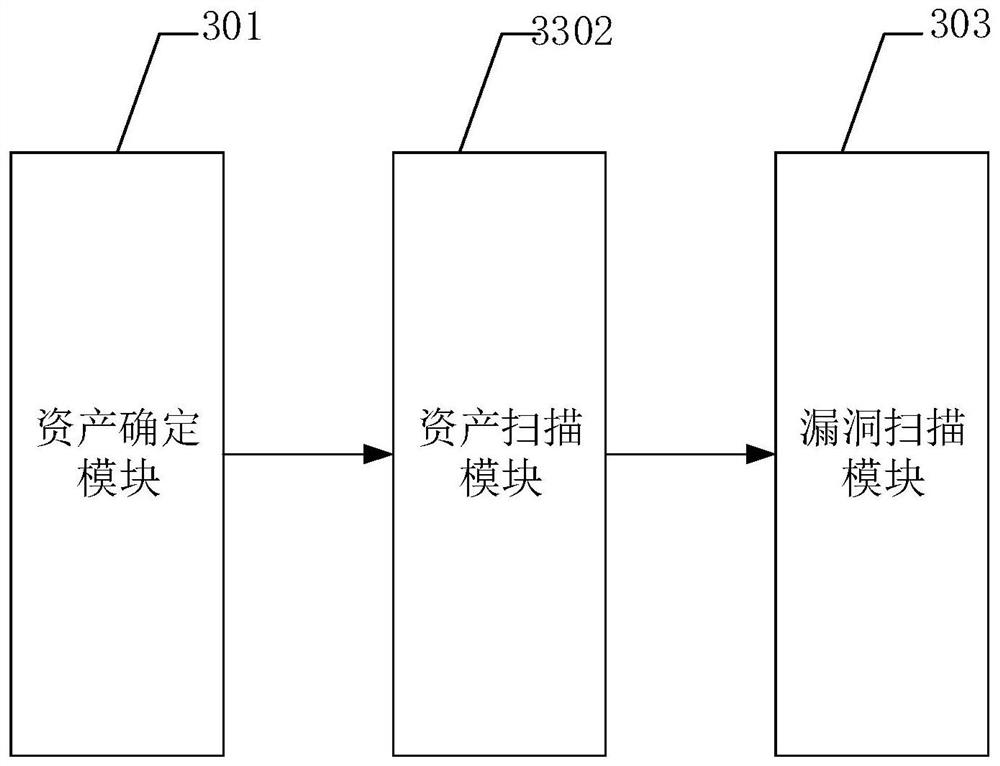
Network asset scanning method, device and equipment based on active detection technology
PendingCN112637159AEfficient managementImprove scanning efficiencyTransmissionComputer networkActive detection
The invention discloses a network asset scanning method based on an active detection technology. The method comprises the steps: determining network assets to be scanned; scanning a plurality of ports of the network assets at the same time to obtain asset information of the network assets; carrying out the vulnerability scanning on the network assets to obtain vulnerability scanning results of the network assets; and carrying out notification alarm on the network assets with the vulnerabilities. Therefore, the method can automatically discover assets in the network, significantly improve the asset scanning efficiency, discover vulnerabilities of the assets in time, avoid loss caused by the vulnerabilities, and realize effective management of the network assets. In addition, the invention further provides a network asset scanning device and equipment based on the active detection technology and a readable storage medium, and the technical effects of the network asset scanning device and equipment correspond to those of the method.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
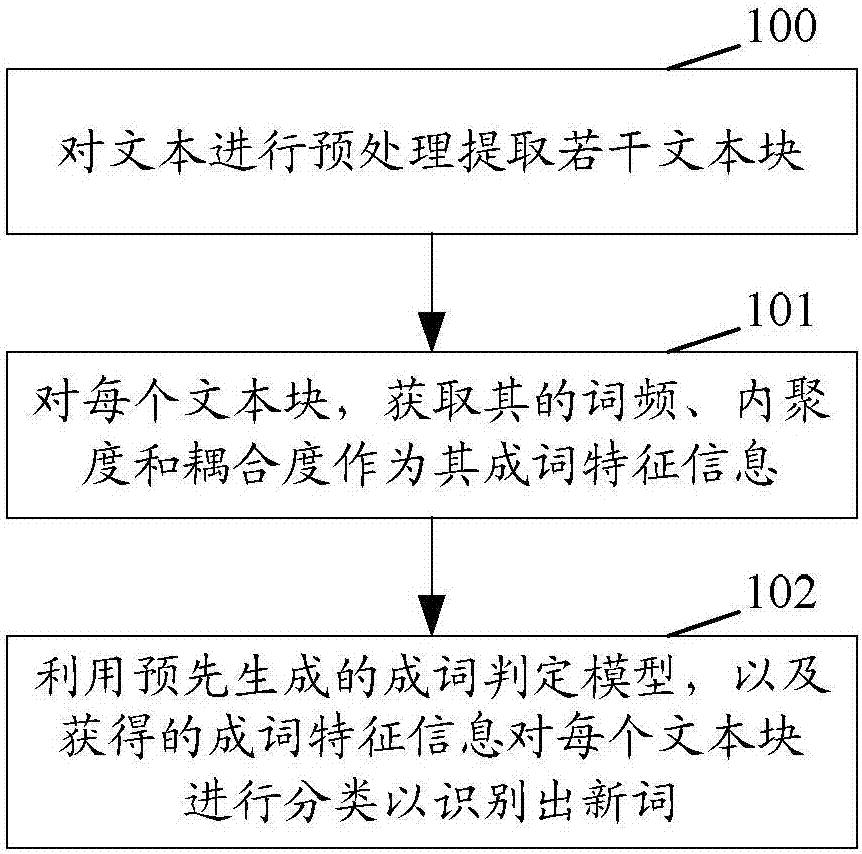
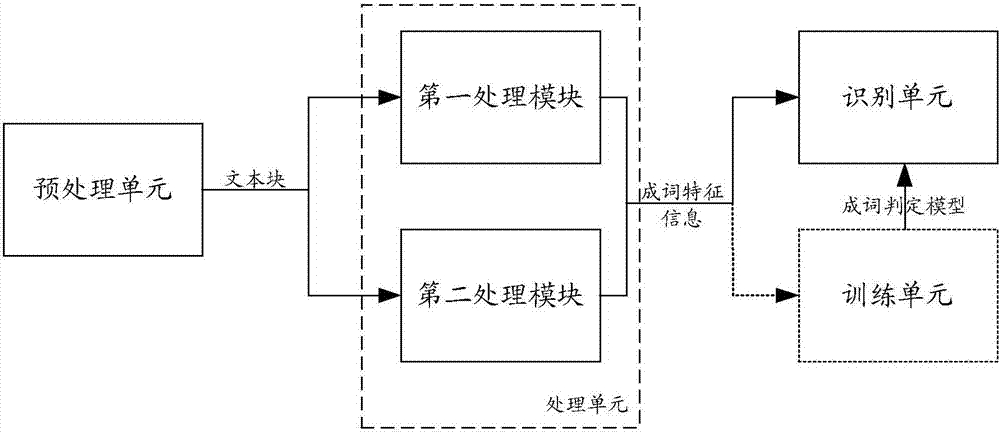
Word forming determination model generation method, and new word discovery method and device
InactiveCN107515849AImprove accuracyAutomatic discoveryNatural language data processingSpecial data processing applicationsWord recognitionLexical frequency
The invention discloses a word forming determination model generation method, and a new word discovery method and device. The new word discovery method includes: performing pre-processing on a text so as to extract a plurality of text blocks; acquiring the word frequency, the cohesion degree and the coupling degree of each text block as word forming feature information of each text block; using a pre-generated word forming determination model and the word forming feature information to classify each text block so as to recognize new words. Automatic discovery of the new words can be achieved, the word forming feature information of each block includes the word frequency, the cohesion degree, and the coupling degree; and the accuracy of new word recognition can be improved.
Owner:CAINIAO SMART LOGISTICS HLDG LTD
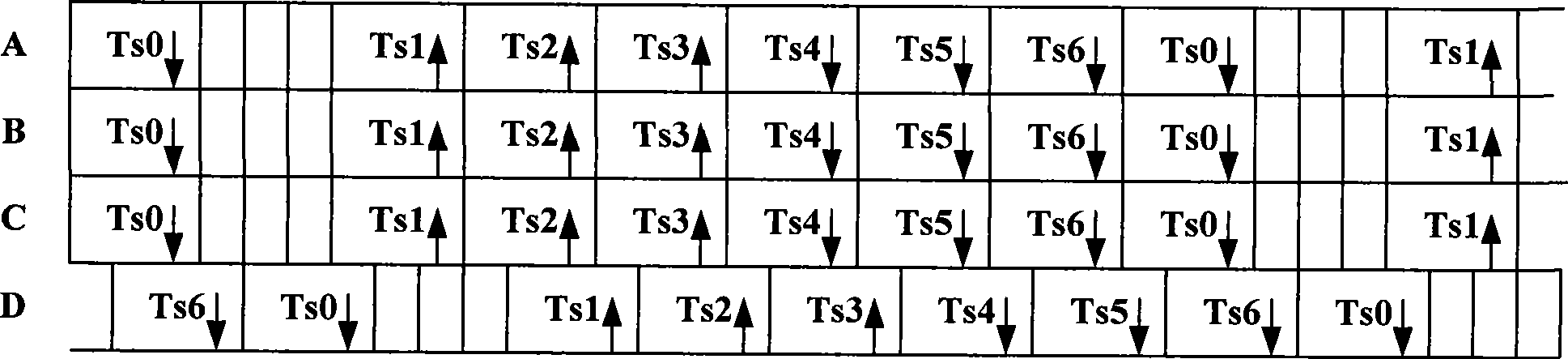
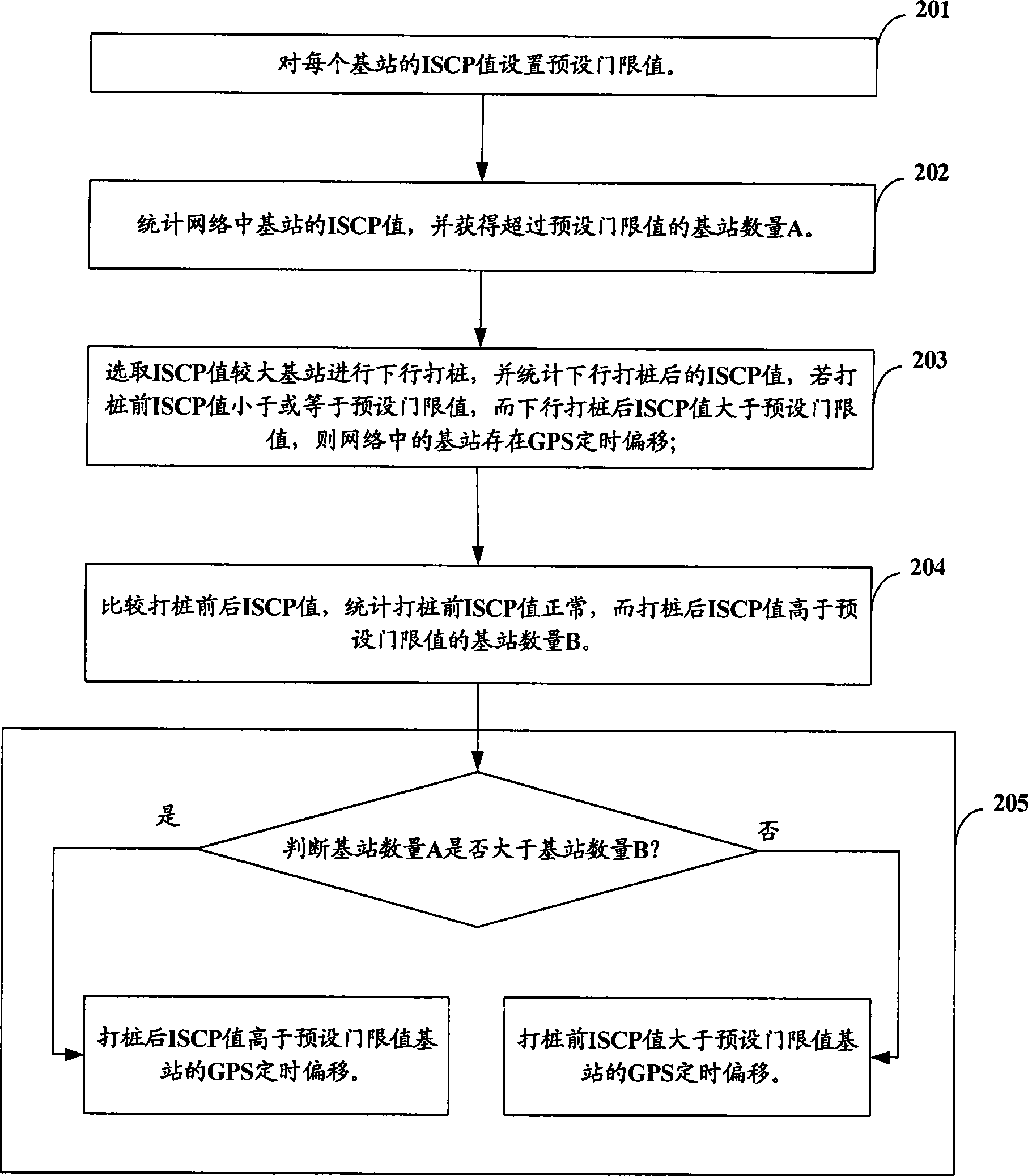
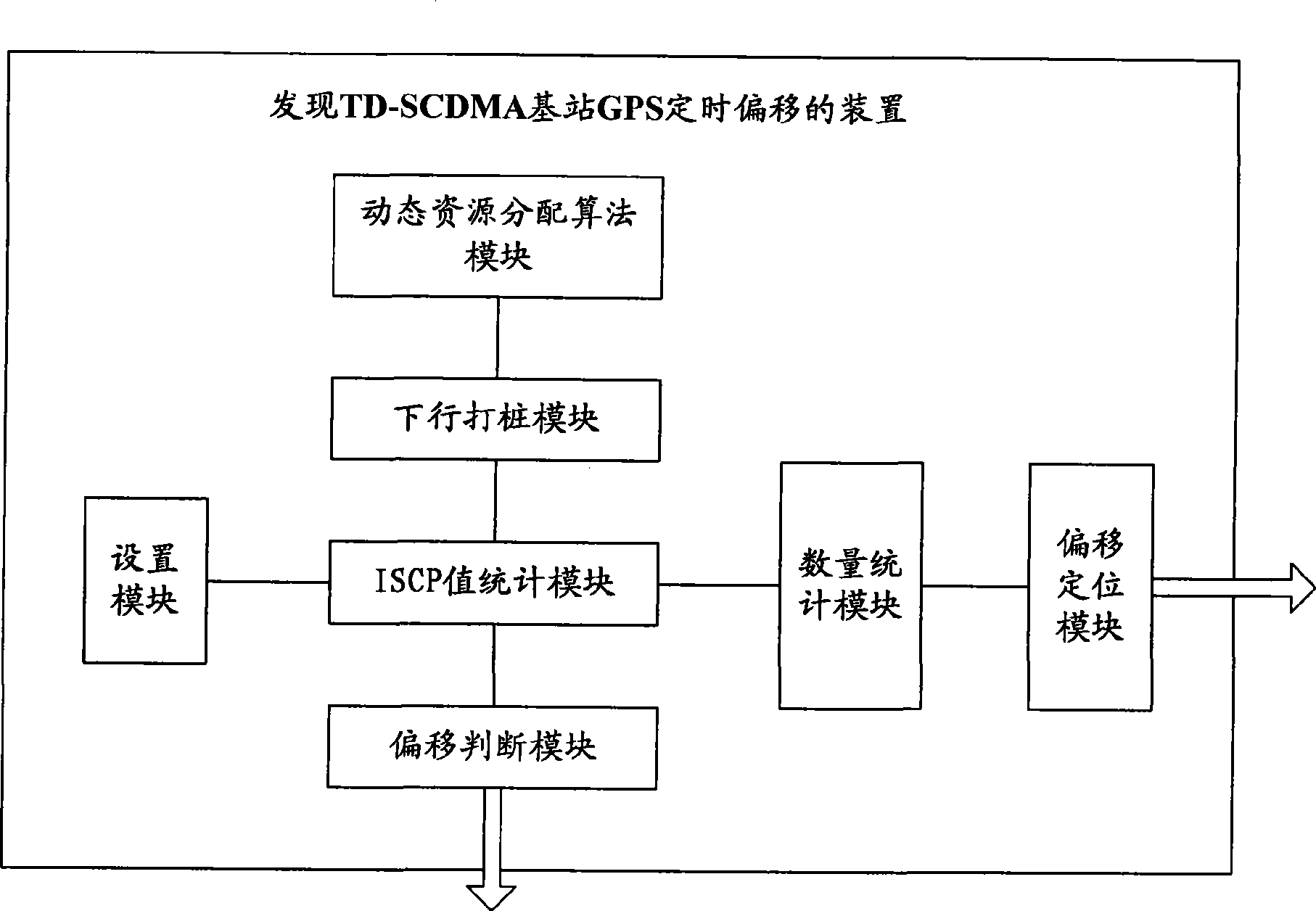
Method for finding GPS timing offset of TD-SCDMA base station and device thereof
InactiveCN101447824ADiscovered in timeAutomatic discoveryRadio transmission for post communicationTD-SCDMAEngineering
The invention provides a method for finding GPS timing offset of a TD-SCDMA base station and a device thereof, and belongs to the telecommunication technical field. The method comprises the following steps: setting a threshold of an interference signal code power value of each base station, counting a time slot interference signal code power value of a network side, selecting a base station in which a frequency point with a higher time slot interference signal code power value is located to perform downlink piling on the frequency point, and then recounting the time slot interference signal code power value of the whole network; if the time slot interference signal code power value of a certain frequency point of a certain base station is normal before the piling, while the time slot interference signal code power value is more than the threshold after the piling, then the GPS timing offset of the base station occurs in the network. The method can be widely applicable to a GPS synchronization technology in a TD-SCDMA system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and method for digging non-recalled type error correction word of searching engine
InactiveCN104102633AAutomatic discoverySave human effortSpecial data processing applicationsType errorSearch words
The invention provides a method for digging a non-recalled type error correction word of a searching engine. The method comprises the following steps: the searching engine obtains a conversation log of a user, wherein the conversation log at least comprises a first conversation and a second conversation, and the first conversation and the second conversation respectively comprise a first searching word and a second searching word; the searching engine obtains related relation information between the first searching word and the second searching word; the searching engine judges whether the first searching word is the non-recalled type error correction word or not according to the related relation information. The invention further provides a device for digging the non-recalled type error correction word of the searching engine. According to the method and the device, modeling analysis on a user searching word sequence and a searching result is carried out so that the non-recalled type error correction word can be automatically found, and the recalling efficiency is considerably higher than that of manual searching; the manpower cost for finding out the non-recalled type error correction word is greatly reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
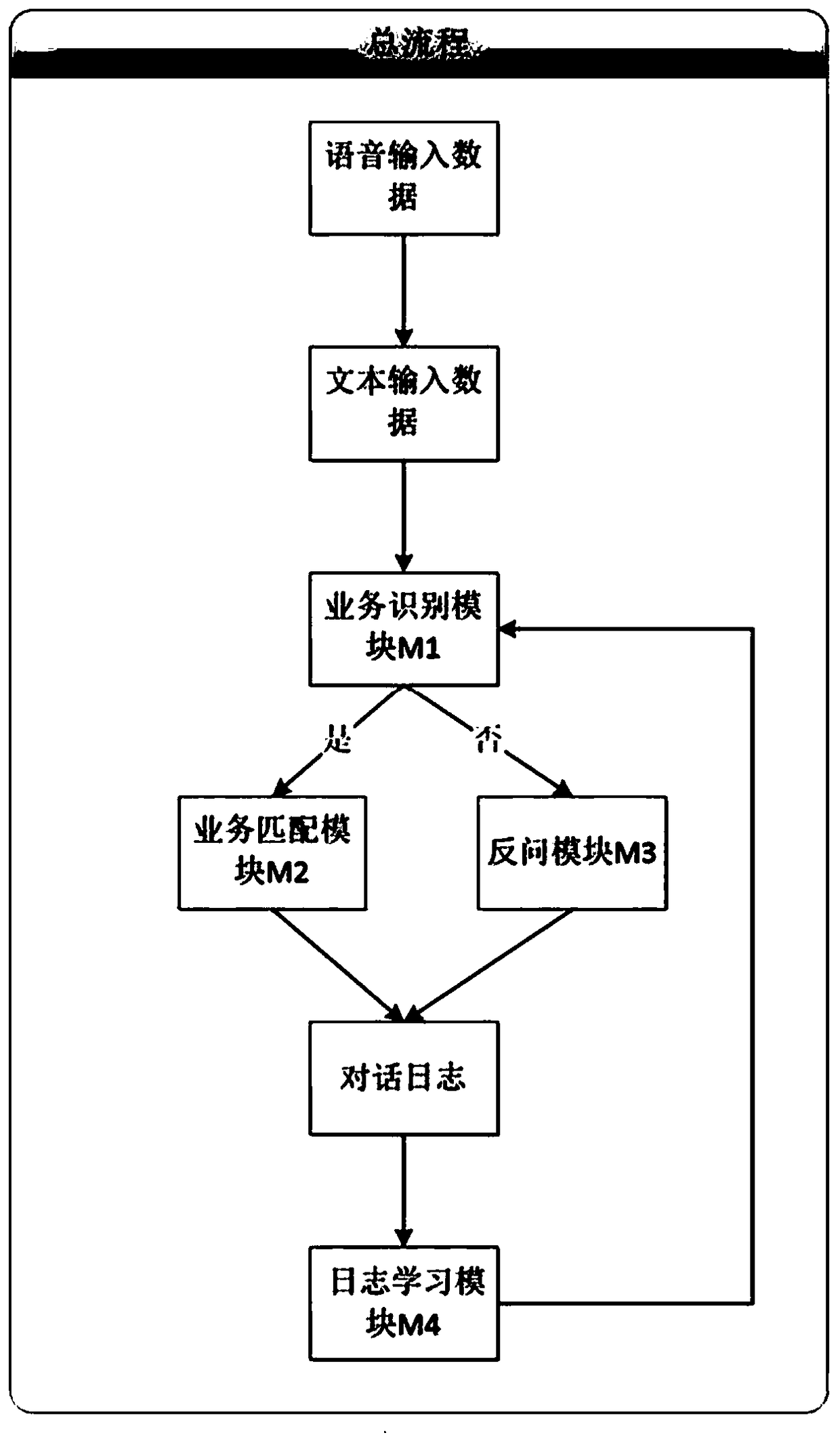
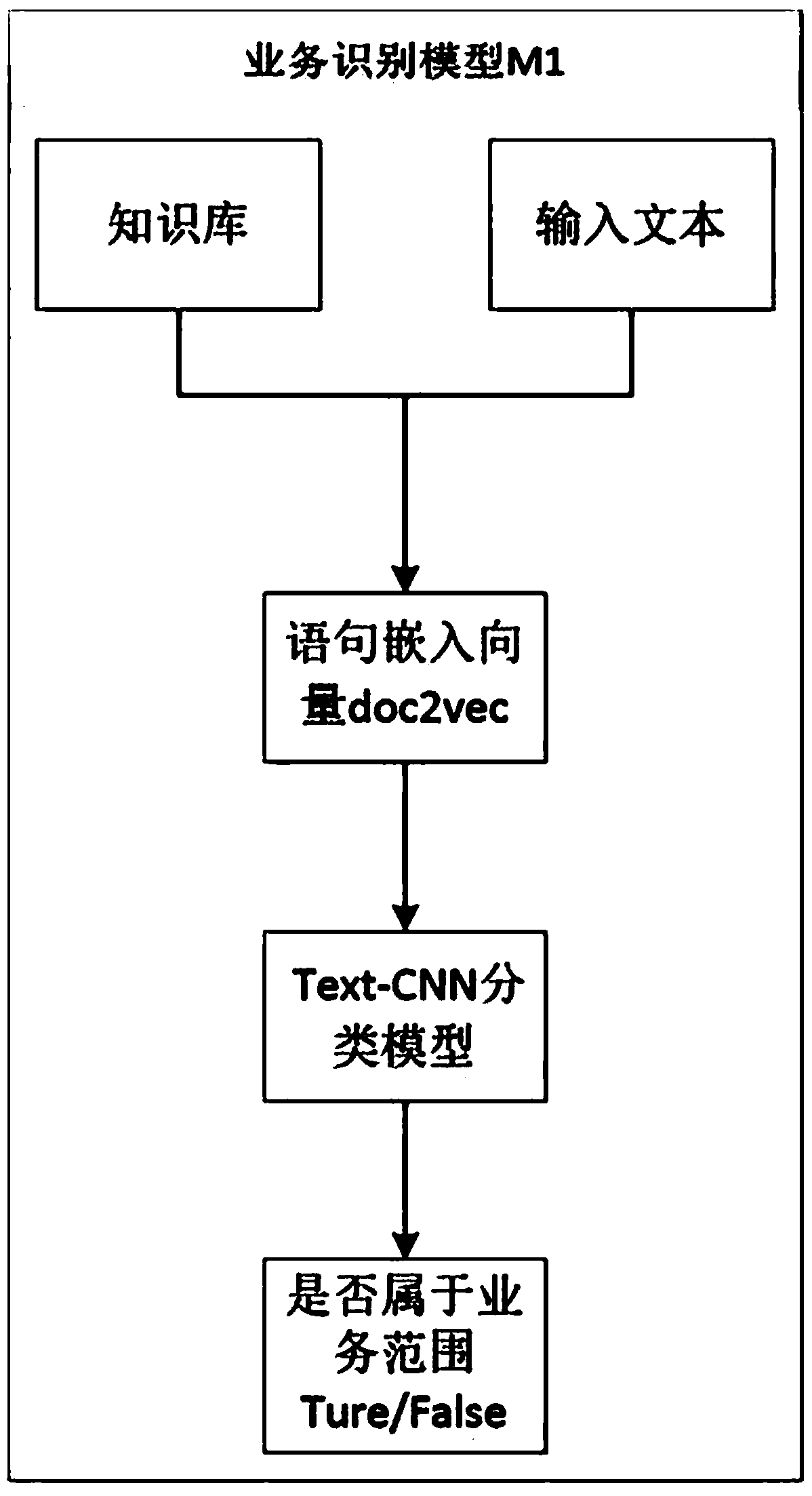
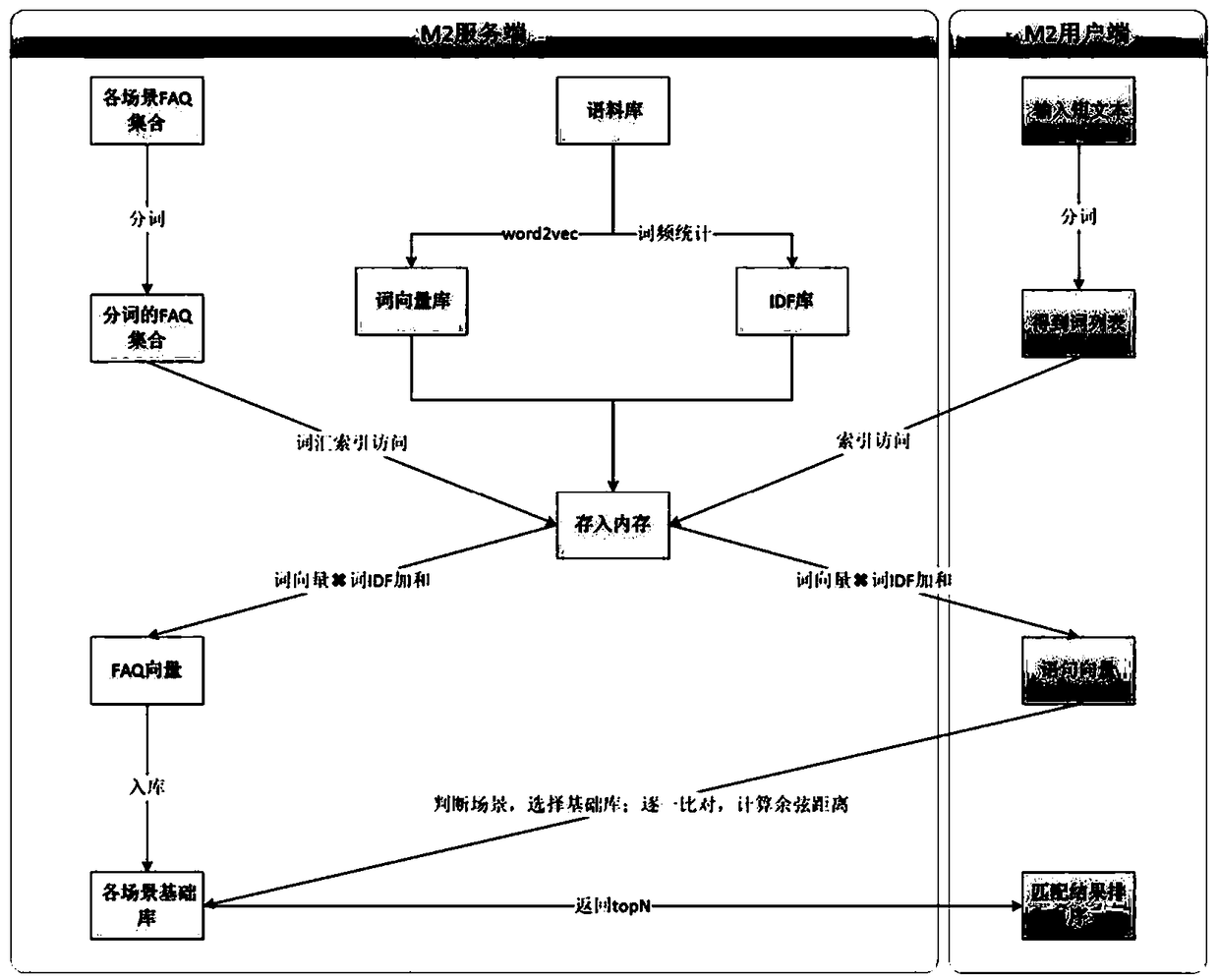
A dialog system automatic optimization method based on log learning
ActiveCN109460459AAutomatic discoveryReduce workloadSemantic analysisSpecial data processing applicationsDialog systemSystem maintenance
The invention discloses a dialog system automatic optimization method based on log learning, Based on log analysis, semantic recognition and knowledge extraction technology, the knowledge base in thebackground of the system will automatically expand with the gradual increase of dialogue records, and the robot will know more and more, and eventually cover all the dialogue scenarios that may be involved in the interaction, and improve the user experience. The method realized by the invention has a high level of automation, and compared with the method of using pure human power to collect and edit, the invention can greatly reduce the manpower and material resources required for system maintenance.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
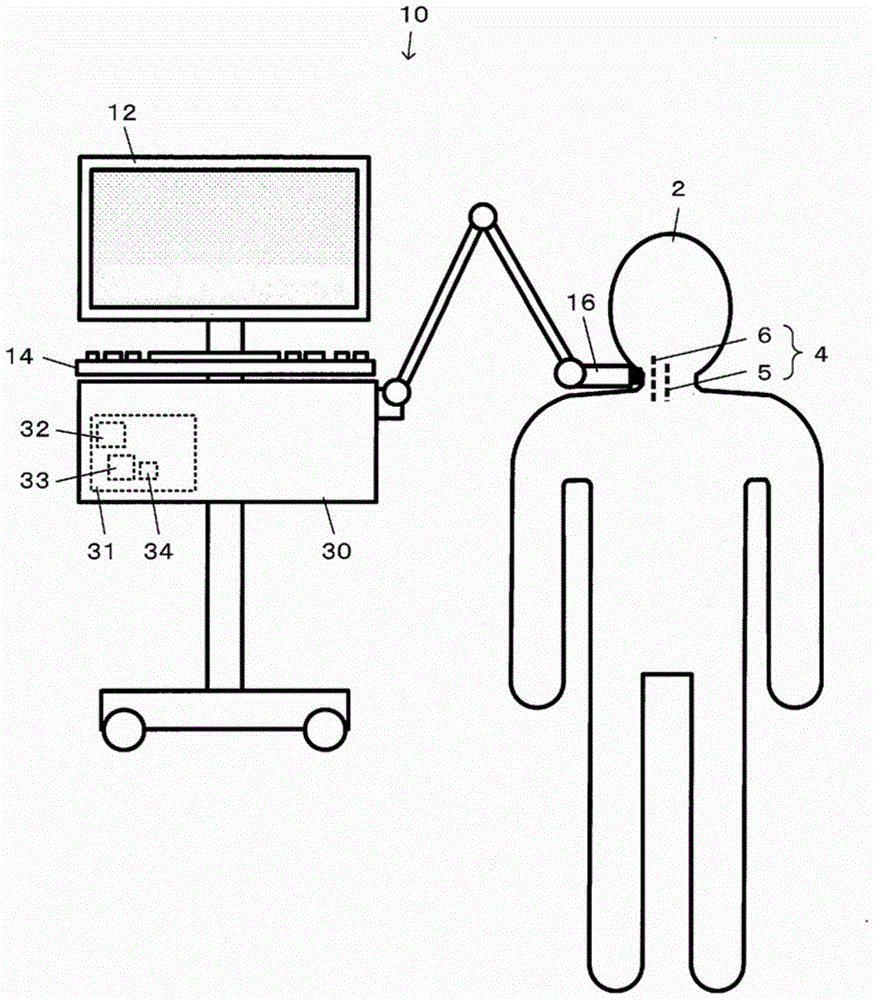
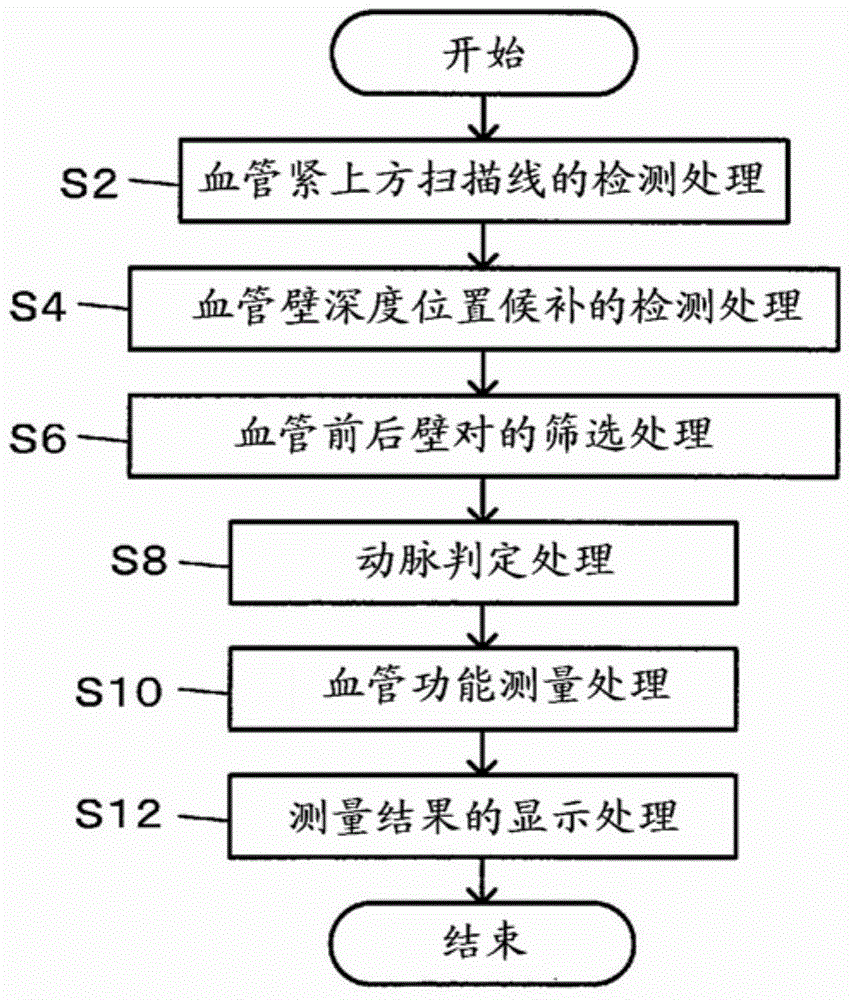
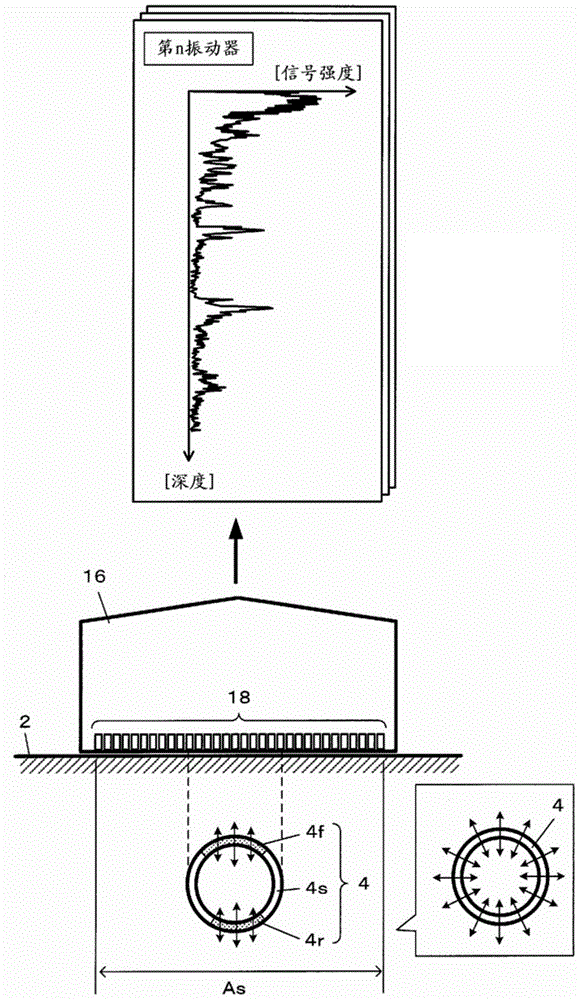
Ultrasonic measurement apparatus and ultrasonic measurement method
InactiveCN104905823AAutomatic discoveryUltrasonic/sonic/infrasonic diagnosticsHealth-index calculationVeinReflected waves
A scanning line immediately above a blood vessel is detected using a received signal of a reflected wave of an ultrasonic wave transmitted to the blood vessel, and candidates for front and rear walls of the blood vessel are detected based on the received signal of the scanning line. Then, vascular front and rear walls pairs of front and rear walls among the candidates are narrowed down, and the narrowed-down vascular front and rear walls pair is regarded as one blood vessel and artery / vein identification is performed for each blood vessel. Measurement of vascular function information is performed for the blood vessel determined to be an artery.
Owner:SEIKO EPSON CORP
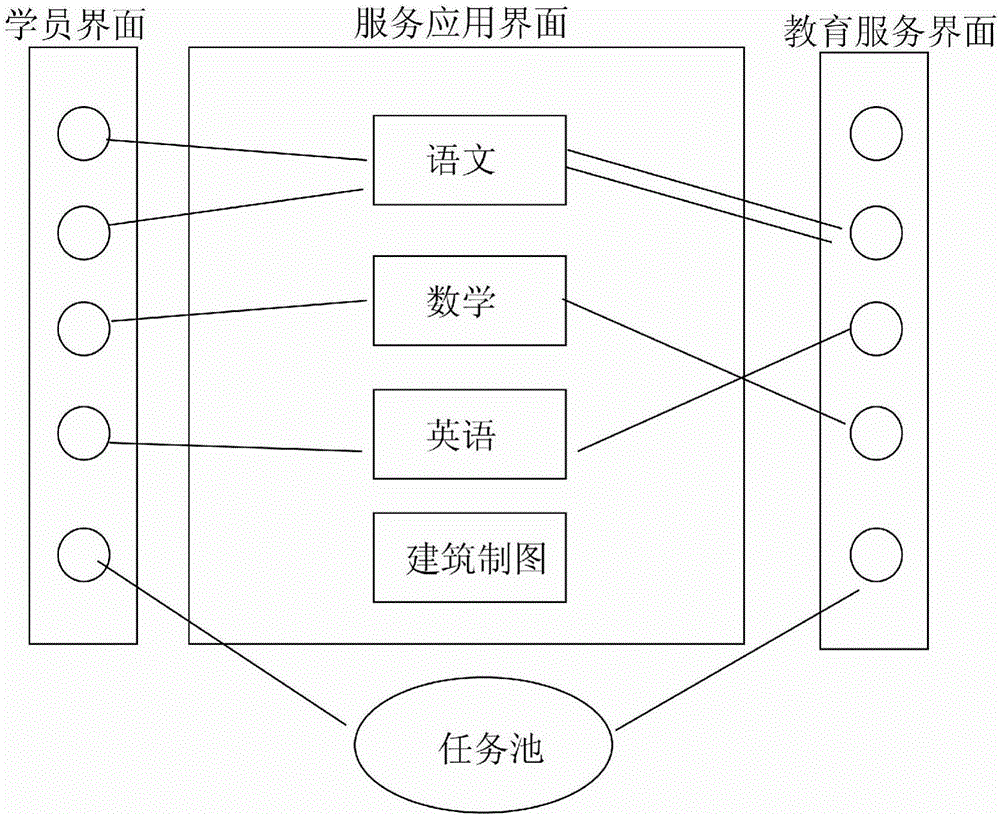
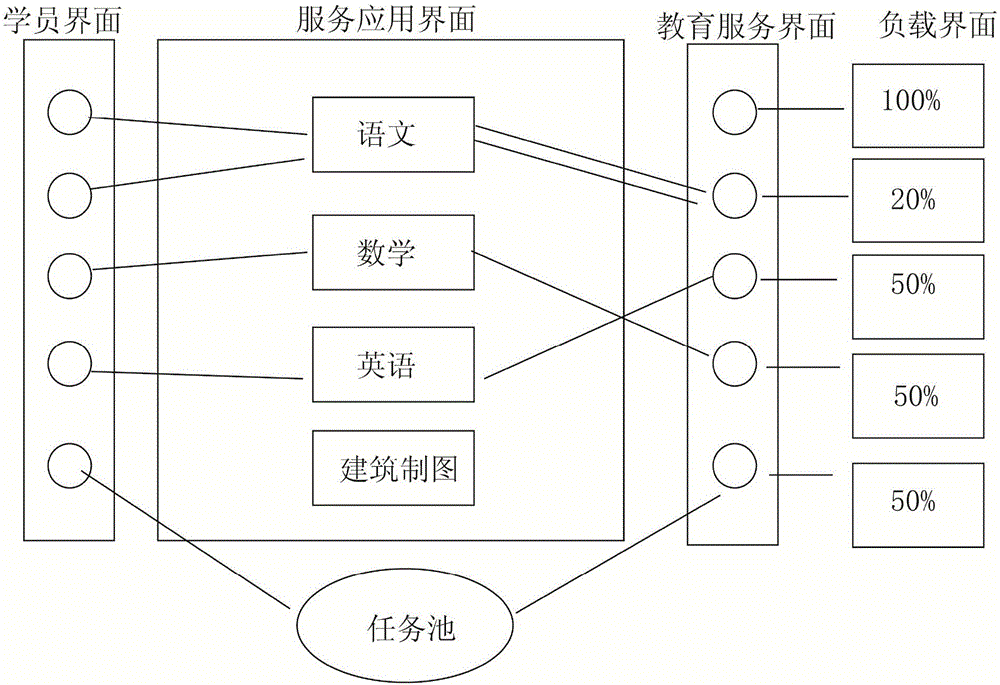
Hadoop based learning cloud paas (platform-as-a-service) platform construction method
InactiveCN106384318AEfficient use ofEasy to useData processing applicationsRating systemManagement system
The invention discloses a hadoop based learning cloud paas (platform-as-a-service) platform construction method, which is characterized by comprising the steps of 1) establishing a service website on a paas platform, building a service application interface, a student interface and an education service interface, and setting up connection between the student interface and the service application interface and connection between the service application interface and teacher interface by applying hadoop; 2) establishing an account management system, wherein the student interface and the teacher interface establish independent accounts corresponding to an individual student and an individual teacher respectively; and 3) setting a plurality of teaching modules in the service application interface, and establishing a scoring system in each teaching module, wherein the scoring system automatically connects a student to a corresponding teacher account according to a scoring result after the student completes the scoring system, thereby realizing point-to-point teaching.
Owner:LIUZHOU CITY VOCATIONAL COLLEGE
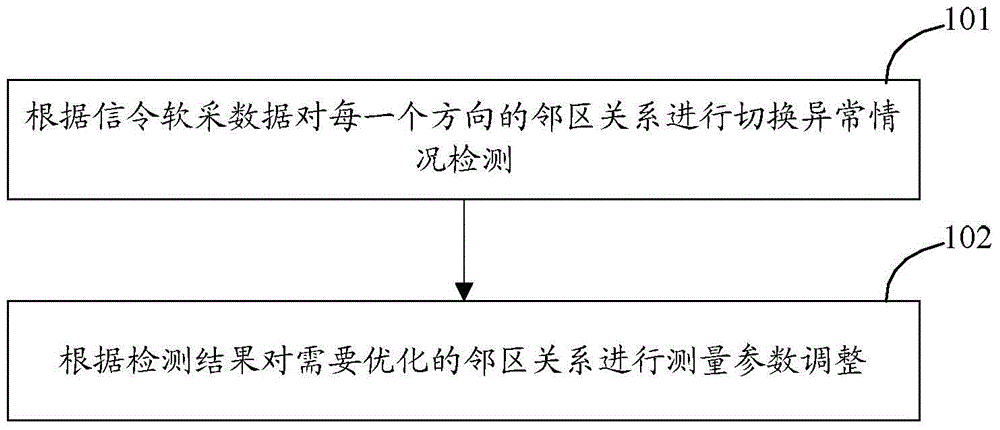
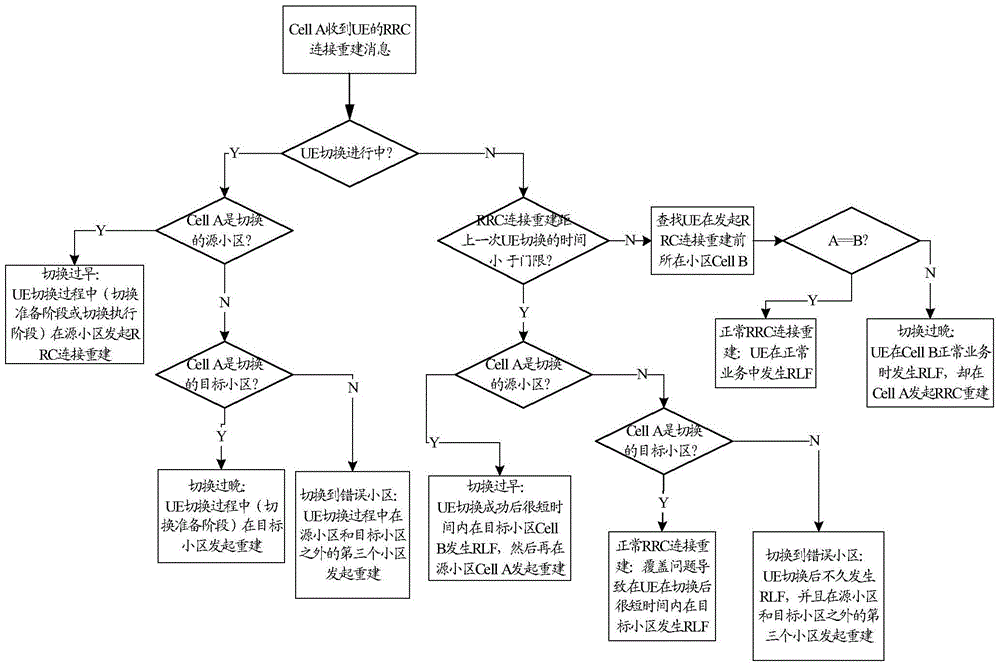
Switching and optimization method and device
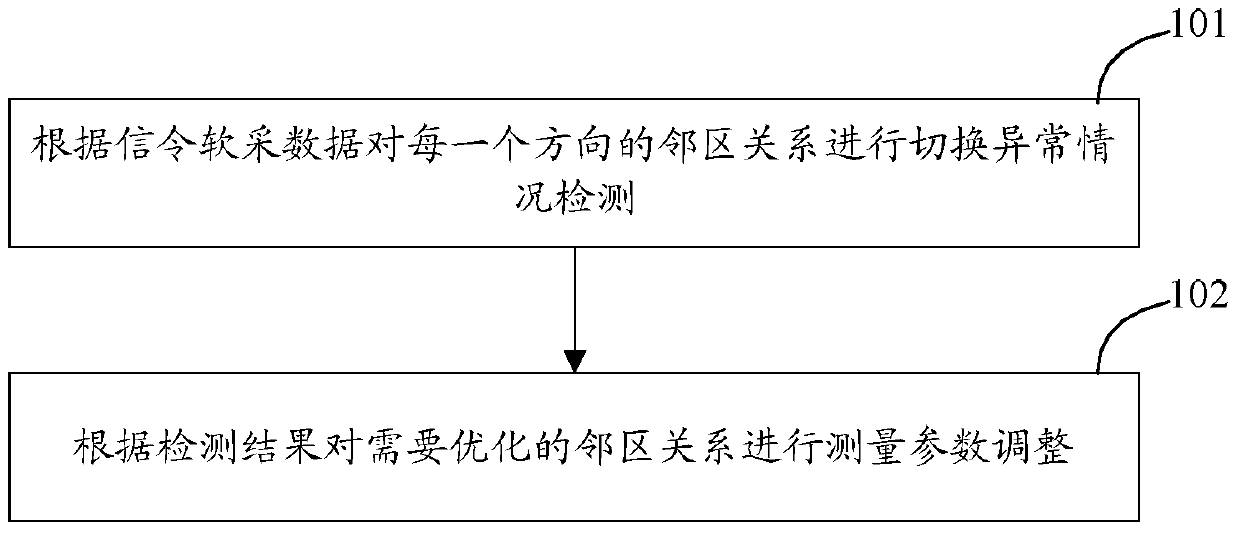
ActiveCN105992251AAutomatic discoveryAccurate discoveryWireless communicationNeighbor relationSoftware acquisition
The invention discloses a switching and optimization method. In the method, according to signaling software acquisition data, switching abnormal condition detection is carried on a neighbor relation in each direction, and according to the detection result, measurement parameter adjustment is carried out on the neighbor relation in need of optimization. The invention also discloses a switching and optimization device.
Owner:ZUNYI BRANCH OF CHINA MOBILE GRP GUIZHOU COMPANY
Learning cloud paas platform modeling method based on hadoop
InactiveCN106204381AEfficient use ofEasy to useData processing applicationsWeb siteManagement system
The invention discloses a learning cloud paas platform modeling method based on hadoop. The method is characterized by comprising the following steps that 1, a service network is set up on the paas platform, a service application interface, a student interface and an education service interface are established, and connection between the student interface and the service application interface and between the service application interface and a teacher interface is built by utilizing the hadoop; 2, an account management system is set up, and separate accounts are set up for the student interface and the teacher interface for individual students and individual teachers respectively; 3, multiple teaching modules are arranged in the service application interface, a scoring system is set up in the teaching module, after students complete the scoring system, the scoring system automatically connects the students to the corresponding teacher accounts according to score results, and point-to-point teaching is achieved; 4, for a teacher load system in the service application interface, when one teacher account displays that the load is 90%, the system automatically cancel matching to the teacher.
Owner:LIUZHOU CITY VOCATIONAL COLLEGE
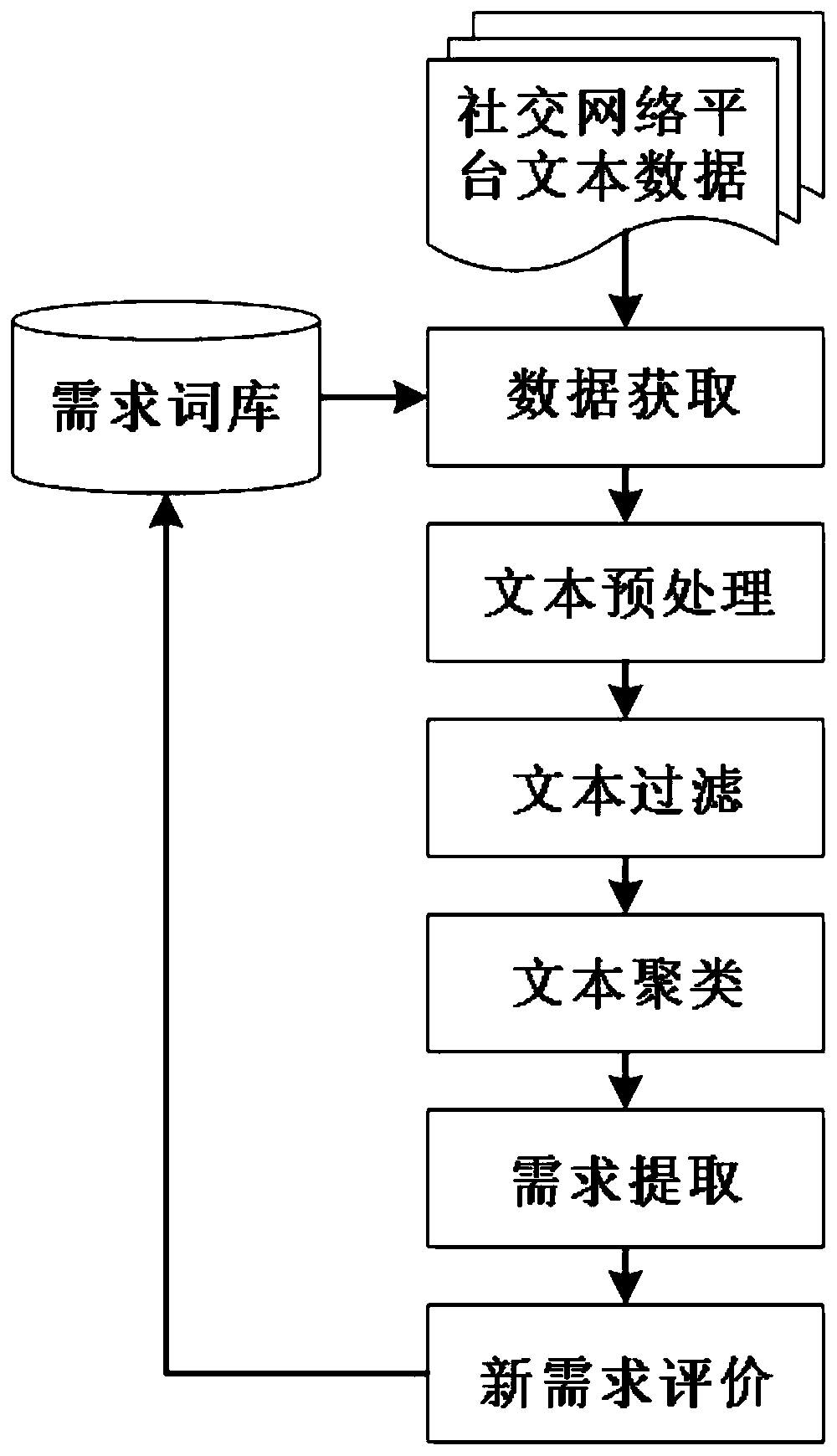
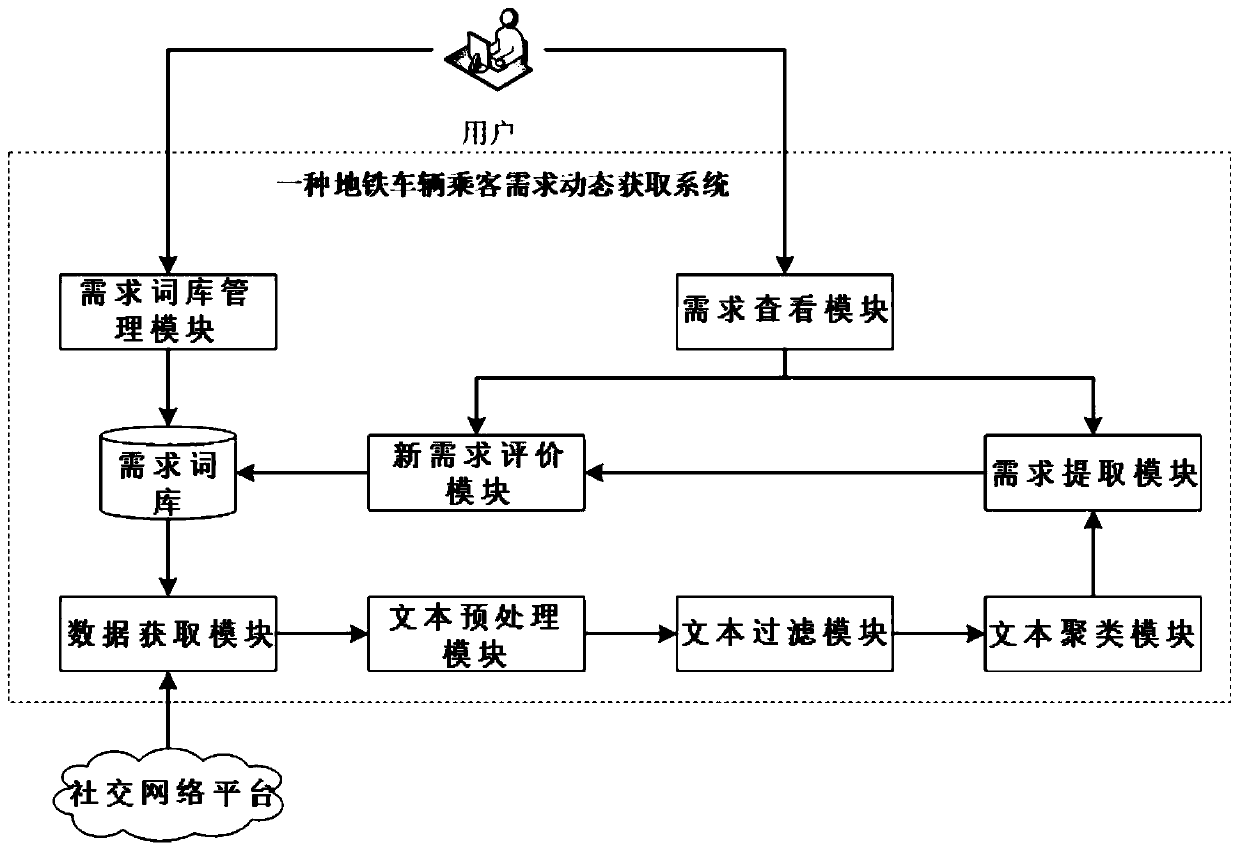
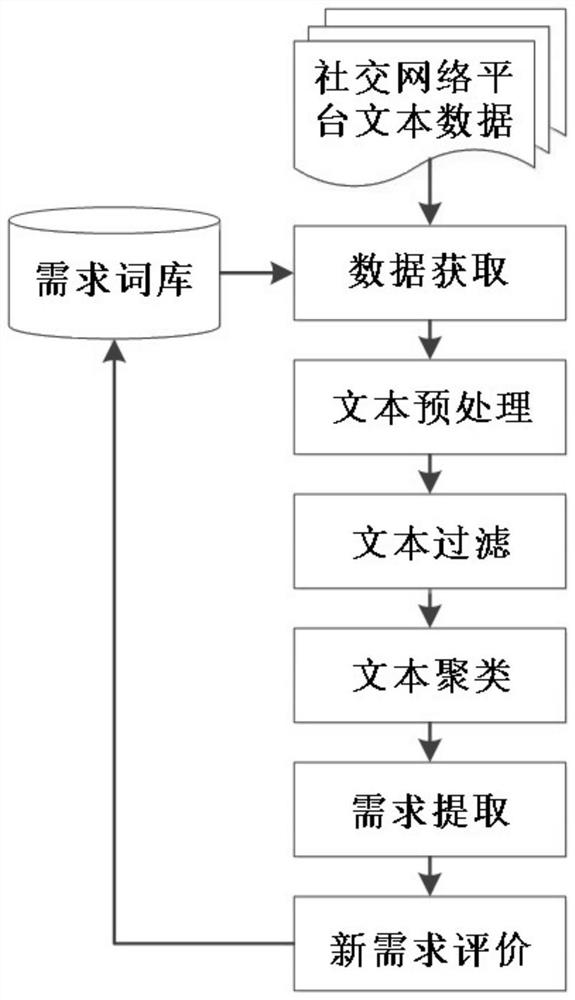
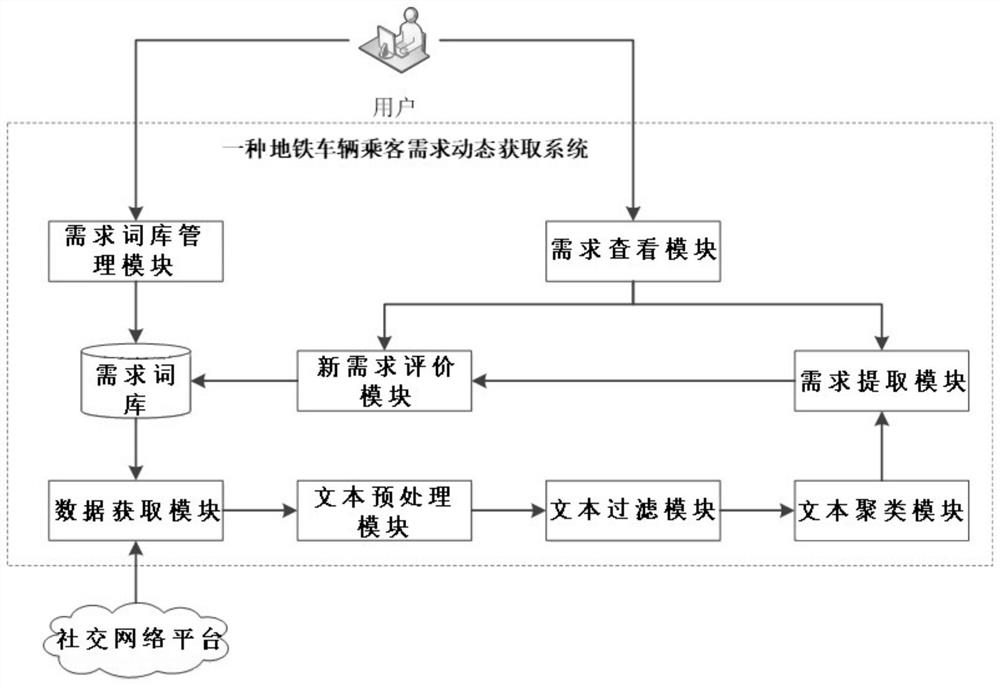
Subway passenger demand dynamic acquisition method and acquisition system thereof
ActiveCN110347828AImprove the efficiency of demand acquisitionReduce subjectivityWeb data indexingCharacter and pattern recognitionCorrelation clusteringLexicon
The invention discloses a subway passenger demand dynamic acquisition method and an acquisition system thereof. The subway passenger demand dynamic acquisition method comprises the following steps: 1,building a demand lexicon, and obtaining user message sending data from a social network platform; 2, preprocessing the obtained data; 3, filtering texts irrelevant to subway passenger demands by adopting a support vector machine classifier; 4, performing correlation clustering; 5, for each clustering cluster, giving a label as a demand item, and calculating the importance of the demand item; 6,firstly judging whether the demand item exists in the demand word bank, if so, exiting, and if not, judging whether the importance degree and the relative propagation persistence of the demand item simultaneously meet a preset threshold value, if so, discovering a new demand item, adding the new demand item into the demand word bank; and if not, exiting. According to the invention, a large numberof user sentences can be processed; the user demand acquisition efficiency is improved; and the subjectivity is low; demand preferences and potential user demands can be obtained from massive user sentences in real time.
Owner:SOUTHWEST JIAOTONG UNIV
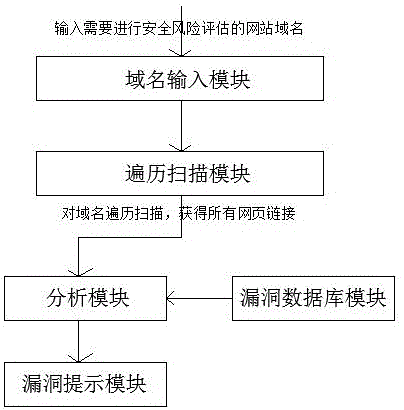
Website security risk assessment system
The present invention relates to a website security risk assessment system and belongs to the information security technical field. The website security risk assessment system of the invention is scientific, advanced and reasonable, and the use method of the system is simple. When the system of the invention is used, a website domain name required to be assessed is inputted a domain name input module; traversal scanning is performed on the website domain name required to be assessed by the traversal scanning module; and all webpage links under the website domain name required to be assessed can be obtained. According to the website security risk assessment system, the scores of each of a plurality of vulnerabilities stored in a vulnerability database module are obtained based on a hundred mark system; corresponding test functions are called to carry out simulation attack on all the web pages under the website domain name required to be assessed according to rules in the vulnerability database module; and the score of website security risk assessment is obtained according to the number of the vulnerabilities. With the system of the invention adopted, the vulnerabilities of websites can be quickly, automatically and accurately found out, and the security inspection efficiency of an information system can be greatly improved. The system of the invention has a high market application and promotion value.
Owner:安徽云图信息技术有限公司
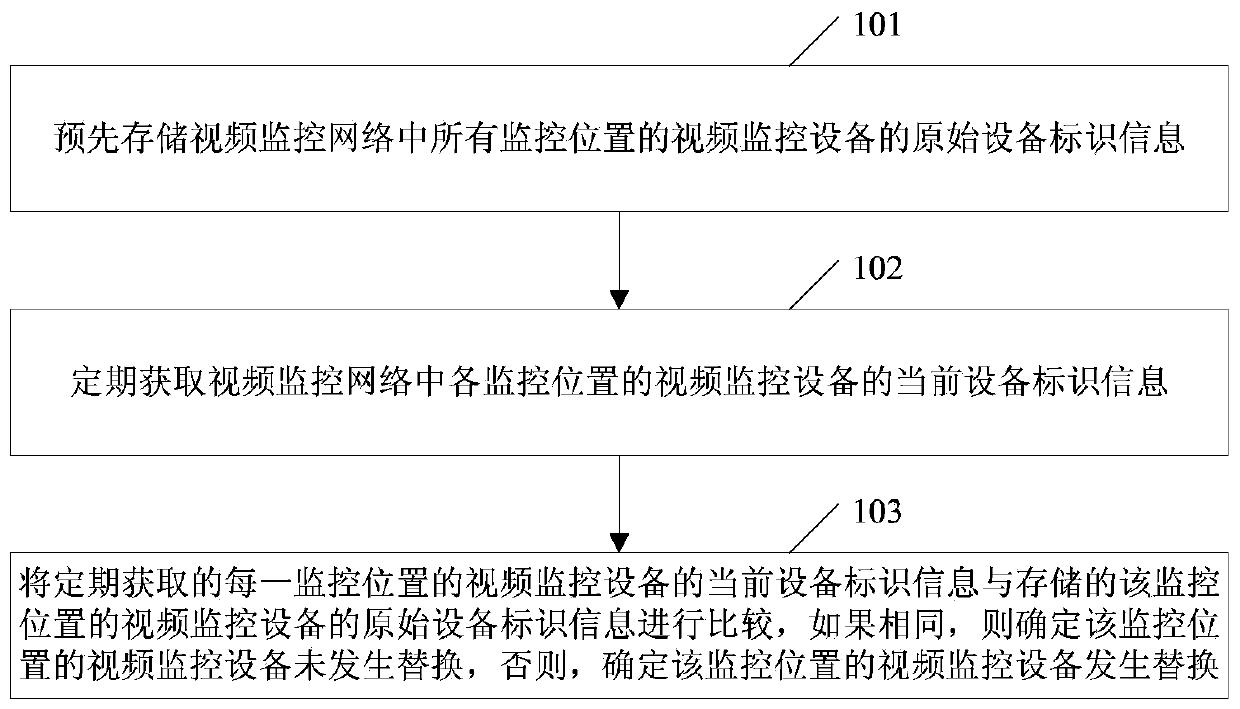
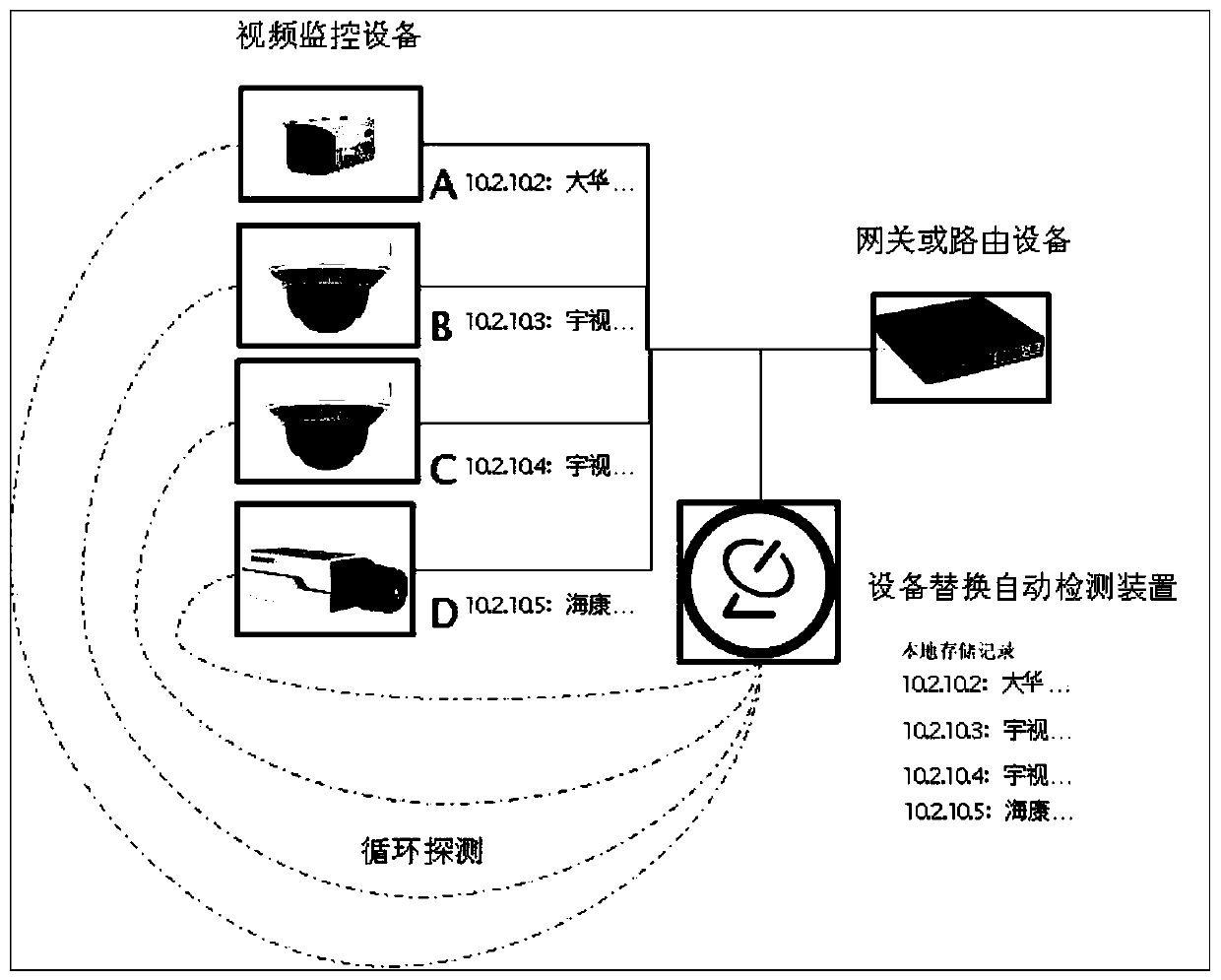
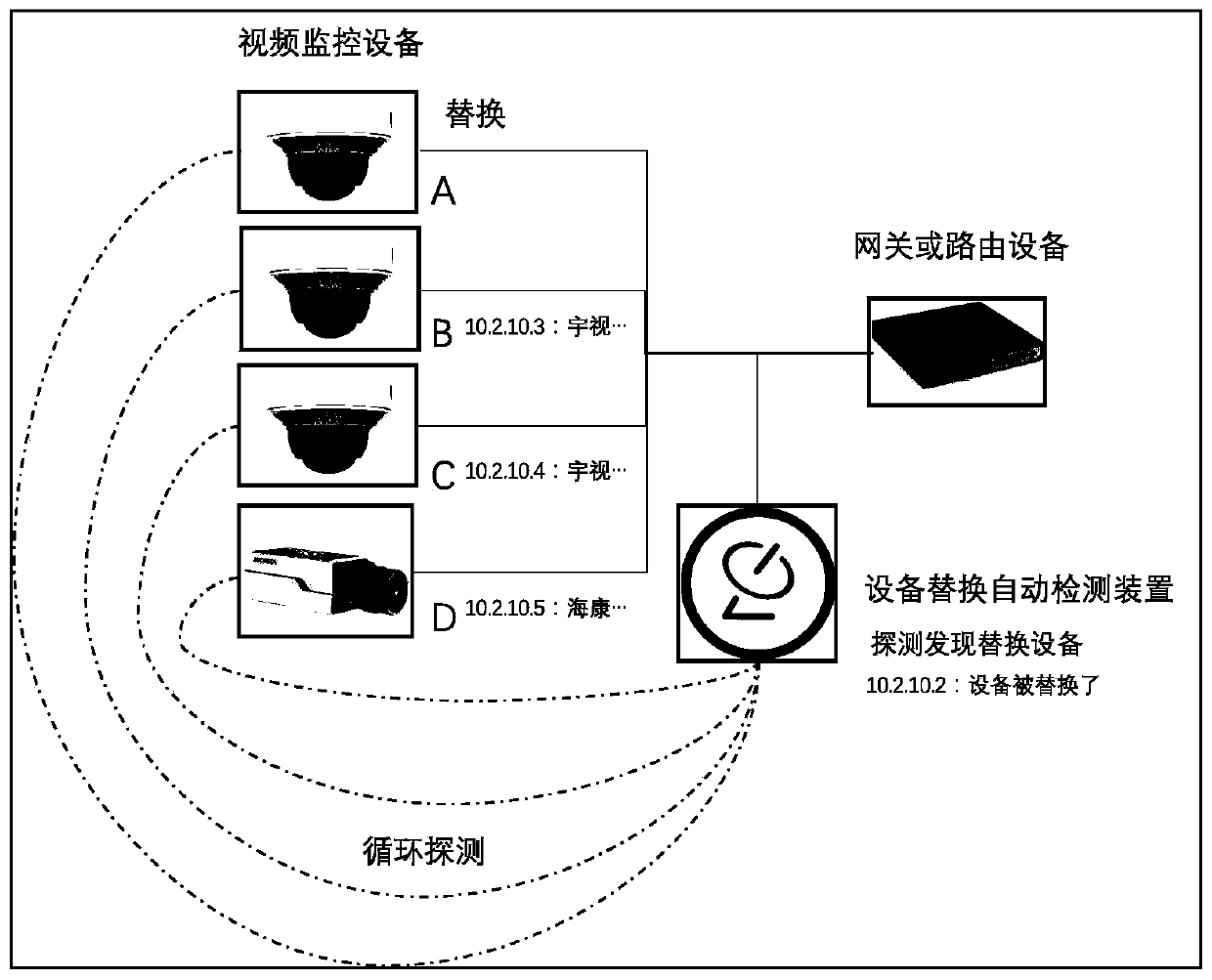
Automatic detection method and device for replacement of video monitoring equipment
InactiveCN110505443AAutomatic discoveryDiscovered in timeClosed circuit television systemsVideo monitoring
The invention provides an automatic detection method and device for replacement of video monitoring equipment which are applied to a video monitoring network, and the technical scheme is that the method comprises the steps of storing original equipment identification information of video monitoring equipment at all monitoring positions in the video monitoring network in advance; periodically acquiring current equipment identification information of the video monitoring equipment at each monitoring position in the video monitoring network; comparing the periodically acquired current equipmentidentification information of the video monitoring equipment at each monitoring position with the stored long-range equipment identification information of the video monitoring equipment at the monitoring position; and if yes, determining that the video monitoring equipment at the monitoring position is not replaced, otherwise, determining that the video monitoring equipment at the monitoring position is replaced. According to the invention, the video monitoring equipment which is maliciously replaced can be automatically and timely discovered.
Owner:HANGZHOU HIKVISION DIGITAL TECH
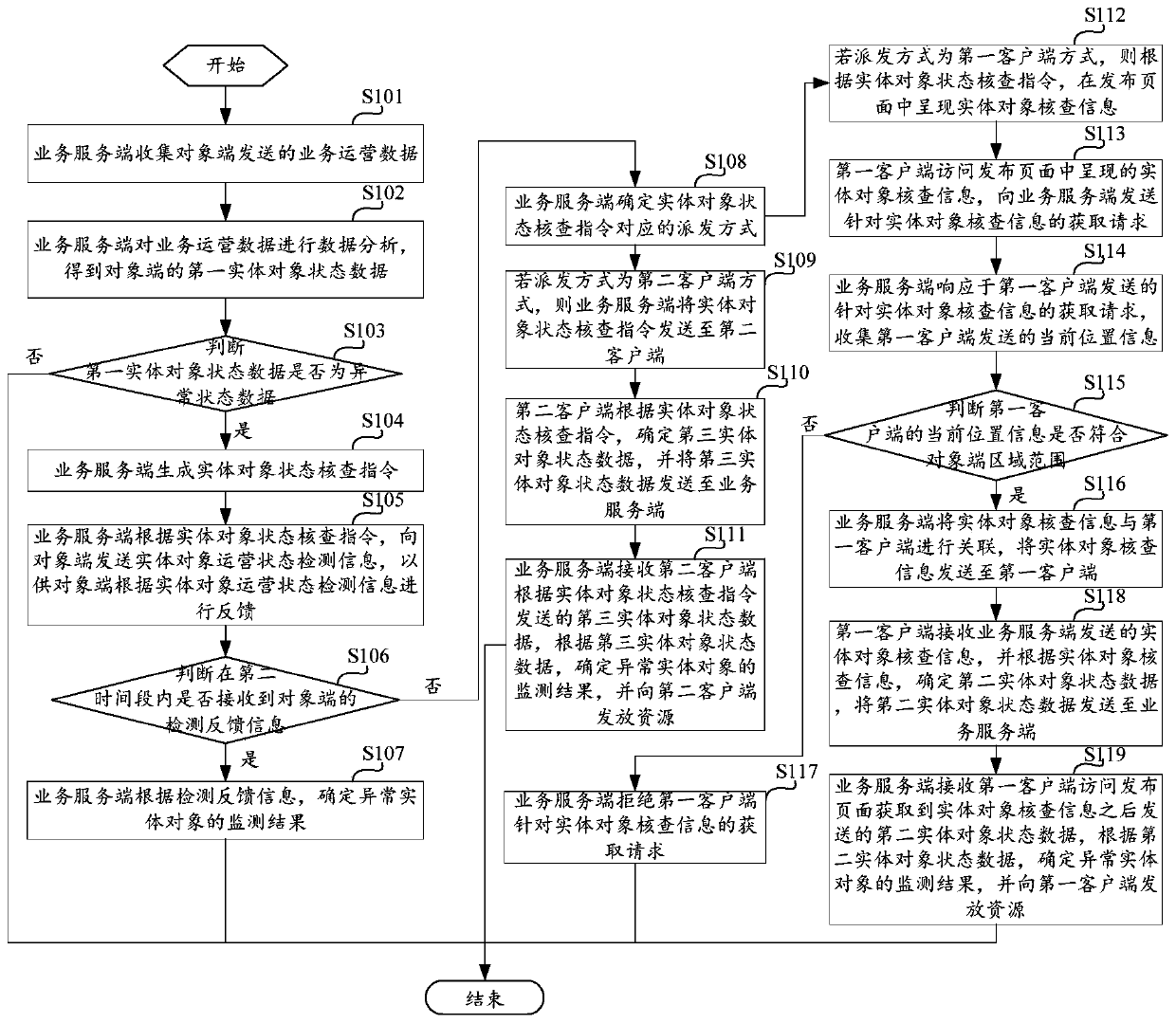
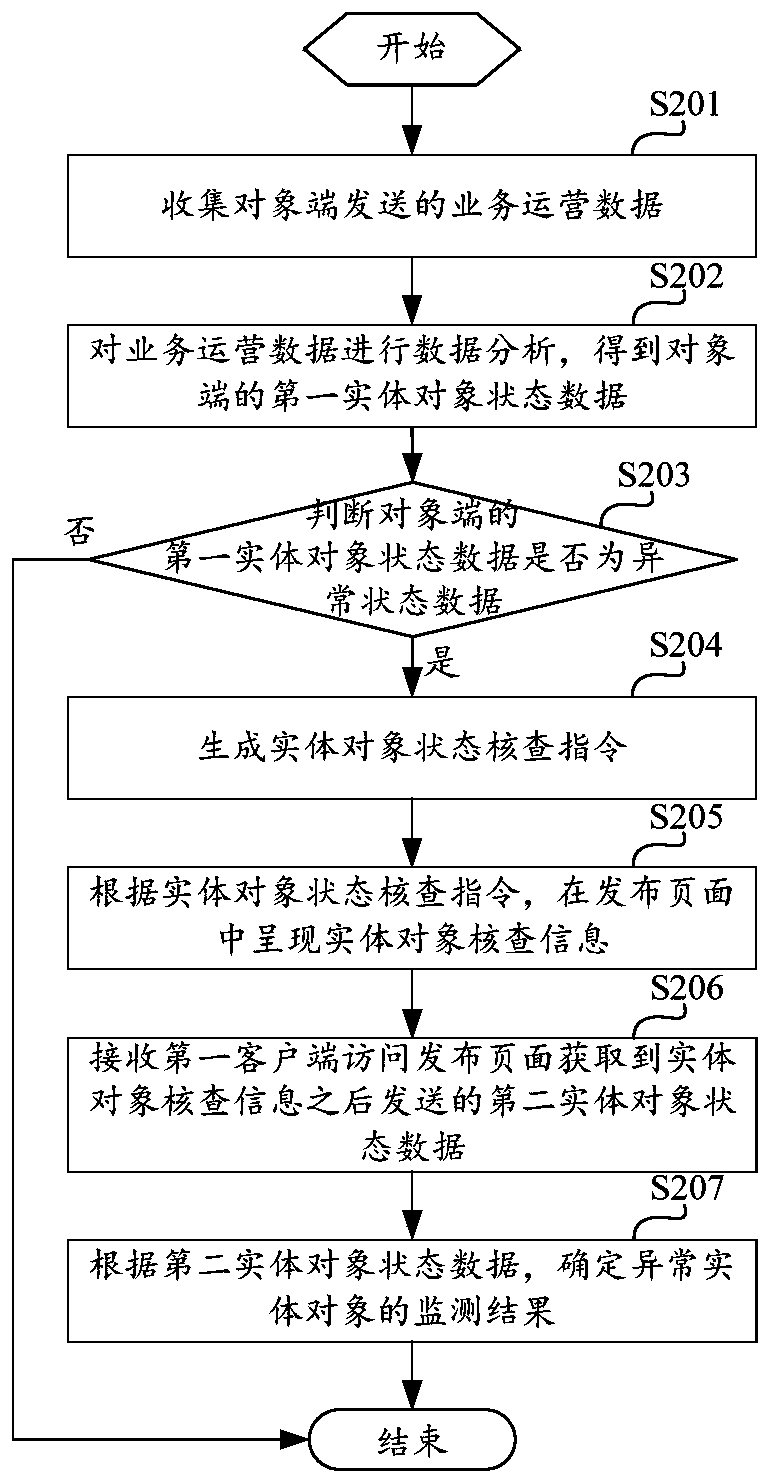
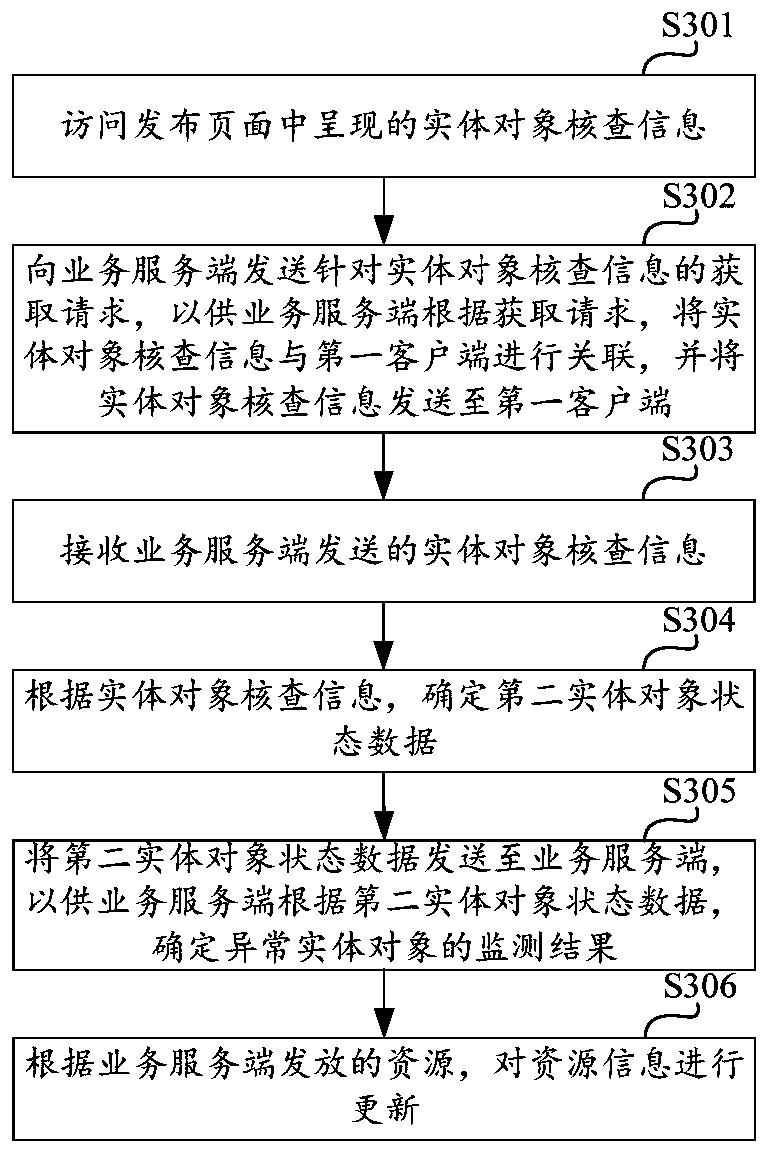
Abnormal entity object monitoring method and device
InactiveCN111047355AImprove Condition Monitoring EfficiencyEasy to handleMarket predictionsEngineeringMonitoring methods
The invention discloses an abnormal entity object monitoring method and device, and the method comprises the steps: collecting business operation data transmitted by an object end; performing data analysis on the business operation data to obtain first entity object state data of the object end; judging whether the first entity object state data of the object end is abnormal state data or not, ifyes, generating an entity object state checking instruction, and presenting entity object checking information in a release page according to the entity object state checking instruction; receiving second entity object state data sent after the first client accesses the release page to obtain entity object check information; and determining a monitoring result of the abnormal entity object according to the second entity object state data. According to the scheme, exception monitoring for the global data of the object end is realized, the existence of an exceptional entity object can be quicklyand automatically discovered, and entity object check information can be conveniently processed by the first client.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
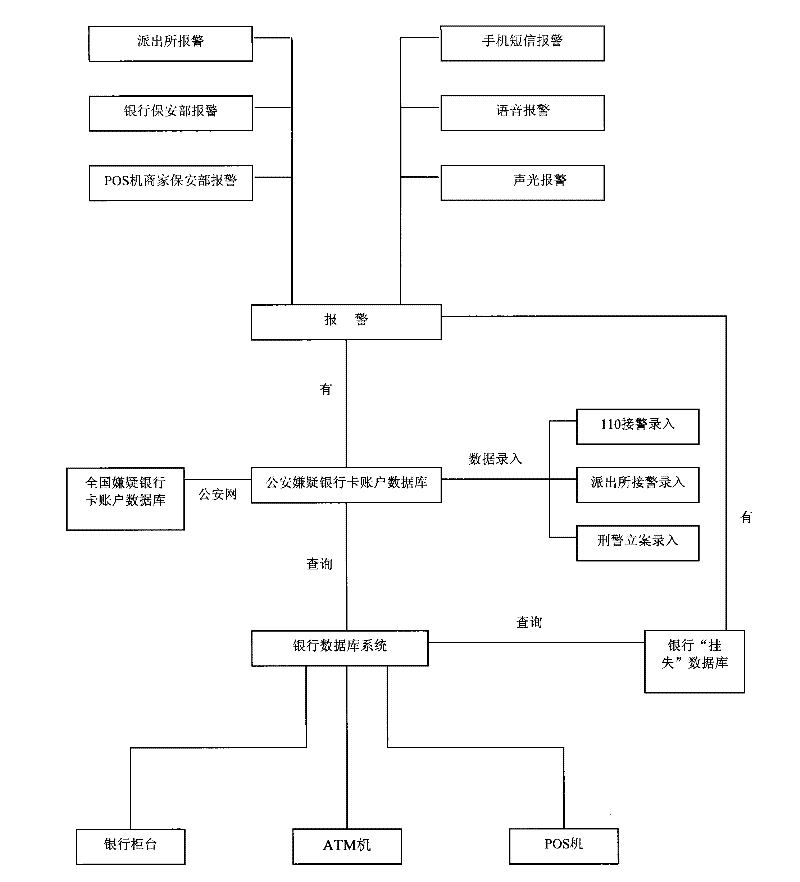
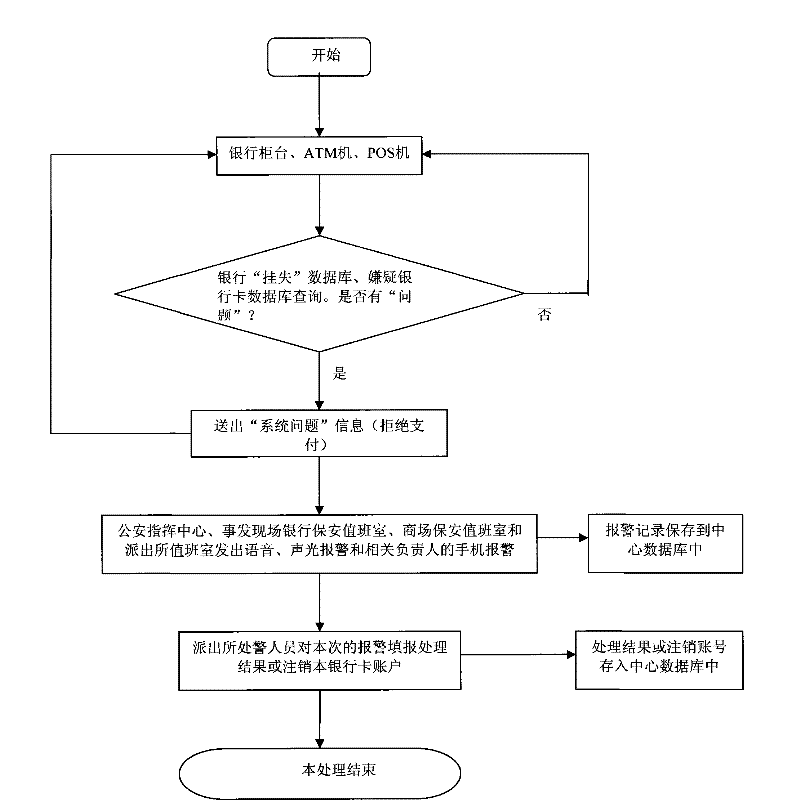
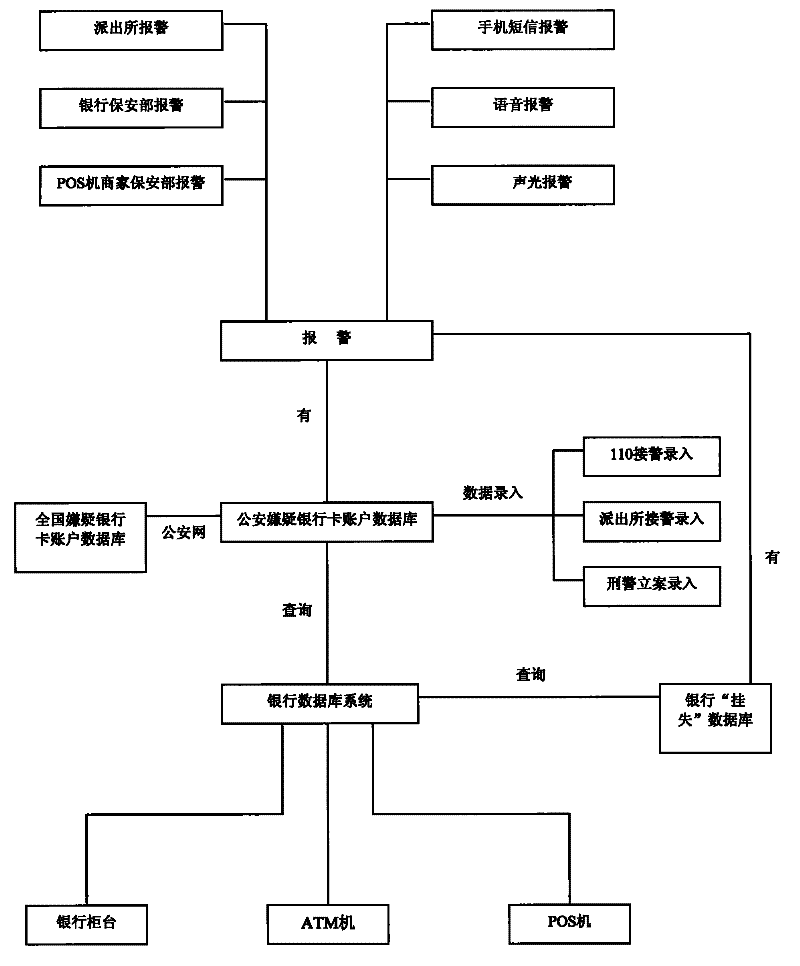
Bank card crime monitoring system and method
ActiveCN101645191BAutomatic discoveryInstant discoveryComplete banking machinesFinanceDatabase serverMonitoring system
The invention discloses a bank card crime monitoring system and a method. A suspicion bank card information verification and storage module of a local central database server receives the suspicion bank card information of a suspicion bank card information entering terminal, stores the suspicion bank card information to a suspicion bank card account database, uploads the suspicion bank card information to a superior center server, and meanwhile, receives the off-site suspicion bank card information from the superior center server; the suspicion bank card information verification and storage module receives the bank card account information of a bank database system and carries out check analysis between the bank card account information and the suspicion bank card information, an analyzedresult is inputted to a check warning module, and then the check warning module sends a warning command to a warning unit according to the result. The invention can automatically discover suspicion bank cards immediately and alarms at bank counters, ATM machines, POS machines and the like.
Owner:北京市振隆科技股份有限公司
Hotspot detection method and device, monitoring server and storage medium
PendingCN113489776AAutomatic discoveryQuick and accurate discoveryData switching networksQueries per secondEngineering
The invention provides a hotspot detection method and device of a distributed storage system, a monitoring server and a storage medium, and belongs to the technical field of distributed storage. The hotspot detection method comprises the following steps: obtaining a per-second query rate of a data fragment in a storage node, wherein the per-second query rate comprises a current per-second query rate and a historical per-second query rate; determining the state of the current per-second query rate based on the historical per-second query rate; and in response to the state of the current query rate per second as a target state, determining that the storage node corresponding to the data fragment is a hotspot. Therefore, the hot spot can be found automatically, quickly and accurately, and the problems of complexity, time consumption and low accuracy caused by speculating the position of the hot spot in a manual observation mode are effectively solved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD +1
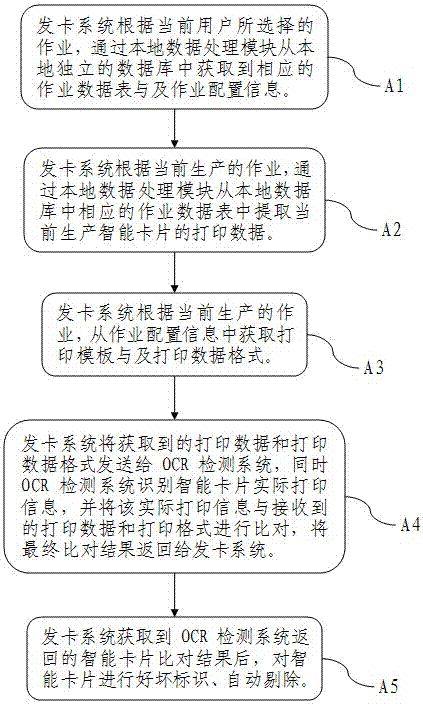
Printing online real-time detection method of a smart card issuing system
ActiveCN103942547BImprove detection and recognition efficiencyReduce the intensity of random inspectionCharacter and pattern recognitionSpecial data processing applicationsIdentifying problemsQuality assurance
Owner:EASTCOMPEACE TECH
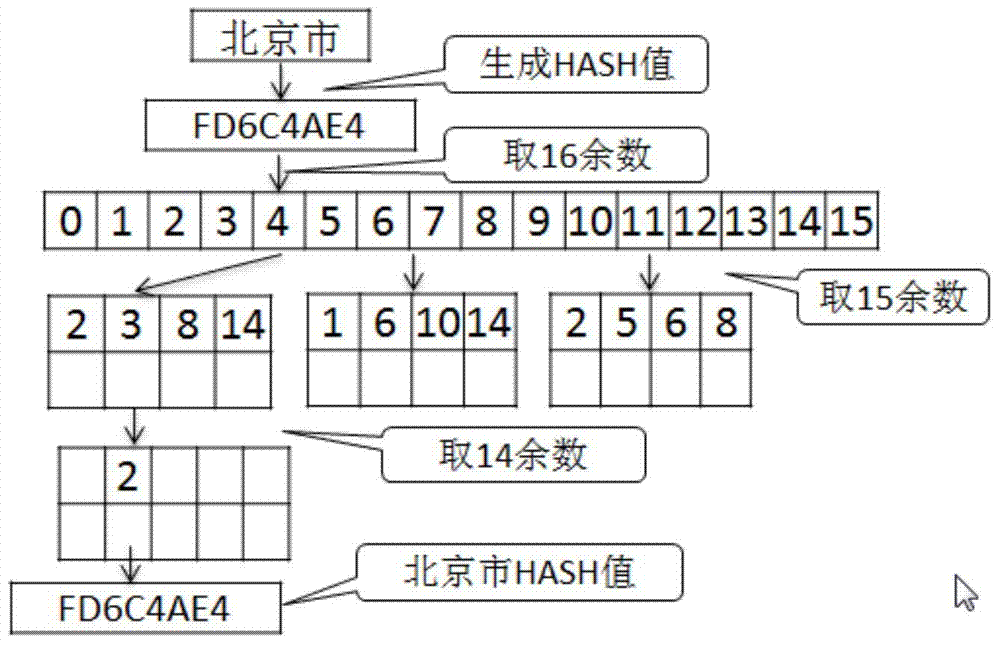
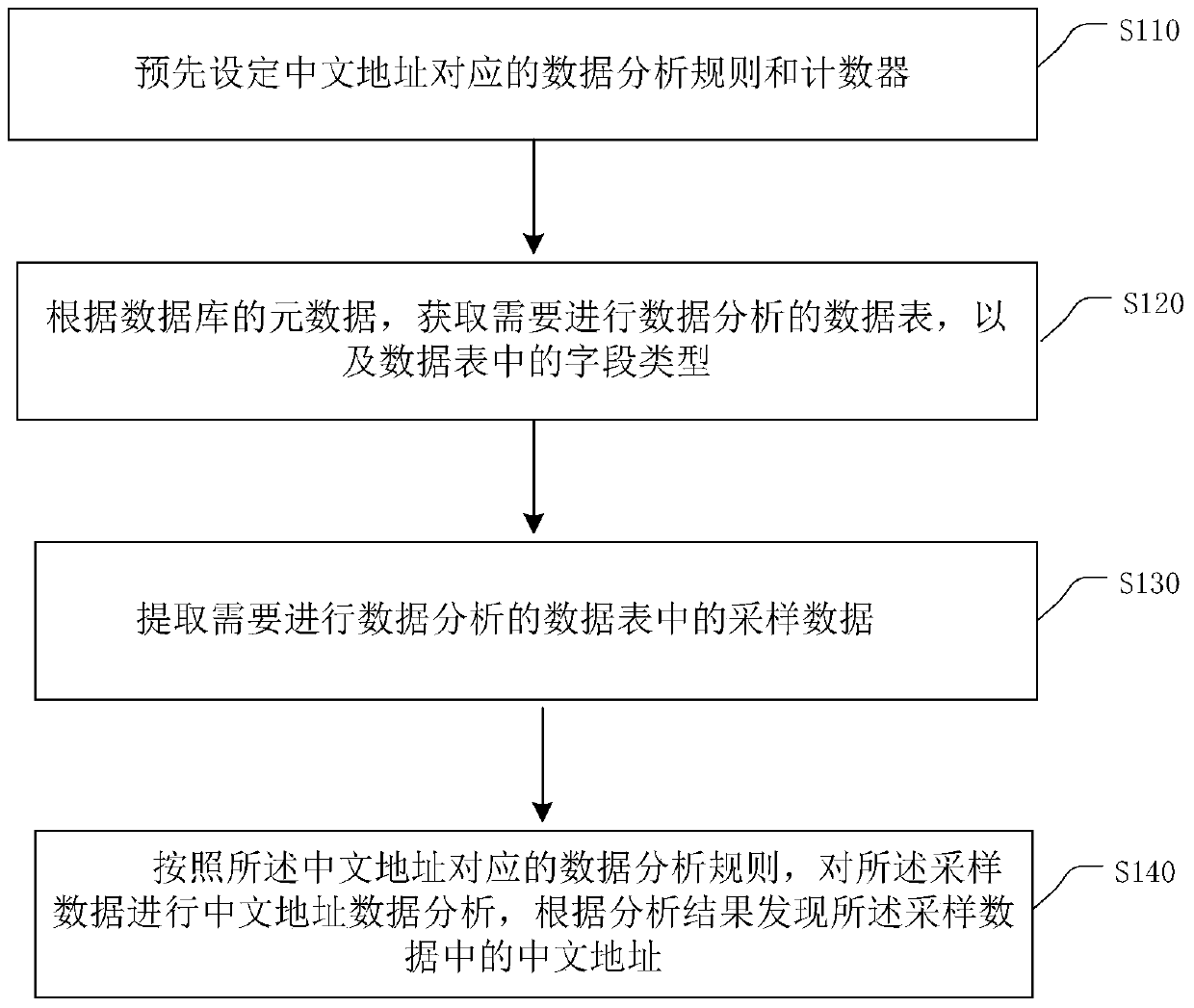
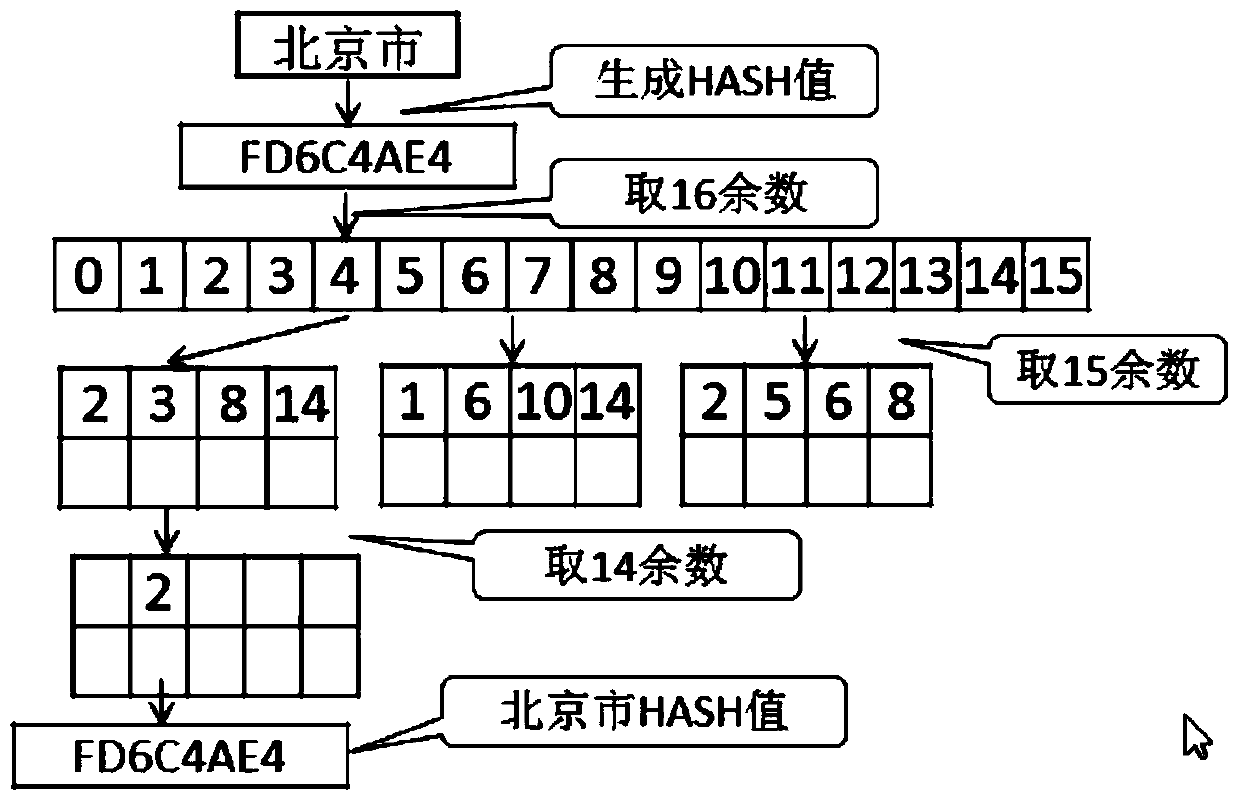
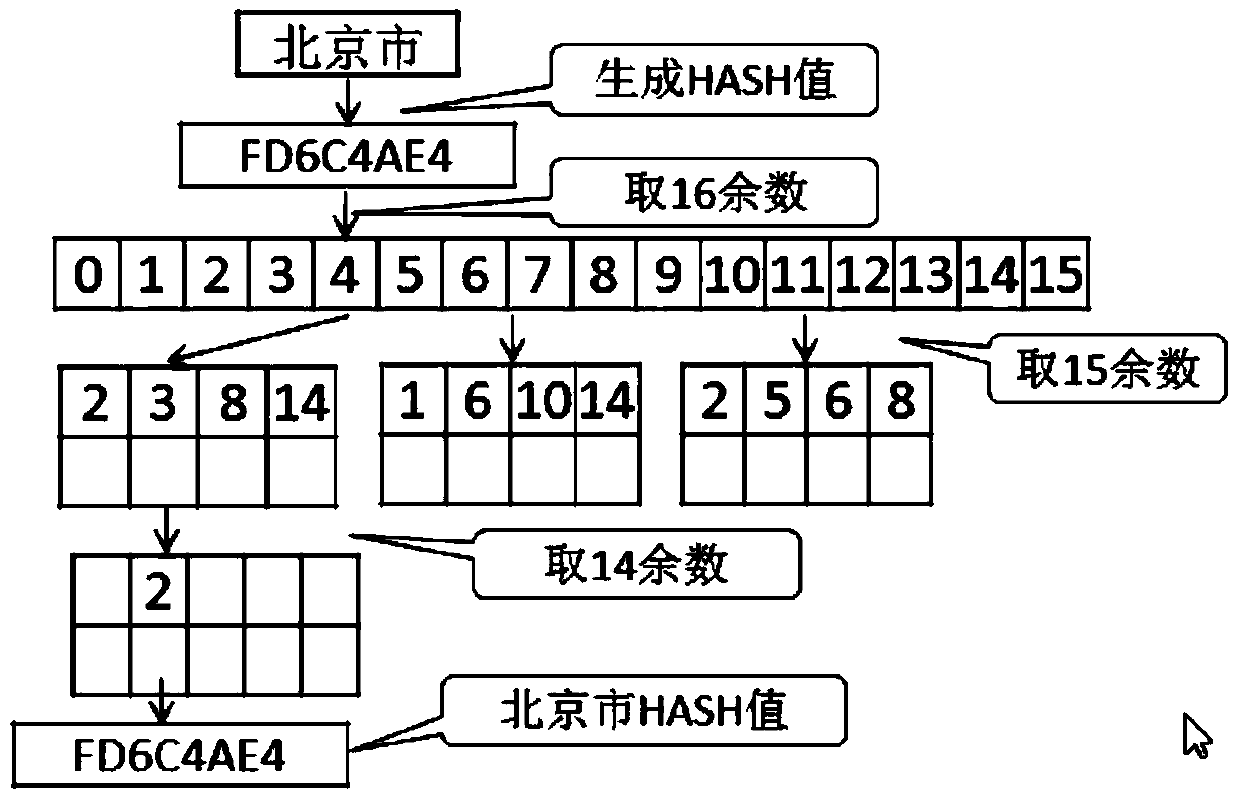
Discovery and Classification of Chinese Address Data
ActiveCN104750852BAutomatic discoveryEfficient discoverySpecial data processing applicationsClassification methodsData profiling
The embodiment of the invention provides a method for finding and classifying Chinese address data. The method mainly comprises the steps of presetting data analyzing rules corresponding a Chinese address; extracting sampling data in a data sheet; analyzing Chinese address data of the sampling data according to the data analyzing rules corresponding to the Chinese address; finding out the Chinese address in the sampling data according to the analyzing result. With the adoption of the method, the type of Chinese address data in the data sheet of an enterprise application database can be automatically and effectively found; the key data of the Chinese addresses in the data sheet of the enterprise application database can be efficiently found out and classified; therefore, the workload is greatly reduced, and the working hours can be decreased.
Owner:MASSIVE CLOUD BEIJING DATA TECH
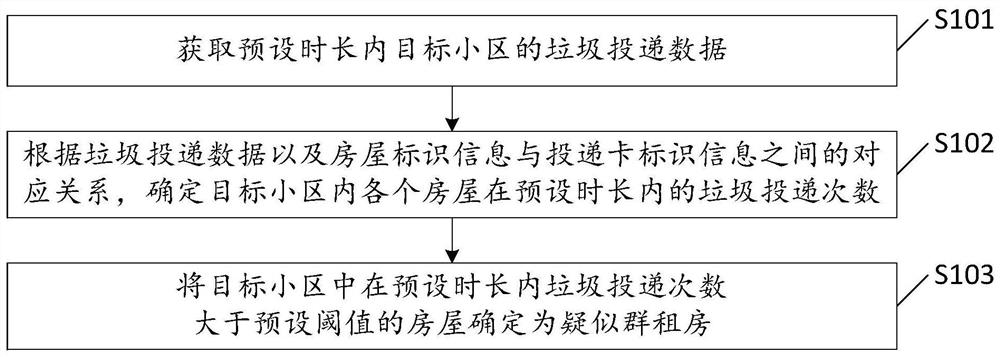
Group renting identification method, device and equipment
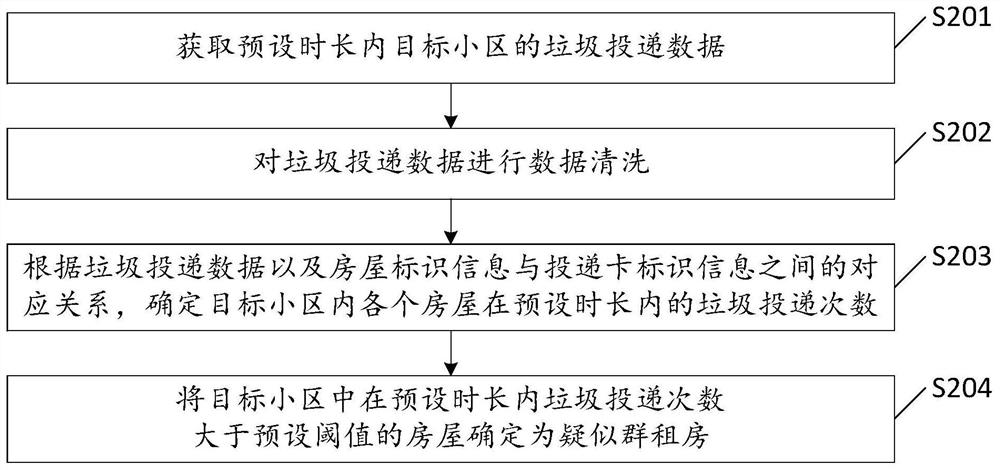
PendingCN112988837AImprove recognition efficiencyImprove the accuracy of judgmentDigital data information retrievalBuying/selling/leasing transactionsComputer scienceRenting
A group renting identification method, device and equipment, wherein and method comprises the steps of obtaining garbage delivery data of a target community within a preset duration, wherein the garbage delivery data is at least used for recording the delivery time, delivery card identification information and garbage can identification information of each garbage delivery; according to the garbage delivery data and the corresponding relationship between the house identification information and the delivery card identification information, determining the garbage delivery times of each house in the target community within a preset duration; and determining the houses of which the garbage delivery times are greater than a preset threshold value in a preset time length in the target community as suspected group rental houses. Whether a certain house generates a large amount of garbage or not is judged by counting the garbage delivery times, so that whether the actual population of the house is in a standard exceeding state or not is deduced, suspected group-rented houses can be timely and automatically found, the recognition efficiency of the group-rented houses and the judgment accuracy of the group-rented houses are improved, and related departments are helped to improve the group renting and renovation efficiency.
Owner:SHENZHEN ZTE NETVIEW TECH +1
Pavement maintenance robot
PendingCN114561858ASystematicImprove integrityMixing operation control apparatusPretreatment controlSocial benefitsPavement maintenance
The invention relates to automatic road construction equipment, and discloses a robot for discovering and maintaining a damaged road surface. The pavement maintenance robot comprises a walking system, a positioning detection system, a crushing system, a concrete pouring system, an alarm system, a power supply system, a control system and the like. According to the invention, the work of finding and maintaining the damaged road surface can be automatically, systematically and comprehensively completed, the maintenance cost can be saved, and the maintenance road occupation time is reduced. The method has wide application prospects and remarkable economic benefits and social benefits.
Owner:函鼎科技(成都)有限公司
Discovery and Classification of Telephone Number Data
ActiveCN104731977BAutomatic discoveryEfficient discoverySpecial data processing applicationsTelecommunicationsClassification methods
Owner:MASSIVE CLOUD BEIJING DATA TECH
A switching belt optimization method and device
ActiveCN105992251BAutomatic discoveryAccurate discoveryWireless communicationNeighbor relationSoftware acquisition
The invention discloses a switching and optimization method. In the method, according to signaling software acquisition data, switching abnormal condition detection is carried on a neighbor relation in each direction, and according to the detection result, measurement parameter adjustment is carried out on the neighbor relation in need of optimization. The invention also discloses a switching and optimization device.
Owner:ZUNYI BRANCH OF CHINA MOBILE GRP GUIZHOU COMPANY
Discovery and Classification Method of Chinese Name Data
ActiveCN104731978BAutomatic discoveryEfficient discoveryCharacter and pattern recognitionSpecial data processing applicationsClassification methodsWorkload
The embodiment of the present invention provides a method for discovering and classifying Chinese name data. The method mainly includes: presetting the data analysis rules corresponding to the Chinese names, extracting the sampling data in the data table, performing Chinese name data analysis on the sampling data according to the data analysis rules corresponding to the Chinese names, and finding out according to the analysis results The Chinese name in the sampled data. The embodiment of the present invention can automatically and effectively discover the types of Chinese name data in the data table of the enterprise application database, efficiently find out and classify the key data of the Chinese name in the data table of the enterprise application database, and can greatly reduce the Reduced workload and shortened working hours.
Owner:MASSIVE CLOUD BEIJING DATA TECH
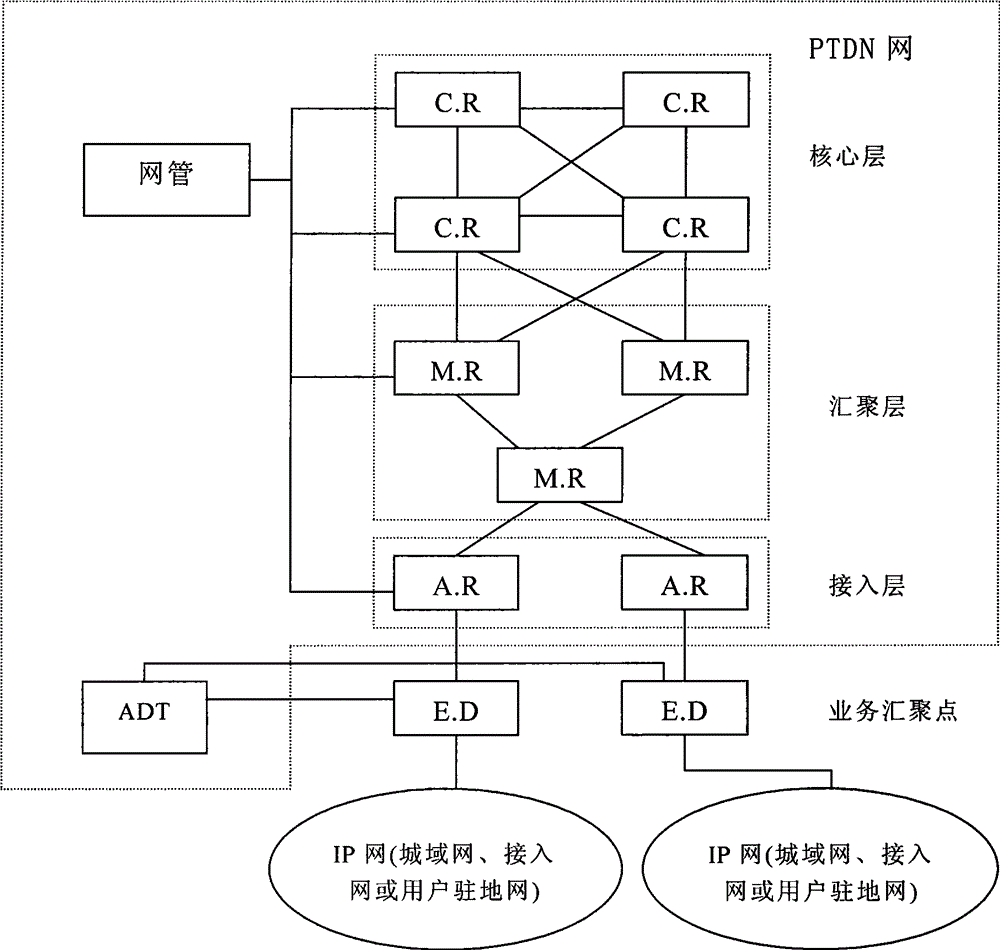
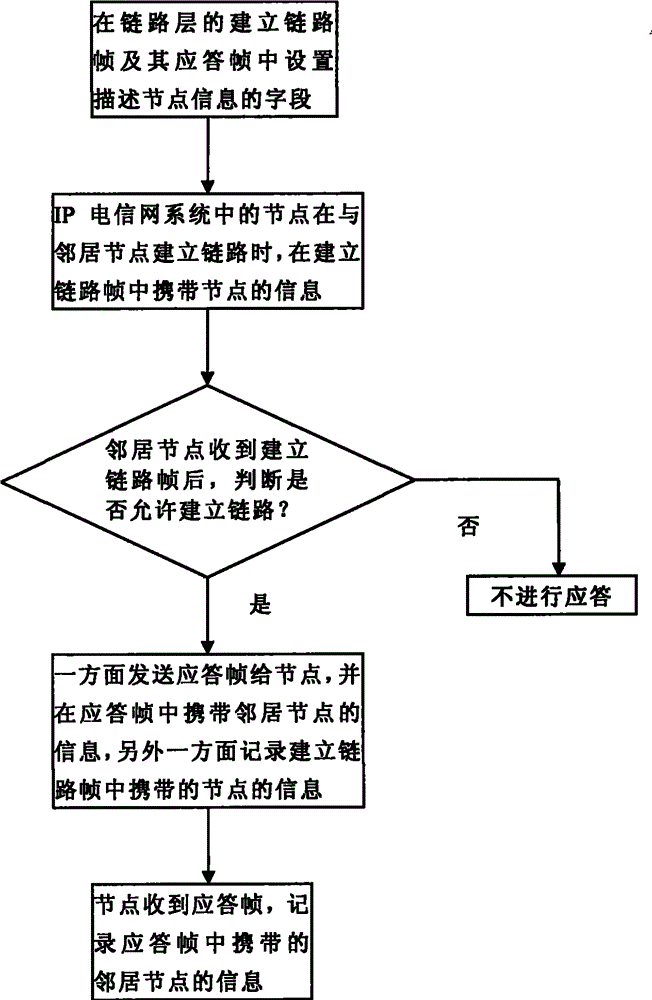
Method for acquiring information of neighbor nodes in IP telecommunication network system
InactiveCN101729515BAutomatic discoveryEfficient discoveryData switching networksTelecommunications networkNetwork topology
The invention discloses a method for acquiring information of neighbor nodes in an IP telecommunication network system, which comprises the following steps: (1) setting fields describing node information in an establishment link frame and a response frame thereof of a link layer; (2) leading the establishment link frame to carry the node information when a link between nodes in the IP telecommunication network system and the neighbor nodes is established; (3) judging whether the link is allowed to be established when the neighbor nodes receive the establishment link frame; sending the response frame to the nodes and carrying the information of the neighbor nodes in the response frame on one hand, and recording the node information carried in the establishment link frame on the other hand when the establishment is allowed to carry out; and not responding when the establishment is not allowed to carry out; and (4) recording the information of the neighbor nodes carried in the response frame when the nodes receive the response frame. The utilization of the method can automatically and high-efficiently find the neighbor relationship of the nodes, thereby automatically providing a technical basis for automatically acquiring a network topology for the network system.
Owner:蒋林涛 +4
A kind of dynamic acquisition method and acquisition system of subway passenger demand
ActiveCN110347828BImprove the efficiency of demand acquisitionReduce subjectivityWeb data indexingCharacter and pattern recognitionUser needsSupport vector machine classifier
Owner:SOUTHWEST JIAOTONG UNIV
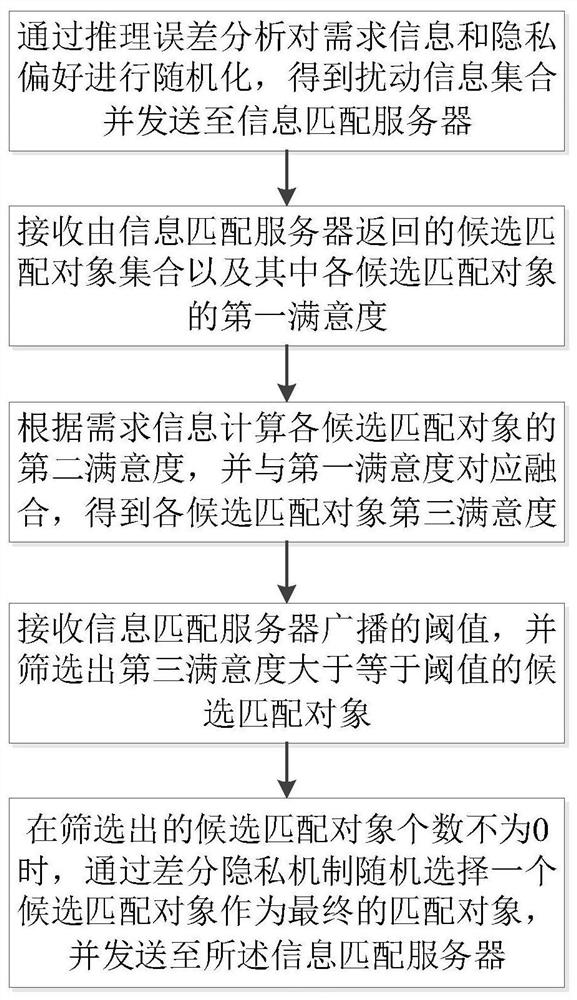
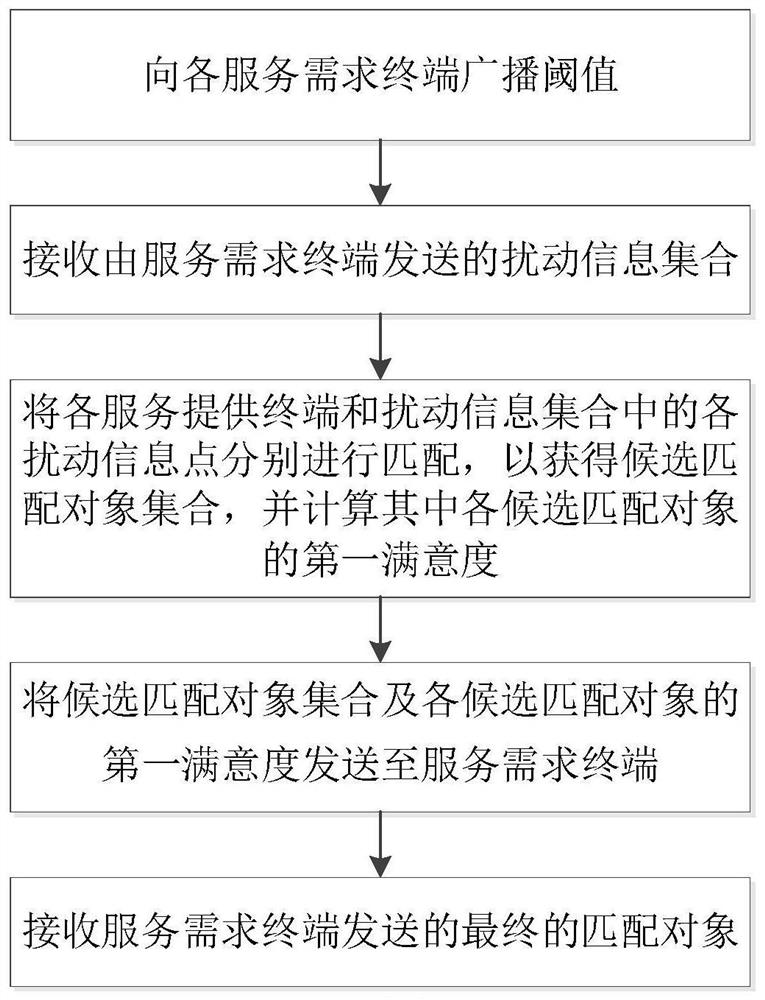
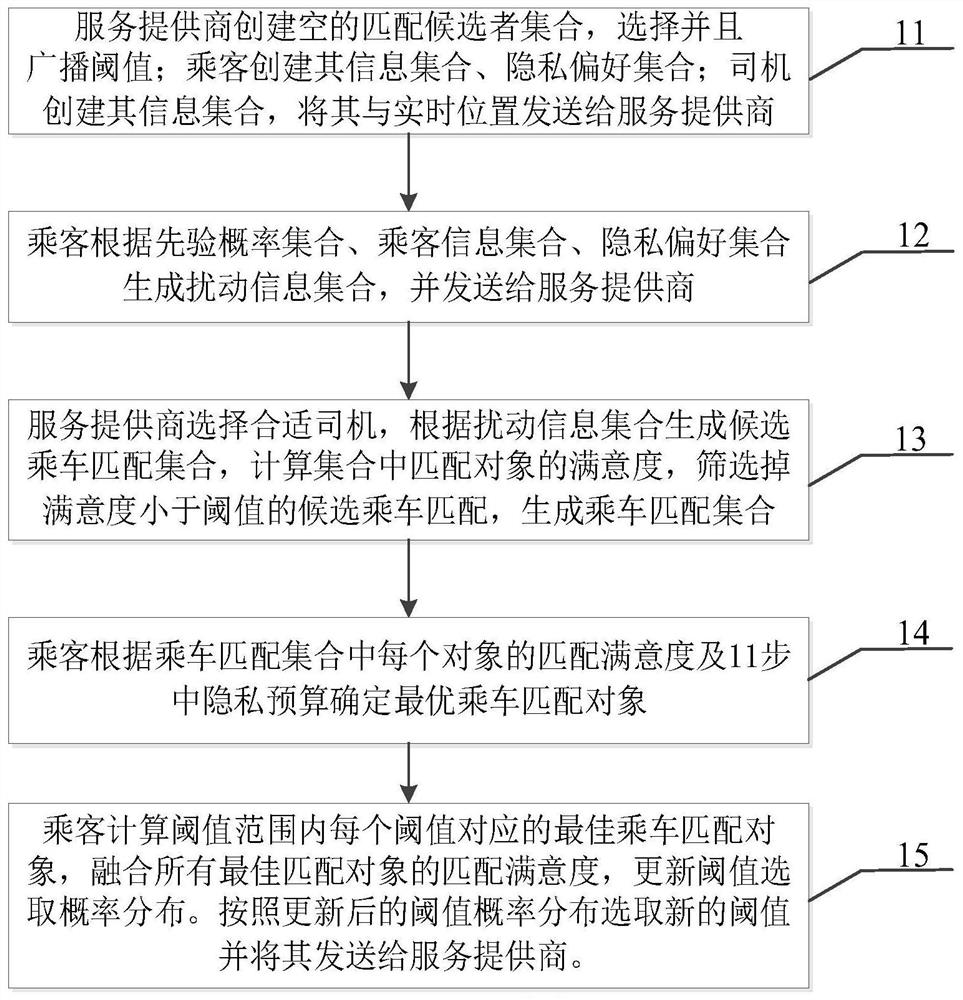
Anti-inference attack privacy protection information matching method and device
PendingCN114021120AEffectively resist inference attacksResistance to inference attacksDigital data protectionPlatform integrity maintainancePersonalizationAttack
The invention discloses an anti-reasoning attack privacy protection information matching method and device, and the method comprises the steps: carrying out the randomization of demand information and privacy preference through reasoning error analysis, obtaining a disturbance information set, and transmitting the disturbance information set to an information matching server; receiving a candidate matching object set returned by the information matching server and a first satisfaction degree of each candidate matching object in the candidate matching object set; calculating a second satisfaction degree of each candidate matching object according to the demand information, and correspondingly fusing the second satisfaction degree with the first satisfaction degree into a third satisfaction degree; receiving a threshold value broadcasted by the information matching server, and screening out candidate matching objects of which the third satisfaction degree is greater than or equal to the threshold value; and when the screening result is not 0, randomly selecting a candidate matching object as a final matching object through a differential privacy mechanism, and sending the candidate matching object to an information matching server. According to the method and device, reasoning attack can be resisted by fusing reasoning error analysis and differential privacy and combining personalized privacy requirements of the user, and dynamic change of the requirements of the user can be adapted.
Owner:HUAZHONG UNIV OF SCI & TECH
Discovery and classification method of private data in data table
ActiveCN104731976BAutomatic discoveryEfficient discoverySpecial data processing applicationsLicense numberEmail address
An embodiment of the present invention provides a method for discovering and classifying private data in a data table. This method mainly pre-sets the privacy data analysis rules corresponding to each privacy data type; extracts the sampling data in the data table; according to the set privacy data type analysis order and the privacy data analysis rules corresponding to each privacy data type, the According to the analysis results, it is found that the ID number, postal code, business license number, organization code, taxpayer identification number, email address, company name, telephone number, Chinese name in the sampled data There are 10 types of private data including addresses, and the key data in the data table of the enterprise application database can be efficiently found and classified, which can greatly reduce the workload and shorten the working time.
Owner:MASSIVE CLOUD BEIJING DATA TECH
A Visual Target Detection and Labeling Method
ActiveCN104217225BKeep boundariesHigh overlap rateCharacter and pattern recognitionPositive sampleData set
The present invention discloses a visual target detection and labeling method. The method includes: an image inputting step, to input an image to be detected; a candidate region extracting step, to extract a candidate window as the candidate region from the image to be detected using selectively search algorithm; a feature description extracting step, to perform feature description on the candidate region using a pre-trained large-scale convolutional neural network and output the feature description of the candidate region; a visual target predicting step, to predict the candidate region based on the feature description of the candidate region using a pre-trained object detection module, to estimate regions having the visual target; and a position labeling step, to labeling the position of the visual target according to the estimated result. Experiments show that, compared with the mainstream week supervision visual target detection and labeling method, the present invention has a stronger ability to excavate positive samples and a more general application prospect, and is suitable for visual target detection and automatic labeling tasks on the large-scale data set.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com