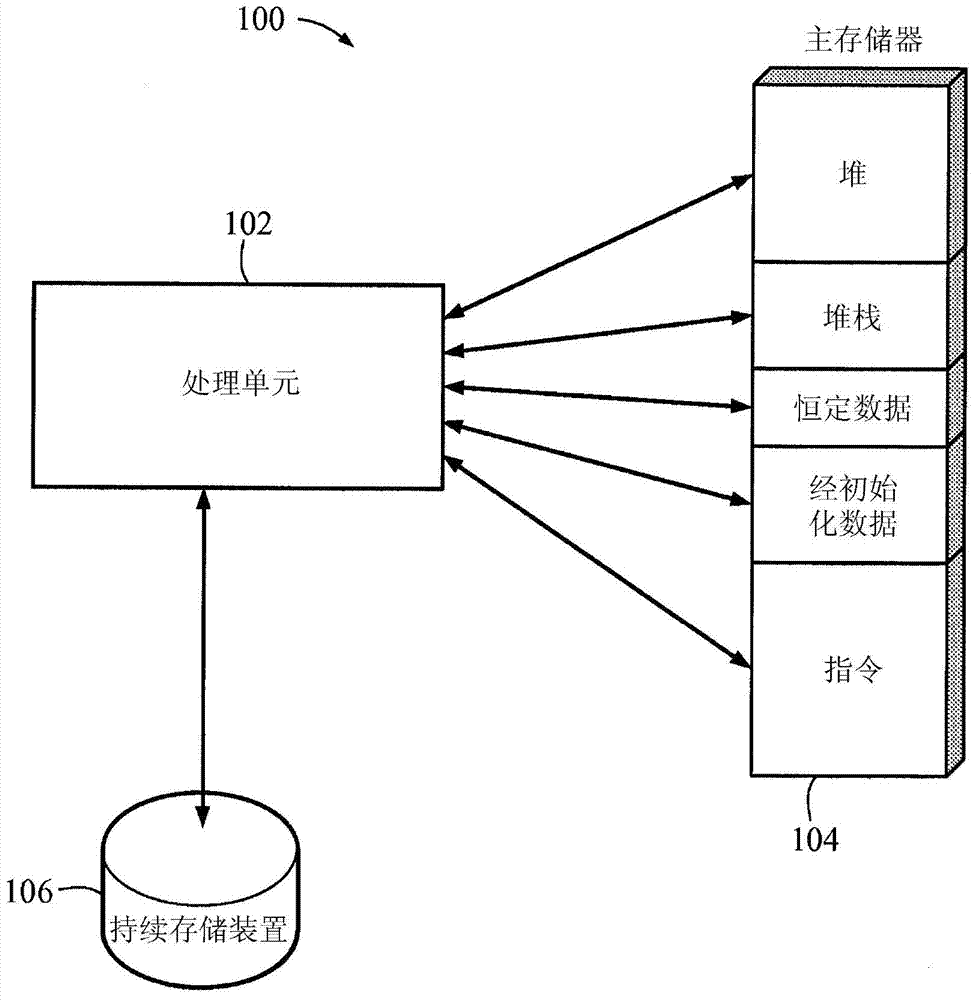
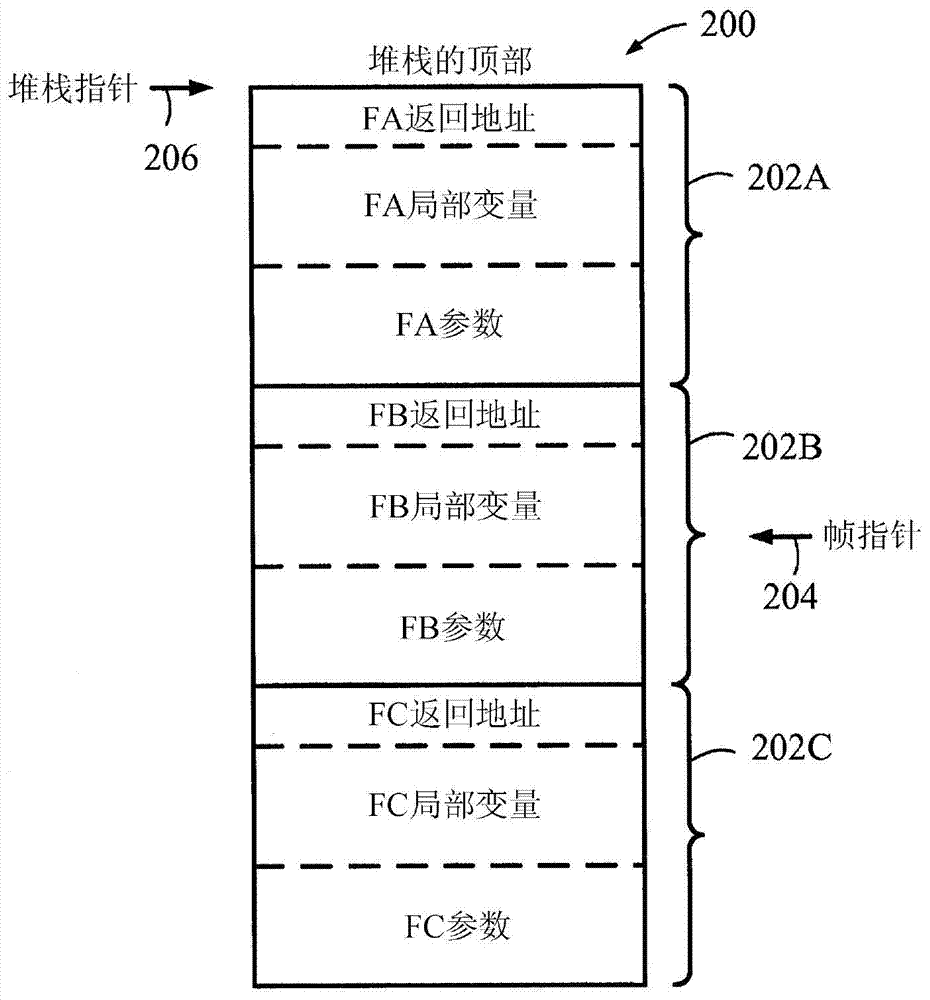
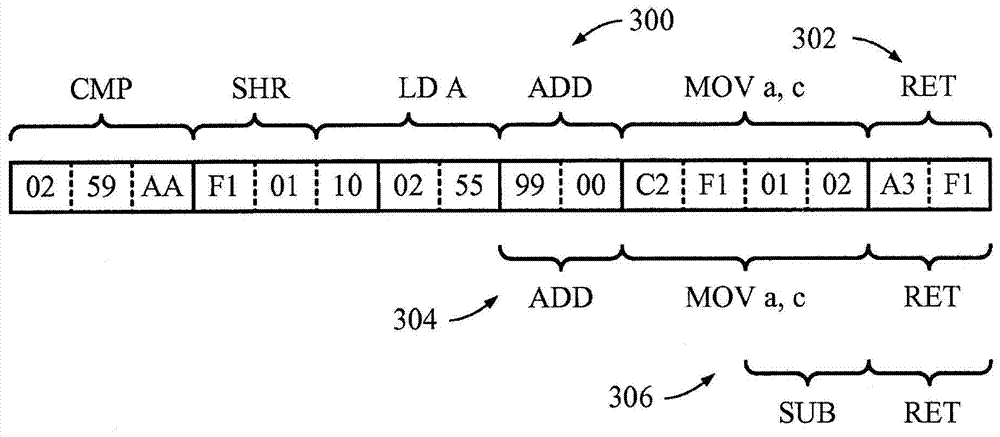
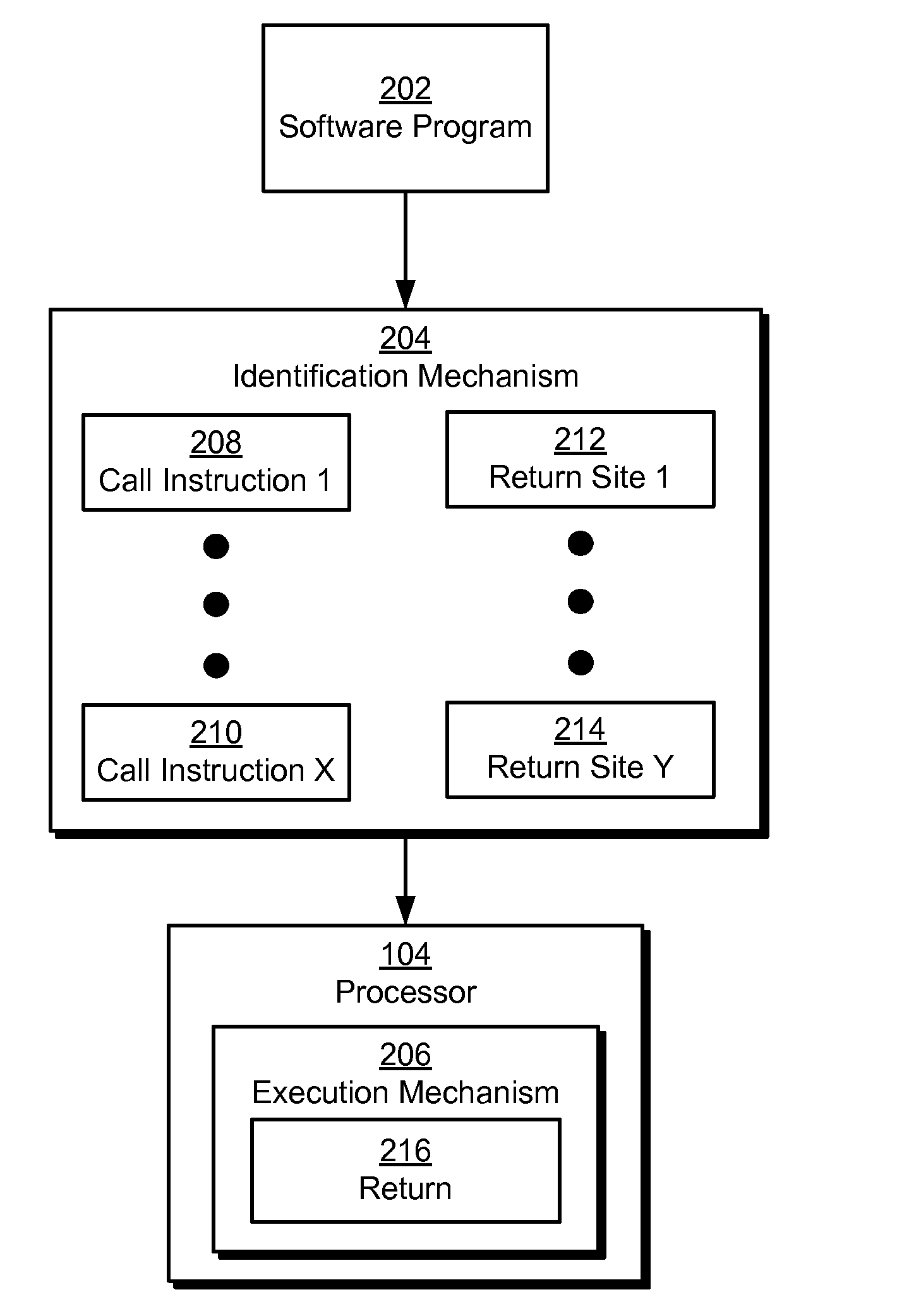
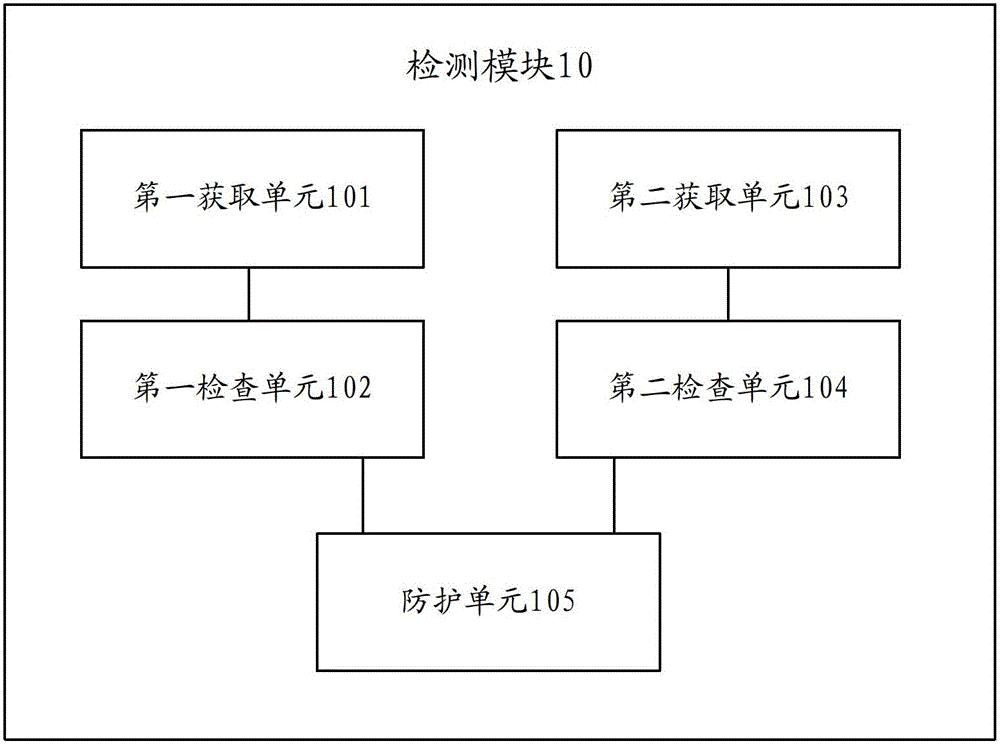
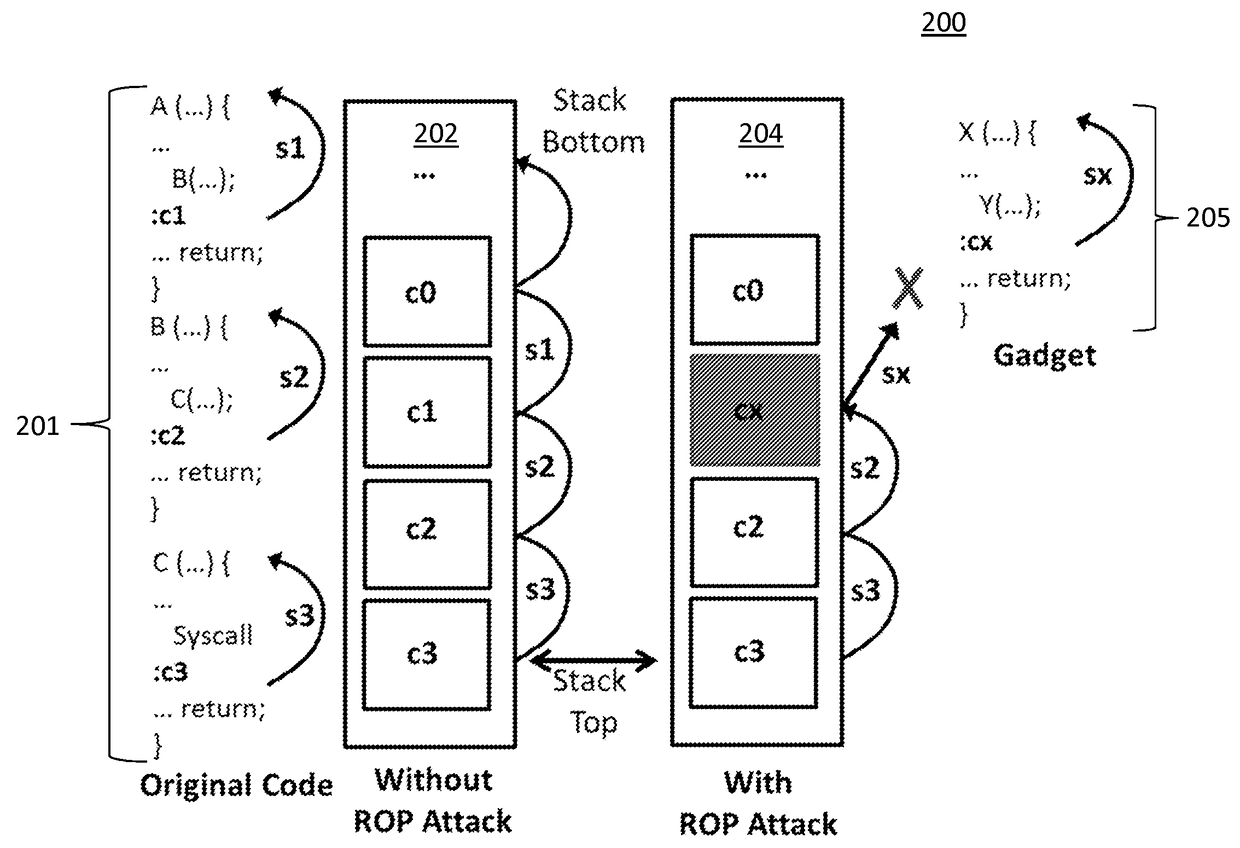
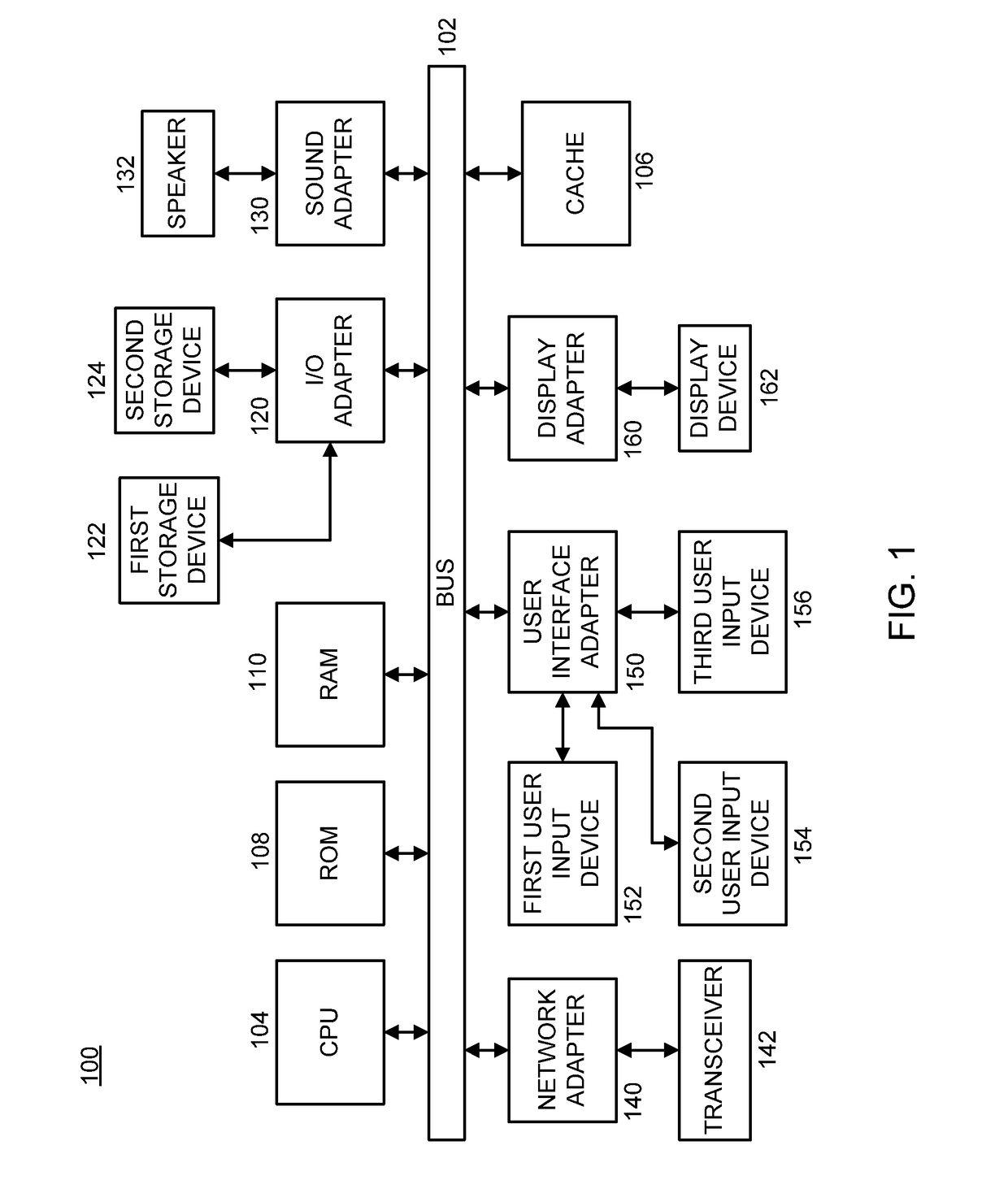
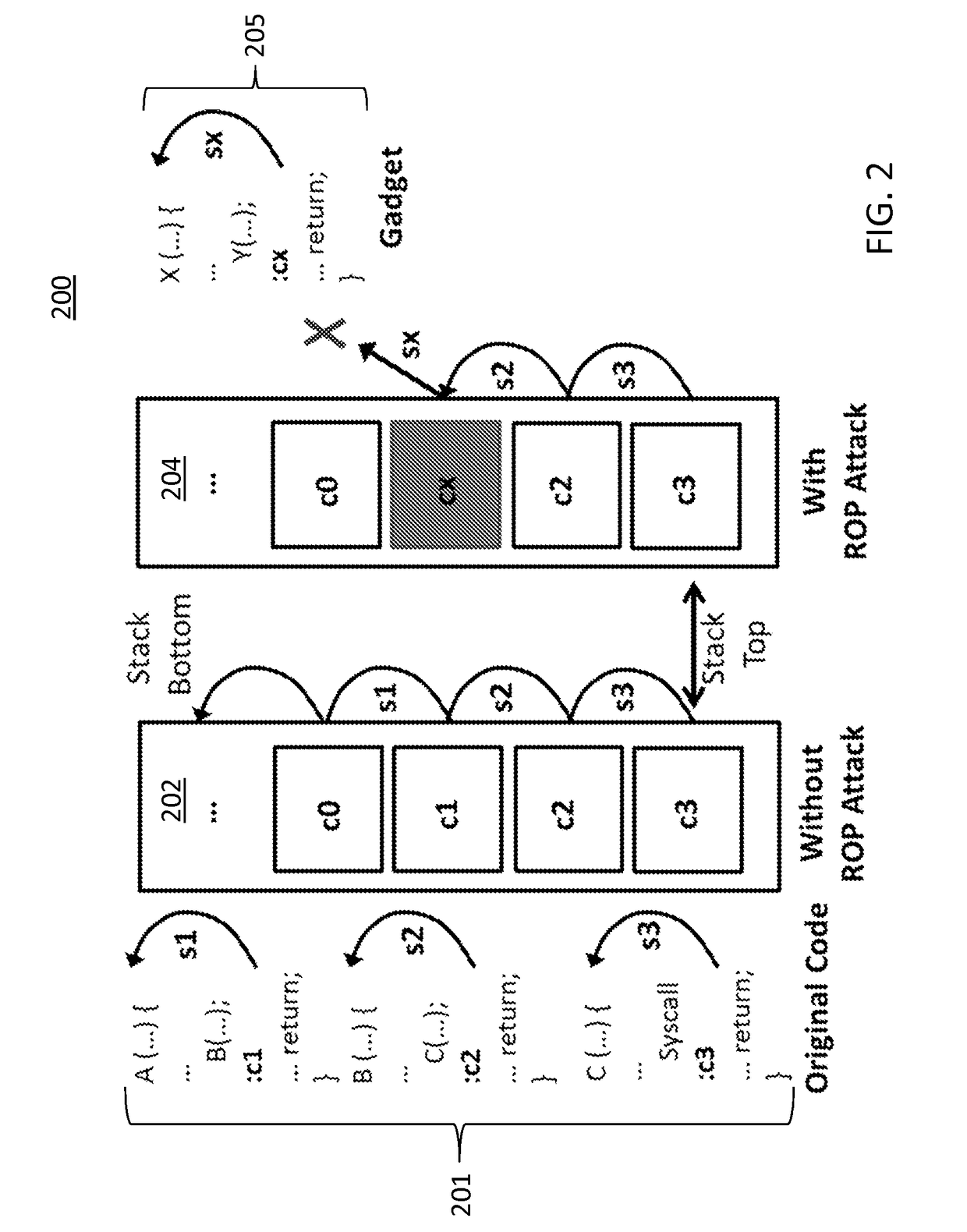
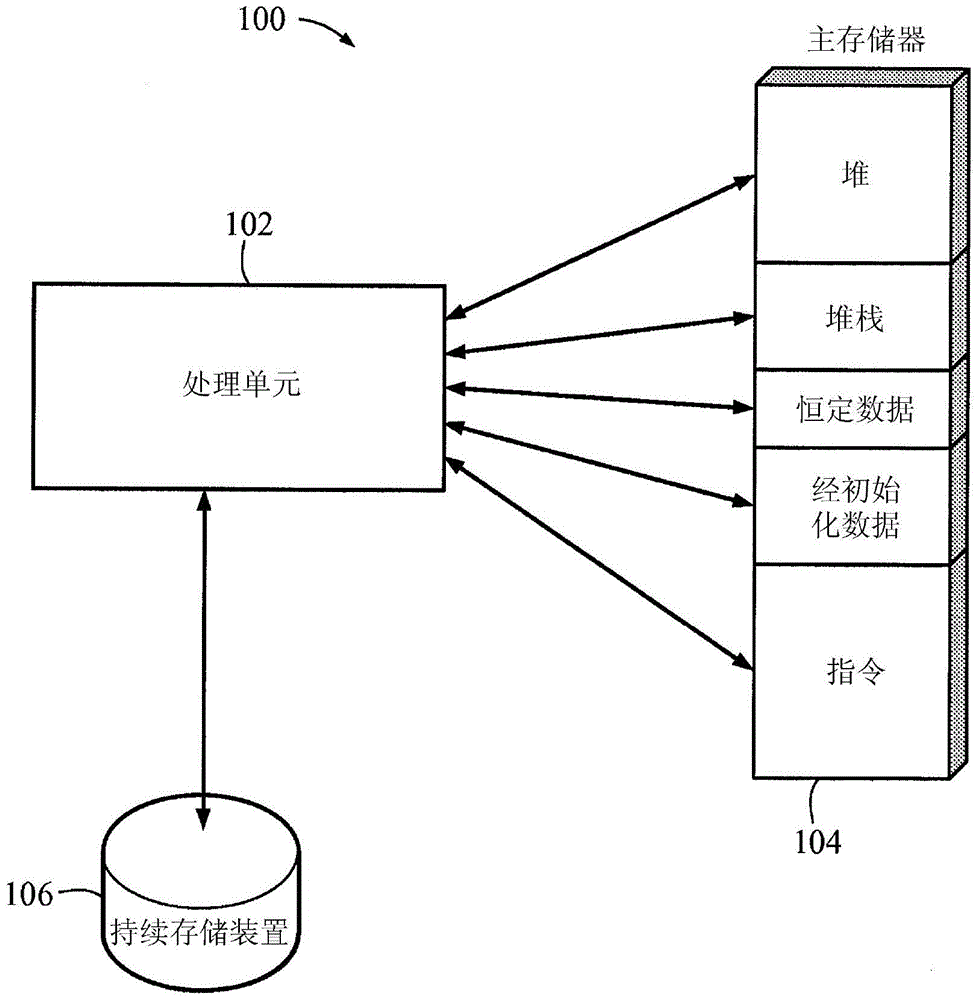
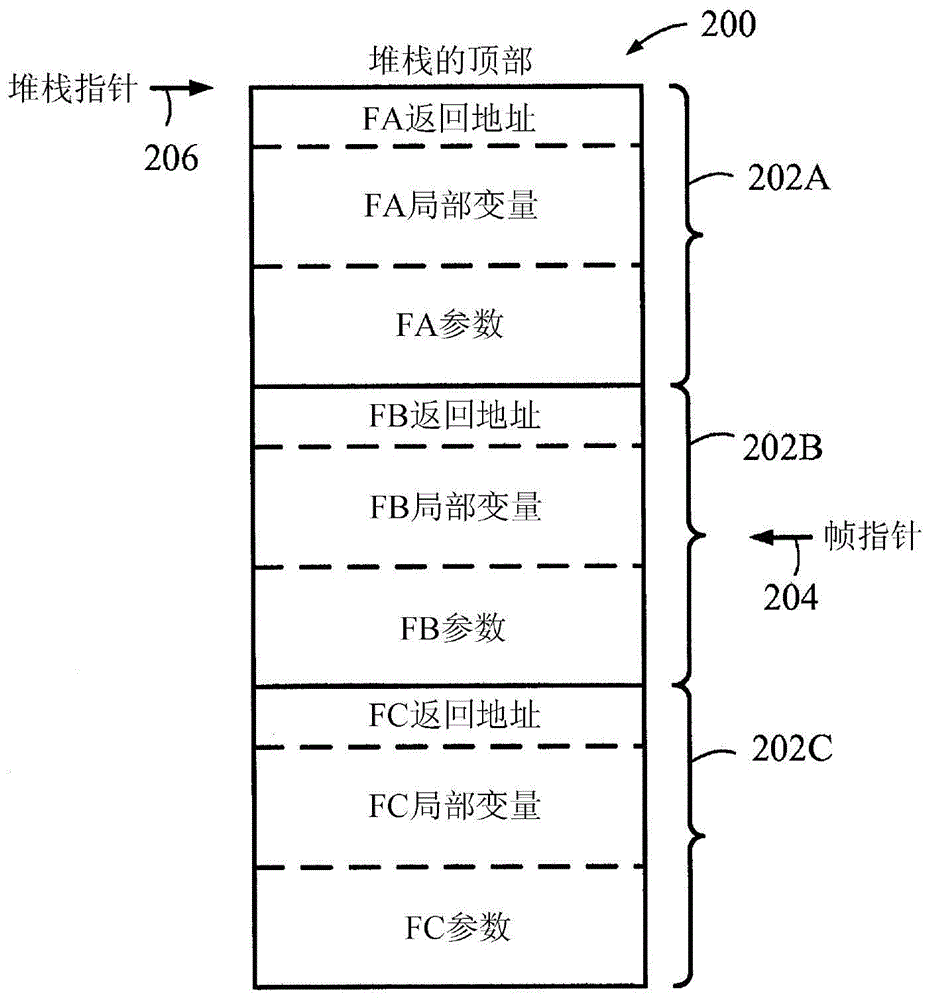
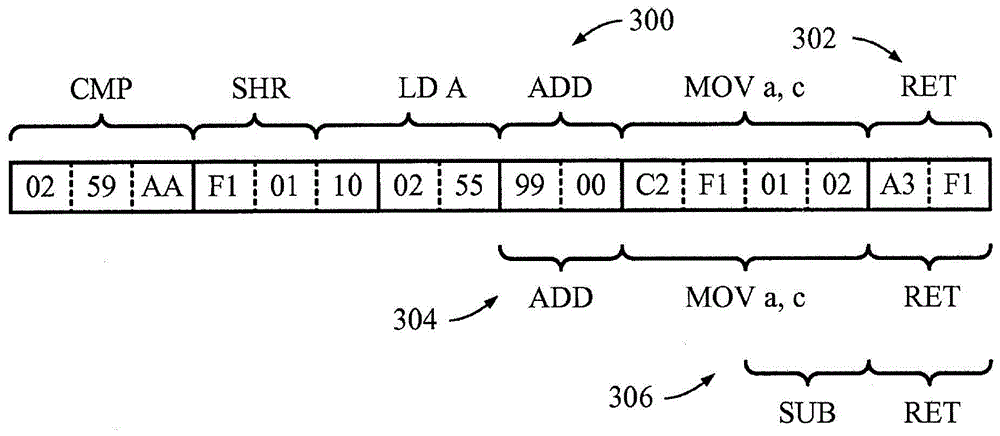
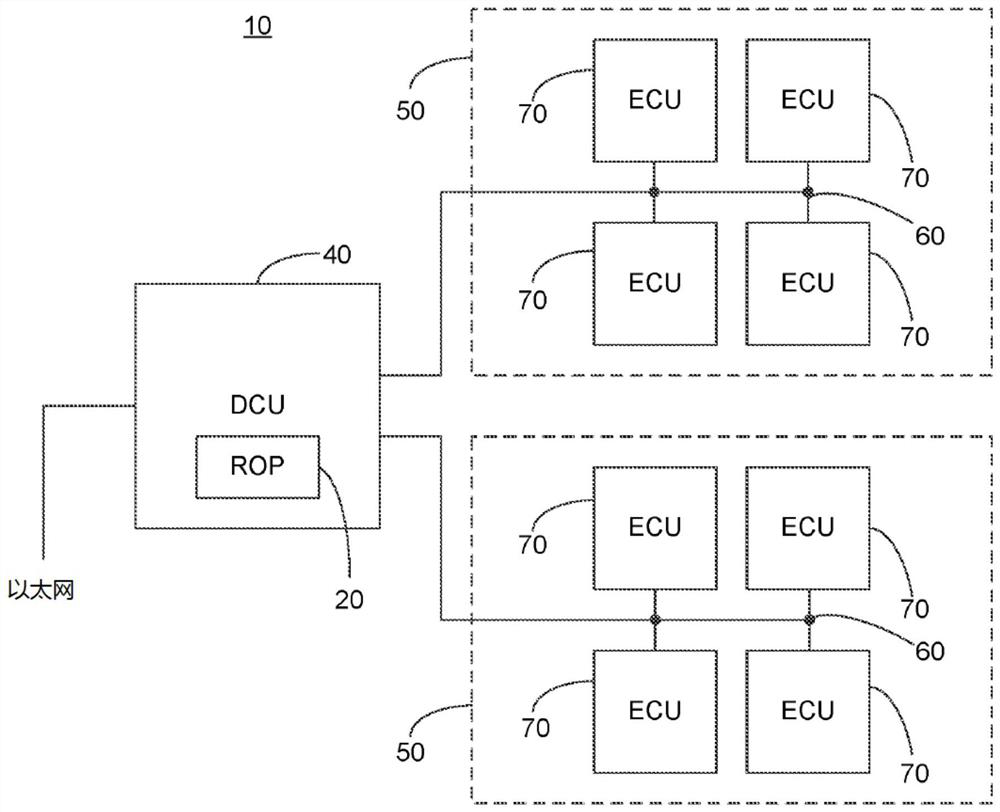
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38 results about "Return-oriented programming" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Return-oriented programming (ROP) is a computer security exploit technique that allows an attacker to execute code in the presence of security defenses such as executable space protection and code signing.
Methods, Devices, And Systems For Detecting Return-Oriented Programming Exploits
InactiveUS20130117843A1Memory architecture accessing/allocationMemory loss protectionCode snippetRemedial action
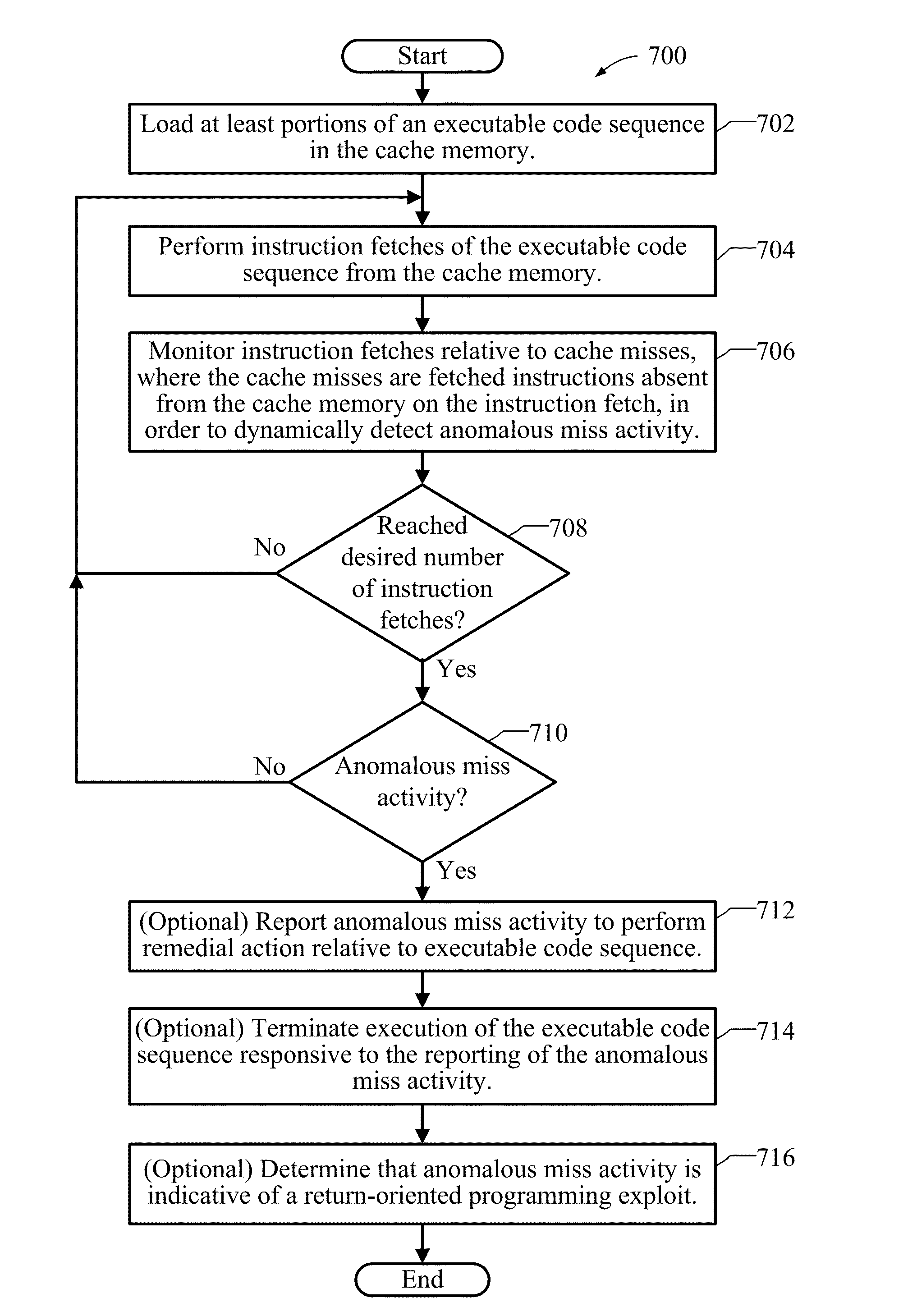
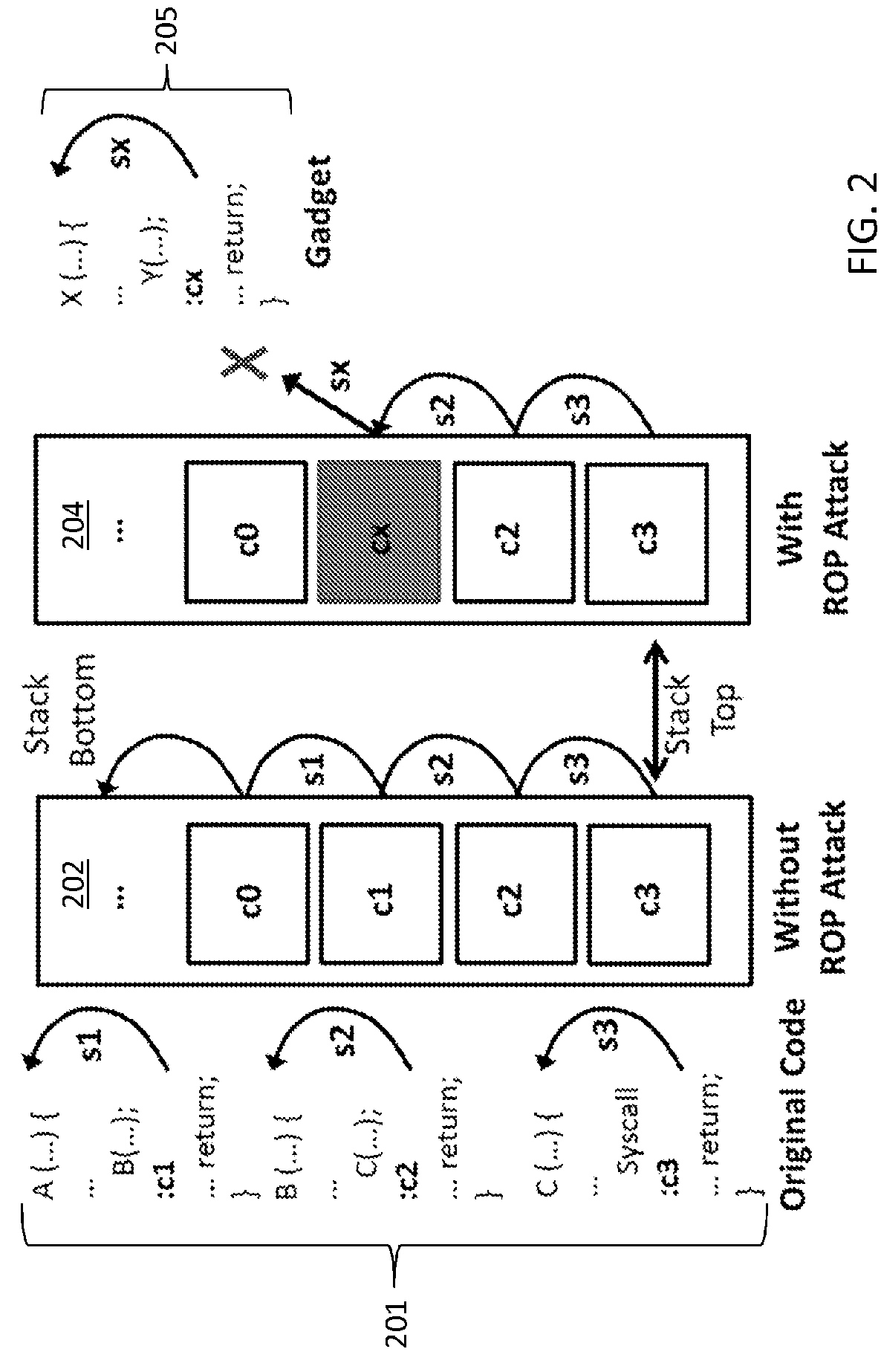
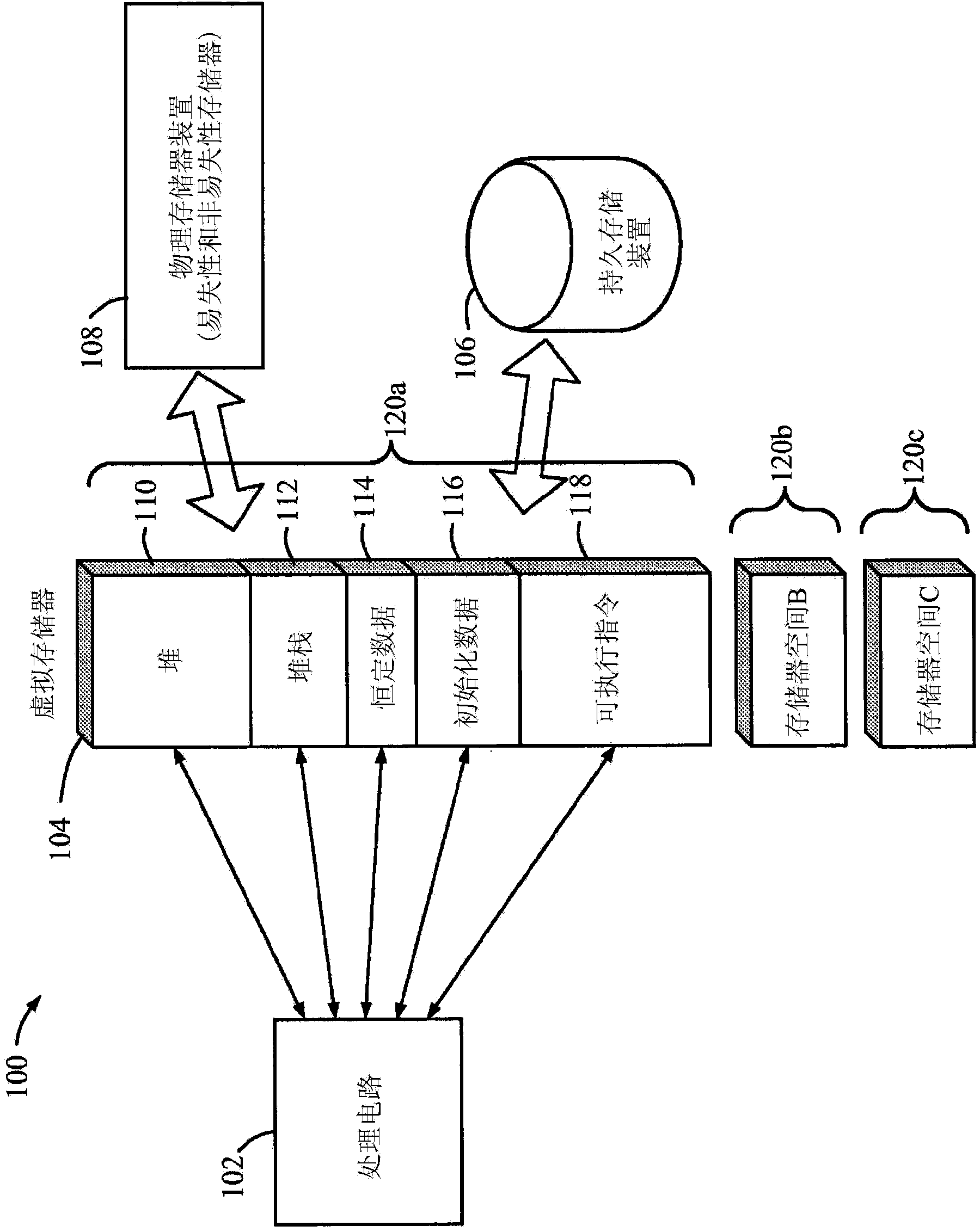
Methods, devices, and systems for detecting return-oriented programming (ROP) exploits are disclosed. A system includes a processor, a main memory, and a cache memory. A cache monitor develops an instruction loading profile by monitoring accesses to cached instructions found in the cache memory and misses to instructions not currently in the cache memory. A remedial action unit terminates execution of one or more of the valid code sequences if the instruction loading profile is indicative of execution of an ROP exploit involving one or more valid code sequences. The instruction loading profile may be a hit / miss ratio derived from monitoring cache hits relative to cache misses. The ROP exploits may include code snippets that each include an executable instruction and a return instruction from valid code sequences.
Owner:QUALCOMM INC
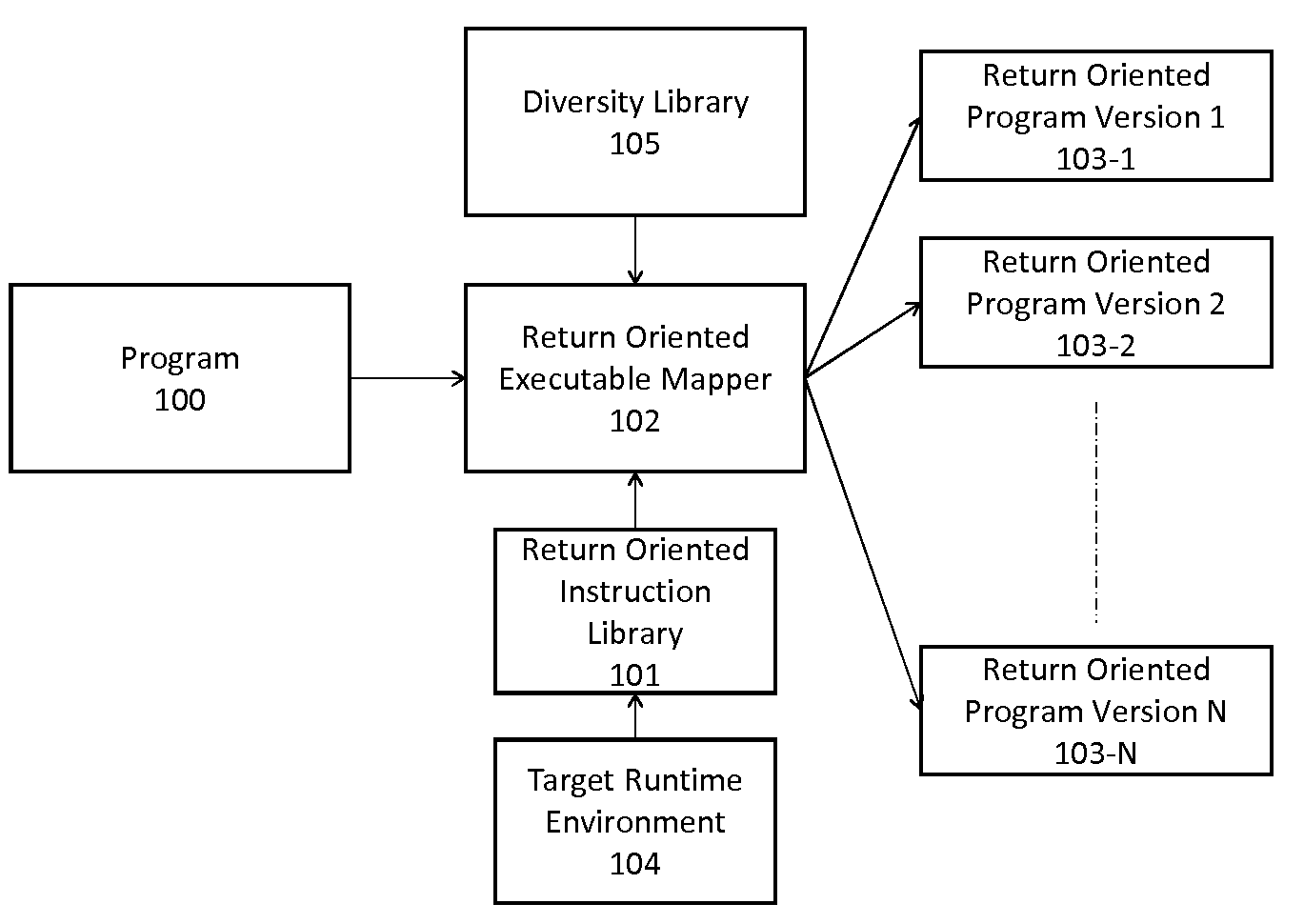
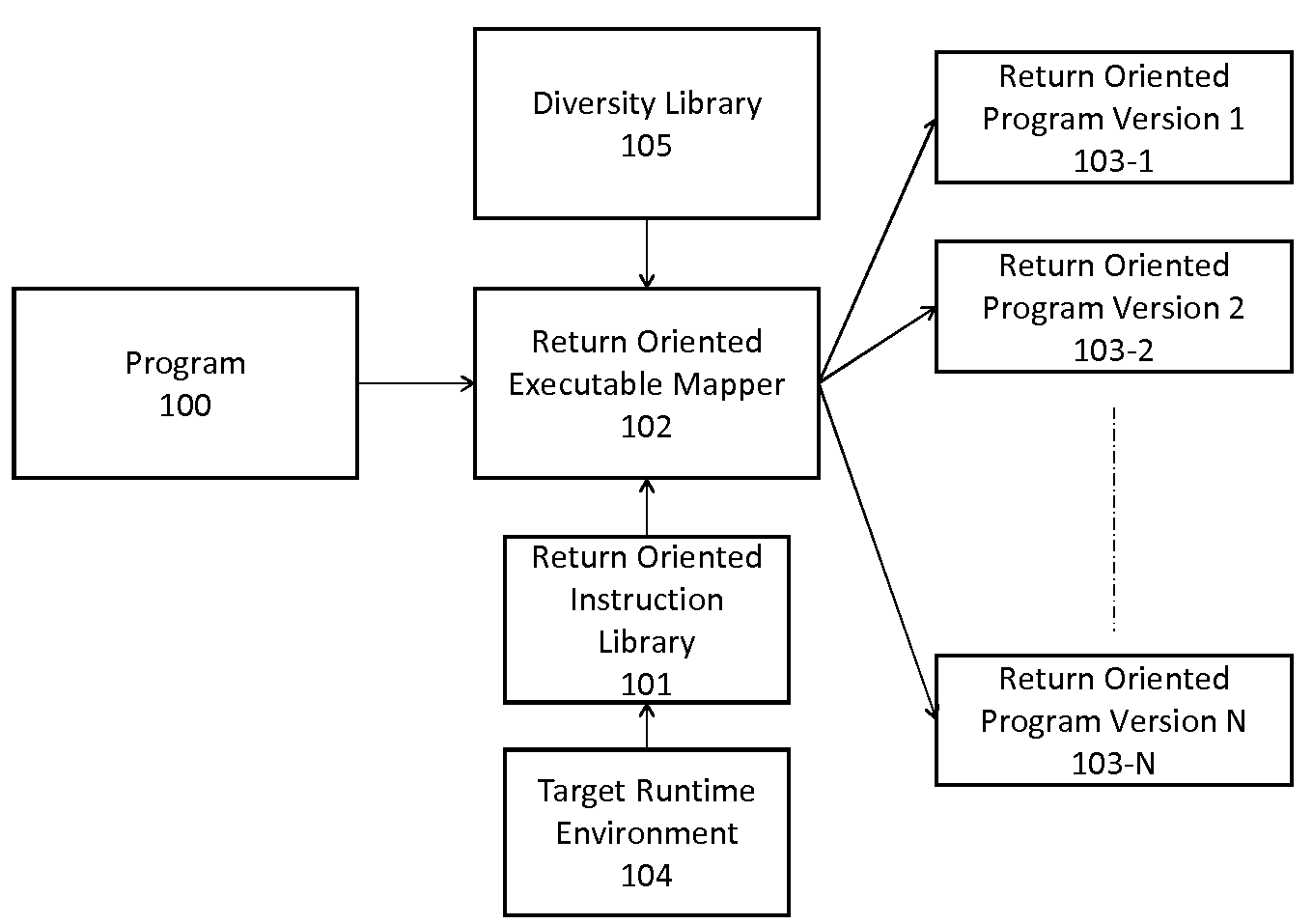
Automated Diversity Using Return Oriented Programming
InactiveUS20120030758A1Avoid hardIncrease the number ofMemory loss protectionError detection/correctionReturn-oriented programmingExecutable
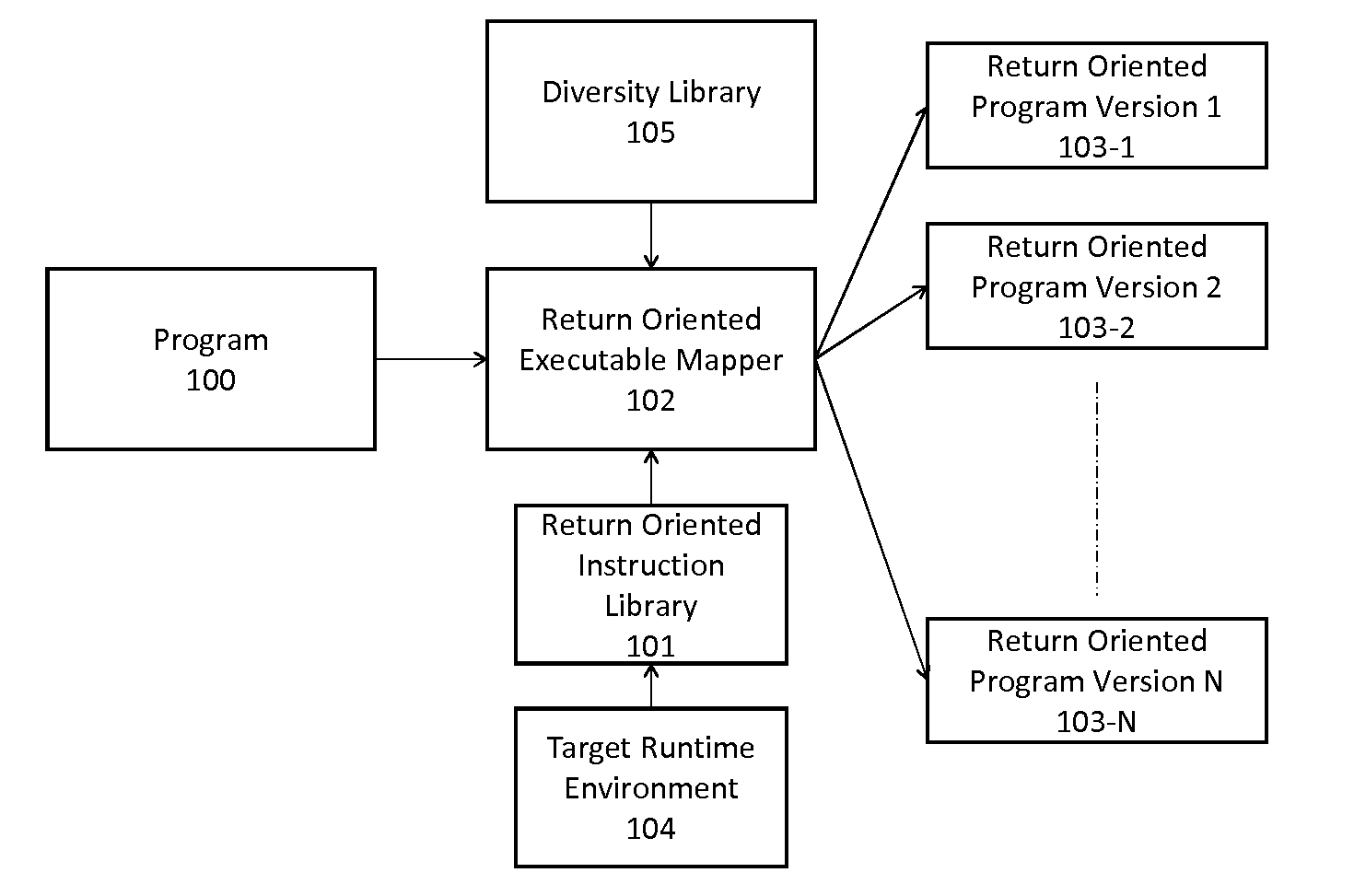
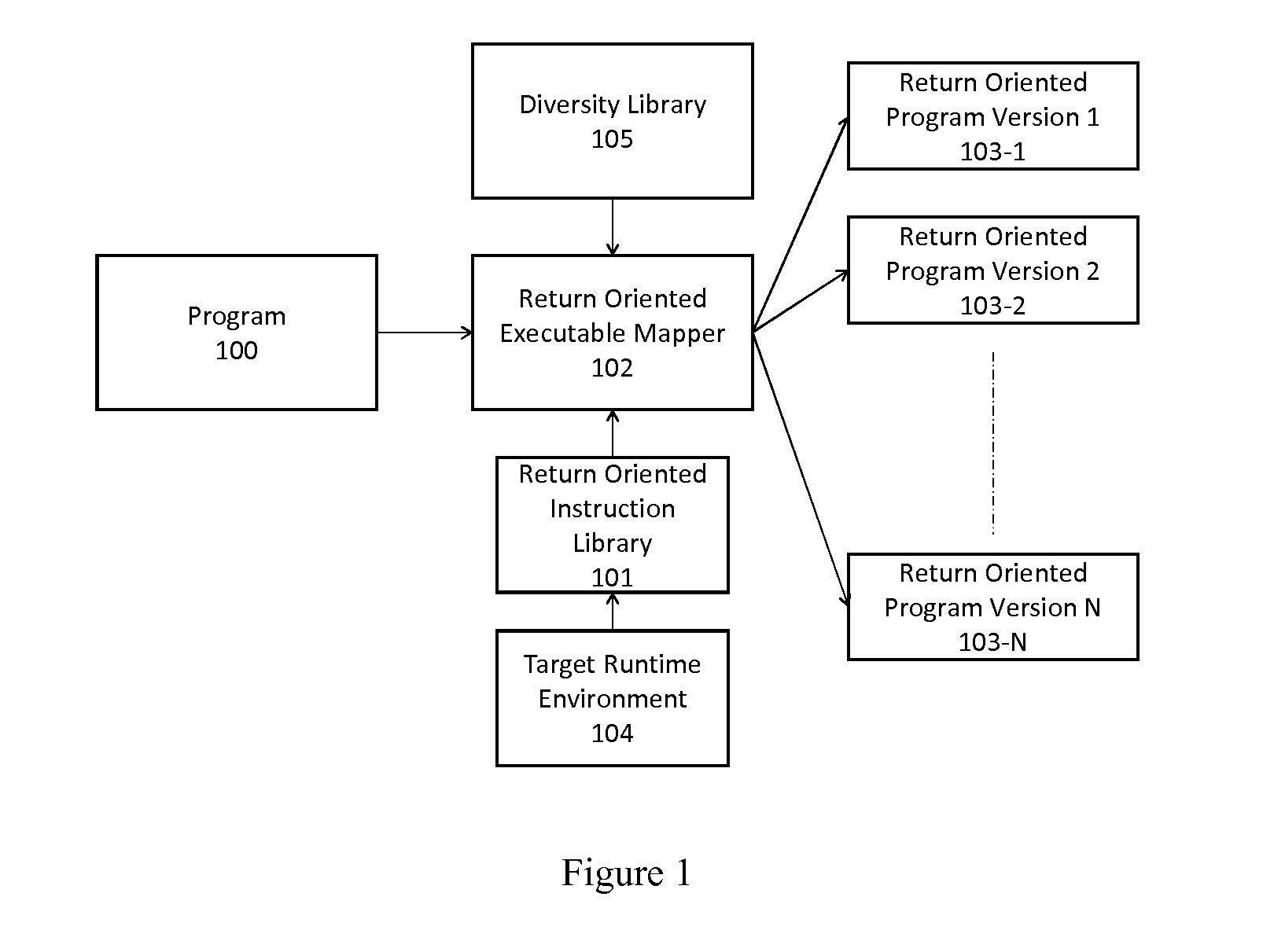
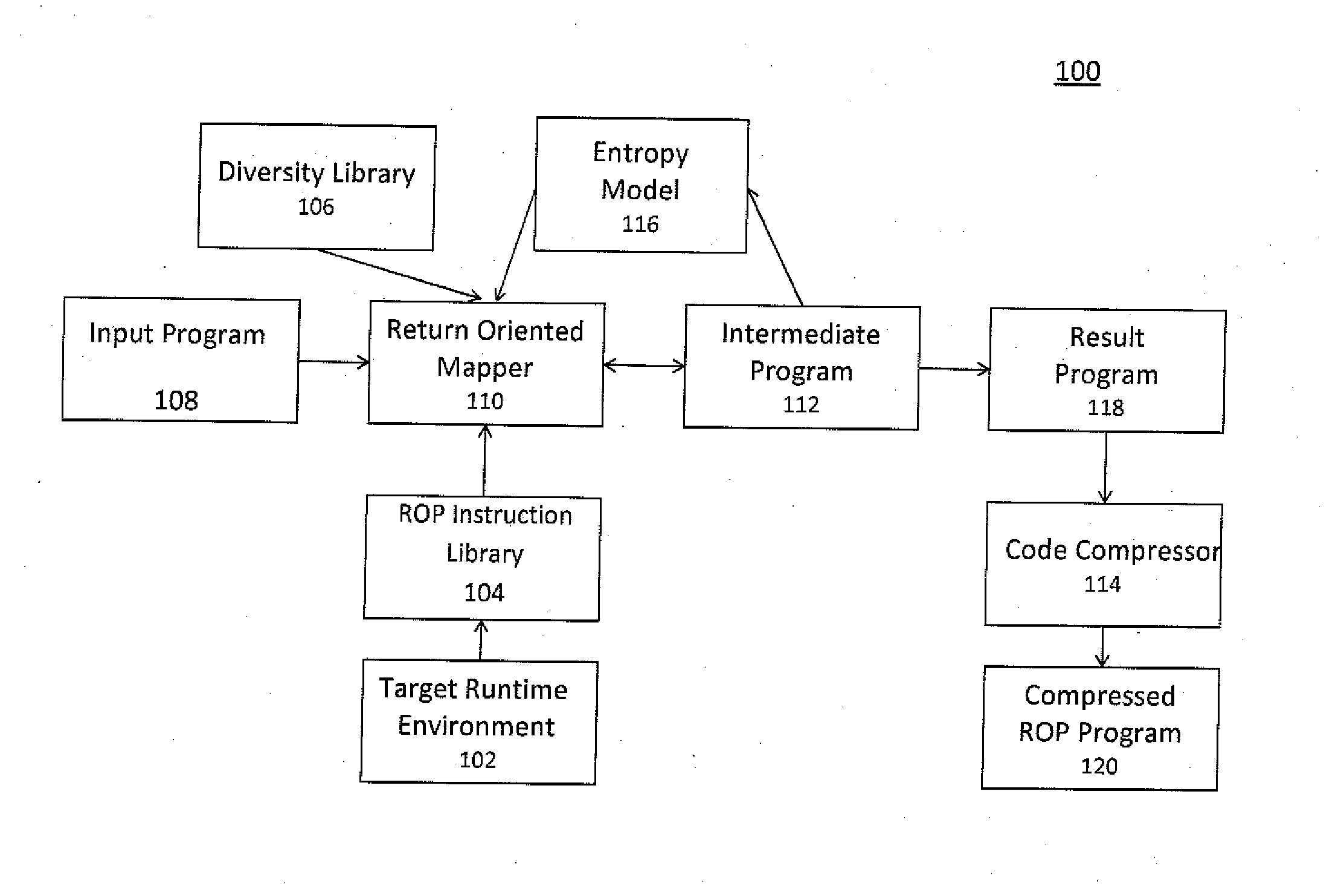
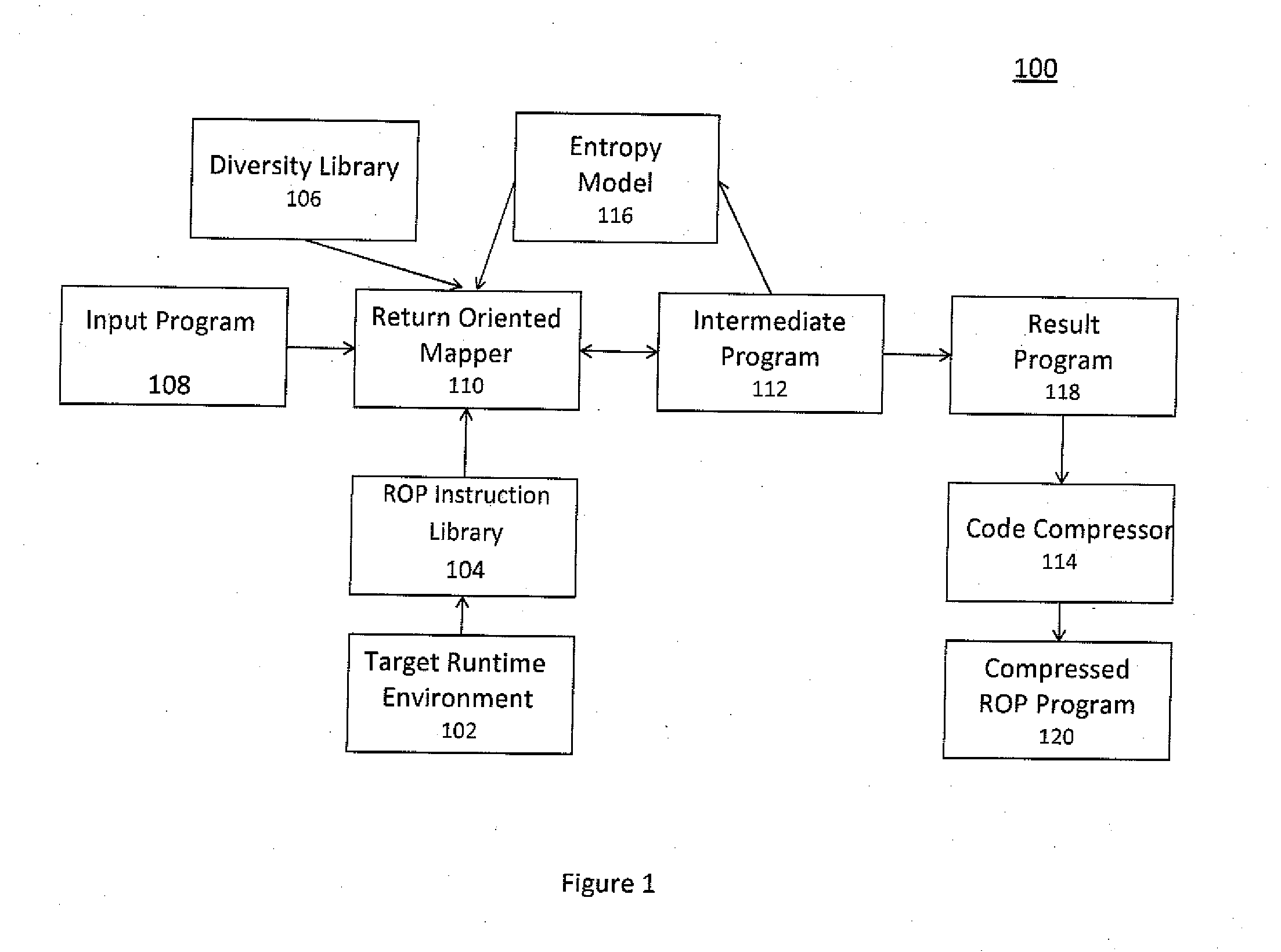
A method of automatically creating functionally and structurally diverse equivalent copies of software executables using return oriented programming for the purpose of passing through a filter and other purposes includes starting with a program and a target runtime environment, creating a return oriented instruction library having a plurality of code fragments which end in a ‘return’ instruction from the program and chaining fragments together to automatically form diverse equivalent copies of software executables using return oriented programming.
Owner:TELCORDIA TECHNOLOGIES INC
Aslr map obfuscation
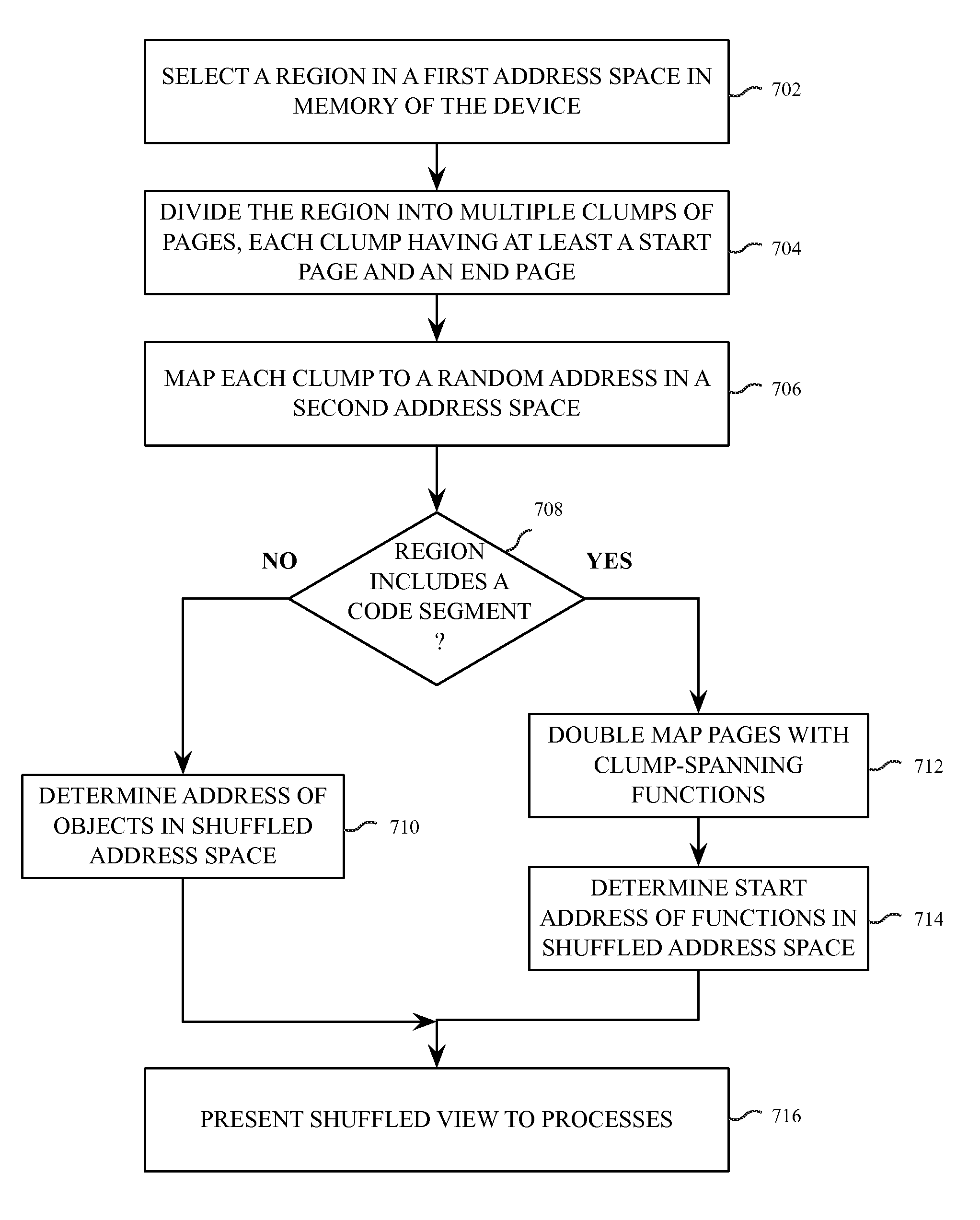
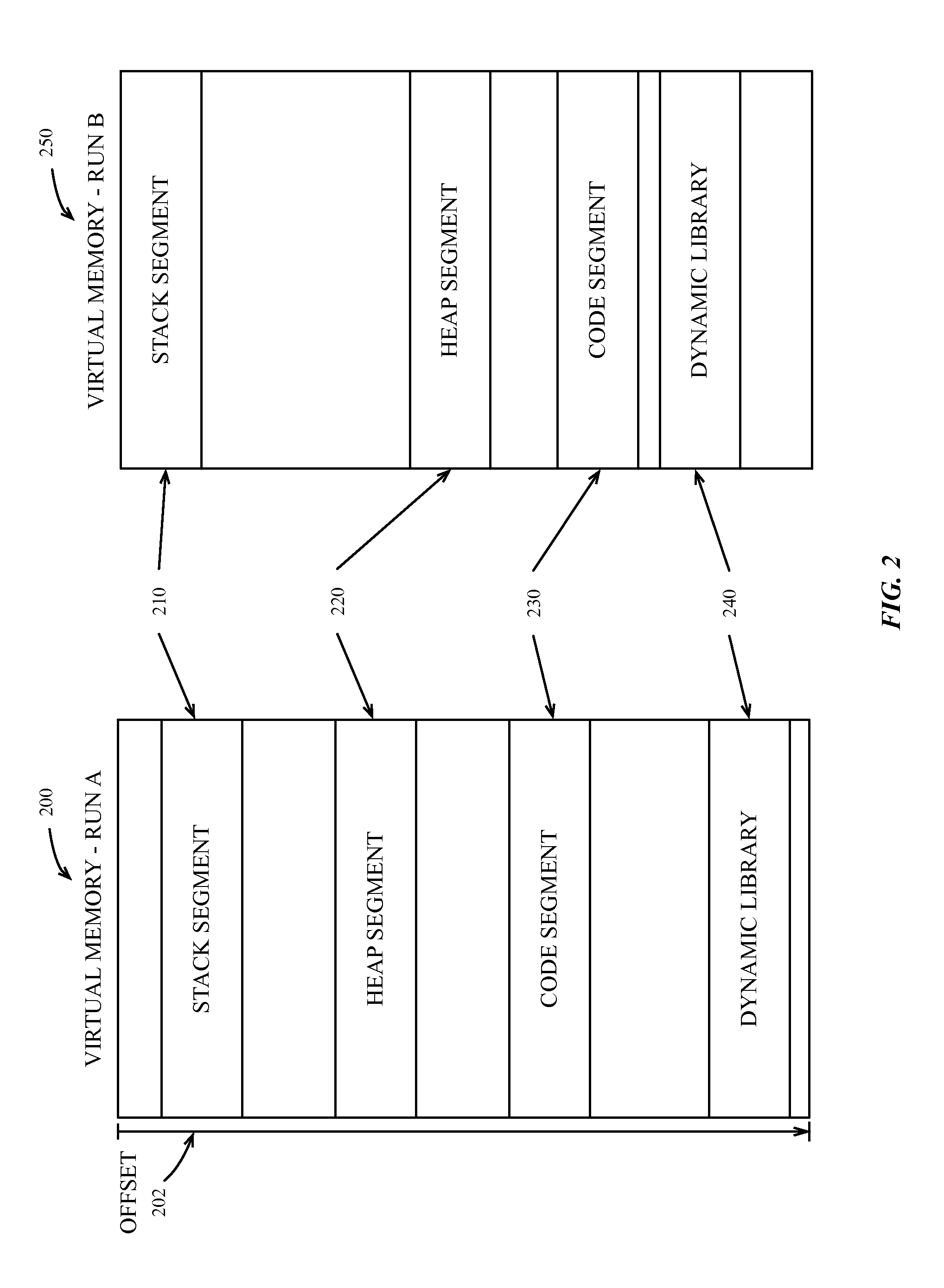
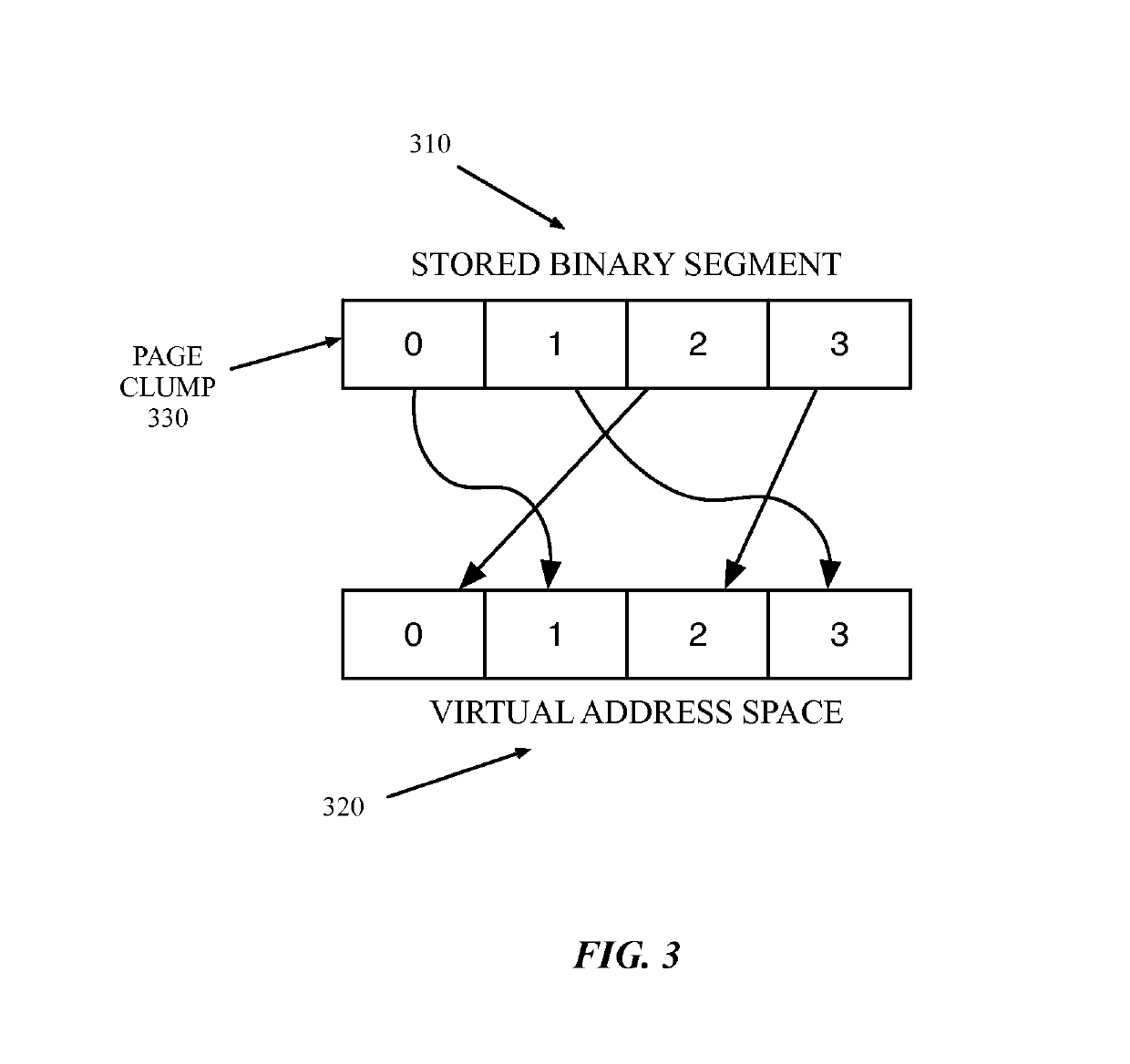
A data processing system can use a method of fine-grained address space layout randomization to mitigate the system's vulnerability to return oriented programming security exploits. The randomization can occur at the sub-segment level by randomizing clumps of virtual memory pages. The randomized virtual memory can be presented to processes executing on the system. The mapping between memory spaces can be obfuscated using several obfuscation techniques to prevent the reverse engineering of the shuffled virtual memory mapping.
Owner:APPLE INC
Fine-grained address space layout randomization
ActiveUS20160092675A1Reduce vulnerabilityMemory loss protectionError detection/correctionObfuscationParallel computing
A data processing system can use a method of fine-grained address space layout randomization to mitigate the system's vulnerability to return oriented programming security exploits. The randomization can occur at the sub-segment level by randomizing clumps of virtual memory pages. The randomized virtual memory can be presented to processes executing on the system. The mapping between memory spaces can be obfuscated using several obfuscation techniques to prevent the reverse engineering of the shuffled virtual memory mapping.
Owner:APPLE INC
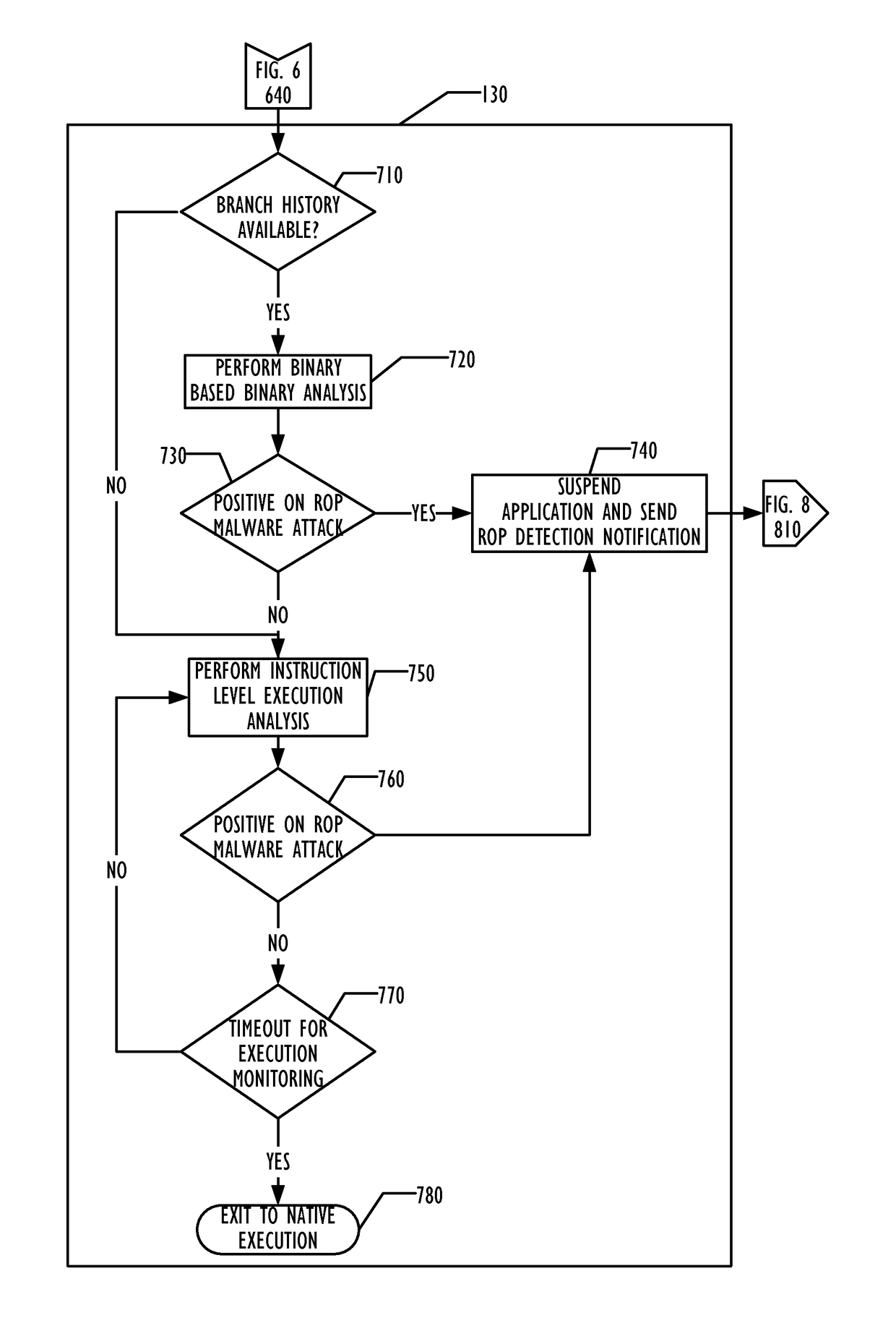
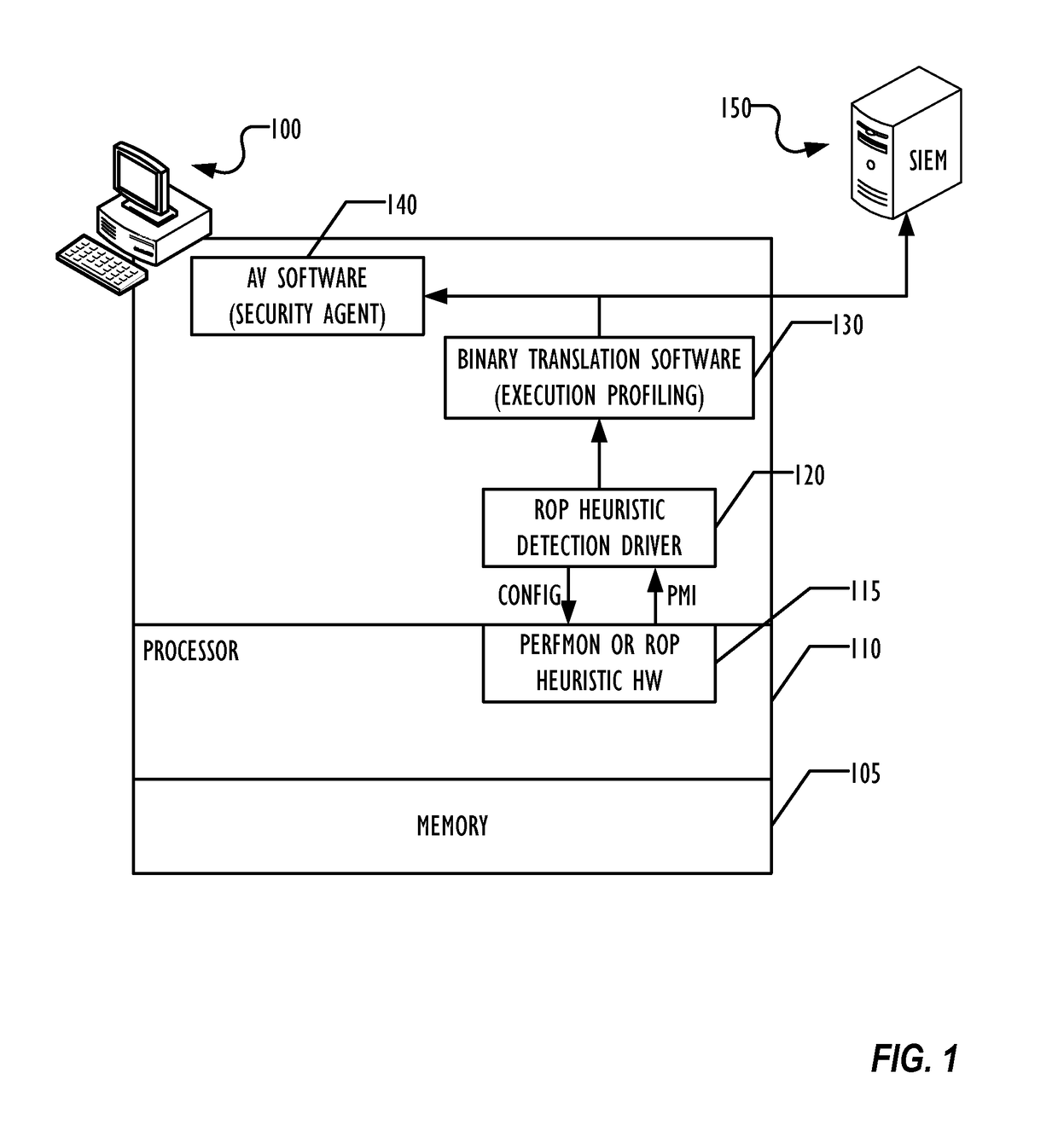
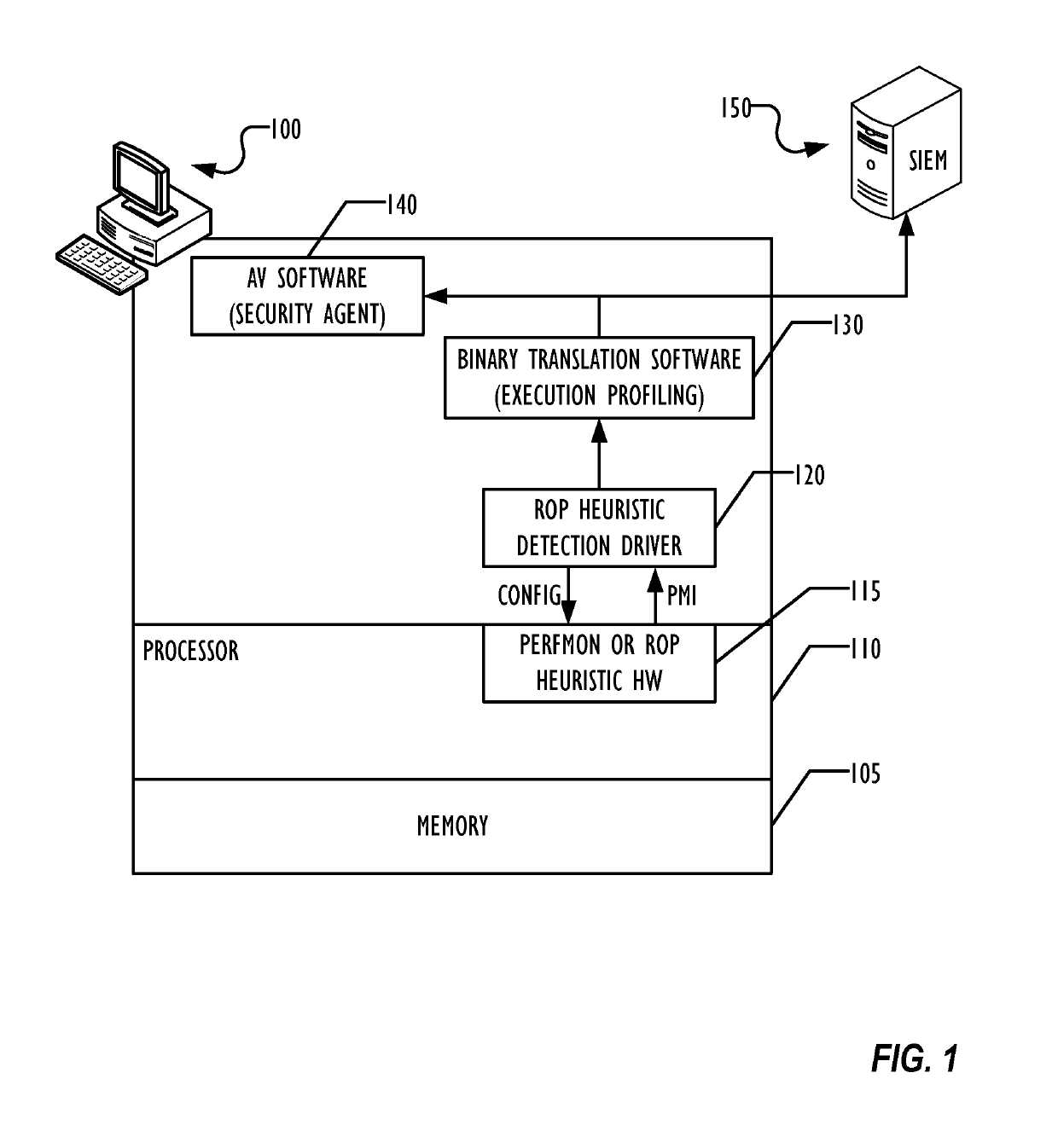
Hardware heuristic-driven binary translation-based execution analysis for return-oriented programming malware detection
A combination of hardware monitoring and binary translation software allow detection of return-oriented programming (ROP) exploits with low overhead and low false positive rates. Embodiments may use various forms of hardware to detect ROP exploits and indicate the presence of an anomaly to a device driver, which may collect data and pass the indication of the anomaly to the binary translation software to instrument the application code and determine whether an ROP exploit has been detected. Upon detection of the ROP exploit, the binary translation software may indicate the ROP exploit to an anti-malware software, which may take further remedial action as desired.
Owner:MCAFEE LLC
Method and device for detecting return-oriented programming attack
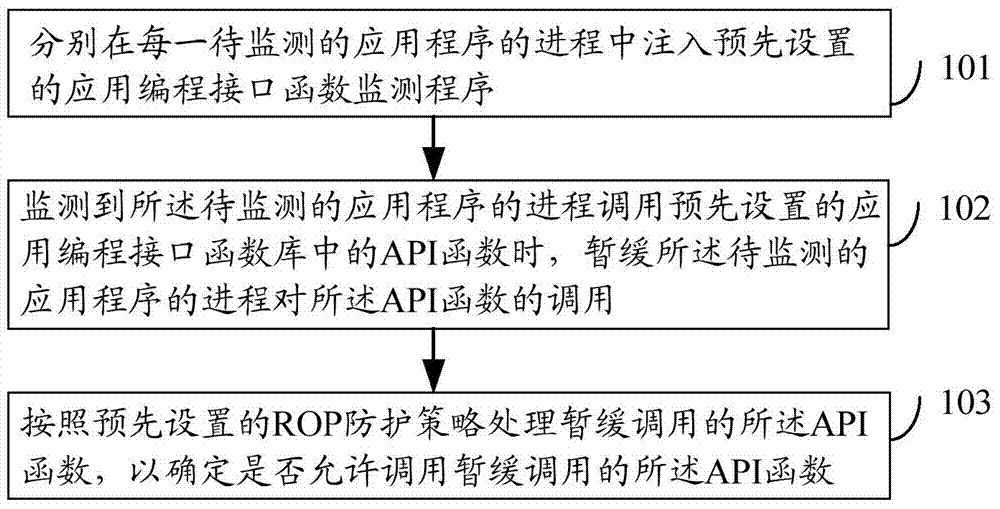
ActiveCN104268471AImprove securityEffective protectionPlatform integrity maintainanceApplication programming interfaceSoftware engineering
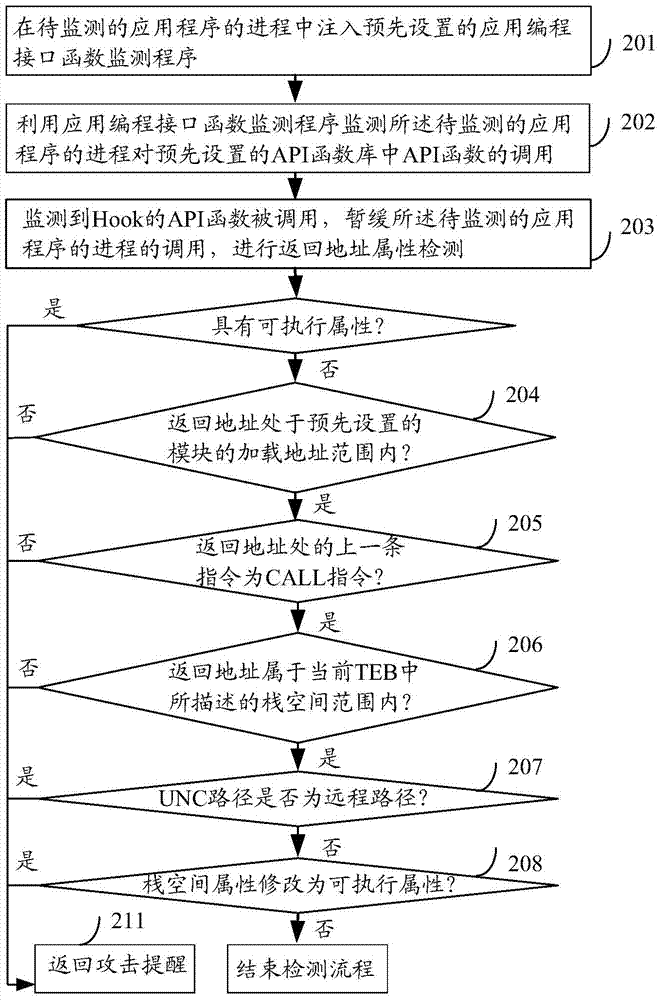
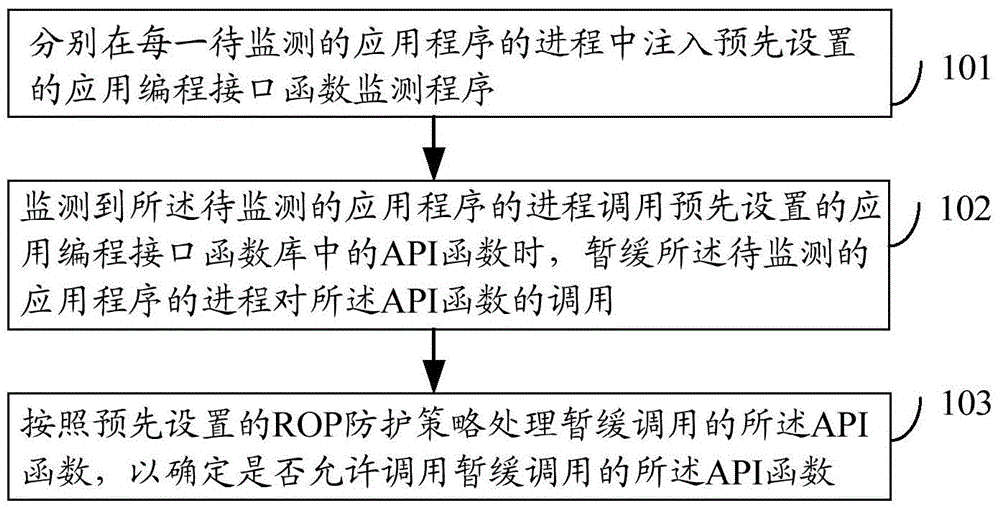
The embodiment of the invention discloses a method and a device for detecting return-oriented programming attack. The method for detecting the return-oriented programming attack comprises injecting preset application programming interface (API) function monitoring programs into the process of every application program to be monitored; when the process of the application program to be monitored calls API functions inside a preset API function library, retarding the process of the application program to be monitored from calling the API functions; processing the calling-retarded API functions according to preset return-oriented programming (ROP) protecting strategies to determine whether calling the calling-retarded API functions is allowed. The method and device for detecting the return-oriented programming attack can effectively detect ROP attack and accordingly improve network security.
Owner:ZHUHAI BAOQU TECH CO LTD
Transparent detection and extraction of return-oriented-programming attacks
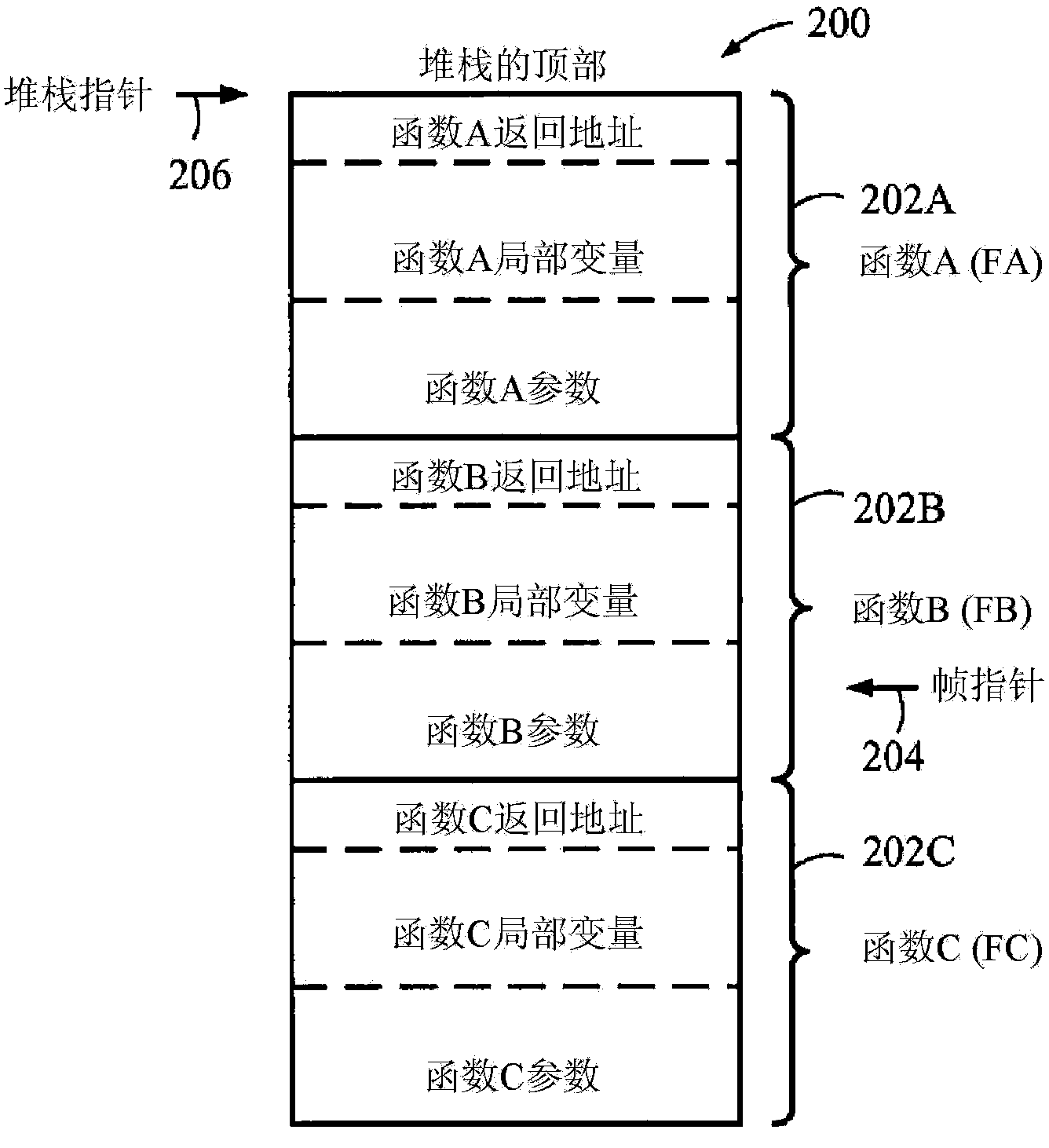
Systems and methods for detection and prevention of Return-Oriented-Programming (ROP) attacks in one or more applications, including an attack detection device and a stack inspection device for performing stack inspection to detect ROP gadgets in a stack. The stack inspection includes stack walking from a stack frame at a top of the stack toward a bottom of the stack to detect one or more failure conditions, determining whether a valid stack frame and return code address is present; and determining a failure condition type if no valid stack frame and return code is present, with Type III failure conditions indicating an ROP attack. The ROP attack is contained using a containment device, and the ROP gadgets detected in the stack during the ROP attack are analyzed using an attack analysis device.
Owner:NEC CORP
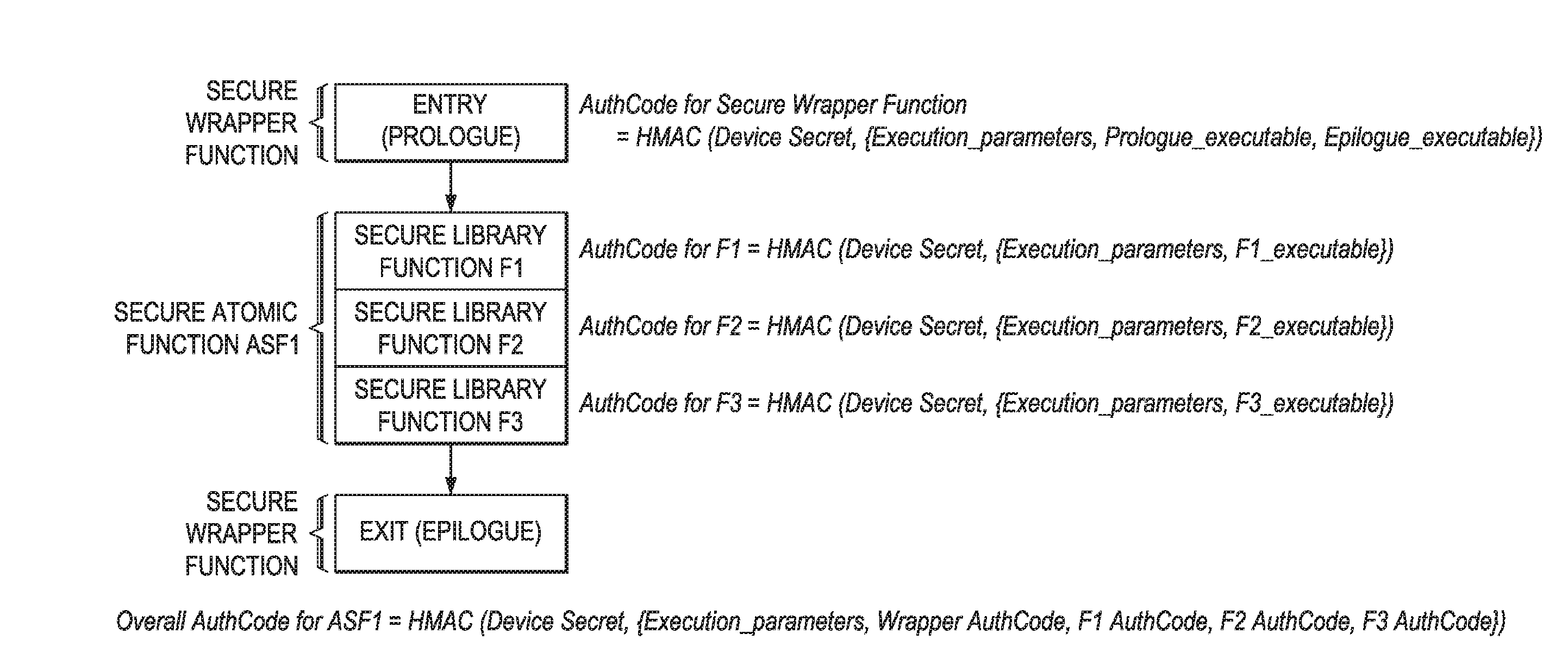
System and method for secure code entry point control
InactiveUS20160188874A1Improve performanceImprove securityMemory loss protectionError detection/correctionProgramming languageCoding block
Owner:RUBICON LABS
Method, device and browser for protecting webpage against malicious attack
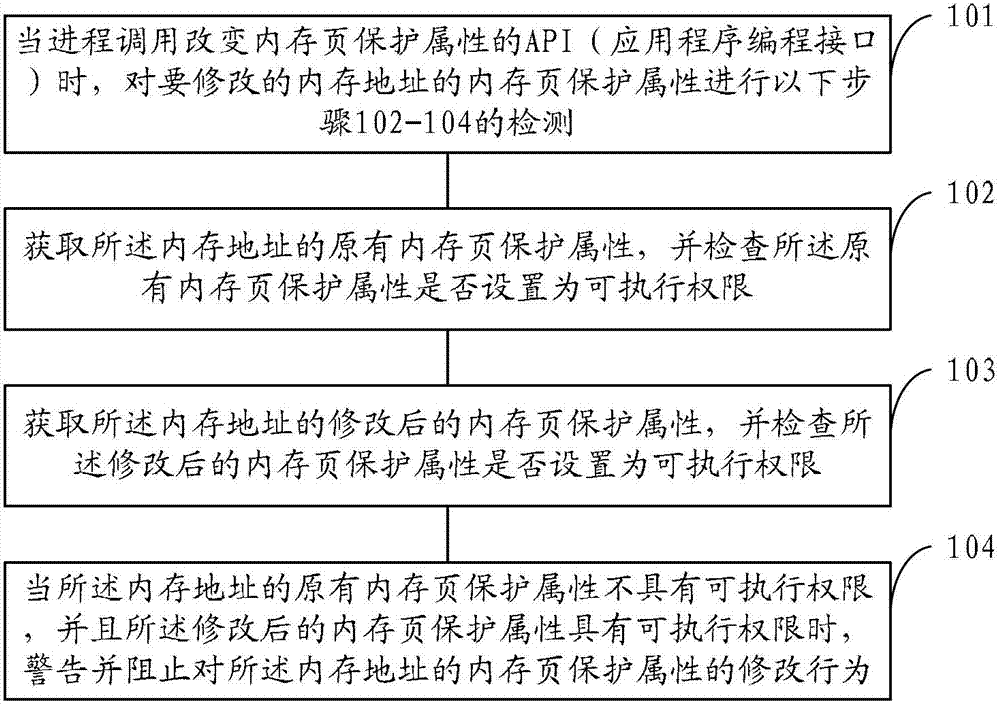
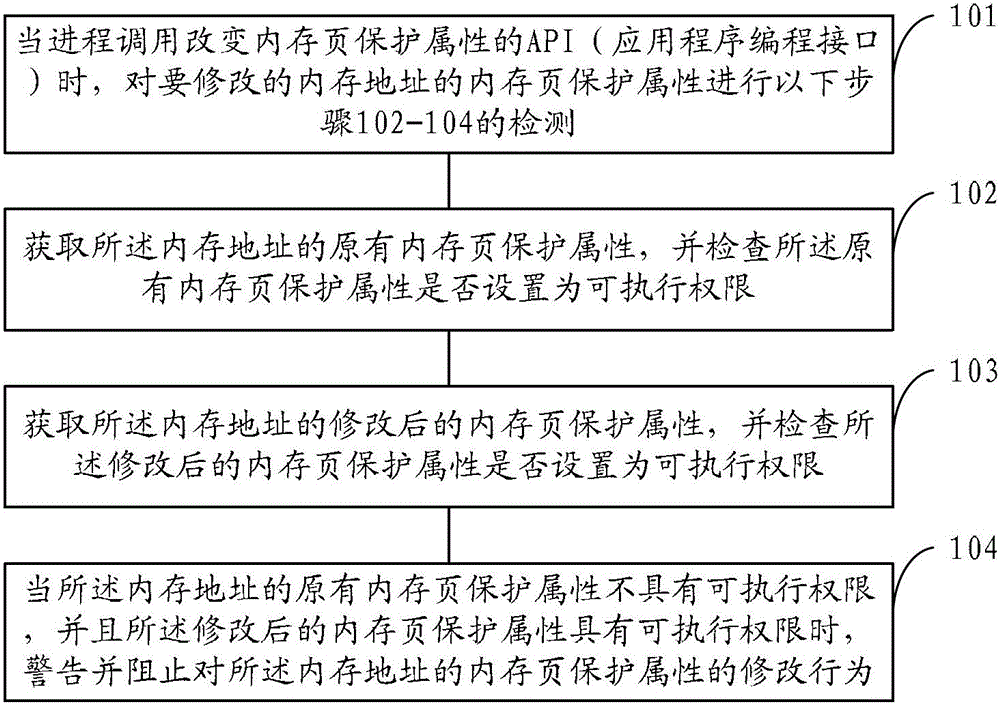
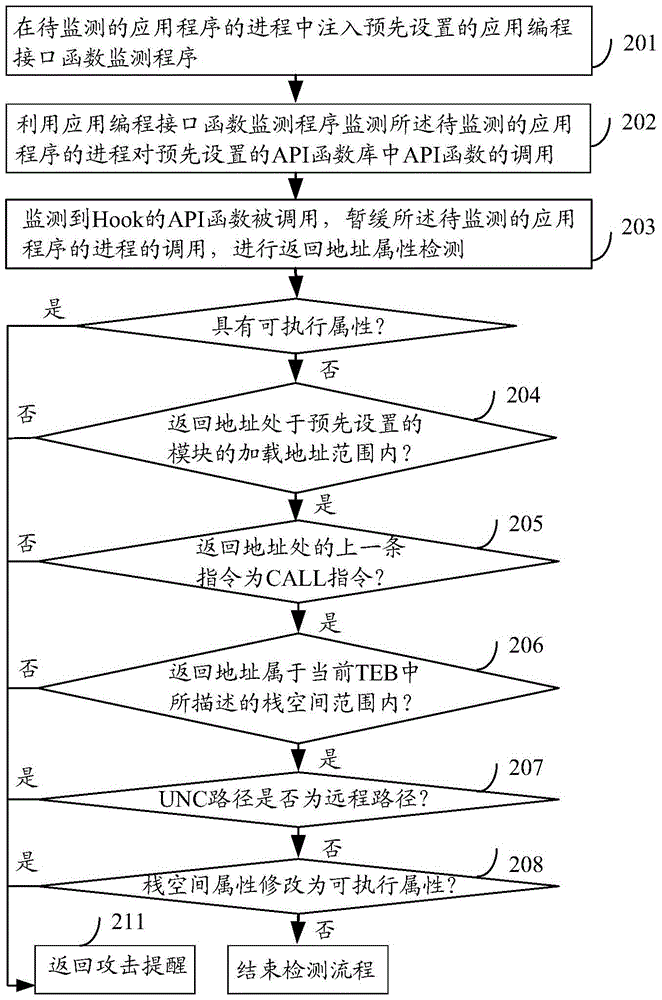
The application provides a method, a device and a browser for protecting a webpage against a malicious attack, which aim to solve the problem that an attacker performs the Trojan horse attack on the webpage through bypassing DEP (Data Execution Protection) by the ROP (Return Oriented Programming) technology. In the application, a memory page protection attribute of a memory address to be modified by a malicious code is pre-detected when an API (Application Programming Interface) of the memory page protection attribute is transferred in the process; and the original memory page protection attribute and the modified memory page protection attribute of the memory address are distinguished through a rule, and a malicious modifying behavior is baffled or warned once found out, so that the conditions that the memory address of a data page is modified into an executable authority and the malicious code is illegally executed can be avoided.
Owner:BEIJING QIHOO TECH CO LTD
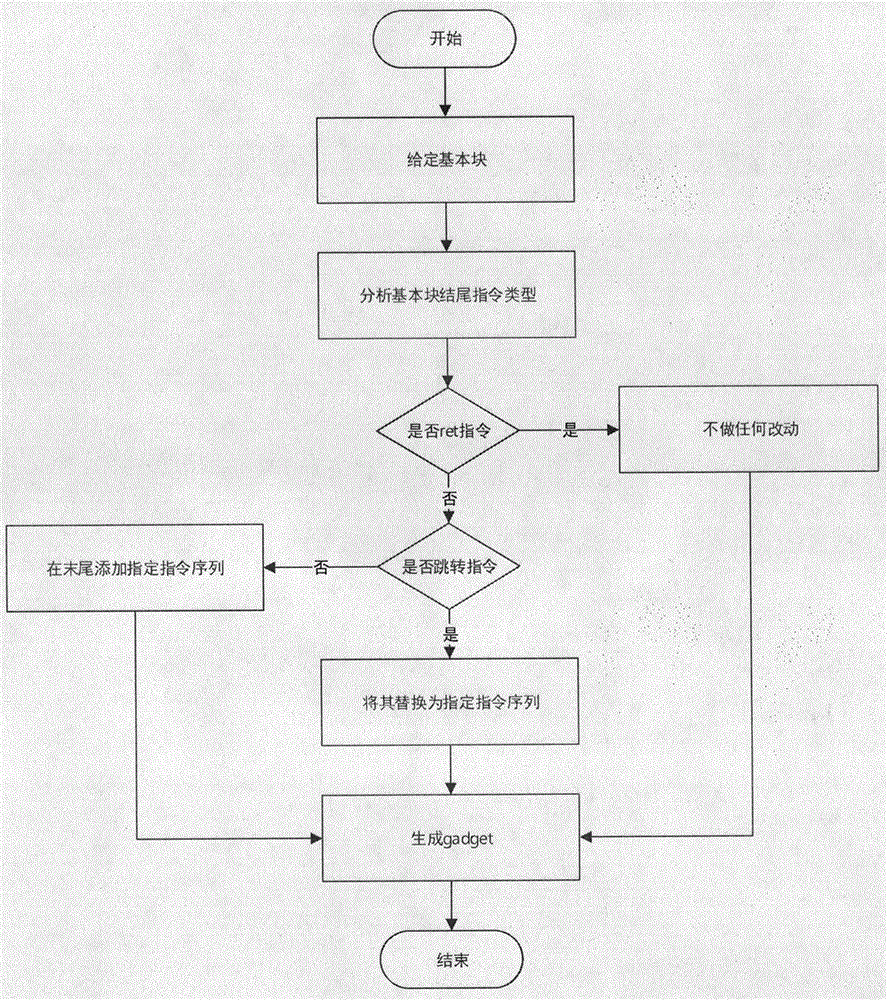
Binary obfuscation method based on ROP (Return Oriented Programming) attack feature
InactiveCN106529224AWide applicabilityStrong deployabilityProgram/content distribution protectionObfuscationSoftware obfuscation
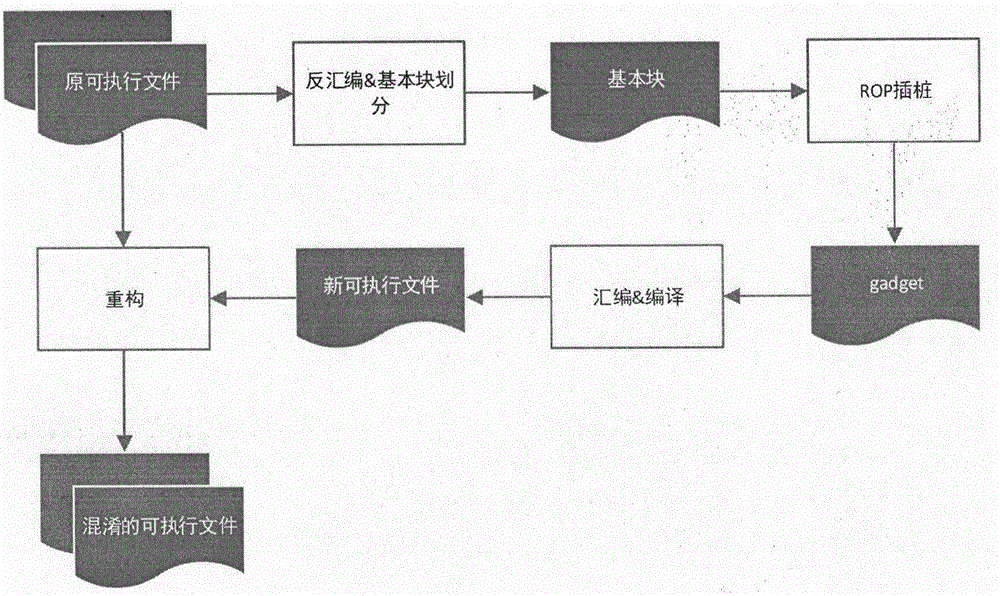
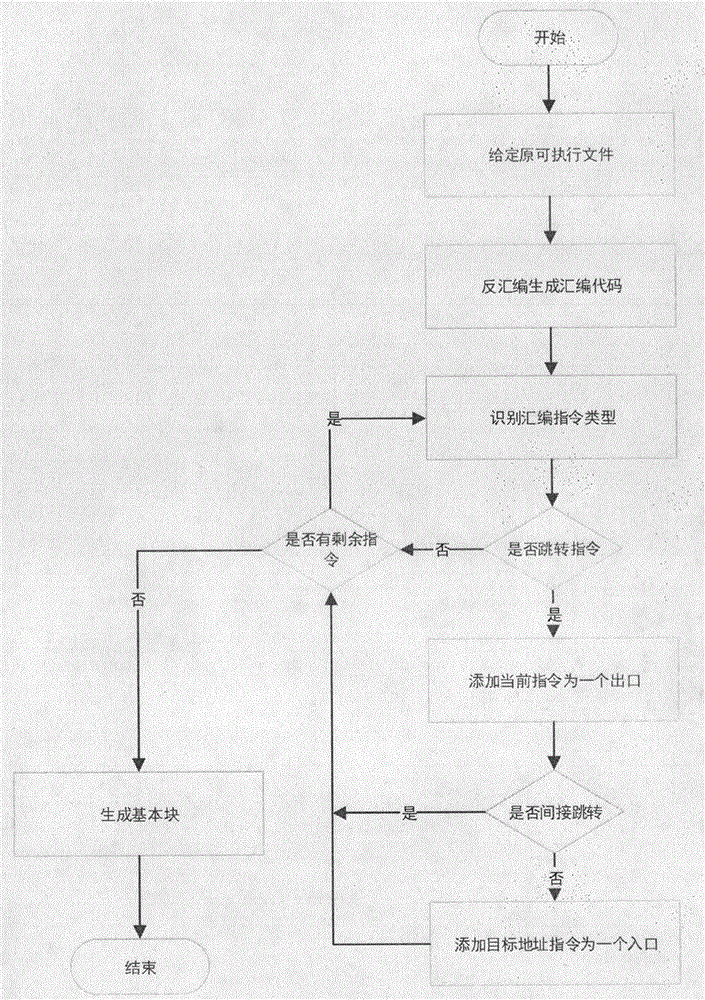
The invention provides a binary obfuscation method based on a ROP (Return Oriented Programming) attack feature. The method comprises the steps of disassembling an original binary file and dividing basic blocks; carrying out ROP form instrumentation on the basic blocks, thereby obtaining gadget form assembly code ended by a ret instruction; and refactoring recompiled new code and the original binary file, and generating a finally obfuscated executable file. According to the method, through application of a mode of converting a code segment of the binary file into a gadget form, an obfuscation purpose is achieved. The software obfuscation performance loss is low. The deployable performance is high. The dependence on a feature of a special hardware processor is removed.
Owner:NANJING UNIV
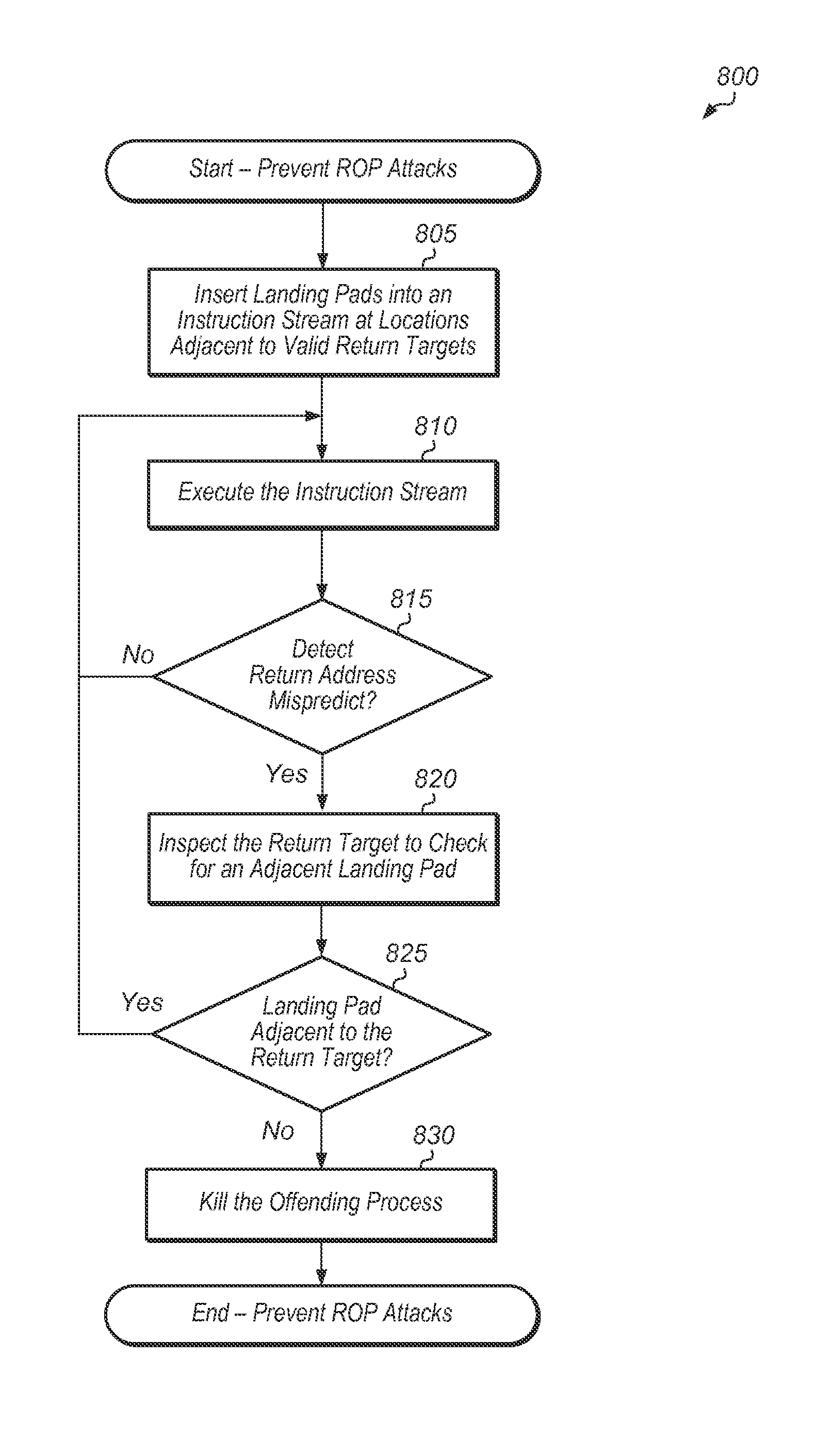
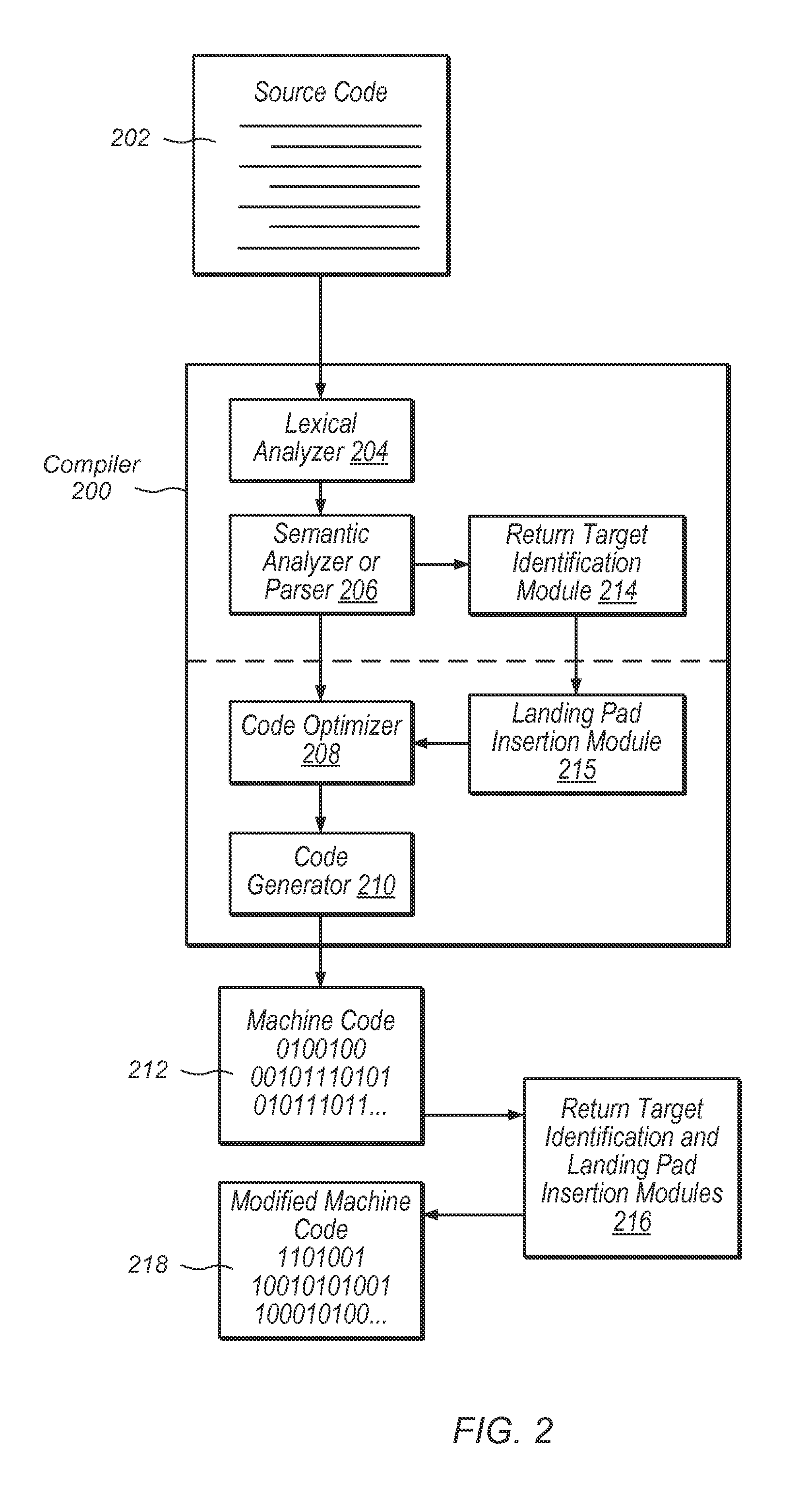
Marking valid return targets
Systems, apparatuses, methods, and computer-readable mediums for preventing return oriented programming (ROP) attacks. A compiler may insert landing pads adjacent to valid return targets in an instruction sequence. When a return instruction is executed, the processor may treat the return as suspicious if the target of the return instruction does not have an adjacent landing pad. Additionally, each landing pad may be encoded with a color, and a colored launch pad may be inserted into the instruction stream next to each return instruction. When a return instruction is executed, the processor may determine if the target of the return has a landing pad with the same color as the launch pad of the return instruction. Return-target pairs with color mismatches may be treated as suspicious and the offending process may be killed.
Owner:APPLE INC
Methods, devices, and systems for detecting return-oriented programming exploits
ActiveCN103946855AMemory architecture accessing/allocationError detection/correctionCode snippetRemedial action
Methods, devices, and systems for detecting return-oriented programming (ROP) exploits are disclosed. A system includes a processor, a main memory, and a cache memory. A cache monitor develops an instruction loading profile by monitoring accesses to cached instructions found in the cache memory and misses to instructions not currently in the cache memory. A remedial action unit terminates execution of one or more of the valid code sequences if the instruction loading profile is indicative of execution of an ROP exploit involving one or more valid code sequences. The instruction loading profile may be a hit / miss ratio derived from monitoring cache hits relative to cache misses. The ROP exploits may include code snippets that each include an executable instruction and a return instruction from valid code sequences.
Owner:QUALCOMM INC
Mitigating vulnerabilities associated with return-oriented programming
InactiveUS20140283060A1Memory loss protectionError detection/correctionParallel computingComputerized system
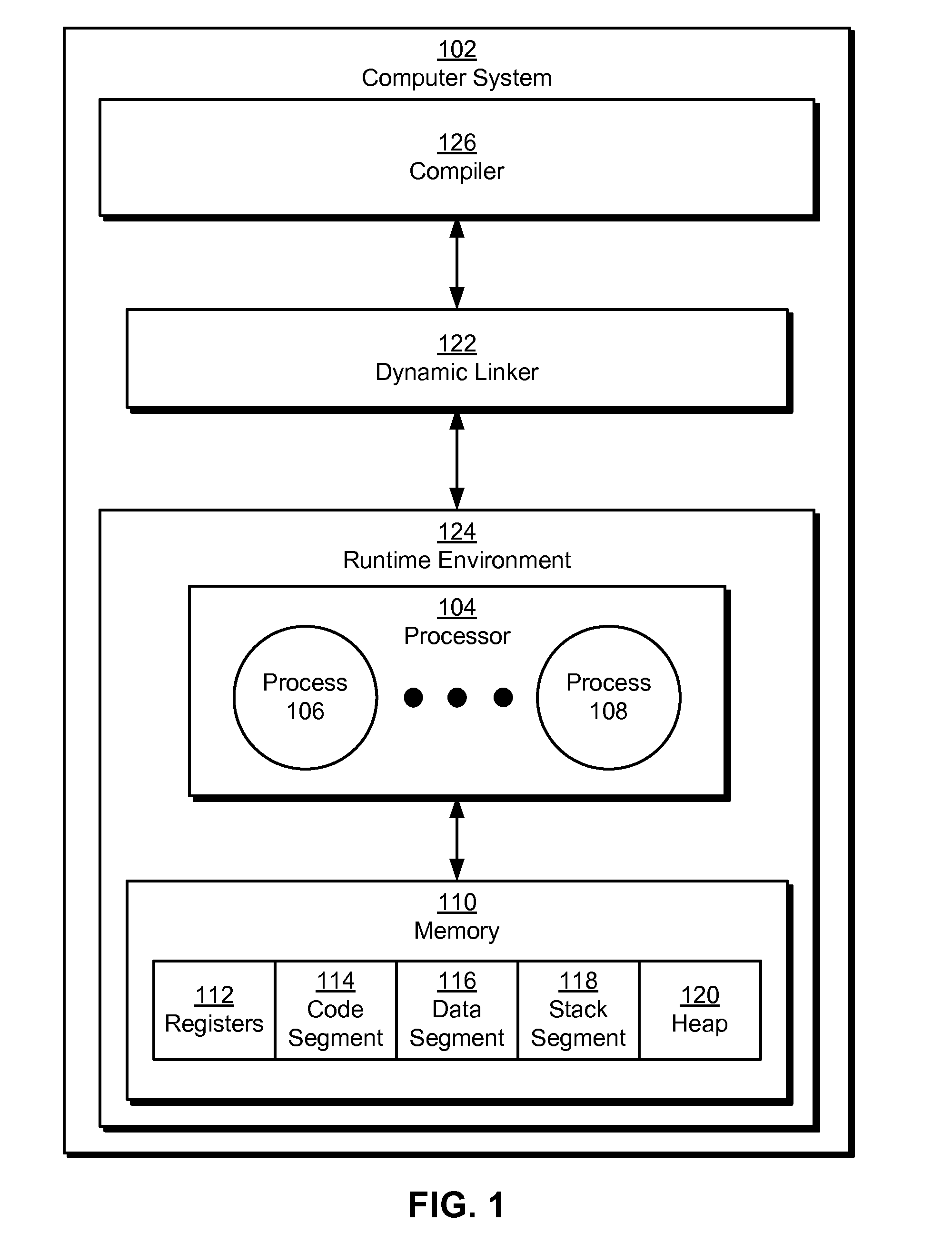
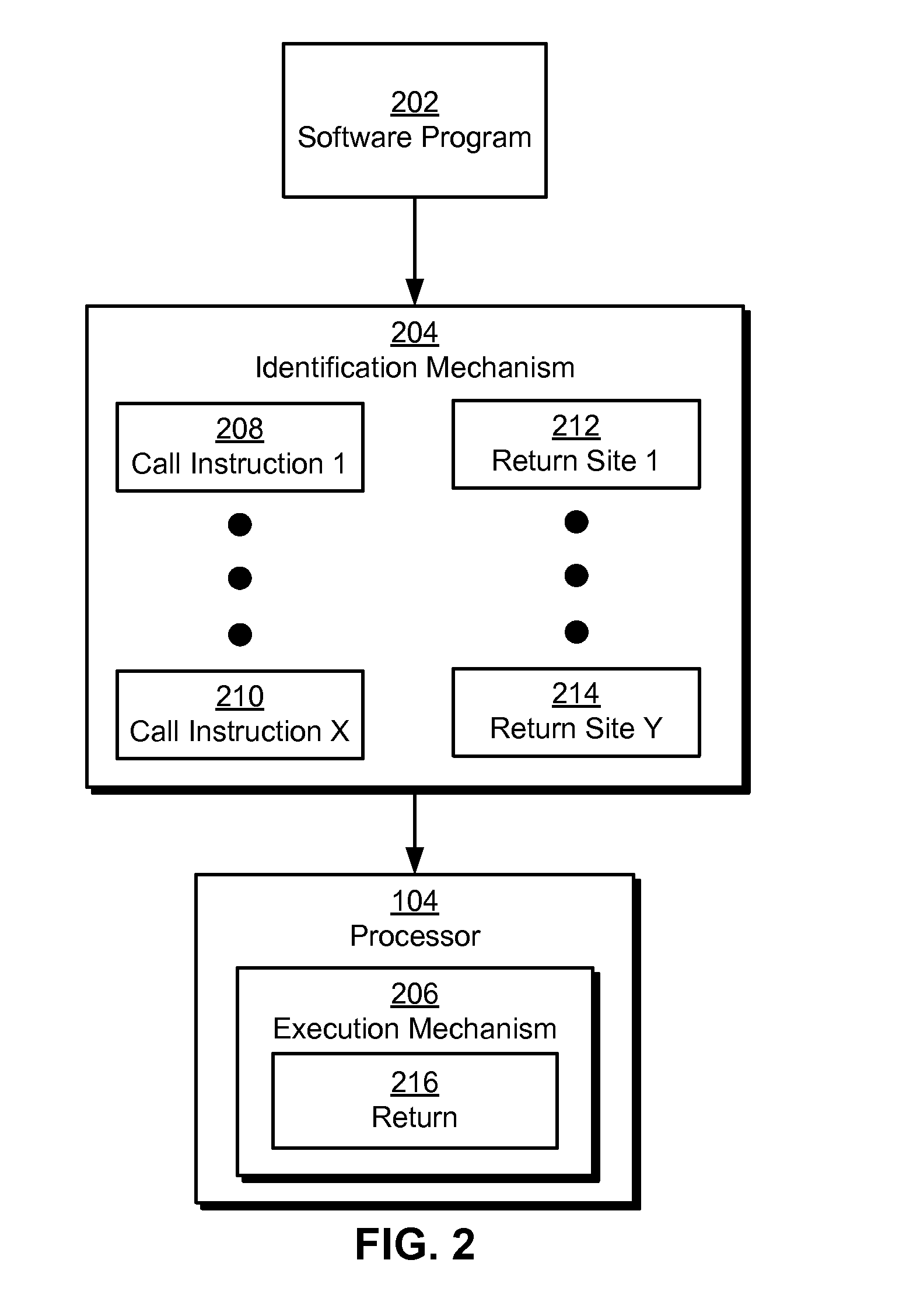
The disclosed embodiments provide a system that operates a processor in a computer system. During operation, the system identifies one or more return sites associated with a call instruction of a software program. Next, the system restricts execution of a return from the call instruction by the processor to the one or more return sites.
Owner:ORACLE INT CORP
Obfuscation of an address space layout randomization mapping in a data processing system
ActiveUS10311227B2Unauthorized memory use protectionPlatform integrity maintainanceObfuscationParallel computing
A data processing system can use a method of fine-grained address space layout randomization to mitigate the system's vulnerability to return oriented programming security exploits. The randomization can occur at the sub-segment level by randomizing clumps of virtual memory pages. The randomized virtual memory can be presented to processes executing on the system. The mapping between memory spaces can be obfuscated using several obfuscation techniques to prevent the reverse engineering of the shuffled virtual memory mapping.
Owner:APPLE INC
Detecting method for ROP (Return-Oriented Programming) attacks
InactiveCN106326747AChange loading locationNo additional burdenPlatform integrity maintainanceGranularityCode segment
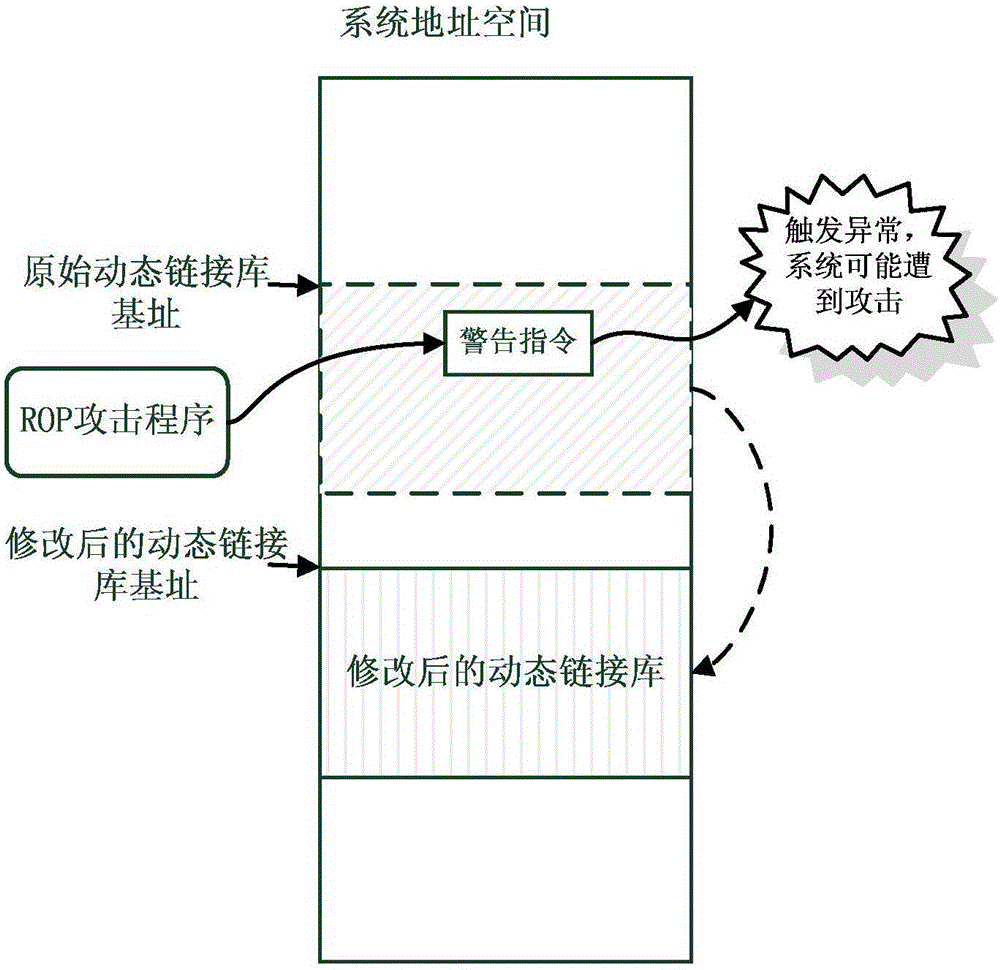
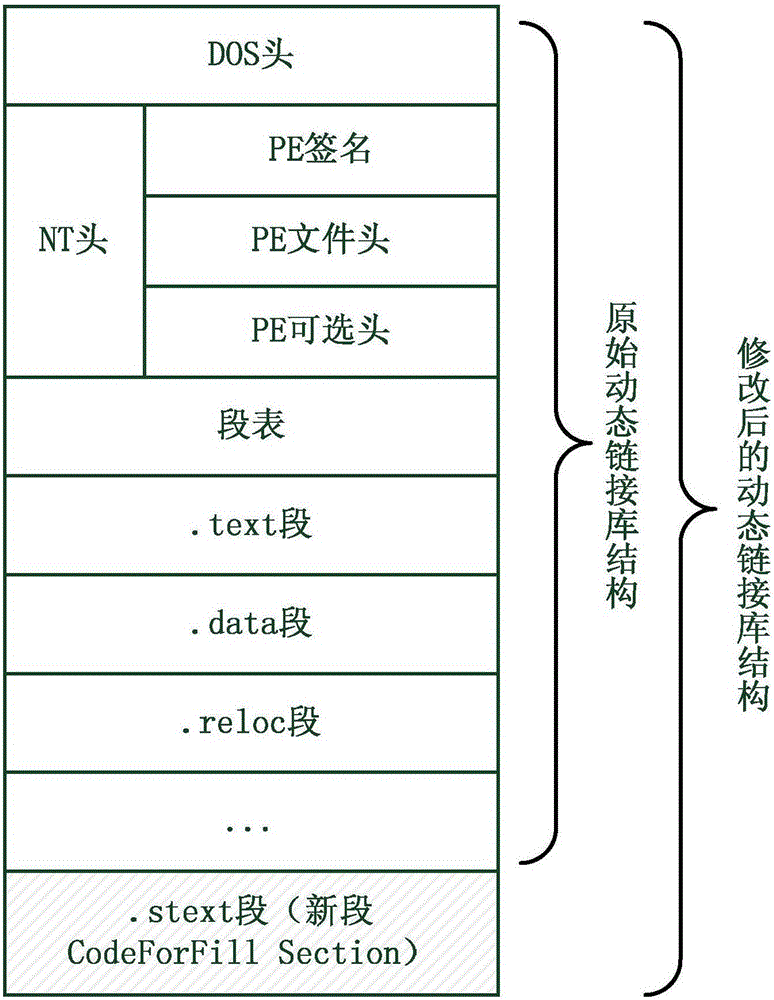
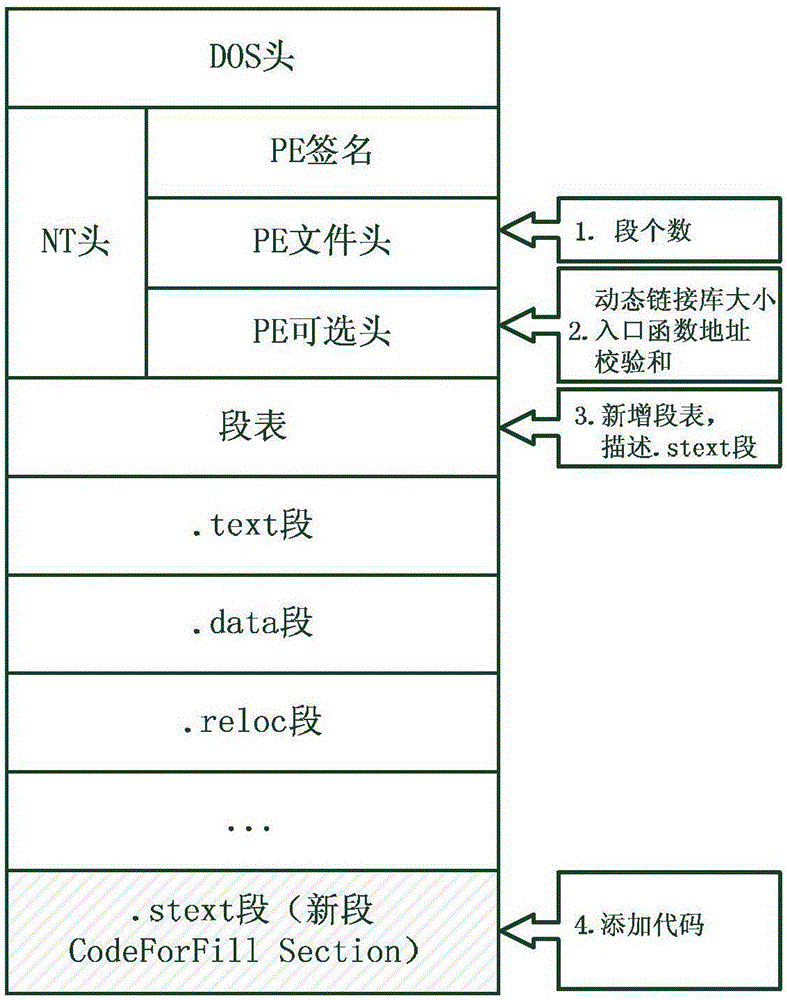
The invention discloses a detecting method for ROP (Return-Oriented Programming) attacks. The method comprises the following steps of obtaining a new base address of a dynamic linking library, wherein the new base address is equal to the sum of an original base address of the dynamic linking library and offset, the offset is random non-zero integral multiples of allocation granularity, and the absolute value of the offset is greater than length of the dynamic linking library; modifying base address fields of the dynamic linking library, and enabling the base address fields to point to the new base address of the dynamic linking library; increasing a code segment into the dynamic linking library, wherein the code segment is used for filling a loading position which corresponds to the original base address of the dynamic linking library with a warning instruction, the tail part of the code section has a jump instruction, and jump distance of the jump instruction is relative distance between the jump instruction and an entry function; and setting the entry address of the dynamic linking library to be the address of the code section. The detecting method disclosed by the invention can be applied to all Windows systems without causing extra burden on the systems, and can be used for detecting all ROP attacks except JIT-ROP.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Automated diversity using return oriented programming
InactiveUS8689201B2Overcome limitationsAvoid hardMemory loss protectionError detection/correctionReturn-oriented programmingExecutable
A method of automatically creating functionally and structurally diverse equivalent copies of software executables using return oriented programming for the purpose of passing through a filter and other purposes includes starting with a program and a target runtime environment, creating a return oriented instruction library having a plurality of code fragments which end in a ‘return’ instruction from the program and chaining fragments together to automatically form diverse equivalent copies of software executables using return oriented programming.
Owner:TELCORDIA TECHNOLOGIES INC
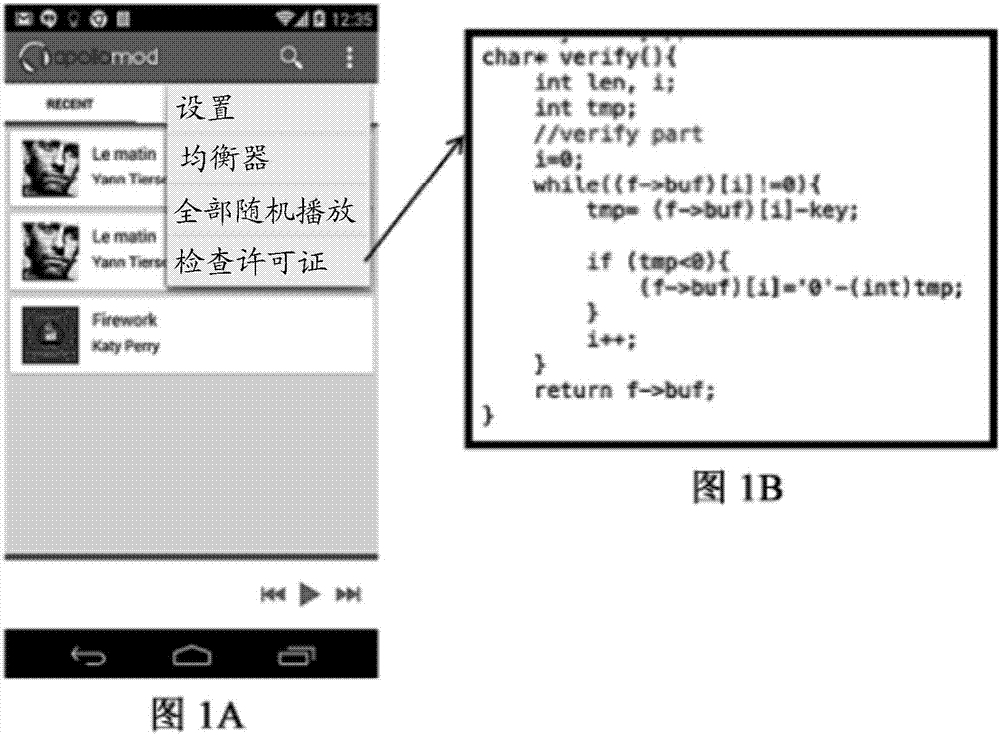
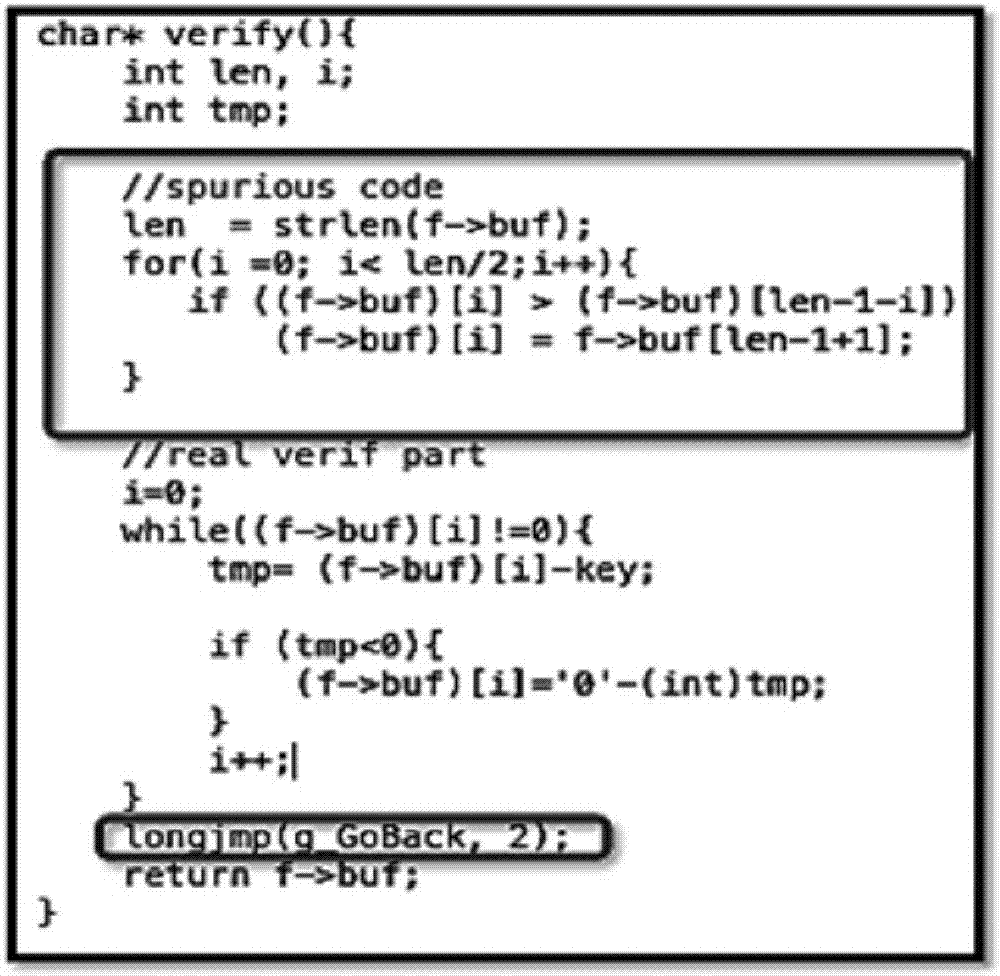
Method for obfuscation of code using return oriented programming
ActiveCN107209815APlatform integrity maintainanceProgram/content distribution protectionControl flowObfuscation
Embodiments of the invention relates to utilization of Return Oriented Programming (ROP) for a non-malicious purpose i.e. code obfuscation to improve security. Program code that is associated with a designated function of sensitive nature may be hidden by creating a ROP code that performs the designated function of the original (unobsfuscated) code and constructing a ROP payload that can be loaded to execute the ROP code. The original code may be replaced by a spurious code unrelated to the designated function, and a control flow instruction is provided to load the ROP payload to execute the ROP code.
Owner:HUAWEI INT +1
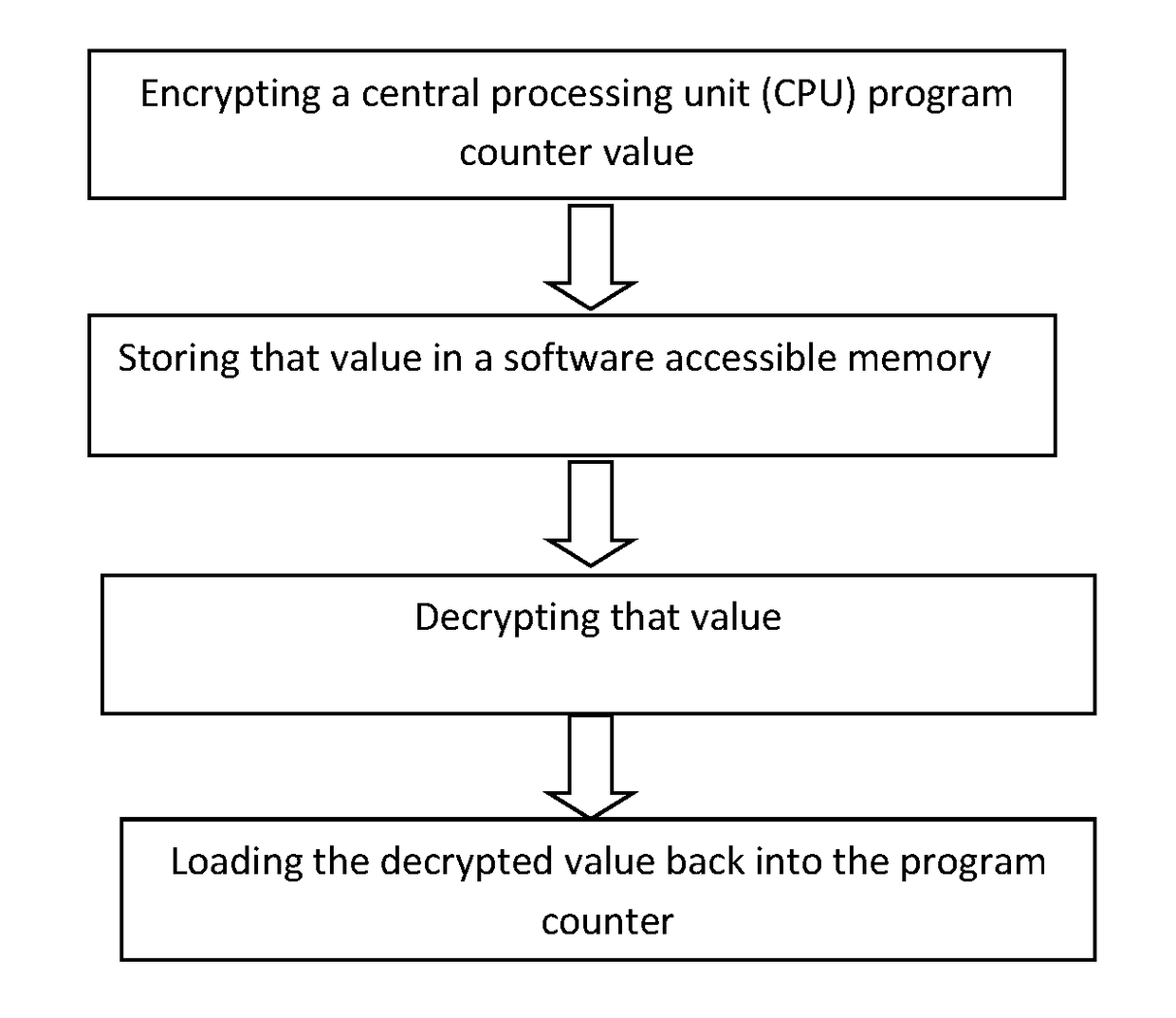
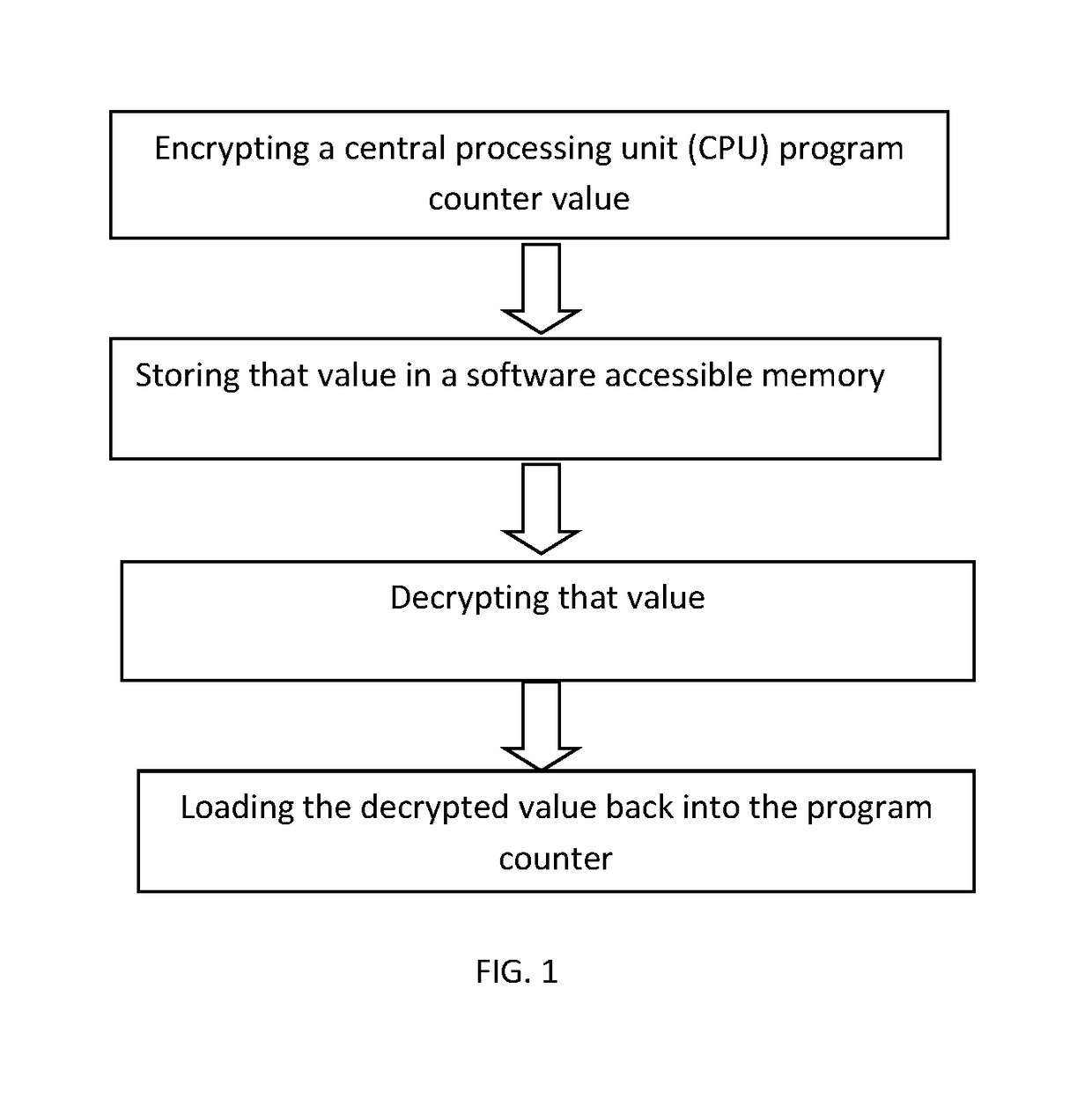
System for program counter encryption
InactiveUS20180060585A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesProcessing elementProgram counter
A method and system for protecting a device against return oriented programming attacks by encrypting a central processing unit (CPU) program counter value when storing that value in a software accessible memory and decrypting that value when loading it back into the program counter; whereby alterations to the value will prevent proper decryption and interoperation with the CPU.
Owner:BATTELLE MEMORIAL INST
Dynamic execution prevention to inhibit return-oriented programming
ActiveCN104054061AUnauthorized memory use protectionPlatform integrity maintainanceParallel computingApplication software
A method, apparatus, and / or system for execution prevention is provided. A state indicator for a first subset of a plurality of memory pages of executable code in a memory device is set to a non-executable state. A state indicator for a second subset of the plurality of memory pages is set to an executable state, where the second subset of the plurality of memory pages includes indirection stubs to functions in the first subset of the plurality of memory pages. Upon execution of an application, a function call is directed to a corresponding indirection stub in the second subset of the plurality of memory pages which modifies the state indicator for a corresponding function in the first subset of the plurality of memory pages prior to directing execution of the called function from the first subset of the plurality of memory pages.
Owner:QUALCOMM INC
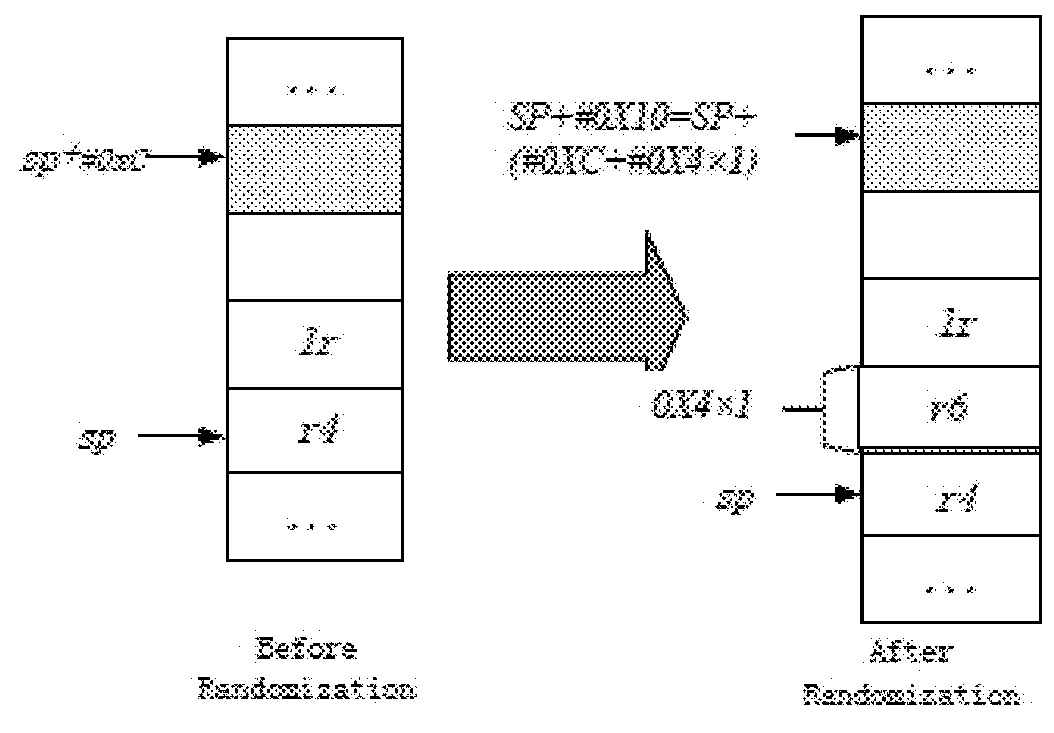
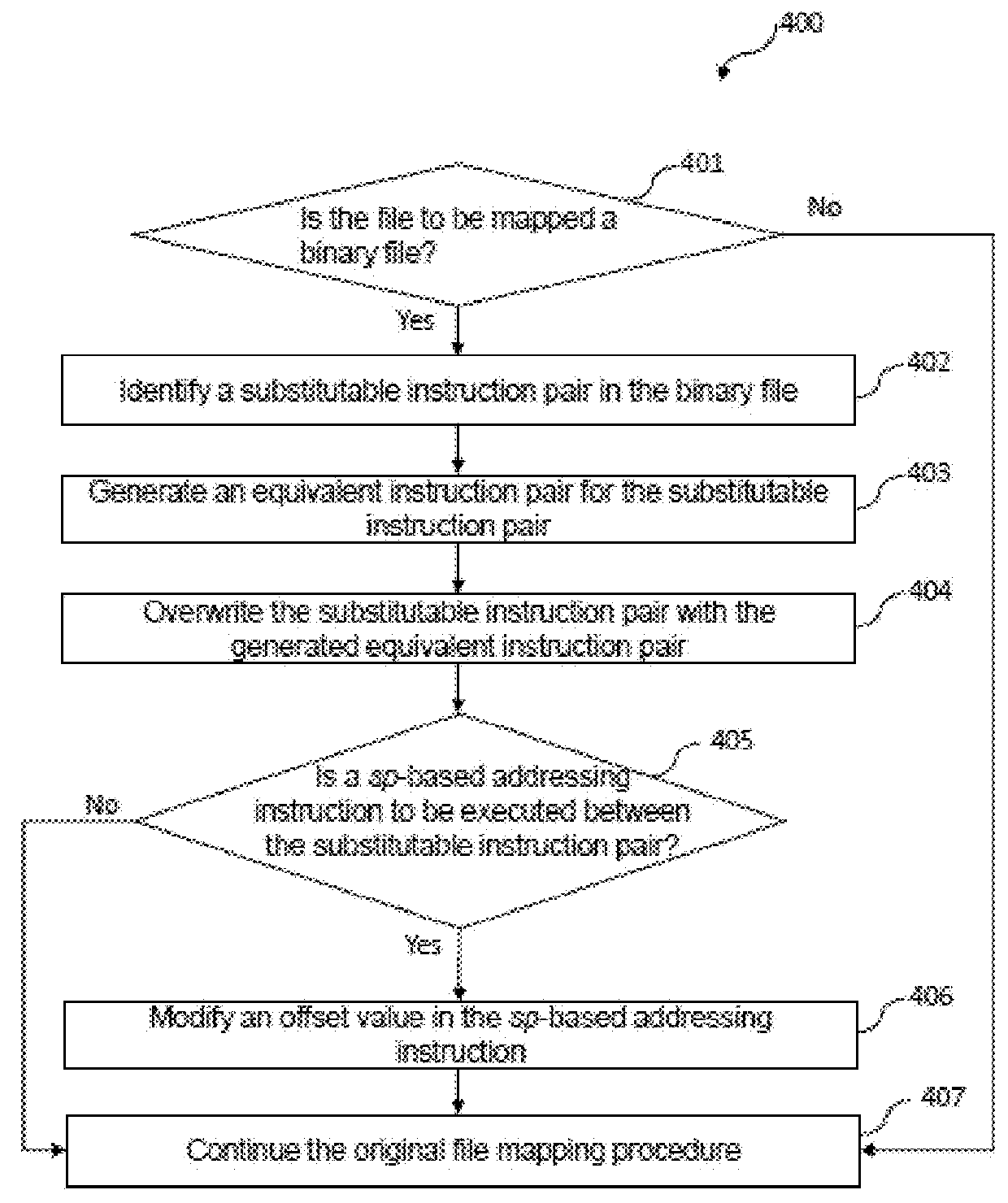
Method and system for defense against return oriented programming (ROP) based attacks
InactiveUS20180096139A1Effective ROP mitigation strategyPlatform integrity maintainanceMachine execution arrangementsProcessor registerParallel computing
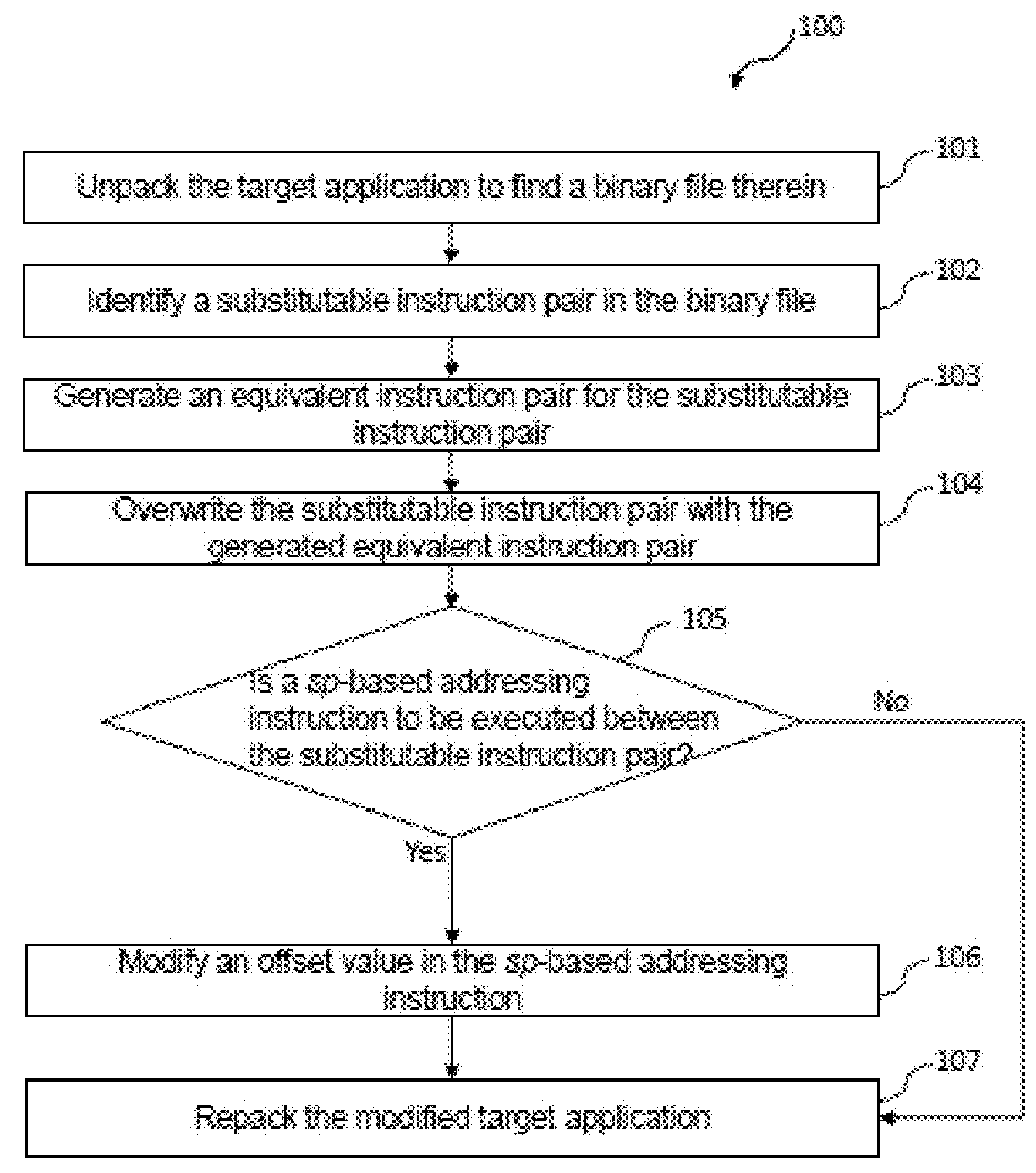
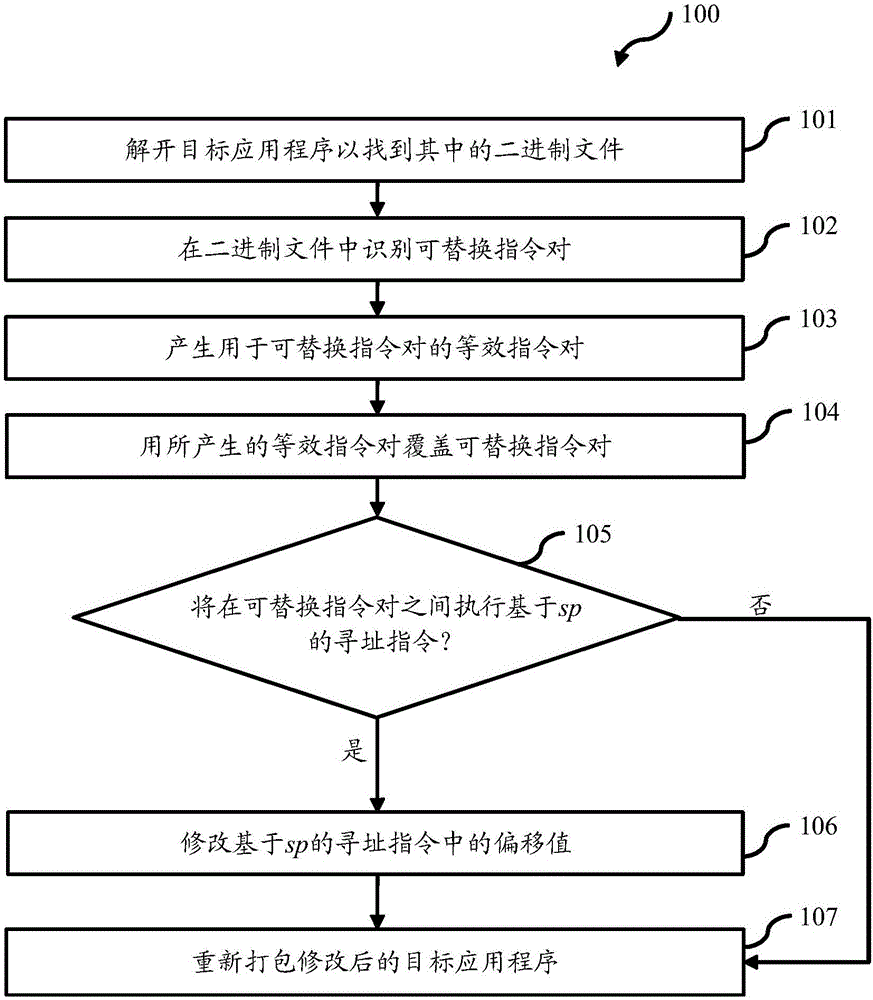
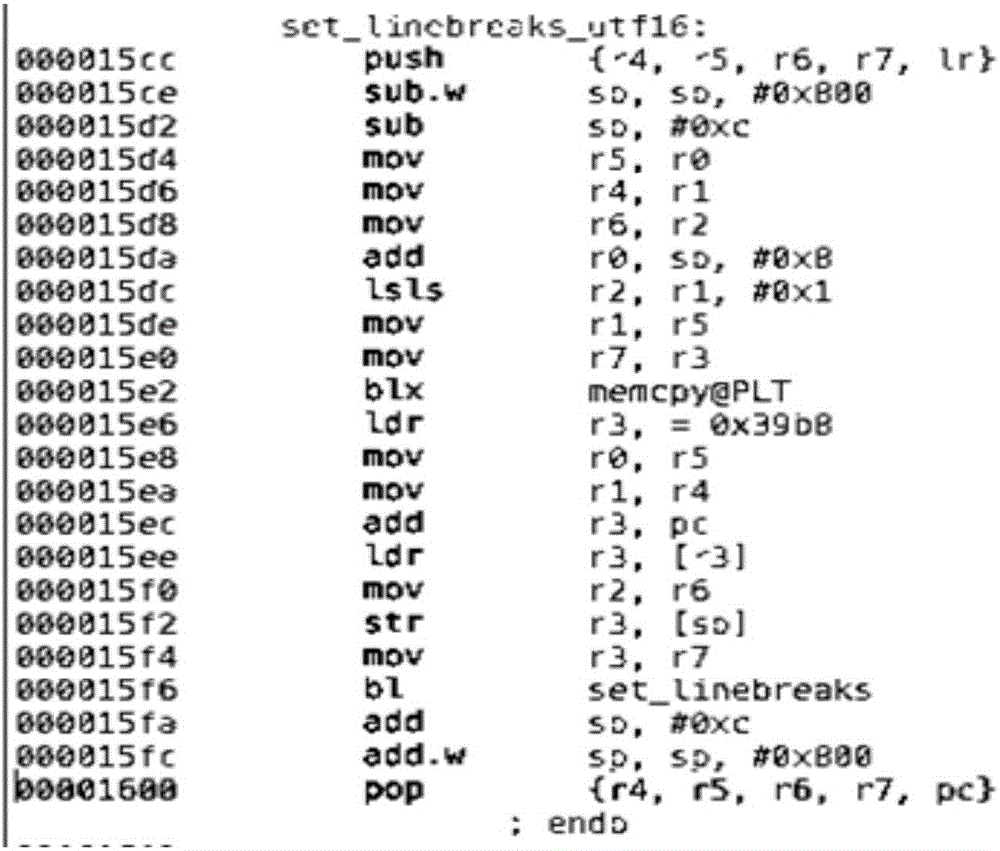
Embodiments of the application provide method and system for defense against ROP attacks. The method comprises: identifying a substitutable instruction pair in a binary file, which includes a first instruction for pushing a first group of registers into a stack memory, and a second instruction for popping the first group of registers off the stack memory, generating an equivalent instruction pair for the substitutable instruction pair, which includes a first equivalent instruction for pushing a second group of registers onto the stack memory, and a second equivalent instruction for popping the second group of registers off the stack memory, wherein the second group of registers includes the first group of registers and at least one additional register which is not used by the substitutable instruction pair, and overwriting the first instruction and the second instruction with the first equivalent instruction and the second equivalent instruction respectively.
Owner:HUAWEI INT +1
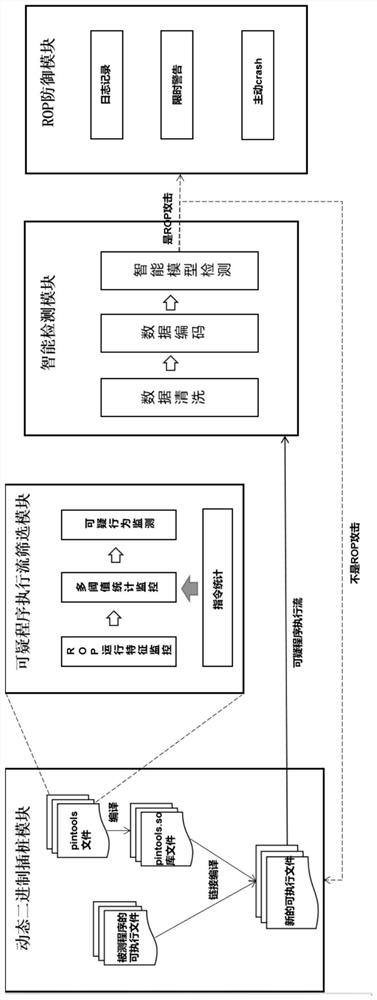
Intelligent detection method and device for return programming attack
ActiveCN114880665ASoftware testing/debuggingPlatform integrity maintainanceAttackCommercial software
The invention relates to the field of security detection, discloses an intelligent detection method and device for a return programming attack, belongs to the field of system underlying security detection, and aims to detect binary executable files of a program and process commercial software without a source code of a detected software program. According to the main scheme, the method comprises the steps that instrumentation is conducted on a tested program, the execution process of the tested program is output in the form of assembly codes through the disassembling technology, and then a program execution stream is obtained; performing real-time monitoring by utilizing the execution streams, and screening out suspicious program execution streams; according to the method, a suspicious program execution flow is subjected to secondary screening, an artificial intelligence model is utilized to accurately judge a suspicious ROP attack, whether ROP defense is started or not is determined according to a judgment result, and a time-limited alarm and active crash strategy is adopted for a program judged to be the ROP attack, so that the detected program is prevented from suffering from greater loss.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Hardware heuristic-driven binary translation-based execution analysis for return-oriented programming malware detection
A combination of hardware monitoring and binary translation software allow detection of return-oriented programming (ROP) exploits with low overhead and low false positive rates. Embodiments may use various forms of hardware to detect ROP exploits and indicate the presence of an anomaly to a device driver, which may collect data and pass the indication of the anomaly to the binary translation software to instrument the application code and determine whether an ROP exploit has been detected. Upon detection of the ROP exploit, the binary translation software may indicate the ROP exploit to an anti-malware software, which may take further remedial action as desired.
Owner:MCAFEE LLC
Applying security mitigation measures for stack corruption exploitation in intermediate code files
ActiveUS20200125378A1Increase in sizeRegister arrangementsConcurrent instruction executionParallel computingEngineering
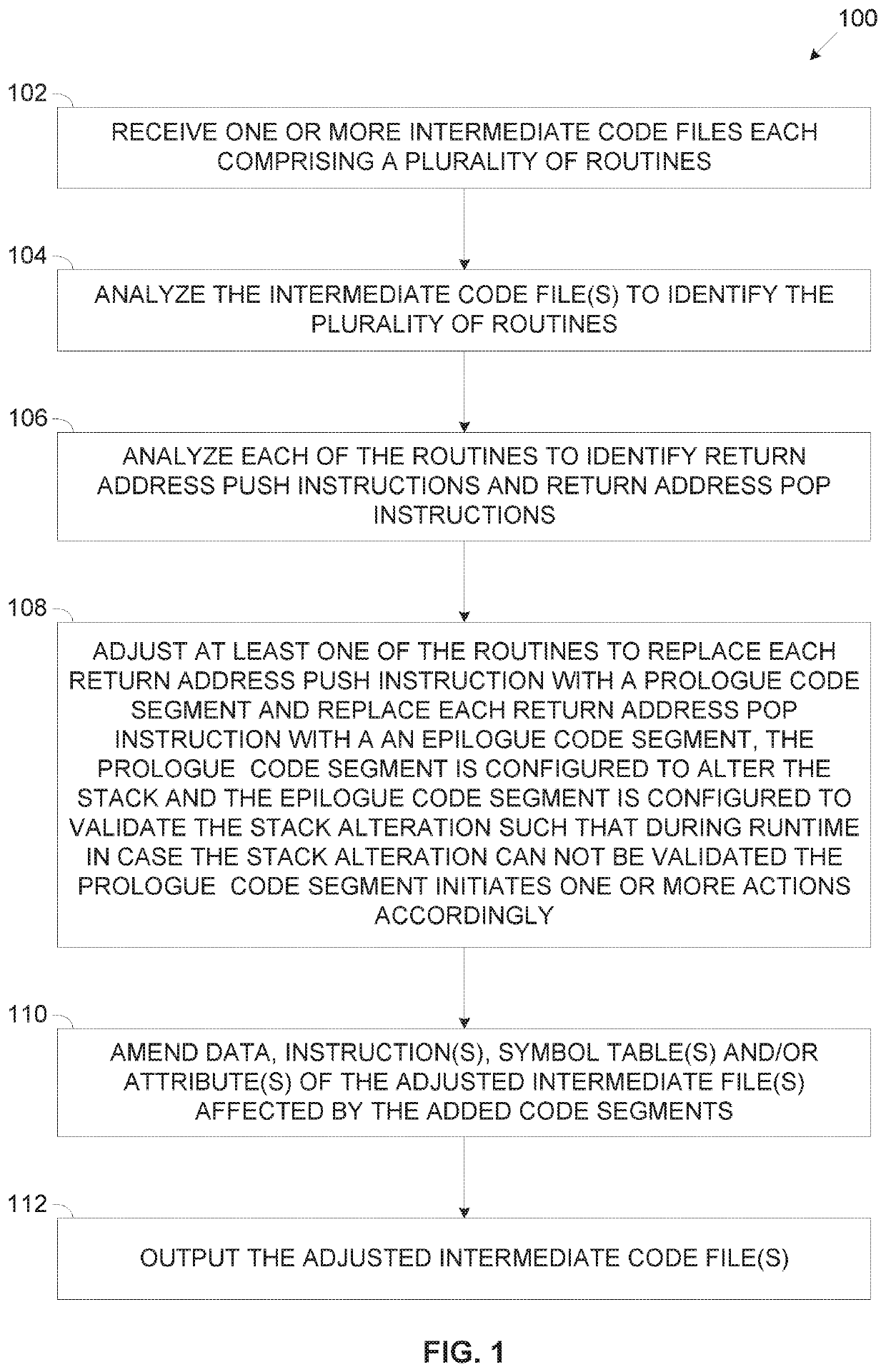
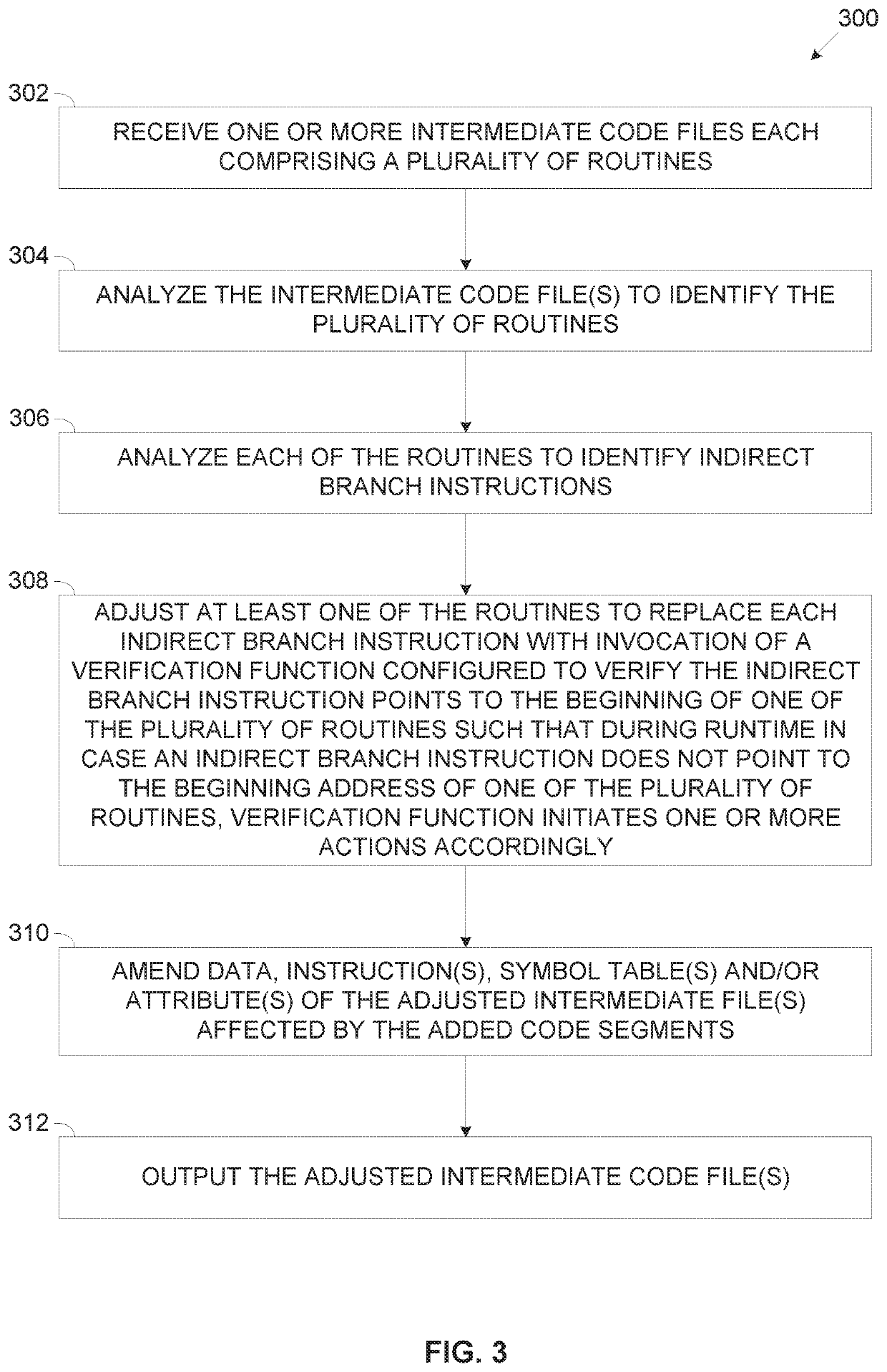
Presented herein are methods and systems for generating intermediate code files adjusted to prevent return oriented programming exploitation, comprising receiving compiled intermediate code file(s) comprise a plurality of routines and adjusting them prior to generation of a respective executable file for execution by one or more processor. The adjusting comprising analyzing a symbol table of the intermediate code file(s) to identify a beginning address of each of the routines, analyzing each of the routines to identify indirect branch instructions in the routines, and replacing each detected indirect branch instruction with invocation of a verification code segment configured to verify that the respective indirect branch instruction points to the beginning address of one of the routines. In runtime, the verification code segment causes the processor(s) to initiate one or more predefined actions in case the indirect branch instruction isn't pointing to the beginning address of one of the plurality of routines.
Owner:STERNUM LTD
Adaptive Diversity for Compressible Return Oriented Programs
InactiveUS20130179869A1Good varietyMaximize and localityBinary to binaryProgram controlFunctional diversitySelf adaptive
A method of transforming return oriented programming executables into functionally equivalent yet different forms with specific structural and / or functional characteristics that can assist in the use of such executables. A method automatically biases the structural and / or functional diversity of the return oriented programming software executables to achieve specific program representation objectives while preserving the programmatic capabilities of the original executable.
Owner:TELCORDIA TECHNOLOGIES INC
Method, device and browser for protecting webpage against malicious attack
The application provides a method, a device and a browser for protecting a webpage against a malicious attack, which aim to solve the problem that an attacker performs the Trojan horse attack on the webpage through bypassing DEP (Data Execution Protection) by the ROP (Return Oriented Programming) technology. In the application, a memory page protection attribute of a memory address to be modified by a malicious code is pre-detected when an API (Application Programming Interface) of the memory page protection attribute is transferred in the process; and the original memory page protection attribute and the modified memory page protection attribute of the memory address are distinguished through a rule, and a malicious modifying behavior is baffled or warned once found out, so that the conditions that the memory address of a data page is modified into an executable authority and the malicious code is illegally executed can be avoided.
Owner:BEIJING QIHOO TECH CO LTD
Transparent detection and extraction of return-oriented-programming attacks
ActiveUS9904780B2Digital data protectionPlatform integrity maintainanceComputer hardwareAttack analysis
Owner:NEC CORP
Method, apparatus and system for detecting return-oriented programming attacks
ActiveCN103946855BMemory architecture accessing/allocationError detection/correctionCode snippetParallel computing
Methods, devices, and systems for detecting return-oriented programming (ROP) exploits are disclosed. A method includes executing an unintended sequence of code snippets in a processing circuit, each code snippet including at least one executable instruction including a control transfer instruction. One or more of the code snippets may include a modified control transfer instruction different from an originally intended control transfer instruction and at least one code snippet of the plurality may be a non-cached code snippet not found in a cache memory. The method also includes developing an instruction loading profile by monitoring instruction fetches relative to cache misses, where the cache misses are fetched instructions absent from the cache memory on the instruction fetch.
Owner:QUALCOMM INC
Return-oriented programming protection
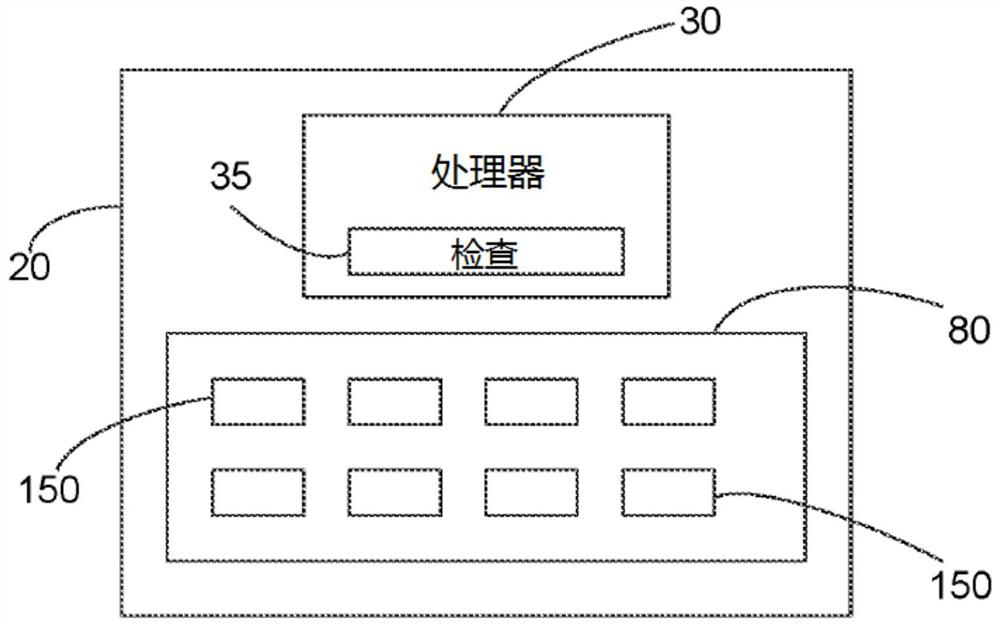
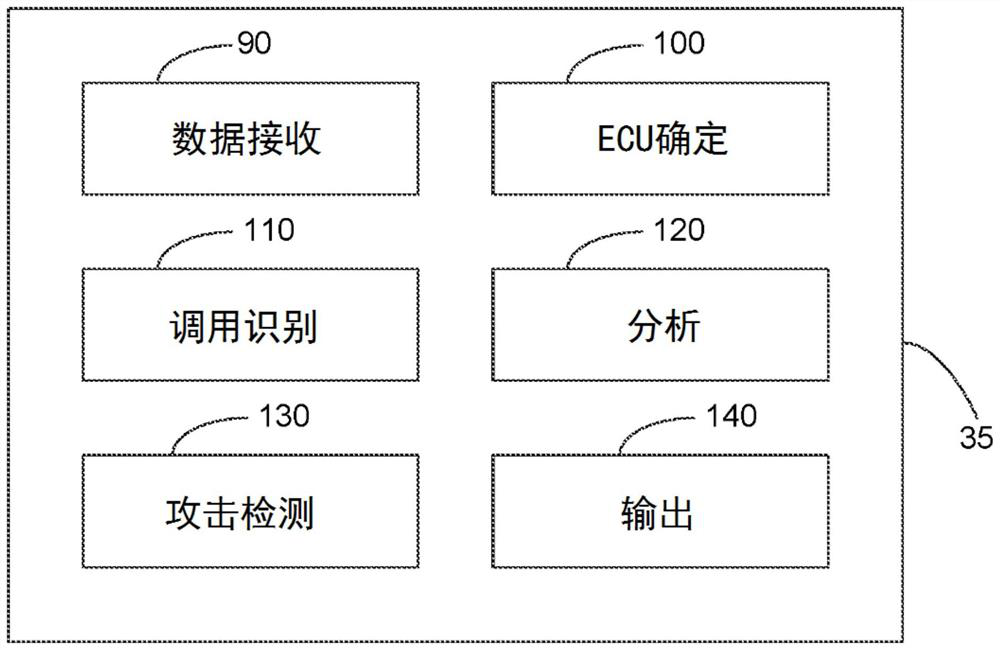
PendingCN113544677AParticular environment based servicesPlatform integrity maintainanceControl flowStatistical analysis
An ROP attack protection method for a plurality of ECUs comprises the steps: receiving data destined for one of the plurality of ECUs; determining which of the plurality of ECUs the received data is destined for; responsive to a unique model associated with the determined ECU, analyzing the received data to identify control flow instructions addressed to one or more predetermined addresses; responsive to the analyzation, generating a statistical analysis of the identified control flow instructions; and responsive to the generated statistical analysis, outputting a signal indicating a possibility of an attack.
Owner:C2A SEC LTD
Method and system for defense against return oriented programming (ROP) based attacks
ActiveCN106687973ASame sizeFree from attackPlatform integrity maintainanceProgram controlProcessor registerParallel computing
Embodiments of the invention provide method and system for defense against ROP attacks. The method comprises: identifying a substitutable instruction pair in a binary file, which includes a first instruction for pushing a first group of registers into a stack memory, and a second instruction for popping the first group of registers off the stack memory, generating an equivalent instruction pair for the substitutable instruction pair, which includes a first equivalent instruction for pushing a second group of registers onto the stack memory, and a second equivalent instruction for popping the second group of registers off the stack memory, wherein the second group of registers includes the first group of registers and at least one additional register which is not used by the substitutable instruction pair, and overwriting the first instruction and the second instruction with the first equivalent instruction and the second equivalent instruction respectively.
Owner:HUAWEI INT +1
A method and device for detecting return-oriented programming attacks
ActiveCN104268471BImprove securityEffective protectionPlatform integrity maintainanceApplication programming interfaceApplication software
The embodiment of the invention discloses a method and a device for detecting return-oriented programming attack. The method for detecting the return-oriented programming attack comprises injecting preset application programming interface (API) function monitoring programs into the process of every application program to be monitored; when the process of the application program to be monitored calls API functions inside a preset API function library, retarding the process of the application program to be monitored from calling the API functions; processing the calling-retarded API functions according to preset return-oriented programming (ROP) protecting strategies to determine whether calling the calling-retarded API functions is allowed. The method and device for detecting the return-oriented programming attack can effectively detect ROP attack and accordingly improve network security.
Owner:ZHUHAI BAOQU TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com