Method and system for defense against return oriented programming (ROP) based attacks
A technology of computer system and application file, applied in the direction of program control design, instrument, electrical digital data processing, etc., can solve the problem that there is no effective ROP mitigation strategy for mobile computer system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In the following description, numerous specific details are set forth in order to provide a thorough understanding of various illustrative embodiments of the invention. However, it will be understood by those skilled in the art that embodiments of the invention may be practiced without some or all of these specific details. It should be understood that the terminology used herein is for the purpose of describing particular embodiments only and is not intended to limit the scope of the invention. In the drawings, the same reference numerals refer to the same or similar functionality or features throughout the several views.
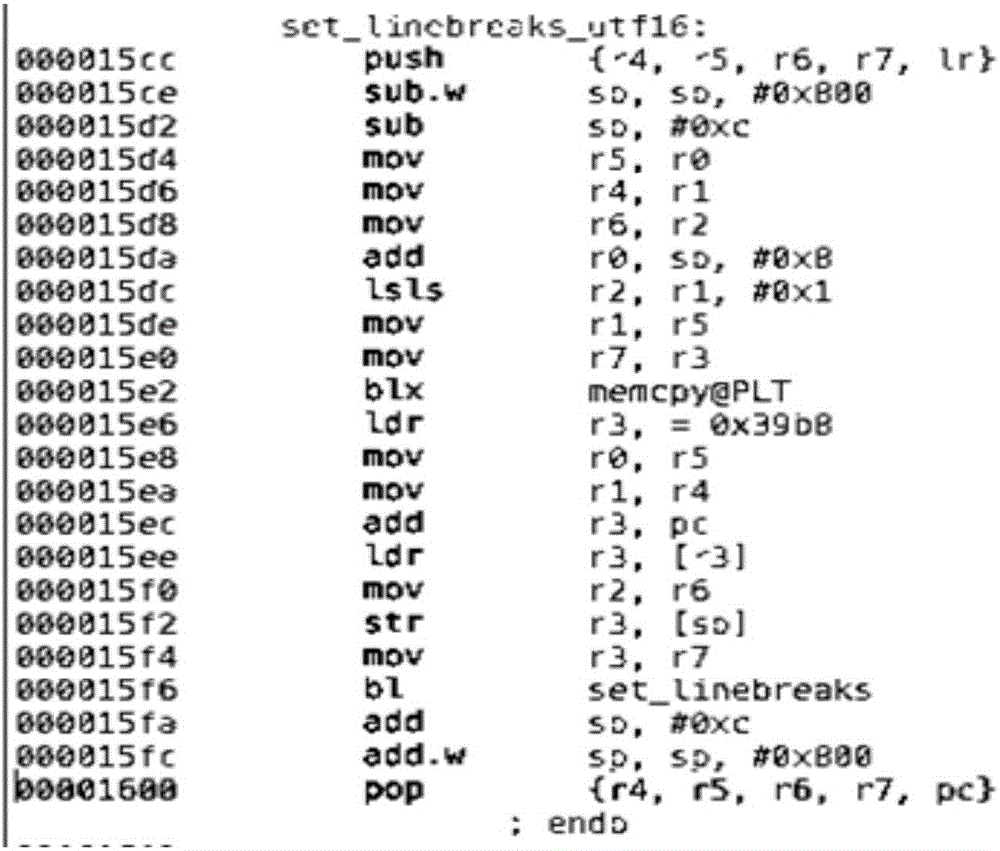
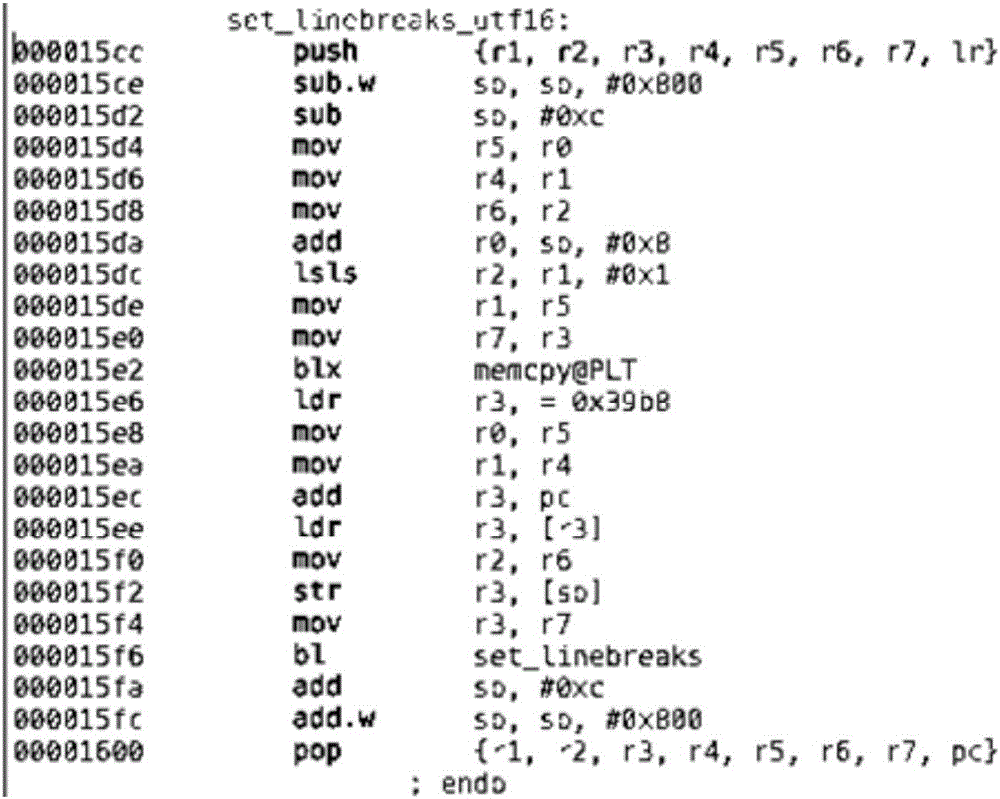
[0027] Embodiments of the present invention provide a ROP mitigation strategy for a computer system, specifically a mobile computer system running on an ARM architecture. This strategy can significantly reduce the likelihood of ROP-based attacks on computer systems.
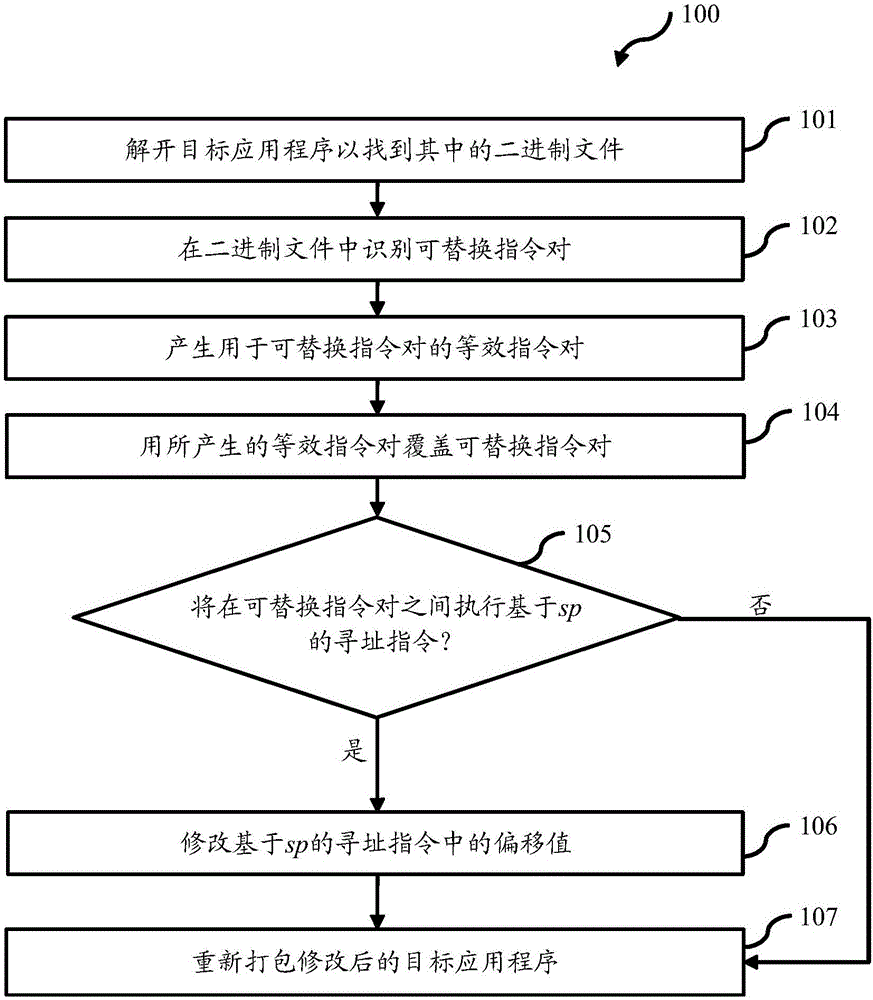
[0028] figure 1 is a flowchart illustrating a method 100 for defending against ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com