Intelligent detection method and device for return programming attack
A technology oriented to return and detection devices, applied in the field of intelligent detection, can solve the problems that cannot directly and effectively solve variant ROP attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
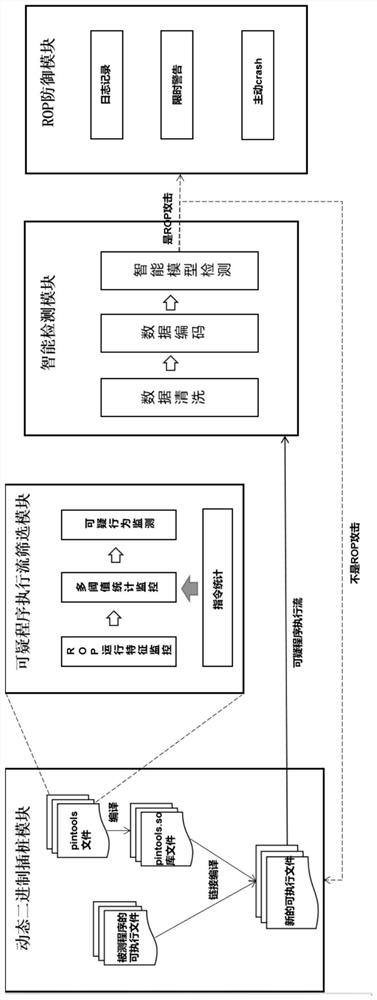
[0083] The present invention, in combination with the actual situation, briefly exemplifies some of the key contents in the technical solutions disclosed in the present invention as follows:
[0084] For the program executable file with buffer overflow vulnerability, the operating system is Ubuntu 18.04 version of the Linux operating system.
[0085] For the instrumentation of the program to be tested, the dynamic binary instrumentation framework Intel PIN is used. The PIN uses the buried point detection technology to bury some instructions in the program execution process, which can facilitate instruction identification and instruction statistics, and the PIN provides The rich API interface is available for users to call, and the dynamic execution flow of the program can be easily displayed in the form of assembly code through disassembly. The APIs used are provided by Intel PIN.
[0086] 1. System initialization: Obtain the executable file of the program software to be teste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com