Binary obfuscation method based on ROP (Return Oriented Programming) attack feature
A binary and characteristic technology, applied in the system and software security, computer field, can solve problems such as performance loss, dependence on specific hardware processor, easy to be cracked, etc., to achieve low execution speed loss, wide applicability, and low program performance loss Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
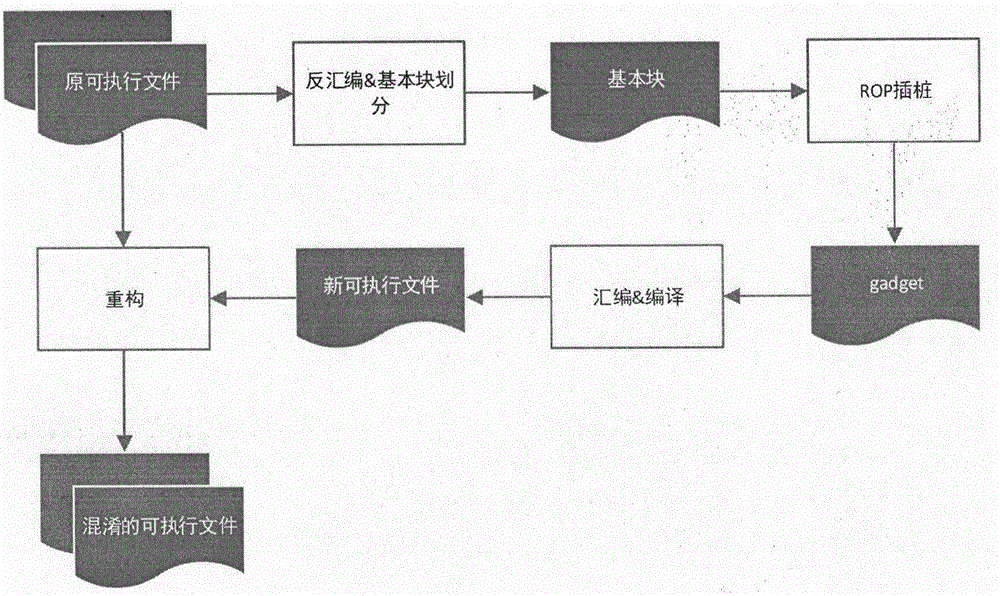
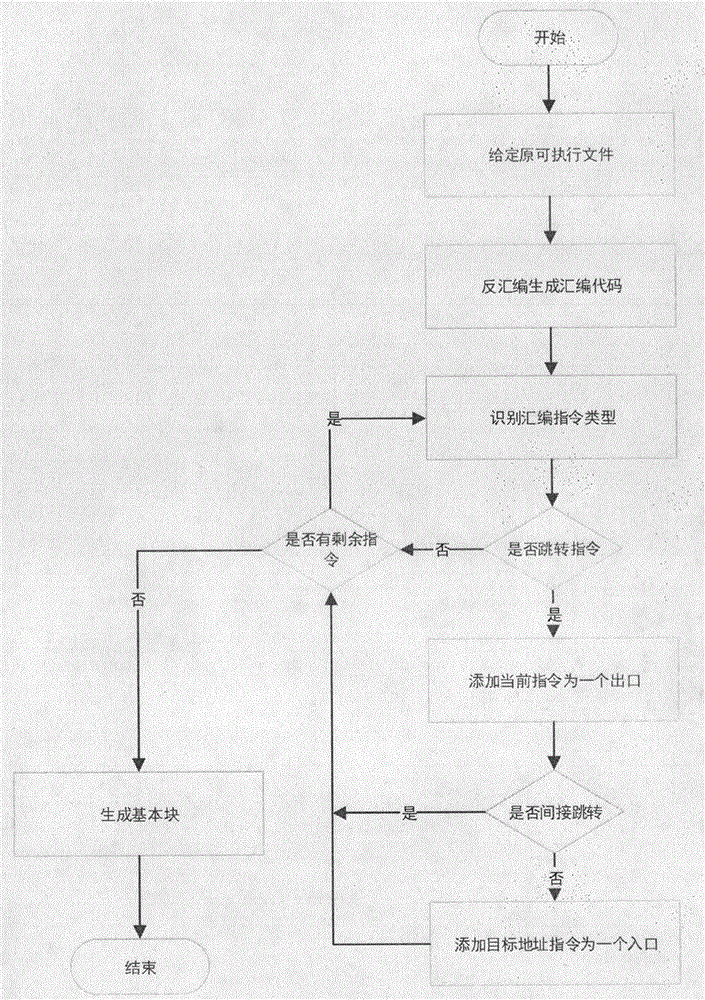
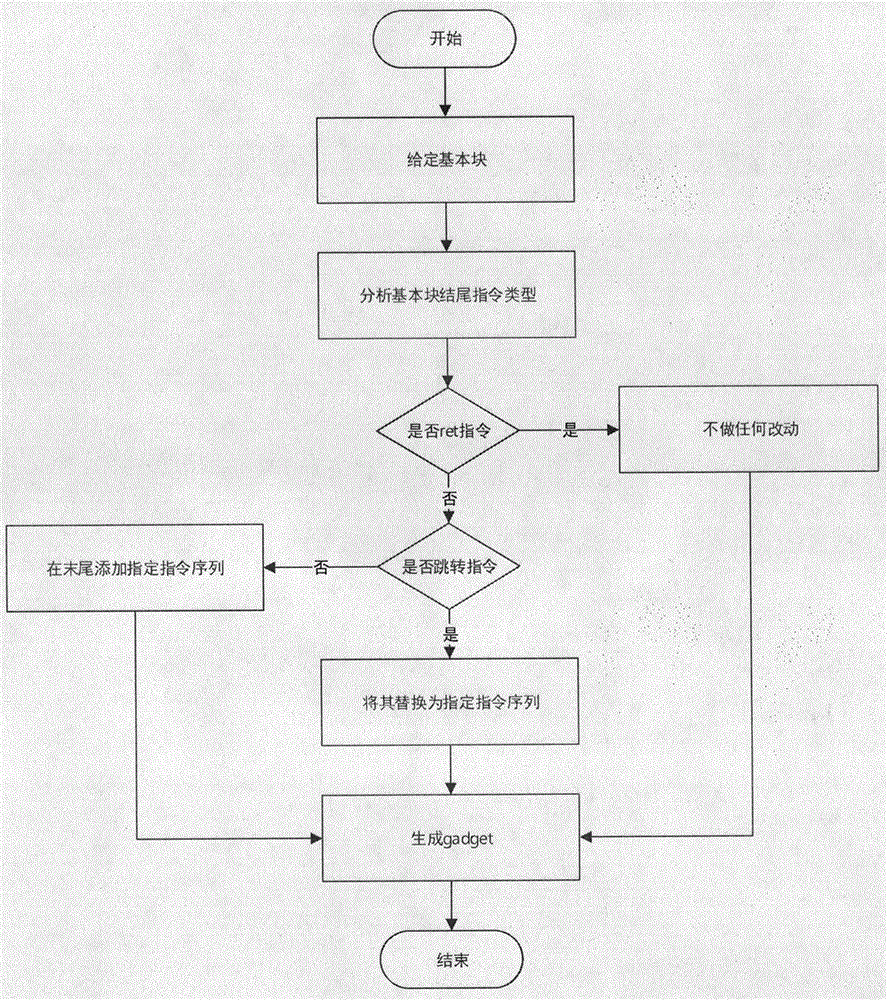
[0033] The method of the present invention at first disassembles the ELF binary file, obtains the assembly code, then divides the assembly code into basic blocks; after obtaining the basic blocks, carries out ROP instrumentation to the basic blocks, so that the basic blocks are converted into gadgets ending with ret instructions, these The code in the gadget form is the code in the obfuscated form; then, based on the assembly code in the gadget form, add the FindNext binary search function code, add the payload data segment and the maptable data segment, generate an asm format assembly file, recompile, and generate a new executable Execute the file; finally, reconstruct the original executable file, fill the content of the original code segment with nop instructions, add a new code segment newtxt to store the obfuscated code, and add a new data segment payload segment to control the gadget The connection between them adds a new data segment maptable segment for address mapping ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com