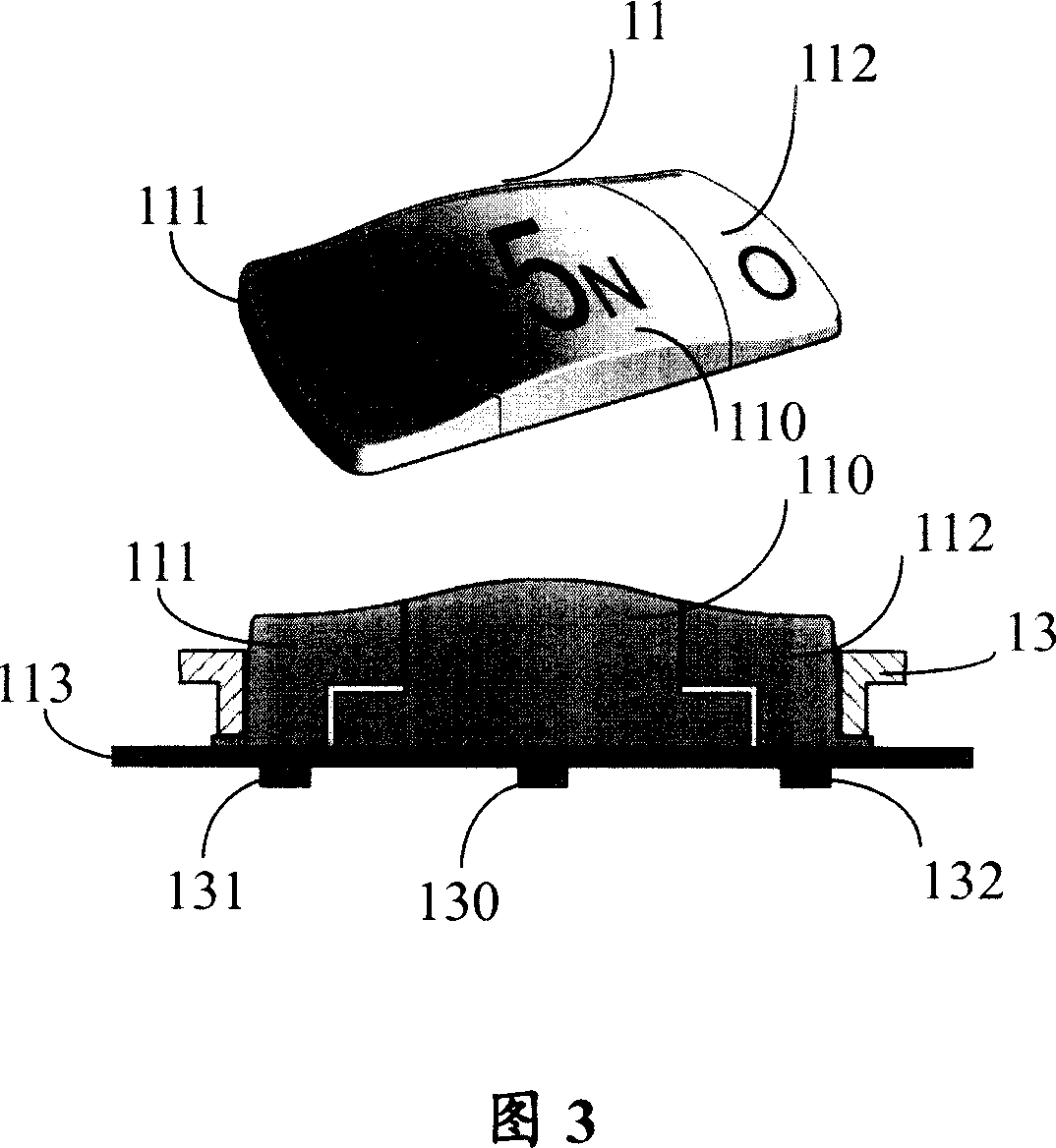
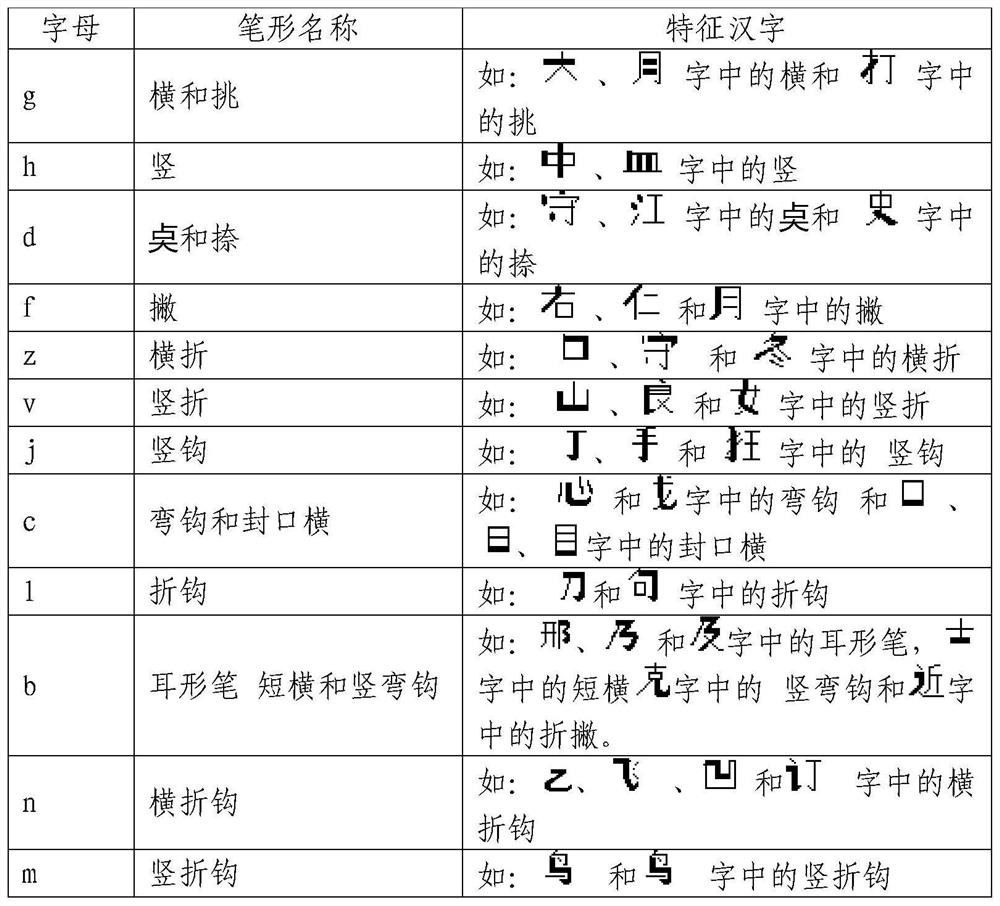
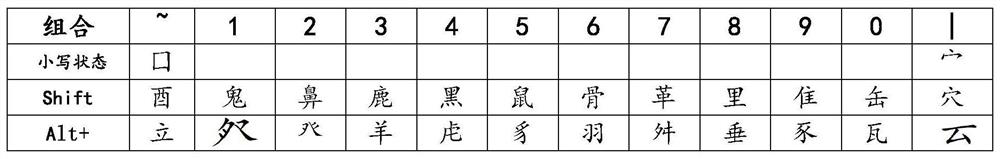
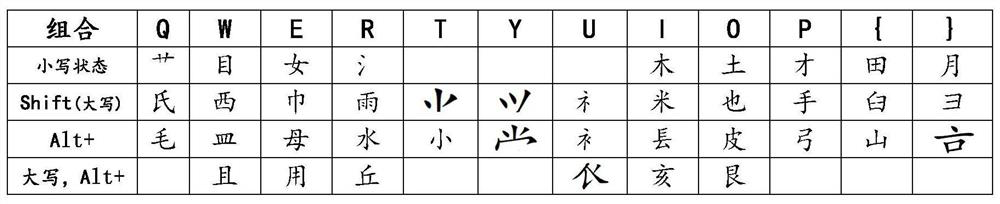
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Compound key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
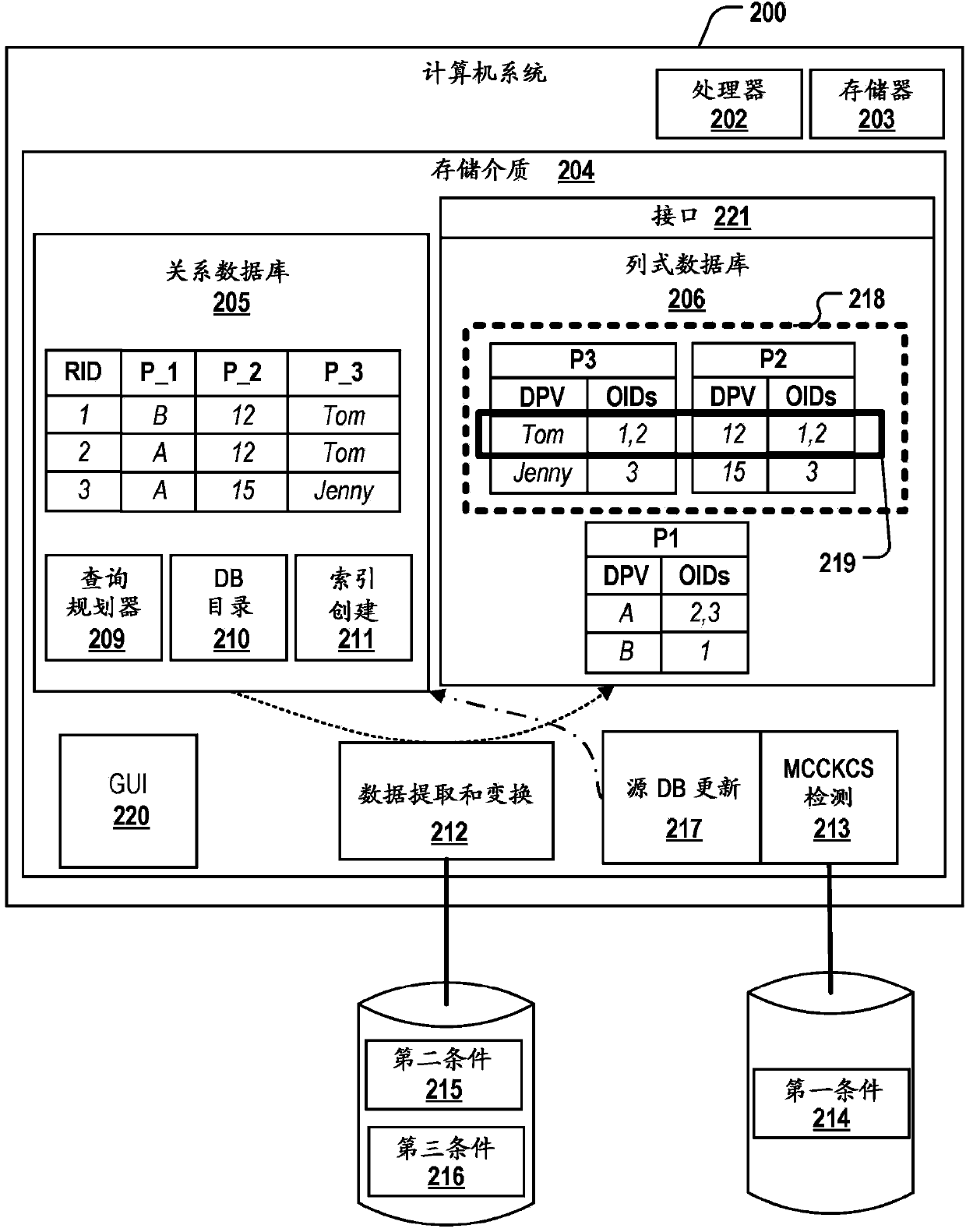
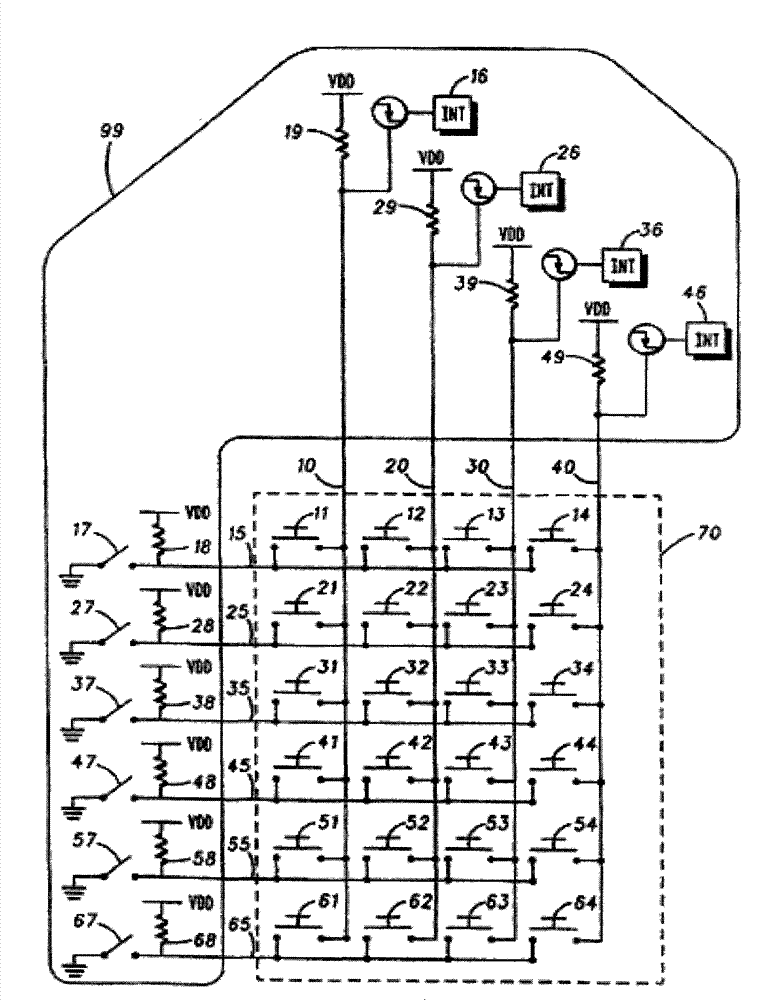
In database design, a composite key is a candidate key that consists of two or more attributes (table columns) that uniquely identify an entity occurrence (table row). A compound key is a composite key for which each attribute that makes up the key is a simple (foreign) key in its own right.
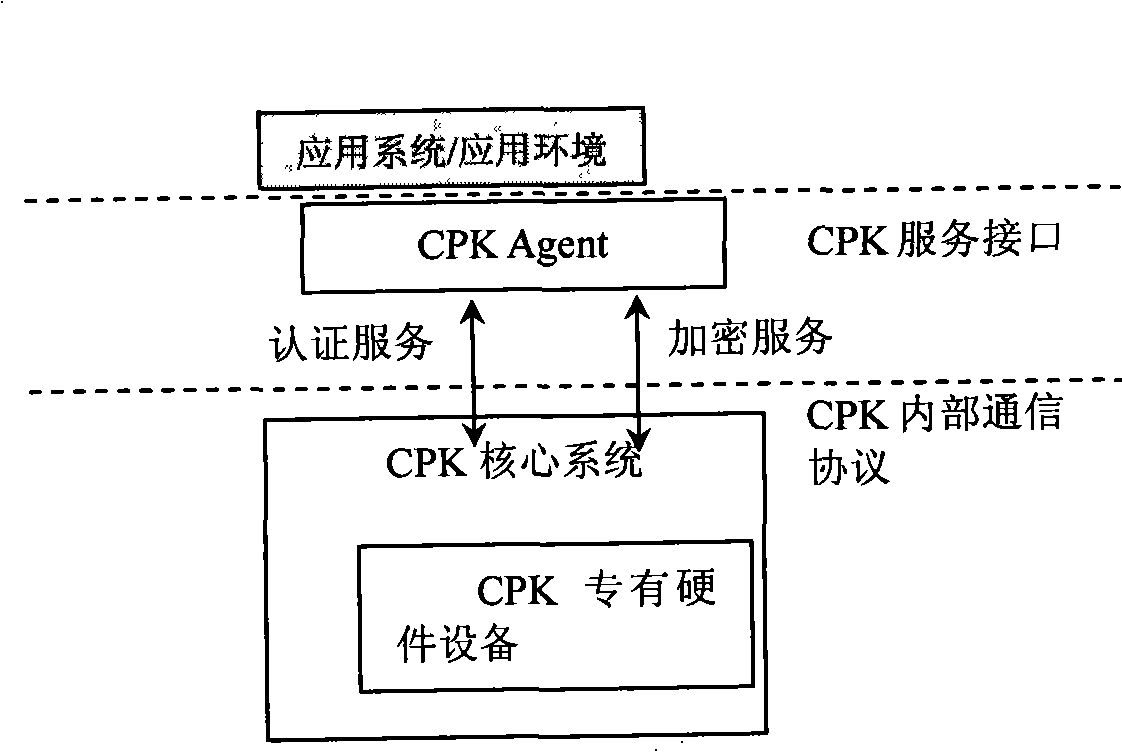
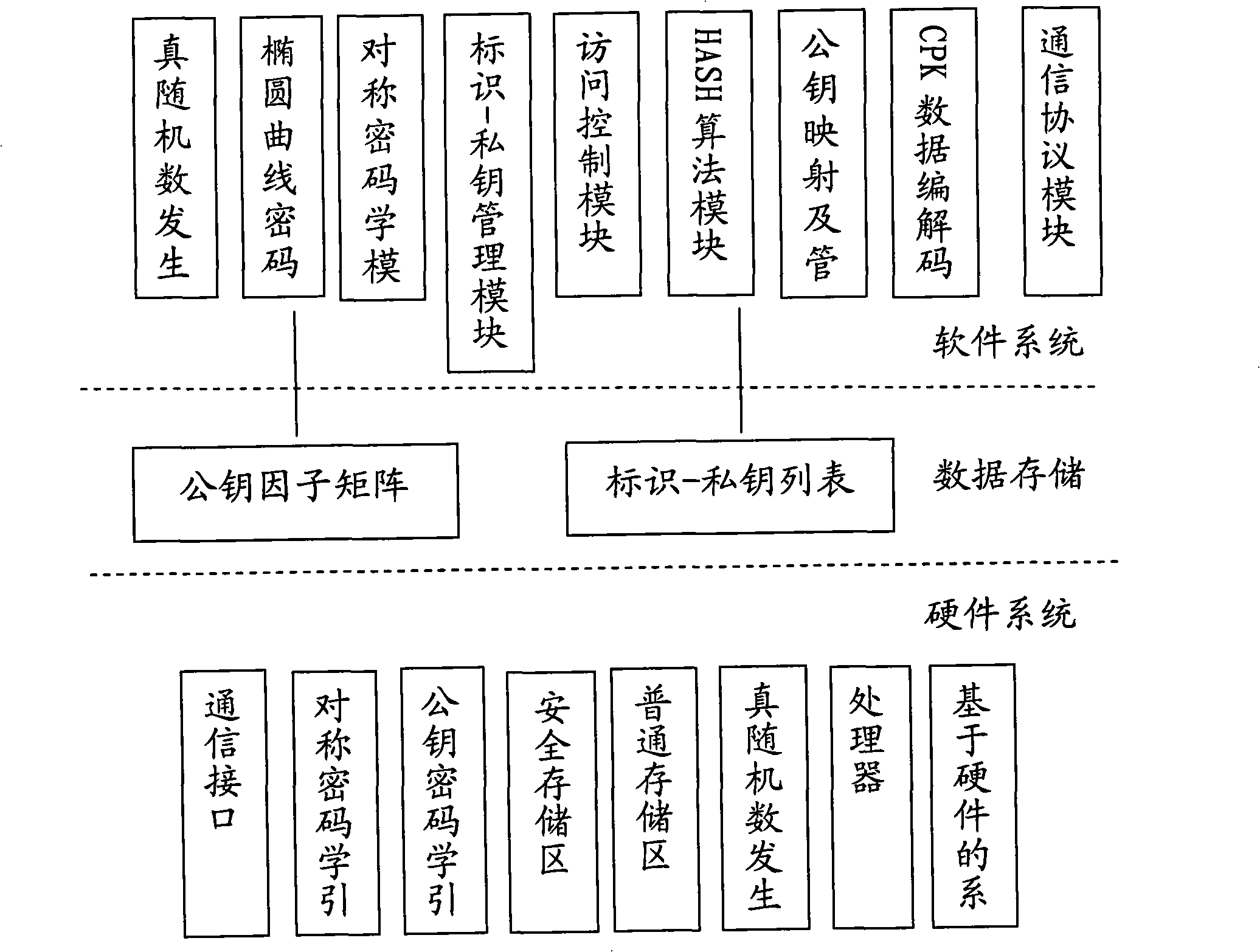
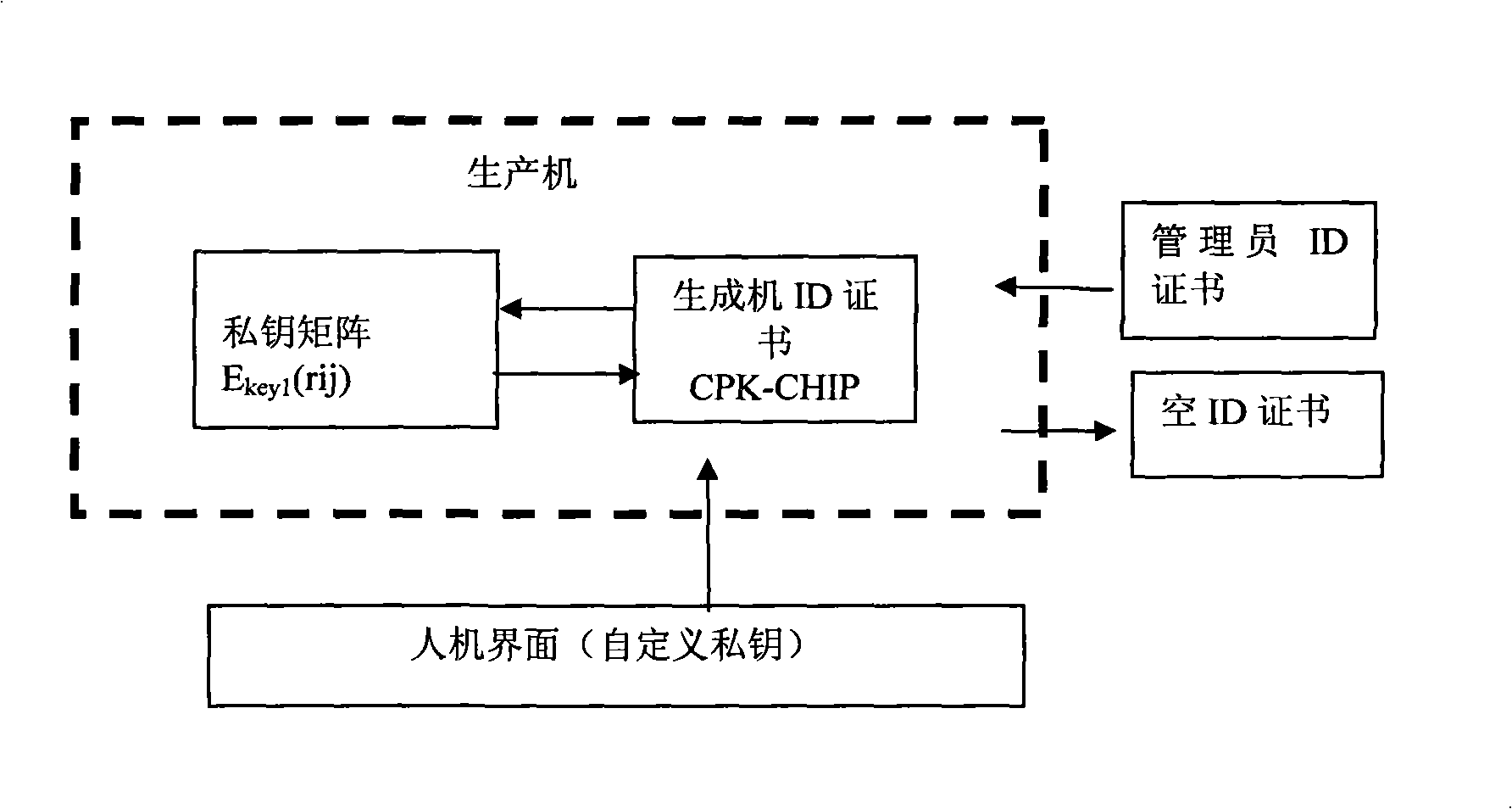
Generation method of composite public key
InactiveCN101340282AExposure that masks linear regularityCover up exposurePublic key for secure communicationUser identity/authority verificationThird partyKey exchange
Owner:BEIJING E HENXEN AUTHENTICATION TECH
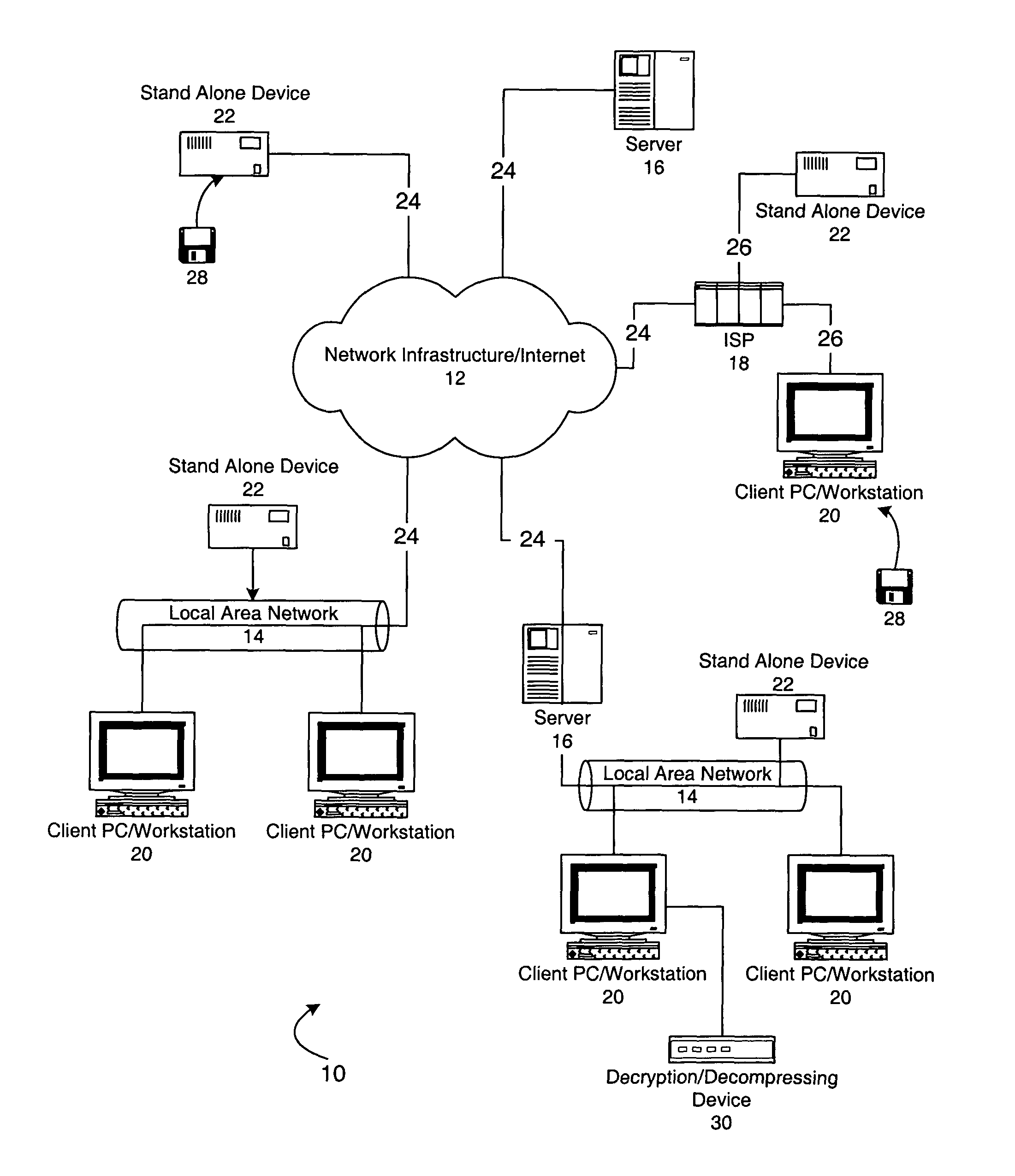
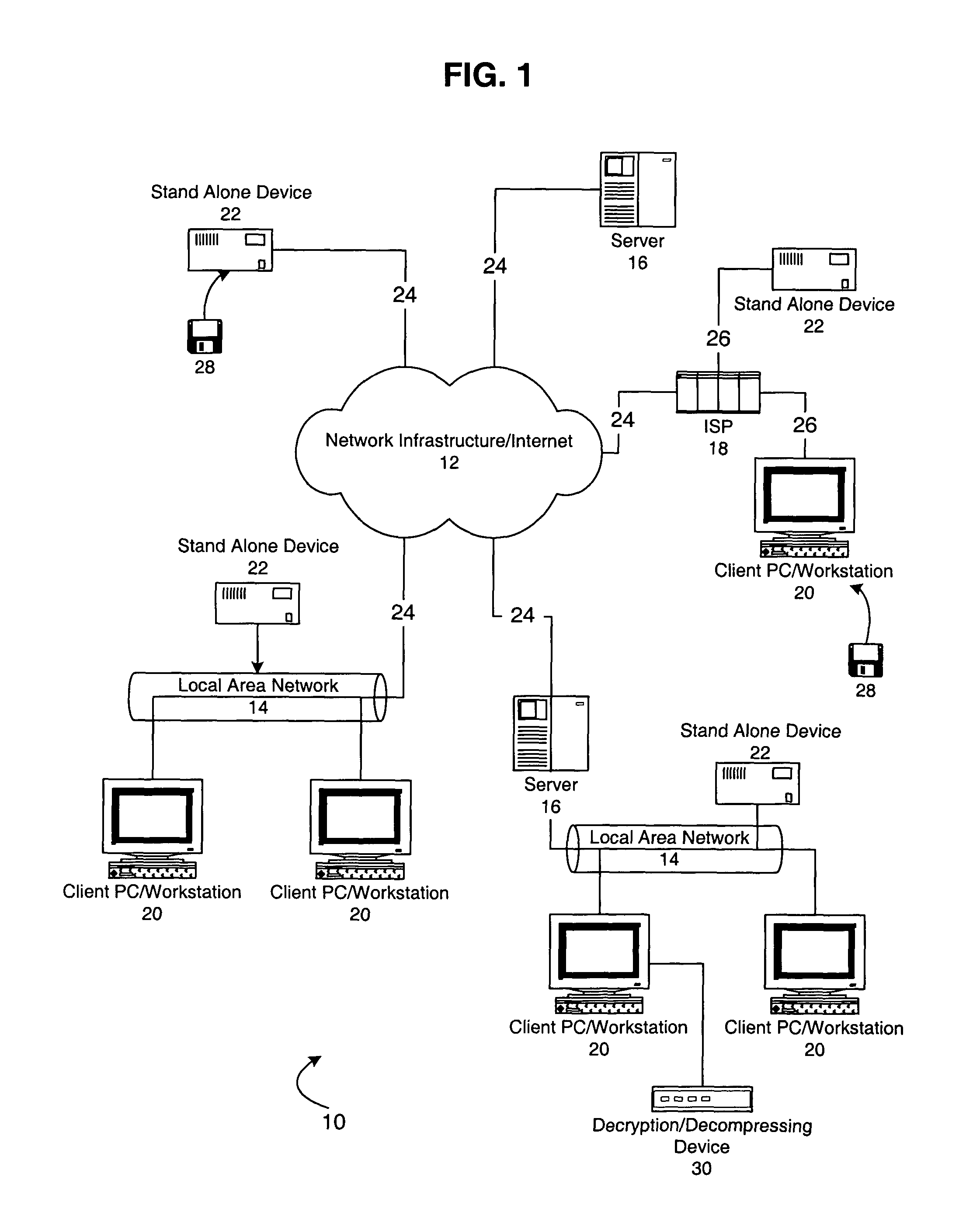
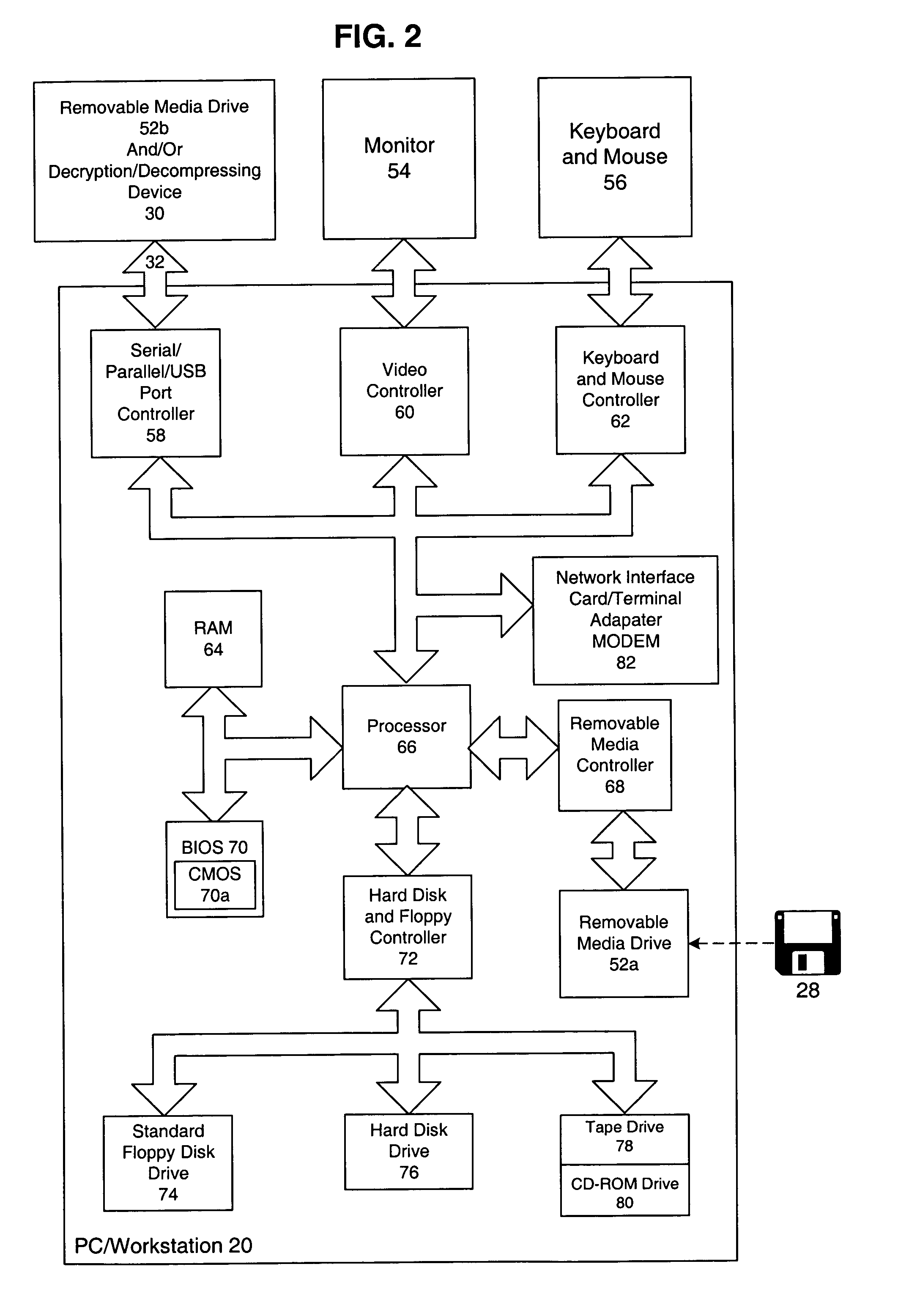
System for keying protected electronic data to particular media to prevent unauthorized copying using a compound key
InactiveUS7246246B2Digital data processing detailsUnauthorized memory use protectionGeneral purpose computerCompound key
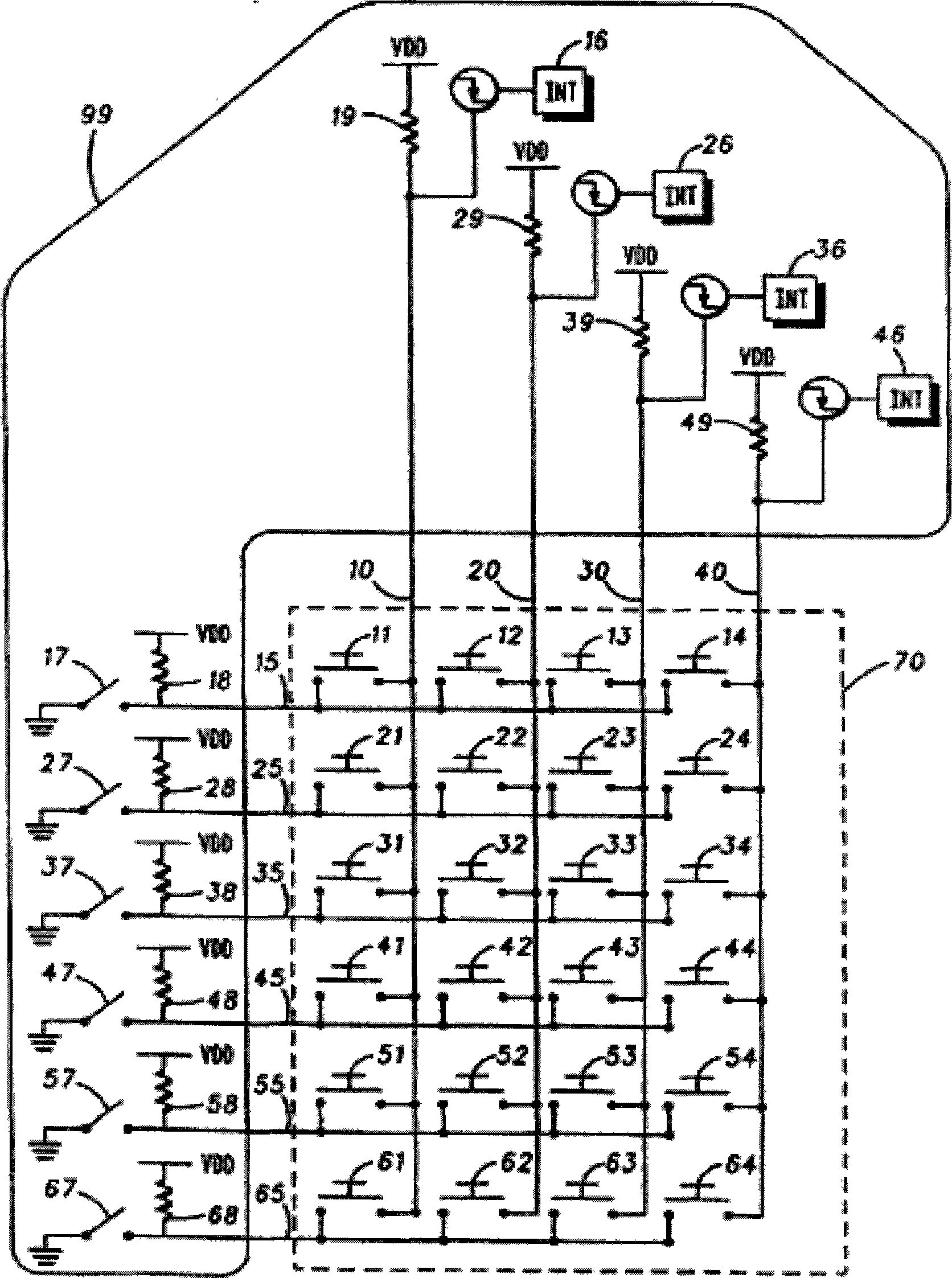
A system an method for distribution of electronic data over a network infrastructure that includes a client device for operation by a user desiring to receive the electronic data and server that contains the electronic data and offering the electronic data for downloading to the client device via the network infrastructure. The client device communicates a compound data key that includes a unique serial number associated with a particular piece of media to which the electronic data is to be stored to the server, vendor information and user information. The server encrypts the electronic data using the compound key, and downloads the encrypted electronic data to the client computer, where the client computer writes the encrypted electronic data to the particular piece of media such that the encrypted electronic data may only be accessed from the particular piece of media. The electronic data is decrypted for use by the apparatus or another device attached to the apparatus using the compound key as a data key, and the data is accessible from only the one piece of media having the unique serial number and is not accessible from any other media having a different or no identifier. In an alternate embodiment, the apparatus for reading the encrypted electronic data is connected to a general purpose computer having a media drive which reads the unique serial number and the electronic data from the one piece of media. The apparatus comprises an application specific integrated circuit which controls and executes instructions to accept the electronic data and the unique serial number from the general purpose computer.
Owner:EMC IP HLDG CO LLC
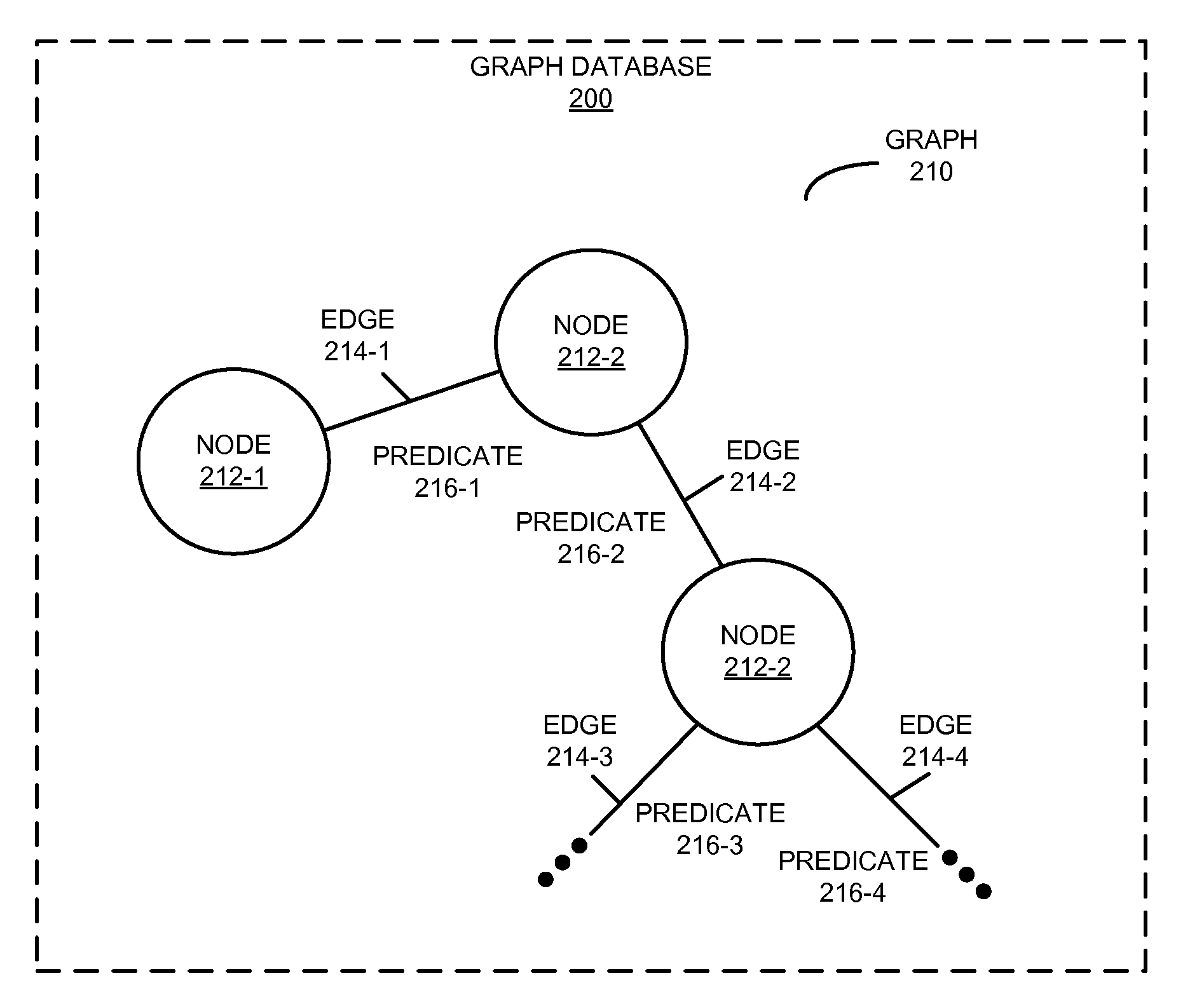
Translating queries into graph queries using primitives
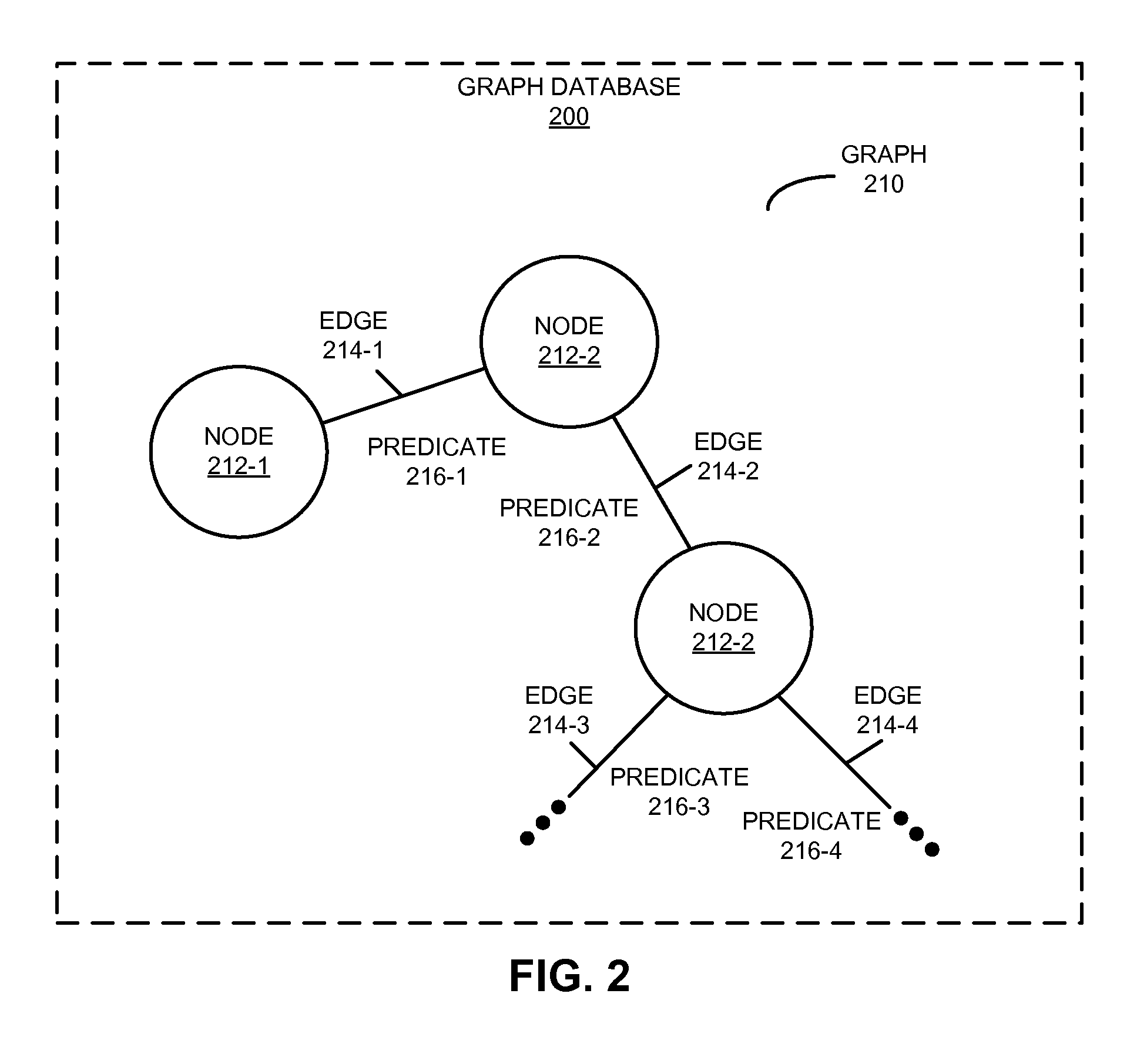
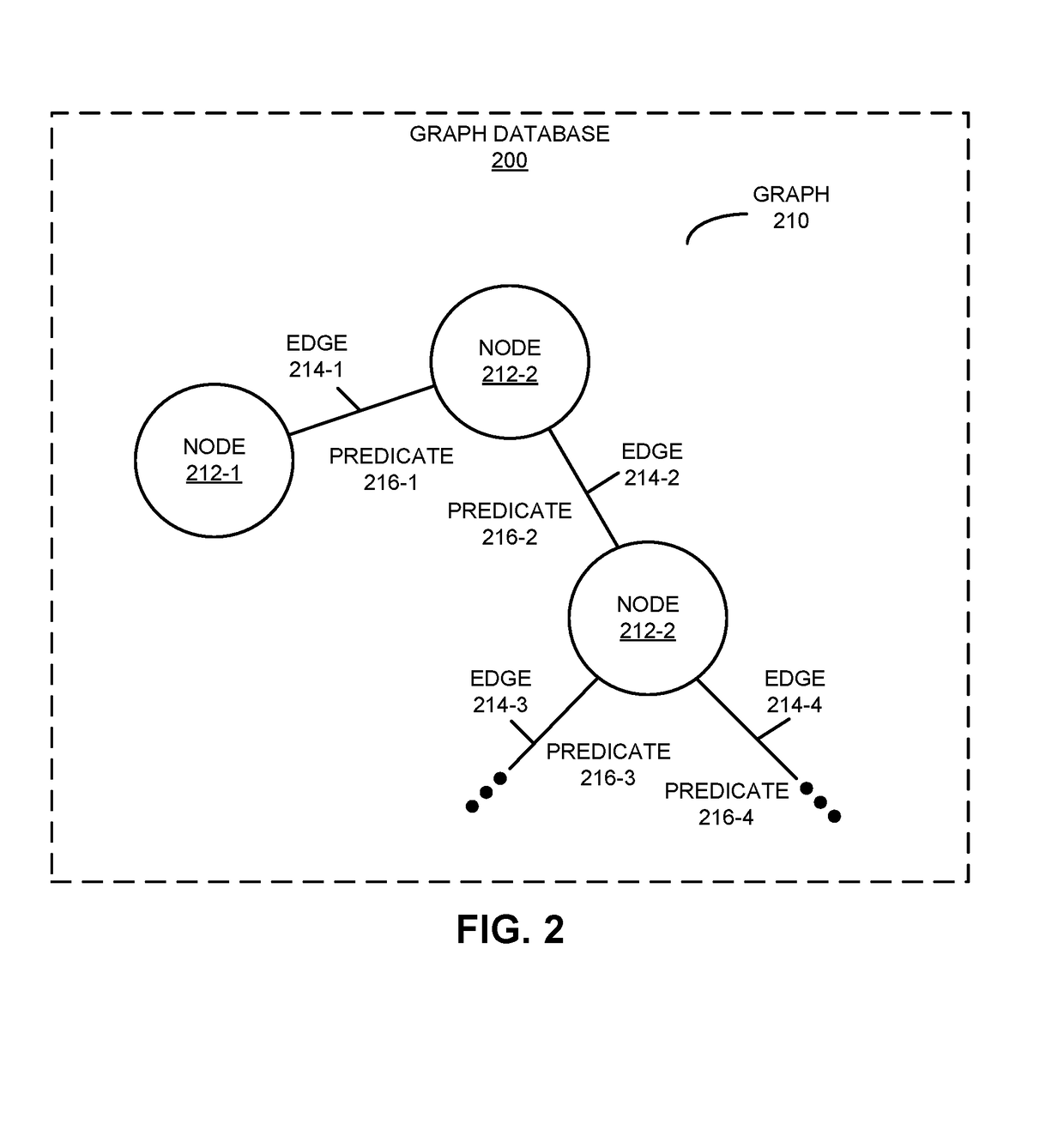
In order to facilitate the requesting of desired information from a graph database that stores a graph, a system may translate an initial query into a query that can be executed against the graph database. In particular, using primitives, the system may translate a query associated with a type of database (such as a relational database) into the query. The graph may include nodes, edges between the nodes, and predicates to represent and store data with index-free adjacency. Moreover, the primitives may include: a rule based on edges in the graph that expresses a relational schema in the type of database, and information associated with a compound key that specifies a relationship between nodes, edges and predicates in the graph corresponding to a table in the type of database. Then, the system may execute the query against the graph database, and may receive a result that includes a subset of the graph.
Owner:MICROSOFT TECH LICENSING LLC
Method, apparatus and chip for implementing keyboard module composite key function
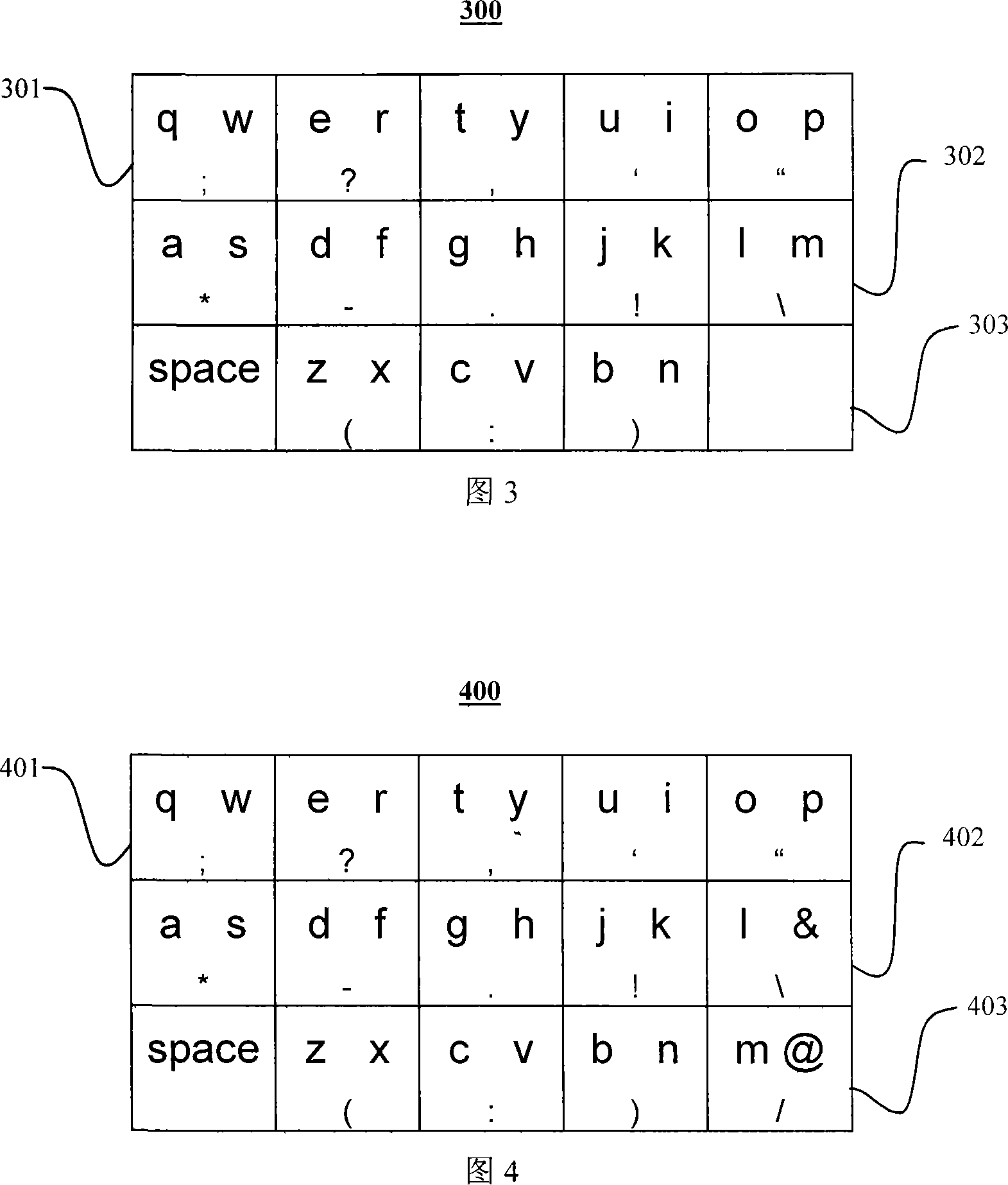
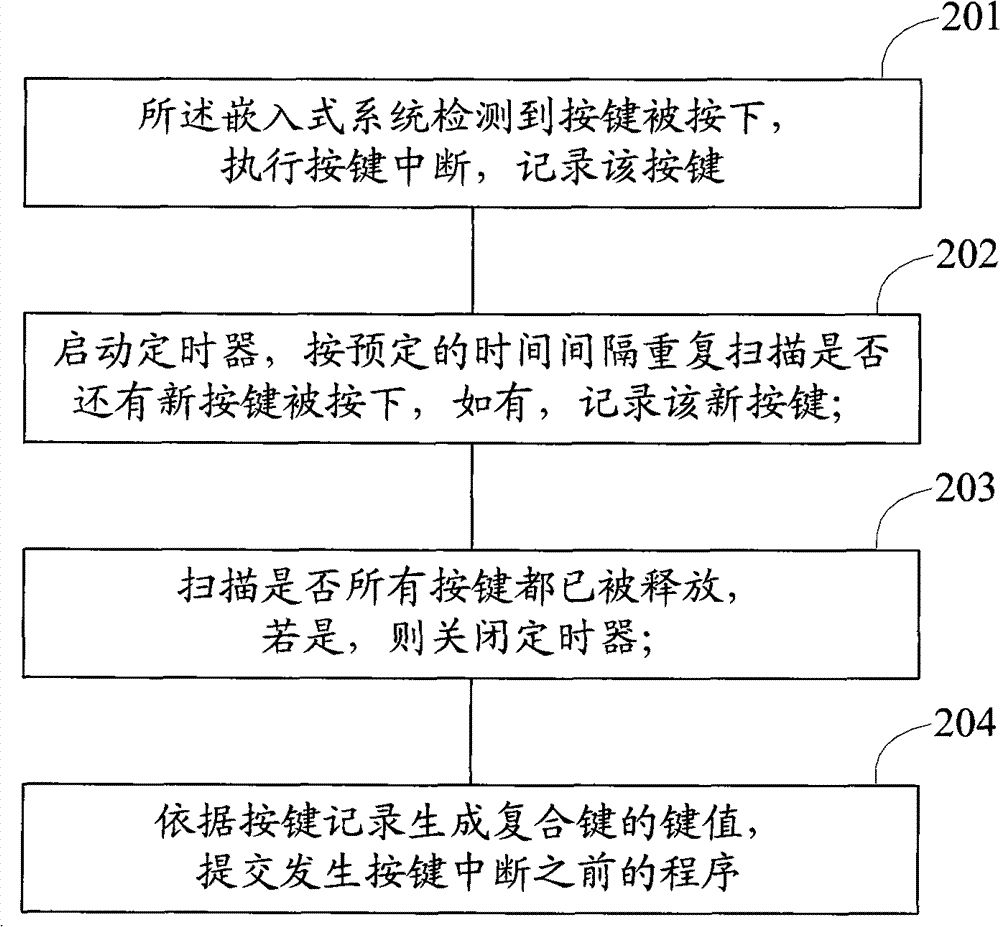
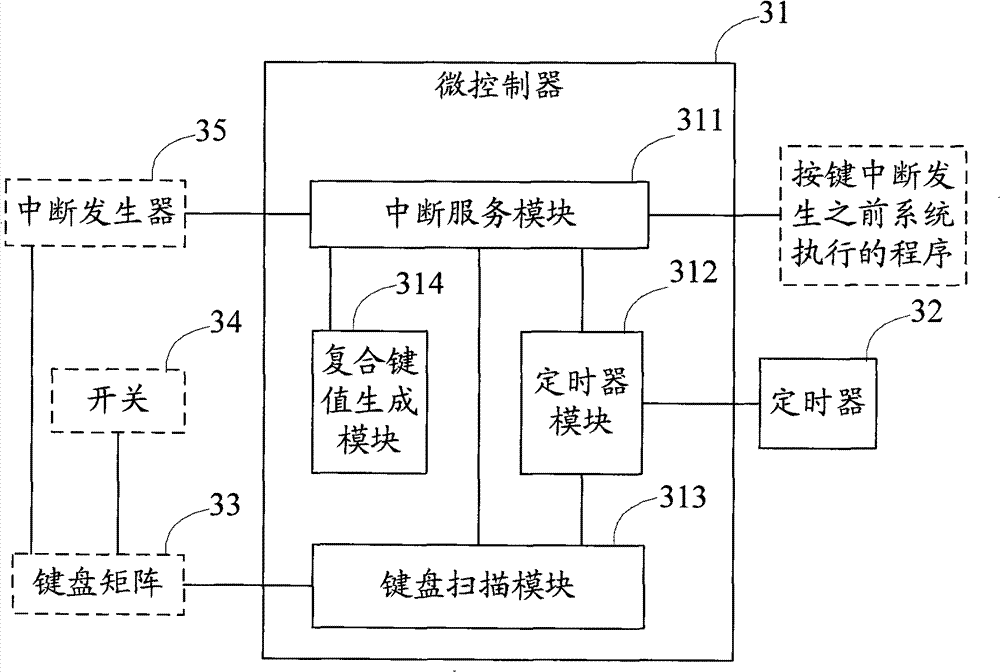
InactiveCN101510127ARealize compound key functionNo orderInput/output processes for data processingKey assignmentCompound key
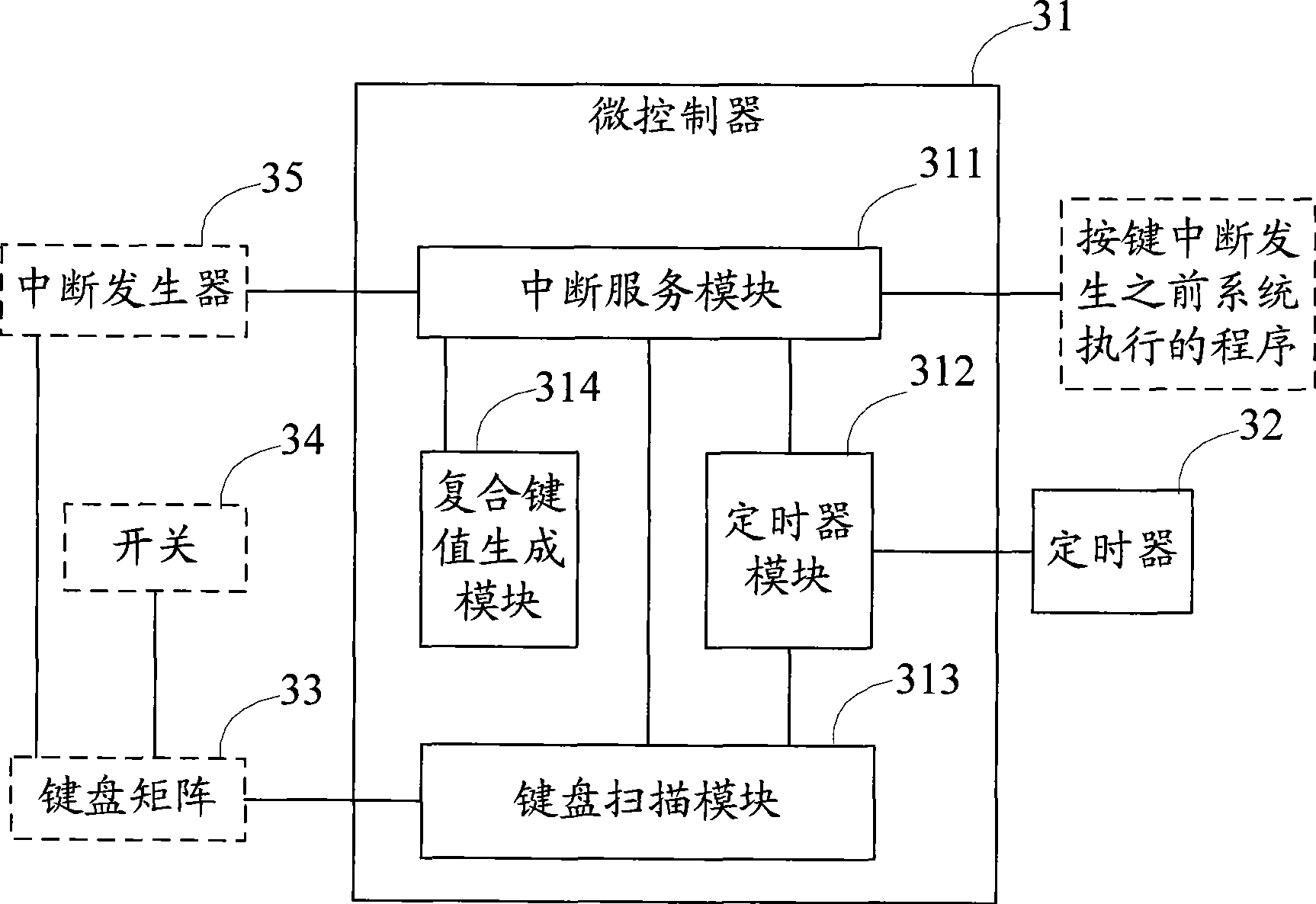
The invention provides a method, a chip and a device for implementing the functions of compound keys of the key module of an embedded system. The method comprises the following steps: the embedded system executes keystroke interruption and records the keystroke after detecting the keystroke is pressed; the embedded system starts a timer and then rescans if other keystrokes are pressed in accordance with scheduled time intervals, if so, records the new keystrokes; the embedded system scans if all the keystrokes are released, and then disables the timer if all the keystrokes are released; then the embedded system produces the key assignments of the compound keys according to the keystroke records and submits the program prior to the keystroke interruption. The timer is additionally arranged in the system on the basis of the existing array keystroke module. The system starts the timer and then rescans and records other keystrokes in accordance with the scheduled time intervals after detecting a keystroke interruption. Therefore, under the condition of one system interrupted, the invention can realize the functions of the compound keys by obtaining the responding of a plurality of keystrokes. Besides, the proposal of the invention has no restriction to the keystroke sequence and quantity, and supports the composite of any keystroke and a plurality of keystrokes.
Owner:WUXI ZGMICRO ELECTRONICS CO LTD
Translating queries into graph queries using primitives
In order to facilitate the requesting of desired information from a graph database that stores a graph, a system may translate an initial query into a query that can be executed against the graph database. In particular, using primitives, the system may translate a query associated with a type of database (such as a relational database) into the query. The graph may include nodes, edges between the nodes, and predicates to represent and store data with index-free adjacency. Moreover, the primitives may include: a rule based on edges in the graph that expresses a relational schema in the type of database, and information associated with a compound key that specifies a relationship between nodes, edges and predicates in the graph corresponding to a table in the type of database. Then, the system may execute the query against the graph database, and may receive a result that includes a subset of the graph.
Owner:MICROSOFT TECH LICENSING LLC
Software keyboard entry method for implementing composite key on screen of electronic equipments
ActiveCN101174190AConvenient and accurate information inputThe implementation process is simpleInput/output processes for data processingCompound keyComputer science
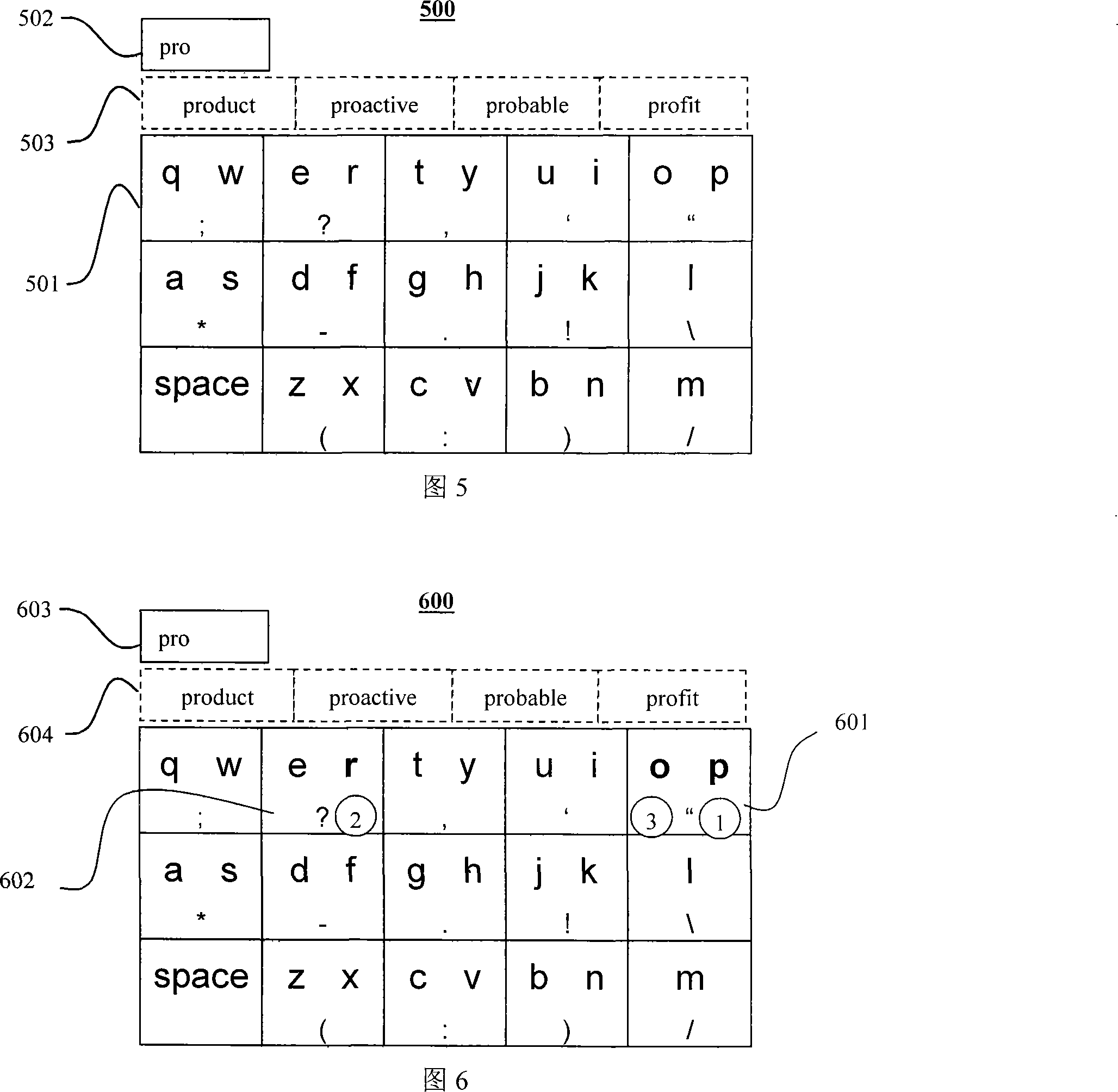
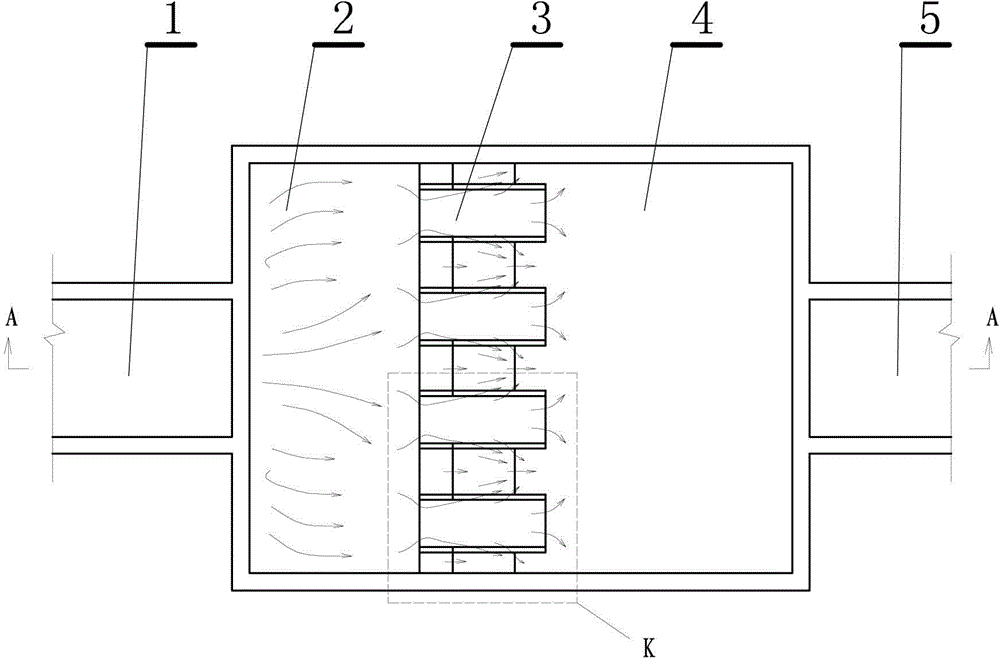
The invention relates to a software-based input method for the onscreen keyboard, which enables compound key-press on the screen of electronic equipment. The invention is realized as follows: two letters are arranged on a key position; the user clicks the key position directly to perform fuzzy input, and then moves the contact to perform exact input; furthermore, the symbols are selected or the capital letters are switched quickly through the contact movement. The invention enables the user to input text quickly, conveniently and efficiently, and has the advantages of convenient and accurate information input on the screen of electronic equipment, and convenient, quick and flexible input.
Owner:SHANGHAI CHULE (COOTEK) INFORMATION TECH CO LTD
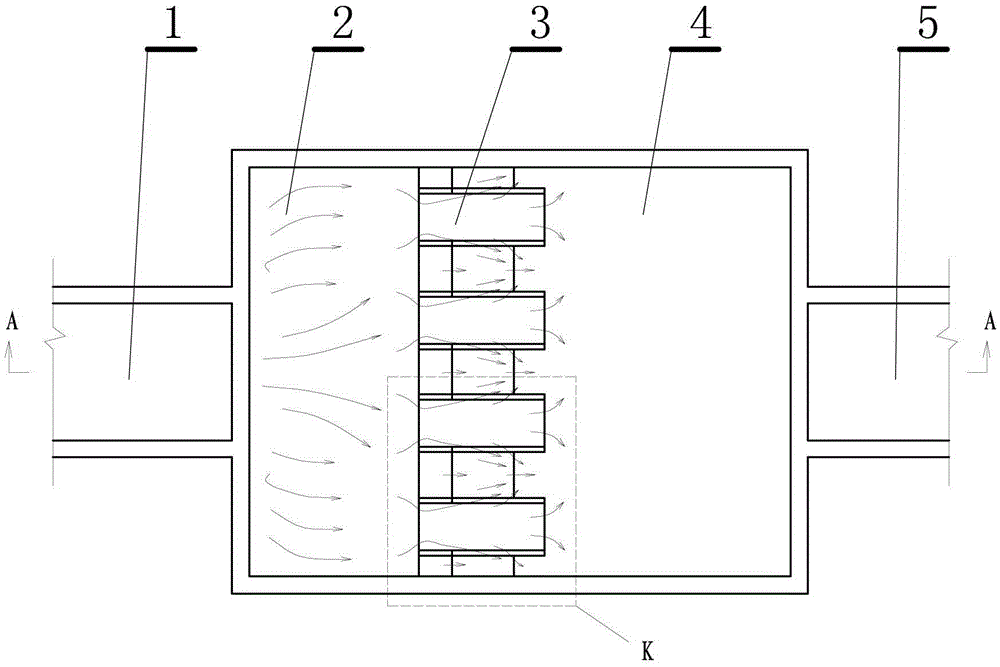
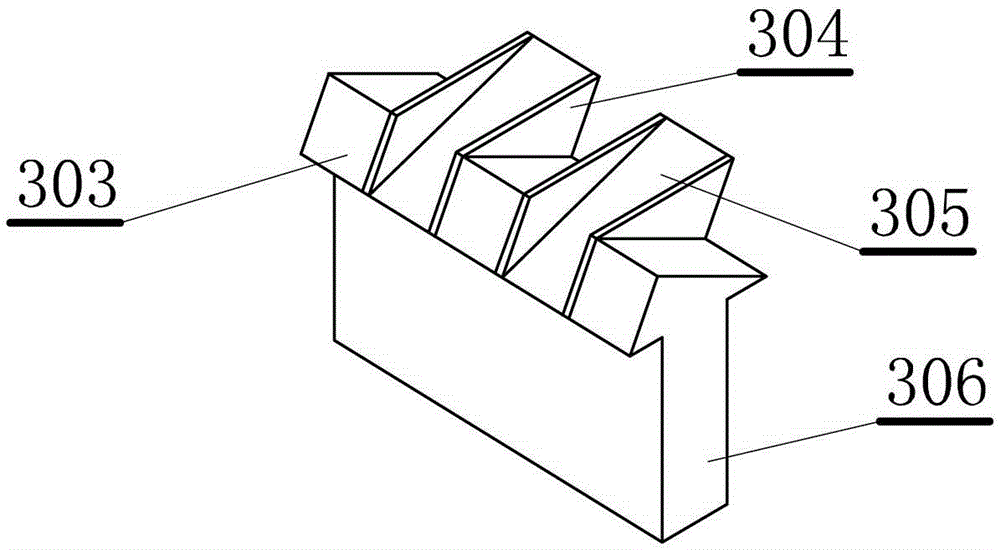
Compound key overflow weir type siphon well and method implemented by same
InactiveCN104563267AEnhanced single-width overcurrent capabilityLow costSewerage structuresSiphonWater flow
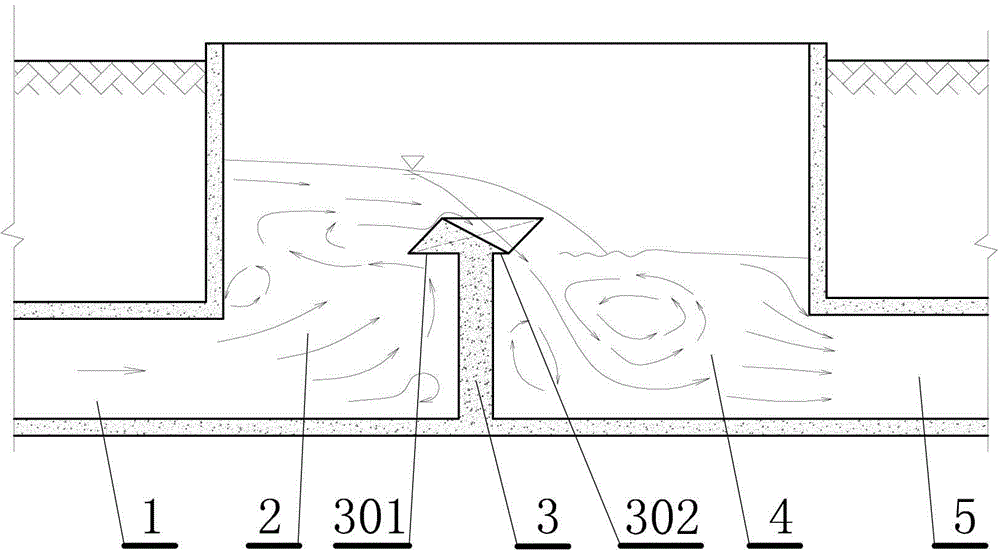
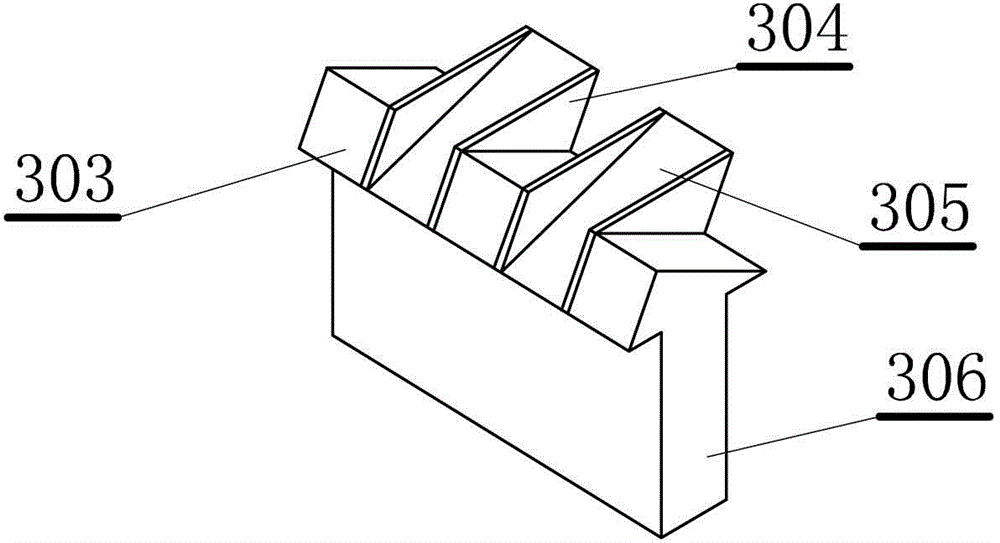
The invention relates to a compound key overflow weir type siphon well which comprises at least one single well combination. Each single well combination comprises a vertical well with a water inlet culvert pipe, the vertical wells are connected with overflow connecting wells, the overflow connecting wells are connected with water delivery culvert pipes, and compound key overflow weirs are arranged between the vertical wells and the overflow connecting wells; the compound key overflow weirs comprise weir bodies, positive triangular piers and reverse triangular piers which are provided with horizontal bottom surfaces are staggered on the tops of the weir bodies, the lengths of the bottom surfaces of the positive triangular piers and the reverse triangular piers along the direction of water flow are larger than the thicknesses of the tops of the weir bodies, and front weir cantilevers and rear weir cantilevers are formed. The compound key overflow weir type siphon well has the advantages that the compound key overflow weirs are used as flow passing facilities and bubble inhibiting schemes, accordingly, the single-width flow passing ability of the overflow weirs of the siphon well can be improved, the drop flow difference between the overflow weirs of the siphon well and open seas can be reduced, bubbles mixed in the water flow which flows through the weirs can be inhibited, and influence on ambient environments can be reduced; the engineering cost can be lowered, energy can be effectively dissipated, the bubbles can be effectively eliminated, and relatively clean water can be drained.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
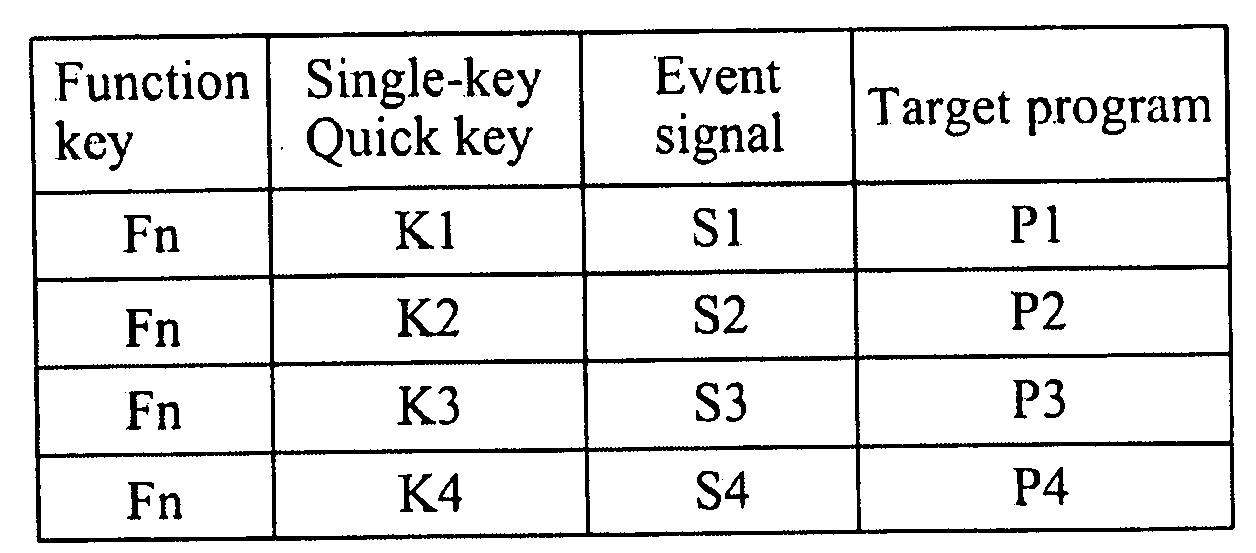
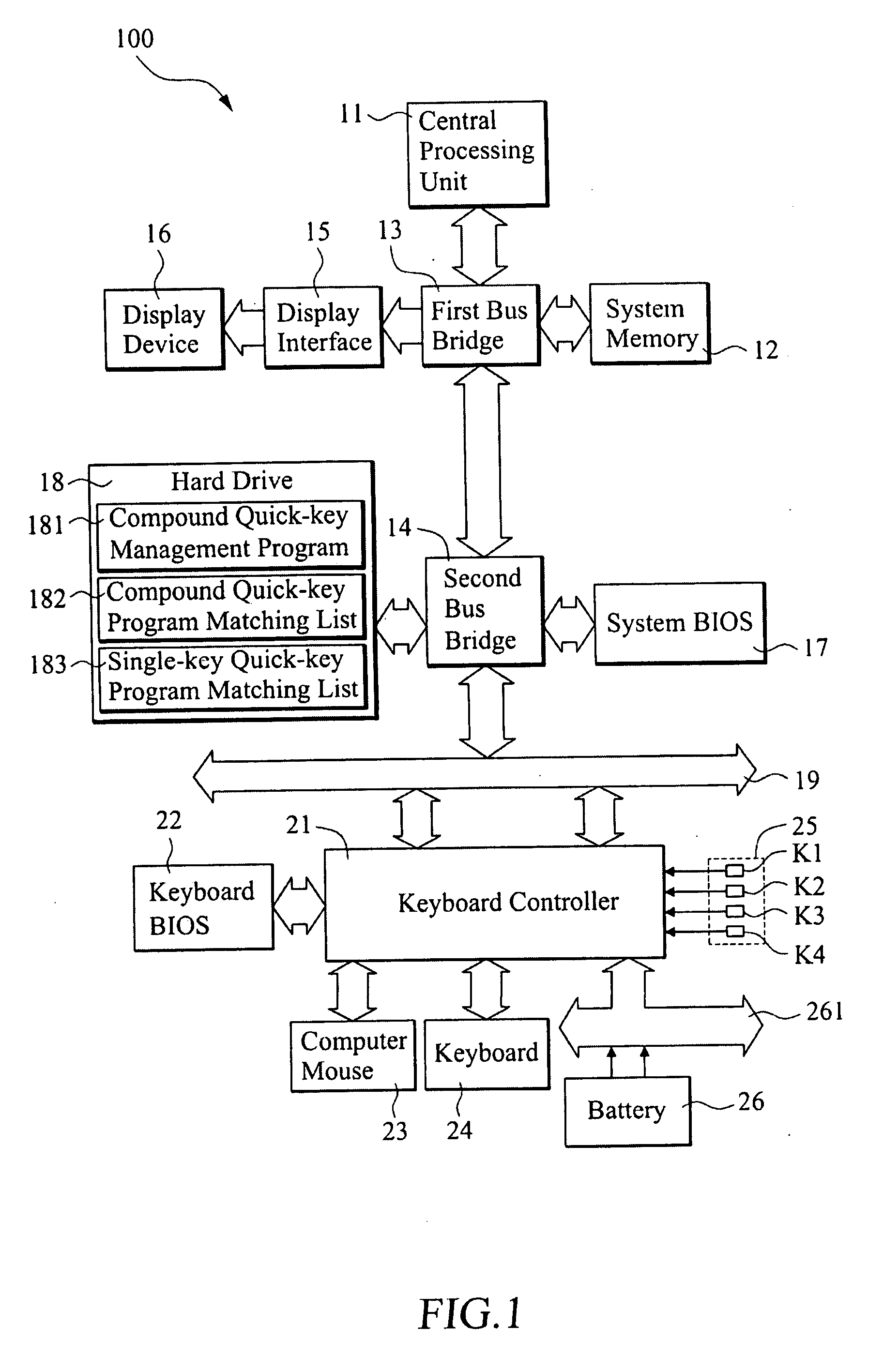
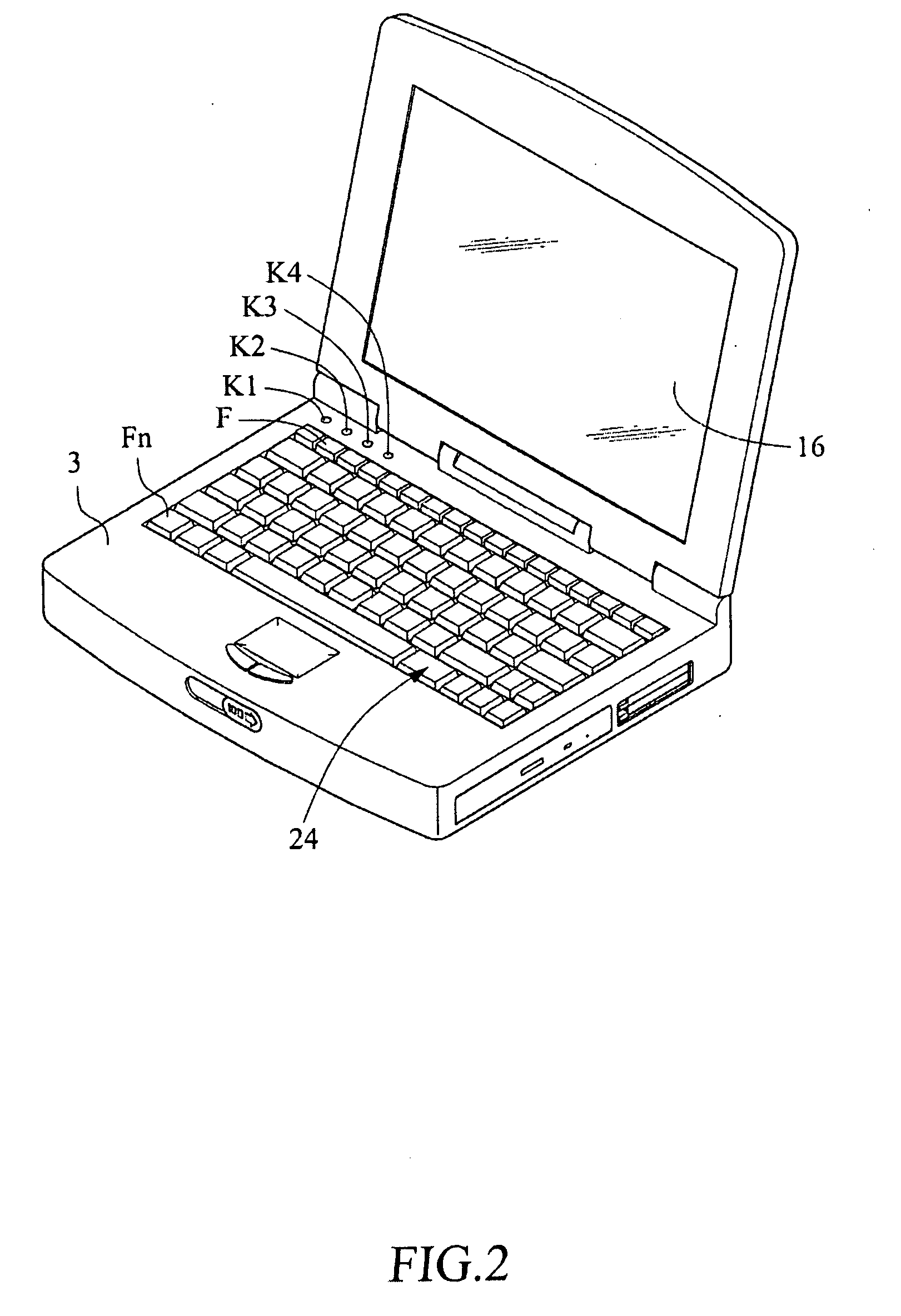
Method for executing target programs with compound quick keys
InactiveUS20090070491A1Easy to set upConvenient and efficient assistanceInput/output for user-computer interactionComputer hardwareOperational system
Disclosed is a method for executing target programs with compound quick keys, which is applicable to a computer that is pre-loaded with a compound quick-key program matching list that contains data of at least one function key, at least one single-key quick key, and an event signal and a target program associated with the quick key. After the computer loads the operating system, a compound quick-key management program is activated to read the compound quick-key program matching list. When a user actuates the function key and the single-key quick key simultaneously, the keyboard controller transmits the event signal associated with the actuated function key and the single-key quick key and executes the target program associated with the actuated function key and the single-key quick key in accordance with compound quick-key program matching list.
Owner:MITAC TECH CORP
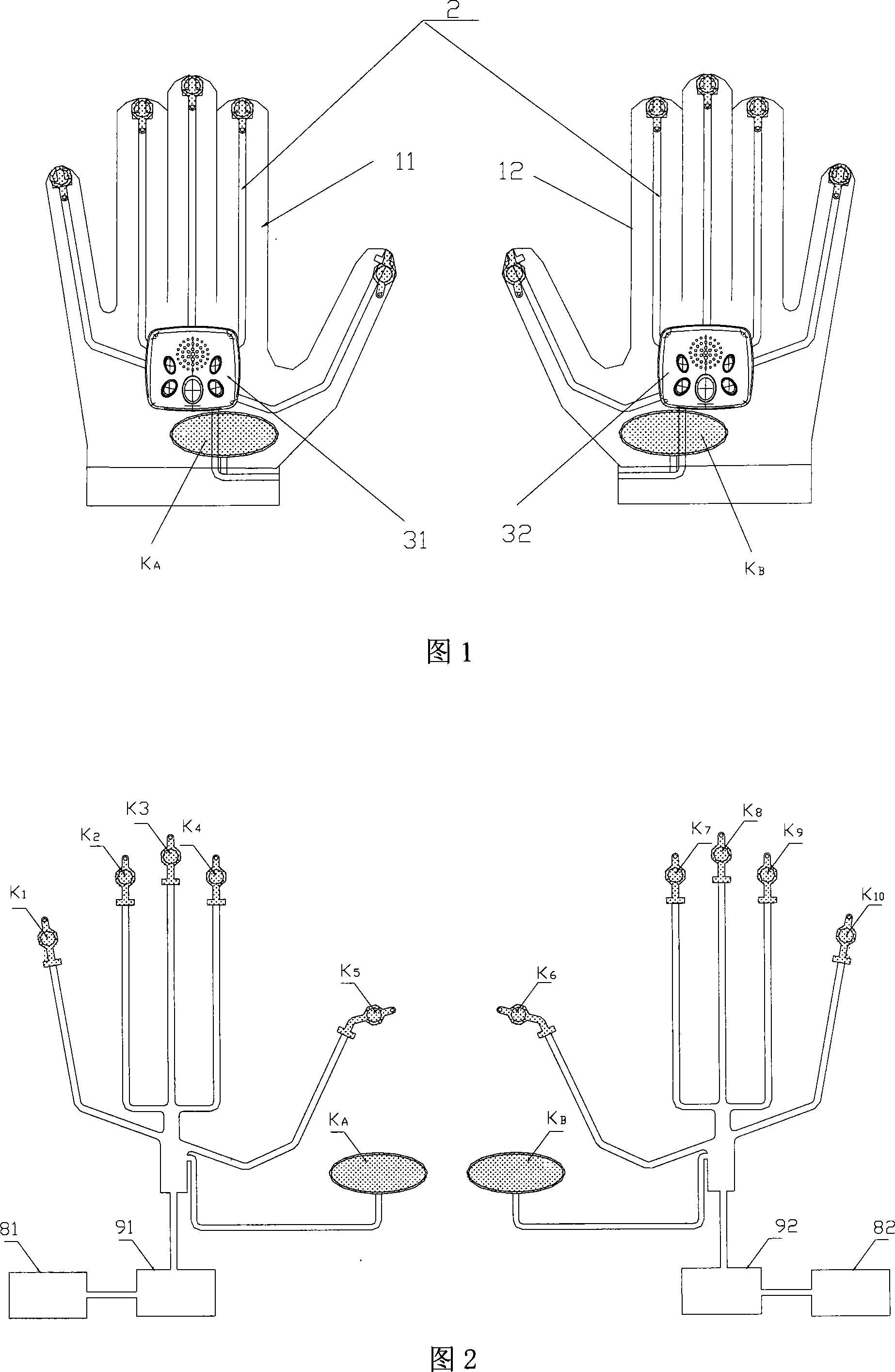
Electronic organ putted on hand
The invention relates to a finger piano, comprising a first glove, a second glove, a plurality of playing keys distributed at each finger tip of the gloves, and a sound box arranged on each glove. The finger piano also comprises compound keys arranged in the position of a palm end of each glove, each sound box is connected with a controller, the playing keys and compound keys arranged on the same glove are all connected on the corresponding controller, wherein the playing keys and the compound keys of one glove are combined to pronounce an octave, and the playing keys and the compound keys of the other glove are combined to pronounce another octave. A gamut controlling switch used for rising or lowering an octave of each glove is arranged on each controller, and with the adjustment of the gamut controlling switch, the finger piano is capable of realizing pronunciation with at least two octaves. The finger piano of the invention steps over gamut with three octaves, more vivid music is displayed, and the controllers are capable of switching over between playing model and teaching model, thereby reinforcing the interactivity between the finger piano and users.
Owner:JUXING ELECTRONICS HUIZHOU
Integrated super-discharge energy-dissipation flood-overflowing unit and method
InactiveCN104695390AIncrease the effective inventory capacity of XinliEasy dischargeBarrages/weirsWater flowEngineering
The invention relates to an integrated super-discharge energy-dissipation flood-overflowing unit. The unit comprises an inlet overflow weir, wherein a chute is formed in the downstream of the inlet overflow weir; a water-falling energy dissipater is formed in the chute; the inlet overflow weir is a compound key overflow weir; the compound key overflow weir comprises a weir body; a forward triangular pier and a reverse triangular pier with horizontal bottom surfaces are staggered at the top of the weir body; the length in the water flow direction of the bottom surfaces of the positive triangular pier and the reverse triangular pier exceeds the thickness of the top end of the weir to form a weir front cantilever and a weir rear cantilever; a partition is arranged between the positive triangular pier and the reverse triangular pier. Compared with the conventional overflow weir, the compound key overflow weir has the advantages that the flow coefficient is remarkably increased; water heads acting on the weir are obviously reduced, so that a condition of heightening the dam for dealing with the exceeding flood caused by dam break and extreme climate. The integrated super-discharge energy-dissipation flood-overflowing unit is simple in structure and low in upgrading, improving and maintaining costs; by virtue of the open type arrangement, the sand is easily discharged; the unit is especially suitable for upgrading and improvement of the built wide-top weirs or practical weir flood spillway.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
Data model processing method based on Spring Data for MongoDB cluster
InactiveCN105956041AEvenly distributedUniform query efficiencyDatabase distribution/replicationSpecial data processing applicationsData centerHigh availability
The invention discloses a data model processing method based on Spring Data for a MongoDB cluster, in particular to a data processing method of a distributed cluster MapReduce. A MongoDB document-oriented NoSQL (Structured Query Language) database is used as bottom data storage, the data of other documents is quoted through the virtual union query of a client side to solve the problem of the union query of unstructured data; data processing adopts a Map / Reduce computational frame provided by the Spring Data for a MongoDB, and a MapReduce task can carry out data concurrent processing on a plurality of nodes so as to improve system processing speed; and on a data storage aspect, the long-term operation of mass data storage service provides a data center of high availability and expansibility. The high-availability data cluster which supports horizontal and longitudinal expansion is designed by the MongoDB technology, a compound key of double fields is used for optimization, so that the operation of CRUD (Create, Retrieve, Update and Delete) can utilize locality to improve query efficiency and support cloud-level flexibility.
Owner:JIANGSU CAS JUNSHINE TECH
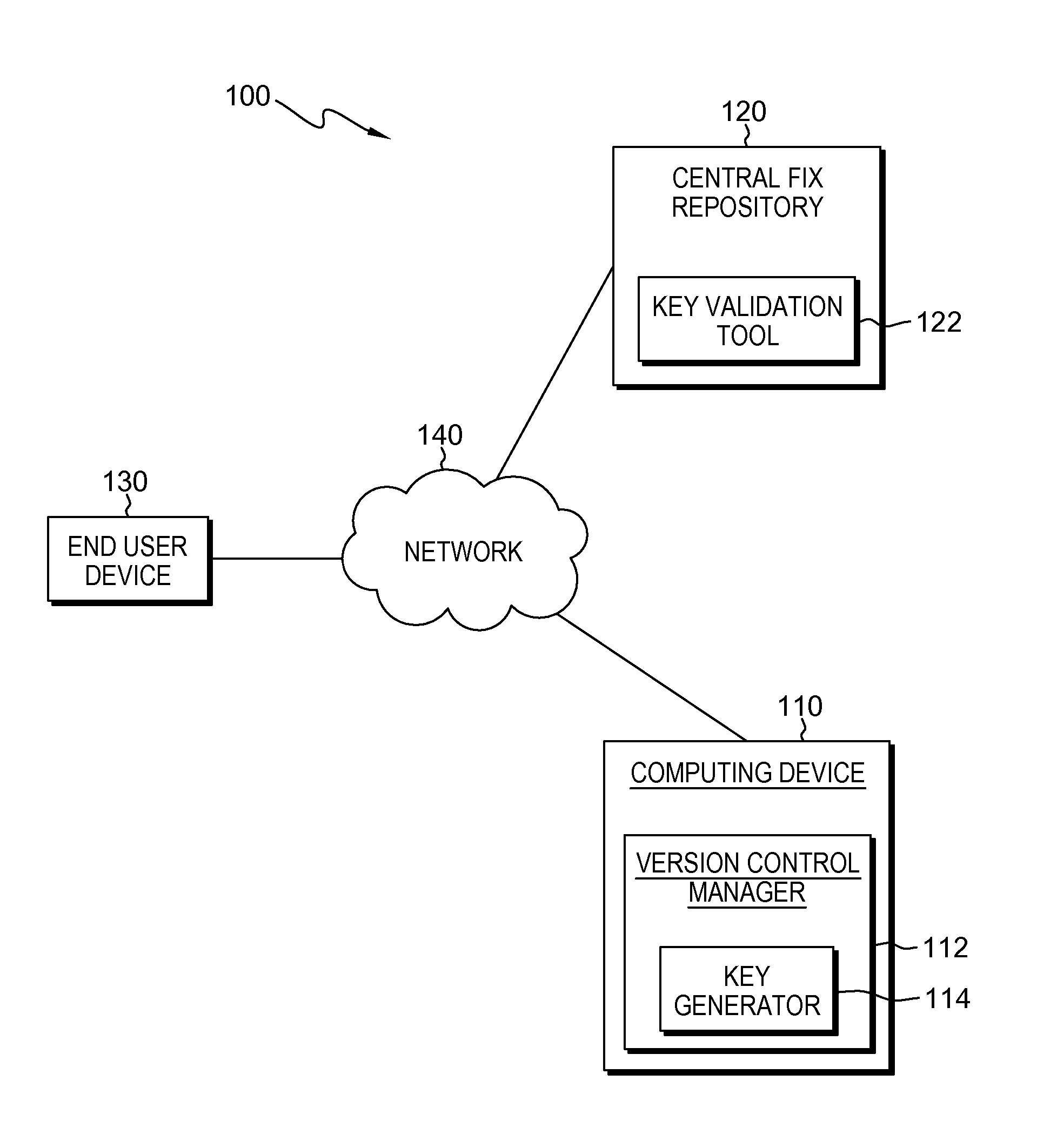
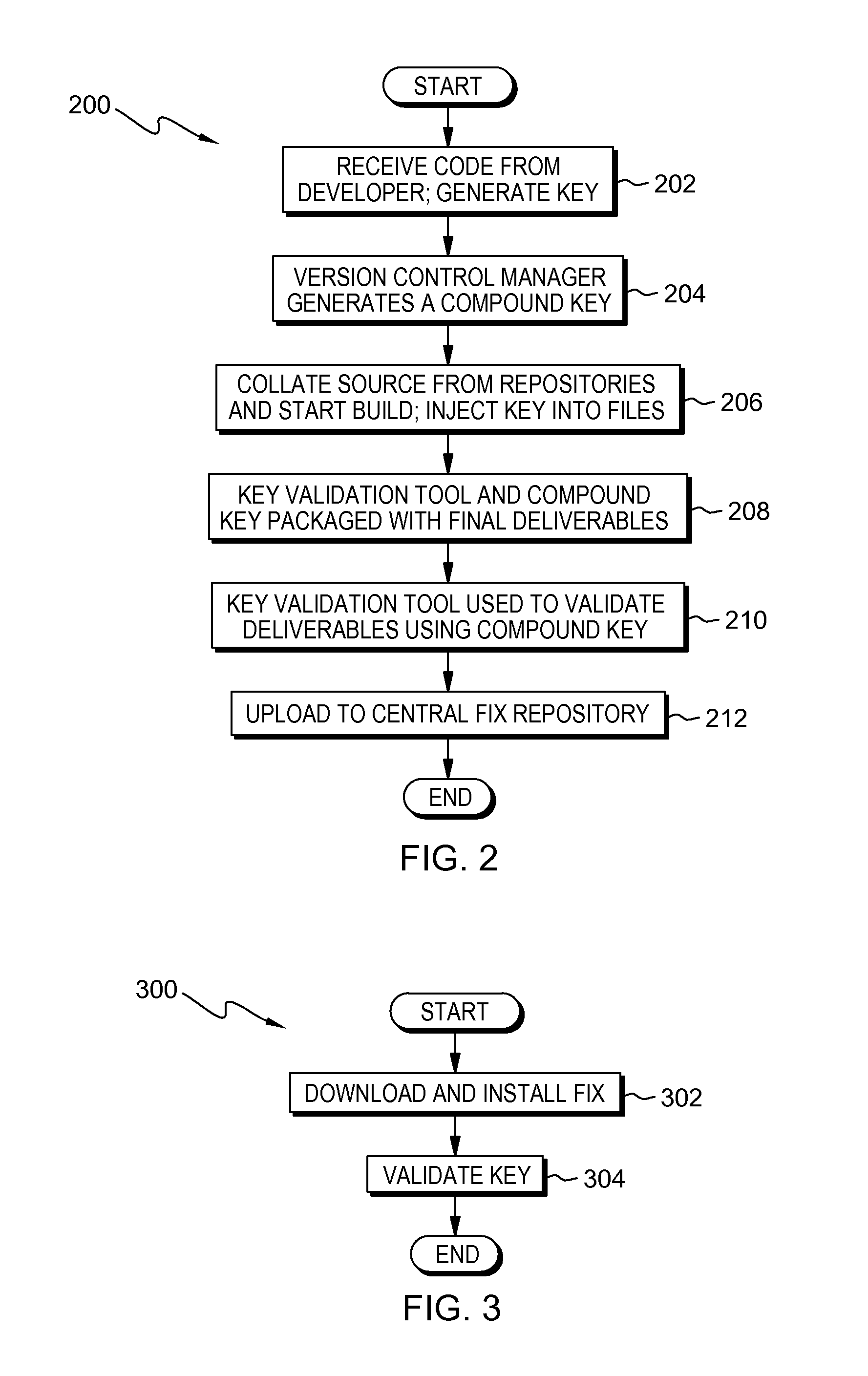
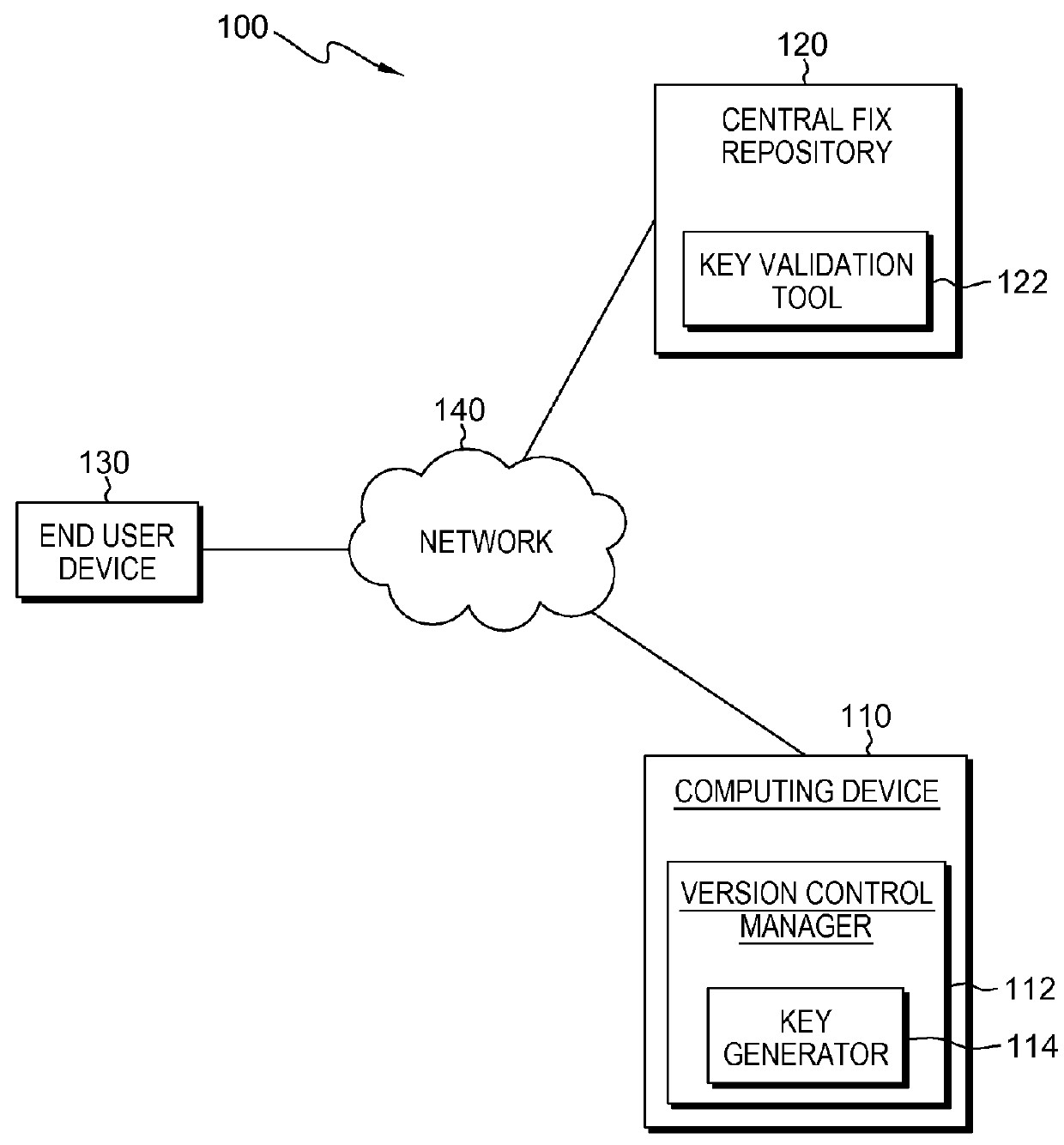
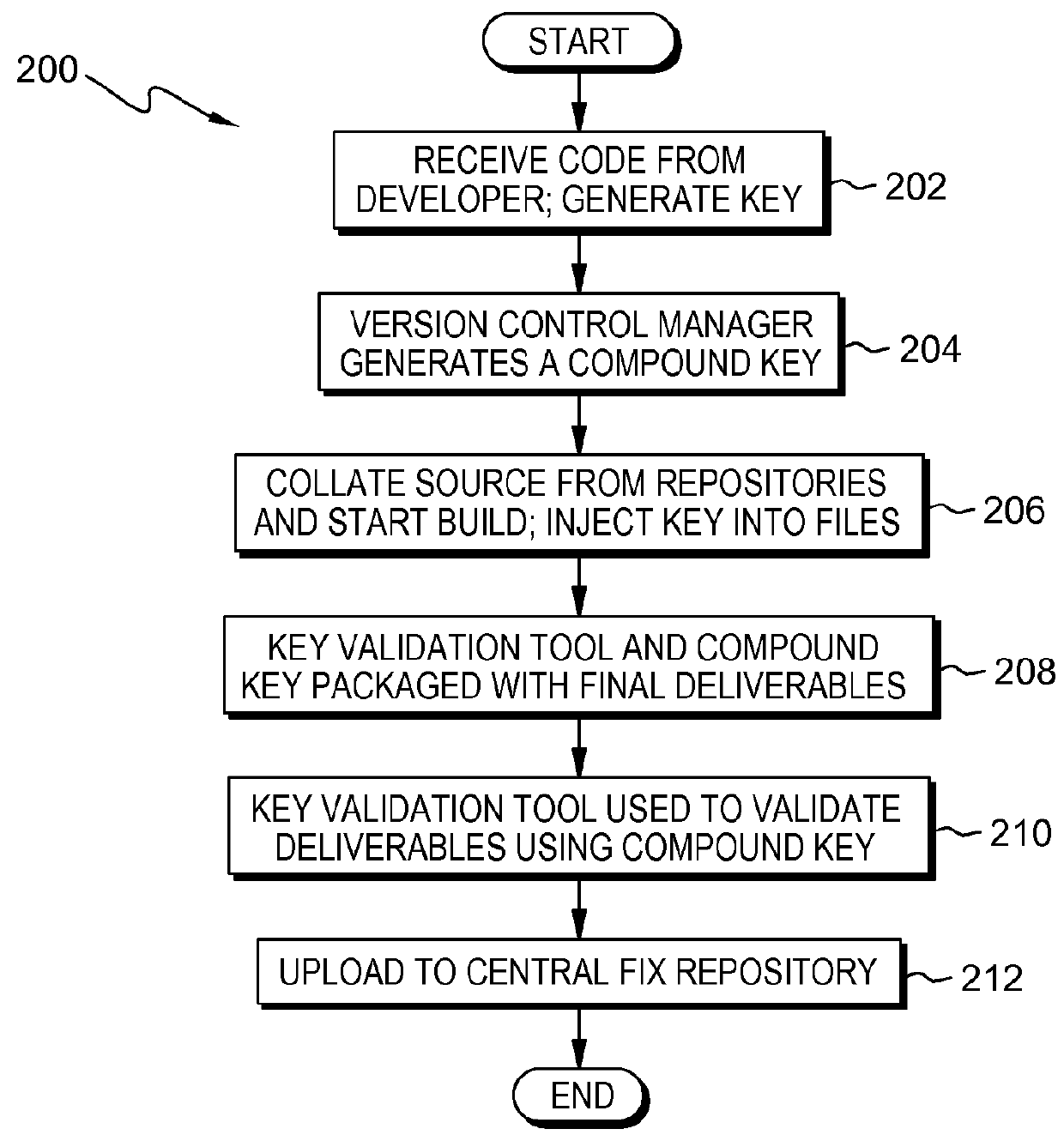
Source authentication of a software product
Embodiments of the present invention provide systems and methods for authenticating the source code of a software end product. The method includes generating a compound key, which is composed of a set of unique keys generated from a source file. A set of files are separately build based on a received source code, and a key generated and embedded into the files at the time of the build. A validation tool is used to compare the values of the generated compound key to the values of the embedded key to determine if the values match.
Owner:IBM CORP
Downsizing keyboard of composite key
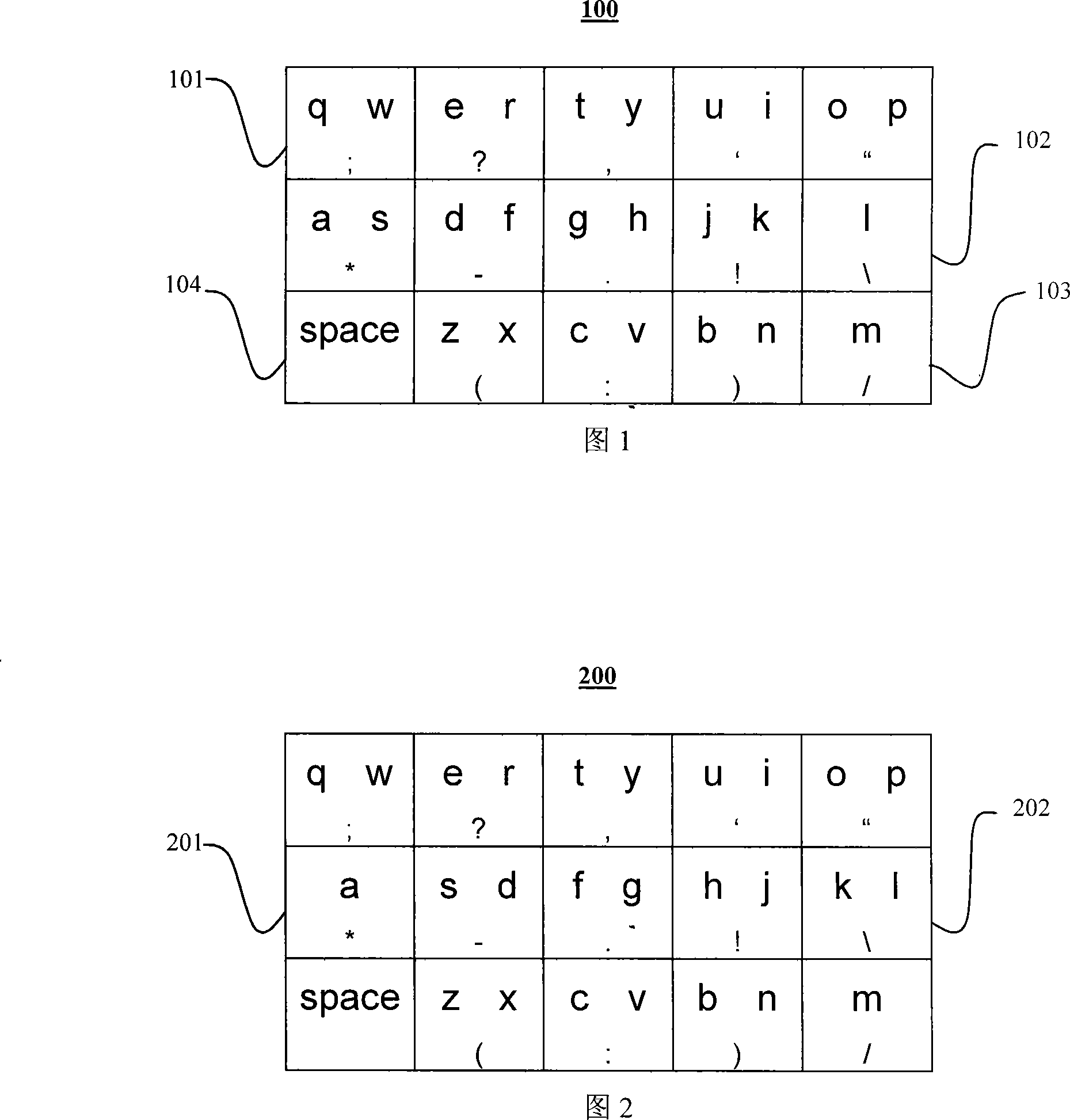
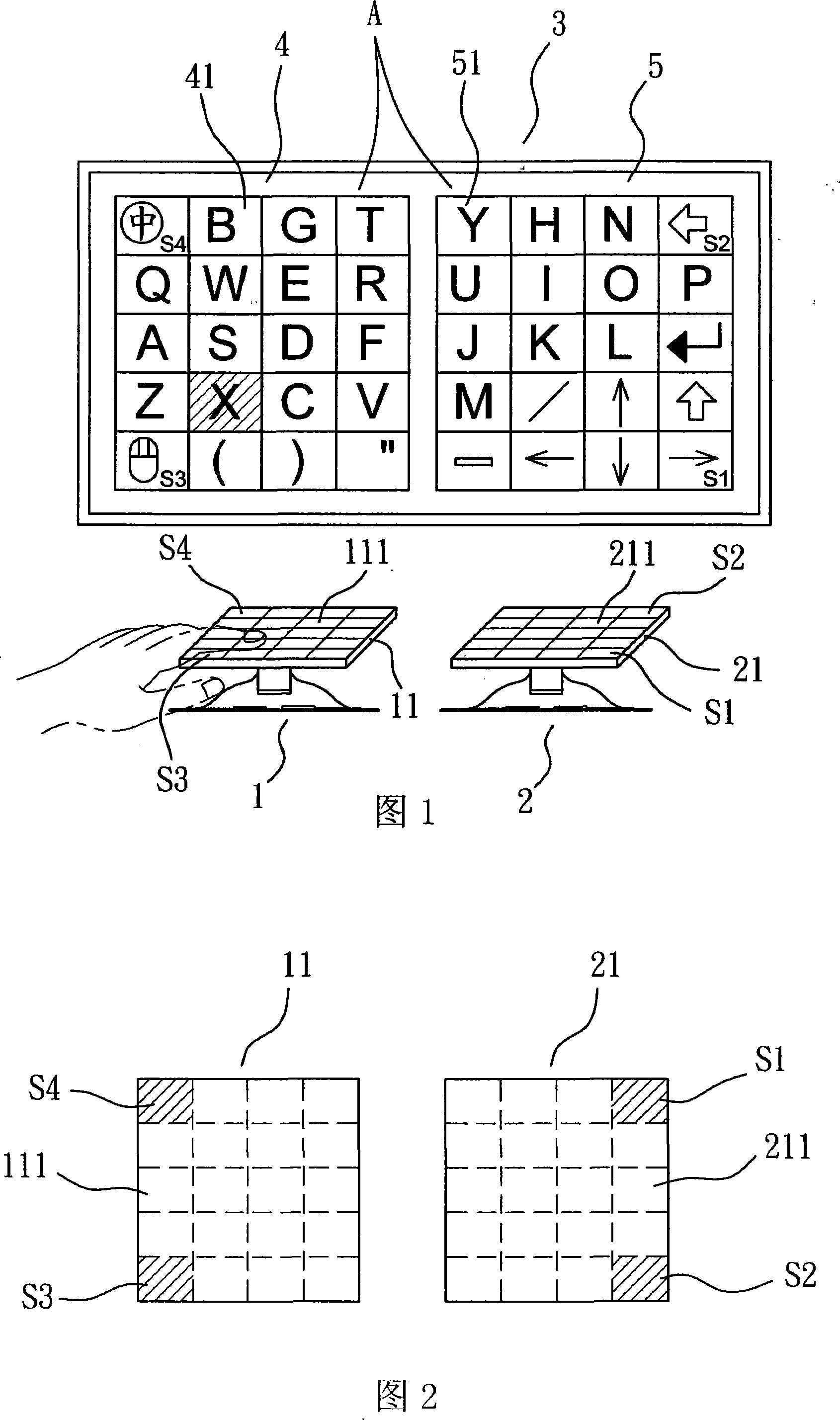
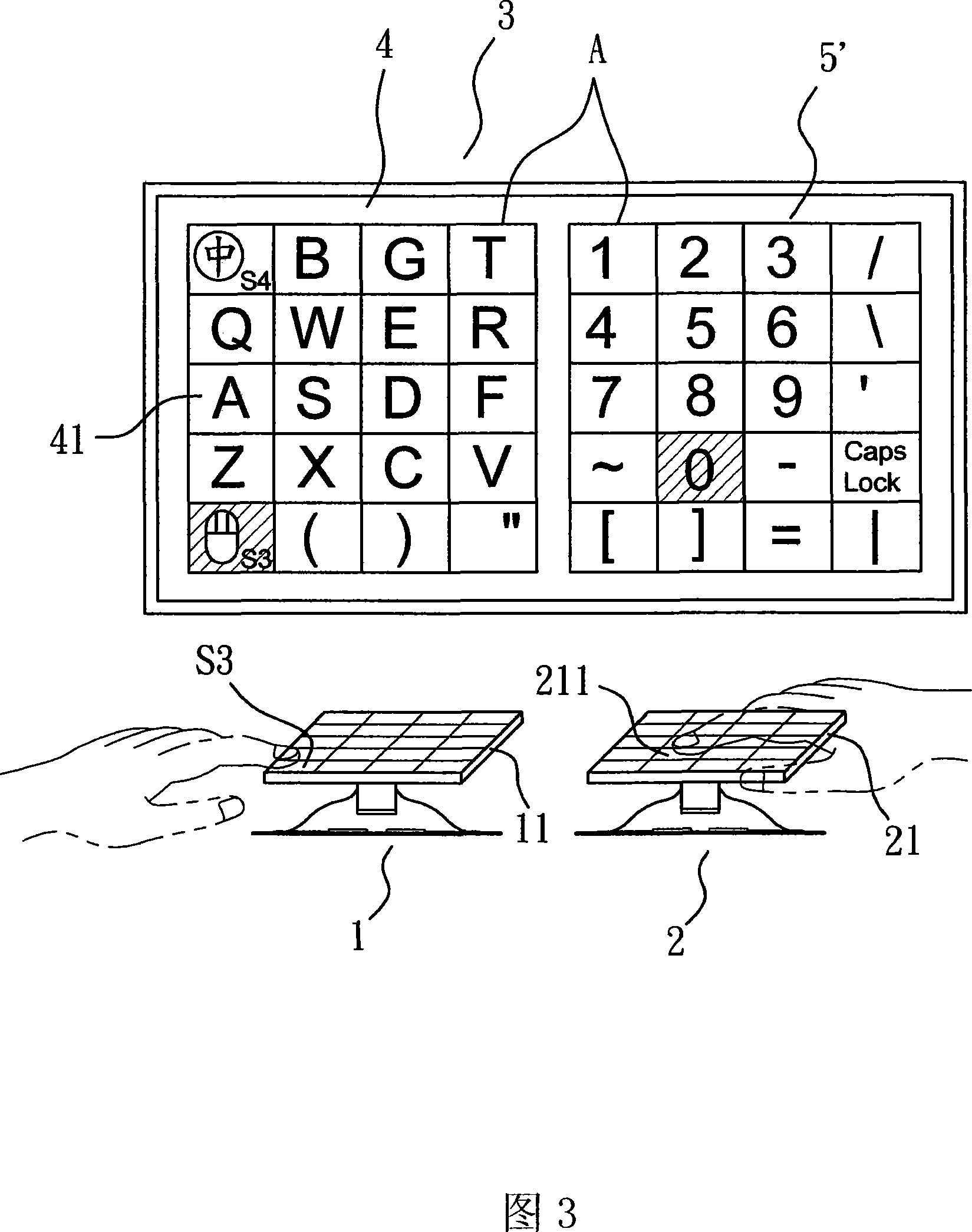
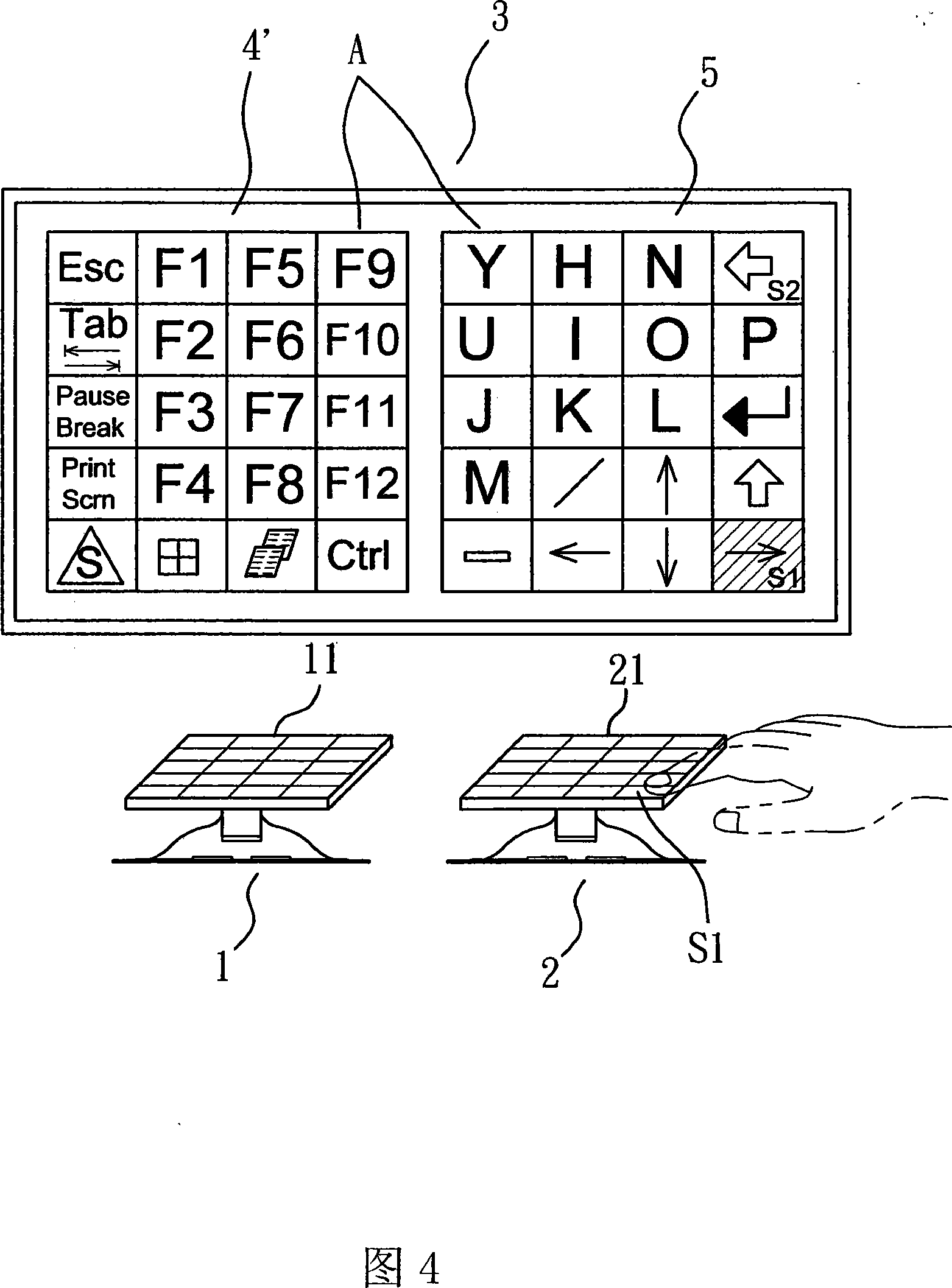
InactiveCN101118475AAvoid clutter and illegible phenomenaInput/output processes for data processingCompound keyComputer science
The present invention discloses a compound key-press downsizing keyboard, which at least comprises a first key-press and a second key-press. The present invention utilizes a control induction area arranged on the keys of the first key-press and the second key-press which are attached with touch-control boards to control and transform the character definition of a character group which corresponds with another key-press, so as to provide the user with the ability to carry on a complete character input operation of the keyboard in adownsizing keyboard, as well as the setting which increases the total amount of the character.
Owner:E LEAD ELECTRONICS
Detecting multi-column composite key column sets
Owner:INT BUSINESS MASCH CORP
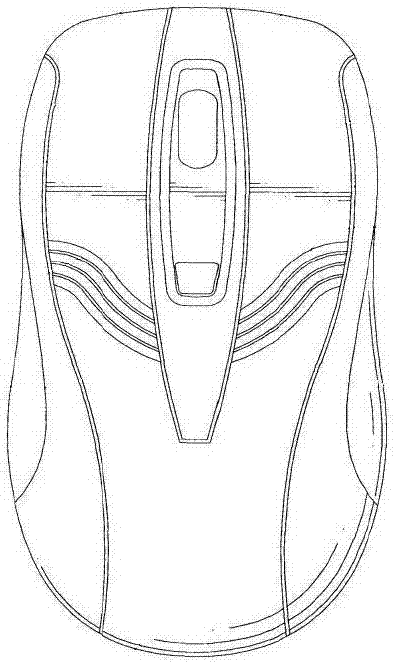
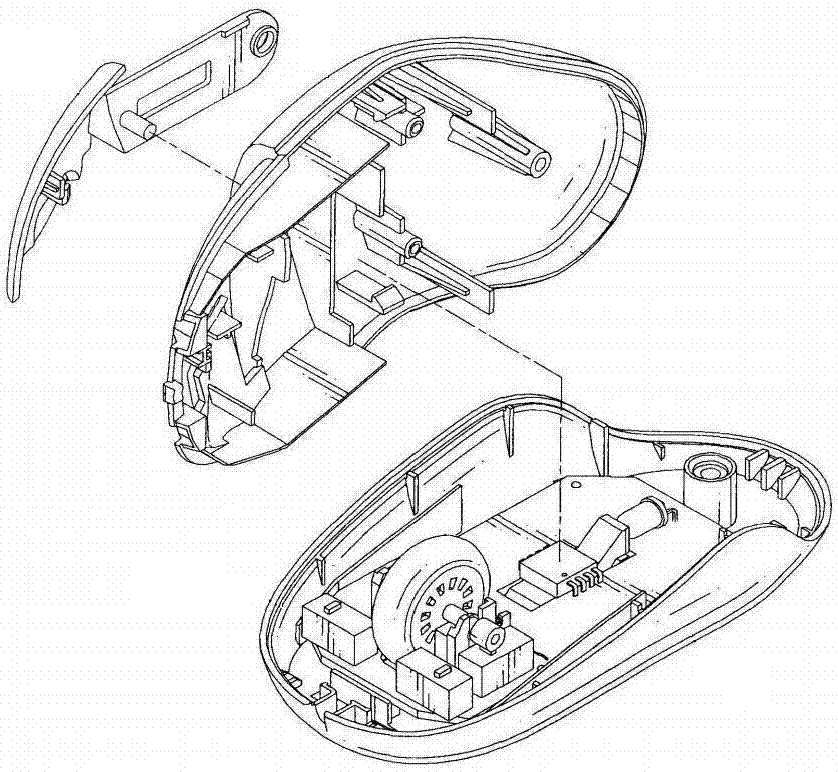
Pen type table and air dual-purpose gyroscope mouse and using method thereof
PendingCN107885353AIn line with daily habitsFlexible operationInput/output processes for data processingKey pressingScroll wheel
The invention discloses a pen type table and air dual-purpose gyroscope mouse and a using method thereof. The dual-purpose gyroscope mouse comprises an inner structure, a key structure and a shell, wherein the key structure comprises a left mouse button, a composite key, a right mouse button, a reset key, an air mouse / pen mouse switching key, a dpi key, a power button and a scroll button; the composite key is a clutch key in a pen mouse mode and is a conventional left mouse button in an air mouse mode; and the inner structure comprises a central processing unit, a gyroscope, an acceleration sensor, a signal transmitter, a data interface and a power supply. According to the technical scheme of the invention, the dual-purpose gyroscope mouse is diversified in functions and capable of realizing one-pen multi-purpose effects, and flexible switching of the table mouse and the air mouse is realized; and the dual-purpose gyroscope mouse can be used in air, can relieve fatigue of using the mouse during long-time working, and has the functions of the mouse and a laser pen in a pioneering form. The convenience is greatly improved, and a comfortable office environment is provided.
Owner:赵武峰
Method, apparatus and chip for implementing keyboard module composite key function
InactiveCN101510127BRealize compound key functionComposite supportInput/output processes for data processingKey assignmentCompound key
The invention provides a method, a chip and a device for implementing the functions of compound keys of the key module of an embedded system. The method comprises the following steps: the embedded system executes keystroke interruption and records the keystroke after detecting the keystroke is pressed; the embedded system starts a timer and then rescans if other keystrokes are pressed in accordance with scheduled time intervals, if so, records the new keystrokes; the embedded system scans if all the keystrokes are released, and then disables the timer if all the keystrokes are released; then the embedded system produces the key assignments of the compound keys according to the keystroke records and submits the program prior to the keystroke interruption. The timer is additionally arrangedin the system on the basis of the existing array keystroke module. The system starts the timer and then rescans and records other keystrokes in accordance with the scheduled time intervals after detecting a keystroke interruption. Therefore, under the condition of one system interrupted, the invention can realize the functions of the compound keys by obtaining the responding of a plurality of keystrokes. Besides, the proposal of the invention has no restriction to the keystroke sequence and quantity, and supports the composite of any keystroke and a plurality of keystrokes.
Owner:WUXI ZGMICRO ELECTRONICS CO LTD
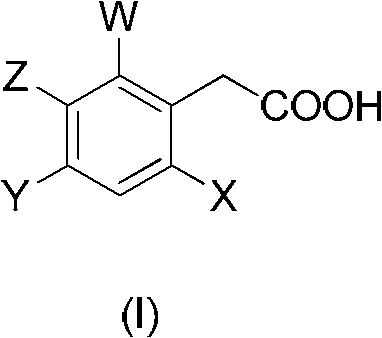
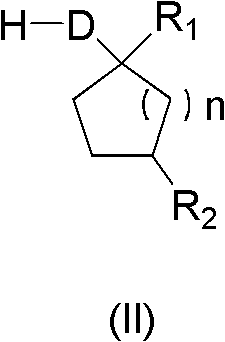
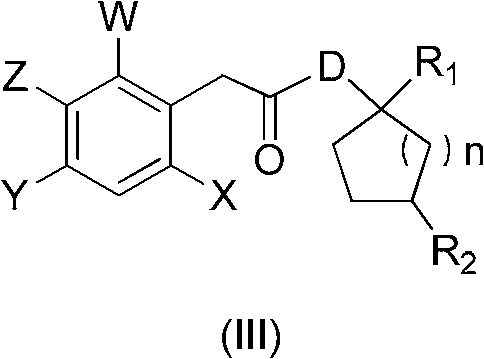
Synthetic method of spirocyclic tetronic acid compound key intermediate
ActiveCN102241590ALow costEnvironmentally friendlyCarboxylic acid nitrile preparationOrganic compound preparationPhenylacetic acidCarboxylic acid
The invention discloses a synthetic method of a spirocyclic tetronic acid compound key intermediate. The method comprises the following steps of: mixing a substituted phenylacetic acid compound (I) with a compound (II); heating the mixture to 50-150 DEG C; adding a carboxylic acid activation reagent; preserving heat at the temperature 50-150 DEG C and reacting fully; and performing post-treatmentto obtain a spirocyclic tetronic acid compound key intermediate compound (III). The invention has the advantages that: (1) an acylation reaction is completed at one step in the preparation method, the reaction time is short, the raw material utilization ratio is high, and the energy consumption and the environmental pressure are lowered; (2) in the preparation method, the costs of raw materials are low, and an acid-binding agent or a catalyst is not invested additionally; and (3) the preparation method has a simple process, a small quantity of side reactions and high yield, and is suitable for large-scale industrial production.
Owner:YONGNONG BIOSCI
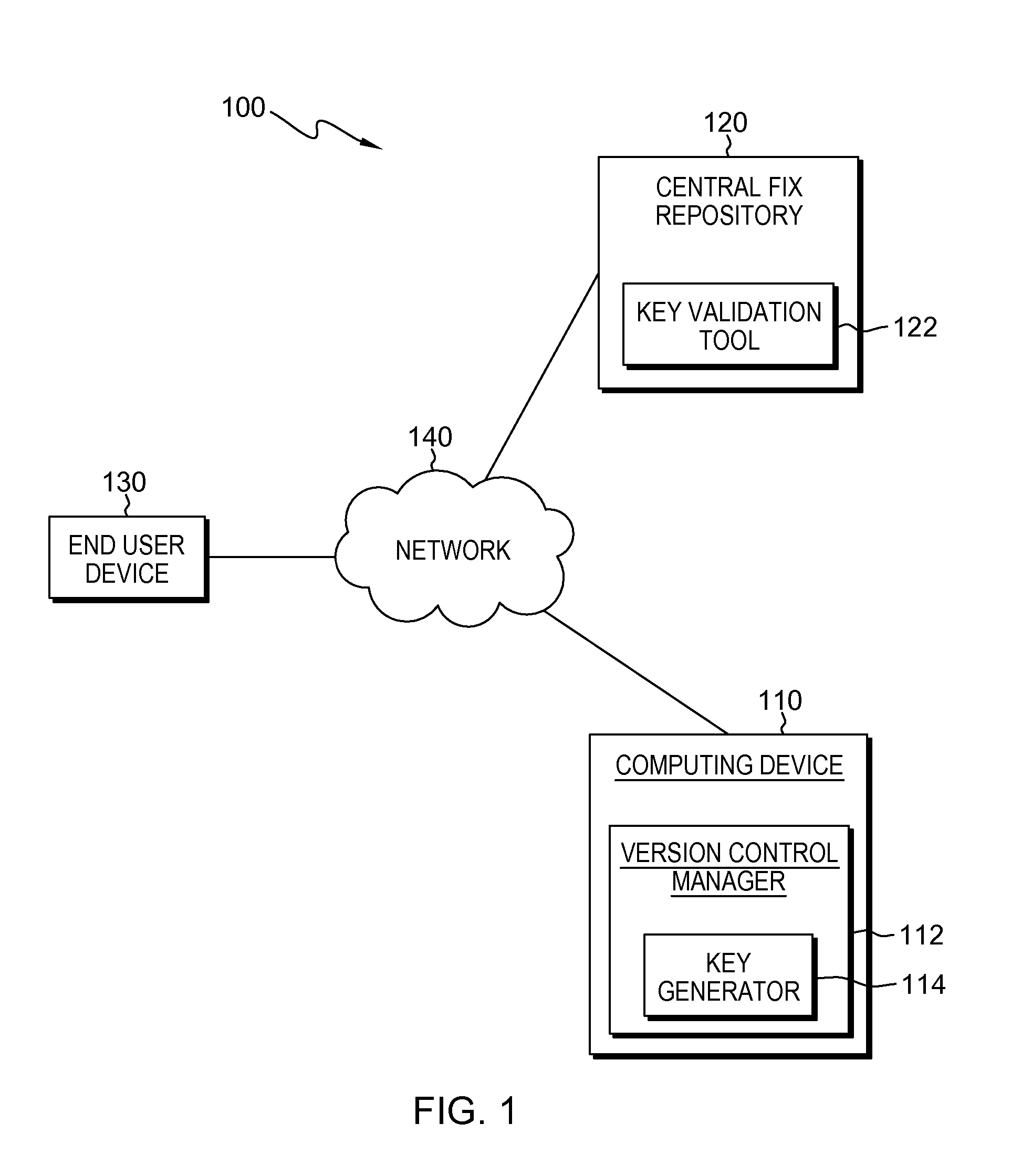
Source authentication of a software product
Embodiments of the present invention provide systems and methods for authenticating the source code of a software end product. The method includes generating a compound key, which is composed of a set of unique keys generated from a source file. A set of files are separately build based on a received source code, and a key generated and embedded into the files at the time of the build. A validation tool is used to compare the values of the generated compound key to the values of the embedded key to determine if the values match.
Owner:IBM CORP
Optimized setup method for function keys of note-book computer mouse
InactiveCN101419507AEasy to replaceIn line with daily habitsInput/output processes for data processingComputer architectureCompound key
The invention belongs to an optimal setting method of function keys of a mouse of a notebook pc and is characterized in that: the keyboard surface (1) and the right side (7) of a computer keyboard are respectively provided with a mouse shifting key (3), a mouse left key (4), a mouse rolling key (5), a mouse right key (6) or a mouse shifting-rolling compound key (8). The invention has convenient operation and flexible use, reduces the area of the keyboard area, and is convenient to be replaced after the mouse is damaged.
Owner:张保华
Fabric-based delivery payment application method and Fabric-based delivery payment application system
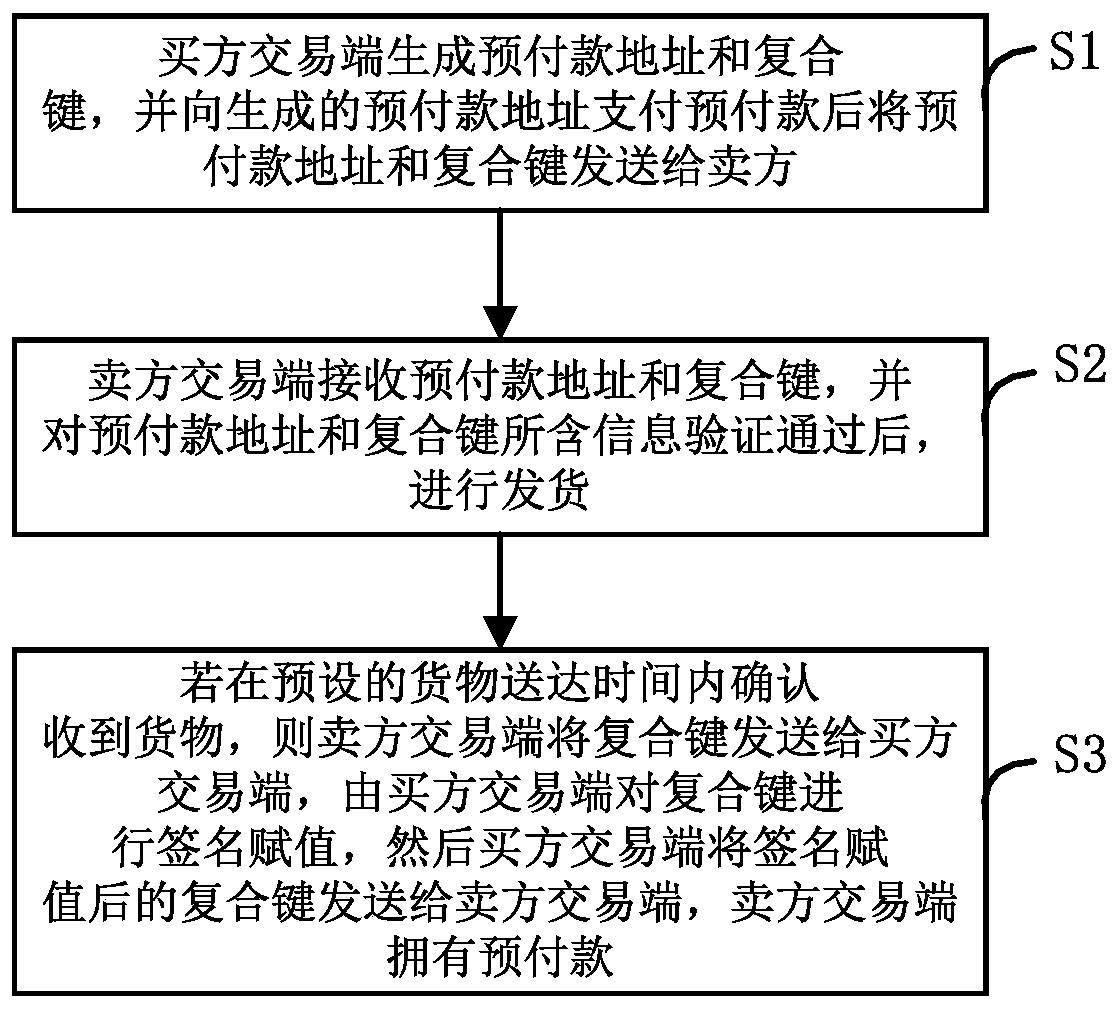
PendingCN111080291AEnsure safetyReduce in quantityProtocol authorisationComputer networkPayment transaction
The invention discloses a Fabric-based delivery payment application method and a Fabric-based delivery payment application system, and relates to the technical field of block chains. The method comprises the steps that a buyer transaction terminal generates a pre-payment address and a composite key, pays pre-payment to the generated pre-payment address and then sends the pre-payment address and the composite key to a seller transaction terminal, and both the pre-payment address and the composite key contain cargo information and preset cargo delivery time; the seller transaction terminal receives the advance payment address and the composite key, and delivers goods after the information contained in the advance payment address and the composite key passes the verification; and if the buyertransaction terminal confirms that the goods are received within the preset goods delivery time, the seller transaction terminal sends the composite key to the buyer transaction terminal, the buyer transaction terminal carries out signature assignment on the composite key, then the buyer transaction terminal sends the composite key after signature assignment to the seller transaction terminal, and the seller transaction terminal owns advance payment and ends the transaction. The method can effectively guarantee the safety of advance payment.
Owner:WUHAN TIANYU INFORMATION IND
Compound key ring
The invention relates to a compound key ring which comprises a fixed ring and a moveable ring, wherein inlets are formed in both of the fixed ring and the moveable ring; blocking pins are arranged on the fixed ring; the quantity of the blocking pins is more than or equal to 2; bayonets are formed on the moveable ring in the positions corresponding to the blocking pins; and the fixed ring and the moveable ring are buckled through the bayonets. After a key hole is inserted into the fixed ring, the moveable ring is inserted into the key hole, and finally, the fixed ring and the moveable ring are buckled in the manner of pressing, so that a key can be easily inserted into the key ring. The key can be easily taken out through a reverse operation.
Owner:梁昌业
A combined super-discharging energy-dissipating flood unit and method
InactiveCN104695390BIncrease the effective inventory capacity of XinliEasy dischargeBarrages/weirsModular unitWater flow
The invention relates to an integrated super-discharge energy-dissipation flood-overflowing unit. The unit comprises an inlet overflow weir, wherein a chute is formed in the downstream of the inlet overflow weir; a water-falling energy dissipater is formed in the chute; the inlet overflow weir is a compound key overflow weir; the compound key overflow weir comprises a weir body; a forward triangular pier and a reverse triangular pier with horizontal bottom surfaces are staggered at the top of the weir body; the length in the water flow direction of the bottom surfaces of the positive triangular pier and the reverse triangular pier exceeds the thickness of the top end of the weir to form a weir front cantilever and a weir rear cantilever; a partition is arranged between the positive triangular pier and the reverse triangular pier. Compared with the conventional overflow weir, the compound key overflow weir has the advantages that the flow coefficient is remarkably increased; water heads acting on the weir are obviously reduced, so that a condition of heightening the dam for dealing with the exceeding flood caused by dam break and extreme climate. The integrated super-discharge energy-dissipation flood-overflowing unit is simple in structure and low in upgrading, improving and maintaining costs; by virtue of the open type arrangement, the sand is easily discharged; the unit is especially suitable for upgrading and improvement of the built wide-top weirs or practical weir flood spillway.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
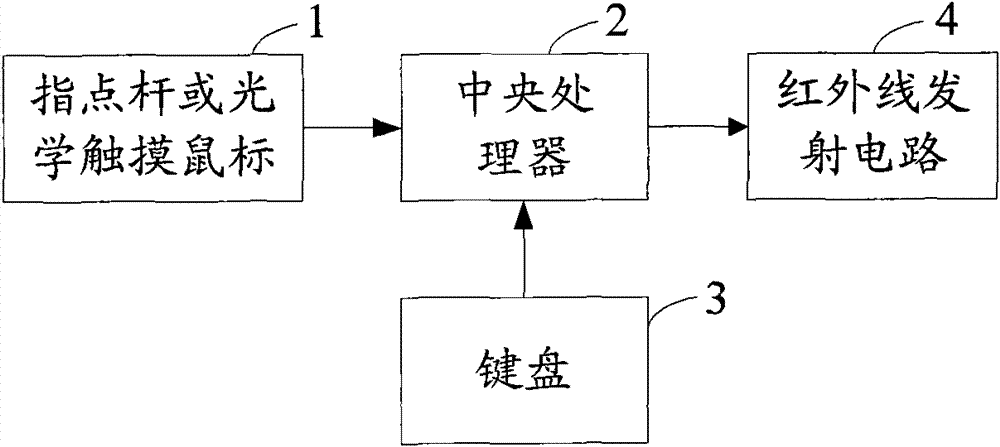
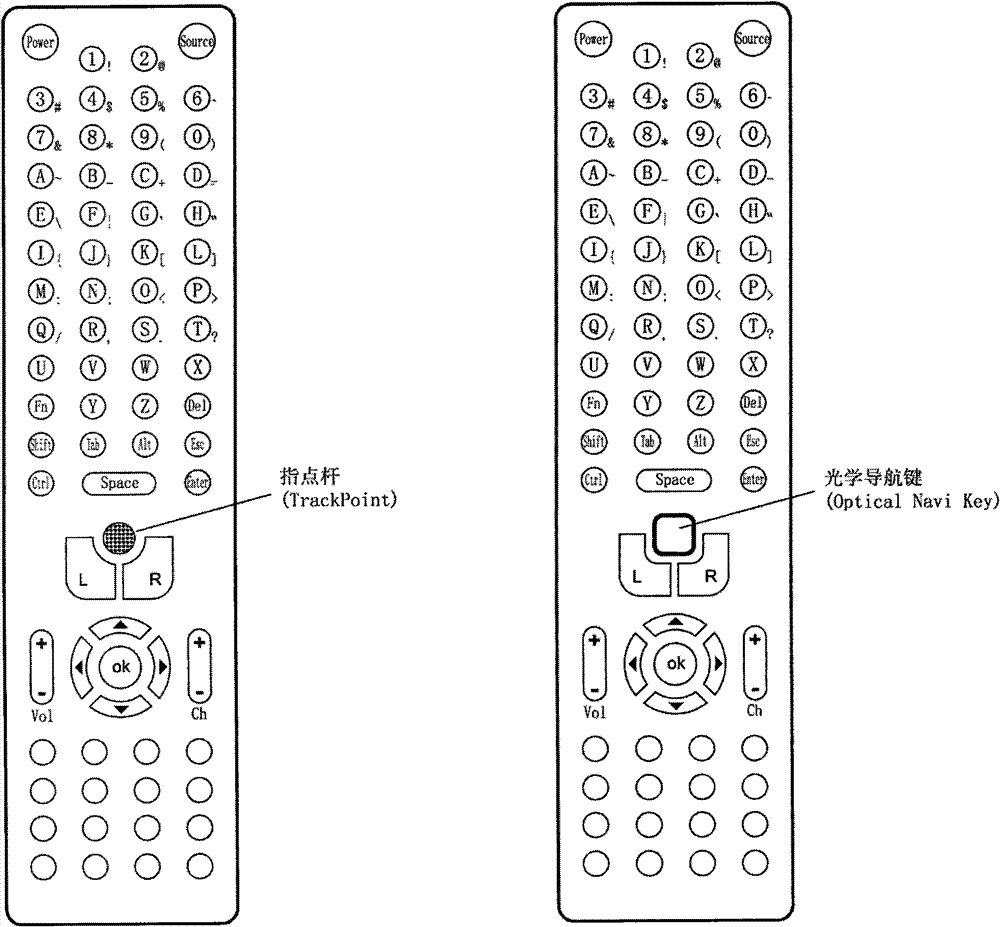
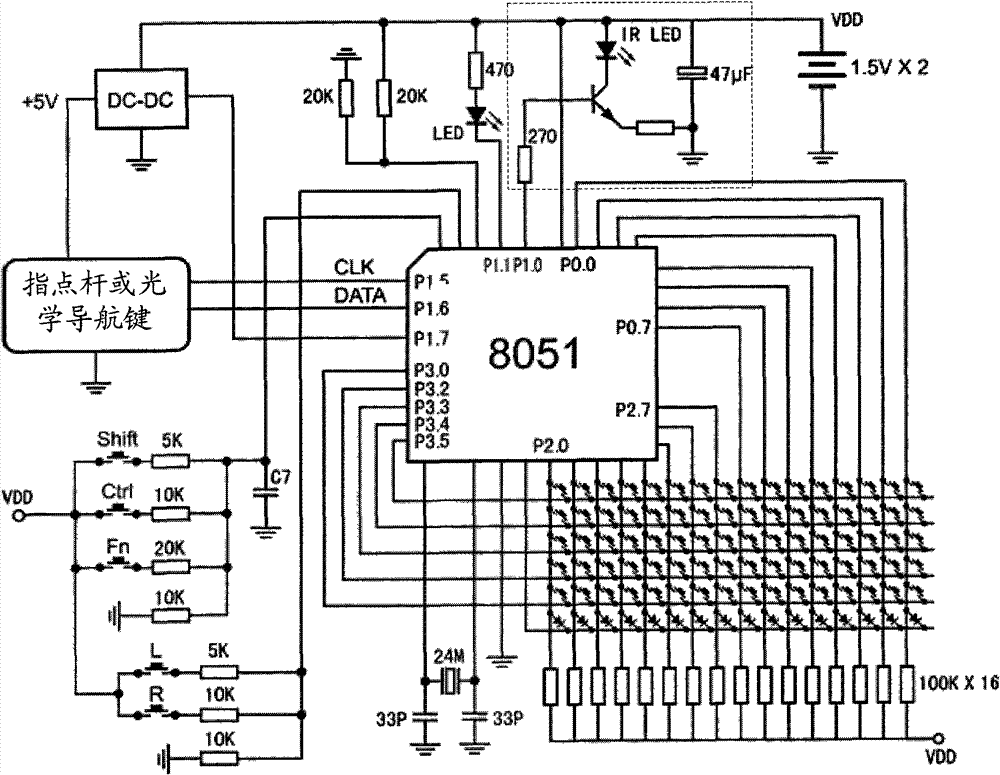
Data transmission method and infrared remote controller
InactiveCN101727738BTelevision system detailsNon-electrical signal transmission systemsComputer hardwareKey pressing
The invention discloses a data transmission method and an infrared remote controller, which belong to the field of wireless communication. The data transmission method comprises that: the infrared remote controller samples cursor moving data from a track point or an optical touch mouse integrated on the infrared remote controller with a period of 54 ms in real time, transmits a notice to a receiving end when a user starts to move a cursor, alternately combines the cursor moving data into a B cursor moving data frame and an A cursor moving data frame with the period of 108 ms and transmits thedata frames to the receiving end; when pressing a composite key down, the user combines key codes of the composite key into a key command frame and transmits the key command frame to the receiving end; when pressing a one-click key down, the user combines the key codes of the one-clock key into a single-key one-click frame and transmits the single-key one-click frame to the receiving end; and when pressing a double-click key down, the user combines the key codes of the double-click key into a single-key double-clock frame and transmits the single-key double-click frame to the receiving end. The data transmission method can enable the infrared remote controller to perform cursor input in an electrical appliance under the remote control of the infrared remote controller.
Owner:张绍祥
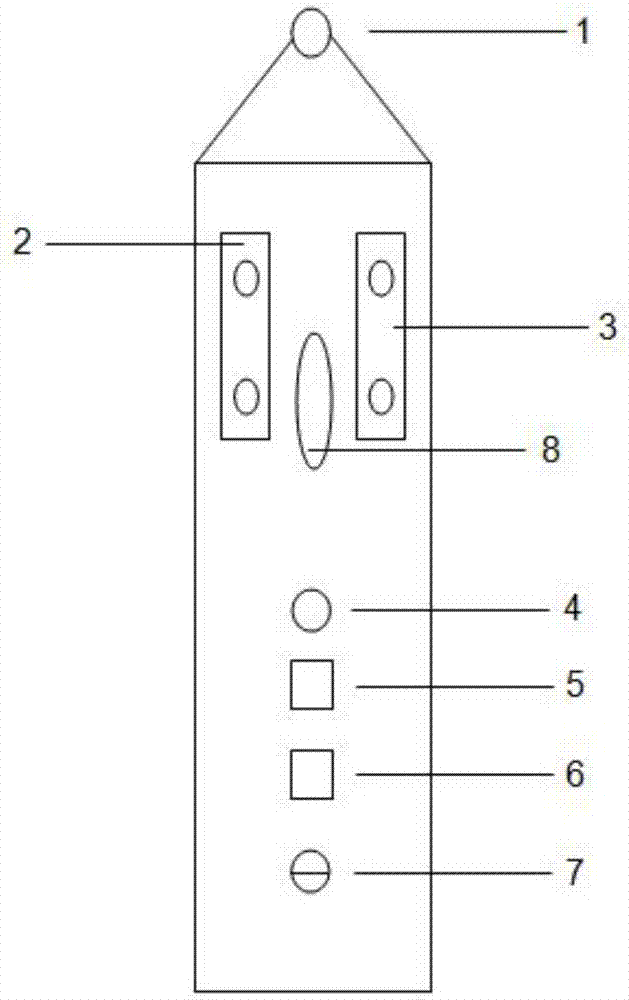
Anti-theft lock
The invention relates to an anti-theft lock which comprises a lock head body as well as a lock core and a lock tongue that are arranged inside the lock head body; wherein the lock core is fixed insidethe lock head body by a lock core fixing pin, the lock core is internally inserted with a key, an opening pin is arranged on the top of a key hole inside the lock core, and the lock tongue is firmlywithstood by the opening pin; the lock tongue is internally provided with a lock tongue spring, and a locating pin is arranged on the lock tongue; the lock core is internally provided with a flat jacket, a flat inner core positioned inside the flat jacket, a marble jacket and a marble inner core positioned inside the marble jacket; the flat jacket and the marble jacket are in butt connection, theflat inner core and the marble inner core are in butt connection, the rear part of the flat jacket is firmly withstood with the spring, and the spring is arranged inside the lock head body. The marbleinner core is hidden inside the marble jacket, and the lock core can be unlocked by the compound key, so that the complexity of the technology for unlocking the lock core can be enhanced, and the lock core has double anti-theft function. The anti-theft structure of the lock can be applied to the interior of various lock head bodies.
Owner:韦志强
Double-layer compound key storage box
Disclosed is a double-layer compound key storage box, which belongs to the technical field of an article of daily necessities. The storage box comprises a box body, and upper and lower box covers. The box body comprises a pair of broadside columns, and a plurality of pairs of upper and lower storage cases, wherein the upper and lower storage cases are symmetrically arranged and are divided by base plates. The adjacent base plates are divided by division bars, and the outer sides of the base plates arranged at the outmost edges are provided with the broadside columns. A gap is formed in one end, near a pin hole, of each base plate and forms a key seat cavity for containing upper and lower key seats. A pin passes through a pin hole in one broadside column, shaft holes in the upper and lower key seats, and pin holes in the division bars, and is pivoted on the other broadside column. The box is small in size and is convenient to carry, can be put, together with a wallet, into a hided pocket of a coat, and has an antitheft function. Keys are convenient to change and are arranged in alignment, are easy to remember and simple to take out, and are convenient to use at night or in a situation with weak light. The box can be carried without sounds; the amount of keys stored in the box is multiply increased; and the box is applicable to a wide range.
Owner:CHANGSHU YONGXIANG ELECTROMECHANICAL
Composite keyboard, electronic device and character input method
InactiveCN1979388ASmall sizeEasy inputEmergency actuatorsOperation facilitationCompound keyComputer science
The invention relates to a combined key-type keyboard, electronic device and the character input method thereof. And the input method comprises the steps of: providing a combined key-type keyboard, which comprises several combined keys, each comprising a main key and at least an auxiliary key, where each main key and each auxiliary key separately stand for a character, and the main and auxiliary keys are adjacent and able to be pressed, separately or together; pressing a combined key; judging whether the auxiliary key of the combined key is pressed; if the auxiliary key is pressed, selecting the character the auxiliary key stands for; otherwise, selecting the character the main key stands for. And it meets the requirement for character input on a portable electronic device.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Chinese character digital keyboard input method based on stroke sequence
PendingCN114063794AFast inputSmooth working environmentNatural language data processingInput/output processes for data processingWord selectionMedicine
The invention discloses a Chinese character digital keyboard input method based on a stroke sequence, which comprises the following specific steps of: classifying stroke shapes of Chinese character writing habits, inputting by representing corresponding English letters on a keyboard, inputting the stroke shapes stroke by stroke according to an input sequence by taking a GB13000.1 stroke order standard as an input sequence basis, and outputting required Chinese characters by a system. The input method can be used for touch typing and is particularly suitable for visually impaired people and character workers; a conversion thinking process before input is avoided, so that the input is smoother, and creative exertion when inspiration exists is not influenced; on the basis of the GB13000.1 stroke order specification, input can be started only by remembering 17 types and 12 types of basic stroke shapes, and entry is easy; meanwhile, the input efficiency is high through combined input of the compound keys, one Chinese character is generally input in 1-4 characters, and meanwhile, the coding mode is flexible and free and easy to master; according to the method, the repeated code rate of coding is extremely low, the input accuracy can be greatly improved, and the word selection time is saved.
Owner:董传飞
Composite piano overflow weir type siphon well and method
InactiveCN104563267BEnhanced single-width overcurrent capabilityLow costSewerage structuresSiphonWater flow
The invention relates to a compound key overflow weir type siphon well which comprises at least one single well combination. Each single well combination comprises a vertical well with a water inlet culvert pipe, the vertical wells are connected with overflow connecting wells, the overflow connecting wells are connected with water delivery culvert pipes, and compound key overflow weirs are arranged between the vertical wells and the overflow connecting wells; the compound key overflow weirs comprise weir bodies, positive triangular piers and reverse triangular piers which are provided with horizontal bottom surfaces are staggered on the tops of the weir bodies, the lengths of the bottom surfaces of the positive triangular piers and the reverse triangular piers along the direction of water flow are larger than the thicknesses of the tops of the weir bodies, and front weir cantilevers and rear weir cantilevers are formed. The compound key overflow weir type siphon well has the advantages that the compound key overflow weirs are used as flow passing facilities and bubble inhibiting schemes, accordingly, the single-width flow passing ability of the overflow weirs of the siphon well can be improved, the drop flow difference between the overflow weirs of the siphon well and open seas can be reduced, bubbles mixed in the water flow which flows through the weirs can be inhibited, and influence on ambient environments can be reduced; the engineering cost can be lowered, energy can be effectively dissipated, the bubbles can be effectively eliminated, and relatively clean water can be drained.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
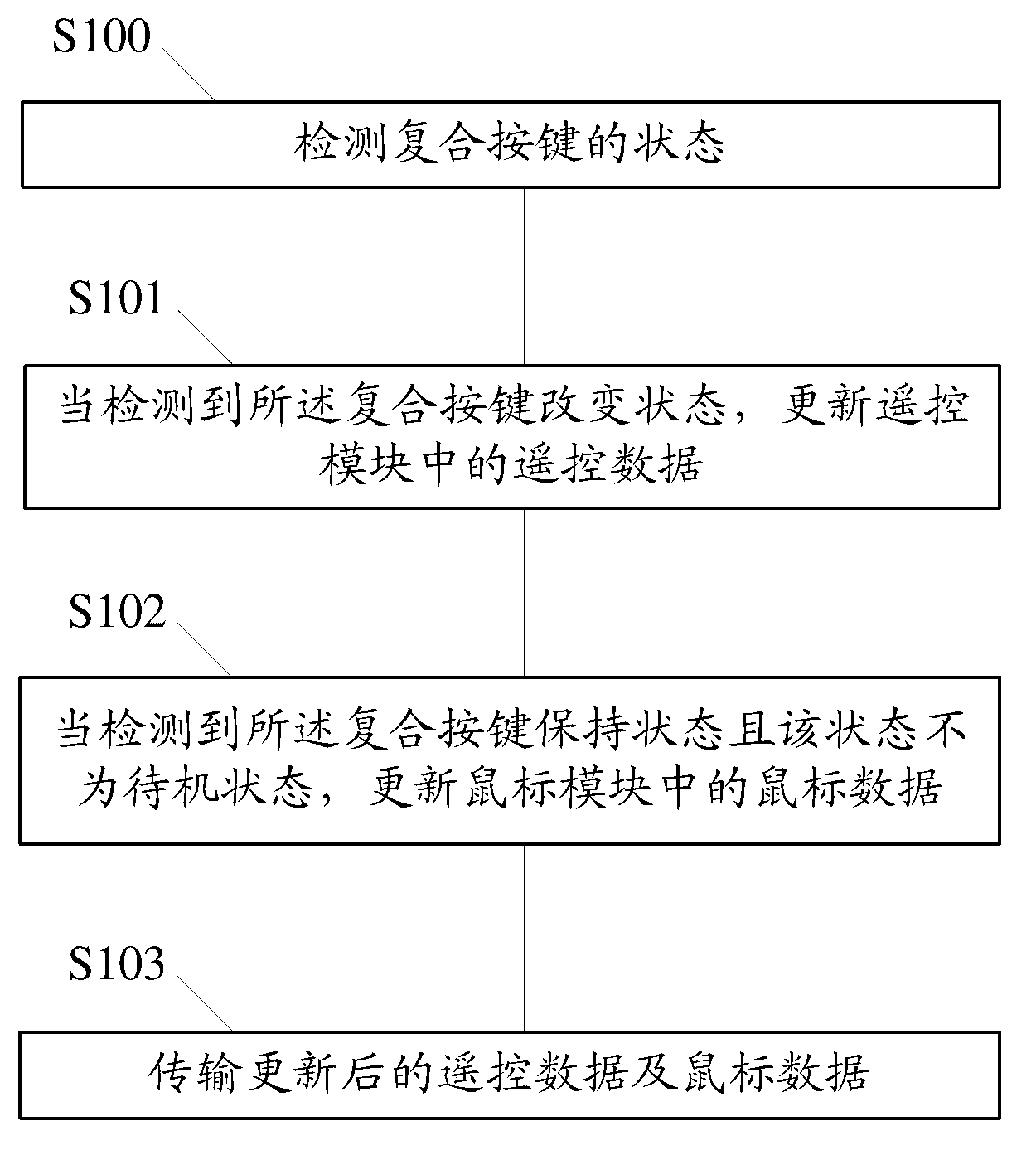
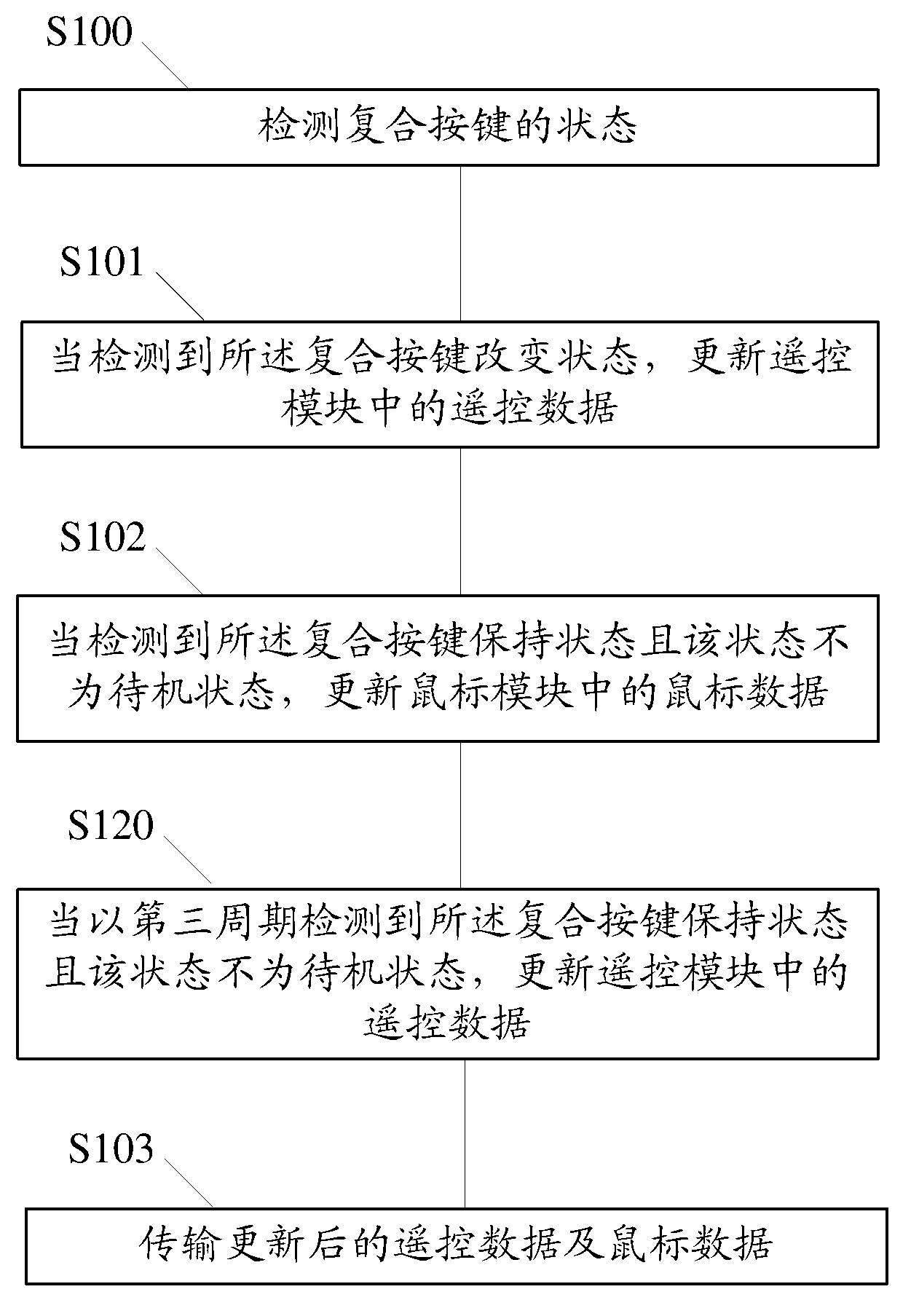
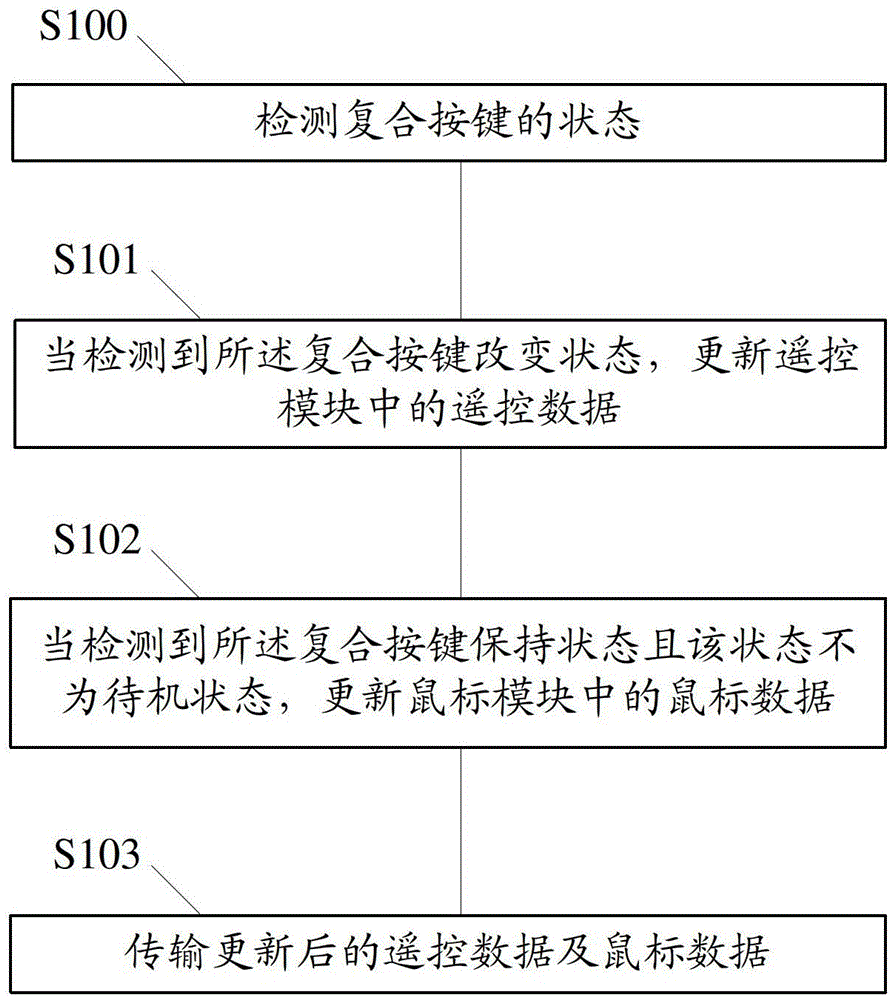
Data transmission method and device and data identification method and device
ActiveCN103324316ALarge amount of data transferSensitiveInput/output processes for data processingRemote controlCompound key
The invention relates to a data transmission method and device and a data identification method and device. The data transmission method comprises detecting states of compound keys; updating remote control data in a remote control module when detecting state changes of the compound keys; updating mouse data in a mouse module when detecting hold states of the compound keys and that the states are not stand-by states; and transmitting the updated remote data and mouse data. The data identification method comprises receiving the remote control data / the mouse data transmitted by corresponding handheld devices through the data transmission method; identifying the remote control data / the mouse data transmitted by the handheld devices through corresponding protocols; and responding to the identified remote control data / the mouse data and performing corresponding operations. By means of the data transmission method and device and the data identification method and device, the validity of data transmission of the handheld devices can be improved.
Owner:JIANGSU HUITONG GRP
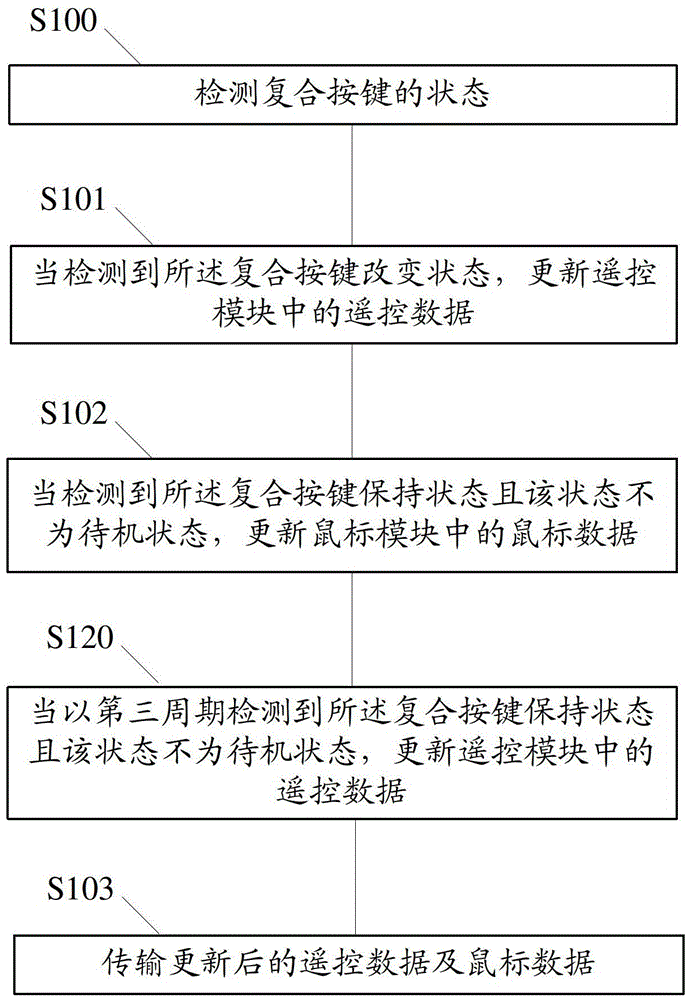
Data transmission method and device, data identification method and device
ActiveCN103324316BImprove reliabilityInput/output processes for data processingRemote controlComputer module
The present invention relates to a data transmission method and device and a data identification method and device. The data transmission method comprises: detecting states of compound keys; updating remote control data in a remote control module when detecting state changes of the compound keys; updating mouse data in a mouse module when detecting hold states of the compound keys and that the states are not stand-by states; transmitting the updated remote control data and mouse data. Accordingly, the data identification method comprises: receiving the remote control data / the mouse data transmitted by corresponding handheld devices through the data transmission method; identifying the remote control data / the mouse data transmitted by the handheld devices through corresponding protocols; responding to the identified remote control data / the mouse data and performing corresponding operations. The present invention can improve the validity of data transmission of the handheld devices.
Owner:JIANGSU HUITONG GRP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com