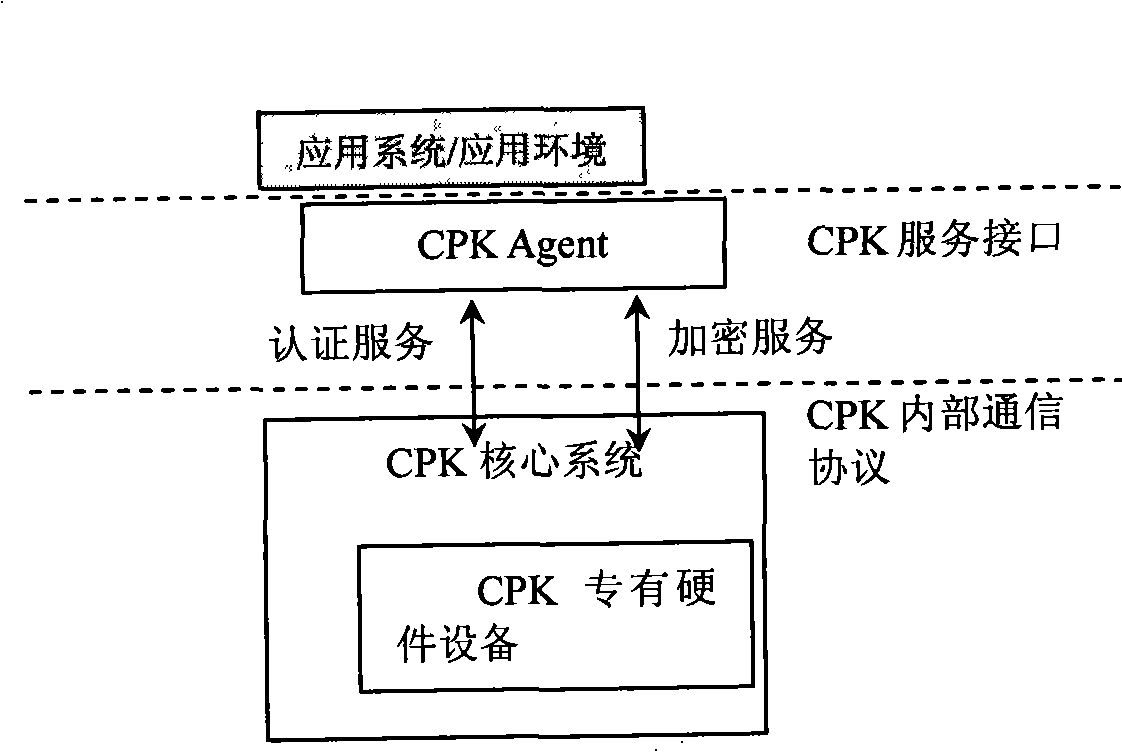
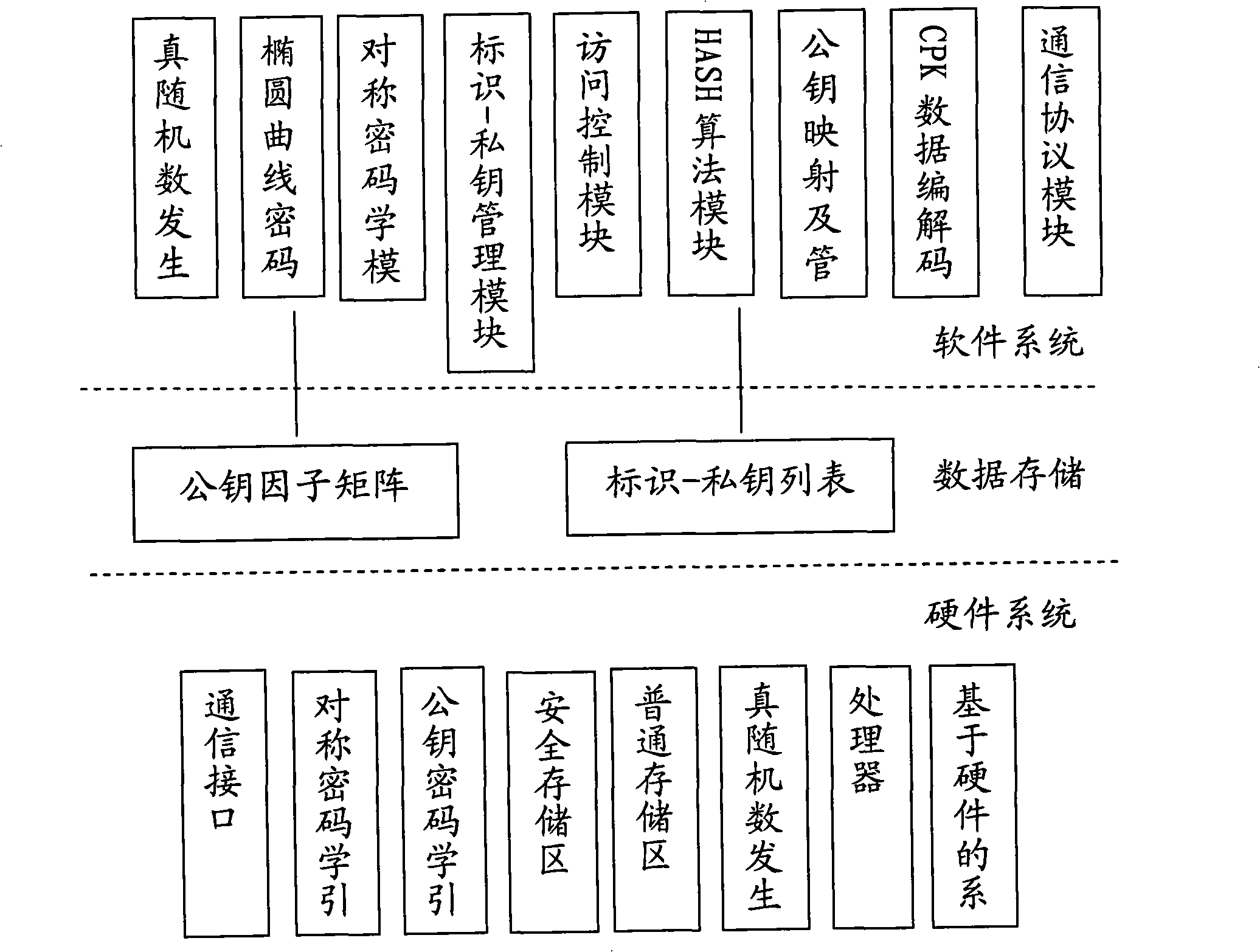
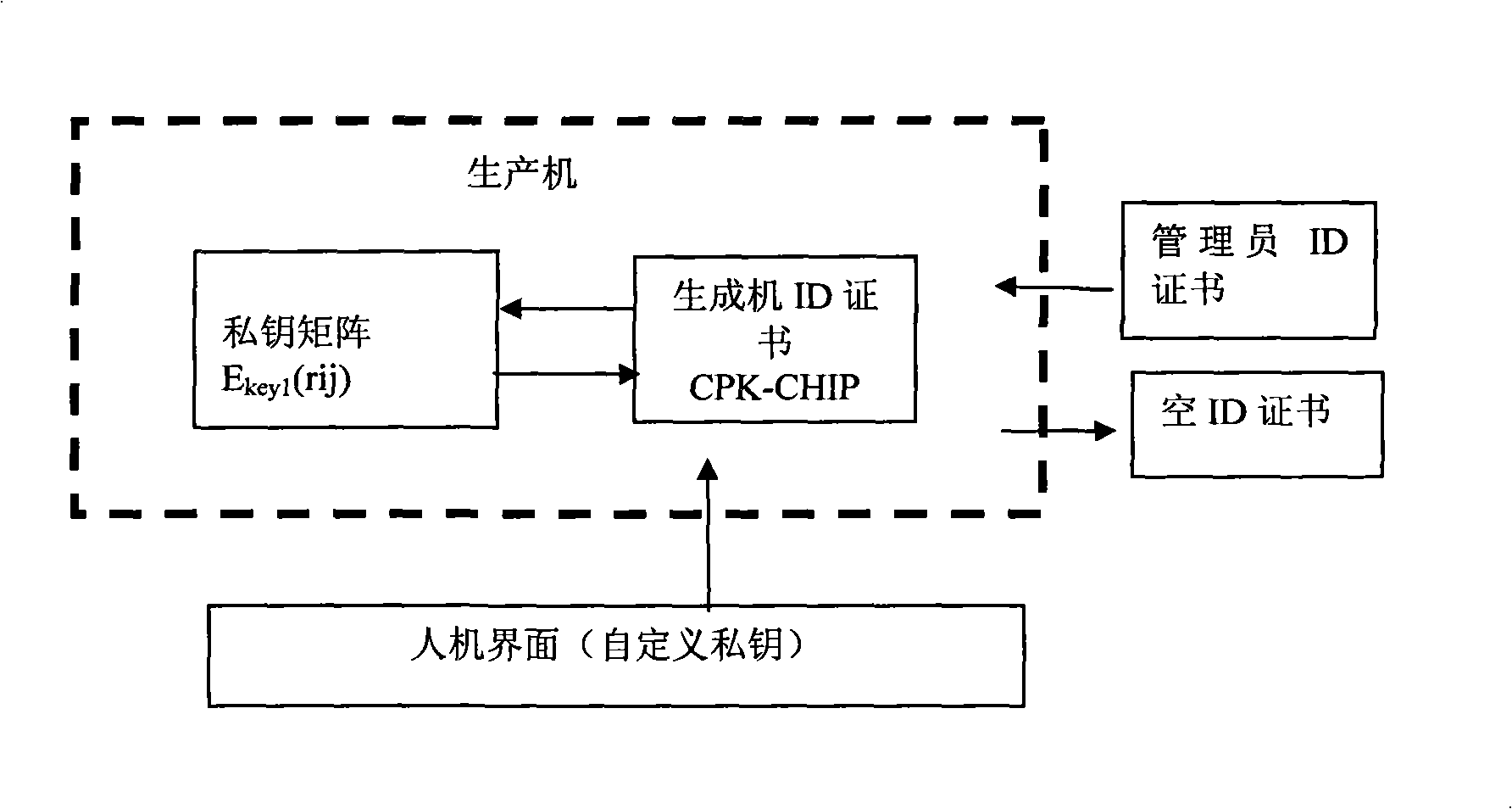
Generation method of composite public key
A technology of compound public key and generation method, which is applied in the direction of public key of secure communication, user identity/authority verification, digital transmission system, etc. Problems such as digital signatures cannot be realized to achieve the effect of ensuring privacy and exclusivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0460] Embodiment 1 Entity ID Authentication
[0461] In the transaction, the entity-to-entity business relationship first occurs, which involves the authentication of entity identification and data authentication. If the data contains seals, such as legal person seals, account seals, bank seals, financial special seals, etc., then seals are also involved Identity certification.
[0462] The initiator of the transaction is the attesting party, who must provide proof of entity identity authenticity and data authenticity. The proof of entity authenticity is the signature of the entity identity on the identity itself, the data authenticity proof is the signature of the entity identity on the data (entity level / user level), and the proof of the authenticity of the seal is the signature of the seal identity on the seal itself (identity level). The proof of the authenticity of the seal is the signature (identity level) of the seal identity on the seal itself. If privacy is required...
Embodiment 2
[0470] Embodiment 2 Electronic bill authentication
[0471] See the applicant's prior application 200610081134.6 "A CPK-Based Trusted Authentication System and Method for Electronic Bills", the full text of which is hereby incorporated by reference.
[0472] In electronic bills, the proof and verification relationship is as follows:
[0473] Account number, name, unit, etc., three signatures are required, such as:
[0474] sign1=SIG 账号 (mac);
[0475] sign2=SIG 姓名 (mac);
[0476] sign3=SIG 单位 (mac);
[0477] Make the bill file and the signature section into one file, such as Figure 5 The ticket file shown.
[0478] The electronic bill is transmitted, and the verification system in the bank server verifies each digital signature.
[0479] Together with the digital signature, electronic bills can be stored in the database in the form of electronic documents, or printed out and turned into paper-based bills, all of which have the same effect as real bills.
Embodiment 3
[0480] Embodiment 3 Software Label Authentication
[0481] See the applicant's prior application 200610081133.1 "A Trusted Authentication System Based on CPK", the full text of which is hereby incorporated by reference.
[0482] The user's transaction is processed by computer, so there is a need for trusted computing. Trusted computing needs to solve three problems: one is whether the program should be loaded, the other is whether the program is loaded correctly, and the third is whether the program runs as expected. As the first gate of trusted computing, it is very important to judge whether the program should be loaded or not. This depends on the identification technology of the process identification. If it is an illegal identification, it will refuse to load. In this way, malicious software such as viruses cannot function even if they invade. Software identification authentication needs to rely on code signing (code signing) technology to solve.
[0483] As far as a ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com