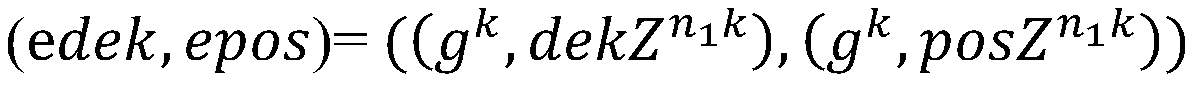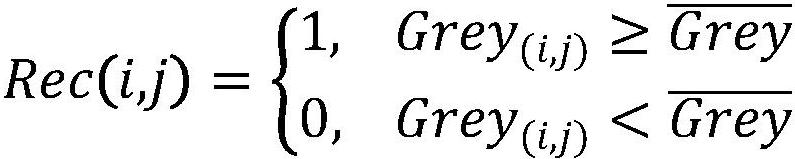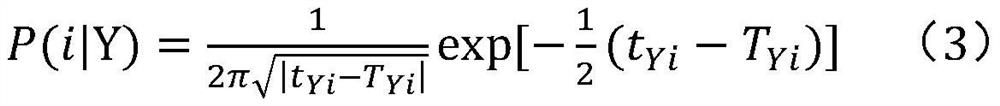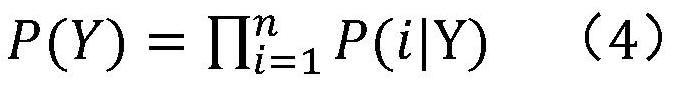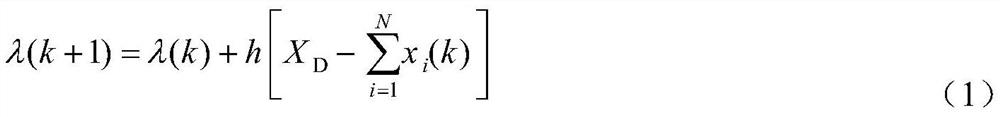Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "With privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Attendance-checking method
InactiveCN102831662ALow application costSimple structureRegistering/indicating time of eventsAccess timeUnique identifier
The invention relates to an attendance-checking method based on a network connectivity technology judging whether equipment used by enterprise personnel is accessed to an enterprise local area network or not. The attendance-checking method particularly comprises the following steps of: initially acquiring a unique identifier of an access point of the enterprise local area network, setting the enterprise local area network, and determining an effective attendance-checking identification point; initially setting the personal information of the enterprise personnel and an information list matched with the unique identifier of the equipment used by the enterprise personnel; initially setting the attendance-checking information of an enterprise; judging whether the equipment used by the enterprise personnel is accessed to / disconnected from the enterprise local area network or not, and recording through an attendance-checking server; determining the time of the equipment used by the enterprise personnel in being accessed to / disconnected from the enterprise local area network, and recording through the attendance-checking server; and matching the unique identifier of the equipment and the access time which are recorded through the attendance-checking server with the personal information data of the enterprise personnel and sorting and recording the attendance-checking conditions of the enterprise personnel according to the set attendance-checking information by the attendance-checking server. The attendance-checking method disclosed by the invention has the advantages of convenience, practicability, high efficiency, low cost and suitability for popularization.
Owner:HENAN YASCN SOFTWARE TECH
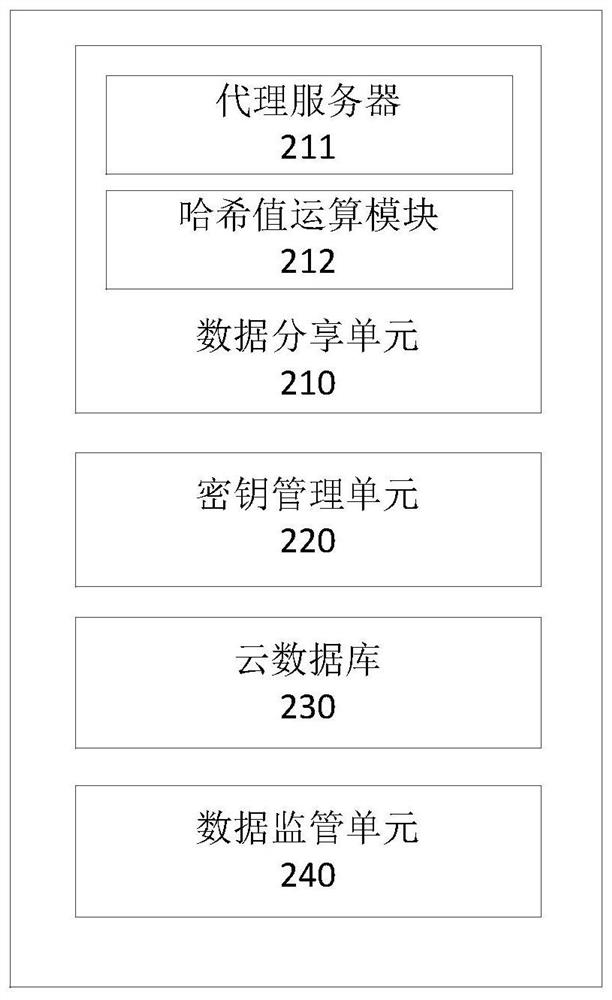
Supervisable data anonymous sharing method and system based on block chain
ActiveCN110430161ARealize privacy sharingAddressing hierarchical regulatory needsUser identity/authority verificationPlaintextCiphertext
The invention discloses a supervisable data anonymous sharing method and a supervisable data anonymous sharing system based on a block chain. The method comprises the steps that when a data using nodeinitiates a data sharing request to a data owning node, the data owning node generates a re-encryption key through a private key of the data owning node and a public key of the data using node, and sends the re-encryption key to a proxy server; the proxy server stores a random key used for encrypting plaintext data in advance by the data owning node and a data ciphertext at the position of the cloud server according to the re-encryption key, encrypts the random key and the data ciphertext according to a public key of the data owning node, then performs re-encryption conversion on the encrypted random key and the encrypted data ciphertext together as a ciphertext, and sends the re-encryption conversion result to the data using node; and the data use node obtains the encryption key of the to-be-shared data and the storage position of the to-be-shared data in the cloud database through decryption of the private key of the data use node, extracts the corresponding position data in the cloud database and obtains the to-be-shared data through decryption according to the encryption key.
Owner:BUBI BEIJING NETWORK TECH CO LTD
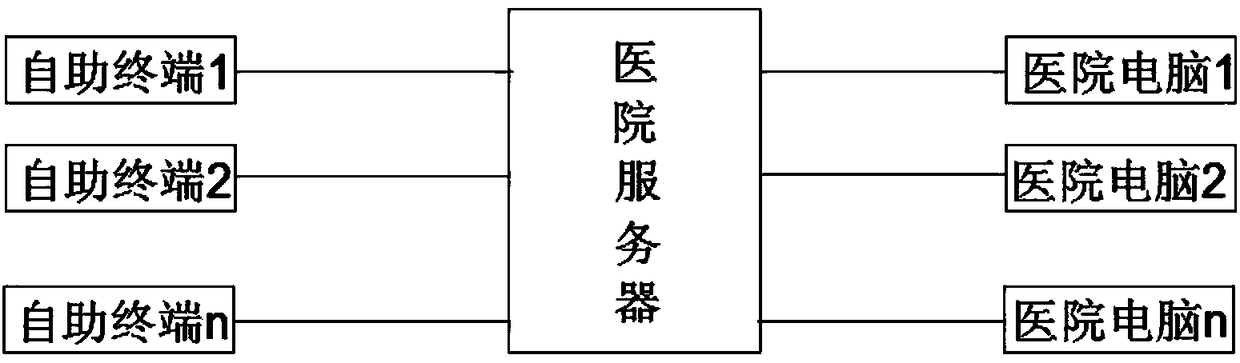
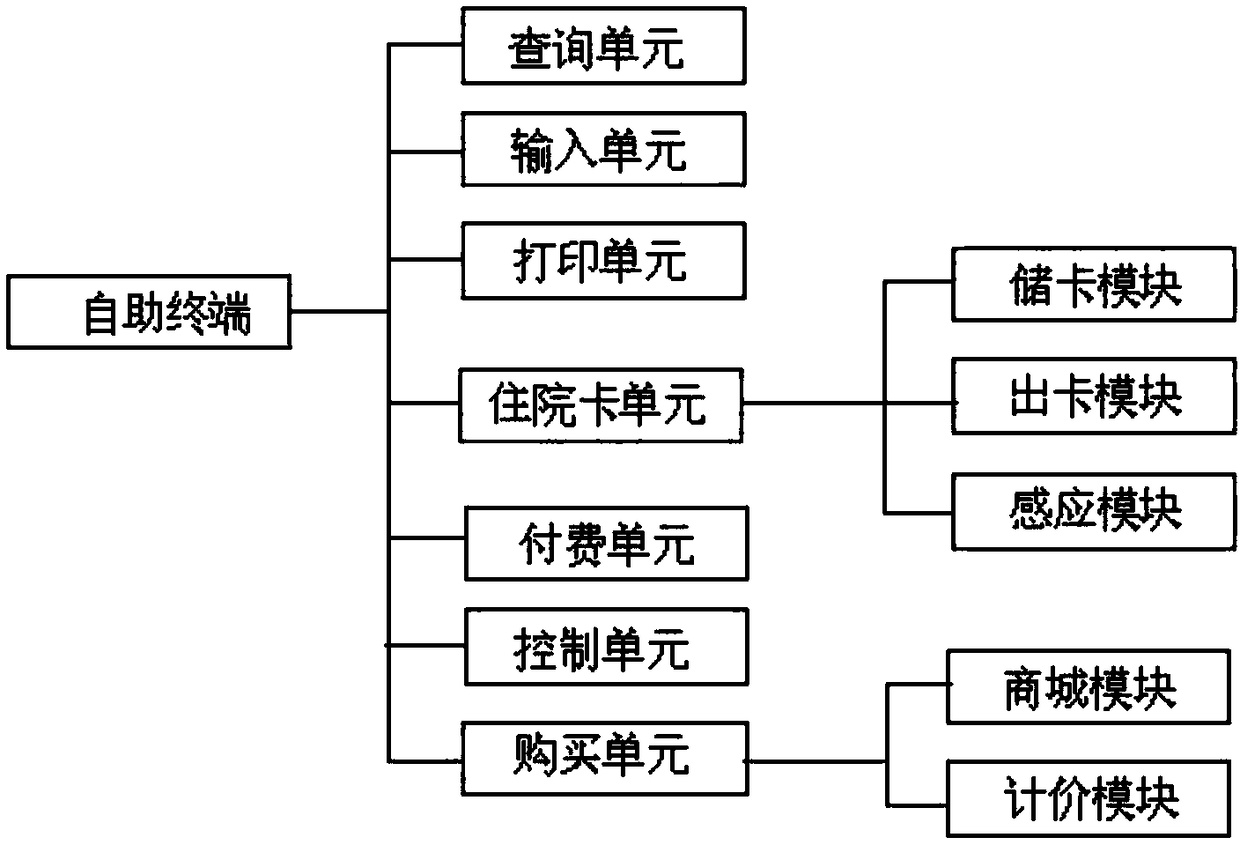
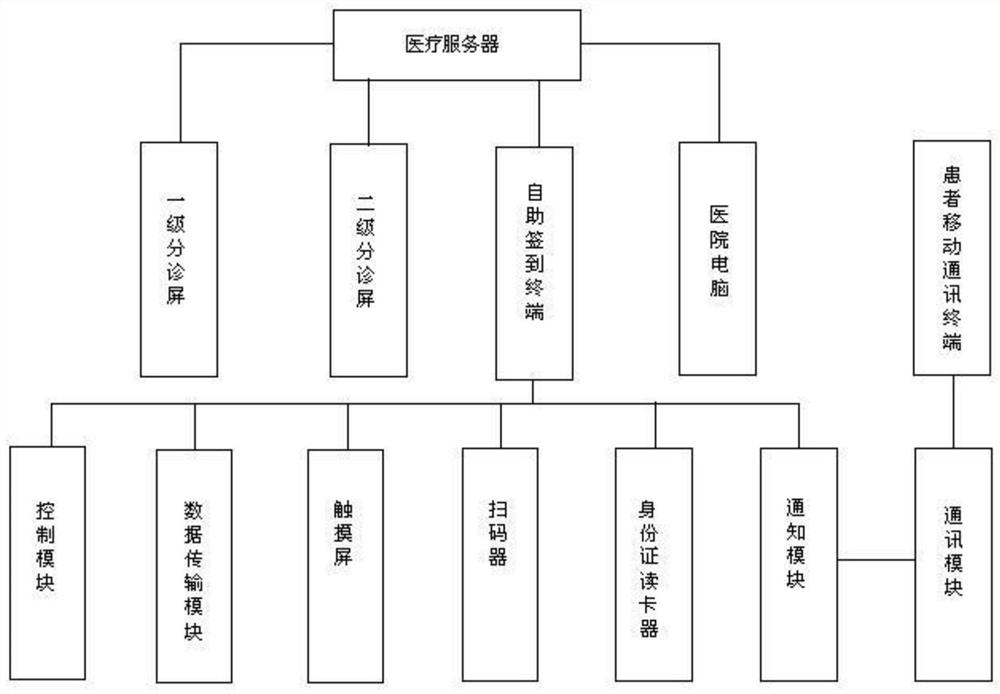
Hospital self-service terminal system and intelligent triage management system thereof
InactiveCN108417257ASave timeSave energyRegistering/indicating time of eventsReservationsTriageMedical ward
The invention discloses a hospital self-service terminal system and an intelligent triage management system thereof. The hospital self-service terminal system comprises a self-service terminal, a hospital server and a hospital computer. The hospital server stores inpatient information, receives a signal of the self-service terminal, and responds to the self-service terminal. The hospital computeris connected to the hospital server through an optical fiber and receives data from the hospital server. The self-service terminal scans a hospitalization certificate issued by a doctor and communicates with the hospital server for verification, and a patient handles a hospital admission procedure and selects a ward bed through the self-service terminal. The hospital server is connected to the self-service terminal through the optical fiber, receives the data of the self-service terminal, and manages a personal account of the patient. The self-service terminal reads the information of the personal account of the patient and provides patient information inquiry and printing services. The self-service terminal has a built-in card warehouse and provides distribution, binding and recharge services of inpatient department magnetic cards. According to the hospital self-service terminal system and the intelligent triage management system, the time and energy of the patient are effectively saved, a hospital admission preparation process is simplified, the quick hospital admission of the patient is facilitated, and a complete purchase service of daily necessities is provided for the patient.
Owner:浙江远图技术股份有限公司
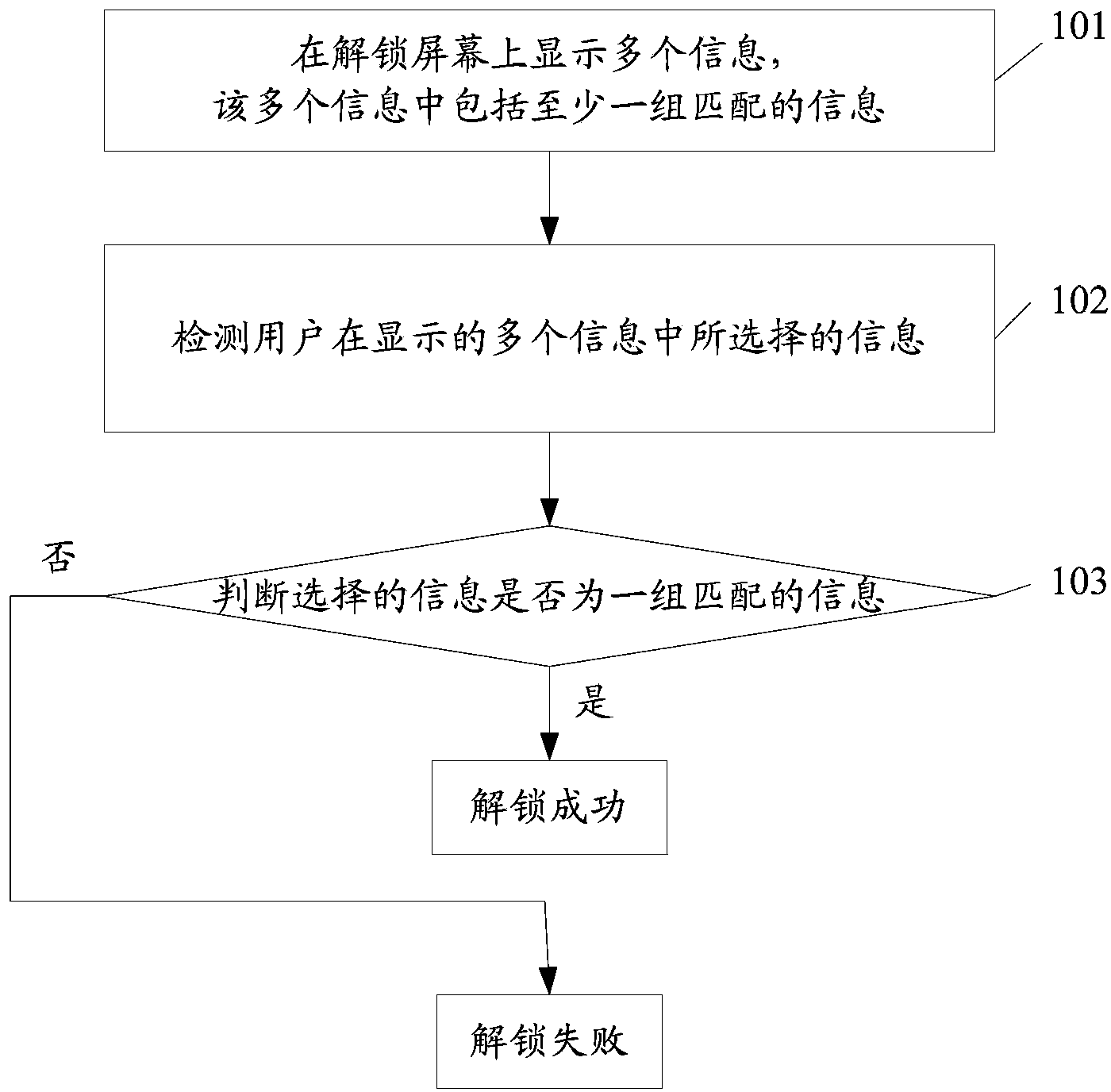
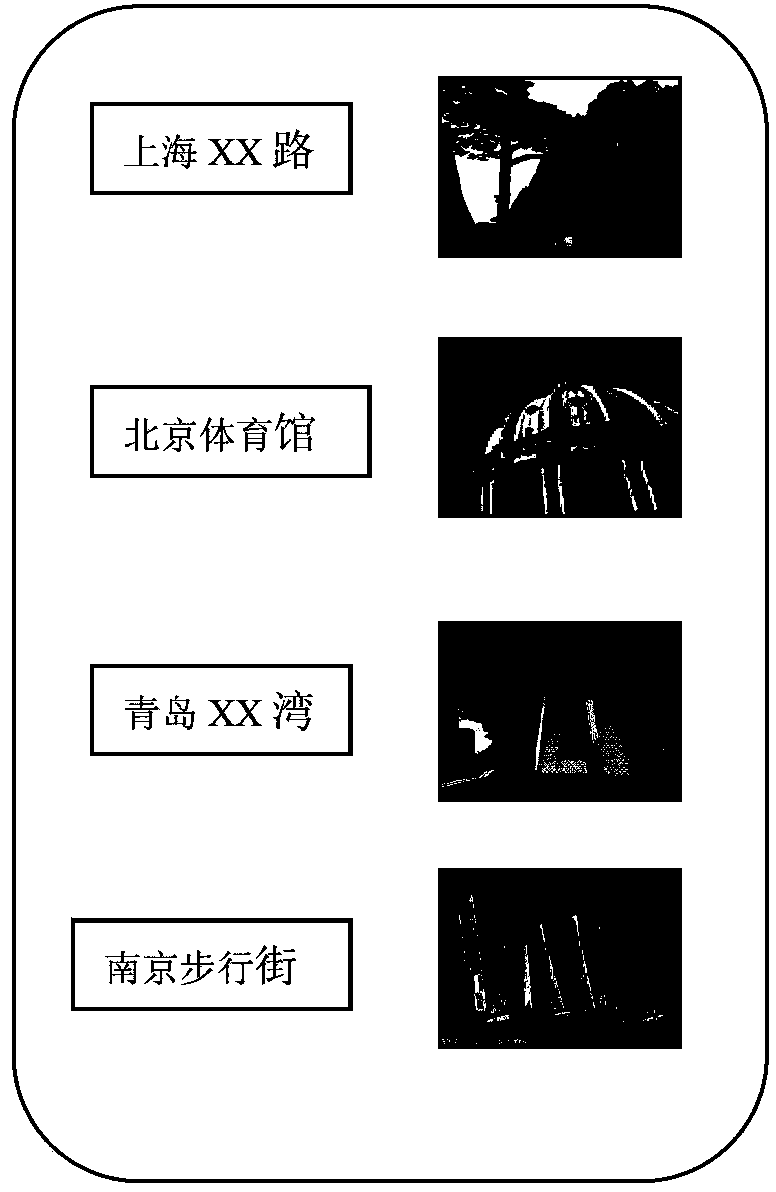
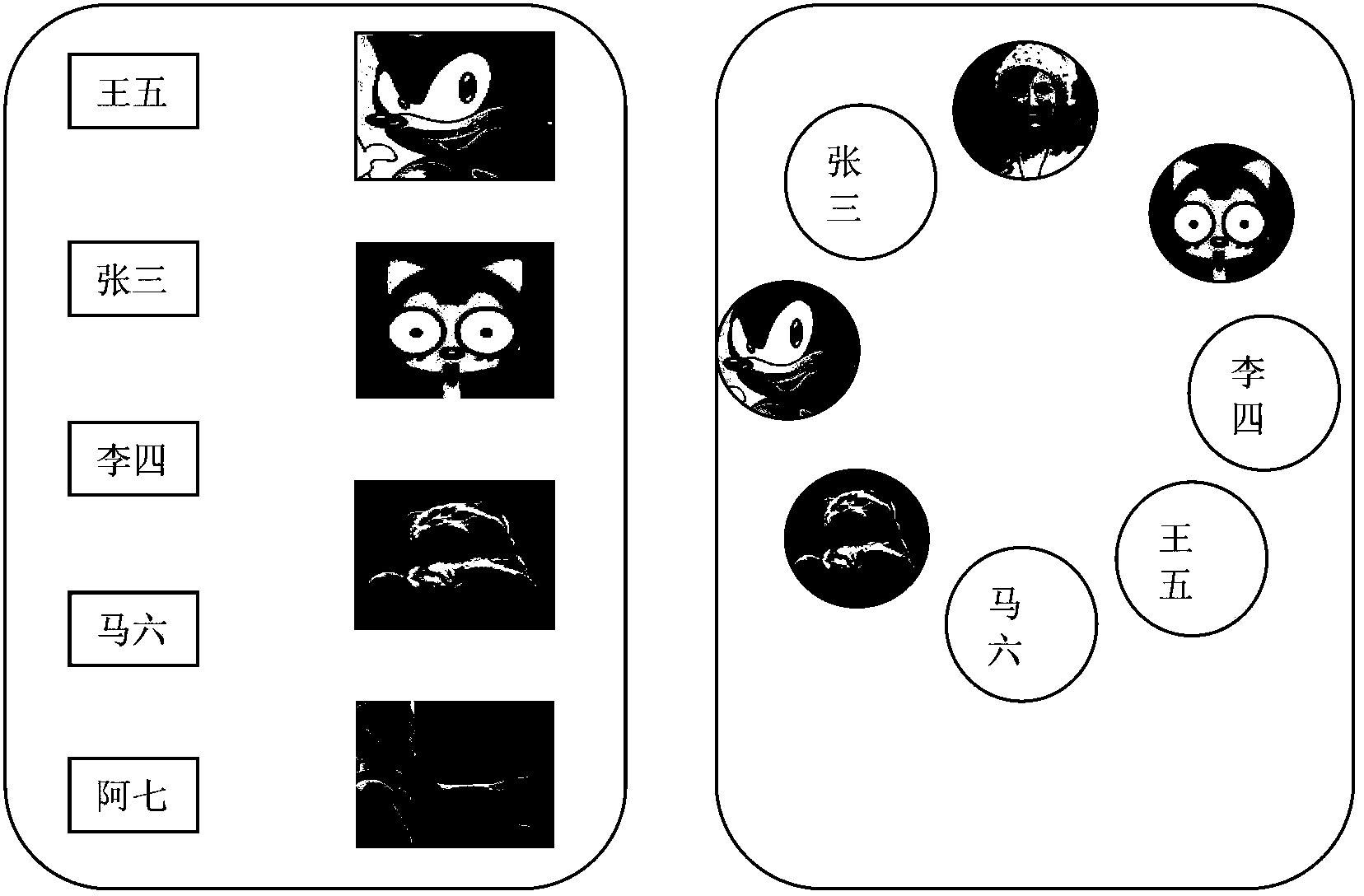
Terminal and unlocking method of terminal
InactiveCN103902175AAchieve unlockWith privacyInput/output processes for data processingComputer hardwareComputer science
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
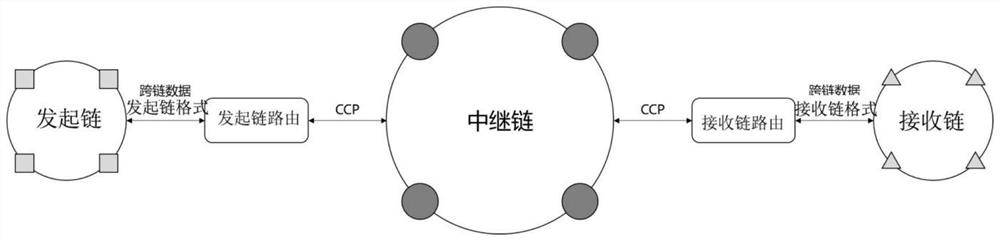
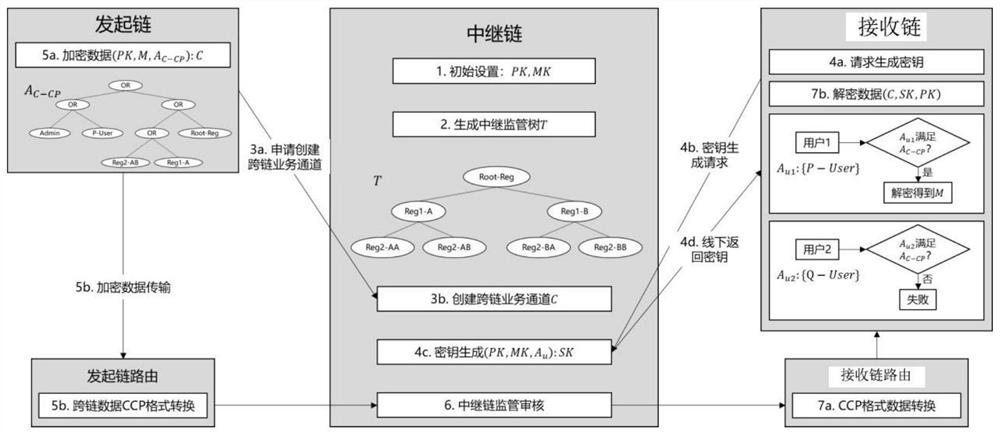
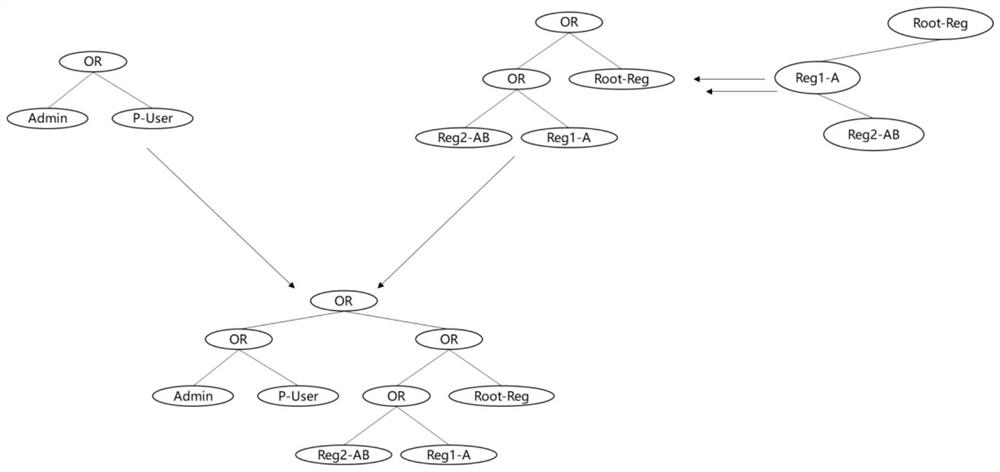
Supervisable privacy protection cross-block chain system based on CP-ABE
ActiveCN113595735AAchieving RegulatoryWith privacyFinanceUser identity/authority verificationPrivacy protectionTrunking
The embodiment of the invention discloses a supervisible privacy protection cross-block chain system based on CP-ABE. The system comprises an initiating chain, an initiating chain route, a relay chain, a receiving chain route and a receiving chain. The initiating chain encrypts a to-be-cross-chain transaction through a preset cross-chain smart contract function supporting CP-ABE to obtain a cross-chain transaction, so that the cross-chain transaction has privacy in a cross-chain transmission process, and the relay chain generates a key and sends the key to a target user in the receiving chain. The receiving chain judges whether the target user successfully decrypts the format-converted cross-chain transaction through the key, and if so, the target user obtains the decrypted cross-chain transaction. Therefore, not all users on the receiving chain can obtain the cross-chain transaction, but only the cross-chain transaction after the format conversion is successfully decrypted can obtain the cross-chain transaction, user-level privacy protection on the cross-chain business is realized, inconvenience brought by multiple times of encryption is avoided, a supervisor participates in the relay chain in a simple manner, hierarchical data visibility is achieved, and the actual service scene is met.
Owner:中债金科信息技术有限公司 +1
Intelligent sunshade integrated system window and control system thereof
PendingCN107165542ASave energyAnti-theftBurglary protectionStatic indicating devicesControl systemEngineering
The invention provides an intelligent sunshade integrated system window and a control system thereof. The intelligent sunshade integrated system window comprises a window frame and a window sash which is rotationally connected with the window frame to open or close the window. A cavity is formed in the window sash, a master controller is arranged in the cavity, and the window sash is fixedly provided with a glass module; the glass module comprises inner-layer glass, outer-layer glass and a plurality of electro-induced liquid crystal films which are glued between the inner-layer glass and the outer-layer glass and distributed in sequence; the master controller is connected with and controls each electro-induced liquid crystal film, and the master controller is arranged in the cavity to achieve the effect of protecting the master controller; the glass module uses a dry-process laminated glass process, and the electro-induced liquid crystal films are glued between the two pieces of glass, so that the heat-preservation and energy-saving effects are improved; the inner-layer glass and the outer-layer glass are glued so that the glass can be broken but not broken into pieces, and the safety performance and the anti-theft function are improved; meanwhile, single control and multiple control over the electro-induced liquid crystal films can be achieved through the master controller, so that various effects of light shielding and the like are achieved.
Owner:南京盈润门窗科技有限公司
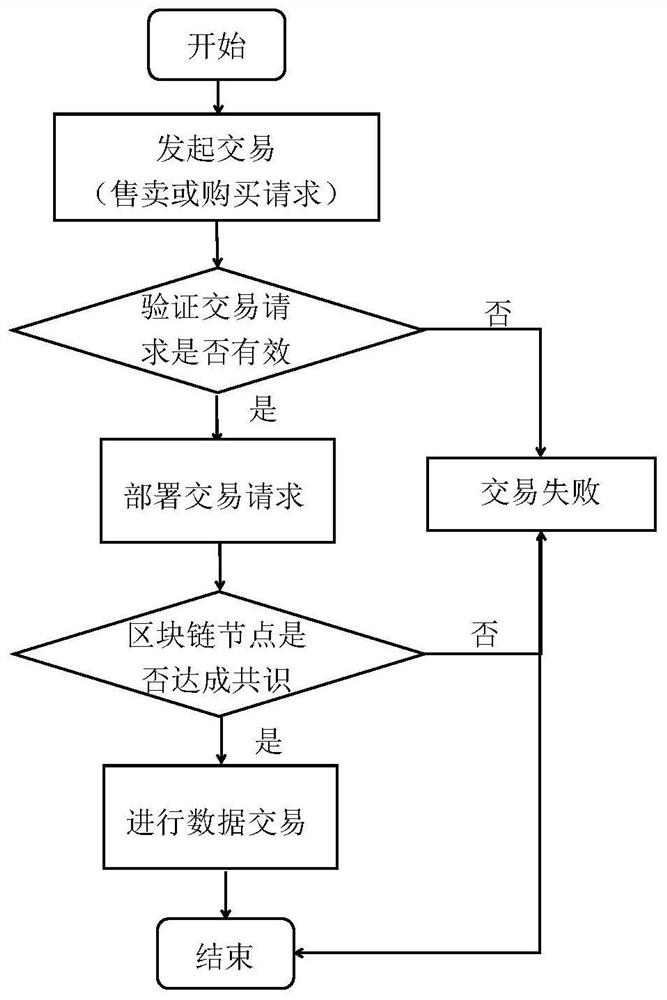
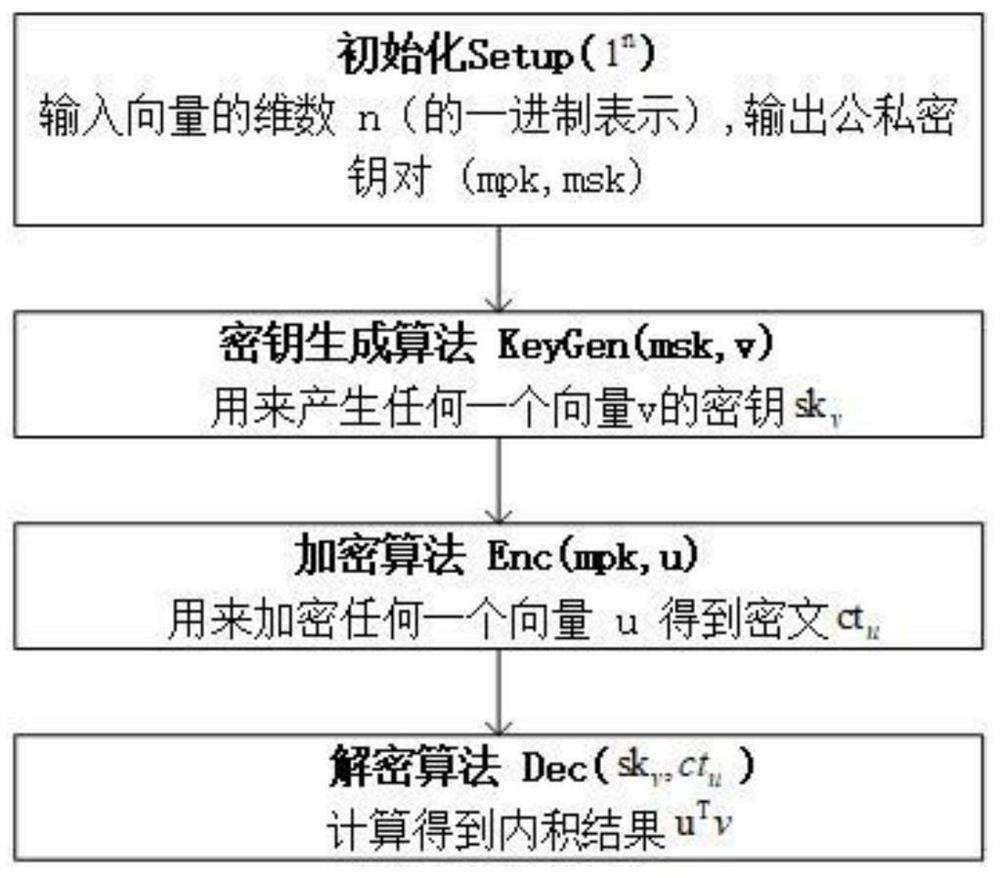
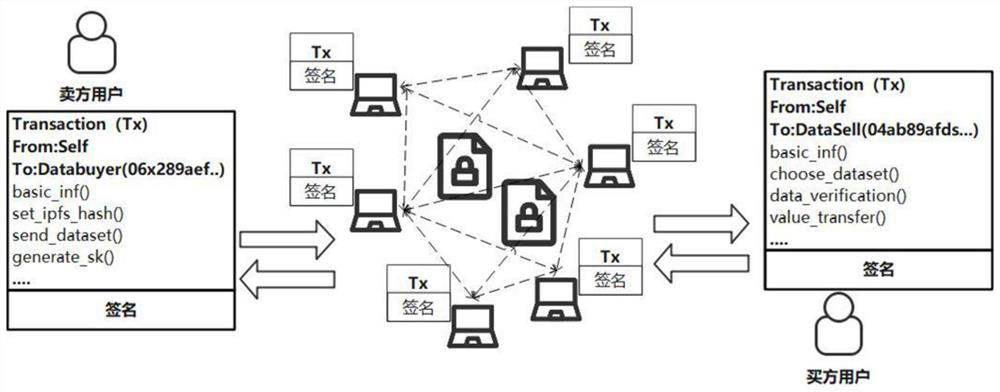
Block chain data transaction method with privacy protection
The invention provides a block chain data transaction method with privacy protection, and relates to the technical field of block chains. The seller user participates in the transaction and stores original data into an interstellar file system after performing public key inner product encryption on the original data, and initiates a transaction request for creating a seller smart contract in a block chain; then the buyer user initiates a transaction request for creating a buyer smart contract in the block chain; the consensus nodes on the block chain perform validity check on the transaction requests initiated by the transaction participating users; if the check is passed, all the consensus nodes on the block chain record the transaction requests in the chain, and the seller user and the buyer user perform data transaction based on the block chain; and if the check is invalid, the transaction application is rejected. The method is based on the block chain, the traceability of the data transaction process is guaranteed, and the rights and interests of buyers and sellers are guaranteed. Meanwhile, the data transaction process is encrypted by using a secret key, so that the transaction platform is ensured not to check and store easy-to-check data.
Owner:NORTHEASTERN UNIV
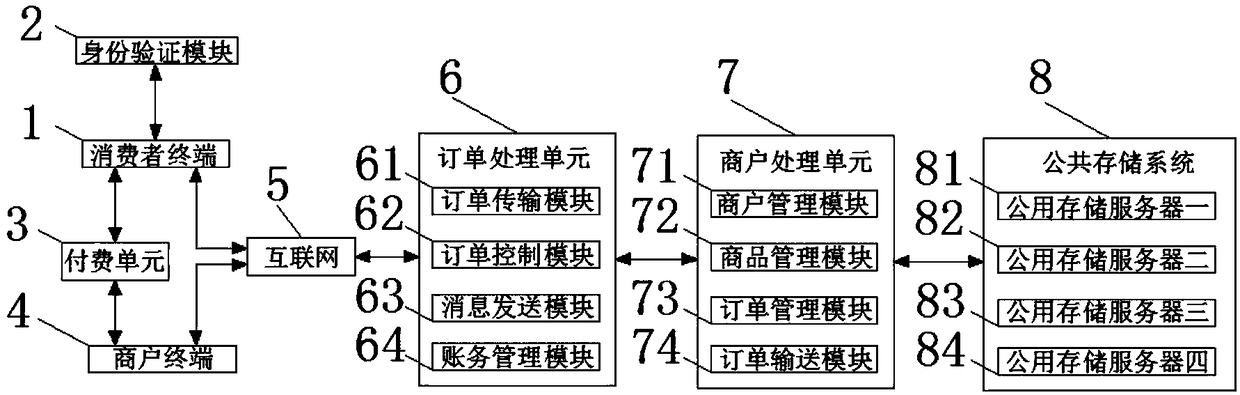
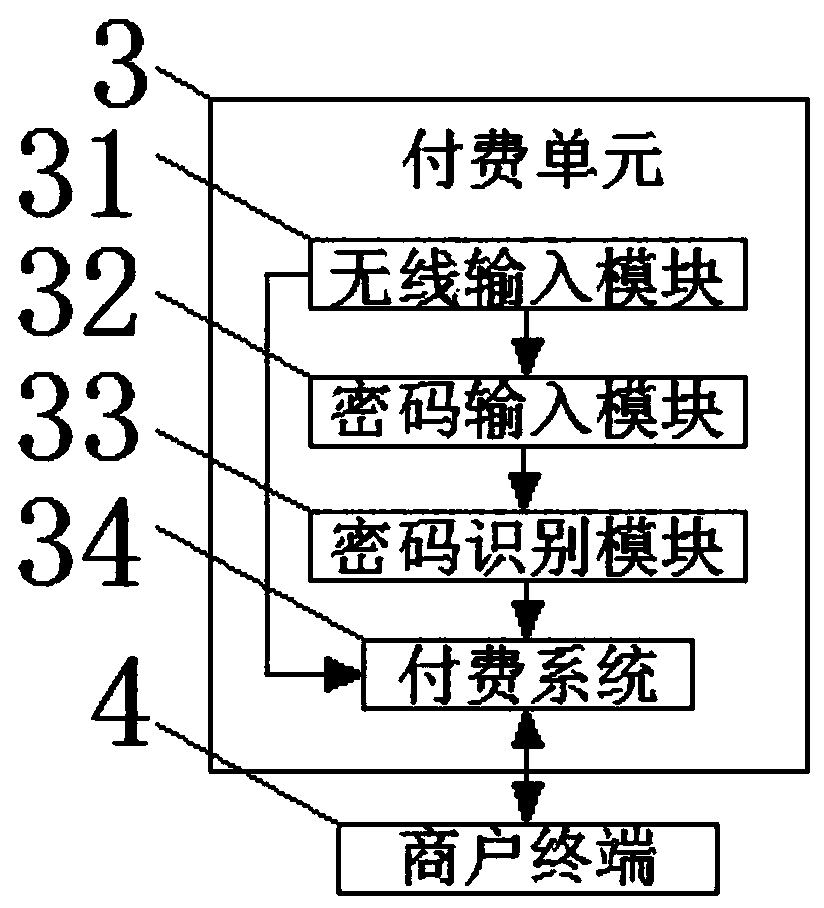
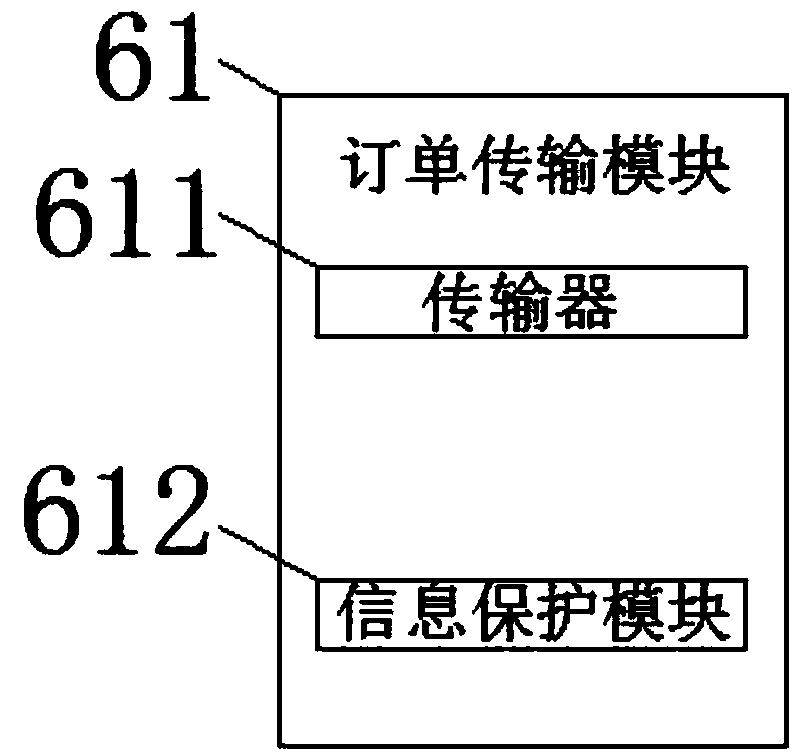
Third-party payment system based on block chain technology
InactiveCN108346040ASafeWith privacyPayments involving neutral partyProtocol authorisationComputer moduleComputer terminal
The invention relates to the technical field of online payment and discloses a third-party payment system based on a block chain technology. The third-party payment system includes a consumer terminal, the output end of the consumer terminal is in signal connection with the input end of an identity verification module, the output end of the identity verification module is in signal connection withthe input end of the consumer terminal, and the output end of the consumer terminal is in signal connection with the input end of a payment unit, and the output end of the payment unit is in signal connection with the input end of the consumer terminal, and the output end of the payment unit is in signal connection with the input end of a commercial terminal, and the output end of the commercialterminal is in signal connection with the input end of the payment unit. The third-party payment system based on the block chain technology achieves the effects of safety, privacy and stability by arranging a first public storage server, a second public storage server, a third public storage server and a fourth public storage server.
Owner:北京智帮帮科技有限公司
Data storage method based on block chain
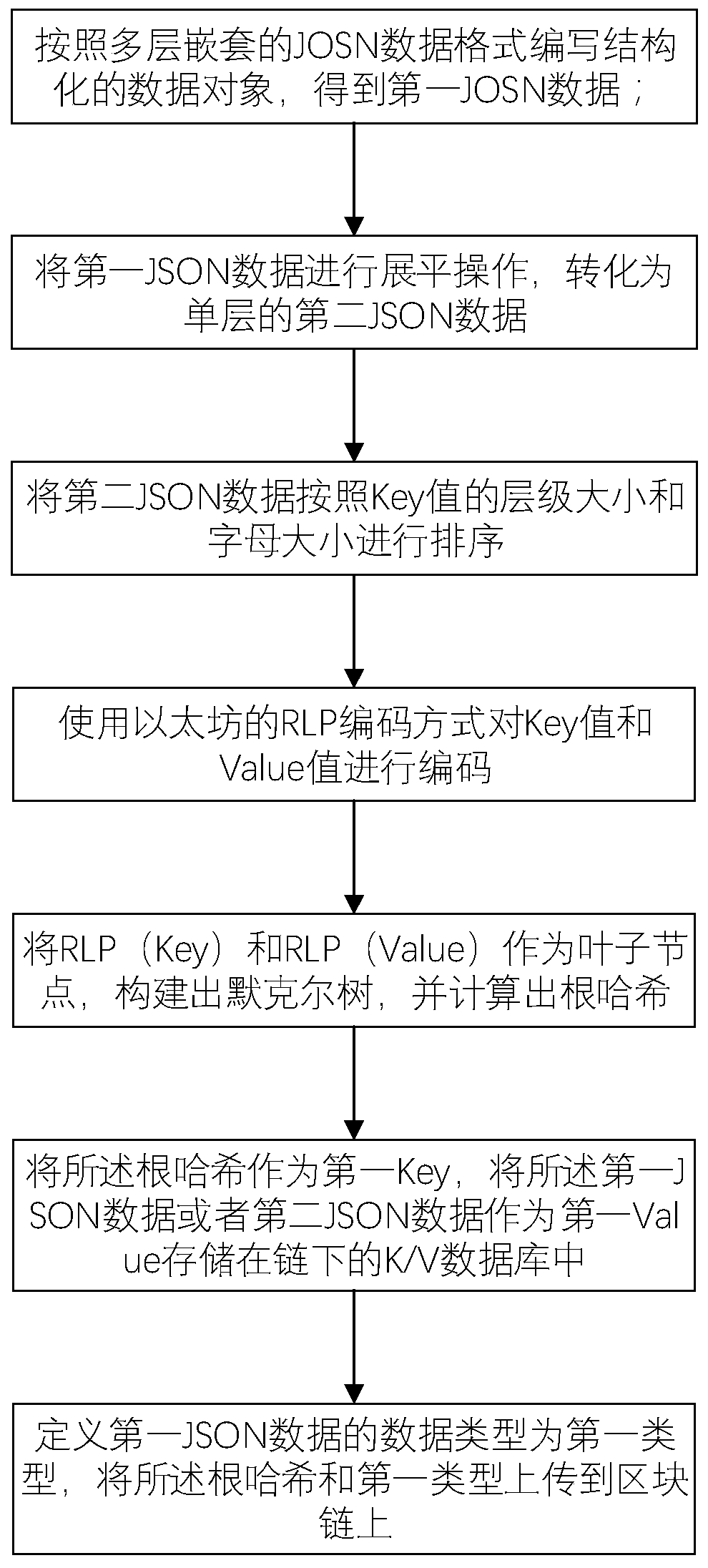
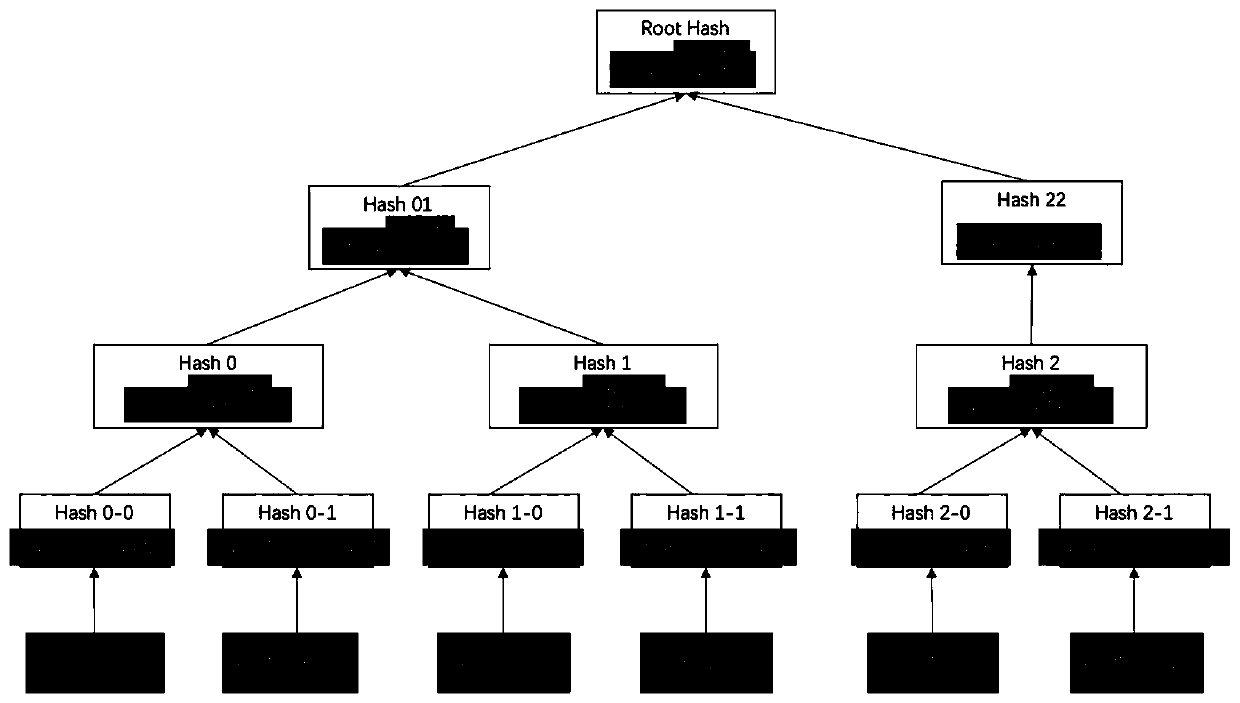
PendingCN111523148ANon-tamperableWith privacyDatabase management systemsDigital data protectionParallel computingTheoretical computer science
The invention provides a data storage method based on a block chain. The data storage method comprises the following steps: S1, compiling a structured data object according to a multi-layer nested JOSN data format; S2, carrying out flattening operation on the first JSON data; S3, sorting the second JSON data according to the hierarchical size and letter size of the Key value; S4, encoding the Keyvalue and the Value value by using an RLP encoding mode of the Ethereum; S5, taking the RLP (Key) and the RLP (Value) as leaf nodes, constructing a Merkel tree, and calculating a root hash; S6, takingthe root hash as a first Key, taking the first JSON data or the second JSON data as a first Value, and storing the first JSON data or the second JSON data in a K / V database under a chain; and S7, defining the data type of the first JSON data as a first type, and uploading the root hash and the first type to a block chain. The data storage method based on the block chain has the advantages of tamper resistance, privacy, verifiability, high efficiency and the like.
Owner:丝链(常州)控股有限公司
Identifiable recording and broadcasting system based on multiple groups of wireless terminals
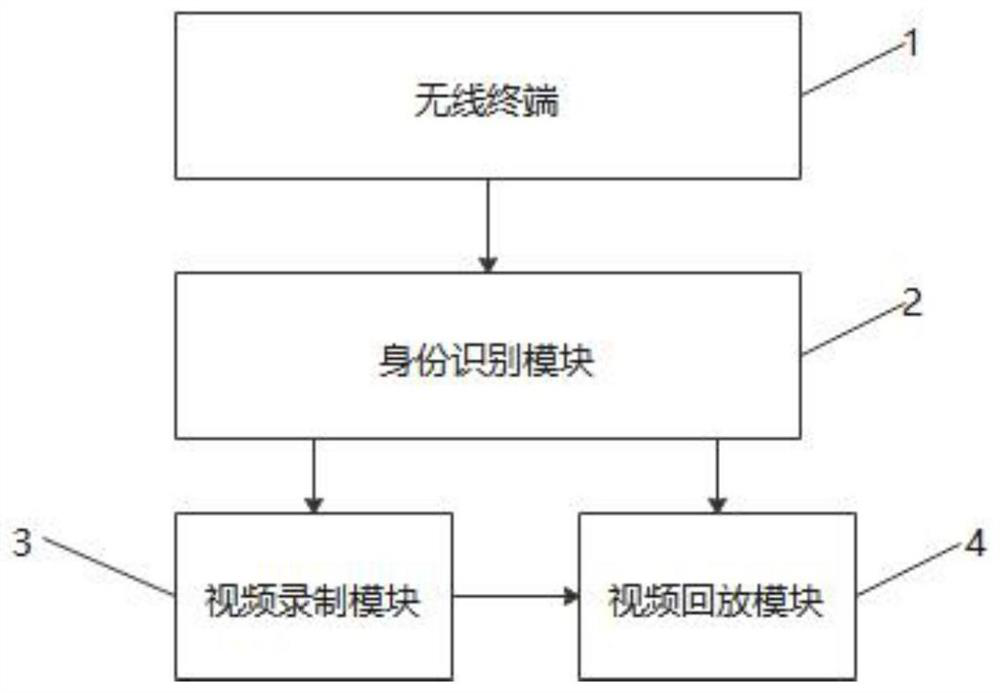
ActiveCN112702738AIncrease flexibilityPrevent malicious swiping of viewing timeTelevision system detailsColor television detailsIdentity recognitionVideo record
The invention provides an identifiable recording and broadcasting system based on multiple groups of wireless terminals. The system comprises the wireless terminals; a identity recognition module connected with the wireless terminal and used for recognizing the identity of the current user; a video recording module connected with the identity recognition module and used for recording and storing the wireless terminal of the user passing verification of the identity recognition module; and a video playback module connected with the identity recognition module and used for providing the video stored by the video recording module for the user passing the verification of the identity recognition module.
Owner:深圳日谦科技有限公司
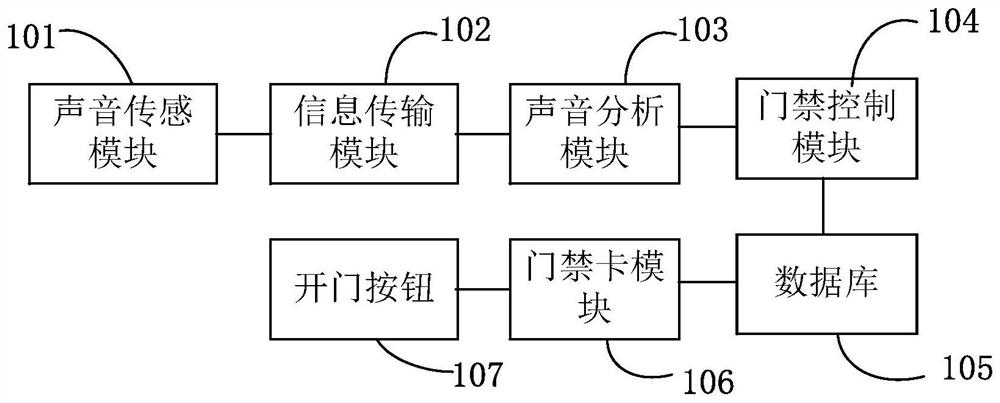
Intelligent access control system for realizing door opening through voice recognition
InactiveCN112349005ARealize safe and controllableSafe and controllableSpeech analysisIndividual entry/exit registersControl systemEngineering
The invention provides an intelligent access control system for realizing door opening through voice recognition, and the intelligent access control system for realizing door opening through voice recognition comprises a sound sensing module which is used for detecting sound data of a current door opening user; a sound analysis module which is used for analyzing the sound data detected by the sound sensing module; and an access control module which is used for controlling opening and closing of the door according to the analysis result of the sound analysis module. According to the intelligentaccess control system for realizing door opening through voice recognition, a single sensing mode at present is changed, non-contact recognition is realized, the information safety can be better ensured, and the detection efficiency is improved; in addition, from the aspect of information collection, sound collection is more convenient, and meanwhile the uniqueness and privacy are better achieved; moreover, from the perspective of security and protection, the security and the controllability of information are realized.
Owner:慧之安信息技术股份有限公司
Air-permeable door with simple umbrella placing function
InactiveCN112443248AAvoid bringing inWith ventilationApparel holdersGas treatmentJambMechanical engineering
Owner:武穴朋来豪门科技有限公司
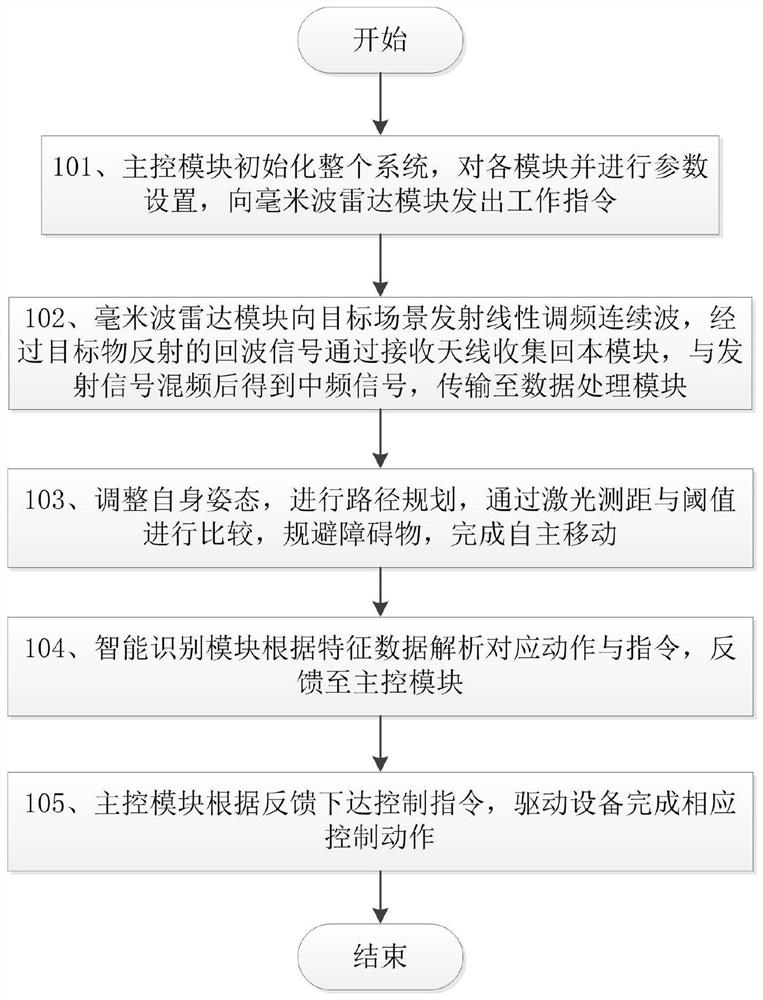
Man-machine interaction method based on millimeter wave radar
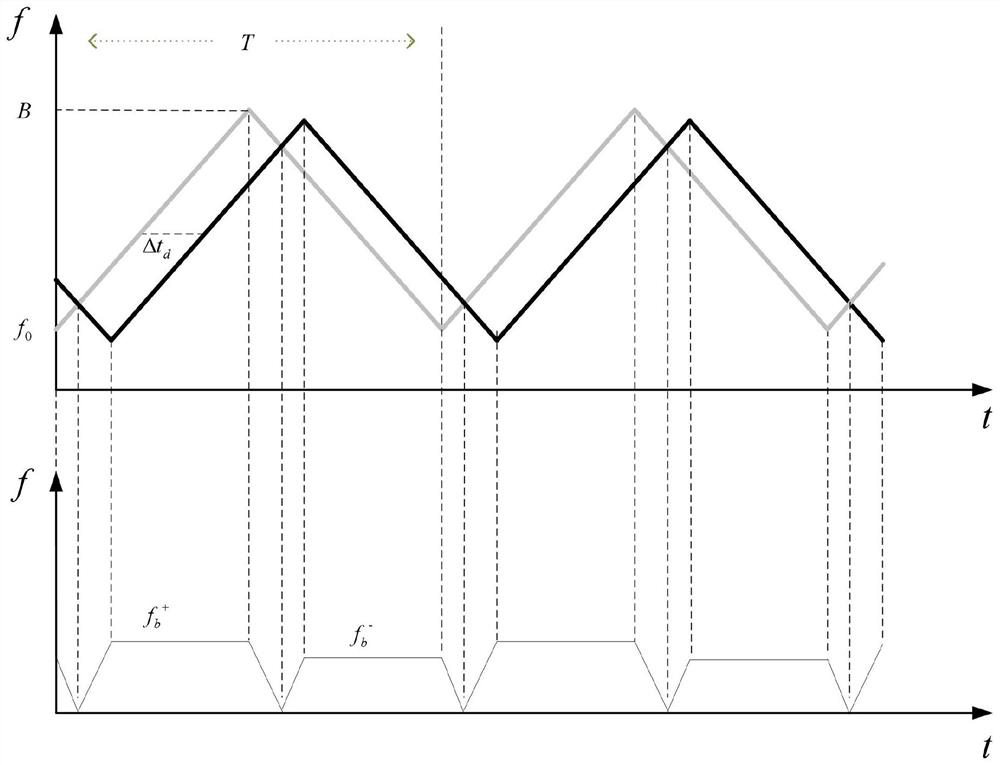
PendingCN112130133AAvoid safety hazardsReduce the risk of transmissionInput/output for user-computer interactionGraph readingIntermediate frequencyFrequency modulation
The invention discloses a man-machine interaction method based on a millimeter wave radar. The method comprises the following steps of: (1) performing initialization through a main control module, performing parameter setting on a millimeter wave radar module, a data processing module and an intelligent identification module, and sending a working instruction to the millimeter wave radar module; (2) transmitting linear frequency modulation continuous waves to a target scene by the millimeter wave radar module, collecting echo signals reflected by a target object to a script module through a receiving antenna, performing frequency mixing with transmitted signals to obtain intermediate frequency signals, and transmitting the intermediate frequency signals to the data processing module; (3) executing a resolving algorithm by the data processing module to obtain feature data, and transmitting the feature data to the intelligent identification module; (4) analyzing corresponding actions andinstructions by the intelligent identification module according to the feature data, and feeding back the corresponding actions and instructions to the main control module; and (5) issuing a controlinstruction by the main control module according to the feedback, and driving equipment to complete corresponding control actions. According to the man-machine interaction method disclosed by the invention, smart home equipment is expanded to perform interaction, so that the smart home equipment can feed back action posture instructions, and specific control operations can be realized according tomodel comparison.
Owner:NANJING PANDA ELECTRONICS MFG +1
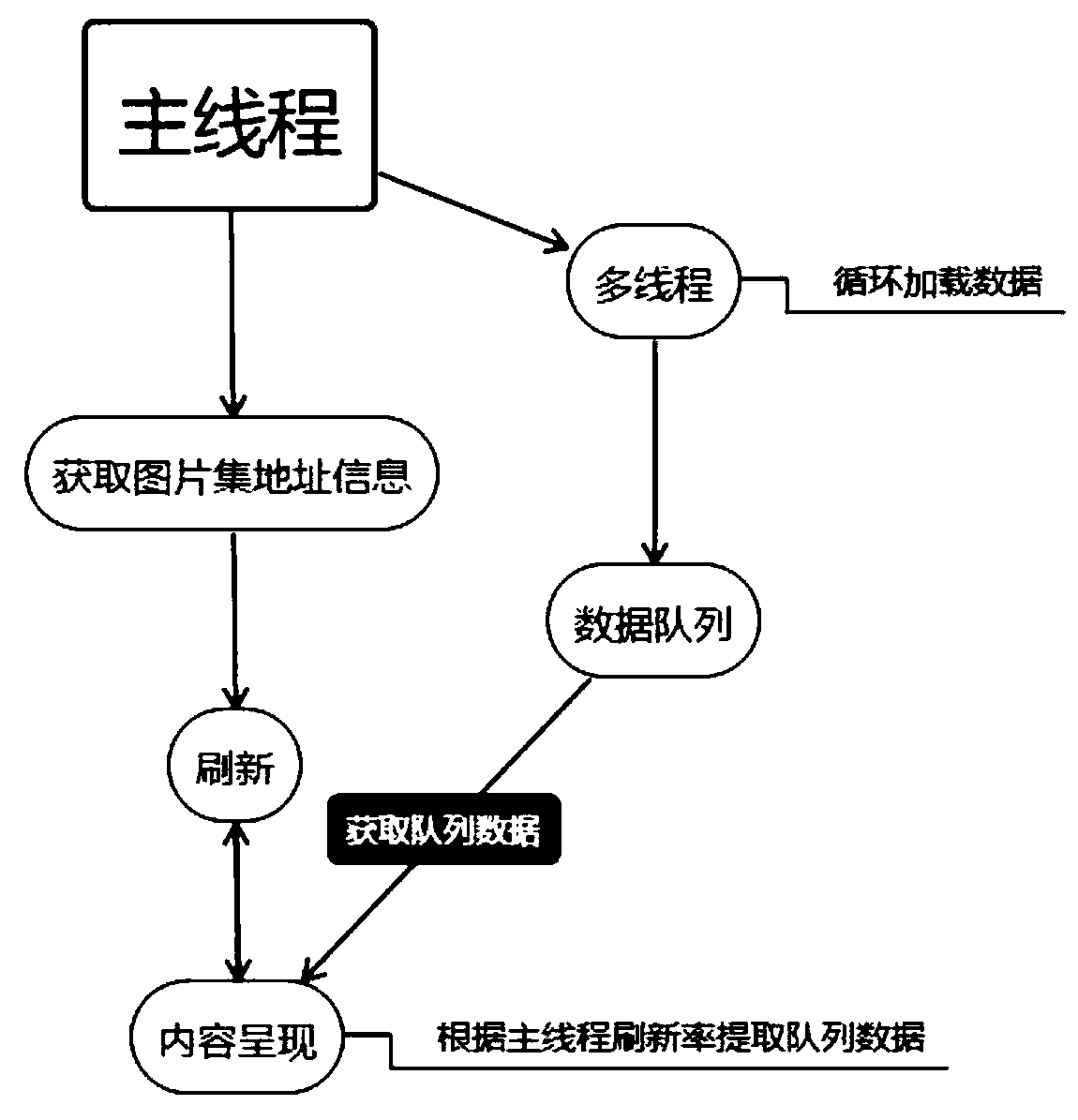
Method for realizing smooth loading of external picture set based on Unity 3D characteristics
The invention discloses a method for realizing smooth loading of an external picture set based on Unity 3D characteristics. The system comprises a main thread and multiple threads; the main thread isused for acquiring picture set address information; the obtained picture set address information is refreshed to realize content presentation; the content presentation extracts team data according toa main thread refresh rate; the main thread is connected with multiple threads, the multiple threads are used for cyclically loading data, the multiple threads are further used for a data queue, the data queue can obtain team data, the output end of the team sequence is connected with content presentation, and the main thread loads picture set file path information at a time. The method for realizing the smooth loading of the external picture set based on the Unity 3D characteristics is applied to a unique operation mechanism of a Unity 3D engine, the constant loading and use of a large numberof picture sets are obviously improved, resources can be flexibly replaced, and the operation fluency is ensured, so that the technical method is relatively excellent in efficiency, universality, fluency and convenience.
Owner:江苏火米互动科技有限公司
Automotive glass with neutral color solar control coating
PendingCN114746374APrecise control of transmission levelsHas a neutral colorGlass/slag layered productsCoatingsColor shiftLow emissivity
Due to the fact that the glass area of a modern vehicle is increased, in particular to a large panoramic glass roof, the use of solar control glass and a coating is greatly increased. The manufacturing cost of the solar glass composition and the coating is very high. While solar coatings are more effective than compositions, it is generally not applicable to single glass, as solar coatings are not durable. A solar coating must be applied to one surface of the inner side of the laminate. Most of these products also introduce undesirable color shifts. The present invention provides a coating that can be used in glass to produce a laminated glass or monolithic glass with a solar controlled neutral gray coating, the coating also having anti-reflection properties and low emissivity.
Owner:AGP AMERICA
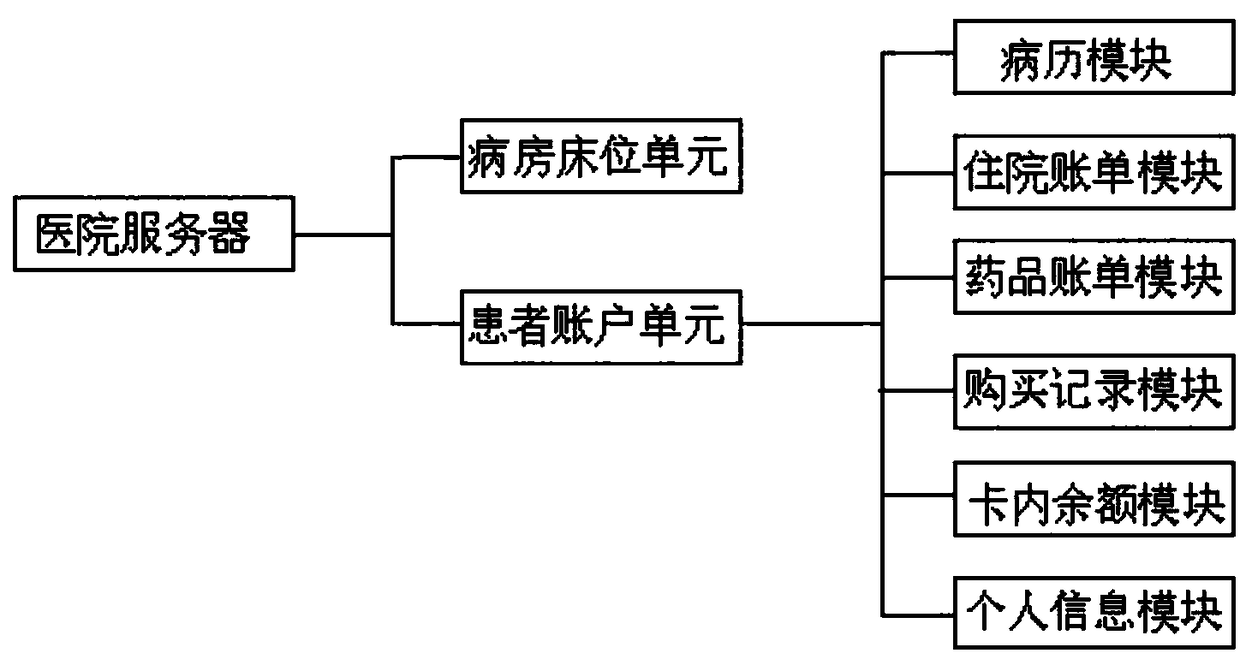
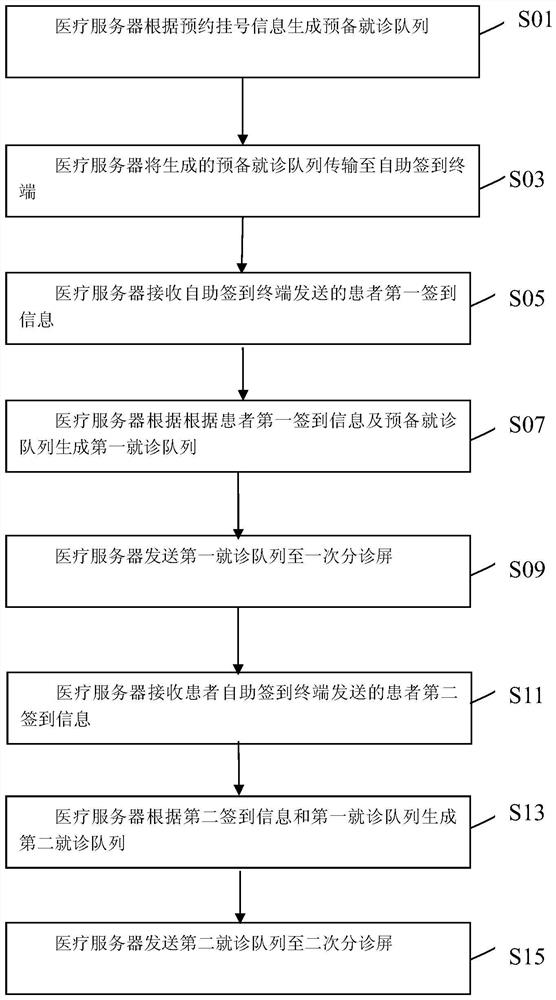
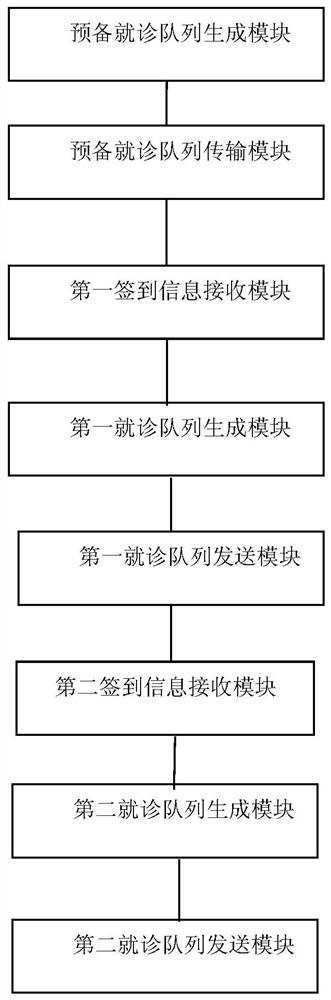
An intelligent triage management system for a hospital and the medical server used therein
ActiveCN108461133BImprove certaintyGood medical orderReservationsChecking apparatusTriageComputer network
Owner:浙江远图技术股份有限公司
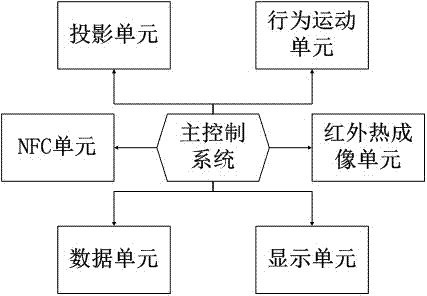
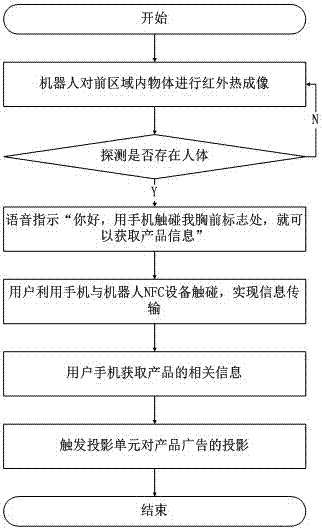
Advertisement acquisition system based on NFC (near field communication)
InactiveCN107068018AWith privacyEnsure safetyAdvertisingDisplay meansInformation transmissionRelevant information
The invention discloses an advertisement acquisition system based on NFC (near field communication). The system comprises a main control system, a projection unit, a behavior movement unit, an infrared thermal imaging unit, a data unit, an NFC unit and a display unit, wherein the main controller is connected to the projection unit, the behavior movement unit, the infrared thermal imaging unit, the data unit, the NFC unit and the display unit. The system provided by the invention has the beneficial effects that a user, by implementing information transmission through touch connection to NFC equipment, can acquire related information of products; meanwhile, a robot is triggered to conduct advertisement projection, so that system's design flexibility is reflected to the greatest extent; the NFC has the characteristics of being private and being safe; and with the application of the NFC, user information, when transmitted, is prevented from being revealed, and marketing and publicity of the products are achieved rapidly, conveniently and intelligently.
Owner:SHENZHEN SANBOT INNOVATION INTELLIGENT CO LTD
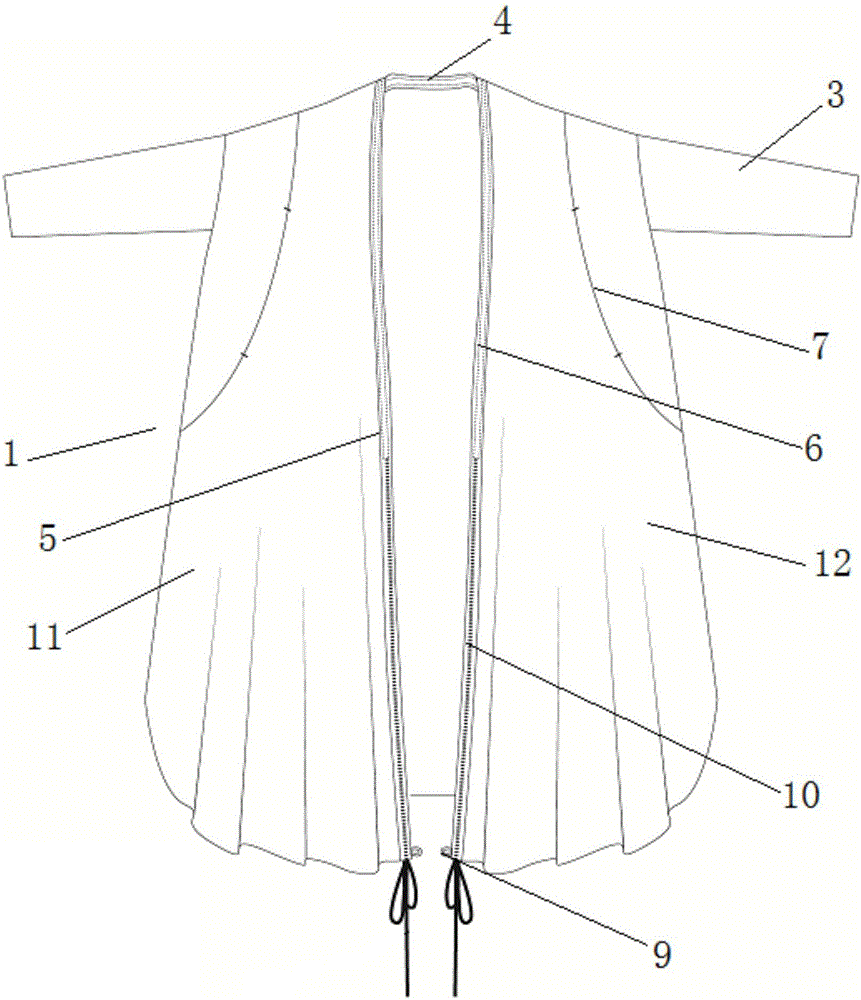
Wind coat for lactation
The invention discloses a wind coat for lactation. The wind coat comprises a front part, a rear part and sleeves. The front part and the rear part are of a sector-shaped structure as a whole. The upper end of the front part and the upper end of the rear part form a neckline, the front part is provided with a front fly, the front part is divided into a front part body A and a front part body B by the front fly, plastic supporting strips are arranged in the neckline and in the front fly, and hidden slots are formed in the positions, close to the left sides and the right sides of the sleeves, of the front part; buttons are arranged at the position, close to the neckline, of the rear part and at the positions, close to the left and right slots, in the back side of the front part respectively; the tail ends of the front fly of the front part bodies A and B are provided with button loops matched with the buttons respectively. The wind coat can be worn and used as a wind coat for daily outgoing, has the functions of covering up the figure and flattering the figure, can also be used as a lactation coat, and can achieve lactation conveniently and quickly. Besides, the wind coat can form a private and spatial lactation space during lactation and has application and popularization value.
Owner:SHANGHAI UNIV OF ENG SCI
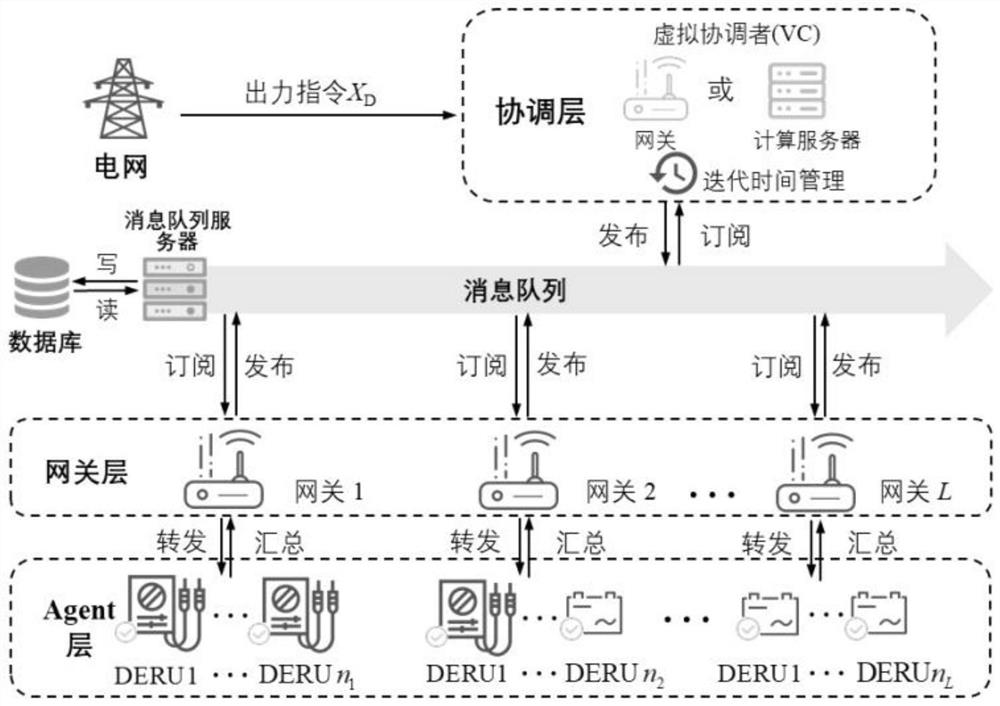
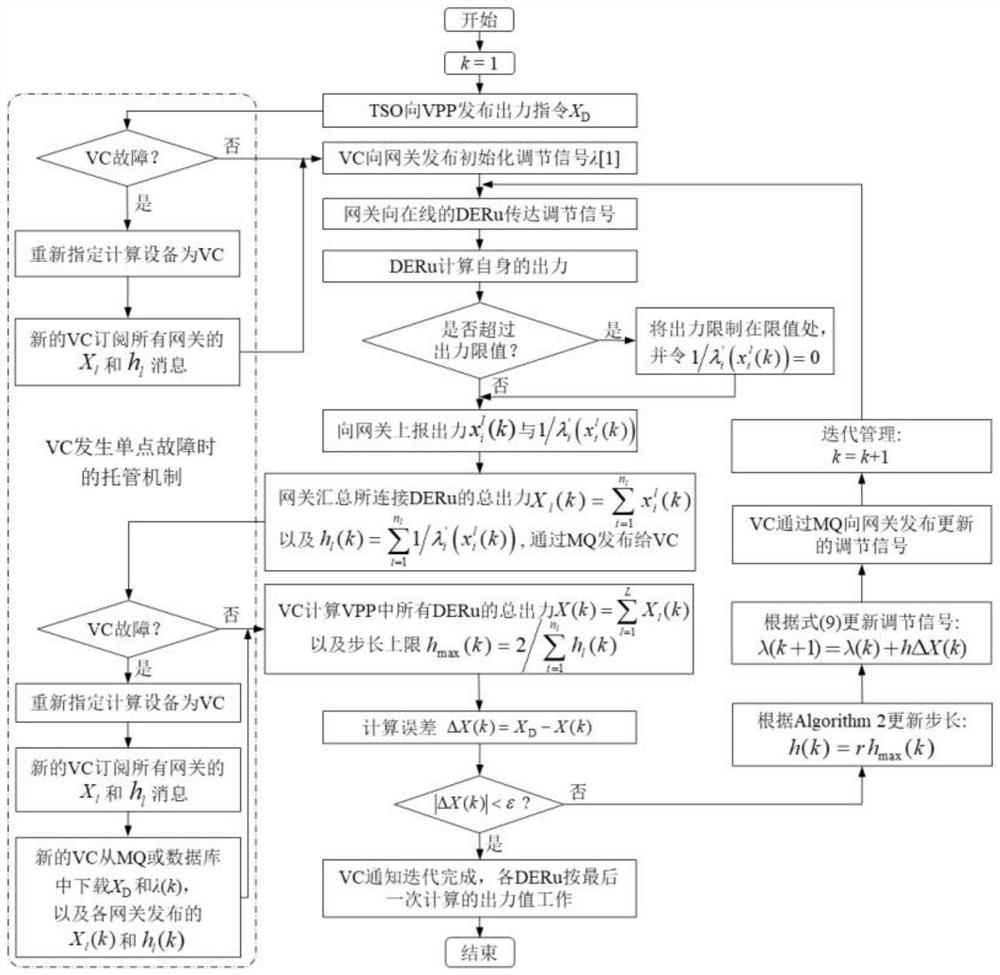
Self-adaptive virtual power plant distributed architecture and economic dispatching method thereof
PendingCN113191680AAdaptableVariableResourcesSystems intergating technologiesSelf adaptivePlug and play
The invention relates to the technical field of electrical engineering and automation thereof. The distributed economic dispatching method provided by the invention has self-adaptability and can adapt to the characteristics of mass and variability of distributed resources in a virtual power plant; the decoupling property and the layered distributed architecture of the step length calculation method can adapt to the dispersive characteristic of distributed resources, plug and play of the distributed resources can be achieved, the method has reliable convergence due to existence of a step length upper bound theoretical value, and meanwhile, the problem of economic dispatching of massive distributed resources can be effectively solved through the self-adaptability of the method; the calculation and communication pressure of the system is dispersed through the lightweight design, and the operation efficiency and the adjusting speed of the virtual power plant are remarkably improved; a hosting processing method when a coordinator has a single-point fault is provided, and the whole method has relatively high fault tolerance in combination with the characteristic of supporting plug and play of distributed resources; and the parameter information of the distributed resources is protected by the updating characteristics of the parameters and the layered architecture, and the privacy is realized.
Owner:SHANGHAI JIAO TONG UNIV +2
Multifunctional intelligent packaging box
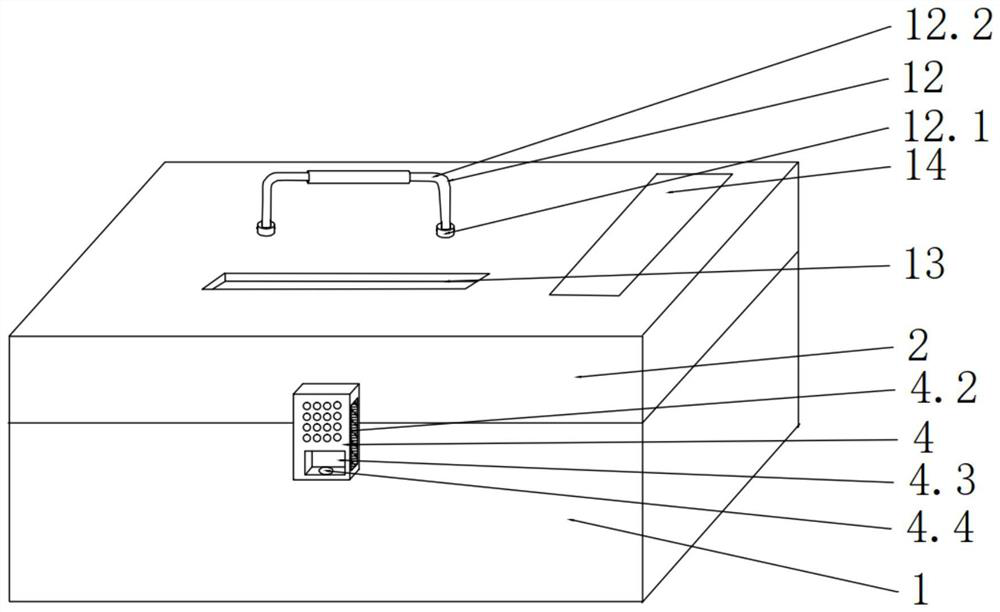
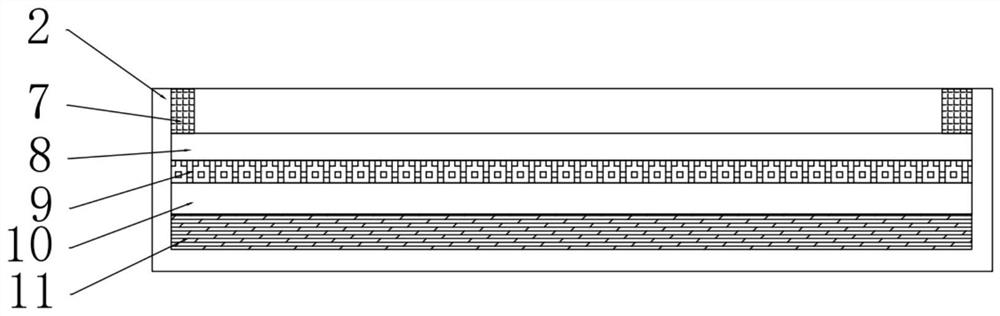
PendingCN113086368AWith privacyPlay the role of anti-collision and shock absorptionContainers preventing decayShock-sensitive articlesPhysicsSmart lock
The invention relates to the technical field of packaging containers, in particular to a multifunctional intelligent packaging box. The multifunctional intelligent packaging box comprises a box body and a box cover, wherein a foam shock absorbing layer is arranged in the box body, an intelligent lock is arranged on one side of the box body, and partition plates are arranged in the box body; and a temperature adjusting knob is arranged on the box cover, a dehumidification layer is arranged in the box cover, a grid shock absorbing layer is arranged in the box cover, a heater is arranged in the box cover, a heat insulation layer is arranged in the box cover, a GPS positioning device is arranged in the box cover, and a second loudspeaker is arranged on the upper surface of the box cover. The multifunctional intelligent packaging box has the advantages that omni-directional shock absorbing protection can be conducted on objects, the most appropriate temperature can be provided for the held objects, when the packaging box is stolen or violently damaged, an alarm can be given out, long-distance information transmission can be conducted, and after the objects are lost, the positions of the lost objects can be locked by locking the position of the packaging box.
Owner:上海乐橘科技有限公司
Entertainment culture management system based on mobile terminal
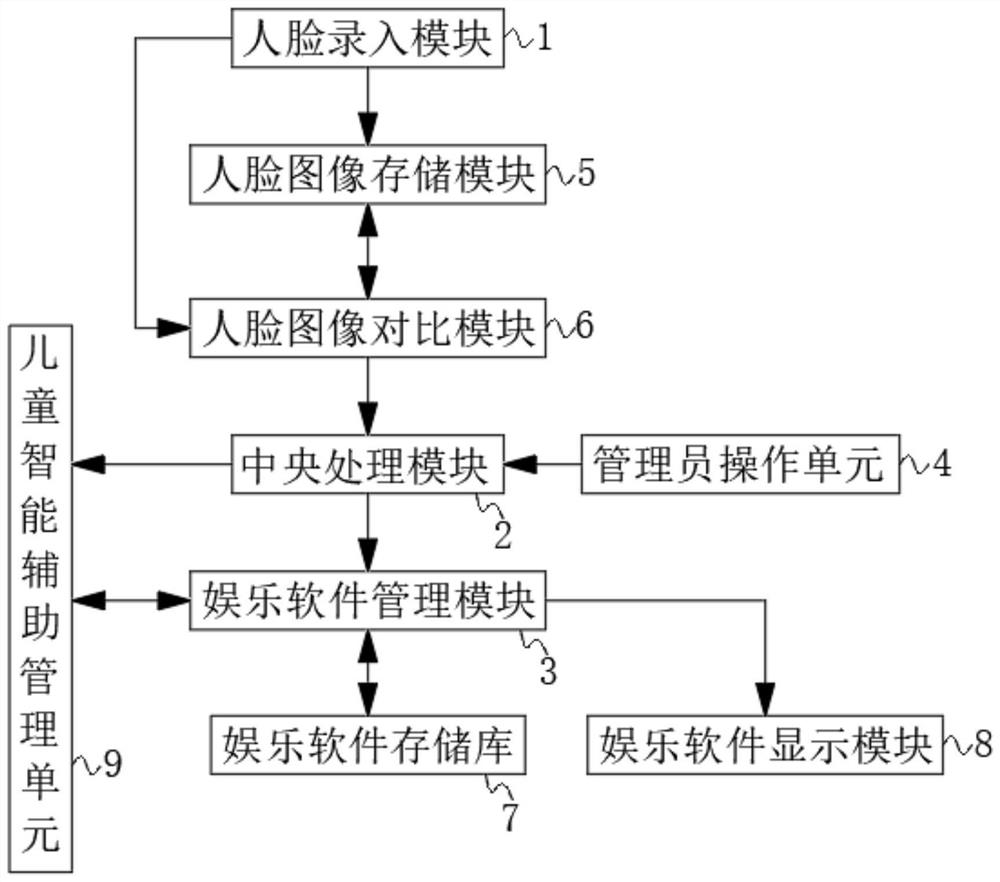
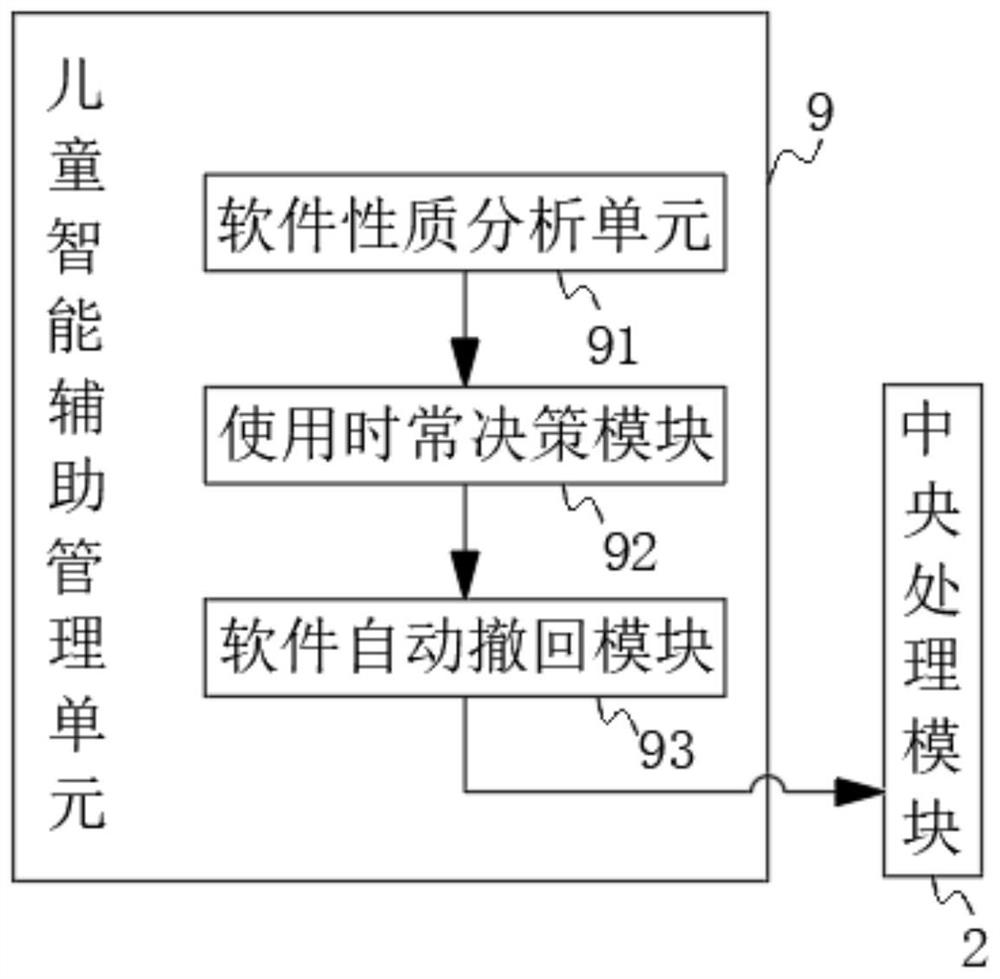
PendingCN113554531AWith privacyProtect personal privacyCharacter and pattern recognitionDigital data protectionEngineeringImage pair
The invention discloses an entertainment culture management system based on a mobile terminal. Theentertainment culture management system comprises a face input module, a central processing module, an entertainment software management unit and an administrator operation unit; the output end of the face input module is connected with the input end of a face image storage module; the output end of the face image storage module is connected with the input end of the face image comparison module, and the output end of the face image comparison module is connected with the input end of the central processing module.The invention relates to the technical field of software management. According to the entertainment culture management system based on the mobile terminal, software in the home mobile terminal can be classified, during classification, after entering an entertainment interface of the mobile terminal through face recognition, the entertainment software is automatically classified, and the entertainment software which is independently used by a person is displayed in front of a user; and therefore, each family member has own privacy.
Owner:南京飞悦文化科技有限责任公司
Data operation device for network and information security software development
PendingCN114468545AWith privacyPlay a protective effectEngine sealsOffice tablesSoftware developmentBevel gear
The invention discloses a data running device for network and information security software development, and belongs to the technical field of software development equipment. A data operation device for network and information security software development comprises a shell, two baffles are hinged to the top face of the shell in a bilateral symmetry mode, a limiting groove is formed in the inner wall of the lower end of the shell, a lead screw is arranged in the limiting groove, a lifting plate is arranged above the lead screw, a damping plate is arranged above the lifting plate, and an operation machine body is fixedly arranged on the top face of the damping plate. When software development is needed, an adjusting handle can be rotated to drive a bevel gear B, and the bevel gear B drives a meshed bevel gear A to rotate, so that a lead screw rotates, an ejector rod rotates by an angle, baffles can be jacked up, the baffles on the two sides are in a vertical state, and an operation machine body is shielded; therefore, the device has certain privacy, people on the two sides can be effectively prevented from seeing codes on the running machine body, and the protection effect is achieved.
Owner:刘金平
Resource index transaction method based on block chain technology
PendingCN111681109AAchieve fairnessTransaction in real timeFinanceDigital data protectionFinancial transactionData mining
The invention discloses a resource index transaction method based on a block chain technology, and the method comprises the following steps: S1, carrying out the identification of a resource index, and carrying out the recognition and information collection of the identified resource index; S2, receiving resource index transaction request information sent to the block chain system by a user; S3, calling out target resource index information meeting requirements from a local database according to the transaction request information; s4, displaying the target resource index information and a transaction node with a block chain system transaction interface to a user; s5, receiving a transaction confirmation request sent to the transaction node by the user, and performing automatic transactionsettlement after each participant confirms the transaction; s6, generating a transaction record according to the automatic transaction settlement behavior; s7, broadcasting the transaction record toeach node in the block chain system to determine legality; and S8, sending the target resource index to the user. According to the invention, the problems of high cost, low transaction efficiency andhigh difficulty of the existing resource index transaction method can be effectively solved.
Owner:山东星云信息科技有限公司
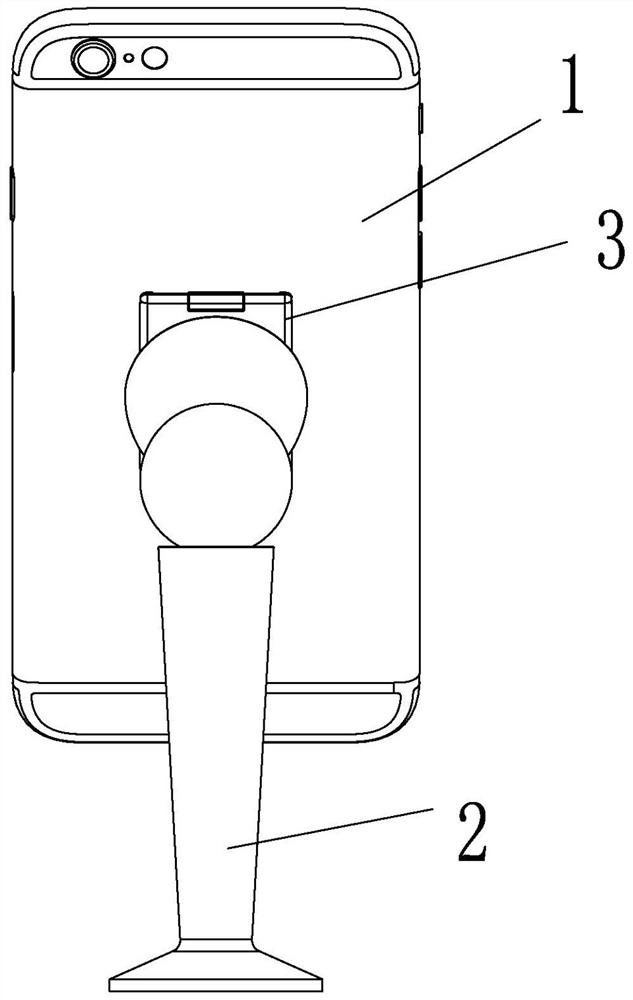
A mobile phone holder for vehicle or desktop use
A mobile phone bracket for vehicle or desktop use, comprising a magnetic base and a connecting piece connected to the mobile phone, the connecting piece includes a lower cover and an upper cover, the lower cover is connected to the mobile phone, the upper cover and the lower The cover is connected to form a cavity, and a magnetically permeable metal sheet is arranged in the cavity, and when the connector is fixed on the magnetic base, the magnetically permeable metal sheet is adsorbed and connected to the magnetic base. It can be compatible with the magnetic base of the car at the same time, or can be used as a mobile phone holder alone, as well as a fulcrum for holding a mobile phone, and has a wide range of applications.
Owner:谢汝周
A method and system for anonymous sharing of supervised data based on blockchain
ActiveCN110430161BRealize privacy sharingAddressing hierarchical regulatory needsUser identity/authority verificationPlaintextCiphertext
The invention discloses a method and system for anonymously sharing supervisable data based on block chain. The method includes: when a data using node initiates a data sharing request to a data owning node, the data owning node uses its own private key and the The data uses the node public key to generate a re-encryption key, and sends the re-encryption key to the proxy server; the proxy server owns the random key used by the node to pre-encrypt the plaintext data and the The data ciphertext is stored in the location of the cloud server, encrypted according to the public key of the data owning node, and then re-encrypted and converted as ciphertext, and sent to the data-using node; the data-using node decrypts through its own private key to obtain the data to be shared The encryption key and its storage location in the cloud database, extract the corresponding location data in the cloud database and decrypt it according to the encryption key to obtain the data to be shared.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Psychological treatment cloud platform based on exercise prescription
PendingCN111599443APromote secretionWith privacyPhysical therapies and activitiesMental therapiesStream dataExercise treatment
The invention discloses a psychological treatment cloud platform based on an exercise prescription. The platform comprises a user side and a platform side, the user side comprises a user module and aninteraction module; the platform side comprises an evaluation module, a treatment module, a shopping mall module, a communication module and a database. The user side is connected with the platform end through the interaction module, the evaluation module is used for evaluating the disease degree of users, the treatment module is used for providing exercise psychological counseling treatment, theshopping mall module is used for purchasing treatment equipment and courses, the communication module is used for communication among users, and the database is used for storing platform data. An online auxiliary psychological treatment mode combining the user side and the platform side is adopted; psychological treatment is more convenient, meanwhile, an exercise treatment unit in the treatmentmodule is used for executing video prompt content and actions to complete action counseling psychological treatment, targeted music and actions for different illness states are adopted for videos, a patient with light symptoms is assisted in psychological treatment in an exercise mode, and the effect is better.
Owner:山西体育职业学院
Data processing method and device and storage medium
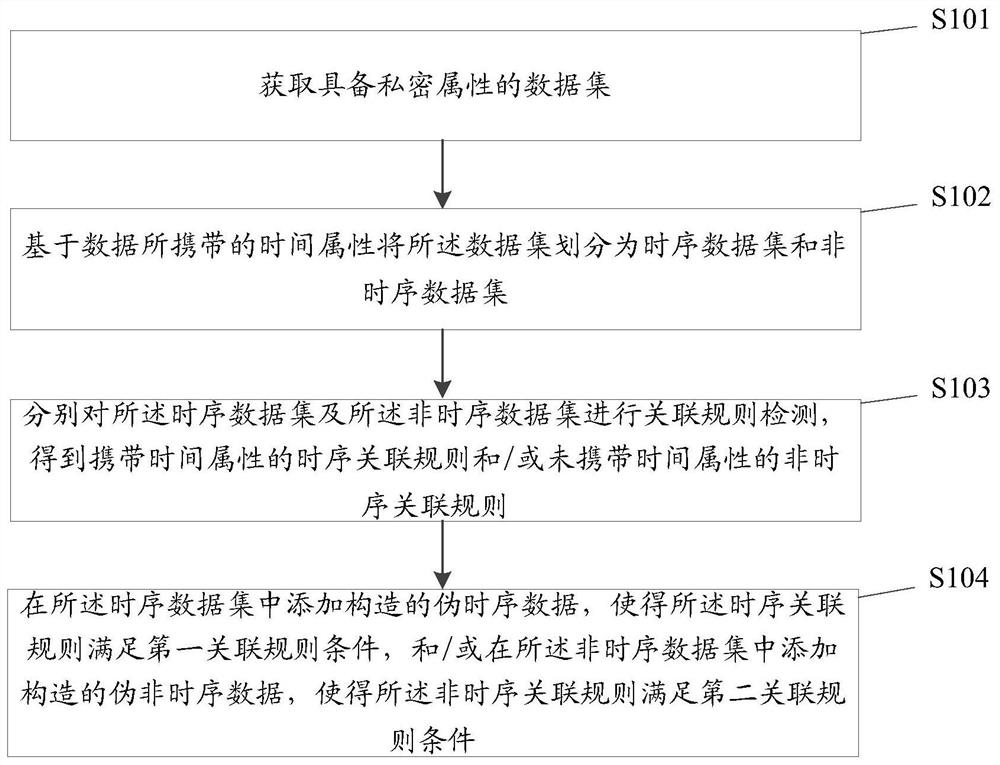
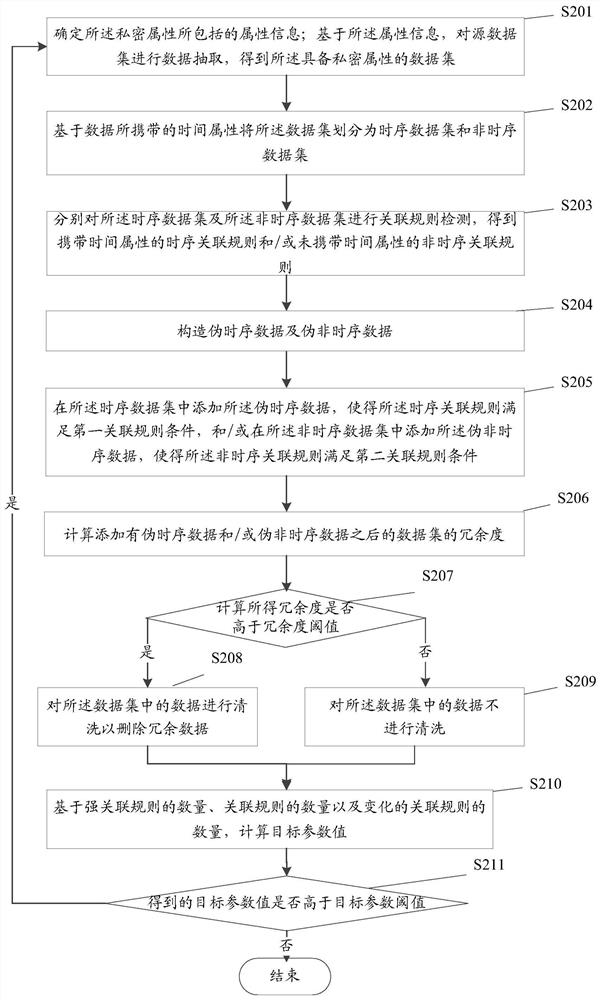
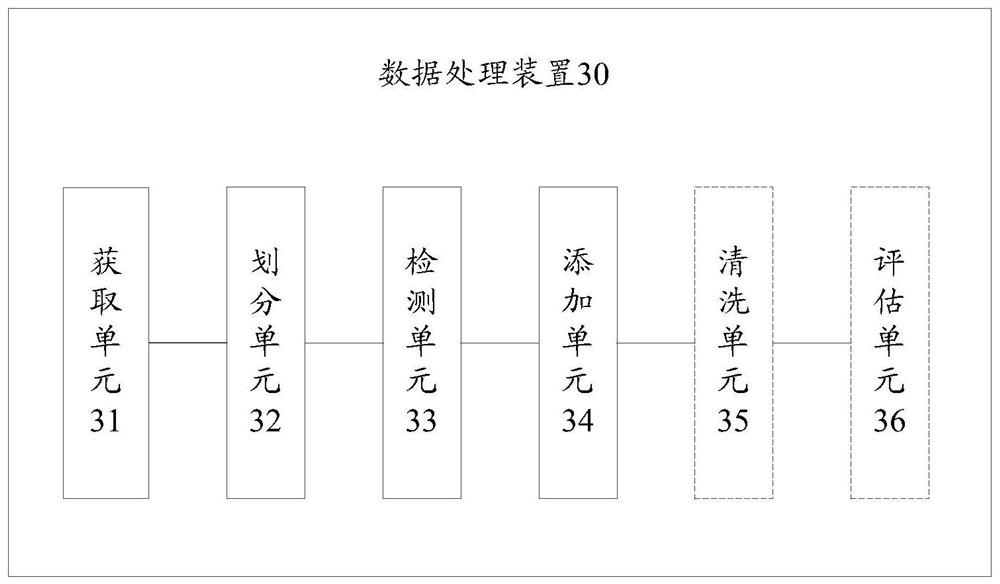
PendingCN112347489AImprove integrityWith privacyDigital data protectionEnergy efficient computingSource dataData processing
The embodiment of the invention provides a data processing method and device and a storage medium. The method comprises the steps of acquiring a data set with private attributes; dividing the data setinto a time series data set and a non-time series data set based on time attributes carried by the data; carrying out association rule detection on the time series data set and the non-time series data set to obtain a time series association rule carrying the time attribute and / or a non-time series association rule not carrying the time attribute; and adding the constructed pseudo time series data into the time series data set to enable the time series association rule to meet a first association rule condition, and / or adding the constructed pseudo non-time series data into the non-time series data set to enable the non-time series association rule to meet a second association rule condition. Thus, the source data is divided into the time series data set and the non-time series data set,the corresponding time series association rules and non-time series association rules are hidden in the mode of adding the constructed pseudo-time series data and pseudo-non-time series data, and thedata is completely protected.
Owner:CHINA MOBILE SUZHOU SOFTWARE TECH CO LTD +1
Project collaboration system based on mobile internet
InactiveCN108428118AImprove convenienceProtect research resultsOffice automationTransmissionComputer moduleAlternating current
The invention discloses a project collaboration system based on mobile internet. The system comprises a mobile device, an uploading module, a central processing module, a data statistics module, a storage module, a supervision module, a communication module and a permission module; the output end of the mobile device is respectively connected with the input ends of the uploading module, the alternating current module and the permission module are connected, the output end of the uploading module is connected to the input end of the central processing module, the output end of the central processing module is respectively connected with the input ends of the monitoring module and the data statistics module, the output end of the supervisory module is connected to the input end of the mobiledevice, and the output ends of the data statistics module and the permission module are connected to the input end of the storage module. The system is efficient and convenient, project team memberscan understand and communicate with one another at any time and place, security performance is high, data is private, and the system can supervise and urge the members to complete the work at any time.
Owner:WUHU LERUISI INFORMATION CONSULTING
A continuous identity authentication method for collecting user interaction behaviors by using a mobile terminal
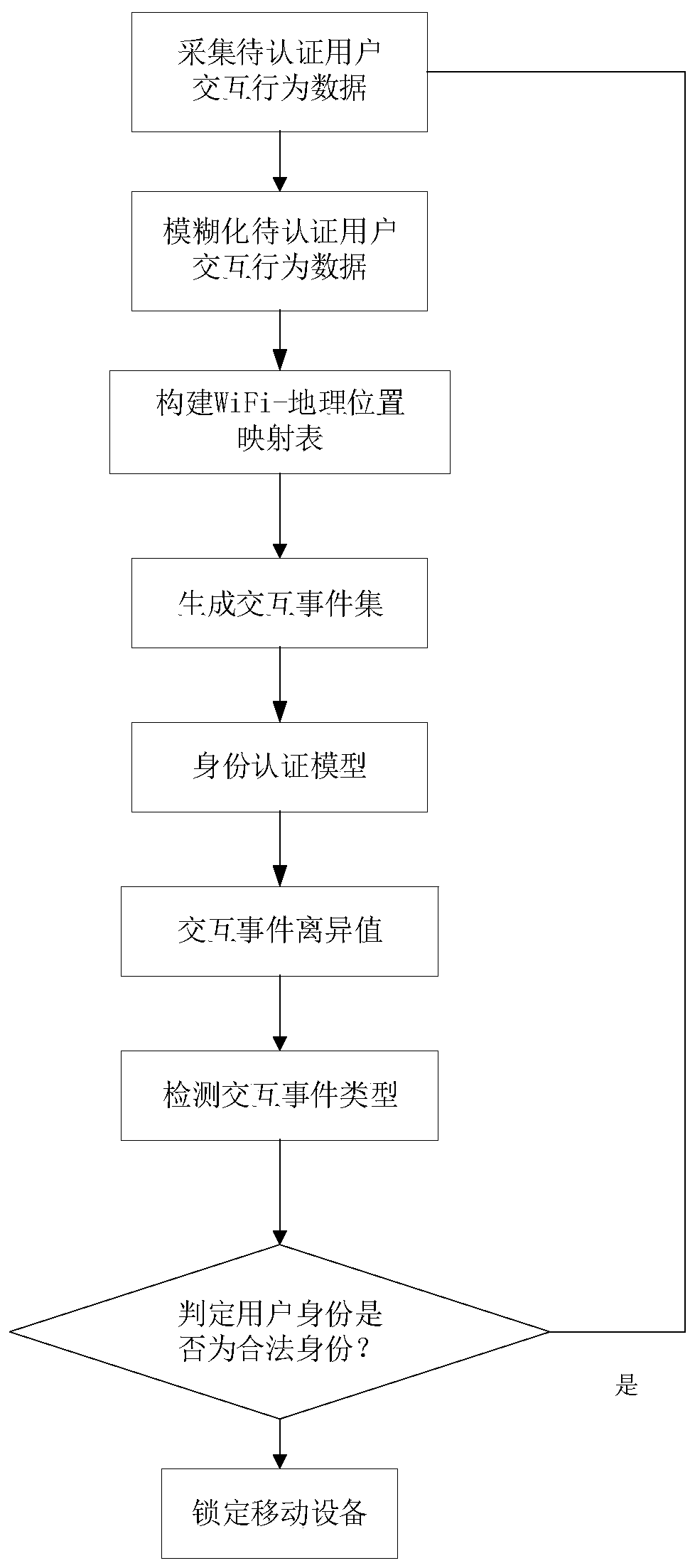
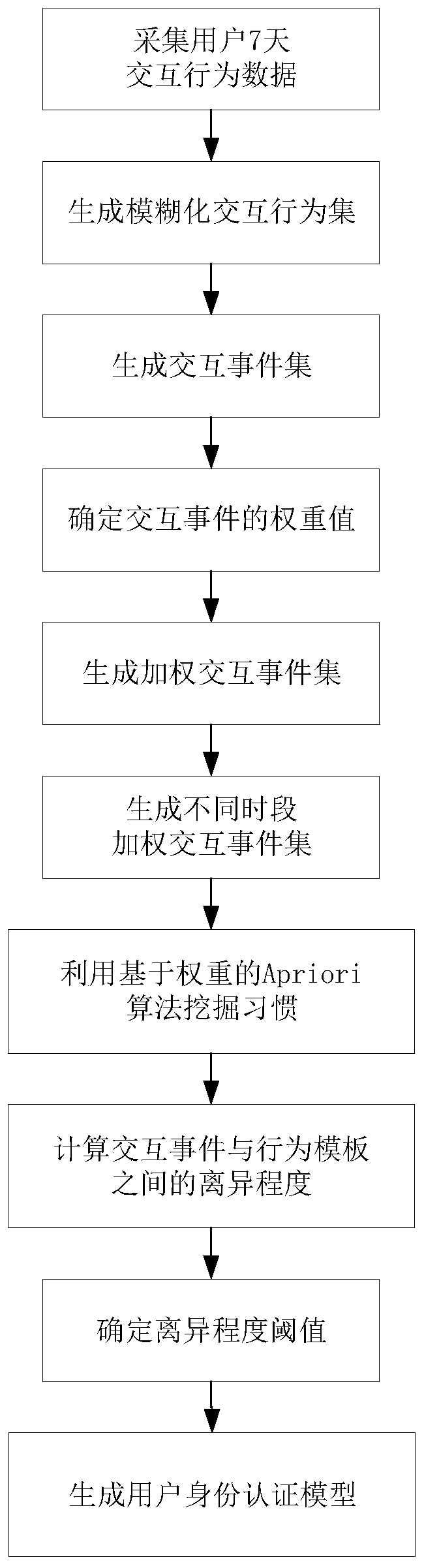
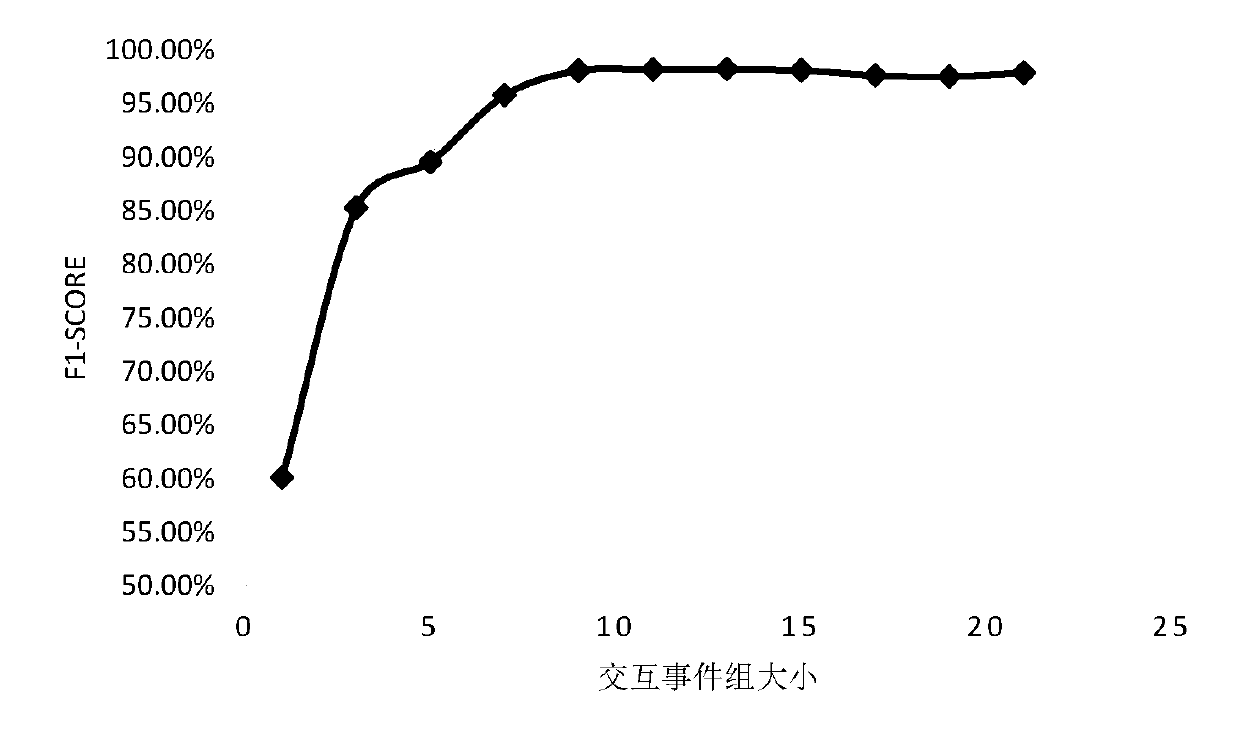
ActiveCN109918873AOvercome the problem of illegal accessResistance securityDigital data authenticationGeographic sitePrivacy protection
The invention discloses a continuous identity authentication method based on a mobile terminal interaction behavior. The method comprises the following steps: (1) collecting user interaction behaviordata; (2) fuzzifying user interaction behavior data; (3) constructing WiFi-geographic position mapping table; (4) generating an interaction event set; (5) constructing a user identity authentication model; (6) obtaining an interaction event departure value; (7) judging the type of the interaction event; And (8) judging the user identity. According to the method, the problem that the user behaviorcollected in the prior art is easily simulated and the problems that the energy consumption is high, the data is not easy to collect and the privacy protection intensity is low when the user behaviordata is collected in the prior art are solved, so that the method has the advantages of safety, practicability and privacy.
Owner:XIDIAN UNIV
Mobile phone holder for vehicle and table top
ActiveCN106453731AWith privacySolve operational problemsVehicle componentsTelephone set constructionsMetal sheetMobile phone
The invention discloses a mobile phone holder for a vehicle and a table top. The mobile phone holder comprises a magnetic base and a connecting piece connected with a mobile phone; the connecting piece comprises a lower cover and an upper cover, wherein the lower cover is connected with the mobile phone, a cavity is formed when the upper cover and the lower cover are connected, and a magnetic-conductivity metal sheet is arranged in the cavity; when the connecting piece is fixed on the magnetic base, the magnetic-conductivity metal sheet is in attaching connection with the magnetic base. The mobile phone holder can be compatible with the functions of being used as a vehicle-mounted magnetic base or singly used as the mobile phone holder at the same time, and the mobile phone holder can be further used as a handheld fulcrum of the mobile phone; and the application range of the mobile phone holder is wide.
Owner:谢汝周
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com