Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85results about How to "Strong privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Indoor positioning system and positioning method for ultrasound radio frequency signal combined processing
InactiveCN103941231AMeet Simultaneous Location ServicesHigh positioning accuracyPosition fixationUltra-widebandSonification
The invention discloses an indoor positioning system and positioning method for ultrasound radio frequency signal combined processing. The indoor positioning system comprises three kinds of basic nodes which are anchor nodes, mobile nodes and display control nodes. The anchor nodes are fixed nodes with spatial positions known, the mobile nodes are active nodes with position coordinates needing to be determined in space, and the display control nodes display a system topological structure and node positioning results in real time and perform coordination control on the whole system. The anchor nodes and the mobile nodes perform contact by adopting radio frequency and ultrasonic signals, data processing is performed on received sound signals on the anchor nodes or the mobile nodes, spatial three-dimensional coordinates of the mobile nodes are solved, and system positioning results are finally displayed on the display control nodes. Compared with ultra-wideband radio frequency, WIFI radio frequency, video images and the like, the ultrasonic positioning system has the advantages of being prominent in performance, low in cost, high in privacy and free of electromagnetic pollution and is a first choice technology for indoor position services.
Owner:江苏坤研电子科技有限公司
Hide display starting device and hide display starting method for application programs
ActiveCN106446632AImprove experienceFull camouflageDigital data authenticationExecution for user interfacesTerminal equipmentComputer terminal
The invention provides a hide display starting device and a hide display starting method for application programs. The method includes: when trigger operations applied by a user to a hide application icon of any application program are detected, starting the application program, and displaying a starting verification interface matched with an application scene pointed by the hide application icon; receiving code information inputted by the user through the starting verification interface; starting the application program if code information verification is successful. By adoption of the technical scheme, high privacy of the user can be guaranteed in the application program even under the condition of unlocking of a screen of terminal equipment, the application program is prevented from being used by any person except for the user of the terminal equipment, and accordingly privacy safety of user data in the application program can be effectively protected, and user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
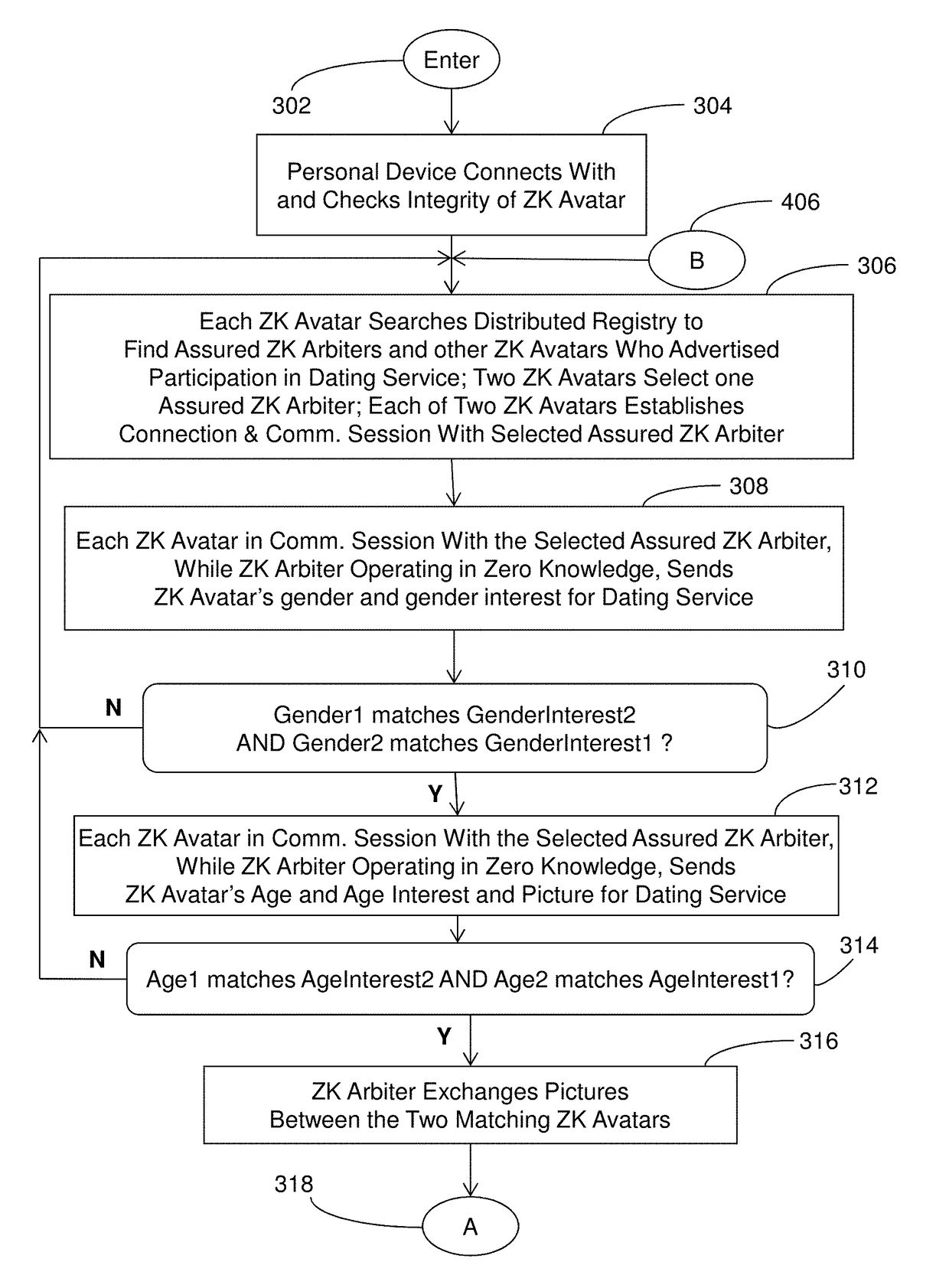
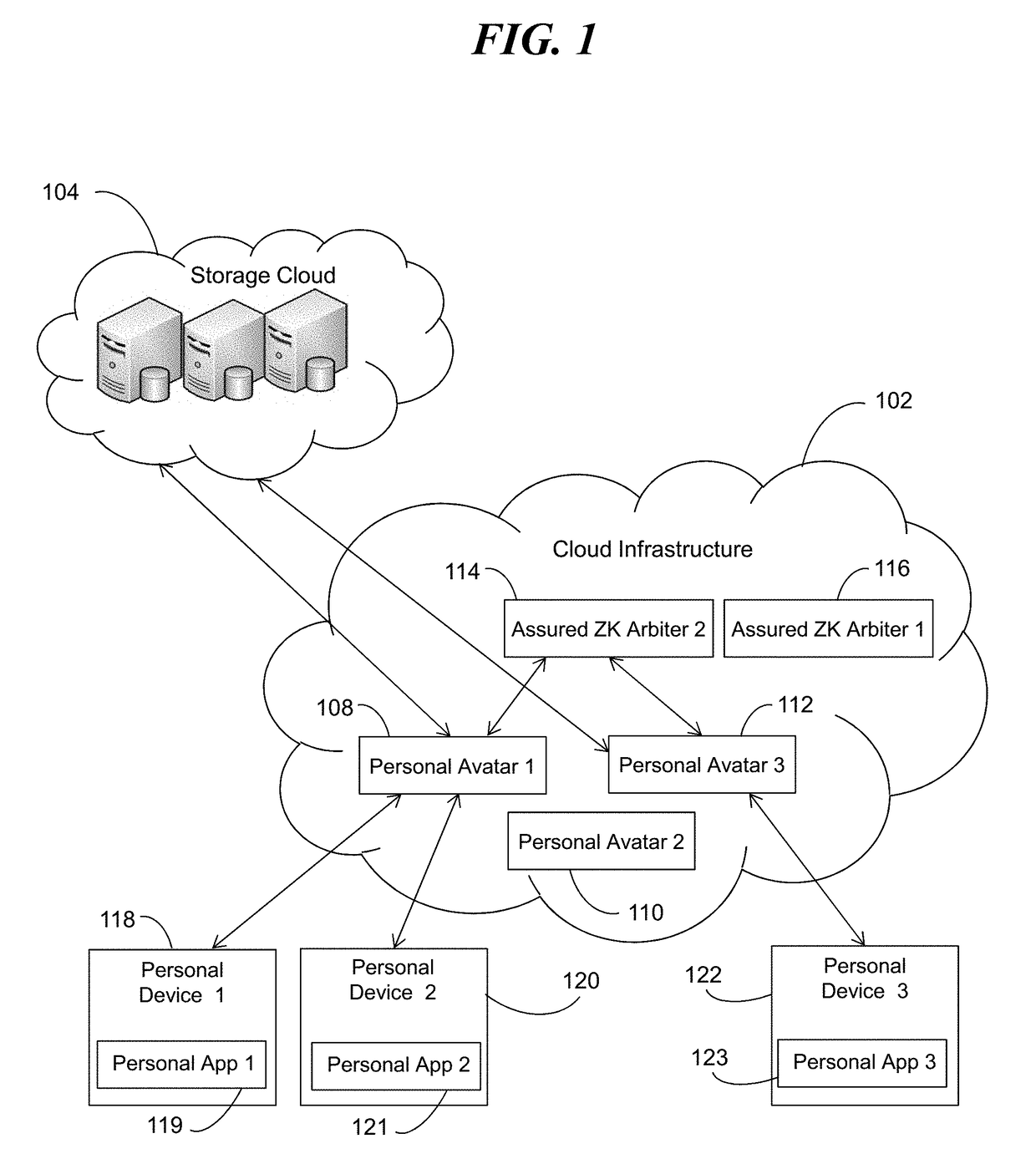
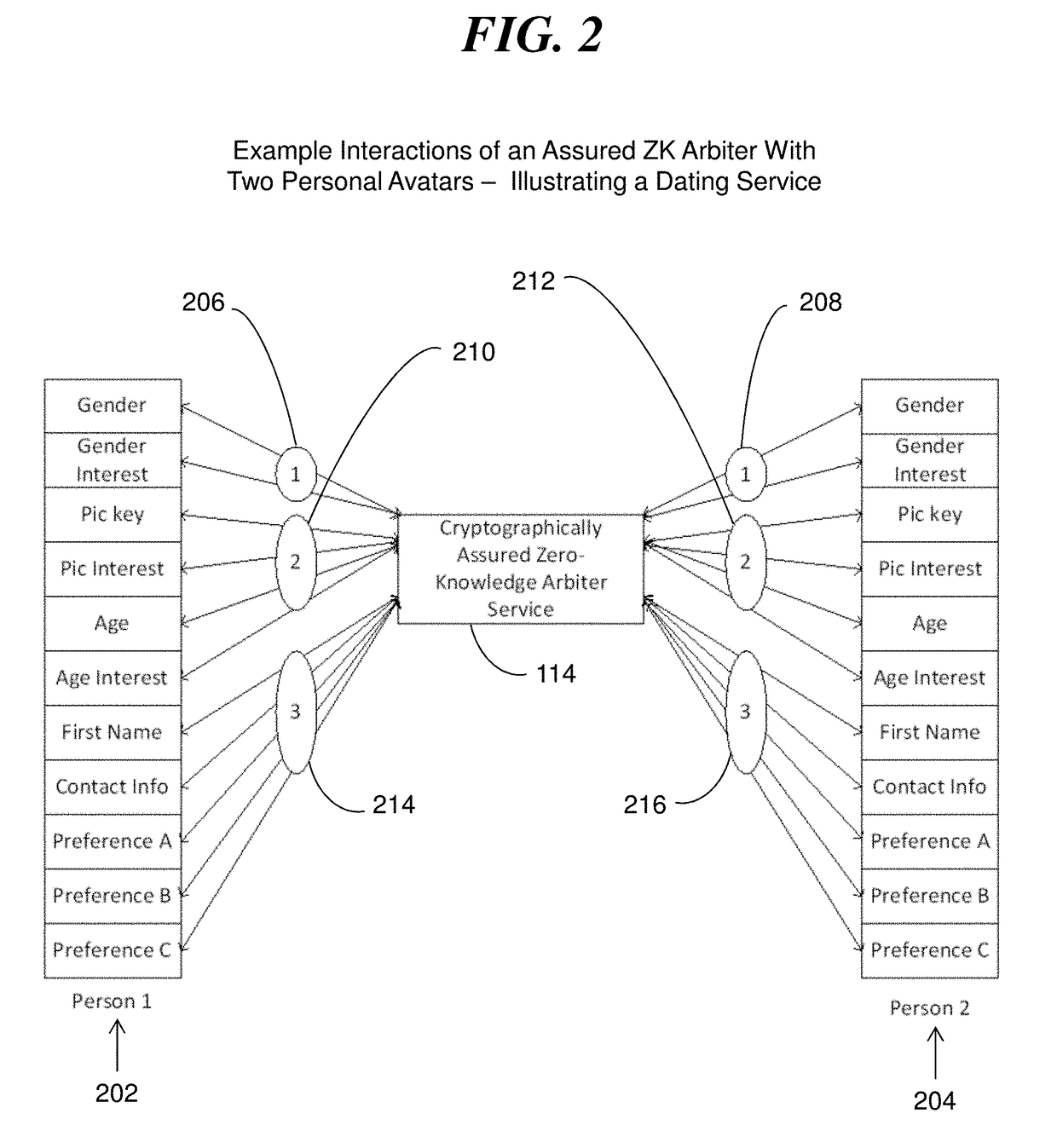
System and method of cryptographically provable zero knowledge social networking
ActiveUS20180019873A1Strong privacy guaranteeZero knowledge assuranceCryptography processingUser identity/authority verificationInternet privacyProtocol for Carrying Authentication for Network Access
A social networking system, computer program product, and methods with a Personal Avatar executing on a first server node and a zero knowledge Arbiter executing on a second server node in a network of the social networking system. The Personal Avatar communicates social networking system messages in a communication session using a zero knowledge protocol with the zero knowledge Arbiter executing on the second server node operating in zero knowledge and using zero knowledge verifiable computing to enforce usage conditions on social networking system messages communicated in a communication session with the zero knowledge Arbiter. The zero knowledge Personal Avatar communicates social networking system messages in a communication session using a zero knowledge protocol with the zero knowledge Arbiter. The methods ensure privacy of an end user of the social networking system.
Owner:IBM CORP
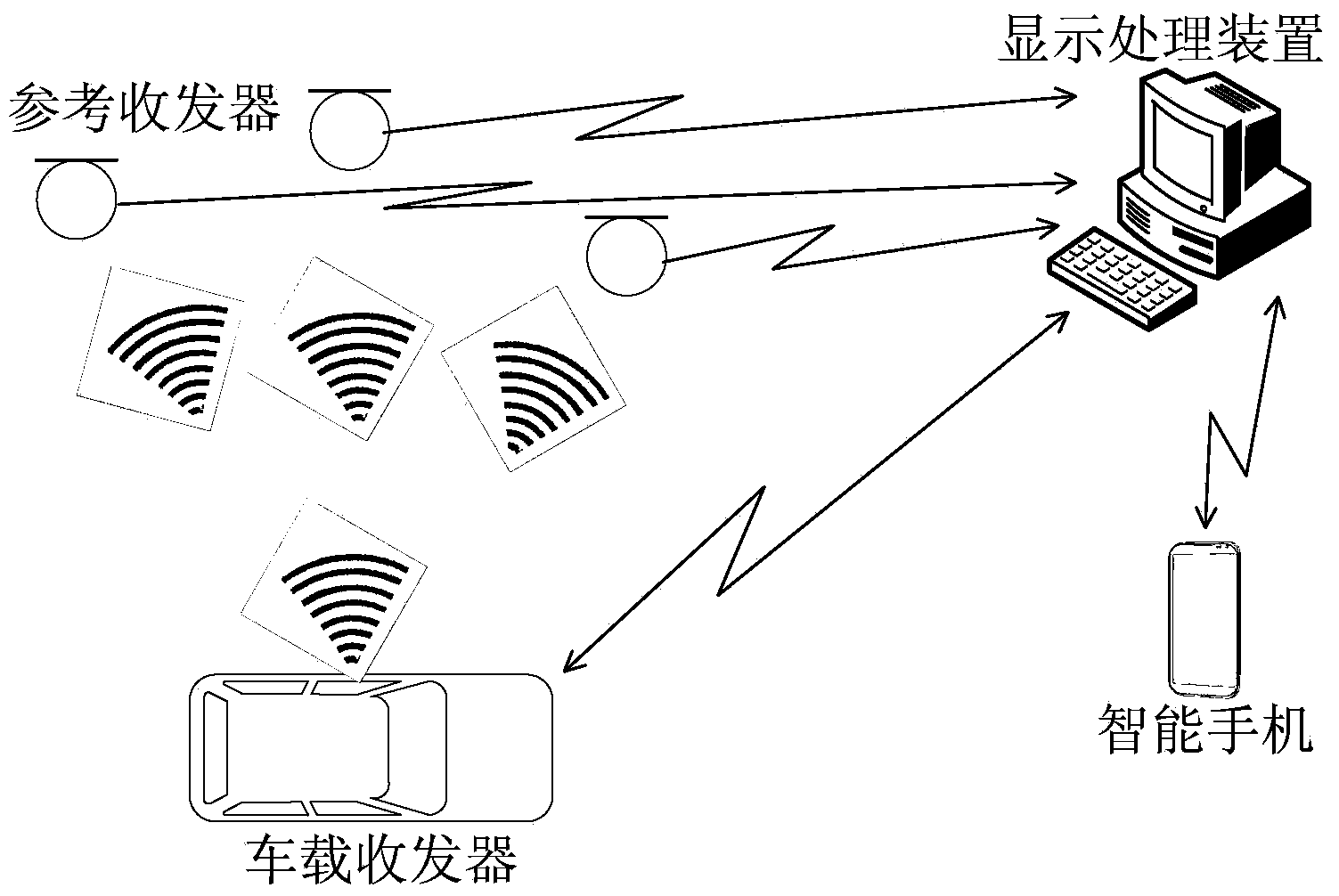
Parking lot automatic guiding system based on position service and implementation method
InactiveCN103956074AMeet simultaneous positioning and navigation servicesPrivacy protectionIndication of parksing free spacesTransceiverParking space
The invention discloses a parking lot automatic guiding system based on the position service and an implementation method. The parking lot automatic guiding system comprises a reference transceiver fixed to the roof of an indoor parking lot, a vehicle-mounted transceiver arranged on a vehicle of a vehicle owner, and a display processing device, wherein the reference transceiver contacts with the vehicle-mounted transceiver through radio-frequency and ultrasonic signals. The reference transceiver and the vehicle-mounted transceiver transmit the signals to the display processing device, and then data processing is conducted so that the space three-dimensional coordinates of the vehicle where the vehicle-mounted transceiver is located can be solved and the target vehicle can be guided according to the space three-dimensional coordinates. The display processing device displays spare stall information of the parking lot in real time, dynamically issues parking space guiding and exit guiding information, and sends the displayed information to a smart phone of the vehicle owner. The parking lot automatic guiding system is based on the ultrasonic positioning mechanism and has the advantages of being accurate in positioning, low in cost, high in privacy, free of electromagnetic pollution, and the like.
Owner:江苏坤研电子科技有限公司
Automatic exit and entry certificate handling device and method thereof
PendingCN106846661AImprove the efficiency of certificate processingSave time and energyData processing applicationsApparatus for meter-controlled dispensingDigital cameraCard reader
The invention discloses an automatic exit and entry certificate handling device and a method thereof. The device comprises a shell, a touch display screen, a digital camera, a picture color printer, a laser printer, an identity card reader, an endorsement module, a control module, a lifting chair, and a lifting part, wherein the touch display screen, the digital camera, the picture color printer, the laser printer, the identity card reader, the endorsement module and the control module are arranged on the rear part in the shell, the lens of the digital camera faces to the front part in the shell, the lifting chair and the lifting part are arranged on the front part in the shell, and the lifting part is used for driving the lifting chair to go up or down; and the touch display screen, the digital camera, the picture color printer, the laser printer, the identity card reader, the endorsement module and the lifting part are respectively connected to the control module. The device disclosed by the invention can enable users to independently apply for new exit and entry certificates and endorse exit and entry certificates for the second time, and thereby, not only is the efficiency of certificate handling increased, but also the time and energy of the users are saved.
Owner:广州市华标科技发展有限公司
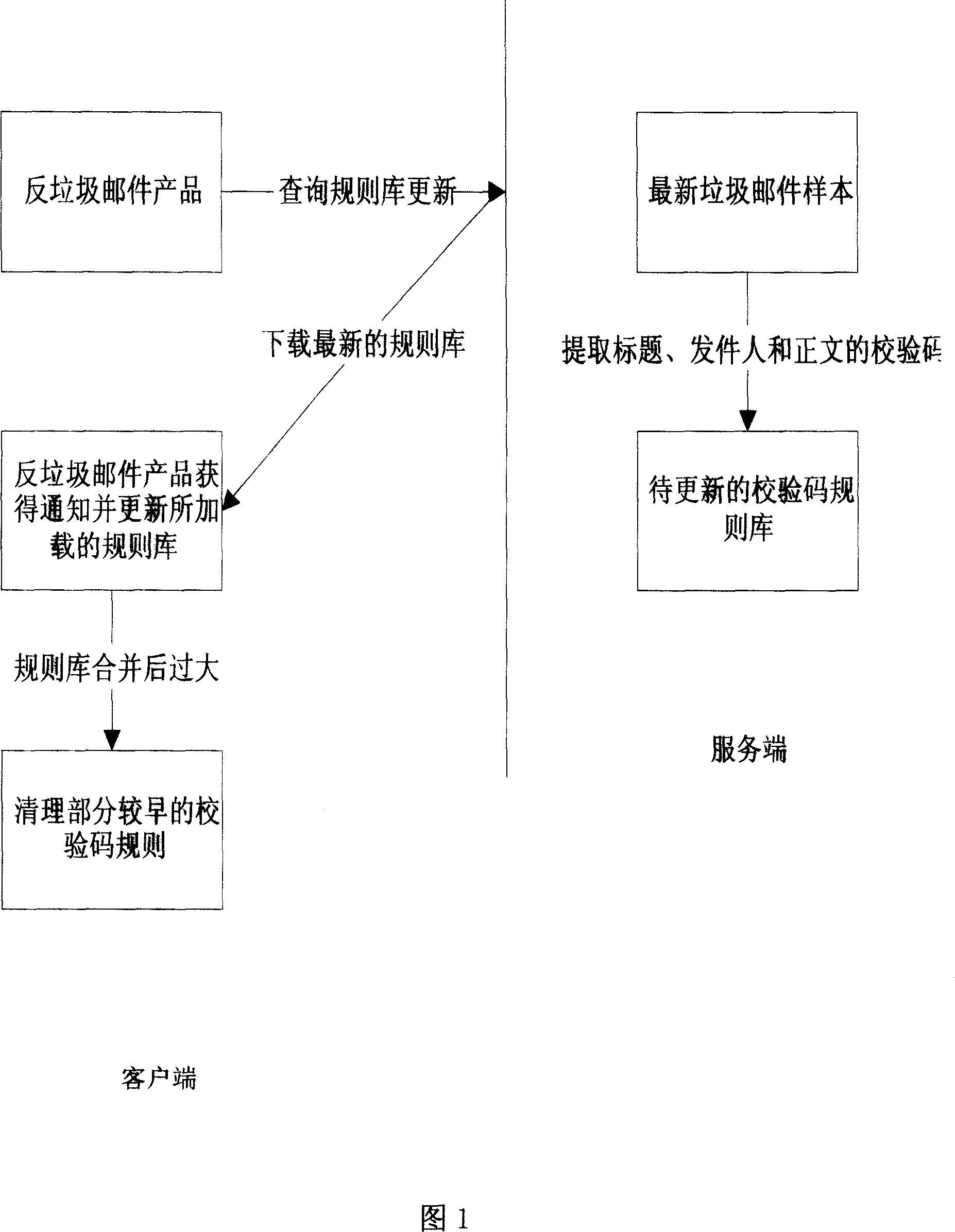
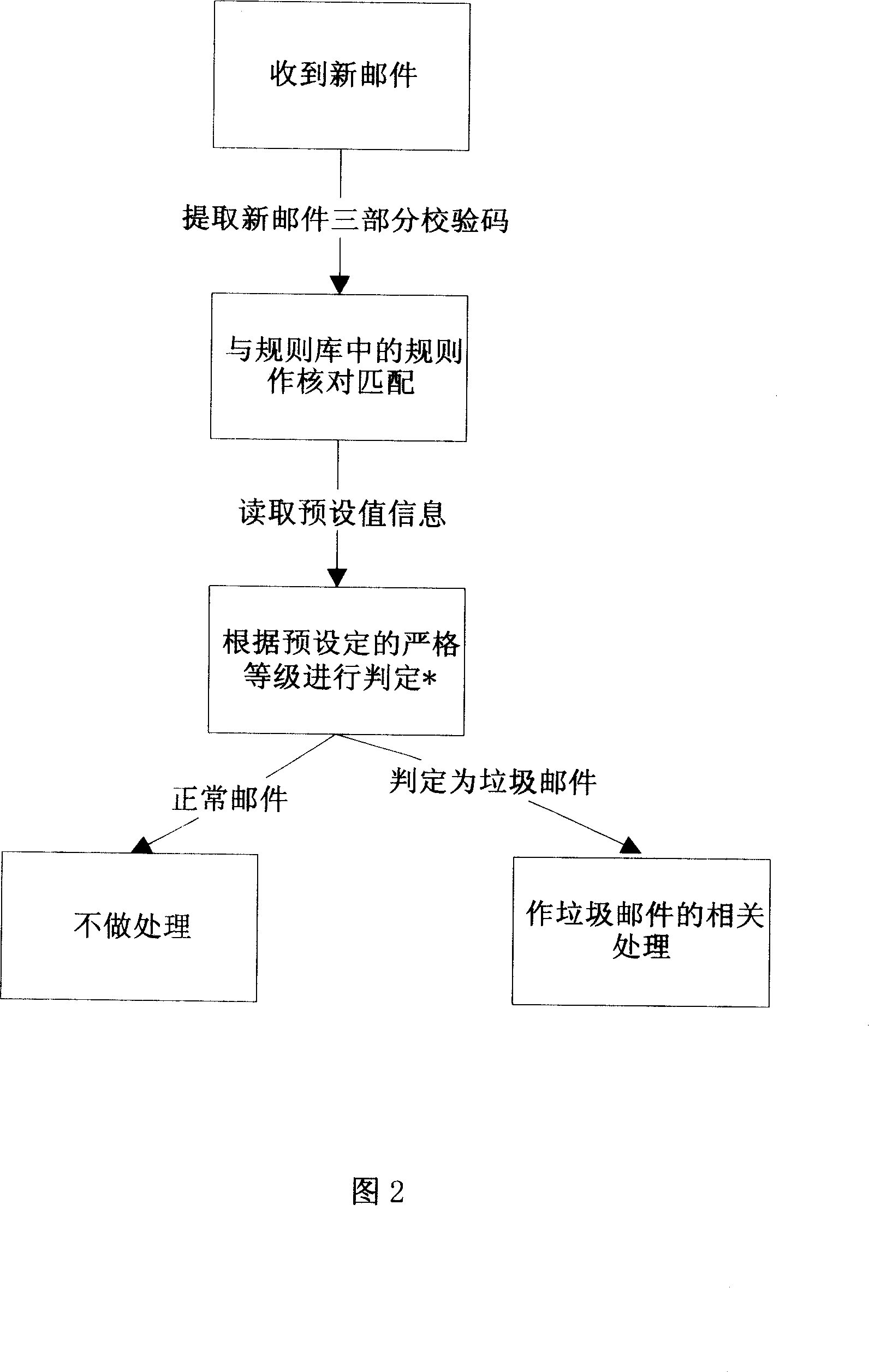
E-mail system and method capable of preventing garbage E-mail
InactiveCN101090357AExplosiveReduce volumeOffice automationData switching networksElectronic mailDatabase
This invention provides a mail system and a method, which can analyze received mails intelligently on PC of users and hold legal mails in an inbox automatically and stores rubbish mails in an isolation region or deletes them, an E-mail system anti-rubbish mails includes a server and multiple kinds of customer ends and an anti-rubbish mail subsystem including: a rubbish mail verifying code rule library set at the server end and customer ends, a rubbish-mail collecting module set at the server end, a module for picking up the verifying codes and an upgrade service end module, a mail monitor module set at the customer end, a match module and a management module of the verifying codes.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
A head-mounted computer and an information input method thereof
PendingCN109683667AStrong privacyPortable and convenientInput/output for user-computer interactionDetails for portable computersRemote controlComputer science
A head-mounted computer is used for remotely controlling a remotely controlled object and at least comprises a gesture sensor and an augmented reality / virtual reality imaging device, and the augmentedreality / virtual reality imaging device is used for constructing a virtual remote controller; And the gesture sensor is used for identifying the spatial position of the fingertip, and matching the spatial position of the fingertip with the position relationship of the keys of the virtual remote controller, and / or the relative spatial position of the fingertip, so as to trigger the head-mounted remote controller to send out a remote control instruction. Through the combination of the augmented reality / virtual reality imaging device and the gesture sensor, the virtual remote controller can be conveniently created and remotely operated, the appearance and parameters of the virtual remote controller can be autonomously set according to a user, the applicability is wide, and the operation is flexible and convenient; The invention further provides a head-mounted computer information input method which is high in variability and flexibility, capable of adapting to different remote control operations and small in fatigue degree after long-time operation.
Owner:上海萃钛智能科技有限公司
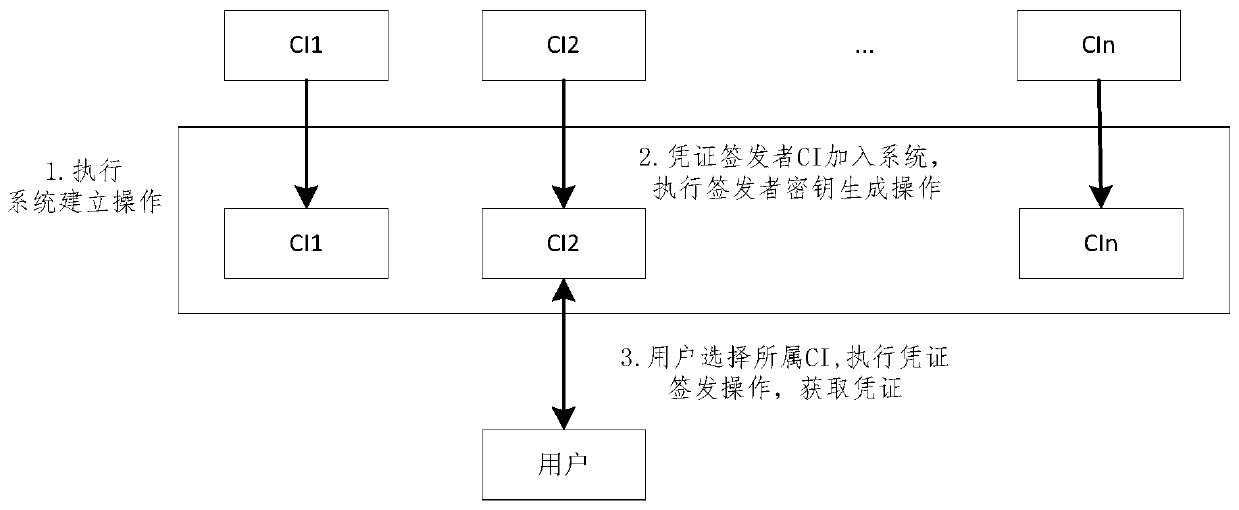
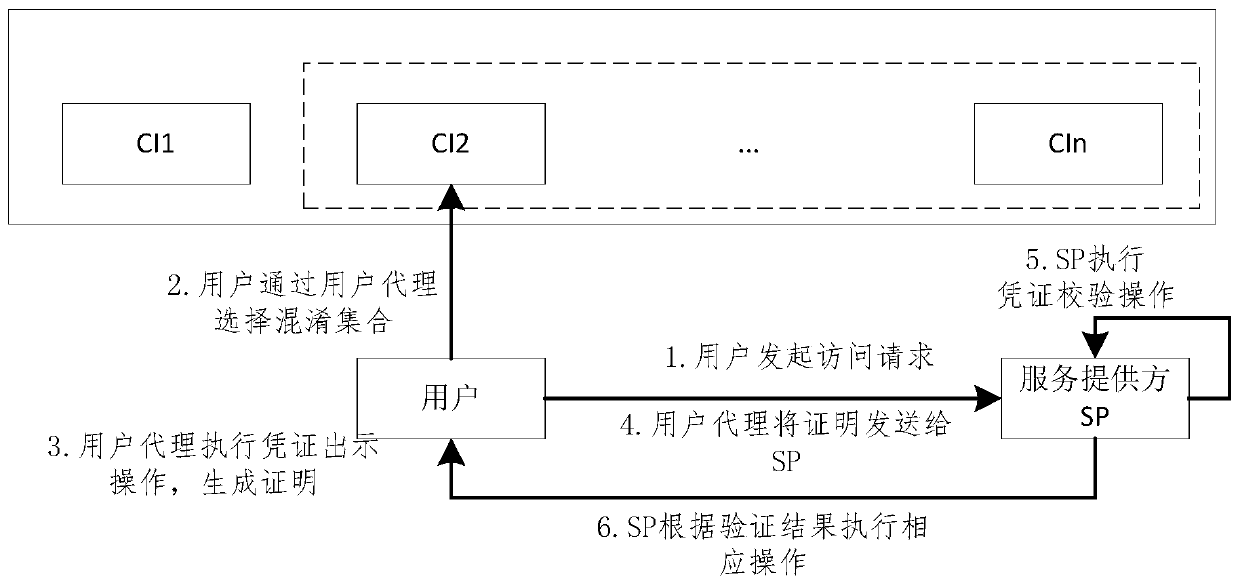
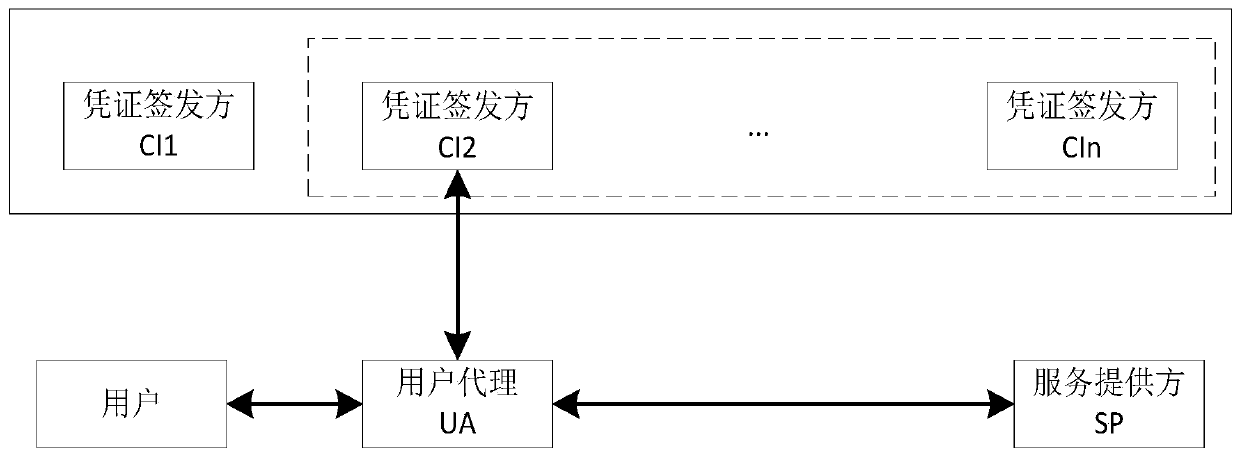
A certificate issuer anonymity entity identification method and system
InactiveCN109902508AEnhanced anonymityStrong privacyDigital data protectionRoot certificateConfusion
The invention discloses a certificate issuer anonymity entity identification method and system. The method comprises the following steps that: 1) each certificate issuer joining a system generates a private key and a public key of the certificate issuer according to system public parameters; 2) the certificate issuer I generates an identity certificate of the user according to the input user identity identifier, the private key of the certificate issuer I and the system public parameters and transmits the identity certificate to the user; 3) the user selects a plurality of certificate issuersto form a confusion set; an anonymous identity certificate of the user is generated according to the public parameters of the system, the public keys of all the selected certificate issuers and the identity certificate held by the user, and sending the anonymous identity certificate to an identity verifier; Wherein the confusion set comprises a certificate issuer I for issuing a user certificate to the user; And 4) the identity verifier verifies the received anonymous identity certificate according to the system public parameters and the public key of each certificate issuer in the confusion set, and determines whether the received anonymous identity certificate is valid or not.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Communication encryption method based on communication network
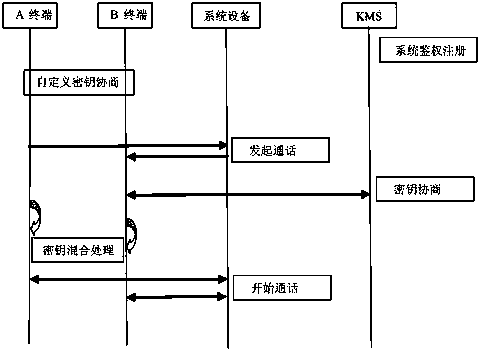
InactiveCN103684783AUnable to monitorPromote generationUser identity/authority verificationSecurity arrangementConfidentialityComputer terminal
The invention discloses a communication encryption method based on a communication network. The communication encryption method based on the communication network is characterized by comprising the following steps that (1) authentication and registration are conducted on the system side of terminals; (2) secret keys are self-defined between the terminals, and the self-defined secret keys are stored in the terminals; (3) the self-defined secret keys of the terminals start to be used; (4) communication encryption is conduced, wherein communication encryption comprises the steps that (41) one terminal makes an encryption call request with an encryption identification to the other terminal, (42) if the called-party terminal judges out self-defined encryption communication according to the encryption identification, a working secret key which is processed through the corresponding self-defined secret key starts to be used, (43) the called party accepts communication, the terminals of the two parties respectively conduct encryption or decryption on communication data with the working secret keys which are processed through the corresponding self-defined secret keys, and encryption communication is conducted. By the adoption of the communication encryption method based on the communication network, the self-defined secret keys can be allocated offline through coordination, so that the confidentiality is higher, the privacy is better, and monitoring of communication cannot be realized on the system side.
Owner:QINGDAO HISENSE ELECTRONICS EQUIP
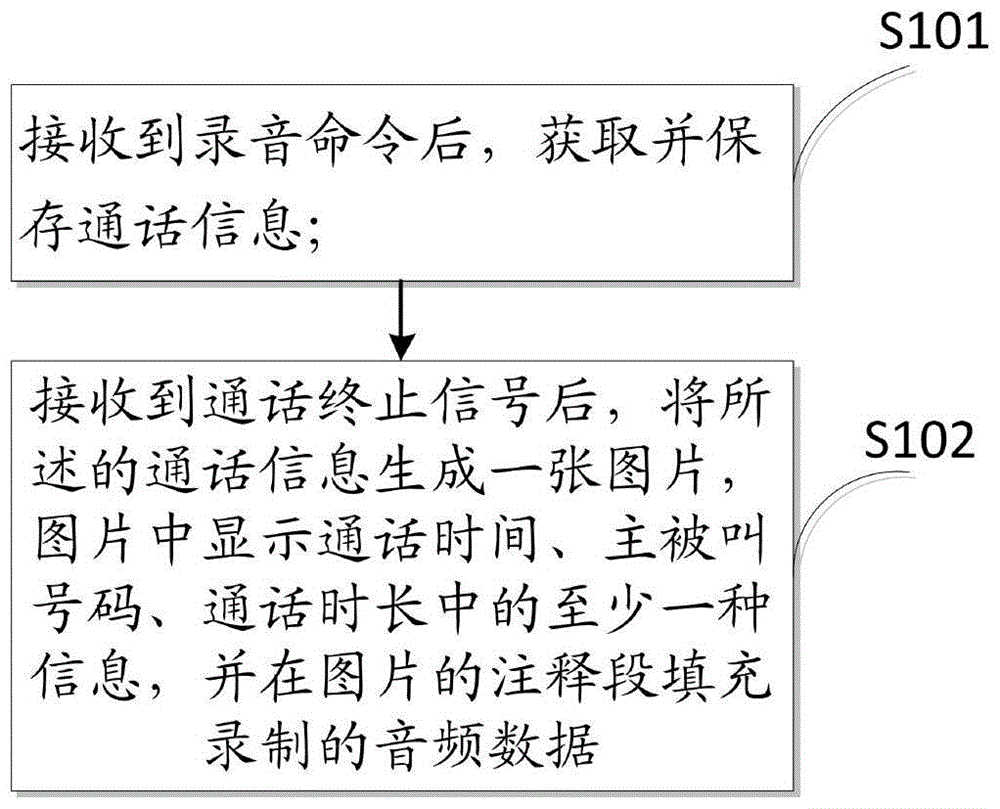
Device and method for saving call recordings and method for displaying call recordings
ActiveCN105049582AStrong privacyImprove experienceSubstation equipmentCall terminationAudio frequency
The invention discloses a device and a method for saving call recordings and a method for displaying the call recordings. The device comprises a start unit set to obtain and save call content and call time after receiving a recording command, and a termination unit set to generate a picture to save the call recording after receiving a call termination signal, wherein at least one information of the call time, calling and called numbers and call duration is displayed in the picture, and the annotation section of the picture is filled with audio data; the audio data is marked in the annotation section by use of an identifier, and the identifier is searched to recognize the recording. Recording files saved by use of the method or device are capable of visually displaying the information such as calling and called parties of calls, call time and call duration; besides, the saved call recordings are highly private.
Owner:NUBIA TECHNOLOGY CO LTD
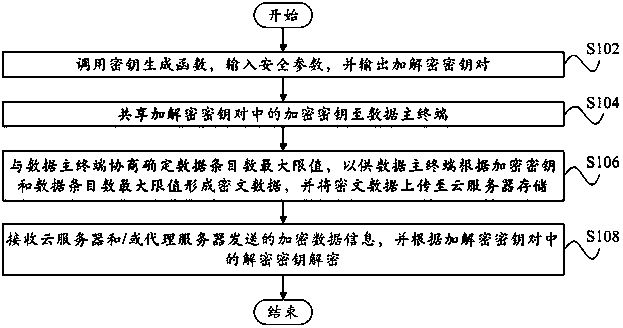
Data security protection method and device based on cloud computing
InactiveCN108449329APrivacy protectionProtection securityDigital data protectionTransmissionComputer hardwareData information
The invention provides a data security protection method and device based on cloud computing. The method comprises the following steps of calling a key generation function, inputting security parameters and outputting an encryption and decryption key pair; sharing an encryption key in the encryption and decryption key pair to a data master terminal; negotiating with the data master terminal to determine a maximum value of the number of data entries in order to make the data master terminal form ciphertext data according to the encryption key and the maximum value of the number of data entries,and uploading the ciphertext data to a cloud server for storage; and receiving encryption data information sent by the cloud server and / or a proxy server, and decrypting according to a decryption keyin the encryption and decryption key pair. According to the technical scheme, the local storage space and the data management cost of the data master terminal are saved, and meanwhile, the faster andmore accurate computing capability is obtained by utilizing the functions of the cloud computing, and the privacy of user data and the privacy of related computing requests are effectively protected.
Owner:中经汇通电子商务有限公司
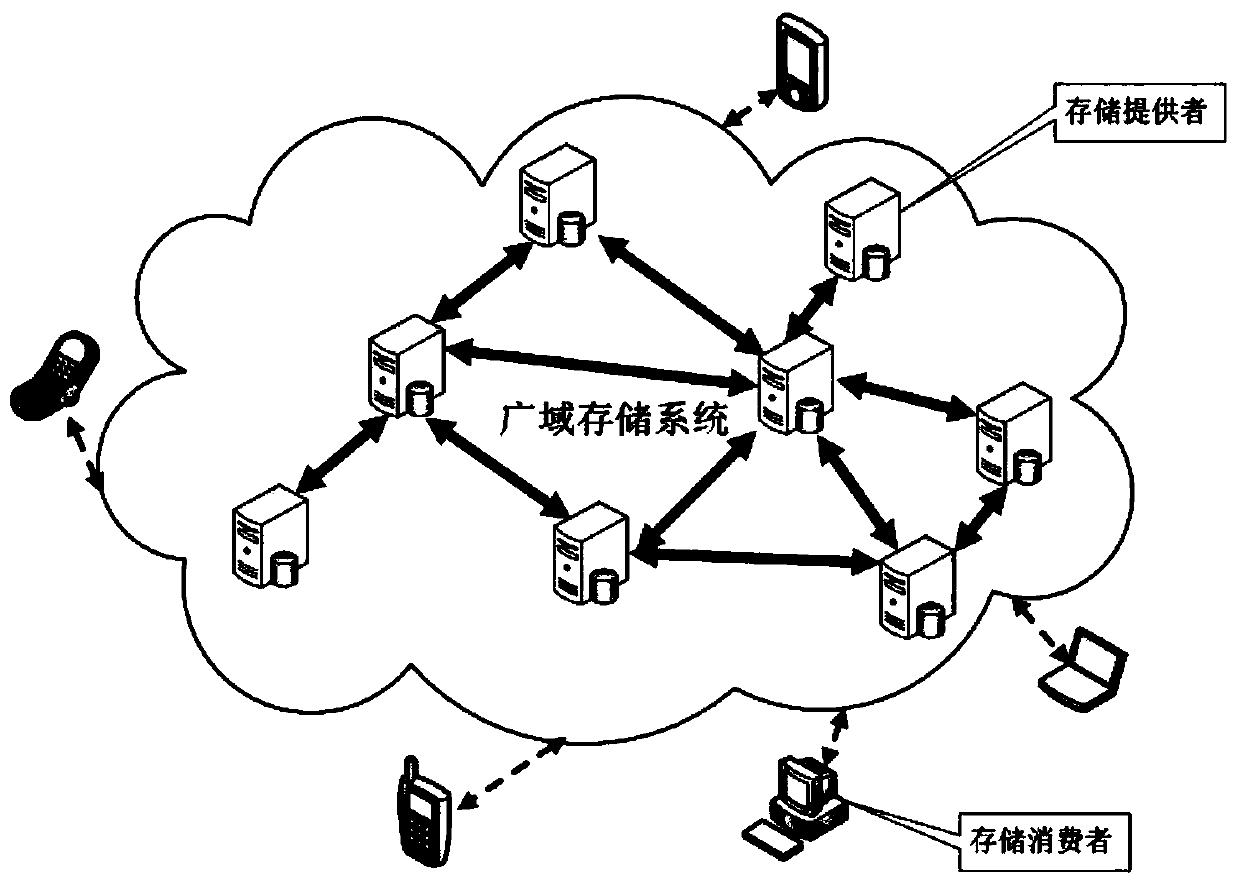
Large-scale distributed secure storage system based on block chain
ActiveCN111209262ASecure Data SharingImprove securityDigital data protectionDigital data authenticationMass storageResource pool
The invention provides a large-scale distributed secure storage system based on a block chain, and belongs to the technical field of computer storage and information security. A large-scale distributed mass storage resource pool which is formed by interconnecting storage resources dispersed on a region and a network, so as to provide high-reliability, high-availability and safe storage service forusers. And by combining a block chain and a distributed secure storage technology, an on-chain and off-chain data storage mode is designed, so that the problem that the data is easily tampered is effectively solved, and the integrity of the data is greatly improved on the premise of ensuring privacy.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
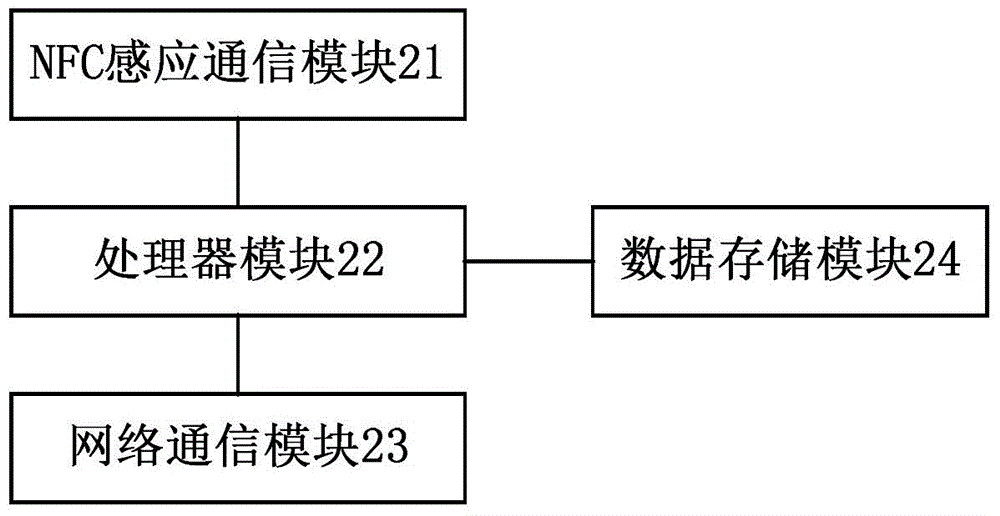
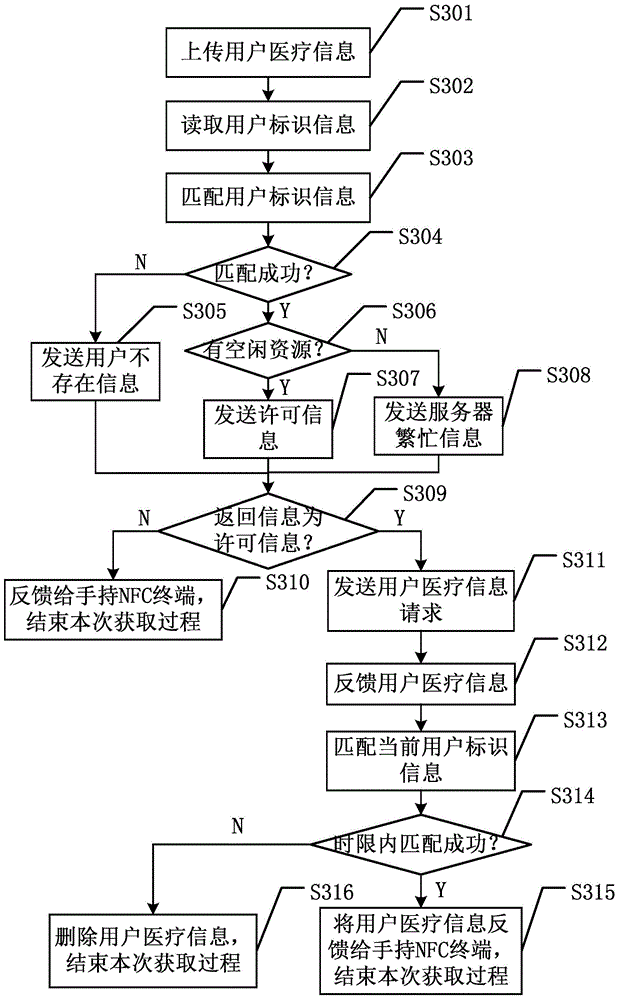
Medical information notice acquiring system and method based on NFC
InactiveCN104462851AAcquiring Efficiency TraditionStrong privacyCo-operative working arrangementsSpecial data processing applicationsComputer terminalComputer science
The invention discloses a medical information notice acquiring system and method based on NFC. Medical staff upload the medical information of a user to a center server through a medical information uploading terminal, connection between the user and a public NFC service terminal is established through a handheld NFC terminal, the public NFC service terminal reads user identification information contained in the handheld NFC terminal and sends the user identification information to the center server, then the medical information of the user is obtained and fed back to the handheld NFC terminal, and the handheld NFC terminal displays the medical information of the user to enable the user to check the medical information. By the adoption of the system and method, people do not need to carry various paper files or medical treatment cards, cost is reduced, convenience and efficiency are improved, and privacy leakage and information loss are avoided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for testing children psychology helping by computer
The invention relates to the technical field of adopting a computer to test children mental health, in particular to a method for testing children psychology helping by the computer, comprising the following steps: selecting the scales to be evaluated; accomplishing the test contents of the scales according to steps; automatically judging by a system and automatically grading; finding out the corresponding evaluating result in background by testing personnel according to the grades; ending up the test and obtaining the solution. Aiming at the characteristics of the testing process of children mental health problems, the invention rationally operates the multi-media technical specialty and fully utilizes the mental theory of the children to design the testing method which meets the children mental health test rules. The method has the characteristics of without fatigue, without emotion factors, without mood swings, strong privacy and unlimited repetition, and the method has wide application in life.
Owner:CHANGZHOU AOBO REHABILITATION EQUIP TECH
Private application program starting method and device
InactiveCN106547590AEnhance camouflageStrong privacyDigital data authenticationProgram loading/initiatingApplication softwarePassword
The invention provides a private application program starting method and device. The method comprises the following steps of: detecting a trigger operation carried out on a disguised application icon of any private application program by a user, and displaying a starting verification interface matched with an application scene pointed by the disguised application icon; receiving password information input by the user through the starting verification interface and verifying the received password information; and when the continuous verification failure frequency of the password information is greater than a predetermined threshold value, starting a shooting application program to shoot the user. According to the technical scheme of the invention, the private application program displays the starting verification interface matched with the application scene pointed by the disguised application icon if a second person except the user of terminal touches the private application program when a screen of the terminal is unlocked, so that the second person cannot know the real content information of the private application program, and the second person does not think that the private application program is disguised or encrypted, thereby achieving a relatively high disguise effect.
Owner:BEIJING QIHOO TECH CO LTD +1
Automatic supporting and winding type sunshade of front windshield
The invention provides an automatic supporting and winding type sunshade of a front windshield. The automatic supporting and winding type sunshade of the front windshield comprises a left group of telescopic roller shutters and a right group of telescopic roller shutters. The key point of the automatic supporting and winding type sunshade of the front windshield is that winding shafts of the leftgroup of telescopic roller shutters and the right group of telescopic roller shutters are symmetrically arranged on the two sides of a base; the base is positioned in the position, at the bottom of the front windshield, on a vehicle body; a left lifting supporting plate and a right lifting supporting plate are limited at the top of the base in a matched manner; and the left lifting supporting plate and the right lifting supporting plate are correspondingly connected with cord fabric free ends of the left group of telescopic roller shutters and the right group of telescopic roller shutters andform a structure, which horizontally moves upwards along the windshield to support a cord fabric and horizontally moves downwards to assist the winding of the cord fabric, by means of lifting drivingmechanisms connected to the left and right lifting supporting plates. The automatic supporting and winding type sunshade of the front windshield is mounted on the front windshield in the vehicle, thelifting driving mechanisms can be of folding types and can be folded and stored to the bottom of the front windshield; and moreover, the automatic supporting and winding type sunshade of the front windshield can be automatically supported; the operation is stable and reliable; the volume is small; the mounting is convenient; the automatic supporting and winding type sunshade of the front windshield does not need to be repeatedly assembled and disassembled; and the automatic supporting and winding type sunshade of the front windshield is safe and reliable.
Owner:刘占峰
Realization method of switchable multi-password local information encryption box
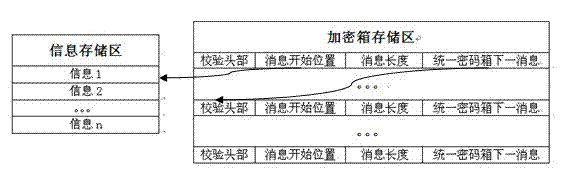
ActiveCN102299800APrivacy protectionStrong privacyUser identity/authority verificationComputer hardwarePassword
The invention relates to a method for realizing a switchable multi-cipher local information encryption box. The traditional encryption method mainly comprises two types: (1) single cipher protection which does not support the form that a plurality of encryption boxes are divided according to information sources or contents; and (2) a plurality of cipher protections by which the number of the encryption boxes can be listed or presumed. In the method, a user can select classify information to a certain encryption box according to information sources and information contents; the encryption boxes can be switched at any time when a certain encryption box is needed to be checked; a cipher is needed to be provided when the encryption boxes are switched; the information is correctly deciphered when the cipher is correct, and blank is displayed when the cipher is wrong; and other people cannot judge whether the cipher is wrong or no corresponding encryption box is provided and cannot also know how many encryption boxes owned by the user, therefore, the aims of information hiding and privacy protection are achieved. The method is suitable for encryption of short messages, instant messages, e-mails, pictures, files and other information and has the advantages of flexibility and good privacy.
Owner:杭州弗兰科信息安全科技有限公司
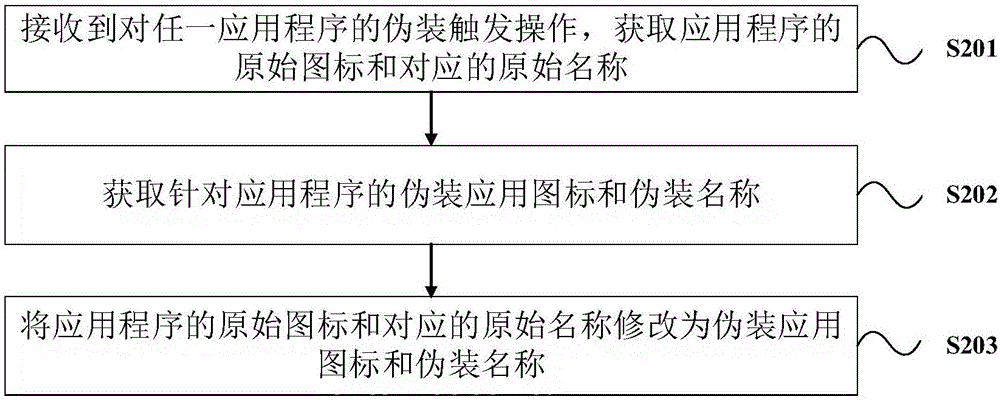
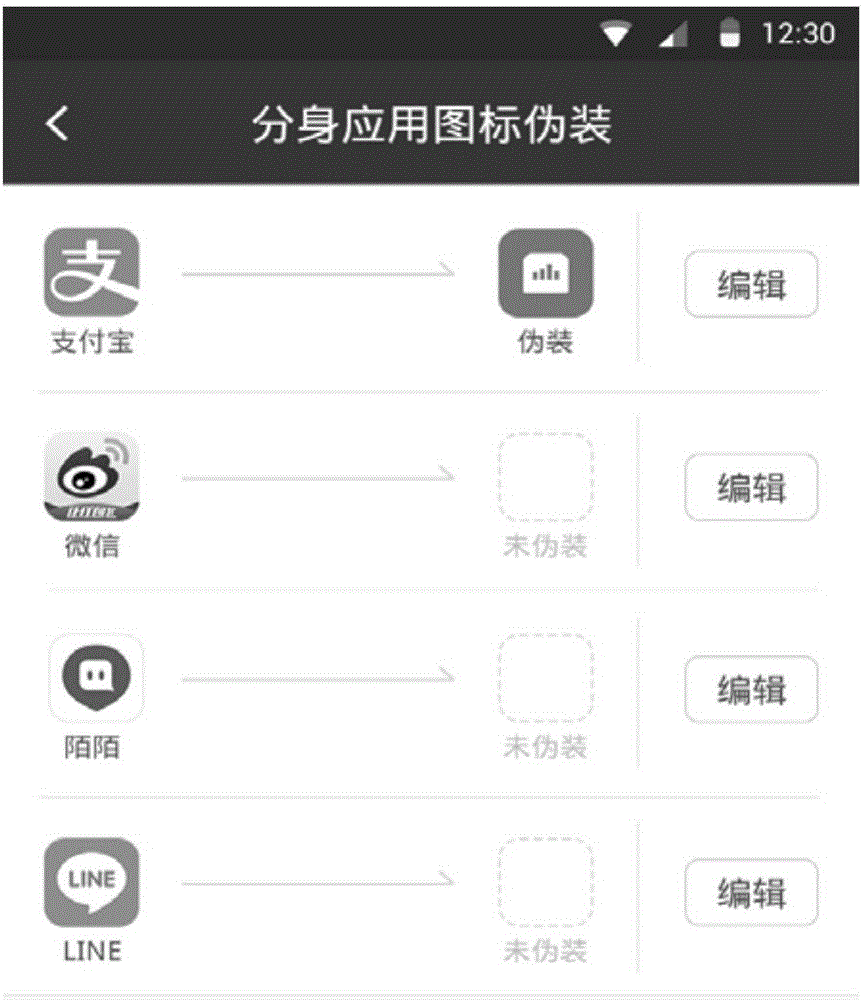
A privacy protection method and a privacy protection device for application programs
InactiveCN106407790AStrong privacyProtect privacy and securityDigital data authenticationPrivacy protectionApplication software
The invention provides a privacy protection method and a privacy protection device for application programs. The privacy protection method comprises the steps of when receiving a disguise trigger operation for any application program, acquiring an original icon and the corresponding original name of the application program; acquiring a disguise icon and a disguise name for the application program; changing the original icon and the corresponding original name of the application program to the disguise icon and the disguise name. According to the technical solution, the disguise for marking information of application programs is realized in a screen of a terminal apparatus, so that greater privacy of the application programs can be guaranteed for the user even when the screen of the mobile terminal is unlocked, the application programs are prevented from being used by another person aside from the user of the terminal, the privacy security of user data in the application programs can be effectively protected and user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
Integrated type slide-support outward-opening aluminum alloy door and window
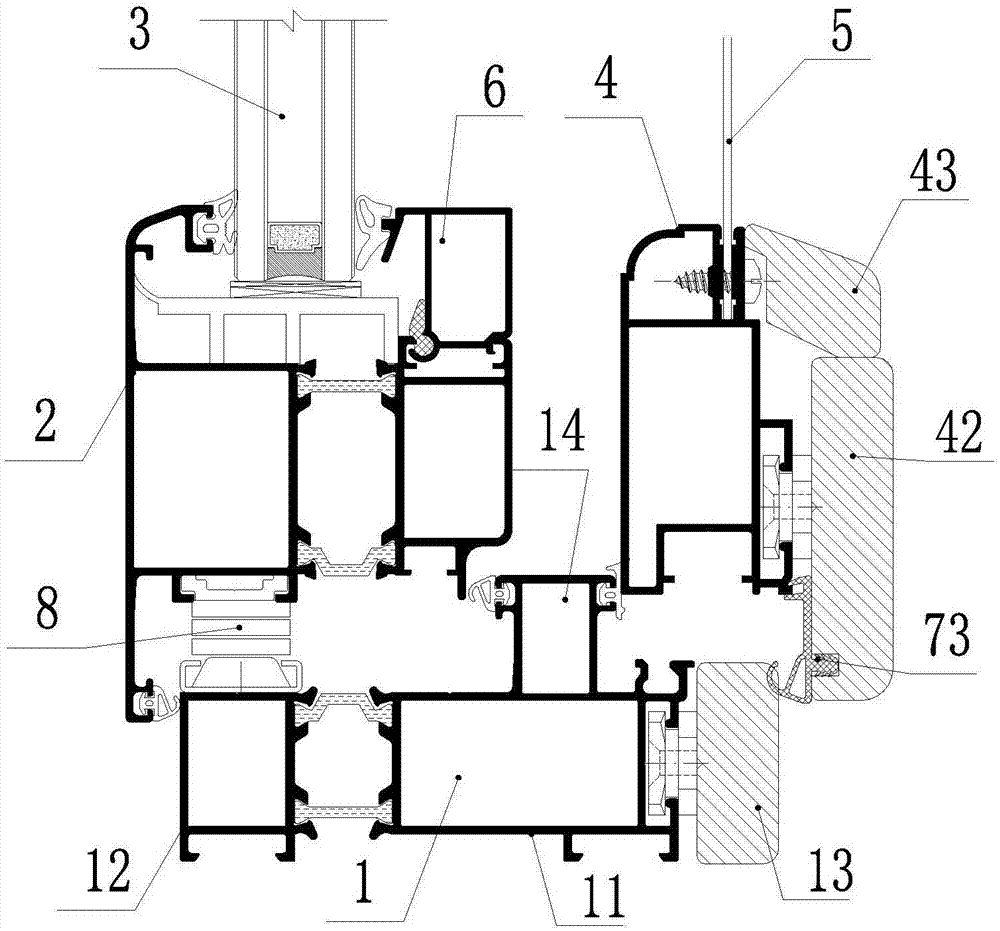
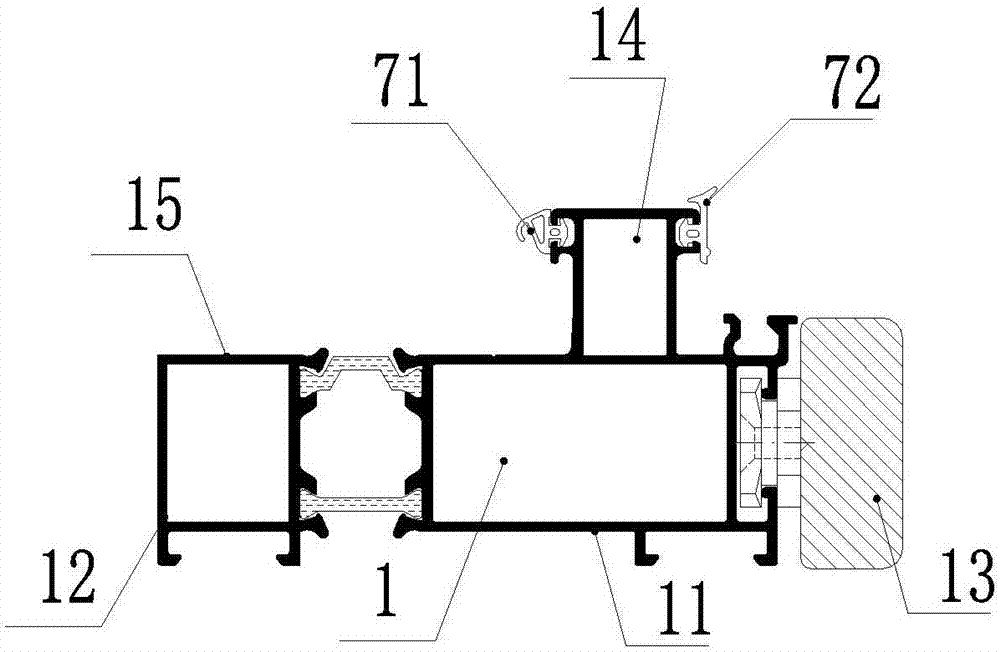
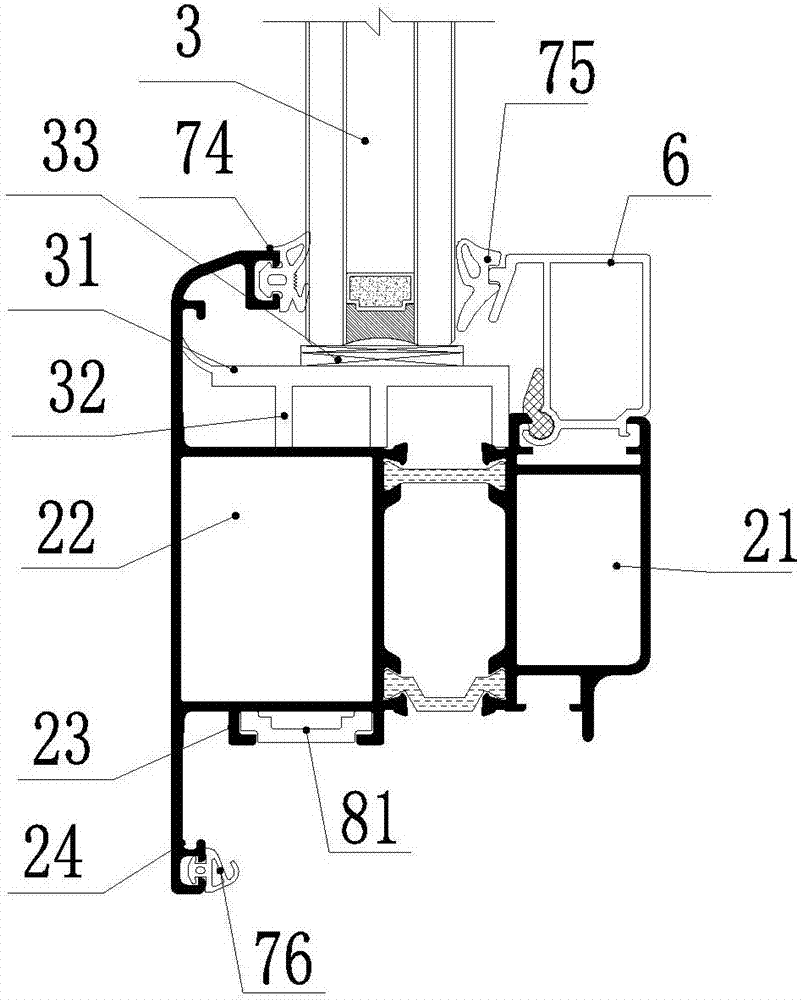
InactiveCN106968553AAvoid affecting the appearanceImprove water tightnessShutters/ movable grillesInsect protectionAluminium alloy
The invention relates to aluminum alloy doors and windows, in particular to an integrated type slide-support outward-opening aluminum alloy door and window which comprises a window frame, a window sash, glass and an aluminum pressing wire. The window frame comprises an aluminum alloy frame profile which is formed by connecting an indoor side aluminum alloy frame profile body and an outdoor side aluminum alloy frame profile body through a broken bridge. The window sash is formed by connecting an indoor side aluminum alloy sash profile and an outdoor side aluminum alloy sash profile through a broken bridge. The lower portion of the outdoor side aluminum alloy sash profile is provided with an extension arm which is provided with a sixth sealing rubber strip. The sixth sealing rubber strip is matched with the outdoor side of the outdoor side aluminum alloy frame profile body. A slide support is arranged between the outdoor side aluminum alloy sash profile and the outdoor side aluminum alloy frame profile body. The bottom of the slide support is connected with the flush part of the outdoor side aluminum alloy frame profile body. The upper portion of the slide support is connected with a C-shaped groove of the outdoor side aluminum alloy sash profile. According to the integrated type slide-support outward-opening aluminum alloy door and window, the portion, corresponding to the mounting position of the slide support, of the aluminum frame is of a flush structure, and the portion, corresponding to the mounting position of the slide support, of the aluminum sash is of a C-shaped groove structure so that a slide support hinge can be directly mounted.
Owner:ZHEJIANG ROOMEYE ENERGY SAVING TECH CO LTD
Radar personnel monitoring and measuring system and method
PendingCN111474537AStrong privacyReduce power consumptionRadio wave reradiation/reflectionReflected wavesRadio wave
The invention discloses a radar personnel monitoring and measuring system and method. The system comprises a millimeter-wave radar which transmits radio waves through an antenna, reflects the radio waves through an obstacle and receives returned reflected waves through the antenna, a signal separation module which is used for separating a plurality of persons from the reflected wave, a DSP which is used for carrying out Fourier transform, fast Fourier transform and smoothing processing on each separated person signal to obtain the number of persons, the position coordinates of each person, thespeed on the position coordinates and the acceleration data on the position coordinates, a 4G wireless module which is used for uploading the number of the persons, the position coordinates of each person, the speed on the position coordinate and the acceleration data on the position coordinate to a network, and a terminal which is used for monitoring the persons in an area in real time accordingto the number of the persons in the network, the position coordinates of each person, the speed on the position coordinate and the acceleration data on the position coordinate. Personnel in an area can be monitored, pre-judgment, prevention and control are performed in advance, and privacy is protected.
Owner:广州桑瑞科技有限公司
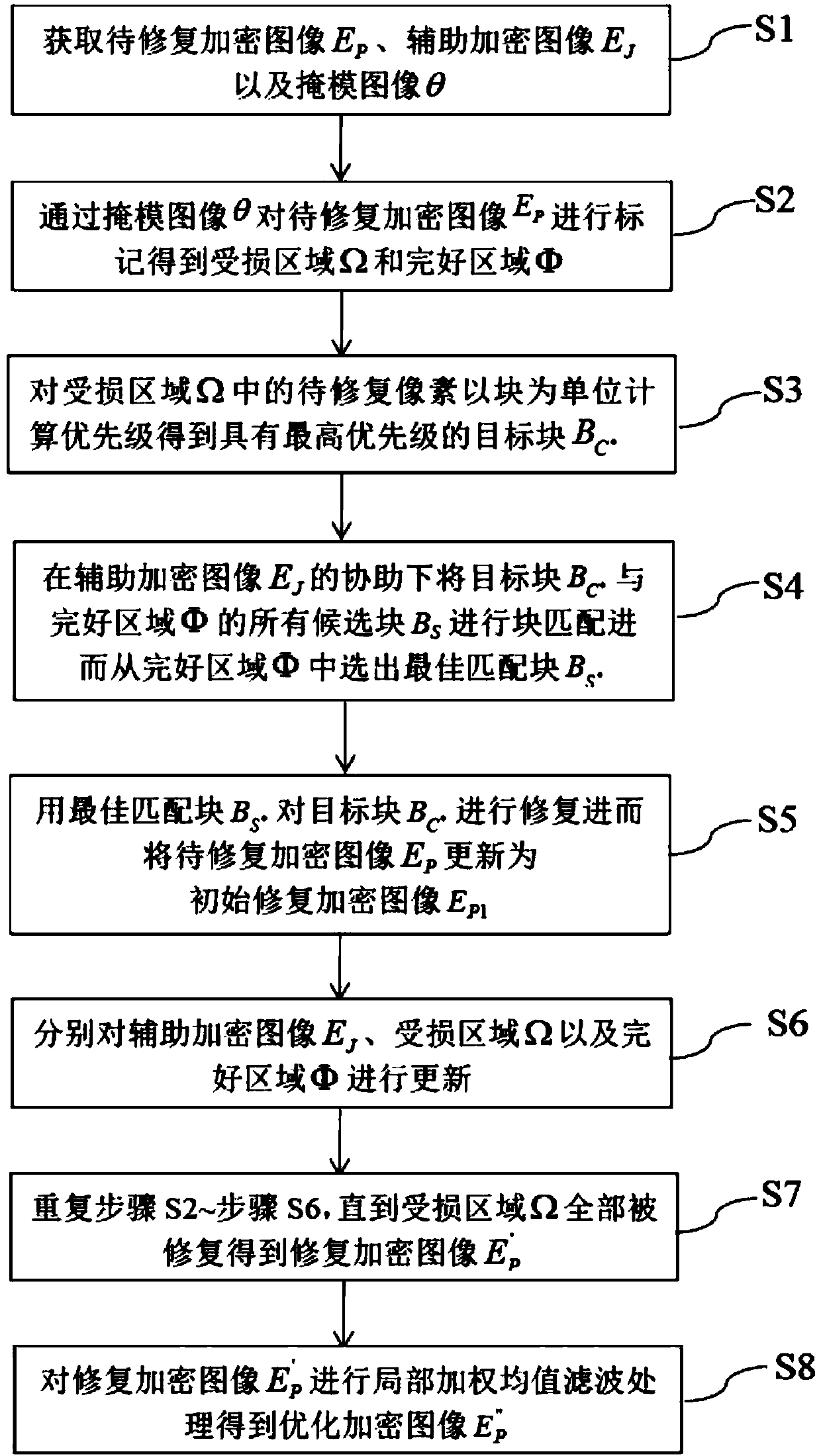
Ciphertext domain image repair method
ActiveCN108846816AStrong privacyGood image restorationImage enhancementDigital data protectionComputer visionEncryption
The invention provides a ciphertext domain image repair method which is used for carrying out repair on a damaged image generated by suffering from damage of a mask image in a ciphertext domain and ischaracterized by comprising the following steps of: S1, acquiring a to-be-repaired encryption image EP, an auxiliary encryption image EJ and a mask image theta; S2, carrying out marking on the to-be-repaired encryption image EP by the mask image theta to obtain a damaged region omega and an undamaged region phi; S3, calculating priorities of to-be-repaired pixels c in the damaged region omega bytaking a block as the unit so as to obtain a target block (with the reference to the specification) with the highest priority; S4, under the assistance of the auxiliary encryption image EJ, carrying out block matching on the target block (with the reference to the specification) and all candidate blocks BS in the undamaged region phi to obtain an optimal matched block (with the reference to the specification); S5, carrying out repair on the target block (with the reference to the specification) by the optimal matched block (with the reference to the specification) to select an initial repairedencryption image EP1; S6, respectively carrying out updating on the auxiliary encryption image EJ, the damaged omega and the undamaged region phi; and S7, repeating the steps S2 to S6, until the damaged region omega is completely repaired to obtain a repaired encryption image E'P.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Method for terminal interaction based on network security and relevant device thereof
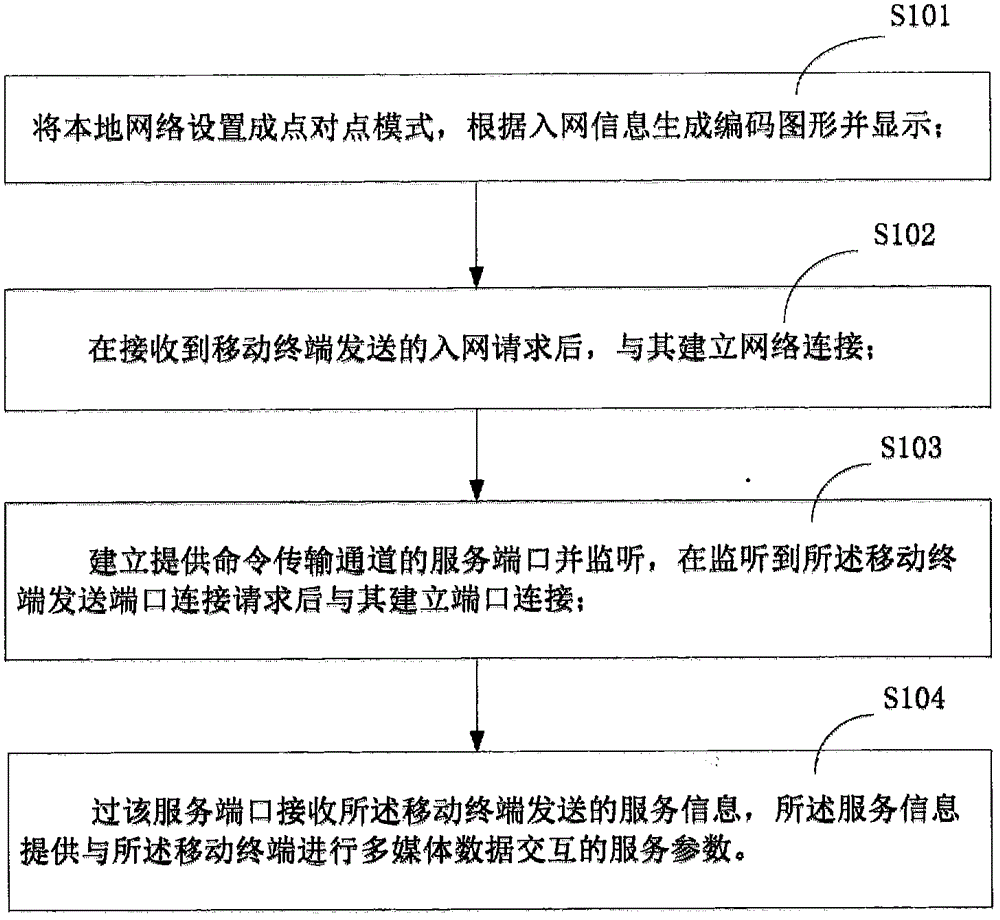
A network security-based terminal interaction method and related equipment, wherein the method includes: setting the local network to a point-to-point mode, generating and displaying coded graphics according to network access information; after receiving a network access request sent by a mobile terminal, and Establish a network connection; establish and monitor a service port that provides a command transmission channel, and establish a port connection with the mobile terminal after listening to the port connection request sent by the mobile terminal; receive the service information sent by the mobile terminal through the service port, and the service information Provide service parameters for multimedia data interaction with the mobile terminal. By adopting the above-mentioned method and related equipment, it has the characteristics of high network security and strong privacy when resource sharing and exchange control are performed, and the resource transmission speed is fast.
Owner:袁斌
Safety door body device with an object receiving and sending function
PendingCN110685577AReduce thicknessDoes not affect appearanceClosed circuit television systemsPeep-holesEngineeringComputer science
The invention relates to a safety door body device with a parcel receiving and sending function. The safety door body device with the parcel receiving and sending function comprises a door body, a door hole, a receiving box and an interaction unit; the door hole is used for taking and placing a parcel; the receiving box is arranged on the back side of the door body; the interaction unit is arranged in the door body and is used for receiving information; the receiving box is a storable folding box; the receiving box and the interaction unit are both slidably arranged in a middle interlayer on the back side of the door body; and if in the normal conditions, the receiving box is folded and stored in the middle interlayer, and the interaction unit is arranged at the door hole and closes the door hole; during parcel throwing, the interaction unit leaves the door hole, the receiving box is unfolded, the front part and the back part of the unfolded receiving box are provided with openings respectively, the front opening of the receiving box is opposite to the door hole, and after the parcel is thrown, the interaction unit goes back into place; and the back side of the receiving box is further provided with a telescopic back plate for closing the back opening of the unfolded receiving box. For the safety door body device provided by the invention, under the condition of guaranteeing the safety and an existing door body structure, accurate, safe and convenient receiving of a parcel can be realized, and structural arrangement of a door can be further ensured.
Owner:上海护虎电子科技有限公司
Lane keeping system and method based on Beidou high-precision positioning
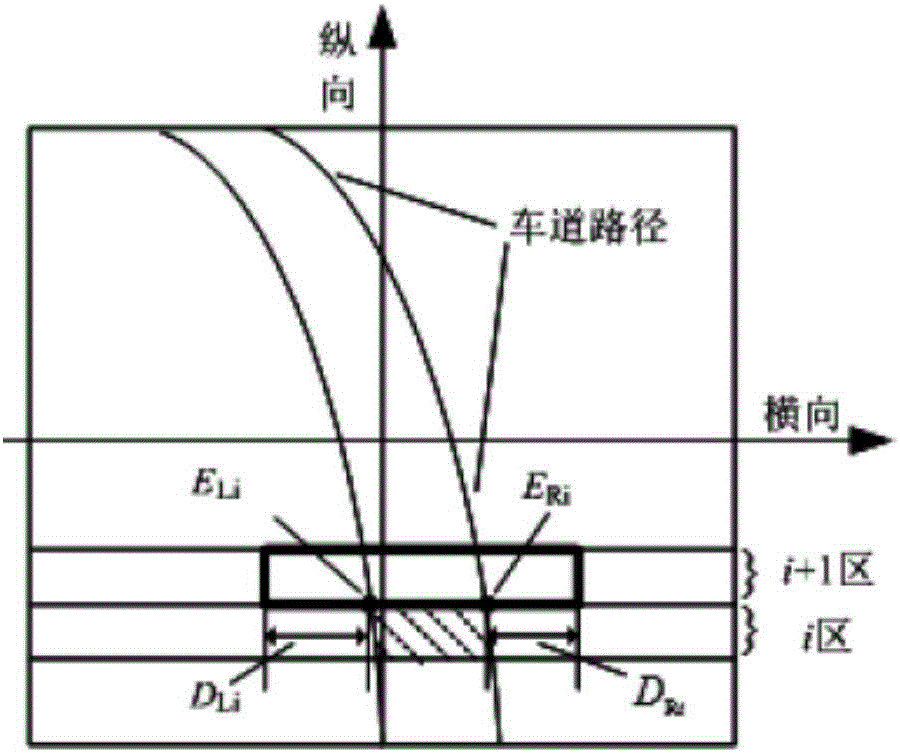
InactiveCN106354135ALow costStrong privacyCharacter and pattern recognitionPosition/course control in two dimensionsComputer control systemTraffic capacity
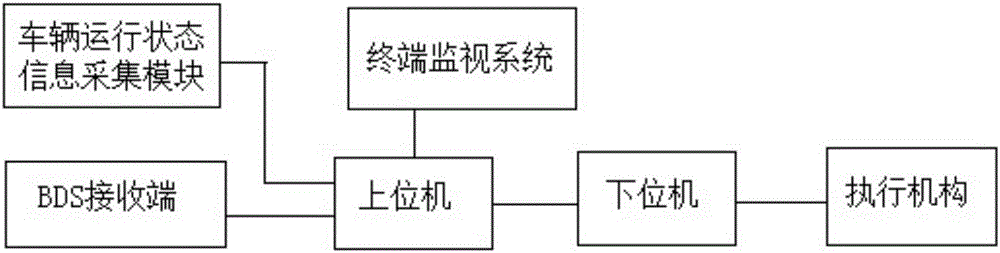
The invention provides a lane keeping system based on Beidou high-precision positioning. The lane keeping system comprises a vehicle running state information acquiring module, a BDS receiving end, an upper computer control system, a lower computer control system and a terminal monitoring system, wherein the vehicle running state information acquiring module acquires parameters of vehicle running states from a vehicle; the BDS receiving end receives position information of the vehicle, a map and road information from a Beidou satellite; the upper computer control system acquires the parameters of the vehicle running states, the position information of the vehicle, the map and the road information through a CAN bus, a suitable lane is selected, the vehicle is tracked in real time according to a vehicle tracking algorithm, and the position information of the vehicle is fed back; the lower computer control system acquires the suitable lane and transmits a control command to the vehicle; and the terminal monitoring system communicates with the upper computer control system through a network. The device is directly mounted in the vehicle, a background server or wireless network bandwidth is not required, the cost is low, and cost for data flow is not required to be paid in a later period.
Owner:WUHAN YIXUN ELECTRONICS INFORMATION TECH
Handbag making machine
PendingCN112537082ARealize automatic processingEasy to useBag making operationsPaper-makingPunchingStructural engineering
The invention discloses a hand bag making machine, which comprises a traction mechanism, a longitudinal slitting mechanism, a release film coating mechanism, a bag body opening mechanism, a punching mechanism and a sealing and cutting mechanism; the traction mechanism comprises a feed roller; the longitudinal slitting mechanism comprises a cutter; the release film coating mechanism comprises a material frame and a guide rod, and the guide rod is arranged at a film coating station; the bag body opening mechanism comprises an opening piece, and the bag body opening mechanism is arranged betweenthe longitudinal slitting mechanism and the release film coating mechanism in a main material conveying direction; and the punching mechanism comprises a punching cutter. The cutter longitudinally cuts, divides a roll material into two parts, cuts the roll material into a left main material and a right main material, punches a hole at a bag opening to form a hand-held hole, is convenient for a user to use, opens the bag openings of the left main material and the right main material, and introduces a release film at the bag opening, so that the processing efficiency is high, wastes are reduced,the environment is protected, and the production cost is reduced.
Owner:浙江超伟机械有限公司
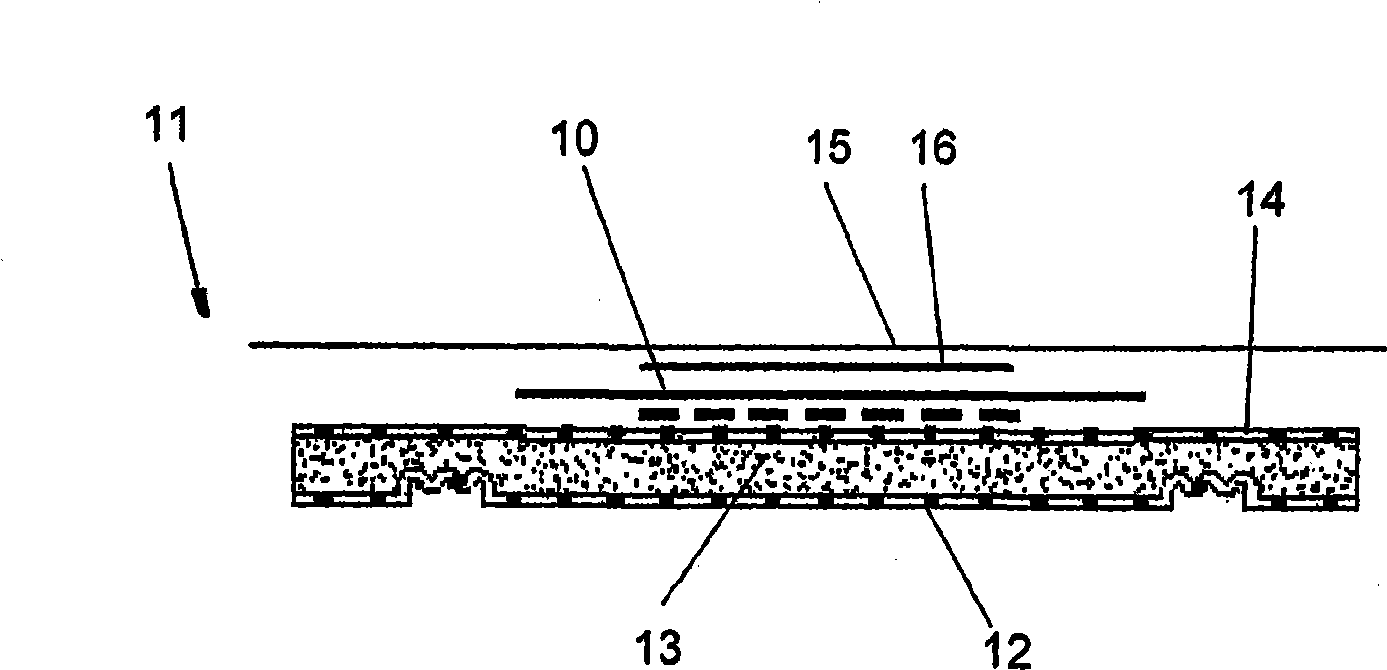
Component for packaging roll-shaped sanitary nursing article and method for producing the same
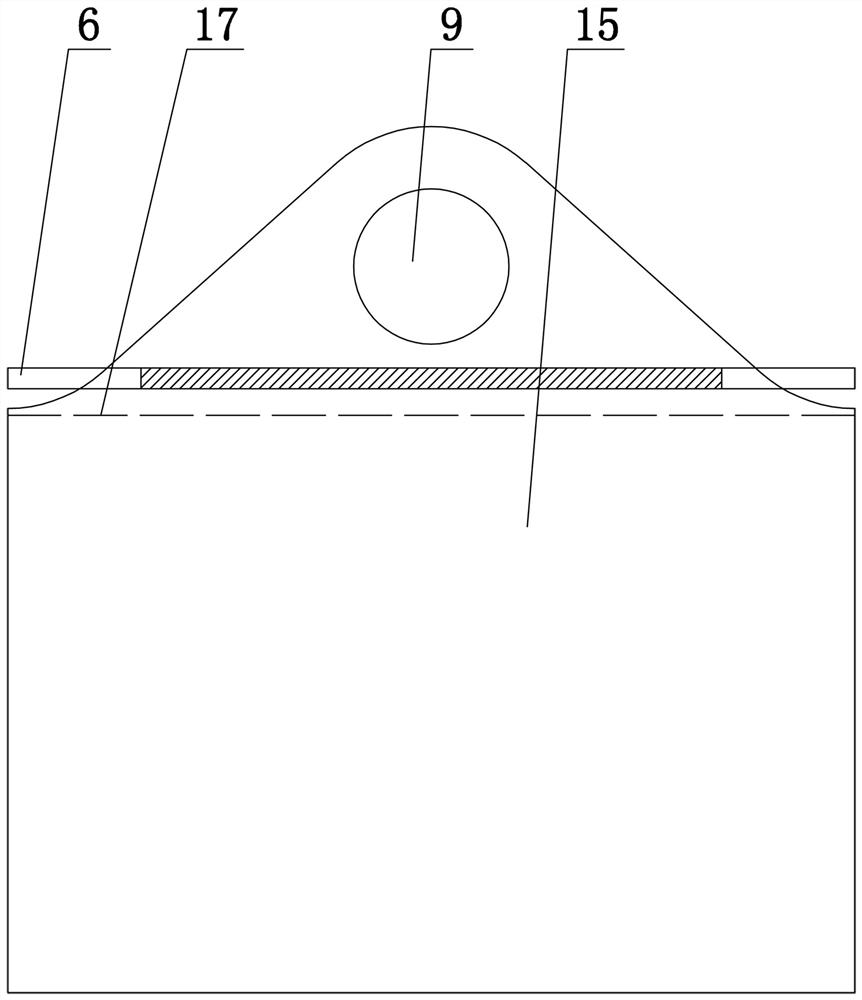
ActiveCN101497385ANot easy to get dirtyEasy to carryFlexible coversWrappersSurface layerBiomedical engineering
The invention provides a rolled health nursing article packing component (1; 11) and a manufacturing method thereof. The packing component (1; 11) comprises a health nursing article which comprises a surface layer (2; 12), an absorbing layer (3; 13), an isolating layer (4; 14) and / or a health nursing article consists of a release paper (10) and a packing film (5; 15) used for packing the health nursing article, wherein the health nursing article can be rolled into a roll shape. In order to ensure the rolled health nursing article is convenient to carry, has stronger privacy, is convenient to open the package and prepare for use, and guarantee the clean ability of the surface layer, the invention specifies that before the packing film (5; 15) and the health nursing article are rolled into a plurality of circles, a first edge (7; 17) and a second edge (8; 18) of the basic flat shape health nursing article are in an overlapped state according to the following mode: the surface layer part near the first edge (7; 17) and the surface layer part near the second edge (8; 18) contact.
Owner:KIMBERLY CLARK (CHINA) CO LTD
Targeted drug delivery fumigation system and method for gynecology department
ActiveCN109009992APrecise positioningPromote absorptionMedical devicesBathing devicesTreatment effectGynecology department
The invention relates to a targeted drug delivery fumigation system and method for the gynecology department. A water inlet pipe with nozzles is fixedly mounted on the inner top wall of a fumigation box, a heating disinfection lamp is fixedly mounted on one side of the water inlet pipe, a bellows box is fixedly mounted on the portion, at the lower end of the heating and disinfection lamp, of the inner wall of the fumigation box, fans are installed in the bellows box, an opening is formed below an oblique pulling support plate, and a targeted positioning fumigation device is mounted in the portion, below the opening, of the interior of the fumigation box. A positioning targeted drug delivery connector is used for drug delivery so that a female private part can be accurately located; moreover, a universal adjustment rod is used for positioning, fixation and adjustment of the corresponding degree, and the positioning targeted drug delivery connector is provided with an upper drug outlet,a middle drug outlet and a lower drug outlet. According to a human body bionic principle, omnibearing fumigation drug therapy treatment is carried out to a precise position and peripheral positions ofthe female private part, precise targeted drug delivery is achieved, and the treatment effect is remarkable.
Owner:NANYANG CITY CENT HOSPITAL
Anonymous file examination and approval method
The invention relates to an anonymous file examination and approval method. The anonymous file examination and approval method is implemented by a server and a client, and the method comprises the following steps: a user authenticated by a CA authentication center and having a certificate issued by the CA authentication center submits a to-be-examined and approved file, uploads the file to the server, selects the number of people requiring examination and approval, and sets an examination and approval sequence; the client fills examination and approval serial numbers and approver names, sendsthe examination and approval serial numbers and the approver names to the server, and randomly allocates an ID; the user provides an examination and approval application for the client, the client queries whether a to-be-examined and approved project exists, meanwhile the server receives a current client certificate and judges whether the current client certificate is correct, thereafter the client receives the information and examines and approves the information, after the examination and approval are accomplished, the client selects a blinding factor for an examination and approval result xand the allocated ID for blinding the examination and approval result x to obtain a blinding result e, and performs signature. The identity information of approvers cannot be obtained in the whole process, thus realizing the anonymity of the result in the examination and approval process, and after all examination and approval is accomplished, the server performs statistics on the stored data andprovides the final examination and approval result.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
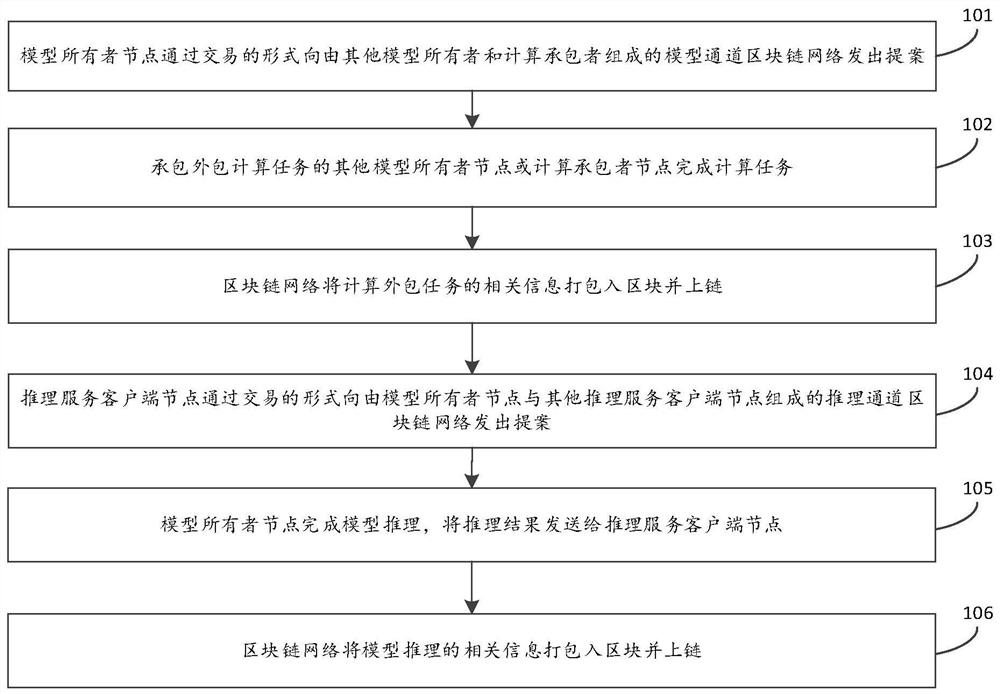
Privacy protection machine learning training and reasoning method and system based on block chain
ActiveCN114118438AEnsure safetyGuaranteed privacyResource allocationDigital data protectionPrivacy protectionEngineering
The invention discloses a privacy protection machine learning training and reasoning method and system based on a block chain. The system comprises a machine learning model training module, a machine learning model reasoning service module, and a block chain service module which is connected with the machine learning model training module and the machine learning model reasoning service module and communicates with the machine learning model training module and the machine learning model reasoning service module. The method is applied to a block chain network, and the block chain network comprises a machine learning model owner node, a calculation contractor node, a trusted arbitration node and an inference service client node. Wherein the machine learning model owner node, the calculation contractor node and the trusted arbitration node form a model channel, and the machine learning model owner node, the reasoning service client node and the trusted arbitration node form a reasoning channel; according to the method, model training and reasoning are separated, reasoning services are separated, and good privacy protection is formed by information isolation between channels; and the safety and credibility of the model training and reasoning process are ensured.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Data sharing system, method and device and data sharing equipment
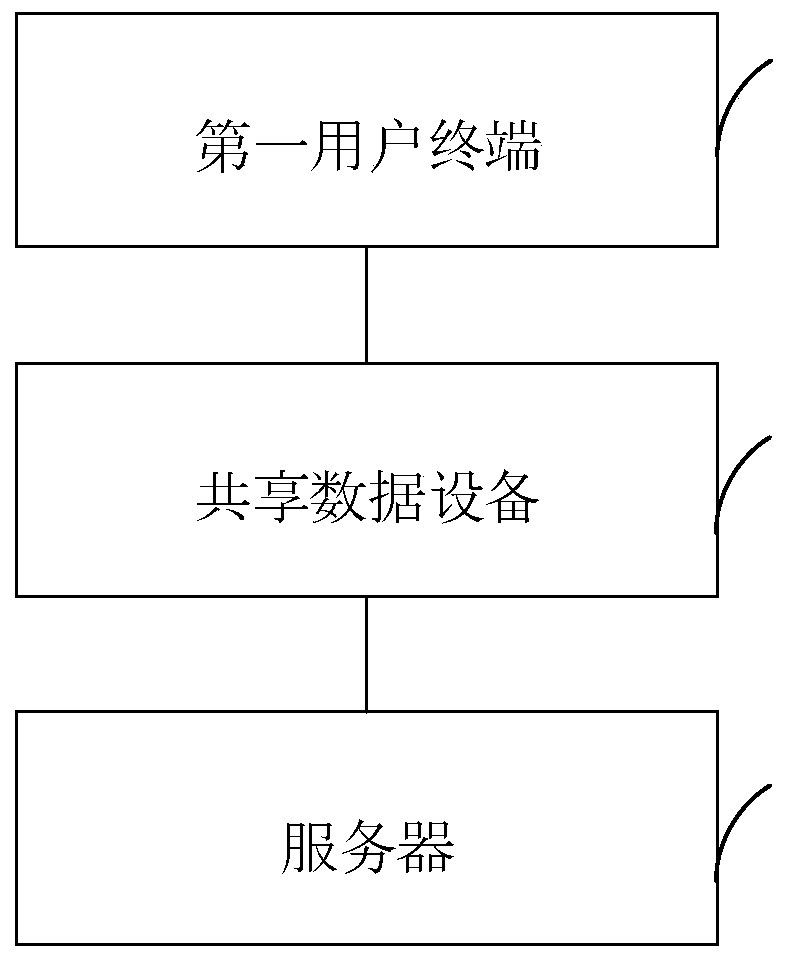
InactiveCN109962985AStrong privacyTransmissionSensing by electromagnetic radiationComputer terminalData sharing
The embodiment of the invention discloses a data sharing system, a data sharing method, a data sharing device and data sharing equipment. The system comprises a first user terminal, the data sharing equipment and a server, wherein the data sharing equipment comprises a carrier and an identification area arranged on the carrier; wherein the identification area comprises a unique code which can be identified by a user terminal; and the first user terminal obtains and identifies the unique code, and stores the shared data shared by the first user terminal in the server in association with the unique code. The method has the characteristics of environmental protection, no dependence on power supply of a user terminal and high privacy.
Owner:巩傅鹏
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com