Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Reduce the chance of misconfiguration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
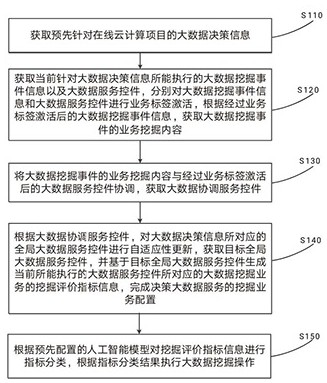
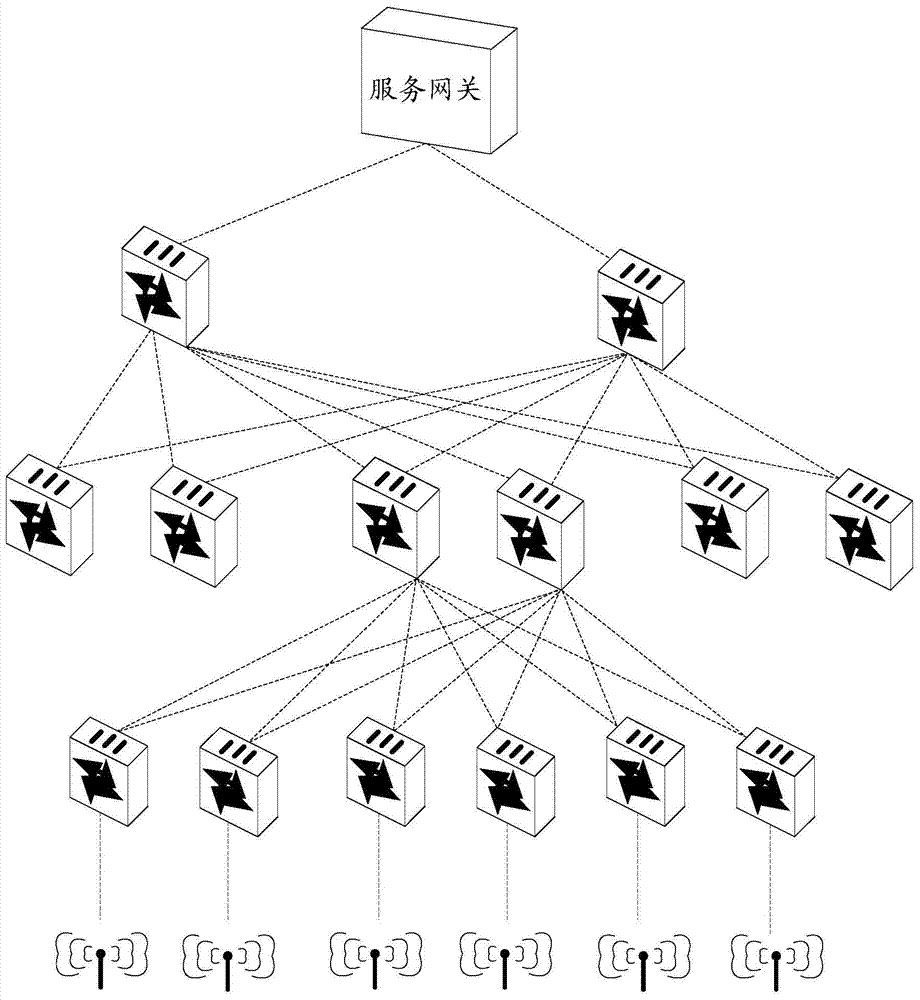
Big data processing method based on artificial intelligence and cloud computing and cloud service center
ActiveCN112163156AOvercome error-prone situationsReduce the chance of misconfigurationText database queryingSpecial data processing applicationsService controlService configuration
The embodiment of the invention provides a big data processing method based on artificial intelligence and cloud computing and a cloud service center, and the method comprises the steps: carrying outthe coordination of big data mining event information activated by a business label and a big data service control activated by the business label, and obtaining a big data coordination service control; therefore, the executable big data service control is optimized. The big data mining event information and the big data service control are coordinated, so that the condition that the big data service control is easy to make mistakes in a business scene of big data service process initialization can be overcome, and business adaptation of big data mining business in the big data service controlis achieved, in addition, a target global big data service control with global consistency can be obtained, so that mining service configuration of decision big data services is completed, and the service configuration error probability of online cloud computing projects in the use process is reduced.
Owner:青岛仁科信息技术有限公司
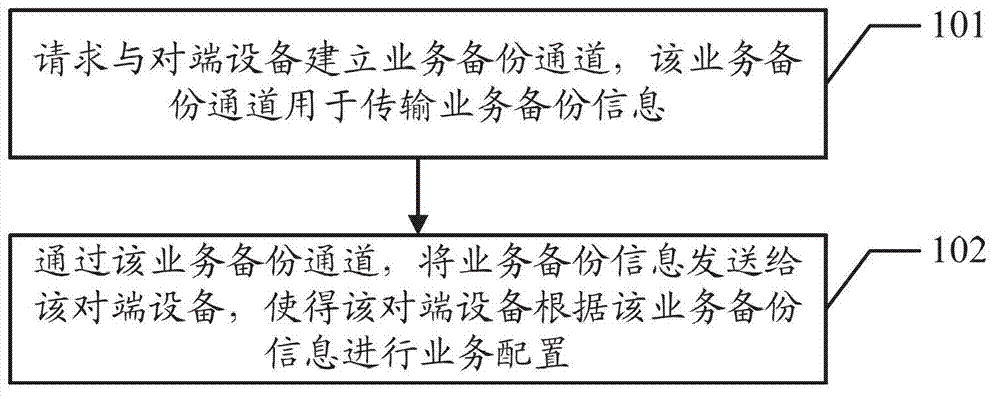
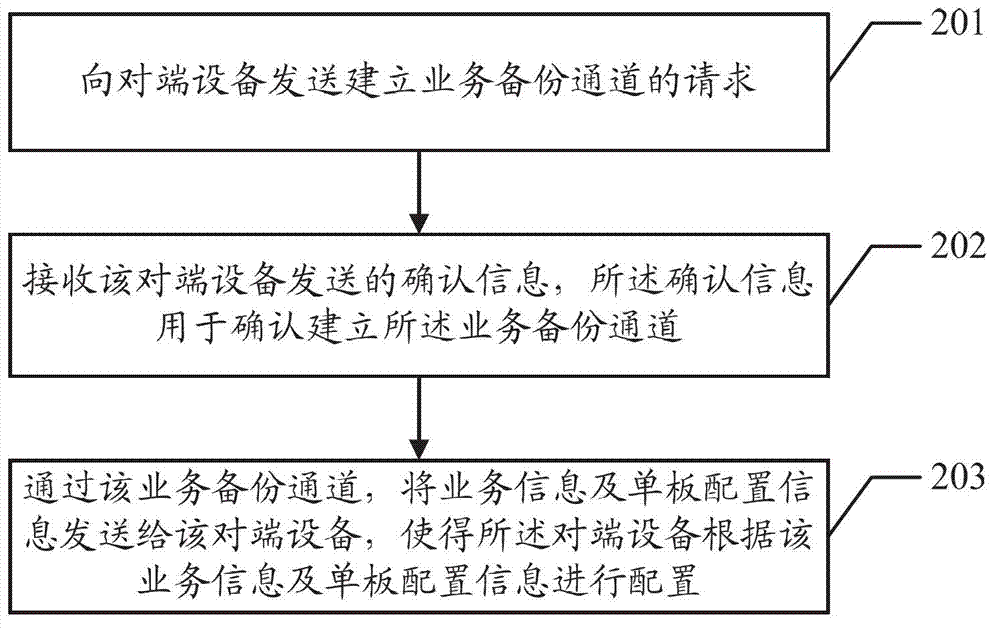
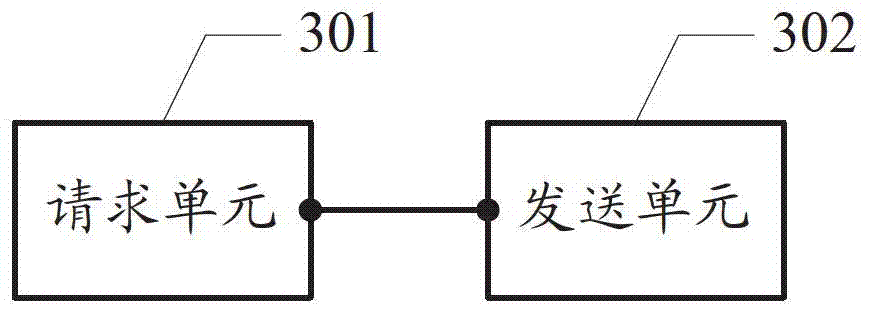
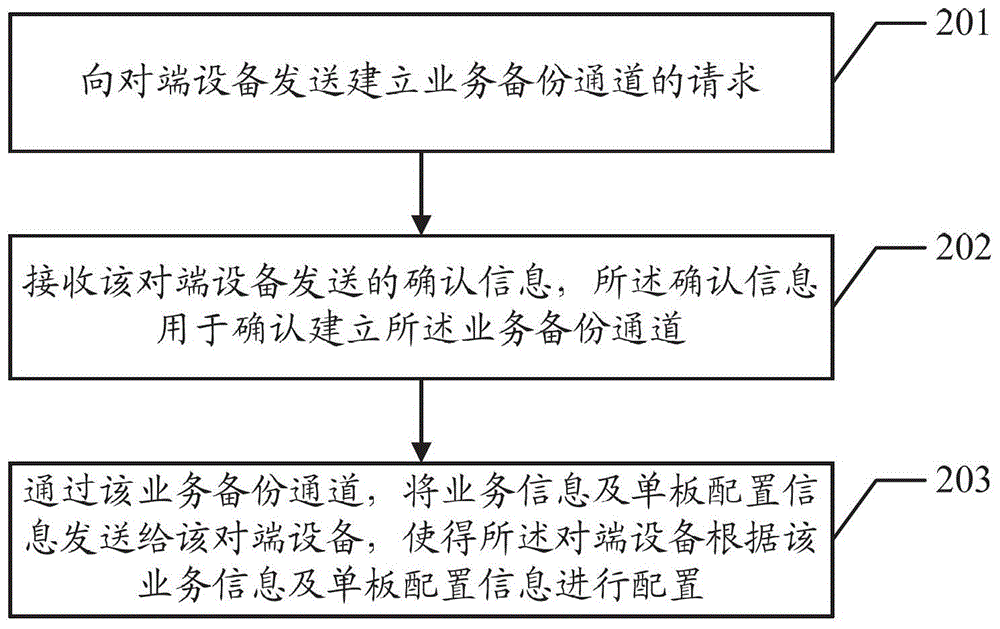
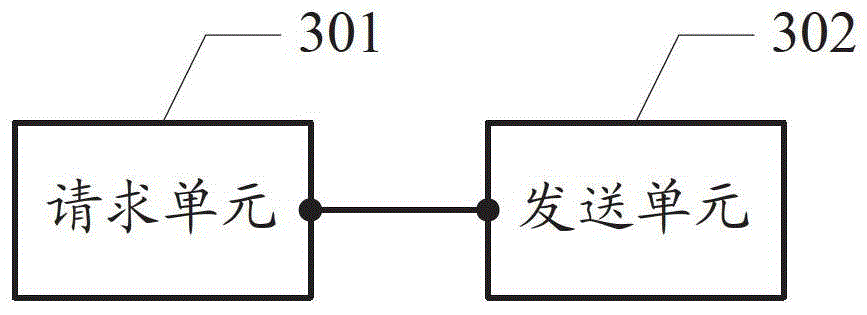
Inter-machine business backup method, device and system
InactiveCN102907037AImplement backupReduce the chance of misconfigurationData switching networksSynchronising arrangementMulti machineBusiness data
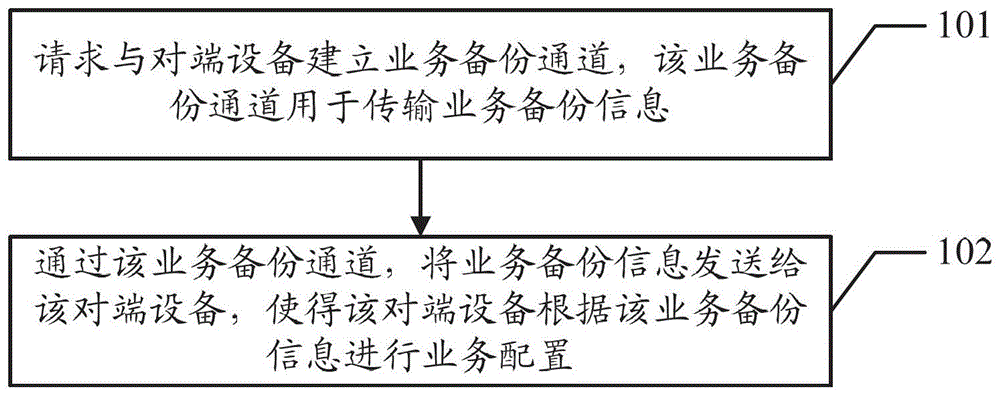
Embodiments of the invention disclose an inter-machine business backup method, a device and a system, which are used to perform automatic synchronous configuration among main backup devices under the multi-machine backup background and to carry out business data backup. The method comprises requesting the establishment of a business backup channel with an opposite-end device, wherein the business backup channel is used to transmit the business backup information; and sending the business backup information to the opposite-end device by means of the business backup channel so that the opposite-end device configures according to the business backup information.
Owner:HUAWEI TECH CO LTD
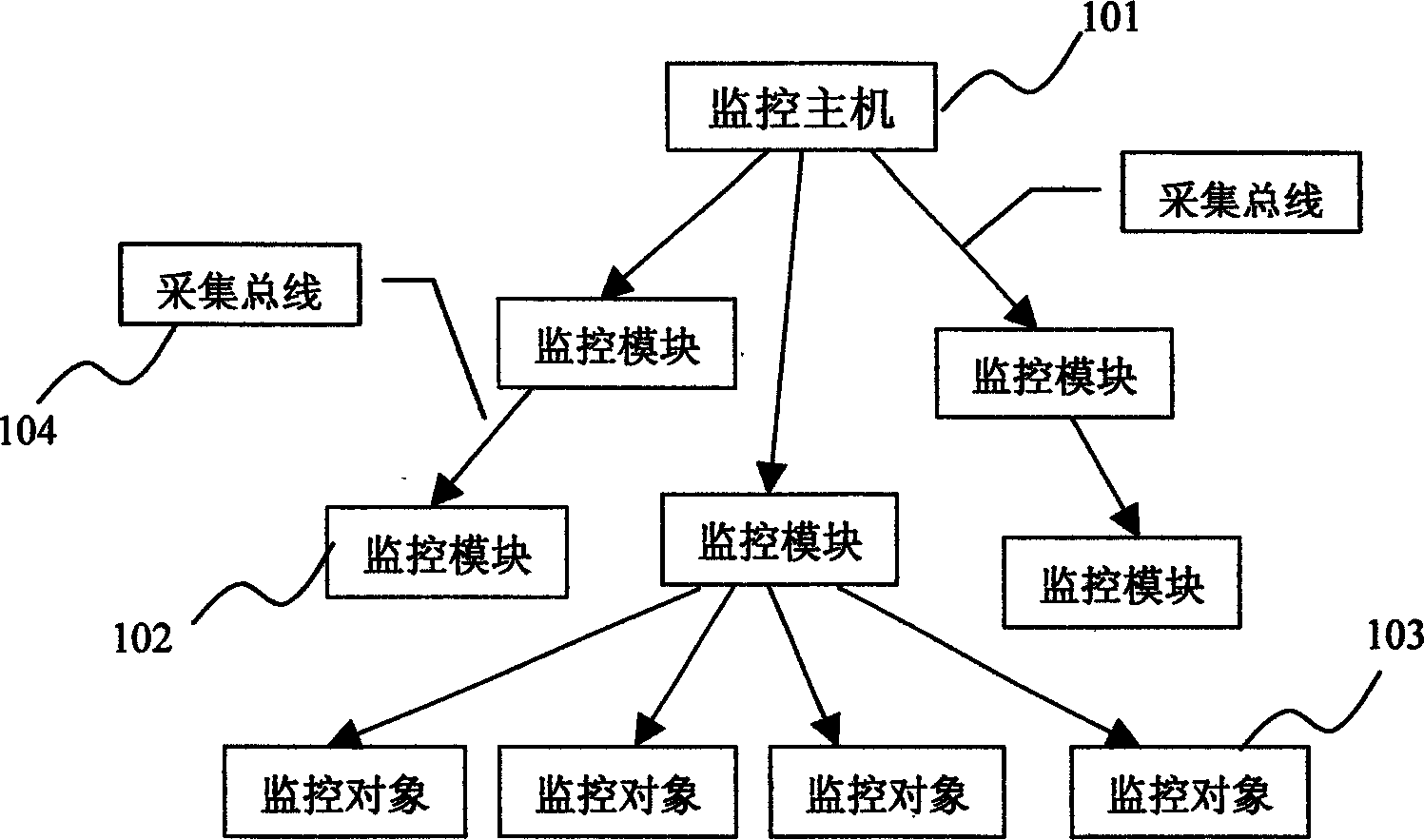
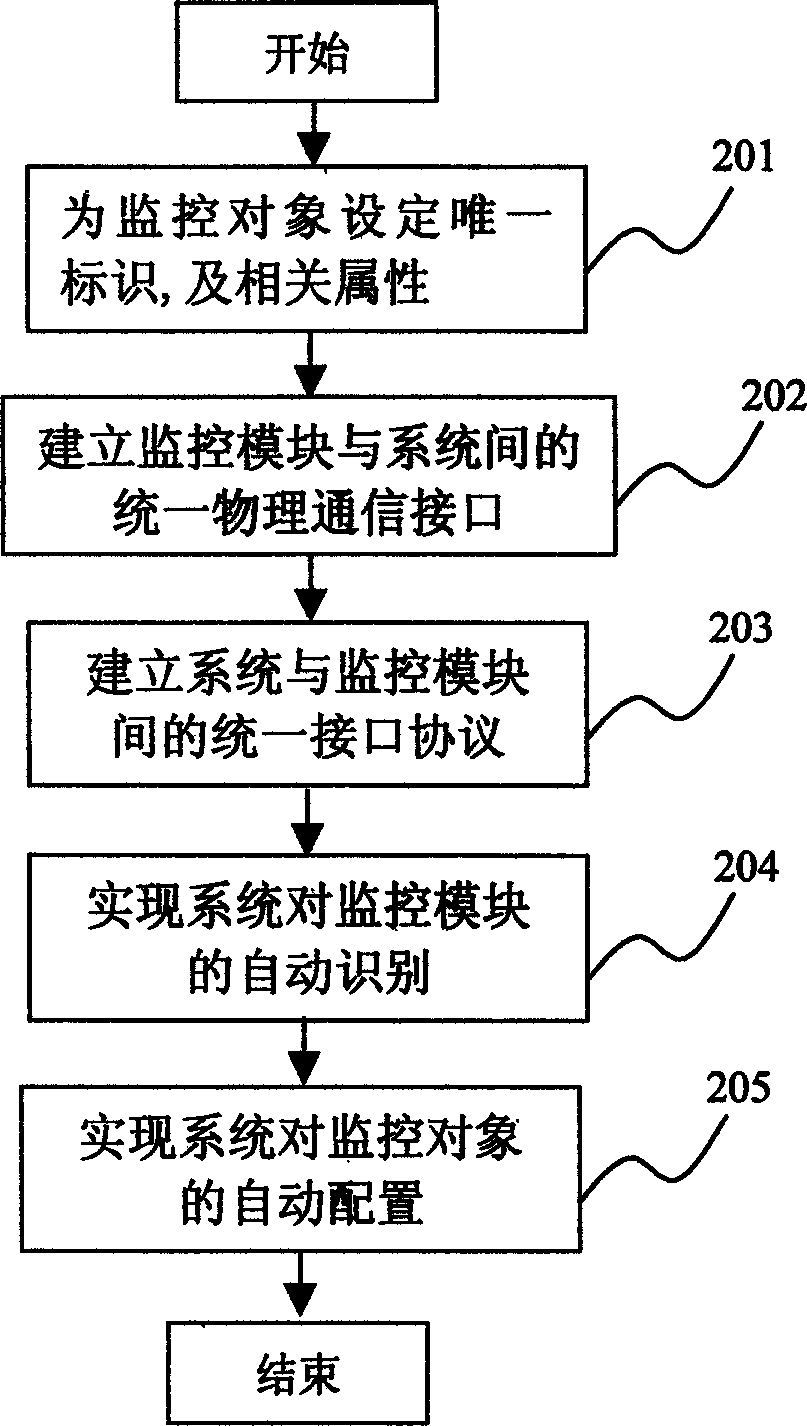
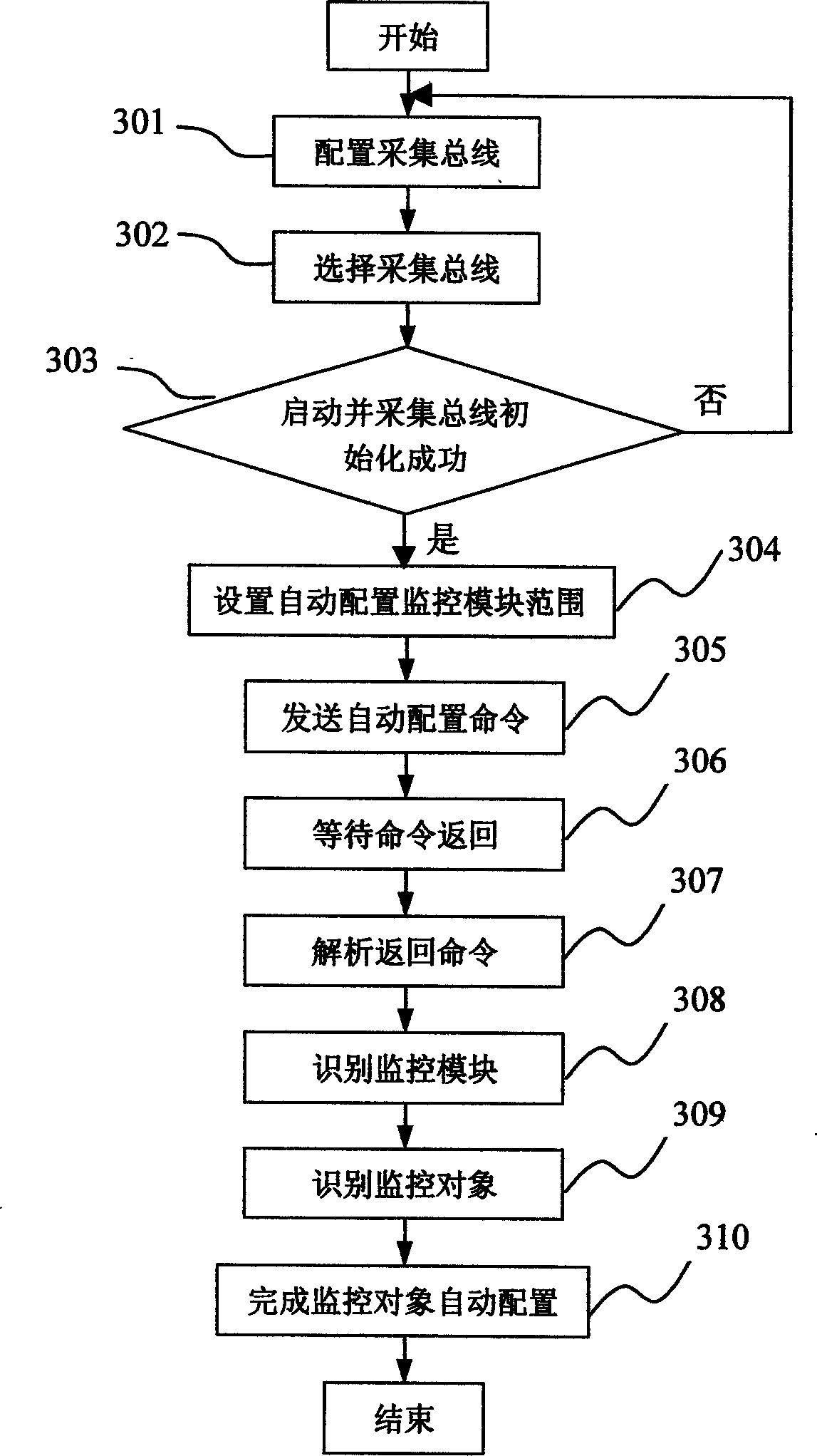
Dynamic layout method of power environment monitoring system
InactiveCN1538644AReduce the degree of manual interventionImprove configuration management efficiencyTransmission monitoringCommunication interfaceMonitoring system
The method of dynamic configuration of power environment monitor system includes setting unique id and related properties for monitored object corresponding to a monitored point; set-up unified physical communication interface between monitoring module and system; set-up unified interface protocol between monitoring module and system; realizing automatic recognizing monitoring module and automatic configuring monitored object by system. The method lowers degree of manual intervention in operating, raises configuration and management efficiency and reduces umstabilizing factor brought by manual operation and error configuration, and save time.
Owner:ZTE CORP
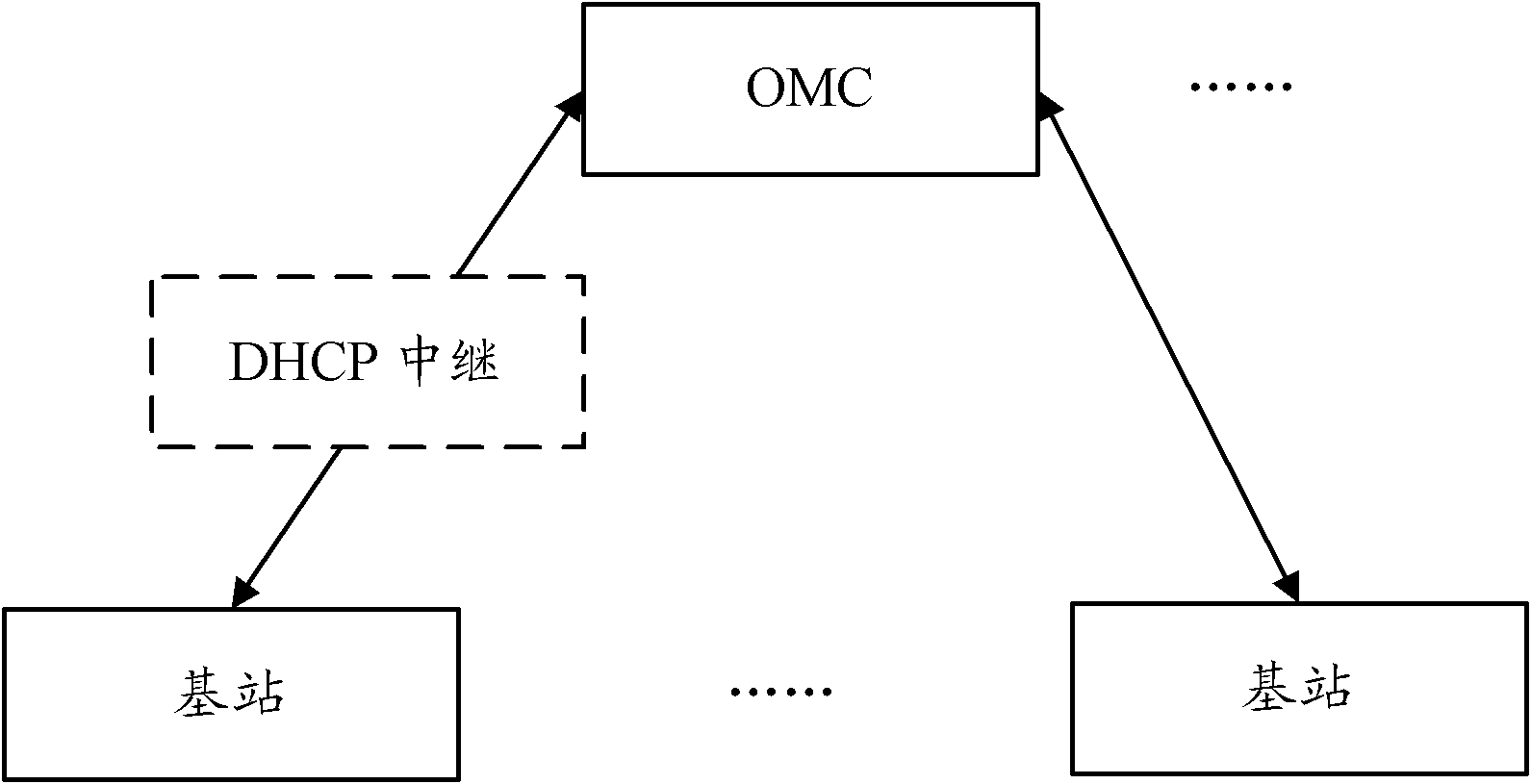
Self-configuration method and device of base station
ActiveCN102857953ASimplify the IP configuration processImprove execution efficiencyWireless communicationError ratioTelecommunications link
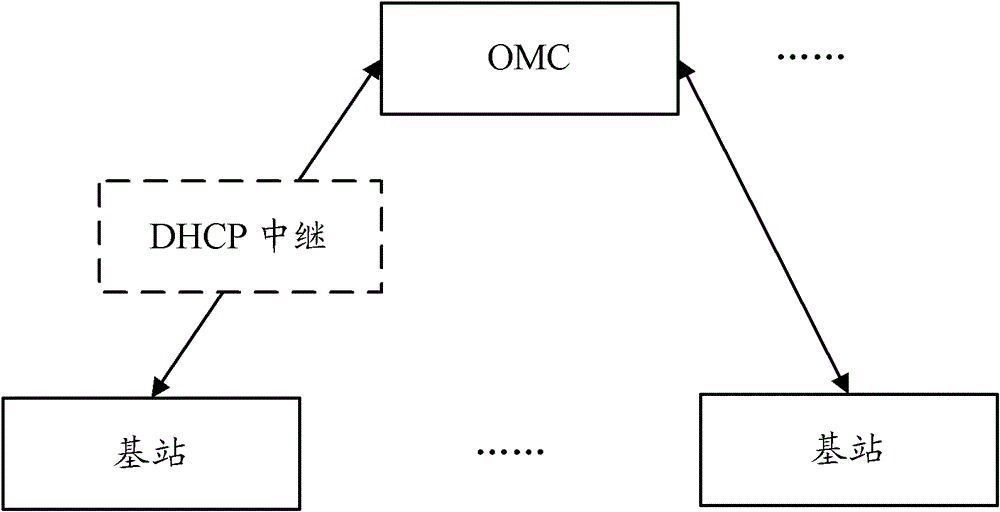
The invention provides a self-configuration method and a self-configuration device of a base station, which are used for improving the execution frequency of a configuration flow and reducing the complexity and the configuration error rate of the configuration flow. The method comprises the steps that a system adopts an OMC (Operation Maintenance Center) to replace a DHCP (Dynamic Host Configuration Protocol) server; a base station can prevent the DHCP server from directly obtaining an IP (Internet Protocol) parameter from the OMC, so as to simplify an IP configuration flow of the base station, improve the execution frequency of the configuration flow, and reduce the execution complexity of the configuration flow; and communication link interrupt caused by the IP parameters configured by the DHCP server and inconsistent IP parameters configured by the OMC is avoided, the configuration error rate is effectively reduced, and the system performance is improved.
Owner:ZTE CORP
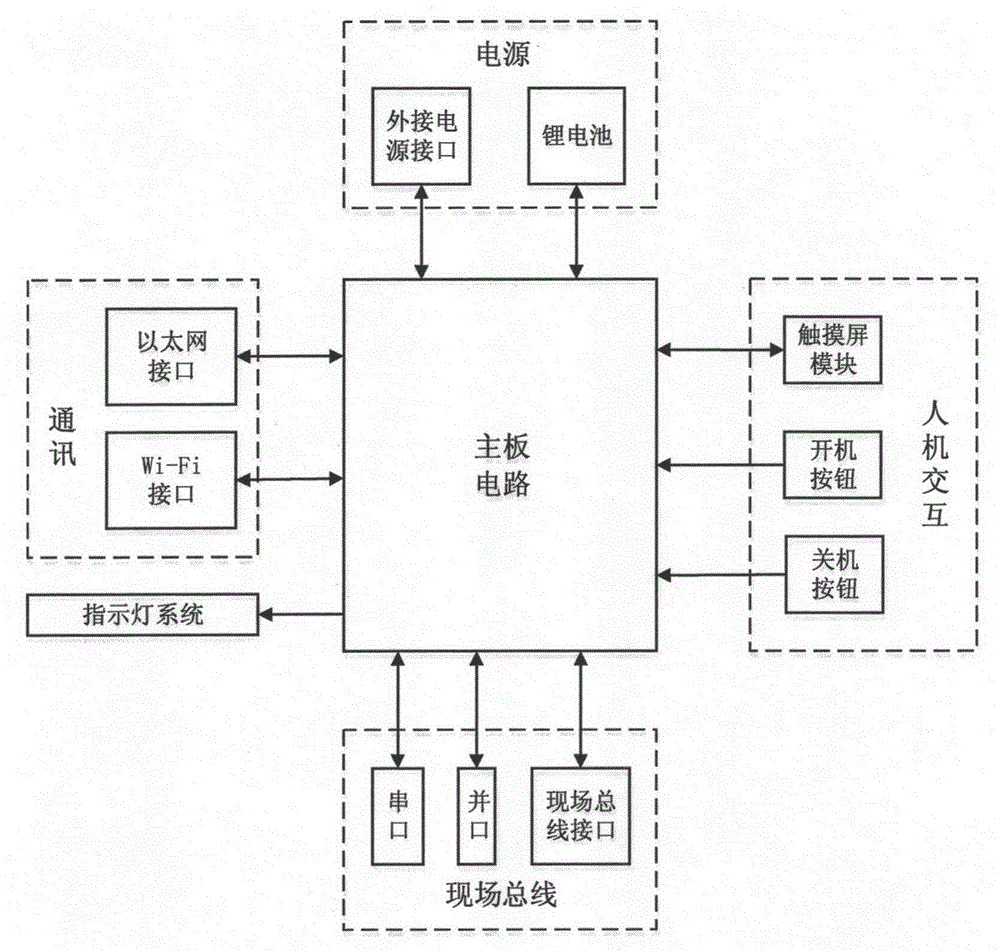
Intelligent industrial network protocol wireless converter
InactiveCN104932373ASimplify intelligent configurationSimplify related configuration workProgramme controlComputer controlIndustrial networkComputer device
The invention discloses an intelligent industrial network protocol wireless converter, comprising a main board circuit. The main board circuit is connected to a power supply, a man-machine interactive circuit, an on-site bus interface and a circuit communication circuit; the power supply supplies power to the main board circuit; the man-machine interactive circuit is used for setting the working state of a converter; the on-site bus interface is used for controlling the communication between the on-site bus and the microprocessor; and the communication circuit is used for converting a signal transmitted by the on-site bus to a wireless Wi-Fi signal. The intelligent industrial network protocol wireless converter can debug various on-site bus networks on the computer lacks of the one-site bus interface.
Owner:DONGHUA UNIV
Right management method and device, and server
ActiveCN108377228AImprove work efficiencyReduce the chance of misconfigurationTransmissionCollections dataDatabase
The invention discloses a right management method and device, and a server. The right management method comprises a right data collection step. The right data collection step comprises steps of S1. acquiring a first account waiting for right configuration; S2. searching a second account corresponding to the first account according to a preset rule; S3. acquiring right data of the second account; and S4. configuring right data of the first account according to the right data of the second account. Through adoption of the right management method and device and the server, a right manager can work more efficiently and reduce errors, and stalling phenomena are solved effectively.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Table batch processing method, system and device and storable medium
PendingCN110287459ATroubleshoot configuration issuesImprove efficiencyNatural language data processingSpecial data processing applicationsBatch processingComputer science
The invention relates to the technical field of data processing, and provides a table batch processing method, system and device and a storage medium, wherein the method comprises the steps of S110, generating a business table of a corresponding format according to a preset business demand; S120, carrying out pattern parameter identification on the cells in the business table, and classifying the cells of the business table according to the identified pattern parameters, wherein the pattern parameters of the cells of all the categories are the same; S130, configuring the style of each category of cells according to a preset service demand, wherein for each category of cells, one of the plurality of cells of the type is determined as a mode cell to carry out corresponding cell style configuration, and a cell format brush is called to uniformly refresh and configure the rest cells in the type for each cell of the configured mode cell according to the style of the mode cell. By utilizing the method, the problems of low table configuration efficiency, high error rate and the like in the prior art can be solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
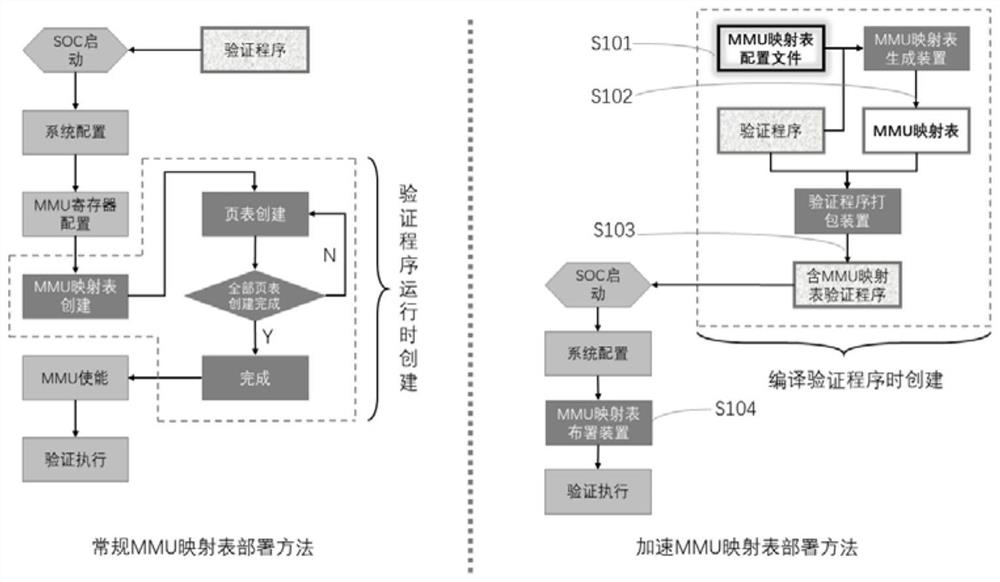
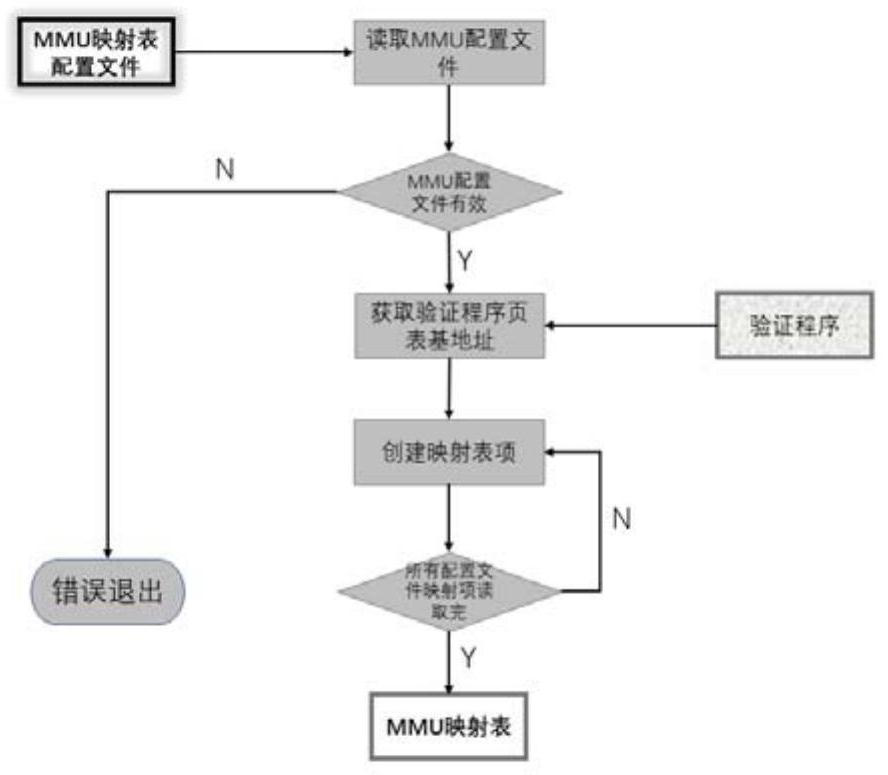
System and method for accelerating MMU mapping table deployment
PendingCN114239448AReduce creation timeReduce the chance of misconfigurationCAD circuit designSpecial data processing applicationsProgramming languageParallel computing
The invention provides a system and a method for accelerating MMU mapping table deployment. The system comprises an MMU mapping table generation device and a verification program packaging device which run on a verification program compiling server, and an MMU mapping table deployment device which runs on a target SOC; the MMU mapping table generation device is used for reading, analyzing and legality checking an MMU mapping table configuration file, and generating an MMU mapping table adaptive to the target SOC according to the MMU mapping table configuration file; the verification program packaging device analyzes an original verification program generated by compiling, obtains an MMU mapping table address specified by the verification program and maximum size information of an MMU mapping table, checks validity of the size of the MMU mapping table adapted to a target SOC, and combines and packages the generated MMU mapping table adapted to the SOC and the verification program into a new verification program containing the MMU mapping table; and the MMU mapping table deployment device analyzes the MMU mapping table adapted to the target SOC, and completes deployment of the MMU mapping table on the target SOC.
Owner:SHANGHAI LINKCHIP SEMICON TECH CO LTD
Method and device for base station self-configuration
ActiveCN102857953BSimplify the IP configuration processImprove execution efficiencyWireless communicationTelecommunications linkSoftware engineering
Disclosed are a base station self-configuration method and device, so as to improve the execution efficiency of a configuration process and reduce the complexity of the configuration process and the configuration error rate. The method is: in a system, an OMC replaces a DHCP server. Therefore, a base station can dodge the DHCP server and directly obtain an IP parameter from the OMC, thereby simplifying the IP configuration process of the base station, improving the execution efficiency of the configuration process, and reducing the execution complexity of the configuration process. In addition, communication link interruption incurred by inconsistence between the IP parameter configured by the DHCP server and the IP parameter configured by OMC is avoided, thereby effectively reducing the configuration error rate and improving the system performance.
Owner:ZTE CORP
MCS configuration method and device, terminal equipment and network equipment
ActiveCN109818716AImprove instruction efficiencyReduce the chance of misconfigurationChannel coding adaptationSignalling characterisationComputer terminalData terminal equipment
The embodiment of the invention provides an MCS configuration method and device, terminal equipment and network equipment. The indication efficiency of an MCS can be improved. The method comprises thesteps that terminal equipment receives a first RRC signaling sent by network equipment, the first RRC signaling carries first indication information, and the first indication information is used forindicating the type of an MCS table; wherein under the condition that the first RNTI is configured, the type of the MCS table indicated by the first indication information does not comprise a first MCS table, and the first MCS table refers to an MCS table corresponding to the first DCI under the condition that the CRC of the first DCI is scrambled by the first RNTI.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
A method, device and system for business backup among multiple machines
InactiveCN102907037BImplement backupReduce the chance of misconfigurationData switching networksSynchronising arrangementMulti machineBackup
Disclosed are a method, device and system for service backup among multiple machines, which are used for automatically completing synchronization configuration and conducting service data backup among main backup devices in the scenario of multi-machine backup. The method comprises: requesting to establish a service backup channel with an opposite-end device, the service backup channel being used for transmitting service backup information; and through the service backup channel, sending the service backup information to the opposite-end device, so as to enable the opposite-end device to conduct configuration according to the service backup information.
Owner:HUAWEI TECH CO LTD
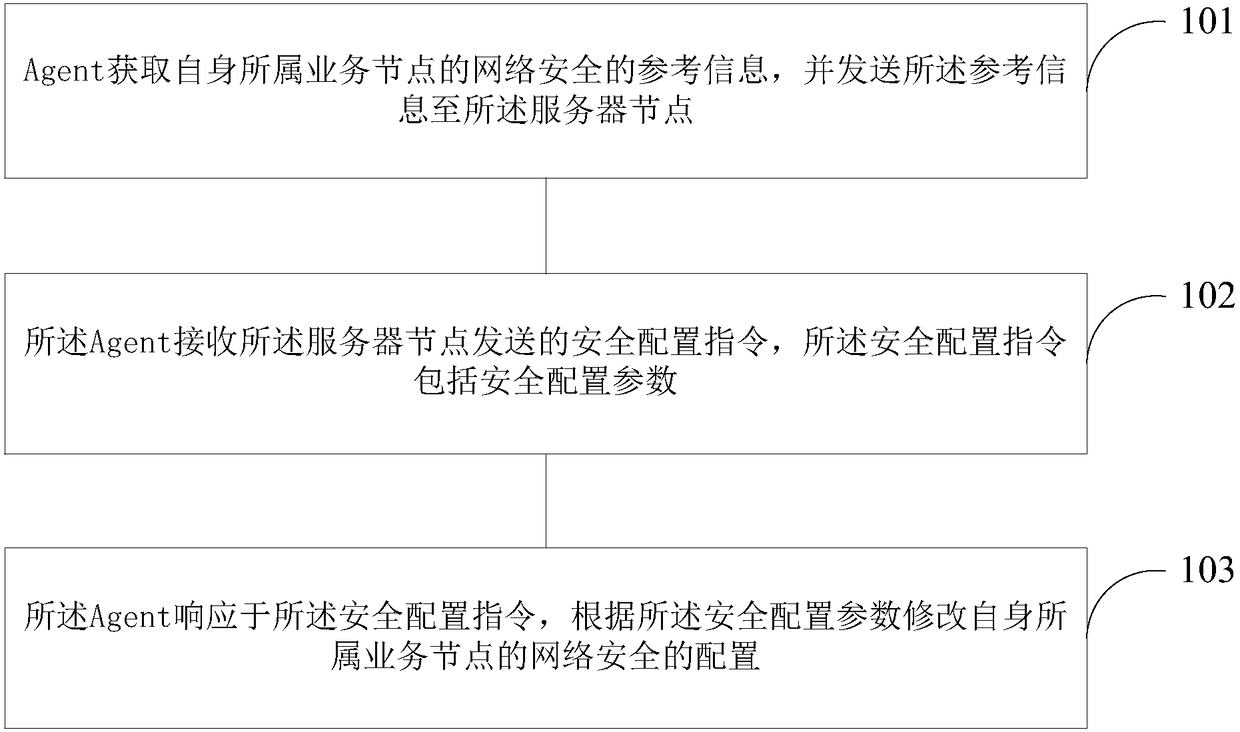
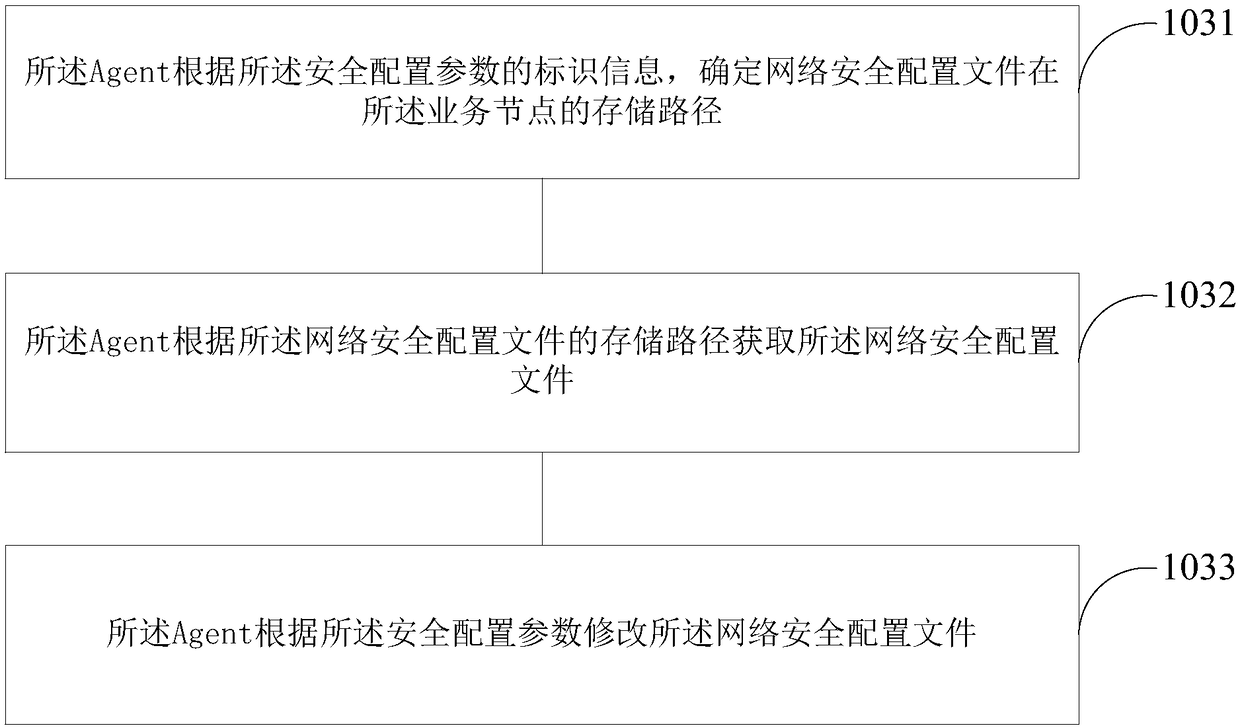
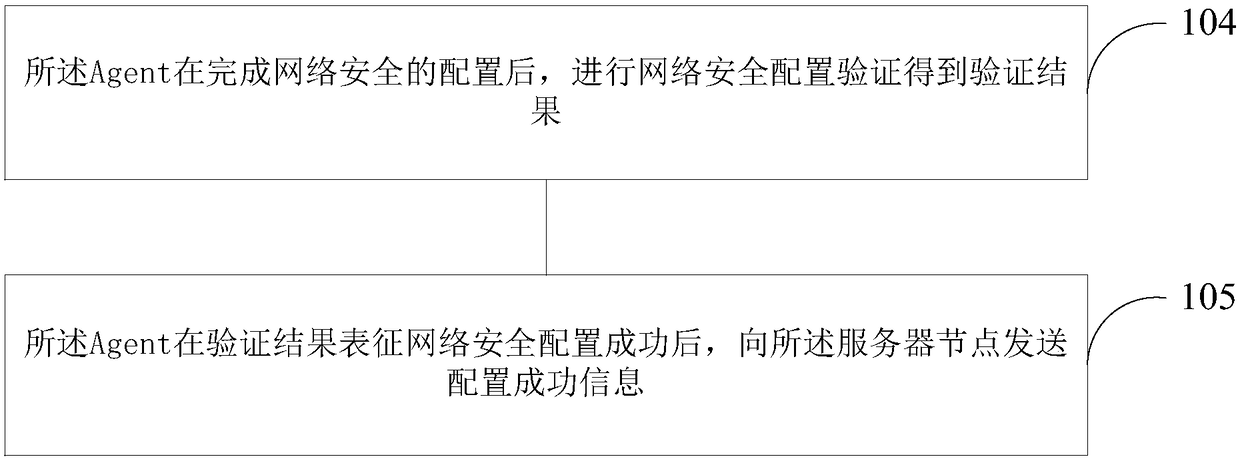
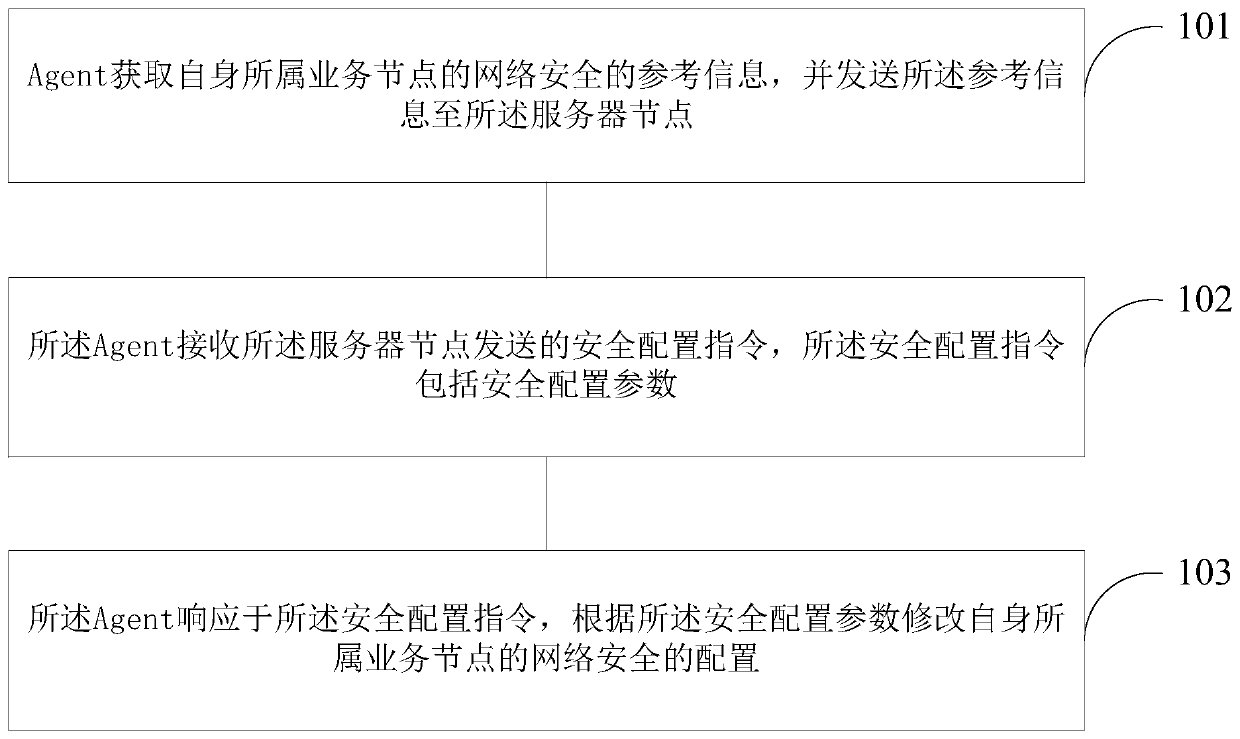
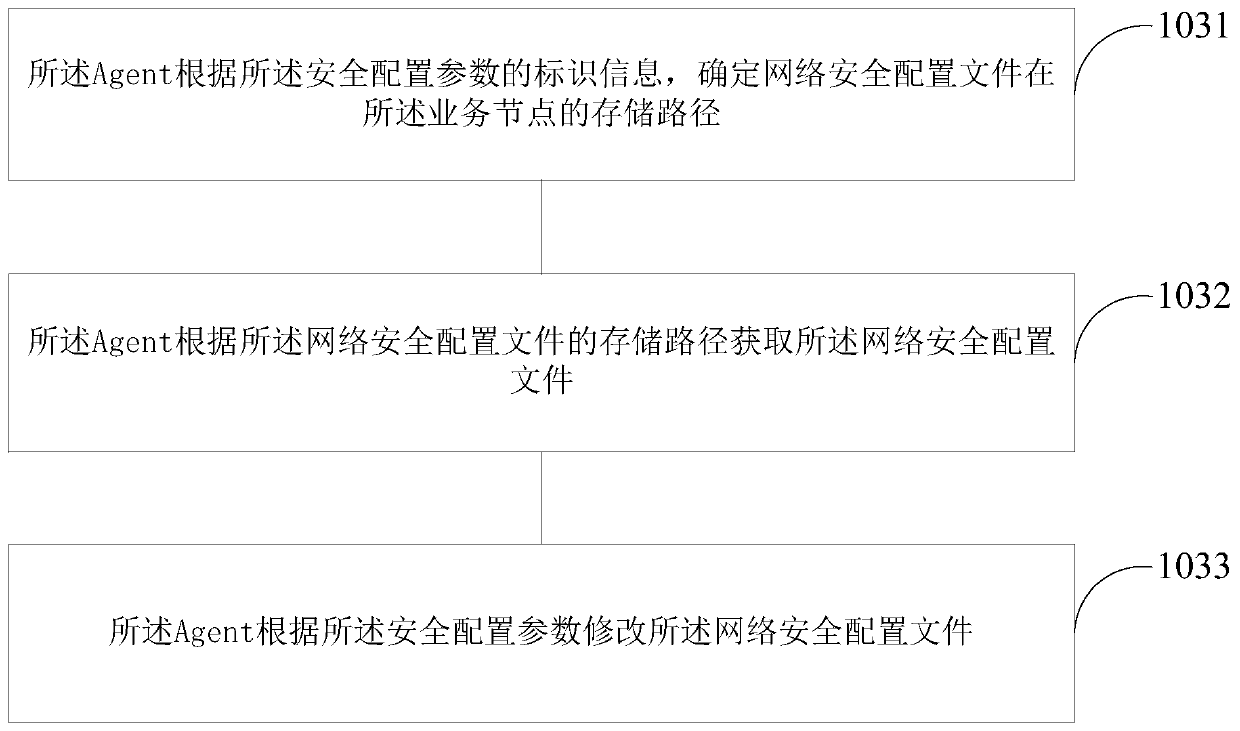
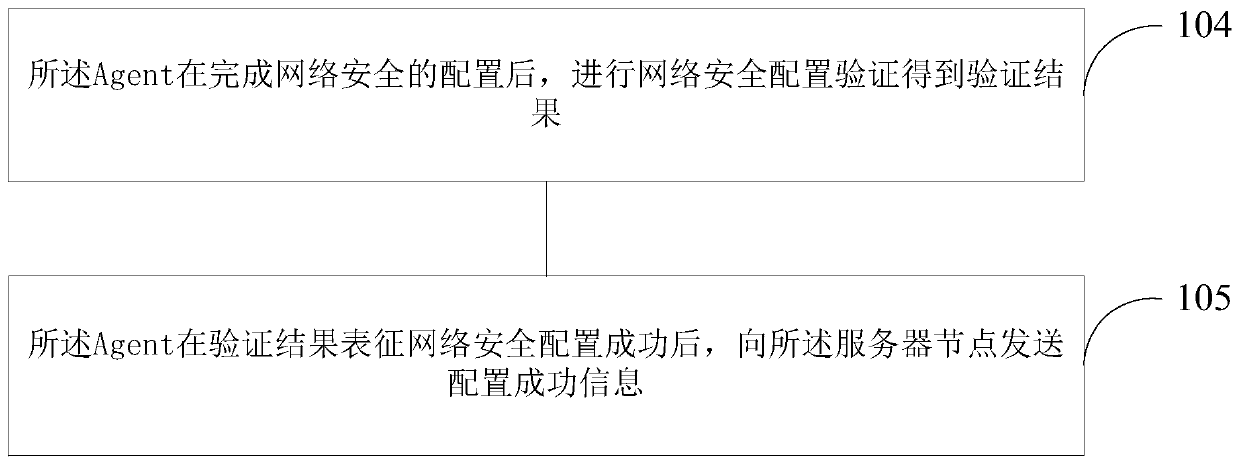
Network security configuration method and apparatus
ActiveCN108400897AImprove configuration efficiencyImprove reliabilityData switching networksBig dataNetwork security
The invention relates to a network security configuration method and apparatus. The method comprises the following steps: an Agent obtains reference information of network security of a service node to which the Agent belongs, and transmits the reference information to the server node; the Agent receives a security configuration instruction sent by the server node, wherein the security configuration instruction comprises a security configuration parameter; and the Agent modifies the configuration of the network security of the service node to which the Agent belongs according to the security configuration parameter in response to the security configuration instruction. According to the network security configuration method and apparatus provided by the embodiment of the invention, the configuration efficiency of network security can be greatly improved, human caused errors are avoided, the configuration error rate is reduced, and the reliability of a big data cluster is greatly improved.
Owner:NEW H3C BIG DATA TECH CO LTD
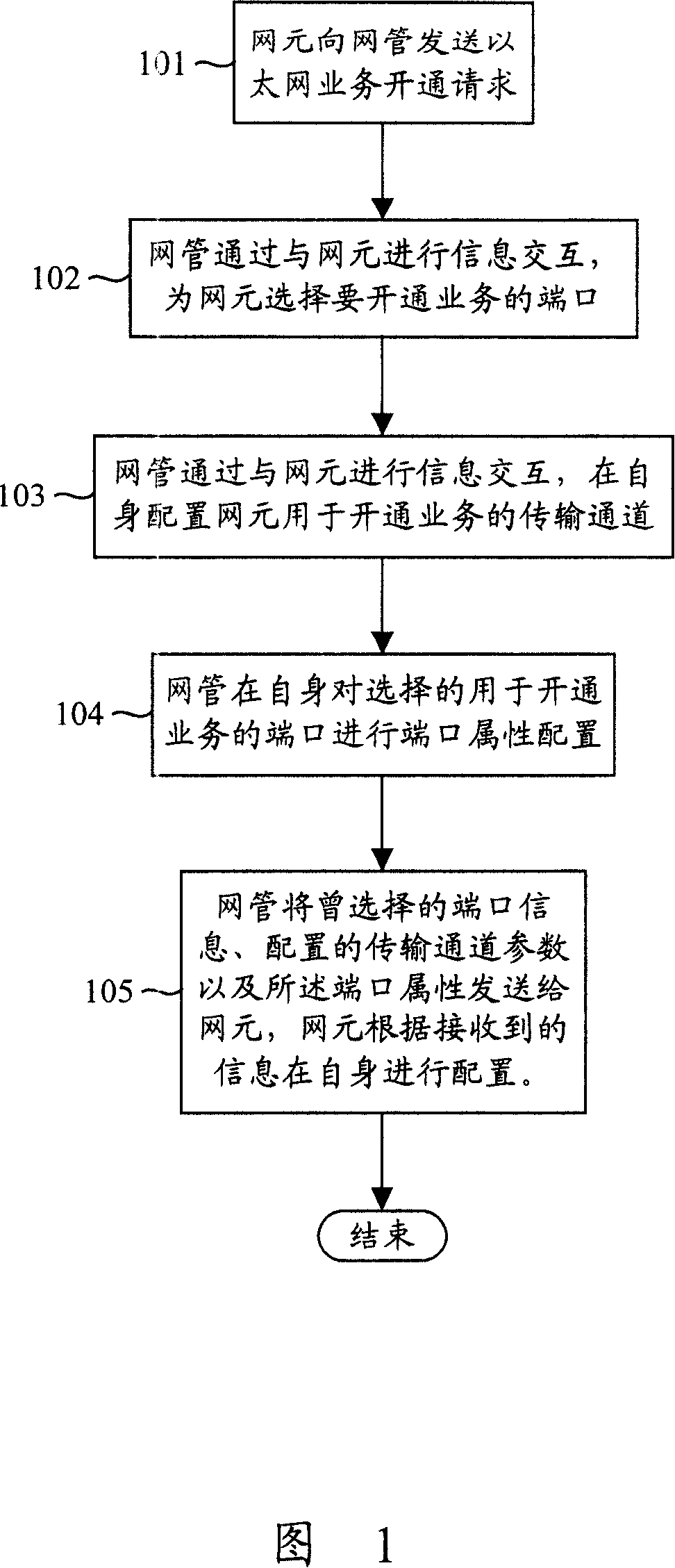
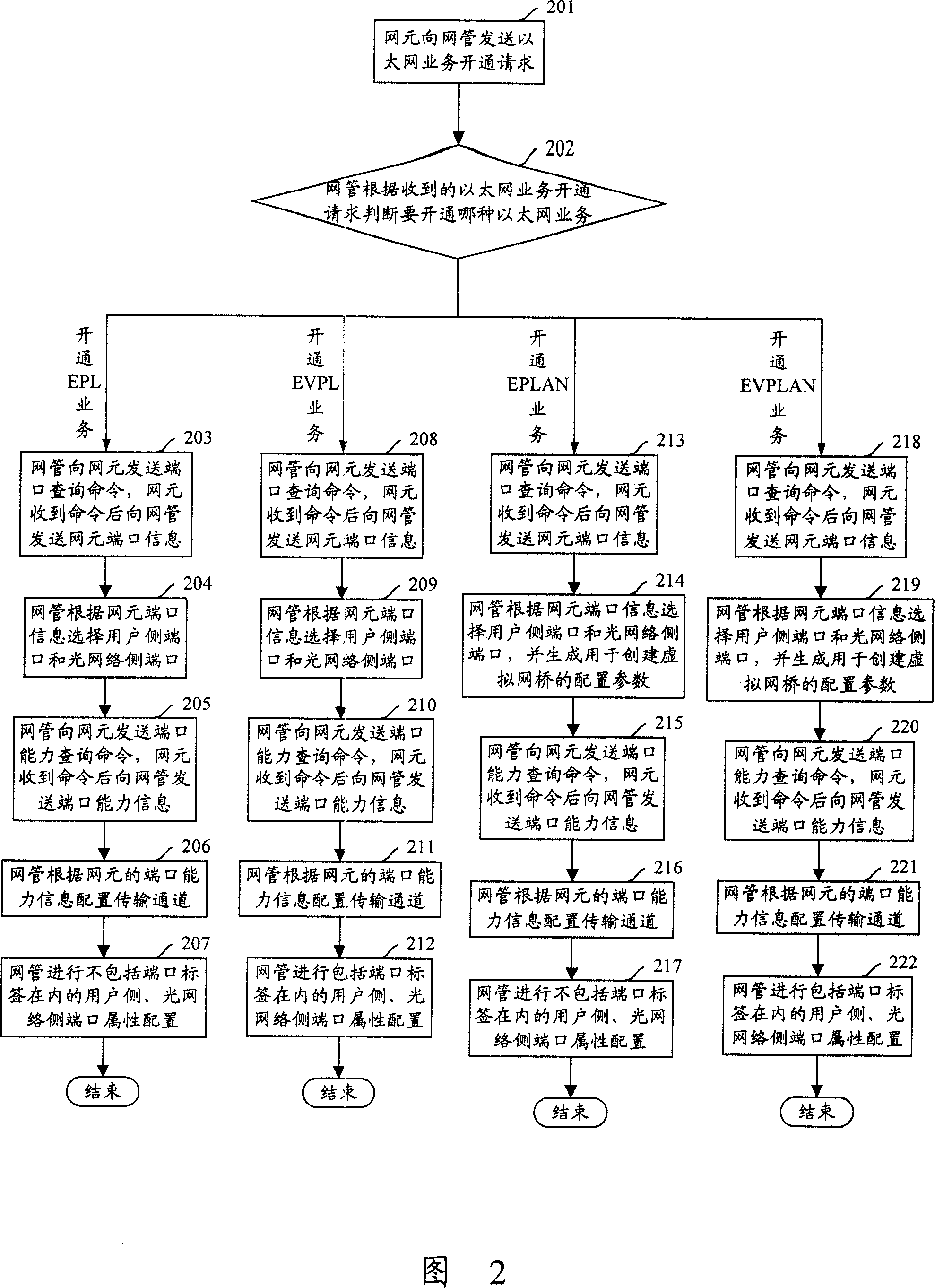
Method for opening Ethernet business
InactiveCN100365995CReduce complexityImprove activation efficiencyData switching by path configurationTransmission channelEngineering
A method for cutting in Ethernet service includes selecting user side port and optical network side port used for cutting in current Ethernet service by carrying out information interaction with network element after Ethernet service cutting in request from network element is received by network management, configuring transmission channel for cutting in service and port attribute of two said side ports by network management, sending port information and configured transmission channel information as well as port attribute to network element by network management for carrying out itself information configuration of network element.
Owner:SHANGHAI HUAWEI TECH CO LTD
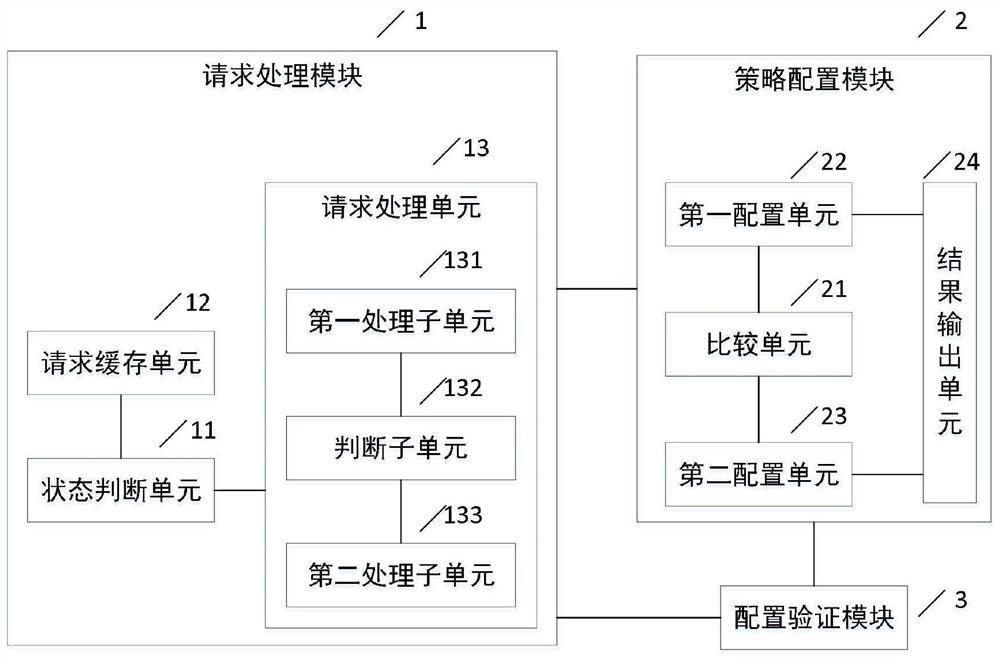
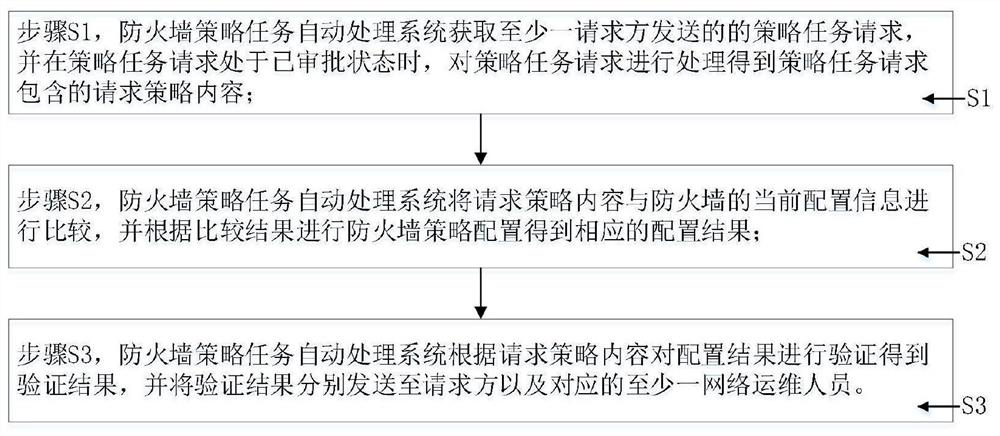
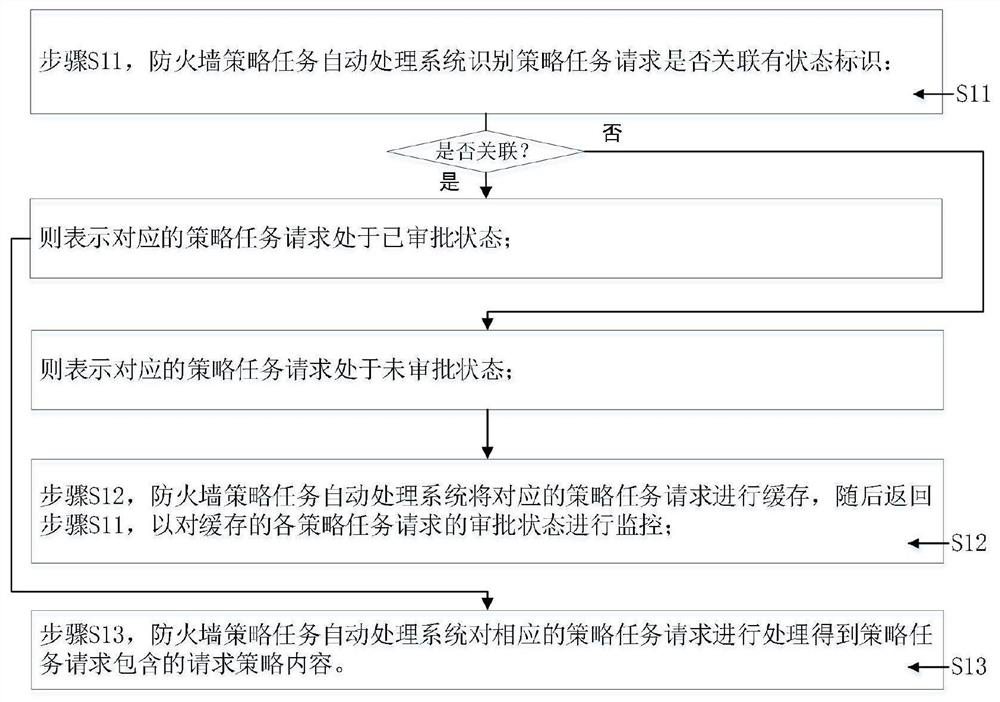
Firewall policy task automatic processing system and method
ActiveCN112787867AAvoid Duplicate Policy ConfigurationTimely communication and processingData switching networksAuto-configurationEngineering
The invention provides a firewall policy task automatic processing system and method, and relates to the technical field of process automation, and the system comprises a request processing module which is used for obtaining a policy task request sent by at least one requester, and when the policy task request is in an approved state, sending the policy task request to the requester, processing the strategy task request to obtain request strategy content contained in the strategy task request; a policy configuration module which is used for comparing the request policy content with the current configuration information of the firewall, and performing firewall policy configuration according to a comparison result to obtain a corresponding configuration result; and a configuration verification module which is used for verifying the configuration result according to the request strategy content to obtain a verification result, and sending the verification result to the requester and at least one corresponding network operation and maintenance person. The method has the beneficial effects that repeated policy configuration can be effectively avoided while automatic configuration of the firewall policy is realized, the configuration error rate of the firewall policy is reduced, and the time for network operation and maintenance personnel to execute repeated work is shortened.
Owner:SHANGHAI HANDPAY INFORMATION & TECH
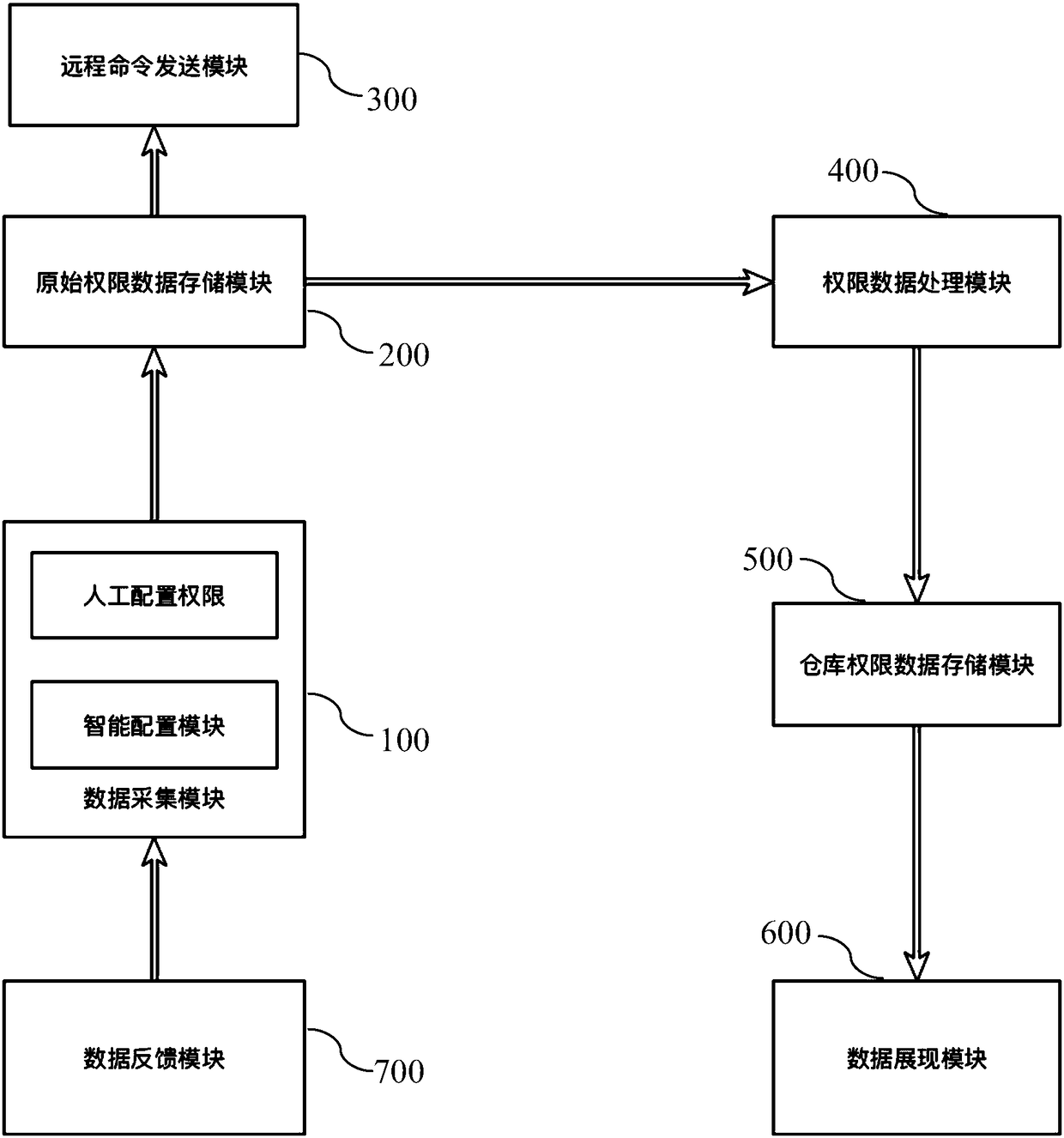
Authority management method, device and equipment and storage medium
PendingCN111310166AImprove configuration efficiencyReduce the chance of misconfigurationDigital data authenticationUser PrivilegeSoftware engineering
Owner:深圳手回科技集团有限公司
A kind of mcs configuration method and device, terminal equipment, network equipment
ActiveCN109818716BImprove instruction efficiencyReduce the chance of misconfigurationChannel coding adaptationSignalling characterisationComputer hardwareTerminal equipment
An embodiment of the invention provides an MCS configuration method and device, terminal equipment and network equipment, which can improve the indication efficiency of an MCS. The MCS configuration method comprises the steps that: the terminal equipment receives a first RRC signaling sent by the network equipment, the first RRC signaling carries first indication information, and the first indication information is used for indicating a type of an MCS table, wherein under the condition that a first RNTI is configured, the type of the MCS table indicated by the first indication information doesnot include a first MCS table, and the first MCS table refers to a MCS table corresponding to the first DCI under the condition that CRC of the first DCI is scrambled by the first RNTI.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
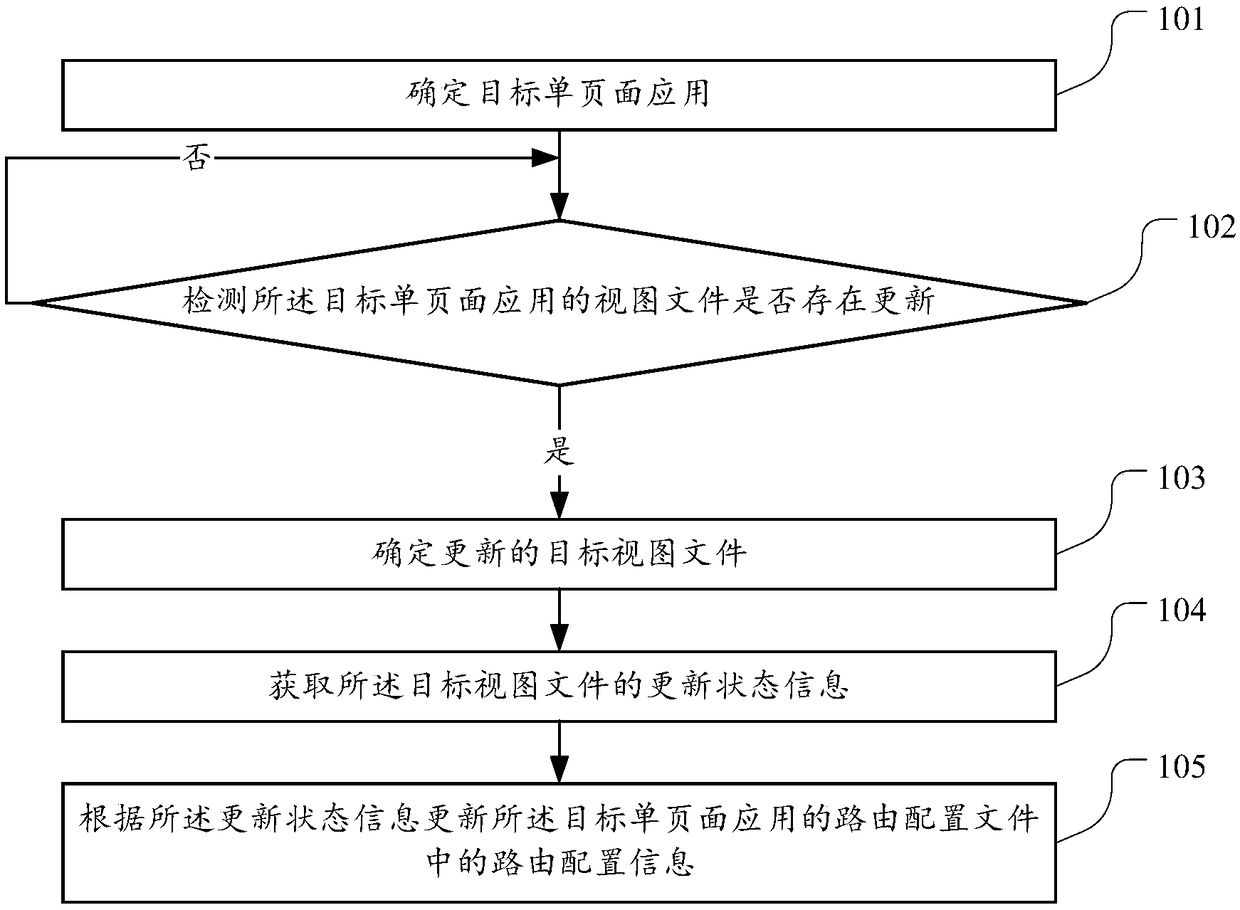
A routing configuration method and device for view files
ActiveCN107800562BReduce the chance of misconfigurationImprove update efficiencyWebsite content managementData switching networksTerminal equipmentOperating system
An embodiment of the present invention discloses a route configuration method for a view file, which is used to solve the problem of low efficiency in manually configuring routing information of a view file and prone to routing configuration errors. The method of the embodiment of the present invention includes: determining the target single-page application; detecting whether there is an update in the view file of the target single-page application; if there is an update in the view file of the target single-page application, determining the updated target view file; obtaining the updated target view file. Update status information of the target view file; update routing configuration information in the routing configuration file of the target single-page application according to the update status information. An embodiment of the present invention also provides a route configuration device for a view file.
Owner:PING AN TECH (SHENZHEN) CO LTD
Network security configuration method and device
ActiveCN108400897BImprove configuration efficiencyImprove reliabilityData switching networksEngineeringDistributed computing
Owner:NEW H3C BIG DATA TECH CO LTD
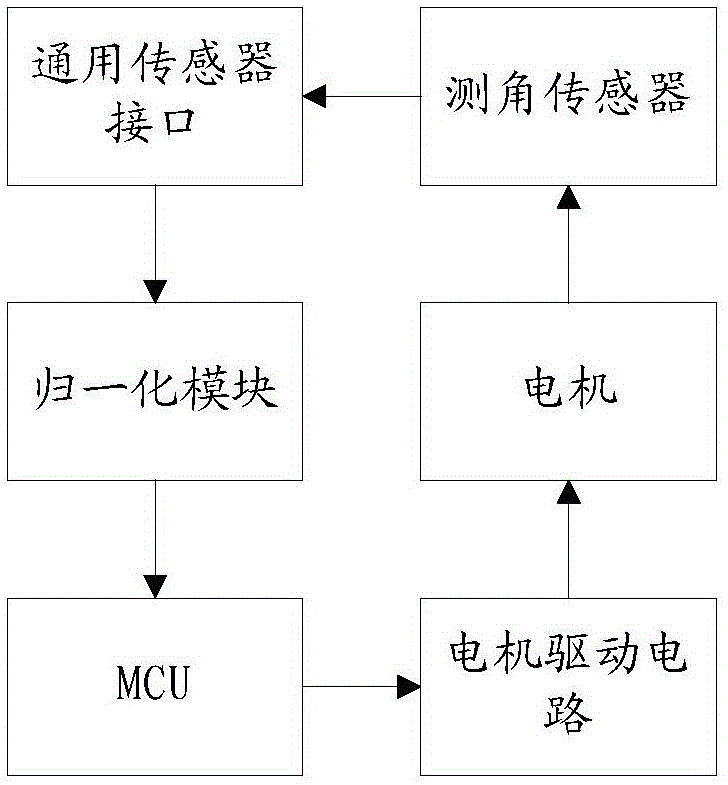
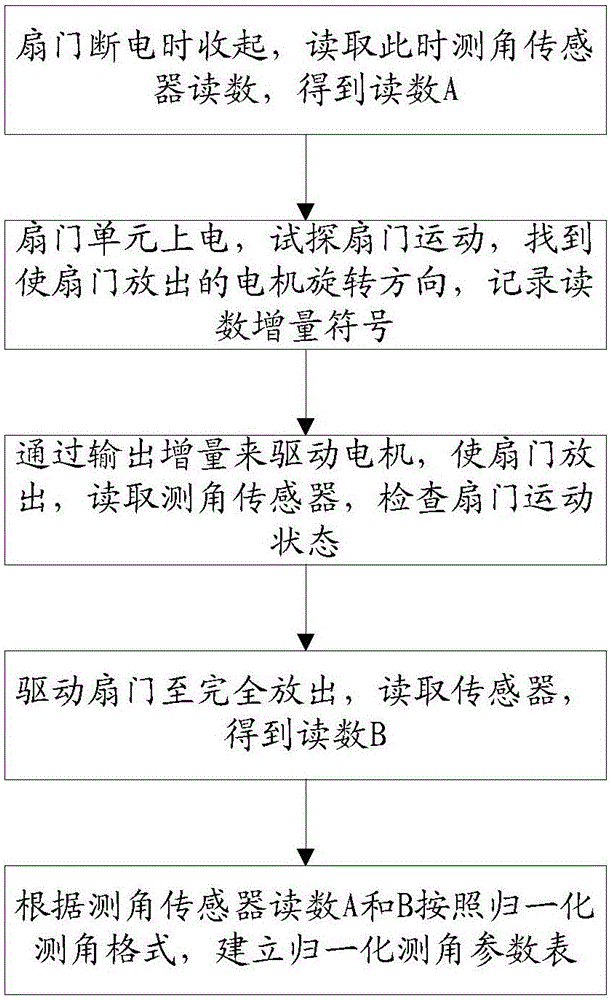
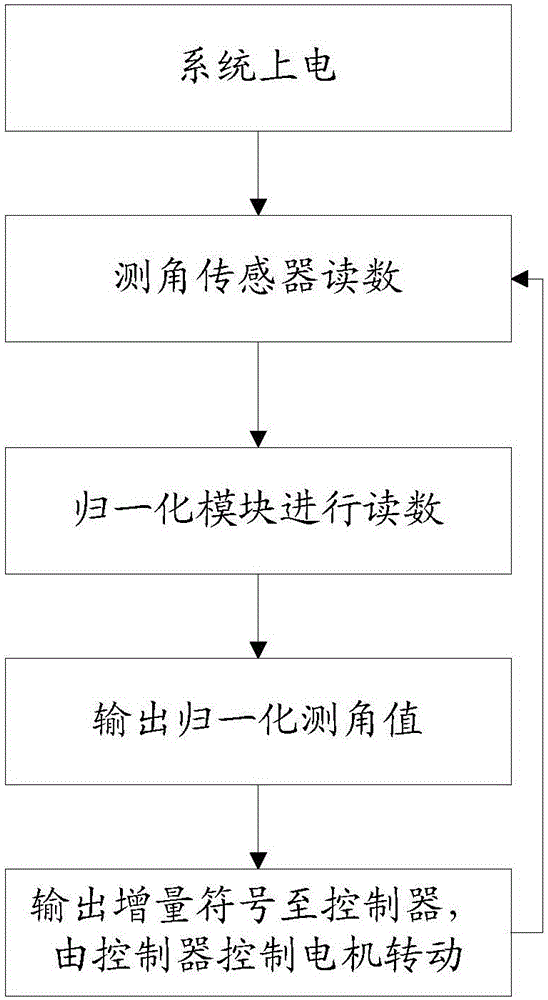
Door configuration system and method
ActiveCN103742020BImprove configuration efficiencyReduce the chance of misconfigurationPower-operated mechanismTransducerEmbedded system
The invention discloses a door sash configuration system. The door sash configuration system comprises a motor and a controller. An angle measurement transducer is installed on the motor. The door sash configuration system further comprises a universal transducer interface and a normalization module. The input end of the universal transducer interface is connected with the angle measurement transducer, and the output end of the universal transducer interface is connected with the normalization module. The normalization module is connected to the controller. The invention further discloses a door sash configuration method. The door sash configuration method includes the following steps that firstly, the system is powered on, the angle measurement transducer measures the angle of the motor, and an angle measurement value is input to the normalization module through the universal transducer interface; secondly, a normalization angle measurement parameter table is searched for a normalization angle measurement value corresponding to the currently acquired angle measurement value through the normalization module, and the found normalization angle measurement value is input to the controller; thirdly, the controller controls the motor to rotate according to the normalization angle measurement value. According to the door sash configuration system and method, calculation cost of the system is saved, and stability of the system and further improvement in the system are facilitated.
Owner:ZHEJIANG UNIV
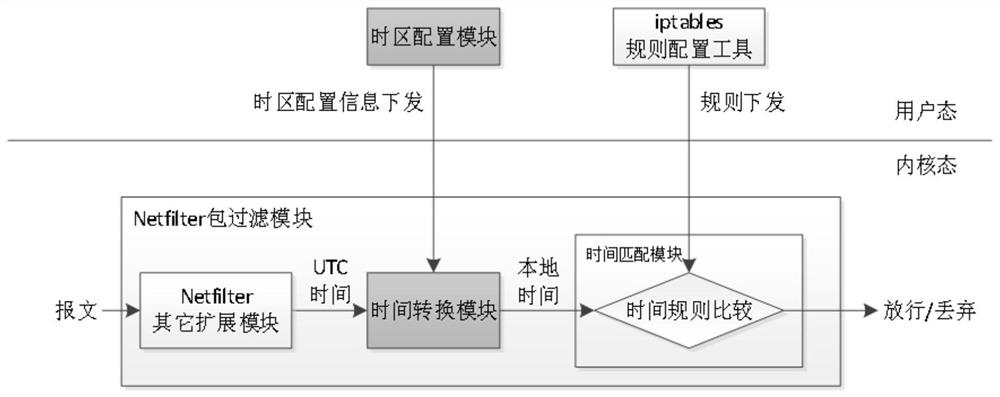
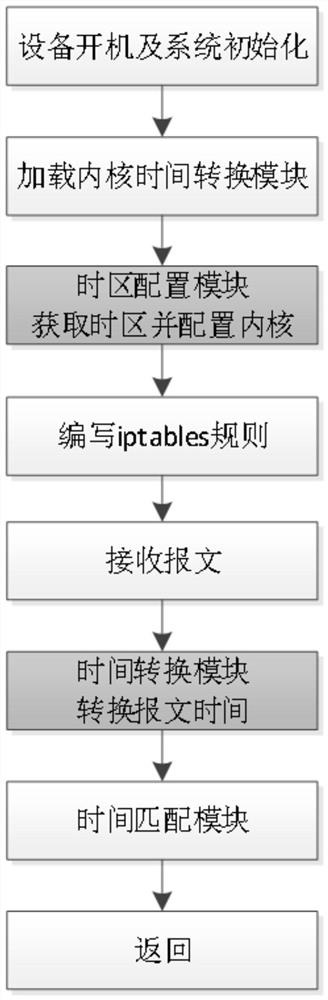
Method and terminal for enabling iptables rule to support local time
ActiveCN111901060ASimplify the difficulty of useImprove work efficiencyTime-division multiplexTransmissionOperational systemInit
The invention provides a method and a terminal for enabling an iptables rule to support local time. The method comprises the following steps of: initializing an operating system, and setting time of the operating system and time zone information of the operating system; acquiring the time of the operating system and the time zone information of the operating system in a user mode; configuring thetime zone information of the operating system to a kernel; setting the iptables rule of the firewall, wherein the iptables rule is a rule about expected time control, and the expected time IS set according to a time zone set by the operating system; receiving a message by means of the kernel; converting world unified time UTC in the message into the time in the time zone set by the operating system according to the configured time zone information by means of the kernel; matching the time obtained by conversion with the expected time to obtain a matching result by means of the kernel; and releasing or discarding the message according to the matching result and the iptables rule of the firewall. The method solves many problems in the prior art, greatly simplifies the use difficulty of the iptables firewall based on time control, improves the work efficiency, and reduces the probability of configuration errors.
Owner:BEIJING CHANGYANG TECH CO LTD
Method and system for obtaining bridge server number
ActiveCN110113556BReduce the chance of misconfigurationEasy to operateTelevision conference systemsTwo-way working systemsEngineeringServer
The embodiment of the present invention provides a method and a device for obtaining a bridging server number. Including: the bridging server receives the first conference number acquisition request and the second conference number acquisition request; according to the first conference number acquisition request and the second conference number acquisition request, acquires the first conference number and the second conference number in an idle state; The bridging server sends the first meeting number to the first regional video networking server, and sends the second conference number to the second regional video networking server; the first regional video networking server forwards the first conference number to the first Pamir software, and the second The regional video networking server forwards the second conference number to the second Pamir software; the first Pamir software connects the first regional terminal to the video networking conference according to the first conference number, and the second Pamir software connects the second regional terminal to the video conference according to the second conference number. Access video conference. The invention reduces the probability of number configuration errors.
Owner:VISIONVERA INFORMATION TECH CO LTD
Bridging server number acquisition method and device
ActiveCN110113556AReduce the chance of misconfigurationEasy to operateTelevision conference systemsTwo-way working systemsComputer terminalComputer science
The embodiment of the invention provides a bridging server number acquisition method and device. The method comprises the steps that a bridging server receives a first conference number obtaining request and a second conference number obtaining request; a first conference number and a second conference number in an idle state are obtained according to the first conference number obtaining requestand the second conference number obtaining request; the bridging server sends the first conference number to a first regional articulated naturality web server and sends the second conference number to a second regional articulated naturality web server; the first area articulated naturality web server forwards the first conference number to the first Pamir software, and the second area articulated naturality web server forwards the second conference number to the second Pamir software; and the first Pamir software accesses the first regional terminal to the Internet of videos conference according to the first conference number, and the second Pamir software accesses the second regional terminal to the Internet of videos conference according to the second conference number. The probabilityof number configuration errors is reduced.
Owner:VISIONVERA INFORMATION TECH CO LTD
A rights management method, device and server
The invention discloses a rights management method, device and server. The authority management method includes a step of collecting authority data: S1, obtaining a first account whose authority is to be configured; S2, retrieving a second account corresponding to the first account according to preset rules; S3, acquiring the authority of the second account data; S4, configuring the permission data of the first account according to the permission data of the second account. Through the authority management method, device and server, the present invention can improve the work efficiency of the authority administrator, reduce the error rate, and facilitate and effectively solve the stuck phenomenon.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
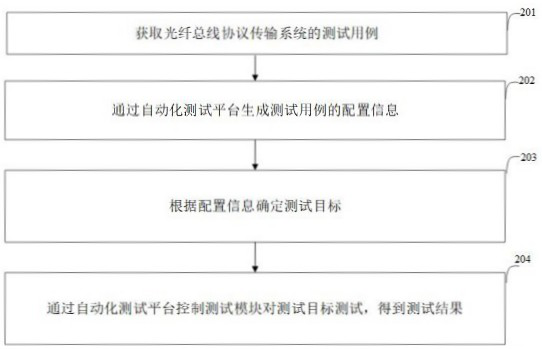
Method and device for automatically testing optical fiber bus protocol transmission system
InactiveCN113794513AImplement automated testingImprove test efficiencyElectromagnetic transmissionTest efficiencyTest platform
The invention discloses a method and a device for automatically testing an optical fiber bus protocol transmission system. The method comprises the following steps: acquiring a test case of the optical fiber bus protocol transmission system; generating configuration information of the test case through the automatic test platform; determining a test target according to the configuration information; and controlling the test module to test the test target through the automatic test platform to obtain a test result. The automatic test platform is used for testing the optical fiber bus protocol transmission system, so that the test efficiency is improved, and the configuration error rate is reduced; and comprehensive automation is realized.
Owner:BEIJING TASSON SCI & TECH CO LTD
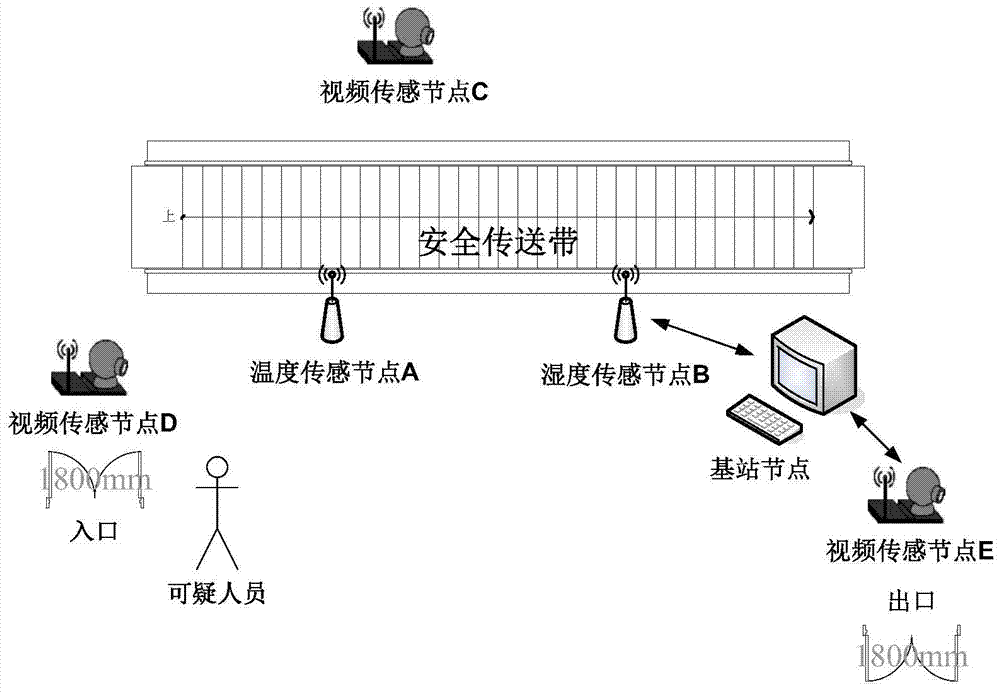
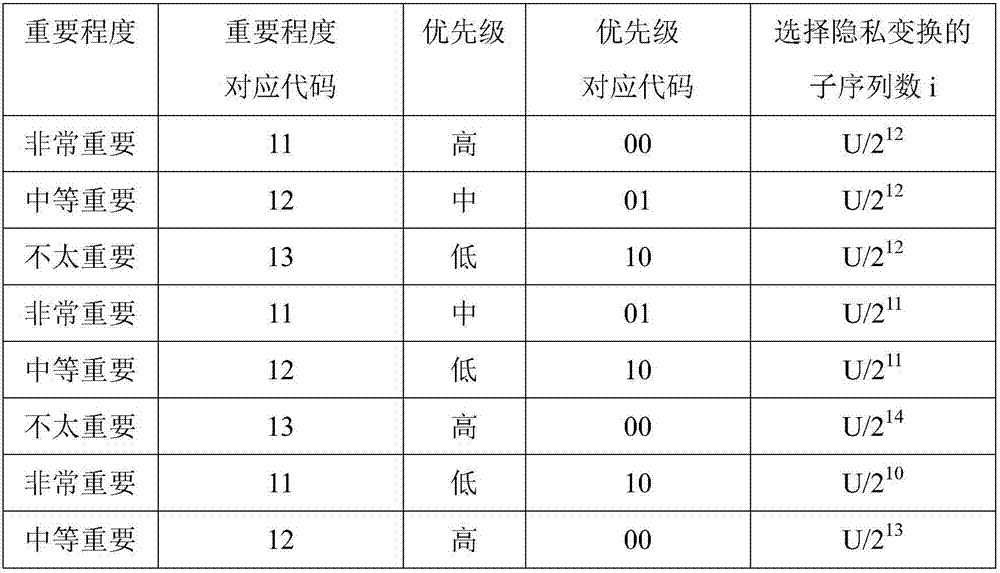
A priority-based data security communication method for ipv6 heterogeneous sensor networks
ActiveCN104219224BGuaranteed service qualityFully consider service qualityTransmissionSecure communicationSecure transmission
The invention provides a priority-based IPV6 heterogeneous sensor network data security communication method. Multimedia sensor nodes and scalar sensor nodes supporting the IPV6 protocol stack form a heterogeneous network, transmitted data are classified according to the importance and priority in different application environments, and the balance between data security transmission and network service quality is achieved through different encryption levels. The method can be applied to the field of airport public security control. According to the method, the data is distinguished according to the priority; compared with that all data are transmitted according to the uniform standard, the method has the advantages that the network service quality is considered fully, and energy consumption is reduced to the certain extent; partial privacy conversion and encryption transmission with importance distinguish are performed on the acquired data, the security is guaranteed, and the computation overhead and network load are reduced as compared with those of full encryption.
Owner:NANJING UNIV OF POSTS & TELECOMM
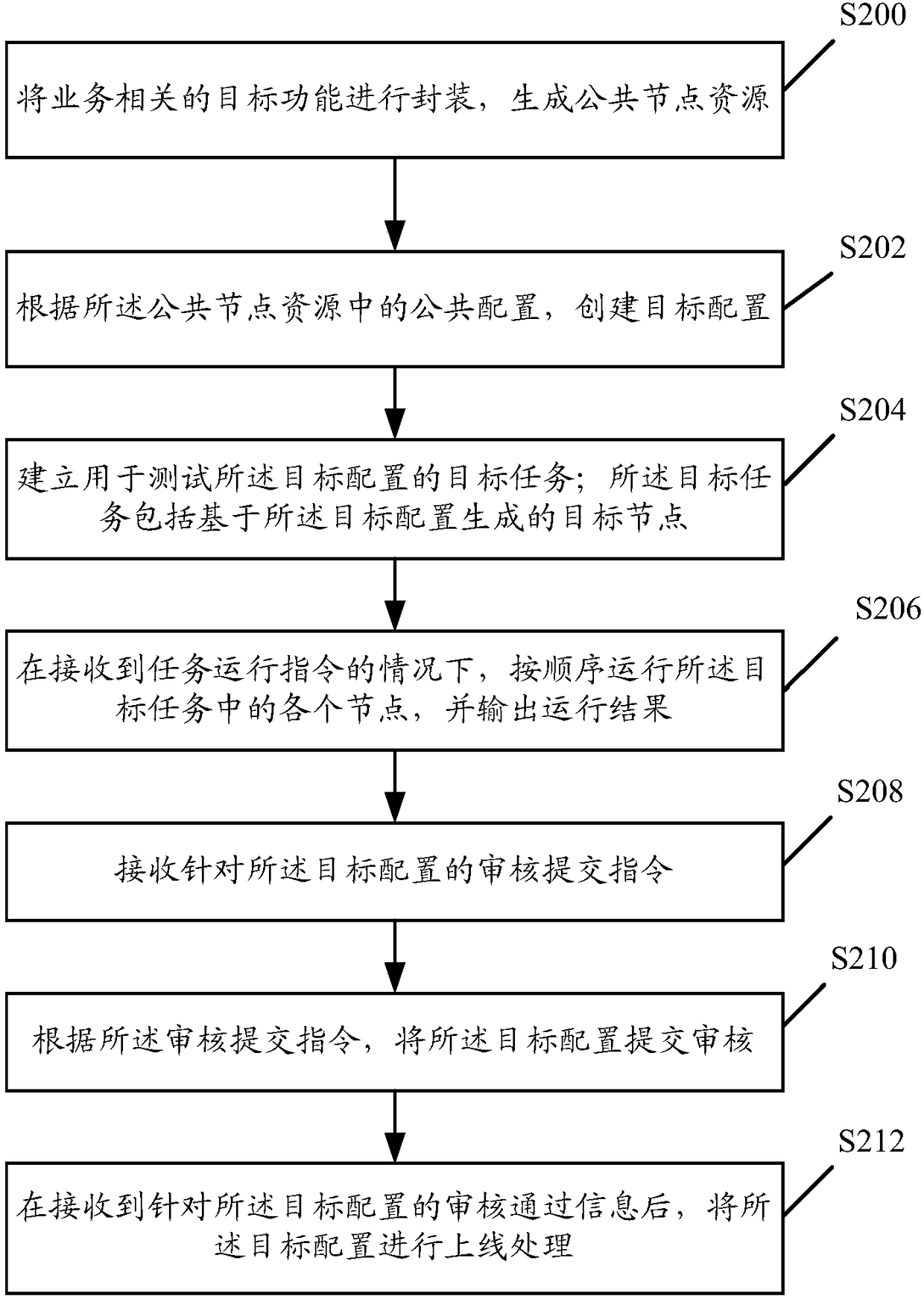
Data processing method and system
ActiveCN108509330AReduce configuration errorsReduce work costsSoftware testing/debuggingData processingData processing system
The invention discloses a data processing method. The method comprises the following steps of: packaging a business-related target function so as to generate a public node resource; creating a targetconfiguration according to a public configuration in the public node resource; establishing a target task for testing the target configuration, wherein the target task comprises a target node generated on the basis of the target configuration; and operating each node in the target task in sequence under the condition that a task operation instruction is received, and outputting an operation result. The invention furthermore discloses a data processing system. According to the data processing method and system, the technical problems that the efficiency is low and the online speed is low as thetest carried out on configurations in a manual manner needs to consume plenty of labor and offline communication time in the prior art are solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A method and smart card for realizing UPS remote monitoring
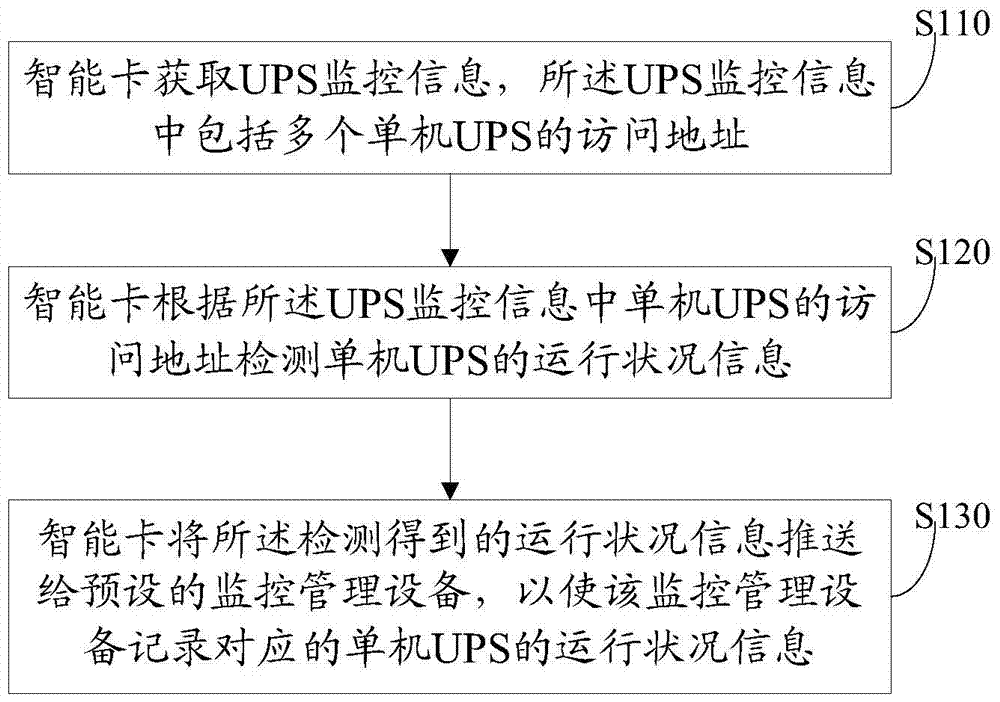
ActiveCN103716377BReduce in quantityReduce the chance of misconfigurationTransmissionSmart cardRemote patient monitoring
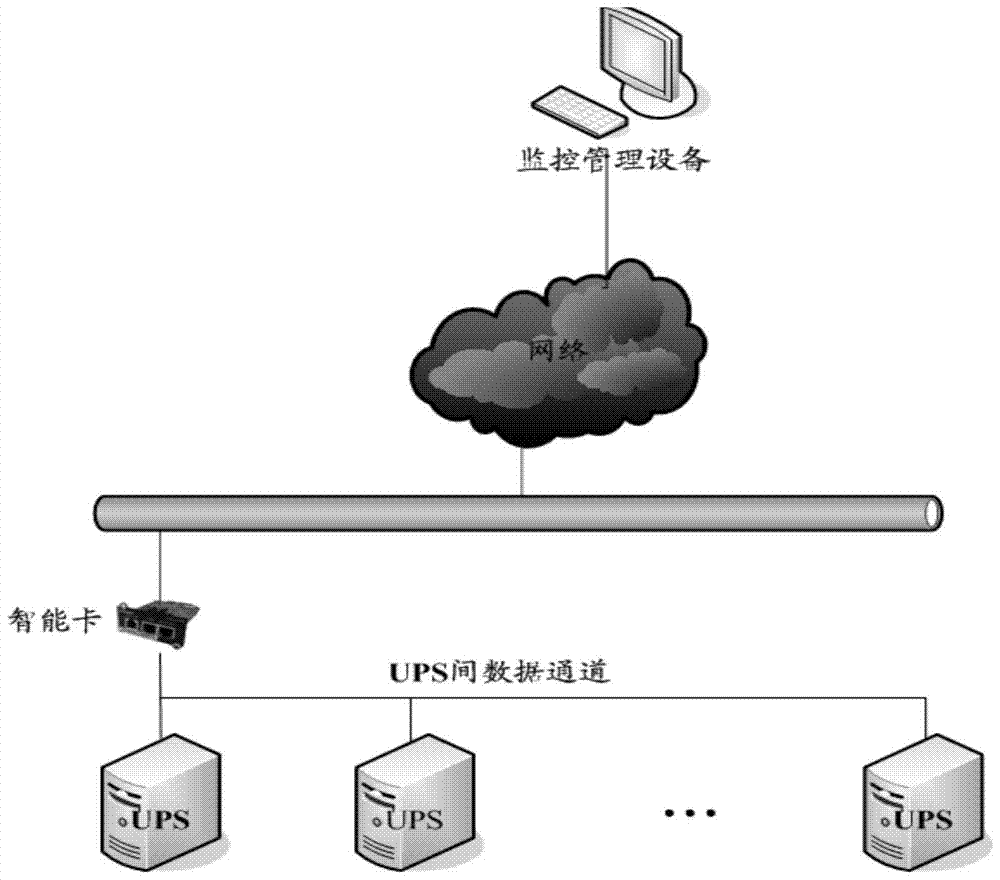
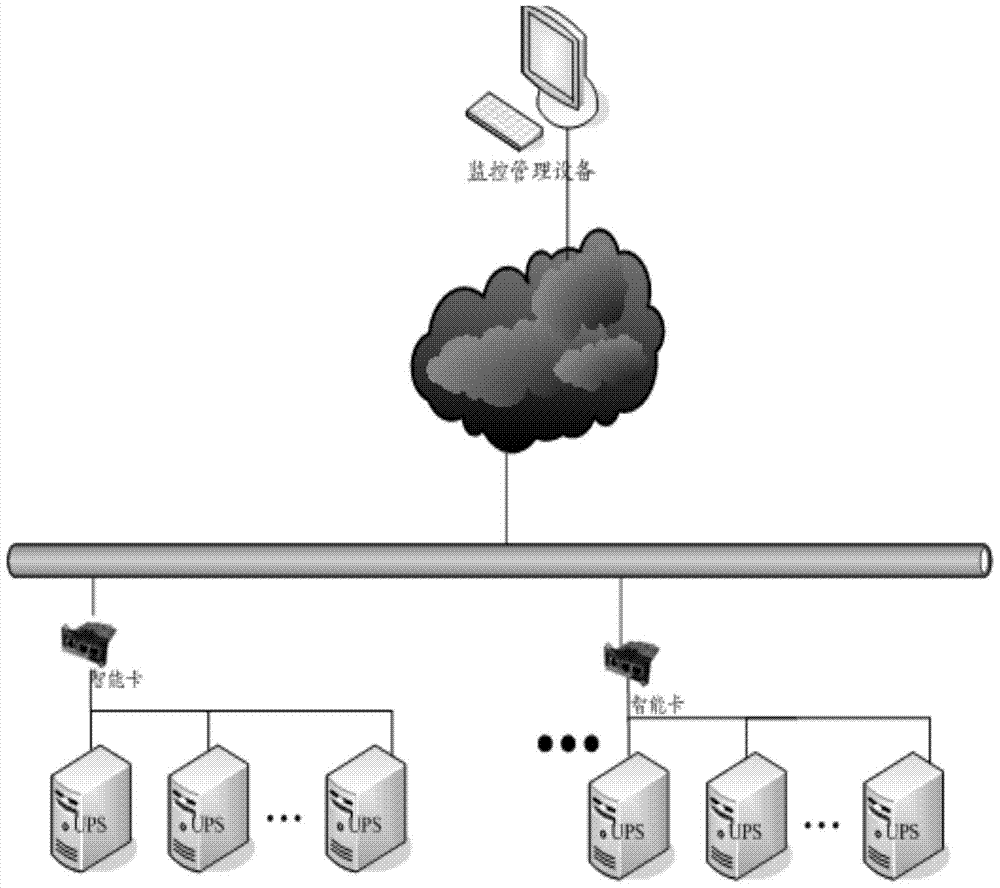
The embodiment of the present invention discloses a method for realizing UPS remote monitoring, comprising: a smart card obtains UPS monitoring information, and the UPS monitoring information includes access addresses of multiple stand-alone UPSs; The address detects the running status information of the stand-alone UPS; the smart card pushes the detected running status information to a preset monitoring and management device, so that the monitoring and managing device records the running status information of the corresponding stand-alone UPS. Correspondingly, the embodiment of the invention also discloses a smart card for realizing UPS remote monitoring. By adopting the embodiment of the present invention, the number of smart cards is greatly reduced for the multi-machine UPS system, thereby reducing the management cost and management workload.
Owner:HUAWEI DIGITAL POWER TECH CO LTD
Routing configuration method and device for virtual private network
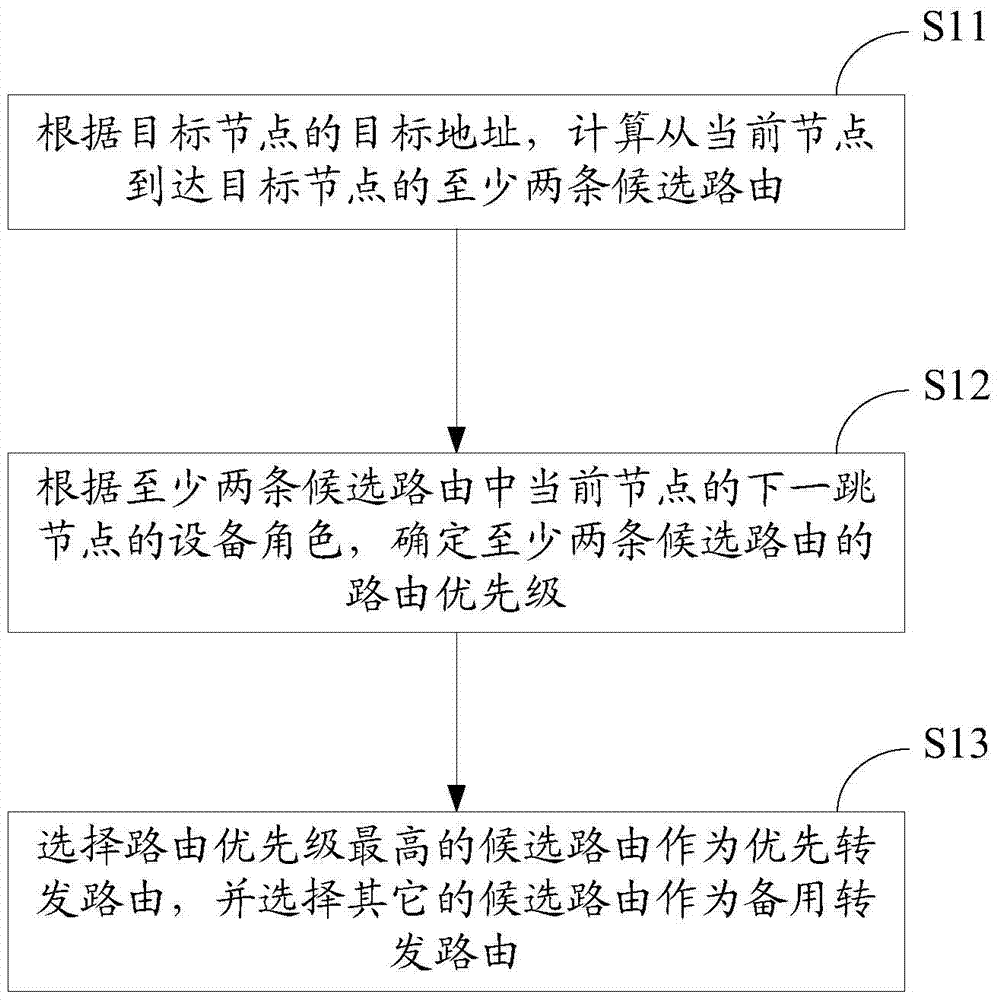
ActiveCN103973567BProfessional skills are not requiredImprove operational efficiencyNetworks interconnectionPrivate networkWorkload
The invention provides a method and device for route configuration of a virtual private network. The method for route configuration of the virtual private network comprises the steps that at least two candidate routes from a current node to a target node are worked out according to the target address of the target node; according to the device role of a next hop node of the current node in the candidate routes, the route priorities of the candidate routes are determined; the candidate route with the highest priority is selected to be used as an optimal transmission route, and other candidate routes are selected to be used as standby transmission routes. In this way, determination of the priorities of the routes is converted into determination of a master and slaves of access nodes; due to the fact that the number of the access nodes is far smaller than the number of the routes in an L3VPN network, the workload generated during configuration is small, operation efficiency is high, the configuration error rate is low, and the requirement for professional skills of configuration personnel is low.
Owner:HUAWEI TECH CO LTD
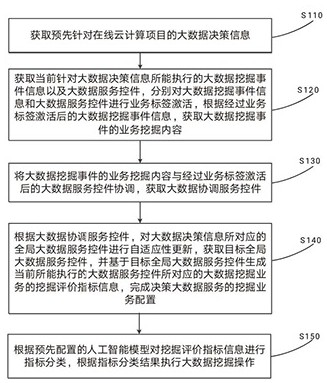
Big data processing method and cloud service center based on artificial intelligence and cloud computing
ActiveCN112163156BOvercome error-prone situationsReduce the chance of misconfigurationText database queryingSpecial data processing applicationsService controlOperations research
The embodiment of the present invention provides a big data processing method based on artificial intelligence and cloud computing and a cloud service center. By coordinating the big data mining event information activated by the business label and the big data service control activated by the business label, Obtain big data coordination service controls, thereby optimizing the big data service controls that can be executed. By coordinating big data mining event information with big data service controls, not only can it overcome the error-prone situation of big data service controls in the business scenario of big data service process initialization, but also realize the big data mining business in big data service controls At the same time of business adaptation, the target global big data service control with global consistency can also be obtained, thereby completing the mining business configuration of decision-making big data services, thereby reducing the probability of business configuration errors during the use of online cloud computing projects.
Owner:青岛仁科信息技术有限公司
Configuration account checking file generation device
PendingCN113591446ASimple configurationStart fastText processingInput/output processes for data processingTheoretical computer scienceData source
The invention belongs to the technical field of computers, particularly relates to a configured account checking file generation device, and aims to solve the problems that in the prior art, only simple data column formats can be processed, configuration is complex, and learning cost is high. A main editing area of the content of the target file is displayed by adopting a graphical table, and field cells of the editing area are directly dragged to the editing area from a data source or edited through a function editor; the data area is used for configuring the value of each column of data, part of columns are obtained through a data source, and part of columns are converted through function calculation based on the actual situation; configuration of the reconciliation file is simplified, the WYSIWYG configuration mode is simplified, an operator can complete configuration through interface dragging and editing, reconciliation file examples are generated at the same time, the final file effect can be seen clearly through the interface, the probability of configuration errors is reduced, configuration complexity is reduced. And both technicians and business operation personnel can quickly operate the method.
Owner:SICHUAN XW BANK CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com