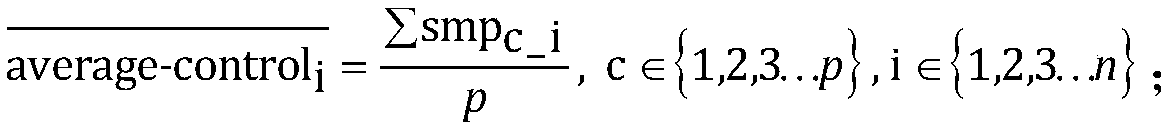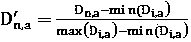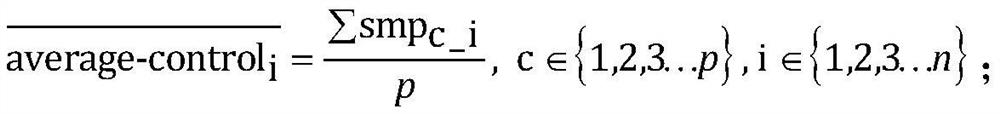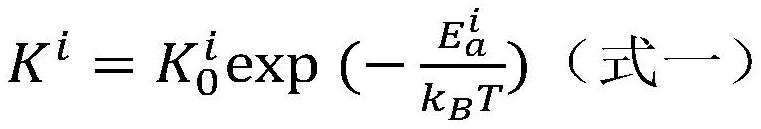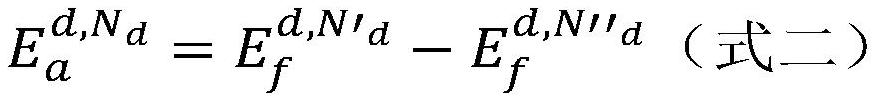Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Reduce Analysis Complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
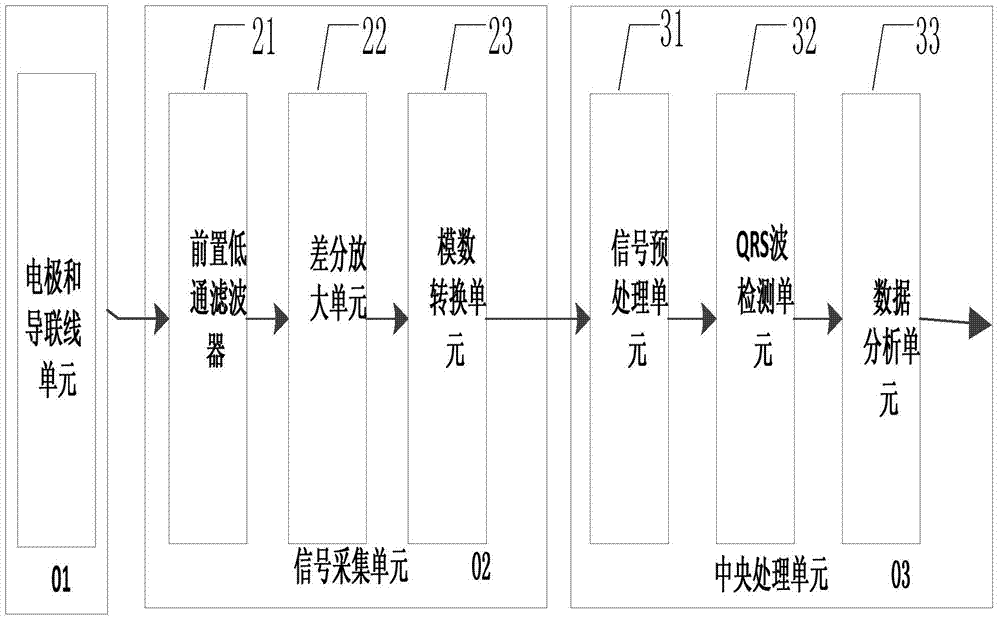
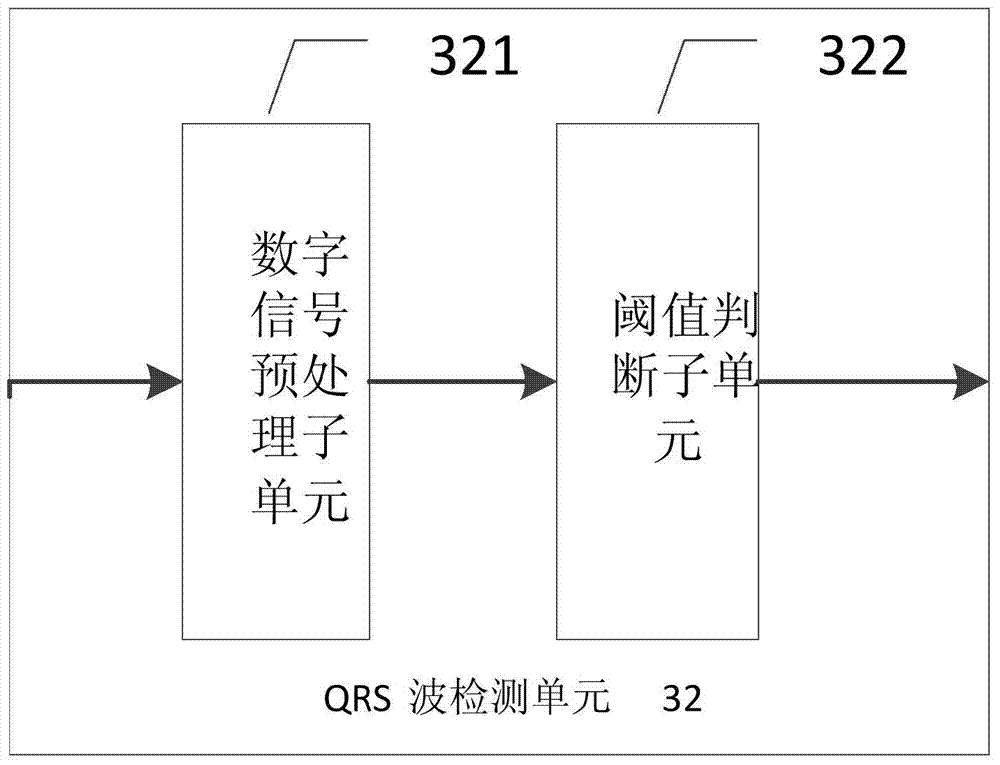
Electrocardiosignal data acquisition and processing method and system
ActiveCN103479349AReduce Analysis ComplexityReduce computationDiagnostic recording/measuringSensorsEcg signalSystems design
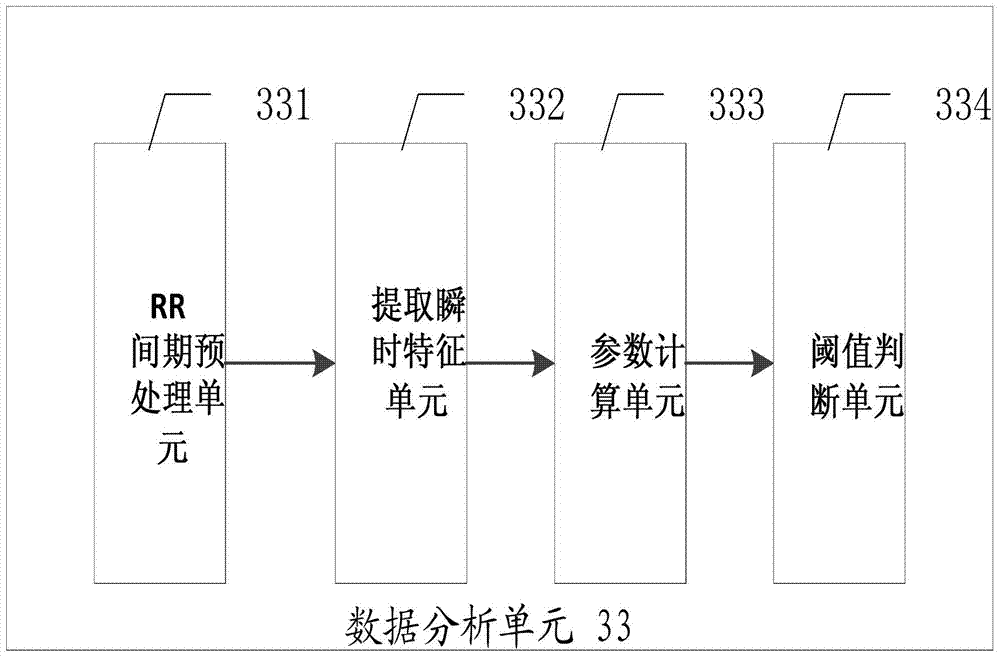
The invention provides an electrocardiosignal data acquisition and processing method and system. The electrocardiosignal data acquisition and processing system comprises a data processing unit which comprises a data analysis unit. The data analysis unit comprises an RR interphase preprocessing unit and an instantaneous feature extraction unit. The RR interphase preprocessing unit is used for preprocessing an RR interphase sequence, so that a signal bandwidth of an RR interphase is enabled to fall in a frequency bandwidth requested by the best amplitude frequency features of the Hilbert transform. The instantaneous feature extraction unit is used for extracting instantaneous amplitude features and instantaneous frequency features of the RR interphase sequence. The electrocardiosignal data acquisition and processing system has the advantages that through acquisition and processing of the electrocardiosignals, complexity of data analysis is reduced, and amount of calculation is decreased; the system is simple in design, low in cost and convenient to apply.
Owner:EDAN INSTR
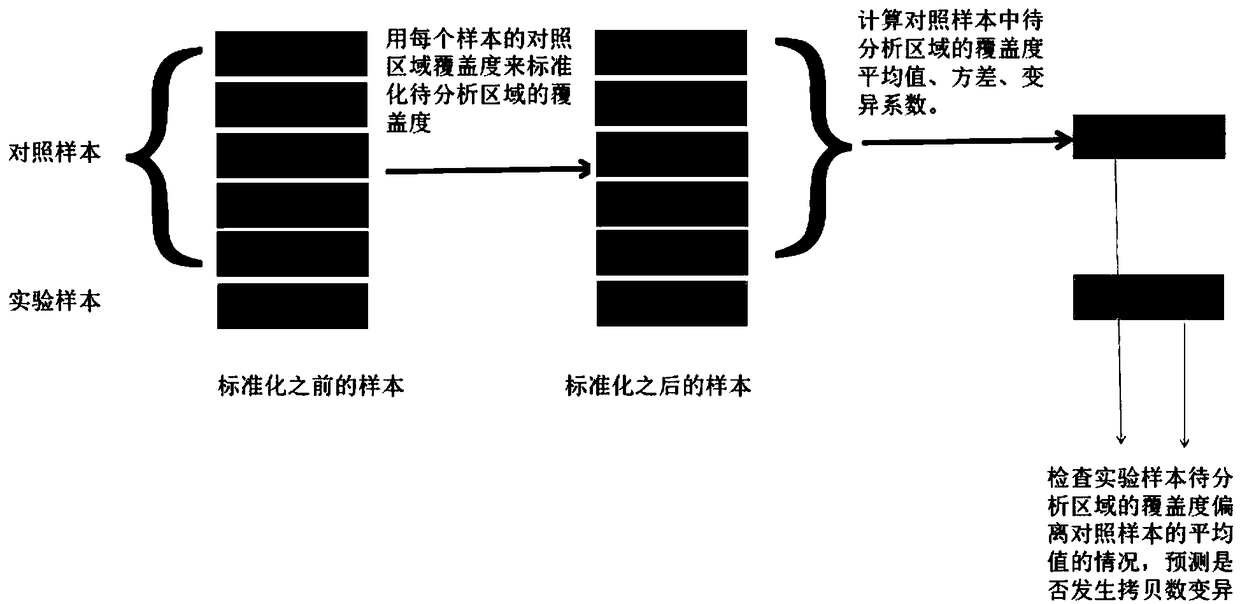
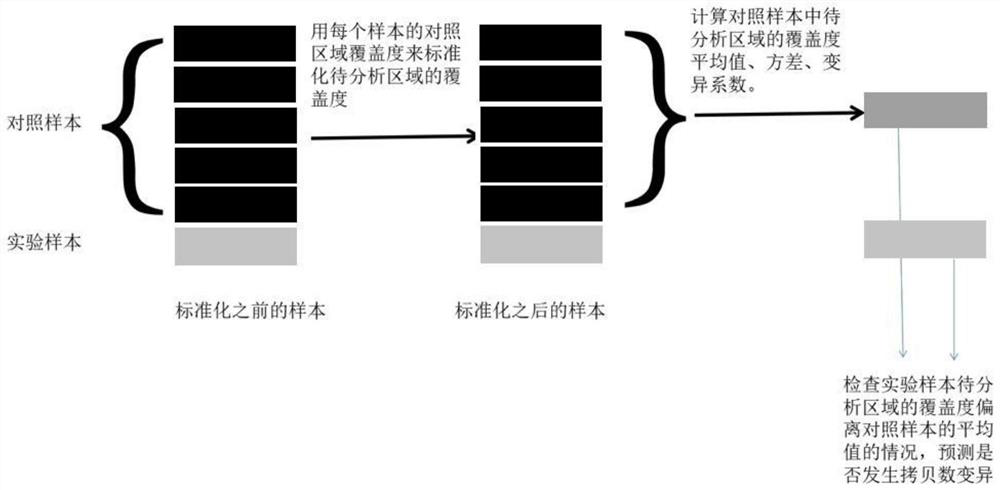
Single exon copy number variation predicting method based on target area sequencing
ActiveCN108920899ALow costReduce Analysis ComplexitySpecial data processing applicationsWhole genome sequencingExon
The invention relates to a single exon copy number variation predicting method based on target area sequencing. The method includes: processing sequencing data; predicting copy number variation, to bemore specific, statistically counting the total number of sequencing sequences and basic groups covering a target area, determining control exon areas, standardizing the coverage of the to-be-analyzed exon areas of each control sample and each experiment sample, calculating the average value, standard deviation and variation coefficient of the standardized coverage of the to-be-analyzed exon areas in the control samples, and predicting the copy number variation of to-be-analyzed exon areas. The method has the advantages that whole genome sequencing is not needed, the copy number variation ofexon level is analyzed by directly using the coverage information of the exon level, and the method is simple in analysis and does not need complex GC correction and modeling.
Owner:杭州迈迪科生物科技有限公司
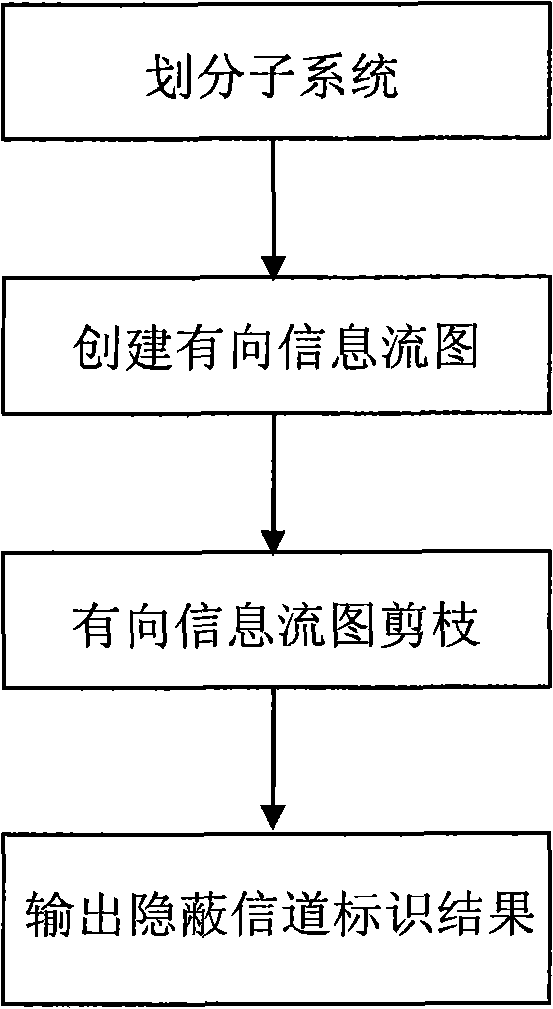
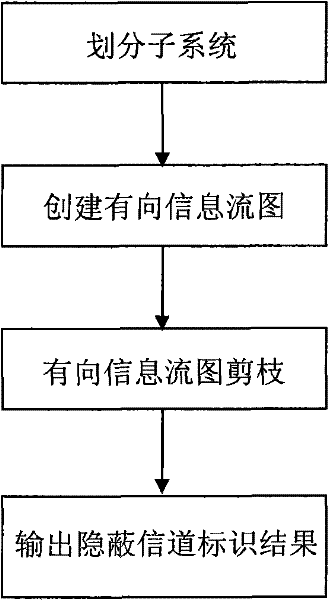
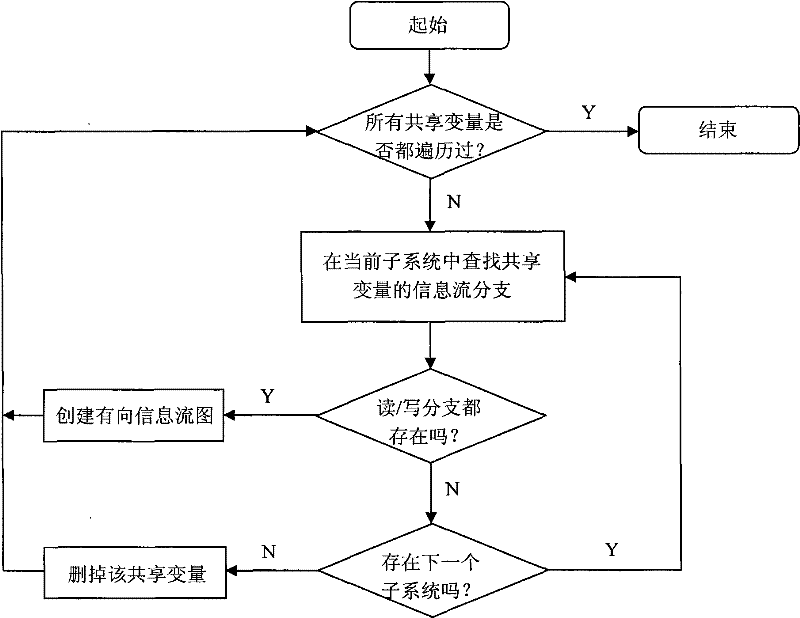
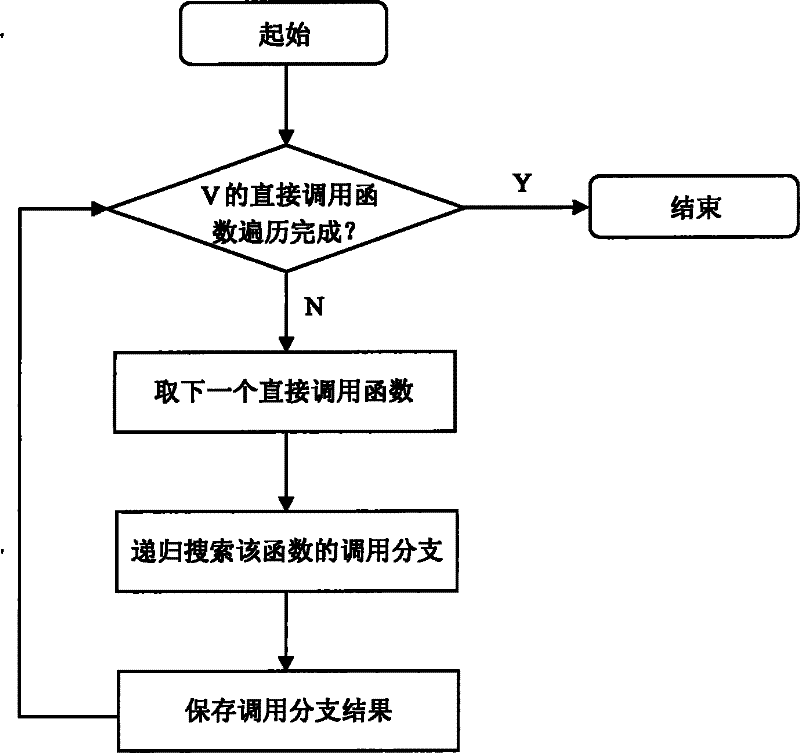
Concealed channel identification method
InactiveCN102045158AMeet the requirements of the analysisReduce analysis sizeSecuring communicationNODALOperational system
The invention discloses a concealed channel identification method. A system source code is used as an analysis object. The method comprises the following steps of: formally describing a concealed channel in a secure information system as (V, PAh, PVl, P); then dividing a system to be analyzed into relatively independent subsystems; searching related function calling branches in the subsystems by using a shared variable as a basic unit, and further constructing directed information flow graphs according to an information flow relationship; and pruning each information flow graph according to the formal description of the concealed channel to eliminate invalid flow branches and variable aliases in the code, wherein all flow nodes and function calling branches in the finally obtained information flow graphs are potential concealed channel forming factors. The method is suitable for source codes of information systems such as an operating system, a database, a network and the like of high security level, has wide application range, high execution efficiency and low error report rate and missing report rate, can identify the potential concealed channel in the system, and meets the requirement of security standards on concealed channel analysis.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
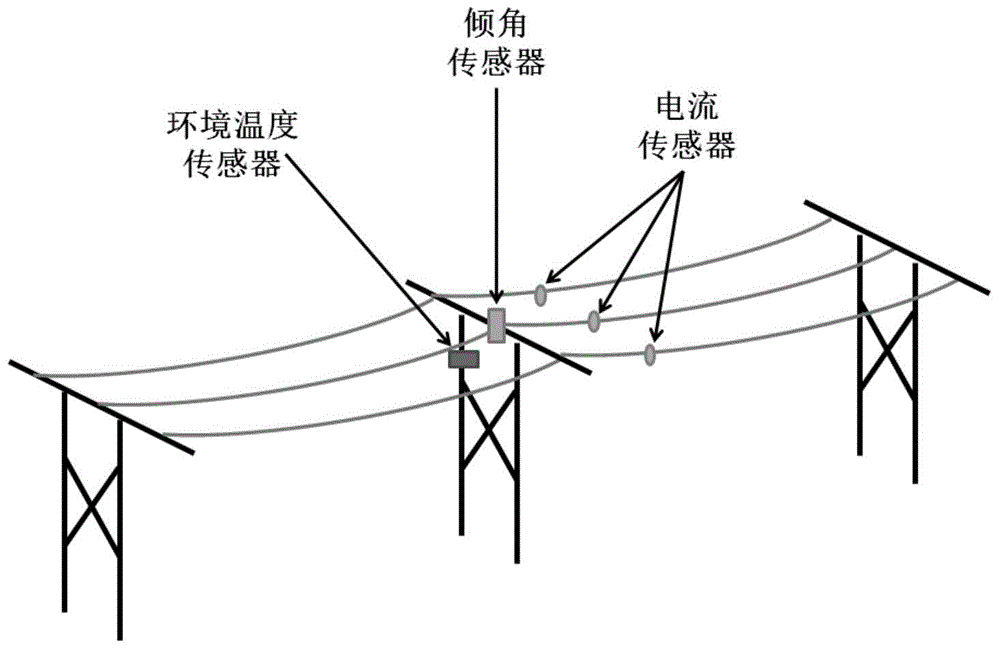
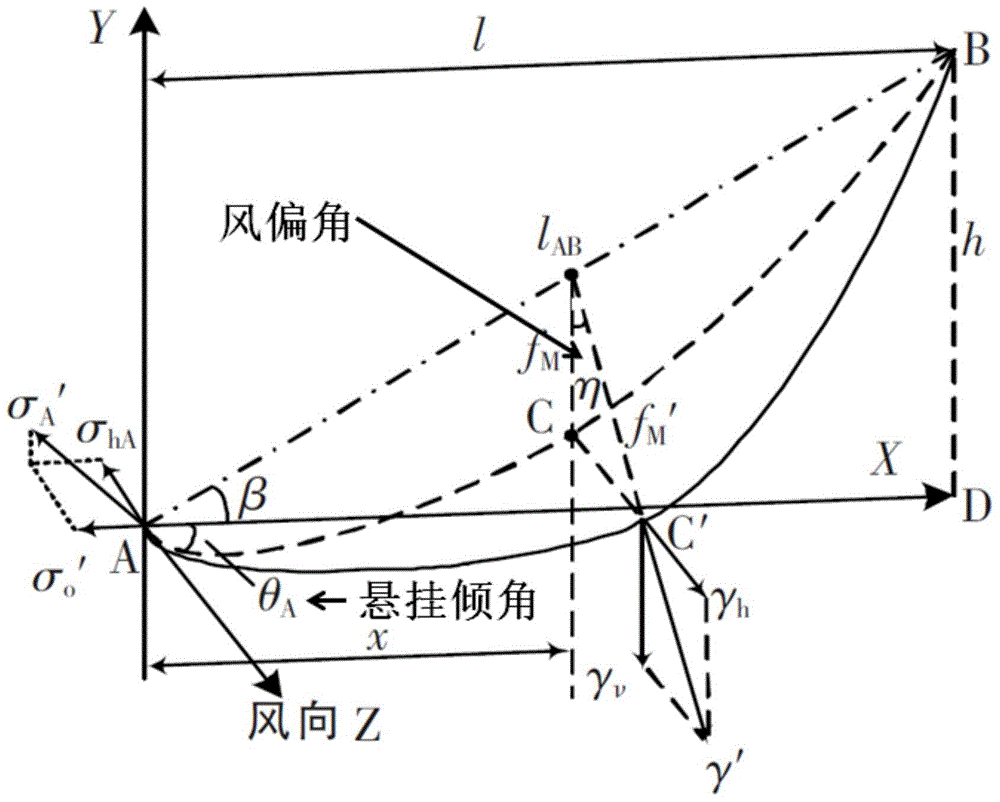
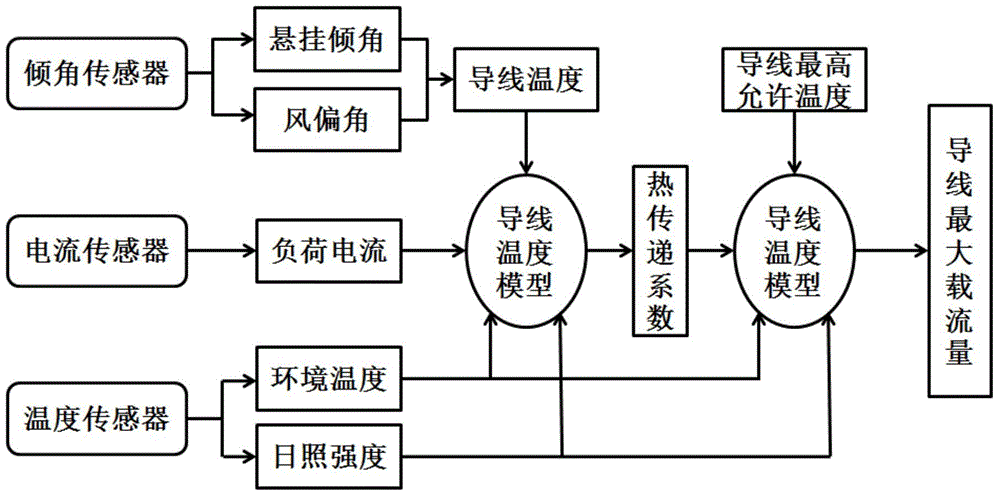
Carrying capacity evaluation method of overhead transmission line
Disclosed in the invention is a carrying capacity evaluation method of an overhead transmission line. A tilt angle sensor is installed at a tower; a lead temperature is calculated based on a lead suspension tilt angle and a wind deflection angle, thereby calculating a lead temperature; a temperature sensor is used for measurement an environmental temperature and a sunlight intensity; current sensors installed at the line are used for measuring real-time loads of the lead; and a heat transmission coefficient is used for representing a combined influence on the lead by microclimate conditions like a wind sped and a wind direction and the like. And then according to the lead temperature model, a real-time maximum carrying capacity of the lead is calculated and evaluated. With the method, an error caused by using the existing lead temperature measurement method can be reduced; the equipment installation time is shortened; the data analysis complexity is reduced; a problem of inaccurate wind speed and wind direction measurement is solved; and reliability of lead carrying capacity calculation is enhanced.
Owner:SHANGHAI JIAO TONG UNIV
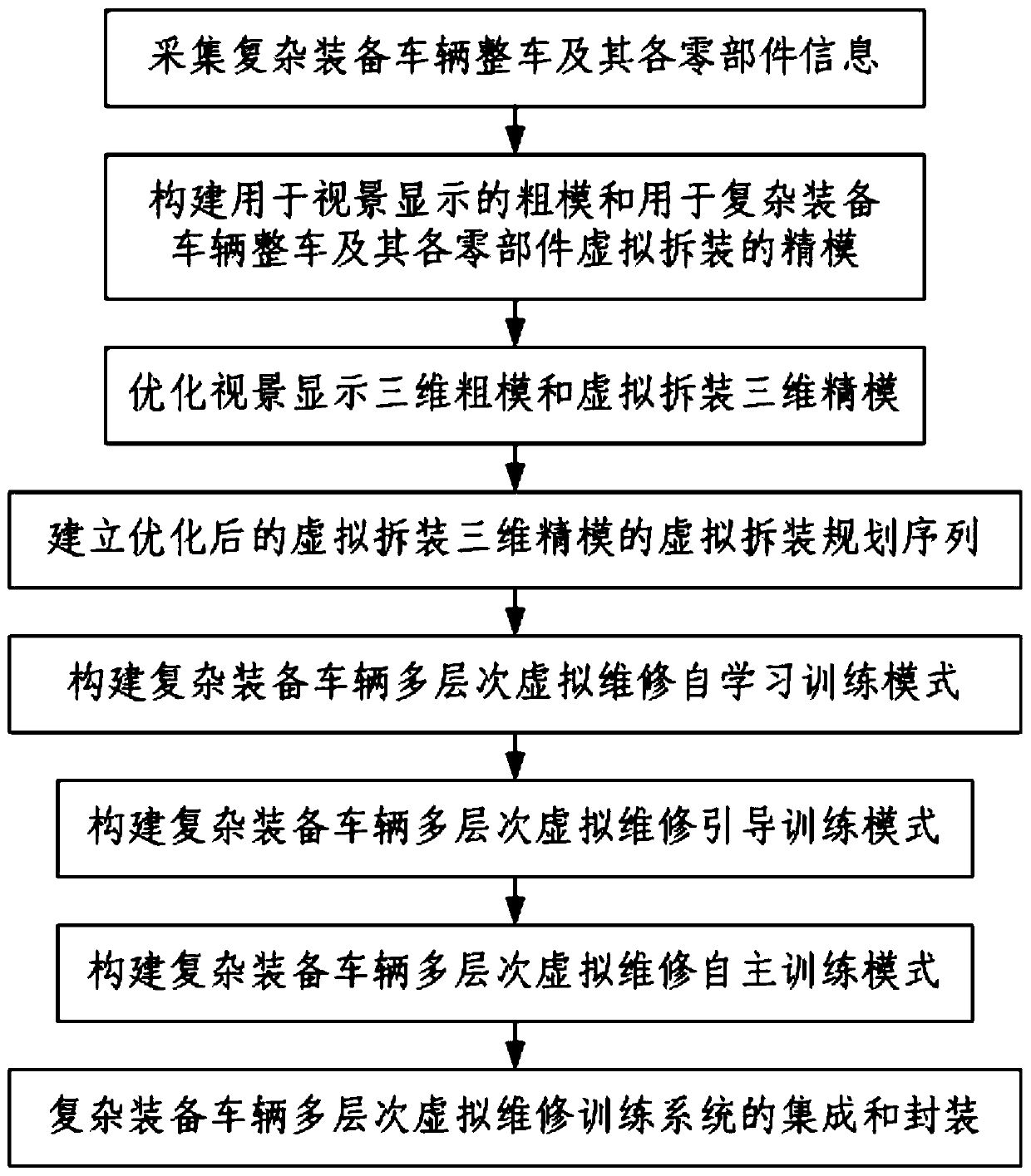
Method for establishing multi-level virtual maintenance training system of complex equipment vehicle
ActiveCN110502868AAvoid running out of memoryIncrease real-time interactionCosmonautic condition simulationsCharacter and pattern recognitionDecompositionSimulation
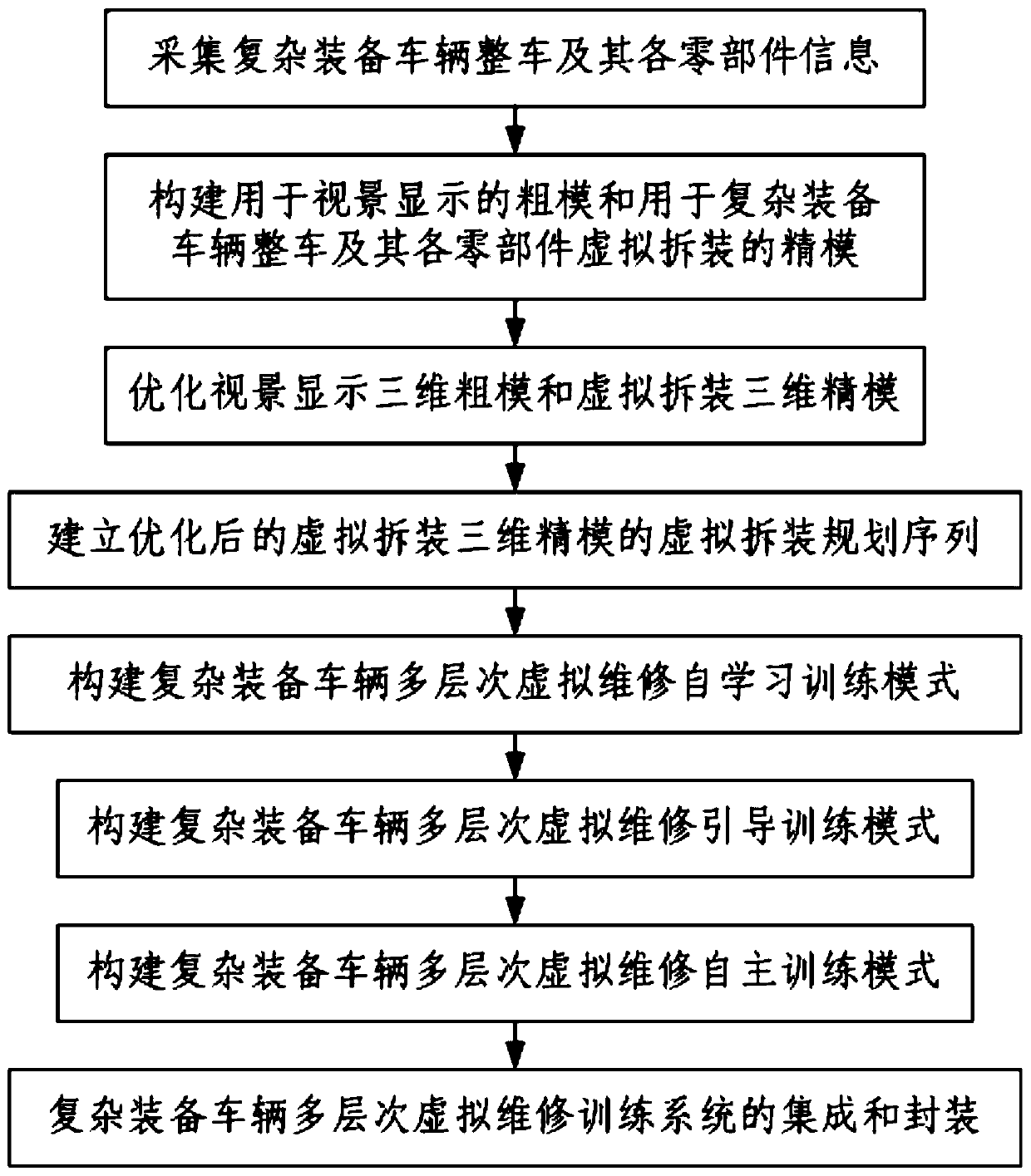
The invention discloses a method for establishing a multi-level virtual maintenance training system of a complex equipment vehicle. The method comprises the following steps: 1, acquiring the information of the whole complex equipment vehicle and each part thereof; 2, constructing a rough mold for visual display and a fine mold for virtual disassembly and assembly of the whole complex equipment vehicle and all parts thereof; 3, optimizing a visual display three-dimensional coarse mold and virtually disassembling and assembling a three-dimensional fine mold; 4, establishing a virtual disassemblyand assembly planning sequence of the optimized virtual disassembly and assembly three-dimensional precision mold; 5, constructing a multi-level virtual maintenance self-learning training mode of thecomplex equipment vehicle; 6, constructing a multi-level virtual maintenance guide training mode of the complex equipment vehicle; 7, constructing a multi-level virtual maintenance autonomous training mode of the complex equipment vehicle; and 8, integrating and packaging the multi-level virtual maintenance training system of the complex equipment vehicle. According to the method, the rough modeland the fine model are established, training is smooth, the truth and immersion are good, the virtual decomposition and assembly object model and the hierarchical relationship thereof are established, and later virtual maintenance training is facilitated.
Owner:中国人民解放军火箭军工程大学
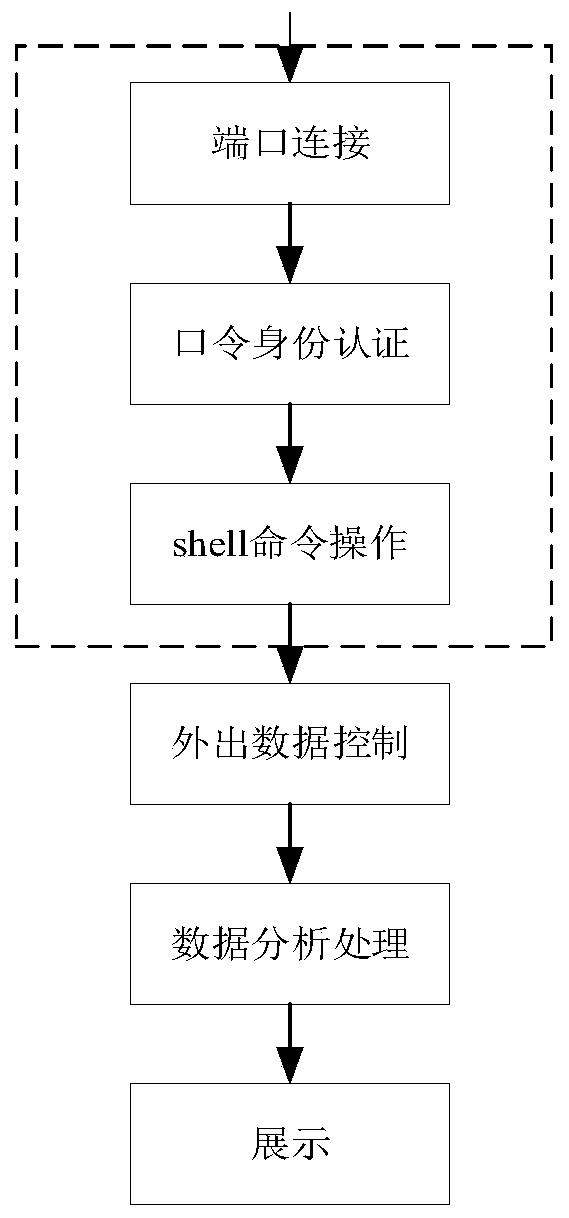
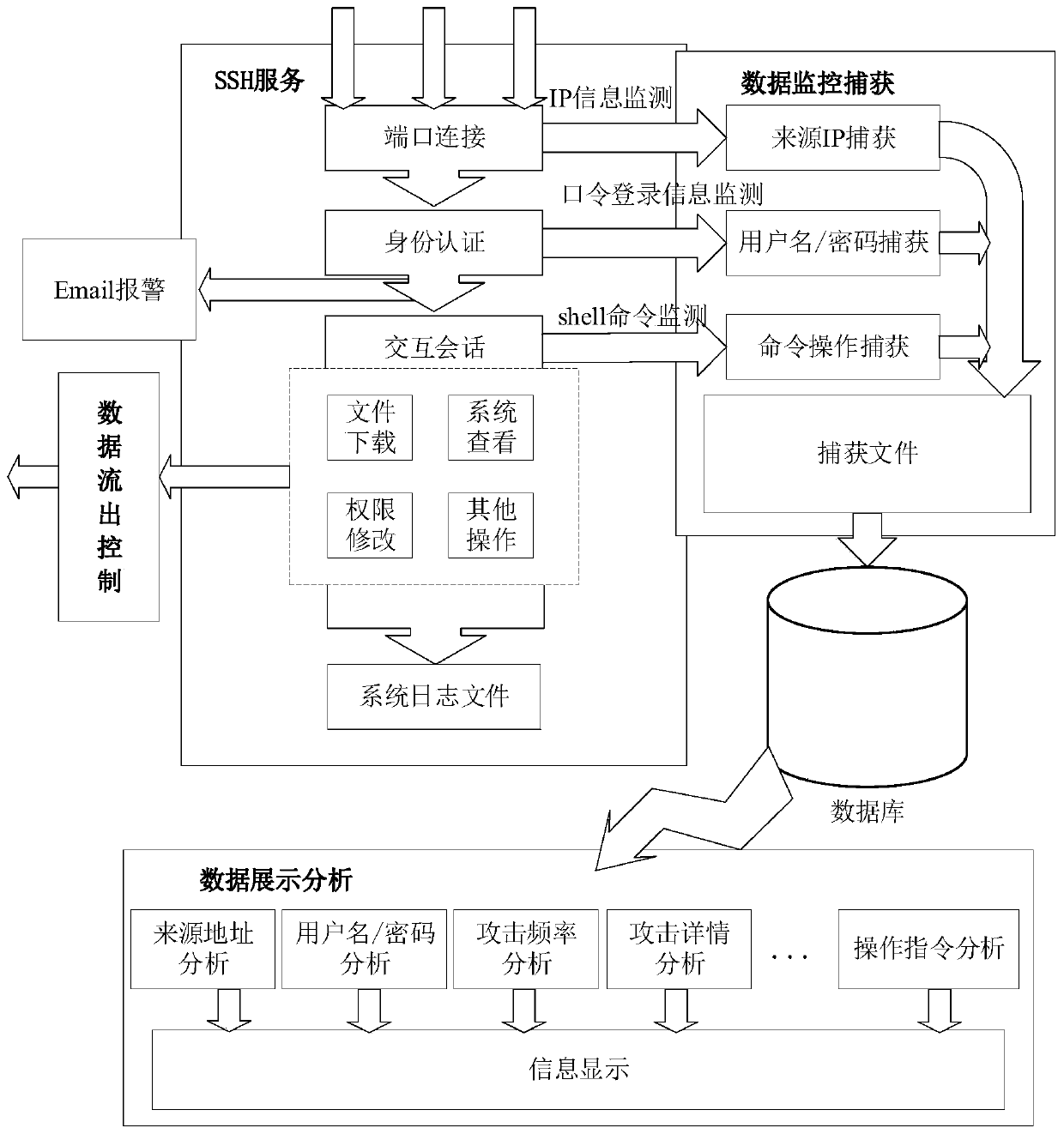
High-interaction SSH honeypot implementation method
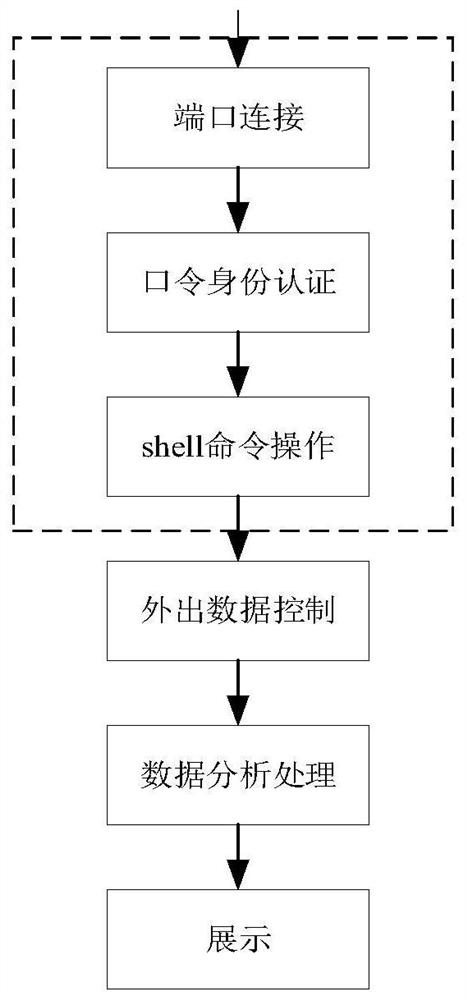
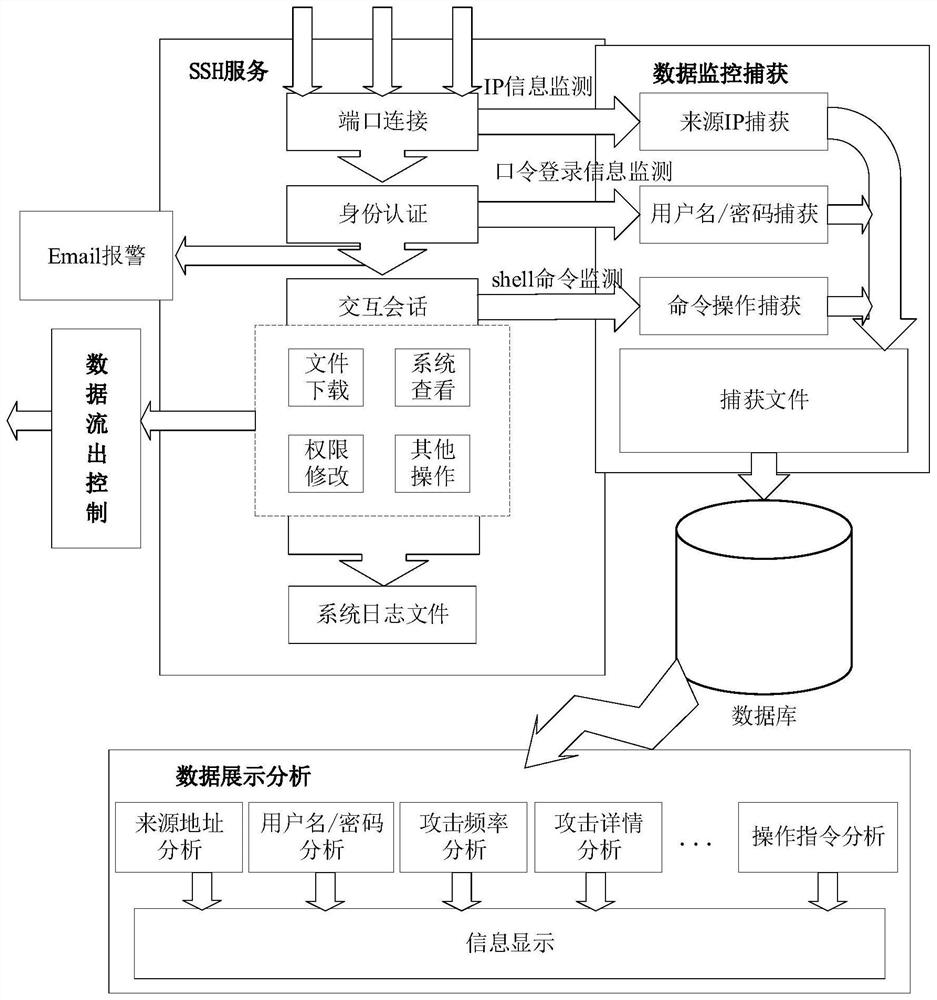
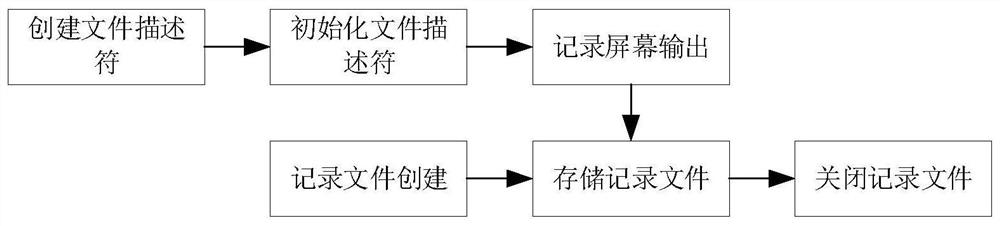
The invention discloses a high-interaction SSH honeypot implementation method which comprises the following steps: connecting a system SSH port, judging whether SSH service exists or not, and enteringthe next step if the SSH service exists; capturing an authenticated user name / password during password identity authentication by utilizing a logit function and an authctxt structure body in the OpenSSH; after the password is successfully authenticated, modifying related module codes by utilizing the characteristic that SSH service processes client data through a pipeline and a user processing interactive session module, so as to record the shell password; controlling the outflow flow of the honeypot system, including two processes of limiting an external data packet and inhibiting an external attack packet; and analyzing, processing and displaying the data captured by the honeypot system by utilizing a javaweb technology. According to the high-interaction SSH honeypot implementation method, the defects that a passive defense technology cannot be used for SSH attacks which are continuously updated and changed due to valleys, and medium and low interaction SSH honeypots are low in interaction degree, insufficient in decorativeness, easy to be broken and the like can be overcome, and the security defense capability for SSH services is improved.
Owner:HOHAI UNIV
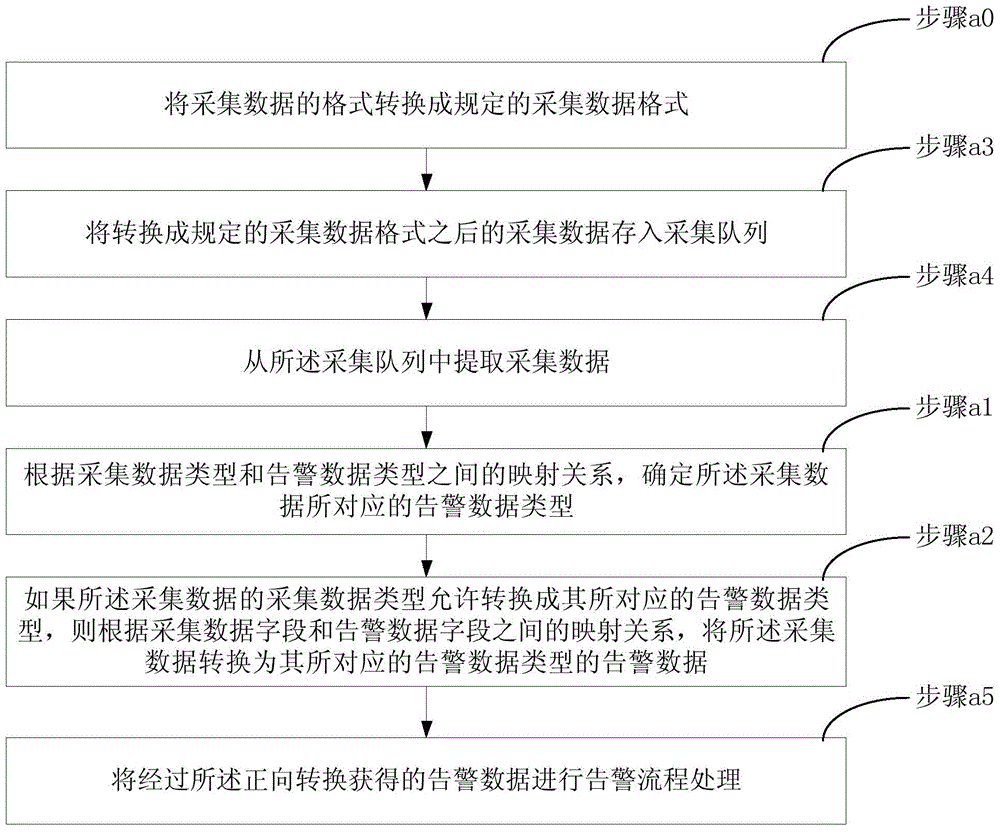
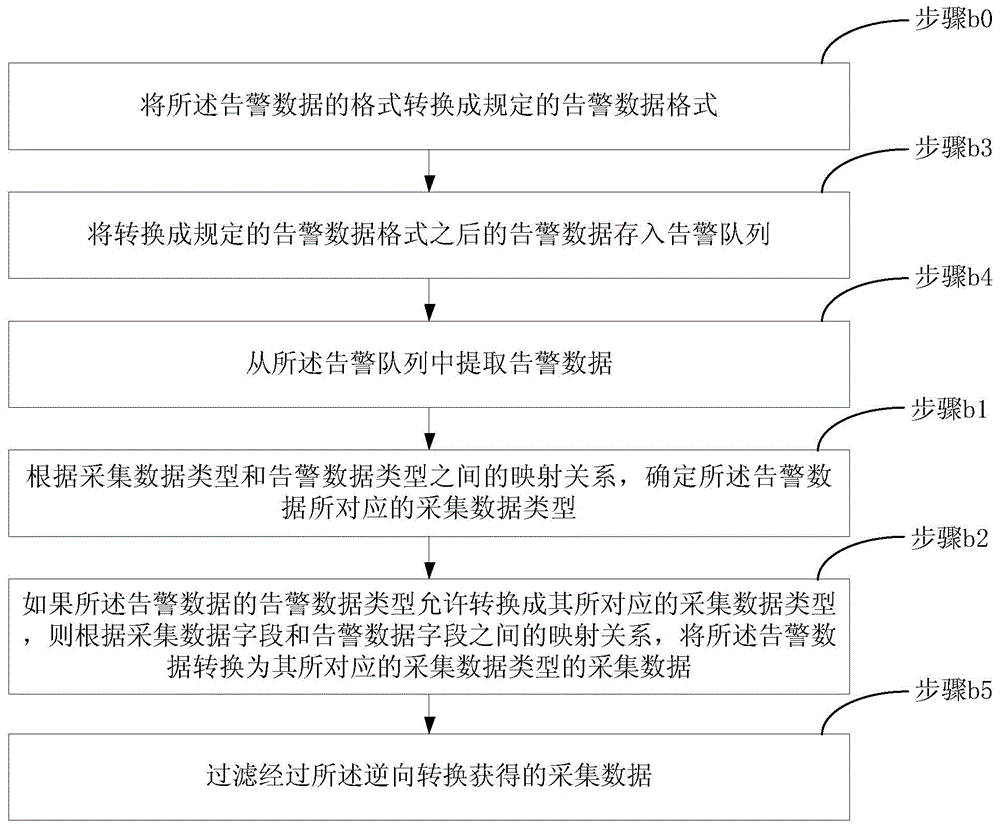
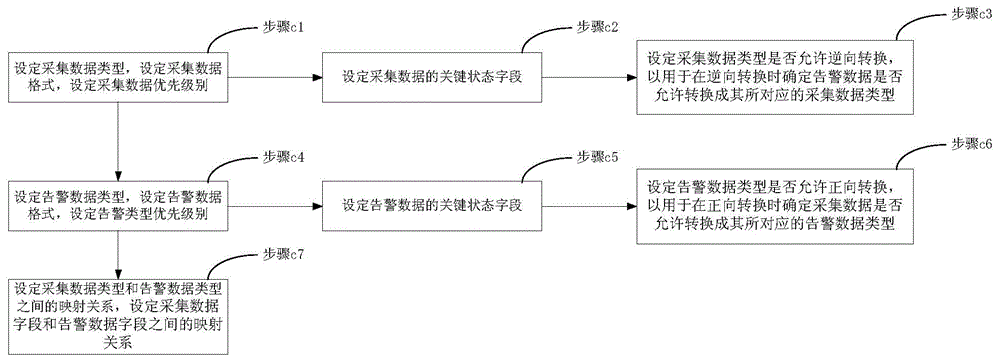
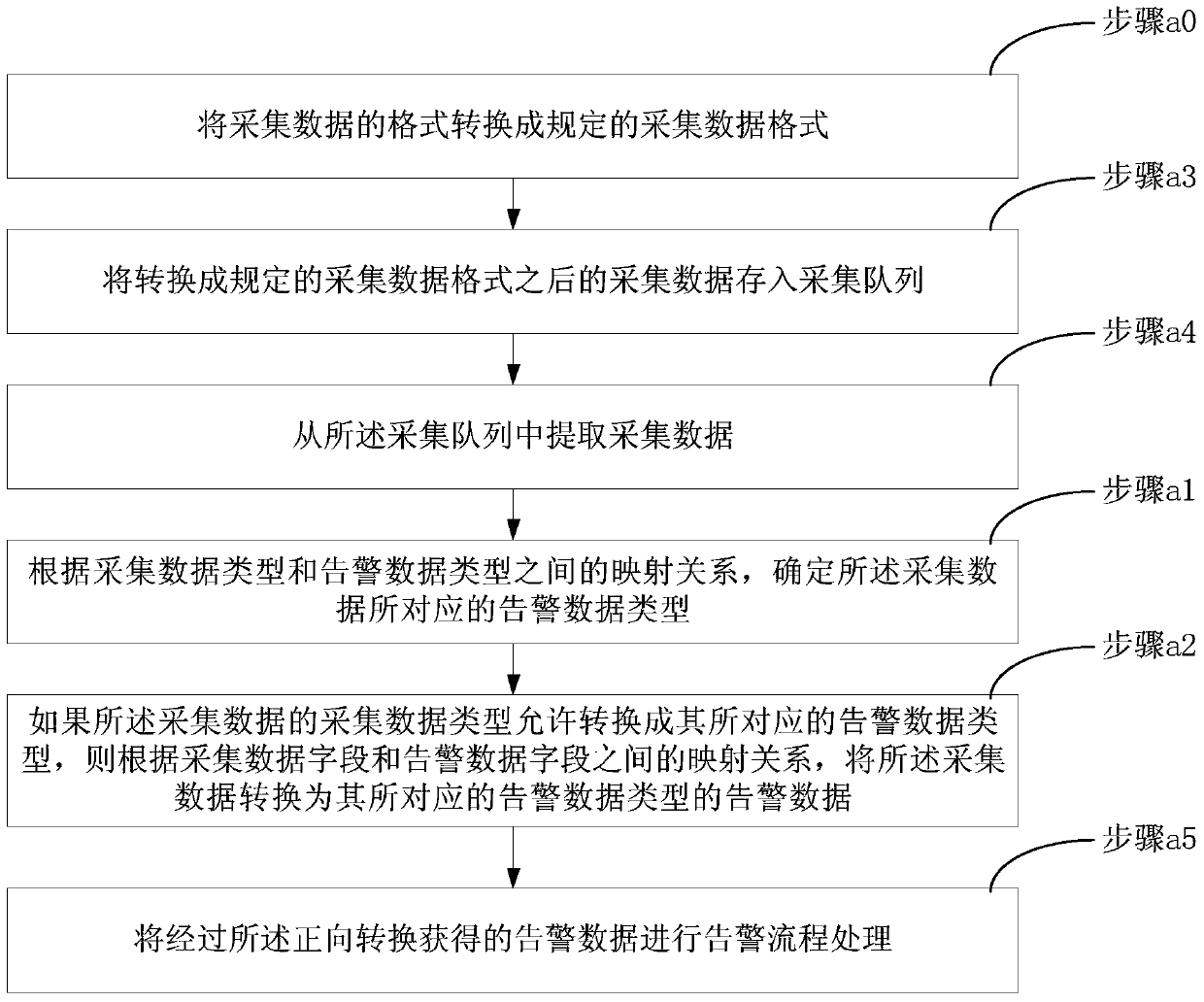
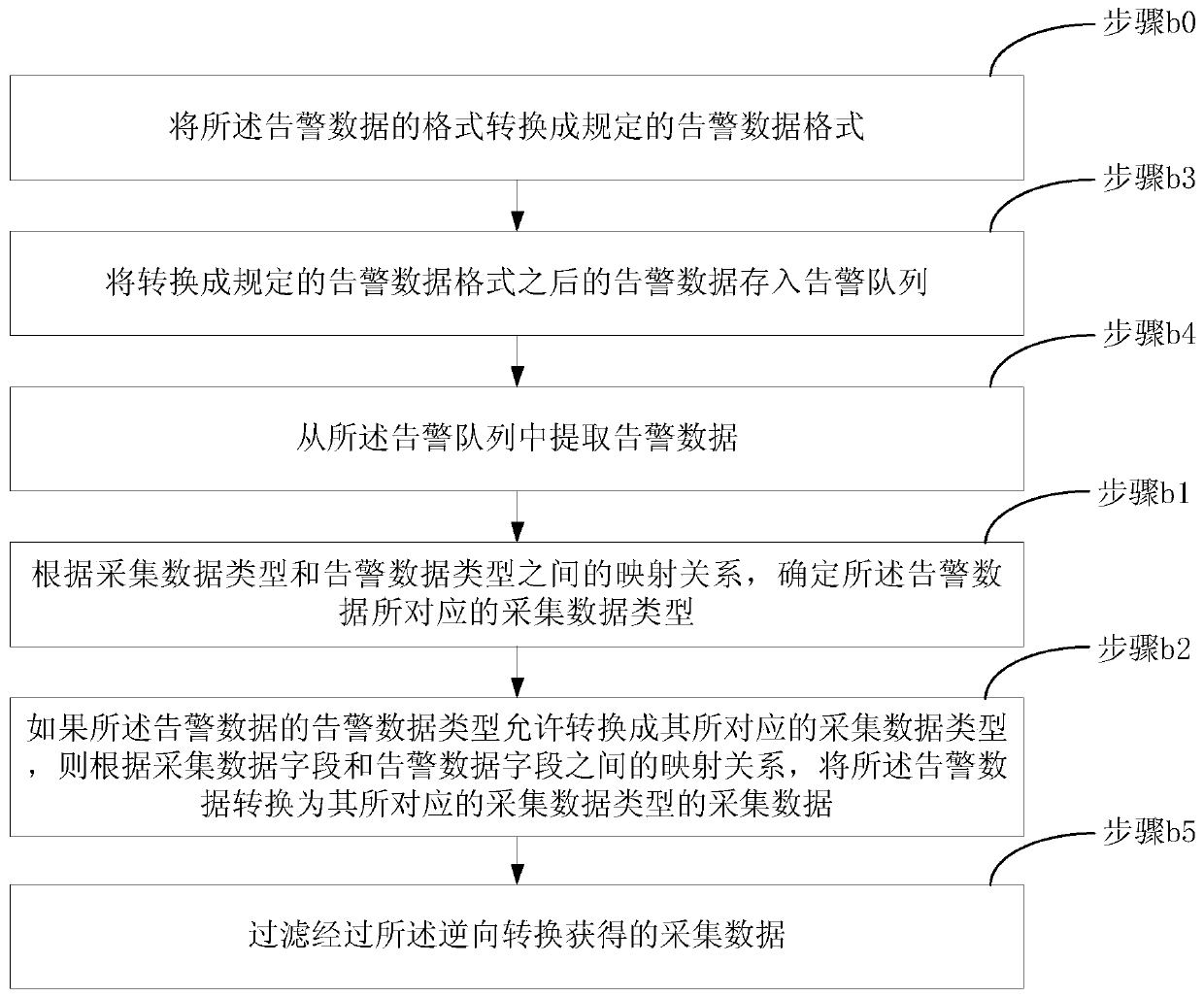
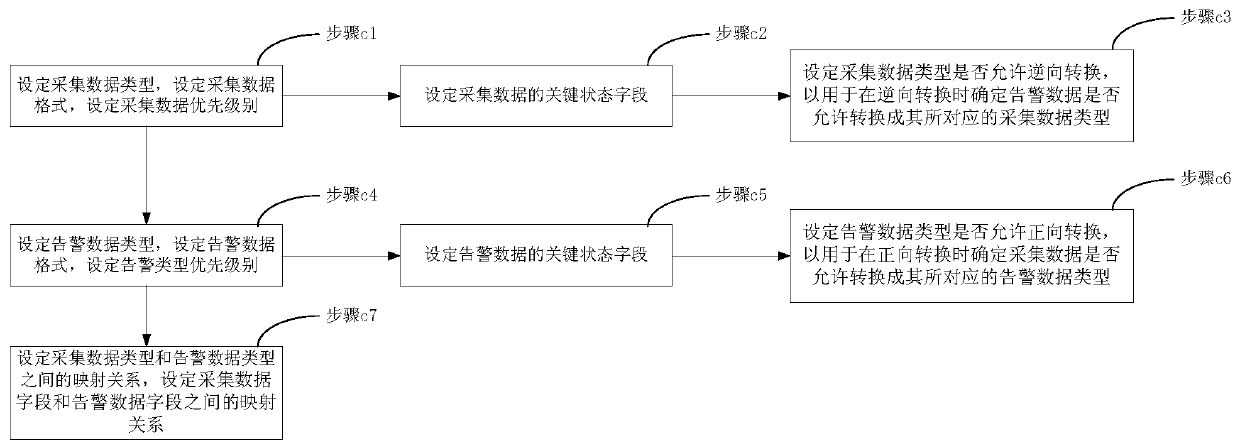
Data conversion method
ActiveCN105446707AReduce Analysis ComplexityReduce operational complexitySpecific program execution arrangementsData conversionData file
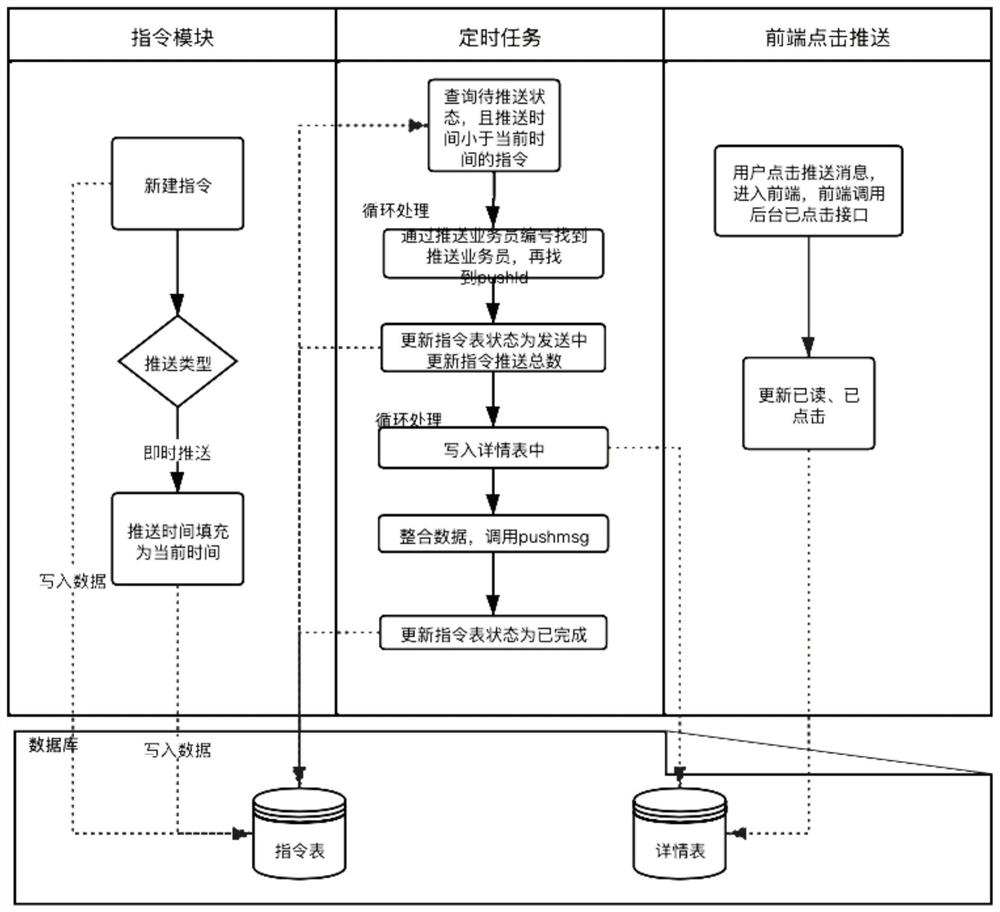
The invention discloses a data conversion method used for data conversion between acquisition data and alarm data of an operation and maintenance system; according to a preset mapping relation between acquisition data type and alarm data type and a mapping relation between acquisition data file and alarm data field, the method can realize positive conversion which is to convert acquisition data into alarm data, and can realize reversed conversion which is to convert alarm data into acquisition data. The alarm data obtained by positive conversion can provide more comprehensive alarm information for operation and maintenance people, thus reducing operation and maintenance data analysis complexity for the operation and maintenance people, solving alarm data loss problems caused by increasing system device, and reducing video cloud storage operation and maintenance platform fault processing flow operation complexity; on the other hand, the acquisition data obtained by reversed conversion can be pushed to the a front end display system, thus enhancing real time display of equipment under abnormal state, and providing more accurate equipment fault information for the operation and maintenance people.
Owner:HANGZHOU HIKVISION SYST TECH
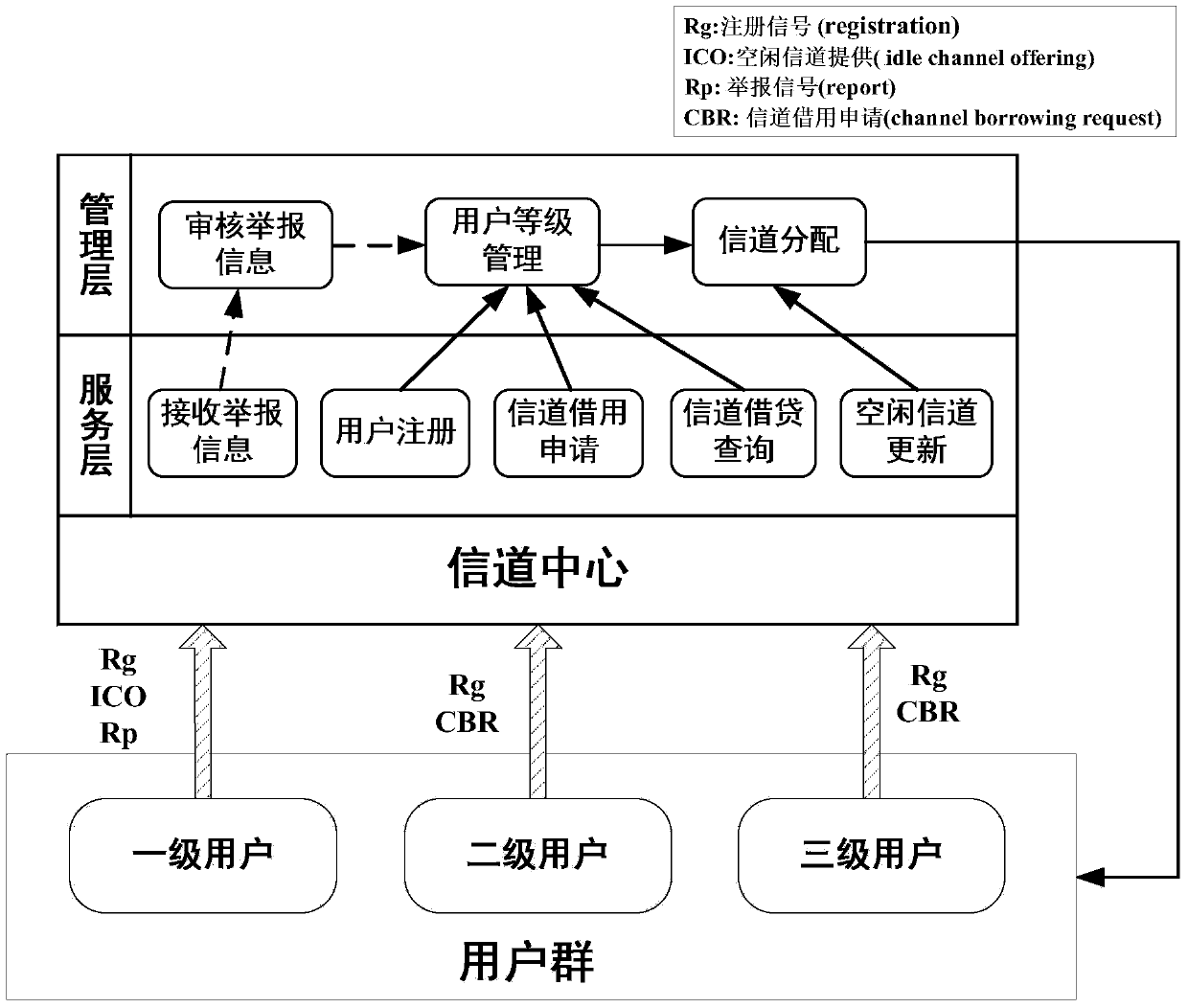
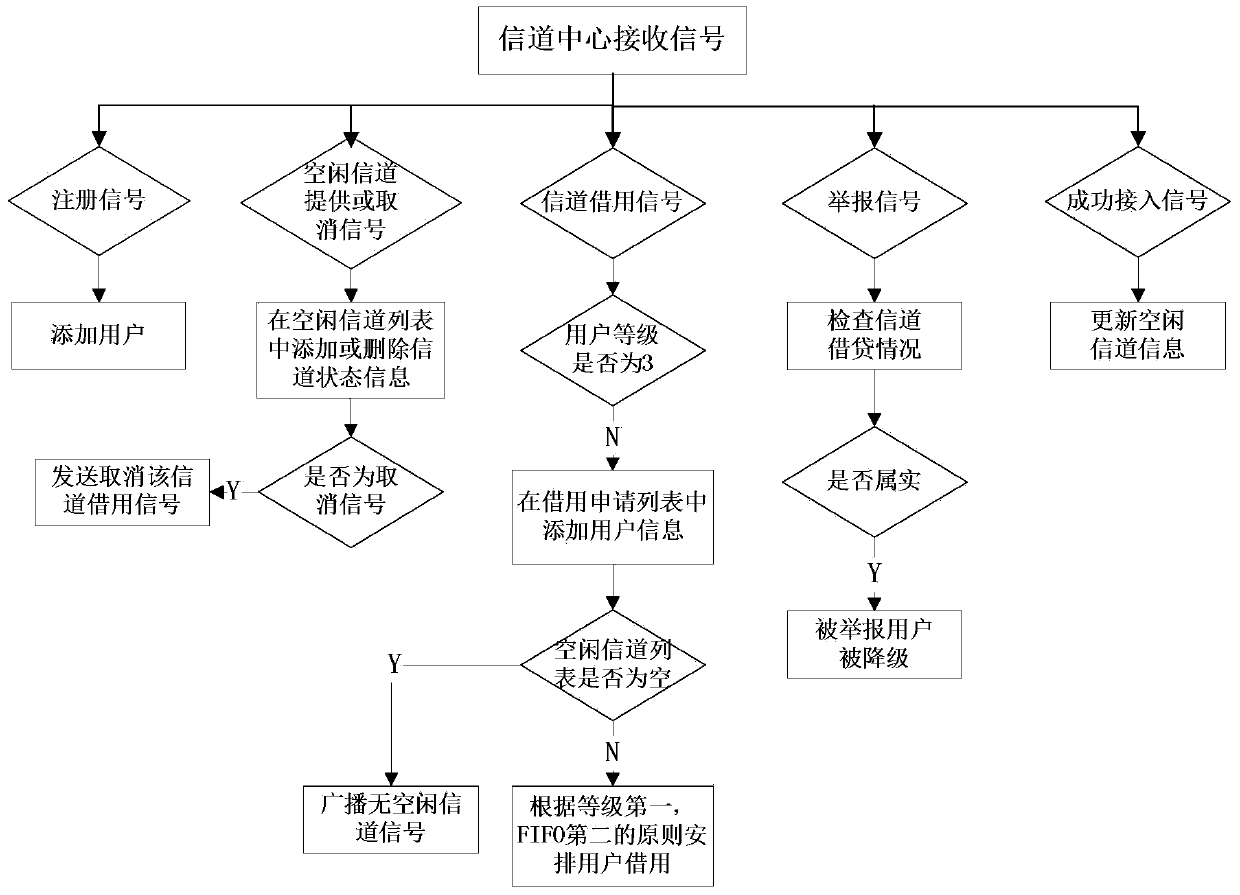
Information channel center system and method for distributing information channels by using information channel center strategy
InactiveCN104202748ARegulated accessRealize managementNetwork planningChannel dataAssignment methods
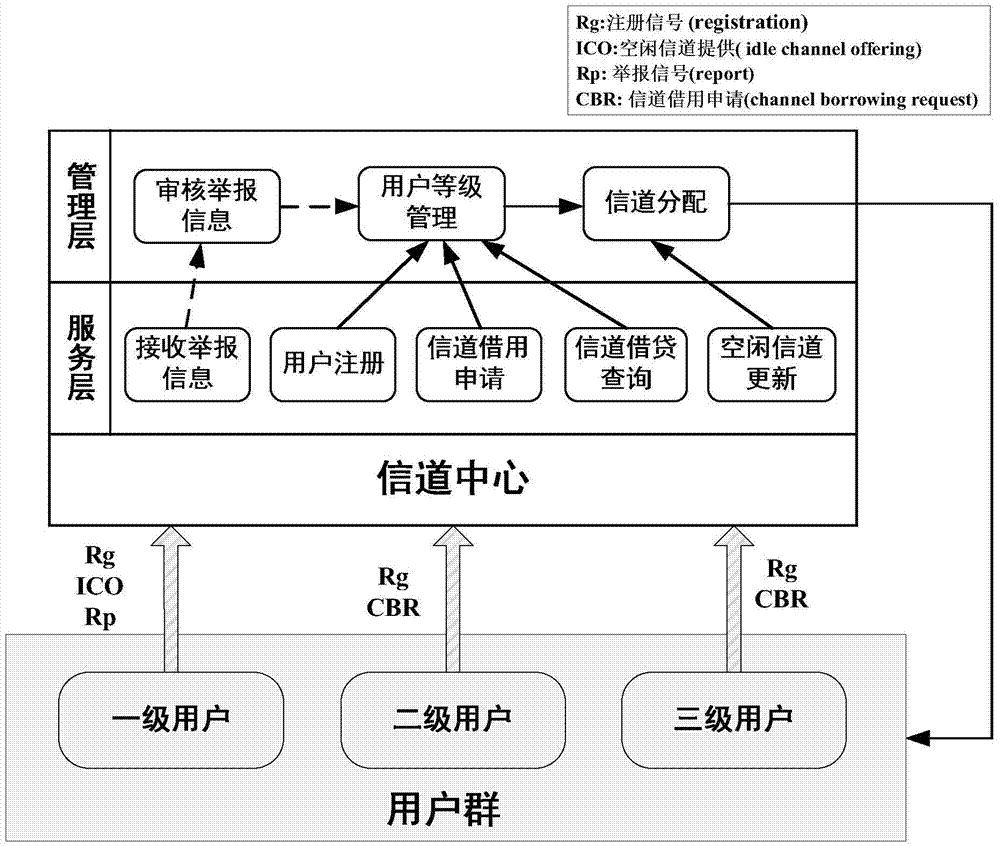
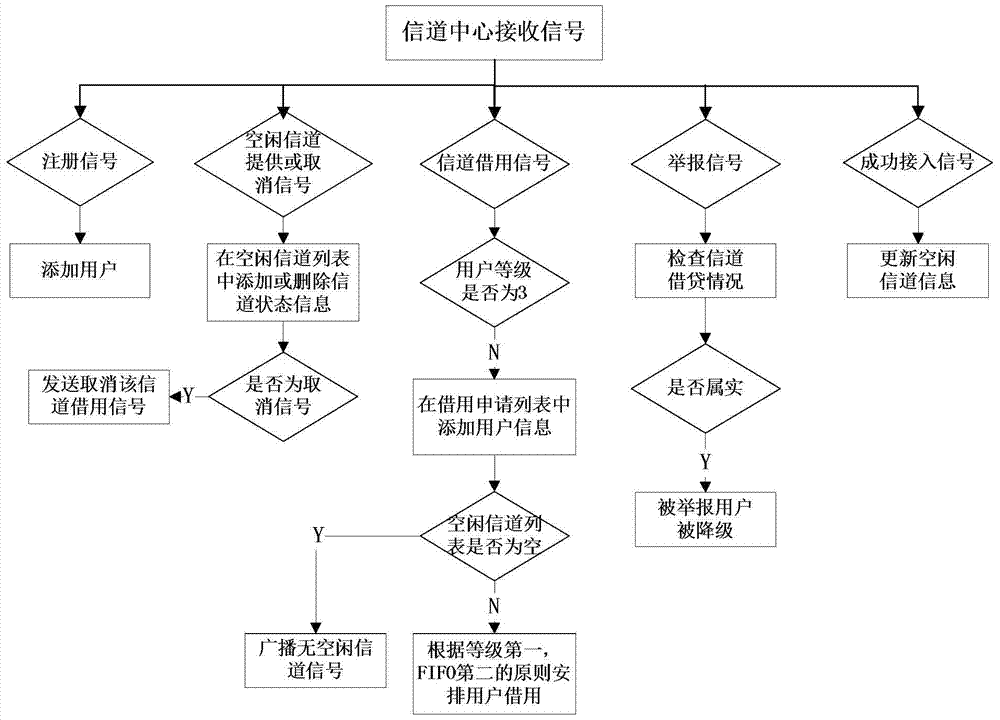
The invention discloses an information channel center system and a method for distributing information channels by using an information channel center strategy. The information channel center system comprises a management layer, a service layer, an information channel center and a user group. The method for distributing the information channels comprises the following steps of classifying users; judging whether idle first-class user information channels are distributed to unlicensed users by using the information channel center according to the class of the users; storing and managing information channel state information by using the information channel center; planning the user class; managing information channel borrowing behaviors of the unlicensed users; providing query services on information channel borrowing conditions; establishing a multi-user and multi-information-channel cognitive radio network under management of the information channel center by using a unit type model based on a Markov chain; and optimizing information channel distribution by using a genetic algorithm. Information channel data and user information are comprehensively managed on the basis of the information channel center; a circumstance that the unlicensed users await an opportunity to occupy information channels viciously can be effectively prevented in the multi-user and multi-information-channel cognitive radio network; on that basis, the information channels are optimally distributed; and the total handling capacity can be maximized.
Owner:NANJING UNIV
A dynamic generation method for a power grid task handling scheme
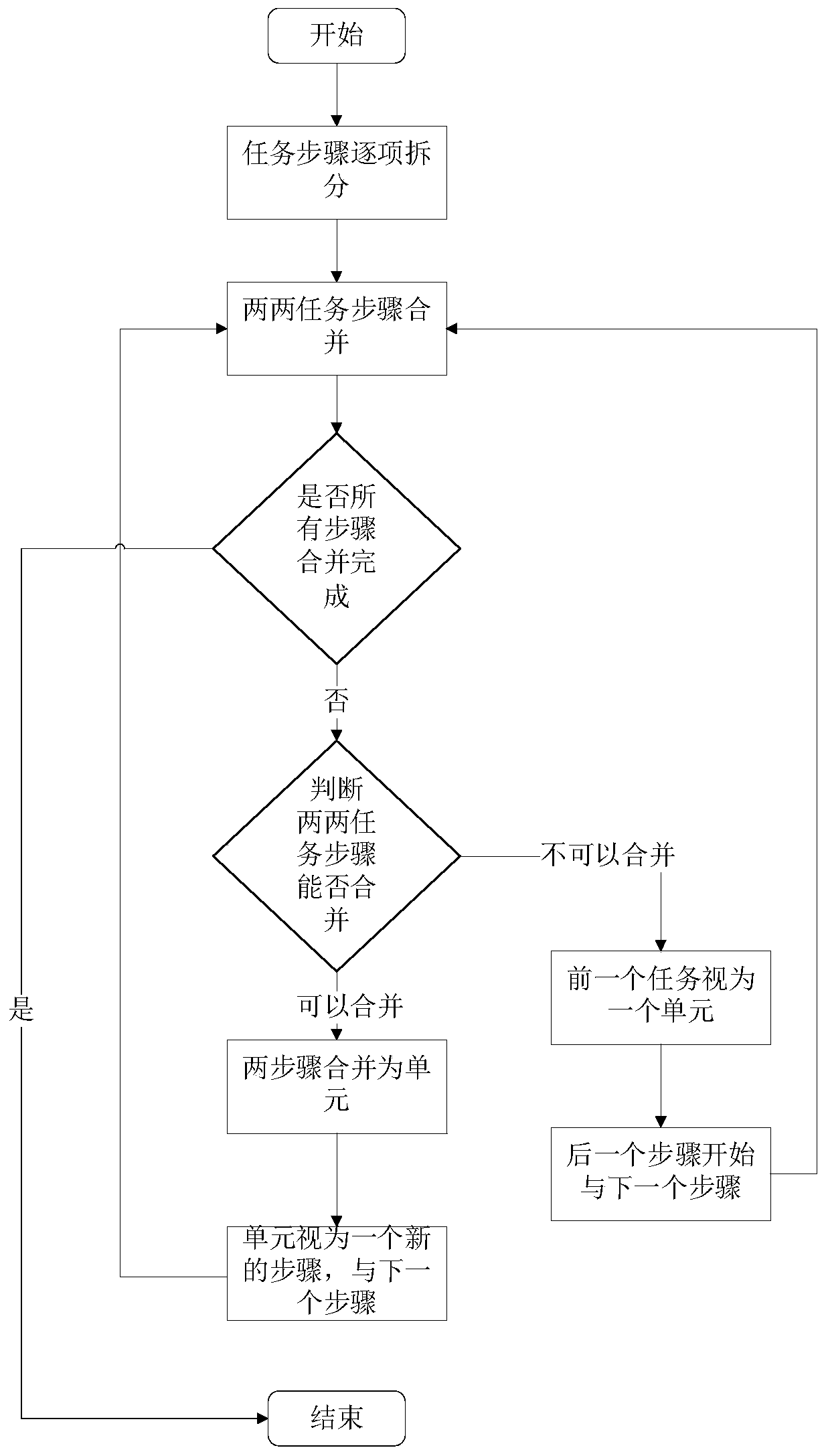
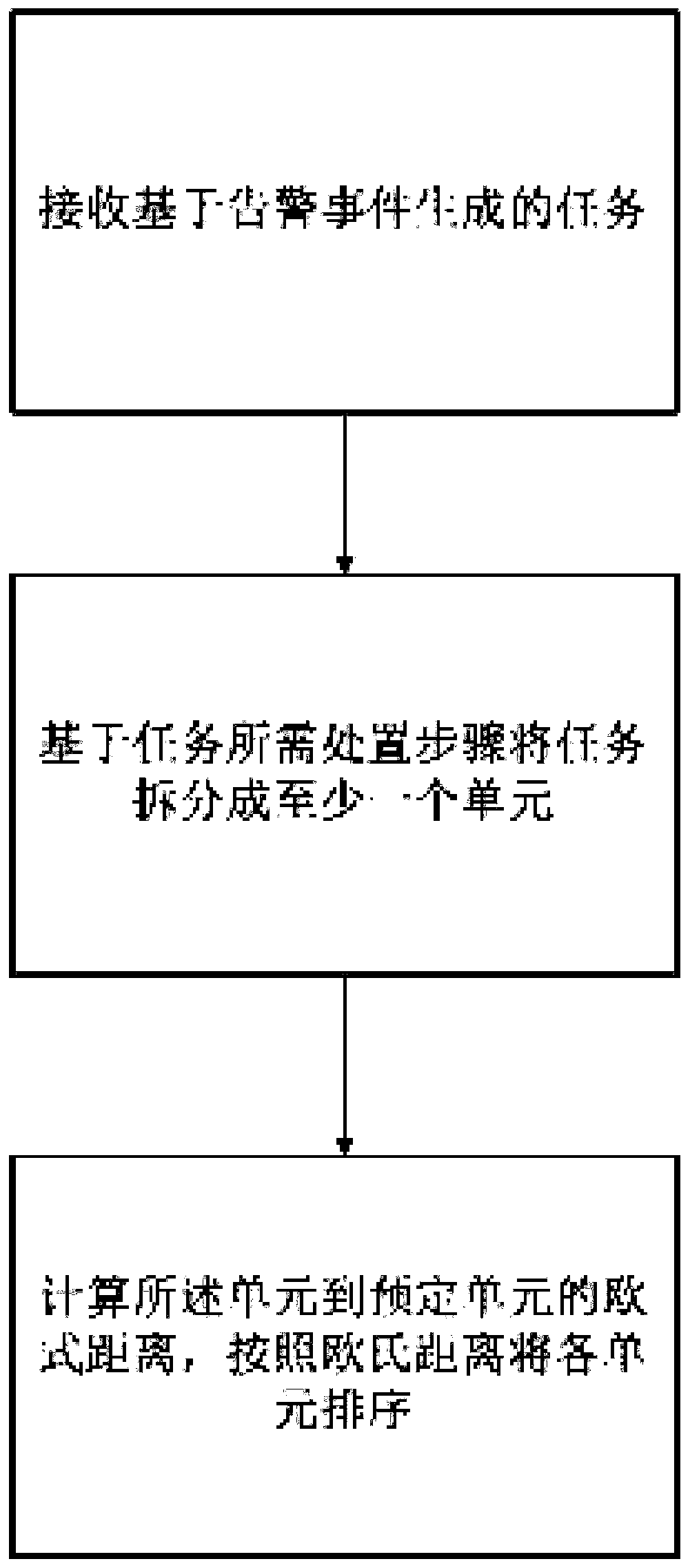
ActiveCN109767062AIncreased processing speedImprove operational efficiencyResourcesInformation technology support systemPower gridComputer science
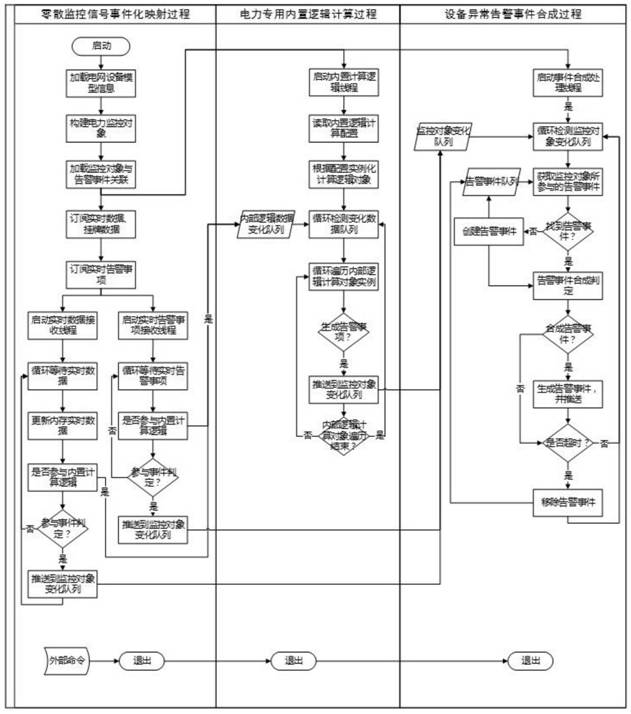
The invention relates to a dynamic generation method for a power grid task disposal scheme, and belongs to the technical field of task sorting. The method comprises the following steps of 1) receivingat least one task generated based on an alarm event; 2) splitting the task into a plurality of independent units based on the processing steps required by the task, and associating and combining intoa new unit according to the relevance among the steps corresponding to the units; 3) performing quantifiable attribute splitting on the units processed in the step 2); obtaining an attribute set of each unit; and calculating the Euclidean distance from each attribute set to the typical sample, and respectively dividing the units corresponding to each attribute set into the nearest typical samplegroup, thereby dividing different crisis handling degrees of each unit, preferentially handling critical units, secondly handling emergency units, and finally handling common units. According to the method, the analysis complexity of the monitoring service event can be greatly reduced, and the operation efficiency of the monitoring service event is improved.
Owner:JIANGSU ELECTRIC POWER CO +2
A method for establishing a multi-level virtual maintenance training system for complex equipped vehicles
ActiveCN110502868BAvoid running out of memoryIncrease real-time interactionCosmonautic condition simulationsCharacter and pattern recognitionControl engineeringDimensional precision
The invention discloses a method for establishing a multi-level virtual maintenance training system for vehicles with complex equipment, comprising the steps of: 1. Collecting information about the entire vehicle with complex equipment and its components; 3. Optimizing the visual display of 3D rough models and 3D fine models for virtual disassembly and assembly; 4. Establishing the optimized virtual disassembly of 3D fine models for virtual disassembly 5. Construct a multi-level virtual maintenance self-learning training mode for complex equipment vehicles; 6. Construct a multi-level virtual maintenance guidance training mode for complex equipment vehicles; 7. Construct a multi-level virtual maintenance autonomous training mode for complex Integration and packaging of multi-level virtual maintenance training system for equipped vehicles. The present invention establishes a rough model and a fine model, the training is smooth, the degree of reality and immersion is good, and the virtual decomposition and assembly object model and its hierarchical relationship are established to facilitate the later virtual maintenance training.
Owner:ROCKET FORCE UNIV OF ENG
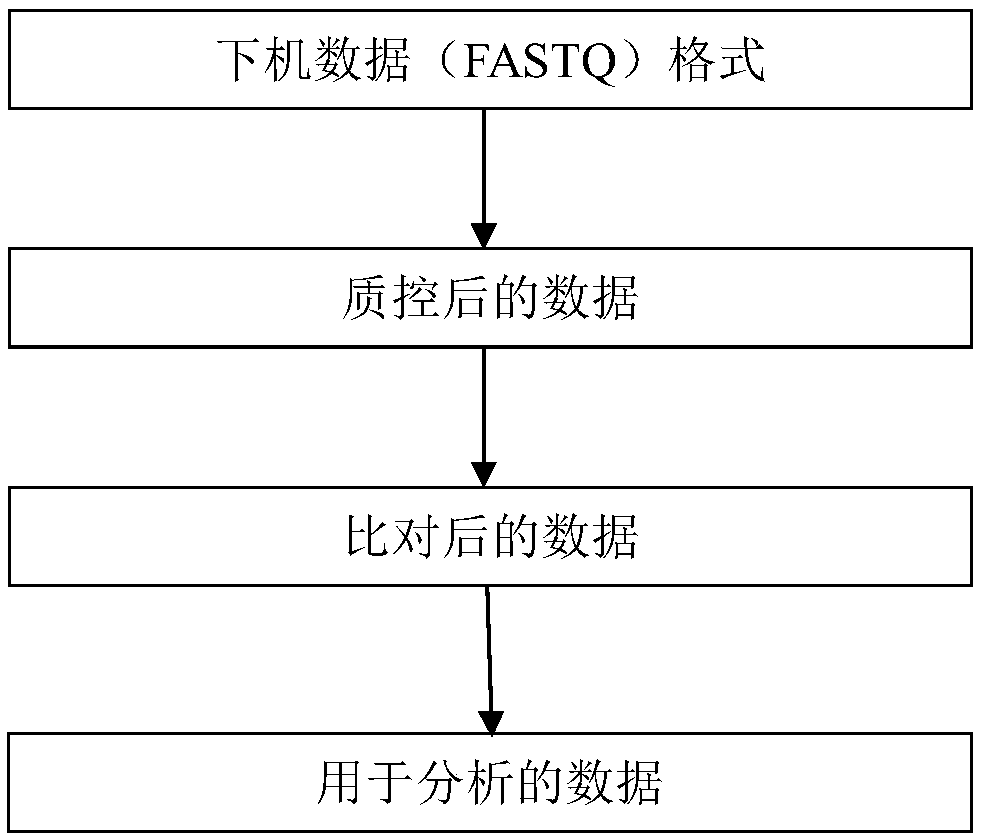
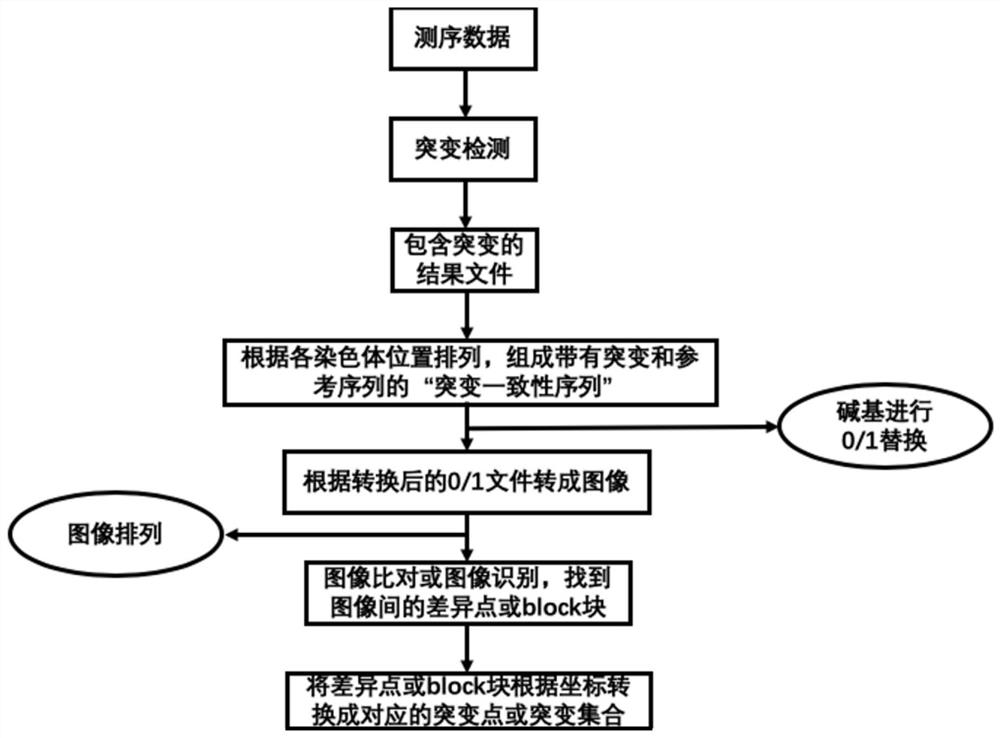
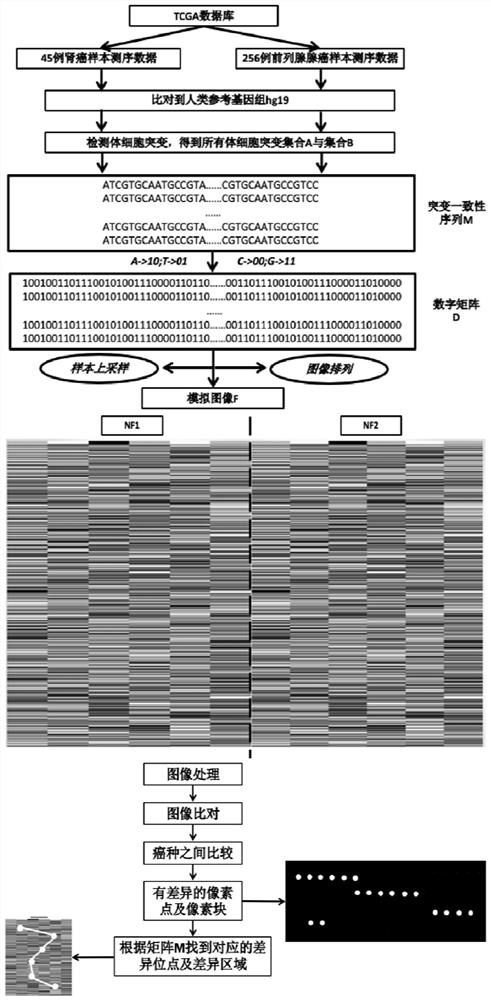
Method and system for analyzing gene sequencing data
PendingCN112435712AReduce Analysis ComplexityLow costImage analysisBiostatisticsSequencing dataConventional analysis
The invention discloses a method and system for analyzing gene sequencing data. According to the method, all detected variation information can be utilized; meanwhile, a visual concept is fused, unprocessed variation information is simulated into an image, variation distribution and intensity can be visually seen, an image comparison or image recognition technology is utilized to directly processthe image to search for differences. Therefore, the analysis complexity can be reduced to the great extent, the analysis time cost is lowered, the analysis time is multiplied compared with a conventional analysis method, and the analysis process is simpler and more visual.
Owner:元码基因科技(苏州)有限公司
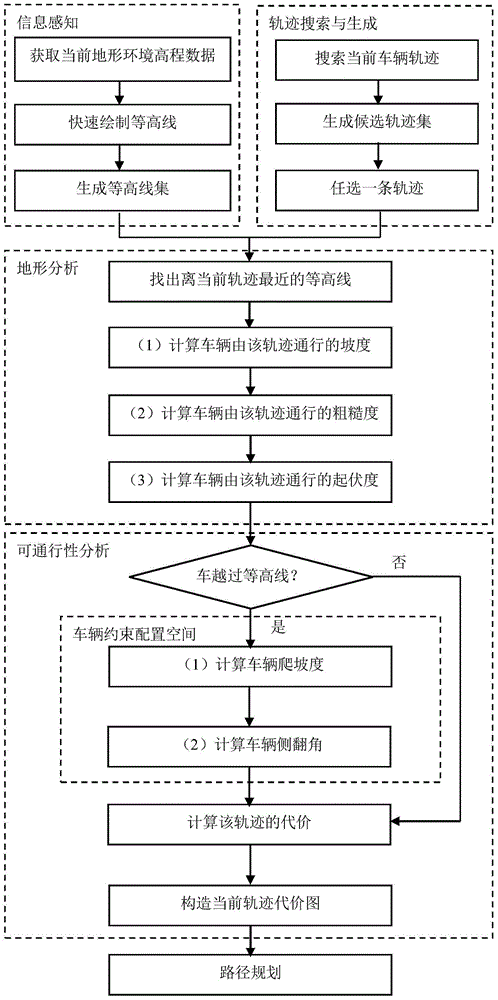
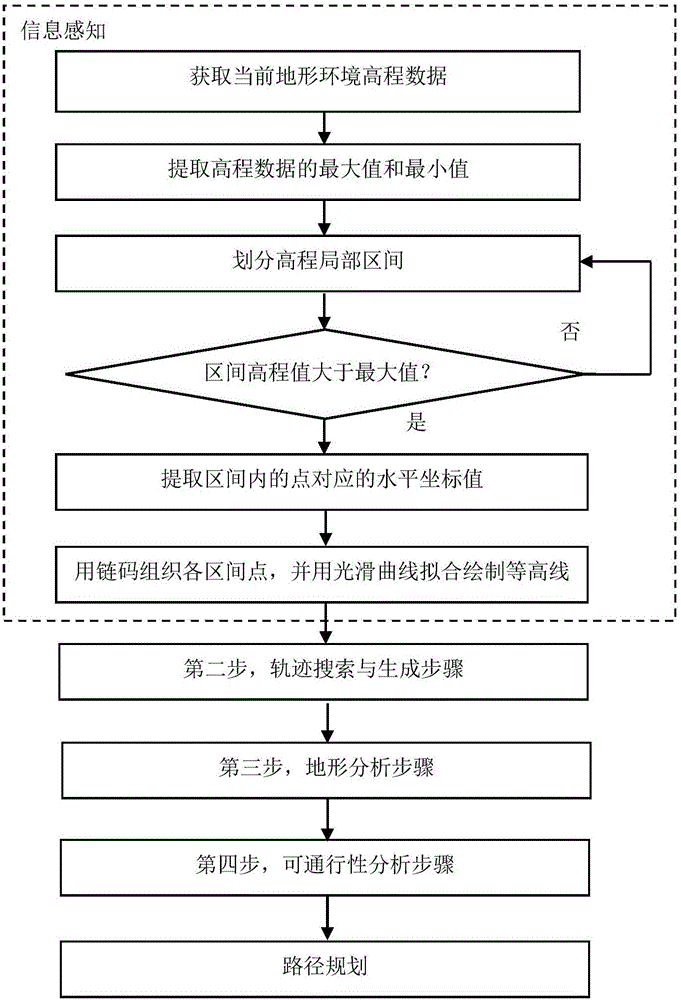
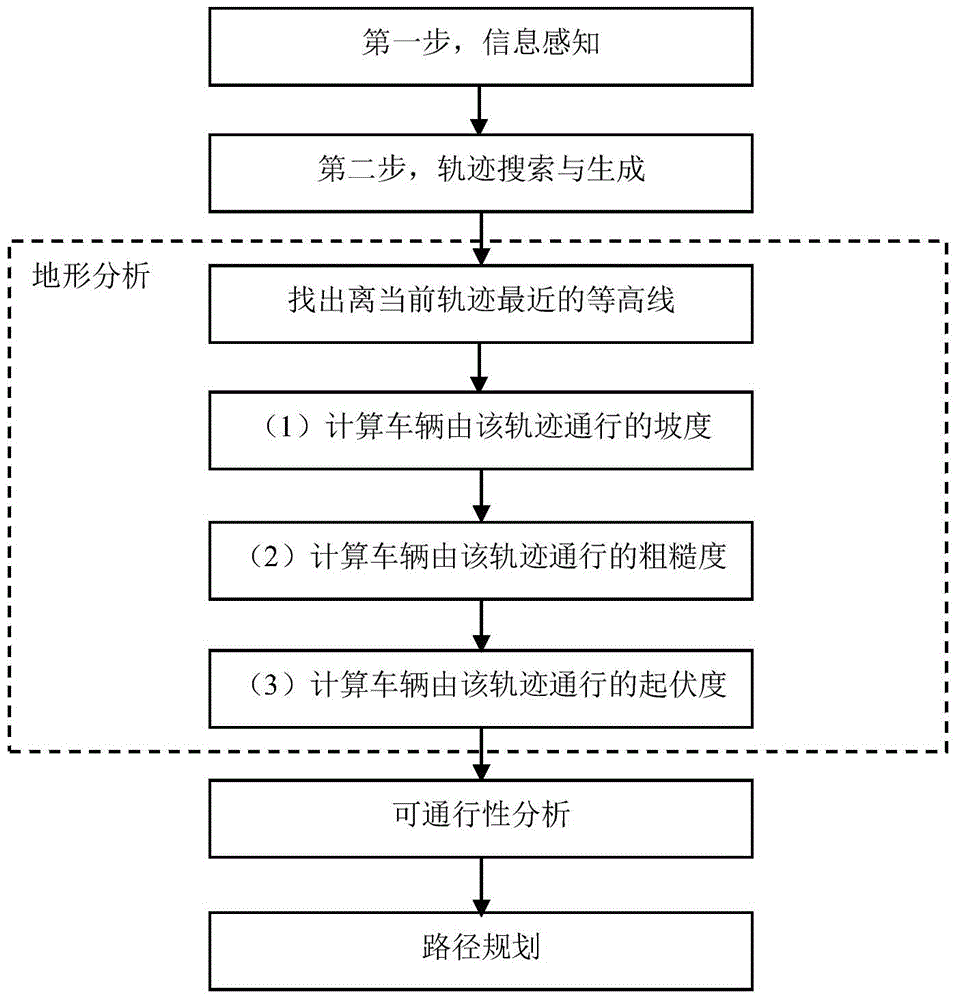
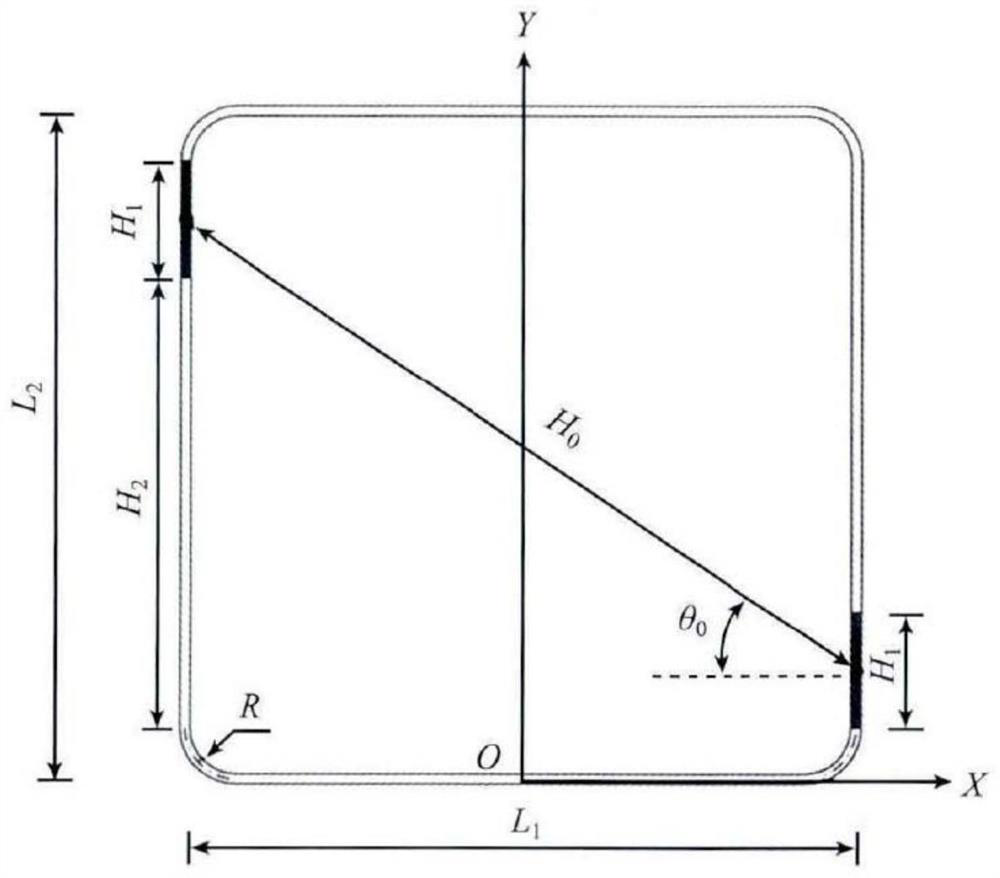
A three-dimensional terrain traversability analysis method for autonomous vehicles
ActiveCN104268862BQuick calculationReduce Analysis ComplexityImage analysisForecastingKinematicsIntersection of a polyhedron with a line
A three-dimensional terrain trafficability analytical method for an autonomous land vehicle comprises the step of information perception, wherein movement state information and environmental information of the current vehicle are obtained; the step of track searching and generation, wherein track preliminary searching is carried out according to the current vehicle position and a final target position, and a local track set of possible movements of the vehicle is generated; the step of terrain analysis, wherein the contour line of the current terrain is drawn according to obtained terrain altitude data, the intersection point of a candidate track and the contour line is found according to a vehicle speed v, the terrain characteristics of track curved sections formed by a lower intersection point of the contour line and the current position of the autonomous land vehicle are analyzed, and a basic terrain factor is calculated; the step of trafficability analysis, wherein the cost of each track curved section formed when the vehicle passes is calculated by combining dynamic constraints and kinematical constraints of the vehicle, so that a cost chart is constructed; and the step of route planning, wherein the optimal route is searched with the cost chart serving as heuristic information. The three-dimensional terrain trafficability analytical method for the autonomous land vehicle has the advantages of being simple in principle, easy and convenient to operate, high in identification accuracy, efficient in calculation and the like.
Owner:NAT UNIV OF DEFENSE TECH
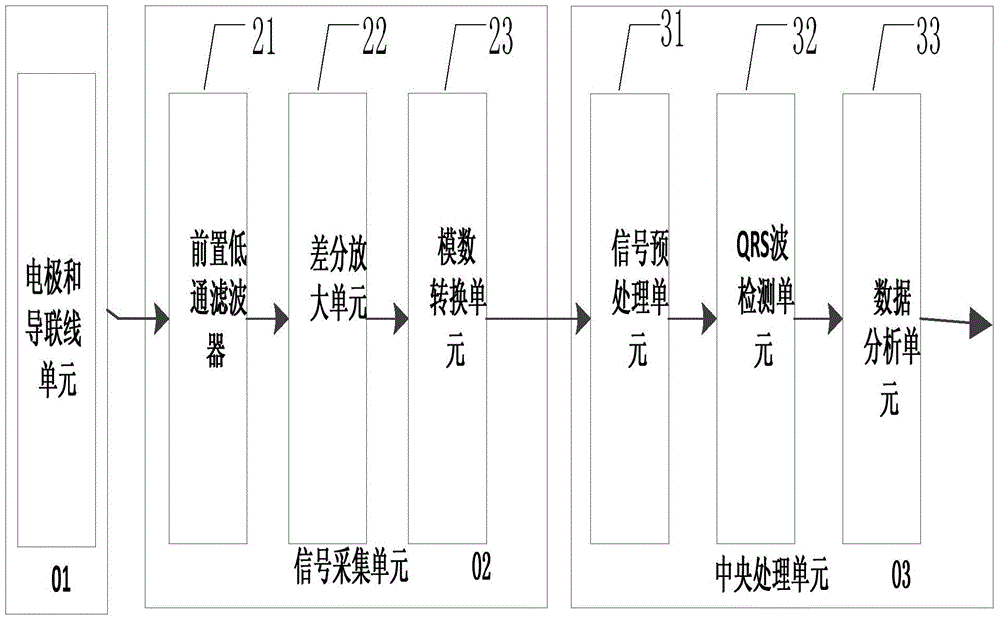
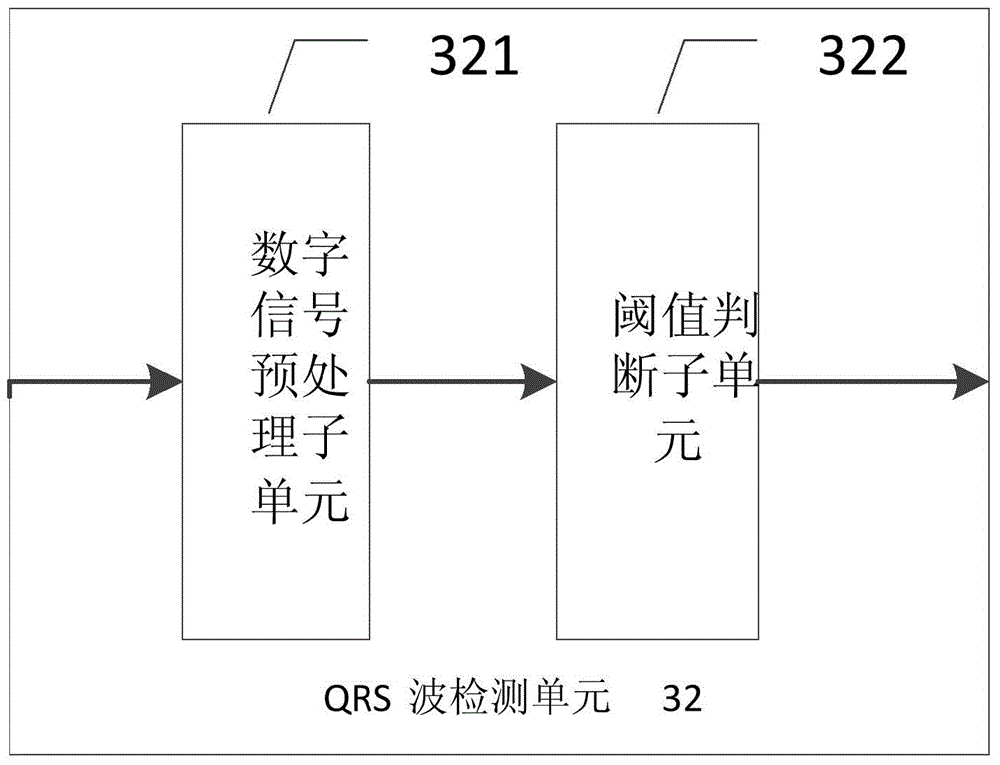
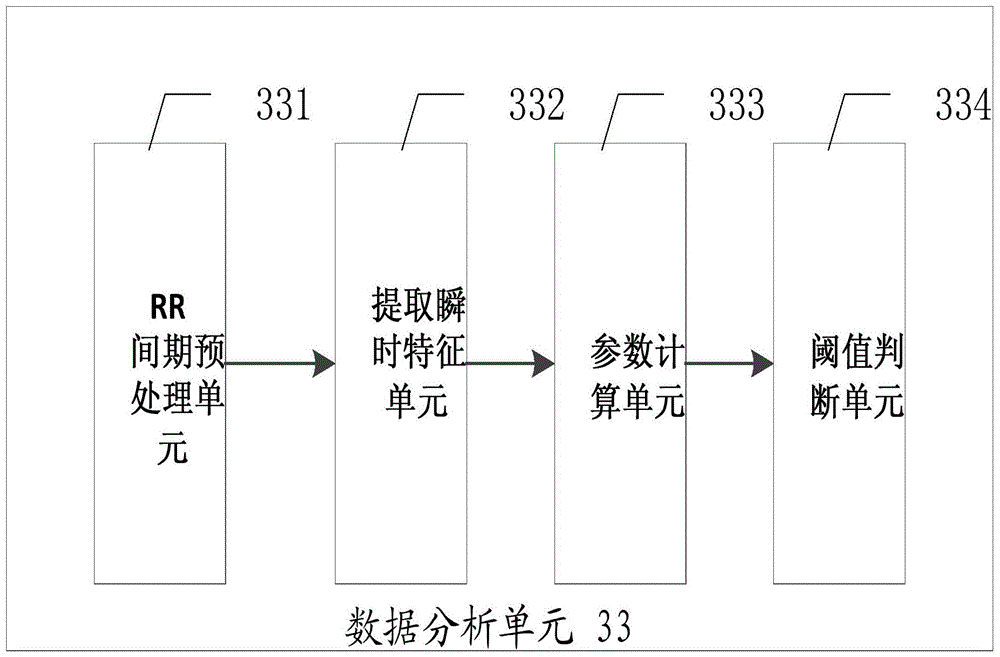
ECG signal data acquisition and processing method and system
ActiveCN103479349BReduce Analysis ComplexityReduce computationDiagnostic recording/measuringSensorsEcg signalFeature extraction
The invention provides an electrocardiosignal data acquisition and processing method and system. The electrocardiosignal data acquisition and processing system comprises a data processing unit which comprises a data analysis unit. The data analysis unit comprises an RR interphase preprocessing unit and an instantaneous feature extraction unit. The RR interphase preprocessing unit is used for preprocessing an RR interphase sequence, so that a signal bandwidth of an RR interphase is enabled to fall in a frequency bandwidth requested by the best amplitude frequency features of the Hilbert transform. The instantaneous feature extraction unit is used for extracting instantaneous amplitude features and instantaneous frequency features of the RR interphase sequence. The electrocardiosignal data acquisition and processing system has the advantages that through acquisition and processing of the electrocardiosignals, complexity of data analysis is reduced, and amount of calculation is decreased; the system is simple in design, low in cost and convenient to apply.
Owner:EDAN INSTR
Flow determination method, device and server for natural circulation loop
ActiveCN110289111BSimplify the analysis processGuaranteed accuracyPlant parameters regulationNuclear energy generationMathematical modelStream flow
The invention provides a flow determining method and device for a natural circulation loop as well as a server. The method comprises the following steps: obtaining a mathematical model of the natural circulation loop of a reactor and parameters of a coolant; according to a computational fluid dynamics principle, a reactor core heat exchange section model and a preset initial loop inlet flow rate, determining the average temperature of various sub-heat exchange section models; according to a natural circulation pressure drop balance principle, the average temperature, the reactor core heat exchange section model, a steam generator heat exchange section, a pipeline section model and the parameters of the coolant, determining a natural circulation steady-state inlet flow rate; then in combination with the natural circulation steady-state inlet flow rate and a preset rocking condition, determining the change function of the average temperature of the various sub-heat exchange section models under the rocking condition; based on a principle similar to the determining of the natural circulation steady-state inlet flow rate, determining the change function of the natural circulation inlet flow rate of the coolant under the rocking condition. According to the invention, the analysis efficiency is improved while the accuracy of the analysis result of the natural circulation flow change under the rocking condition is ensured.
Owner:SHANGHAI JIAOTONG UNIV
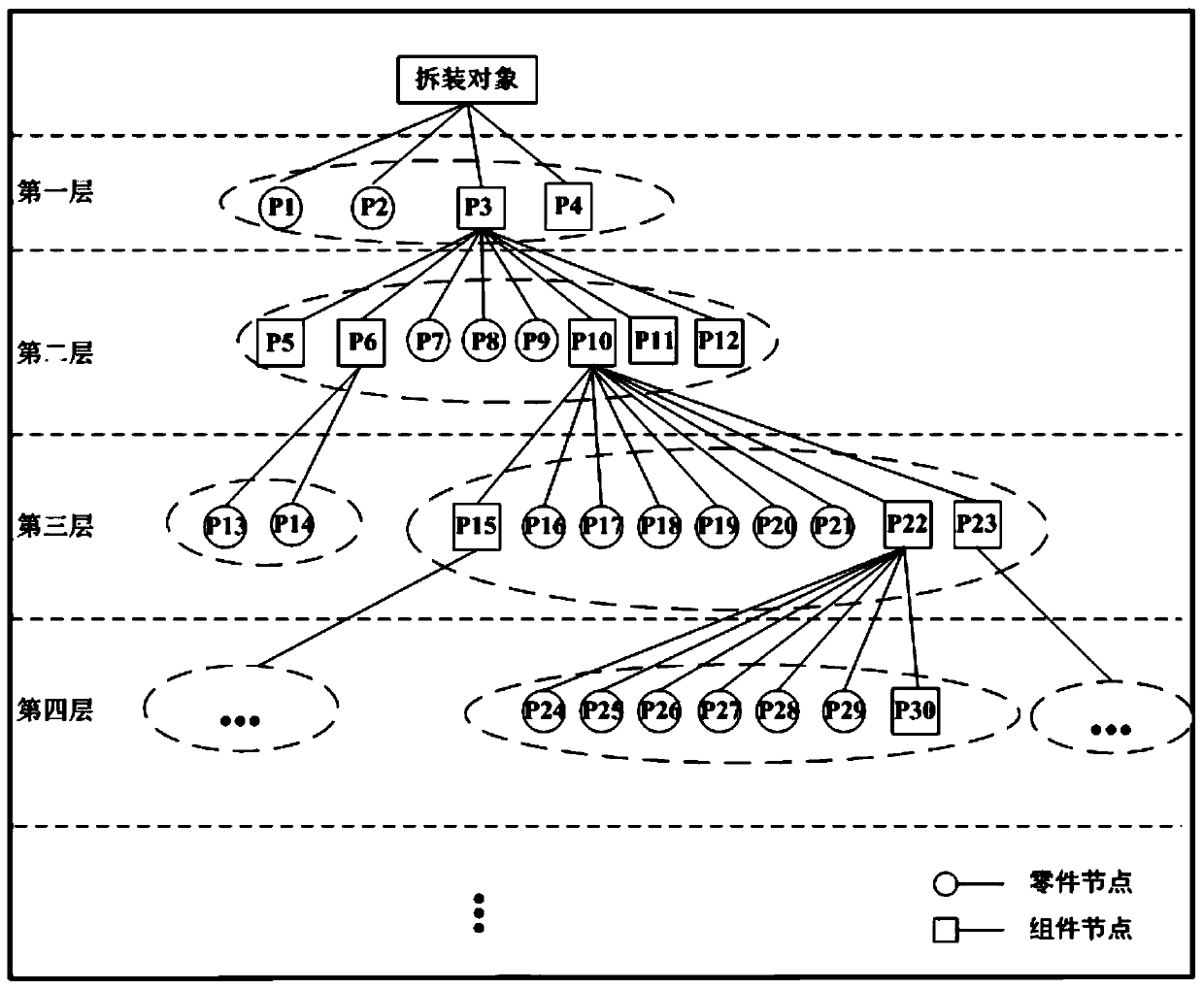
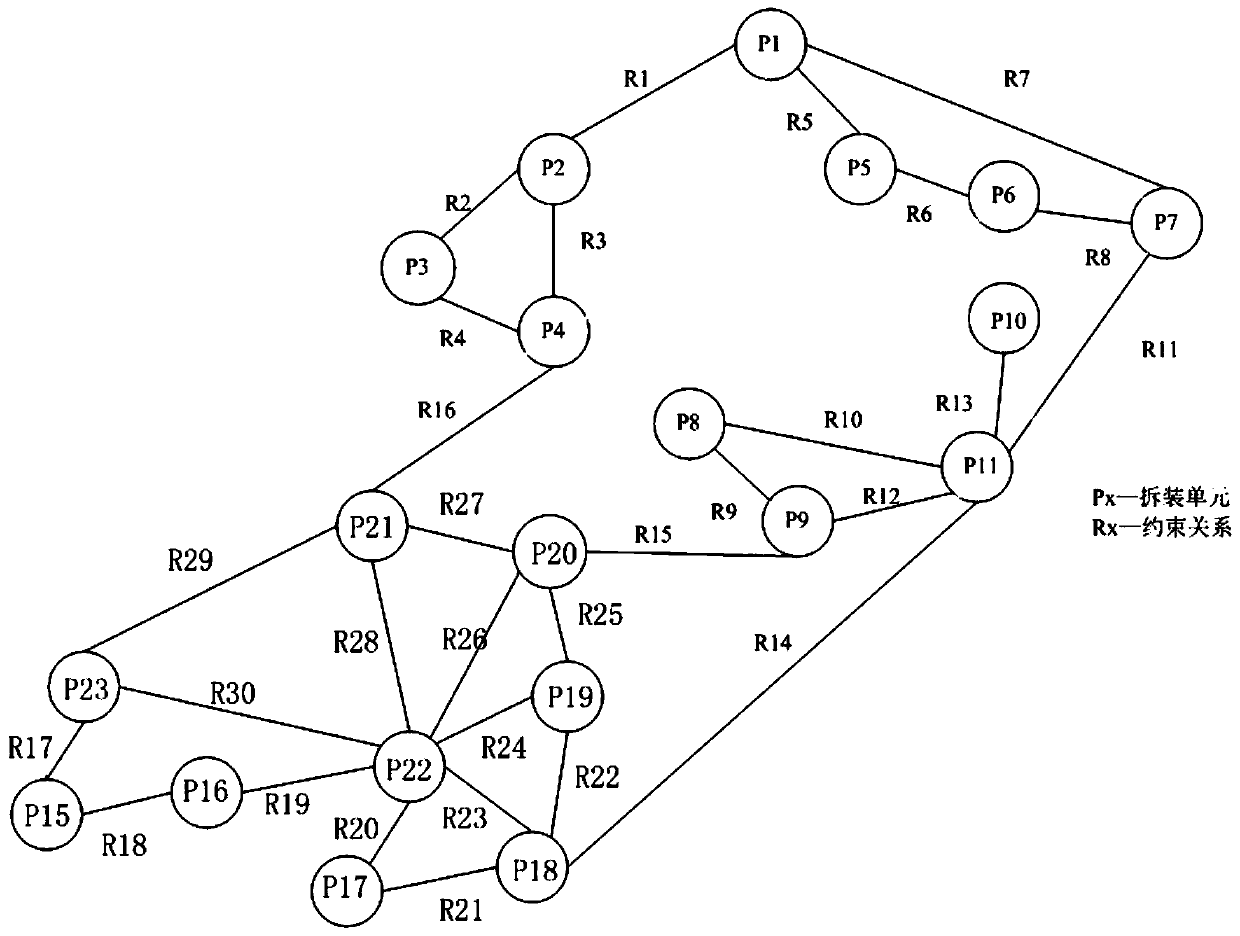
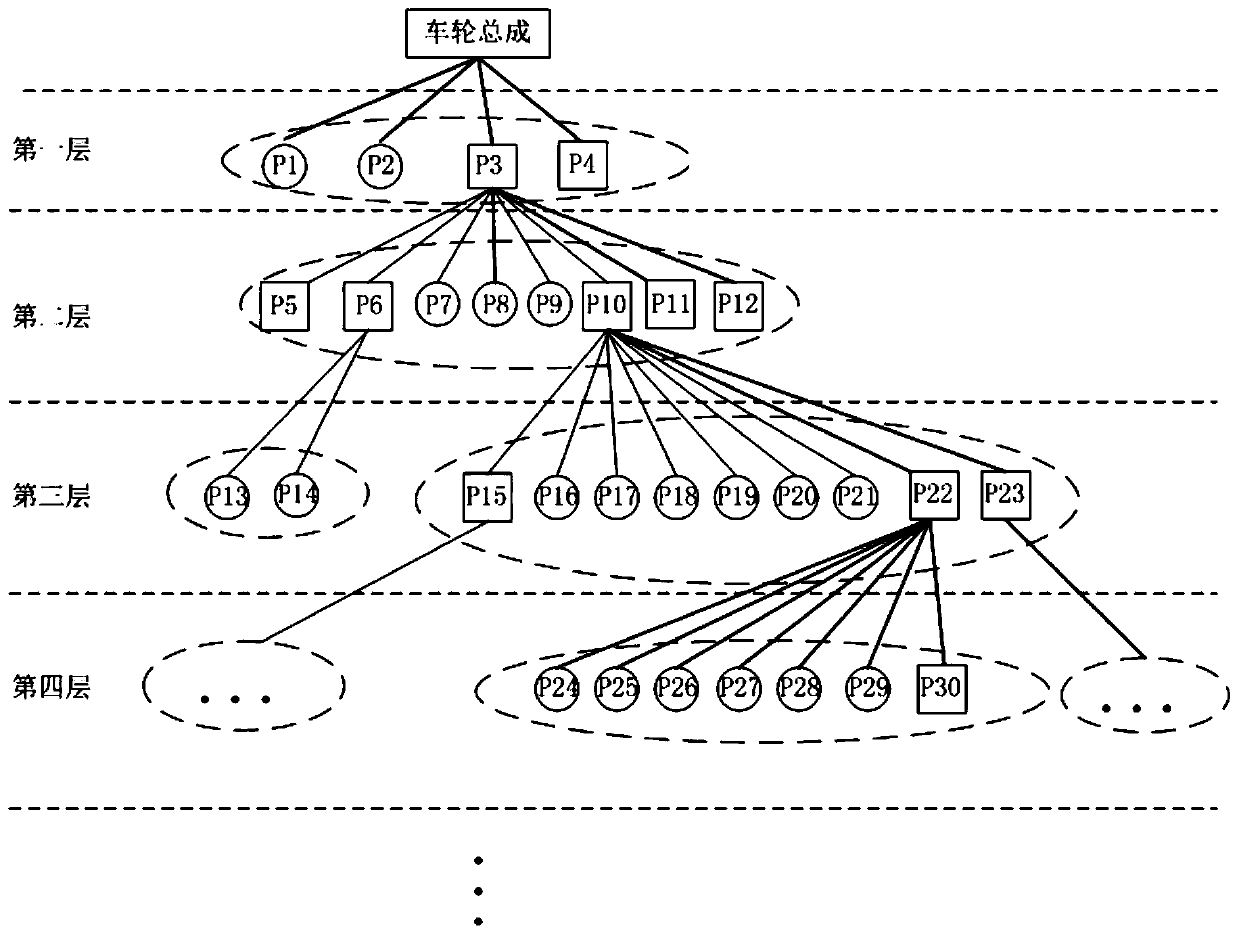
Optimal cut-set virtual disassembly sequence planning method for large-scale and complex equipment
ActiveCN110532718BEmbodied structureReduce in quantityDesign optimisation/simulationSequence planningProcess engineering
The invention discloses a large-scale complex equipment hierarchical association optimal cut set virtual disassembling and assembling sequence planning method. The method comprises the steps of 1, constructing a multi-level relationship disassembling and assembling tree model of a large-scale complex equipment disassembling and assembling object; 2, establishing an association relationship disassembling and assembling network model of disassembling and assembling objects; 3, generating a disassembling cut set; 4, obtaining a mechanical feasibility disassembly initial planning sequence; 5, verifying a mechanical feasibility disassembling initial planning sequence; and 6, obtaining a final planning sequence of mechanical feasibility assembly. According to the method, the hierarchical relationship of the disassembled object is considered; a disassembling and assembling sequence is planned by fusing and describing the mutual association relationship between the disassembling object part nodes and the assembling nodes; the structure of the disassembling and assembling object is well reflected, the number of elements of each layer is reduced, the analysis complexity of the disassemblingand assembling object is reduced, the collision real-time detection method of the space-time correlation tracking strategy is used for verifying the mechanical feasibility disassembling initial planning sequence, and the final disassembling and assemblling sequence between each part node and each assembly node can be planned.
Owner:ROCKET FORCE UNIV OF ENG
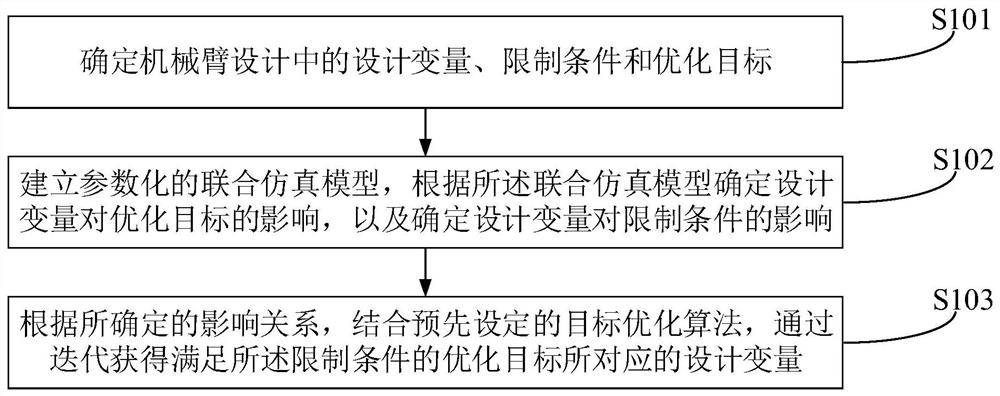
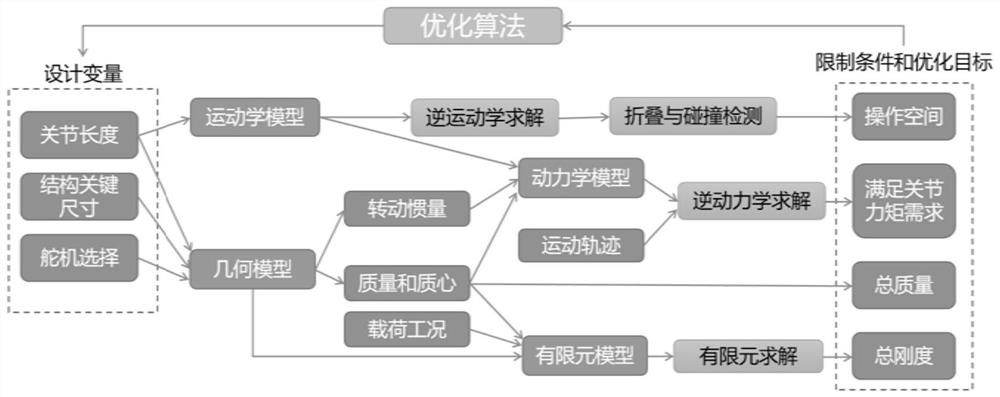
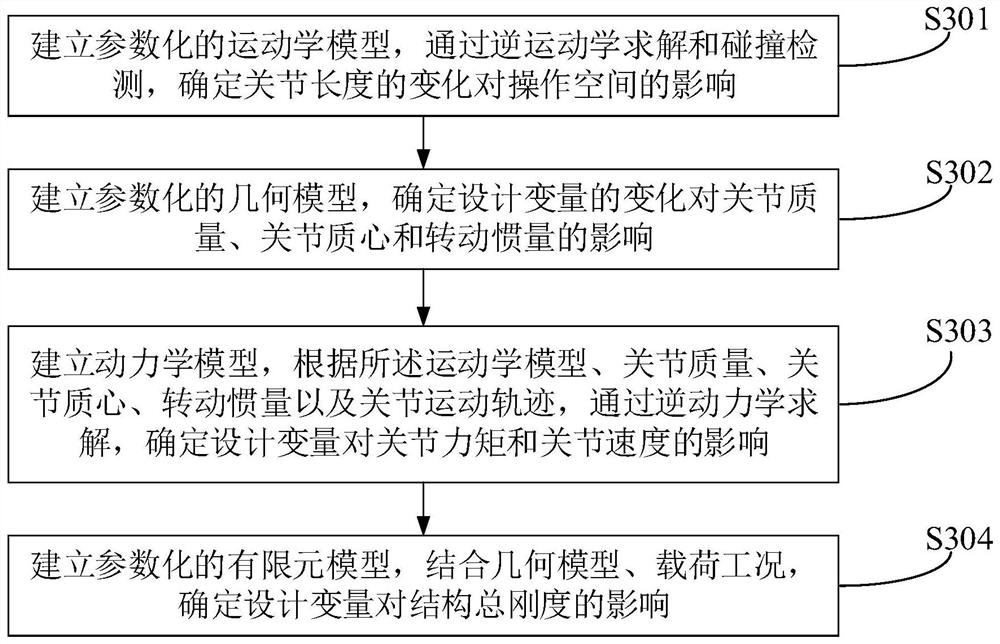
Optimization method, device and equipment for robotic arm design
ActiveCN112743574BReduce the impact of barriersReduce Analysis ComplexityProgramme-controlled manipulatorRoboticsAlgorithm
The present application belongs to the field of robotics, and proposes an optimization method, device and equipment for the design of a manipulator. The method includes: determining the design variables, constraints and optimization objectives in the design of the manipulator; establishing a parametric co-simulation model, according to the The co-simulation model is used to determine the influence of the design variables on the optimization objective and the influence of the design variables on the constraints; according to the determined influence relationship, combined with the pre-set target optimization algorithm, the optimization goal that satisfies the constraints is obtained through iteration the corresponding design variables. The relationship between design variables and optimization objectives and constraints is determined through the co-simulation model, so as to effectively reduce the influence of barriers of different algorithms, reduce the complexity of analysis, reduce the amount of calculation, and reduce the difficulty of collaborative optimization.
Owner:UBKANG (QINGDAO) TECH CO LTD
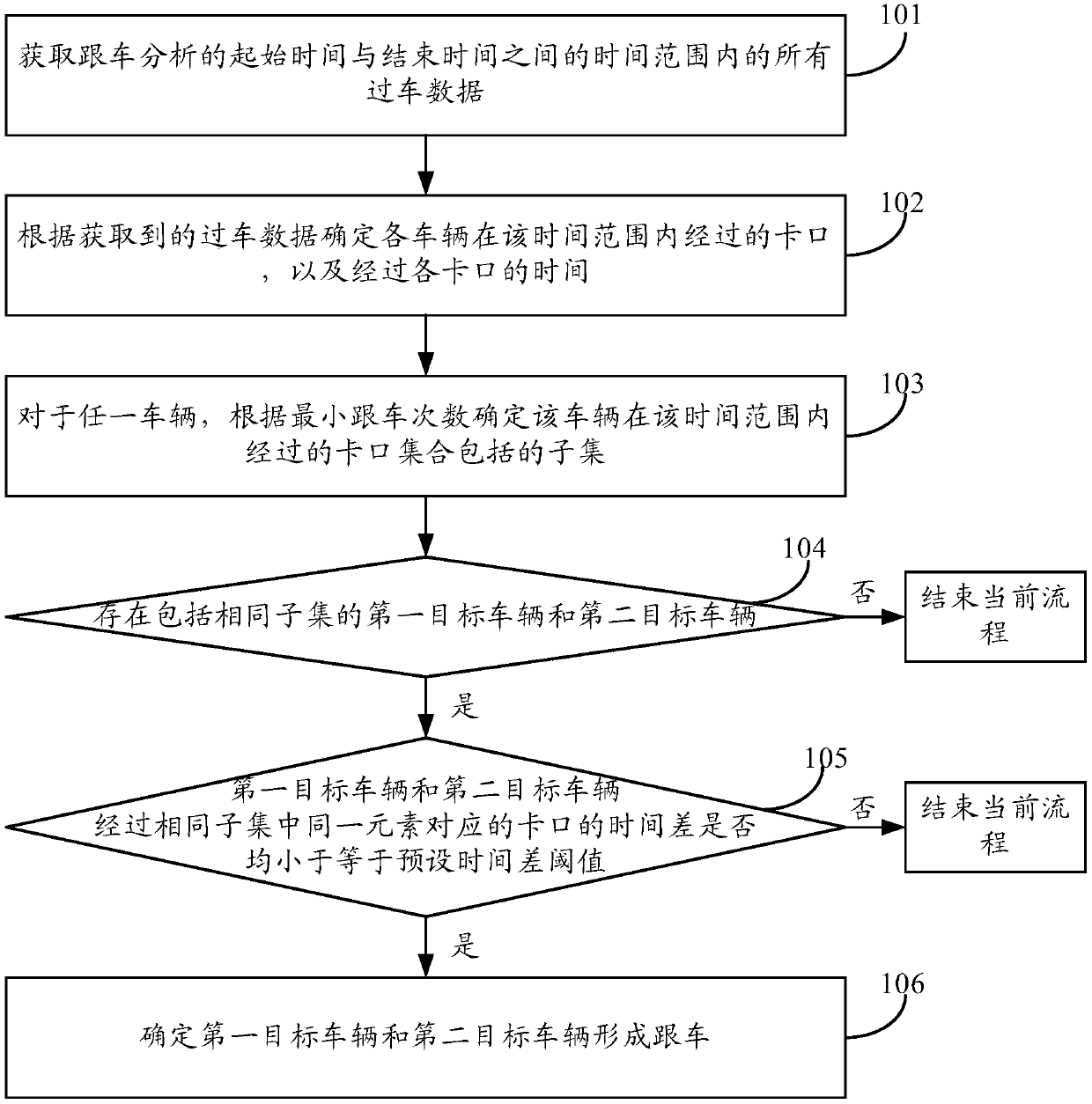
Method and device for determining vehicle following
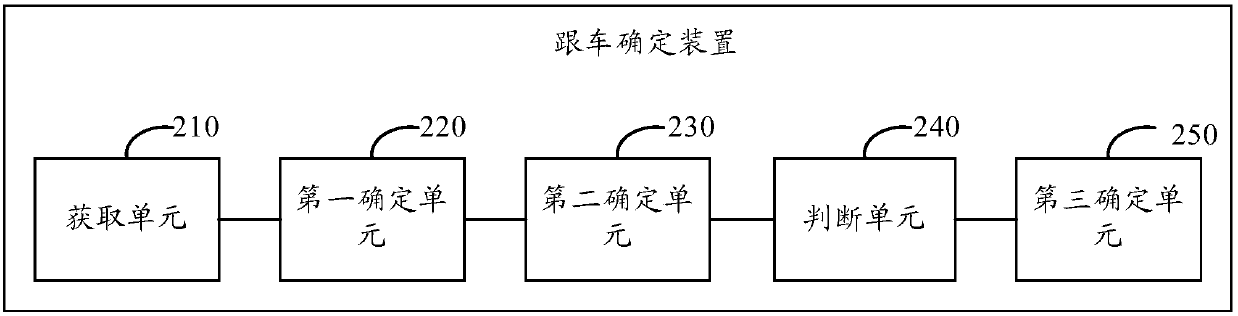
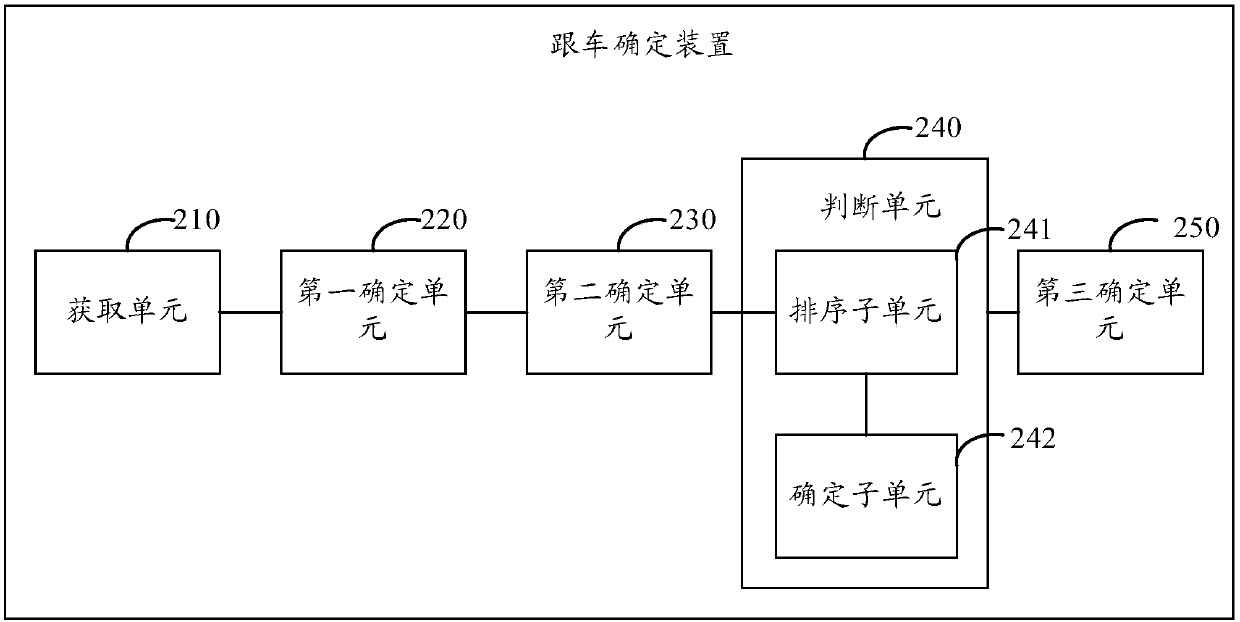
ActiveCN106097708BImprove determination efficiencyReduce data volumeDetection of traffic movementTime rangeStart time
Owner:ZHEJIANG UNIVIEW TECH CO LTD
A data conversion method
ActiveCN105446707BAchieve conversionReduce Analysis ComplexityHardware monitoringData transformationData field
The invention discloses a data conversion method used for data conversion between acquisition data and alarm data of an operation and maintenance system; according to a preset mapping relation between acquisition data type and alarm data type and a mapping relation between acquisition data file and alarm data field, the method can realize positive conversion which is to convert acquisition data into alarm data, and can realize reversed conversion which is to convert alarm data into acquisition data. The alarm data obtained by positive conversion can provide more comprehensive alarm information for operation and maintenance people, thus reducing operation and maintenance data analysis complexity for the operation and maintenance people, solving alarm data loss problems caused by increasing system device, and reducing video cloud storage operation and maintenance platform fault processing flow operation complexity; on the other hand, the acquisition data obtained by reversed conversion can be pushed to the a front end display system, thus enhancing real time display of equipment under abnormal state, and providing more accurate equipment fault information for the operation and maintenance people.
Owner:HANGZHOU HIKVISION SYST TECH
A single exon copy number variation prediction method based on target region sequencing
ActiveCN108920899BLow costReduce Analysis ComplexityProteomicsGenomicsWhole genome sequencingGenetics
Owner:杭州迈迪科生物科技有限公司
A high-interaction ssh honeypot implementation method
The invention discloses a high-interaction SSH honeypot implementation method, comprising the following steps: connecting the system SSH port, judging whether there is SSH service, and entering the next step with the SSH service; using the logit function and the authctxt structure in OpenSSH in Capture the authenticated user name / password during password authentication; after the password authentication is successful, use the SSH service to process the client data through the pipeline and the user processing interactive session module, and modify the relevant module code to complete the shell Record passwords; control the outgoing flow of the honeypot system, including the two processes of external data packet restriction and external attack packet suppression; use javaweb technology to analyze, process and display the data captured by the honeypot system. A high-interaction SSH honeypot implementation method of the present invention can solve the SSH attack that passive defense technology cannot be continuously updated due to the bottom of the valley, and the low-interaction SSH honeypot has low interaction degree, insufficient deception, and is easy to be seen through. Improve the security defense capability of the SSH service.
Owner:HOHAI UNIV
Equipment abnormity alarm event synthesis method of power monitoring system based on signal analysis
PendingCN113447744AReduce Analysis ComplexityRaise the level of security surveillanceElectrical testingElectric power equipmentMonitoring system
The invention discloses an equipment abnormity alarm event synthesis method for an electric power monitoring system based on signal analysis, which is characterized in that initialization and updating from scattered monitoring signals to monitoring events are realized through a model loading process, and special logic calculation normalization processing of the electric power monitoring system is realized through a special built-in logic calculation process of electric power; by monitoring a signal logic calculation process, synthesis of an equipment abnormity alarm event is realized, so that the signal analysis complexity is reduced, and basic data is provided for tracking and processing of an equipment abnormity state. According to a general logic calculation rule, signal action reasons are inferred reversely according to scattered signals, synthesis from the scattered monitoring signals to an equipment abnormity alarm event is achieved, and equipment abnormity can be found in time; a special logic calculation formula for electric power is expanded, a complex configuration process of special calculation logic is shielded, normalized data is provided for a general logic configuration process, and event synthesis calculation logic is simplified; and abnormal state tracking and processing of the power equipment are realized.
Owner:FUZHOU POWER SUPPLY COMPANY OF STATE GRID FUJIAN ELECTRIC POWER
Cash management system
PendingCN113139862ANo need to develop habitsBreak down barriersDigital data information retrievalFinanceStreaming dataFinancial transaction
The invention relates to a cash management system, which comprises an instruction unit, an acquisition unit, a recommendation unit and an analysis unit; the instruction unit is used for receiving a user request and initiating cash flow analysis based on the user request; the acquisition unit is used for acquiring cash flow transaction data of a user from each data source based on a user request; the recommendation unit is used for carrying out financial product modeling based on the cash flow transaction data and recommending a corresponding financial product according to the risk bearing capability of the user; and the analysis unit is used for generating cash flow data of the user based on the cash flow transaction data and the corresponding financial product model and storing the cash flow data to the database. The method has the beneficial effects that the cash flow condition of the salesman can be completely and accurately analyzed and is actively pushed to the salesman, and the use habit of the salesman does not need to be cultivated; user group particularity is achieved, and the analysis complexity can be reduced; and salesman information is obtained by using a company as a main body, and the payment information barrier is broken.
Owner:SHANGHAI ZHONGTONGJI NETWORK TECH CO LTD
Channel-centric system and method for realizing channel allocation by using channel-centric strategy
InactiveCN104202748BRegulated accessRealize managementNetwork planningMarkov chainDistribution method
Owner:NANJING UNIV
Concealed channel identification method
InactiveCN102045158BMeet the requirements of the analysisReduce analysis sizeSecuring communicationNODALOperational system
The invention discloses a concealed channel identification method. A system source code is used as an analysis object. The method comprises the following steps of: formally describing a concealed channel in a secure information system as (V, PAh, PVl, P); then dividing a system to be analyzed into relatively independent subsystems; searching related function calling branches in the subsystems by using a shared variable as a basic unit, and further constructing directed information flow graphs according to an information flow relationship; and pruning each information flow graph according to the formal description of the concealed channel to eliminate invalid flow branches and variable aliases in the code, wherein all flow nodes and function calling branches in the finally obtained information flow graphs are potential concealed channel forming factors. The method is suitable for source codes of information systems such as an operating system, a database, a network and the like of highsecurity level, has wide application range, high execution efficiency and low error report rate and missing report rate, can identify the potential concealed channel in the system, and meets the requirement of security standards on concealed channel analysis.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method, device and electronic equipment for determining distance between interaction target and robot
Owner:山东睿思奥图智能科技有限公司 +1
A distributed information tracking system, information processing method and device
ActiveCN106933724BImprove real-time analysisReduce Analysis ComplexityDigital data information retrievalInterprogram communicationInformation processingReal time analysis
The invention provides a distributed information tracking system, information processing method and device, which collects call information in the business processing stage through information collection equipment, sends the call information to the message channel, and obtains call information from the message channel through information analysis equipment. Information, real-time analysis of the call information to obtain the call information with the same identification information, and obtain the corresponding call chain according to the call information with the same identification information, so the present invention can rely on the call information to obtain the call chain, compared with the prior art In other words, it saves the process of converting the call information into the corresponding log format and writing it into a local file, thereby improving the real-time performance of the analysis, and the information analysis device can obtain the call chain through real-time analysis of the call information. Compared with the existing real-time The analysis of the three sub-steps of analysis, offline analysis and combined analysis can get a call chain, which further improves the real-time performance of the analysis and reduces the complexity of the analysis.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
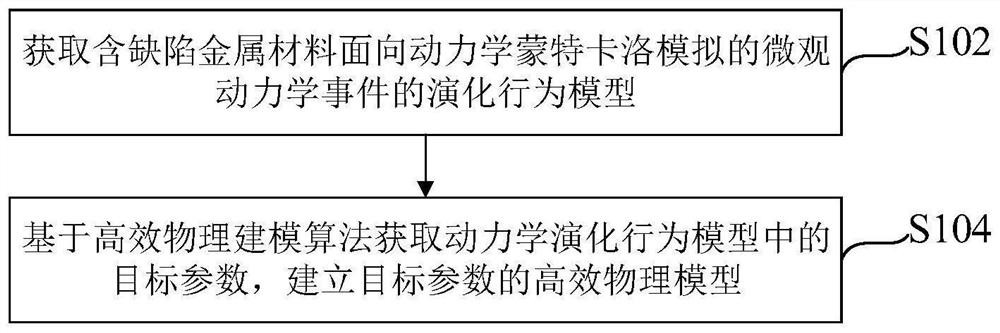
Novel dynamic Monte Carlo modeling method for defective metal material
PendingCN114528698ASimplify the modeling processReduce the amount of parametersDesign optimisation/simulationSpecial data processing applicationsMetallic materialsPhysical model
The invention provides a novel dynamic Monte Carlo modeling method for a defect-containing metal material, and relates to the technical field of microdynamics, and the method comprises the steps: obtaining an evolution behavior model of the defect-containing metal material for a dynamic Monte Carlo simulation microdynamics event; wherein the microdynamics events comprise any one or more of a defect binding / dissociation event, a defect emission / absorption event and a defect diffusion event; obtaining target parameters in the dynamic evolution behavior model based on an efficient physical modeling algorithm, and establishing an efficient physical model of the target parameters; wherein the efficient physical model is an approximate model reflecting a high-probability change rule of the target parameter along with the defect information, and the defect information comprises a defect type and a defect size. According to the method, the dynamic evolution behavior analysis complexity can be reduced, and the modeling efficiency and the analysis efficiency of the dynamic evolution behavior of the defect-containing metal material are improved.
Owner:INST OF APPLIED PHYSICS & COMPUTATIONAL MATHEMATICS +1
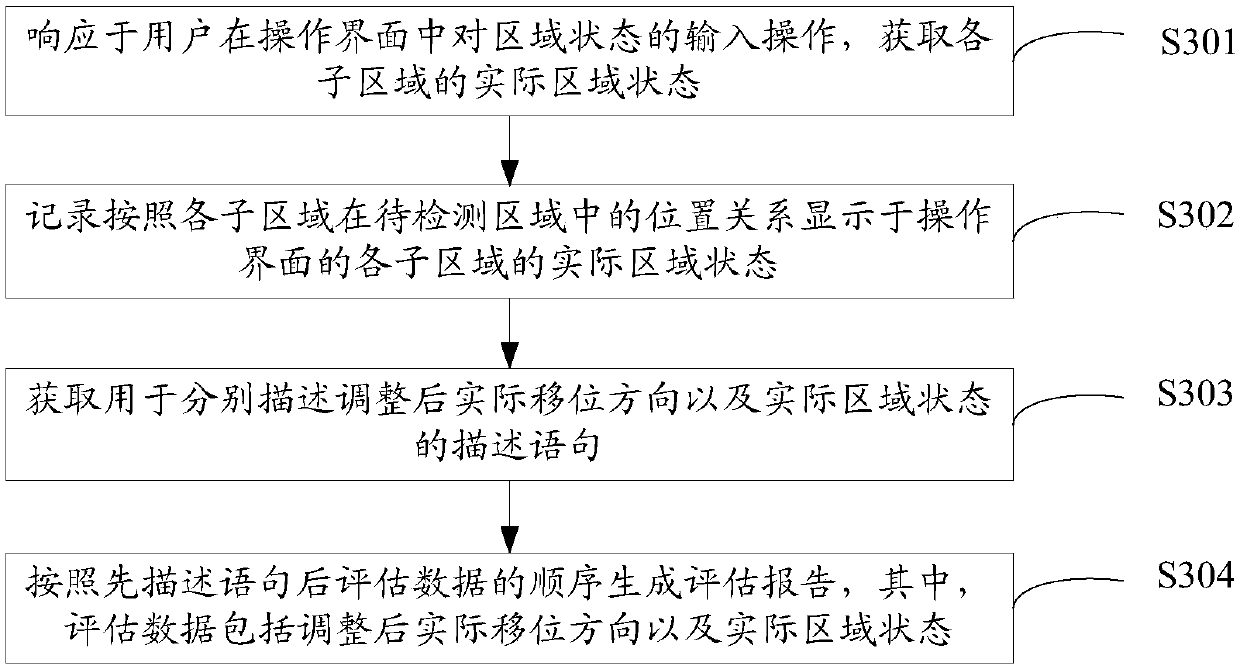
Data processing method and device and electronic equipment
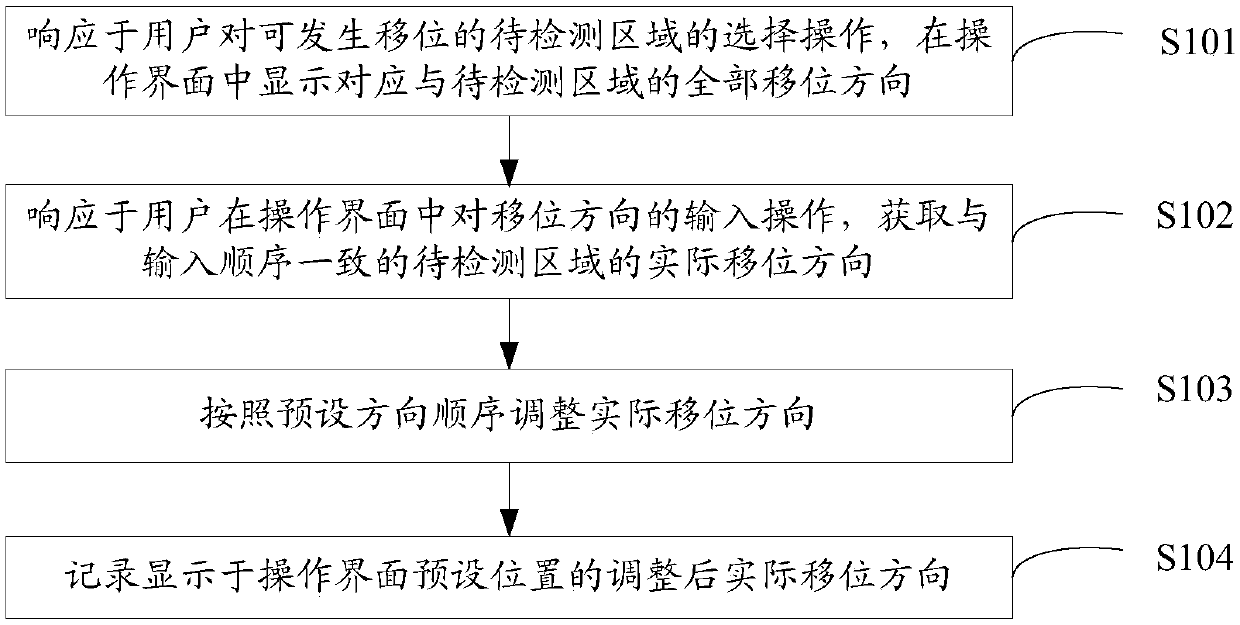
ActiveCN110262727AReduce Analysis ComplexityMedical equipmentExecution for user interfacesUser inputSimulation
The embodiment of the invention provides a data processing method and device and electronic equipment, and the method comprises the steps that data processing equipment responds to the selection operation of a user on a displaceable to-be-detected area, and all the displacement directions corresponding to the to-be-detected area are displayed in an operation interface. Then, in response to an input operation of the user on the shift direction, an actual shift direction consistent with the input sequence is acquired. And the data processing device adjusts the obtained actual displacement direction according to a preset direction sequence. And finally, the adjusted actual displacement direction displayed at the preset position of the operation interface is recorded. No matter how the direction sequence of the actual displacement direction input by the user is, the data processing equipment can ensure that the actual displacement direction input by the user can be recorded in a unified direction sequence by adjusting the actual displacement direction. And by standardizing the direction sequence of the shift direction, the analysis complexity during subsequent analysis of a large amount of shift direction data can be further reduced.
Owner:BEIJING FRIENDSHIP HOSPITAL CAPITAL MEDICAL UNIV +1
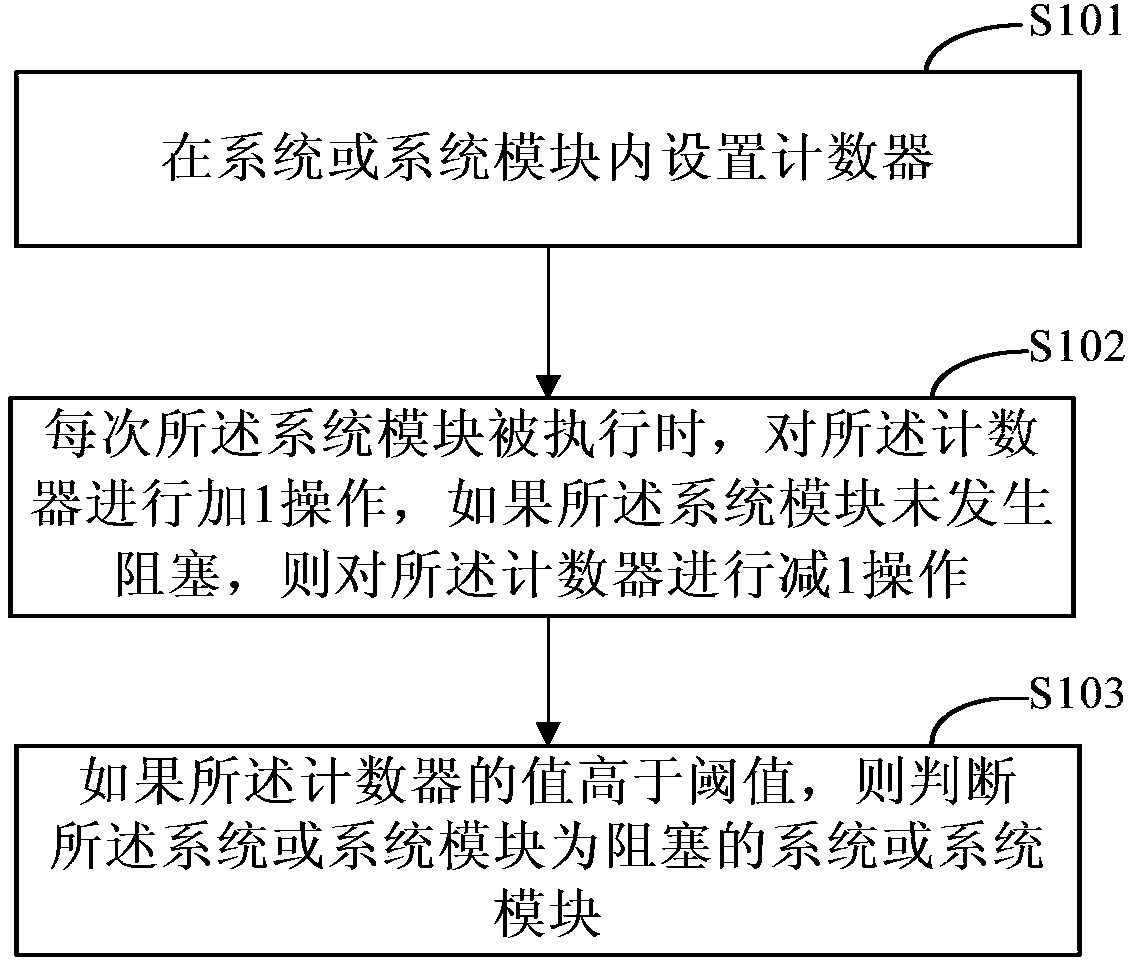
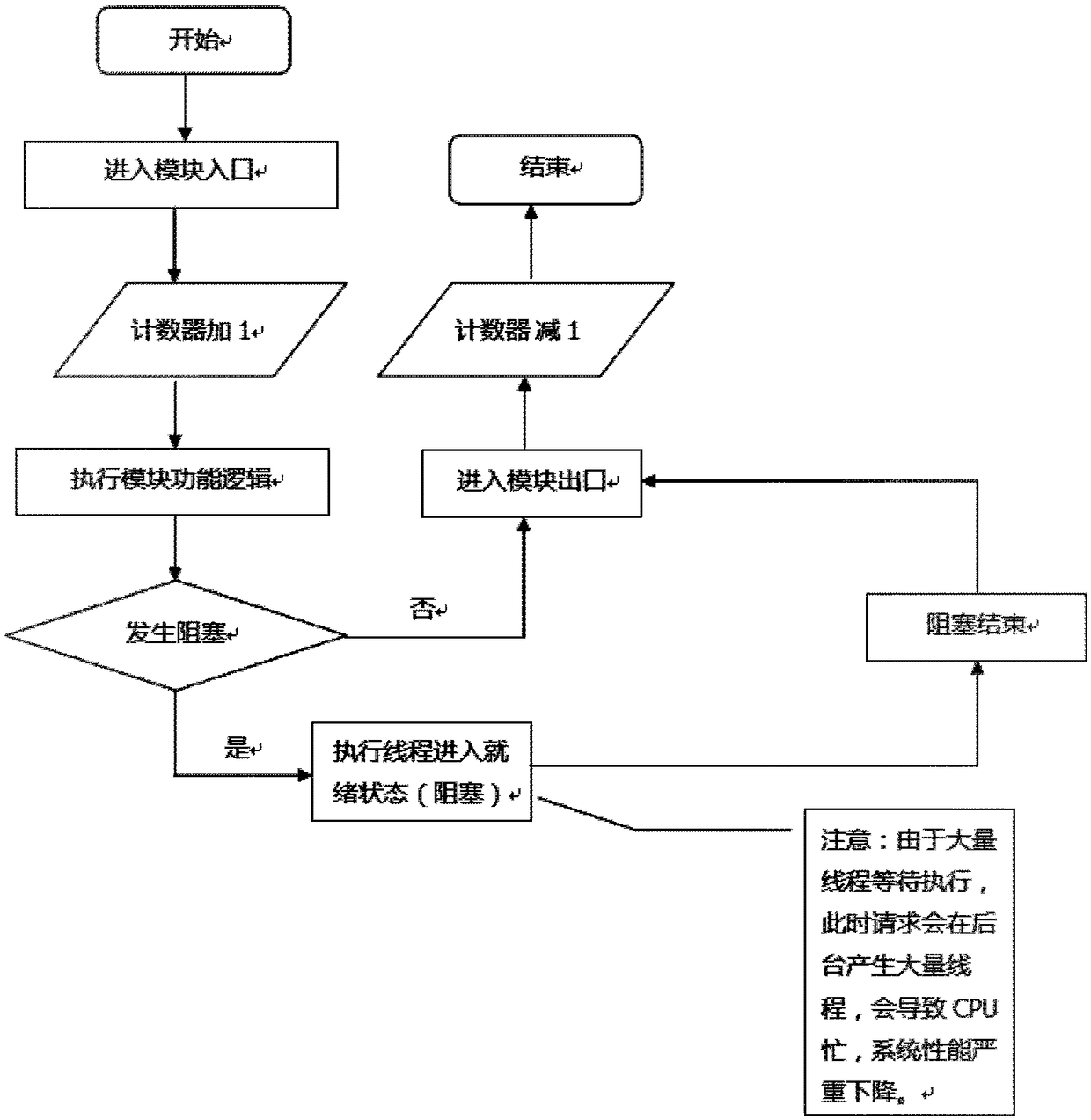
Method and device for judging whether system or system module is blocked or not
InactiveCN108959015AOperational securityAvoid lossHardware monitoringComputer scienceReal-time computing
The invention provides a method and device for judging whether a system or a system module is blocked or not. By the method and the device, the threading blocking condition of the system or the systemmodule can be simply and effectively judged, the performance of the whole system and each module can be monitored, and judgment can be achieved under the condition of extremely low performance loss.The method comprises the steps of arranging a counter in the system or the system module; performing 1-adding operation on the counter each time when the system module is executed, and performing 1-subtraction operation on the counter if the system module is not blocked; and judging whether the system or the system module is a blocked system or system module if a value of the counter is higher than a threshold value.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
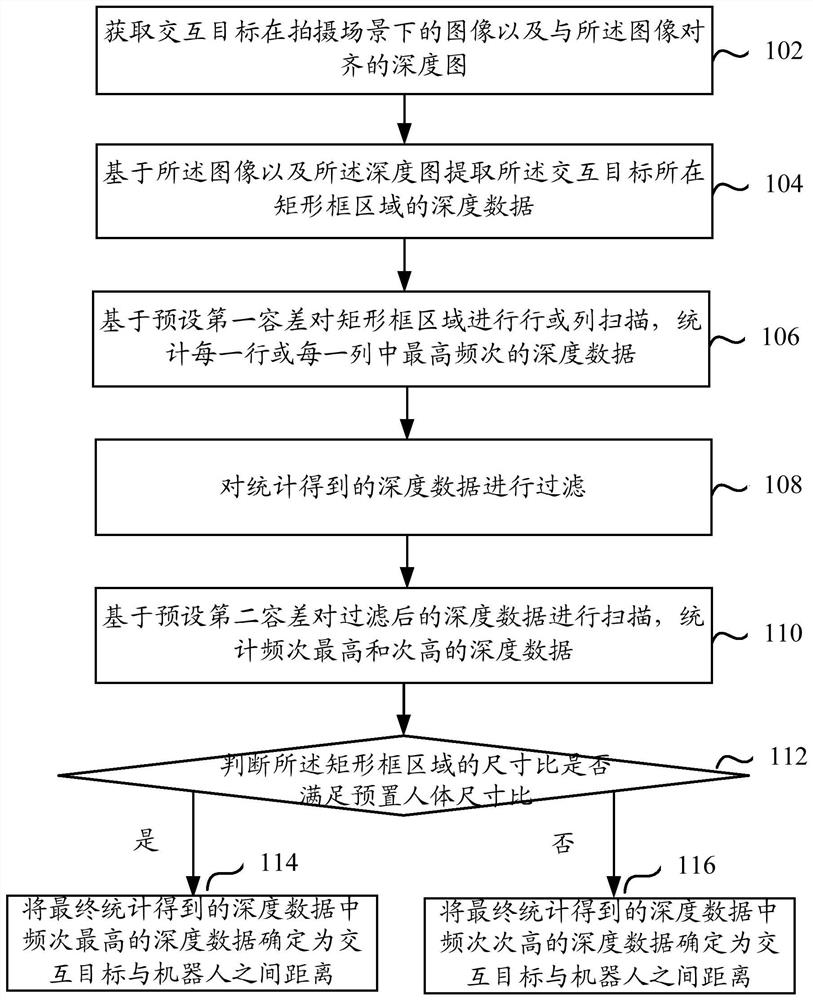
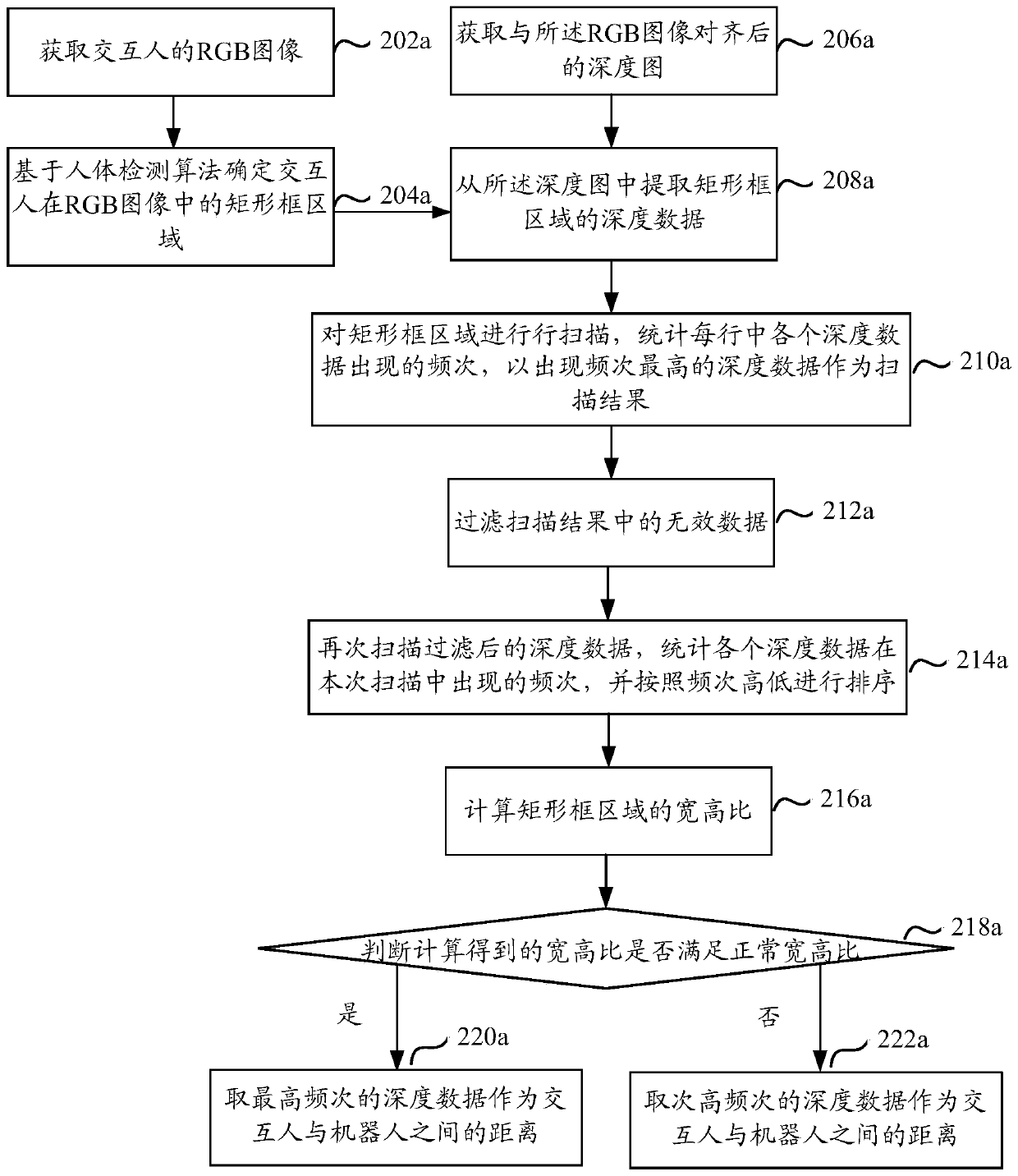
Method and device for determining distance between interactive target and robot, and electronic equipment
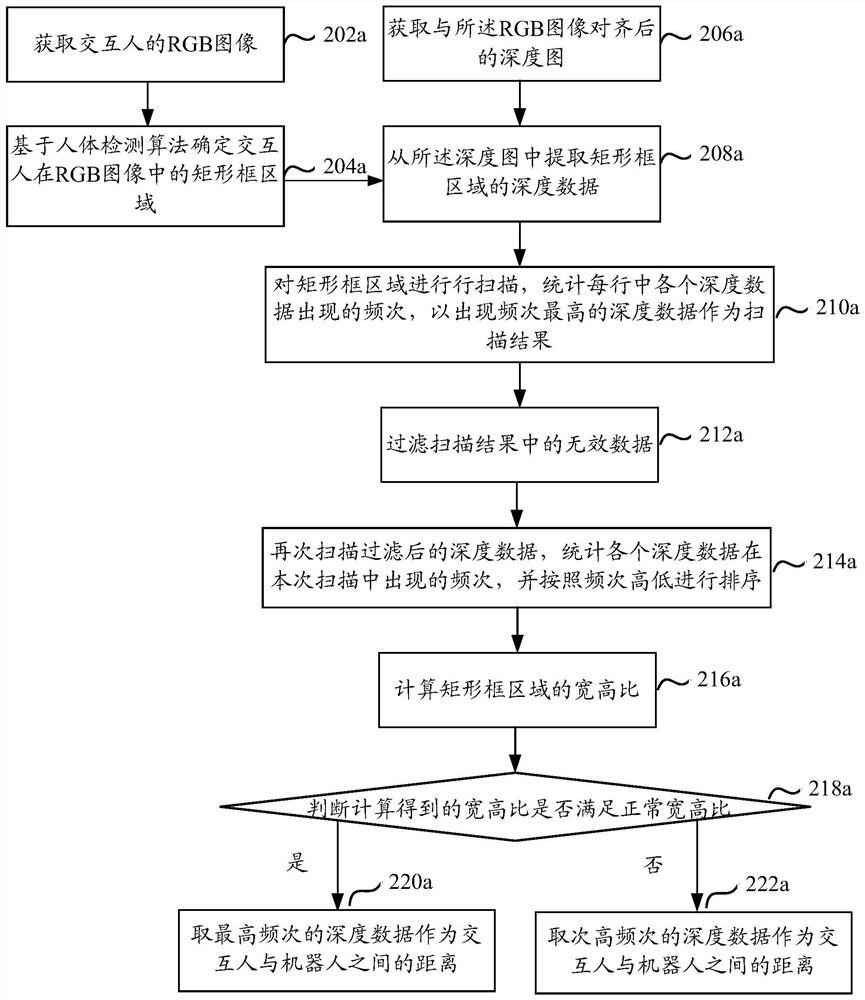
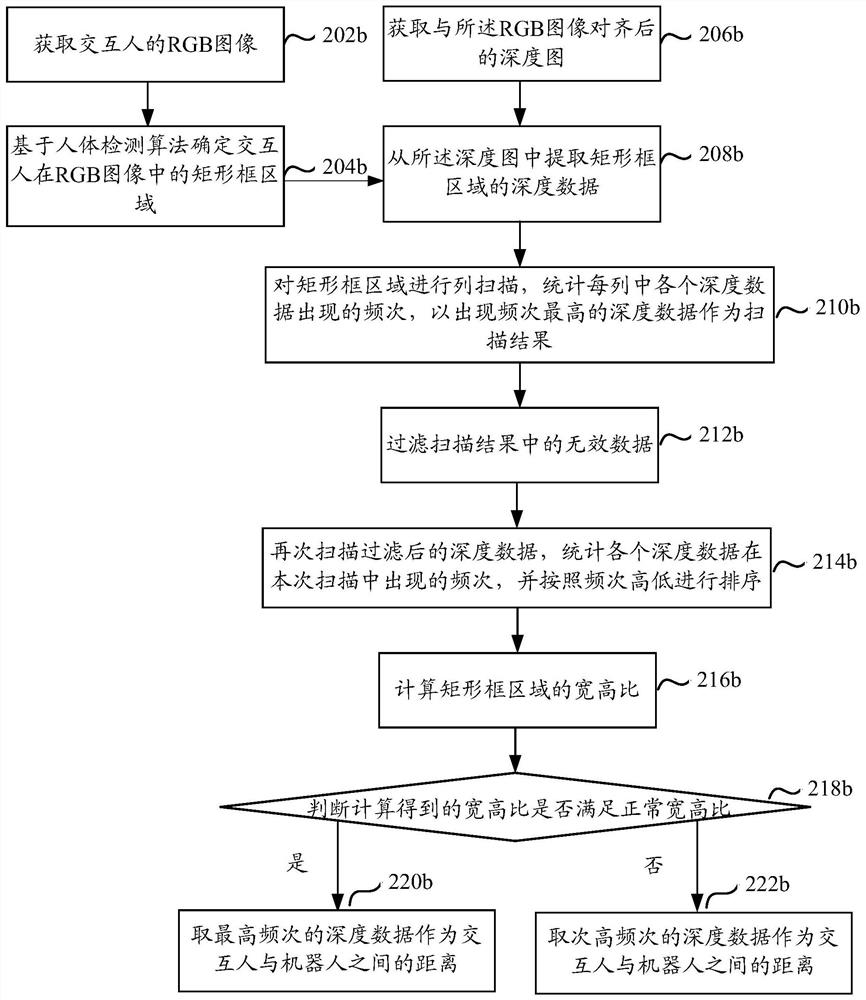
The embodiment of the invention relates to a method and device for determining the distance between an interactive target and a robot, and electronic equipment. The method comprises steps of determining a rectangular frame area where an interaction target is located by adopting a human body detection algorithm; extracting depth data of the rectangular frame area from a depth map, then, reducing analysis complexity in a row scanning mode or a column scanning mode, filtering depth data obtained through scanning statistics, and accurately determining a distance between the interaction target andthe robot according to the appearance frequency of the depth data obtained after filtering. The method is advantaged in that the method can be suitable for various poses and scenes while that a distance is determined through real-time collection is guaranteed.
Owner:山东睿思奥图智能科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com