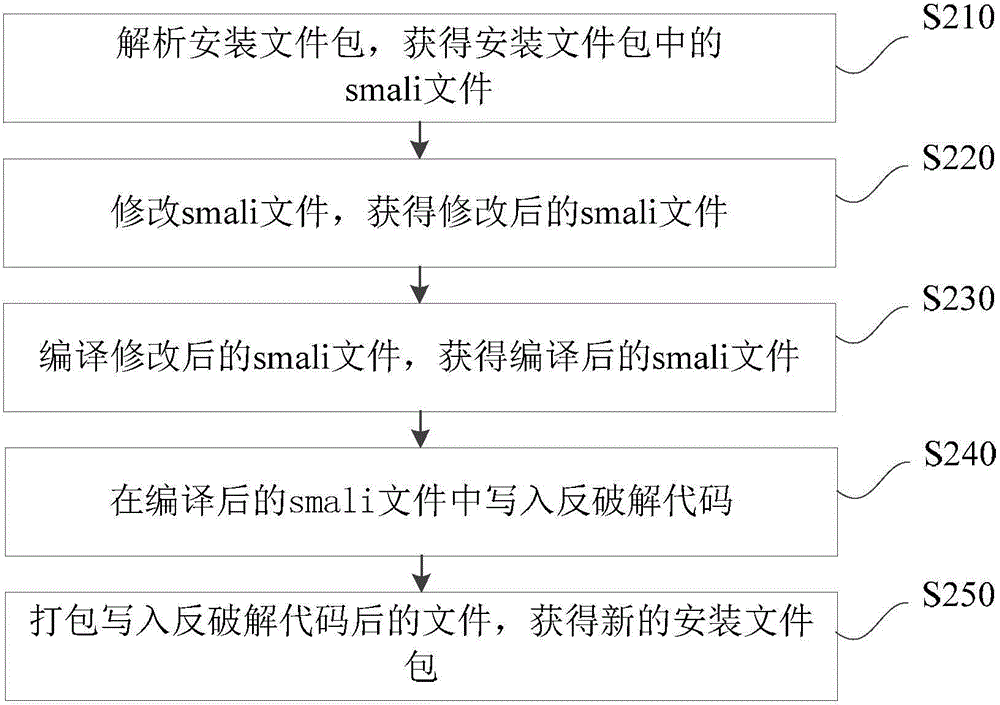
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49results about How to "Prevent decompilation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
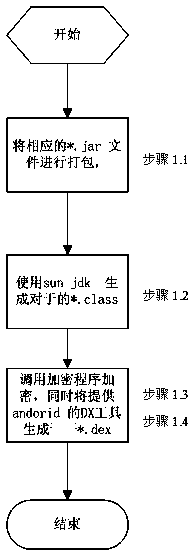
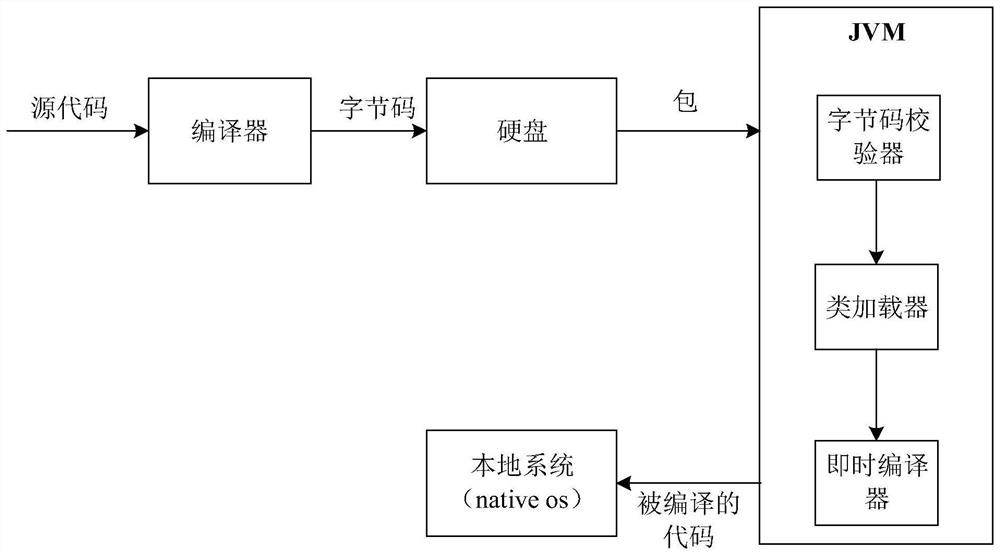
Java source code protection method based on dynamic link library
InactiveCN107992723APrevent decompilationProgram loading/initiatingProgram/content distribution protectionThird partyJava Classloader
The invention discloses a Java source code protection method based on a dynamic link library. A function declaration port and a function implementation main body are extracted and separated from a Java source code file, a port declaration file extracted from the source codes is obtained, the source codes are compiled into a Java bytecode file, and the Java bytecode file is processed to obtain bytecode content information and to generate a dynamic link library file; the extracted port declaration file is compiled to obtain a publication-quality port call file, and the publication-quality port call file can be published to permit a third party to use; the dynamic link library file is deployed to a running environment, a loader corresponding to Java type is used for dynamically loading the bytecode information in the dynamic link library file content into a JVM virtual machine, and the operation of protected codes is completed. The method effectively protects core codes, controls the operation of the core codes, and increases the protection of the Java source codes.
Owner:NANJING LES INFORMATION TECH
Method for preventing application program in intelligent terminal android system from being decompiled
InactiveCN103745141APrevent decompilationImprove securityProgram/content distribution protectionComputer hardwareApplication software
The invention provides a method for preventing an application program in an intelligent terminal android system from being decompiled. An encryption algorithm is introduced into the android system, as a result, a software program is prevented from being decompiled, and the security of android programs can be improved greatly.
Owner:PHICOMM (SHANGHAI) CO LTD
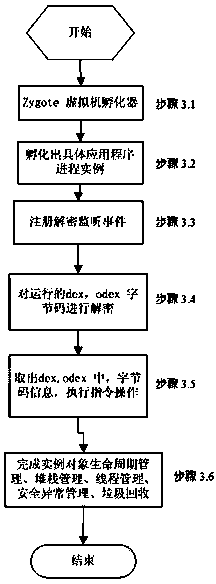
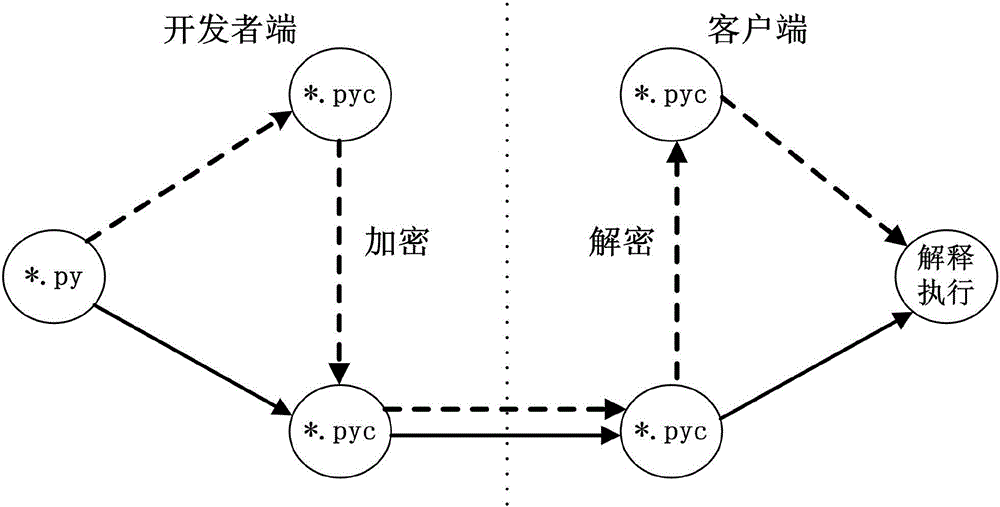
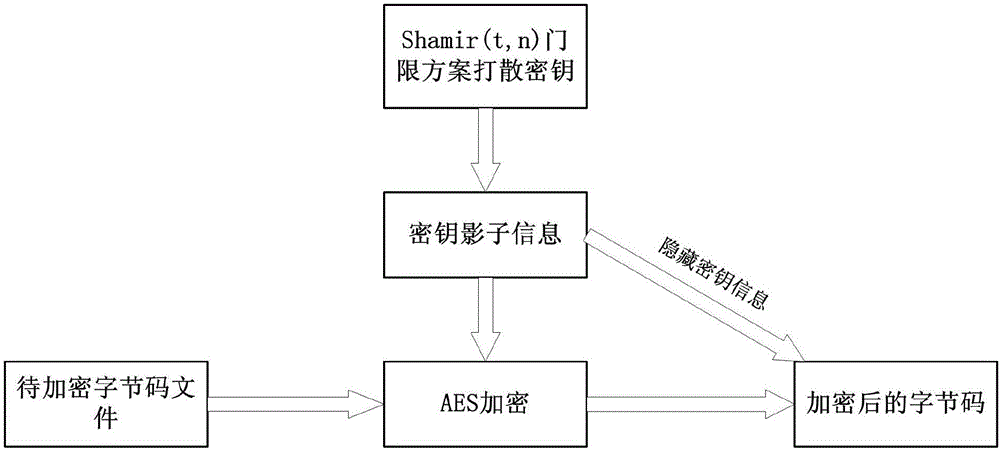
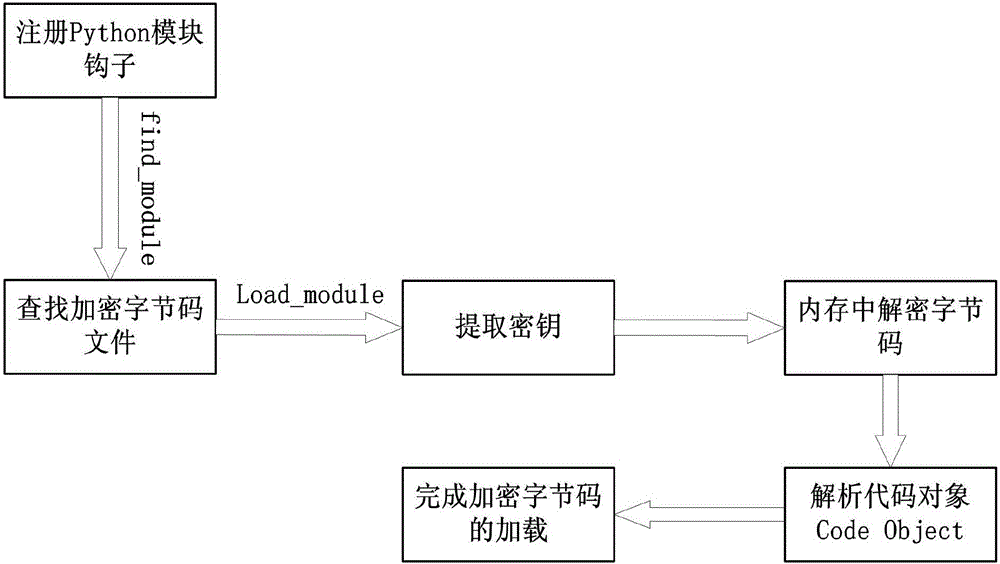
Python byte code file protection method based on module hook
ActiveCN106599628AGuarantee safety and reliabilityImprove reliabilityProgram/content distribution protectionSource code fileEncryption
The invention discloses a Python byte code file protection method based on a module hook. The method comprises the following steps: 1, performing encryption processing on a Python byte code file; 2, designing a Python module hook and a corresponding registration script; 3, adding the Python module hook and the corresponding registration script to a source code file of a Python interpreter of a client; 4, releasing a main program and the encrypted Python byte code file to the client by a developer terminal, and providing a new source code file of the Python interpreter; 5, compiling the source code file of the Python interpreter with the Python module hook and the corresponding registration script added to obtain a compiled Python interpreter; and 6, executing the main program by the client by using the compiled Python interpreter. By adoption of the Python byte code file protection method disclosed by the invention, decompilation is effectively defended, and the protection strength of Python software programs is improved.
Owner:赵志铎
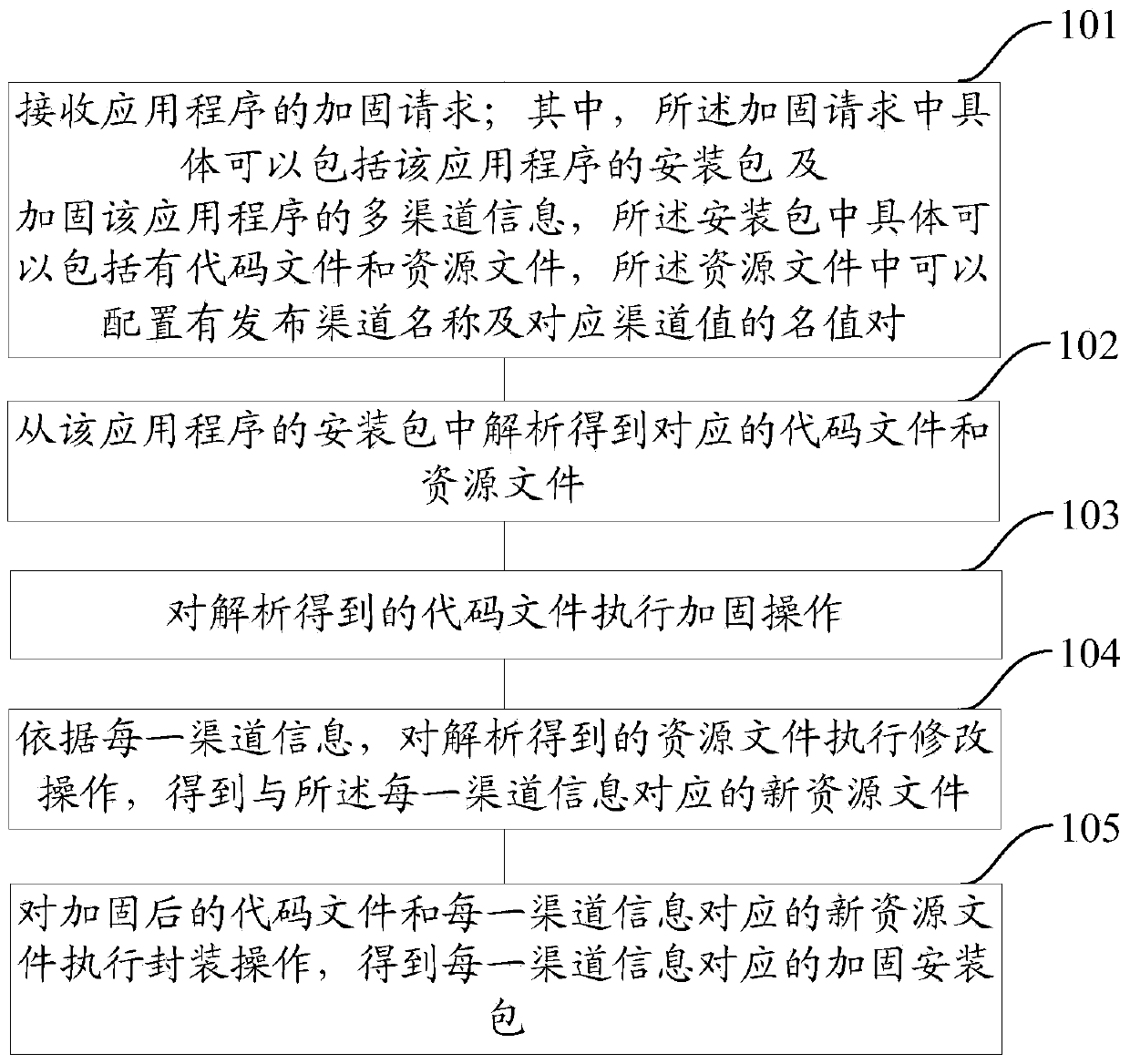
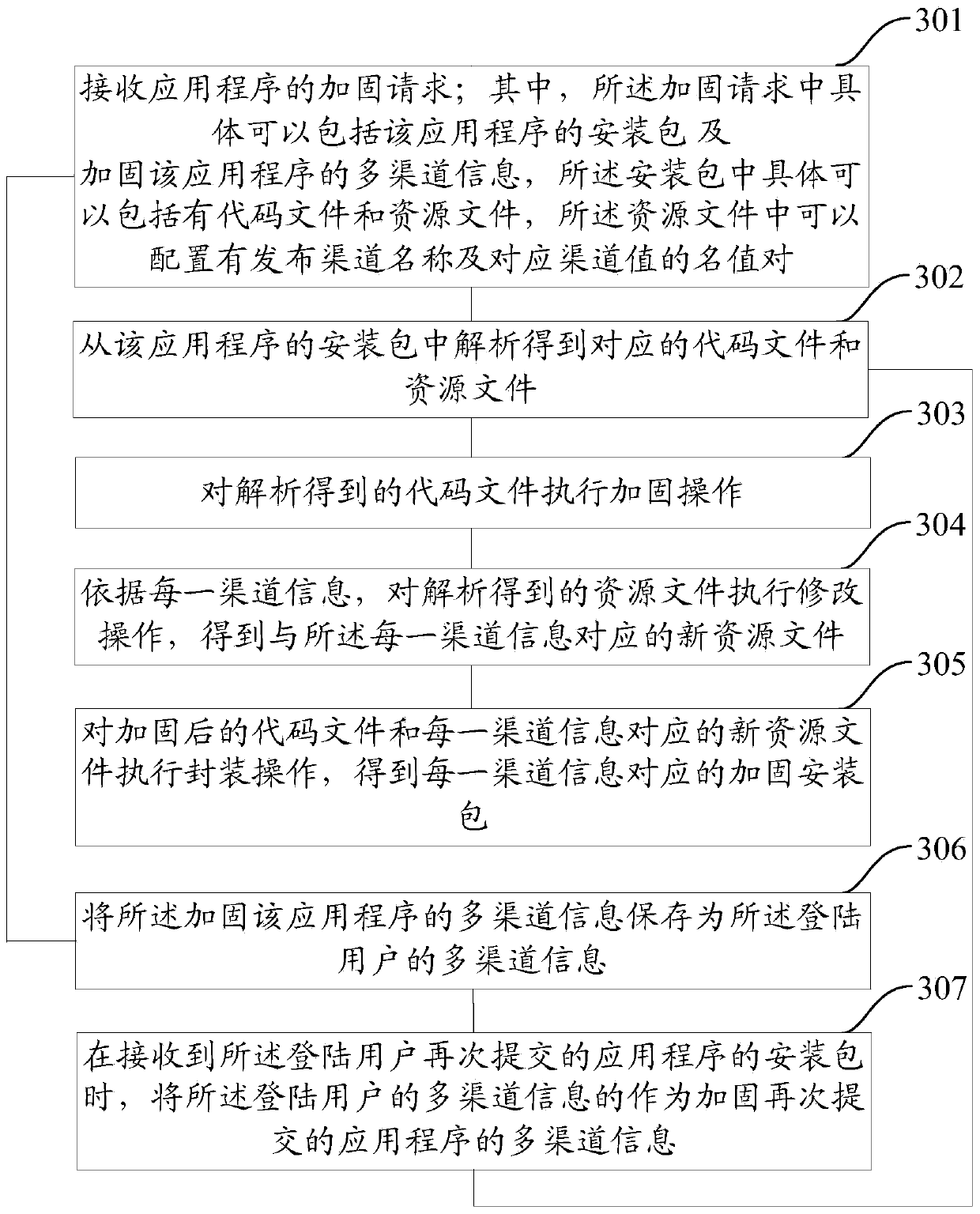
Method and device for reinforcing application program
ActiveCN104217140AImprove securityPrevent decompilationProgram/content distribution protectionOperating systemResource file
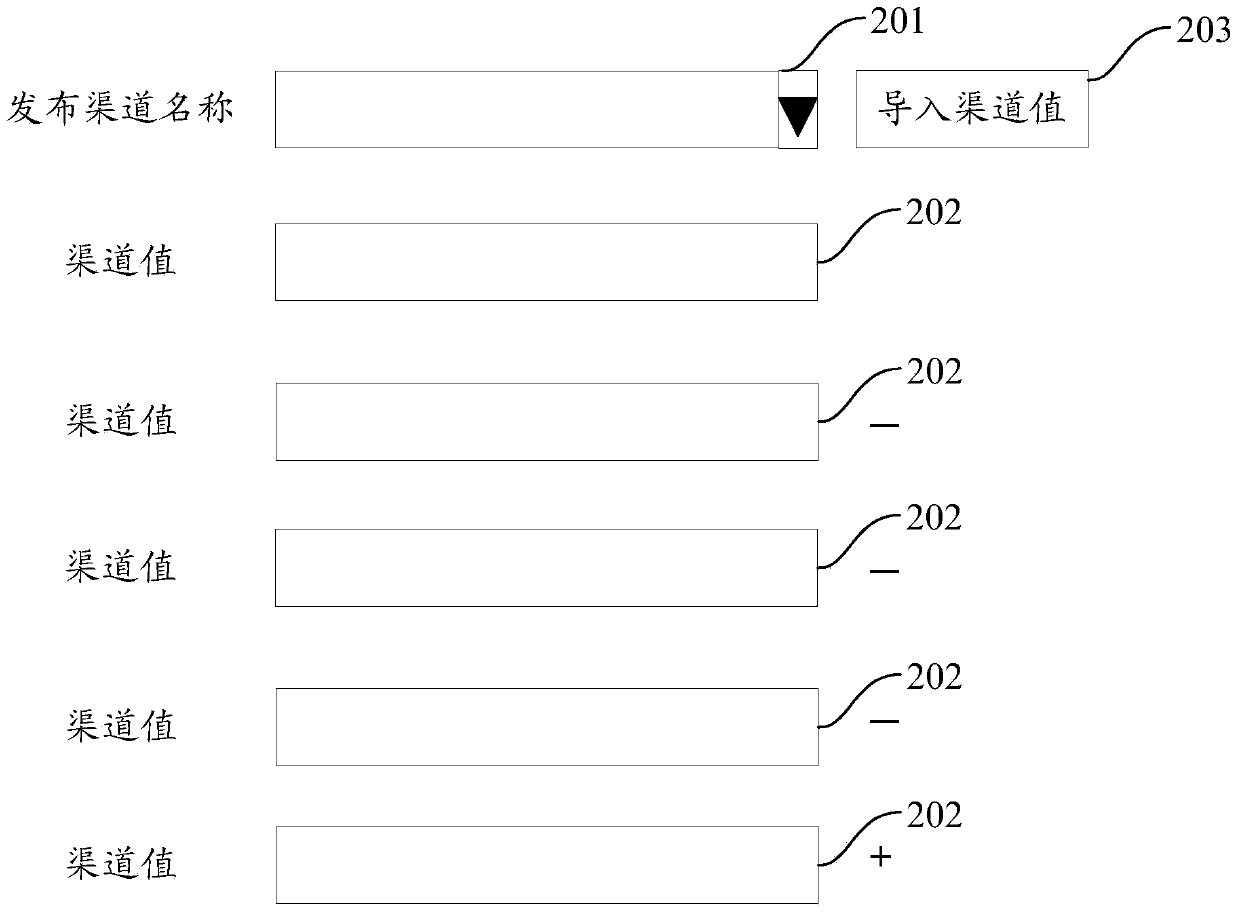
The embodiment of the invention provides a method and a device for reinforcing an application program. The method comprises the following steps of receiving a reinforcing request of the application program, wherein the reinforcing request comprises an installation package of the application program and multi-channel information for reinforcing the application program, the installation package comprises code files and resource files, and release channel names and corresponding channel values are configured in the resource files; analyzing to obtain corresponding code files and resource files from the installation package of the application program; executing reinforcing operation on the code files obtained through analysis; executing retouching operation on the resource files obtained through analysis according to each piece of channel information to obtain a new resource file corresponding to each piece of channel information; executing packaging operation on the reinforced code files and the new resource file corresponding to each piece of channel information to obtain a reinforced installation package corresponding to each piece of channel information. According to the method and the device, the safety of the application program can be improved and the efficiency of reinforcing multiple release channels is improved.
Owner:BEIJING QIHOO TECH CO LTD
Method and device for protecting class files
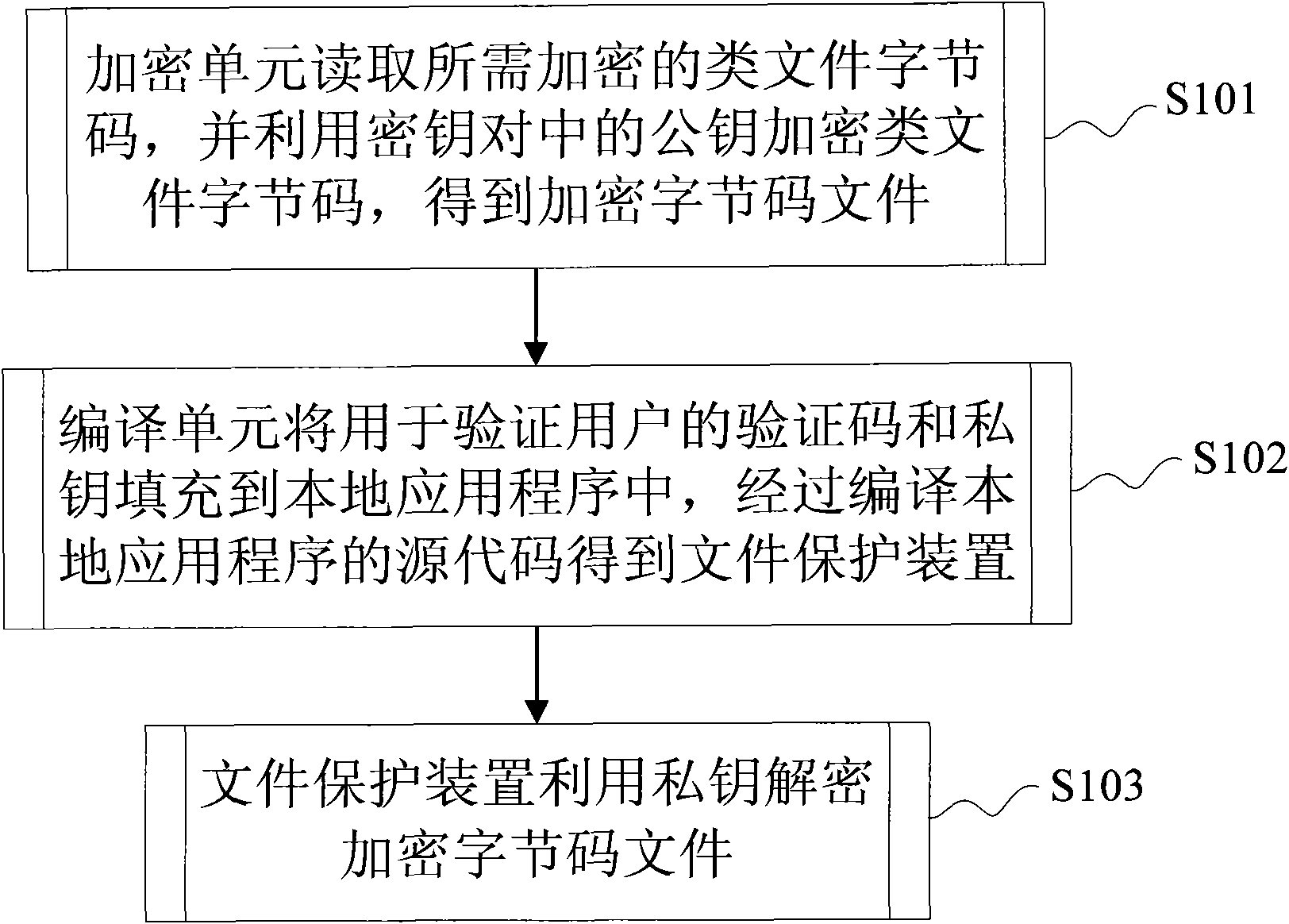
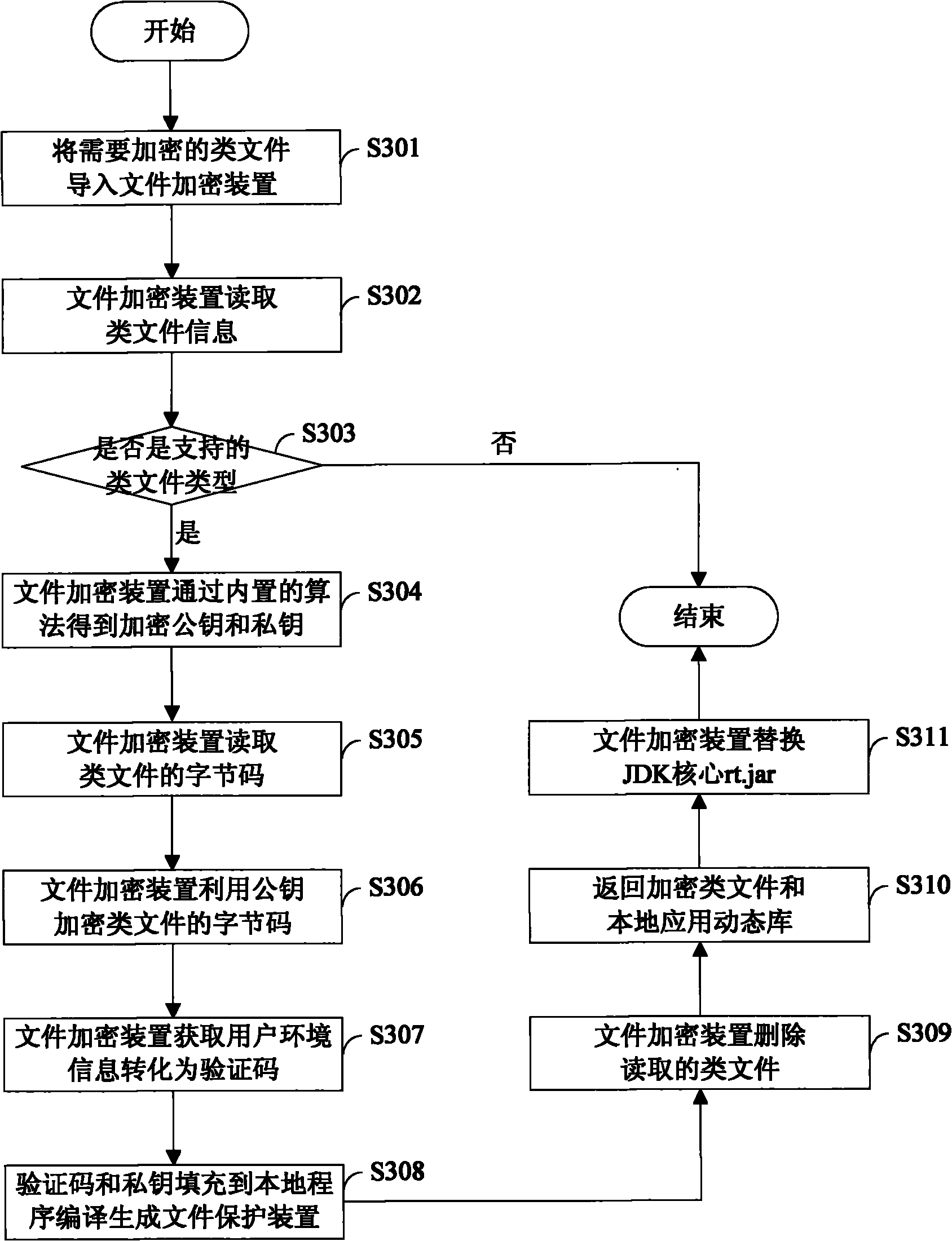
InactiveCN101957903APrevent decompilationKeep it cross-platformDigital data protectionApplication softwareByte
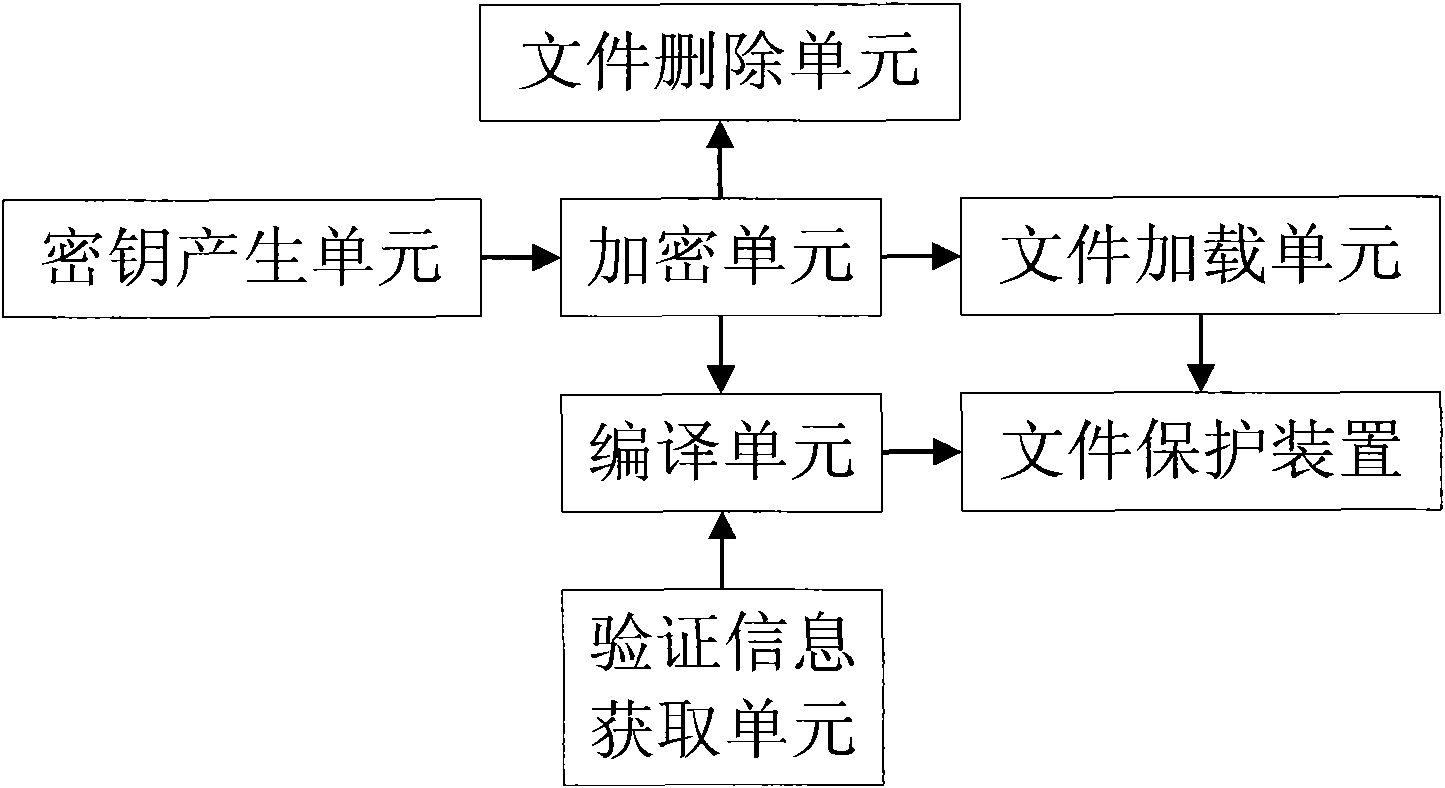
The invention discloses a method and device for protecting class files. The method comprises the following steps: an encryption unit reads the byte codes of a class file to be encrypted, a key pair is used to encrypt the byte codes of the class file to obtain an encrypted byte code file; a compilation unit fills the verification code and key pair used for verifying the user in a local application program, a file protection device is obtained by compiling the source codes of the local application program; and the file protection device uses the key pair to decrypt the encrypted byte code file. In the method of the invention, the file encryption unit is adopted to encrypt the byte codes of the class file and the file protection device generated in the encryption process is used to decrypt the byte codes, thus the class file is effectively prevented from decompiling, the cross-platform characteristic of the program can be maintained and the operation of the user can be more convenient.
Owner:ZTE CORP
Installation file protection method and apparatus
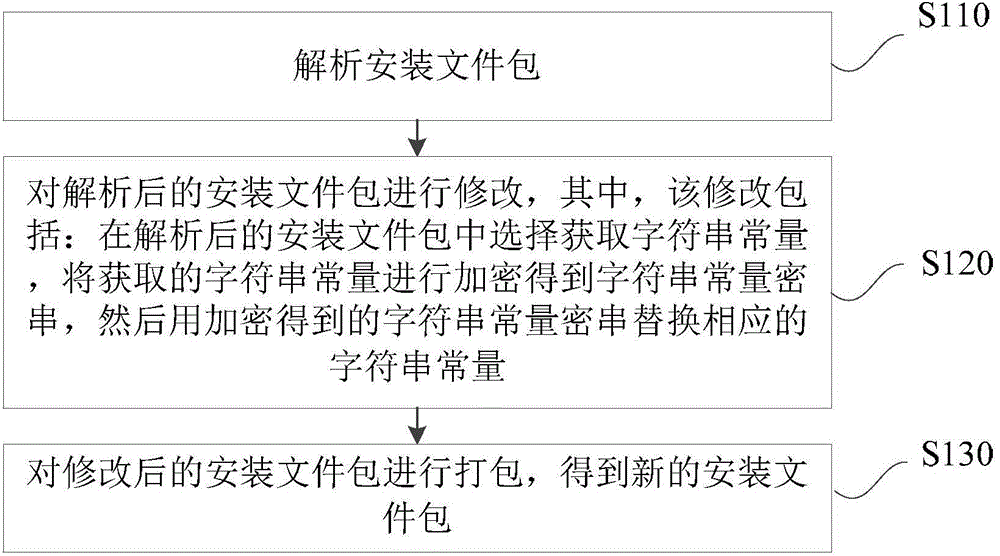
InactiveCN105335151APrevent tamperingPrevention of secondary packagingSpecific program execution arrangementsSoftware engineeringComputer science
The invention provides an installation file protection method and apparatus. The method comprises: analyzing an installation file package; modifying the analyzed installation file package, wherein the modification comprises: selecting and obtaining a character string constant in the analyzed installation file package, encrypting the selected and obtained character string constant to obtain an encrypted character string constant string, and replacing a corresponding character string constant with the encrypted character string constant string; and packing the modified installation file package to obtain a new installation file package. Through the installation file protection method and apparatus, an installation file can be prevented from being subjected to tampering, secondary packing and decompilation, so that the purpose of better protecting the installation file is achieved.
Owner:GUANGZHOU AIJIUYOU INFORMATION TECH
Bytecode encryption method, bytecode decryption method and terminal
ActiveCN109784007AEffective protectionPrevent decompilationDigital data protectionProgram/content distribution protectionJava classesByte
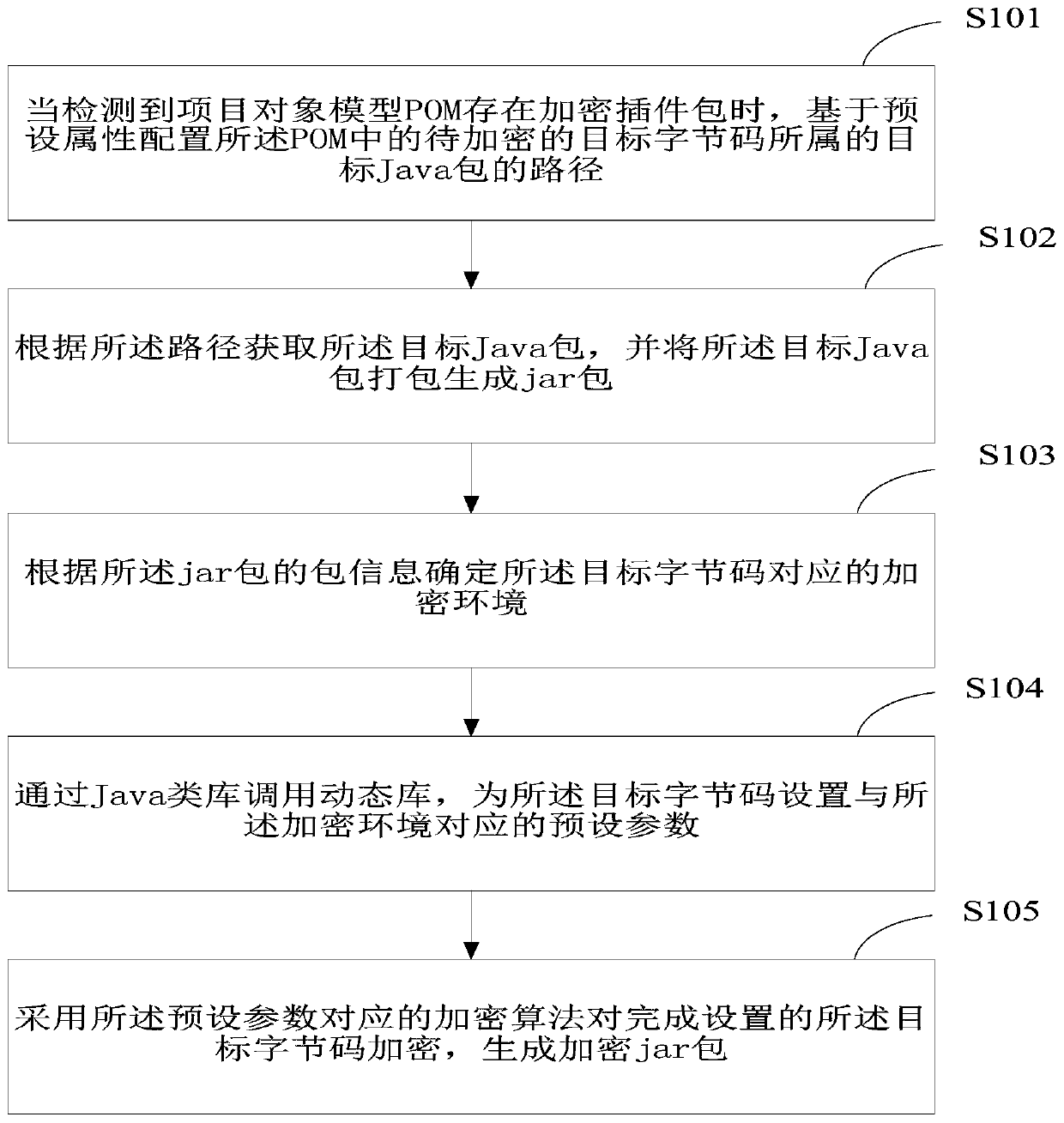
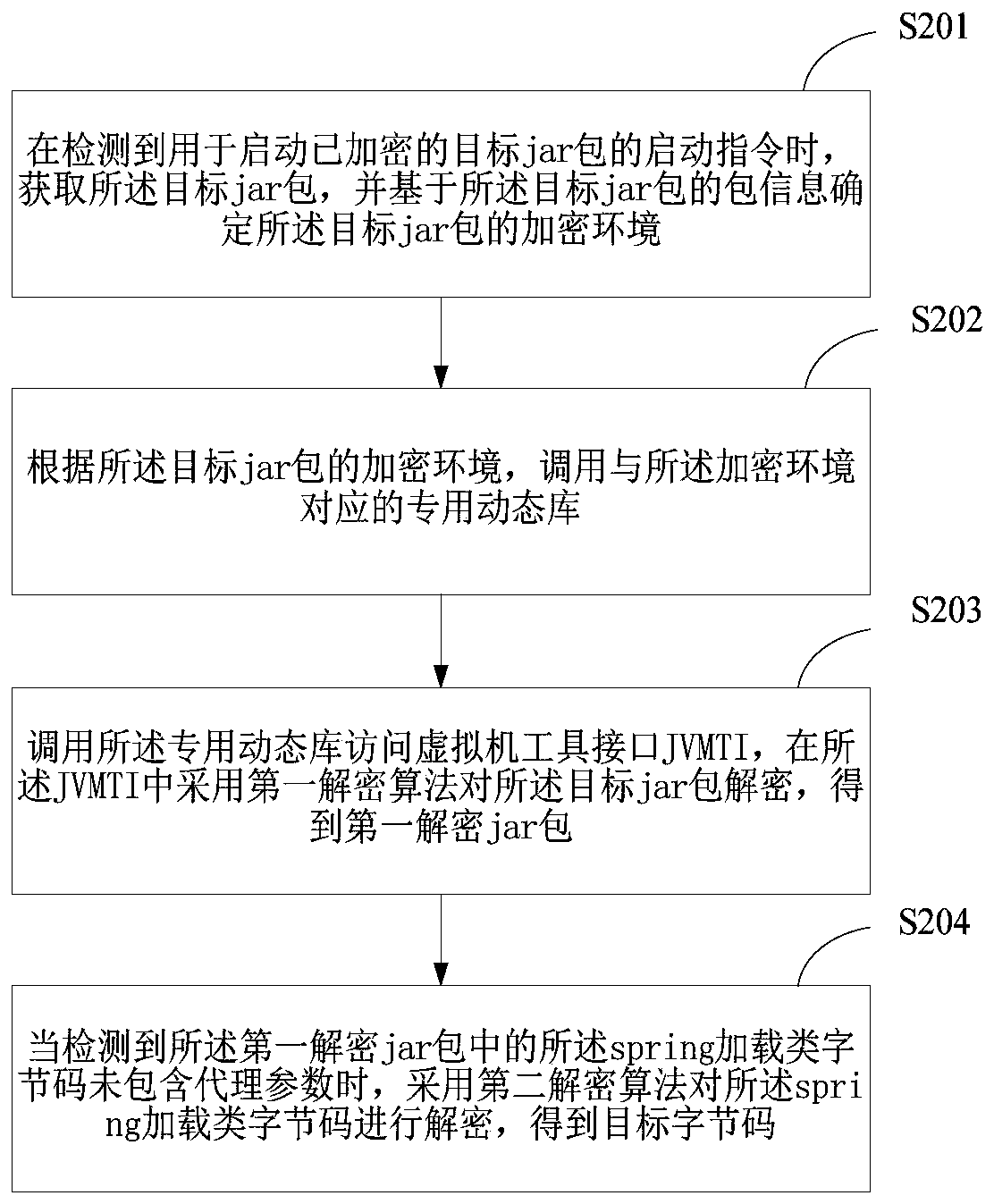
The invention is applicable to the technical field of computers, and provides a byte code encryption method, a byte code decryption method and a terminal, and the method comprises the steps: configuring a path of a target Java packet to which a to-be-encrypted target byte code belongs in a POM (Project Object Model) based on a preset attribute when detecting that an encrypted plug-in packet existsin the POM; Obtaining a target Java packet, and packaging the target Java packet to generate a jar packet; Determining an encryption environment corresponding to the target byte code according to thepacket information of the jar packet; Calling a dynamic library through the Java class library, and setting a preset parameter corresponding to the encryption environment for the target byte code; And encrypting the set target byte code by adopting an encryption algorithm corresponding to the preset parameter to generate an encrypted jar package. According to the scheme, different encryption algorithms are adopted to encrypt the byte codes in different encryption environments, the byte codes are not prone to being cracked by agents, the byte code files are effectively protected, decompilationis prevented, and therefore source codes are effectively protected.
Owner:厦门熵基科技有限公司
APK reinforcing protection method and system
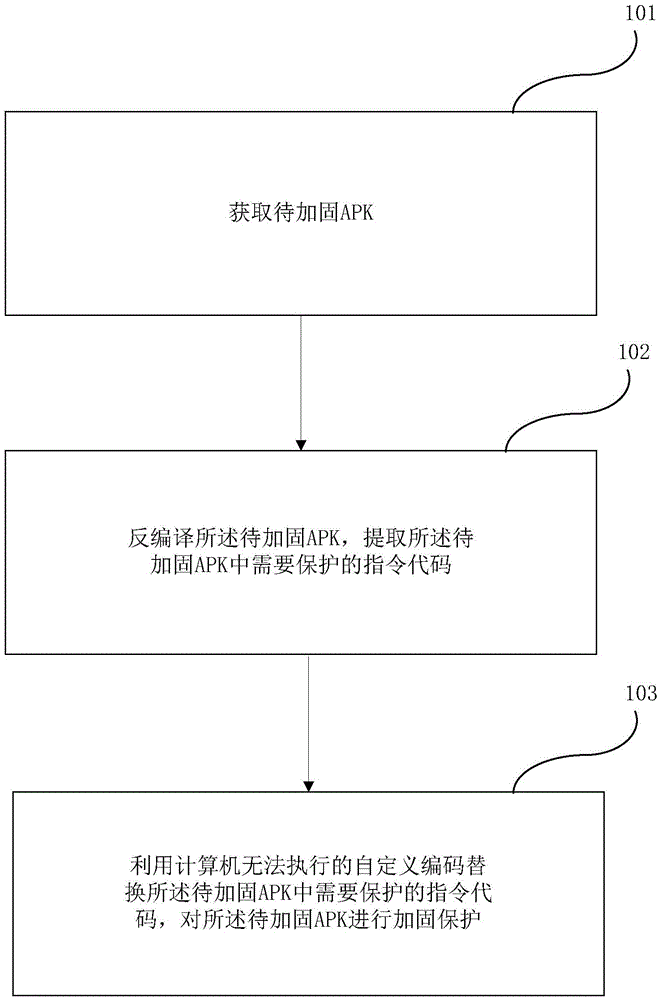
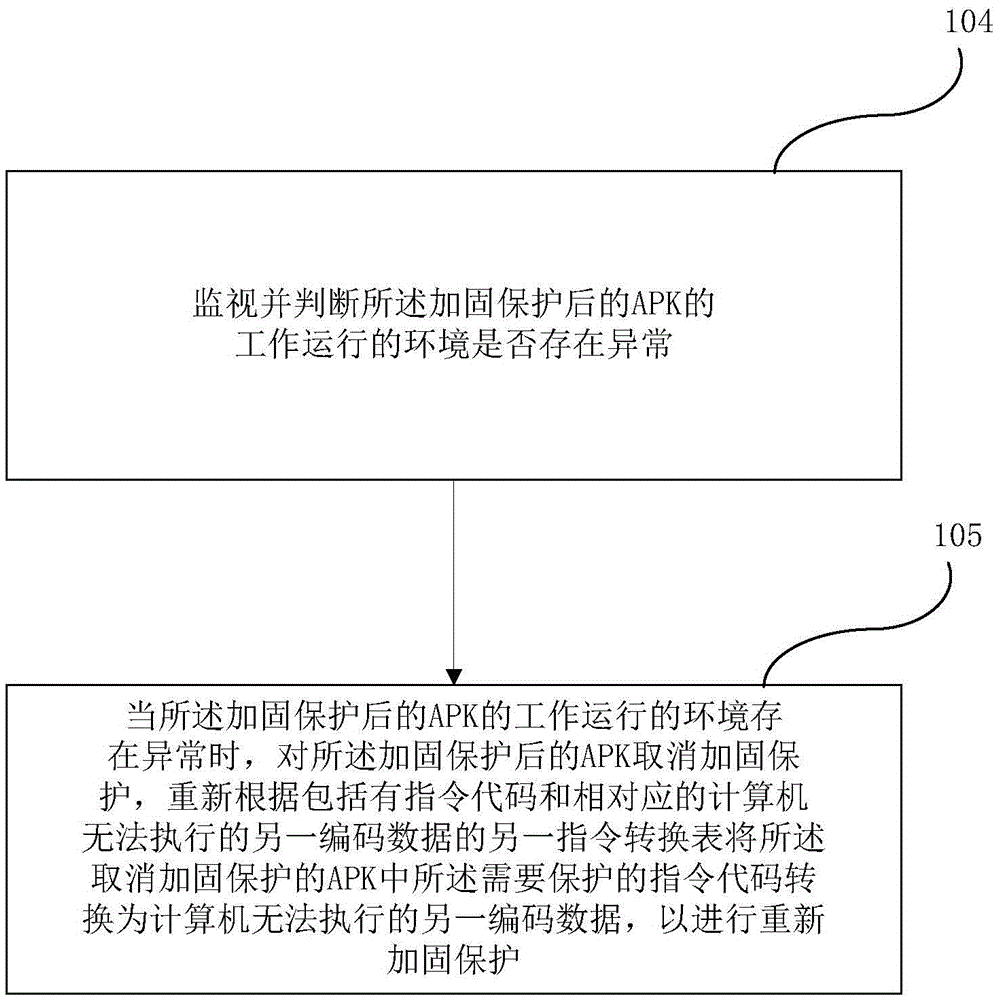
ActiveCN105631251AReal-time monitoring of privacyEnsure safetyProgram/content distribution protectionUser-defined codesSoftware engineering
The embodiment of the invention provides an APK reinforcing protection method. The method is characterized by comprising the steps that an APK to be reinforced is obtained; the APK to be reinforced is decompiled, and an instruction code needing to be protected in the APK to be reinforced is extracted; the instruction code needing to be protected in the APK to be reinforced is replaced with a user-defined code, wherein the user-defined code comprises code data incapable of being executed by a computer, and the APK to be reinforced is subjected to reinforcing protection. The embodiment of the invention further provides an APK reinforcing protection system. Reinforcing protection on the APK is achieved, and the APK is effectively prevented from being reversely analyzed or tampered or secondarily packaged.
Owner:BEIJING QIHOO TECH CO LTD
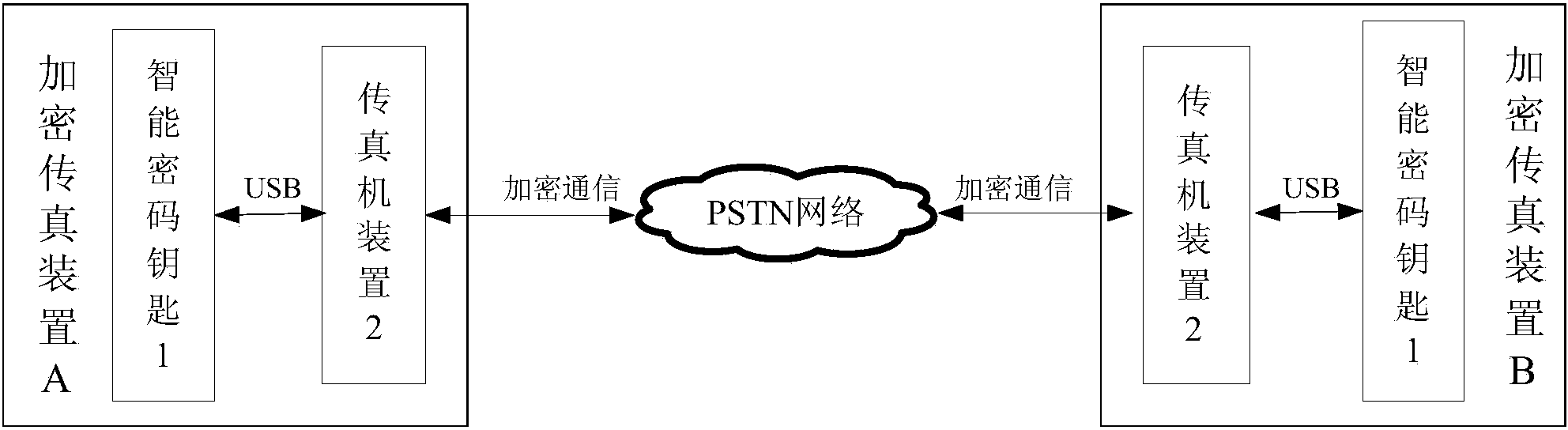
Fax encryption device based on intelligent encryption key and implementation method of fax encryption device
The invention discloses a fax encryption device based on an intelligent encryption key and an implementation method of the fax encryption device, and relates to the field of encrypted fax communication. Hardware encrypted faxes are realized through a traditional PSTN (public switched telephone network), a custom command is added in the fax implementation process to realize the fax encryption method on the basis of the fax T.30 protocol, fax data encryption is organically integrated in the fax communication process, and the hidden danger of guard type secret leakage is eliminated. The adopted intelligent encryption key is approved and certificated by the State Encryption Administration, adopts the state commercial cryptographic algorithm and can effectively ensure the reliability and the high efficiency of the cryptographic algorithm; the device can automatically switch unencrypted and encrypted faxes, is higher in safety, working efficiency and compatibility and can be widely applied to various industries such as government agencies, military, finance, telecom, enterprises and the like as well as users.
Owner:TOEC ANCHEN INFORMATION TECH
Method for guaranteeing self-security of JAVA program
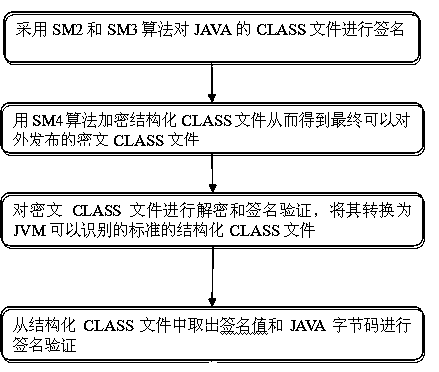
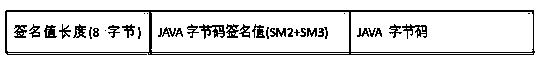
InactiveCN104200137APrevent decompilationNot be obtained illegallyProgram controlProgram/content distribution protectionAttackSoftware engineering
The invention provides a method for guaranteeing the self-security of a JAVA program. GM algorithms SM2 and SM3 are used for signing a CLASS file of the JAVA, then a GM algorithm SM4 is used for encrypting the CLASS file, and the CLASS file is effectively prevented from being decompiled and tampered maliciously. The method can effectively protect the JAVA program, and the self-security is high. According to the encrypted CLASS file, a JAVA source program corresponding to the CLASS file can not be decompiled by any decompiling tools. For the signed CLASS file, any illegal change to the signed CLASS file can be timely found and is prevented from operating, attacks made by maliciously modifying codes are prevented, and the security level of the JAVA program is greatly improved.
Owner:中电科网络安全科技股份有限公司
Safety protection method of application programs and server
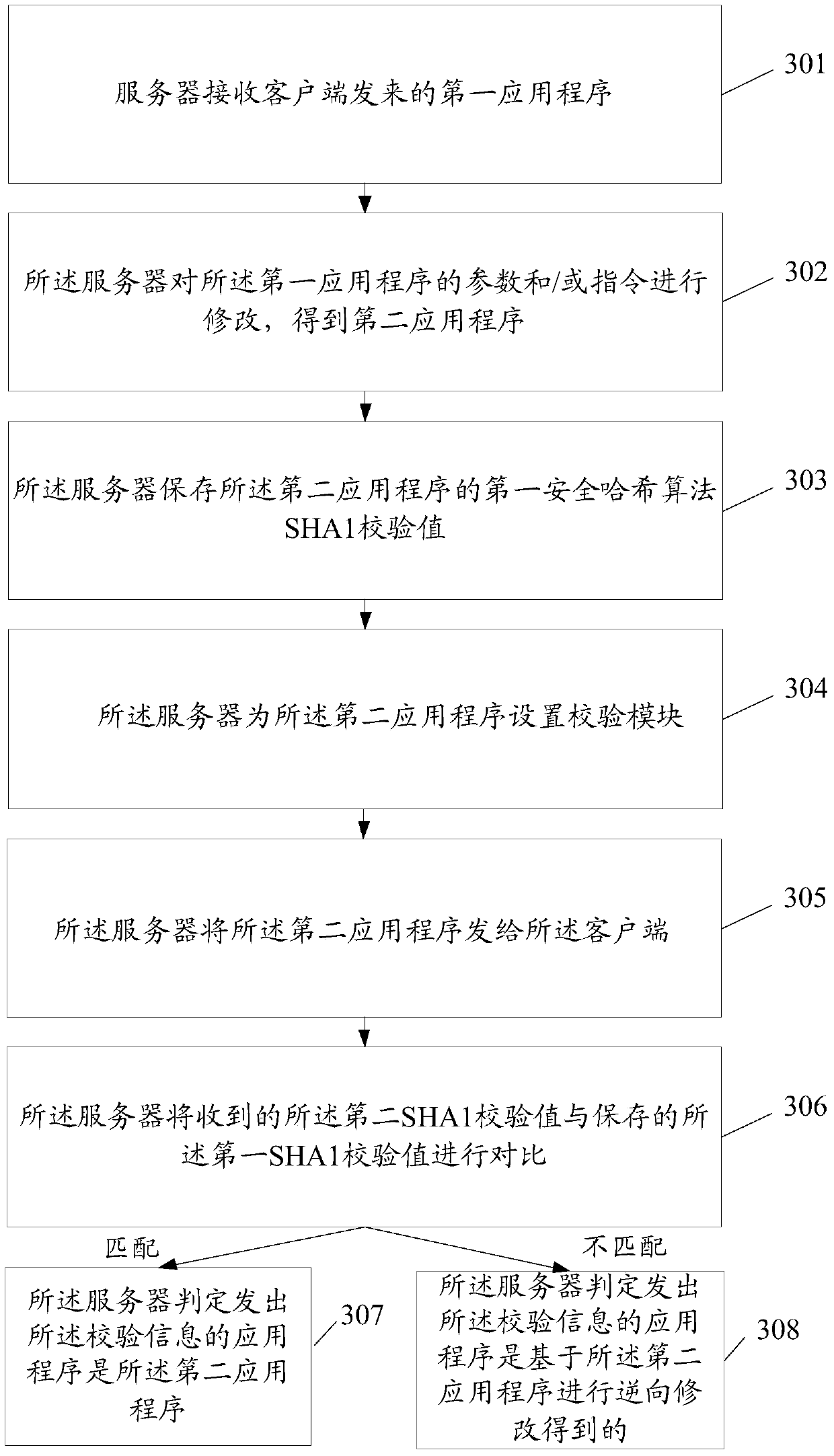
ActiveCN105678120ATo achieve the purpose of security protectionPrevent decompilationTransmissionProgram/content distribution protectionApplication softwareComputer science
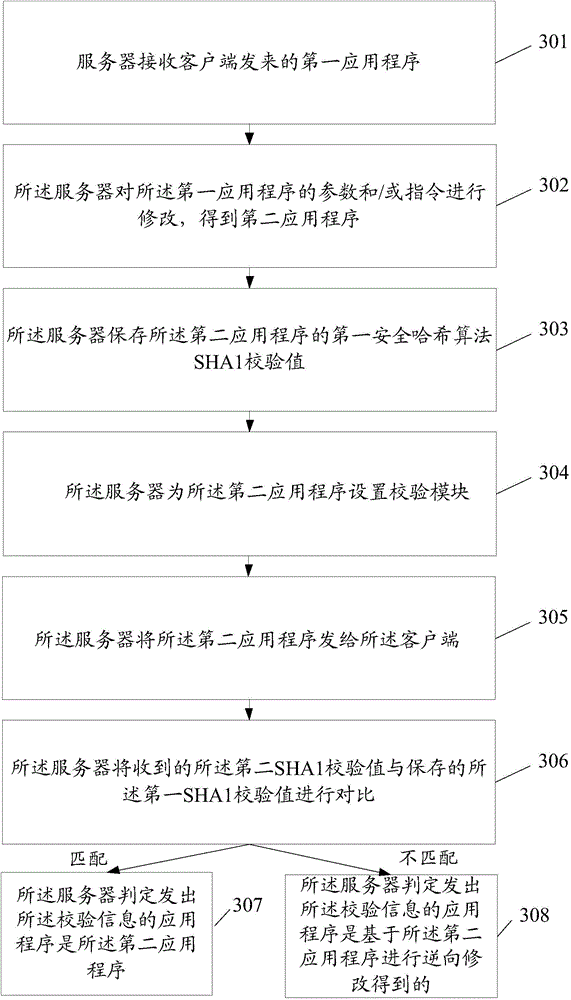
The invention discloses a safety protection method of application programs and a server. The method comprises following steps: receiving a first application program sent from a client by the server; collecting parameters / instructions of the first application program by the server in order to obtain a second application program such that the second application program can normally operate and enable a reverse tool to exit by fault when the reverse tool is utilized for analyzing the second application program; and sending the second application program to the client by the server.
Owner:CHINA MOBILE COMM GRP CO LTD
APK file strengthening method
InactiveCN104462883AImprove securityPrevent decompilationProgram/content distribution protectionCore functionSource code
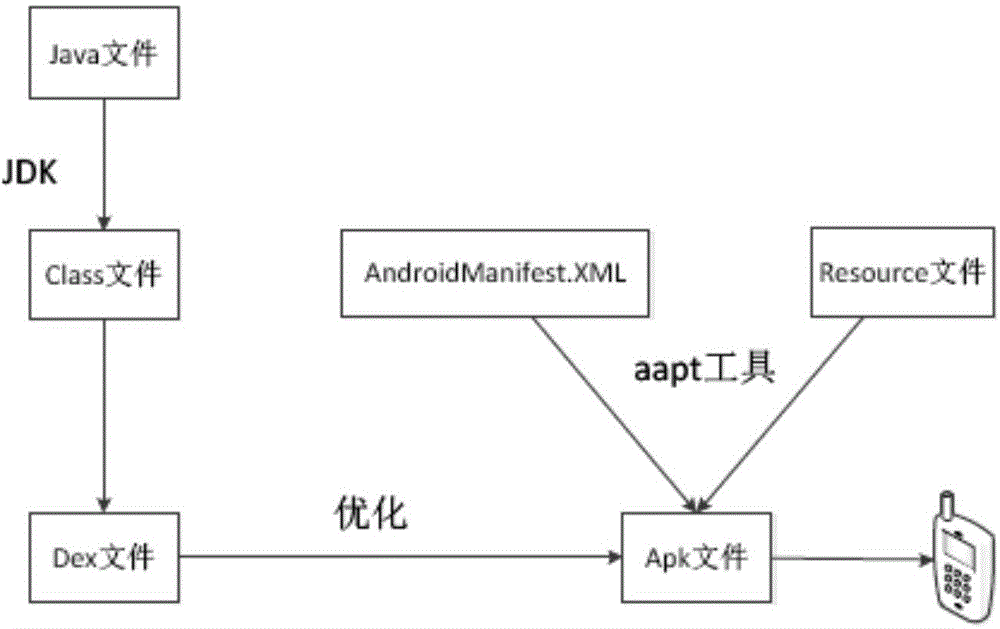
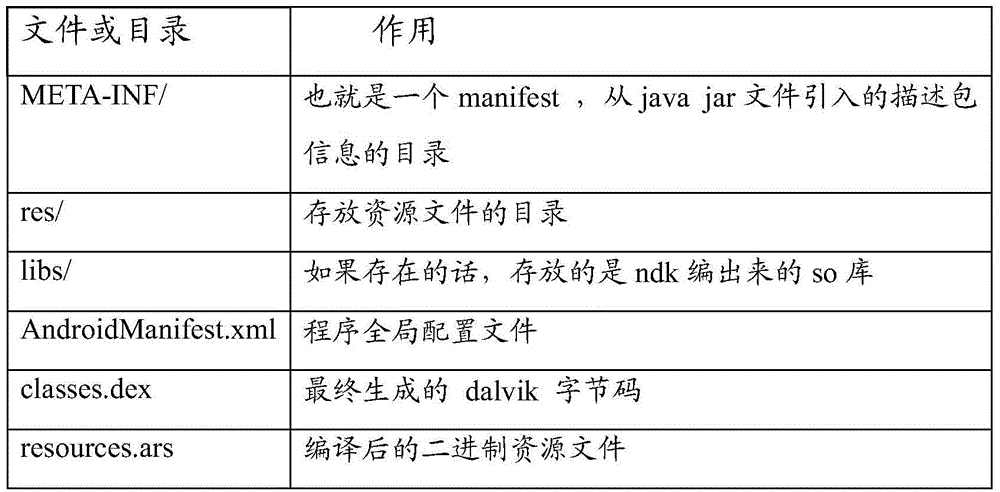
The invention discloses an APK file strengthening method. The APK file strengthening method comprises the steps that a source code of an APK file needing to be strengthened is divided into a first source code serving as a body part and a second source code serving as a core function part; the first source code and the second source code are coded into a first APK file and a second APK file respectively; the first APK file is decompressed, and a first classes.dex file in the first APK file is extracted; encryption processing is conducted on the second APK file, and statistics is conducted on the file length information of the encrypted second APK file; the encrypted second APK file and the file length information of the second APK file are added to the tail part of the first classes.dex file; file head information in the first classes.dex file is recalculated and updated, the first APK file is signed through a signing tool provided in an Android SDK, and the strengthened APK file is obtained. By means of the APK file strengthening method, decompilation of an existing Android reverse tool can be avoided, the difficulty of decompilation is increased, and thus the safety of the APK file can be improved to a great degree.
Owner:刘鹏
Method for protecting software distribution security by applying strong symmetric encryption
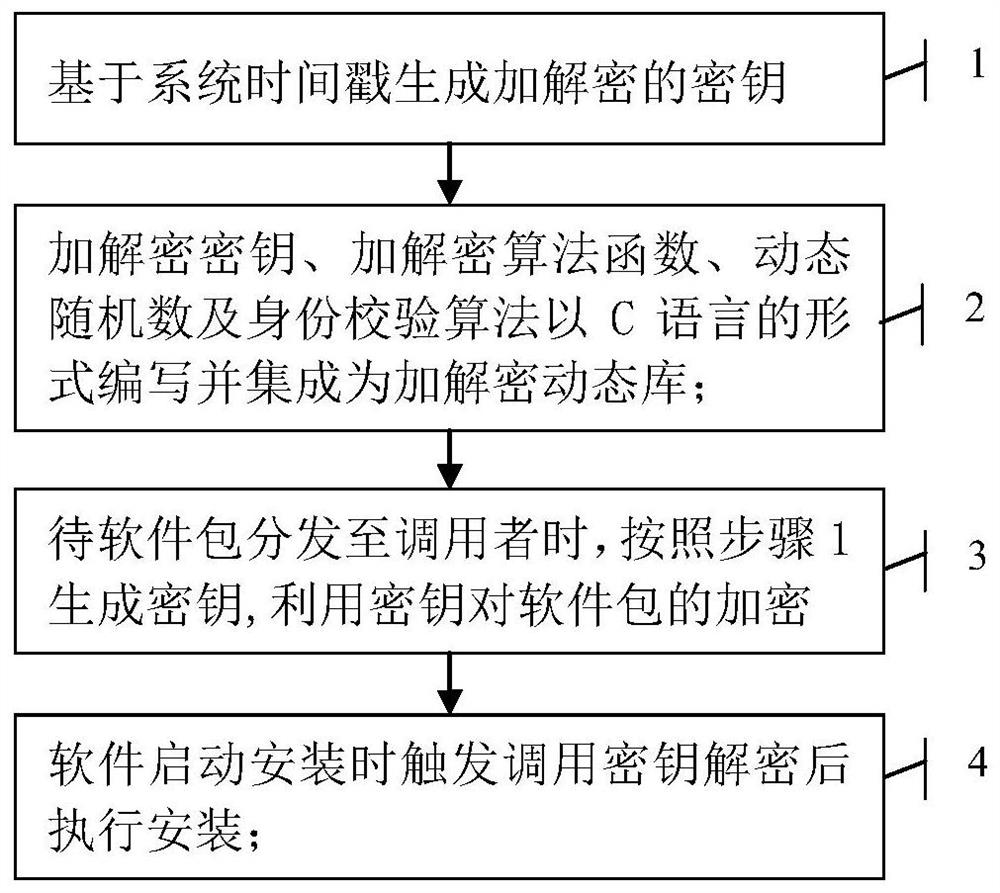
ActiveCN112100582APrevent decompilationPrevent unauthorized authorizationProgram/content distribution protectionSoftware distributionTimestamp
The invention discloses a method for protecting software distribution security by applying strong symmetric encryption. The method is characterized by comprising the following steps of: 1, generatingan encryption and decryption key based on a system timestamp by utilizing a pseudo random number generation algorithm; 2, compiling and integrating the encryption and decryption key, an encryption anddecryption algorithm function, a dynamic random number and an identity verification algorithm into an encryption and decryption dynamic library in a C language form; 3, automatically generating a secret key according to the step 1, and encrypting a software package by using the generated secret key; and 4, sequentially calling the identity verification algorithm and the encryption and decryptionalgorithm function of the encryption and decryption dynamic library to verify a software installer. Thus, decompilation is high in difficulty, an encryption and decryption module realizes multiple protection measures such as encryption, verification, confusion and the like, and the effect of preventing an application from being decompiled and illegally authorized to the greatest extent is achieved.
Owner:FOCUS EDUCATION TECHNOLOGY CO LTD
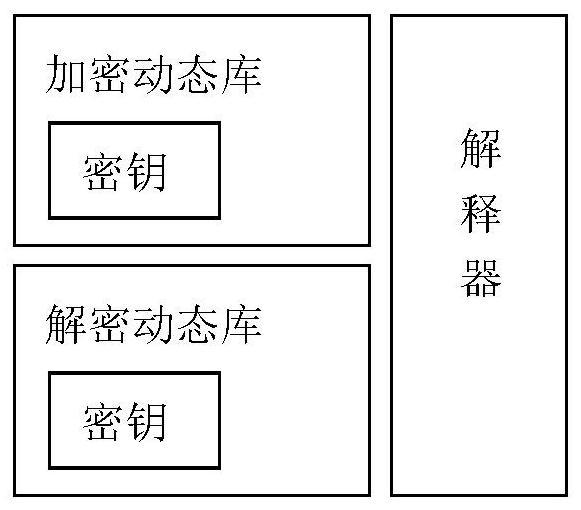
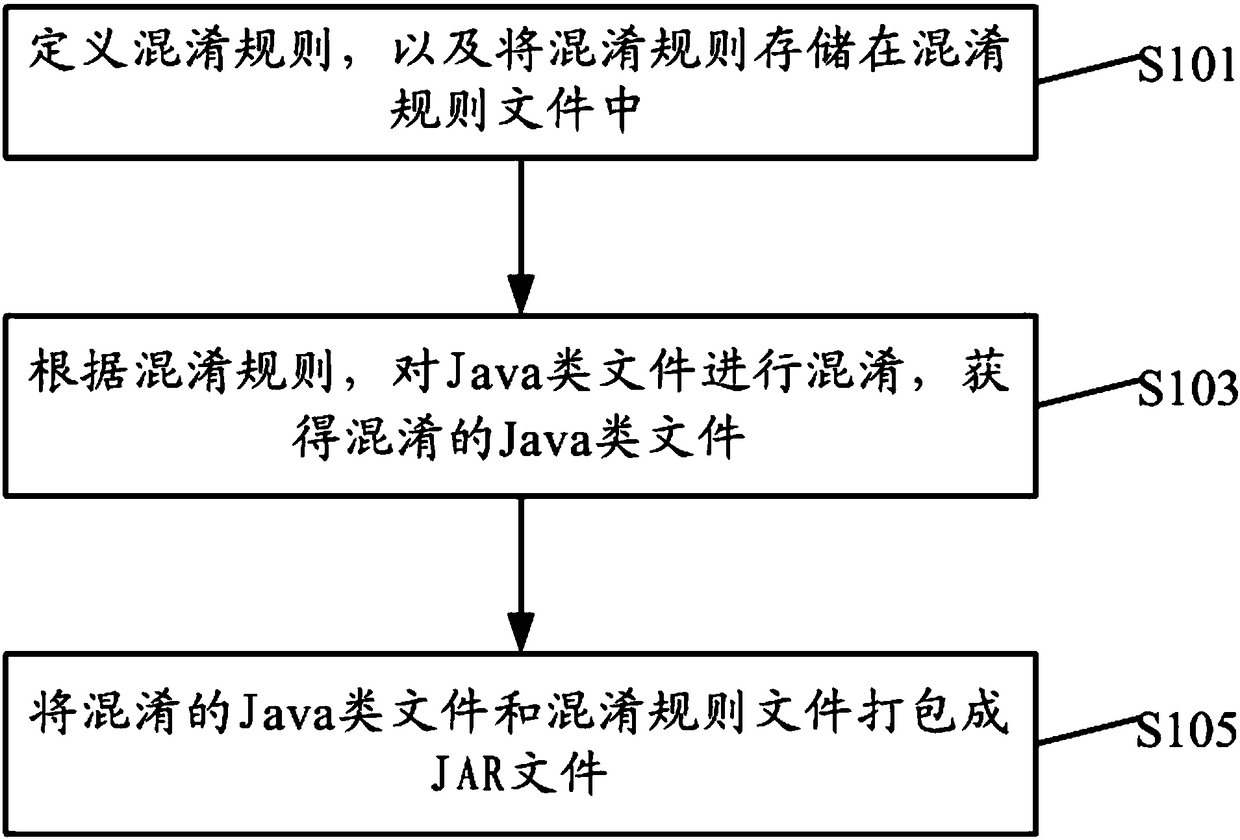
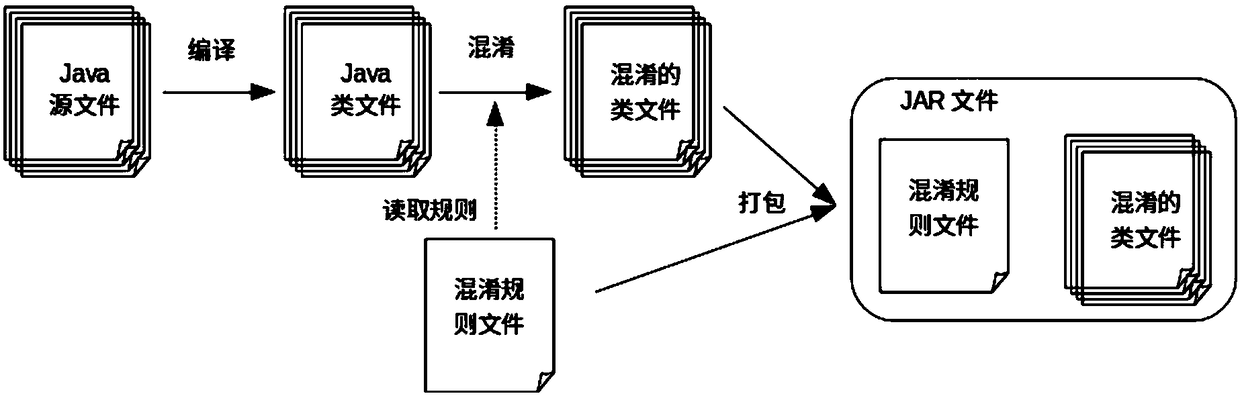
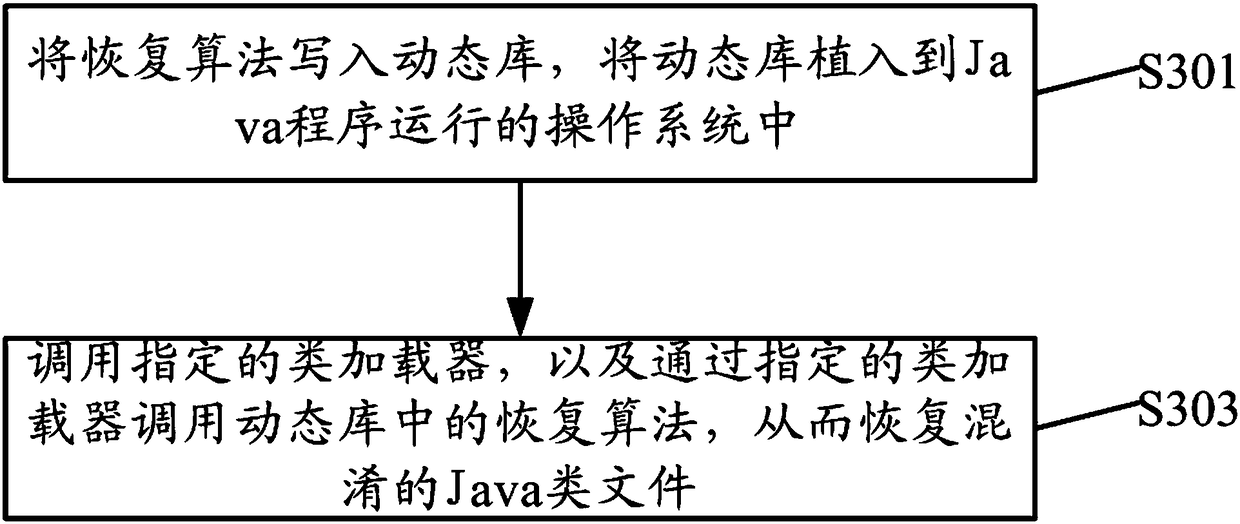
Java code confusion and recovery methods and apparatuses
InactiveCN108170433ANo errorPrevent decompilationProgram/content distribution protectionCode compilationJava codeThird party
The invention discloses Java code confusion and recovery methods and apparatuses. The Java code confusion method comprises the steps of defining a confusion rule, and storing the confusion rule in a confusion rule file; according to the confusion rule, confusing Java class files to obtain confused Java class files; and packaging the confused Java class files and the confusion rule file into a JARfile. By defining the confusion rule, which Java class files need to be confused is flexibly configured; in addition, the confused Java class files realize detail confusion, so that the confused Javaclass files are prevented from being decompiled; and the confused Java class files still meet Java class file format standards, so that the confused Java class files can participate in compilation anderrors during operation of other third-party frameworks and class libraries which a Java program depends on are not caused.
Owner:上海五行嘉信息技术有限公司
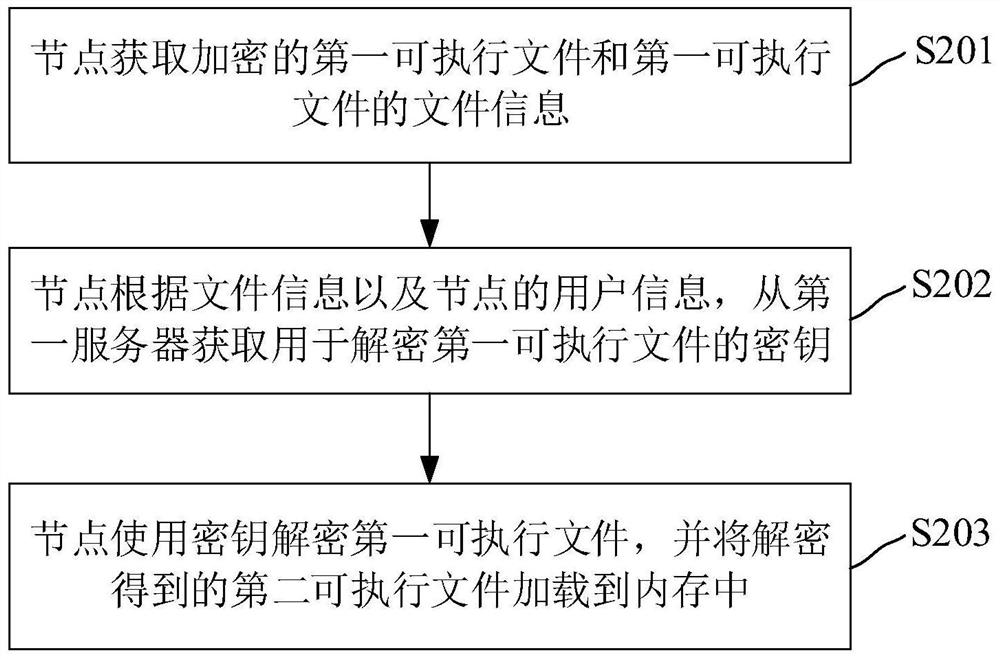
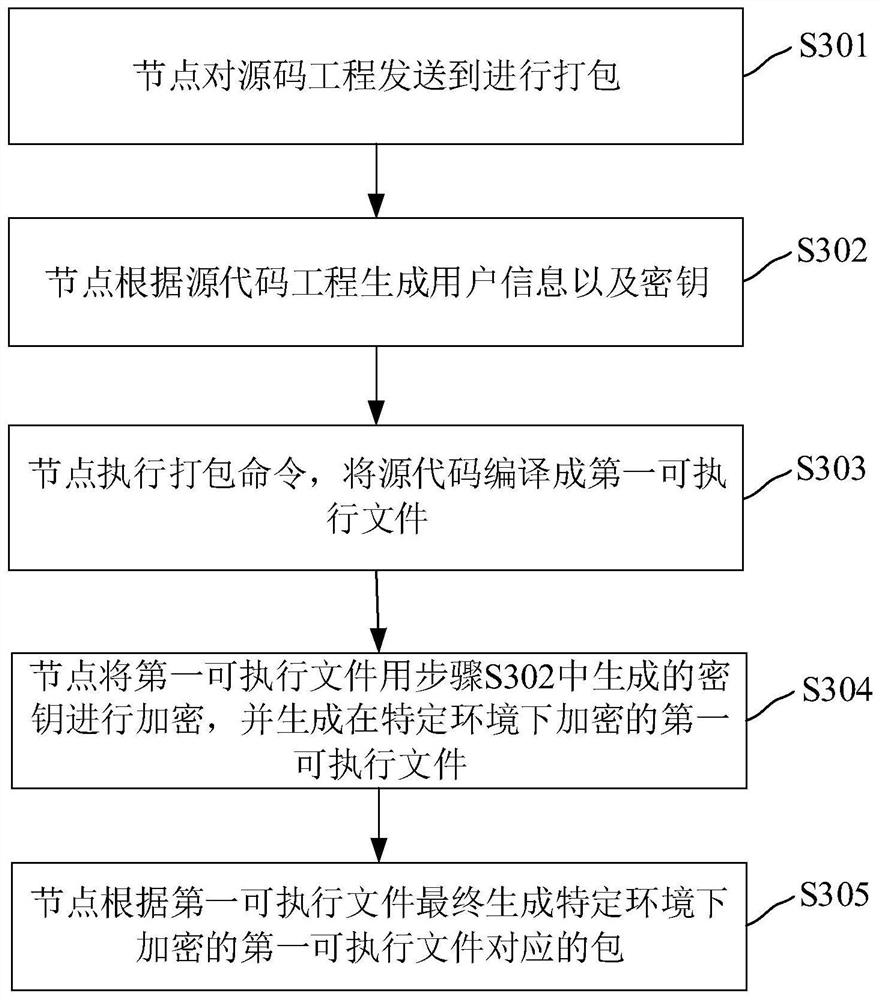
Method and device for preventing decompilation of executable file, computer equipment and medium
PendingCN111639311ATroubleshoot leaked technical issuesImprove securityProgram/content distribution protectionSoftware engineeringTerm memory
The invention relates to a method and device for preventing decompilation of executable files, computer equipment and a medium. The method for preventing decompilation of the executable file comprisesthe steps that a node acquires an encrypted first executable file and file information of the first executable file; the node obtains a secret key used for decrypting the first executable file from the first server according to the file information and the user information of the node; and the node decrypts the first executable file by using the key, and loads the second executable file obtainedby decryption into the memory. Through the method and the device, the technical problem of source code leakage in related technologies is solved, and the safety of the source code is improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
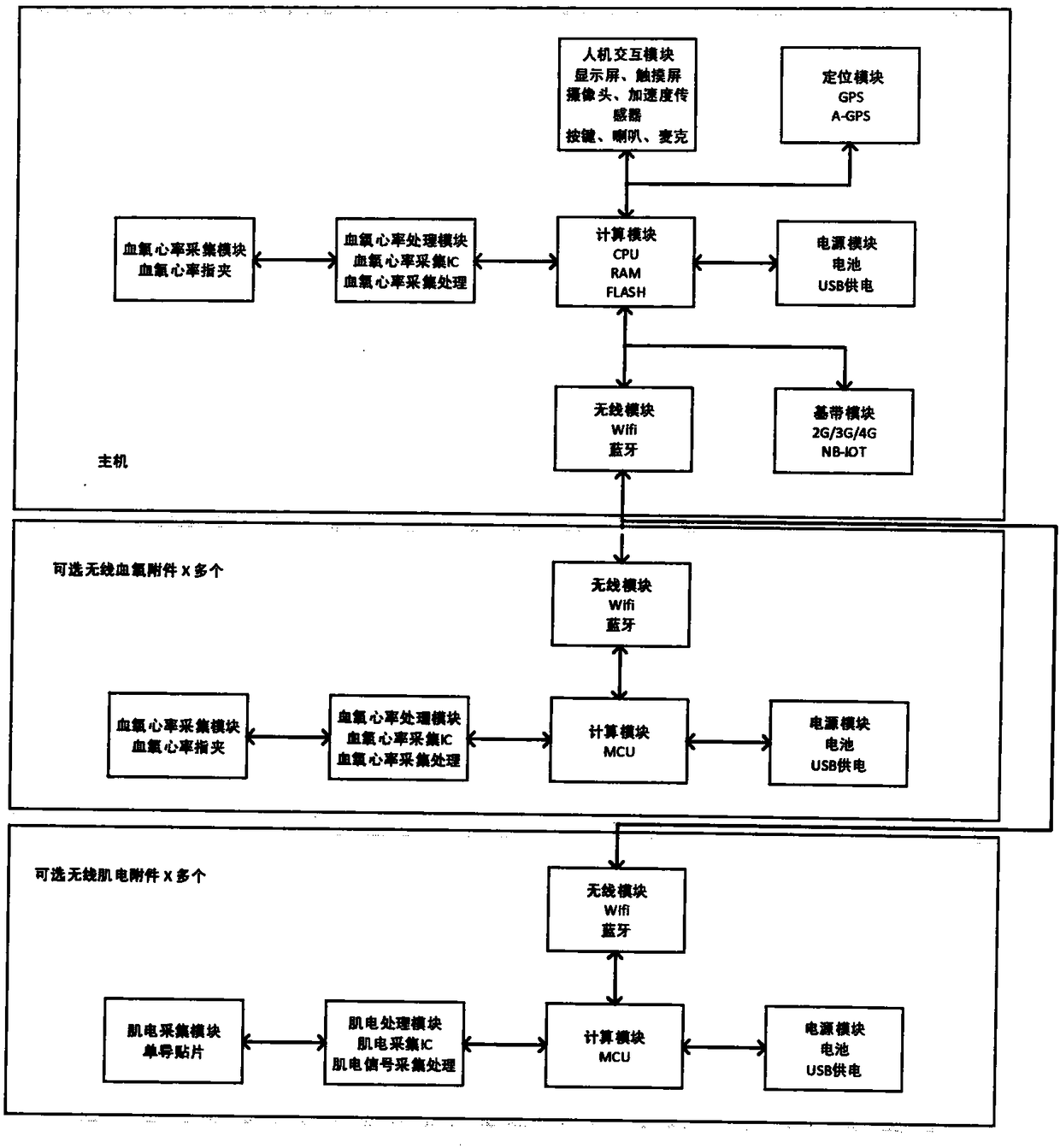
Blood oxygen monitoring device
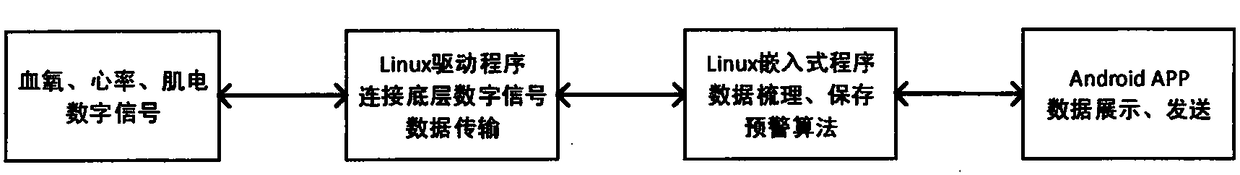
PendingCN108354615AImprove sending success rateStrong coverageDiagnostic recording/measuringSensorsOxygen monitoringEngineering
The invention provides a blood oxygen monitoring device. The blood oxygen monitoring device comprises a host, an optional wireless blood oxygen accessory and an optional wireless myoelectricity accessory; the host comprises a first computing module, the first computing module is connected with a human-machine interaction module, a first wireless module, a baseband module, a first power module, a first blood oxygen and heart rate processing module and a positioning module, and a first blood oxygen and heart rate acquisition module is connected with the first blood oxygen and heart rate processing module; the optional wireless blood oxygen accessory comprises a second computing module, the second computing module is connected with a second wireless module, a second blood oxygen and heart rate processing module and a second power module, and a second blood oxygen and heart rate acquisition module is connected with the second blood oxygen and heart rate processing module; the optional wireless myoelectricity accessory comprises a third computing module, the third computing module is connected with a third wireless module, a myoelectricity processing module and a third power module, anda myoelectricity acquisition module is connected with the myoelectricity processing module. The blood oxygen monitoring device has the advantages of simple structure, high use flexibility, high detection data accuracy and good safety, and can be used for exercise monitoring.
Owner:SHANGHAI LEPU CLOUDMED CO LTD
System for preventing java program from being decompiled
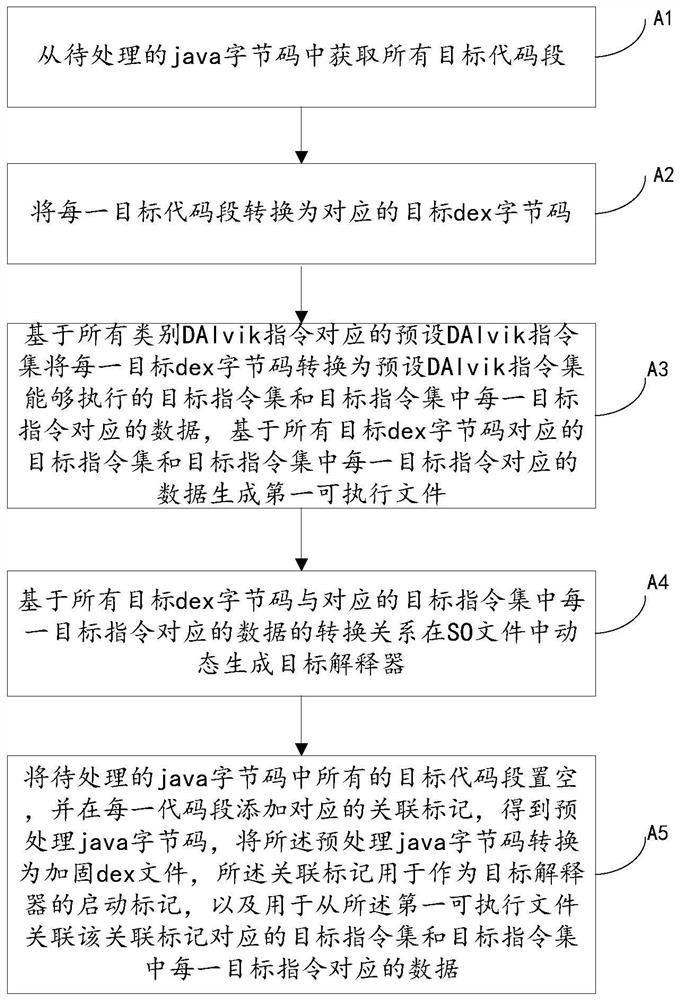
ActiveCN113094667AFairly technologically advancedQuite practicalProgram/content distribution protectionObject codeSoftware engineering
The invention relates to a system for preventing a java program from being decompiled, which comprises a preset DAlvik instruction set, a processor and a memory in which a computer program is stored; when the computer program is executed by the processor, the method includes: A1: acquiring all target code segments from java byte codes to be processed; A2, converting each target code segment into a corresponding target dex byte code; A3, converting each target dex byte code into a target instruction set and data corresponding to each target instruction based on a preset DAlvik instruction set, and generating a first executable file; A4, dynamically generating a target interpreter in the SO file based on a conversion relationship between all the target dex byte codes and data corresponding to each target instruction in the target instruction set; A5, emptying all target code segments in the to-be-processed java byte codes, adding corresponding association marks to obtain pre-processed java byte codes, and converting the pre-processed java byte codes into a reinforced dex file. According to the method and the device, the java program can be prevented from being decompiled, and the security of the java program is improved.
Owner:ZHEJIANG MEIRI HUDONG NETWORK TECH CO LTD
An application security protection method and server
ActiveCN105678120BTo achieve the purpose of security protectionPrevent decompilationTransmissionProgram/content distribution protectionApplication securityOperating system
The invention discloses a safety protection method of application programs and a server. The method comprises following steps: receiving a first application program sent from a client by the server; collecting parameters / instructions of the first application program by the server in order to obtain a second application program such that the second application program can normally operate and enable a reverse tool to exit by fault when the reverse tool is utilized for analyzing the second application program; and sending the second application program to the client by the server.
Owner:CHINA MOBILE COMM GRP CO LTD
Source code reinforcement method and device, computer equipment and storage medium
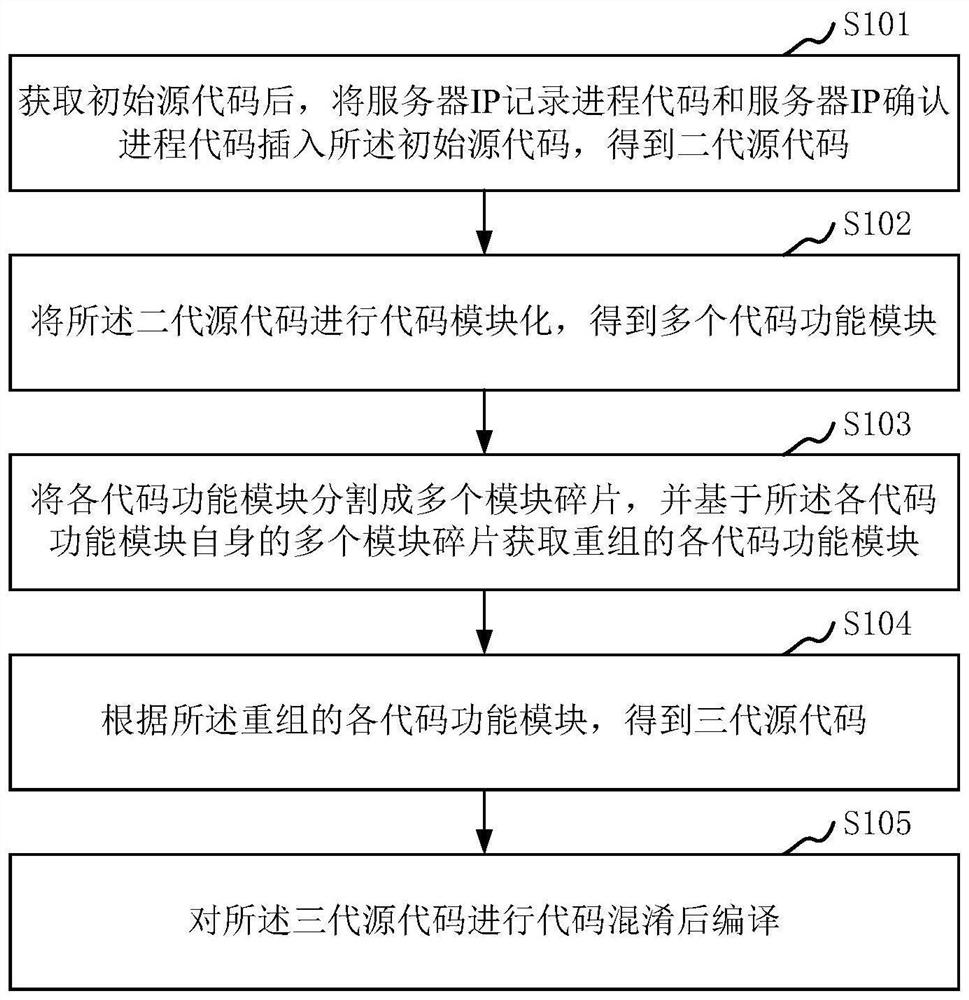
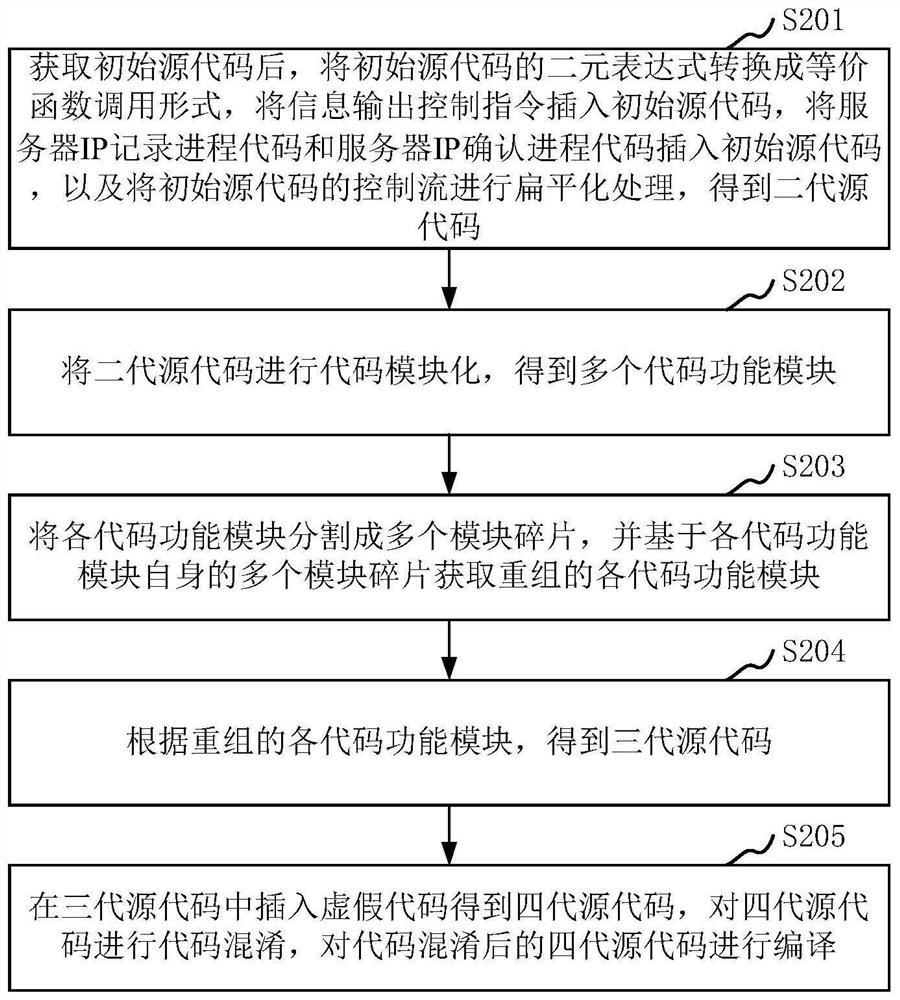
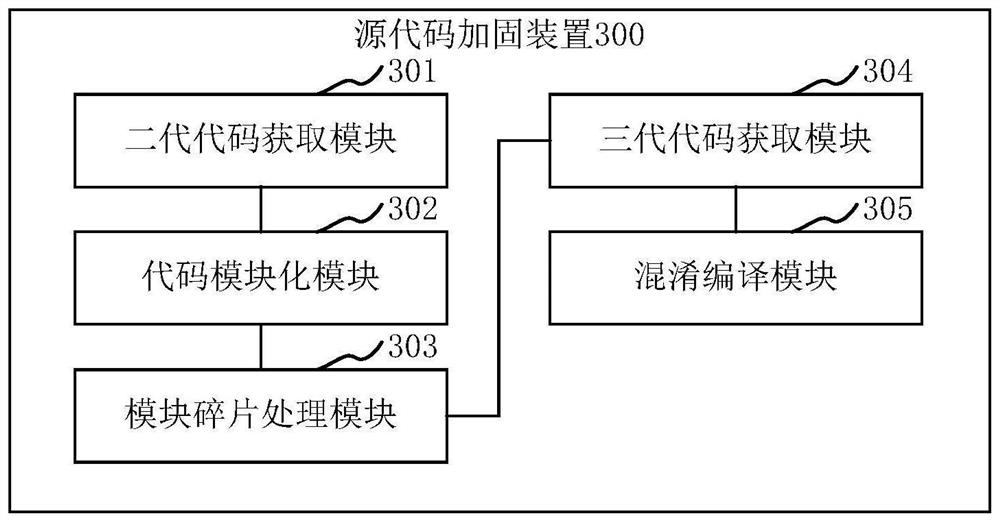
PendingCN113282893ADifficult to readImprove securityProgram/content distribution protectionModularityComputer equipment
The invention relates to the technical field of information security, and provides a source code reinforcement method and device, computer equipment and a storage medium. The source code security can be comprehensively improved. The method comprises the steps that after an initial source code is obtained, a server IP record process code and a server IP confirmation process code are inserted into the initial source code to obtain a second-generation source code, then the second-generation source code is subjected to code modularization to obtain a plurality of code function modules, each code function module is divided into a plurality of module fragments, and each recombined code function module is obtained based on a plurality of module fragments of each code function module, wherein each recombined code function module is composed of a plurality of module fragments after position adjustment, and function link codes are inserted among the plurality of module fragments after position adjustment; third-generation source codes are obtained according to the recombined code function modules, and compilation is carried out after code obfuscation is carried out on the third-generation source codes.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD
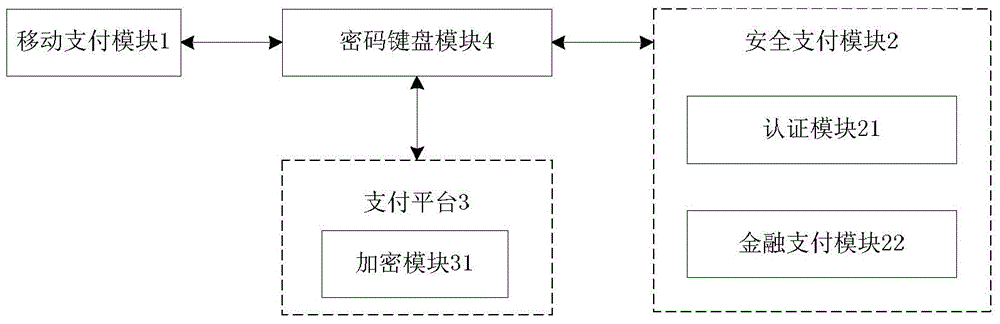
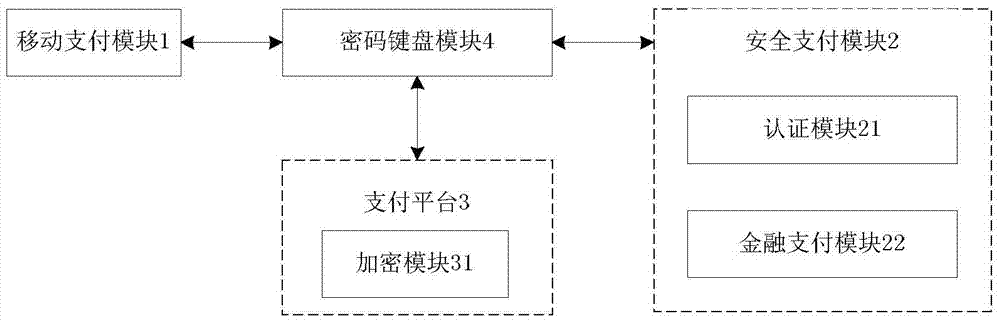
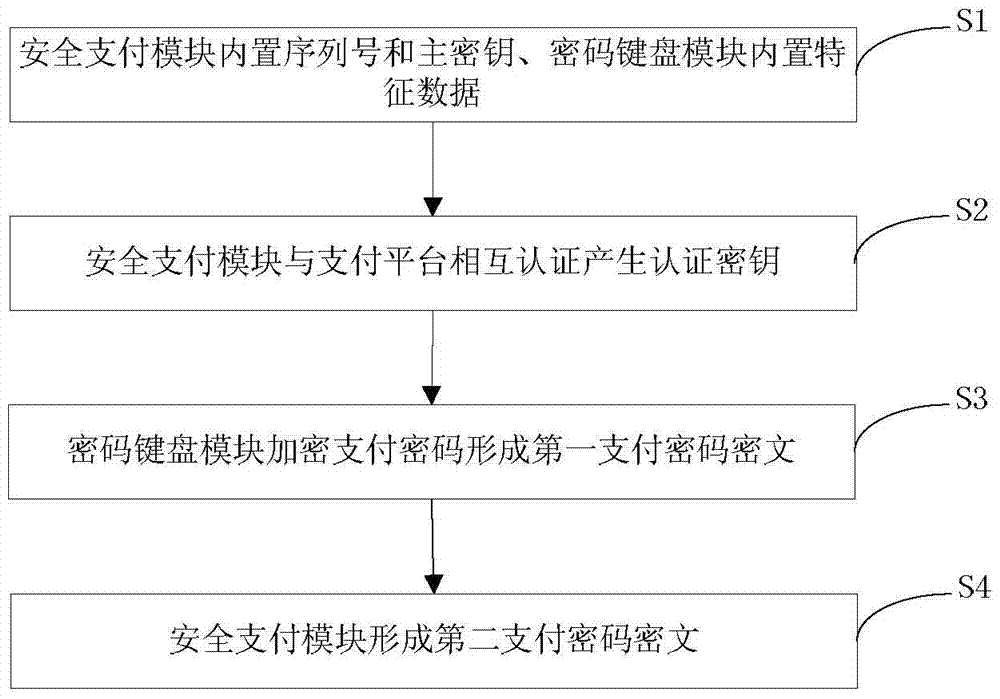
Mobile terminal?payment password?transmission system and method
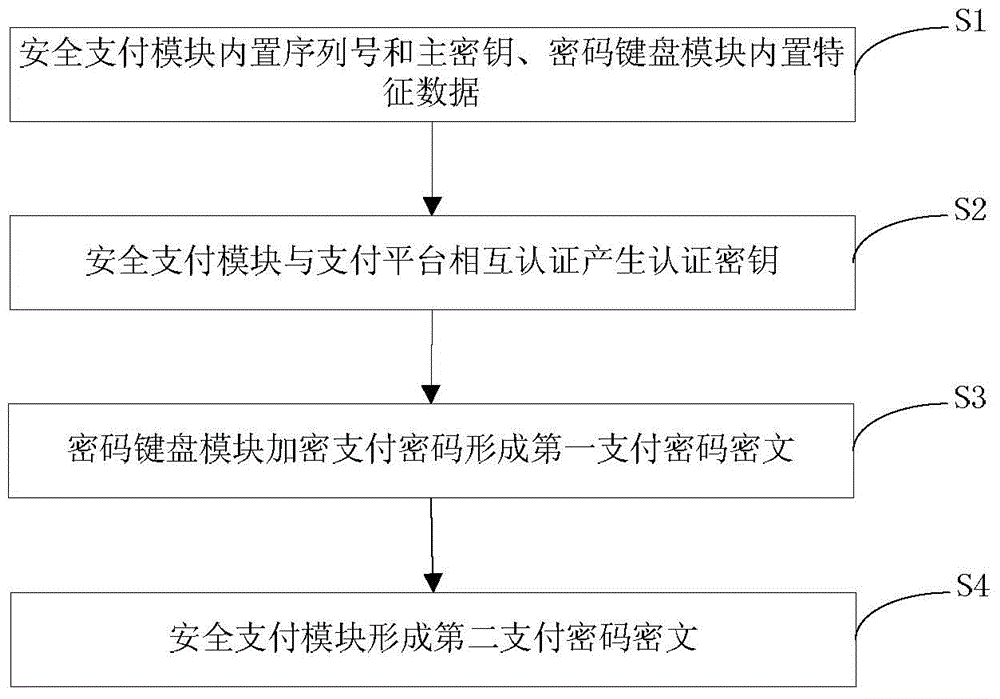
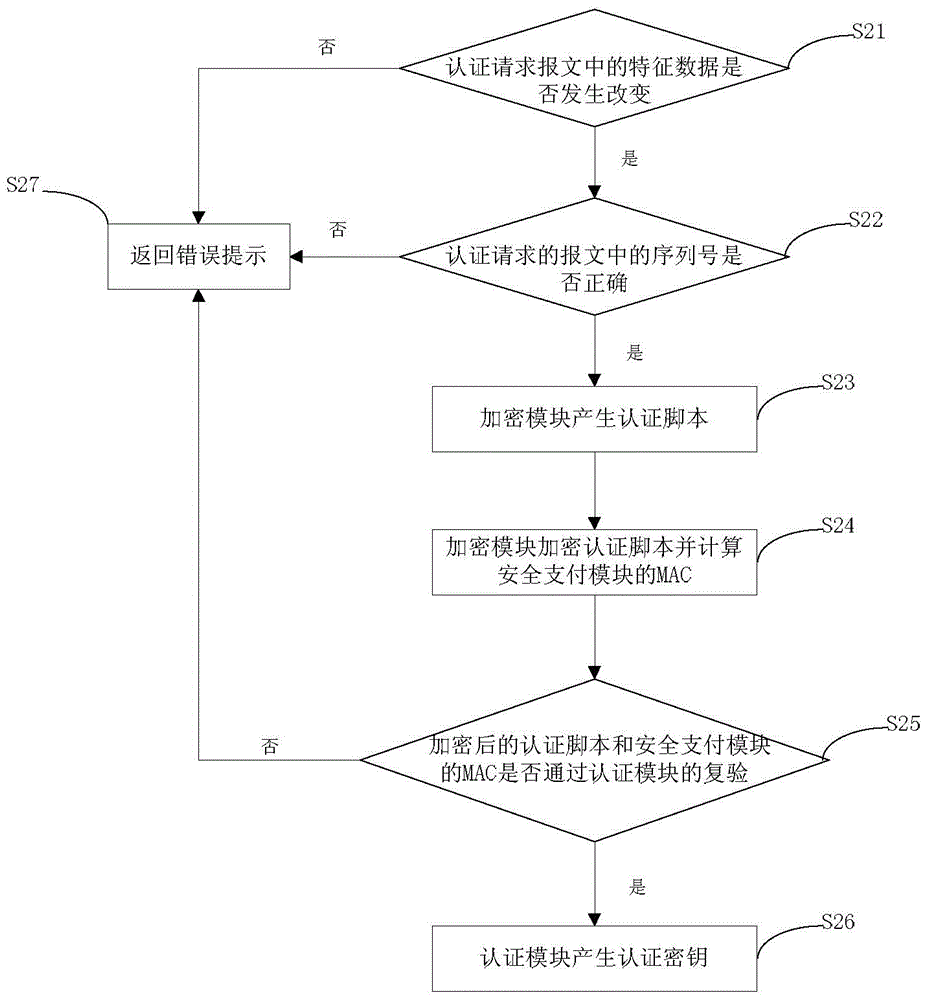
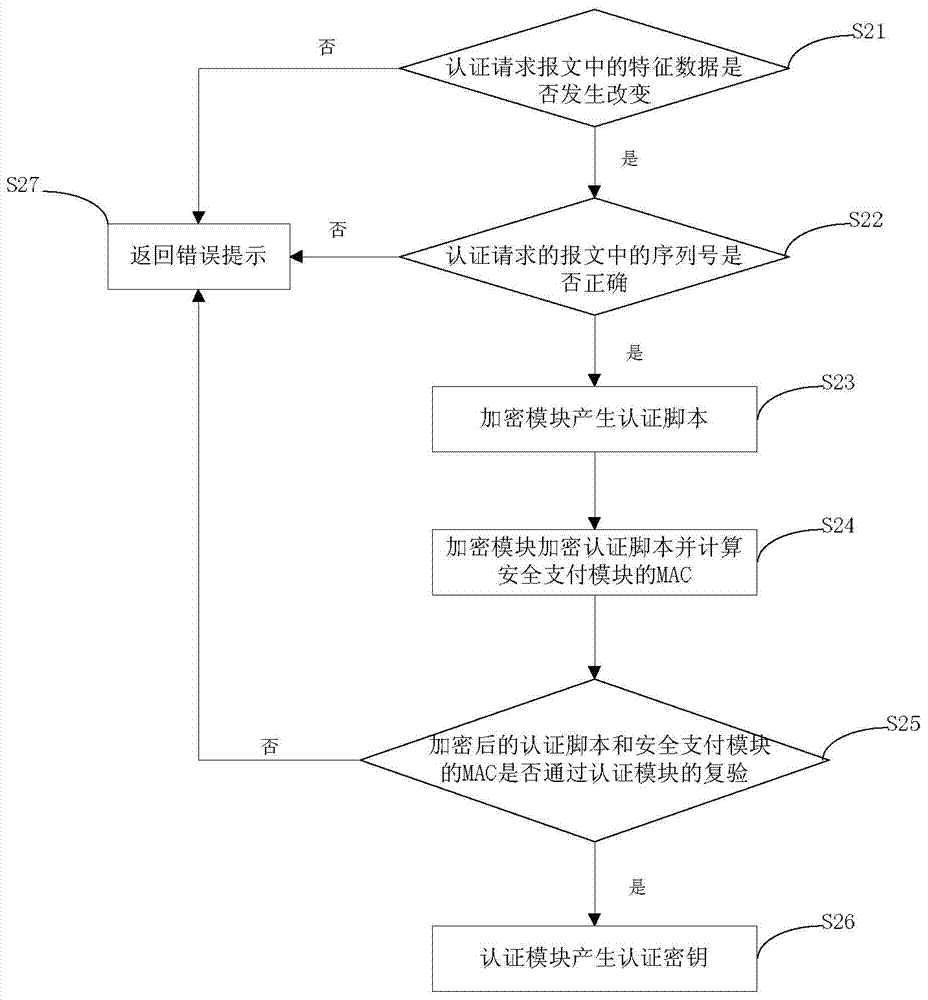
InactiveCN103825740AAvoid the risk of being leakedEnsure safetyUser identity/authority verificationProtocol authorisationPlaintextPassword
The invention discloses a mobile terminal?payment password?transmission system and a method, and relates to the field of mobile payment. The payment password?transmission system comprises a mobile payment?module,?a payment platform, a safety payment?module, and a password keyboard module for inputting a payment password. According to the payment password?transmission method, the safety payment?module and the payment platform are mutually authenticated and an authentication key is generated; the payment password is inputted via the password keyboard module and uses the authentication key for encryption; decryption and encryption again are carried out via the safety payment?module, a payment password ciphertext is formed to be transmitted to the password keyboard module, and the password keyboard module transmits the payment password ciphertext to the mobile payment?module for use. During the payment password use process, the mobile payment?module can not touch a payment password plaintext, and the risk that the payment password is leaked can thus avoided.
Owner:武汉擎动网络科技有限公司
Verification release method for software running
InactiveCN108280329AAvoid crackingPrevent decompilationProgram/content distribution protectionProgram validationRandom seed
The invention relates to a verification release method for software running. The method comprises the steps that a client side and a verification side of software are involved; the client side comprises a program embedding module, and the verification side comprises a program verification module; a verification release program is composed of a code conversion split check module, wherein the code conversion split check module in the verification side converts a digital file into a variable code, takes any random value of the variable code as a random seed and splits a segmentation code of the verification release program, and split codes are packaged into the program embedding module of the client side and the program verification module of the verification side respectively; when the verification side conducts verification, the program verification module loads the program embedding module of the client side, and after the codes are merged, the verification release program runs. According to the verification release method for software running, the codes need to be merged and then the program runs during verification, the situation can be avoided that the verification release program is broken and decompiled, so that the client side and the verification side have unique congruity, and the safety factor is higher. From the code level, the method is easy and ingenious to implement, the expenditure of complex hardware is not needed, and the whole method is more efficient.
Owner:北京数科网维技术有限责任公司
Data processing method and device for application program
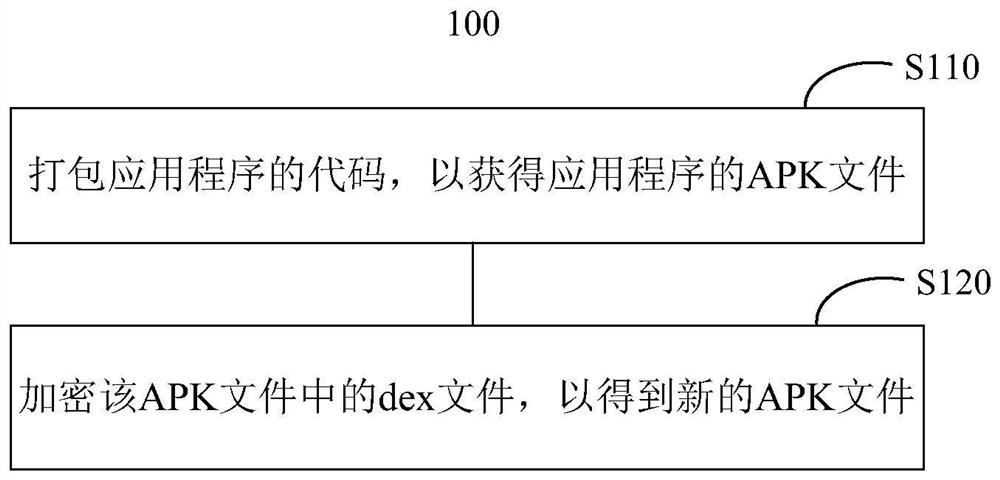
PendingCN112765567AImprove securityPrevent decompilationDigital data protectionProgram/content distribution protectionSoftware engineeringApplication procedure
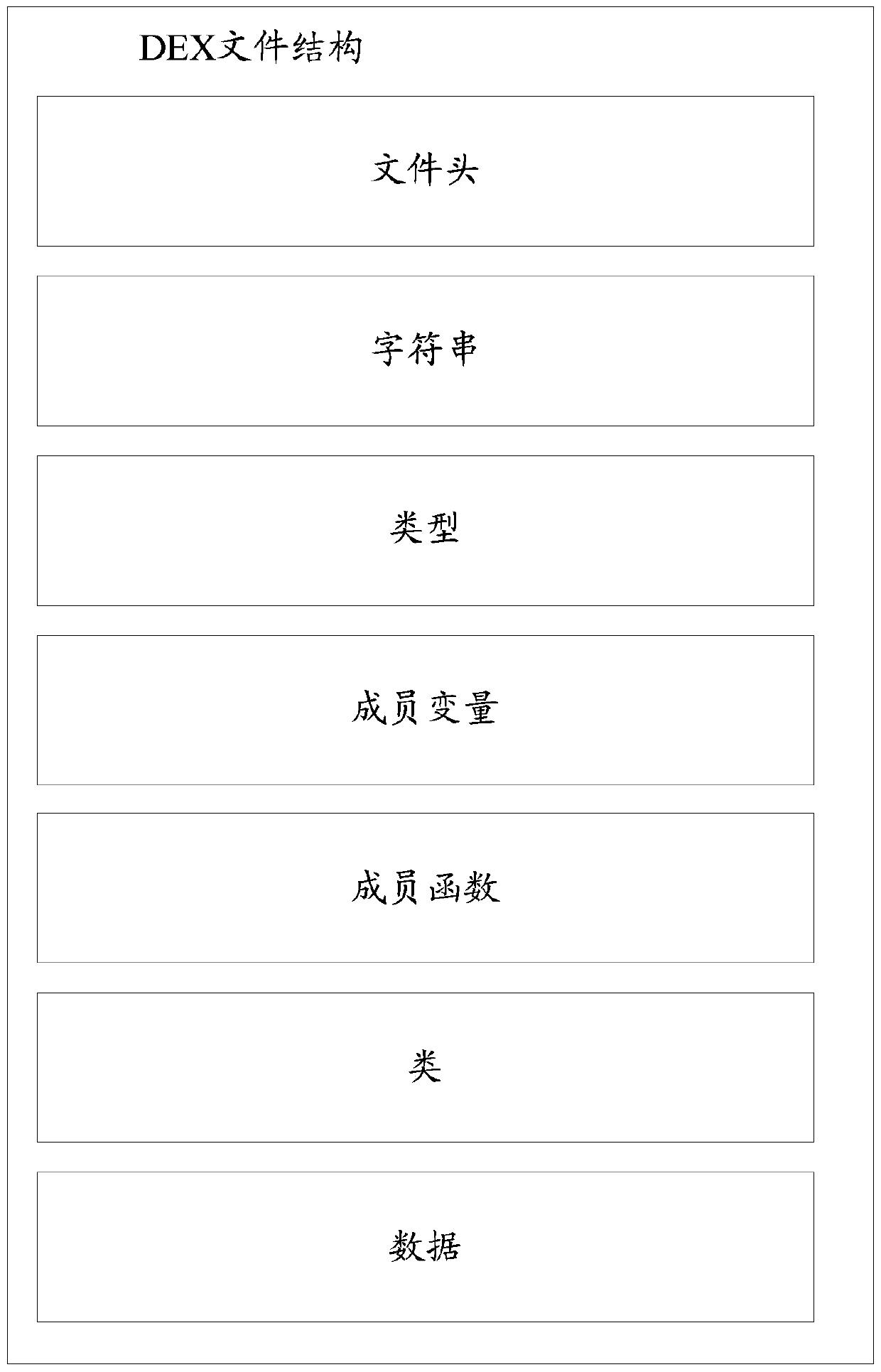
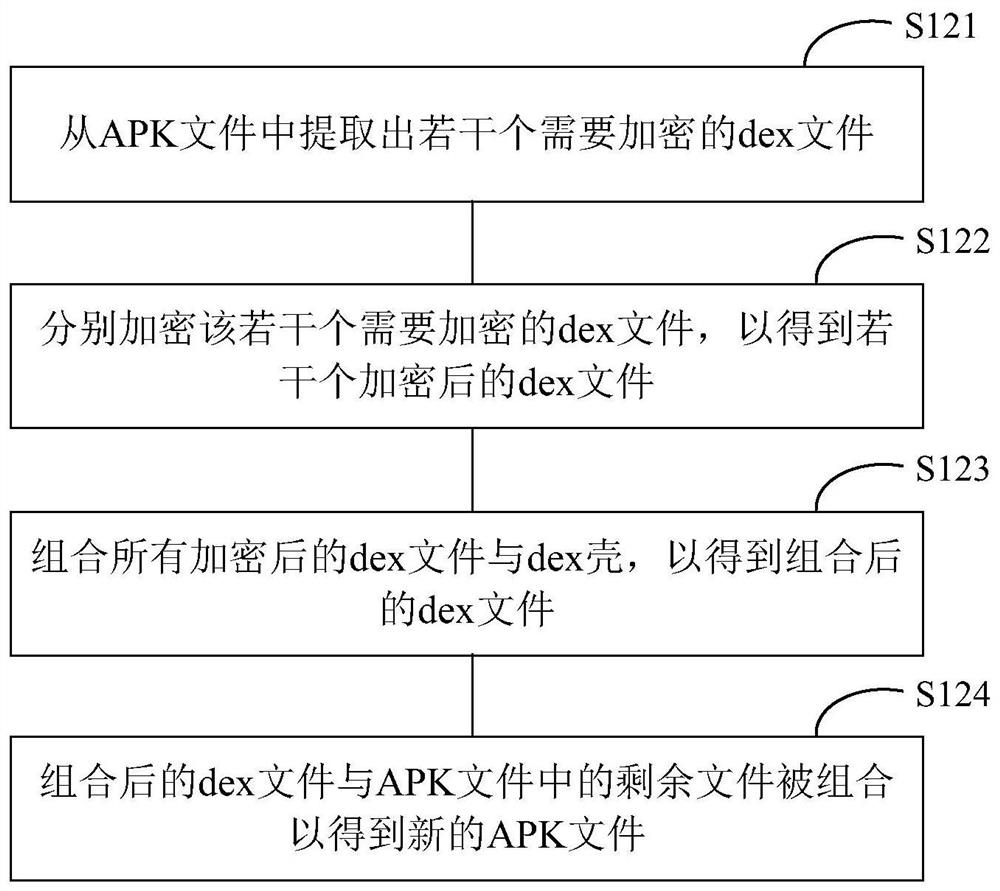
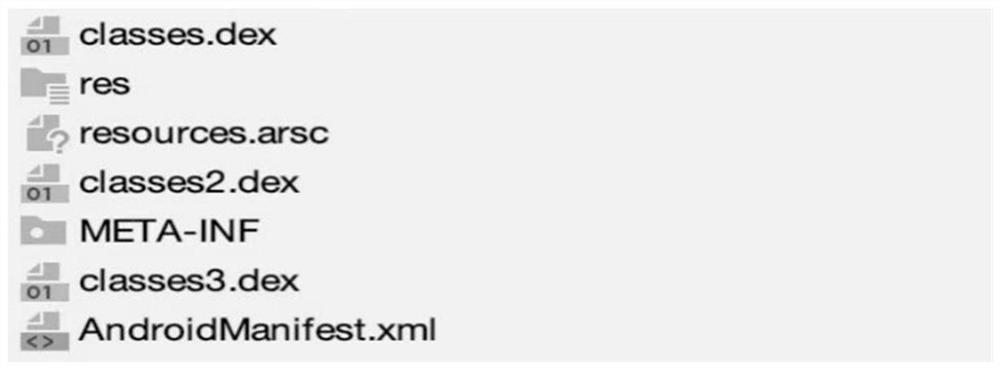
The invention provides a data processing method and device for an application program. The data processing method of the application program comprises the following steps of packaging a code of the application program to obtain an APK file of the application program; and encrypting a dex file in the APK file to obtain a new APK file.
Owner:SHANGHAI QINGGAN INTELLIGENT TECH CO LTD
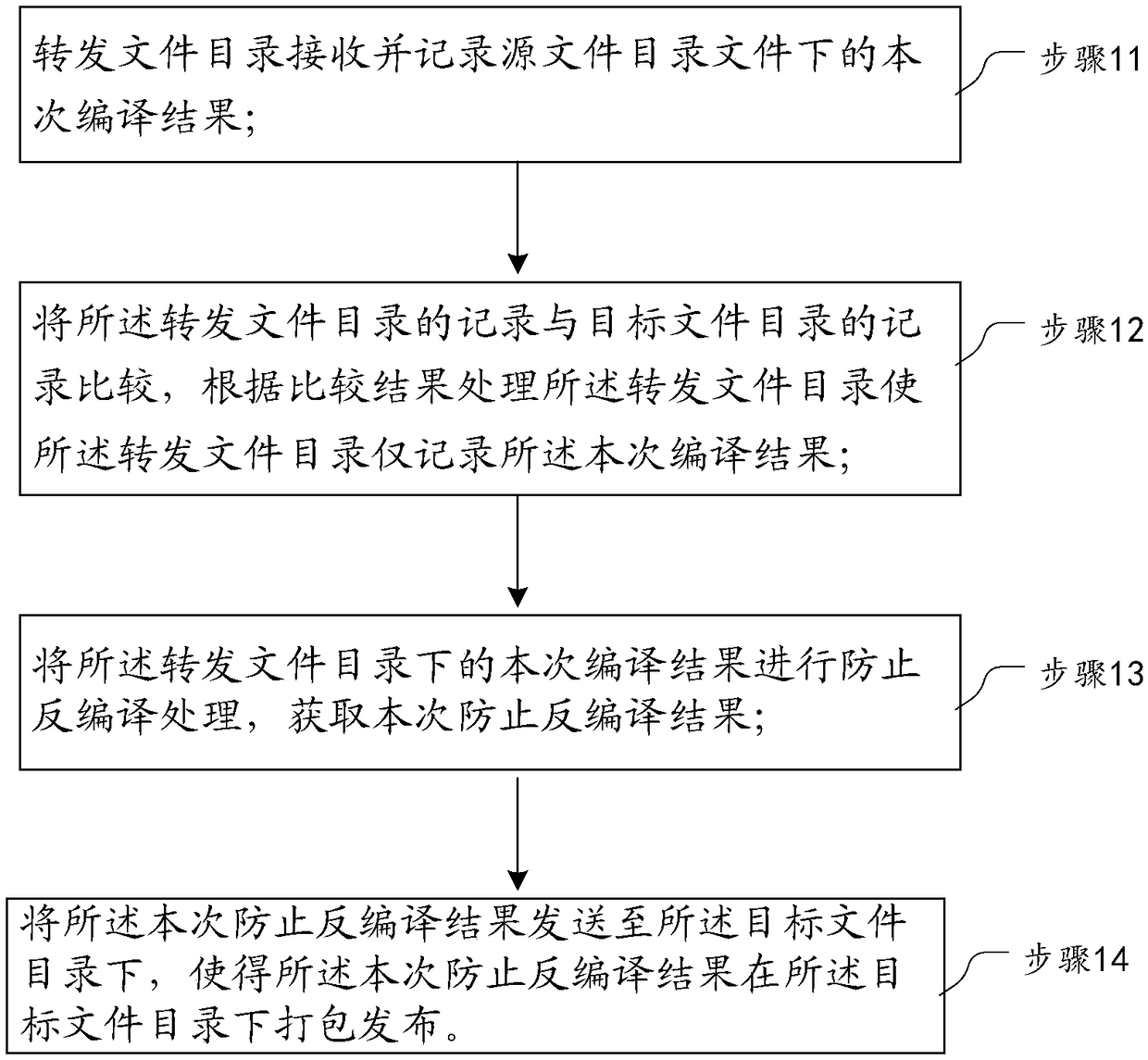
A continuous integration method and system
ActiveCN109446083APrevent decompilationPrevent decompilation processingSoftware testing/debuggingEnergy efficient computingContinuous integrationFile size
Embodiments of the present invention provide a continuous integration method and system. The method comprises the steps of receiving and recording the compilation result under the source file directory file through the forwarding file directory; comparing the record of the forwarding file directory with the record of the target file directory, and processing the forwarding file directory accordingto the comparison result so that the forwarding file directory only records the current compilation result; performing anti-decompilation processing on the current compilation result under the forwarding file directory to obtain the current anti-decompilation result; sending the present prevention decompilation result to the target file directory, so that the present prevention decompilation result is packaged and issued in the target file directory, and the problem of error of comparison result caused by small difference in file size is solved well when processing new files generated by incremental codes.
Owner:AEROSPACE INFORMATION
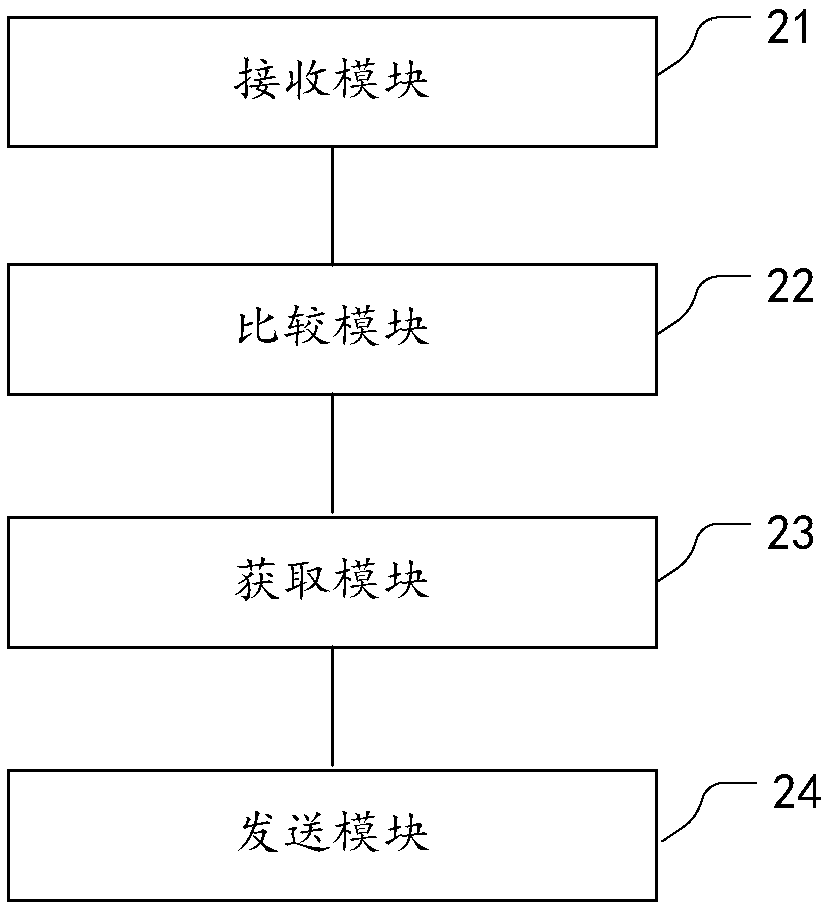
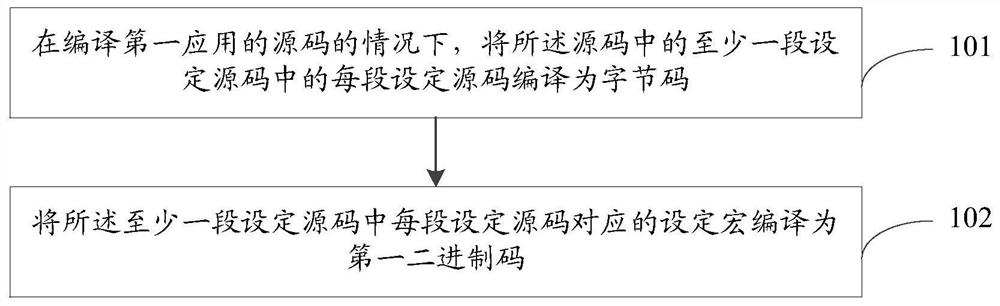
Application compiling method, application running method and electronic equipment
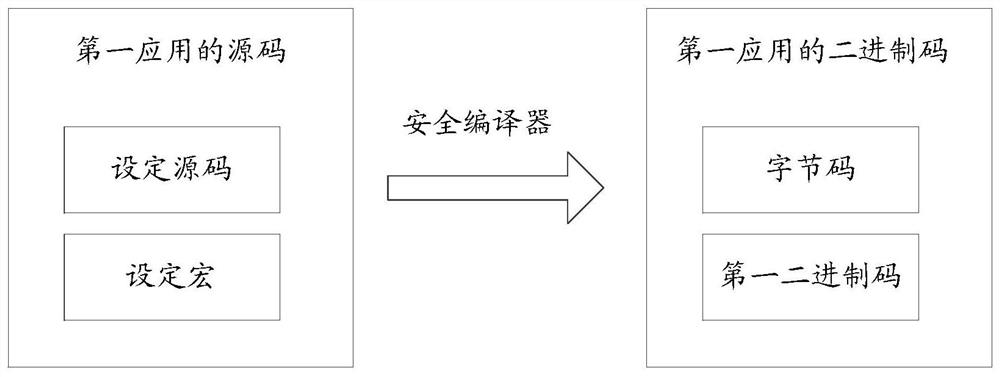
PendingCN113076106APrevent decompilationPrevent tamperingSoftware simulation/interpretation/emulationCode compilationSource codeByte
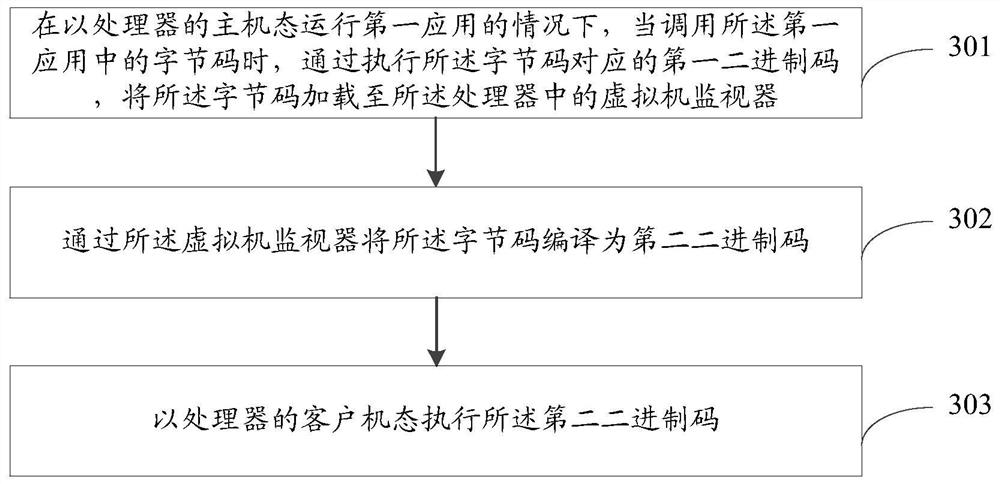
The invention discloses an application compiling method, an application running method and electronic equipment. The application compiling method comprises the steps: under the condition of compiling a source code of a first application, compiling each section of set source code in at least one section of set source code in the source code into a byte code; compiling a setting macro corresponding to each section of setting source code in the at least one section of setting source code into a first binary code, wherein the first binary code is used for being executed when a corresponding byte code is called under the condition that the first application is operated in a host state of a processor; when the first binary code is executed, using the first binary code for triggering a virtual machine monitor of the processor to compile a corresponding byte code into a second binary code, and triggering and switching to a client state of the processor to execute the second binary code.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Source code protection method, application server and computer-readable storage medium
ActiveCN108399319BEnsure safetyImprove experienceProgram/content distribution protectionApplication serverUser input
The invention discloses a source code protection method. The method includes: receiving a code encryption program input by a user, and using the code encryption program to encrypt the source code to obtain an encrypted file; obtaining a JDK, and using The code decryption program corresponding to the code encryption program processes the JDK to obtain the processed JDK; runs the processed JDK; and transfers the encrypted file through the processed JDK and performs decrypt. The invention also provides an application server. The source code protection method and the application server provided by the invention can effectively prevent the source file from being decompiled, ensure the security of the source file, maintain the cross-platform characteristic of the program, and improve user experience.
Owner:PING AN TECH (SHENZHEN) CO LTD
A mobile terminal payment password transmission system and method
InactiveCN103825740BAvoid the risk of being leakedEnsure safetyUser identity/authority verificationProtocol authorisationPlaintextCiphertext
The invention discloses a mobile terminal?payment password?transmission system and a method, and relates to the field of mobile payment. The payment password?transmission system comprises a mobile payment?module,?a payment platform, a safety payment?module, and a password keyboard module for inputting a payment password. According to the payment password?transmission method, the safety payment?module and the payment platform are mutually authenticated and an authentication key is generated; the payment password is inputted via the password keyboard module and uses the authentication key for encryption; decryption and encryption again are carried out via the safety payment?module, a payment password ciphertext is formed to be transmitted to the password keyboard module, and the password keyboard module transmits the payment password ciphertext to the mobile payment?module for use. During the payment password use process, the mobile payment?module can not touch a payment password plaintext, and the risk that the payment password is leaked can thus avoided.
Owner:武汉擎动网络科技有限公司
An Encryption Method Based on rc4 Algorithm for Encryption of Code
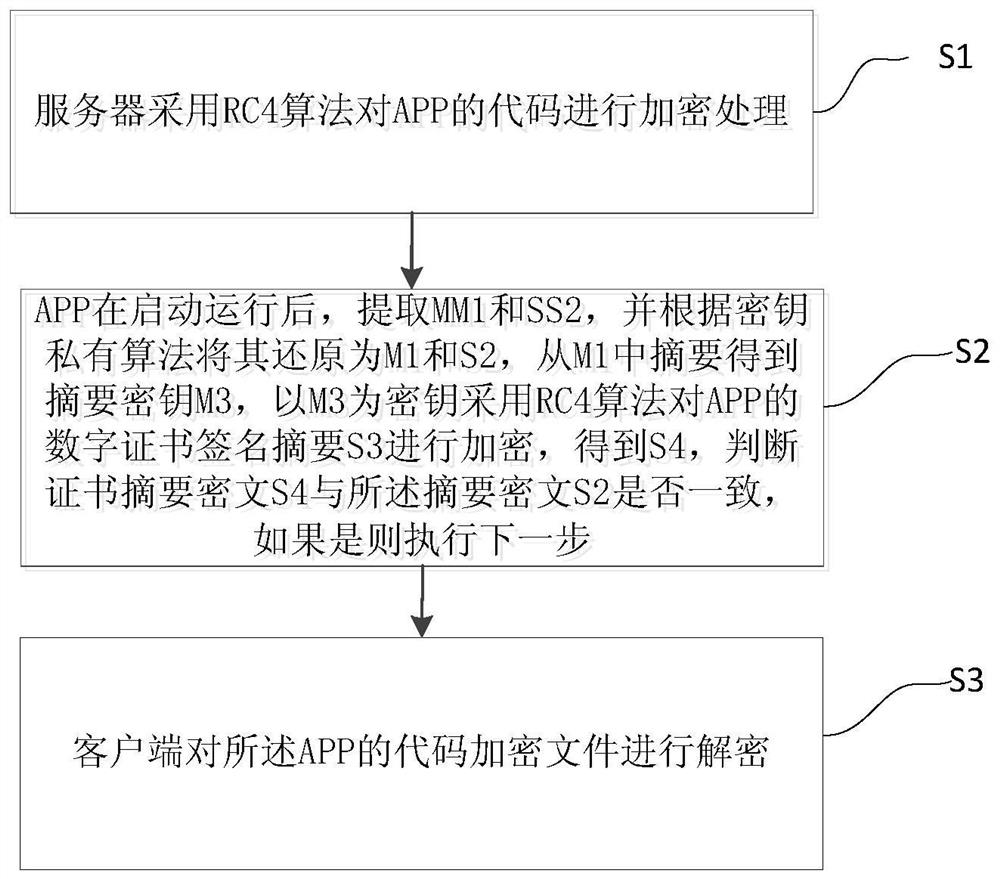
ActiveCN107257282BProtection securityTaking into account efficiencyKey distribution for secure communicationUser identity/authority verificationRC4Algorithm
The invention provides an RC4 algorithm-based code full-packet encryption method. The method comprises the steps of subjecting the codes of an APP to encryption treatment by a server based on an RC4 algorithm; after the APP is started to run, extracting an MM1 and an SS2, and restoring the MM1 and the SS2 to a global ciphertext secret key M1 and an abstract ciphertext S2 based on a secret key private algorithm; obtaining an abstract secret key M3 from the abstract of the M1, and adopting the M3 as a secret key to encrypt the digital certificate signature digest S3 of the APP based on the RC4 algorithm so as to obtain a certificate abstract ciphertext S4; judging whether the certificate abstract ciphertext S4 is consistent with the abstract ciphertext S2 or not; and decrypting the code encryption file of the APP by a client. According to the invention, based on the combination of a standard RC4 symmetric encryption algorithm and a private key generation algorithm, the effects of high efficiency and good safety are achieved at the same time.
Owner:YONYOU NETWORK TECH CO LTD
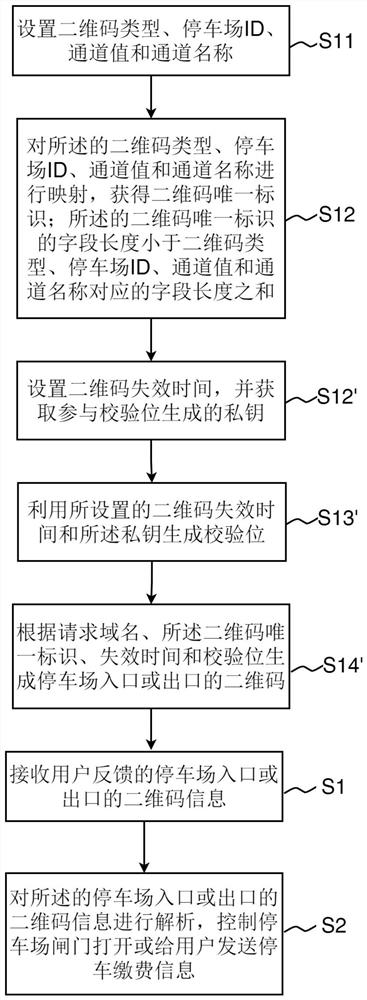
Method, system and equipment for controlling vehicle to enter and exit from parking lot and storage medium
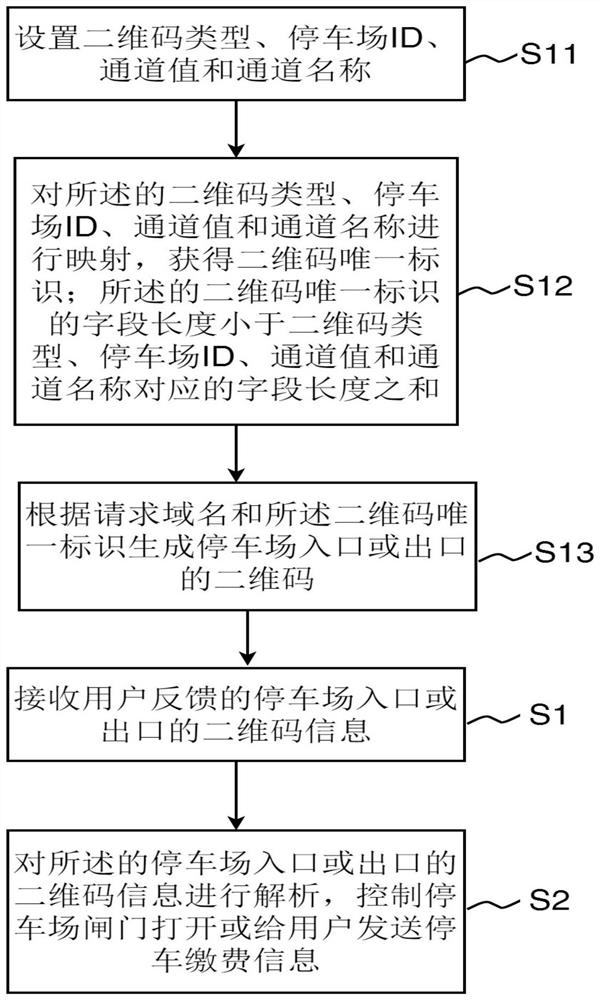
PendingCN114358230AReduce contentModerate densityTicket-issuing apparatusCo-operative working arrangementsParallel computingUnique identifier
The invention relates to a control method, system and device for vehicle access to a parking lot, and a storage medium. The method comprises the steps of receiving two-dimensional code information, fed back by a user, of an entrance or an exit of the parking lot; the two-dimensional code information of the entrance or the exit of the parking lot is analyzed, and a gate of the parking lot is controlled to be opened or parking payment information is sent to a user; wherein the two-dimensional code of the entrance or exit of the parking lot is generated by the following method: setting a two-dimensional code type, a parking lot ID, a channel value and a channel name; mapping the two-dimensional code type, the parking lot ID, the channel value and the channel name to obtain a two-dimensional code unique identifier; the field length of the unique identifier of the two-dimensional code is smaller than the sum of the field lengths corresponding to the two-dimensional code type, the parking lot ID, the channel value and the channel name; and generating a two-dimensional code of the entrance or exit of the parking lot according to the request domain name and the unique identifier of the two-dimensional code. The intensity of the finally generated two-dimensional code is moderate, and the two-dimensional code can be scanned more easily.
Owner:SHENZHEN CHINAROAD NETWORK TECH
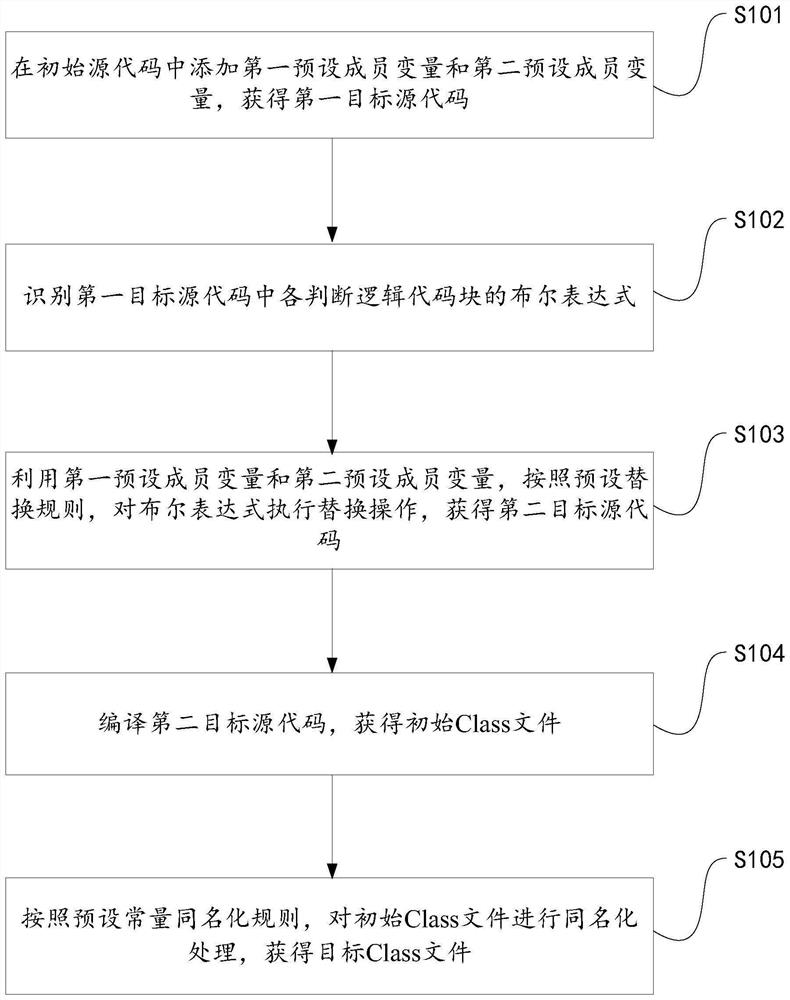
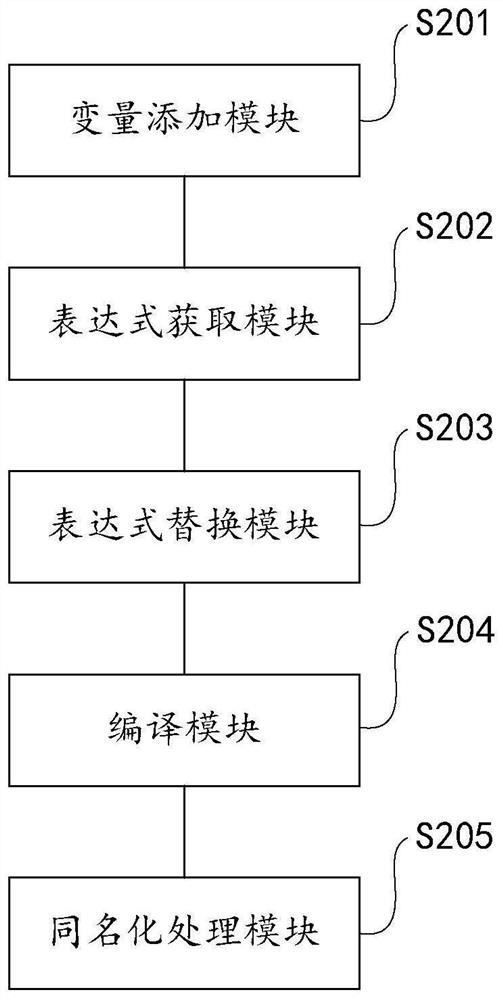
Method, system and device for preventing decompilation and storage medium
PendingCN114707125APrevent decompilationDoes not affect normal operationProgram/content distribution protectionCoding blockMember variable
The embodiment of the invention provides a method, system and device for preventing decompilation and a storage medium, and the method comprises the steps: adding a first preset member variable and a second preset member variable in an initial source code, obtaining a first target source code, obtaining a Boolean expression of each judgment logic code block in the first target source code, and utilizing the first preset member variable and the second preset member variable to perform replacement operation on the Boolean expression according to a preset replacement rule to obtain a second target source code, compiling the second target source code to obtain an initial Class file, and performing homonymy processing on the initial Class file according to a preset constant homonymy rule to obtain a target Class file. Based on the difference between Java language specifications and virtual machine specifications, the target Class file can be normally operated by the virtual machine and cannot be decompiled into legal Java source codes with readability through replacement operation and homonymy processing. Therefore, the Java source code can be prevented from being decompiled.
Owner:HANGZHOU PINGPONG INTELLIGENT TECH CO LTD
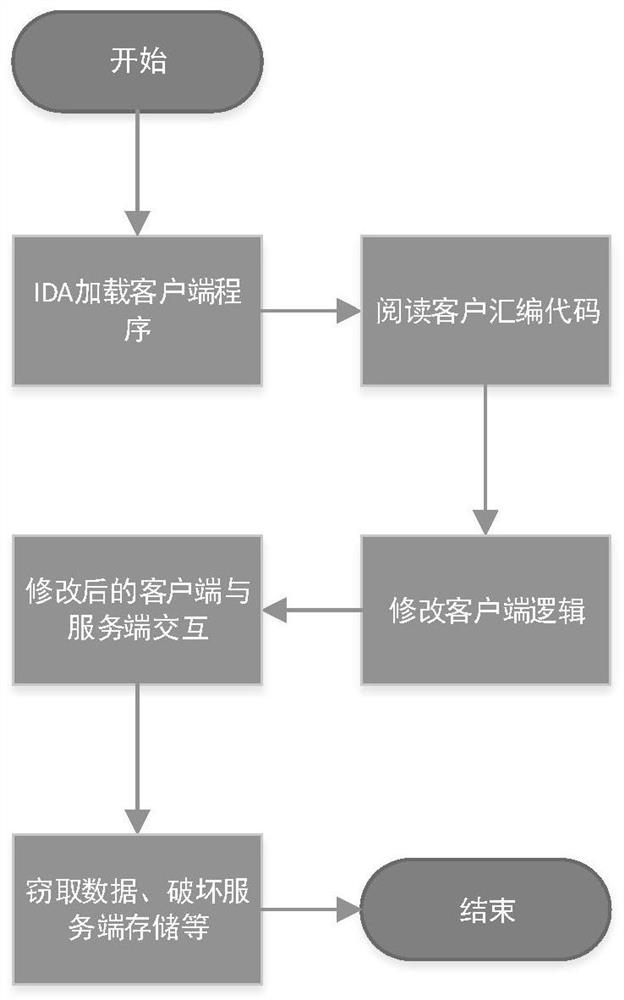
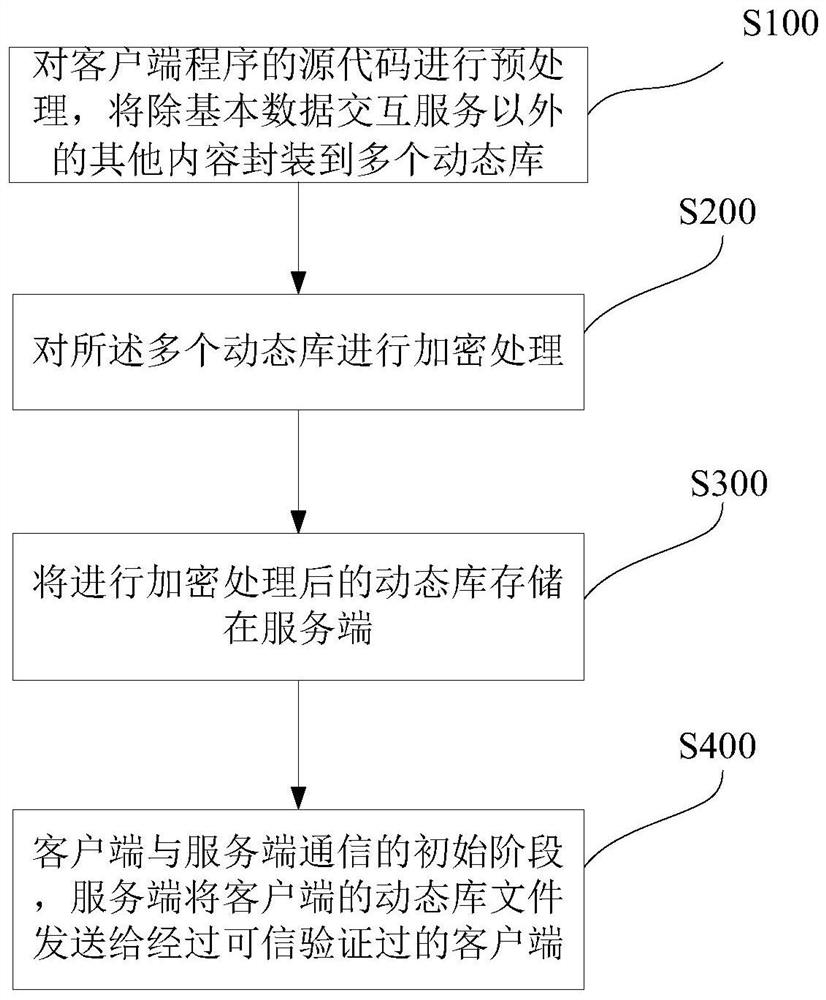
Client program disassembly prevention protection method
The invention relates to a client program disassembly prevention protection method, which comprises the following steps of: preprocessing a source code of a client program, and packaging other contents except a basic data interaction service into a plurality of dynamic libraries; performing encryption processing on the plurality of dynamic libraries; storing the encrypted dynamic library in a server; and in the initial stage of communication between the client and the server, sending the dynamic library file of the client to the client subjected to credibility verification by the server . Through the above protection measures, the client program installed in the application terminal only has one lightweight executable program which does not involve any service logic, and the main logic function dynamic library of the client is stored in the server and is dynamically obtained during operation, so that decompilation by a network attacker is fundamentally avoided. The source code constantof the client and the compiled dynamic library are encrypted, so that the client cannot be decompiled again.
Owner:XUJI GRP +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com