Safety protection method of application programs and server
An application and security protection technology, applied in the field of communication, can solve the problems of poor application security and difficulty in tracing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
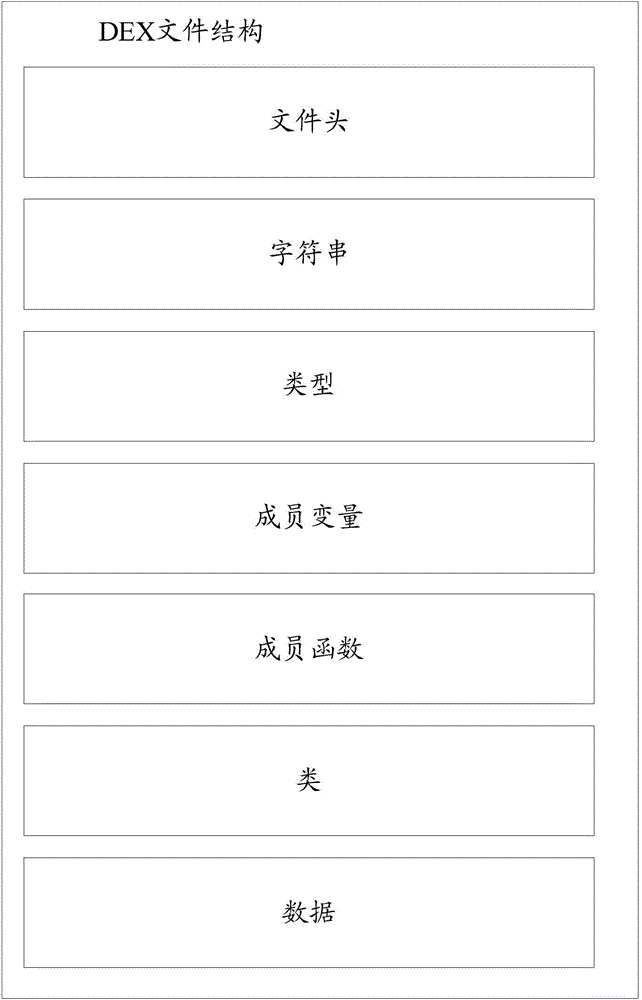
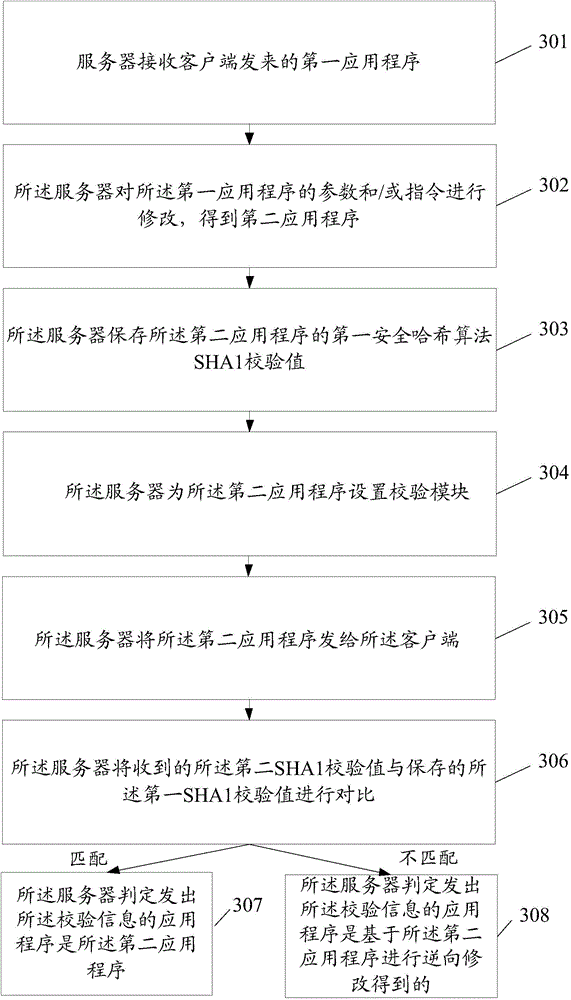
[0078] An application program security protection method provided by the embodiment of the present invention can be implemented in the following manner: by modifying the encryption flag in the application program to deceive the reverse tool, but this security reinforcement method is easy to analyze and restore, and the security is poor , and the reverse modification of the application cannot be traced, and the traceability is poor.
[0079] Another application security protection method provided by the embodiment of the present invention can be implemented in the following manner: the real application program is encrypted, and the shell program decrypts and starts it when running, but the shell program will also be analyzed by the reverse tool , so the security is poor. In addition, this method has strict restrictions on the version and operating environment of the mobile platform, and cannot adapt to multiple versions of the mobile platform, and has poor compatibility.
[008...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com