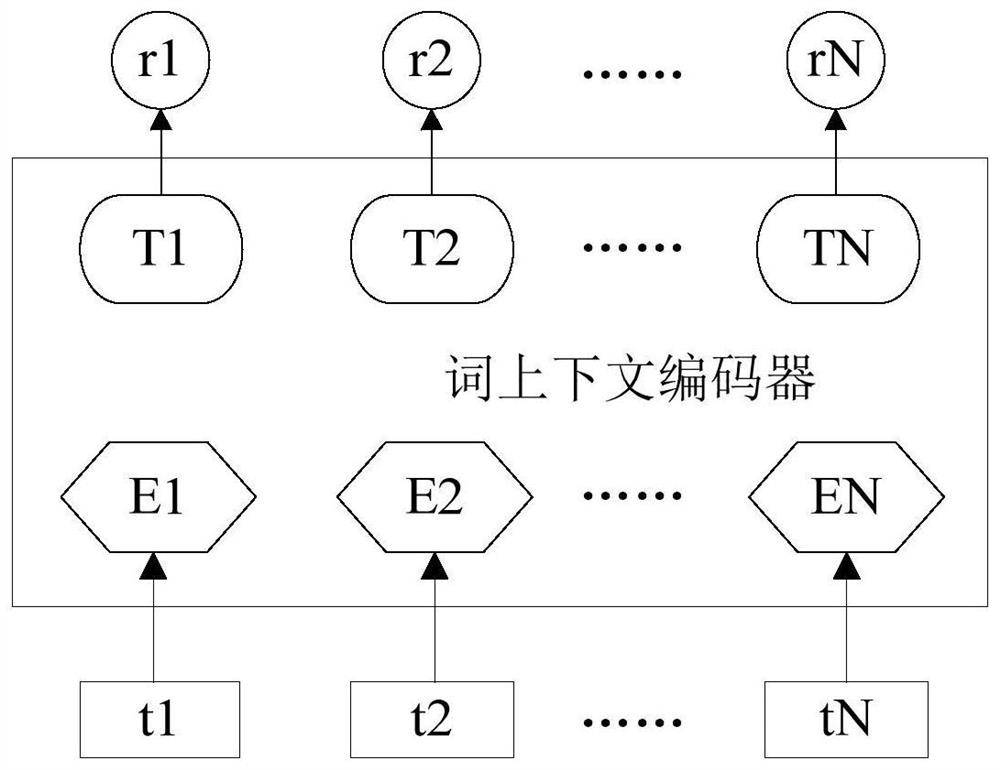
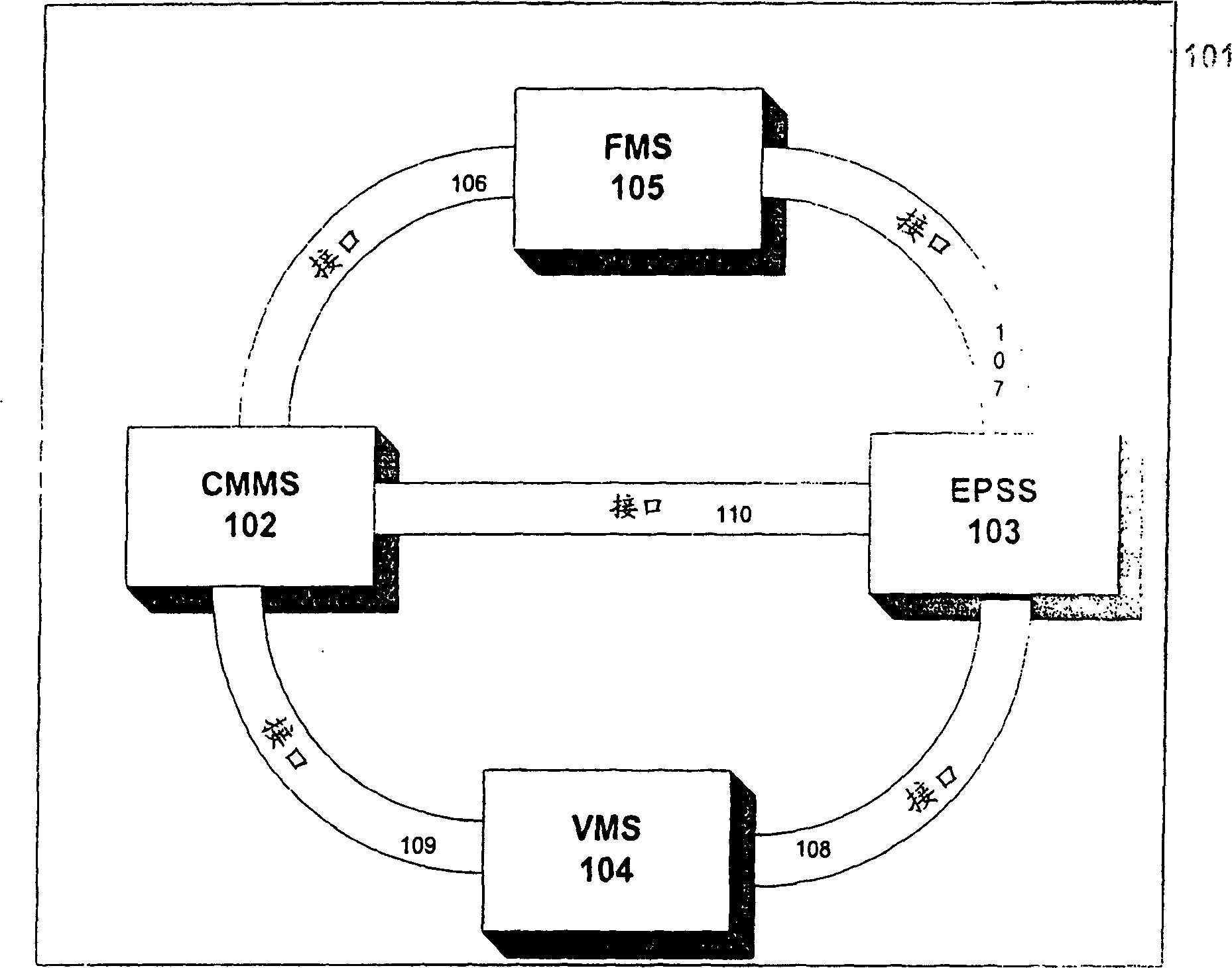
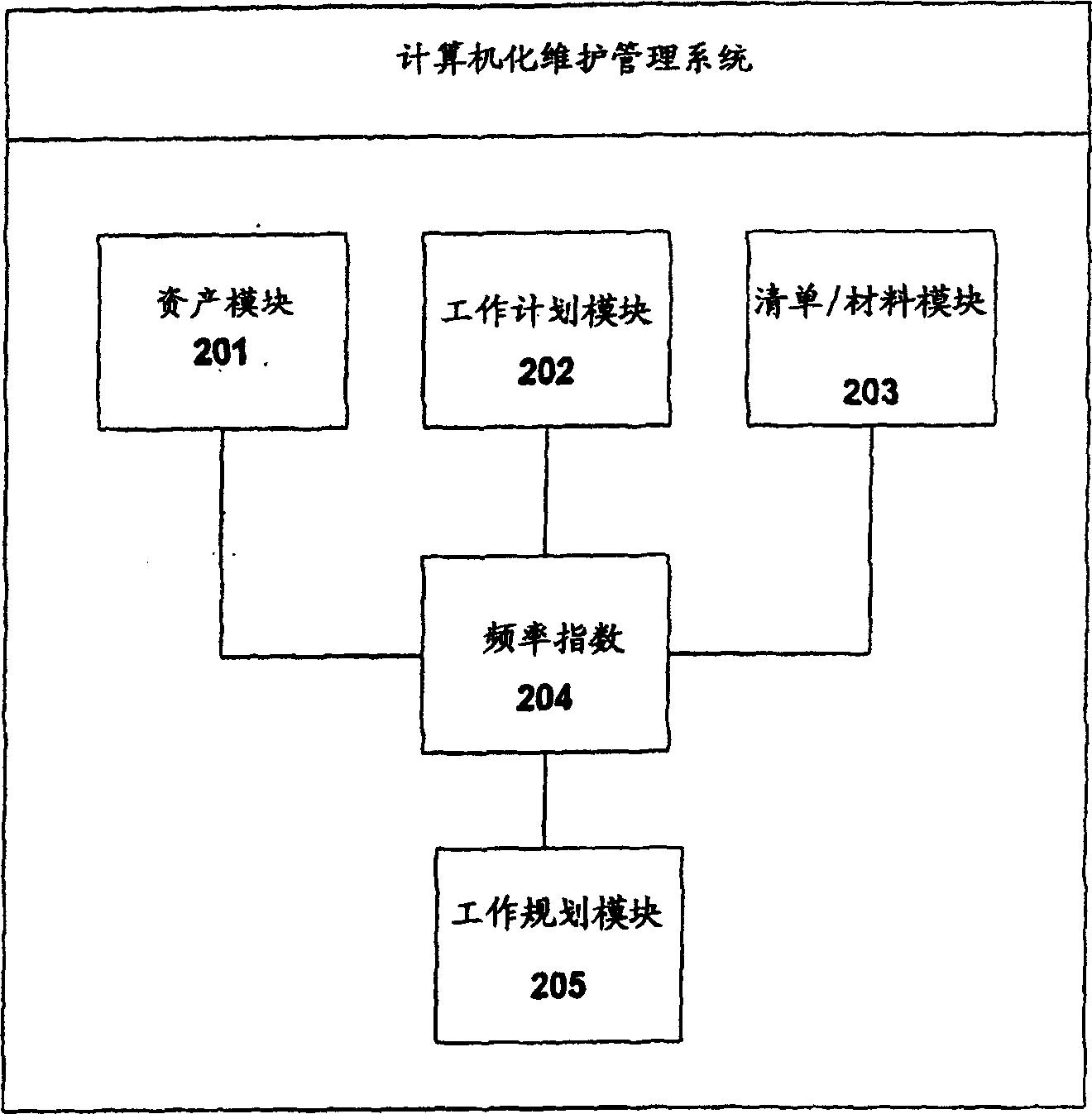
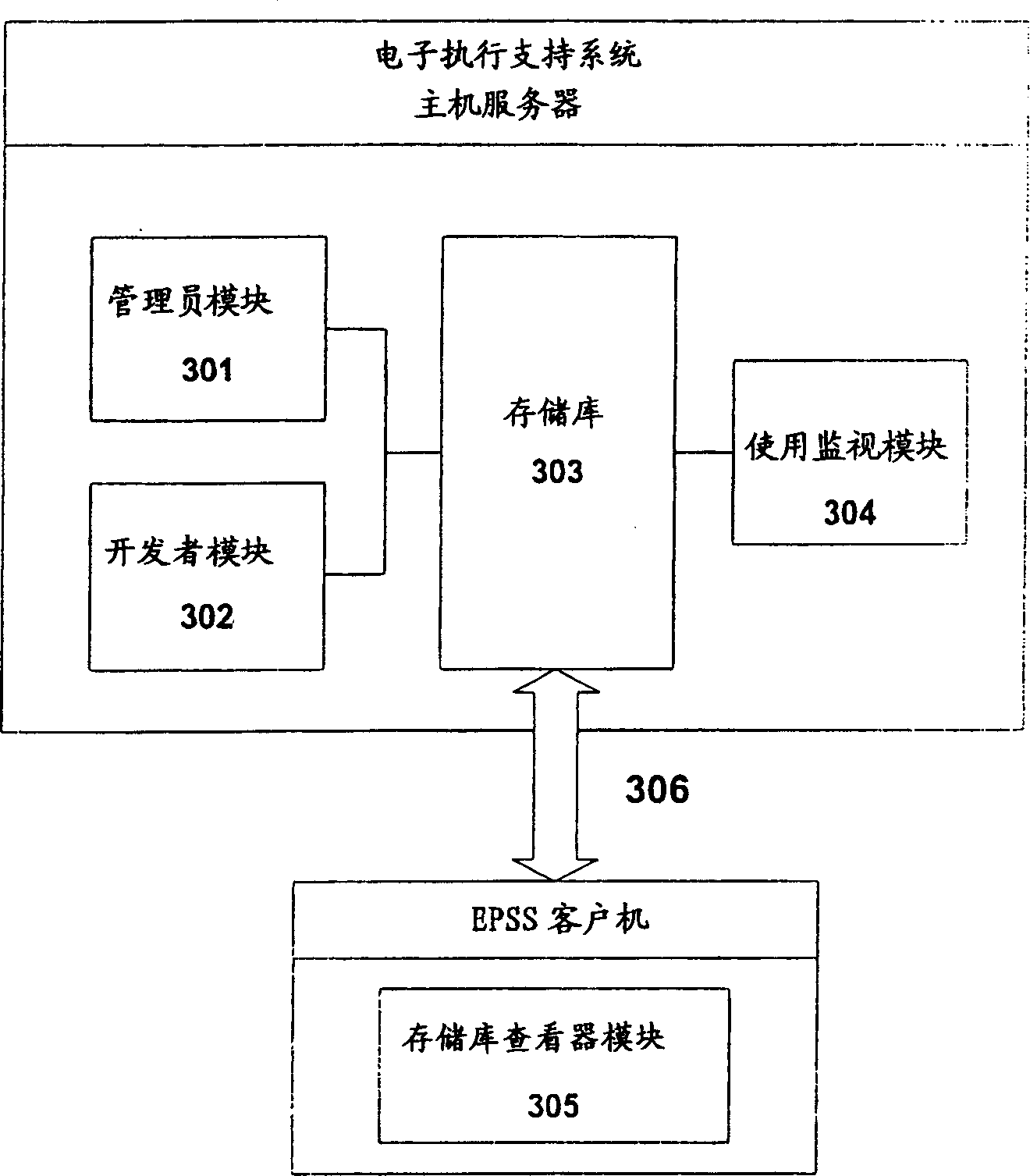
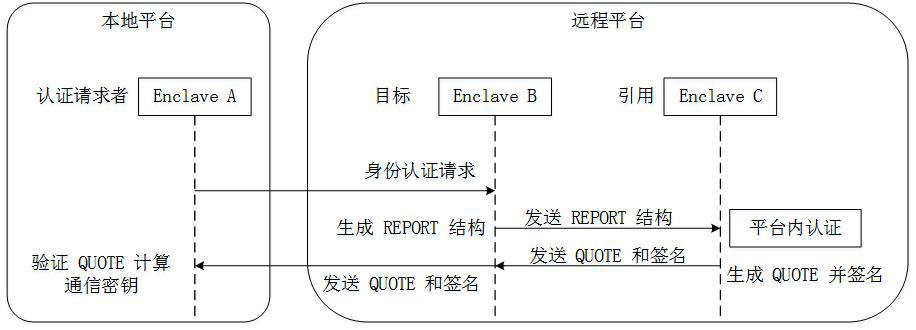
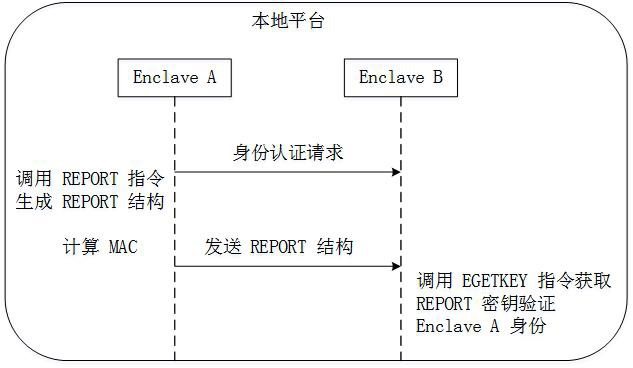
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Improve audit effect" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
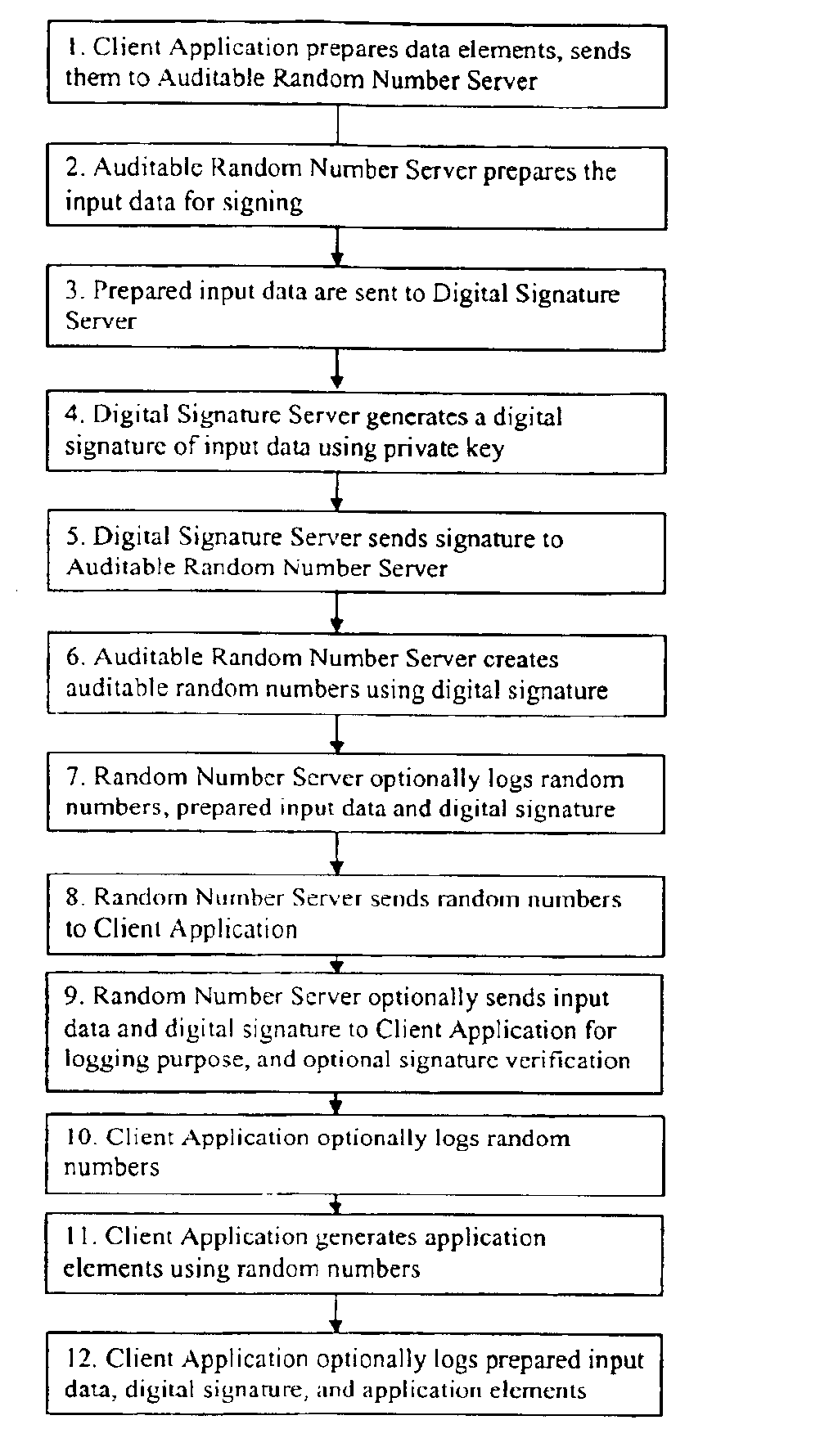
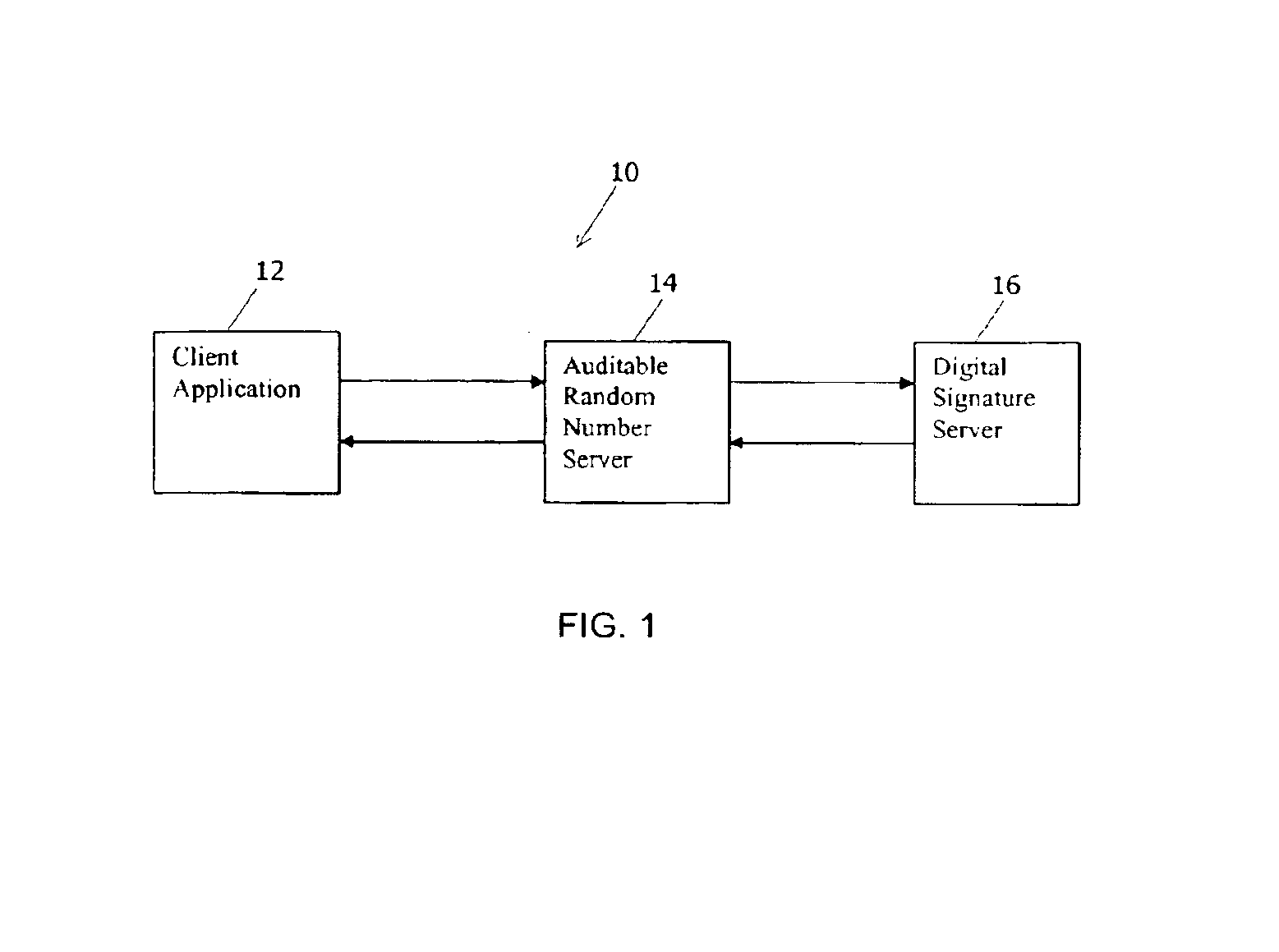
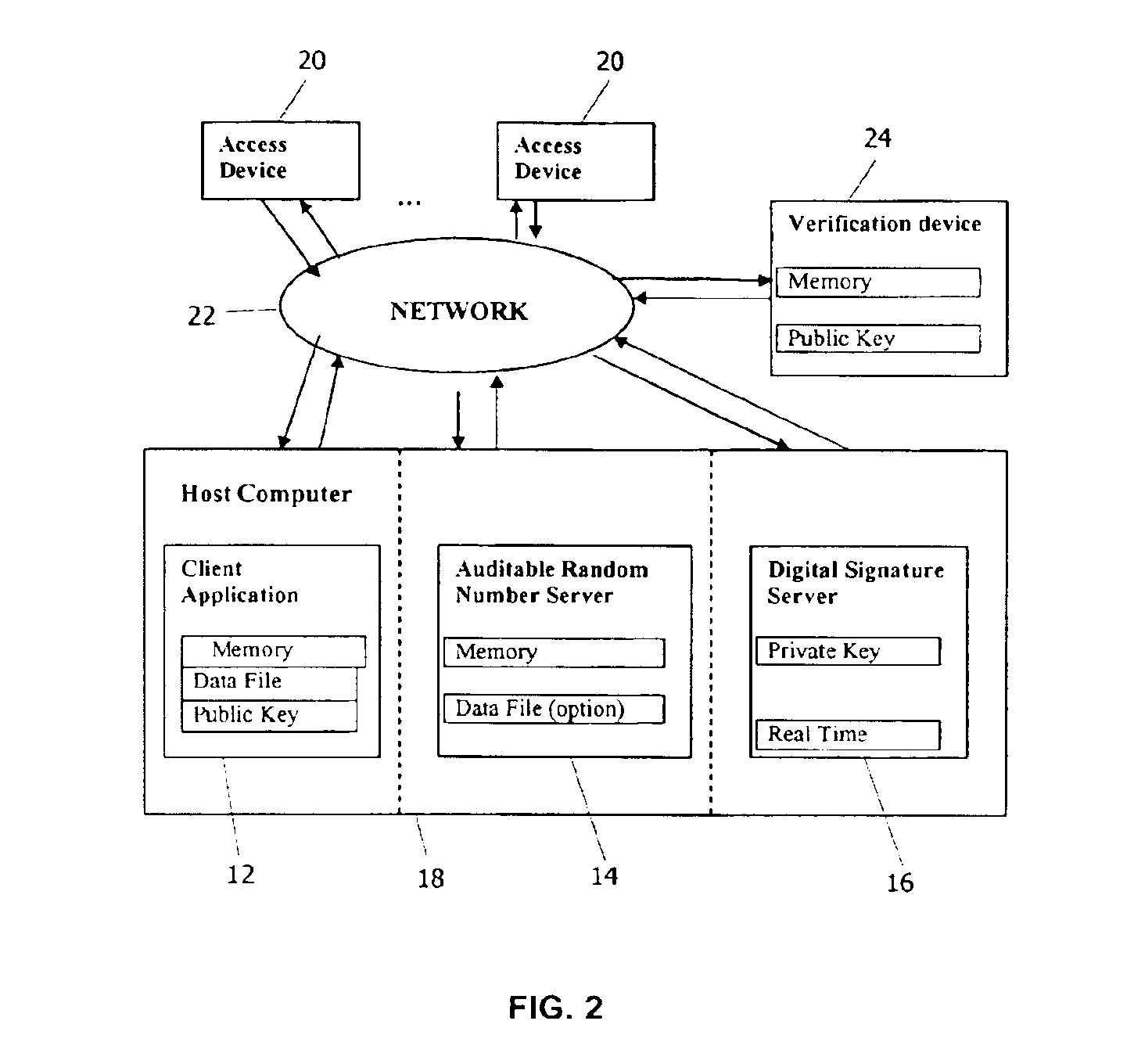
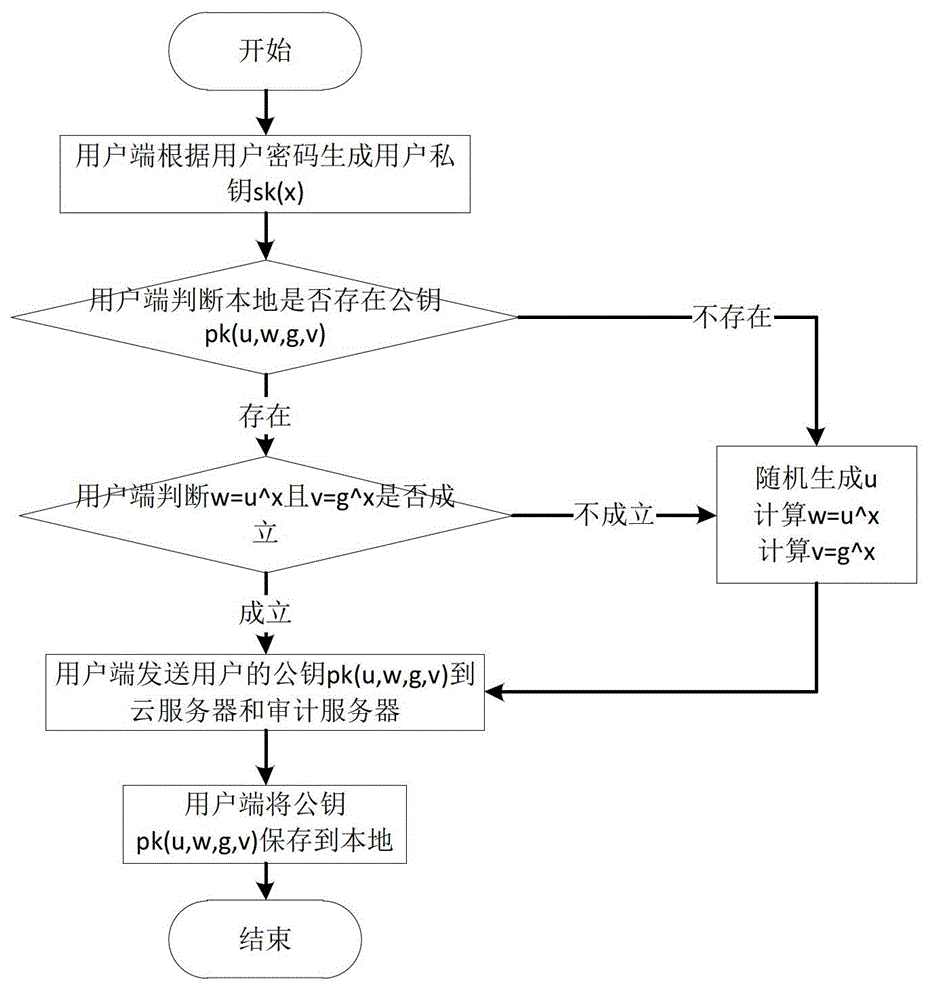
Method of generating unpredictable and auditable random numbers
InactiveUS6934846B2Preserve integrityImprove performanceLottery apparatusRandom number generatorsDigital signatureTheoretical computer science
A system and method for generation of unpredictable and auditable random numbers includes a host computer, a digital signature server and a verification device. The host computer provides data to the digital signature server; obtains digital signature for this data; uses elements of this signature for random numbers generation; logs relevant data for audit. The verification device uses logged data for auditing of the random number generation process. This invention can be applied in gaming and gambling industries where the random numbers are used for generation of game / play elements and of winning numbers elements. The game / play elements and winning numbers elements generated using this invention can be audited.
Owner:SZREK WALTER +1
Cloud storage data auditing method for preventing secret key from being revealed
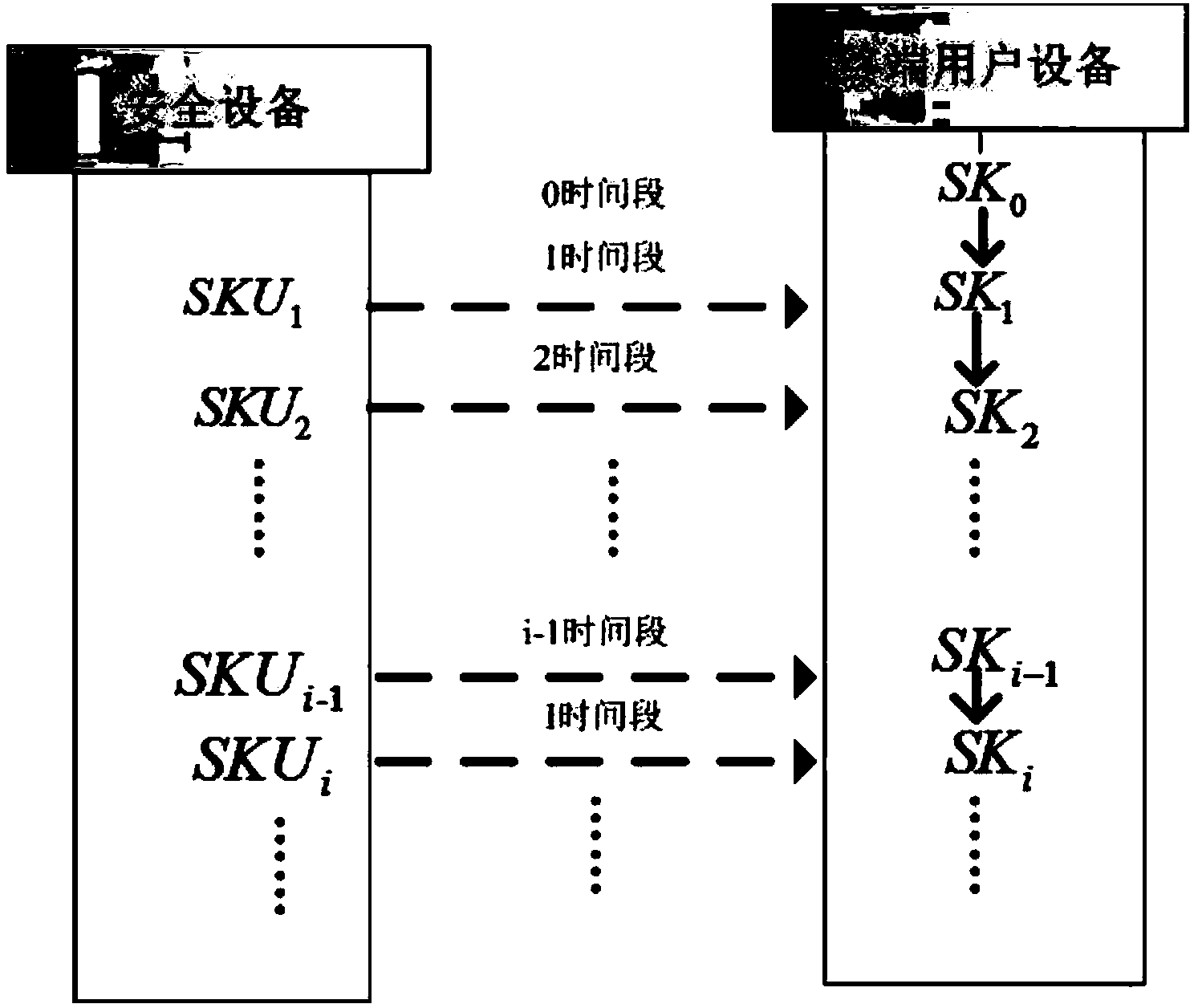
ActiveCN103986732AImprove audit efficiencyImprove efficiencyTransmissionPhysical securityTime segment
The invention provides a cloud storage data auditing method for preventing a secret key from being revealed. The method comprises the first step of system parameter generating, the second step of secret key updating and the third step of file uploading and auditing. According to the method, a physically safe safety device is introduced to help a user to periodically update the secret key, and therefore data auditing in other time periods is still safe even when an attacker attacks the user at one time period and obtains the user secret key at the time period.
Owner:SHANDONG ZHENGZHONG COMP NETWORK TECH CONSULTING
Document auditing method, device and system, equipment and storage medium
PendingCN110852065AEasy to useMeet audit needsNatural language data processingMachine learningInformation retrievalNumbered musical notation
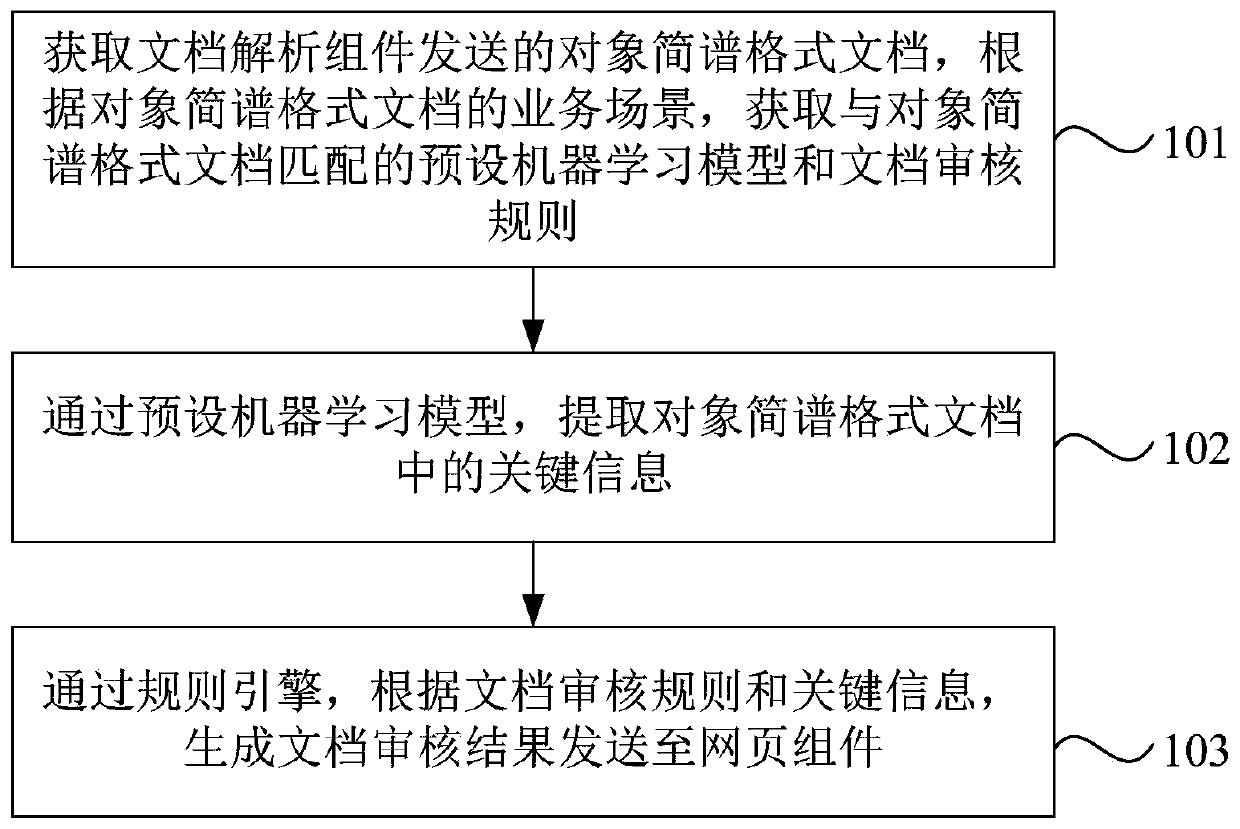
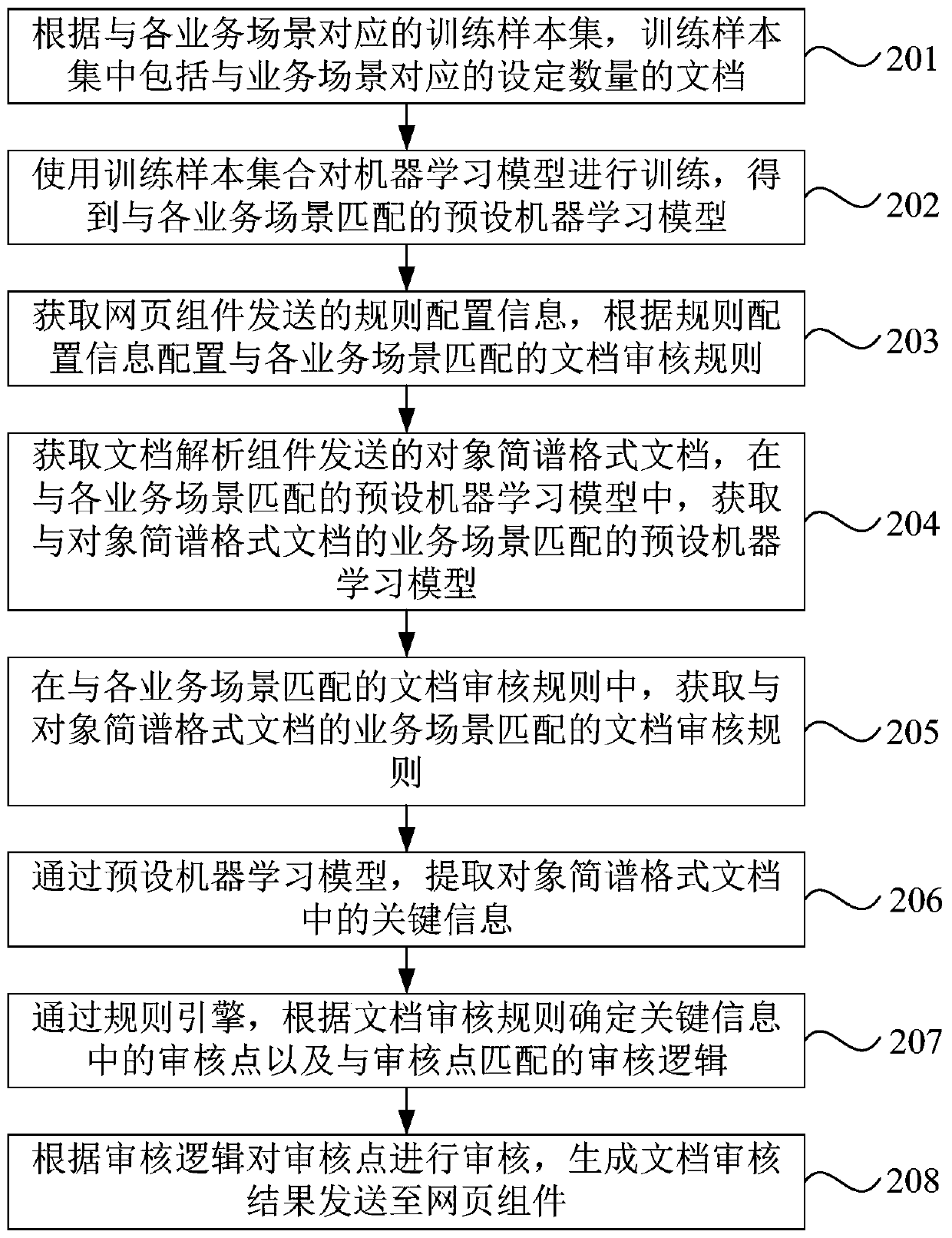
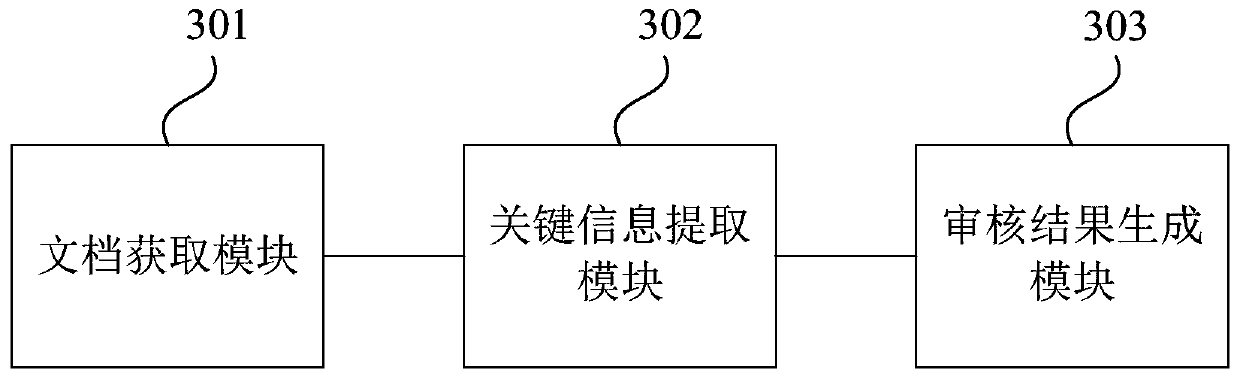
The embodiment of the invention discloses a document auditing method, device and system, equipment and a storage medium. The method comprises the following steps: acquiring an object numbered musicalnotation format document sent by a document analysis component, and acquiring a preset machine learning model and a document auditing rule matched with the object numbered musical notation format document according to a business scene of the object numbered musical notation format document; extracting key information in the object numbered musical notation format document through a preset machinelearning model; and generating a document auditing result through a rule engine according to the document auditing rule and the key information, and sending the document auditing result to the webpagecomponent. According to the embodiment of the invention, the matched preset machine learning model and document auditing rule can be obtained according to the business scene. The key information in the object numbered musical notation format document can be accurately extracted through the preset machine learning model, and then document auditing is carried out through the rule engine according to the document auditing rule and the key information, so that the document auditing requirements under different business scenes are met, and the document auditing effect and the document auditing efficiency are improved.
Owner:DATAGRAND TECH INC
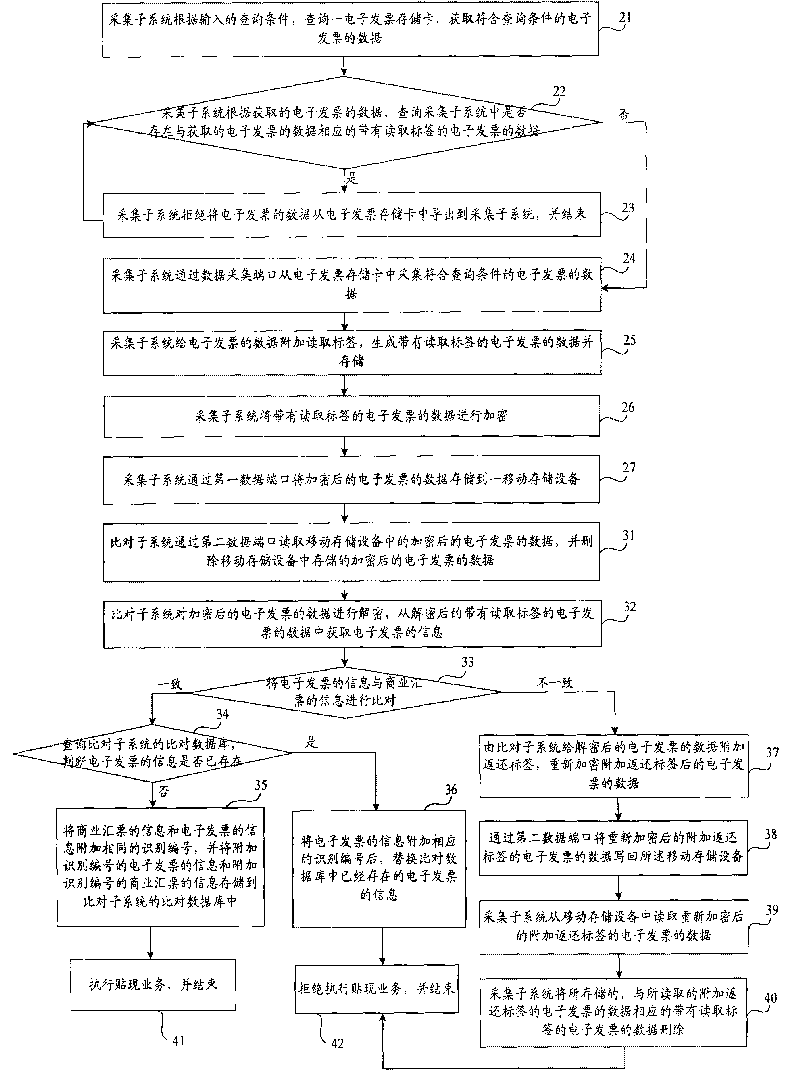
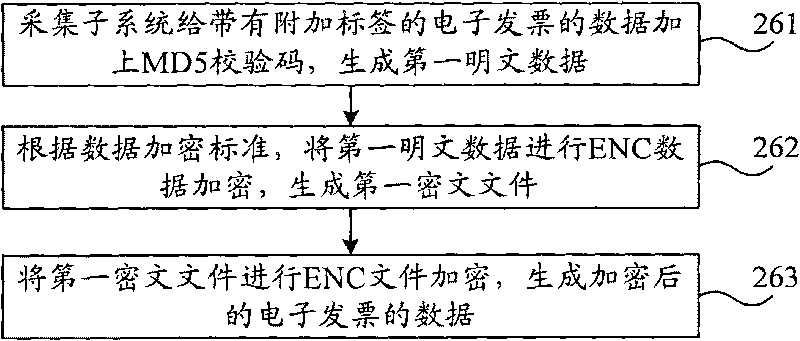
Comparing method and comparing system of electronic invoice
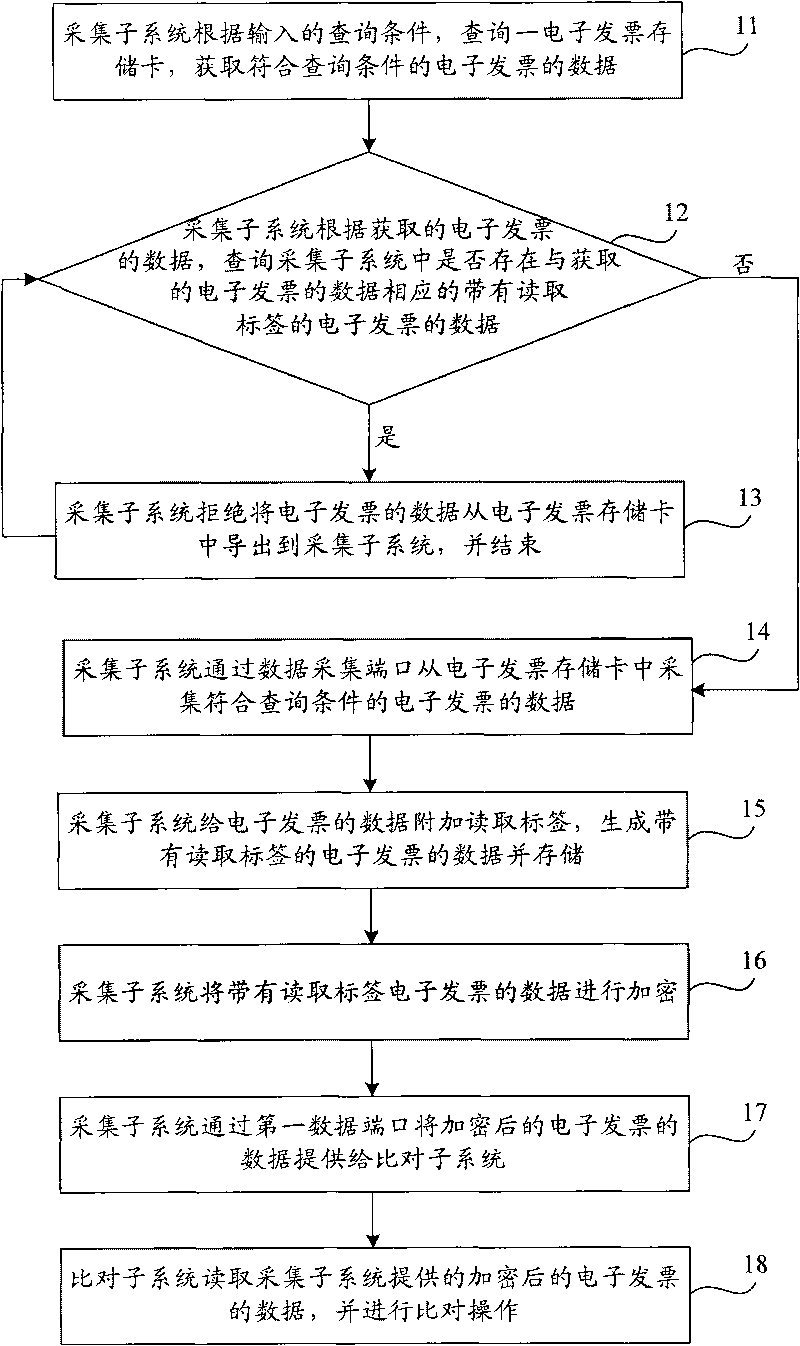
The invention relates to comparing method and comparing system of electronic invoices, wherein the comparing method comprises the following steps of: inquiring an electronic invoice storage card, and obtaining the data of the electronic invoice conforming to an inquiry condition; inquiring whether the electronic invoice which corresponds to the obtained data of the electronic invoice and is provided with a reading tag exists in an acquisition subsystem, and if so, then reject to lead out the data of the electronic invoice and ending, wherein the reading tag is used for marking that the data of the electronic invoice is read by the acquisition subsystem from the electronic invoice storage card; otherwise, acquiring the data of the electronic invoice, and generating and storing the data of the electronic invoice with the reading tag; and transmitting the encrypted data of the electronic invoice to a comparing subsystem for carrying out comparing operation. The comparing system comprises the acquisition subsystem and the acquisition subsystem. The comparing method and the comparing system of the electronic invoices provided by the invention improve the auditing capability for invoice authenticity and simultaneously overcome the defect that the same invoice can be accepted for many times in the prior art.
Owner:MINSHENG BANKING CORP
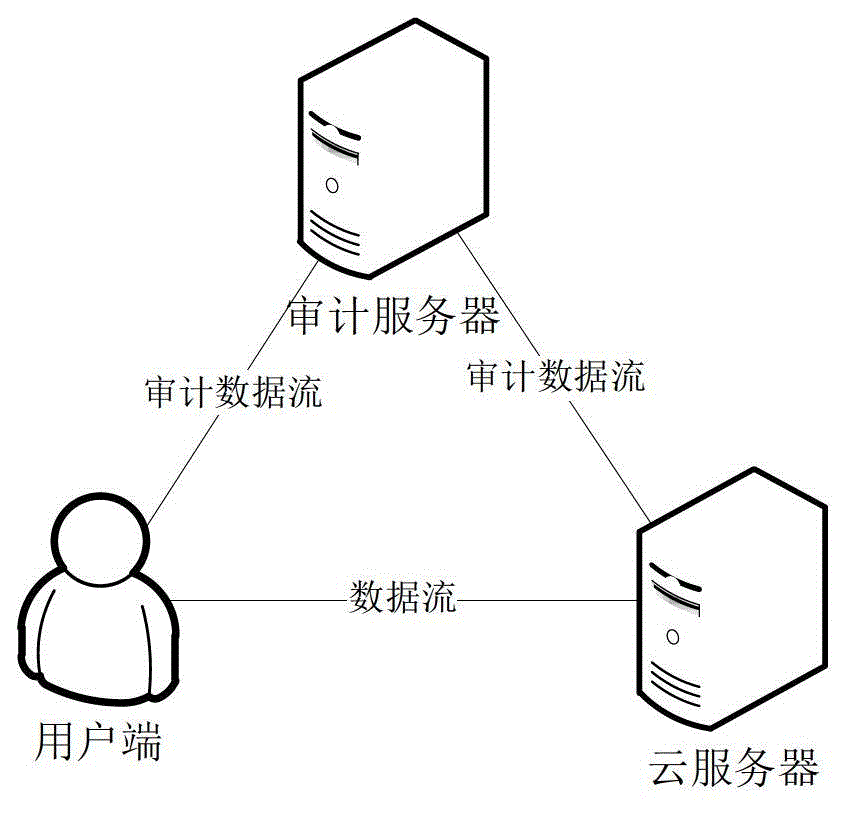
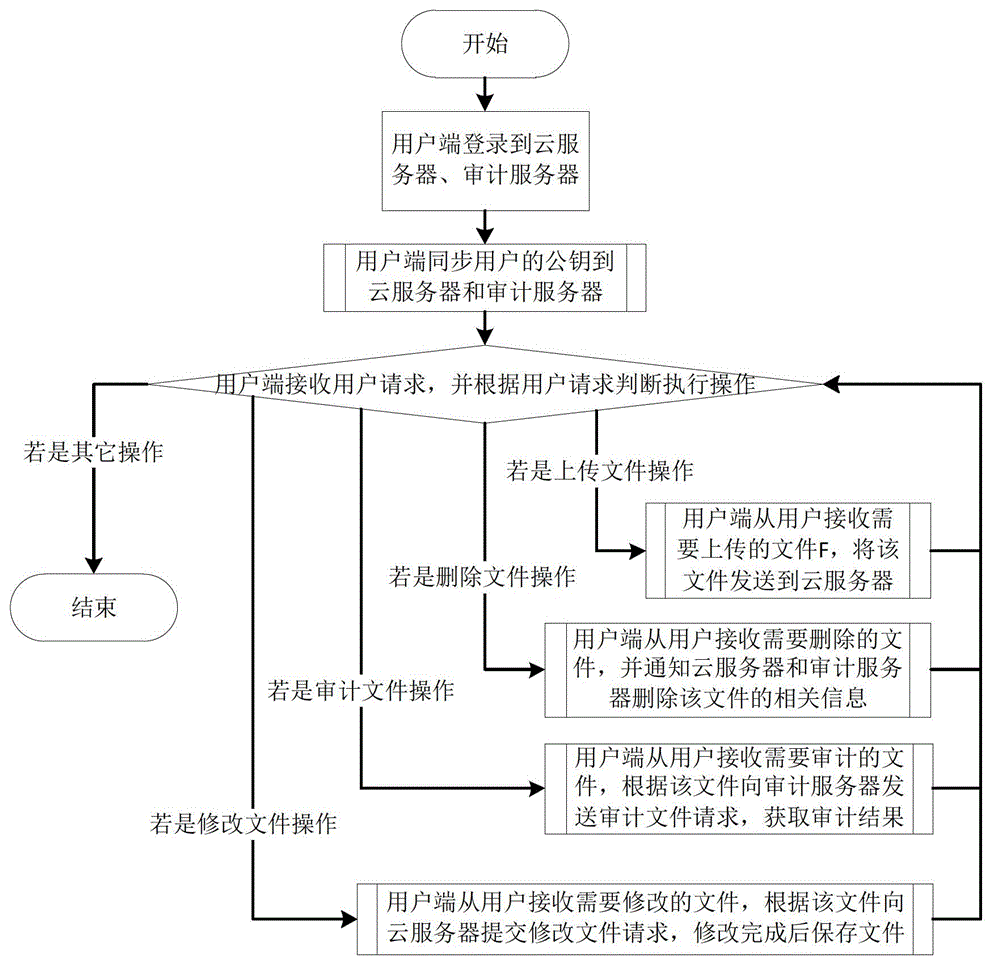
Index conversion method for public data integrity checking
ActiveCN103067363AImprove audit effectImprove efficiencyTransmissionPrivacy preservingOperating system
The invention discloses an index conversion method for public data integrity checking. The index conversion method for the public data integrity checking includes the following steps: a user side logs in a cloud server and an audit server, synchronizes a public key of a user to the cloud server and the audit server, receives a user request, and judges whether the user side is requested to execute the operation of uploading a file or requested to execute the operation of deleting the file according to the user request; if the user side is requested to execute the operation of uploading the file, the user side receives the file needing to be uploaded from the user, segments the file needing to be uploaded according to the public key and a private key of the user, calculates a label of each segment, and uploads the file needing to be uploaded and the label of each segment to the cloud server; and if the user side is requested to execute the operation of deleting the file, the user side receives the file needing to be deleted from the user, and deletes files, file labels and relevant file information in the cloud server and the audit server, wherein the files, the file labels and the relevant file information correspond to the file needing to be deleted. The index conversion method for the public data integrity checking is an improvement based on an existing privacy-preserving public auditing (PPPA) scheme, and the problem that the existing scheme does not support dynamic updating of data can be solved.
Owner:HUAZHONG UNIV OF SCI & TECH
General information acquisition system for internal network security monitoring
ActiveCN103749002BImprove efficiencyDoes not affect acquisition efficiencyData switching networksBiological activationSecurity monitoring
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
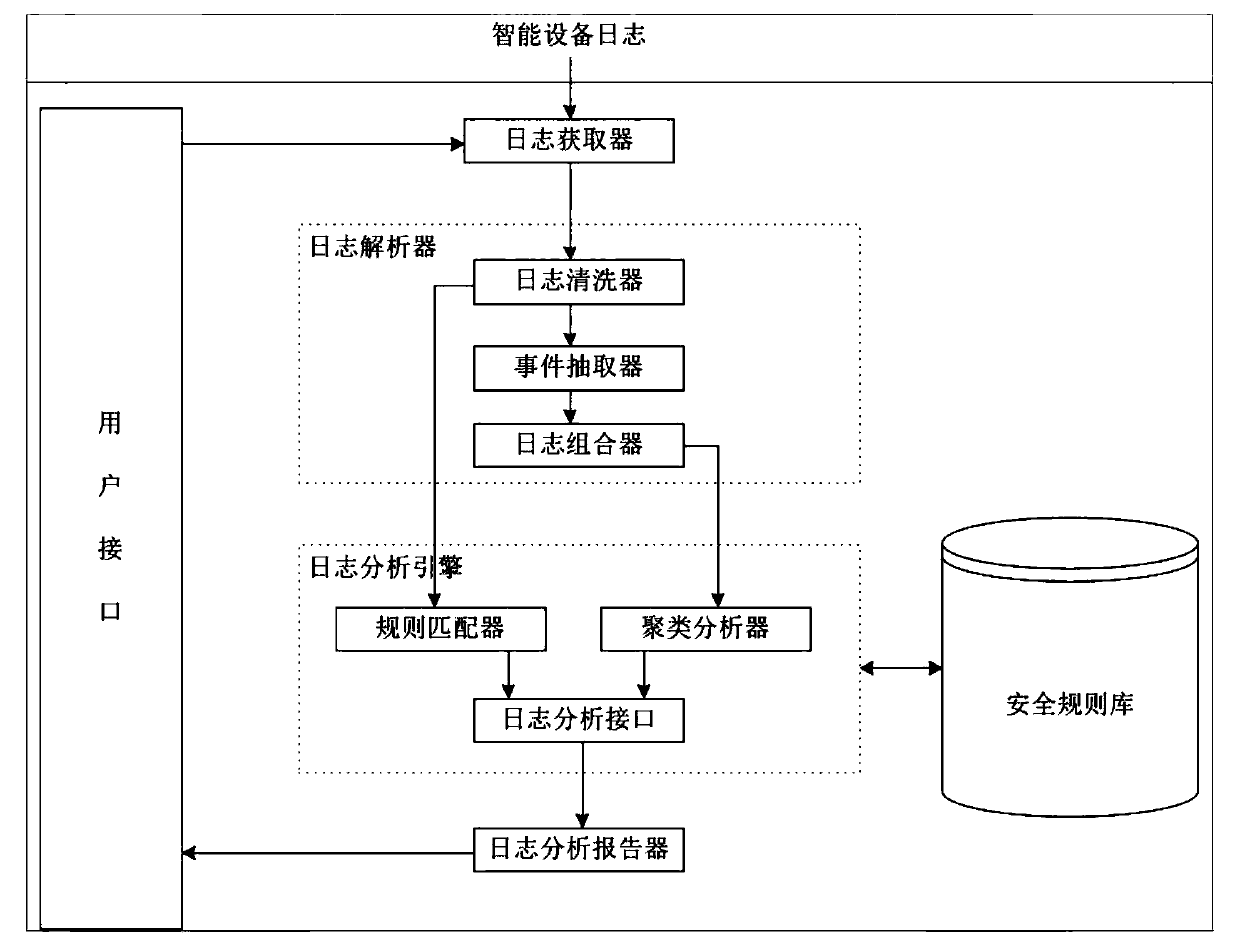
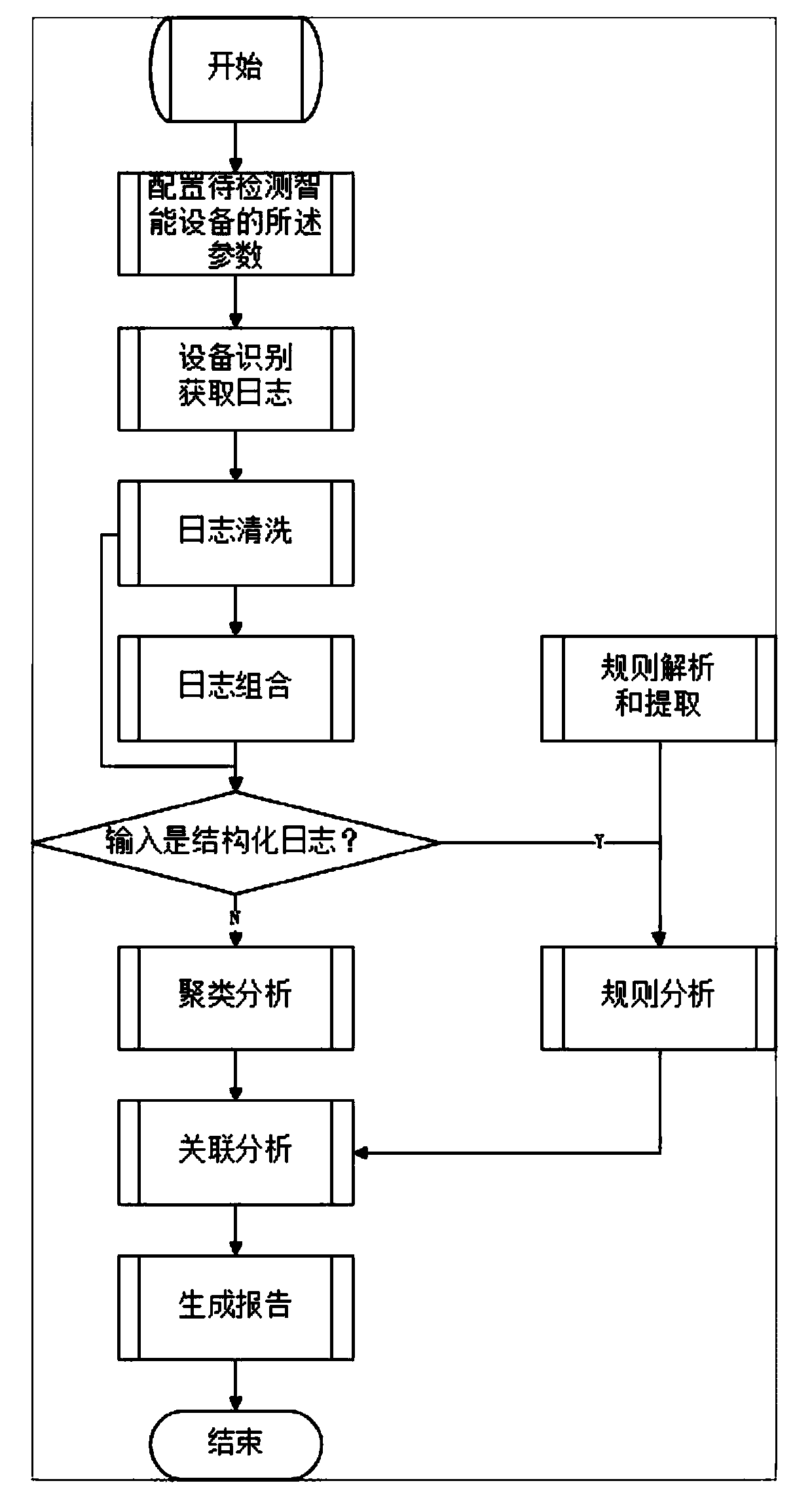
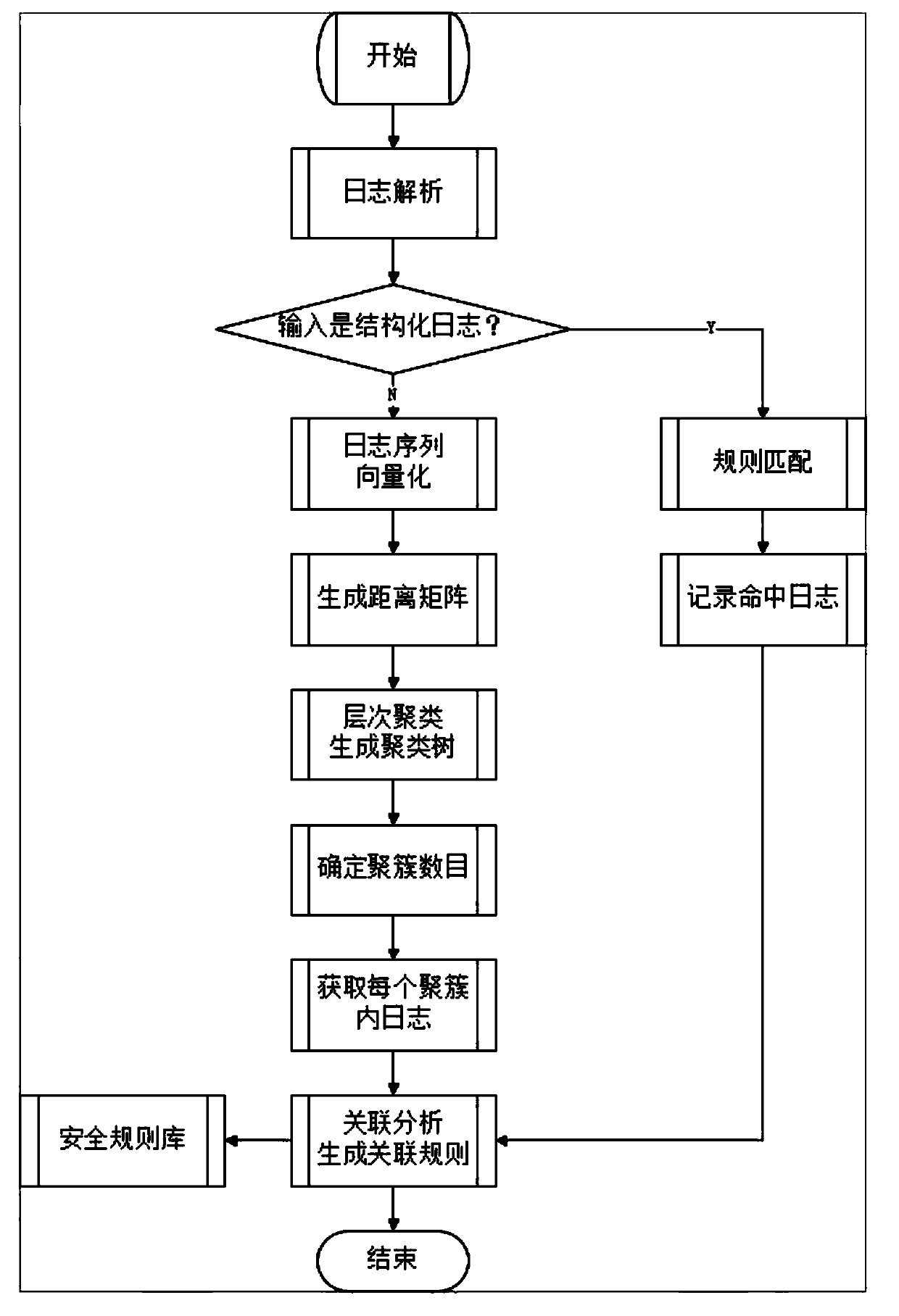
Intelligent device log processing system and method
InactiveCN110262949ALog acquisition is efficientLog acquisition is simpleHardware monitoringCharacter and pattern recognitionHandling systemSecurity rule
The invention discloses an intelligent device log processing system and method, and relates to an Internet of Things intelligent device log processing system. The system comprises a log obtaining device used for obtaining an original log of an intelligent device according to parameters of the intelligent device; a log parser used for receiving the original log, parsing the unstructured or semi-structured original log into a structured log and generating a log sequence; a security rule base comprising log analysis rules; a log analysis engine used for receiving the structured logs and the log sequences, carrying out rule matching on the structured logs according to log analysis rules of the security rule base, and carrying out hierarchical clustering on the log sequences; a log analysis reporting device used for generating a report according to the result of the log analysis engine and the security rule base; and a user interface module used for interacting with a user, receiving the parameters of the intelligent equipment and outputting the report to the user. The intelligent device log processing system and method are efficient, simple and accurate in log obtaining.
Owner:BEIJING UNIV OF POSTS & TELECOMM
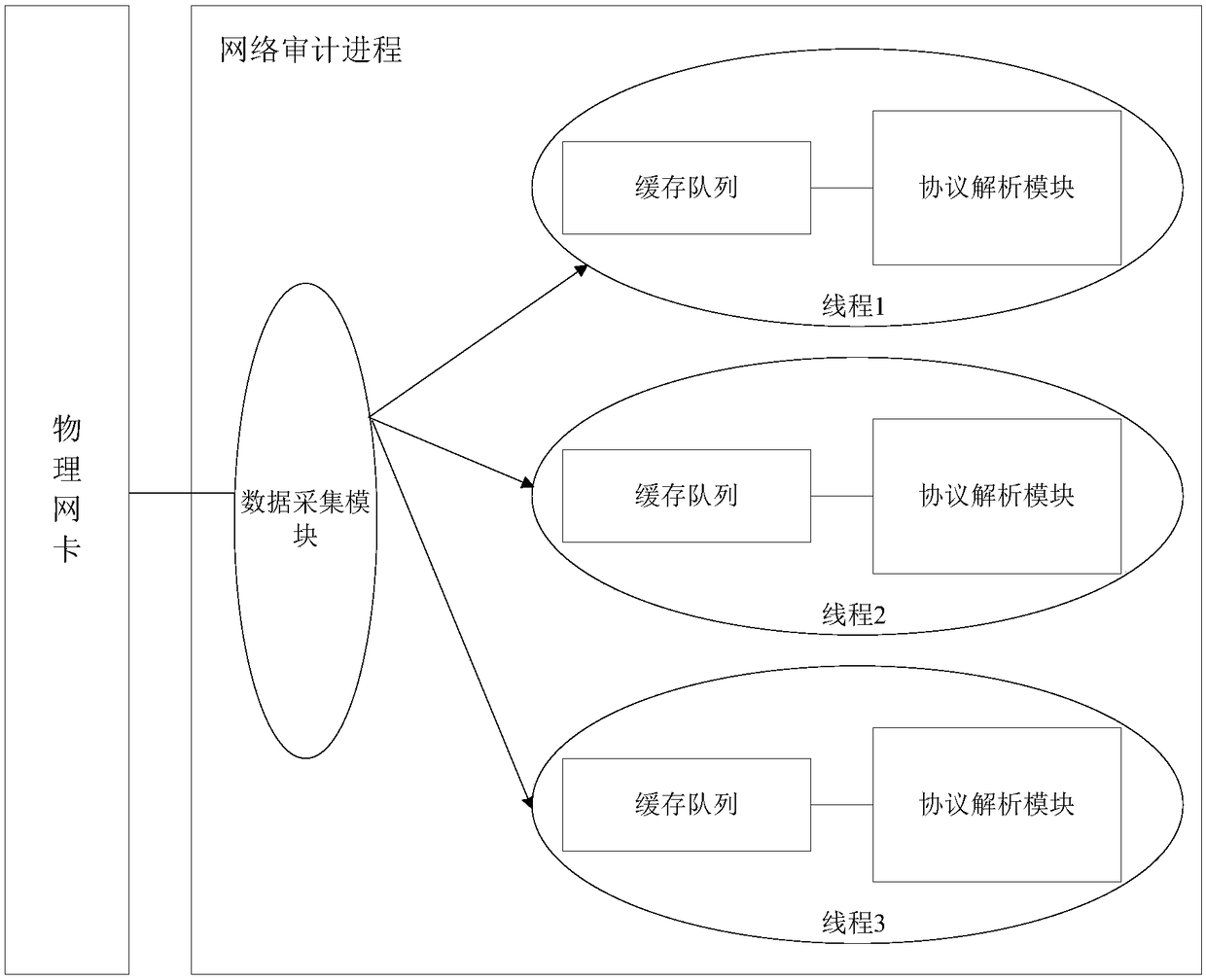
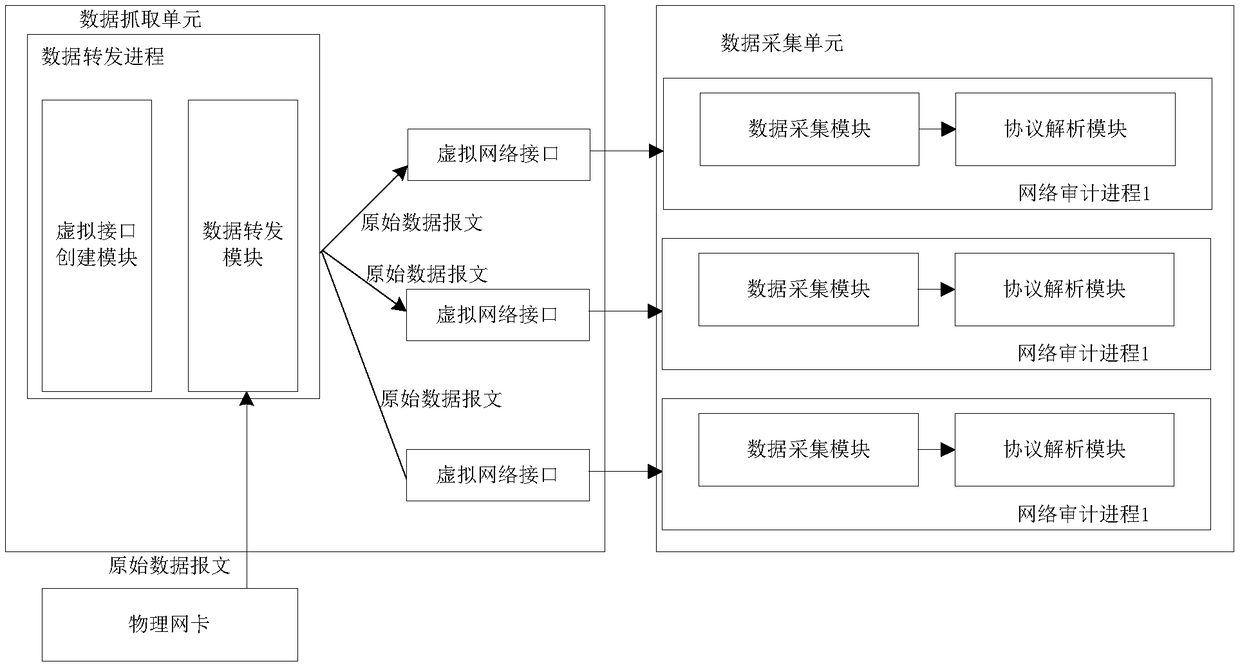
Network audit data collection method, corresponding device and equipment, and storage medium
InactiveCN108809748AImprove audit effectImprove fault toleranceData switching networksFault toleranceTraffic capacity
The invention discloses a network audit data collection method, a corresponding device and equipment and a storage medium. The device comprises a data capture unit, which is used for starting a data forwarding process, creating a plurality of virtual network interfaces through the data forwarding process, capturing an original data message from a physical network card and sending the original datamessage to each virtual network interface; and a data collection unit, which is used for starting a plurality of network auditing processes, and obtaining corresponding original data message from thecorresponding virtual network interface through each network auditing process. The network audit data collection method, the corresponding device and equipment and the storage medium in the inventioneffectively improve the auditing performance of network flow, increase the fault tolerance of the network auditing system, and reduce the probability of network auditing time audit missing.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
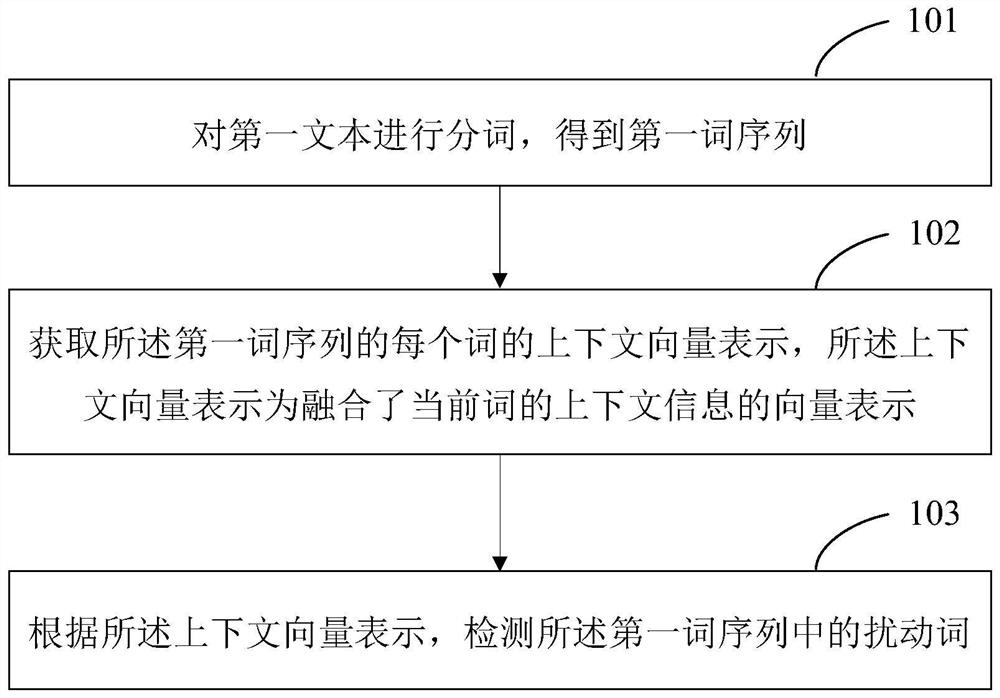
Text disturbance detection method, disturbance restoration method, disturbance processing method and devices
PendingCN111783443AEliminate text noiseReduce text review riskCharacter and pattern recognitionNatural language data processingMachine learningNatural language
The invention discloses a text disturbance detection method, a disturbance restoration method and a disturbance processing method and devices, and relates to the technical field of natural language processing. The text disturbance detection method comprises the steps of performing word segmentation on a first text to obtain a first word sequence; obtaining context vector representation of each word of the first word sequence; and detecting disturbance words in the first word sequence according to the context vector representation. According to the invention, the disturbance word in the text isdetected according to the context vector representation, so that text disturbance detection is realized. After the disturbance word is detected, mask processing is carried out on the disturbance word, and a replacement word of the disturbance word is determined by obtaining estimated context vector representation of a mask mark so as to realize text disturbance restoration. Through the text disturbance detection and text disturbance restoration processes, the text disturbance can be effectively eliminated, so that the text auditing effect can be improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Maintenance and inspection system and method
InactiveCN1573762AQuality improvementComprehensive use of simplification and enhancementDigital computer detailsOffice automationComputerized maintenance management systemElectronic performance support systems
A maintenance and inspection system integrates at least two software modules including a computerized maintenance management system, an electronic performance support system, forms management system, and video messaging system running on a host sever thus allowing a maintenance and inspection user with complementary software modules the ability to collect and access data and communicate with experts not in the field.
Owner:XYBERNAUT +1
Multi-party secure computing implementation method based on block chain technology
PendingCN112115204AEnhanced authenticationImprove audit effectDatabase updatingFinanceData securitySmart contract
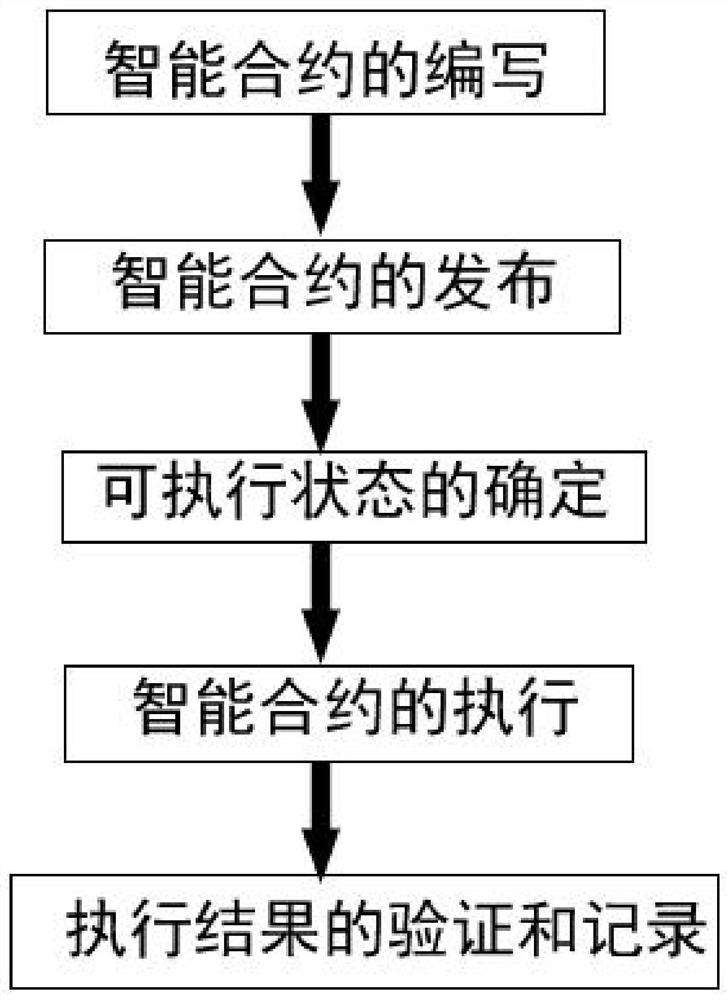
The invention discloses a multi-party security computing implementation method based on a blockchain technology. The method specifically comprises the following steps: step 1, compiling an intelligentcontract, wherein the intelligent contract comprises node information of each contract party, tasks of each contract party for executing the intelligent contract and task execution relationships among the tasks; step 2, publishing the intelligent contract: publishing the intelligent contract on the block chain; 3, determining an executable state: after the intelligent contract is authorized by related nodes of each contract party of the intelligent contract, determining the intelligent contract as the executable state; step 4, executing the intelligent contract, wherein different contract parties have own unique business accounts, log in node servers of nodes through node accounts of the nodes and execute tasks of the intelligent contract on the blockchain; and step 5, carrying out verification and recording of an execution result, wherein the nodes which do not participate in the intelligent contract carry out verification and state recording of the contract execution result. According to the invention, the problems of data security and privacy in the data cooperation process are solved.
Owner:DATANG NETWORK CO LTD
Smart contract auditing method and device, computer device and storage medium
ActiveCN110727948AReduce security risksImprove audit effectPlatform integrity maintainanceCode compilationSmart contractSource code
The invention relates to a smart contract auditing method and device, a computer device and a storage medium, and relates to the technical field of network security. The method comprises the followingsteps: a server receiving a source code of a smart contract uploaded by an editing terminal; acquiring audit parameters of the smart contract, compiling the source code of the smart contract according to the compiling parameters, performing security problem scanning on the smart contract according to the scanning parameters after the source code of the smart contract is successfully compiled, acquiring a scanning audit result, and returning the scanning audit result to the editing terminal. According to the scheme, the compiling parameters and the scanning parameters of the intelligent contract are obtained at the server side, and the source code of the smart contract is compiled and the security problem is scanned according to the obtained compiling parameter and scanning parameter, thereby realizing scanning of the security problem of the smart contract at the server side, effectively reducing the potential safety hazard of the smart contract, and improving the auditing effect of the smart contract.
Owner:TENCENT TECH (SHENZHEN) CO LTD
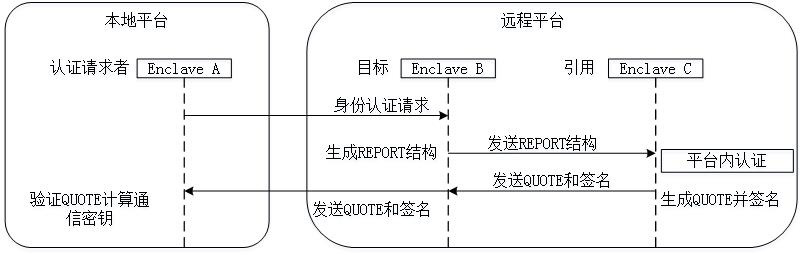
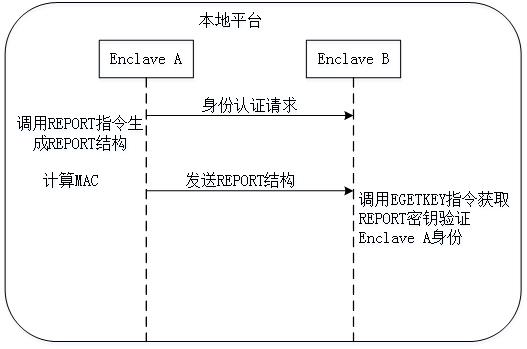
Cloud storage self-auditing method based on SGX and Ethereum block chain
InactiveCN113285812ASupport for Integrity StatusGuaranteed verifiable randomnessUser identity/authority verificationDigital data protectionData packThird party
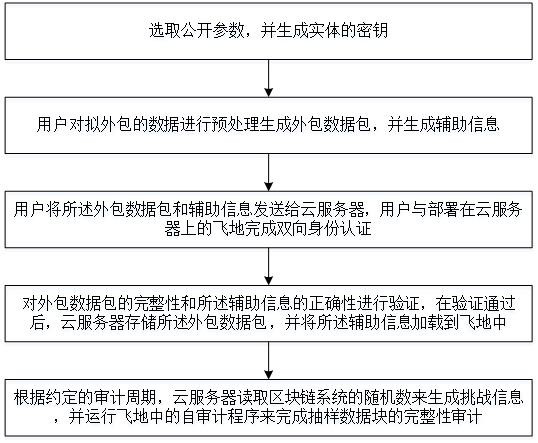
The invention discloses a cloud storage self-auditing method based on an SGX and an Ethereum block chain, and the method comprises the steps: public parameters are selected, and a key of an entity is generated; the user preprocesses data to be outsourced to generate an outsourced data packet and generate auxiliary information; the user sends the outsourcing data packet and the auxiliary information to the cloud server, and bidirectional identity authentication is completed between the user and an enclave deployed on the cloud server; the integrity of the outsourcing data packet and the correctness of the auxiliary information are verified, and after verification is passed, the cloud server stores the outsourcing data packet and loads the auxiliary information into the enclave; and according to a preset auditing period, the cloud server reads the random number of the block chain system to generate challenge information, and operates a self-auditing program in the enclave to complete integrity auditing of the sampled data block. According to the method disclosed by the invention, on the premise of not depending on any trusted third-party participant, the data owner is supported to periodically acquire the integrity state of the outsourcing data packet when the resources are limited.
Owner:SOUTHWEST PETROLEUM UNIV
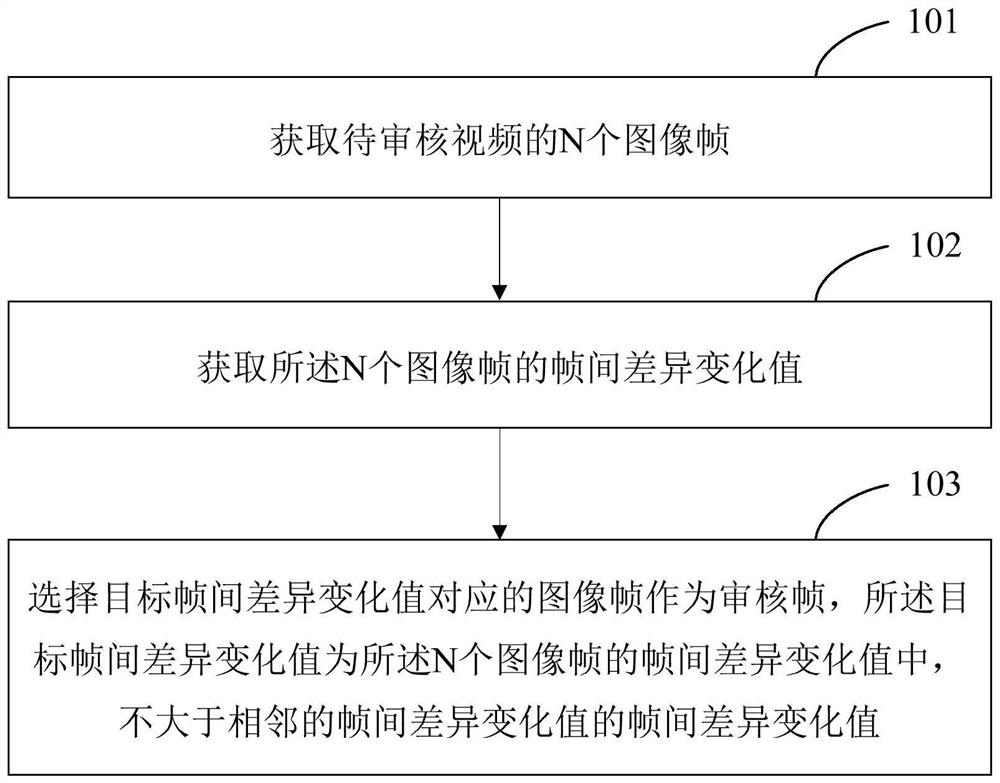
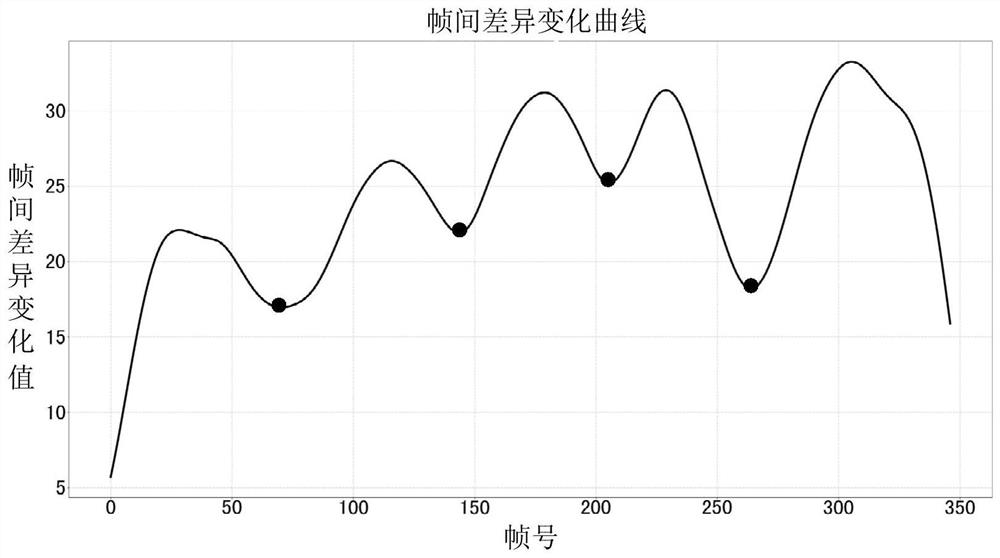
Video auditing method, video auditing device and electronic equipment
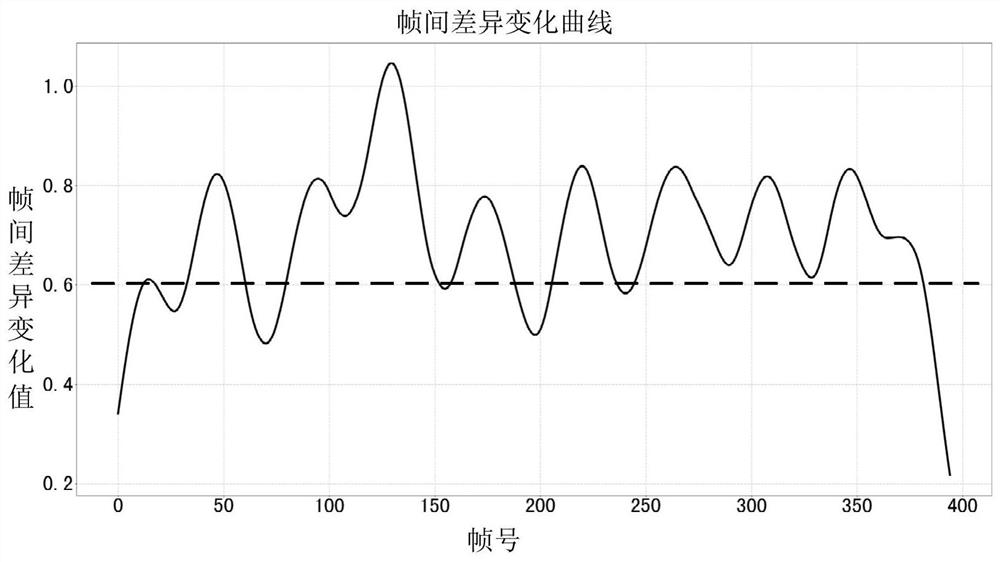
PendingCN113542725AImprove stabilityImprove the effectTelevision systemsDigital video signal modificationEngineeringComputer graphics (images)
The invention discloses a video auditing method, a video auditing device and electronic equipment, and relates to the technical field of video auditing. The video auditing method comprises the steps: acquiring N image frames of a video to be audited, wherein N is an integer greater than 1; obtaining an inter-frame difference change value of the N image frames, wherein the inter-frame difference change value is used for representing a difference degree between two adjacent image frames; and selecting an image frame corresponding to a target inter-frame difference change value as an auditing frame, wherein the target inter-frame difference change value is an inter-frame difference change value which is not greater than the adjacent inter-frame difference change value in the inter-frame difference change values of the N image frames. According to the method and the device, the inter-frame difference change value of the plurality of image frames of the to-be-audited video is acquired and is used as the basis for selecting the audit frame, so that the selected audit frame has relatively high stability, the video audit effect can be improved, and the problem that the video audit effect is relatively poor in the prior art is solved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Background live video auditing method
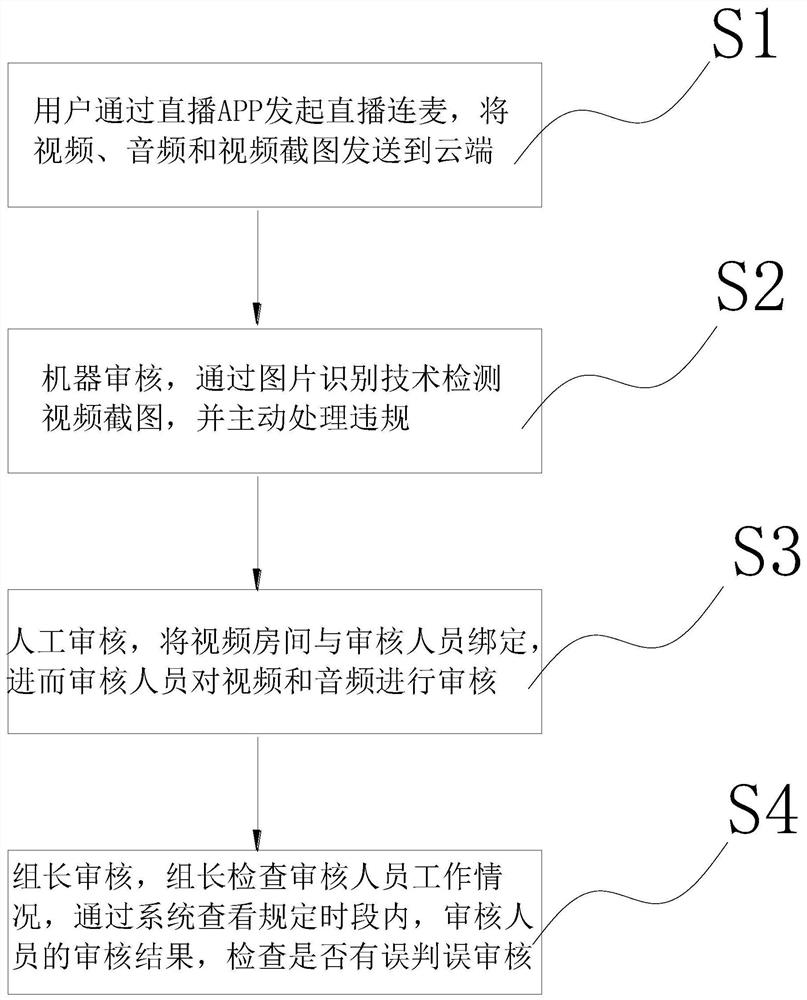
PendingCN113422975AAddress difficult-to-moderate contentImprove audit effectCharacter and pattern recognitionTransmissionSoftware engineeringPicture recognition
The invention discloses a background live video auditing method, which comprises the following steps that: a user initiates microphone connection, and sends a video, an audio and a video screenshot to a cloud end; machine auditing: performing detection through a picture recognition technology, and actively processing violation; manual auditing: binding a video room with an auditing worker, and then performing auditing by the auditing worker; group leader auditing: enabling the group leader to check the working condition of the auditing worker; and checking the auditing result of the auditing worker in a specified time period through the system, and checking whether misjudgment and misauditing exist or not. The method has the beneficial effects that machine auditing and manual auditing are combined, on one hand, the auditing efficiency is improved through machine auditing, the situation that manual auditing is not timely is avoided, and the labor intensity of manual auditing is reduced; the manual auditing solves the problem that content is difficult to audit through machine auditing; the auditing effect on the auditing content is improved; group leader auditing is mainly used for auditing an auditing result of the manual auditing, so that user actions are misjudged and the user is forced to be offline caused by subjective errors of manual auditing is prevented.
Owner:武汉氪细胞网络技术有限公司
Medical prescription auditing system and method
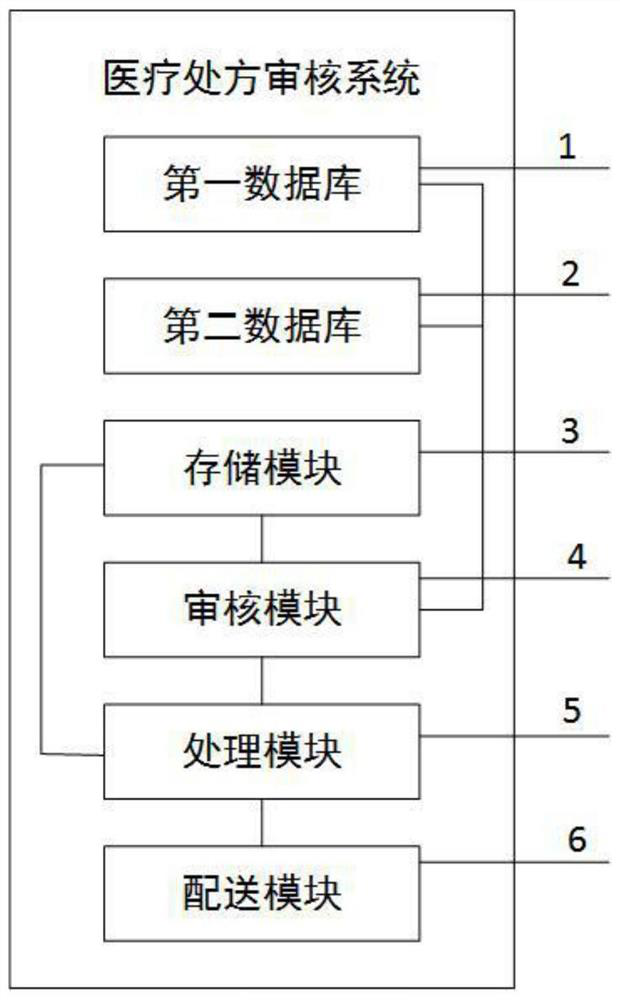
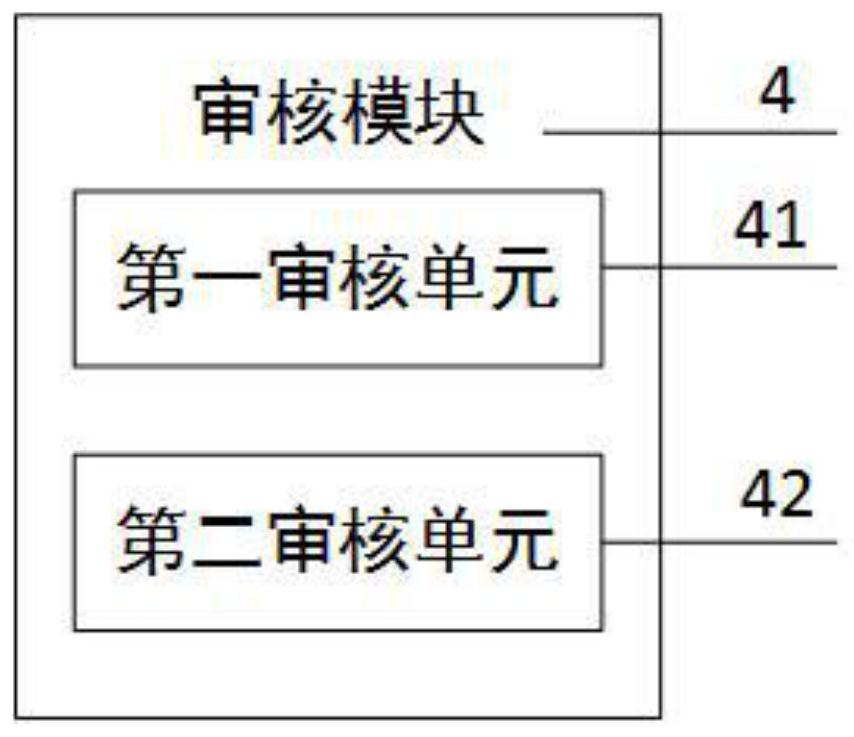
PendingCN112259253AImprove audit effectSolve the disadvantages of low efficiency during manual reviewDrug and medicationsDrug referencesDrug utilisationDatabase
The invention discloses a medical prescription auditing system and method, and relates to the technical field of medical treatment. The medical prescription auditing system comprises a first databasein which standard prescription information is pre-stored, a second database pre-storing historical treatment information, a storage module used for storing prescription information uploaded by a doctor, an auditing module used for auditing whether the prescription information is compliant, and a processing module used for outputting the final prescription to a distribution module used for distributing the medicines. The technical scheme provided by the invention has the beneficial effects that the requirements of policies are met, the existing electronic prescription circulation path is modified, the medication decision knowledge base is creatively built, the defect of low efficiency during original manual auditing is overcome, the auditing effect on the prescription reasonability is improved, the uniform auditing standard is realized, and the auditing efficiency is improved. Prescription external distribution of Internet hospitals and social pharmacy and prescription auditing in medical association are realized, subsequent prescription commenting work can be carried out, and rules of a medication decision knowledge base are maintained.
Owner:SHANGHAI SIXTH PEOPLES HOSPITAL
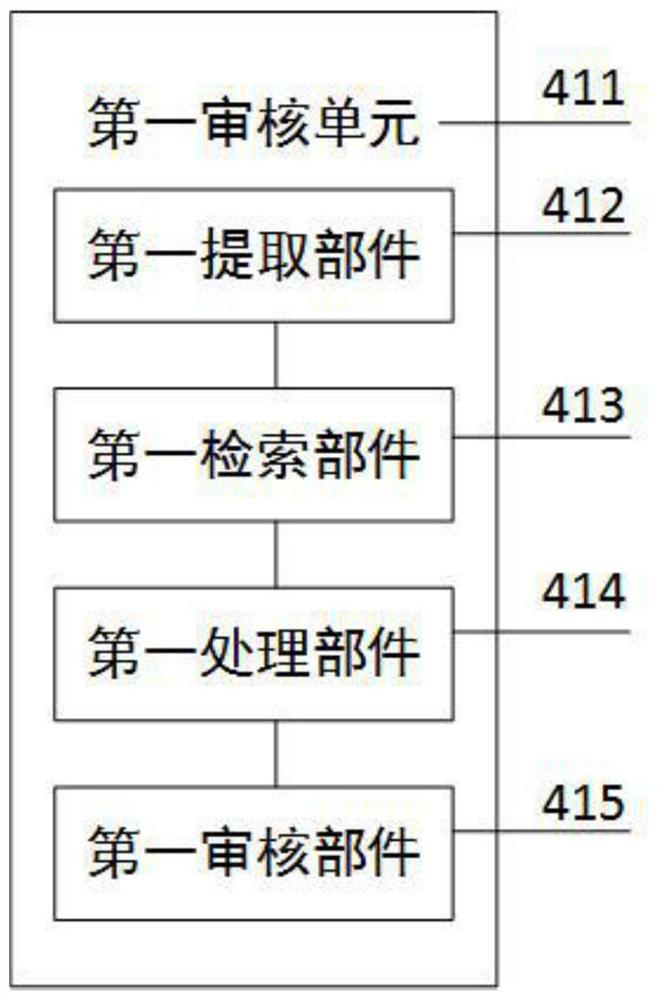
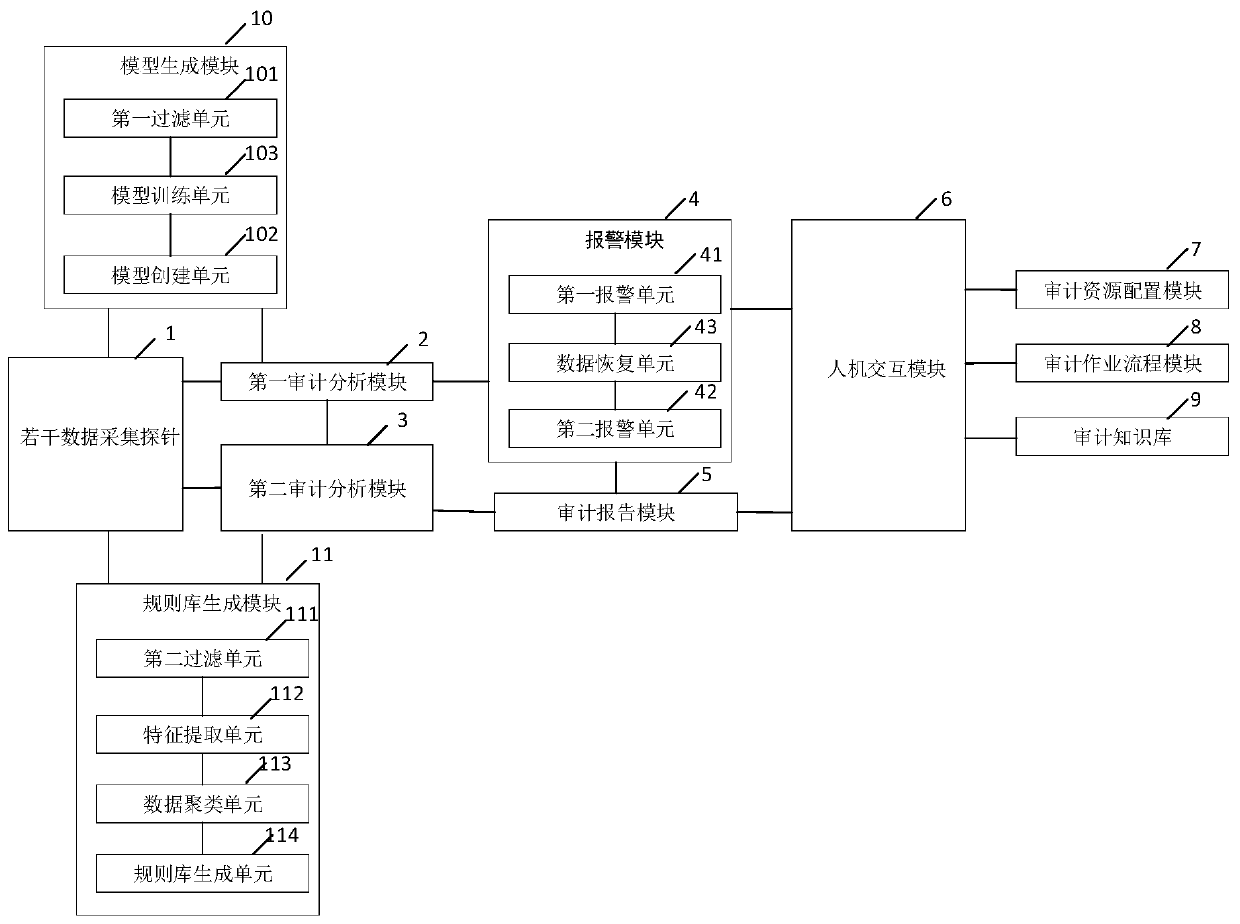
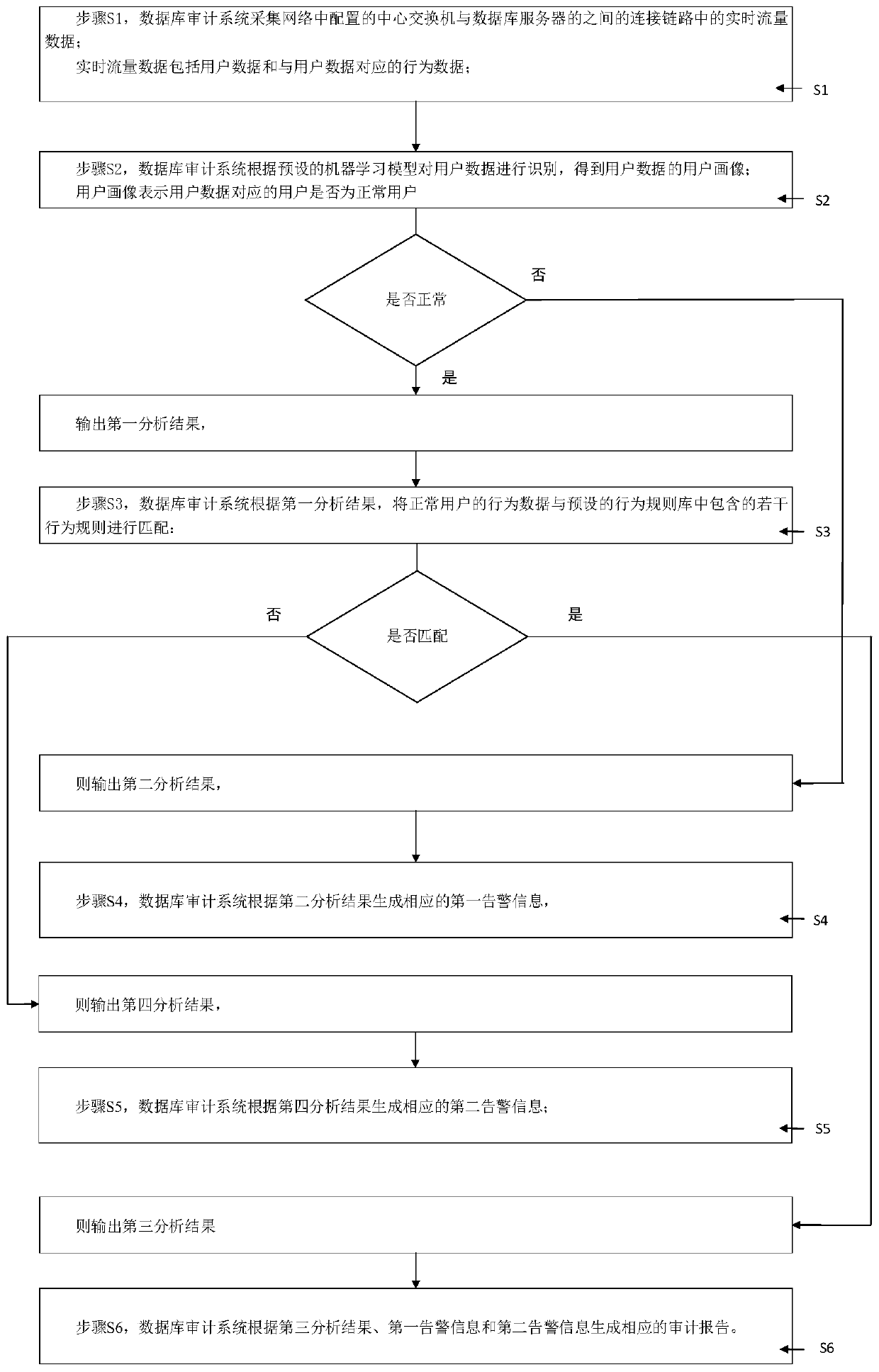
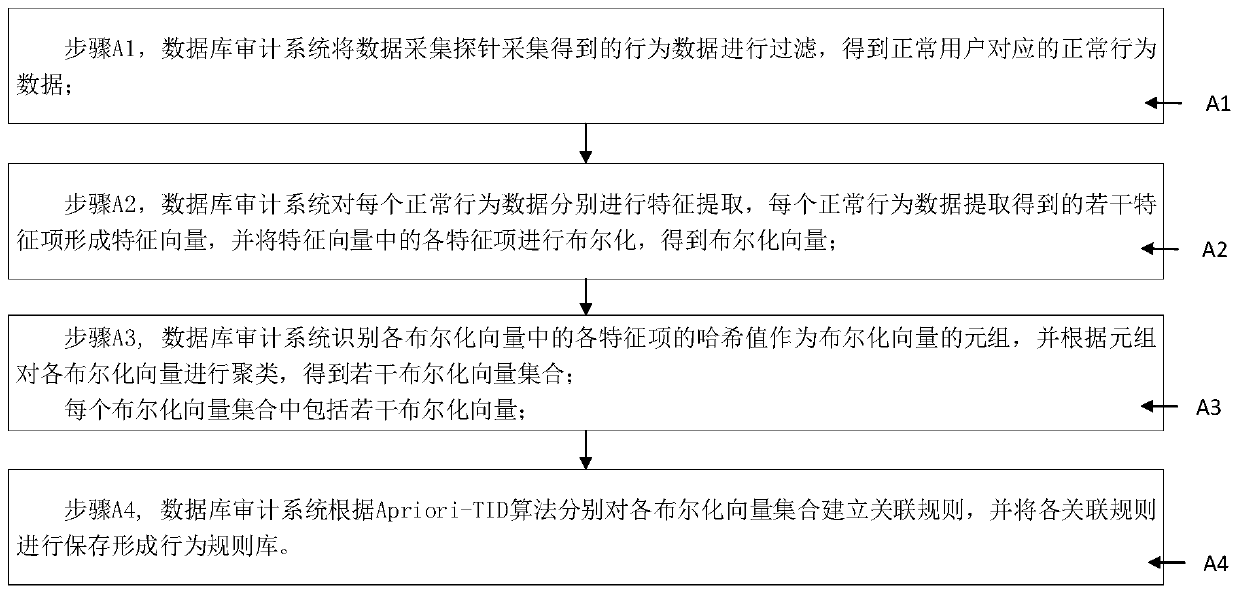
Database auditing system and method based on clustering analysis and association rules
ActiveCN111274227AImprove audit effectImprove efficiencyRelational databasesSpecial data processing applicationsData acquisitionEngineering
The invention discloses a database auditing system and method based on clustering analysis and association rules, and relates to database auditing. The data acquisition probes are used for acquiring and outputting user data and behavior data; the first audit analysis module is used for identifying the user data by the machine learning model to obtain a user portrait, outputting a first analysis result when the user portrait is a normal user, otherwise, outputting a second analysis result; the second audit analysis module is used for matching the behavior data of the first analysis result witha rule base, outputting a third analysis result when matching is carried out, and outputting a fourth analysis result when matching cannot be carried out; the first alarm unit generates first alarm information according to the second analysis result; the second alarm unit generates second alarm information according to the fourth analysis result; and the audit report module generates an audit report according to the third analysis result, the first alarm information and the second alarm information. The performance of the database is improved, a guarantee is provided for safe operation of thedatabase, and real-time auditing and safety detection are achieved.
Owner:上海市大数据中心
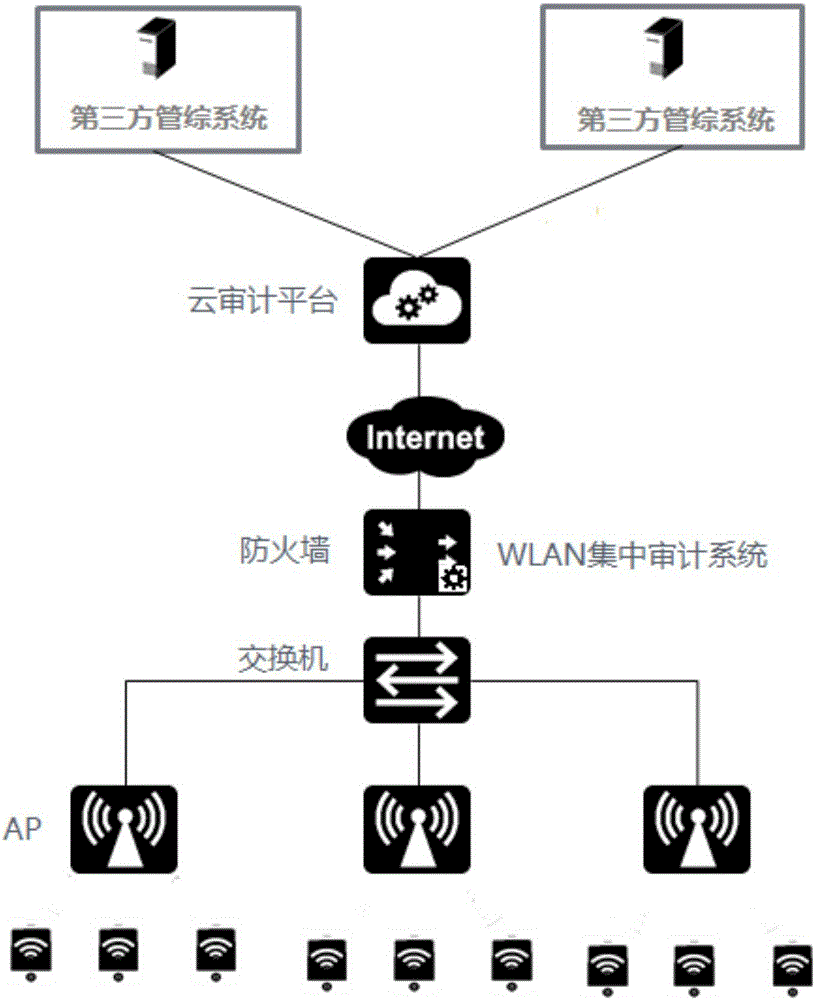
Centralized WLAN auditing method and device
The invention provides a centralized WLAN auditing method. The centralized WLAN auditing method comprises the following steps: collecting an original data packet, performing recognition processing on the original data packet, and generating a formatted log; storing the formatted log in a storage module; sensing the formatted log stored in the storage module to a cloud auditing platform; and sending a heartbeat signal to the cloud auditing platform, and displaying a working state of a centralized WLAN auditing device. According to the centralized WLAN auditing method provided by the invention, the original deployment structure of the equipment generates no change, the original data are analyzed in the local of the front end of the equipment, and the original data are not uploaded to the cloud auditing platform, thereby greatly reducing the network bandwidth consumed by the auditing data, improving the internet access experience of users and realizing a high auditing effect; and full audit of internet access behaviors of terminal users is accomplished on the front end equipment, the audited data are directly transmitted to the cloud auditing platform, and the cloud auditing platform transmits the audited data to a third party management system.
Owner:SURFILTER NETWORK TECH
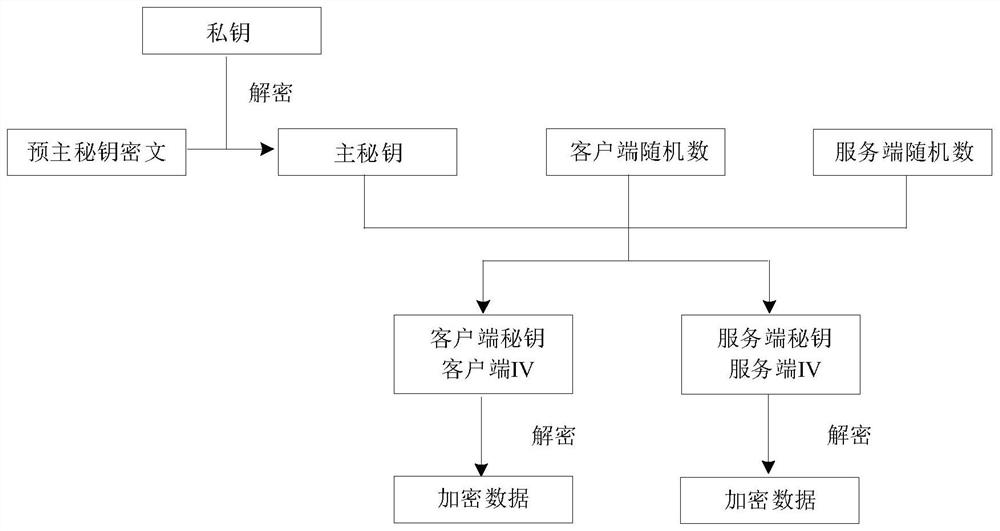
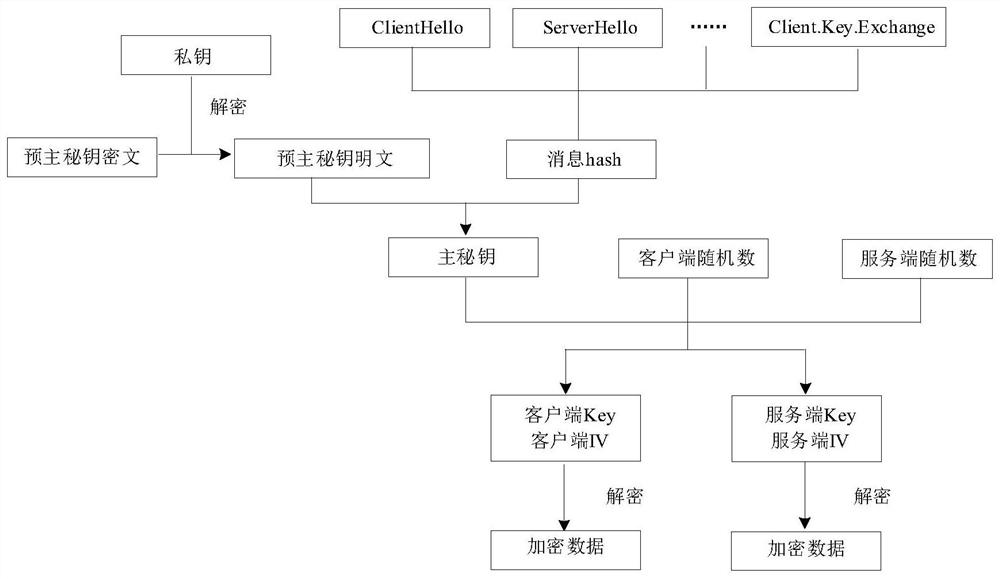
Method, system and terminal for encrypting data by bypass audit compatible with extended main secret key
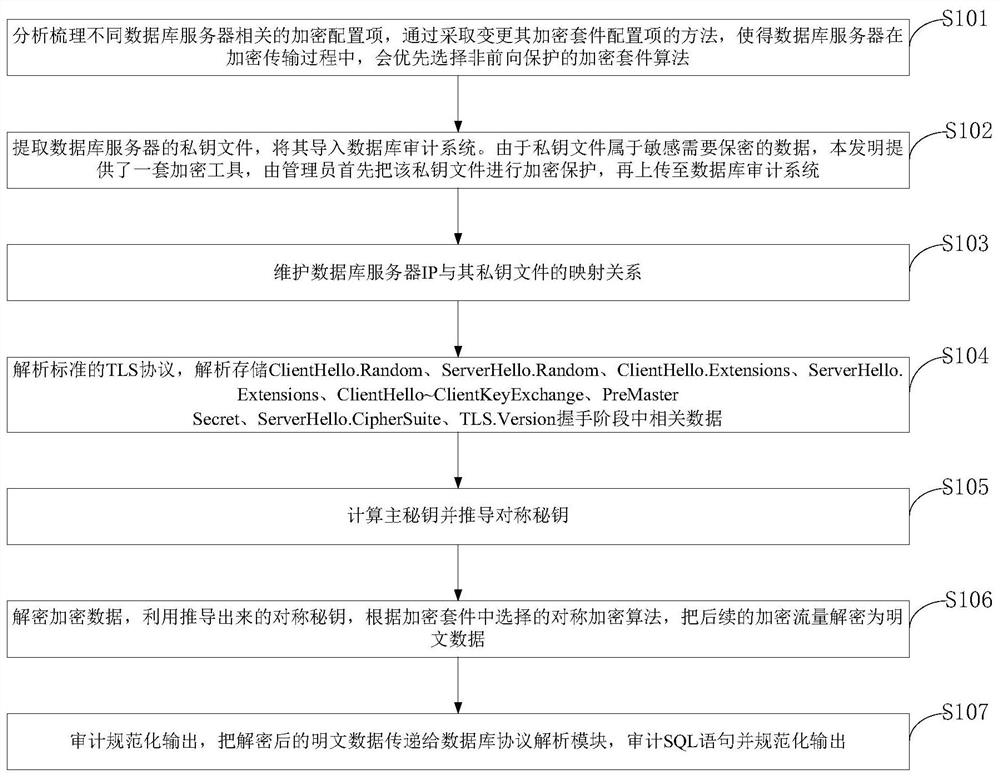
PendingCN114679260AExpand Audit CapabilitiesDecryption function expansionKey distribution for secure communicationHigh level techniquesProtocol for Carrying Authentication for Network AccessSQL
The invention belongs to the technical field of data processing, and discloses a data encryption method and system compatible with a bypass audit expansion main secret key, and a terminal. And on the basis of analyzing standard TLS protocol data, calculating a main key in an extended key calculation mode, deducing a symmetric key according to the main key, and decrypting subsequent encrypted traffic by using the symmetric key. And a symmetric key derivation method in a general main key calculation mode of the TLS is integrated to realize decryption and auditing of the TLS encrypted database traffic in a non-forward security encryption suite configuration item. According to the TLS traffic decryption method under the non-forward security encryption suite, the decrypted plaintext is transmitted to the protocol analysis module, SQL statement auditing and standardized output are achieved, and the auditing capability of a database auditing system is effectively expanded.
Owner:北京亿赛通科技发展有限责任公司
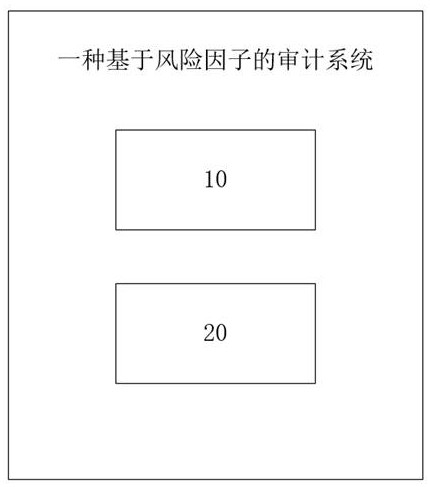
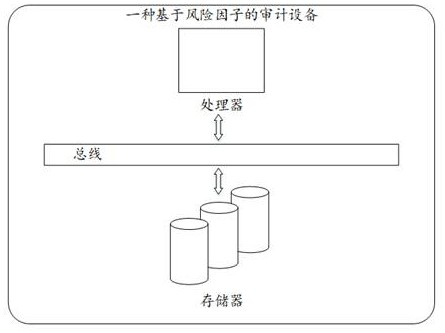
An audit system and equipment based on risk factors
ActiveCN114022053BSolve the time-consuming and labor-intensive problem of manual risk auditImprove efficiencyFinanceResourcesData processing systemInformation processing
This application relates to the technical field of data processing systems or methods specially applicable to the financial field, and discloses an audit system and equipment based on risk factors, including: the collection module obtains the financial statements of the enterprise, the type of main business, and the financial statements contained in the financial statements The processing module determines the corresponding business data according to the fund change information, selects the corresponding risk factor set from the pre-stored risk factor database according to the main business type, and judges whether there is any relationship between the risk factor set and the business based on the business data. The risk factor corresponding to the data; if it exists, list the documents to be proved according to the risk factor, and select the corresponding witnesses; build the first audit process; if it does not exist, expand the variable according to the risk orientation corresponding to the business data, and list it in the enterprise personnel structure list Select the corresponding business personnel, obtain the risk rating of the business personnel, and mark the risk rating in the fund change information corresponding to the business personnel.
Owner:鲁信科技股份有限公司
Intelligent health privacy protection system
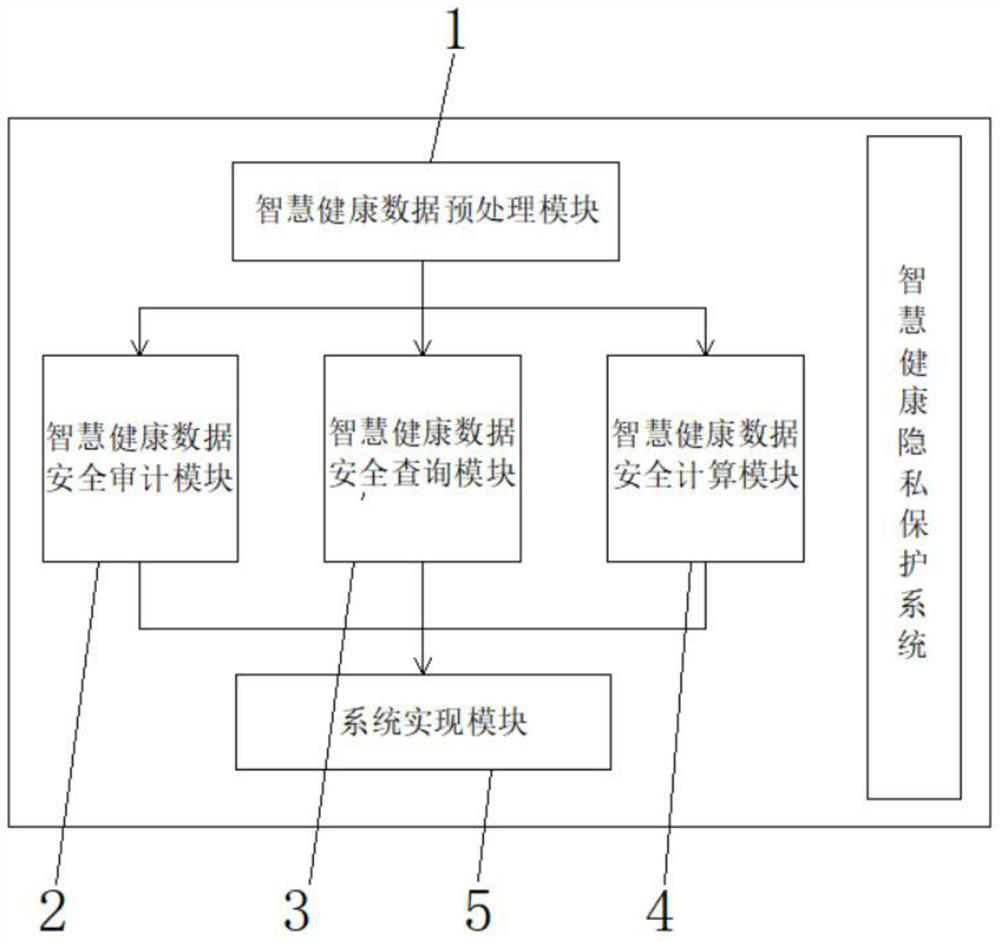
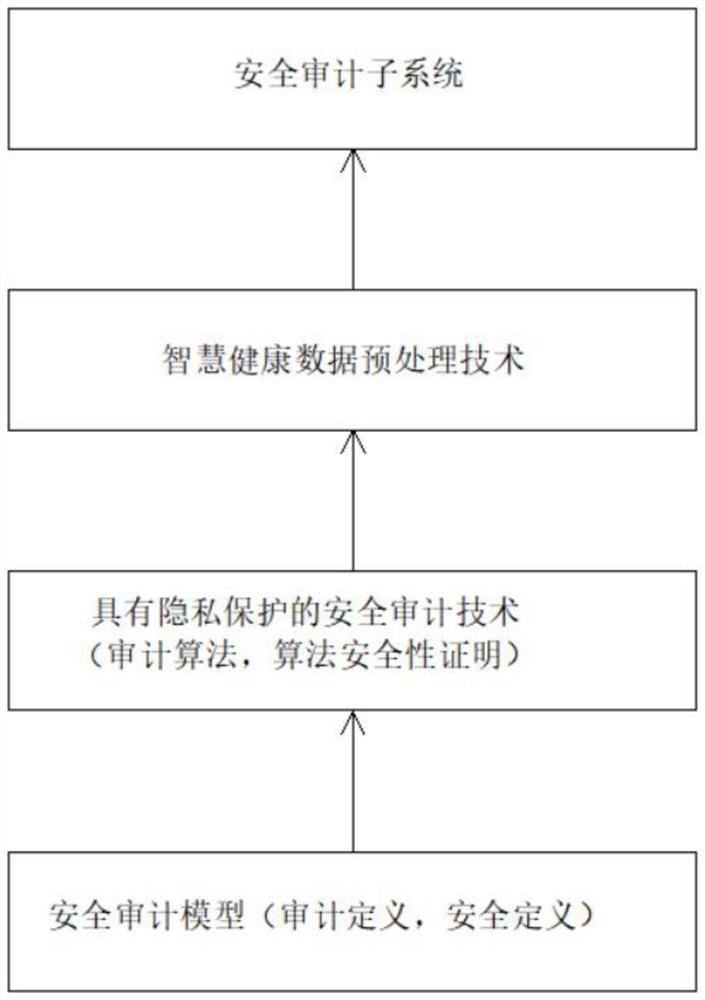
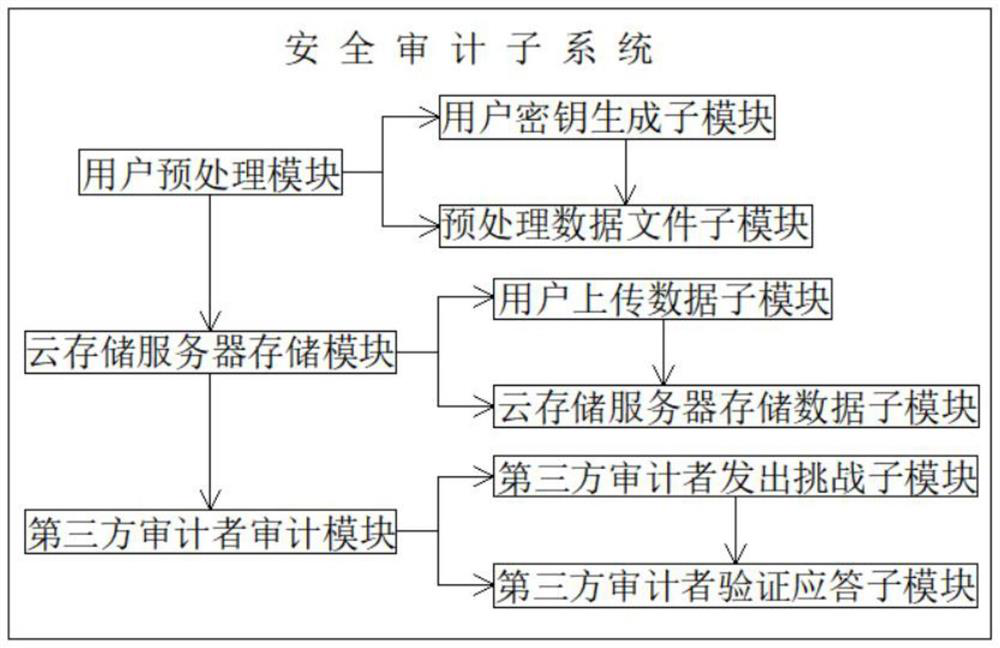
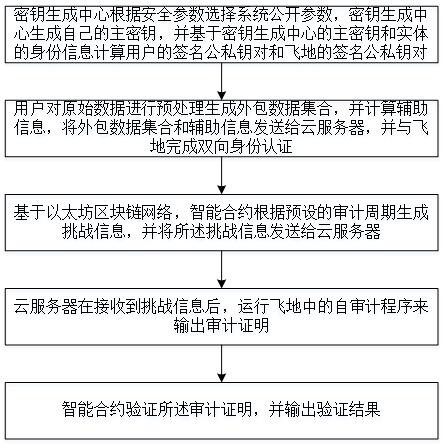
InactiveCN112329061AHigh audit securityImprove audit effectDigital data protectionData informationPrivacy protection
The invention discloses an intelligent health privacy protection system, and relates to the technical field of privacy protection, in particular to an intelligent health privacy protection system which comprises an intelligent health data preprocessing module. The output end of the intelligent health data preprocessing module is electrically connected with an intelligent health data security auditmodule, an intelligent health data security query module and an intelligent health data security calculation module. The output ends of the intelligent health data security auditing module, the intelligent health data security query module and the intelligent health data security calculation module are electrically connected with a system implementation module. According to the intelligent healthprivacy protection system, safety calculation of the intelligent health data with privacy protection has data confidentiality, and the safety calculation of the intelligent health data with privacy protection must ensure that intelligent health data information and a safety calculation result are not leaked; results of correctness and safety calculation must be correct; and results must be obtained in reasonable time for efficiency and safety calculation.
Owner:河北上晟医疗科技发展有限公司
A fast audit method for cloud storage data
ActiveCN113422688BGuaranteed verifiable randomnessImprove audit effectUser identity/authority verificationDigital data protectionData setOriginal data
The invention discloses a fast audit method for cloud storage data, including: Step S1. The key generation center selects system public parameters, and generates the user's signature public-private key pair and the enclave's signature public-private key pair; Step S2. The user pairs The original data is preprocessed to generate an outsourced data set, and auxiliary information is calculated, and the outsourced data set and auxiliary information are sent to the cloud server, and two-way identity authentication is completed with the enclave; step S3. Based on the Ethereum blockchain network, the smart contract is based on The preset audit cycle generates challenge information and sends the challenge information to the cloud server; Step S4. After receiving the challenge information, the cloud server runs the self-audit program in the enclave to output the audit certificate; Step S5. Smart contract verification audit Prove and output the verification result. The invention can resist the replacement attack and forgery attack of the malicious cloud server without introducing a trusted third party.
Owner:SOUTHWEST PETROLEUM UNIV
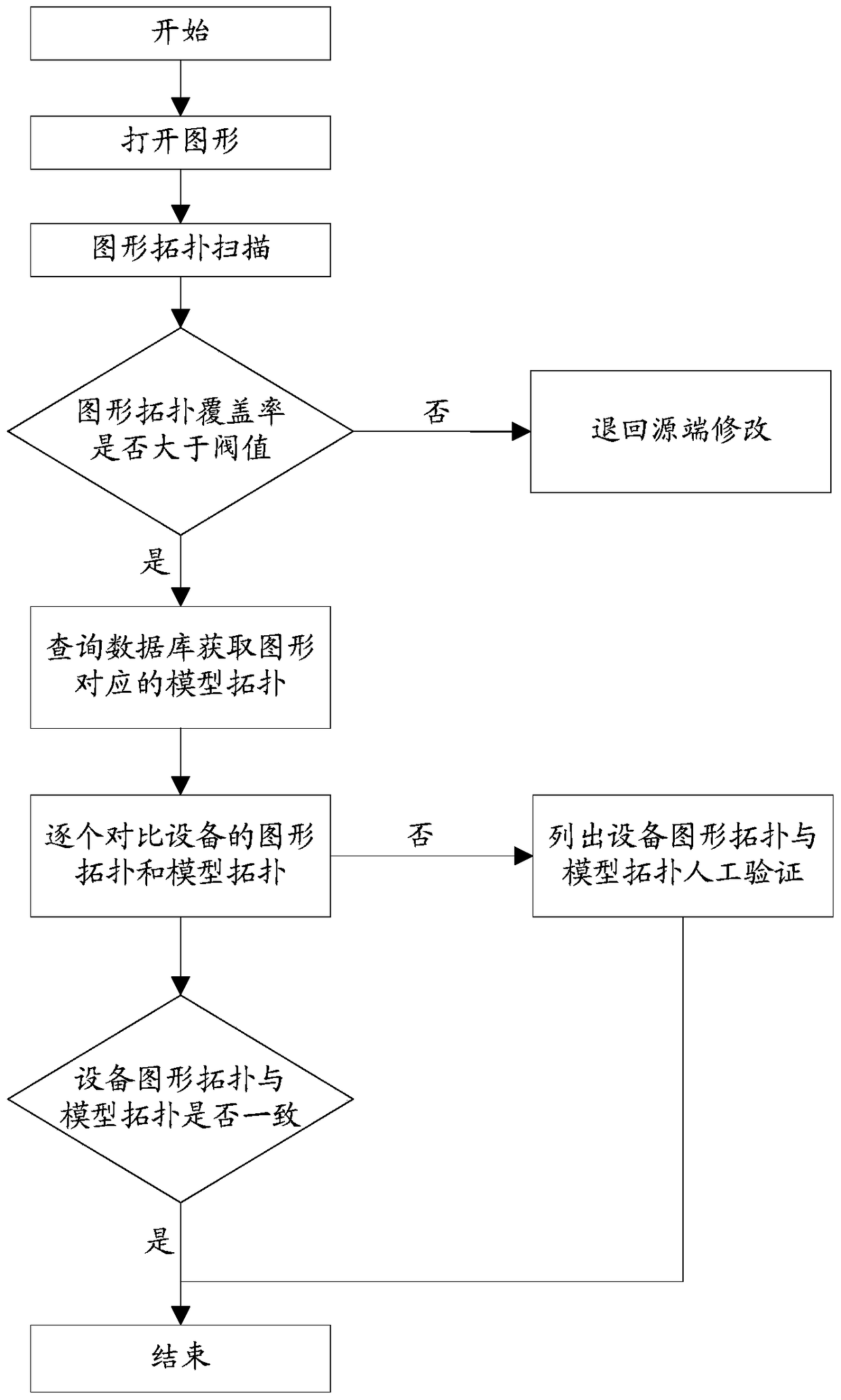
A Method of Realizing Change Process Comparison of Distribution Network Equipment Based on Graphics and Models
ActiveCN105160132BImprove audit effectStandardize the review processSpecial data processing applicationsGraphicsOpen graph
The invention provides a graph and model based method for realizing distribution network device difference process comparison. In a distribution network, a graph is based on an svg graphic format, and a model file is based on an xml format; and graphic topologies in the distribution network are connection relationships between graphic elements in the svg graph, and the graphic elements represent a device. The method specifically comprises: opening the graph in the distribution network; extracting the graphic topologies; querying a distribution network database to obtain model topologies corresponding to the opened graph; comparing the graphic topologies and the model topologies of the device one by one; judging whether the graphic topologies and the model topologies of the device are same or not; if so, not performing operation and accepting a process; or otherwise, listing differences of the graphic topologies and the model topologies of the device, and performing artificial verification. According to the method, the check effect of the graph and the model is improved; the check process is standardized; and the check efficiency is improved and the labor cost is reduced.
Owner:FUJIAN AUTOMATION ELECTRIC POWER TECH
Man-machine cooperation intelligent auditing analysis method for incomplete data
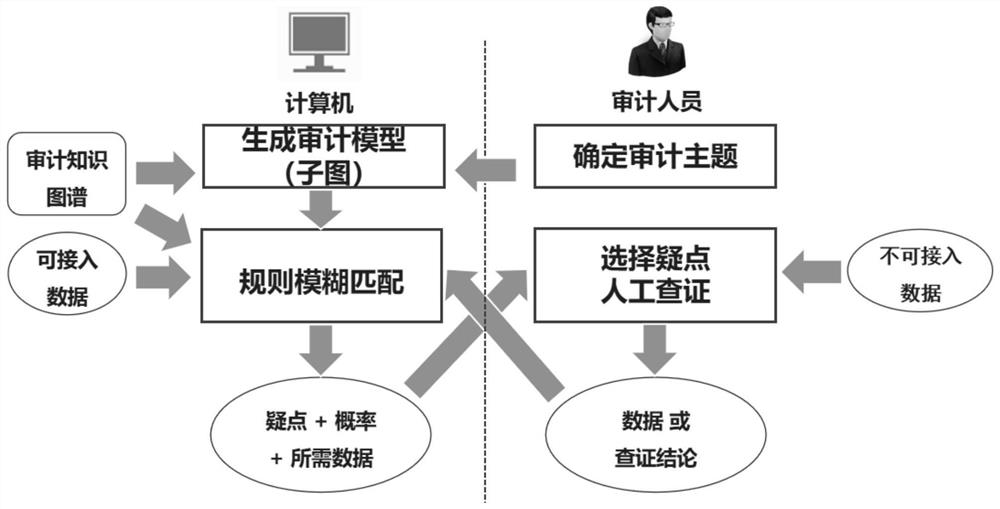
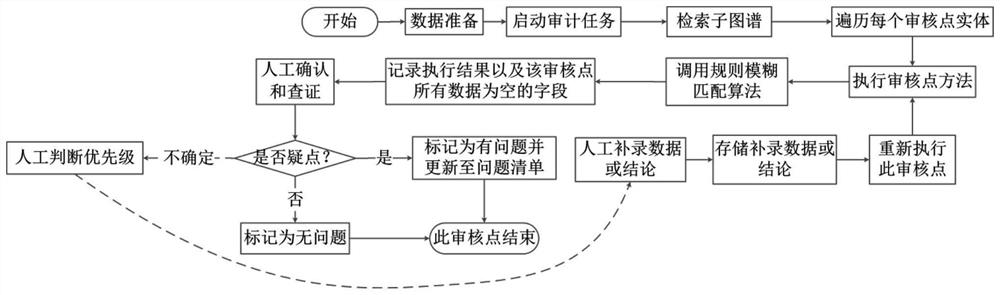
PendingCN113657854AAchieve full process coverageEasy accessOffice automationSpecial data processing applicationsMissing dataKnowledge graph
The invention discloses a man-machine cooperation intelligent auditing analysis method for incomplete data, and belongs to a core method in a digital auditing process. The method mainly comprises eight steps which are respectively completed by auditing personnel and a computer and sequentially comprise the following steps: constructing an auditing knowledge graph, integrating and preparing data, determining an auditing theme, generating an auditing model, generating a doubtful point list and calculating a compliance probability, confirming doubtful points and manually checking, additionally recording missing data or checking a conclusion and generating an auditing manuscript. According to the method, the limitation that the auditing cannot be carried out for incomplete data in the existing digital auditing technology is broken through, the compliance probability of the auditing point can be calculated through the current existing data, and auditing personnel are helped to determine the importance of doubtful points. After the auditor completes data additional recording, the auditing model can perform a new round of fuzzy matching and output a result, a progressive iteration type auditing point study and judgment process is formed, powerful reference is provided for the auditor to quickly identify and position problem points, and the auditor is assisted in performing compliance check.
Owner:ZHEJIANG LAB
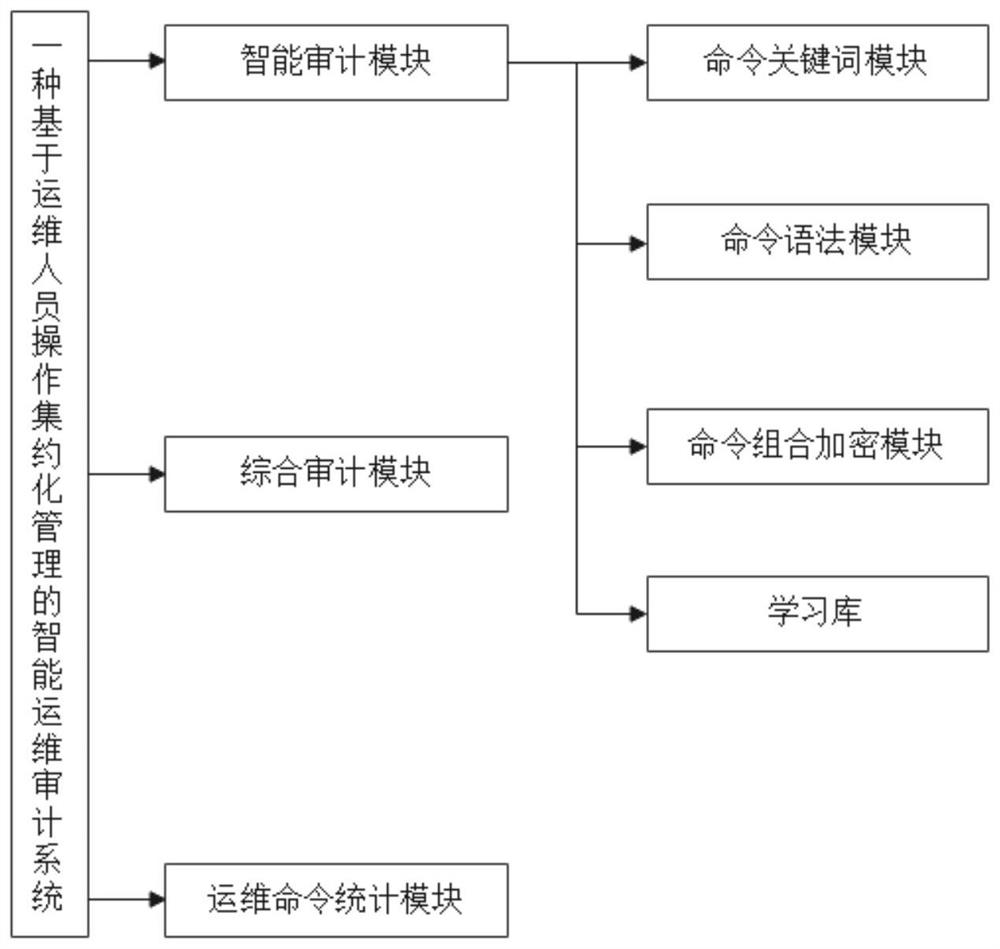
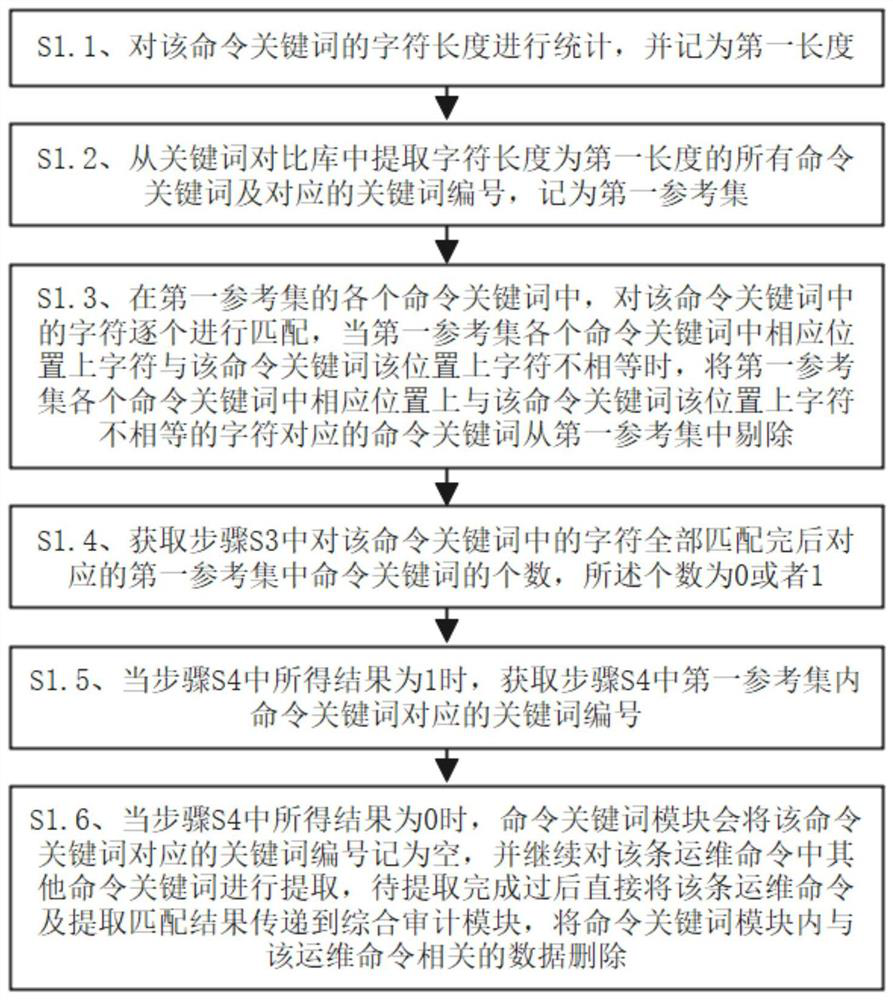
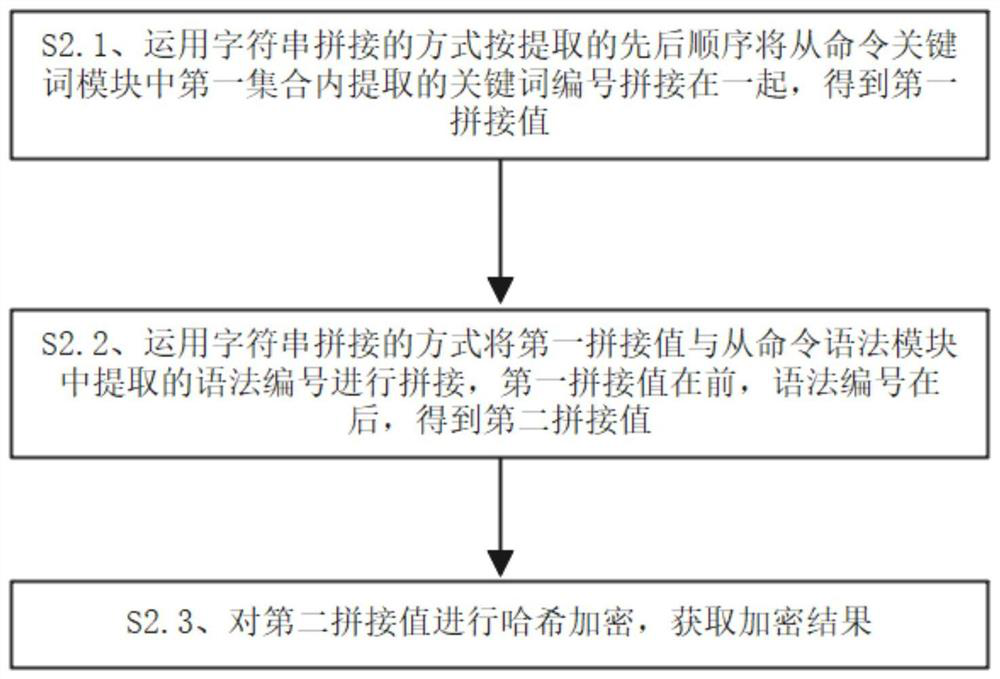
Intelligent operation and maintenance auditing system based on intensive management of operation and maintenance personnel operation
ActiveCN113360926AImprove audit effectSlow processingDigital data protectionMachine learningServer-sideReliability engineering
The invention discloses an intelligent operation and maintenance auditing system based on intensive management of operation and maintenance personnel operation, which is characterized in that the system is erected between a client side and a server side, is respectively connected with the client side and the server side, and comprises an intelligent auditing module, a comprehensive auditing module and an operation and maintenance command statistics module, the intelligent auditing module comprises a command keyword module, a command grammar module, a command combination encryption module and a learning library. According to the method, the client and the server are separated by adopting a fortress machine mechanism, so that intrusion of outsiders is effectively avoided, the operation and maintenance command is managed by adopting a machine learning mode from the operation and maintenance command, the operation condition of operation and maintenance personnel is supervised, malicious damage of the operation and maintenance personnel to data is avoided, and the operation and maintenance efficiency is improved. And the pressure of the operation and maintenance personnel is relieved, and the time for the operation and maintenance personnel to check the operation and maintenance command is saved.
Owner:珠海市鸿瑞信息技术股份有限公司
Smart contract audit method, device, computer equipment and storage medium
ActiveCN110727948BReduce security risksImprove audit effectPlatform integrity maintainanceCode compilationSmart contractSource code
This application relates to a smart contract audit method, device, computer equipment and storage medium, and relates to the technical field of network security. The method includes: the server obtains the audit parameters of the smart contract by receiving the source code of the smart contract uploaded by the editing terminal, compiles the source code of the smart contract according to the compilation parameters, and after the source code of the smart contract is compiled successfully, according to the scanning parameters Scan the smart contract for security issues, obtain the scanning audit results, and return the scanning audit results to the editing terminal; this solution obtains the compilation parameters and scanning parameters of the smart contract on the server side, and performs the smart contract according to the obtained compilation parameters and scanning parameters. The source code of the contract is compiled and the security issue is scanned, which realizes the security issue scanning of the smart contract on the server side, which can effectively reduce the security risks of the smart contract, thereby improving the audit effect of the smart contract.
Owner:TENCENT TECH (SHENZHEN) CO LTD
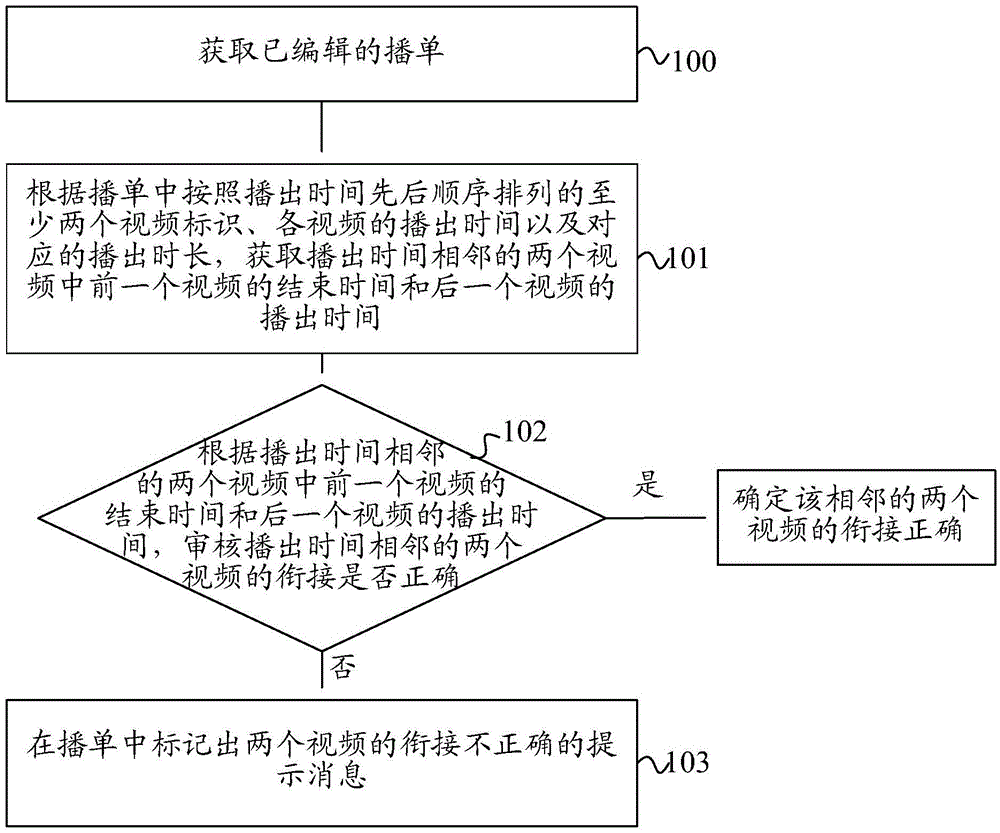
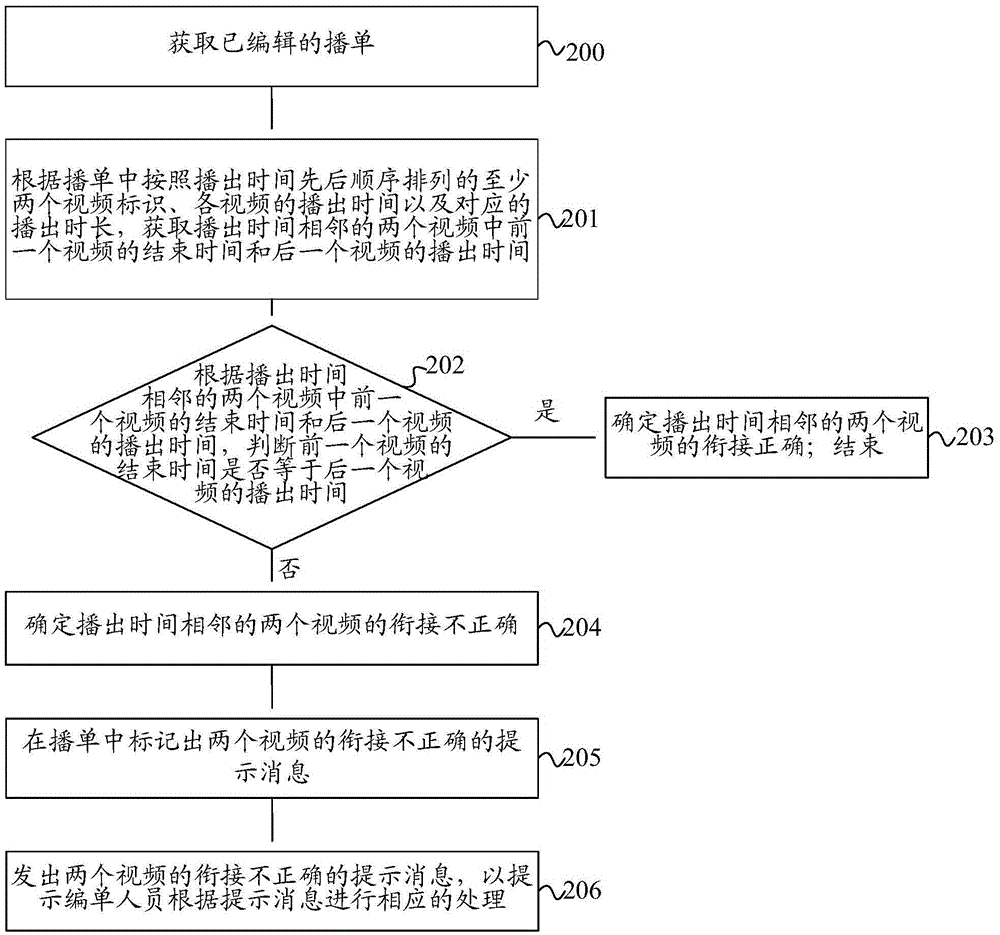
Method and device for auditing broadcast list
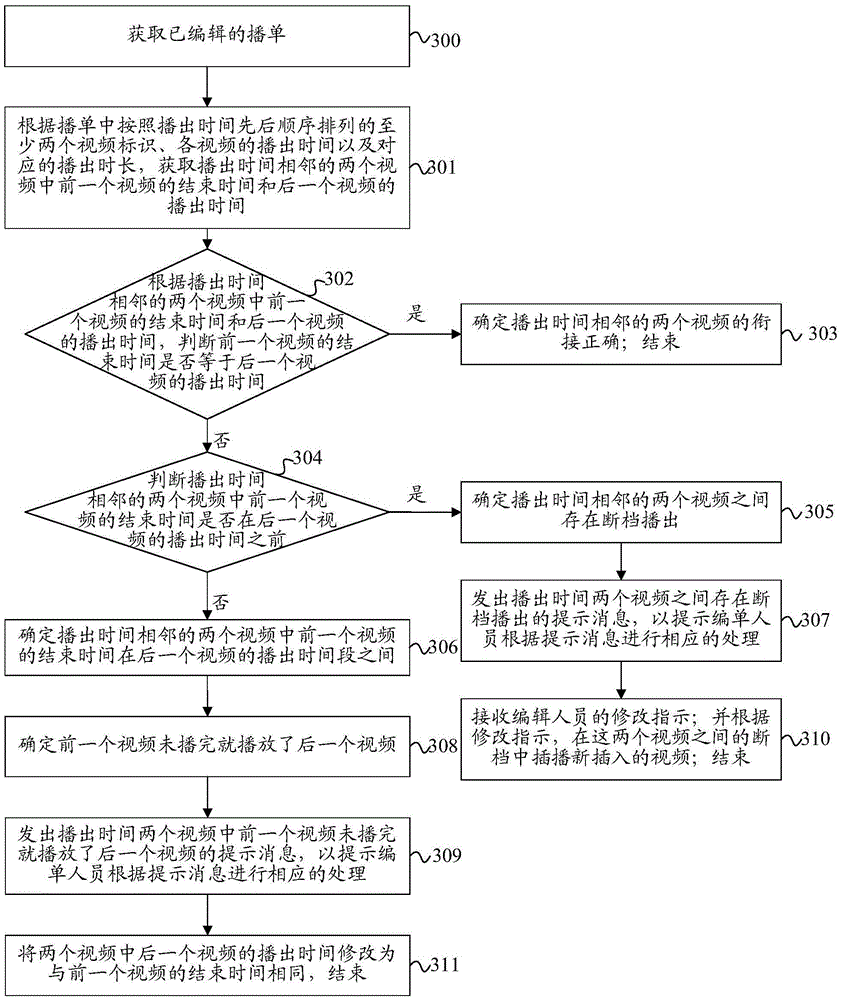
InactiveCN105430450AAutomatic Review ProcessingImprove audit effectSelective content distributionTelecommunicationsComputer science
The invention discloses a method and a device for auditing a broadcast list. The method comprises the following steps: obtaining an edited broadcast list; obtaining an end time of a former video and a broadcast time of a latter video in two videos with adjacent broadcast times according to at least two video identifiers that are arranged according to the sequence of the broadcast times in the broadcast list, the broadcast times of the videos and corresponding broadcast durations; auditing whether a link of the two videos with the adjacent broadcast times is correct according to the end time of the former video and the broadcast time of the latter video in the two videos with the adjacent broadcast times; and when the link of the two videos with the adjacent broadcast times is incorrect, marking a prompt message prompting that the link of the two videos is incorrect in the broadcast list. The invention further discloses a device used for realizing the method. The auditing scheme of the broadcast list disclosed by the invention can be used for automatically auditing the broadcast list, thereby improving the auditing effect of the broadcast list and guarantee the play continuity of the videos in the broadcast list; and the labor cost can also be saved.
Owner:WUXI TVMINING MEDIA SCI & TECH
Method and device for restoring parameters in Oracle database access traffic
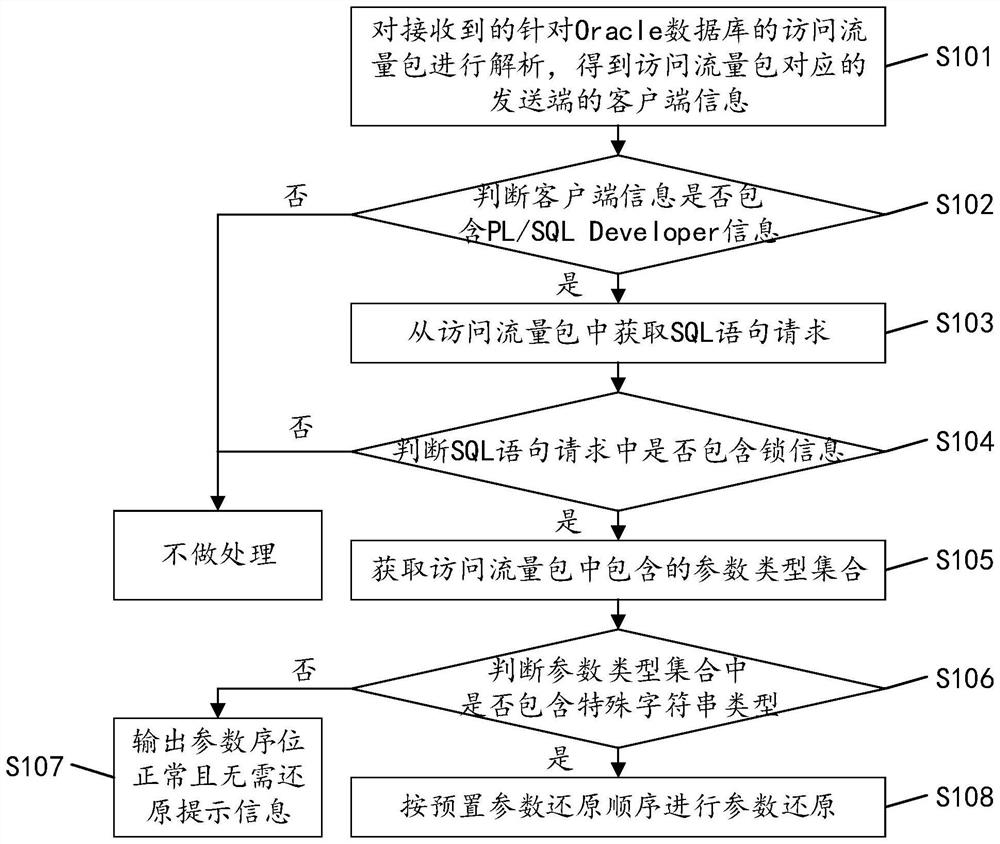
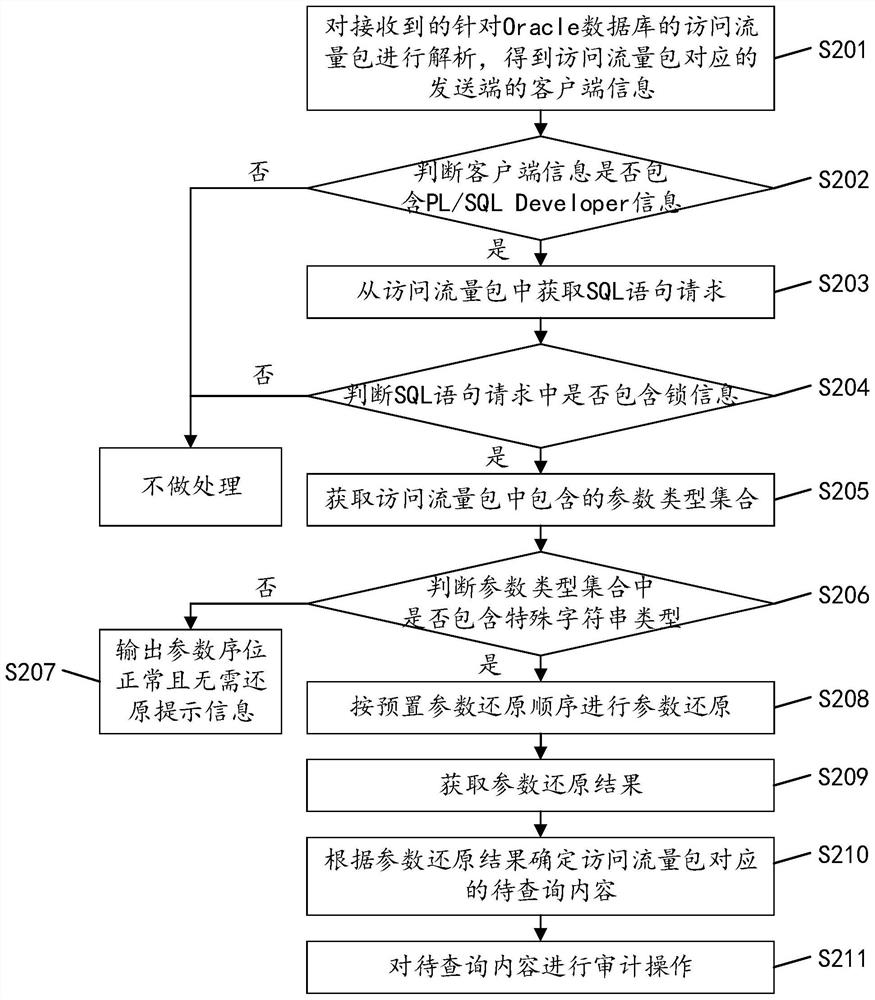
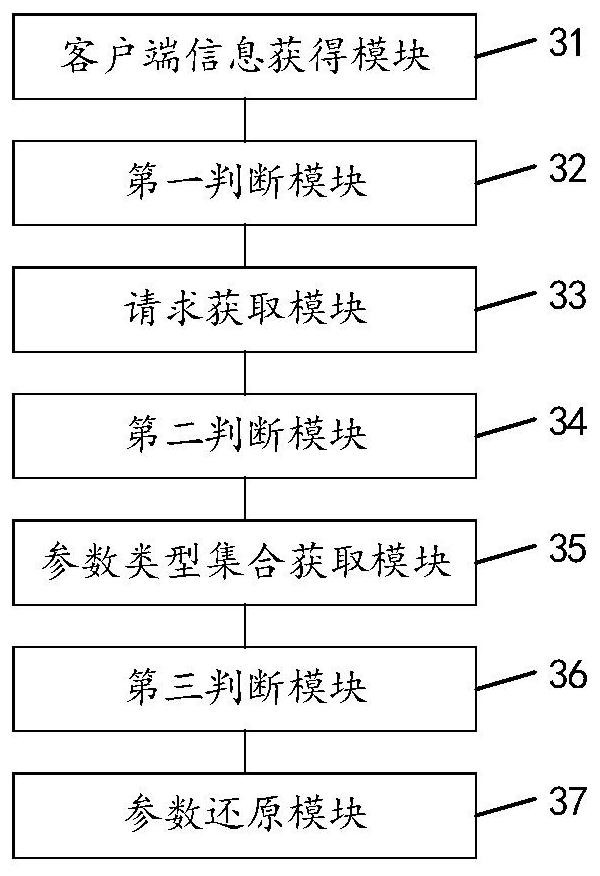
PendingCN113722351AImprove audit effectRestore accuratelyDigital data protectionSpecial data processing applicationsEngineeringOracle database
The invention discloses a method for restoring parameters in Oracle database access traffic, which comprises the following steps: analyzing a received access traffic packet aiming at an Oracle database to obtain client information of a sending end corresponding to the access traffic packet; judging whether the client side information contains the PL / SQLDEVELOPER information or not; if yes, obtaining an SQL statement request from the access traffic packet; judging whether the SQL statement request contains lock information or not; if yes, acquiring a parameter type set contained in the access traffic packet; judging whether the parameter type set contains a special character string type or not; and if yes, performing parameter reduction according to a preset parameter reduction sequence. According to the invention, the parameters contained in the access traffic packet are accurately restored, and the audit effect of the access traffic packet is improved. The invention further discloses a device, equipment and a storage medium, which have corresponding technical effects.
Owner:杭州安恒信息安全技术有限公司
A mail audit method, device and computer-readable storage medium
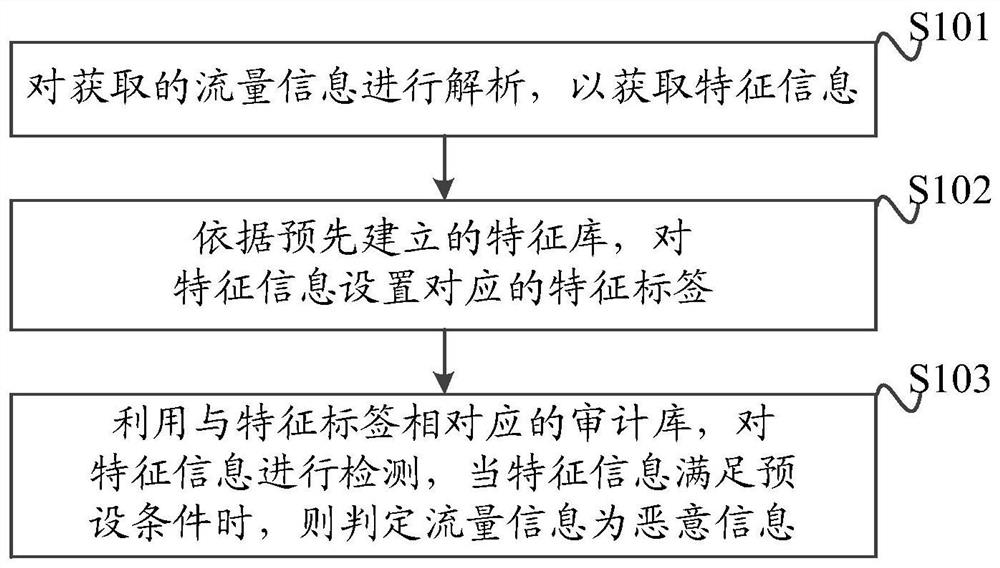
ActiveCN108965350BNarrow detection rangeImprove accuracyData switching networksEngineeringData mining
The embodiment of the present invention discloses a mail auditing method, device and computer-readable storage medium, which analyze the acquired traffic information to obtain characteristic information; set corresponding characteristic labels for characteristic information according to the pre-established characteristic database; use and The audit library corresponding to the feature label detects the feature information, and when the feature information meets the preset conditions, it is determined that the traffic information is malicious information. In this technical solution, traffic information is classified according to the feature database, so that special detection is performed according to the audit database corresponding to the feature label, which makes the selected audit database more targeted and improves the accuracy of phishing email monitoring. And by setting the characteristic label, the scope of detecting the characteristic information is narrowed, thereby shortening the time spent on detection, reducing unnecessary detection, and further improving the performance of mail auditing.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method for auditing safety of internet video
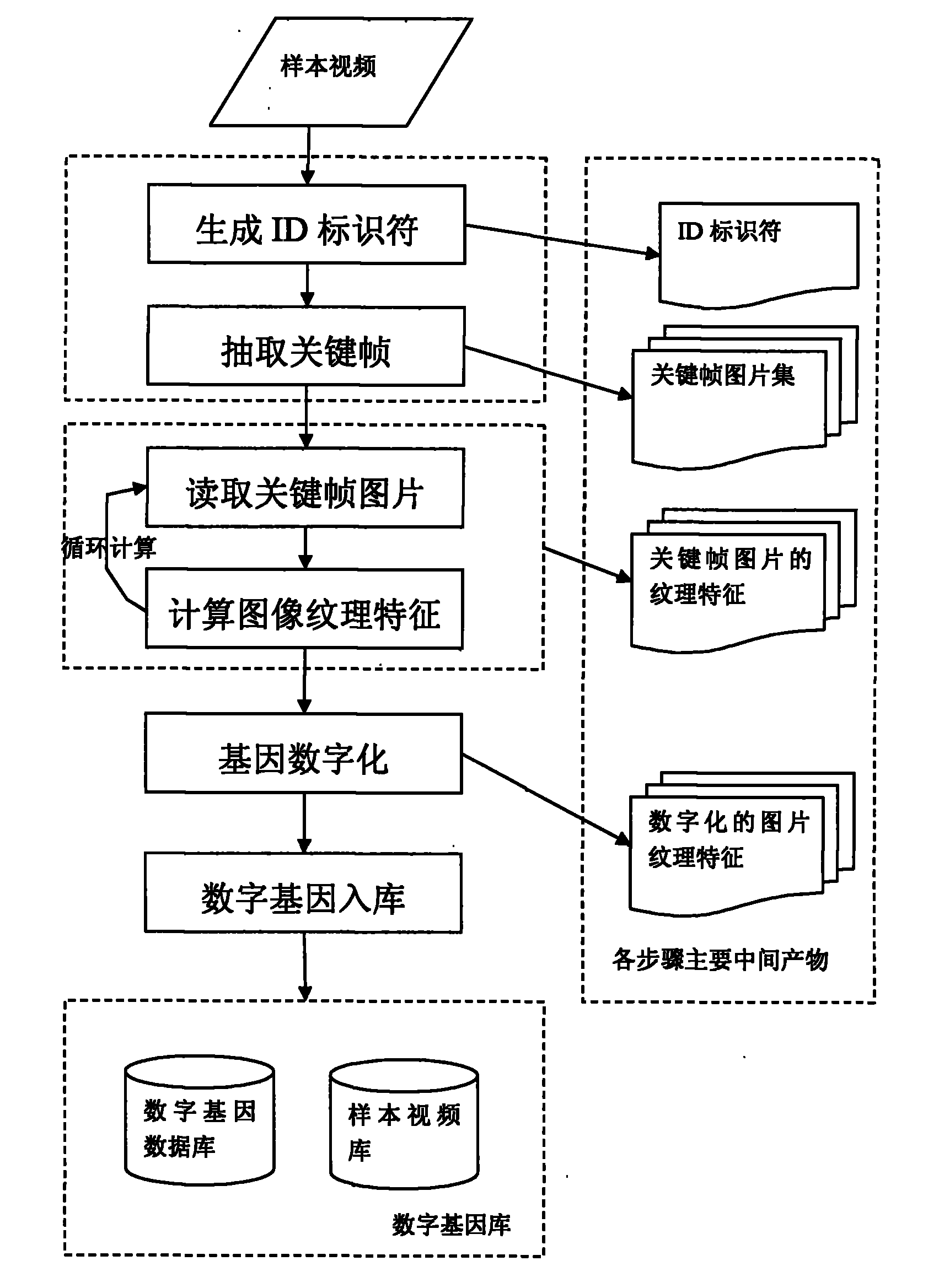
InactiveCN101540907BImprove retrieval efficiencyImprove matching efficiencyTelevision systemsData switching networksComputerized systemSample image
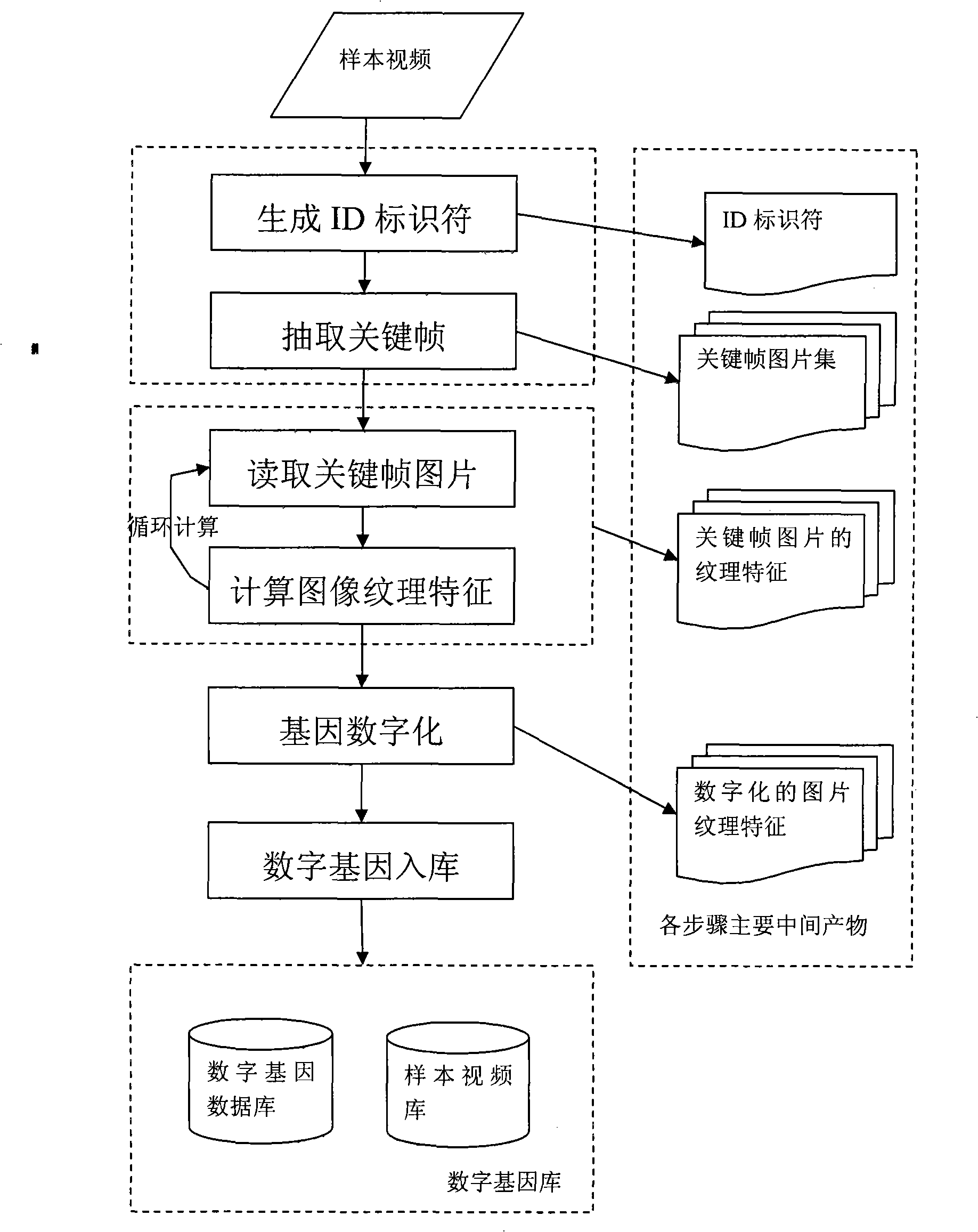
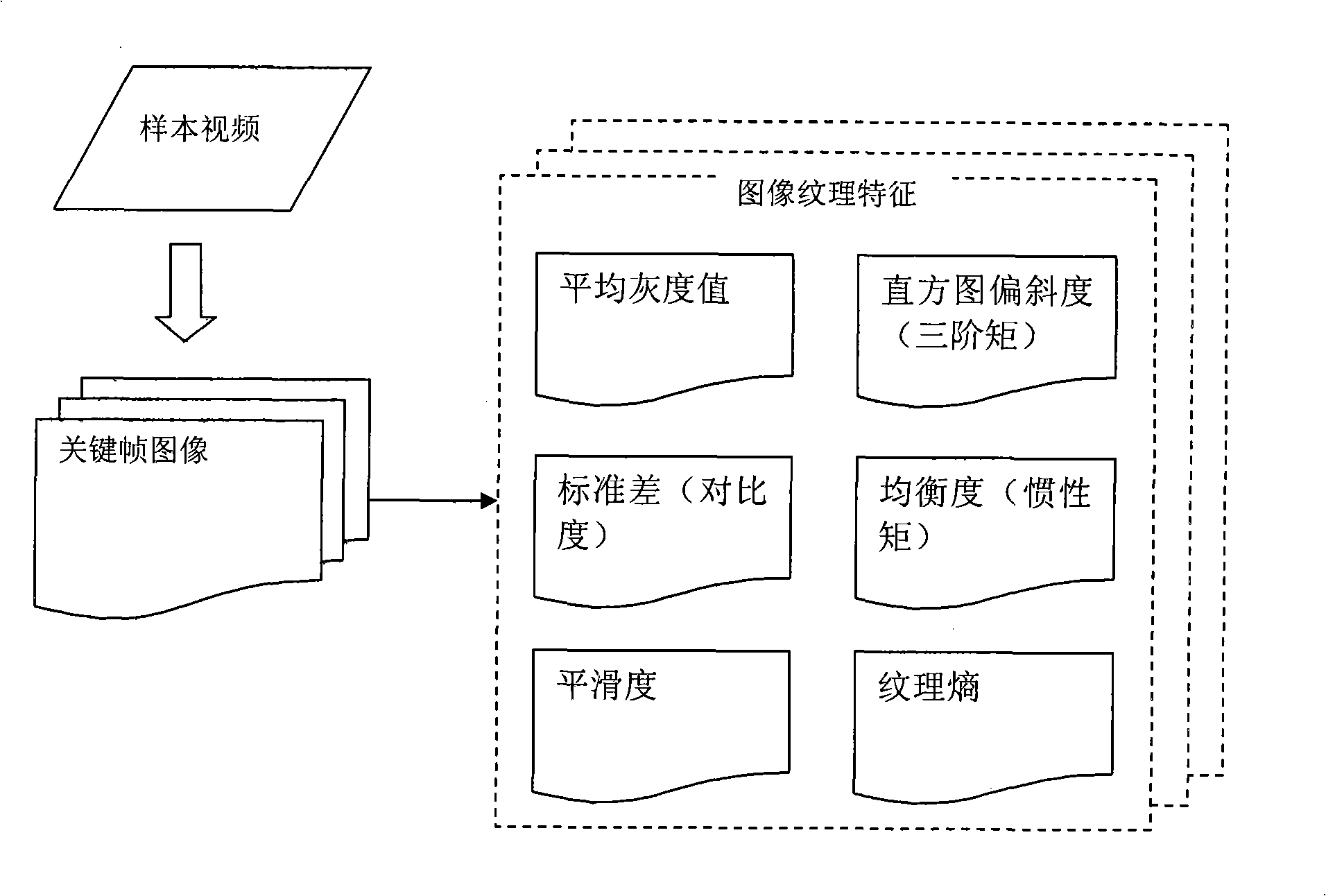
The invention discloses a method for auditing the safety of an internet video by using a computer system. Digital genes are formed by extracting the characteristics of a sample image or video. Each gene represents all samples with similar characteristics so that the validity and the availability of the samples are improved through abstraction. In the process of detection comparison, a four-step detection method, i.e. slicing and screening, preliminary detection comparison of a maximum sample, a secondary detection comparison of a minimum sample, result feedback and alarming, is adopted, therefore, screening is carried out first, then a large-scope comparison is fast carried out so that the number of the video images to be detected is reduced, and then the detection with pertinence is carried out so as to greatly improve the audition efficiency and increases the accuracy, validity and completeness of the audition.
Owner:WUXI TVMINING MEDIA SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com