Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
386 results about "Networking hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
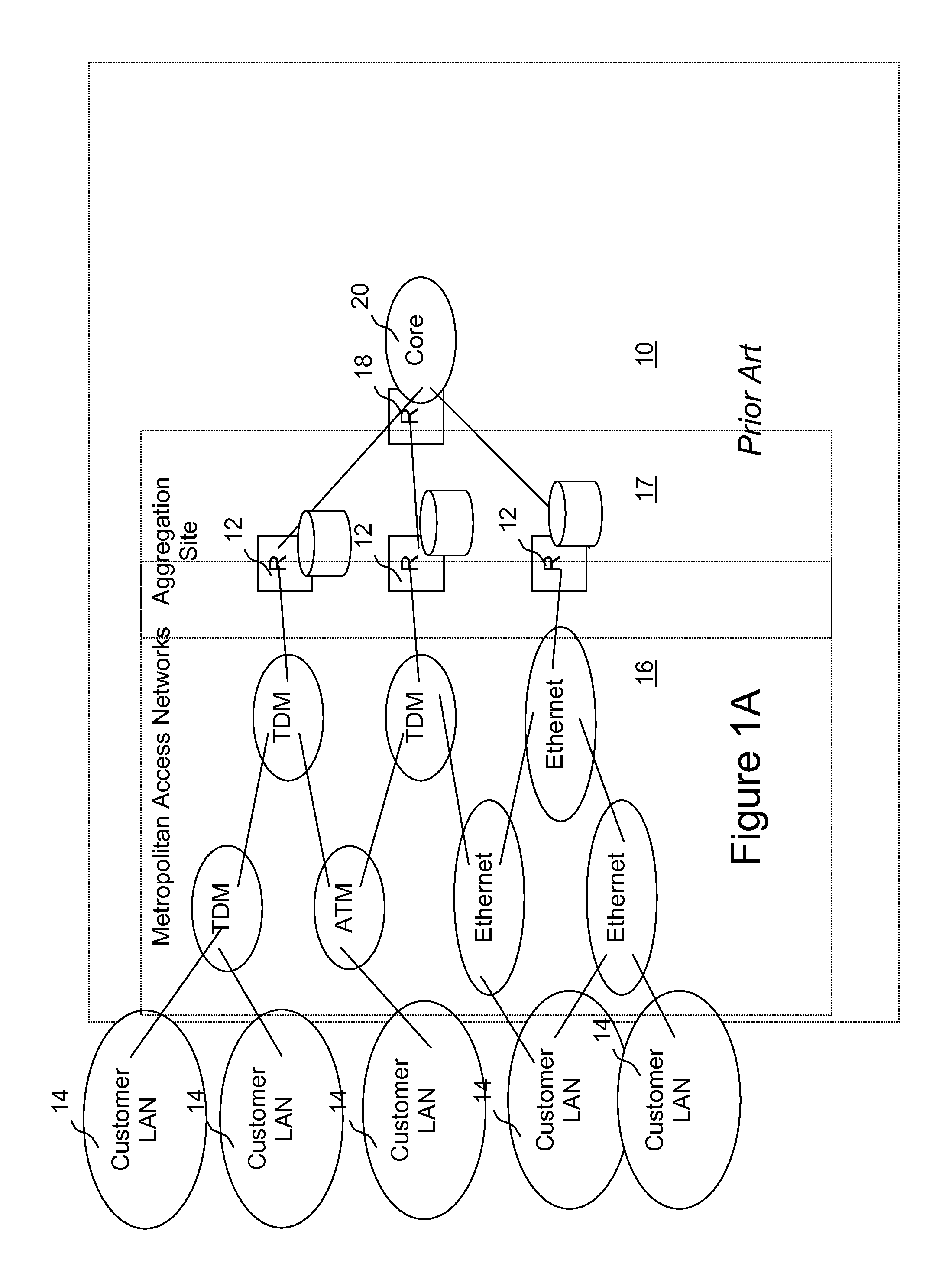
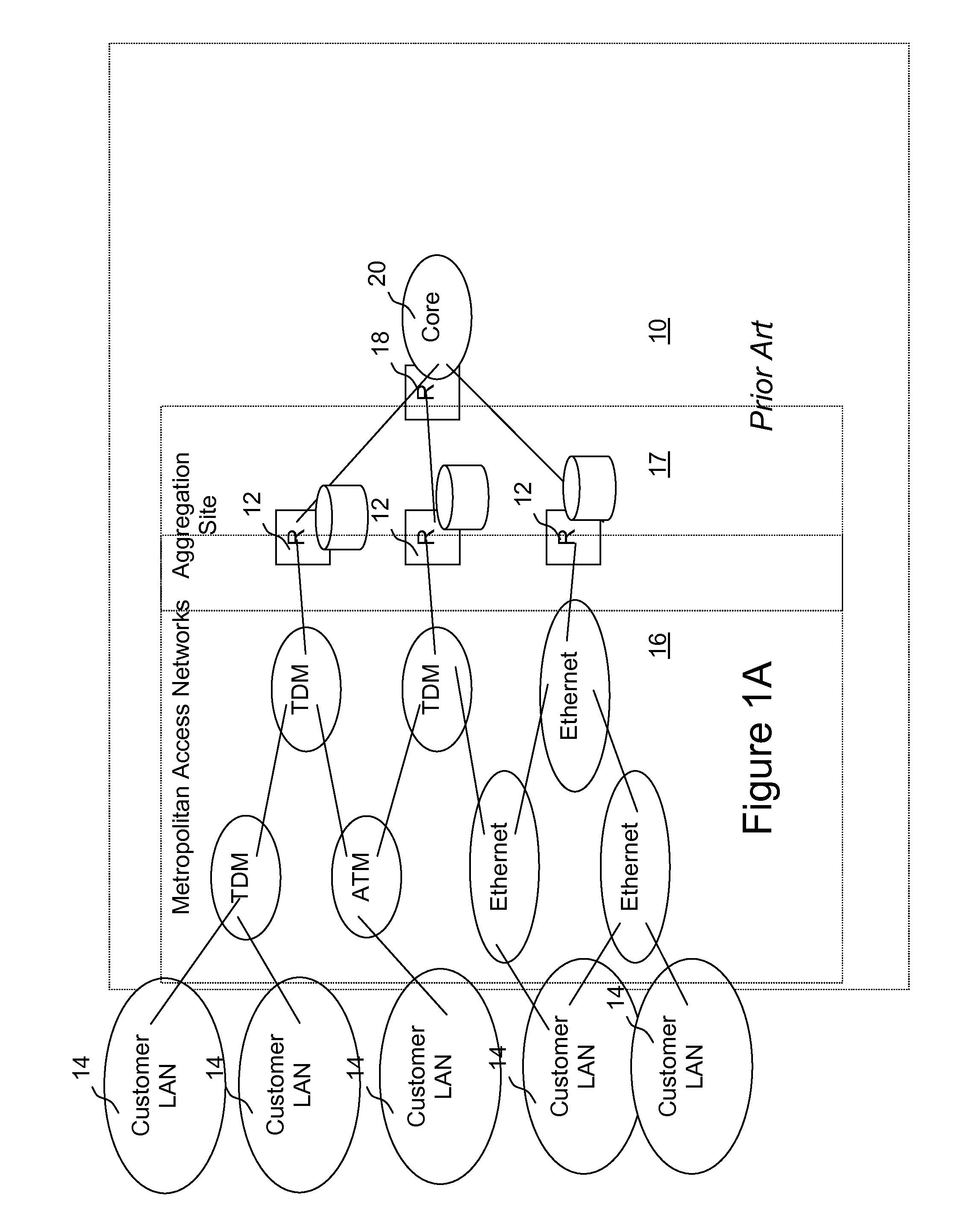
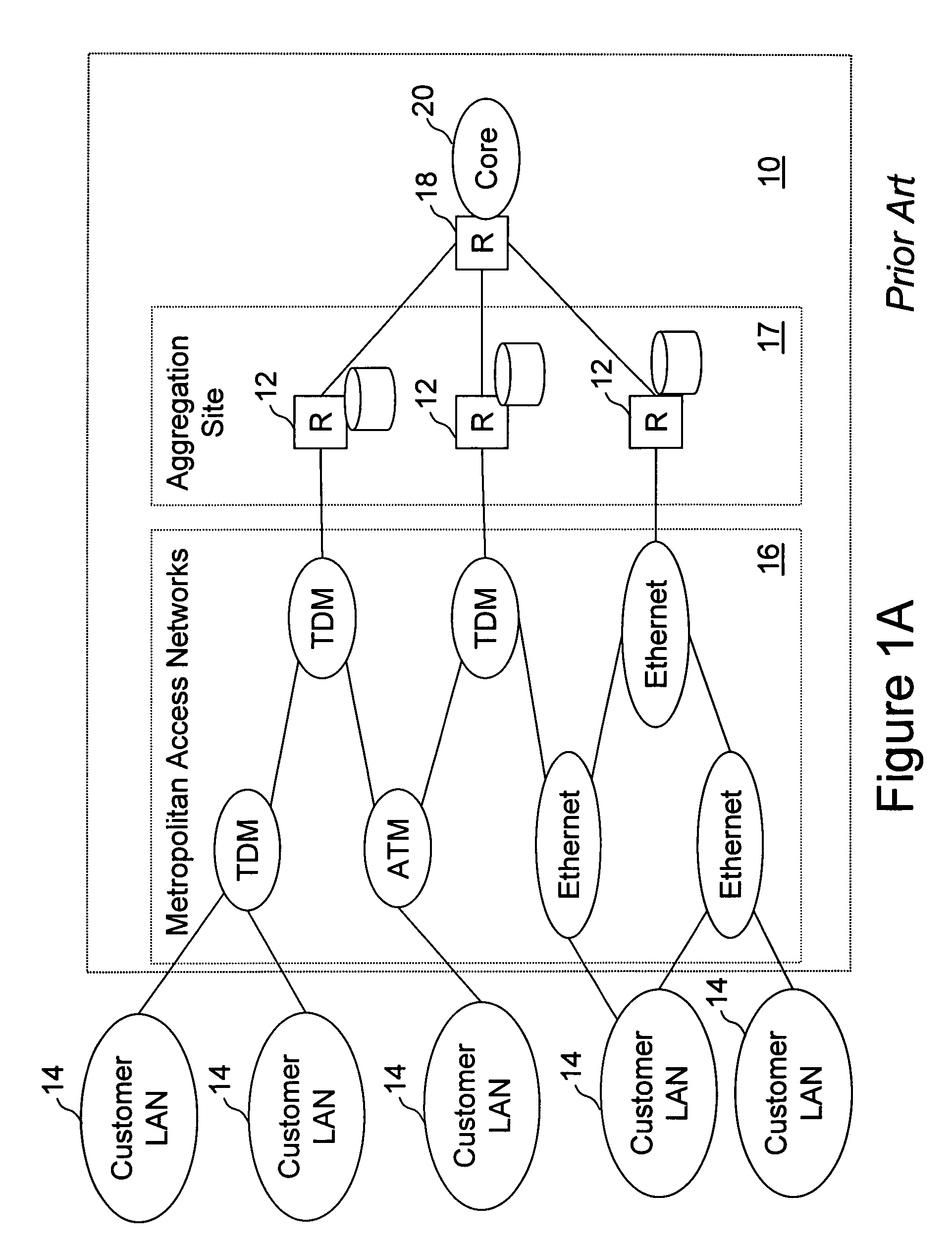
Networking hardware, also known as network equipment or computer networking devices, are electronic devices which are required for communication and interaction between devices on a computer network. Specifically, they mediate data transmission in a computer network. Units which are the last receiver or generate data are called hosts or data terminal equipment.
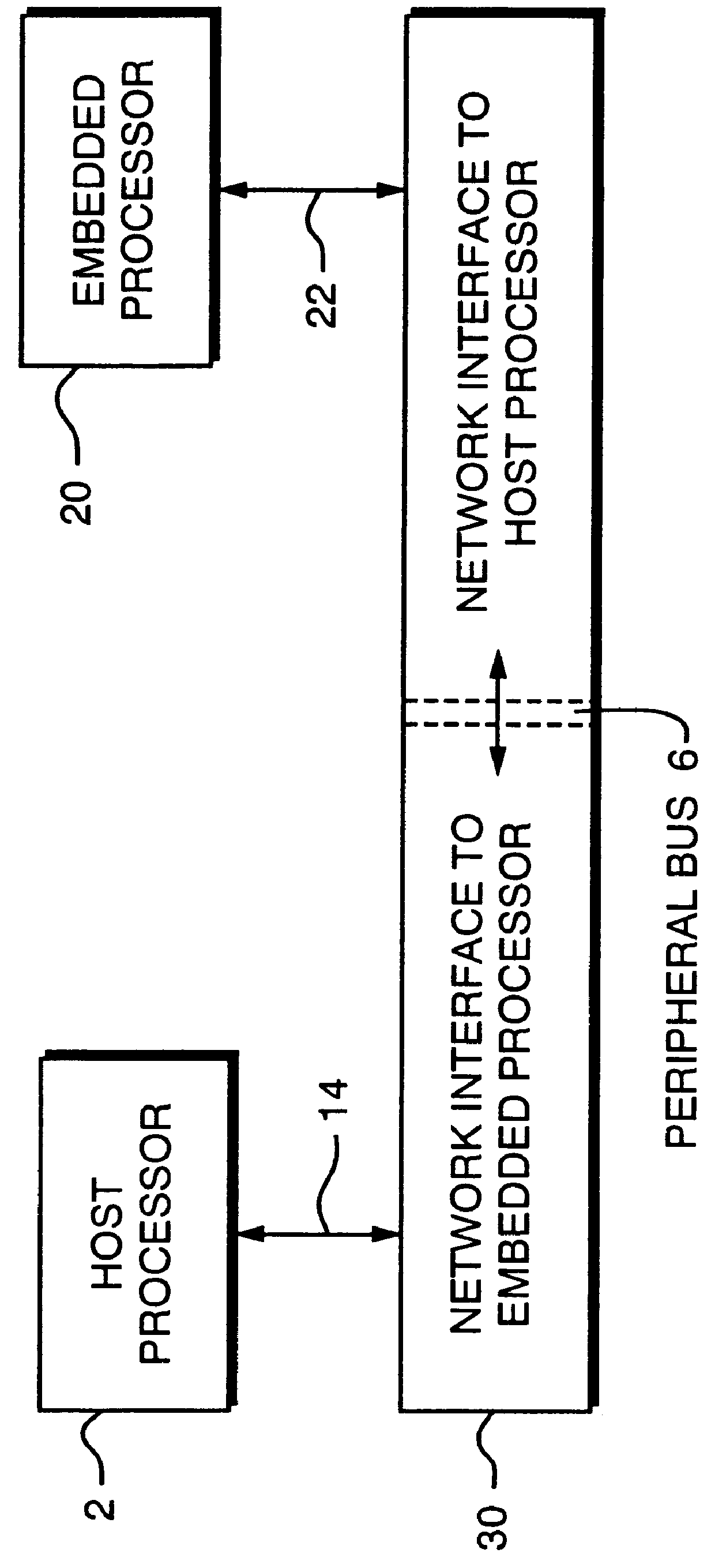
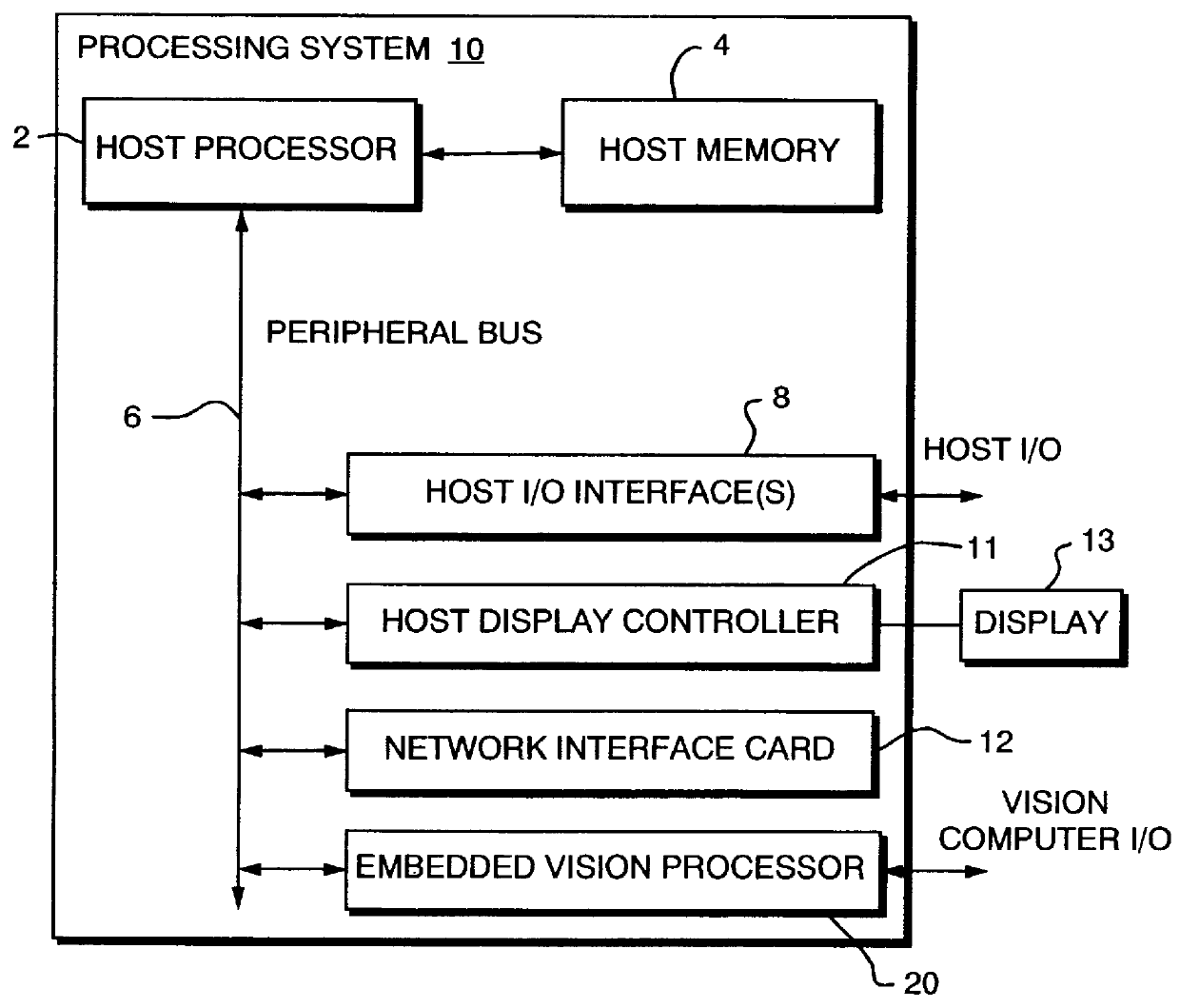
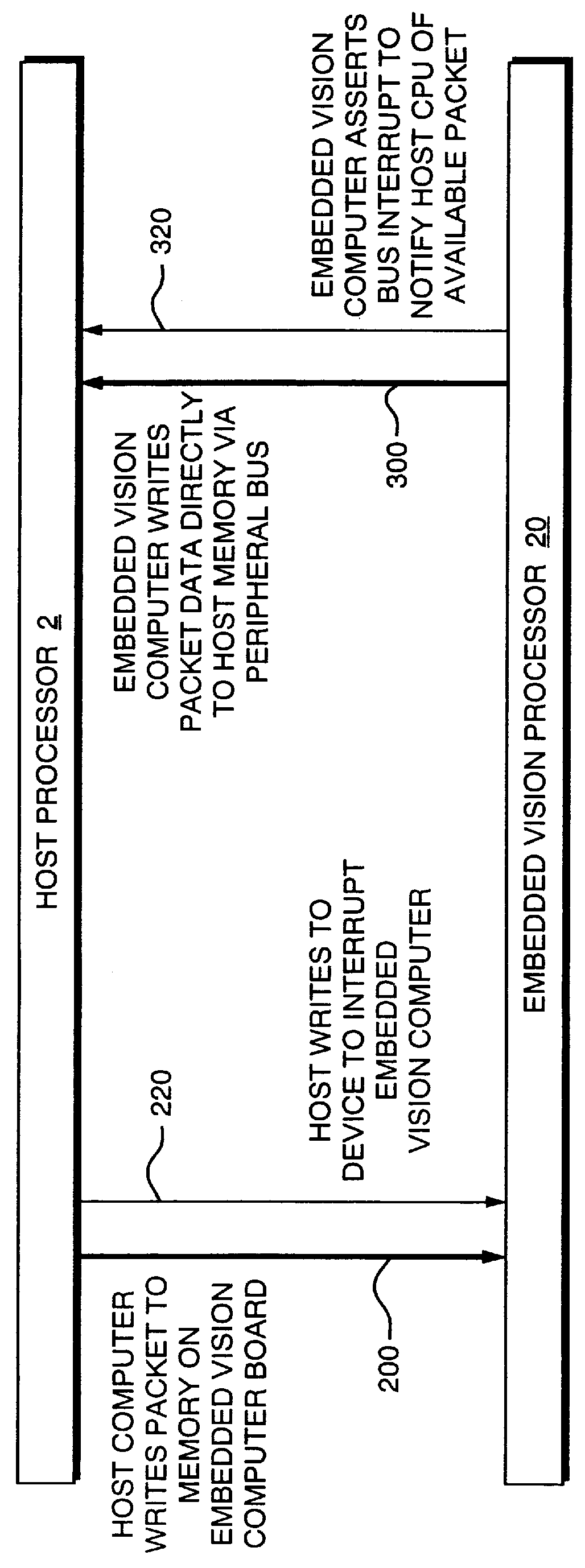
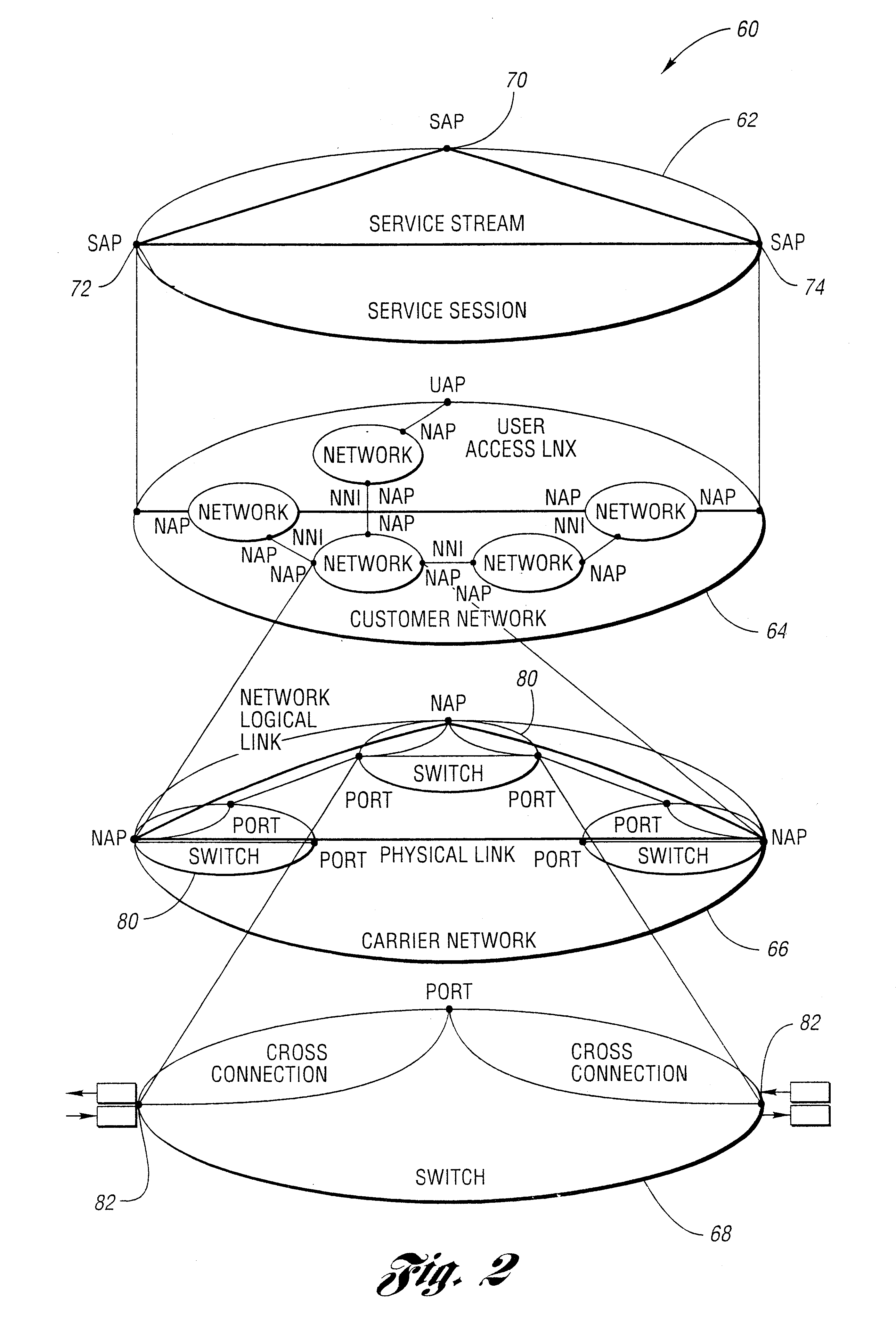
Apparent network interface for and between embedded and host processors
InactiveUS6058434ASignificant comprehensive benefitsMultiple digital computer combinationsElectric digital data processingPerformance enhancementWeb service
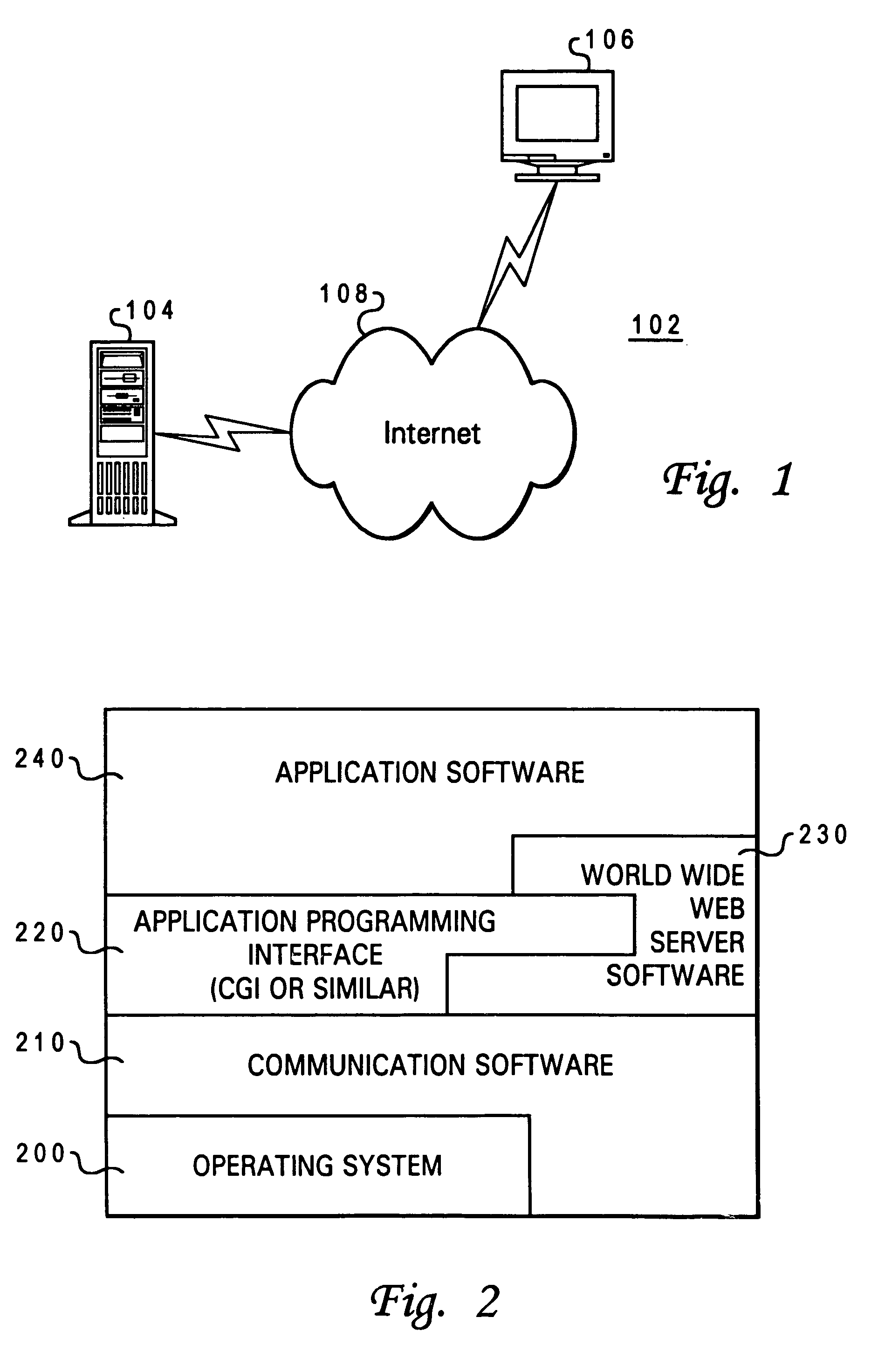
An apparent network interface permits one processor such as a processor embedded within a larger processing system (an embedded processor) to communicate to a host processor or other processors and devices on the network to which the embedded processor is attached, using standard network communication mechanisms / protocols such as TCP / IP, NFS, FTP, HTTP, etc. The web server protocol HTTP is particularly useful because it permits the embedded computer to publish a user interface for remote monitoring and remote control using a standard web browser application. The invention provides the host computer with an apparent network interface that appears to be a standard network device, such as an Ethernet interface card. This apparent interface communicates directly with the embedded processor, which appears to be a device on this apparent network. Significant cost savings and performance enhancements are realized by implementing the communication directly over the host computer's peripheral bus rather than using standard network hardware such as Ethernet hardware.
Owner:MICROSCAN SYSTEMS
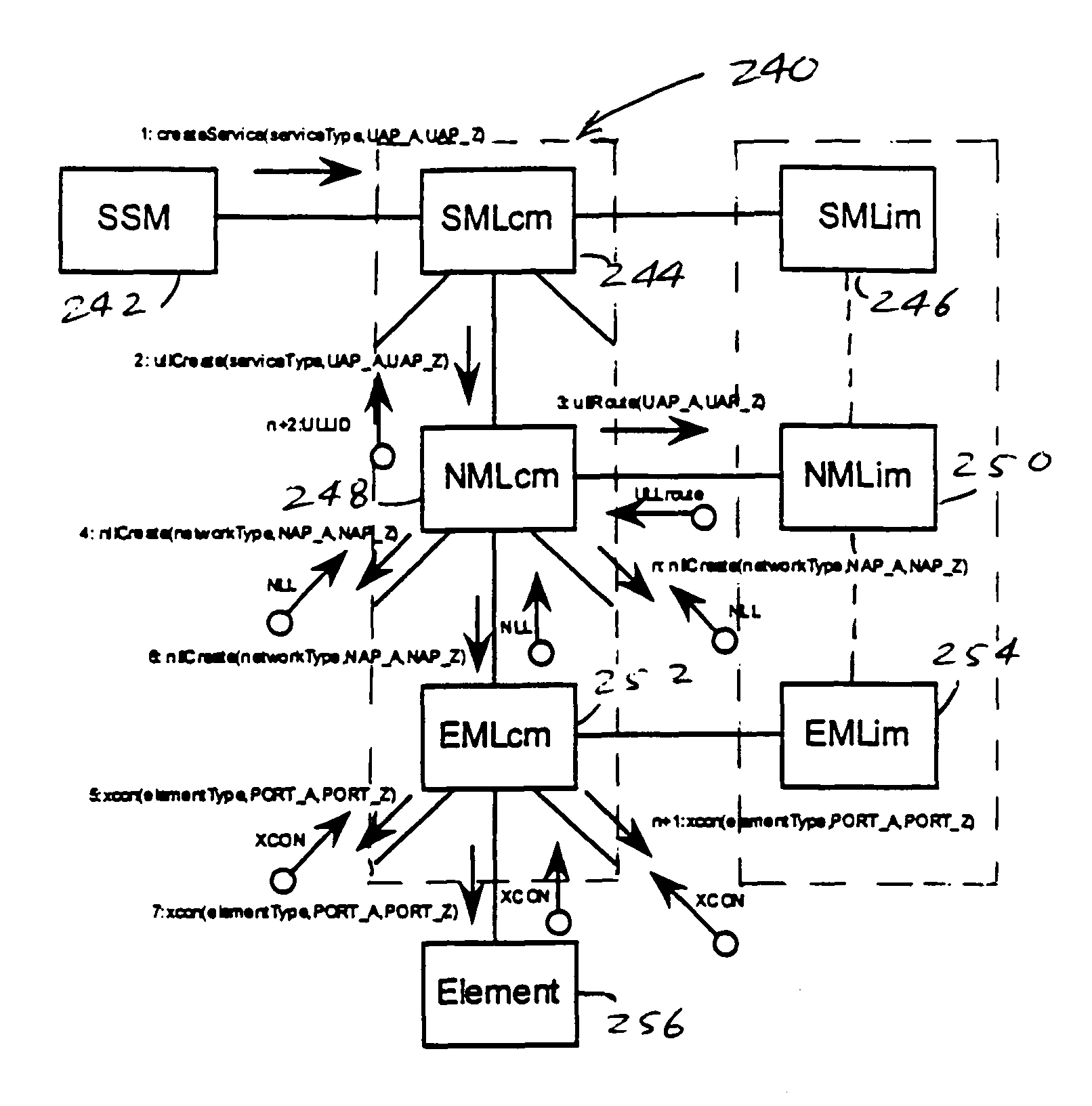
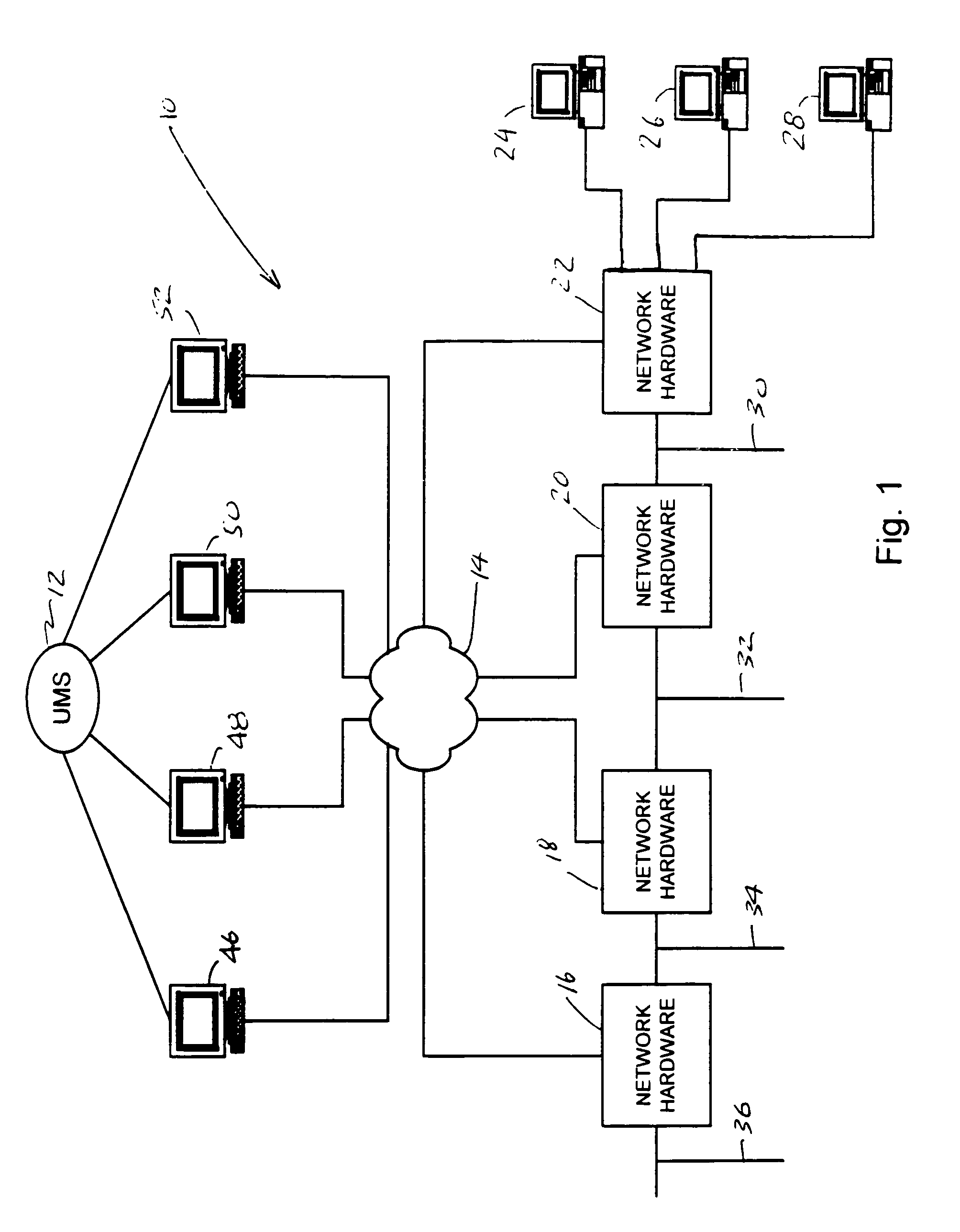
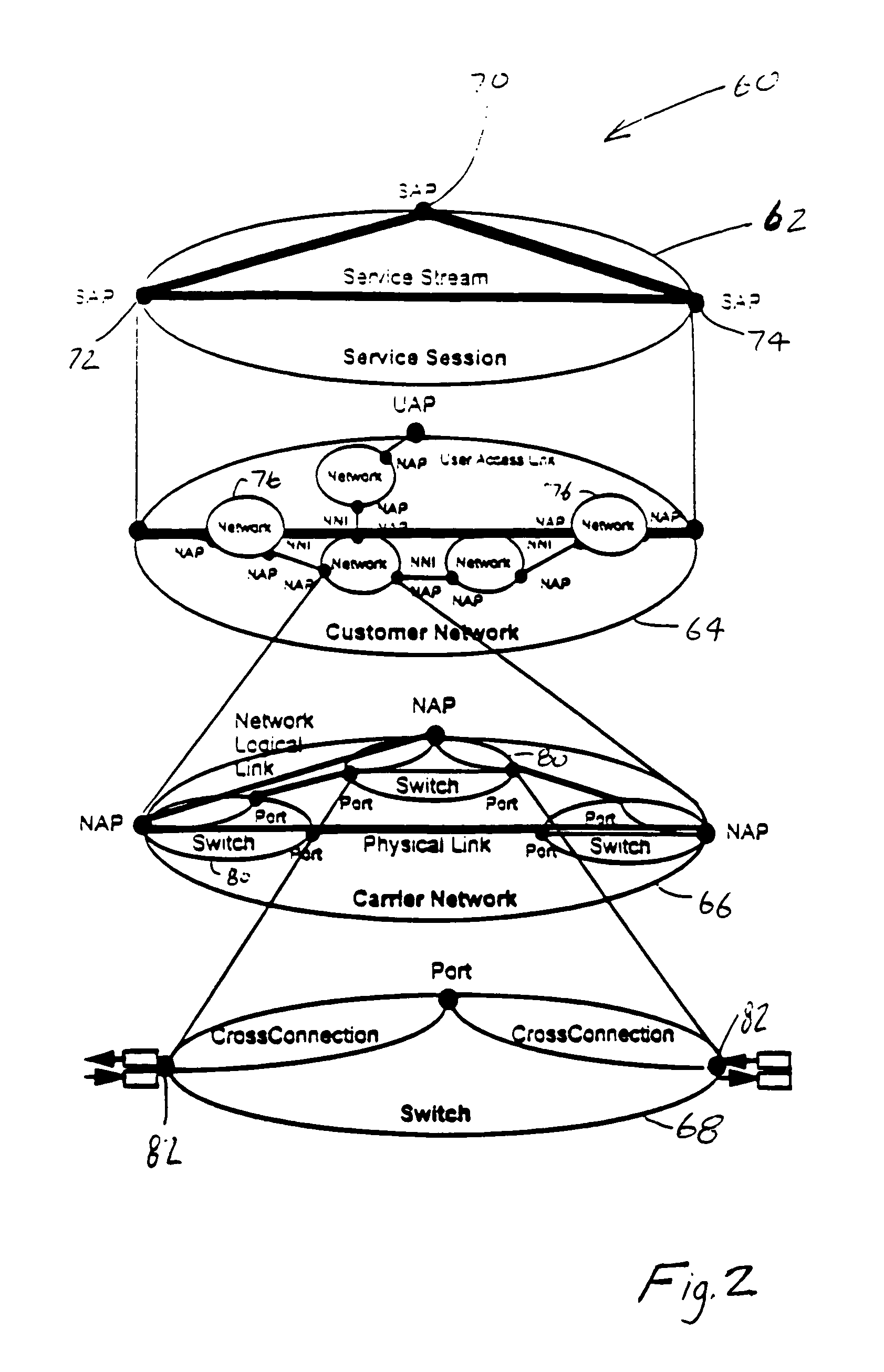
Network management system and graphical user interface
InactiveUS7966388B1Change is minimalError preventionTransmission systemsNetwork connectionNetworking hardware
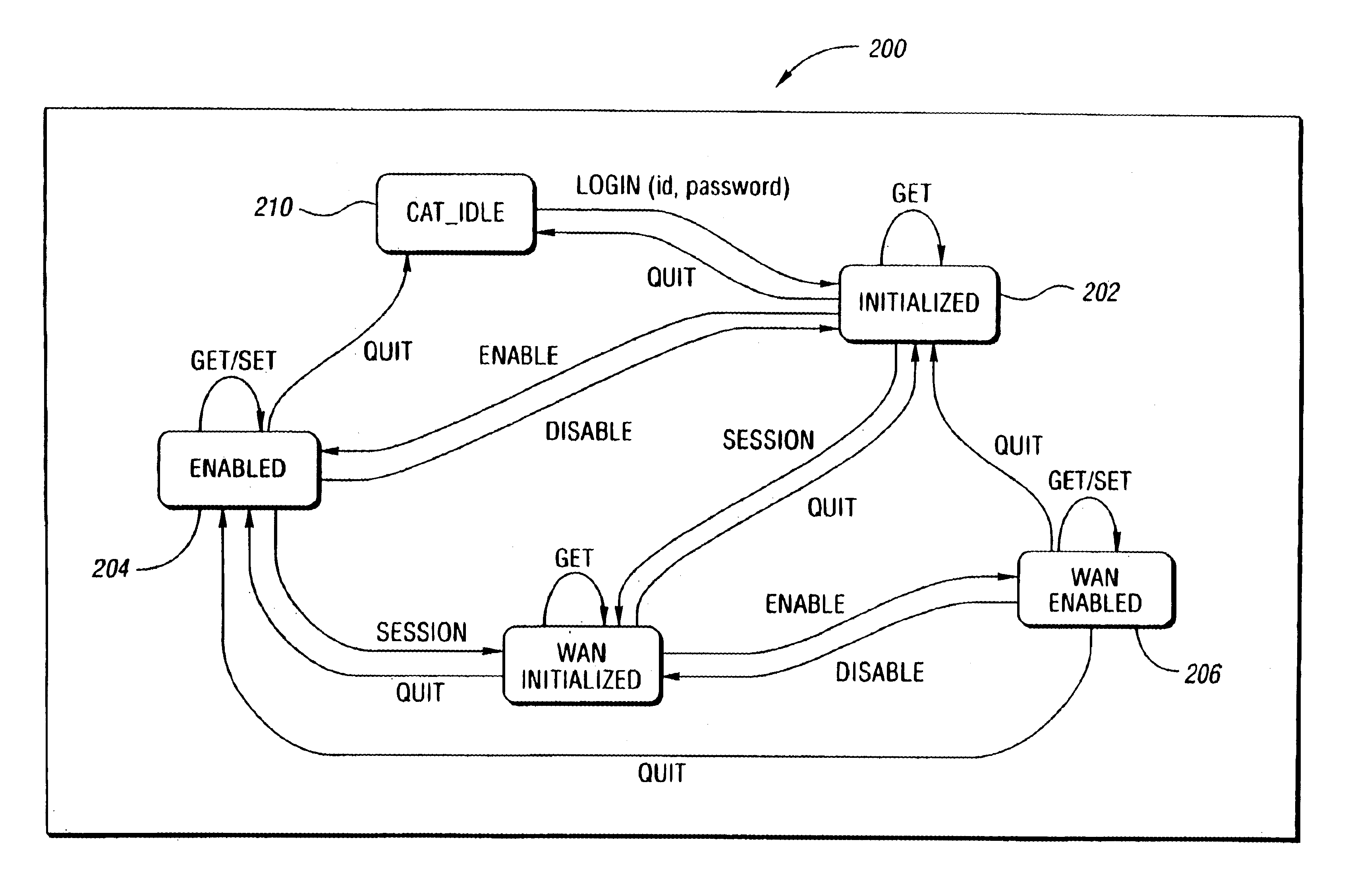
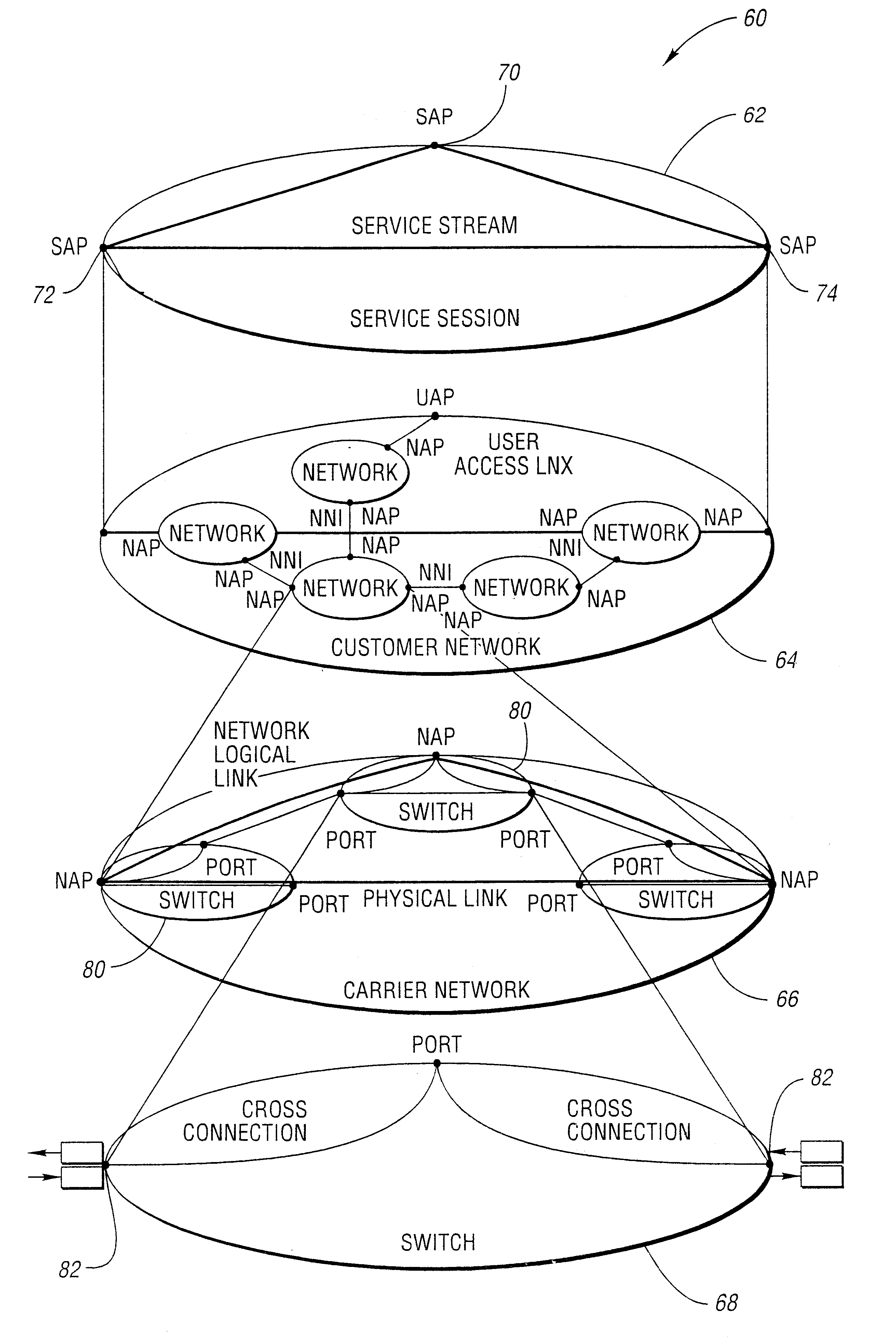
A network management system and graphical user interface for configuring a network connection between first and second service access points utilizes a configuration manager and information manager to provide a generic set of models so that different manufacturer's nodal processors and other network hardware can be inserted into the network with minimal changes to the software which controls the device. The system comprises an information manager including routing information for the network. The configuration manager operates to establish a connection across each subnet on the route by sending requests to element managers to program the subnet elements.
Owner:QWEST
Network virtualization
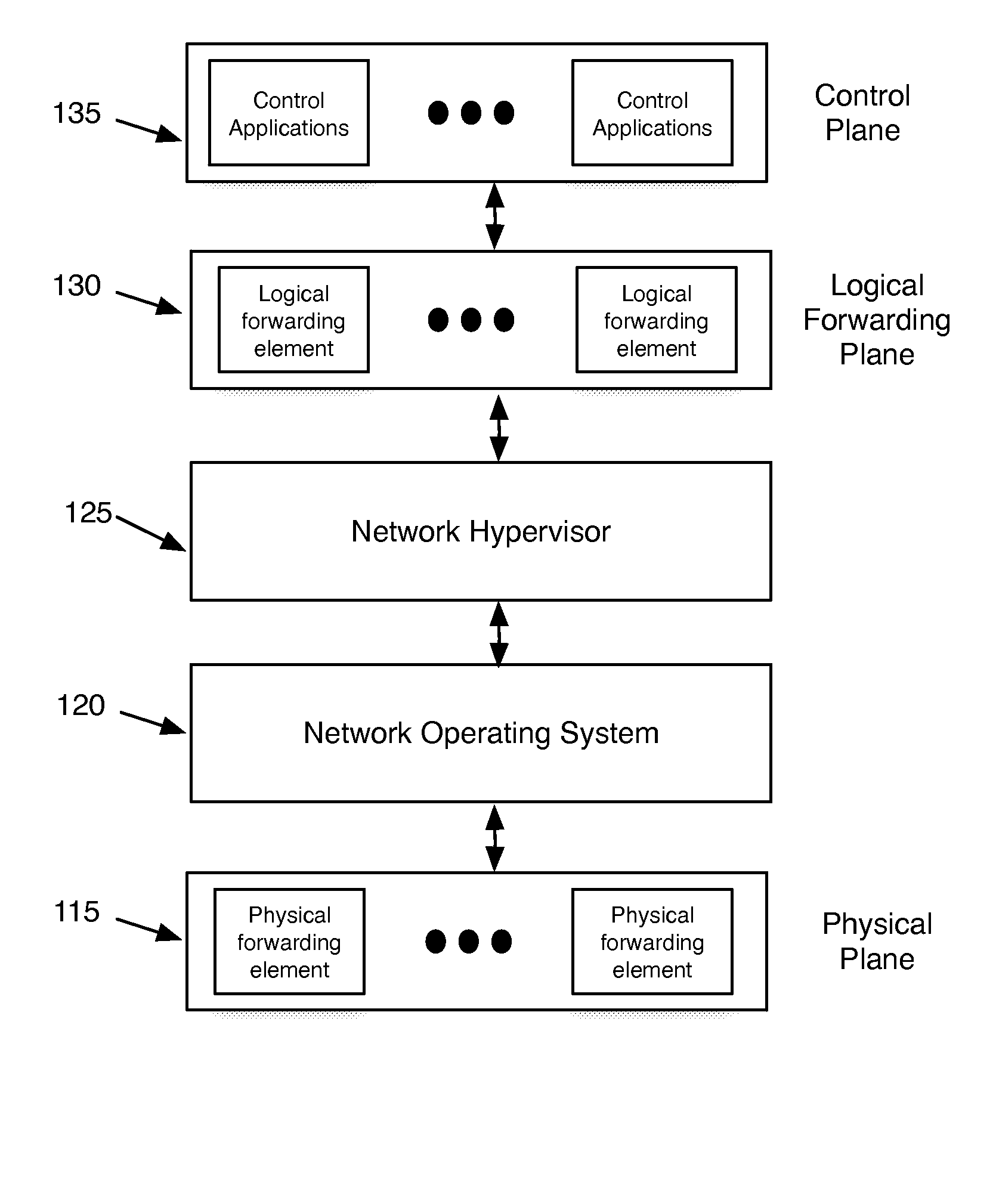
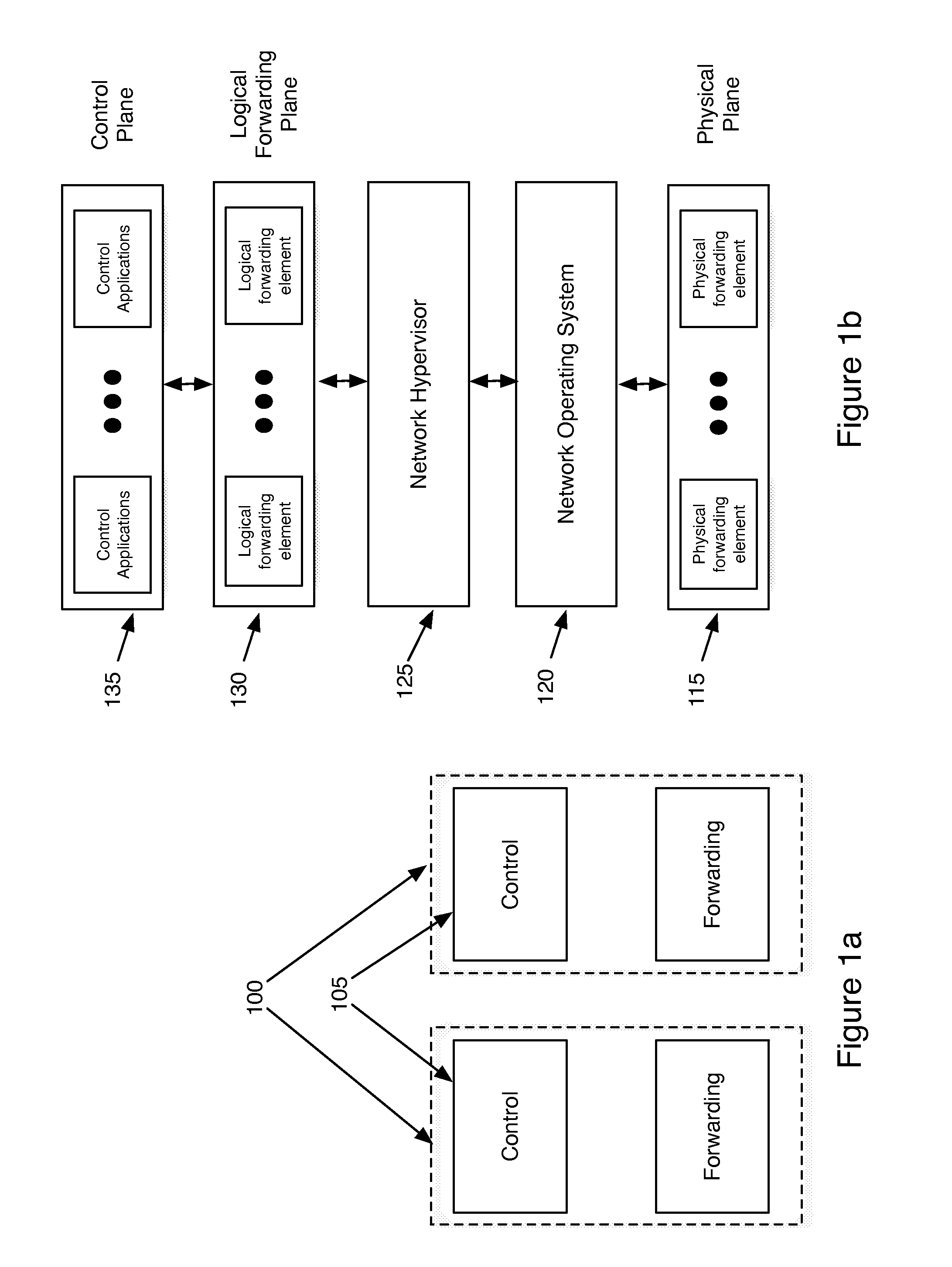
ActiveUS20130060940A1Fault responseMultiple digital computer combinationsCyber operationsNetworking hardware
Some embodiments of the invention provide a robust scaling-out of network functionality by providing a software layer, called the network hypervisor, that sits between the network forwarding functions (i.e., the forwarding plane) and the network control interfaces (i.e., the control plane). The network hypervisor of some embodiments provides a logical abstraction of the network's forwarding functionality, so that network operators make their control decisions in terms of this abstraction, independent of the details of the underlying networking hardware. The network hypervisor of some embodiments may then “compile” commands placed against this abstraction into configurations of the underlying hardware. Accordingly, in some embodiments, there are two design challenges: (1) the choice of the network abstraction, and (2) the technology needed to compile the logical “abstract” controls into low-level configurations.
Owner:NICIRA
System and method for highly scalable high-speed content-based filtering and load balancing in interconnected fabrics
InactiveUS7346702B2Digital computer detailsMultiprogramming arrangementsTraffic capacityNetworking hardware
In some embodiments of the present invention, a system includes one or more server computers having multi-channel reliable network hardware and a proxy. The proxy is able to receive packet-oriented traffic from a client computer, to convert a session of the packet-oriented traffic into transactions, and to send the transactions to one of the server computers. The transactions include remote direct memory access messages.
Owner:MELLANOX TECH TLV
Methods and apparatus for enabling bus connectivity over a data network
ActiveUS20060059287A1Facilitate communicationSelectively leverage operating system capabilitiesProgram synchronisationMemory addressAbstraction layer
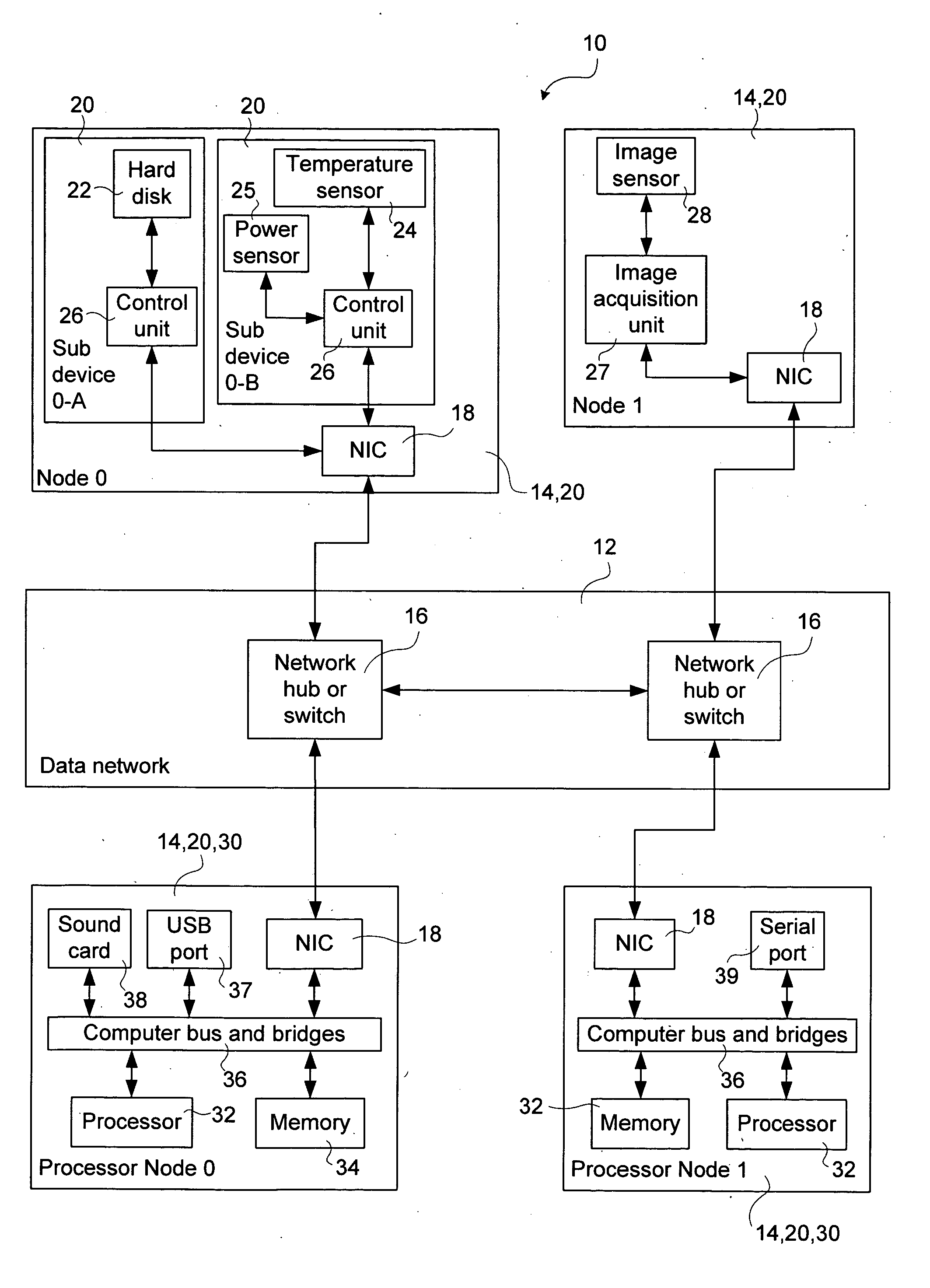
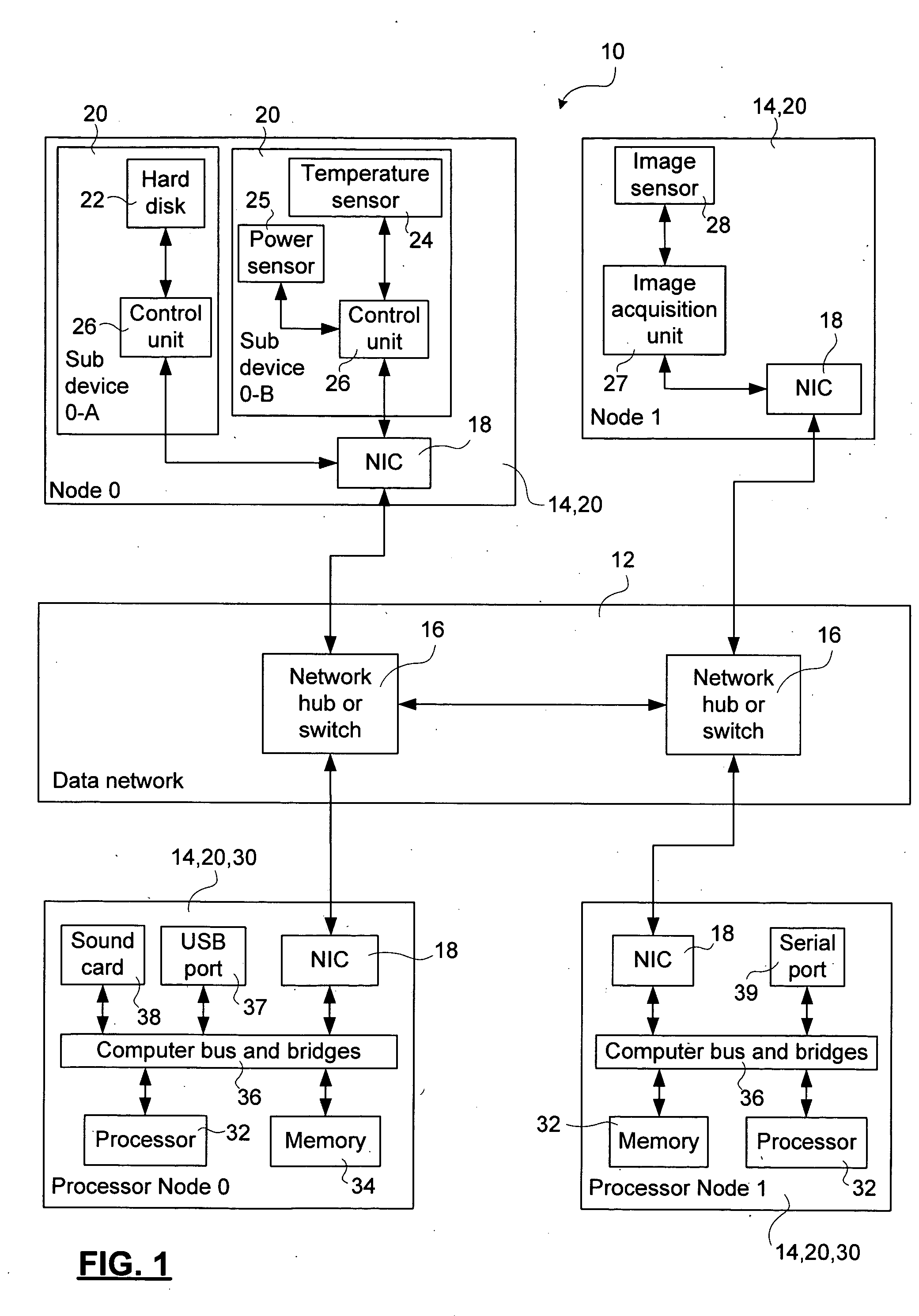
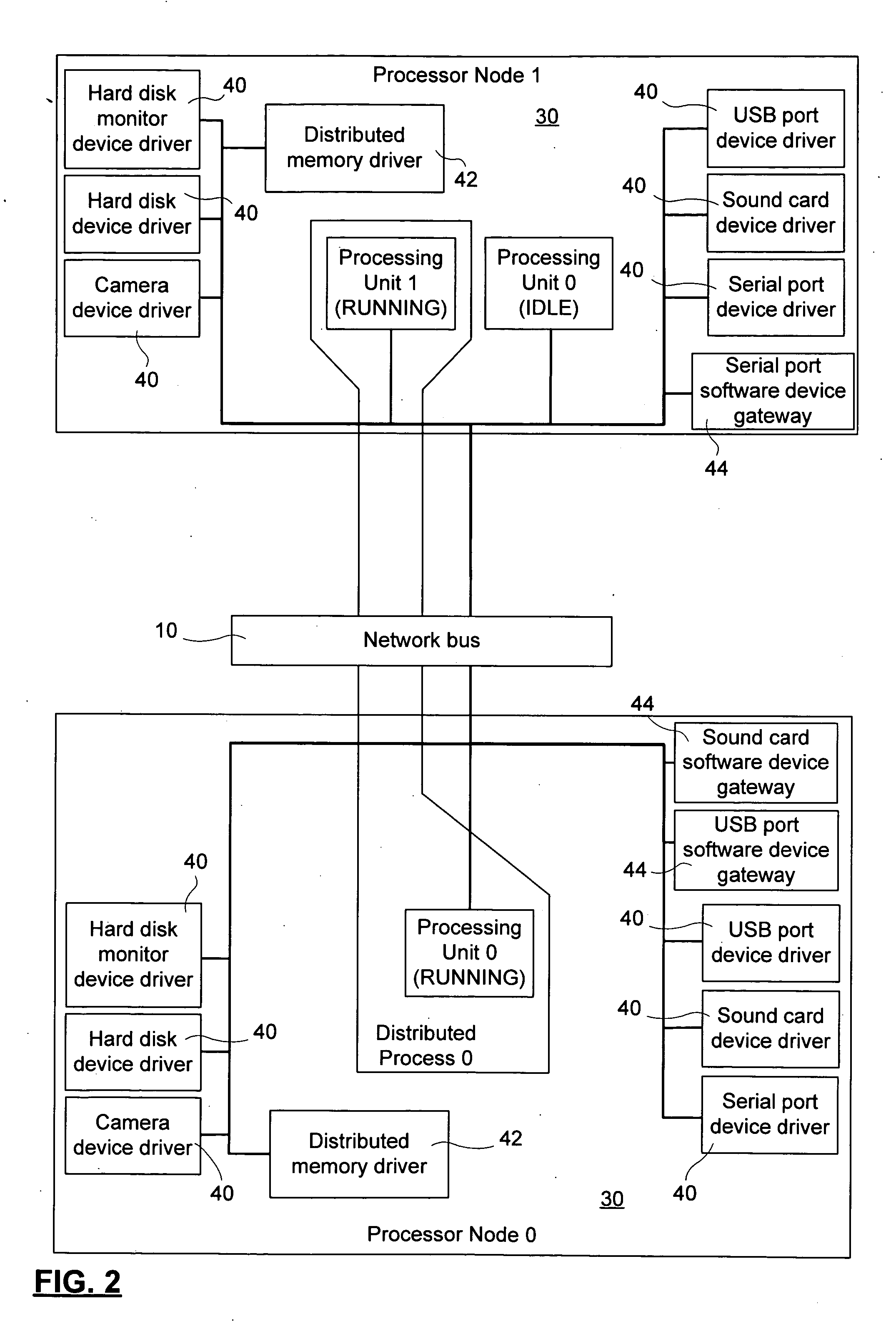
A method and system for interconnecting peripherals, processor nodes, and hardware devices to a data network to produce a network bus providing OS functionality for managing hardware devices connected to the network bus involves defining a network bus driver at each of the processor nodes that couples hardware device drivers to a network hardware abstraction layer of the processor node. The network bus can be constructed to account for the hot-swappable nature of the hardware devices using a device monitoring function, and plug and play functionality for adding and, removing device driver instances. The network bus can be used to provide a distributed processing system by defining a shared memory space at each processor node. Distributed memory pages are provided with bus-network-wide unique memory addresses, and a distributed memory manager is added to ensure consistency of the distributed memory pages, and to provide a library of functions for user mode applications.
Owner:PLEORA TECH
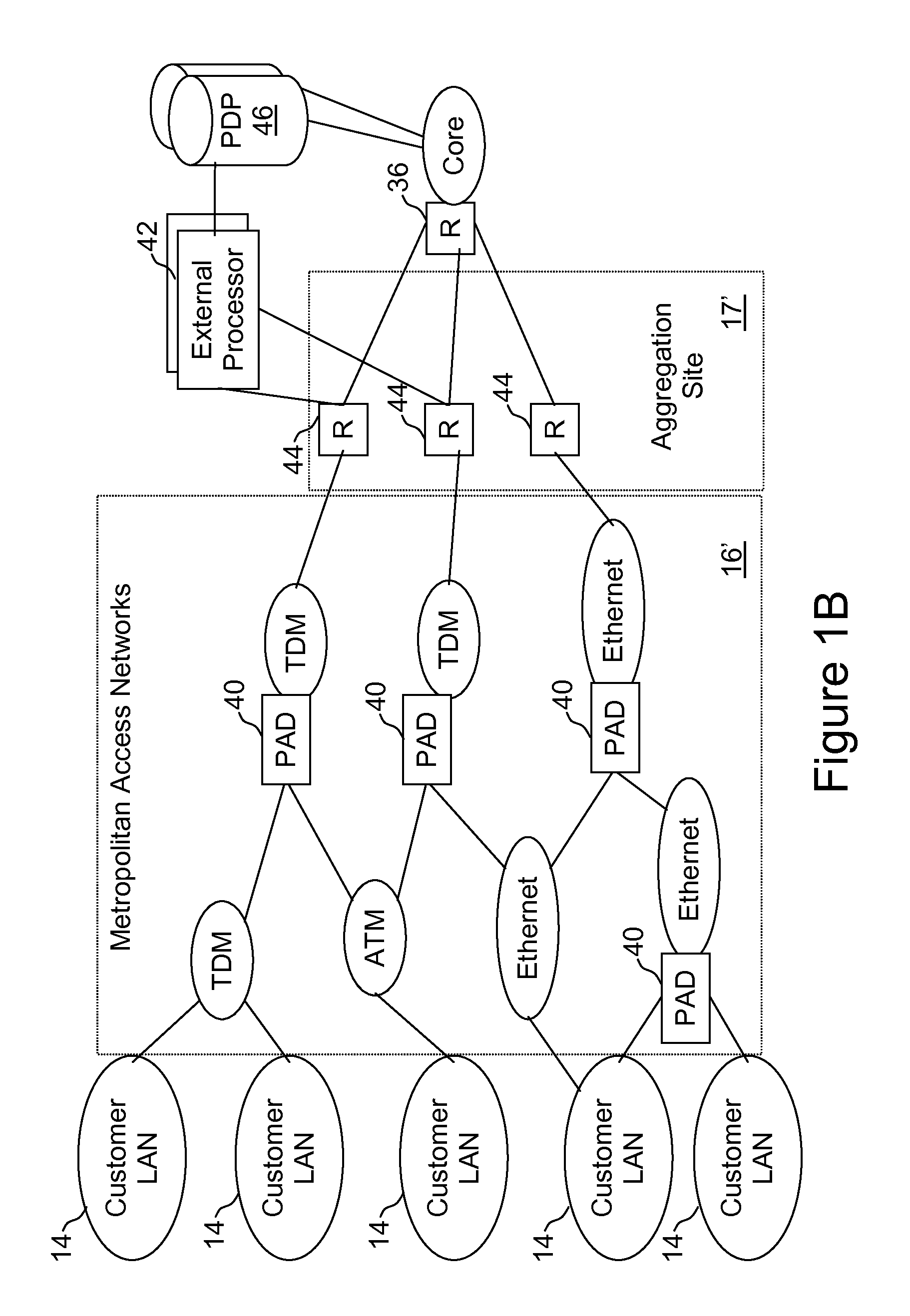
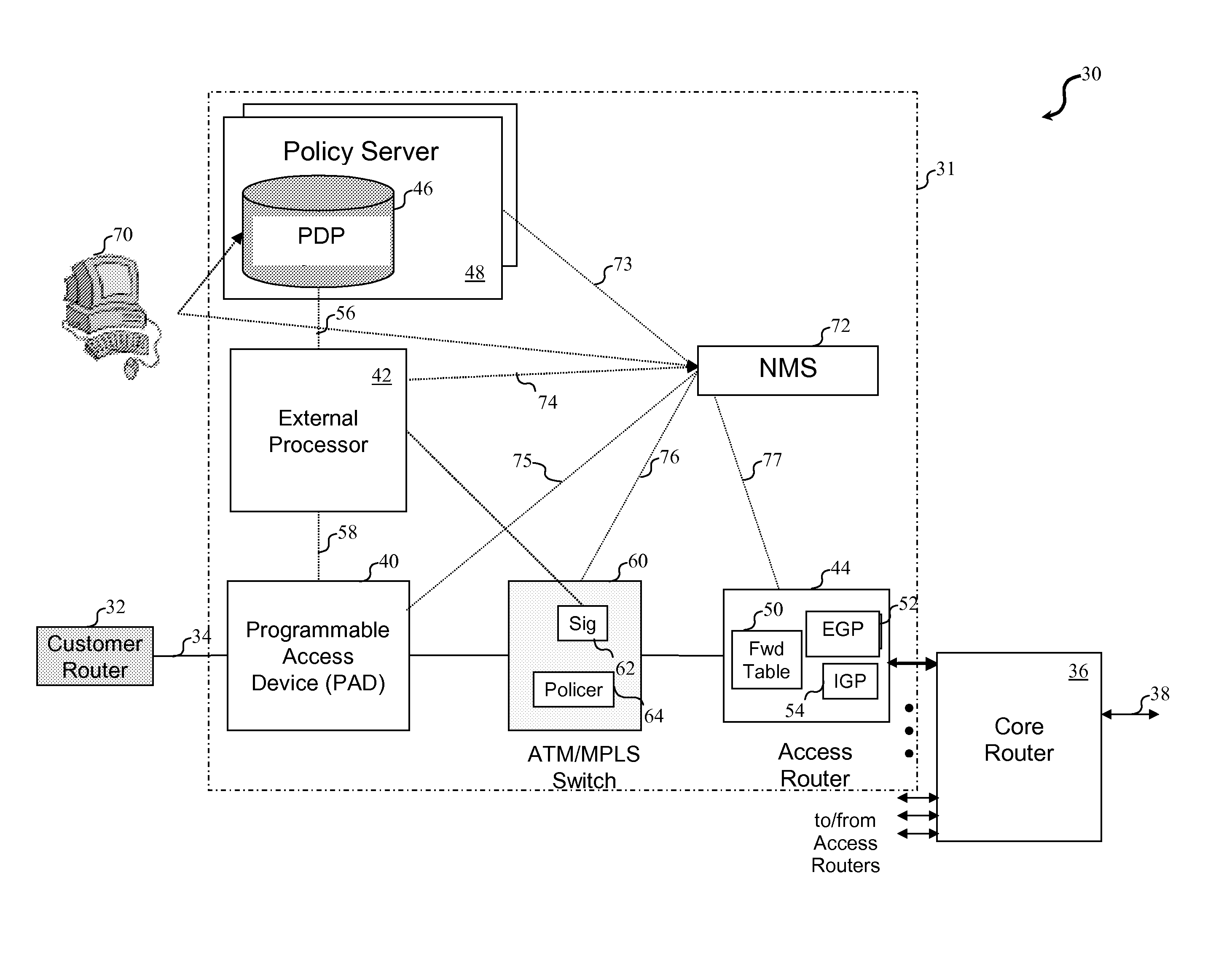
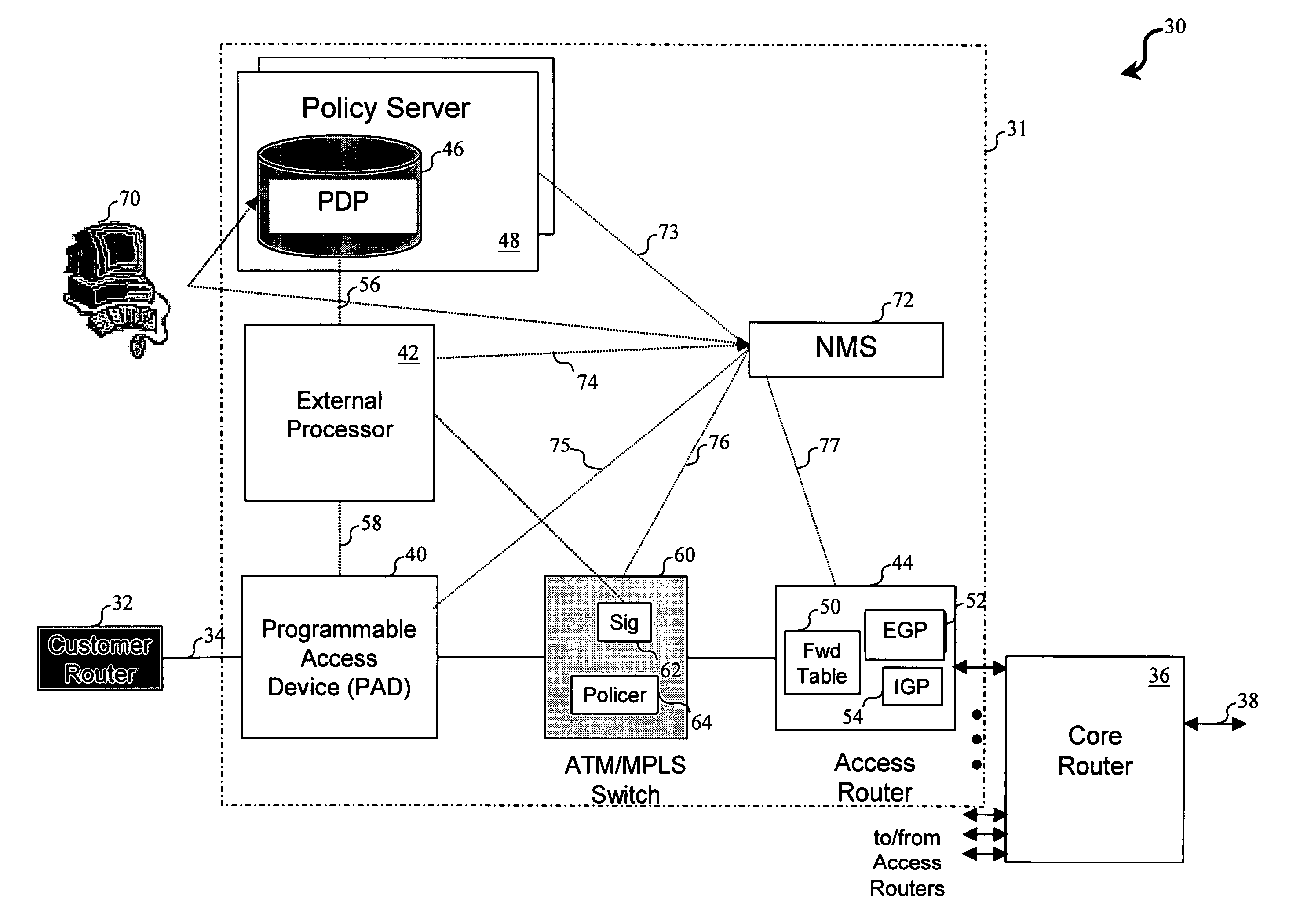
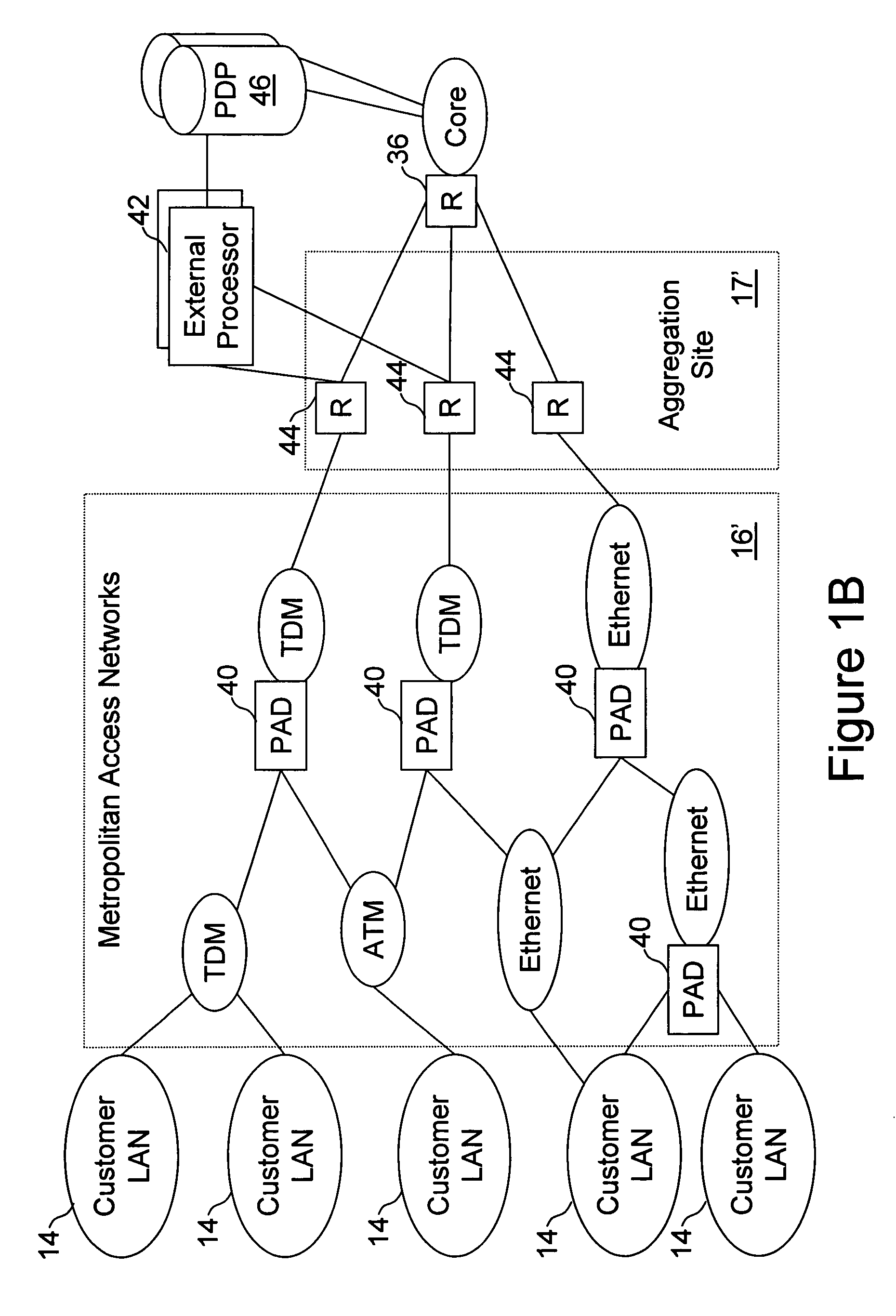
External processor for a distributed network access system
InactiveUS20100211678A1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationTraffic capacityPolicy decision
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
External processor for a distributed network access system
InactiveUS20110270956A1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationPolicy decisionTraffic capacity
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
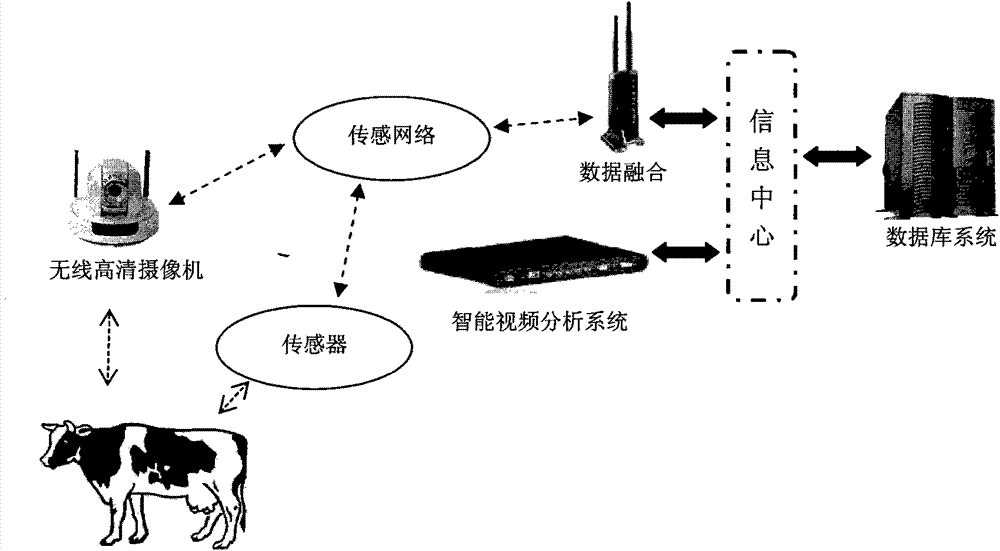
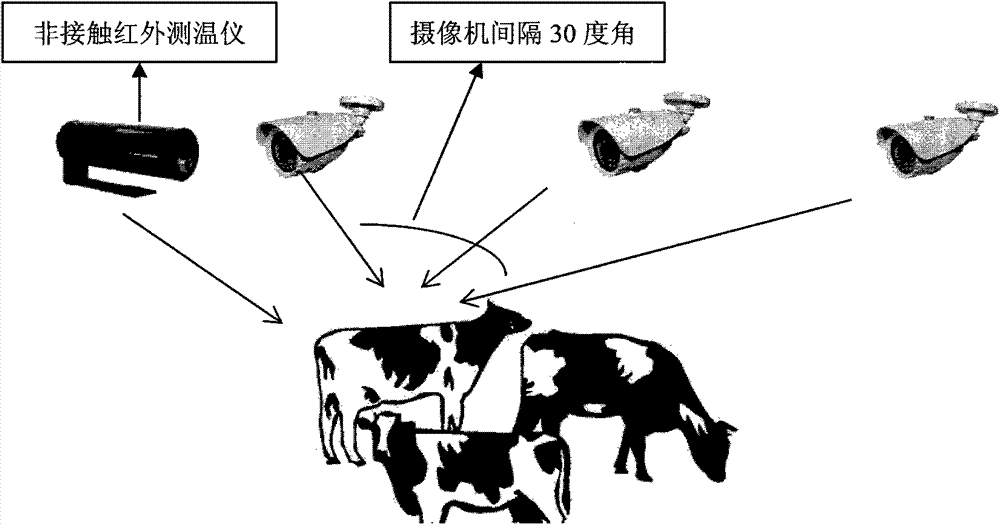
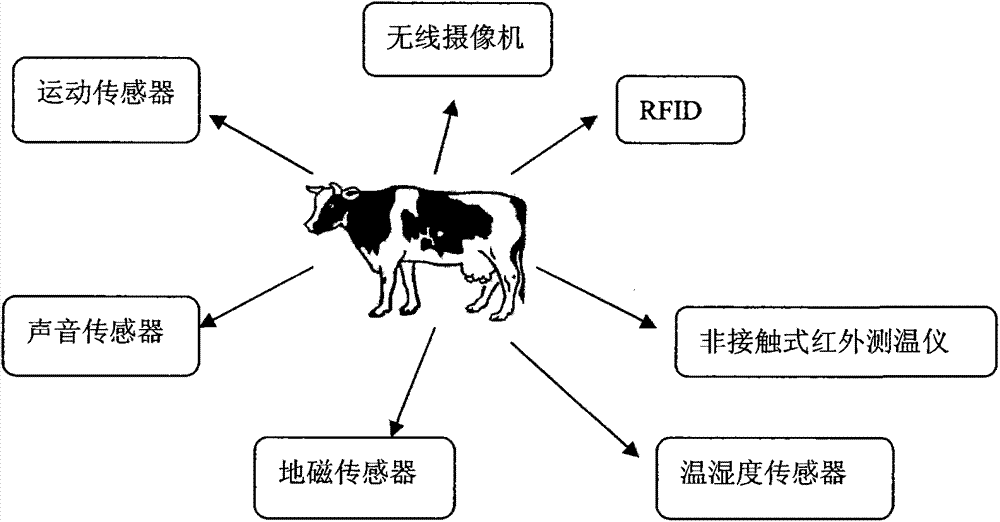
Intelligent livestock behavior monitoring system based on internet of things and computer vision
InactiveCN103488148AMeasurement devicesProgramme total factory controlVideo monitoringSoftware system
The invention discloses an intelligent livestock behavior monitoring system. According to the system, the aim that monitoring and analysis are carried out on livestock behaviors on a real farming scene by fusing the internet of things and the computer vision technology is achieved for the first time, a video monitoring and sensor network hardware and software system based on the WiFi technology is constructed for the first time, the problems that a traditional cable is high in installation cost, long in consumed time and hard to expand are solved, the monitoring and analysis on the behaviors of dairy cows on the real farming scene is achieved by fusing the internet of things and the computer vision technology, and the monitoring and analysis on several kinds of daily behaviors, such as ingestion, drinking, rumination, excretion, exercise, rest and exploration are achieved. Meanwhile, occurrences of abnormal events are monitored, and the alarm is automatically given on the abnormal behaviors.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
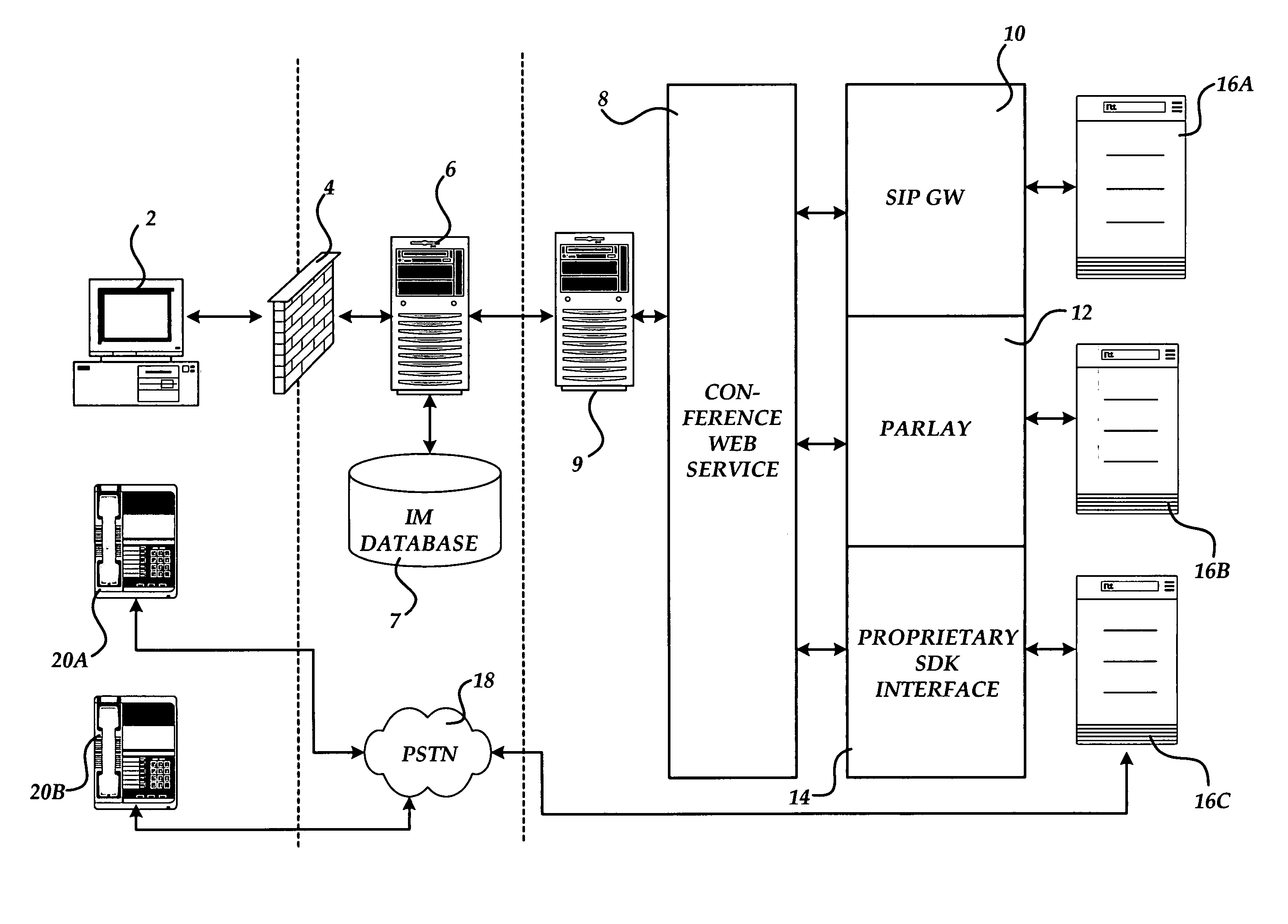
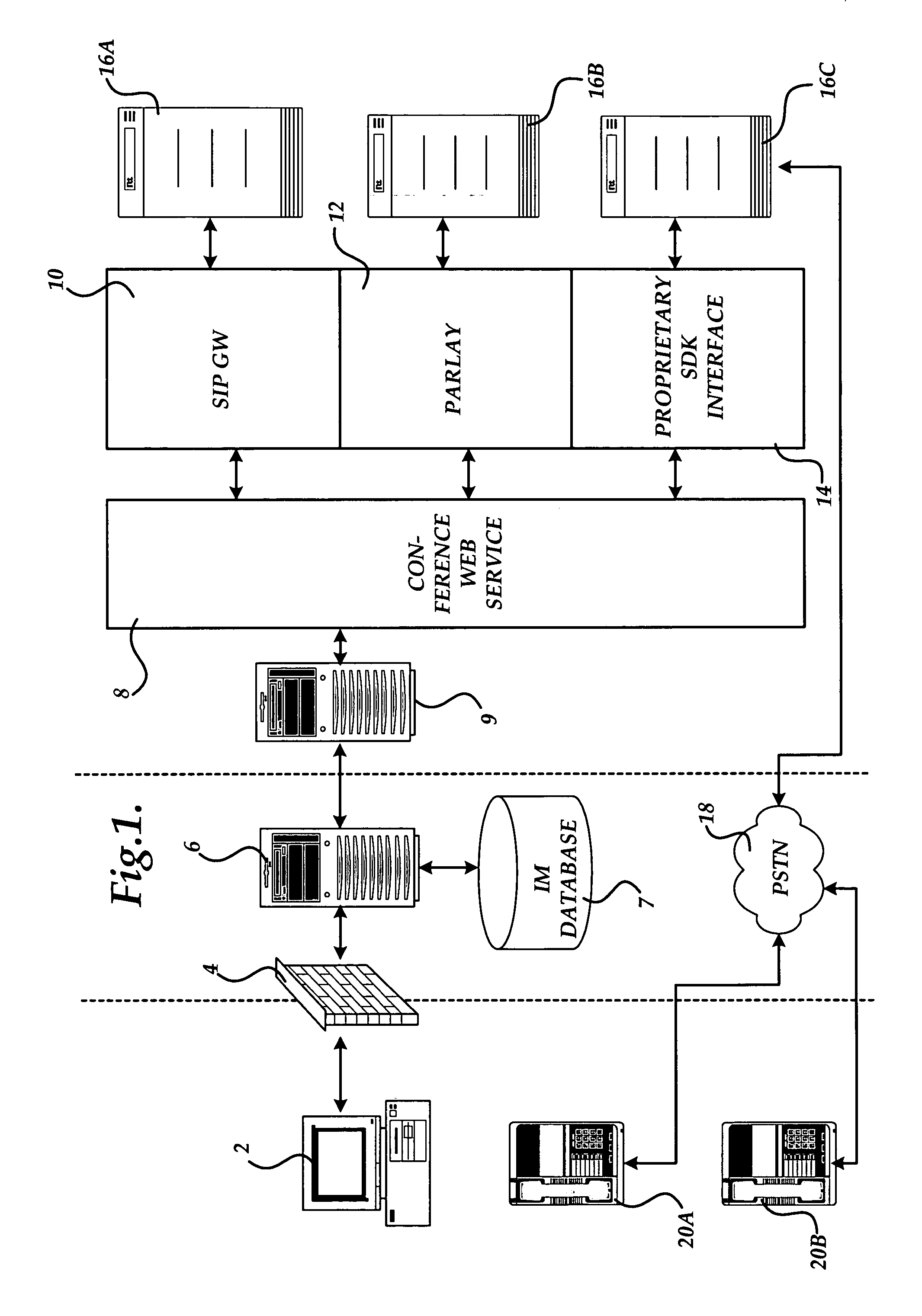
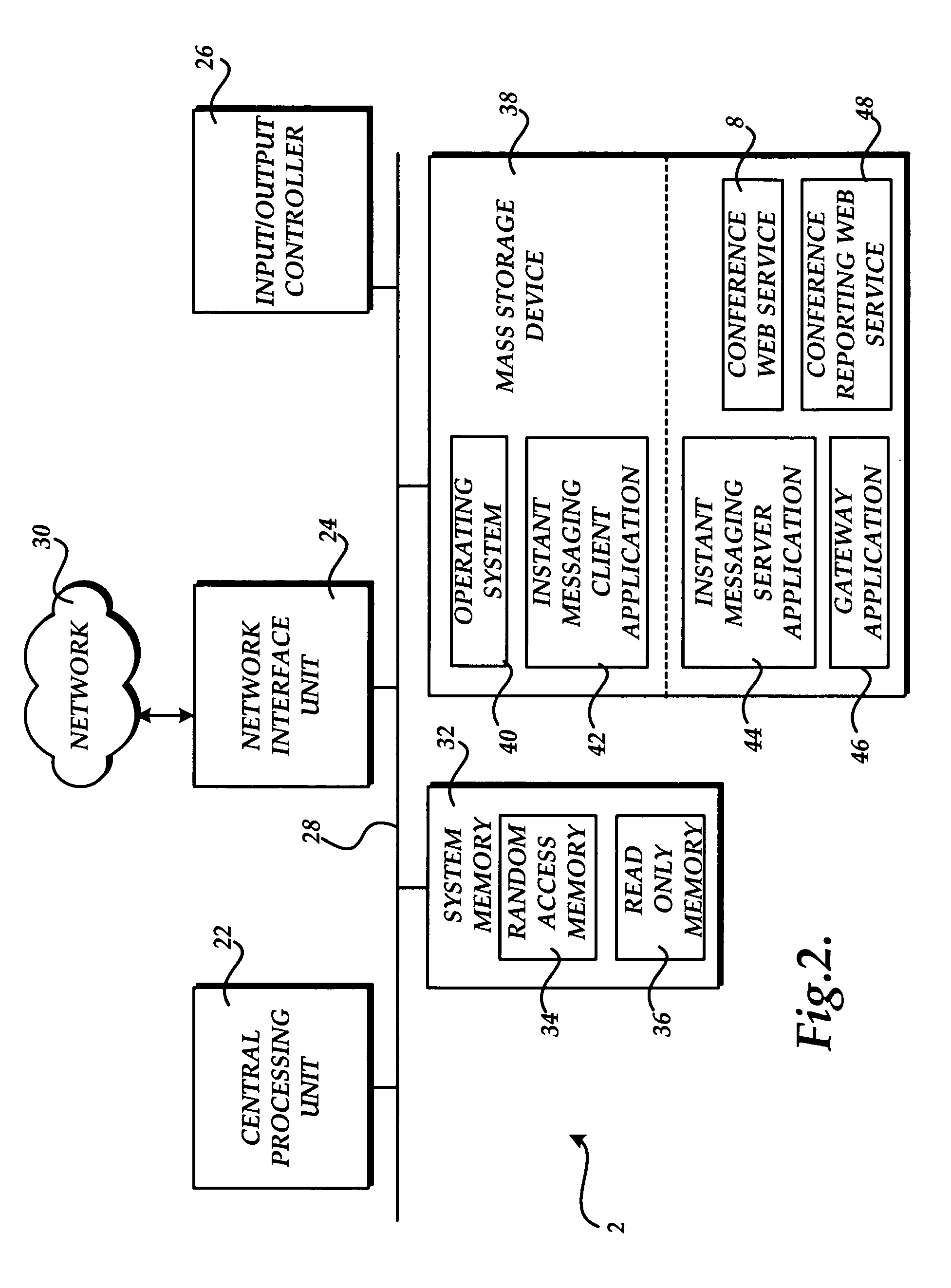
Method and system for providing an improved communications channel for telephone conference initiation and management
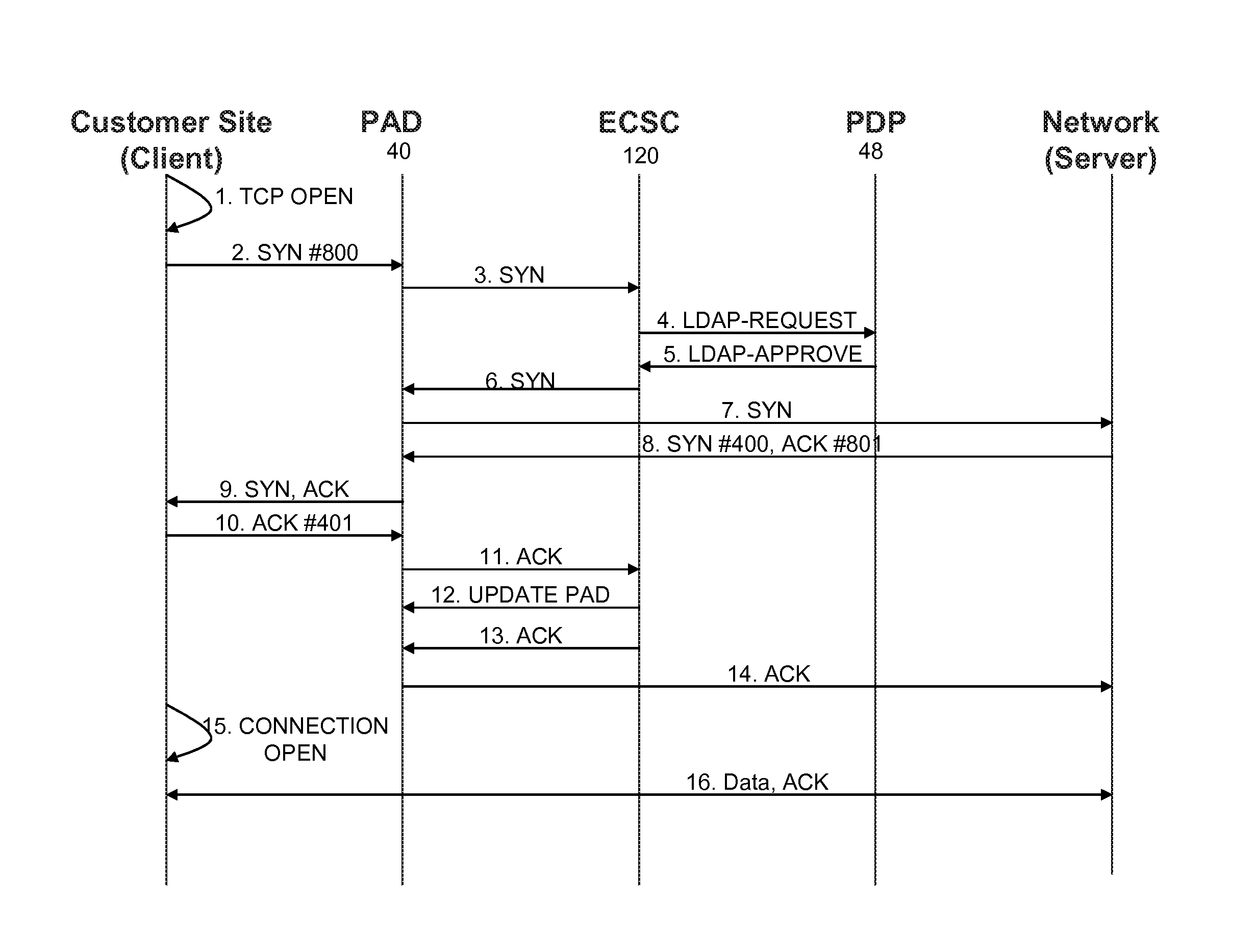
ActiveUS20050213724A1Facilitate communicationMultiplex system selection arrangementsInterconnection arrangementsWeb serviceNetworking hardware
Methods and systems for providing an improved communications channel for telephone conference initiation and management are provided. Messages for initiating and managing a telephone conference are exchanged between a client computer and a gateway computer utilizing XML formatted messages transmitted over an instant messaging compatible protocol. The gateway computer converts the messages to web services requests and communicates with telephone conference network hardware utilizing the web services-based request. Status indicators from the telephone conference equipment is converted from web services requests to XML by the gateway and transmitted back to the client computer via the instant messaging protocol.
Owner:MICROSOFT TECH LICENSING LLC
External processor for a distributed network access system
ActiveUS7657628B1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationTraffic capacityPolicy decision
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
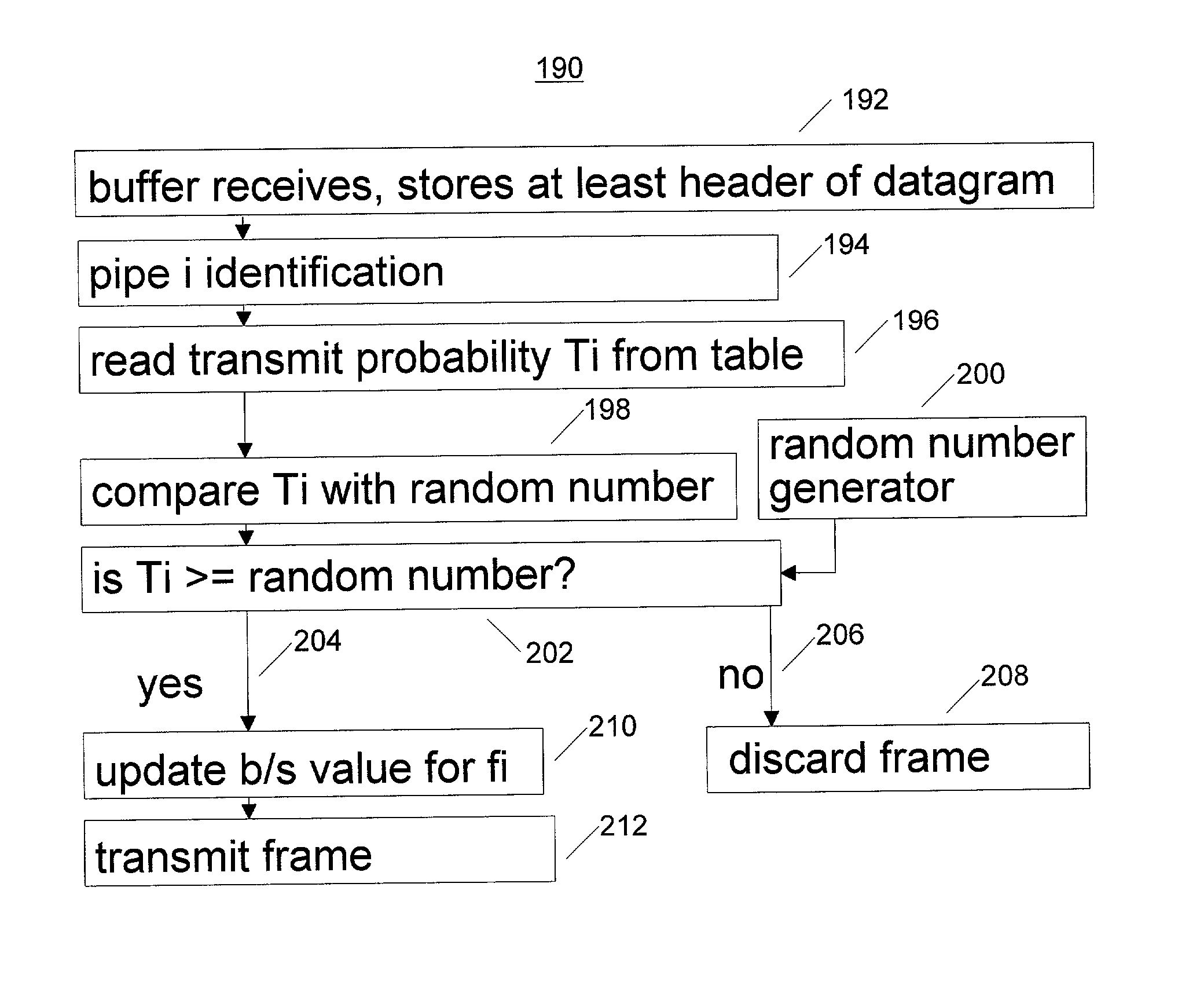
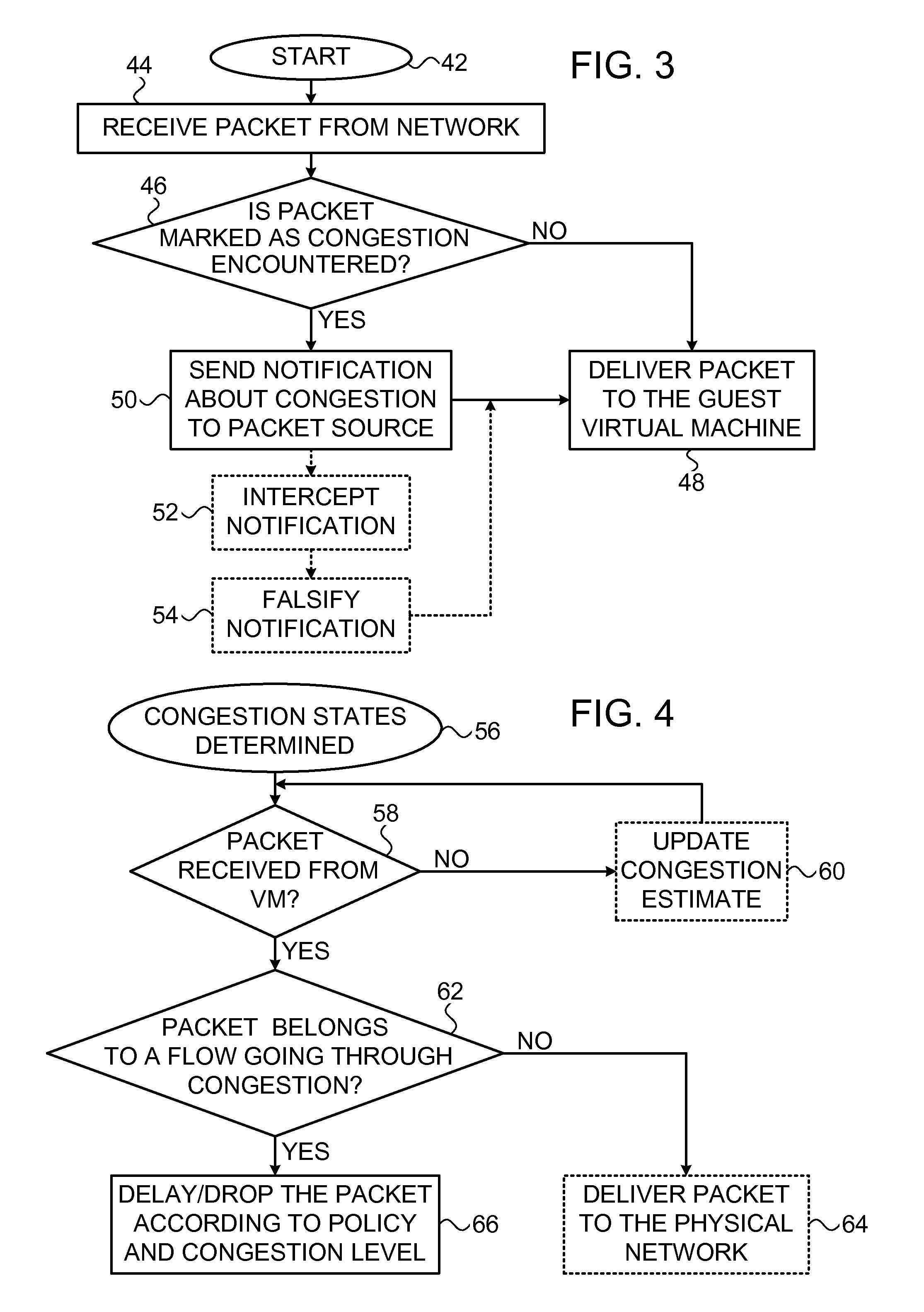
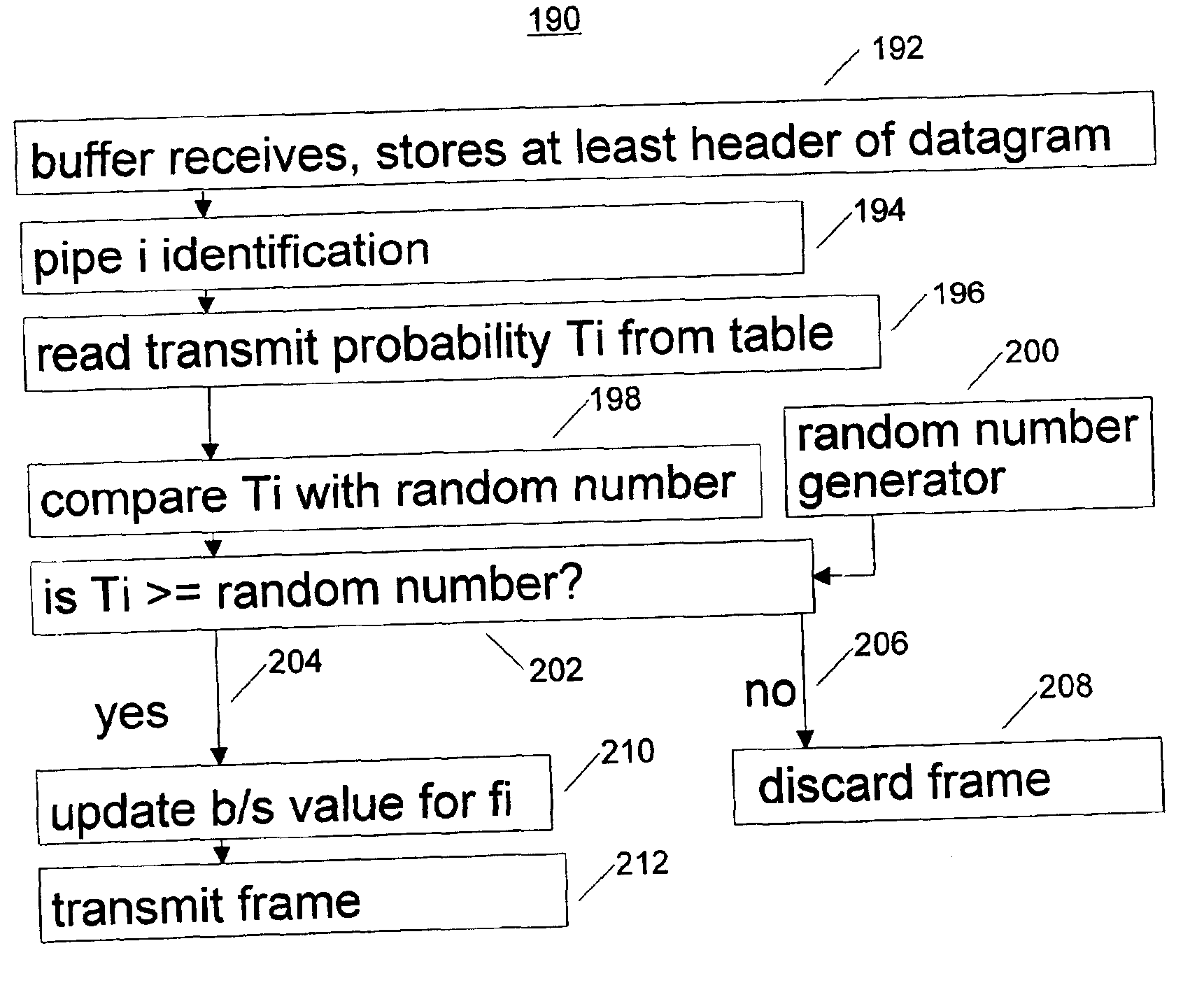
Quality of service functions implemented in input interface circuit interface devices in computer network hardware
The decision to discard or forward a packet is made by a flow control mechanism, upstream from the forwarding engine in the node of a communication network. The forwarding engine includes a switch with mechanism to detect congestion in the switch and return a binary signal B indicating congestion or no congestion. The flow control mechanism uses B and other network related information to generate a probability transmission table against which received packets are tested to determine proactively whether a packet is to be discarded or forwarded.
Owner:IBM CORP
Bandwidth efficient wireless network modem
InactiveUS20090310619A1Easy to useEasy to processError prevention/detection by using return channelTime-division multiplexMulti user interferenceModem device
A modem that provides efficient use of wireless network bandwidth in the presence of multiuser interference and noise is disclosed. The modem design provides for compatibility with existing network hardware and protocols so that new efficient modems may be added to the network without removing installed hardware and software.
Owner:COLLISION COMM INC
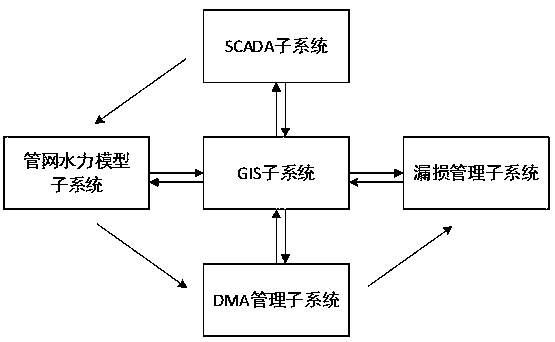
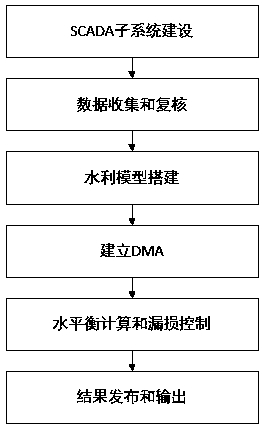
Water supply pipe network leakage management system and establishment method and system application thereof
InactiveCN107767012ALeak management rationalizationImprove distributionResourcesSpecial data processing applicationsData acquisitionNetworking hardware
The invention belongs to the field of water supply pipe network leakage management systems, in particular to a water supply pipe network leakage management system and an establishment method and system application thereof. In the prior art, through DMA (District Metering Area) zone metering, the independent metering and management of a complex pipe network is realized, and common DMA zone meteringhas the problems of high hardware investment, insufficient hardware laying reasonability, extensive leakage management, shortage of leakage economic evaluation system, imperfect data releasing and sharing mechanism. The water supply pipe network leakage management system comprises a pipe network hydraulic model subsystem, an SCADA (Supervisory Control And Data Acquisition) subsystem, a DMA management subsystem, a leakage management subsystem and a water affairs GIS (Geographic Information System) management subsystem. Through the guidance of basic data, an optimal hydraulic model is established, independent metering zone division is guided through the hydraulic model, pipe network hardware laying is guided, the economic benefit of a laying scheme is accurately evaluated, leakage management is reasonably carried out, and multiple pieces of system data can be shared.
Owner:浙江钛合工程技术有限公司
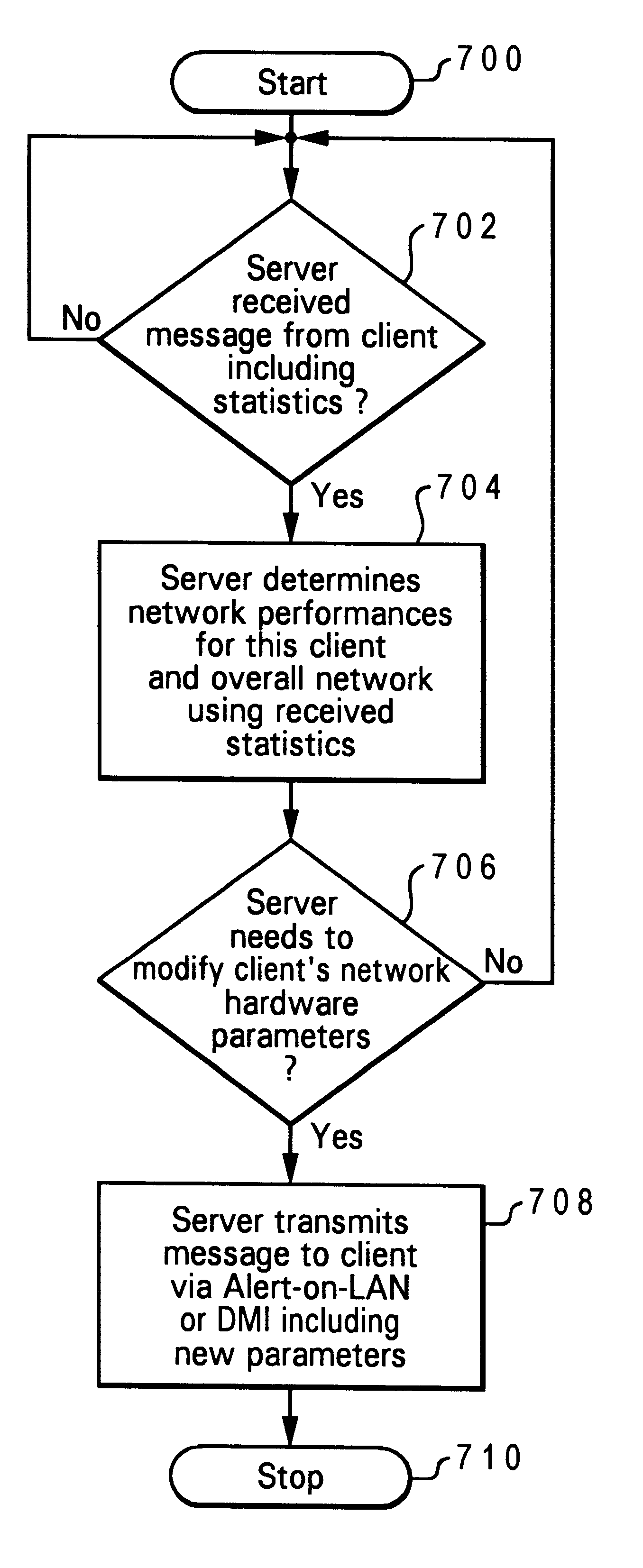
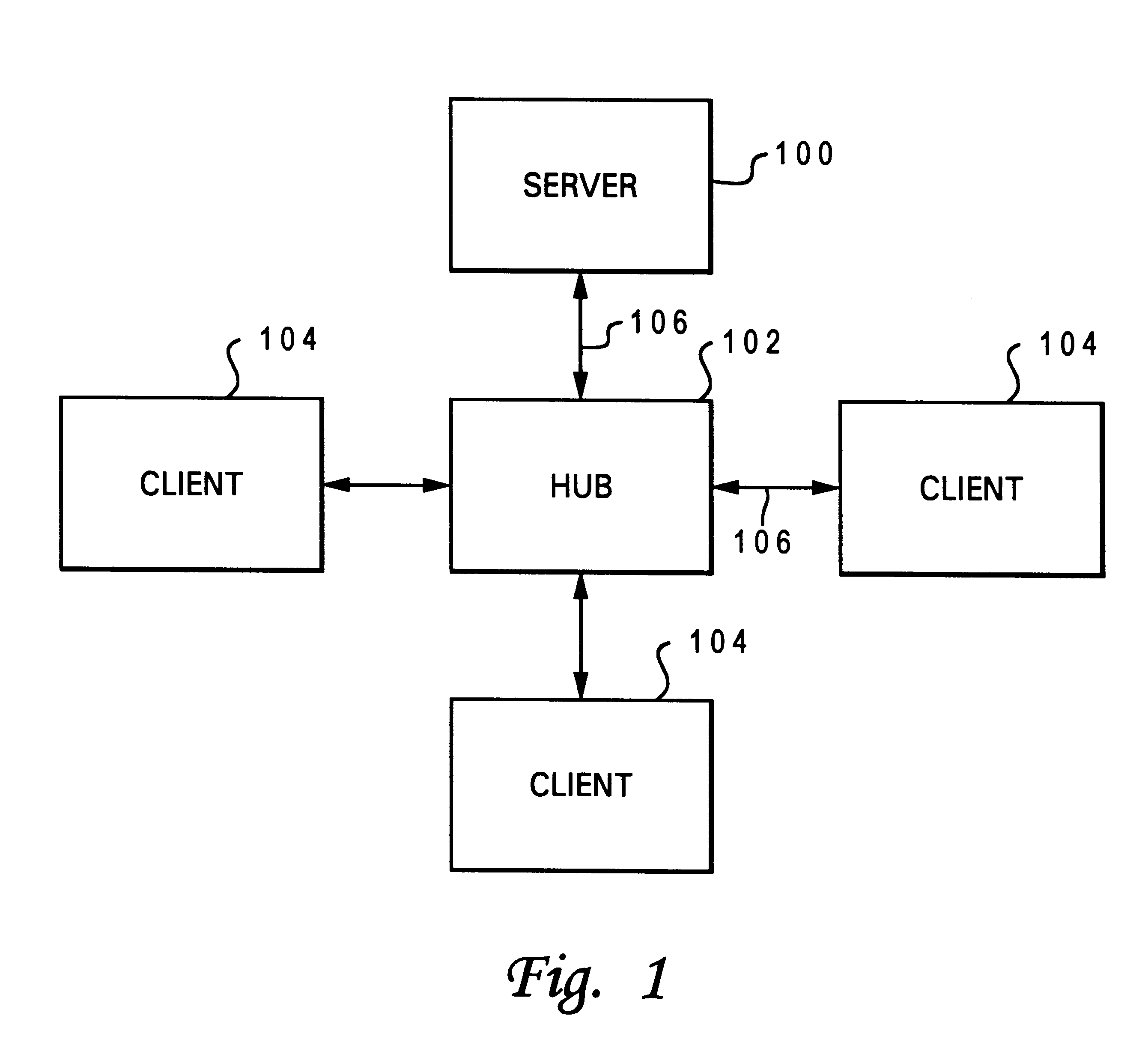
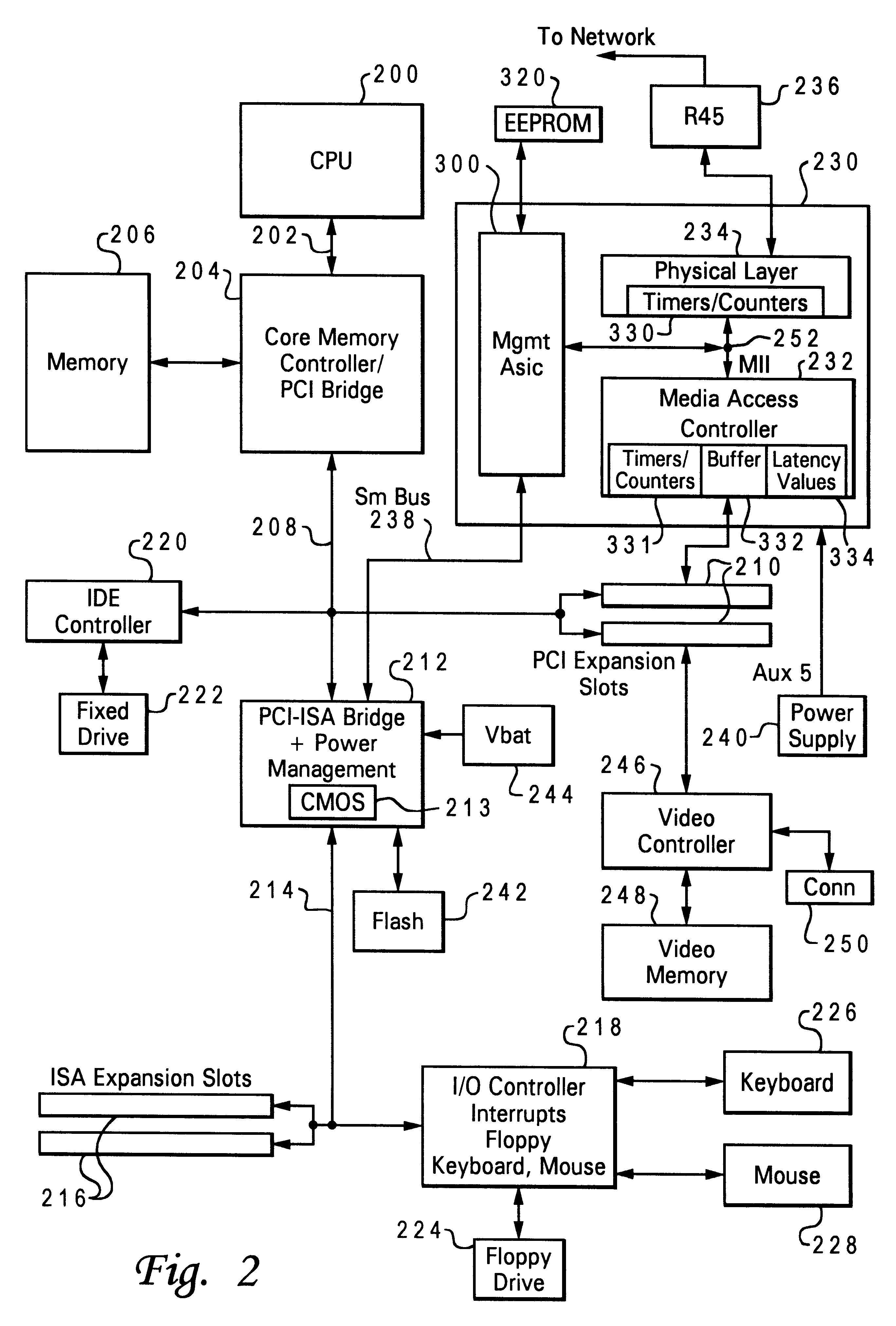
Data processing system and method for permitting a server computer system to remotely modify operation of a client computer system's network hardware
InactiveUS6304900B1Digital computer detailsHardware monitoringData processing systemComputerized system
A data processing system and method are described for permitting a server computer system coupled to a client computer system utilizing a network to remotely modify operation of the client computer system's network hardware. A counter is established within the client computer system for counting a plurality of network events. A counter threshold is established. Upon the counter reaching the counter threshold, the client computer system's network hardware transmits a message to the server computer system including network statistics information. The network statistics information includes an indication of the counter reaching the counter threshold. In response to a receipt of the message, the server computer system determines whether to modify the operation of the client's network hardware. In response to a determination to modify operation of the network hardware, the server remotely modifies operation of the client's network hardware.
Owner:LENOVO PC INT
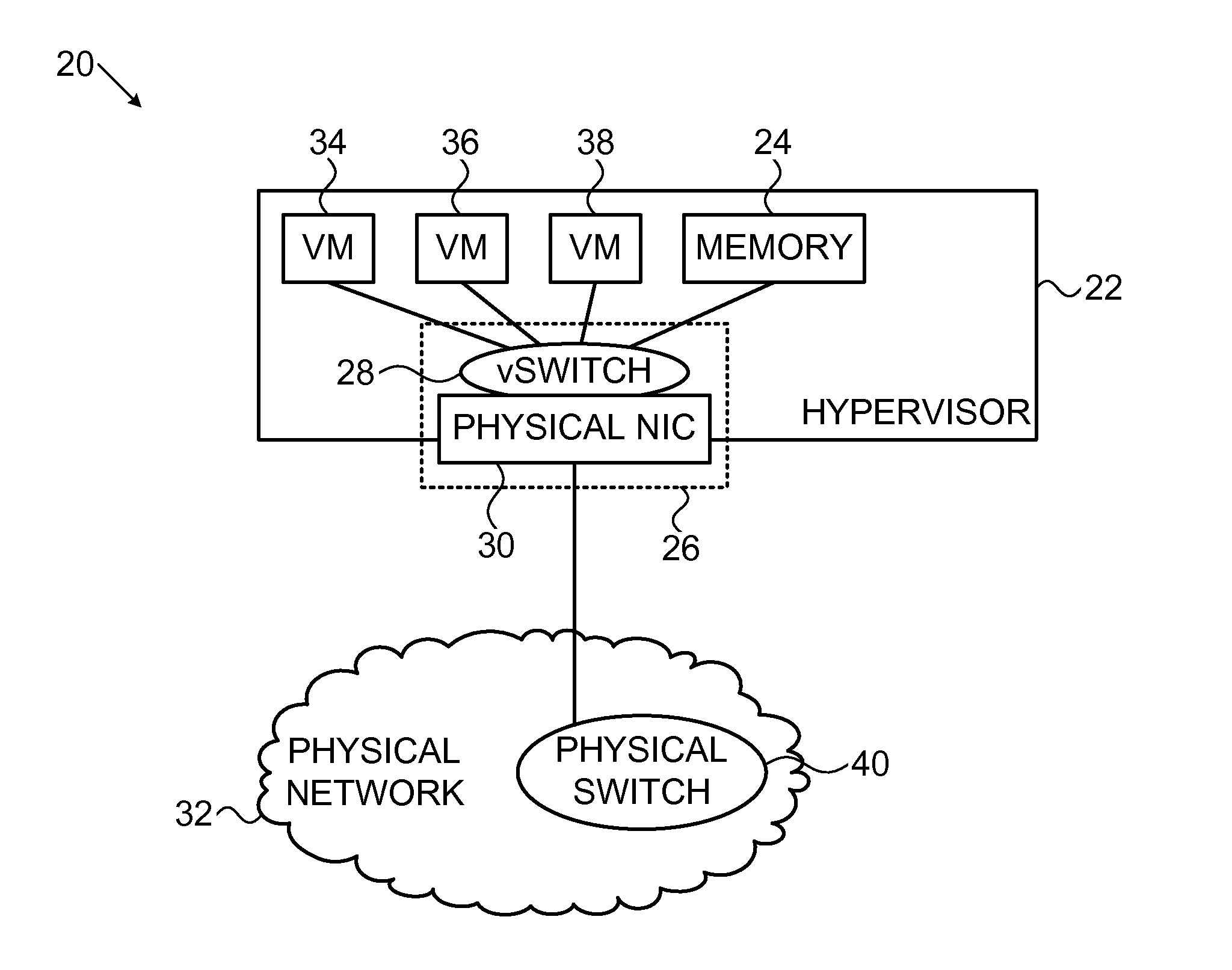
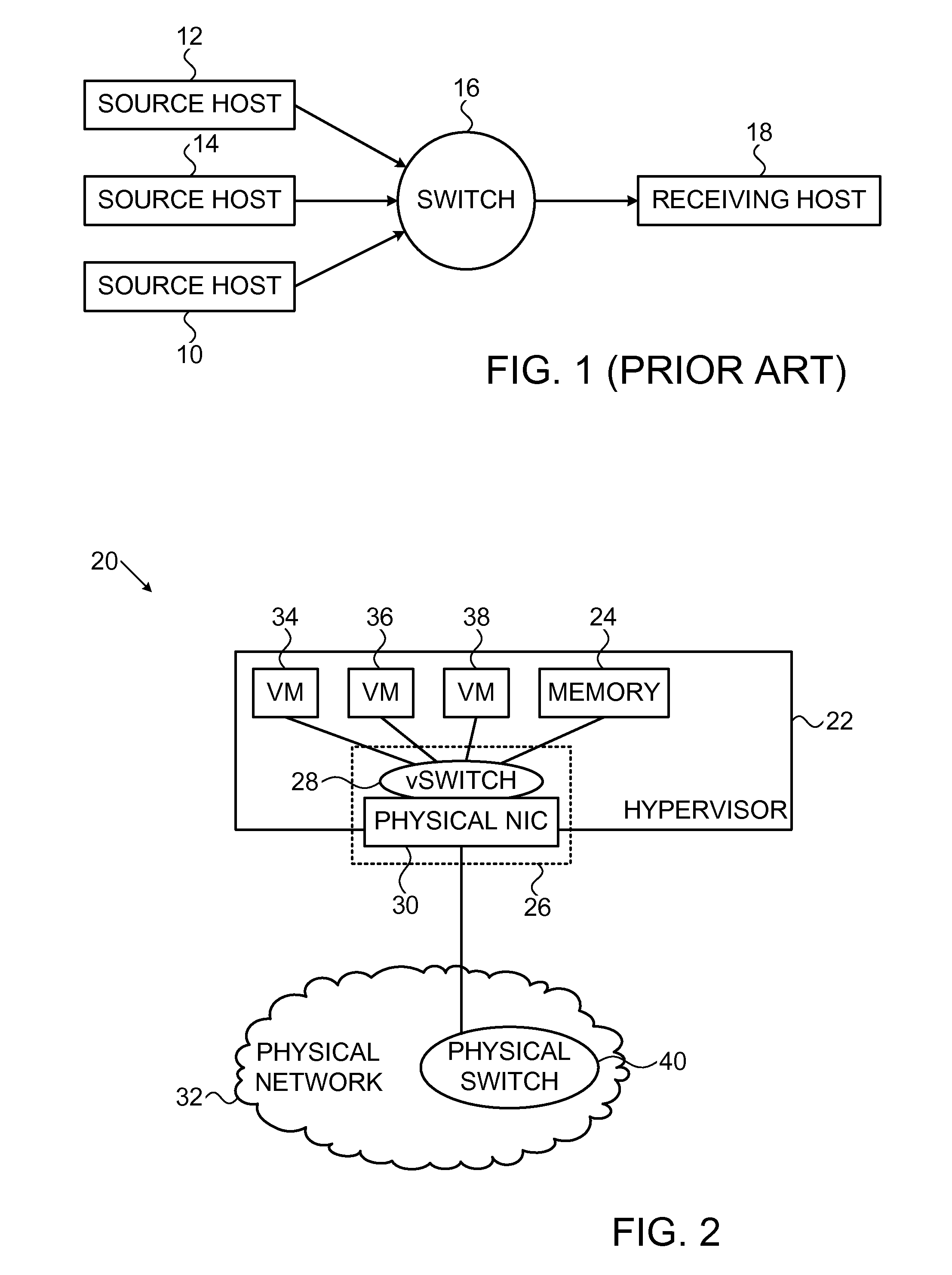
Congestion control enforcement in a virtualized environment
ActiveUS20150029853A1Facilitate transmissionImprove fairnessError preventionTransmission systemsTrusted componentsPacket loss
In a data network congestion control in a virtualized environment is enforced in packet flows to and from virtual machines in a host. A hypervisor and network interface hardware in the host are trusted components. Enforcement comprises estimating congestion states in the data network attributable to respective packet flows, recognizing a new packet that belongs to one of the data packet flows, and using one or more of the trusted components and to make a determination based on the congestion states that the new packet belongs to a congestion-producing packet flow. A congestion-control policy is applied by one or more of the trusted components to the new packet responsively to the determination.
Owner:MELLANOX TECHNOLOGIES LTD
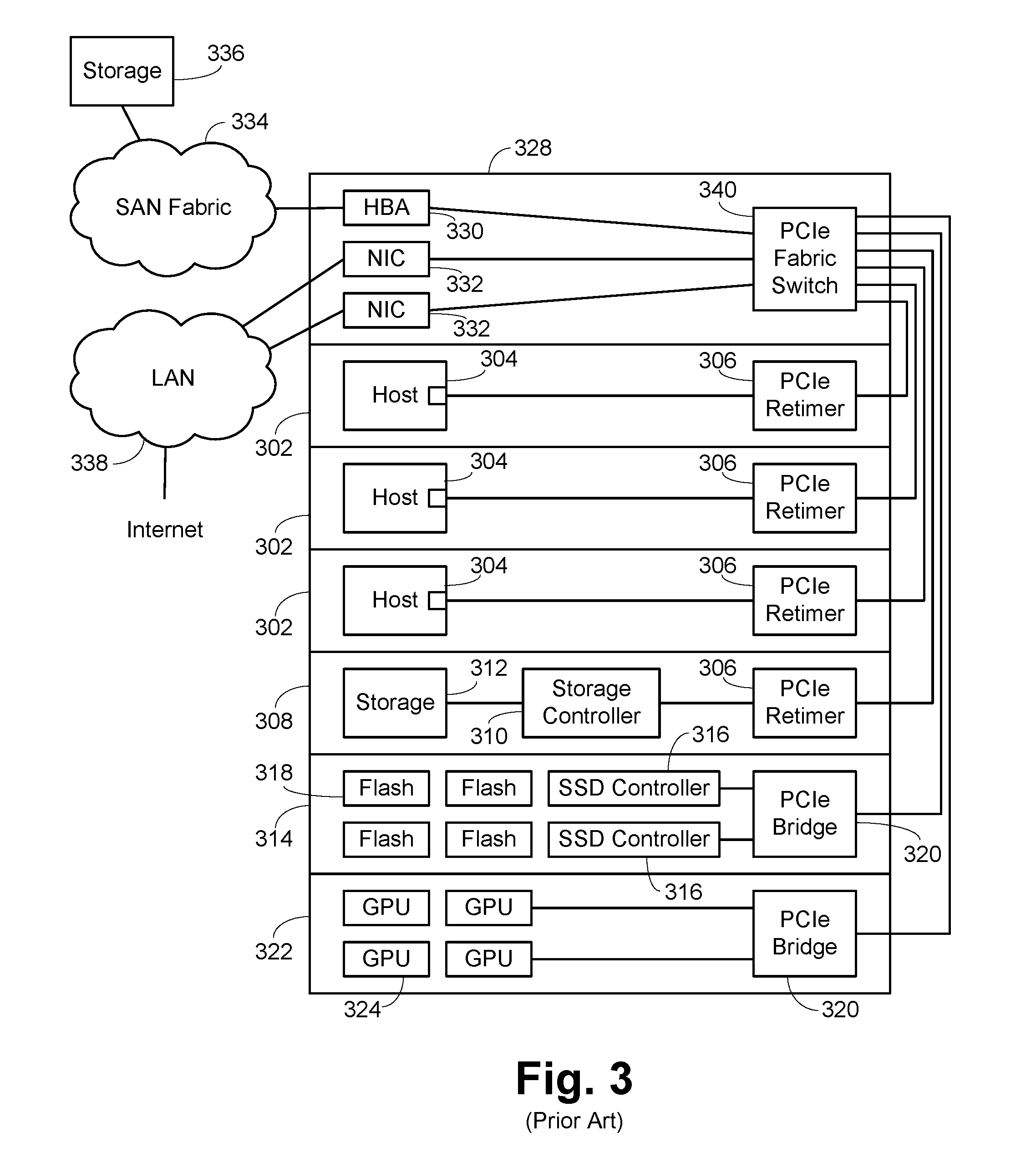
PCI Express Connected Network Switch
ActiveUS20170052916A1Low costSave spaceElectric digital data processingNetworking protocolNetwork packet
A host connected to a switch using a PCI Express (PCIe) link. At the switch, the packets are received and routed as appropriate and provided to a conventional switch network port for egress. The conventional networking hardware on the host is substantially moved to the port at the switch, with various software portions retained as a driver on the host. This saves cost and space and reduces latency significantly. As networking protocols have multiple threads or flows, these flows can correlate to PCIe queues, easing QoS handling. The data provided over the PCIe link is essentially just the payload of the packet, so sending the packet from the switch as a different protocol just requires doing the protocol specific wrapping. In some embodiments, this use of different protocols can be done dynamically, allowing the bandwidth of the PCIe link to be shared between various protocols.
Owner:AVAGO TECH INT SALES PTE LTD
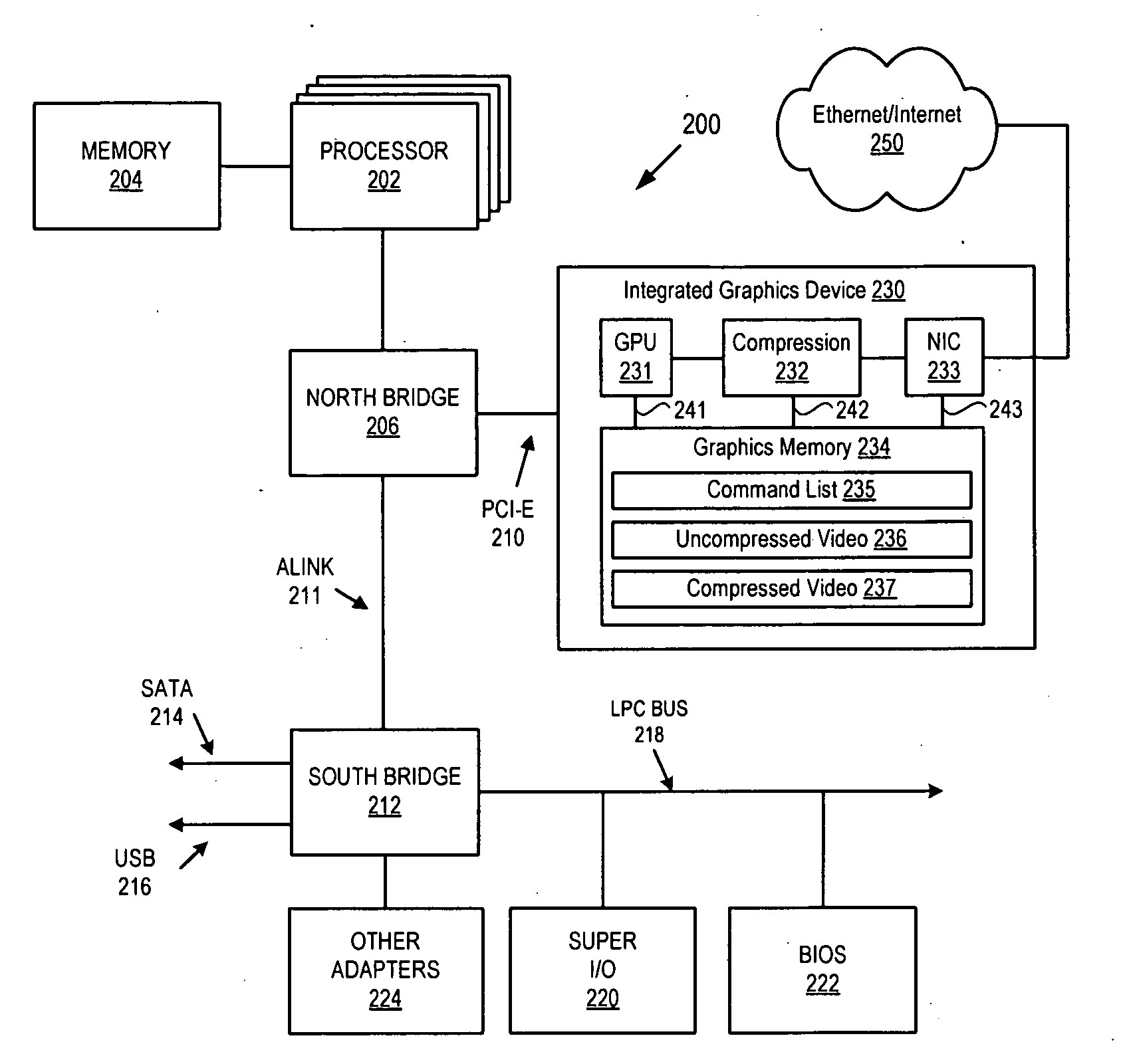
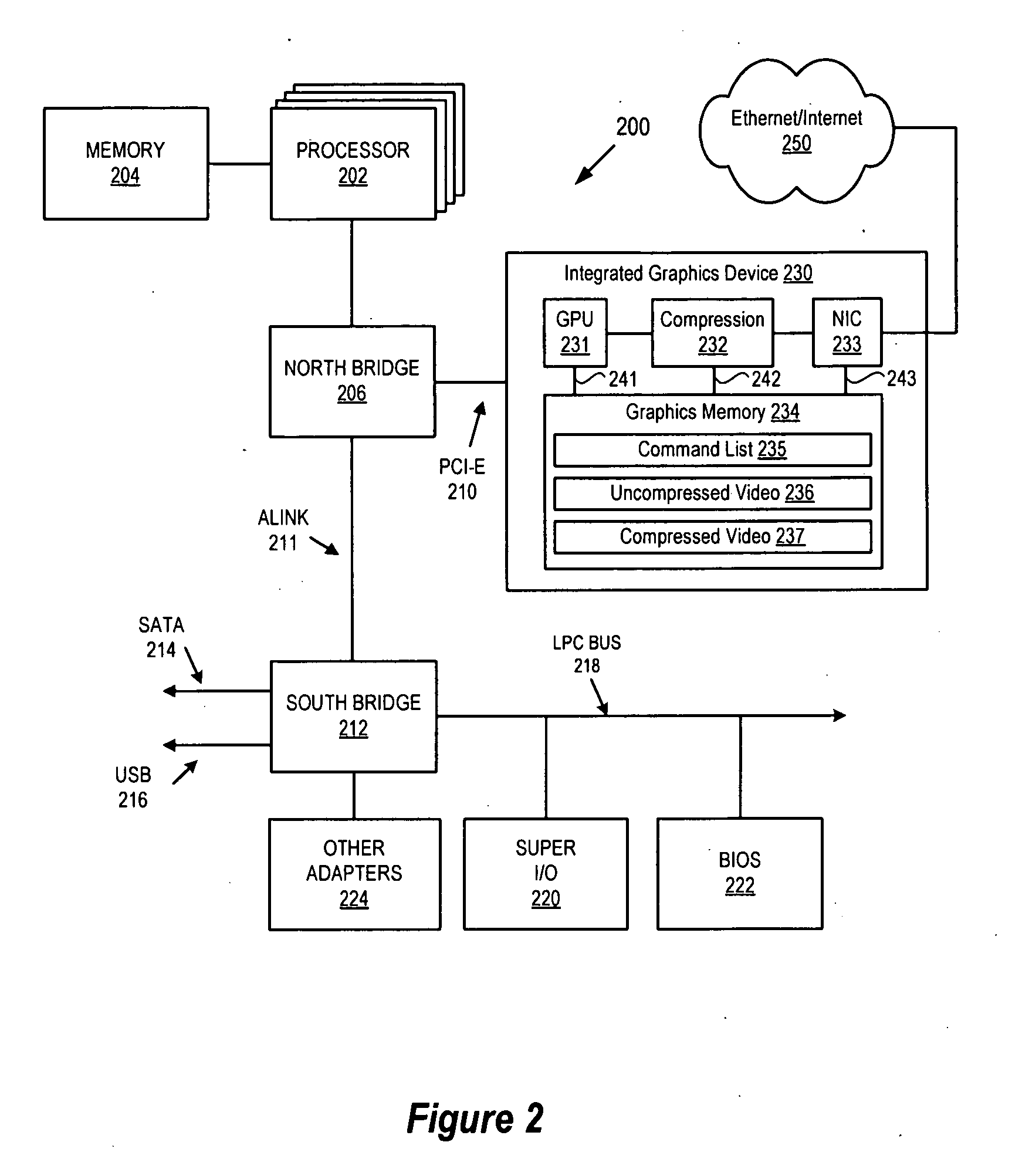
Integrated GPU, NIC and Compression Hardware for Hosted Graphics
InactiveUS20100013839A1Increases graphic processing speedSimplified communication protocolMultiple digital computer combinationsProcessor architectures/configurationCommunication interfaceGraphics
A computer graphics processing system includes an integrated graphics and network hardware device having a PCI Express interface logic unit, a graphics processor unit, a graphics memory, a compression unit and a network interface unit, all connected together on a PCI Express adapter card using one or more dedicated communication interfaces so that data traffic for graphics processing and network communication need not be routed over a peripheral interface circuit which has a communications bandwidth that must be shared with other system components.
Owner:ADVANCED MICRO DEVICES INC
Network management system and graphical user interface
InactiveUS6903755B1Change is minimalDigital computer detailsData switching networksNetwork connectionNetworking hardware
A network management system and graphical user interface for configuring a network connection between first and second service access points utilizes a configuration manager and information manager to provide a generic set of models so that different manufacturer's nodal processors and other network hardware can be inserted into the network with minimal changes to the software which controls the device. The system comprises an information manager including routing information for the network. The configuration manager operates to establish a connection across each subnet on the route by sending requests to element managers to program the subnet elements.
Owner:QWEST
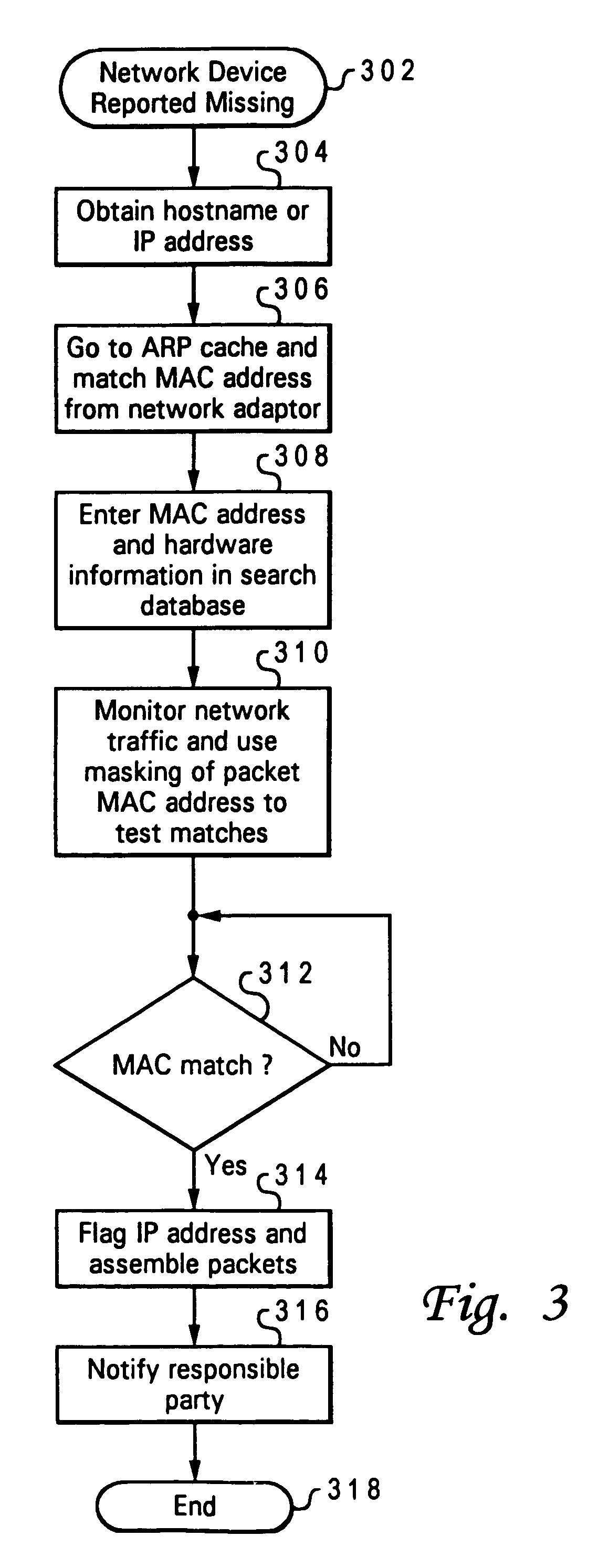
Method and system for tracing missing network devices using hardware fingerprints
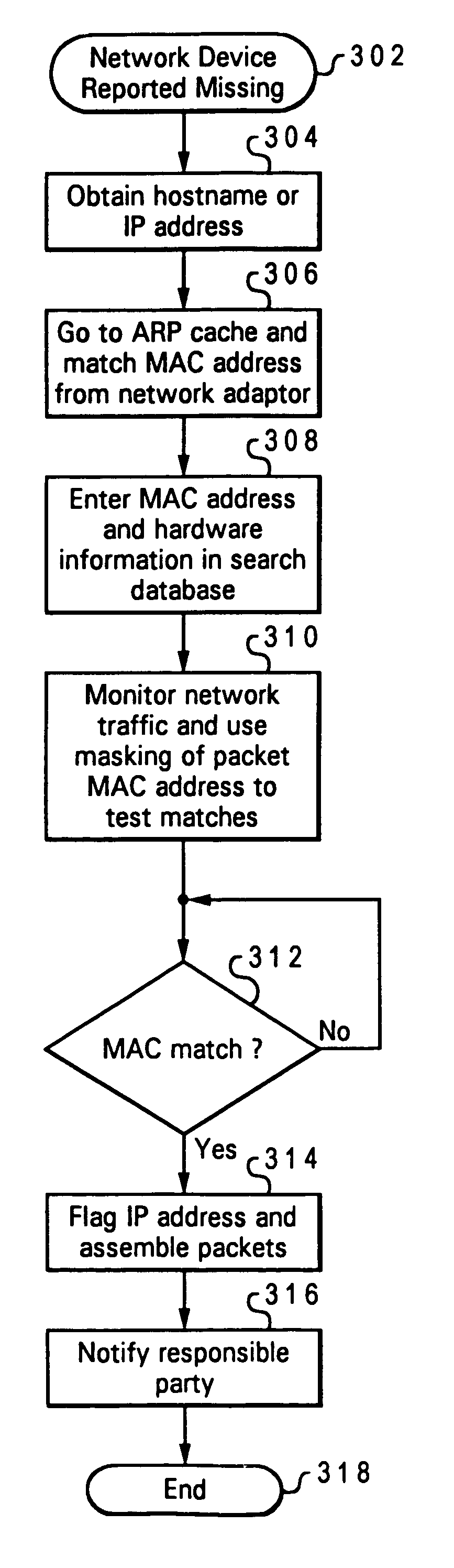
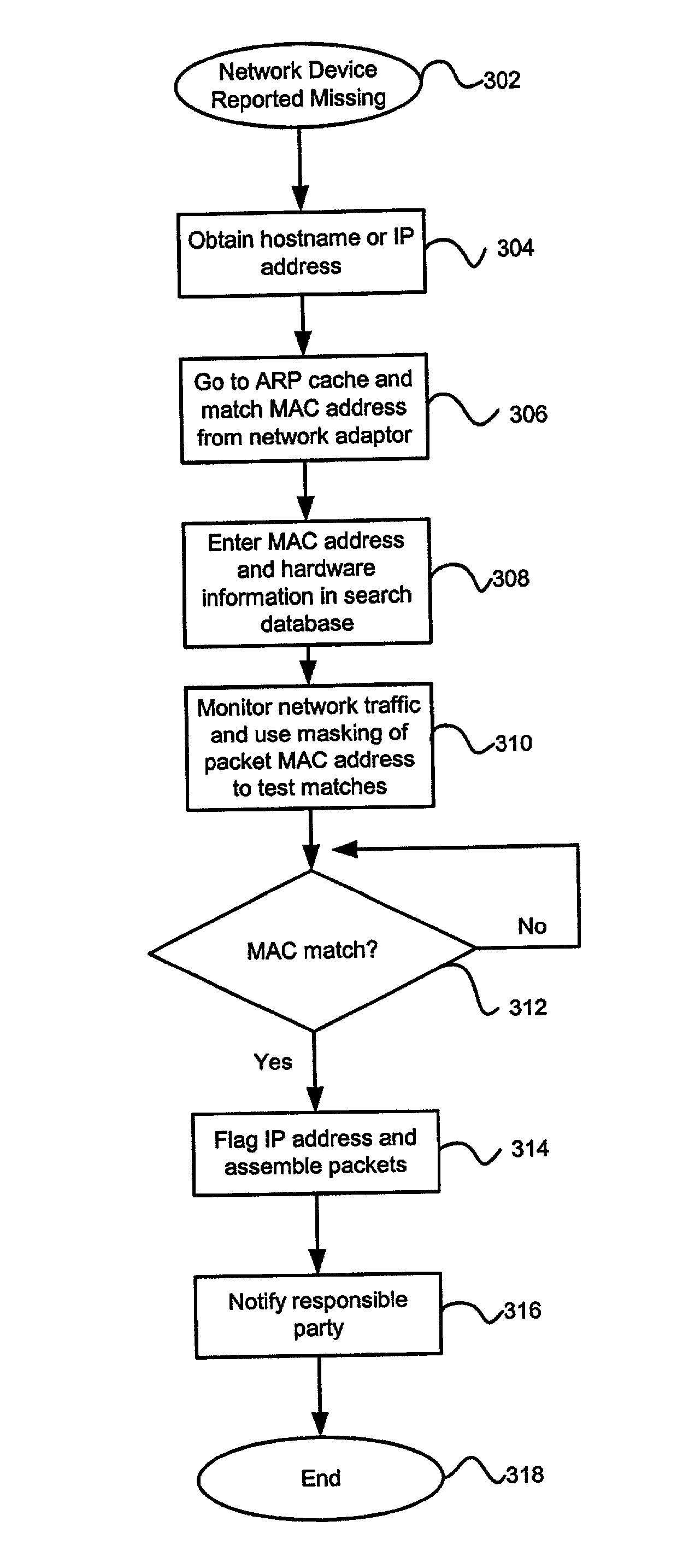
InactiveUS7181195B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareInternet traffic
When a piece of network equipment is determined to be stolen or missing, a hardware tracing tool mounted within the network detects the distinctive hardware fingerprints of the missing hardware within Internet traffic and extracts the device's IP address to trace the location of the missing equipment. As Internet messages or data packets cross through servers containing the tracing tool, the data packets are decompiled to retrieve unique identifier indicia (hardware fingerprints), such as a computer's MAC address, for example. The extracted fingerprints are then compared with fingerprints stored in a database of missing hardware using a hashing or mapping function, and the server system is alerted to a match. The IP address of the device transmitting the matching indicia is then extracted to determine the location of the missing or stolen network hardware. In this way, a method of tracing missing network hardware is provided that does not increase the cost of network equipment or unnecessarily effect network bandwidth.
Owner:RAKUTEN GRP INC
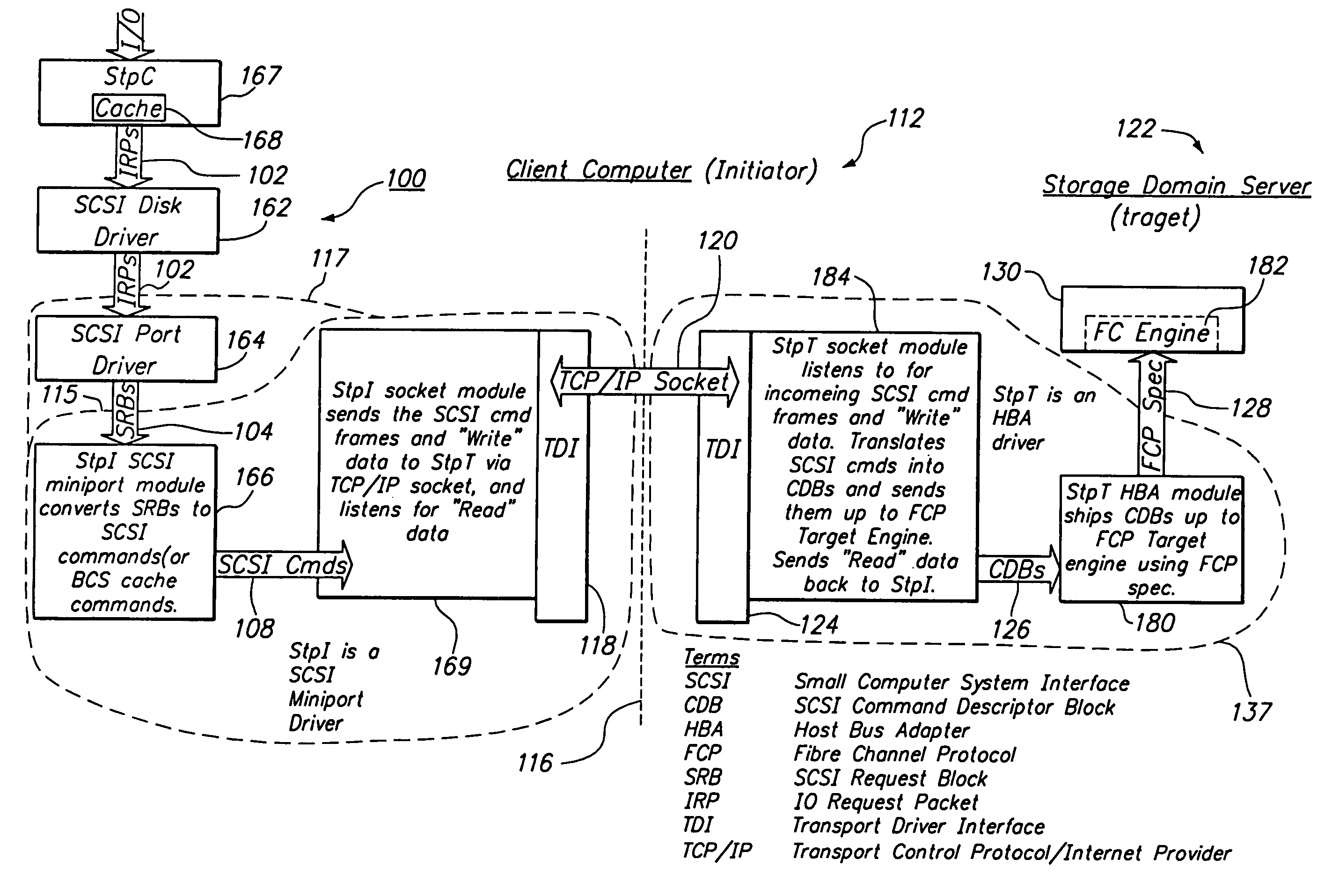
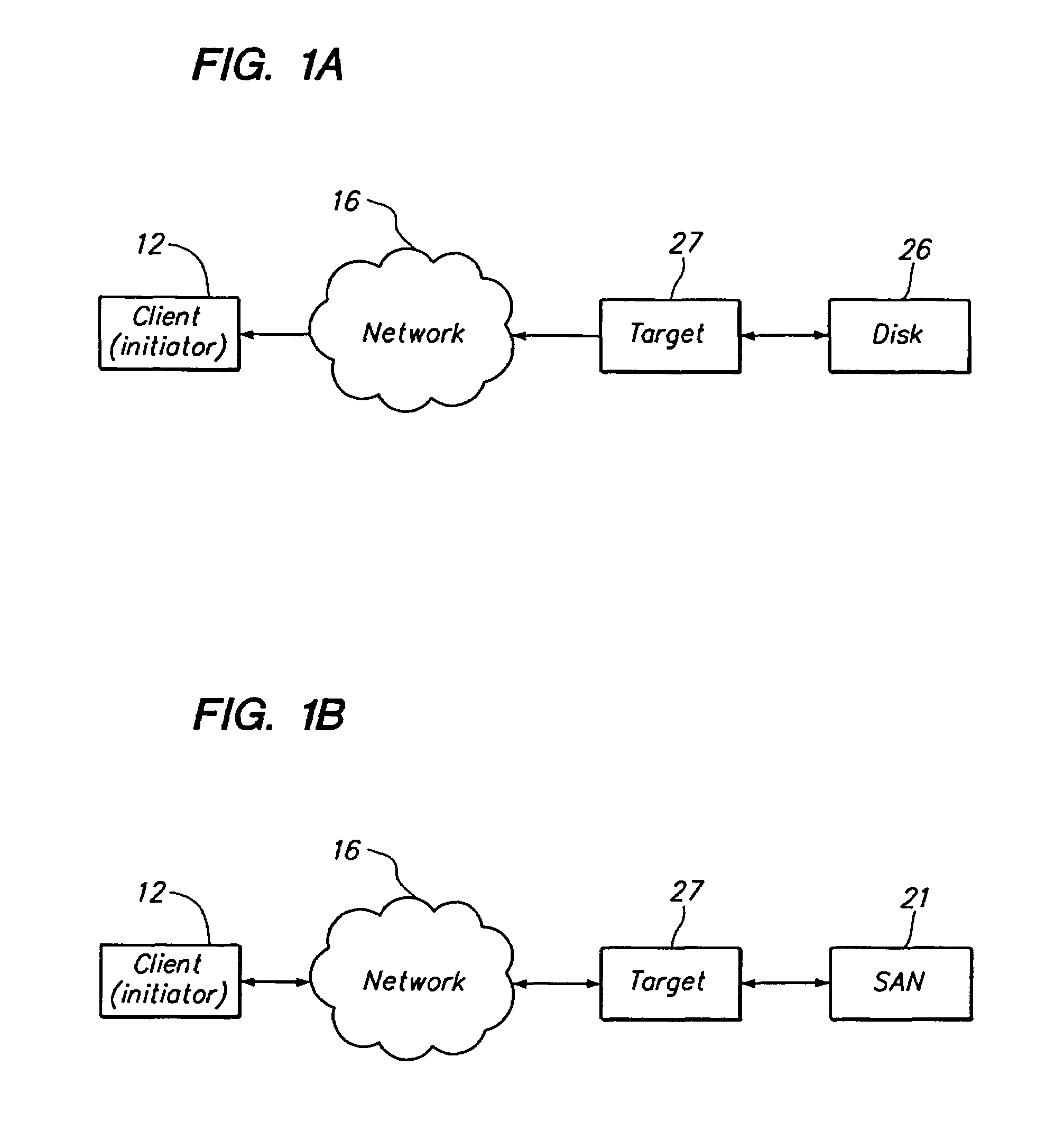
SCSI transport protocol via TCP/IP using existing network hardware and software
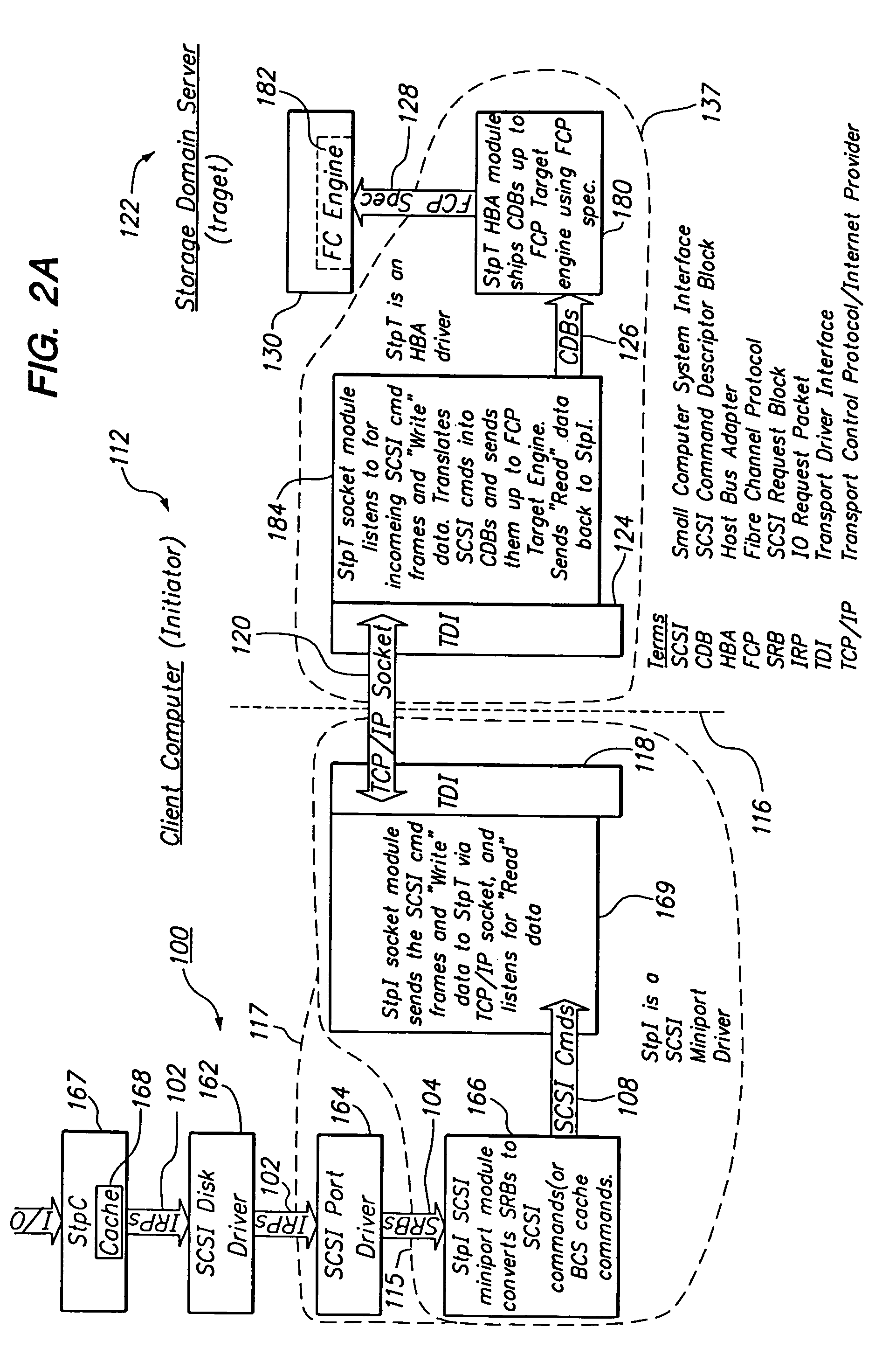
ActiveUS7177912B1Reduce overall network-related I/O latencyReduce I/O LatencyDigital computer detailsTransmissionSCSINetworking hardware
A computer network system includes a client-server architecture, where the client transmits SCSI commands over a network using TCP / IP to a server to request input and output operations for a physical storage device that is communicatively coupled to a storage device. The client perceives the storage device to be a local disk drive, even though the storage device is located on the target side of a network. The system includes a client-side disk-based cache.
Owner:DATACORE SOFTWARE
Methoe for realizing object sharing in network storage service based on instant communication tool
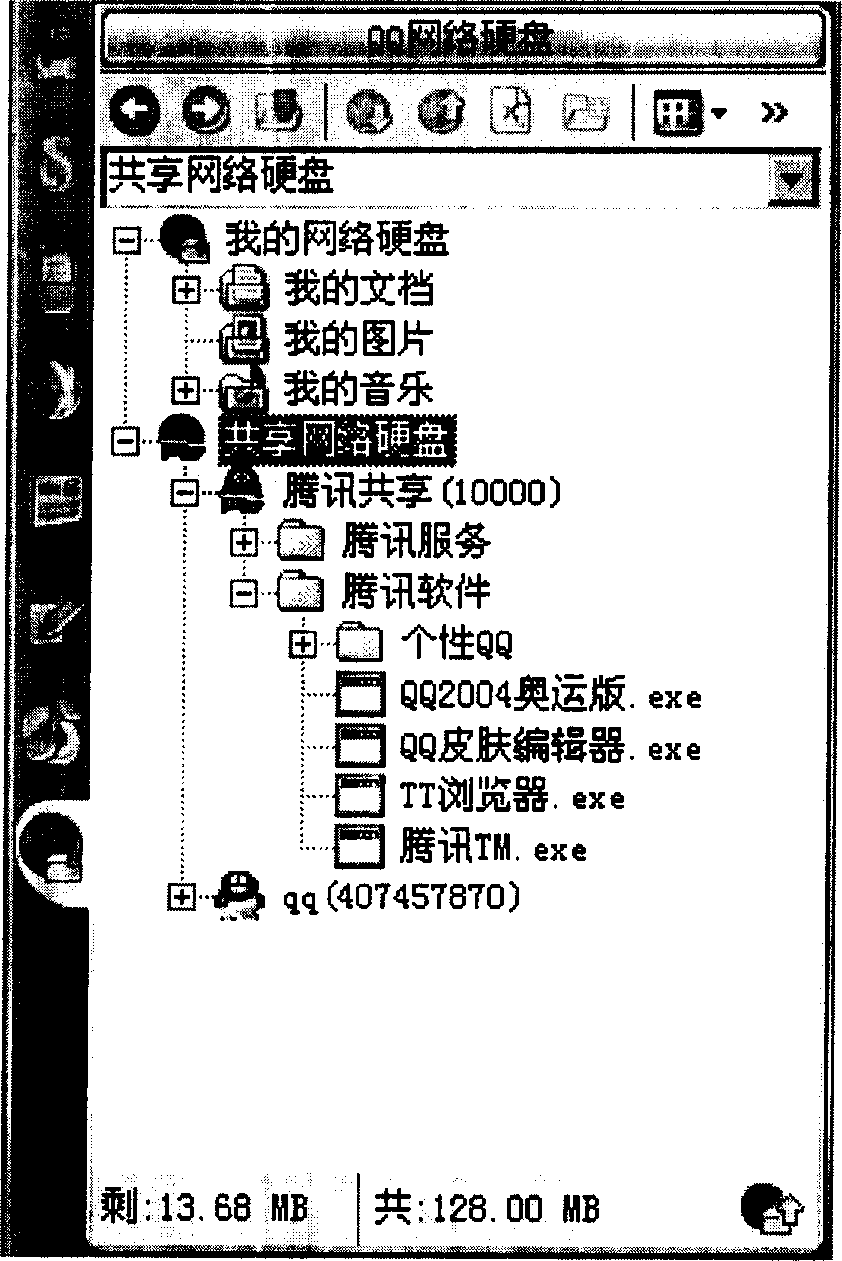
ActiveCN1744557AEasy to shareEasy way to share dataStore-and-forward switching systemsSpecial data processing applicationsThird partyNetworking hardware
Based on hardware of instant communication network system, in order to solve security and complicated operation etc. issues existed in current remote file sharing, the invention discloses method for realizing friend sharing files stored in network hardware disk based on remote storage service of network hard disk in instant communication mode. Through simple setting, user can share files stored own instant communication network hard disk directly with own good friend. Since third party sharing based on storage service of instant communication is adopted in instant communication network system, the invention provides facile data sharing approach for users.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for tracing missing network devices using hardware fingerprints
InactiveUS20030153328A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareIp address
When a piece of network equipment is determined to be stolen or missing, a hardware tracing tool mounted within the network detects the distinctive hardware fingerprints of the missing hardware within Internet traffic and extracts the device's IP address to trace the location of the missing equipment. As Internet messages or data packets cross through servers containing the tracing tool, the data packets are decompiled to retrieve unique identifier indicia (hardware fingerprints), such as a computer's MAC address, for example. The extracted fingerprints are then compared with fingerprints stored in a database of missing hardware using a hashing or mapping function, and the server system is alerted to a match. The IP address of the device transmitting the matching indicia is then extracted to determine the location of the missing or stolen network hardware. In this way, a method of tracing missing network hardware is provided that does not increase the cost of network equipment or unnecessarily effect network bandwidth.
Owner:RAKUTEN GRP INC
Network management system and graphical user interface
InactiveUS6963916B1Change is minimalMultiple digital computer combinationsData switching networksNetwork connectionNetworking hardware
A network management system and graphical user interface for configuring a network connection between first and second service access points utilizes a configuration manager and information manager to provide a generic set of models so that different manufacturer's nodal processors and other network hardware can be inserted into the network with minimal changes to the software which controls the device. The system comprises an information manager including routing information for the network. The configuration manager operates to establish a connection across each subnet on the route by sending requests to element managers to program the subnet elements.
Owner:QWEST
Validating packets in network communications
ActiveUS20120017265A1Digital data processing detailsMultiple digital computer combinationsComputer hardwareVirtualization
A method for validating packets in network communications includes receiving, at networking hardware of a device, a packet communicated from another device over a network; intercepting, by virtual dispersive routing (VDR) software loaded on the device, the packet as it is passed from the networking hardware; determining, by the VDR software, that a destination address of the packet corresponds to an address associated with the device; and determining, by the VDR software, using a virtual machine for a network connection that virtualizes network capabilities of the device, that the packet belongs to a valid application running on the device.
Owner:ASSET RECOVERY ASSOC +1
Hardware shunt method of IP report
ActiveCN101540727AImprove performanceAvoid congestionResource allocationData switching networksHardware threadChannel scheduling
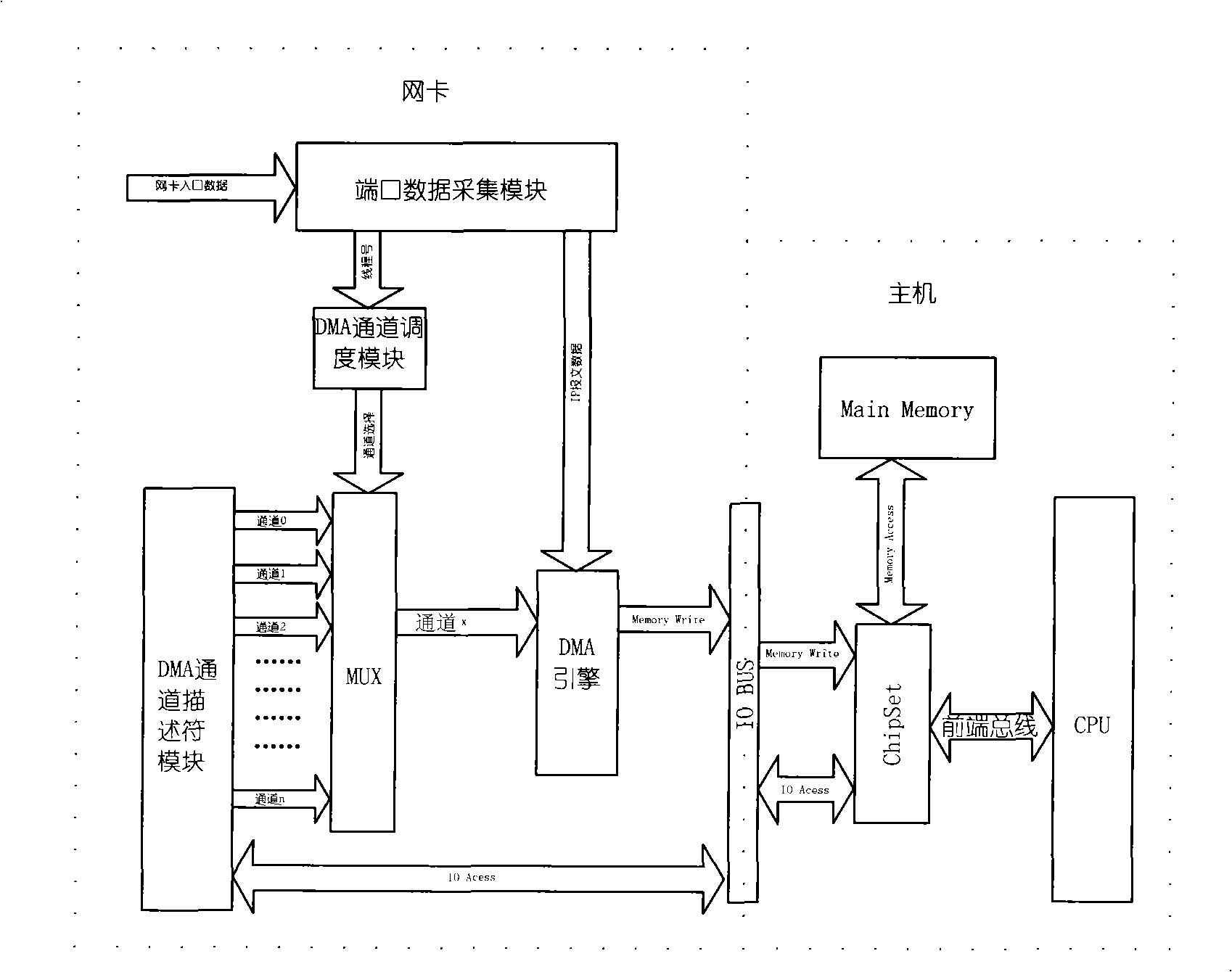
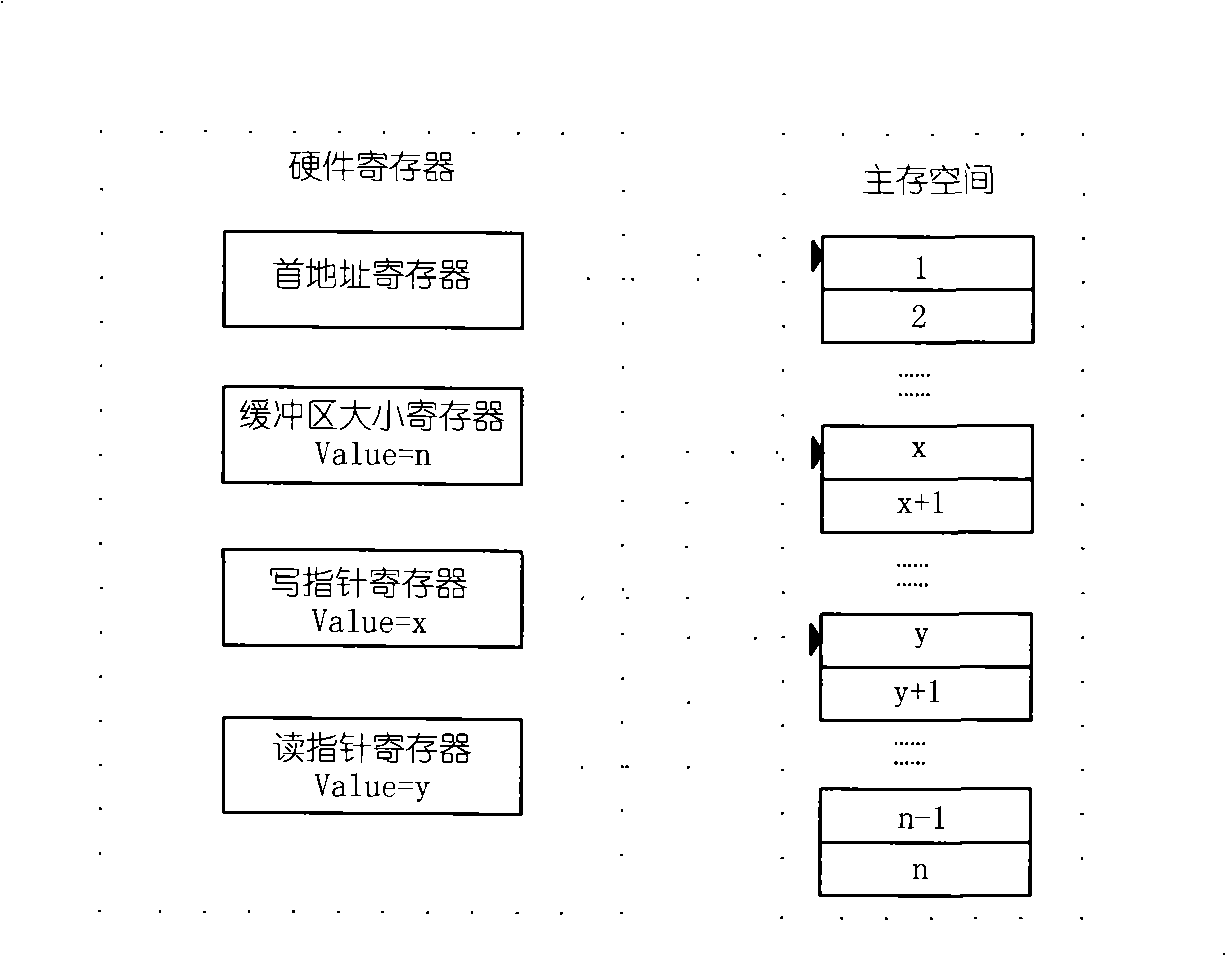
The invention relates to a hardware shunt method of an IP report. In the technical scheme of the invention, a received IP report is shunted by a piece of network card hardware; the source address and the target address of an IP report title are extracted when the IP report is received by a network card; Hash algorithm is then employed to calculate tread to which the IP report belongs; and a DMA channel scheduling module starts up a DMA engine according to tread number to transmit the report to a main storage buffer area to which the tread belongs; in order to support hardware shunt strategy of the IP report, an upper-layer software ensures each tread to have a special main storage buffer area; the network card starts up the threads of a plurality of IP packages to correspond to the treads of host processing IP packages one to one; the treads of the host processing IP packages directly acquires data from a memory buffer area for processing; therefore, the transmission of intermediate data does not need a CPU, thereby reducing the CPU load. The hardware tread number supported by the method is as high as 1024 and even as higher as 4096 or 8192. The best configuration is that each CPU is corresponding to one tread, so that each tread operates independently without mutual interference; moreover, the best performance is achieved due to the least system resource sharing.
Owner:WUXI CITY CLOUD COMPUTING CENT
Column network hardware management system
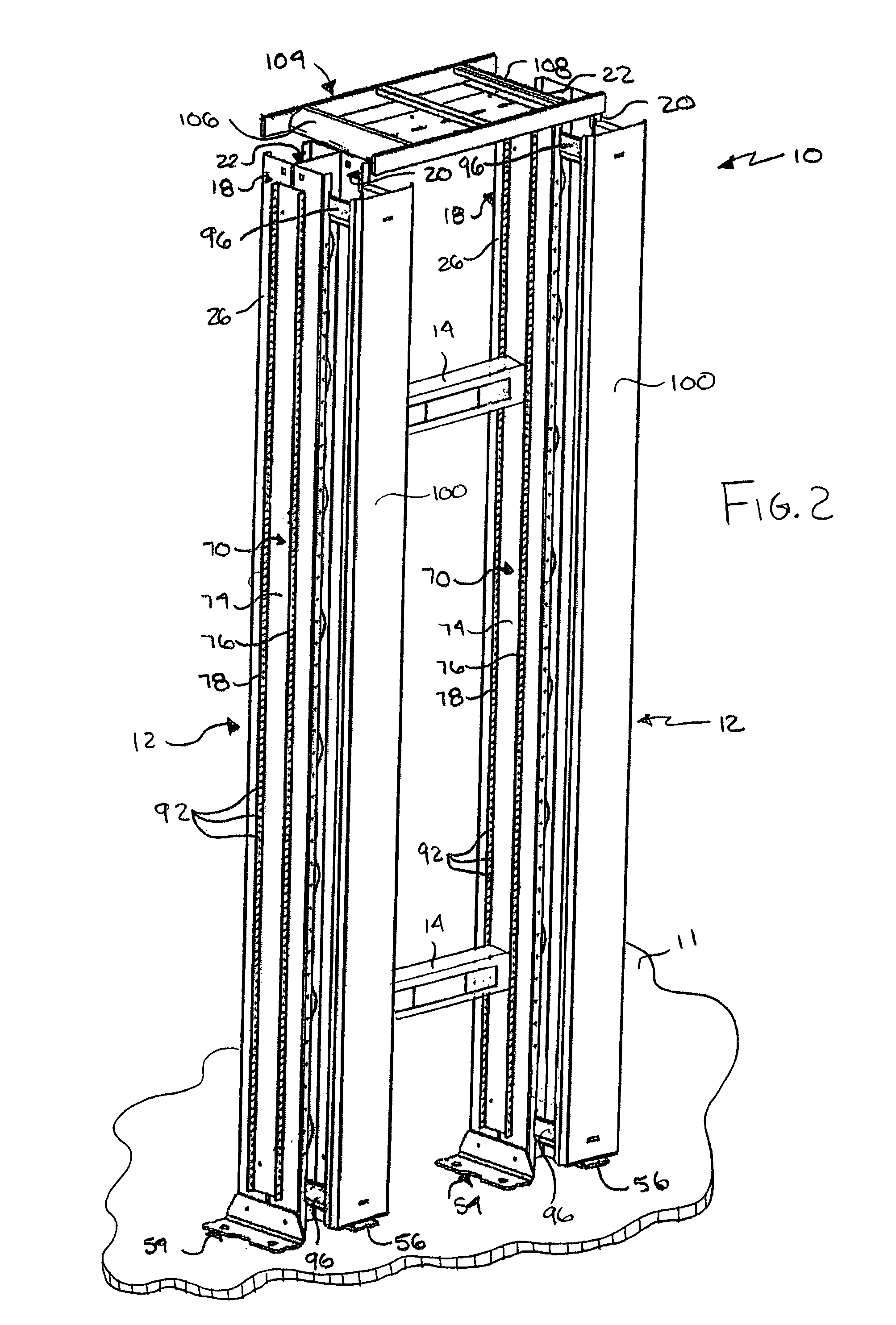
ActiveUS7172078B2Effective supportLess costlyBus-bar/wiring layoutsShow shelvesNetworking hardwareManagement system
Owner:HUBBELL INC
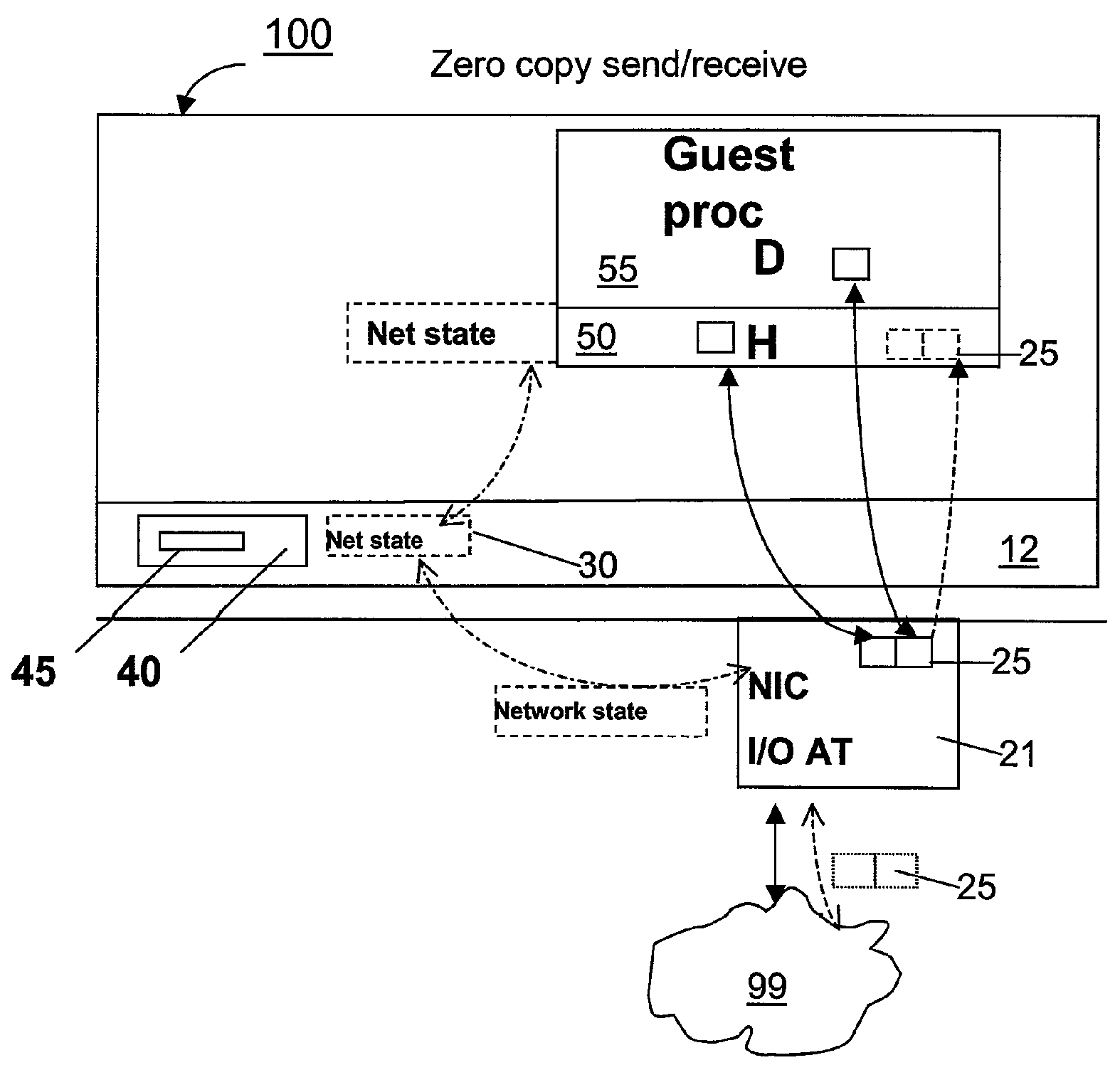
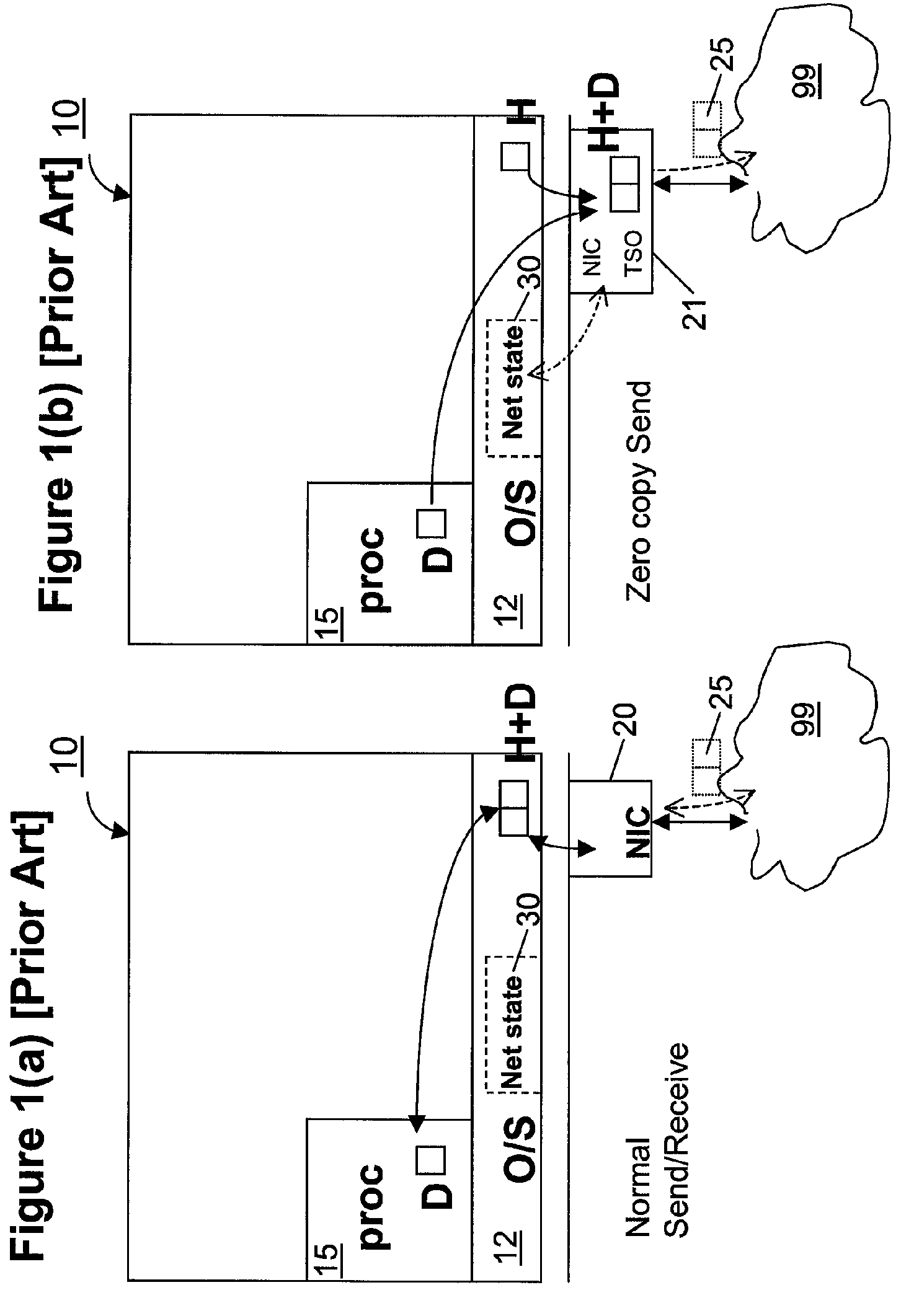
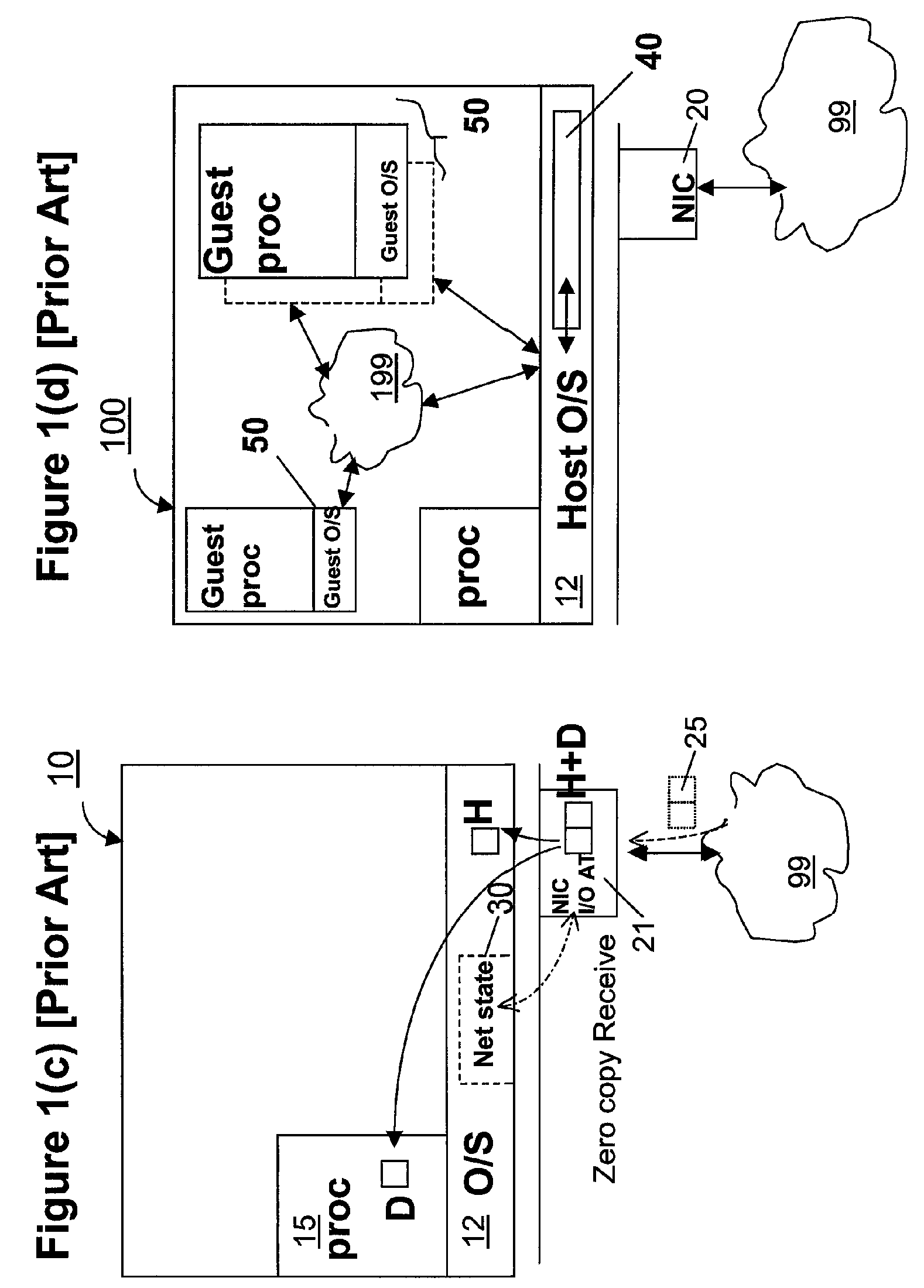
Zero-copy network I/O for virtual hosts
ActiveUS7721299B2Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionComputer hardwareVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
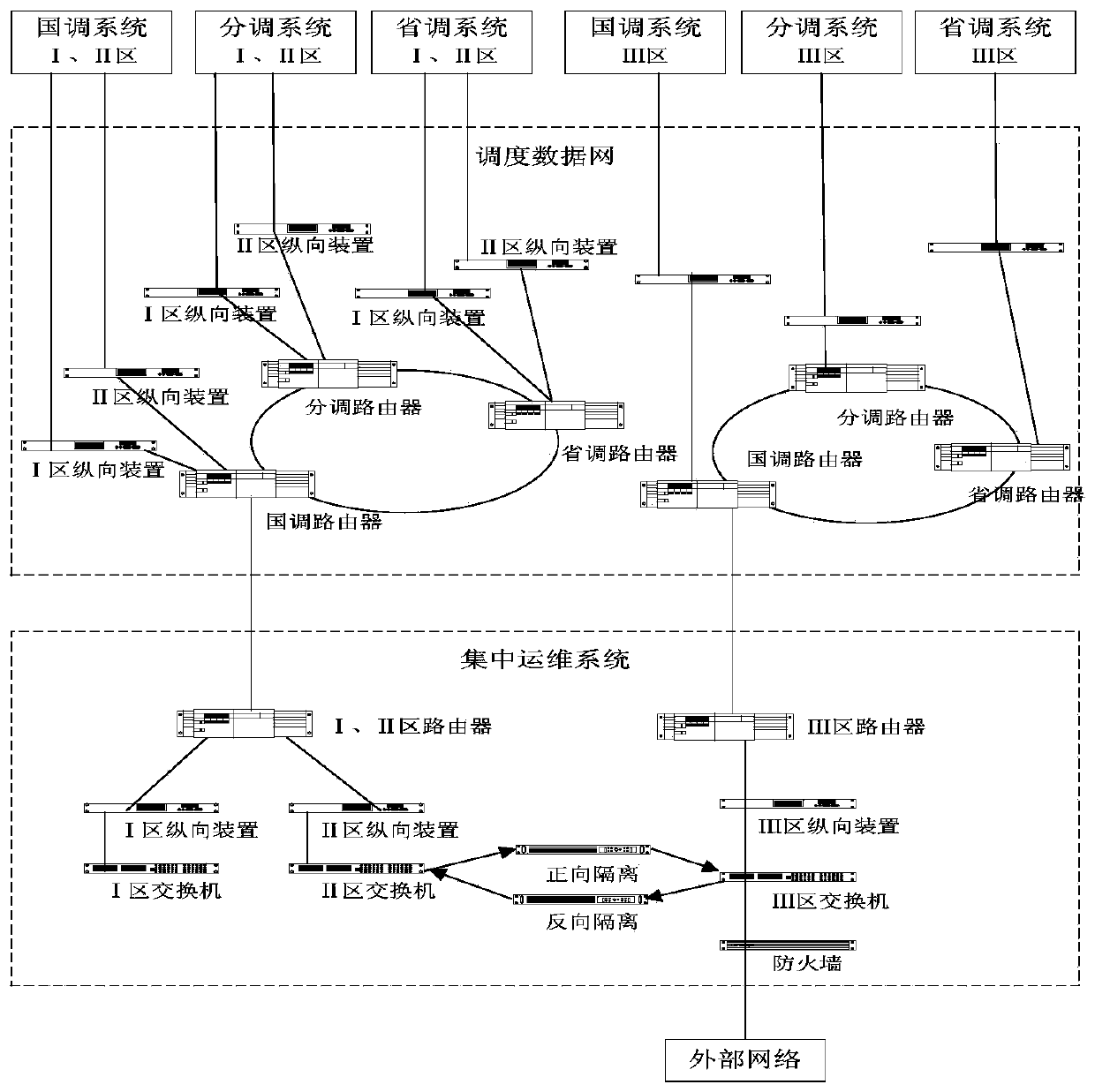
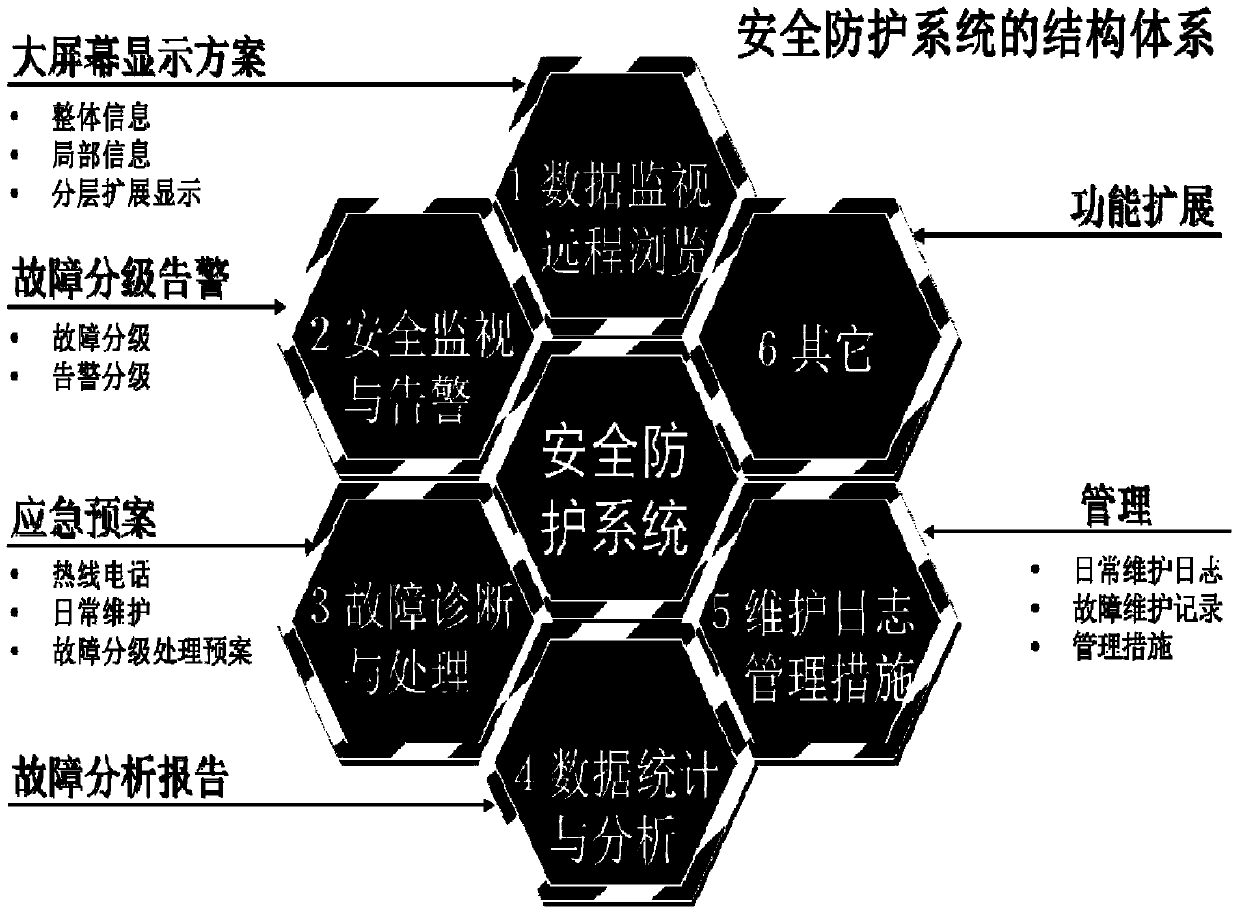
Security protection method based on integrated dispatching data network operation and maintenance system
InactiveCN103473626AEnsure safetyGuaranteed reliabilityResourcesData switching networksNetworking hardwareSoftware development
The invention relates to a security protection method based on an integrated dispatching data network operation and maintenance system. A security protection system adopted in the method comprises a remote data monitoring browsing module, a security monitoring and alarming module, a fault diagnosis and processing module, a data counting and analyzing module, a maintenance log management measure module and a function extension module; the method comprises the following steps: (1) configuring security network hardware accessed to a dispatching data network; (2) determining the range and the content of security protection; (3) determining a security protection software development scheme; (4) determining security protection management measures of the operation and maintenance system; (5) determining a security protection scheme. The integrated operation and maintenance security protection work can be developed in a manner of accessing to the dispatching data network, so as to provide the security technology basis for the construction of the integrated operation and maintenance system; the working content of security protection personnel can be cleared, and the security stability operation can be guaranteed; the security protection and monitoring functions of the system can be clear, the working flow can be specified so as to provide the guarantee for the system security.
Owner:STATE GRID CORP OF CHINA +1
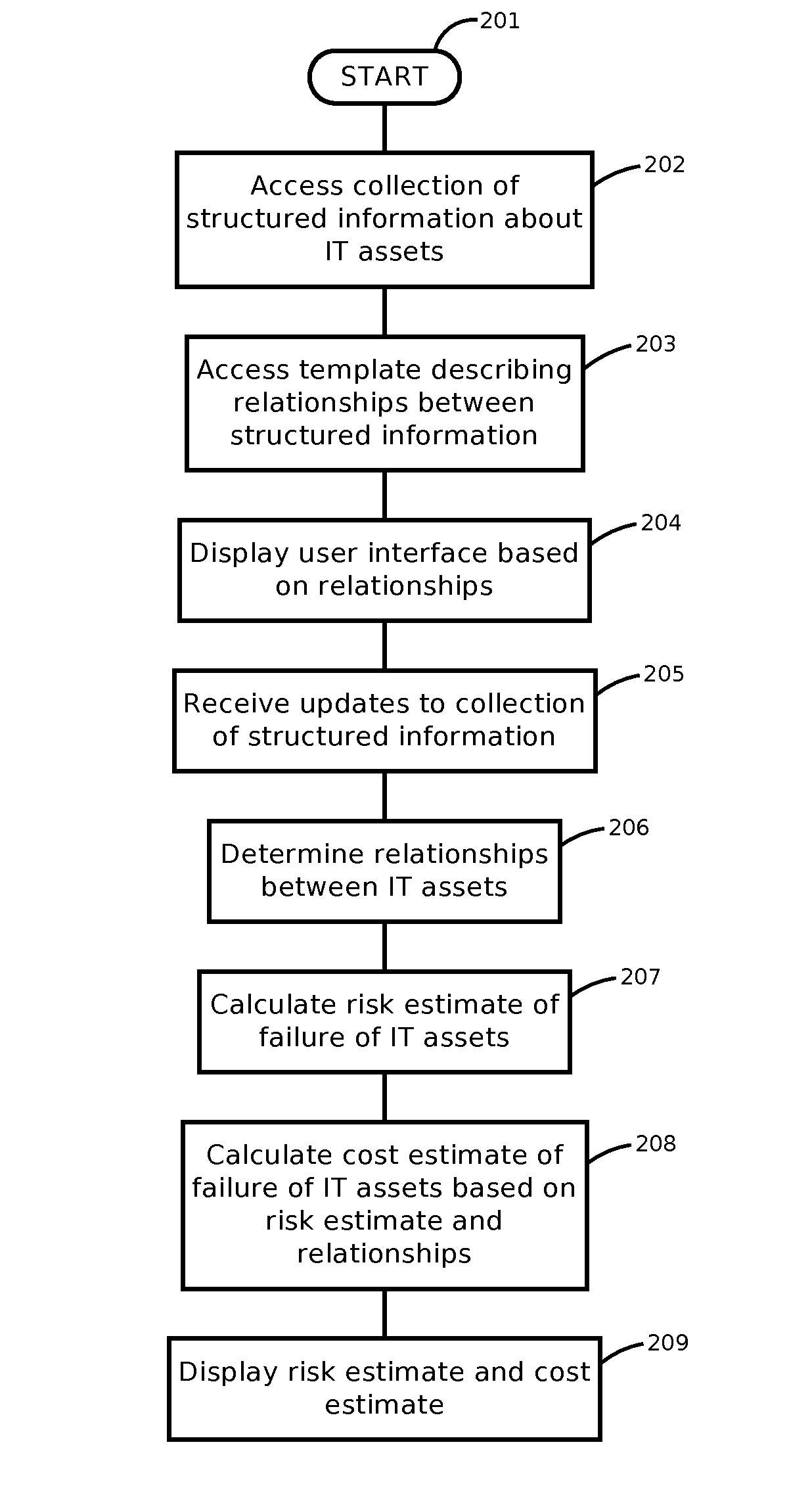
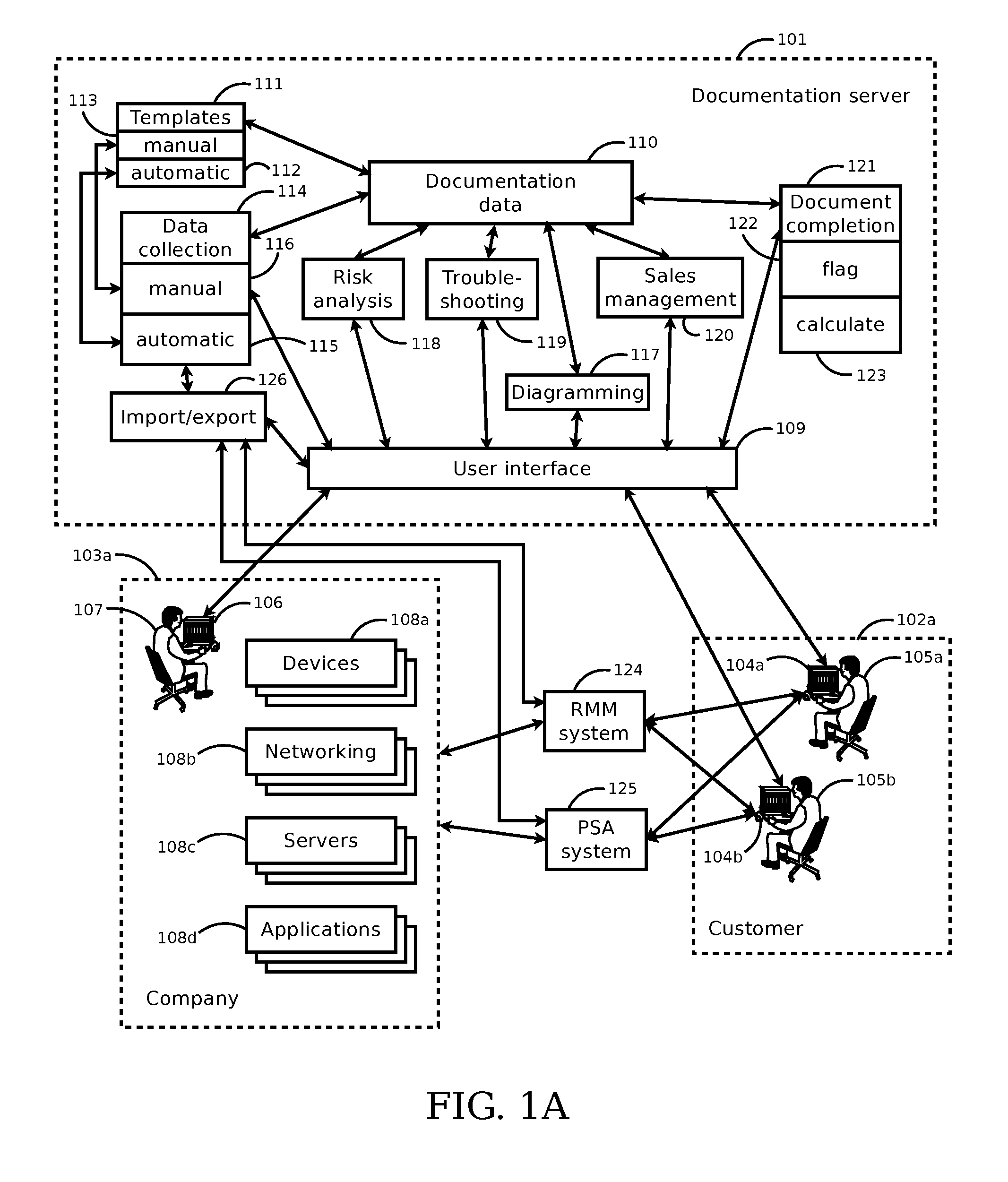
Systems and methods for documenting, analyzing, and supporting information technology infrastructure
ActiveUS20150278219A1Easy diagnosisPrediction is simpleWeb data indexingDigital data processing detailsNetworking hardwareInformation infrastructure
Systems and methods of the present disclosure facilitate managing information technology (IT) infrastructure. The system can include a server configured to retrieve data records for first and second IT assets, each asset comprising at least one of a computing device, a software application, an end user, a business unit, a piece of networking hardware, or an agreement for an IT service. The server can select a template comprising a relationship between the first and second data records. The system can include a link generator configured to generate a different relationship, absent from the template, between the first and second data records. The system can include a search engine configured to identify third and fourth IT assets that satisfy the second relationship, determine an indices of completeness for the third and fourth IT assets, and rank the third and fourth IT assets based on the indices to generate an ordered list.
Owner:CONNECTWISE LLC
Quality of service functions implemented in input interface circuit interface devices in computer network hardware
InactiveUS6870811B2Prevents and reduces congestionError preventionTransmission systemsQuality of serviceRelevant information
The decision to discard or forward a packet is made by a flow control mechanism, upstream from the forwarding engine in the node of a communication network. The forwarding engine includes a switch with mechanism to detect congestion in the switch and return a binary signal B indicating congestion or no congestion. The flow control mechanism uses B and other network related information to generate a probability transmission table against which received packets are tested to determine proactively whether a packet is to be discarded or forwarded.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com