Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
90 results about "It assets" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Definition - An IT asset is any company-owned information, system or hardware that is used in the course of business activities.
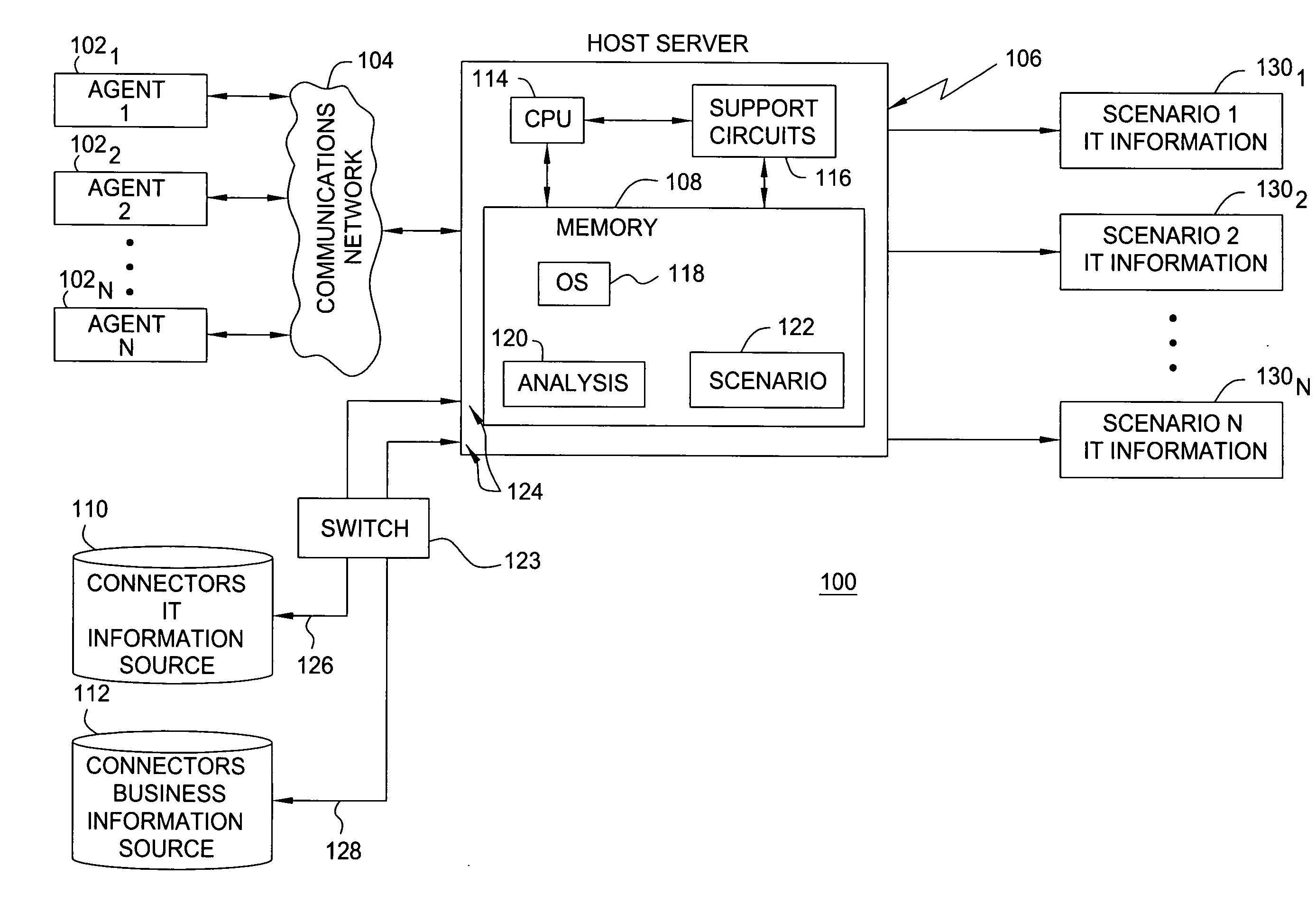
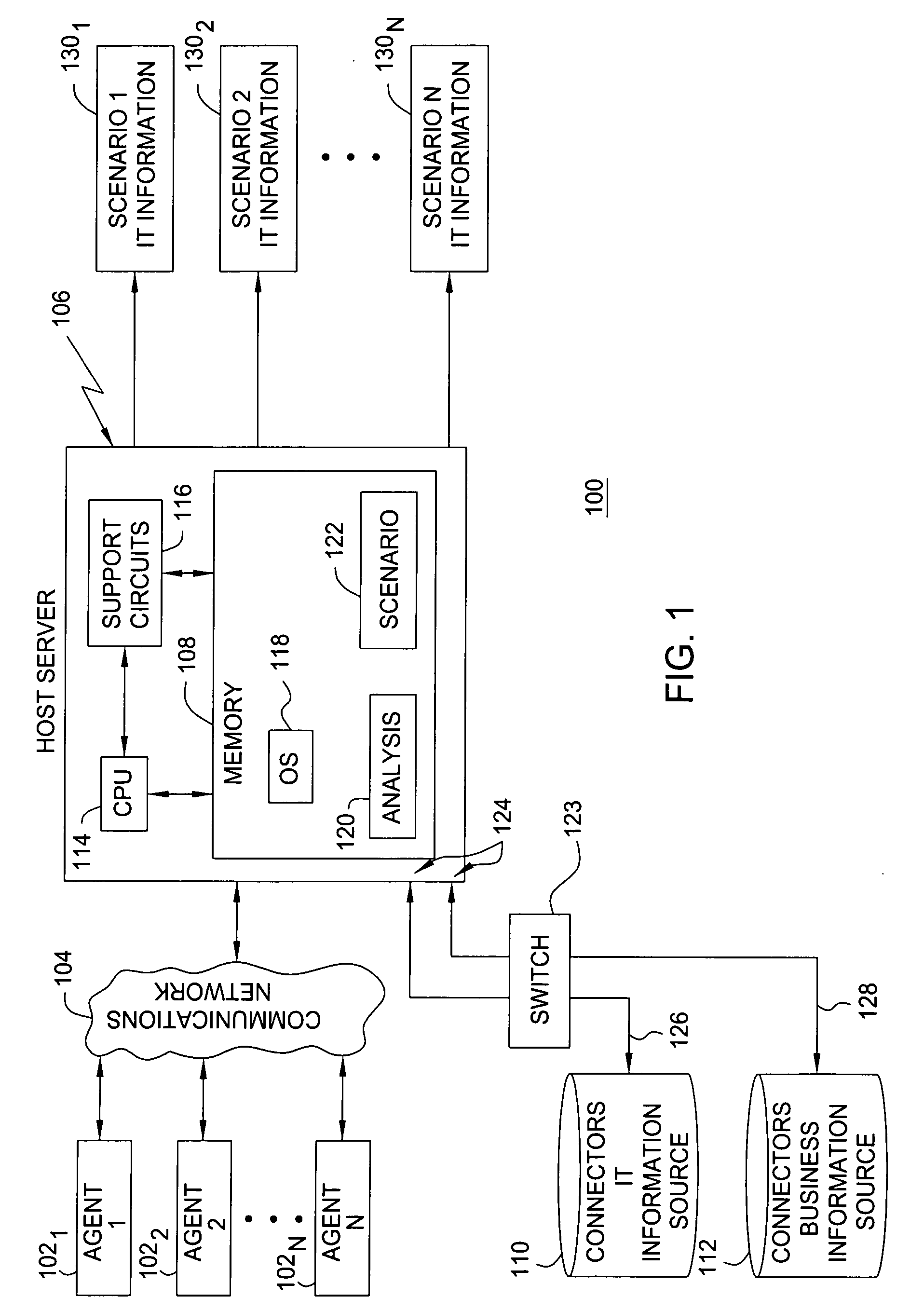
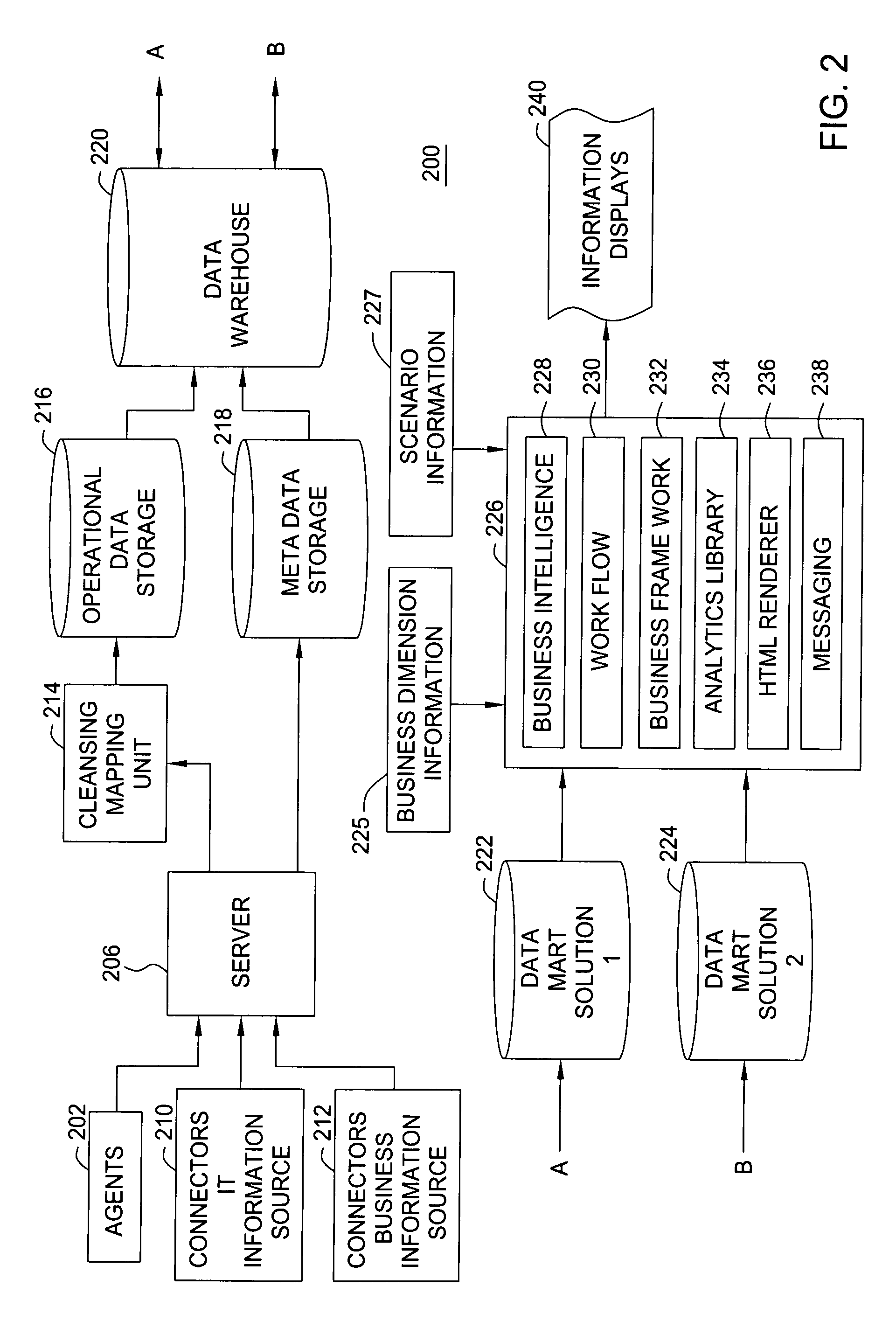
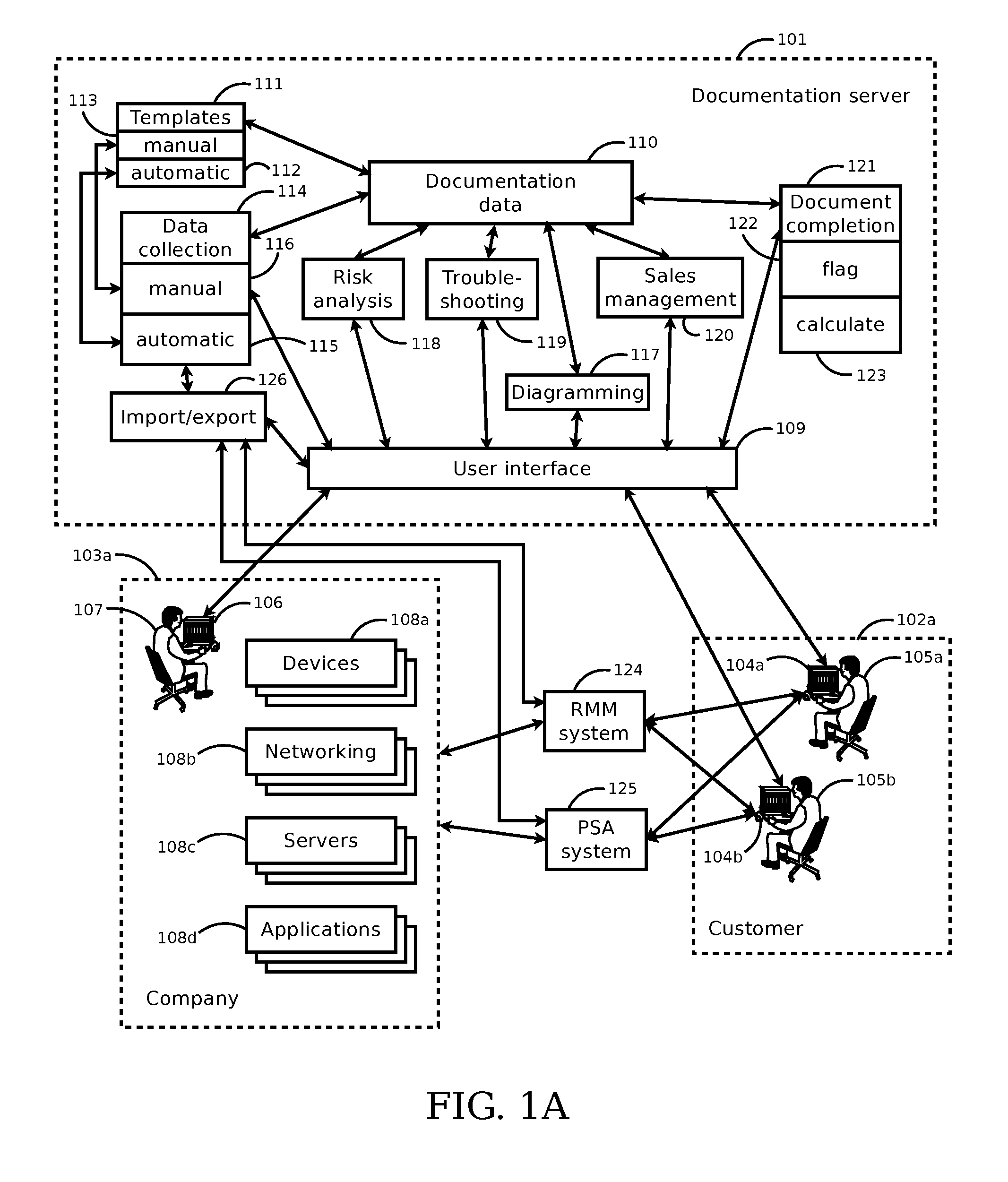
Method and system for filtering, organizing and presenting selected information technology information as a function of business dimensions
A method and system for filtering, organizing and presenting selected information technology (IT) information as a function of business dimensions, through guided analysis, are disclosed. The method and system may be based on the needs and role of the viewer requesting such IT asset information at the time of the request.
Owner:BLAZENT INC
System and method to identify abnormalities to continuously measure transaction risk
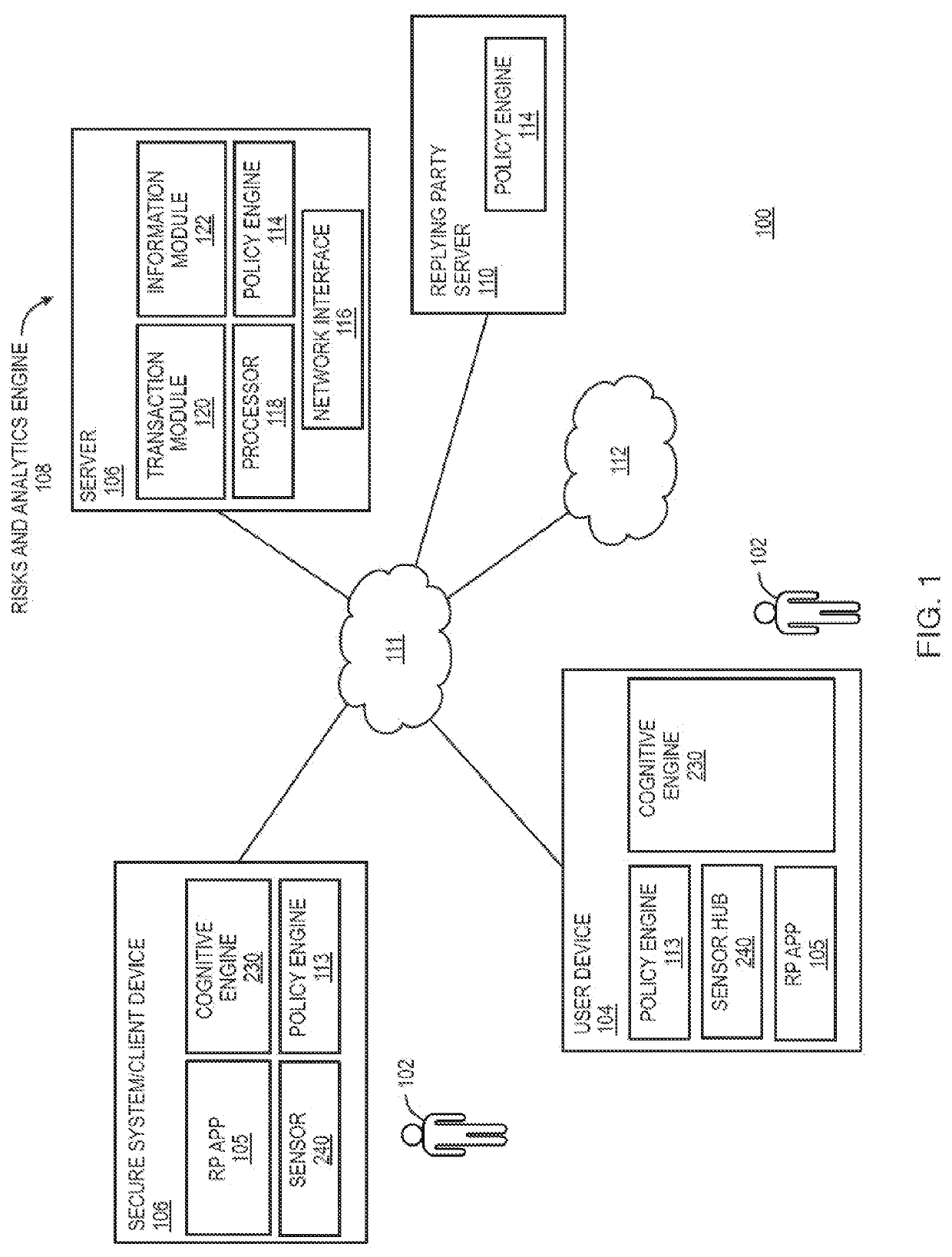
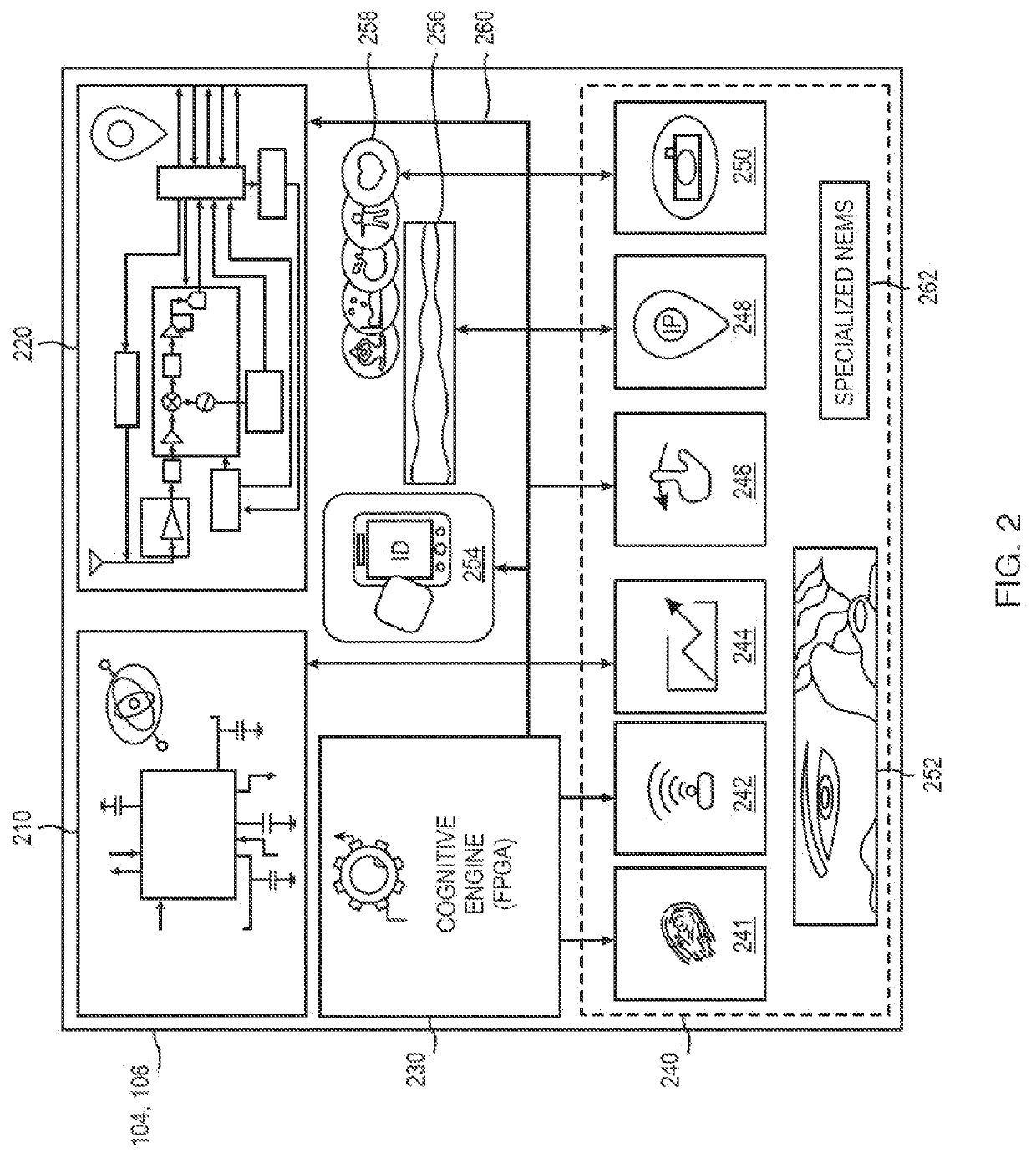
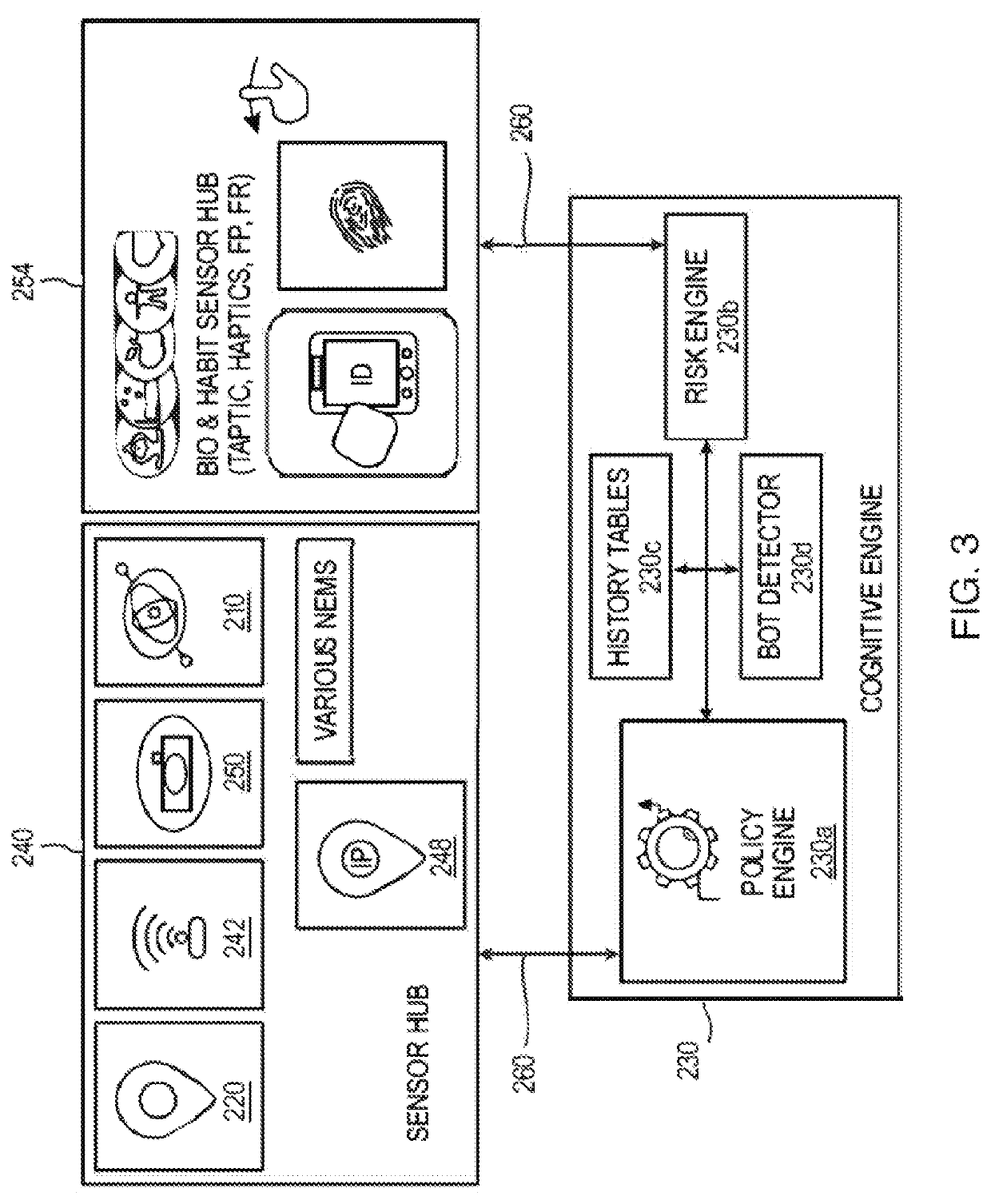
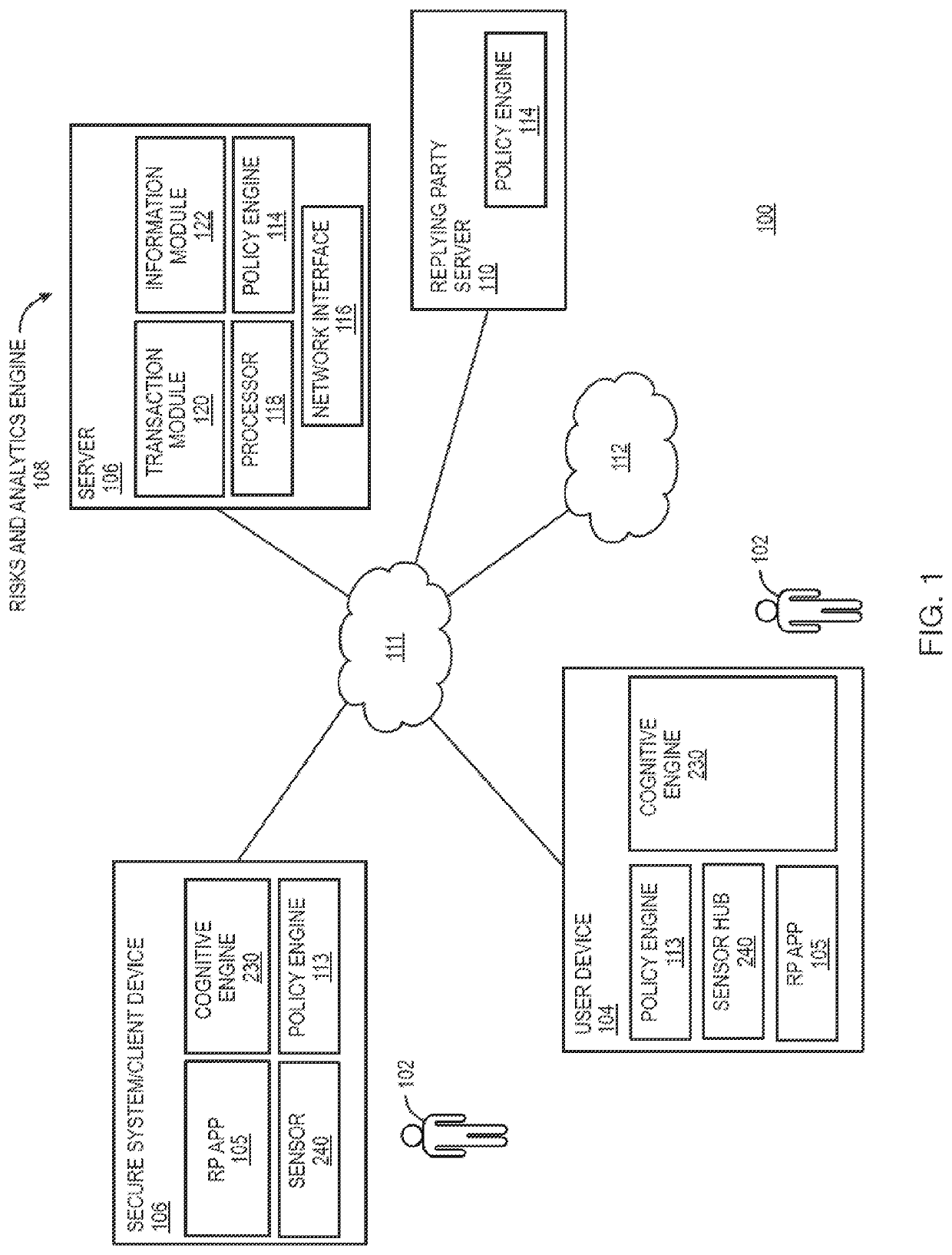
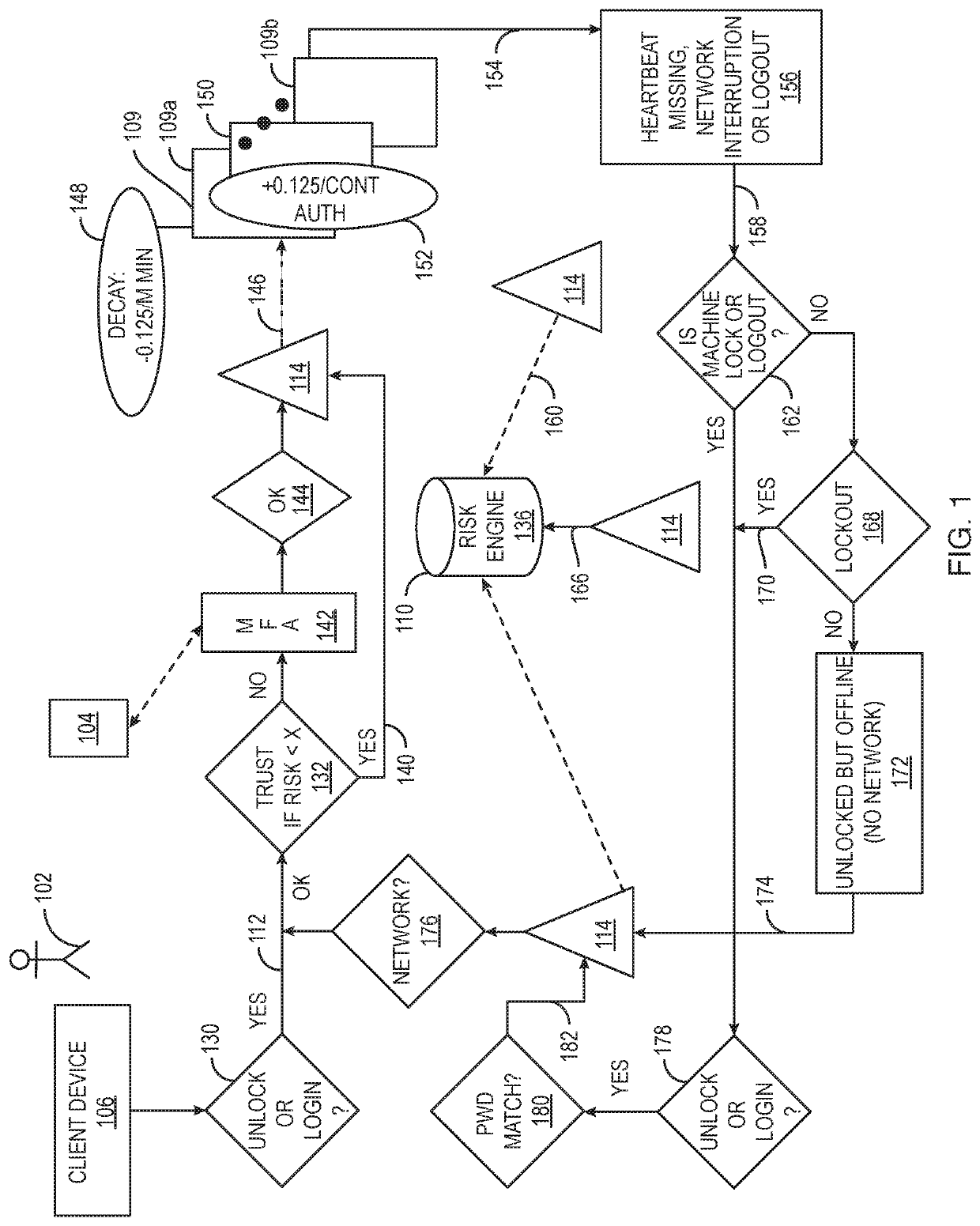
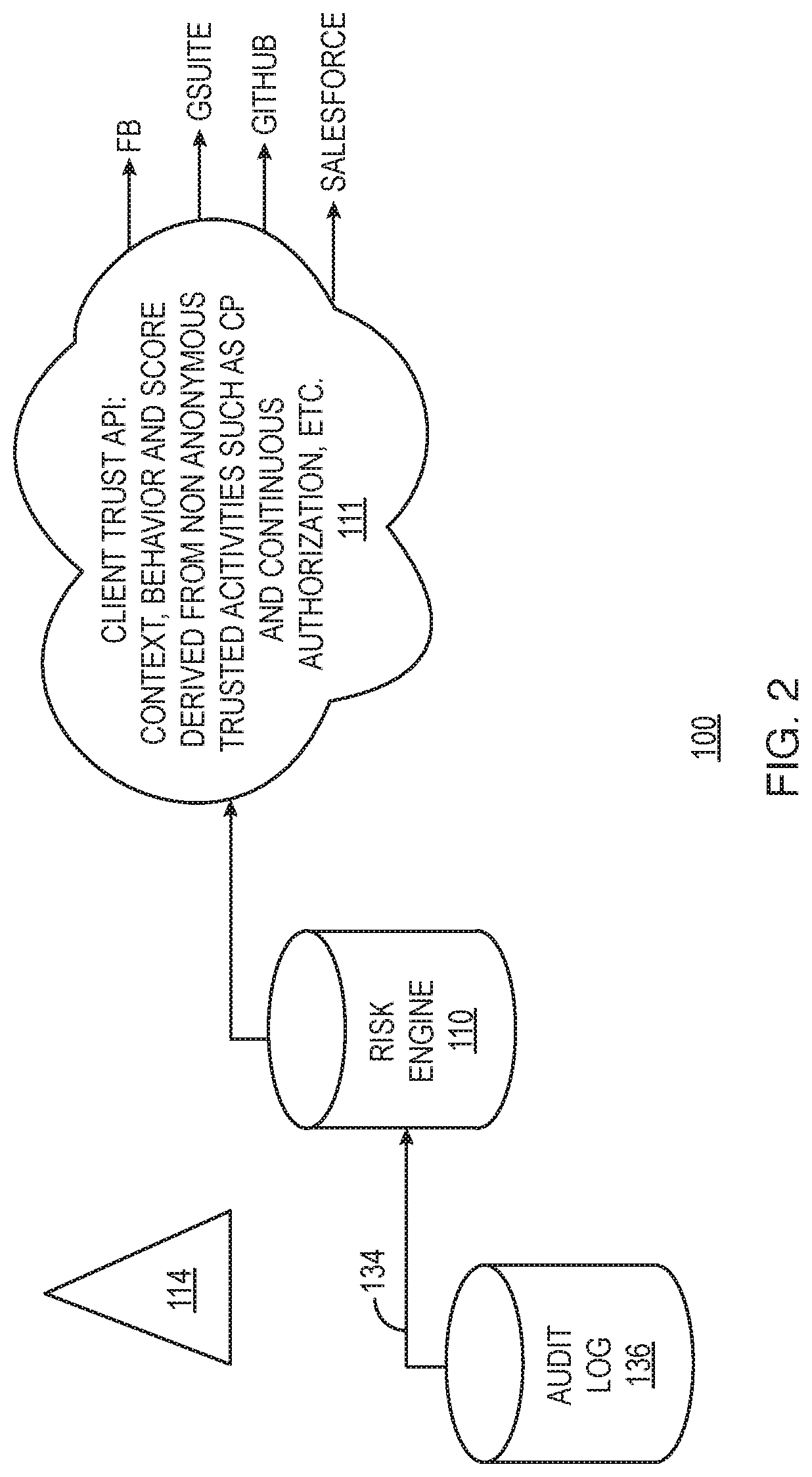
Aspects of the disclosure provide techniques for using behavior based information for providing and restricting access to a secure website, or computer network and its assets to a user. Components of the system may include the following. Client remote computing device, network and browser unique attribute data collection and fingerprinting. Method for capturing user habits and fingerprinting with ability to detect abnormalities through AIML using mobile and wearable device applications. System for detection of normality of user behavior based on habits, and cyber transactions, device access and determining a confidence score associated with each transaction. Method for calculating individual transaction risk based on contextual factors such as user behavior, device, browser and the network traffic and request for authentication by account owner when risk greater than allowed threshold. Method and system to identify user device, browser, and behavior unique attributes, storing and later matching to infer change upon consequent transactions and measuring transaction risk through a search and match against classified set of static and dynamic attributes using a user, browser traffic, device search and match engine.
Owner:SECUREAUTH CORP
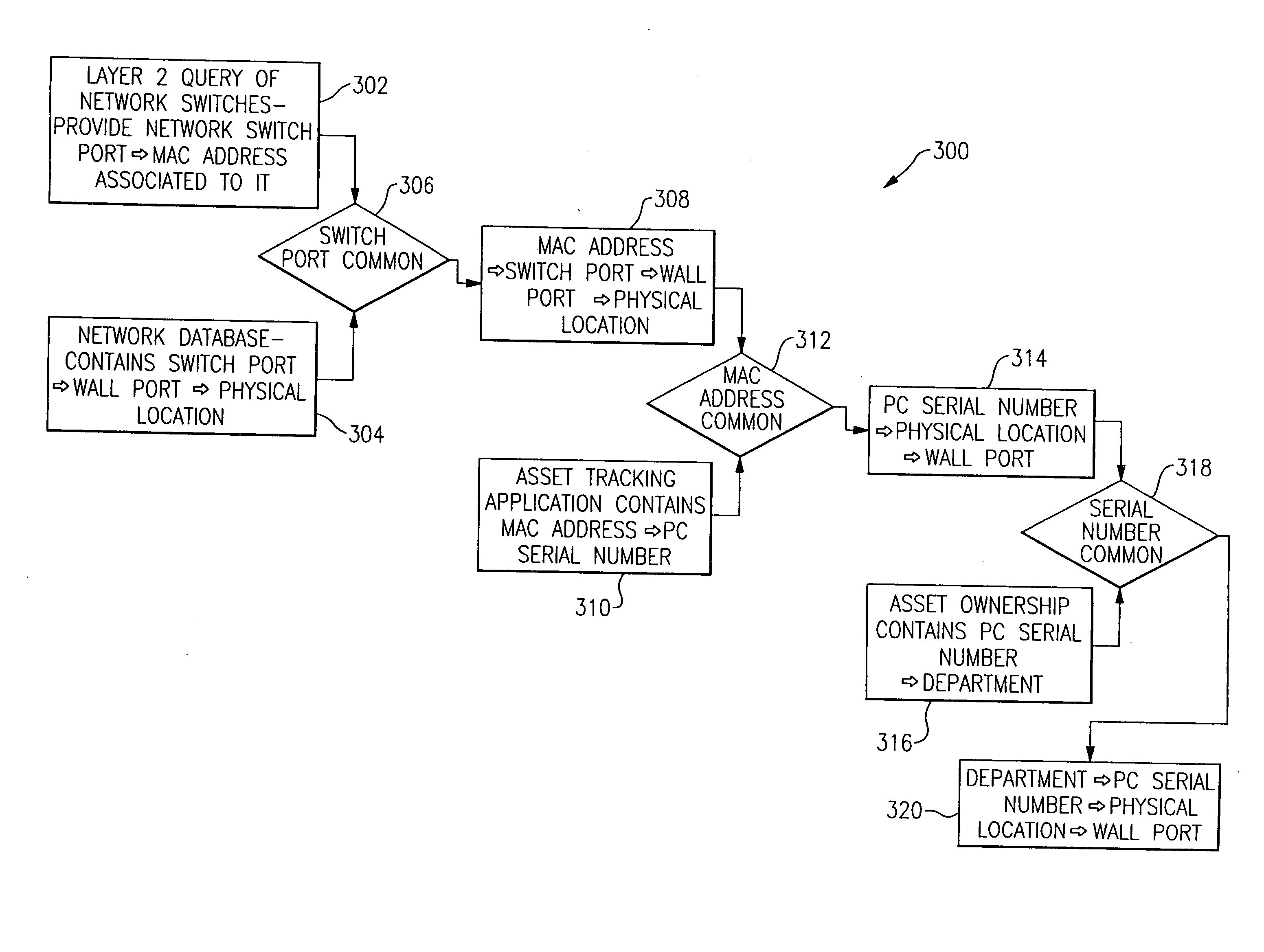
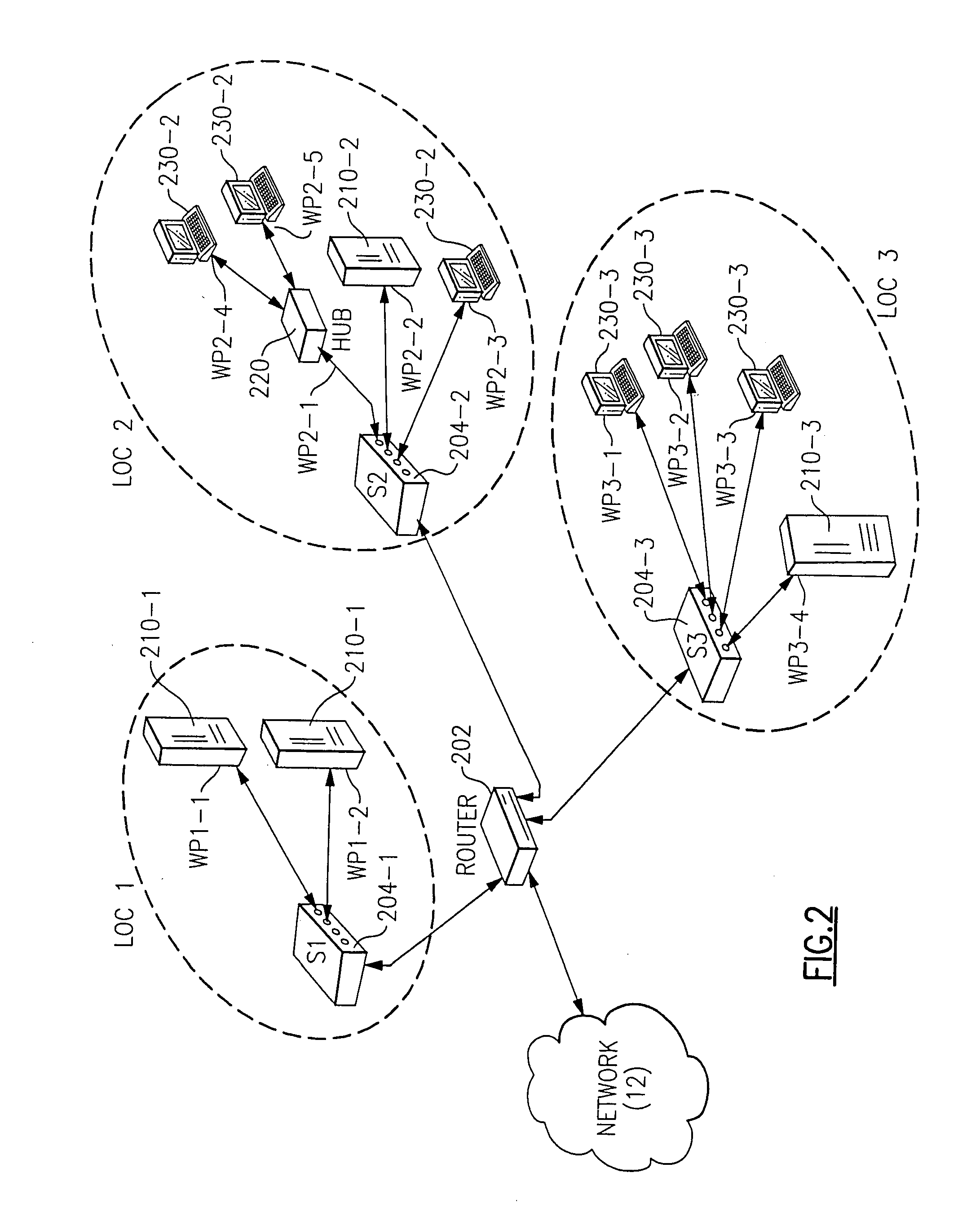
Automated IT asset location system
The present invention is directed to a computerized method for locating and tracking devices in a network. The method including the step of querying the network to obtain network device connectivity data for each device coupled to the network. Device relational data is retrieved from at least one database. The network device connectivity data is correlated with the device relational data to obtain an asset tracking record for each device. The asset tracking record includes device location data, device identification data, and device responsibility data.
Owner:LOCKHEED MARTIN CORP
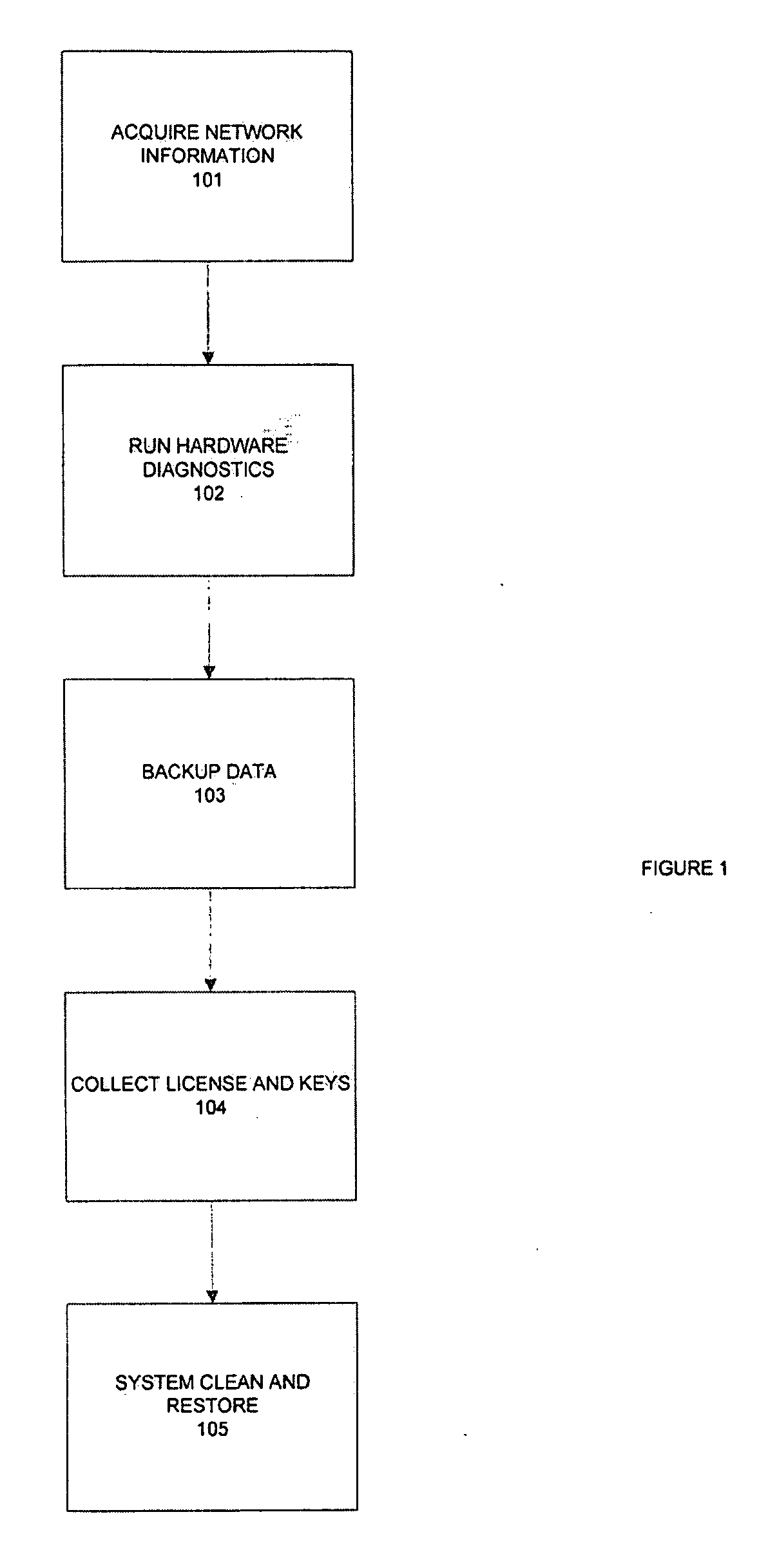
It asset management system
InactiveUS20080177598A1Enhanced resale valueIncrease valueSustainable waste treatmentResourcesHard disc driveOperational system
The system provides a method to automate the complex processes that occur at the end-of-life of IT hardware assets, and at the same time, increase the resale value of these assets. Using the system, an IT manager is able to identify a scalable number of systems for Secure Disk Wiping, Diagnostic Testing, Hardware Audit, License Recovery and Backup. These tasks are schedule driven in one embodiment, performed on multiple systems simultaneously, and minimizing the usage of network bandwidth. (In one embodiment, the system is agentless). At the same time, an IT manager can increase resale value by; restoring operating systems to hard drives once wiped, diagnostically testing systems, and capturing detailed hardware information all of which can be supplied to potential buyers or new users of repurposed / refurbished components.
Owner:DAVIE ROBERT
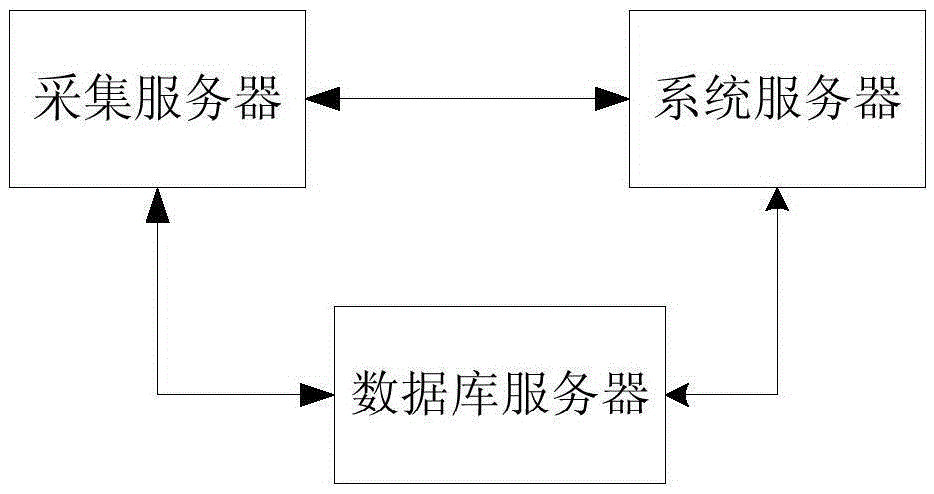
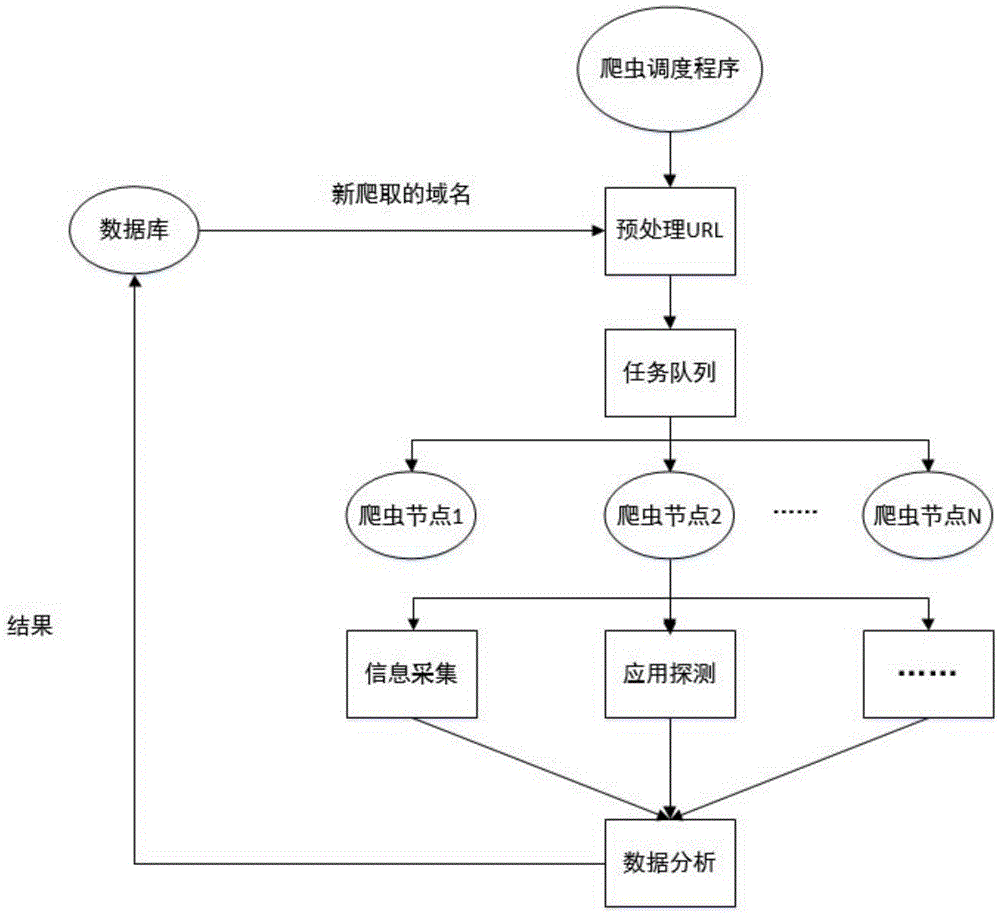
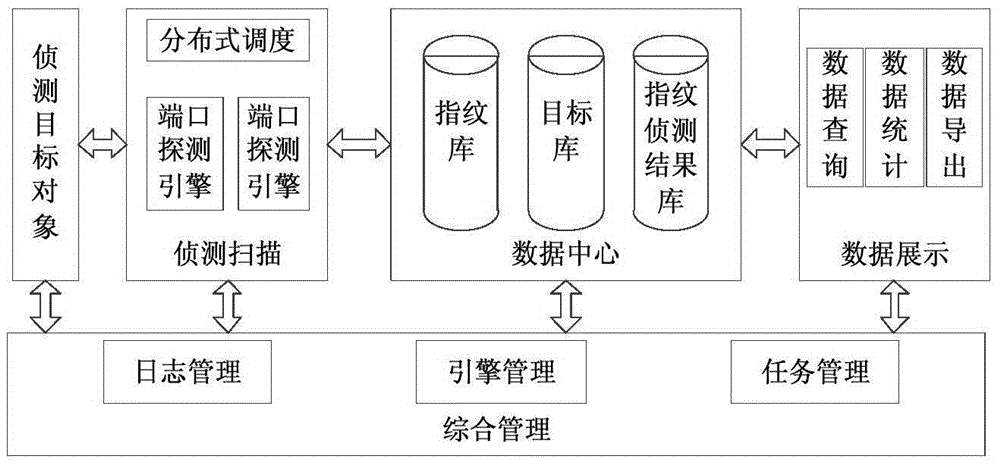
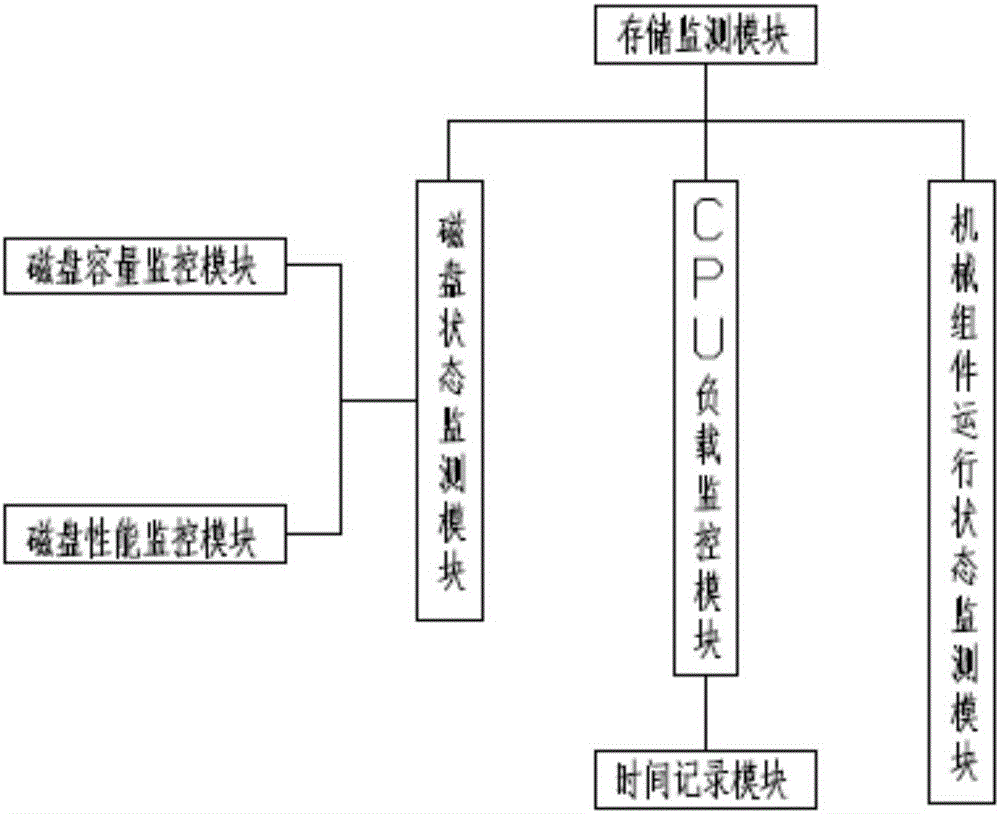
Intelligent power grid IT asset safety monitoring system based on distributed scheduling
InactiveCN106888194ACapable of self-discoveryImprove security policy guidance capabilitiesTransmissionDatabase serverData information
The invention discloses an intelligent power grid IT asset safety monitoring system based on distributed scheduling. The system comprises multiple acquisition servers, multiple system servers and multiple database servers, wherein the acquisition servers are used for acquiring the IT asset data information and comparing the acquired IT asset data information to find vulnerability, the system servers are used for distributing received detection tasks to each acquisition server, and the database servers are used for realizing storage, update, query and statistics of a vulnerability database, a target database and a vulnerability detection result database. The system is advantaged in that through constructing a distributed database, establishing a detection cluster and realizing distributed degree scheduling, distributed operation and analysis in a real sense are realized, and high-efficiency safety monitoring on intelligent power grid IT assets is accomplished.
Owner:STATE GRID CORP OF CHINA +5
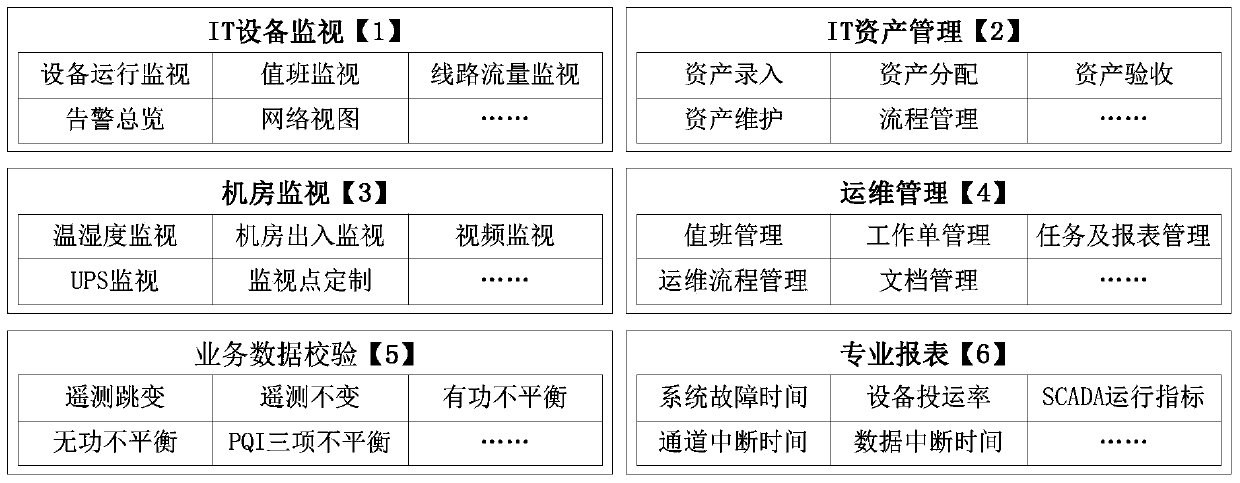
Province-city secondary system integrated comprehensive monitoring and process management system in power dispatching and implementation method for system
InactiveCN103745322AFull displaySolve the problem of managing processes that do not form a closed loopResourcesData informationClosed loop
The invention discloses a province-city secondary system integrated comprehensive monitoring and process management system in power dispatching and an implementation method for the system. The system is designed on the basis of SOA (service-oriented architecture), a bottom layer is programmed by adopting standard C, a front end is constructed by applying a J2EE (java 2 enterprise edition) technology, and the system is a cluster-type integrated architecture system which is arranged on a plurality of servers; the system is characterized by comprising a real-time monitoring module and a management function module, wherein the real-time monitoring module is used for IT (information technology) monitoring, machine room environment monitoring and service data validating (RTU (remote terminal unit) and OCS (office communication server) monitoring); the management function module comprises IT asset management, operation and maintenance management and professional reports. The system and the implementation method have the beneficial effects that a comprehensive platform is realized, and the automatic monitoring situations can be displayed comprehensively; province-city two-level automatic system data sharing is realized, and valuable data information can be provided for operators on duty automatically; the problem that a closed-loop process is not formed in the conventional automatic internal management is solved.
Owner:YUNNAN ELECTRIC POWER DISPATCH CONTROL CENT +1
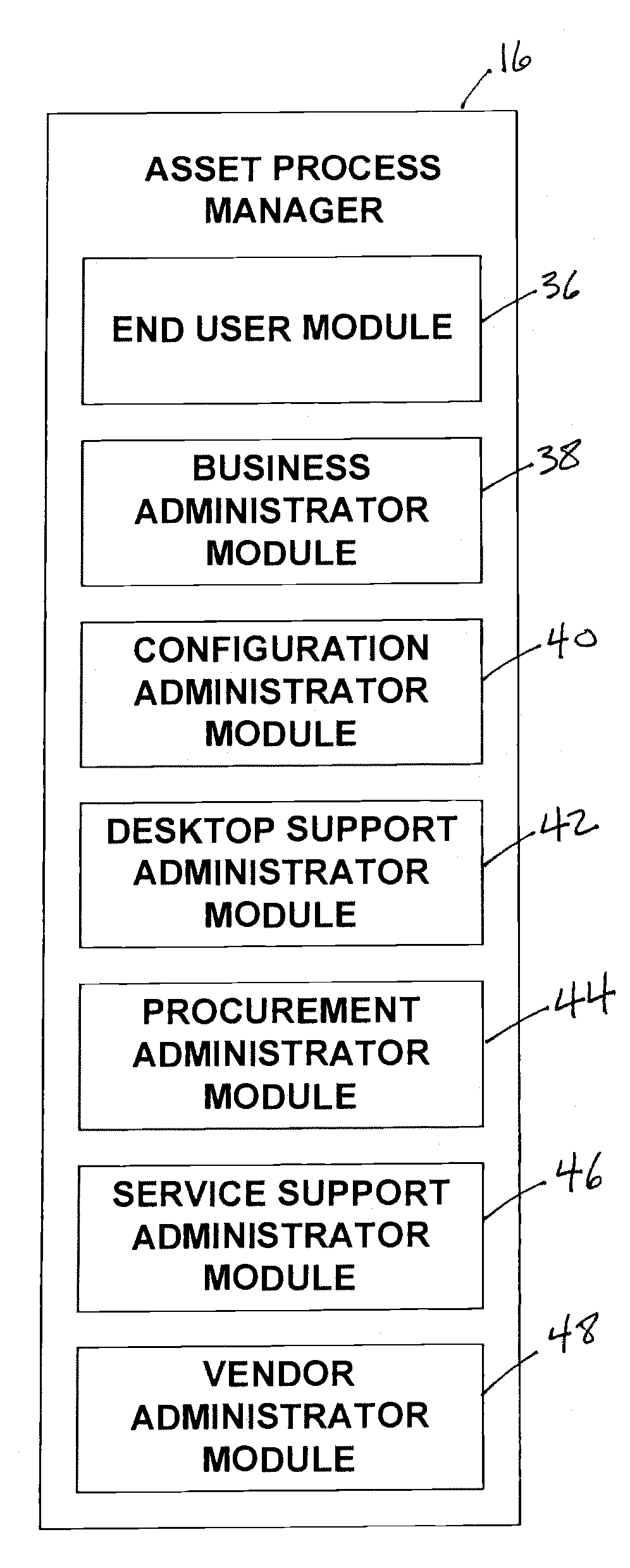
System and method for managing IT assets
InactiveUS7747738B2Improve efficiencyReduce the amount requiredFinanceDigital computer detailsAmbulatory systemRelevant information
Owner:CA TECH INC
Systems and methods for documenting, analyzing, and supporting information technology infrastructure
ActiveUS20150278219A1Easy diagnosisPrediction is simpleWeb data indexingDigital data processing detailsNetworking hardwareInformation infrastructure
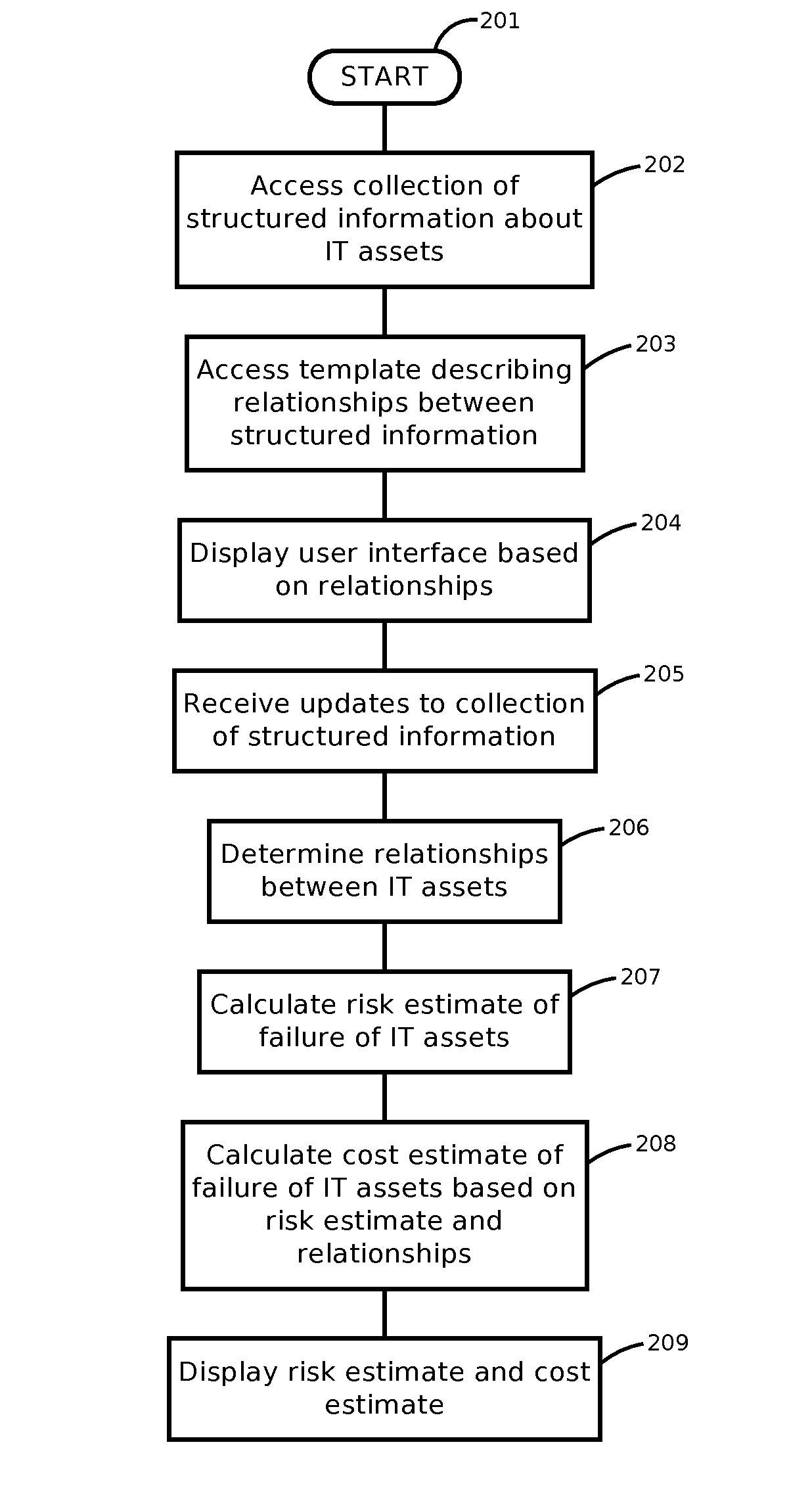
Systems and methods of the present disclosure facilitate managing information technology (IT) infrastructure. The system can include a server configured to retrieve data records for first and second IT assets, each asset comprising at least one of a computing device, a software application, an end user, a business unit, a piece of networking hardware, or an agreement for an IT service. The server can select a template comprising a relationship between the first and second data records. The system can include a link generator configured to generate a different relationship, absent from the template, between the first and second data records. The system can include a search engine configured to identify third and fourth IT assets that satisfy the second relationship, determine an indices of completeness for the third and fourth IT assets, and rank the third and fourth IT assets based on the indices to generate an ordered list.
Owner:CONNECTWISE LLC
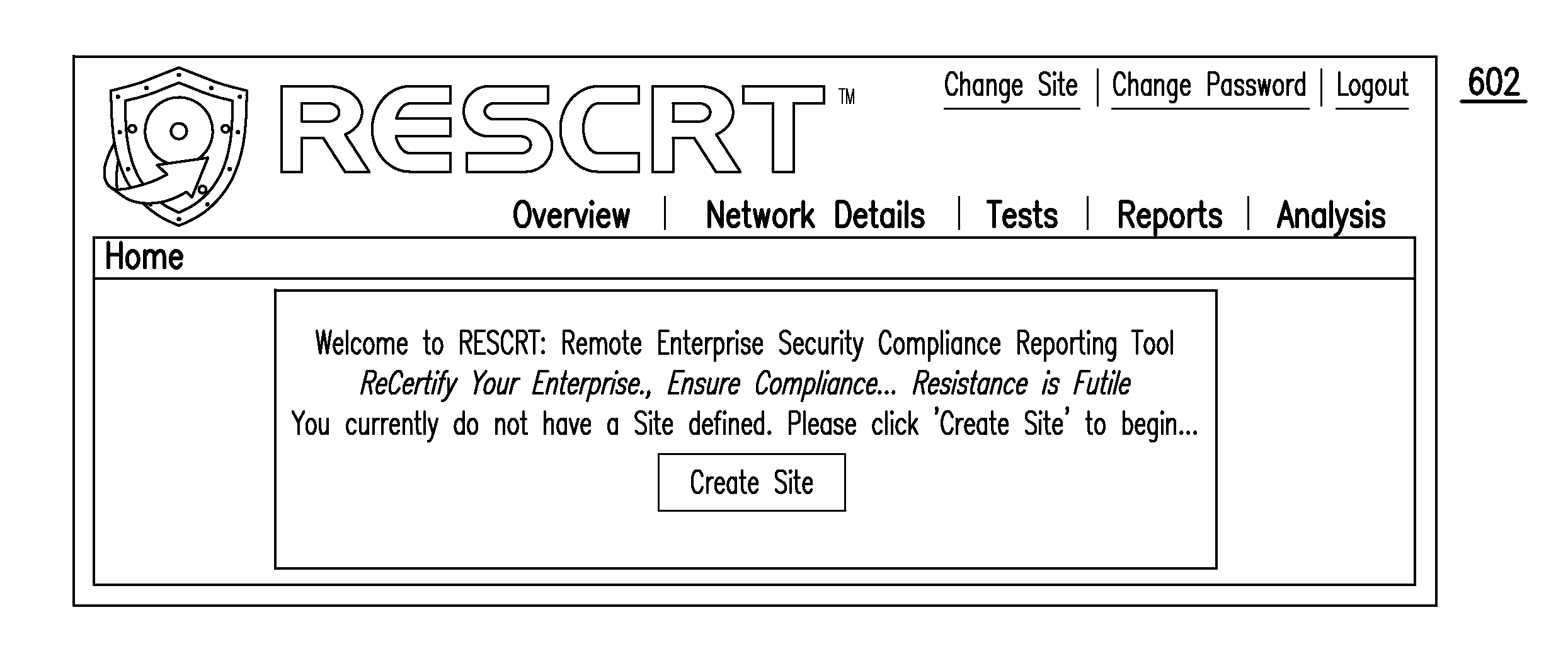
Remote enterprise security compliance reporting tool
Described is a method for cross-referencing one or more defined entities against a system configuration, system component configuration and / or system IT asset configuration to thereby validate applicability, non-applicability, compliance and / or non-compliance of a policy, set of policies, and / or policy checks with respect to the system, system component and / or system IT asset configuration. Also described are an apparatus and a machine-readable medium for performing this method.
Owner:SMARTRONIX
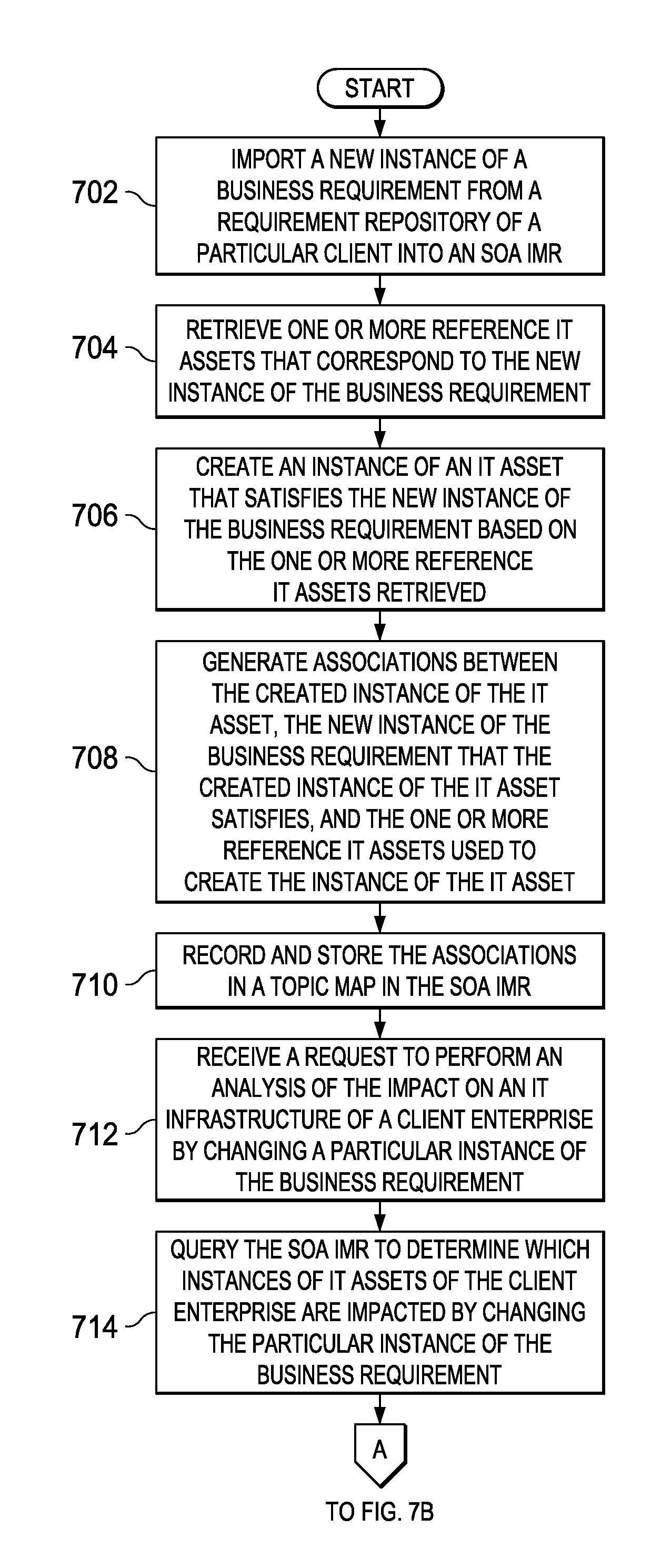
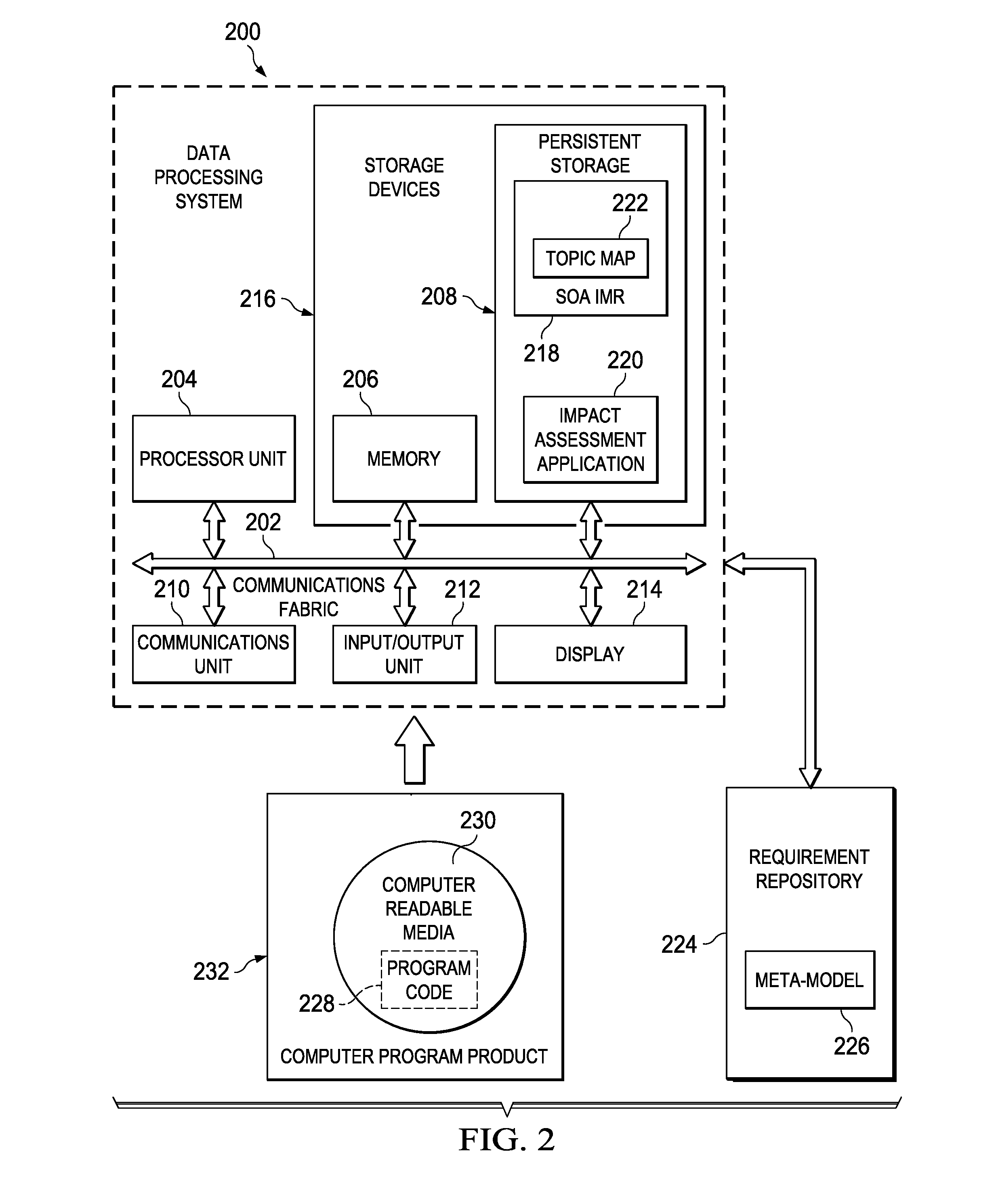
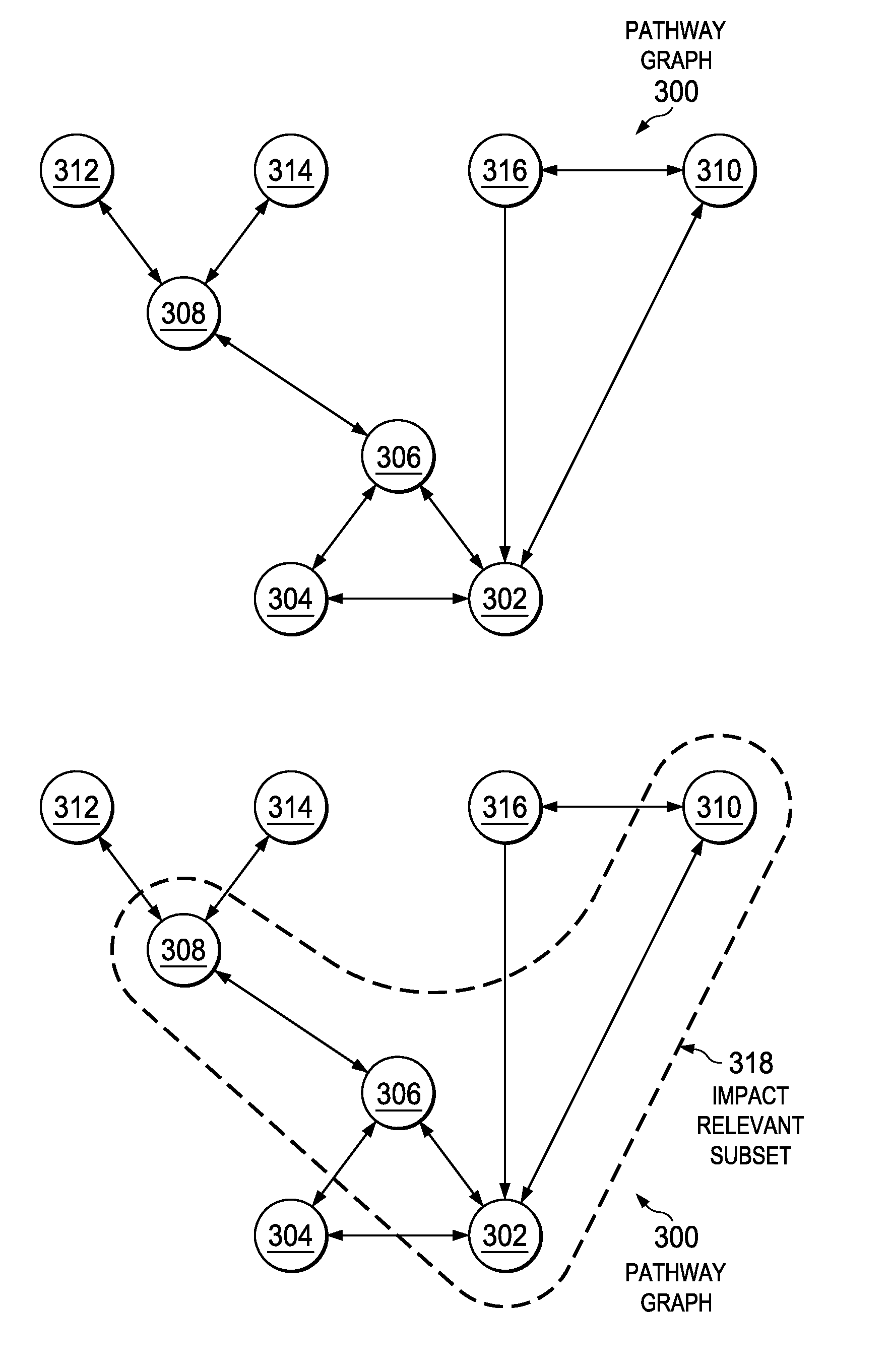
Cross Repository Impact Analysis Using Topic Maps
An apparatus for automatically analyzing the impact of changing a business requirement on an IT infrastructure of an enterprise. A request is received to perform an analysis of an impact on the enterprise by changing a particular instance of the business requirement. A model repository is queried to determine which IT assets of the enterprise are impacted by changing the particular instance of the business requirement. An impact relevant subset of a topic map is received from the model repository representing the impact on the enterprise by changing the particular instance of the business requirement that includes the particular instance requirement as a root node and only those specific assets impacted by changing the particular instance requirement as connected nodes. Then, the impact relevant subset of the topic map representing the impact on the enterprise by changing the particular instance of the business requirement is outputted on an output device.
Owner:IBM CORP
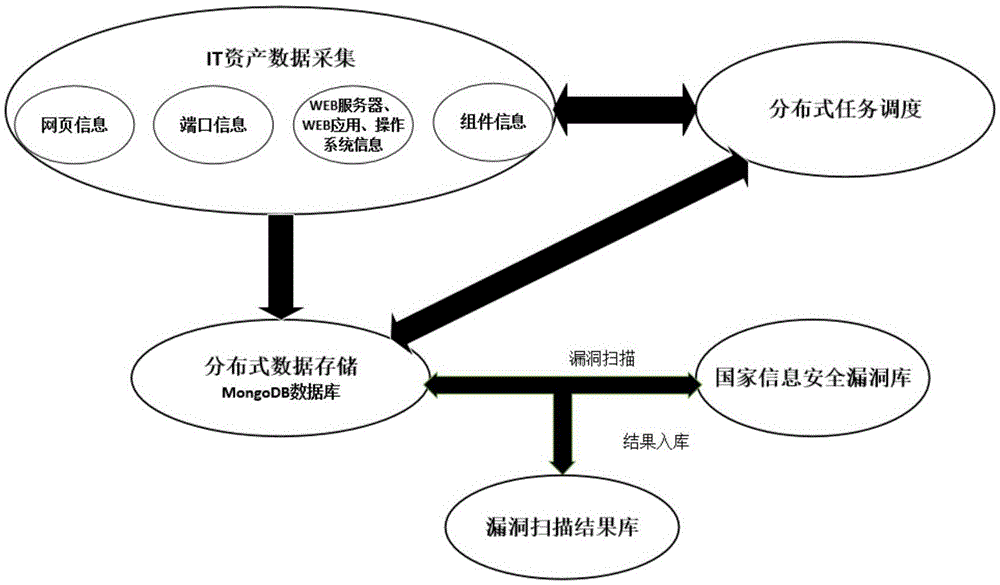
IT asset large-scale detection system of smart power grid
InactiveCN106888106ACapable of self-discoveryFull detectionData switching networksDatabase serverPower grid
The invention discloses an IT asset large-scale detection system of a smart power grid. The detection system comprises a scheduling server, a database server and multiple network equipment fingerprint acquiring servers, wherein the scheduling server is used for acquiring detection tasks and distributing the detection tasks to the various network equipment fingerprint acquiring servers according to certain rules, the network equipment fingerprint acquiring servers are used for carrying out assembly fingerprint detection scanning for IP targets of the smart power grid after receiving the detection tasks distributed by the scheduling server and sending acquired identification data to the database server, and the database server is used for saving the identification data sent by the network equipment fingerprint acquiring servers into a target database. The detection system is advantaged in that autonomous discovery capability for IT assets of the smart power grid and omnibearing information positioning capability are realized, and comprehensive, real-time and accurate detection on the intelligent power grid space can be realized.
Owner:STATE GRID CORP OF CHINA +5
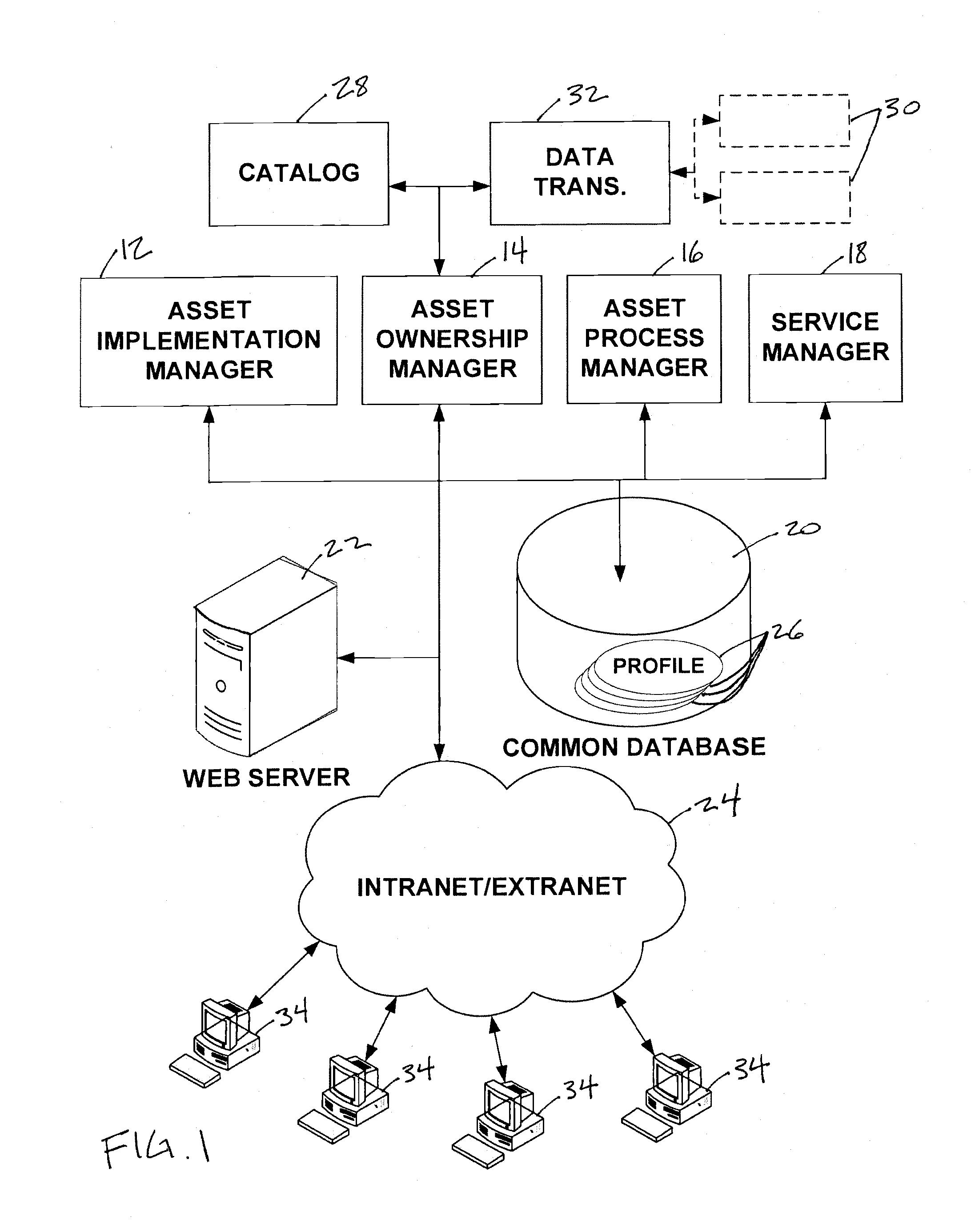
System and Method for Managing IT Assets
InactiveUS20080243921A1Improve efficiencyReduce the amount requiredFinanceDigital computer detailsRelevant informationTelenet
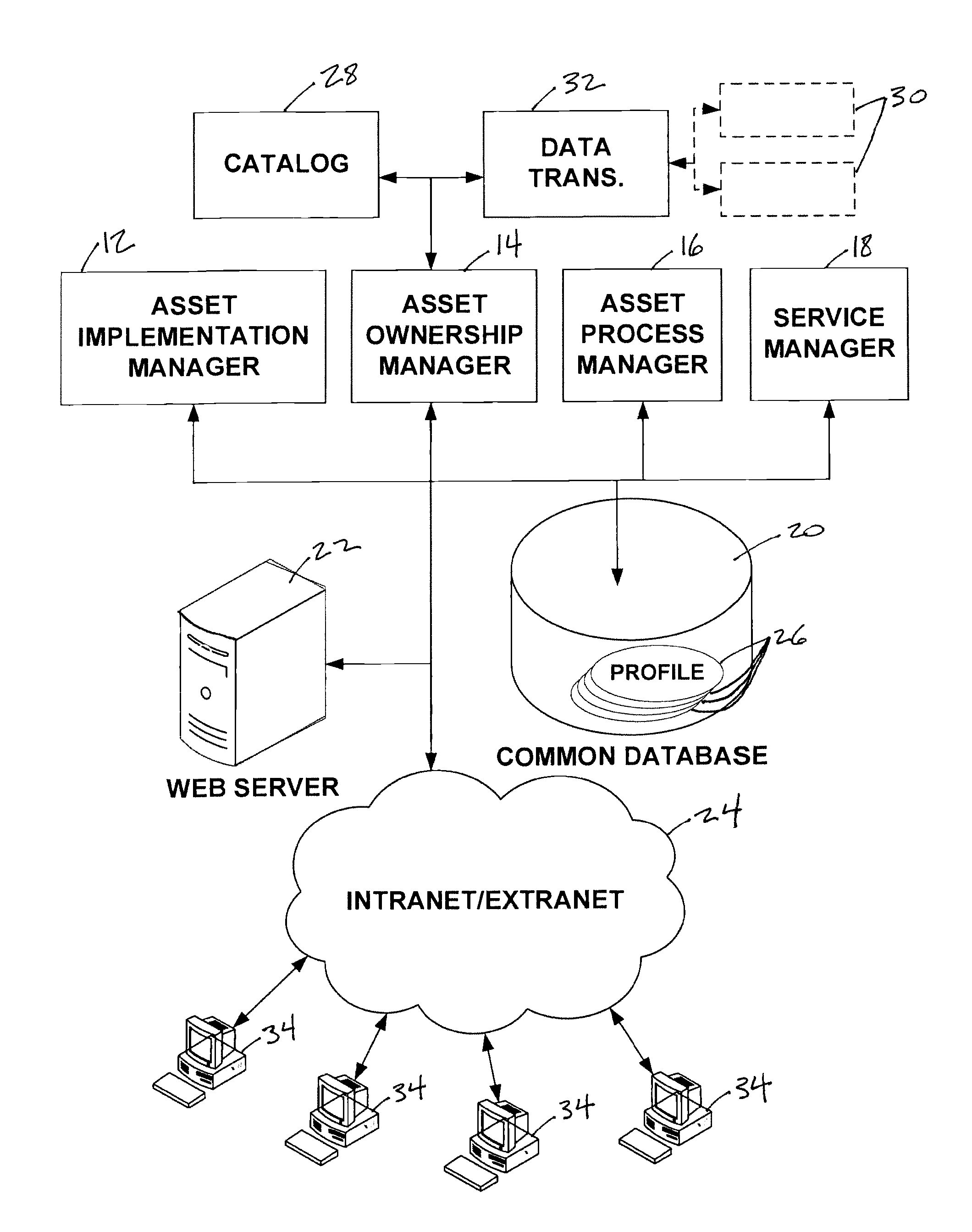
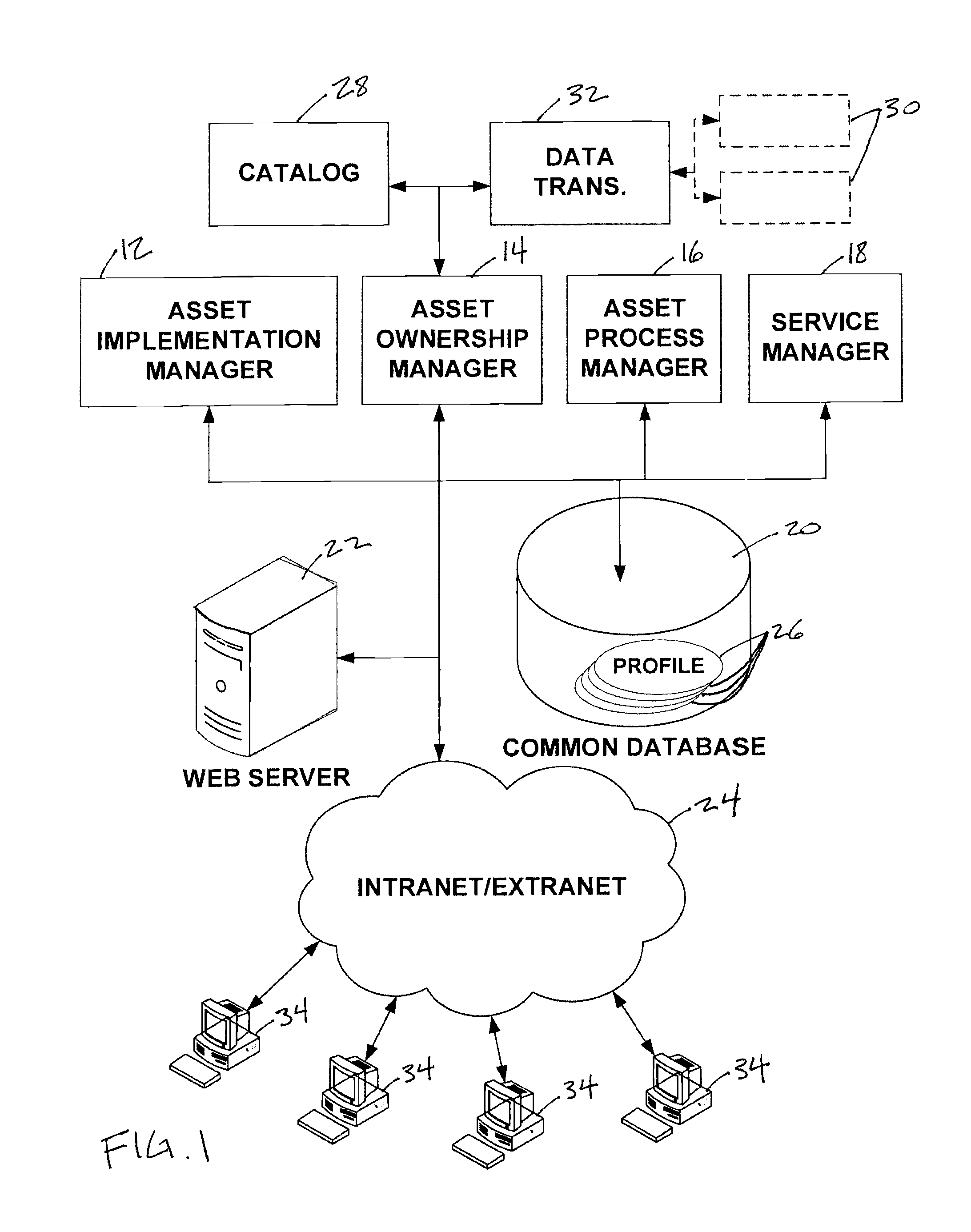
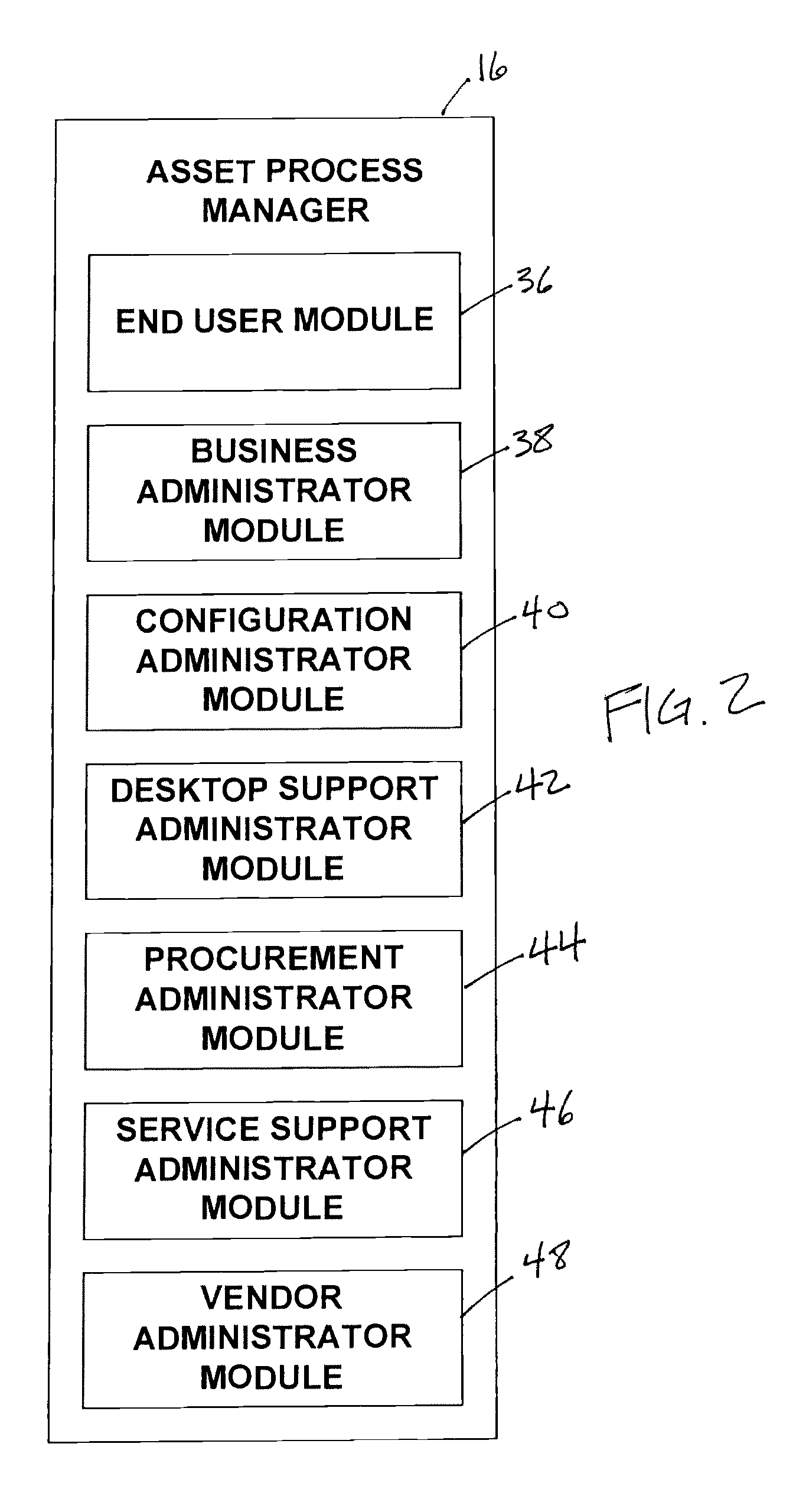
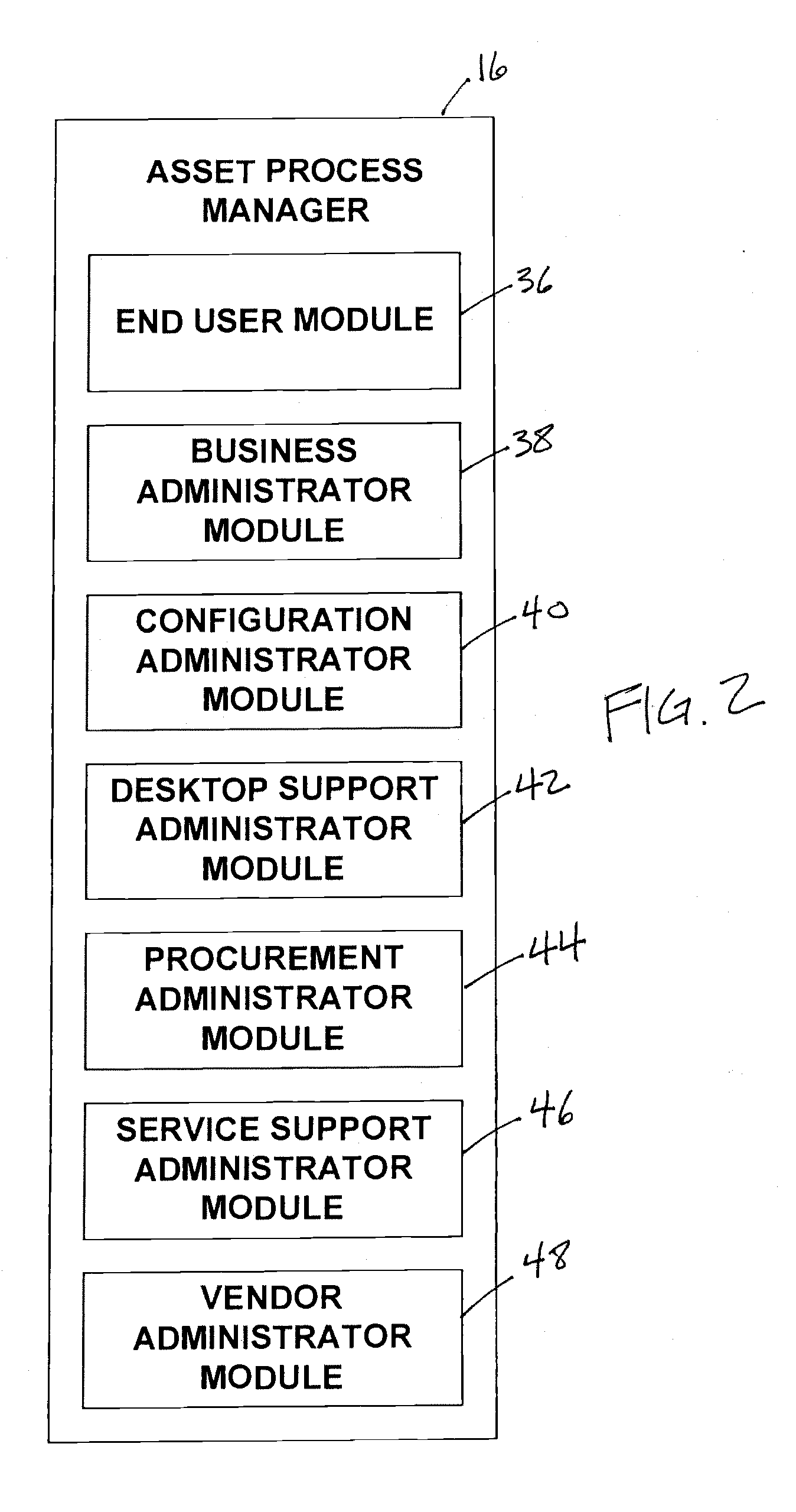
A system configured to manage IT assets associated with an entity (e.g., a company, an institution, etc.), in accordance with one or more embodiments of the invention. The IT assets may include hardware assets, software assets, telecommunications assets, and / or other IT assets. The system enables substantially all of the information relevant to the individual IT assets to be organized within a single repository throughout the life cycle of the IT assets (e.g., from order to disposal). By organizing the relevant information within a single repository, automation and dynamic system interaction may be leveraged during the life cycle of a given IT asset to track and / or monitor the given IT asset with an enhanced efficiency. In some embodiments, the system may include a common database, and an asset implementation manager, an asset ownership manager, an asset process manager, a service manager in operative communication with the common database.
Owner:CA TECH INC
Cross repository impact analysis using topic maps
An apparatus for automatically analyzing the impact of changing a business requirement on an IT infrastructure of an enterprise. A request is received to perform an analysis of an impact on the enterprise by changing a particular instance of the business requirement. A model repository is queried to determine which IT assets of the enterprise are impacted by changing the particular instance of the business requirement. An impact relevant subset of a topic map is received from the model repository representing the impact on the enterprise by changing the particular instance of the business requirement that includes the particular instance requirement as a root node and only those specific assets impacted by changing the particular instance requirement as connected nodes. Then, the impact relevant subset of the topic map representing the impact on the enterprise by changing the particular instance of the business requirement is outputted on an output device.
Owner:INT BUSINESS MASCH CORP
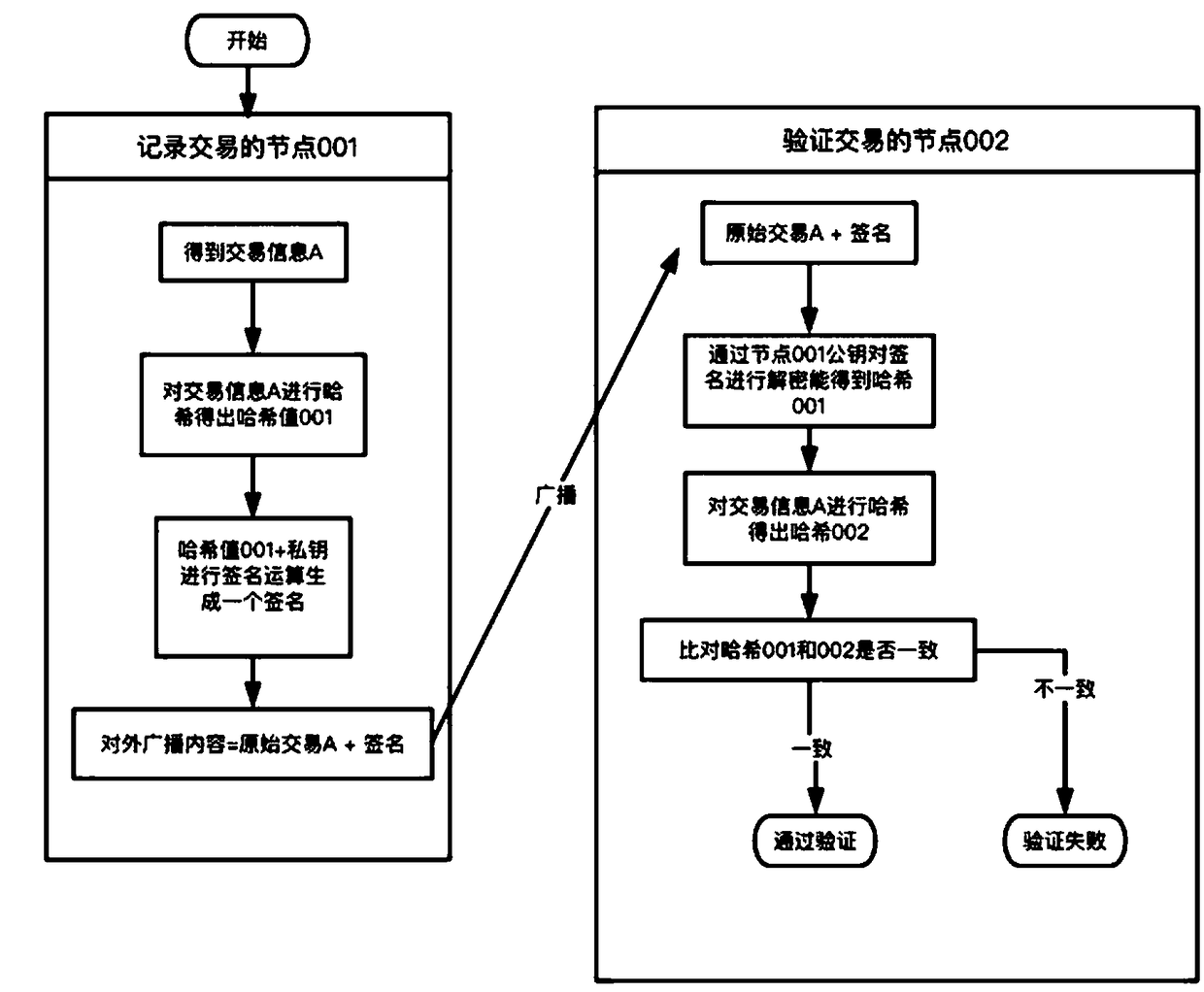
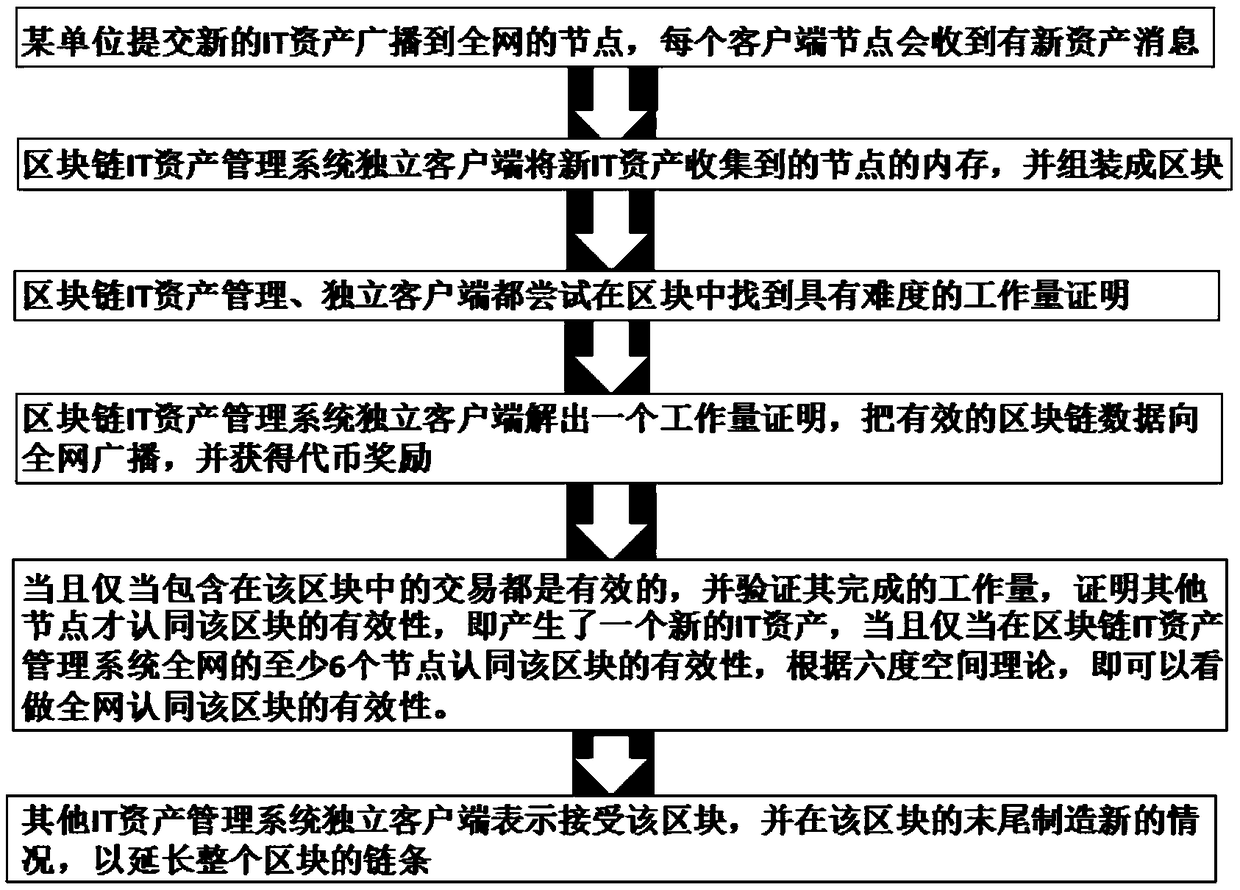
An IT asset management method based on a block chain
InactiveCN109409749ASolve storage problemsValue maximizationResourcesProblem managementAccident management
The invention discloses an IT asset management method based on a block chain. The invention solves the problem of decentralized accounting and unified server storage by building an economic system centered on competition-bookkeeping-reward. The IT asset management system builds a forward circulation economic system by means of a block chain, so that the IT asset management system naturally grows and develops and expands under the condition that no powerful centralization mechanism or organization promotion exists. The method is applicable to owned management organizations; Hardware, software and information assets which can play a value for organizing services are also suitable for management of the whole process including but not limited to IT asset demand proposing, type selection, fundbudget and preparation, purchasing, contract, registration and entry, installation, use, asset accident management, problem management, maintenance, upgrade, change, migration, transfer, spare part management, scrapping and the like.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
System and method to identify user and device behavior abnormalities to continuously measure transaction risk
Aspects of the disclosure provide techniques for using behavior based information for providing and restricting access to a secure website, or computer network and its assets to a user. Components of the system may include the following. Client remote computing device, network and browser unique attribute data collection and fingerprinting. Method for capturing user habits and fingerprinting with ability to detect abnormalities through AIML using mobile and wearable device applications. System for detection of normality of user behavior based on habits, and cyber transactions, device access and determining a confidence score associated with each transaction. Method for calculating individual transaction risk based on contextual factors such as user behavior, device, browser and the network traffic and request for authentication by account owner when risk greater than allowed threshold. Method and system to identify user device, browser, and behavior unique attributes, storing and later matching to infer change upon consequent transactions and measuring transaction risk through a search and match against classified set of static and dynamic attributes using a user, browser traffic, device search and match engine.
Owner:SECUREAUTH CORP
System and method for continuous passwordless authentication across trusted devices
ActiveUS10824702B1Digital data protectionDigital data authenticationEngineeringArtificial intelligence
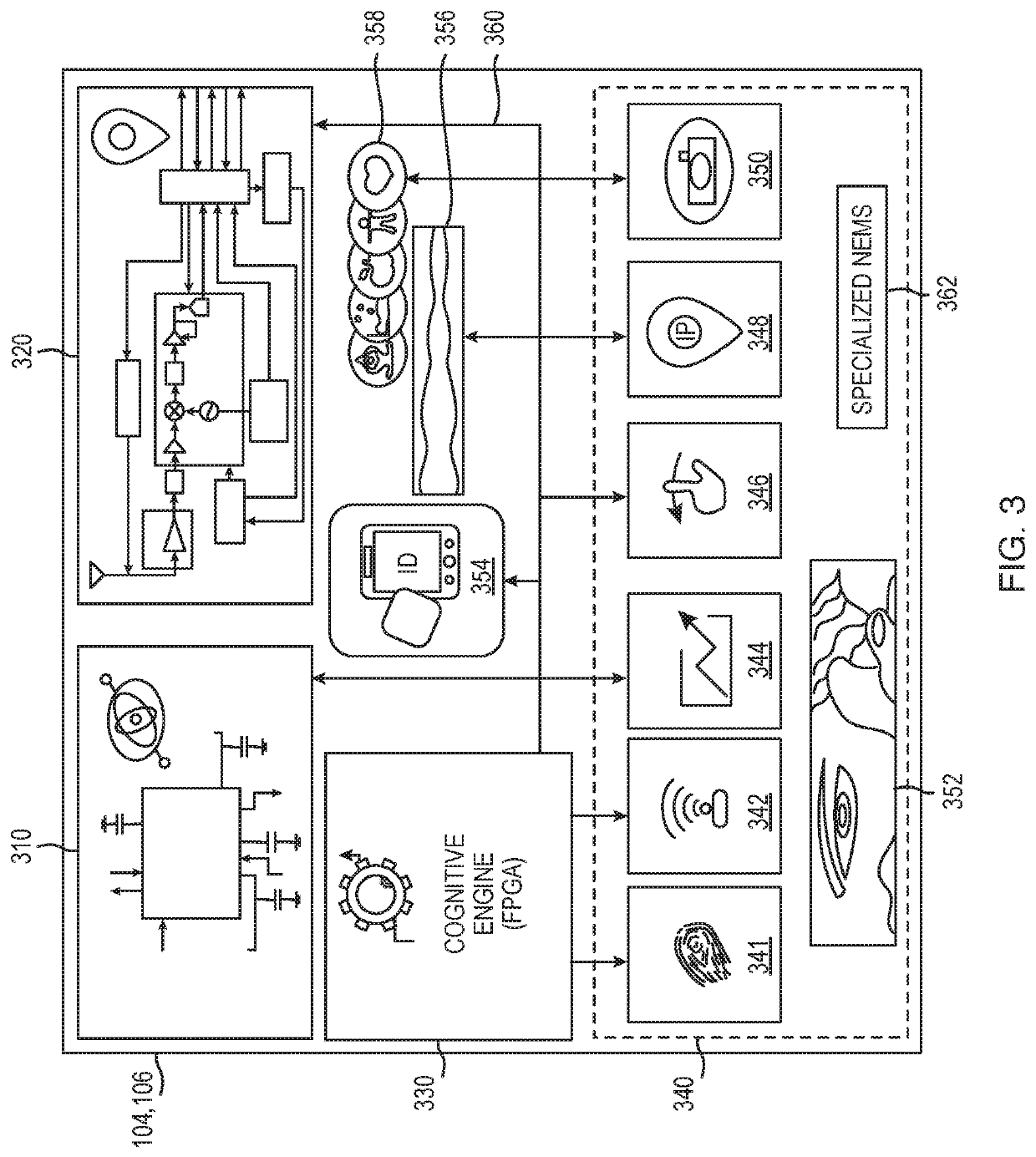
Aspects of the disclosure provide techniques for using egocentric and allocentric information for providing and restricting access to a secure network and its assets to a user entity. The system may include capturing user habits and fingerprinting with ability to detect abnormalities through artificial intelligence / machine learning (AIML) using mobile and wearable device applications.
Owner:SECUREAUTH CORP
IT asset management system
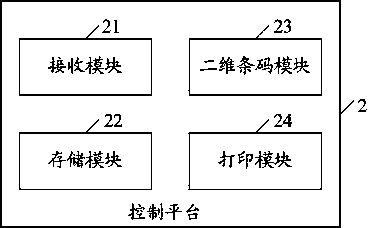
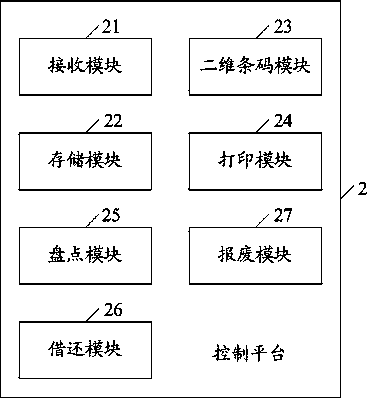
InactiveCN103440547AStrong error correction abilityIncrease reflectionResourcesCode moduleSoftware engineering
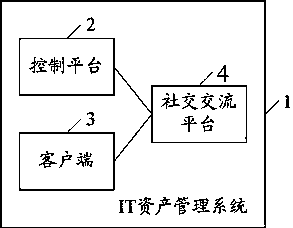
The invention discloses an IT asset management system which comprises a control platform, a client terminal and a social interaction communication platform. The control platform comprises a receiving module, a storage module, a two-dimensional bar code module and a printing module, wherein the receiving module is used for receiving the asset information of the IT asset uploaded by a user, the storage module is used for storing the asset information, the two-dimensional bar code module is used for generating a two-dimensional bar code according to the asset information, the printing module is used for printing the two-dimensional bar code, the client terminal is used for obtaining the asset information of the IT asset through the two-dimensional bar code and obtaining the geometrical information of the IT asset through LBS, and the social interaction communication platform is used for carrying out information forwarding. According to the IT asset management system, the two-dimensional bar code technology, the LBS technology and the social interaction technology are combined to carry out IT asset management, a user can rapidly and accurately conduct statistics of real-time geometrical information and asset information through a hand-held client terminal, great convenience is brought to the close connection between the user and a manager, and real-time forwarding of information is achieved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT +1
Method, apparatus and program to link users to manufacturers
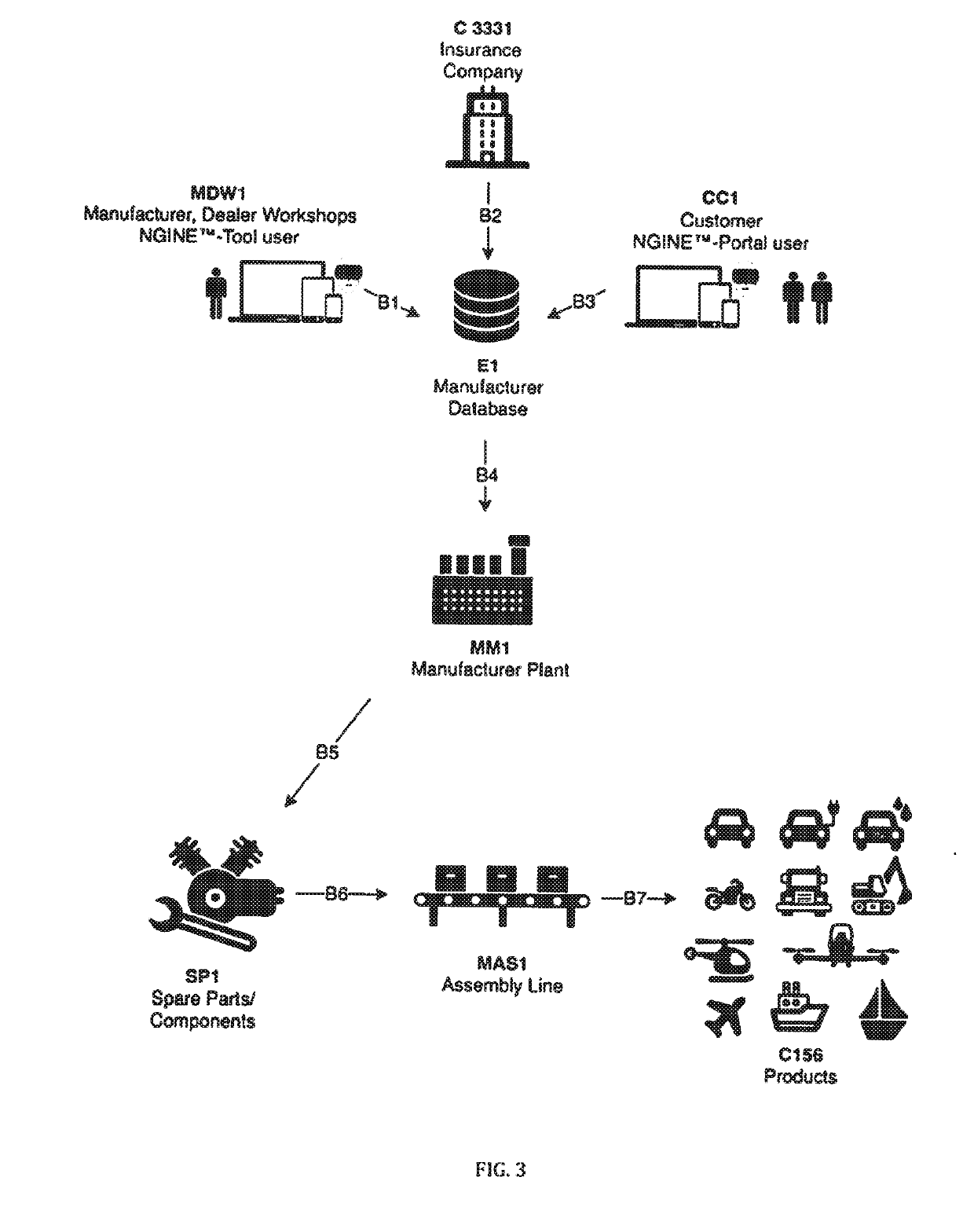
InactiveUS20190287162A1Quick changeEasy to useOffice automationBuying/selling/leasing transactionsProduction lineSingle vehicle
A novel user interface between a vehicle user and a manufacturer providing a transfer of consumer data to the manufacturer to change production line parameters based on safety, service and consumer experience with the vehicle. The user interface which can include a virtual reality module further provides an automated system allowing manufacturer, user and workshops managing their assets and services with an electronically adjustable database to complete the entire lease purchase application process of the customer and / or workshop service request online including negotiations, financing, bank approvals, insurance package, vehicle registration service, workshop services and delivery of the vehicle to the customer after a lease / purchase contract is concluded with online transaction processing. The interface can provide a workshop service in which the customer has the option to request a car for fleet purchase / lease or a single vehicle for a group of lessors and optionally allow a customer to trade in their vehicle and present an offer directly to dealerships.
Owner:MI SOFTTECH INC
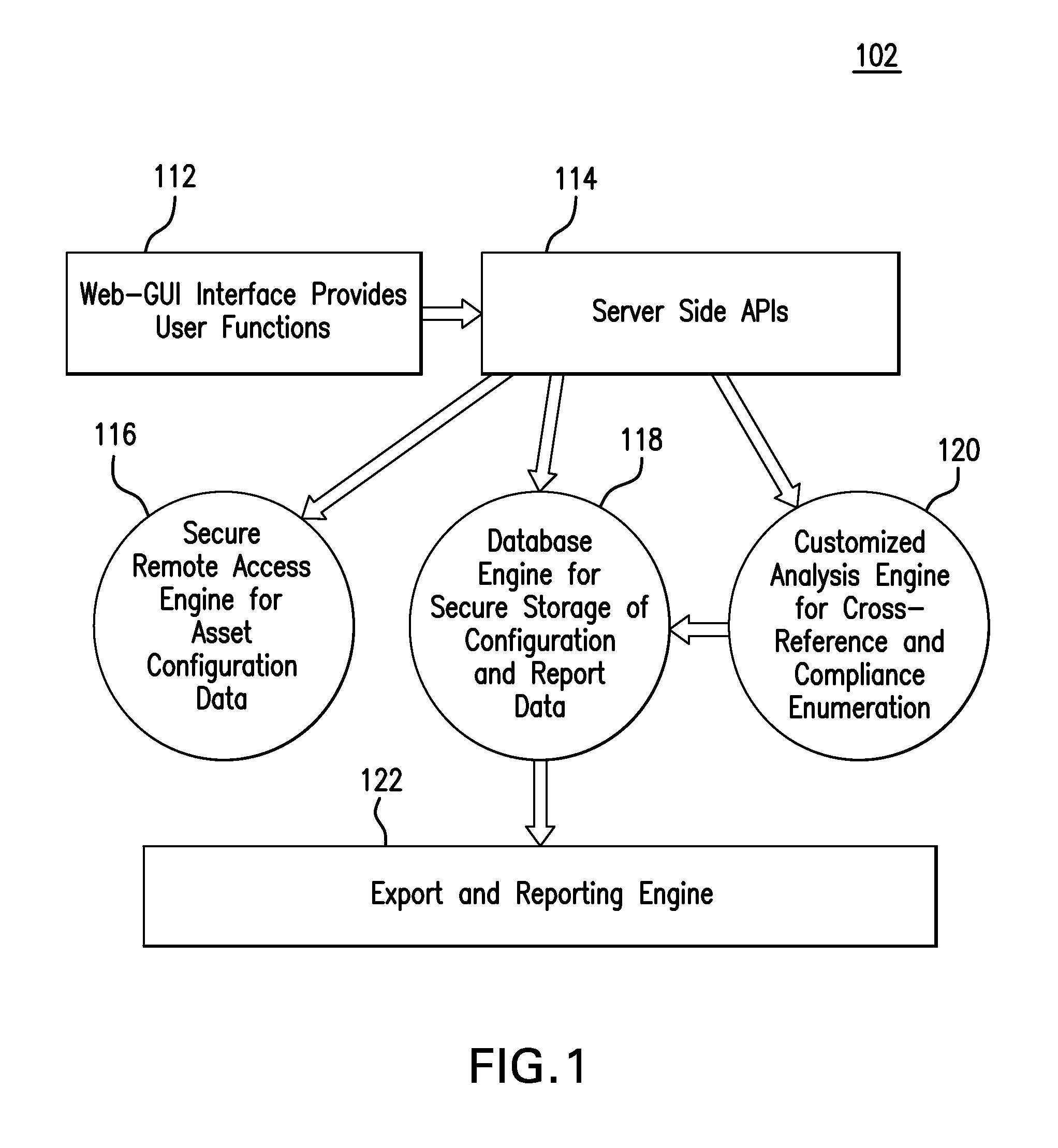
System for Aggregation and Prioritization of IT Asset Field Values from Real-Time Event Logs and Method thereof
The invention relates to a system and a method of identifying and managing IT assets that aggregates fields and their associated values from multiple event log data sources that share one or more common IT asset identifiers and leverages a prioritization approach to determine the most appropriate values for each of the fields. The system utilizes two inputs, namely event log data source inputs and prioritization inputs. Through aggregation of data from different input data sources, the system pieces together a more comprehensive record of field values for a given IT asset, to generate in real-time the updated asset inventory output.
Owner:DISCOVERED INTELLIGENCE INC
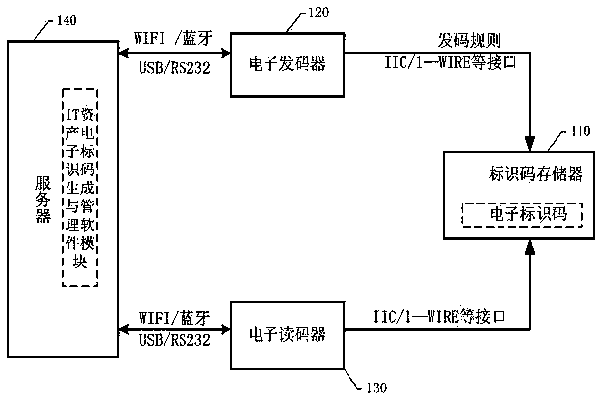
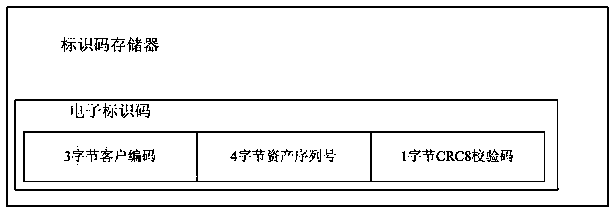
Data center IT asset electronic identification code generating and managing system and implementation method
InactiveCN103971203AEasy to manage centrallyFor long-term storageCo-operative working arrangementsResourcesProgramming languageElectronic identification
The invention discloses a data center IT asset electronic identification code generating and managing system and an implementation method. The data center IT asset electronic identification code generating and managing system comprises identification code memorizers, an IT asset electronic identification code generating and managing software module, a server, an electronic code sender and an electronic code reader, wherein the IT asset electronic identification code generating and managing software module is used for sequentially generating electronic identification codes without repetition according to code sending rules, the electronic code sender is used for writing a unique electronic identification code in each identification code memorizer under the control of management software, each identification code memorizer with the unique electronic identification code is in permanent physical bonding with an IT device, and the electronic identification codes of the IT devices are used for identifying the bonded IT devices, and the electronic code reader is used for reading the electronic identification codes and checking whether the electronic identification codes of the identification code memorizers are correct or not. According to the data center IT asset electronic identification code generating and managing system and the implementation method, the data center IT asset electronic identification codes are easy to generate, capable of being saved a in long time, not prone to damage and high in reliability, and the electronic identification codes capable of identifying different IT assets can be generated and managed.
Owner:SHENZHEN XBROTHER TECH
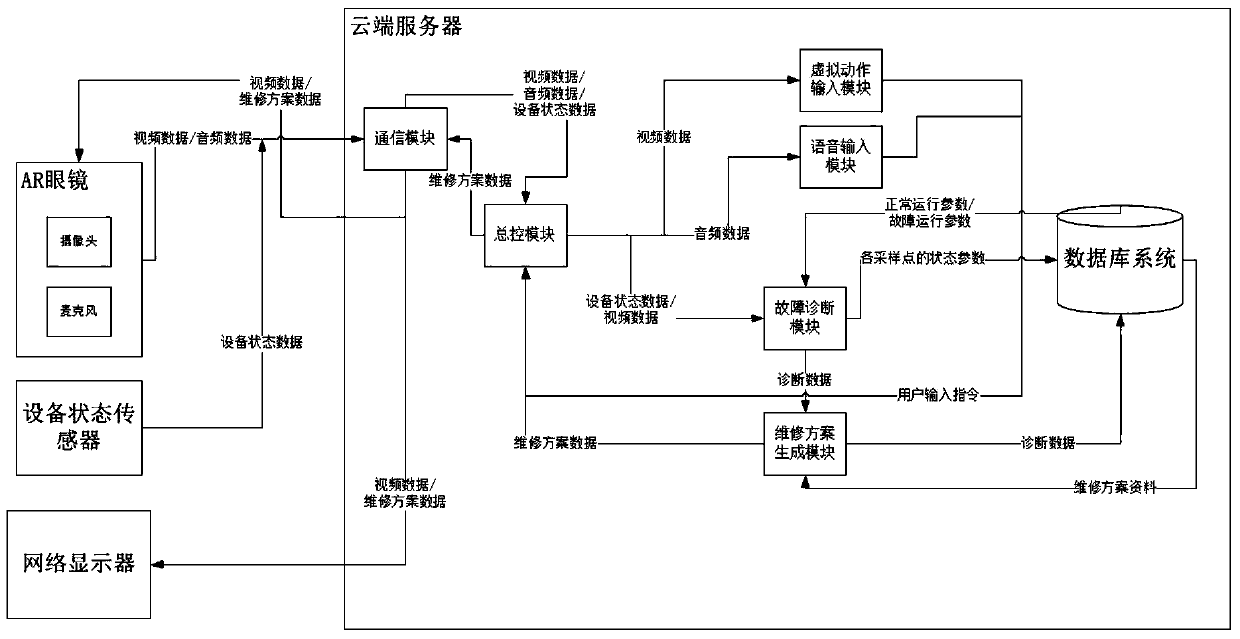
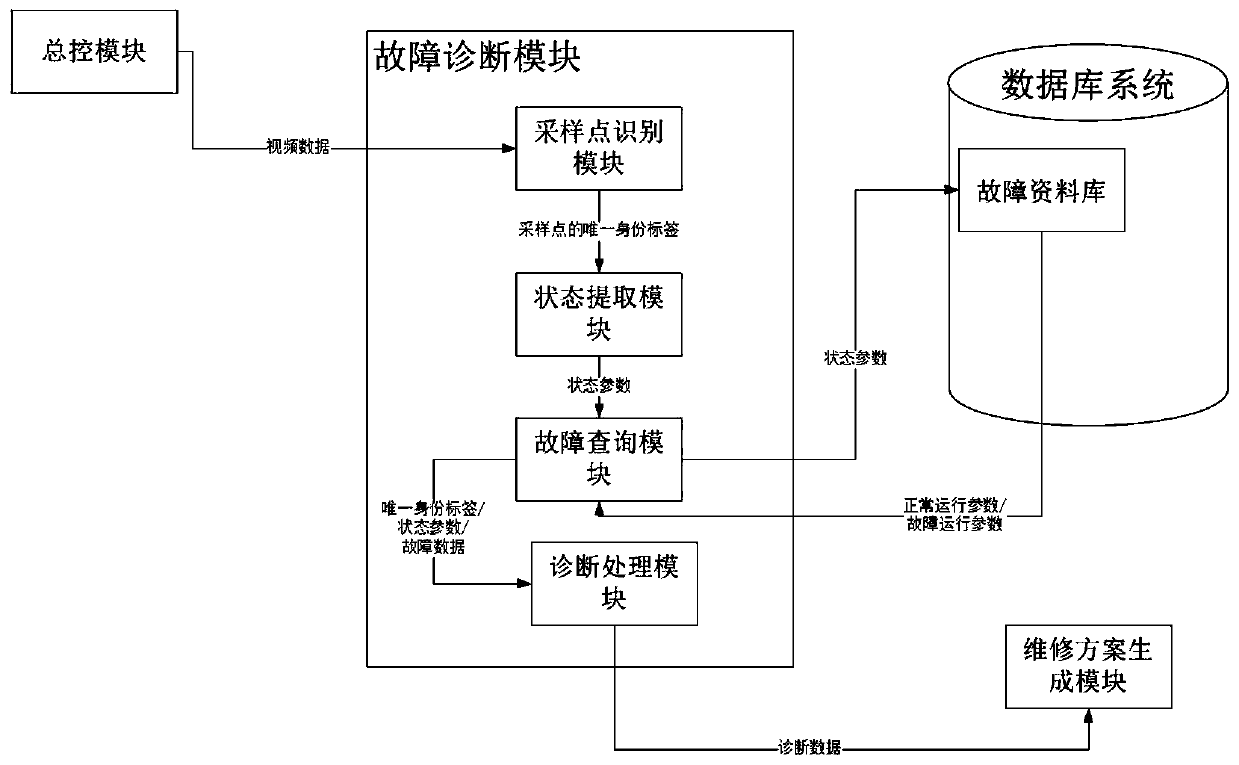
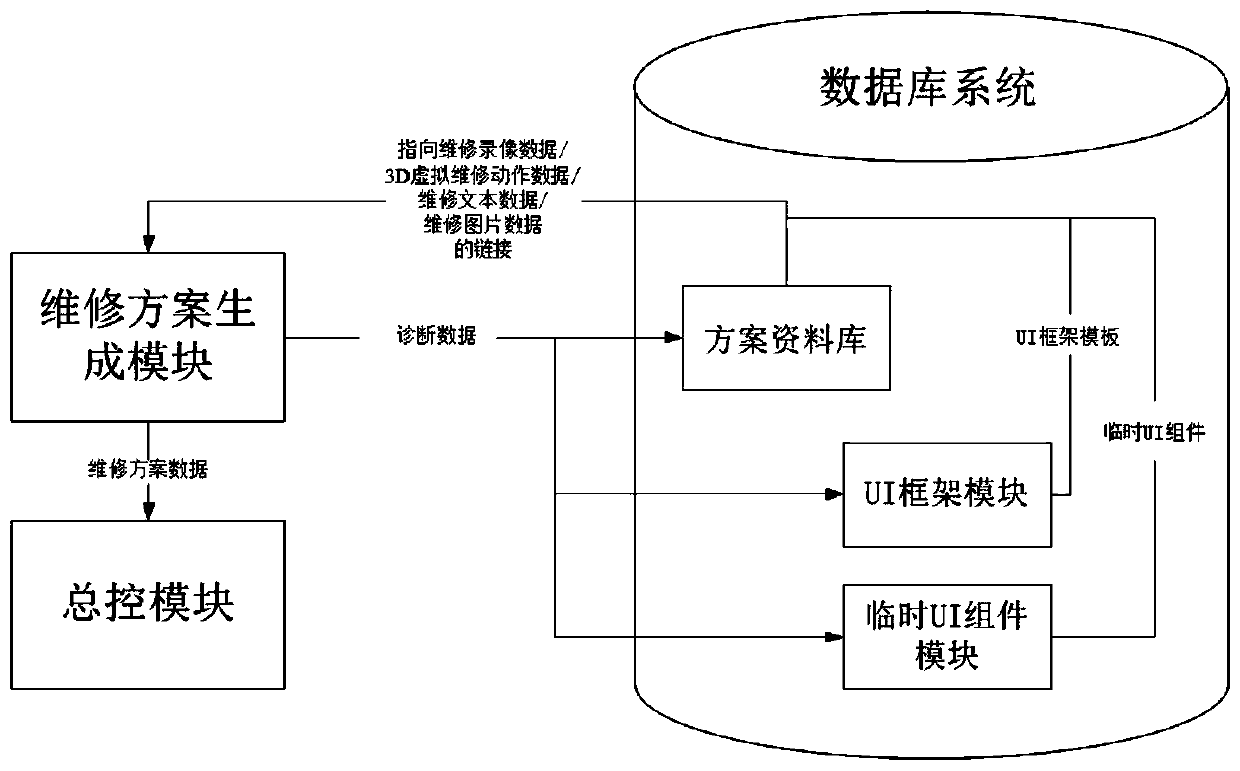
Zero-knowledge bank machine room fault diagnosis and maintenance guidance system and method based on AR glasses
PendingCN110909898AEliminate expertiseEliminate demandFinanceImage data processingDiagnostic dataMaintenance management
The invention relates to a zero-knowledge bank machine room fault diagnosis and maintenance guidance system based on AR glasses. The zero-knowledge bank machine room fault diagnosis and maintenance guidance system comprises an equipment state sensor, AR glasses, a database system, a fault diagnosis module, a maintenance scheme generation module, a communication module and a master control module.The invention further relates to a zero-knowledge bank machine room fault diagnosis and maintenance guidance method based on the AR glasses. The zero-knowledge bank machine room fault diagnosis and maintenance guidance method comprises the steps that the master control module forwards equipment state data and video data to the fault diagnosis module; the fault diagnosis module obtains diagnosis data; and the maintenance scheme generation module obtains maintenance scheme data and sends the maintenance scheme data to the AR glasses. The zero-knowledge bank machine room fault diagnosis and maintenance guidance system adopts zero knowledge, fundamentally eliminates the requirements of professional skills and working experience, saves the training cost, reduces the labor cost, reduces the maintenance time and the repair rate, is adapted to understanding habits of different people, and provides an intelligent, efficient and safe solution for traditional IT asset operation and maintenance management in combination with national strategic level layout.
Owner:武汉农村商业银行股份有限公司
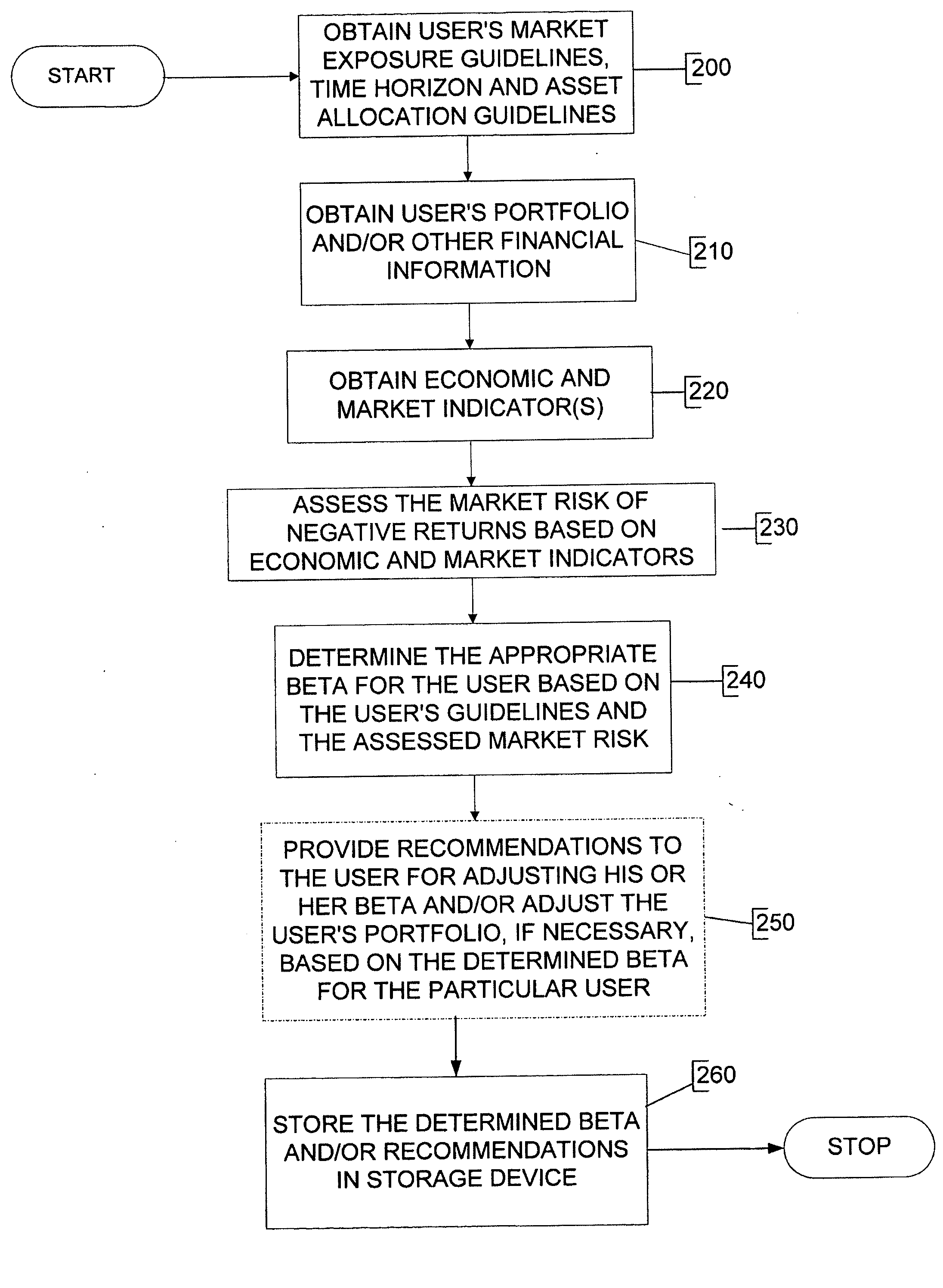
Process, system and financial engine for determining a level of risk in the market, and for adjusting user's market exposure based on the level of risk
InactiveUS20090099978A1Increasing or decreasing the portfolio's exposure to equity investmentsFinanceRisk levelGuideline
A process, system and financial engine which determine a portfolio's sensitivity to market risk based on market conditions are described. In particular, with these process, system and financial engine, first data representative of time horizon information and second data representative of risk tolerance information are first received, and guidelines data based on the first and second data are established. Economic and market data underlying the quantitative indicators and factors determining the qualitative indicators are received. Market risk signals based on the indicator(s) is then established. The portfolio's sensitivity is determined based on the established guidelines data and the market risk signal. Using these process, system and financial engine, it is possible to determine the current market risk level, and then recommend changes to (or adjust) the user's portfolio market risk sensitivities based on the user's time horizon (i.e., the need to access their assets within a particular time) and the determined market risk level.
Owner:MANNING WILLIAM +2
Asset management method, device and system and medium
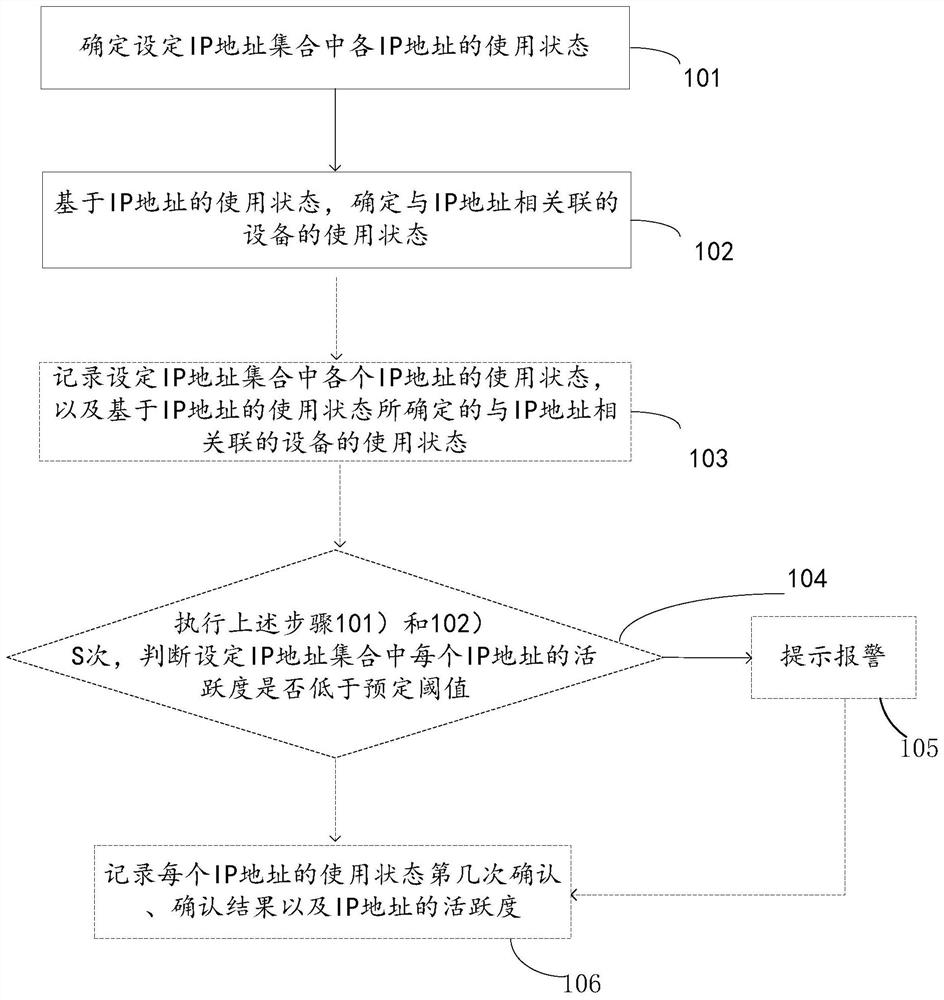
The invention relates to an asset management method. The method comprises the following steps: determining the use state of each IP address in a set IP address set; and based on the use state of the IP address, determining the use state of a device associated with the IP address. According to the method, statistics and management are carried out on assets, especially IT assets, such as network equipment in a set network segment by taking an IP address as a dimension, so that the stability and change conditions of the IT assets in the given network segment can be known in real time.
Owner:BEIJING SHU AN XINYUN TECH CO LTD
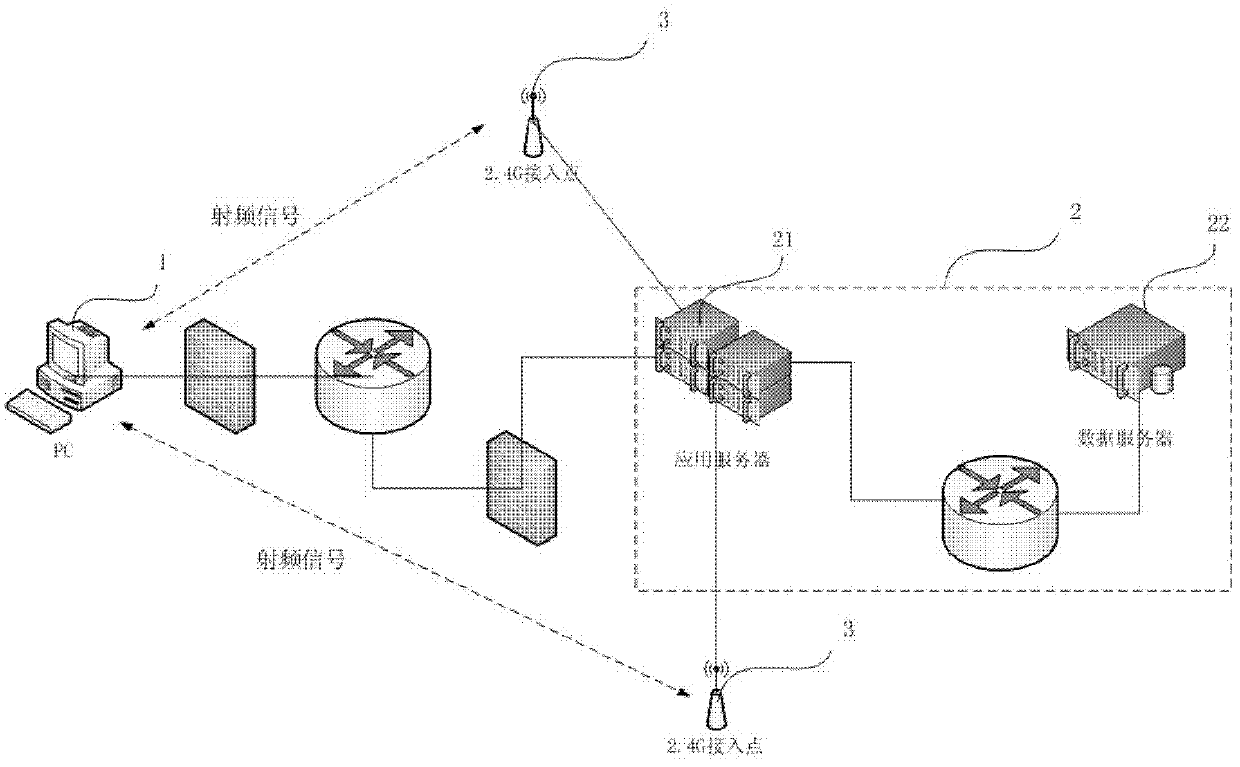
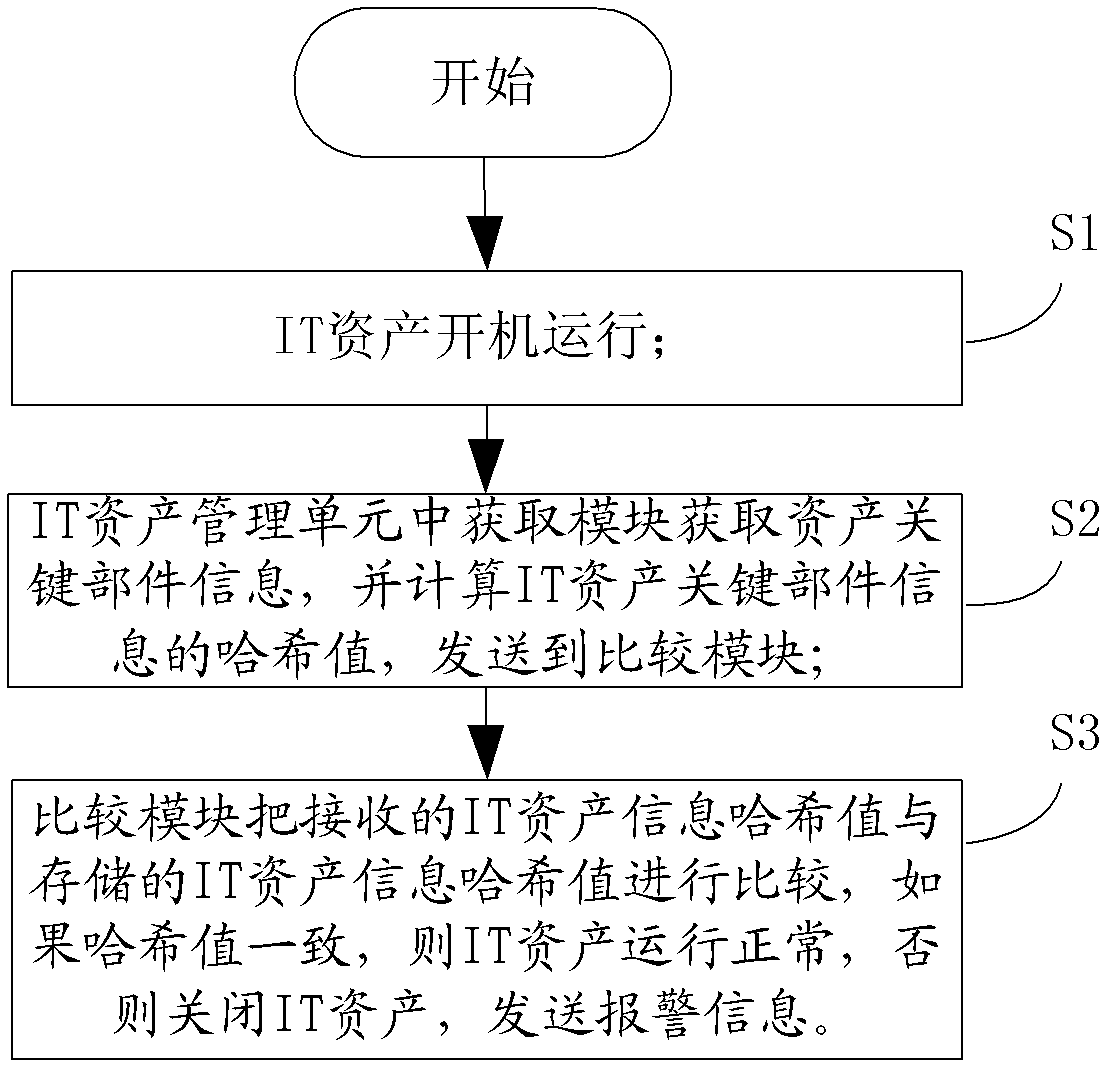
IT asset management unit, IT asset management system and IT asset management method
InactiveCN103377410AImprove management abilityShort processResourcesRadio frequency signalComputer science
The invention discloses an IT asset management unit, an IT asset management system and an IT asset management method. IT asset information is stored through the IT asset management unit, therefore, input errors cannot occur, the IT asset information is not prone to damage, stain-resistant performance is strong, the IT asset information can be stored for a long time, and viewing is convenient. The IT asset information is transmitted through radio frequency signals, and therefore the distance range for reading data is effectively increased. The IT asset management system is used for managing IT assets, therefore, the capacity to manage the IT assets can be effectively improved, and the conditions of the IT assets can be searched quickly and conveniently. The procedures of IT asset management are saved and working efficiency is improved. Meanwhile, position information management of the IT assets can also be realized according to the strength of received radio frequency signals. Therefore, the problem that the IT assets of an enterprise are prone to being lost due to the fact that the IT assets are not managed by specially-assigned persons is solved.
Owner:NATIONZ TECH INC
Marketing System and Method for Customer Specific Promotions
InactiveUS20090088245A1Readily promote growth and profitabilityApparatus for meter-controlled dispensingVideo gamesManagement toolEngineering
A marketing system and method for customer specific promotions providing a yield management tool for casino resort properties to more effectively manage entertainment related assets and inventories to build new and existing customer business. The system provides a convenient method for consumers to realize promotional incentives proportional to their player wagering status at a broader level within the casino resort industry while simultaneously delivering casino resort operators a cost effective tool to maximize the value of their assets. The system utilizes register user supplied player wagering and comp data, and historical waging data on said registered users collected by the system from participating casino resort properties to build a broad-based casino customer database defining the waging profiles of individual gaming customers. Built on the foundation of this industry-wide database resource, the system's electronic transaction platform construction provides casino resort properties a facility to interact directly with gaming oriented customers to present compelling, customer specific promotional offers at the point of purchase where said customers make casino resort air / room travel plans and review purchase decision options.
Owner:C2 REWARDS INC
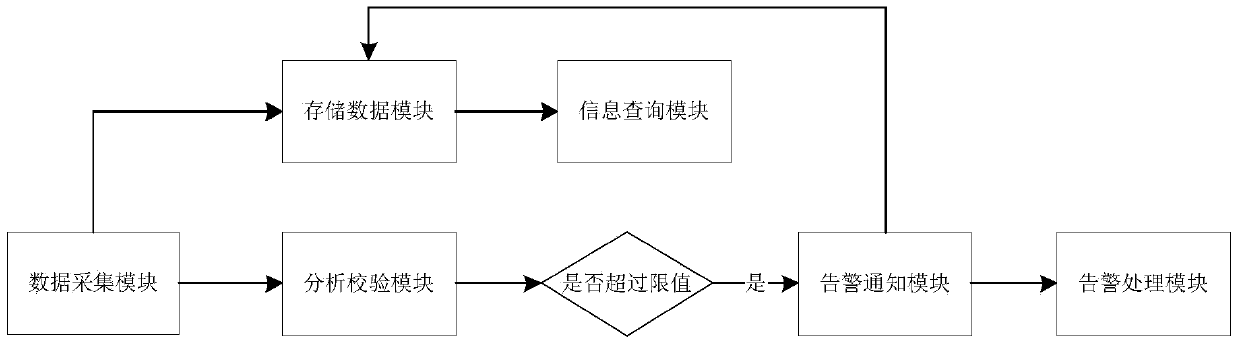
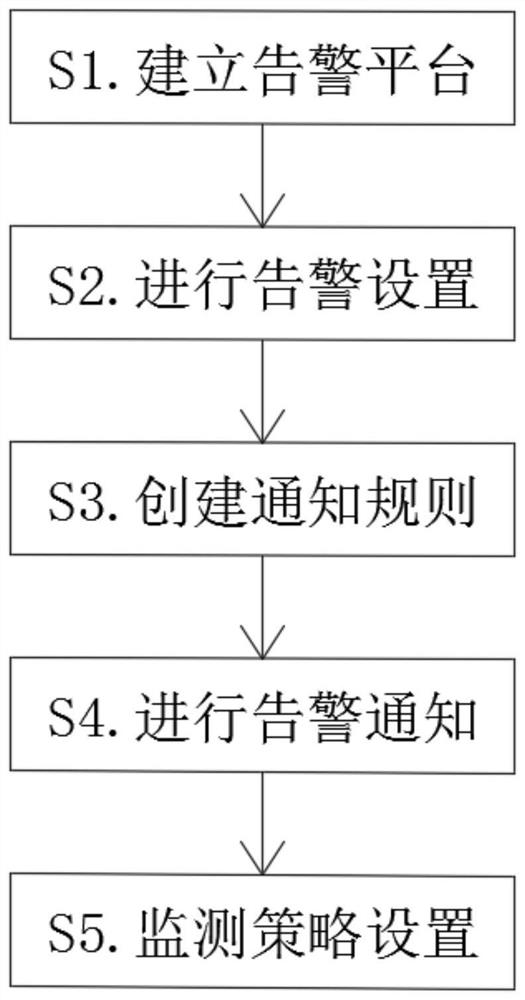
Monitoring method for automatic early warning and warning functions of IT assets
PendingCN112688796ATimely detection of asset changesStatistical OccupancyResourcesData switching networksMonitoring systemManagement system
The invention discloses a monitoring method for automatic early warning and warning functions of IT assets. The monitoring method comprises the following steps: S1, establishing a warning platform; S2, performing alarm setting, wherein IT resources needing to be alarmed are classified, and defining the levels of objects and events needing to be alarmed; S3, creating a notification rule: selecting an alarm category, and setting a corresponding notification condition; S4, performing alarm notification: performing alarm through WeChat, short messages, mails, voice and pop-up windows, and automatically sending out information to remind related personnel when the alarm occurs; S5, setting a monitoring strategy: S51, setting monitoring strategies in batches; and S52, setting a monitoring strategy for a single resource. According to the invention, asset real-time monitoring and automatic early warning, warning and management systems can realize real-time monitoring of the U-bit space and assets of the cabinet, asset transaction can be discovered in time, early warning is carried out on the U-bit allowance and the power load of the cabinet, and warning information is pushed to related warning monitoring systems.
Owner:GUIZHOU POWER GRID CO LTD
Power distribution control with asset assimilation and optimization
ActiveUS20200176984A1Programme controlGeneration forecast in ac networkDistribution controlPower control system
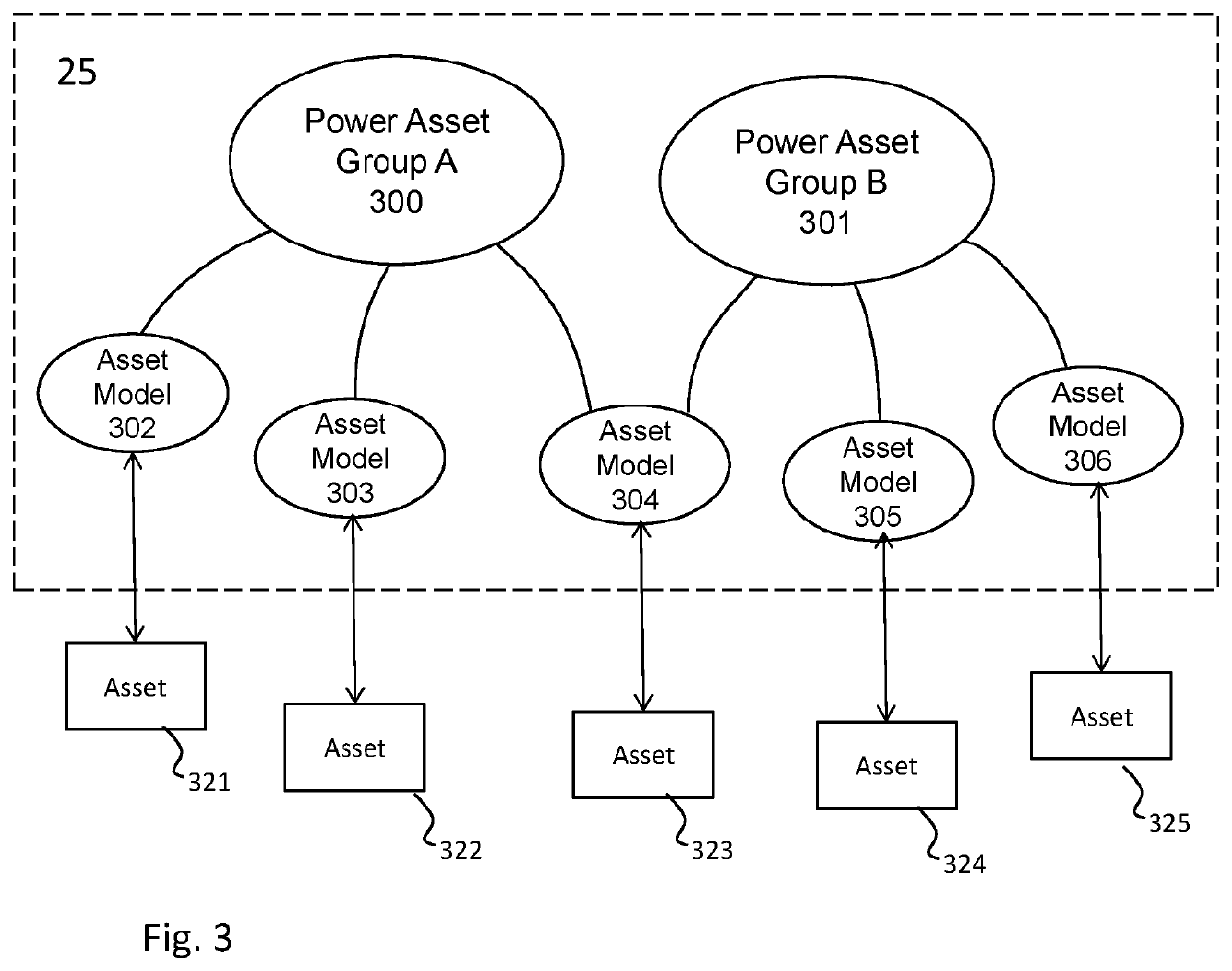
In a power control system a server maintains asset models that represent asset behaviour, each asset model being in real-time communication with its asset to dynamically inform the model of the status of the asset. A test is performed at the server by issuing a command to an asset requesting the asset to perform a function. Sensors at the asset measure physical parameters at the asset and report these to the server. The server determines whether the asset responded to the command and, if the asset responded, how it responded over time. The server establishes a model for the asset in terms of an energy capacitance and a time constant based on the measured response. An optimizer determines which assets are to participate in which service models. The server sends instructions to the selected assets to attempt to fulfill the services.
Owner:ORIGAMI ENERGY
IT asset cooperation monitoring system based on unified view
InactiveCN106209444AFacilitate communicationStrong targetingData switching networksOperational systemData center
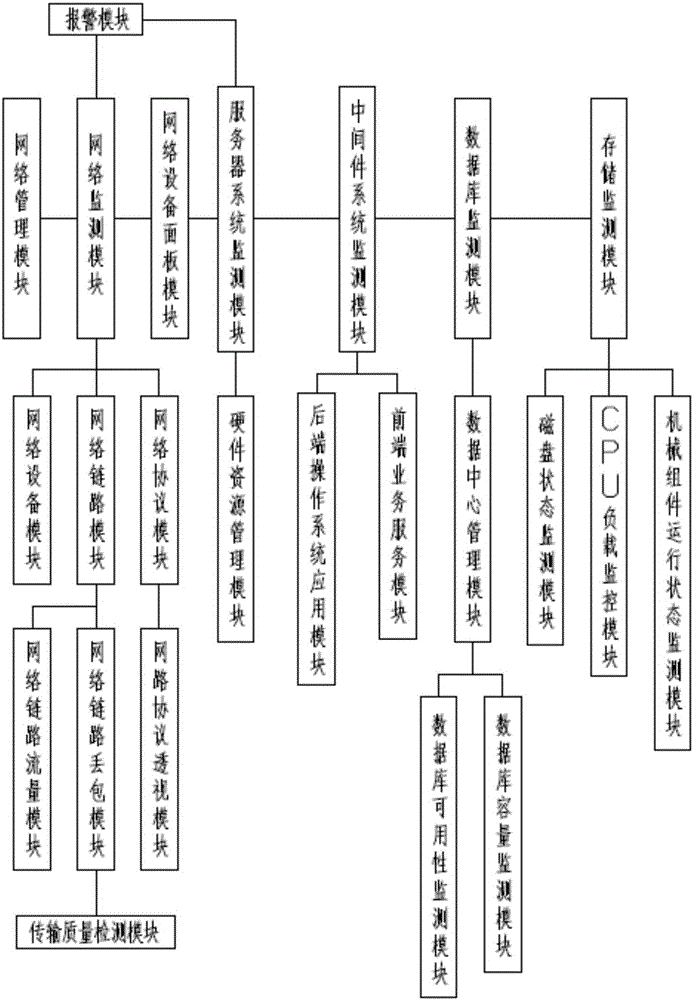
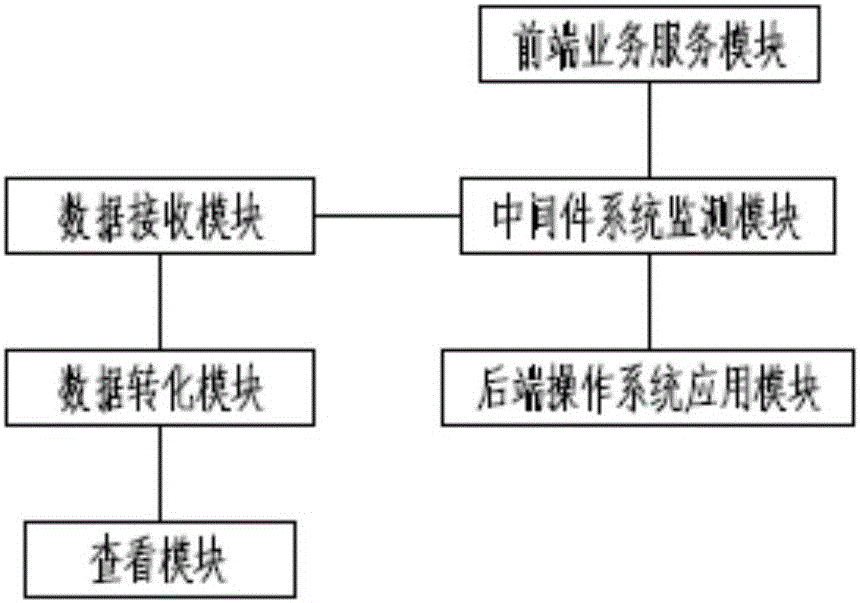
The invention discloses an IT asset cooperation monitoring system based on a unified view. The system comprises a network monitoring module, a server system monitoring module, a middleware system monitoring module, a database system monitoring module and a storage monitoring module. The network monitoring module is connected to a network management module and an alarm module respectively. The alarm module is connected to the server system monitoring module. The server system monitoring module is connected to a hardware resource management module. The middleware system monitoring module is connected to a front-end business service module and a rear-end operation system application module respectively. The database system monitoring module is connected to a data center management module. The system possesses advantages that the system is visual and clear; pertinency is high; a monitoring capability is good; early warning can be performed timely; real-time performance is good; work efficiency is high; manual intensity is saved and stable operation of an IT system is guaranteed.
Owner:ZHEJIANG SCI-TECH UNIV
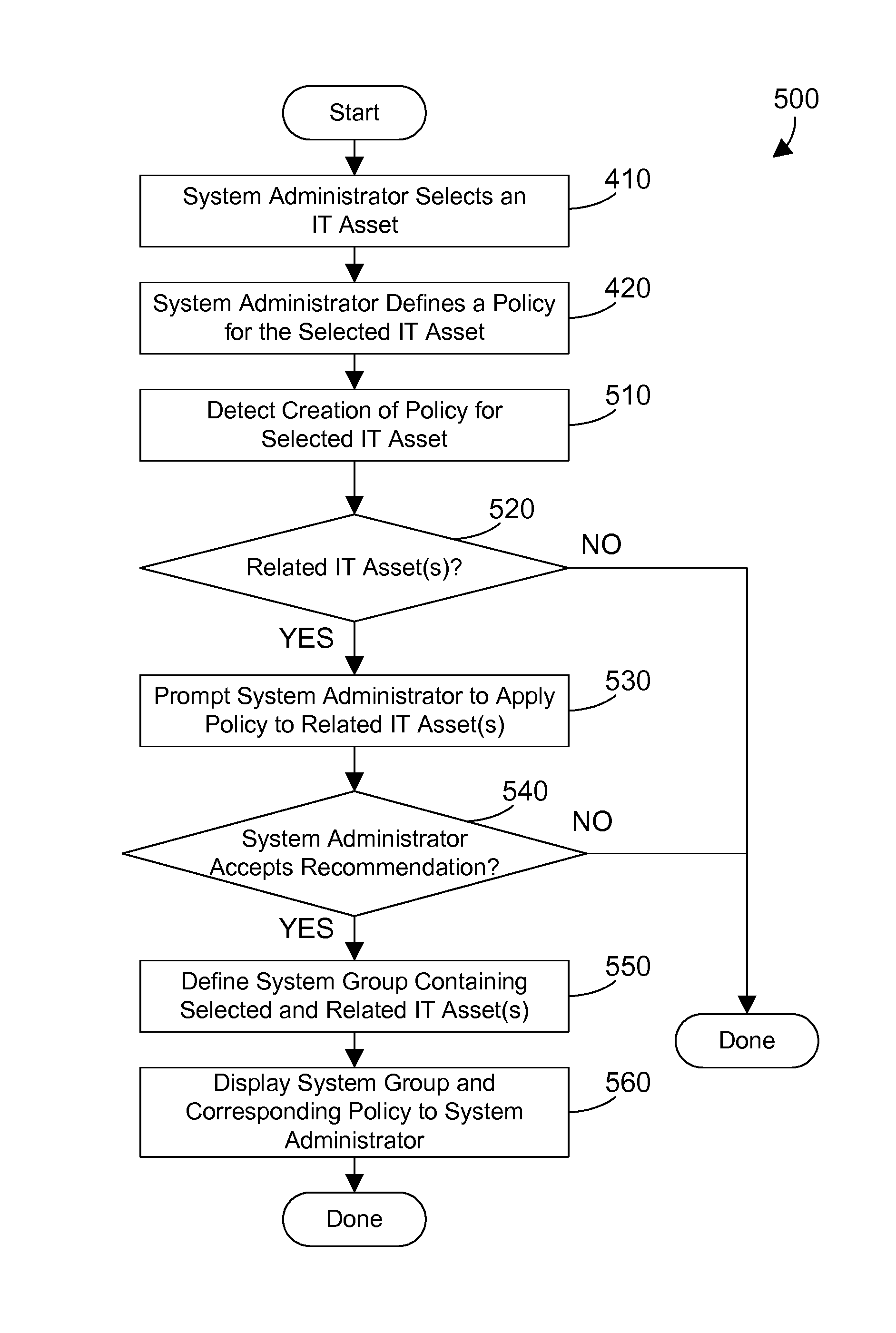
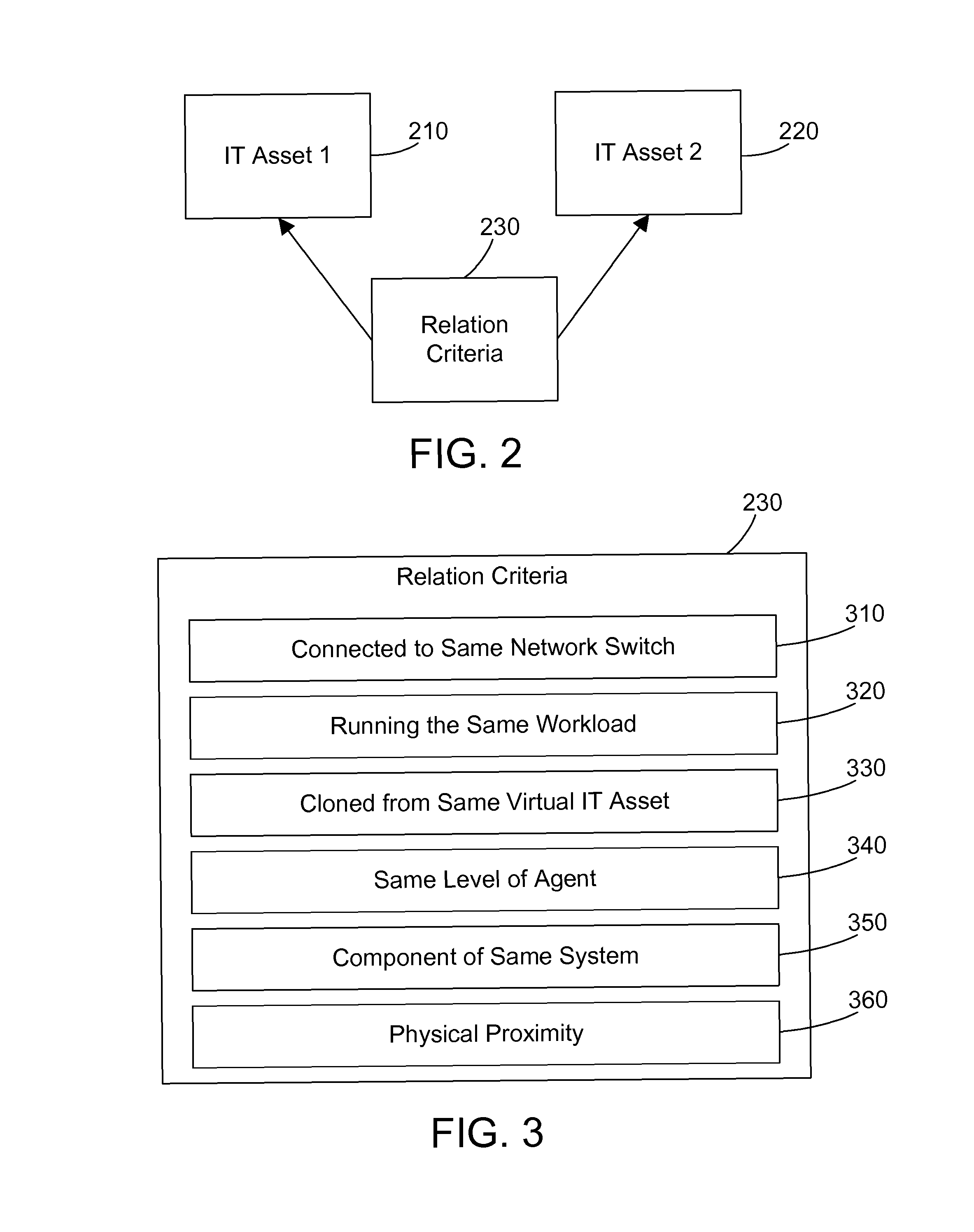
Recommending a policy for an IT asset
When a policy for an IT asset is created in a system manager that manages one or more IT assets, other IT assets that are related to the selected IT asset are determined based on at least one relation criteria related to system topology. The system administrator is prompted to apply the same policy to the related systems. When the system administrator accepts the recommendation to apply the same policy to the related systems, a system group is defined that includes the selected computer system and the related systems, and the system group and its corresponding policy are displayed to the system administrator.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com