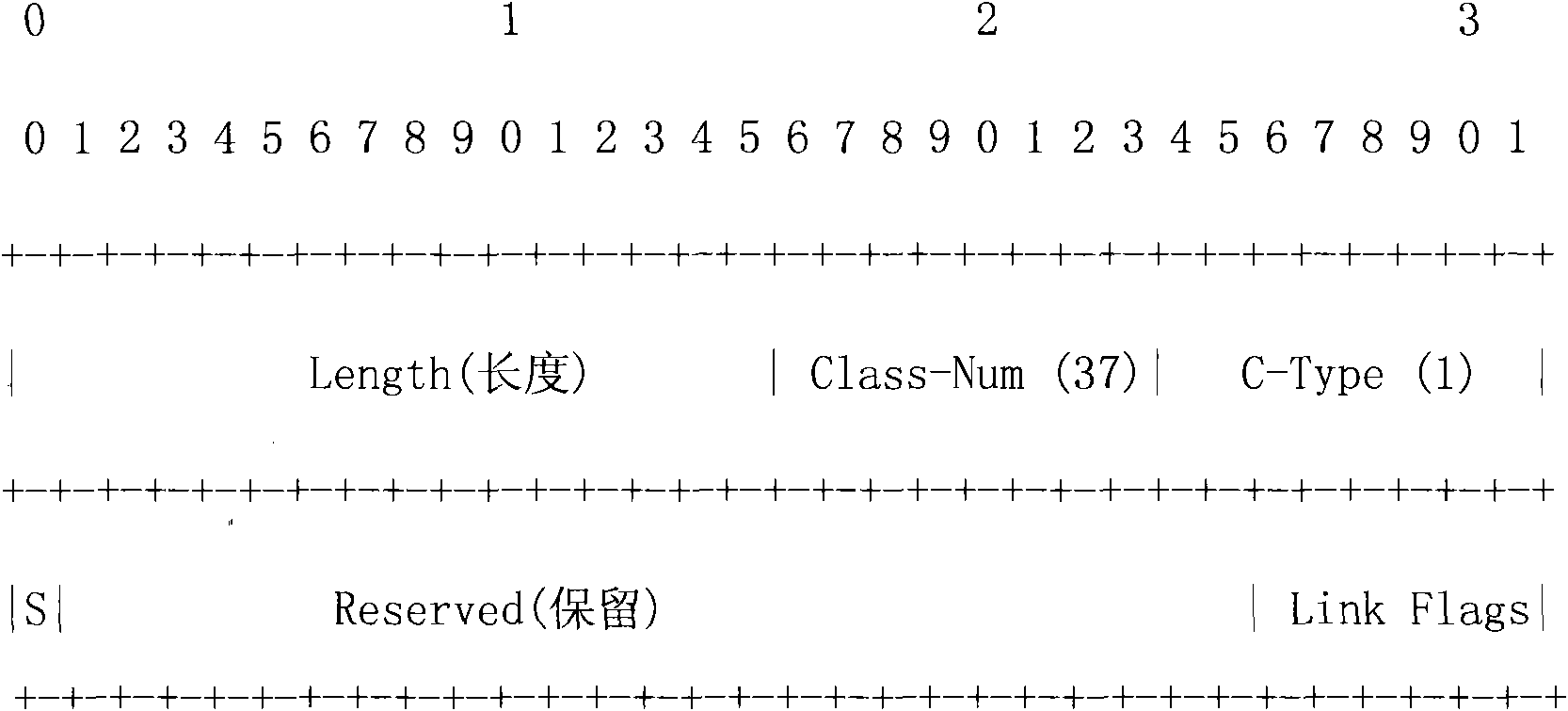
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
60 results about "Layered Service Provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
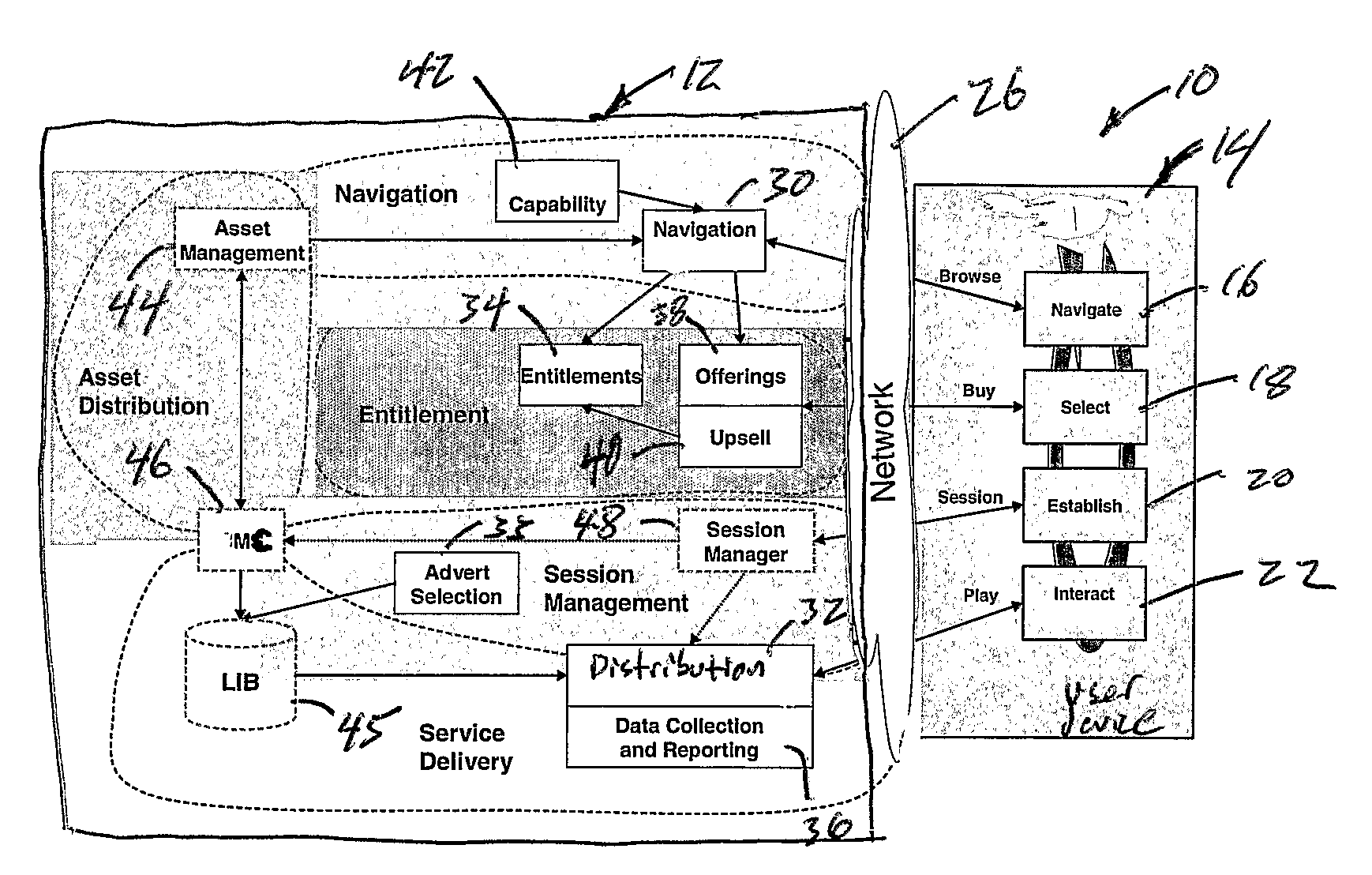
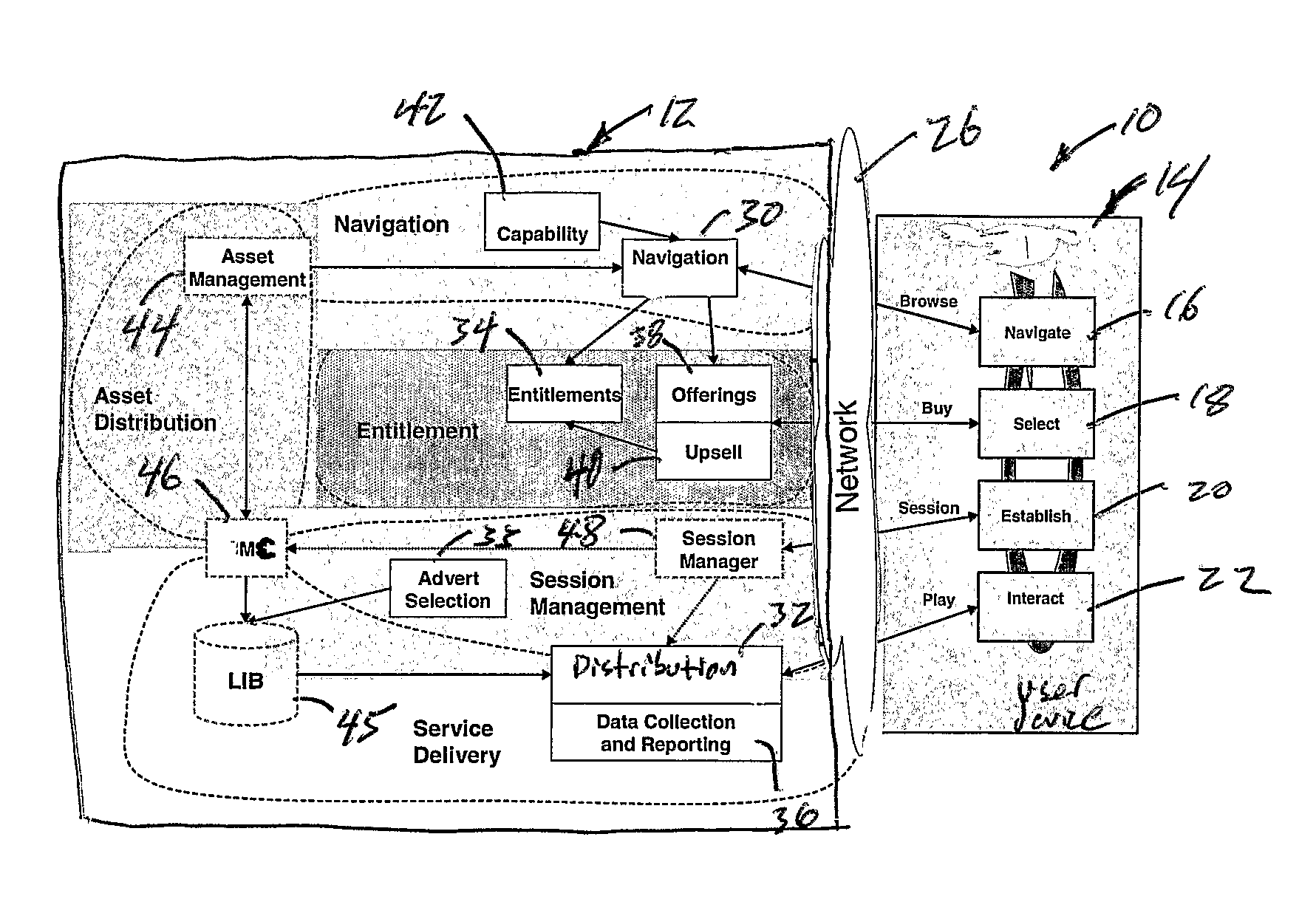
Layered Service Provider (LSP) is a deprecated feature of the Microsoft Windows Winsock 2 Service Provider Interface (SPI). A Layered Service Provider is a DLL that uses Winsock APIs to attempt to insert itself into the TCP/IP protocol stack. Once in the stack, a Layered Service Provider can intercept and modify inbound and outbound Internet traffic. It allows processing of all the TCP/IP traffic taking place between the Internet and the applications that are accessing the Internet (such as a web browser, the email client, etc.). For example, it could be used by malware to redirect web browers to rogue websites, or to block access to sites like Windows Update. Alternatively, a computer security program could scan network traffic for viruses or other threats. The Winsock Service Provider Interface (SPI) API provides a mechanism for layering providers on top of each other. Winsock LSPs are available for a range of useful purposes, including parental controls and Web content filtering. The parental controls web filter in Windows Vista is an LSP. The layering order of all providers is kept in the Winsock Catalog.
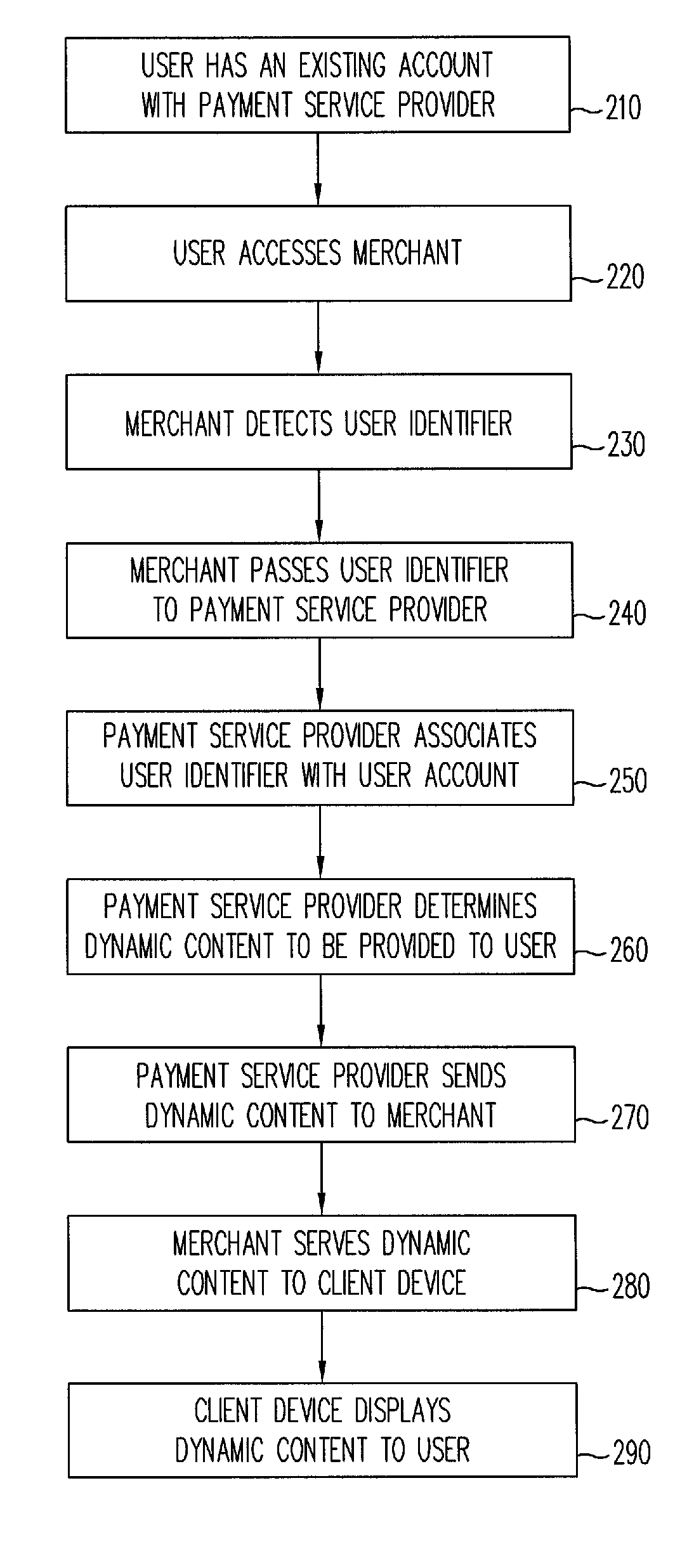
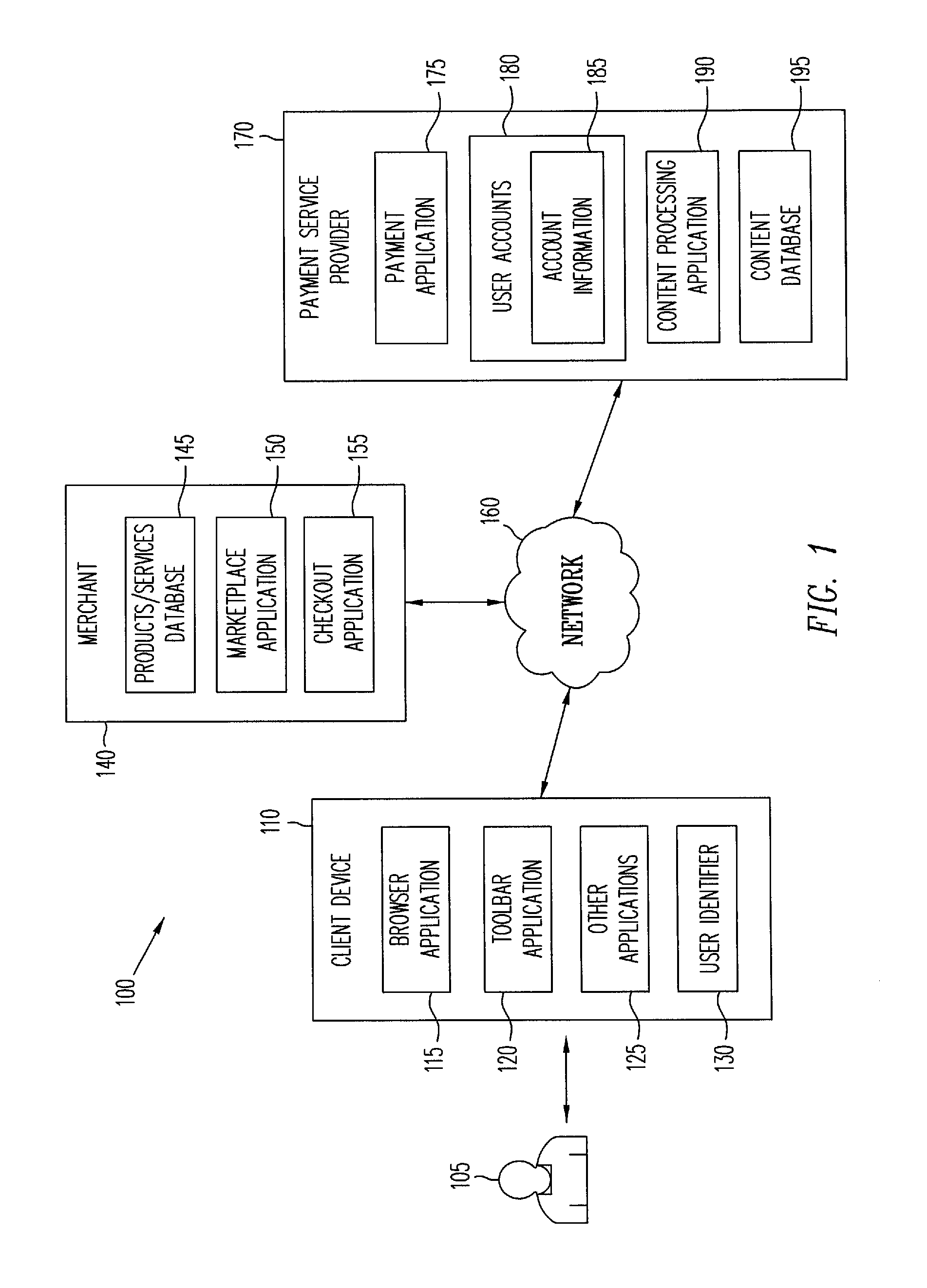
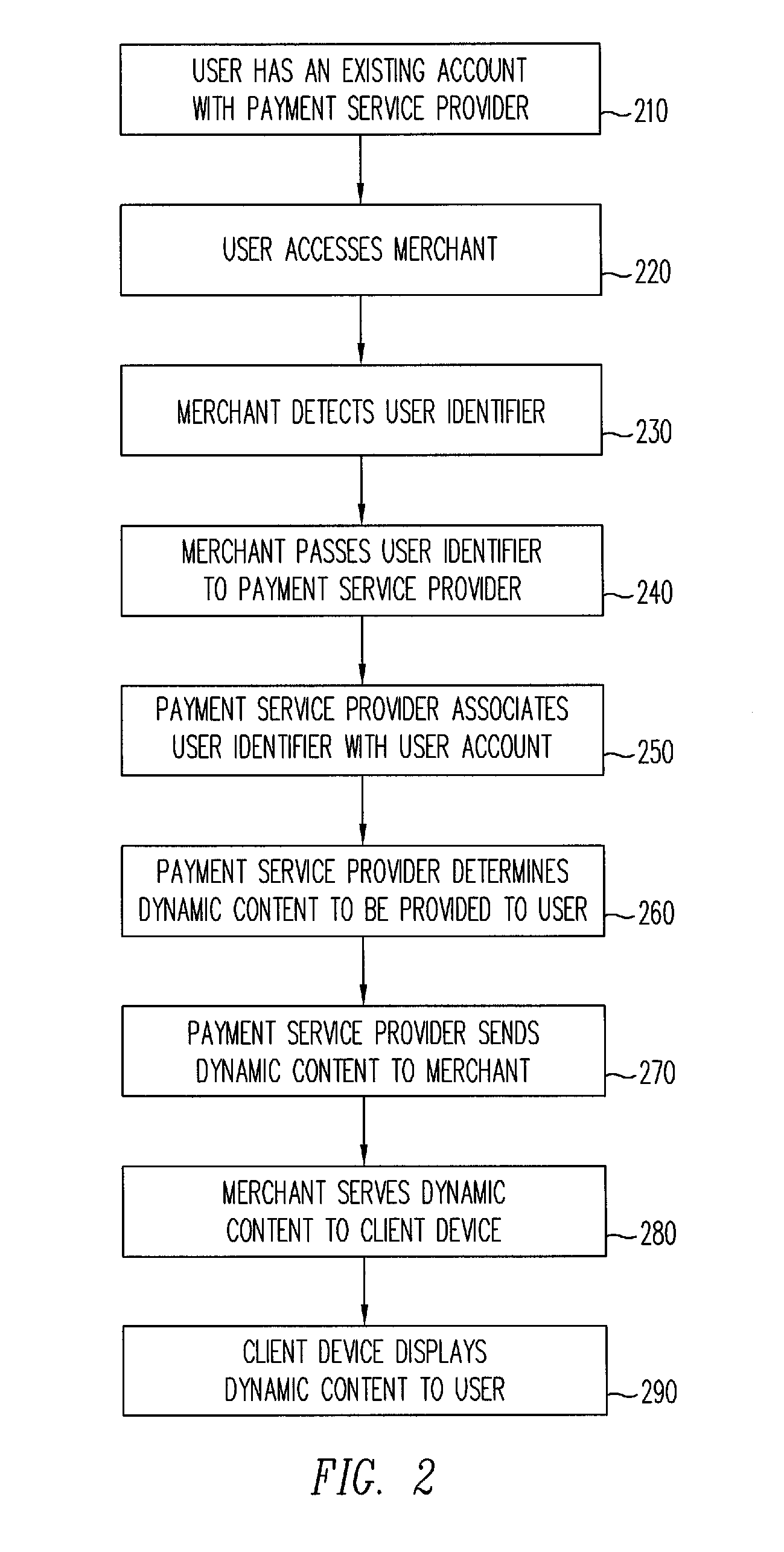
Dynamic content for online transactions
ActiveUS20070245022A1Promote disseminationFinanceMultiple digital computer combinationsClient-sideUser identifier
Various methods and systems are disclosed to provide dynamic content to users of online payment service providers without requiring users to log in or otherwise actively engage the payment service providers. In one example, a method of providing dynamic content includes providing a client device with access to an online marketplace over a network. The method also includes facilitating transmission of a user identifier stored by the client device to a payment service provider. The method further includes receiving dynamic content from the payment service provider in response to the user identifier. In addition, the method includes serving the dynamic content to the client device over the network.
Owner:PAYPAL INC
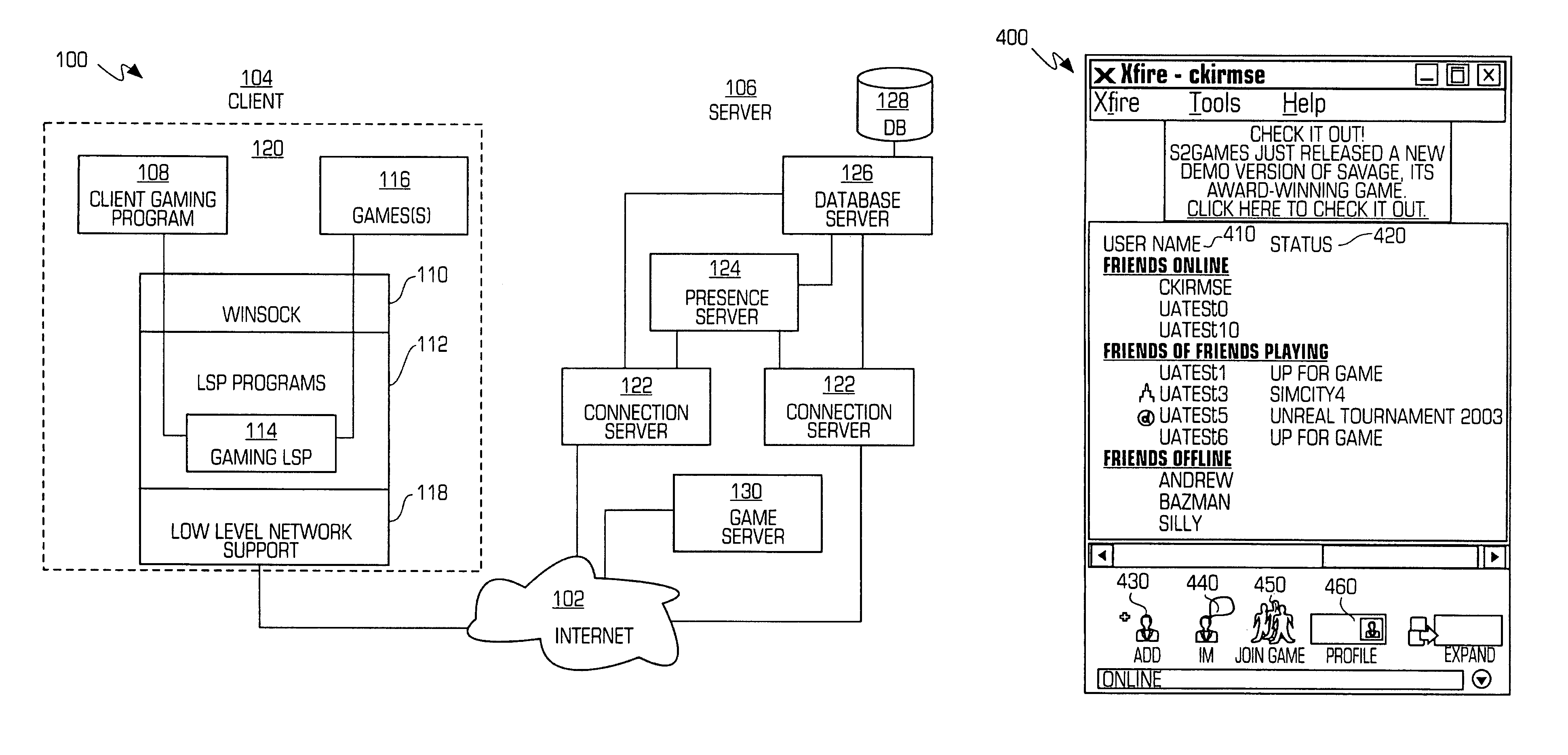
System and method for facilitating multiplayer online gaming
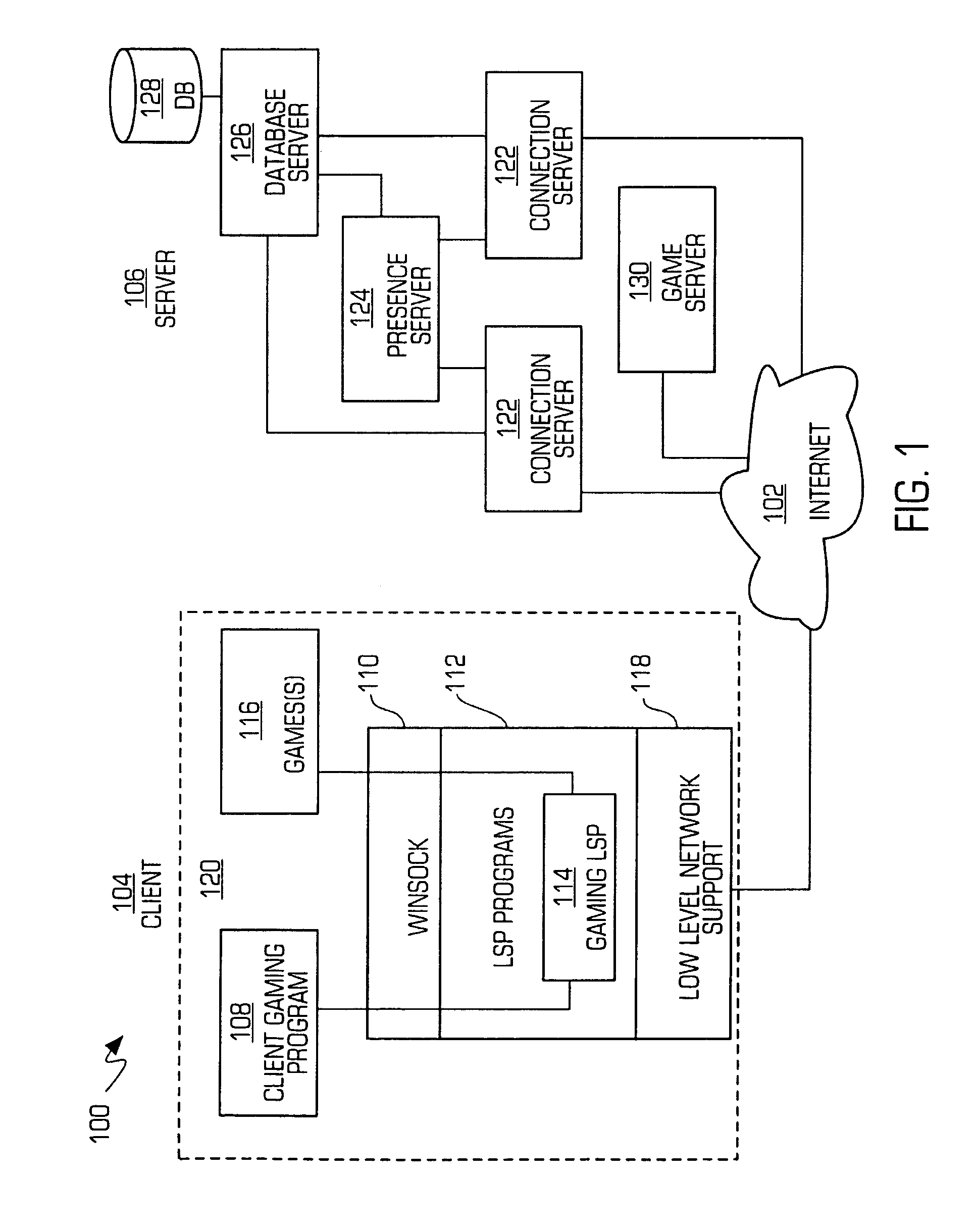
ActiveUS7914381B2Easy to joinOptimize networkDigital computer detailsRadio transmissionComputer terminalLayered Service Provider
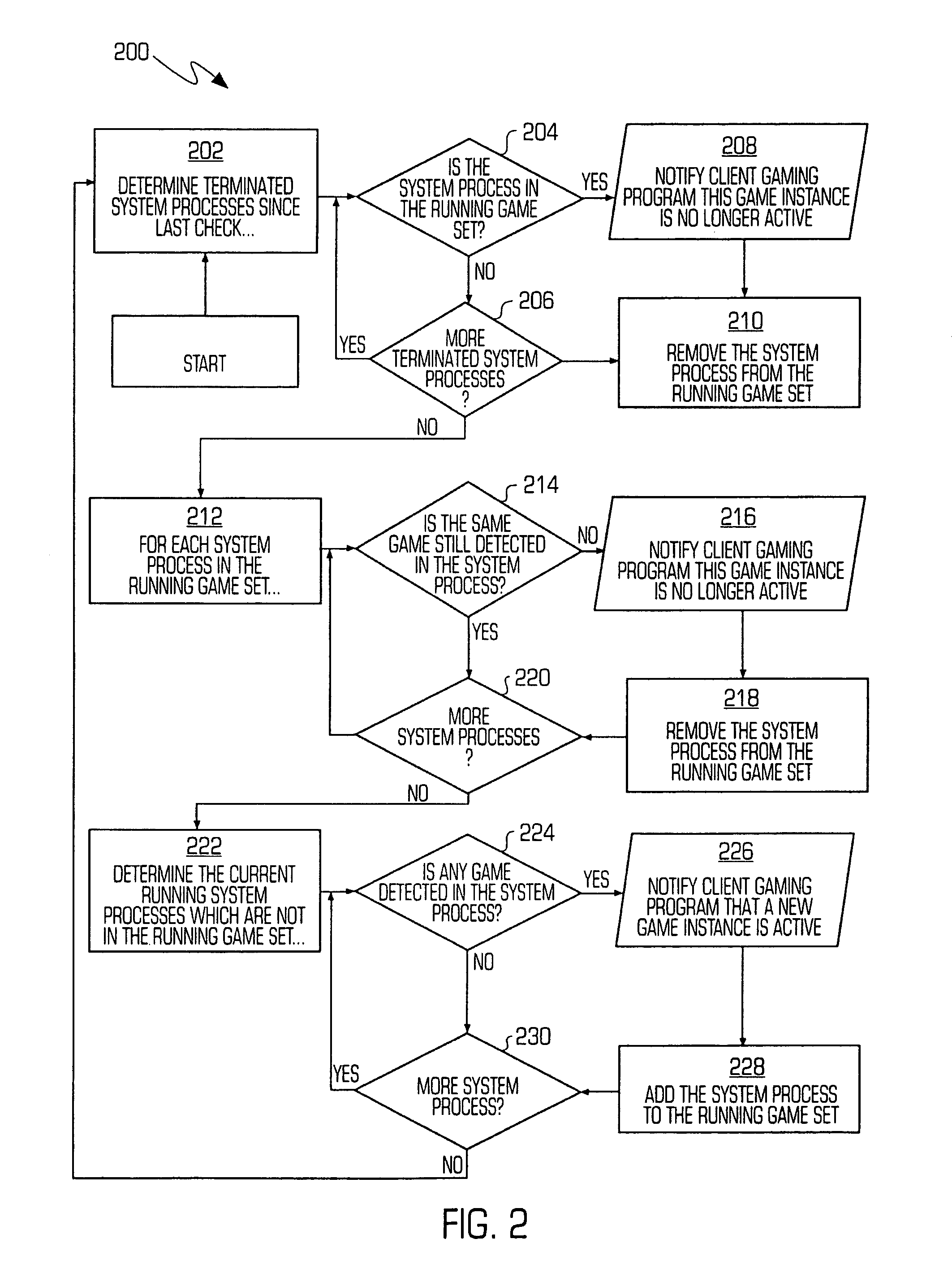
A system and method for facilitating multiplayer online gaming is disclosed. The system 100 includes a client gaming program 108 and a gaming layered service provider (“LSP”) 114, which are stored and operate on a client computer terminal 120. The client gaming program 108 detects when certain individuals identified by a user are playing online games and notifies the user of the individuals currently playing games online and the games that the individuals are playing. The client gaming program 108 allows the user to easily join the games in progress. The gaming program 108 and LSP 114 also monitor and detect games that are running on the terminal 120 and the connection status of the games. The gaming program 108 communicates data regarding the user, games and connection status over the computer network for receipt by selected individuals.
Owner:AG 18
LSP (Layered Service Provider) information flooding method and equipment in SPBM (Shortest Path Bridging MAC)
ActiveCN102882784AFast convergenceIncrease the speed of floodingData switching networksLayered Service ProviderNetwork topology
The invention discloses an LSP (Layered Service Provider) information flooding method and equipment in an SPBM (Shortest Path Bridging MAC). A data plane of each backbone network bridging equipment in the SPBM network is maintained by a unicast FDB (Forwarding Database) table. The method comprises the following steps of: generating new LSP information according to the variation of network topology after the variation of the network topology is detected; and using B-MAC (Multiplexed Analogue Components) addresses and corresponding B-VLANs (Virtual Local Area Network) of all the other backbone network bridging equipment locally saved to create an IS-IS (Intermediate System to Intermediate System) LSP message with the new LSP information and sending out the IS-IS LSP message by a transceiving port corresponding to the B-MAC address in the unicast FDB table, wherein the B-MAC address in the IS-IS LSP message refers to the B-MAC address of the other backbone network bridging equipment, and a B-VLAN tag is filled with the B-VLAN corresponding to the B-MAC address of the other backbone network bridging equipment. According to the invention, the flooding speed is raised, time spent in the flooding process is shortened, and the convergence performance of the SPBM network is improved.
Owner:紫光恒越技术有限公司
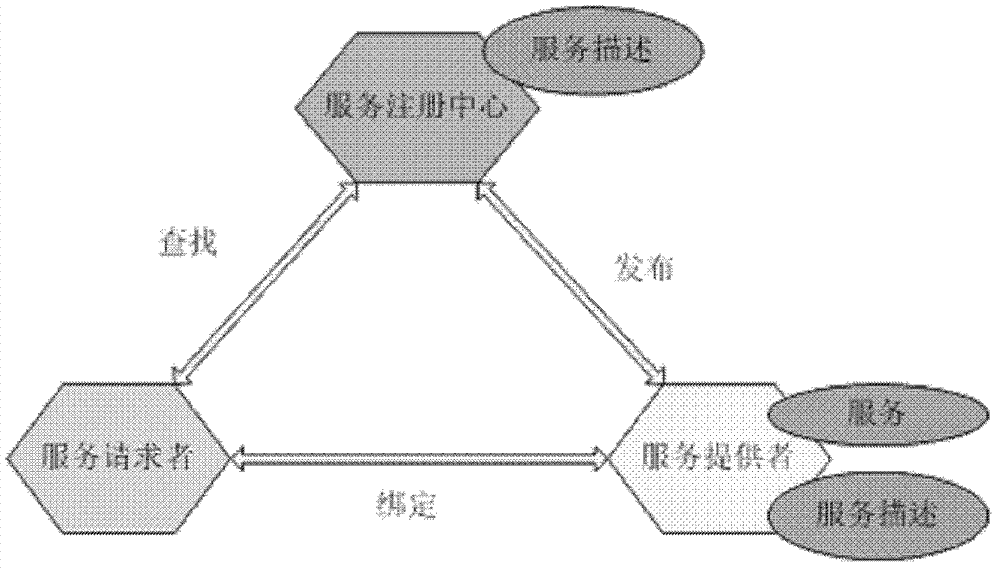
Data service request response method and data service protocol stack
ActiveCN103117983AInternal implementation details are simpleEfficient internal implementation detailsTransmissionResponse methodHyper text transport protocol
The invention discloses a data service request response method and a data service protocol stack, wherein the method comprises the steps that a service requester encapsulates a service index parameter into a simple object access protocol (SOAP) data packet, and the service requester sends the encapsulated SOAP data packet to a service provider to enable the service provider to obtain an service query order and service data from the database after conducting analysis processing to the SOAP data packet or a hyper text transport protocol (HTTP) data packet. The data service request response method and the data service protocol stack can not only achieve the decoupling of application and data, but also achieve the decoupling inside the data service to enable the details inside the data service to be simpler, more effective, clearer, more flexible and extensible.
Owner:CHINA MOBILE COMM GRP CO LTD +1
Network route convergence processing method and network route convergence processing device
The invention discloses a network route convergence processing method. According to the method, a preset non-pruning multicast distribution tree is utilized as a fast channel, when network topology is changed, after adjacent devices of a topological change source detect the topological change, a layered service provider (LSP) message is generated according to topological change type, and the LSP message is sent out through the fast channel, and then convergence processing modules on the adjacent devices continue to carry out route convergence process to the topological change event. After a device on the fast channel receives the LSP message, the message is transmitted, and at the same time, the message is sent to the convergence processing modules for route convergence process. The invention further provides a corresponding network route convergence processing device. By means of the network route convergence processing method and the network route convergence processing device, convergence of a whole network is enabled basically not to be limited by network size and topological change positions, and the convergence performance of the whole network is close to the convergence performance of a single device.
Owner:HUAWEI TECH CO LTD
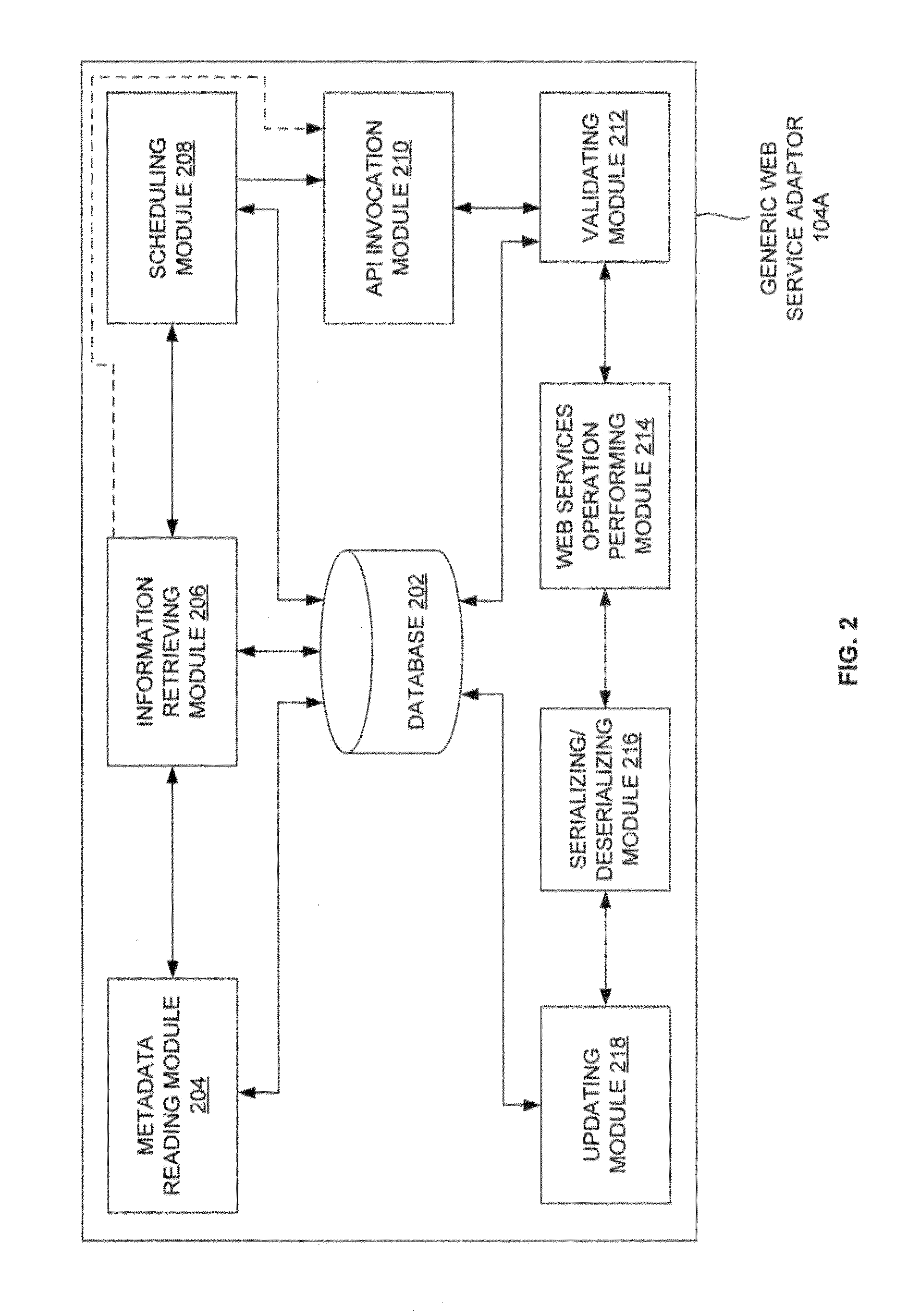
Generic web service adaptor for performing web service operations for multiple web service providers
Approaches for extracting data from data sources using a generic web service adaptor that implements a web services processing framework. Metadata stored in the database is read to identify specified named entities from a plurality of web service providers. Application protocol interface (API) semantics and configurations are retrieved from the metadata. Metadata objects for the specified named entities are fetched. Web services operation API signatures of the metadata objects are validated by comparing with predefined web services operation API signatures stored in the metadata. Web services operations for the specified named entities of the web service providers comprising the data sources are performed to obtain returned result objects. The returned result objects are serialized to XML using the same framework as used by the source web service. An adaptor may be configured to support the plurality of web service providers based on configurations.
Owner:DIGITAL AI SOFTWARE INC
Message forwarding method and system in information center network
InactiveCN105812261ASign up for reliefReduce updateData switching networksResource managementLayered Service Provider
An embodiment of the invention provides a message forwarding method and system in an information center network. The method mainly includes that an explorer inquires a service registry managed by the explorer according to a service mark in a service request packet; the service request packet is forwarded to a corresponding outlet according to service provider information corresponding to the service mark in the service registry when that the service corresponding to the service mark is in the autonomous domain is determined through inquiry; when that the service corresponding to the service mark is not in the autonomous domain is determined through inquiry, an inter-domain path mark directing to the next autonomous domain of the service provider corresponding to the service mark and related forwarding port information are obtained and the service request packet is forwarded to the next autonomous domain. According to the embodiment of the invention, analysis, searching and forwarding in the explorer of the service request packet in the information center network are realized. Each RM only needs to manage registered information including service marks and the like, so that RM load of operation of registration, update, deletion and like of service content is reduced.
Owner:BEIJING JIAOTONG UNIV
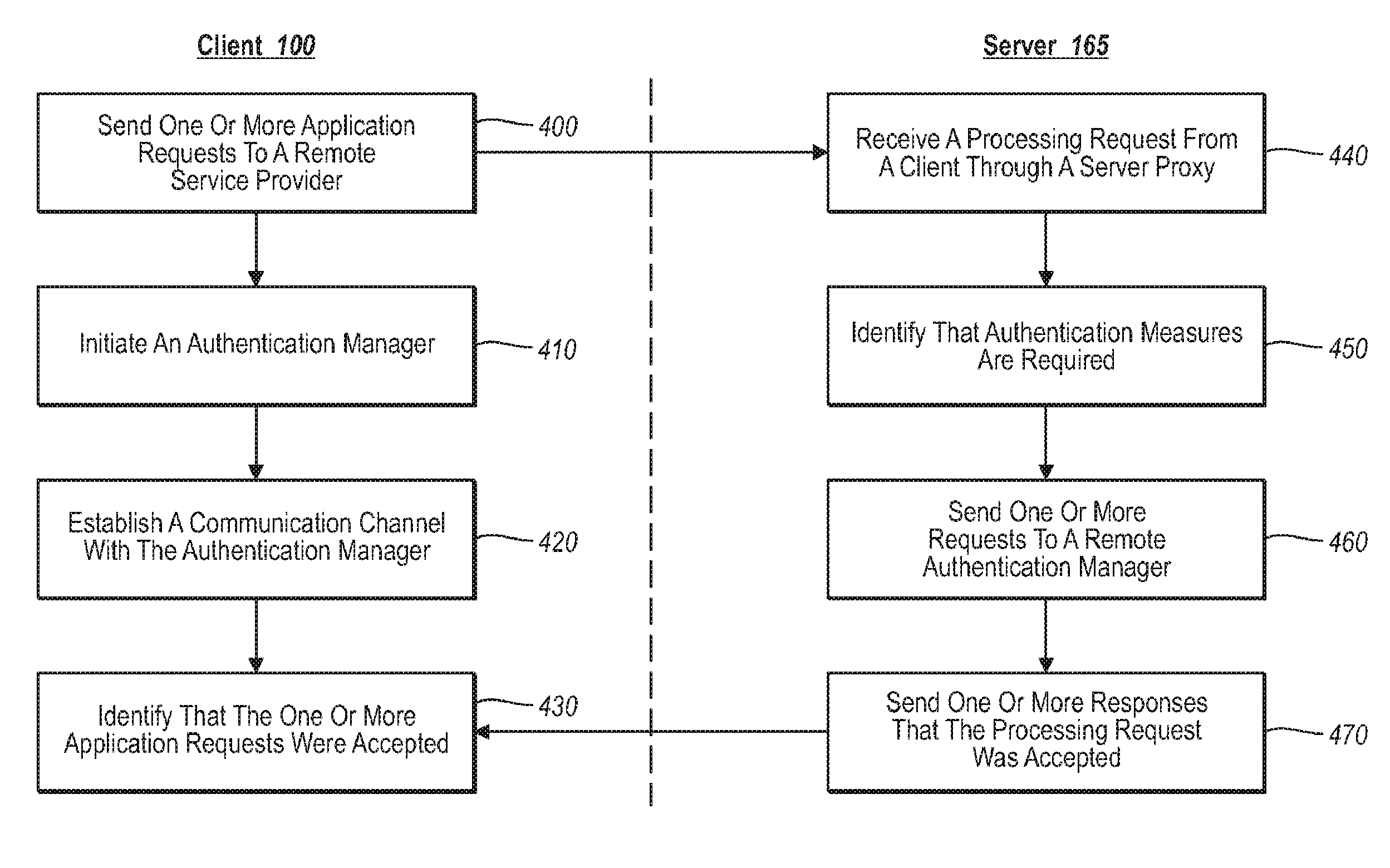
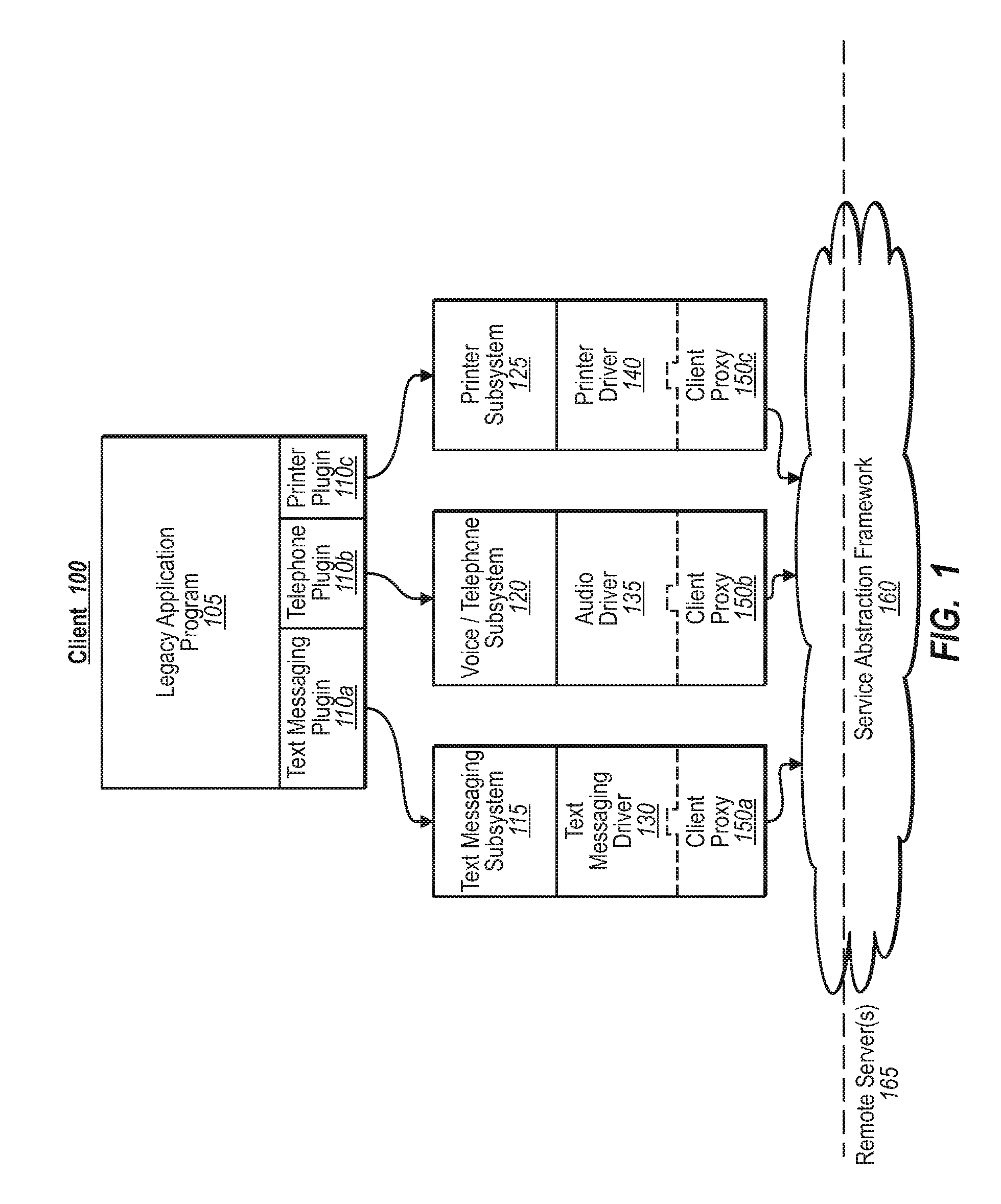
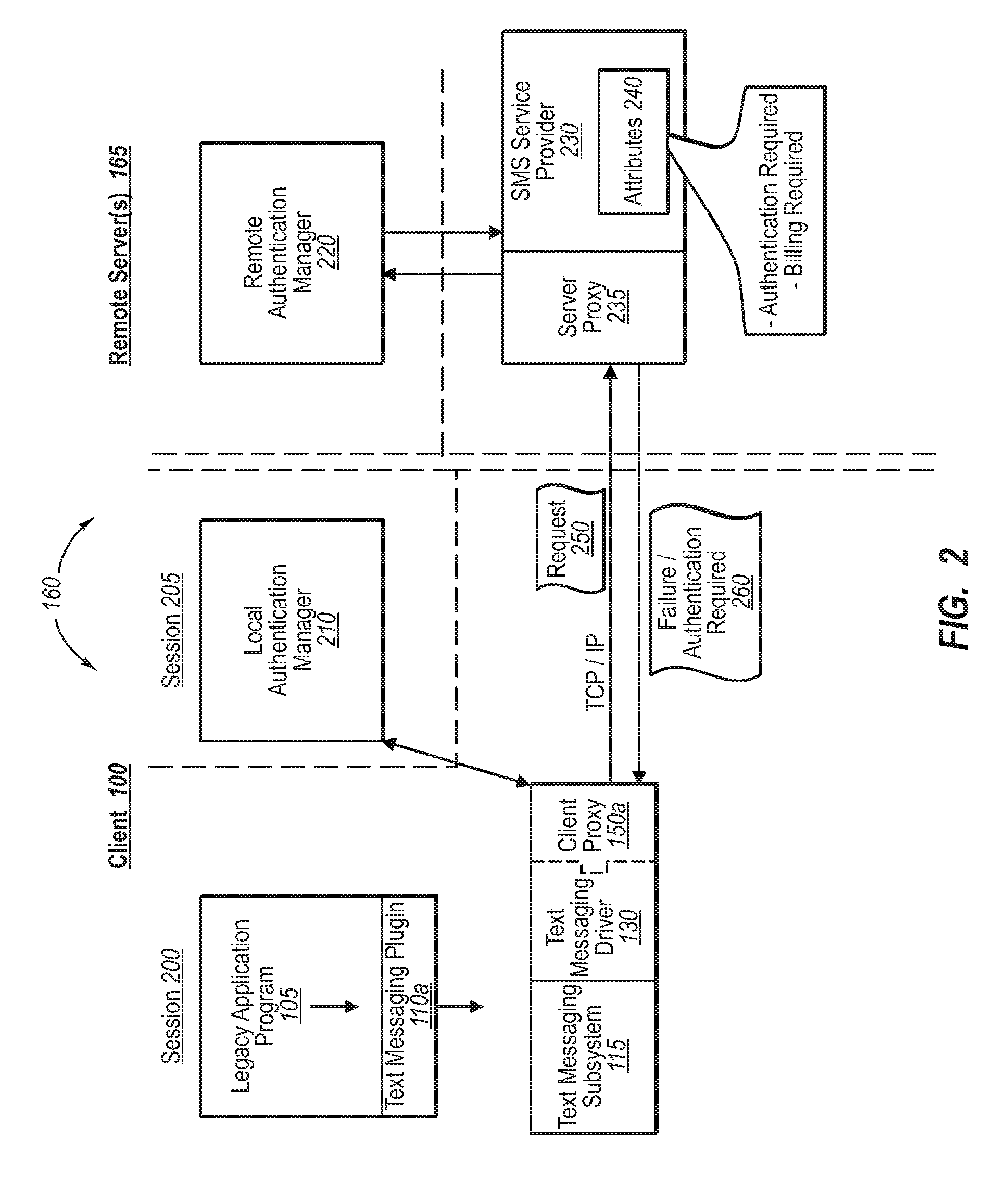
Providing remote services to legacy applications
ActiveUS7945949B2Digital data processing detailsComputer security arrangementsServer agentVoice communication
A developer can provide complex services to existing legacy applications using one or more components configured to tap into a service abstraction framework. In one implementation, for example, a developer of a remote service provider adds one or more authentication attributes to the remote service provider, and further creates a local client driver that incorporates a client proxy. When a legacy application generates a function request (e.g., to print, send a text message, initiate a voice communication), the client proxy intercepts the request through an appropriate communication subsystem, and relays the request to the server proxy. The server proxy determines the extent to which authentication measures may be required. If required, the client proxy can initiate out-of-band processing with various authentication managers to validate / process the request at the remote service provider.
Owner:MICROSOFT TECH LICENSING LLC
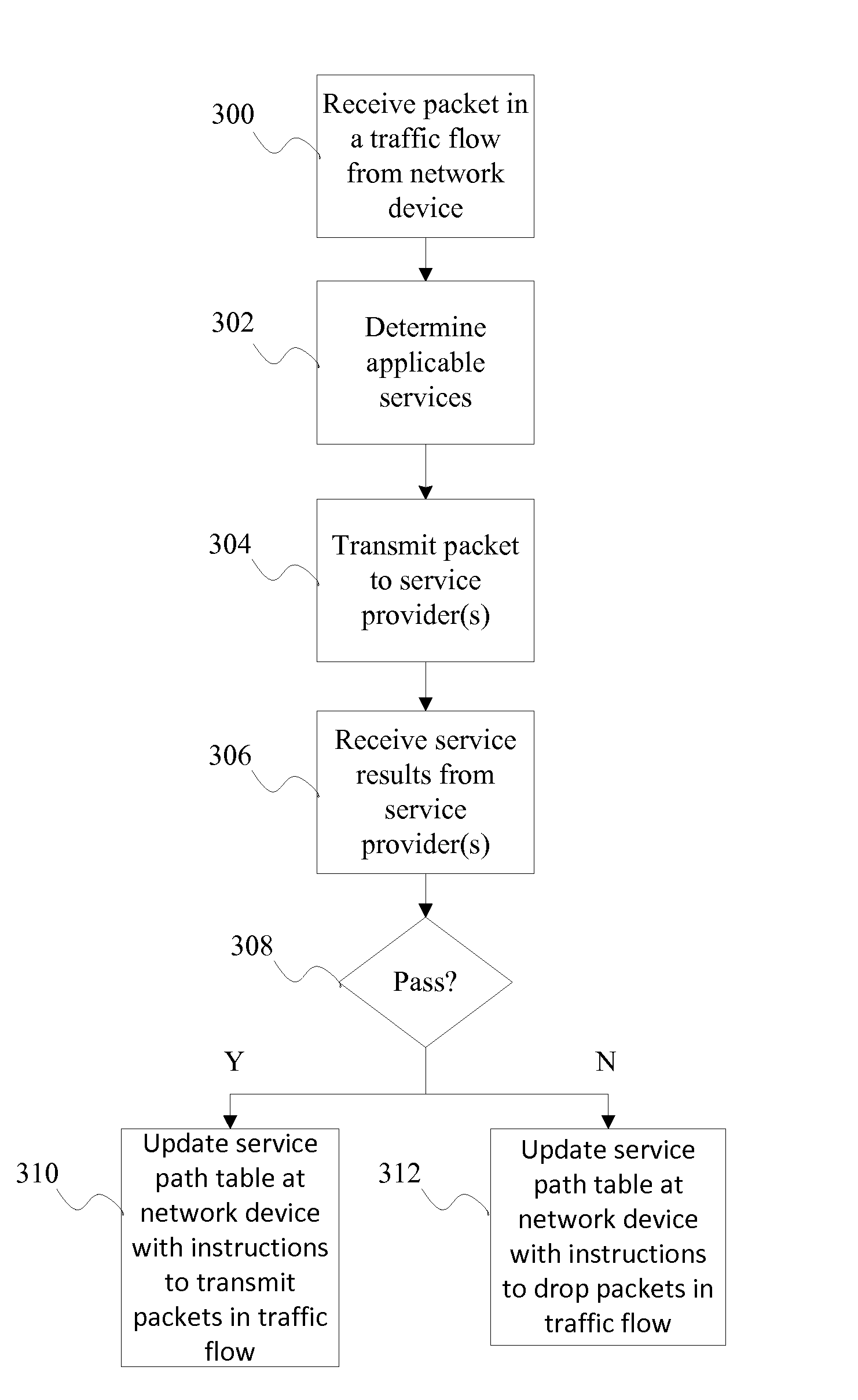
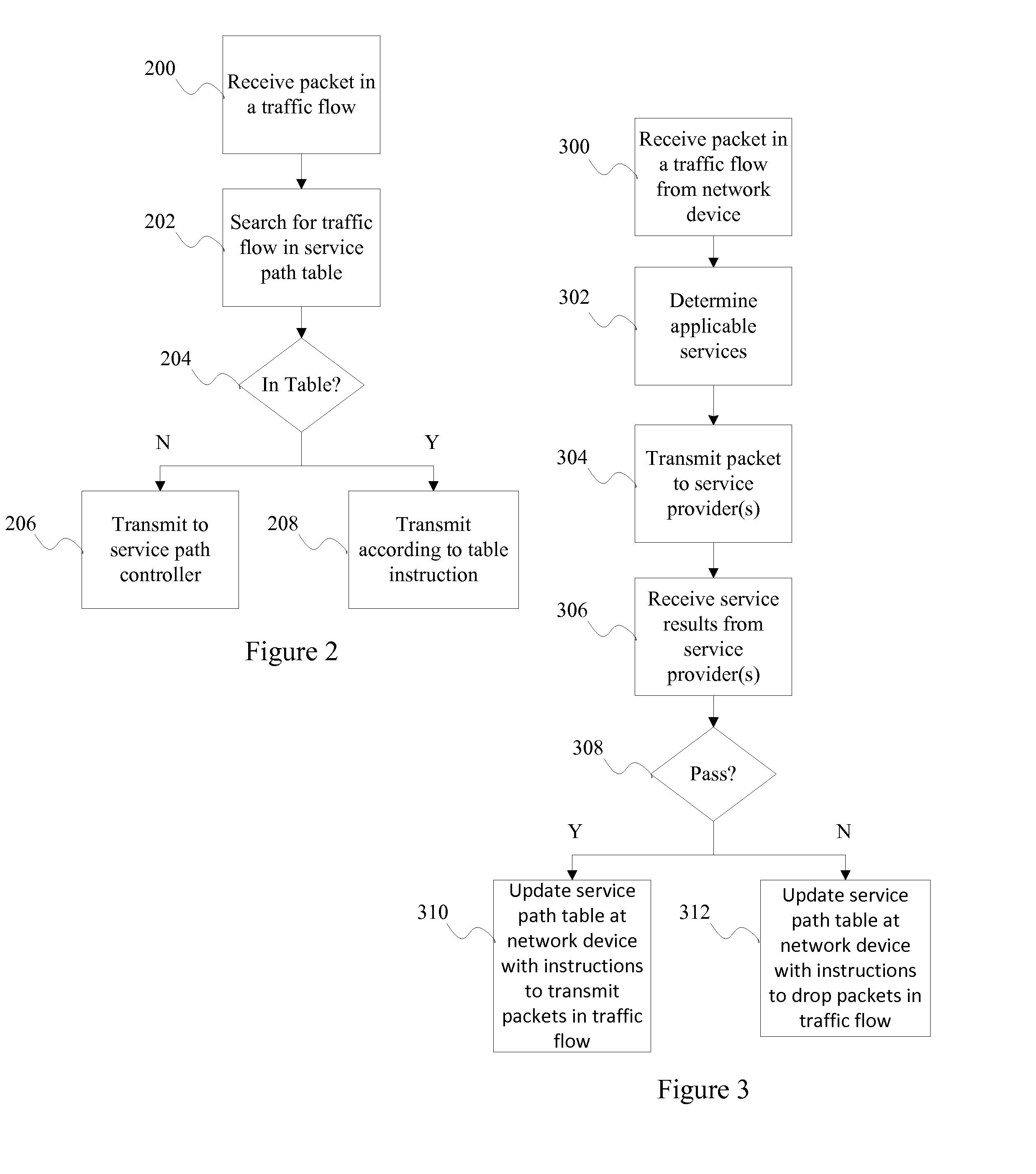
Intelligent Software-Defined Networking Based Service Paths
ActiveUS20150009809A1Error preventionFrequency-division multiplex detailsRadio Network ControllerTraffic flow
An example method embodiment for networking includes managing, by a network controller, network services for one or more network devices connected to the network controller. Managing network services includes receiving a packet in a traffic flow from a network device. The network device is one of the one or more network devices connected to the network controller. Managing network services further includes determining applicable services for the packet, transmitting the packet to a service provider in accordance with the applicable services for the packet, receiving, from the service provider, service results corresponding to the packet, and creating a forwarding entry providing instructions for handling the traffic flow in a service path table at the network device in accordance with the service results corresponding to the packet.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
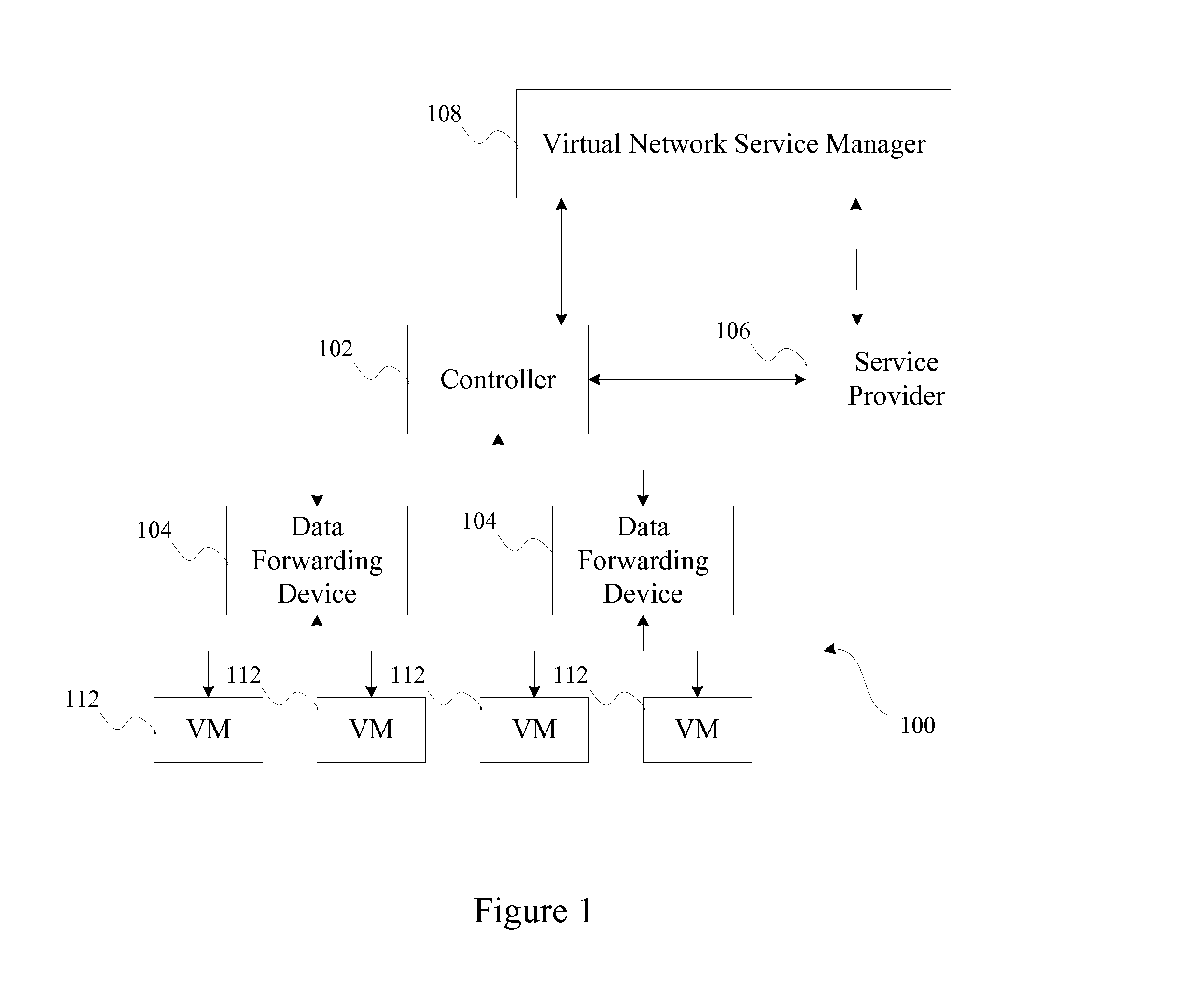
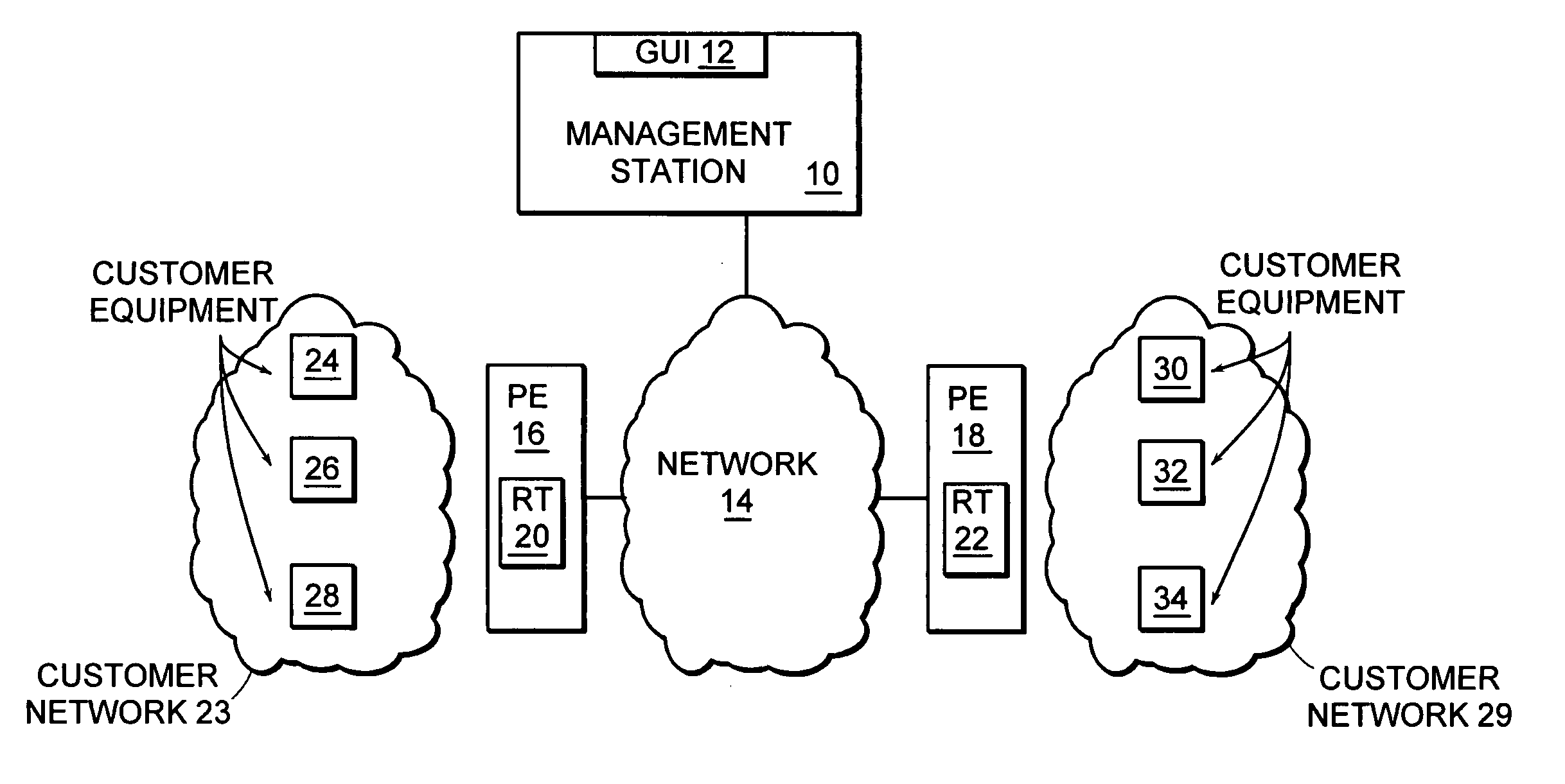
Method and system for providing configurable route table limits in a service provider for managing VPN resource usage
ActiveUS8868745B1Avoid overuseAccurate chargesDigital computer detailsHybrid transportRouting tableStructure of Management Information
A number of route tables are stored in a server at the edge of a service provider network, and are used to connect a set of customer sites to VPNs provided by the service provider. The forwarding entries in the route tables describe how packets conveyed over associated VPNs are to be forwarded between the service provider network and customer equipment systems. The disclosed system provides a configuration process for the route table including a route count limit as a parameter. The route count limit parameter provided through the configuration process is associated with the route table, and may be stored at the provider edge system, as well as at each other packet forwarding device within the network infrastructure of the service provider. Each forwarding device in the service provider infrastructure stores the route count limit, and further operates to keep track of the current number of routes inserted into the route table. Once the route table reaches the route count limit associated with it, new route requests can be either rejected, or accepted, based on a predetermined policy configuration. If new route requests are accepted, then the number of routes exceeding the route count limit is taken into account when charging the associated customer for service.
Owner:AVAYA INC
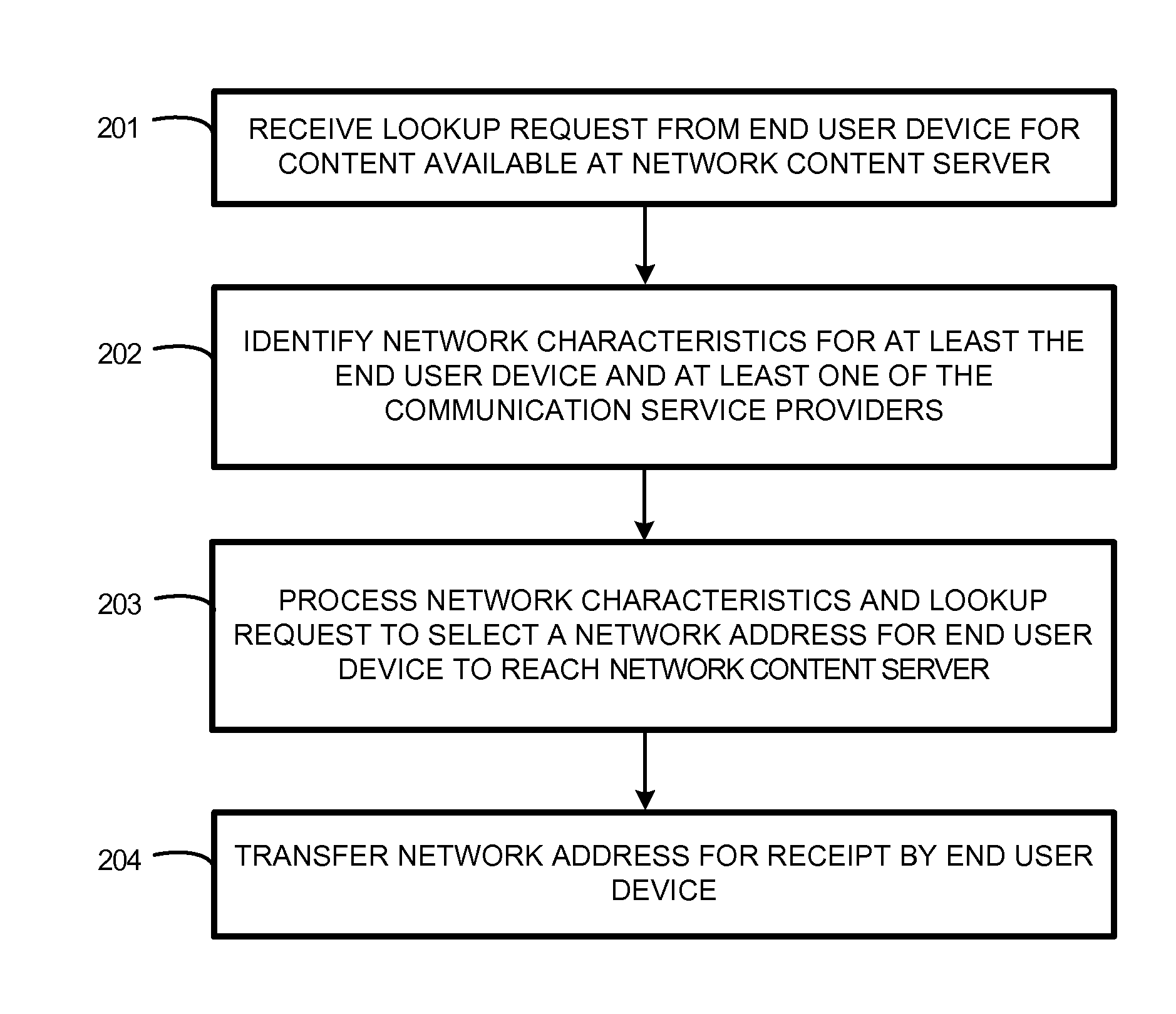
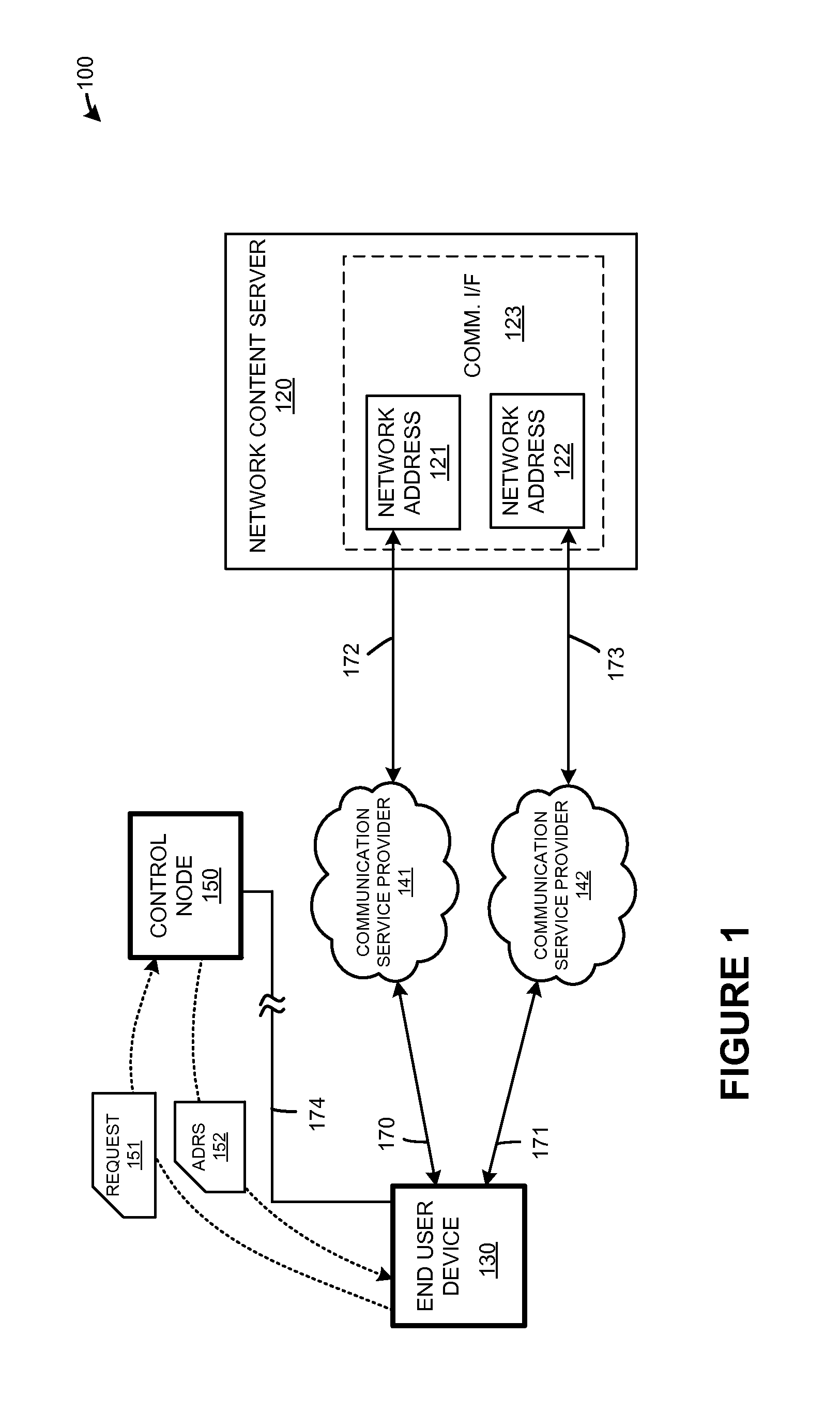
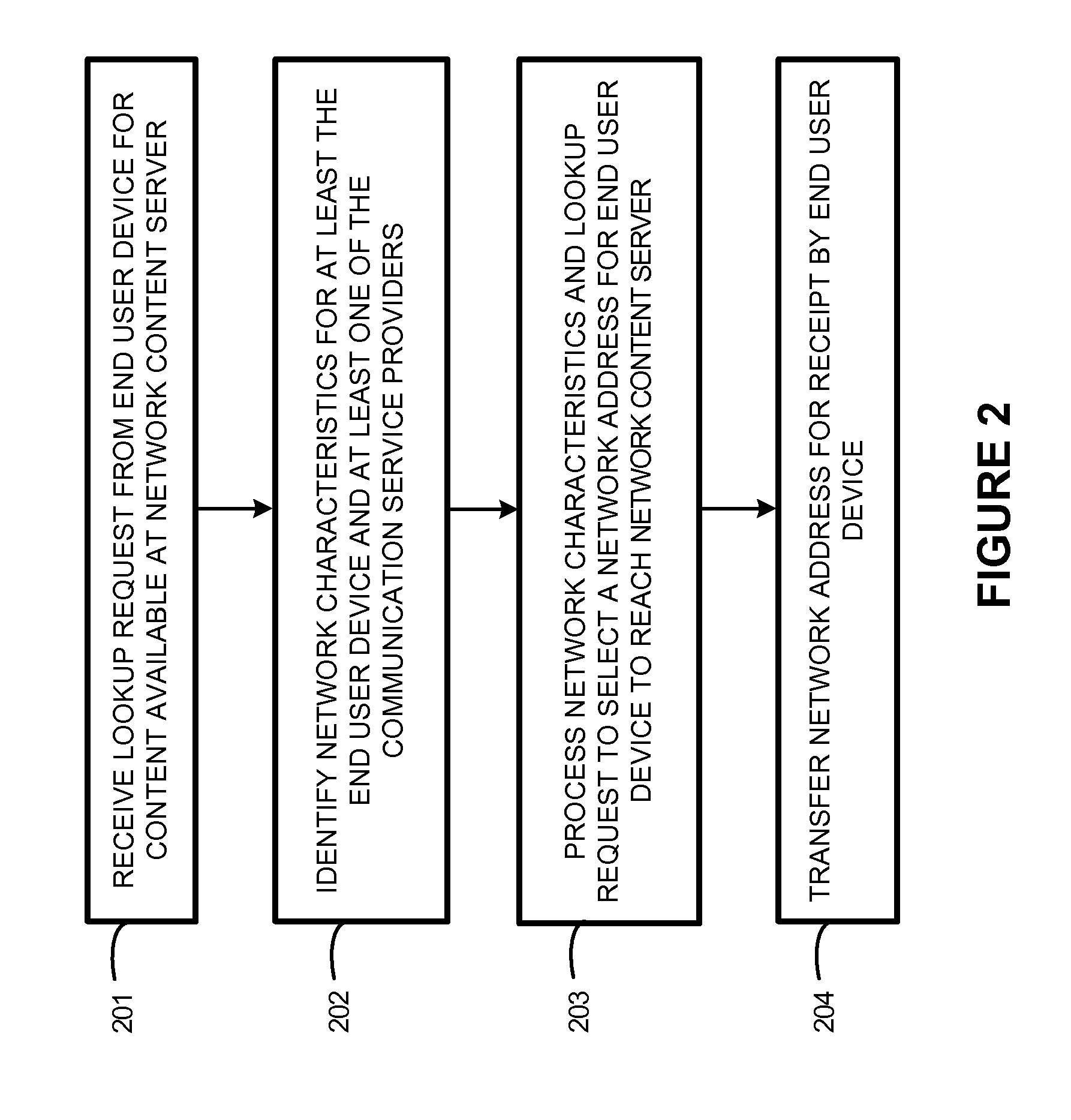
Server network address selection based on network characteristics of service providers
Systems, methods, apparatuses, and software that select network addresses of a network content server are provided herein. In one example, a method of operating a control node to perform network address selection that selects between different communication service providers according to network characteristics is presented. The control node receives a domain name lookup request from an end user device to reach a network content server. The control node processes network characteristics and the domain name lookup request to select a network address that corresponds to one of the communication service providers. The end user device can use the selected network address to reach the network content server over the selected communication service provider.
Owner:FASTLY
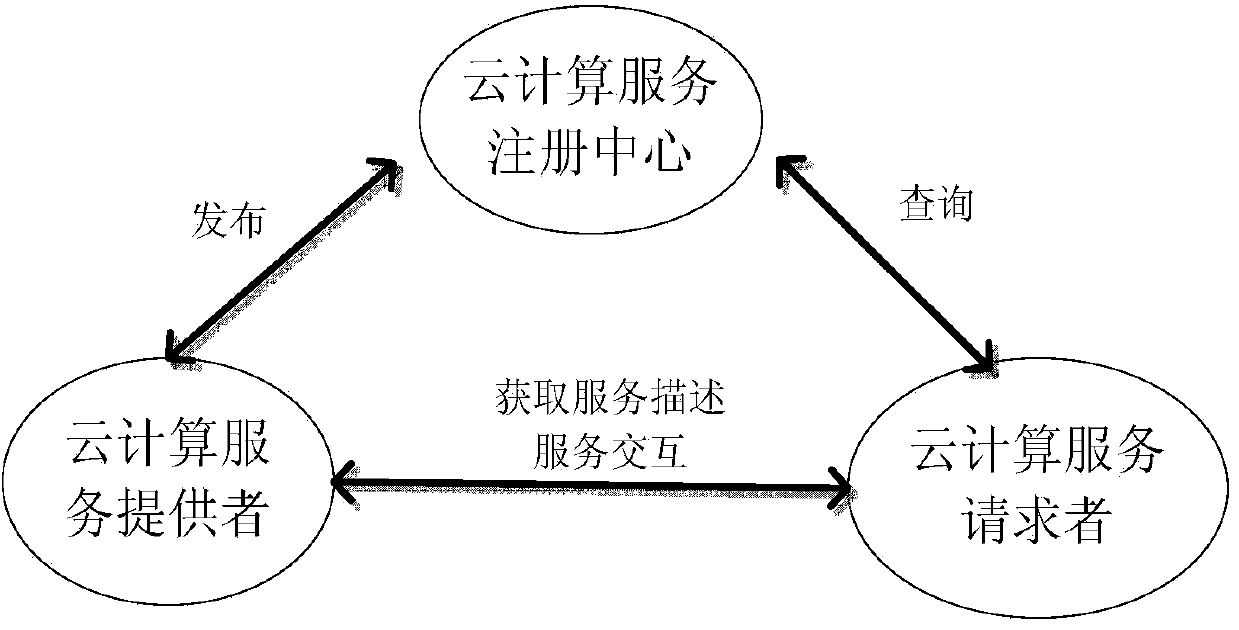
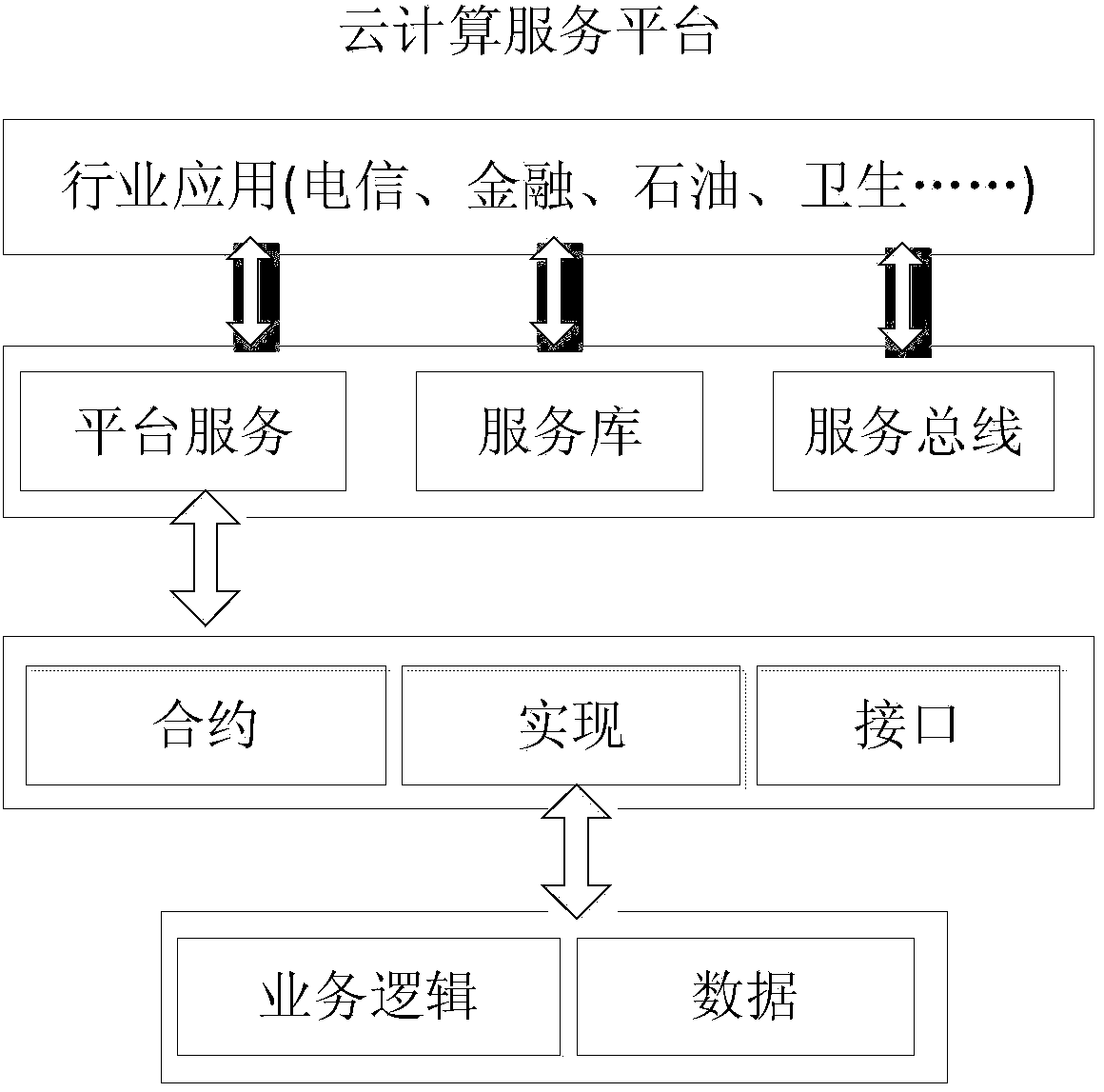
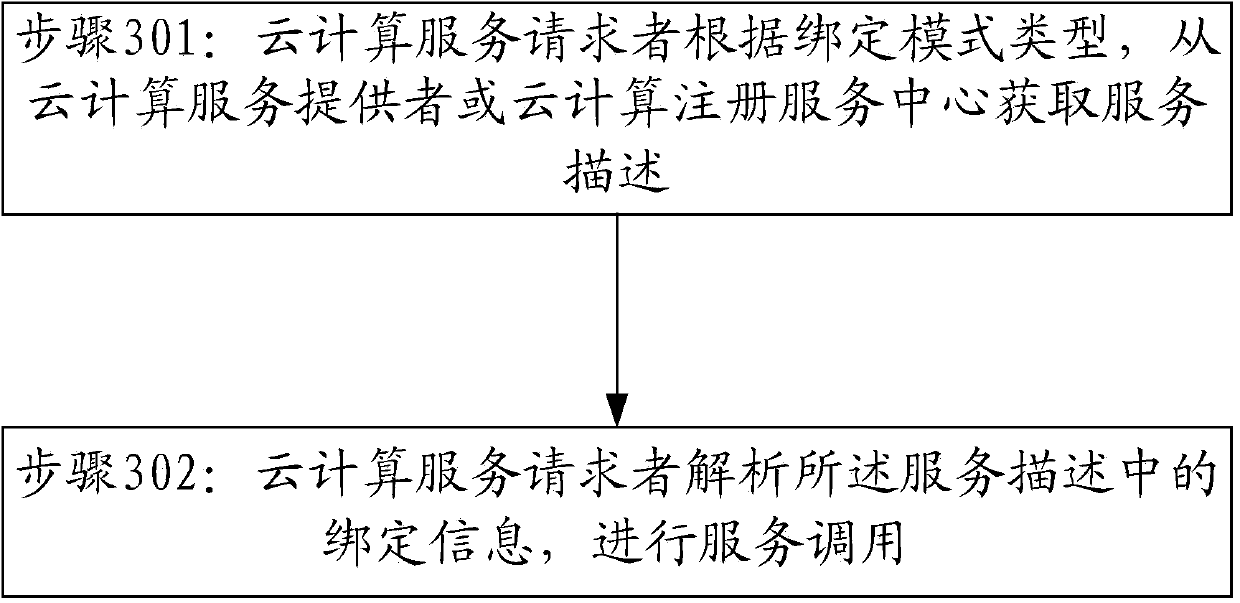
Construction method and system of cloud computing service platform
InactiveCN103701935AImprove scalabilityMeet build requirementsTransmissionLoose couplingLayered Service Provider
The invention provides a construction method and system of a cloud computing service platform, which is applied to the technical field of computer applications. The method comprises the following steps: a cloud computing service requester obtains service description from a cloud computing service provider or a cloud computing registration service center according to the type of binding mode, and analyzes binding information in the service description to perform service calling. According to the method provided by the invention, existing IT (information technology) infrastructures of an enterprise are protected with the help of an SOA (service-oriented architecture) and the loose coupling property thereof in the cloud computing service platform; by using a cloud computing service architecture of the SOA mode, the enterprise can add new services or update the existing services according to a modularization way to solve new business requirements, provide choices to provide the services through different channels, take the existing applications of the enterprise as the services and further protect existing IT infrastructure investment.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
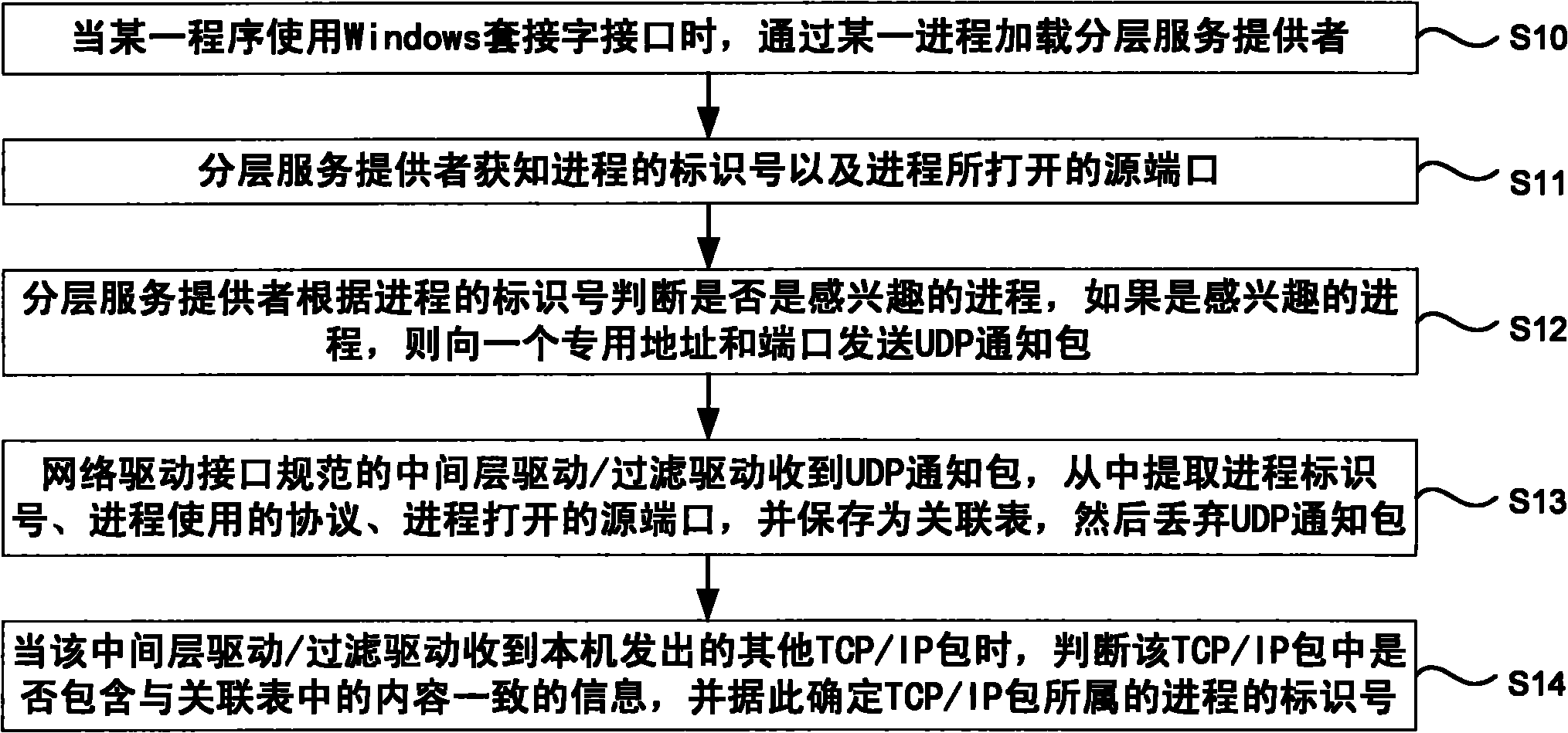
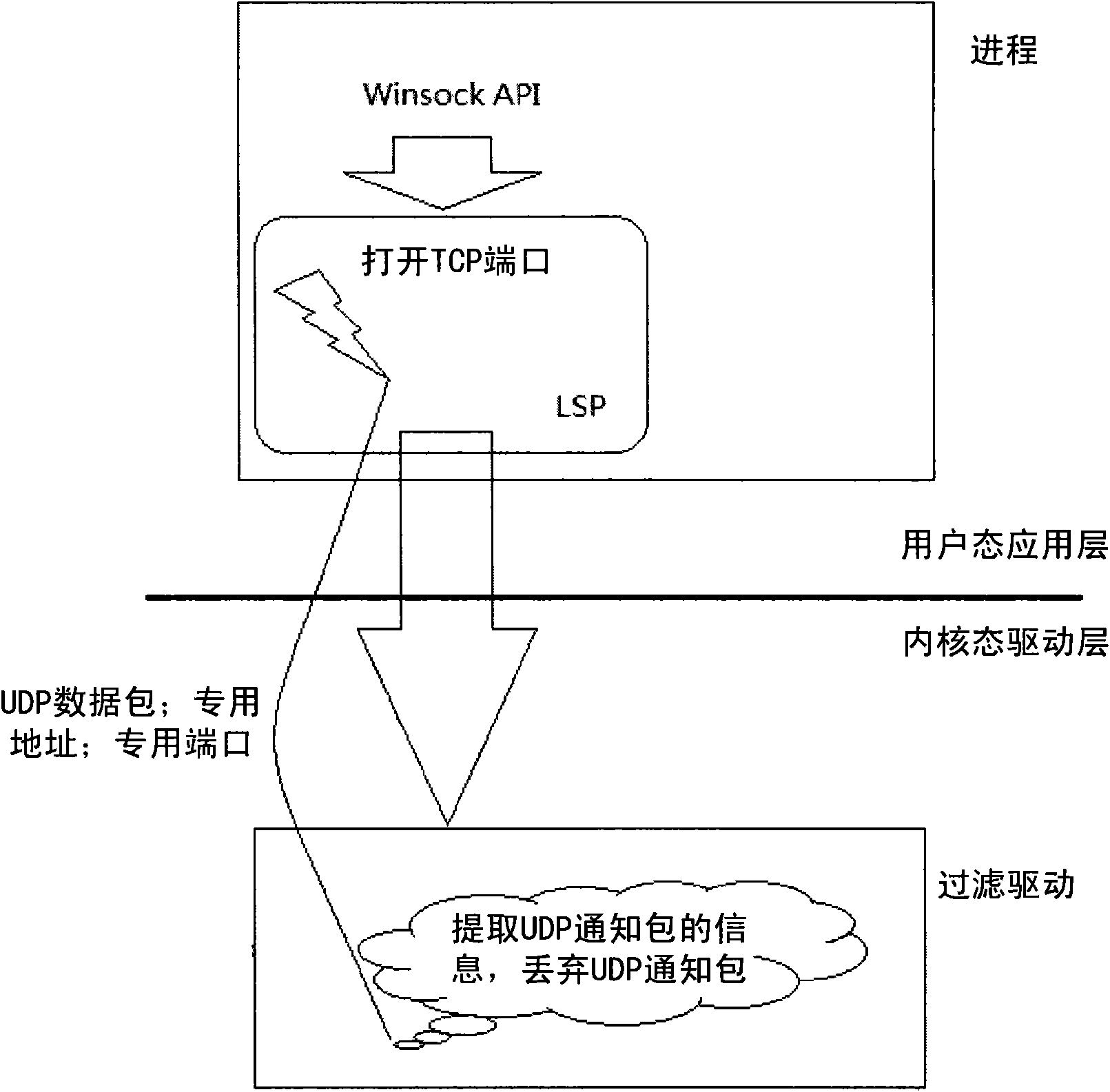
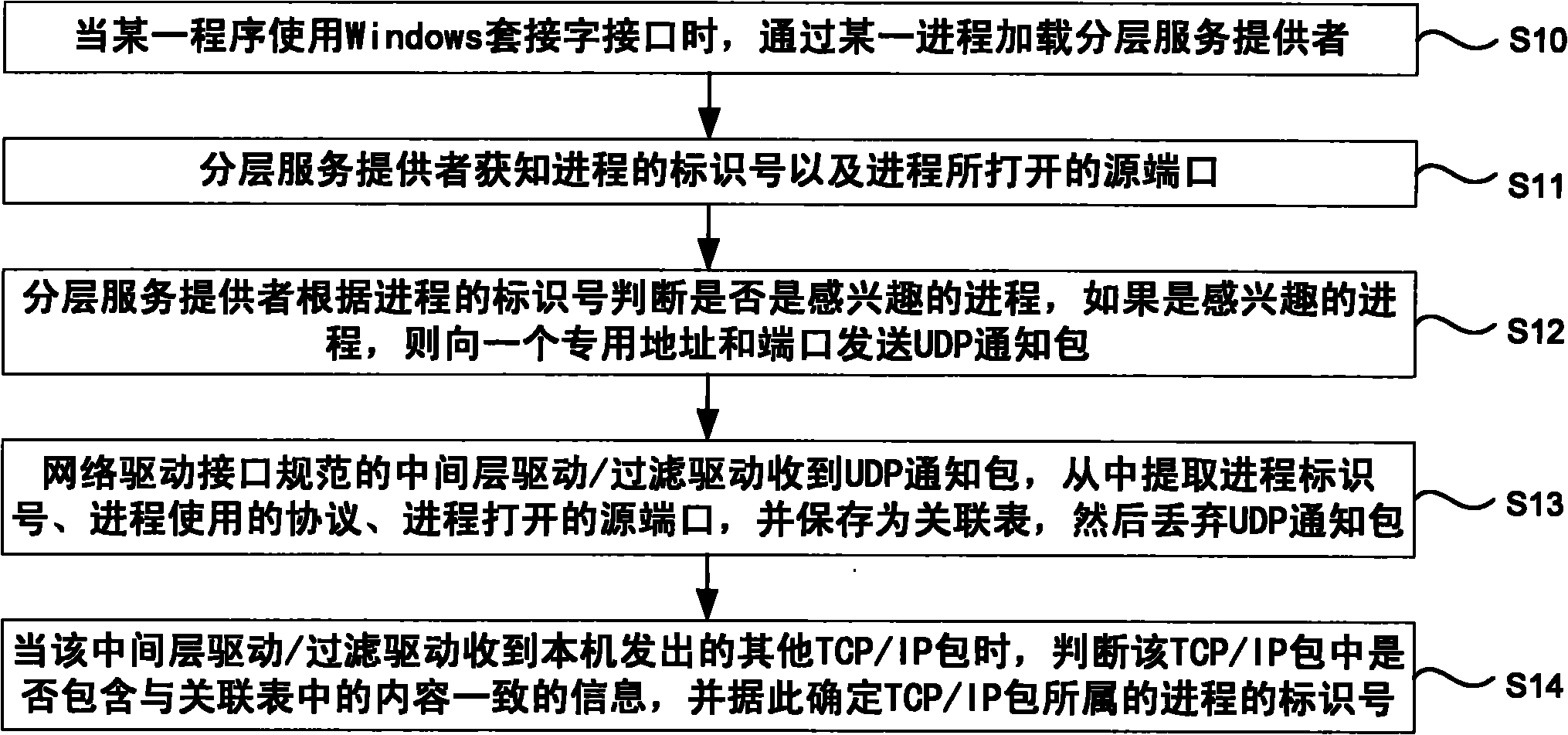
Method for judging process of TCP/IP packet in driver layer
The invention discloses a method for judging a process of a TCP / IP packet in a driver layer, which can accurately distinguish the process of a packet in a network driver interface specification (NDIS) filter driver. The technical scheme comprises that the method comprises the following steps of: when a certain program uses a Windows socket interface, loading a layered service provider through a certain process; acquiring an identification number of the process and a source port opened by the process by the layered service provider; judging whether the process is an interested process according to the identification number of the layered service provider; if the process is the interested process, transmitting a user datagram protocol (UDP) notification packet to a specific address and a port; receiving the UDP notification packet, extracting the identification number of the process, a protocol used by the process and the source port opened by the process from the UDP notification packet, saving the identification number of the process, the protocol used by the process and the source port opened by the process as an association table, and discarding the UDP notification packet by using an intermediate layer driver / filter driver normalized by a network driver interface; and when the intermediate layer driver / the filter driver receives another TCP / IP packet transmitted by a local host, judging whether the TCP / IP packet comprises the information consistent with the contents in the association table, and determining the identification number of the process to which the TCP / IP packet belongs according to the judgment.
Owner:CHINANETCENT TECH
Multiprotocol label-switched path APS (Active Protection System) protection and management method, equipment and system
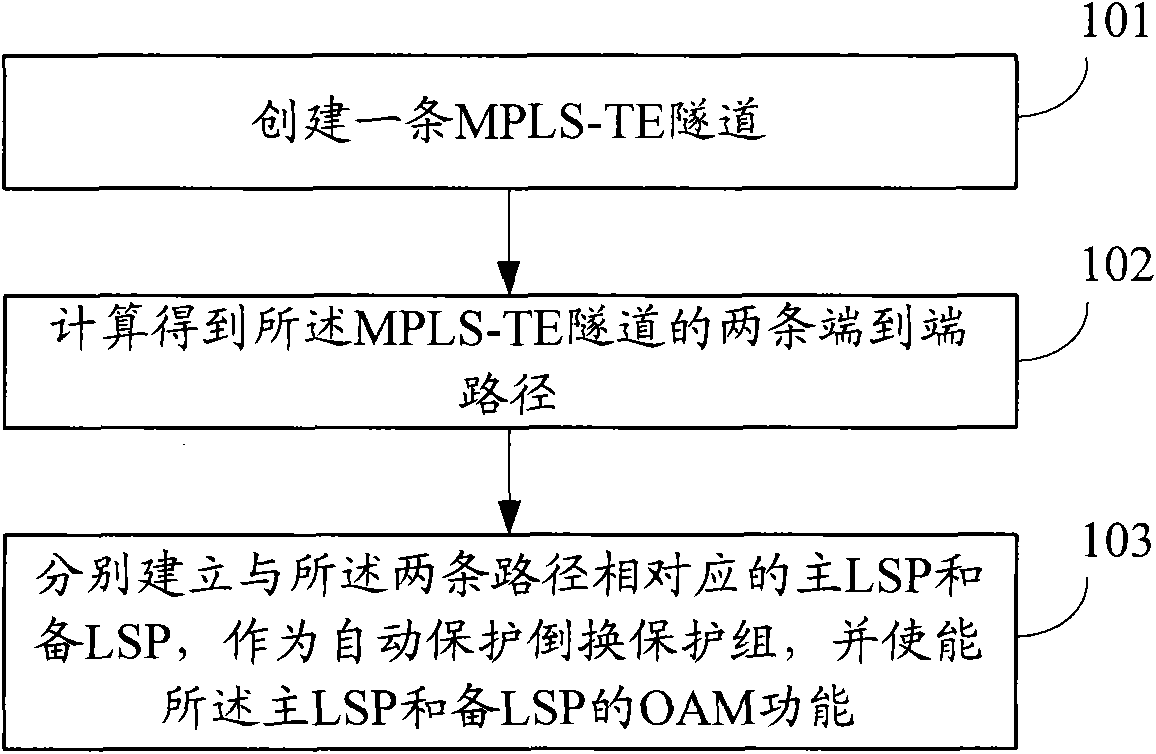
InactiveCN101964743ASimple configurationRealize automatic protection switchingNetworks interconnectionMultiprotocol Label SwitchingAutomatic protection switching
The invention relates to the technical field of network communication, and discloses multiprotocol label-switched path APS protection and management method, equipment and system, wherein the method comprises the following steps of: establishing an MPLS-TE (Multiprotocol Label Switching-Traffic Engineering) tunnel; computing to obtain the two end-to-end paths of the MPLS-TE tunnel; and respectively establishing a main LSP (Layered Service Provider) to one path in the two paths and a spare LSP corresponding to the other path in the two paths to be used as an automatic protection switching protection group, and enabling the OAM (Operation, Administration and Maintenance) functions of the main LSP and the spare LSP. The invention can be utilized for simplifying the configuration for the APS protection of the MPLS-TE tunnel and effectively realizing the automatic protection switching of the MPLS-TE tunnel.
Owner:HUAWEI TECH CO LTD
Mobile application, identity interface
ActiveUS9081951B2Digital data processing detailsMultiple digital computer combinationsApplication softwareLayered Service Provider
Techniques for managing identities are provided. In some examples, identity management, authentication, authorization, and token exchange frameworks may be provided for use with mobile devices, mobile applications, cloud applications, and / or other web-based applications. For example a mobile client may request to perform one or more identity management operations associated with an account of a service provider. Based at least in part on the requested operation and / or the particular service provider, an application programming interface (API) may be utilized to generate and / or perform one or more instructions and / or method calls for managing identity information of the service provider.
Owner:ORACLE INT CORP
Method and device for posting information in layered service provider (LSP) zone message
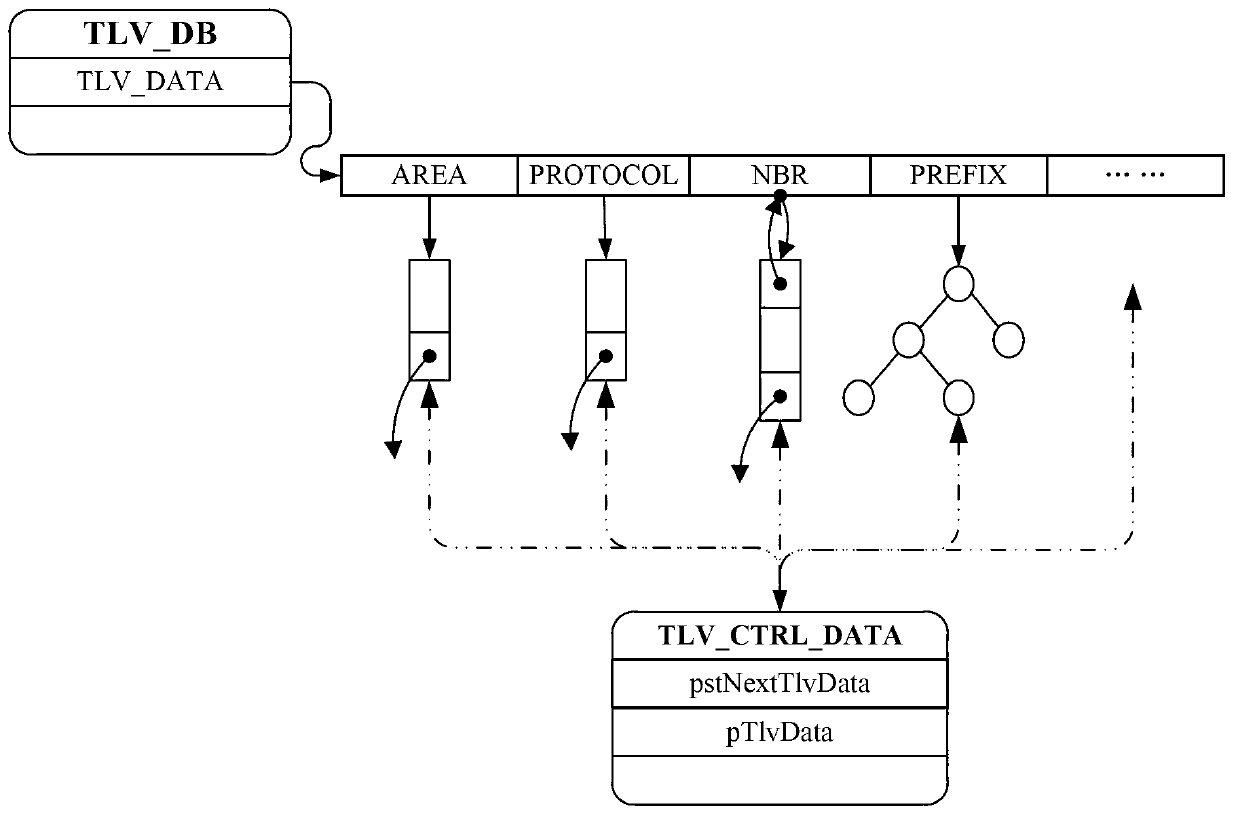
ActiveCN103001865AEffective maintenanceFlexible maintenanceData switching networksLayered Service ProviderDatabase
The invention discloses a method for posting information in layered service provider (LSP) zone message. The method includes that a device stores data information to be posted into a data information database in, generates control information according to stored data information and current course environment trend and stores the information in a control information database. The device packages data information belonging to an identical LSP zone and stored in the data information database according to corresponding types to generate LSP zone message and post the message according to the control information stored in the control information database. The device based on identical invention conception is further provided. The method and the device are capable of effectively and flexibly maintaining the data information and the control information posting LSP zone message.
Owner:NEW H3C TECH CO LTD
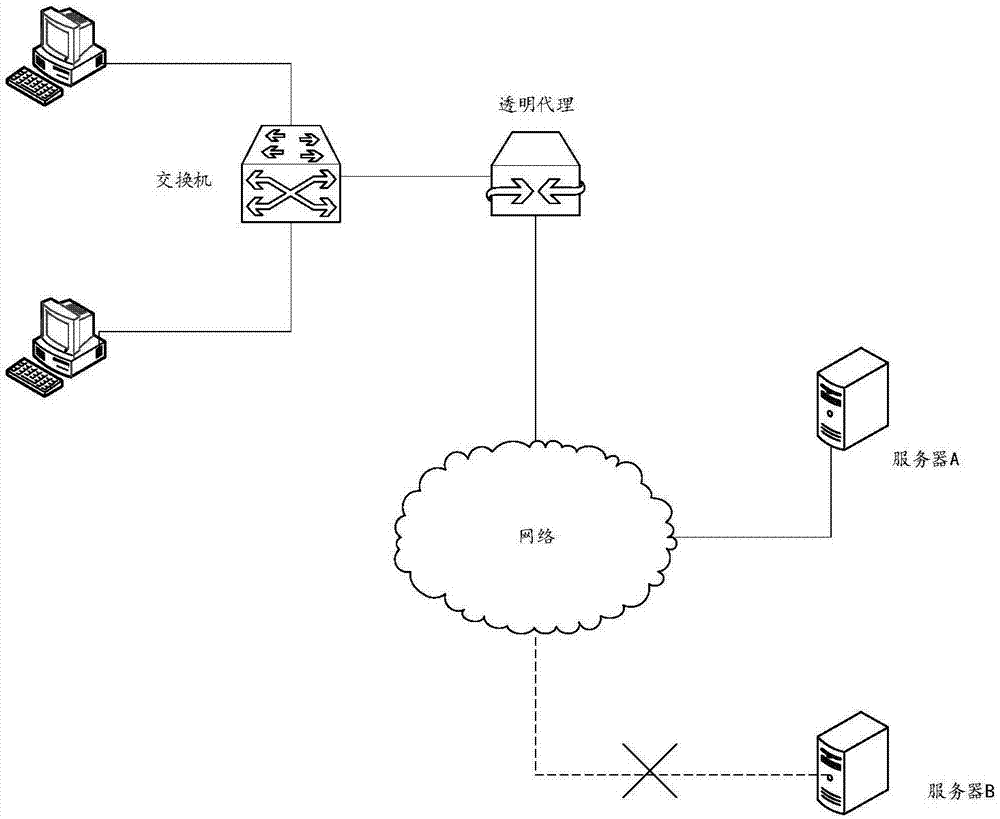
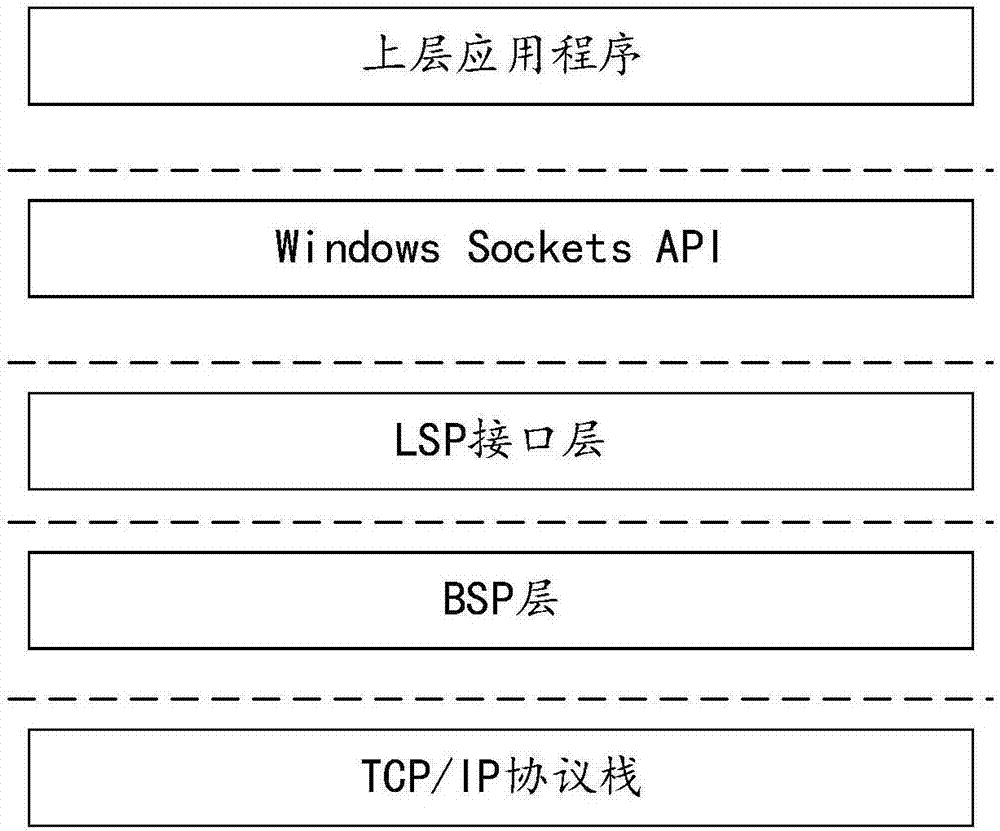
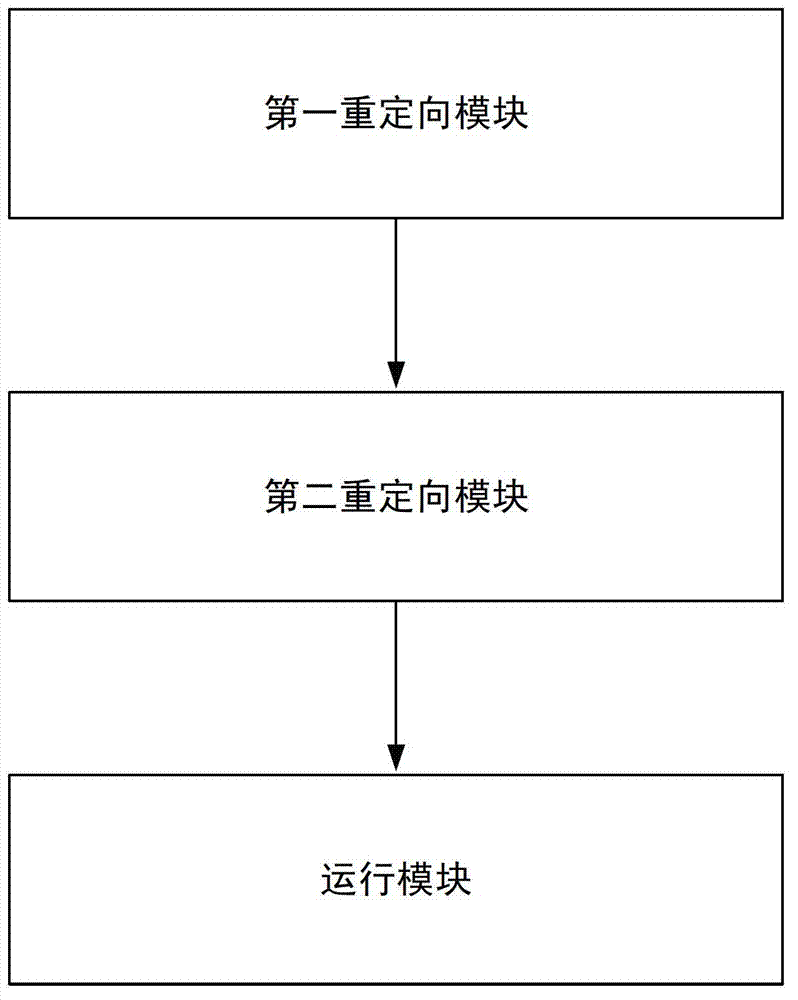
Transparent proxy implementation method, device and client
The invention discloses a transparent proxy method, device and a client. The method comprises the following steps: a layered service provider (LSP) layer modifies a transmission address of first application layer data to an address of a transfer loop layer, and sends the application layer data to the transfer loop layer; the transfer loop layer receives the first application layer data sent from the LSP layer, and modifies the first application layer data to second application layer data based on a preset proxy protocol; the transfer loop layer sends the second application layer data to a basic service provider (BSP) layer; and the BSP layer pushes the second application layer data to a TCP / IP protocol stack according to the proxy protocol information contained in the second application layer data. Based on the technical scheme disclosed by the embodiment of the invention, the LSP layer can be decoupled from the application layer data modification function, the complexity of the LSP layer can be reduced, and thus the problem of LSP conflicts caused by modifying the application layer data or the problem that an upper application cannot be executed due to model missing can be avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Selective exclusion of LSPs on a per-packet basis
InactiveUS20060224749A1Multiple digital computer combinationsTransmissionData packLayered Service Provider
A method is provided for selectively loading a layered service provider (LSP). The method includes registering at least one category for an installed LSP and registering a list of permitted categories of LSPs for an installed application. The application is then loaded, and the list of permitted categories of LSPs for the installed application is read. The installed LSP is loaded only if the at least one category is included in the list of permitted categories of LSPs.
Owner:MICROSOFT TECH LICENSING LLC
Registry redirecting method and device
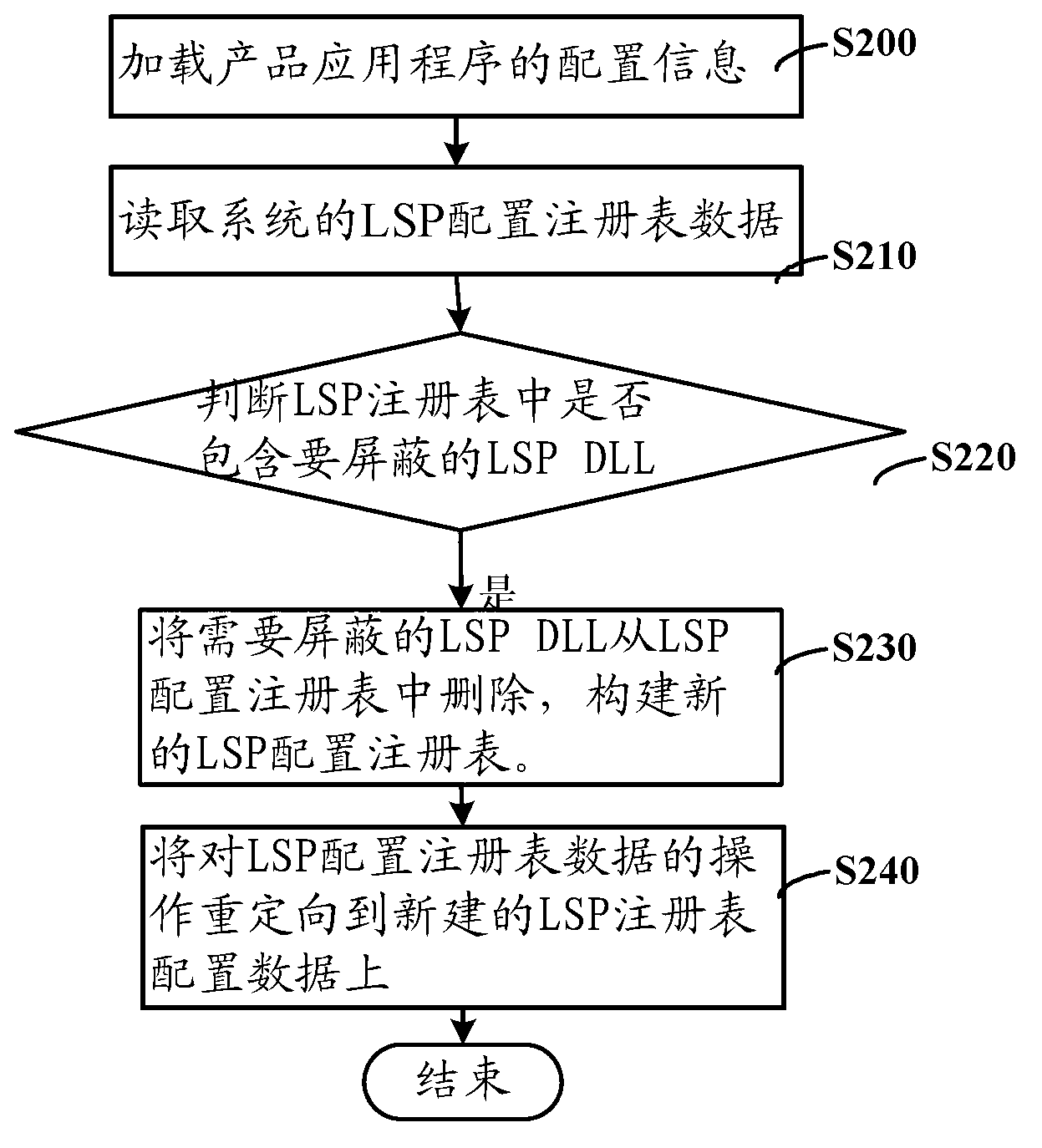
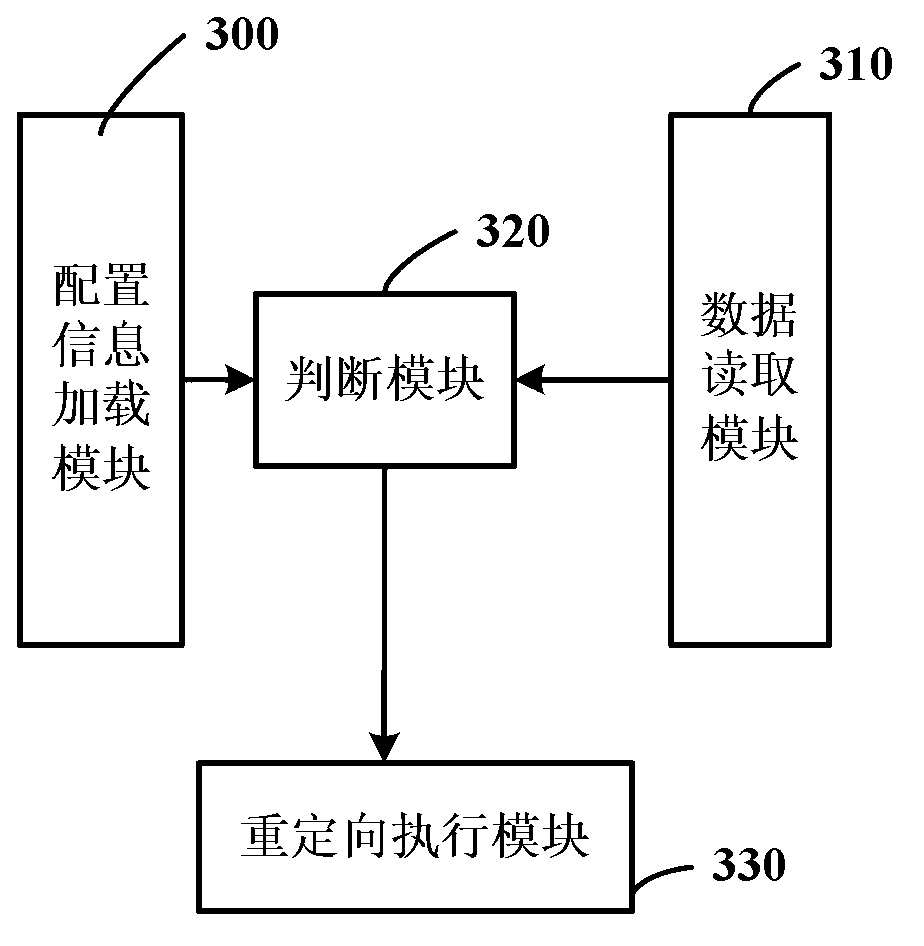
ActiveCN103019674AAvoid loadImprove stabilityData switching networksSpecific program execution arrangementsRegistry dataApplication software
The invention discloses a registry redirecting method and device. The method comprises the following steps of: loading configuration information of an application program; judging whether layered service provider (LSP) configuration registry data comprises LSP dynamic link library (DLL) which needs to be shielded or not according to the loaded configuration information; if the LSP configuration registry data comprises the LSP DLL which needs to be shielded, deleting the information of the LSP DLL from the LSP configuration registry data to construct new LSP configuration registry data; and redirecting the operation of the LSP configuration registry data onto the newly constructed LSP configuration registry data. According to the method disclosed by the invention, through utilizing a registry redirecting mechanism, specific or all LSP DLLs are shielded by aiming at specific or all processes in a Windows system, and therefore, the LSP DLLs are prevented from being loaded into the processes, and the stability and the safety of the application program are improved.
Owner:BEIJING QIHOO TECH CO LTD
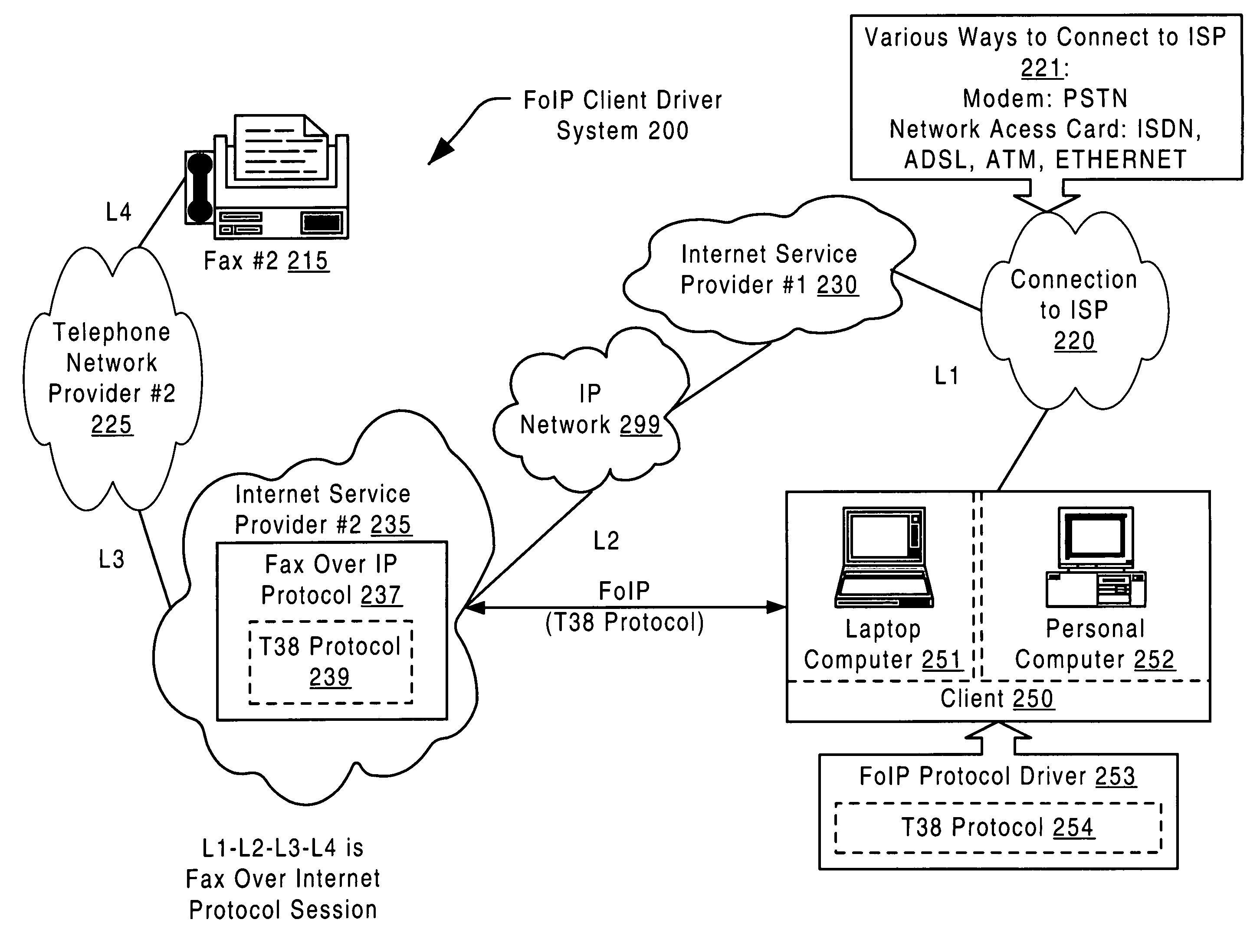
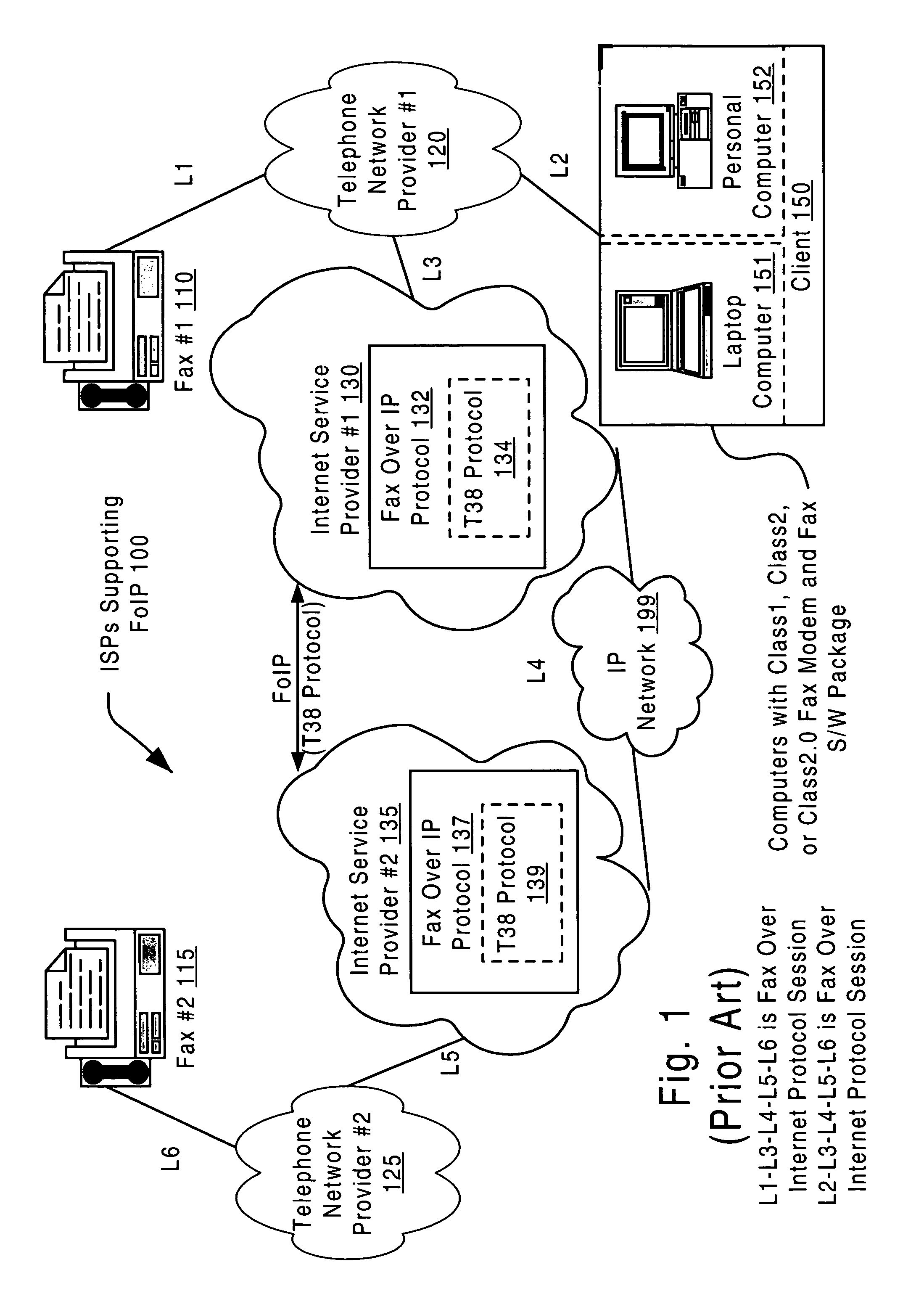
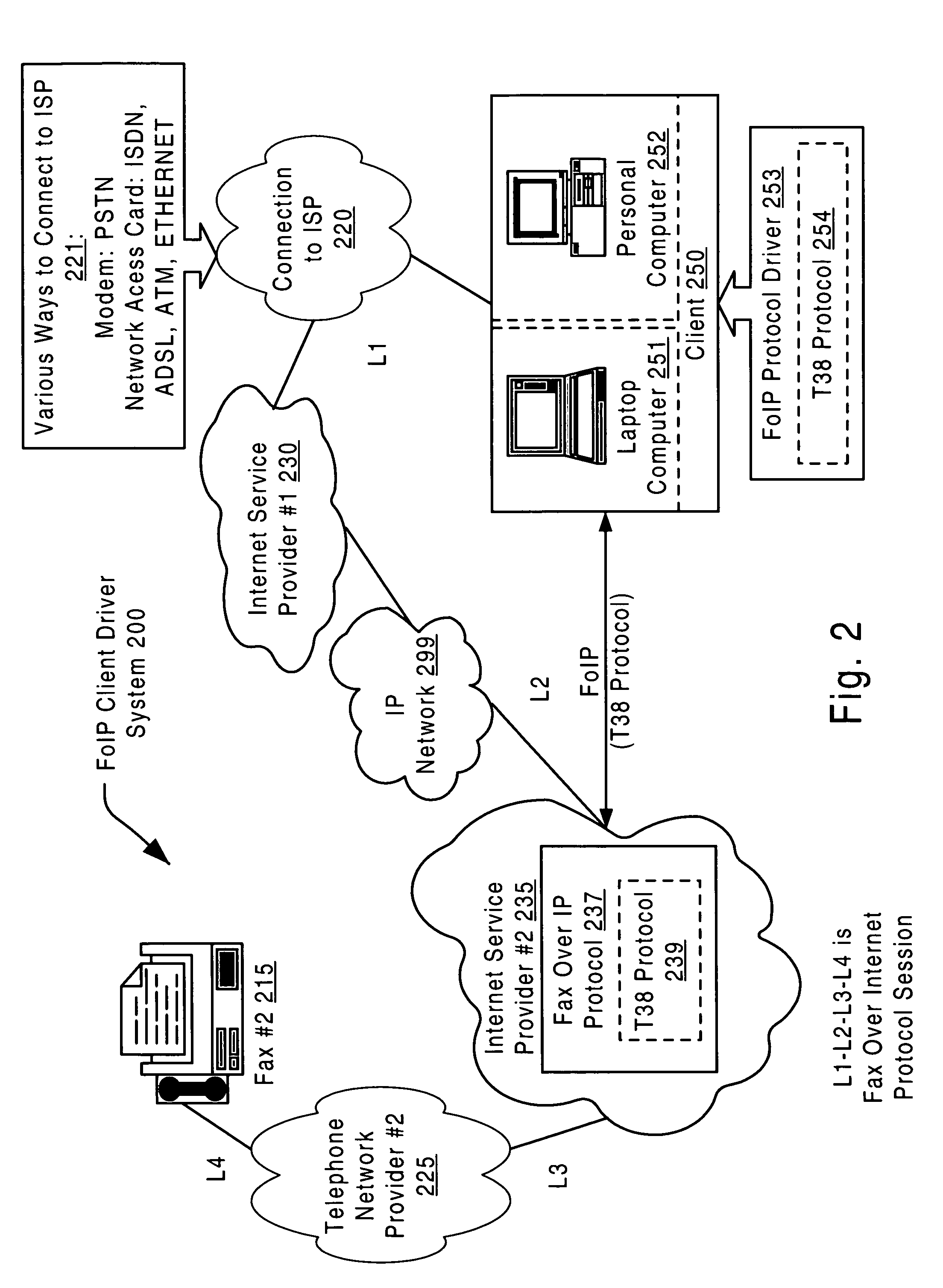
Fax over internet protocol client driver
InactiveUS7085021B1Digital computer detailsTelephonic communicationInternet protocol suitePersonal computer
A fax over Internet protocol client driver. The present invention enables a client to support a fax over Internet protocol. Whereas conventional systems commonly rely upon an Internet service provider (ISP) to support the fax over Internet protocol functionality, the invention ensures that a client can perform multiple Internet sessions, one of which is a fax over Internet protocol session. There is no need to disconnect from a current Internet session, and then re-establish another Internet session. The client is any number of devices including a personal computer, a laptop computer, a pen based computer, an Internet capable fax machine, or any other fax capable device. By providing a fax over Internet protocol driver within the client, the client can send a fax transmission over the Internet, even in the situation where the ISP that the client solicits does not support that particular functionality.
Owner:MACOM TECH SOLUTIONS HLDG INC
Mobile application, identity interface
ActiveUS20150310202A1Digital data processing detailsMultiple digital computer combinationsApplication softwareLayered Service Provider
Techniques for managing identities are provided. In some examples, identity management, authentication, authorization, and token exchange frameworks may be provided for use with mobile devices, mobile applications, cloud applications, and / or other web-based applications. For example a mobile client may request to perform one or more identity management operations associated with an account of a service provider. Based at least in part on the requested operation and / or the particular service provider, an application programming interface (API) may be utilized to generate and / or perform one or more instructions and / or method calls for managing identity information of the service provider.
Owner:ORACLE INT CORP
Method and system of managing subscriber access to services associated with services provider
ActiveUS9037494B2Analogue secracy/subscription systemsTwo-way working systemsLayered Service ProviderPayment service provider
Owner:TIVO CORP
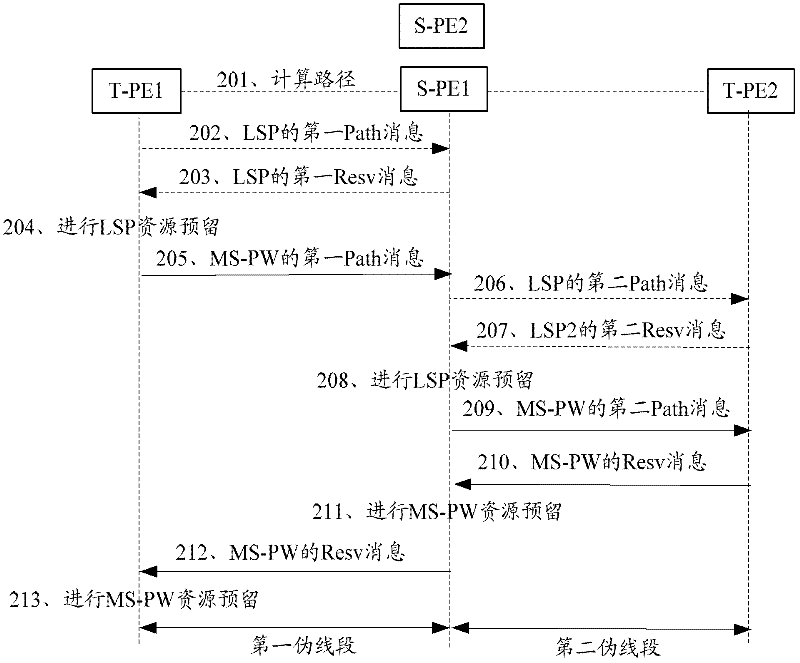
Multi-segment pseudo-wire establishing and recovering method and device as well as system
ActiveCN102404199AEfficient use ofAvoid the build processData switching networksMulti segmentPseudo-wire
The invention provides a multi-segment pseudo-wire establishing method which comprises the following steps that by calculation, a head end node obtains a path of a MS-PW (Multi-Segment Pseudo-Wire) which reaches a destination end node through a switching node; the head end node establishes a LSP (Layered Service Provider) between the head end node and the switching node of a next hop as a service layer; the head end node issues the Path information of establishing a pseudo-wire segment of the MS-PW to the switching node of the next hop on the established LSP layer till the destination end node receives the Path information of establishing the pseudo-wire segment of the MS-PW; the destination end node obtains the resource Resv (Reserve) information of the MS-PW according to the Path information; and the switching node receiving the Resv information of the MS-PW forwards the Resv information of the MS-PW to nodes of a previous hop, and the nodes establishes the PW as a client layer according to the received Resv information of the MS-PW. The invention also discloses a multi-segment pseudo-wire recovering method and a device as well as a system, thereby realizing the reestablishment of a new MS-PW when faults occur and avoiding the establishment of the standby MS-PW when no faults occur so as to more effectively use the communication resources of the system.
Owner:ZTE CORP
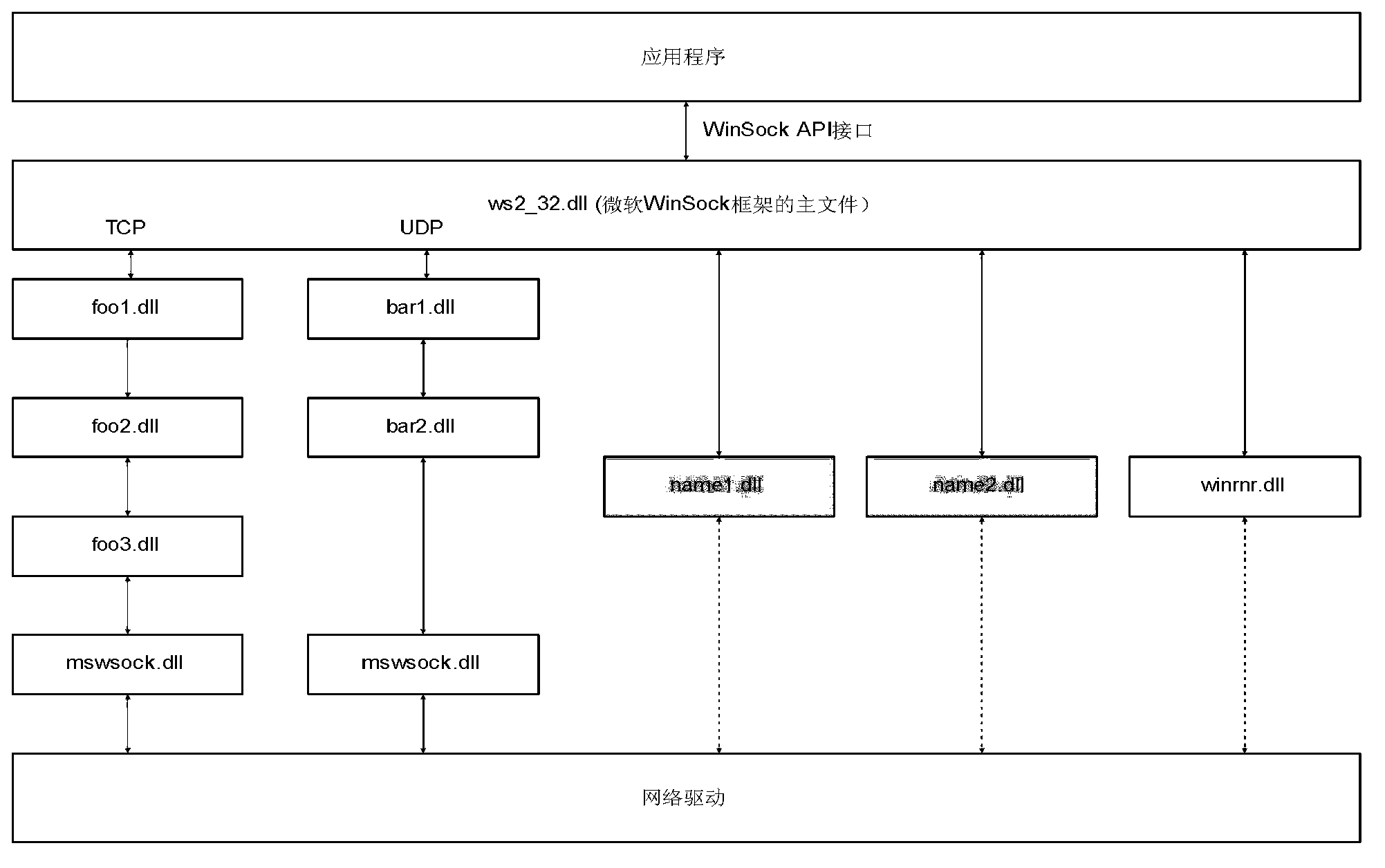
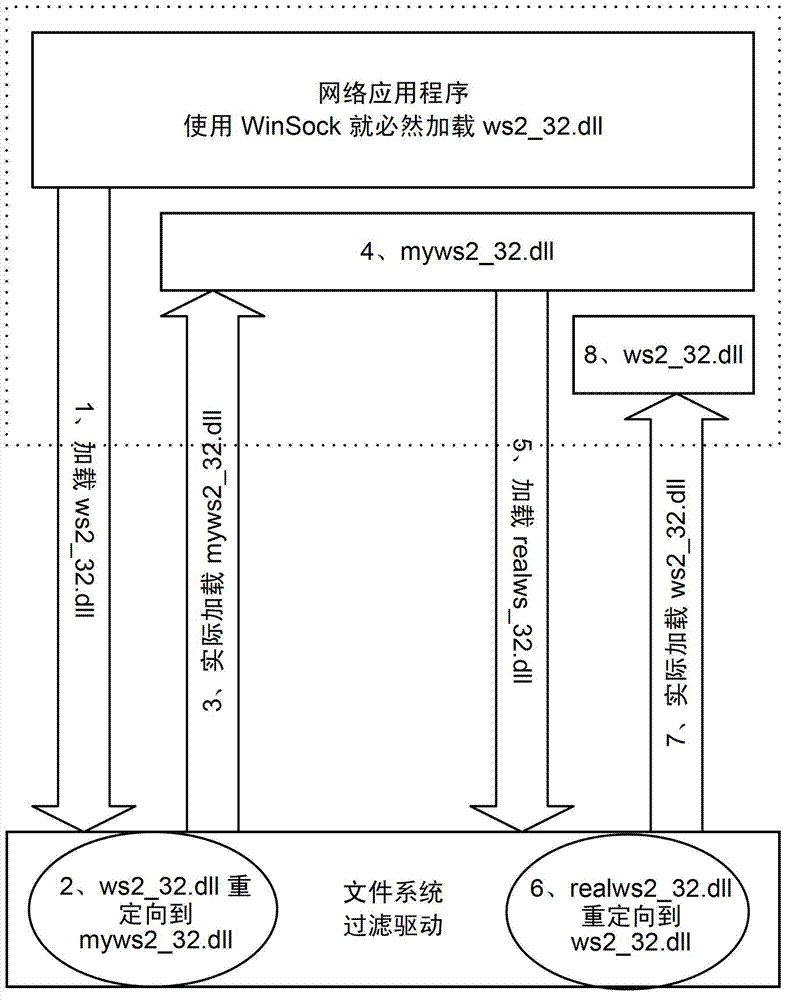
Filter method and device for application layer network communication
The invention discloses a filter method and device for application layer network communication. The method and the device have the advantages of an LSP (Layered Service Provider) and do not have installation difficulty of the LSP. The technical proposal is that the method comprises the following steps: a network application calls a window socket application program interface; a file system filter driver orientates a preset weight loading on a ws2_32.d 11 file to loading on a my ws2_32.d 11 file, wherein the ws2_32.d 11 file is from a Winsock 2.0 database; the my ws2_32.d 11 file directly calls utility functions in the ws2_32.d 11 file; the my ws2_32.d 11 file is operated, so that the file system driver orientates the weight loading on a real ws2_32.d 11 file to the loading for the ws2_32.d 11 file; and the ws2_32.d 11 file is operated.
Owner:XIAMEN WANGSU CO LTD
ISIS (Intermediate System to Intermediate System) LSP (Link State Protocol Data Unit) publishing method and equipment
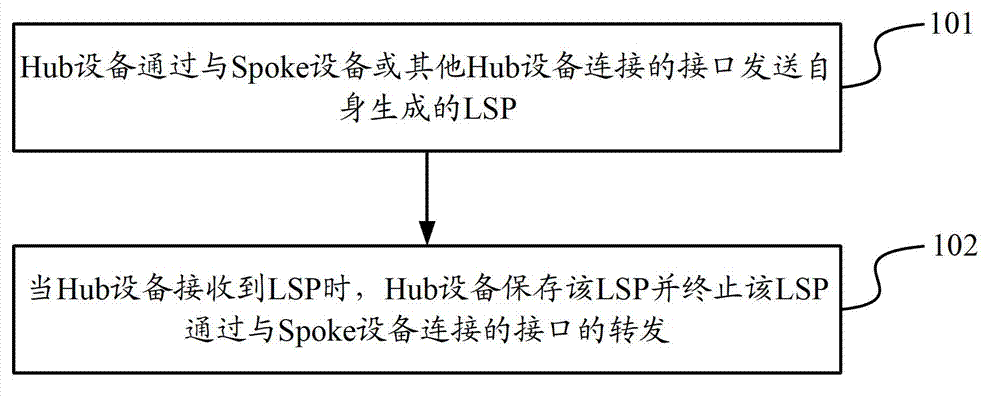
ActiveCN103078792AReduce flooding overheadReduce capacityData switching networksExtensibilityLayered Service Provider
The invention discloses an ISIS (Intermediate System to Intermediate System) LSP (Layered Service Provider) publishing method and equipment. The method comprises the following steps that a self generated LSP is sent by Hub equipment through an interface connected with Spoke equipment or other Hub equipment, wherein the self generated LSP of the Hub equipment contains default routing information, so that a default route, the next hop of which is the Hub equipment, is generated by the Spoke equipment, which is used for receiving the self generated LSP of the Hub equipment, in accordance with the default routing information; and when the LSP is received by the Hub equipment, the LSP is preserved by the Hub equipment, and the forwarding of the LSP through an interface connected with the Spoke equipment is terminated. According to the ISIS LSP publishing method and the equipment, the LSP flooding overhead of the Hub equipment is reduced, and the LSDB (Link State Database) capacity and the routing computation overhead of the Spoke equipment are reduced, thereby improving the stability and the expandability of a network.
Owner:NEW H3C TECH CO LTD
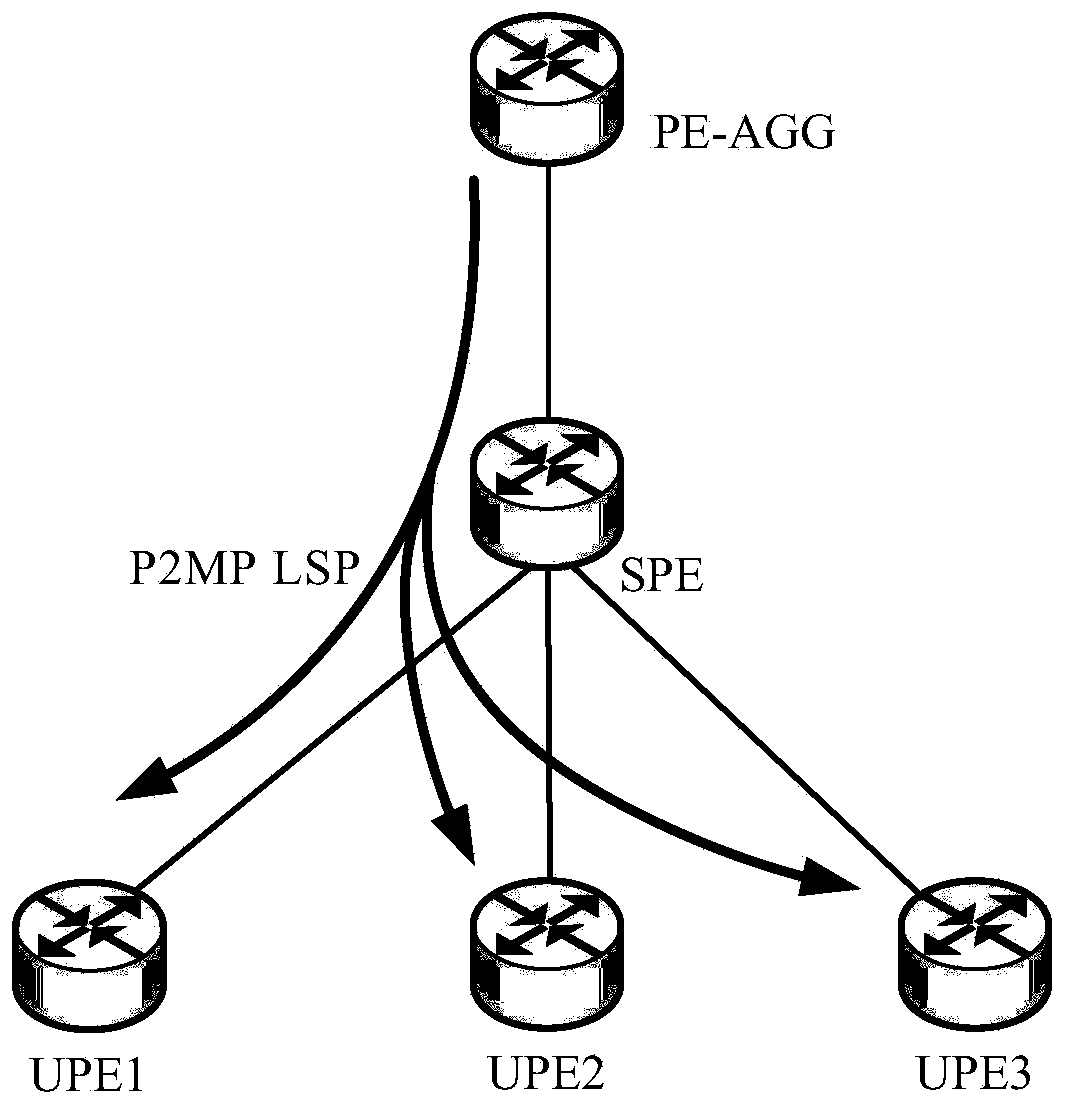
Method and device for realizing multicast in hierarchy of virtual private LAN (Local Area Network) service (H-VPLS) network
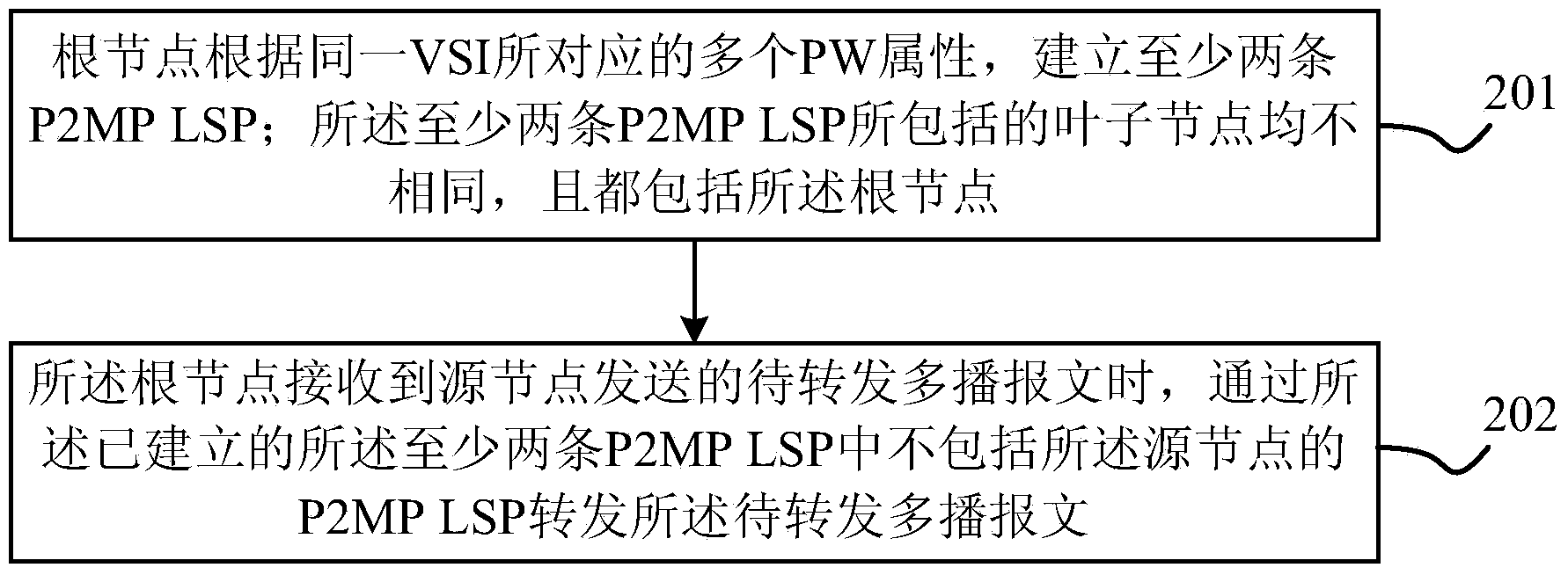
ActiveCN103532862AAvoid formingImprove multicast forwarding performanceNetworks interconnectionIP multicastPseudo-wire
The embodiment of the invention provides a method and a device for realizing multicast in hierarchy of a virtual private LAN (Local Area Network) service (H-VPLS) network. According to the method and the device for realizing multicast in the H-VPLS network provided by the embodiment of the invention, a P2MP LSP (Point-to-MultiPoint Layered Service Provider) is established for at least two PW (Pseudo Wire) attributes corresponding to the same VSI (Virtual Switch Instance) respectively, and all leaf nodes included by each P2MP LSP are different and all comprise root nodes; when a multicast message to be forwarded transmitted by a source node is received, the multicast message to be forwarded is forwarded by other P2MP LSPs other than the P2MP LSP with the source node as the leaf node, so that a loop is prevented from being formed during forwarding of the multicast message, and the multicast forward performance during adoption of the P2MP LSP technology in the H-VPLS network is improved.
Owner:HUAWEI TECH CO LTD
Enabling users to select between secure service providers using key escrow service
Systems and methods are described herein for enabling users to select from available secure service providers (each having a Trusted Service Manager ("TSM")) for provisioning applications and services on a secure element installed on a device of the user. The device includes a service provider selector ("SPS") module that provides a user interface for selecting the secure service provider. In one embodiment, the SPS communicates with a key escrow service that maintains cryptographic keys for the secure element and distributes the keys to the user selected secure service provider. The key escrow service also revokes the keys from deselected secure service providers. In another embodiment, the SPS communicates with a central TSM that provisions applications and service on behalf of the user selected secure service provider. The central TSM serves as a proxy between the secure service providers and the secure element.
Owner:GOOGLE LLC
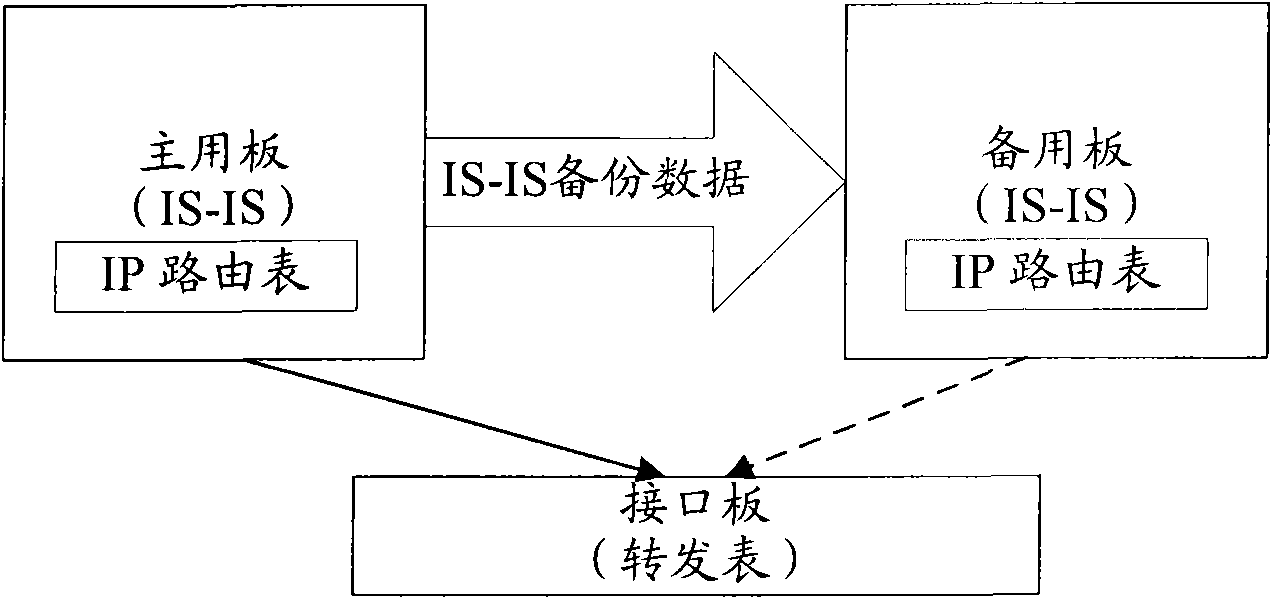
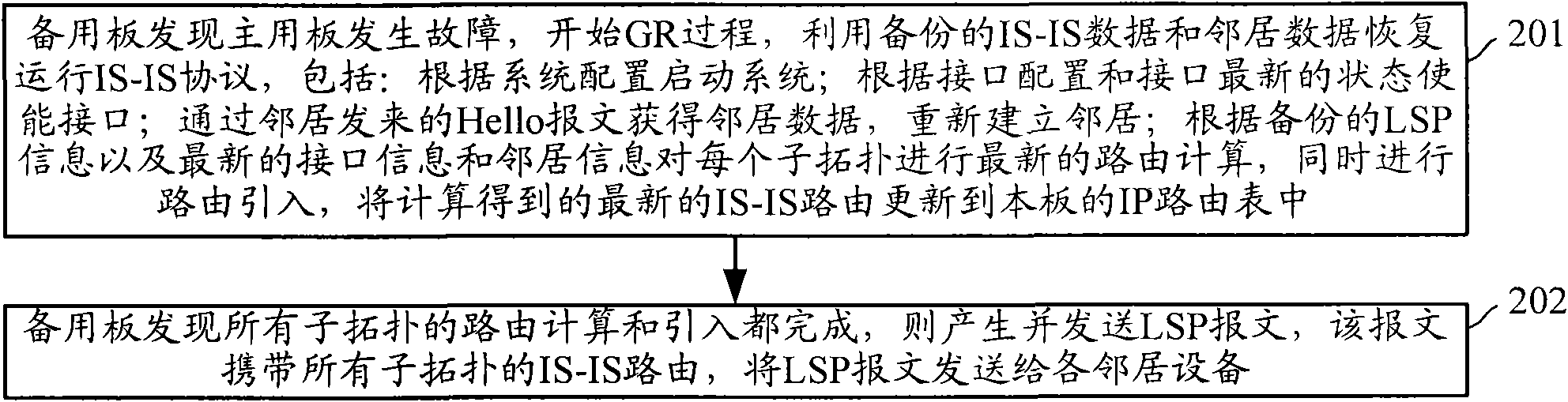
Main and standby switching method of device supporting multi-topology routing as well as master control board
ActiveCN102404189BShorten the timeError preventionData switching networksEngineeringLayered Service Provider
The invention discloses a main and standby switching method of a device supporting multi-topology routing as well as a master control board. The main and standby switching method of the device comprises the following steps that when a standby board of the device supporting MTR (Multi-Topology Routing) finds that a main board goes wrong, the standby board enters a main and standby switching process, a backup intermediate system is used for interconnecting IS-IS (Intermediate System-to-Intermediate System) data so as to carry out routing computation and introduction on each sub-topology; when the standby board finds that the routing computation and the introduction of one sub-topology are completed, the standby board generates a LSP (Layered Service Provider) message, and for the sub-topology subjected to the routing computation and the introduction, a routing computation and introduction completing mark of each sub-topology is arranged in the LSP message; and the standby board sends the LSP message to a neighborhood device so that the neighborhood device carries out local routing computation on each sub-topology subjected to the routing computation and the introduction on the standby board according to the routing computation and introduction completing mark in the LSP message. By adopting the main and standby switching method, the routing convergence time is reduced when the main and standby switching occurs in the device supporting multi-topology routing.
Owner:NEW H3C TECH CO LTD
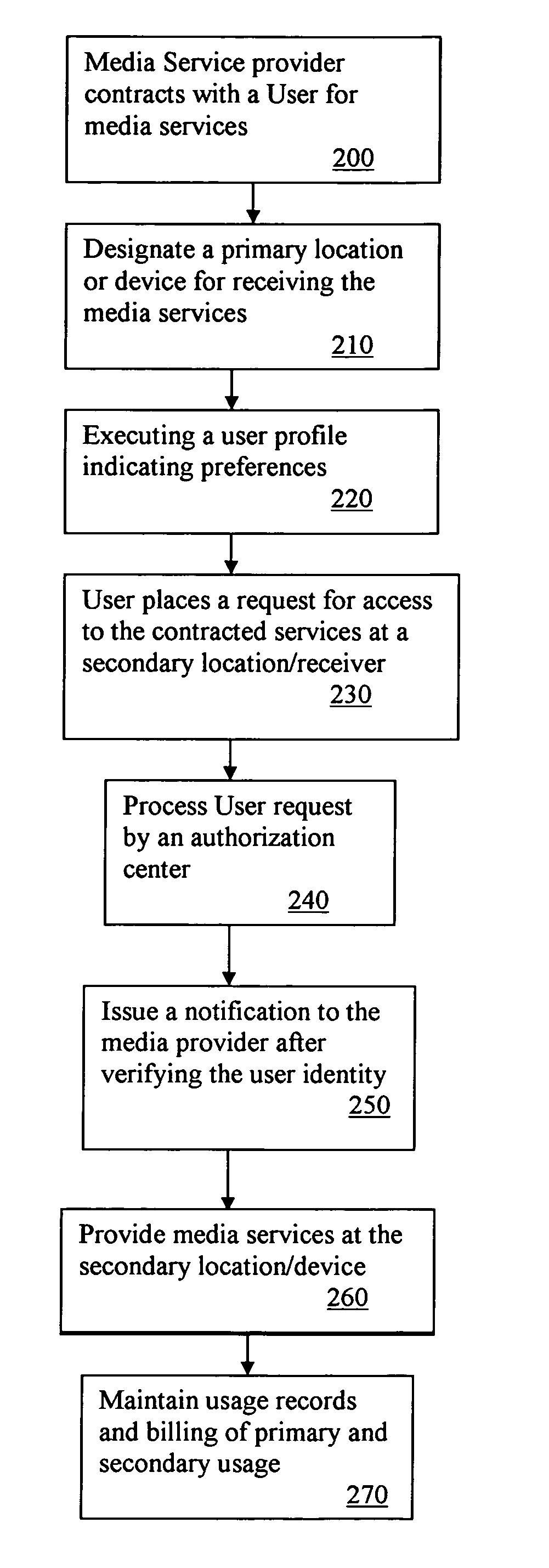
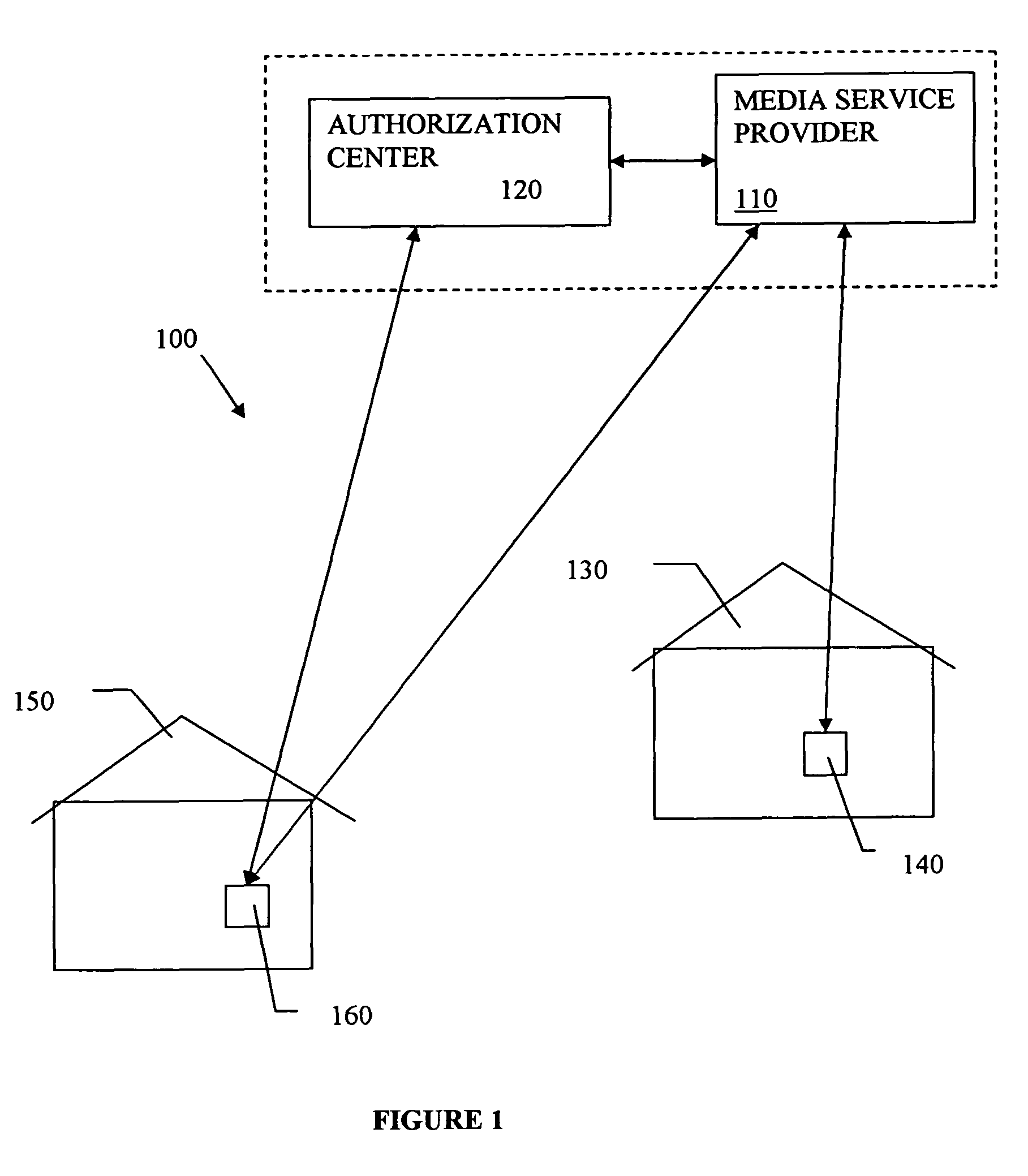
Media services with access control
InactiveUS8706082B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPayment service providerLayered Service Provider
Owner:AT&T INTPROP I LP
System for automatically matching a service requestor with a service provider based on their proximity and establishing a voice call between them
InactiveCN104885485ARoad vehicles traffic controlLocation information based serviceMatch algorithmsMinutiae
A system for automatically matching a service requestor with a service provider based on their physical proximity to each other. A client requesting a service (e.g. Taxi service) using a cellular telephone calls an automatic server. The server interfaces with the cellular operator(s) systems and acquires the client's location. The server also regularly keeps track of the locations and availability of pre-registered service providers (e.g. Taxi Cabs) through the same interface with the cellular operator(s). The server then matches the service requestor with a service provider based on the physical proximity of the latter to the former through a matching algorithm. Once the matching is performed, the server establishes a voice call where the service requestor is the call originator (A-Party) and the service provider is the call recipient (B-Party) so both parties can verbally agree on the details of their transaction.
Owner:STONETHROW TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com